Patents
Literature
33 results about "Compliance level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The term compliance describes the ability to act according to an order, set of rules or request. In the context of financial services businesses compliance operates at two levels. Level 1 - compliance with the external rules that are imposed upon an organisation as a whole.
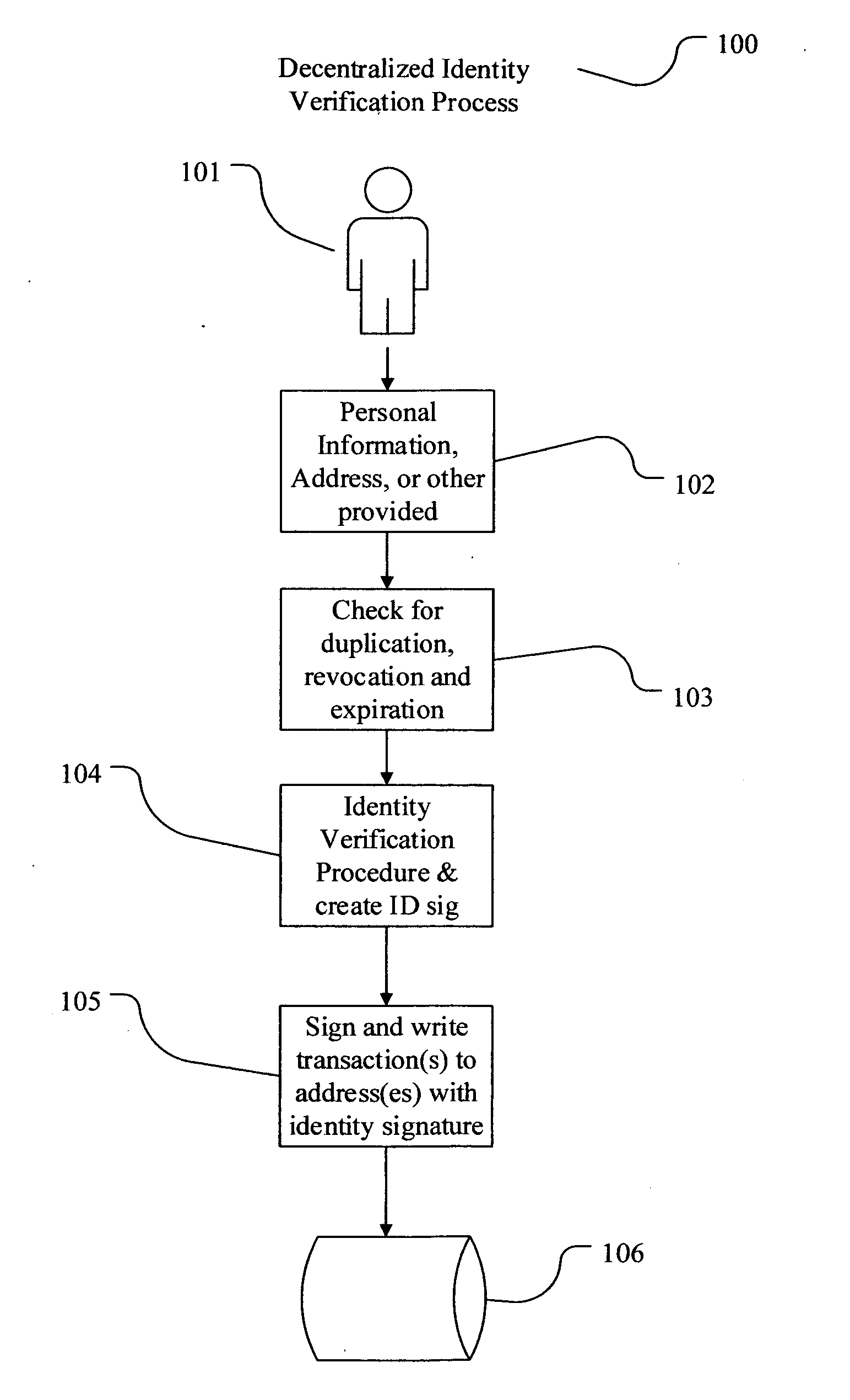
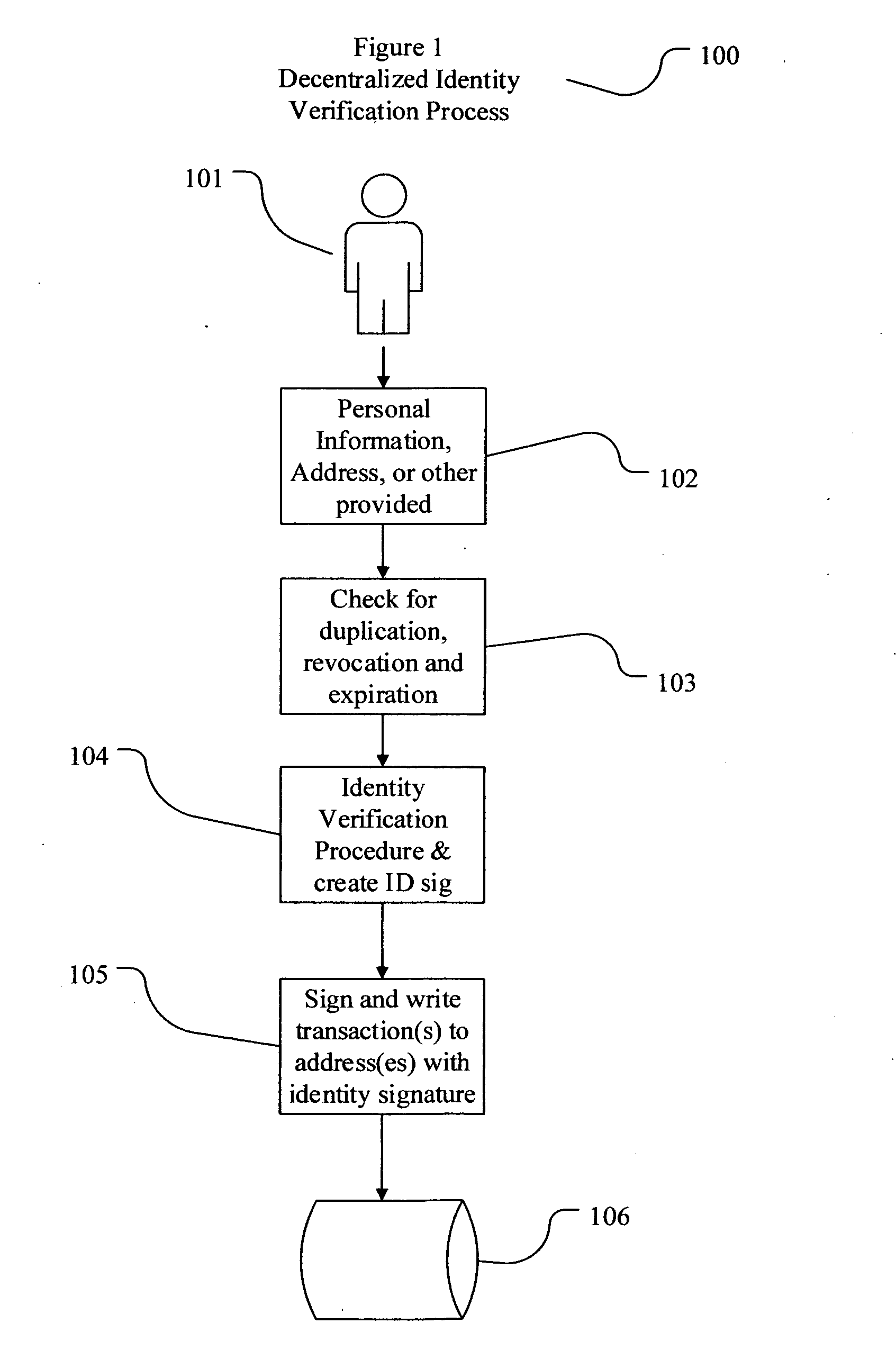
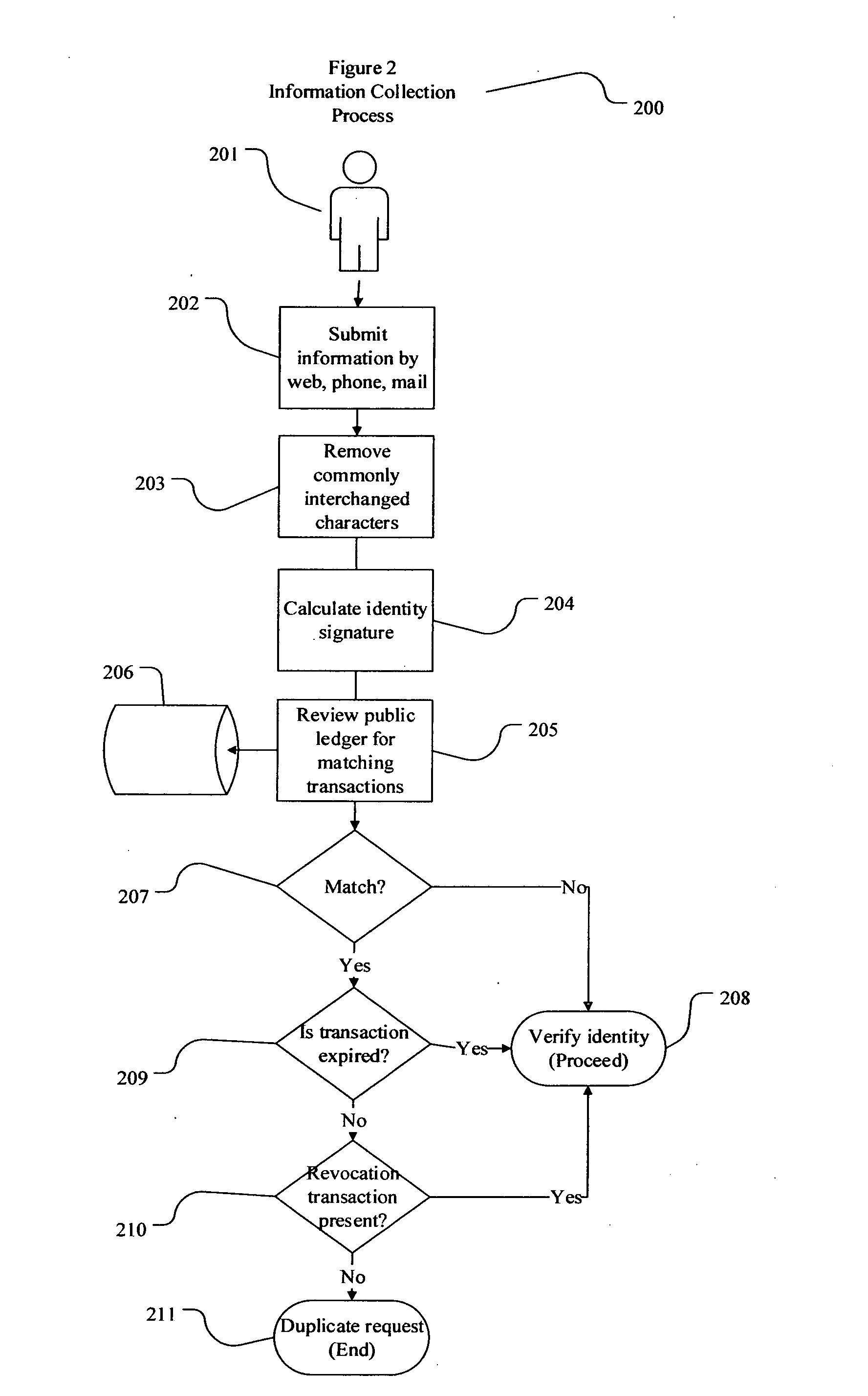
Decentralized identity verification systems and methods
InactiveUS20150356523A1Cryptography processingUser identity/authority verificationRegulatory authorityFinancial transaction
The present invention involves systems and methods that allow participants in cryptocurrency networks to exchange cryptocurrency for traditional currency legally and safely without requiring the use of a traditional exchange or online brokerage as a fiduciary. The invention accomplishes this through the use of a decentralized identity verification protocol that allows a service provider to verify the identity of a participant and then publish an identity signature on the participant's cryptocurrency address or addresses. The invention enables full compliance with Country specific customer identification program and anti-money laundering requirements, and maintains the ability to independently satisfy requests for information or data retention requirements if requested by legally authorized parties, but does not require that the participant store the private keys or access controls to their cryptocurrency on an exchange or brokerage service.The invention serves to verify a participant's identity in full compliance with US Bank Secrecy and Patriot Act provisions or similar regulations where identification may be achieved through non-documentary or documentary identity verification procedures. After passing the applicable verification procedure, the service provider stamps the participant's cryptocurrency address with a transaction containing an identity signature. This identity signature within the transaction consists of a public indicator of the participant's Country and subdivision, a compliance level code, an ID type indicator, and an identity hash. The identity hash is created from the digests of cryptographic hash functions where the participant's personal information is used as an input. The service provider signs the transaction with their authorized private key that corresponds to their publicly accessible public key. This serves as a publicly verifiable confirmation that the identity associated with the address in question was validated by the service provider authorized to act on behalf of the regulatory authority.The participant may then purchase and sell cryptographic currency from and to a third party exchange or brokerage service legally and safely when using their verified cryptocurrency address. This is because the third party is able to confirm compliance by openly referencing and verifying the identity verification transaction present on the address. Subsequent transactions where the third party sells or purchases cryptocurrency for the verified participant are similarly stamped with a transaction conforming to the identity verification protocol. This allows the third party interacting with the verified participant's address to observe any regulations limiting the amount or frequency of transactions over a variable period of time. It follows that this address could be used with any third party or participant in the cryptocurrency network that observes the decentralized identity verification protocol, all without requiring the third party or participant to collect and verify personal information redundantly. The ability to verify an identity remotely also eliminates the need for the third party to act as a fiduciary holding the private keys or access controls to the verified address. Lawful requests for information by authorized authorities are served to the service provider as digitally signed transactions that may then be linked to the participant's identity and transactions, allowing the protocol to observe subpoenas or similar lawful requests for information. The encrypted personal information may be held in escrow by the service provider indexed to the verified cryptocurrency address for such purposes. An alternate embodiment would store the encrypted personal information in a decentralized network of other participants, with the information accessible for retrieval using the public key of the verified cryptocurrency address and decryption using the corresponding private key, decentralizing the process entirely except for the identity verification step.
Owner:CHAINID
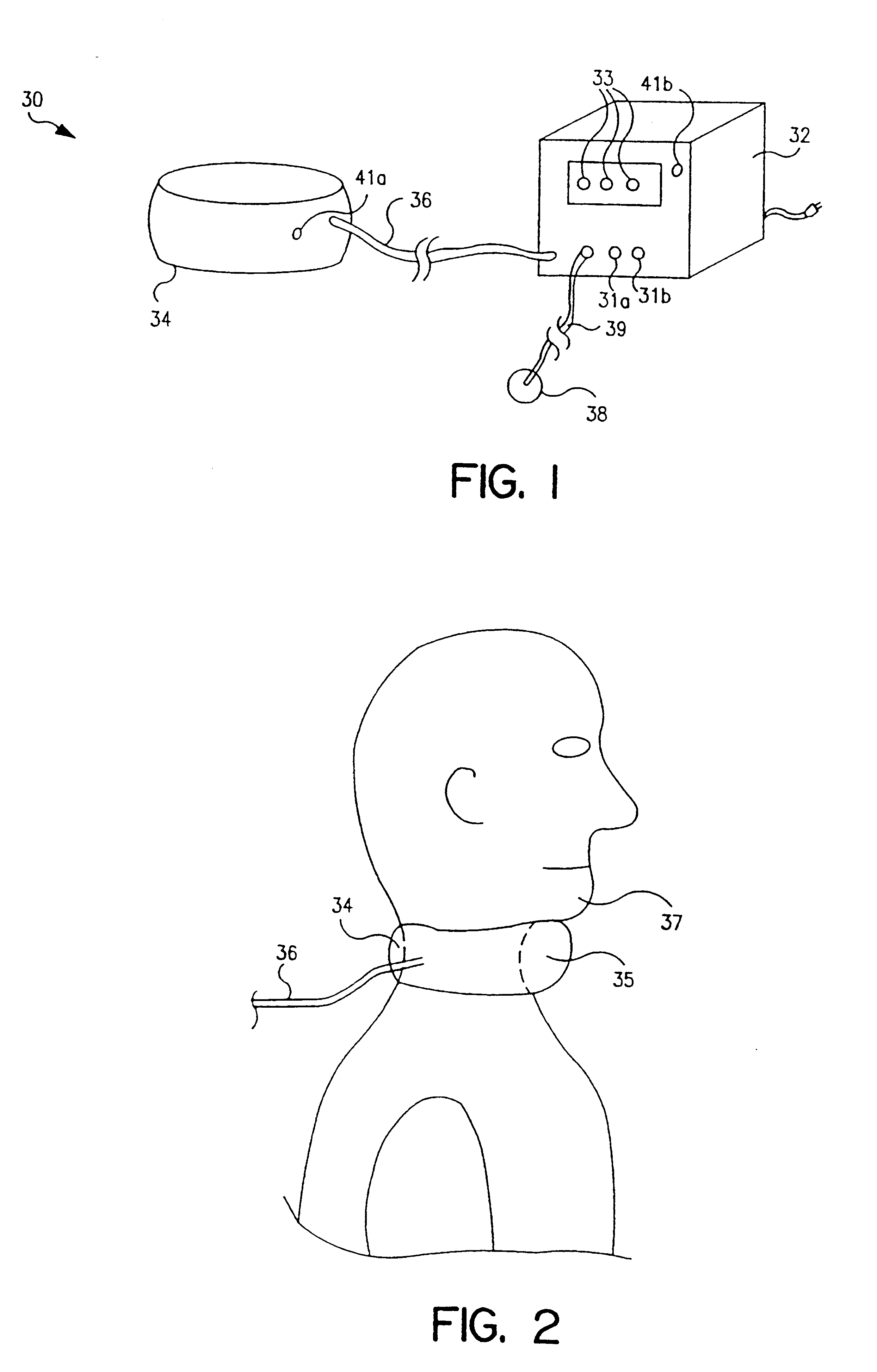
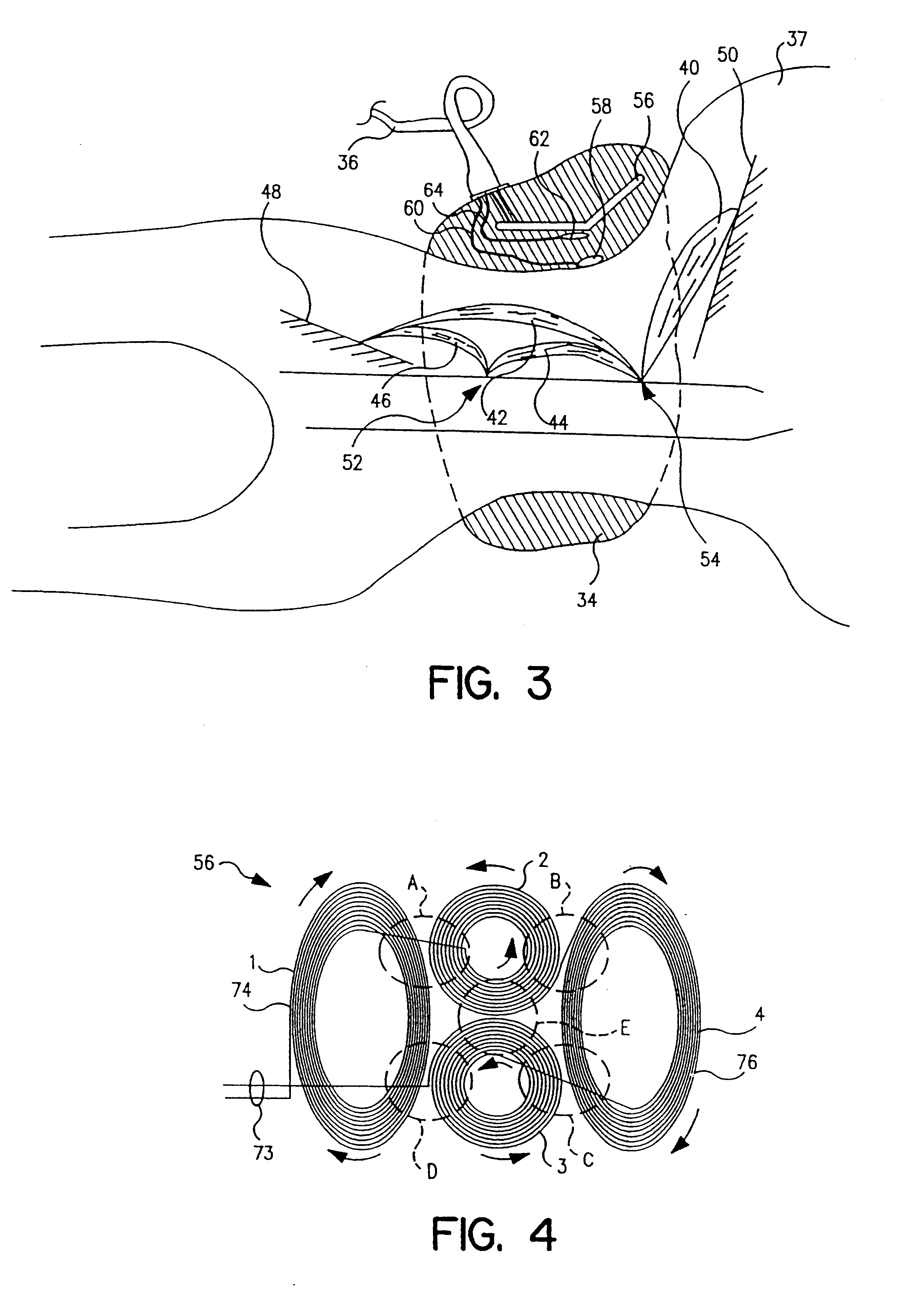
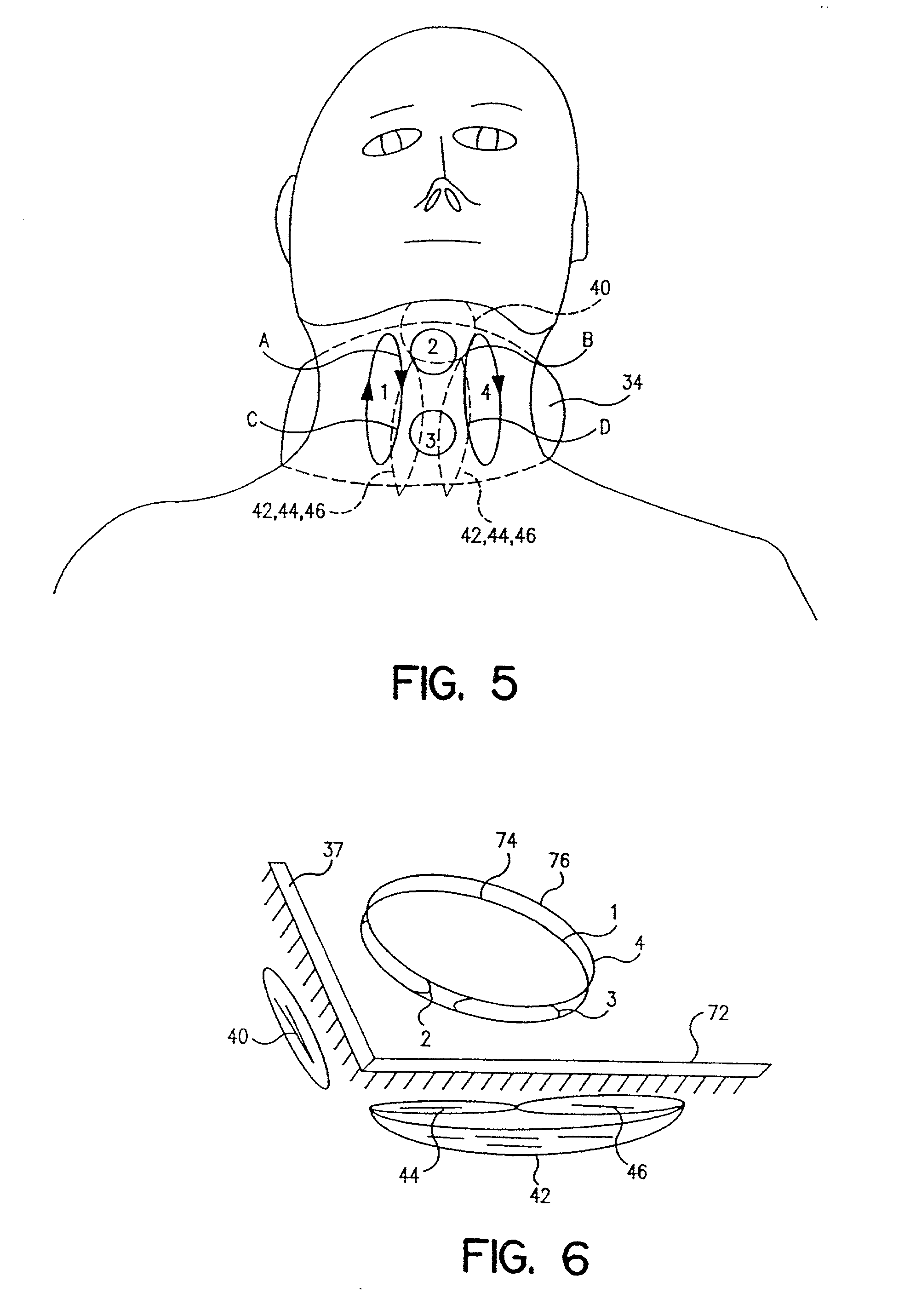
Muscle stimulating device and method for diagnosing and treating a breathing disorder
Owner:RIC INVESTMENTS LLC
Muscle stimulating device and method for diagnosing and treating a breathing disorder
InactiveUS20010018547A1Reduce heatExcessive heatElectrotherapySurgeryMuscle toneIntensive care medicine
A device and method for magnetic stimulation of muscles for the diagnosis and relief of a breathing disorder, such as obstructive sleep apnea. Magnetic stimulation is used to stimulate muscles which serve to stabilize the upper airway of an individual whose nocturnal apneic events are related to diminished muscle tone. A sensor monitors a physiologic characteristic of the patient, a coil is energized to stimulate the appropriate muscles associated with the upper airway, a power supply provides power for energizing the coil, and a control system controls the application of power to the coil based on the output of the sensor. Diagnosis of obstructive sleep apnea is accomplished by measuring the subject's compliance in the presence and absence of the magnetic stimulation of the upper airway muscles. The smaller the difference between these two compliance levels, the more likely that patient suffers from obstructive sleep apnea.
Owner:RIC INVESTMENTS LLC
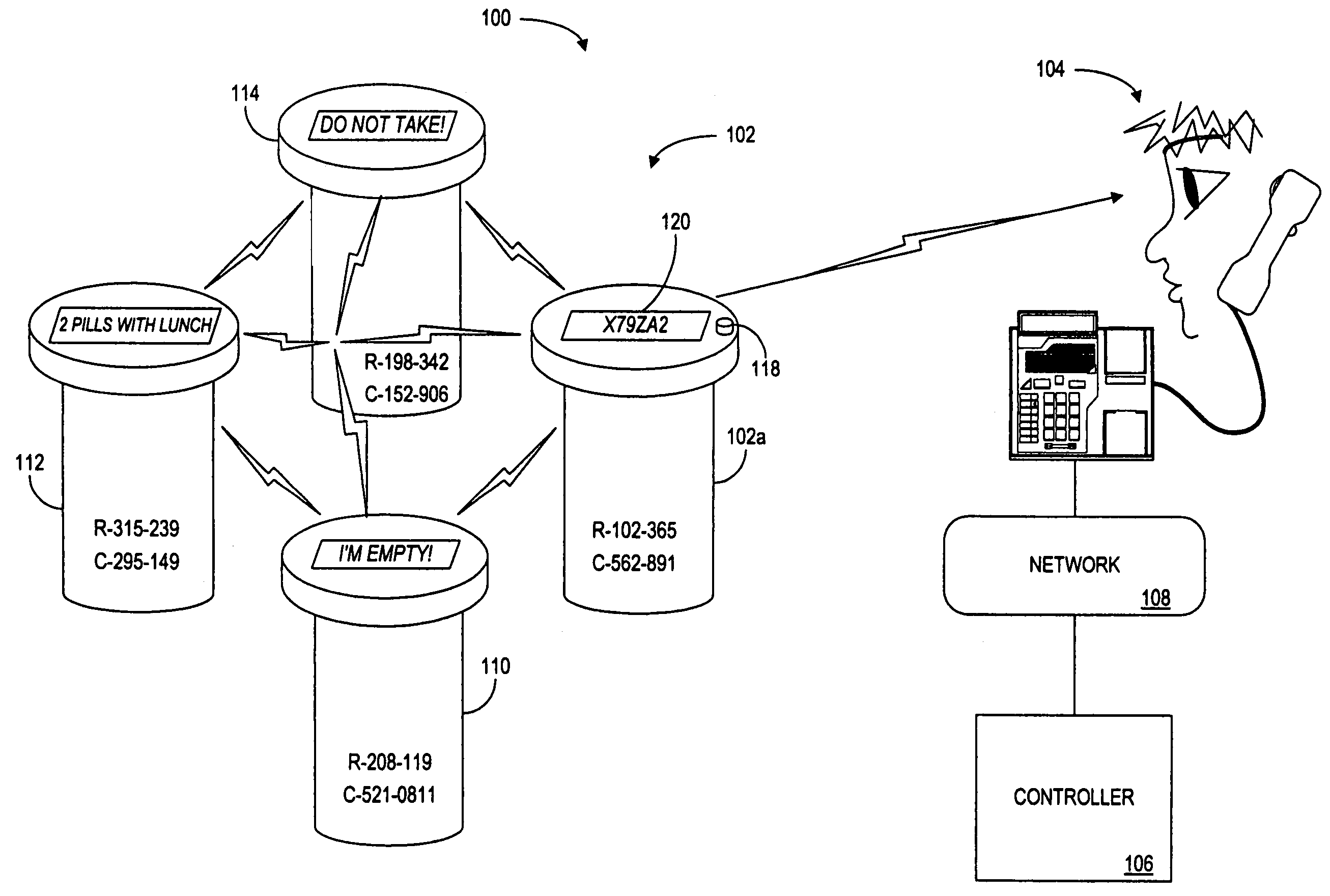
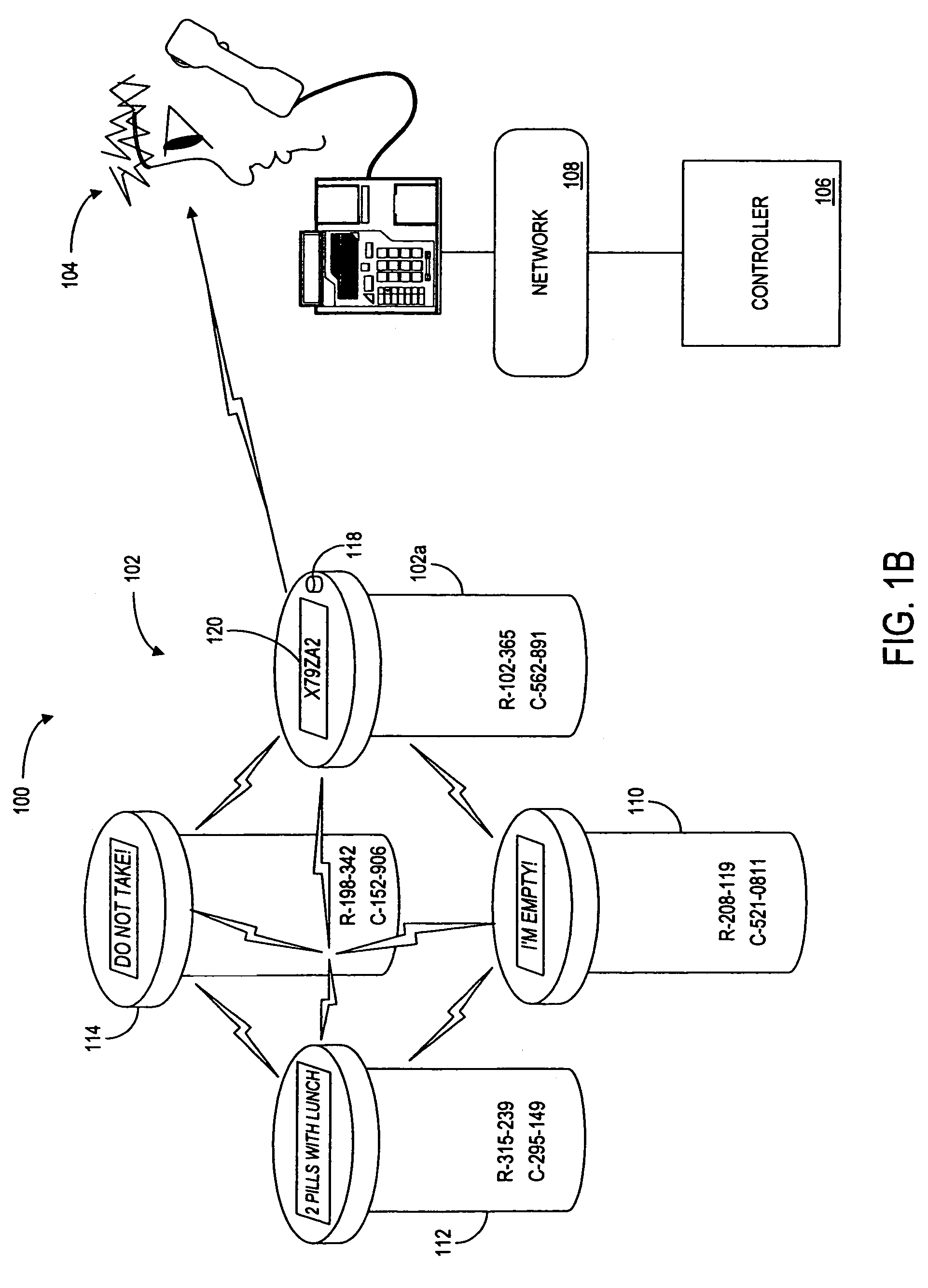
Methods and apparatus for increasing, monitoring and/or rewarding a party's compliance with a schedule for taking medicines
Methods and apparatus are provided for increasing and / or for monitoring a party's compliance with a schedule for taking medicines. In a first embodiment, a method is provided that includes receiving information regarding whether at least two medicine containers were able to communicate during a pre-determined time period, and determining a level to which the party complied to a medicine schedule based on the information. The method further includes rewarding the party based on the party's level of compliance. Systems, apparatus and computer program products are provided for carrying out the above-described embodiments and numerous other embodiments.
Owner:INVENTOR HLDG
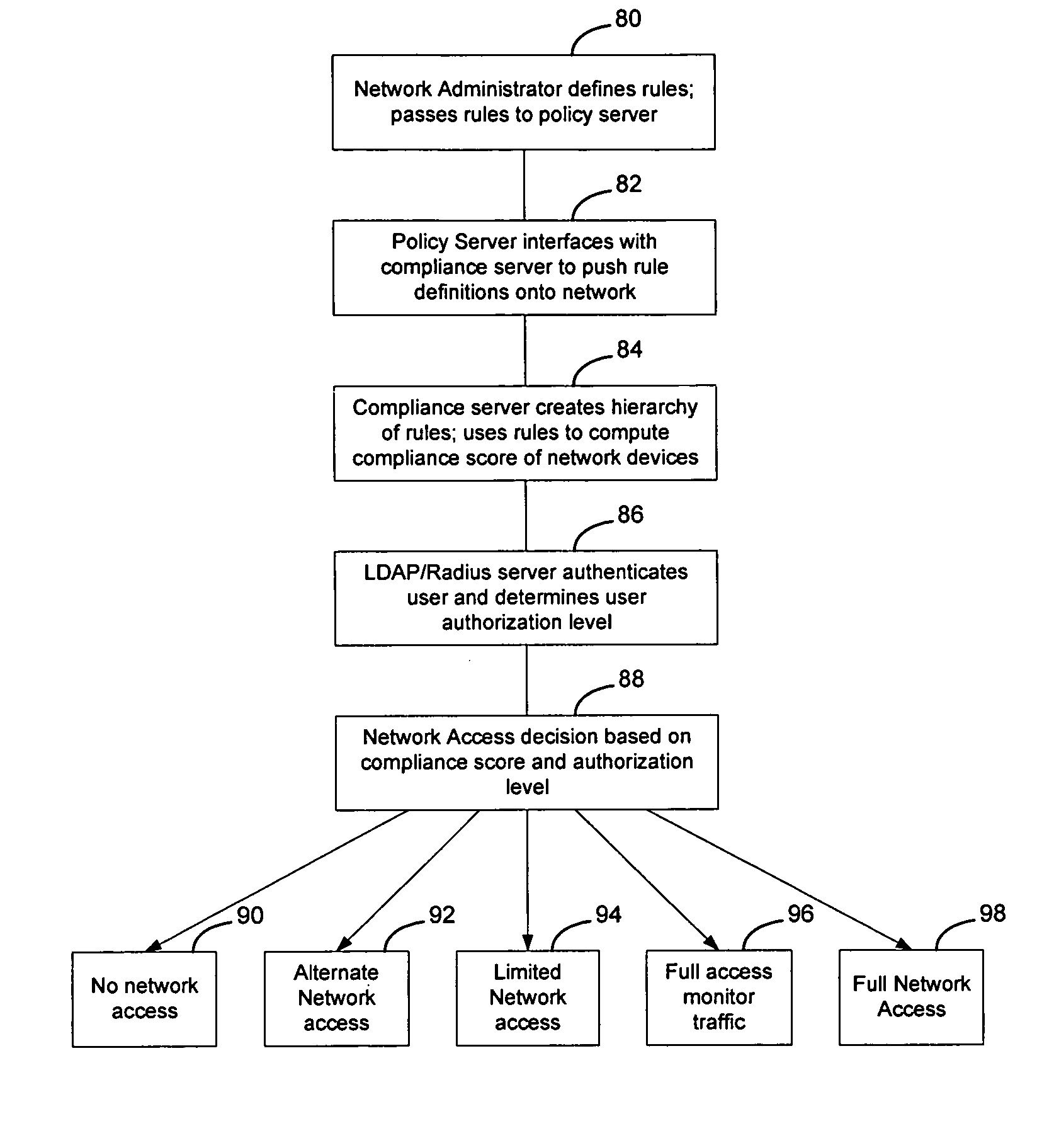
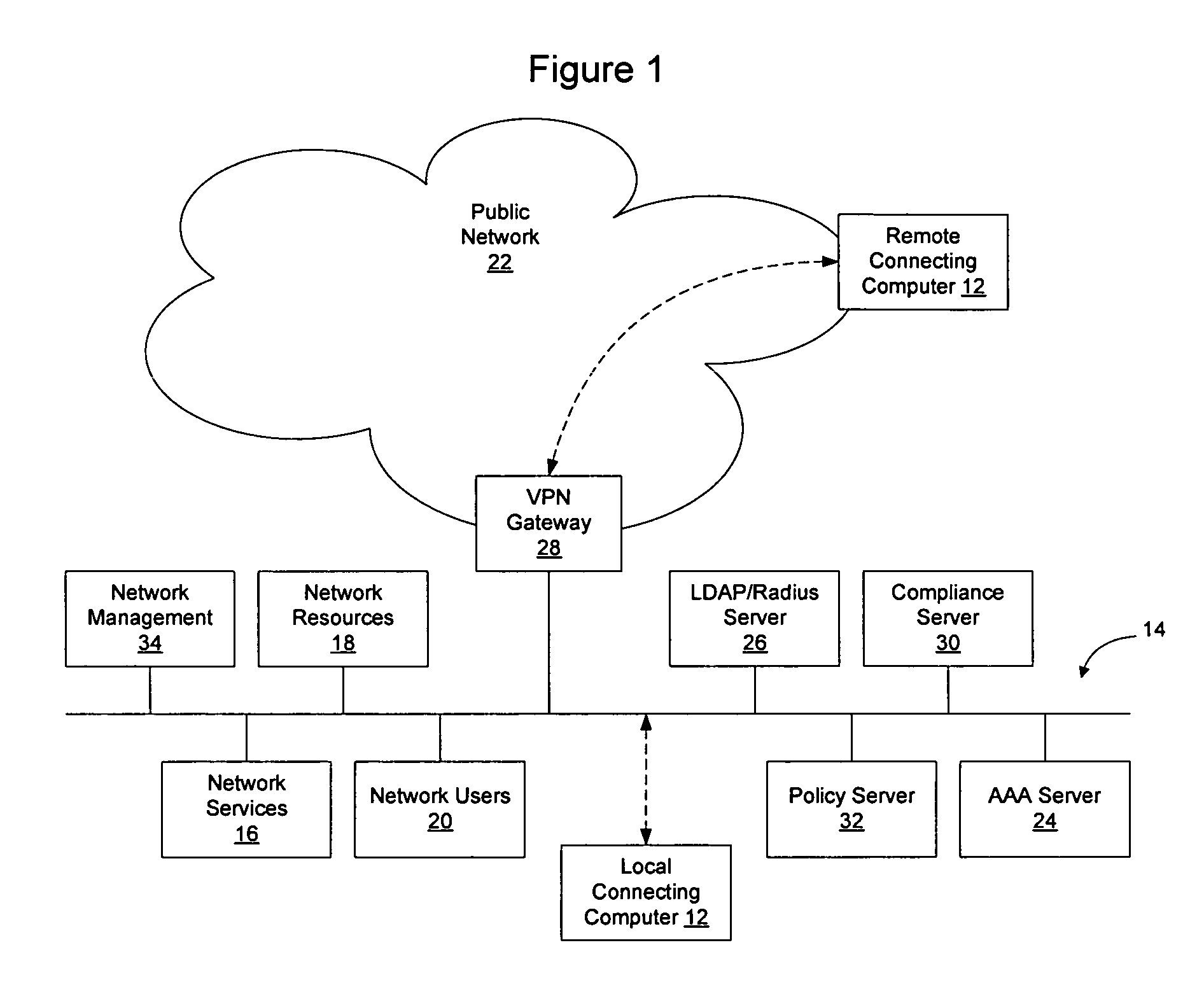
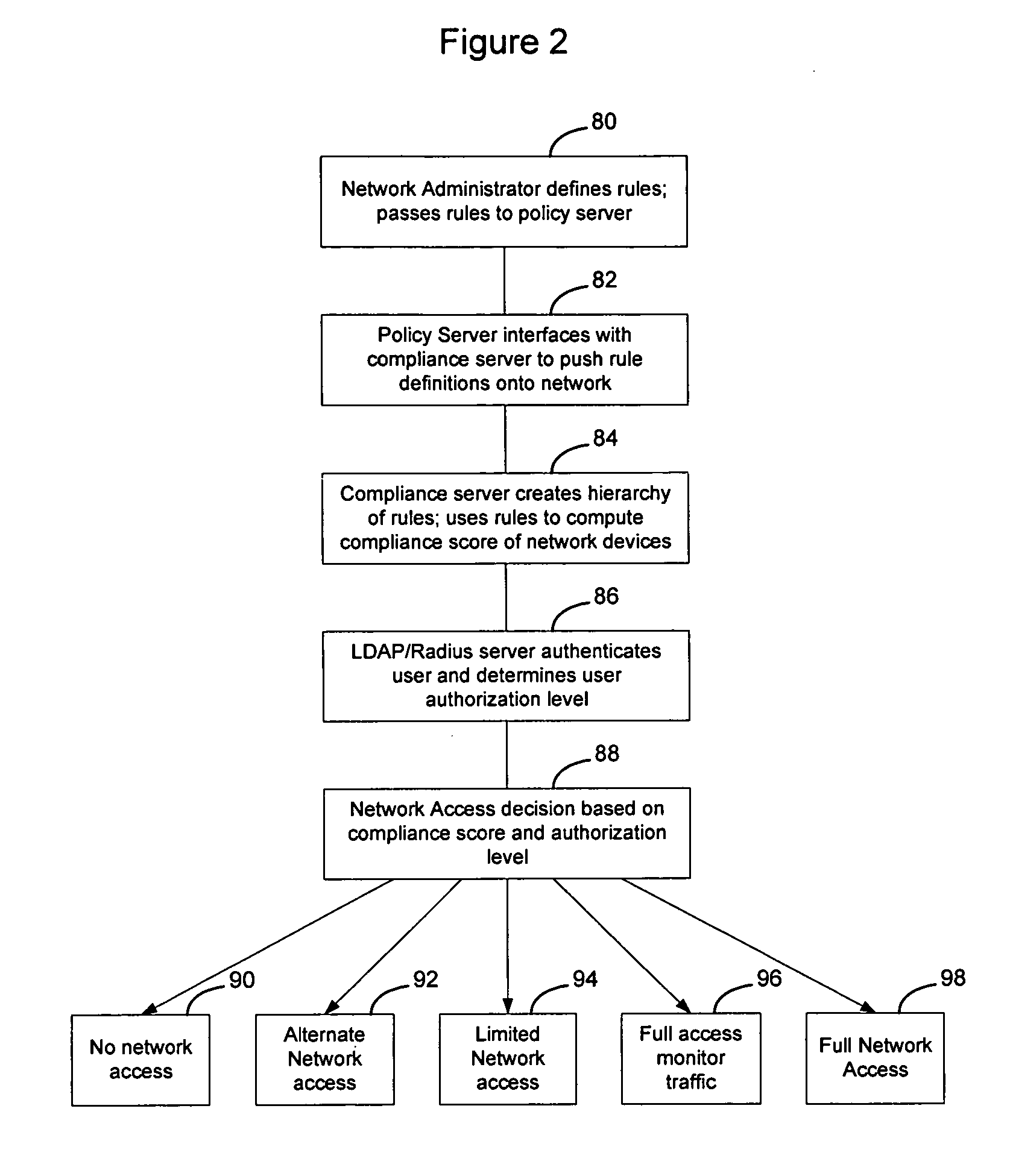
Method and apparatus for rating a compliance level of a computer connecting to a network
InactiveUS20070124803A1MoreOvercomes drawbackRandom number generatorsMemory loss protectionUser PrivilegeCompliance level
Rules are used to determine a compliance level for a computing device attempting to access a network. The compliance level may have multiple categories or facets, that may be determined individually or collectively, to determine a score for the computing device. The score may be used to determine whether the computing device should obtain access to the network, the type of access to be granted, or whether remediation should occur and what type of remediation should occur on the computing device to enable the computing device to enjoy greater network privileges. Optionally, the score may be weighted in connection with the user privileges associated with the user as determined during the authentication process, to enable users with greater network access privileges to access the network in situations where other users may not be able to access the network.
Owner:AVAYA INC
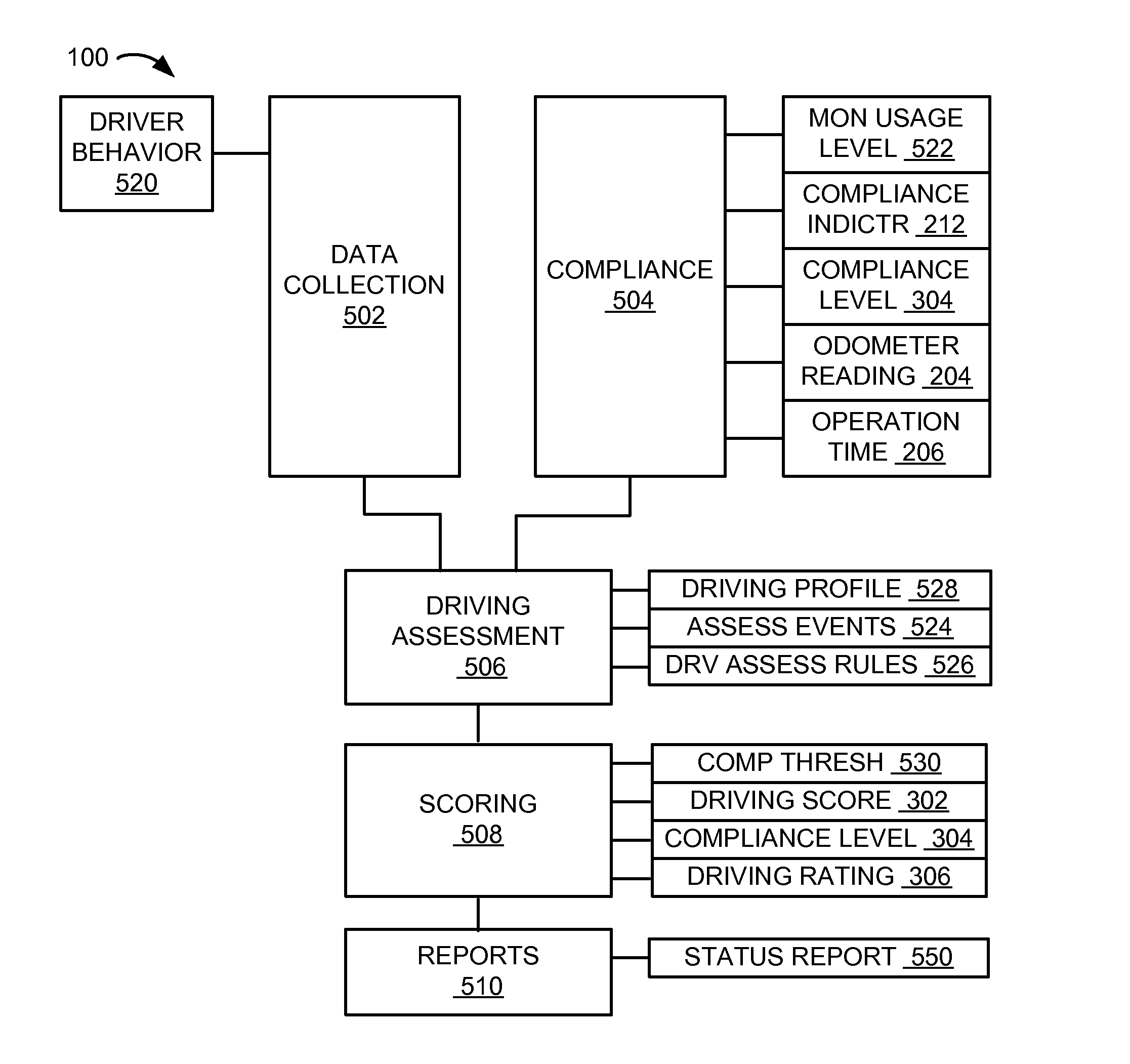
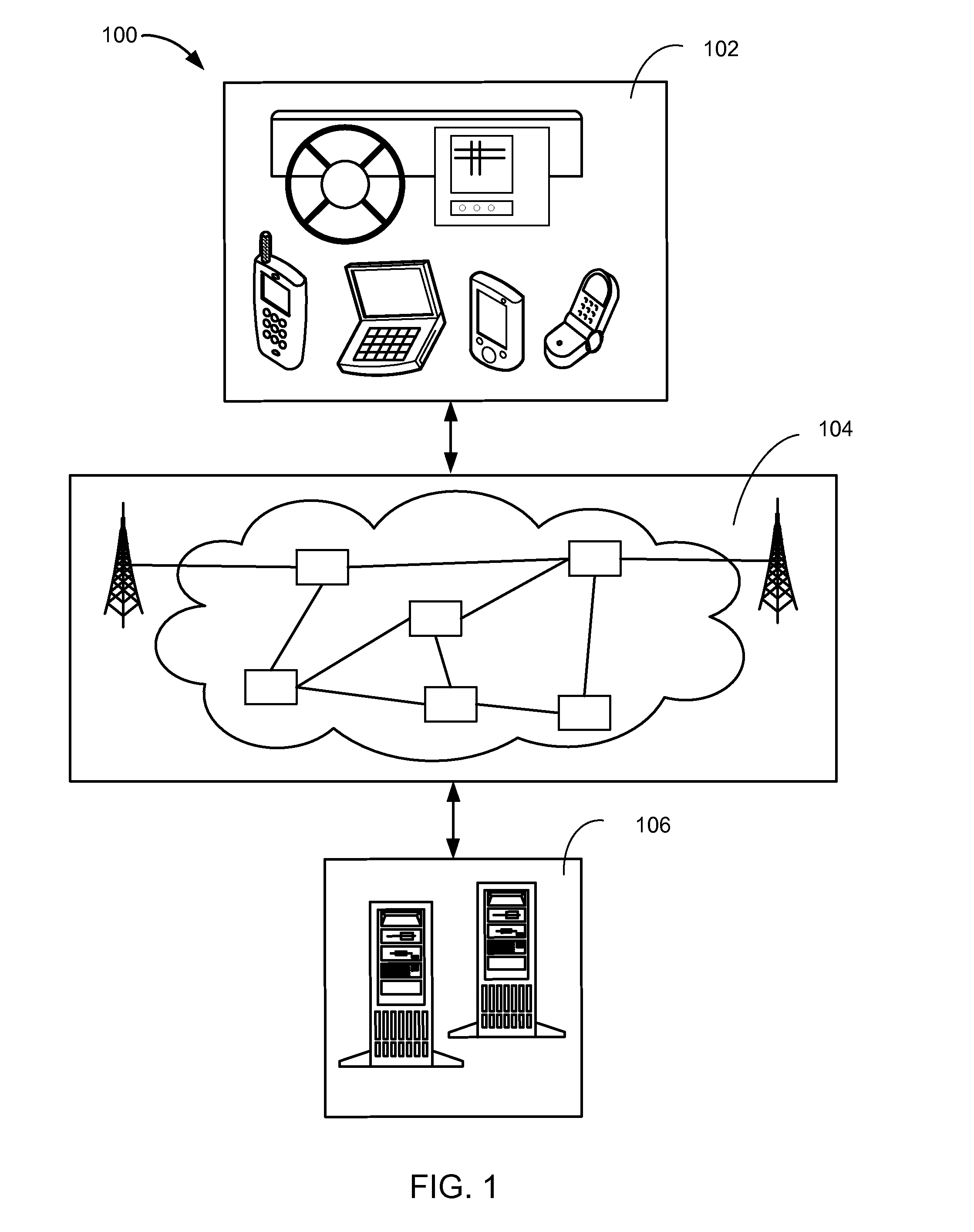
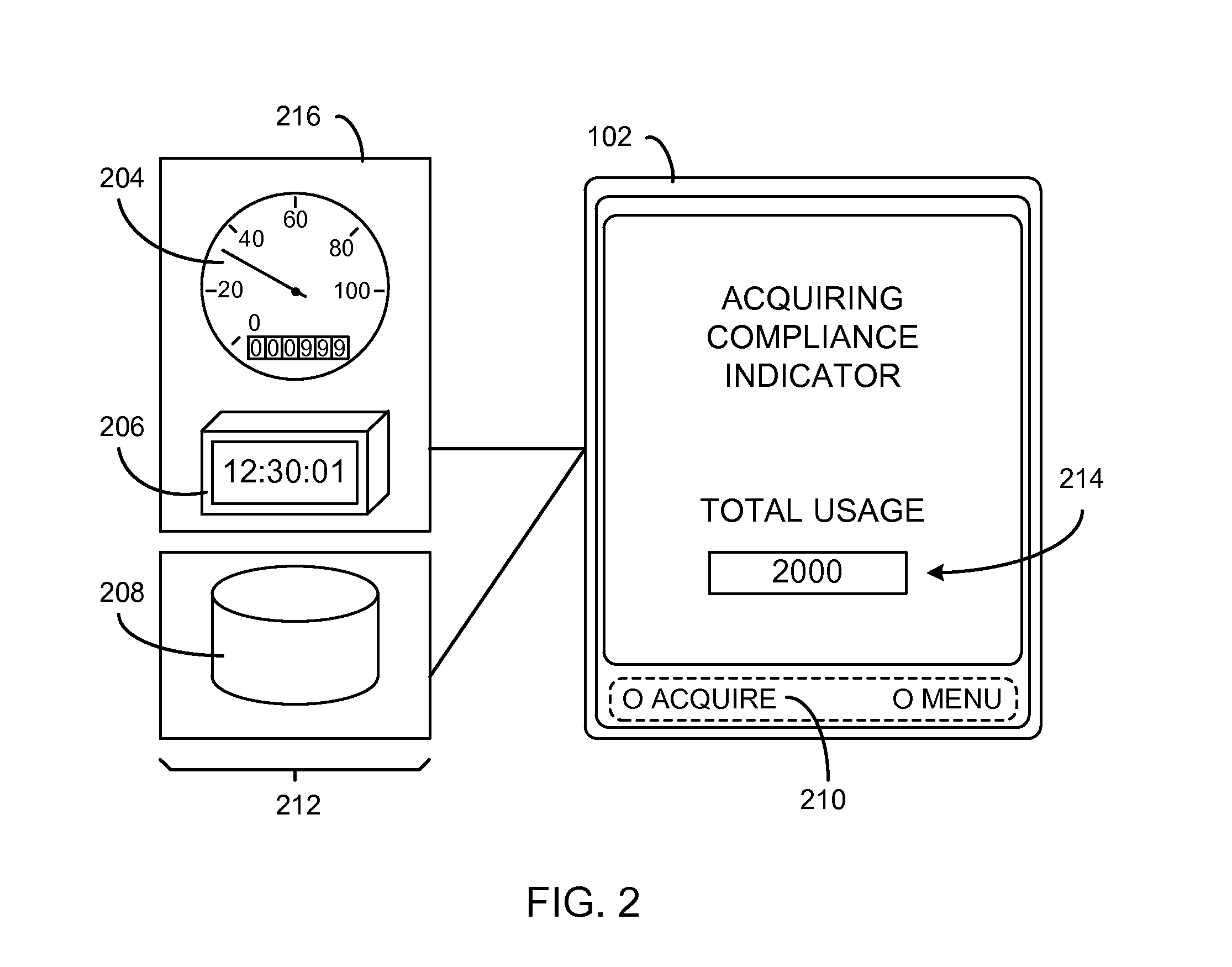
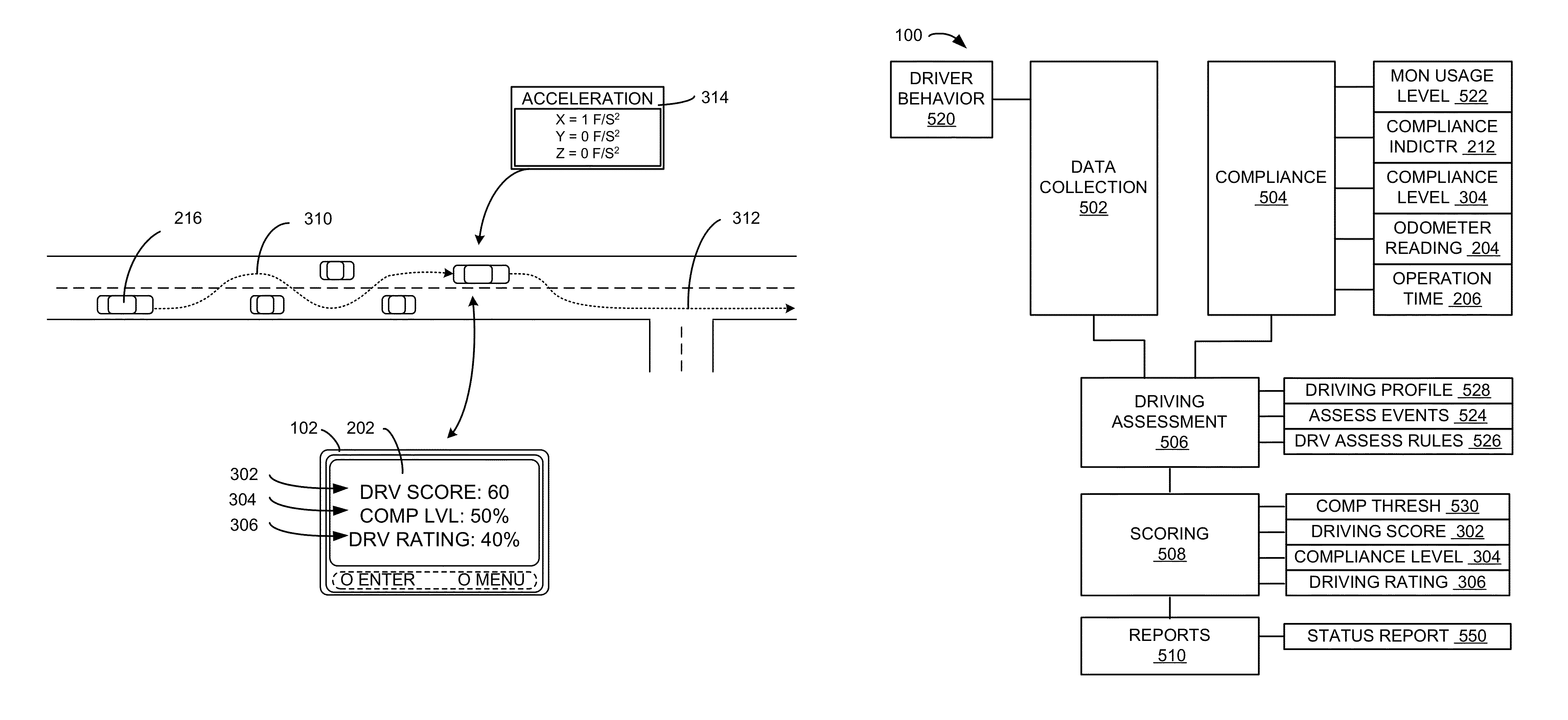
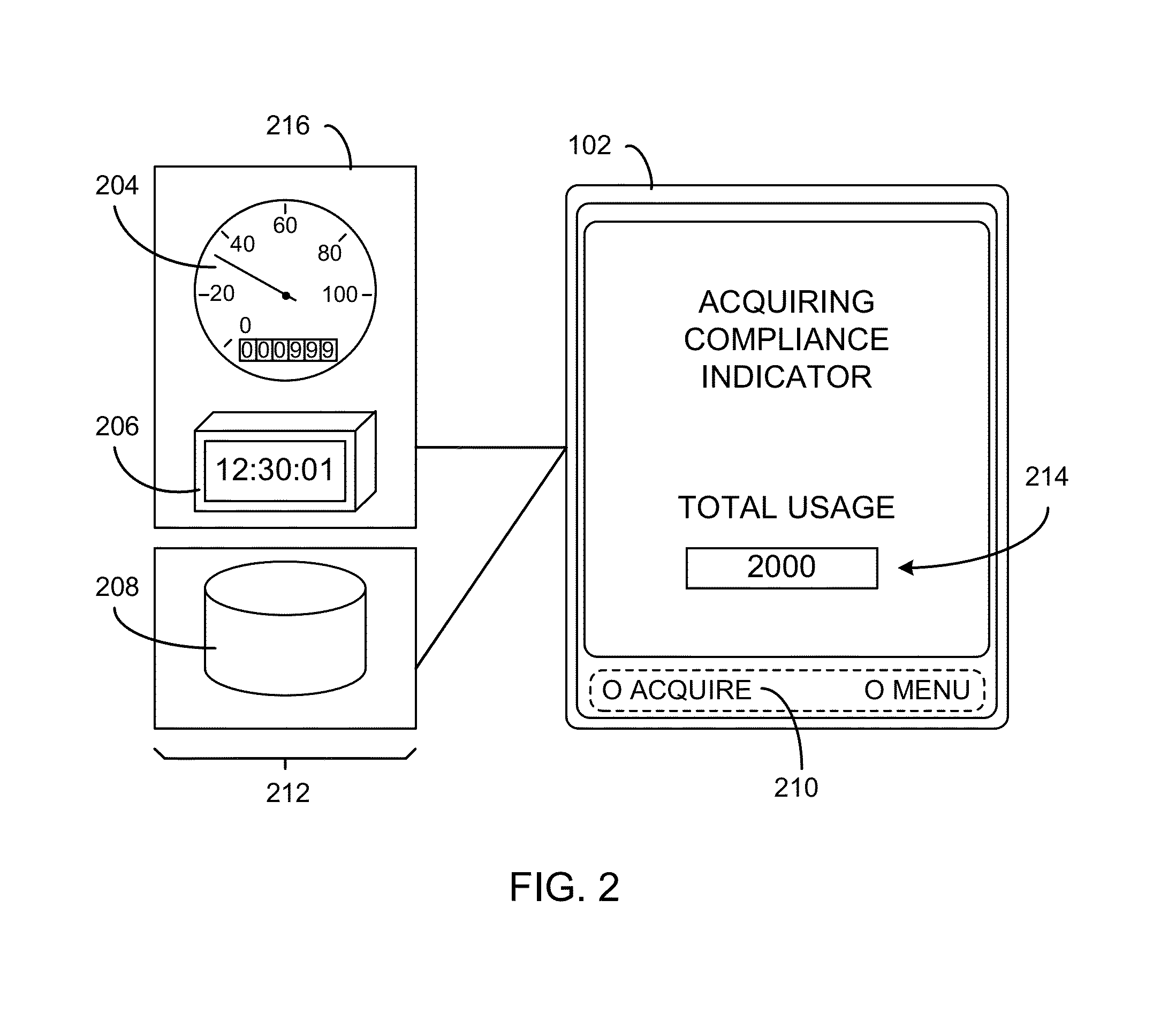
Navigation system with compliance reporting and method of operation thereof
ActiveUS20130110310A1Digital data processing detailsNavigation instrumentsEngineeringNavigation system
A method of operation of a navigation system includes: collecting a driving behavior for determining a driving profile of a vehicle; acquiring a compliance indicator for measuring a total usage of the vehicle; calculating a compliance level based on a monitoring usage level and the compliance indicator; generating a driving score based on the driving profile having an assessment event detected based on the driving behavior; and calculating a driving rating based on the driving score and the compliance level for displaying on a device.
Owner:TELENAV
Trainable record searcher
InactiveUS20060047650A1Digital data information retrievalSpecial data processing applicationsData miningCompliance level
A trainable record searcher is described. The trainable record searcher includes an iterative rules engine including at least an existing knowledge set, a plurality of rules, developed and entered to the iterative rules engine by at least one expert in at least one field of interest, a plurality of records for review by the iterative rules engine, where the plurality of rules are iteratively applied by the iterative rules engine to at least one training record. Also, the iterative application of the plurality of rules results in at least one rule modification in accordance with the existing knowledge set, where the plurality of rules, including the at least one rule modification, are applied by the iterative rules engine to a batch selected from the plurality of records to assess a compliance level for the batch of the plurality of records.
Owner:FREEMAN THOMAS M +1
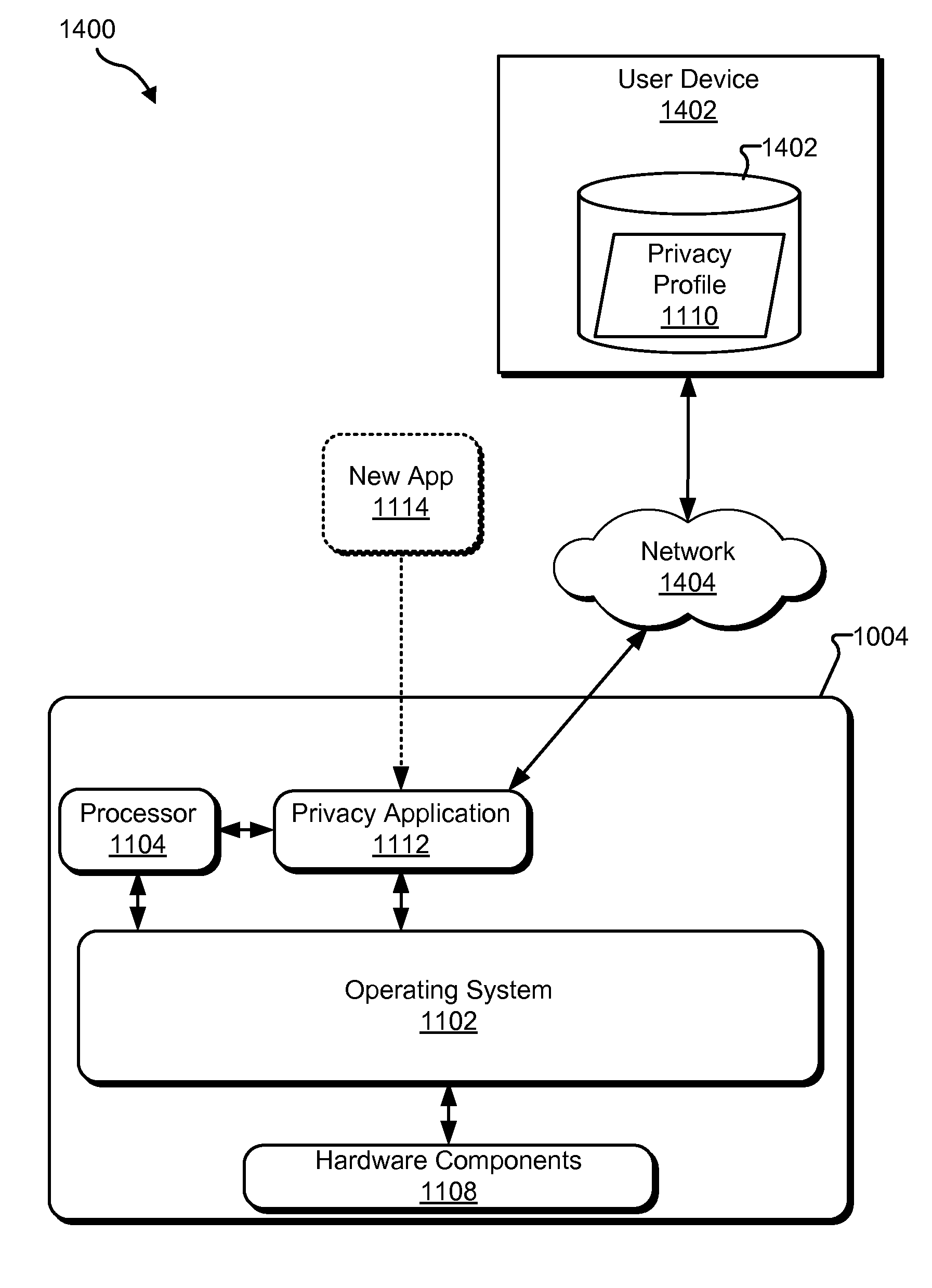
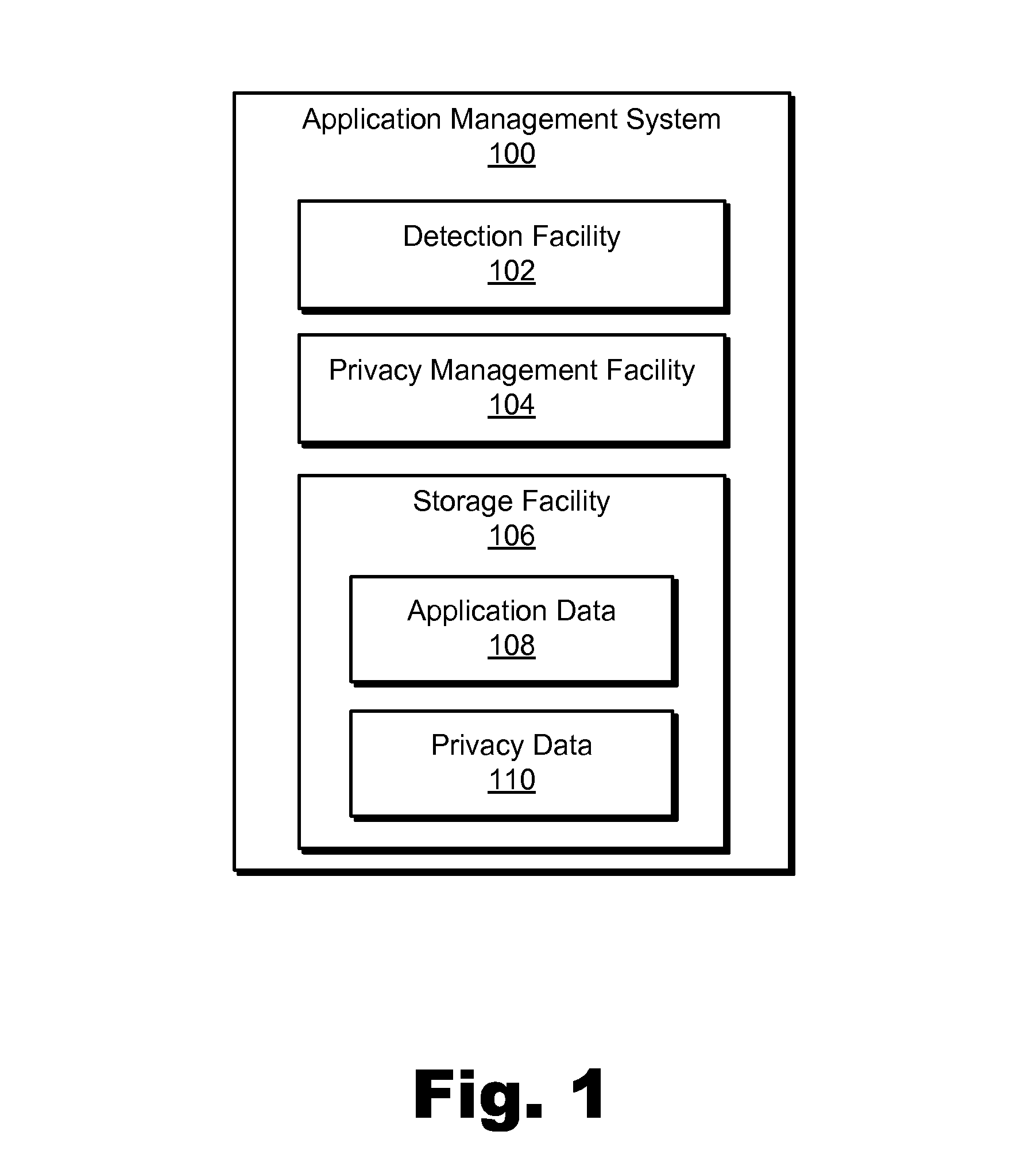
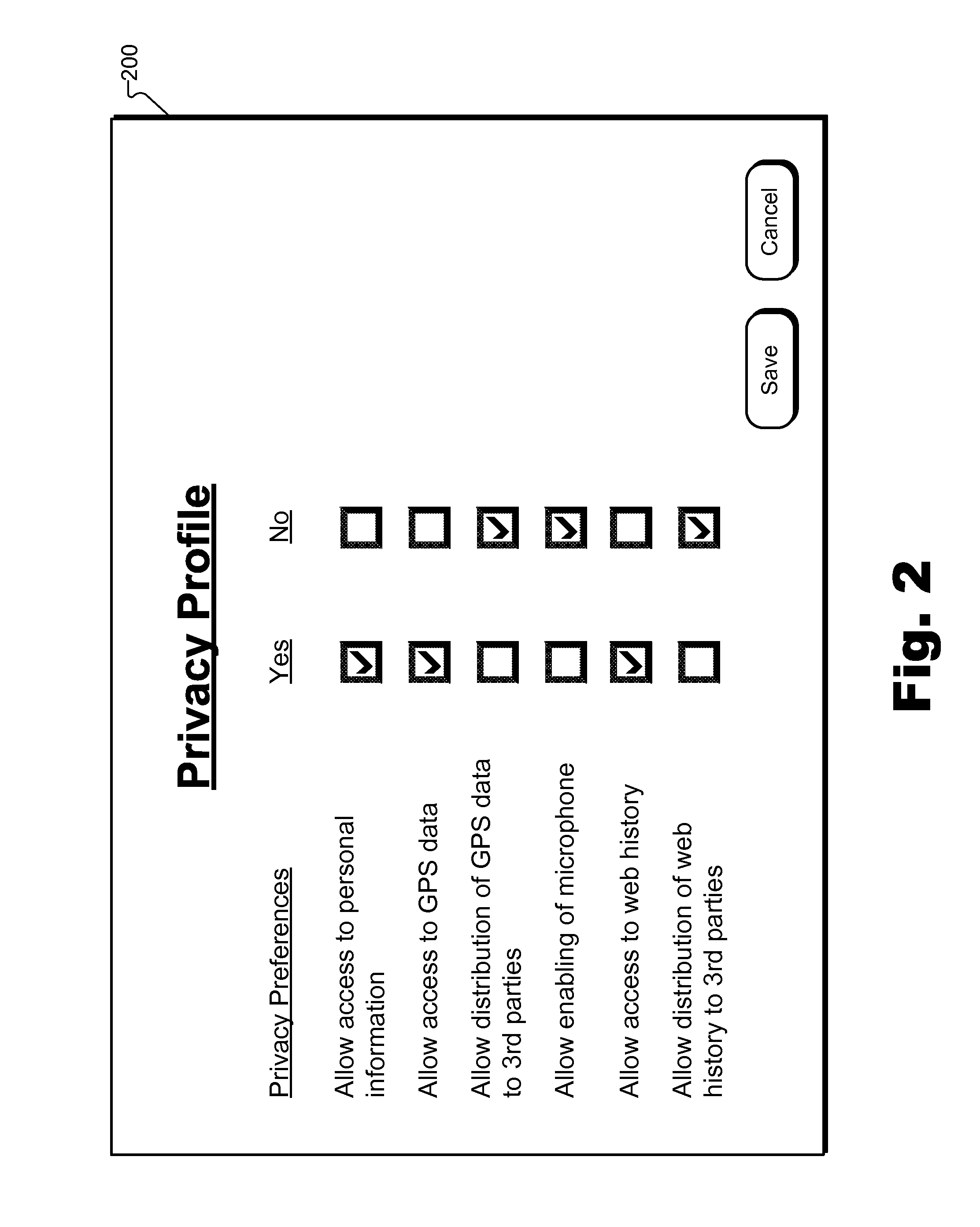
Methods and Systems for Providing a Notification of a Compliance Level of an Application With Respect to a Privacy Profile Associated With a User
ActiveUS20130305379A1Digital data processing detailsAnalogue secracy/subscription systemsGraphicsUser device
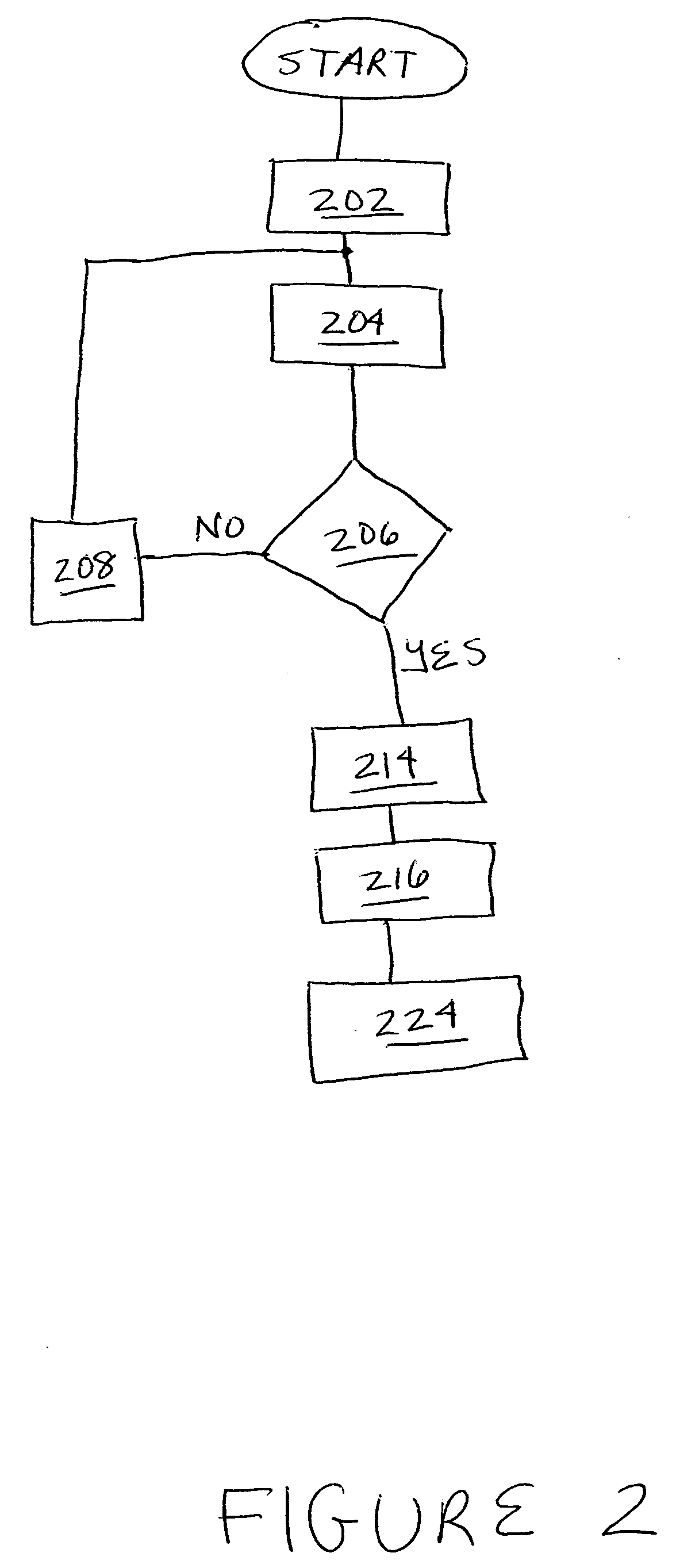
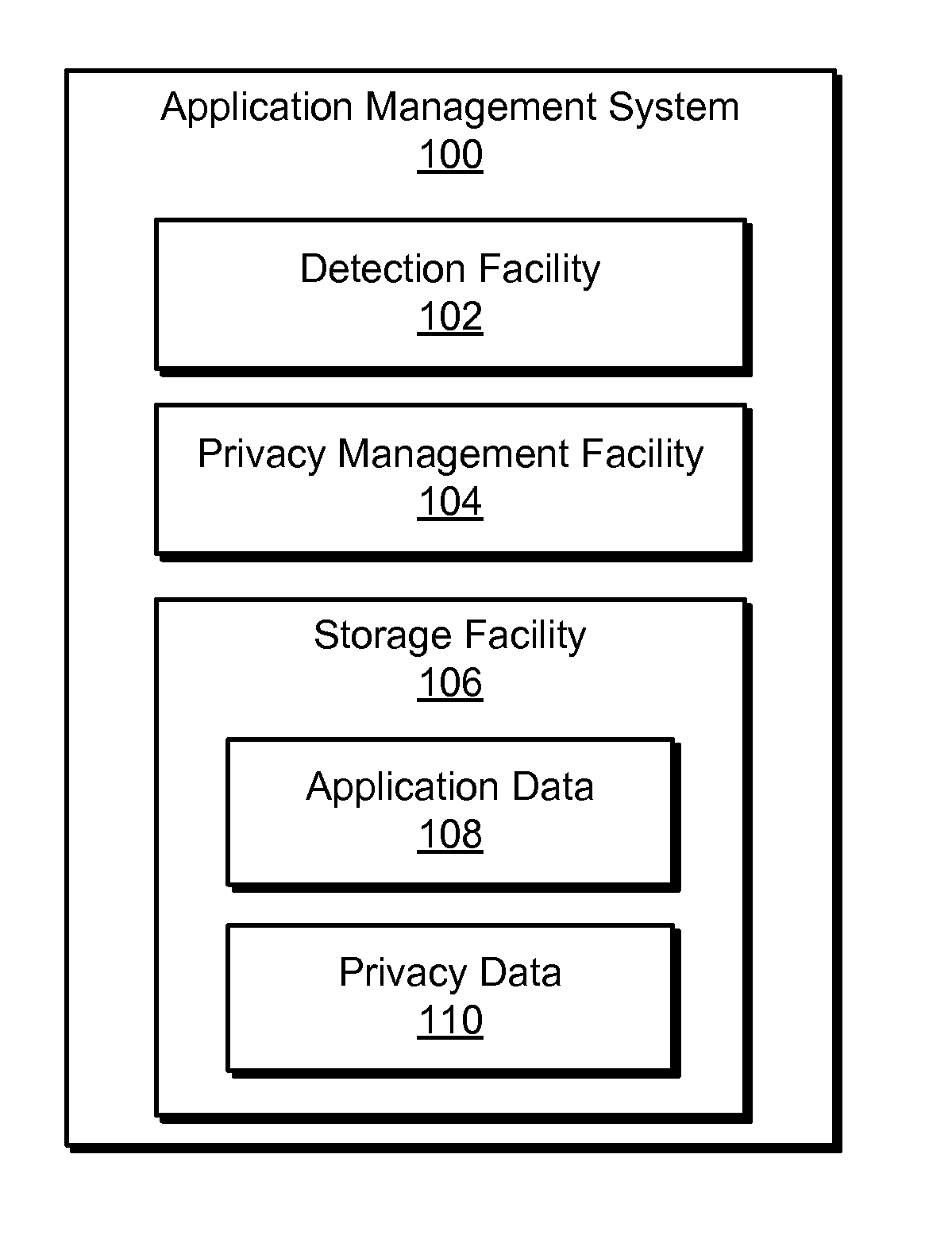
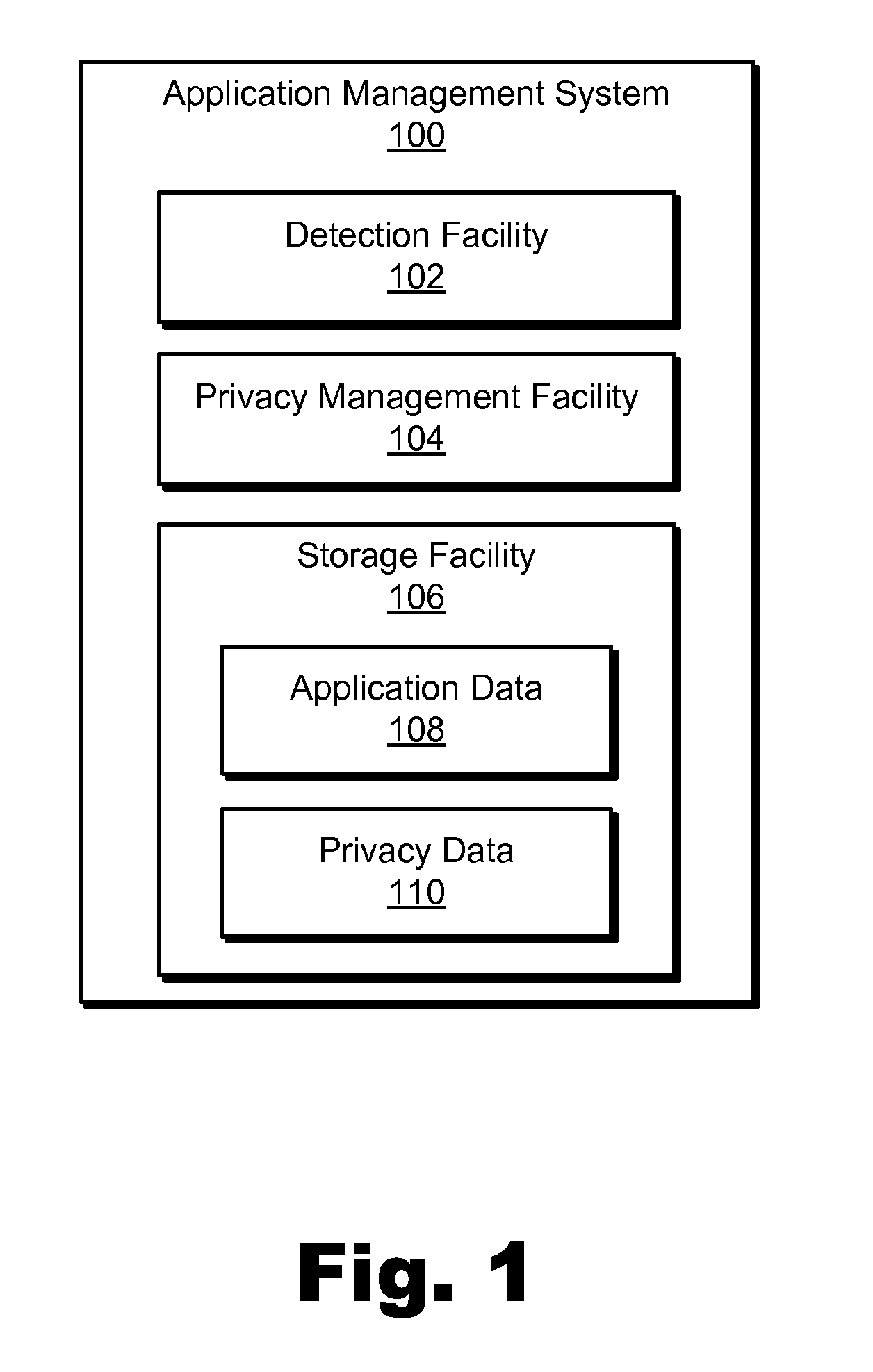
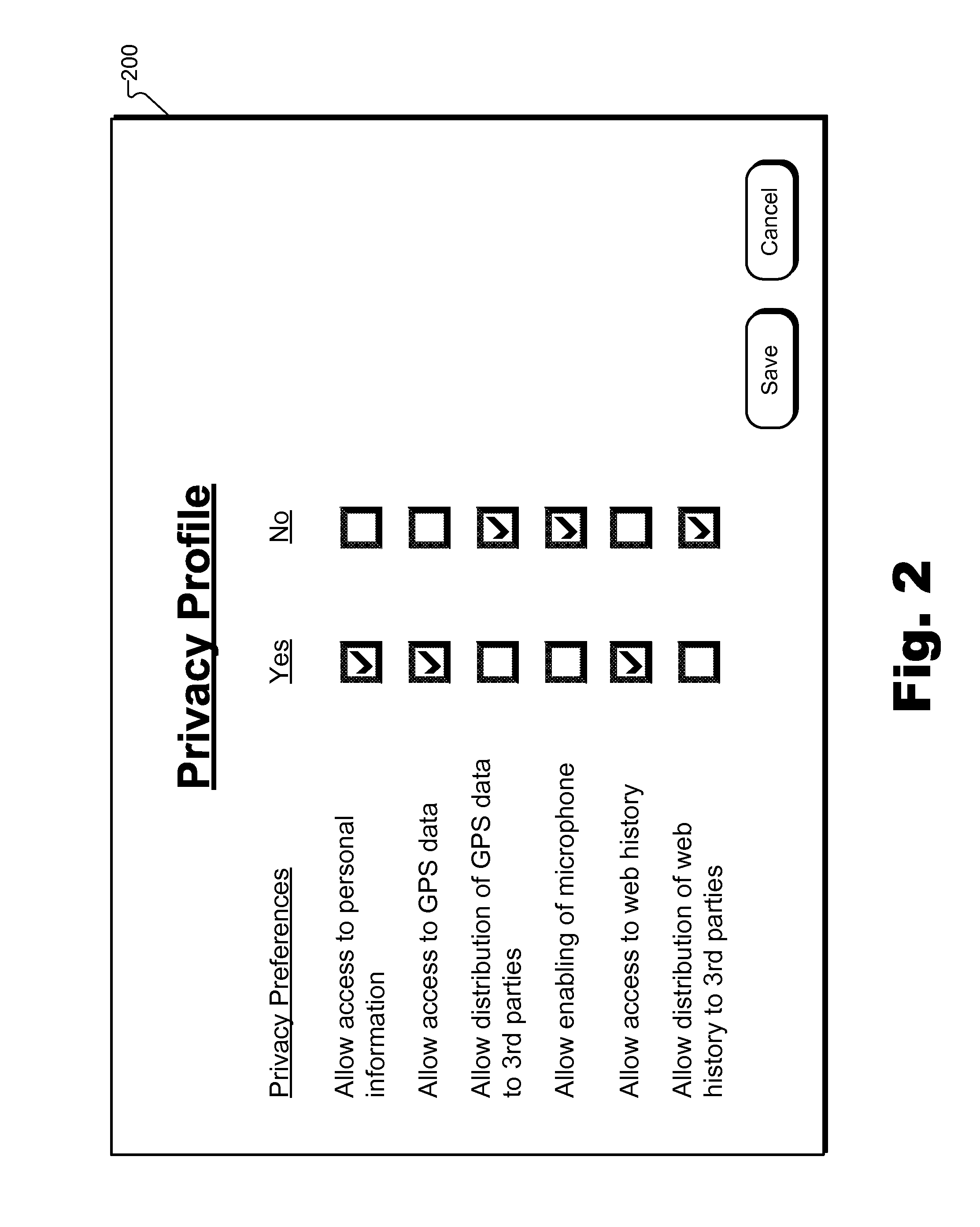
An exemplary method includes an application management system 1) detecting a request provided by a user to install an application on a user device, 2) identifying a plurality of privacy attributes of the application, 3) determining, based on the identified privacy attributes, a compliance level of the application with respect to a privacy profile associated with the user, the compliance level representing a degree to which the application complies with the privacy profile associated with the user, and 4) directing, prior to the installation of the application, the user device to present a graphic that represents the determined compliance level of the application. Corresponding methods and systems are also disclosed.
Owner:VERIZON PATENT & LICENSING INC
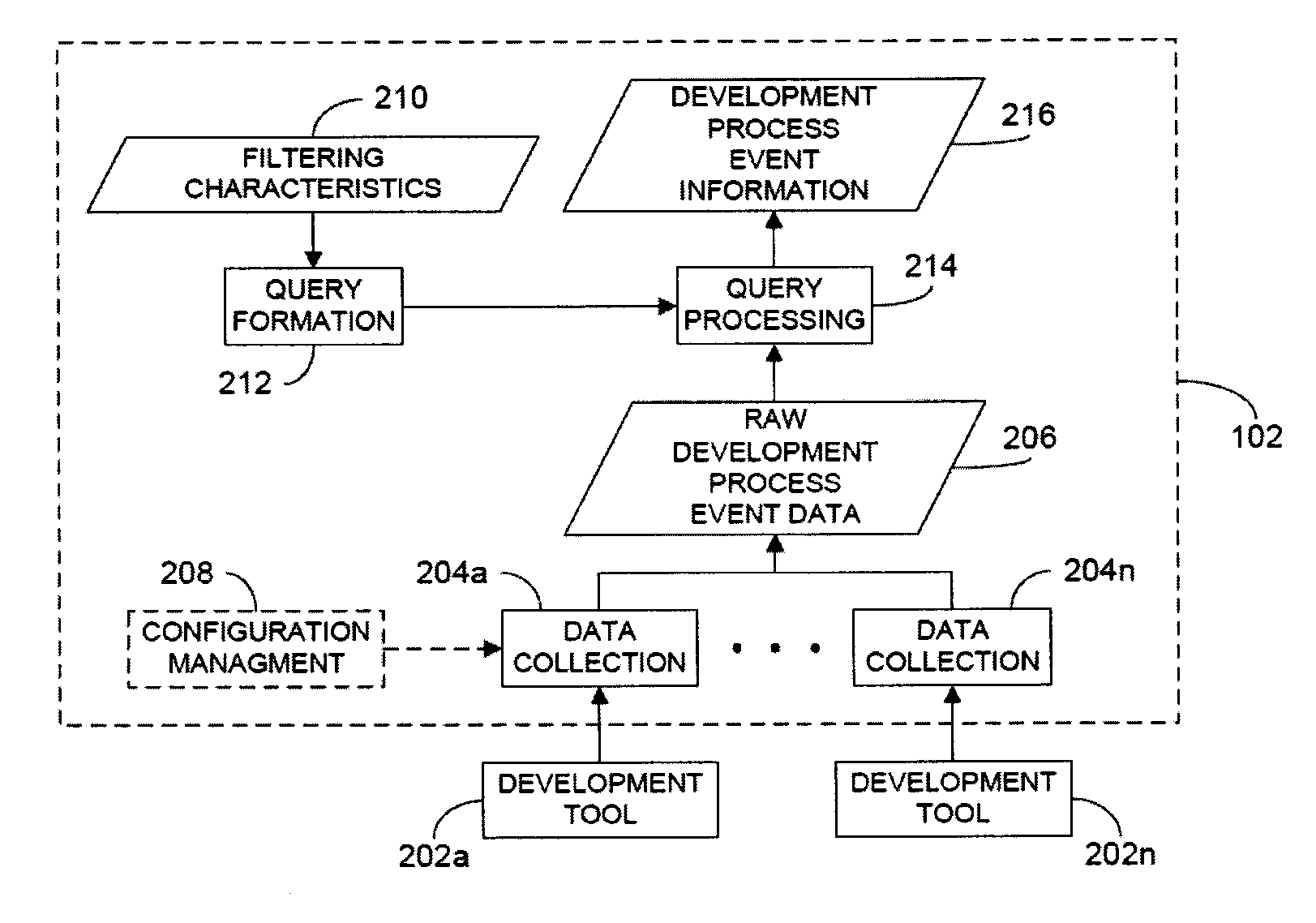
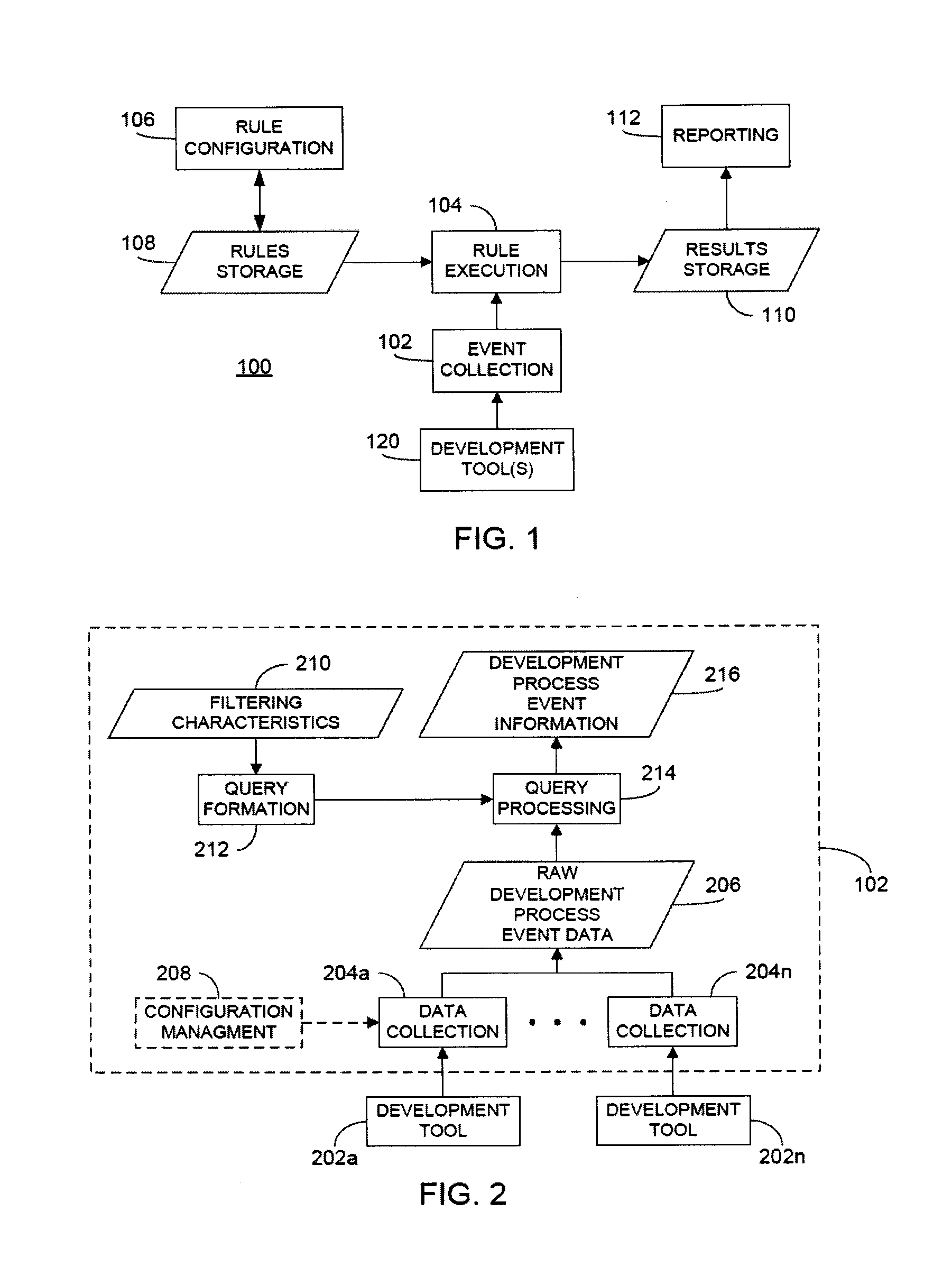
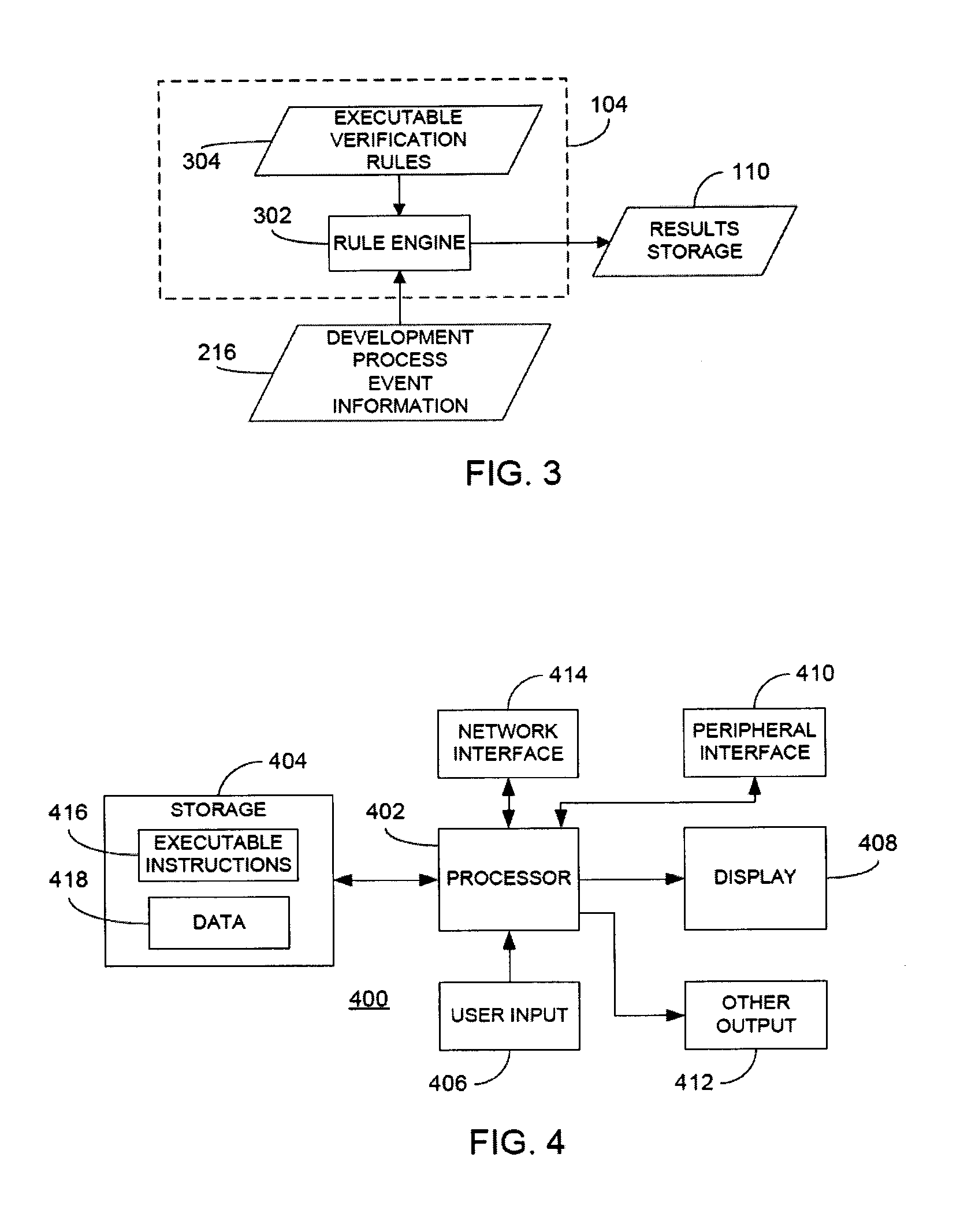
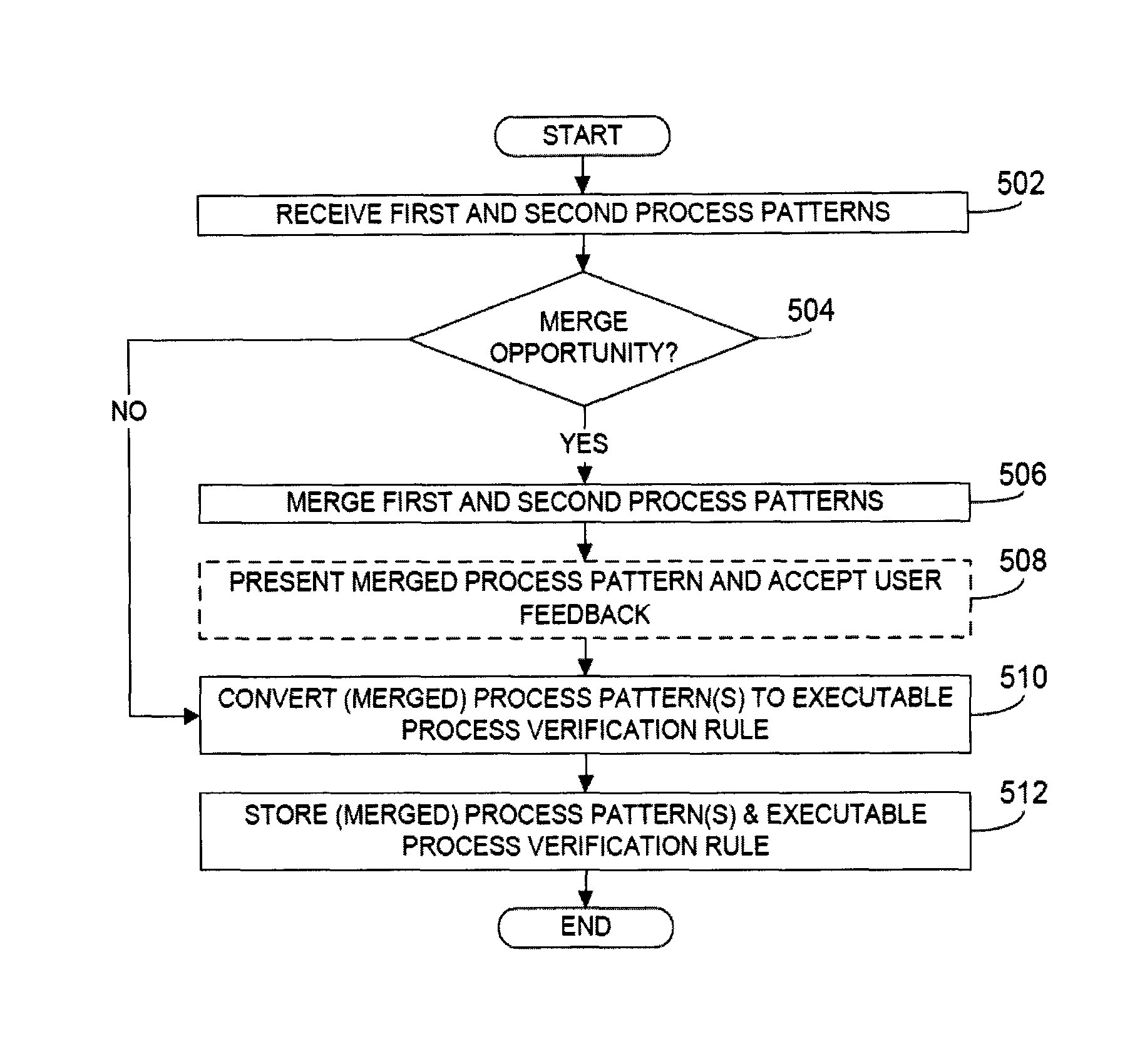
Rule merging in system for monitoring adherence by developers to a software code development process
ActiveUS20120317541A1Improve efficiencyMagnifies processing burdenNuclear monitoringDigital computer detailsSoftware development processSubject-matter expert
In a rule-based system for monitoring process adherence, first and second processing patterns are received and merged to provide a merged processing pattern. Each processing pattern, which may be expressed in a state graph representation, embodies at least a portion of a desired software code development process. Optionally, the merged processing pattern may be presented to a subject-matter expert to obtain feedback thereon. The merged processing pattern may then be converted into an executable process verification rule for use in monitoring process adherence. In an embodiment, development process event data is compared to the executable process verification rules. Violations of the rules result in the generation of failure indications that may be stored and subsequently reported as needed. In this manner, efficiency of automated process adherence monitoring systems may be improved when determining the level of compliance by developers with one or more software code development processes.
Owner:ACCENTURE GLOBAL SERVICES LTD
Methods and systems for providing a notification of a compliance level of an application with respect to a privacy profile associated with a user
ActiveUS8832846B2Digital data processing detailsAnalogue secracy/subscription systemsGraphicsUser device
An exemplary method includes an application management system 1) detecting a request provided by a user to install an application on a user device, 2) identifying a plurality of privacy attributes of the application, 3) determining, based on the identified privacy attributes, a compliance level of the application with respect to a privacy profile associated with the user, the compliance level representing a degree to which the application complies with the privacy profile associated with the user, and 4) directing, prior to the installation of the application, the user device to present a graphic that represents the determined compliance level of the application. Corresponding methods and systems are also disclosed.
Owner:VERIZON PATENT & LICENSING INC
Systems, methods, and devices for providing guidance and feedback based on location and performance
ActiveUS20190008270A1Easy to FeedbackProvide feedbackBrushesTeaching apparatusOral hygieneBiomedical engineering
Systems, methods, and devices for providing feedback to an individual based on brushing performance, and providing guidance for the individual's brushing, are provided herein. In one exemplary embodiment, after an oral hygiene device is orientated, a determination is made as to a segment within the individual's mouth that a brush head of the oral hygiene device is located. Upon this determination being made, a sub-segment within the individual's mouth where the brush head is located is also determined. A brushing performance within the sub-segment is calculated and displayed to the user. A level of compliance for the particular segment is determined based on the brushing performance of the various sub-segments within the particular segment. If the level of compliance exceeds a pre-set compliance level for that segment, the individual is guided to a different segment within their mouth for brushing.
Owner:KONINKLJIJKE PHILIPS NV
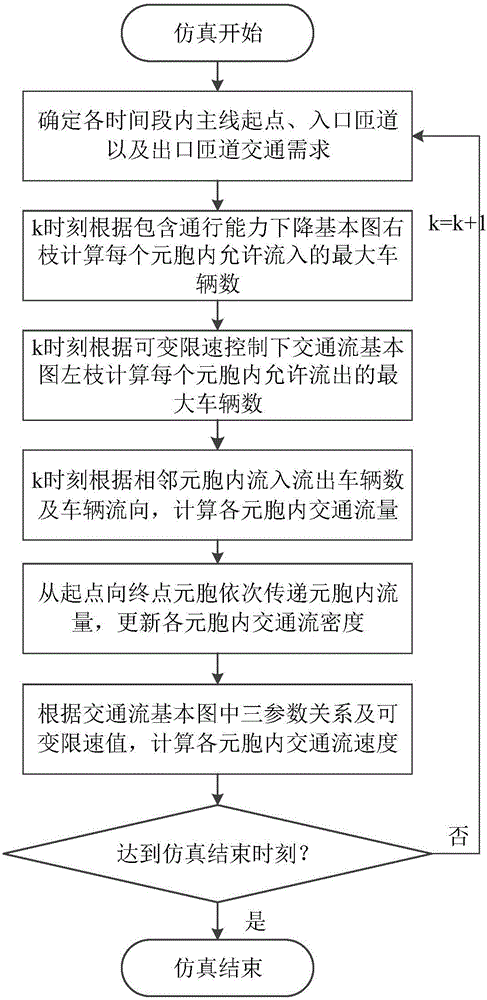
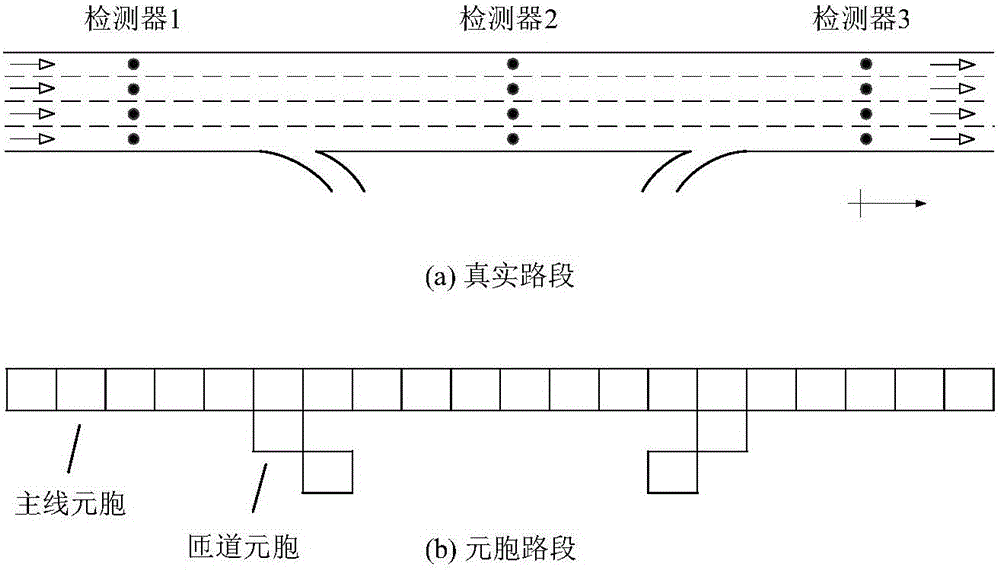
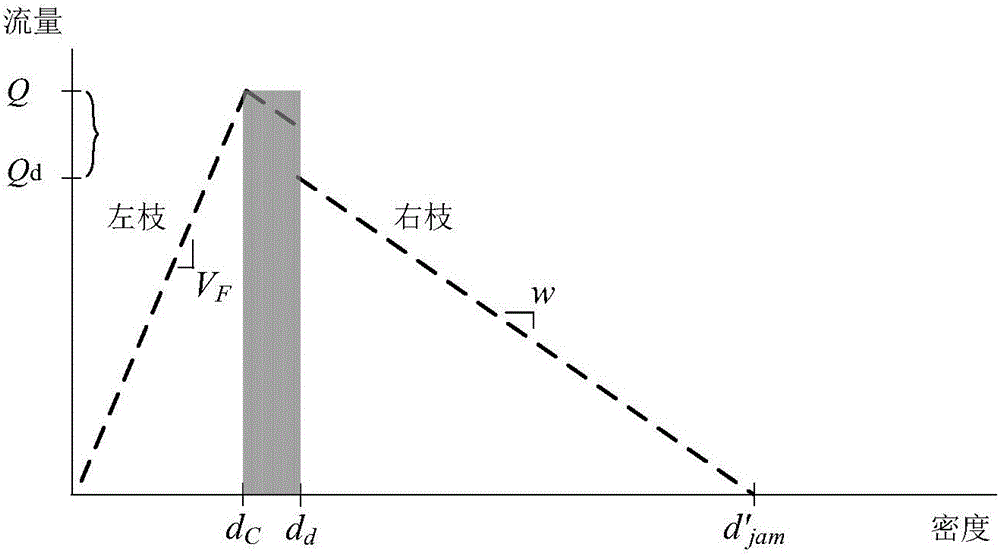
Cell transmission simulation model improved method aiming at variable speed limit control
InactiveCN105975705AInternal combustion piston enginesSpecial data processing applicationsTraffic capacityDriver/operator
A cell transmission simulation model improved method aiming at variable speed limit control comprises the following steps: firstly detecting traffic flow density, flow rate and speed of certain section of rapid road comprising inlet / outlet ramps; using the optimal linearity fitting method to respectively fit data so as to obtain a traffic flow basic map containing dropping pass capability under variable speed limit control; determining traffic demands of a main line origin and inlet / outlet ramps in each period according to the real time traffic flow data; using two types of basic maps to respectively calculate the maximum vehicle number flowing in / out each cell in each simulation step, and updating traffic flow, density and speed in each cell. A basic cell transmission model is overly simple in hypothesis, and cannot consider variable speed limit control influences; the novel improved method can solve said problems, and can simulate variable speed limit control influences on the traffic flow operation under the bottleneck area pass capability dropping condition, jam traffic flow stopping and going phenomenon, and different driver compliance levels, thus providing basis for calculating (simulation-based) variable speed limit control influences on traffic safety and efficiency.
Owner:SOUTHEAST UNIV
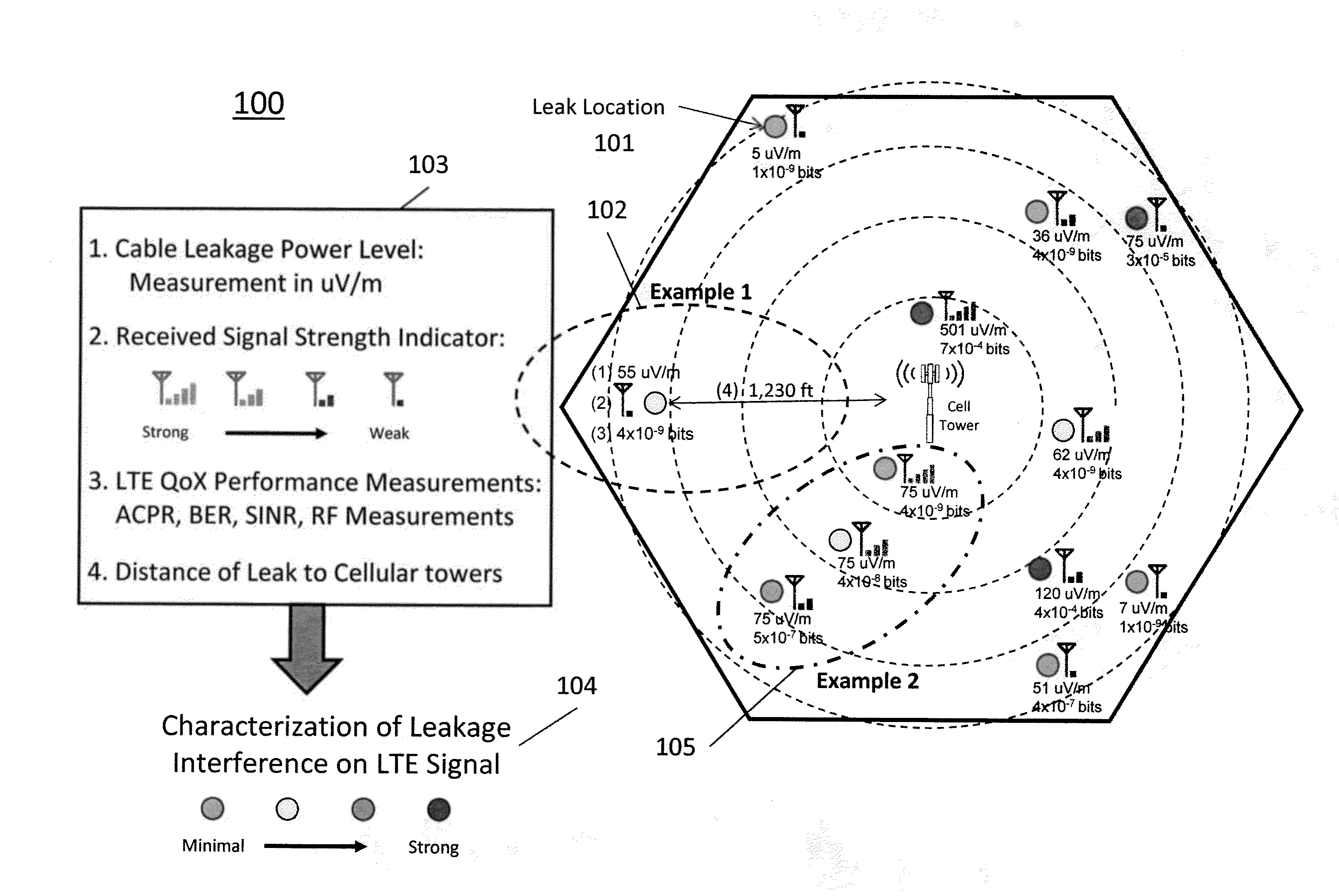
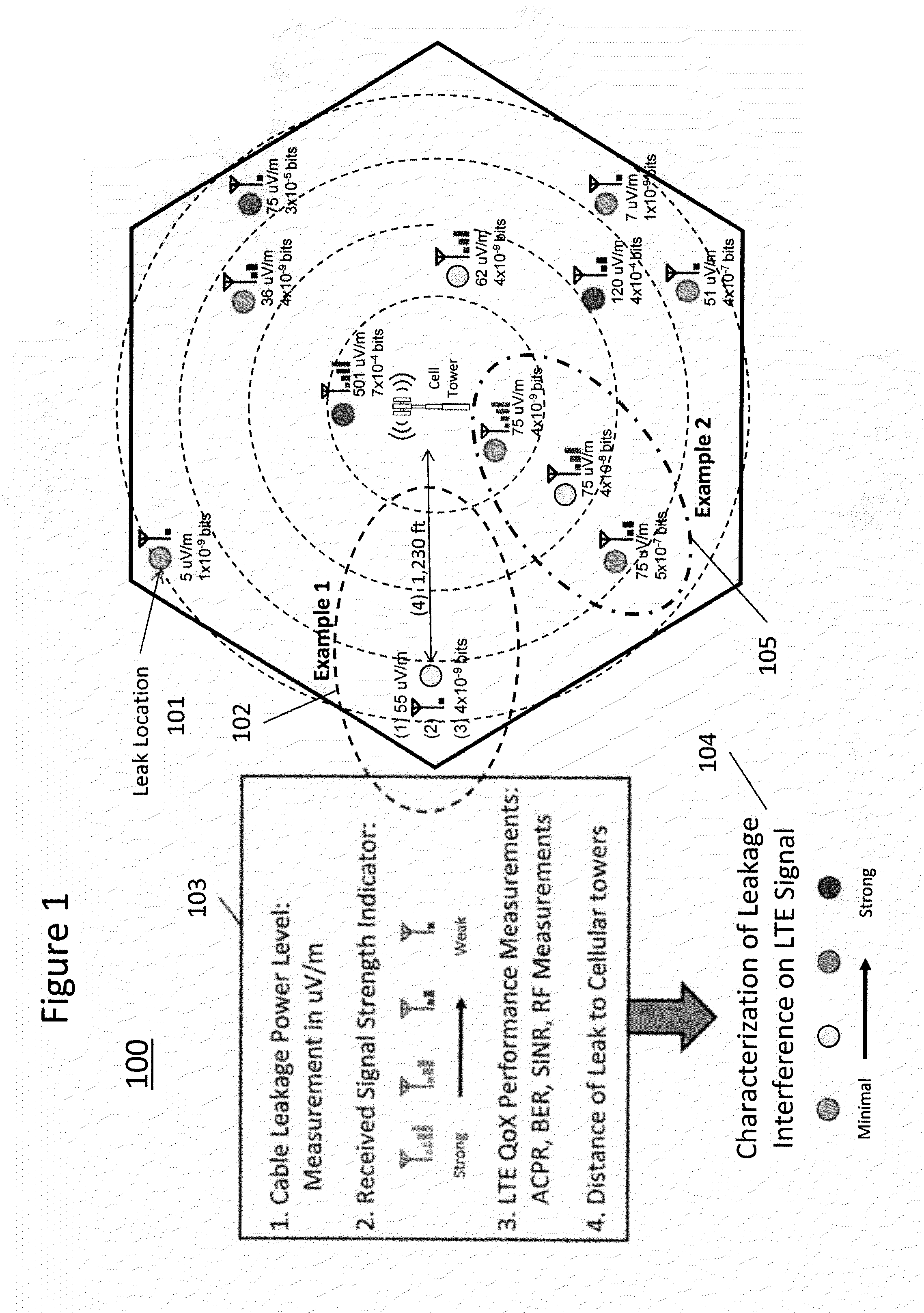
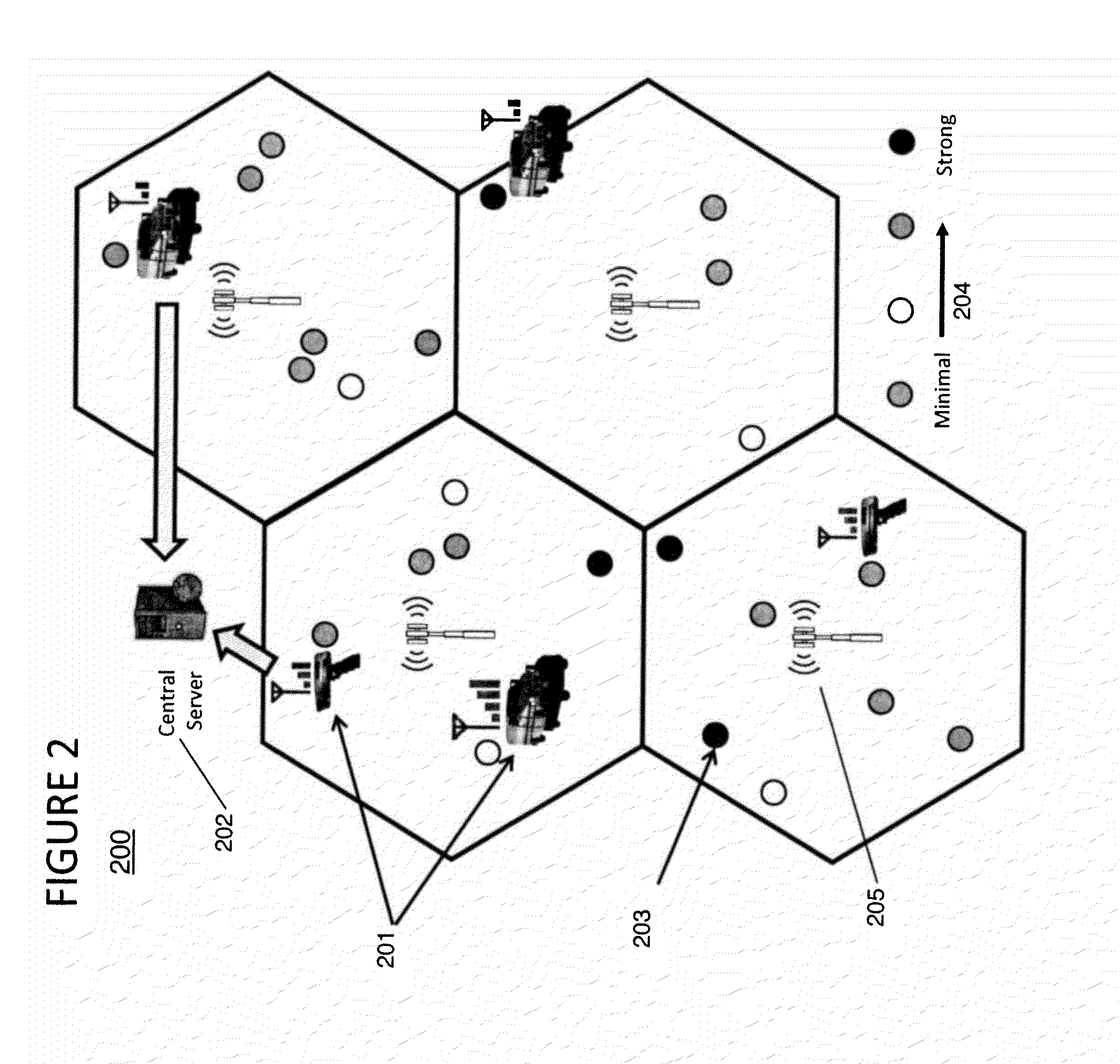
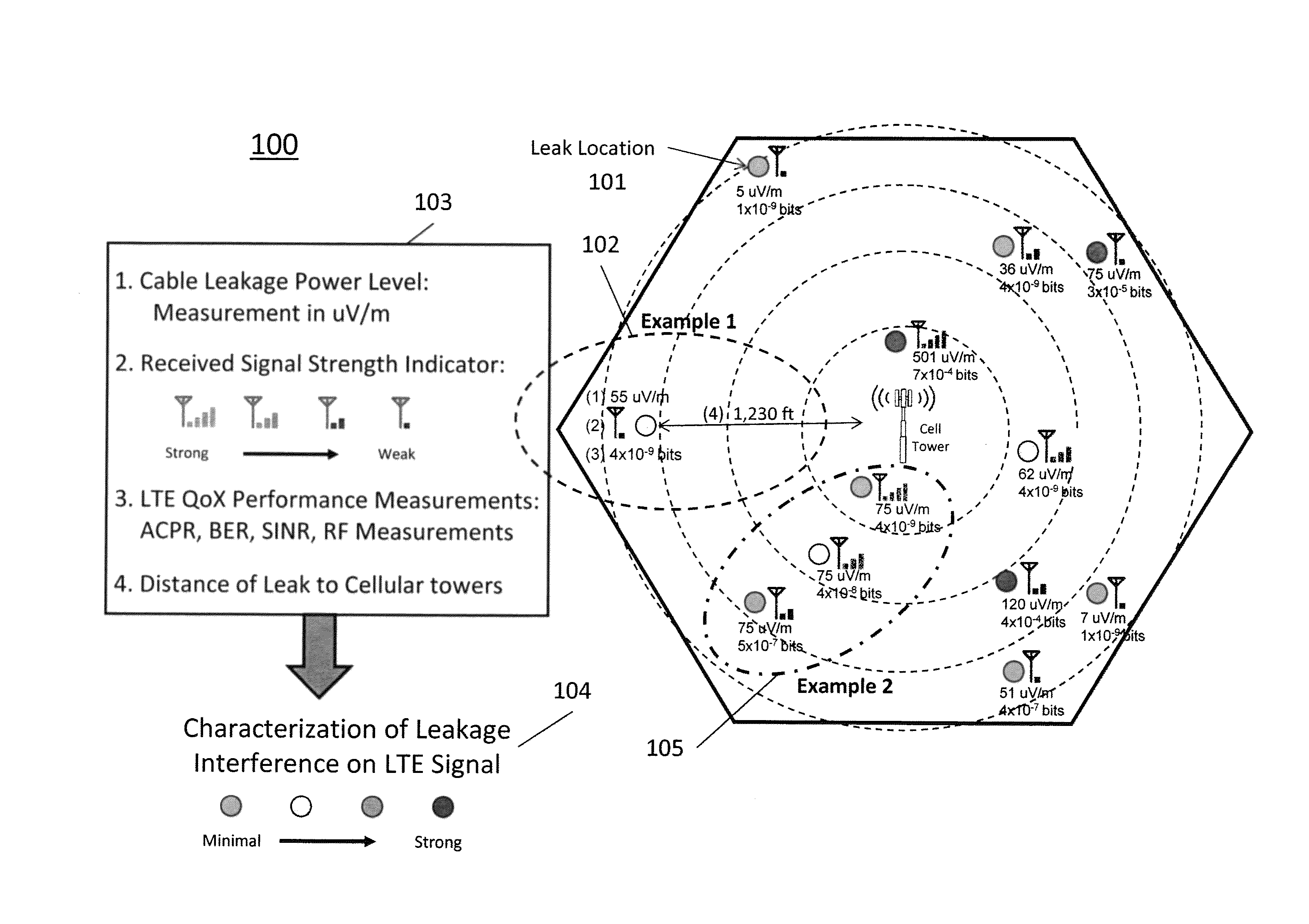
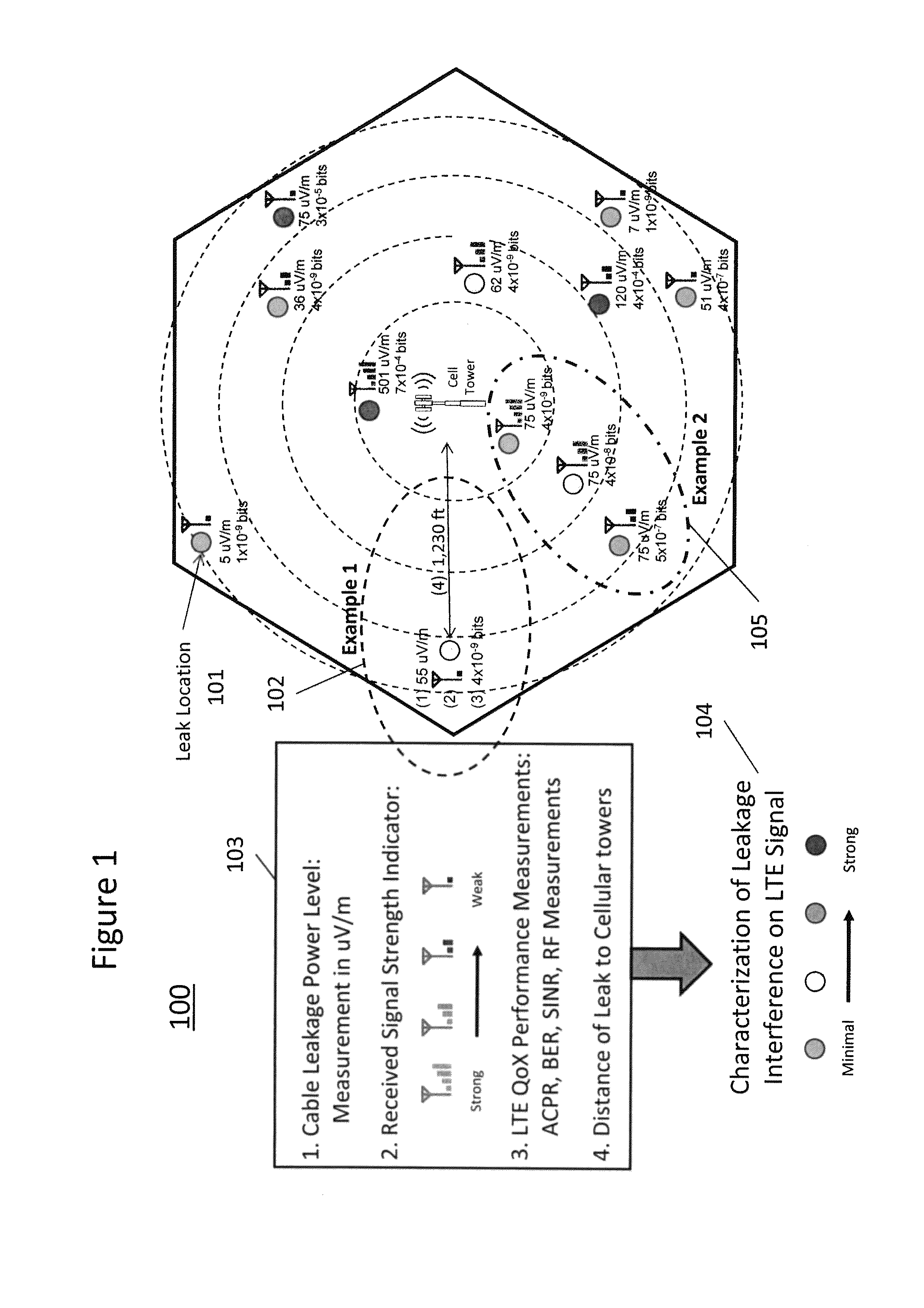
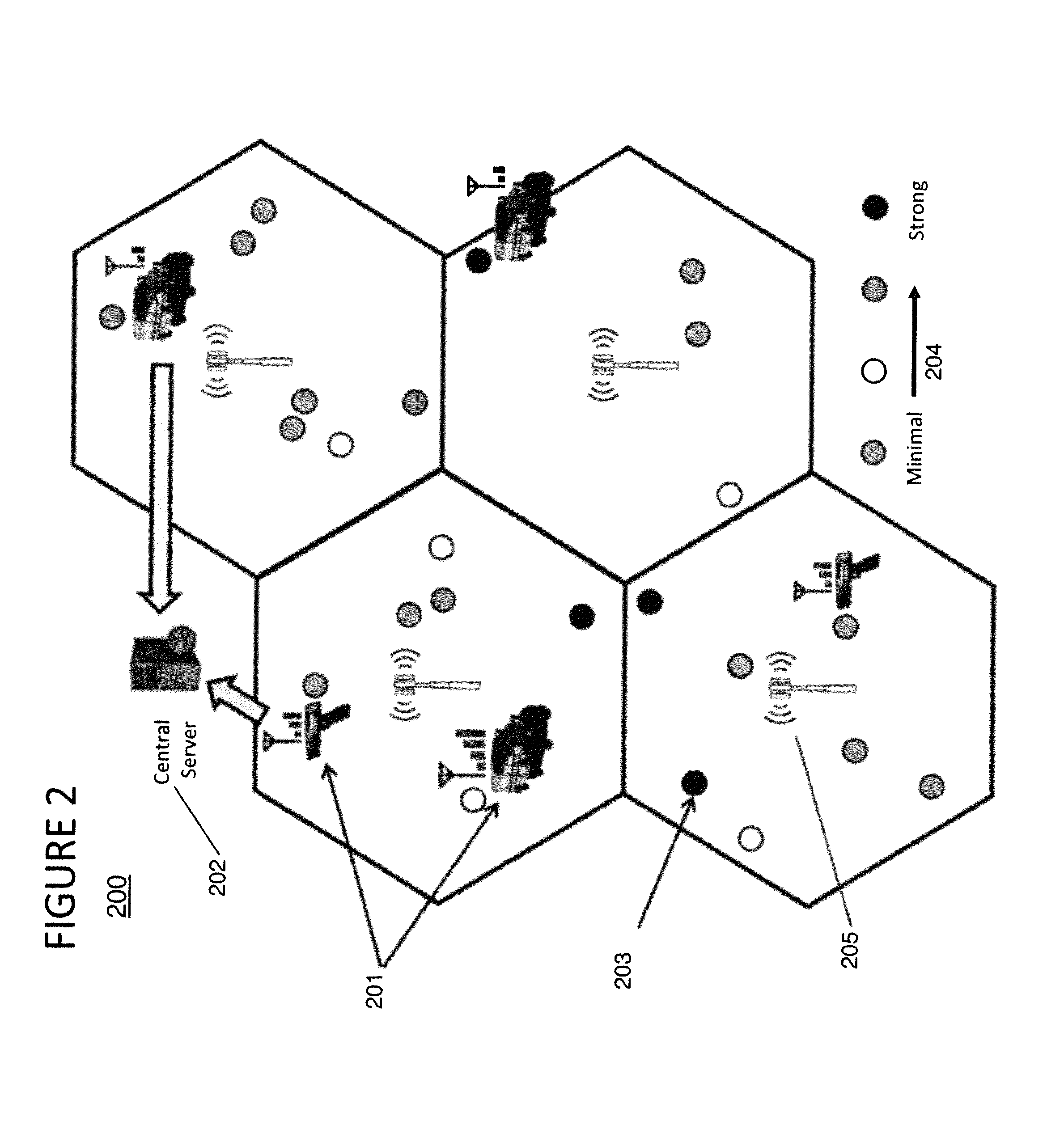
Characterizing cable leakage interference priorities on LTE
A method and structure for conforming to cable leakage compliance level requirements includes calculating, using a processor on a computer, a priority of repairs for cable leakage over a cable operator service area. A result of the priority calculation is provided, thereby permitting higher priority leaks to be identified and repaired. The calculating of priority includes storing geographical locations of cell towers affecting a service area being evaluated, receiving data related to cable leakage sources, receiving data related to wireless service quality, if available, and exercising, using the processor on the computer, a prioritizing algorithm that calculates a relative severity of each cable leakage source.
Owner:COMSONICS
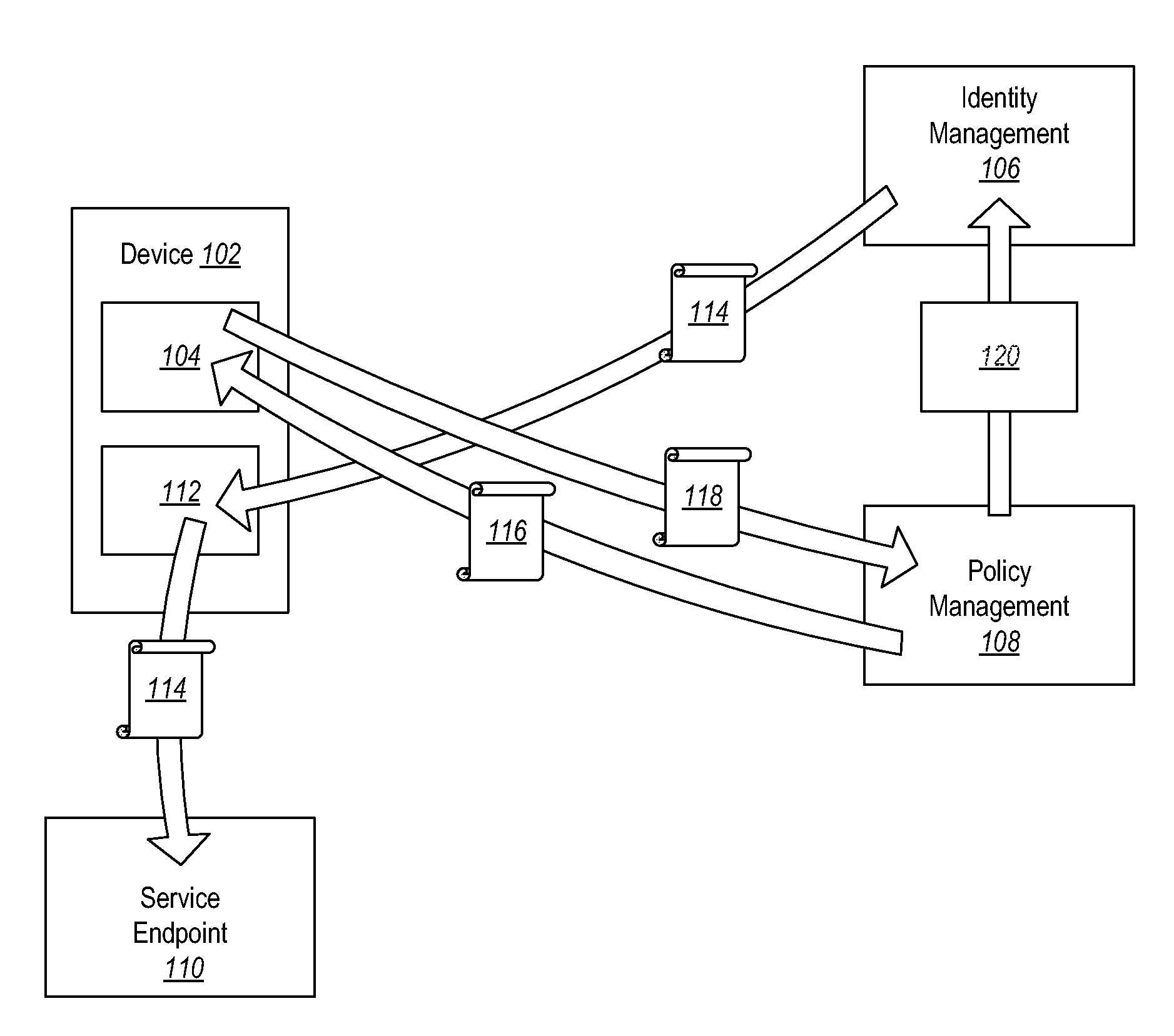
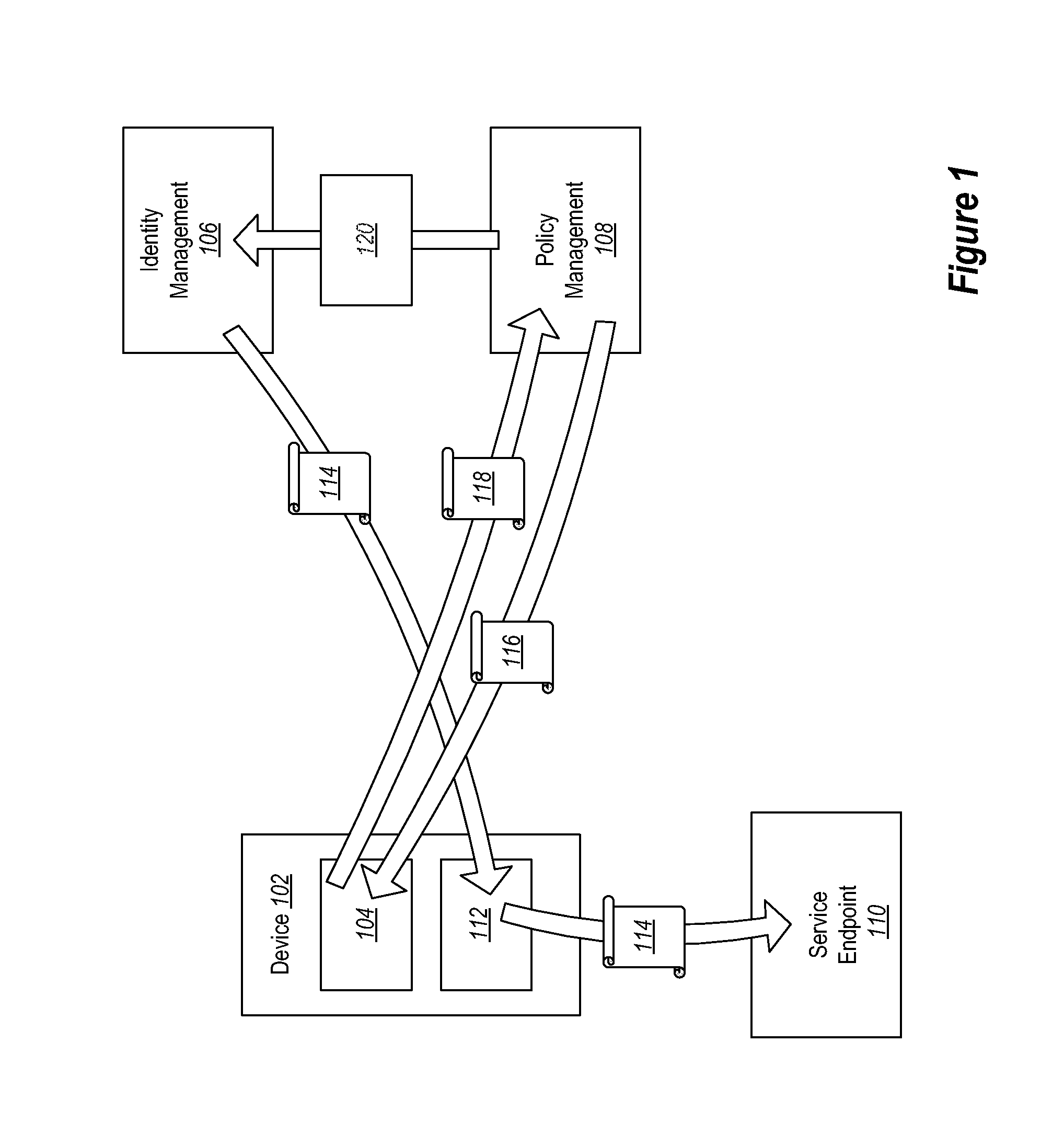
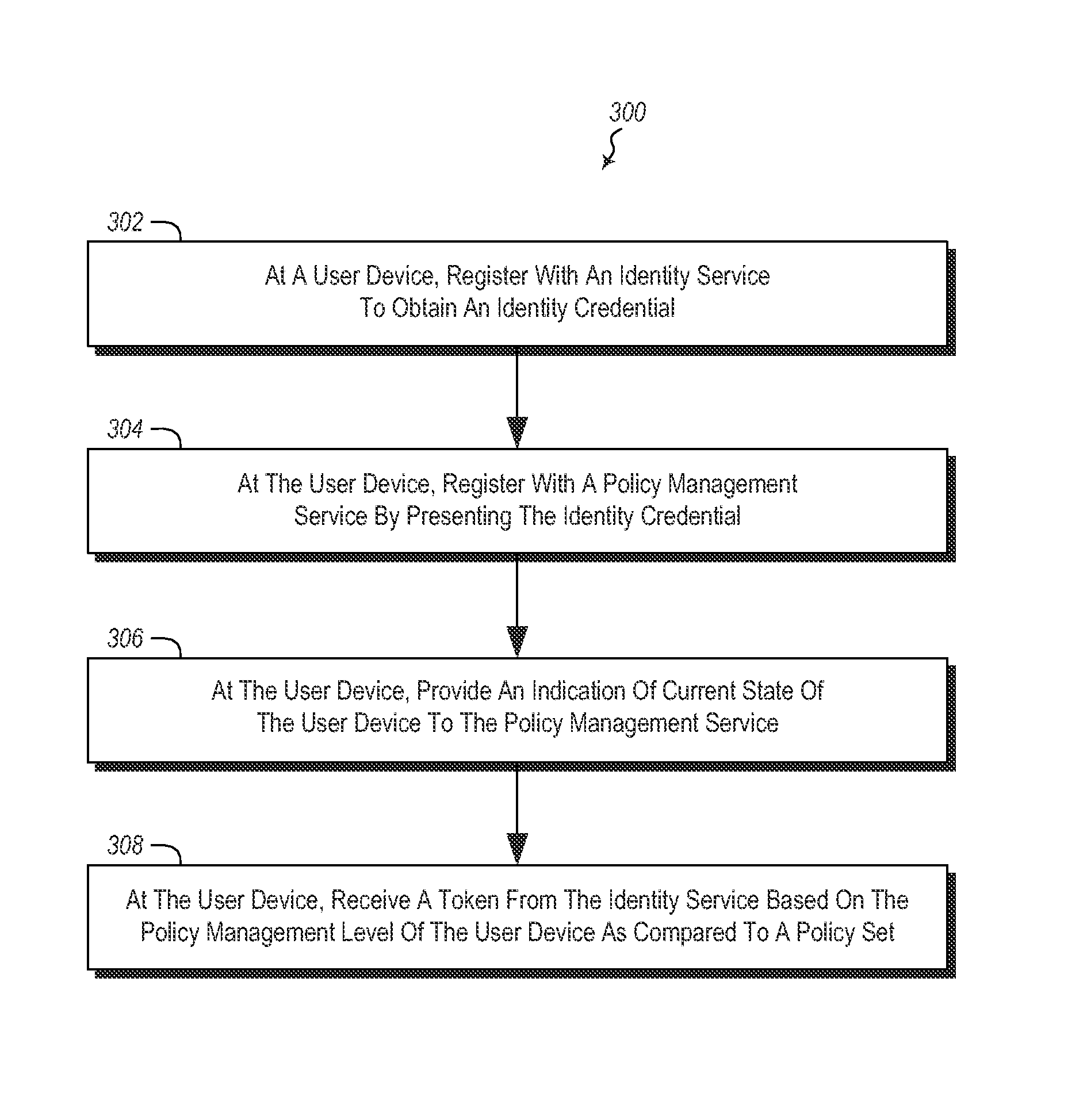
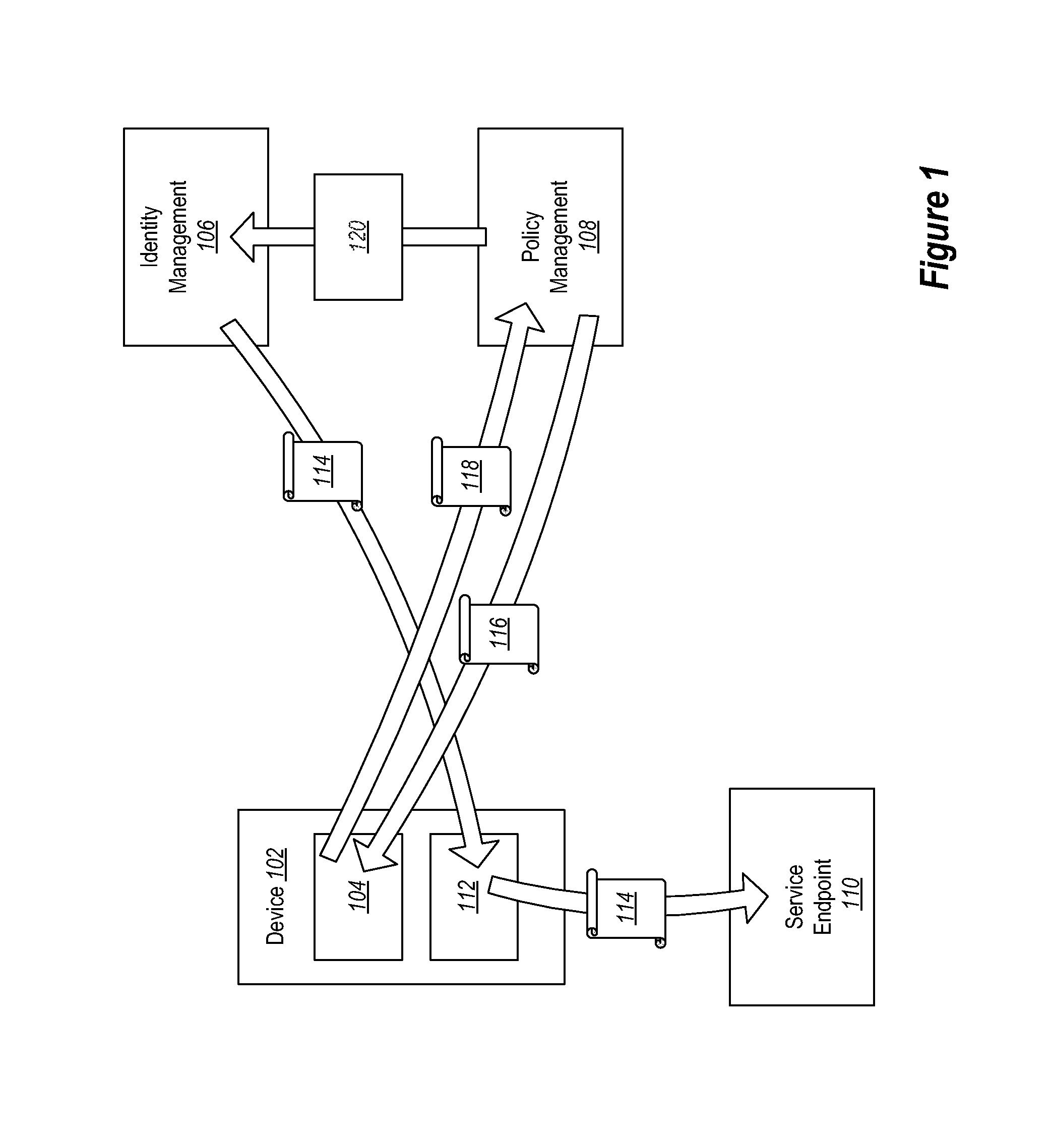
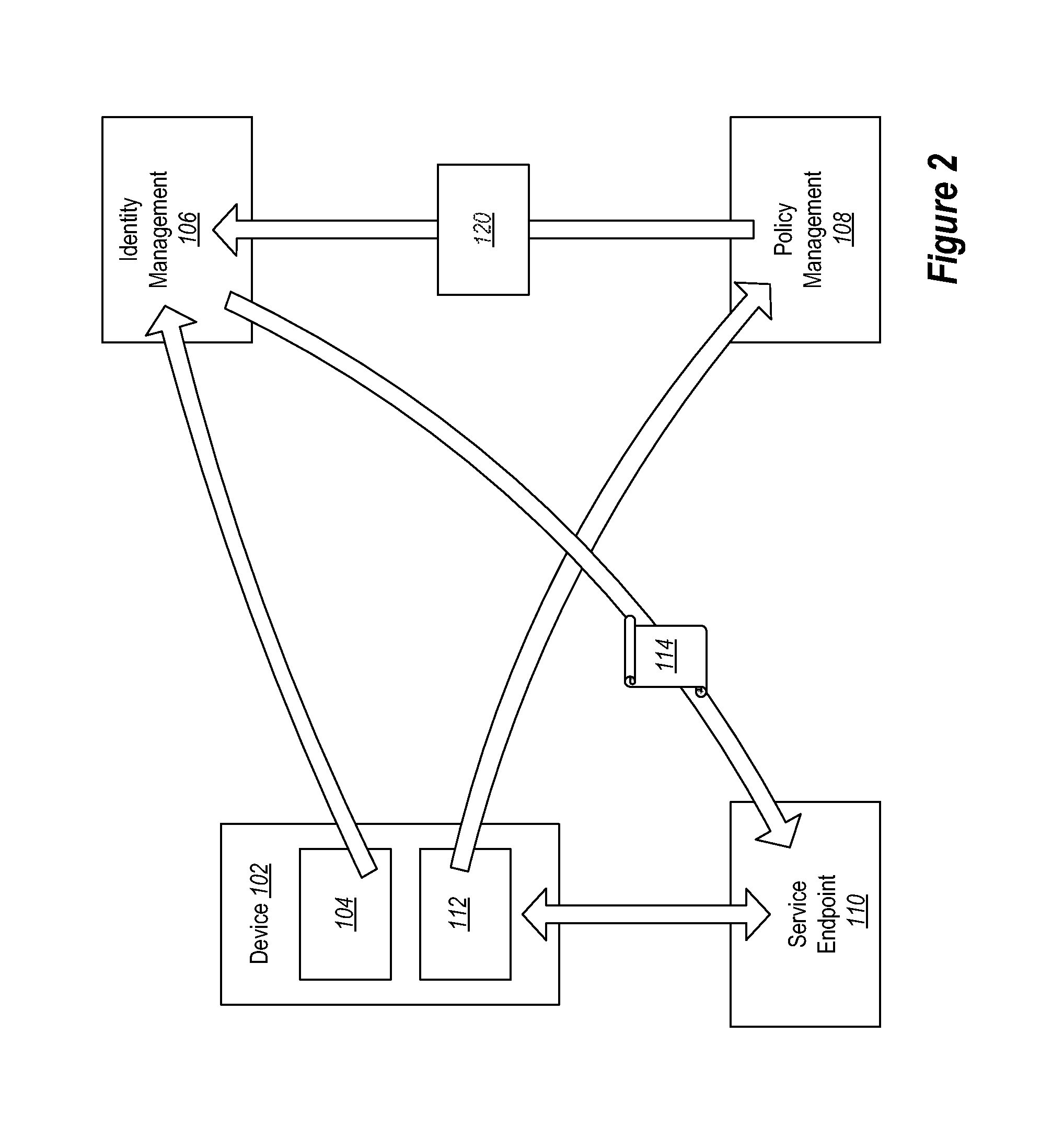
Conditional Access to Services Based on Device Claims
Providing access to one or more resources to a user device. A method includes at a user device, registering with an identity service to obtain an identity credential. The method further includes at the user device, registering with a policy management service by presenting the identity credential. The method further includes at the user device, providing an indication of current state of the user device to the policy management service. The policy management service can then indicate to the identity service the compliance level of the user device. The method further includes the user device receiving a token from the identity service based on the policy management level of the user device as compared to a policy set.
Owner:MICROSOFT TECH LICENSING LLC
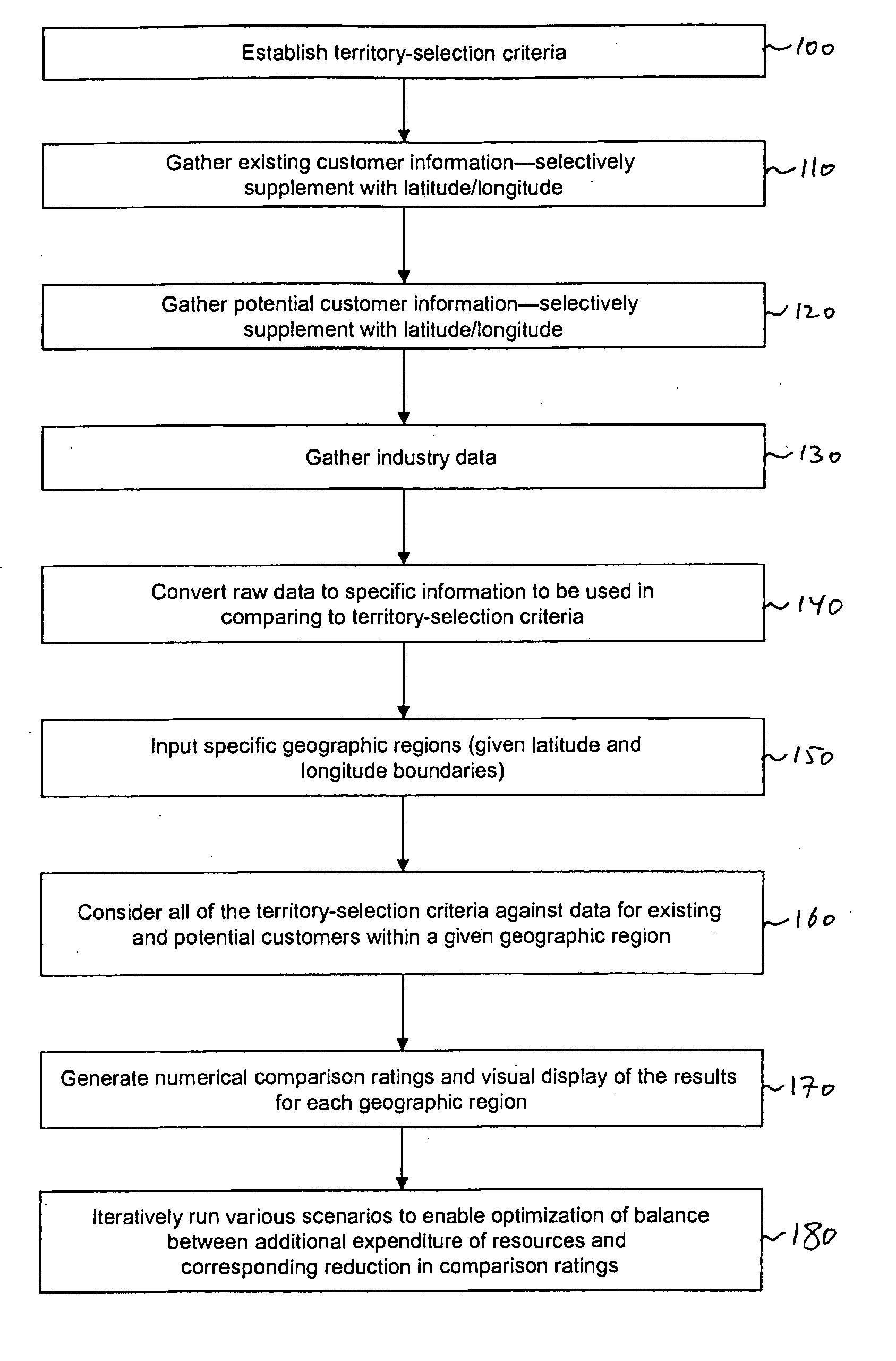
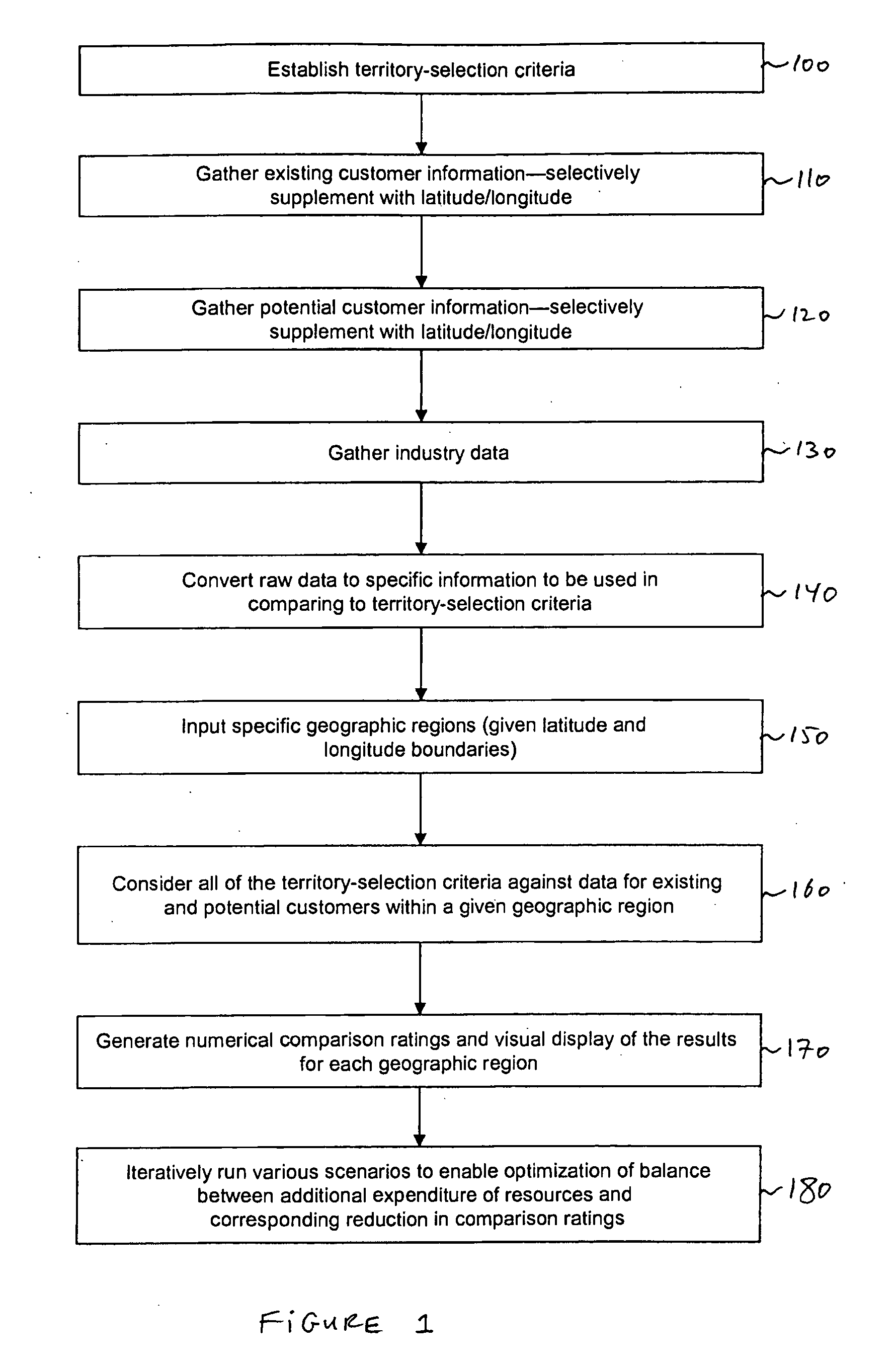
System and method for optimizing allocation of resources
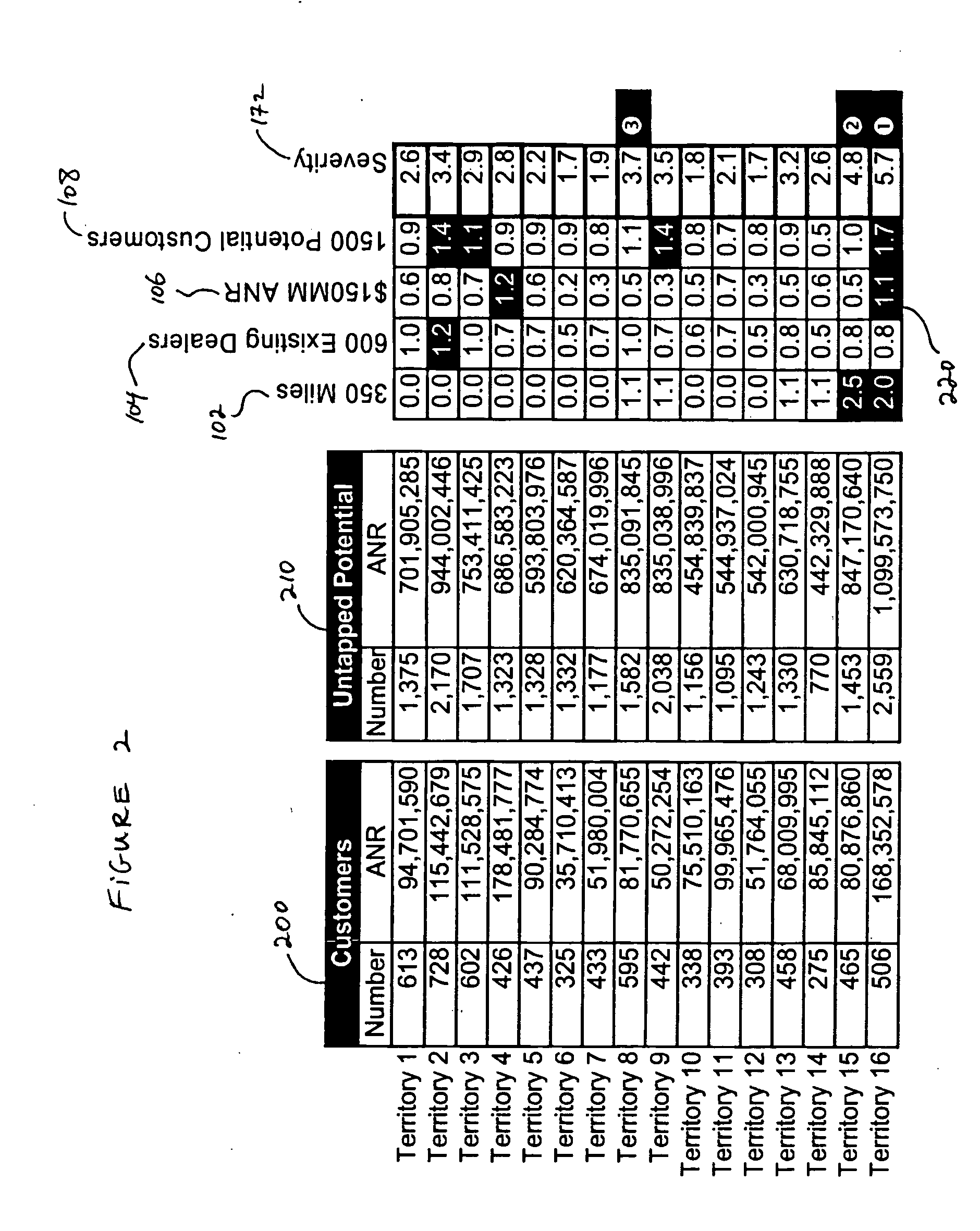
A system and method are disclosed for optimizing allocation of an entity's resources based on an existing set of the entity's geographical service territories, wherein each territory includes both existing and potential customers. A plurality of territory-selection criteria are established and existing and potential customer data are compiled for each of the entity's existing territories. Customer data are quantified, and an overall rating indicative of the relative level of compliance between each existing territory's customer data and the territory-selection criteria is calculated. Based on the magnitude of the average overall rating for all existing territories, the geographical boundaries of at least one of the entity's existing territories are reconfigured to generate a new set of territories in such a way as to reduce the average rating. The process is then iteratively repeated until it is determined that further reductions in the average rating would not justify additional reconfiguration of the territories.
Owner:TEXTRON FINANCIAL CORP
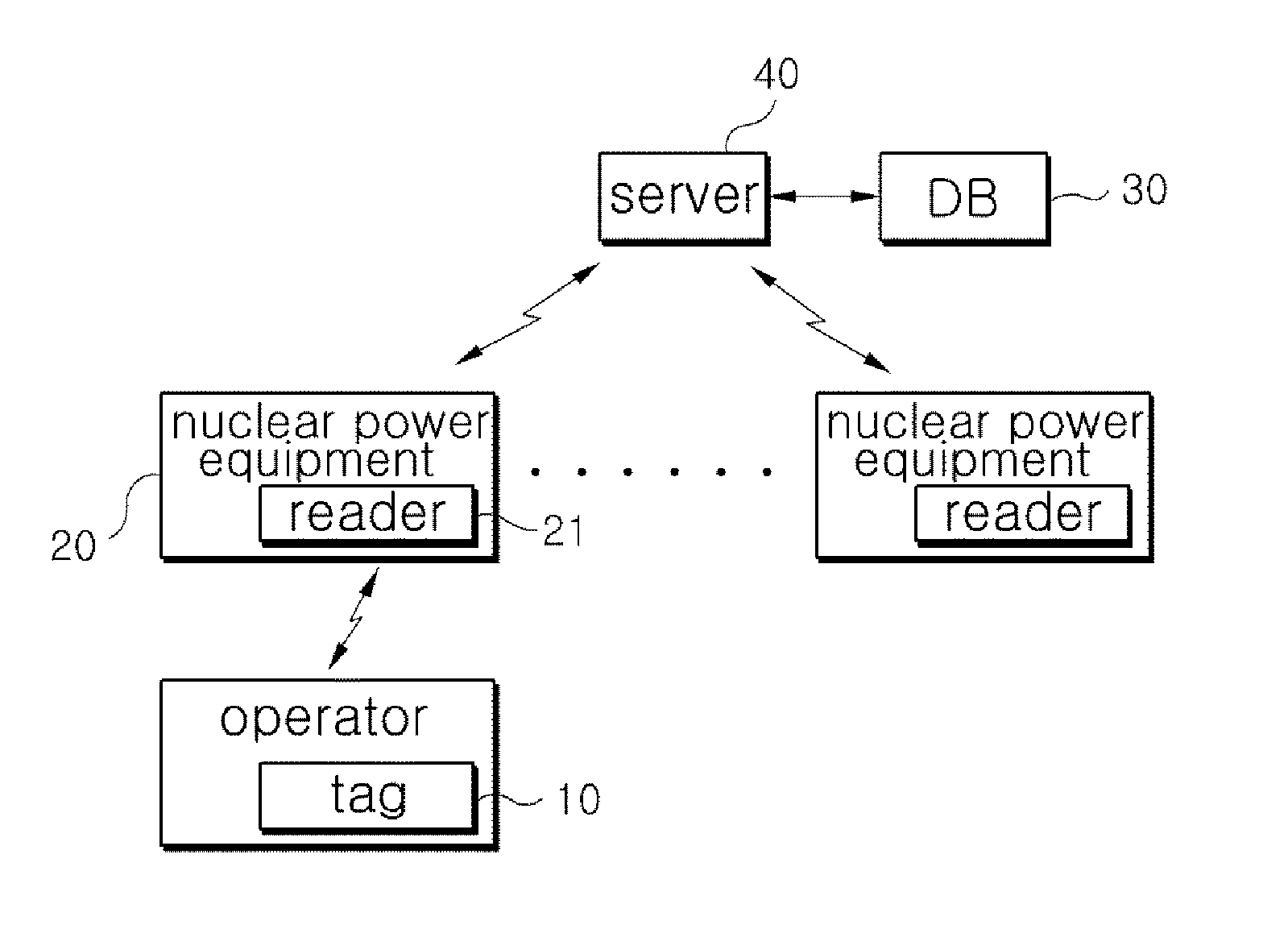
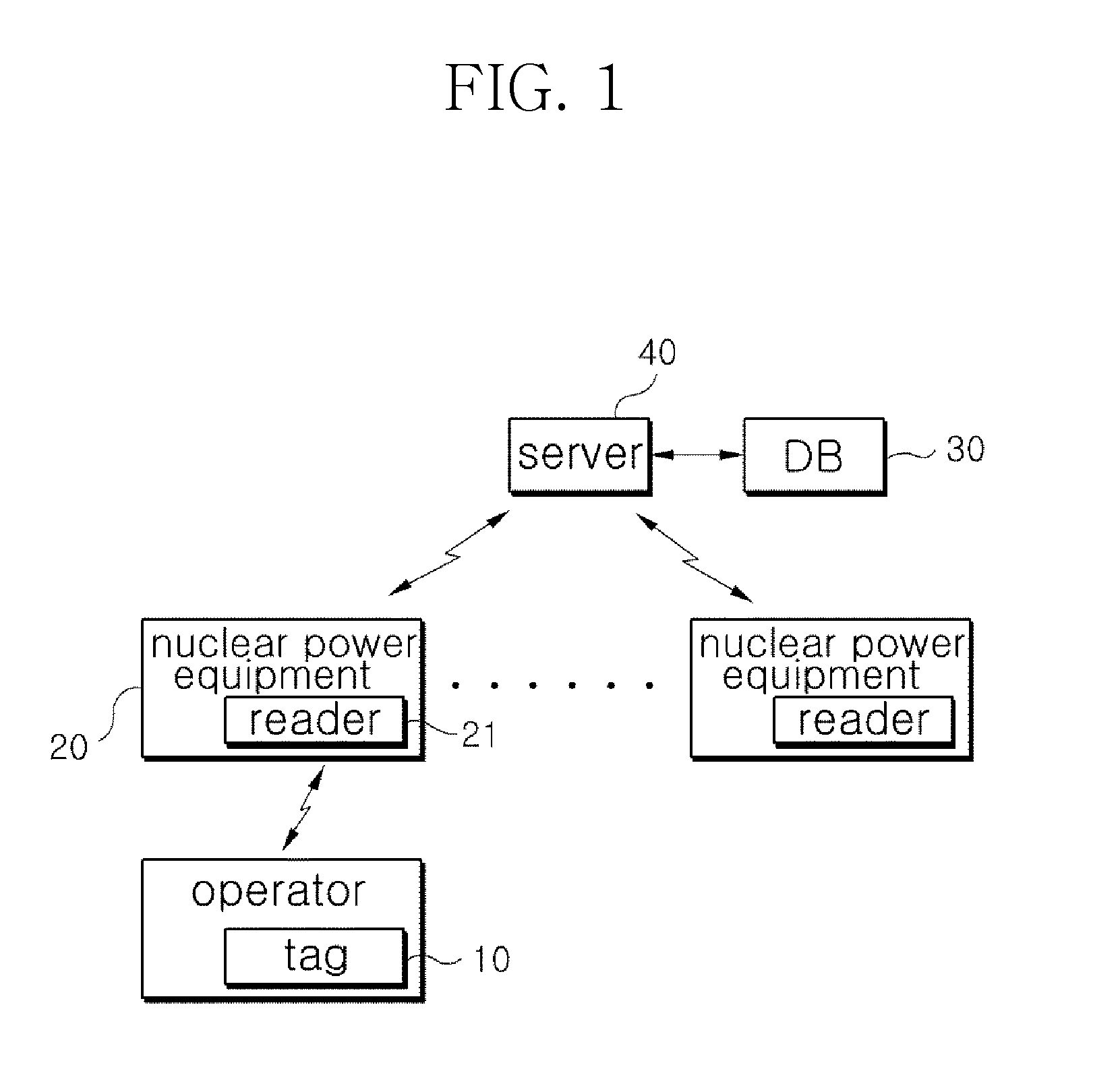
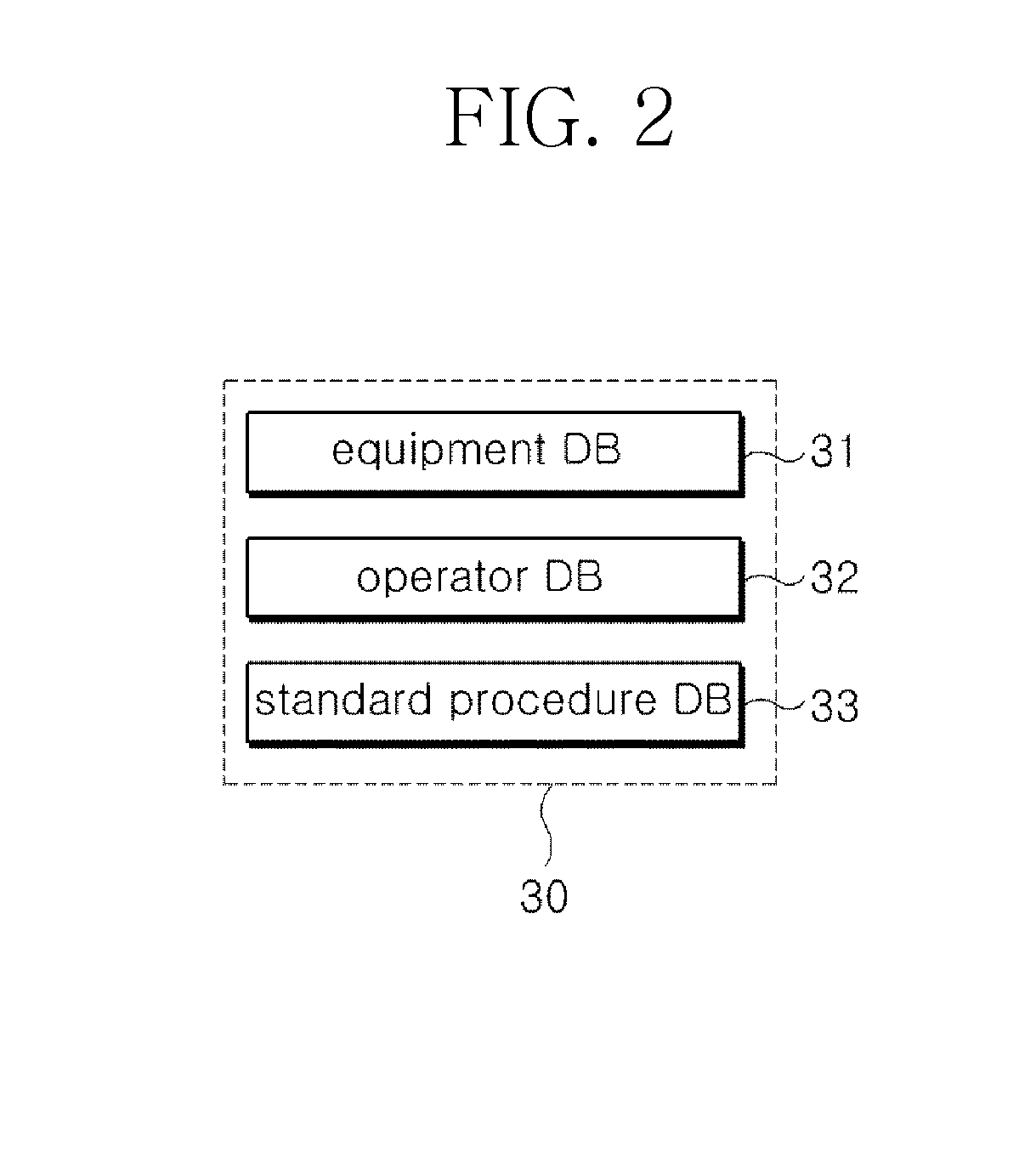
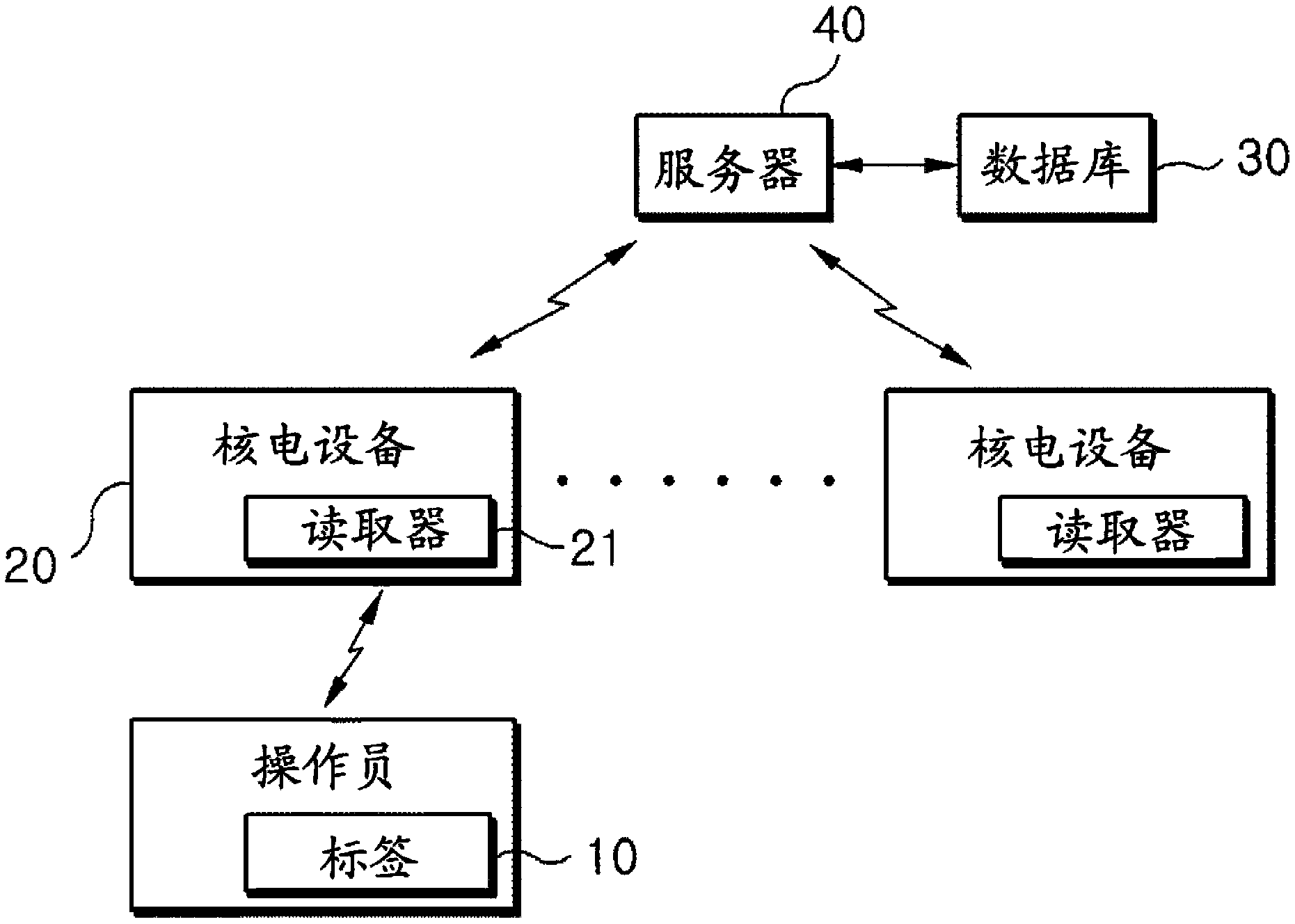
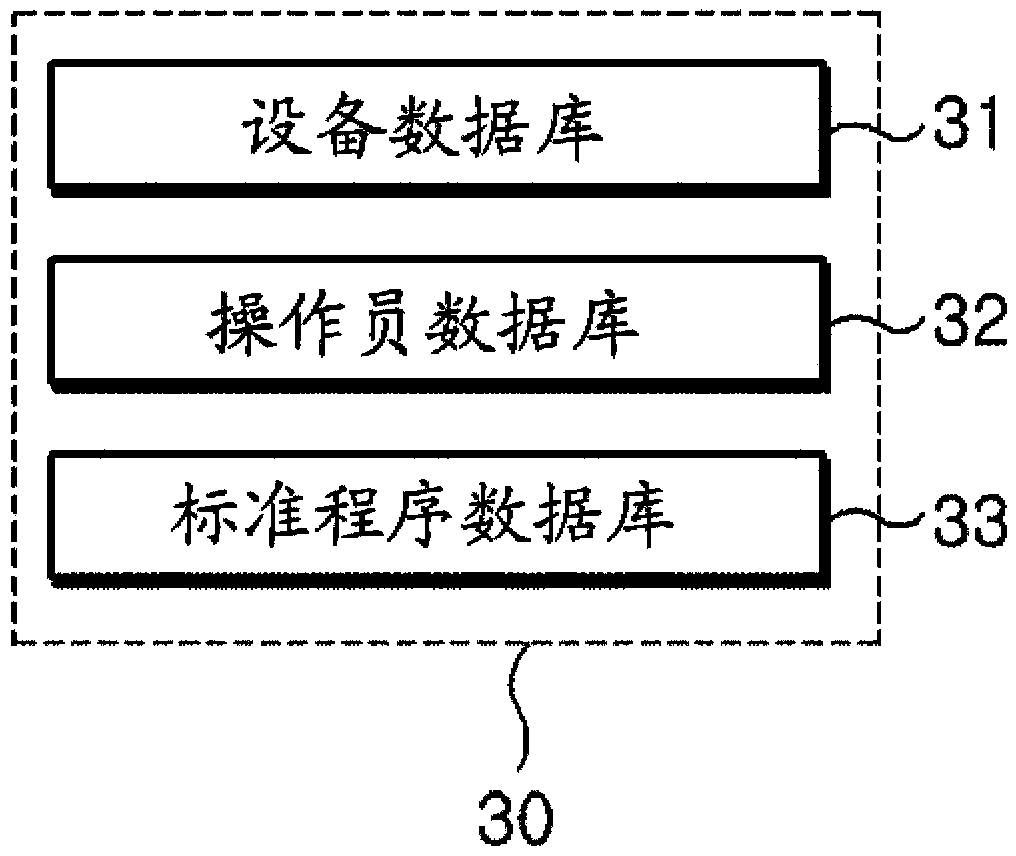
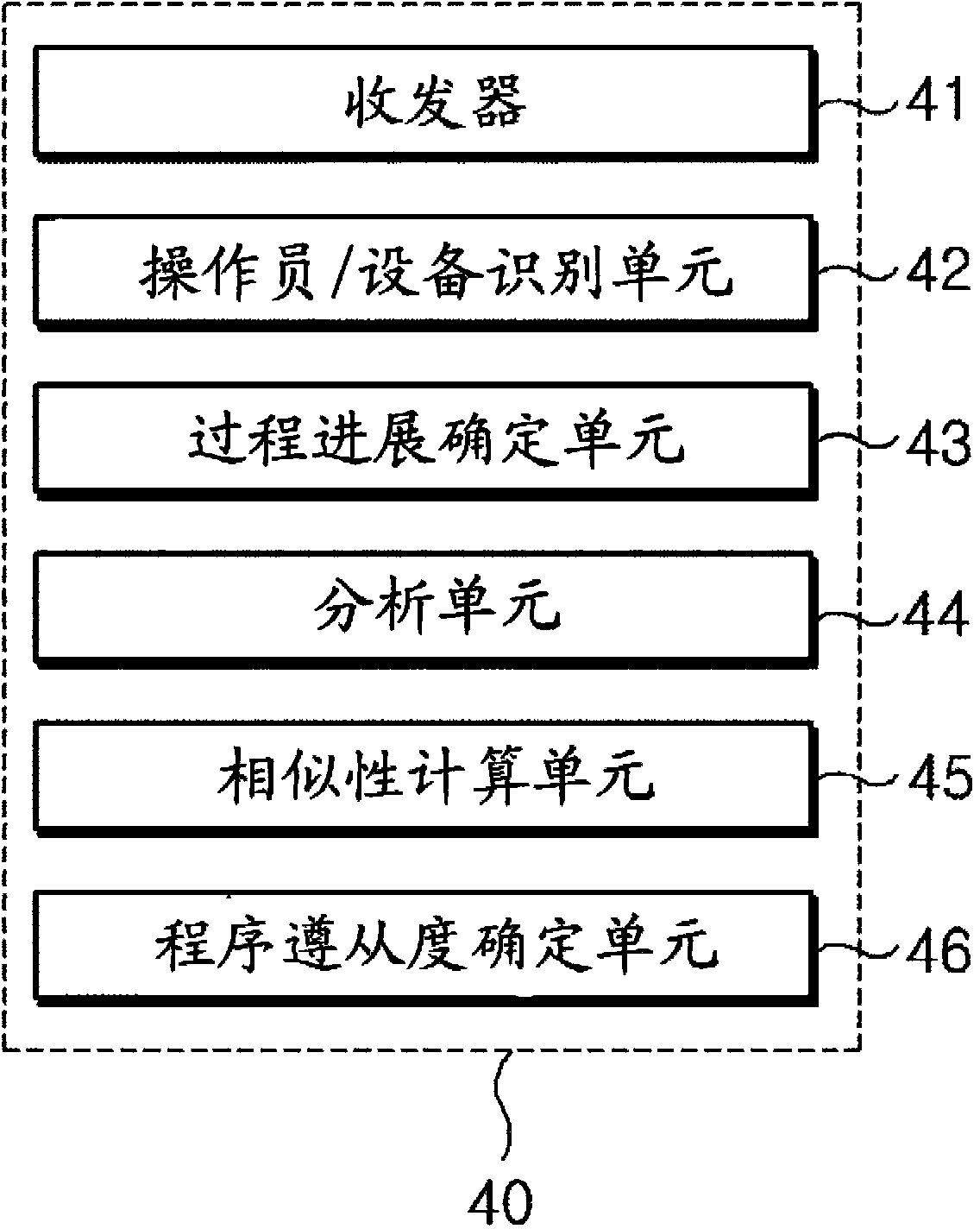
System for assessing procedure compliance level of human operators in nuclear power plants and method thereof
Disclosed are a system for assessing the procedure compliance level of a human operator in a nuclear power plant, which quantitatively detects if the human operator complies with a standard procedure written in an emergency procedure guideline for the nuclear power plant, and a method thereof. The system includes a first recognizing unit attached to each of human operators, a second recognizing unit that is mounted on each of nuclear power equipments and able to make communication with the first recognizing unit, a database storing information of a standard procedure to be performed by the human operator with respect to the nuclear power equipment, and a server that is able to make communication with the second recognizing unit, and assesses the standard procedure stored in the database and an actual procedure performed by the human operator, which is received from the second recognizing unit.
Owner:KOREA ATOMIC ENERGY RES INST +1
Rule merging in system for monitoring adherence by developers to a software code development process
ActiveUS8621417B2Shorten the timeImprove efficiencyDigital computer detailsNuclear monitoringSoftware development processSubject-matter expert
In a rule-based system for monitoring process adherence, first and second processing patterns are received and merged to provide a merged processing pattern. Each processing pattern, which may be expressed in a state graph representation, embodies at least a portion of a desired software code development process. Optionally, the merged processing pattern may be presented to a subject-matter expert to obtain feedback thereon. The merged processing pattern may then be converted into an executable process verification rule for use in monitoring process adherence. In an embodiment, development process event data is compared to the executable process verification rules. Violations of the rules result in the generation of failure indications that may be stored and subsequently reported as needed. In this manner, efficiency of automated process adherence monitoring systems may be improved when determining the level of compliance by developers with one or more software code development processes.
Owner:ACCENTURE GLOBAL SERVICES LTD
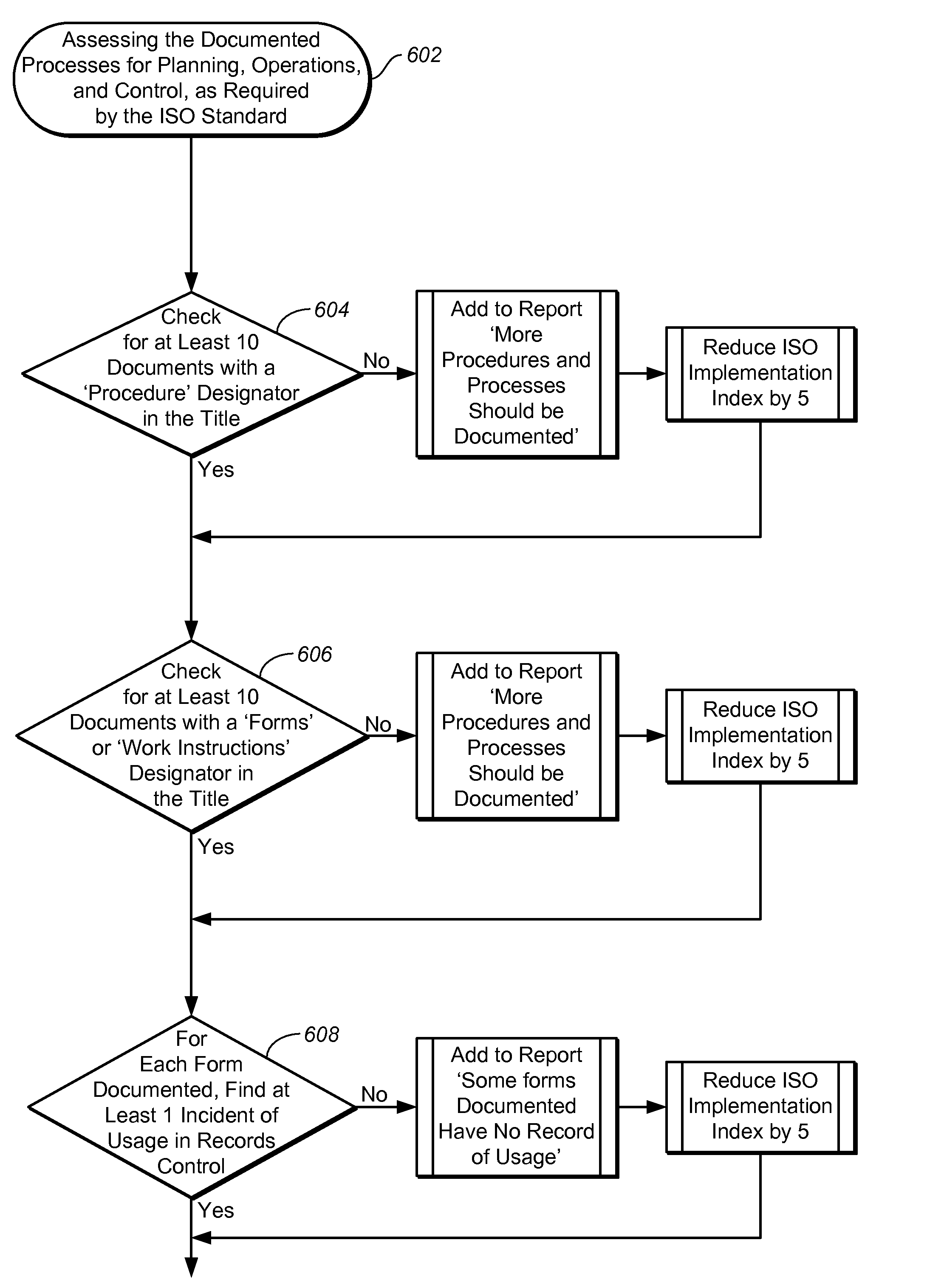
System and method of automatic data search to determine compliance with an international standard
Systems and methods of automatic data search to determine compliance with international standard are disclosed here. One embodiment includes automatically searching through data of an organization for predetermined data to determine if the organization is compliant with an international standard and generating a score based on data identified from the search, the score to indicate a compliance level of the organization based on a predetermined scale of the international standard.
Owner:INTELLIGENT DATA TECH INC IDTI
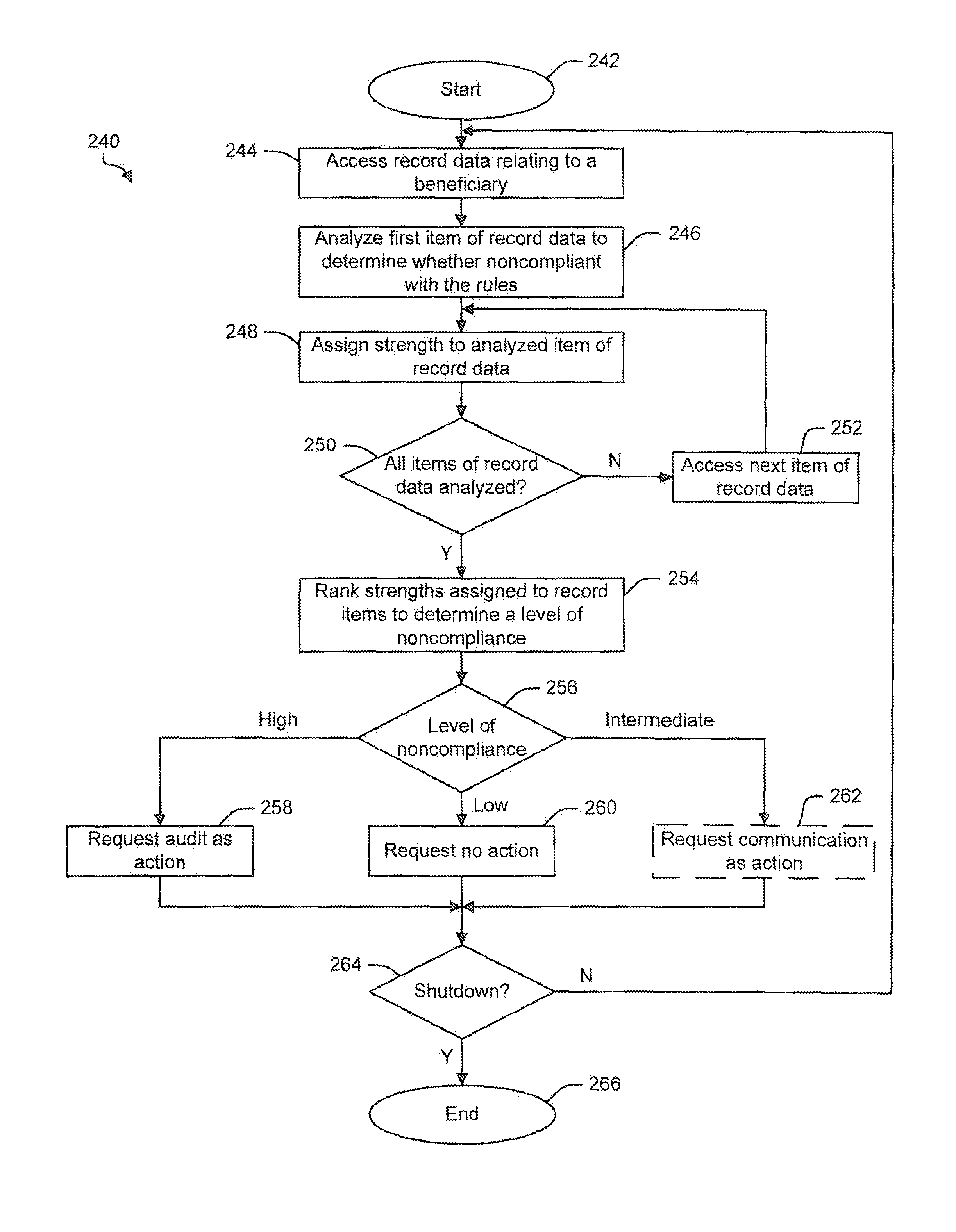
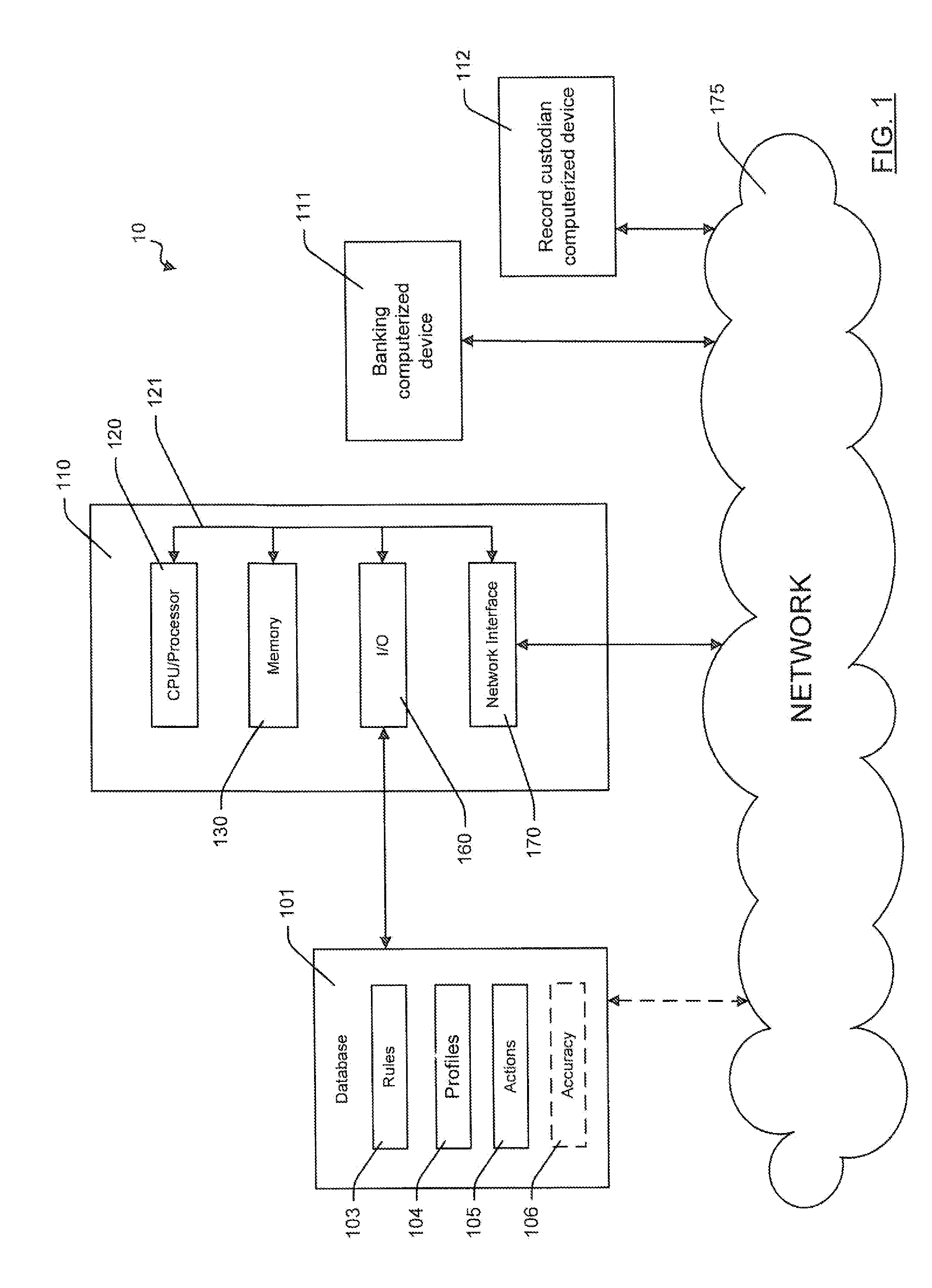
Method for detecting ineligibility of a beneficiary and system
Owner:WILLARD MARY JOAN +1
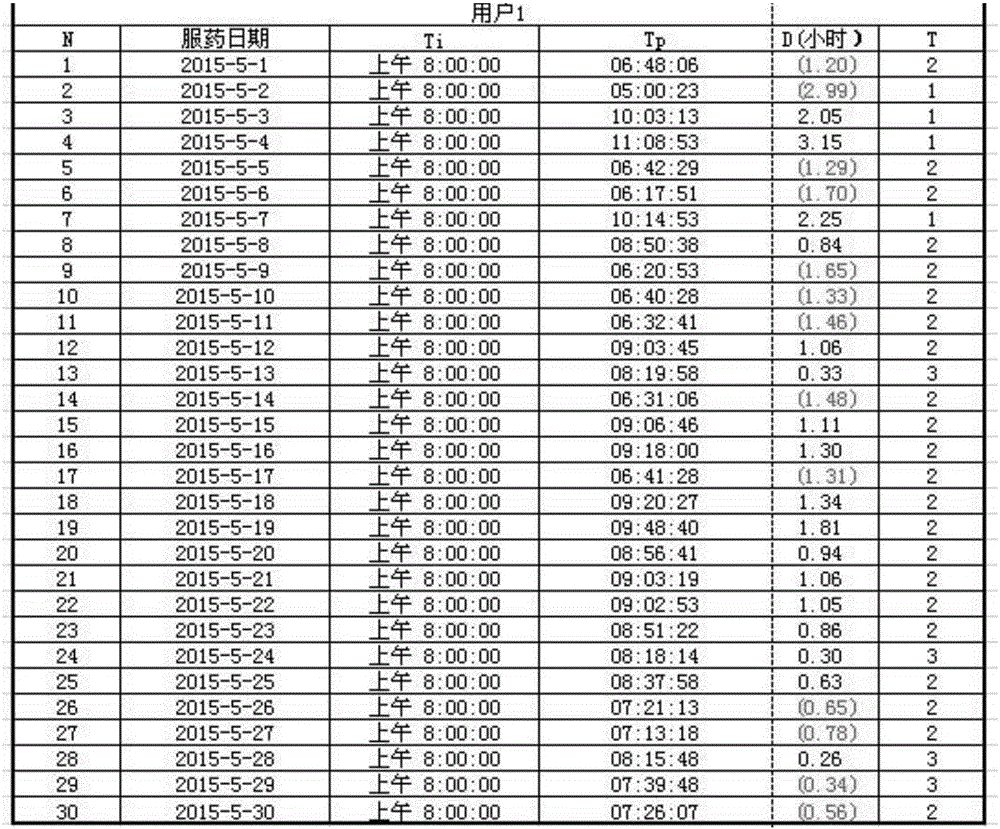
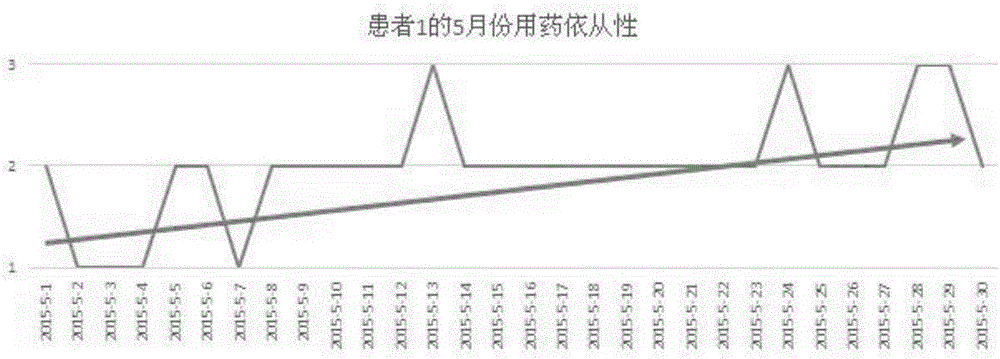
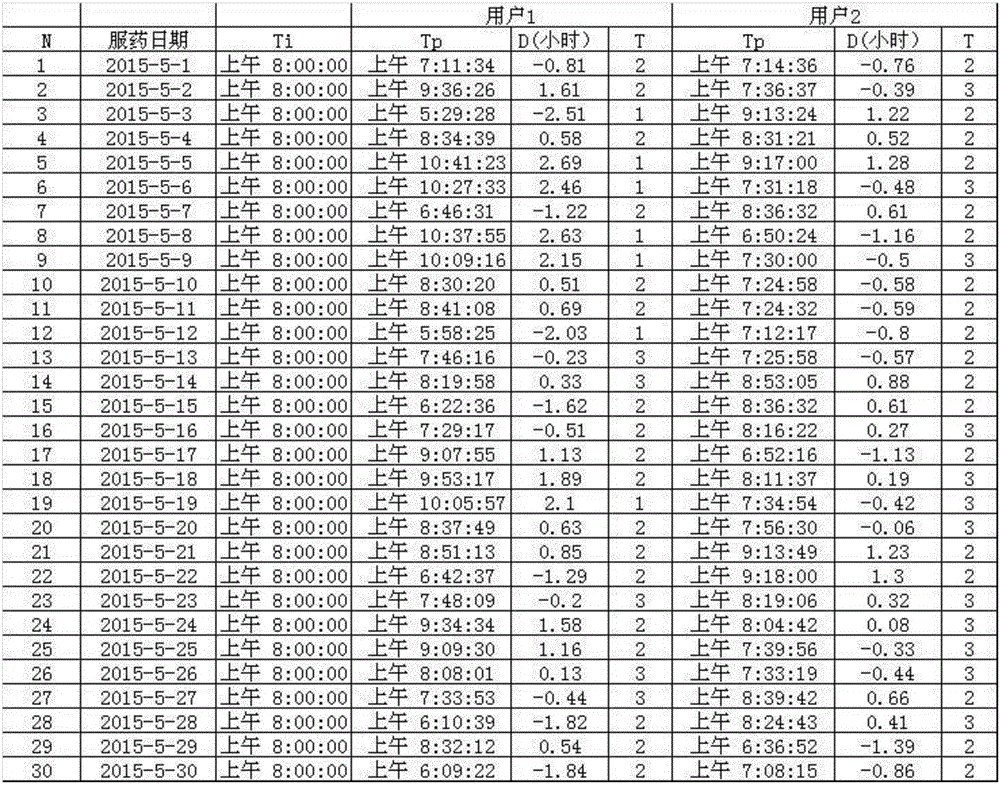
Patient medication compliance judging method
InactiveCN105701356ALinear display complianceIntuitive Adherence TrendsComputer-assisted medicine prescription/deliverySpecial data processing applicationsDrug complianceNursing
The invention discloses a method for judging a patient's medication compliance, comprising the following steps: determining the ideal medication time t i ;Record the user's actual medication time t p ;Calculate medication compliance D=t p -t i ;Judging medication compliance level T, medication compliance level T=the corresponding level of medication compliance D on the drug compliance level table; according to step (d) record the user's compliance level T within a fixed time period N , N is the number of days of taking medicine; draw a user compliance chart, the abscissa is N, and the ordinate is T N ; or calculate the average adherence of a user over a fixed period of time Judge the user's medication compliance according to the trend in the chart or the level of average compliance. It has the following advantages: it can linearly display the user's compliance, and the user's compliance trend can be seen intuitively from the linear table; because the data collected by different users is in the same time period, it is convenient for comparison of different users' compliance .
Owner:黄文佳
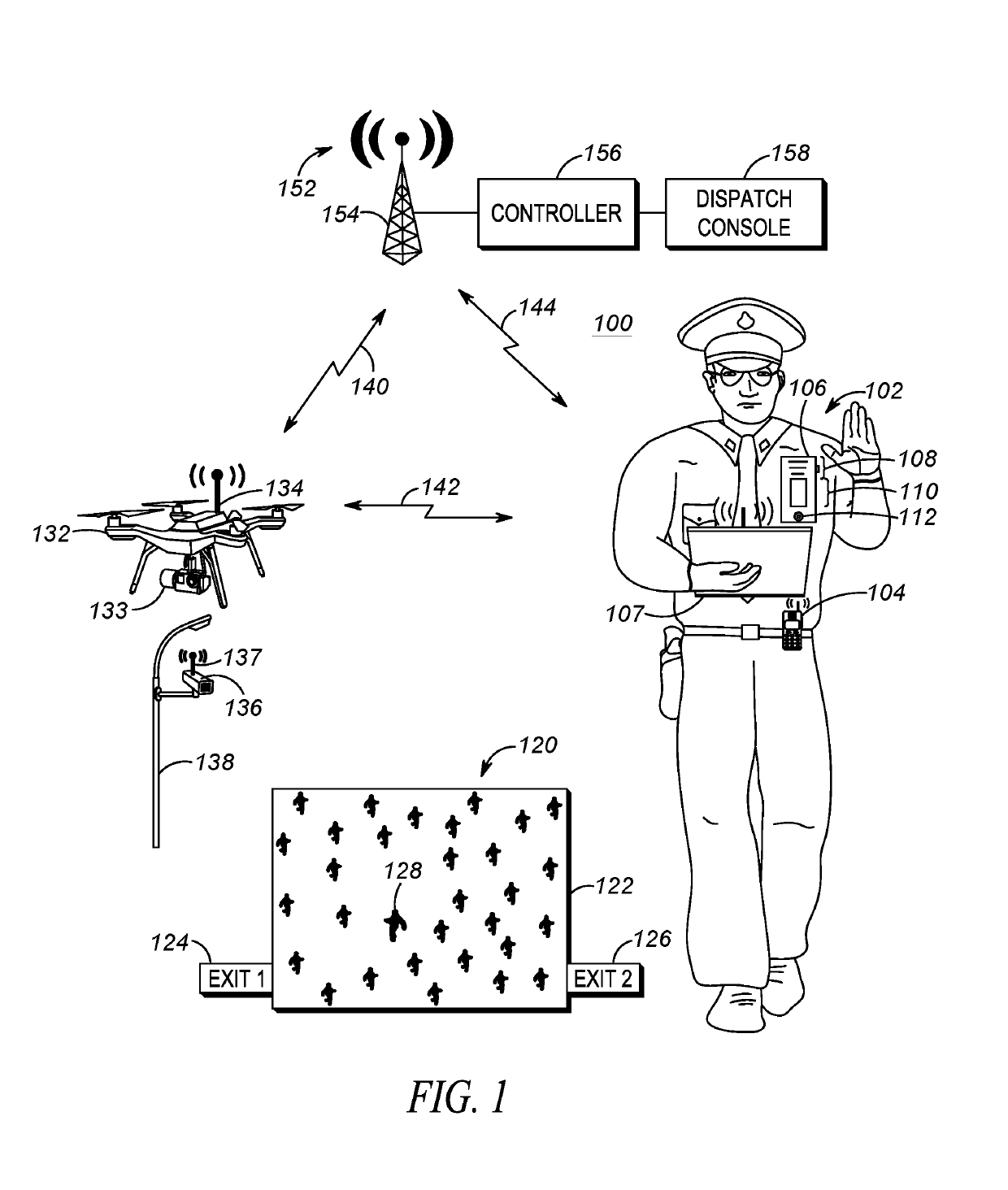
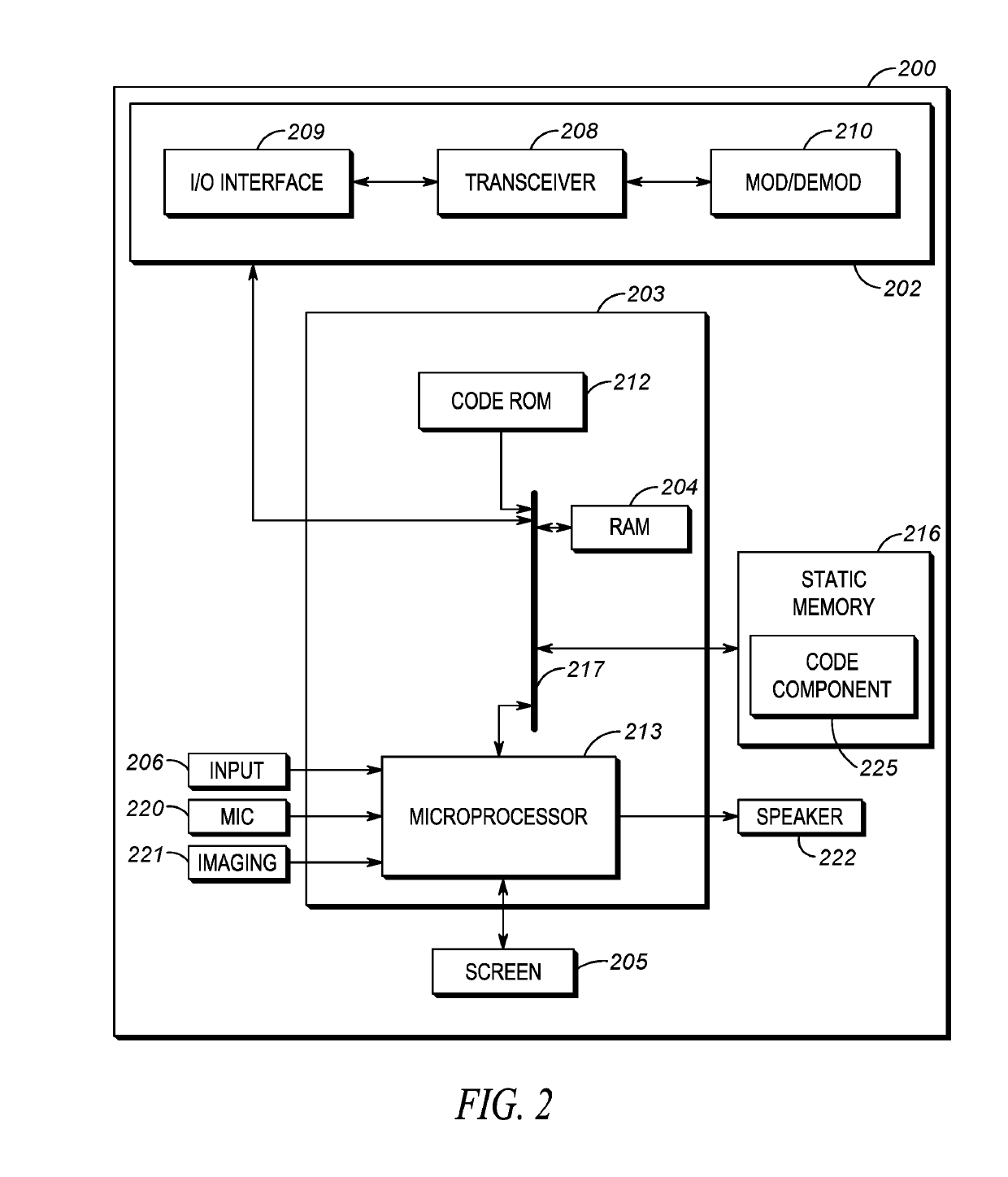
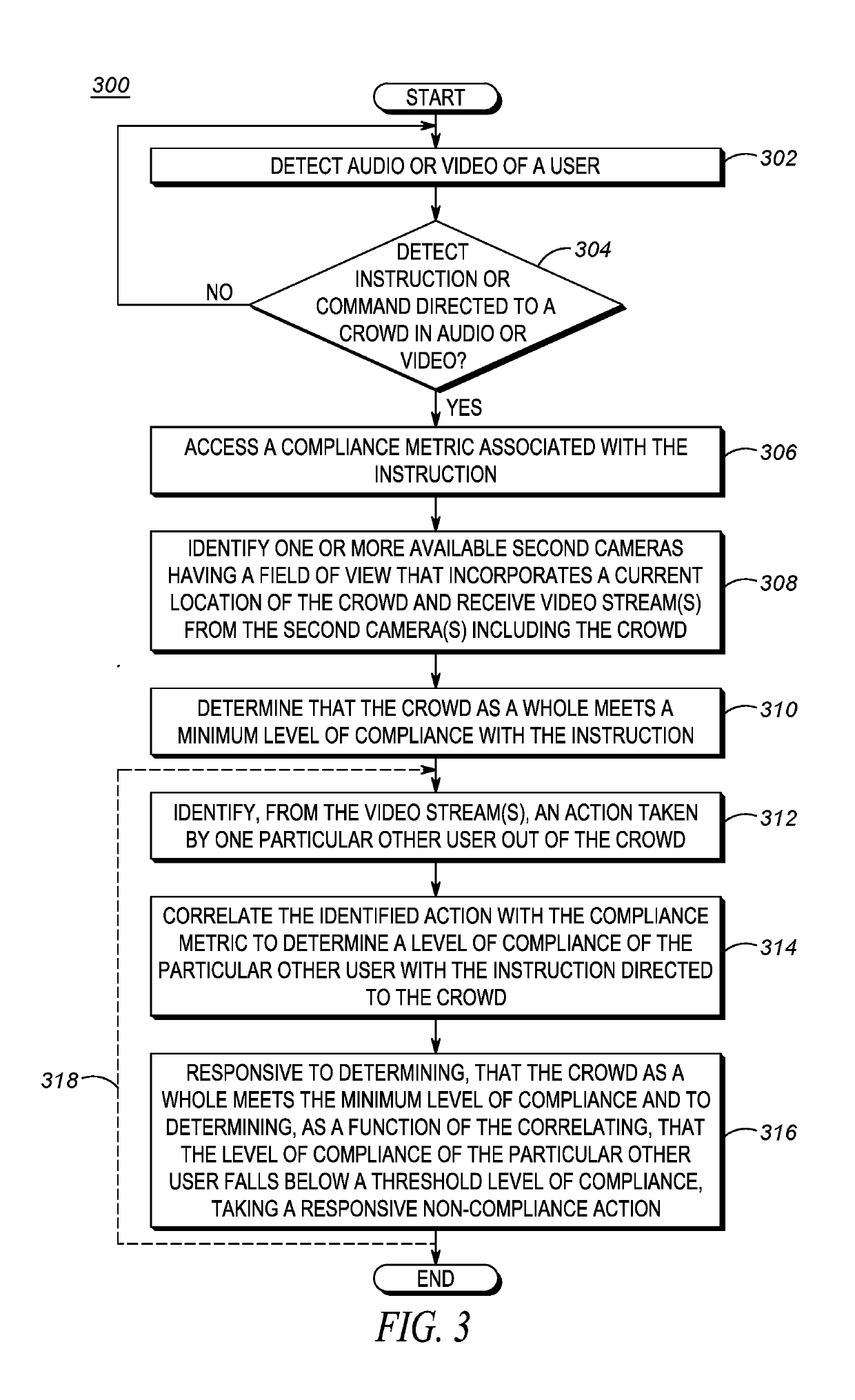
Guardian system in a network to improve situational awareness at an incident
A process for improving situational awareness at an incident scene includes first receiving audio or video of a user and detecting, in one or both of the audio and video, an instruction directed to a crowd. A compliance metric associated with the instruction is then accessed and one or more available second cameras having a field of view that incorporates a current location of the crowd are identified. One or more video streams from the second cameras are received that include the crowd. From the one or more video streams, determinations are made that the crowd as a whole meets a minimum level of compliance with the instruction and that a level of compliance of a particular other user in the crowd has fallen below a threshold level of compliance. In response, a computing device performs a noncompliance action.
Owner:MOTOROLA SOLUTIONS INC
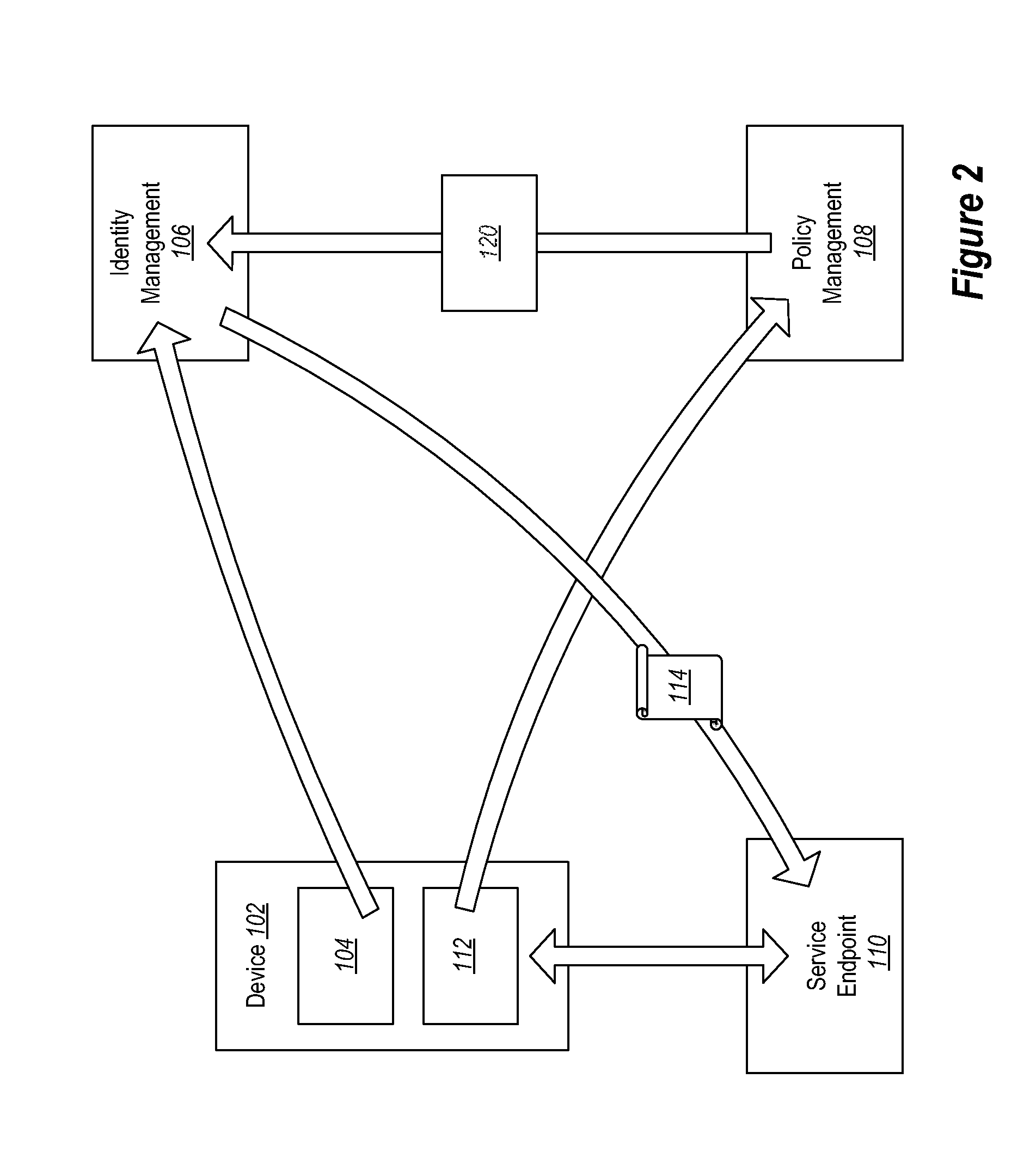
Conditional access to services based on device claims
Providing access to one or more resources to a user device. A method includes at a user device, registering with an identity service to obtain an identity credential. The method further includes at the user device, registering with a policy management service by presenting the identity credential. The method further includes at the user device, providing an indication of current state of the user device to the policy management service. The policy management service can then indicate to the identity service the compliance level of the user device. The method further includes the user device receiving a token from the identity service based on the policy management level of the user device as compared to a policy set.
Owner:MICROSOFT TECH LICENSING LLC
Enterprise console
ActiveCN1791871AEasy to measureMultiple digital computer combinationsProgram loading/initiatingSubject matterCritical system
Owner:IBM CORP
Method for detecting ineligibility of a beneficiary and system
Owner:WILLARD MARY JOAN +1
System for assessing procedure compliance level of human operators in nuclear power plants and method thereof
Disclosed are a system for assessing the procedure compliance level of a human operator in a nuclear power plant, which quantitatively detects if the human operator complies with a standard procedure written in an emergency procedure guideline for the nuclear power plant, and a method thereof. The system includes a first recognizing unit attached to each of human operators, a second recognizing unit that is mounted on each of nuclear power equipments and able to make communication with the first recognizing unit, a database storing information of a standard procedure to be performed by the human operator with respect to the nuclear power equipment, and a server that is able to make communication with the second recognizing unit, and assesses the standard procedure stored in the database and an actual procedure performed by the human operator, which is received from the second recognizing unit.
Owner:KOREA ATOMIC ENERGY RES INST +1
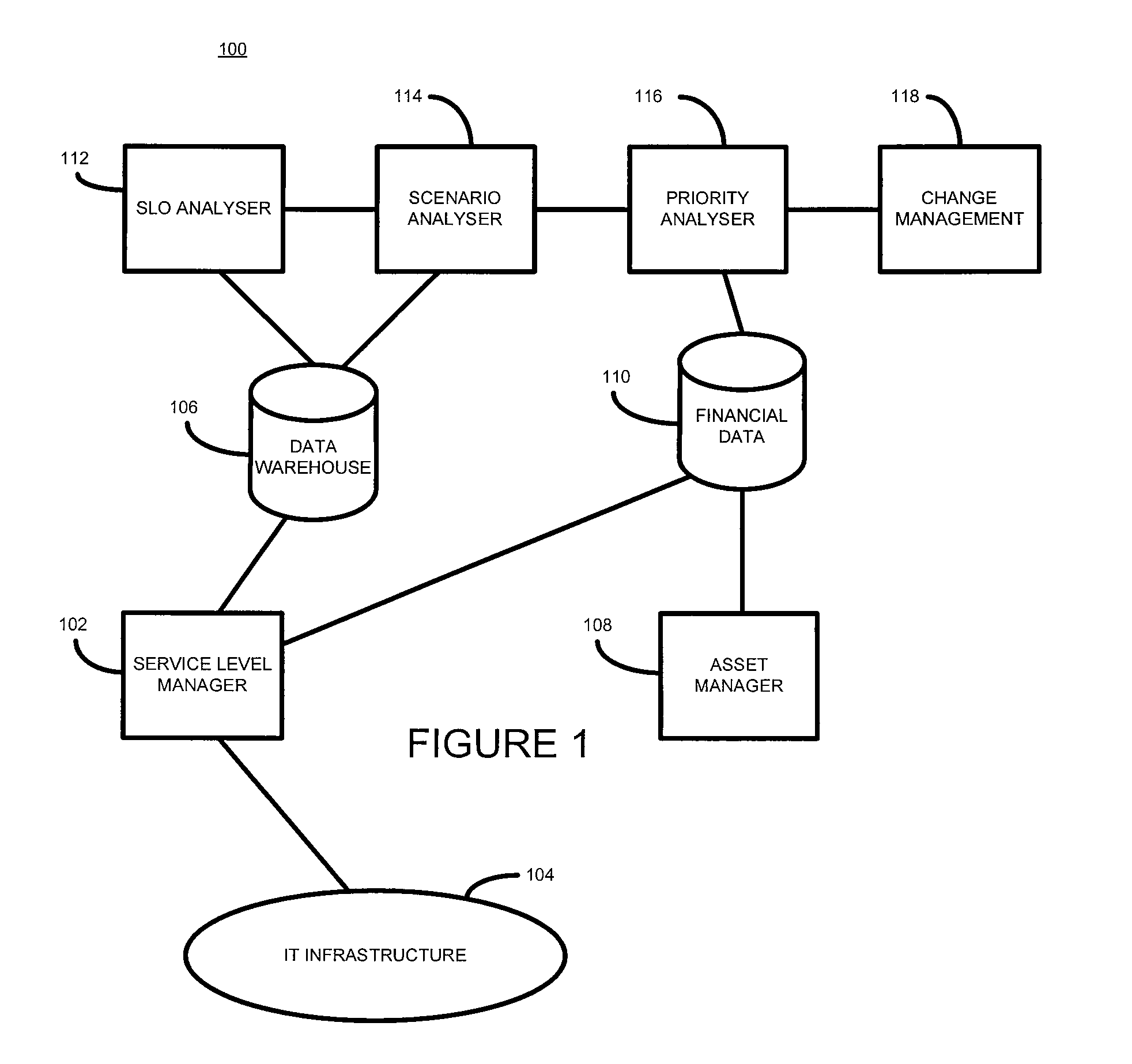
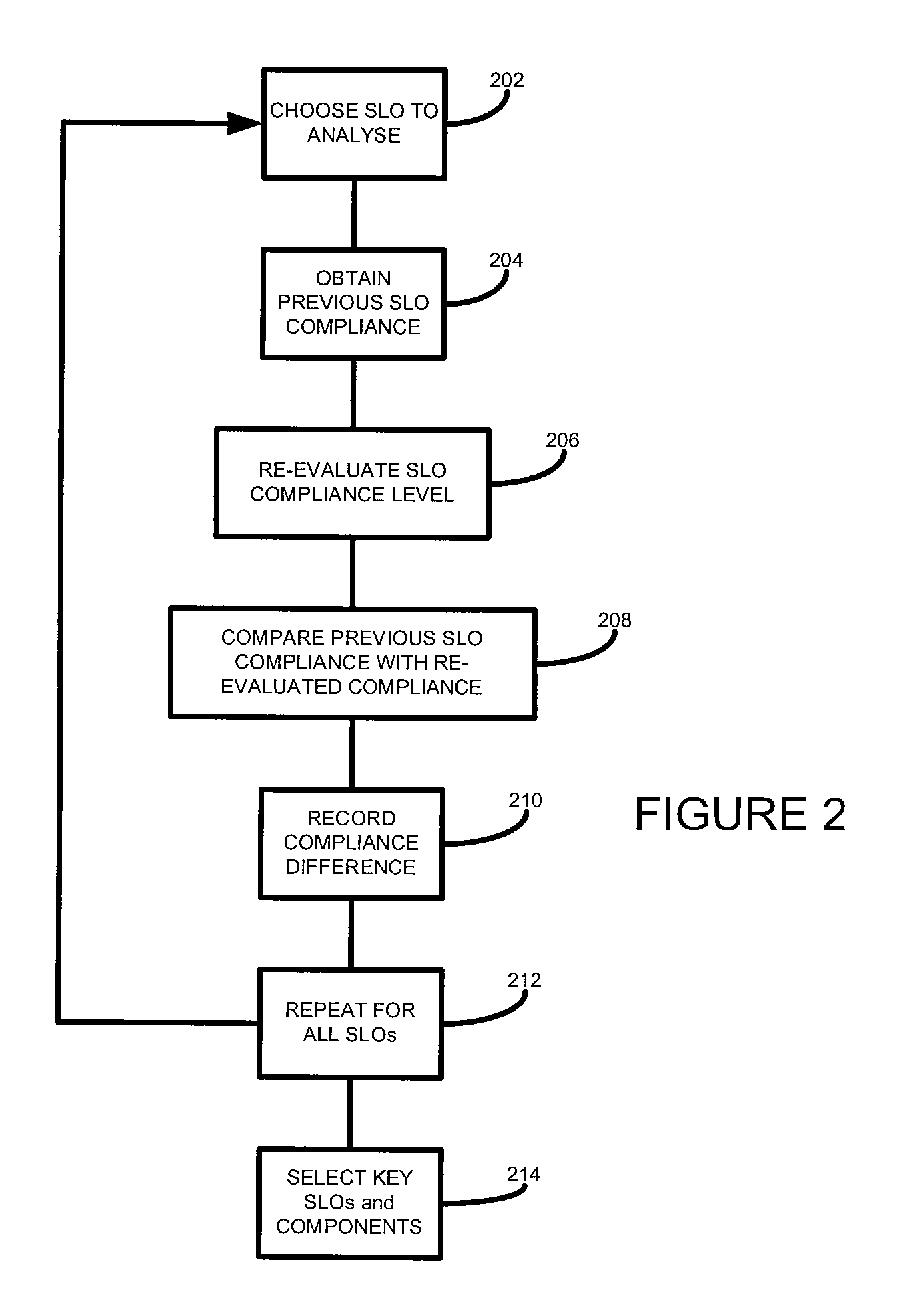
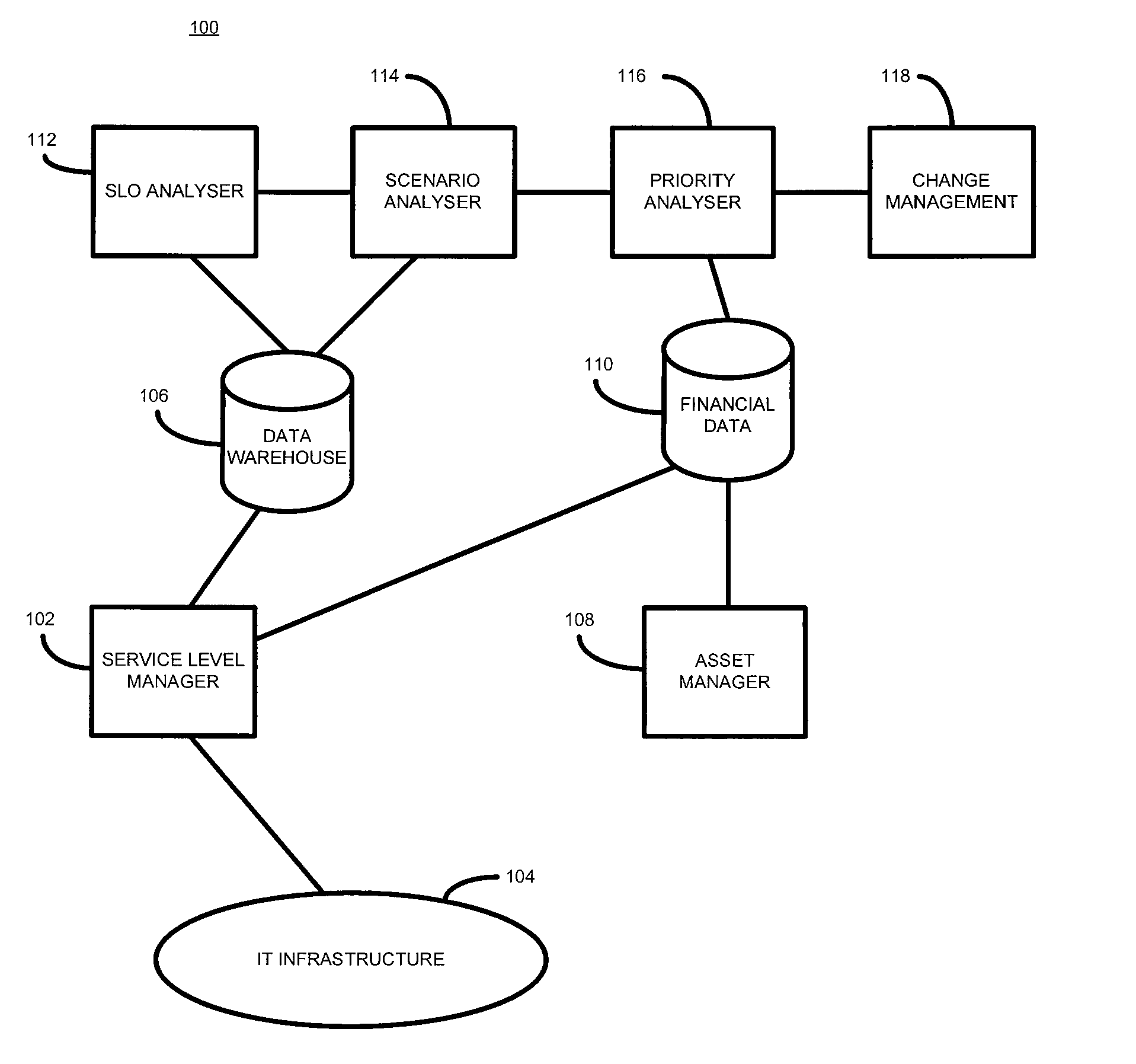
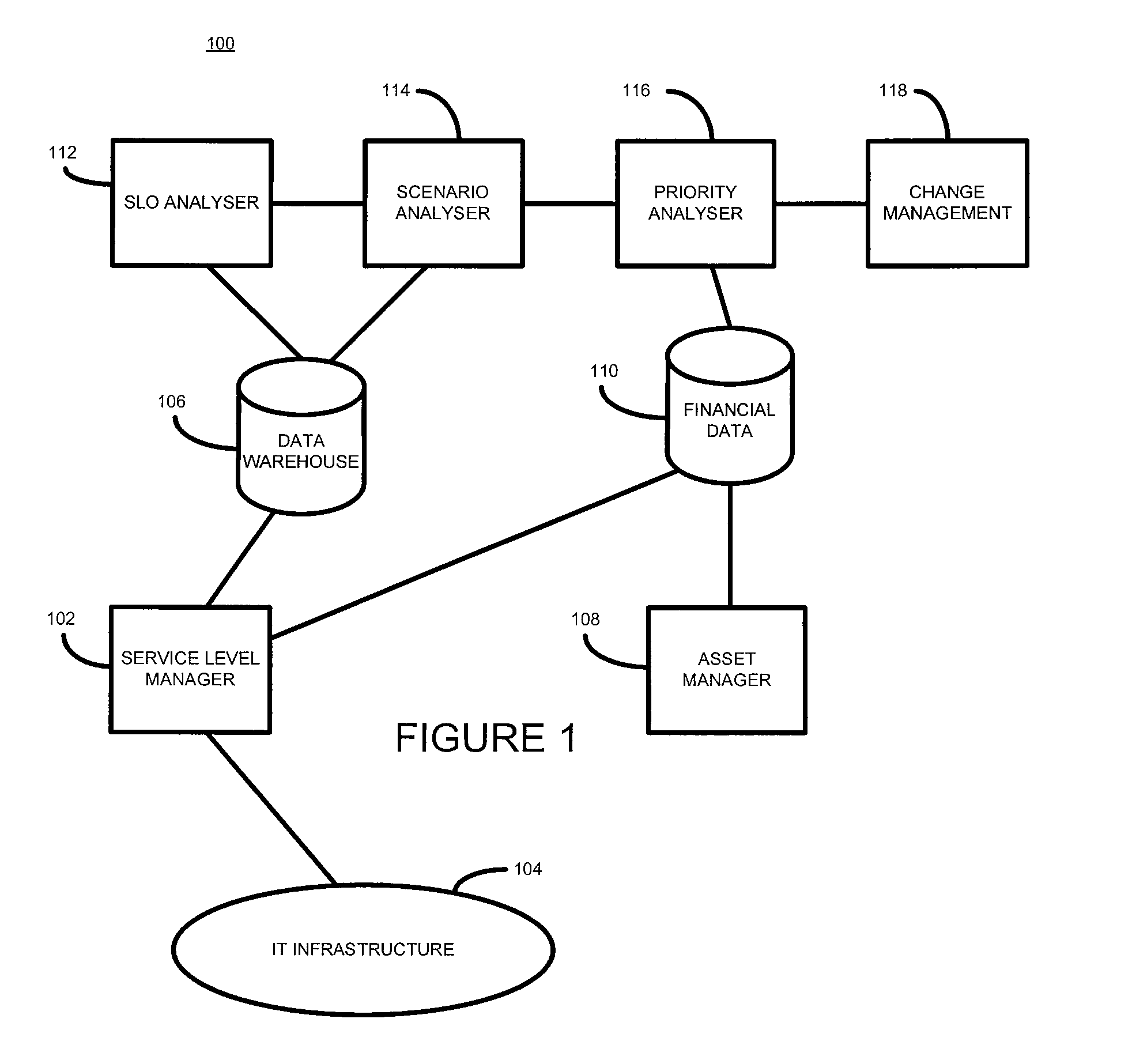
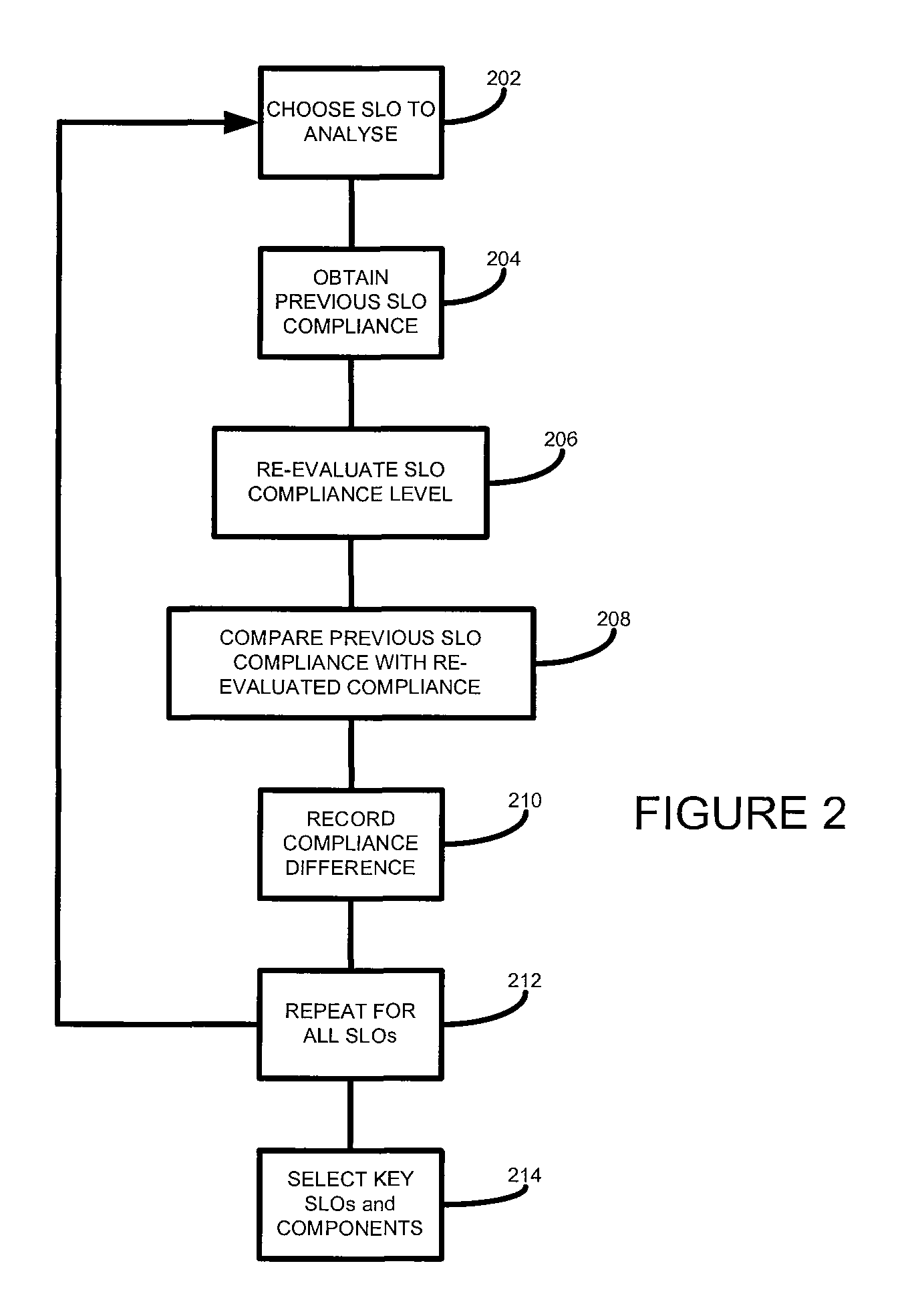
Computer networks
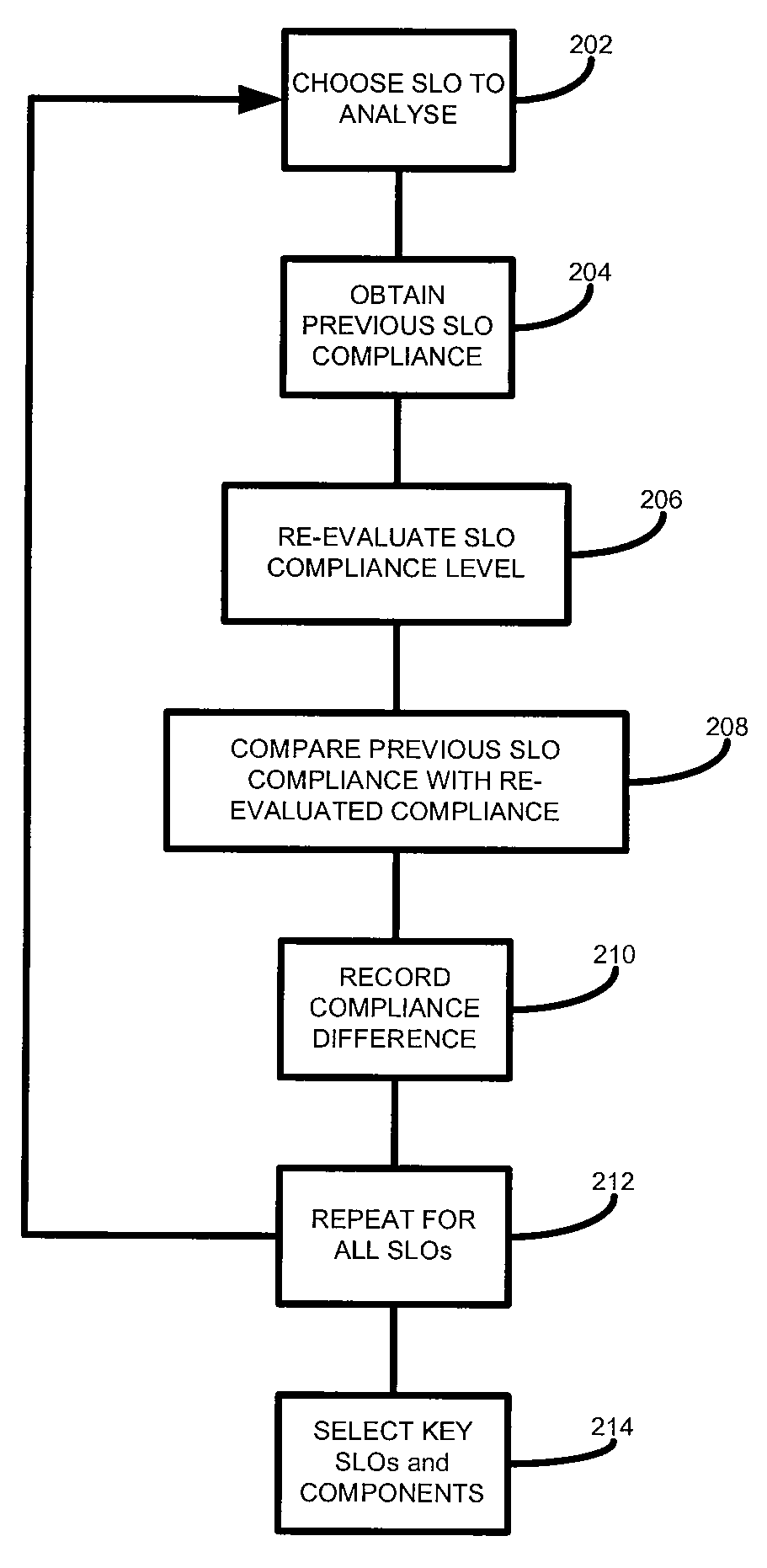
ActiveUS20080208653A1Suitable for modificationResourcesTransmissionQuality levelService level objective
According to one embodiment of the present invention, there is provided a method of analysing a computer infrastructure providing a service, an intended quality level of the service being defined by at least one service level objective defining a service level quality objective and a related compliance level, the computer infrastructure comprising a plurality of components, the method comprising: obtaining first service level objective compliance data for a selected service level objective, the compliance data being calculated using data collected from the computer infrastructure; calculating second service level objective compliance data for the selected service level objective using in part the collected data and for a selected service level quality objective a value that meets that objective; calculating a difference between the first and second data; and identifying, based on the calculated difference, one or more components suitable for modification.
Owner:MICRO FOCUS LLC
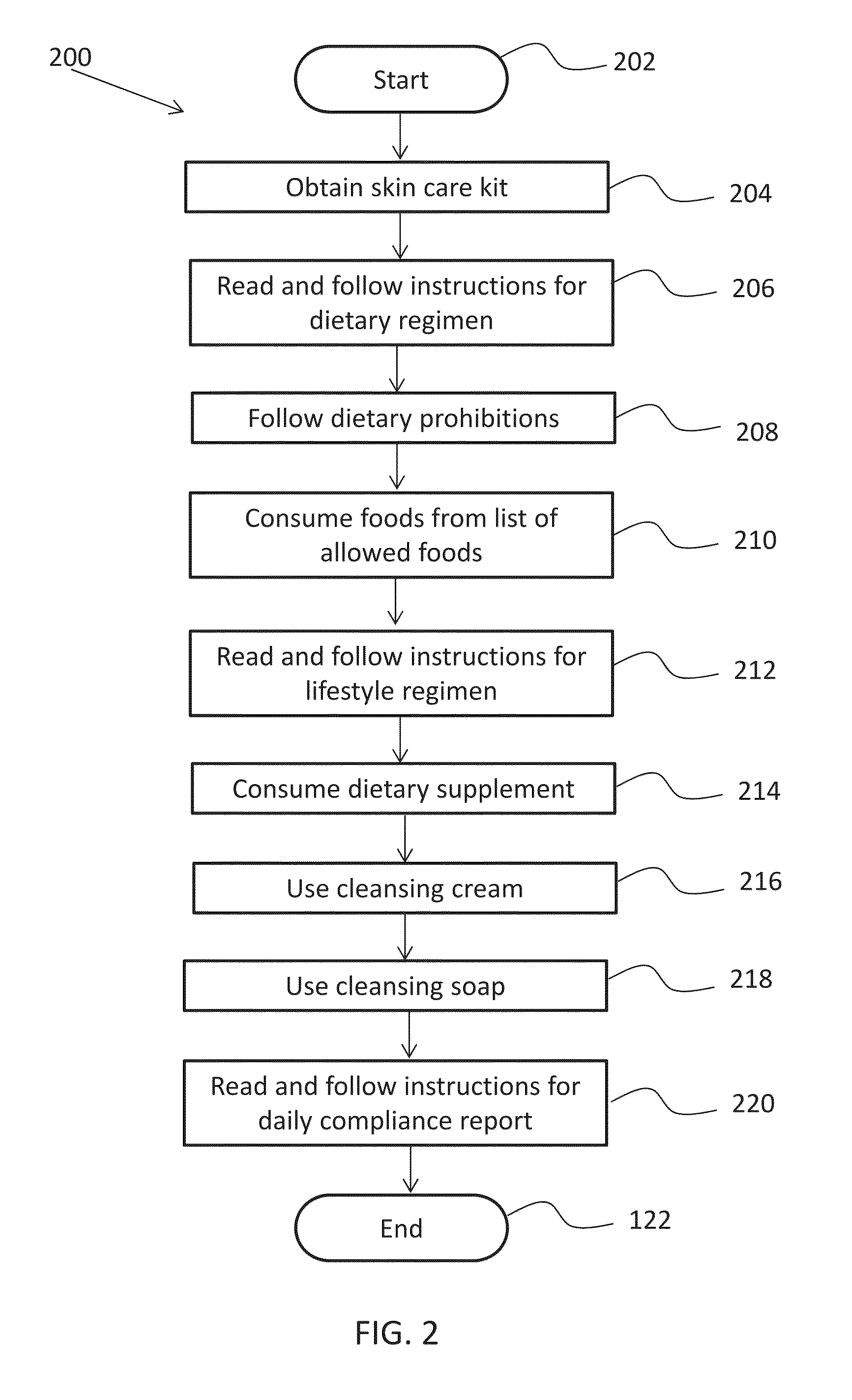
Skin care method and kit
A skin care method and kit is disclosed that includes instructions for a dietary skin care regimen. The regimen includes a list of prohibited and allowed foods. The list of prohibited foods includes red meat, chocolate, eggs, confections, alcoholic beverages, shellfish, fried foods, and tomatoes. The list of allowed foods includes chicken, turkey, non-fried fish, vegetables, fruit other than a tomato, and olive oil as a salad dressing. The skin care kit further includes a compliance report including the list of prohibited and allowed foods with corresponding data input fields for each food in the list of prohibited and allowed foods. The user indicates an amount of each prohibited and allowed food item consumed by the user in the corresponding data input field. A compliance rating system is disclosed in which the total number of servings of prohibited and allowed foods consumed by the user determines the user's compliance level.
Owner:ELEVATOR LAB
Navigation system with compliance reporting and method of operation thereof
A method of operation of a navigation system includes: collecting a driving behavior for determining a driving profile of a vehicle; acquiring a compliance indicator for measuring a total usage of the vehicle; calculating a compliance level based on a monitoring usage level and the compliance indicator; generating a driving score based on the driving profile having an assessment event detected based on the driving behavior; and calculating a driving rating based on the driving score and the compliance level for displaying on a device.
Owner:TELENAV INC
Characterizing cable leakage interference priorities on LTE
A method and structure for conforming to cable leakage compliance level requirements includes calculating, using a processor on a computer, a priority of repairs for cable leakage over a cable operator service area. A result of the priority calculation is provided, thereby permitting higher priority leaks to be identified and repaired. The calculating of priority includes storing geographical locations of cell towers affecting a service area being evaluated, receiving data related to cable leakage sources, receiving data related to wireless service quality, if available, and exercising, using the processor on the computer, a prioritizing algorithm that calculates a relative severity of each cable leakage source.
Owner:COMSONICS
Computer networks
According to one embodiment of the present invention, there is provided a method of analyzing a computer infrastructure providing a service, an intended quality level of the service being defined by at least one service level objective defining a service level quality objective and a related compliance level, the computer infrastructure comprising a plurality of components, the method comprising: obtaining first service level objective compliance data for a selected service level objective, the compliance data being calculated using data collected from the computer infrastructure; calculating second service level objective compliance data for the selected service level objective using in part the collected data and for a selected service level quality objective a value that meets that objective; calculating a difference between the first and second data; and identifying, based on the calculated difference, one or more components suitable for modification.
Owner:MICRO FOCUS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com