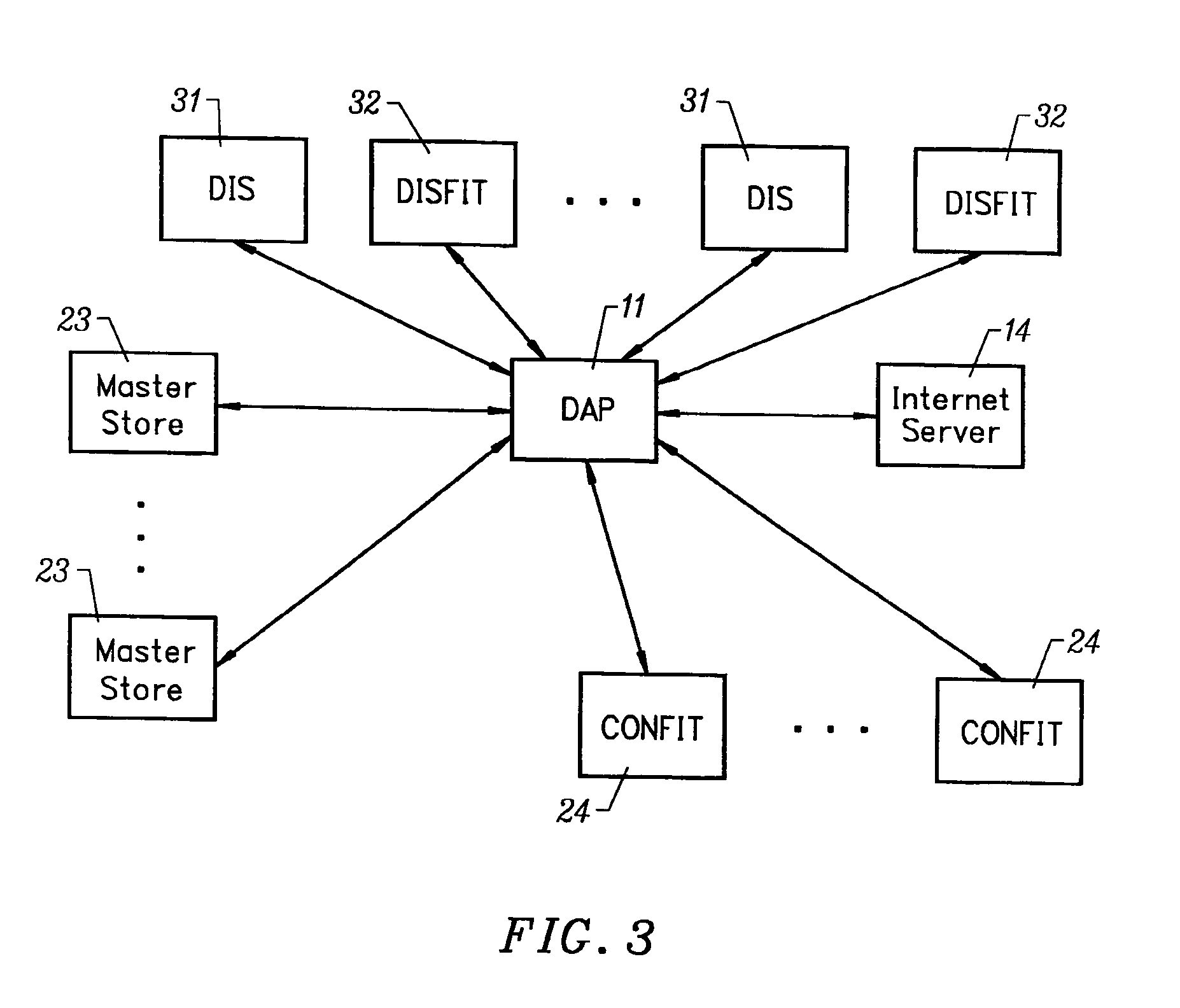
Patents
Literature
371 results about "Unique key" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
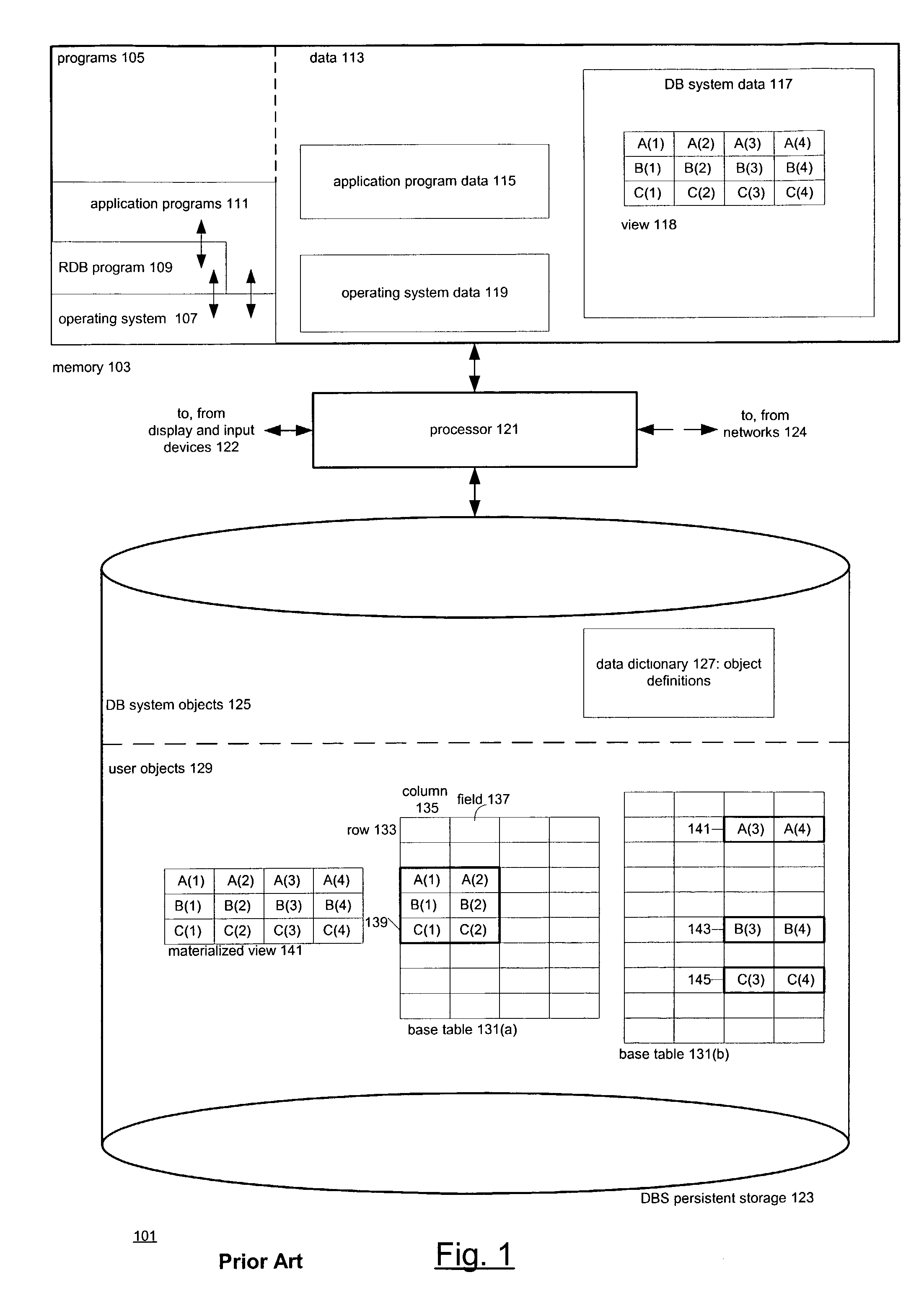
In database relational modeling and implementation, a unique key (also known as a candidate key, primary key, alternate key or more generally just a key) of a relation is a minimal superkey for that relation; that is, a set of attributes such that...
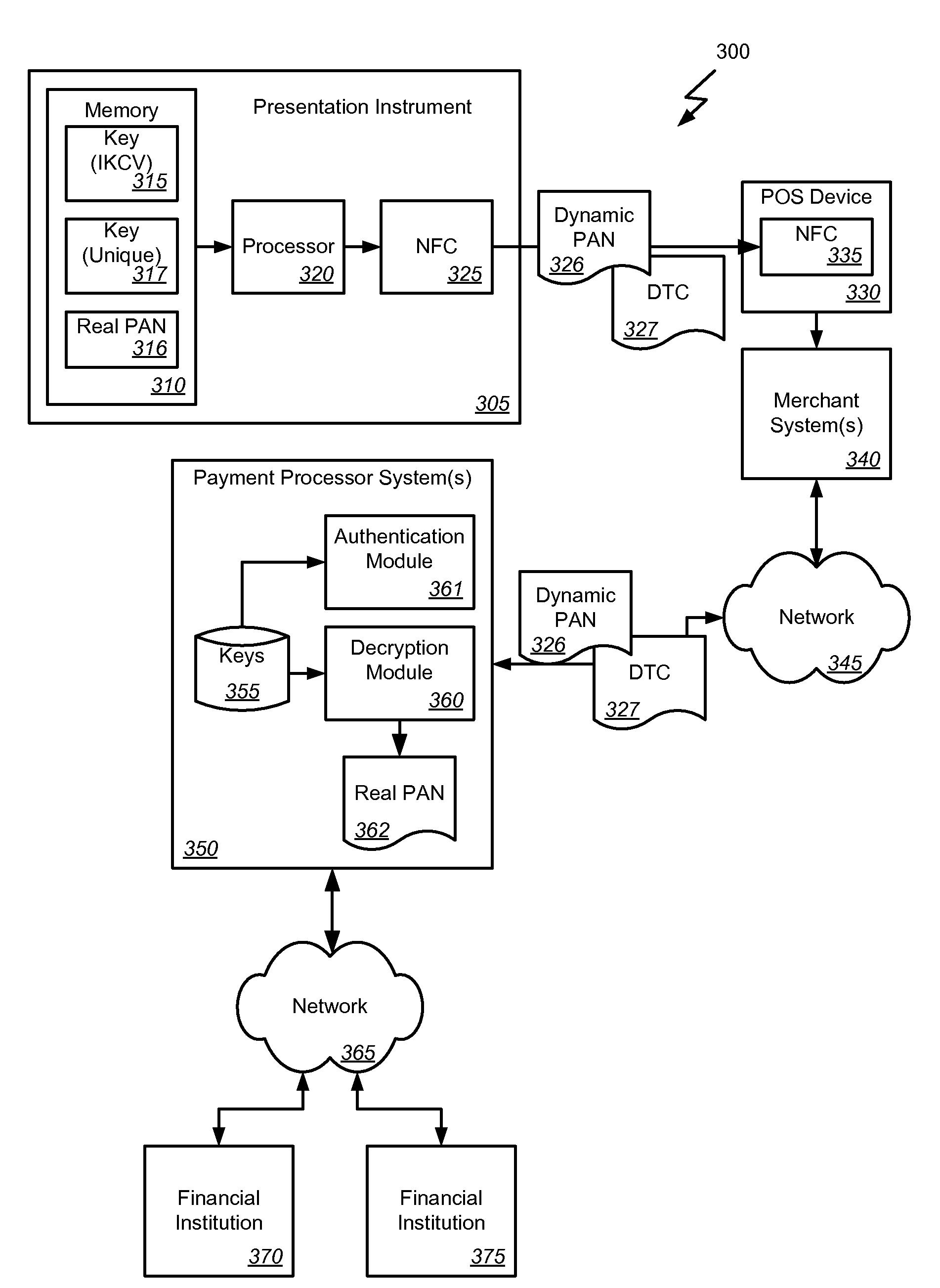
Dynamic primary account number (PAN) and unique key per card
Methods, systems, and machine-readable media are disclosed for handling information related to a financial transaction including utilizing dynamic cryptograms. According to one embodiment, a method of processing a financial transaction related to a financial account can comprise detecting initiation of the transaction with a device used as a presentation instrument in the transaction. A Dynamic Transaction Cryptogram (DTC) and a dynamic PAN can be generated at the device. The DTC can be used to authenticate the transaction and the dynamic PAN can comprise an encrypted form of a real PAN of the financial account that is valid for a single transaction. The DTC and the dynamic PAN can be provided by the device for use in the transaction.
Owner:FIRST DATA
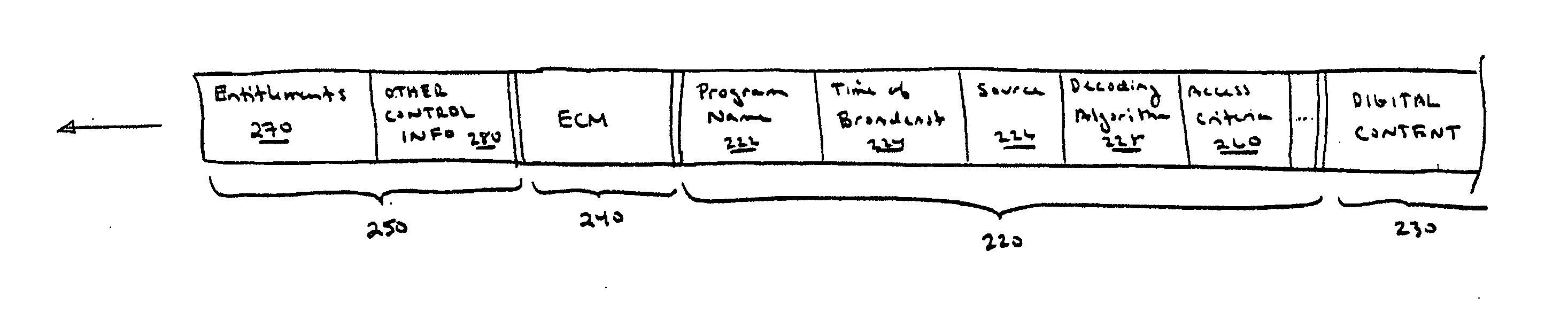
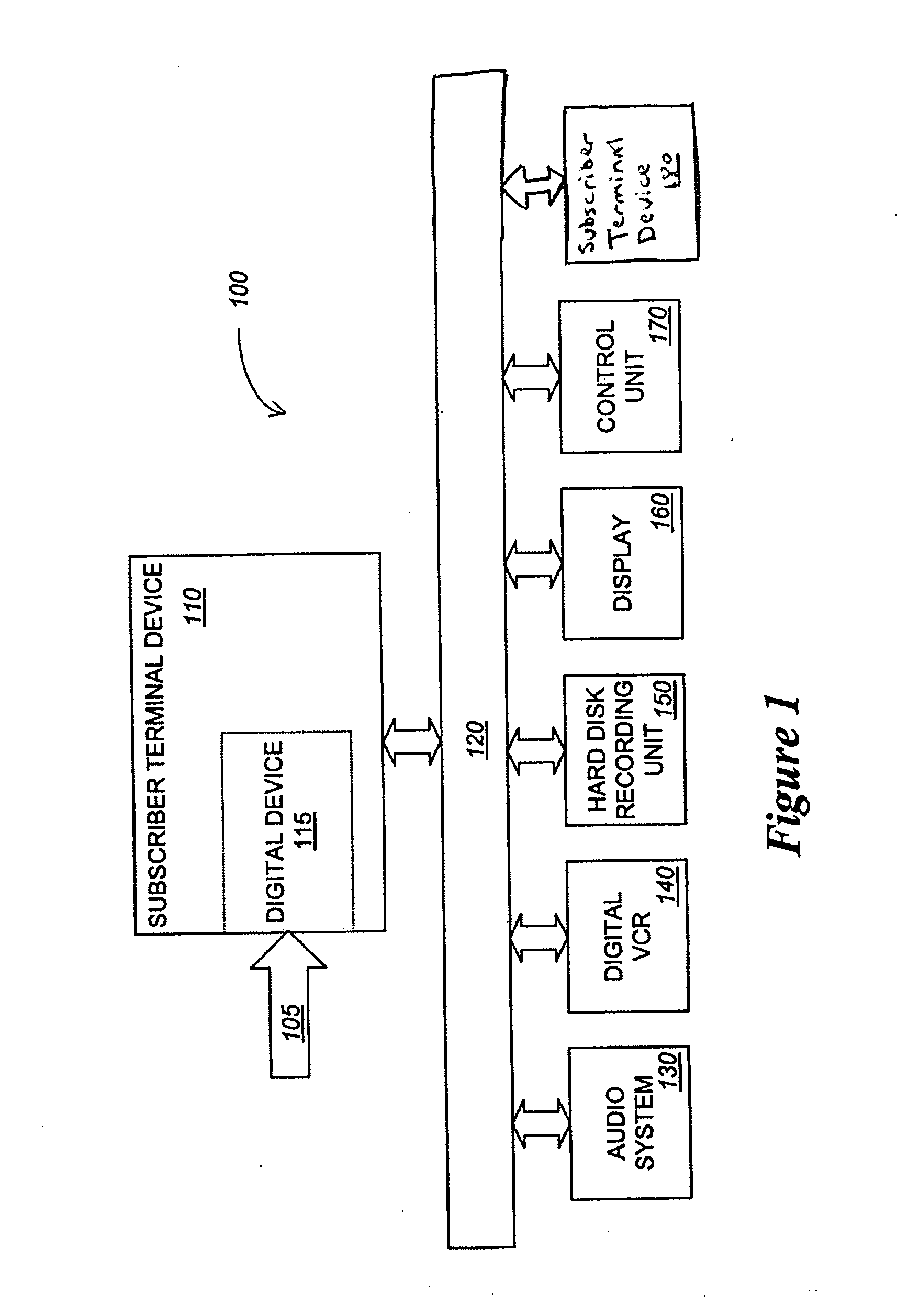
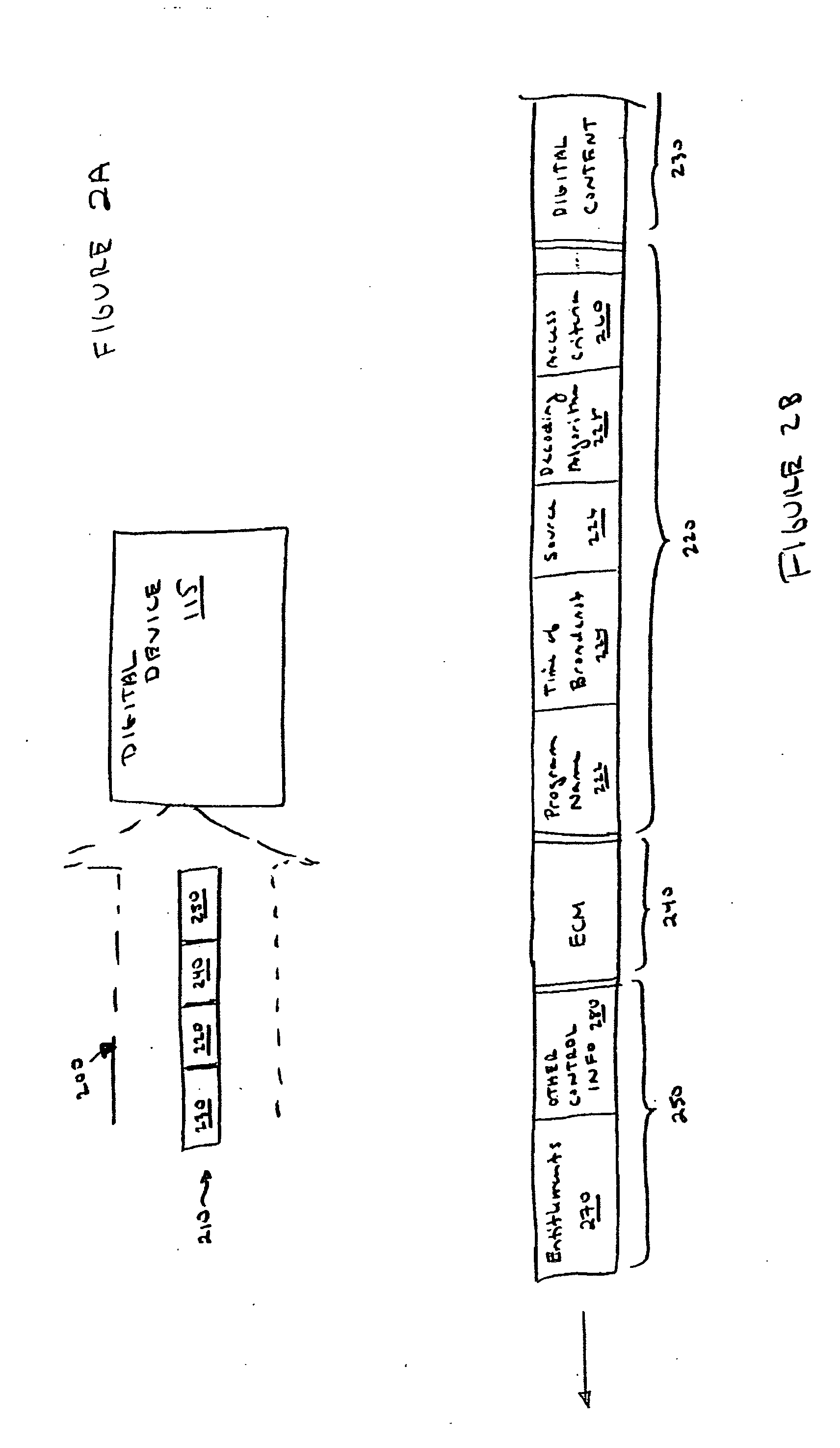
Digital rights management of a digital device
ActiveUS20050063541A1Television system detailsUnauthorized memory use protectionDigital contentRights management
According to one embodiment, an apparatus involves the descrambling of scrambled digital content using a one-time programmable key and digital rights management. The apparatus comprises a processor and a descrambler. The processor is adapted to execute a Digital Rights Management (DRM) function in order to determine whether each entitlement needed to access the digital content is pre-stored. The descrambler is adapted to decrypt encrypted information using a Unique Key stored within the one-time programmable memory. After determining that each entitlement needed to access the digital content is pre-stored, the decrypted information is used to generate a key, which is used to decrypt at least one service key for descrambling the scrambled digital content.
Owner:SONY CORP +1
Method and system for distributing and reconciling electronic promotions
A method and system for distributing and redeeming electronic promotions to a consumer through the Internet is provided. An account which is associated with a unique key is maintained for each consumer account. Access is permitted to the consumer account upon presentation of the unique key over the Internet. The consumer is presented discount or other promotional choices of items available in at least one store associated with the key, or a collection of such stores, over the Internet and the selections of the discount or promotional choices made by the consumer over the Internet are recorded. Upon purchase of items at the associated store by the consumer, such data are received, and the selections and purchases are reconciled to record a credit in the customer account. Unlike paper or electronic coupons, no consumer action other than the selection of promotions desired is required for item purchase.
Owner:DS IQ
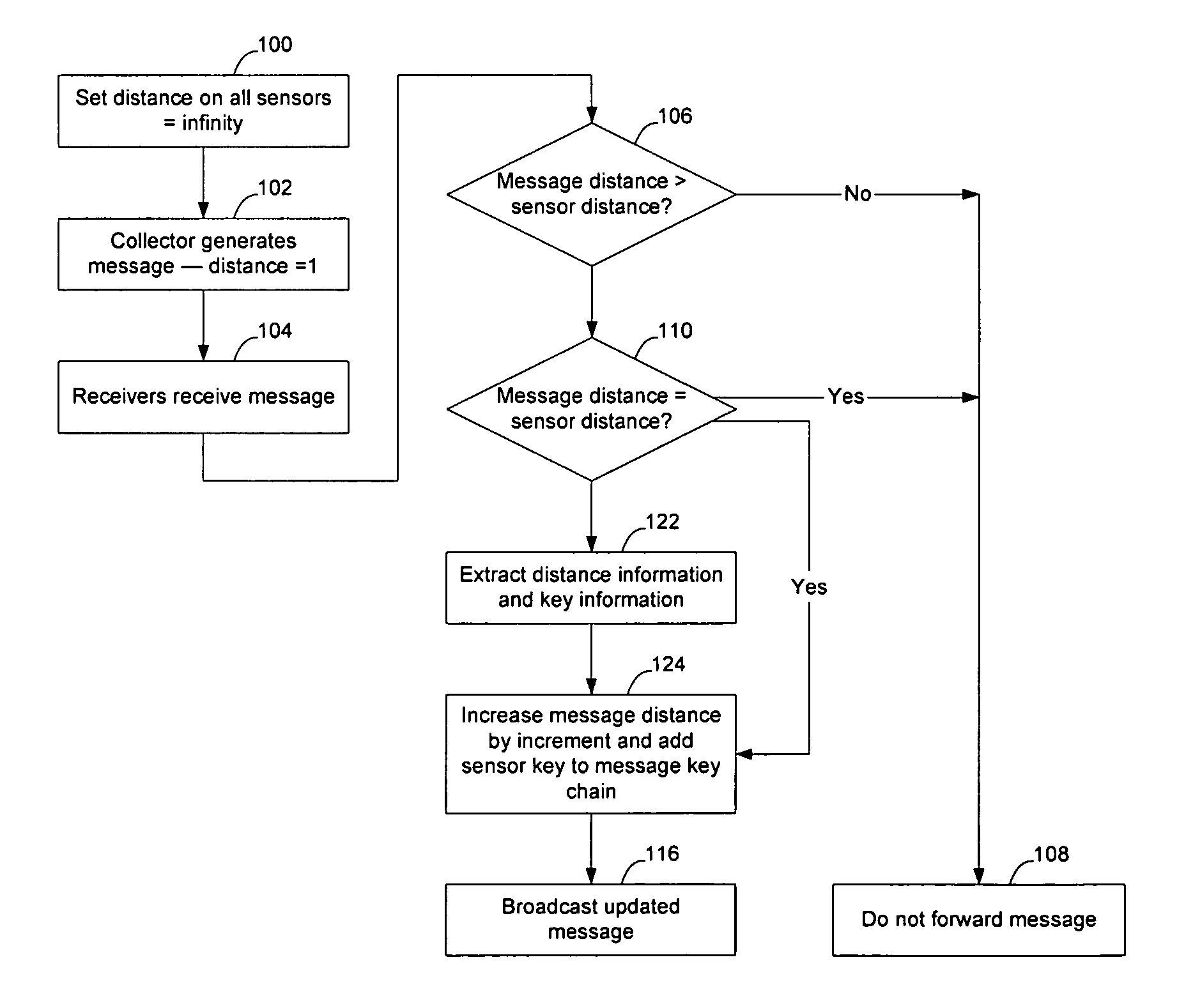
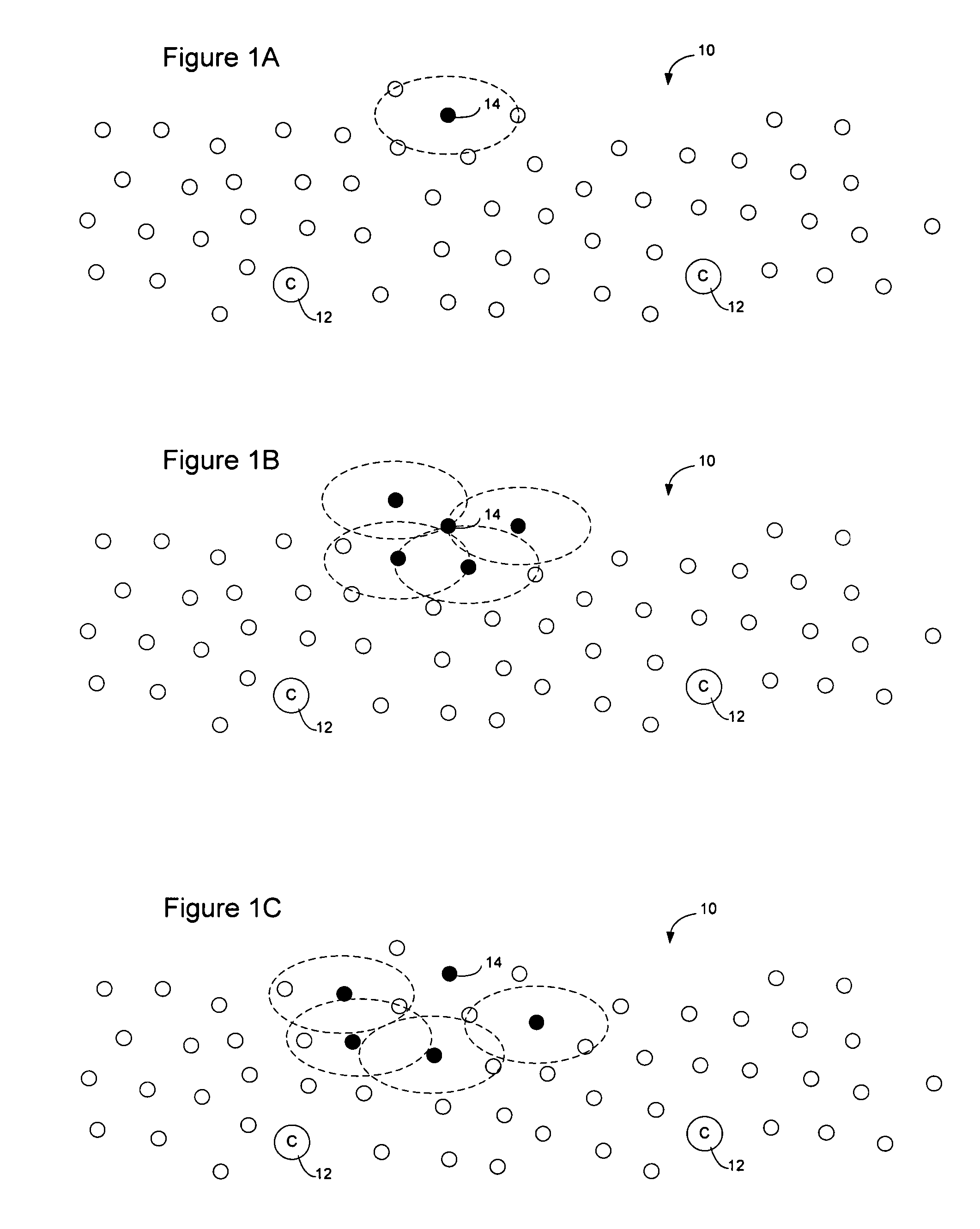
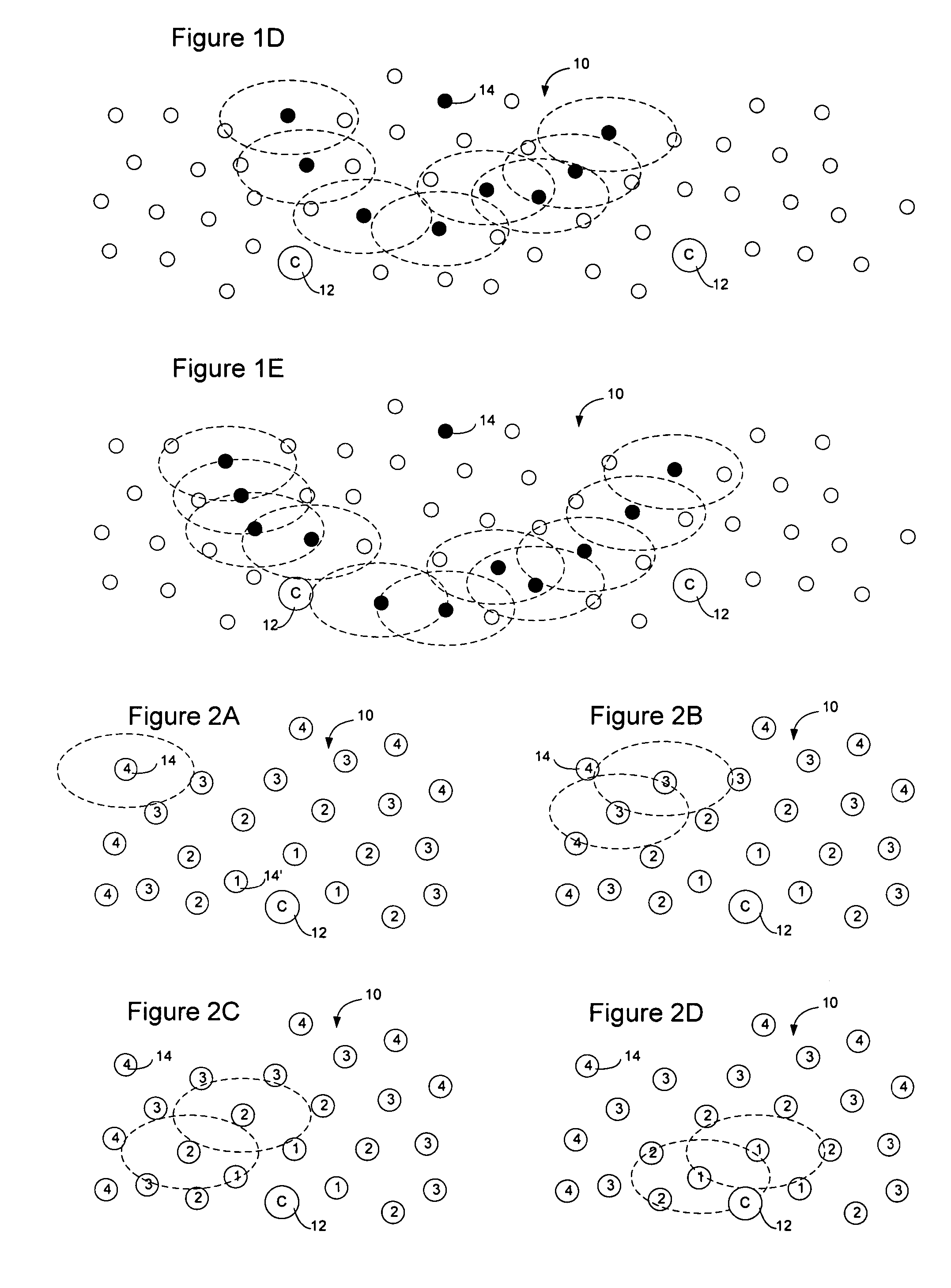
Method and apparatus for sensor network routing
InactiveUS20050207376A1Reduce multiplicityOvercome limitationsNetwork topologiesData switching by path configurationBroadcastingTraffic conditions
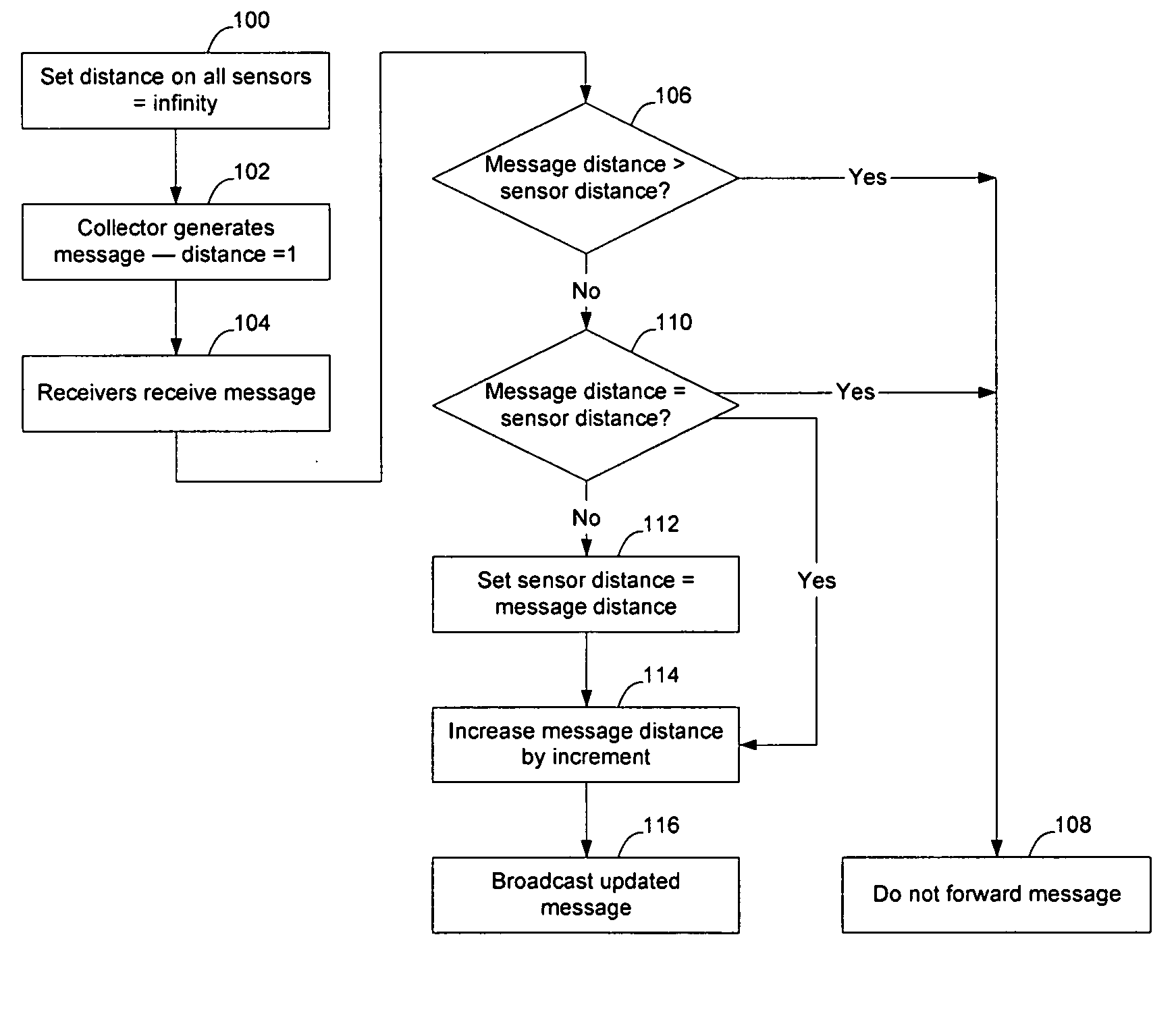
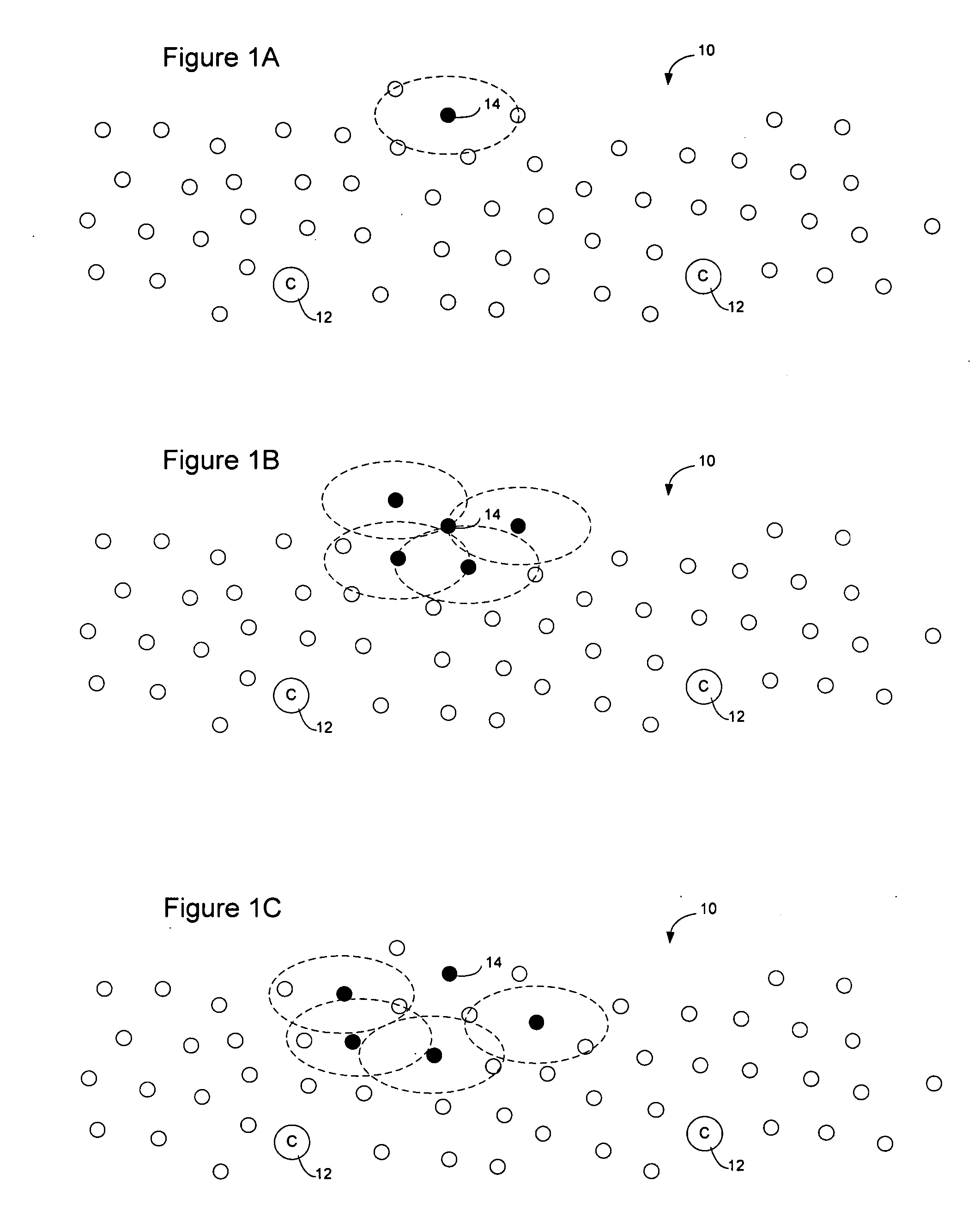
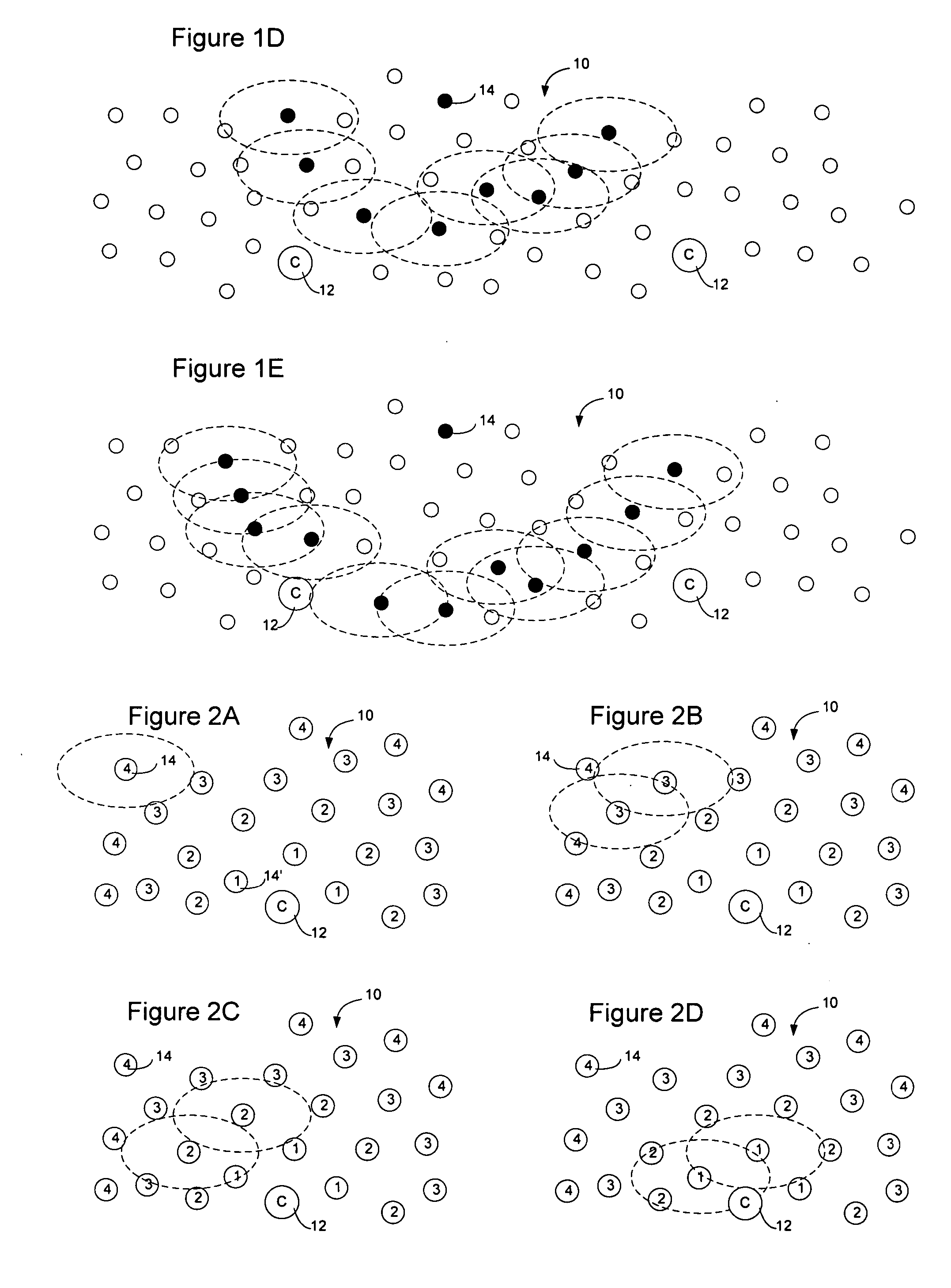
Sensor network routing uses distance information of sensors relative to a collector node, optionally along with non-unique key information, to route broadcasts from addressless sensors to a selected addressless collector. Distance calculation messages (DCMs) are used to set distance values on sensors relative to collectors. The distance values enable messages to propagate toward collectors to reduce the number of broadcasts. Self-assigned key information may be added to DCMs propagating in the network to enable routes to be determined through the network without assigning addresses to the participants. By storing the key information associated with the route, and causing sensors to only rebroadcast a message if the message contains a matching key at the matching distance position, broadcast paths may be created on the network. Optionally, diverse collectors and paths may be selected on the network by exchanging traffic condition indications and preferentially selecting paths with better traffic conditions.
Owner:RPX CLEARINGHOUSE
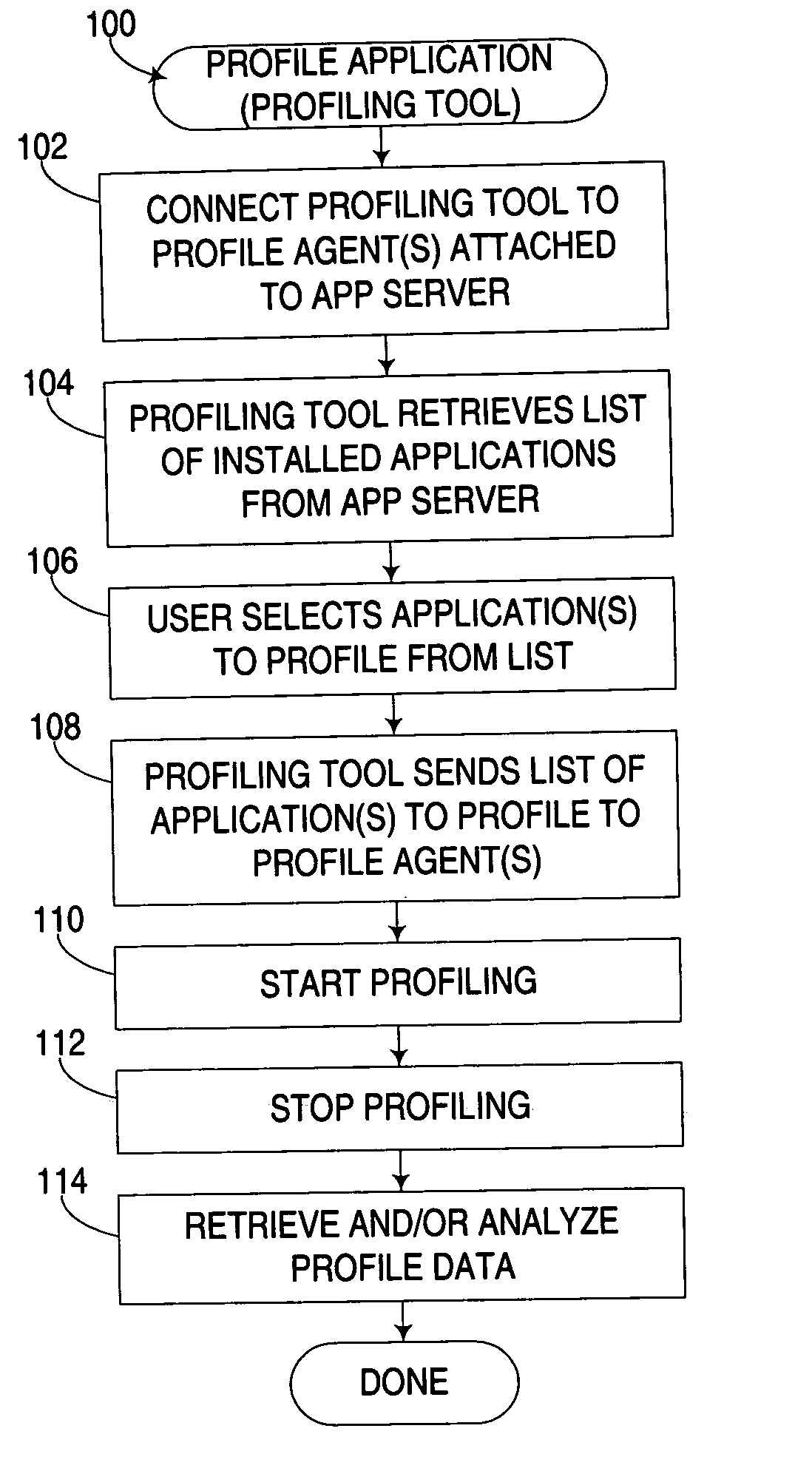
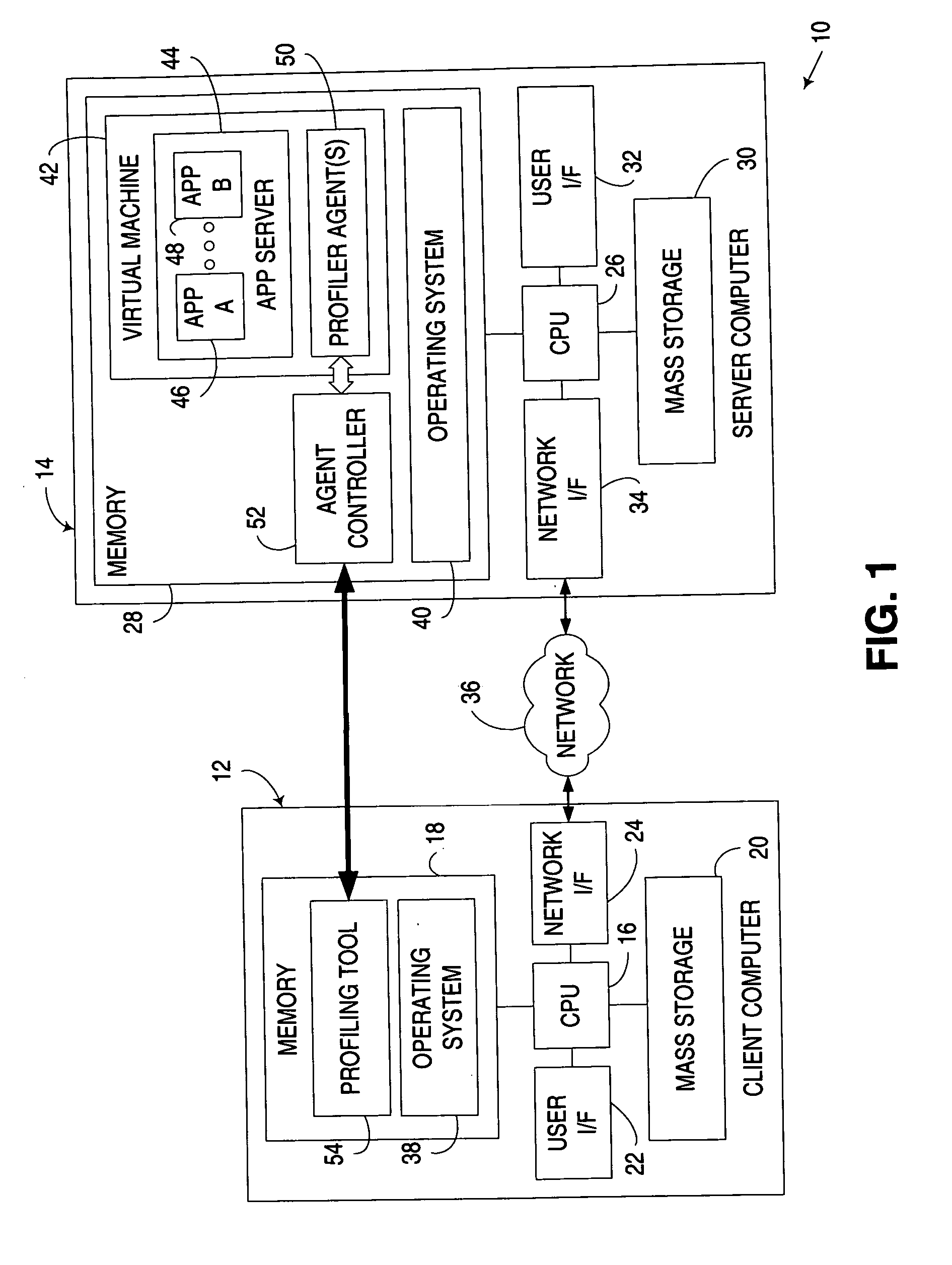
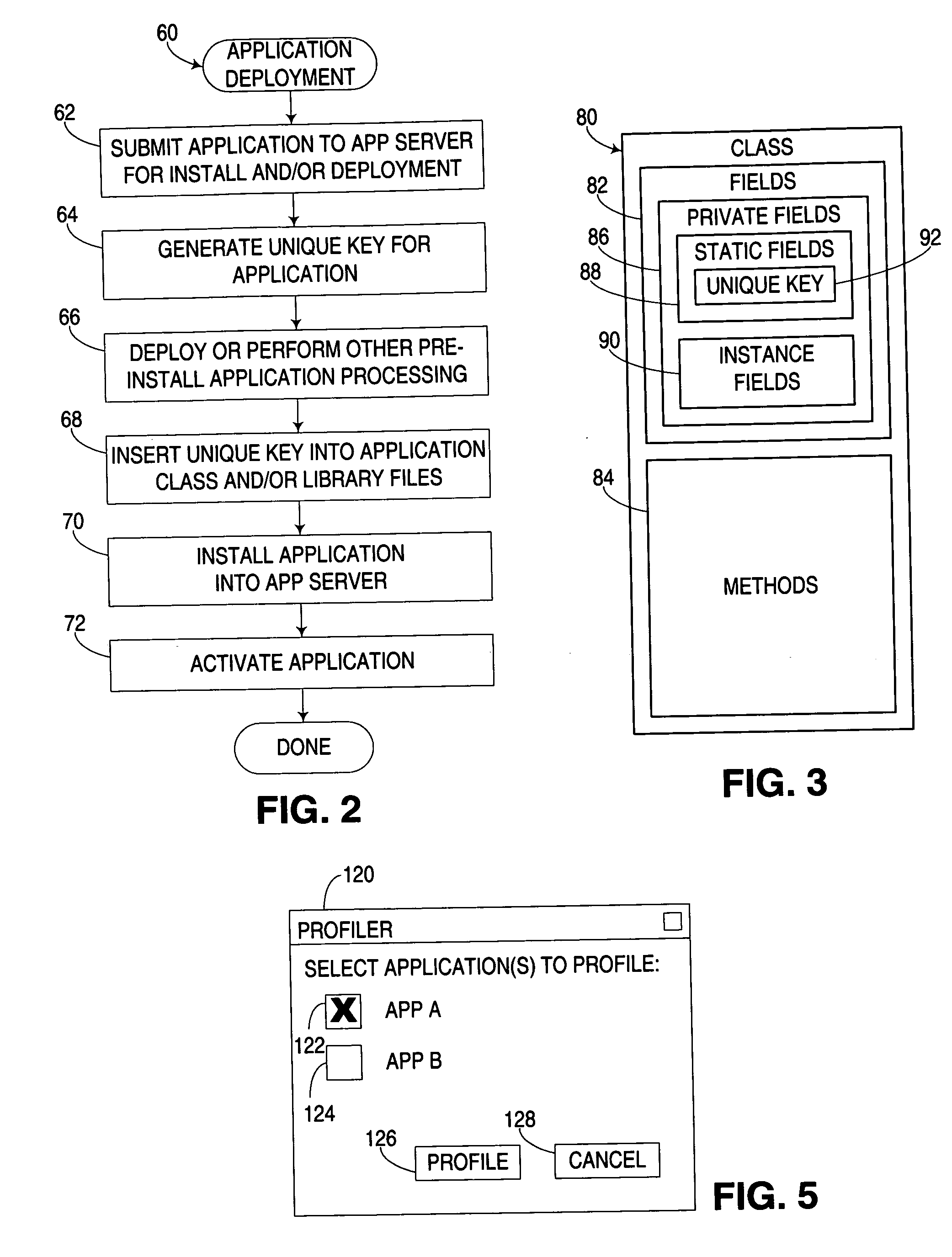
Selective profiling of program code executing in a runtime environment
ActiveUS20070169003A1Error detection/correctionSpecific program execution arrangementsApplication serverParallel computing
An apparatus, program product and method associate a unique key with routines in an application to enable a profiler to ascertain whether to collect profile information for a routine during its execution. A key may be generated, for example, during deployment or installation of an application in an application server or other runtime environment, and subsequently associated with the routines in the application, e.g., by storing the key in the class and / or library files for the application. By doing so, each application in a runtime environment may be uniquely identified by a profiler during execution, such that profile information will only be collected for those applications for which profiling has been enabled.
Owner:IBM CORP
Unified geographic database and method of creating, maintaining and using the same
InactiveUS20050283503A1Increase addressing resolutionInstruments for road network navigationNavigational calculation instrumentsDomain nameCredit card
The present invention involves a Universal Geographic Database (“UGD”). The UGD is an automated, central or distributed, registry of real-world locations and location-related information for businesses and other entities, analogous to the registry of domain names for Internet and web sites. By this central registry, businesses and other entities are facilitated to post their location and location-related information in a single place, for all users who need or want it; and users can refer to this single place, via the Internet, Web, and other telecommunications devices, to obtain accurate, complete and timely location and location-based information about the registered businesses and other entities. Each record of the UGD is keyed by a proprietary location address (PLA) based on the World Geographic Referencing System (WGRS), and optionally may have one or more proprietary location addresses (PLAs), which also may serve as keys. Associated with the PLA keys, each UGD record generally includes the full name for the business or other entity, its street address, and miscellaneous contact information (e.g., telephone number, facsimile number, e-mail address, internet website address, wireless website address). Other more dynamic, customized information (e.g., store hours, credit cards accepted, inventory, prices, specials, hours, parking) also may be available in the UGD record or linked to the UGD record. Users of any device or service can access the UGD through one or more location name servers (LNS), which can provide access to the UGD or other location-based information linked to the UGD or LNS. Based on the WGRS, PLAs provide, in addition to unique keys for UGD records, a user-friendly notation for location naming in the real-world and on all types of location-sensitive electronic devices, from web phones to in-car navigation systems. Given the UGD, these ULA / PLAs are as important to real-world businesses as their domain names because these WGRS addresses drive real-world commerce to physical business locations just as domain names drive e-commerce Internet or web sites.
Owner:WGRS LICENSING
Secure fiber optic network keyed connector assembly
InactiveUS7390203B2Prevent rotationAvoid damageLive contact access preventionOptical light guidesFiberEngineering
Owner:ORTRONICS INC +1
Methods for embedding image, audio and video watermarks in digital data
InactiveUS6983057B1Less coefficientTelevision system detailsRecord information storageDigital dataThe Internet
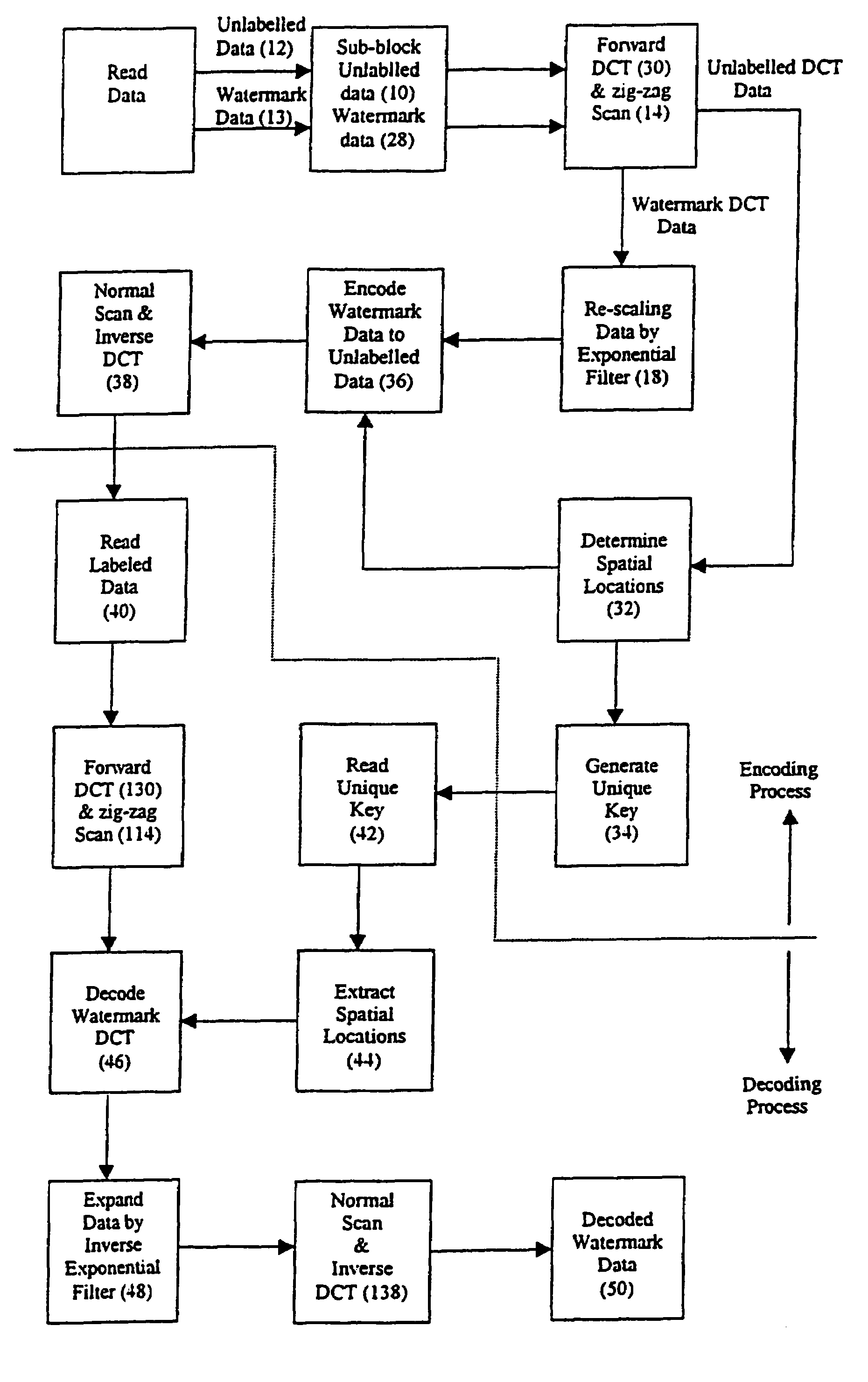
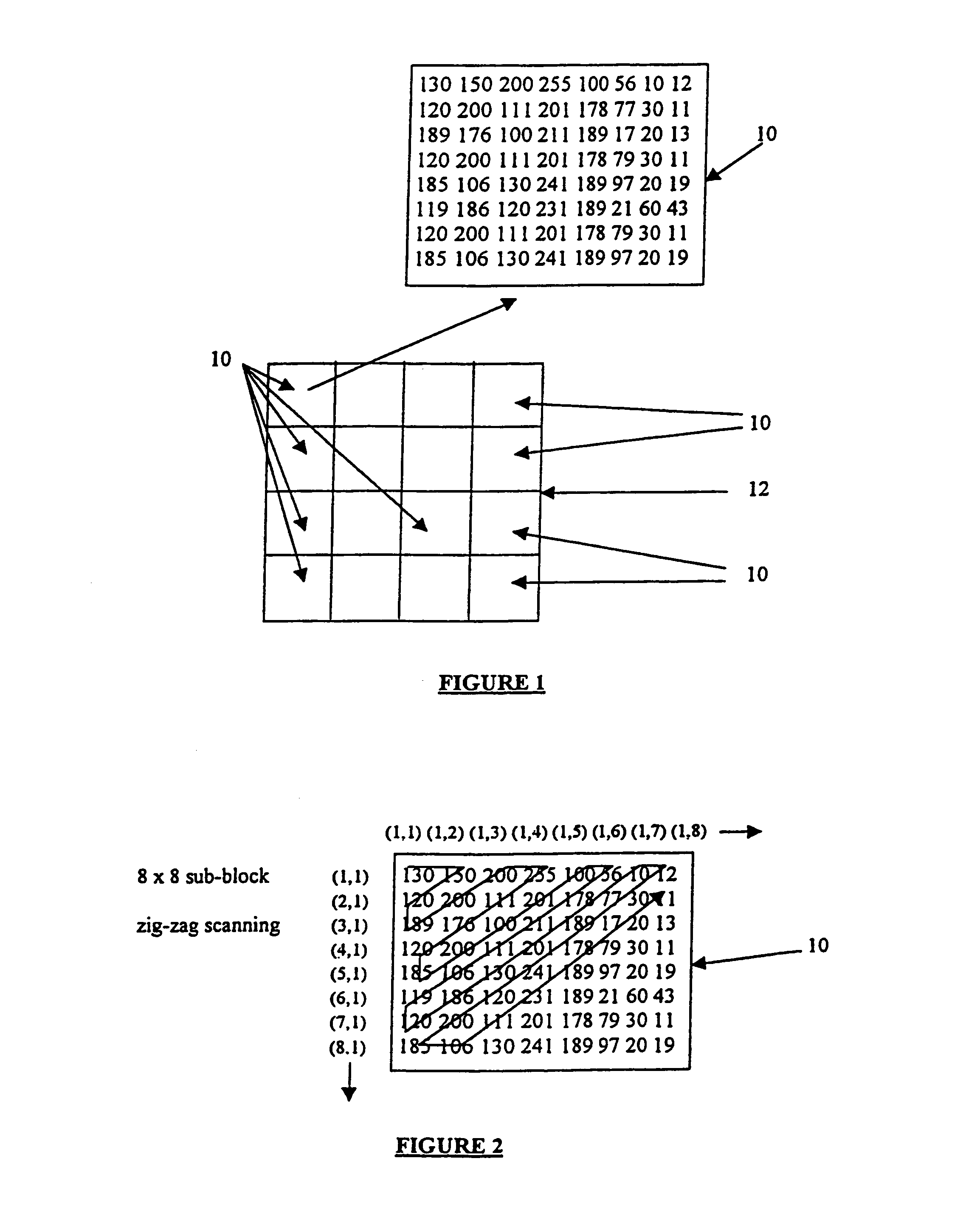
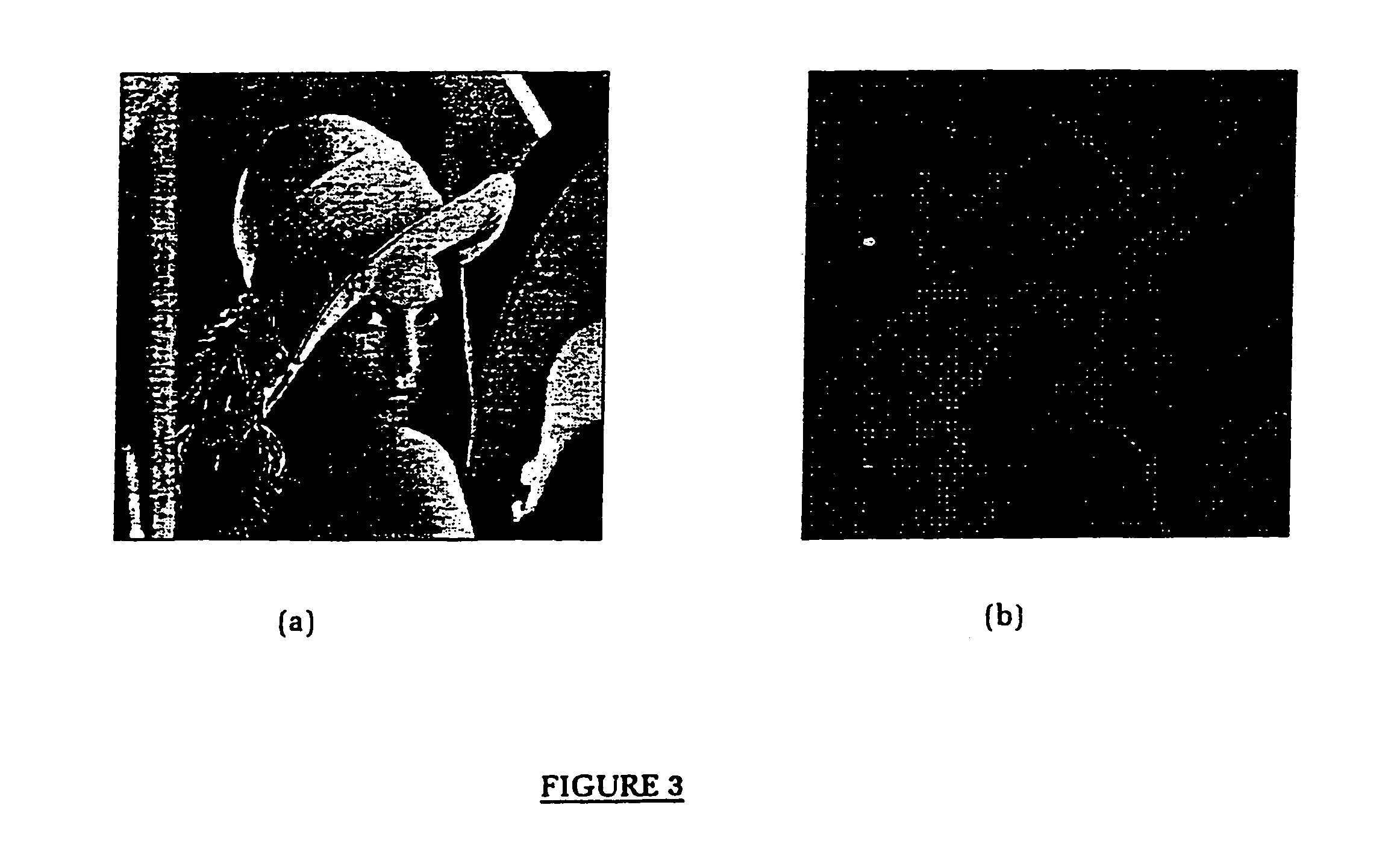
A method for embedding an entire image, audio or video watermark sequence within another image, audio or video data sequence with minimum loss of data quality is presented. The method exploits the de-correlation property of data coefficients in the orthogonal transform domain, similar to the application in data compression through transform coding. The present invention describes the usage of a Discrete Cosine Transform as the embedding domain. However, other orthogonal transforms such as Fourier, Walsh-Hadamard, Haar, Sine and Wavelet can also be used for this operation. A unique key derived adaptively from spatial locations registering the thresholds of the ac transform energies is used to unlock or de-watermark the embedded image or audio sequence. Moreover, an exponential filter has been developed to compress and expand the watermark coefficients prior to the embedding and retrieval process. The method can be used in resolving multimedia copyright protection issues arising on the Internet and in the music industry, such as the inclusion of a company's logo or an artist's recorded voice. The method can also be incorporated as a built-in feature for digital recording devices, such as still and video cameras, as well as more recent devices such as VCD and DVD players. Moreover, the method can be applied to the commercial and service sectors, where security in transmission and reception of private information in terms of speech or image is of the utmost importance.
Owner:ST ELECTRONICS INFO SECURITY
Digital content cryptograph and process
InactiveUS6892306B1Easy to optimizeLimited abilityKey distribution for secure communicationData processing applicationsDigital contentS/KEY
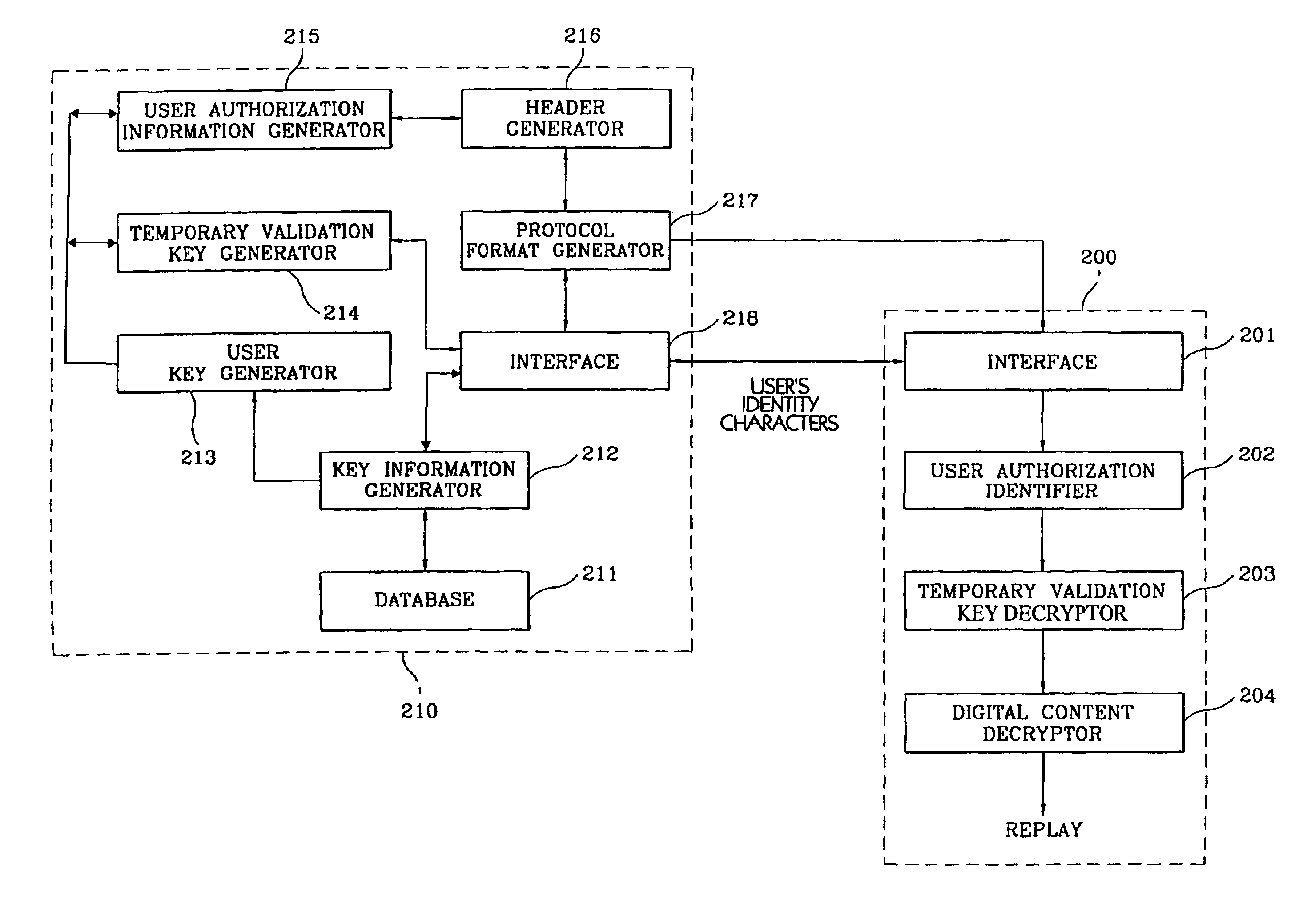
A digital cryptograph and encryption process encrypts and transmits in a digital format specific items of information requested by a user of a digital content transmission system by using key information, a user's key and a temporary validation key, to decrypt and replay the encrypted digital information at the user's terminal by using the key information and the user's authorization information. Each registered subscribing user is provided with unique key information. The user key is generated by applying the key information to a key generation algorithm. The temporary validation key that is created when the registered user accesses the server, is encrypted with the user key. The digital information is encrypted by using the temporary validation key in an encryption algorithm. The decryption algorithm allows the user to decrypt and replay the encrypted digital information upon receipt of the key information that has a one-to-one correspondence to the identity characters of the registered subscribing user.
Owner:SAMSUNG ELECTRONICS CO LTD
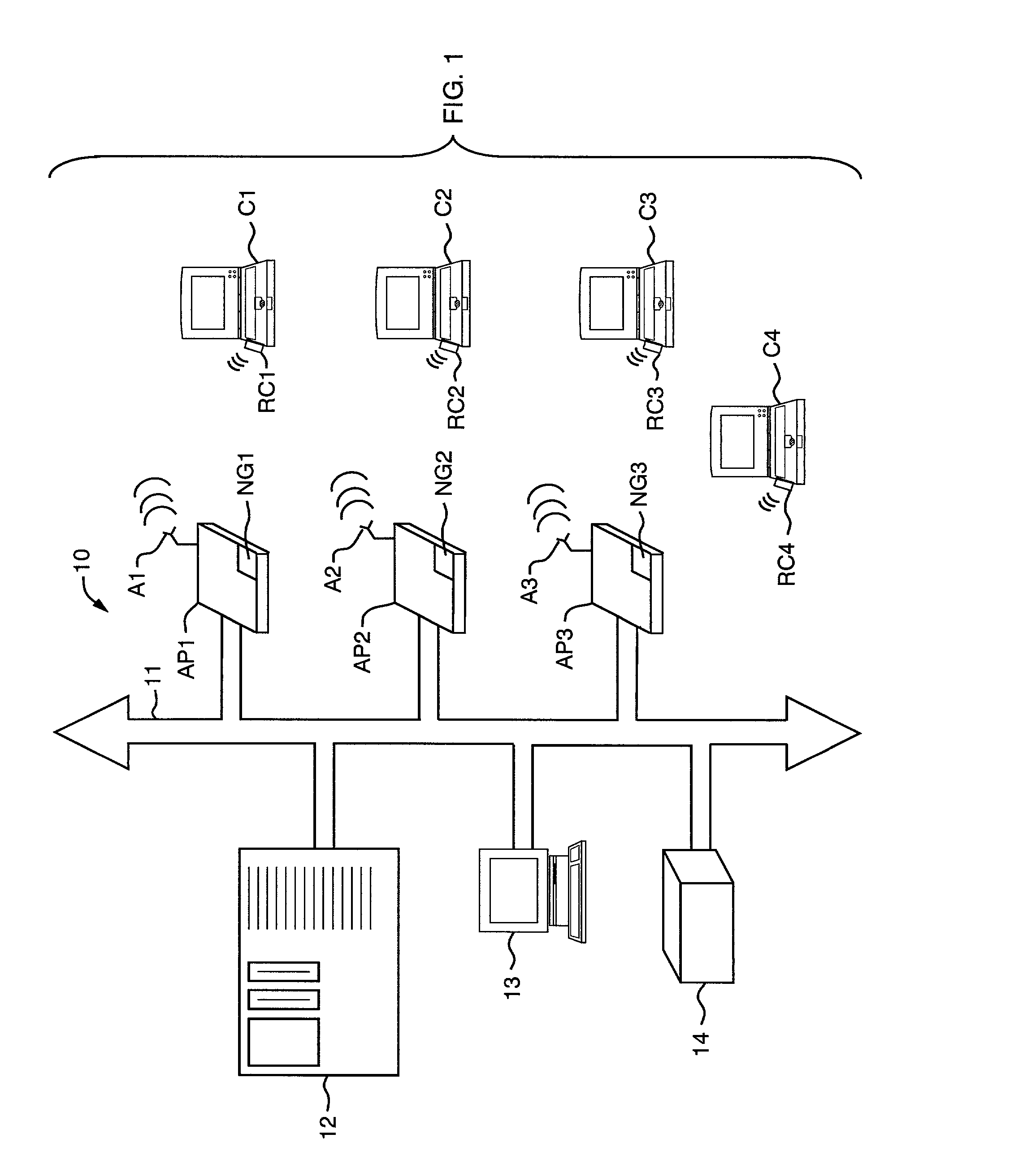
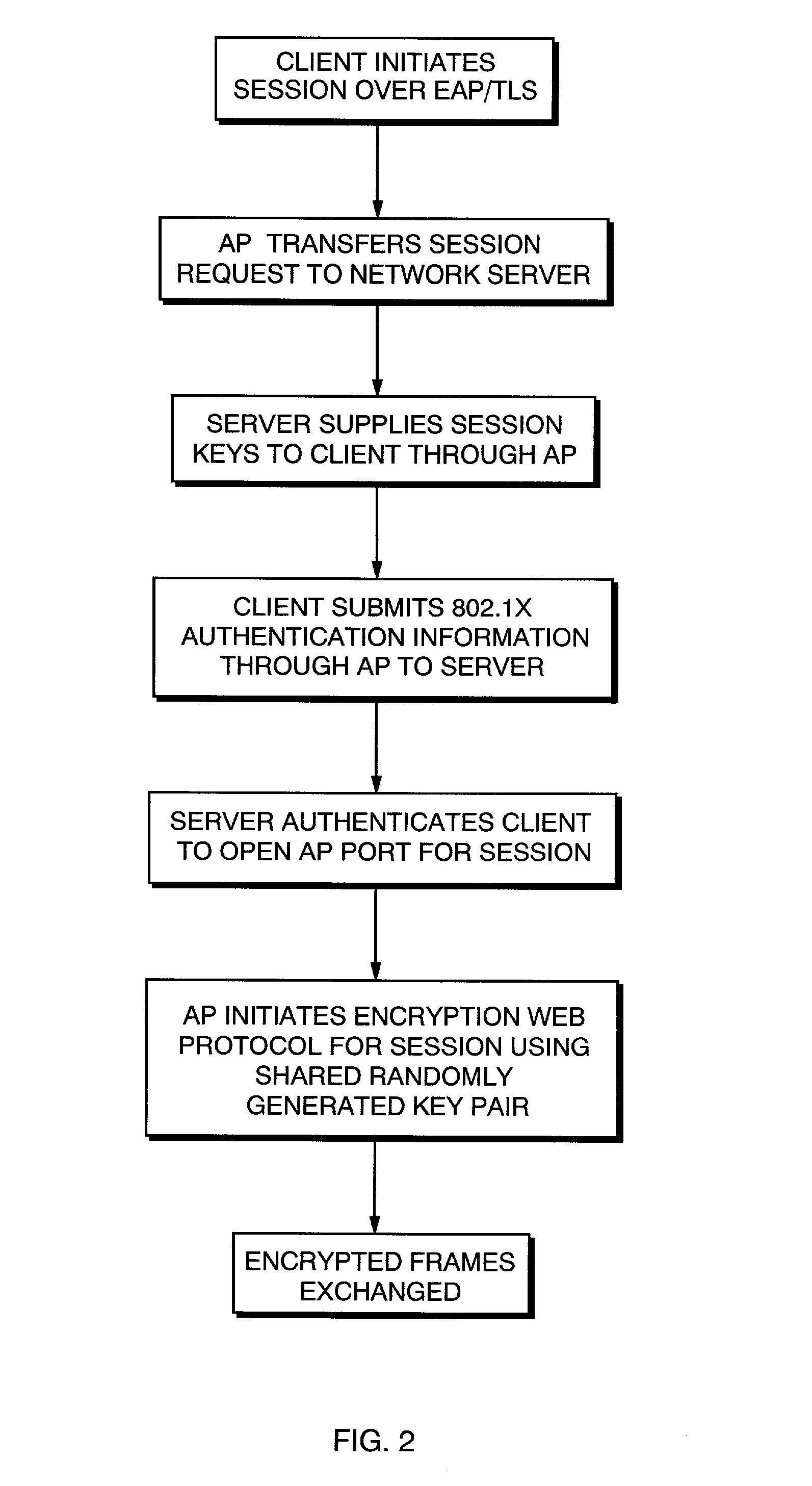
System and method to provide enhanced security in a wireless local area network system
InactiveUS20030095663A1User identity/authority verificationNetwork topologiesClient-sideNetwork access point
A system and method for enhancing Wireless Local Area Network (WLAN) security. The system and method include the generation of a pair of WEP-based encryption keys by a network access point. The key pair is transmitted to one or more clients associated with the access point after the client has been authenticated for access to the network. Each key is preferably randomly generated and the pair is further changed periodically. The timing of the changing of the keys is dependent upon the existing crypto analysis attack capabilities. Individual clients may have unique key pairs or a plurality of clients associated with an access point may share the key pair.
Owner:ENTERASYS NETWORKS
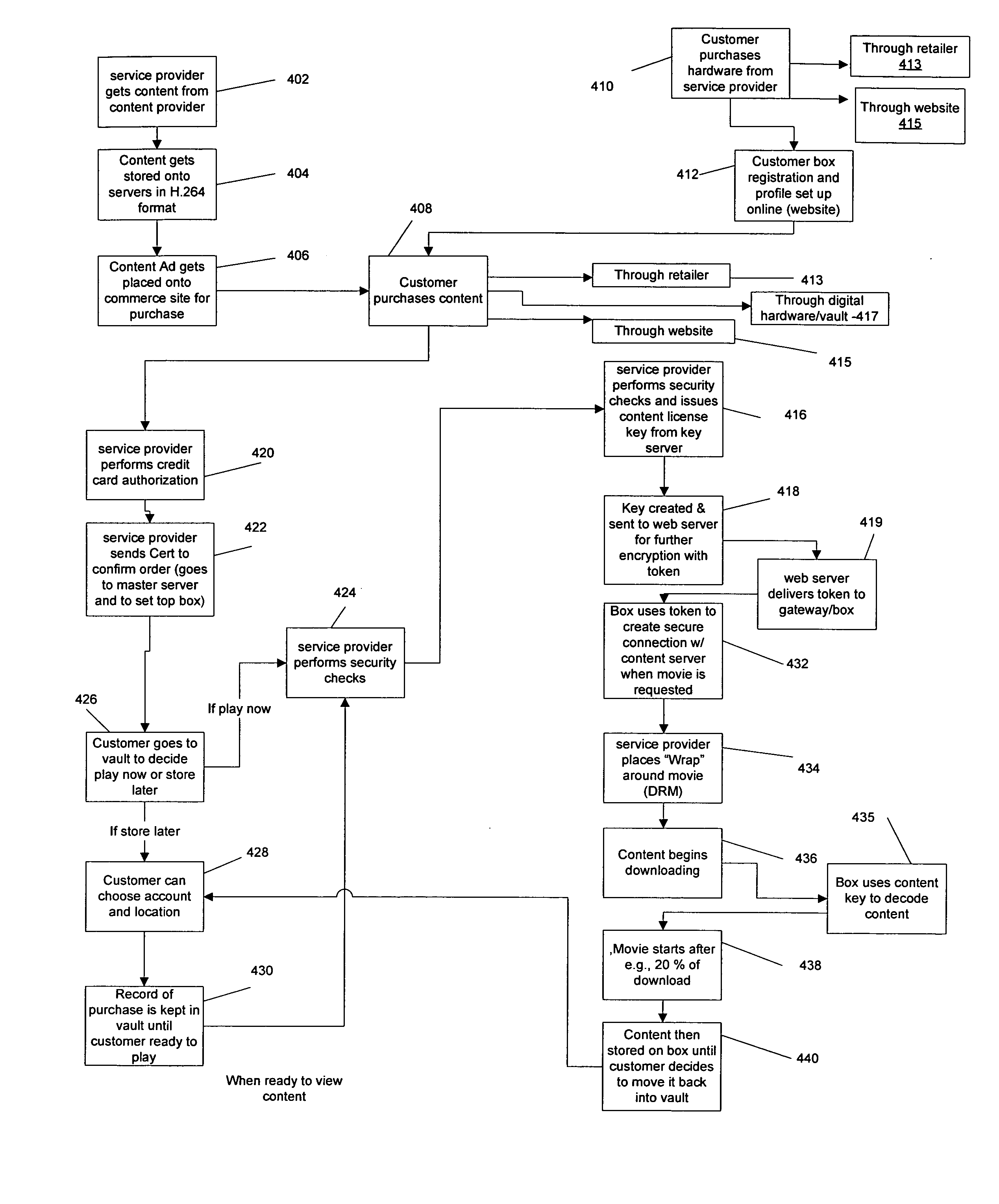
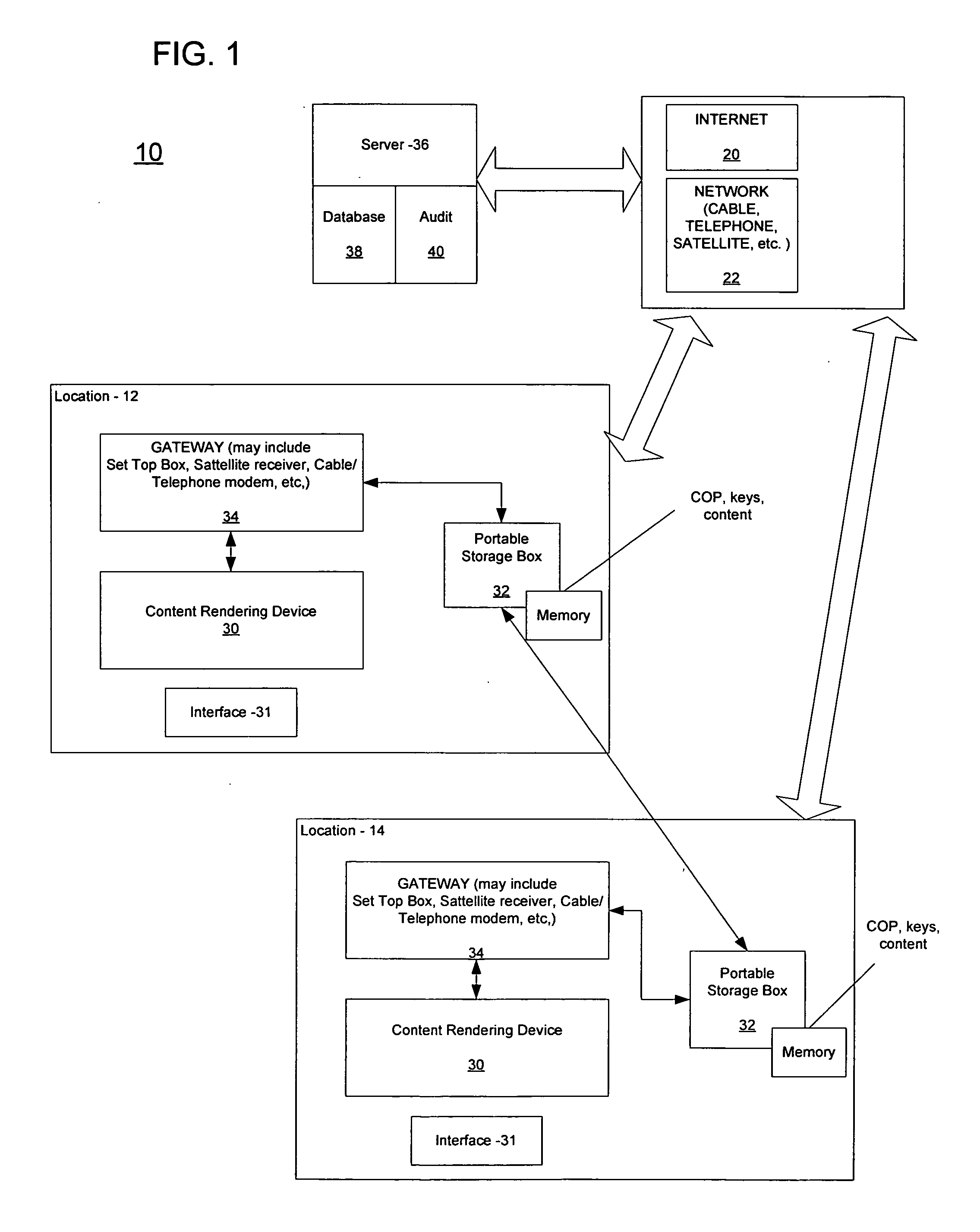
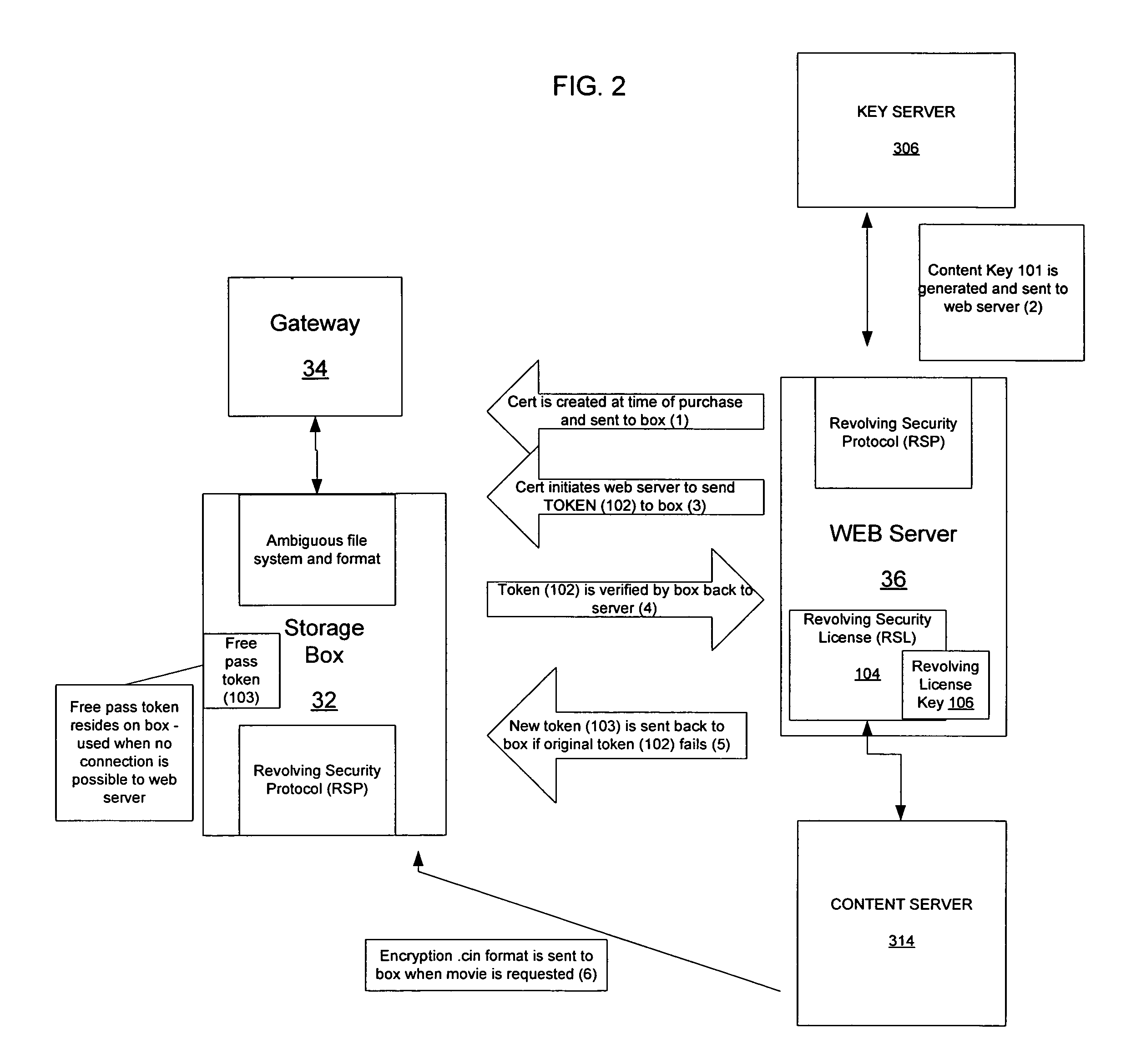
Delivery and storage system for secured content library
A system for maintaining a secure content library includes a server, which manages requests for copyrighted content and encrypts the content using a key server, which generates unique keys and associates the keys with the copyrighted content to create a token. A gateway receives the token and interacts with the server over a network. A client storage box interacts with the gateway to decode the token in accordance with a security protocol and sends a content key back to the server to enable the content to be downloaded and decoded, the storage box including memory for storing downloaded content. The client storage box has a use key that is updated by the server after a predetermined number of accesses to the content to enable further accessing of the content.
Owner:VCINEMA
Method and apparatus for sensor network routing
InactiveUS7466681B2Reduce multiplicityNetwork topologiesData switching by path configurationTraffic conditionsComputer science
Owner:RPX CLEARINGHOUSE
Systems and methods for embedding media forensic identification markings
InactiveUS20050154892A1Improve certaintySimilar quantized statisticsUser identity/authority verificationCharacter and pattern recognitionDegree of certaintyForensic identification
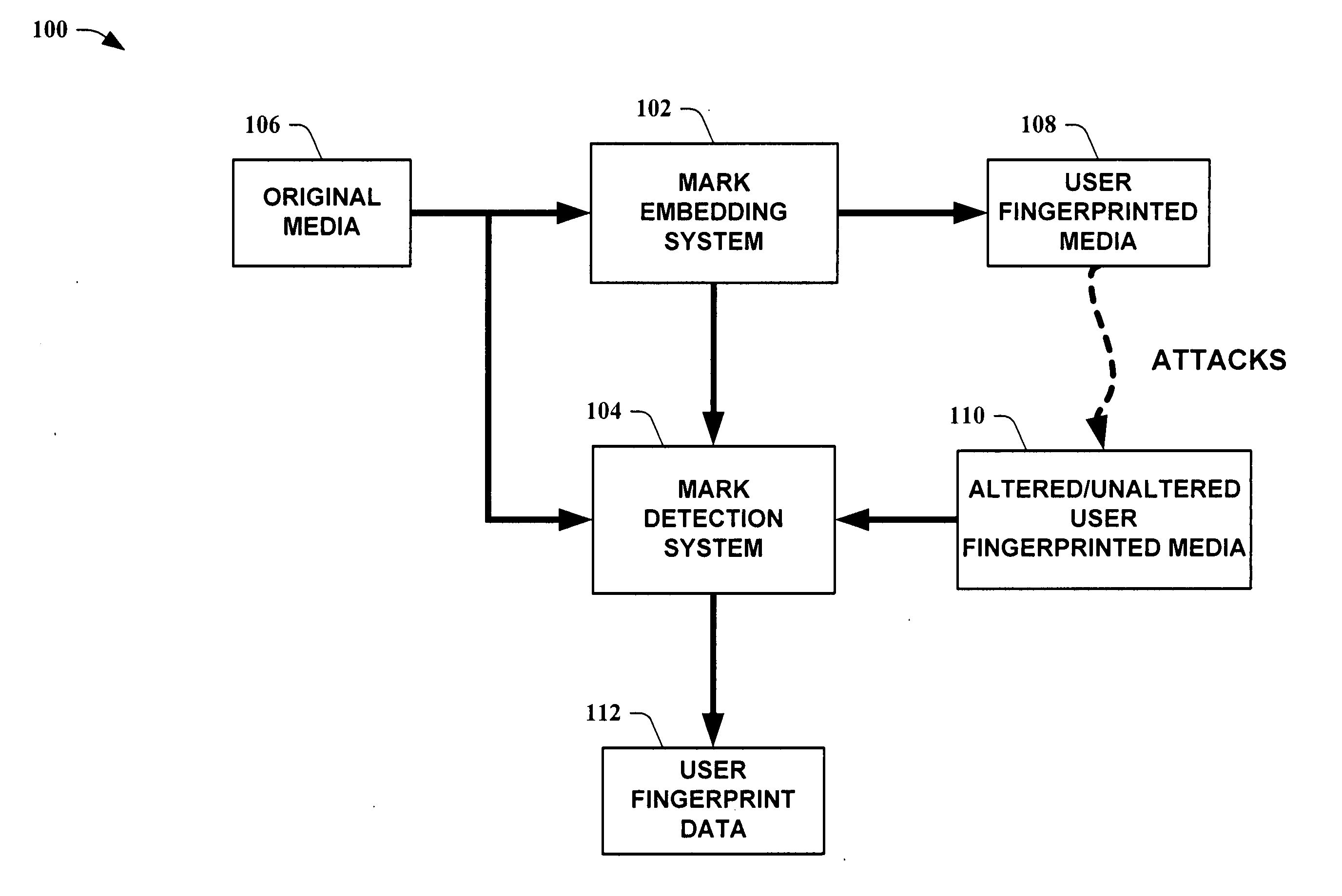
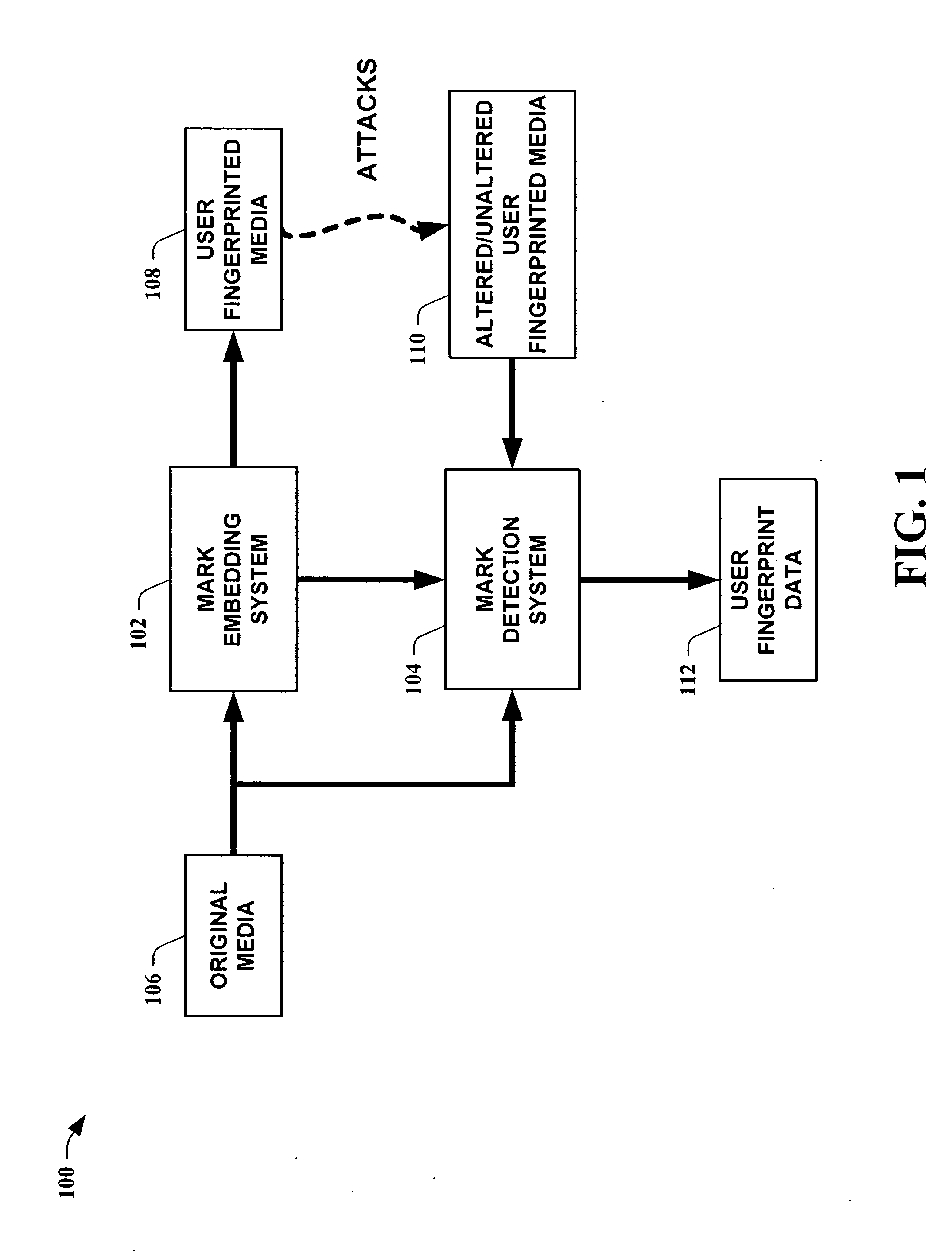
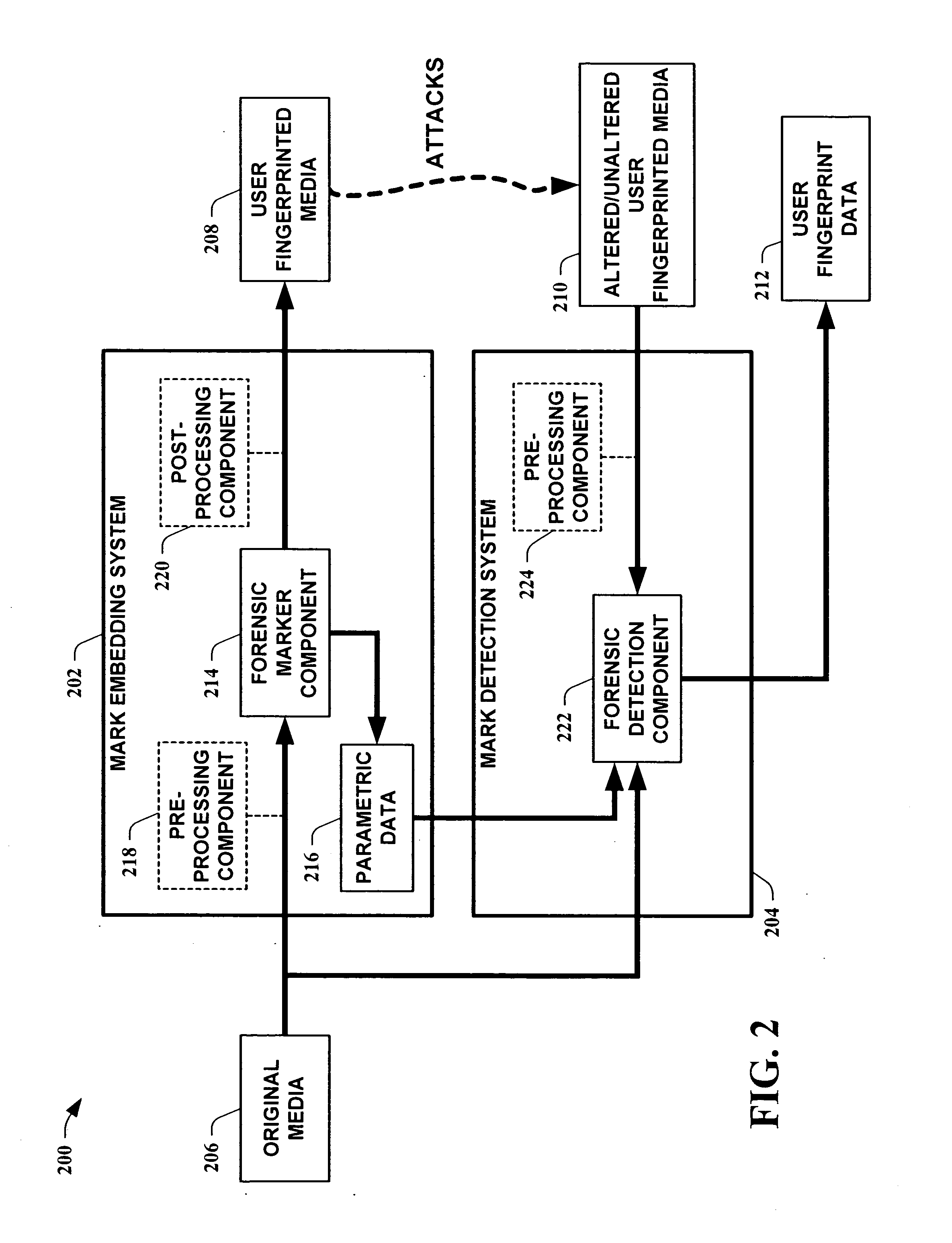
The present invention leverages a series of media watermark locations to provide information relating to media ownership and / or distribution source. This provides a forensic means to establish a source of media with a high degree of certainty despite malicious and / or non-malicious attacks. By providing embedded user unique identification, a source of copied media can be determined without the embedded information substantially interfering with the intended purpose of the media itself. In one instance of the present invention, digital media is transformed into an N-dimensional media signal. User unique keys are then utilized along with a master key to determine locations for embedding a watermark signal that possesses substantially similar quantized statistics as the transformed media signal. The watermark signal is then embedded into the media signal, fingerprinting the media.
Owner:MICROSOFT TECH LICENSING LLC
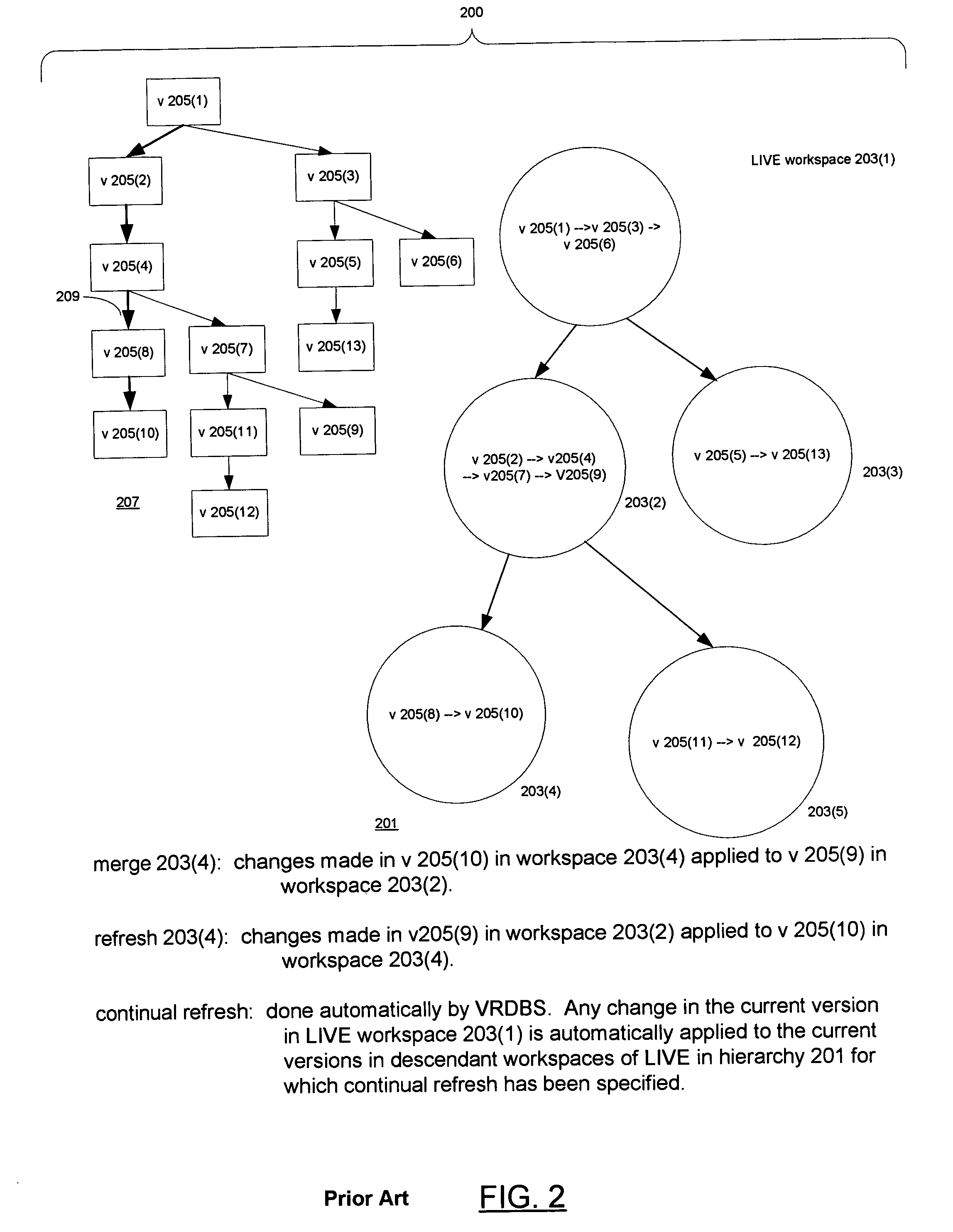
Versioned relational database system with an optimistic constraint model
InactiveUS7028057B1Data processing applicationsDigital data information retrievalTheoretical computer scienceWorkspace
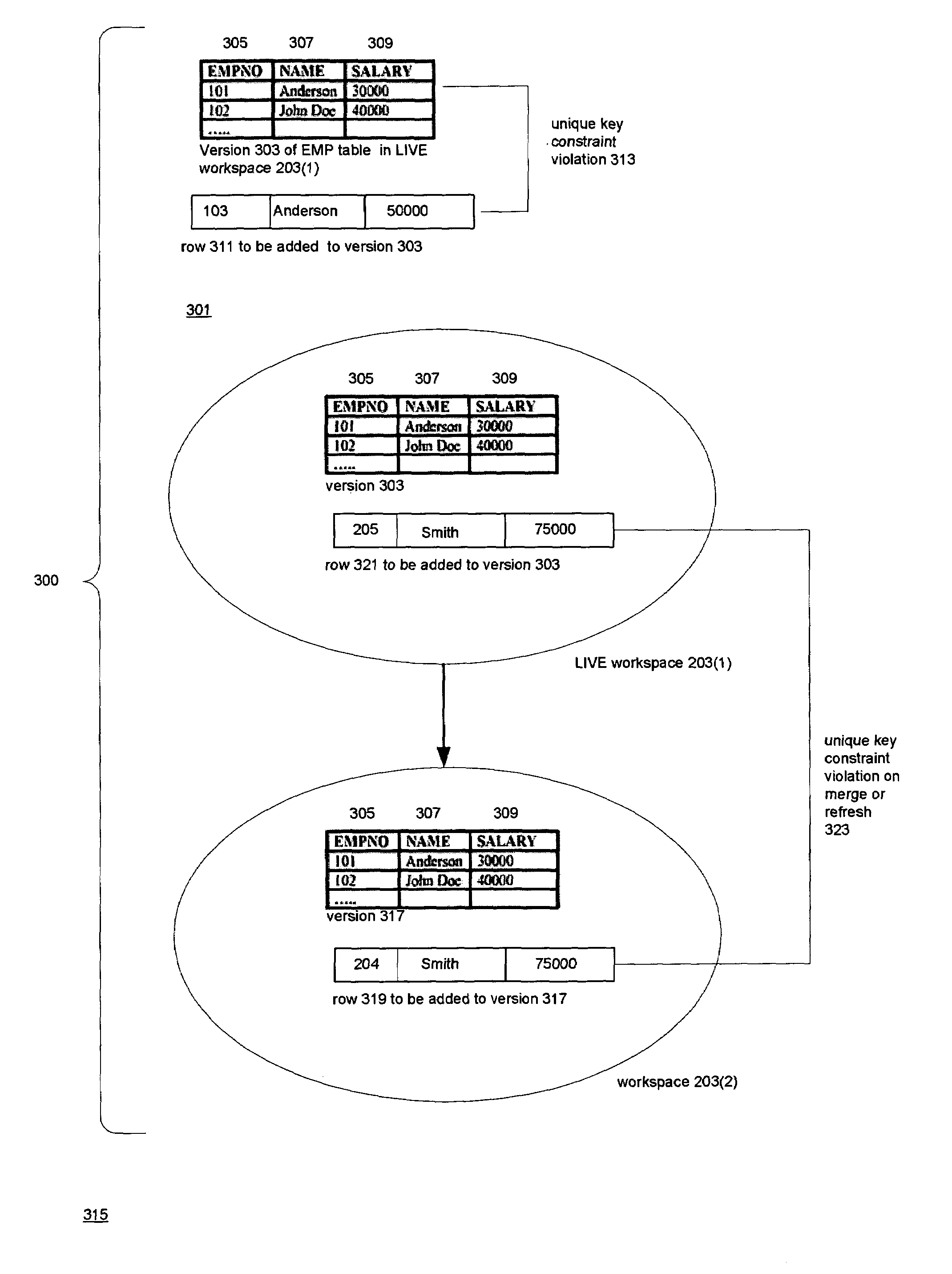
Techniques for doing optimistic constraint checking in a versioned relational database system. The techniques find a subset of the versions of a table that contain all of the rows that need be checked for violation of a constraint when a given version is modified. When the versions of a table are organized into a directed acyclic graph (DAG), the subset for a given version is the ancestry of the given version, that is, the given version plus the ancestors of the given version in the DAG. Within the ancestry, the set of rows that must be checked is termed the version view. A row that belongs to the set has a primary key that is the latest version of the primary key in the given version's ancestry. The technique may be used for constraints including the referential integrity constraint and the unique key constraint. The metadata used to compute the version view is disclosed, as well as the manner in which the constraint checking techniques interact with the workspaces that provide access to the versions. The workspaces may be organized as a DAG. The manner in which the workspaces are organized determines how changes are propagated in the versioned relational database and thus the versions whose ancestry has to be checked for constraint violations.
Owner:ORACLE INT CORP
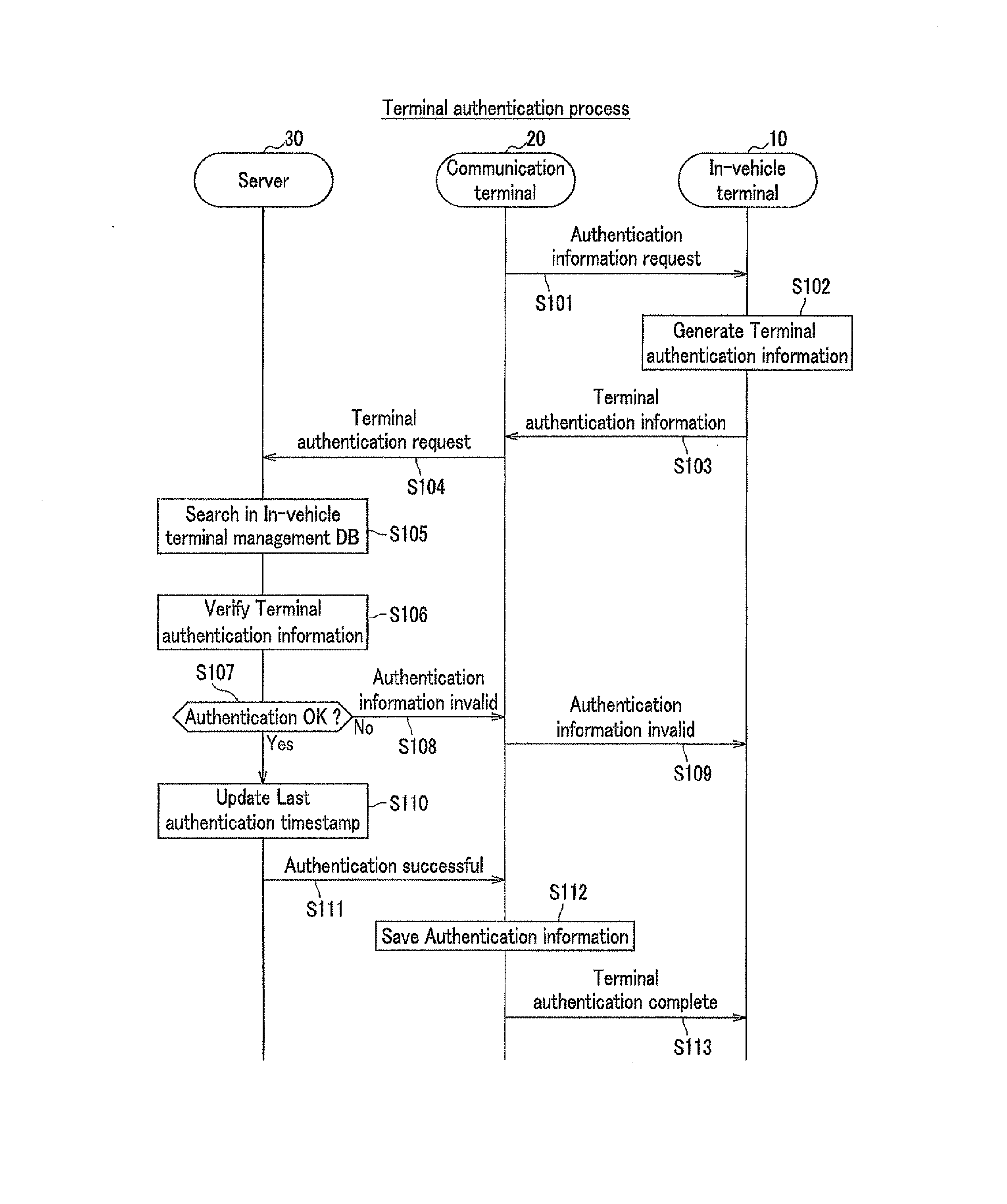
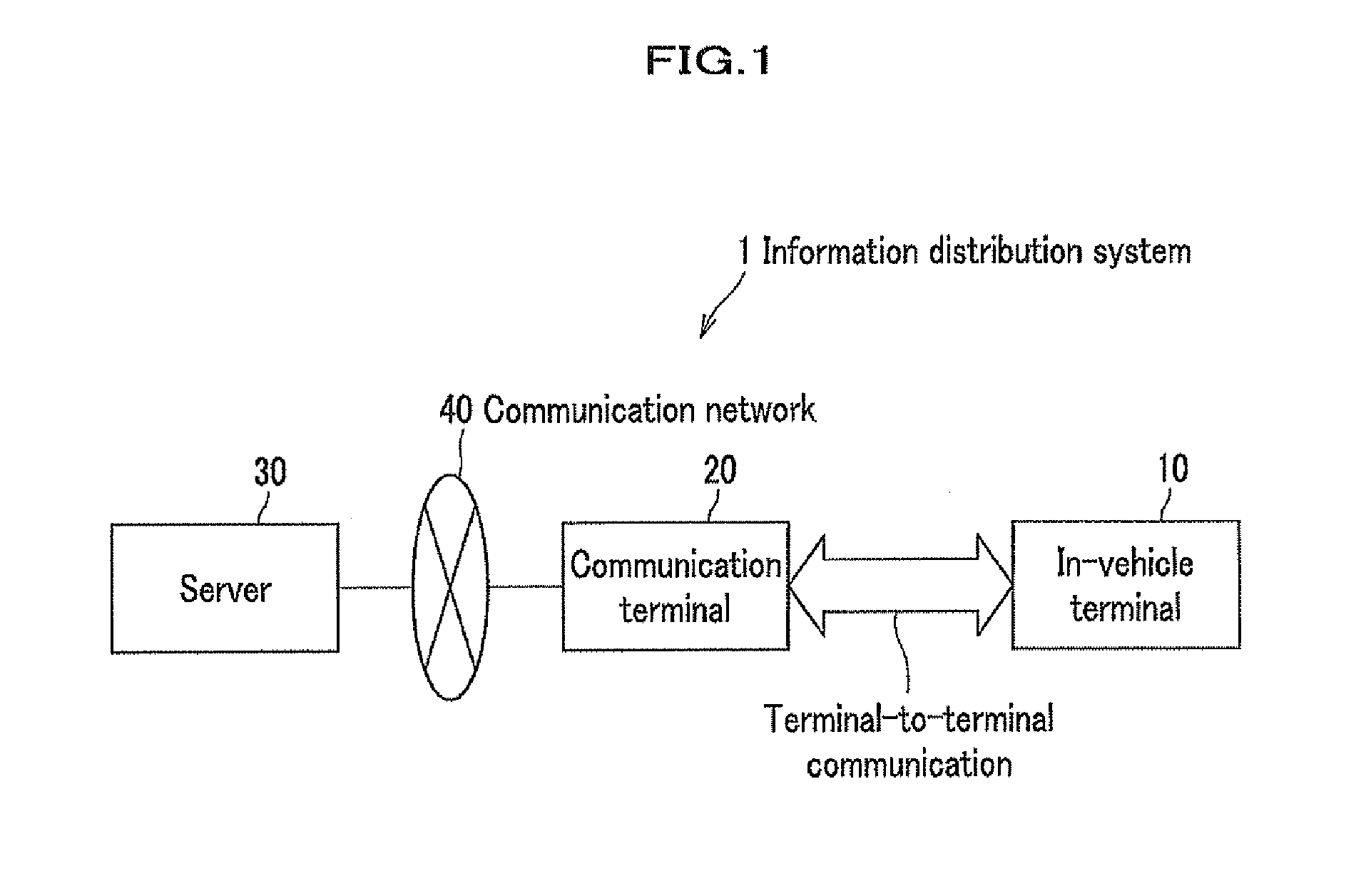
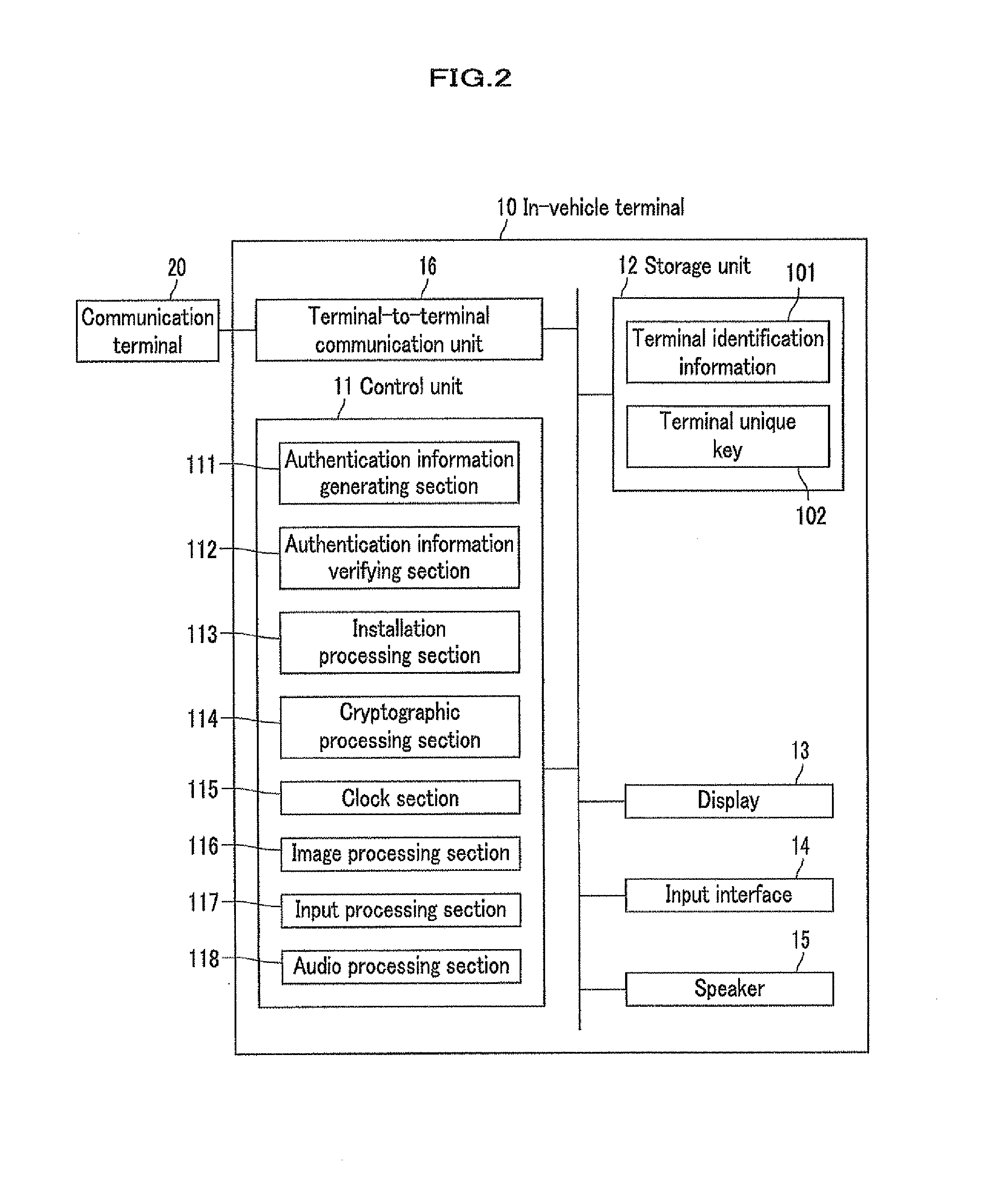
Information distribution method, information distribution system and in-vehicle terminal
ActiveUS20130179689A1Shorten the timeReduce effortService provisioningKey distribution for secure communicationDistribution methodIn vehicle
[Objective] When installing software into an in-vehicle terminal from a server, it is required to prevent the software from being installed into an unsuitable terminal, and to reduce time and efforts for data input and download, thereby improving the convenience of the user.[Solution] In an information distribution system, terminal identification information and a terminal unique key for an in-vehicle terminal are stored in a server as well as in itself. The in-vehicle terminal transmits the terminal identification information to the server for terminal authentication via a communication terminal after encrypting with the terminal unique key, and then the server transmits encrypted software to the communication terminal. The communication terminal transmits the encrypted software to the in-vehicle terminal, which in turn obtains a software unique key encrypted with the terminal unique key from the server and decrypts the encrypted software for installation using the software unique key.
Owner:CLARION CO LTD
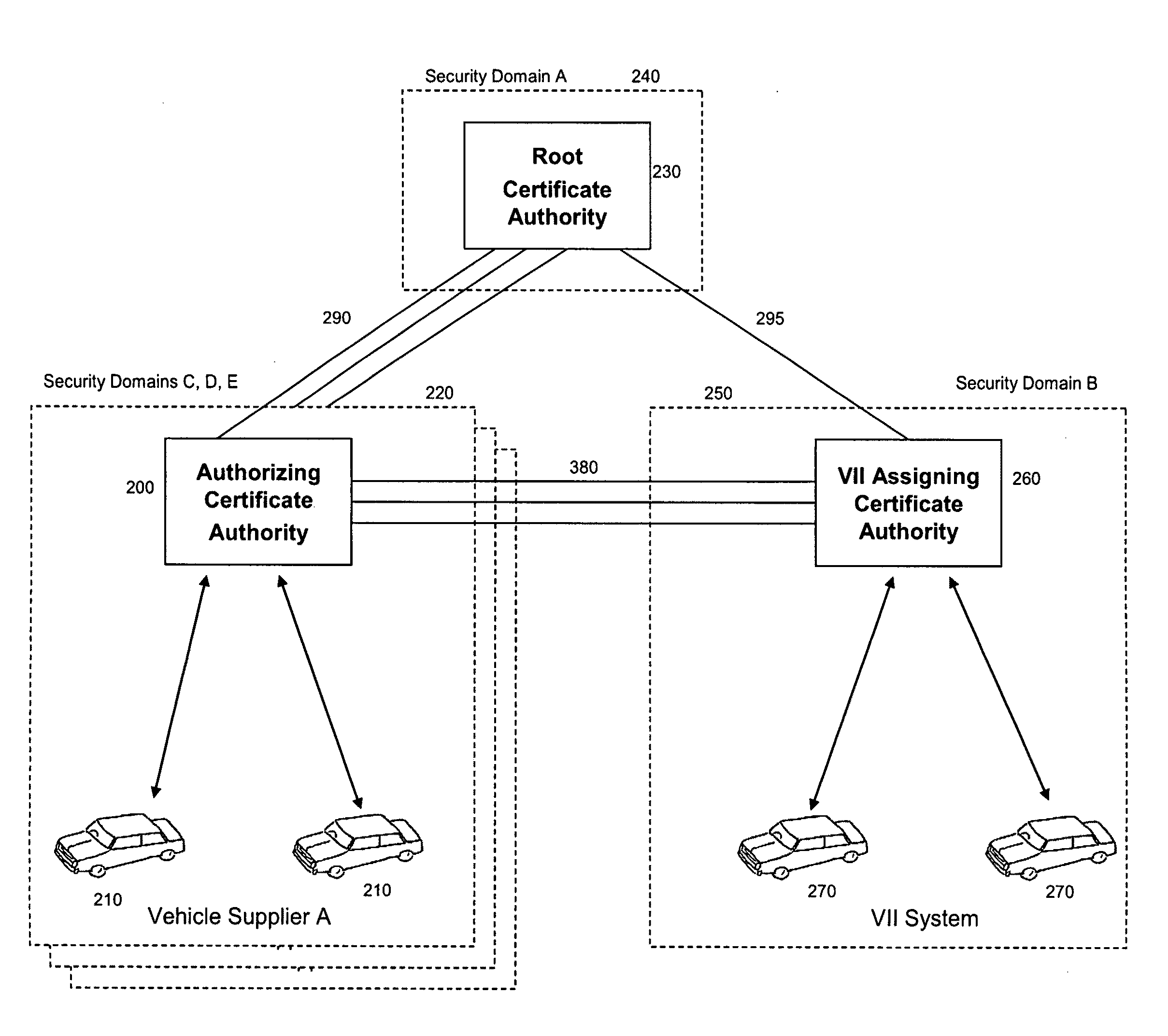
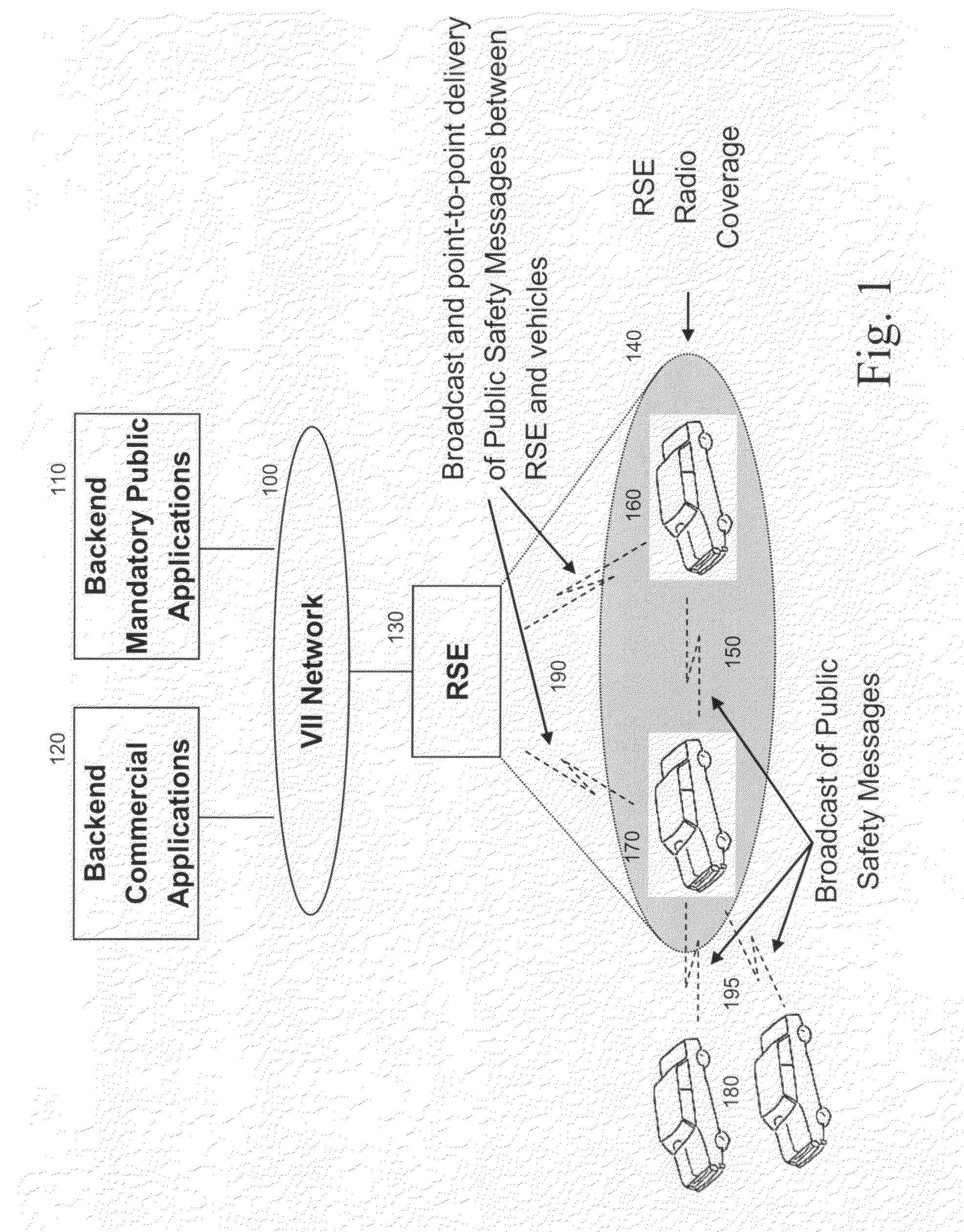
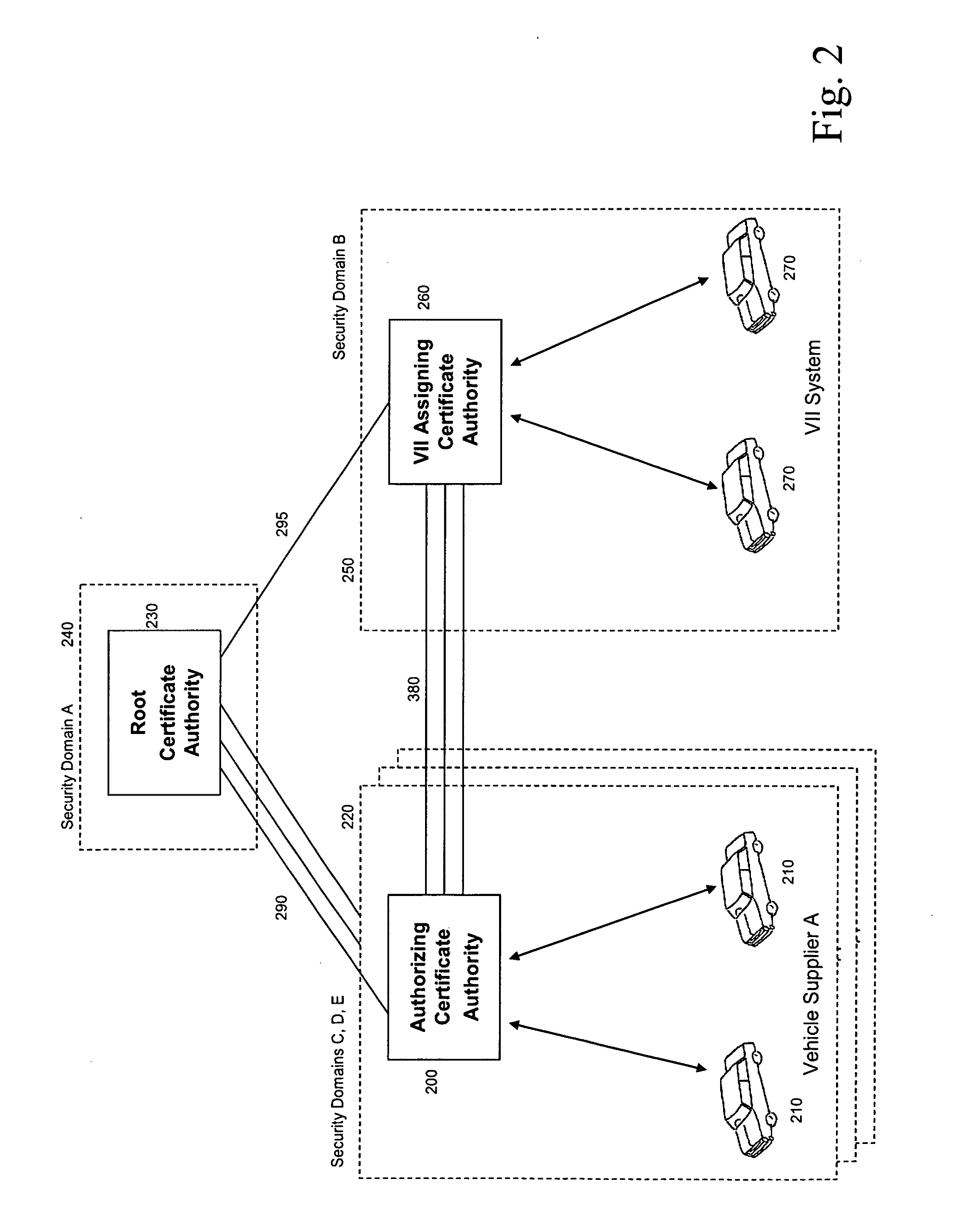
Method and system to authorize and assign digital certificates without loss of privacy, and/or to enhance privacy key selection
A method and system for public key infrastructure key and certificate management provides anonymity to certificate holders and protects the privacy of certificate holders from the compromise of a certificate authority. Functional separation is provided in the authorization of a certificate request and the assignment of certificates and key pairs. The authorizing certificate authority approves or denies each certificate request from a requestor whose identity is not made available to the assigning certificate authority. The assigning certificate authority, upon approval from the authorizing certificate authority, issues one or more certificates and optionally generates and provides the associated key pairs to the requester without disclosing these certificates and key pairs to the authorizing certificate authority. In another aspect, a distributed method is disclosed that allows individual nodes and / or units in a network to select certificates for broadcasting messages to a community of interest with a non-unique key.
Owner:TELCORDIA TECHNOLOGIES INC
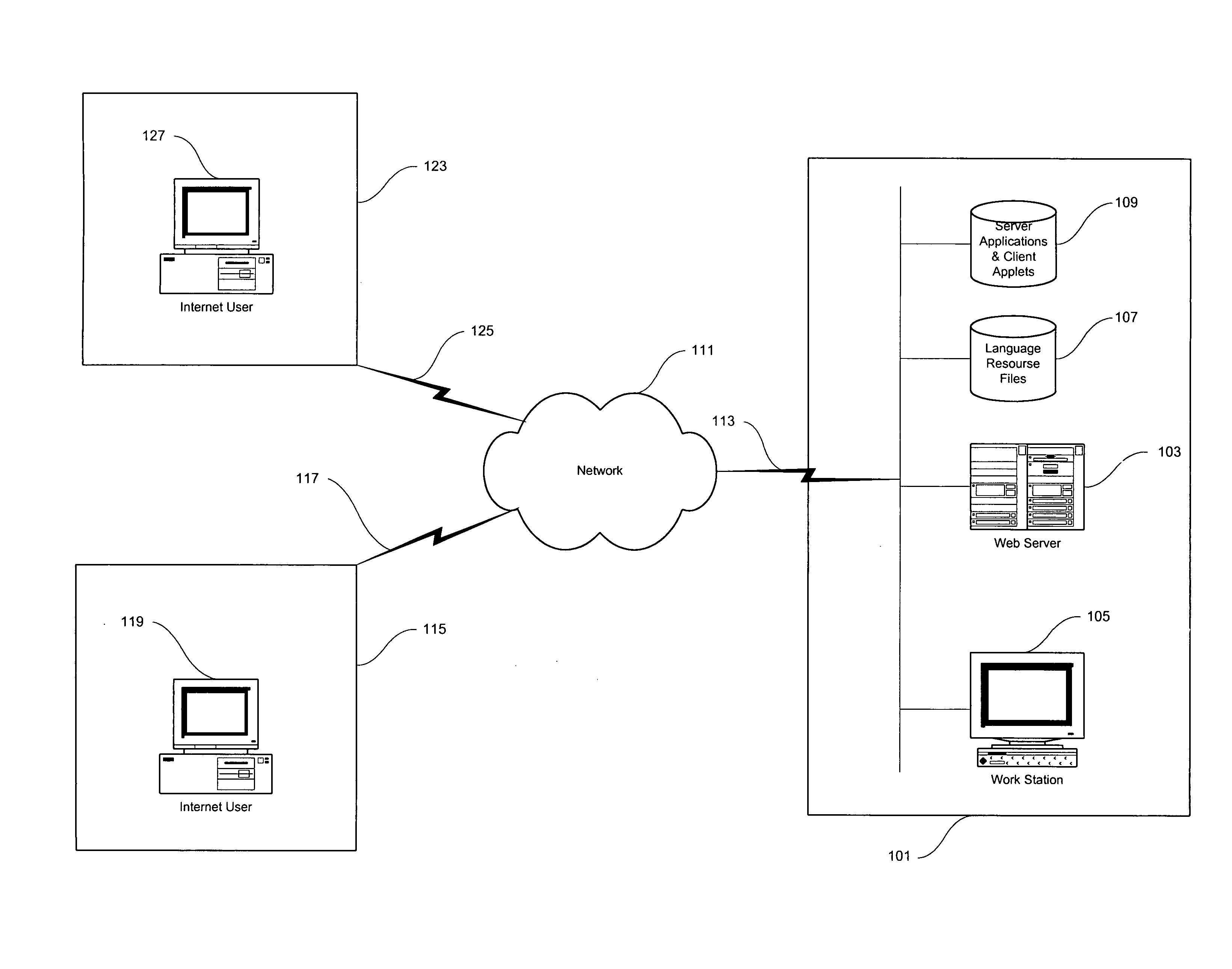
Multi-language system for online communications
ActiveUS7418390B1Improve effectivenessLimited effectivenessNatural language translationSpeech analysisCommunications systemMulti language
An online communications system for converting language. The language conversion is achieved by first storing words and phrases corresponding to a language key and a unique key value in a table at both the transmit and receive ends of the communication. The computer located at the transmit end receives and converts the word or phrase into the unique key value and transmits the unique key value to the computer at the receiving end. The computer at the receiving end receives and converts the unique key value into the corresponding word or phrase.
Owner:R2 SOLUTIONS
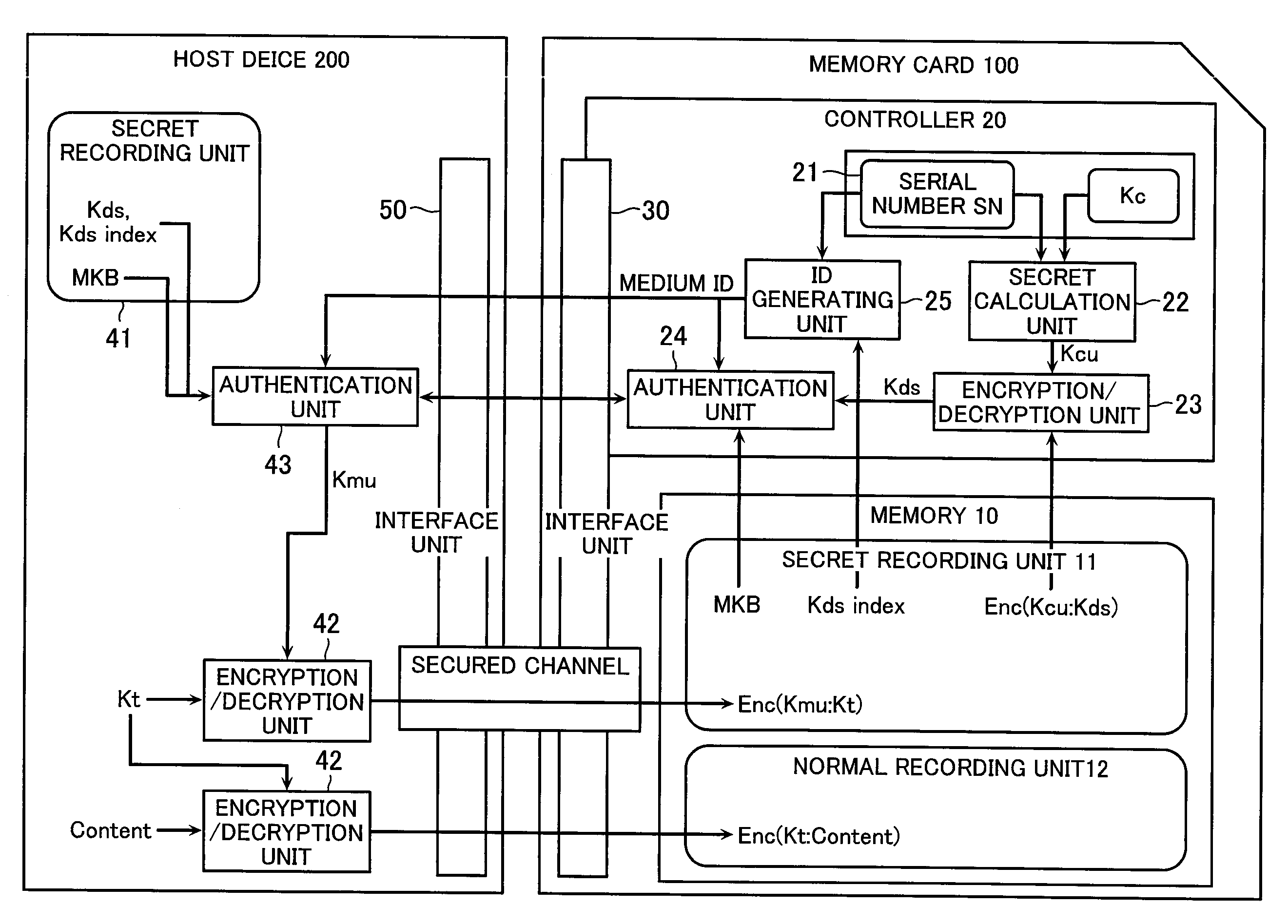
Recording device, and content-data playback system
InactiveUS20100268953A1Key distribution for secure communicationMultiple keys/algorithms usageComputer hardwareAuthentication
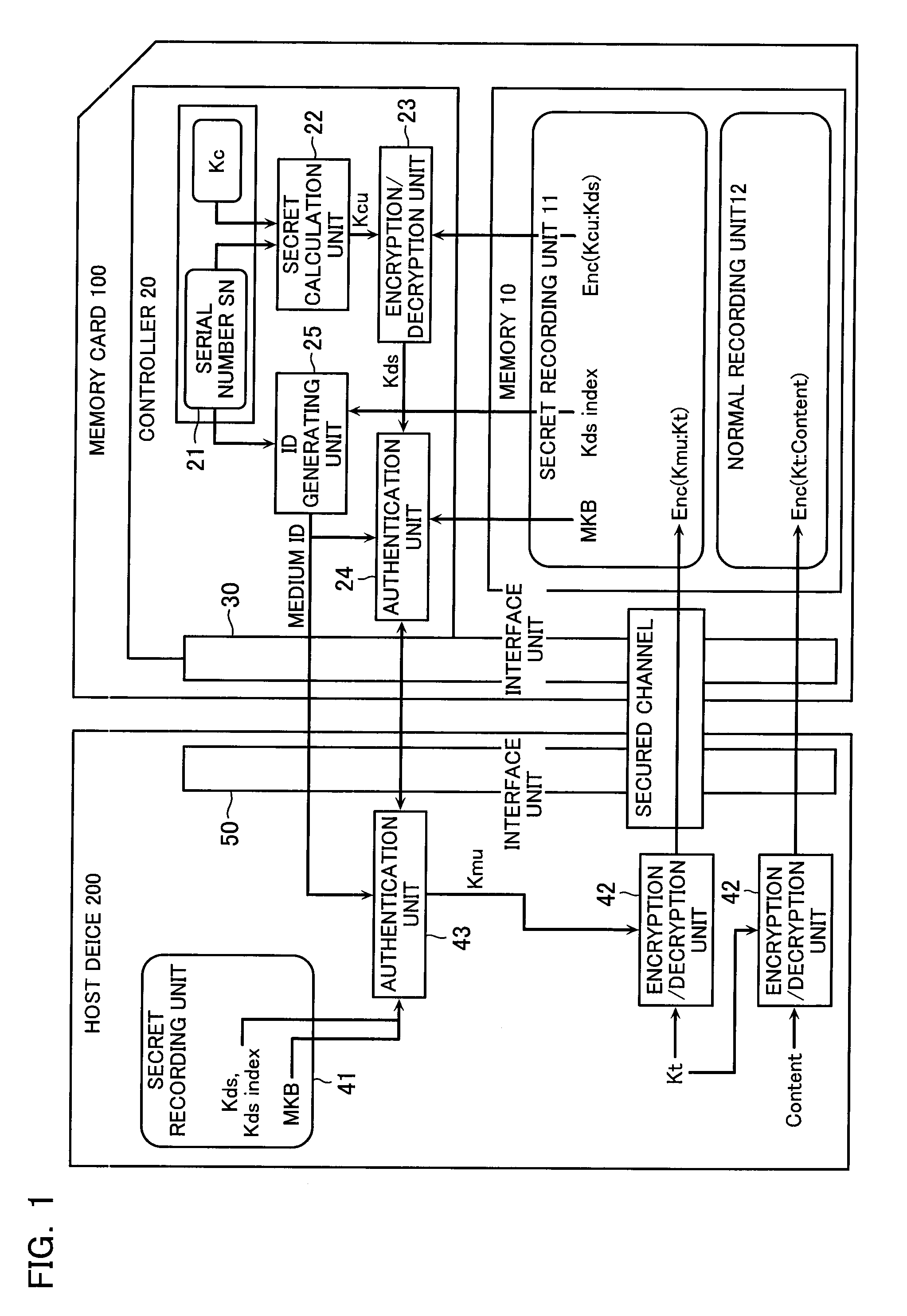
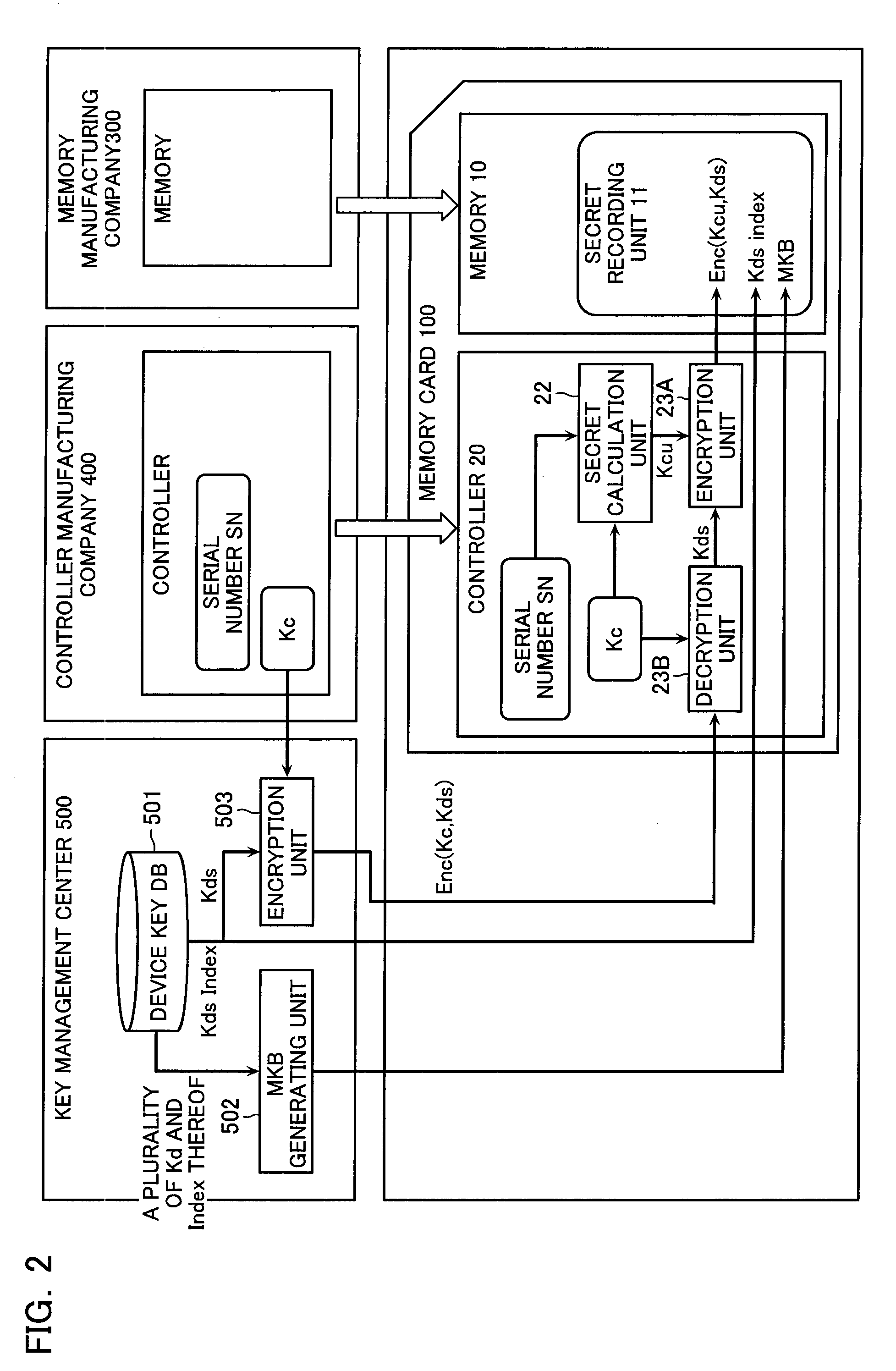
A recording device configured to store content data in an encrypted manner, the recording device comprises a memory unit which stores various data, and a controller which controls the memory unit. The controller possesses a controller key and unique identification information, and is configured to generate a controller-unique key unique for each controller in accordance with the controller key and the identification information. The memory unit stores an MKB generated by encrypting a medium key with a device key set that is a collection of a plurality of device keys, an encrypted device key set generated by encrypting the device key set with the controller-unique key, and a device-key-set index which uniquely identifies the device key set. The controller comprises a decryption unit which obtains a device key set by decrypting the encrypted device key set with the controller-unique key, an ID generating unit which generates a medium ID from the identification information and the device-key-set index, and an authentication unit which executes an authentication process with an exterior in accordance with the device key set, the medium ID and the MKB.
Owner:KK TOSHIBA
System and method for DRM regional and timezone key management
InactiveUS20060200412A1Television systemsSelective content distributionComputer hardwareKey management
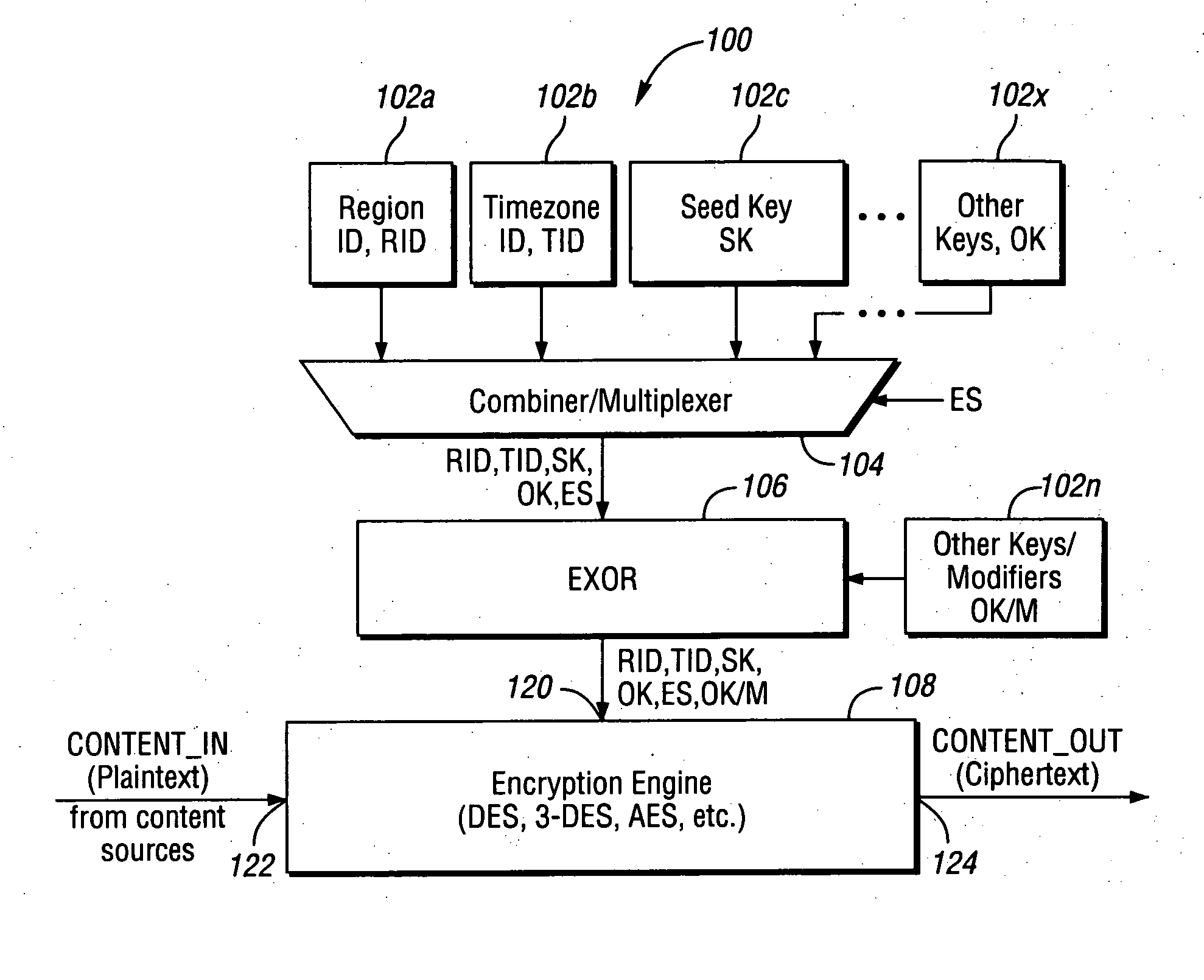
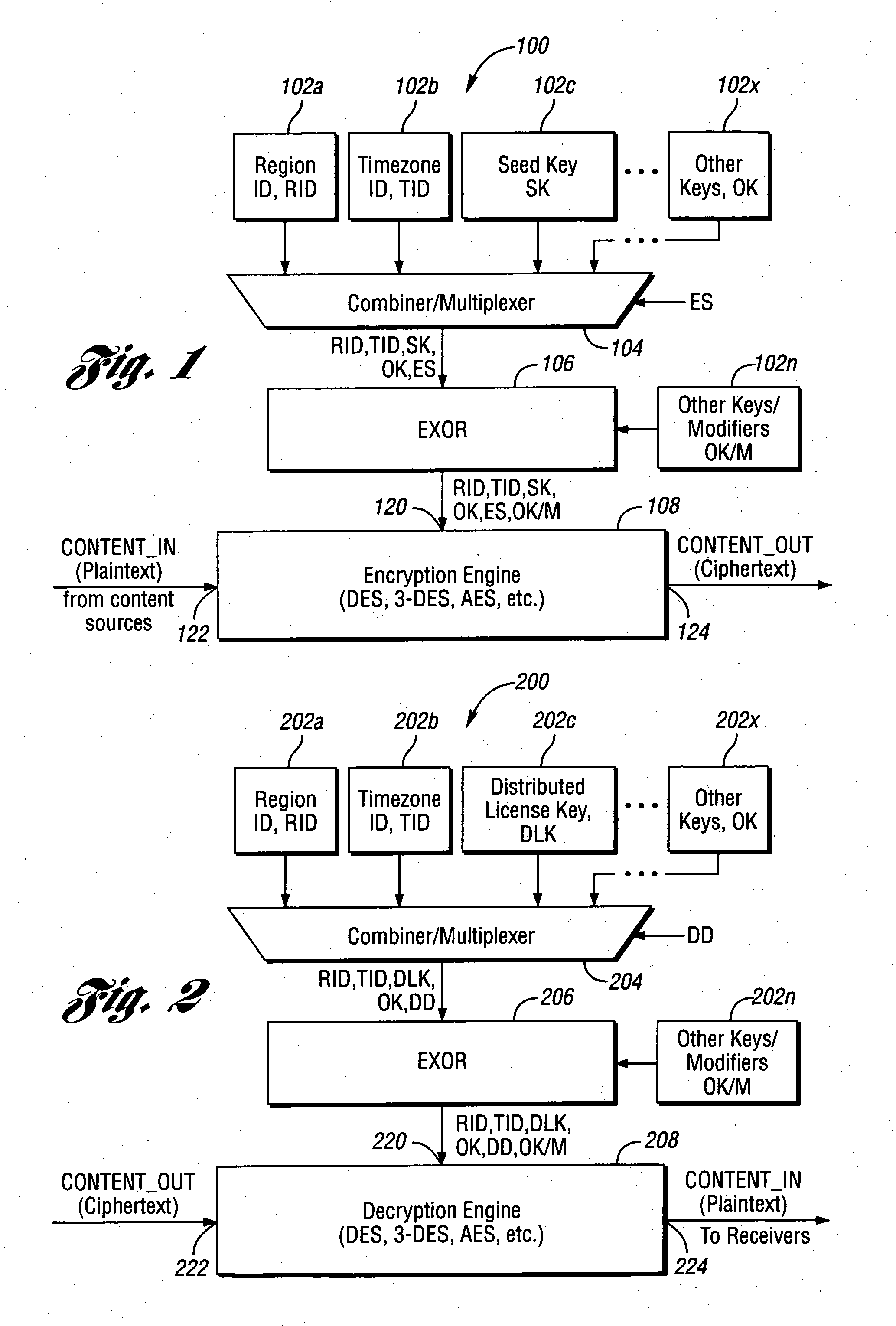
A cryptographic media stream system for ensuring media stream content is only consumed in authorized regions. The system includes at least one encryption / decryption key source configured to provide at least one of a regional key and a timezone key, where the regional key and the timezone key are globally unique keys, a media encryption engine that receives an unencrypted media stream and encrypts the encrypted media stream, and a media decryption engine that receives the encrypted media stream, and decrypts the encrypted media stream in response to at least one of the regional key and the timezone key.
Owner:COMCAST CABLE COMM LLC
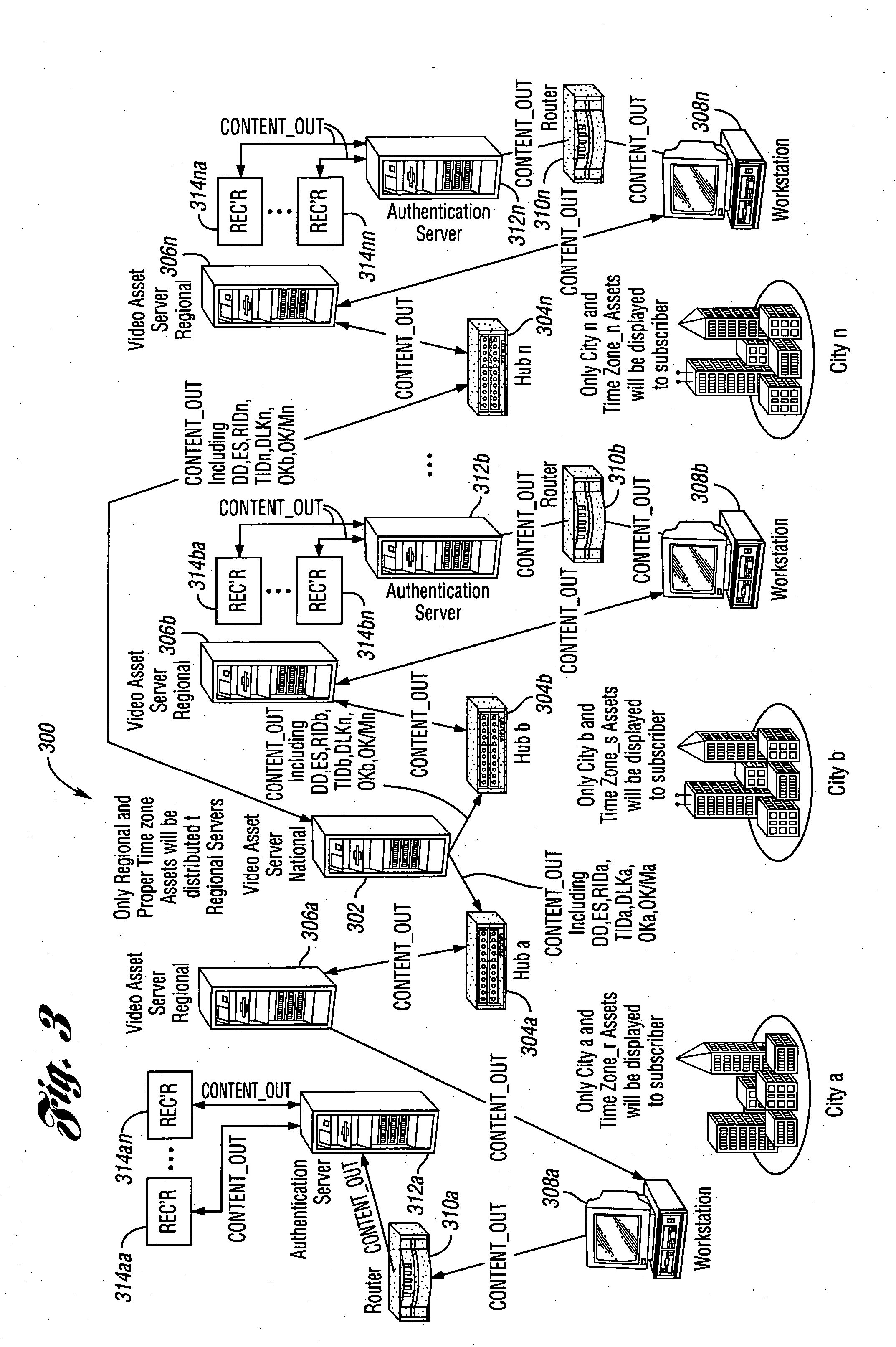
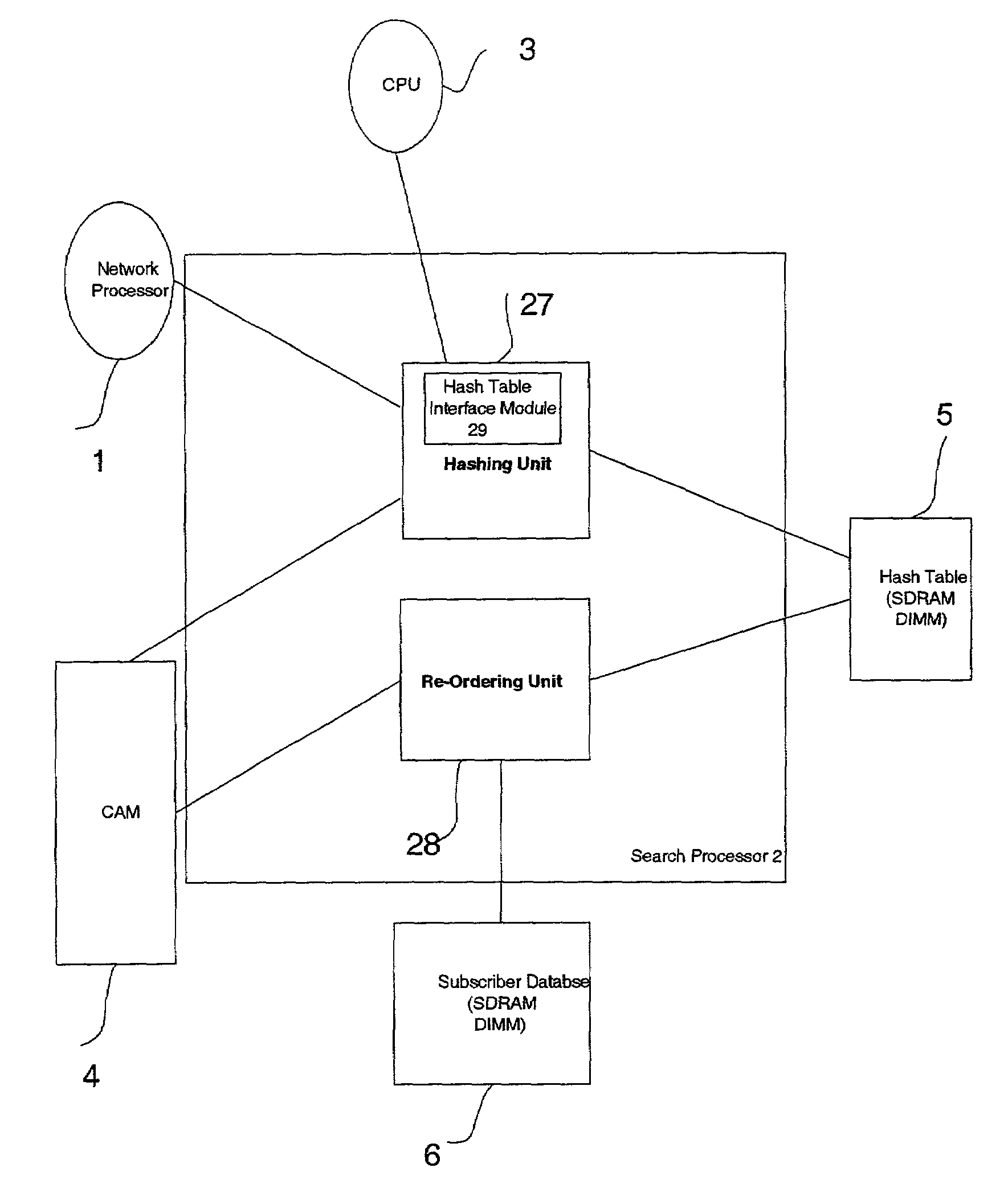
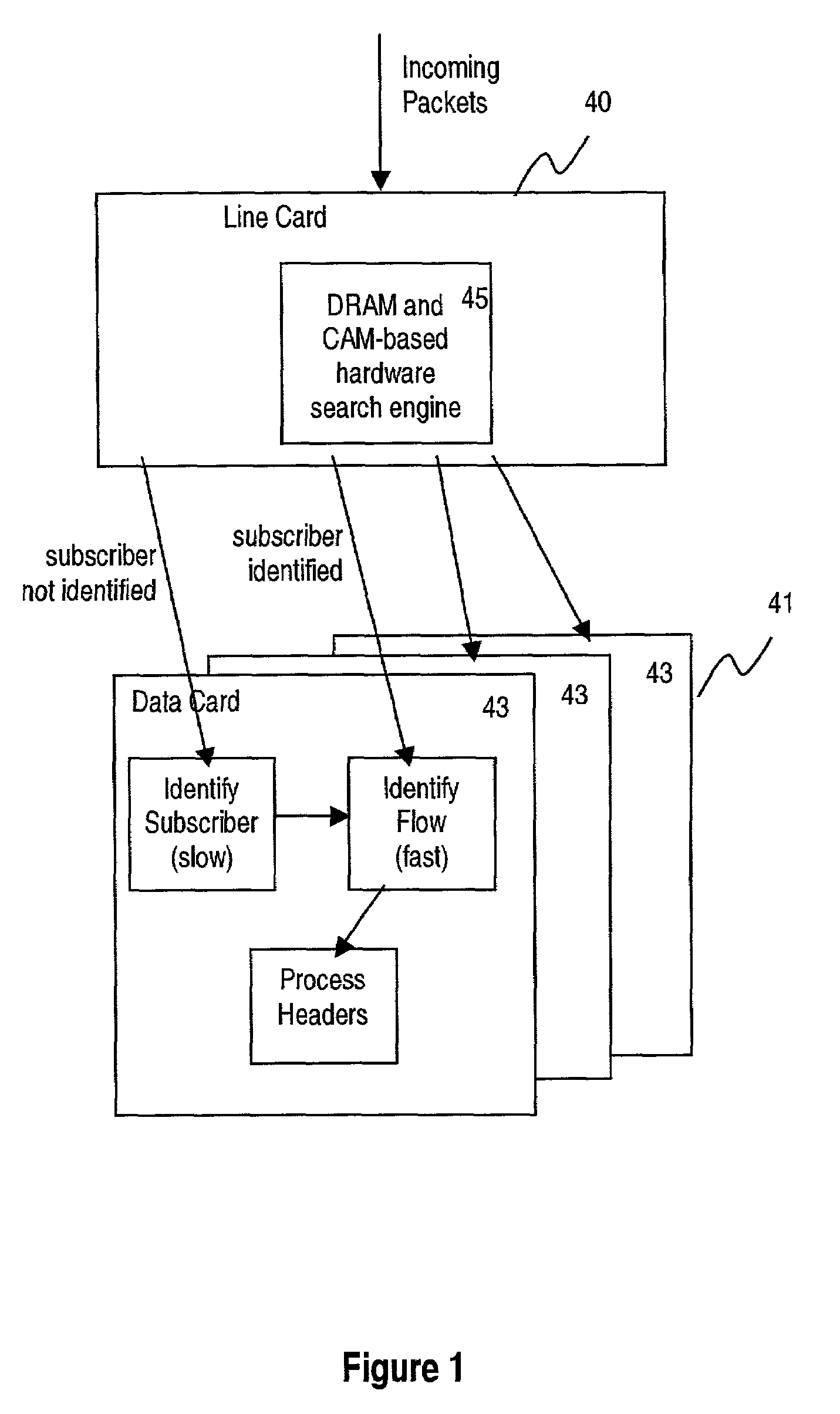
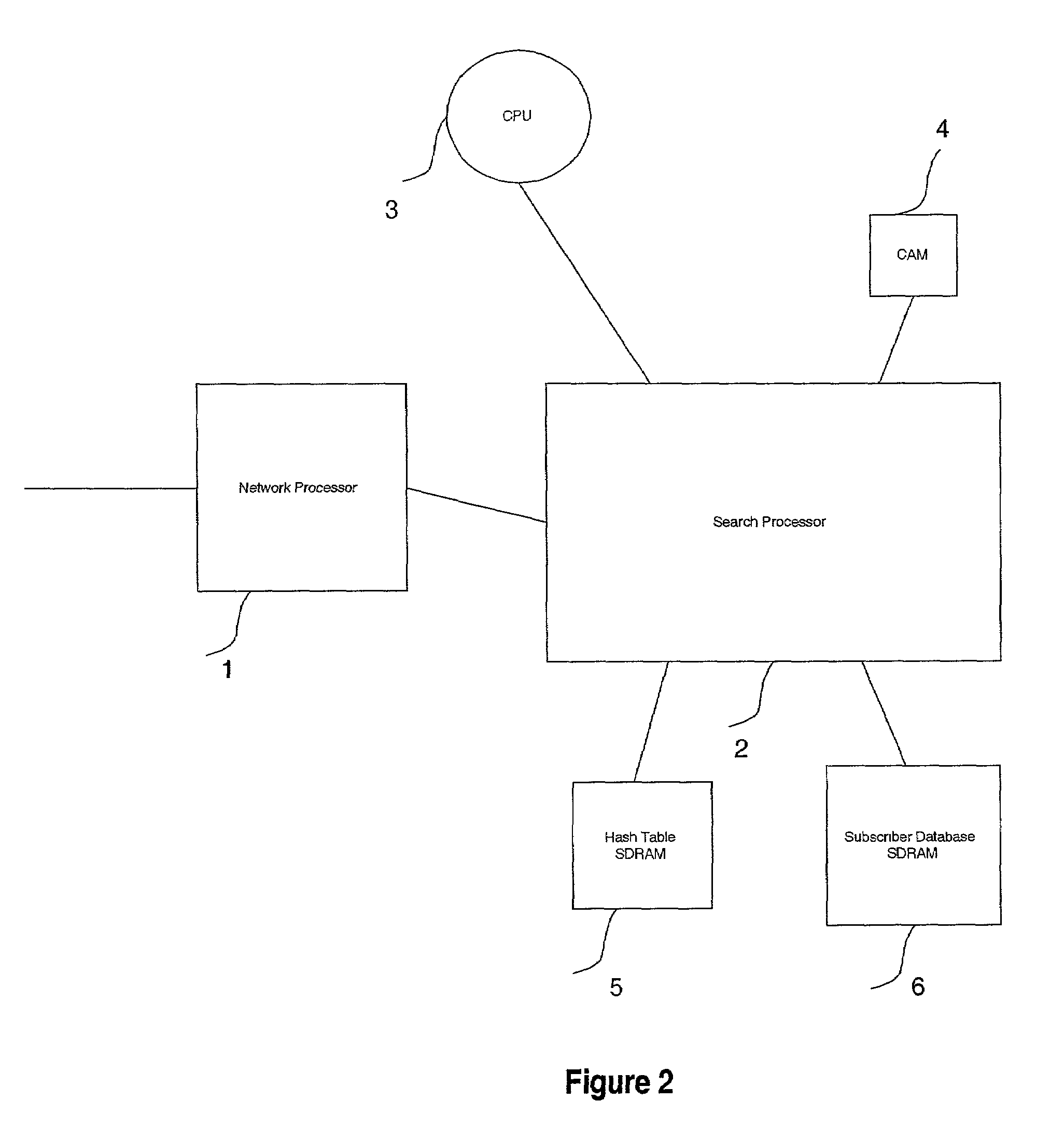
Near-perfect, fixed-time searching algorithm using hashing, LRU and cam-based caching
ActiveUS7039764B1Digital data information retrievalSpecial data processing applicationsComputer scienceFixed time
A method and a search engine are described. A unique key is received. A hash is searched for a match to the unique key. Concurrently with searching the hash, a cache is searched for the match to the unique key. And information regarding the unique key is obtained.
Owner:NOKIA TECHNOLOGLES OY
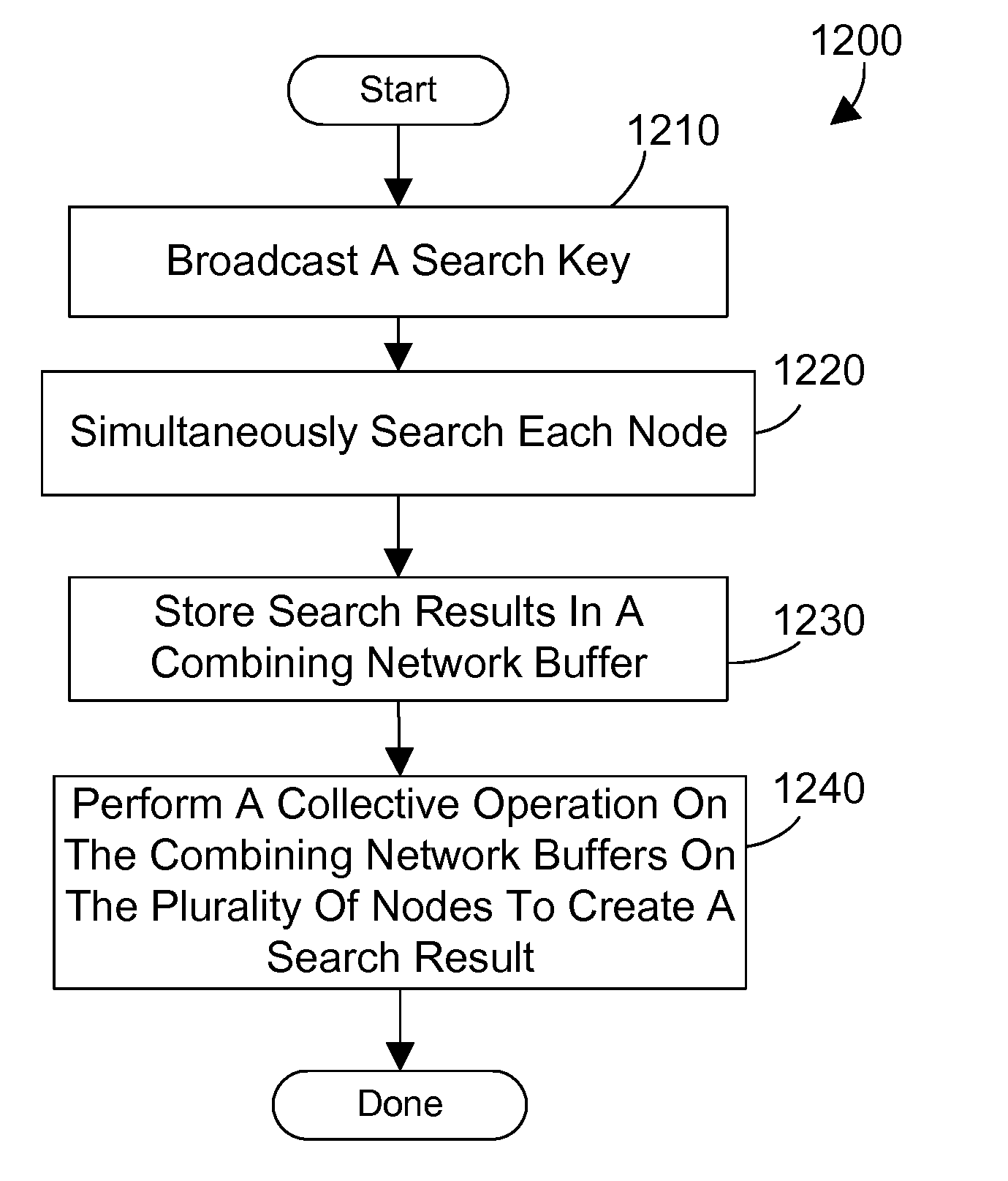
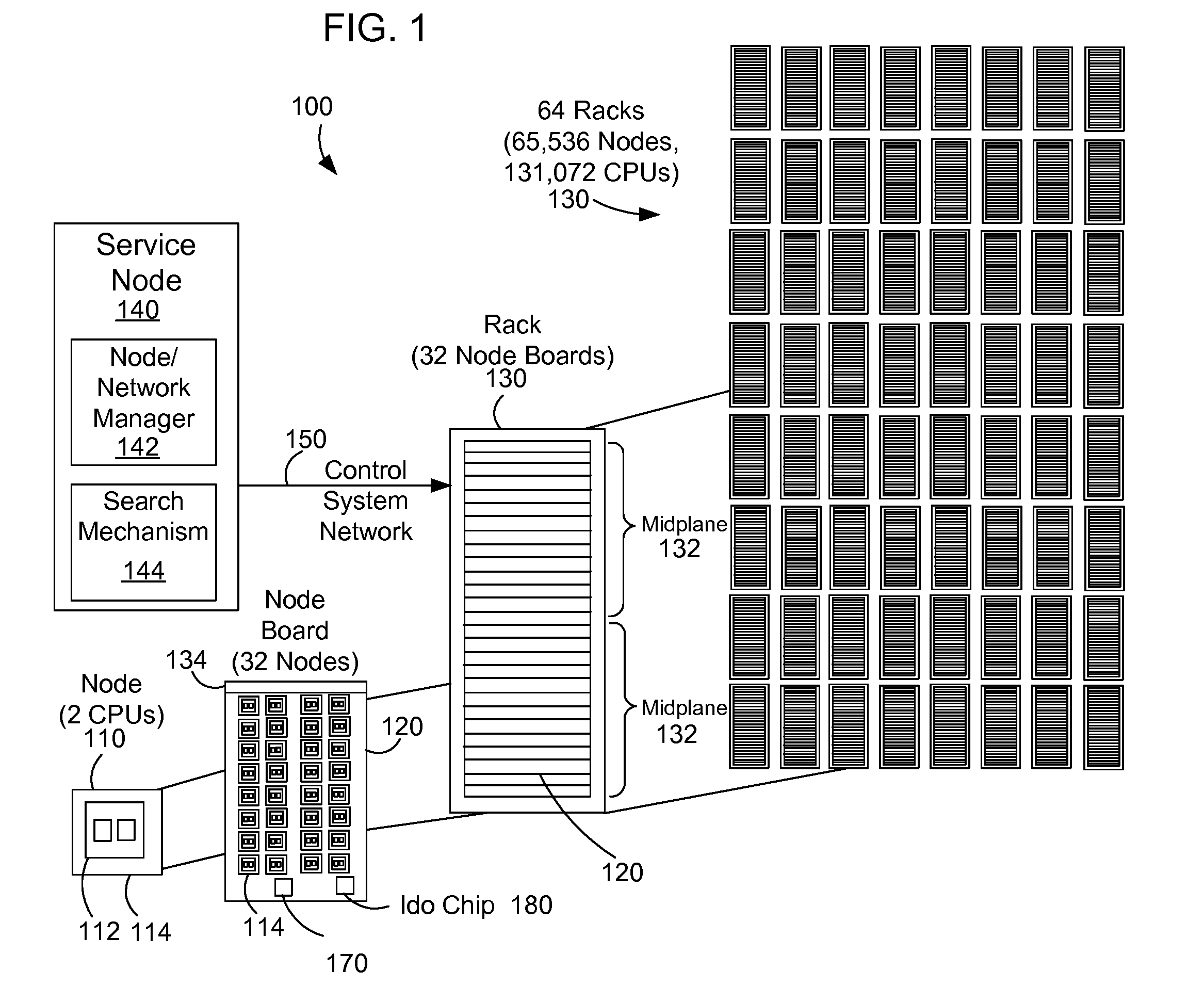
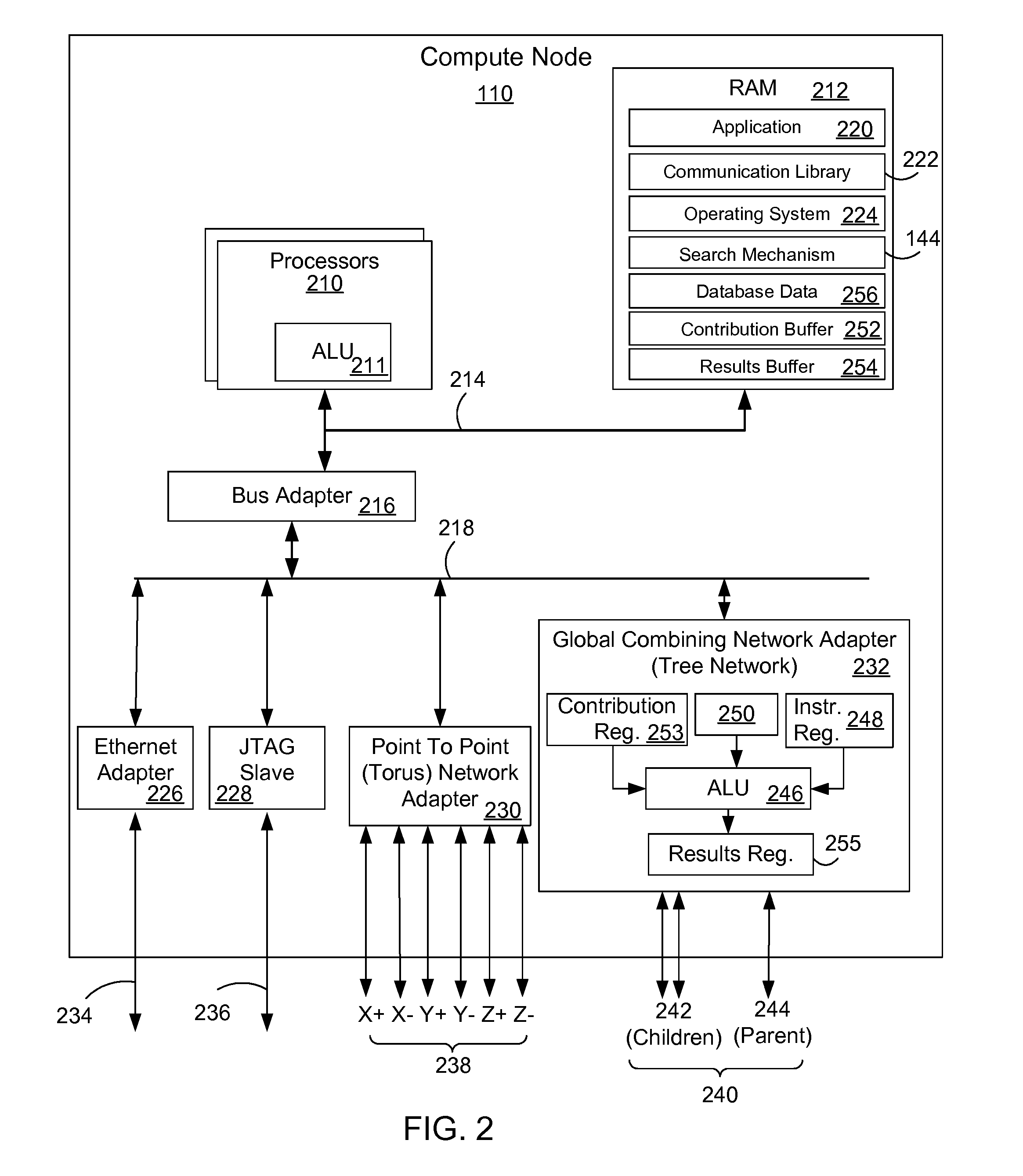
Database retrieval with a non-unique key on a parallel computer system
InactiveUS20090037377A1Efficiently and quickly searchDigital data information retrievalDigital data processing detailsIn-memory databaseComputerized system
An apparatus and method retrieves a database record from an in-memory database of a parallel computer system using a non-unique key. The parallel computer system performs a simultaneous search on each node of the computer system using the non-unique key and then utilizes a global combining network to combine the local results from the searches of each node to efficiently and quickly search the entire database.
Owner:IBM CORP
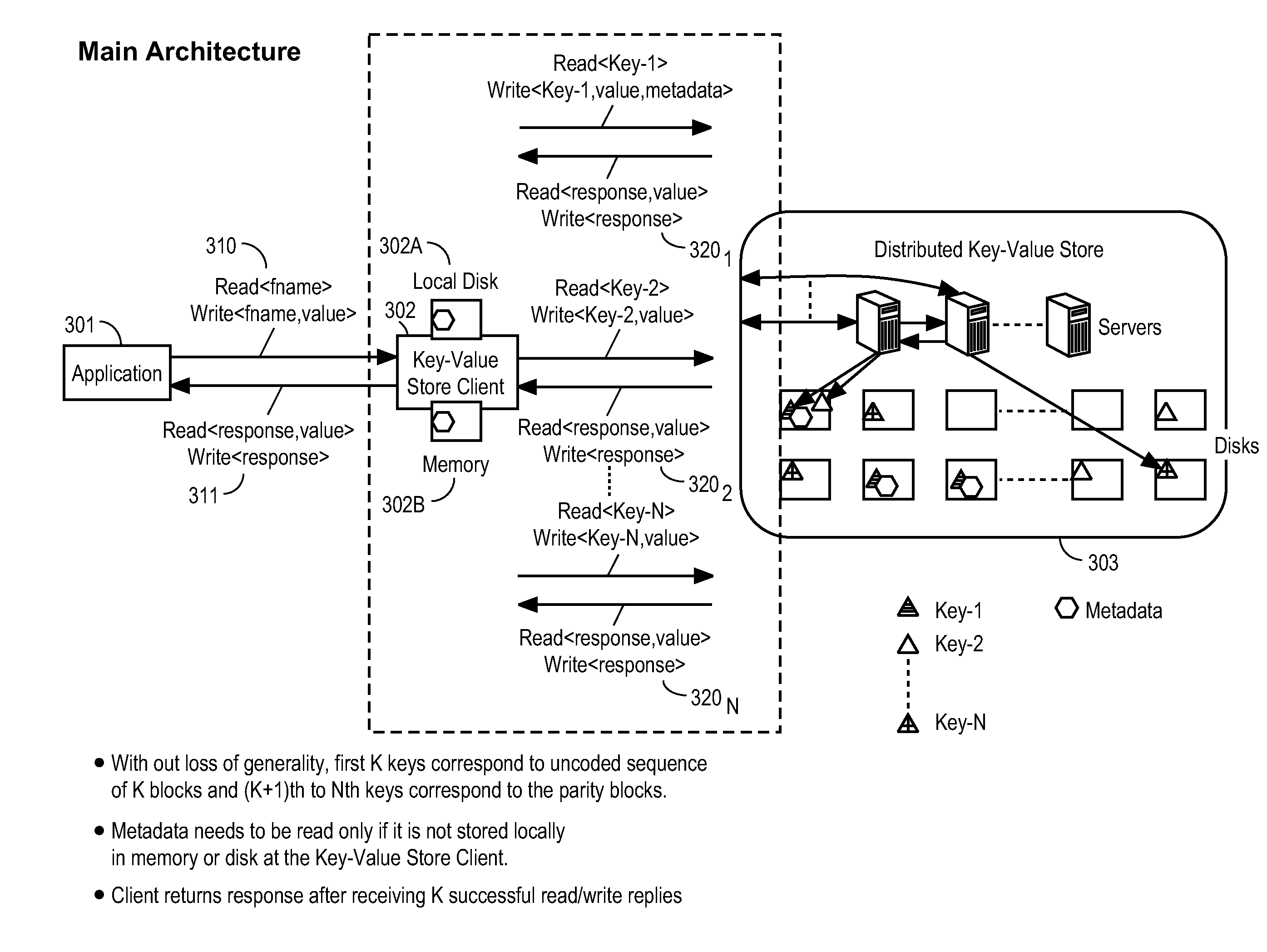
Method and apparatus for low delay access to key-value based storage systems using fec techniques
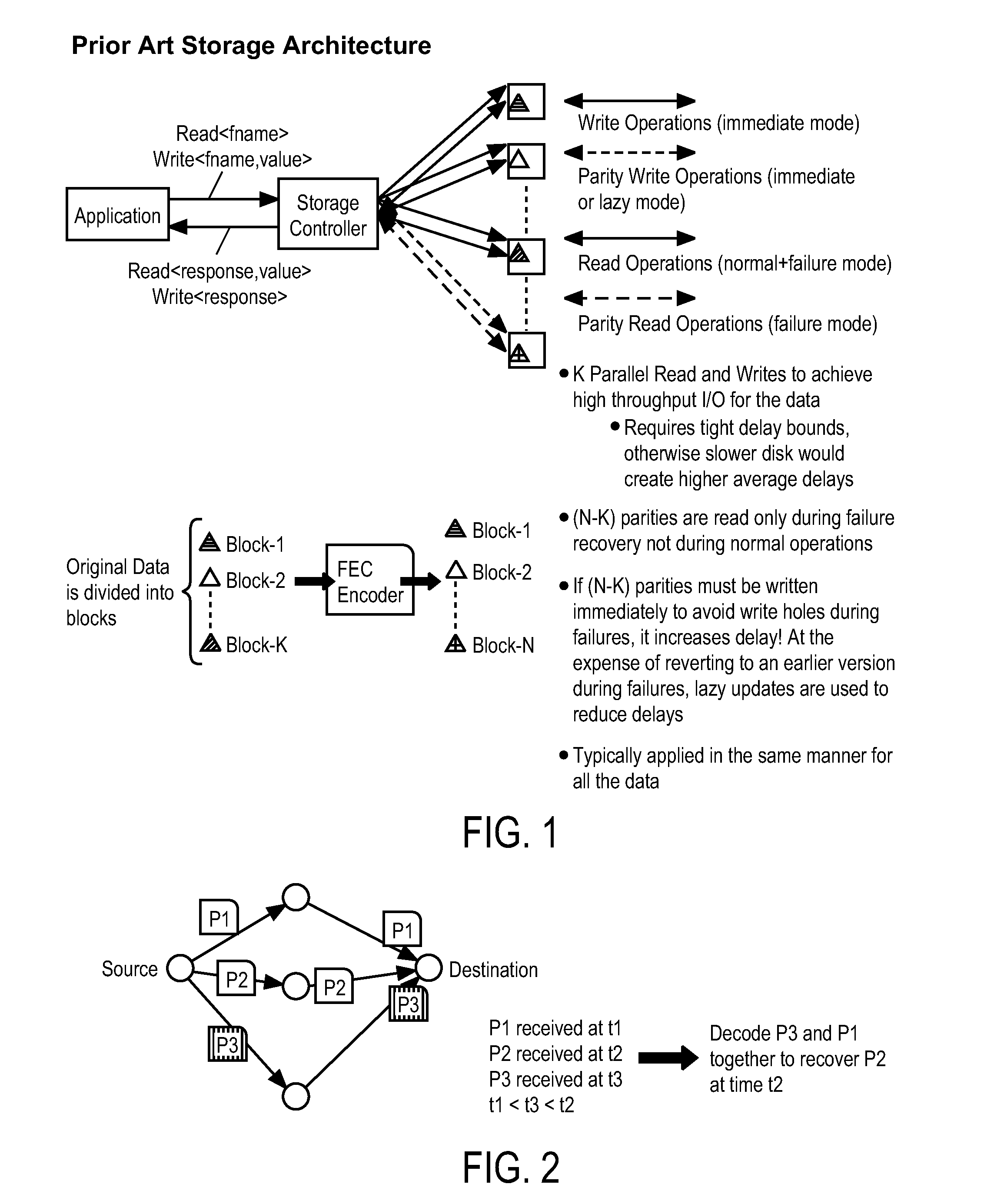
ActiveUS20150149870A1Lower latencyStatic storageForward error control useComputer architectureHybrid storage system
A method and apparatus is disclosed herein for low delay access to key-value based storage systems. In one embodiment, the method for putting data into a key-value store comprising dividing the data into K portions, where K is an integer; selecting an erasure coding to apply to the K portions as a function of delay performance of the key-value based storage system including determining a number of parity blocks to generate to satisfy one or both of a delay target of putting the object into the key-value store and a delay target of subsequent read requests based on an offline performance simulation of delay performance when different numbers of parity blocks are used given the delay distributions obtained through measurements for different request types and object sizes; applying the erasure coding to the K portions to create N blocks of data; sending the N write requests to write blocks of data to the storage system, where each block is assigned a unique key in the key-value store.
Owner:NTT DOCOMO INC
Systems and methods for securing multimedia transmissions over the internet
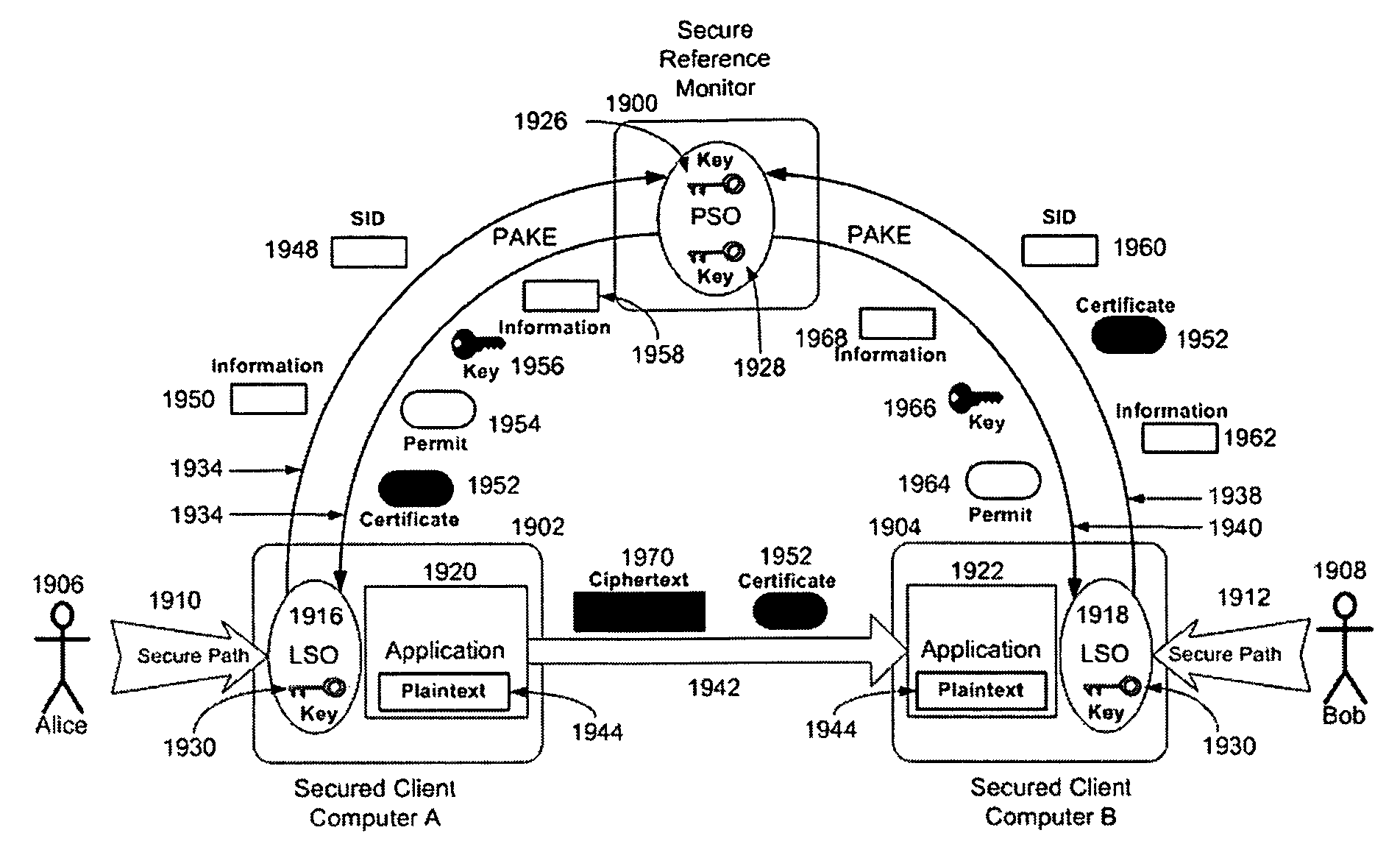
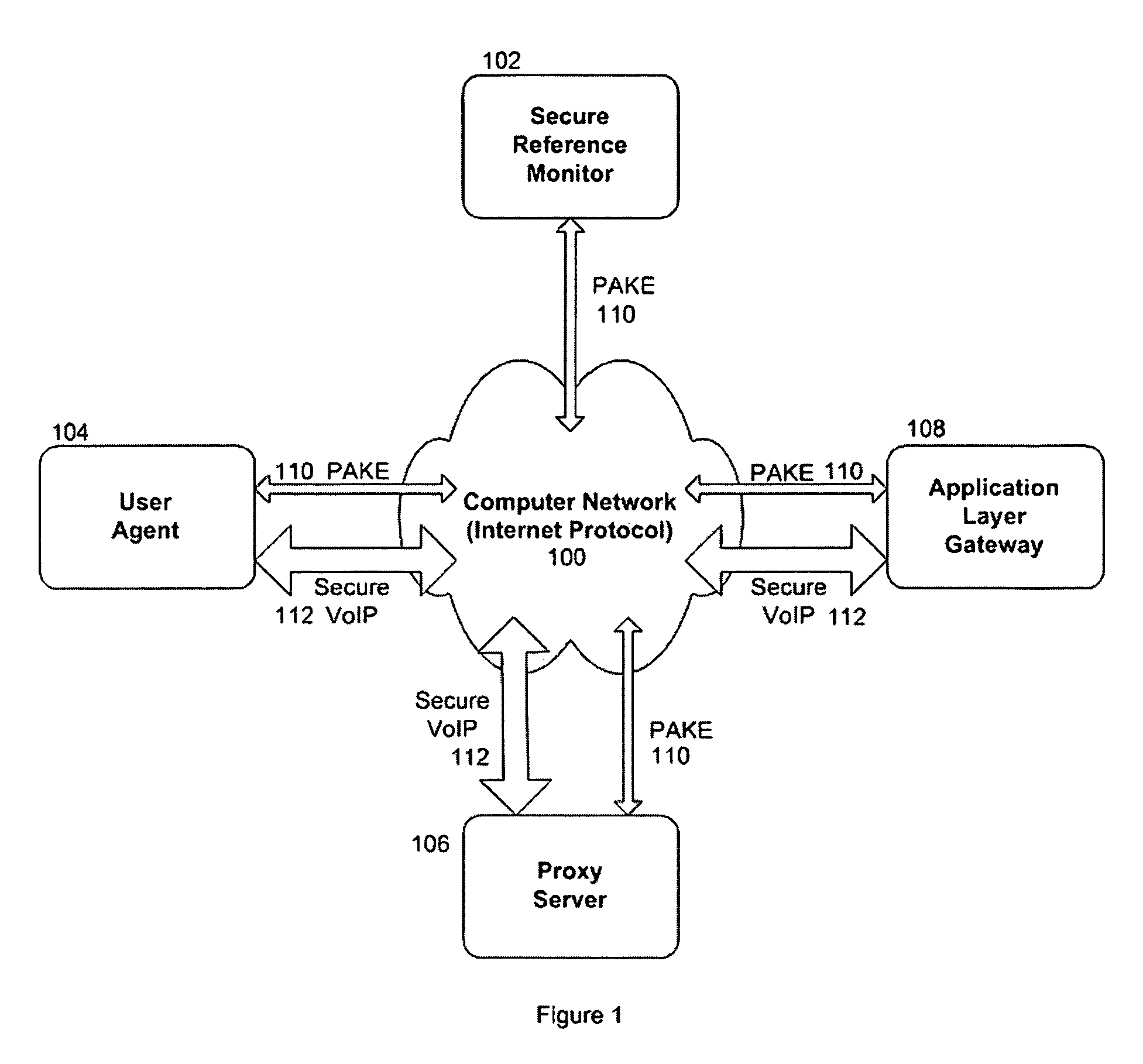
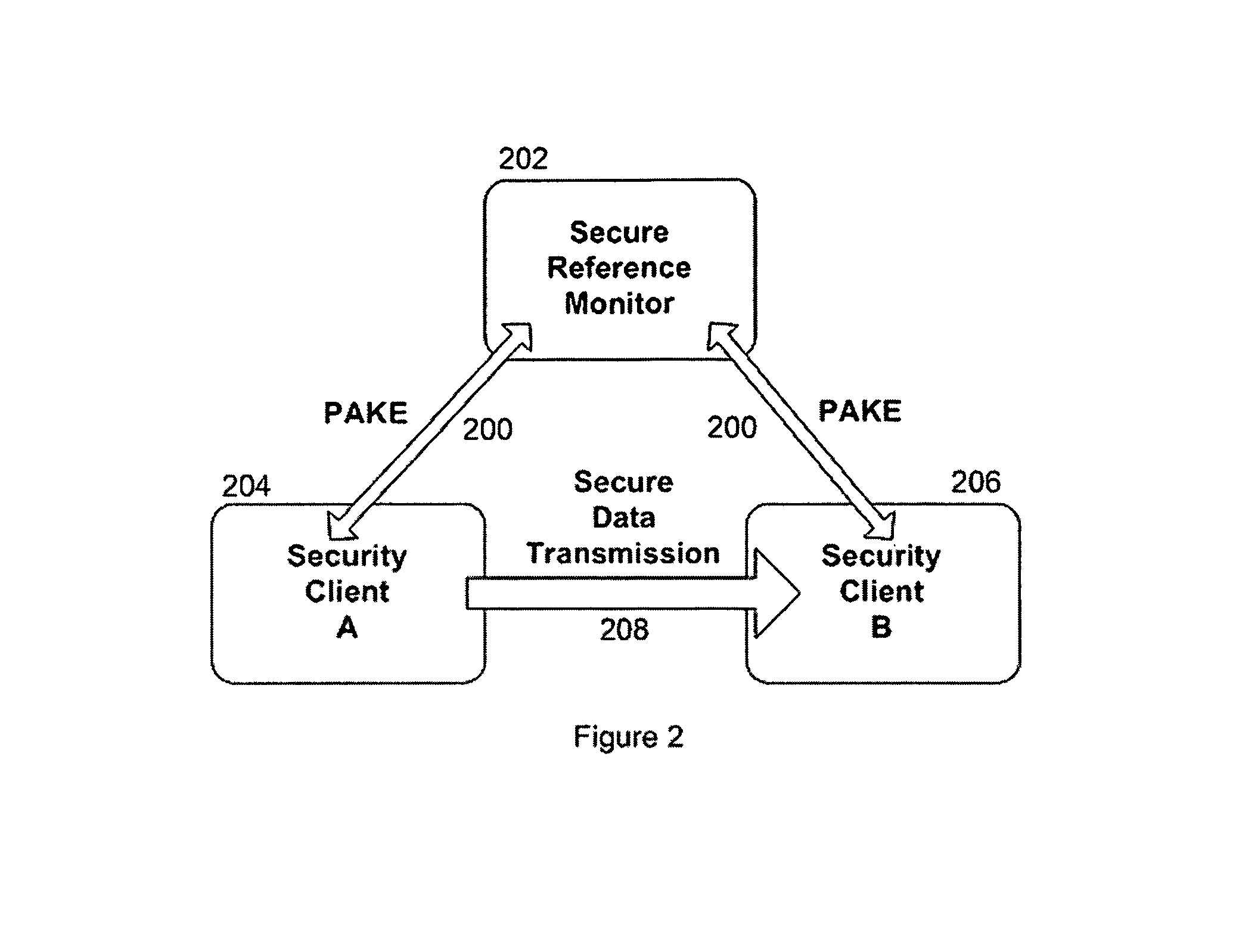
InactiveUS8024560B1Communication securityUser identity/authority verificationUnauthorized memory use protectionSecure communicationThe Internet
In one embodiment, the systems and methods utilizes an enciphered permit identification number, called a session certificate, to reference the policy attribute values and session key that are stored in a secured, online reference monitor (SRM). The session key is used to encipher confidential communications, such as voice and audio communications over the Internet (VoIP), between computers. Each computer uses a unique key with a cryptographic transaction protocol for authentication and key agreement (PAKE) to securely communicate with the SRM. A sender computer uses PAKE to get a session certificate and a session key from the SRM. It sends the session certificate to a receiver computer. The receiver computer sends the session certificate to the SRM and gets back the session key. The sender computer encrypts its VoIP message with the session key and transmits it to the receiver computer. The receiver computer decrypts the VoIP message.
Owner:ALTEN ALEX I
Efficient techniques for sharing a secret
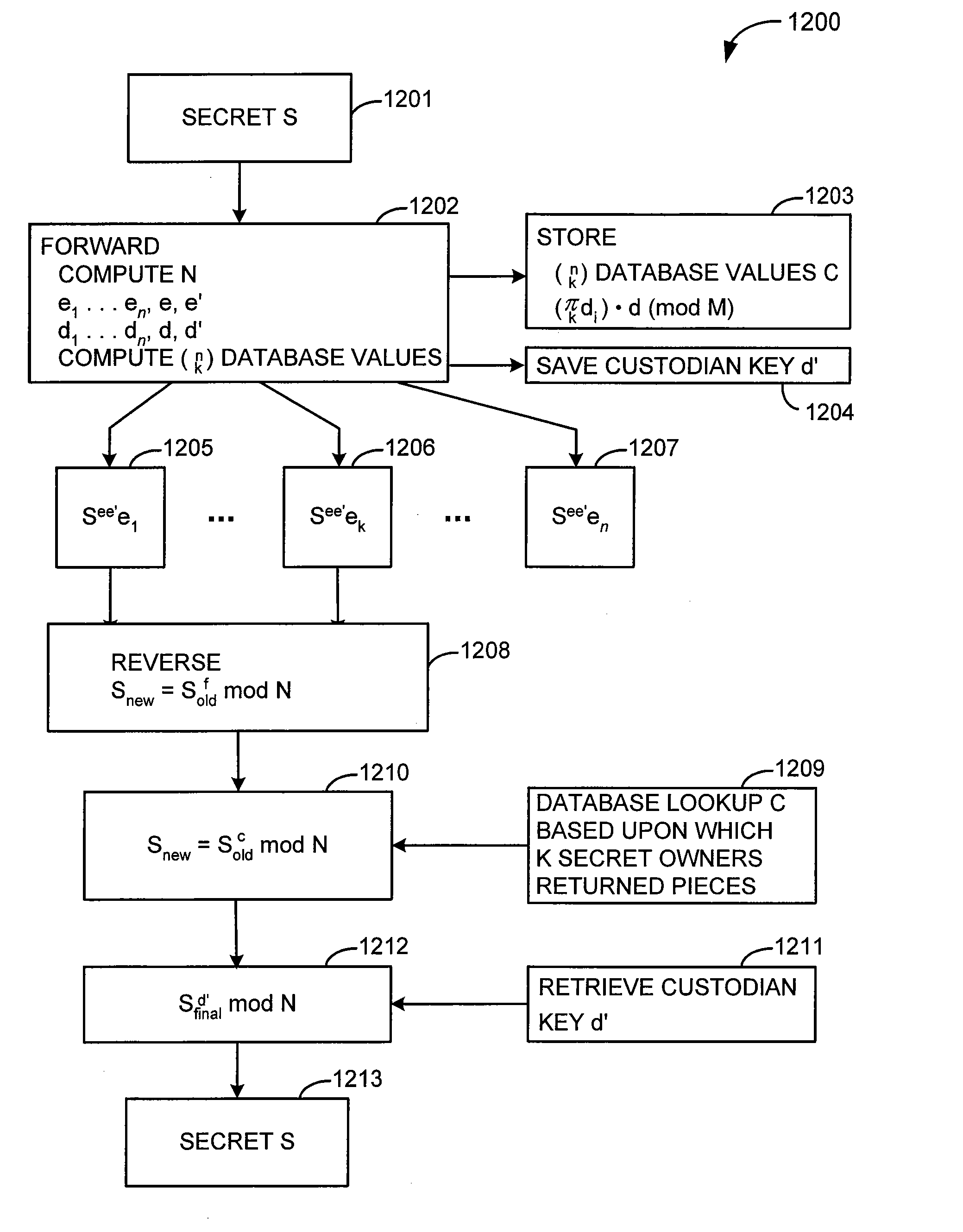
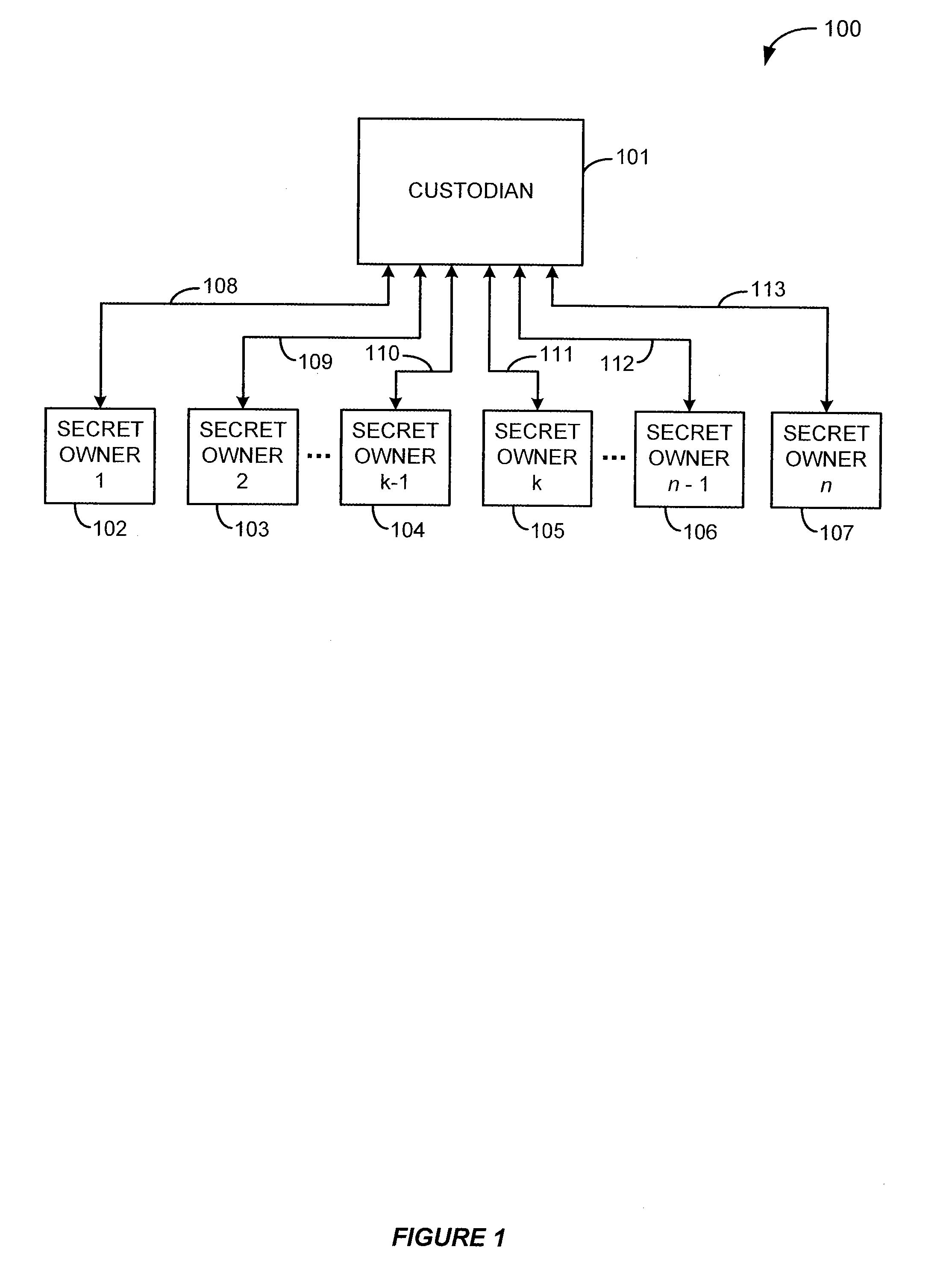
InactiveUS7167565B2Adequate protection against disk attackComputationally efficientKey distribution for secure communicationMultiple keys/algorithms usageKey distributionModulo operation
An n person secret sharing solution computes n unique keys to be distributed to the secret owners along with an exponentiated version of the secret. The custodian performs an exponent / modulo operation each time one of the keys is received from one of the secret owners. Alternatively, n+1 keys are created by the custodian, and the custodian retains one key after distributing the remaining n keys to the secret owners. After the custodian has received and processed the n keys from the secret owners, he performs an exponent / modulo operation using his own retained key. According to another aspect, a k out of n secret sharing solution involves computing and storing a database having an entry for each unique combination of k keys that could be returned from among the n keys. After k keys have been received, the custodian looks up in the database the entry corresponding to the particular unique combination of secret owners who returned keys. The custodian performs another exponent / modulo operation using the entry retrieved from the database in order to reconstruct the original secret. According to an embodiment, the custodian computes n+1 keys, distributes n of the keys to the secret owners, and keeps one of the keys for himself. The custodian retrieves his own key and performs a final exponent / modulo operation in order to reconstruct the original secret. According to another aspect, a k out of n secret sharing solution involves encrypting the original secret before applying any conventional k out of n secret sharing solution.
Owner:CA TECH INC
System and method for protecting a title key in a secure distribution system for recordable media content
InactiveUS20050177740A1Less complexEliminate interactionKey distribution for secure communicationDigital data processing detailsComputer hardwareDistribution system
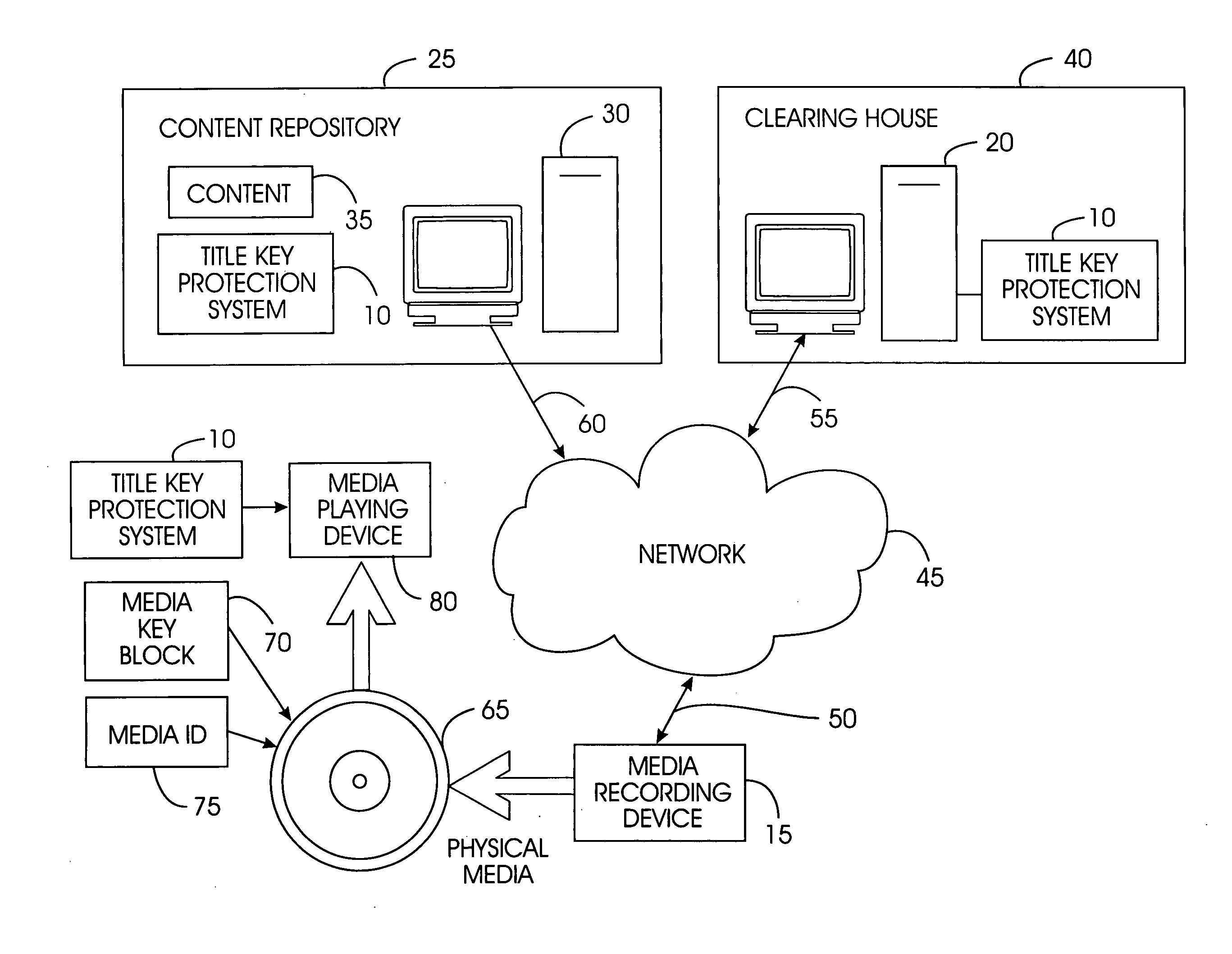
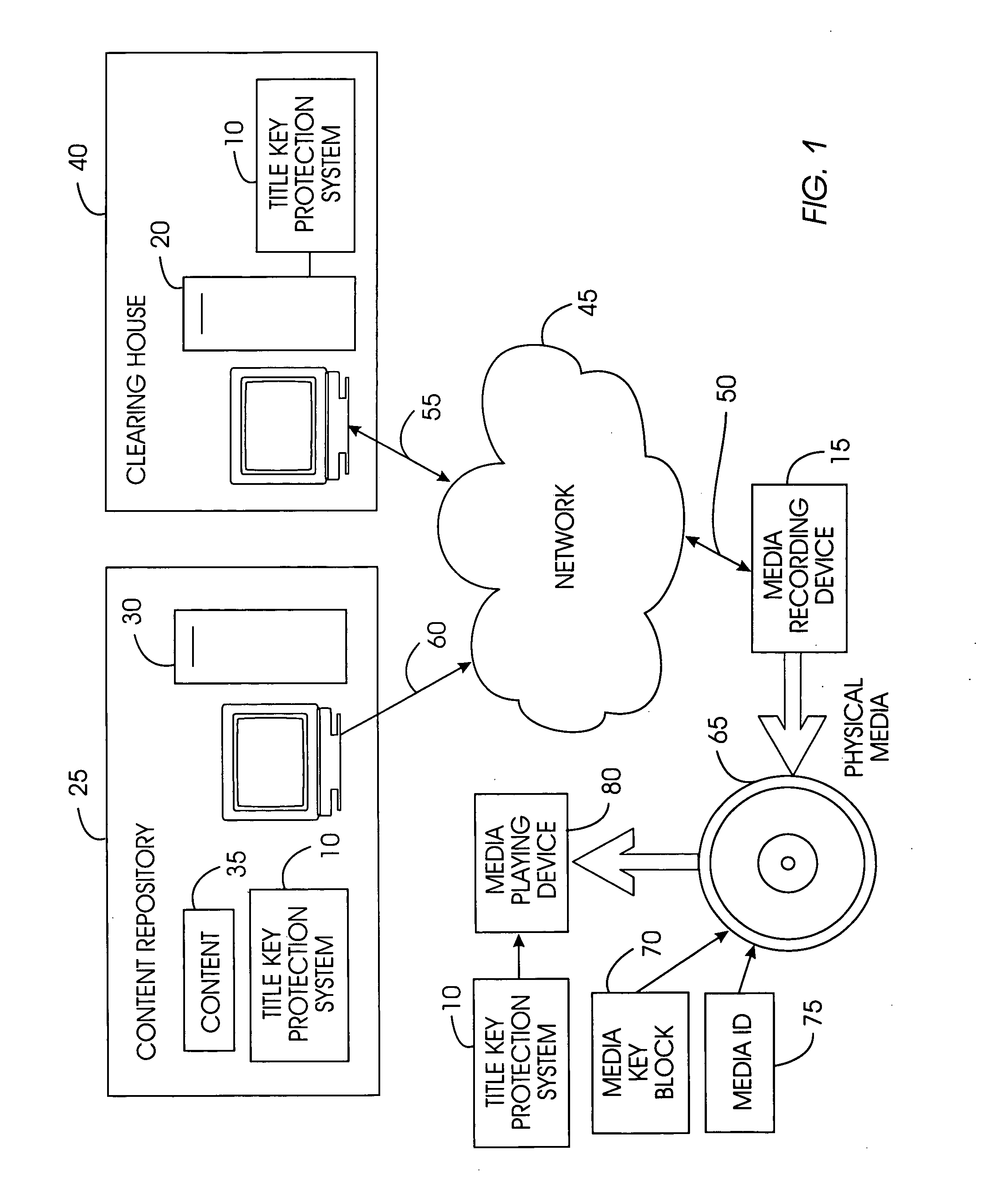
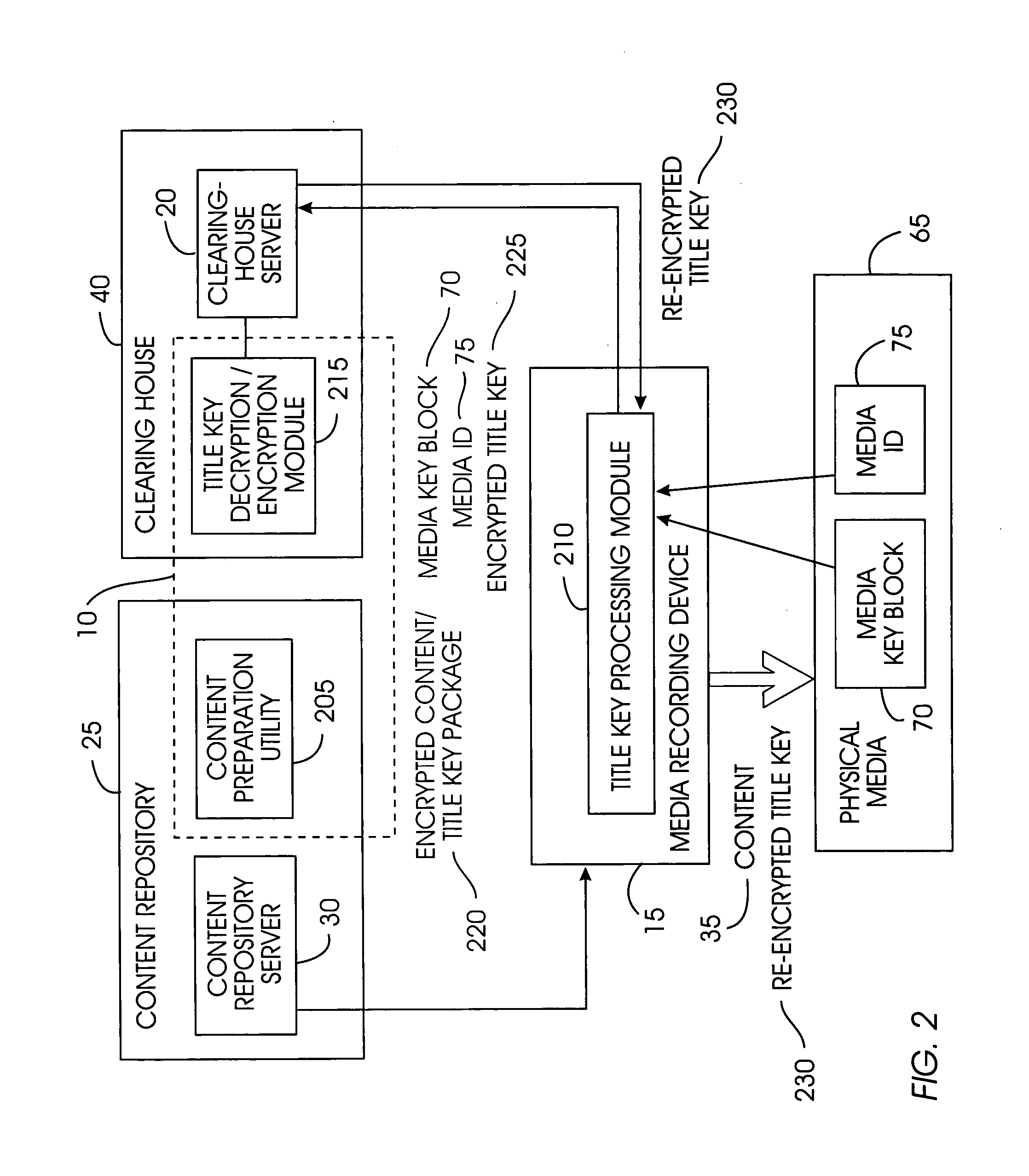
A title key protection system includes a title key with recordable media content; storage in a repository is not required. The title key is decrypted when needed by a clearinghouse, and then re-encrypted. The title key confers rights from the content owners to the user to play and copy the content for personal use. A user downloads encrypted content from a content repository. The user's media recording device extracts an encrypted title key from the content and obtains a media key block and media ID from the physical media on which the content will be recorded. The encrypted title key, media key block, and media ID are transmitted to a clearinghouse. The clearinghouse decrypts the title key and derives a media unique key from the media key block and media ID. The clearinghouse re-encrypts the title key with the media unique key and returns this re-encrypted title key to the media recording device for recording with the content on the physical media.
Owner:IBM CORP
On-chip storage, creation, and manipulation of an encryption key
ActiveUS20050232415A1Energy efficient ICTKey distribution for secure communicationPasswordData treatment
A system and method of creating and managing encryption keys in a data processing device generates subsequent encryption keys by combining the existing encryption key with an existing password and seed value. In the preferred embodiment, the initial encryption key is embedded during manufacture and is unknown to the user and manufacturer, thus ensuring that all subsequent encryption keys are derived from an unknown value. When a subsequent encryption key is generated, all data encrypted using the existing encryption key is decrypted using the existing encryption key and re-encrypted using the subsequent encryption key before the existing encryption key is overwritten. In a further aspect, during encryption / decryption the encryption key is combined with the sector address of the data to be encrypted / decrypted in order to generate a unique key for each sector of data to be encrypted / decrypted.
Owner:MALIKIE INNOVATIONS LTD
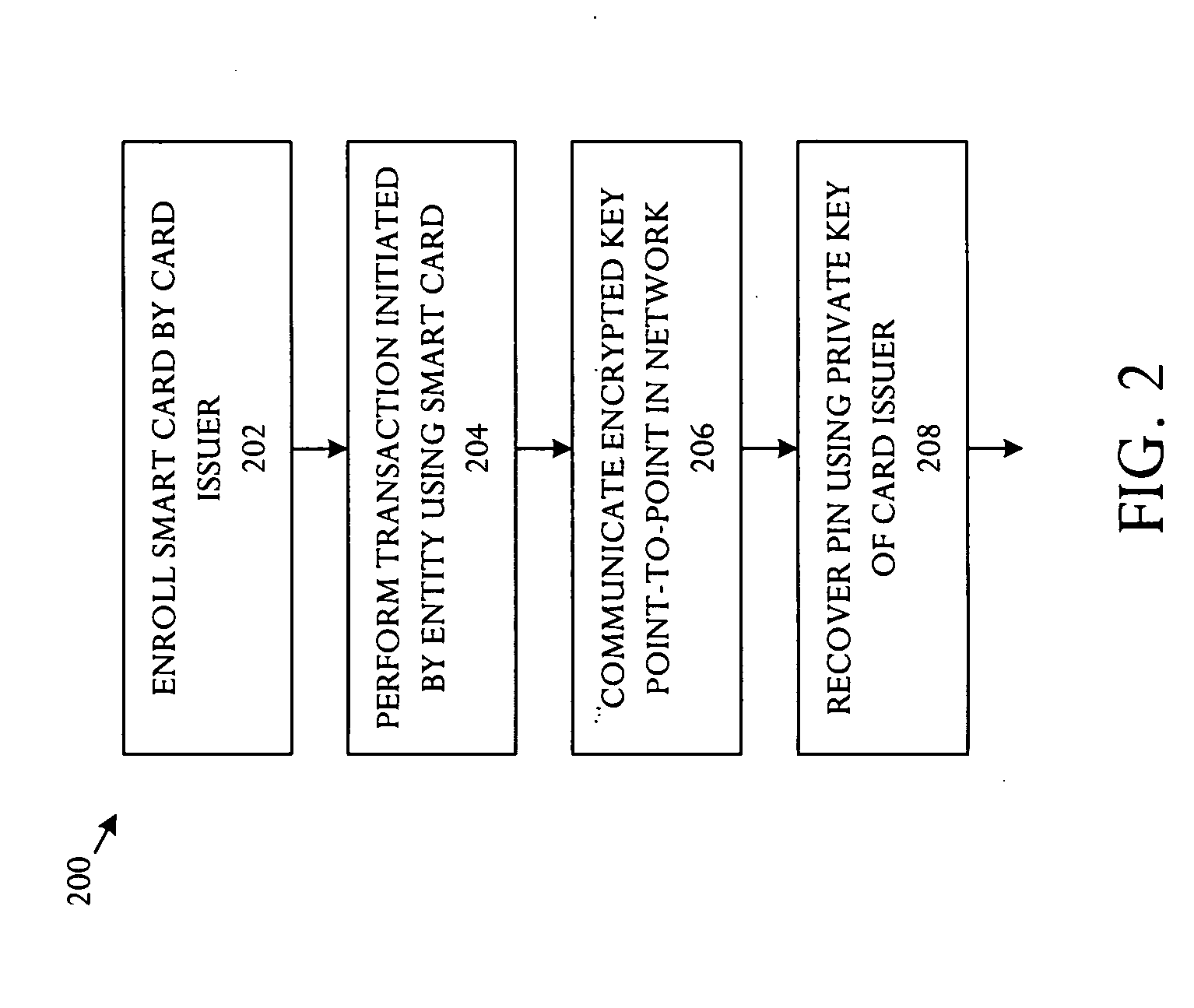
Key management technique for establishing a secure channel
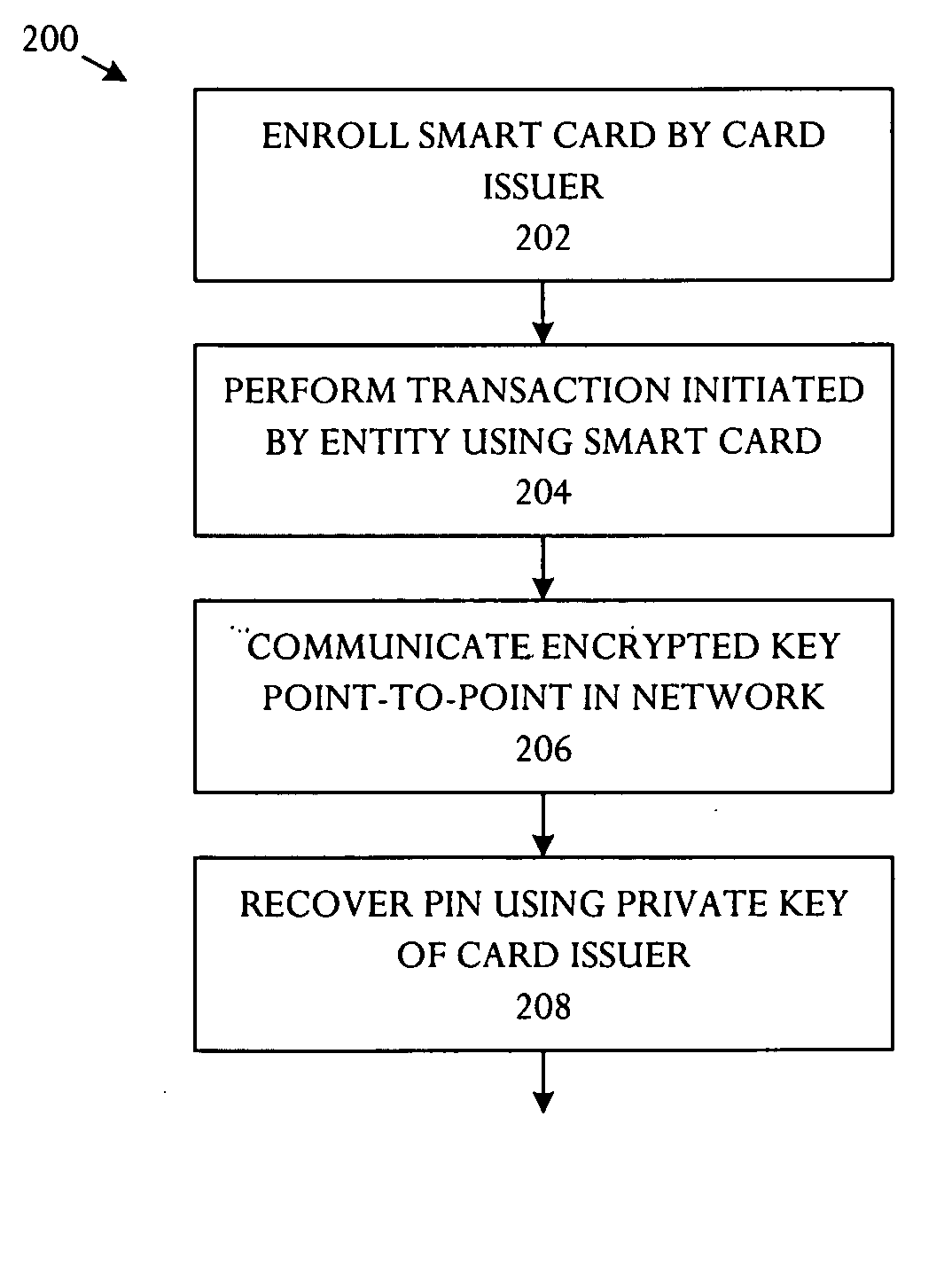
InactiveUS20050172137A1Eliminate operationKey distribution for secure communicationPublic key for secure communicationSmart cardFinancial transaction
A key management technique establishes a secure channel through an indeterminate number of nodes in a network. The technique comprises enrolling a smart card with a unique key per smart card. The unique key is derived from a private key that is assigned and distinctive to systems and a card base of a card issuer. An enrolled smart card contains a stored public entity-identifier and the secret unique key. The technique further comprises transacting at a point of entry to the network. The transaction creates a PIN encryption key derived from the smart card unique key and a transaction identifier that uniquely identifies the point of entry and transaction sequence number. The technique also comprises communicating the PIN encryption key point-to-point in encrypted form through a plurality of nodes in the network, and recovering the PIN at a card issuer server from the PIN encryption key using the card issuer private key.
Owner:MICRO FOCUS LLC
Trusted support processor authentication of host bios/uefi
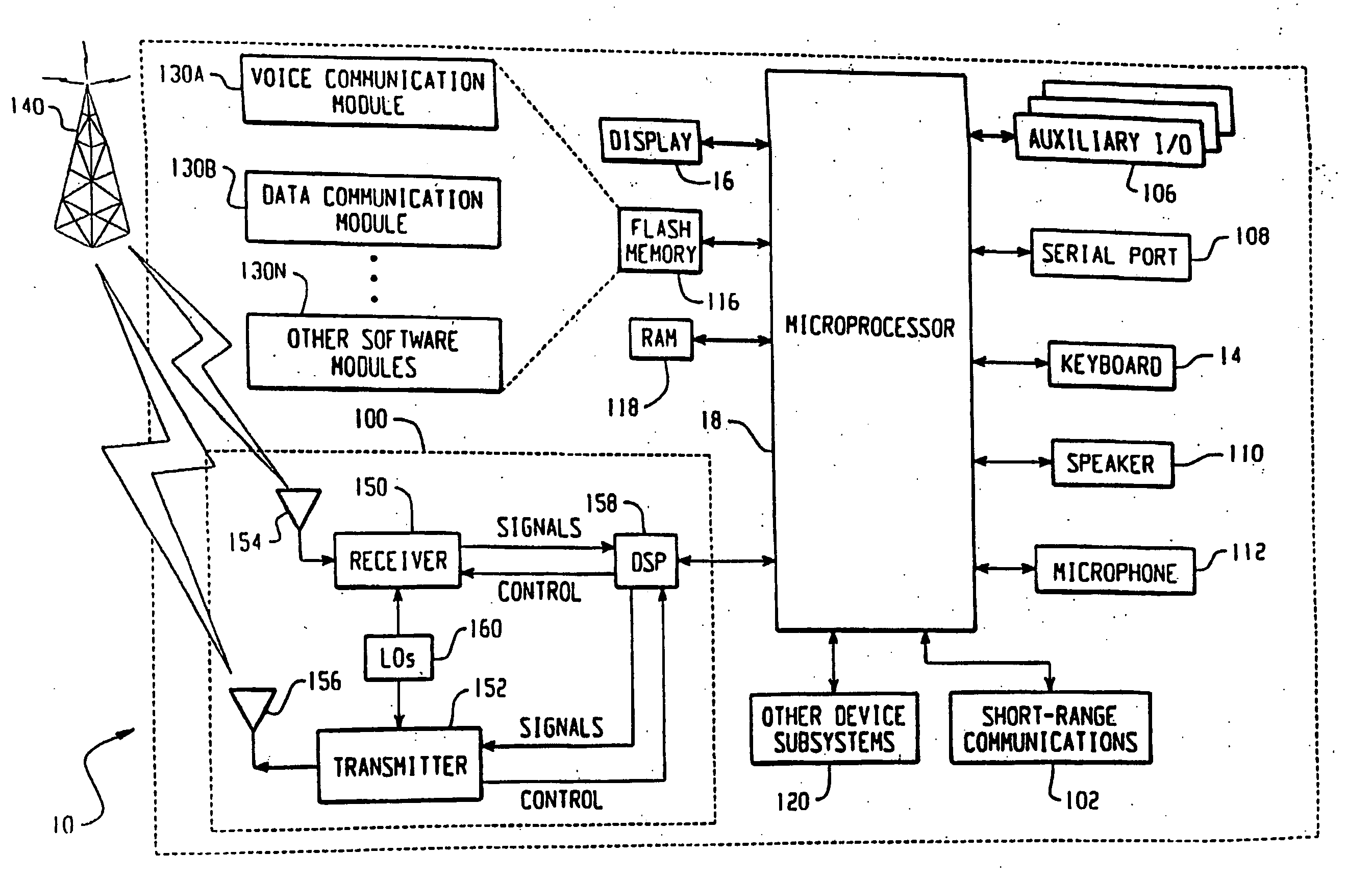
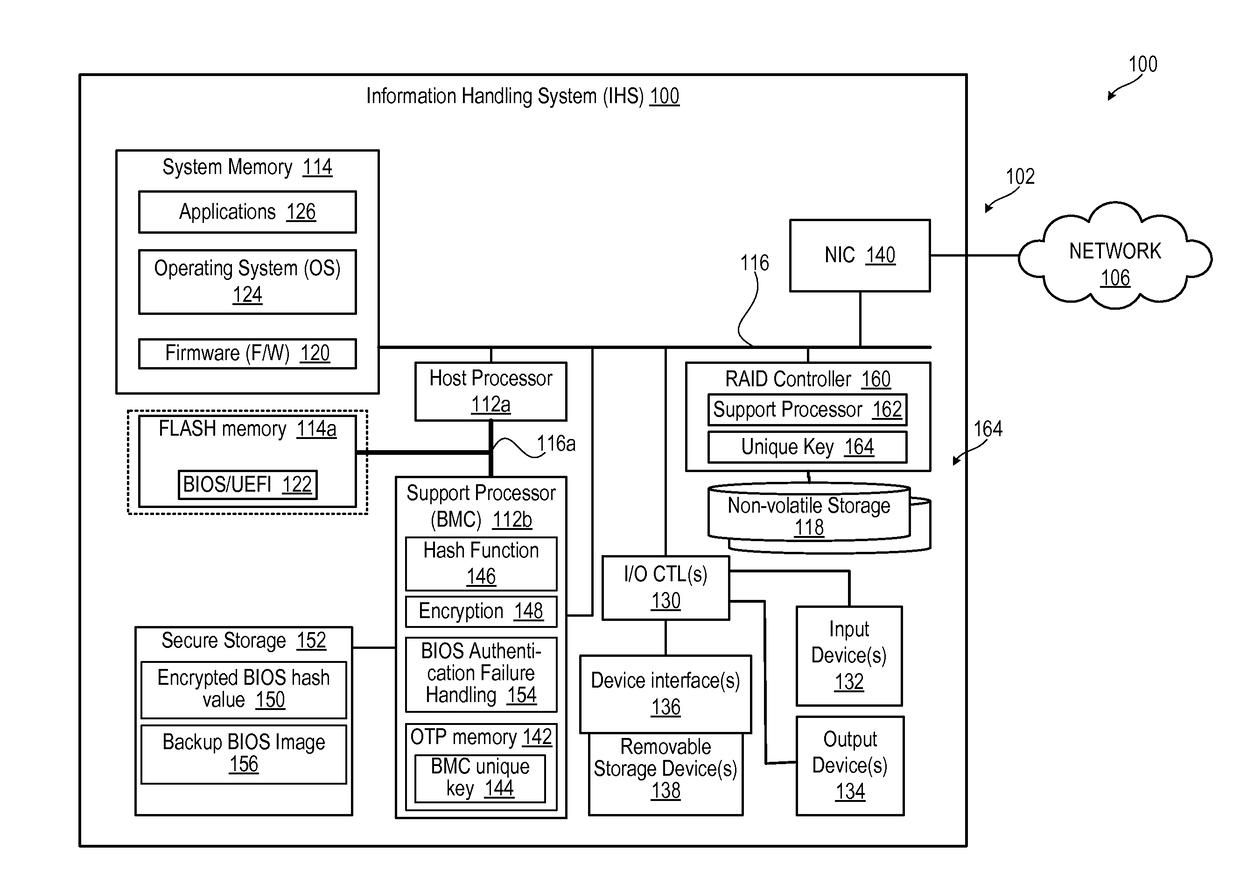
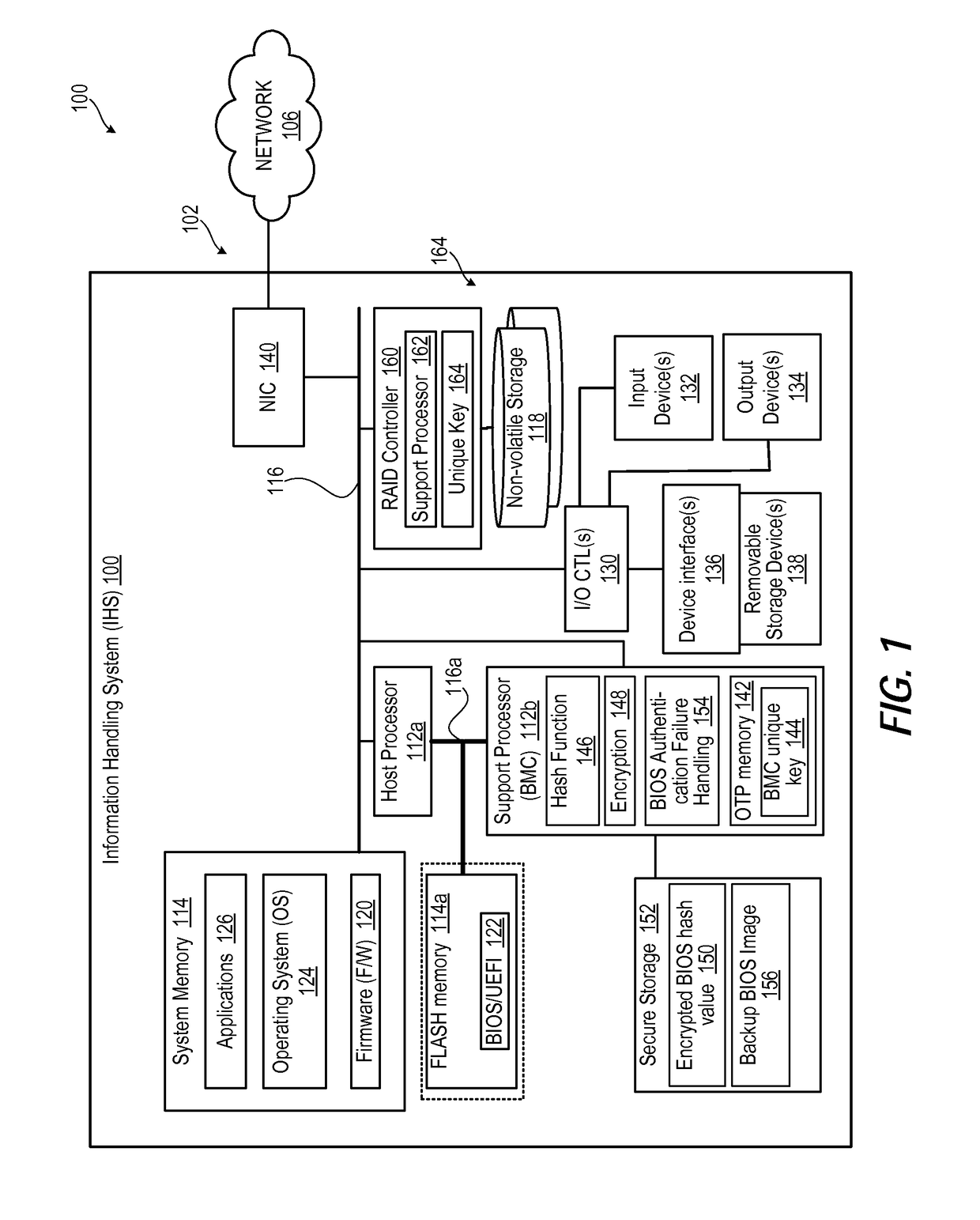
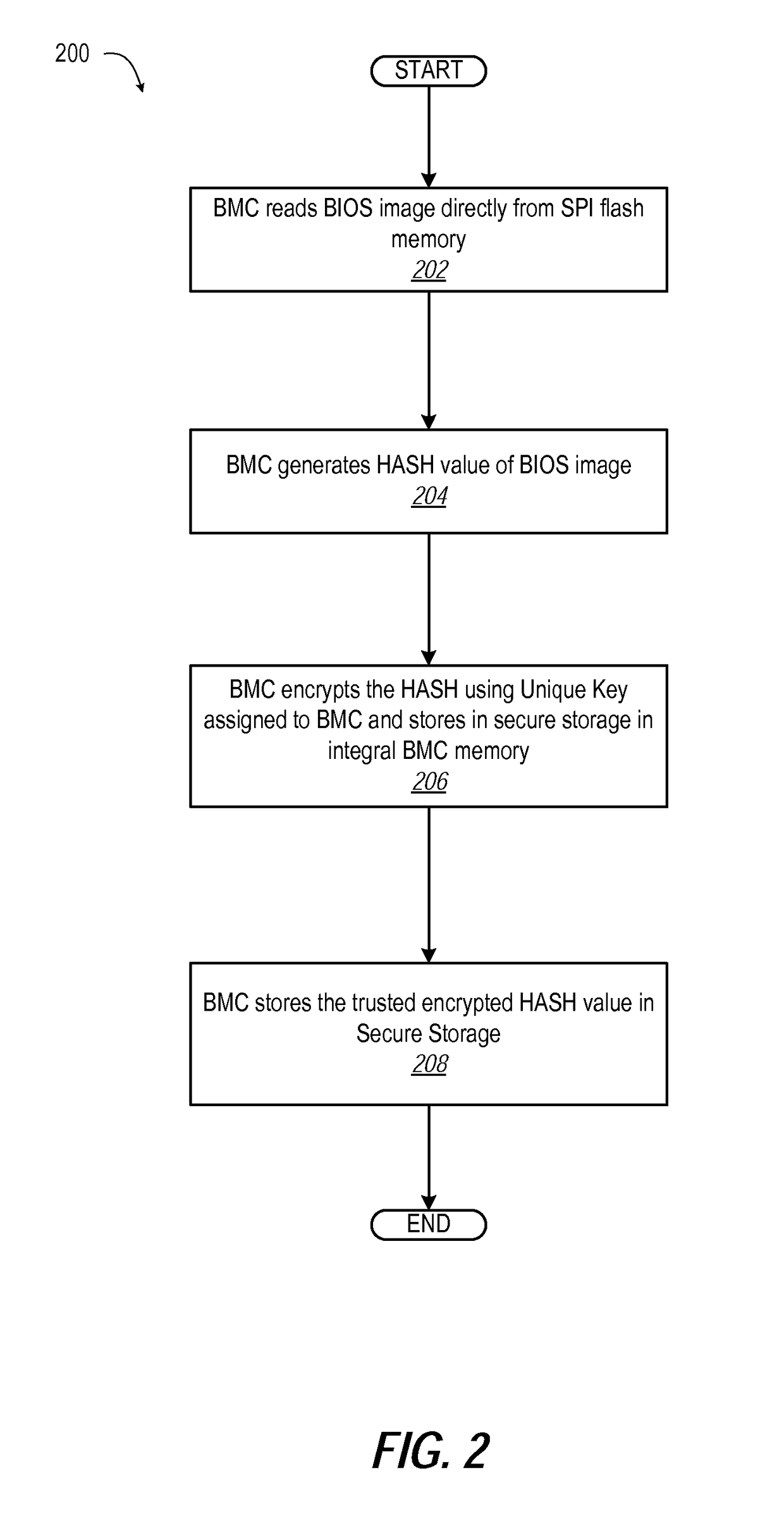
ActiveUS20170085383A1Preventing executionInput/output to record carriersSoftware engineeringHandling systemBIOS
An information handling system (IHS) prevents execution of corrupted bootup instructions in flash memory. A memory component contains basic input / output system (BIOS) instructions to execute during boot up of the IHS. A host processor is in communication with the memory component via the system interconnect to execute the BIOS instructions to configure the IHS. A support processor executes instructions to configure the IHS to: (a) calculate a current hash value for the BIOS instructions; (b) access a trusted encrypted hash value and the unique key from a secure storage; (c) decrypt the trusted encrypted hash value using the unique key to obtain a trusted hash value; (d) determine whether the current hash value is identical to the trusted hash value; and (e) allow execution of the BIOS instructions by the host processor in response to determining that the encrypted current hash value is identical to the trusted hash value.
Owner:DELL PROD LP
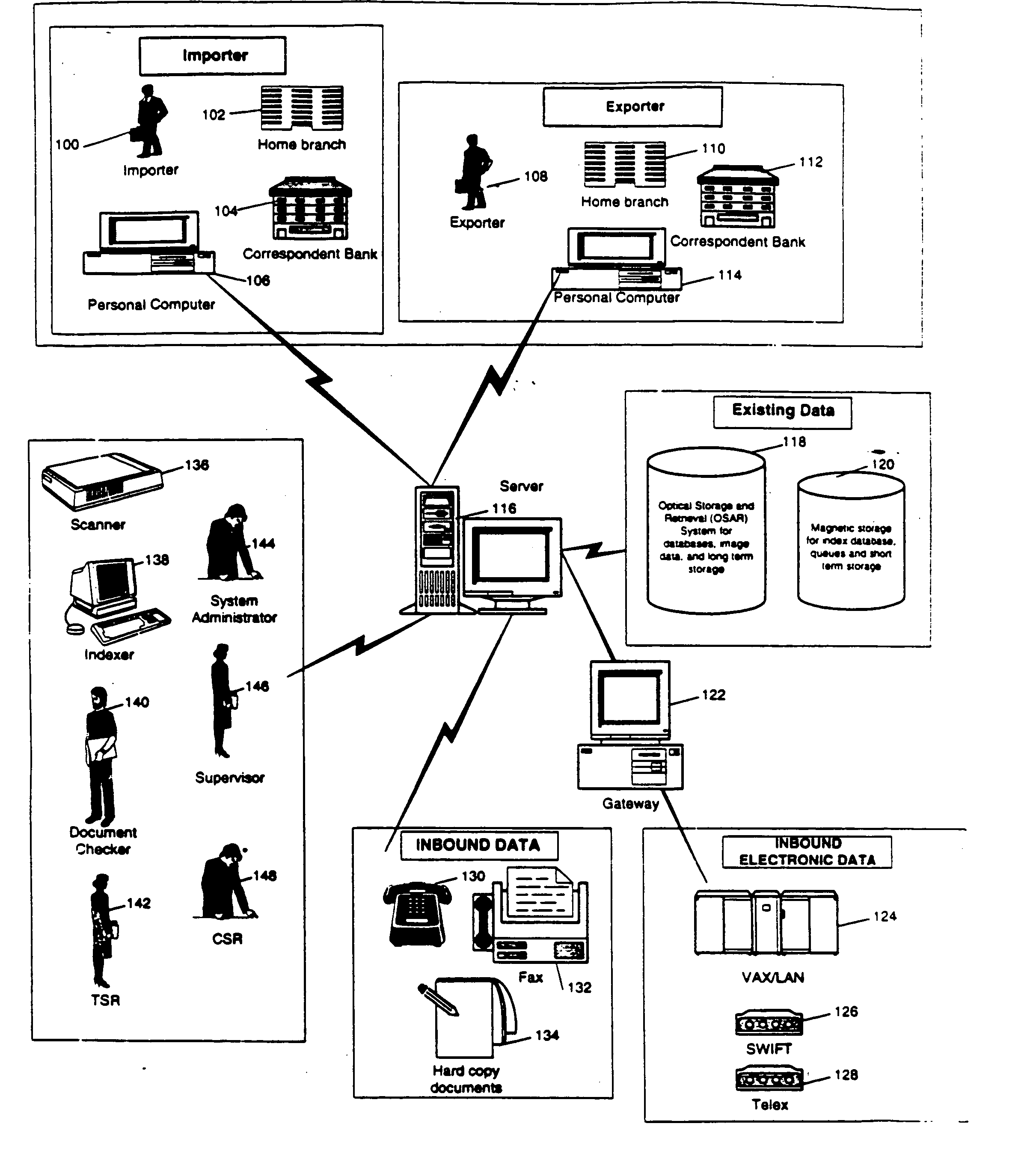
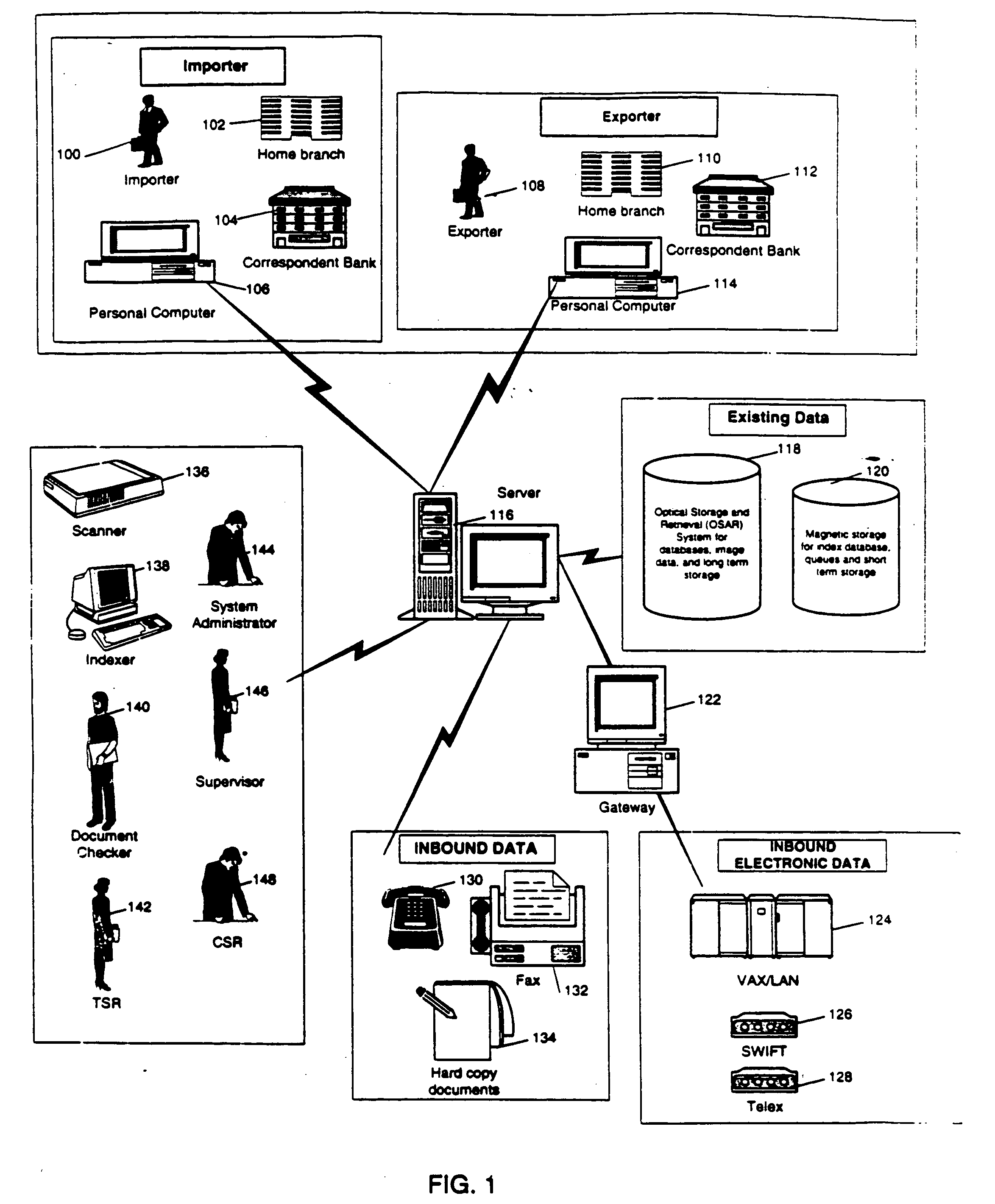
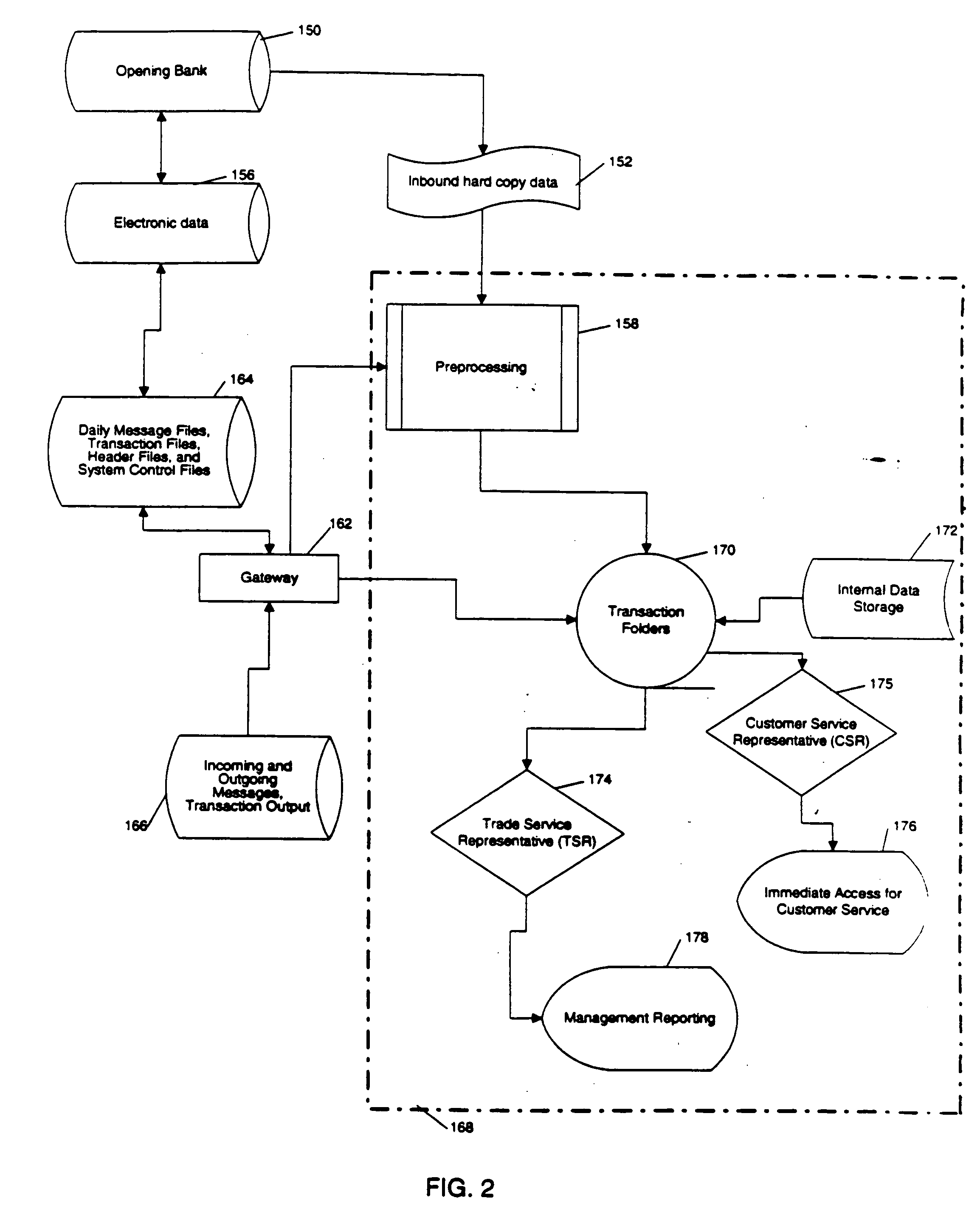
Trade records information management system
InactiveUS20050075964A1Faster turnaroundImprove customer serviceFinanceSpecial data processing applicationsSystem maintenancePaper document
An information management system for storing related documents, messages, and customer inquires as electronic images for retrieval in a controlled and secure manner. The system is centrally maintained, and provides the capability to manage and integrate different forms of information among multiple remote offices. Information is treated as transaction-related items and are linked together by transaction folders. Inbound paper-based documents are scanned, indexed and reviewed by preprocessing. Document processing from folders is conducted by assigning the item to a Trade Service Representative (TSR) based on routing rules defined by the System Administrator. The TSR has a queue containing documents and inquiries for processing, providing the transaction service representative with a single point of reference to data related to a Letter of Credit, a reimbursement, a collection, and a guarantee. Document work flow can be monitored for backlog and assigned work levels. Transaction folders contain the components related to particular trade services transactions. The folders include all physical input and output media associated with transactions, such as electronic messages, mail items, inquiry history records, system user entered messages, and inbound facsimile messages. The system maintains an internal unique key identifier, to identify each folder and document with the image transaction ID number unique to each item when available from the image management system.
Owner:CITIBANK
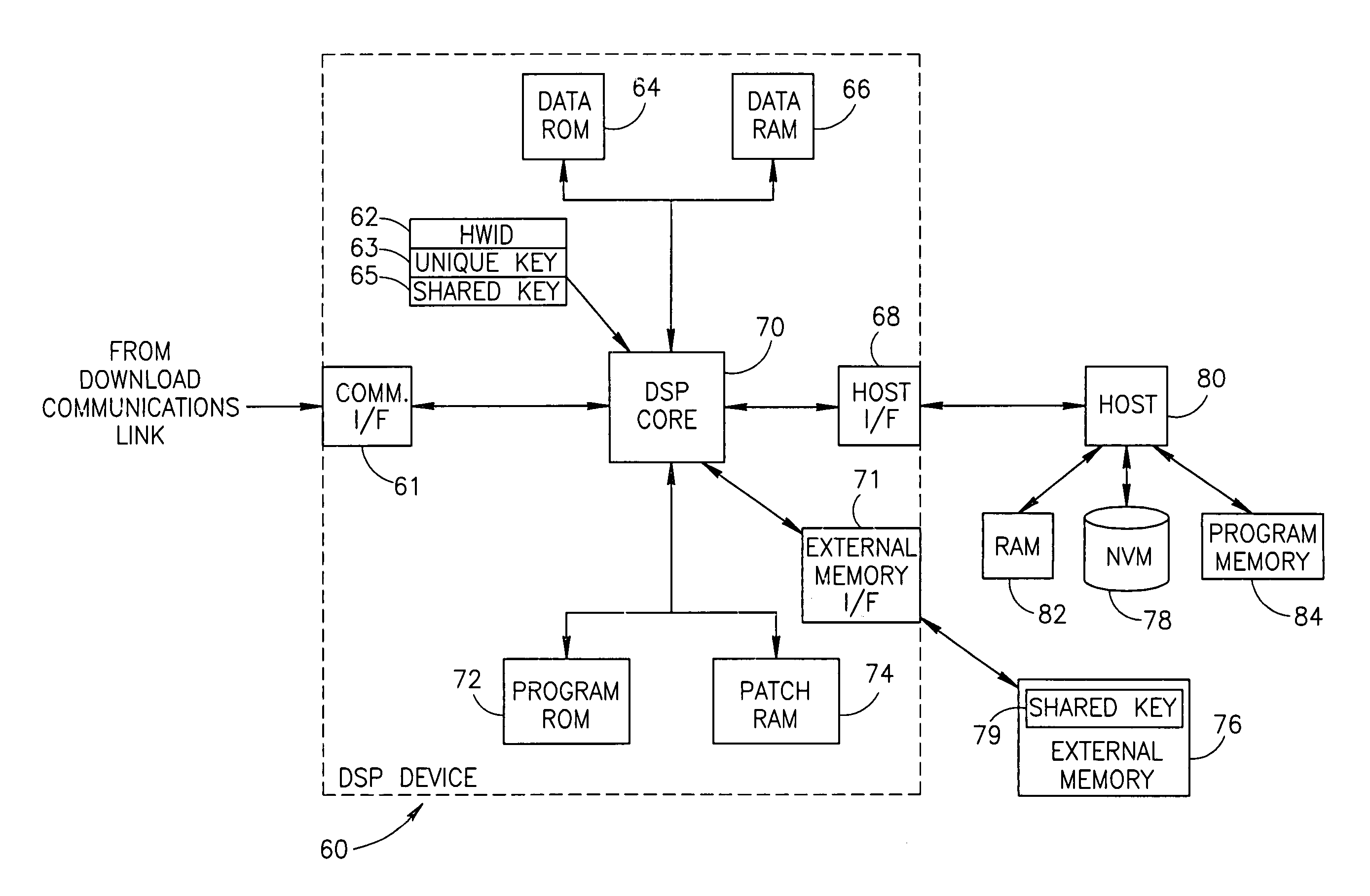
Apparatus for and method of securely downloading and installing a program patch in a processing device
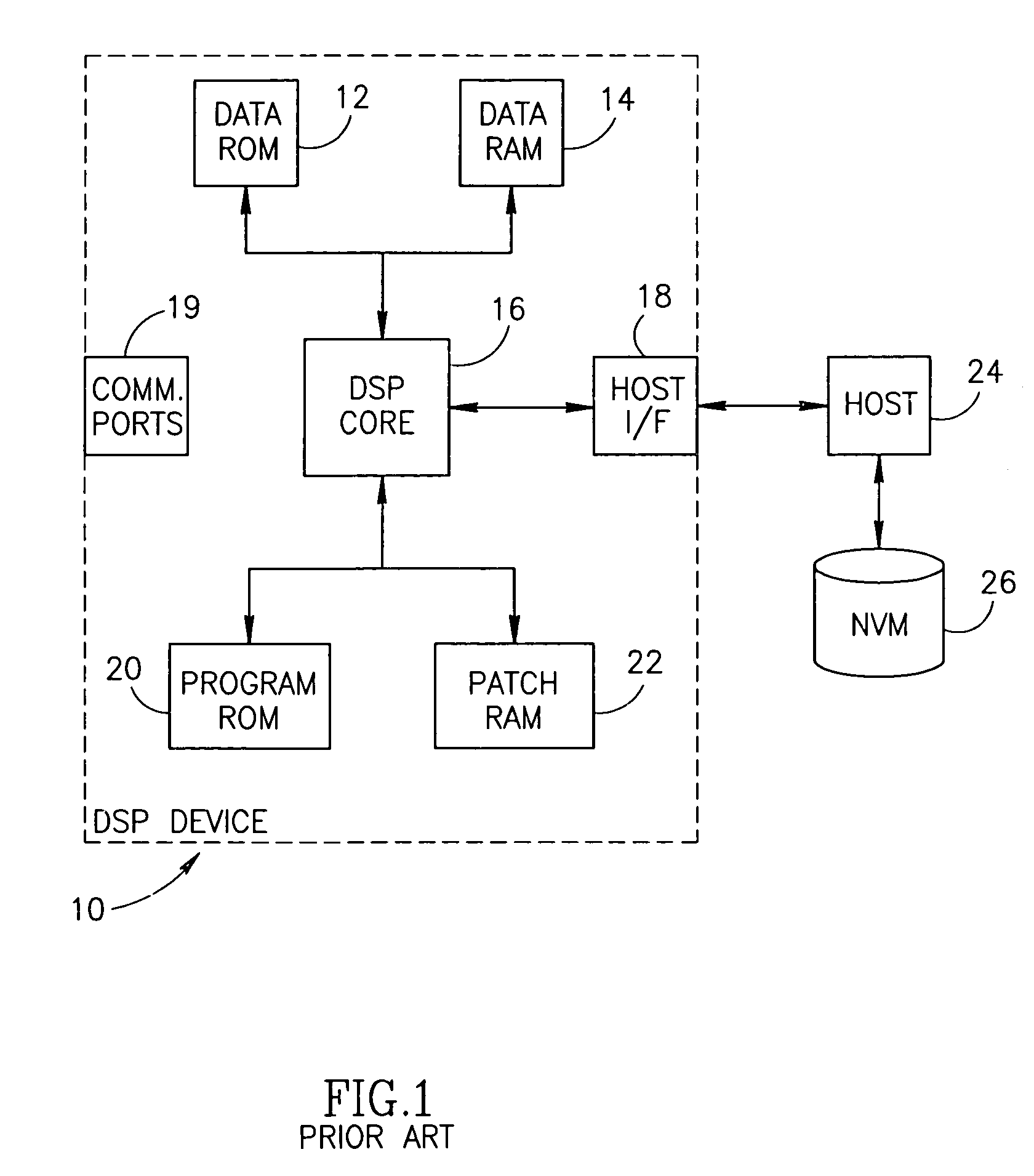
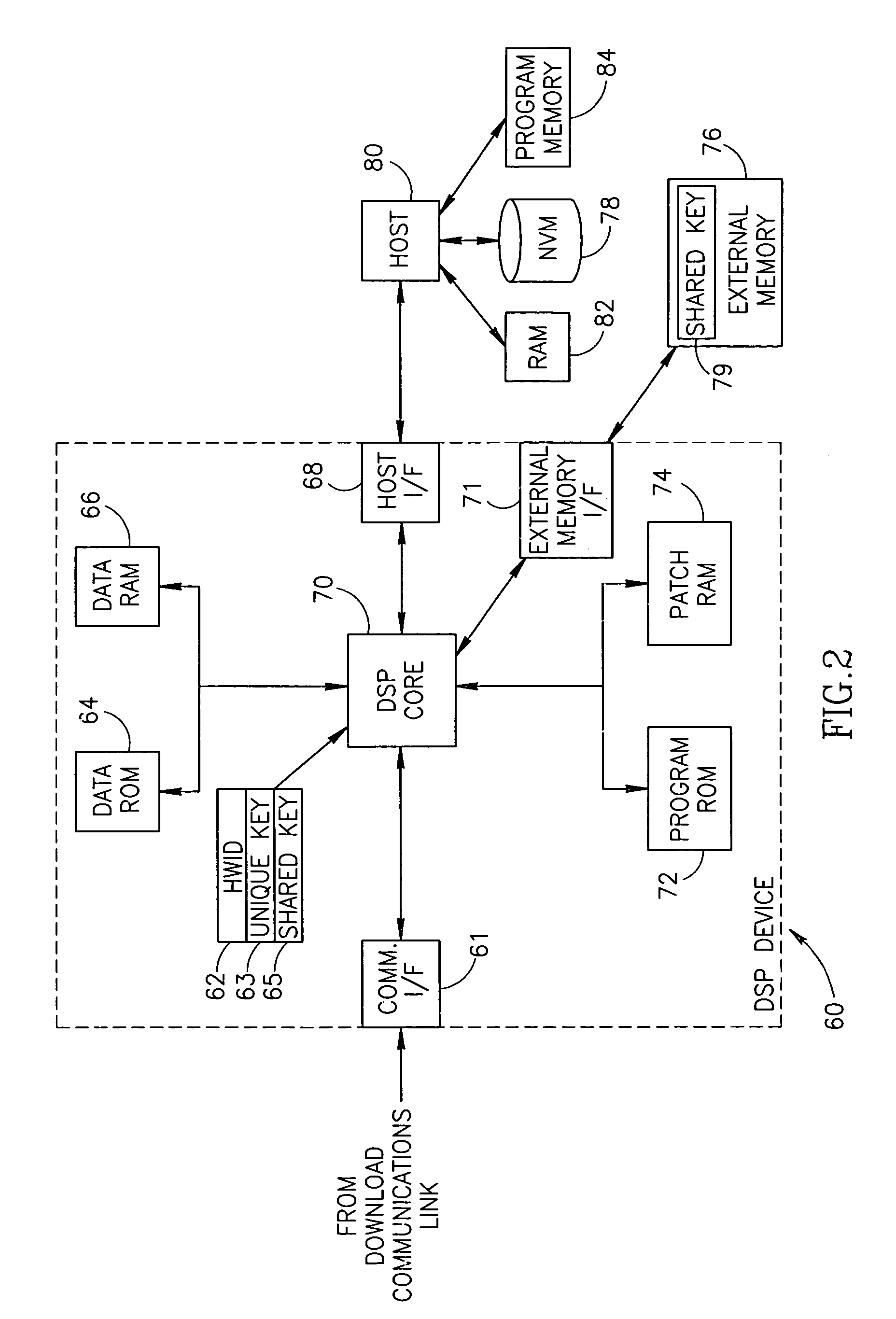
InactiveUS6970565B1Reduce vulnerabilityNone of methods is secureSecret communicationPlatform integrity maintainanceSatellite radioTelecommunications link
A novel and useful apparatus for and method of securely downloading and installing a patch program in a processing device. Each processing device is assigned a unique key embedded therein during manufacture and has knowledge of a shared key. The program patch is encrypted using the shared key and transmitted over a communication link, such as a satellite radio link, to each device. The patch is decrypted using the shared key and re-encrypted using the unique key known only to the device itself. The re-encrypted patch program is stored in nonvolatile memory and upon reset of the device, the encrypted patch contents are read out of the nonvolatile memory, decrypted using the unique key and loaded into patch memory for execution by the processing device.
Owner:SIRIUS XM RADIO INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com