Patents
Literature
2353 results about "Document processing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Document processing involves the conversion of typed and handwritten text on paper-based & electronic documents (e.g., scanned image of a document) into electronic information using one of, or a combination of, intelligent character recognition (ICR), optical character recognition (OCR) and experienced data entry clerks.
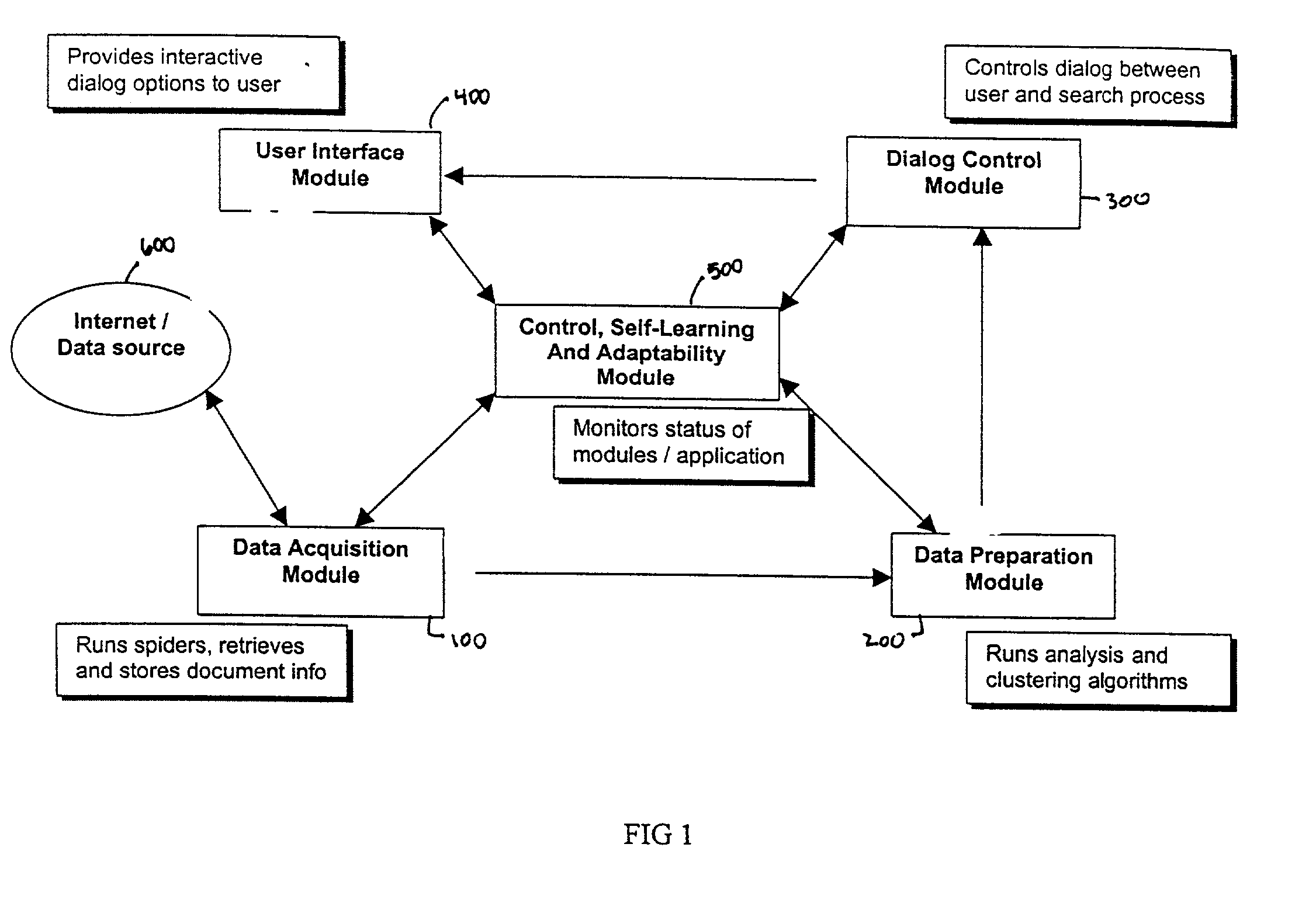
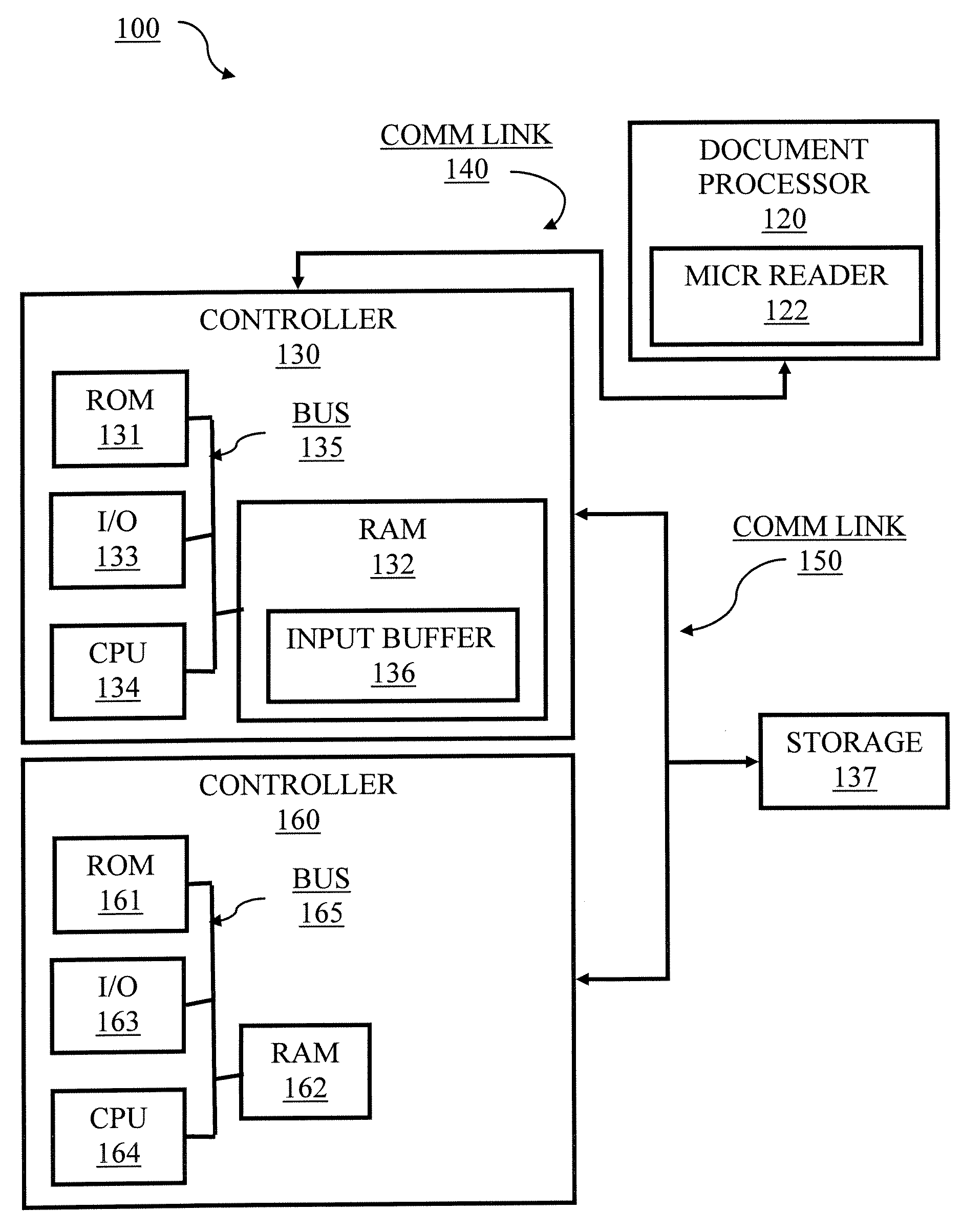
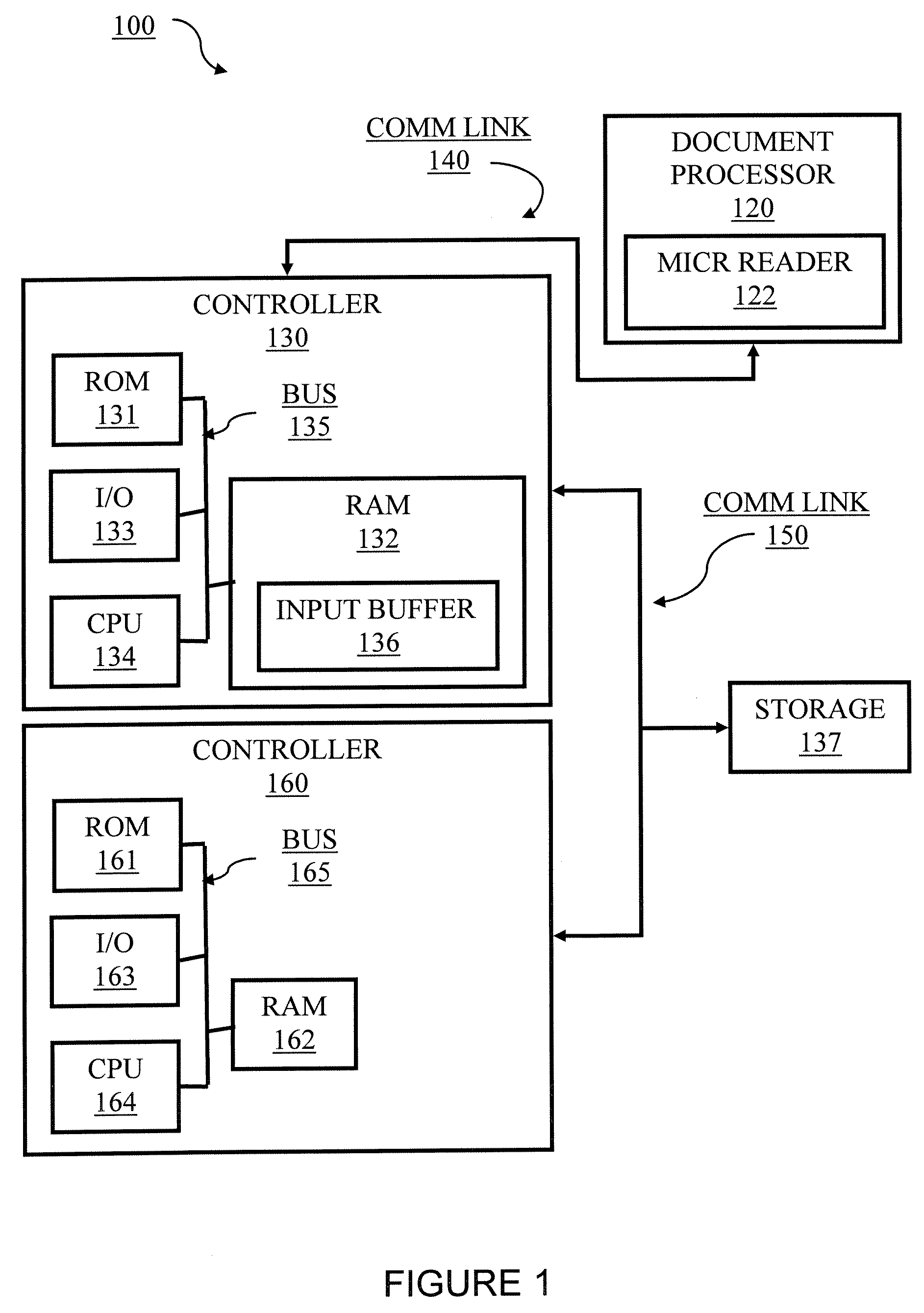
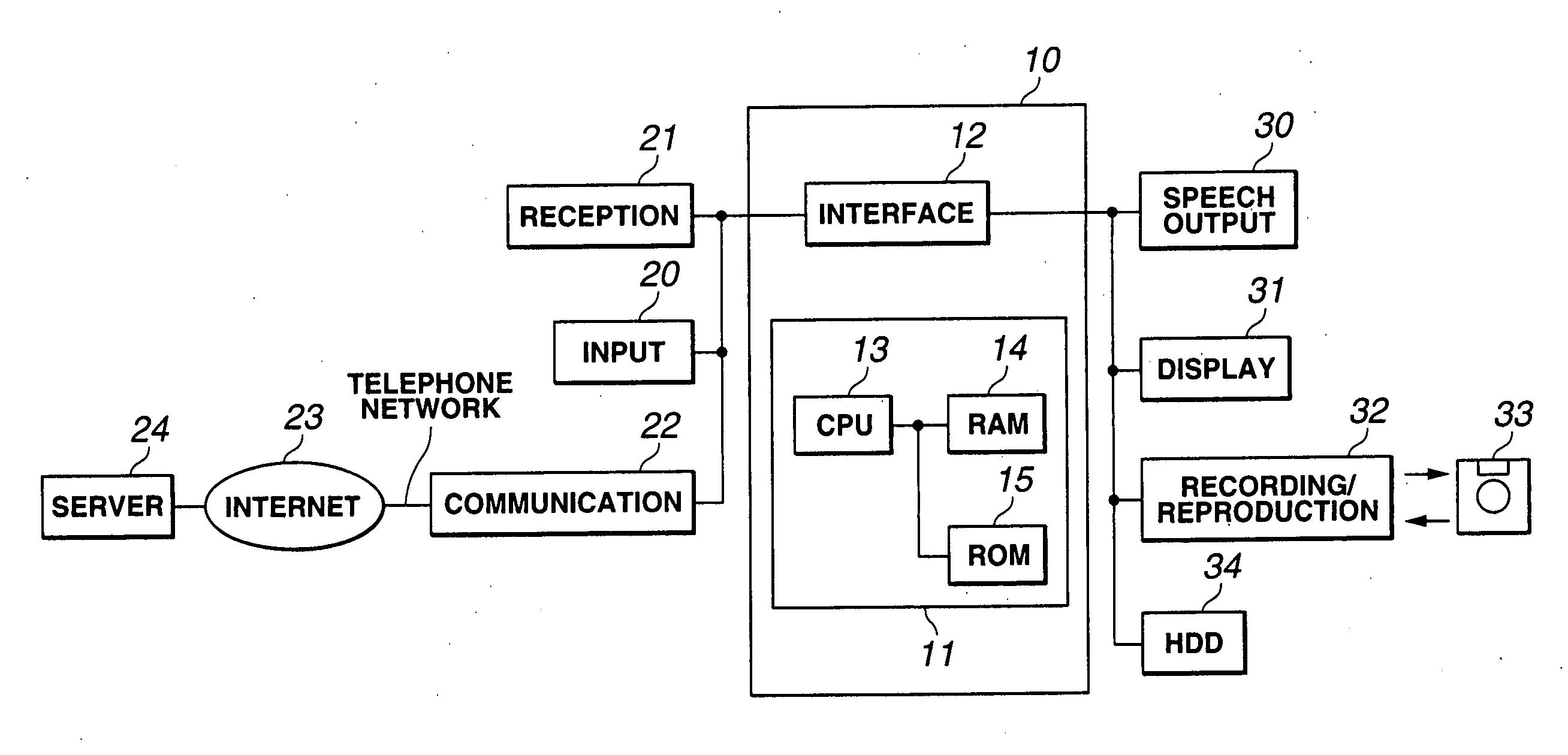
System and method for document processing
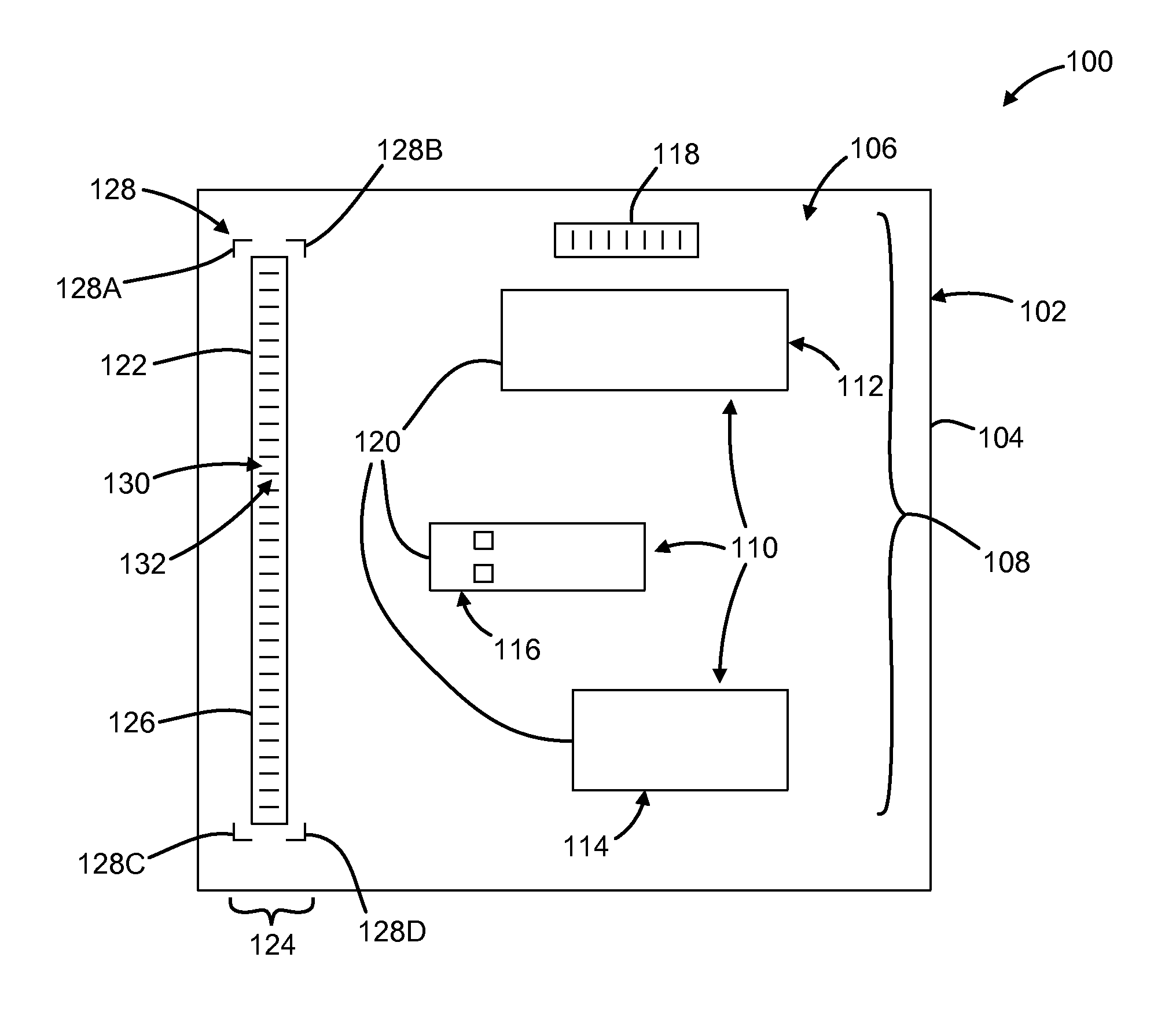
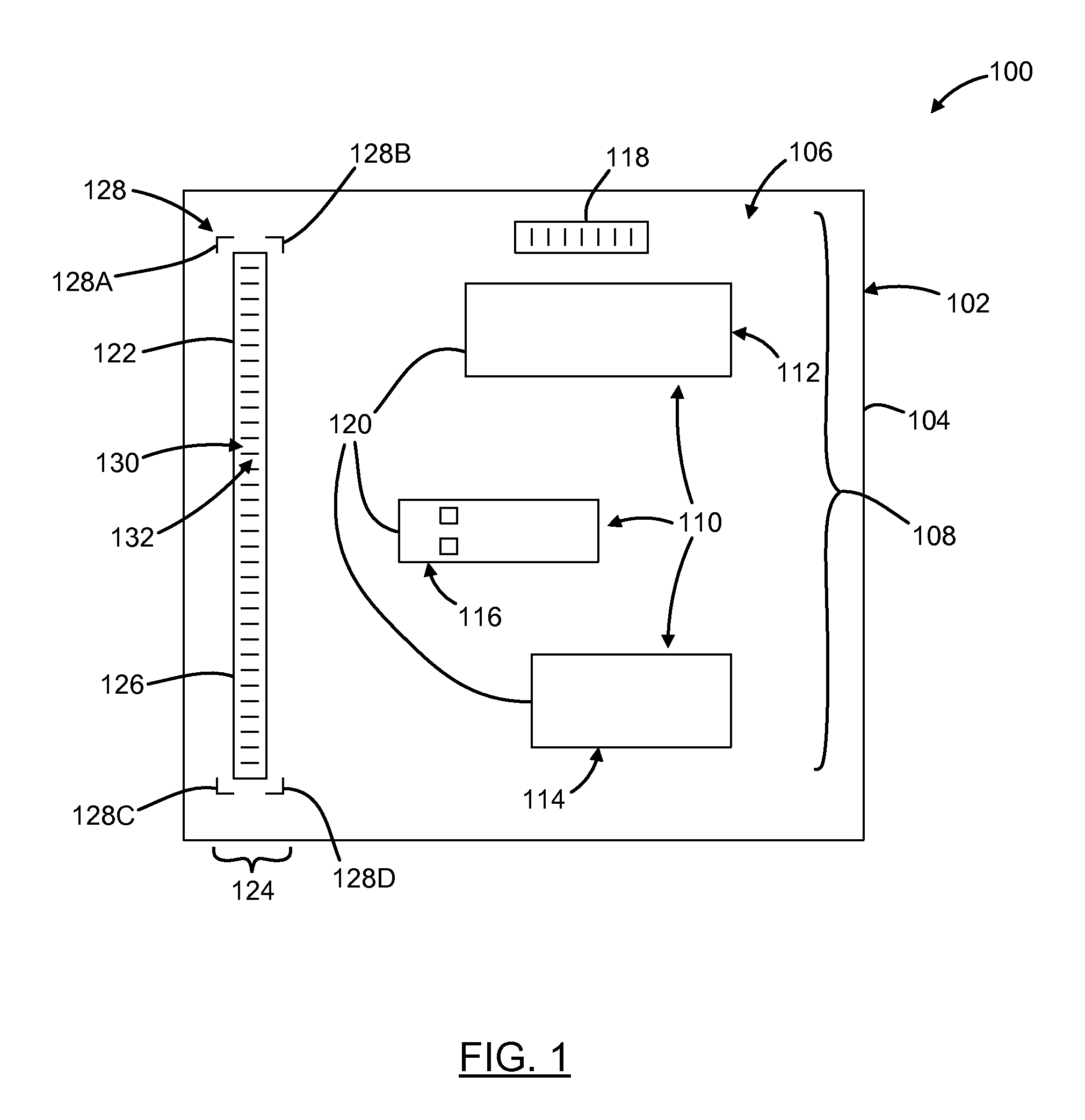
ActiveUS8910870B2Record carriers used with machinesSensing by electromagnetic radiationBarcodeDocument preparation
Embodiments of the present invention are directed to document processing, and more particularly to systems and methods that can utilize relative positions between the content of the document and a decodable indicia affixed to the document. In one embodiment, indicia reading terminals are provided that include an imaging module for capturing a frame of image data of a document. The document can include one or more decodable indicia such as a form barcode and various content fields, which delineate particular content of the document. The form barcode can include information respecting the form design and form design data. This information can be used to process the content of the document such as by providing coordinates or similar location and positioning metrics for use in processing the content of the document. In one example, the frame of image data is analyzed to identify the form barcode, from which the relative location of the content fields can be discerned without extensive processing of the frame of image data.
Owner:HAND HELD PRODS
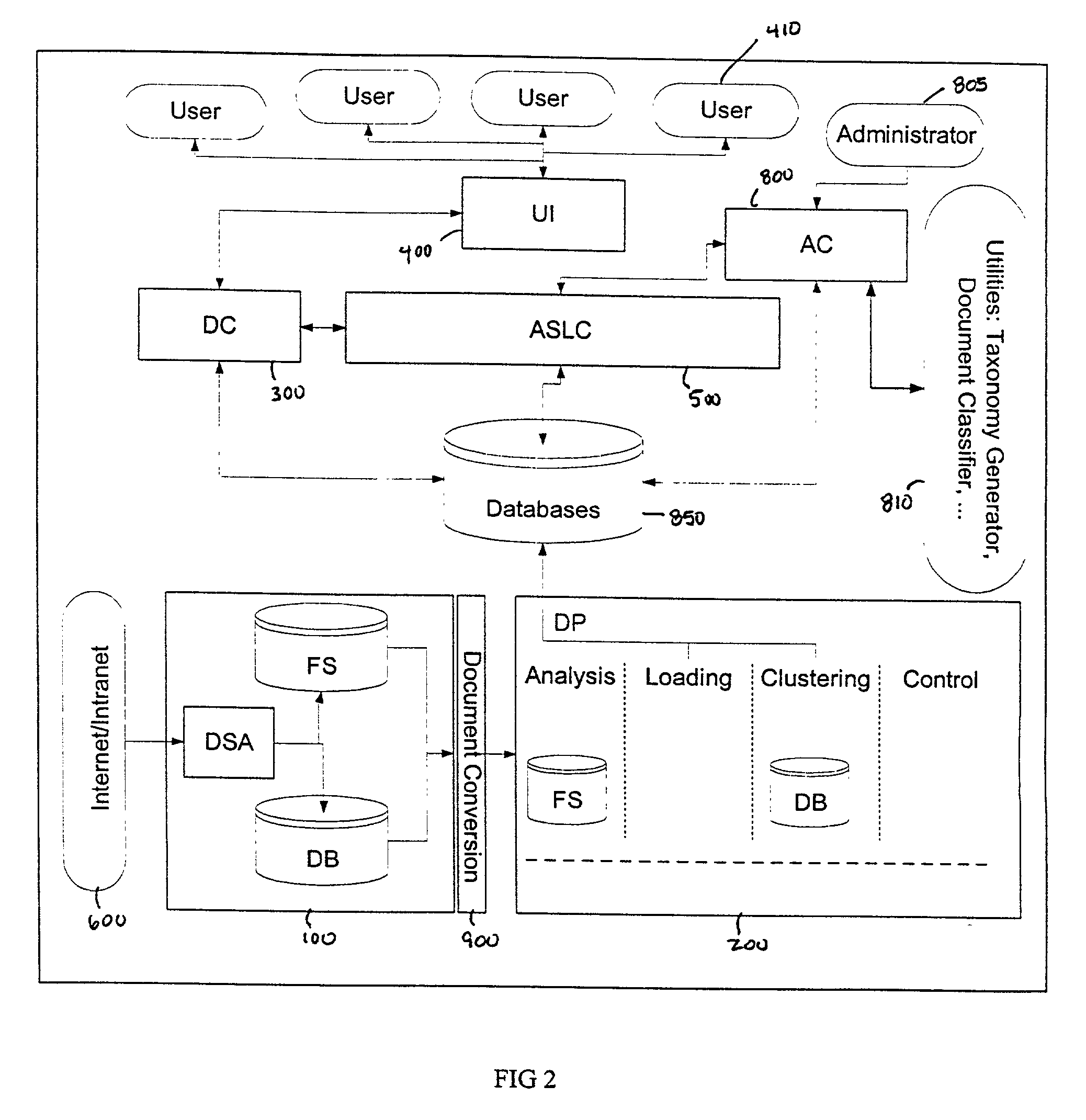
System and method for analysis and clustering of documents for search engine
InactiveUS20020065857A1Digital data information retrievalSpecial data processing applicationsDocument analysisComputational intelligence
A system and method for searching documents in a data source and more particularly, to a system and method for analyzing and clustering of documents for a search engine. The system and method includes analyzing and processing documents to secure the infrastructure and standards for optimal document processing. By incorporating Computational Intelligence (CI) and statistical methods, the document information is analyzed and clustered using novel techniques for knowledge extraction. A comprehensive dictionary is built based on the keywords identified by the these techniques from the entire text of the document. The text is parsed for keywords or the number of its occurrences and the context in which the word appears in the documents. The whole document is identified by the knowledge that is represented in its contents. Based on such knowledge extracted from all the documents, the documents are clustered into meaningful groups in a catalog tree. The results of document analysis and clustering information are stored in a database.
Owner:NUTECH SOLUTIONS
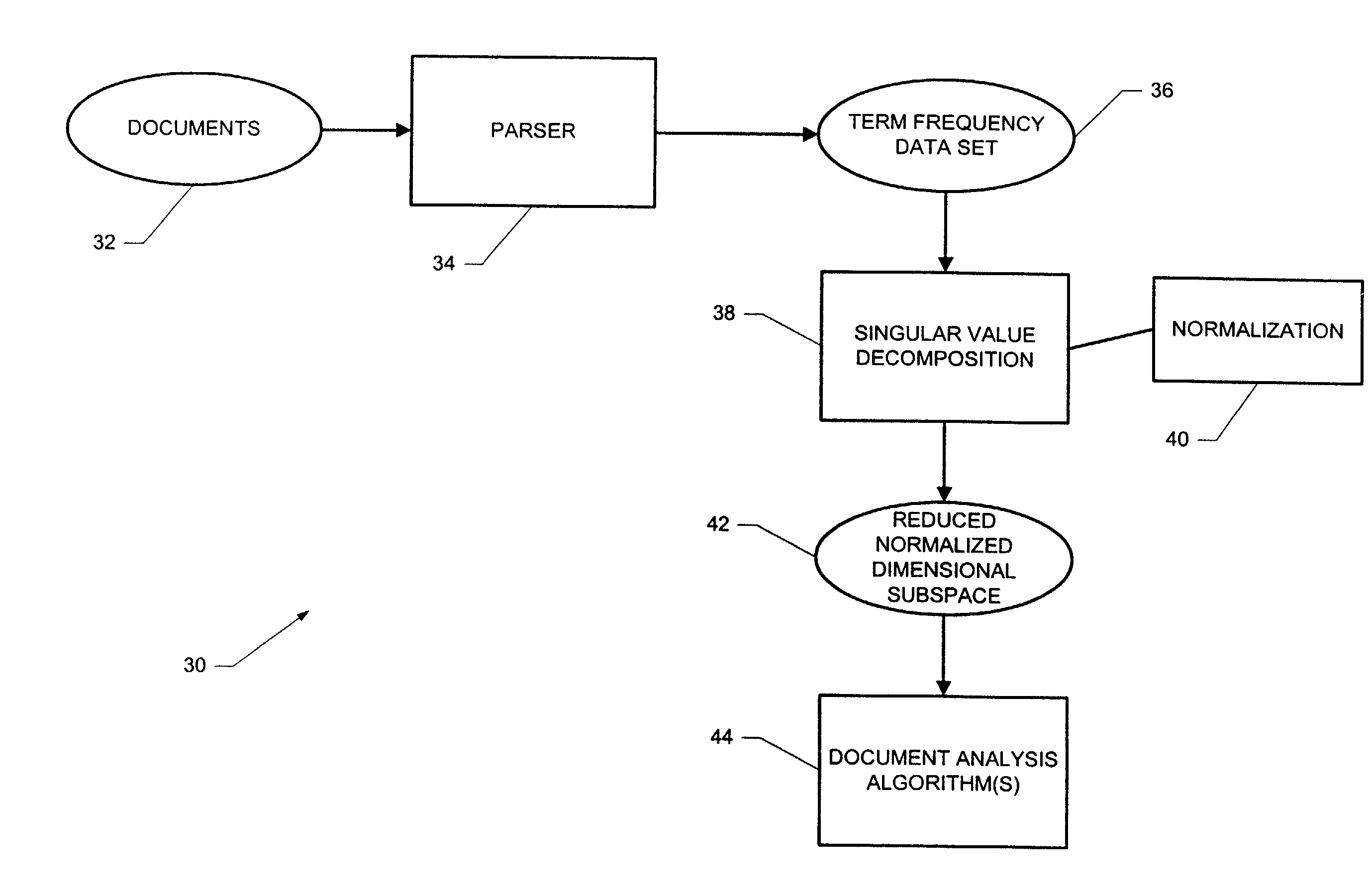
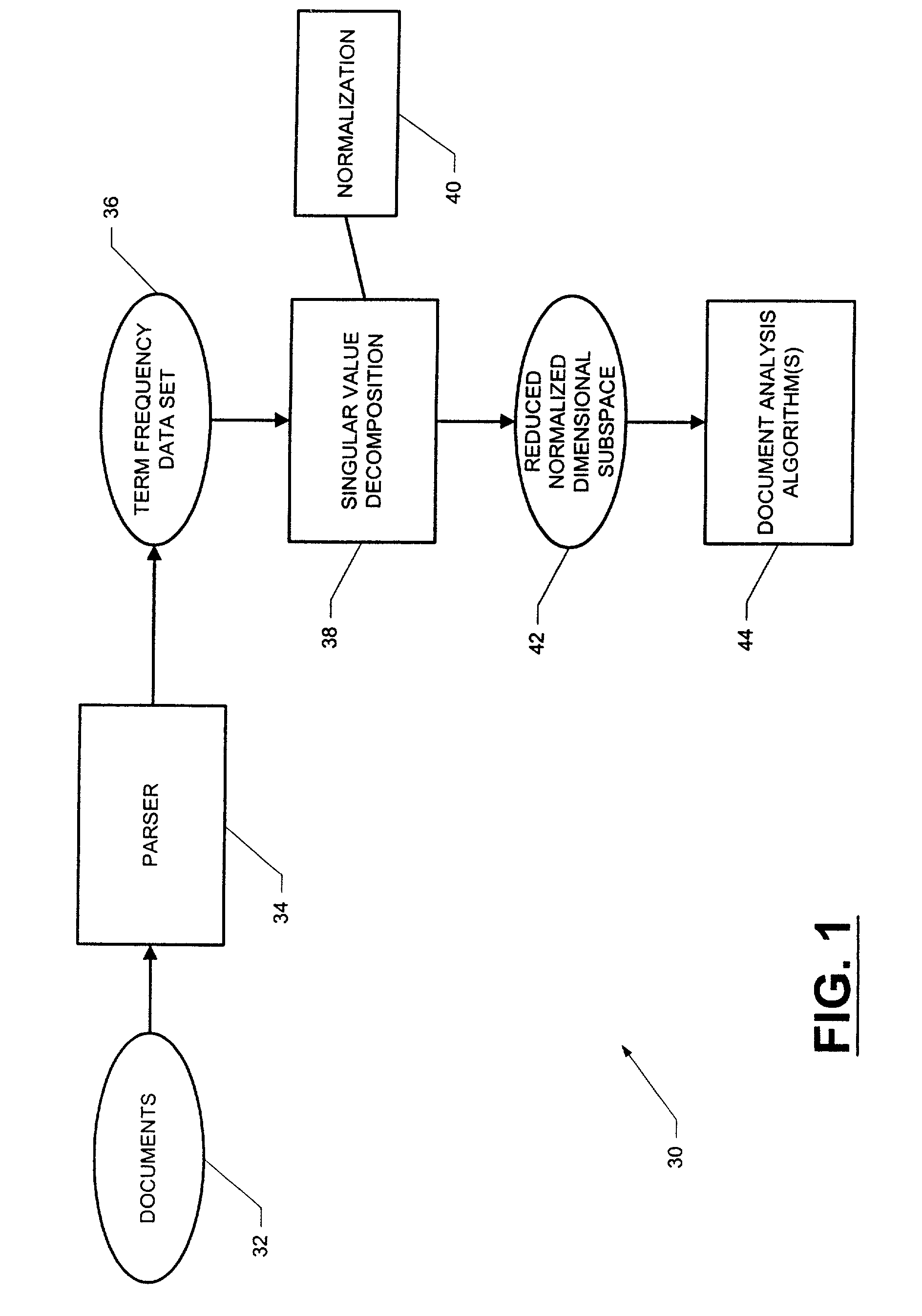
Computer-implemented system and method for text-based document processing
ActiveUS6996575B2Data processing applicationsDigital data processing detailsSingular value decompositionData set
A computer-implemented system and method for processing text-based documents. A frequency of terms data set is generated for the terms appearing in the documents. Singular value decomposition is performed upon the frequency of terms data set in order to form projections of the terms and documents into a reduced dimensional subspace. The projections are normalized, and the normalized projections are used to analyze the documents.
Owner:SAS INSTITUTE
Decision-support expert system and methods for real-time exploitation of documents in non-english languages
ActiveUS20090157382A1Reduce in quantityReduce the burden onNatural language translationDigital data processing detailsDocument preparationDocumentation
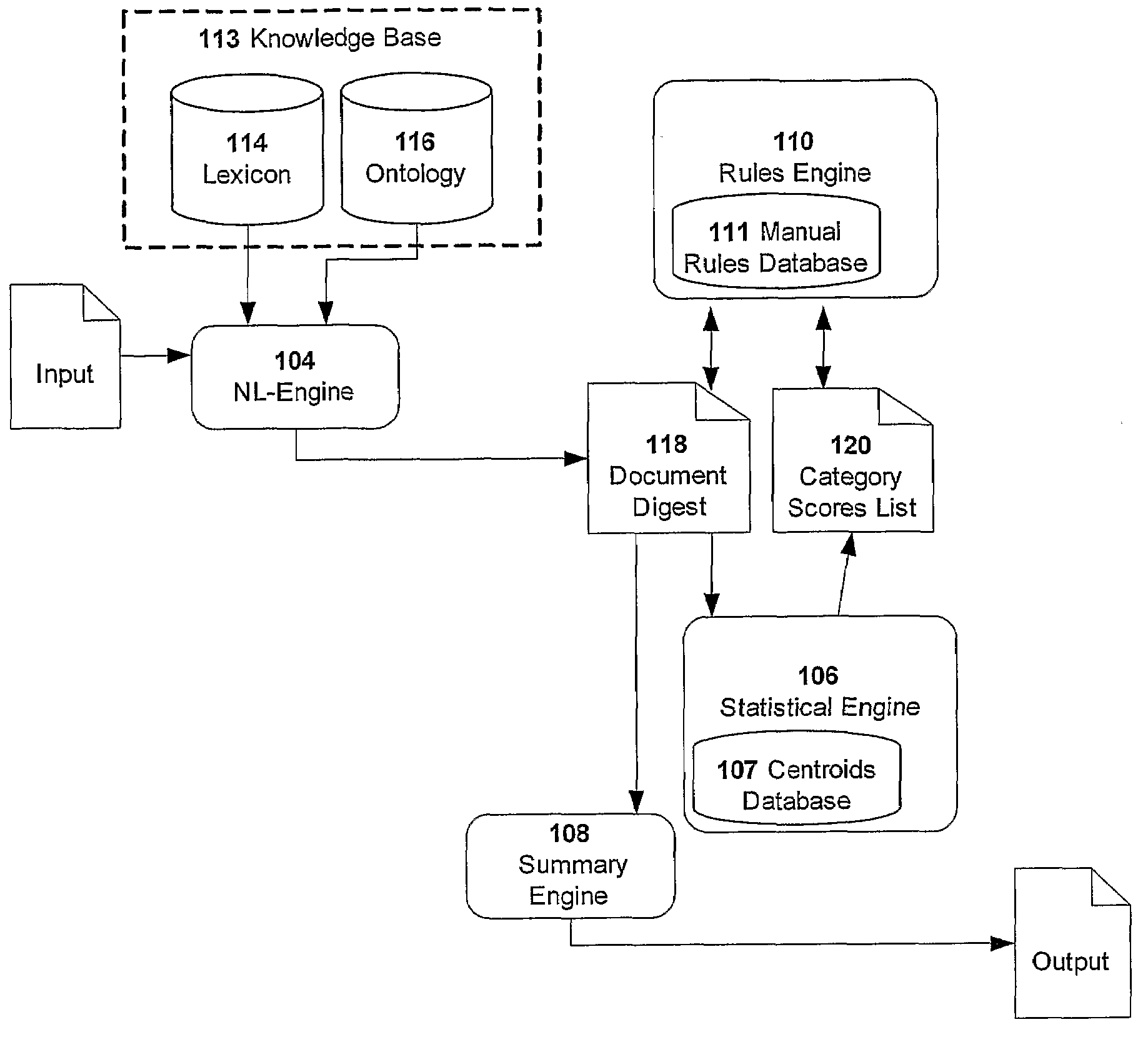
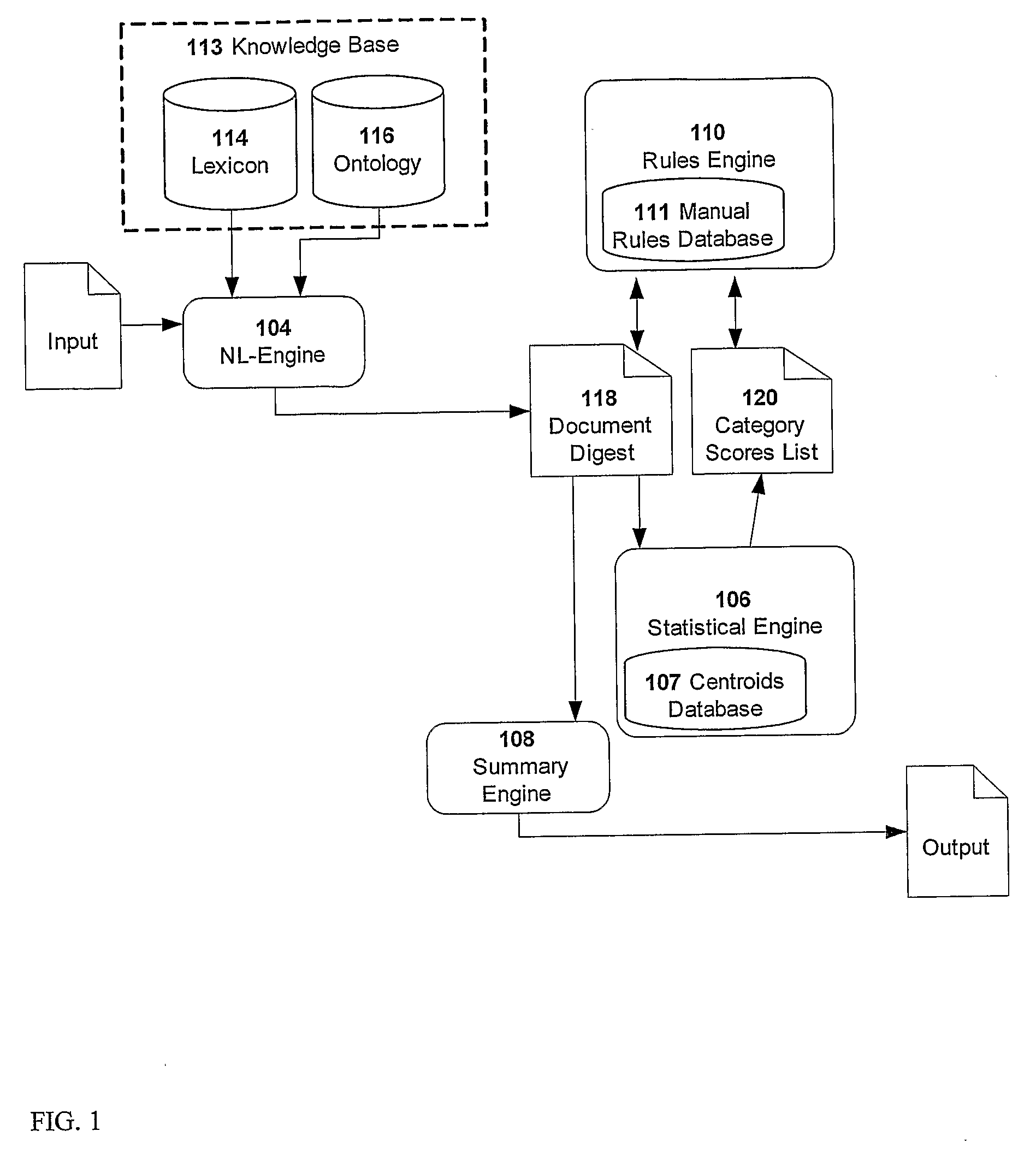
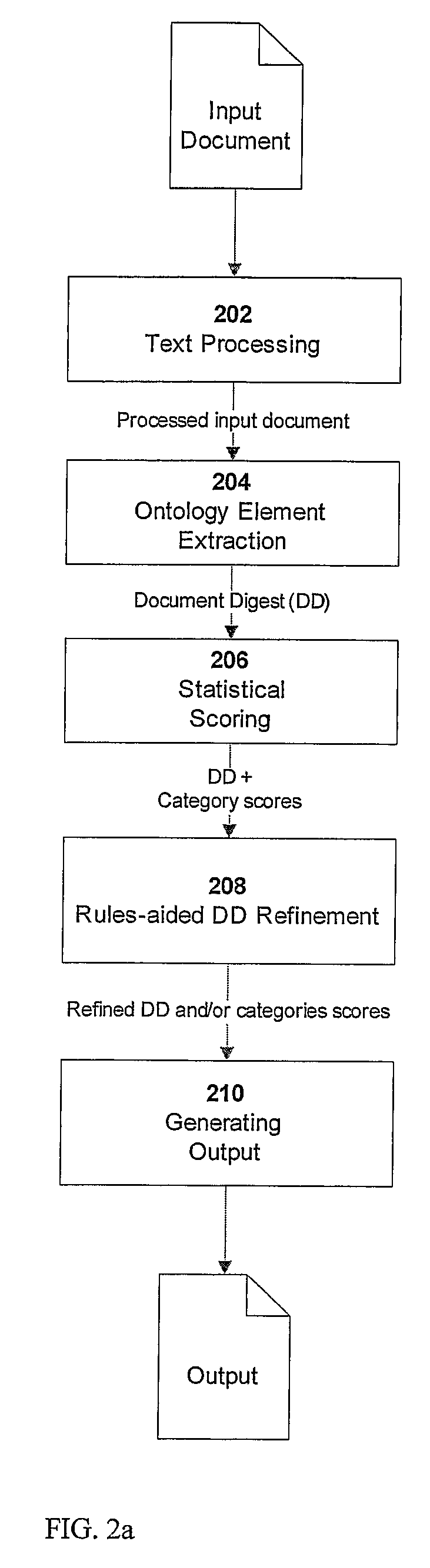
A method for real-time exploitation of documents in non-English languages includes processing an input document in into a processed input document, extracting ontology elements from the processed input document to obtain a document digest (DD), statistically scoring each DD to obtain a DD with category scores, refining the DD and the category scores to obtain a summary of each document in the form of a refined DD with refined category scores. The summary allows a user to estimate in real-time if the input document warrants added attention.
Owner:INTUVIEW
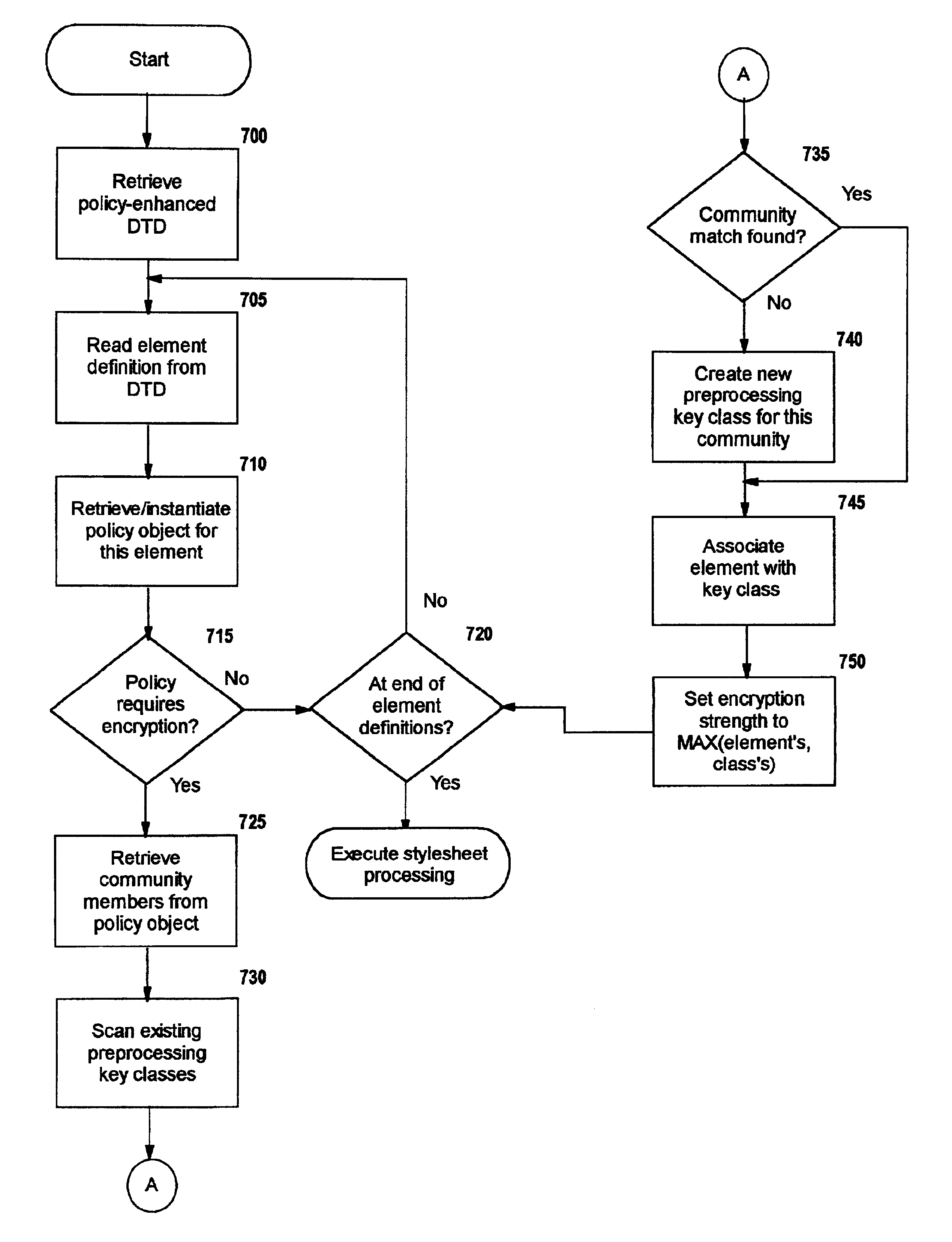
Selective data encryption using style sheet processing for decryption by a client proxy
InactiveUS6978367B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureDocument preparation
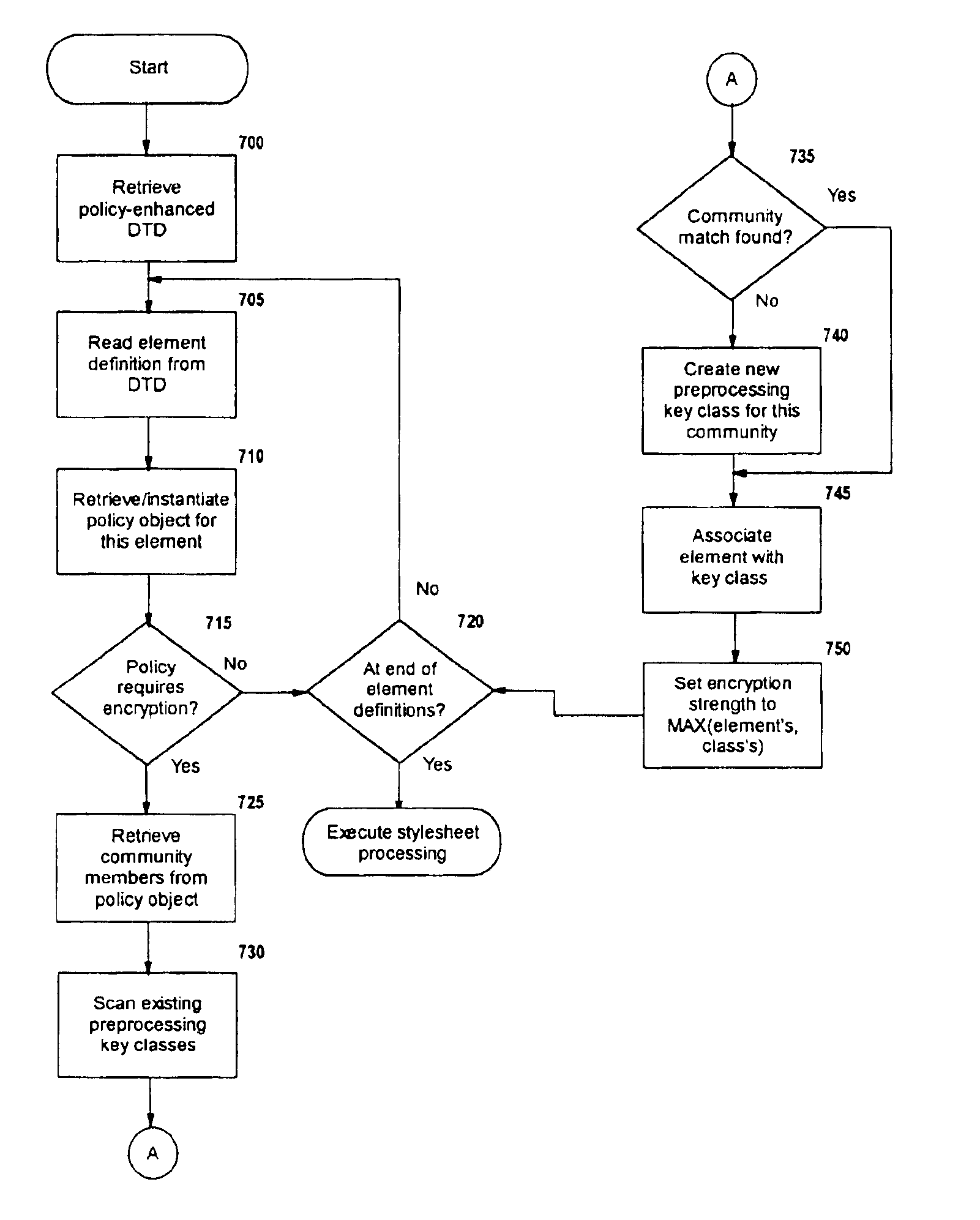
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
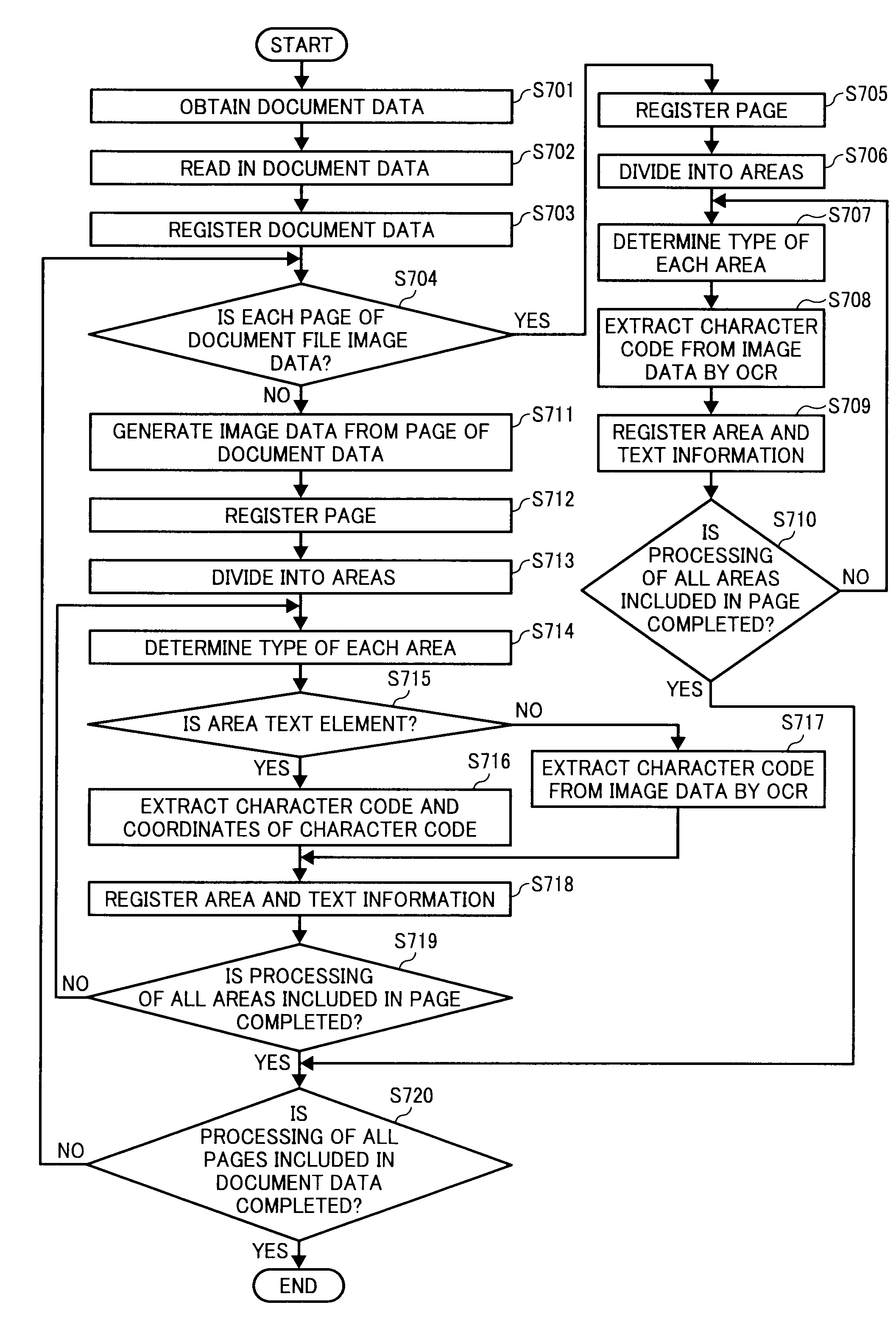
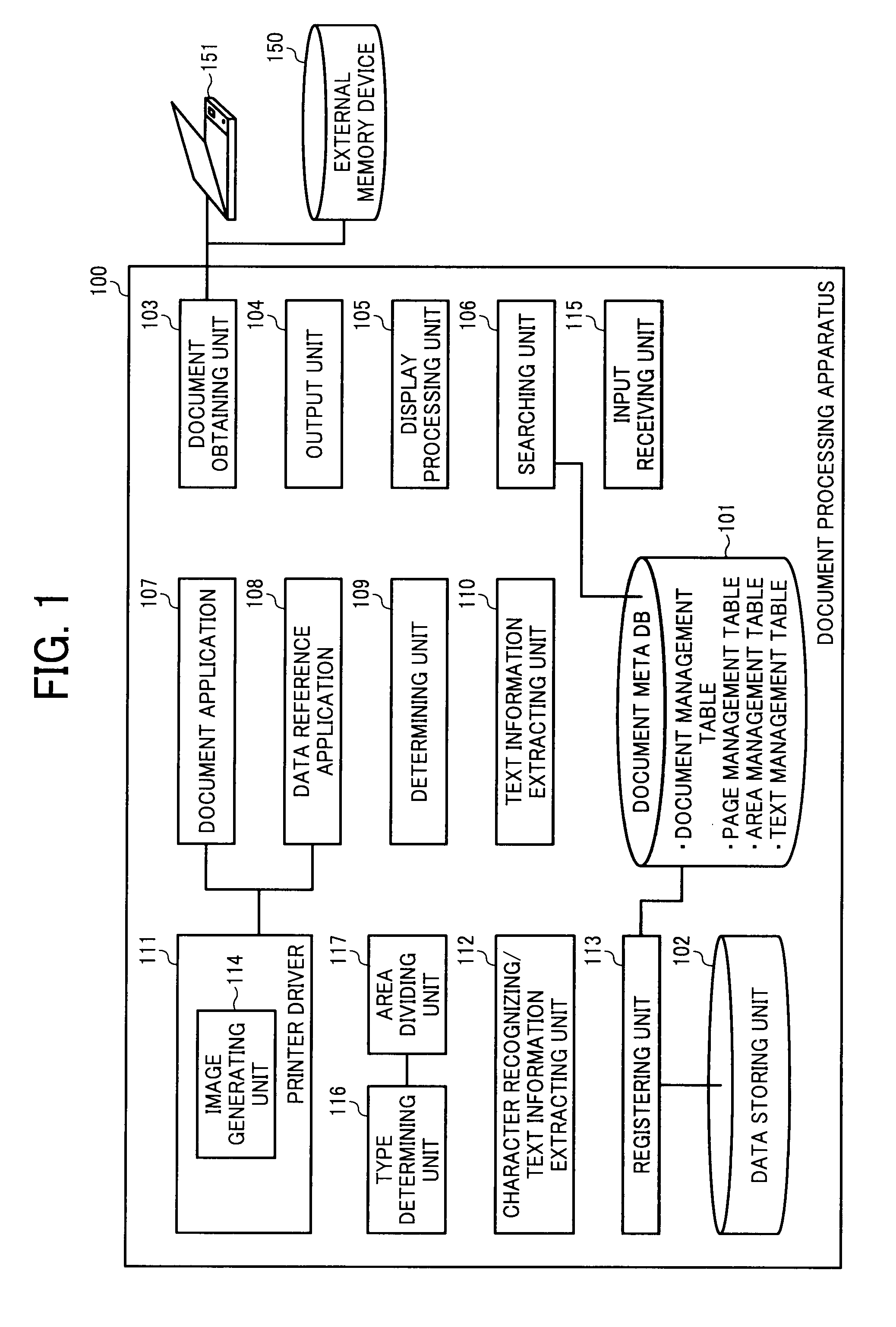
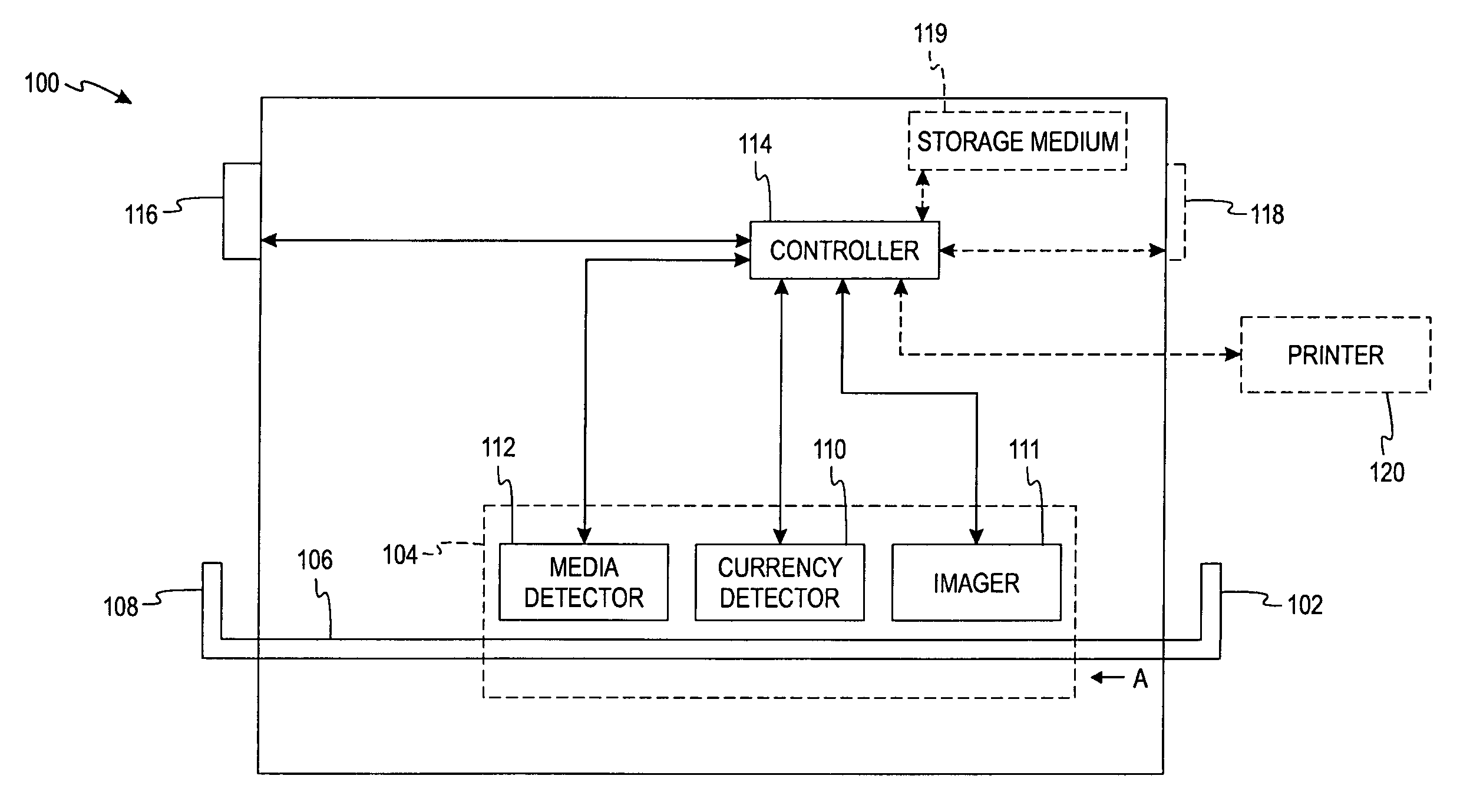
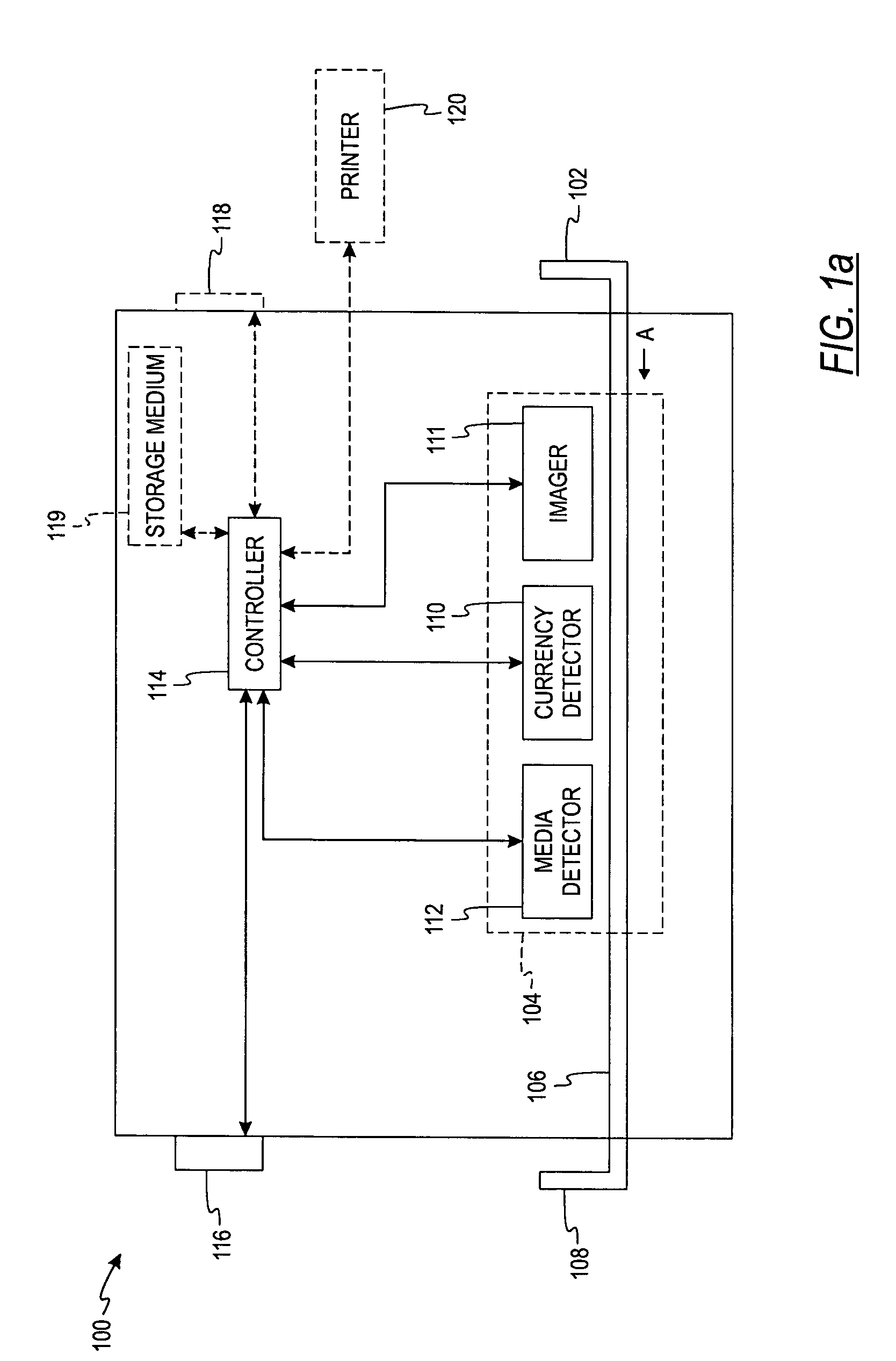
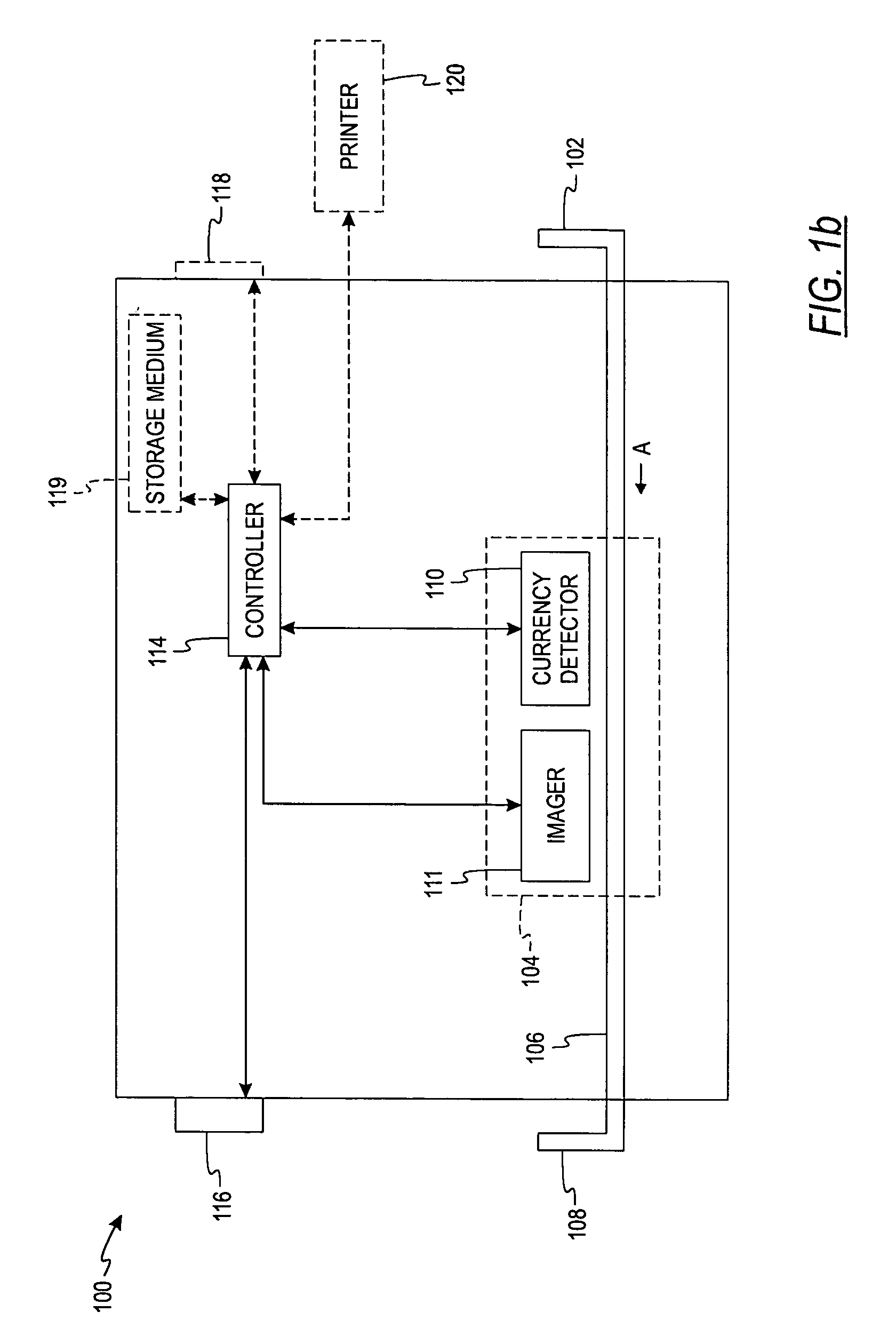
Document processing apparatus, document processing method, and computer program product
ActiveUS20090123071A1Solve problemsCharacter recognitionInput/output processes for data processingDocument preparationDocumentation
In a document processing apparatus, a first character information extracting unit extracts, for a first area that is an area determined to be a character extractable area in divided areas of a document information, first character information from the area; a second character information extracting unit extracts, for a second area that is an area not determined to be the character extractable area in the divided areas, a character code by performing a character recognition processing on a document image generated from the document information as second character information; and a storing unit stores therein the first character information, the second character information, and at least one of the document information and the document image in association with each other.
Owner:RICOH KK
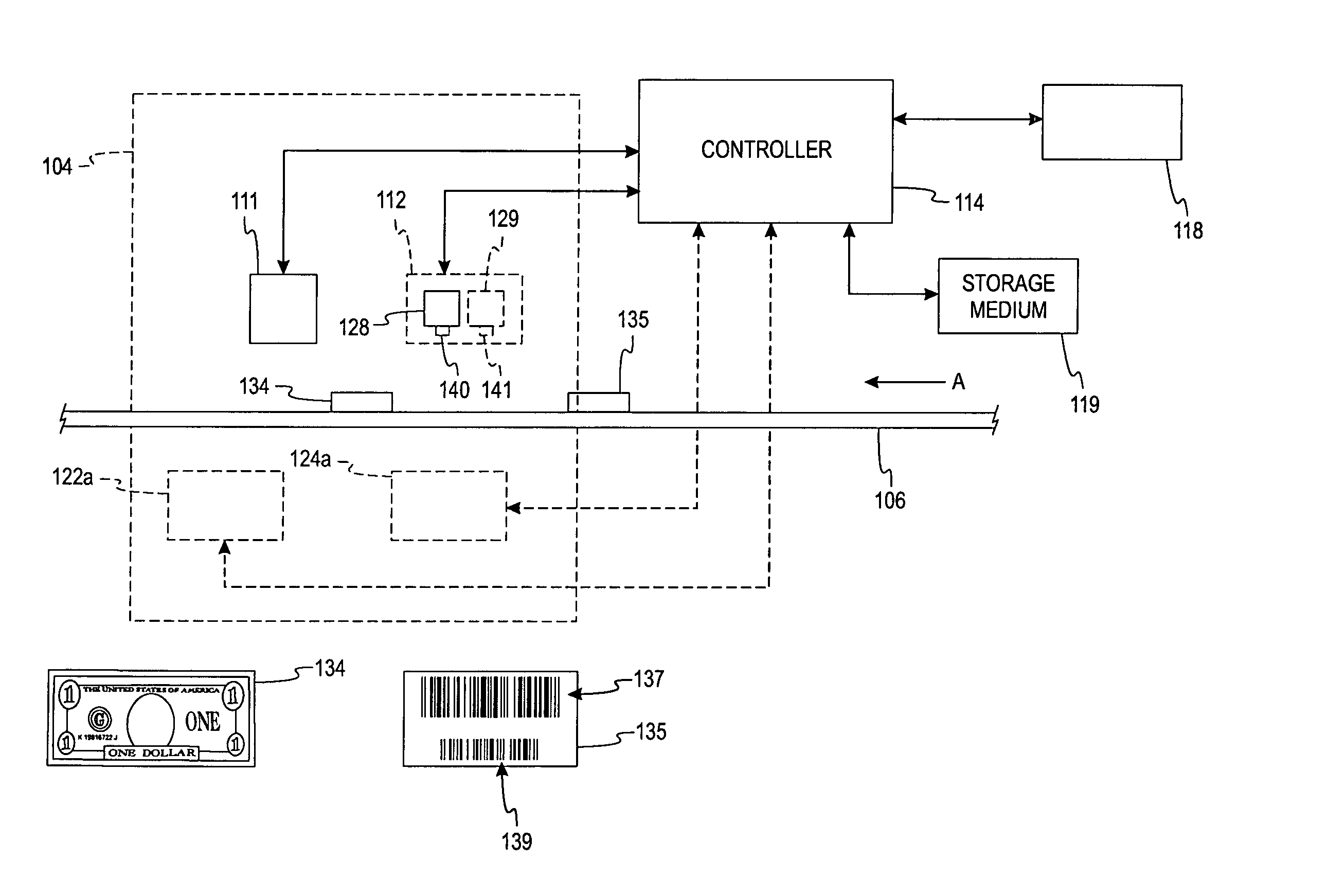
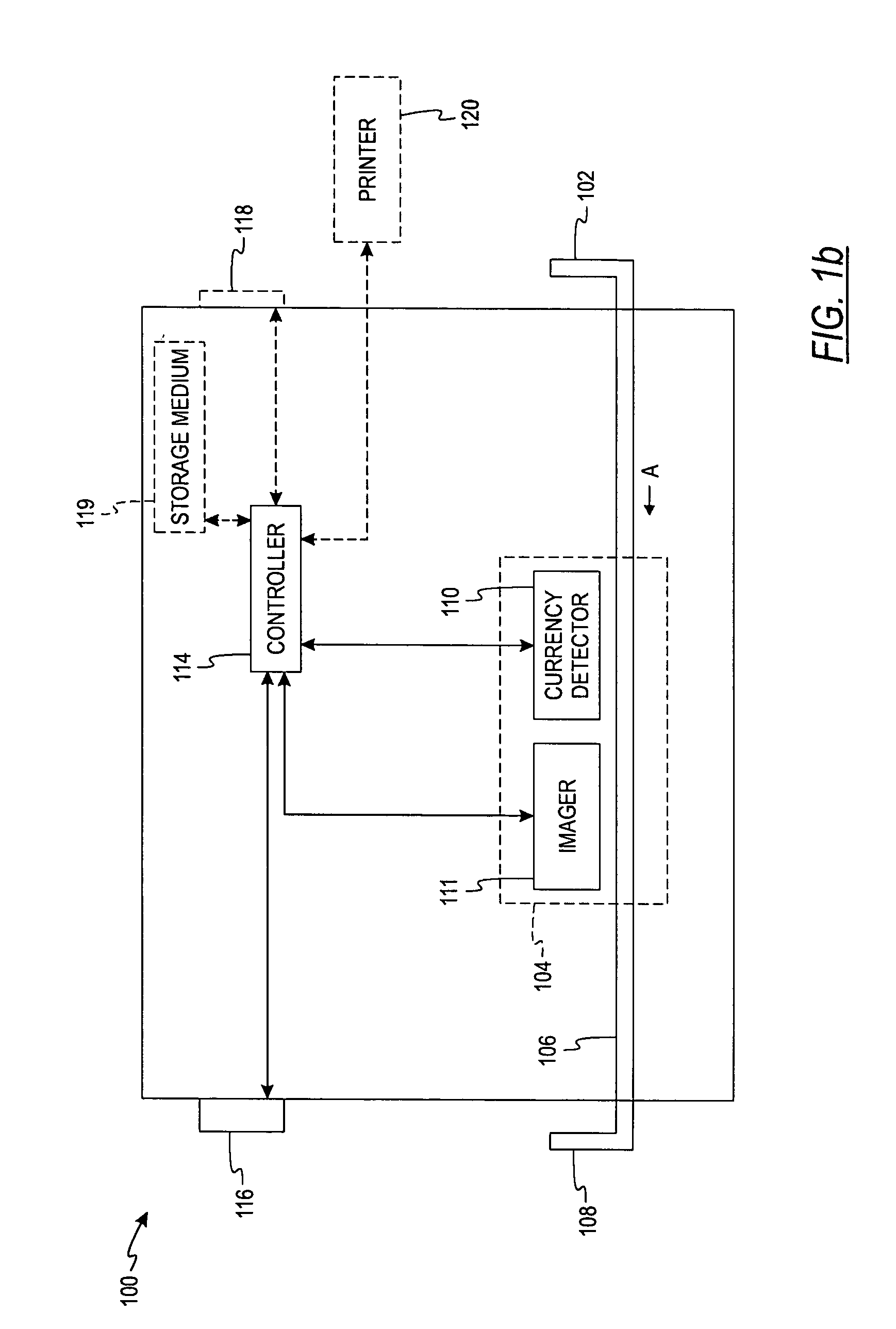
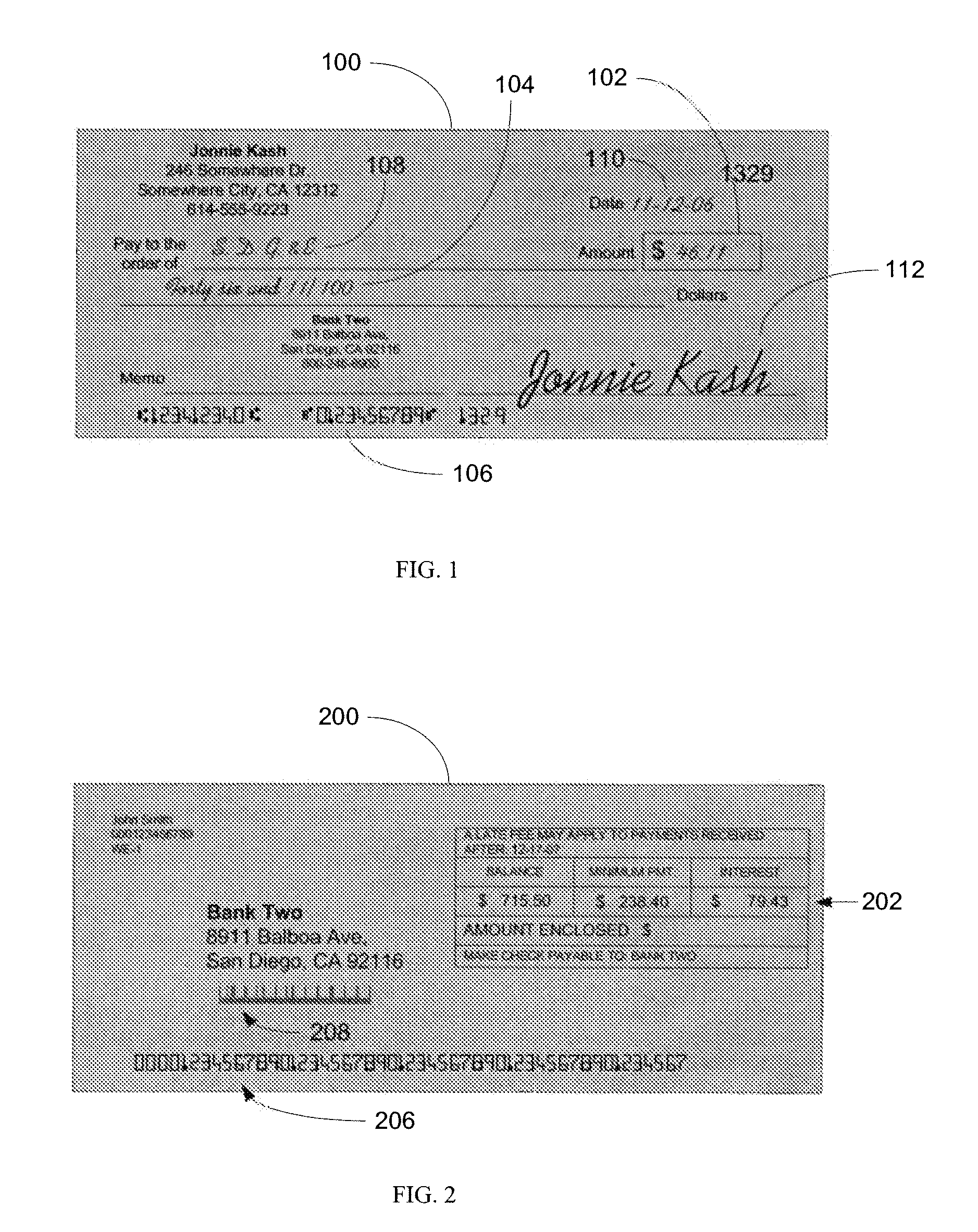
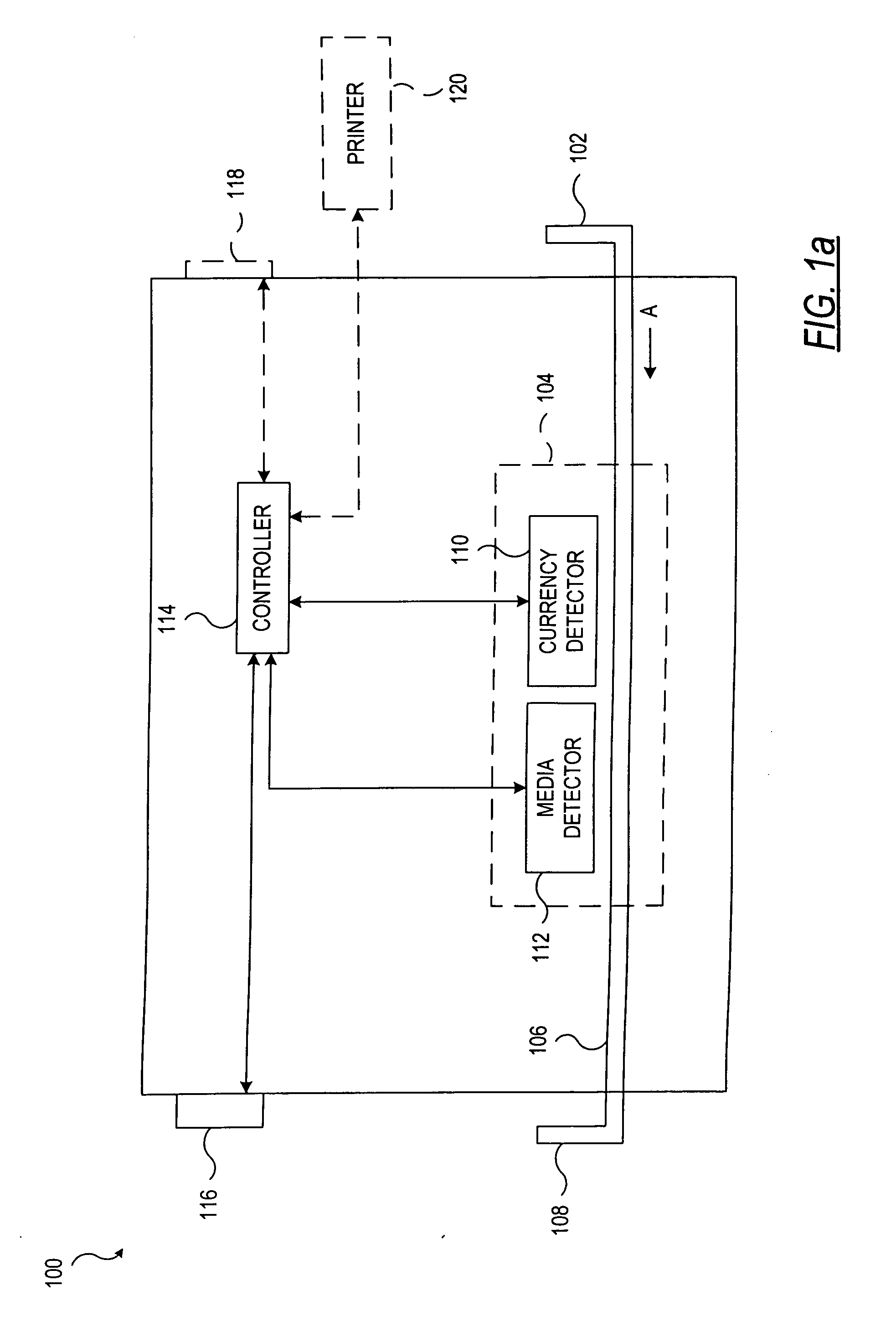
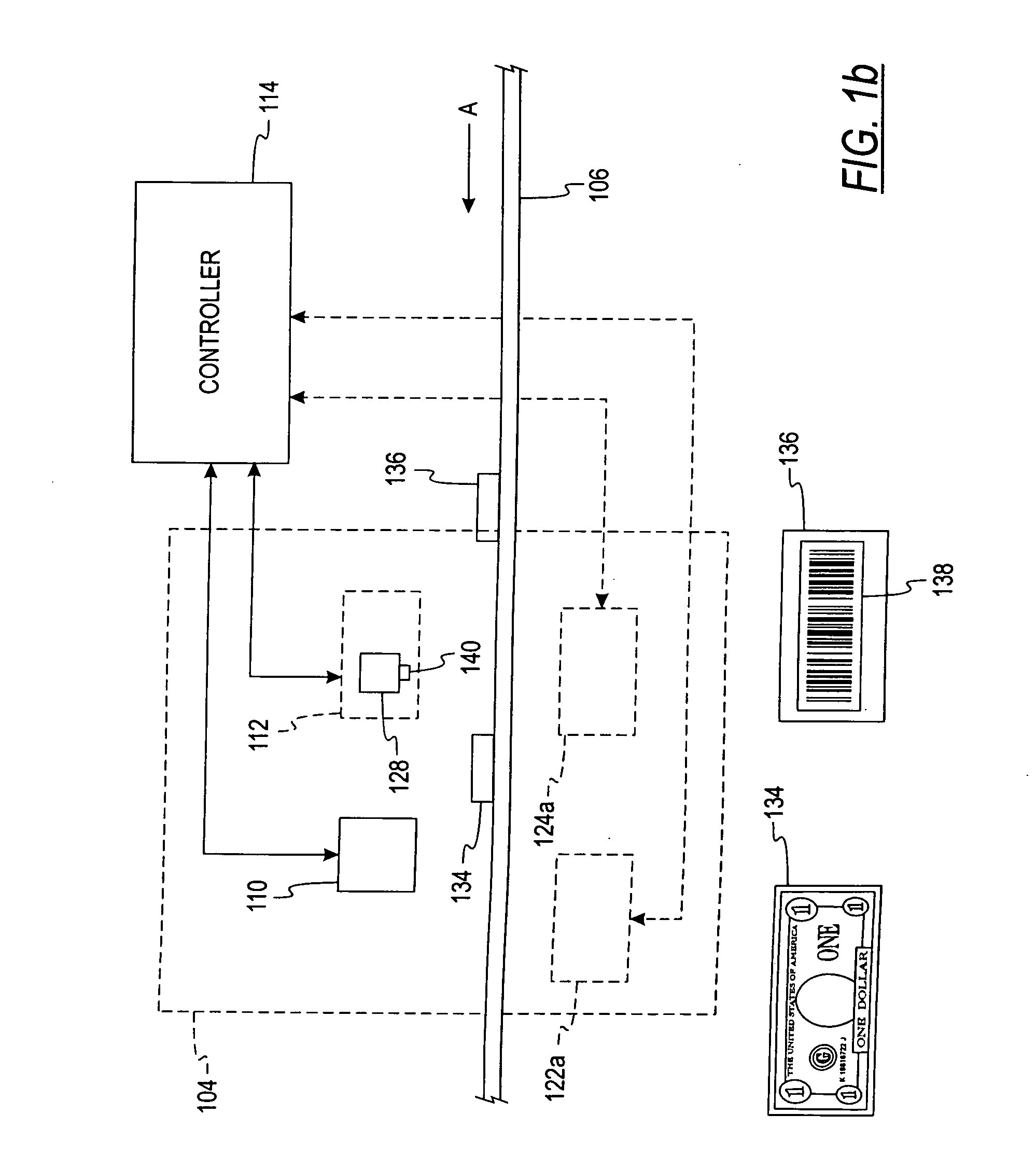
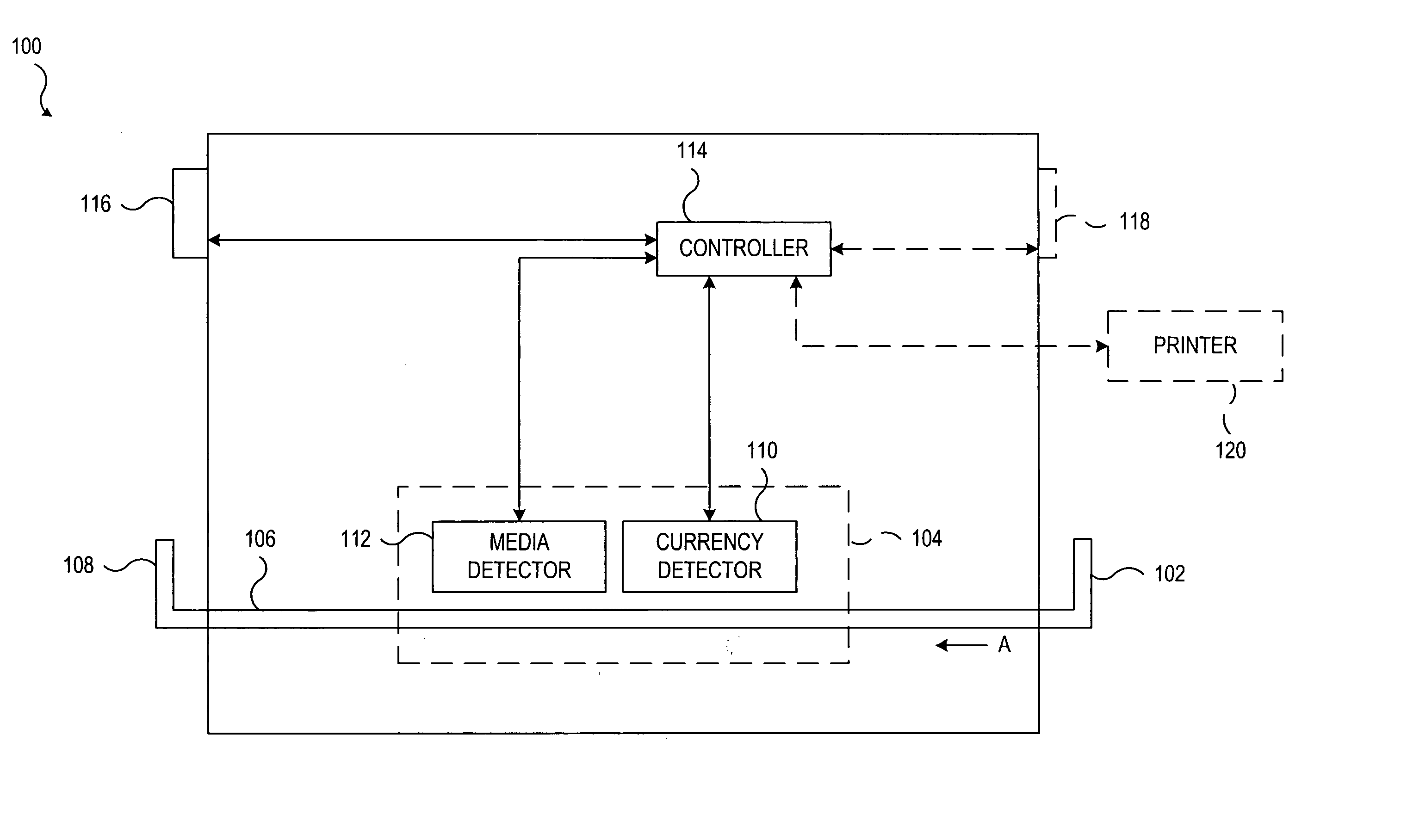
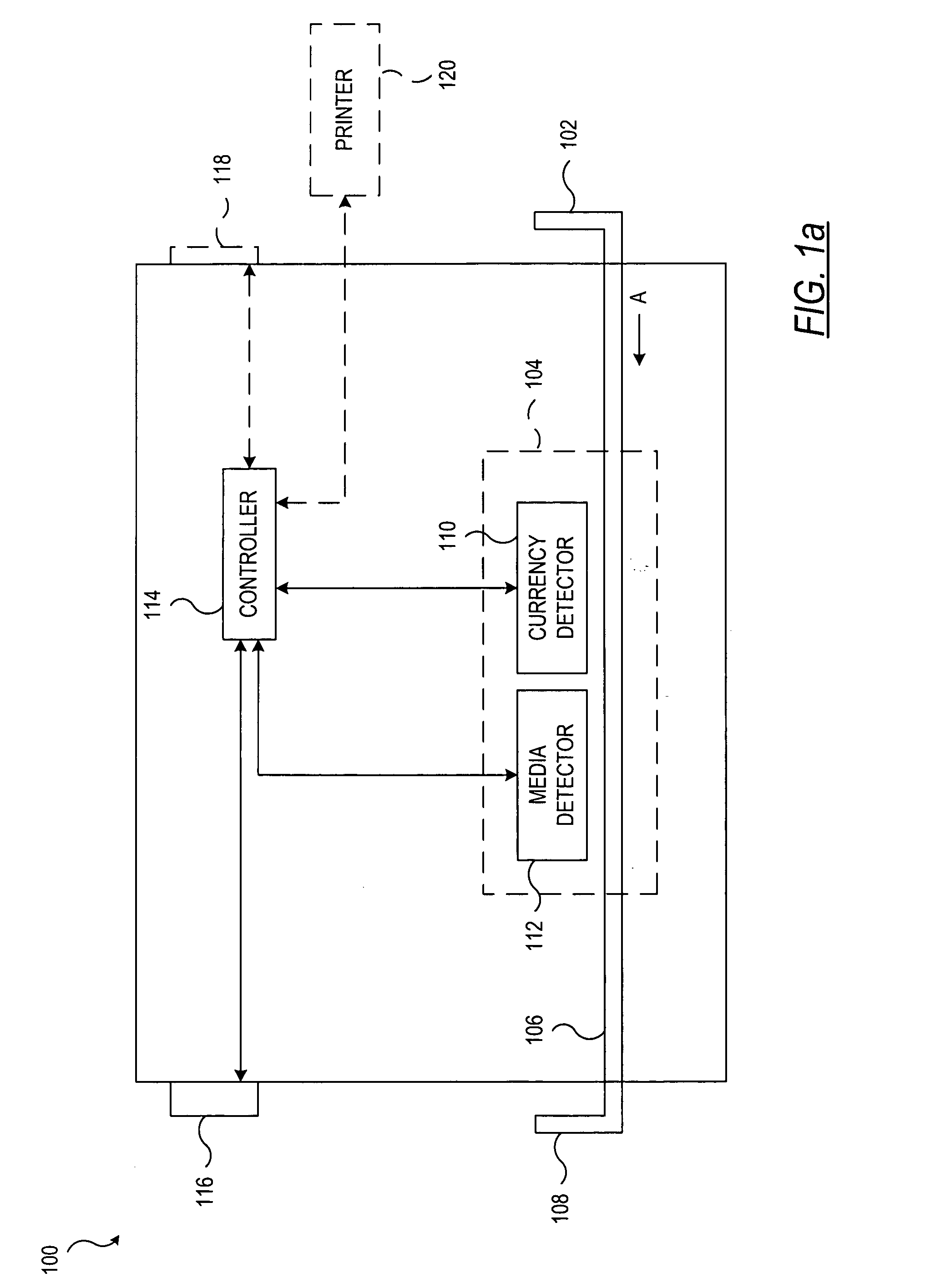
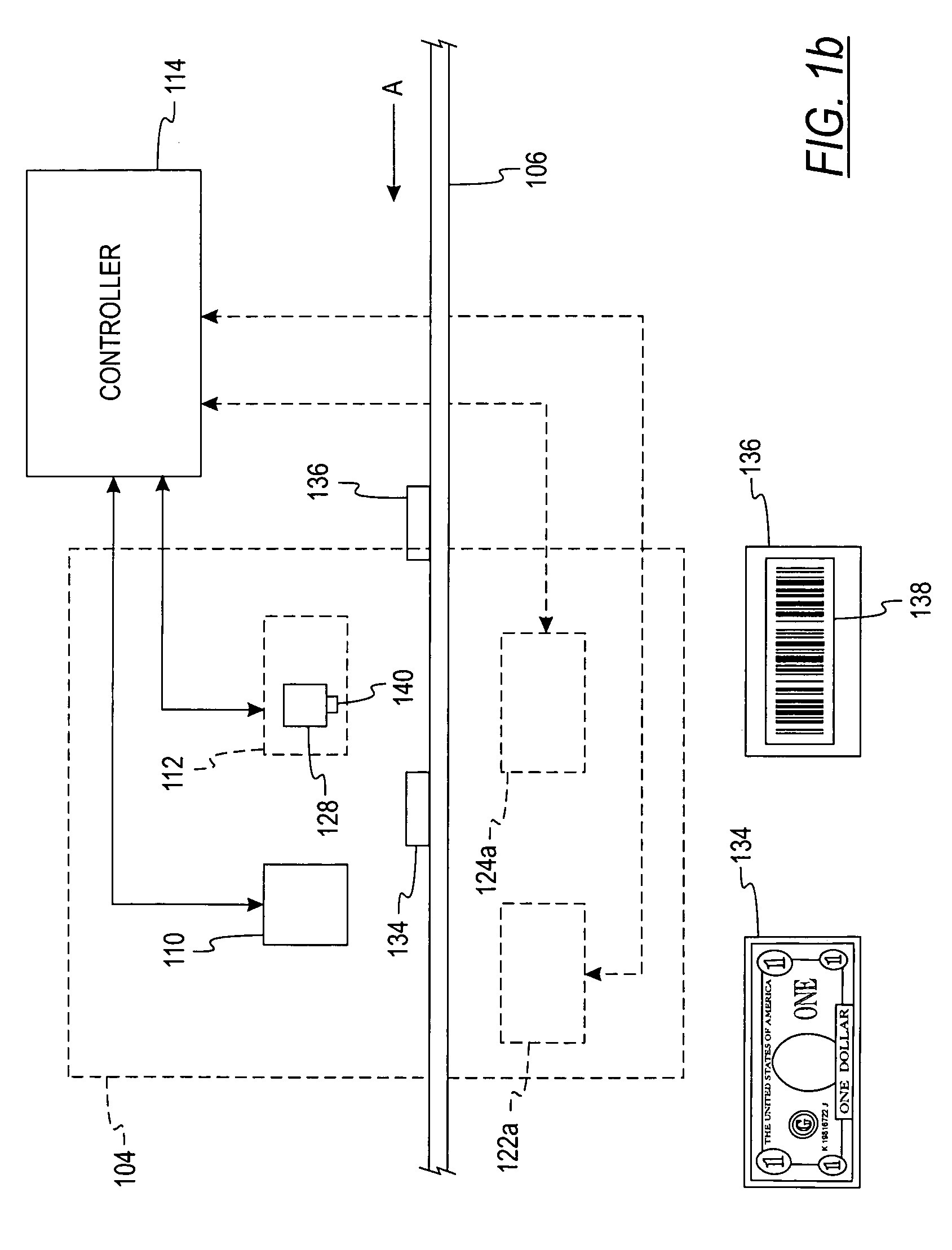
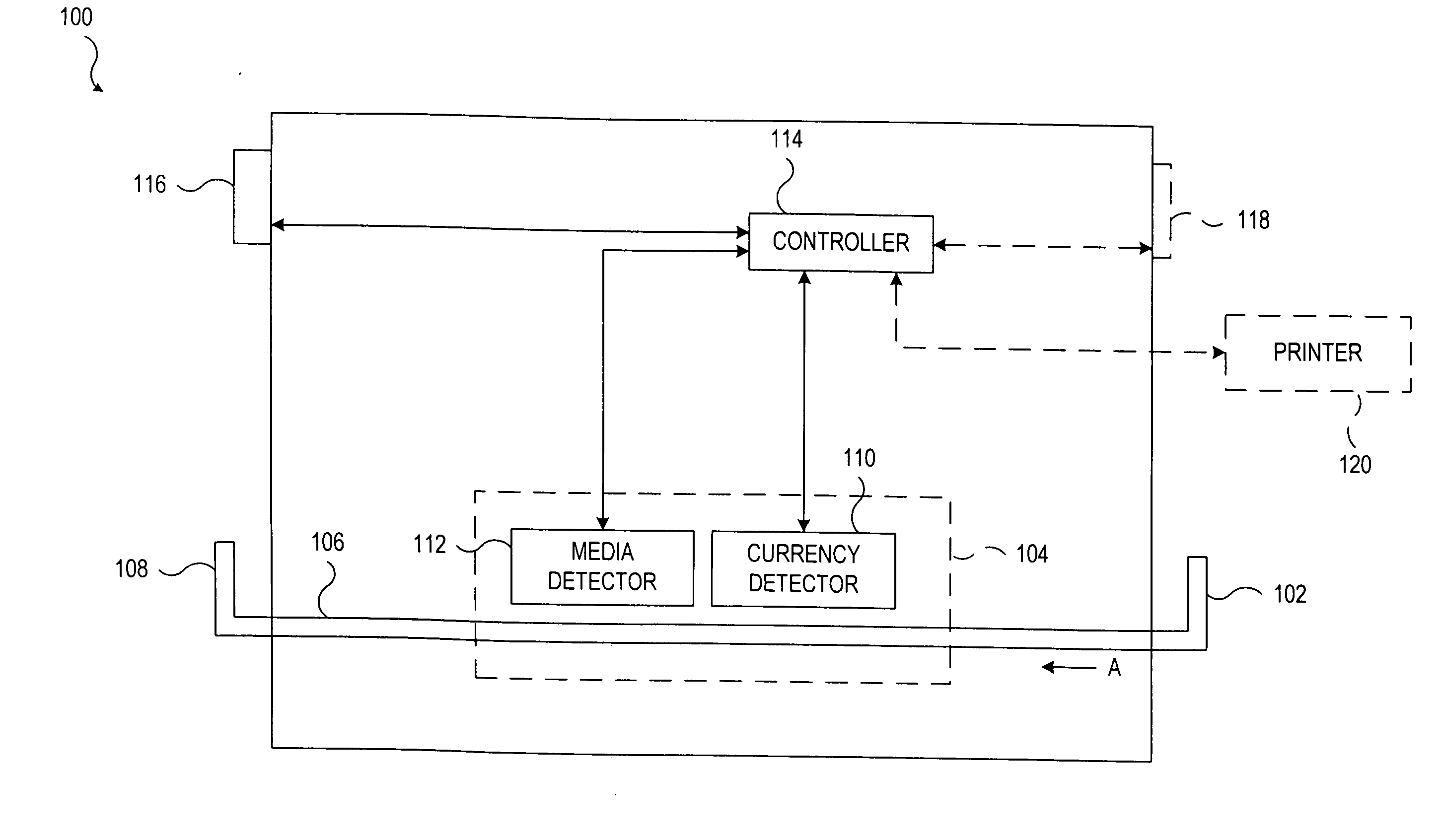
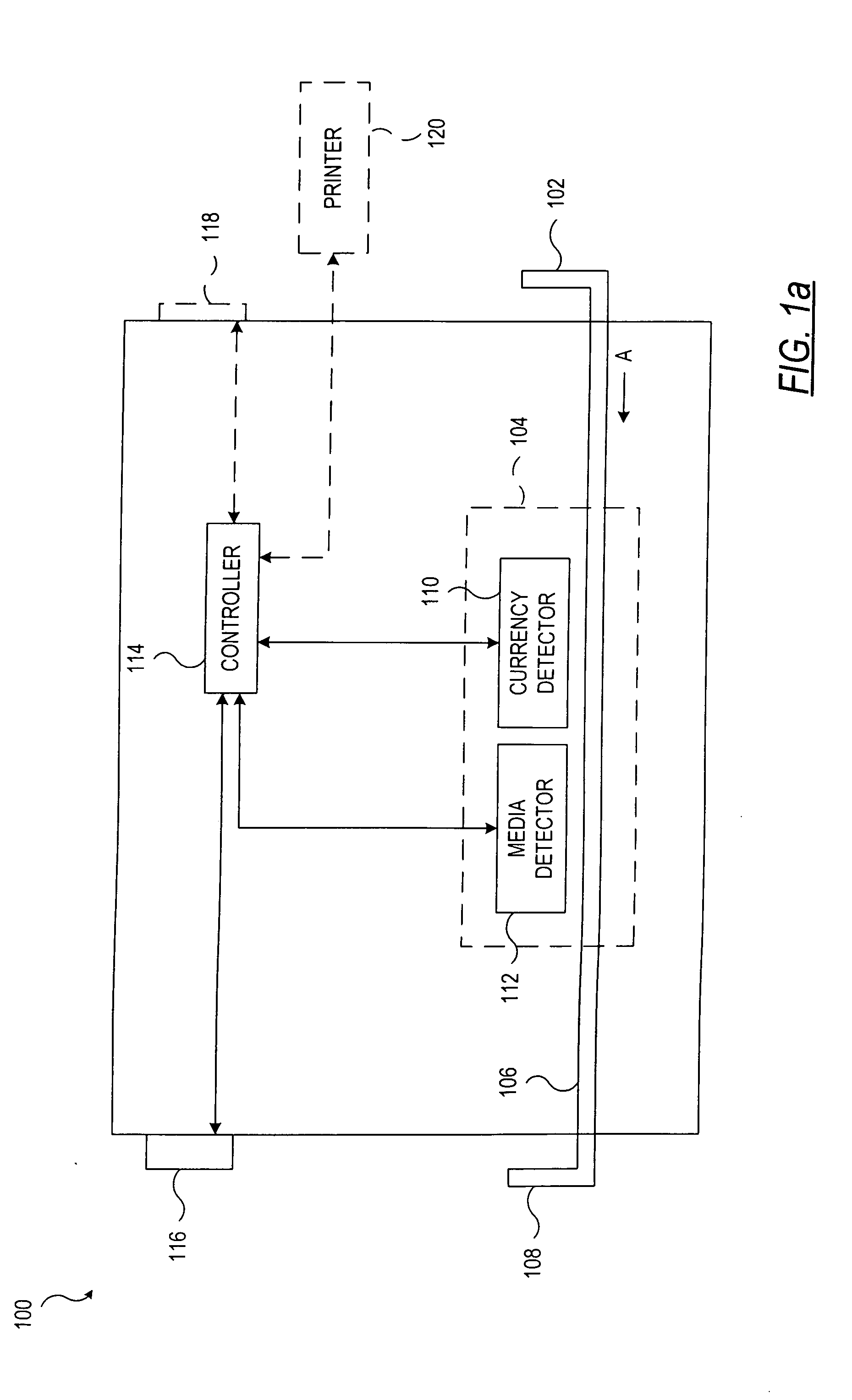
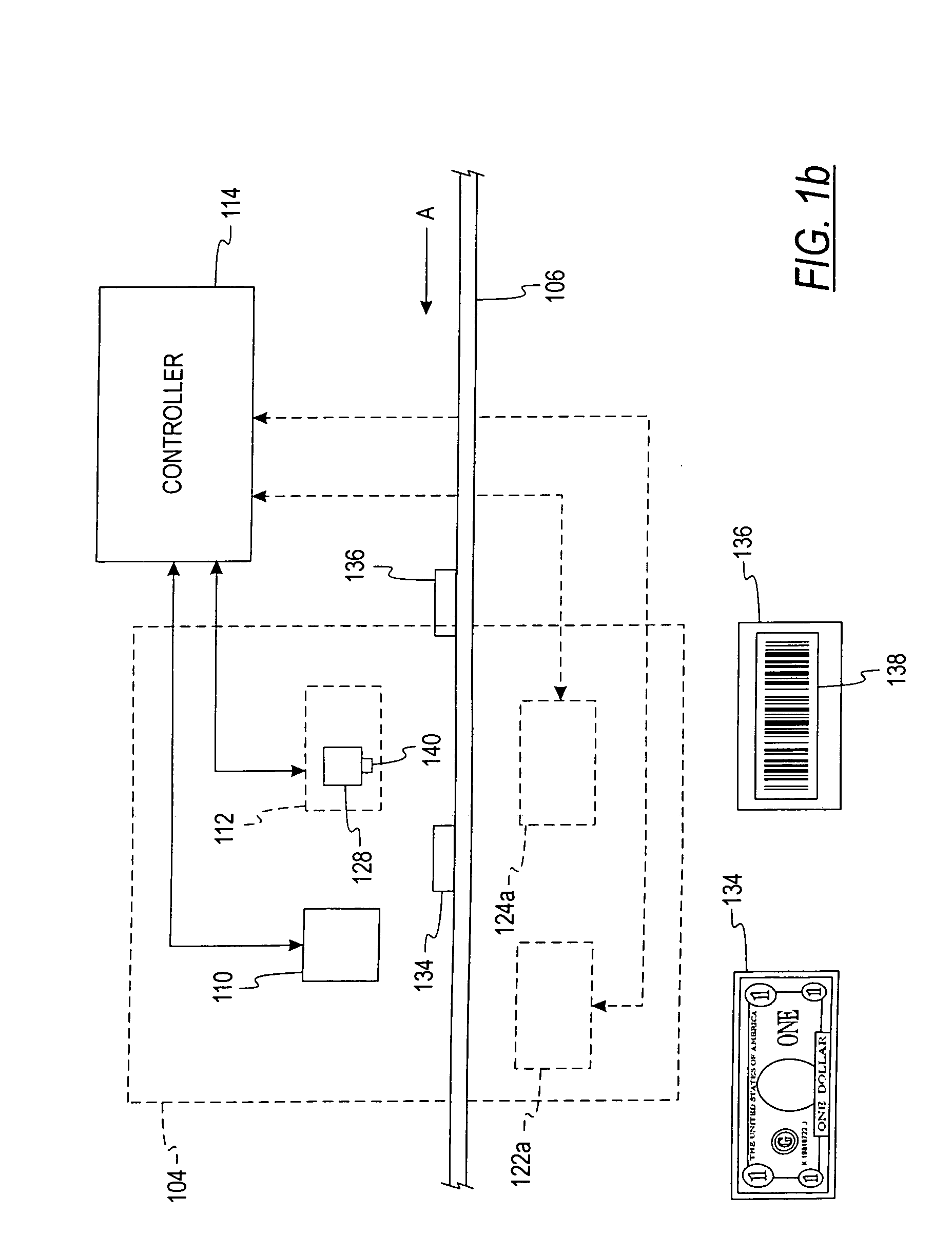
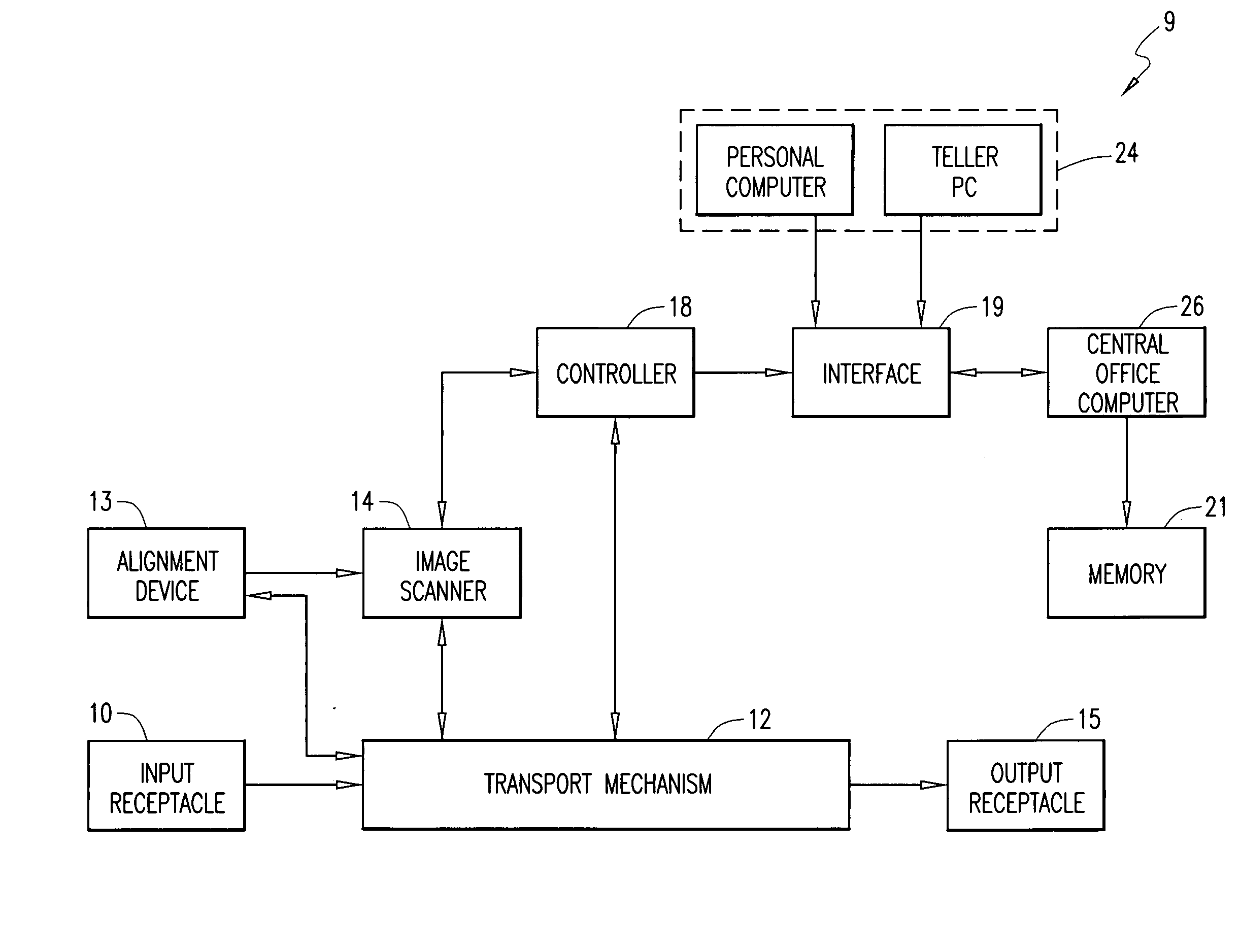
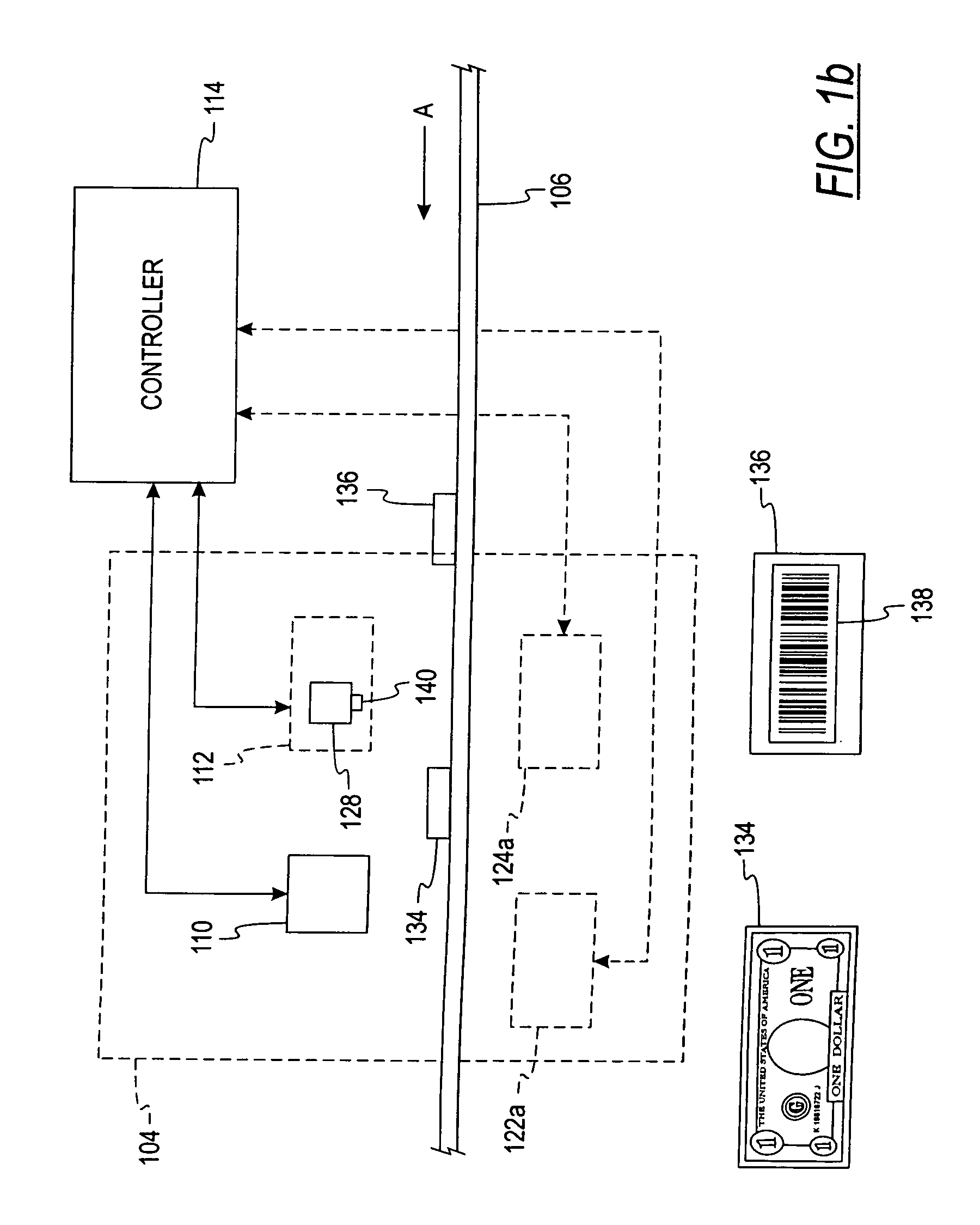
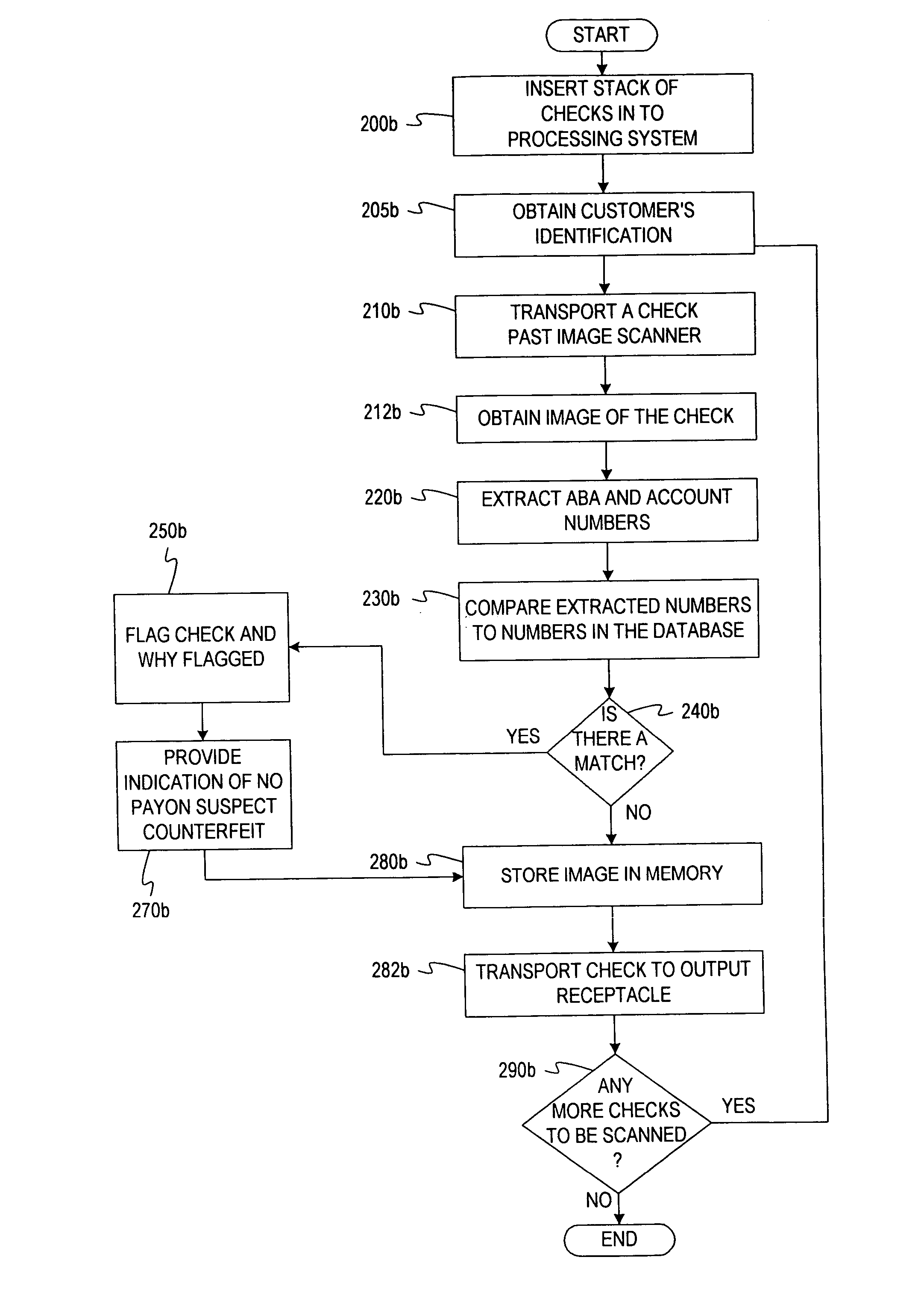
System and method for processing currency bills and documents bearing barcodes in a document processing device
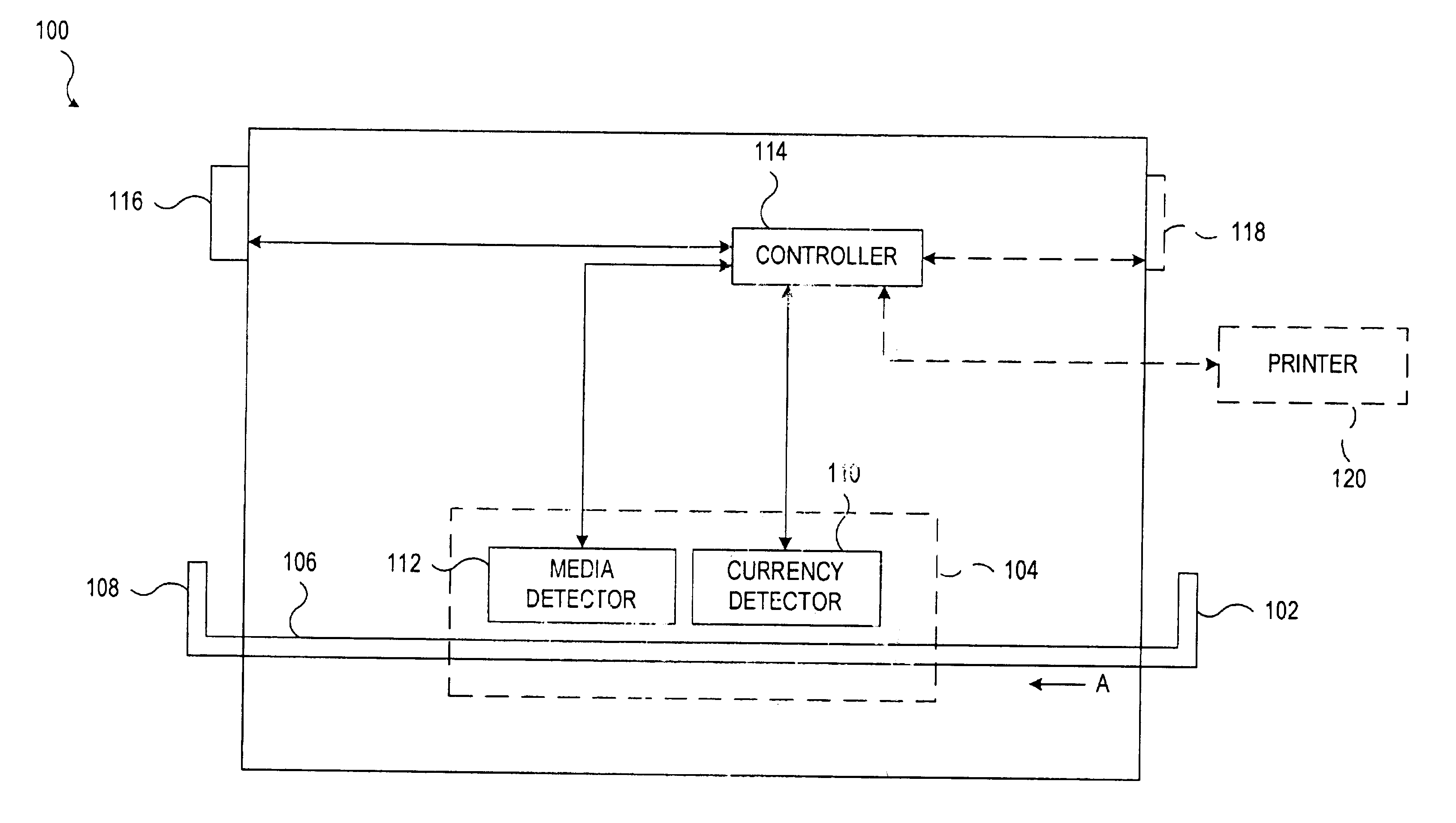
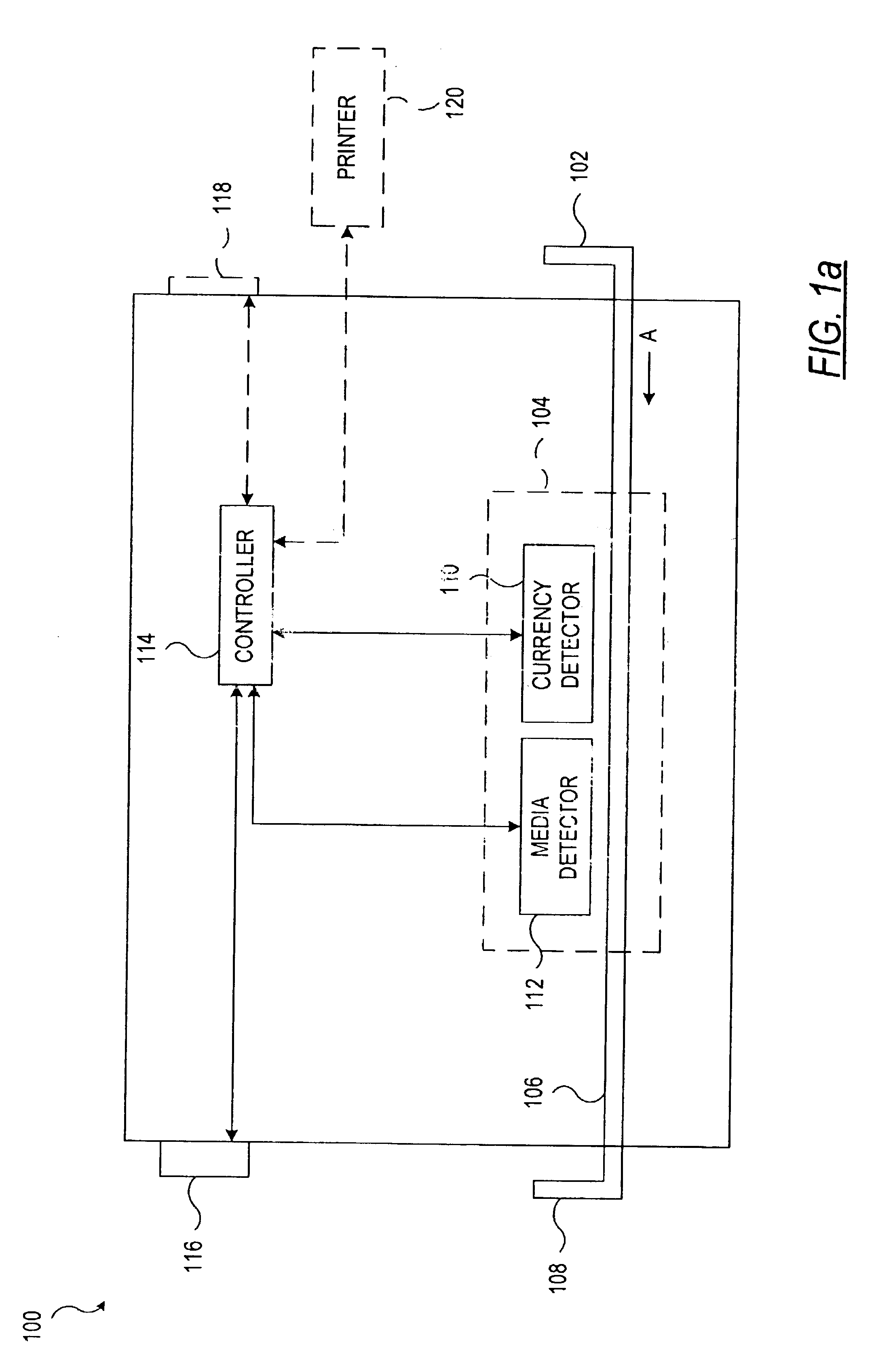
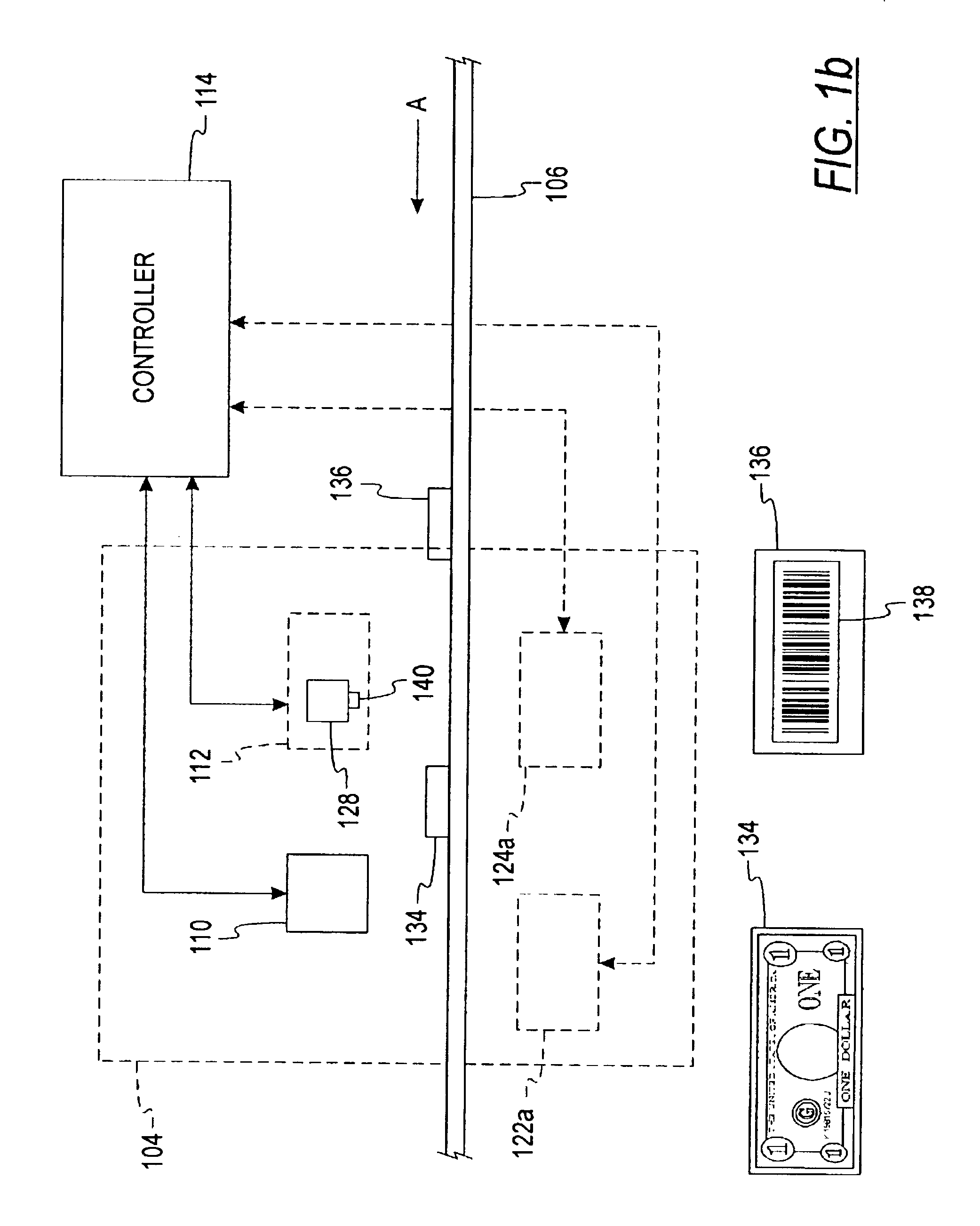
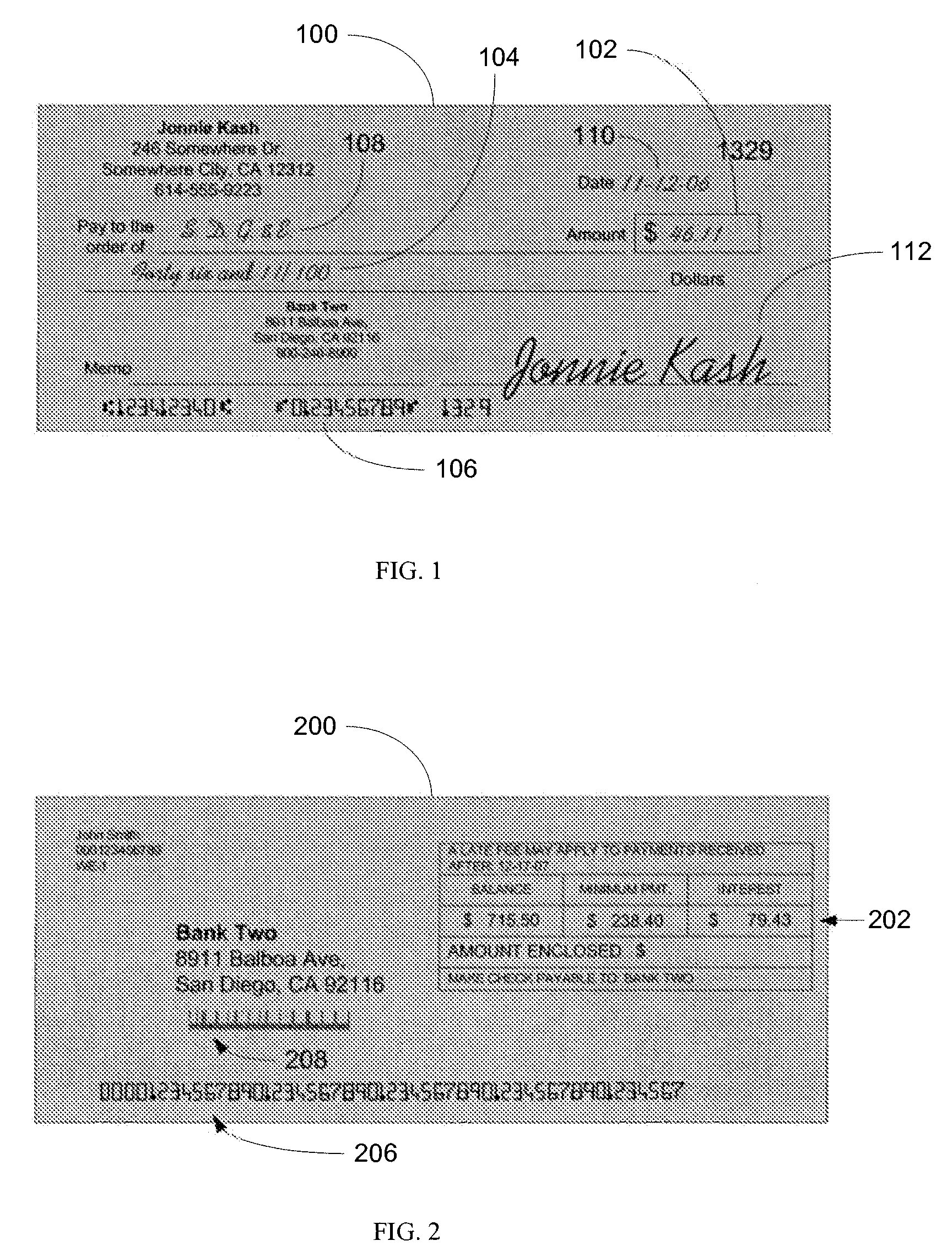
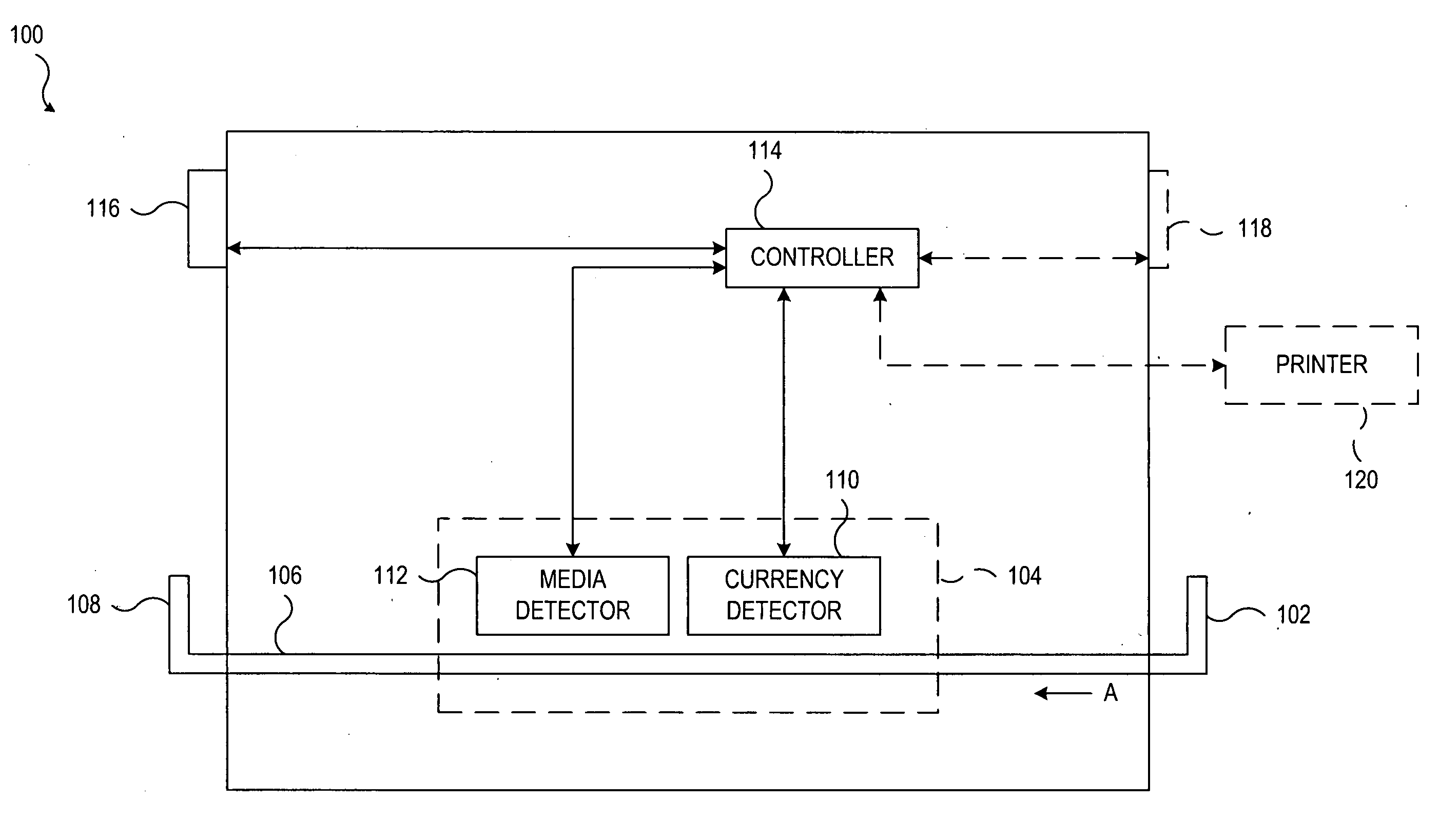
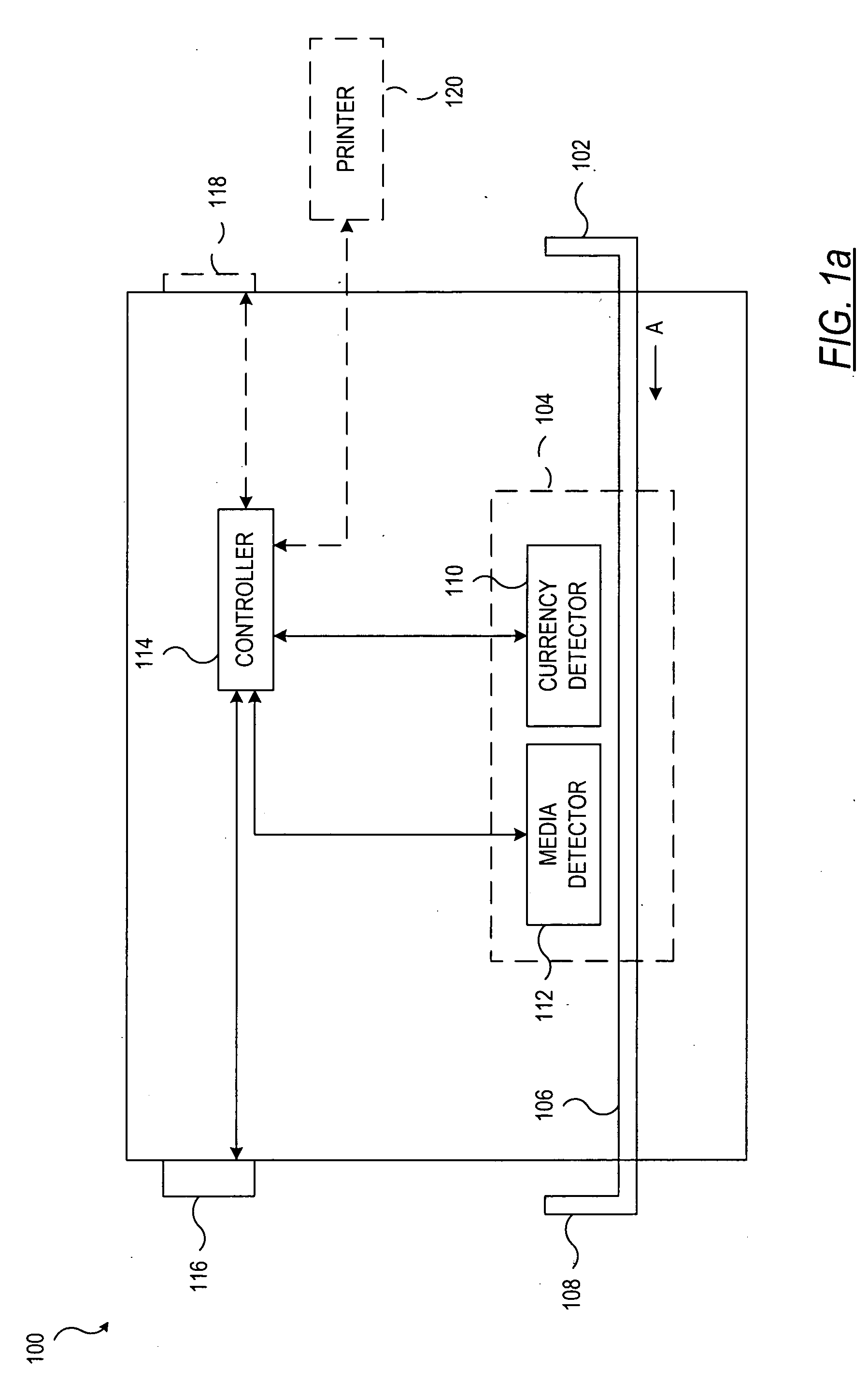
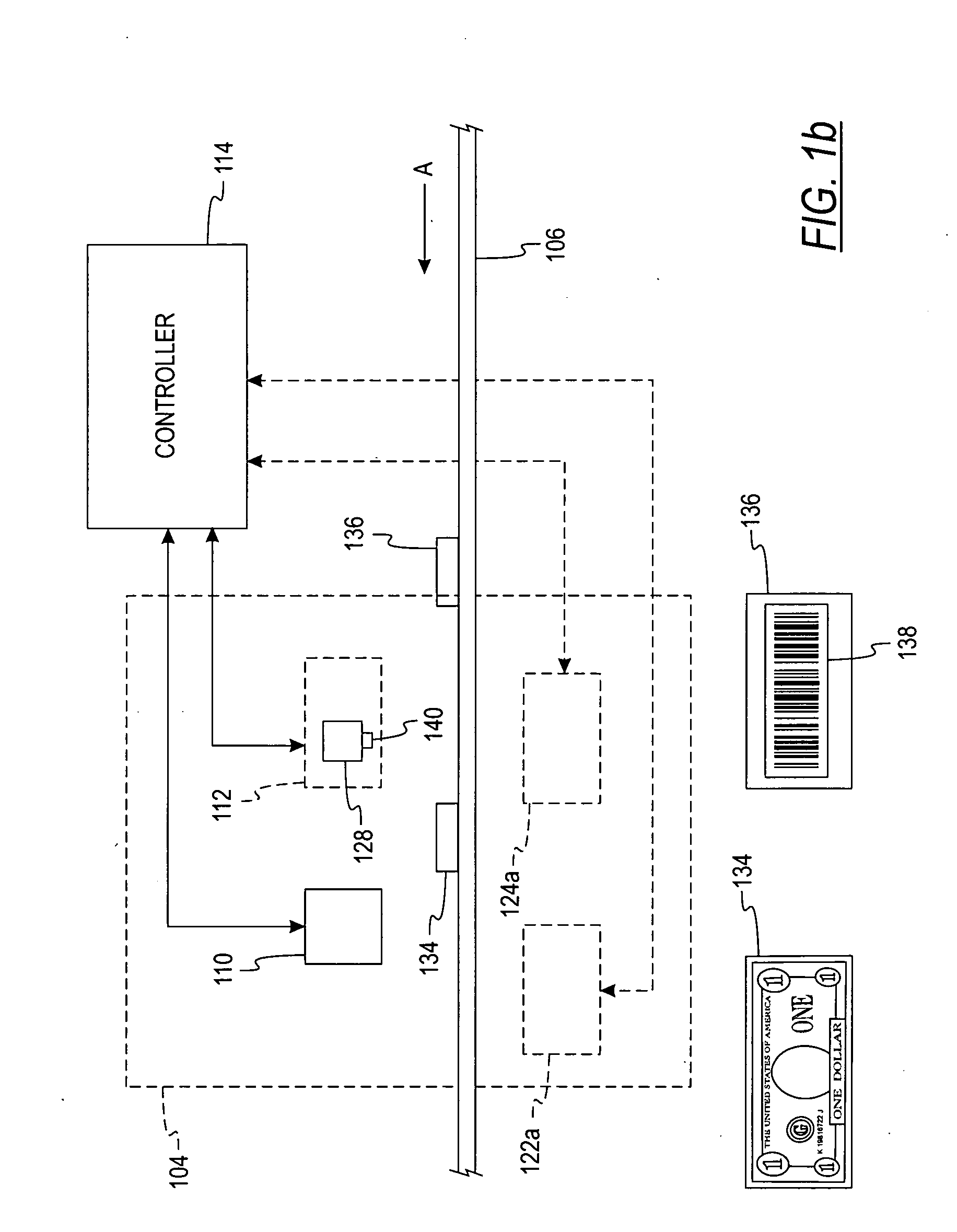
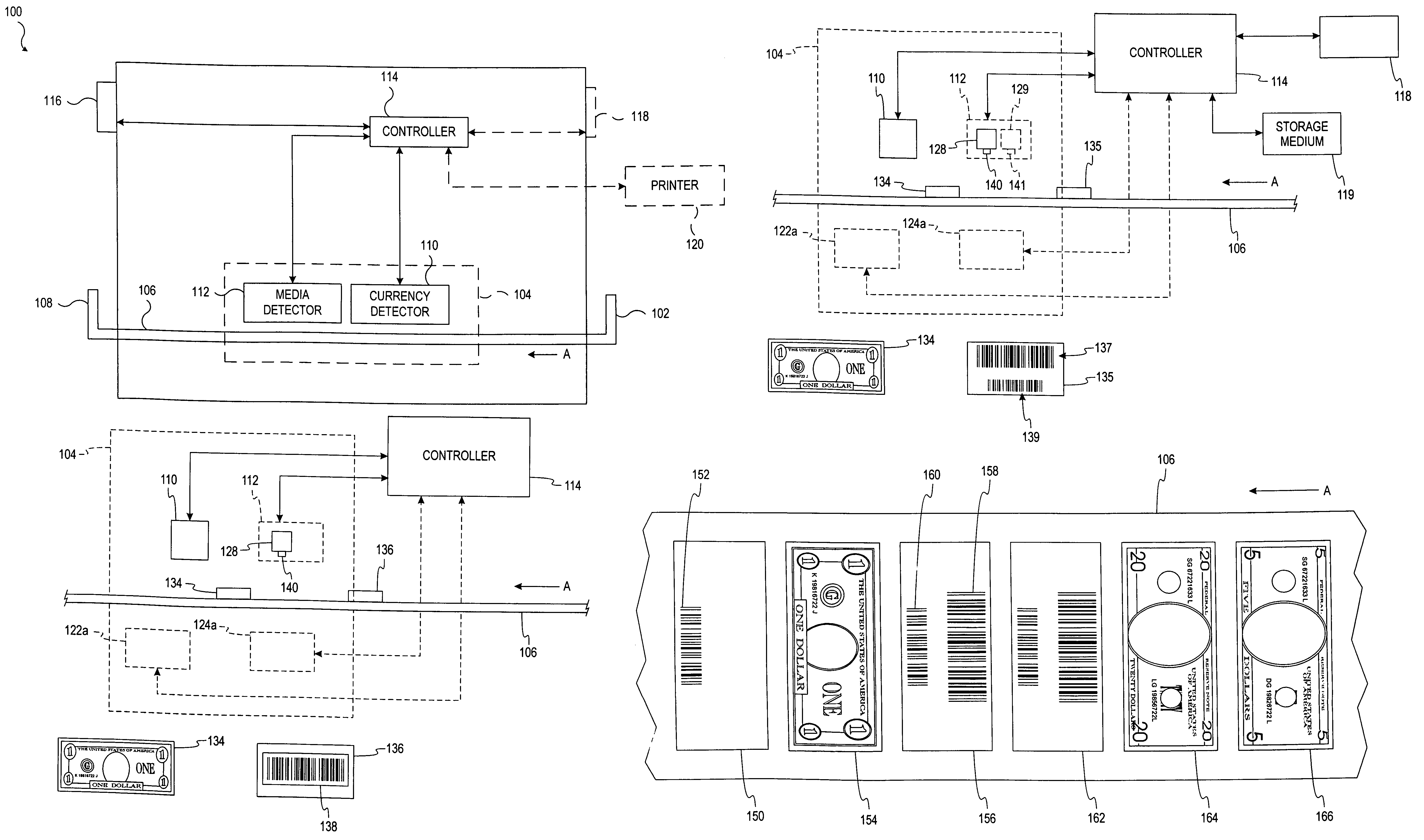
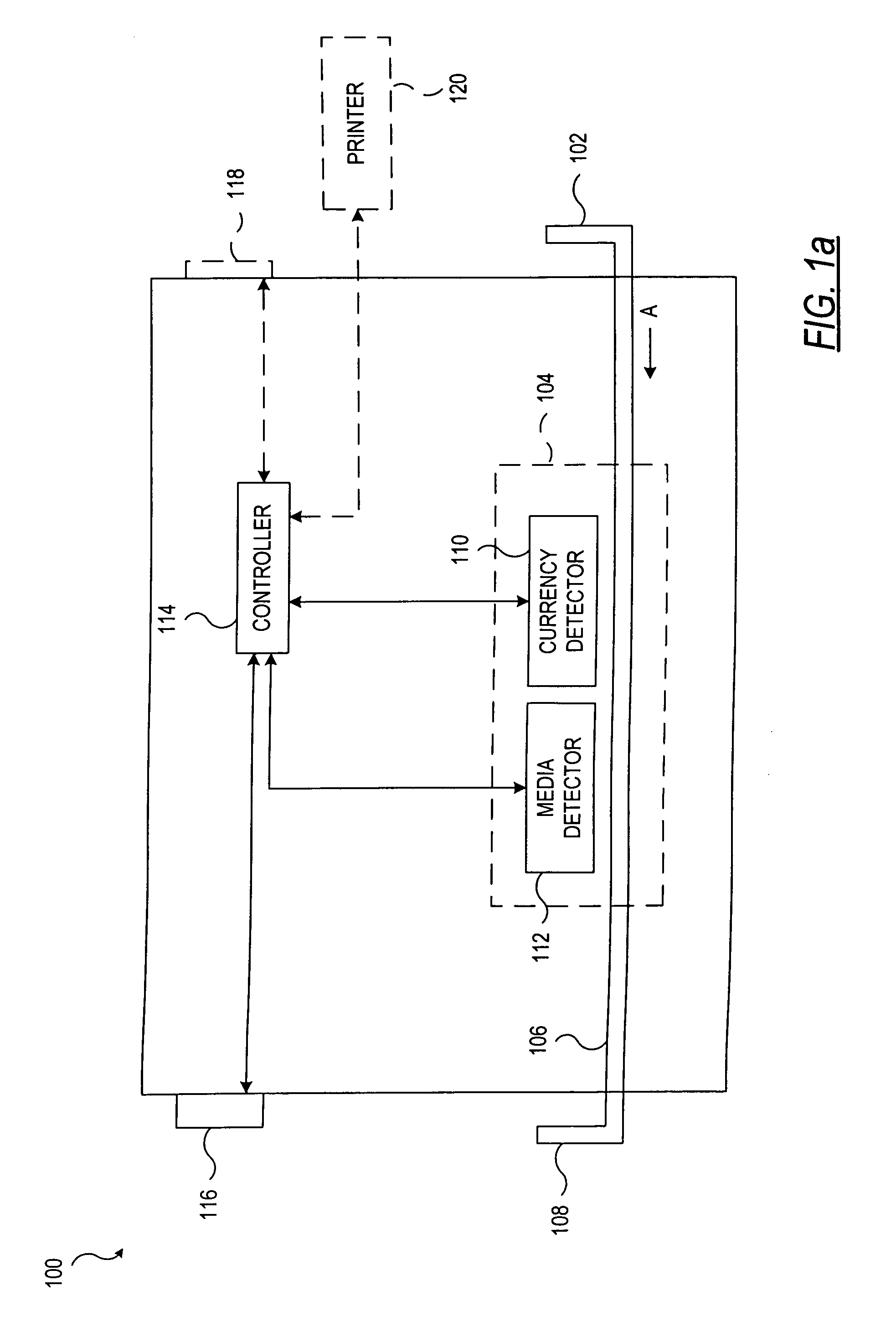
A document processing device having an evaluation region disposed along a transport path between an input and output receptacle capable of processing both currency bills and substitute currency media having at least one indicia. The evaluation region includes at least one of a currency detector, a media detector, and an imager for detecting predetermined characteristics of currency bills and substitute currency media. A controller coupled to the evaluation region controls the operation of the document processing device and receives input from and provides information to a user via a control unit. In some embodiments, the document processing device may have any number of output receptacles, and the control unit allows the user to specify which output receptacle receives which type of document. An optional coin sorter may be coupled to the document processing device to allow document and coin processing. The document processing device may be coupled to a network to communicate information to devices linked to the network.
Owner:CUMMINS-ALLISON CORP
Document processing system and method
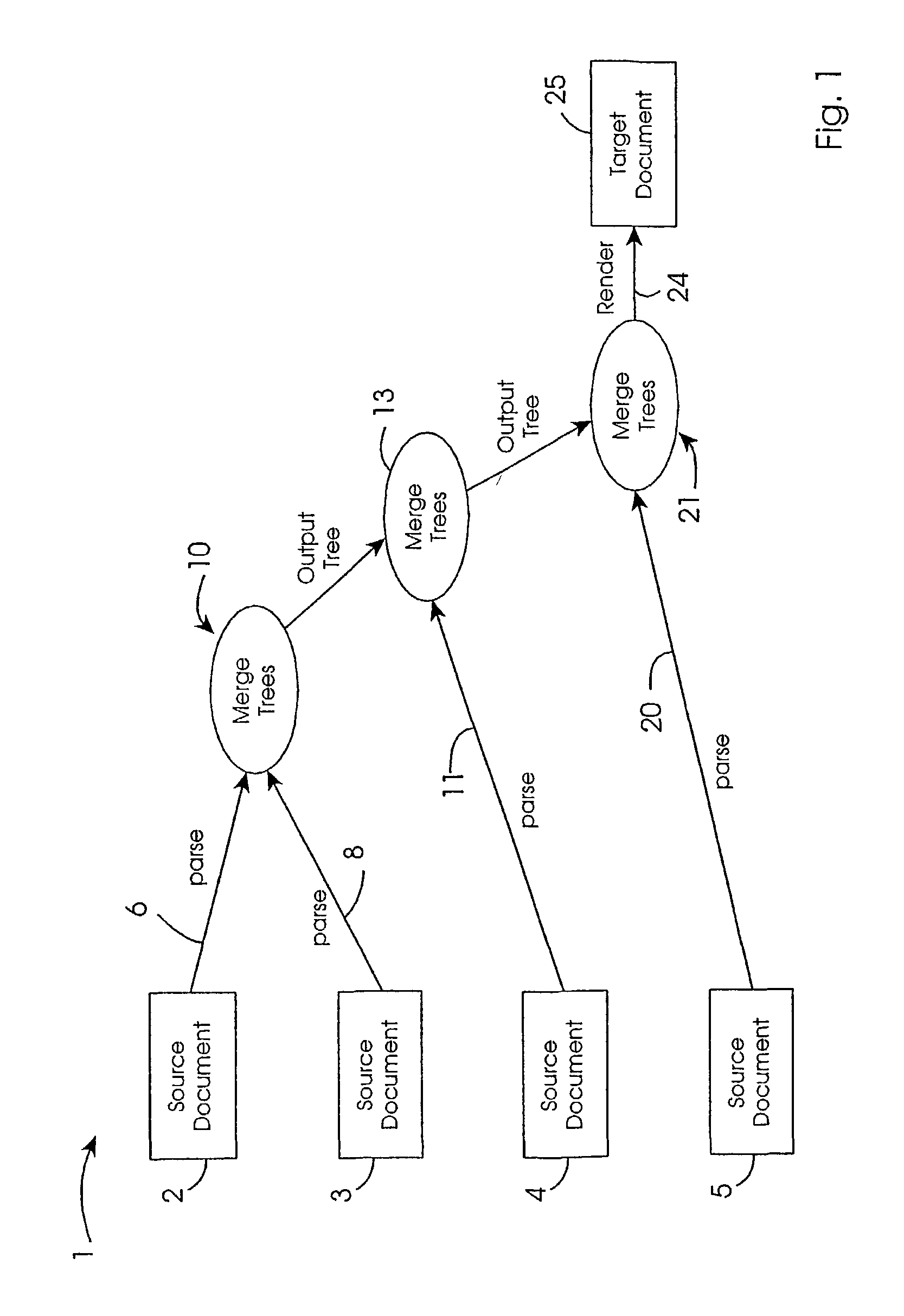
InactiveUS20030093755A1Change structureData processing applicationsDigital computer detailsDatabaseSource document
A target document (25) is generated by merging four source documents (2-5). There are three merge operations, an operation (10) for two source documents (2, 13), an operation (13) for an intermediate target document and a source document (4), and an operation (21) for a second intermediate target document and a final source document (5). In each merge operation one source document inherits from the other. An inheriting instruction is embedded within the inheriting document. Merging is performed by parsing a document (6, 8, 11, 20) into a hierarchical tree if it is not already in that form, and merging the trees. Matching nodes are identified and are combined or replaced according to a policy.
Owner:MEC MANAGEMENT LLC
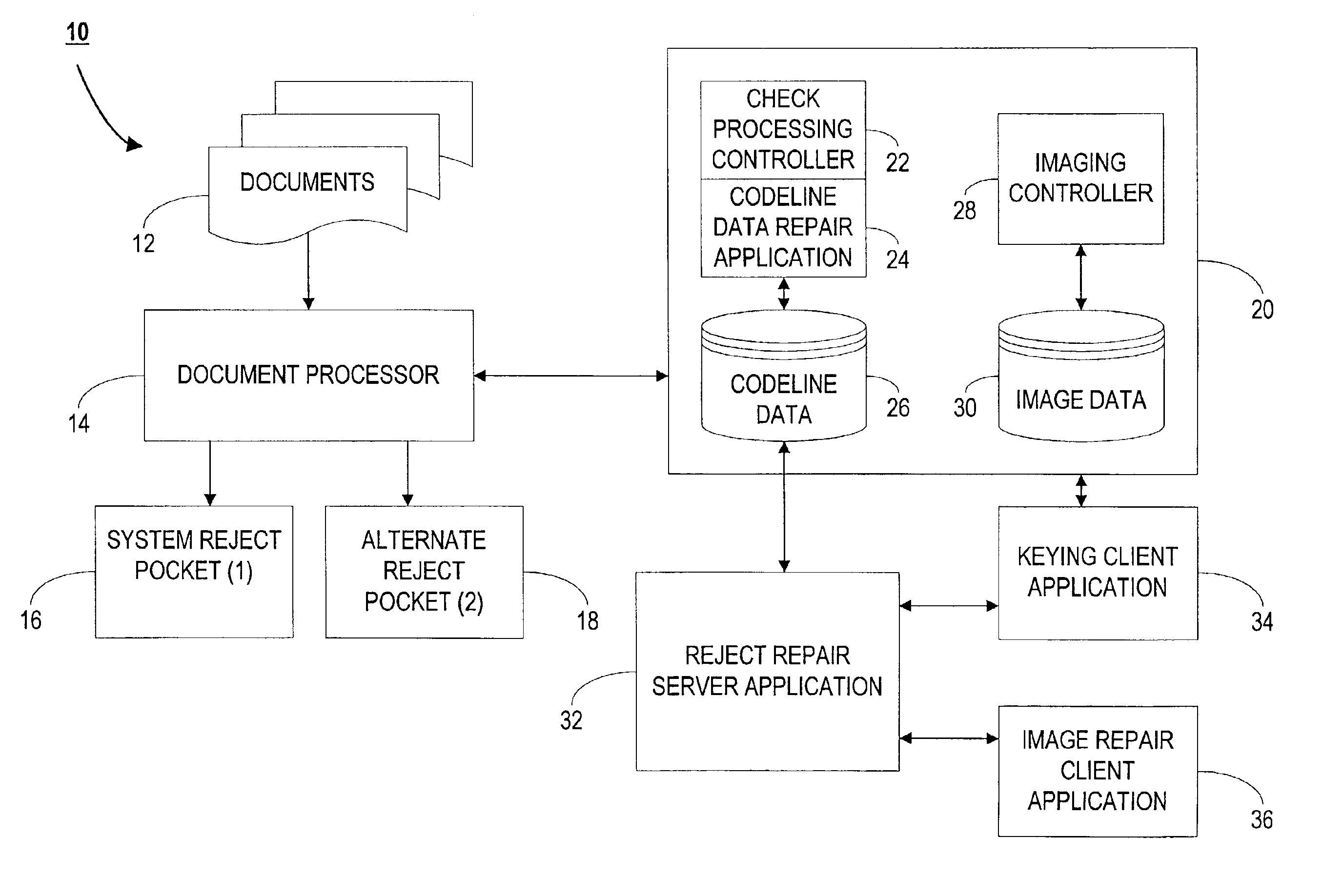
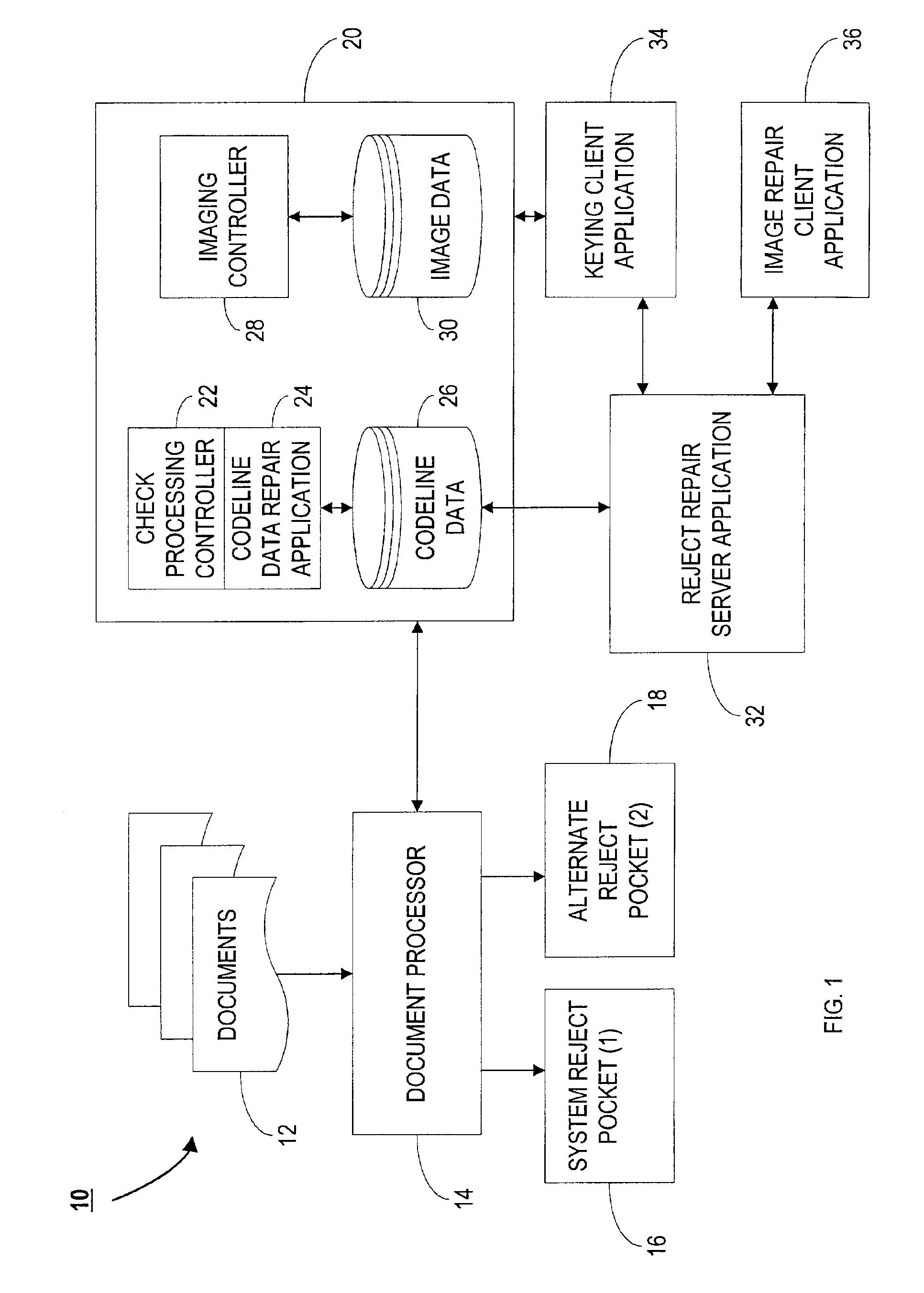
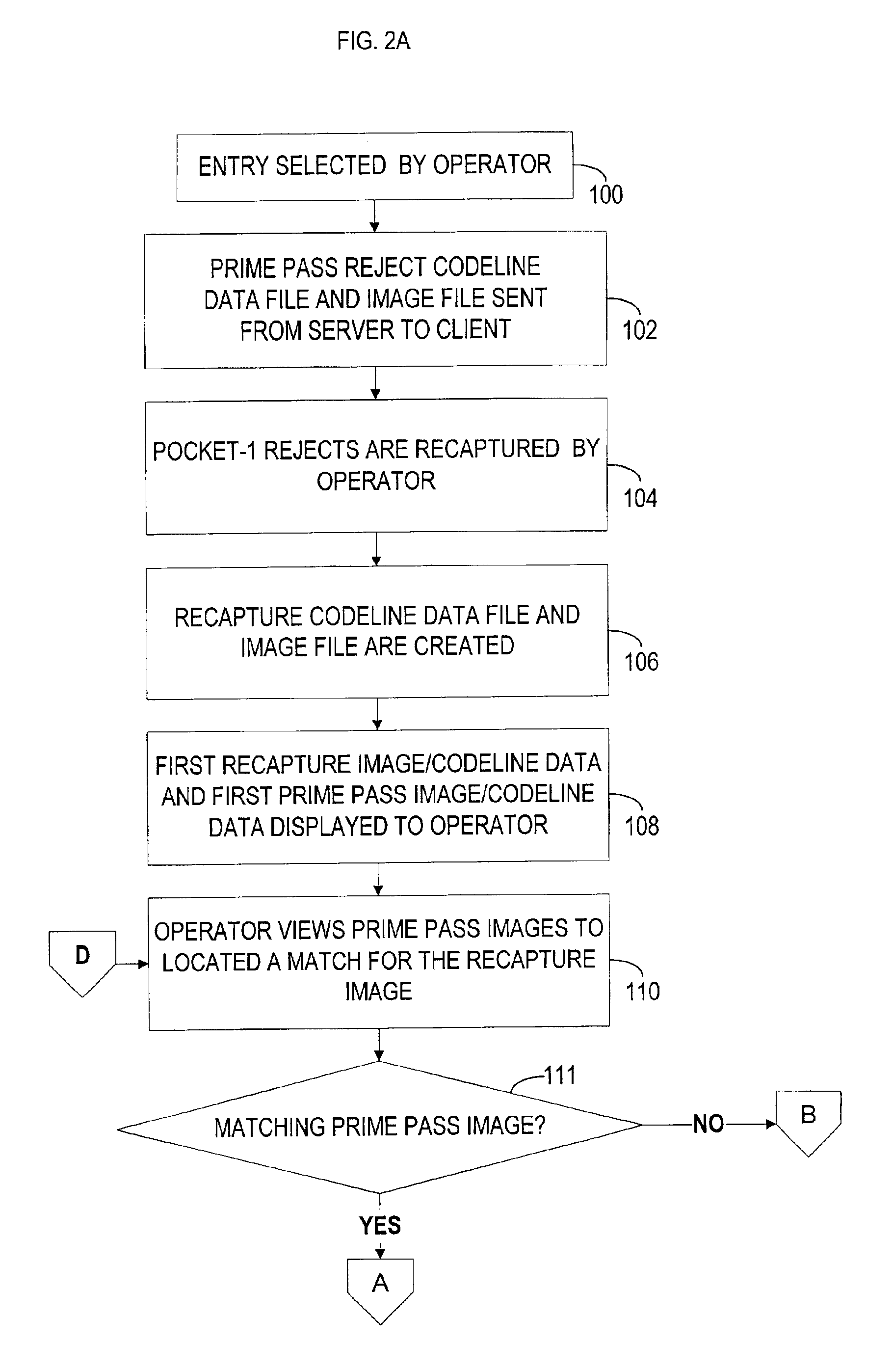
Image enabled reject repair for check processing capture
A method and apparatus for processing a plurality of financial documents, comprising, a document processor, wherein, for each financial document, the document processor captures data encoded on the financial document and an image of the financial document during a prime pass, and assigns a prime pass sequence number to each financial document. The apparatus includes a computer database in which the prime pass data and image is stored in association with the prime pass sequence number for the financial document. The document processor is adapted to determine whether the financial document should be rejected because the data and document image needs to be repaired or the data only needs to be repaired. If the data and image needs to be repaired, the document processor, or a desktop scanner / reader, recaptures the data and image, assigns a recapture sequence number to the financial document, and the recaptured data and image is stored in the computer database in association with the recapture sequence number. An image repair application is adapted to permit an operator to locate a prime pass image that matches the recaptured image, and to repair the document image by visually comparing the recaptured image with the prime pass image. The repaired document image is then stored in the computer database in association with the corresponding prime pass sequence number.
Owner:WELLS FARGO BANK NA
Systems for mobile image capture and processing of documents
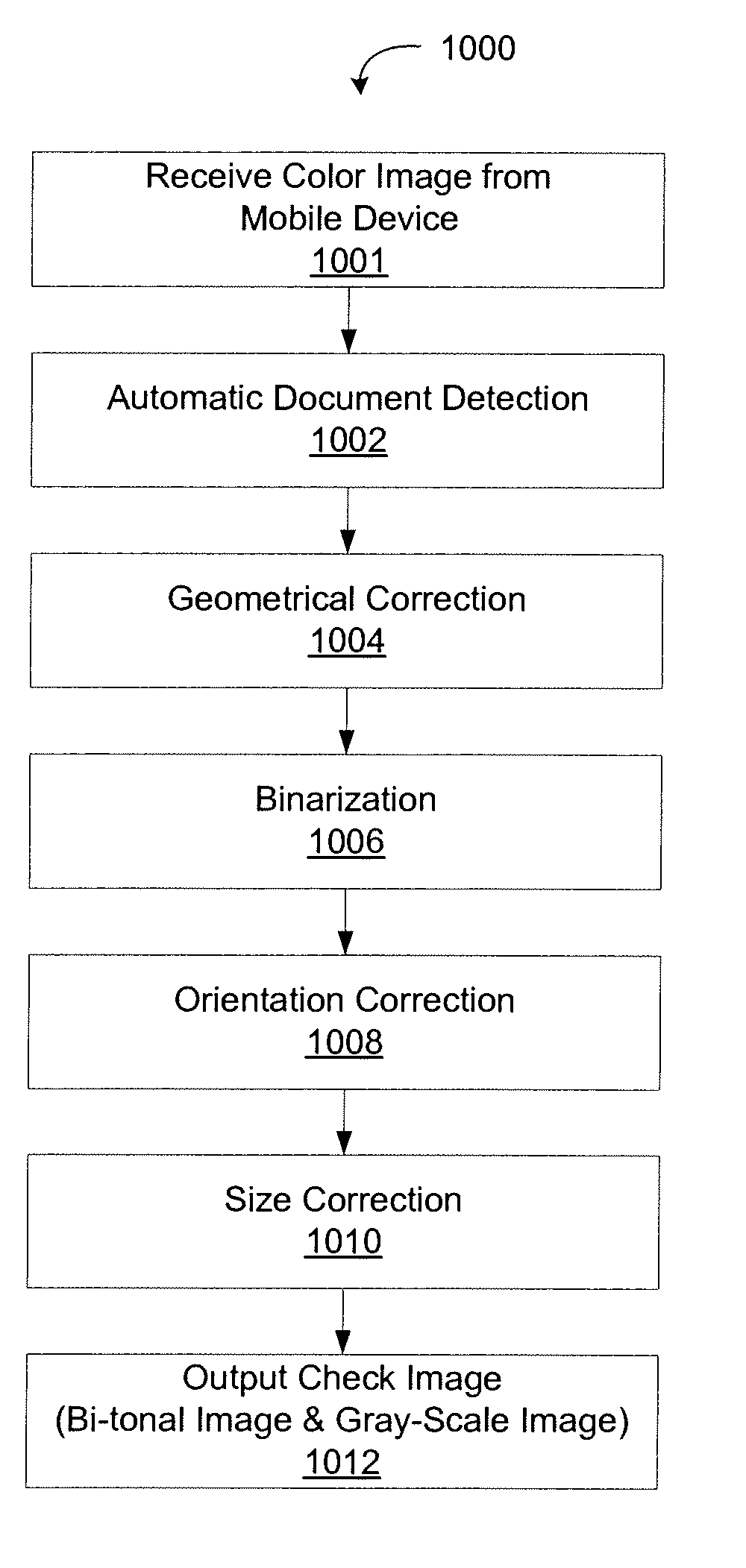
ActiveUS20090185241A1Optimized and enhanced imageEnhance the imageCharacter and pattern recognitionPayment architectureImage transferMobile device
The present invention relates to automated document processing and more particularly, to methods and systems for document image capture and processing using mobile devices. In accordance with various embodiments, methods and systems for document image capture on a mobile communication device are provided such that the image is optimized and enhanced for data extraction from the document as depicted. These methods and systems may comprise capturing an image of a document using a mobile communication device; transmitting the image to a server; and processing the image to create a bi-tonal image of the document for data extraction. Additionally, these methods and systems may comprise capturing a first image of a document using the mobile communication device; automatically detecting the document within the image; geometrically correcting the image; binarizing the image; correcting the orientation of the image; correcting the size of the image; and outputting the resulting image of the document.
Owner:MITEK SYST
System and method for searching and verifying documents in a document processing device
ActiveUS20050060055A1Paper-money testing devicesDigital data processing detailsDocument IdentifierBarcode
A method of processing barcoded tickets in a document processing device including receiving a stack of barcoded tickets in an input receptacle of a document processing device. Each barcoded ticket includes a document-identifier or ticket number that identifies the barcoded ticket. At least one specific document-identifier is inputted by the operator to search for a specific document in a stack of documents. Each of the documents are transported, one at a time, past a detector, which detects the document-identifier of each ticket. A determination is made whether a detected document-identifier matches the specific document-identifier requested by the operator, and if so, the ticket in question is directed to a pre-programmed or user-specified output receptacle.
Owner:CUMMINS-ALLISON CORP
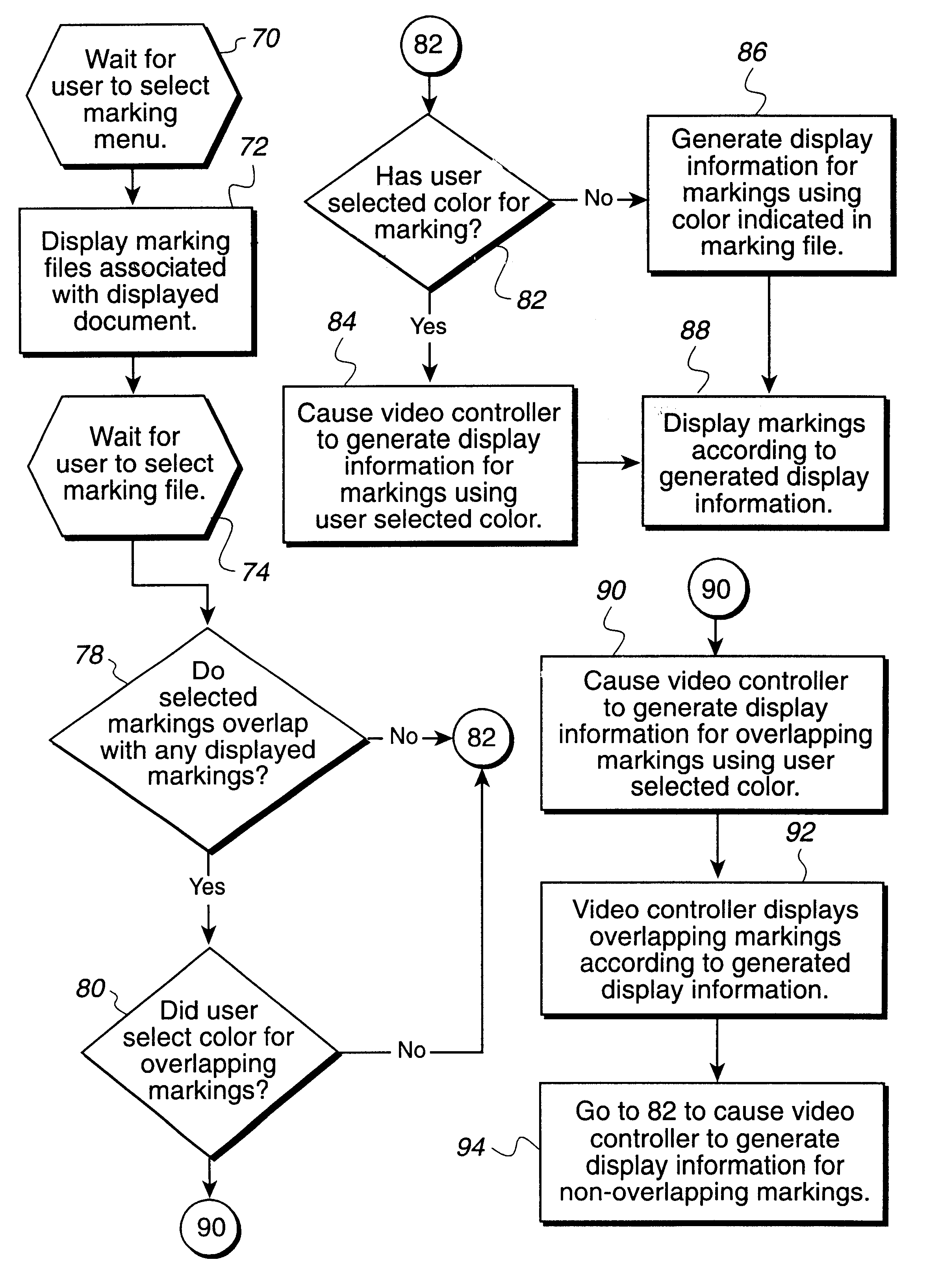
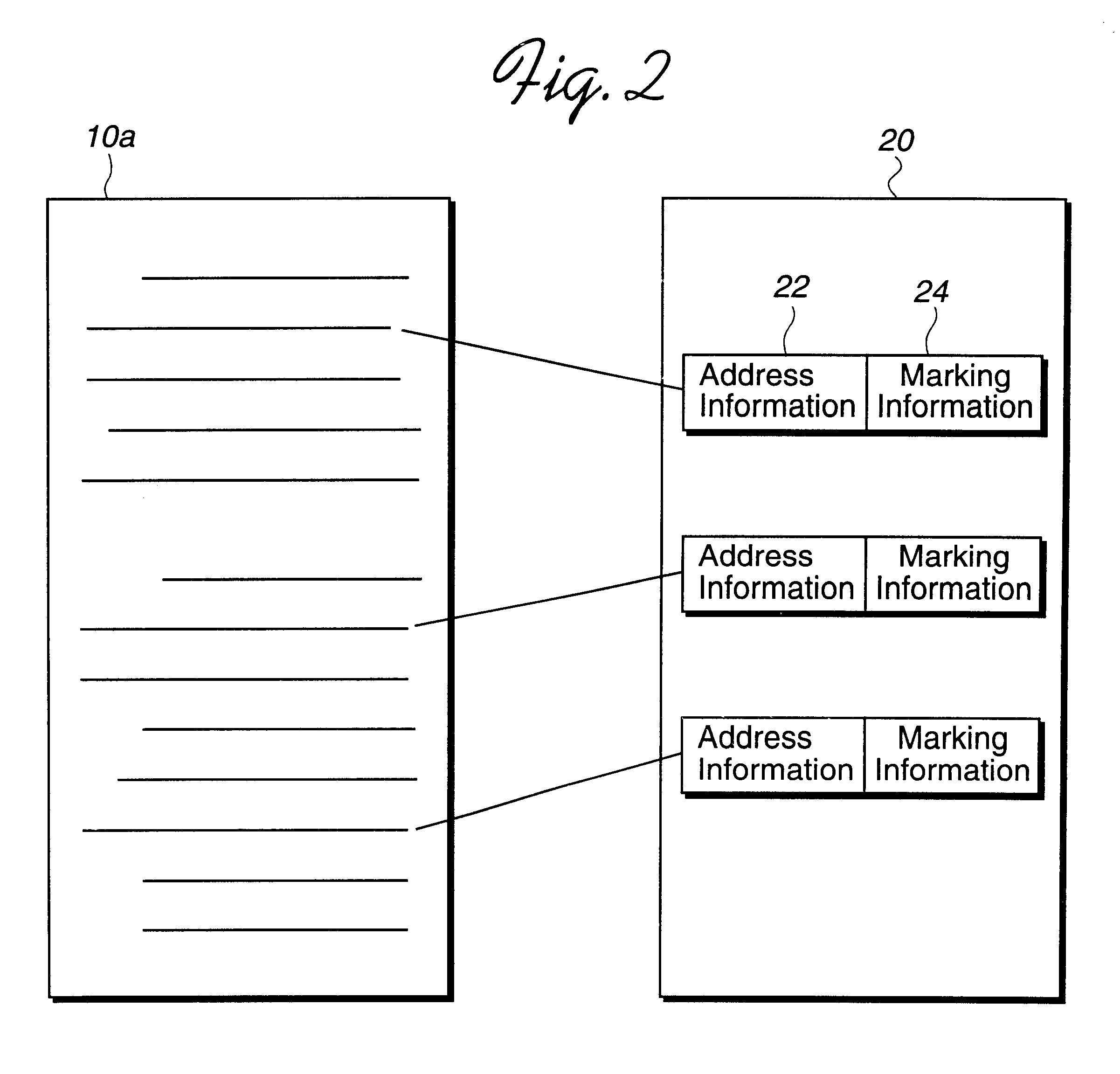
Method, system, and program for storing and retrieving markings for display to an electronic media file
InactiveUS6551357B1Digital computer detailsCathode-ray tube indicatorsGraphicsGraphical user interface
Disclosed is a method, system, and program for displaying markings to electronic media, such as text, images, video clips, audio clips, etc., in an electronic media file. A marking file includes markings and address information indicating locations of electronic media in the electronic media file to which the markings apply. The marking file is created by receiving marking input entered into a graphical user interface (GUI) window displaying the electronic media on a monitor attached to the computer. The marking file is then stored as a separate file from the electronic media file. The electronic media file and marking file are processed to display the markings indicated in the marking file superimposed on the electronic media from the electronic media file on the monitor.
Owner:IBM CORP
System and method for processing currency bills and documents bearing barcodes in a document processing device
A document processing device having an evaluation region disposed along a transport path between an input and output receptacle capable of processing both currency bills and barcoded media having at least two barcodes. One of the barcodes encodes a ticket number and another barcode encodes a payout amount associated with that ticket number. The evaluation region includes detectors for detecting predetermined characteristics of currency bills and a barcode reader for scanning the barcodes printed on the barcoded media. A controller coupled to the evaluation region controls the operation of the document processing device and receives input from and provides information to a user via a control unit In some embodiments, the document processing device may have any number of output receptacles, and the control unit allows the user to specify which output receptacle receives which type of document An optional coin sorter may be coupled to the document processing device to allow document and coin processing The document processing device may be coupled to a network to communicate information to devices linked to the network.
Owner:CUMMINS-ALLISON CORP
Selective data encryption using style sheet processing for decryption by a key recovery agent
InactiveUS6941459B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:PHONENICIA INNOVATIONS LLC SUBSIDIARY OF PENDRELL TECH
System and method for processing batches of documents
A method of processing documents by receiving at least a batch of documents and a separator card in an input receptacle of a document processing device. The separator card includes a conductive material disposed on one side, and a barcode indicative of the source of the batch of documents. The documents and separator card are transported via a transport mechanism past an evaluation unit and a field-effect sensor, respectively. The document processing device evaluates each document, determines whether the document meets or fails predetermined criteria, and detects the presence of the conductive material when a separator card is transported past the sensor. The source identification information from each separator card is entered into a memory of the document processing device after all the documents from the corresponding batch of documents have met the predetermined criteria. Feeder operation is paused between each batch long enough to verify that the previous batch closed successfully. Pausing feeder operation to address document anomalies before subsequent batches are processed promotes batch integrity and reduces operator confusion.
Owner:CUMMINS-ALLISON CORP
System and method for processing currency and identification cards in a document processing device
A document processing device having an evaluation region disposed along a transport path between an input and output receptacle capable of processing both currency bills and identification cards. An evaluation unit enables entry of source identification information before or after processing currency bills. Memory is adapted to store source identification information for multiple batches of currency. Multiple batches are placed in the processing device for multiple batch processing. The evaluation region includes detectors for detecting predetermined characteristics of currency bills and distinguishing identification cards from currency. During processing, the identification card, or other separator card, is sent to a predetermined output receptacle designated as a reject receptacle. Currency that is rejected is sent to the reject receptacle. Rejected currency is separated into batches by the identification cards sent to the reject receptacle during processing.
Owner:CUMMINS-ALLISON CORP
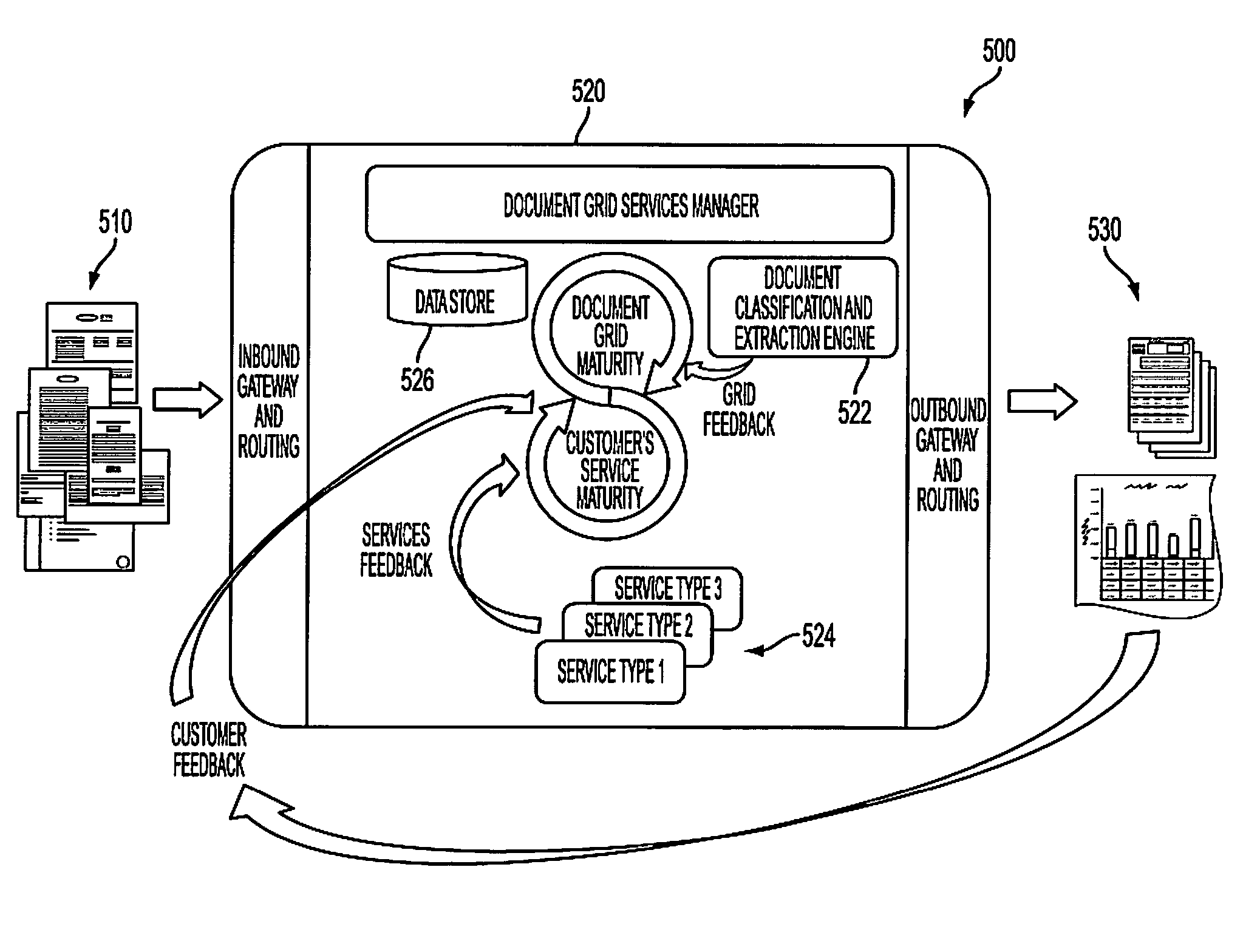
System and method of on-demand document processing
InactiveUS8473454B2Digital data processing detailsDigital computer detailsElectronic documentApplication software
A document processing method includes receiving, at a server with a network interface, electronic documents from a user. The server includes a software application adapted to recognize a class of electronic documents to which the electronic documents belong. The method also includes processing the electronic documents received from the user to extract data therefrom based on a recognition that the electronic documents belong to the class of electronic documents. The extracted data corresponds to a service being provided to the user. The method also includes automatically mapping the extracted data from the processed electronic documents to a data repository on the server. The data repository is accessible by the user through the network interface. The method also includes electronically generating output data based on the mapped data from the data repository to the user. The output data corresponds to the service being provided to the user.
Owner:XEROX CORP
Document processing system using primary and secondary pictorial image comparison
InactiveUS20050169511A1Precise processingManner is significantPaper-money testing devicesCharacter and pattern recognitionComputer graphics (images)Paper document
A document identification system having an input and output receptacle, a transport path, and an image scanner. Primary visible pictorial images and secondary invisible pictorial images are captured by the image scanner. A processor compares the primary and secondary captured pictorial images with master primary and secondary pictorial images to determine the identity of the document, such as denomination or authentication.
Owner:CUMMINS-ALLISON CORP
Image exchange without full micr qualification
InactiveUS20060186194A1Improving image exchange processAdditional exchangeComplete banking machinesFinanceChequePaper document
A system and related methods of correcting errors during check or financial document processing by a bank of first deposit or other entity receiving a paper check or financial document, or by a second bank on whose accounts the checks were written. These corrections can be performed by the computer system of the bank of first deposit, the computer system of the second bank, or both. MICR data may be sent in electronic format from the bank of first deposit or other entity without qualification.
Owner:DIGICOR
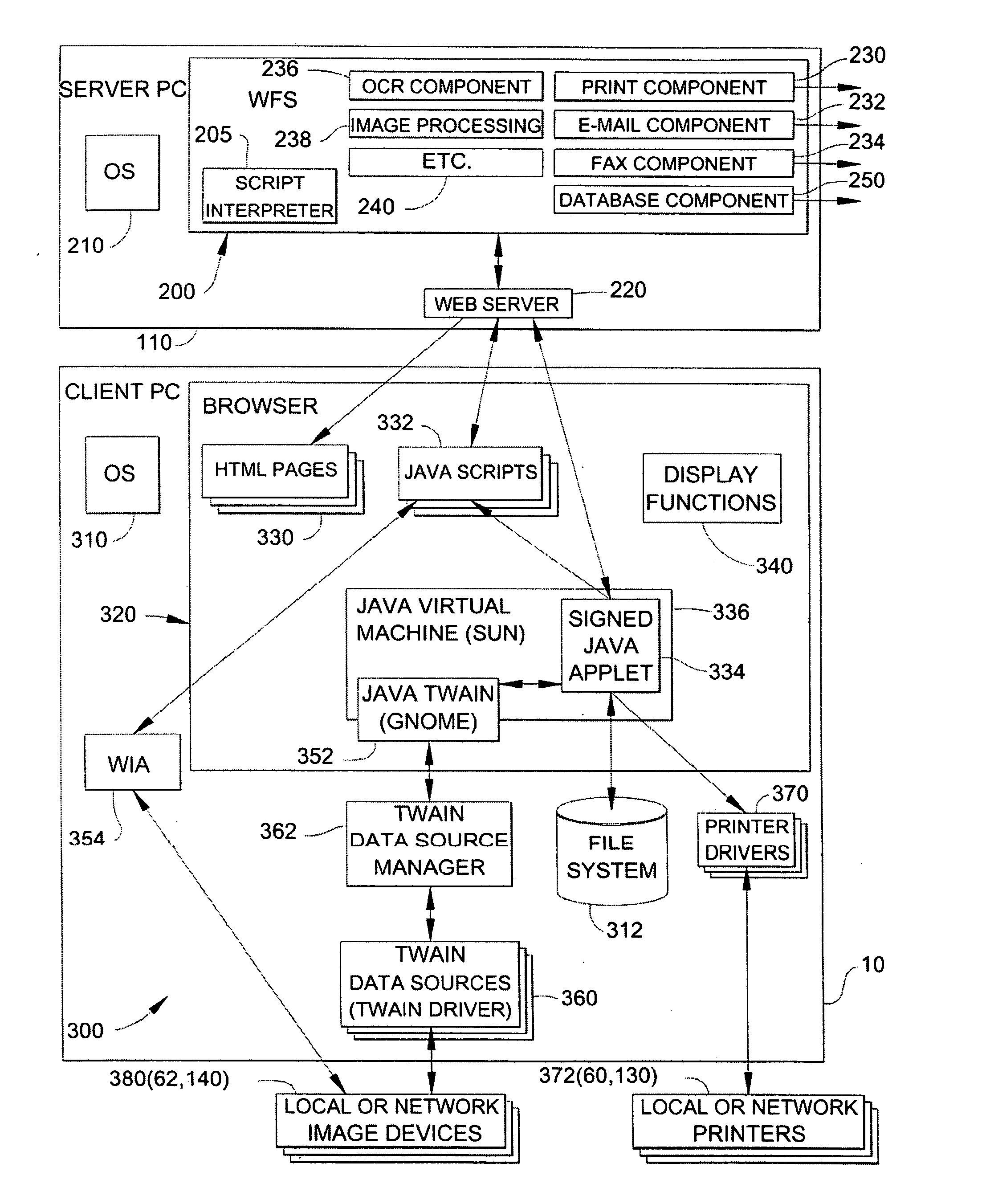
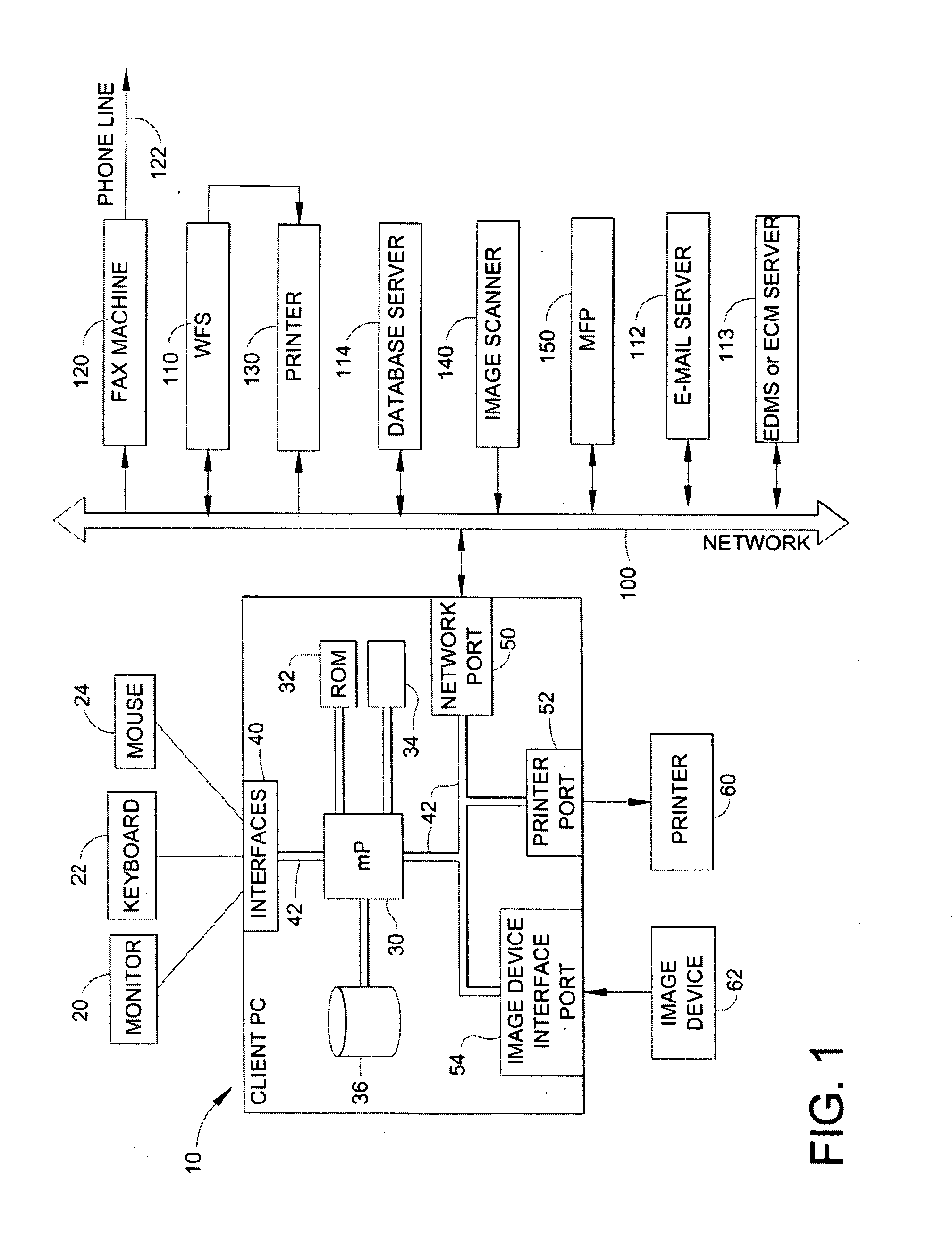
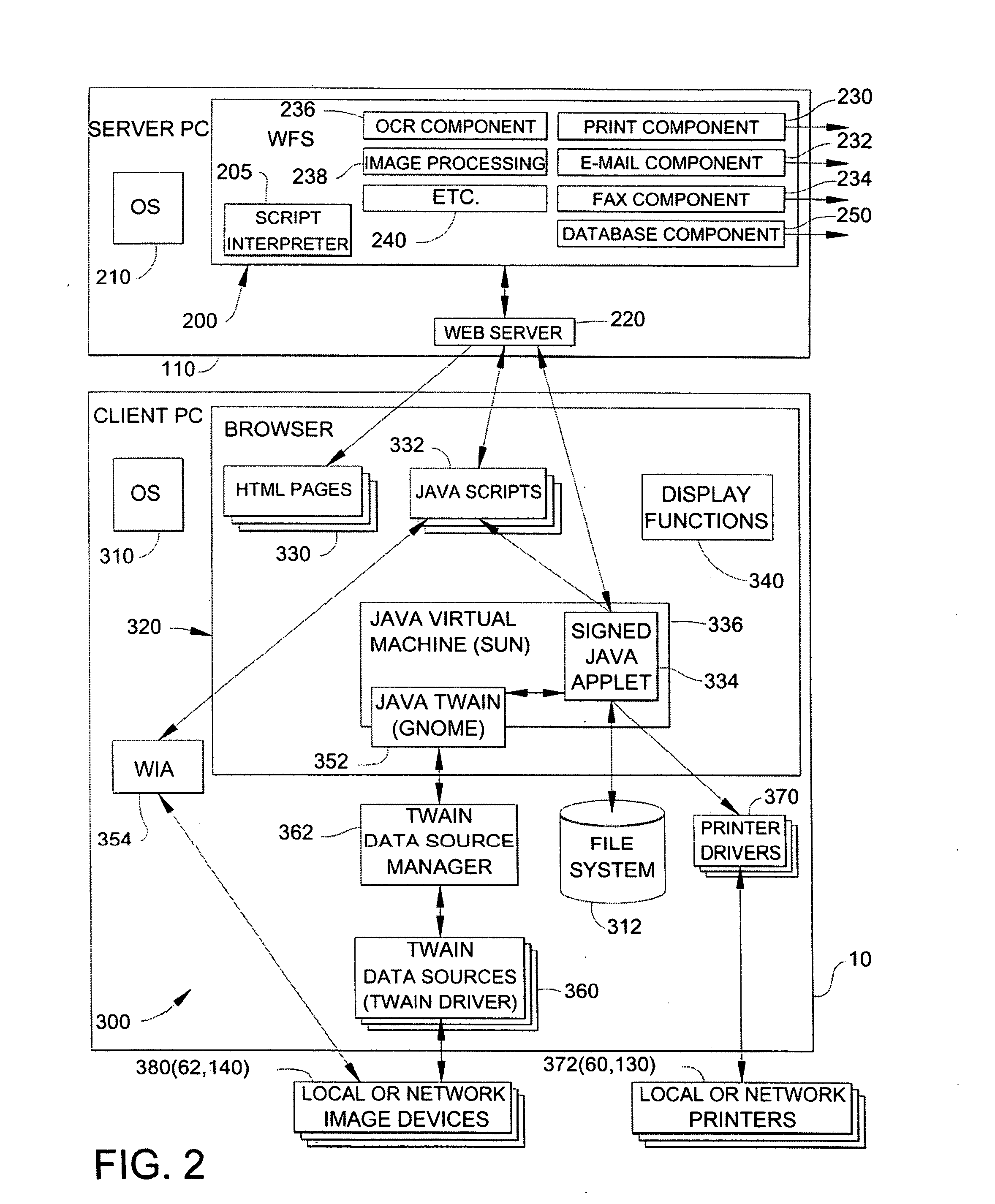
Method and apparatus for providing a work flow web application that receives image data via a web browser and exports the image data to a document processing server
InactiveUS20060085516A1Multiple digital computer combinationsOffice automationApplication softwareUniform resource locator
An improved image processing system is provided which receives image data at a computer and transfers that image data to a work flow server for image processing and document distribution. The system uses a work flow web application computer program that receives image data from a scanner, transfers that image data via a native interface or a driver on a client computer to a browser on the client computer, and then sends the data to a network document distribution server which is addressed from the client computer using URL's.
Owner:LEXMARK INT INC
Methods for mobile image capture and processing of checks
ActiveUS20090185738A1Optimized and enhanced imageEnhance the imageCharacter and pattern recognitionPayment architectureImage transferMobile device
The present invention relates to automated document processing and more particularly, to methods and systems for document image capture and processing using mobile devices. In accordance with various embodiments, methods and systems for document image capture on a mobile communication device are provided such that the image is optimized and enhanced for data extraction from the document as depicted. These methods and systems may comprise capturing an image of a document using a mobile communication device; transmitting the image to a server; and processing the image to create a bi-tonal image of the document for data extraction. Additionally, these methods and systems may comprise capturing a first image of a document using the mobile communication device; automatically detecting the document within the image; geometrically correcting the image; binarizing the image; correcting the orientation of the image; correcting the size of the image; and outputting the resulting image of the document.
Owner:MITEK SYST
System and method for processing currency and identification cards in a document processing device
A document processing device having an evaluation region disposed along a transport path between an input and output receptacle capable of processing both currency bills and identification cards. An evaluation unit enables entry of source identification information before or after processing currency bills. Memory is adapted to store source identification information for multiple batches of currency. Multiple batches are placed in the processing, device for multiple batch processing. The evaluation region includes detectors for detecting predetermined characteristics of currency bills and distinguishing identification cards from currency. During processing, the identification card, or other separator card, is sent to a predetermined output receptacle designated as a reject receptacle. Currency that is rejected is sent to the reject receptacle. Rejected currency is separated into batches by the identification cards sent to the reject receptacle during processing.
Owner:CUMMINS-ALLISON CORP
System and method for searching and verifying documents in a document processing device
ActiveUS7103438B2Paper-money testing devicesDigital data processing detailsDocument IdentifierBarcode
A method of processing barcoded tickets in a document processing device including receiving a stack of barcoded tickets in an input receptacle of a document processing device. Each barcoded ticket includes a document-identifier or ticket number that identifies the barcoded ticket. At least one specific document-identifier is inputted by the operator to search for a specific document in a stack of documents. Each of the documents are transported, one at a time, past a detector, which detects the document-identifier of each ticket. A determination is made whether a detected document-identifier matches the specific document-identifier requested by the operator, and if so, the ticket in question is directed to a pre-programmed or user-specified output receptacle.
Owner:CUMMINS-ALLISON CORP
System and method for processing currency bills and documents bearing barcodes in a document processing device
A document processing device having an evaluation region disposed along a transport path between an input and output receptacle capable of processing both currency bills and substitute currency media having at least one indicia. The evaluation region includes at least one of a currency detector, a media detector, and an imager for detecting predetermined characteristics of currency bills and substitute currency media. A controller coupled to the evaluation region controls the operation of the document processing device and receives input from and provides information to a user via a control unit. In some embodiments, the document processing device may have any number of output receptacles, and the control unit allows the user to specify which output receptacle receives which type of document. An optional coin sorter may be coupled to the document processing device to allow document and coin processing. The document processing device may be coupled to a network to communicate information to devices linked to the network.
Owner:CUMMINS-ALLISON CORP
Electronic document processing apparatus
InactiveUS20050055212A1Easy retrievalShorten the lengthSound input/outputSpecial data processing applicationsElectronic documentPaper document
On receipt of a tagged file, as a tagged document, at step S1, a document processing apparatus at step S2 derives the attribute information for read-out from tags of the tagged file and embeds the attribute information to generate a speech read-out file. Then, at step S3, the document processing apparatus performs processing suited for a speech synthesis engine, using the generated speech read-out file. At step S4, the document processing apparatus performs processing depending on the operation by the user through a user interface.
Owner:SONY CORP
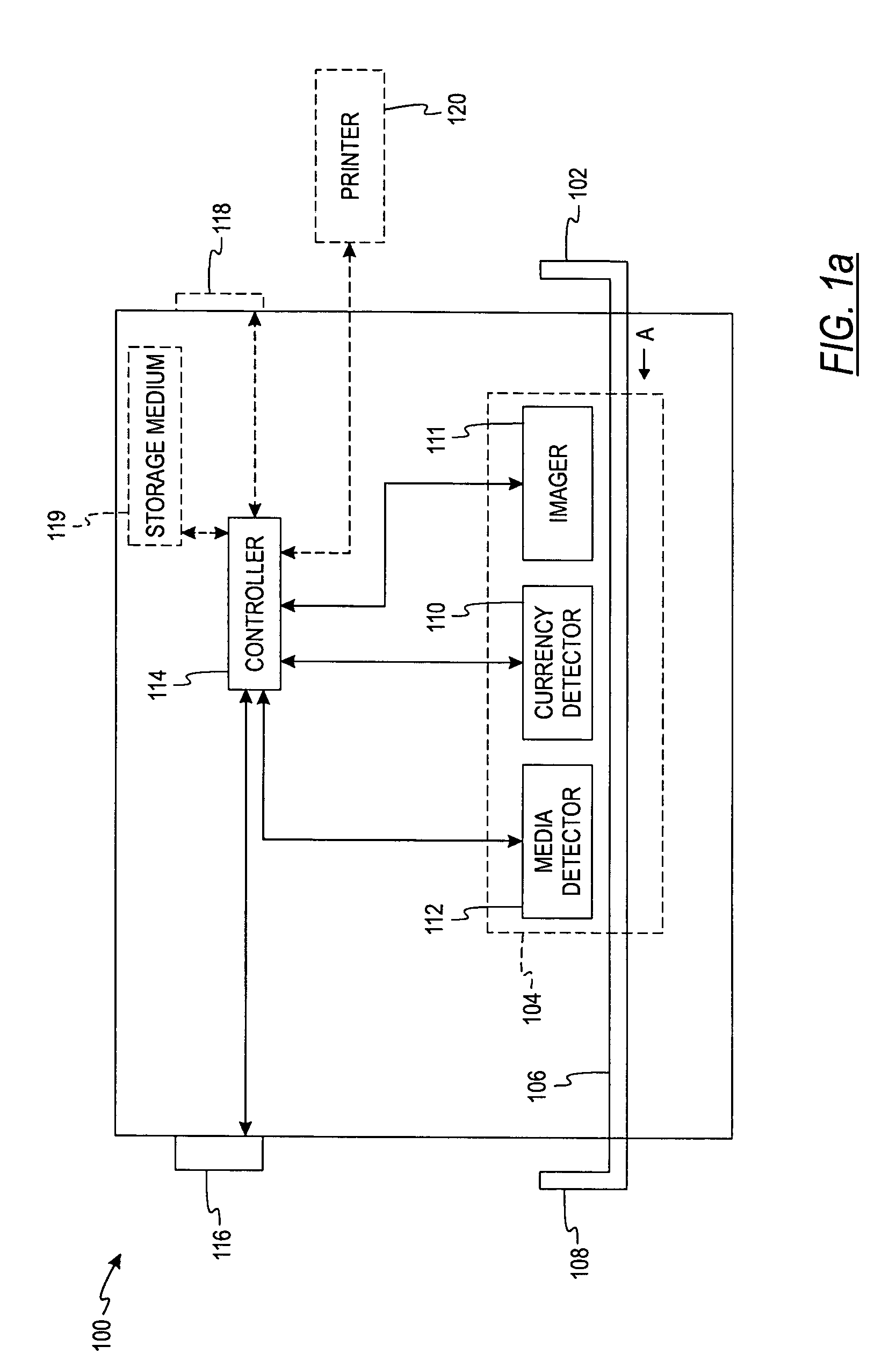
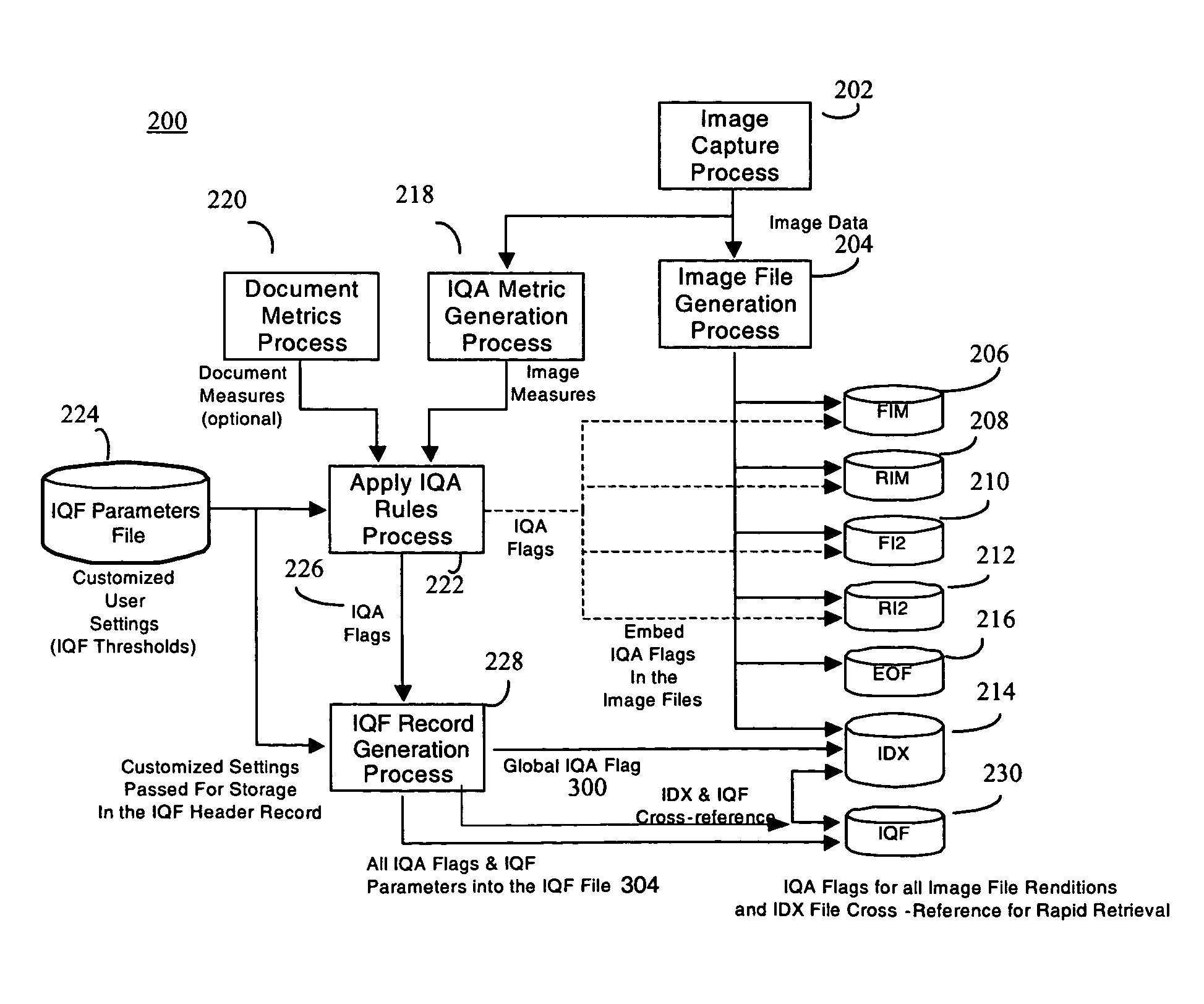
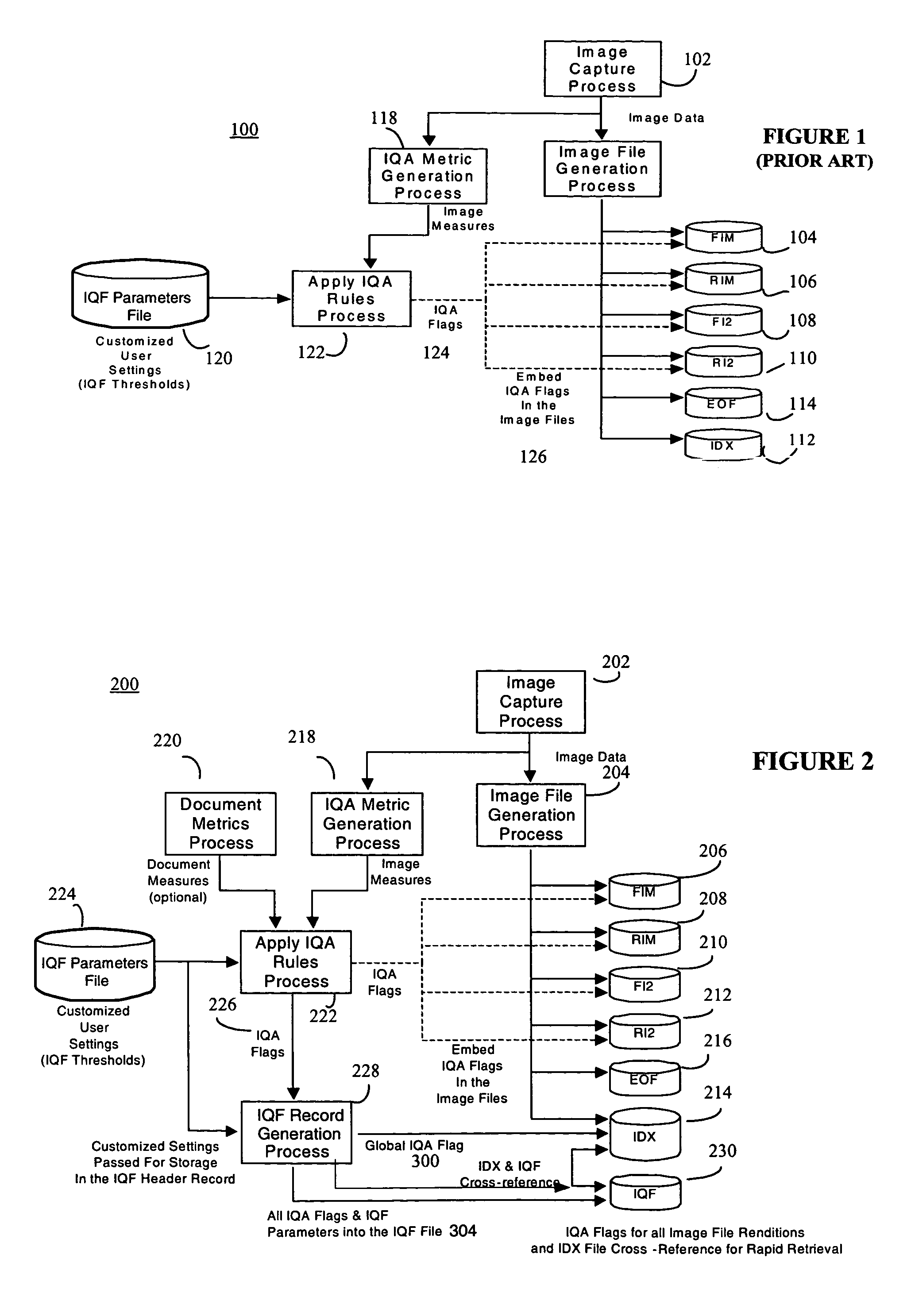
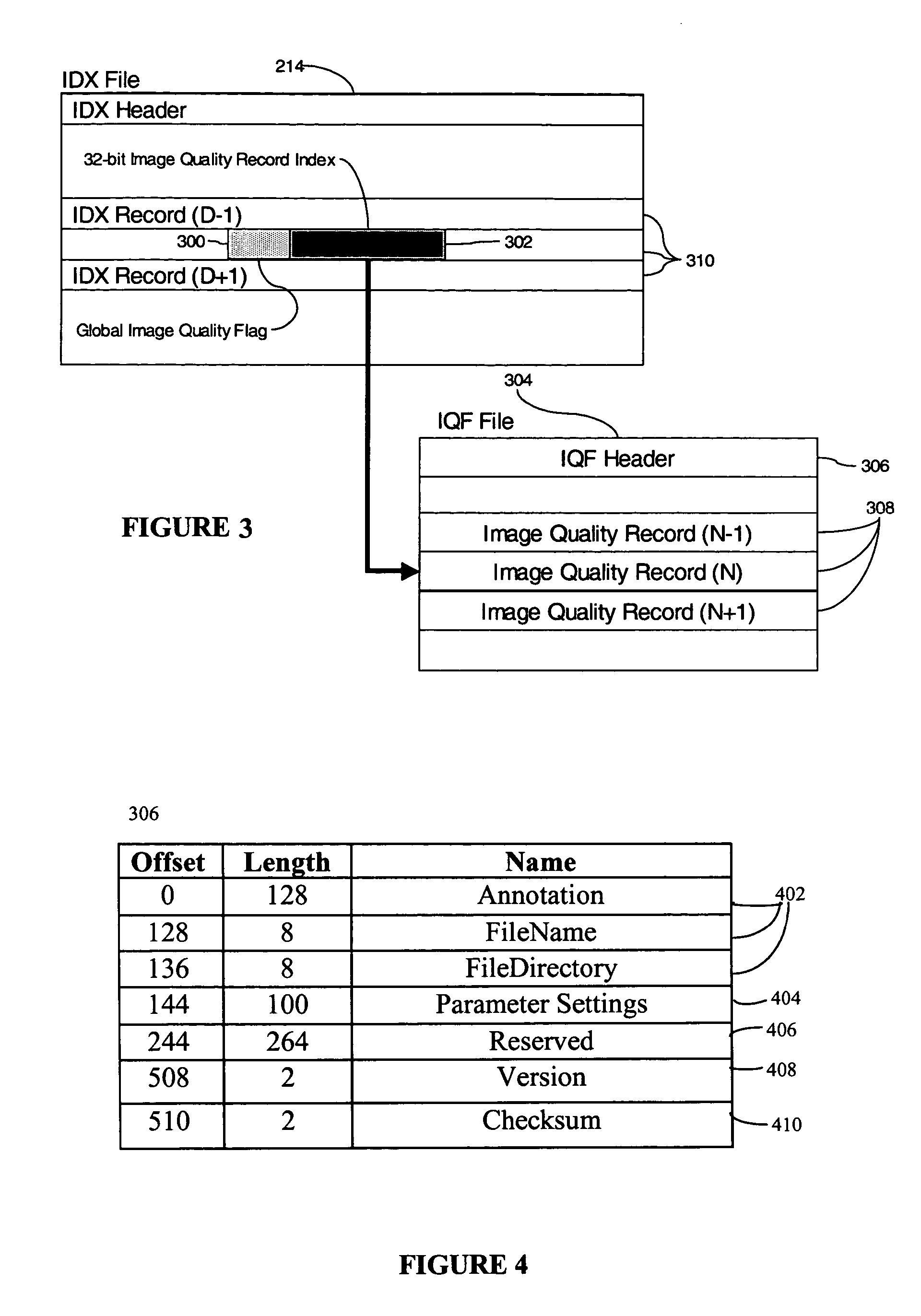
Document processing system with improved image quality assurance
ActiveUS7433098B2Improve image qualityEasy to identifyComplete banking machinesImage enhancementQuality assuranceComputer graphics (images)
A document processing system comprising an image capture subsystem for capturing selected image metrics and at least one image rendition from a plurality of documents and for determining if at least one of the selected image metrics for any of the at least one image rendition does not successfully compare against preselected image quality metric threshold values. An image quality flag is generated for any of the at least one image rendition if it does not successfully compare, and a record entry for each imaged document having at least one flagged image rendition is created in an image quality flag file. An image index file for individually accessing the image renditions is modified to include a reference to the corresponding image quality flag file record entry The document processing system may optionally compare selected document metrics against preselected document metrics in a similar manner. Image defects in the plurality of documents can be identified by examining the record entries in the image quality flag file.
Owner:DIGITAL CHECK CORP
Systems and methods for generating visual representations of graphical data and digital document processing
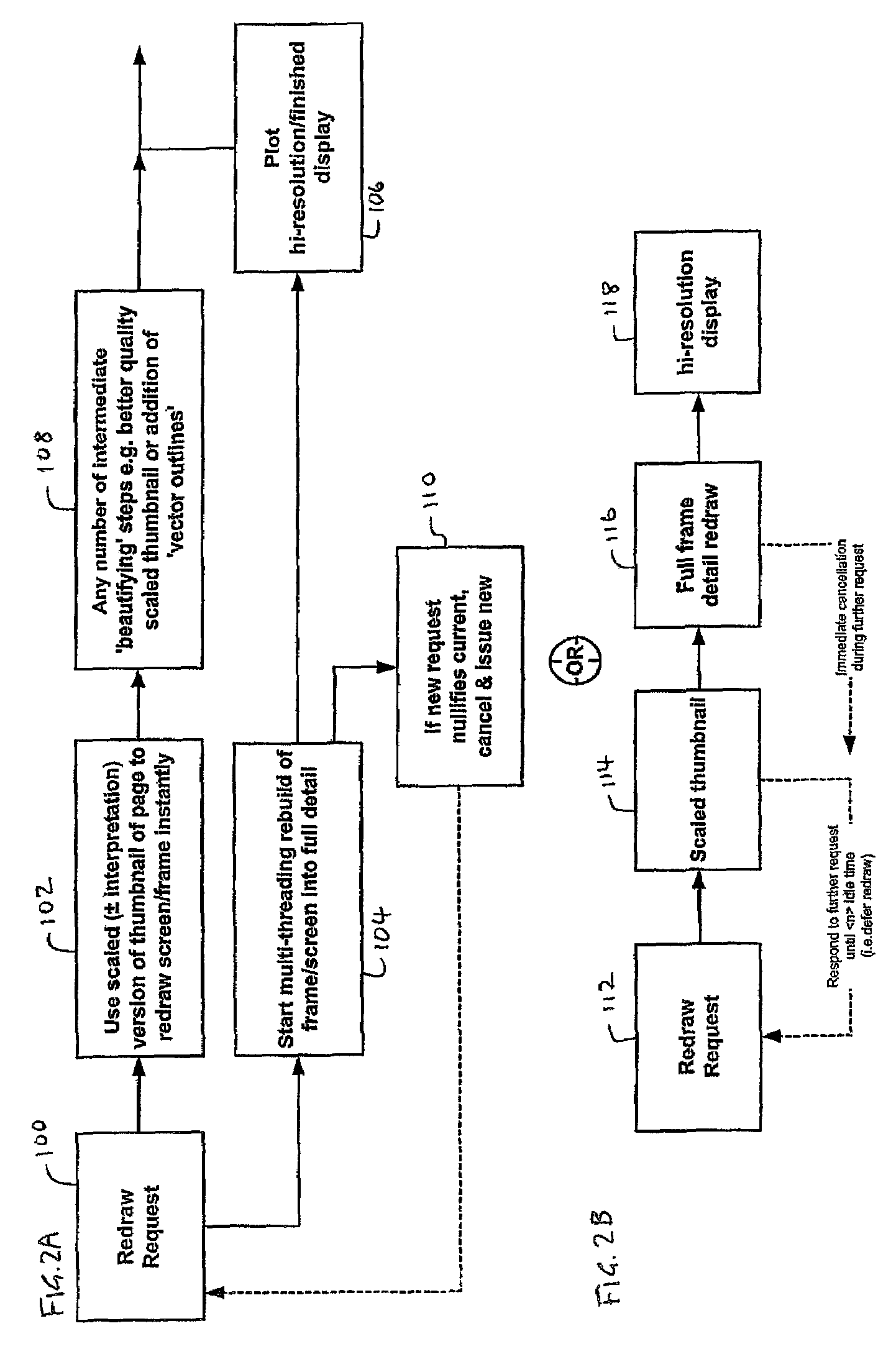
InactiveUS7009626B2Mitigate aforesaid disadvantageDigital data processing detailsCathode-ray tube indicatorsGraphicsDocumentation
Systems and methods for generating visual representations of graphical data and digital document processing, including:A method of redrawing a visual display of graphical data whereby a current display is replaced by an updated display, comprising, in response to a redraw request, immediately replacing the current display with a first approximate representation of the updated display, generating a final updated display, and replacing the approximate representation with the final updated display.A method of generating variable visual representations of graphical data, comprising dividing said graphical data into a plurality of bitmap tiles of fixed, predetermined size, storing said tiles in an indexed array and assembling a required visual representation of said graphical data from a selected set of said tiles.A method of processing a digital document, said document comprising a plurality of graphical objects arranged on at least one page, comprising dividing said document into a plurality of zones and, for each zone, generating a list of objects contained within and overlapping said zone.Digital document processing systems adapted to implement the methods.
Owner:SAMSUNG ELECTRONICS CO LTD
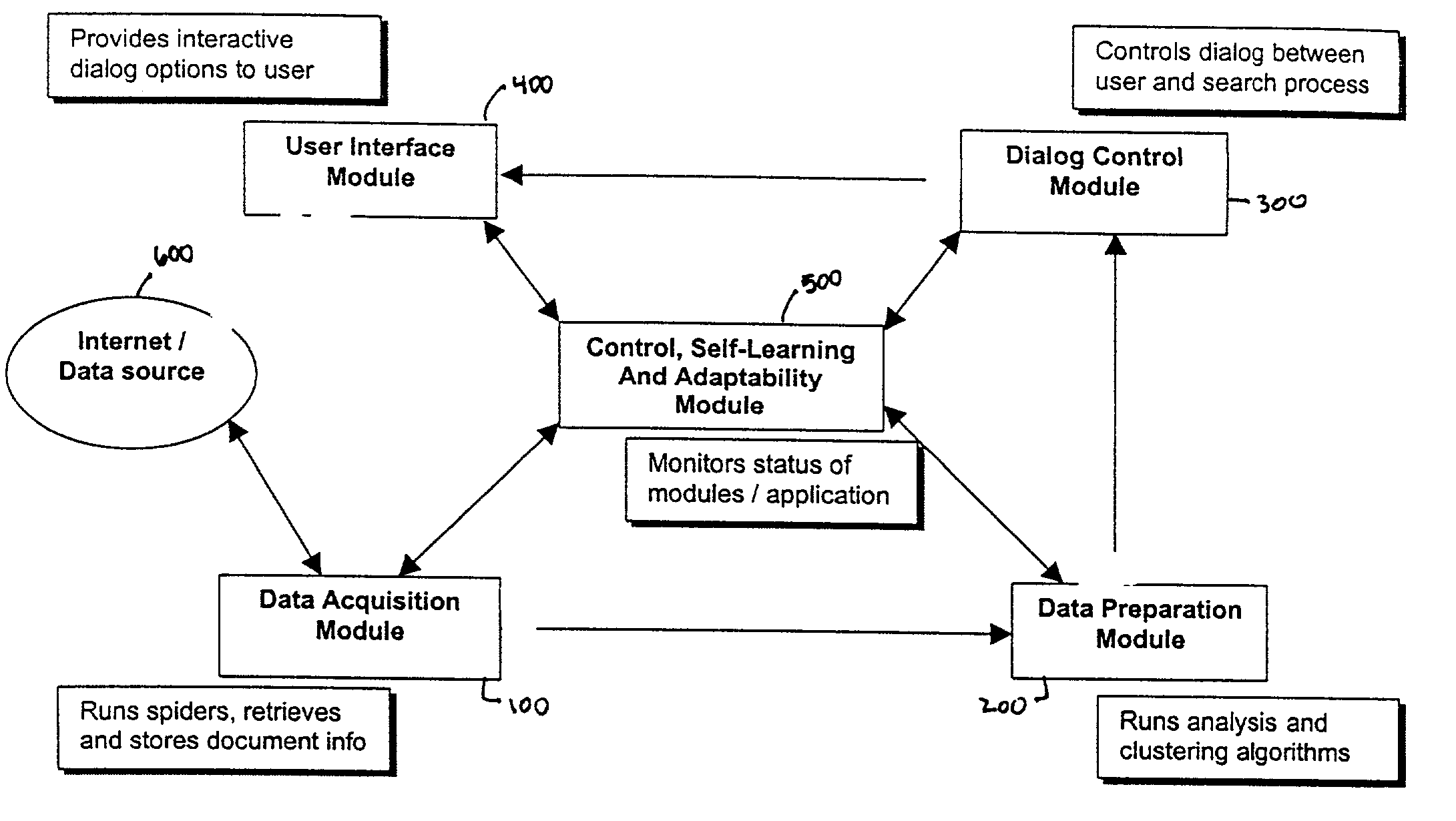
Agent architecture employed within an integrated message, document and communication system
InactiveUS20050060638A1Multiplex communicationMultiple digital computer combinationsCommunications systemAgent architecture
A system is described for managing messages, communications and / or documents comprising: a plurality of task agents, each task agent to perform one or more specified message processing actions, document processing actions, and / or communications processing actions on different types of messages, documents and / or communication channels, respectively; and one or more manager agents to coordinate the actions of the plurality of task agents responsive to a plurality of message and / or document processing rules.
Owner:CATALYSTWEB
Document processing system using full image scanning
Owner:CUMMINS-ALLISON CORP
Systems for mobile image capture and processing of checks
ActiveUS20090185737A1Optimized and enhanced imageEnhance the imageCharacter and pattern recognitionPayment architectureDocumentationMobile device
The present invention relates to automated document processing and more particularly, to methods and systems for document image capture and processing using mobile devices. In accordance with various embodiments, methods and systems for document image capture on a mobile communication device are provided such that the image is optimized and enhanced for data extraction from the document as depicted. These methods and systems may comprise capturing an image of a document using a mobile communication device; submitting the image to a server; and processing the image to create a bi-tonal image of the document for data extraction. Additionally, these methods and systems may comprise capturing a first image of a document using the mobile communication device; automatically detecting the document within the image; geometrically correcting the image; binarizing the image; correcting the orientation of the image; correcting the size of the image; and outputting the resulting image of the document.
Owner:MITEK SYST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com