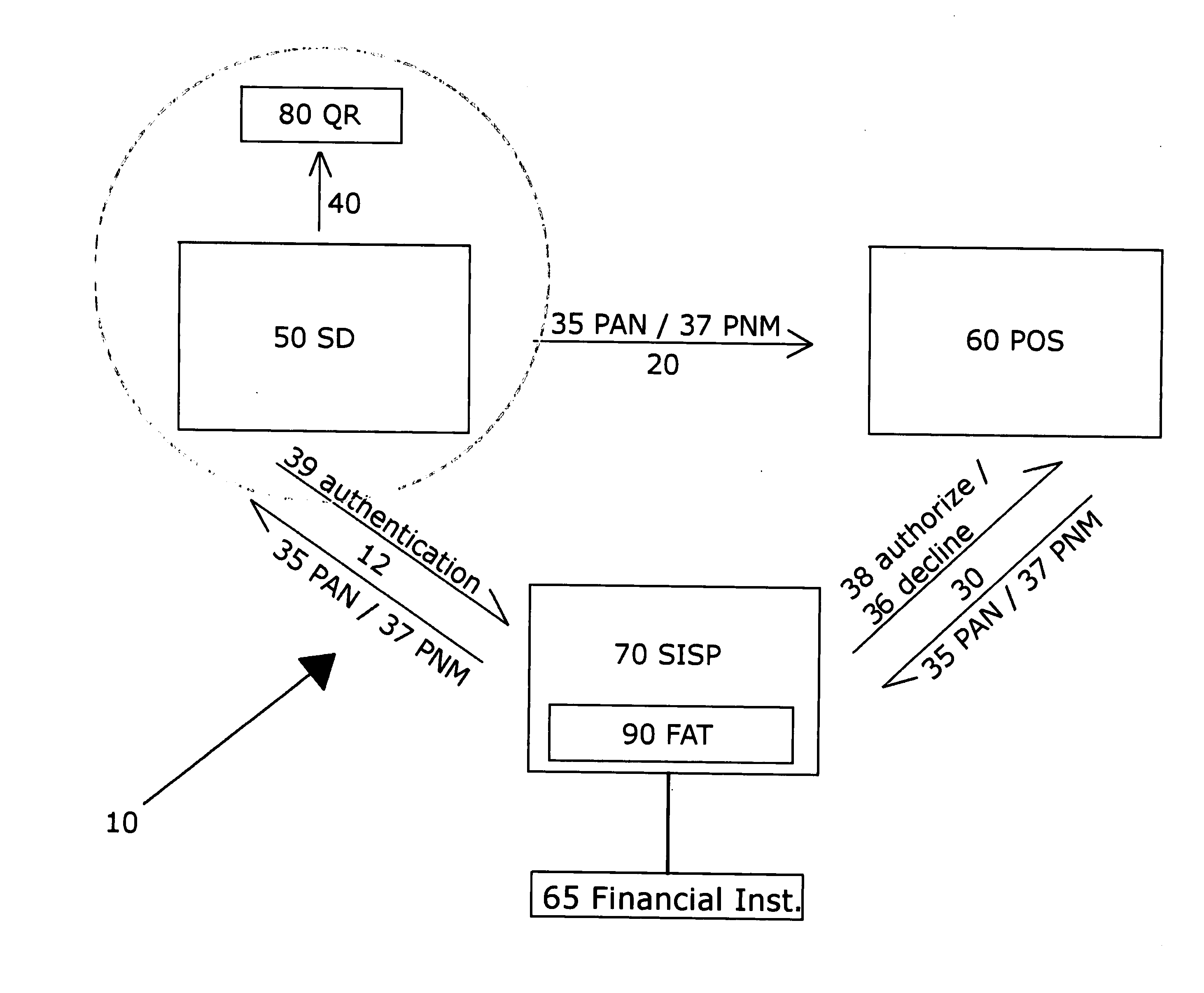
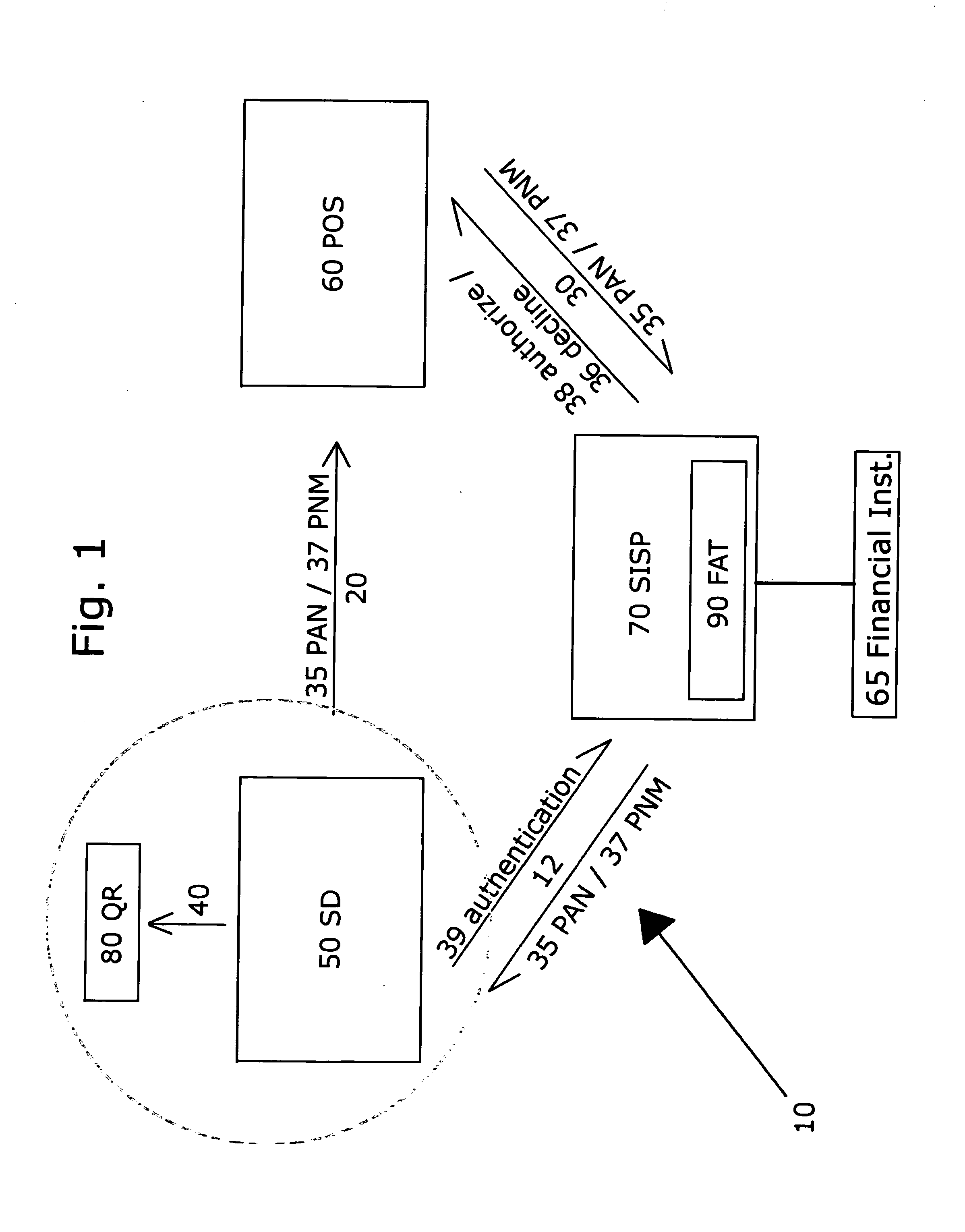
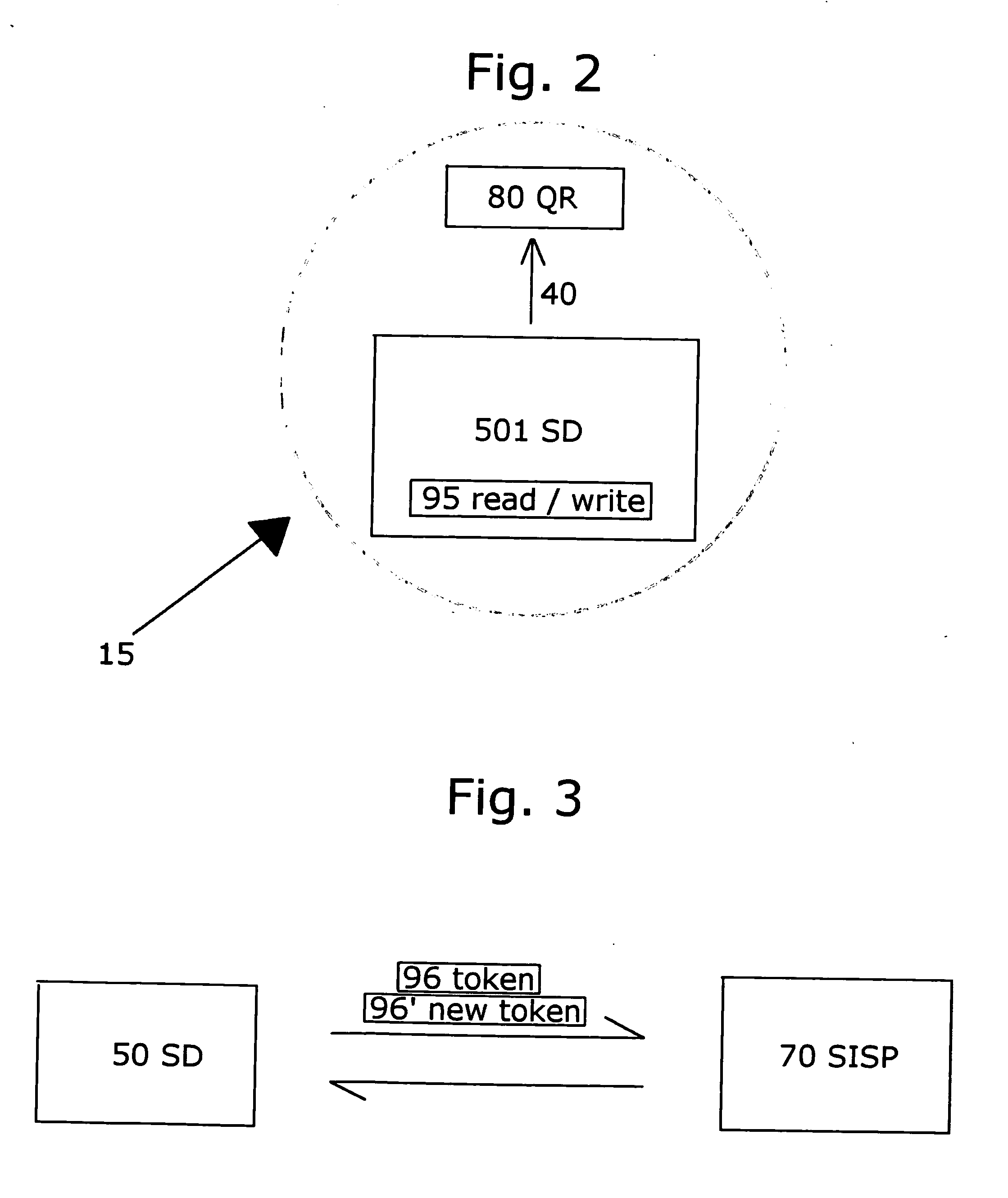
Patents
Literature
512results about "Anonymous user systems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
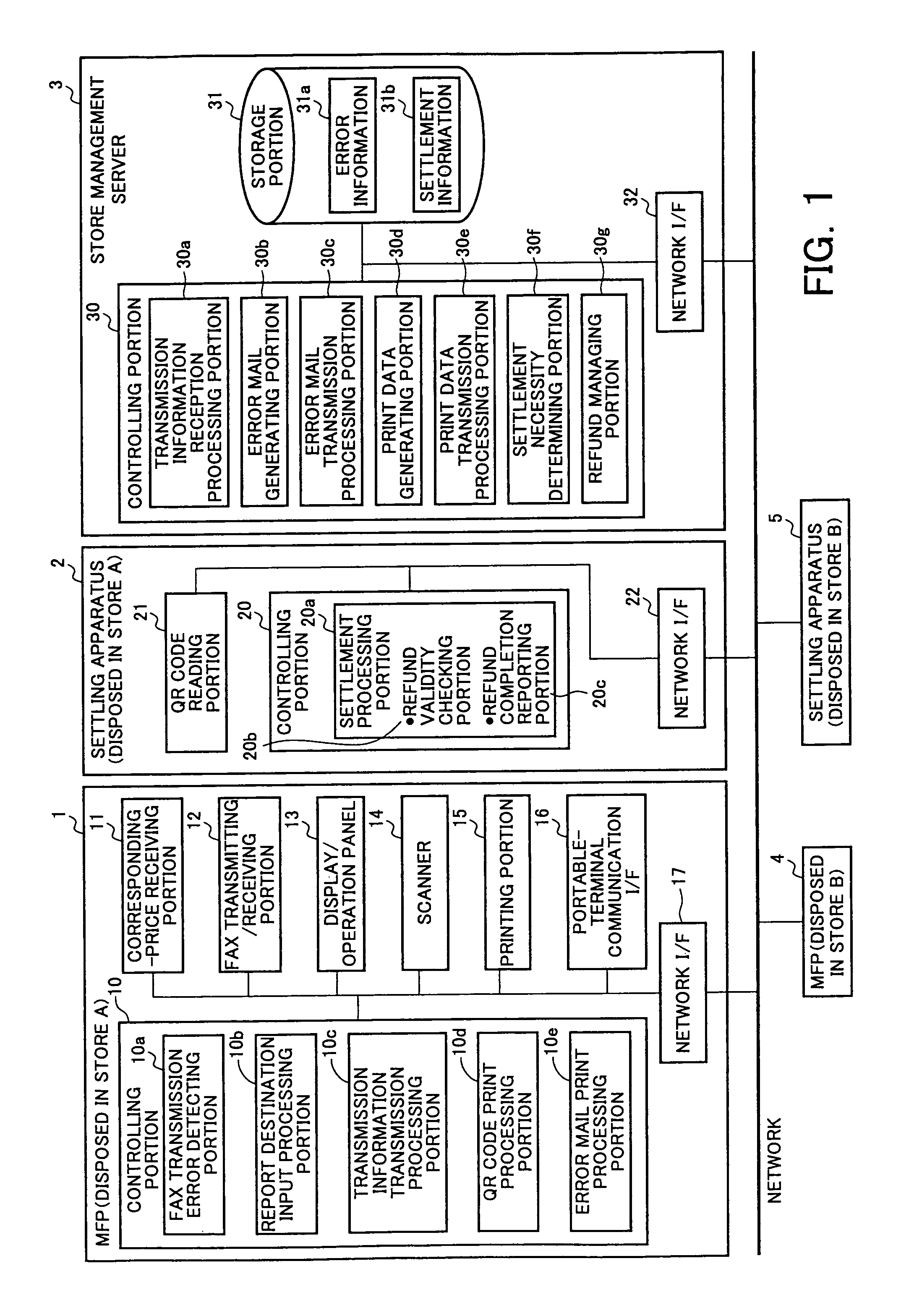
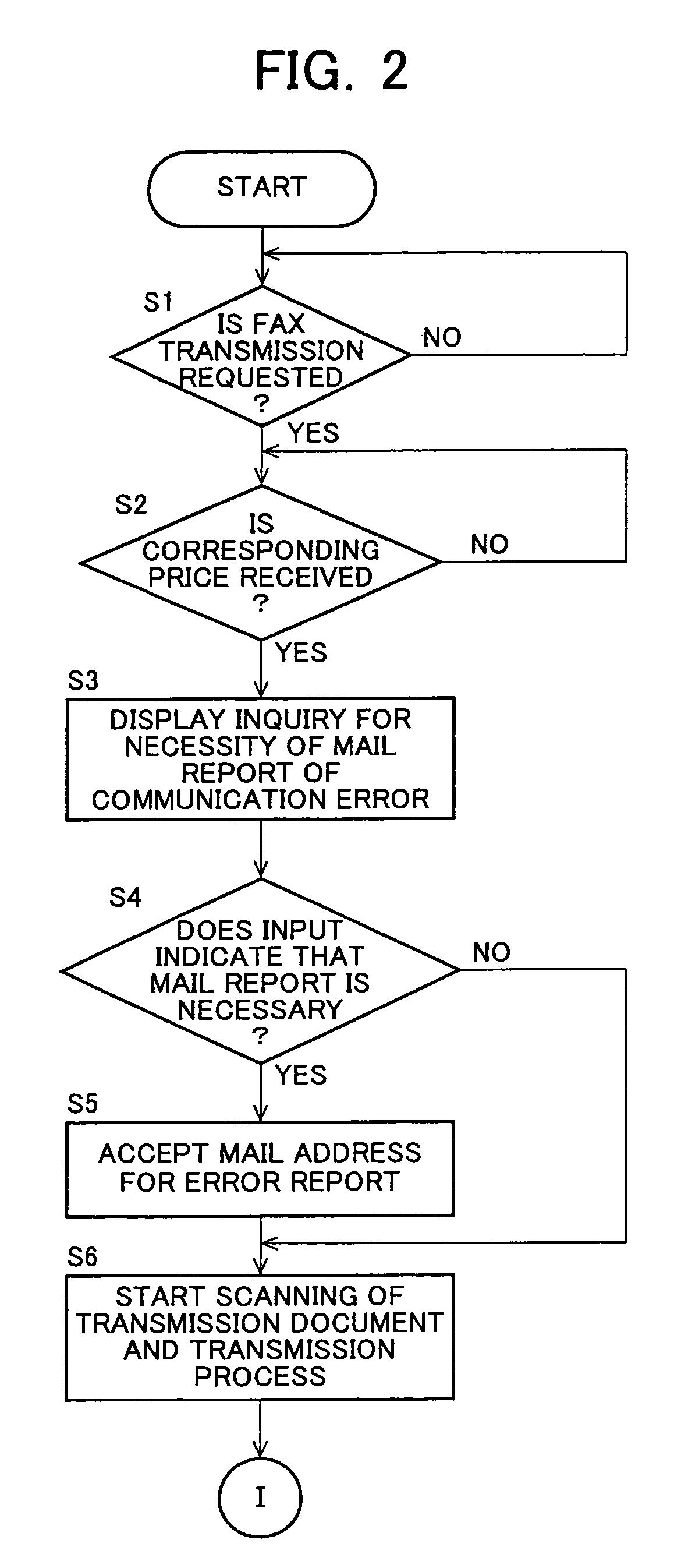
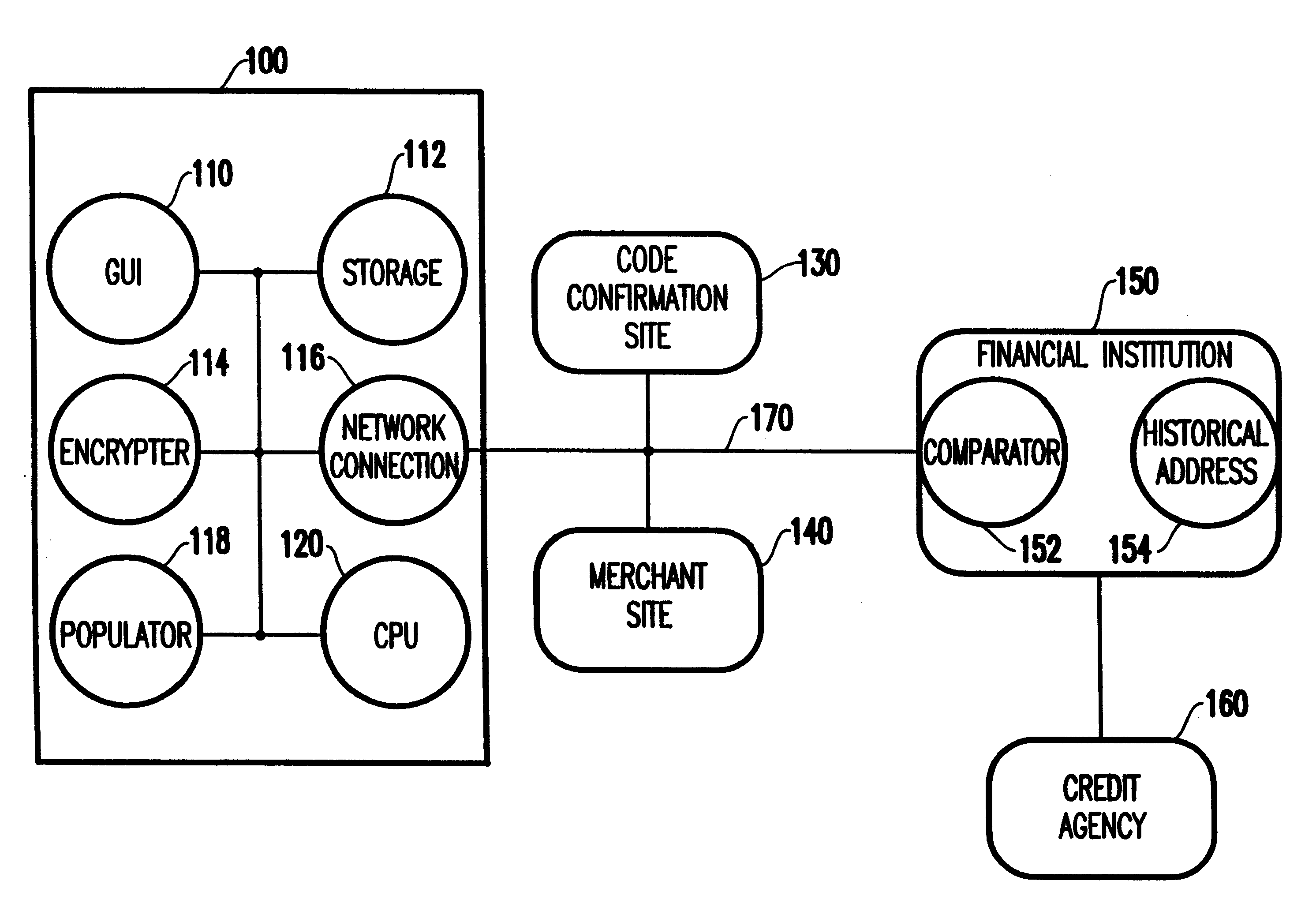
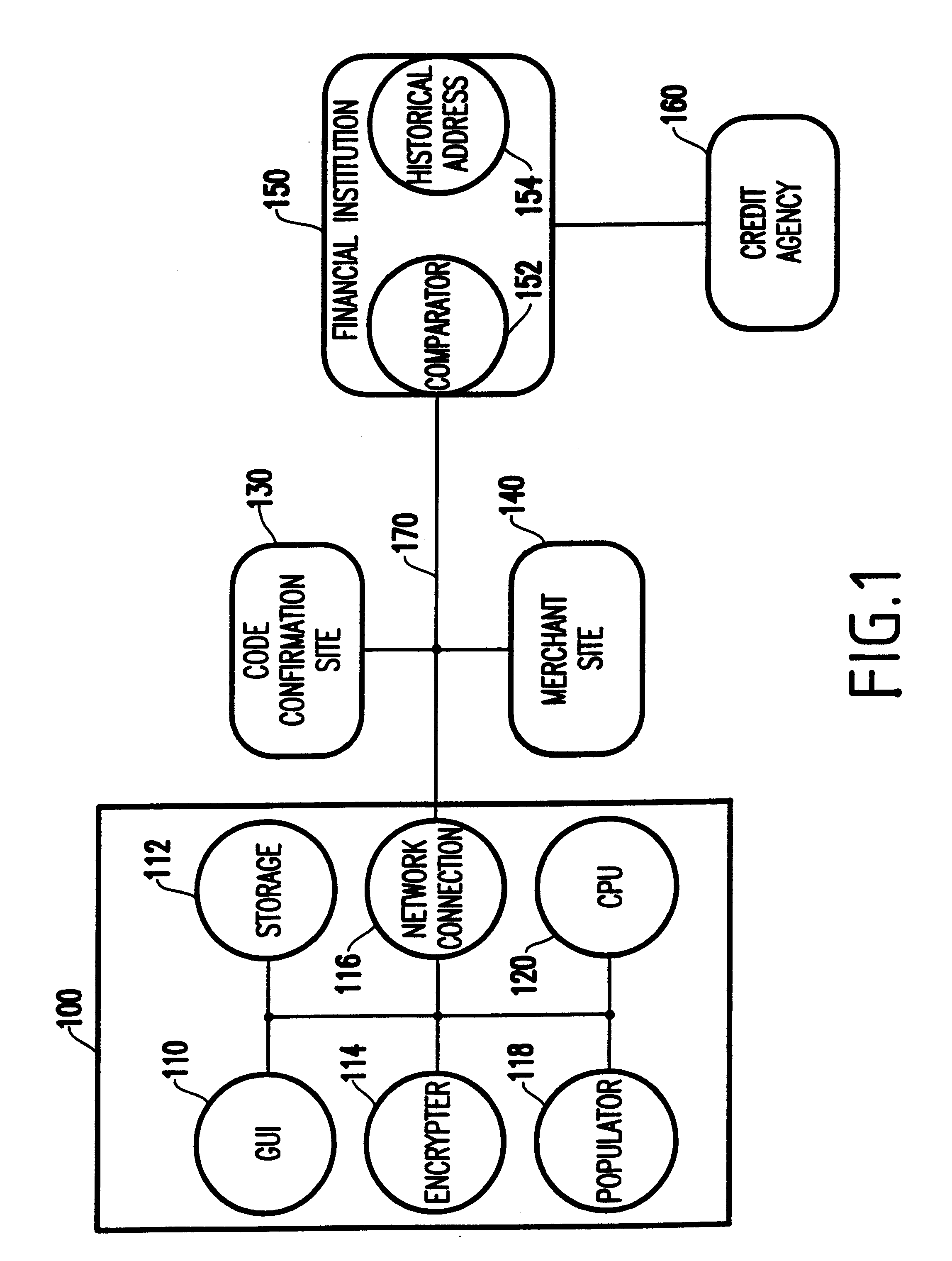
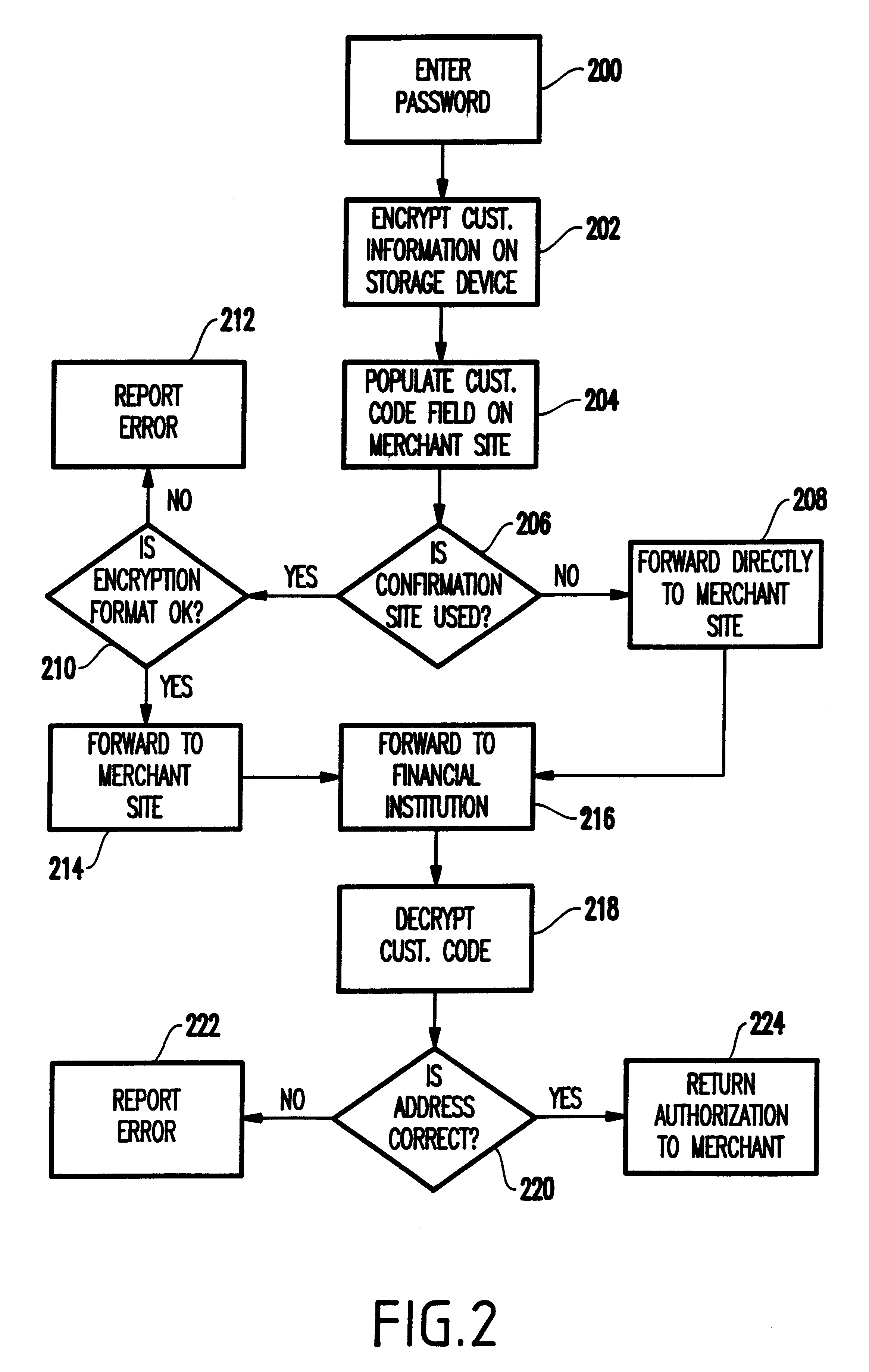
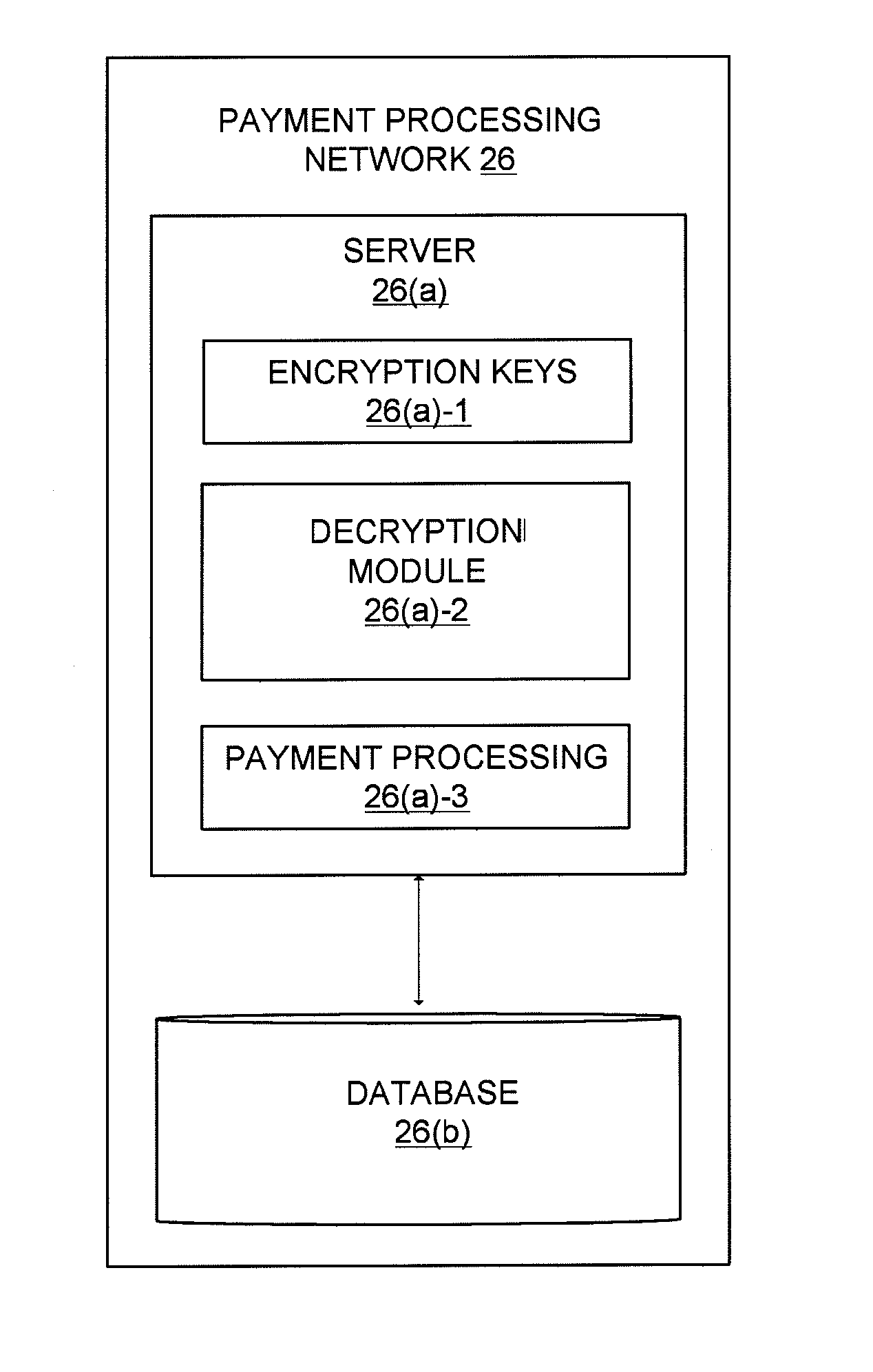
System and method for scheduling broadcast of and access to video programs and other data using customer profiles
InactiveUS6088722AMinimize memory requirementFacilitate text retrievalTelevision system detailsAnalogue secracy/subscription systemsTelevision systemData source
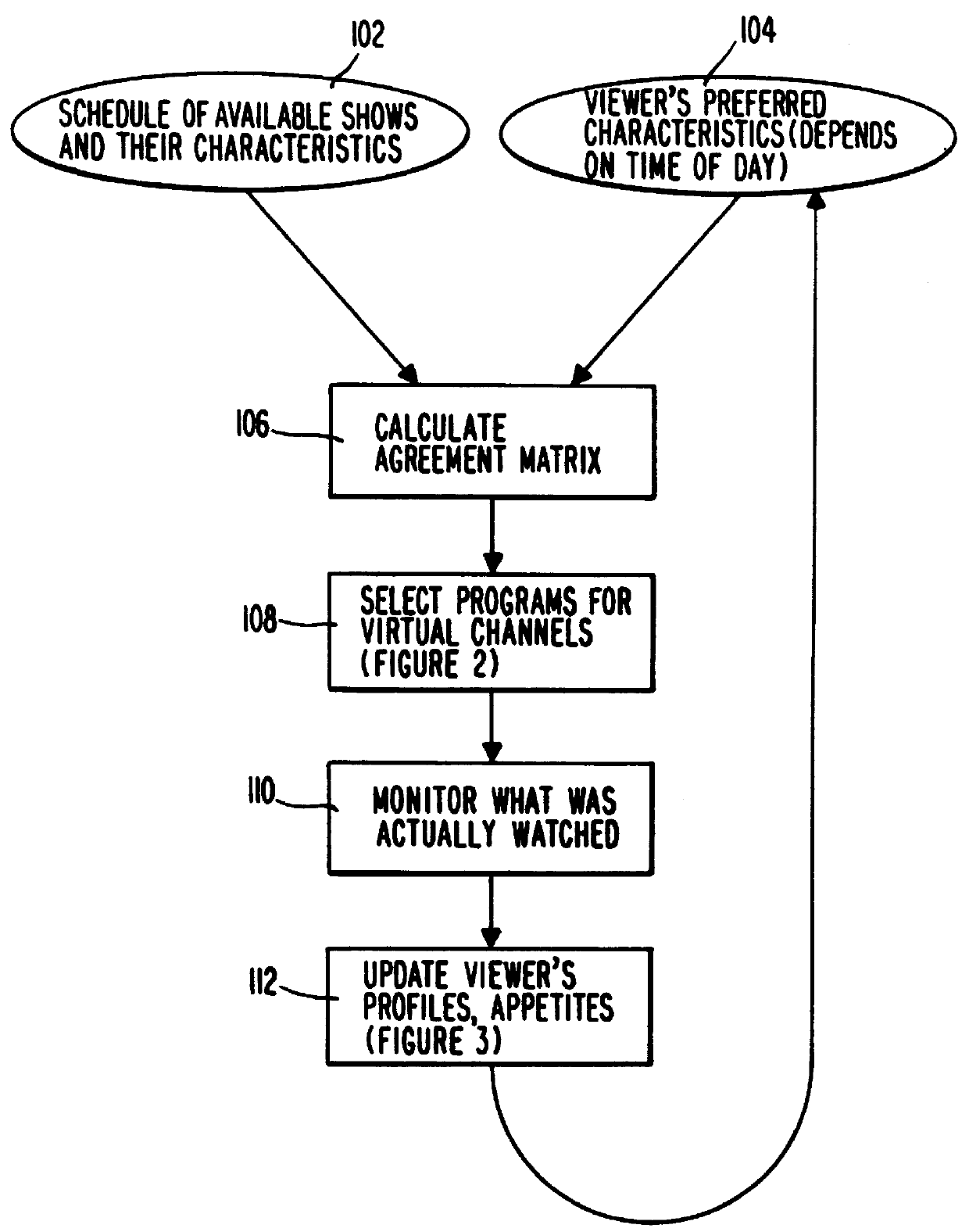
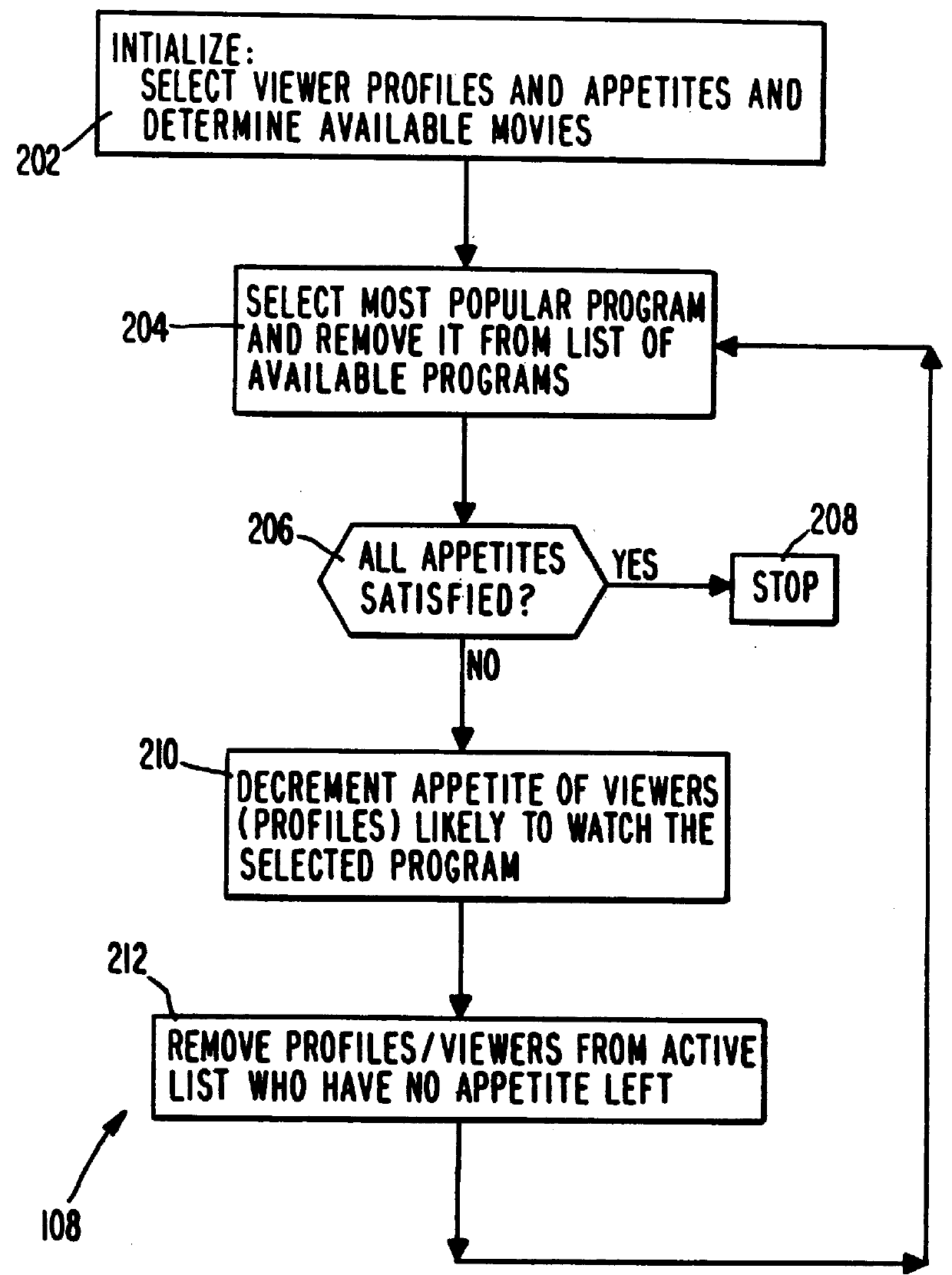
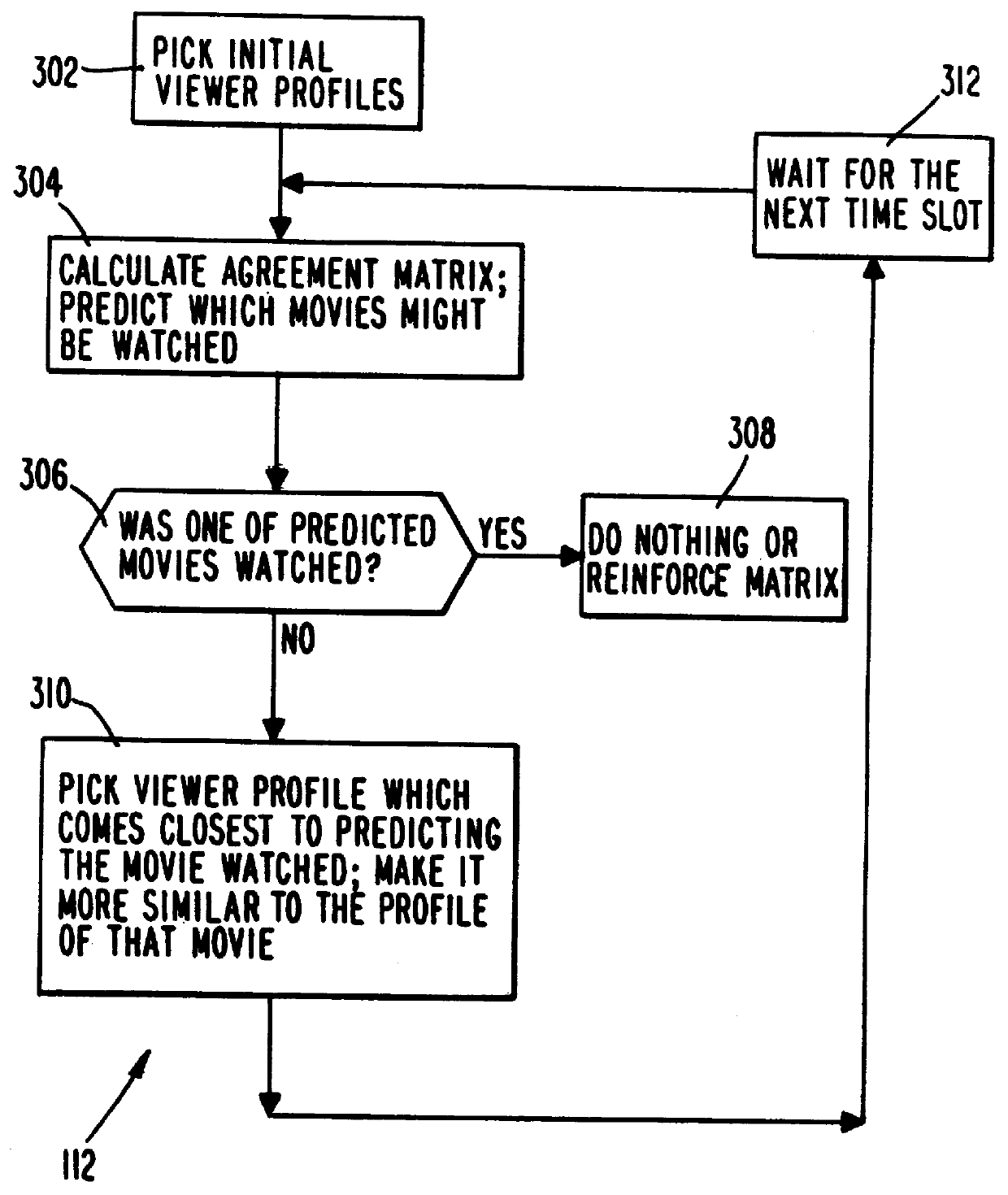
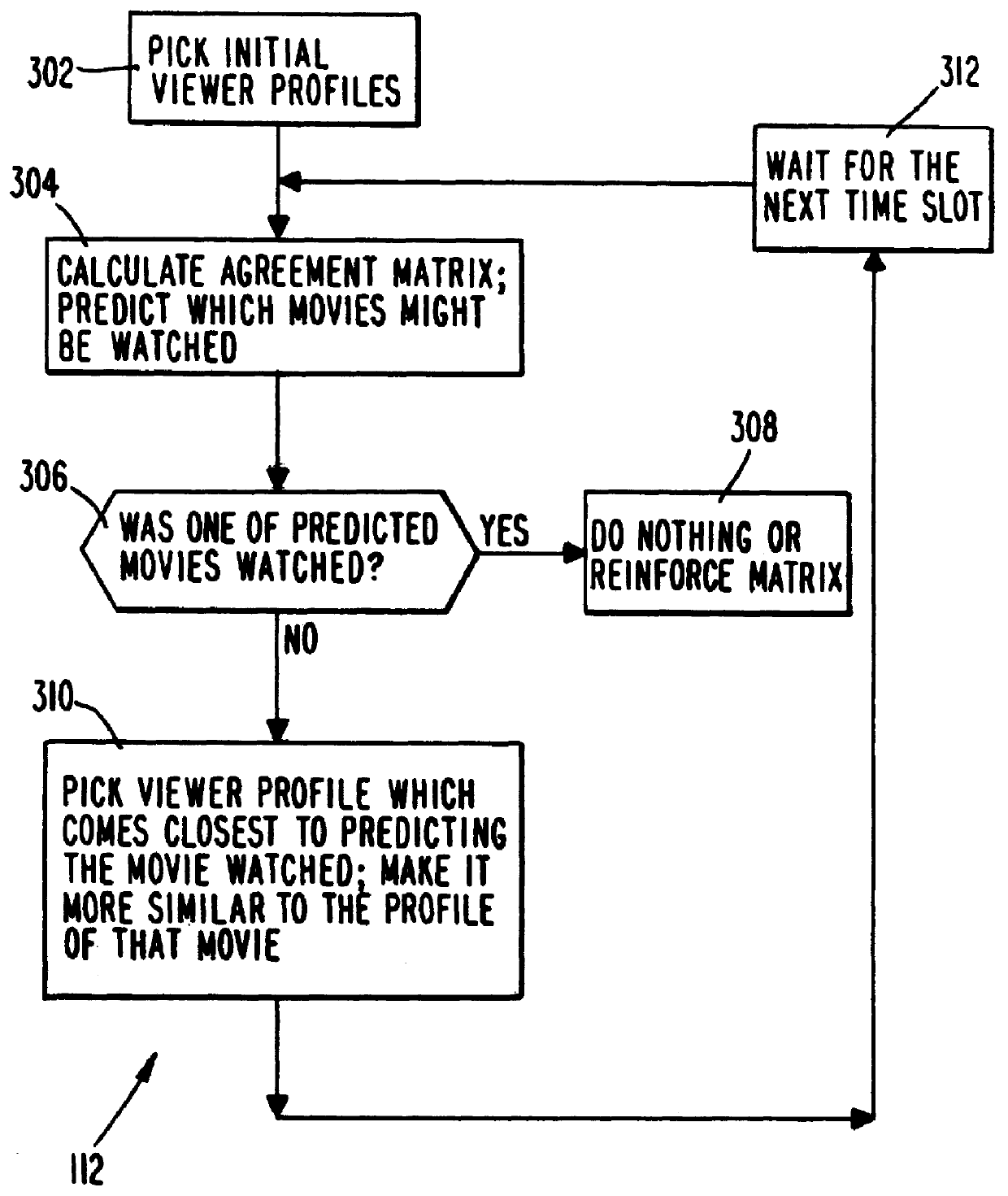
PCT No. PCT / US95 / 15429 Sec. 371 Date Dec. 24, 1997 Sec. 102(e) Date Dec. 24, 1997 PCT Filed Nov. 29, 1995 PCT Pub. No. WO96 / 17467 PCT Pub. Date Jun. 6, 1996A system and method for scheduling the receipt of desired movies and other forms of data from a network, which simultaneously distributes many sources of such data to many customers, as in a cable television system. Customer profiles are developed for the recipient describing how important certain characteristics of the broadcast video program, movie, or other data are to each customer. From these profiles, an "agreement matrix" is calculated by comparing the recipient's profiles to the actual profiles of the characteristics of the available video programs, movies, or other data. The agreement matrix thus characterizes the attractiveness of each video program, movie, or other data to each prospective customer. "Virtual" channels are generated from the agreement matrix to produce a series of video or data programming which will provide the greatest satisfaction to each customer. Feedback paths are also provided so that the customer's profiles and / or the profiles of the video programs or other data may be modified to reflect actual usage, and so that the data downloaded to the customer's set top terminal may be minimized. Kiosks are also developed which assist customers in the selection of videos, music, books, and the like in accordance with the customer's objective profiles.
Owner:FRED HERZ PATENTS
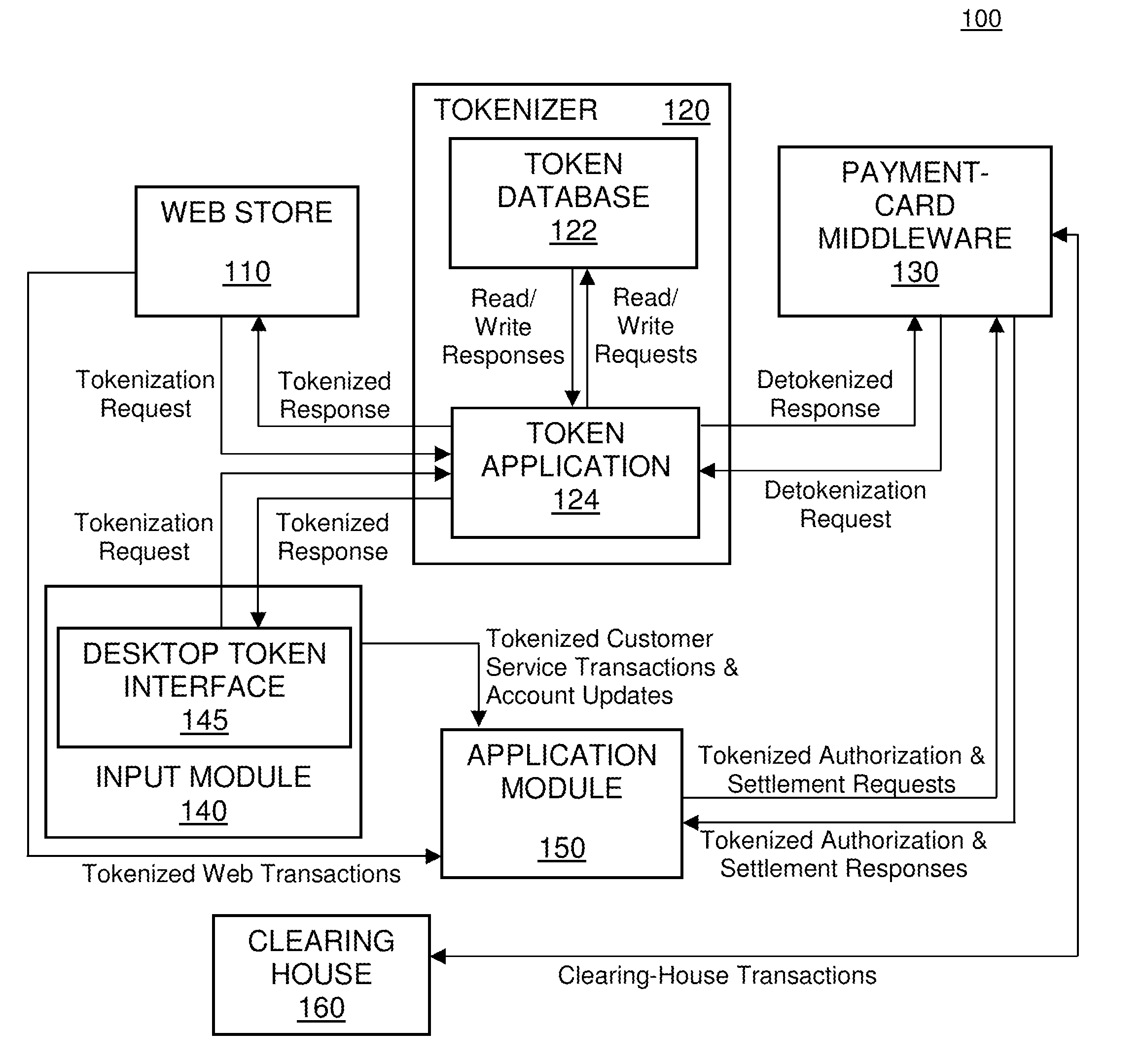
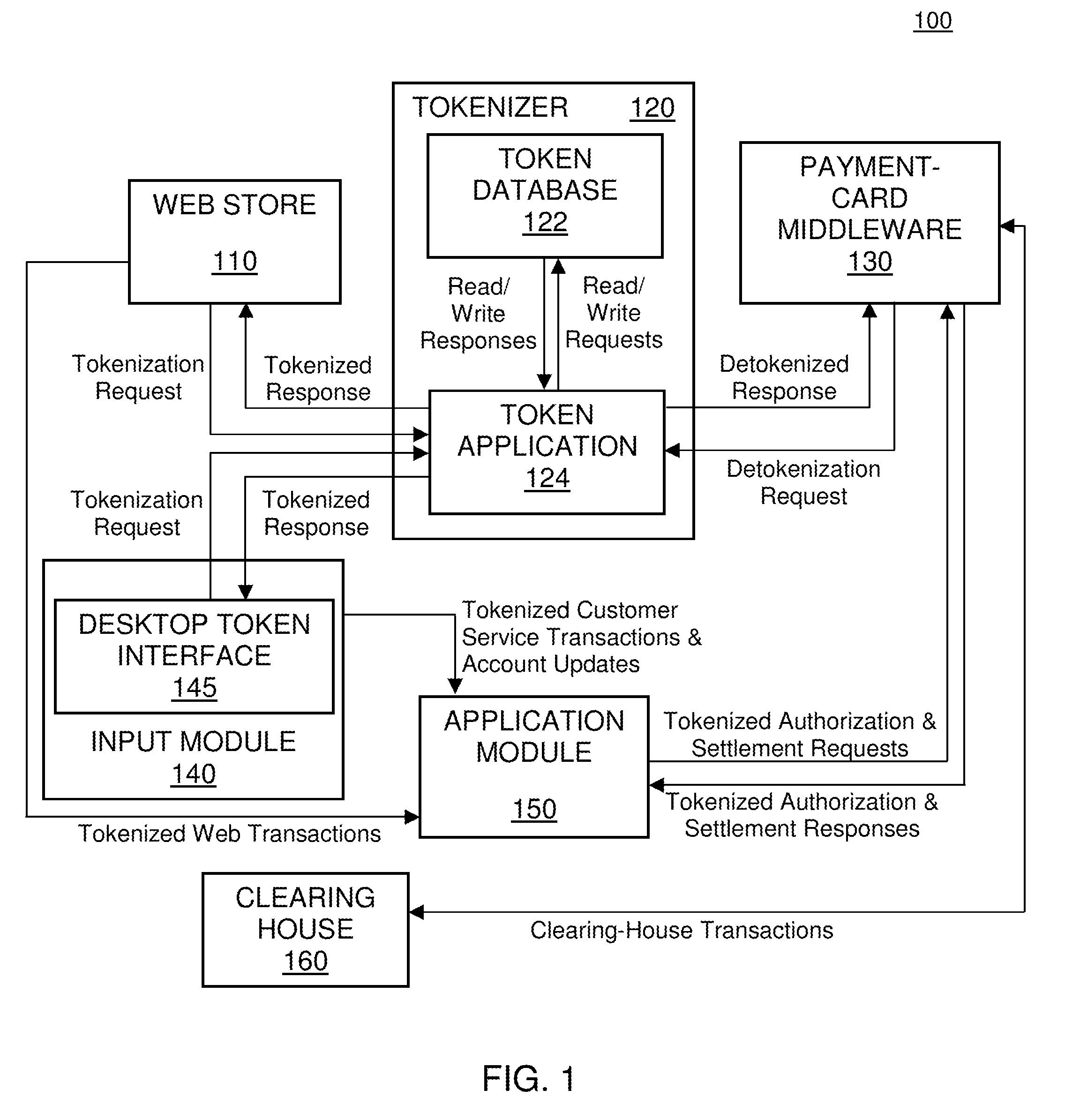
Data transmission system and data transmitting method
Owner:SHARP KK
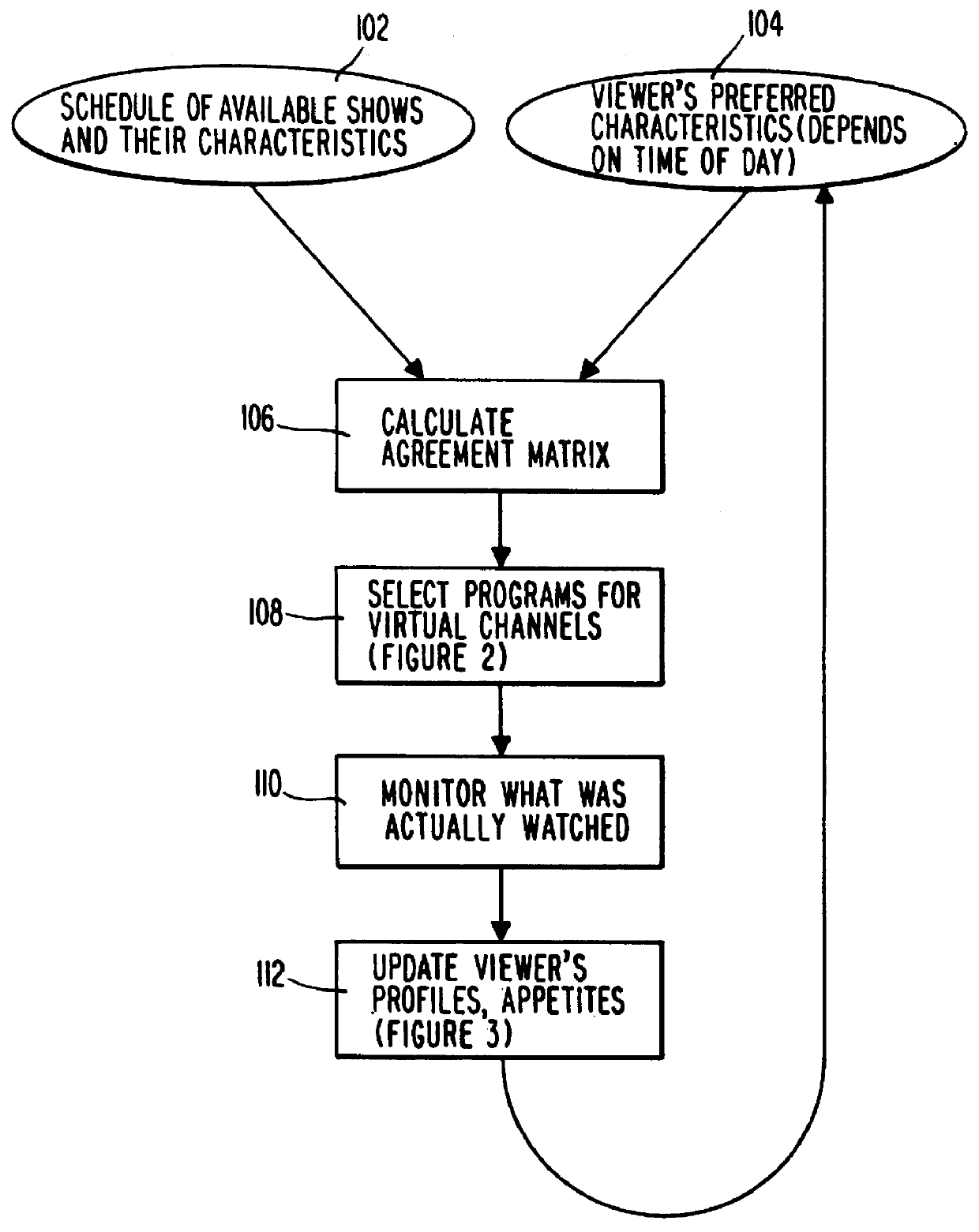
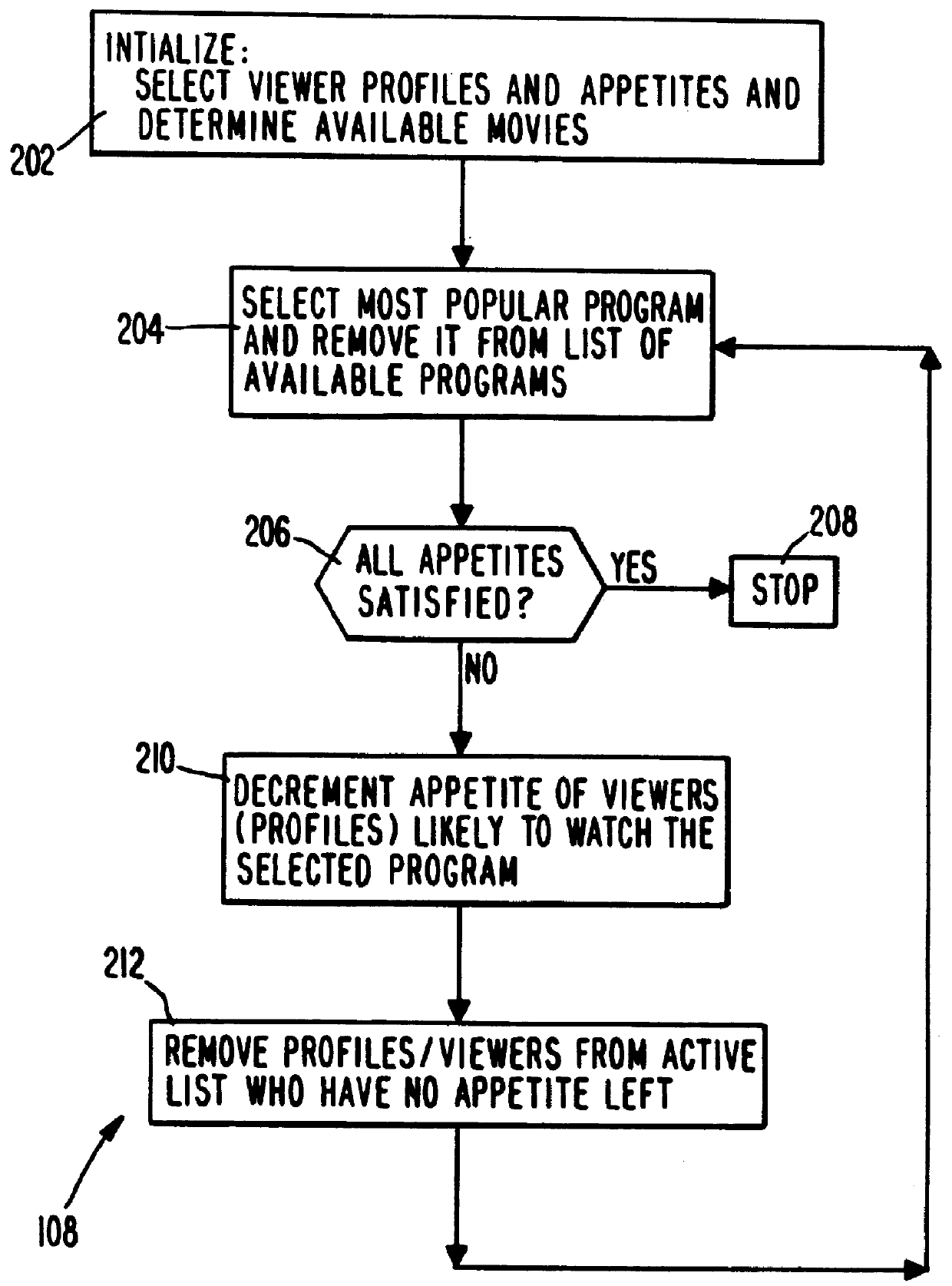
System and method for scheduling broadcast of and access to video programs and other data using customer profiles
InactiveUS6020883ATelevision system detailsAnalogue secracy/subscription systemsTelevision systemData source
A system and method for scheduling the receipt of desired movies and other forms of data from a network which simultaneously distributes many sources of such data to many customers, as in a cable television system. Customer profiles are developed for the recipient describing how important certain characteristics of the broadcast video program, movie or other data are to each customer. From these profiles, an "agreement matrix" is calculated by comparing the recipient's profiles to the actual profiles of the characteristics of the available video programs, movies, or other data. The agreement matrix thus characterizes the attractiveness of each video program, movie, or other data to each prospective customer. "Virtual" channels are generated from the agreement matrix to produce a series of video or data programming which will provide the greatest satisfaction to each customer. Feedback paths are also provided so that the customer's profiles and / or the profiles of the video programs or other data may be modified to reflect actual usage. Kiosks are also developed which assist customers in the selection of videos, music, books, and the like in accordance with the customer's objective profiles.
Owner:PINPOINT
System, method, and business methods for enforcing privacy preferences on personal-data exchanges across a network
ActiveUS7478157B2Digital data processing detailsDigital computer detailsInternet privacyData exchange
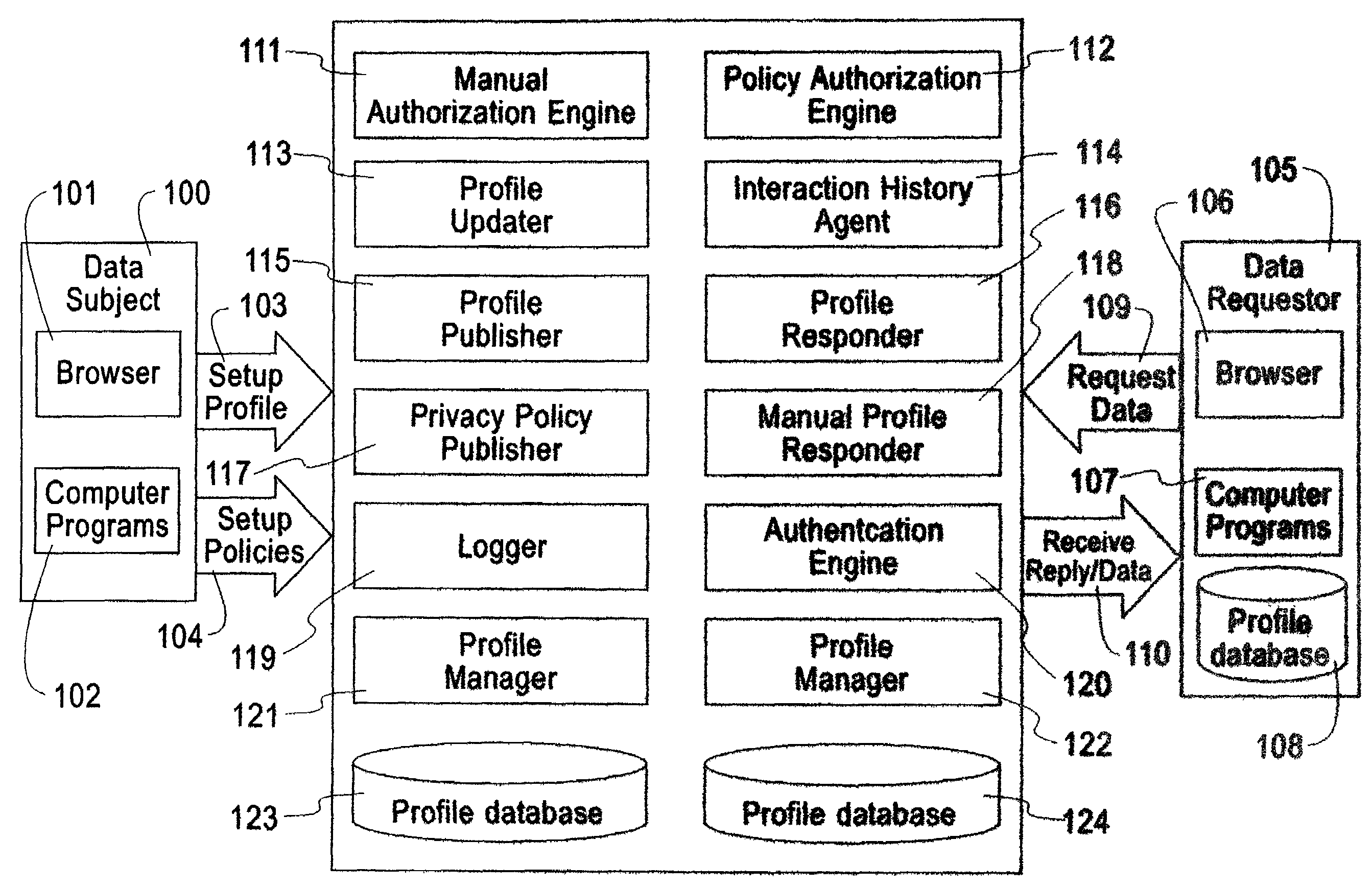
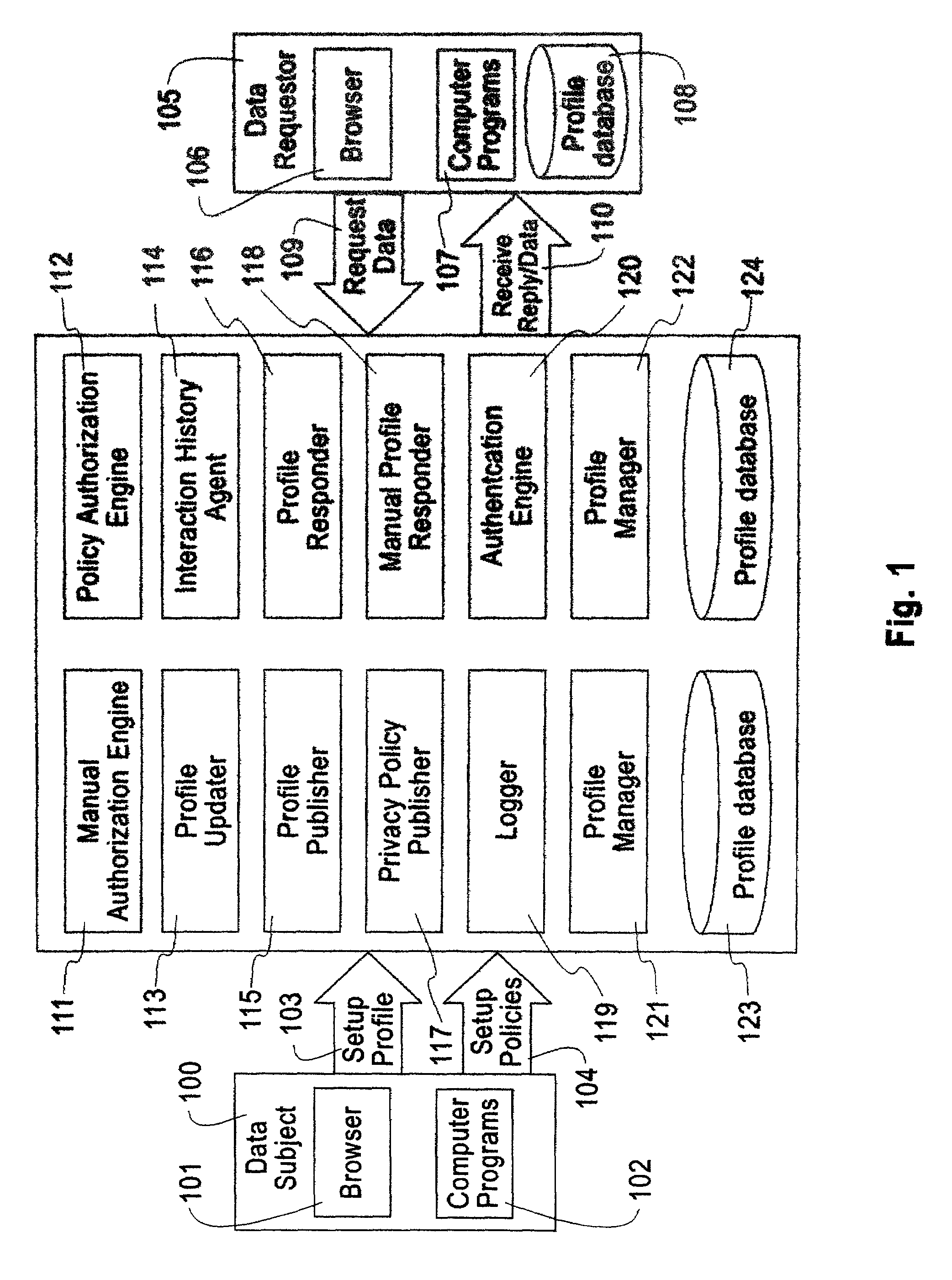
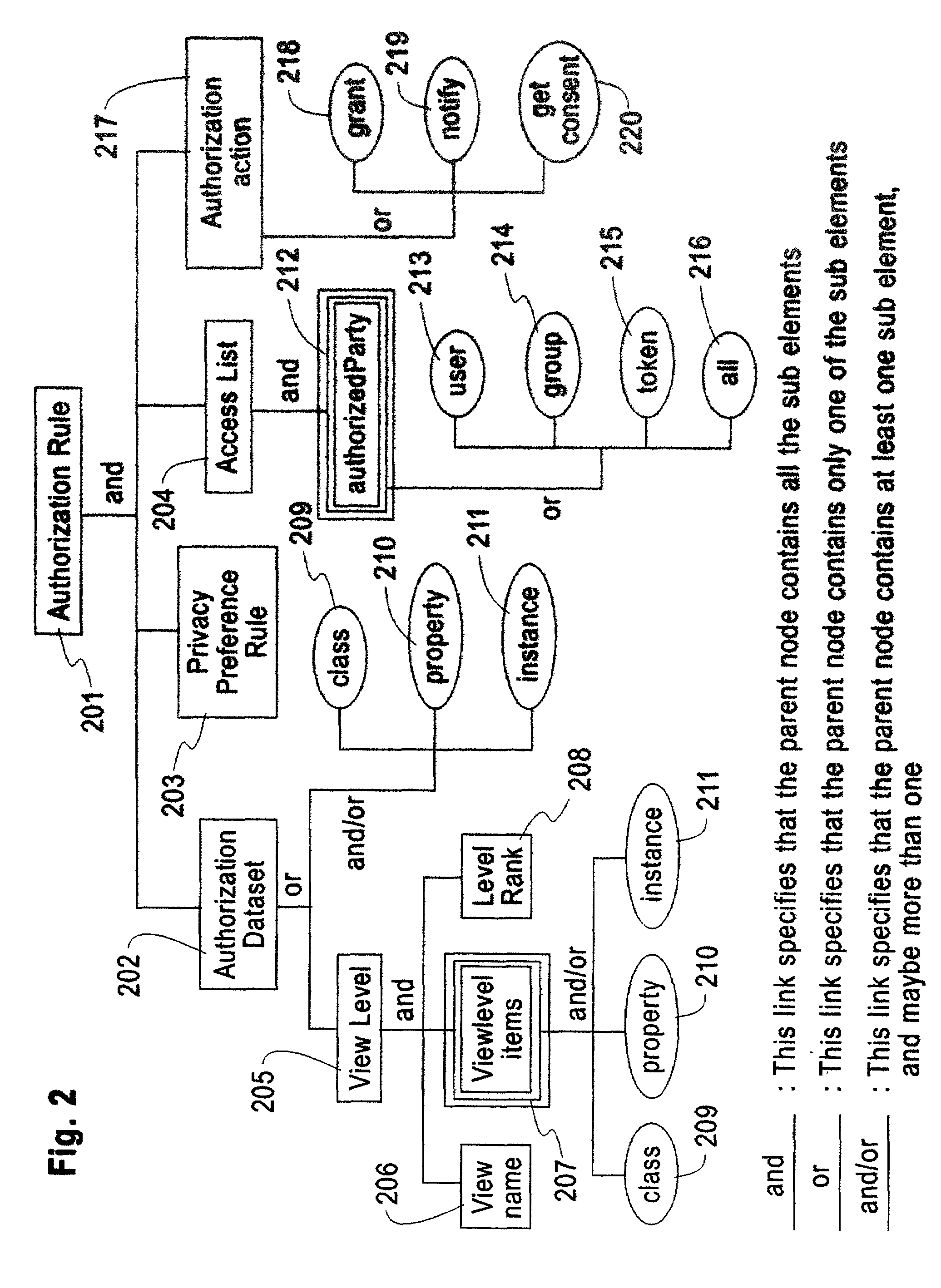
An exemplary embodiment of the present invention includes a method to enforce privacy preferences on exchanges of personal data of a data-subject. The method comprises the steps of: specifying data-subject authorization rule sets having subject constraints, receiving a request message from a requester and a requester privacy statement, comparing the requester privacy statement to the subject constraints, and releasing the data-subject data in a response message to the requester only if the subject constraints are satisfied. The requester privacy statement includes purpose, retention, recipient, and access information, wherein the purpose information specifies the purpose for which the requested data is acquired, the retention information specifies a retention policy for the requested data, the recipient information specifies the recipients of the requested data, and the access information specifies whether the requested data should be accessing to the data-subject after the data has been released.
Owner:IBM CORP
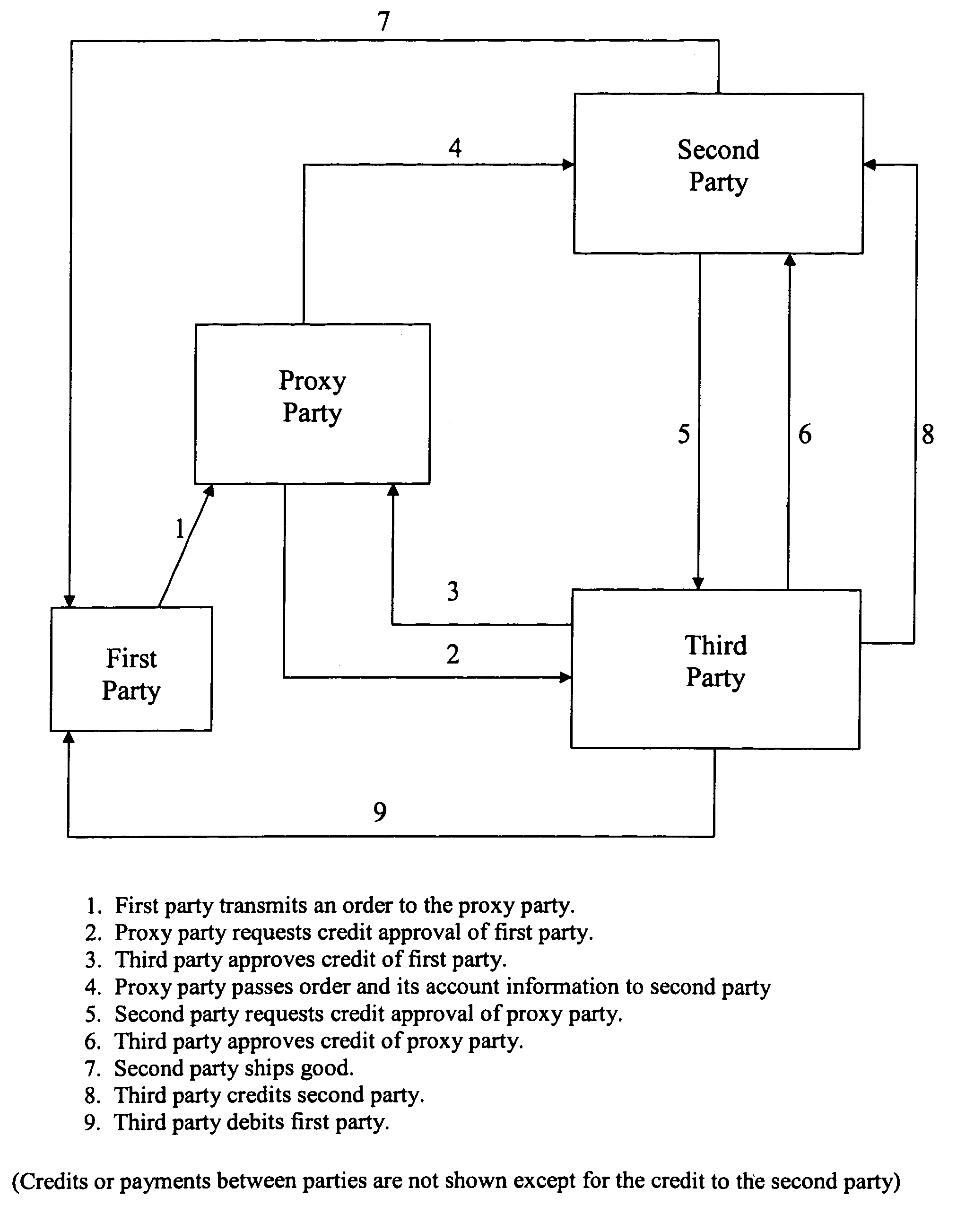
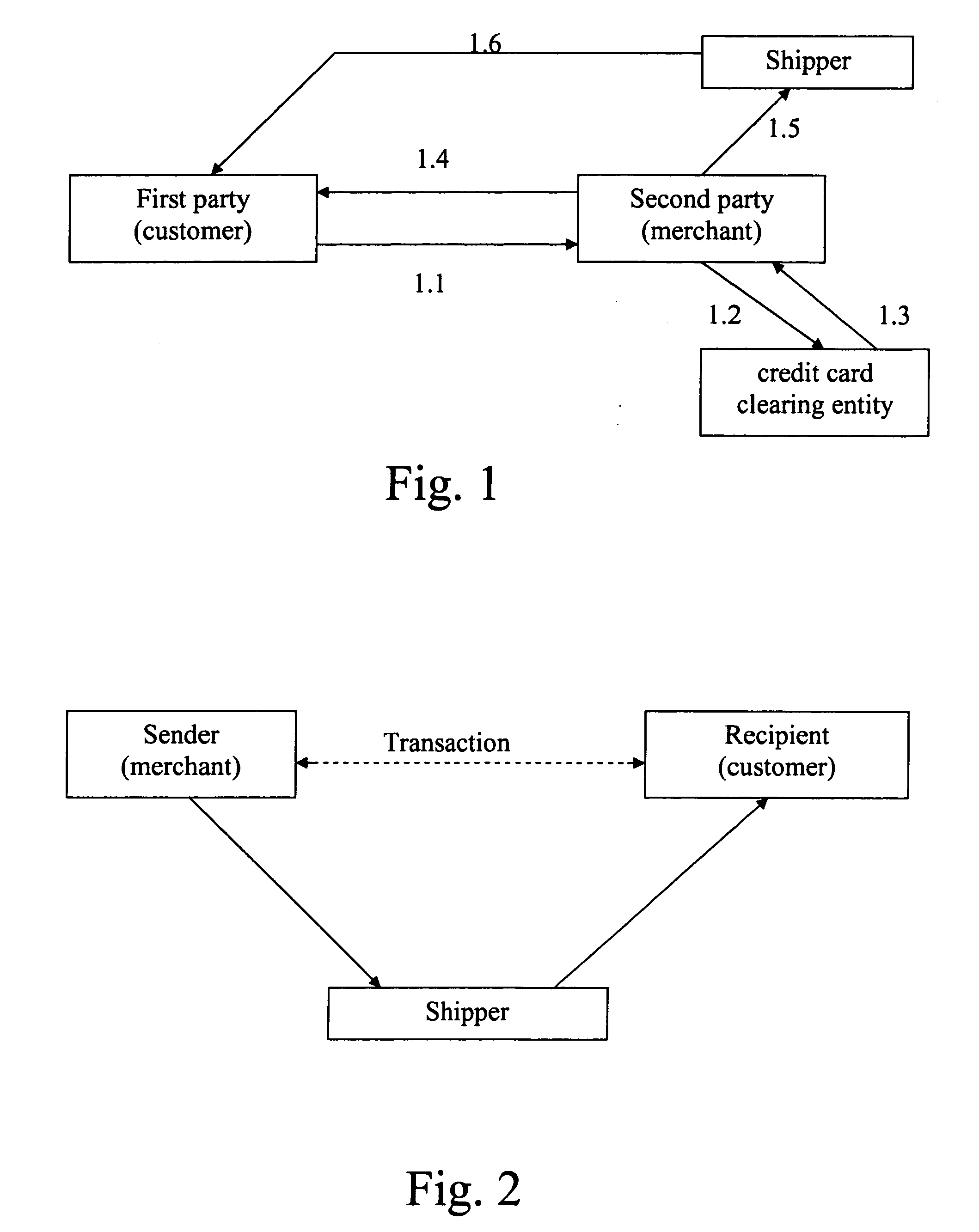
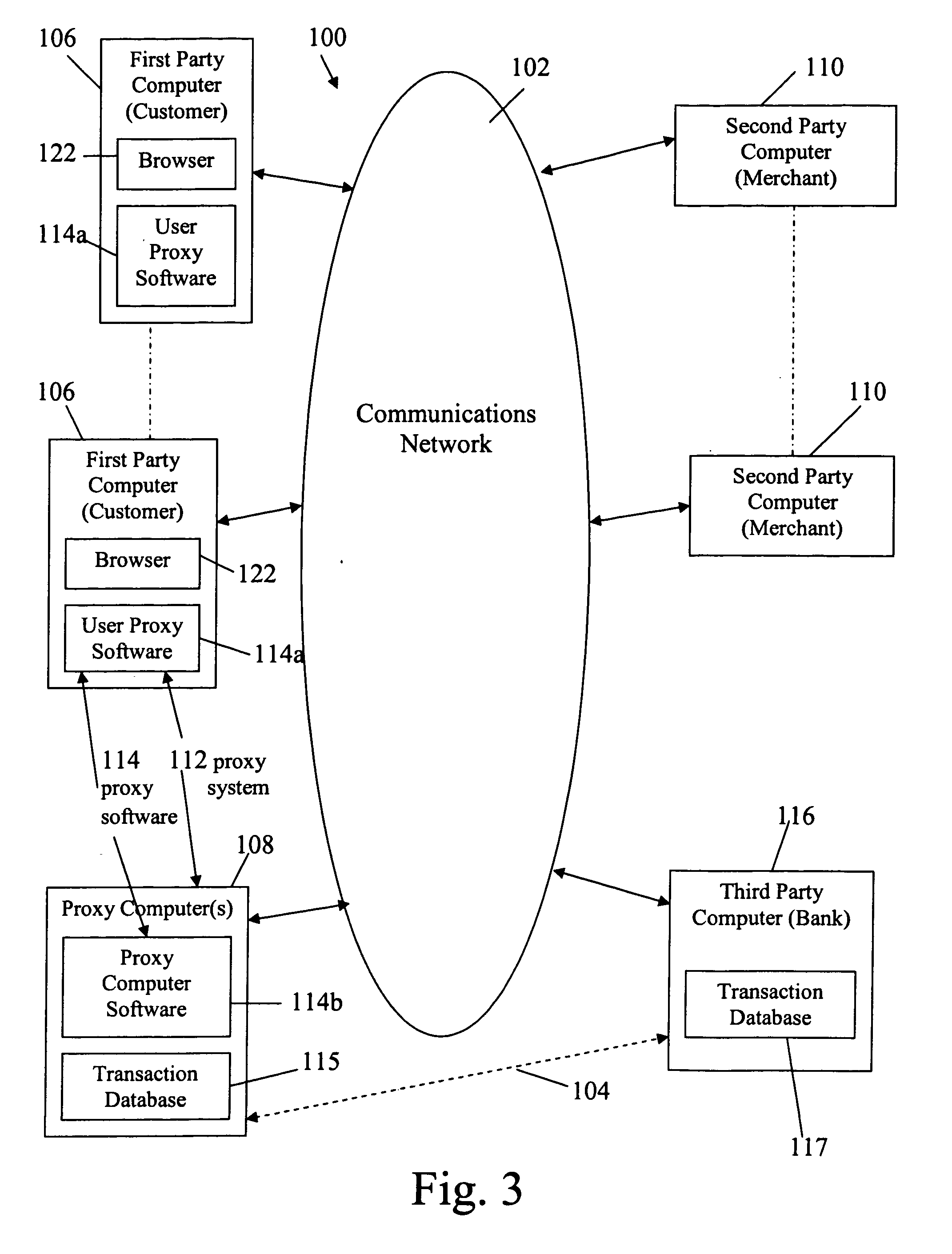
Electronic purchase of goods over a communications network including physical delivery while securing private and personal information of the purchasing party
InactiveUS7069249B2Improve privacy protectionReduce collectionSecret communicationBuying/selling/leasing transactionsPaymentComputer network
E-commerce which may include delivery of a good ordered or purchased over a network (e.g., the Internet) to a purchaser / user, and / or arranging for electronic payment of the good is accomplished while securing private and personal information of purchasers / users. Proxy software is provided for user computers, one or more proxy computers, or both, for users to communicate with vendors anonymously over the network, provide for delivery of an ordered good and provide for electronic payment, while securing the user's private information.
Owner:IPRIVACY
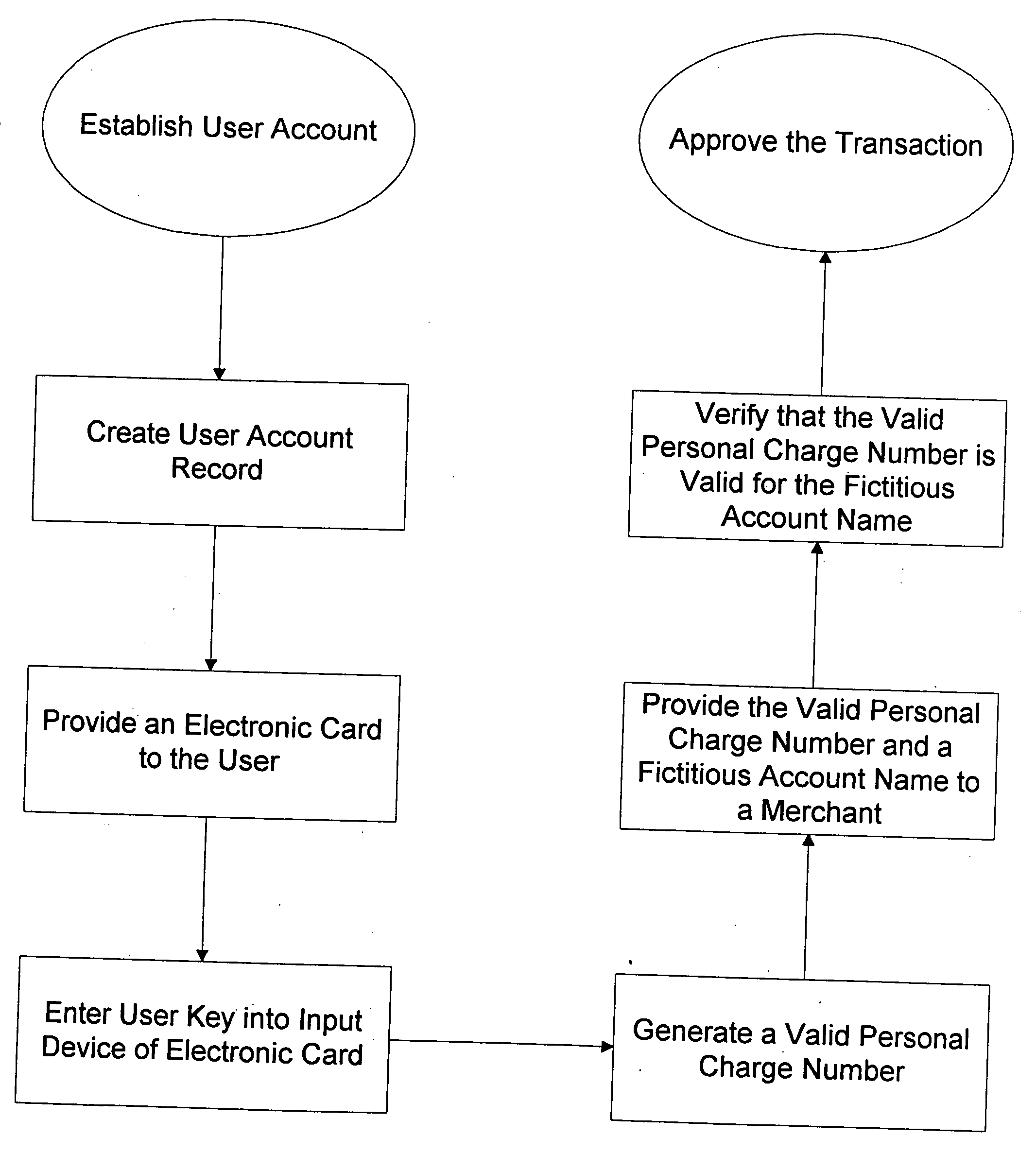
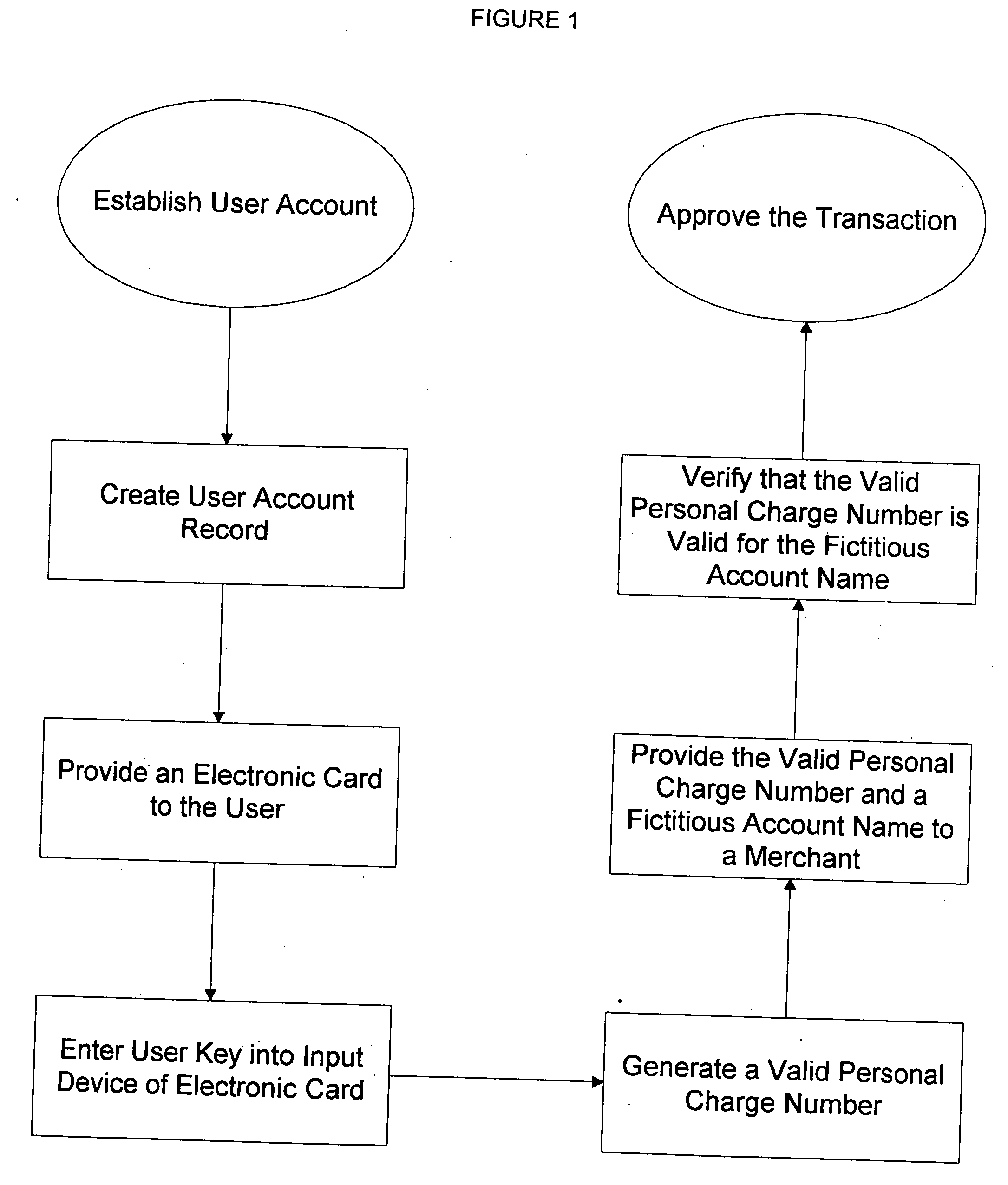
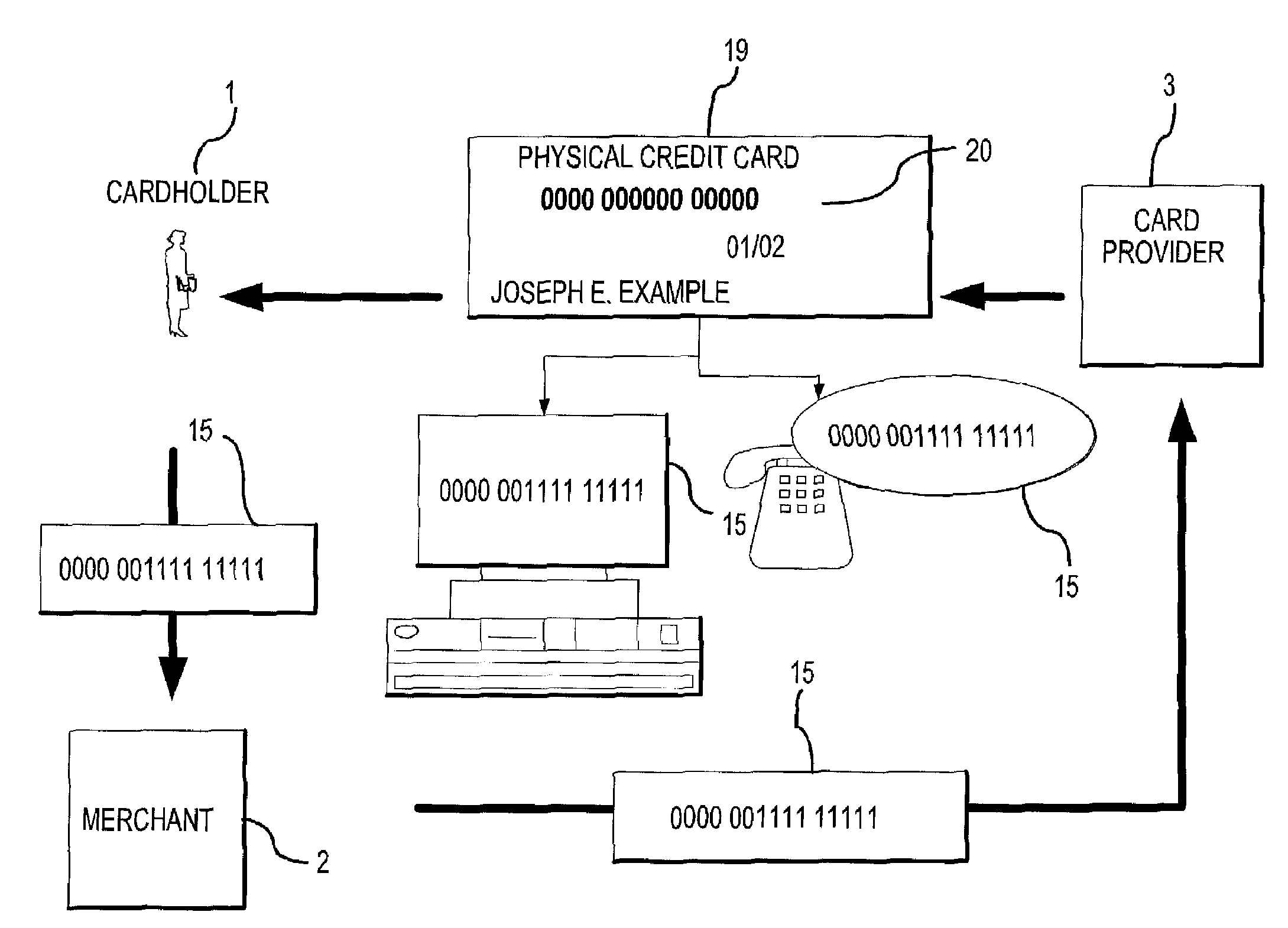
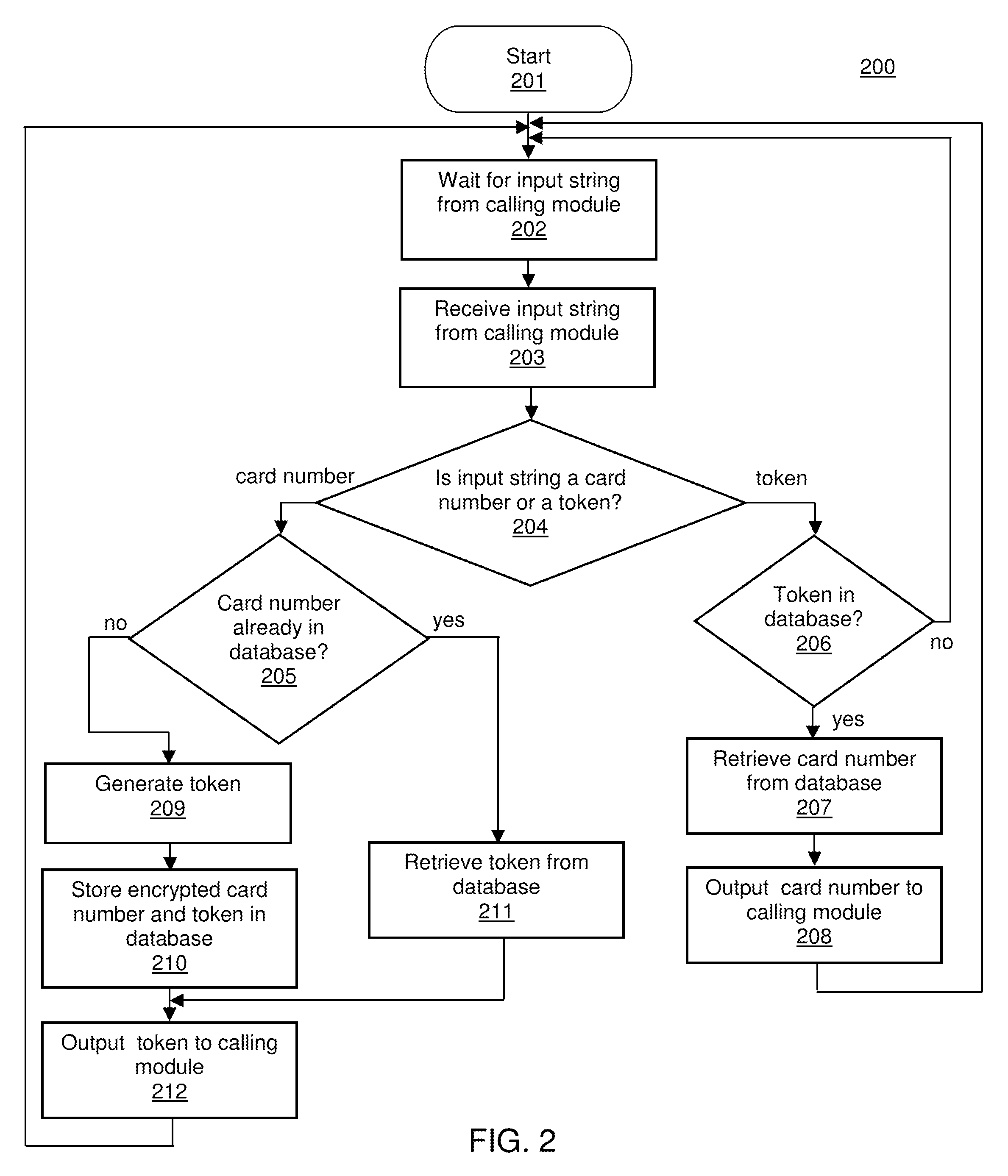
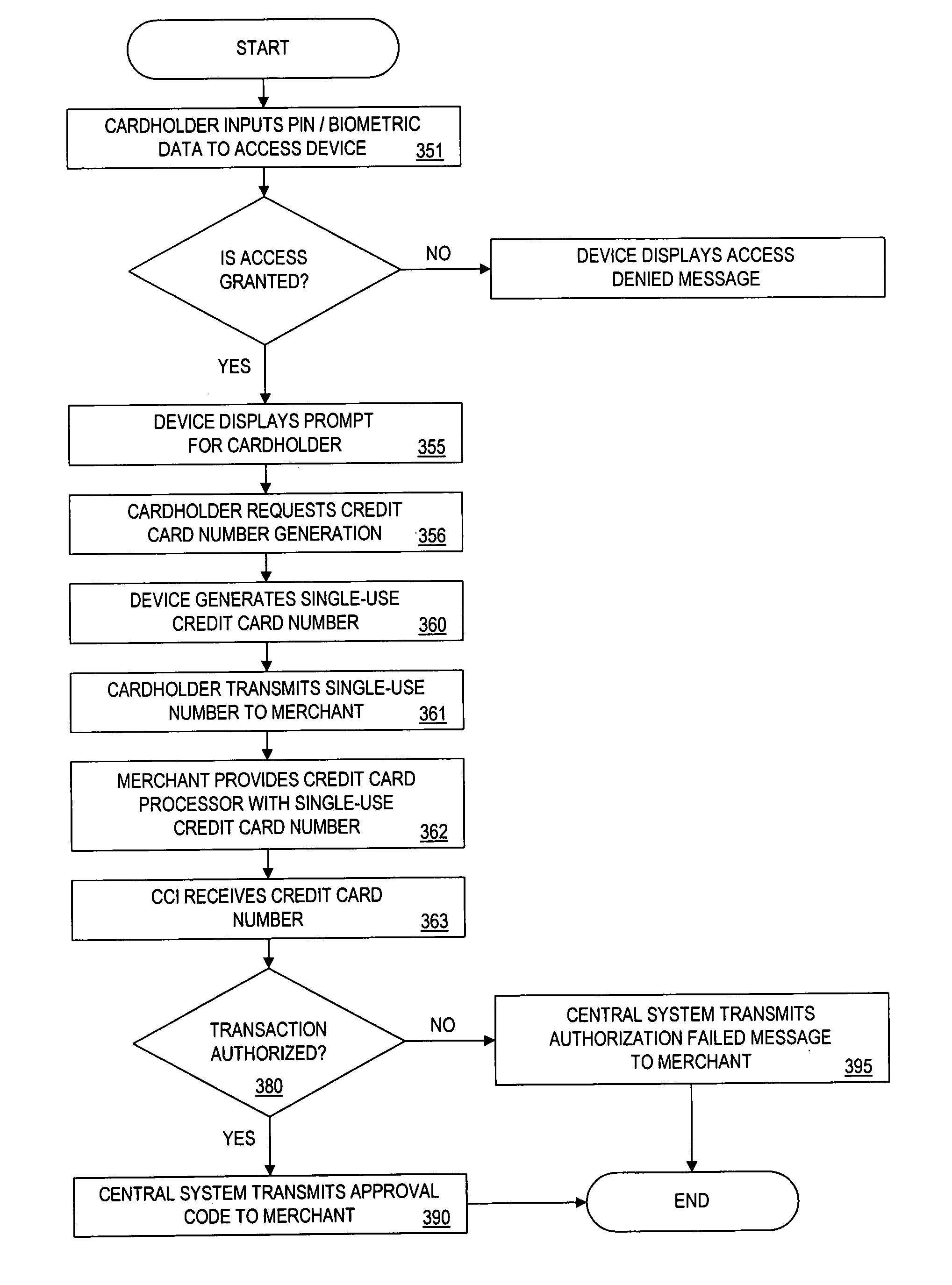
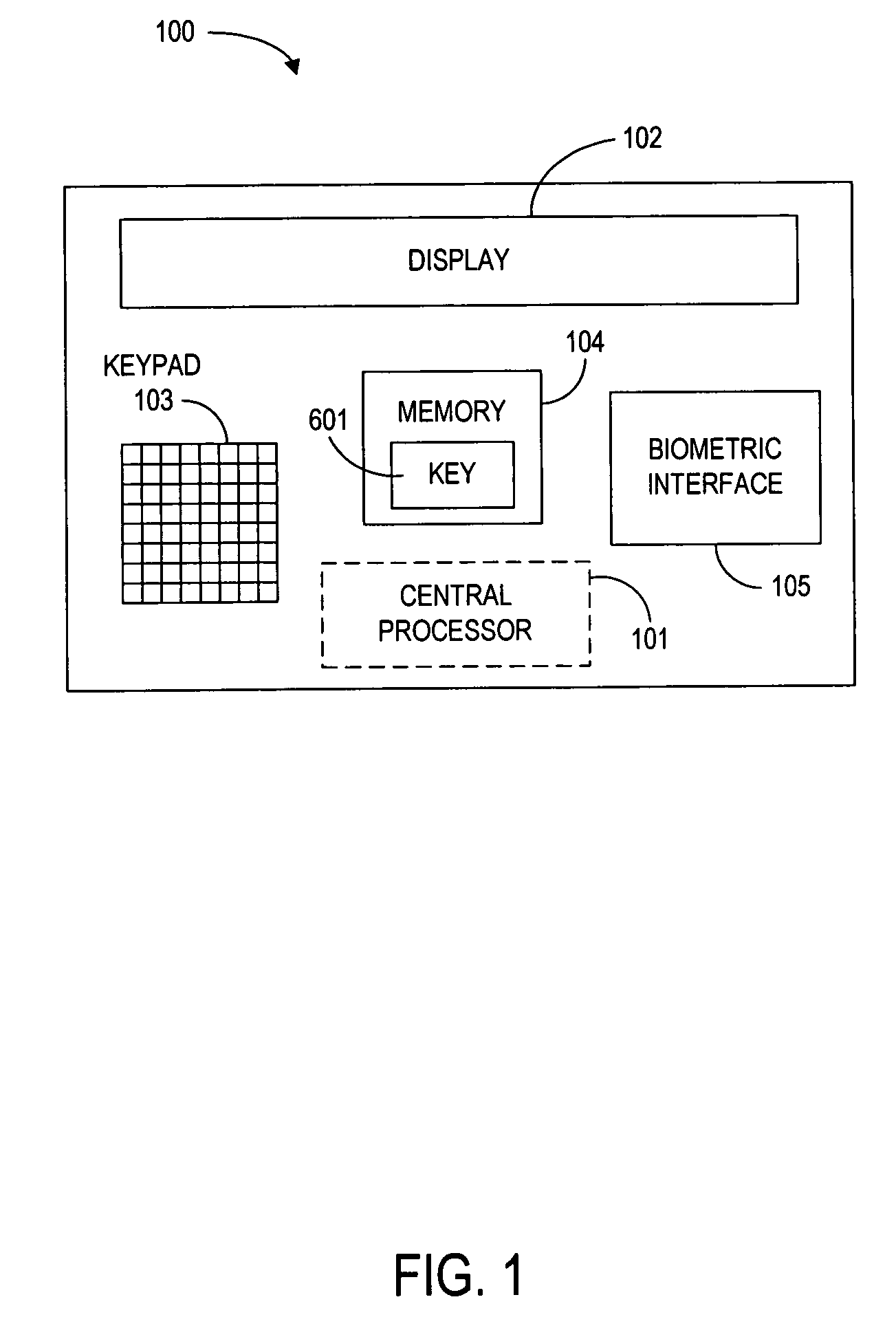
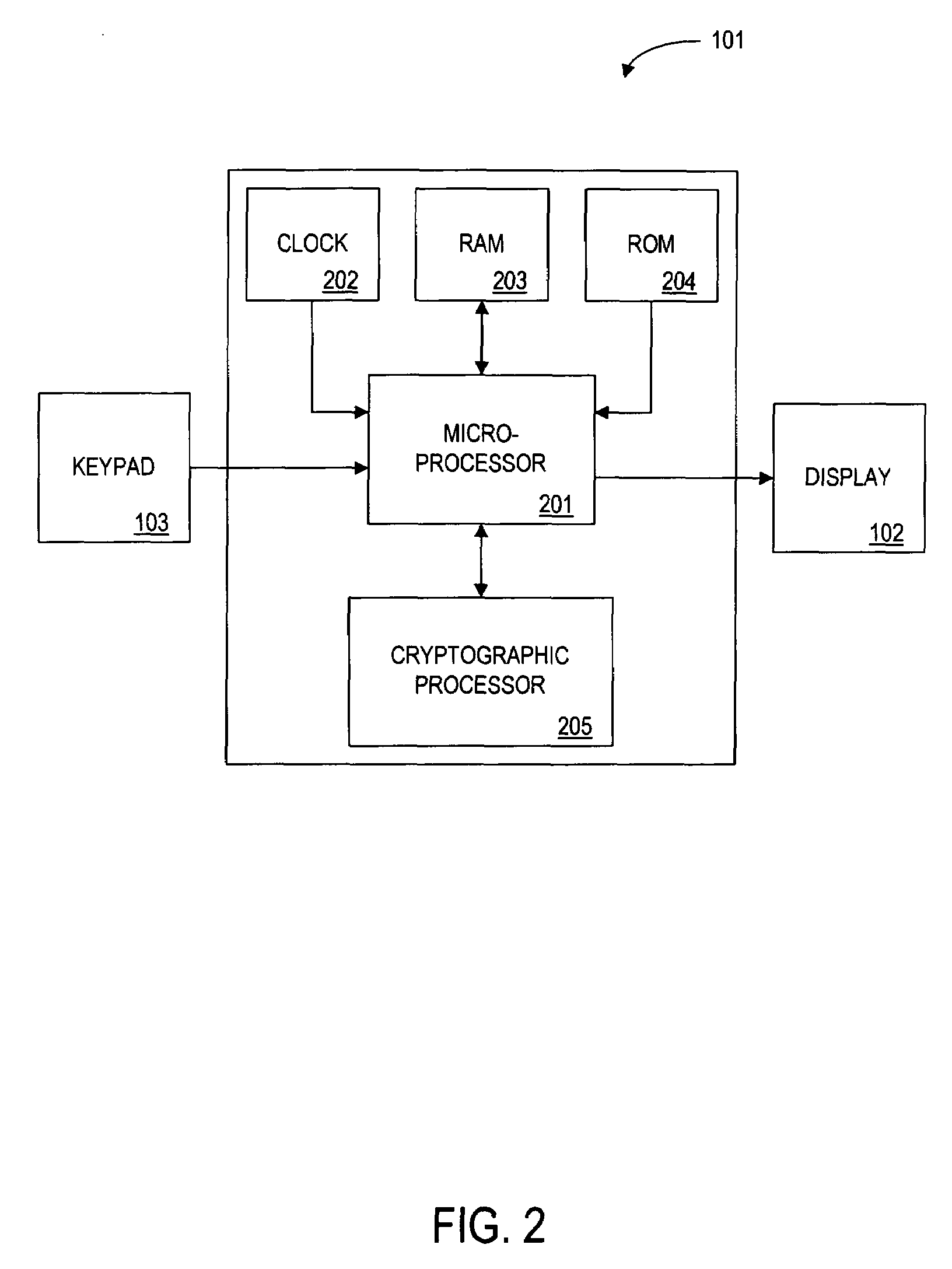
Method for implementing anonymous credit card transactions using a fictitious account name
InactiveUS20050086160A1Electric signal transmission systemsDigital data processing detailsCredit cardInternet privacy
A method for implementing an anonymous face to face or Mail Order Telephone Order credit card transaction by a user who has established a user account associated with a fictitious name. The user generates a valid personal charge number by executing an algorithm in a computer affixed to the electronic credit card that uses a user key and a card number as input variables. A merchant is provided with the valid personal charge number and the fictitious name that is submitted for approval to a credit approval center. The electronic credit card is sized such that a standard magnetic stripe reader can read it.
Owner:WONG JACOB Y +1
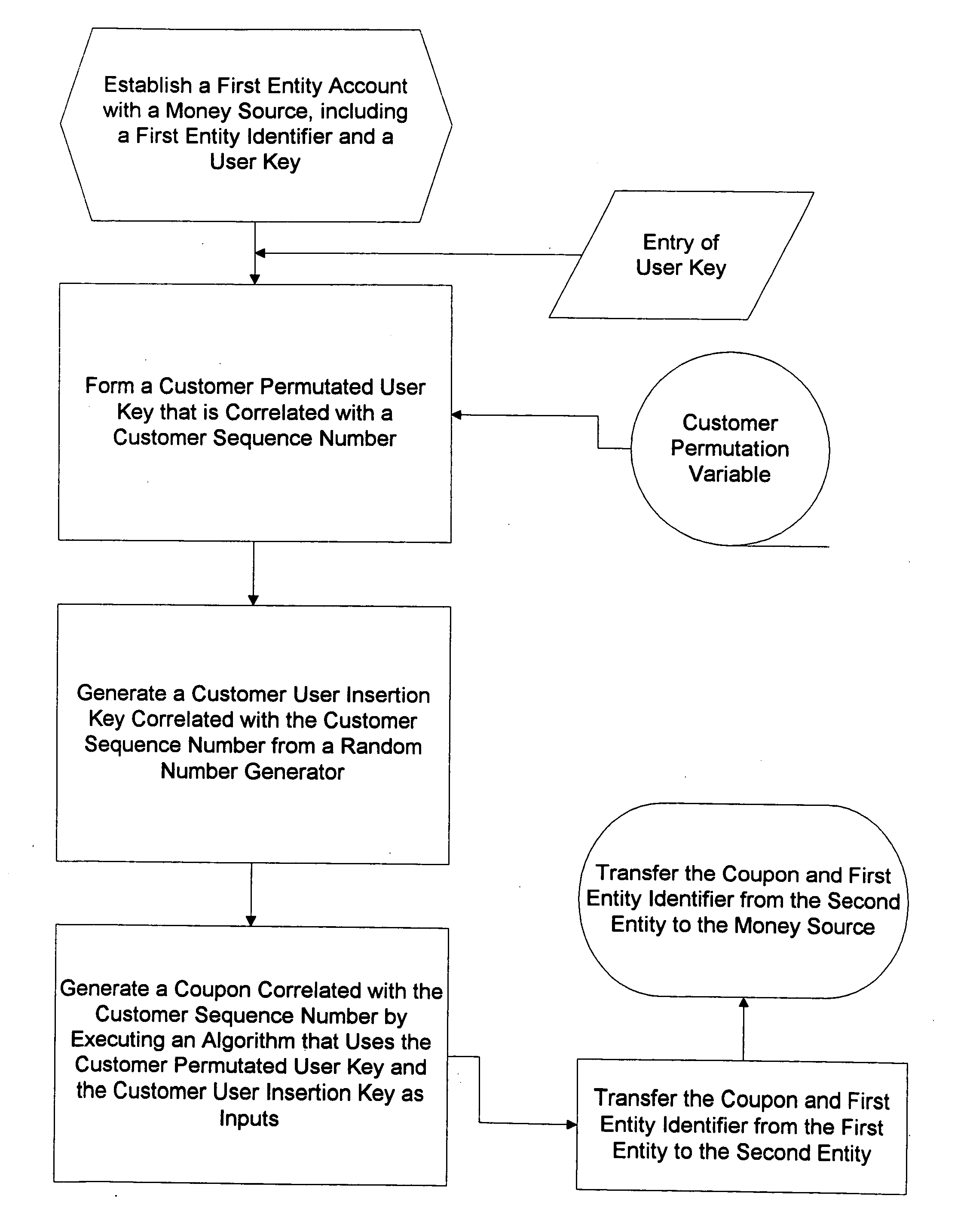
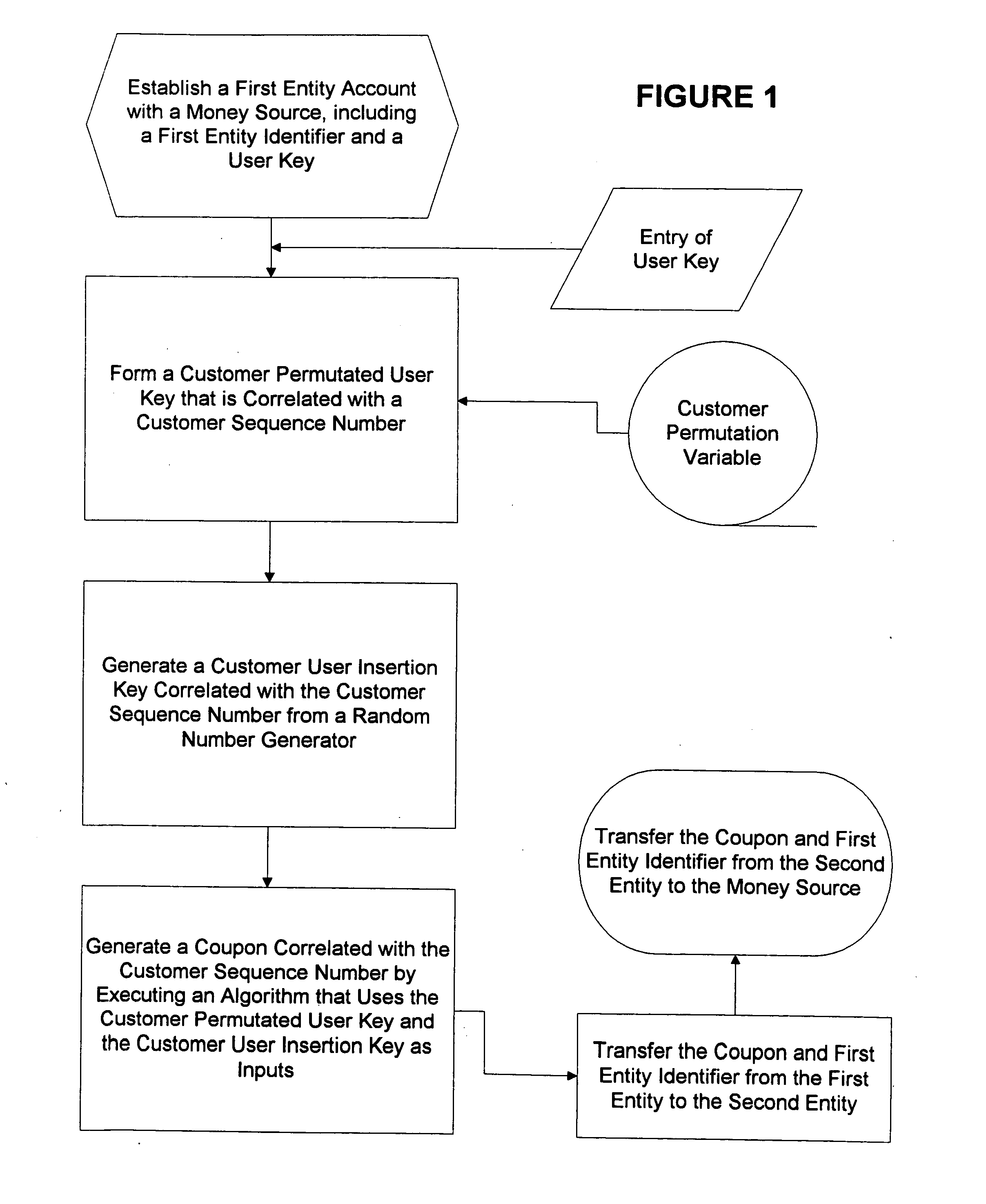
Method for generating customer one-time unique purchase order numbers
InactiveUS20050080747A1Anonymous user systemsRecord carriers used with machinesCredit cardPersonal identification number
Multiple secure transactions are provided through use of a method that uses customer one-time unique purchase order numbers (“Coupons”) generated by an algorithm that uses a permutated user key and a user insertion key as input variables. A user key (such as a Personal Identification Number, or “PIN”) is combined with a permutation variable that is correlated with a customer sequence number to create the permutated user key. A random number generator is used to generate the user insertion key correlated with the customer sequence number. The algorithm can insert the permutated user key into a user account number through use of the user insertion key. A Coupon is validated by confirming that it is contained in a set of money source Coupons generated by a money source using the user key and a random number generator that is synchronized with the random number used to generate Coupons. Once a Coupon is validated, the matching money source Coupon and all earlier generated money source Coupons are deleted from the set, and a new set is generated. If a preselected number of Coupons are not validated for a chosen entity, an invalid user account number will be set. Coupons can be used for credit card or bank card transactions, and they can be generated without changing fixed digits of traditional twenty digit account numbers.
Owner:PRIVASYS
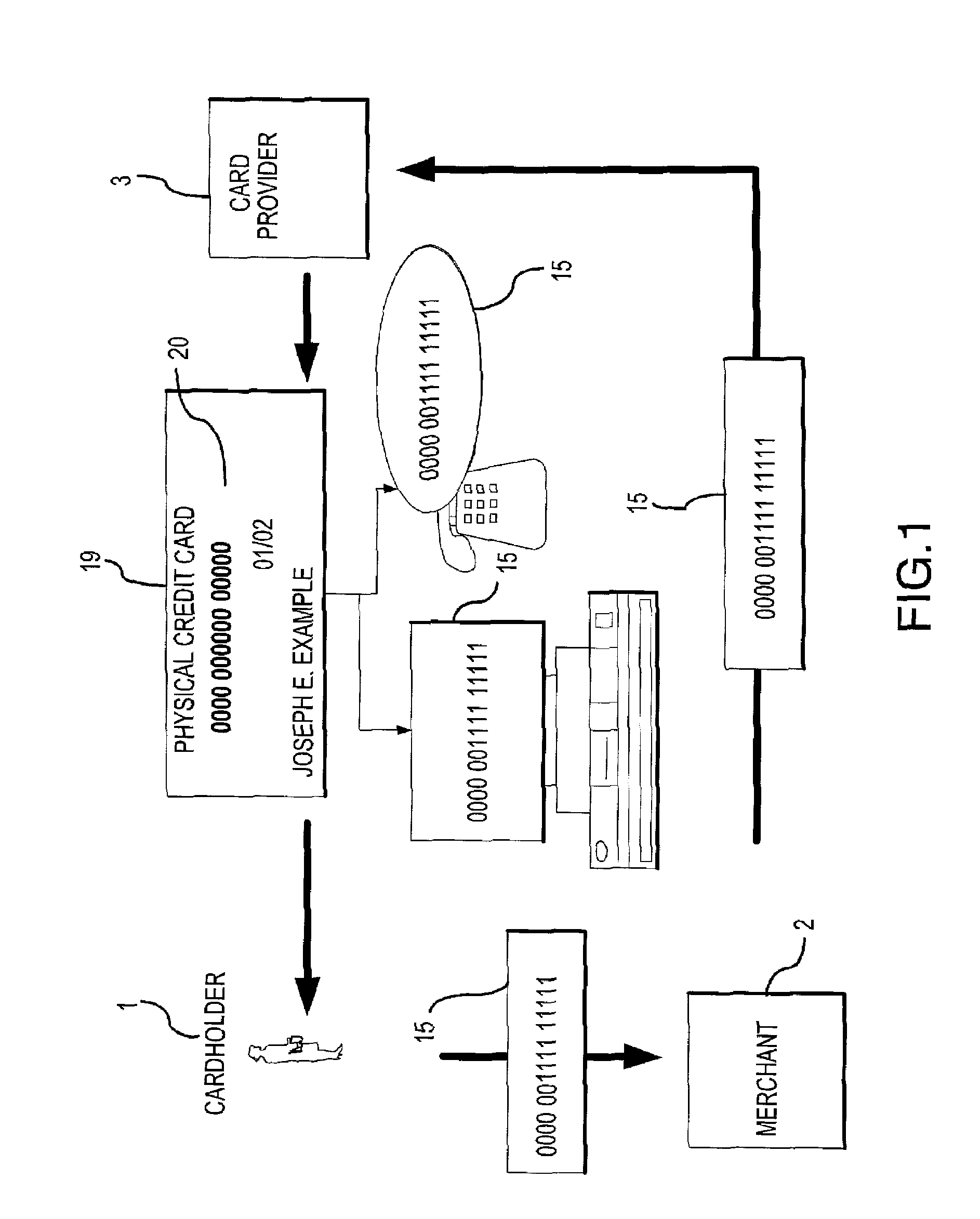
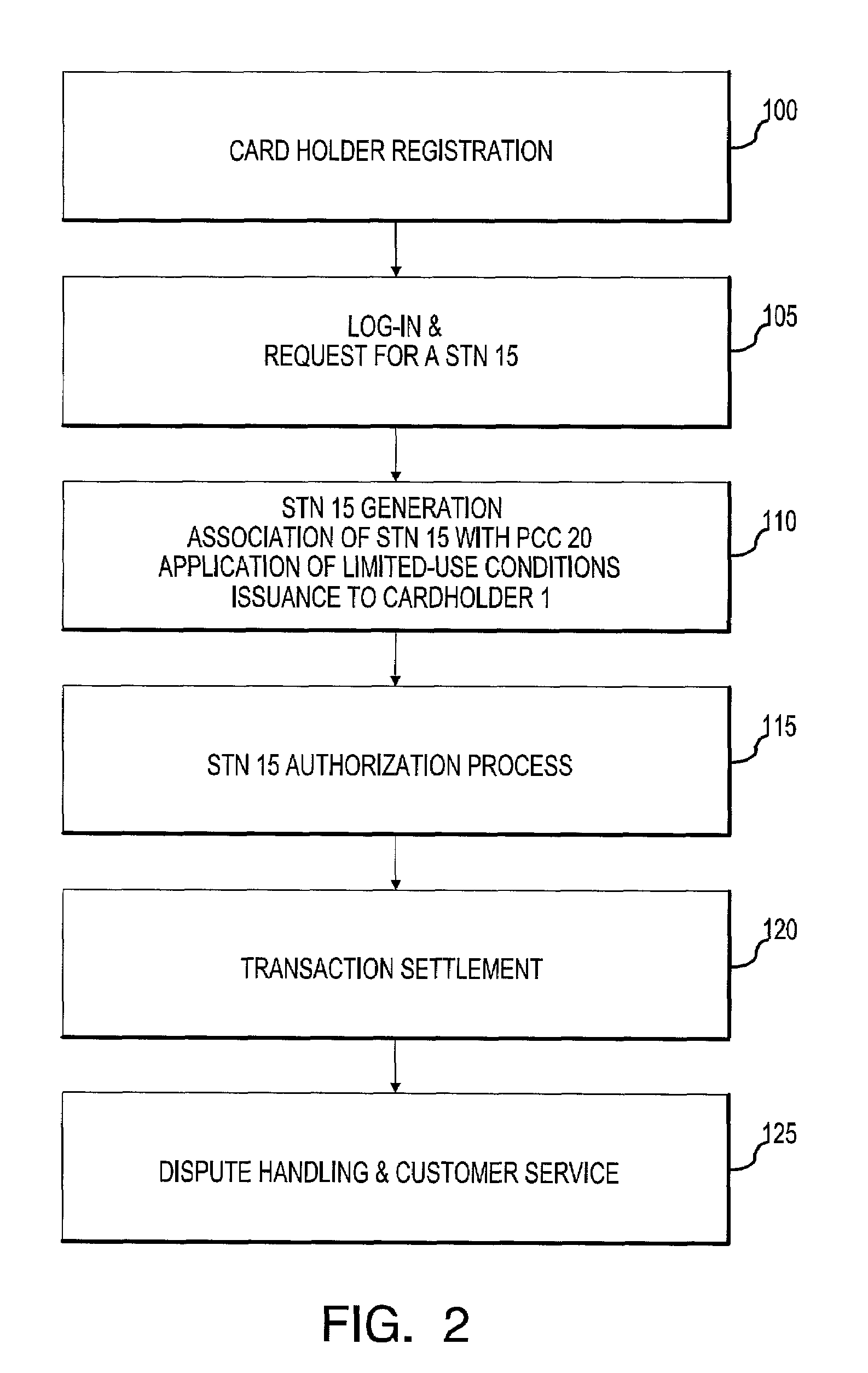
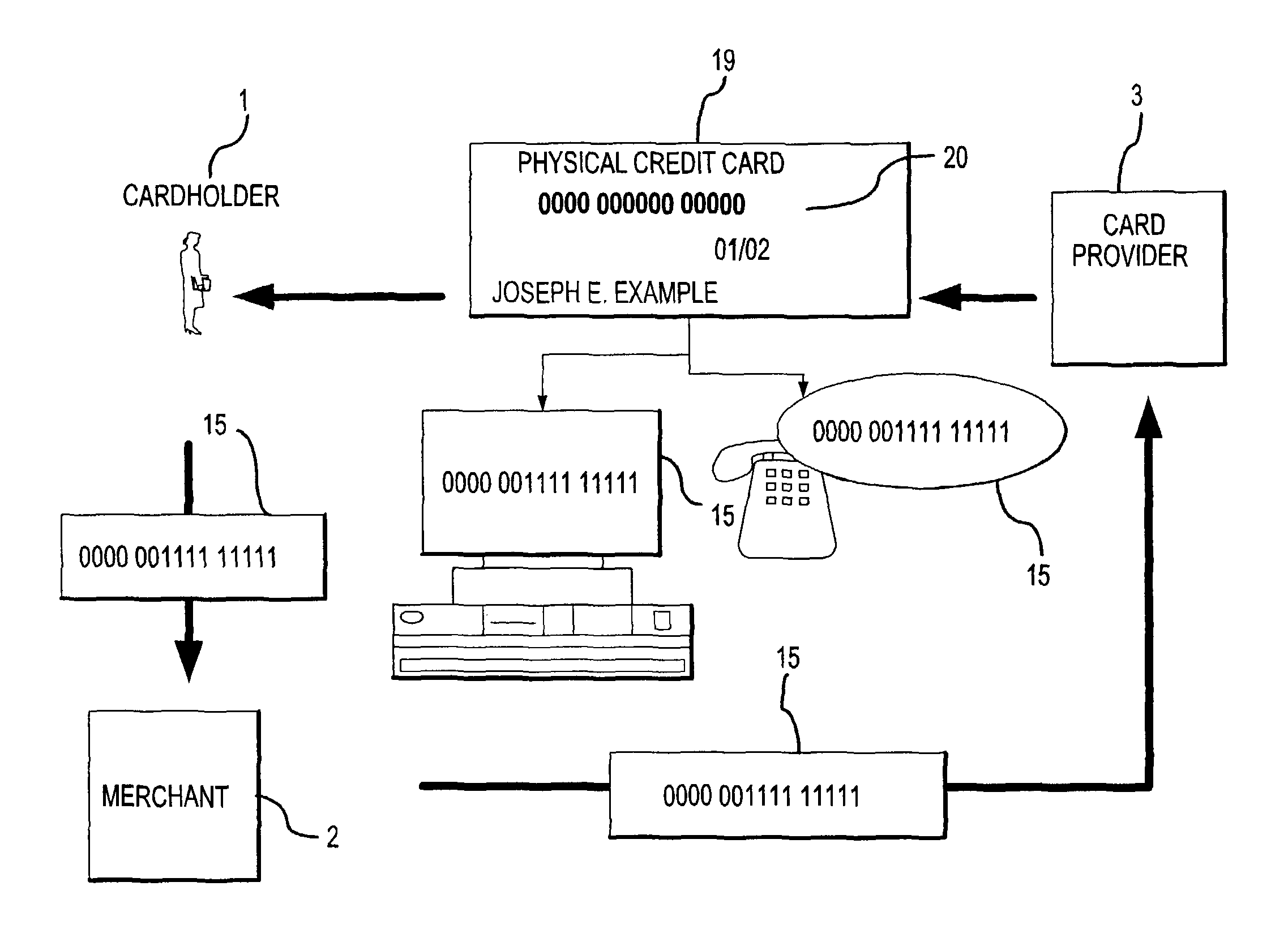
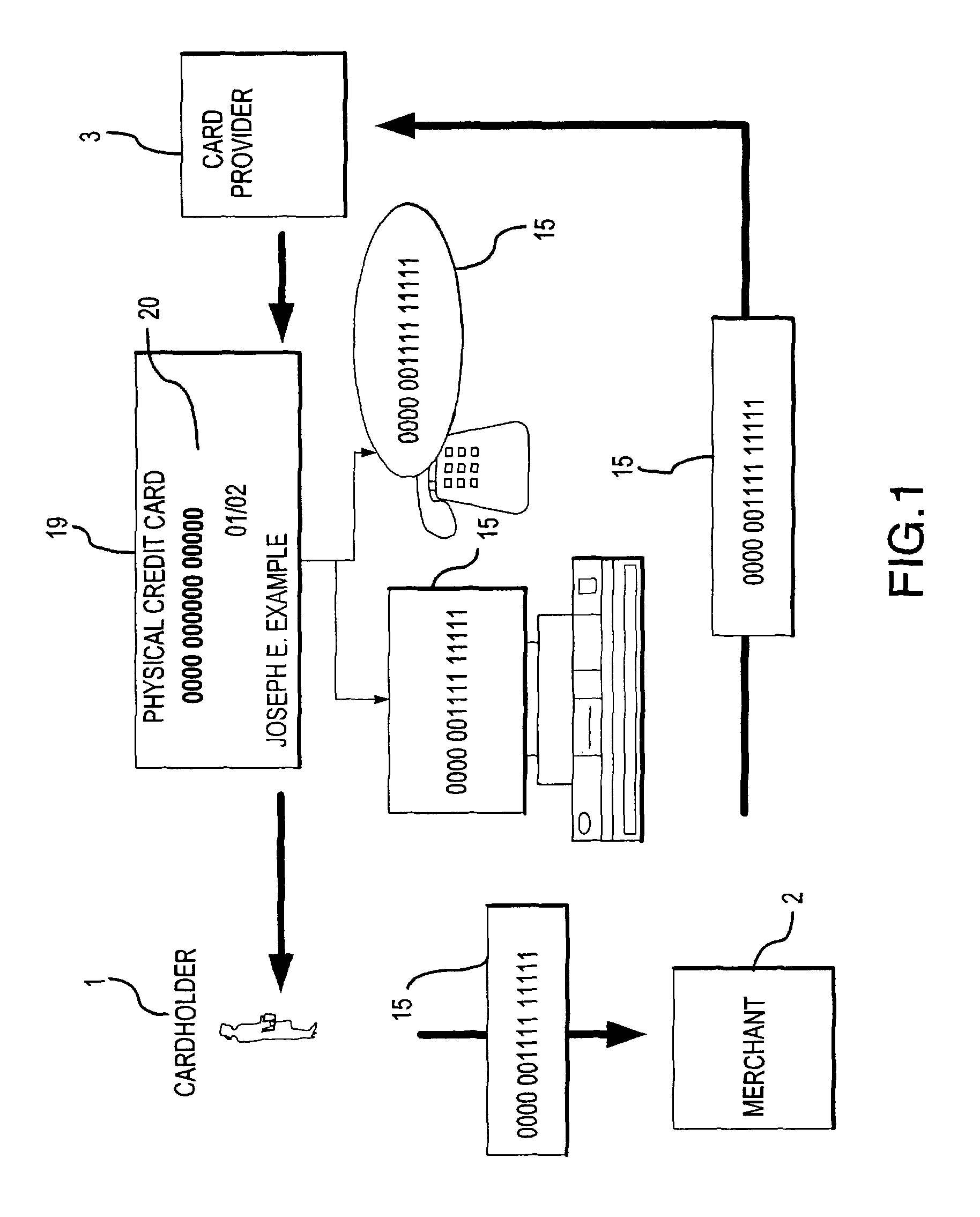
System for facilitating a transaction
The present invention provides a system and method for facilitating a transaction using a secondary transaction number that is associated with a cardholder's primary account. The cardholder provides the secondary transaction number, often with limited-use conditions associated therewith, to a merchant to facilitate a more secure and confident transaction.
Owner:LIBERTY PEAK VENTURES LLC
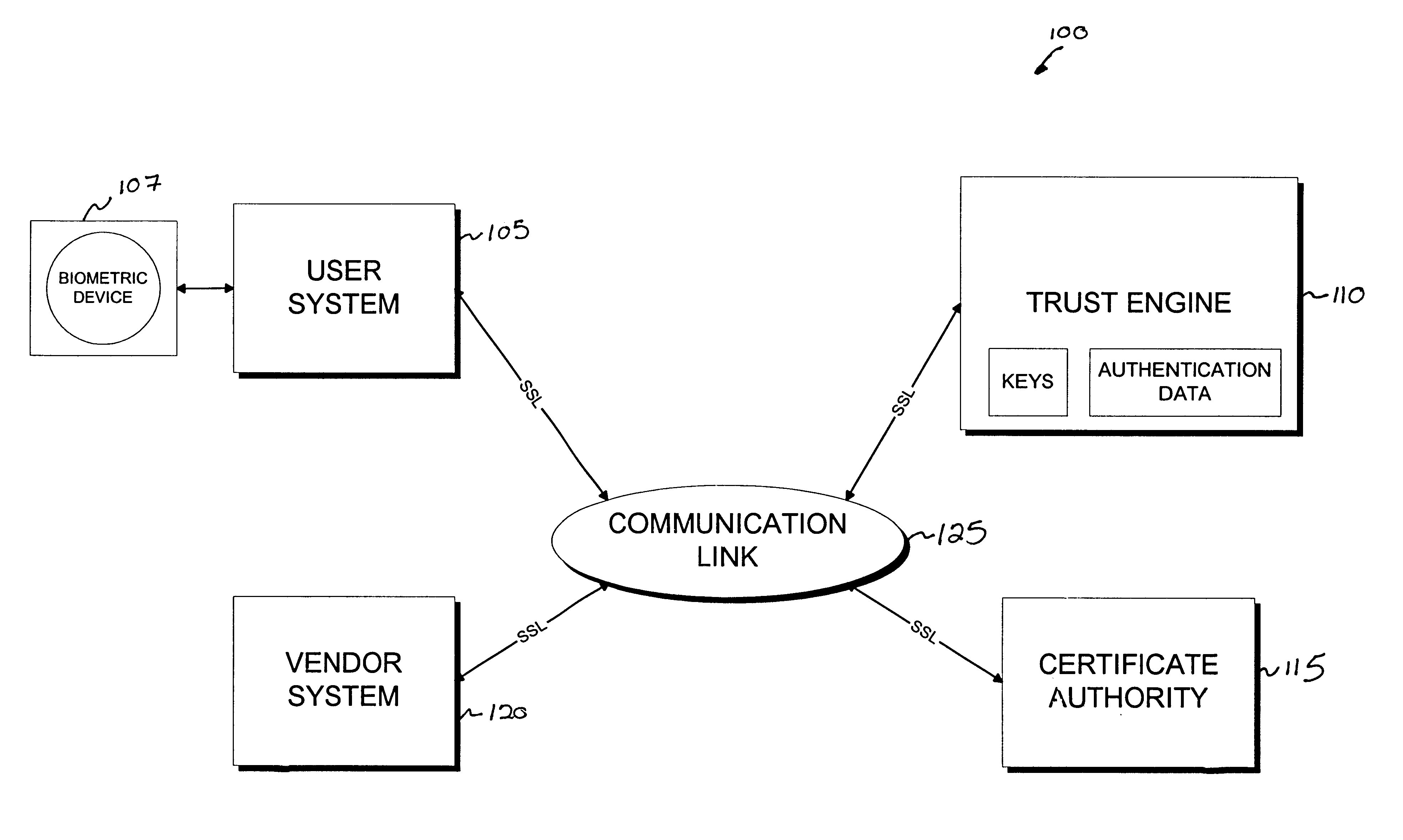
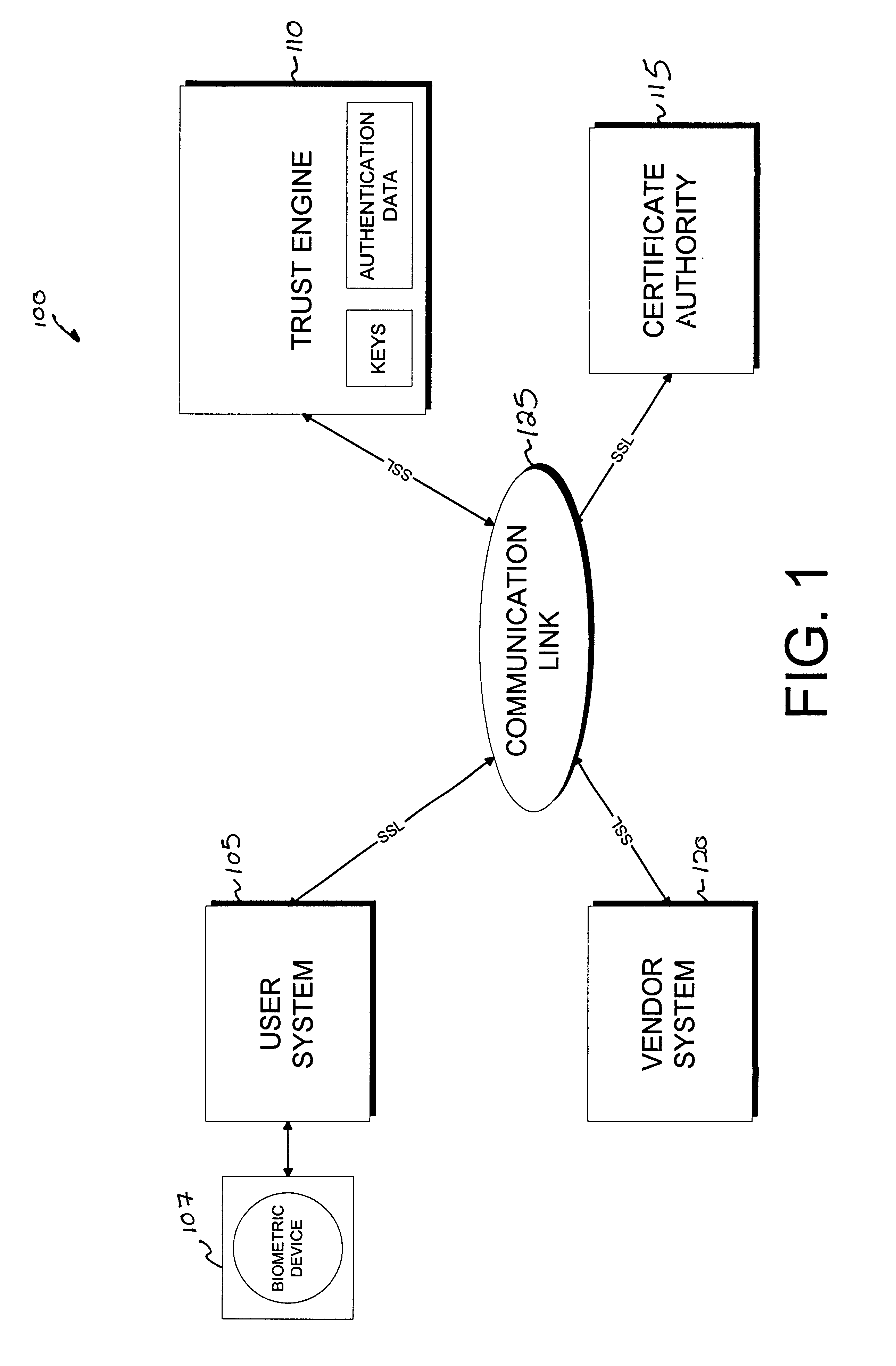
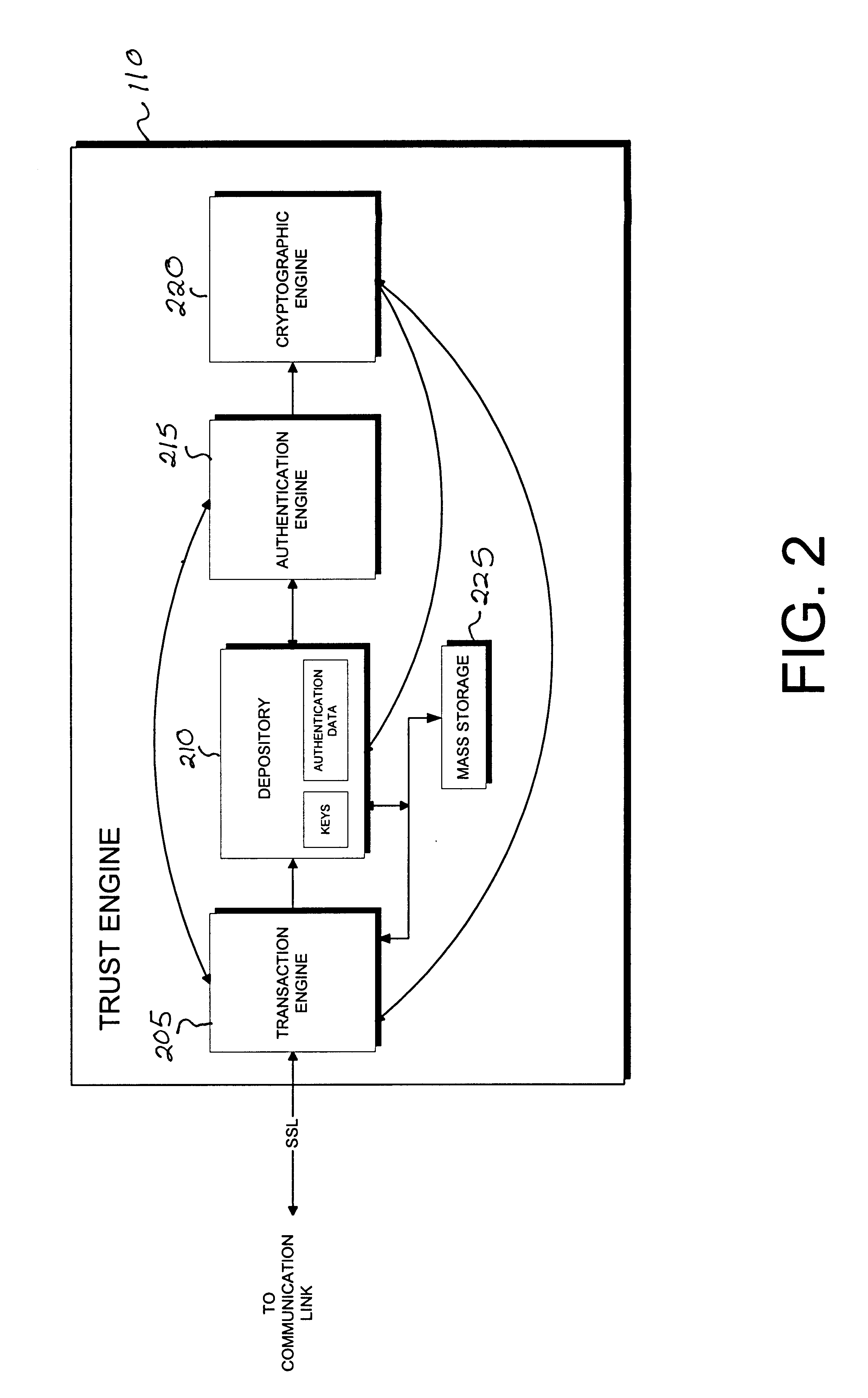
Cryptographic server with provisions for interoperability between cryptographic systems
InactiveUS6853988B1Reduce the number of timesMinimal compute resourceDigital data authenticationBuying/selling/leasing transactionsComputer hardwareKey storage
The invention is a cryptographic server providing interoperability over multiple algorithms, keys, standards, certificate types and issuers, protocols, and the like. Another aspect of the invention is to provide a secure server, or trust engine, having server-centric keys, or in other words, storing cryptographic keys on a server. The server-centric storage of keys provides for user-independent security, portability, availability, and straightforwardness, along with a wide variety of implementation possibilities.
Owner:SECURITY FIRST INNOVATIONS LLC
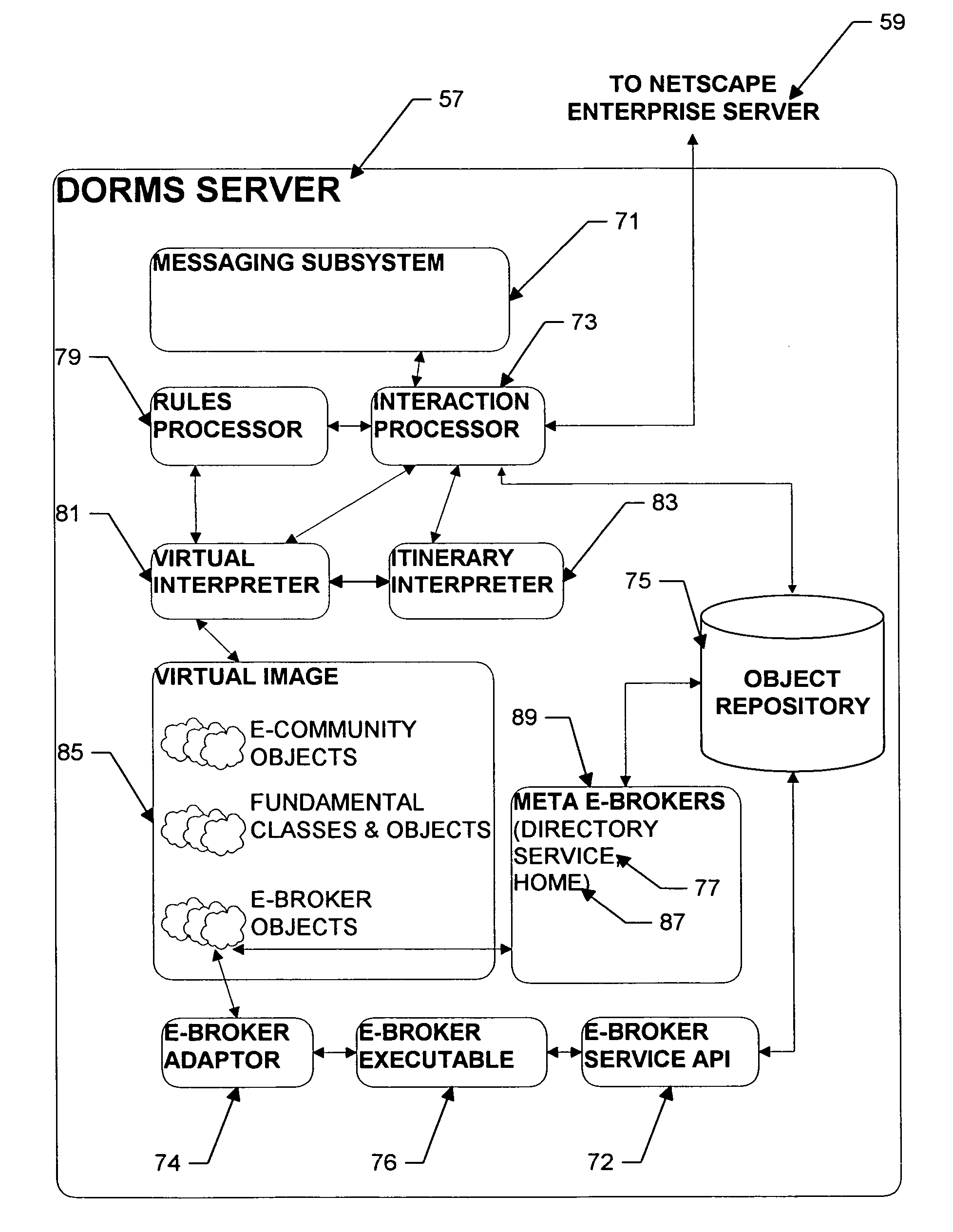
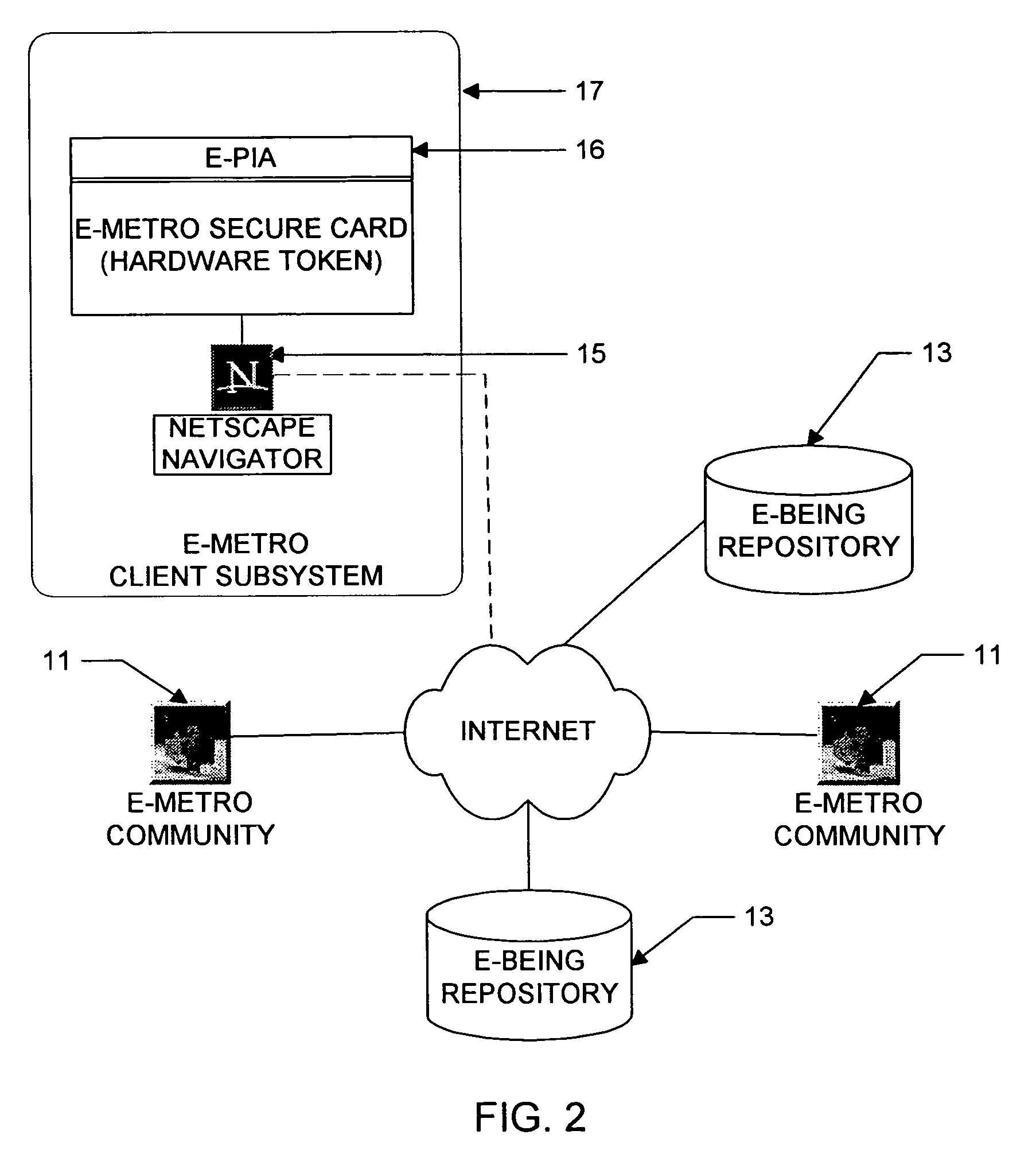
Personal information security and exchange tool
InactiveUS7289971B1Facilitates formation and useEasy to useFinanceComputer security arrangementsCommand and controlElectricity market
Utilization of the E-Metro Community and Personal Information Agents assure an effective and comprehensive agent-rule based command and control of informational assets in a networked computer environment. The concerns of informational privacy and informational self-determination are addressed squarely by the invention affording persons and entities a trusted means to author, secure, search, process, and exchange personal and / or confidential information in a networked computer environment. The formation of trusted electronic communities wherein members command and control their digital persona, exchanging or brokering for value the trusted utility of their informational assets is made possible by the invention. The present invention provides for the trusted utilization of personal data in electronic markets, providing both communities and individuals aggregate and individual rule-based control of the processing of their personal data.
Owner:CYVA RES HLDG
Method for customizing payment card transactions at the time of the transactions
InactiveUS20050086177A1Anonymous user systemsRecord carriers used with machinesThird partyTransaction data
A user can customize use of a payment card, which can be an electronic card, by selecting a customization variable for any given transaction. The customization variable involves at least one of the following steps: (1) customizing generation of a one-time card number; (2) customizing a user identifier; or (3) inclusion of a customization variable with information transmitted to a verification agency for validation of the given use. Multiple payment card transactions can be processed differently depending upon which customization variable is chosen for a given transaction. Different customization variables can be used for different accounts, different types of transactions, or to classify the transactions. A user can receive one bill, or multiple bills. Different levels of privacy can be accorded to transactions that use different customization variables. A user may pay the issuer for increased security, or the user may be paid by the issuer to allow transaction data to be distributed to third parties.
Owner:ANDERSON ROY L +2
Method and system for conducting secure payments over a computer network
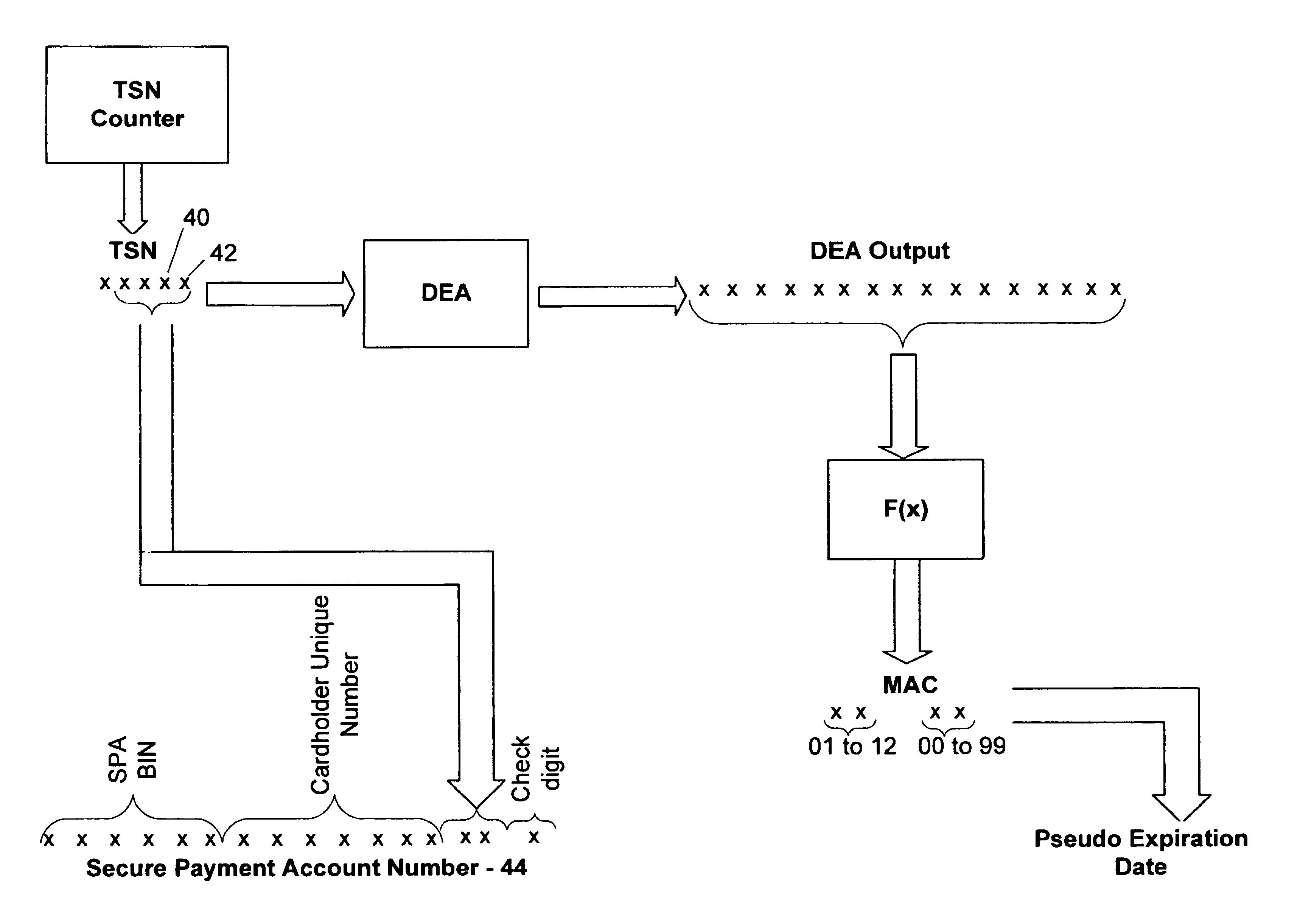
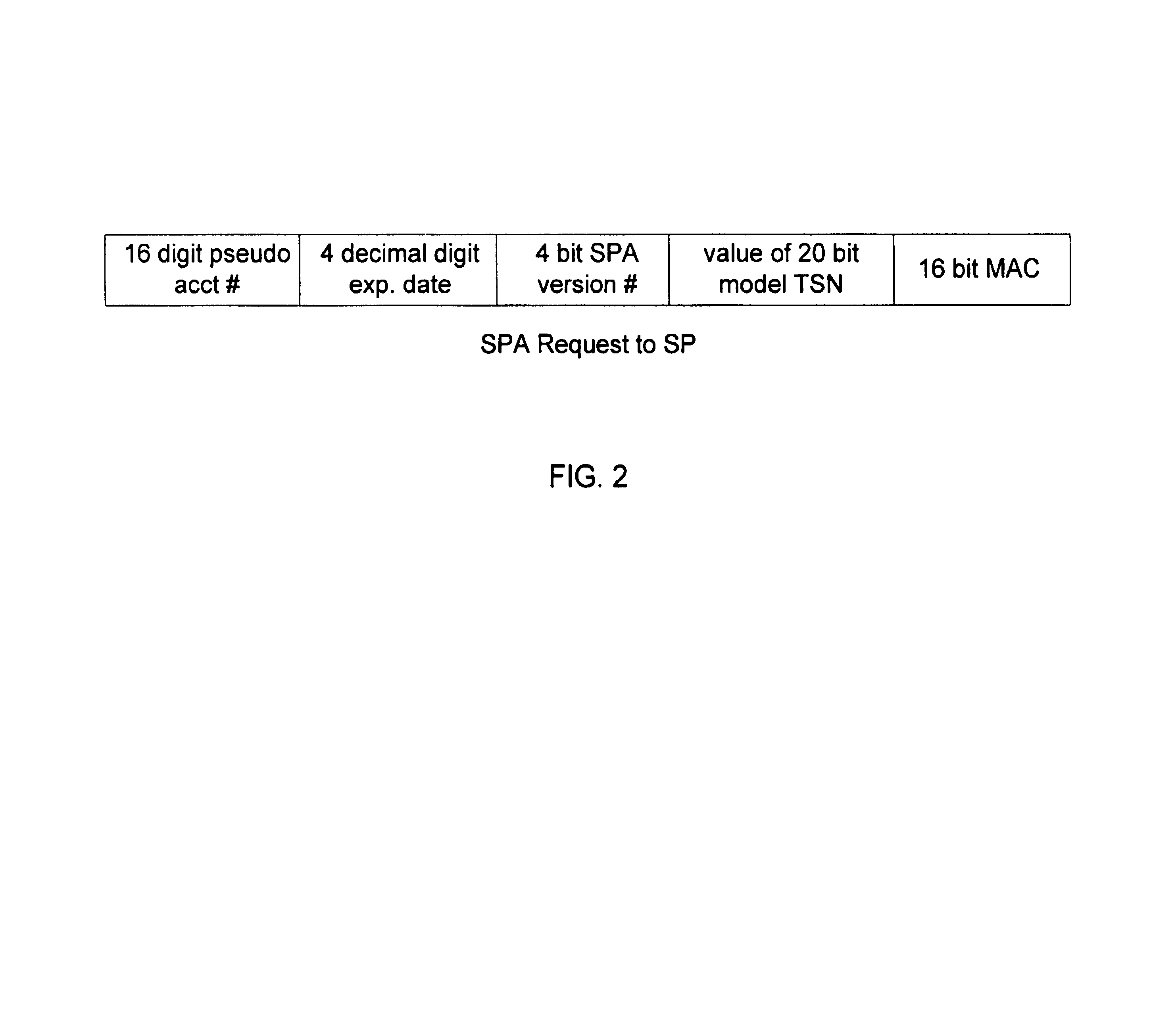
A secure method of conducting an electronic transaction over a public communications network is provided which utilizes a pseudo-expiration date in the expiration date field of an authorization request. One of the preferred methods comprises:generating a per-card key associated with an account number;generating a message authentication code using the per-card key;converting the message authentication code into a pseudo expiration date;generating an authorization request for the transaction, the request having an expiration date field containing the pseudo expiration date; andverifying the message authentication code based on the pseudo expiration date.Another embodiment of the invention includes a method of conducting an electronic transaction over a public communications network, with a payment account number having an associated pseudo account number, comprising:(a) providing the pseudo account number with a control field indicating one of a plurality of key-generation processes to be used to generate an authentication key;(b) generating an authentication key associated with the pseudo account number using one of the plurality of key-generation processes indicated in the control field of the pseudo account number;(c) using the authentication key to generate a message authentication code specific to the transaction;(d) generating an authorization request message including the message authentication code and the pseudo account number; and(e) verifying the message authentication code using the indicated key-generation process and the authentication key.
Owner:MASTERCARD INT INC
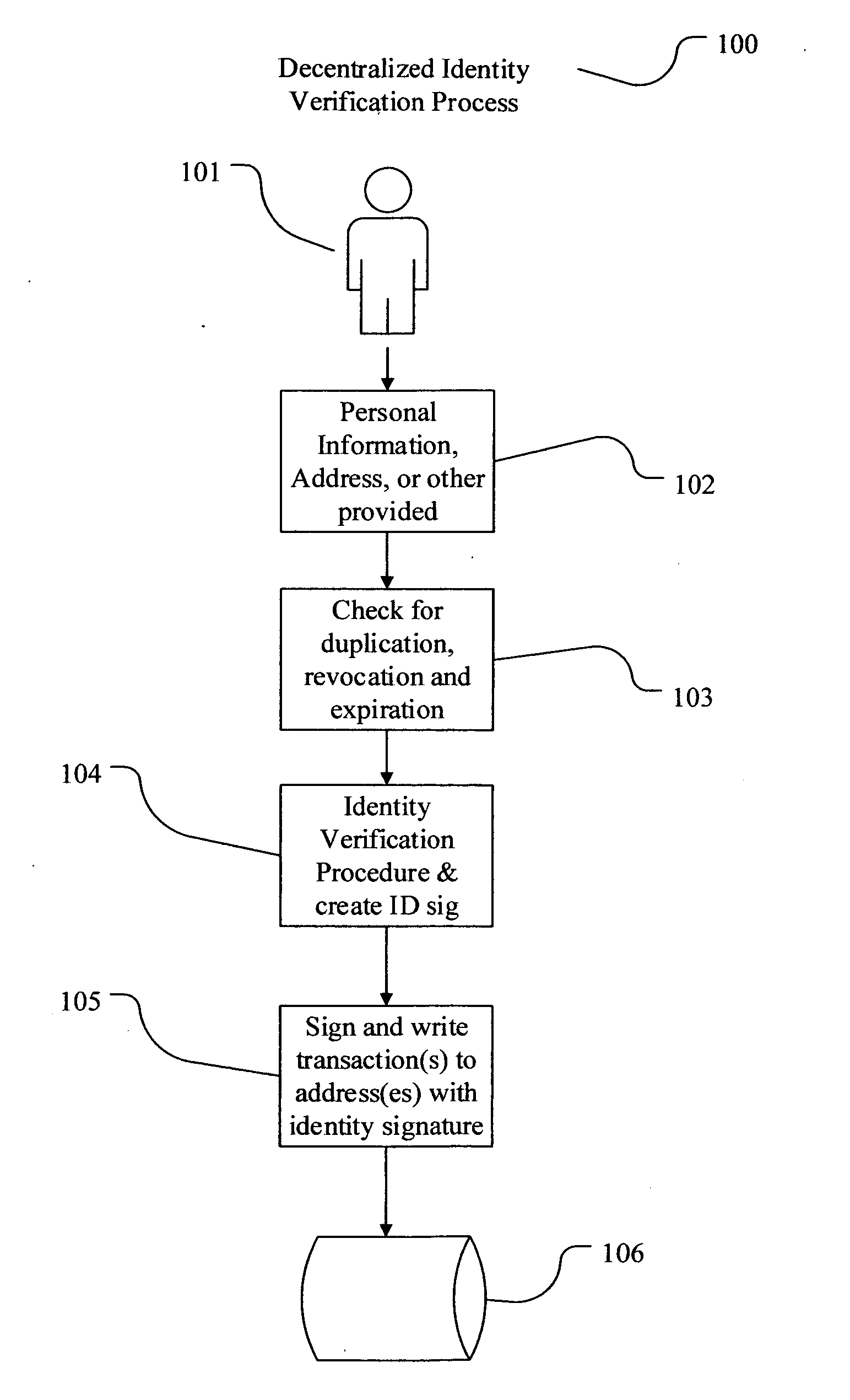
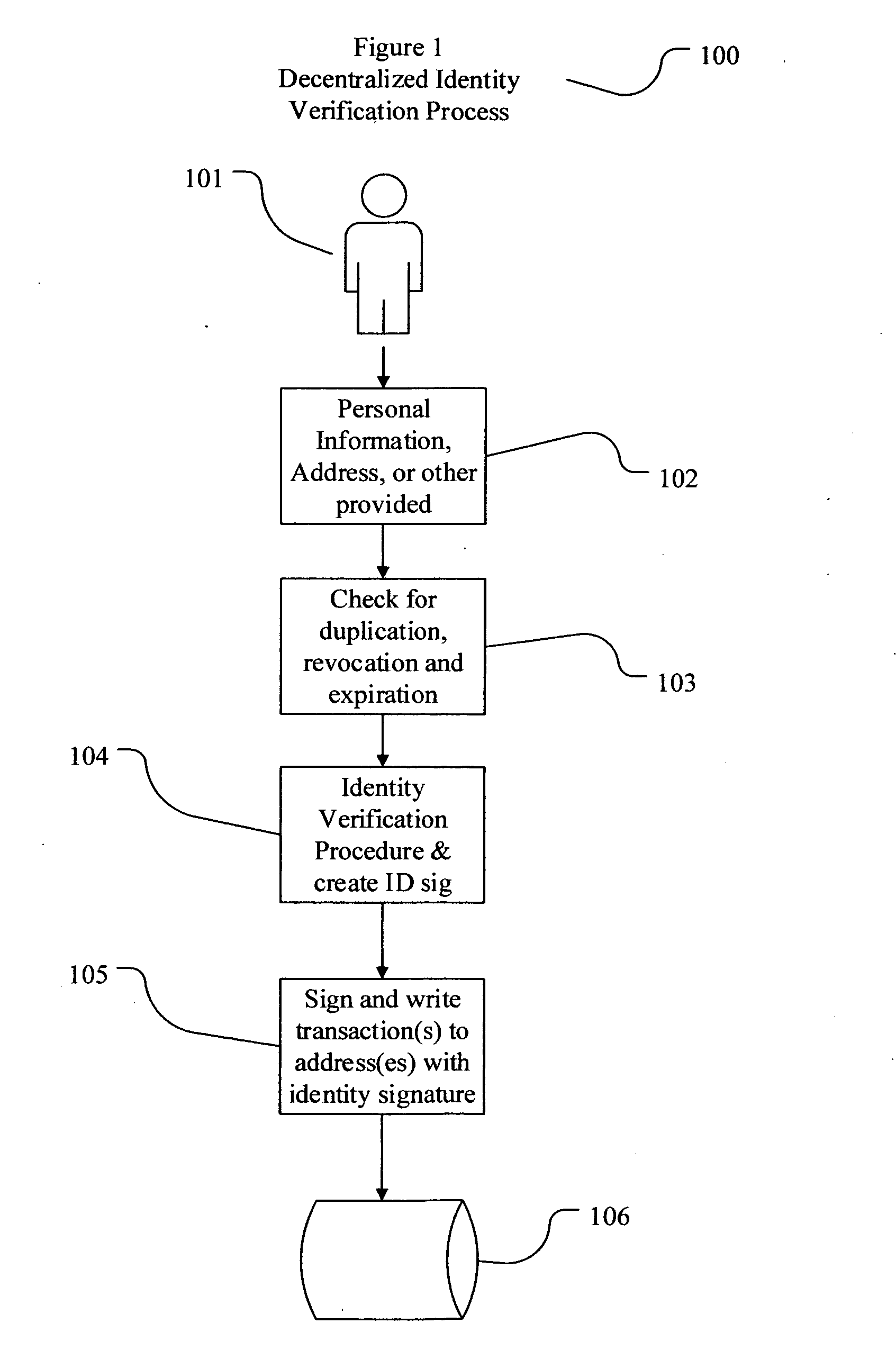
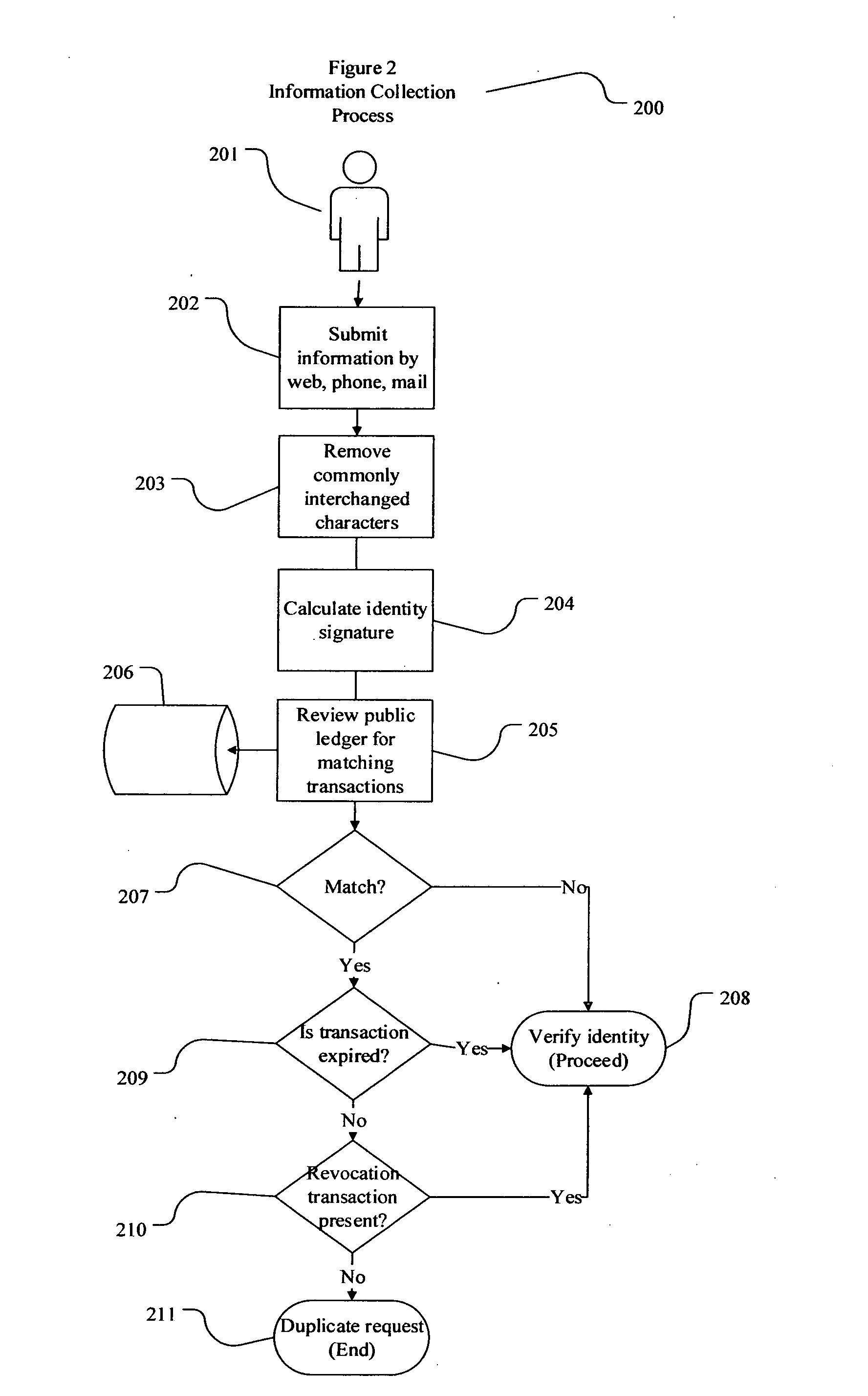
Decentralized identity verification systems and methods
InactiveUS20150356523A1Cryptography processingUser identity/authority verificationRegulatory authorityFinancial transaction
The present invention involves systems and methods that allow participants in cryptocurrency networks to exchange cryptocurrency for traditional currency legally and safely without requiring the use of a traditional exchange or online brokerage as a fiduciary. The invention accomplishes this through the use of a decentralized identity verification protocol that allows a service provider to verify the identity of a participant and then publish an identity signature on the participant's cryptocurrency address or addresses. The invention enables full compliance with Country specific customer identification program and anti-money laundering requirements, and maintains the ability to independently satisfy requests for information or data retention requirements if requested by legally authorized parties, but does not require that the participant store the private keys or access controls to their cryptocurrency on an exchange or brokerage service.The invention serves to verify a participant's identity in full compliance with US Bank Secrecy and Patriot Act provisions or similar regulations where identification may be achieved through non-documentary or documentary identity verification procedures. After passing the applicable verification procedure, the service provider stamps the participant's cryptocurrency address with a transaction containing an identity signature. This identity signature within the transaction consists of a public indicator of the participant's Country and subdivision, a compliance level code, an ID type indicator, and an identity hash. The identity hash is created from the digests of cryptographic hash functions where the participant's personal information is used as an input. The service provider signs the transaction with their authorized private key that corresponds to their publicly accessible public key. This serves as a publicly verifiable confirmation that the identity associated with the address in question was validated by the service provider authorized to act on behalf of the regulatory authority.The participant may then purchase and sell cryptographic currency from and to a third party exchange or brokerage service legally and safely when using their verified cryptocurrency address. This is because the third party is able to confirm compliance by openly referencing and verifying the identity verification transaction present on the address. Subsequent transactions where the third party sells or purchases cryptocurrency for the verified participant are similarly stamped with a transaction conforming to the identity verification protocol. This allows the third party interacting with the verified participant's address to observe any regulations limiting the amount or frequency of transactions over a variable period of time. It follows that this address could be used with any third party or participant in the cryptocurrency network that observes the decentralized identity verification protocol, all without requiring the third party or participant to collect and verify personal information redundantly. The ability to verify an identity remotely also eliminates the need for the third party to act as a fiduciary holding the private keys or access controls to the verified address. Lawful requests for information by authorized authorities are served to the service provider as digitally signed transactions that may then be linked to the participant's identity and transactions, allowing the protocol to observe subpoenas or similar lawful requests for information. The encrypted personal information may be held in escrow by the service provider indexed to the verified cryptocurrency address for such purposes. An alternate embodiment would store the encrypted personal information in a decentralized network of other participants, with the information accessible for retrieval using the public key of the verified cryptocurrency address and decryption using the corresponding private key, decentralizing the process entirely except for the identity verification step.
Owner:CHAINID
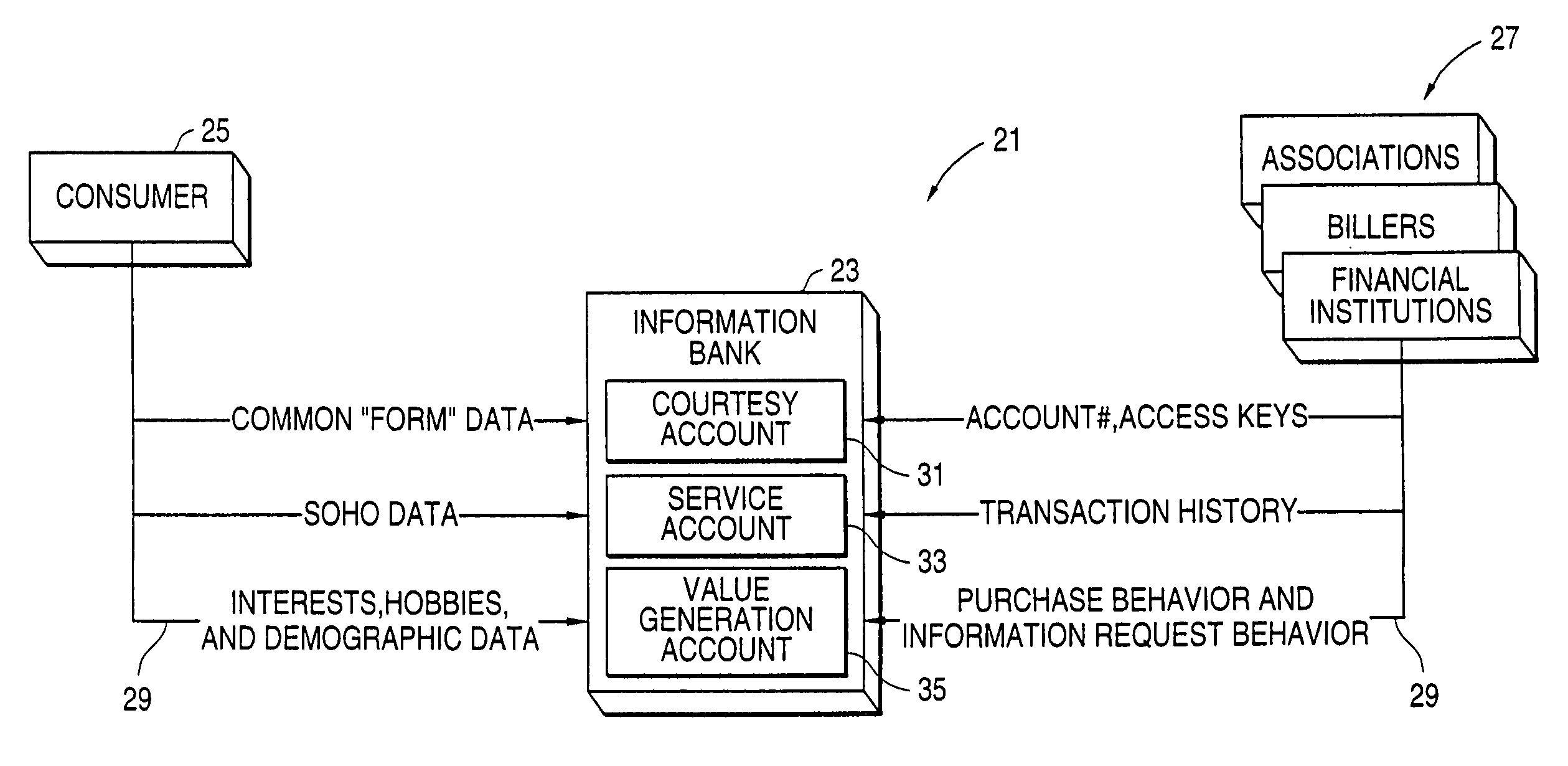
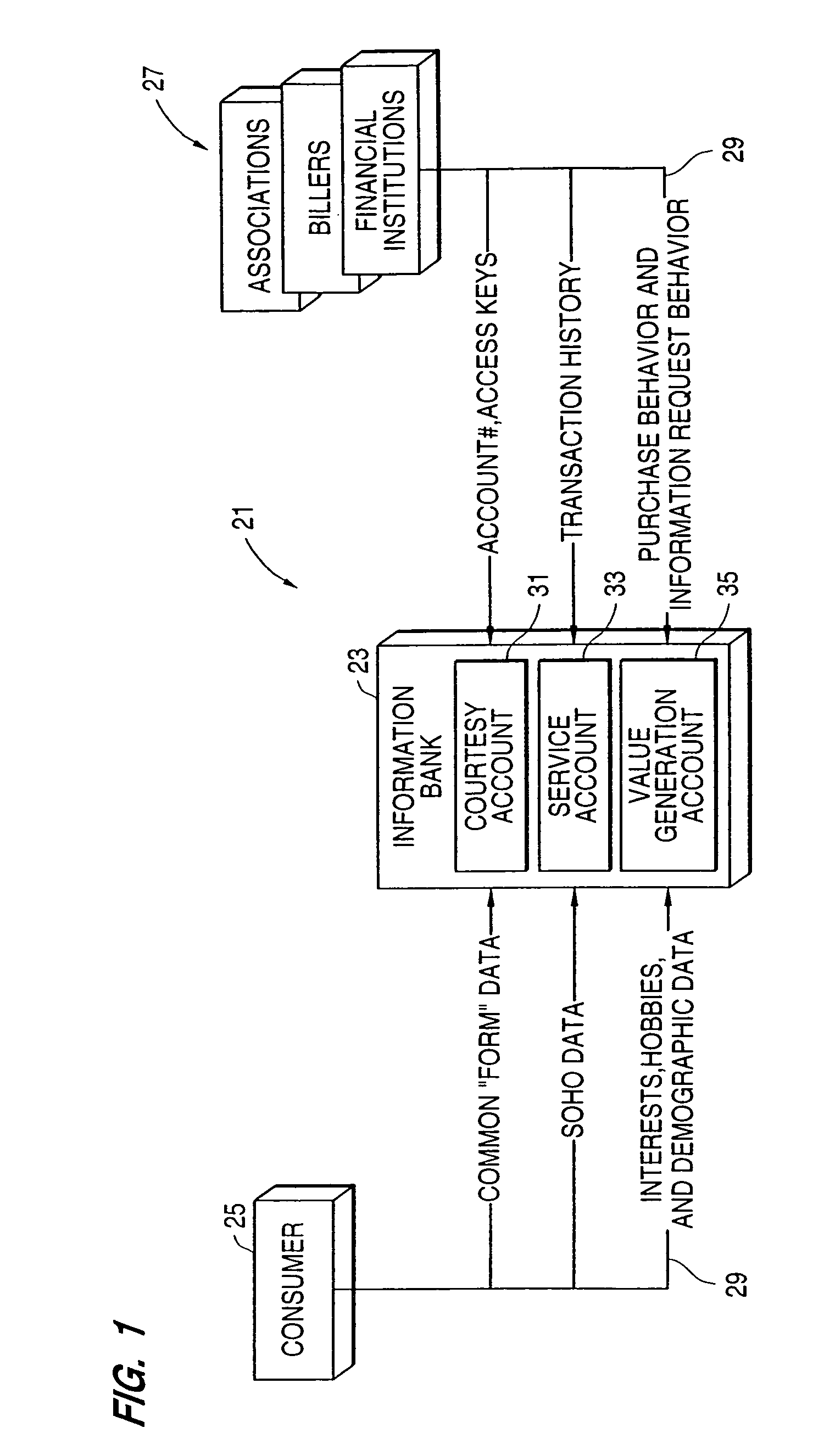
Method and system for anonymizing purchase data
InactiveUS7200578B2Easy accessEliminate needComplete banking machinesFinanceInternet privacyData storing
A system, in which information is the primary asset and in which investments may be made in information, includes multiple data stores for storing different types of a user's information. The safe, secure and properly authorized transfer of information while preserving individual privacy is provided. The system also provides for secure backup and storage, as well as for ubiquitous and nomadic access to information while maintaining the privacy of such information. A first data store includes static identification data about a user. A second data store includes moderately dynamic personal data about the user. A third data store includes dynamic demographic information data about the user. An electronic wallet can be used with the system to download selected portions of the data for use by the user. A method of use of the data includes using the data for billing out forms, providing services to the user and allowing merchants to selectively target users for sales while maintaining user anonymity.
Owner:CITICORP CREDIT SERVICES INC (USA)
Banking computer account system with lock for secure payment via telephone
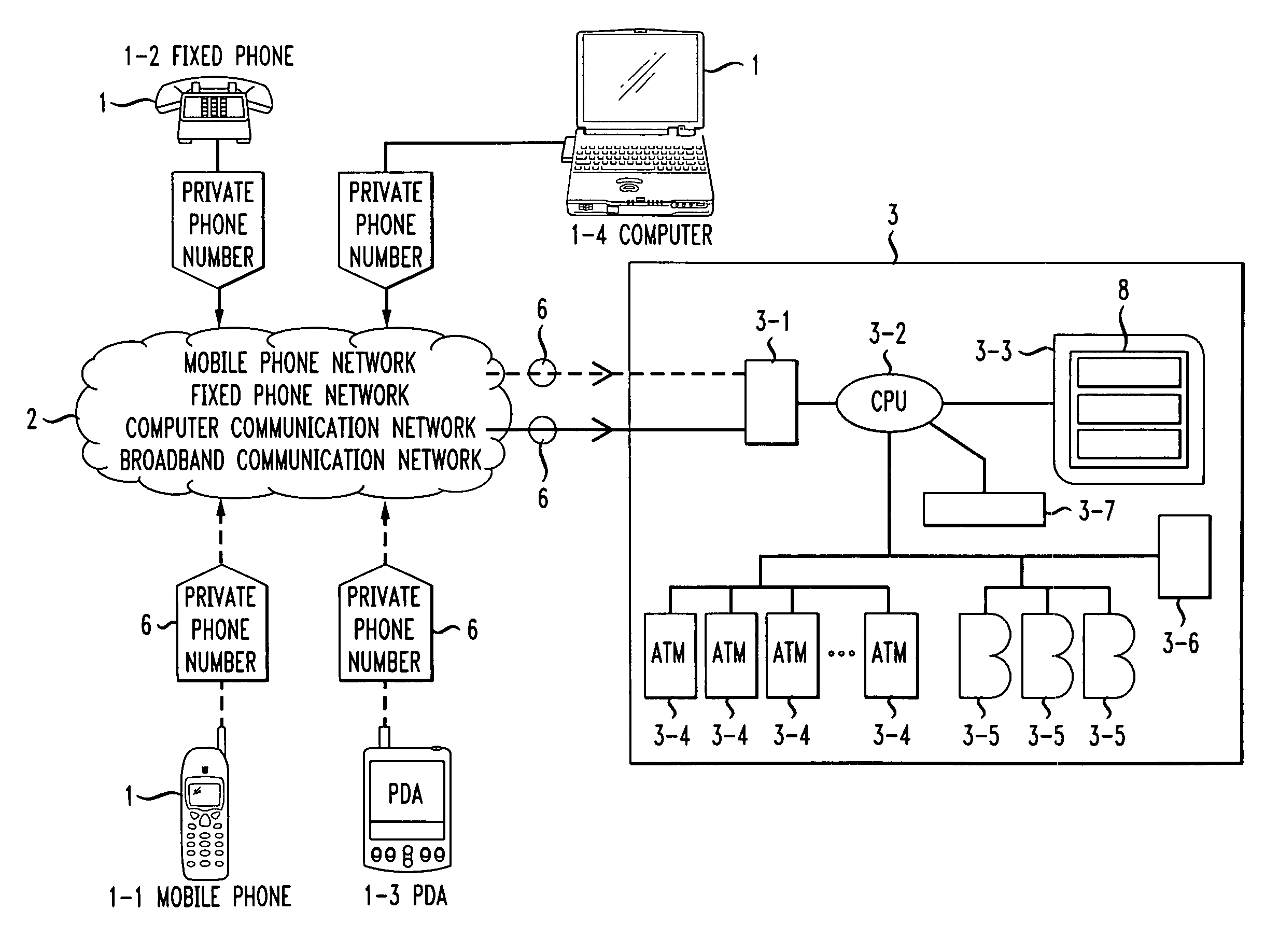
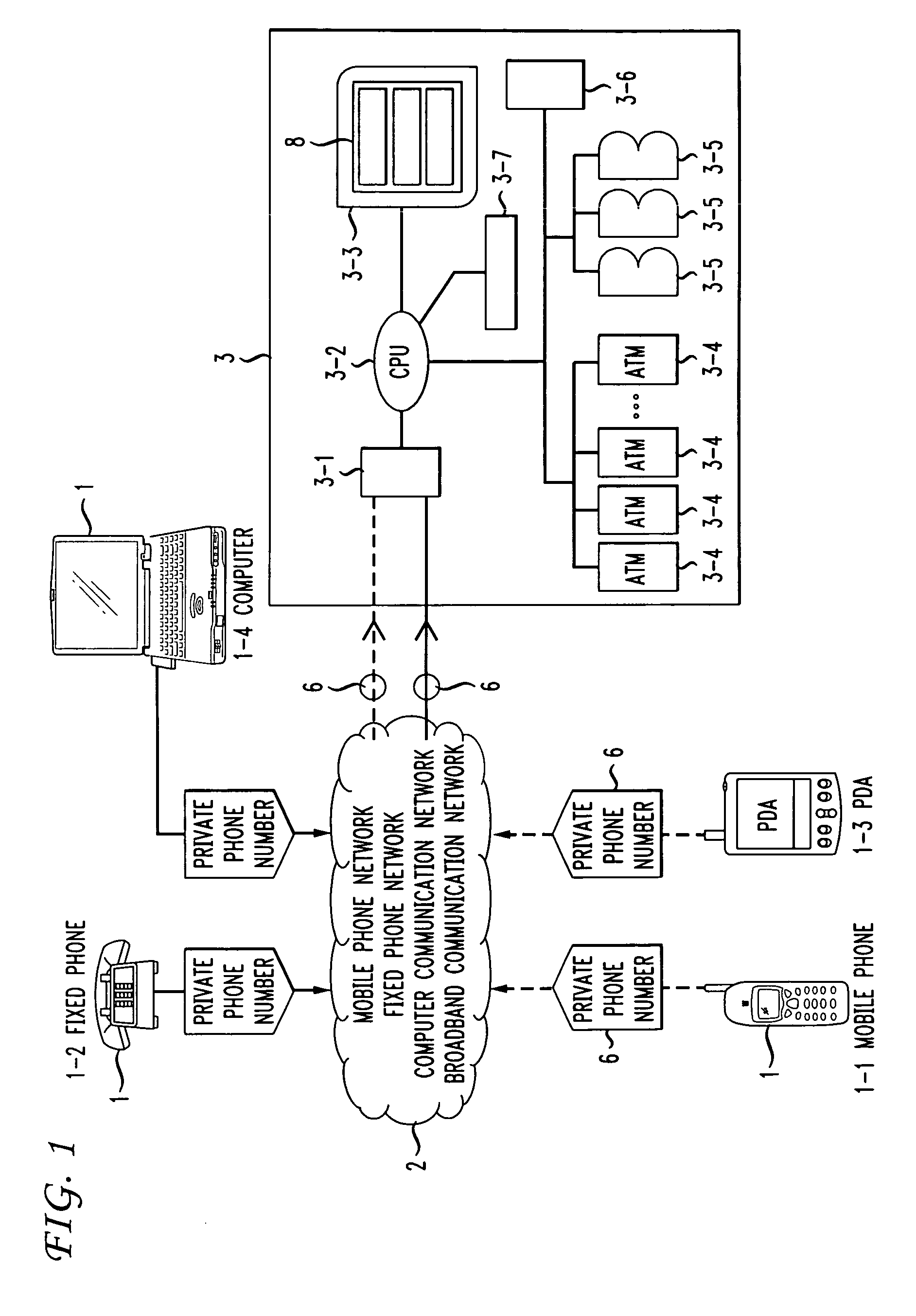
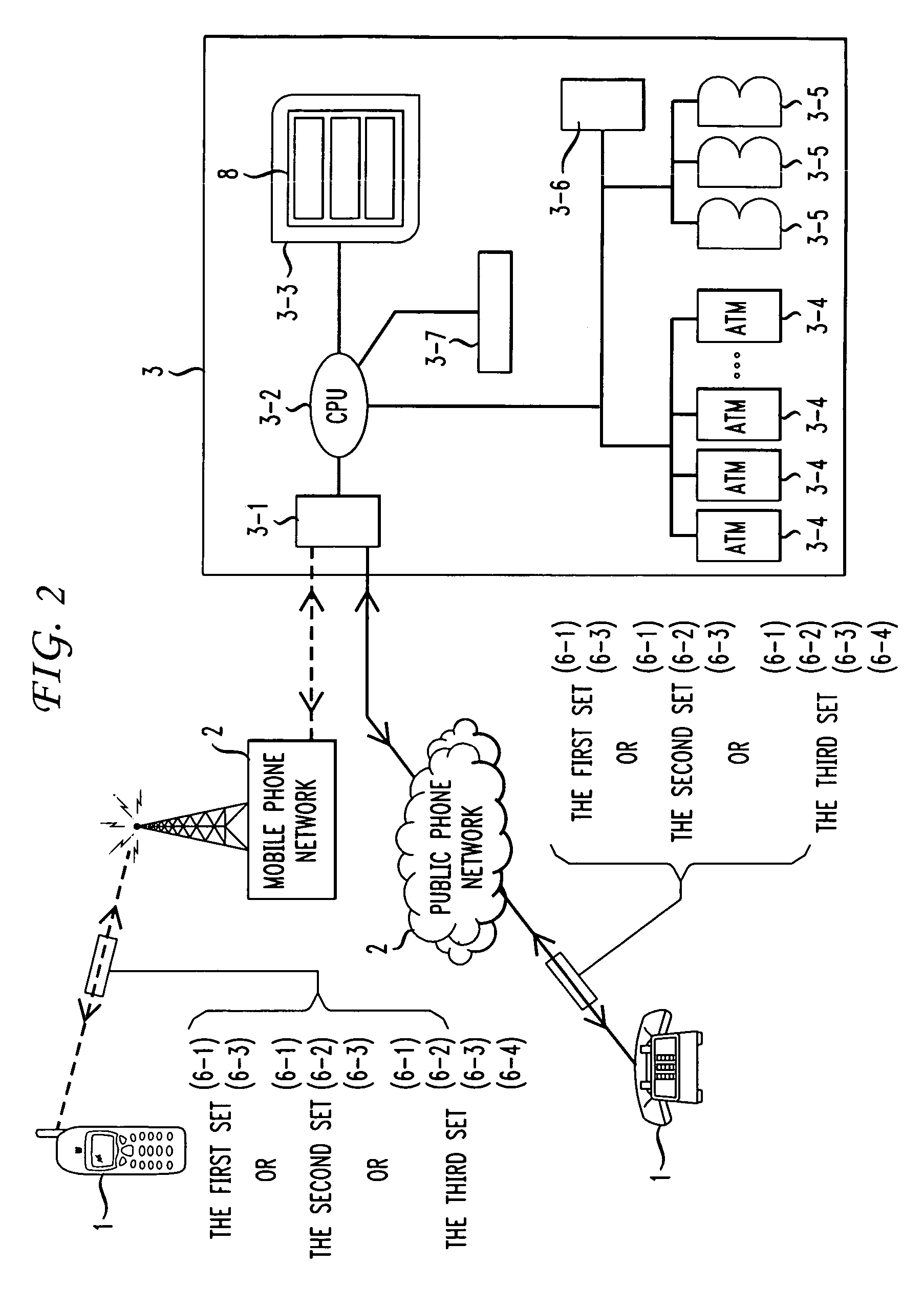
InactiveUS7712655B2Improve securityLow costComplete banking machinesFinancePaymentCommunications system
A banking computer system with lock for secure payment via telephone and corresponding method, the system includes a telephone (1), a public communication system (2), a financial computer account system (3), wherein the financial computer account system (3) usually locks its user account (3-7), assigns a private phone number (6) to a user, and sets unlock information (8) associated with the user account (3-7) in the system. Once the user is connected to the financial computer account system (3) using the telephone (1) with the private phone number (6) through the public communication system (2), the financial computer account system (3) will check the unlock information (8) according to a predefined program, if the unlock information (8) is authenticated, the user account (3-7) will be unlocked for a predefined time, otherwise, the user account cannot be unlocked, the secure payment is therefore achieved by adding an unlock procedure which can be controlled by user.
Owner:WONG KAMFU
System for facilitating a transaction
The present invention provides a system and method for facilitating a transaction using a secondary transaction number that is associated with a cardholder's primary account. The cardholder provides the secondary transaction number, often with limited-use conditions associated therewith, to a merchant to facilitate a more secure and confident transaction.
Owner:LIBERTY PEAK VENTURES LLC
Method and system for monitoring online behavior at a remote site and creating online behavior profiles
InactiveUS6983379B1Amount of timeHardware monitoringComputer security arrangementsInternet privacyTransaction data
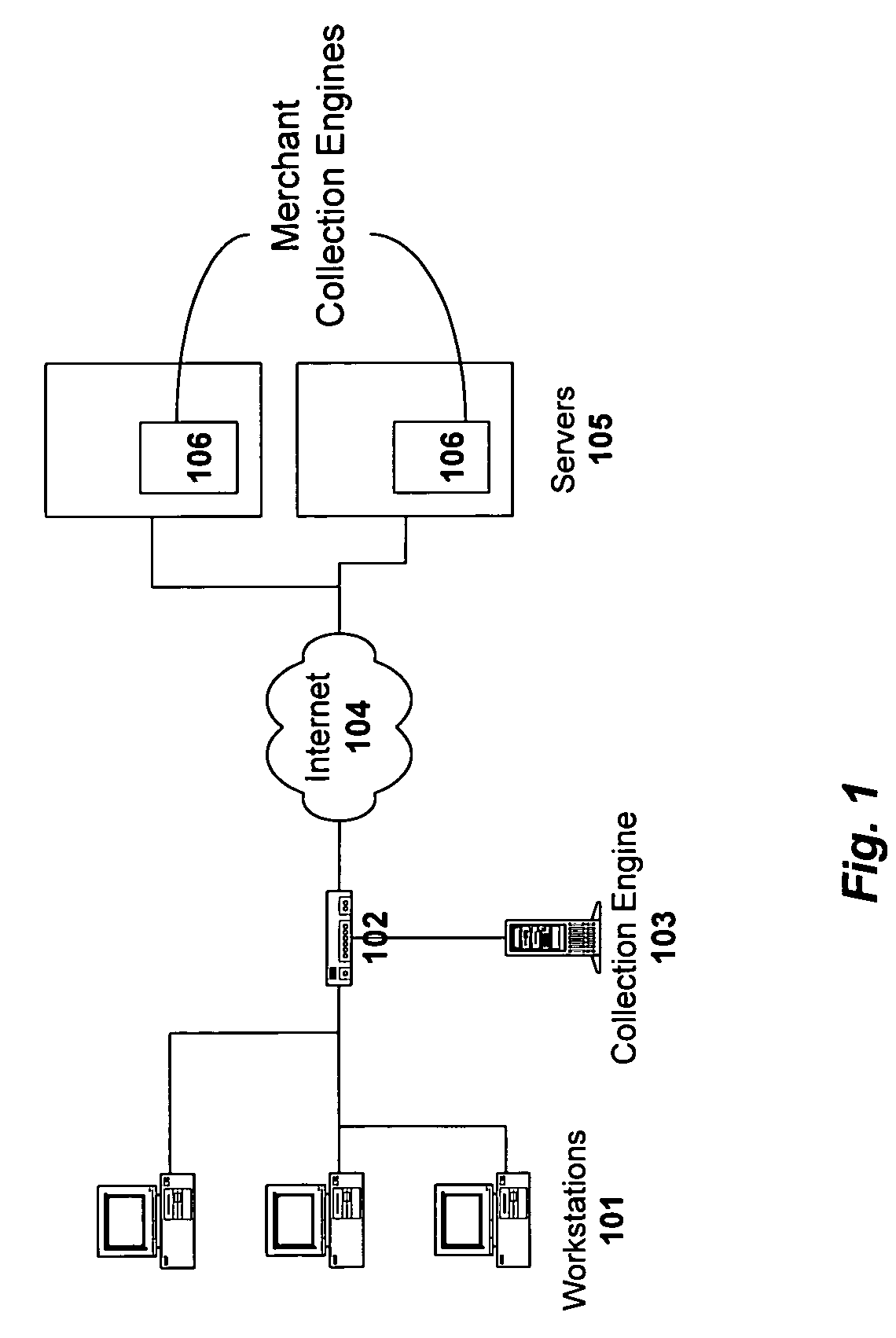
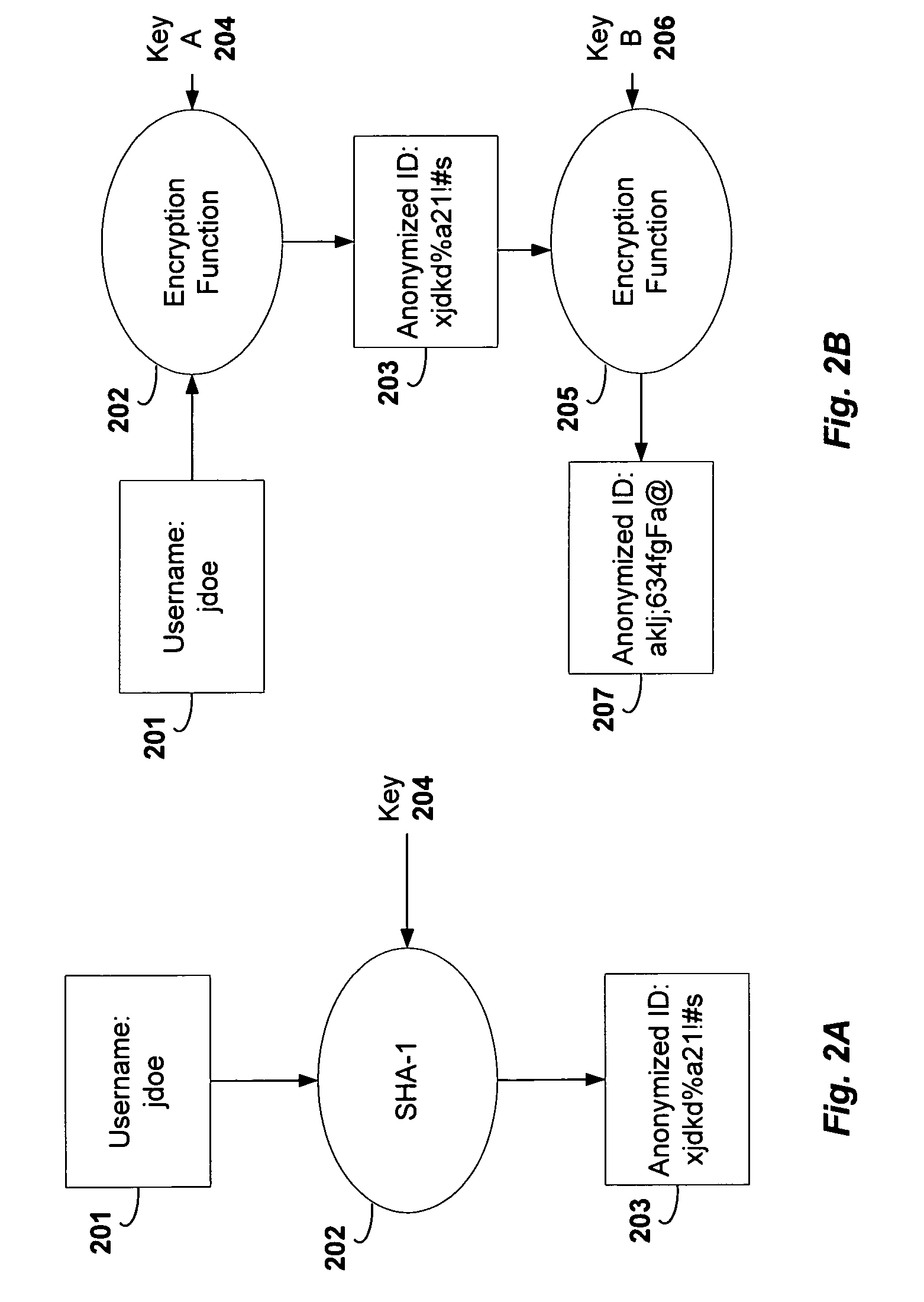
A method and system for monitoring users on one or more computer networks, disassociating personally identifiable information from the collected data, and storing it in a database so that the privacy of the users is protected. The system includes monitoring transactions at both a client and at a server, collecting network transaction data, and aggregating the data collected at the client and at the server. The system receives a user identifier and uses it to create an anonymized identifier. The anonymized identifier is then associated with one or more users' computer network transactions. The data is stored by a collection engine and then aggregated to a central database server across a computer network.
Owner:PLURIMUS CORP +1
Method and apparatus for optimizing networking potential using a secured system for an online community
The present invention provides a method and apparatus for users to search networks, both their own network and their peers' networks, all under the umbrella of a “multiple level access” security system. The present invention has been designed to optimize networking capabilities among users in a comprehensive online community. Networking among such a secured environment will allow users an opportunity to enhance their networking potential by expanding their networks to their peers' and beyond. A user registers with the online community and personally adds individuals that they know to their personal networking database. While adding these peers to the networking database, the user grants a specific level of access to each individual. This security measure is devised to discourage solicitation from other unwanted online users. The levels of access give the user an opportunity to control the amount of personal information, including contacts that they make, available to their individual peers. Based on the level of access granted by the user, the peer may or may not be able to access the users information or the user's personal databases for potential networking. The level of access granted by two individuals need not be the same for each other.
Owner:MICROSOFT TECH LICENSING LLC
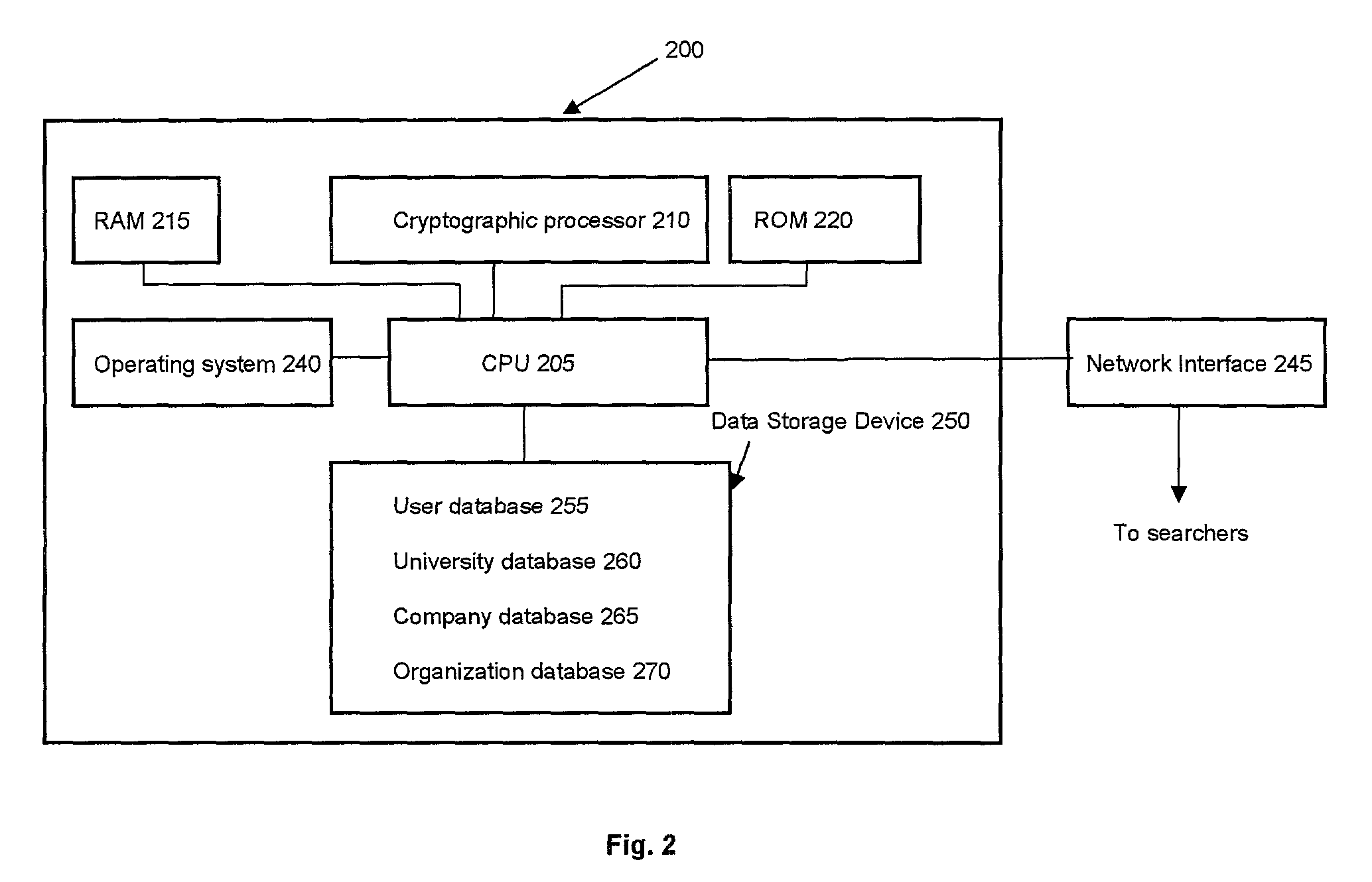
Token-based payment processing system
InactiveUS8584251B2Digital data processing detailsAnalogue secracy/subscription systemsData processing systemPayment
A data-processing system, such as a payment processing system, including a tokenizer, such as a card encryption and storage system (CES) employing a tokenization feature. In one embodiment, the present invention provides a first-computer-implemented method for preventing the transmission of confidential information between a first computer and a second computer in communication with the first computer. The method includes the steps of: (a) the first computer receiving information for performing a transaction, the information including confidential information manually entered by a user; (b) the first computer sending the confidential information to a third computer; (c) the first computer receiving, from the third computer, a token having no algorithmic relationship to the confidential information; and (d) the first computer sending to the second computer (i) the information for performing the transaction, except for the confidential information, and (ii) the token.
Owner:CARDCONNECT LLC
Smart communication device secured electronic payment system
InactiveUS20130204793A1Prevent fraudMinimizes likelihood of liabilityFinanceAnonymous user systemsPayment transactionDocumentation
Systems, apparatuses, and methods enabling secure payment transactions, and methods for sharing secure documents, via a mobile device, for example a mobile telephone, smartphone, cellular telephone, other wireless device, a Near Field Communications (NFC) device, or the like. Actual user account information is substituted with temporary account information such that the temporary account information may be manipulated in a manner similar to actual user account information, with the result that actual account information is masked thereby greatly reducing the likelihood of misuse.
Owner:KERRIDGE KEVIN S +1
Process for making a payment using an account manager
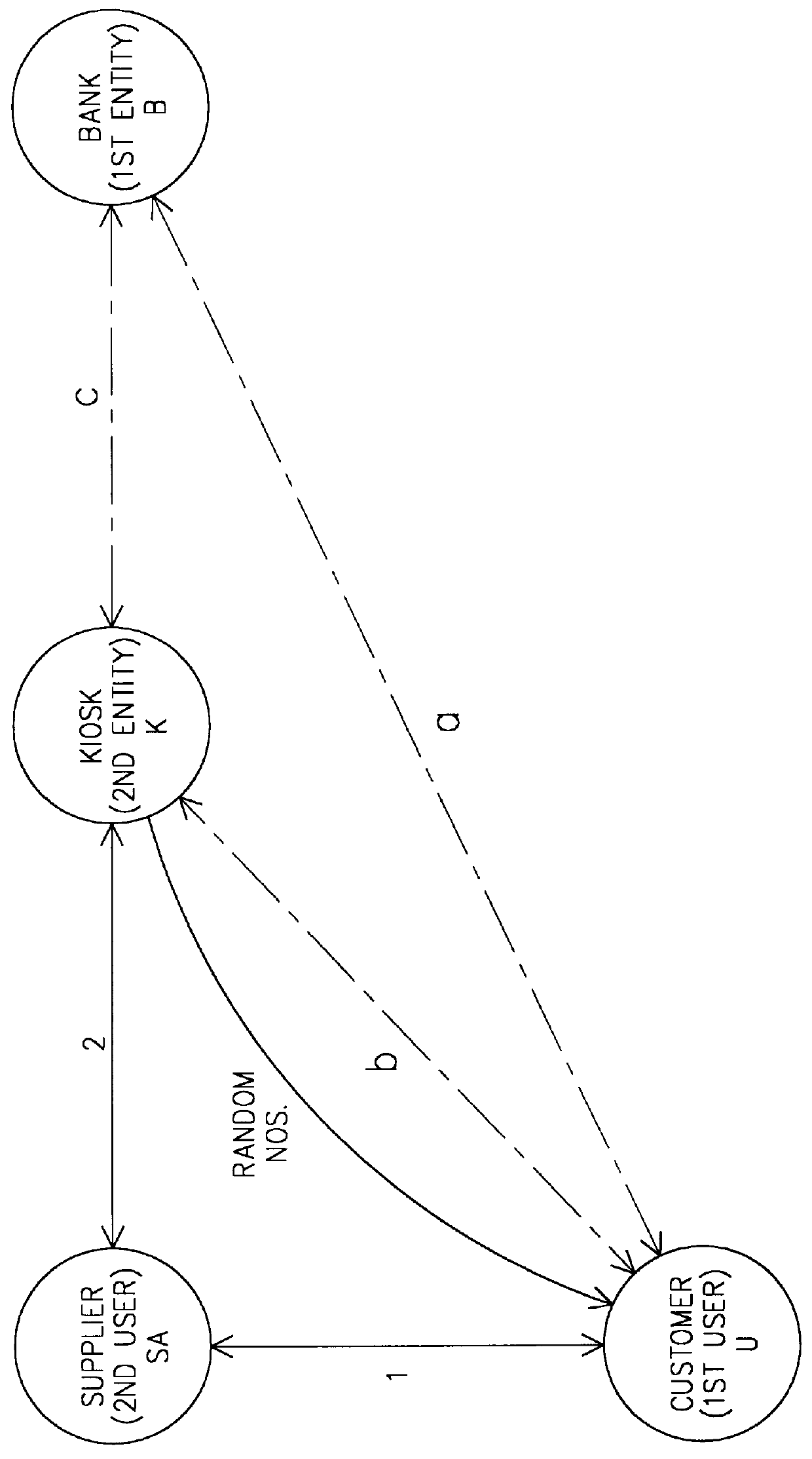
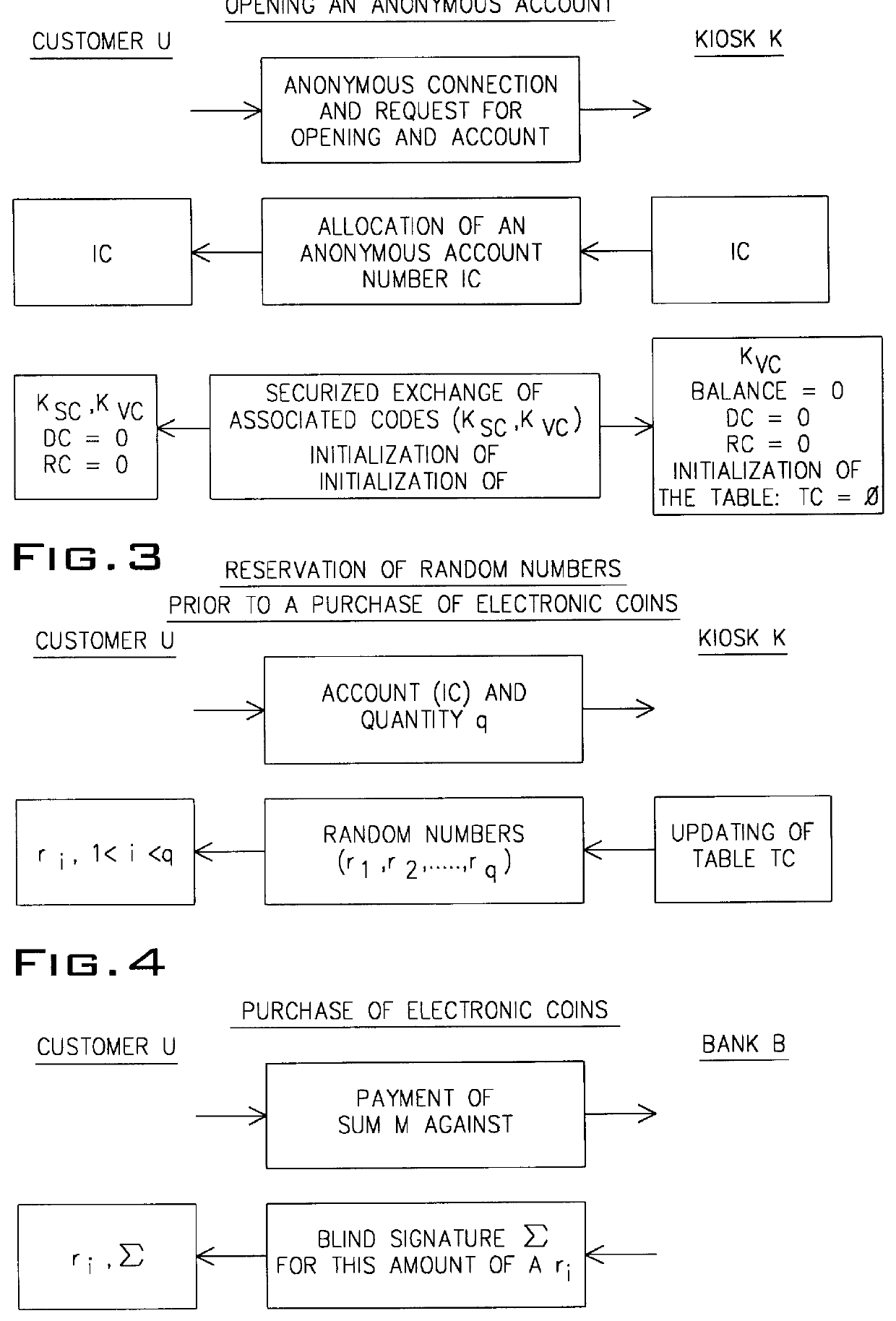
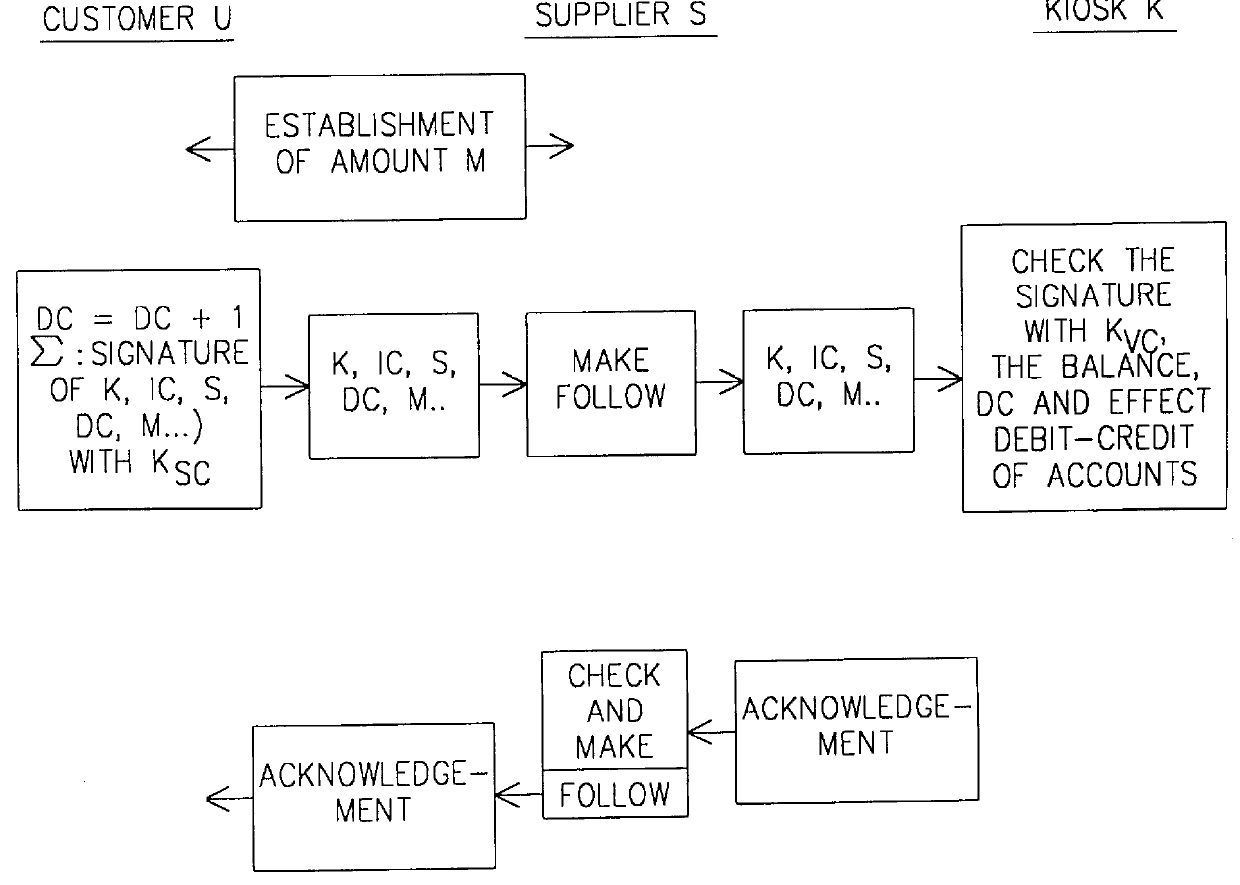
The present invention relates to a process for making a payment using an account manager or kiosk, the process guaranteeing the payment of the supplier and the anonymity of the customer. A customer (U) withdraws from his bank (B) a sum in the form of "blind" electronic coins or cash, deposits the latter in one or more anonymous accounts in a kiosk (K) and finally uses said account or accounts for paying suppliers of goods or services (SA). The invention has application to streamline and voice telepayment.
Owner:FRANCE TELECOM SA
Method and system for managing personal and financial information
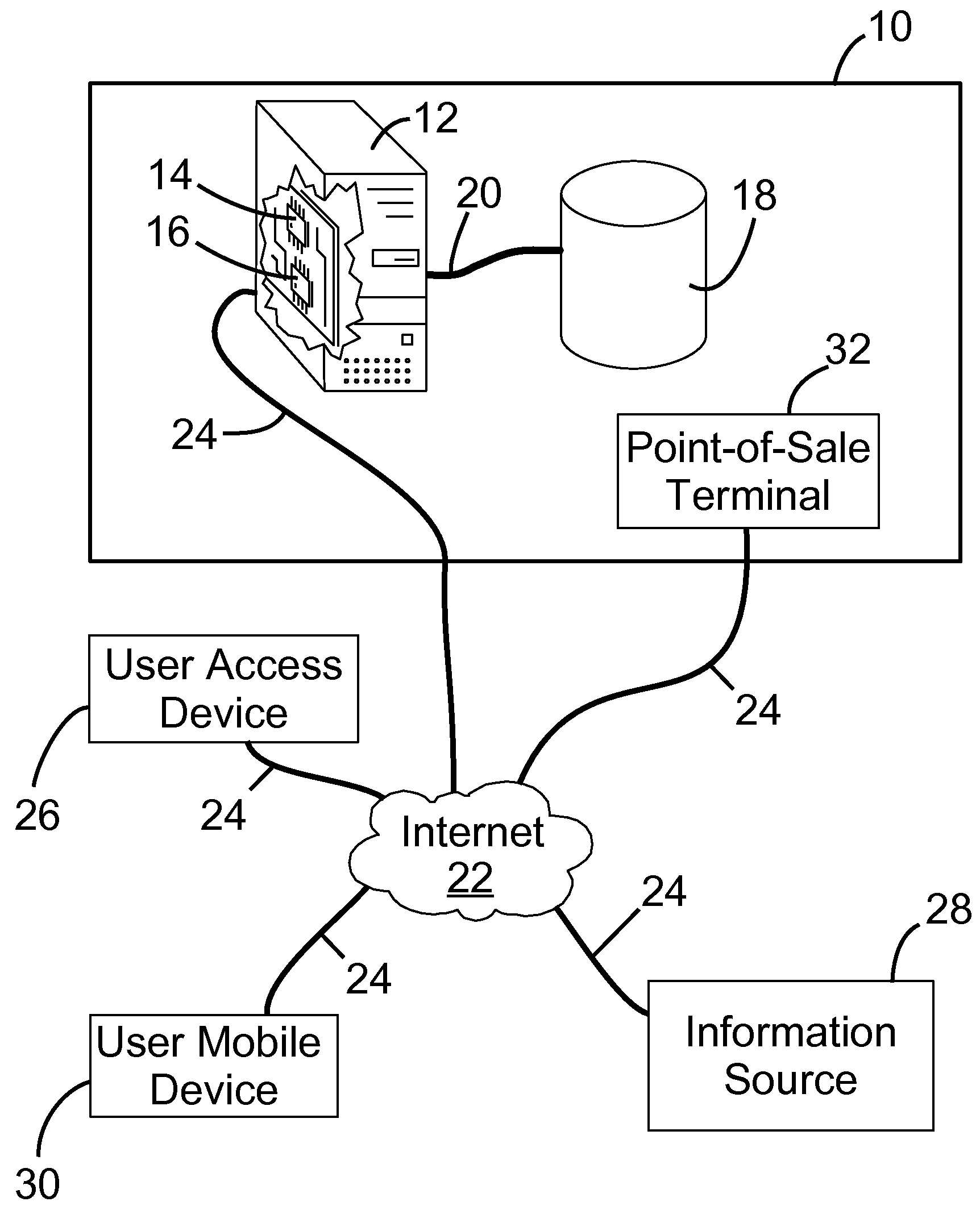
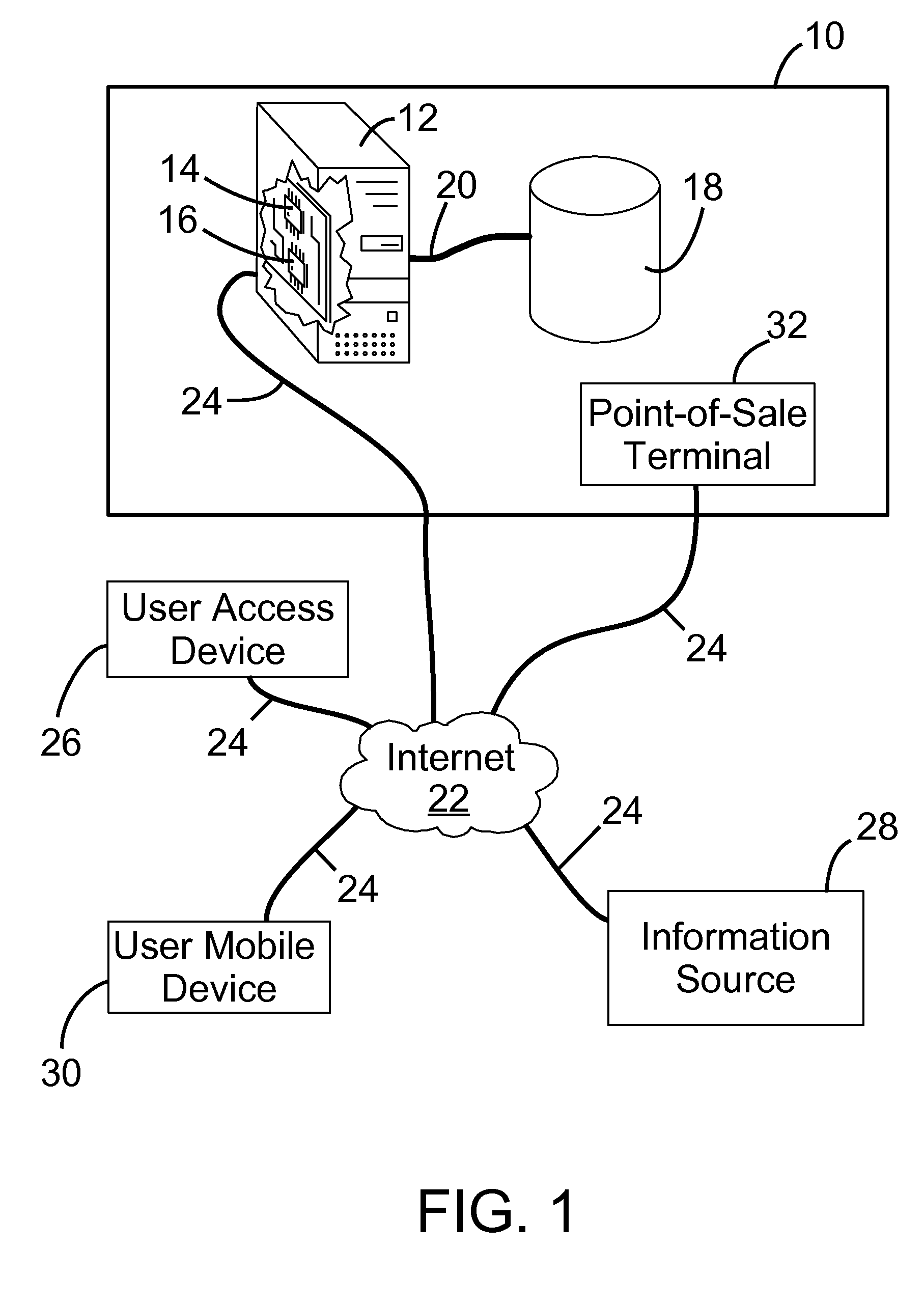
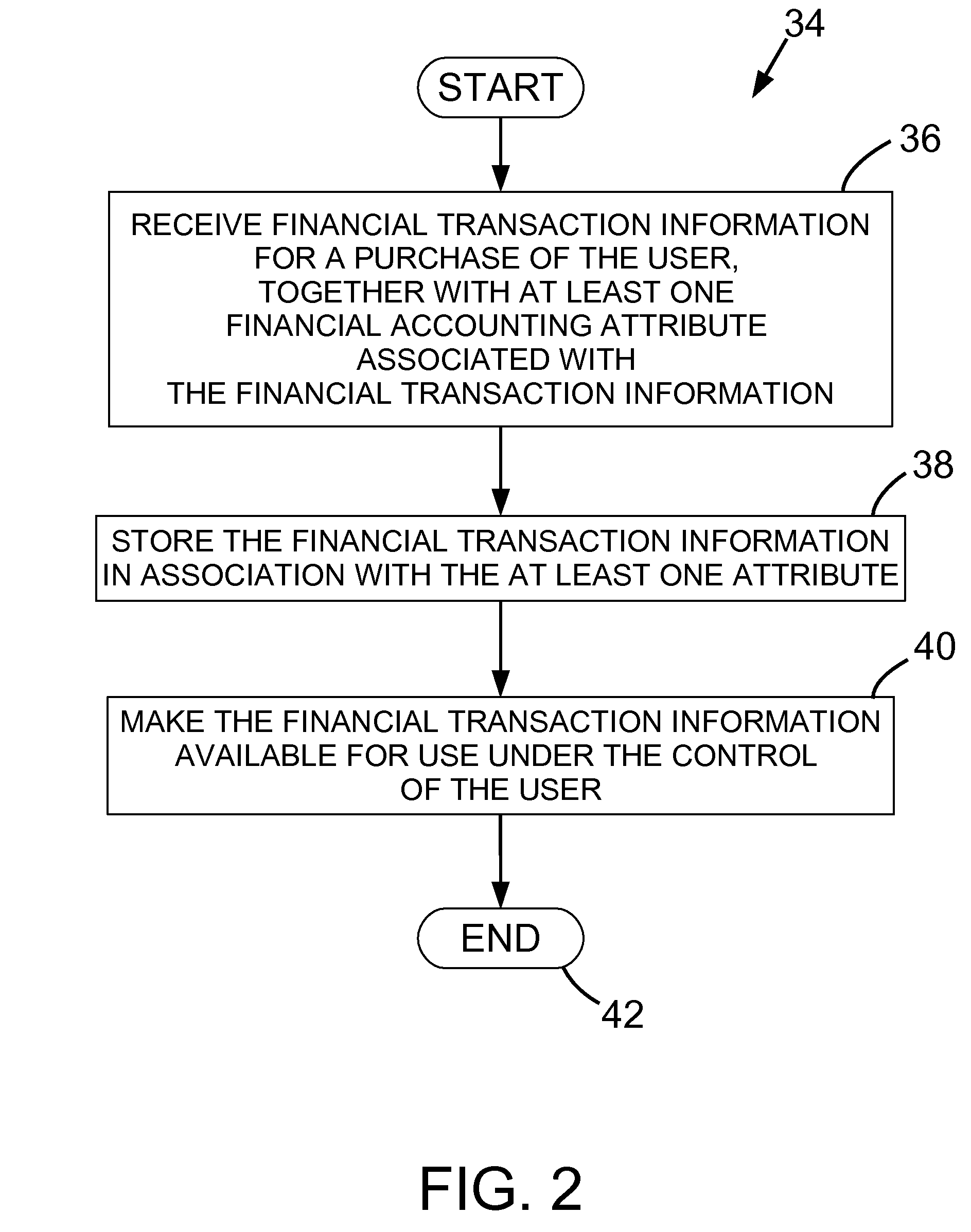
InactiveUS20090254476A1Available for useFinancePoint-of-sale network systemsFinancial transactionMobile device
A system and method for managing personal and financial information is provided. The method involves: receiving financial transaction information for a purchase of the user, together with at least one attribute associated with the financial transaction information; storing the financial transaction information in association with the at least one attribute; and making the financial transaction information available for use under the control of the user. The attribute may be a financial account identifier, a financial account type, a purchase type or a purchase identifier. The method may also involve receiving a purchase location attribute defining a location for the purchase; determining a current location associated with a user mobile device using a global positioning system; and transmitting, if the purchase location attribute does not match the current location, a message to the mobile device for fraud detection purposes.
Owner:QUICKRECEIPT SOLUTIONS
Method and device for generating a single-use financial account number
InactiveUS7177835B1Improve security levelReduce riskFinanceCredit schemesFinancial transactionData element
Owner:PAYPAL INC +1
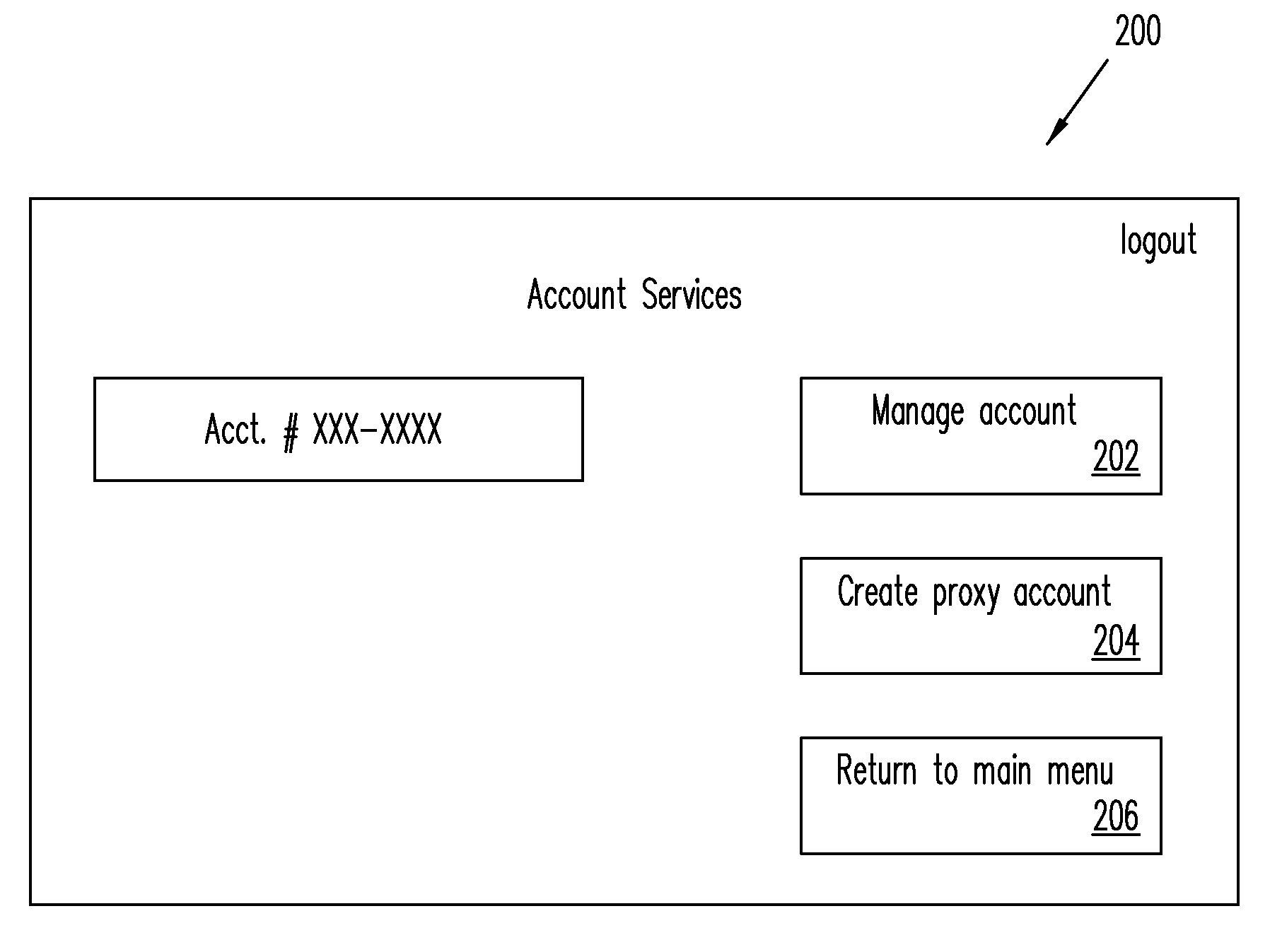
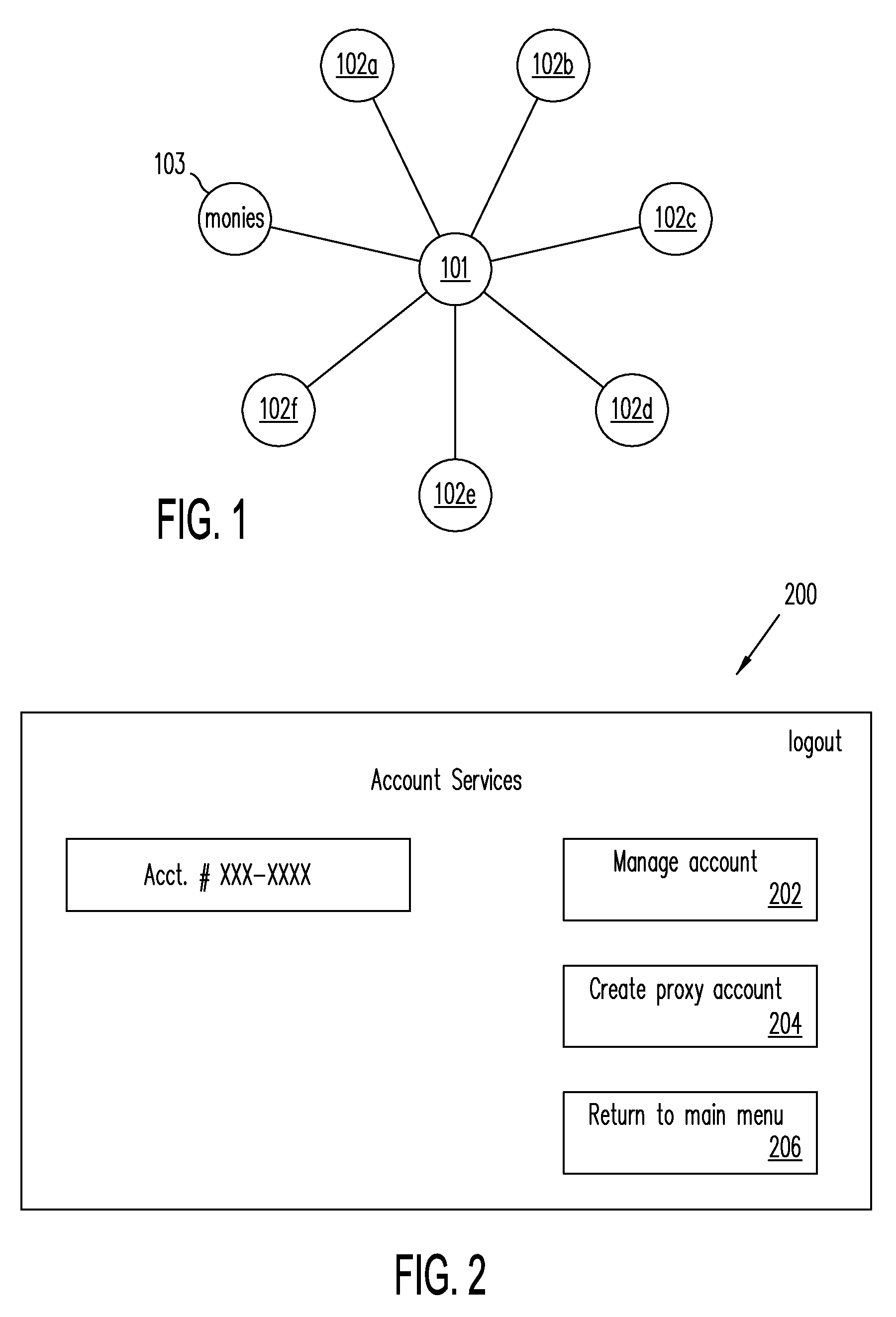
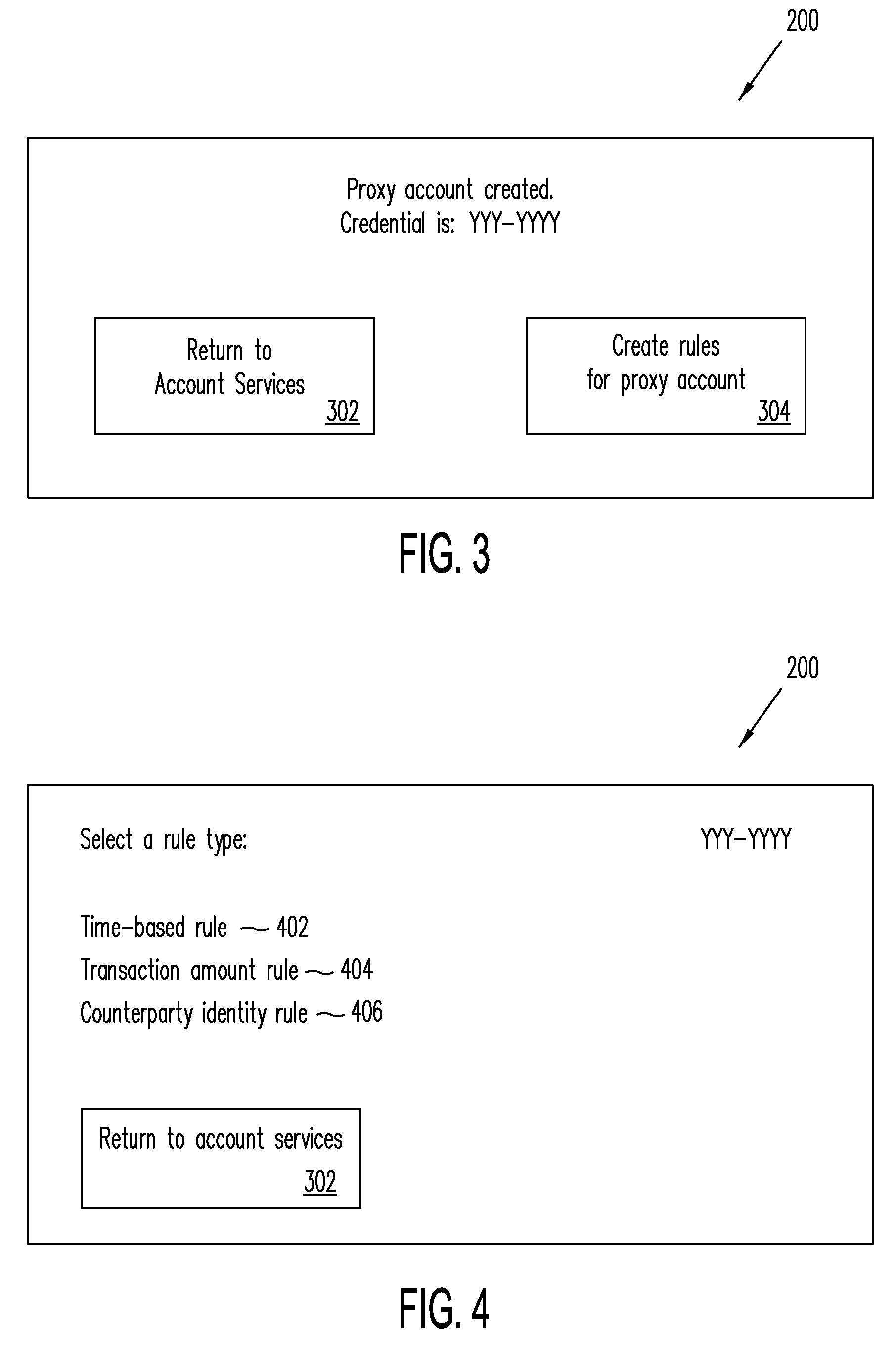
Systems, Methods, and Computer Program Products for Using Proxy Accounts
The present disclosure involves a method including creating a primary payment account for an account owner, in which the primary payment account is linked to a method of payment, and creating a proxy payment account, in which the proxy payment account is linked to the primary account but is not linked directly to the method of payment, in which payments to and from the proxy payment account are cleared through the primary account, further in which the primary payment account has first credentials, and in which the proxy payment account has second credentials, the first and second credentials being different.
Owner:PAYPAL INC
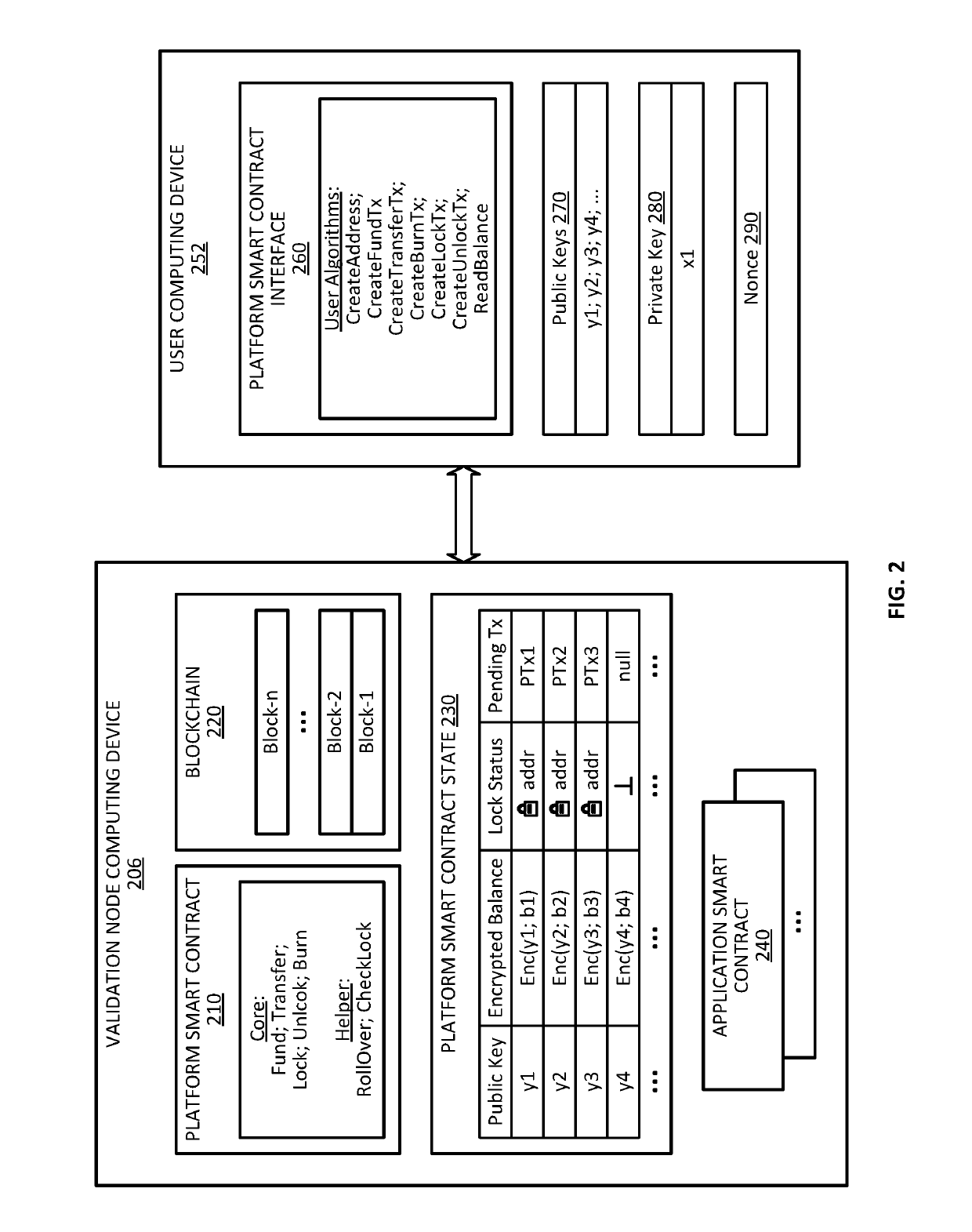
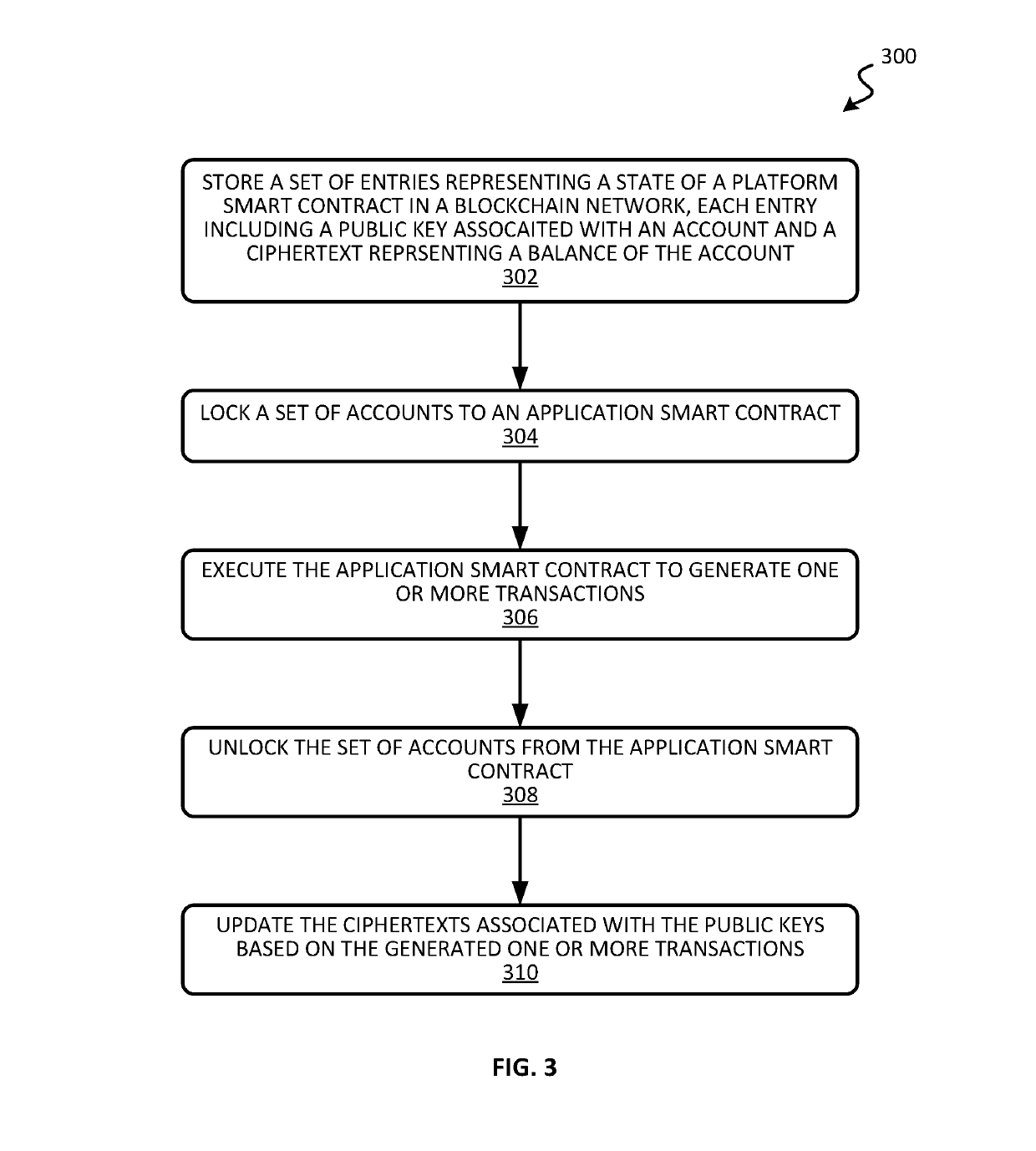
Blockchain system for confidential and anonymous smart contracts
ActiveUS20190164153A1Improve confidentialityEnhanced anonymityEncryption apparatus with shift registers/memoriesCryptography processingInternet privacyPrivacy preserving
Blockchain-based, smart contract platforms have great promise to remove trust and add transparency to distributed applications. However, this benefit often comes at the cost of greatly reduced privacy. Techniques for implementing a privacy-preserving smart contract is described. The system can keep accounts private while not losing functionality and with only a limited performance overhead. This is achieved by building a confidential and anonymous token on top of a cryptocurrency. Multiple complex applications can also be built using the smart contract system.
Owner:VISA INT SERVICE ASSOC +1
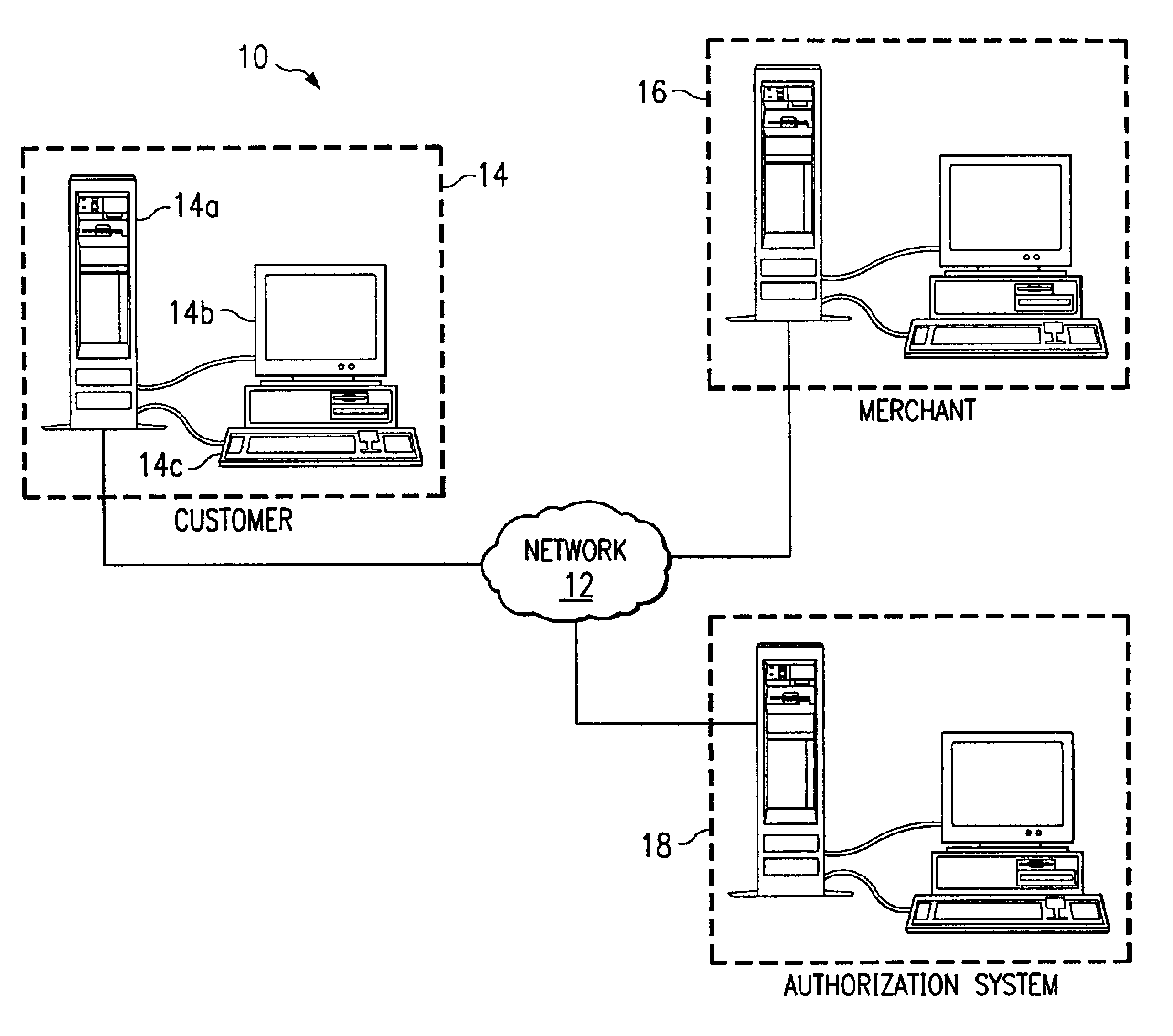
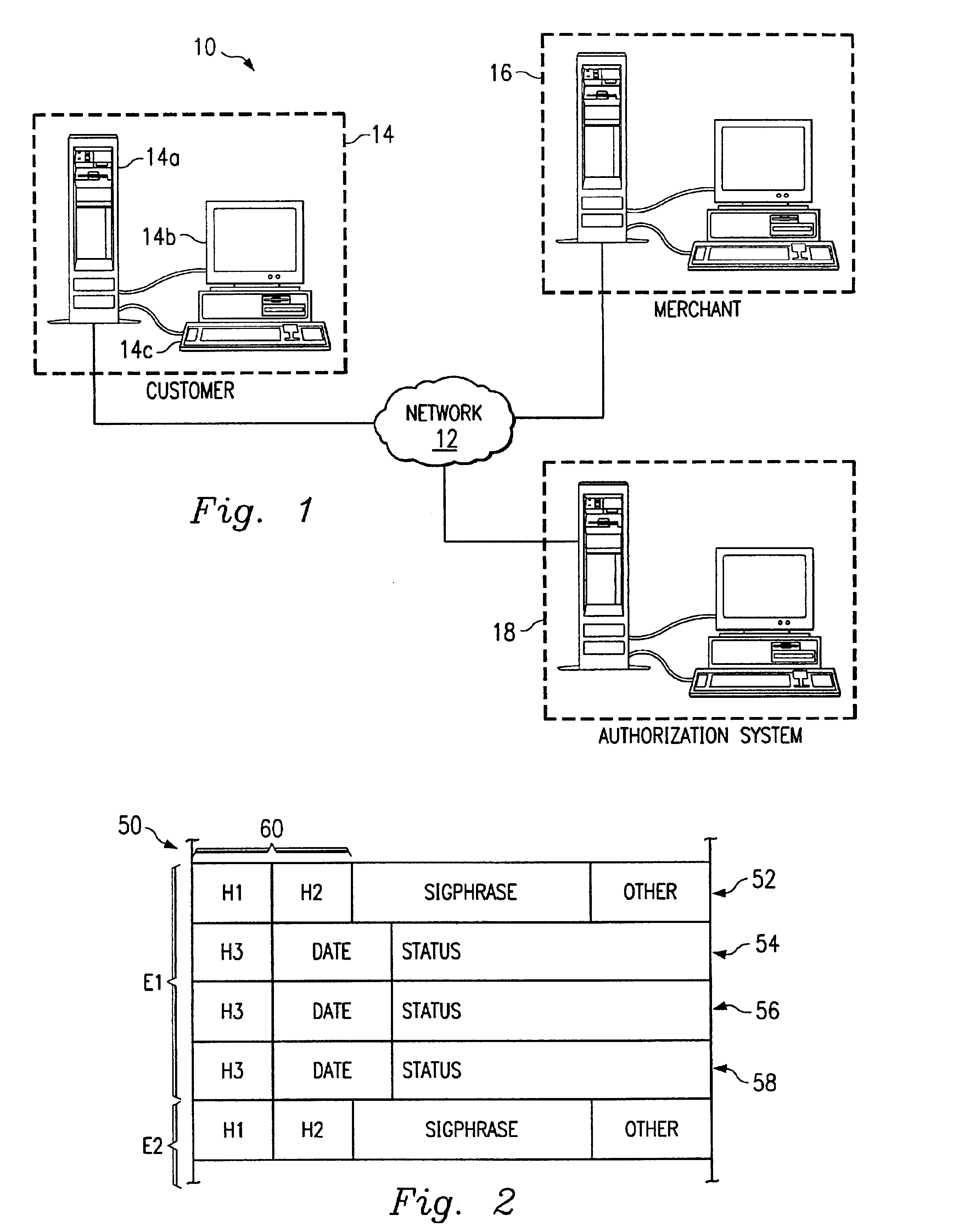
Centralized authorization and fraud-prevention system for network-based transactions
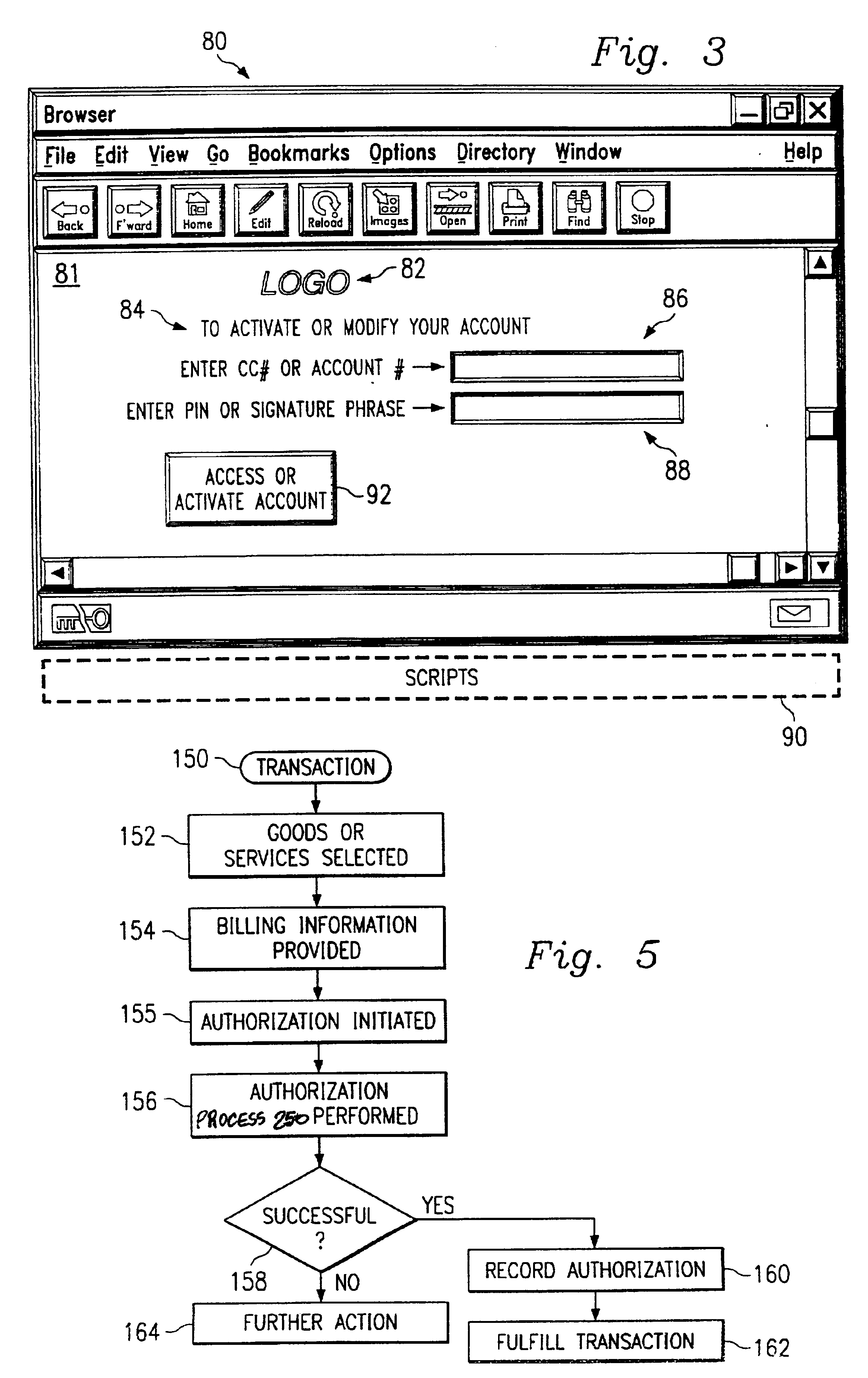
A system and method for authorizing certain aspects of network based transactions between a customer and a merchant is disclosed. The system utilizes an account code for identifying rights to use an account identified by an account number, and a database for storing the account number, account code, and a Signature Phrase. The Signature Phrase is stored when rights to use the account have been positively identified. The customer can complete an e-commerce transaction using the customer's account by providing a Signature Phrase without the Signature Phrase or account code actually residing in the database or being provided to the merchant. The account code, account number, and Signature Phrase may be received through one or more external interfaces with the customer. In some embodiments, the database stores the account number, account code, and the Signature Phrase in a hashed format.
Owner:KIOBA PROCESSING LLC
Electronic identifier payment systems and methods
InactiveUS7107249B2Optimize locationCredit registering devices actuationDiscounts/incentivesPaymentElectronic identification
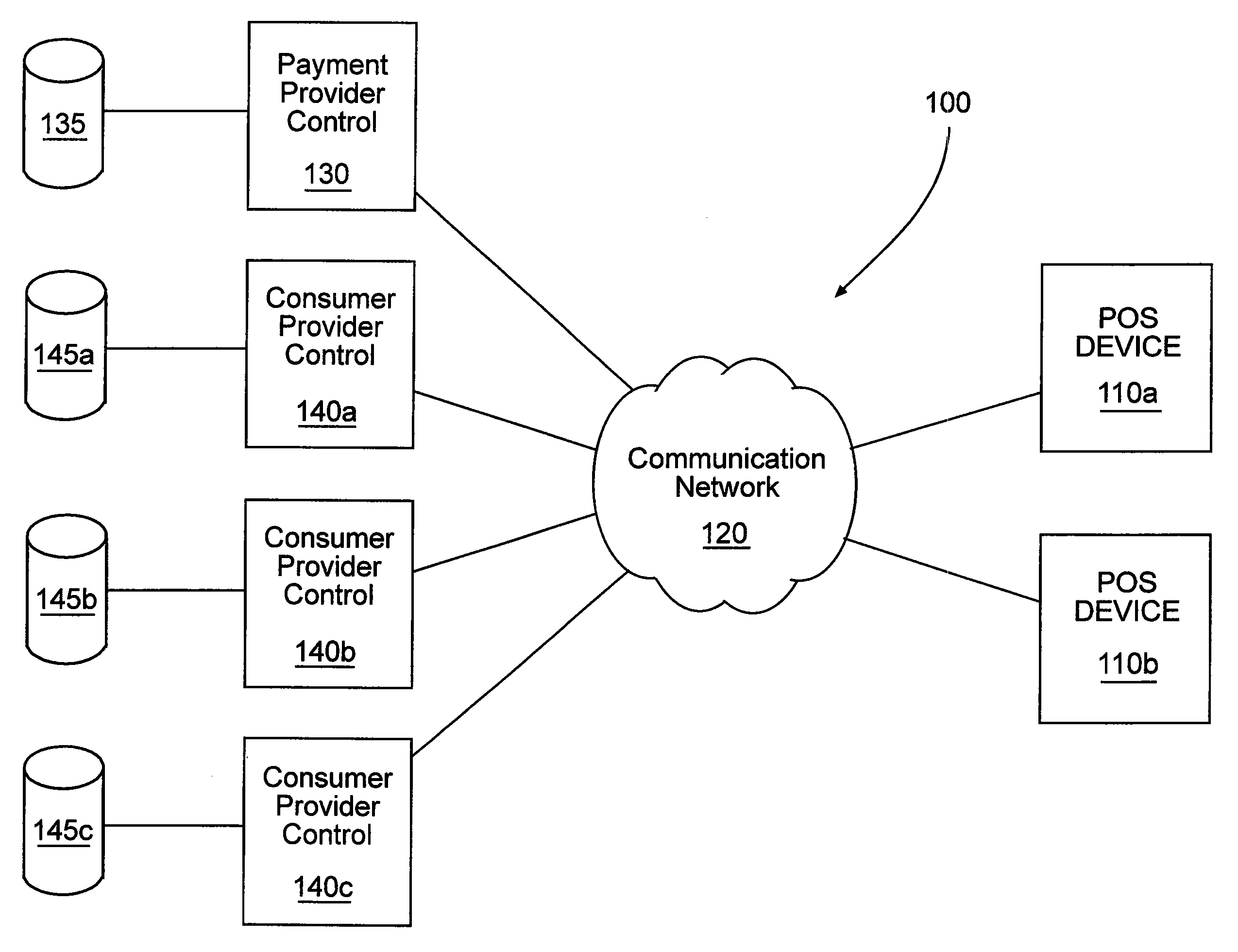
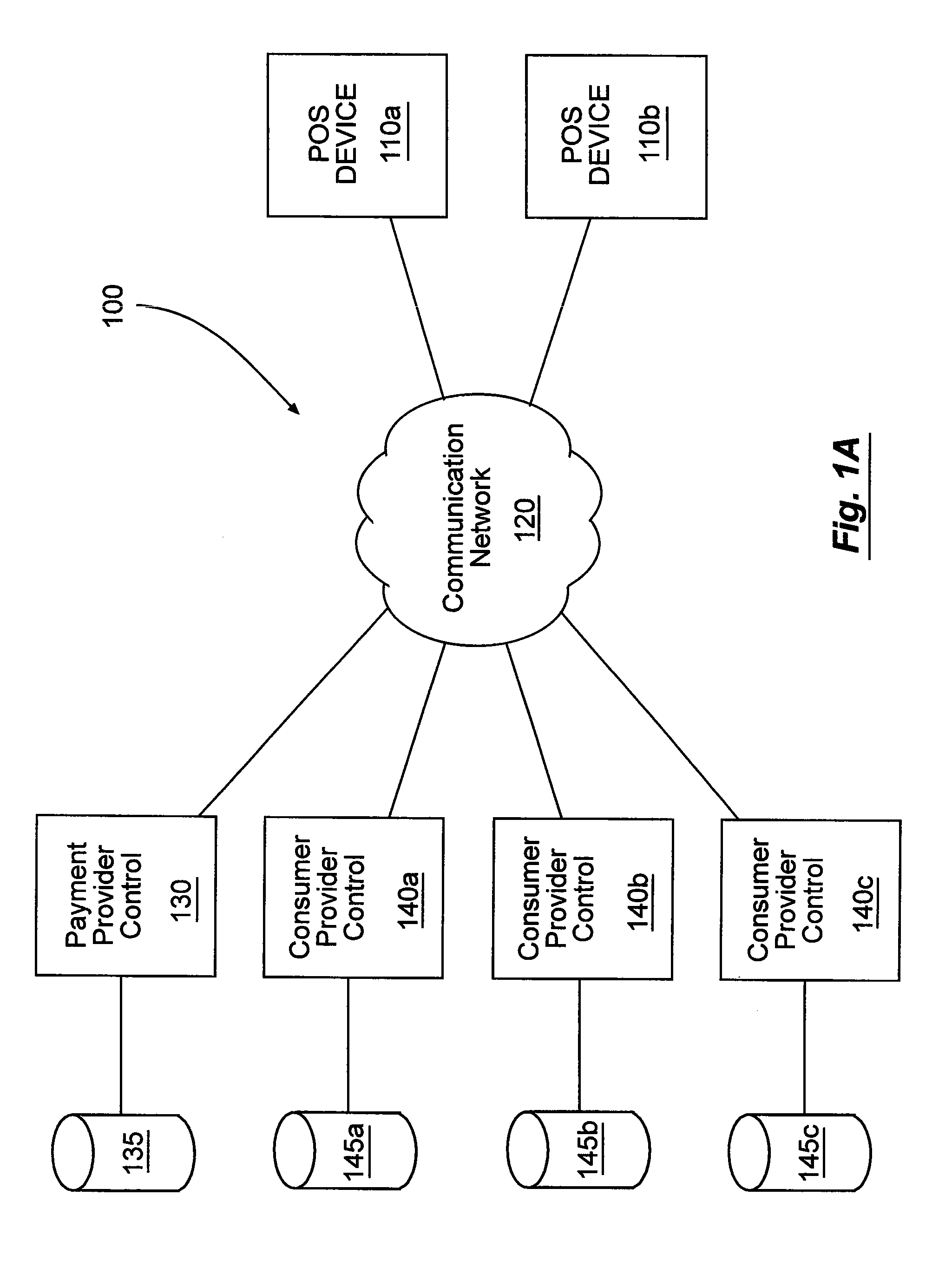
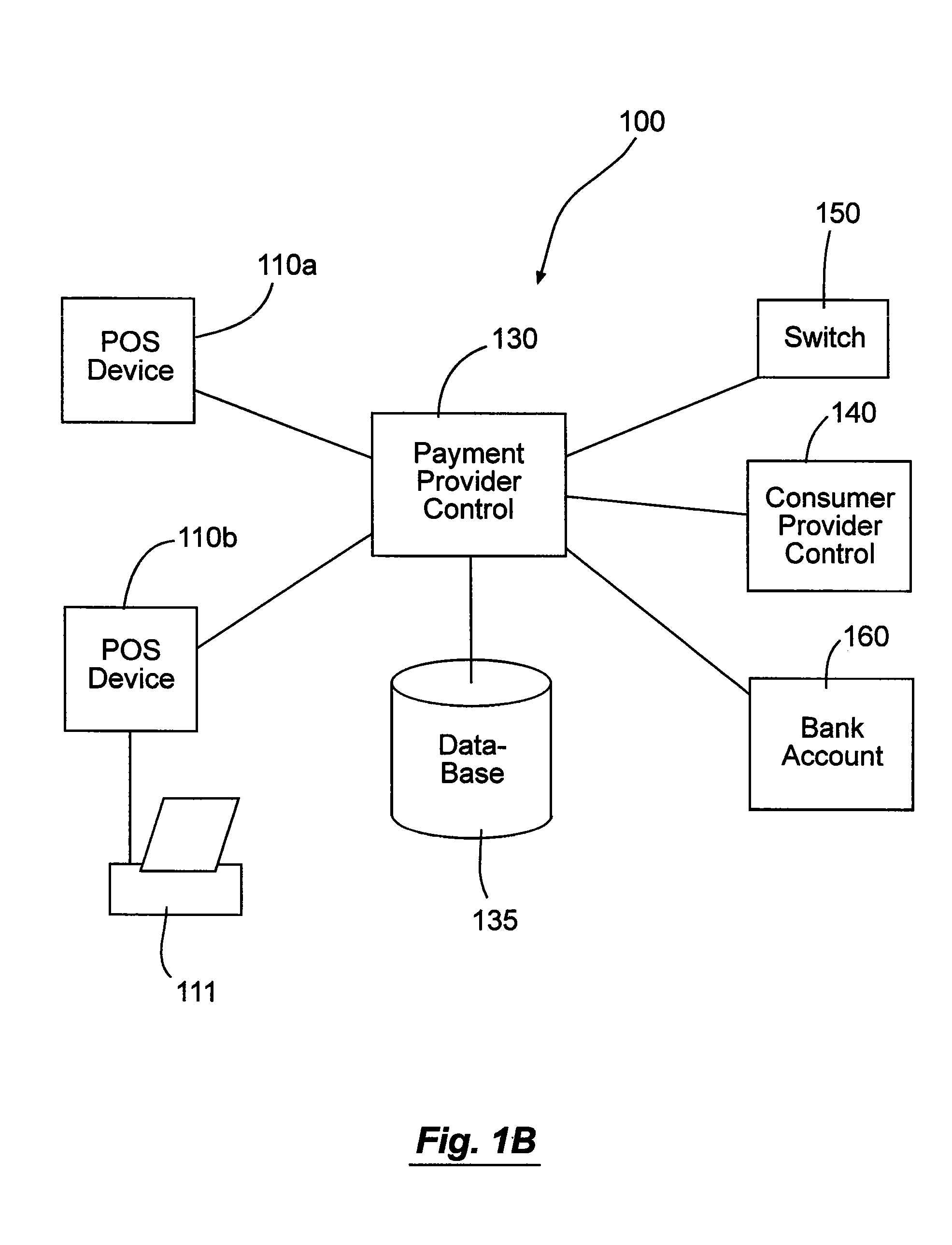
Systems and methods for accepting payments for goods and services provided by a consumer provider. The methods can include associating consumers and consumer providers with a payment provider. The payment provider can receive payments destined for the consumer provider, associate the payments with one or more identifiers, and transfer at least portions of the receive payments to the consumer provider. The systems can include a point-of-sale device configured to accept payments from consumers on behalf of consumer providers. In some cases, the systems include a plurality of such point-of-sale devices in communication with a payment provider control. The payment provider control can be in communication with one or more consumer provider controls.
Owner:THE WESTERN UNION CO
Method and apparatus to provide secure purchase transactions over a computer network
Owner:BENEDORTSE
Device including encrypted data for expiration date and verification value creation
ActiveUS20100299267A1Difficult to obtainFinanceUser identity/authority verificationPayment transactionFinancial transaction
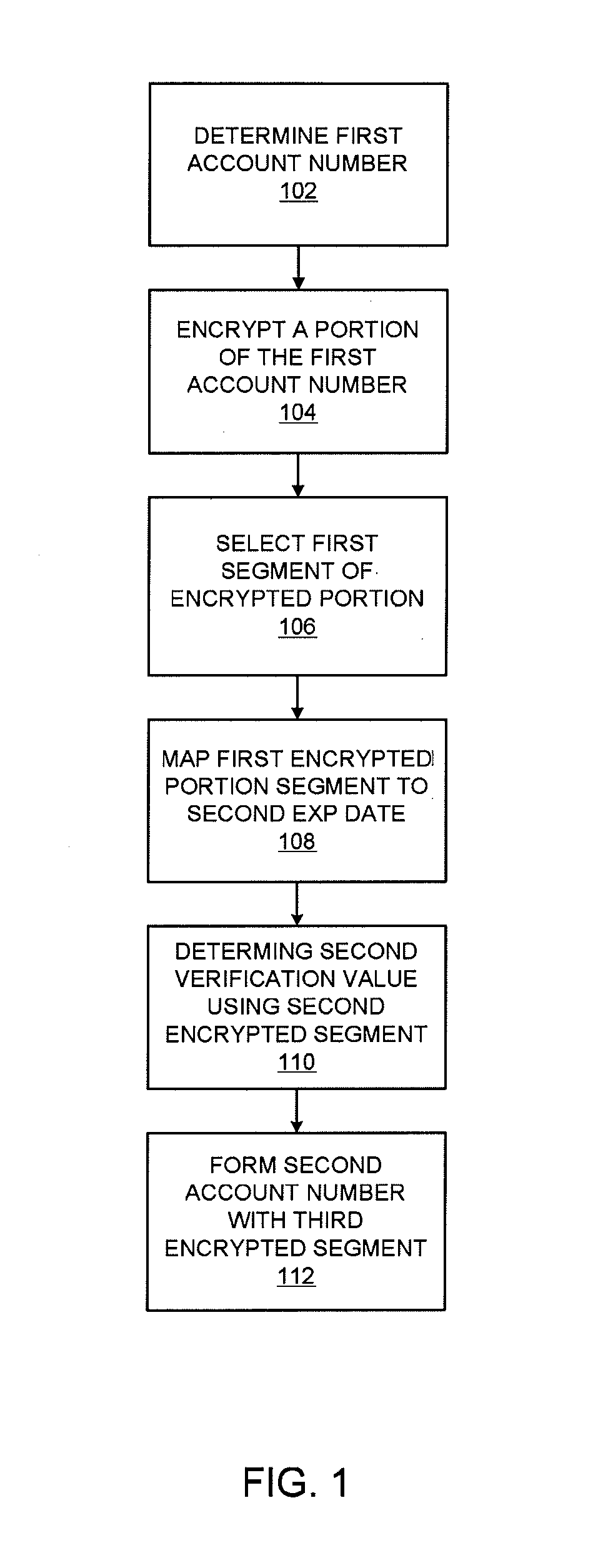
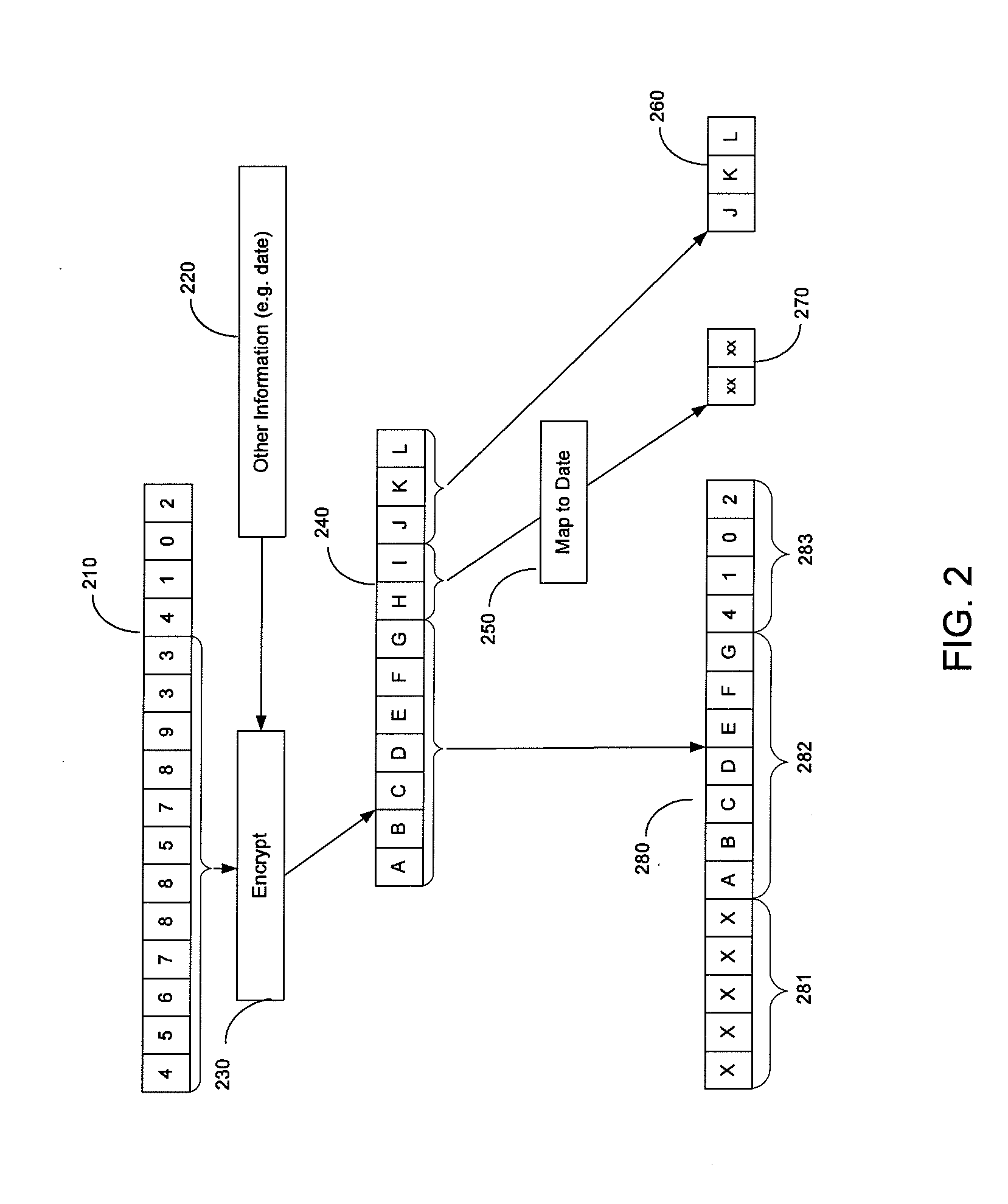
In order to make it more difficult to obtain numbers that can be used to conduct fraudulent transactions, a portion of a real account number is encrypted. The encrypted portion of the account number is used to generate a new account number, a new expiration date, and a new verification value. This information can be determined using processor that may reside in a point of sale terminal, a smart card, or a computer operated by a user. The new account number, the new expiration date, and the new verification value can be used in a payment transaction. A server computer in a central payment processing network may determine that the new account information is not the real account information, and may subsequently generate a modified authorization request message using the real account information and may send it to an issuer for approval. The transmission of data is more secure, since real account information is not sent from the merchant to the payment processing network.
Owner:VISA INT SERVICE ASSOC
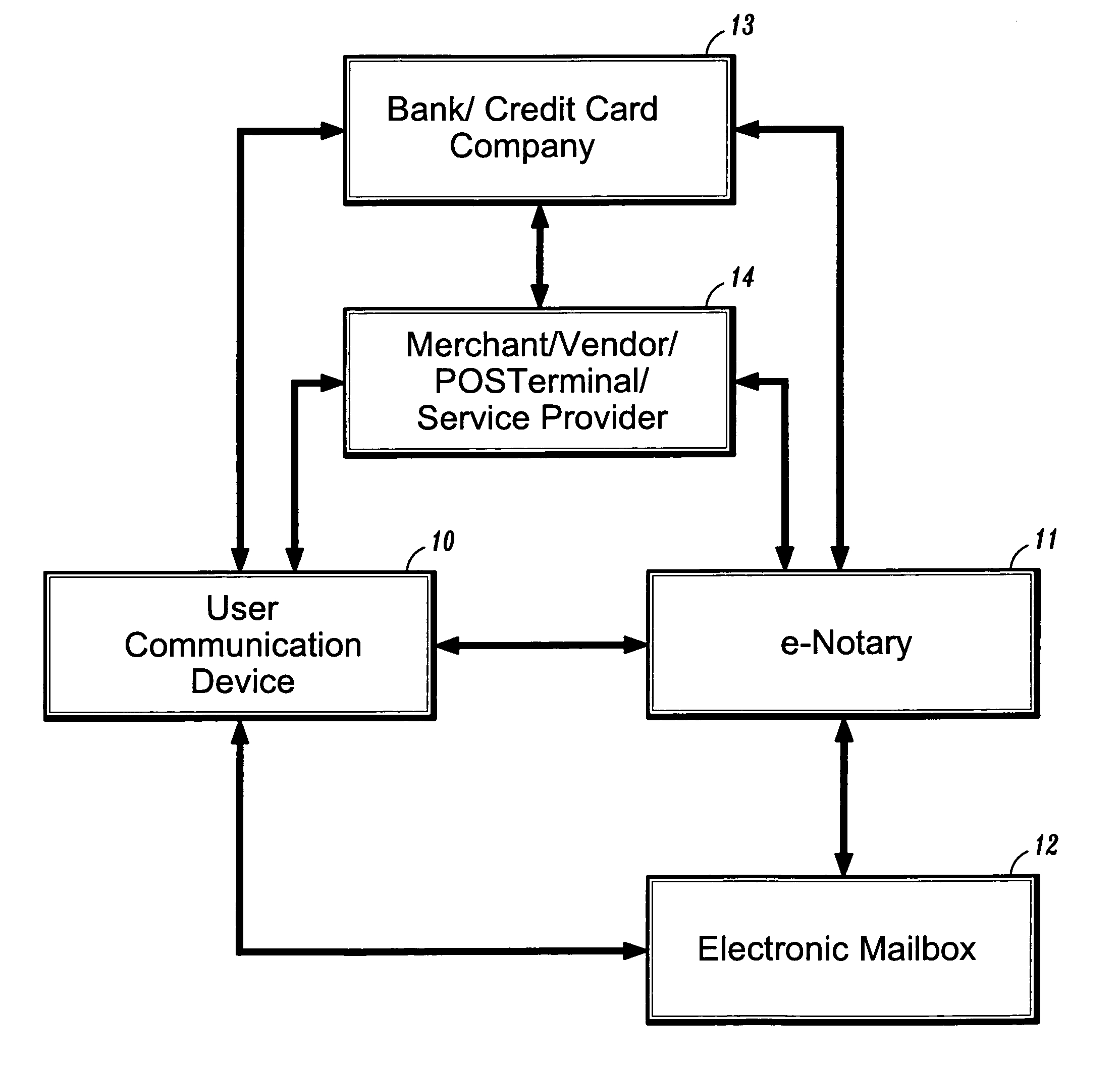
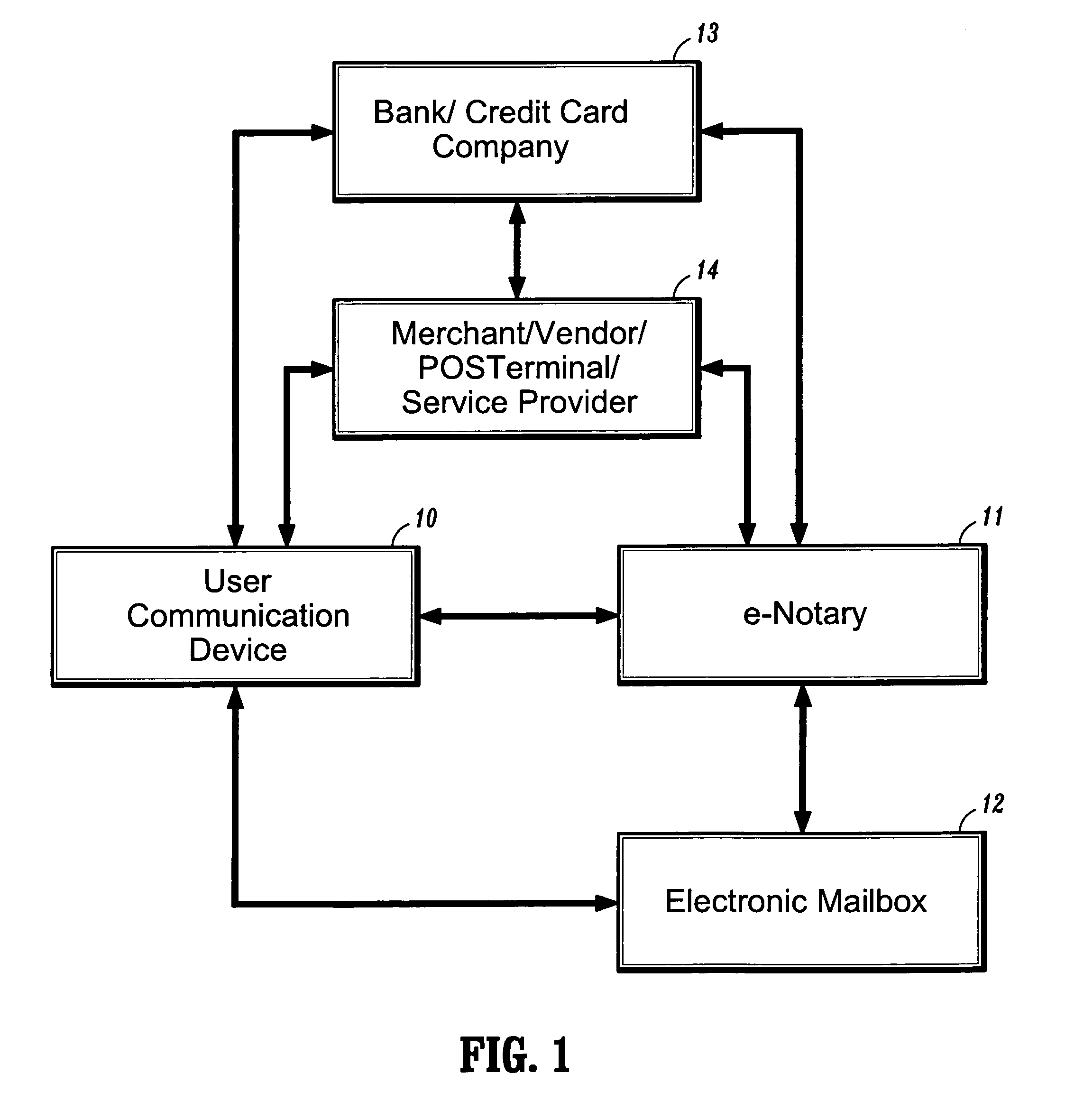
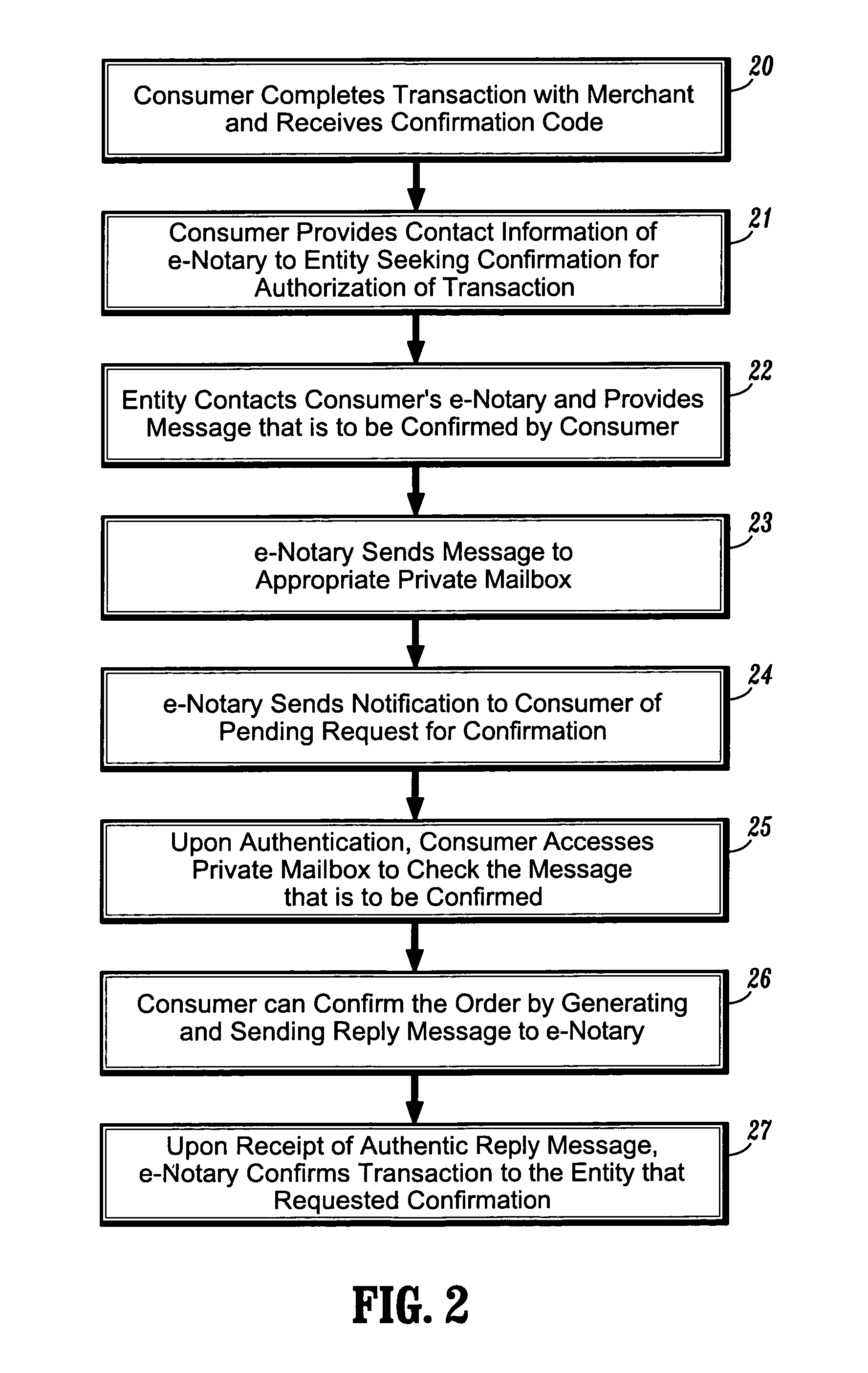
System and method for confirming electronic transactions
Systems and methods for providing user-confirmation of an electronic transaction and in particular, protocols for enabling electronic signatures and confirmation of electronic documents and transactions such as electronic financial transactions and credit card payment. In one aspect, a method for confirming an electronic transaction, comprises the steps of: performing an electronic transaction between a first party and a second party; sending, by the second party, a request for confirmation of the electronic transaction to a predetermined, private mailbox associated with the first party; accessing the private mailbox by the first party; and sending, by the first party, a reply message to the request for confirmation to thereby confirm authorization of the electronic transaction.
Owner:PHONENICIA INNOVATIONS LLC SUBSIDIARY OF PENDRELL TECH +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com