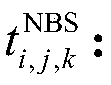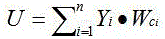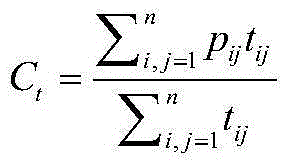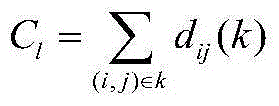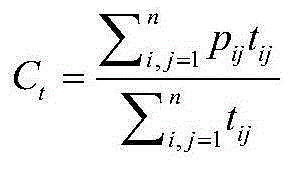Patents
Literature
189 results about "Computational intelligence" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The expression computational intelligence (CI) usually refers to the ability of a computer to learn a specific task from data or experimental observation. Even though it is commonly considered a synonym of soft computing, there is still no commonly accepted definition of computational intelligence.
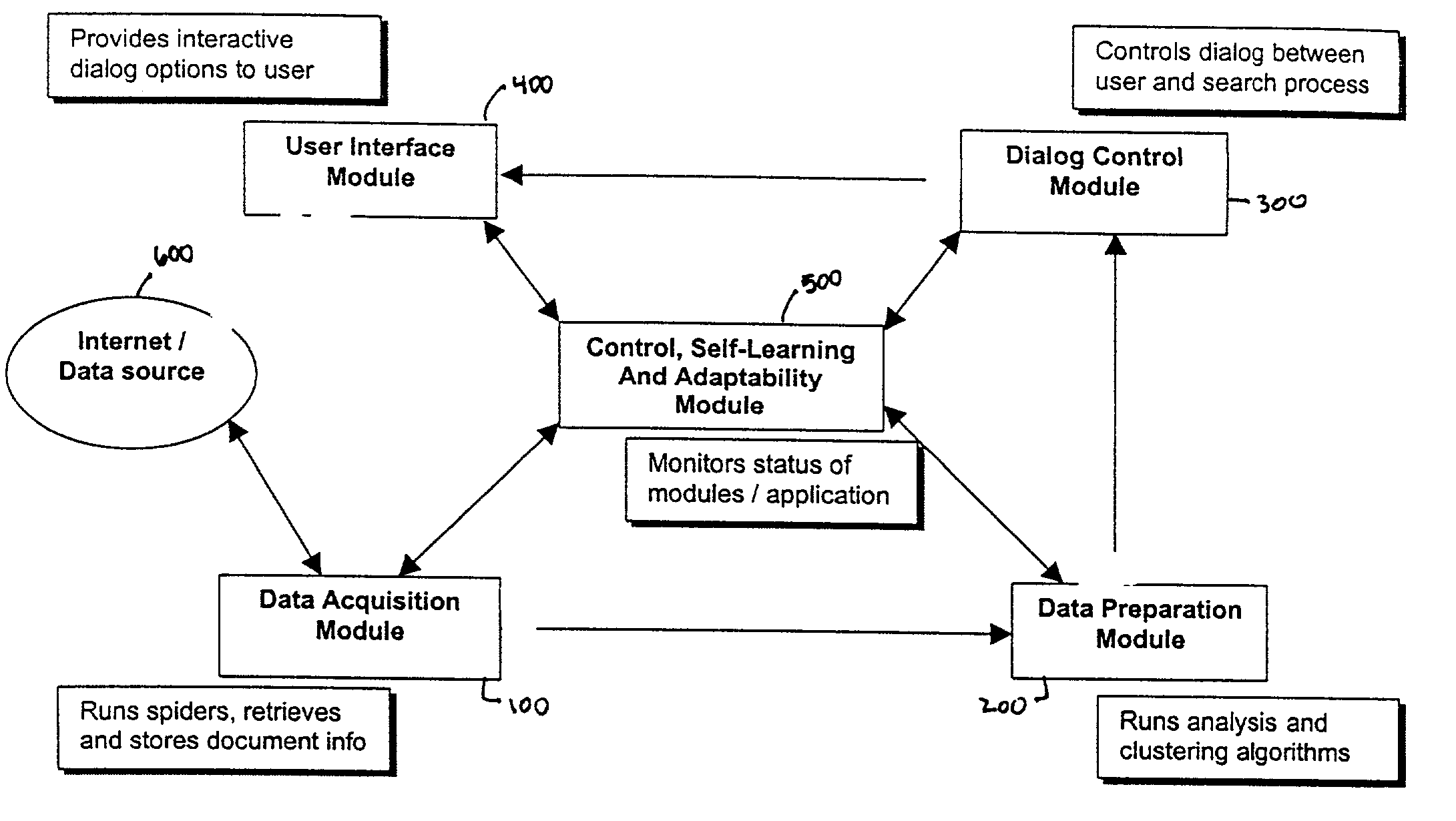
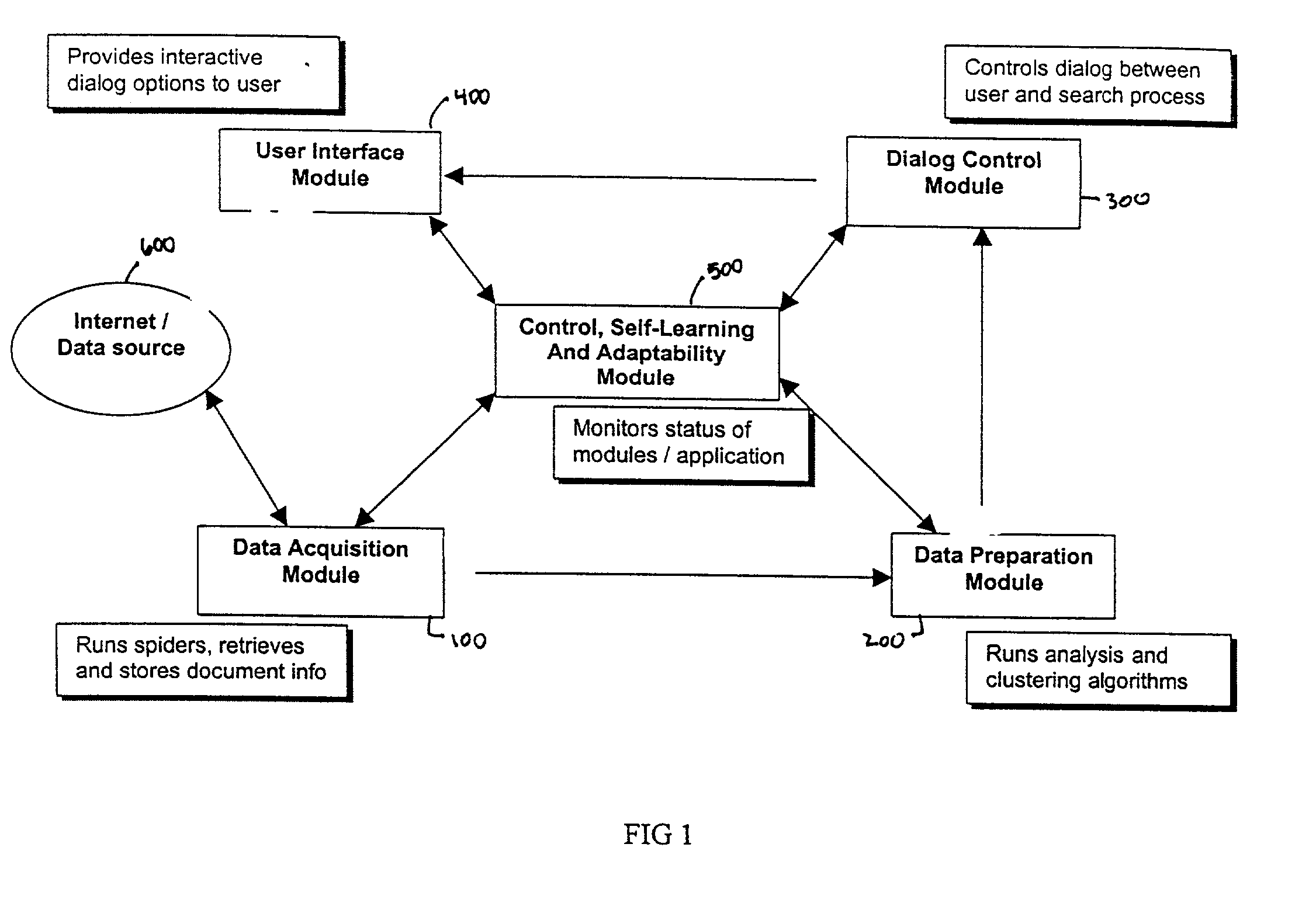
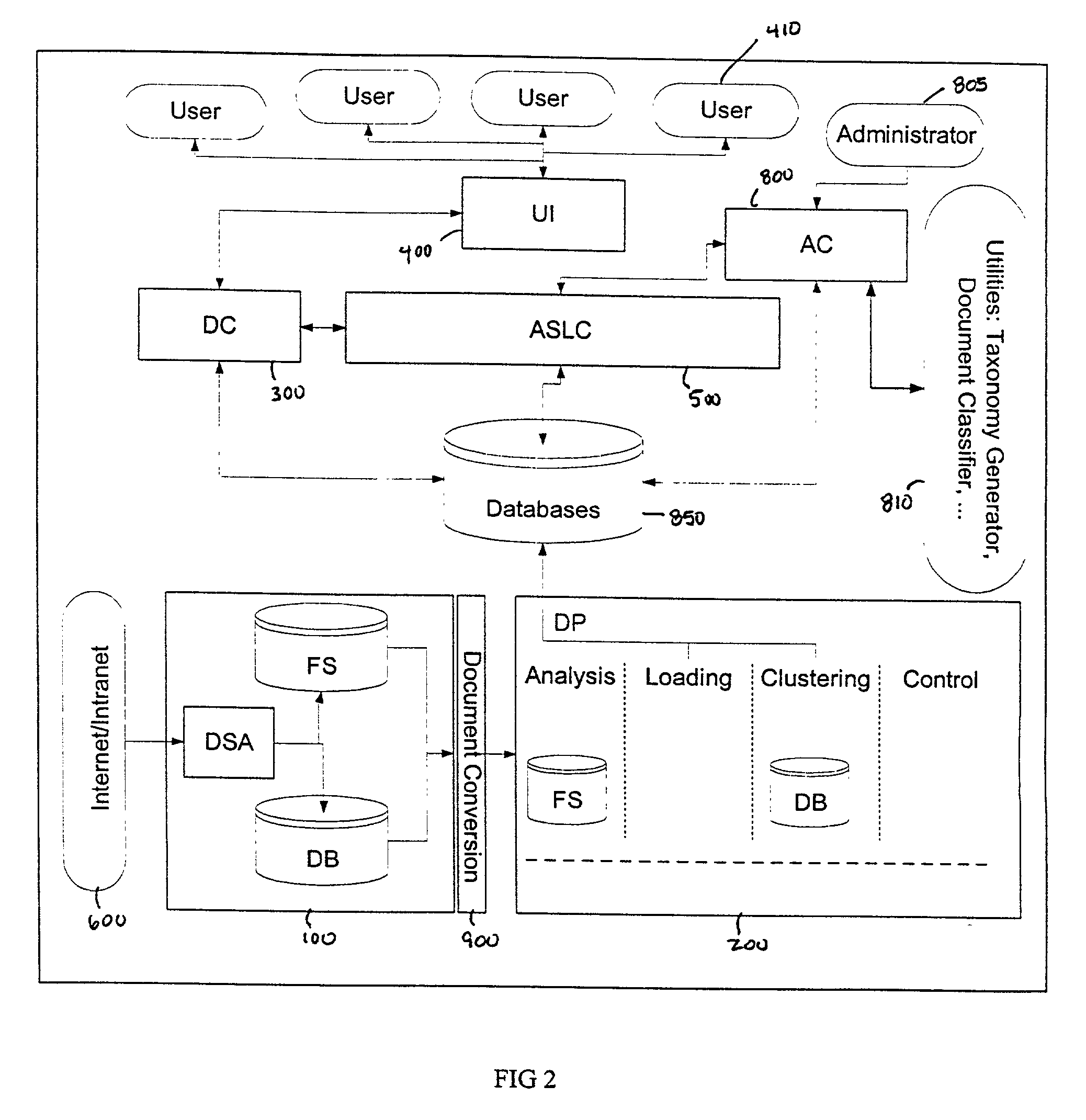
System and method for analysis and clustering of documents for search engine
InactiveUS20020065857A1Digital data information retrievalSpecial data processing applicationsDocument analysisComputational intelligence
A system and method for searching documents in a data source and more particularly, to a system and method for analyzing and clustering of documents for a search engine. The system and method includes analyzing and processing documents to secure the infrastructure and standards for optimal document processing. By incorporating Computational Intelligence (CI) and statistical methods, the document information is analyzed and clustered using novel techniques for knowledge extraction. A comprehensive dictionary is built based on the keywords identified by the these techniques from the entire text of the document. The text is parsed for keywords or the number of its occurrences and the context in which the word appears in the documents. The whole document is identified by the knowledge that is represented in its contents. Based on such knowledge extracted from all the documents, the documents are clustered into meaningful groups in a catalog tree. The results of document analysis and clustering information are stored in a database.
Owner:NUTECH SOLUTIONS
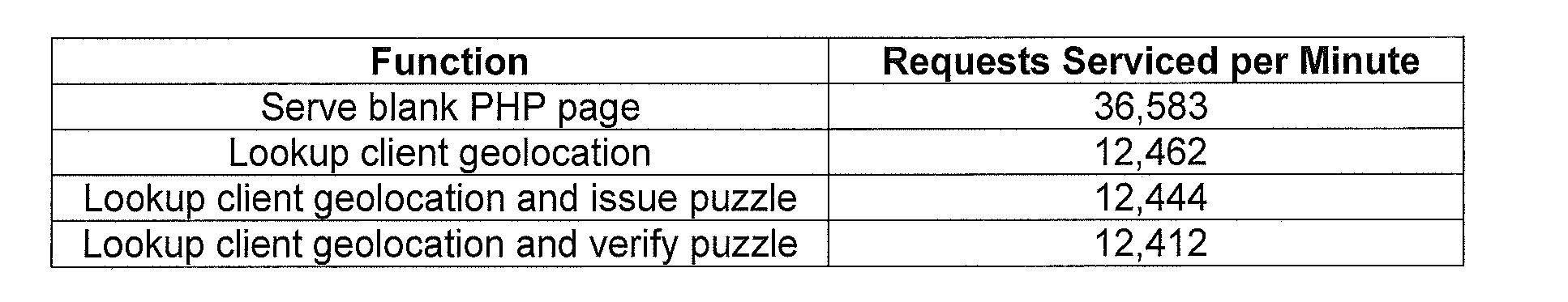
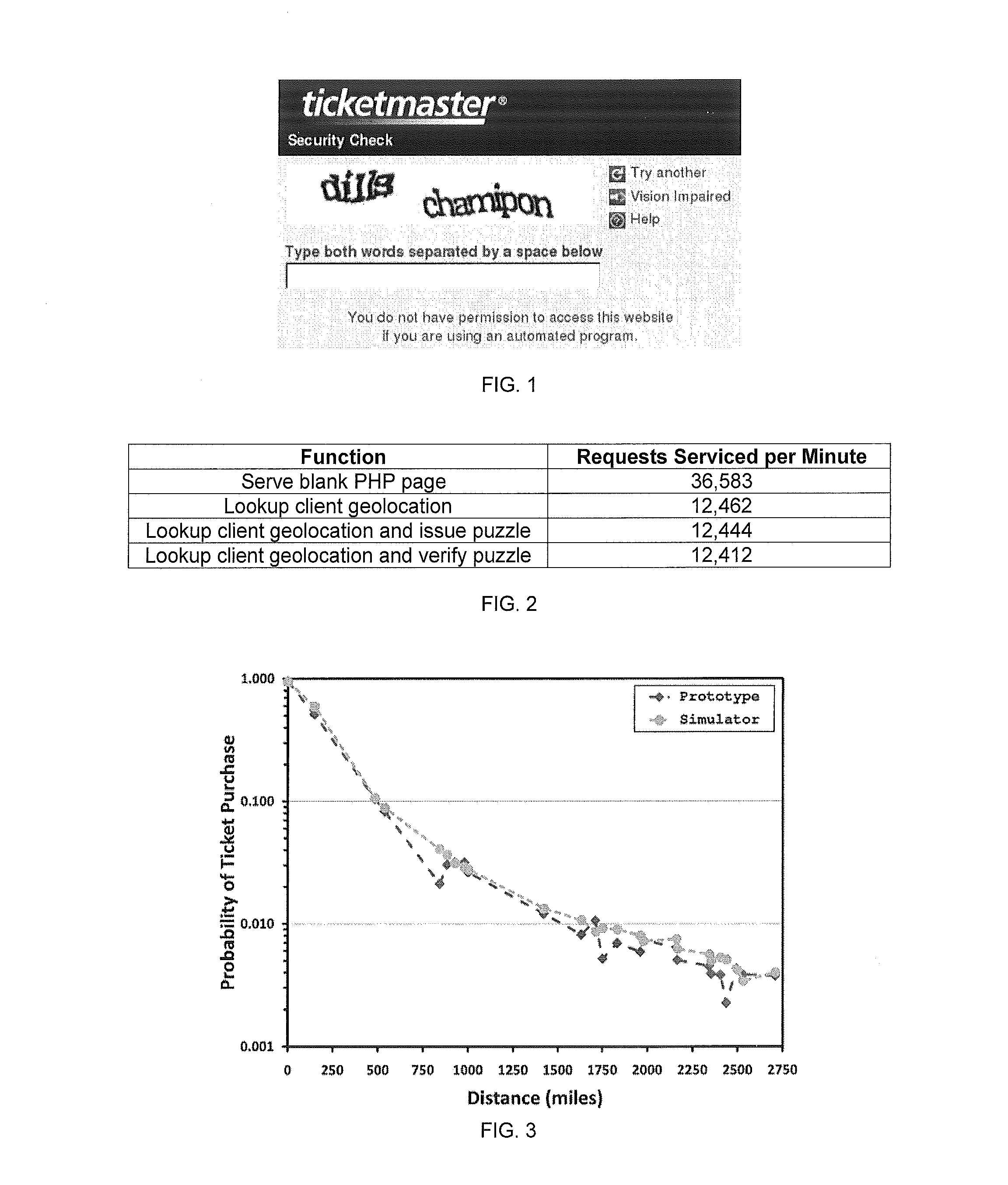
System and methods of determining computational puzzle difficulty for challenge-response authentication
InactiveUS20110231913A1Low costEnsure correct executionDigital data processing detailsMultiple digital computer combinationsGeographic siteComputational intelligence
Computational puzzles are parameterized by a difficulty variable which may be assigned based on at least one component from the group of components: time component, location component, reputation component, usage component, content component, and social networking component. For example, in one embodiment, the proof-of-work puzzle comprises a location component directed by the geographic location of the client that can be applied to any web transaction or application. One such application involves online ticket sales including those that employ purchasing robots. Another application involves accessing and using webmail.
Owner:THE OREGON STATE BOARD OF HIGHER EDUCATION ACTING BY & THROUGH PORTLAND STATE UNIV
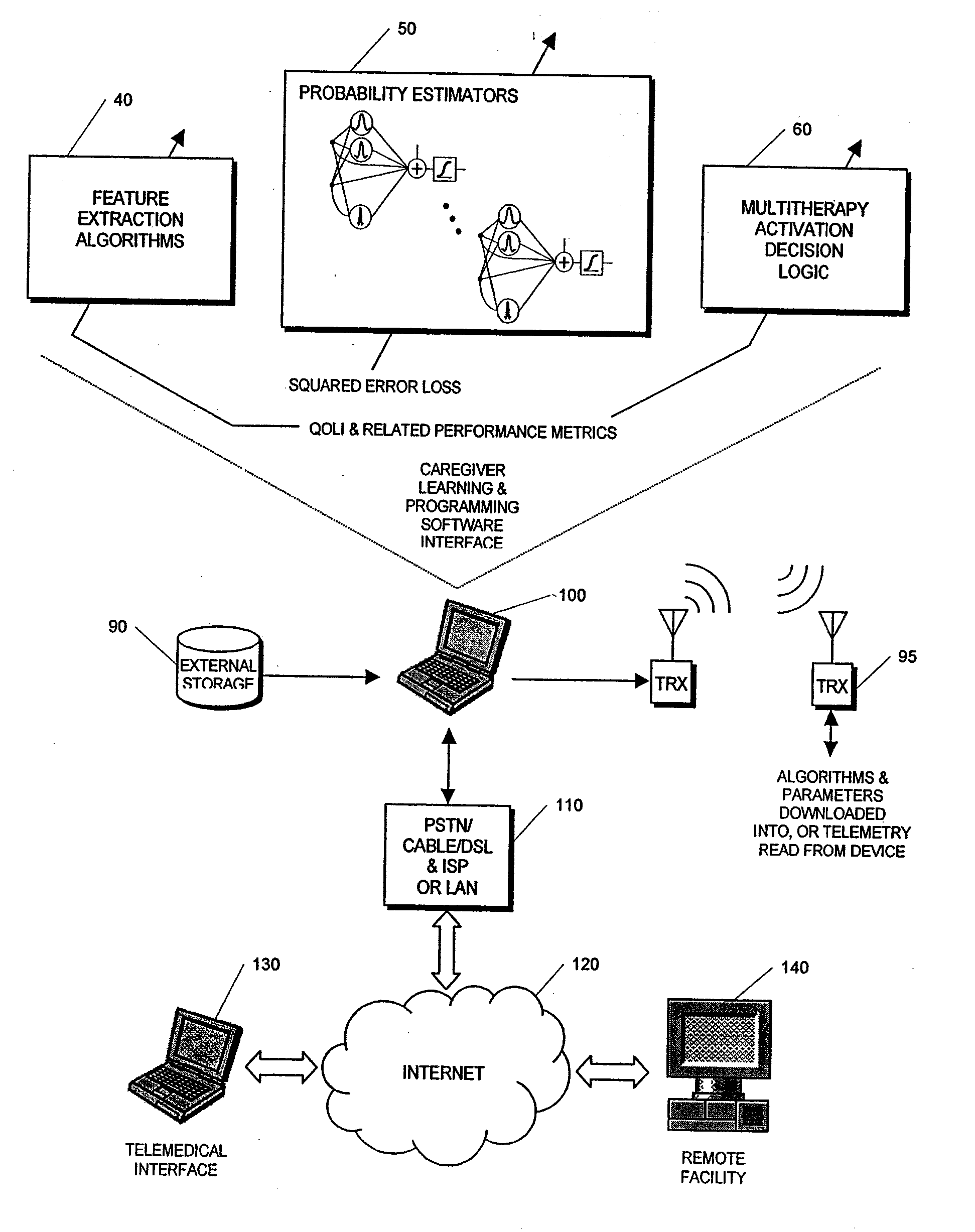
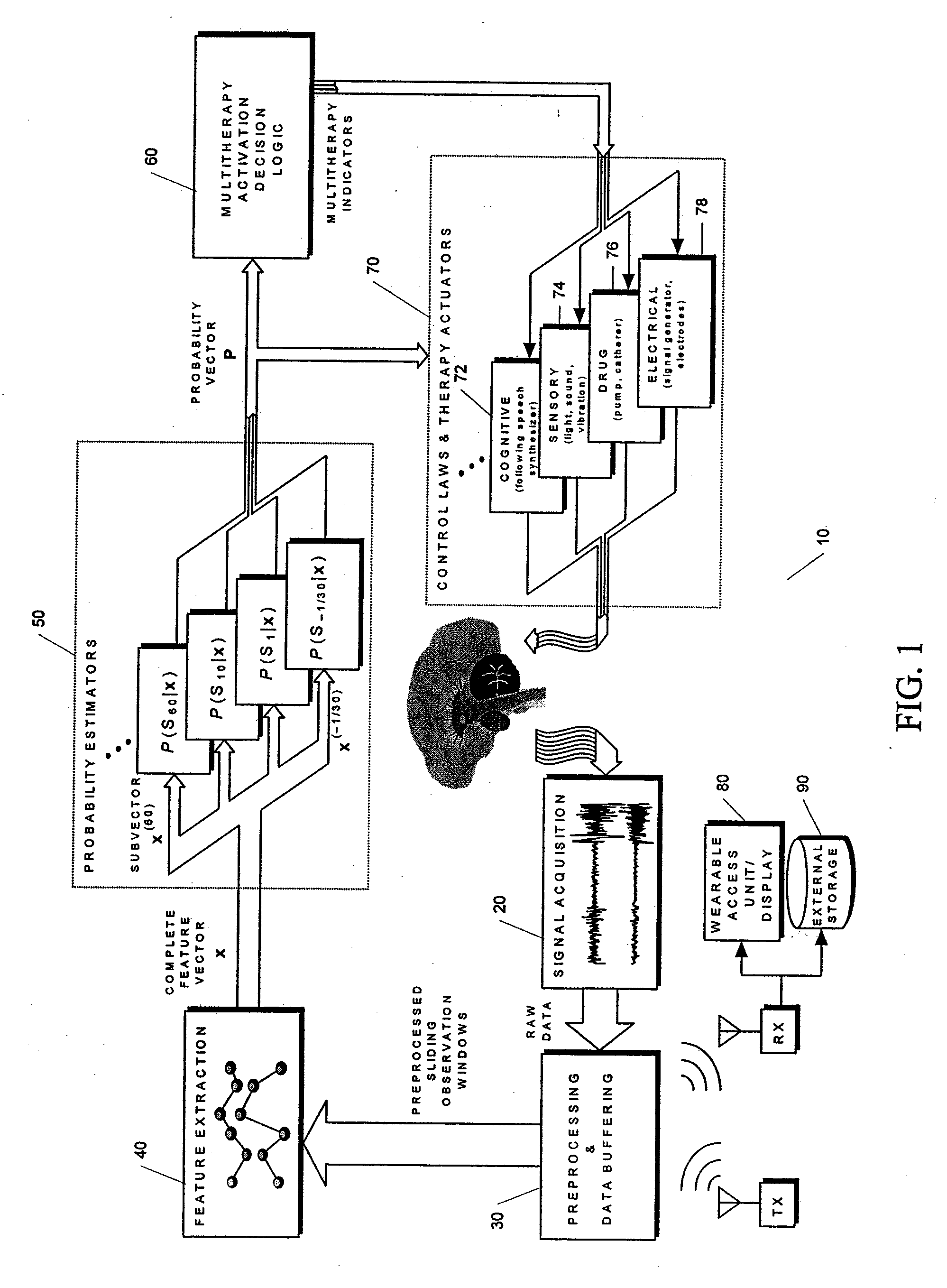
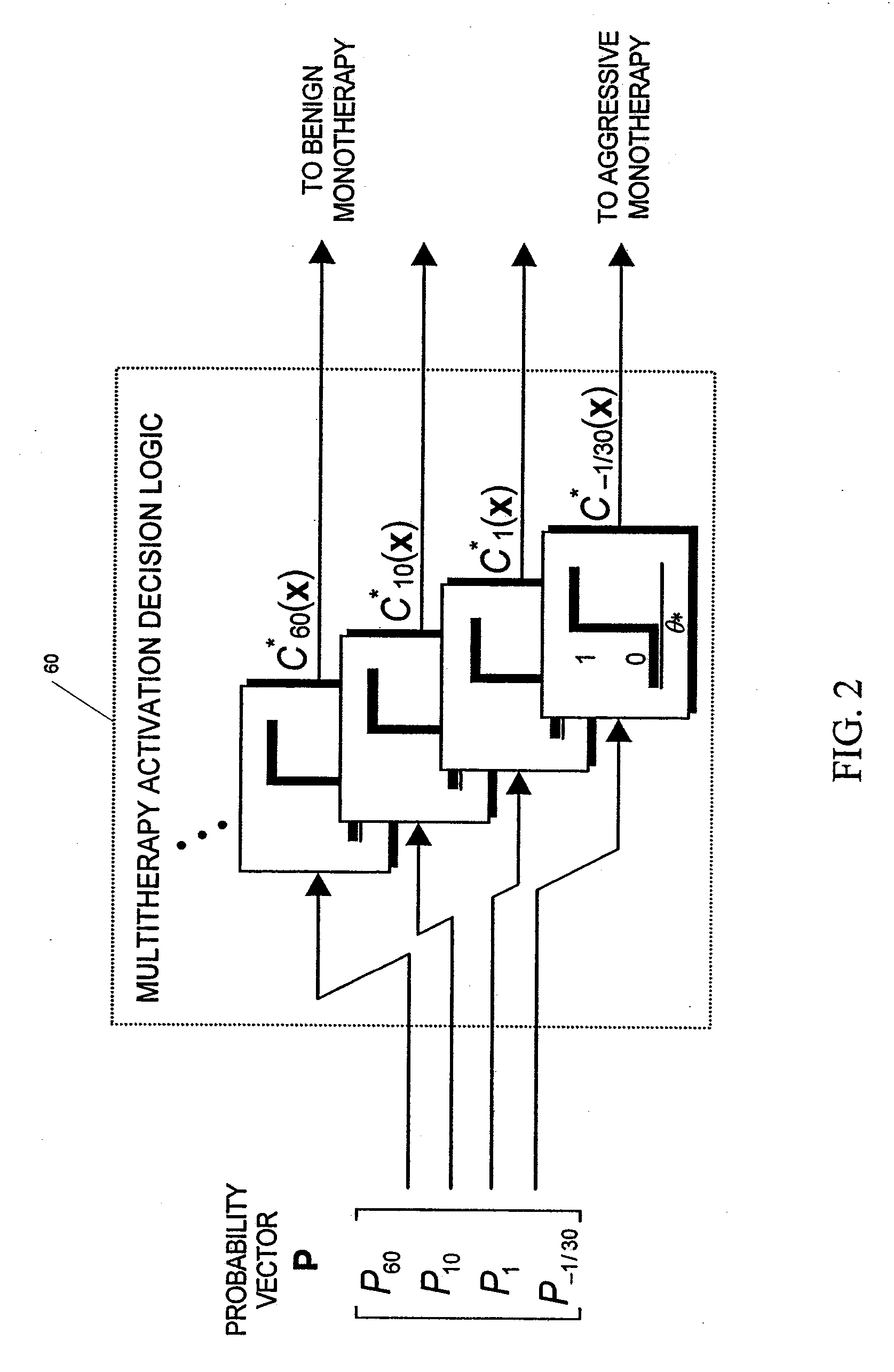
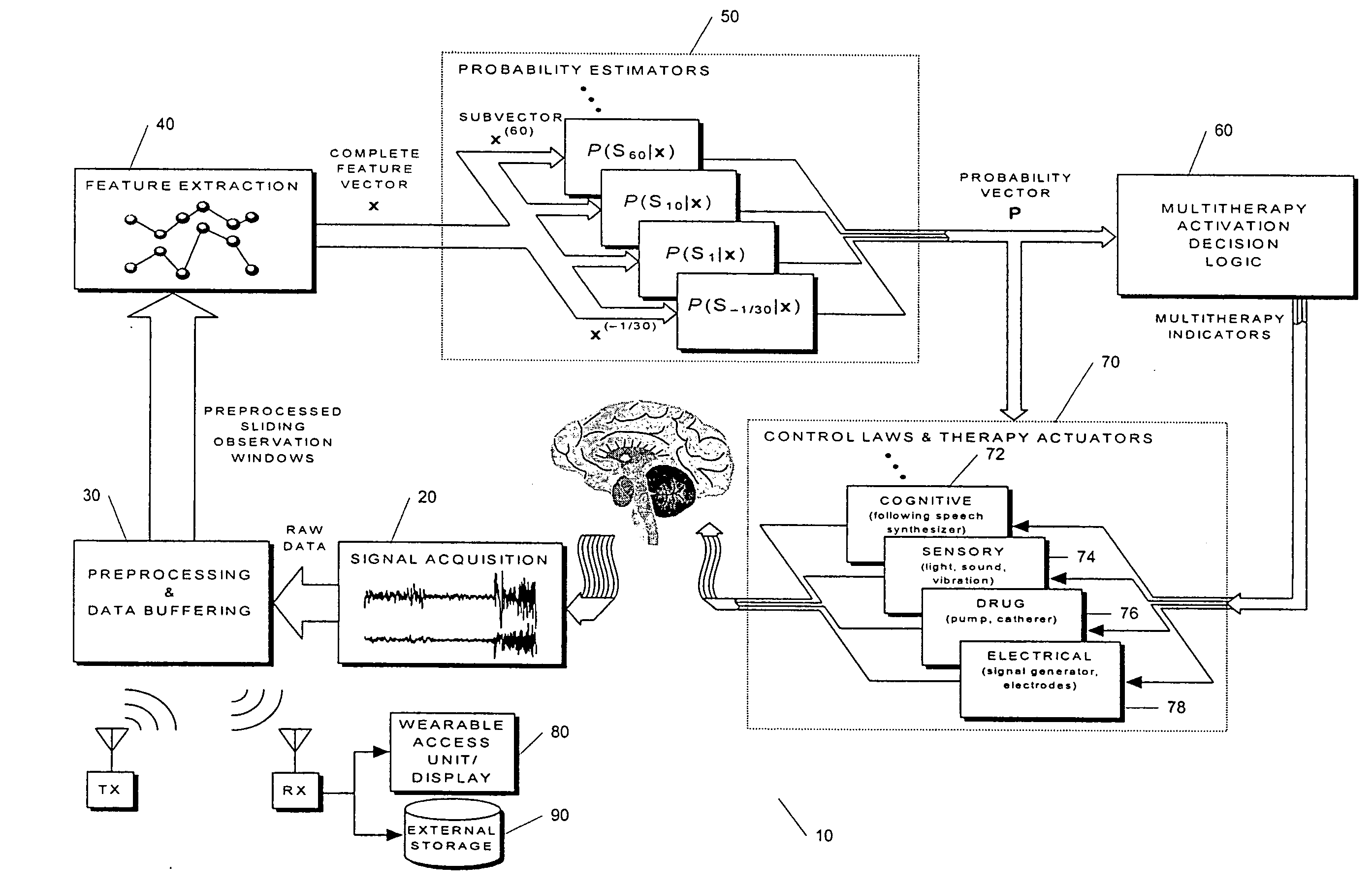
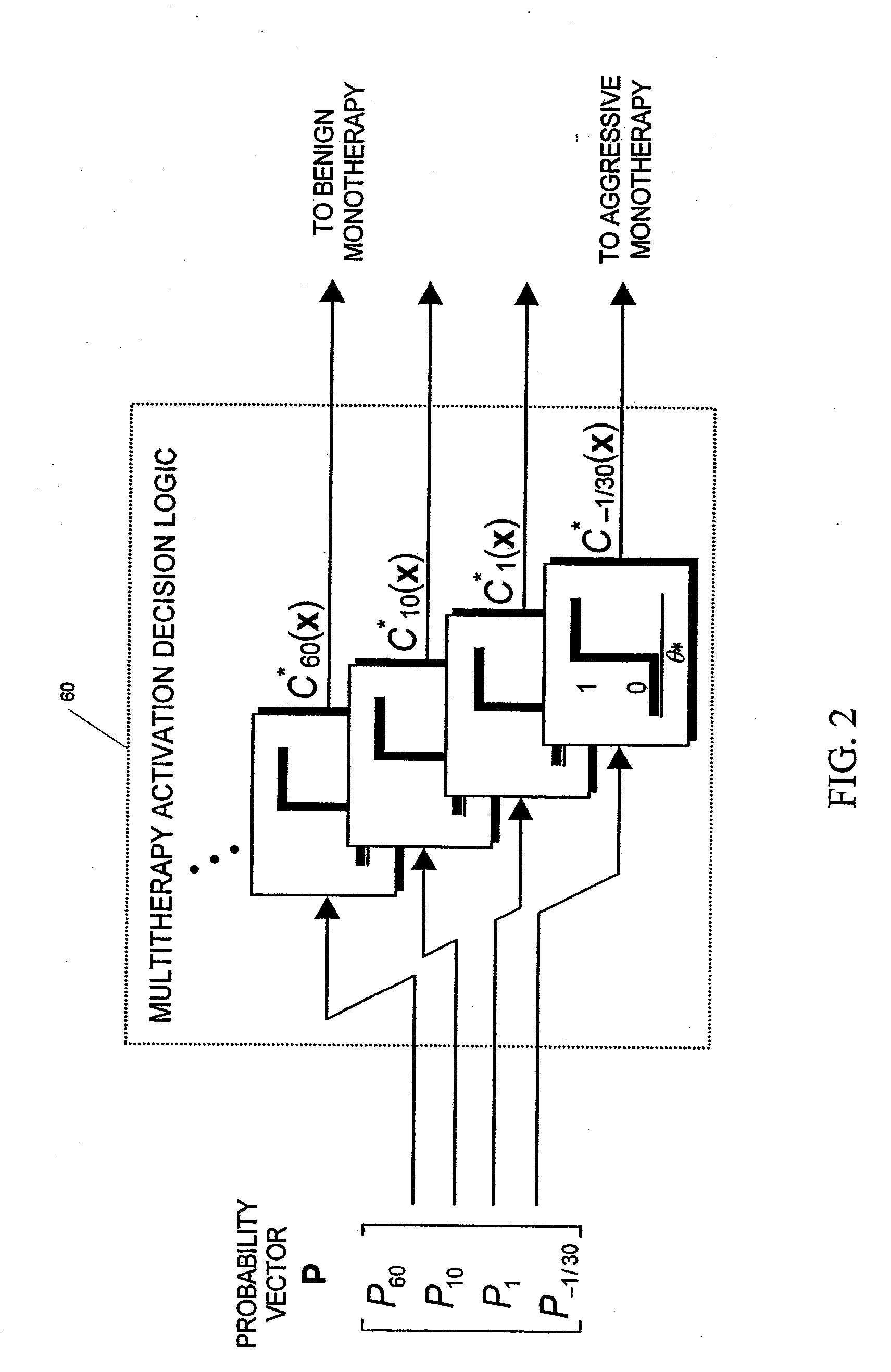
Unified Probabilistic Framework For Predicting And Detecting Seizure Onsets In The Brain And Multitherapeutic Device
InactiveUS20070276279A1Avoid seizuresEnough timePhysical therapies and activitiesElectrotherapyRegimenMultiple therapy
A method and an apparatus for predicting and detecting epileptic seizure onsets within a unified multiresolution probabilistic framework, enabling a portion of the device to automatically deliver a progression of multiple therapies, ranging from benign to aggressive as the probabilities of seizure warrant. Based on novel computational intelligence algorithms, a realistic posterior probability function P(ST|x) representing the probability of one or more seizures starting within the next T minutes, given observations x derived from IEEG or other signals, is periodically synthesized for a plurality of prediction time horizons. When coupled with optimally determined thresholds for alarm or therapy activation, probabilities defined in this manner provide anticipatory time-localization of events in a synergistic logarithmic-like array of time resolutions, thus effectively circumventing the performance vs. prediction-horizon tradeoff of single-resolution systems. The longer and shorter prediction time scales are made to correspond to benign and aggressive therapies respectively. The imminence of seizure events serves to modulate the dosage and other parameters of treatment during open-loop or feedback control of seizures once activation is triggered. Fast seizure onset detection is unified within the framework as a degenerate form of prediction at the shortest, or even negative, time horizon. The device is required to learn in order to find the probabilistic prediction and control strategies that will increase the patient's quality of life over time. A quality-of-life index (QOLI) is used as an overall guide in the optimization of patient-specific signal features, the multitherapy activation decision logic, and to document if patients are actually improving.
Owner:THE TRUSTEES OF THE UNIV OF PENNSYLVANIA
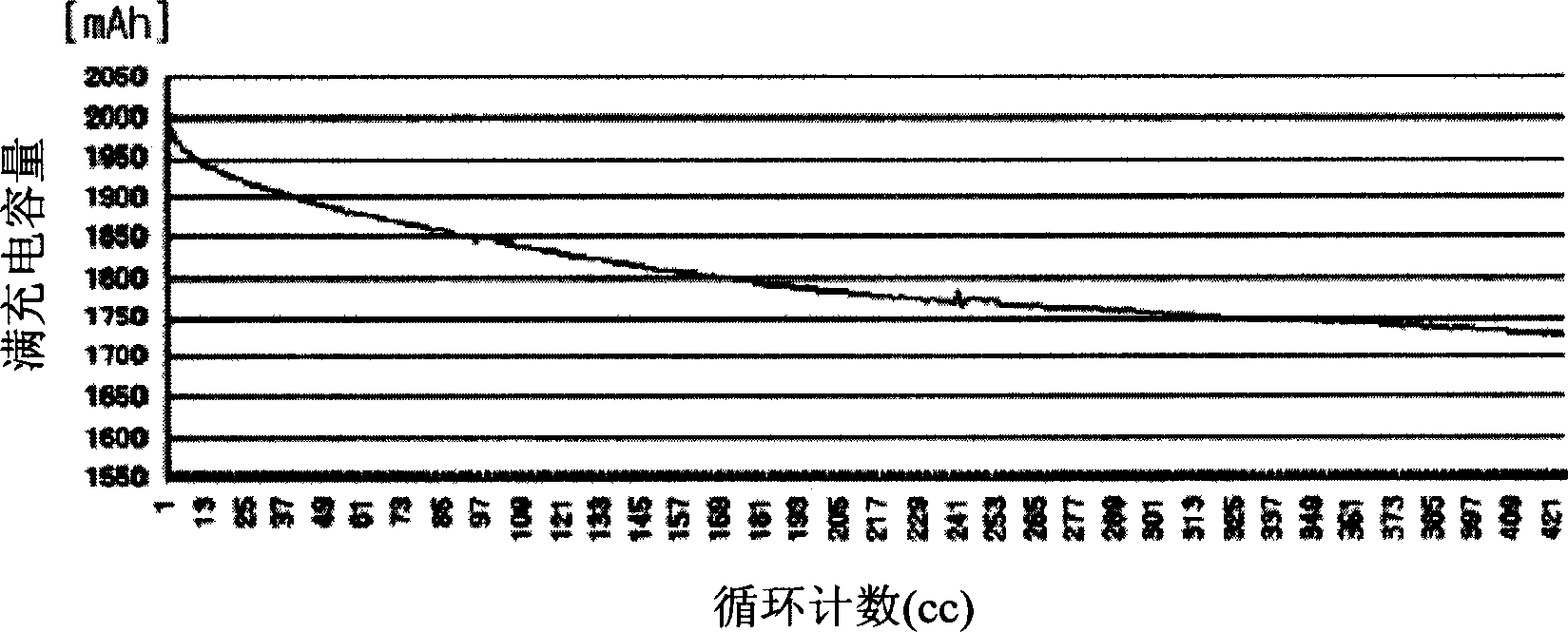
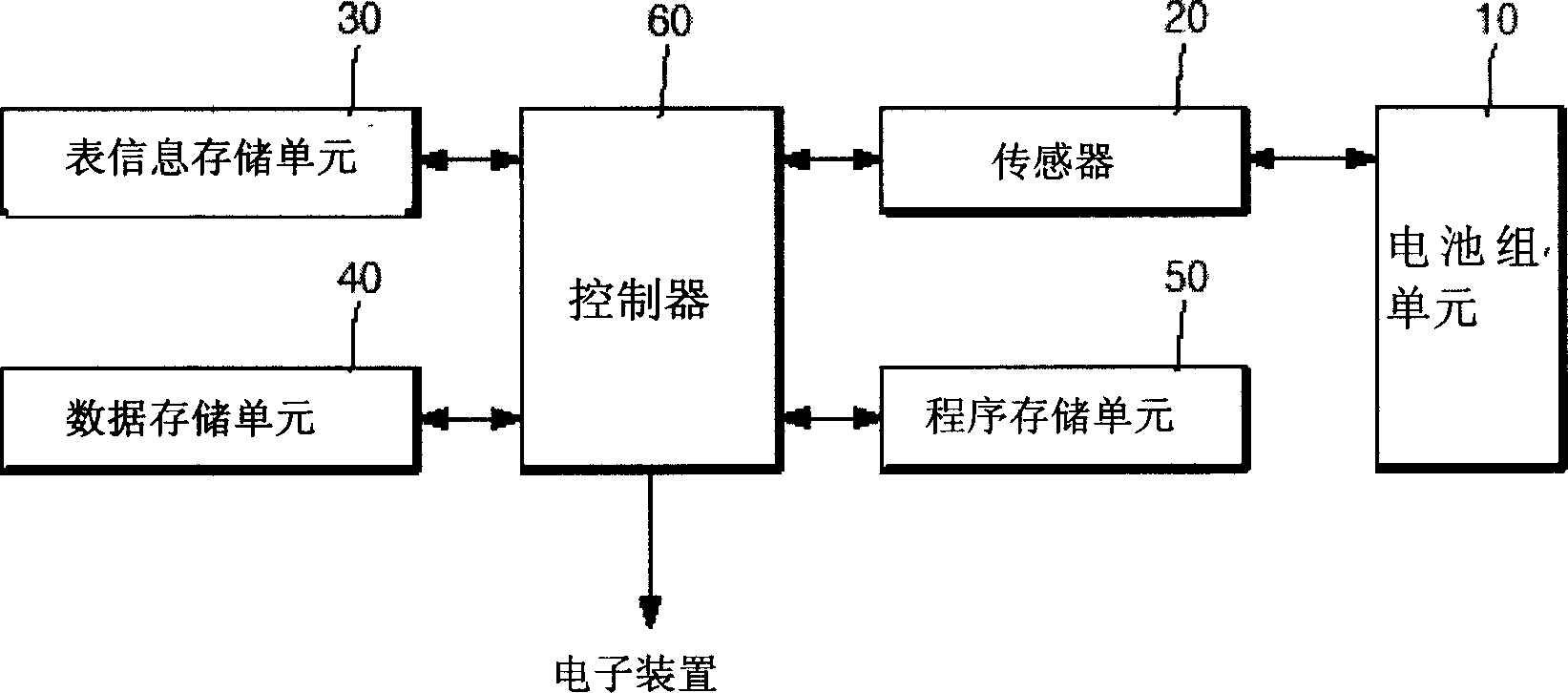
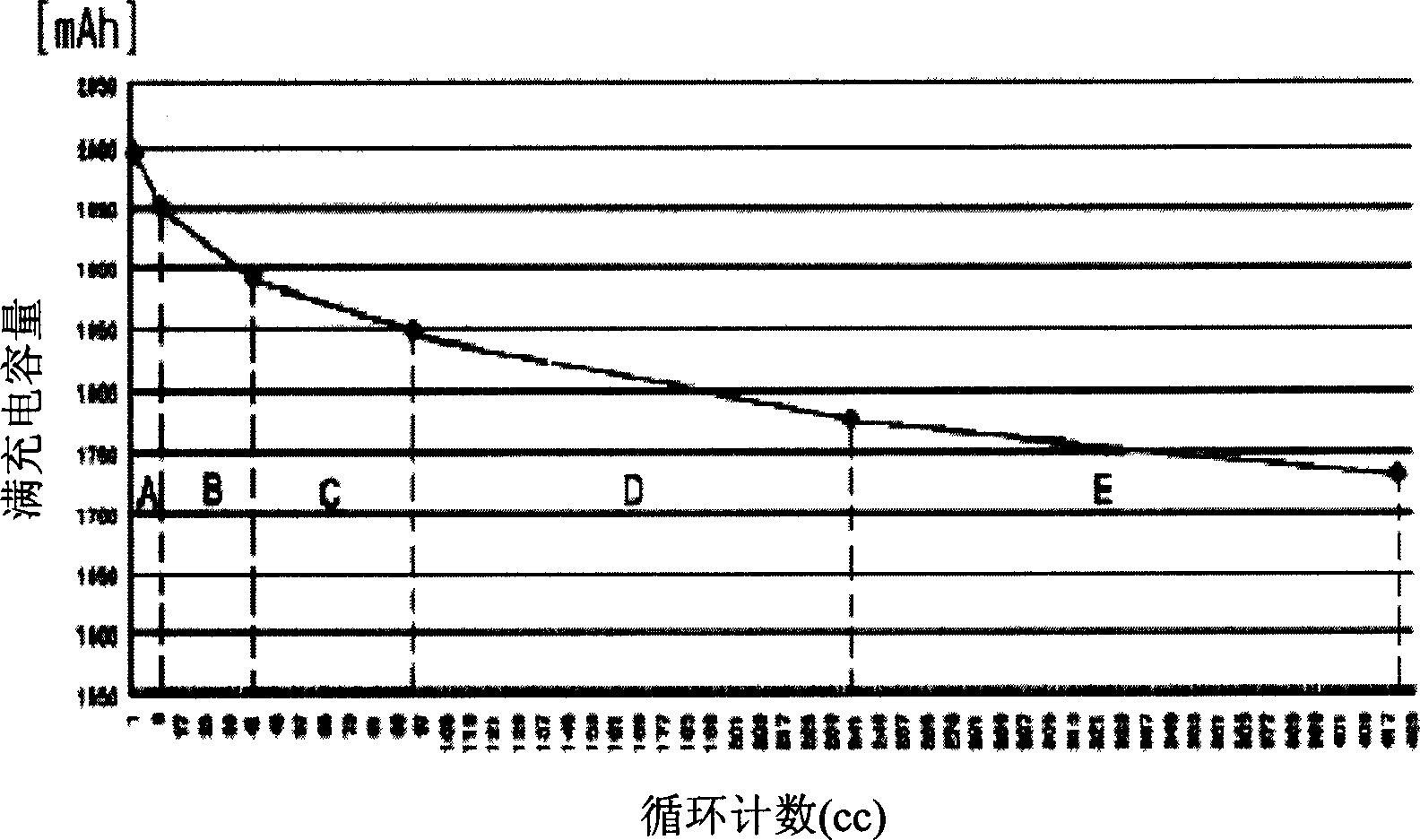
Method for caculating circulation type of intelligent battery, method and equipment for correcting full recharge capacity to intelligent battery using said method
InactiveCN1503000ARegardless of state of chargeHigh precisionElectrical testingComputational intelligenceLinearization
A method for counting cycle count of a smart battery, a method and device for correcting full charge capacity of a smart battery, which is used as reference capacity for indicating correct remaining capacity of the battery, are disclosed. The present invention increase cycle count that is a standard for updating FCC in gradual floating variables in consideration of SOC to obtain continuous cycle count. FCC information is updated when the battery has been fully charged or the integer of the cycle count increases 1 using a predetermined FCC correction table in which FCC correction values varying with the cycle count are linearized by sections. This improves reliability in actually corrected FCC information and increases accuracy in the remaining capacity indicated on the basis of the FCC information.
Owner:MTEQ SYST
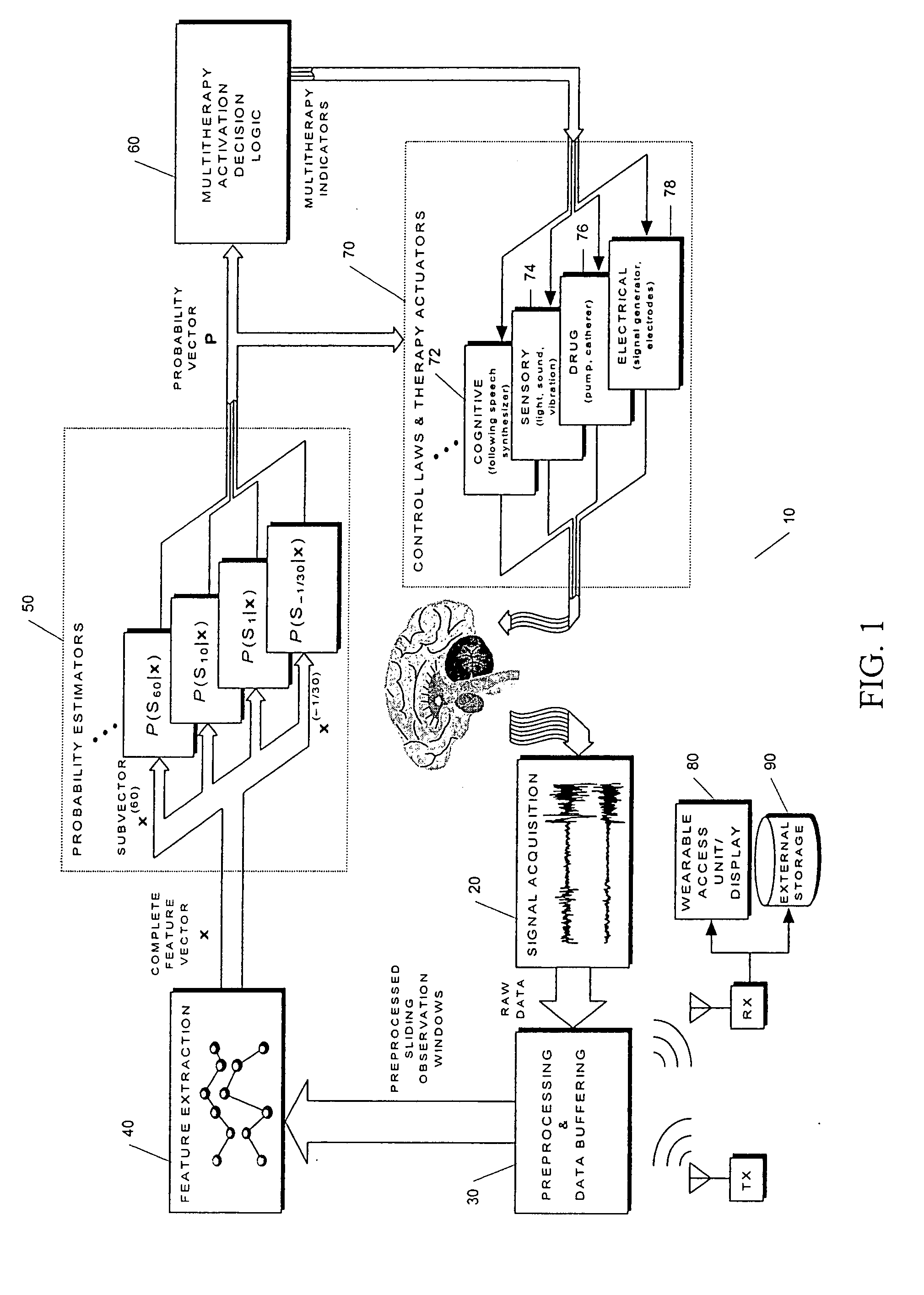
Unified Probabilistic Framework For Predicting And Detecting Seizure Onsets In The Brain And Multitherapeutic Device
ActiveUS20080021342A1Avoid seizuresEnough timePhysical therapies and activitiesElectrotherapyRegimenMultiple therapy
A method and an apparatus for predicting and detecting epileptic seizure onsets within a unified multiresolution probabilistic framework, enabling a portion of the device to automatically deliver a progression of multiple therapies, ranging from benign to aggressive as the probabilities of seizure warrant. Based on novel computational intelligence algorithms, a realistic posterior probability function P(ST|x) representing the probability of one or more seizures starting within the next T minutes, given observations x derived from IEEG or other signals, is periodically synthesized for a plurality of prediction time horizons. When coupled with optimally determined thresholds for alarm or therapy activation, probabilities defined in this manner provide anticipatory time-localization of events in a synergistic logarithmic-like array of time resolutions, thus effectively circumventing the performance vs. prediction-horizon tradeoff of single-resolution systems. The longer and shorter prediction time scales are made to correspond to benign and aggressive therapies respectively. The imminence of seizure events serves to modulate the dosage and other parameters of treatment during open-loop or feedback control of seizures once activation is triggered. Fast seizure onset detection is unified within the framework as a degenerate form of prediction at the shortest, or even negative, time horizon. The device is required to learn in order to find the probabilistic prediction and control strategies that will increase the patient's quality of life over time. A quality-of-life index (QOLI) is used as an overall guide in the optimization of patient-specific signal features, the multitherapy activation decision logic, and to document if patients are actually improving.
Owner:THE TRUSTEES OF THE UNIV OF PENNSYLVANIA
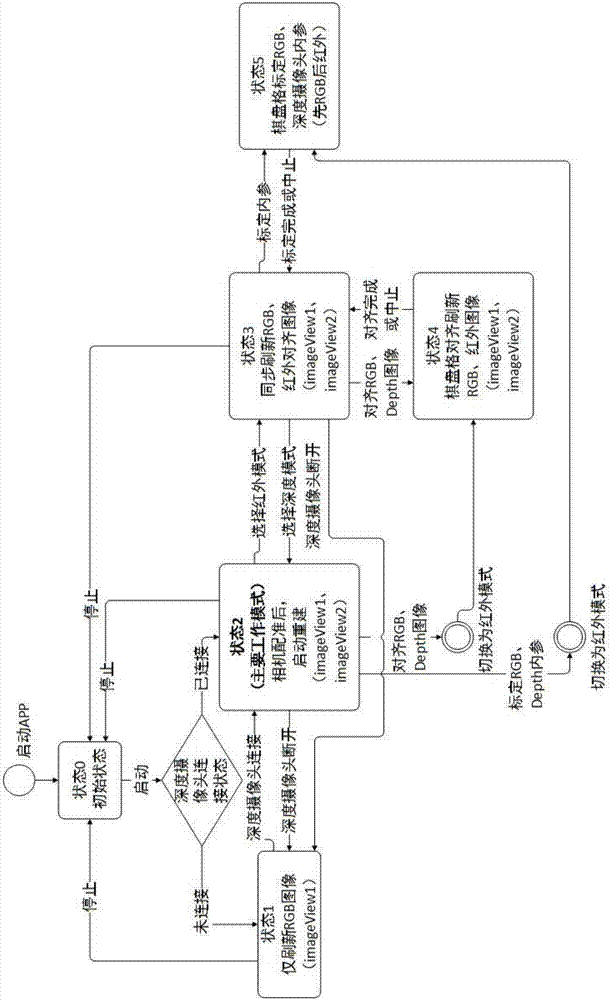
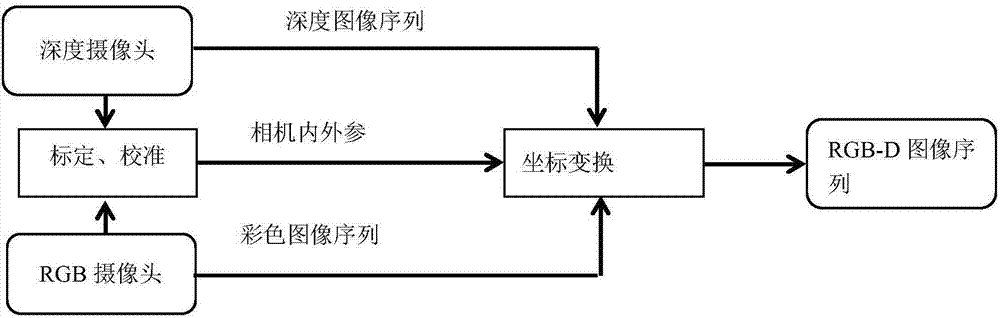
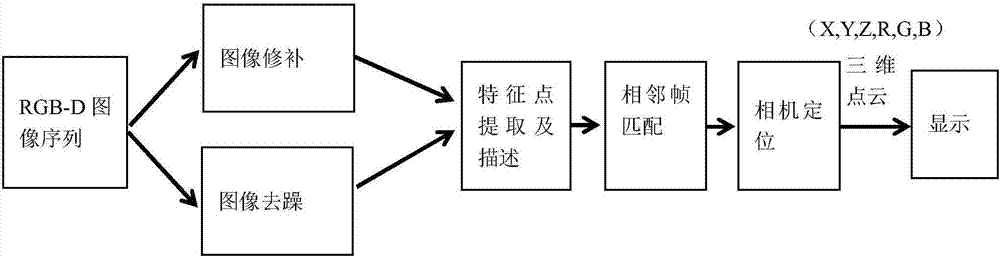
Scene reconstruction method based on smart phone
InactiveCN107103626ASolve the inability to virtualizeAddress effectivenessImage enhancementImage analysisPoint cloudThree-dimensional space
The invention discloses a scene reconstruction method based on a smart phone. The method comprises: 1) calculating the internal camera parameter matrix of the color camera of a smart phone; 2) connecting and fixing a depth camera with the smart phone; and calculating the internal camera parameter matrix and its zoom factor corresponding to the depth camera; 3) calculating the external parameter matrix of the color camera corresponding to the depth camera; 4) using the panorama videos of the scene photographed by the color camera of the smart phone and the depth camera; then, converting the videos into image sequences; and through the obtained external parameter matrix and the internal parameter matrix, combining the image sequences into an RGB-D four-channel sequence; 5) calculating the transform matrixes corresponding to the adjacent two frames in the RGB-D; and 6) through the RGB-D and the transform matrixes, creating the three-dimensional space point cloud sets for the scene and then, through the affine transformation, displaying the point cloud sets on the display screen of the smart phone. The invention can be portably carried and easily shaped.
Owner:HANGZHOU DIANZI UNIV
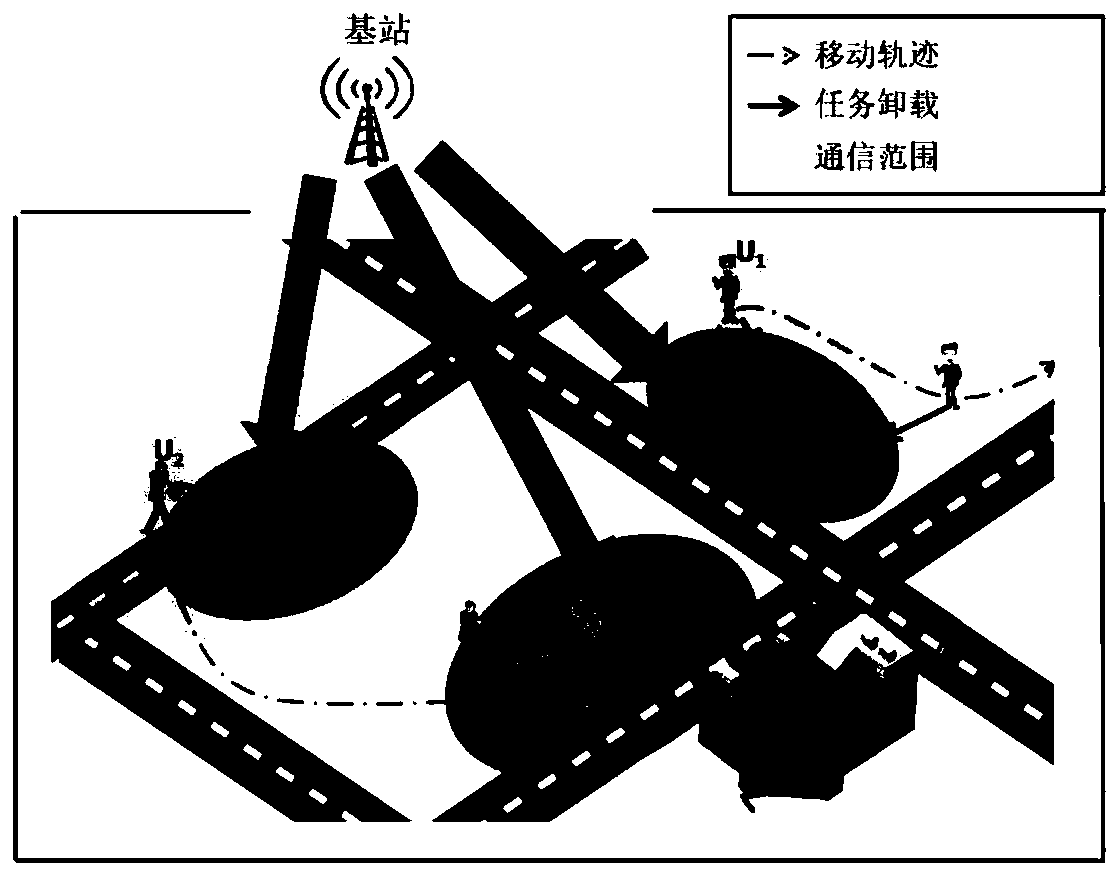
A resource management and scheduling method in a mobile edge computing environment based on multi-base-station cooperation
ActiveCN109862592AIncrease flexibilityImprove processing efficiencyNetwork traffic/resource managementManagement algorithmReal-time computing
The invention discloses a resource management and scheduling method in a mobile edge computing environment based on multi-base-station cooperation. The method comprises the following steps that: a mobile edge computing intelligent base station allocates and schedules resources by utilizing five units of a receiving unit, a controlling unit, a caching unit, a computing unit and a sending unit. Whenthe mobile terminal has a new computing task, uploading a migration request to the intelligent base station to which the mobile terminal belongs; If the task is determined to be executed in the intelligent base station by the management algorithm and the task data is cached, the task is directly executed; If the task data is not cached, the data request of the task is sent to the cloud; If the algorithm determines to execute the task in the adjacent base station, the intelligent base station sends a calculation migration request to the adjacent base station, and the judgment on the cache is the same as before; And if the algorithm determines to execute the task at the cloud, the intelligent base station sends the migration request to the cloud. Therefore, the method provided by the invention can optimize transmission and calculation of time delay, cache distribution, system revenue and the like at the same time.
Owner:BEIJING UNIV OF POSTS & TELECOMM
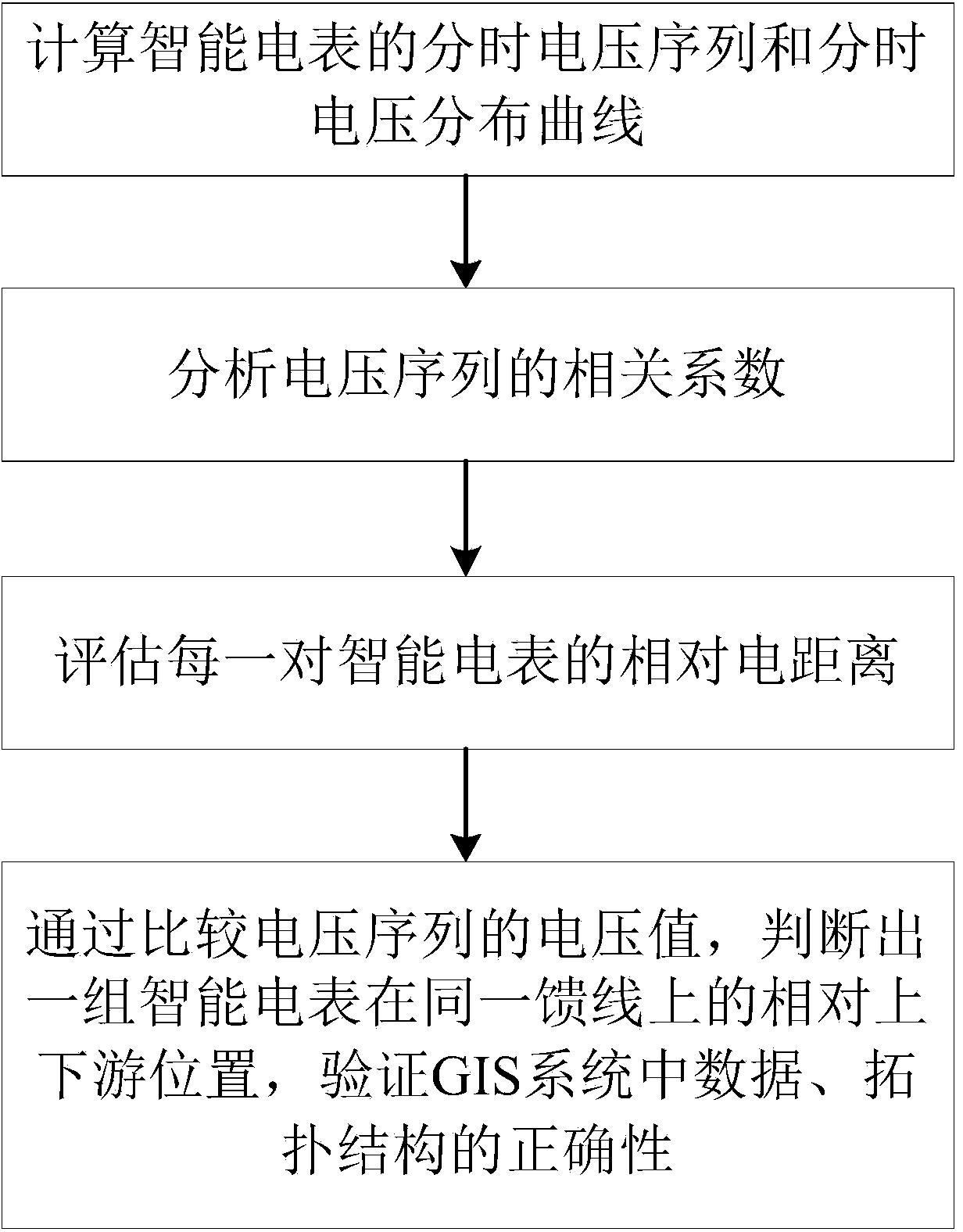
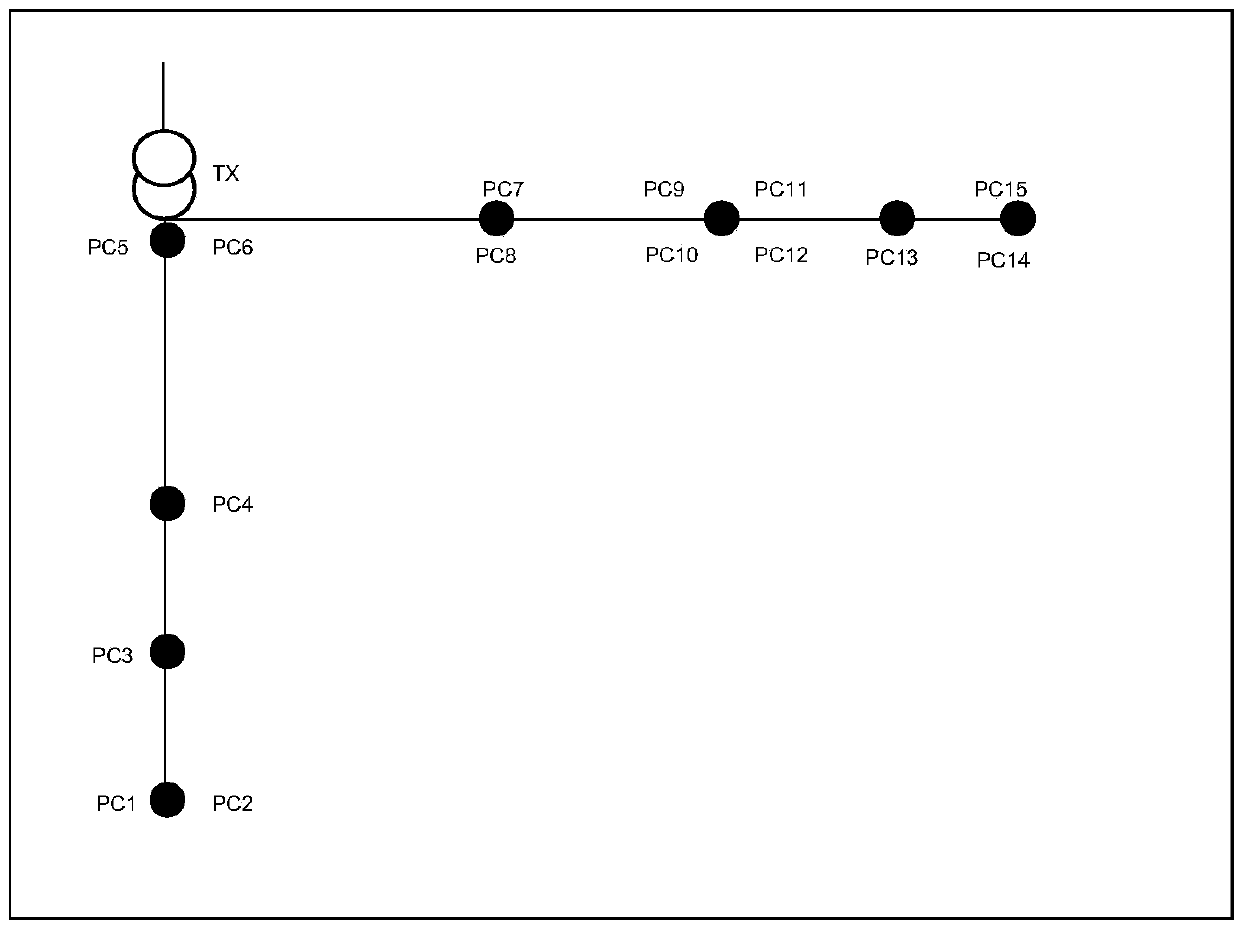
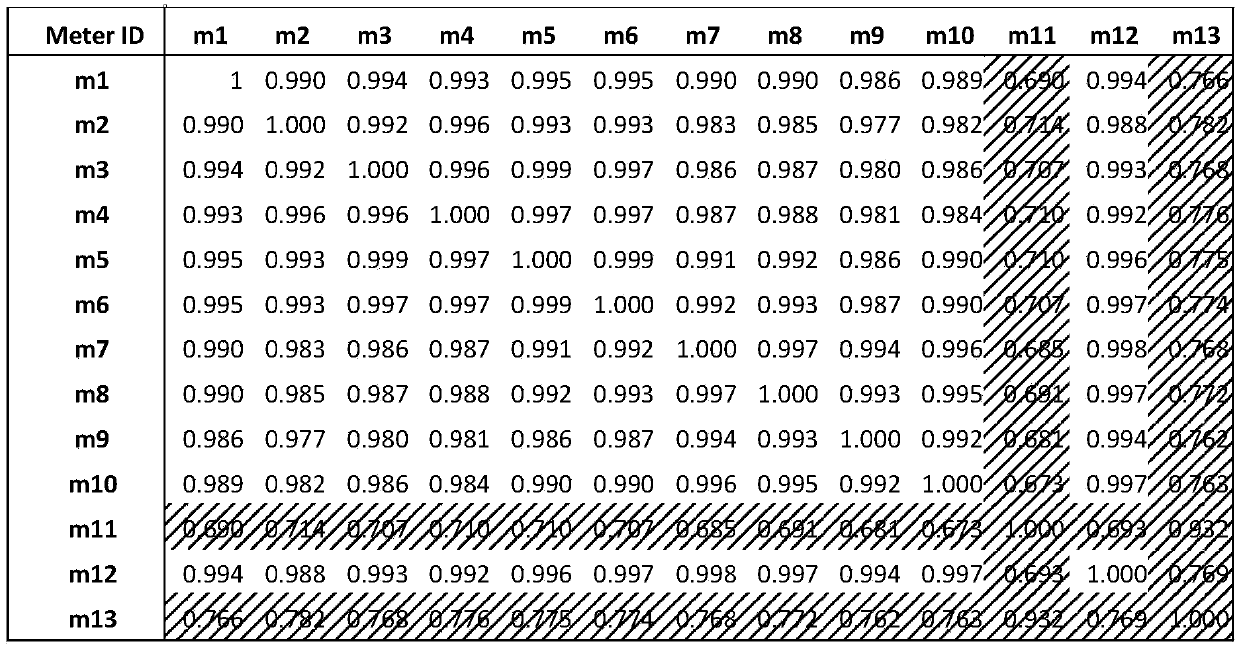
Method for verifying power distribution network topology structure by utilizing measurement data
InactiveCN104218581AEffectively verify correctnessImprove accuracyAc network circuit arrangementsTransformerComputational intelligence
The invention relates to a method for verifying a power distribution network topology structure by utilizing measurement data. The method comprises the steps of: (1) calculating time-sharing voltage sequences and time-sharing voltage distribution curves of smart meters; (2) analyzing relevant coefficients of each voltage sequence; (3) estimating a relative electric distance between each pair of the smart meters; (4) judging relative upstream and downstream positions of a group of the smart meters on the same feed line through comparing voltage values of the voltage sequences, and verifying correctness of data and topology structure in a GIS (Geographic Information System). Through calculation of the relative coefficients and relative voltage size between the time sequence voltages, and contrastive analysis with data in same type obtained under other transformers in the same region, the correctness of the data and the topology structure in the GIS can be verified efficiently, existing errors and faults can be verified and corrected. The verifying method needs low material source and manpower cost, and is high in accuracy and good in operability.
Owner:STATE GRID CORP OF CHINA +3
Infrastructure health monitoring and analysis
InactiveUS20080082470A1Improve modeling accuracyFewer false alarmsDigital computer detailsDigital dataComputational intelligenceInstrument Data
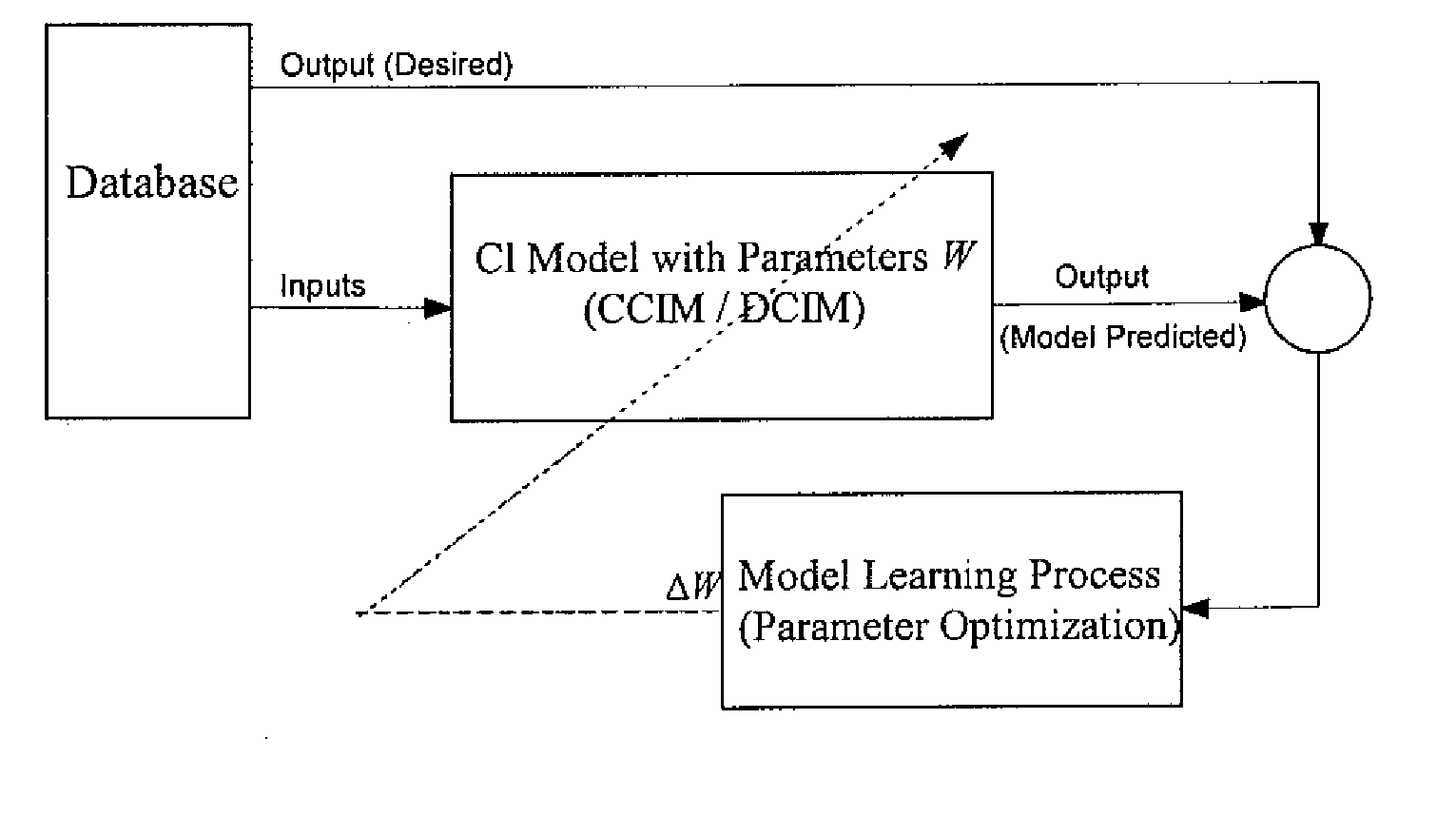
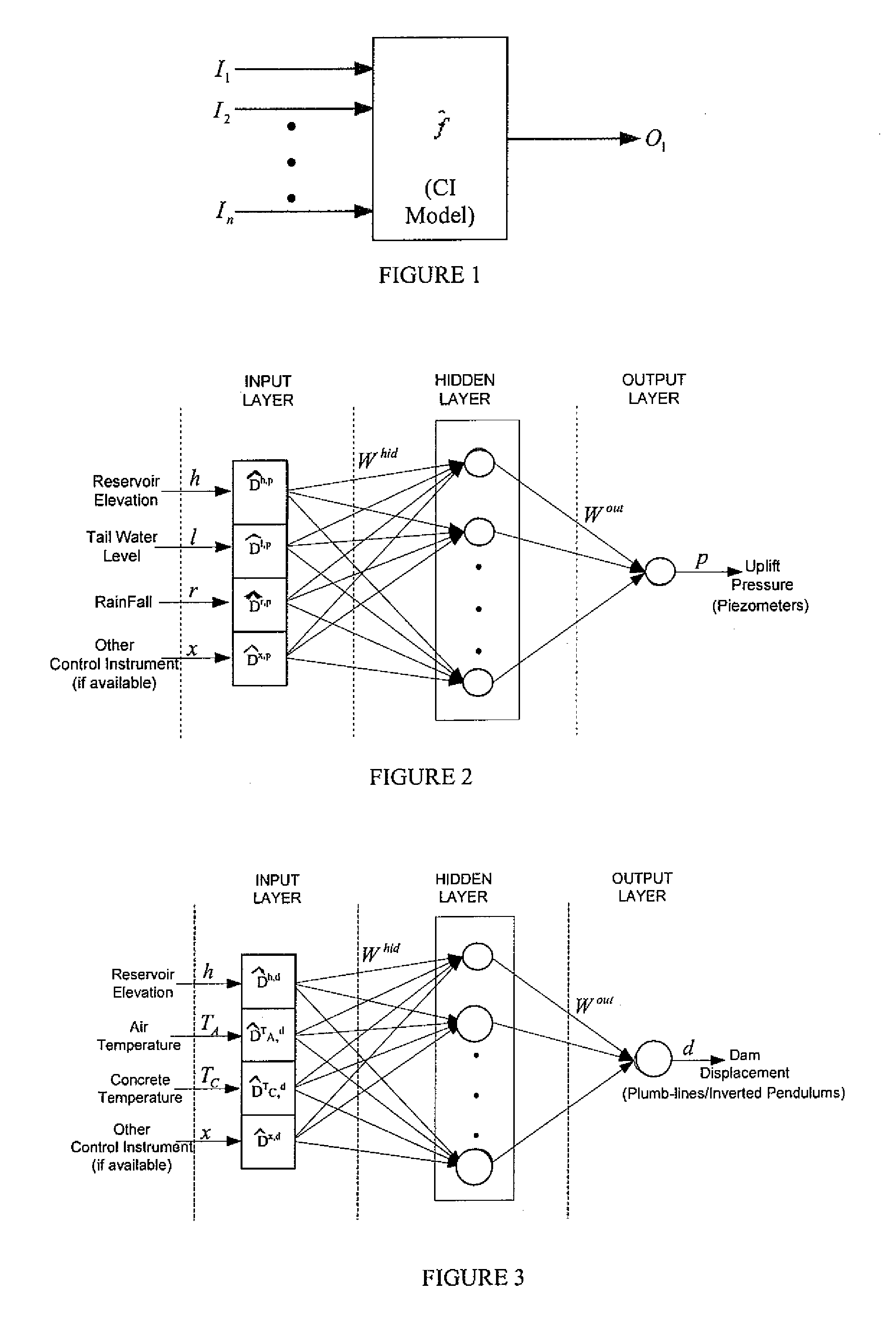
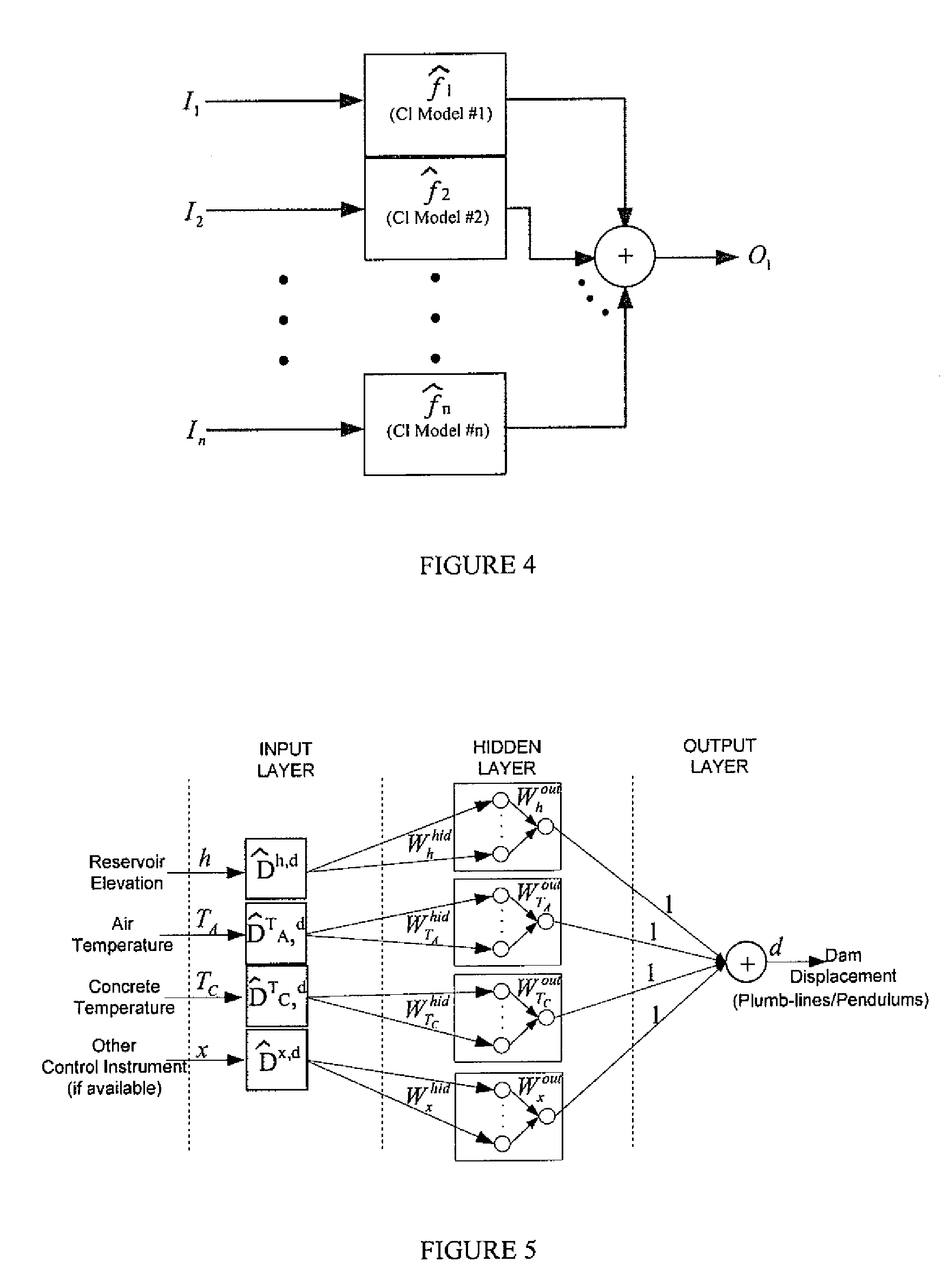
There is described herein a method for detecting anomalies in an infrastructure, the method comprising: providing a computationally-intelligent analysis model to model a behaviour of at least one detection instrument in said infrastructure; inputting control instrument data into said analysis model, said control instrument data being provided by control instruments in said infrastructure; outputting an estimated behaviour for said at least one detection instrument from said analysis model; comparing actual data from said at least one detection instrument to said estimated behaviour and generating a set of residuals representing a difference between said actual data and said estimated behaviour; and identifying anomalies when said residuals exceed a predetermined threshold.
Owner:GLOBVISION
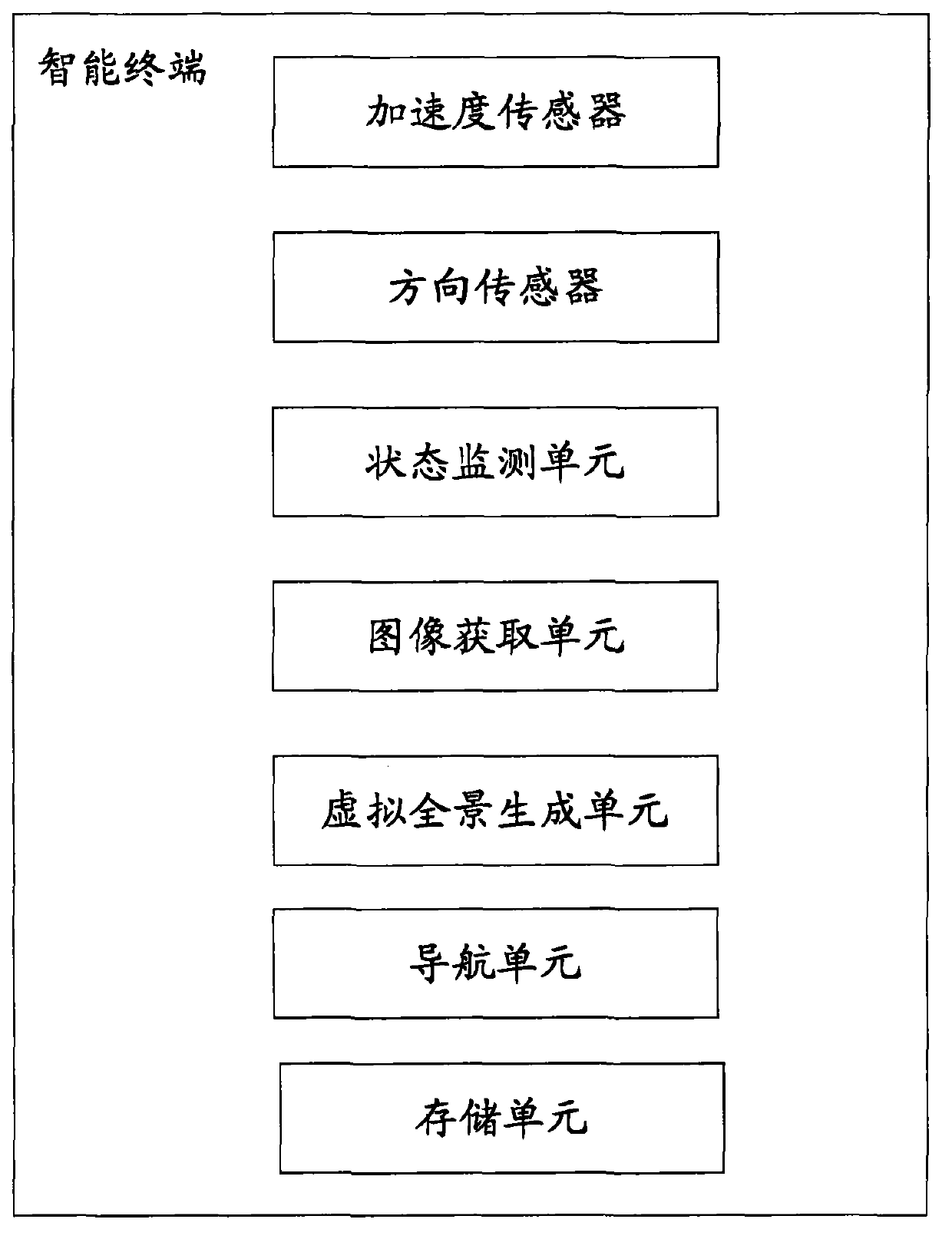
Method for constructing multi-scene virtual panorama space and intelligent terminal
ActiveCN103279187AEasy to operateEasy to carryInput/output for user-computer interactionImage data processingComputational intelligenceComputer science
The invention relates to a method for constructing a multi-scene virtual panorama space on the basis of an intelligent terminal. The method comprises the following steps: utilizing an acceleration sensor to acquire acceleration data of the intelligent terminal; utilizing a direction sensor to acquire direction data of the intelligent terminal; a state monitoring unit confirming operation states of the intelligent terminal through the acceleration data and the direction data, wherein the operation states comprise a real image acquiring state and a navigation state; if the intelligent terminal is in the real image acquiring state, an image acquiring unit utilizing the acceleration data and the direction data to acquire the panorama image, and then a virtual panorama generation unit utilizing the panorama image to generate the multi-scene virtual panorama space; if the intelligent terminal is in the navigation state, a navigation unit utilizing the acceleration data and the direction data to calculate the moving distance and the moving direction of the intelligent terminal, and generating navigation information indicating the moving distance and the moving direction in the original multi-scene virtual panorama space.
Owner:XIDIAN UNIV
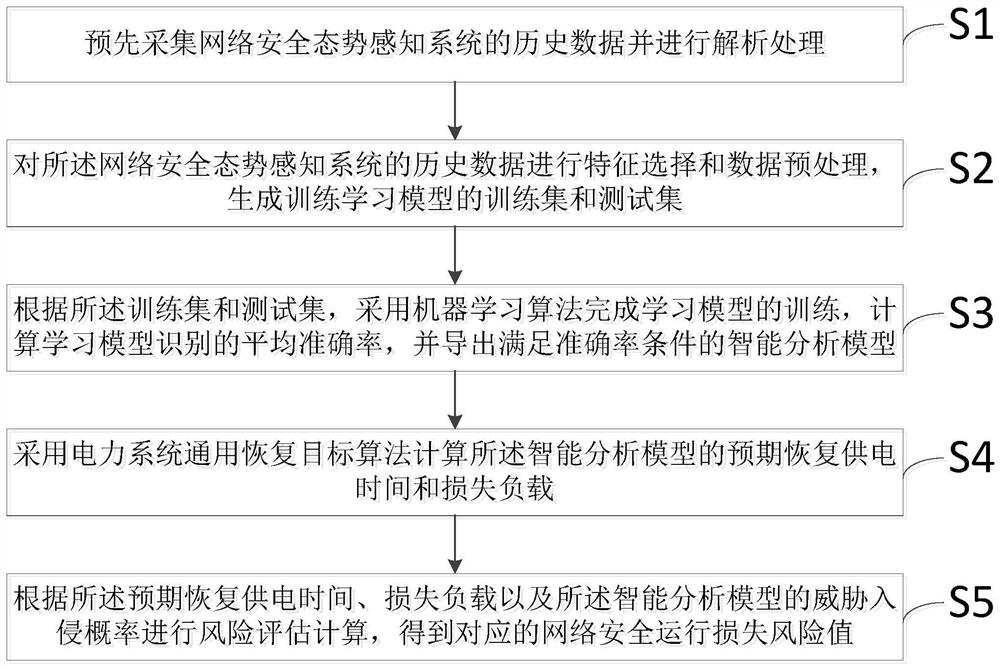
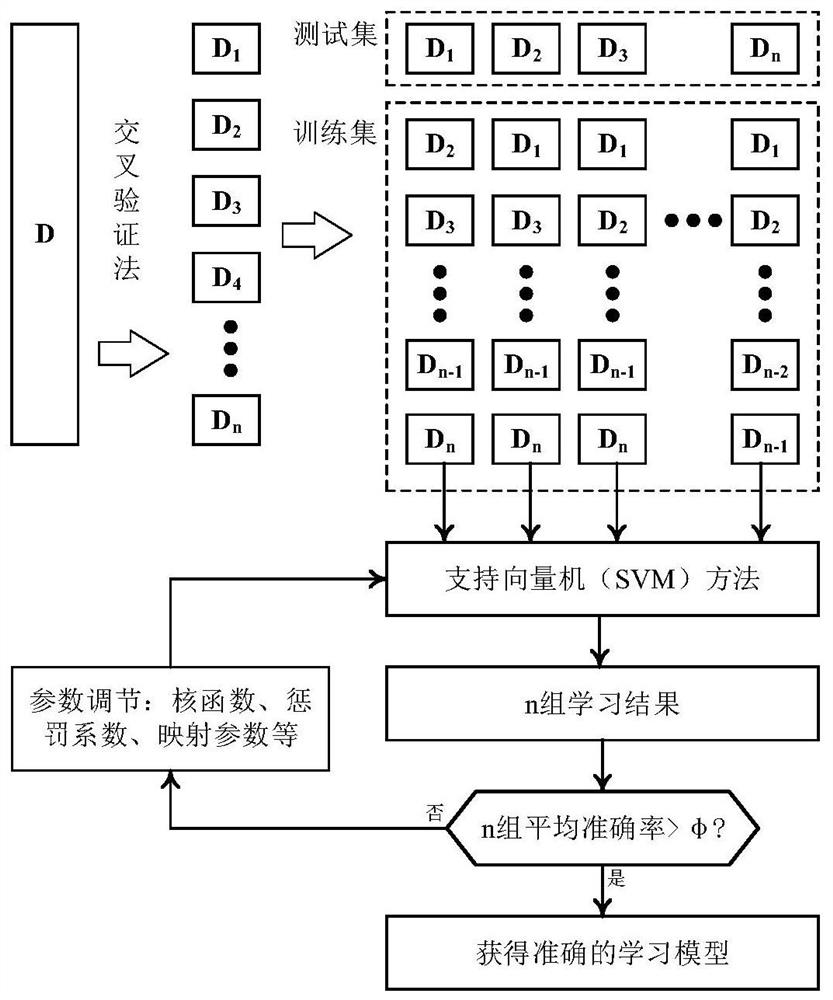
Operation risk assessment method and device based on network security situation awareness system
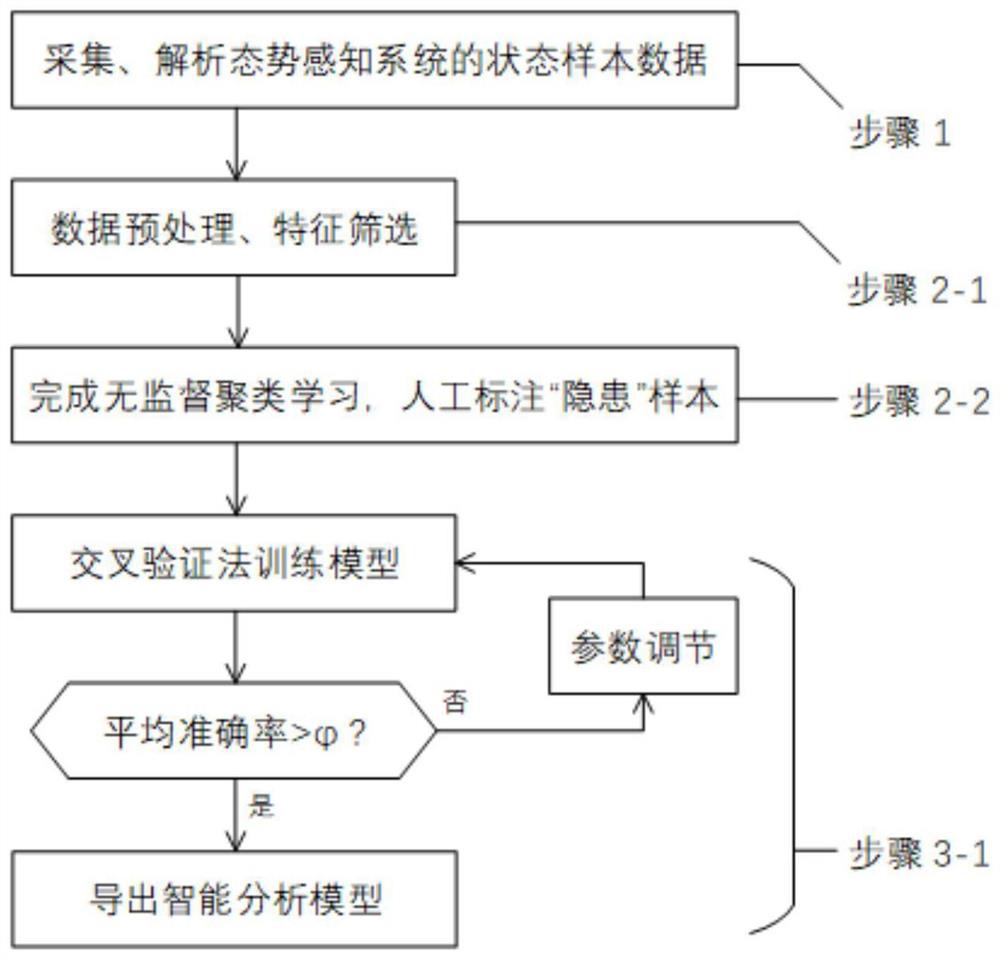
PendingCN111652496AImprove accuracyIncrease diversityKernel methodsCharacter and pattern recognitionAnalytic modelComputational intelligence
The invention discloses an operation risk assessment method and device based on a network security situation awareness system. The method comprises the steps: collecting historical data of the networksecurity situation awareness system in advance and analyzed; performing feature selection and data preprocessing on historical data of the network security situation awareness system to generate a training set and a test set for training a learning model; completing training of a learning model by adopting a machine learning algorithm, and exporting an intelligent analysis model after the learning model meets the average accuracy requirement; calculating expected recovery power supply time and loss load of the intelligent analysis model by adopting a general recovery target algorithm of the power system; and performing risk assessment calculation according to the expected power restoration time, the loss load and the threat intrusion probability of the intelligent analysis model to obtaina corresponding network security operation loss risk value. The method and device can combine the power system intrusion probability model and the network security situation awareness system to evaluate and calculate the operation risk, thus improving the risk evaluation accuracy.
Owner:CHINA ENERGY ENG GRP GUANGDONG ELECTRIC POWER DESIGN INST CO LTD
Method for laser-assisted automatic focusing, and apparatus
ActiveCN105554363AImprove autofocus accuracyImprove experienceTelevision system detailsColor television detailsComputational intelligenceLaser assisted
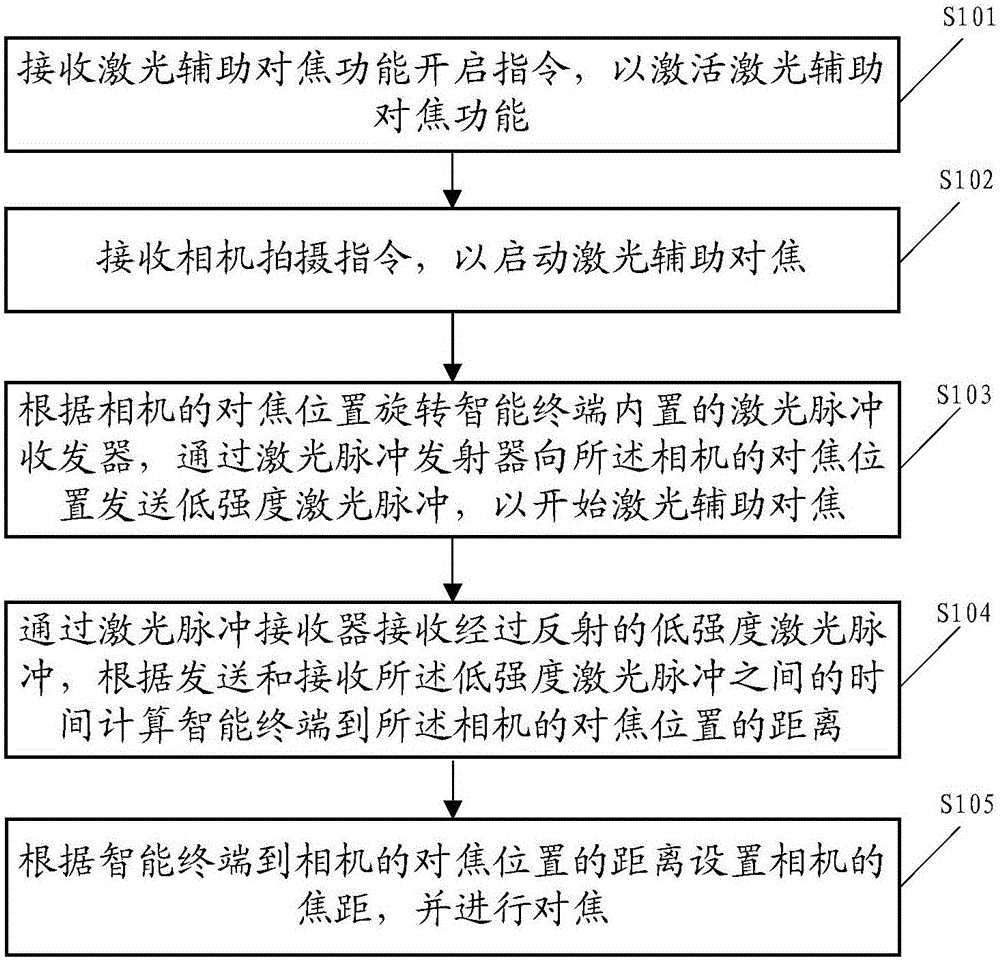
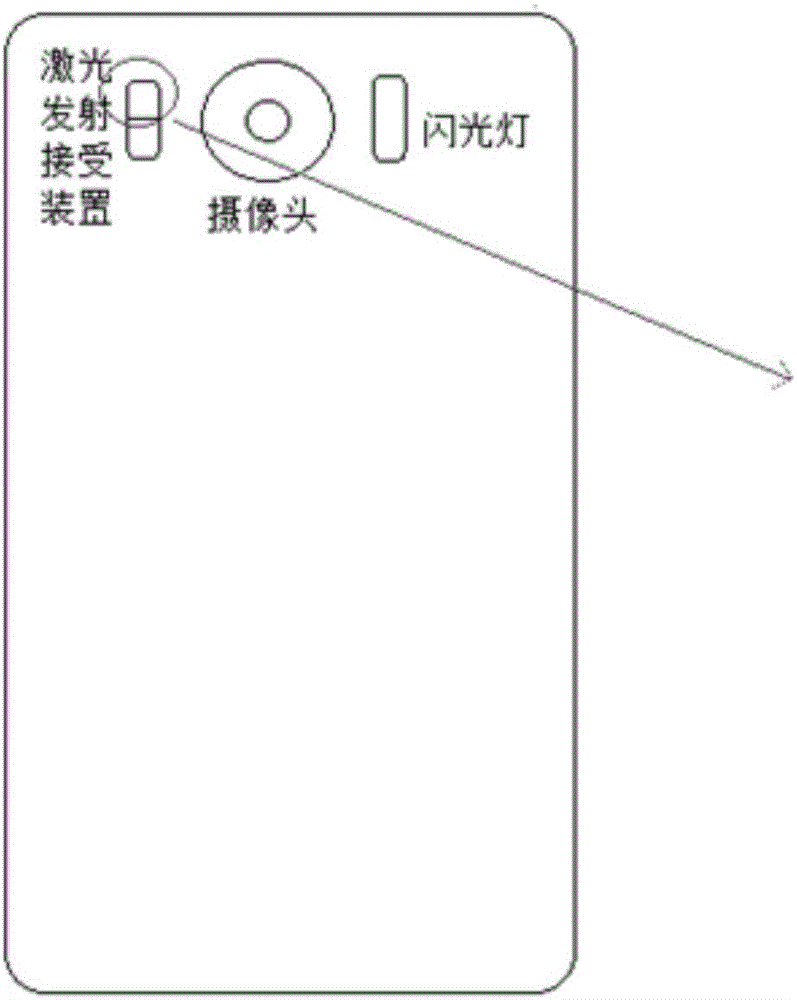
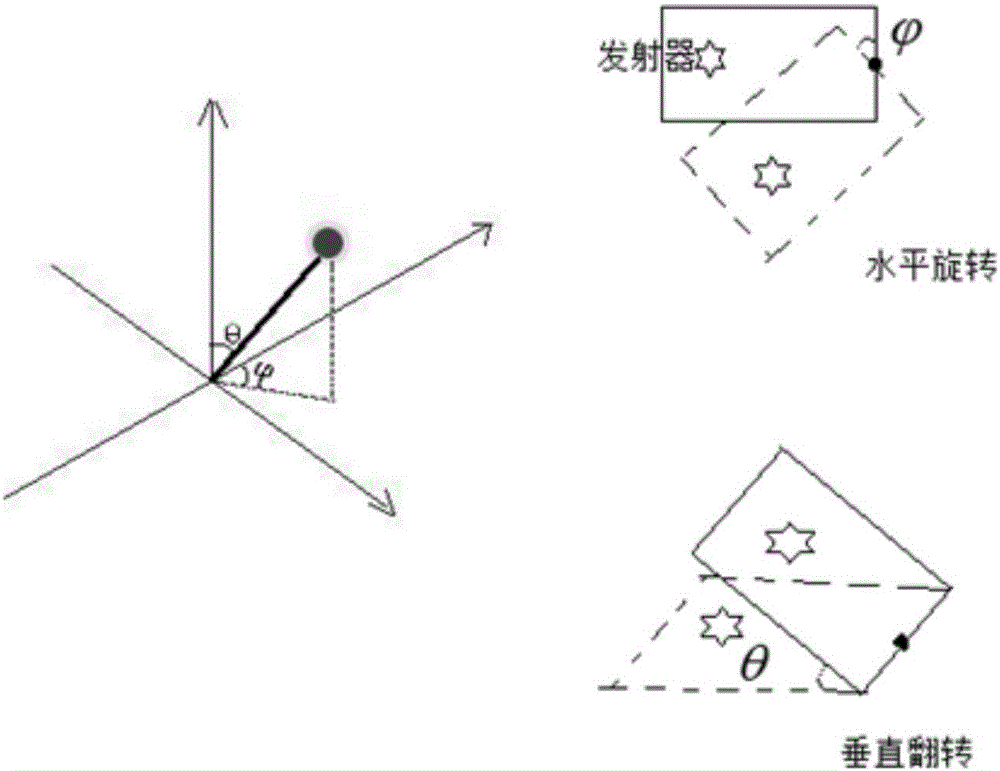
The embodiment of the invention discloses a method for laser-assisted automatic focusing. The method comprises: a laser-assisted focusing function starting instruction is received to activate a laser-assisted focusing function; a camera shooting instruction is received to start laser-assisted focusing; according to the focusing position of the camera, laser pulse transmitter and receiver are rotated and a low-intensity laser pulse is sent to the focusing position of the camera by the laser pulse transmitter; the laser pulse receiver receives the reflected low-intensity laser pulse, and a distance between an intelligent terminal and the focusing position of the camera is calculated according to time between sending the low-intensity laser pulse and receiving the low-intensity laser pulse; and according to the distance between the intelligent terminal and the focusing position of the camera, an image distance of the camera is set and focusing is carried out. According to the technical scheme provided by the embodiment of the invention, the laser pulse transmitter and receiver can be rotated according a focusing position needed by a user and laser-assisted automatic focusing at different focusing positions is supported, so that the automatic focusing precision of the intelligent terminal is improved and thus the user experience is improved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
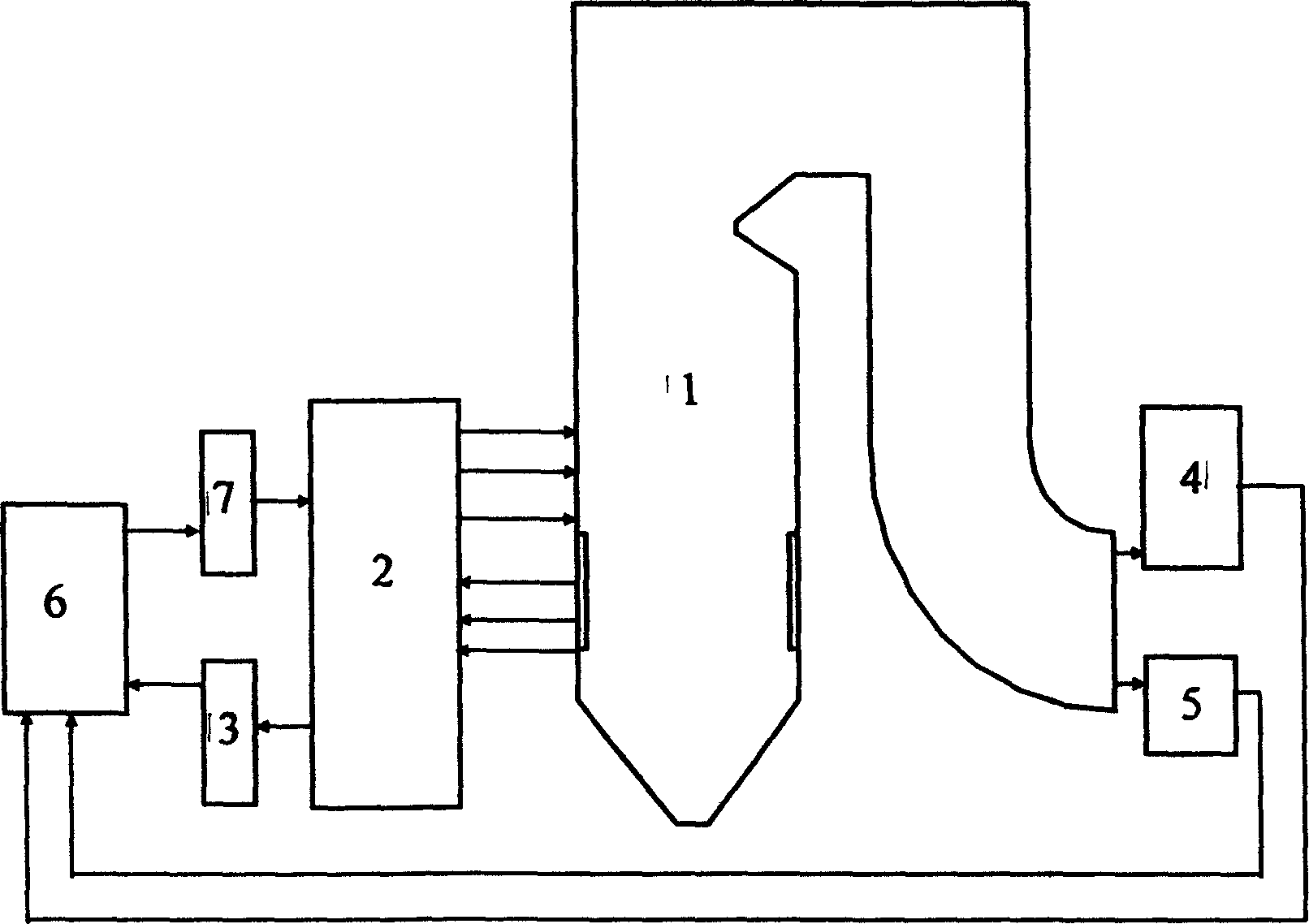
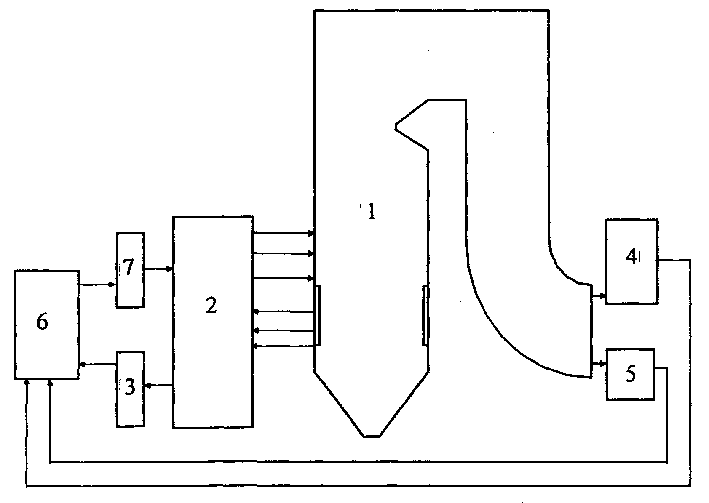
In-situ boiler combustion optimizing control system based on computational intelligence
InactiveCN1453669ARealize online adaptive optimization controlAdaptive controlComputational intelligenceDistributed control system
The present invention is in-situ boiler combustion optimizing control system based on computational intelligence. The control system has download interface to download the operation parameters from the distributed control system, in-situ boiler tail fume monitoring system to obtain the fume components of the boiler, flyash carbon content monitoring system in the tail of boiler to obtain the carbon content in flyash and data base to store all the parameters and data for learning, establishing non-linear model and global optimization calculation. The present invention can obtain boiler optimizing operation scheme with least pollutant exhaust, reach the maximum boiler efficiency in certain boiler pollutant exhaust limitation, and reach multipurpose optimization scheme.
Owner:ZHEJIANG UNIV
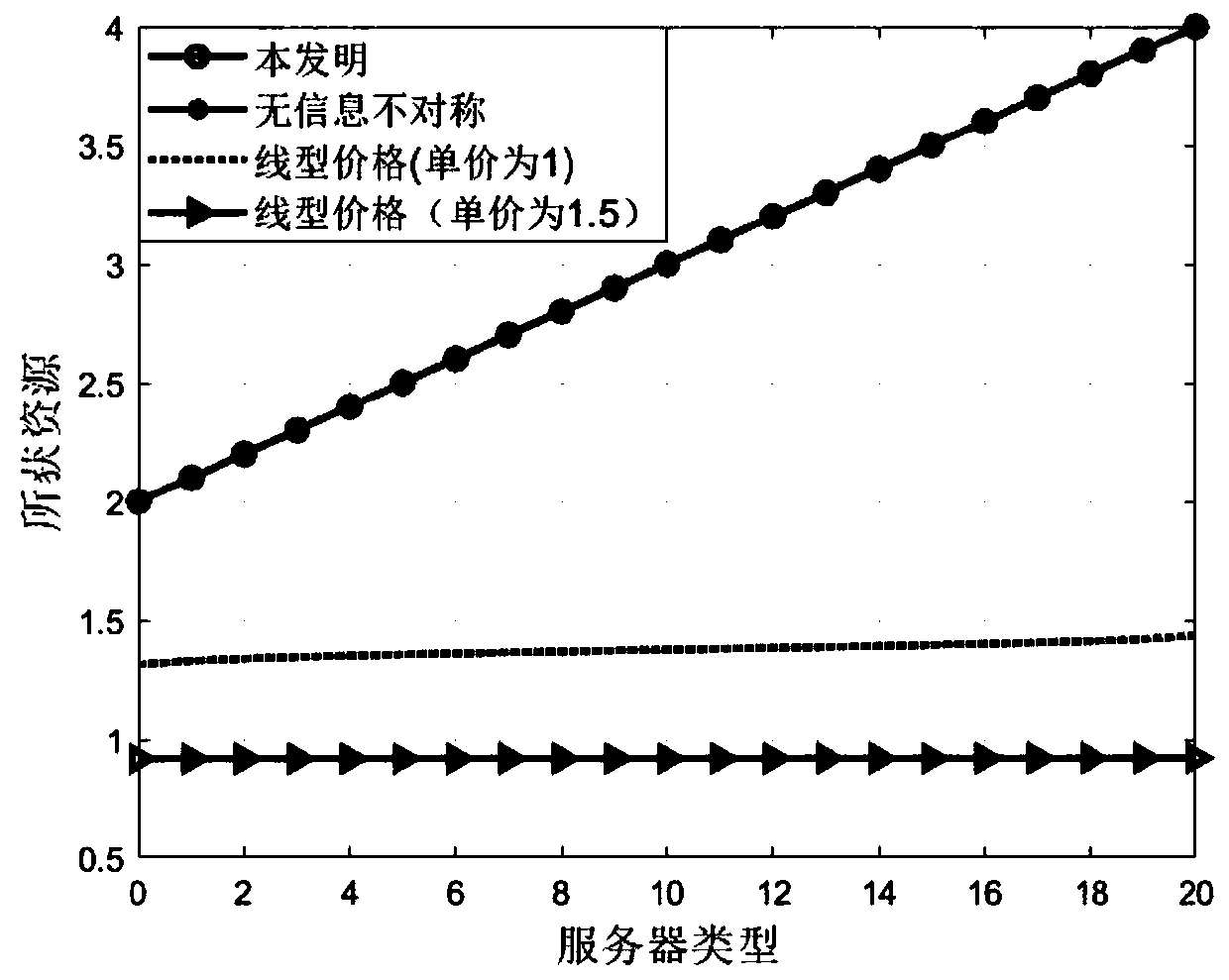
Task unloading mechanism under information asymmetry and uncertainty in internet of things fog computing
ActiveCN109951873ANetwork traffic/resource managementMachine learningConfidence intervalThe Internet
Along with the rapid development of intelligent equipment and computing intensive applications, fog computing becomes a promising solution meeting ever-increasing computing requirements. In particular, at peak times, computing tasks can be offloaded from an overload base station (BS) to a fog server by utilizing computing resources that are not fully utilized on the demand side. However, there aretwo main obstacles that hinder the wide deployment of fog computing in the Internet of Things (IoT), i.e., lack of effective incentive mechanisms and task offload algorithms. In the invention, a taskunloading mechanism under information asymmetry and uncertainty in internet of things fog computing is developed by combining a contract theory with computing intelligence. In the first stage, an effective incentive mechanism is provided, and the server is encouraged to share the remaining computing resources through the contract theory. In the second stage, a distributed task unloading algorithmis provided by utilizing the online learning capability of a multi-arm gambling machine (MAB). Specifically, we propose a fluctuation confidence interval algorithm with distance perception, server occurrence time perception and task attribute perception to minimize long-term delay task unloading.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
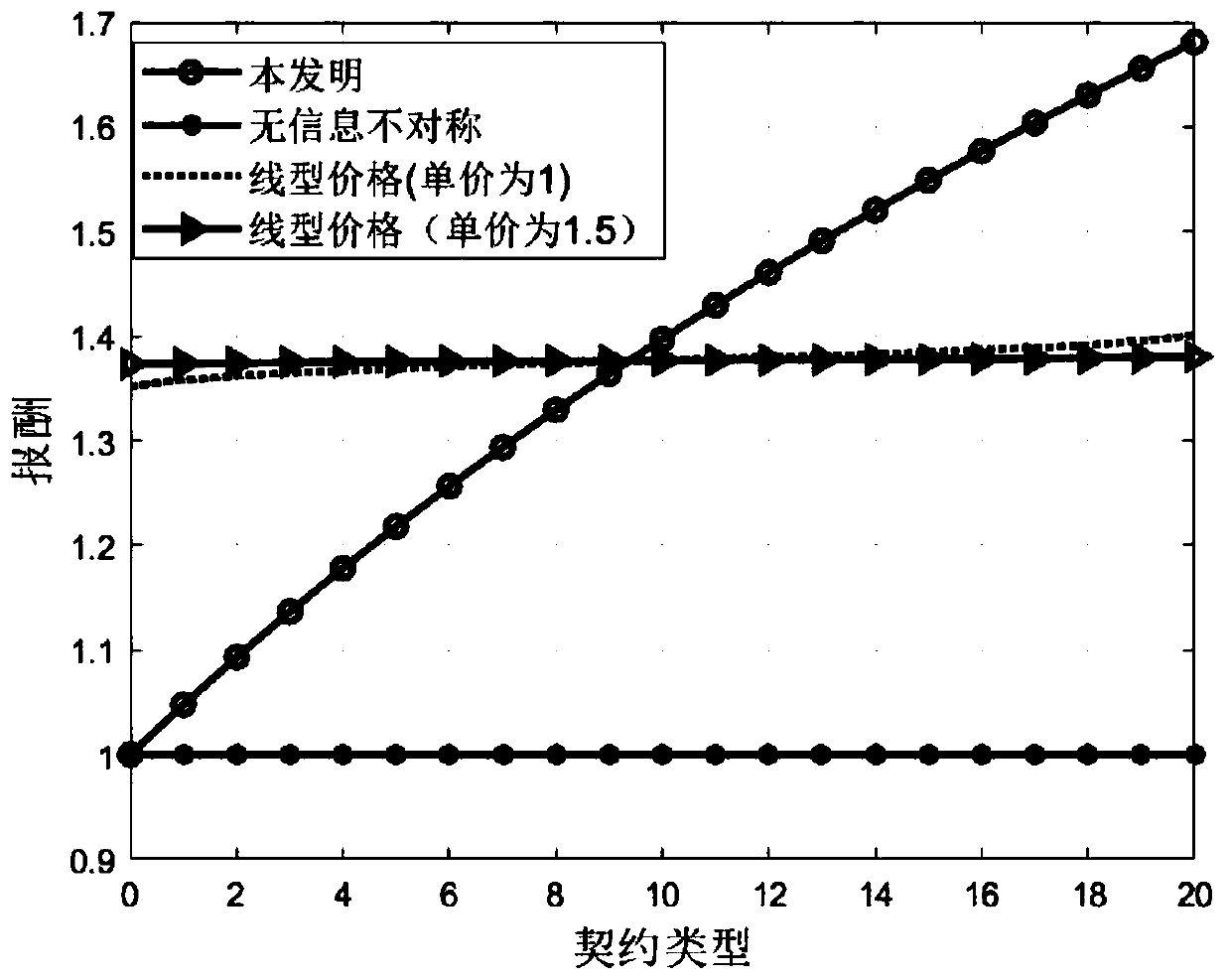
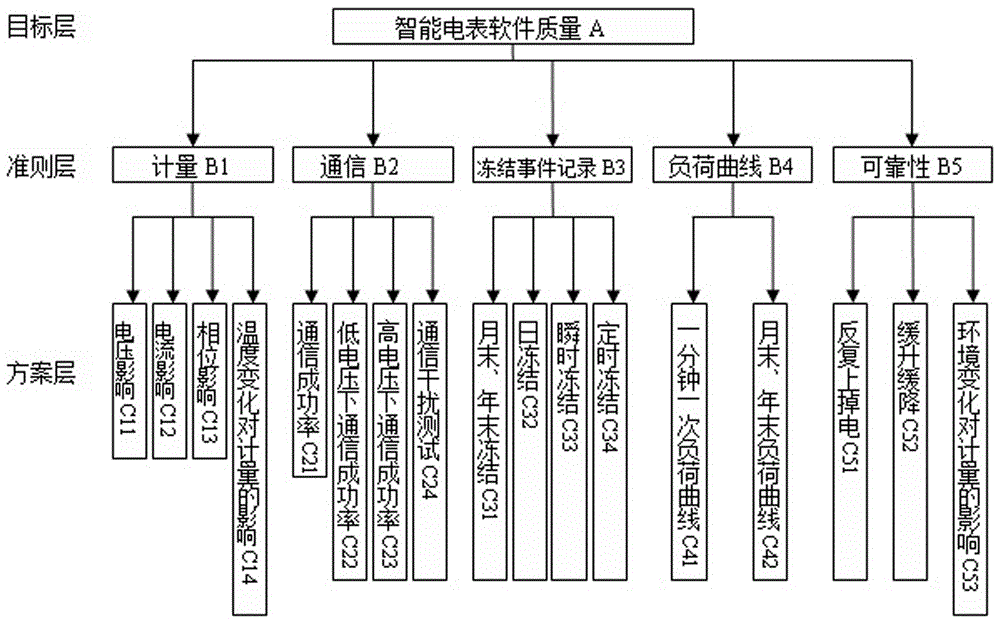
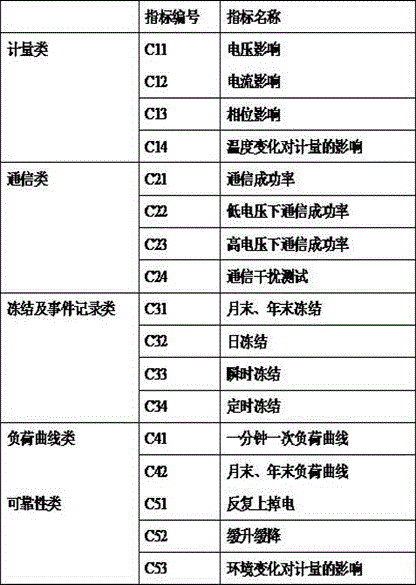
AHP (Analytic Hierarchy Process) based intelligent electricity meter software quality evaluation method
InactiveCN106447212AComprehensive evaluationEvaluation scienceResourcesComputational intelligenceIndex system
The invention discloses an AHP (Analytic Hierarchy Process) based intelligent electricity meter software quality evaluation method. The method comprises the steps of S1, building an intelligent electricity meter software quality evaluation index system; S2, building an intelligent electricity meter software quality evaluation model; S3, determining the relative weight of each evaluation index; S4, determining evaluation levels of the evaluation indexes and evaluation standards corresponding to the evaluation levels, and then determining a score of each evaluation index in a scheme layer; and S5, calculating a comprehensive score of the intelligent electricity meter software quality according to the score of each evaluation index and the relative weight of each evaluation index. According to the invention, the blank of the intelligent electricity meter software quality evaluation method is filled up, an evaluation system for the intelligent electricity meter software quality is established, the quality of software in electricity meters from different suppliers and of different versions can be evaluated comprehensively and scientifically, and then references are provided for evaluating the quality of software in intelligent electricity meters from different suppliers.
Owner:ELECTRIC POWER RES INST OF GUANGXI POWER GRID CO LTD
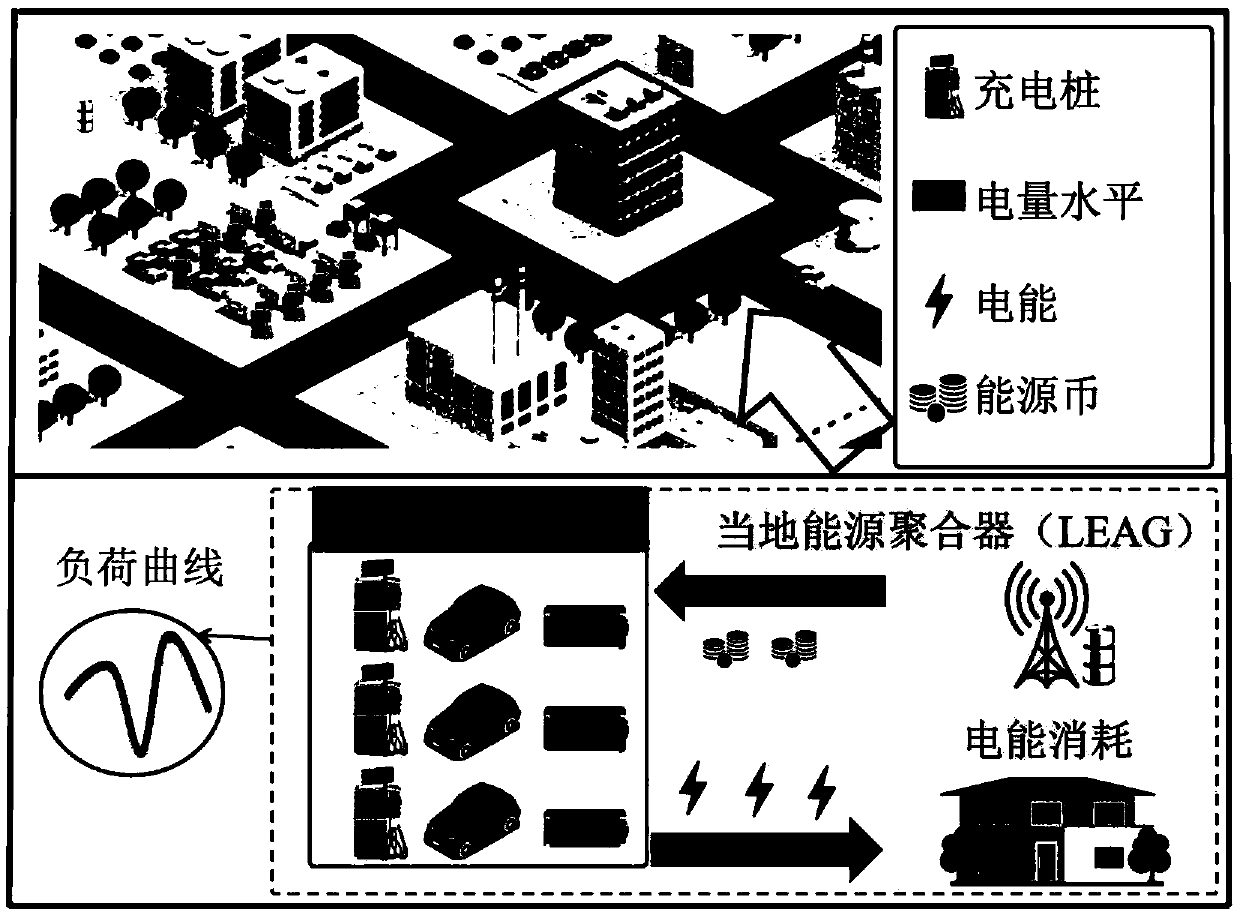
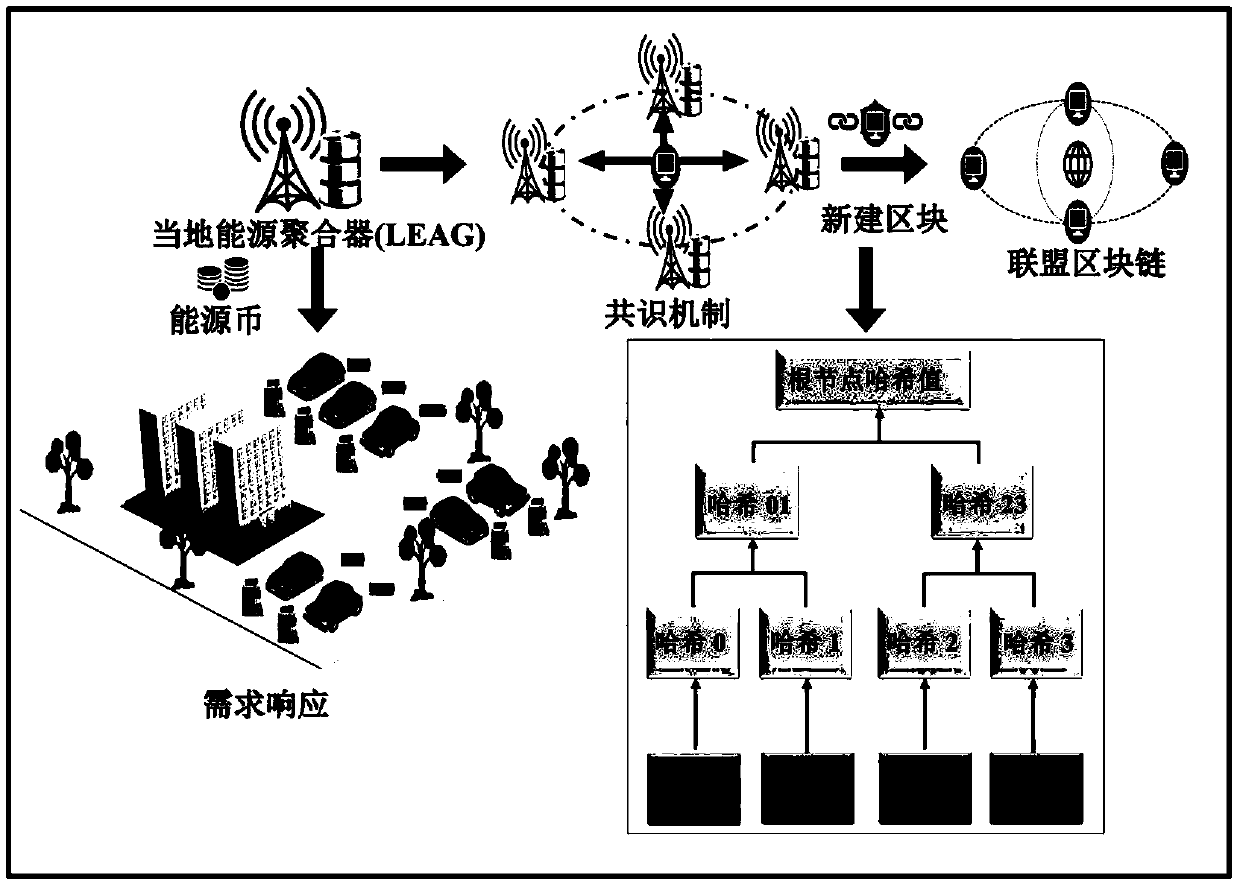
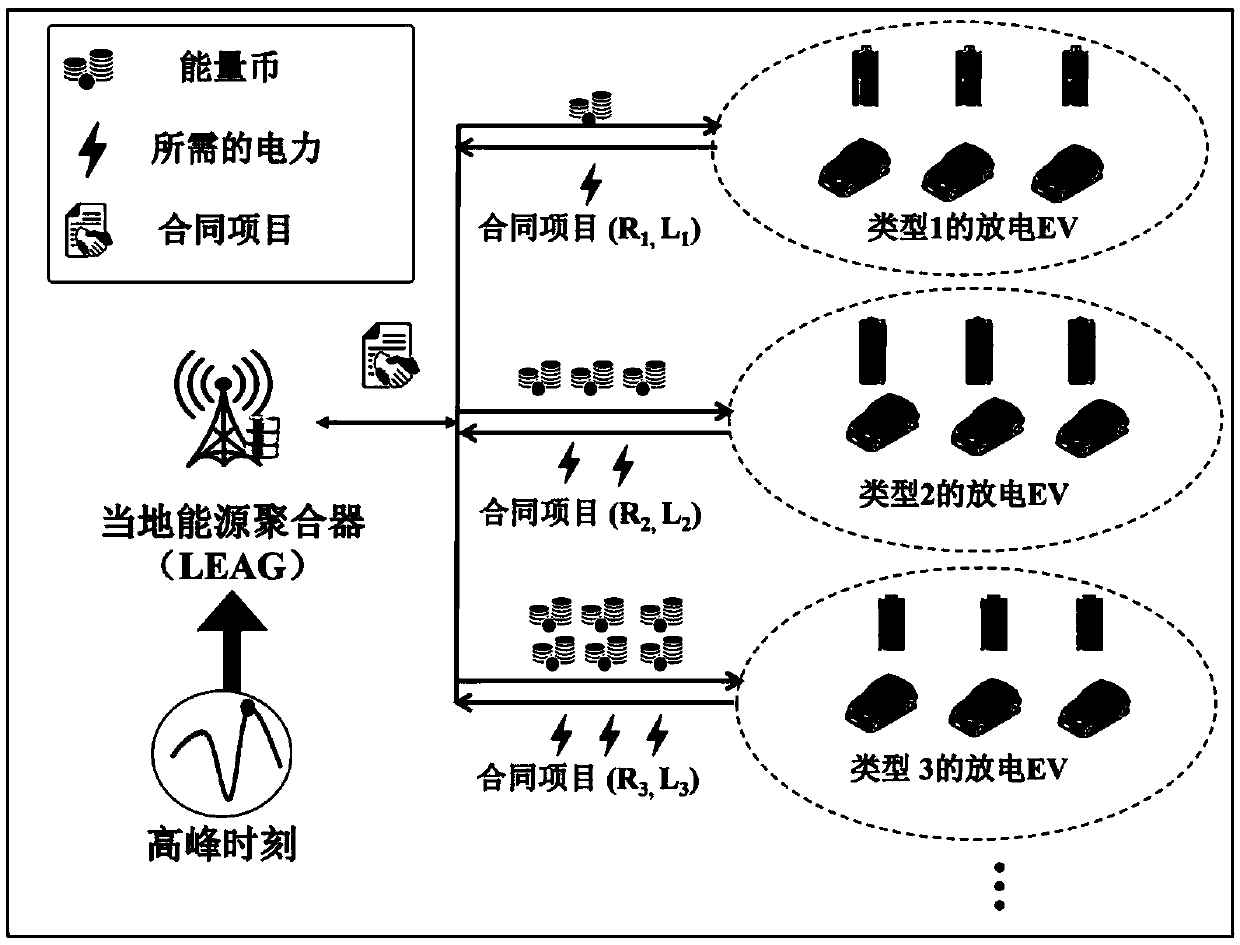
Electric vehicle charging incentive mechanism based on block chain and machine learning
The invention relates to an electric vehicle Internet scene applied to a local energy aggregator and an electric vehicle for carrying out demand response, and a method for jointly solving the problemsof how to protect the safety of transaction information and the privacy of both parties of the transaction, how to design an incentive mechanism, and how to predict the private information of the electric vehicle. We propose a transaction method based on coalition block chain, which protects the security of transaction information and the privacy of both parties, and reduces the cost of consensusprocess in the process of building a transaction information block. In order to encourage electric vehicles to participate in demand response, we propose an incentive-compatible demand response mechanism based on contract theory modeling. In order to maximize social welfare, the contract is tailored to the unique characteristics of each type of electric vehicles. The optimization problem is solved by using the iterative convex-concave programming algorithm. In order to predict the private information of electric vehicles, we derive the probability distribution of EV type by exploring the computationally intelligent state-of-charge (SoC) estimation technology. Finally, the relationship among social welfare, EV type, incentive, emission power and SoC estimation errors is illustrated by numerical results.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Intelligent home control system based on bluetooth
InactiveCN104777750AStrong sense of interactionStrong user experienceComputer controlTotal factory controlComputational intelligenceControl system
The invention relates to an intelligent home, and provides an intelligent home control system based on bluetooth. The intelligent home control system is characterized by comprising an intelligent home and an intelligent terminal, wherein a bluetooth transmitting module and a control module are arranged on the intelligent home, a bluetooth receiving module and a direction computing module are arranged on the intelligent terminal; the bluetooth transmitting module is used for providing a bluetooth base station and transmitting the status information of the intelligent home, and the status information at least comprises the operating state and the position information of the intelligent home; the direction computing module is used for computing the direction information, relative to the intelligent home, of the intelligent terminal, and feeding back the direction information to the bluetooth transmitting module; the bluetooth receiving module is used for receiving the direction information, relative to the intelligent home, of the intelligent terminal, and transmitting the direction information to the control module; the control module is used for regulating the current operation state of the intelligent home according to the direction information, which is relative to the intelligent home, of the intelligent terminal. The intelligent home control system based on the bluetooth is suitable for intelligent home control systems based on bluetooth.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Urban public transport route selection method
ActiveCN105023426ASolve multi-objective optimization problemsEasy to analyzeRoad vehicles traffic controlMulti objective modelTraffic flow
The invention provides an urban public transport route selection method. The method solves urban traffic congestion by fully utilizing an computational intelligence advantage, closely associates various interactive units of a urban intelligent transportation system, solves correlative problems as viewed from a system perspective, accurately predicts road condition information, reasonably plans public transport routes according to a traffic condition, enlarges the coverage of public transport, shortens the waiting time of passengers and the running periods of the public transport, and adjusts traffic flow to be in an optimal state. The method comprises establishing a multi-object model and using the average travel time of a passenger and the total length of a route as two measurement indexes; and planning an optimal public transport route by means of a heuristic algorithm in order to achieve wider coverage and better connectivity. The method may dynamically treat a urban public transport route selection problem and is better in adaptability and wider in application range.
Owner:NANJING UNIV OF POSTS & TELECOMM
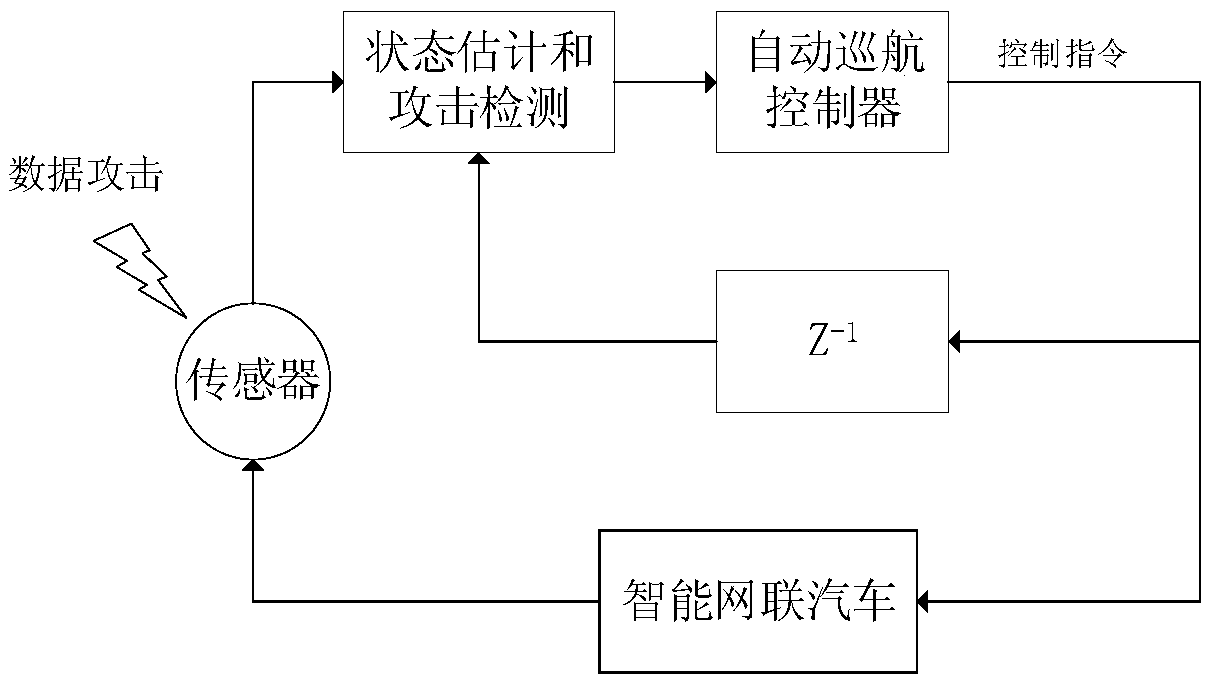
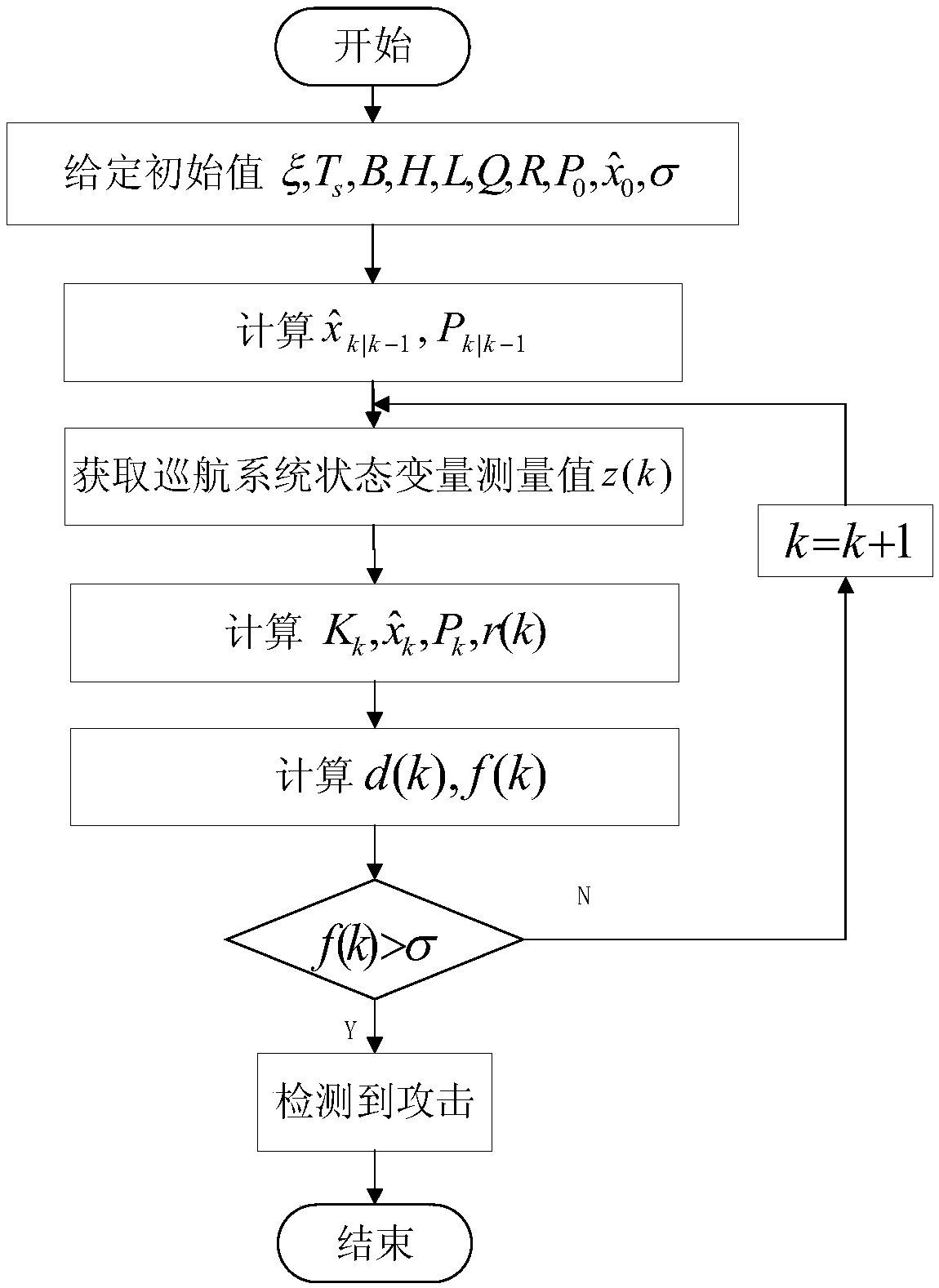
False data injection attack detection method of intelligent networked automobile automatic cruise system
ActiveCN109361678AQuick checkAnti-traffic accidentTransmissionIntelligent NetworkComputational intelligence
The invention discloses a false data injection attack detection method of an intelligent networked automobile automatic cruise system, aiming at solving the problem of false data injection attack existed in the process of network transmission of sensor measured data of the intelligent networked automobile automatic cruise system. Firstly, a discrete-time state space model of the networked automobile automatic cruise system is established, and a filter value of the measured data at each moment is calculated according to the Kalman filter formula; then the sum of noise standard deviations of measuring sensors of the automatic cruise system is taken as a detection threshold; if no data injection attack exists, the Kalman filter value gradually tends to a true value; and when the error betweenthe Kalman filter value and the measured value exceeds a given threshold, it is detected that a false data injection attack is existed at the intelligent networked automobile automatic cruise system.The invention only needs to calculate the state filter value of the intelligent networked automobile automatic cruise system in real time according to the newly obtained observation data, and processthe observation result in real time online, so that the accident that the state data of the intelligent networked automobile automatic cruise system is attacked can be quickly detected.
Owner:ZHEJIANG UNIV OF TECH
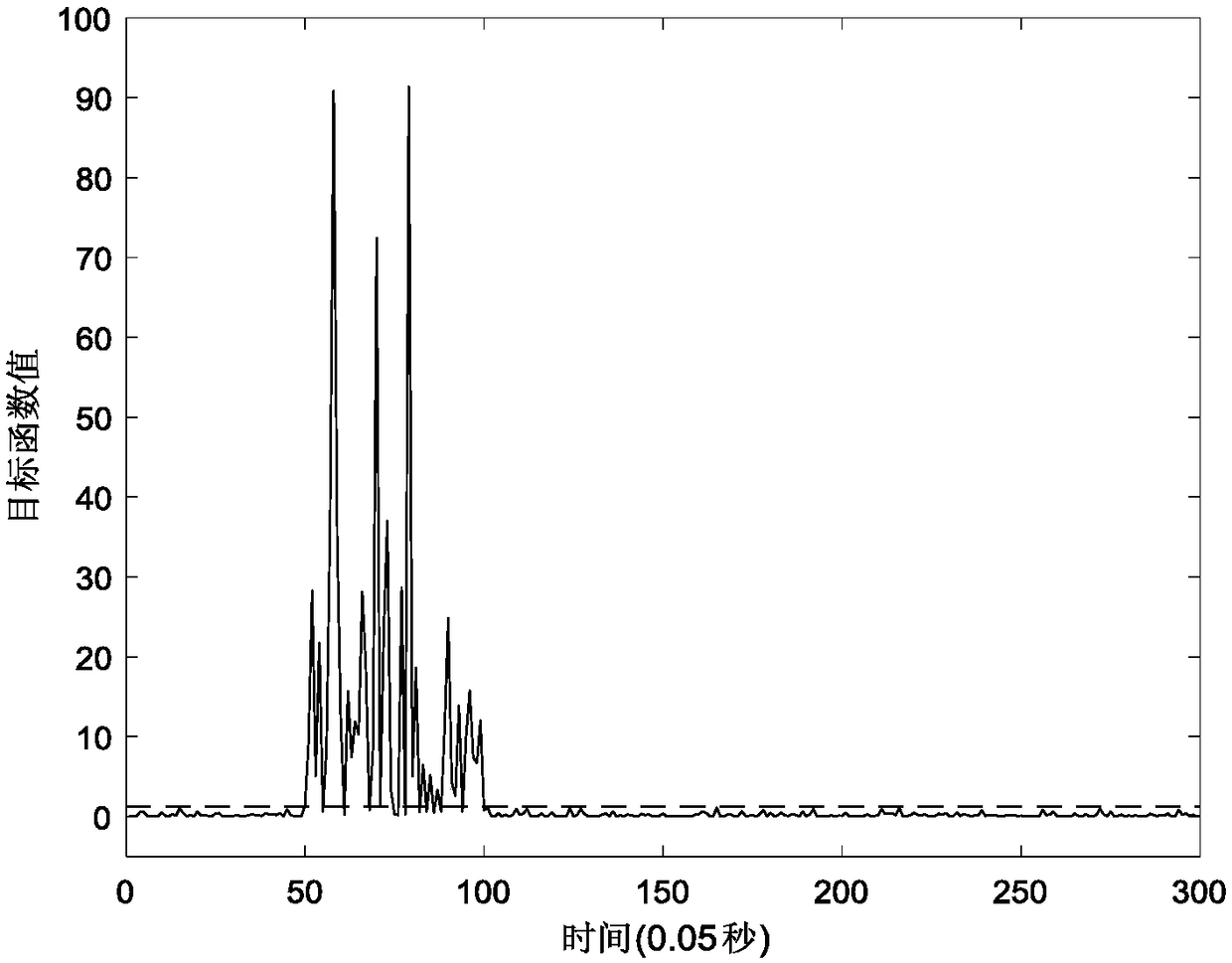
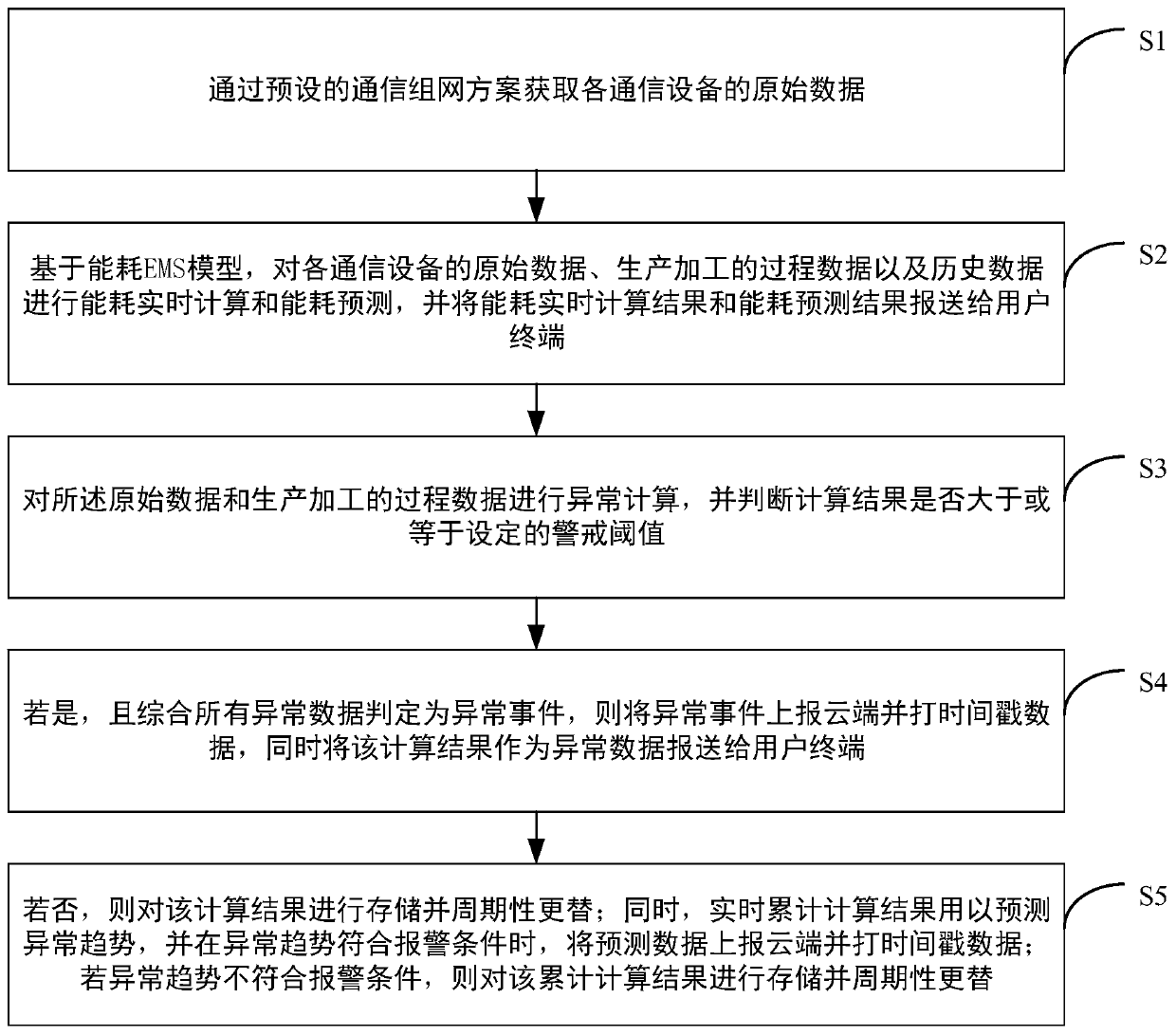
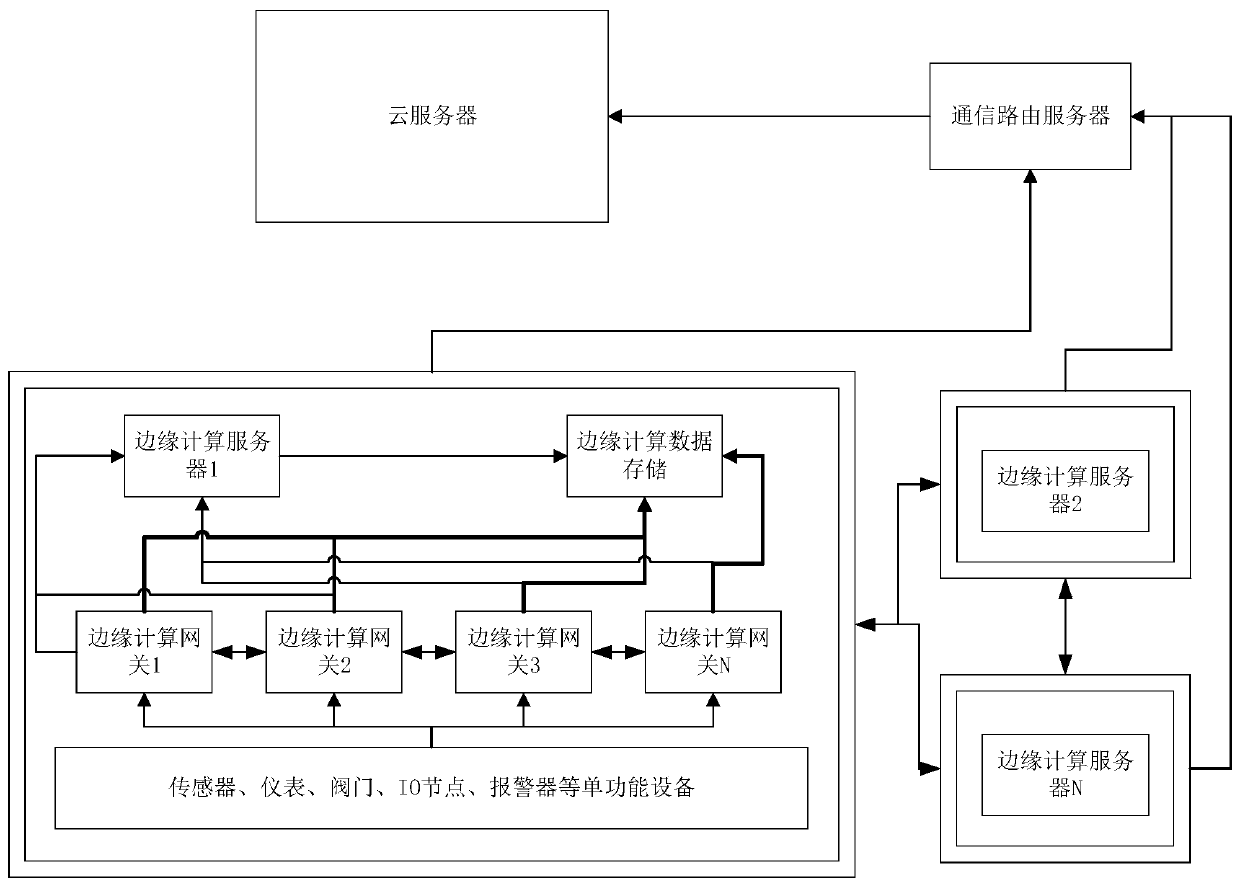
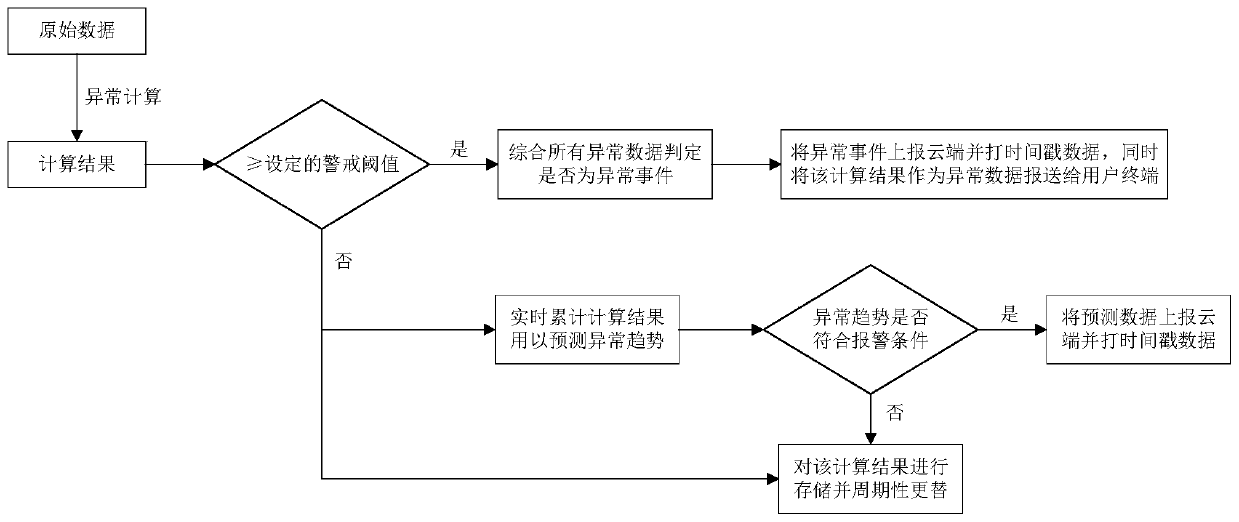
Edge computing intelligent gateway service processing method and edge computing intelligent gateway
ActiveCN110365529AImprove processing efficiencyLower latencyNetwork connectionsOriginal dataEdge computing
The invention discloses an edge computing intelligent gateway service processing method and an edge computing intelligent gateway. The method comprises the following steps: acquiring original data ofeach communication device through a preset communication networking scheme; based on the energy consumption EMS model, performing energy consumption real-time calculation and energy consumption prediction on the original data of each communication device, the production and processing process data and the historical data, and reporting an energy consumption real-time calculation result and an energy consumption prediction result to a user terminal; and performing anomaly calculation on the original data and the production and processing process data, executing a series of judgment operations,and reporting corresponding data to a user terminal. According to the invention, the edge computing intelligent gateway is used for processing and analyzing the industrial data, and the edge end is used for communicating with the cloud end, so that the data processing efficiency is improved, the cloud computing pressure is reduced, and the data delay is reduced.
Owner:广州博依特智能信息科技有限公司
Method and system for achieving vibration navigation on smart wearable device
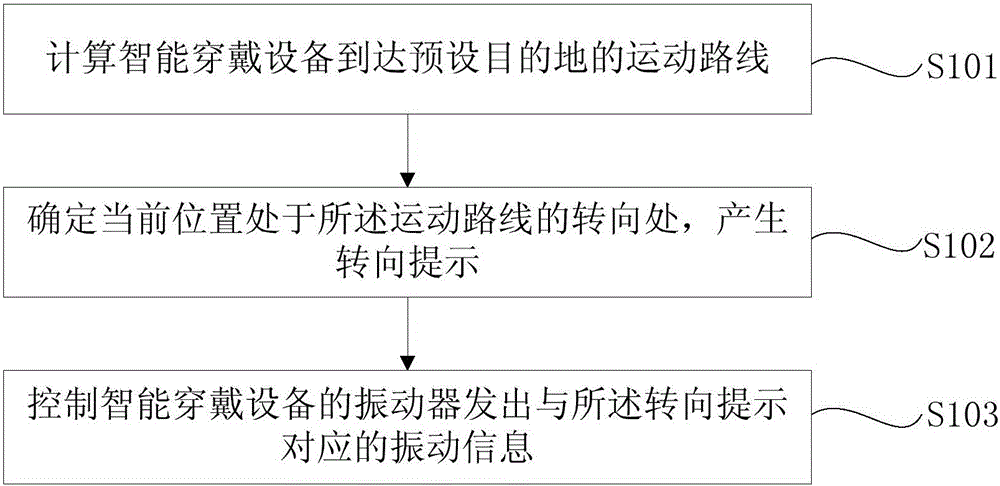
InactiveCN106092089AImprove discriminationImprove experienceNavigation instrumentsComputational intelligenceEngineering
The invention discloses a method and system for achieving vibration navigation on a smart wearable device. The method comprises the steps that the movement route that the smart wearable device arrives at a preset destination is calculated; when it is determined that the current position is located at the turning place of the movement route, a turning prompt is generated; multiple vibrators of the smart wearable device are controlled to send vibration information corresponding to the turning prompt, wherein the vibration information comprises the fact that the vibrators vibrate according to a preset sequence. According to the method and system, a navigation prompt function is achieved through the vibration information that the vibrators vibrate according to the preset sequence, a user can quickly, easily and accurately perceive the navigation orientation without needing to view a navigation interface, and distinguishing on navigation can be promoted.
Owner:XIAOTIANCAI TECH
Automatic fire extinguishing method and system for intelligent gun employing compressed air foam
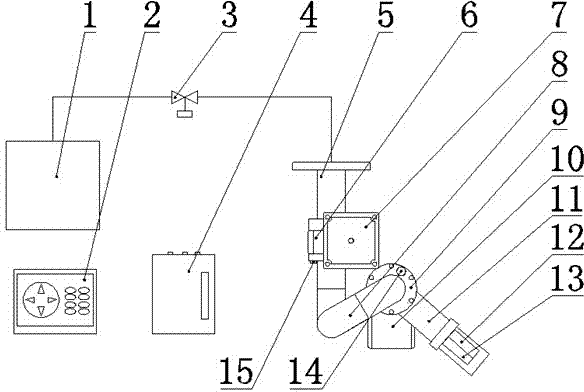
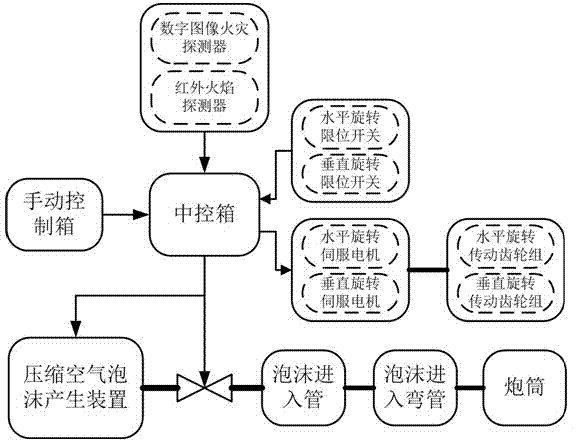
ActiveCN104740818APrecise applicationRealize automatic monitoringFire rescueStopped workComputational intelligence
The invention discloses automatic fire extinguishing method and system for an intelligent gun employing compressed air foam. The automatic fire extinguishing method comprises the following steps: firstly, detecting and positioning a fire source; once a fire occurs, immediately starting a fire source positioning procedure, and calculating the jet pitching angle of the intelligent gun, so as to automatically adjust the direction and angle of a gun muzzle; receiving a fire extinguishing instruction by a foam generating device, beginning to work, and turning on an electric control valve; and after the fire source is put out, enabling the foam generating device to stop working, and turning off the electric control valve. According to the automatic fire extinguishing method and system, automatic monitoring of the fire and fire extinguishing in an accurate positioning manner can be realized. The system is simple in structure, convenient to mount, large in protection range, timely in fire detection response, and high in fire extinguishing efficiency; the fire can be put out at an initial stage; the amount of a foam extinguishing agent and water is reduced; through controlling horizontal swinging of the intelligent gun around a fire source point as a center, the coverage range of the foam is greatly increased, the technical problem of extinguishing of large-area flowing fire caused by liquid fuel leakage is solved, and the reliability and the application range of the automatic fire extinguishing method for the intelligent gun employing the compressed air foam are improved.
Owner:应急管理部天津消防研究所
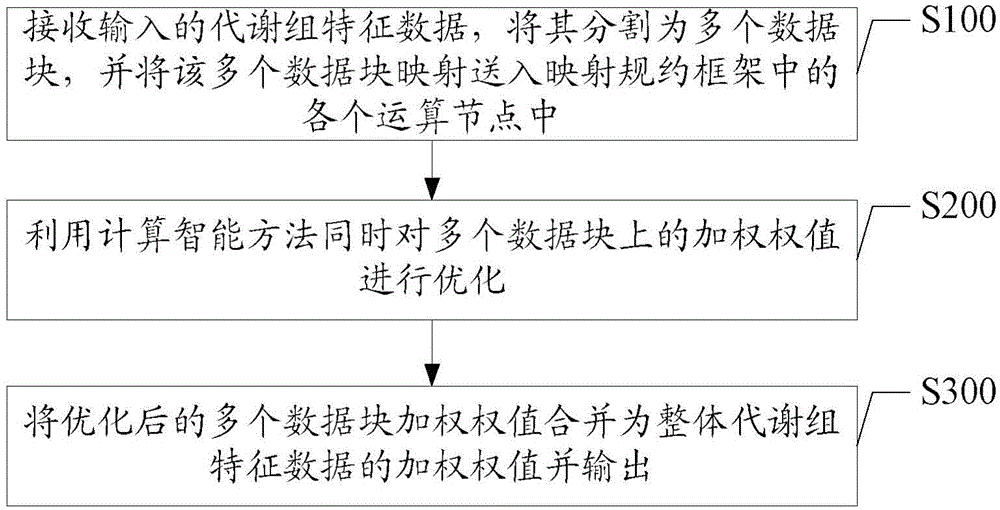
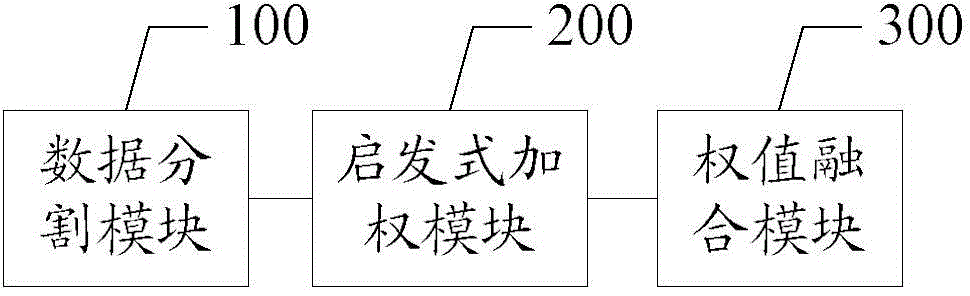
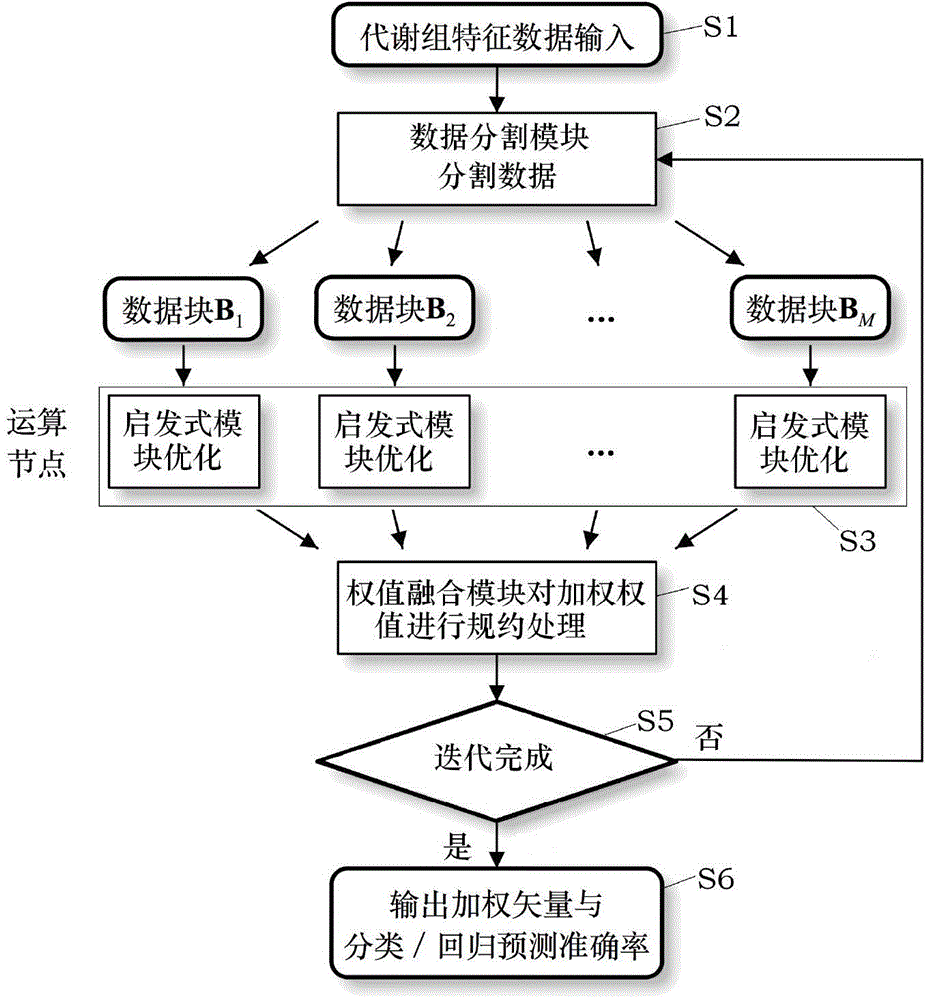
Big data-oriented metabolome characteristic data analysis method and system thereof
InactiveCN104063631AReduce the difficulty of weighted analysisShorten operation timeBiostatisticsSpecial data processing applicationsNODALComputational intelligence
The invention discloses a big data-oriented metabolome characteristic data analysis method and a system thereof. The method comprises the following steps: A) receiving inputted metabolome characteristic data, cutting into multiple data blocks, and mapping and sending the data blocks into each operation node of a mapping protocol frame; B) utilizing a computational intelligence method to simultaneously optimize weighting values on the data blocks; C) merging the optimized weighting values of the data blocks into a weighting value of the whole metabolome characteristic data and outputting. A data block-dividing processing mechanism of the system provided by the invention is capable of reducing the weighting analysis difficulty and efficiently increasing the forecast accuracy. Due to a parallelization structure, the system can be deployed to multiple computational nodes, so that the operation time is obviously reduced while the efficiency and the stability of the system are ensured. According to the computational intelligence method applied by the system, the complex large-scale optimizing problem is effectively solved. The forecast accuracy is better than the forecast accuracy of the present algorithm, so that more effective forecasting for the target physiological status is realized.
Owner:周家锐 +4
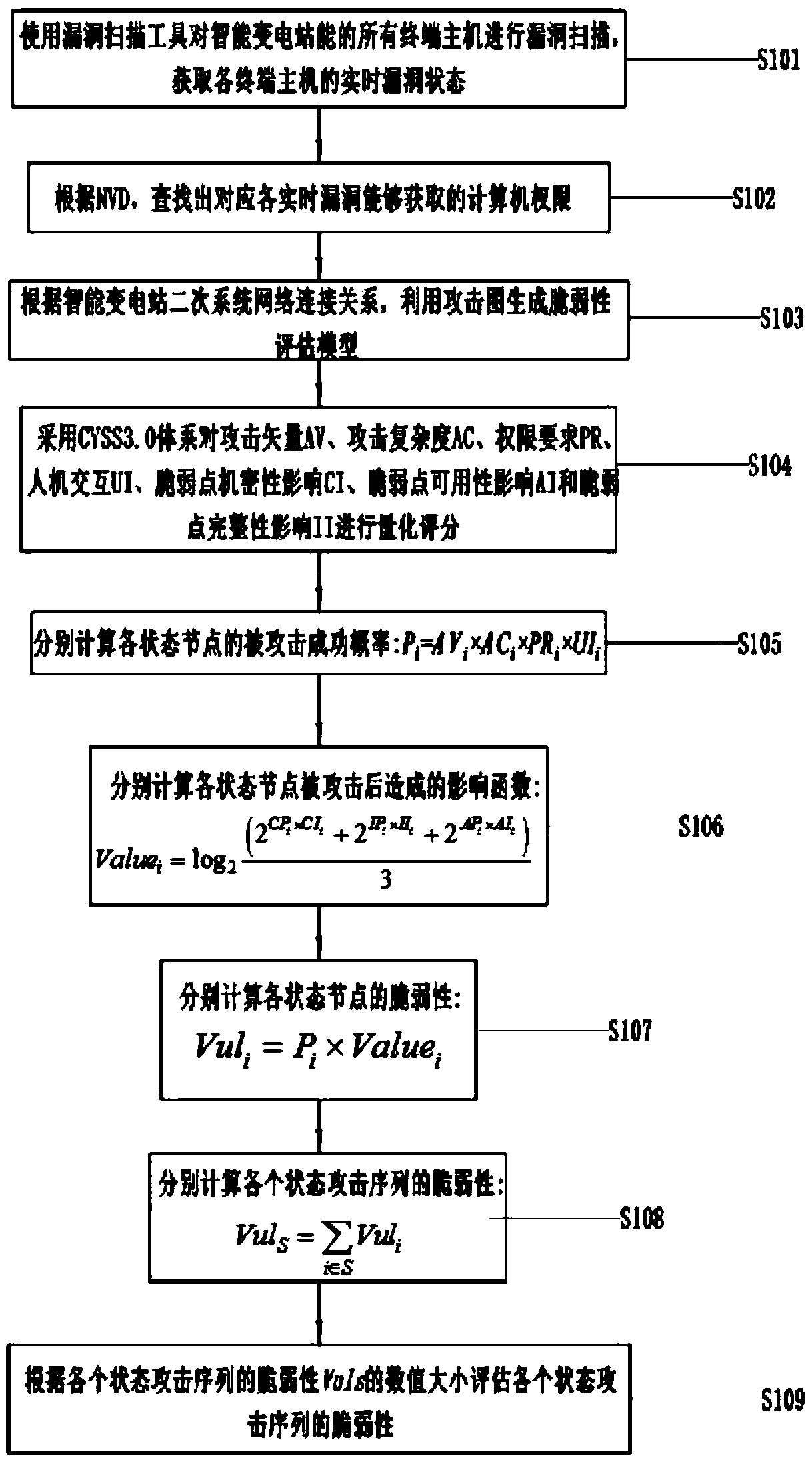
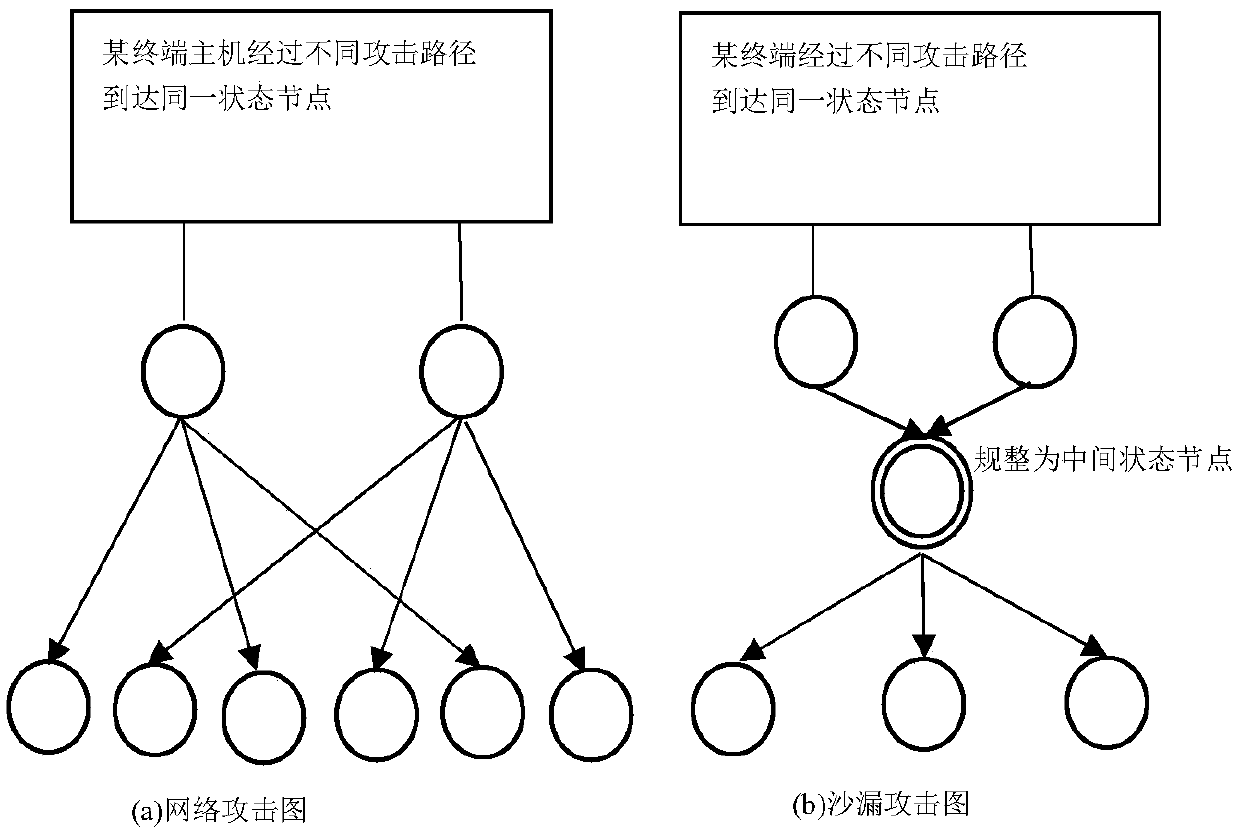
An intelligent substation relay protection vulnerability assessment method
The invention discloses an intelligent substation relay protection vulnerability assessment method, which comprises the following steps: obtaining real-time vulnerabilities of terminal hosts and corresponding computer authorities, generating a vulnerability assessment model by utilizing an attack graph in combination with an intelligent substation secondary system network connection relationship,and carrying out scoring quantification on related indexes by adopting a CVSS3.0 system; The attack success probability of each state node is calculated respectively, the influence function caused bythe attack of the vulnerability of each state node is calculated respectively, the vulnerability of each state node is calculated respectively, the vulnerability of each state attack sequence is calculated respectively, and the overall vulnerability of the information network in the intelligent substation to protection rejection / misoperation is calculated respectively; The method has high evaluation accuracy, plays an important role in guiding the design of the secondary system of the intelligent substation, and is high in practicability and innovativeness.
Owner:GUANGDONG UNIV OF TECH
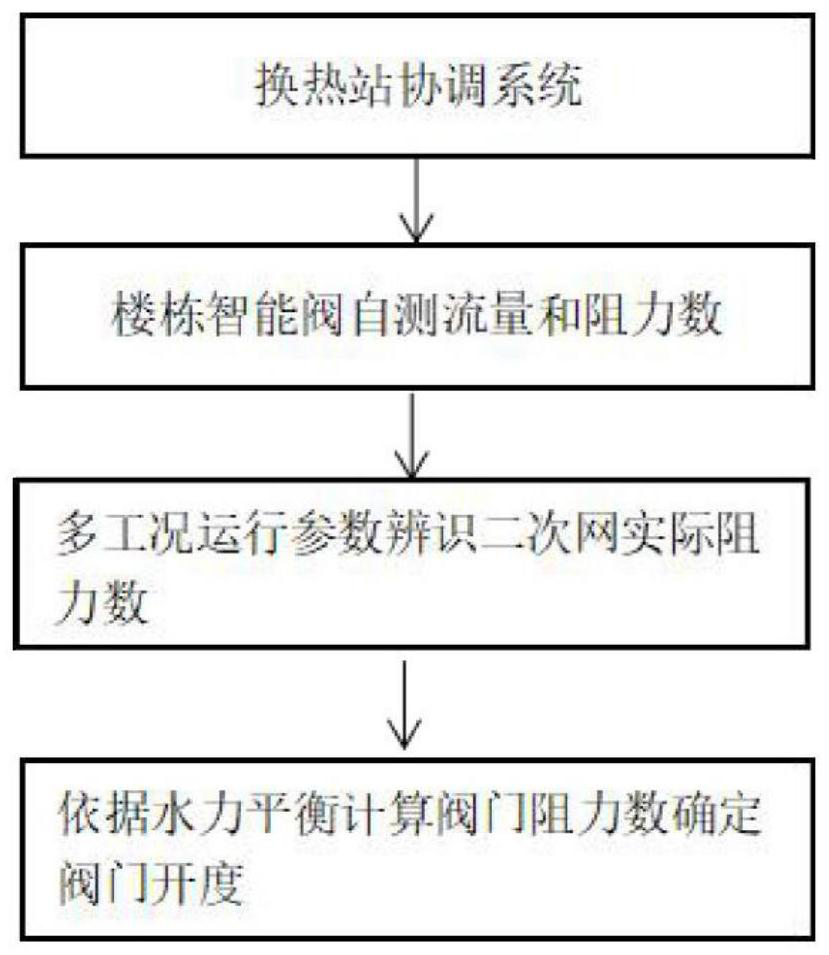
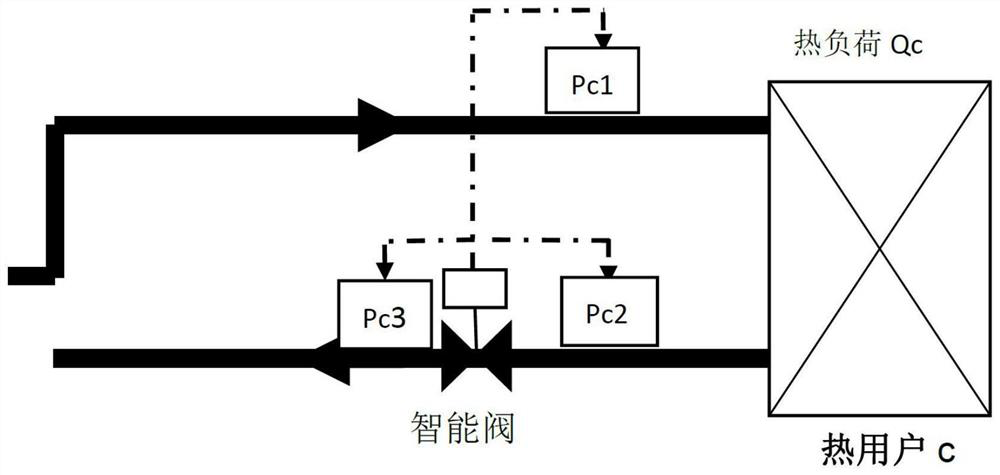
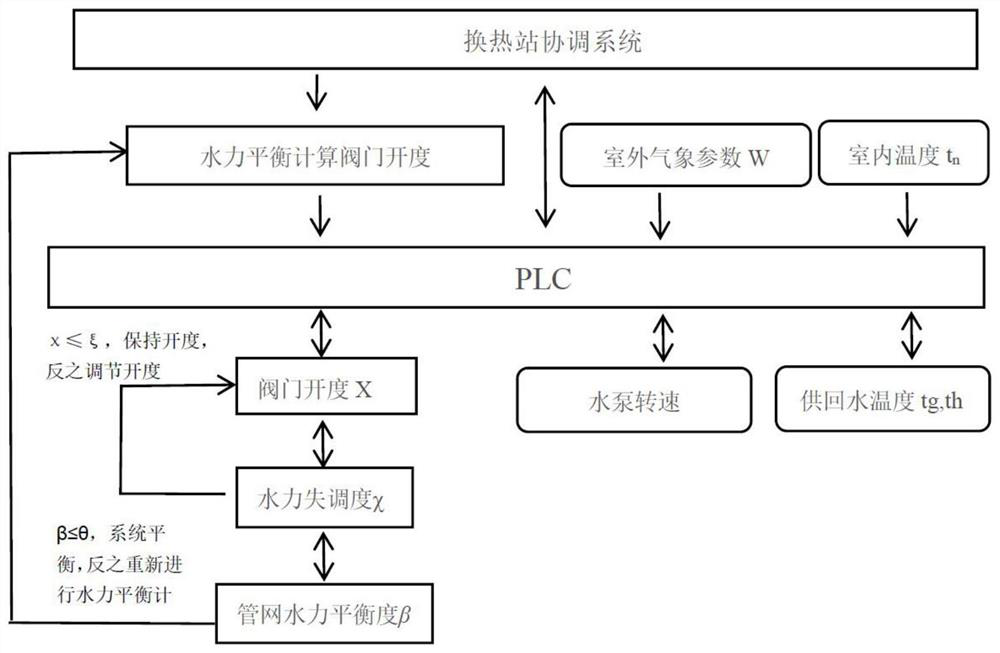
Intelligent valve based secondary network hydraulic equilibrium method
ActiveCN111928335AAutomatic hydraulic balance adjustmentAutomatic calculation of openingLighting and heating apparatusSpace heating and ventilation detailsDirected graphGraph theoretic
The invention discloses an intelligent valve based secondary network hydraulic equilibrium method and belongs to the field of heat-supply engineering. The scheme of the intelligent valve based secondary net hydraulic equilibrium method comprises the following steps: utilizing monitoring data of an intelligent valve to automatically calculate the resistance number of the valve and a building through an algorithm; based on a pipe network topology structure and a graph theory principle, setting up the pipe network into a digraph model composed of nodes and pipe segments; based on the actual operating condition of the pipe network, recording the pipe network operating conditions under multiple working conditions; calculating the actual resistance numbers of all pipe segments of the pipe network; and automatically adjusting the opening degree of the valve through a hydraulic equilibrium algorithm to realize hydraulic equilibrium of a secondary network. The intelligent valve based secondarynetwork hydraulic equilibrium method has the following benefits: the valve opening degree is determined through the resistance number to really reflect the characteristic of the hydraulic condition ofthe pipe network, so that the phenomenon that the flow rate is determined through the opening degree to cause serious hydraulic power distortion is avoided; and the opening degree of the intelligentvalve is automatically calculated, so that the labor cost and time cost for manual secondary network balance debugging are saved, and nondeterminacy and inaccuracy caused by inconsistent personnel quality of manual debugging are also avoided.
Owner:大连海心信息工程有限公司
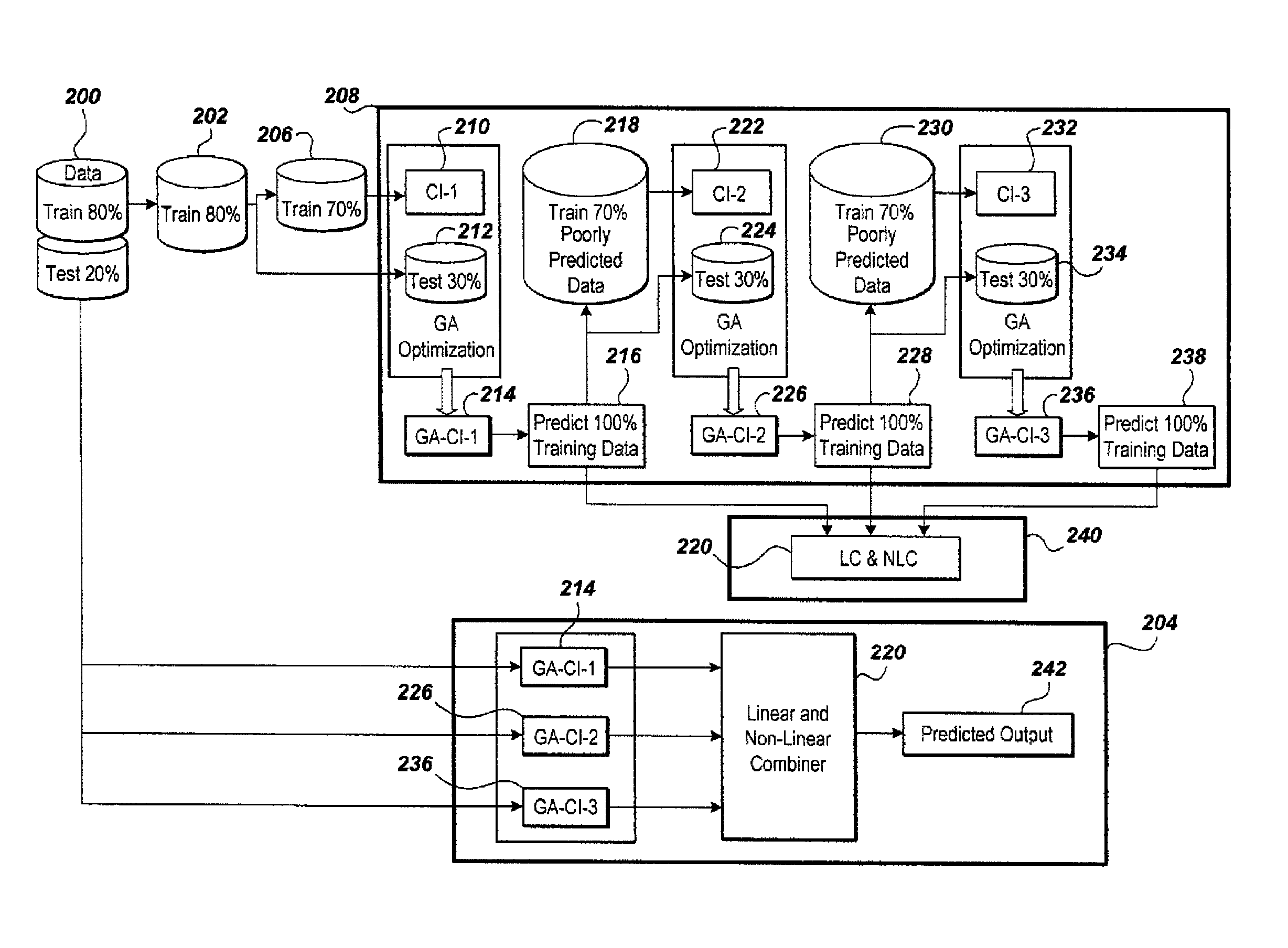
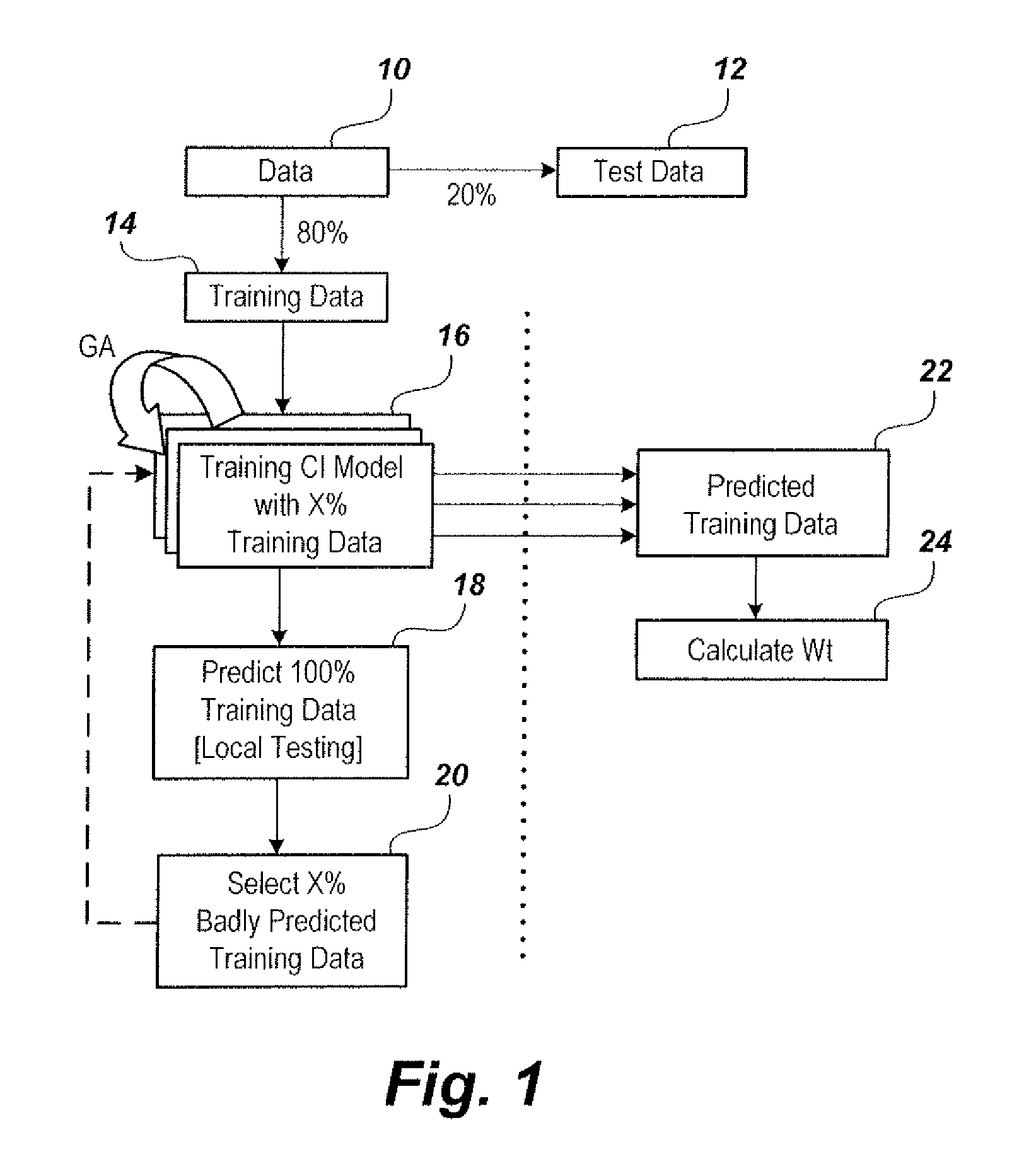
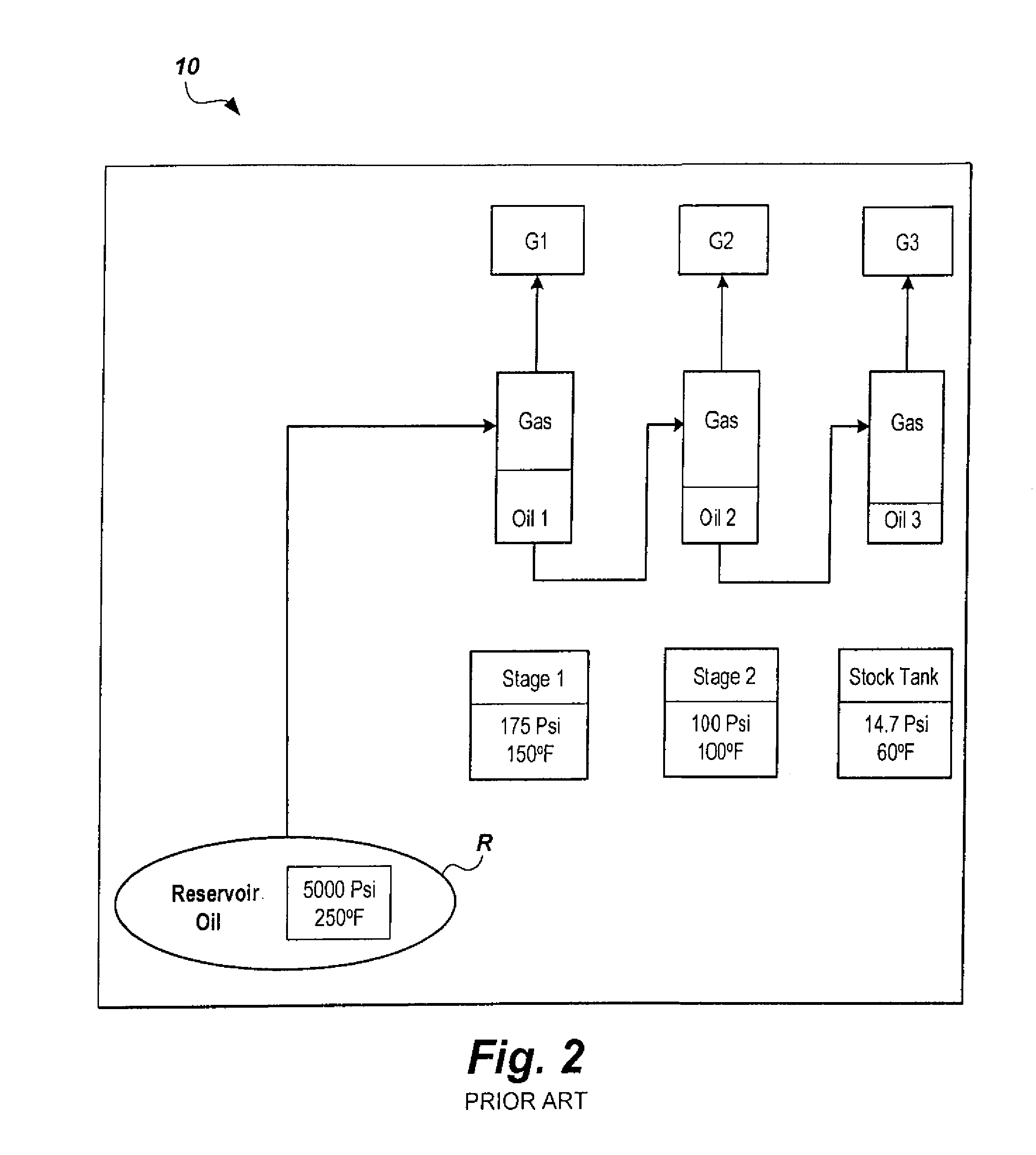
Method of predicting gas composition
The method of predicting gas composition in a multistage separator includes solutions to the regression problem of gas composition prediction that are developed using an ensemble of hybrid computational intelligence (CI) models. Three separate homogeneous and one heterogeneous ensemble of hybrid computational intelligence (EHCI) models are developed using a parallel scheme. The homogeneous models have the same types of CI models used as base learners, and the heterogeneous model has of different types of CI models used as base learners. Various popular CI models, including multi-layer perceptron (MLP), support vector regression (SVR) and adaptive neuro-fuzzy inference system (ANFIS), are used as base learners of ensemble models.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS
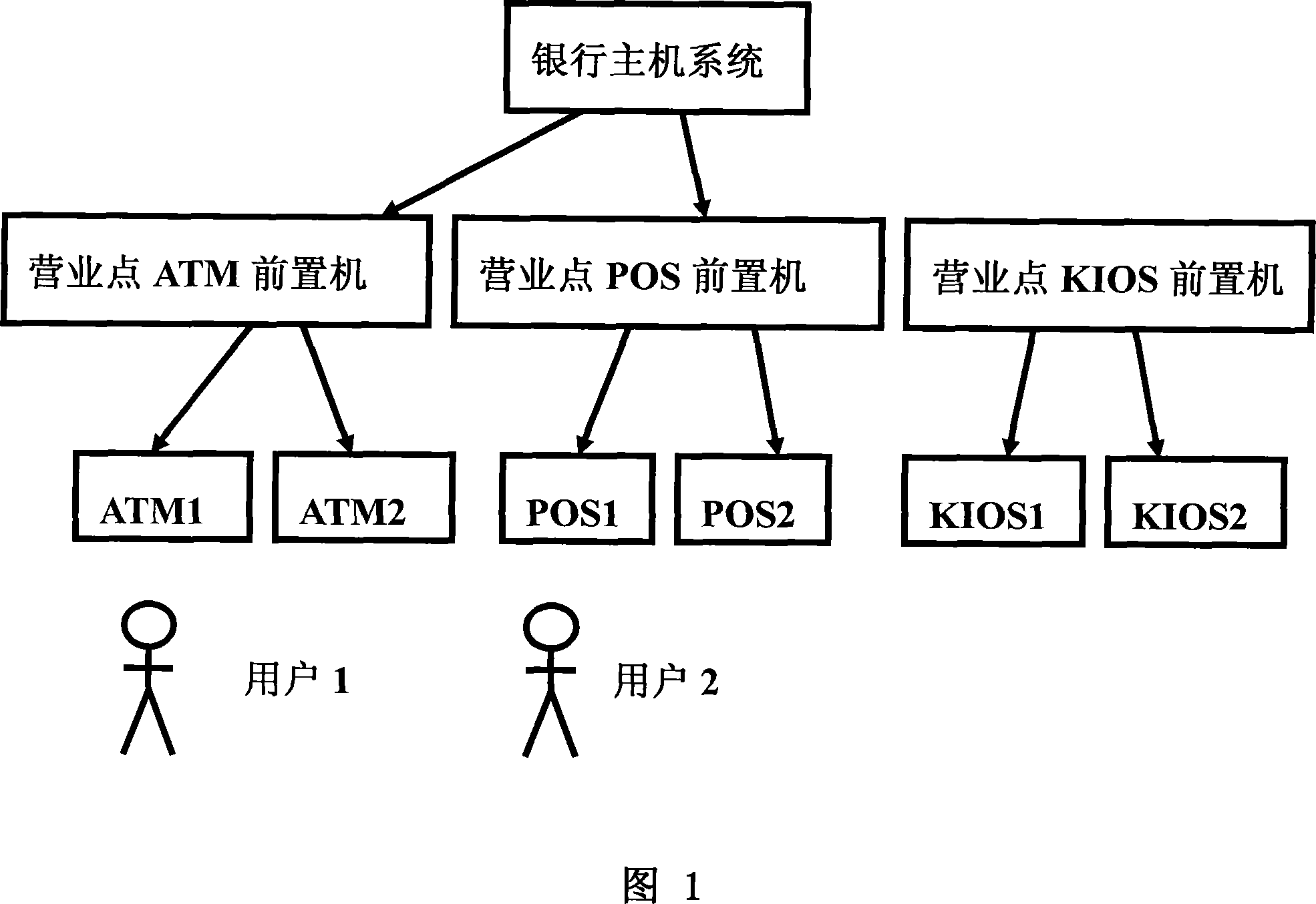
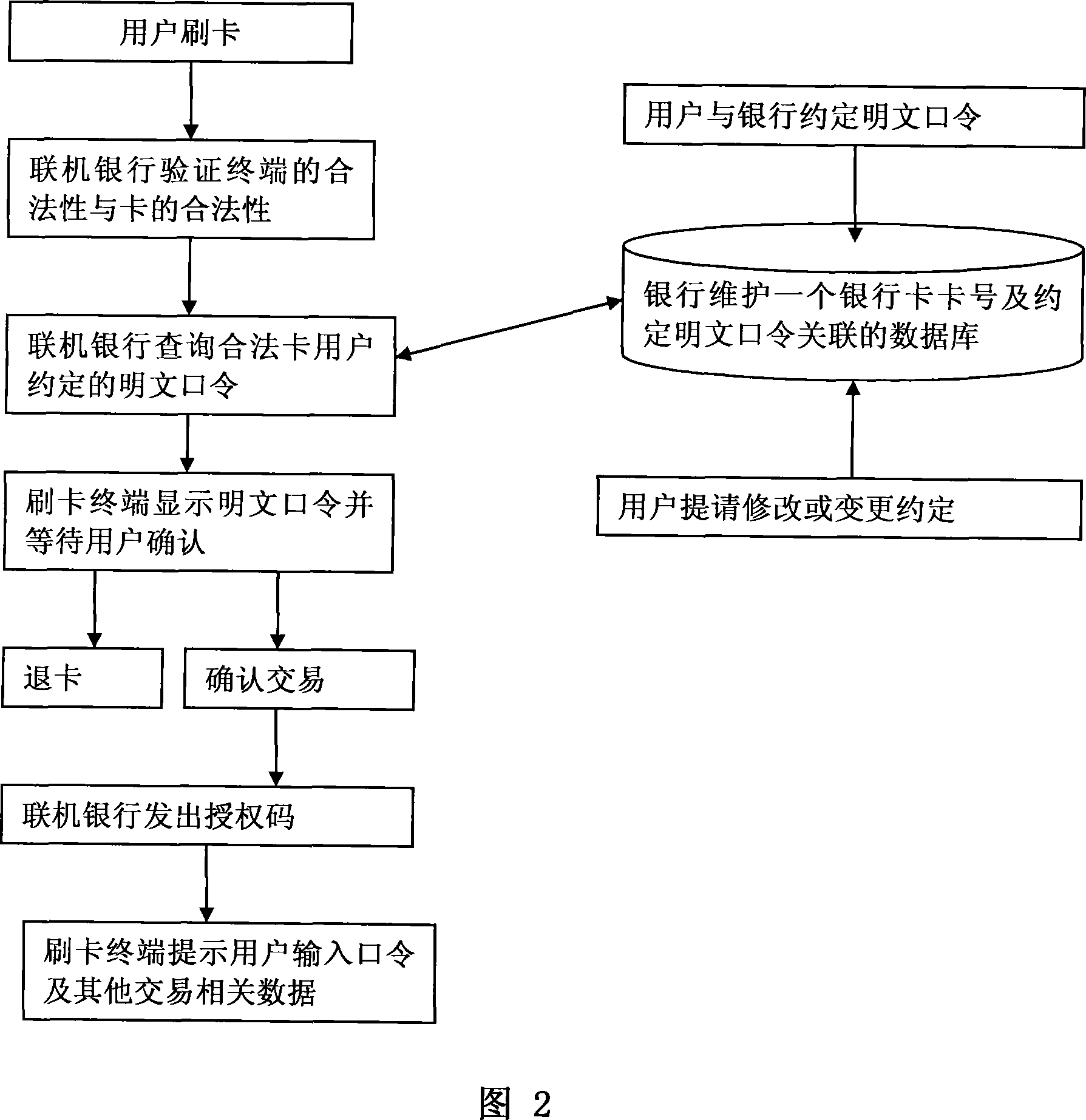
Method supporting user verifying legitimacy of bank brushing card terminal equipment
The invention relates to a method for a user to check the legitimacy of a bank card reading terminal equipment. After a card reading machine gets on line, the password that the user and the card issuing bank agreed on is displayed to check the legitimacy of the card reading machine. When applying for the bank card, the user and the card issuing bank agree on a certain form of password. Being obligated to judge and check the legitimacy of the card reading machine according to the password displayed by the card reading machine before entering the password for bank card consumption, the user can decide in time whether to continue entering the password in order to avoid the bank card password that is stolen by the illegal bank card reading terminal. The invention has the advantages of embodying the system mode of man-machine intelligent synthetic integration in modern system engineering and organically combining the mental judgment of the cardholder with the computational intelligence of the online service center instead of totally depending on the techniques. The invention adds the cooperation of the user to check the safety of the card reading terminal equipment, so as to avoid the traps made by the illegal card reading terminal equipment.
Owner:SUNYARD SYST ENG CO LTD
Power circuit component optimization method based on orthogonal learning particle swarm
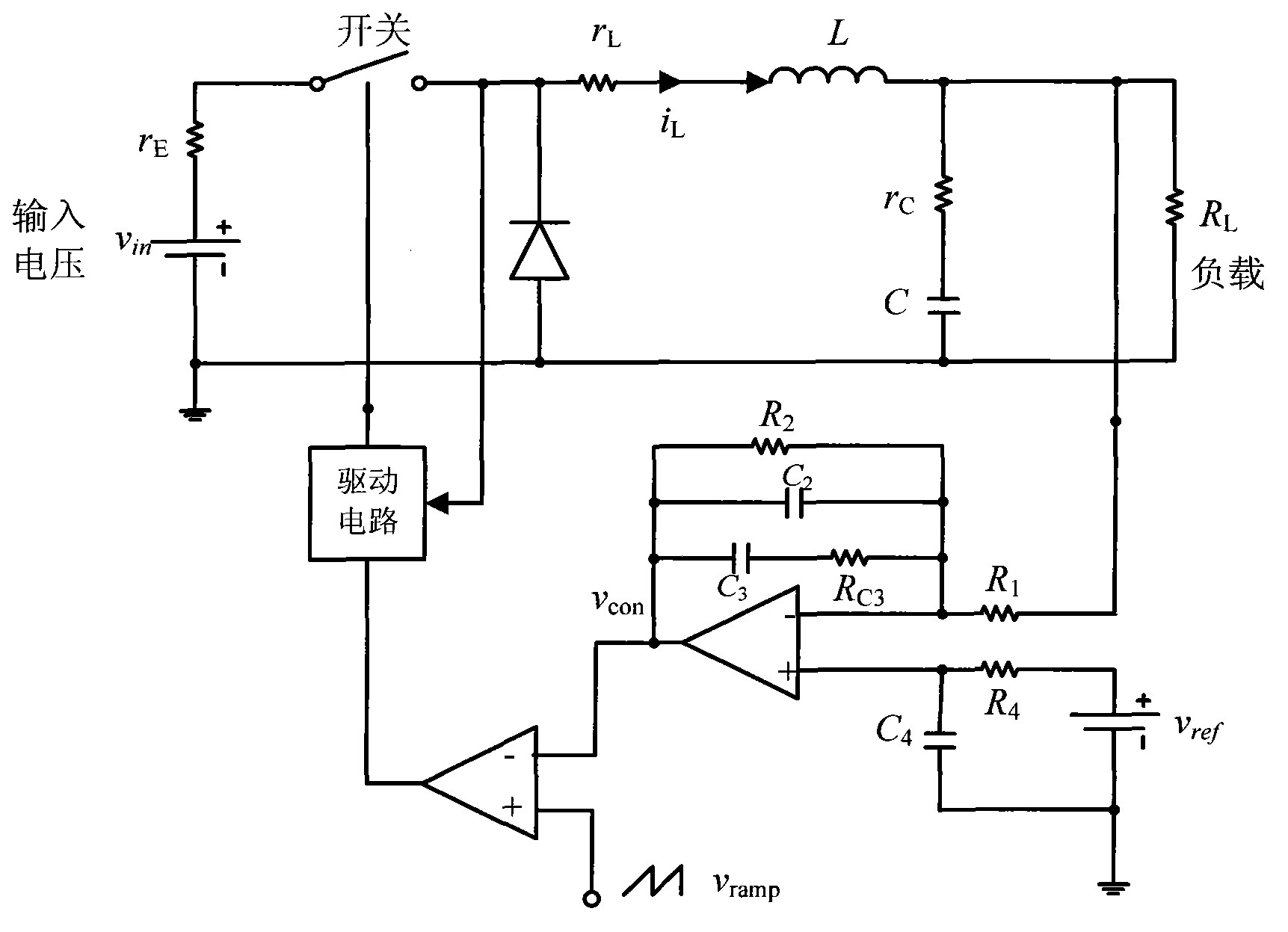
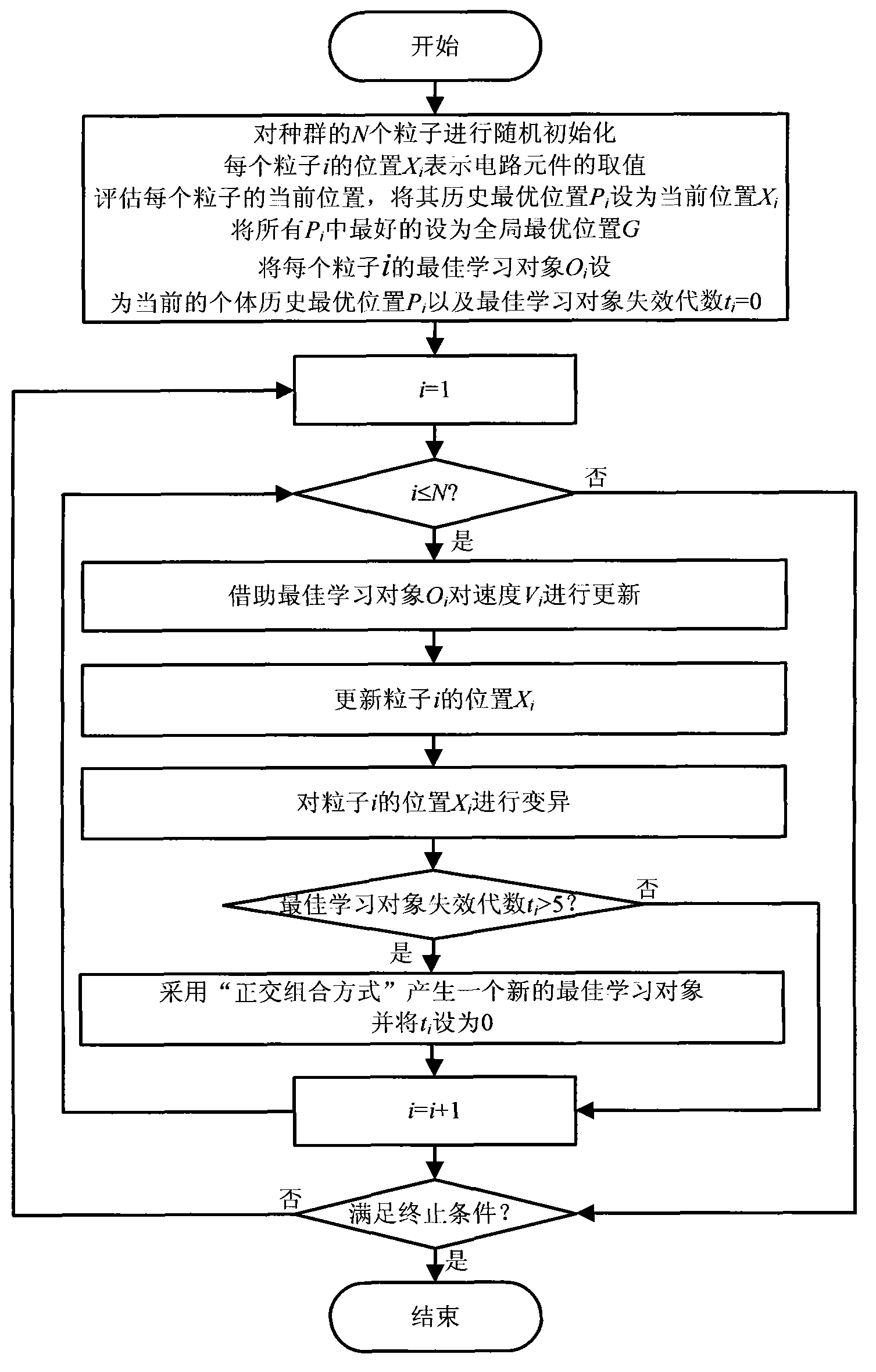
InactiveCN103258131AOptimize valueOvercome the defect that it is easy to fall into local optimumSpecial data processing applicationsObject basedParticle swarm algorithm
The invention discloses a power circuit component optimization method based on an orthogonal learning particle swarm, and belongs to the power electronic technology and the field of computational intelligence. An orthogonal learning particle swarm optimization with a mutation strategy is used for carrying out optimization on an optimal component design of a power electronic circuit. Firstly, a method of generating a new optimal learning object based on an orthogonal combination mode is designed, and is used for mining information of a historical optimal solution of a particle individual and information of a globally-optimal solution of a swarm in the orthogonal learning particle swarm optimization, and combining a learning object which can guide particles to develop in a better direction, secondly, a mutation operator which can improve diversity of the orthogonal learning particle swarm optimization is designed, and the defect that the orthogonal learning particle swarm optimization easily falls into local optimum is overcome. All components of the power electronic circuit serve as variables needing to be optimized and are coded into individuals of the orthogonal learning particle swarm optimization, optimization is carried out on values of the components of the power electronic circuit through specific optimization processes such as update of the speed, update of the location, mutation operation and update of the optimal learning object of the orthogonal learning particle swarm optimization, and the power circuit component optimization method based on the orthogonal learning particle swarm has important application value in the existing large-scale circuit design and optimization field.
Owner:SUN YAT SEN UNIV
Auto-dialing distress method used after user falling detected by smart phone
InactiveCN104243656AHigh fall detection accuracyImprove accuracySubscriber signalling identity devicesTelephone set constructionsStopwatchComputational intelligence
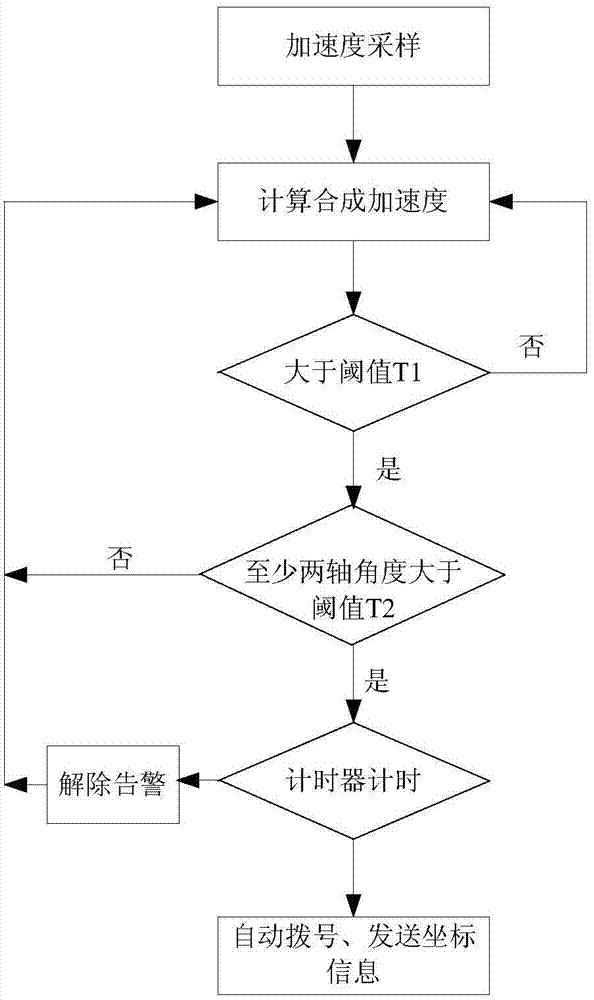
The invention discloses an auto-dialing distress method used after user falling detected by a smart phone. The auto-dialing distress method includes the steps that 1, the smart phone samples the accelerations and calculates a resultant acceleration a; 2, the resultant acceleration a is judged whether or not to be larger than an acceleration threshold value T1, if so, go to the step 3; if not, back to the step 1; 3, three axis attitude angles of the smart phone are calculated, and two of the three-axis attitude angles are judged whether or not to be larger than an angle threshold value T2, if so, go to the step 4; if not; back to the step 1; 4, the smart phone prompts an alarm, and a timer starts, if the alarm is manually released within 10s, back to the step 1; or not, go to the step 5; 5, a preset number is automatically dialed, and a short message showing the position of the smart phone is sent.
Owner:北京大学工学院南京研究院
Method for automated analysis of submaximal F-waves
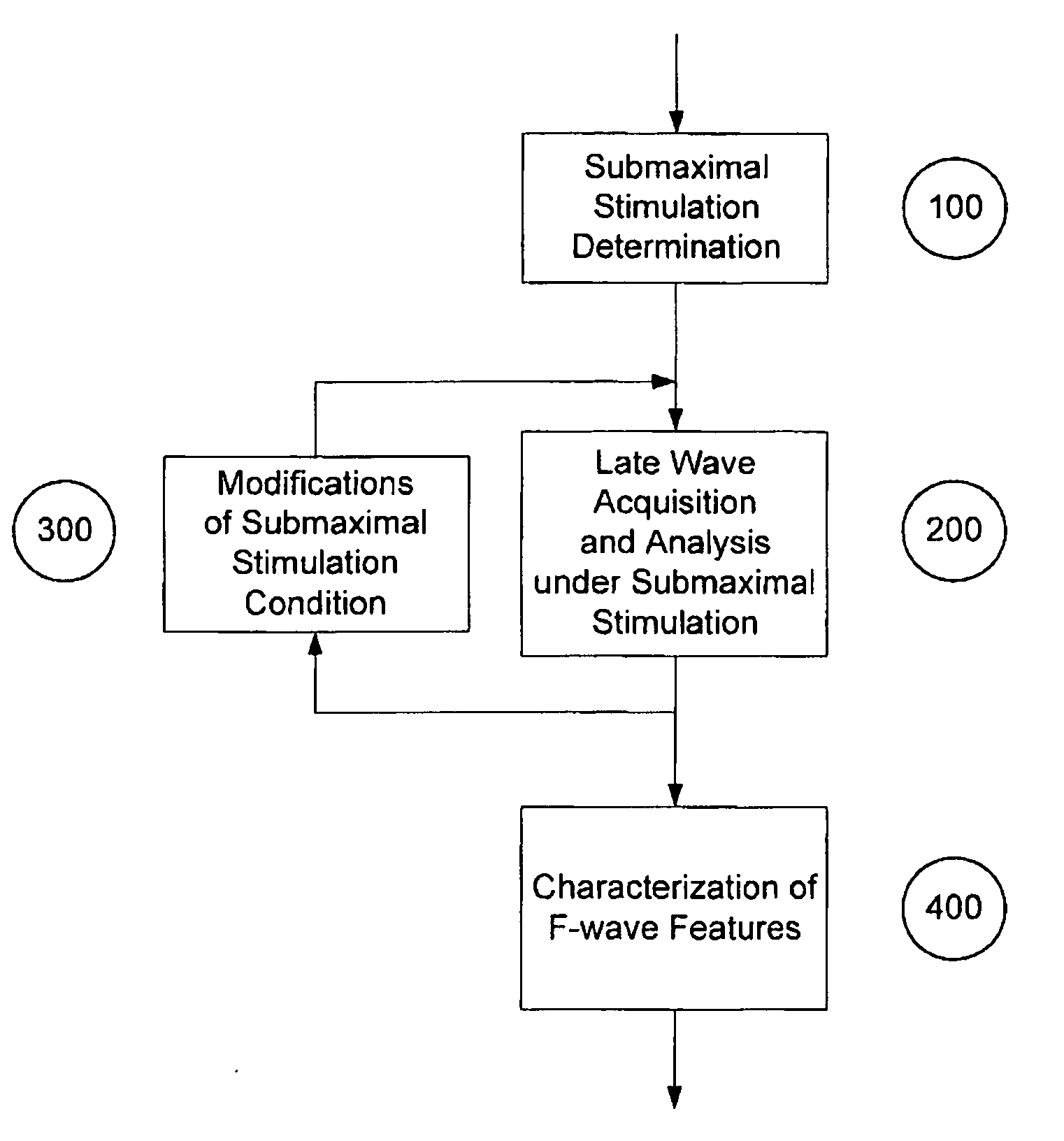
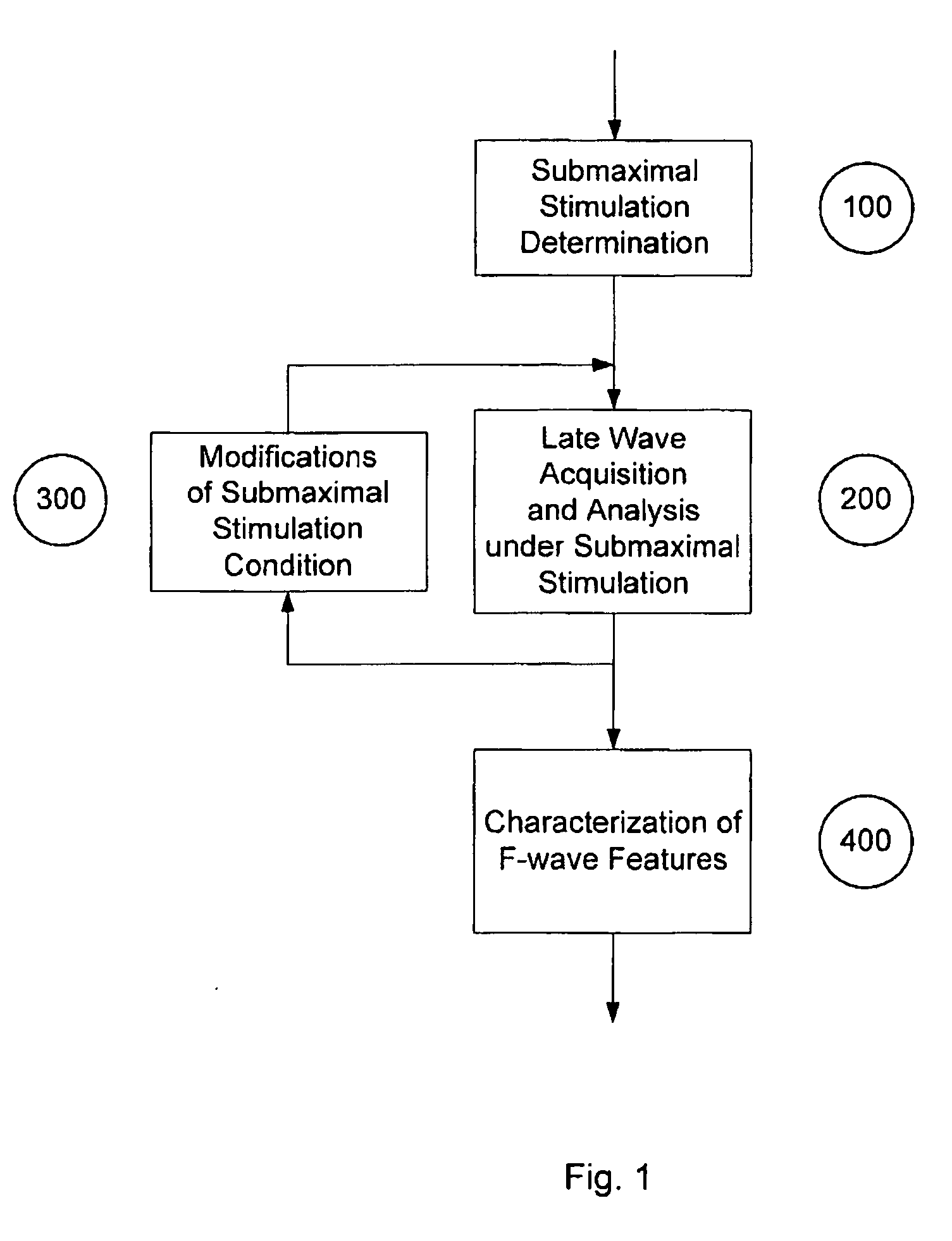
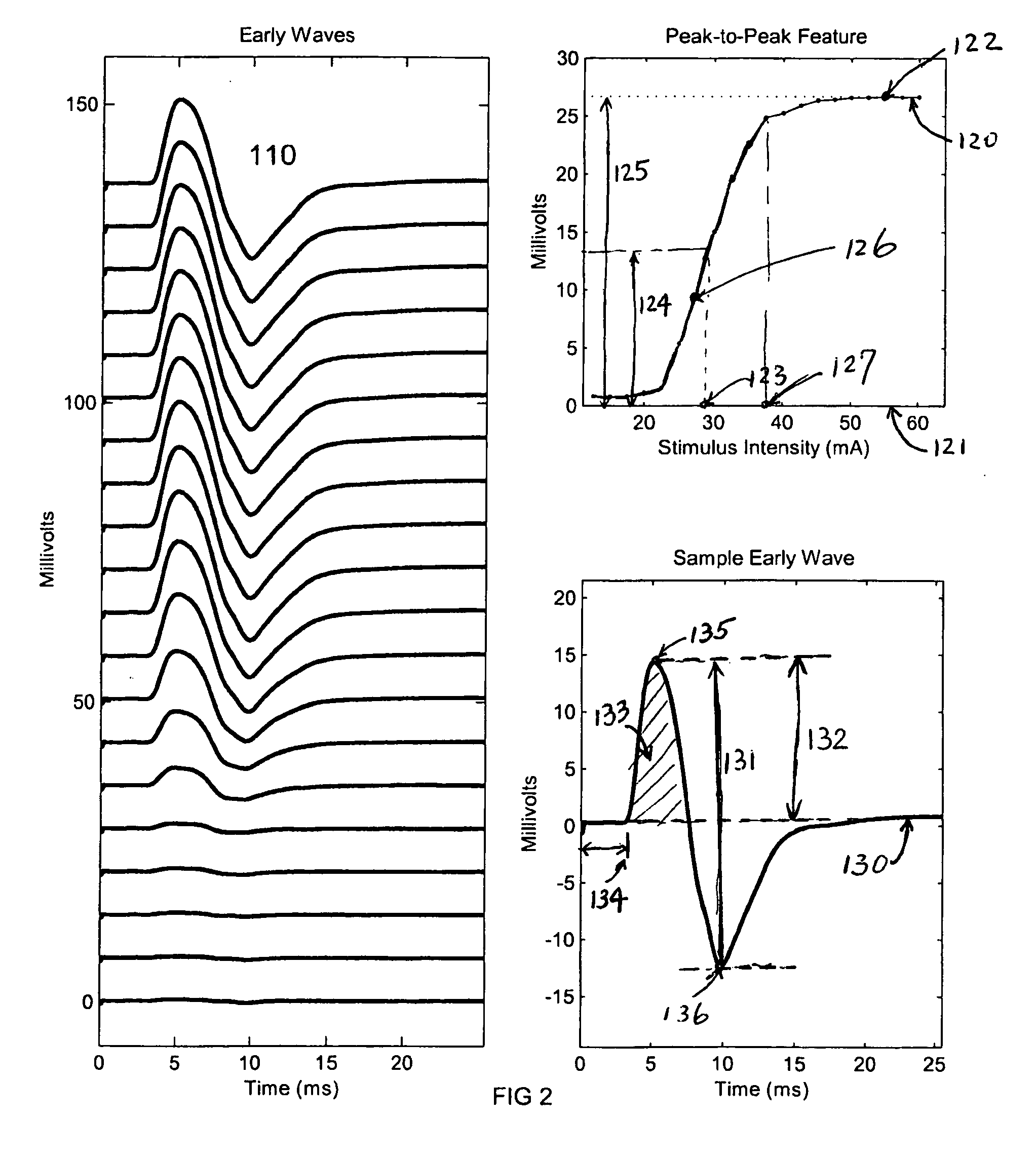
InactiveUS20060217631A1Eliminate needReliable estimateElectromyographySurgeryComputational intelligenceComputer science
A novel submaximal F-wave acquisition and analysis system that employs computational intelligence to set up submaximal F-wave acquisition conditions and to extract submaximal F-wave features automatically, without operator intervention.
Owner:NEUROMETRIX
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com