Patents
Literature
224 results about "Critical system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
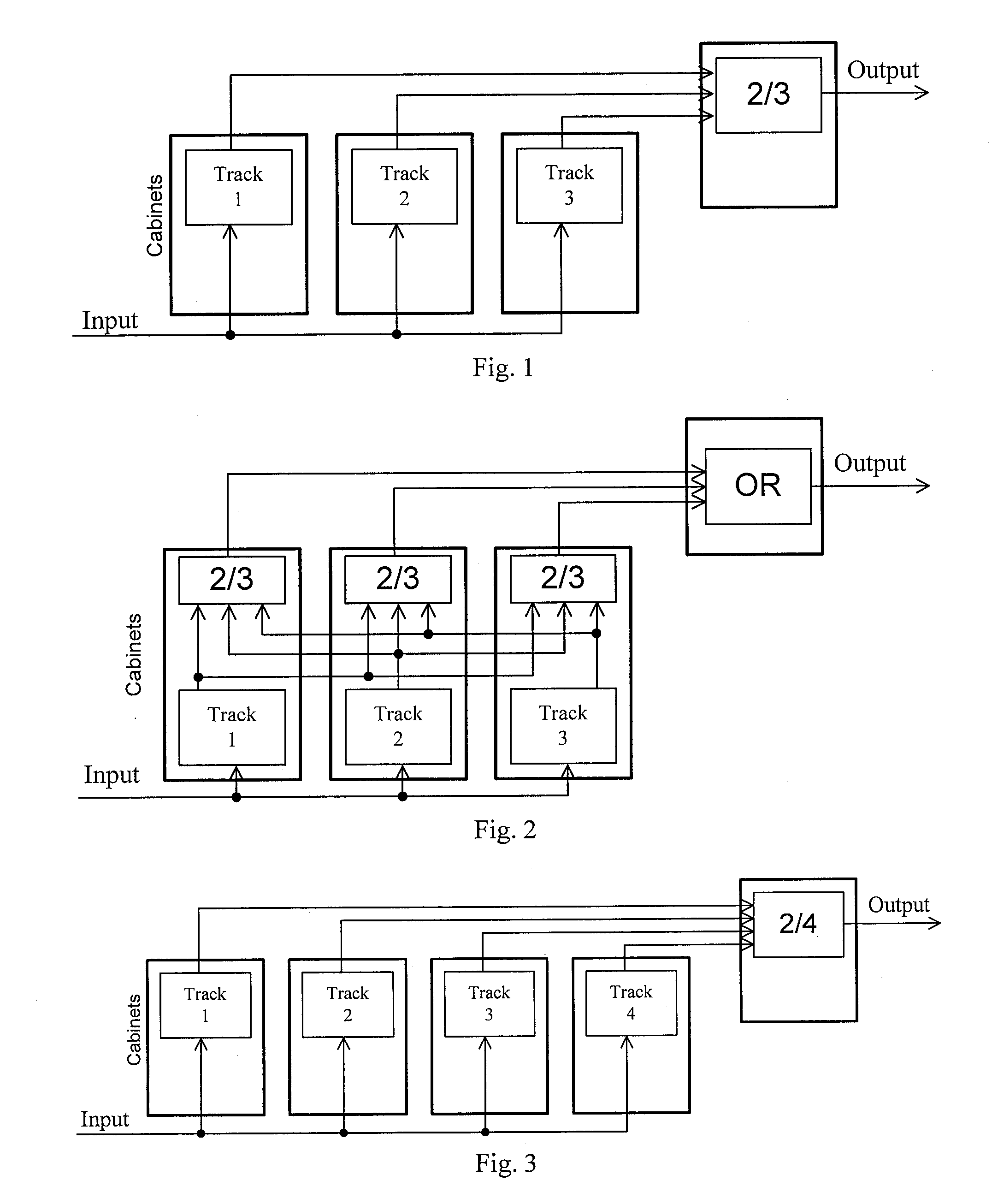
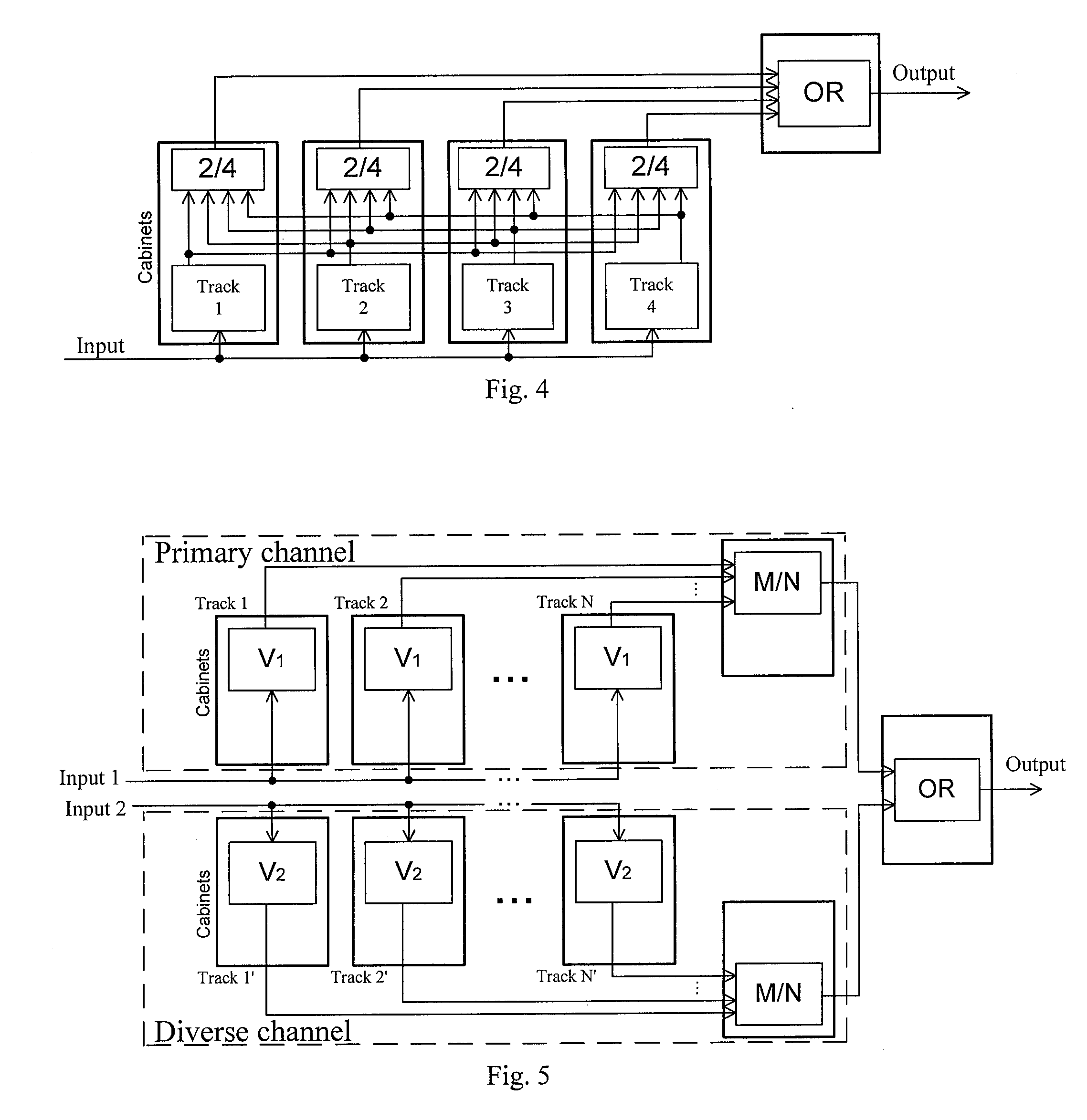
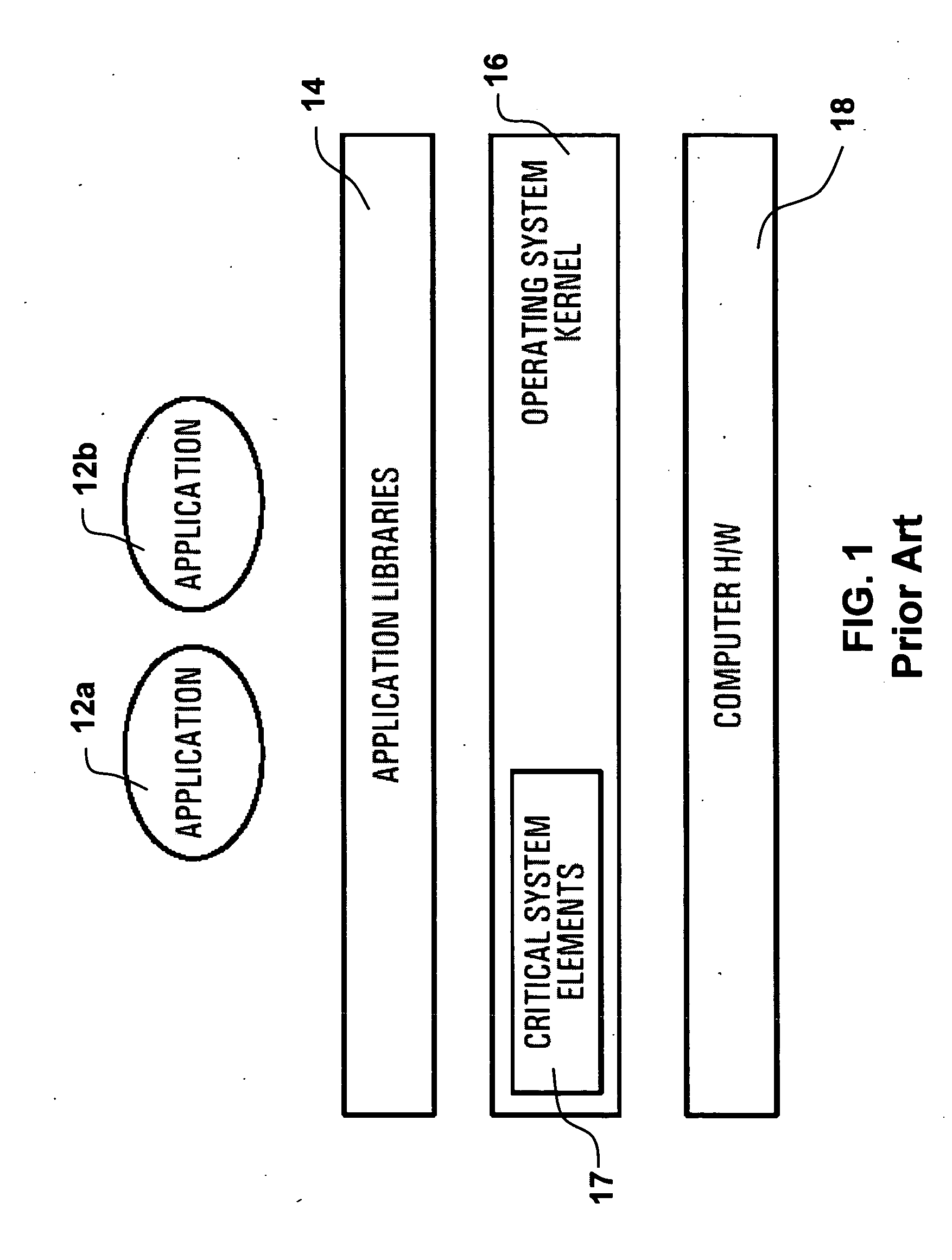
A critical system is a system which must be highly reliable and retain this reliability as they evolve without incurring prohibitive costs. There are four types of critical systems: safety critical, mission critical, business critical and security critical.
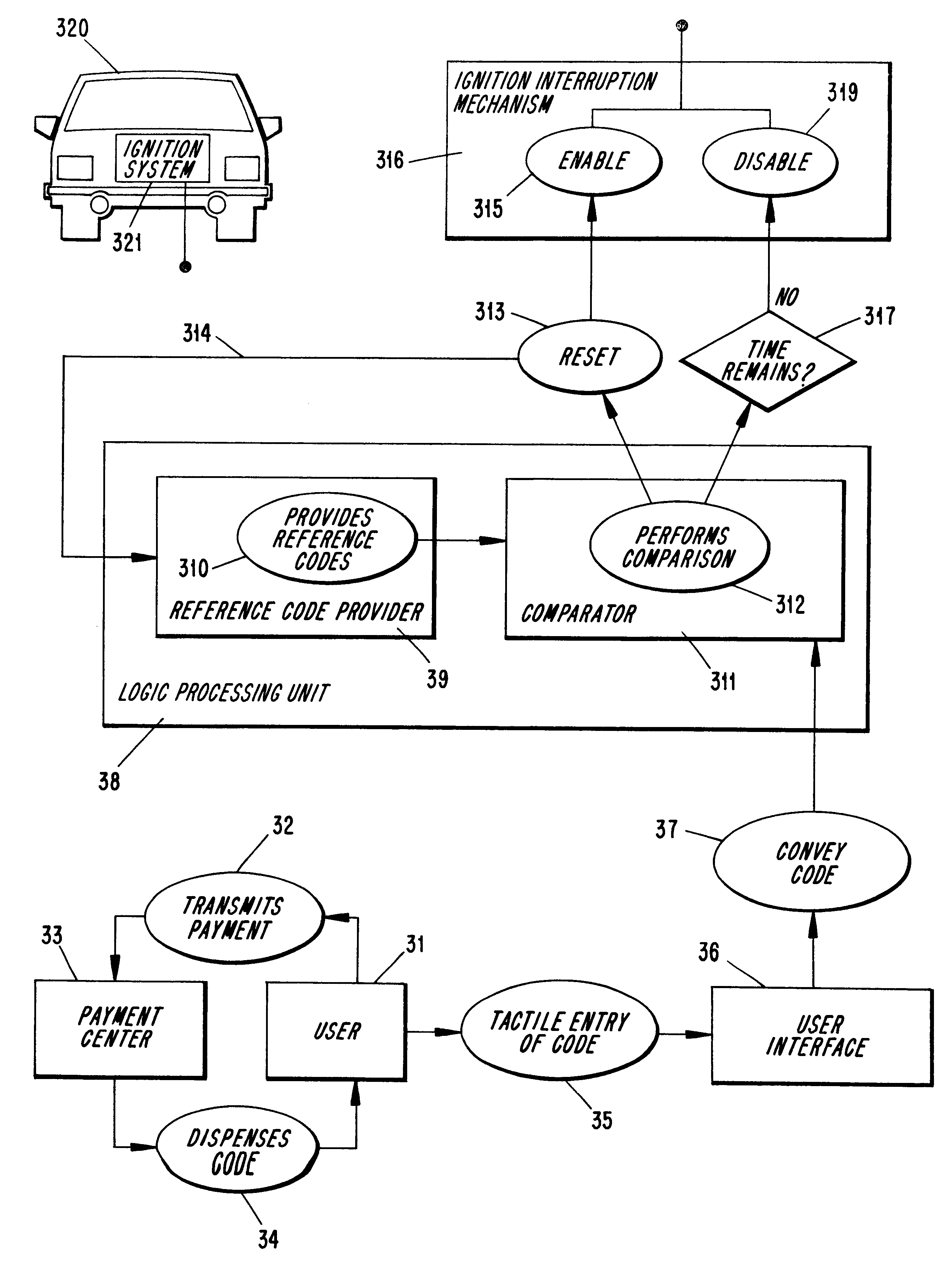
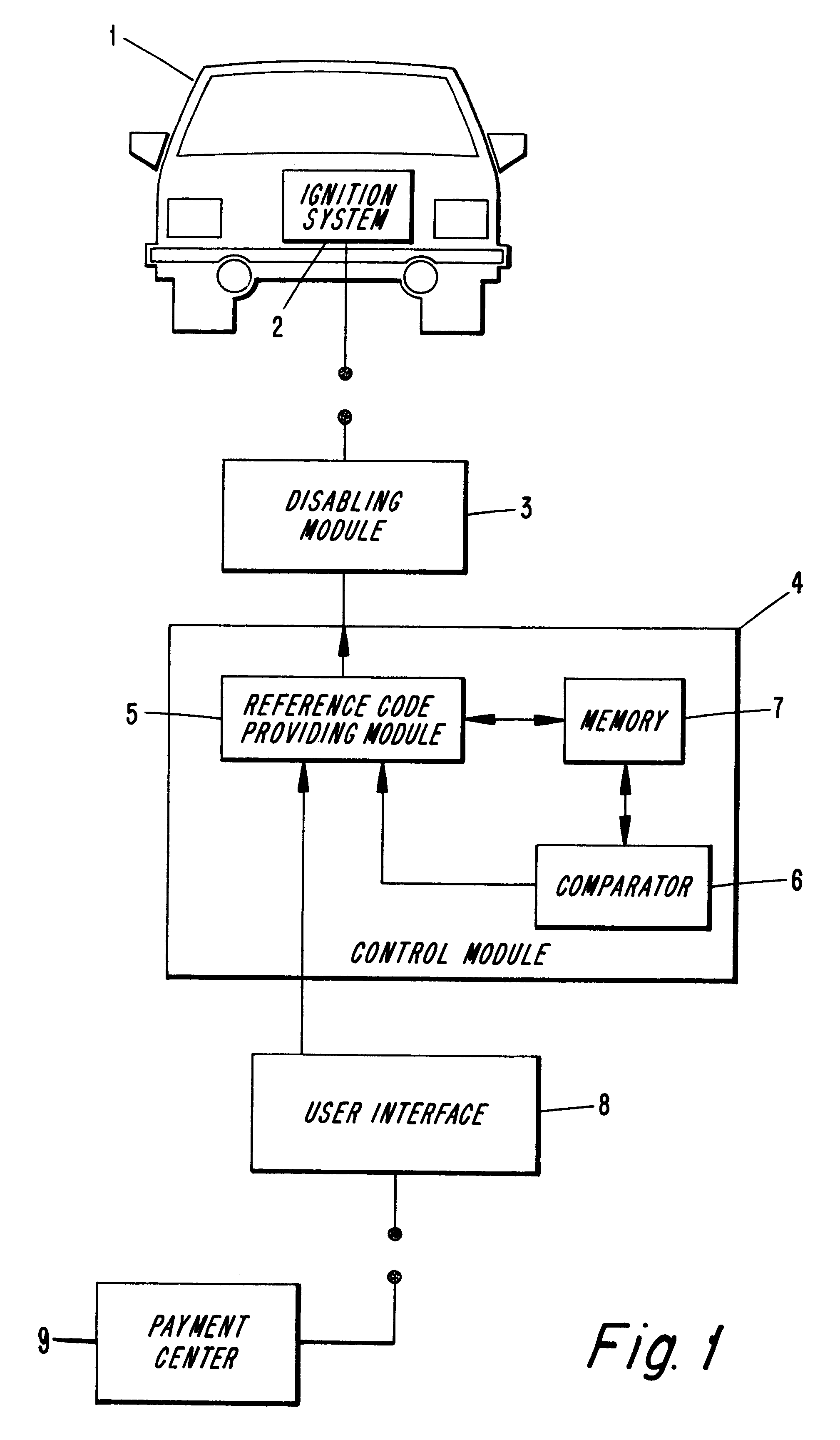
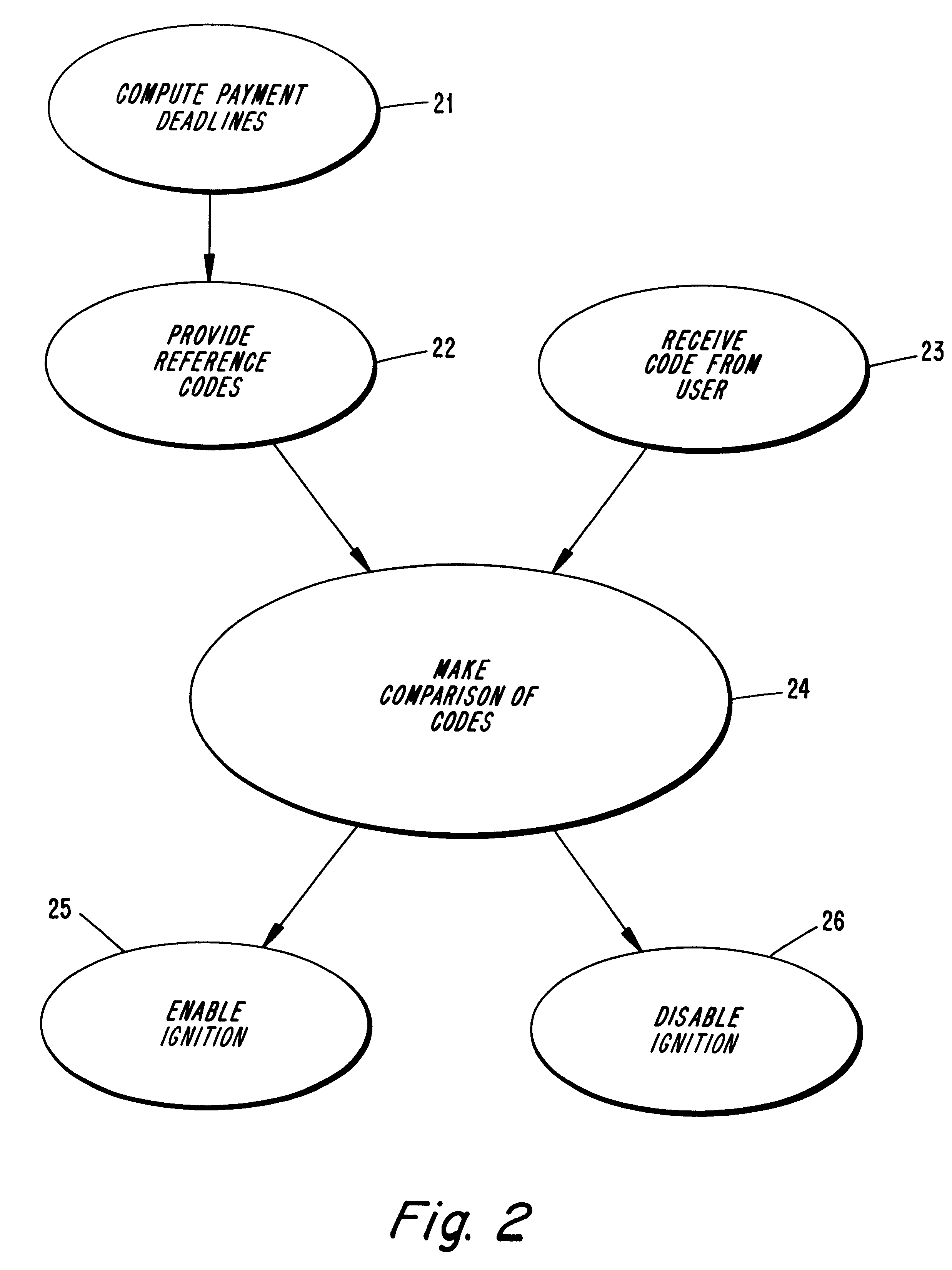
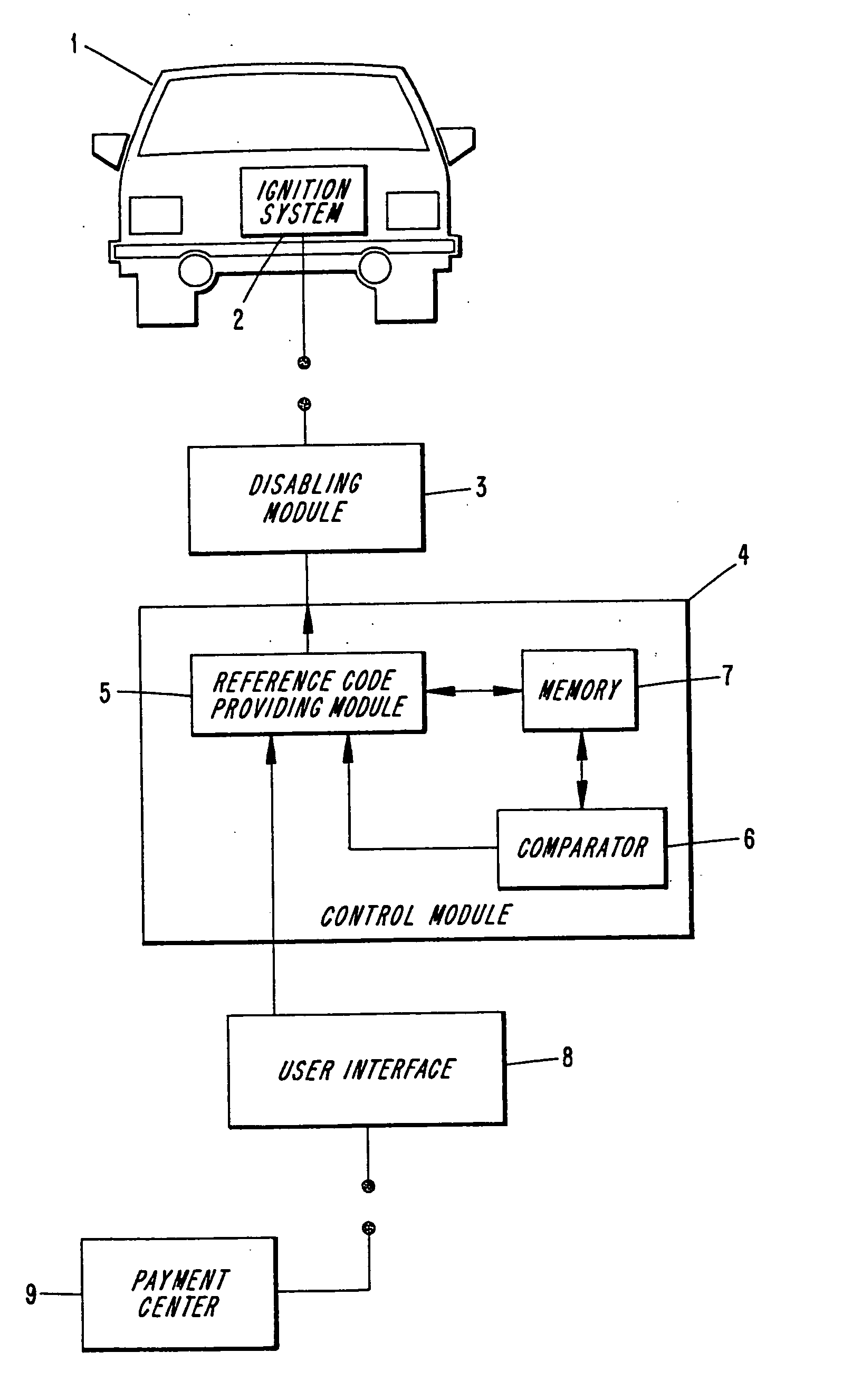
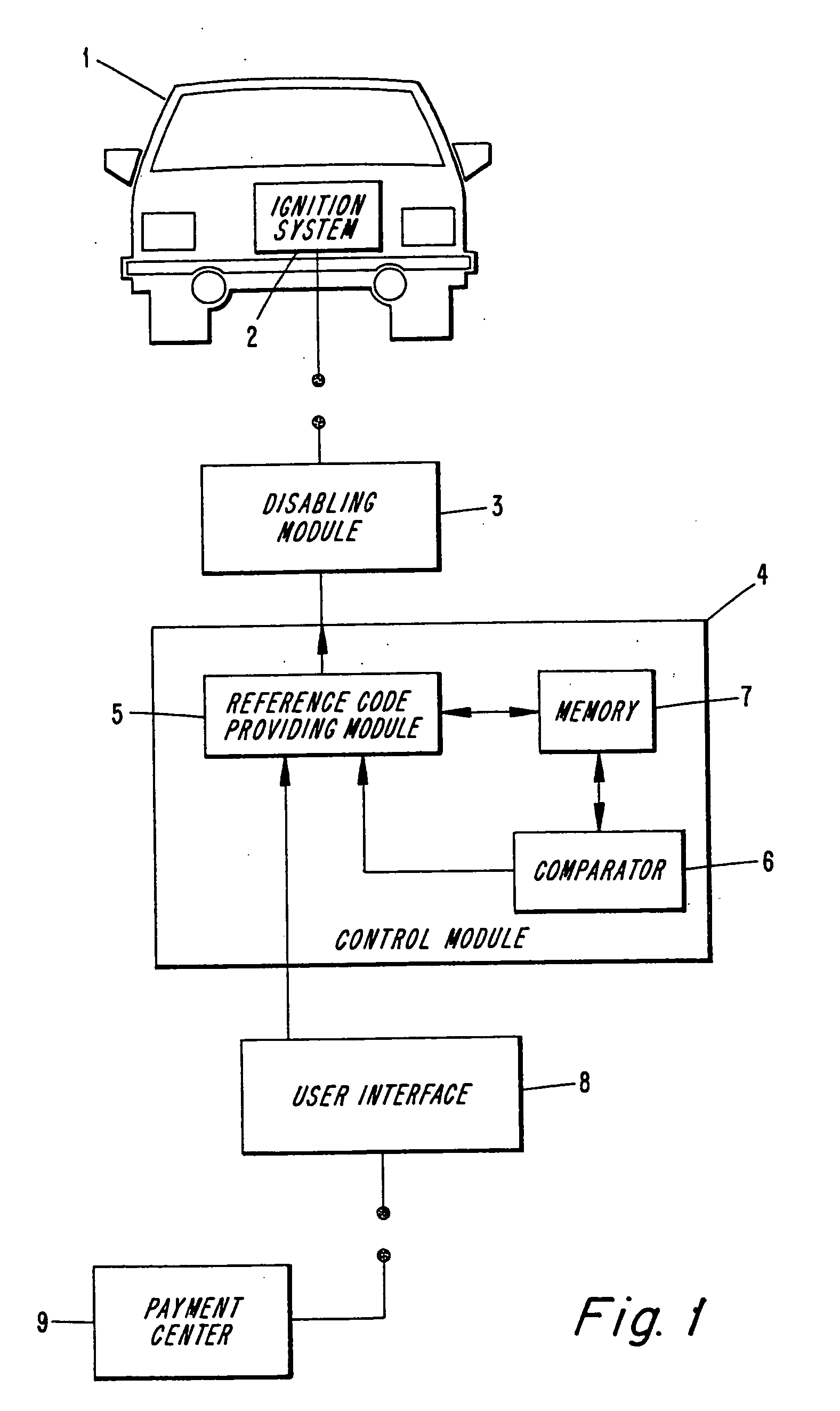
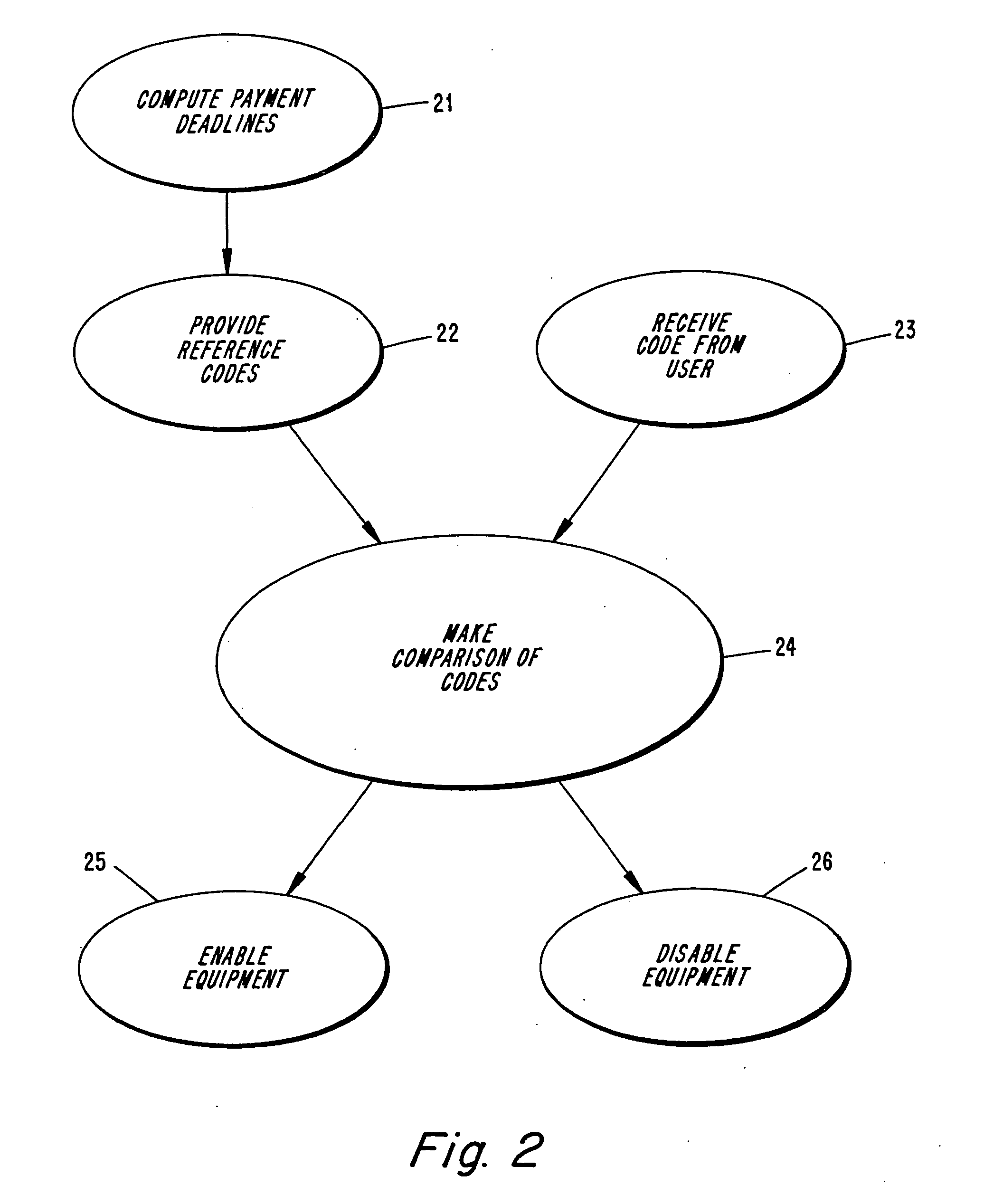
Loan repay enforcement system
InactiveUS6195648B1Improve timely repaymentElectric signal transmission systemsTicket-issuing apparatusOperator interfacePayment
A system to encourage on time repayment of loans includes electronic apparatus coupled to a critical system of certain equipment; for example, the ignition system of an automobile. Apparatus includes mechanism whereby a user-operator is able to enter a code. Entry of a correct code serves as indication that a payment has been made and enables further use of the equipment. On failure to timely make payments, a user is prevented from using the equipment as the apparatus is arranged to disable the equipment by way of the critical system to which it is coupled. Both a user-operator interface and critical system interruption circuit are coupled to a logic processor which is easily mounted onto equipment subject to the program.
Owner:MUELLER RON +1
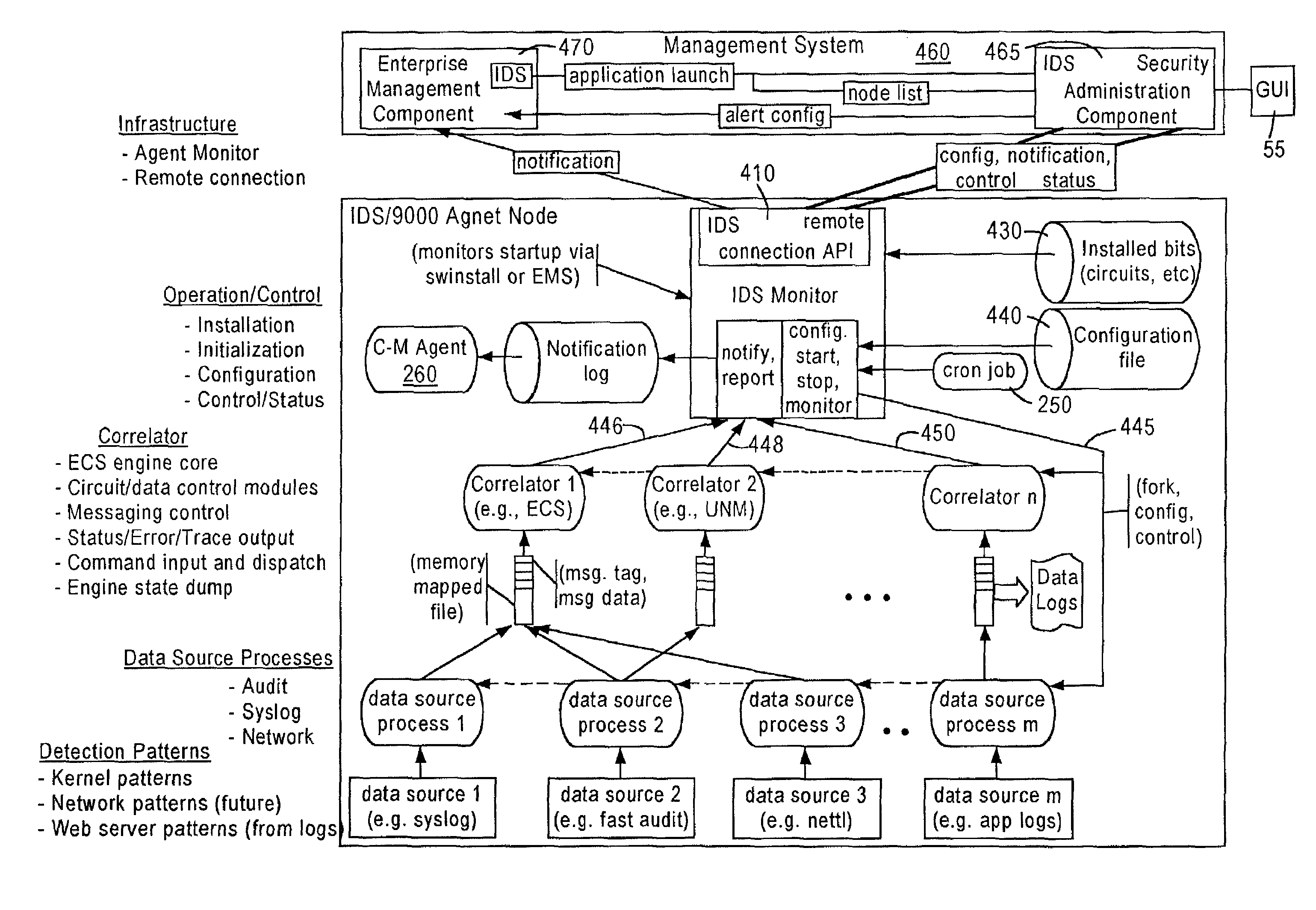
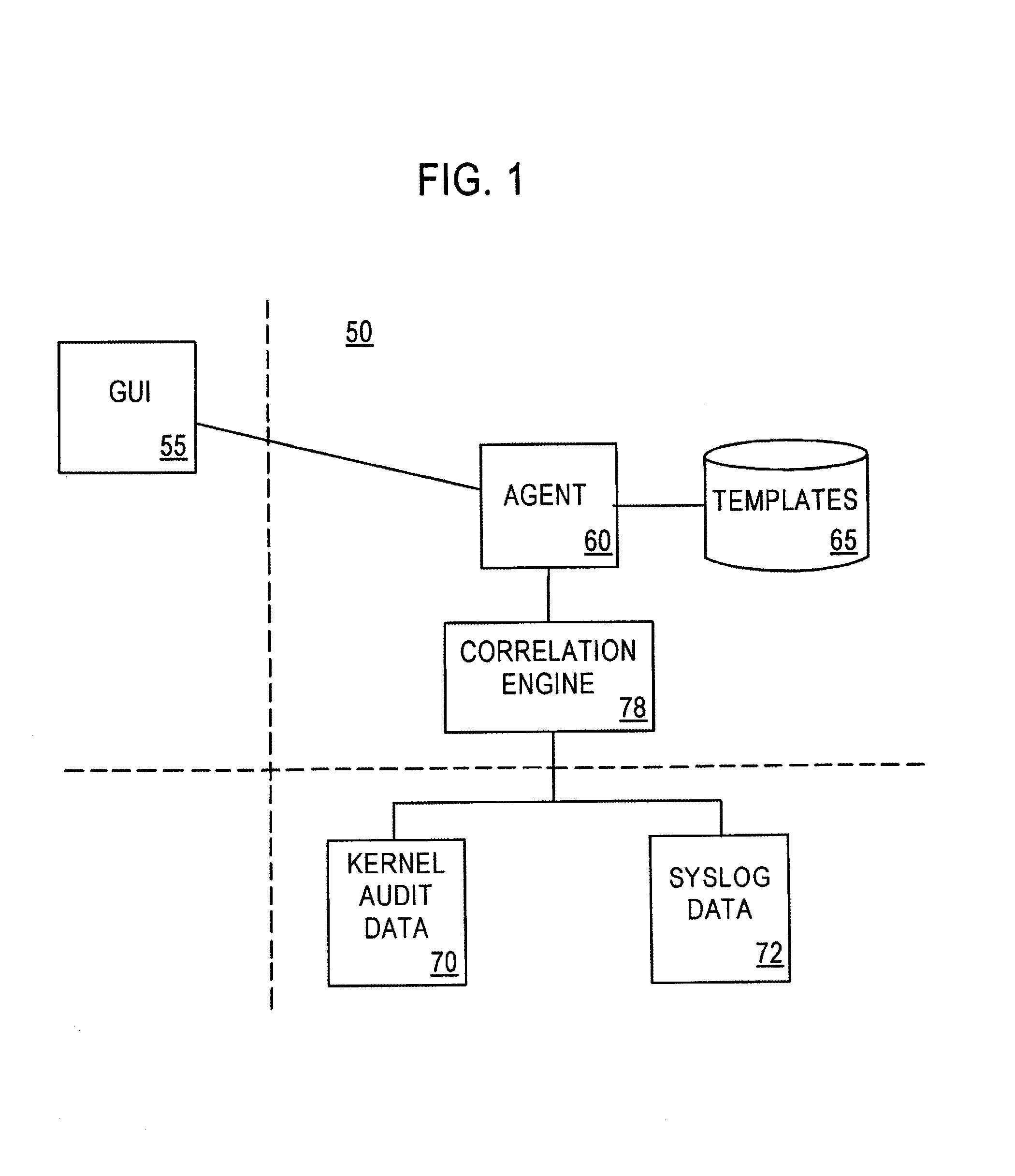
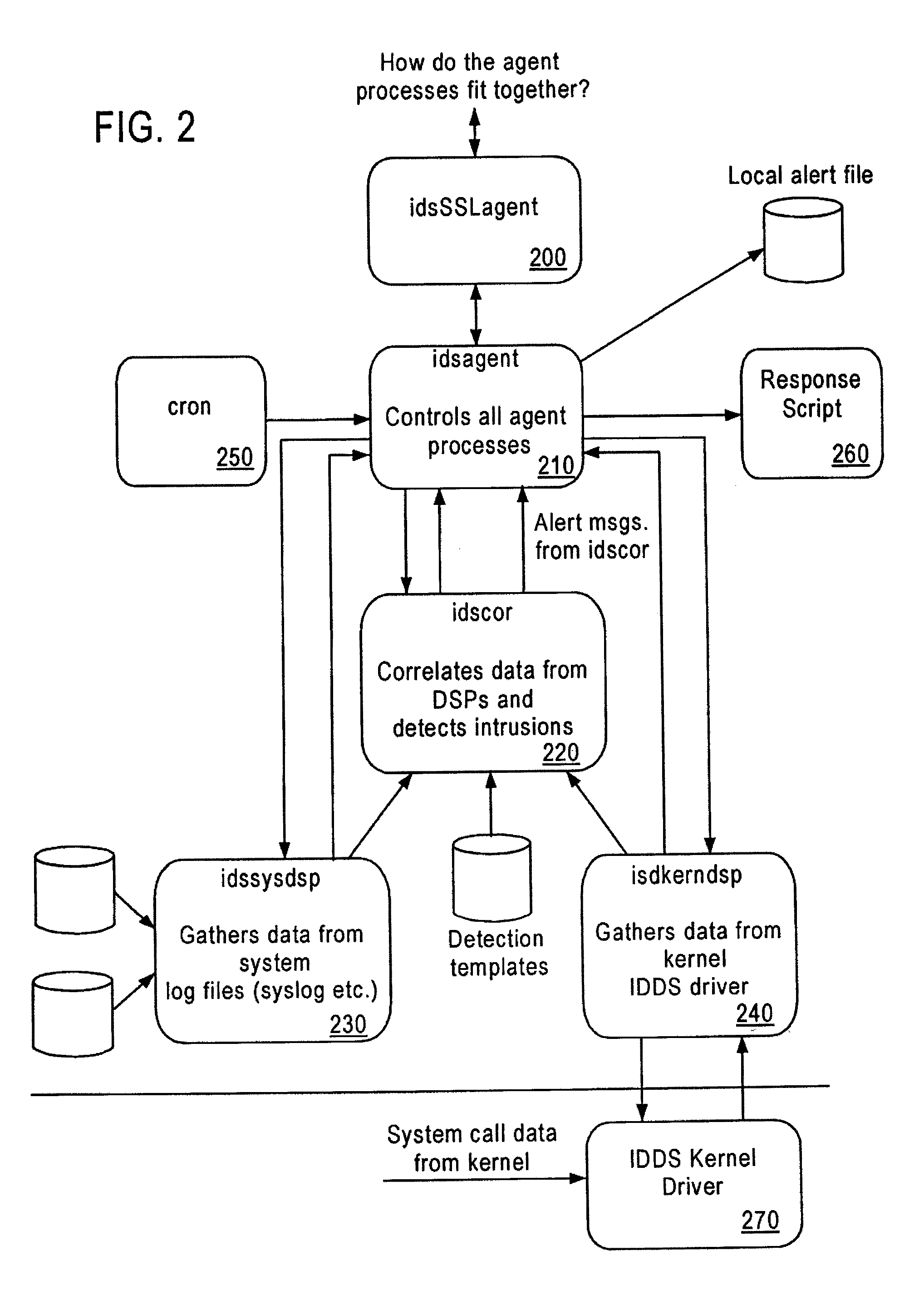
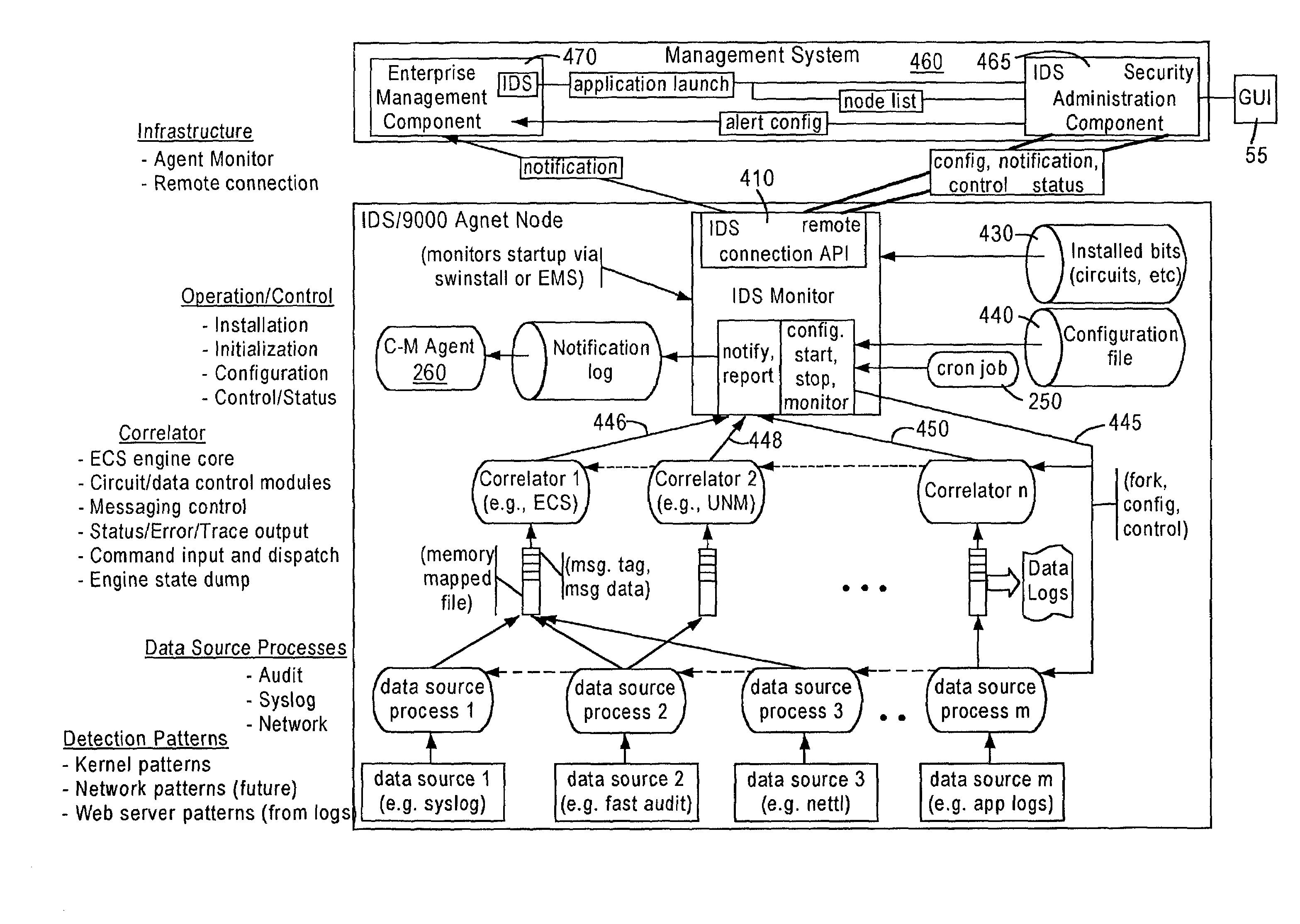
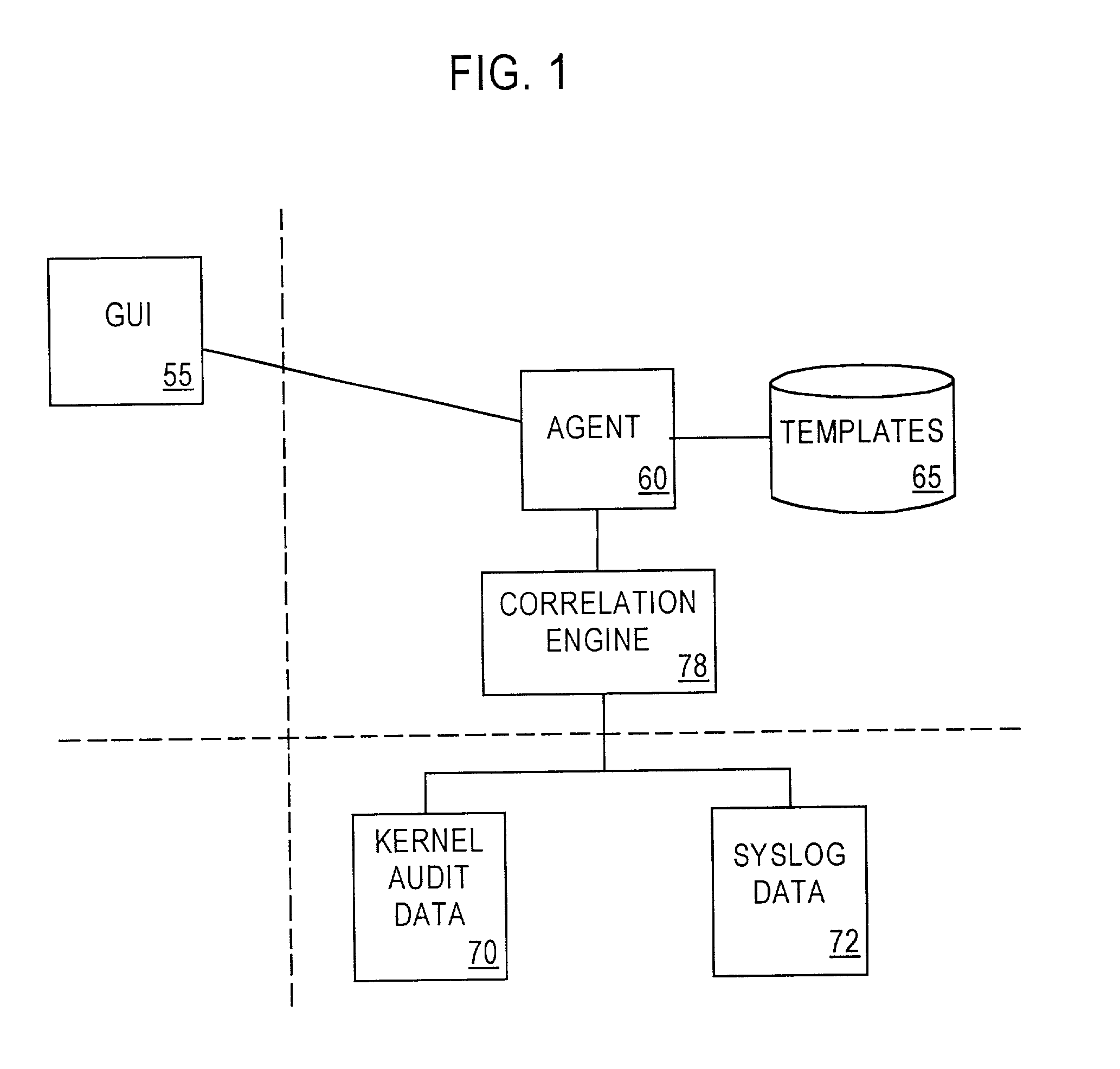
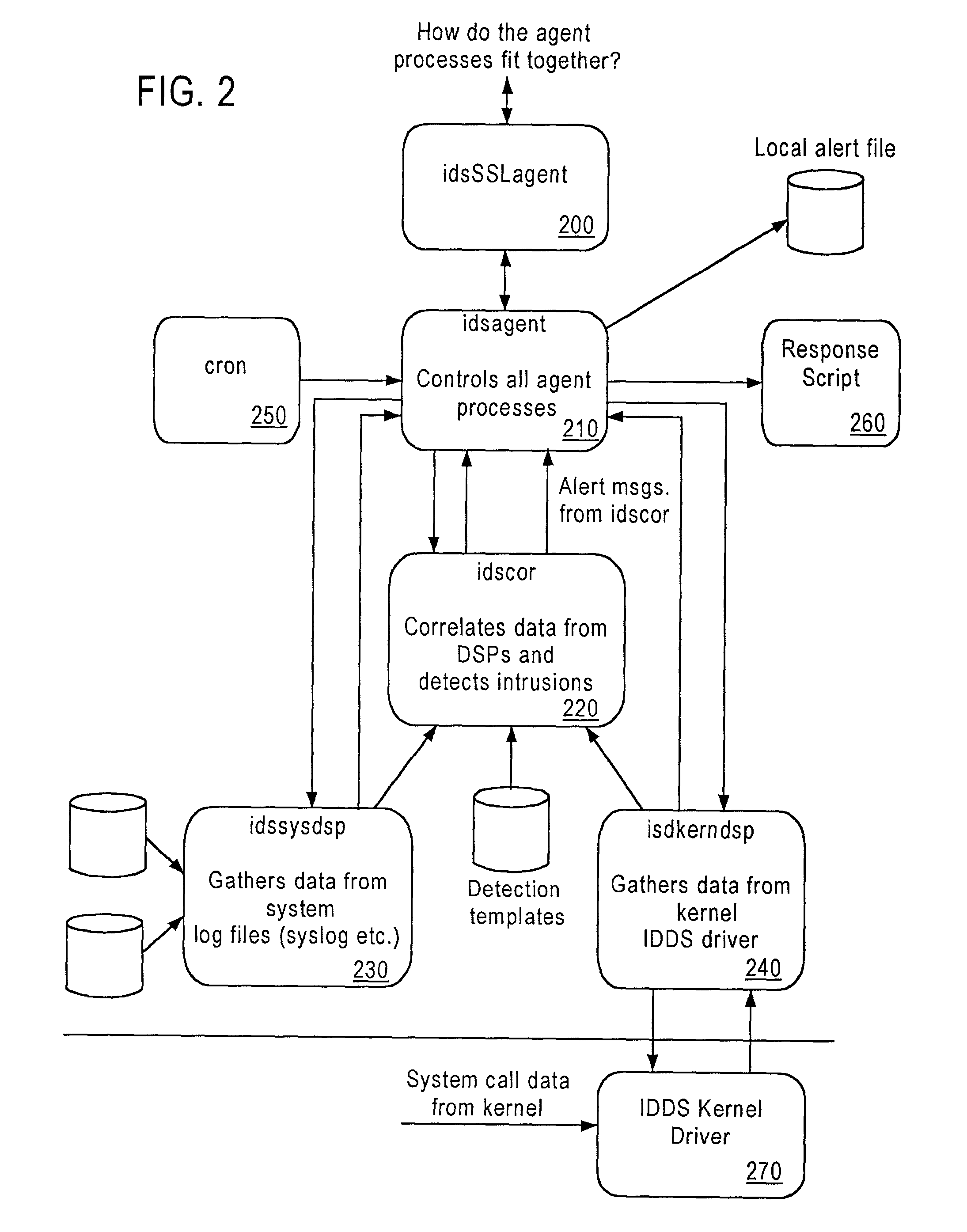
System and method for host and network based intrusion detection and response
InactiveUS7134141B2Accurate measurementFewer false positivesData processing applicationsMemory loss protectionOperational systemCritical system
The present application is directed to a host-based IDS on an HP-UX intrusion detection system that enhances local host-level security within the network. It should be understood that the present invention is also usable on, for example, Eglinux, solaris, aix windows 2000 operating systems. It does this by automatically monitoring each configured host system within the network for possible signs of unwanted and potentially damaging intrusions. If successful, such intrusions could lead to the loss of availability of key systems or could compromise system integrity.
Owner:HEWLETT PACKARD DEV CO LP
Computer architecture for an intrusion detection system
InactiveUS7007301B2Provide protectionAccurate measurementData processing applicationsMemory loss protectionOperational systemCritical system
The present application is directed to a host-based IDS on an HP-UX intrusion detection system that enhances local host-level security within the network. It should be understood that the present invention is also usable on, for example, Eglinux, solaris, aix windows 2000 operating systems. It does this by automatically monitoring each configured host system within the network for possible signs of unwanted and potentially damaging intrusions. If successful, such intrusions could lead to the loss of availability of key systems or could compromise system integrity.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
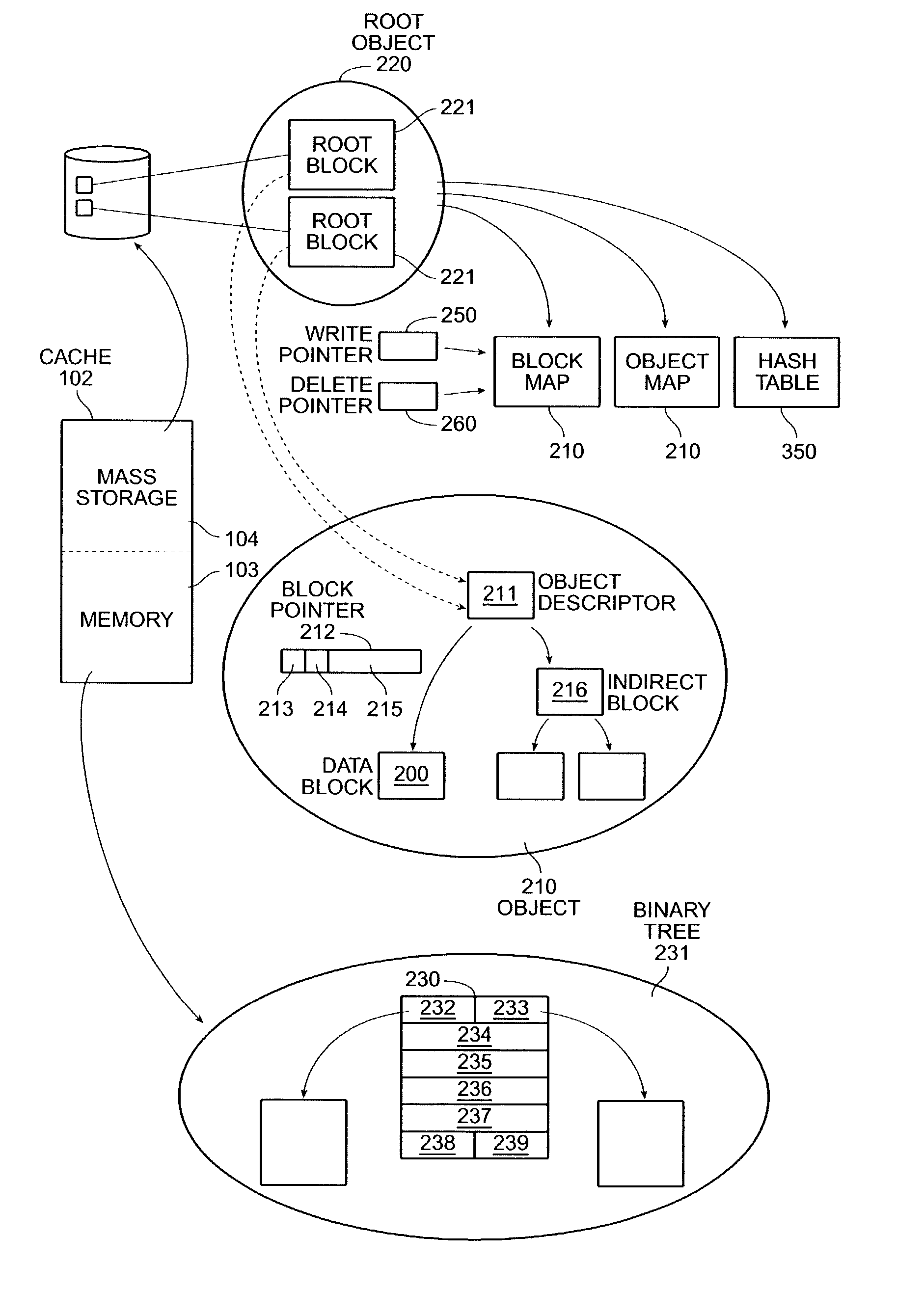
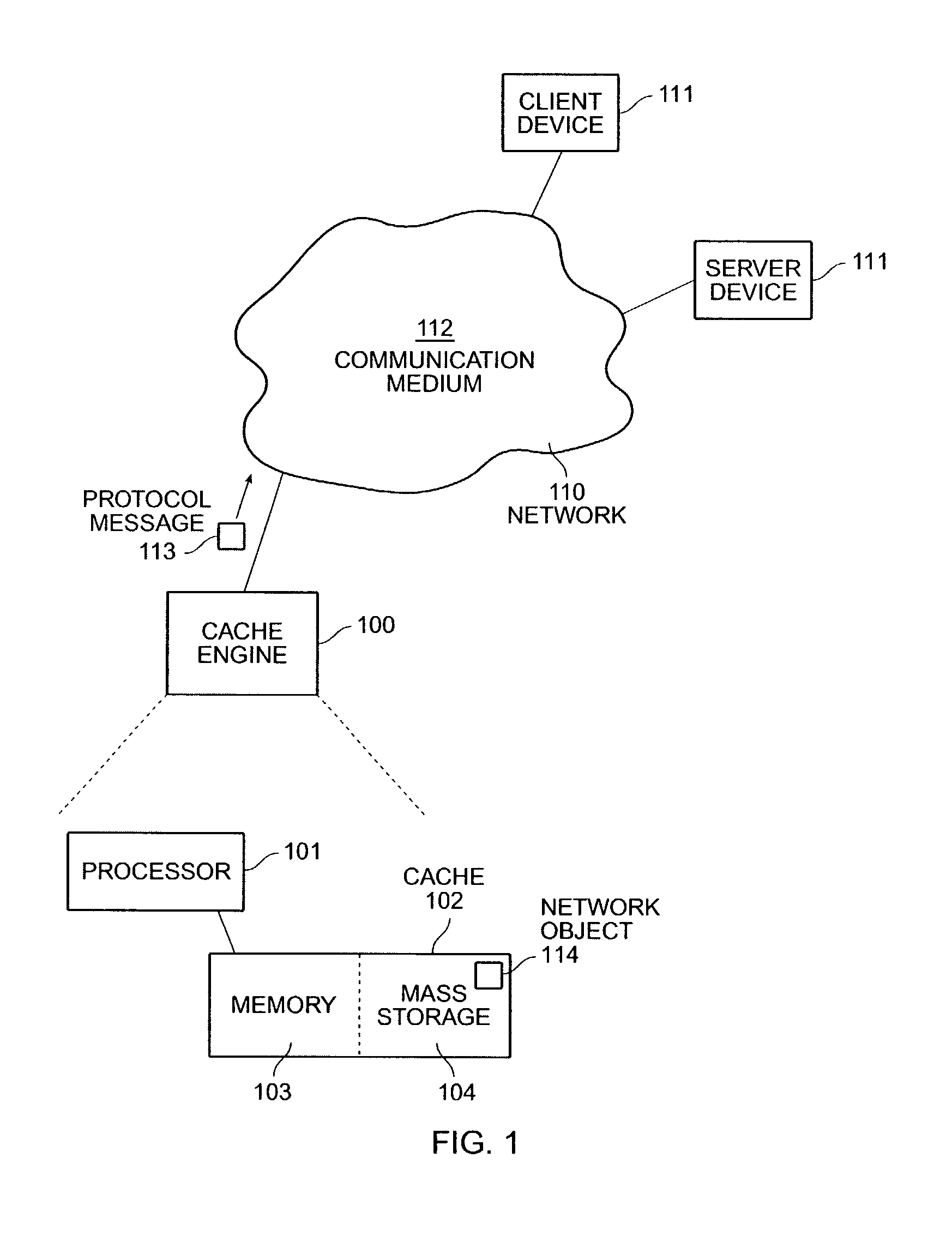
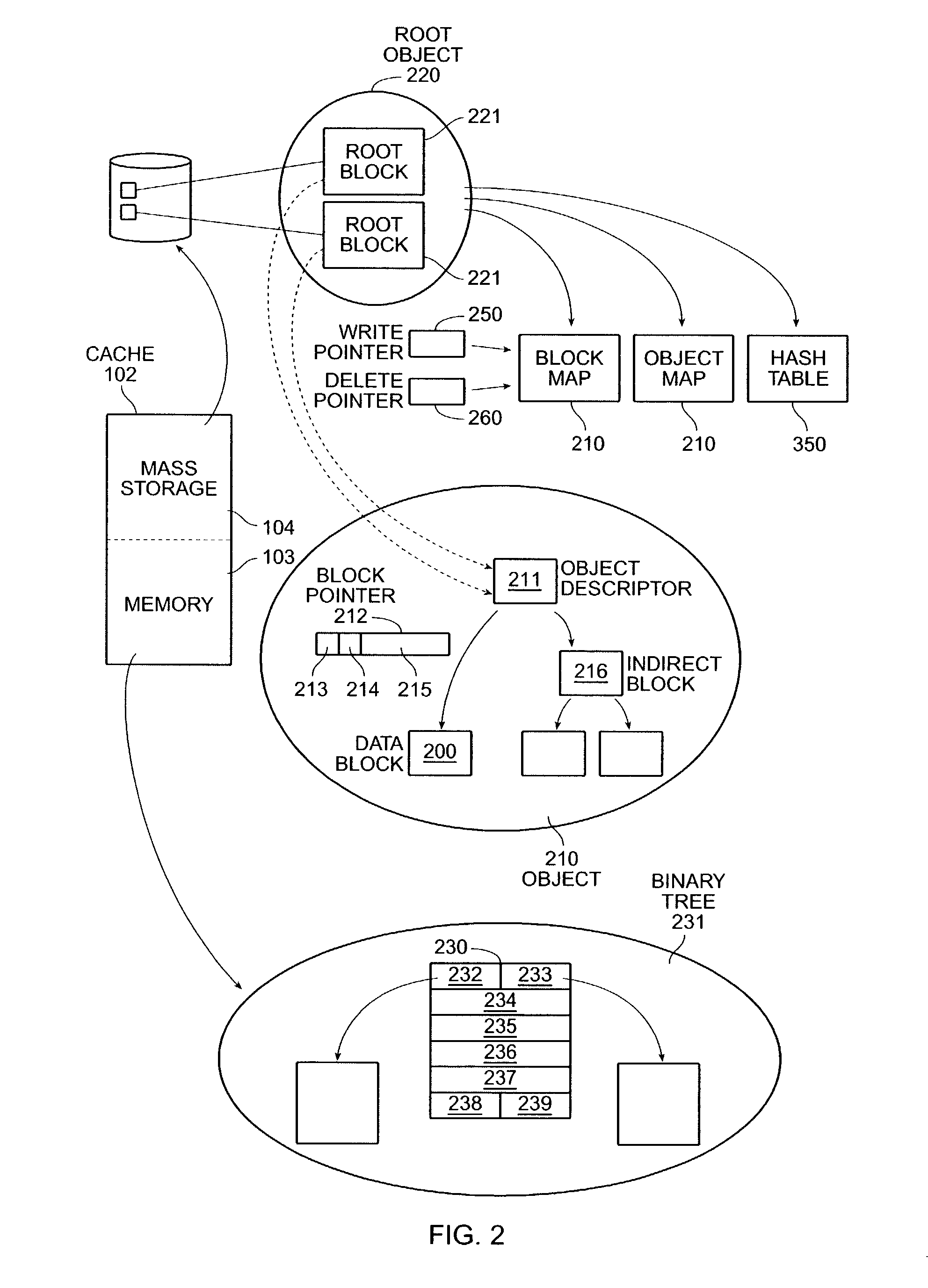
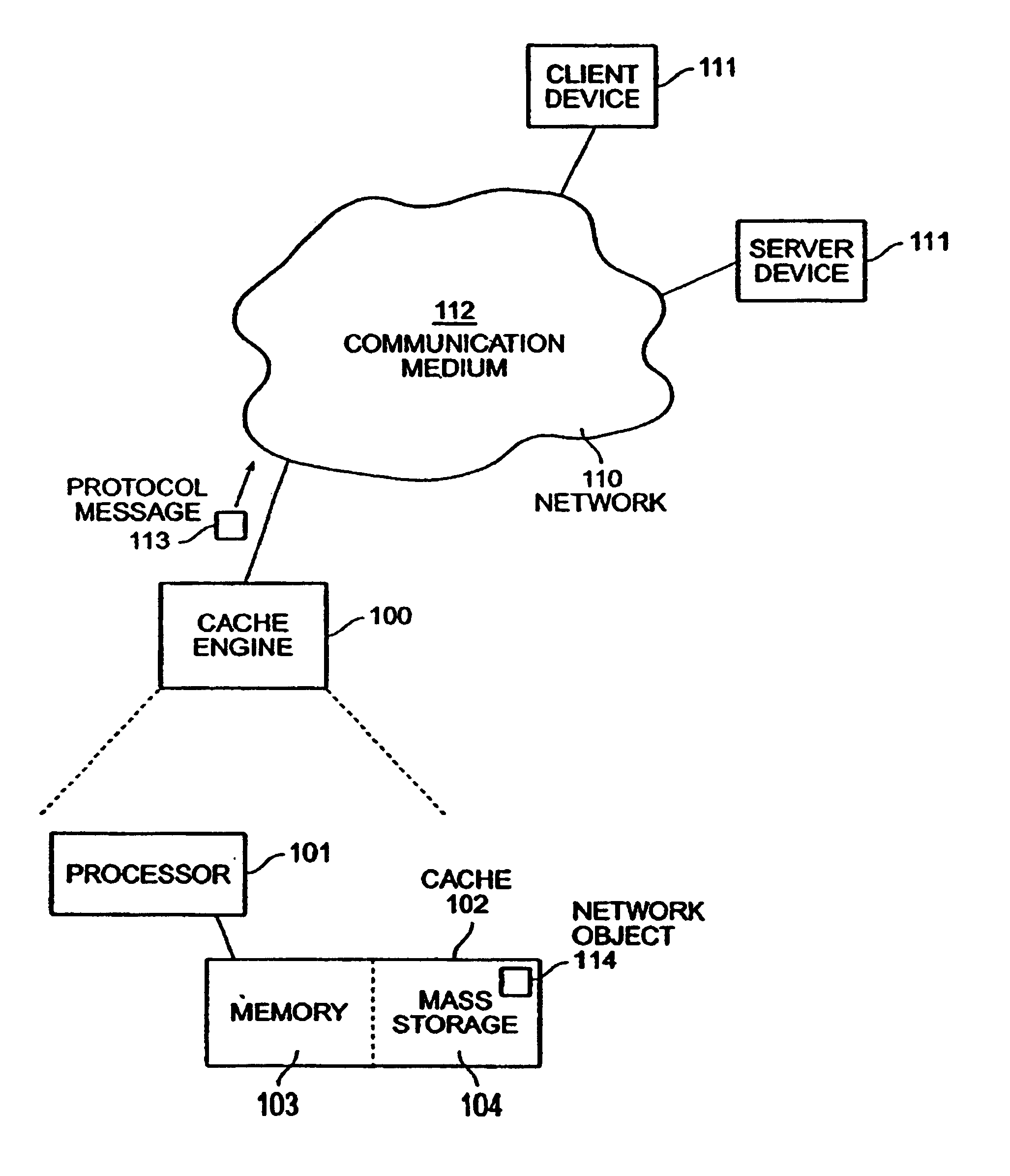
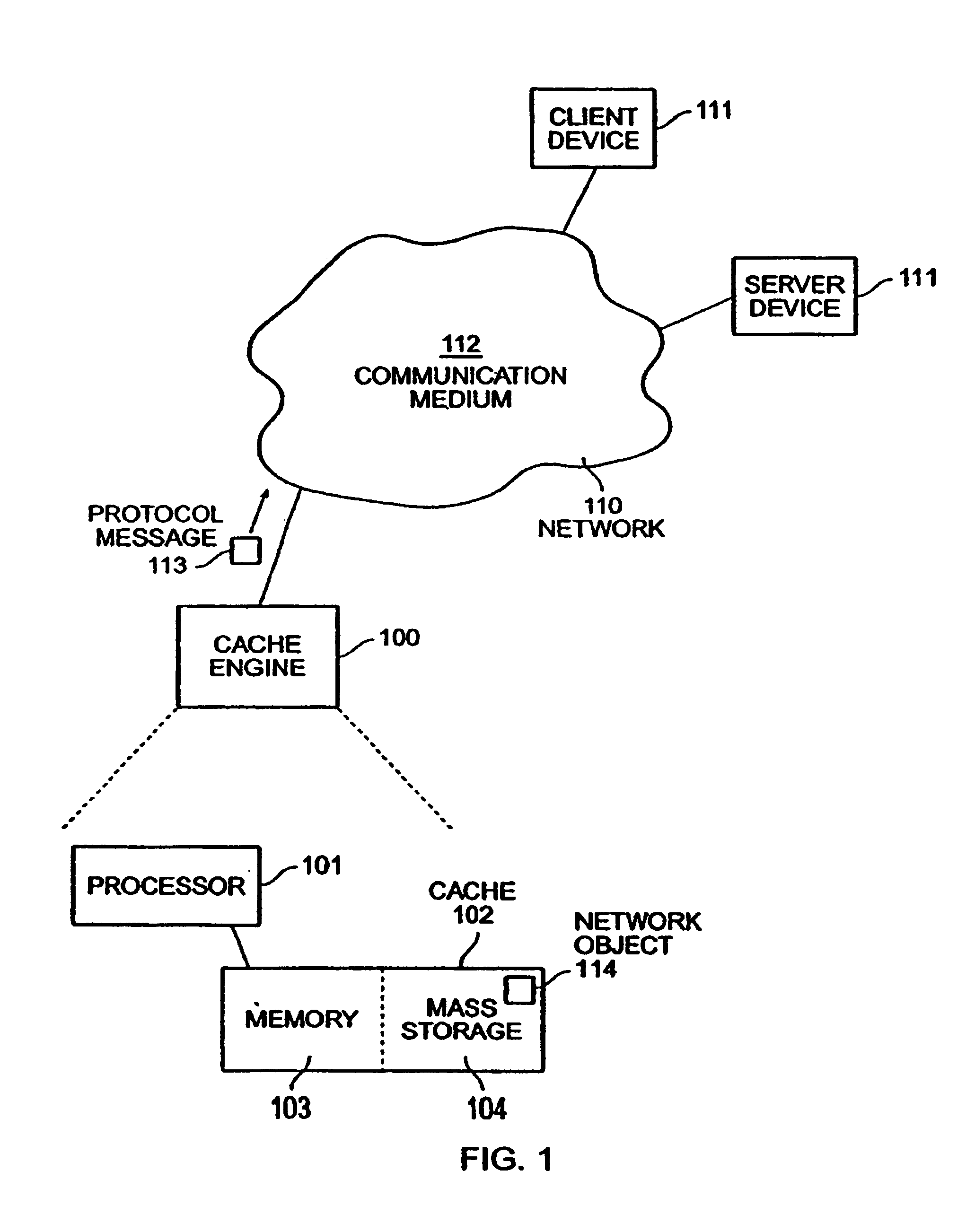
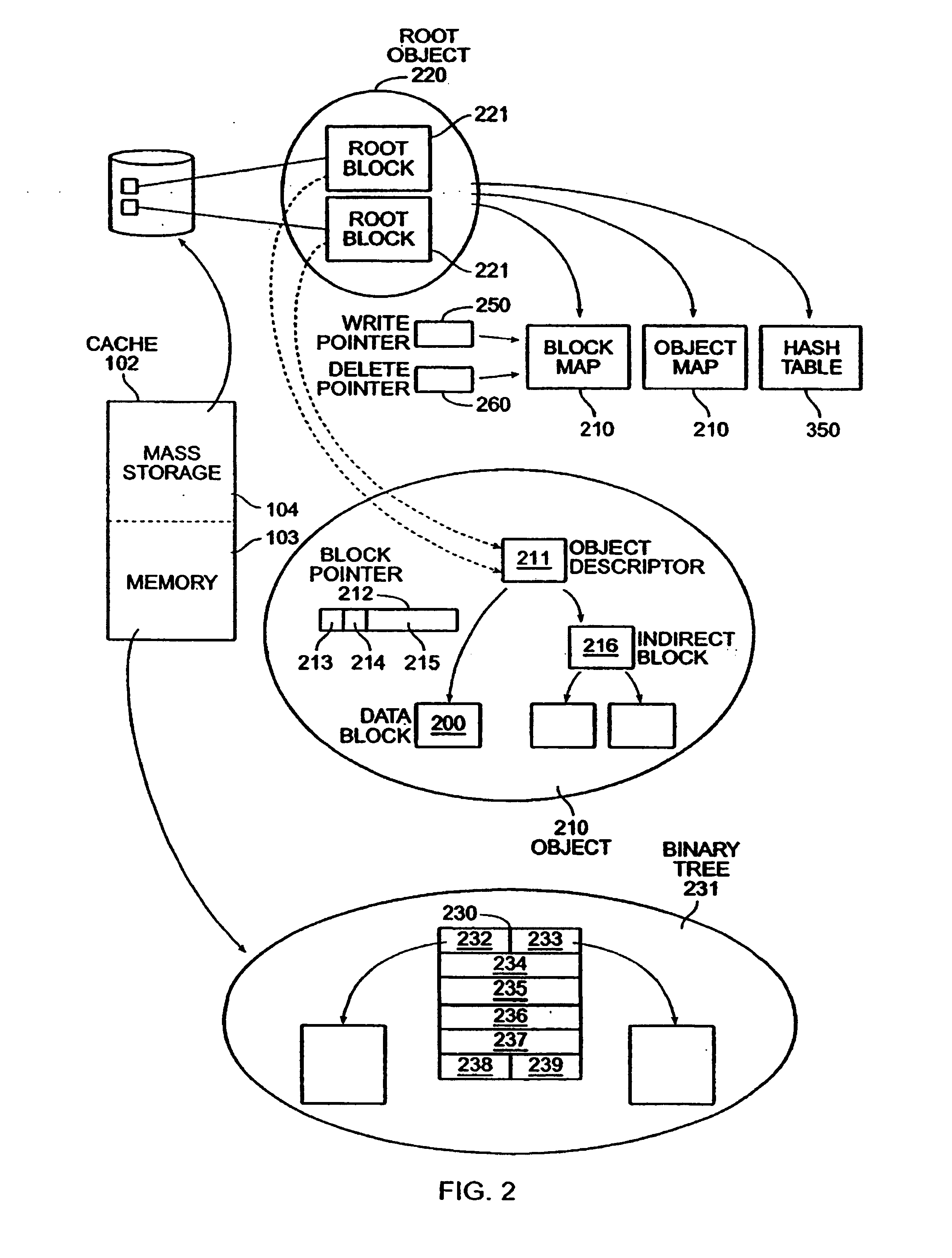
Network object cache engine
InactiveUS20030041280A1Reduce amountMaximize efficiencyDigital data information retrievalMemory loss protectionMass storageInformation object
The invention provides a method and system for caching information objects transmitted using a computer network. A cache engine determines directly when and where to store those objects in a memory (such as RAM) and mass storage (such as one or more disk drives), so as to optimally write those objects to mass storage and later read them from mass storage, without having to maintain them persistently. The cache engine actively allocates those objects to memory or to disk, determines where on disk to store those objects, retrieves those objects in response to their network identifiers (such as their URLs), and determines which objects to remove from the cache so as to maintain sufficient operating space. The cache engine collects information to be written to disk in write episodes, so as to maximize efficiency when writing information to disk and so as to maximize efficiency when later reading that information from disk. The cache engine performs write episodes so as to atomically commit changes to disk during each write episode, so the cache engine does not fail in response to loss of power or storage, or other intermediate failure of portions of the cache. The cache engine also stores key system objects on each one of a plurality of disks, so as to maintain the cache holographic in the sense that loss of any subset of the disks merely decreases the amount of available cache. The cache engine also collects information to be deleted from disk in delete episodes, so as to maximize efficiency when deleting information from disk and so as to maximize efficiency when later writing to those areas having former deleted information. The cache engine responds to the addition or deletion of disks as the expansion or contraction of the amount of available cache.
Owner:BLUE COAT SYSTEMS
System and method for allocating server resources
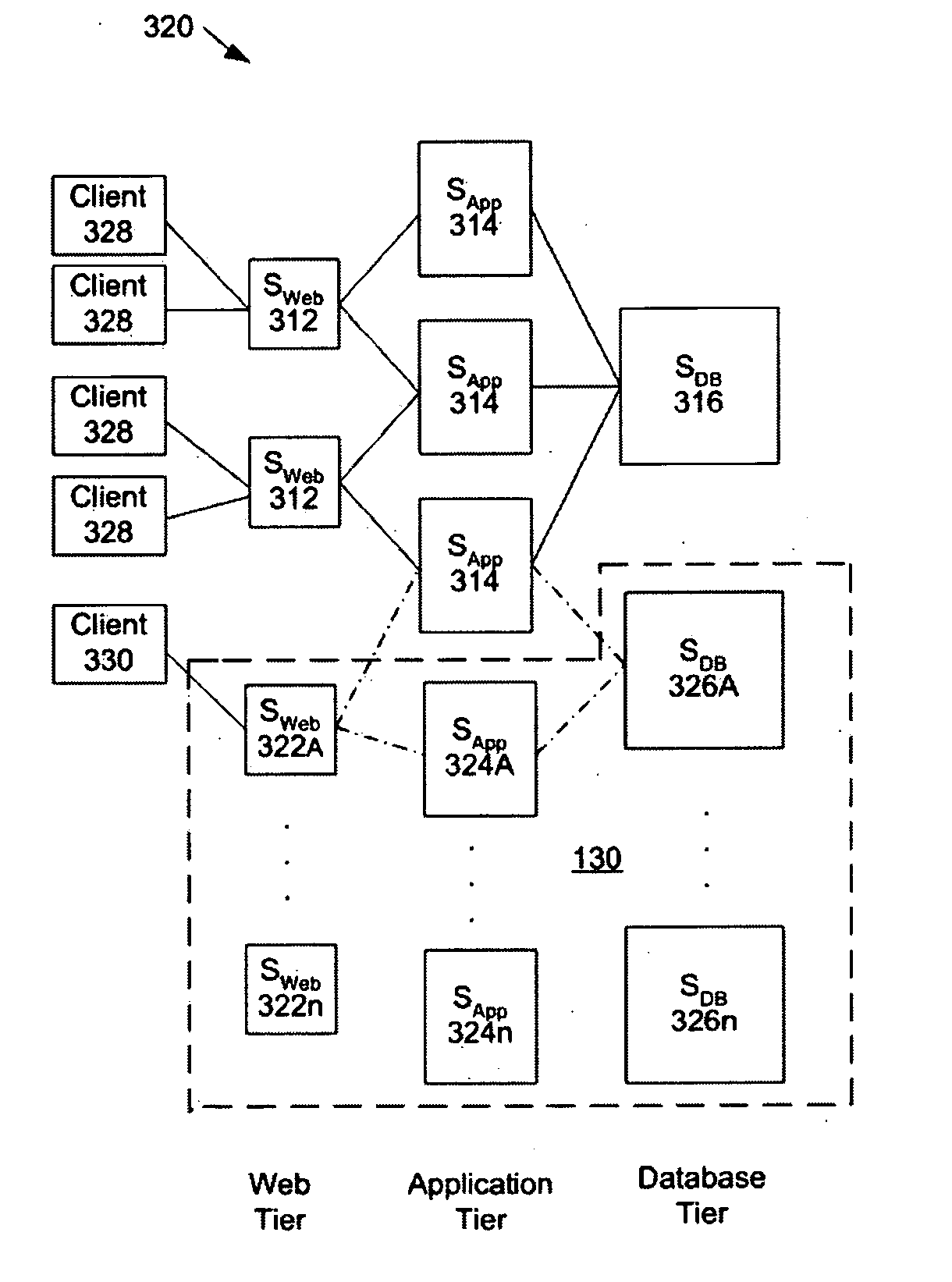
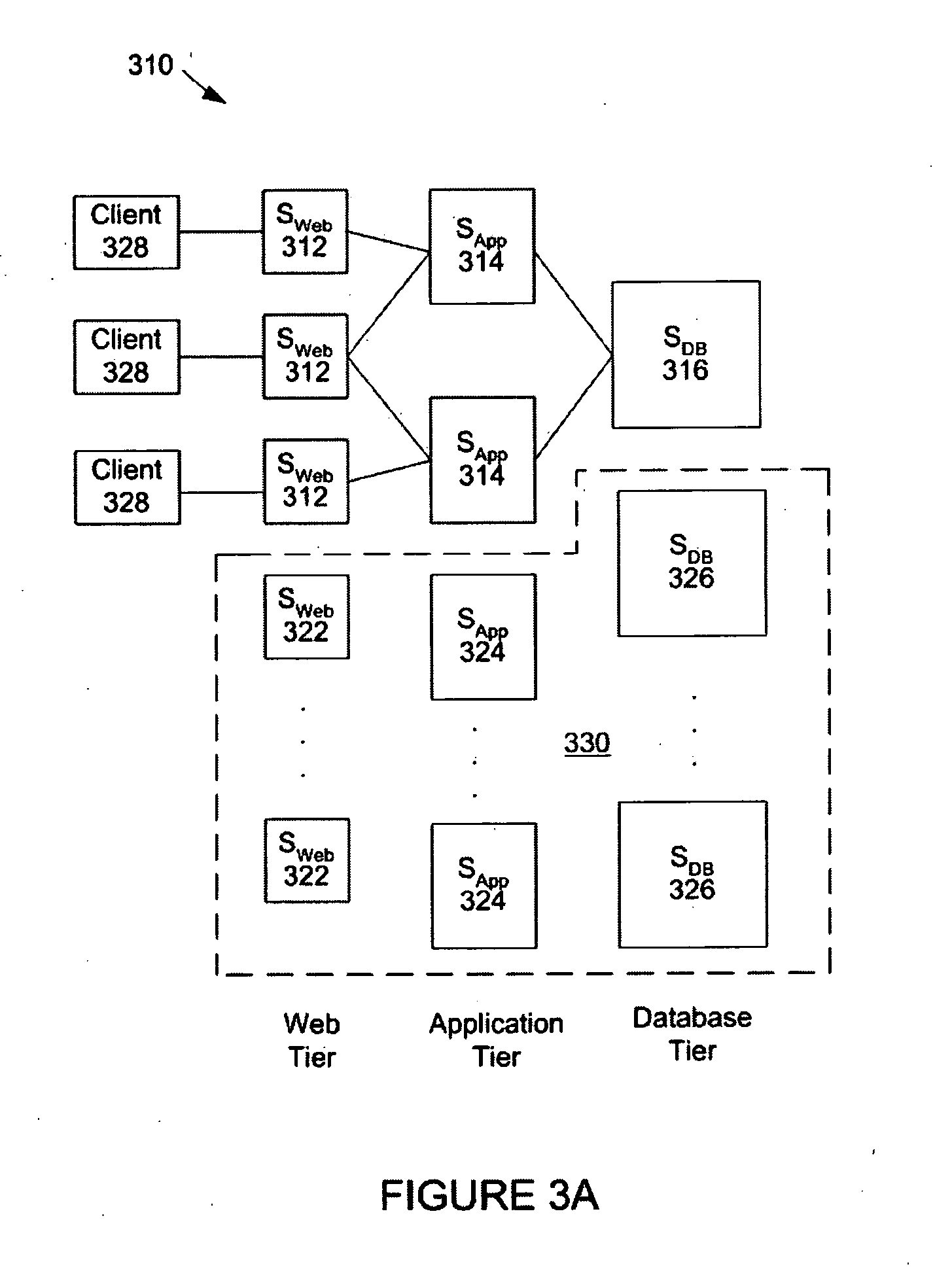
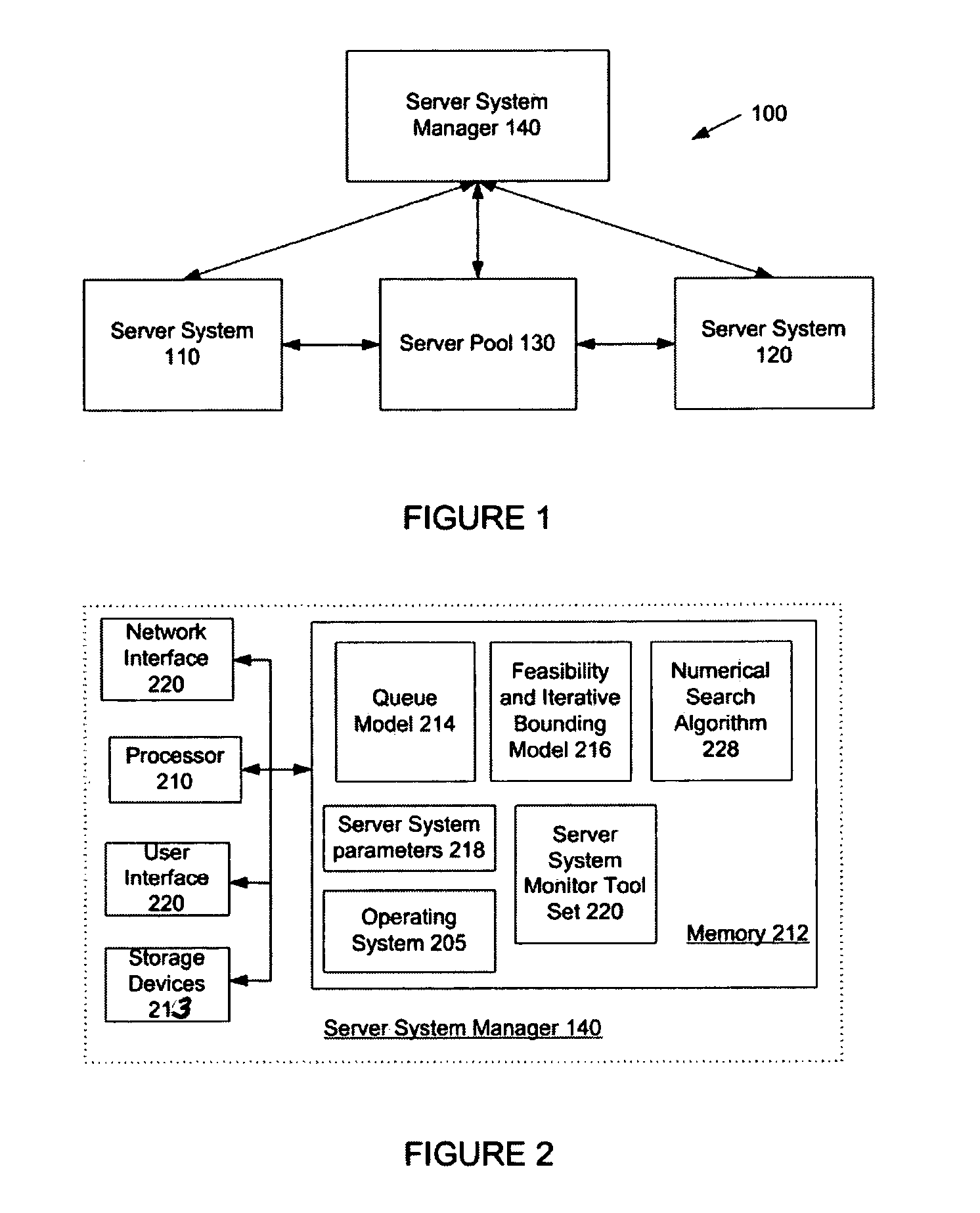
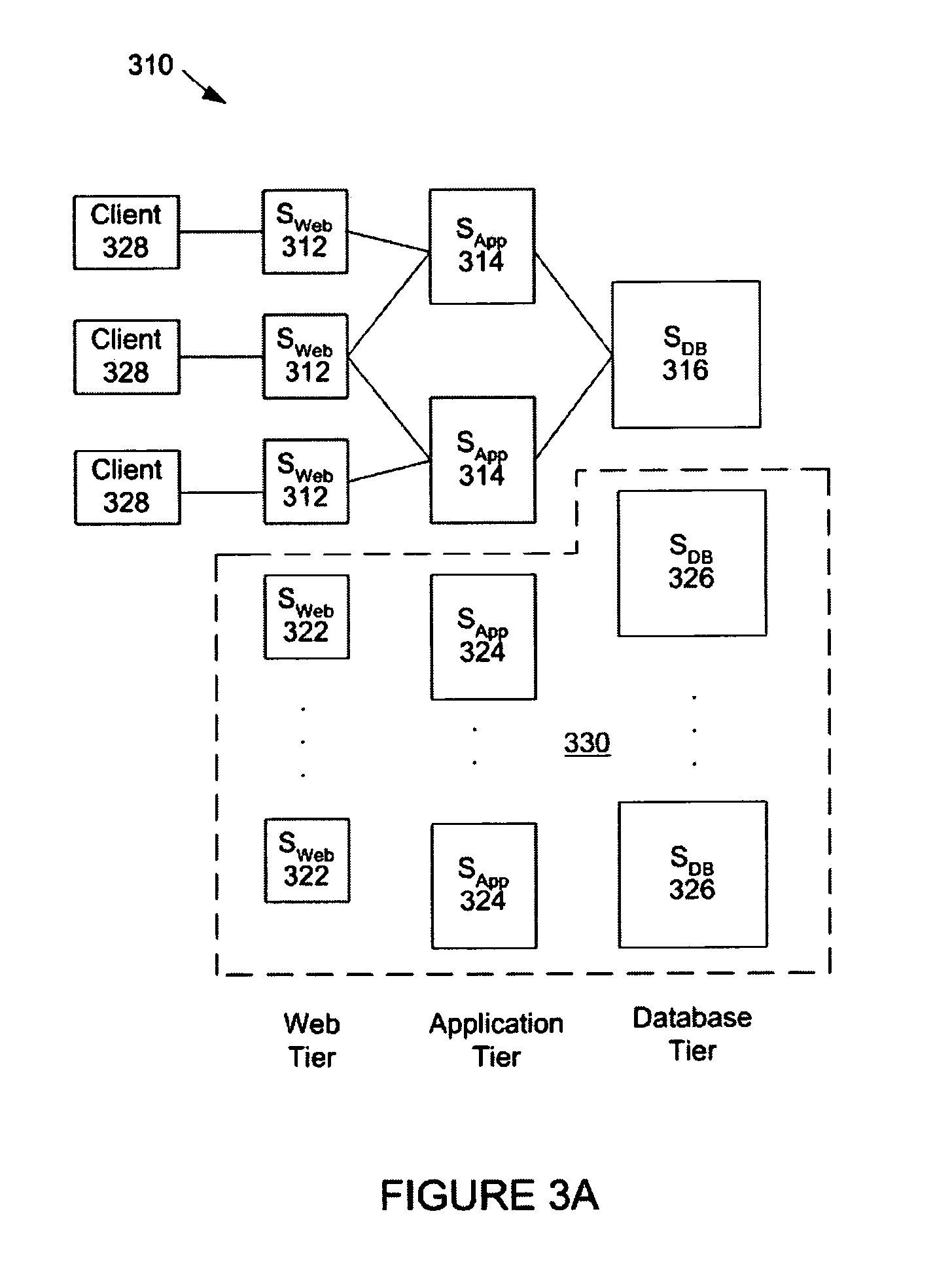
ActiveUS20050102398A1Digital computer detailsComputation using non-denominational number representationCritical systemReal-time computing
A system and method employing an allocation process for determining the number of server machines at each tier of a multiple tiered server system. The allocation process evaluates the number of server machines at each tier sufficient to achieve an average response time of a transaction request to be processed by the server system in response to changes in the average number of transaction requests. The allocation process also identifies shadow pricing enabling analysis of the cost associated with incremental changes in the average response time or other critical system resources.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Method and platform to implement safety critical systems
A method of monitoring and controlling plant operations, which receive input signals from sensors monitoring parameters of plant operation to generate output signals to actuators, comprising; reducing the input signals to a selected group of input functions; reducing the output signals to a selected group of output functions; processing the input signals using FPGA to generate the output signals. The invention also relates to the platform and system embodying the method.
Owner:BAKHMACH LEVGENII
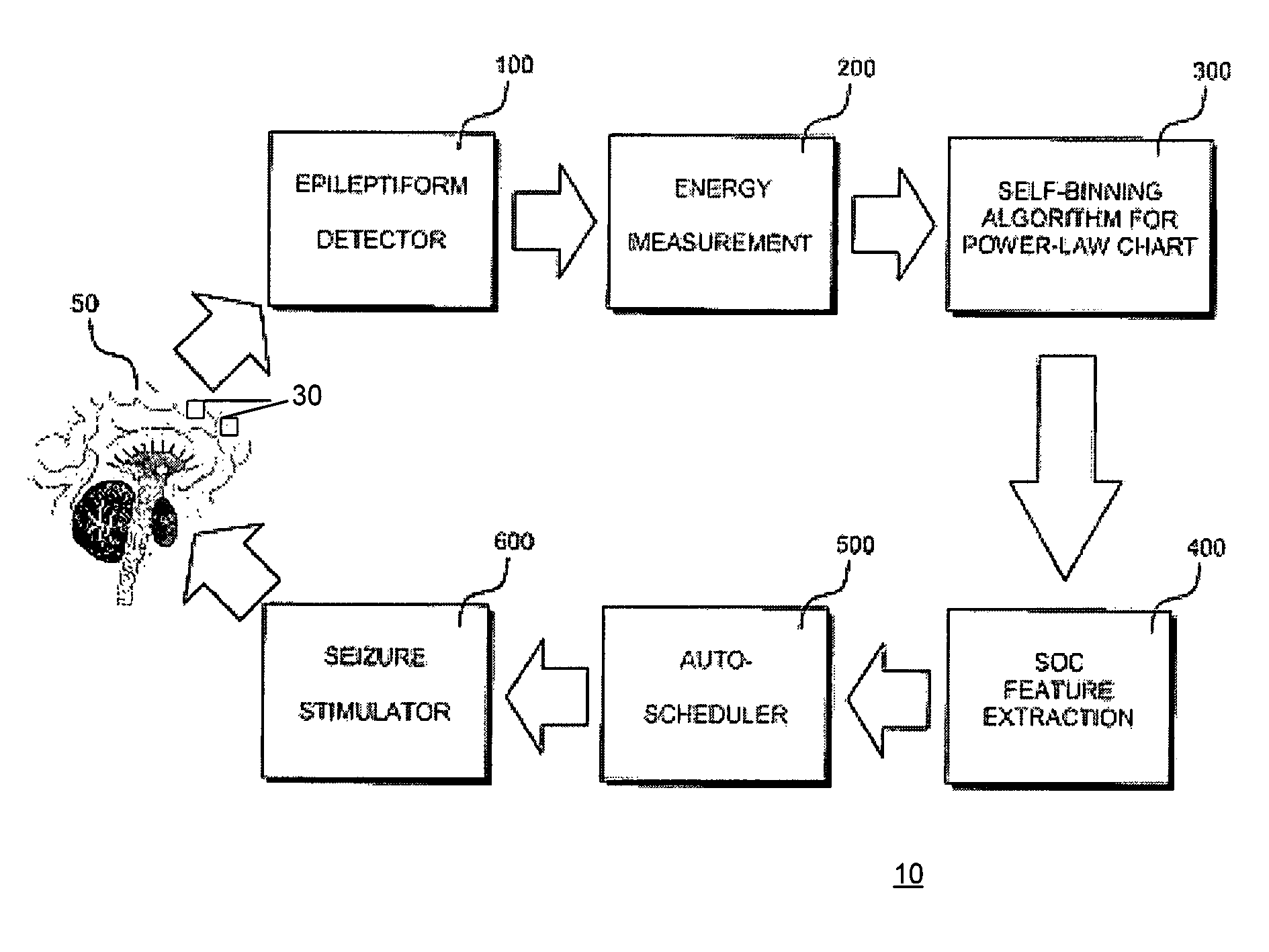
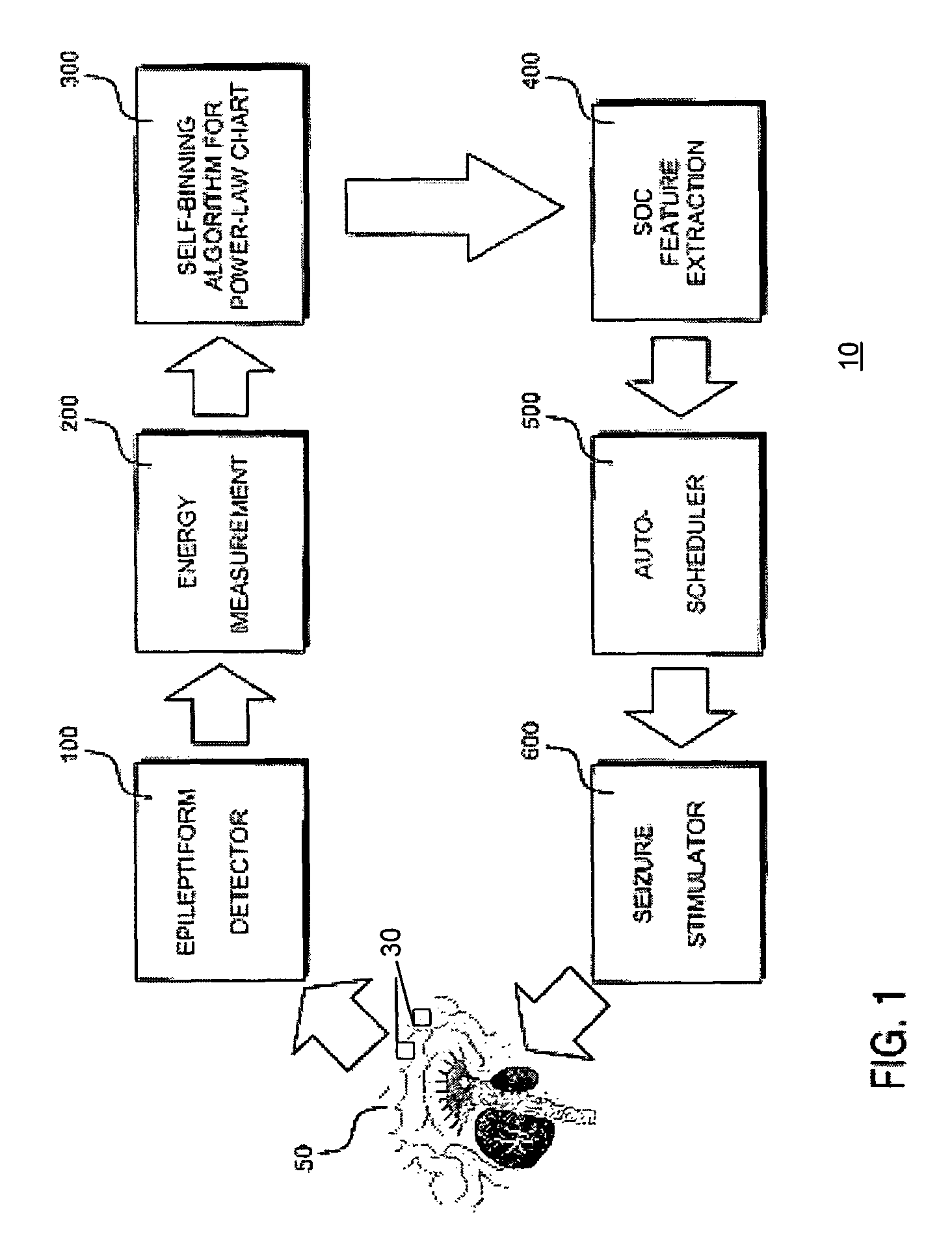
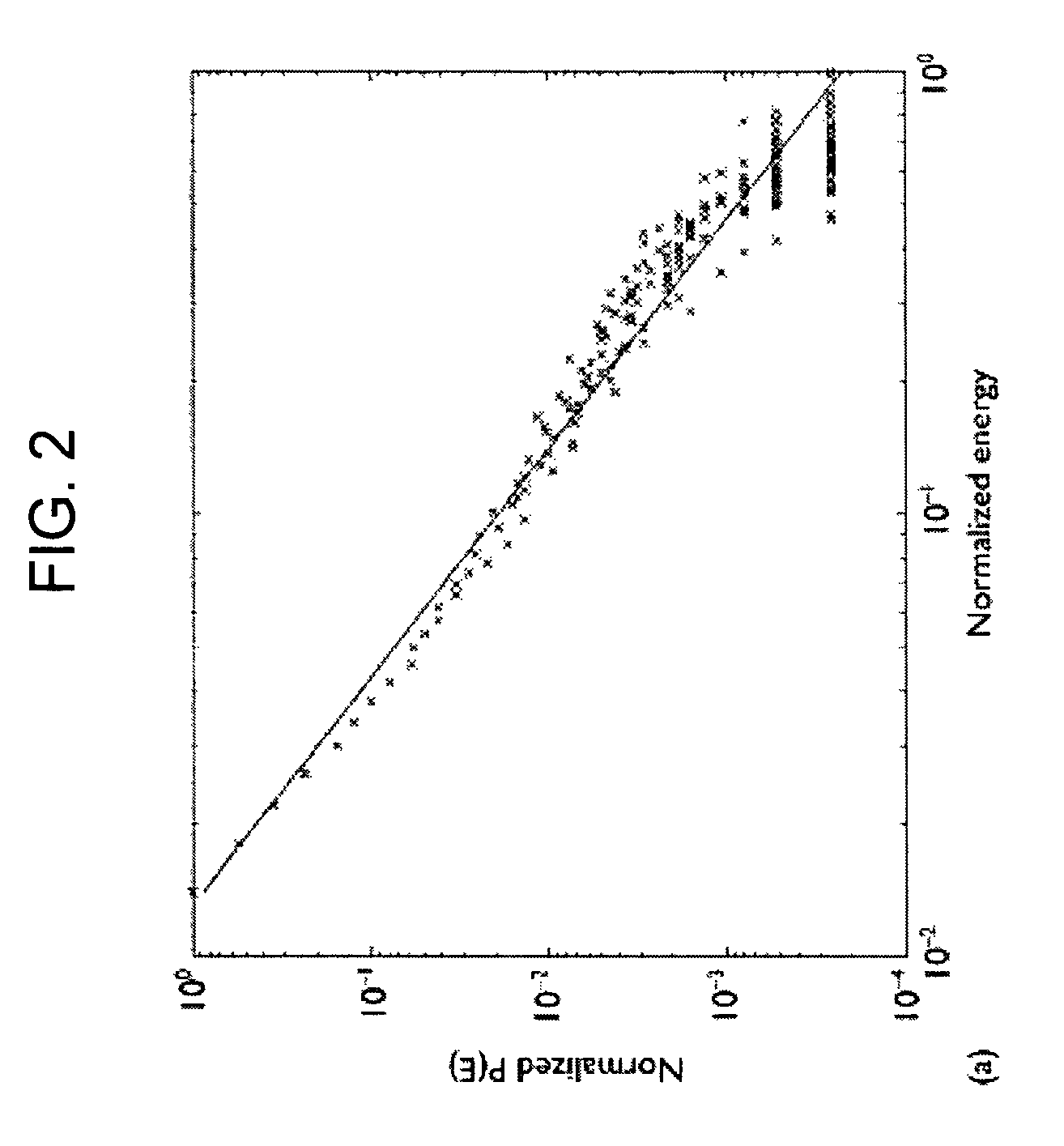
Active control of epileptic seizures and diagnosis based on critical systems-like behavior
ActiveUS8150522B2Avoid it happening againMinimize and guide epilepsyElectrotherapyDiagnostic recording/measuringMedicineSeizure onset zone
Developing a measure of critical systems-like behavior in an epilepsy patient in order to map epileptic networks, either passively or evoking responses through subthreshold stimulation, and to apply “therapeutic” stimulations to the patient that cause smaller, but more frequent dissipations of “energy,” a transcription product, subclinical electrophysiological activity or seizures in order to raise the clinical seizure initiation threshold, through releasing accumulated interictal energy in a seizure onset zone or elsewhere in the epileptic network, thereby preventing occurrence of larger more debilitating seizures.
Owner:THE TRUSTEES OF THE UNIV OF PENNSYLVANIA
Network object cache engine
InactiveUS7103794B2Reduce amountMaximize efficiencyDigital data information retrievalMemory adressing/allocation/relocationMass storageInformation object
The invention provides a method and system for caching information objects transmitted using a computer network. A cache engine determines directly when and where to store those objects in a memory (such as RAM) and mass storage (such as one or more disk drives), so as to optimally write those objects to mass storage and later read them from mass storage, without having to maintain them persistently. The cache engine actively allocates those objects to memory or to disk, determines where on disk to store those objects, retrieves those objects in response to their network identifiers (such as their URLs), and determines which objects to remove from the cache so as to maintain sufficient operating space. The cache engine collects information to be written to disk in write episodes, so as to maximize efficiency when writing information to disk and so as to maximize efficiency when later reading that information from disk. The cache engine performs write episodes so as to atomically commit changes to disk during each write episode, so the cache engine does not fail in response to loss of power or storage, or other intermediate failure of portions of the cache. The cache engine also stores key system objects on each one of a plurality of disks, so as to maintain the cache holographic in the sense that loss of any subset of the disks merely decreases the amount of available cache. The cache engine also collects information to be deleted from disk in delete episodes, so as to maximize efficiency when deleting information from disk and so as to maximize efficiency when later writing to those areas having former deleted information. The cache engine responds to the addition or deletion of disks as the expansion or contraction of the amount of available cache.
Owner:CA TECH INC
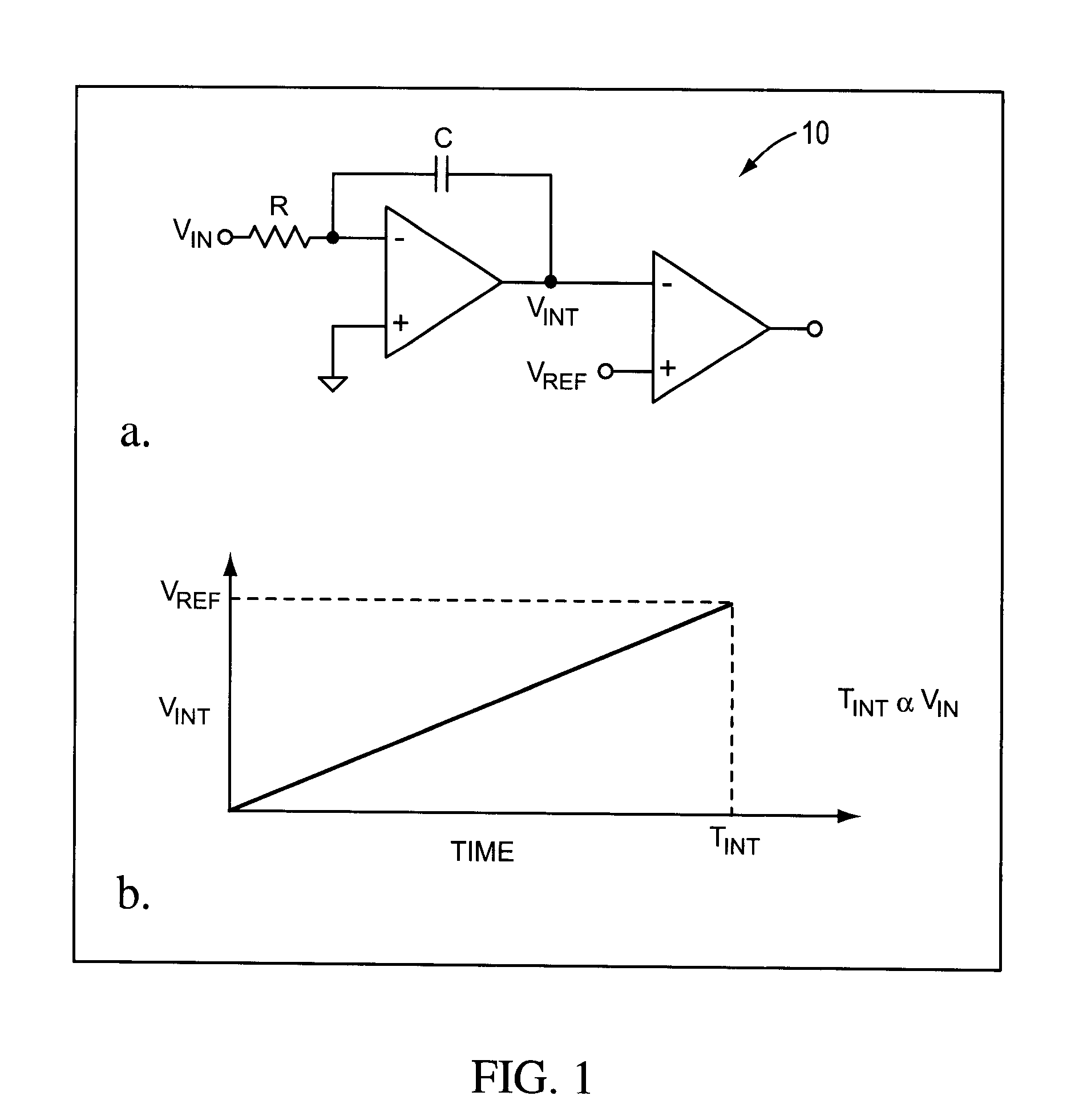
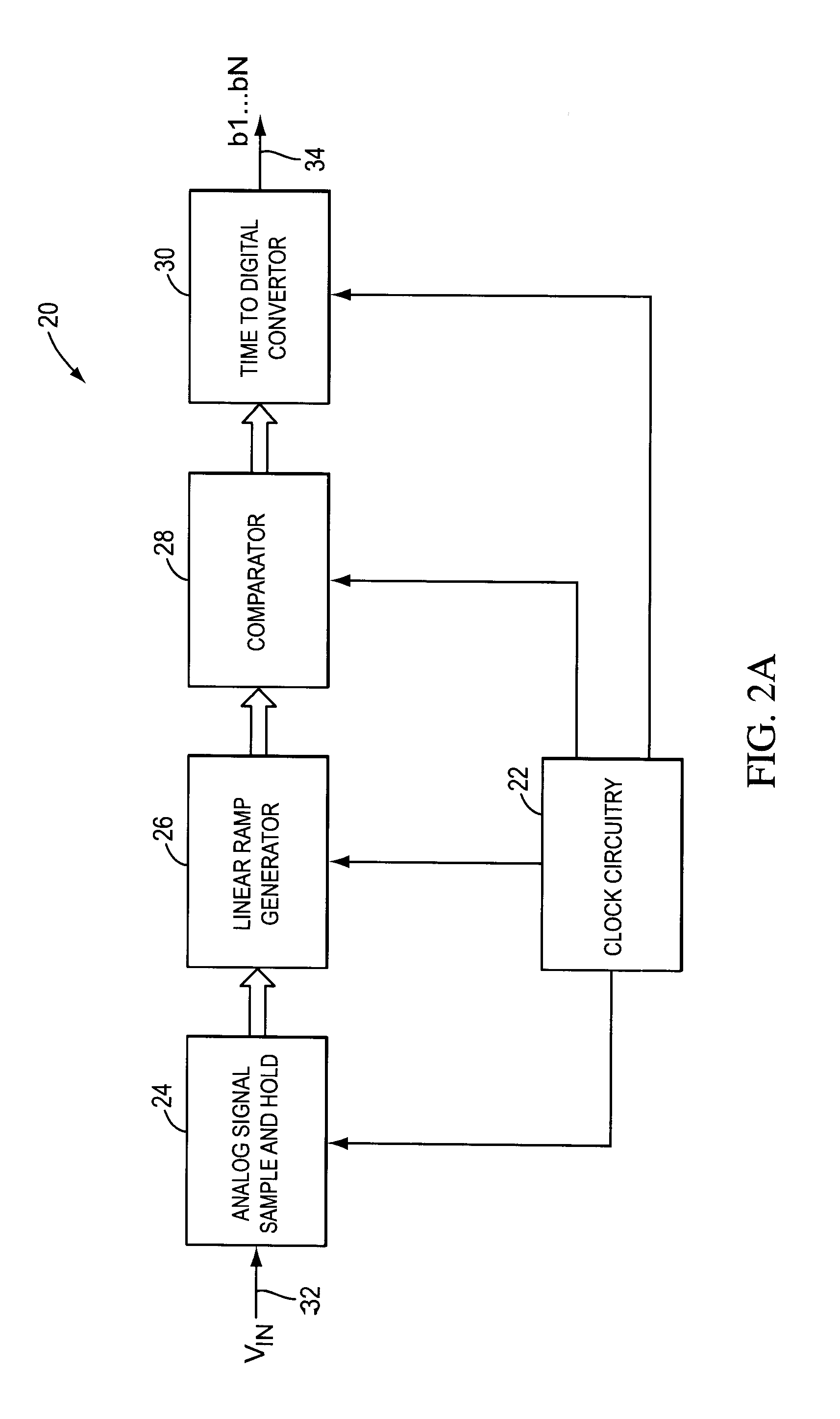
Rotary clock flash analog to digital converter system and method
ActiveUS7609756B2Electric signal transmission systemsPulse automatic controlDigital down converterEngineering
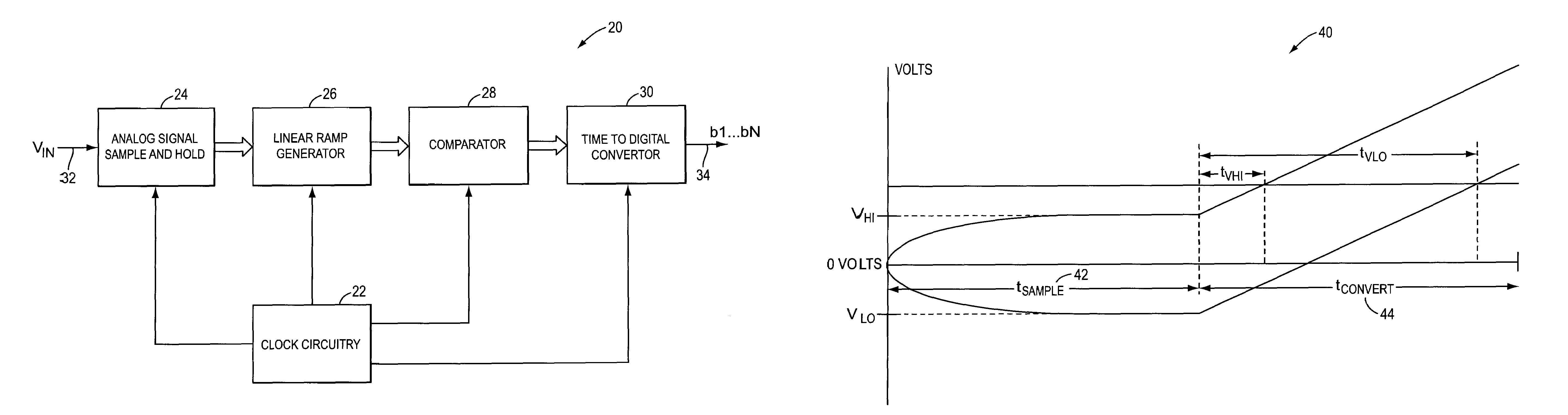
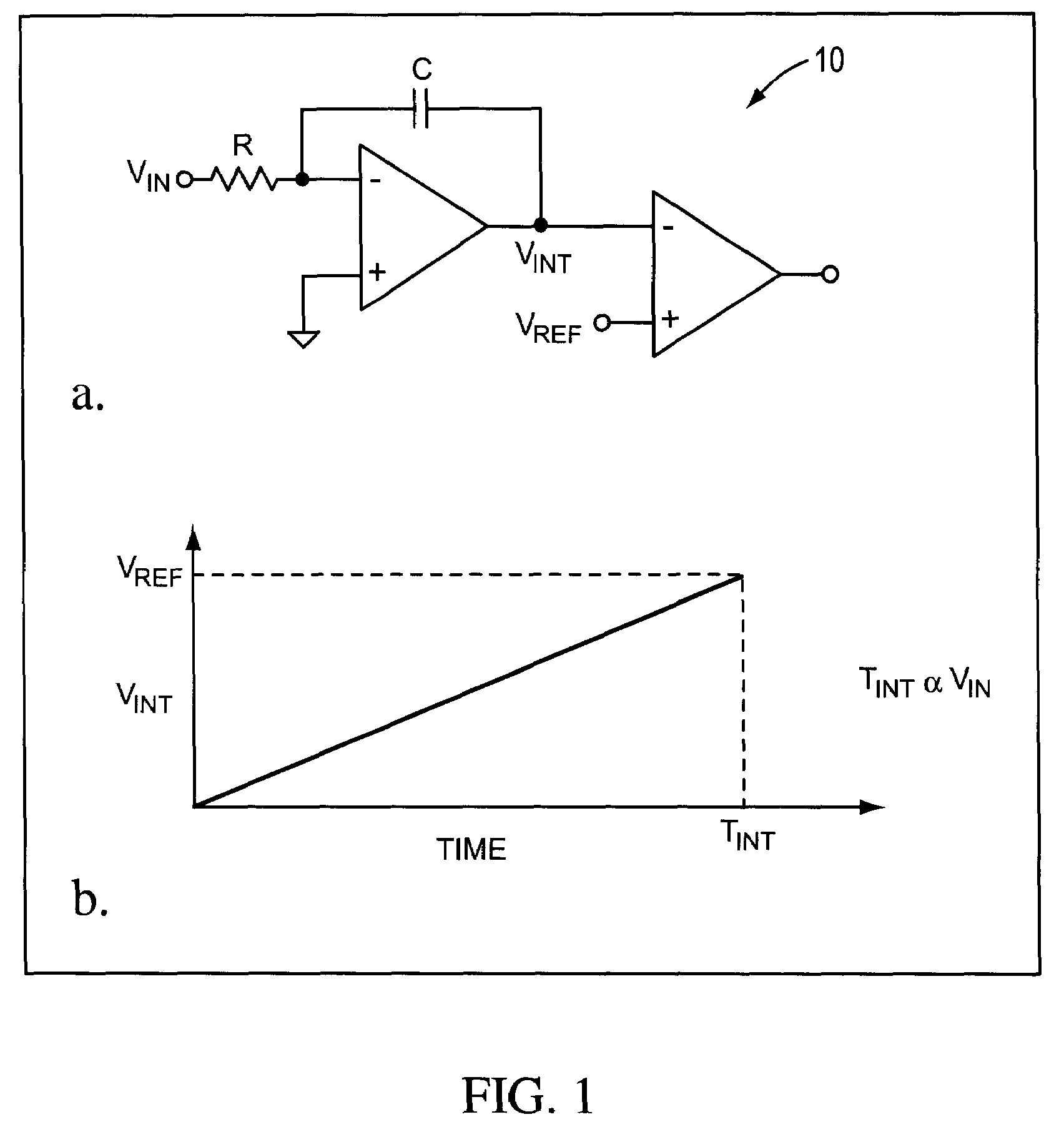
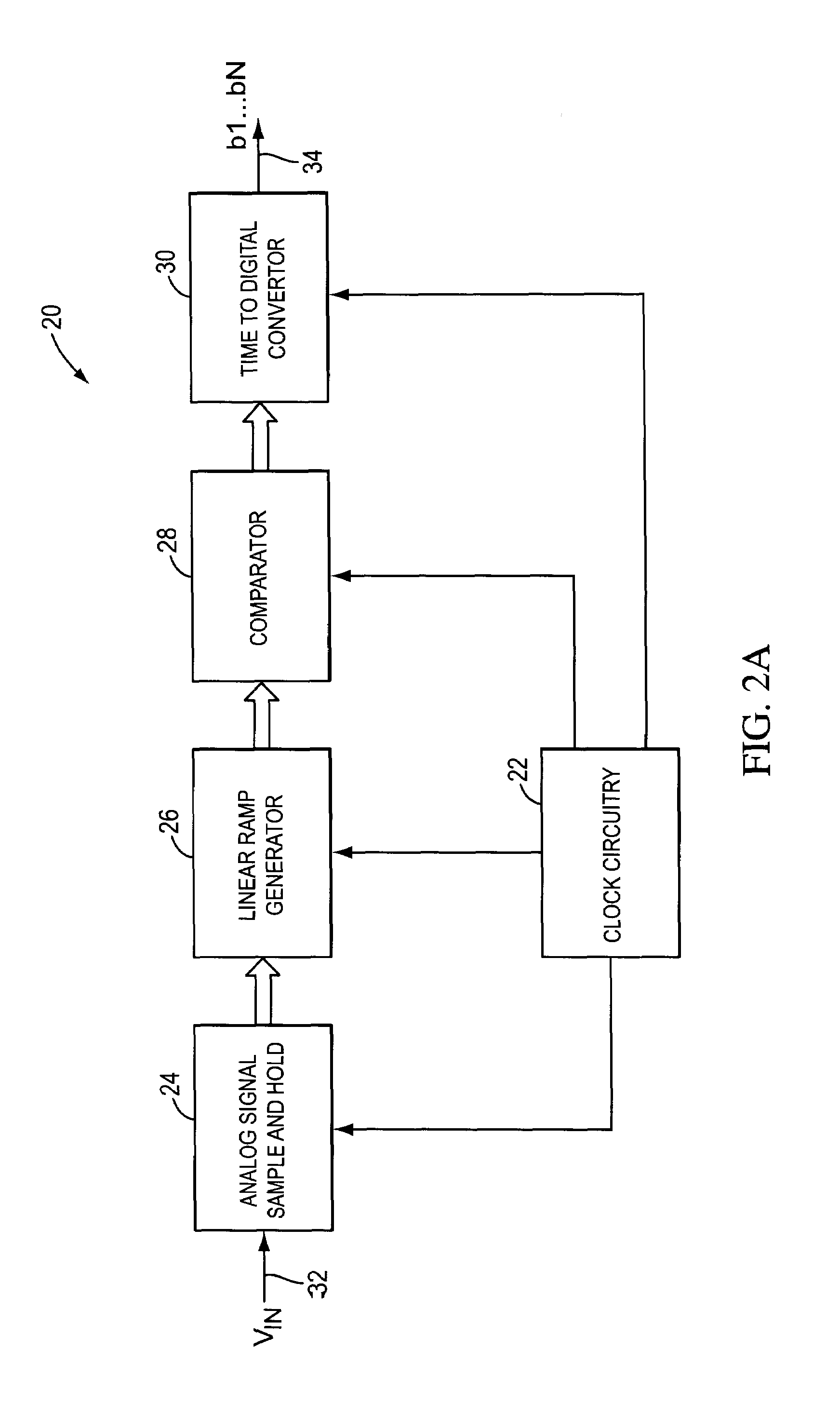
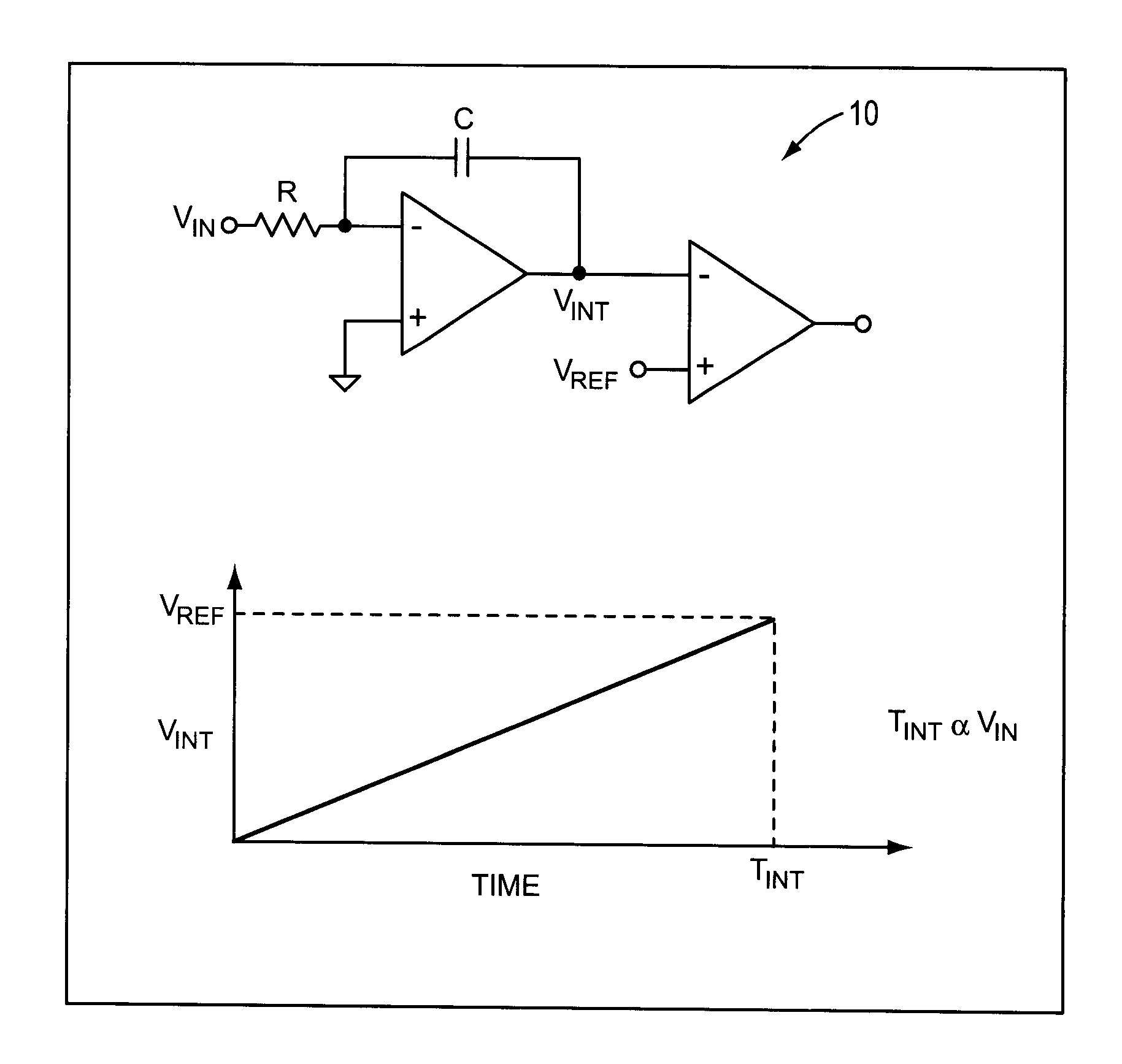
System and method for converting an analog voltage to a digital signal. The system includes an input voltage sampler, a ramp generator, a comparator, a time-to-digital converter (TDC), and a multiphase oscillator, preferably a rotary traveling wave oscillator, that provides the critical system timing. The phases of the multiphase oscillator define a sampling interval during which the input voltage is sampled and held and a conversion interval during which the ramp generator, comparator, and TDC operate to convert the sampled voltage to the digital signal. The TDC samples at times provided by the phases of the multiphase oscillator to form the bits of the digital signal. The sampler, ramp generator, and comparator can be constructed from multiple fragments, one of which is selectable for calibration while the rest of the fragments are joined for normal operation. Multiple converters can be interleaved to increase the sampling rate.
Owner:ANALOG DEVICES INC
Rotary clock flash analog to digital converter system and method
ActiveUS20080272952A1Electric signal transmission systemsPulse automatic controlDigital down converterEngineering
System and method for converting an analog voltage to a digital signal. The system includes an input voltage sampler, a ramp generator, a comparator, a time-to-digital converter (TDC), and a multiphase oscillator, preferably a rotary traveling wave oscillator, that provides the critical system timing. The phases of the multiphase oscillator define a sampling interval during which the input voltage is sampled and held and a conversion interval during which the ramp generator, comparator, and TDC operate to convert the sampled voltage to the digital signal. The TDC samples at times provided by the phases of the multiphase oscillator to form the bits of the digital signal. The sampler, ramp generator, and comparator can be constructed from multiple fragments, one of which is selectable for calibration while the rest of the fragments are joined for normal operation. Multiple converters can be interleaved to increase the sampling rate.
Owner:ANALOG DEVICES INC
Loan repay enforcement system
A system to encourage on time repayment of loans includes electronic apparatus coupled to a critical system of certain equipment; for example, the ignition system of an automobile. Apparatus includes mechanism whereby a user-operator is able to enter a code. Entry of a correct code serves as indication that a payment has been made and enables further use of the equipment. On failure to timely make payments, a user is prevented from using the equipment as the apparatus is arranged to disable the equipment by way of the critical system to which it is coupled. Both a user-operator interface and critical system interruption circuit are coupled to a logic processor which is easily mounted onto equipment subject to the program.
Owner:PAYMENT PROT SYST
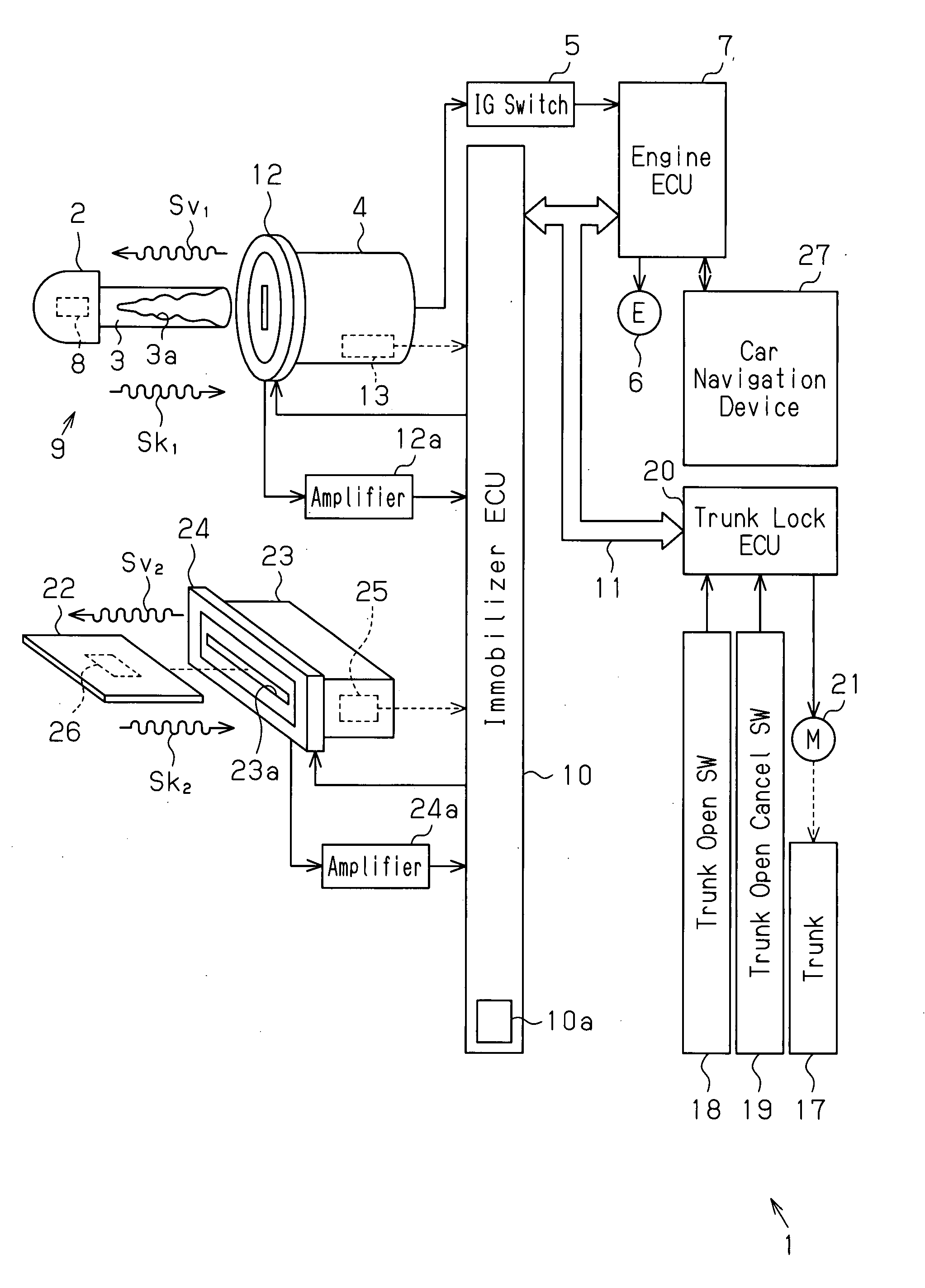
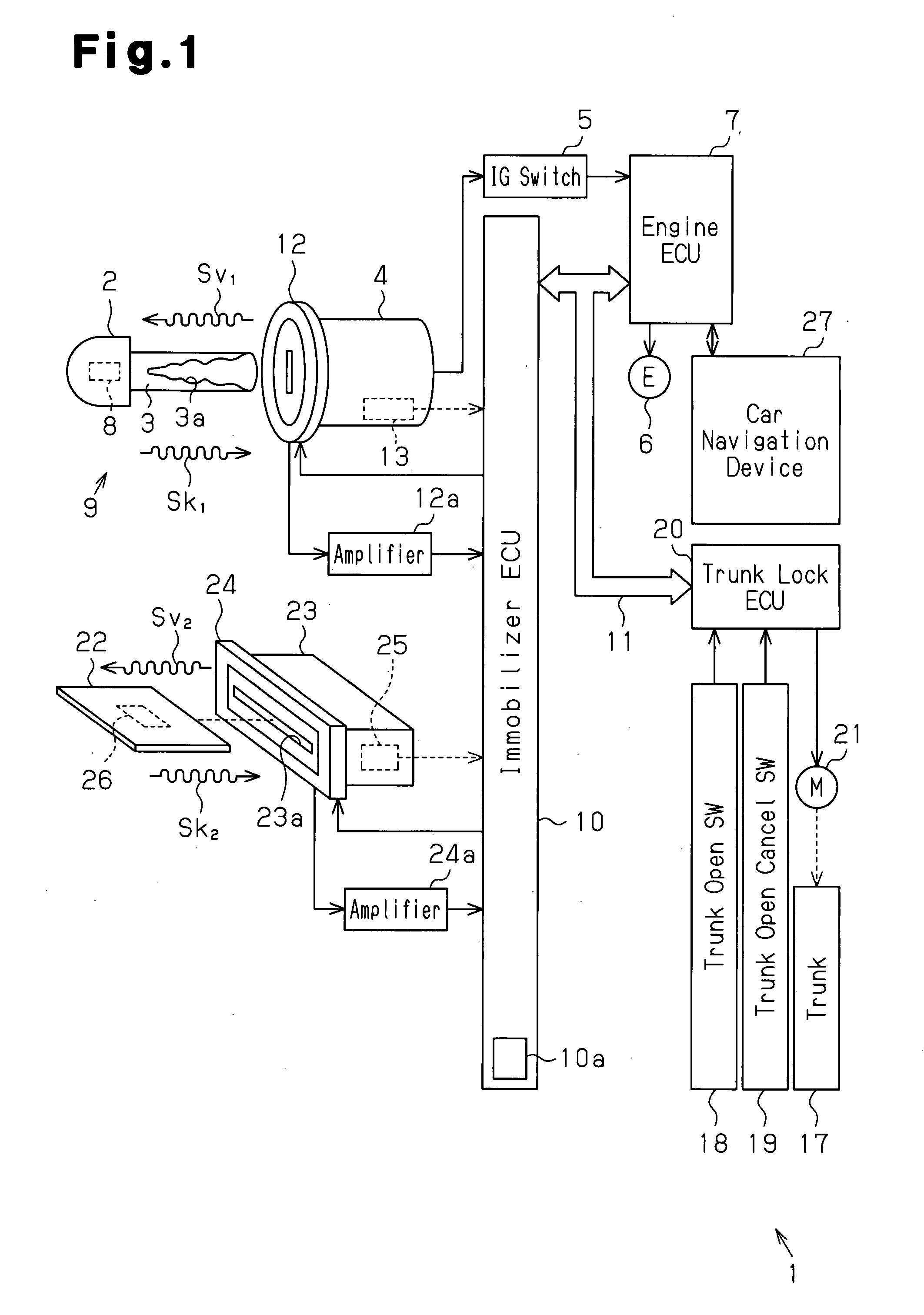
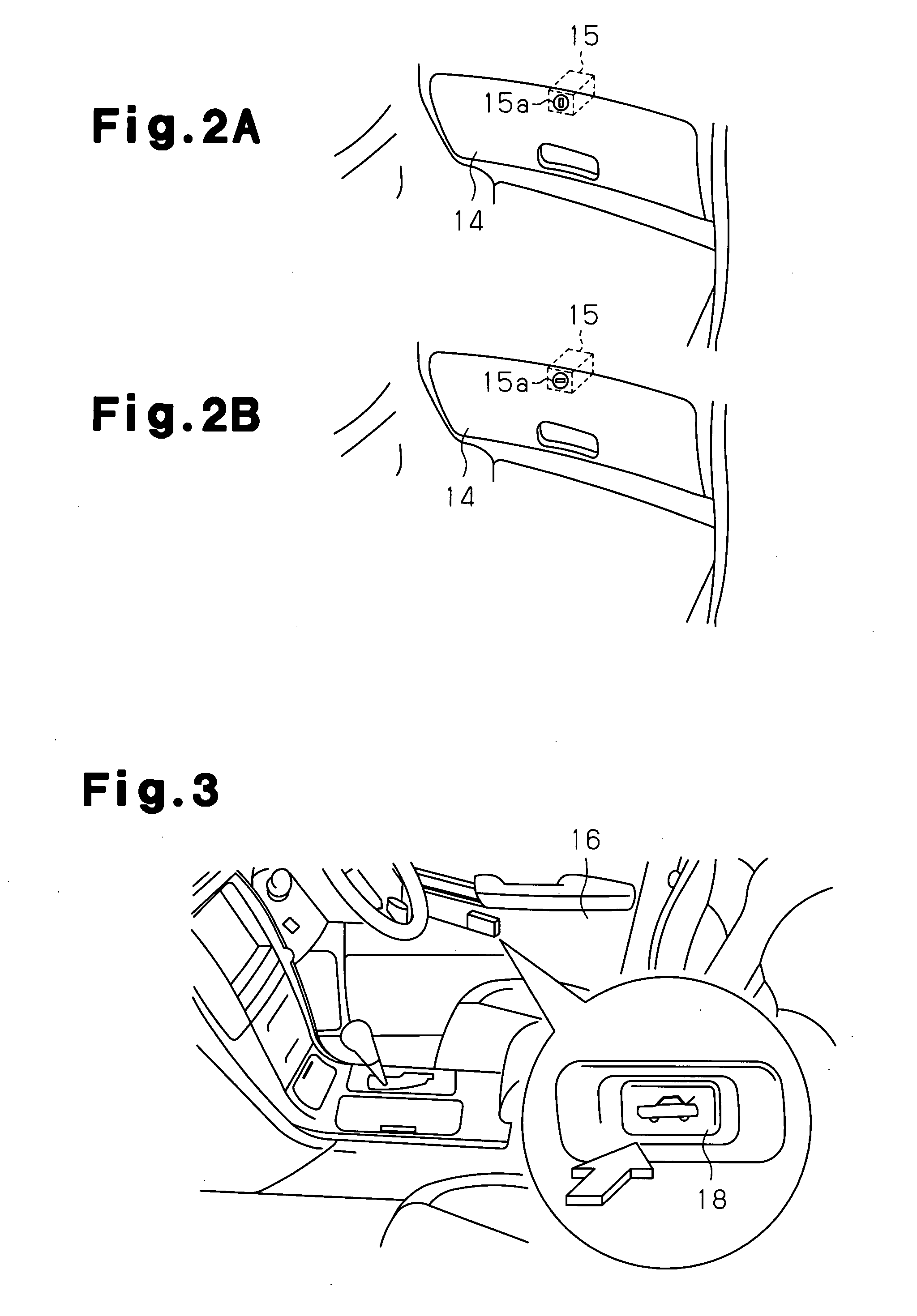
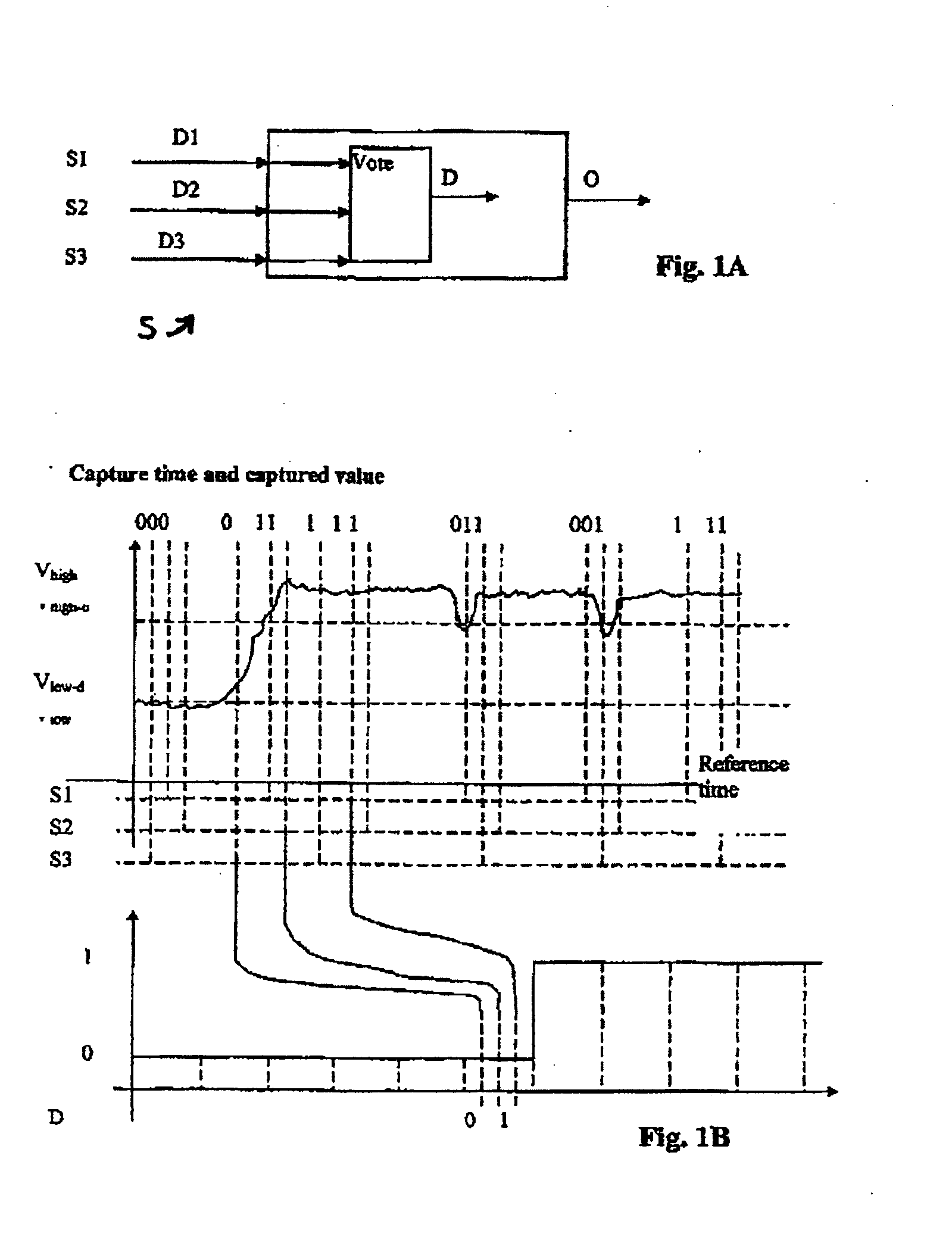
Key system
ActiveUS20080024270A1Eliminate needLock applicationsDigital data processing detailsComputer hardwareCritical system
A key system includes a first authentication part configured to perform first authentication for determining whether or not a unique key code of a key is registered in the operation subject and to permit an operation subject to operate in a state in which a first group of functions is operative when the first authentication generates an affirmative result. A wireless signal receiver is configured to receive a medium code unique to a portable communicable data medium through wireless communication. A second authentication part is configured to perform second authentication for determining whether or not the medium code received by the wireless signal receiver is registered in the operation subject. A condition-imposing part is configured to limit operative functions of the operation subject to a second group of functions that is more limited than the first group of functions when at least either one of the first authentication and the second authentication generates a negative result.
Owner:KK TOKAI RIKA DENKI SEISAKUSHO
Transmission and detection of preamble signal in OFDM communication system
InactiveUS20080095277A1Readily apparentError preventionTransmission path divisionPreambleCritical system
A wireless communication method using wireless signals including a preamble, the method comprising: acquiring a first symbol of the preamble by searching a common waveform; progressively acquiring subsequent symbols of the preamble using information from previous symbols including the first symbol; and acquiring critical system configuration information embedded in the preamble using the first symbol and the subsequent symbols.
Owner:CHENG LIXIN
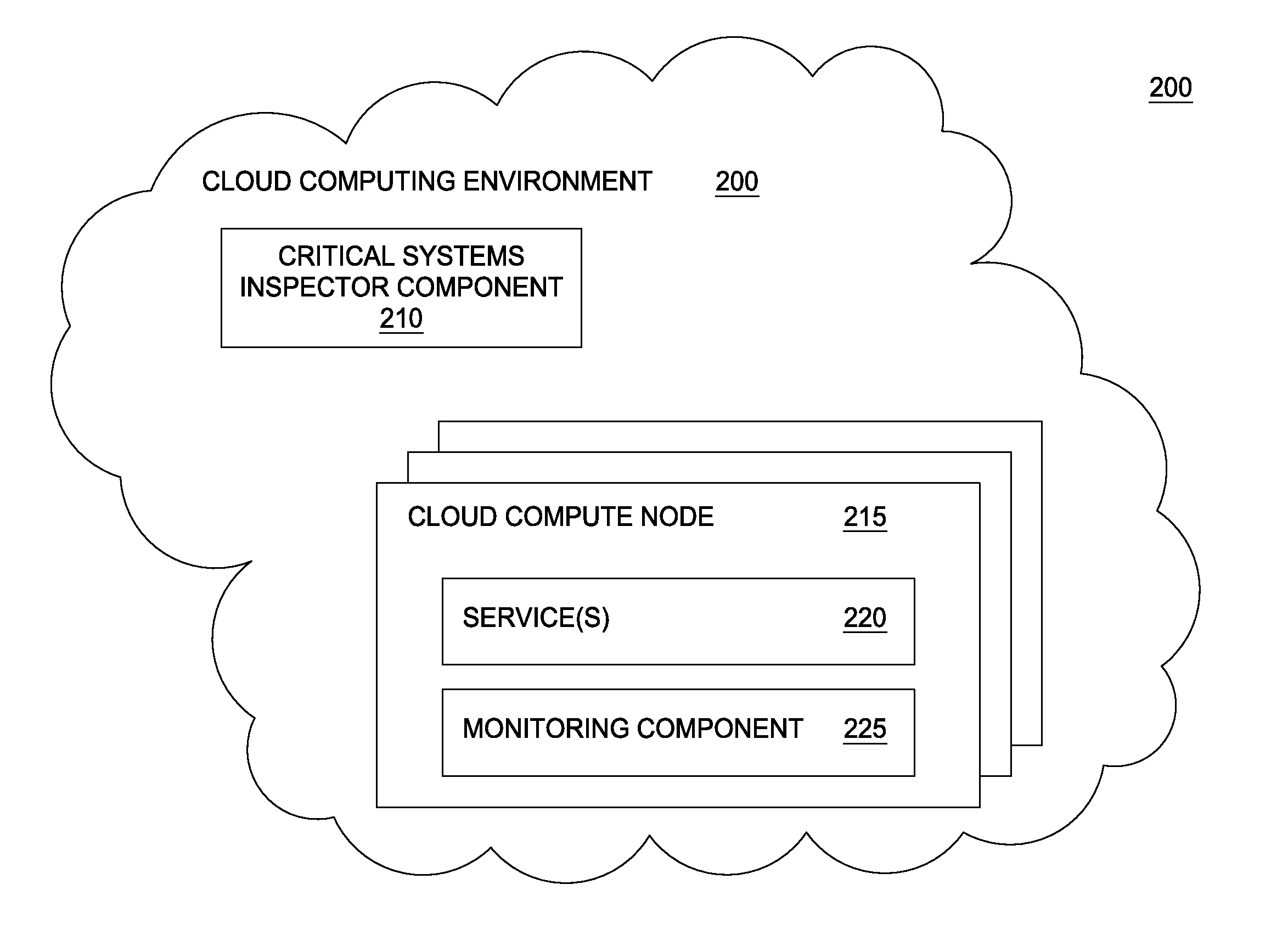
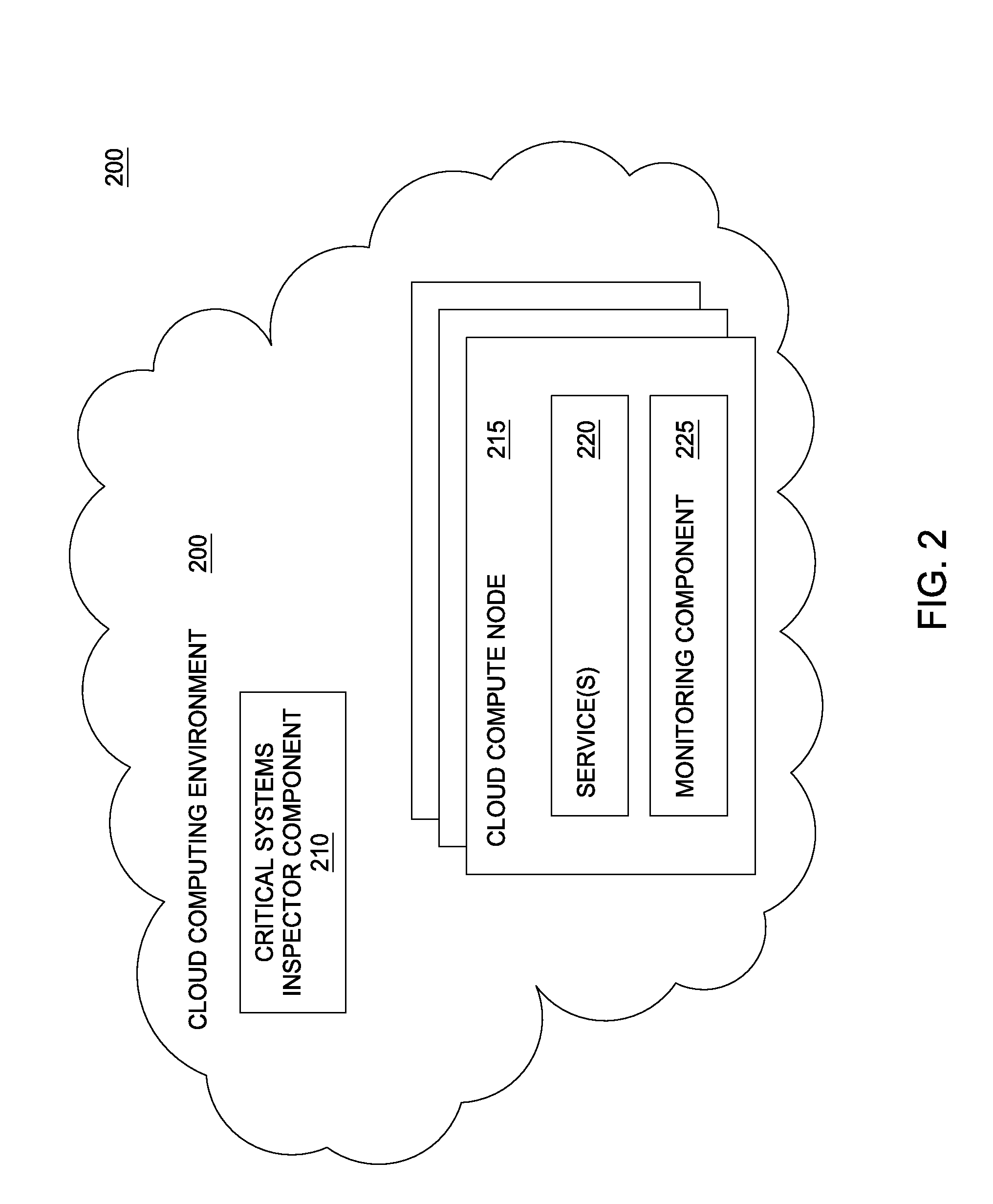
Critical systems inspector
Techniques are described for identifying a root cause of a pattern of performance data in a system including a plurality of services. Embodiments provide dependency information for each of the plurality of services, where at least one of the plurality of services is dependent upon a first one of the plurality of services. Each of the plurality of services is monitored to collect performance data for the respective service. Embodiments further analyze the performance data to identify a cluster of services that each follow a pattern of performance data. The first one of the services in the cluster of services is determined to be a root cause of the pattern of performance data, based on the determined dependency information for each of the plurality of services.
Owner:NETFLIX
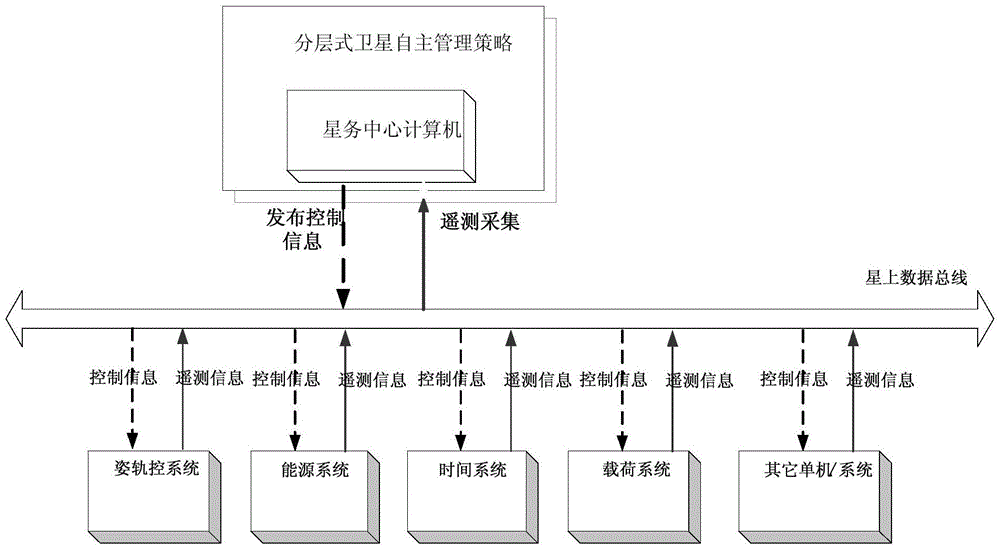
On-orbit autonomous management system for satellite and autonomous management method
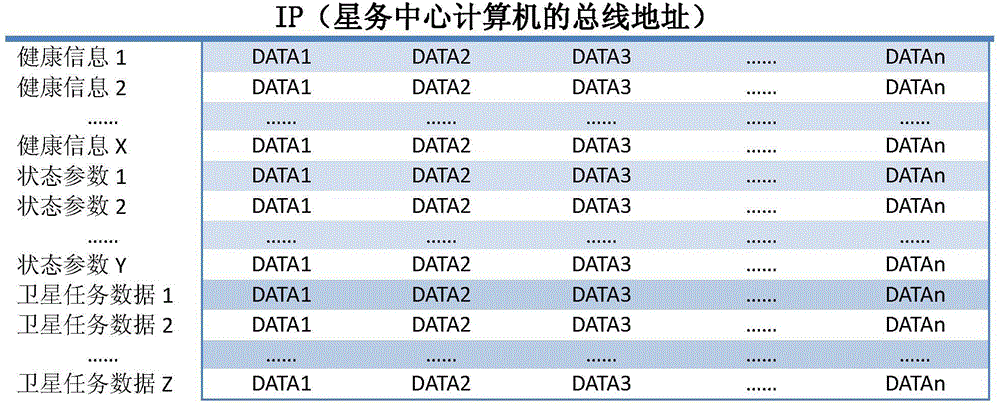
ActiveCN104821894AShorten the timeImprove troubleshooting efficiencyRadio transmissionData switching networksTime-sharingData management
The invention relates to an on-orbit autonomous management system for a satellite and an autonomous management method. Through a method of innovatively leading a bus data monitoring unit and performing state data issuing through unified scheduling for a sub-system on each satellite, state information is directly collected to the bus data monitoring unit, and data extraction by a satellite mission central computer is not required. The bus data monitoring unit directly combines related information for forming alarm information and transmits the alarm information to the satellite mission central computer, thereby saving time in time-sharing acquisition remote sensing and state information data extraction, buying expensive time for treating the fault in time, and improving a fault treating efficiency. A distributed data management method is used for optimizing the operation process of the satellite mission central computer and can simultaneously treat multiple fault alarms which simultaneously occur, thereby realizing intelligent operation for sequencing according to the damage degree and emergency degree of the fault, and maximally ensuring in-time recovery of key system states such as satellite energy and satellite gesture when multiple faults simultaneously occur.
Owner:AEROSPACE DONGFANGHONG SATELLITE
Automated security assessment of business-critical systems and applications
ActiveUS20130174263A1Reduce the risk of fraudReduce audit costsMemory loss protectionWeb data indexingApplication softwareApplication security
Systems and methods which provide a new application security assessment framework that allows auditing and testing systems to automatically perform security and compliance audits, detect technical security vulnerabilities, and illustrate the associated security risks affecting business-critical applications.
Owner:ONAPSIS
Method, System, and Apparatus for Modular Central Plant
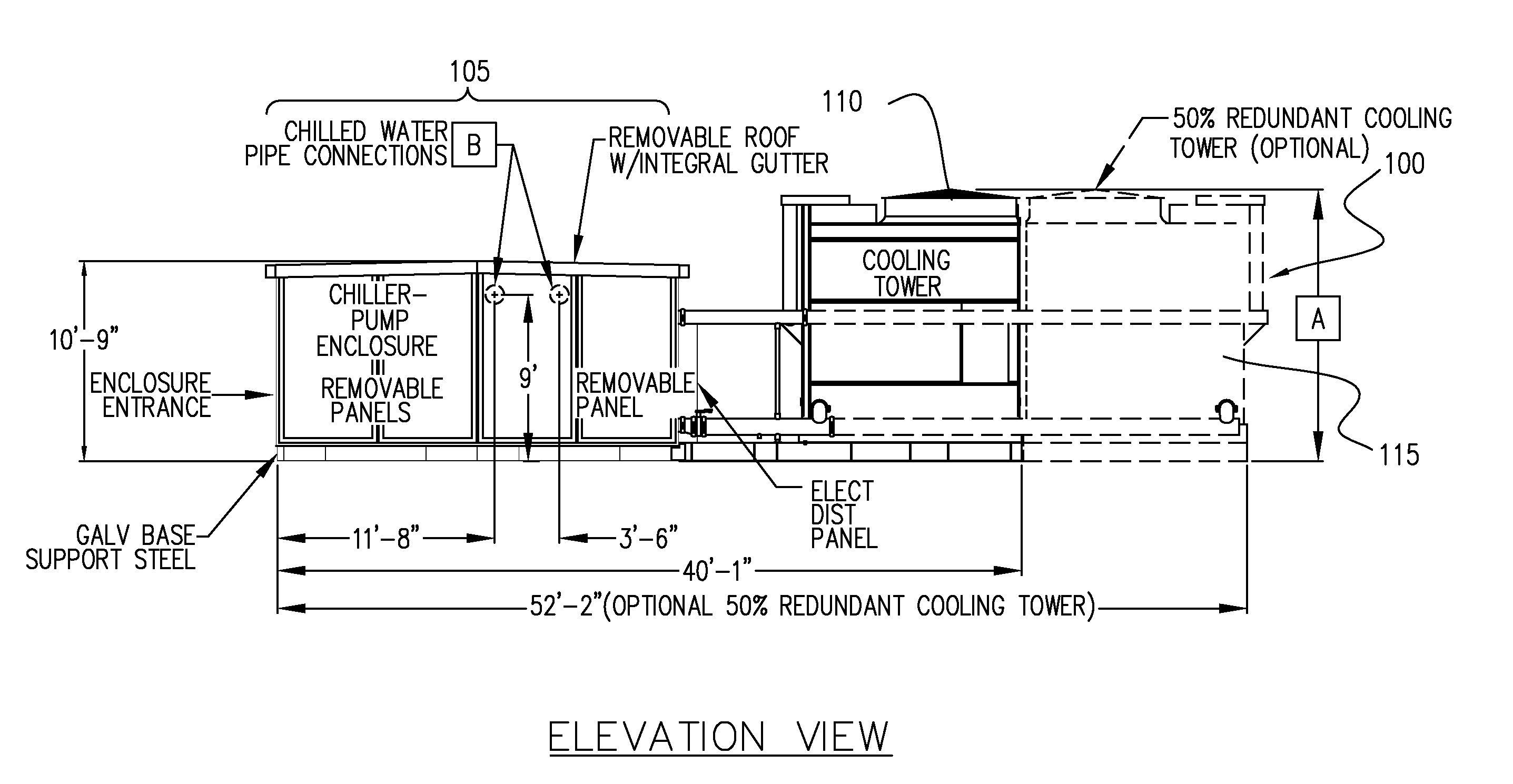
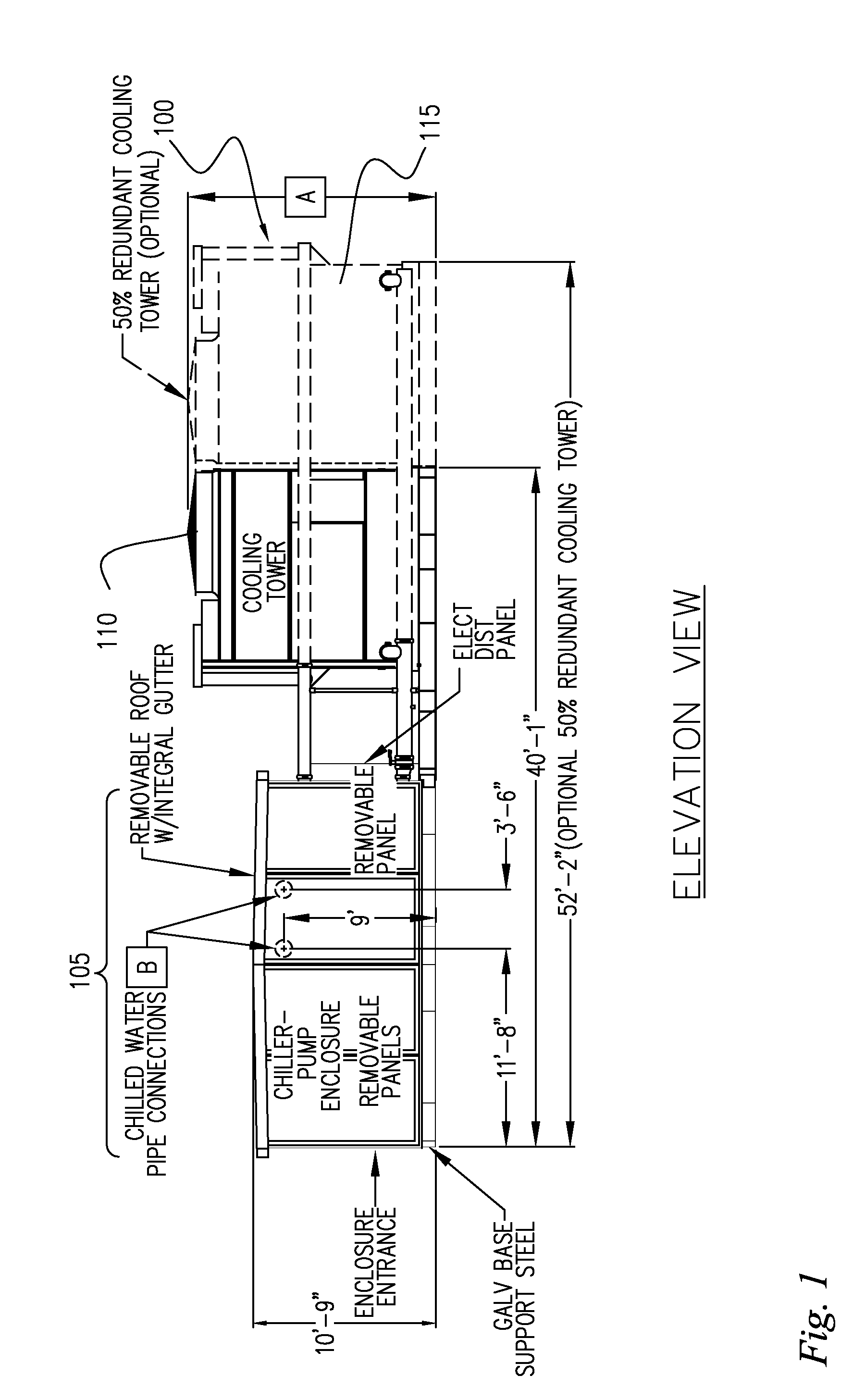
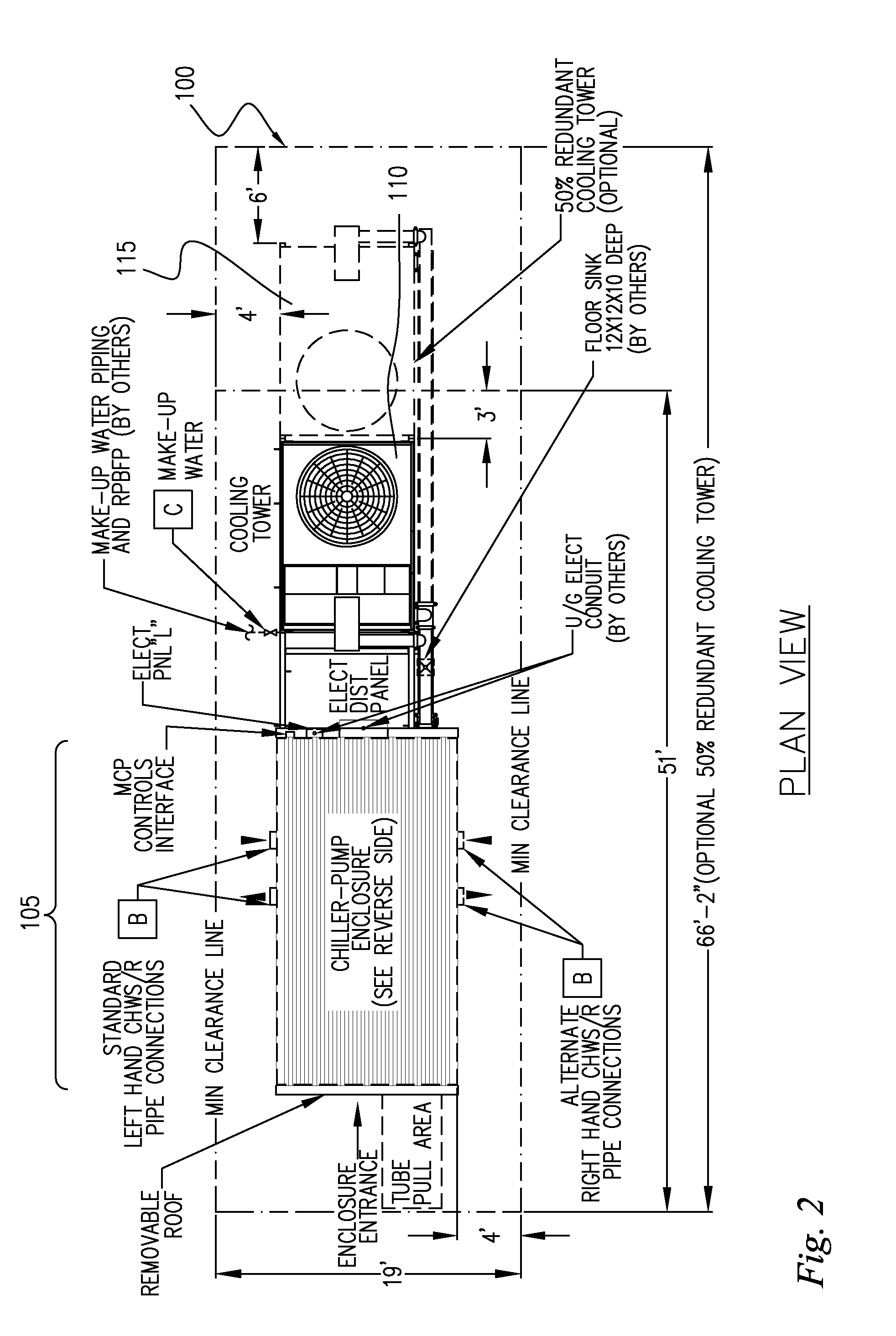
InactiveUS20080127662A1Shorten assembly timeDecreasing cost timeUsing liquid separation agentMixing methodsCooling towerMaintainability
There is provided a system and method for a modular central plant. In one implementation, the inventive system includes a chiller unit and cooling tower that are designed to be modularly assembled, transported, and interconnected, thereby decreasing system cost and assembly time, increasing system maintainability, and improving scalability for increasing capacity at a future date. The removable wall panels and roof of an embodiment of the present invention aid in maintainability by providing enhanced access to critical system components such as the chiller assembly. The modular architecture of the present invention allows for speedy delivery and installation, and with only external electrical and water connections needed, the system can become rapidly operational.
Owner:AAF MCQUAY INC
Downhole hydraulic control system with failsafe features
ActiveUS20080066921A1Fail safeOperating means/releasing devices for valvesFluid removalControl systemControl line
A control system for a subsurface safety valve addresses normal open and closed operation and a failsafe operation if key system components fail. It features a single control line from the surface that splits at the subsurface safety valve and goes to one end of two discrete piston chambers that are aligned and isolated from tubing pressure. The piston in one chamber is larger than in the other and the pistons are connected for tandem movement. Each side of the unbalanced system's piston has a seal mounted to it and another for the rod attached to it that exits the chamber. A jumper line connects the chambers at a point between the seals in each chamber and features a large reservoir. The jumper line is filled with a compressible fluid. Fail safe closure of the valve occurs if any of the four seals fail.
Owner:BAKER HUGHES INC
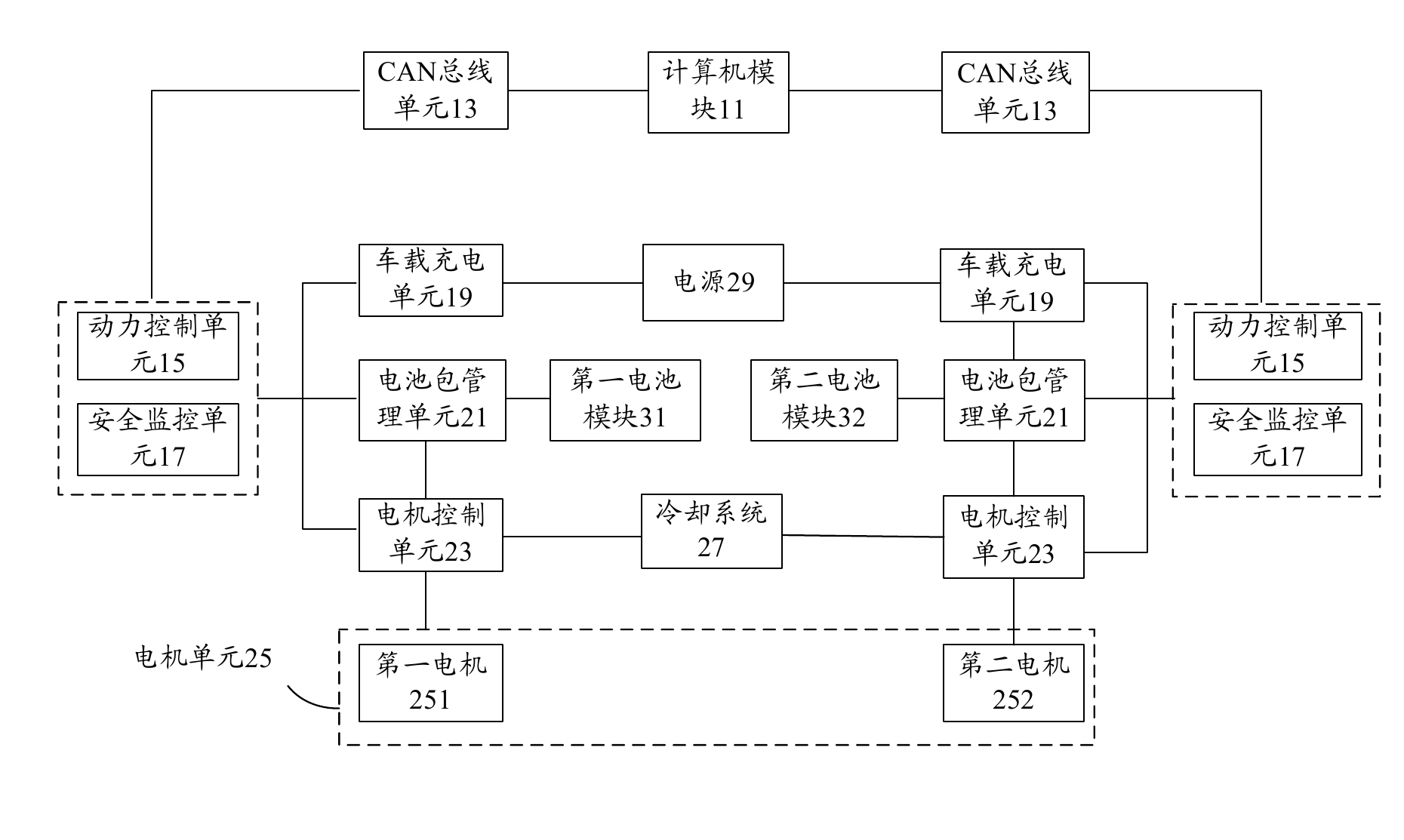
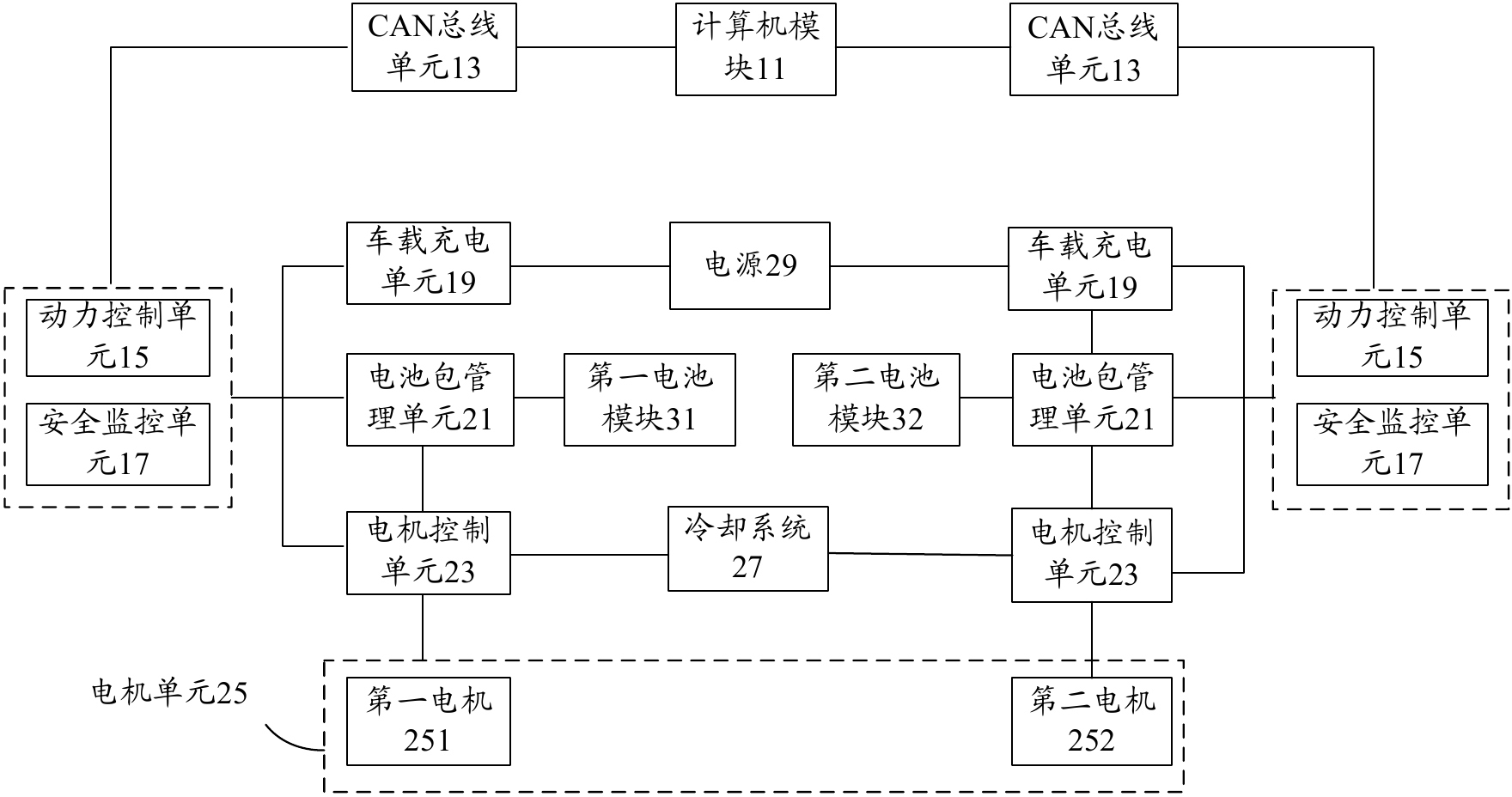
System for testing electric automobile power system assembly
The invention provides a system for testing an electric automobile power system assembly. The system comprises a computer module, a power source, CAN (Control Area Network) bus units, power controlling units, safety monitoring units, vehicle-mounted charger units, battery pack management units, motor controlling units, a motor unit, a first battery module and a second battery module. The motor unit comprises a first motor and a second motor, and rotors of the first motor and the second motor are mutually connected. According to the invention, two identical sets of the motor units, the motor controlling units, the battery pack management units and the vehicle-mounted charger units are combined together. By serially connecting two motors together, energy interacting in the motor unit is realized. Except for inherent operation loss in the system, energy is mutually converted and exchanged among the first battery module, the second battery module and the motor unit, thus the energy is maximally saved, meanwhile, loading testing, service life loading testing and function verifying for core power critical systems of two sets of new-energy automobiles are realized.
Owner:SHENZHEN HANGSHENG ELECTRONICS
System and method for allocating server resources
ActiveUS7581008B2Digital computer detailsComputation using non-denominational number representationCritical systemReal-time computing
A system and method employing an allocation process for determining the number of server machines at each tier of a multiple tiered server system. The allocation process evaluates the number of server machines at each tier sufficient to achieve an average response time of a transaction request to be processed by the server system in response to changes in the average number of transaction requests. The allocation process also identifies shadow pricing enabling analysis of the cost associated with incremental changes in the average response time or other critical system resources.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
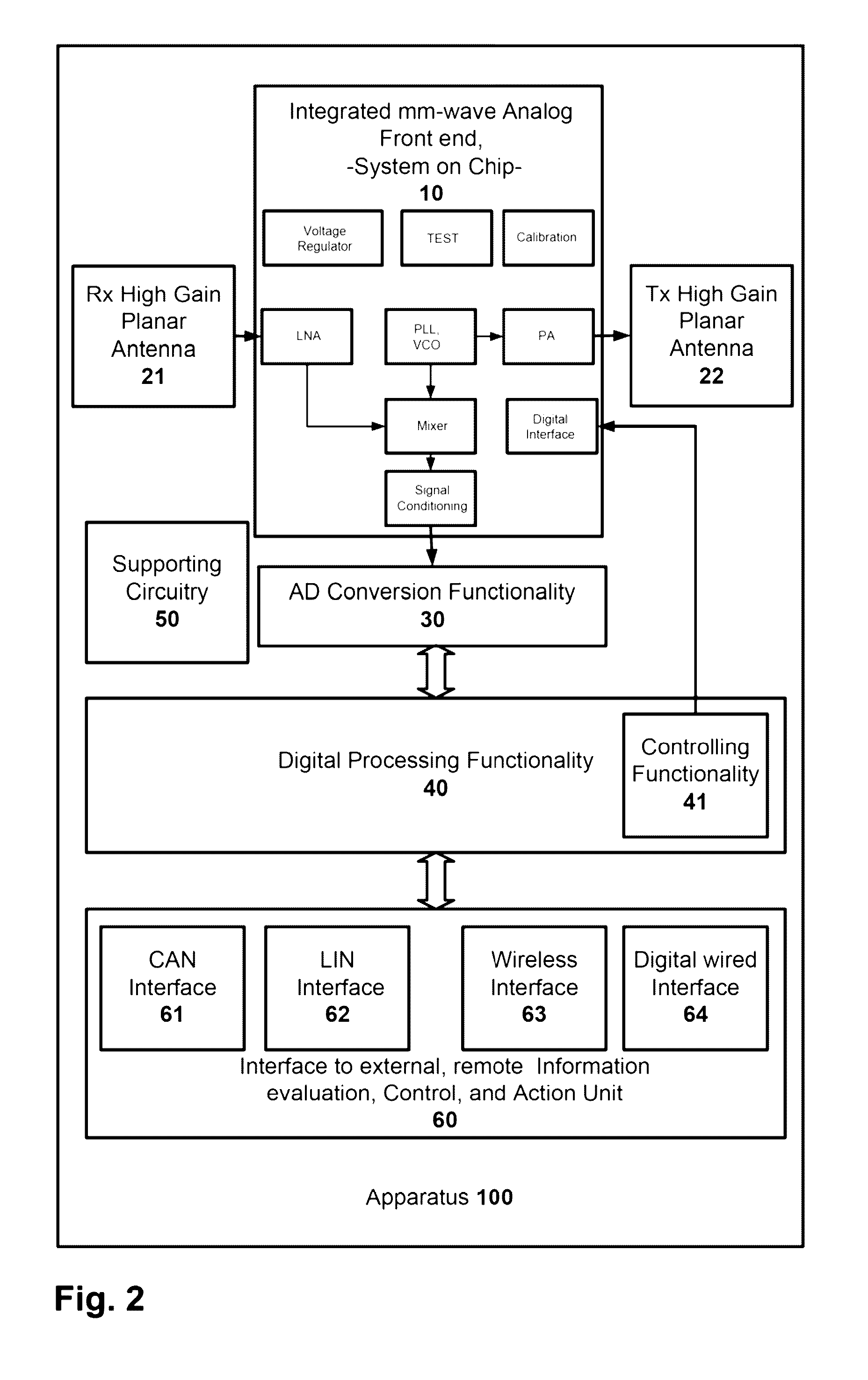
Millimetre-wave seat occupation radar sensor
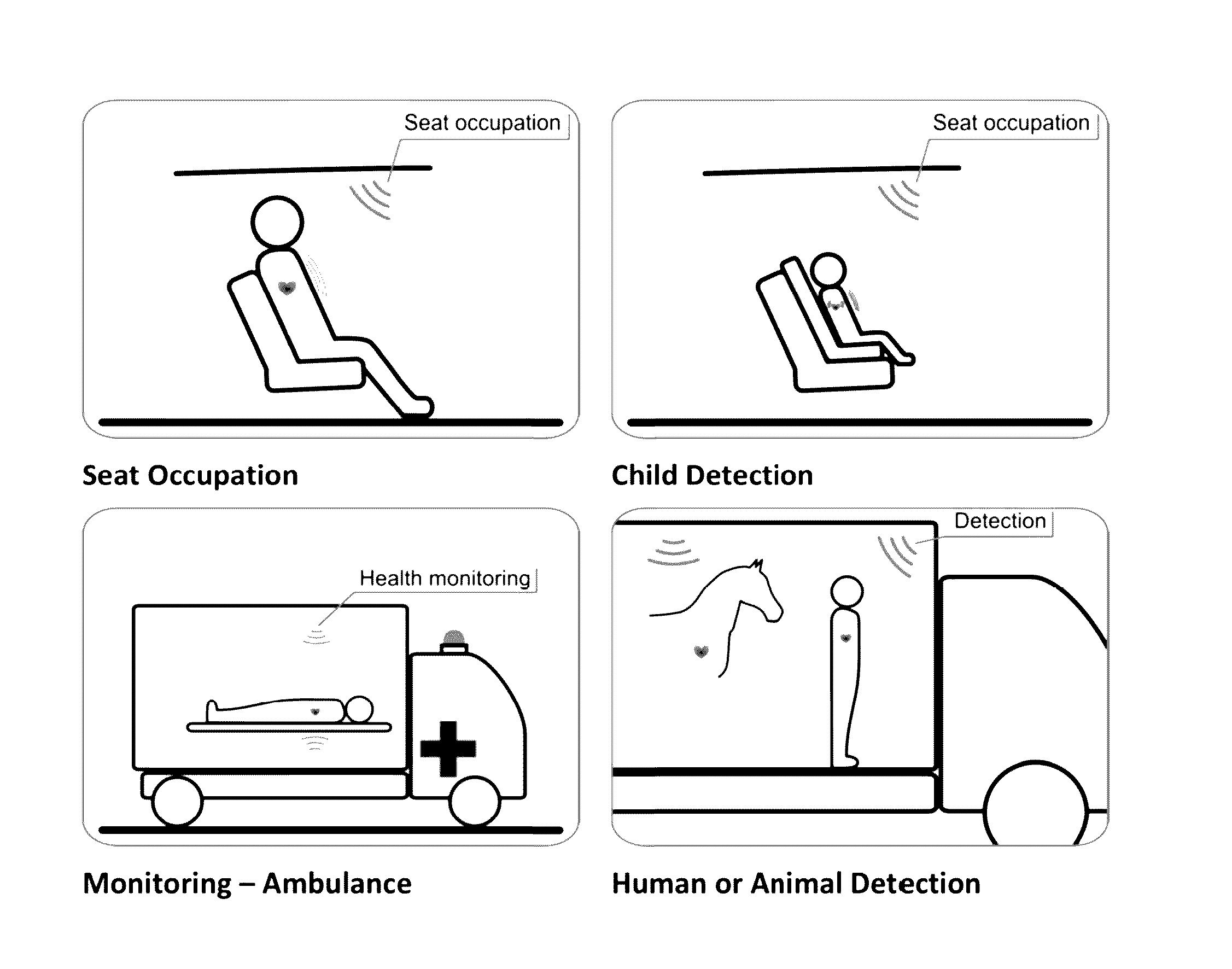
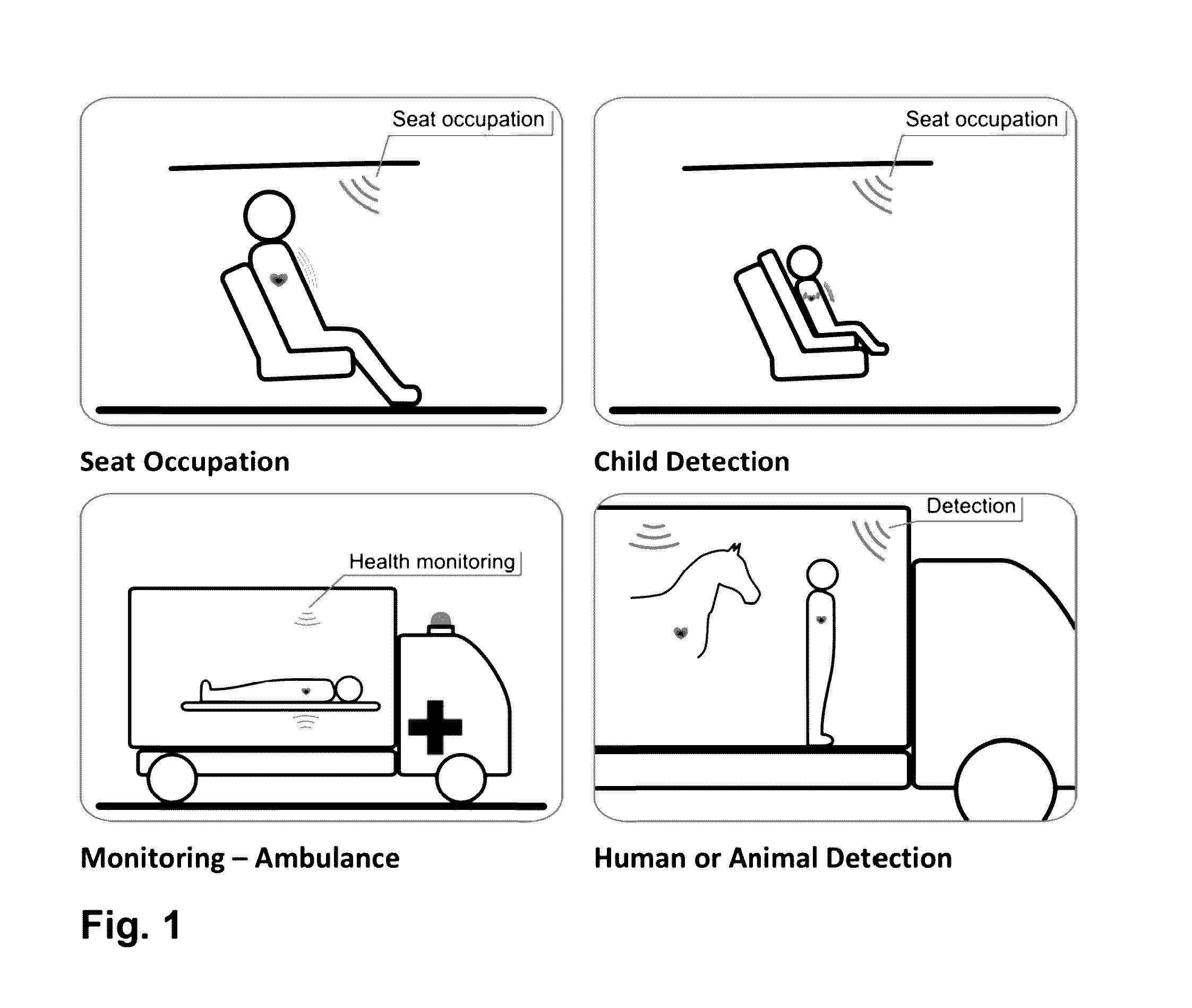
ActiveUS20170039835A1Improve securityVehicle seatsAntenna supports/mountingsTime informationHigh-gain antenna
The present invention discloses a mm-wave radar sensor to be deployed in the vehicles for seat occupation detection applications. The key system relevant components are utilization of mm-wave integrated radar, specific planar high-gain antenna radiation pattern, and analyzing of the heartbeat and optionally also respiratory dynamics. The method of operation calculates probability of the seat occupation event regarding: detection of the passenger on the seat, detection of a baby or a child on the seat, detection of the presence of a baby or a child in the vehicle after the driver has left the vehicle, detection of the human or animal presence of intrusion in specific vehicle environment. In case that probability is above a predefined threshold, typically the interaction with vehicle control system is initiated using arbitrary automotive interfaces. Corresponding predefined actions are taken in that case. The predefined actions could be one or combination of the following: audio signal alerts to driver, inside cabin light condition change, engine operation condition change, opening of the windows or corresponding communication using arbitrary wireless means to outside vehicle environment. Optionally, the system is utilizing additional parameters like vehicle cabin temperature and / or timing information about engine stop and driver leaving the car. Preferably, the system is using 60 GHz or 77-79 GHz integrated radar front end working in Doppler operation mode, with 4×4 Tx and Rx planar radiation elements, with physical size typically in the range 4×2×1 cm, or smaller.
Owner:NOVELIC D O O
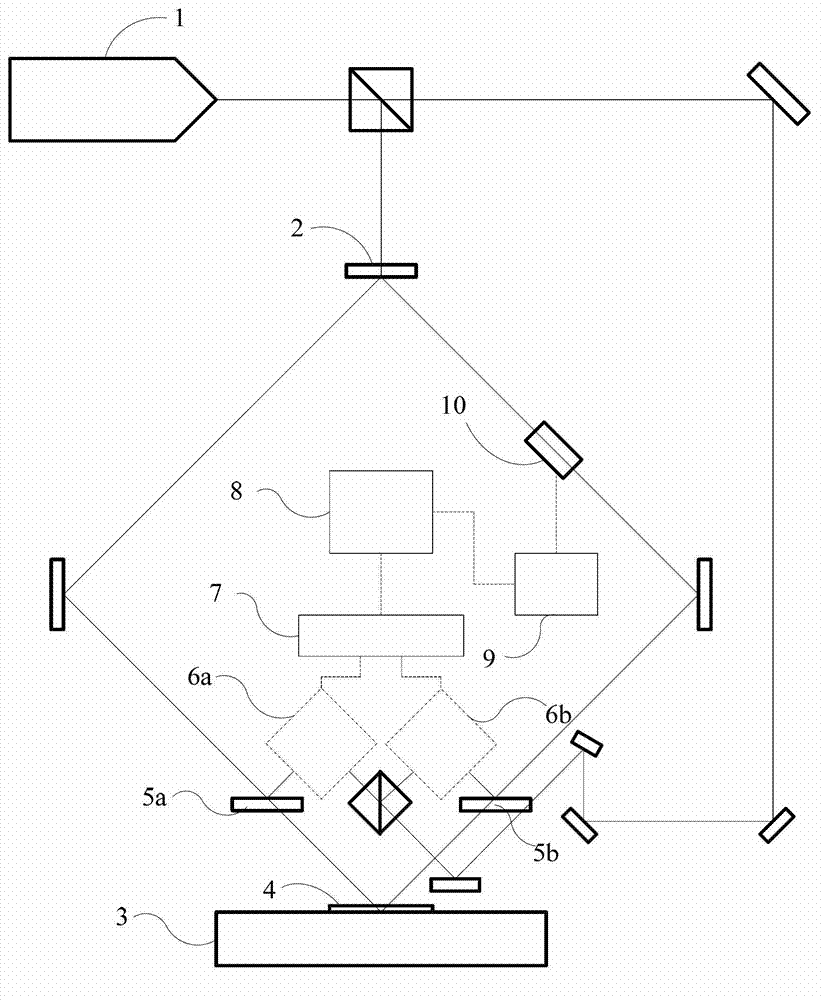
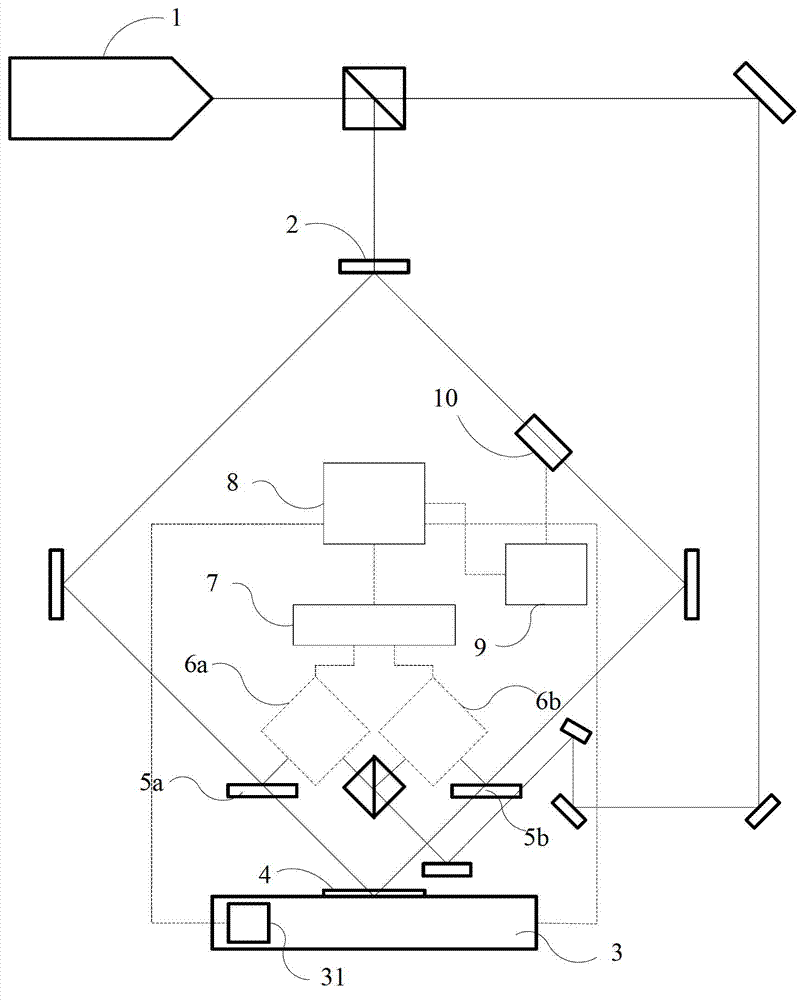
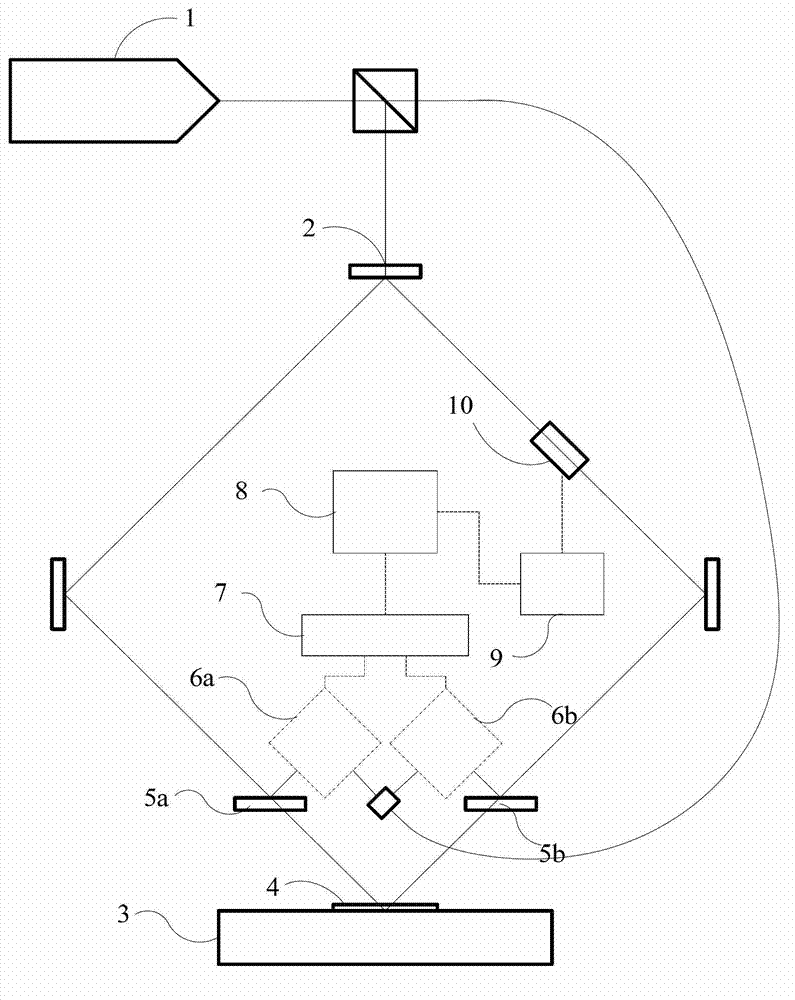
Laser interference lithography system with pattern locking function
ActiveCN103092002AWith graphics lock functionLock high speedPhotomechanical exposure apparatusMicrolithography exposure apparatusGratingBeam splitter
A laser interference lithography system with a pattern locking function comprises a laser, a reflector, a beam splitter, a substrate stage, a substrate and a pattern locking device. A laser beam emitted by the laser is split into an exposure beam and a reference beam by a spectroscope; the exposure beam passes through the beam splitter, and is reflected to the substrate on the substrate stage by the reflector to realize interference; the interference patterns can realize pattern record transfer by exposing the substrate; and the patterns are locked by the pattern locking device to prevent pattern drift during exposure. The pattern locking device includes a null phase meter, an electronic signal processing component, a controller, a driver and a phase modulation executing, wherein the null phase meter is used for measuring pattern phase drift; the pattern phase drift is fed back to the controller through the signal processing component; and the controller controls the phase modulation executer to realize phase locking through the driver. The laser interference lithography system provided by the invention has the advantages of simple structure, high pattern locking accuracy and the like, and is a key system for realizing large-area high-accuracy grating fabrication.
Owner:TSINGHUA UNIV +1
Multiple-redundancy variable master-slave fire alarm monitoring system and method
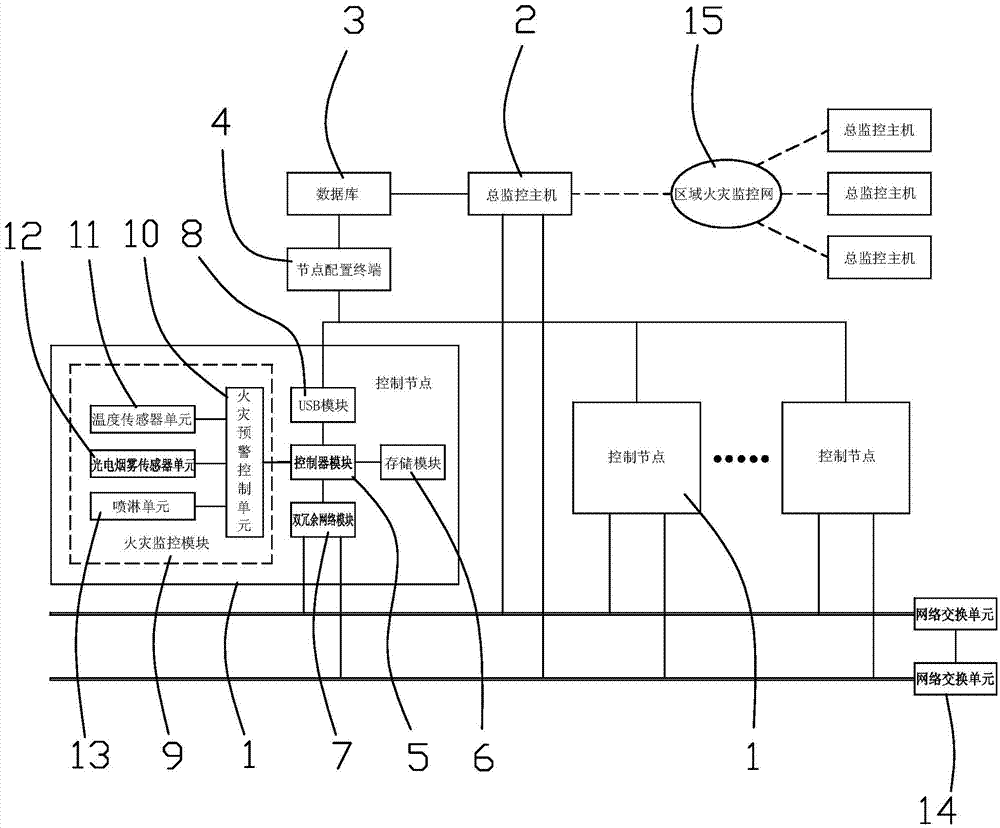
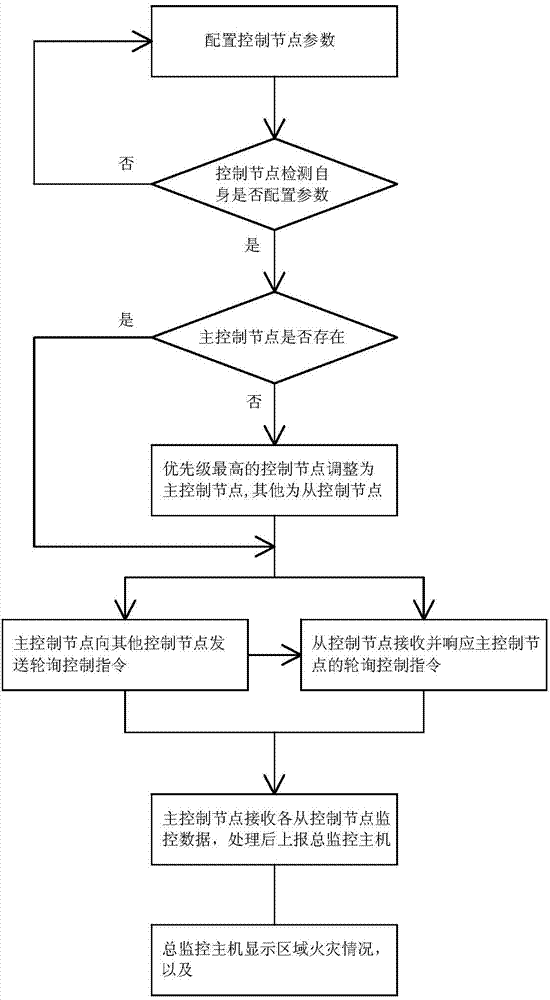
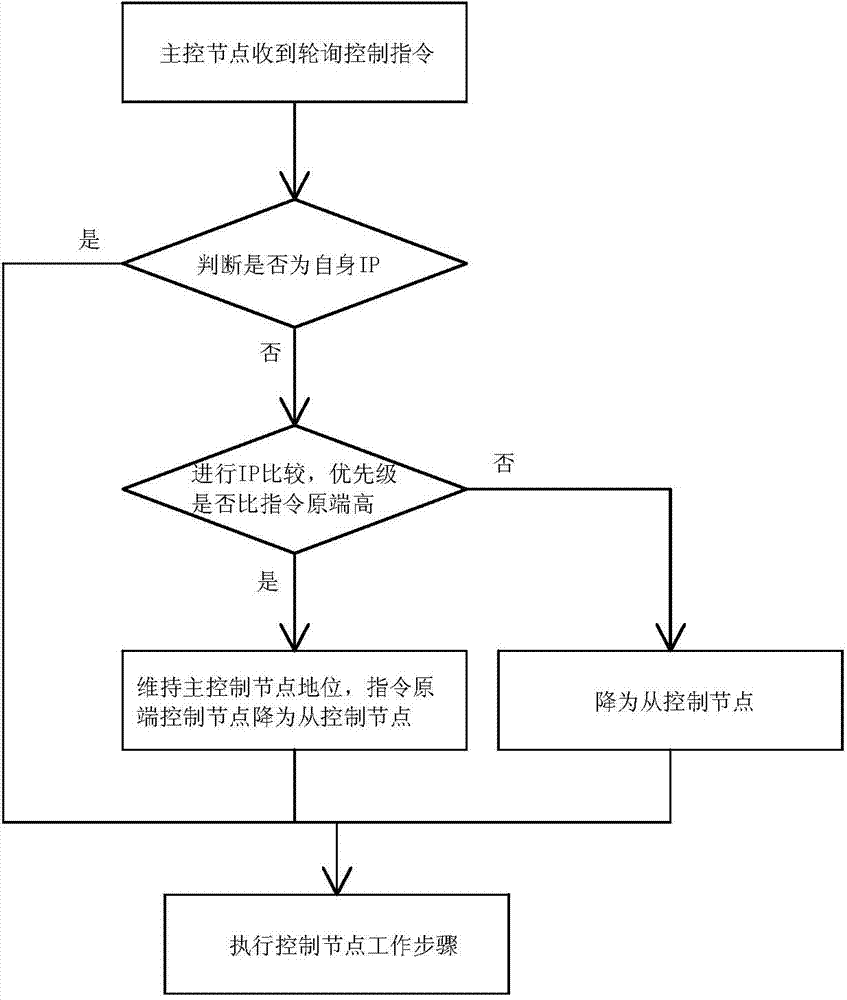
The invention relates to a multiple-redundancy variable master-slave fire alarm monitoring system and method. The multiple-redundancy variable master-slave fire alarm monitoring system solves the problems that a monitoring system in the prior art is weak in real-time performance, is free of key prevention and control differentiation, and fails to work easily when a fault occurs. The system comprises a plurality of control nodes, a master monitoring master computer, a database and a node configuration terminal. Each control node comprises a controller module, a double-redundancy network module, a USB module, a storage module and a fire monitoring module. Each double-redundancy network module is provided with two network interfaces, each network interface is connected to one network exchange unit, the node configuration terminal is connected with the USB module of each control node, the database is connected with the node configuration terminal and the master monitoring master computer respectively, and the master monitoring master computer is connected with the two network exchange units respectively. The system can automatically adjust master-slave relationships according to fault situations and automatically switch the network interfaces and the network exchange units, and therefore the reliability and stability of key systems like the fire alarm monitoring system are greatly improved.
Owner:杭州航海仪器有限公司
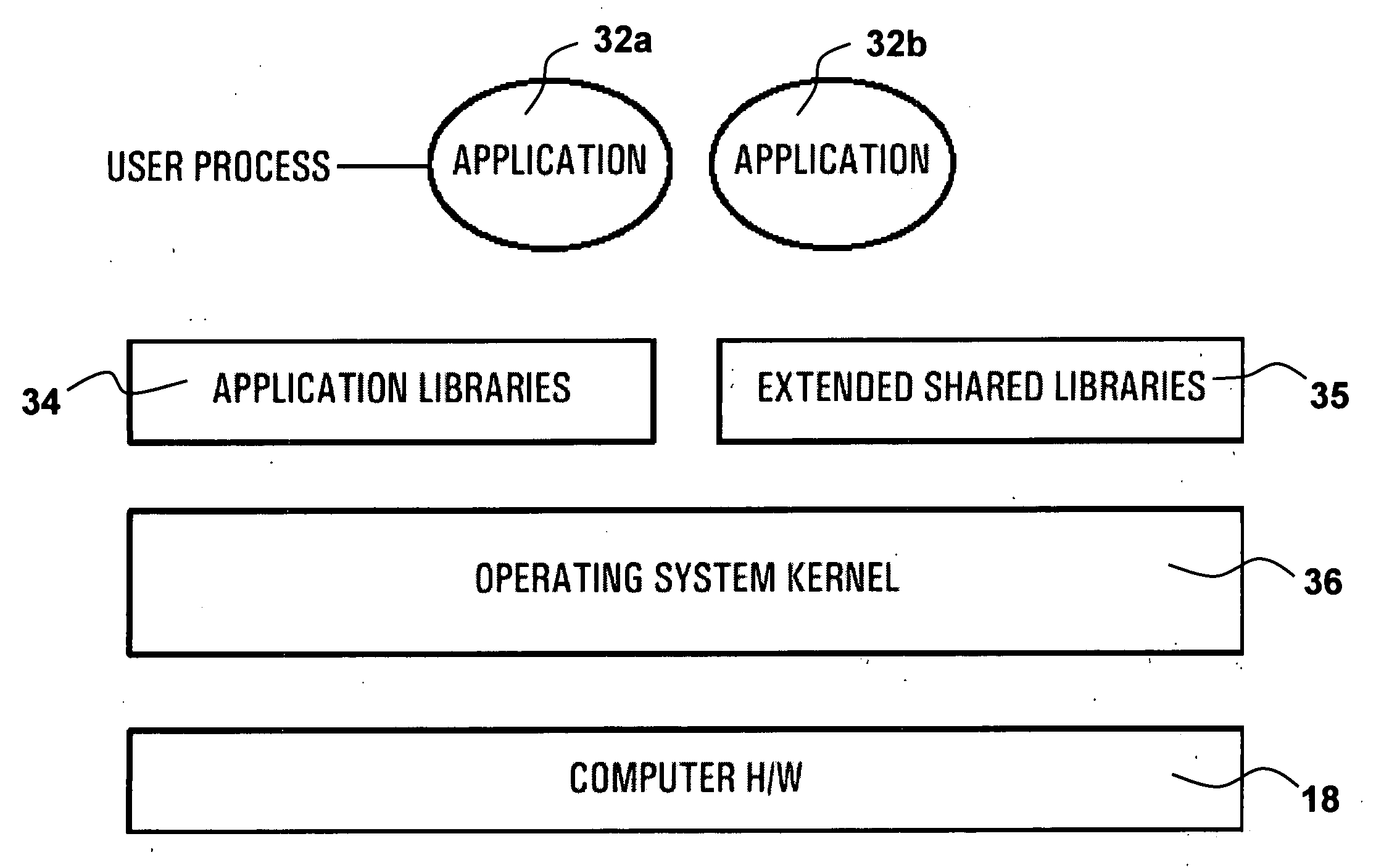
Computing system having user mode critical system elements as shared libraries
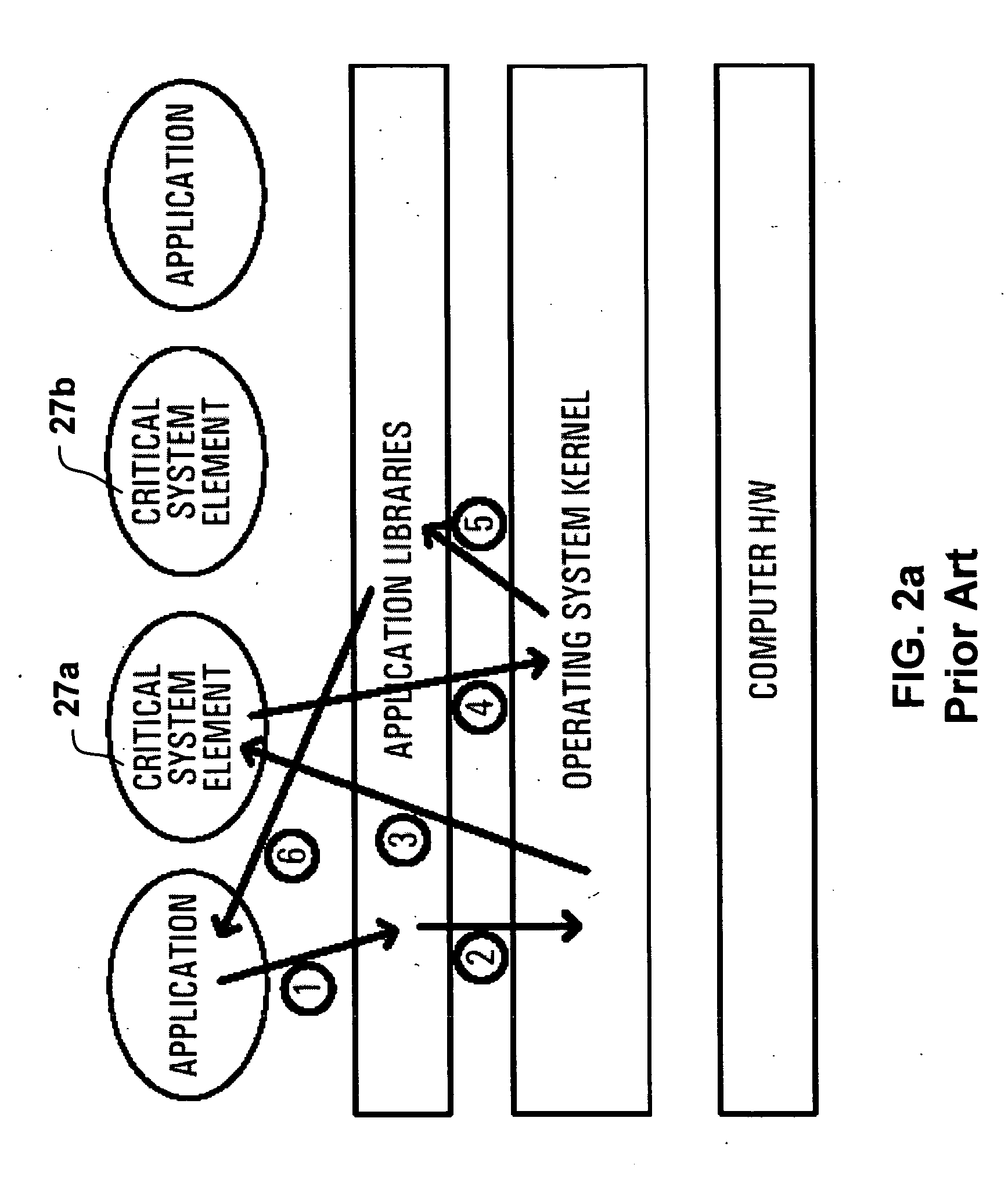
ActiveUS20050066303A1Easy to operateMultiprogramming arrangementsProgram loading/initiatingOperational systemCritical system
A computing system and architecture is provided that affects and extends services exported through application libraries. The system has an operating system having an operating system kernel having OS critical system elements (OSCSEs) for running in kernel mode; and, a shared library having critical system elements (SLCSEs) stored within the shared library for use by the software applications in user mode. The SLCSEs stored in the shared library are accessible to the software applications and when accessed by a software application forms a part of the software application. When an instance of an SLCSE provided to an application from the shared library it is ran in a context of the software application without being shared with other software applications. The other applications running under the operating system each have use of a unique instance of a corresponding critical system element for performing essentially the same function, and can be run simultaneously.
Owner:TRIGENCE CORP
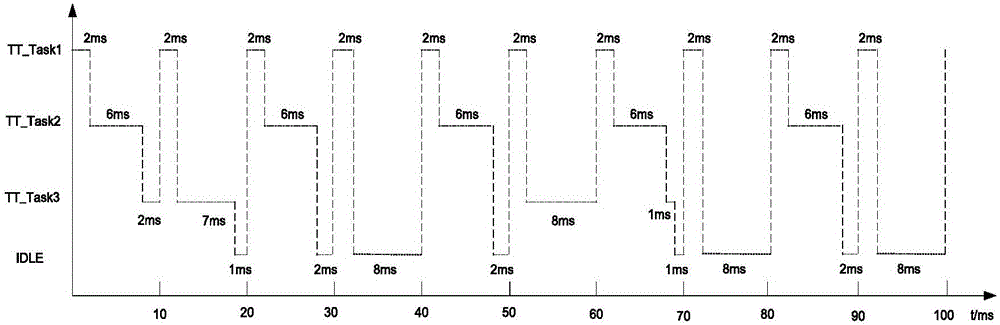
Time-triggered embedded task scheduling device and method
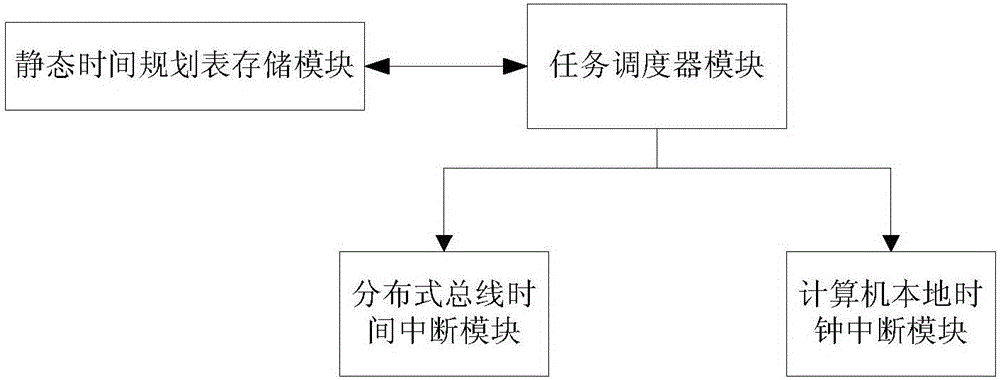
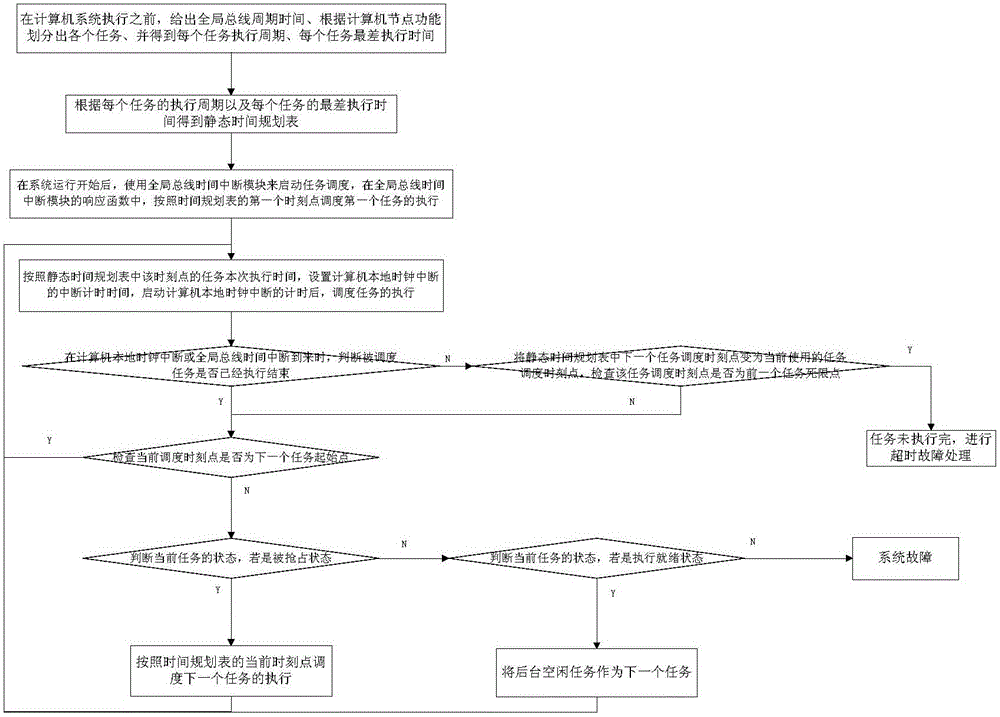
ActiveCN106293919AImprove safety and reliabilityProgram initiation/switchingTime scheduleCritical system
The invention discloses a time-triggered embedded task scheduling device and a time-triggered embedded task scheduling method. The device comprises a static time schedule storage module, a distributed bus time interruption module, a computer local clock interruption module and a task scheduler module. The device and the method disclosed by the invention have the advantages that the task scheduler module is used for switching attributes of a time point according to all tasks predefined in a static time schedule, realizing synchronous execution of distributed nodes by utilization of the distributed bus time interruption module, and monitoring whether task execution time is beyond the worst execution time or not by utilization of the computer local clock interruption module, so that the certainty of the operation of a safety-critical system is guaranteed by utilization of less system overhead.
Owner:XIAN FLIGHT SELF CONTROL INST OF AVIC
Design of safety critical systems
InactiveUS20070168096A1Produced in advanceSafety arrangmentsDigital data processing detailsHardware structureFault tolerance
A method is disclosed of producing a system architecture comprising a plurality of electrical devices connected to each other, said system preferably comprising a fault tolerant system, the method including: a) identifying a set of undesirable events and ascribing to each of said undesirable events an indicator of their severity; b) associating where possible each said undesirable event with one or more actuators of said system architecture; c) developing a functional specification of an initial architecture proposed for implementation of said system architecture; d) refining on said functional specification the fault tolerance requirements; e) producing replicates in said functional specification together with attached indicators of independence of said replicates, f) defining a hardware structure for said system architecture; g) mapping of said functional specification onto said hardware structure; and h) verifying automatically that said indicators of independence are preserved during mapping.
Owner:RENAULT SA
Method for automatically decomposing dynamic system models into submodels
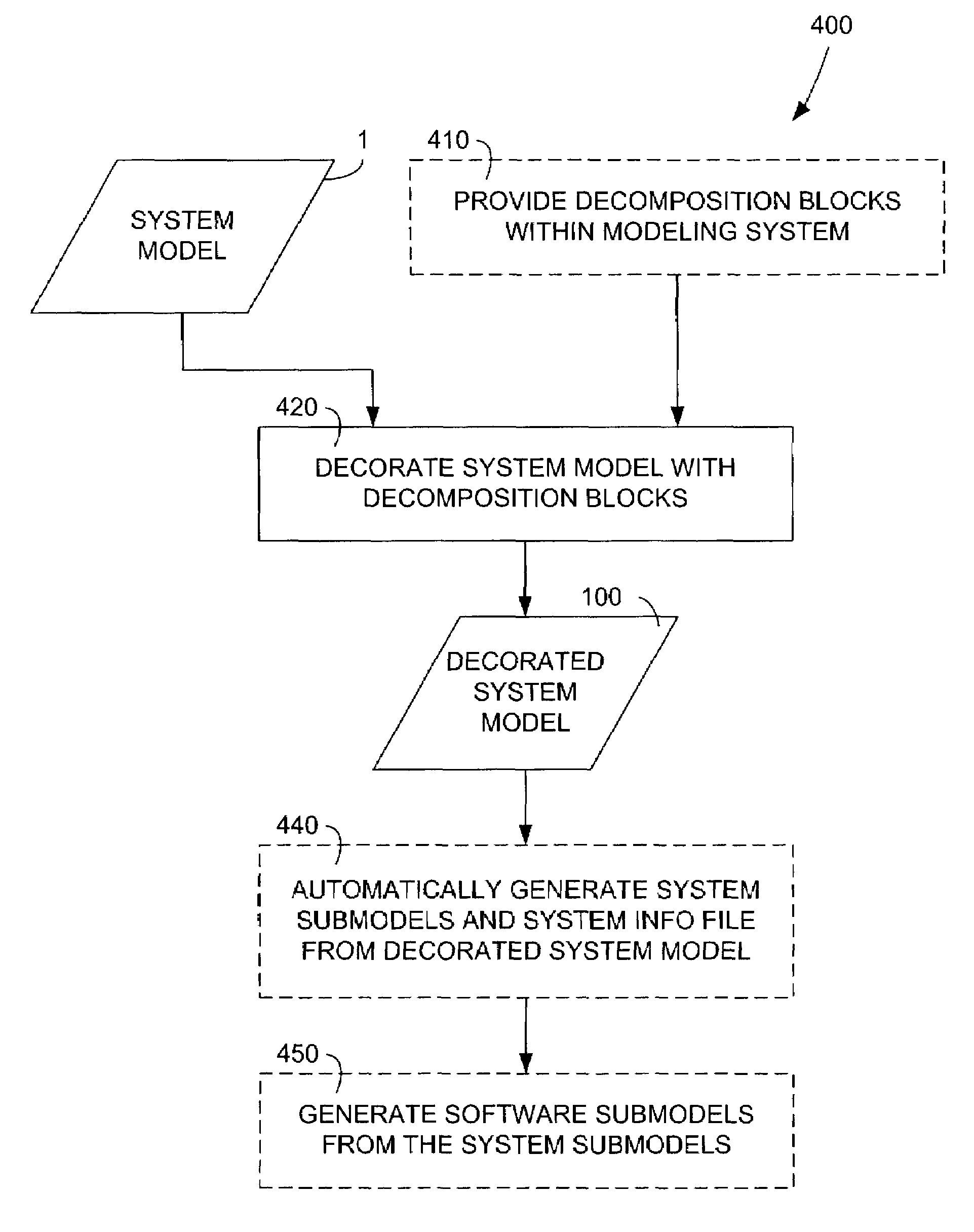
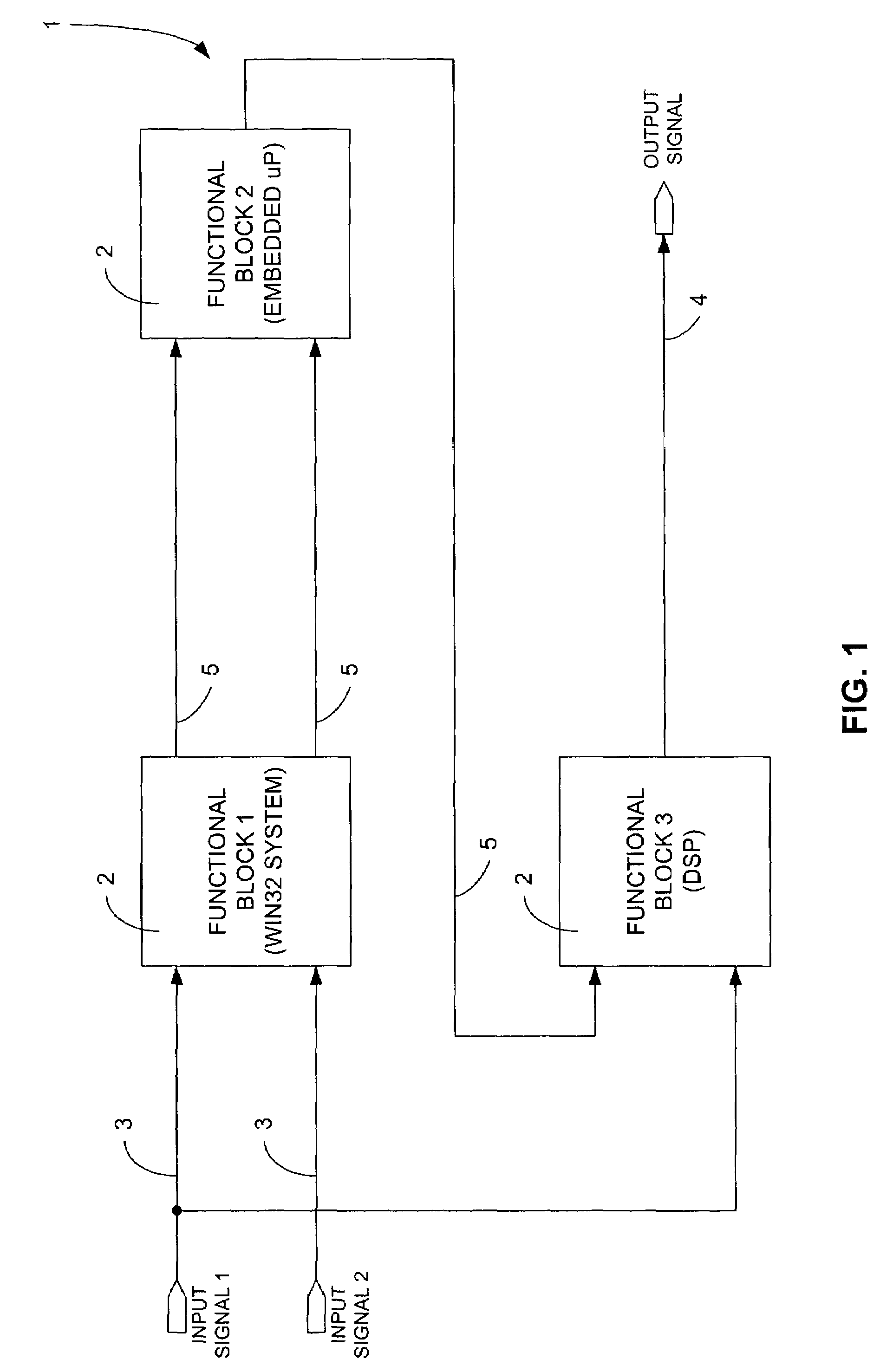
InactiveUS7194726B2Facilitate communicationAvoid deadlockDesign optimisation/simulationSpecific program execution arrangementsDynamic system modelCritical system
A method for automatically decomposing a dynamic system model into separate submodels for ultimate execution on diverse target platforms is provided. Embodiments of the invention provide a way for a system designer to indicate which portions of a previously-specified system model are to become submodels. Optionally, the designer may also indicate the associated target platform for the execution of each submodel. A system submodel for each portion designated by the designer is generated, keeping all critical system-level information consistent throughout the entire system model. Each of these system submodels may then be employed to generate a software version of each system submodel. Each software submodel may then be transferred to its specified target platform and executed in cooperation with the other software submodels to effect an overall system simulation executing across the associated target platforms. Alternately, one or more system submodels may be replaced by the actual components of the dynamic system represented by those system submodels.
Owner:AGILENT TECH INC
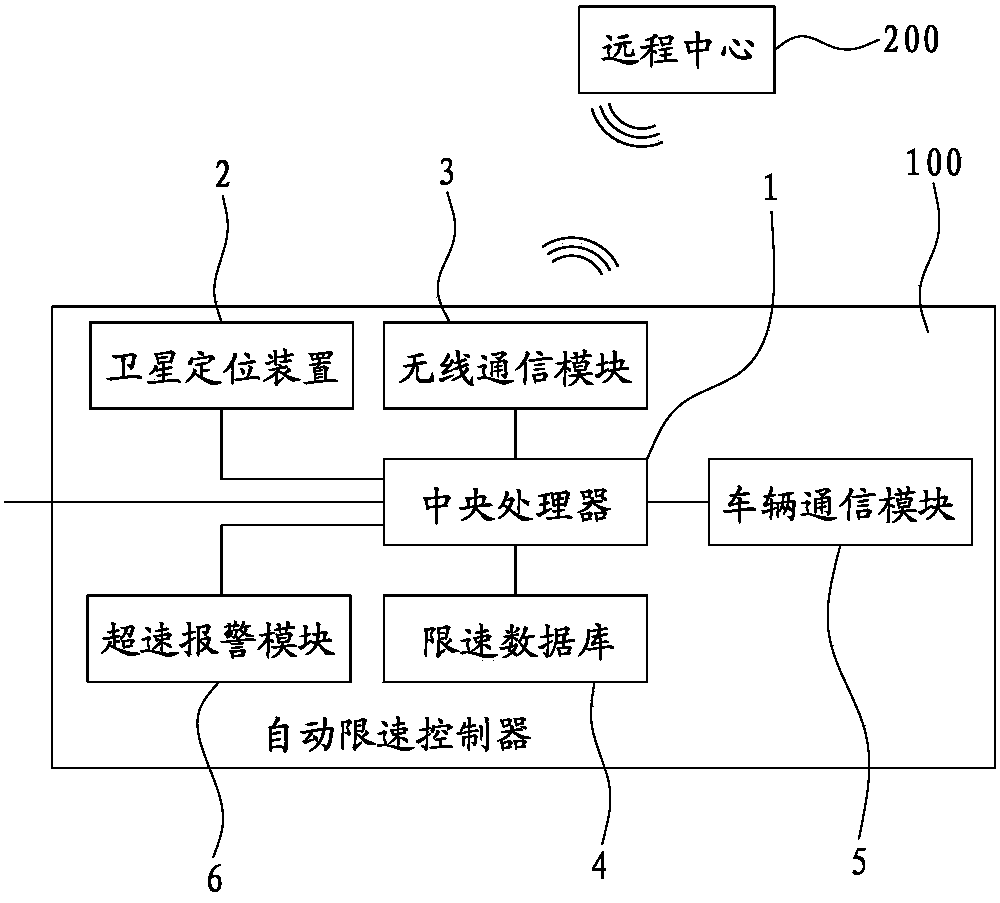
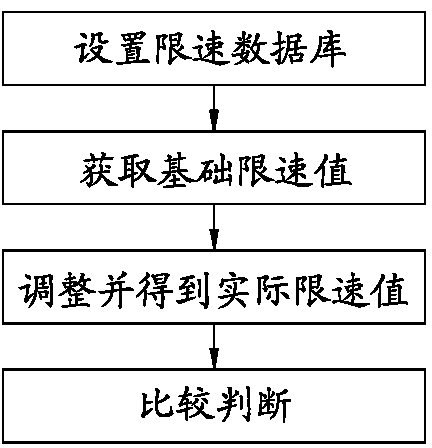
Automatic vehicle speed limit control system and control method
InactiveCN103818258ASpeed limit reachedMinor changesVehicle fittingsSpeed/accelaration controlTime informationThrottle control
The invention discloses an automatic vehicle speed limit control system and control method. The automatic vehicle speed limit control system comprises an automatic speed limit controller and a remote control center. The automatic speed limit controller comprises a central processor, a satellite positioning device, a wireless communication module, a speed limit database, a vehicle communication module and an overspeed alarming module, wherein the satellite positioning device, the wireless communication module, the speed limit database, the vehicle communication module and the overspeed alarming module are connected with the central processor, the satellite positioning device acquires longitude and latitude information and time information of a vehicle and transmits the longitude and latitude information and the time information to the central processor, the central processor is in communication connection with the remote control center through the wireless communication module, the vehicle communication module acquires working states of the vehicle and provides the working states of the vehicle to the central processor, speed limit values matched with the longitude and latitude information and the time information of the vehicle are prestored in the speed limit database, and the central processor is connected with an engine through a bus. Compared with the prior art, additional modification does not need to be carried out on the vehicle, a sensor does not need to be added either, key systems such as throttle control are not changed, and extreme convenience is achieved.
Owner:XIAMEN KING LONG UNITED AUTOMOTIVE IND CO LTD
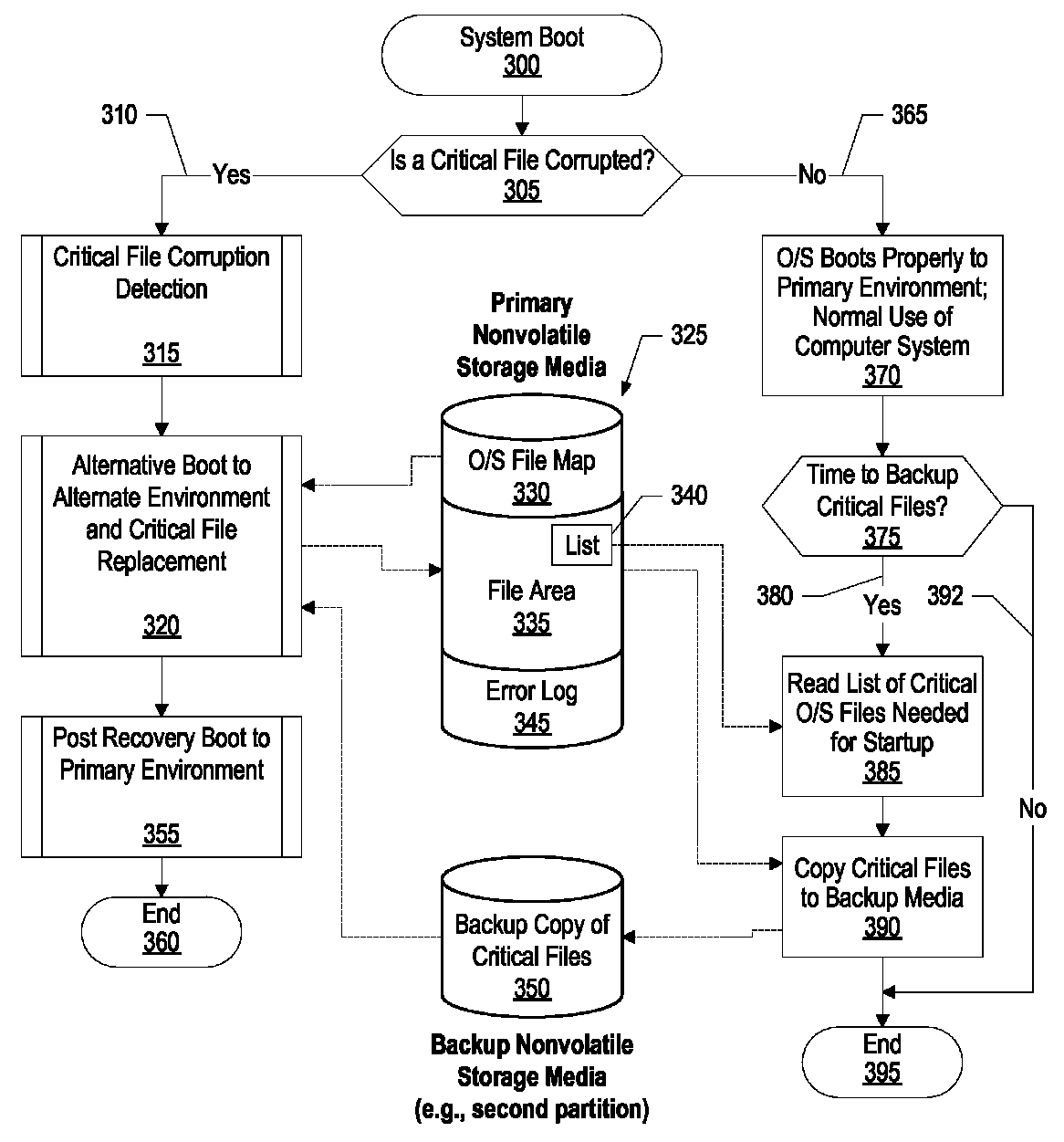
Recovering from hard disk errors that corrupt one or more critical system boot files
A system, method, and program product is provided that recovers from a sector error affecting a critical file. A damaged sector prevents a critical file from being read prevents the computer system from booting. A controller records a sector number corresponding to the damaged sector. The system is rebooted using an alternative boot media. The system accesses the primary nonvolatile storage media after the rebooting. The damaged sector number is read from the error log and a file map is used to determine the critical file that is stored in the damaged sector. A backup copy of the critical file is retrieved from a backup media. The backup copy is written to the primary media using undamaged sectors and the critical file is mapped to the undamaged sectors. The system is subsequently booted successfully from the primary nonvolatile storage media.
Owner:LENOVO PC INT
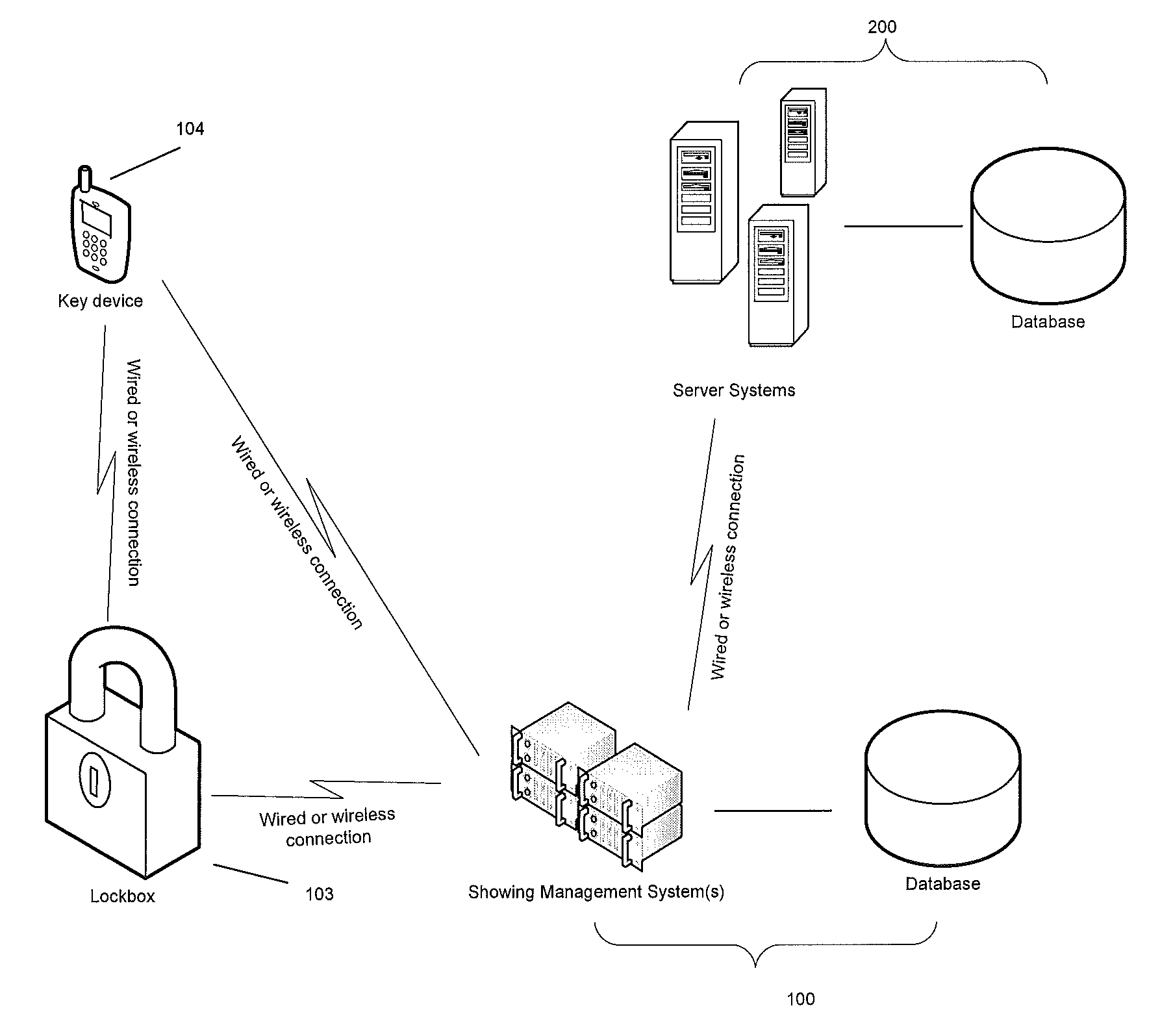
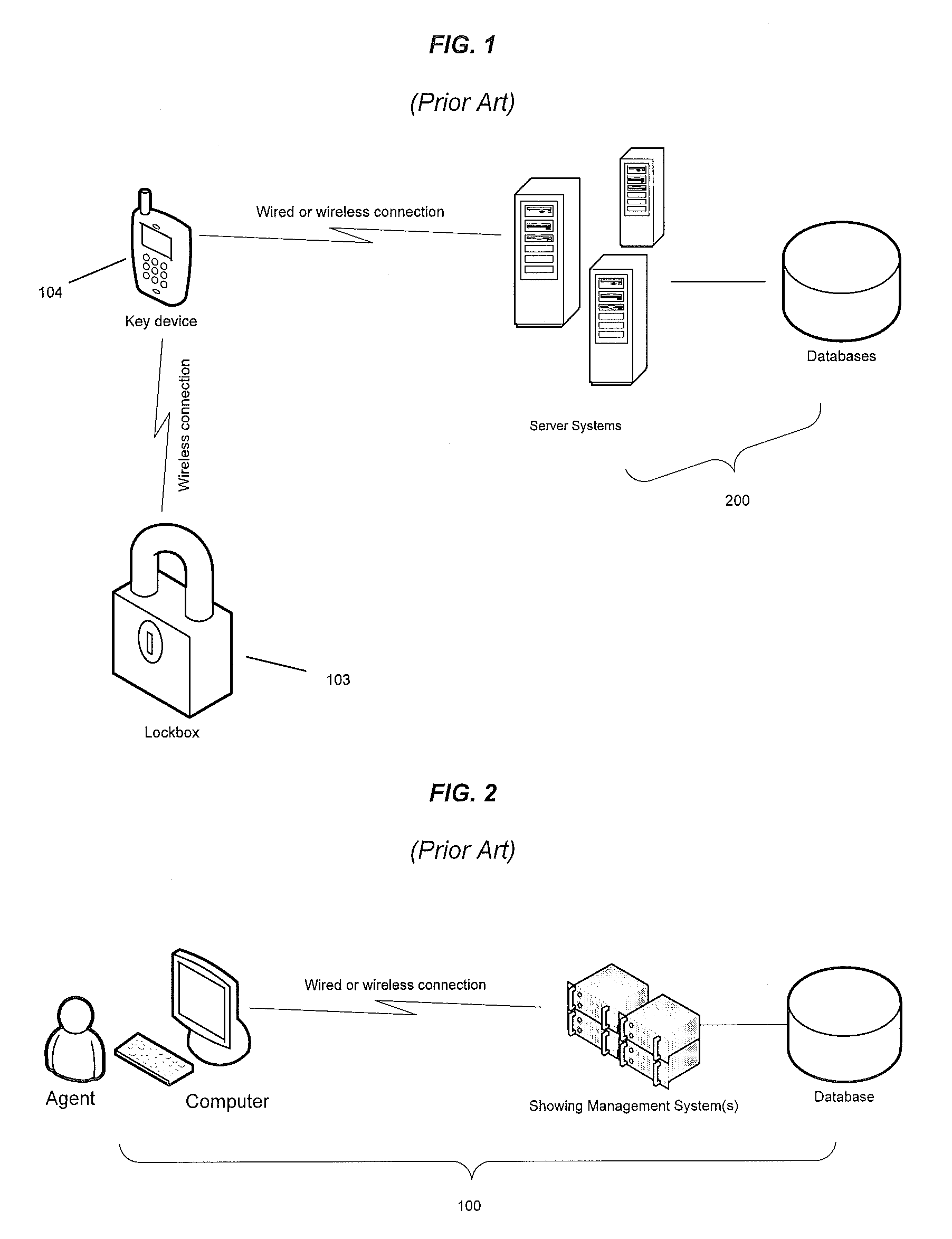
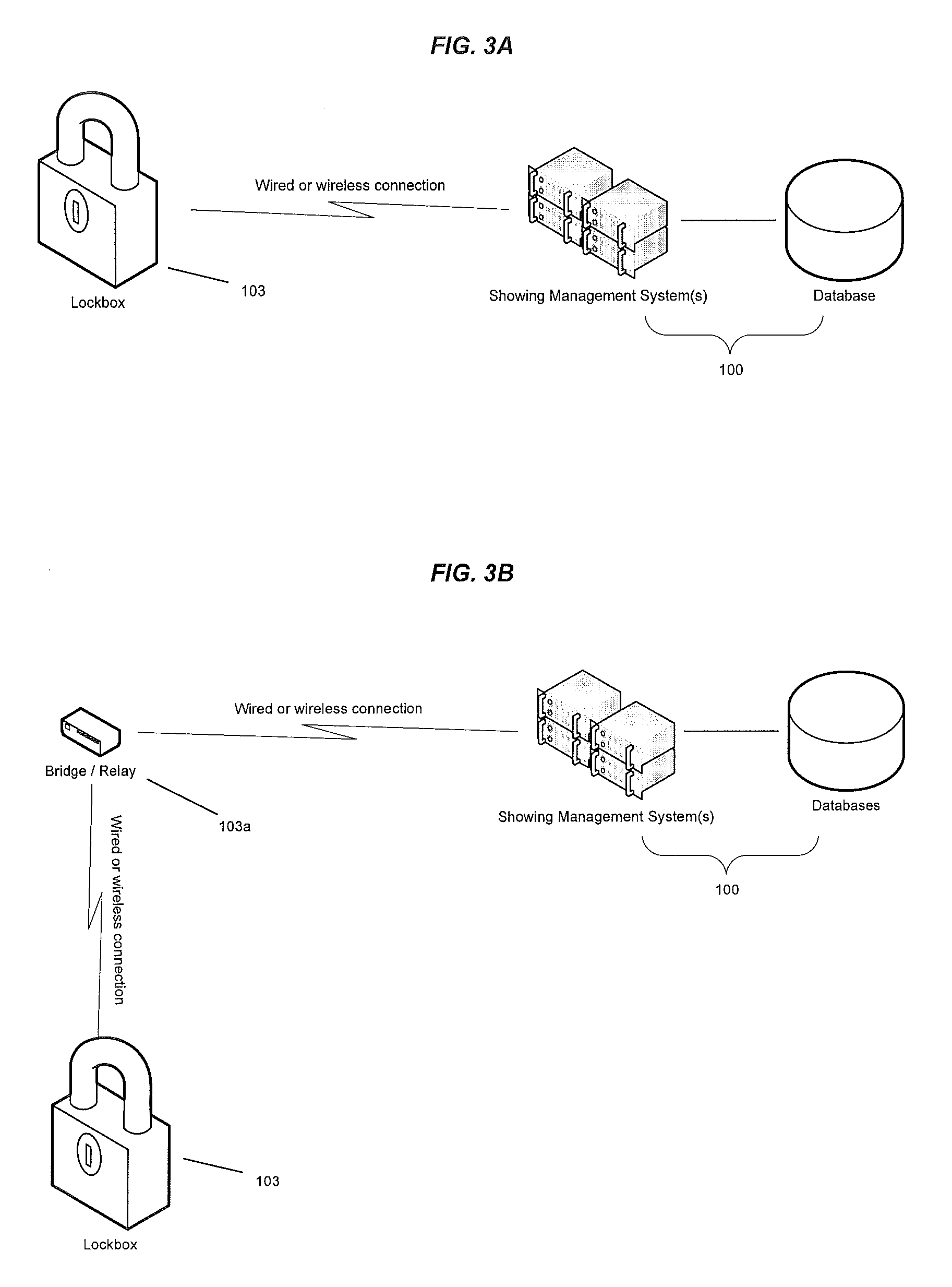
Integrated real estate showing scheduling and key management system
A system and method for dispensing a key from a key kiosk disposed at a realtor's office near a real property based on a showing appointment scheduled with a showing scheduling system. The appointment, including a date and time, as well as an authorized user is communicated from the showing scheduling system to the key kiosk. The user then authenticates herself or himself to the kiosk at the appropriate time, and the key is dispensed. The kiosk authenticates the user by scanning a QR code or using the physical location of the user. The kiosk will not dispense the key if the user has a different key that is checked out, but not returned yet. The key can be returned to the kiosk where it is dispensed, or a different key kiosk. The kiosk also dispenses a single common key when the user shows multiple properties.
Owner:MFTB HOLDCO INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com