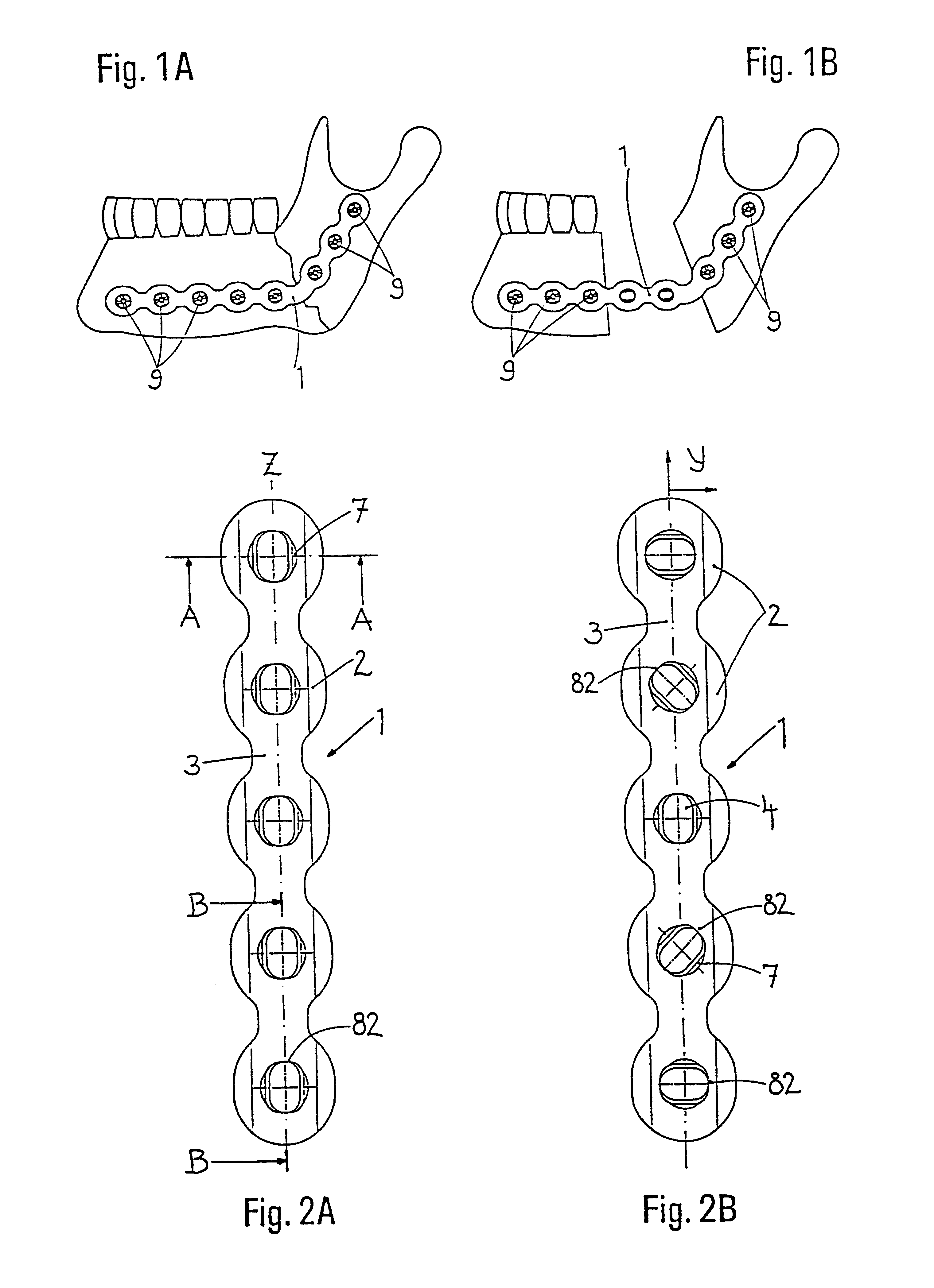Patents
Literature
2813results about How to "Ensure correct execution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
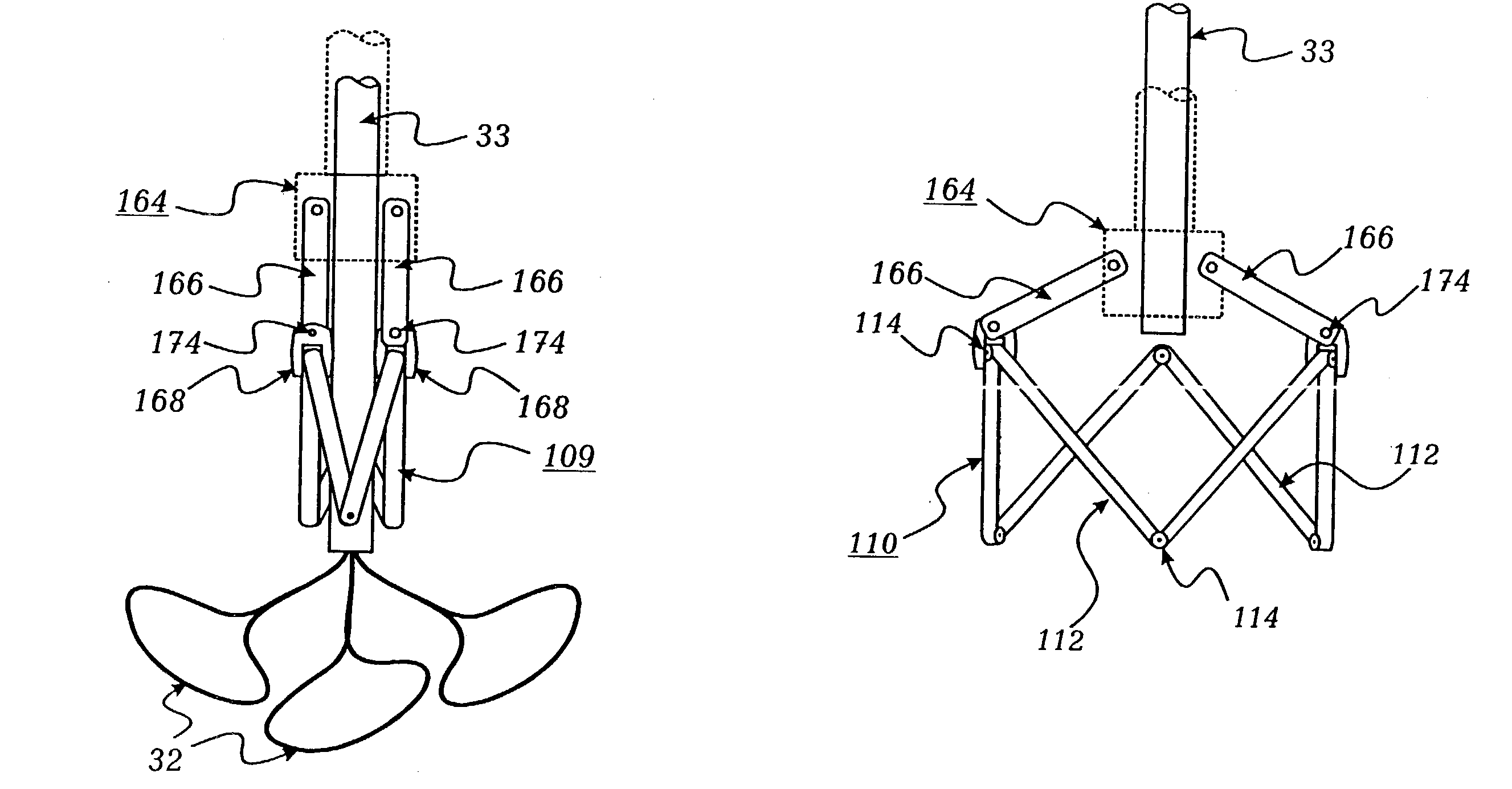
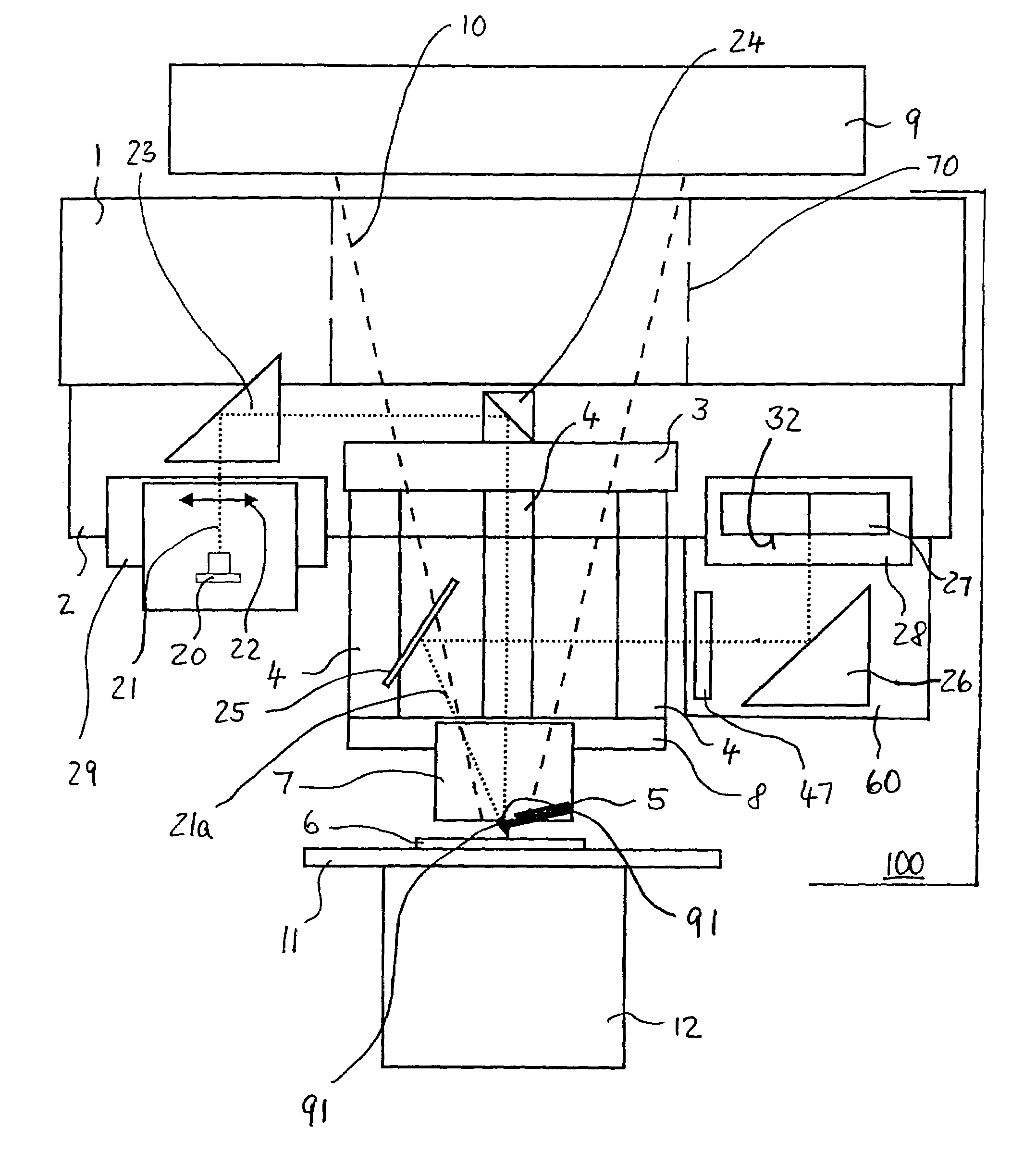
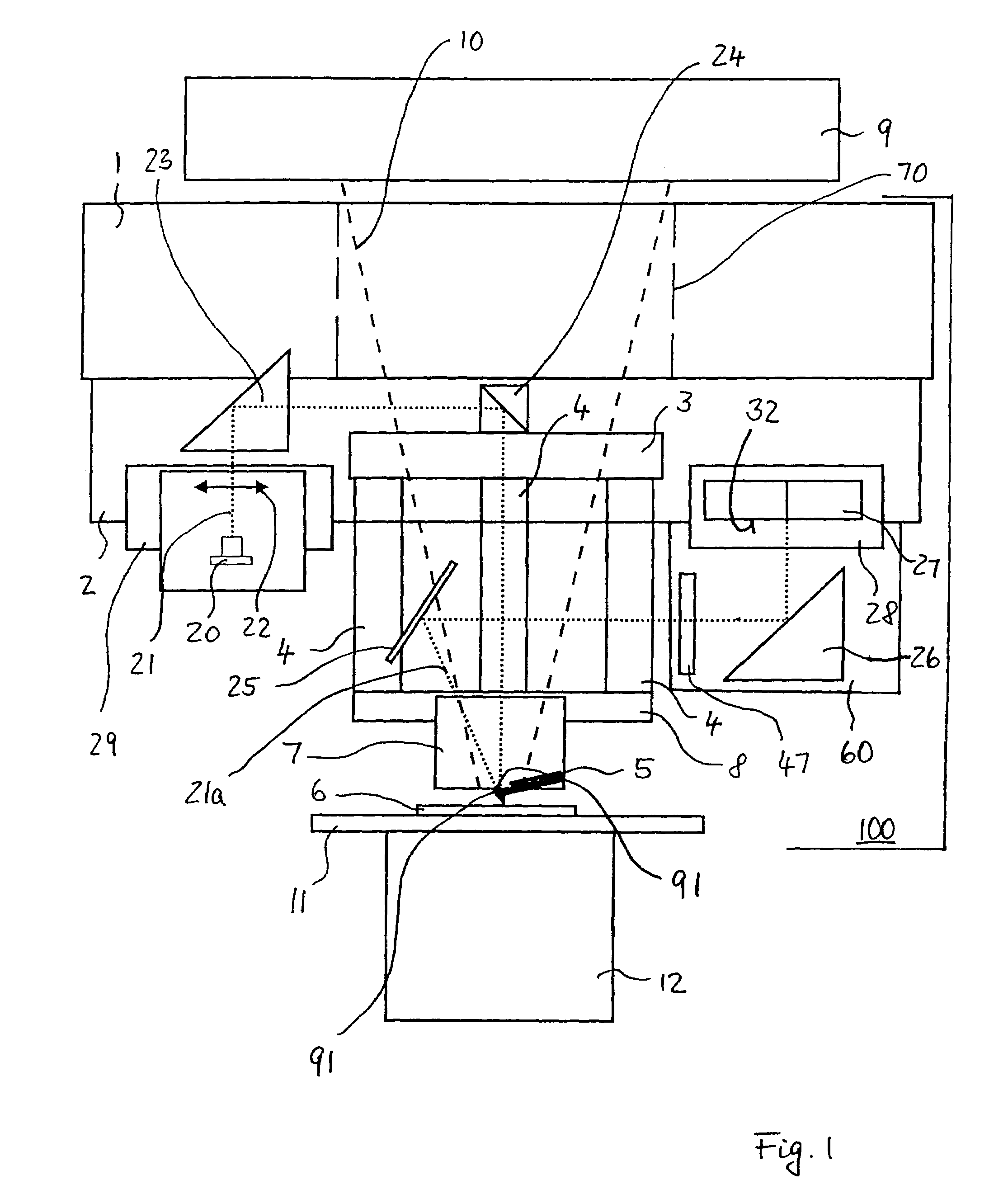
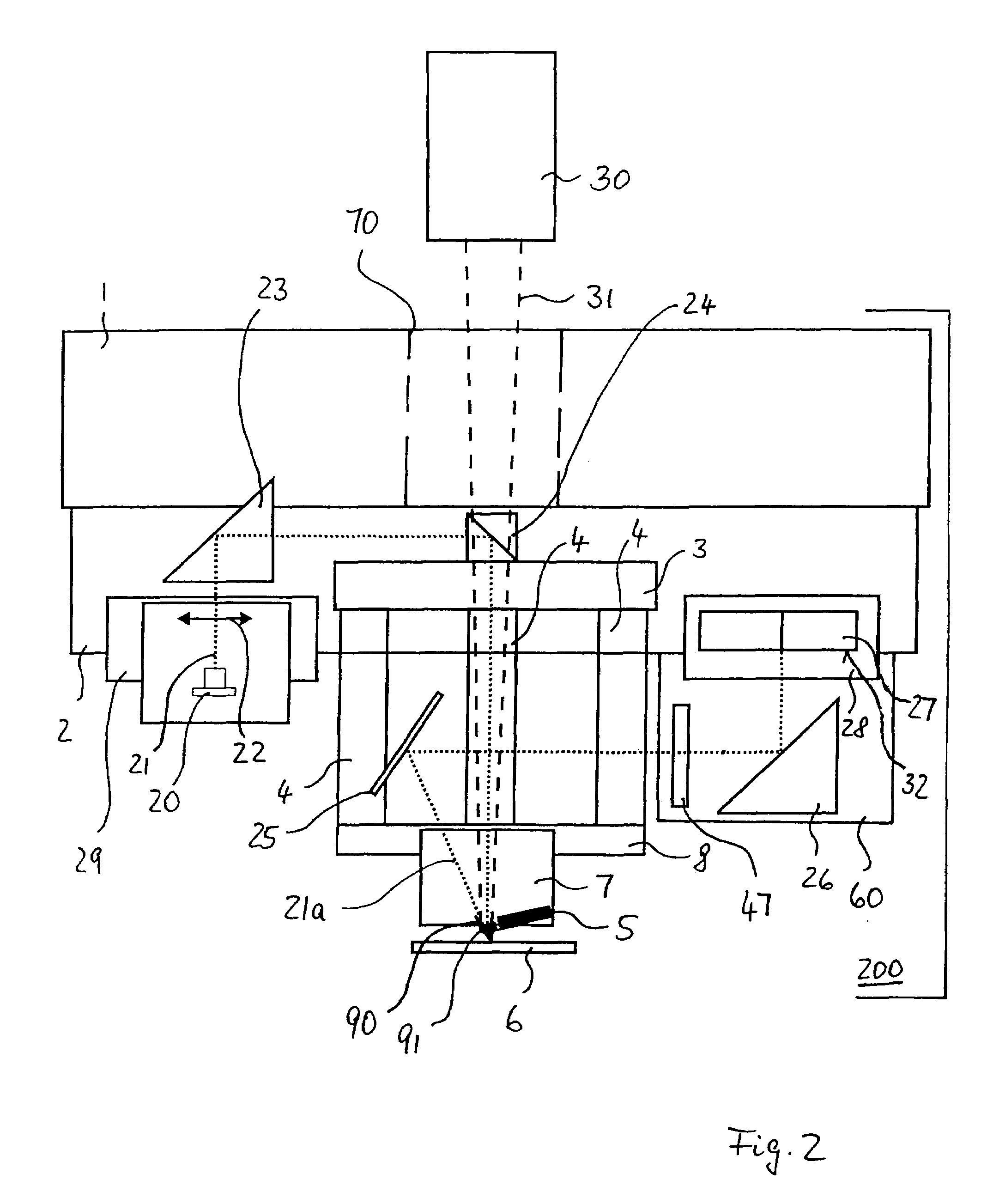
Bioprosthetic cardiovascular valve system
InactiveUS7011681B2Ensure correct executionSafe and convenient removal and replacementEar treatmentHeart valvesProsthesisEngineering
A cardiovascular valve system including a permanent base unit that is affixed to the patient using conventional sutures or staples, and a collapsible valve having a collapsible frame that mates with the permanent base unit, and supports valve leaflets. An installed collapsible frame may be re-collapsed and disengaged from the permanent housing. A new collapsible valve is then installed, to resume the function of the prosthesis.
Owner:THE CLEVELAND CLINIC FOUND
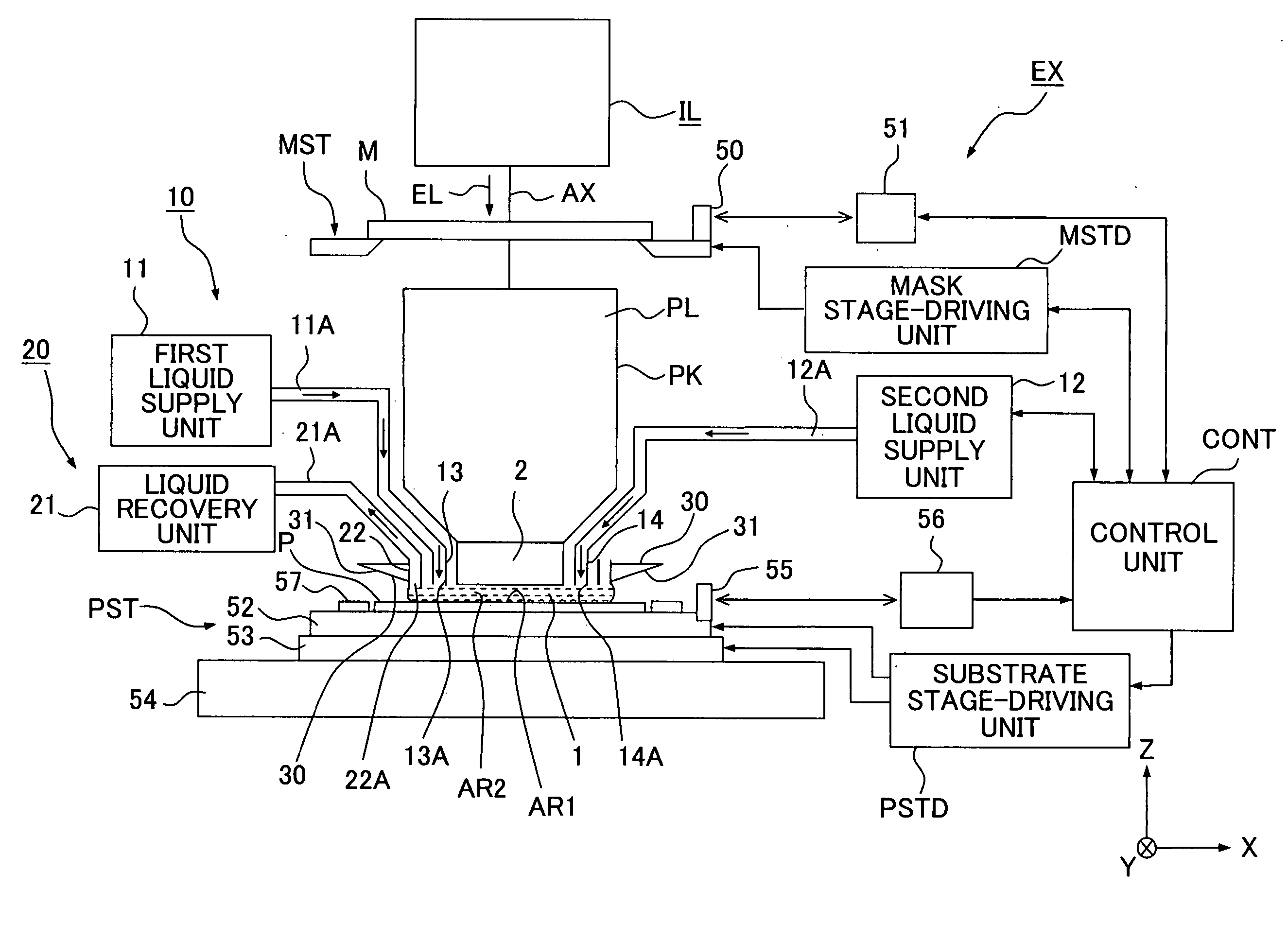
Exposure apparatus, exposure method, and method for producing device
ActiveUS20050280791A1Ensure correct executionSemiconductor/solid-state device manufacturingPhotomechanical exposure apparatusBiomedical engineering
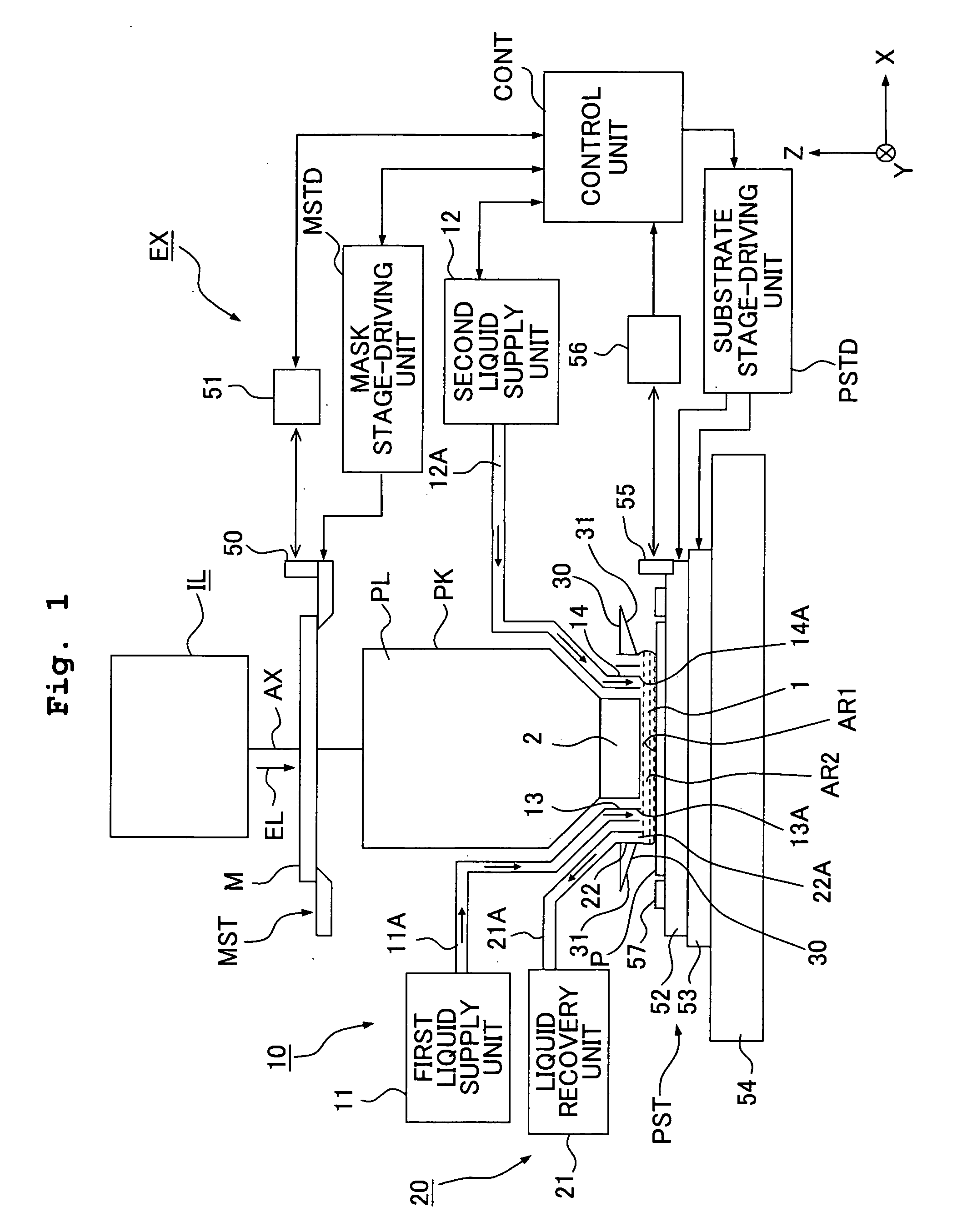
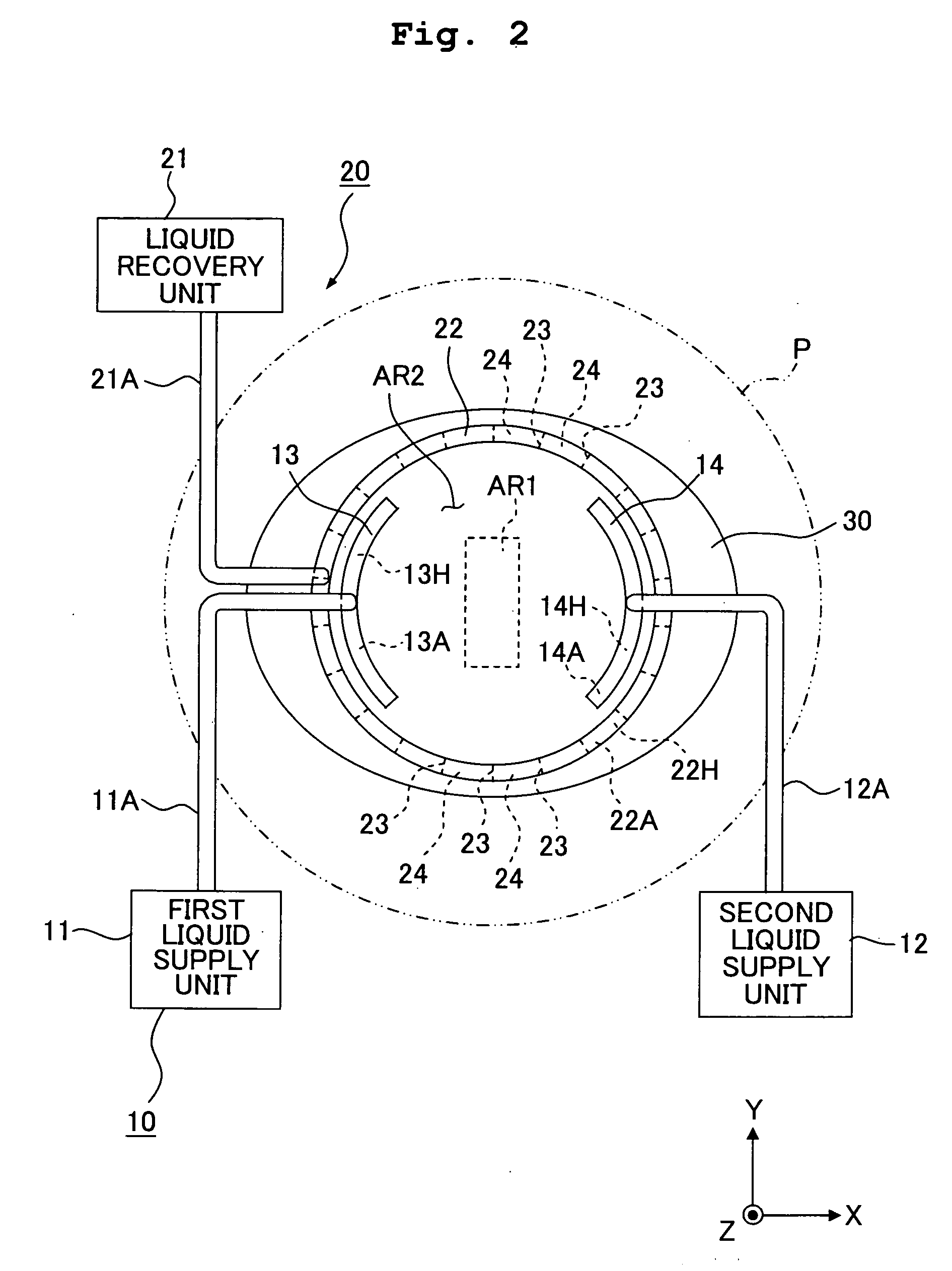
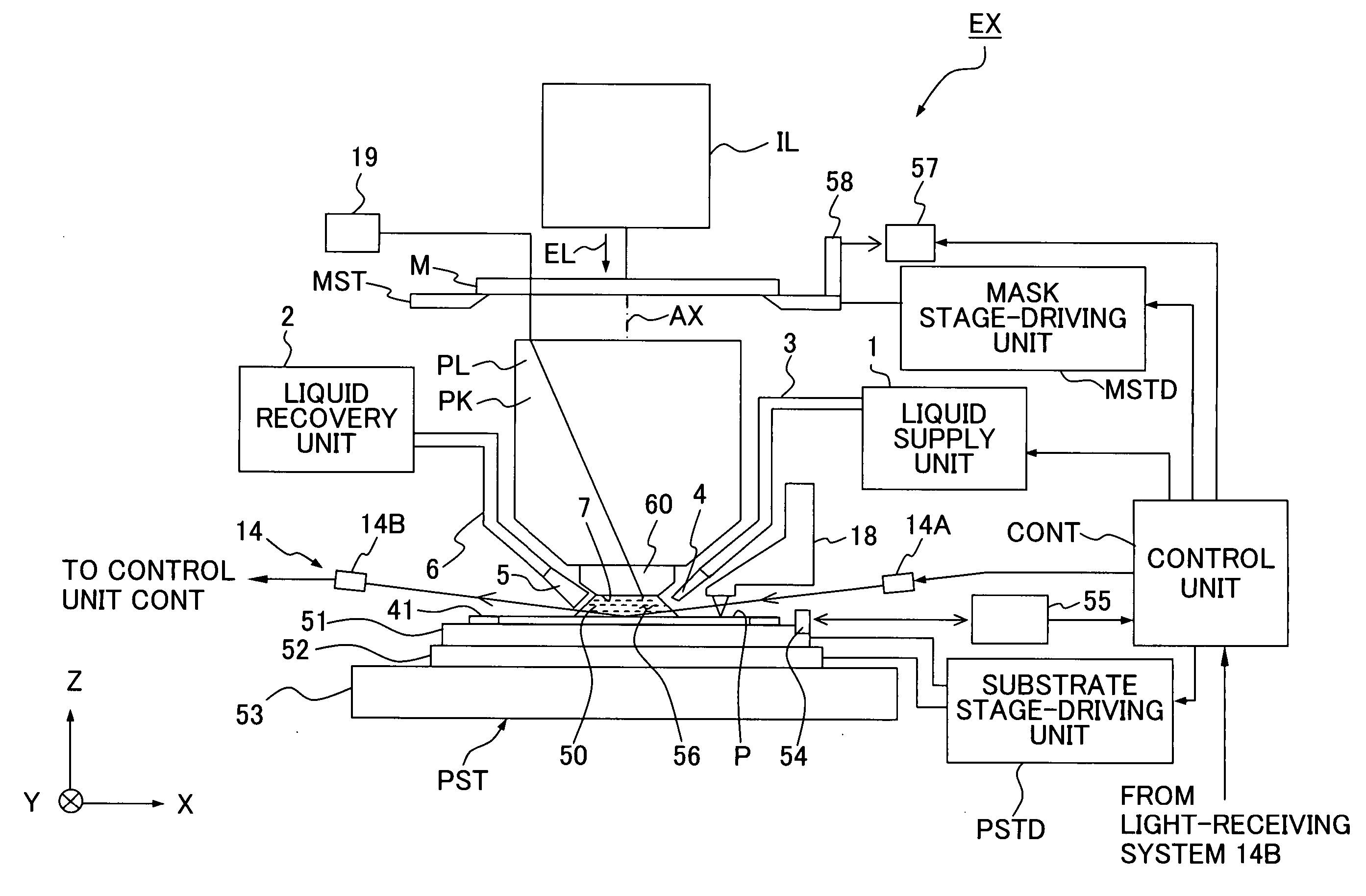
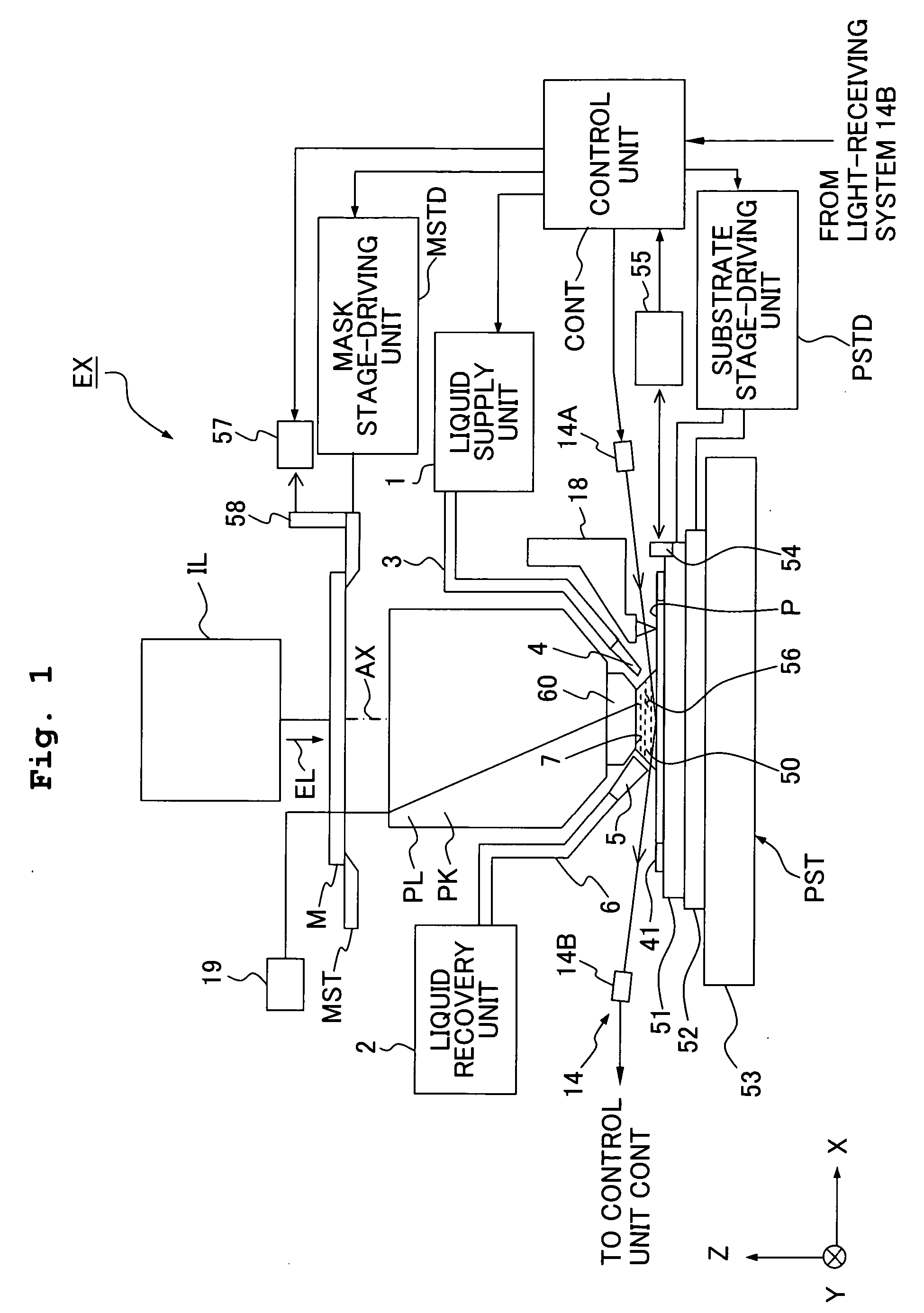
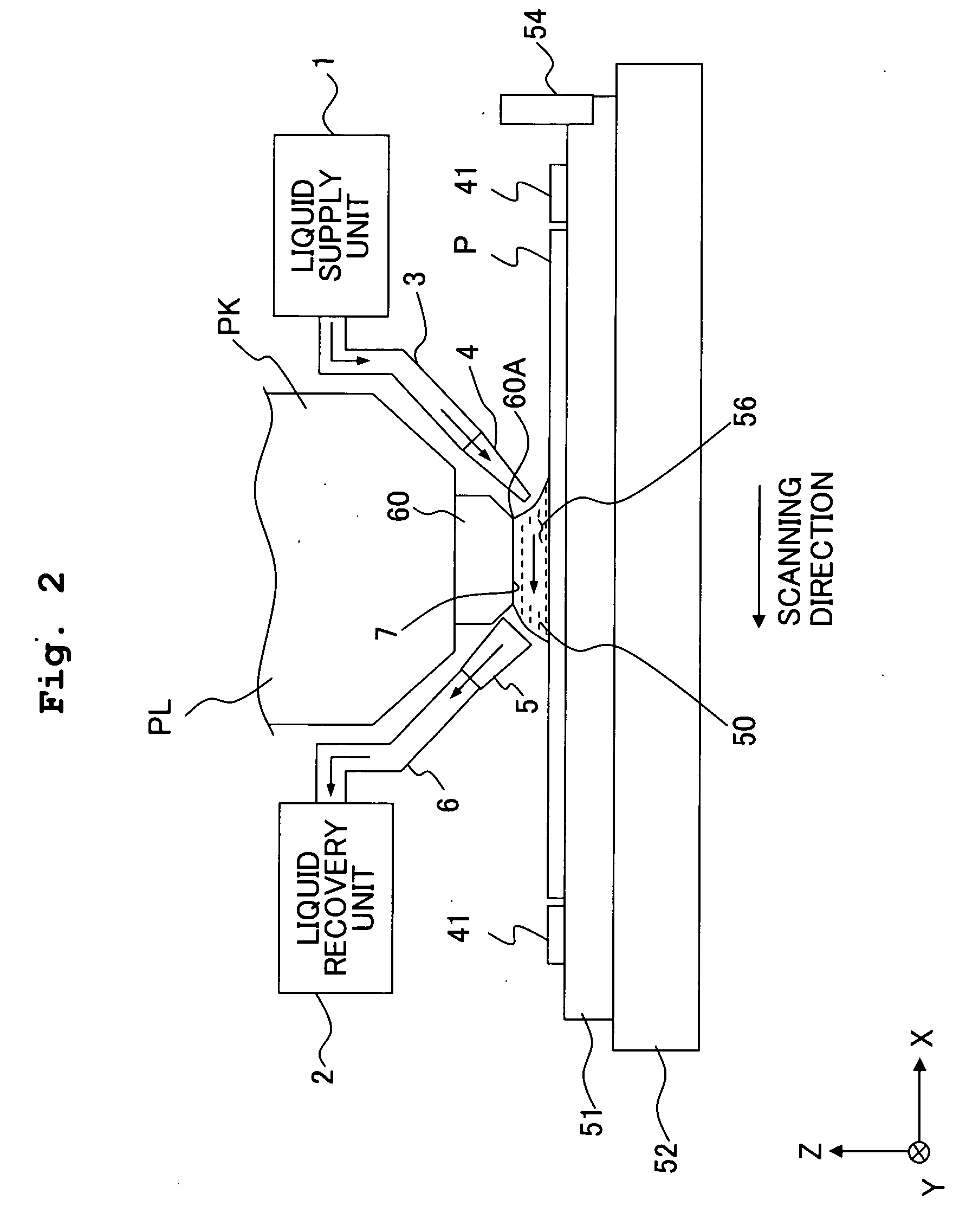
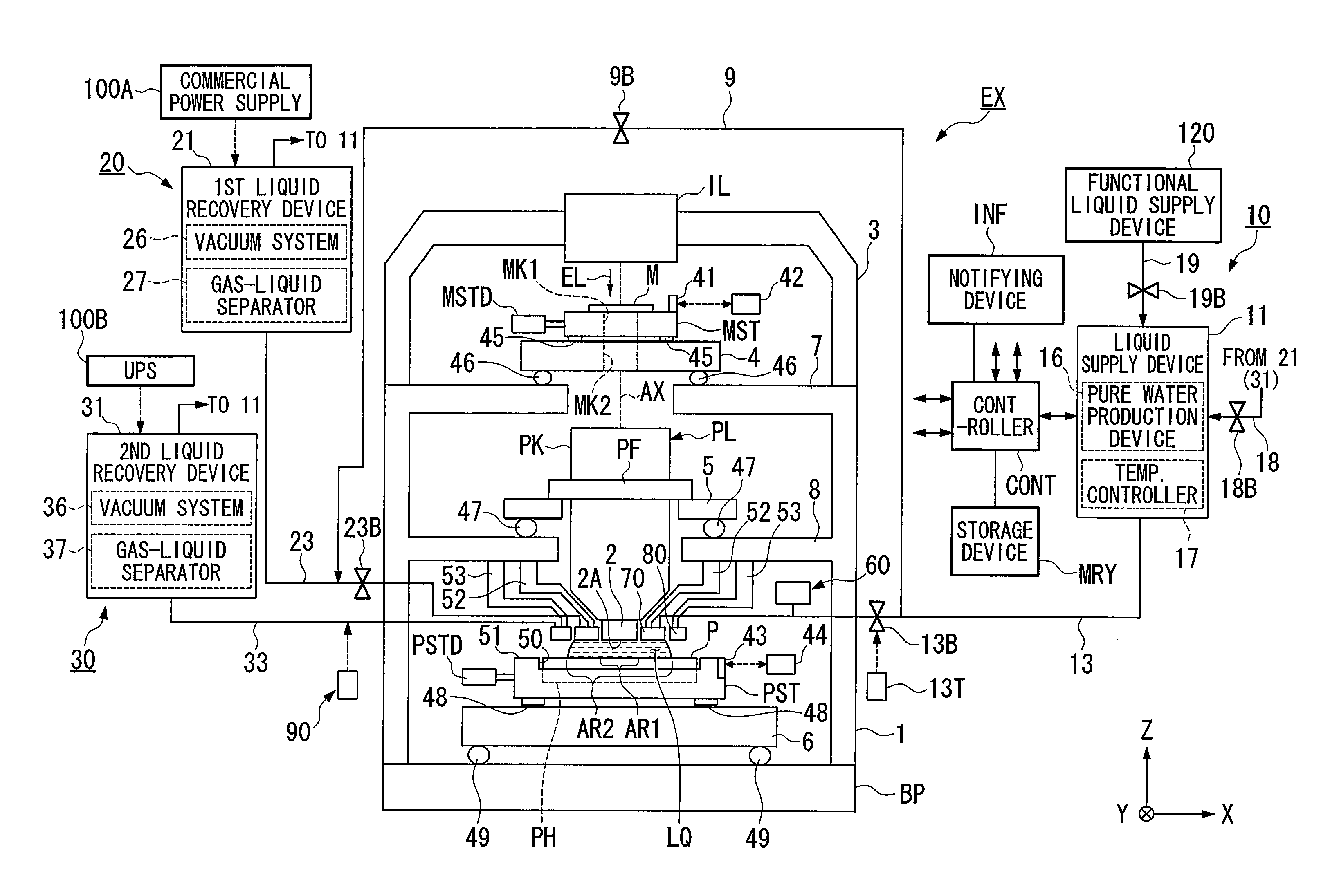
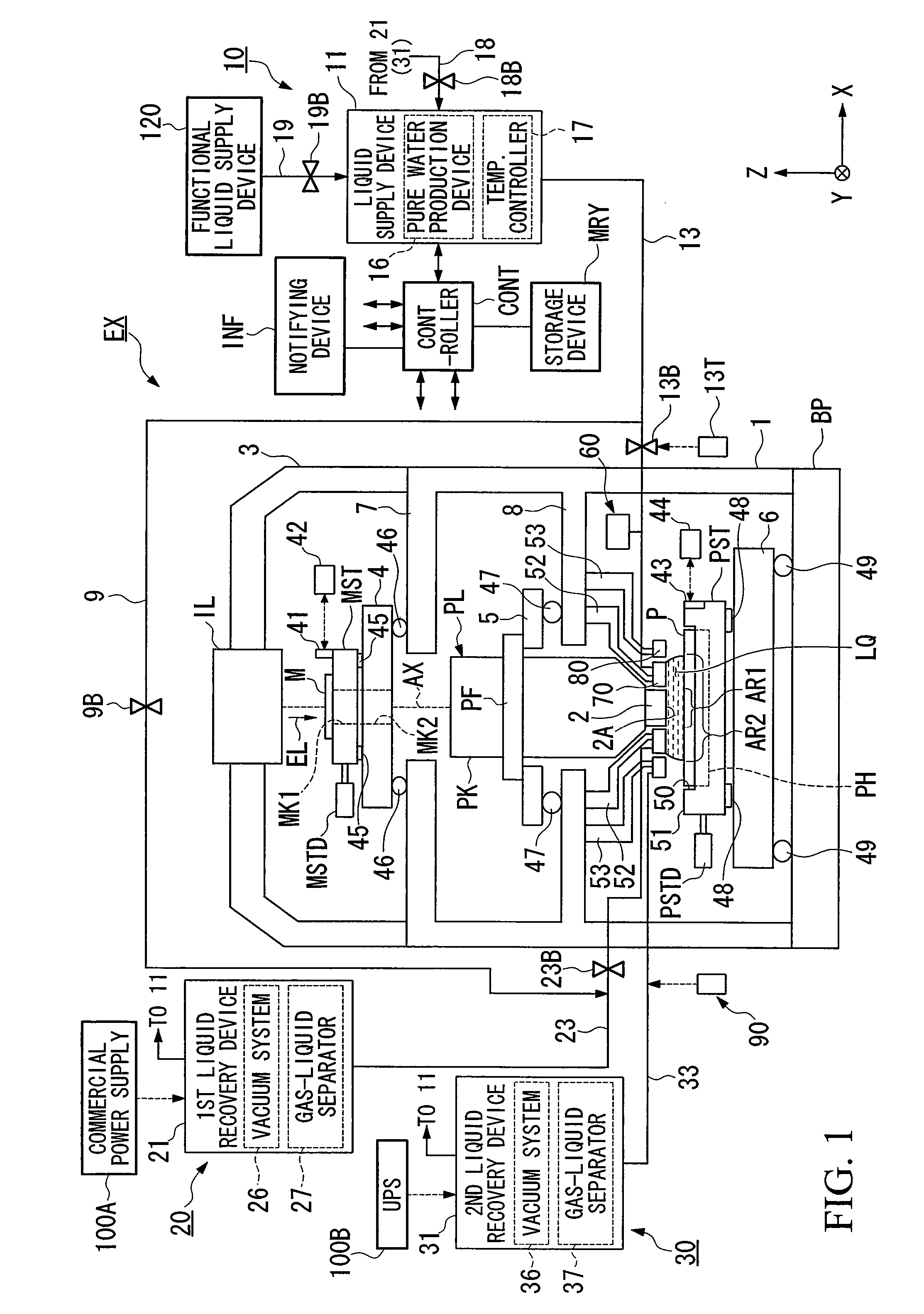
An exposure apparatus EX exposes a substrate P by projecting an image of a predetermined pattern through a liquid 1 onto the substrate. The exposure apparatus includes a projection optical system which performs the projection, and a liquid supply mechanism 10 which supplies the liquid onto the substrate to form a liquid immersion area AR2 on a part of the substrate. The liquid supply mechanism supplies the liquid 1 onto the substrate P simultaneously from a plurality of positions which are apart, in a plurality of different directions, from the projection area AR1. The exposure apparatus is capable of forming the liquid immersion area stably and recovering the liquid satisfactorily. It is possible to perform the exposure process accurately while avoiding, for example, the outflow of the liquid to the surroundings.
Owner:NIKON CORP
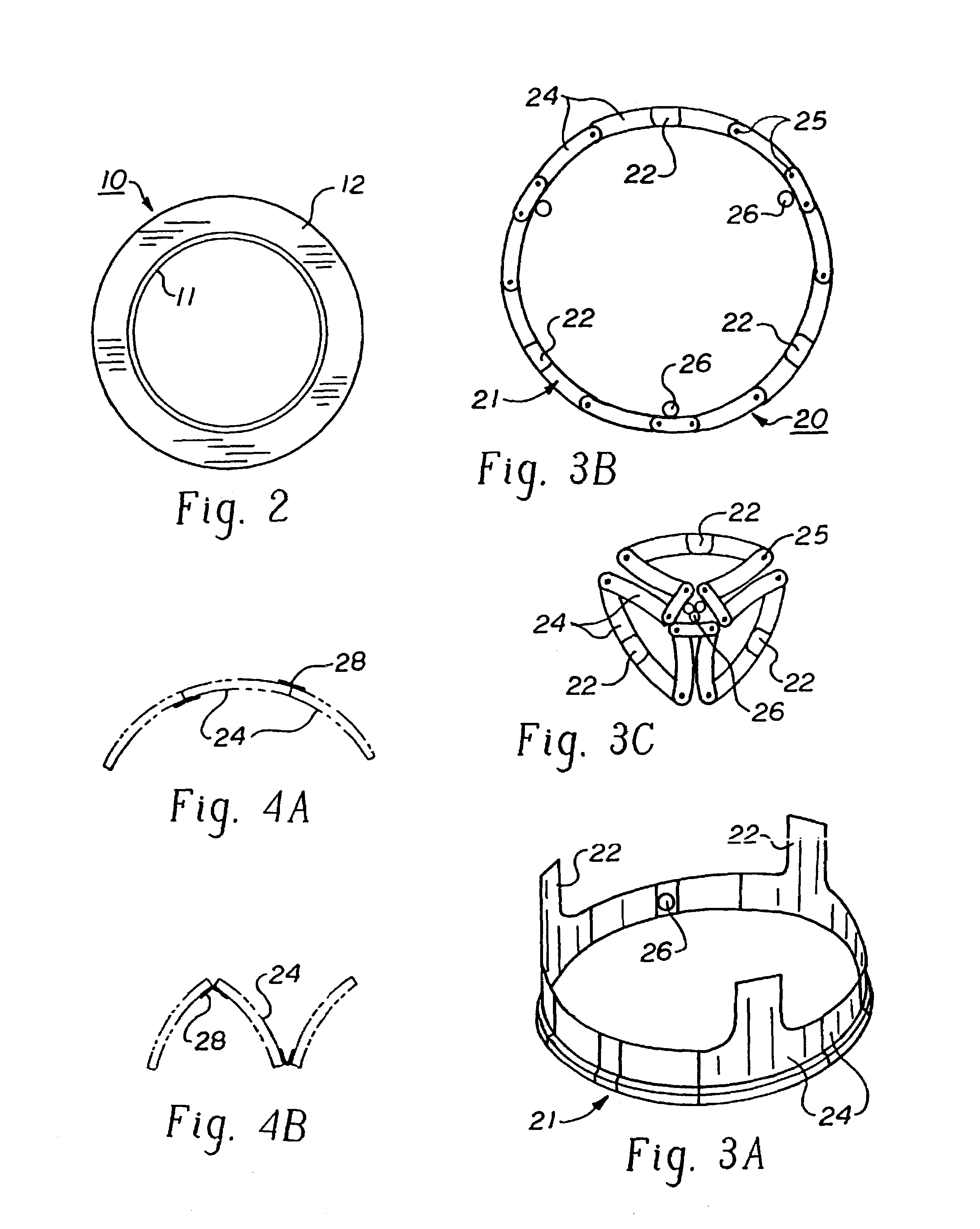
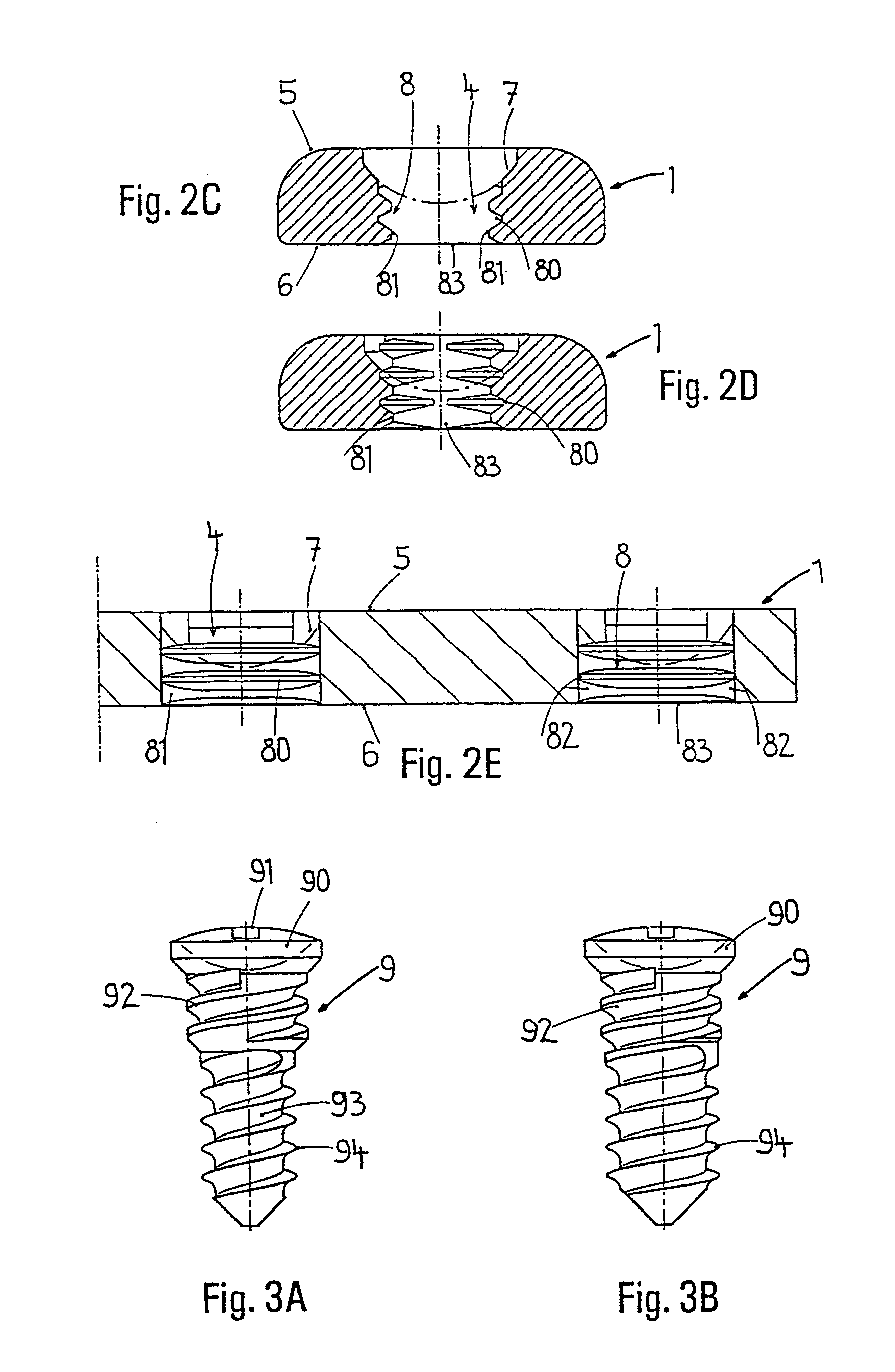
Blockable bone plate
InactiveUS6730091B1Cost effective productionLow costSuture equipmentsInternal osteosythesisEngineeringIliac screw
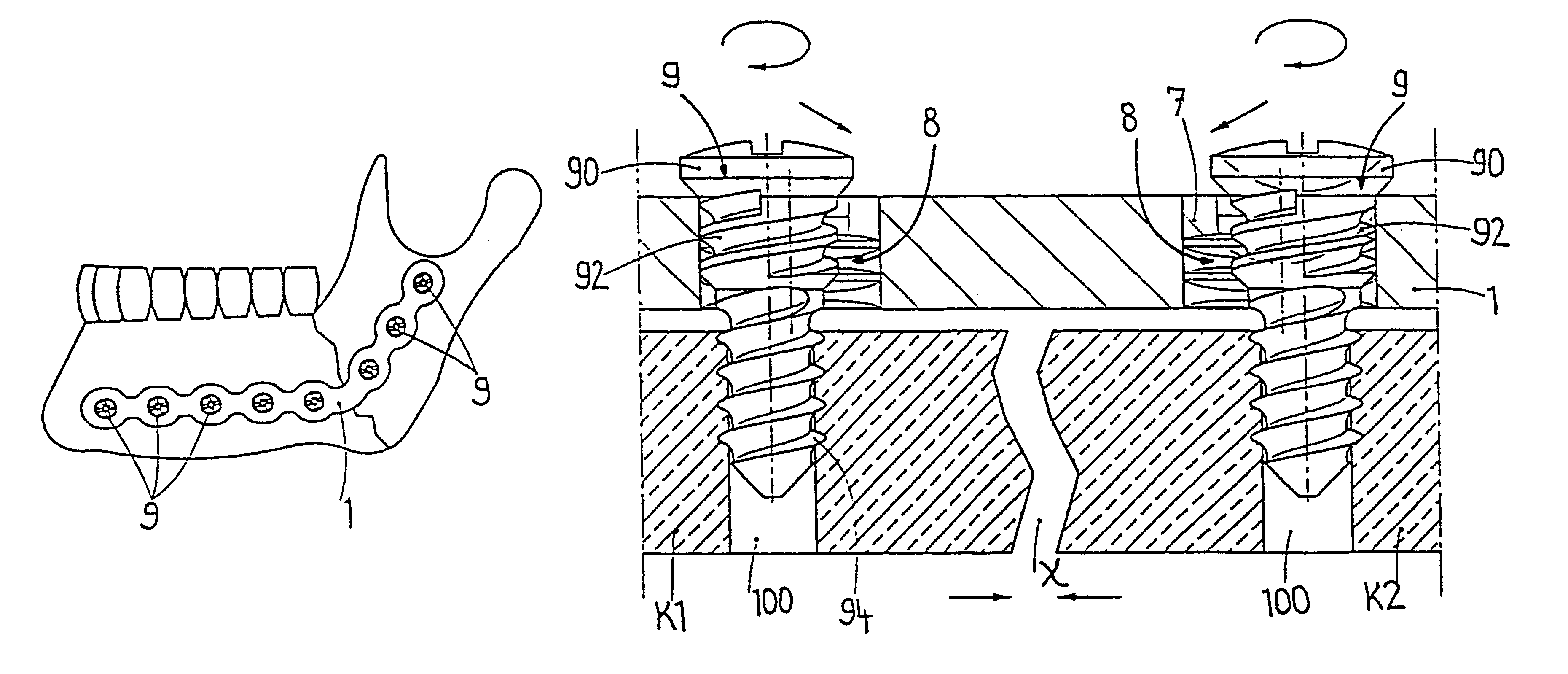
The blockable bone plate consists of a plurality of plate members which are connected to each other via webs. A screw hole is provided in at least some plate members, preferably in each plate member. The screw hole is surrounded by a spherical countersink on the upper surface of the plate. Provided internally in the screw hole there is an engagement contour which consists of contour valleys and contour peaks partially running in a horizontal and radial peripheral direction on the wall of the screw hole. The engagement contour is preferably produced by milling and has for example a pointed, round, trapezoidal or serrated configuration. A blocking thread is provided under the screw head of the screw intended for blocking. As the screw is screwed in, the blocking thread engages in the engagement contour. The particular advantages lie in increased security against the screw coming loose and in the possibility of also inserting the screw through the plate at an inclination. Furthermore, a bone plate is proposed which has the shape of an arc of a circle in the longitudinal axis of the plate and which requires less bending, particularly on the human lower jaw, and adapts to the bone in a more ideal manner.
Owner:MEDARTIS AG
Unit for varying a temperature of a test piece and testing instrument incorporating same
ActiveUS7115838B2Easy to control temperatureUniform temperature distributionDrying solid materials with heatDomestic cooling apparatusInstrumentationCoolant
Owner:ESPEC CORP
Exposure apparatus and method for producing device
ActiveUS20050219489A1Reduce equipment costsWide depth of focusPhotomechanical exposure apparatusMicrolithography exposure apparatusImage plane
An exposure apparatus performs exposure for a substrate by filling a space between a projection optical system and the substrate with a liquid and projecting an image of a pattern onto the substrate through the liquid by using the projection optical system. The exposure apparatus includes a substrate stage for holding the substrate, a liquid supply unit for supplying the liquid to a side of an image plane of the projection optical system, and a focus / leveling-detecting system for detecting surface information about a surface of the substrate not through the liquid. The exposure apparatus performs liquid immersion exposure for the substrate while adjusting a positional relationship between the surface of the substrate and the image plane formed through the projection optical system and the liquid, on the basis of the surface information detected by the focus / leveling-detecting system. The liquid immersion exposure can be performed at a satisfactory pattern transfer accuracy.
Owner:NIKON CORP
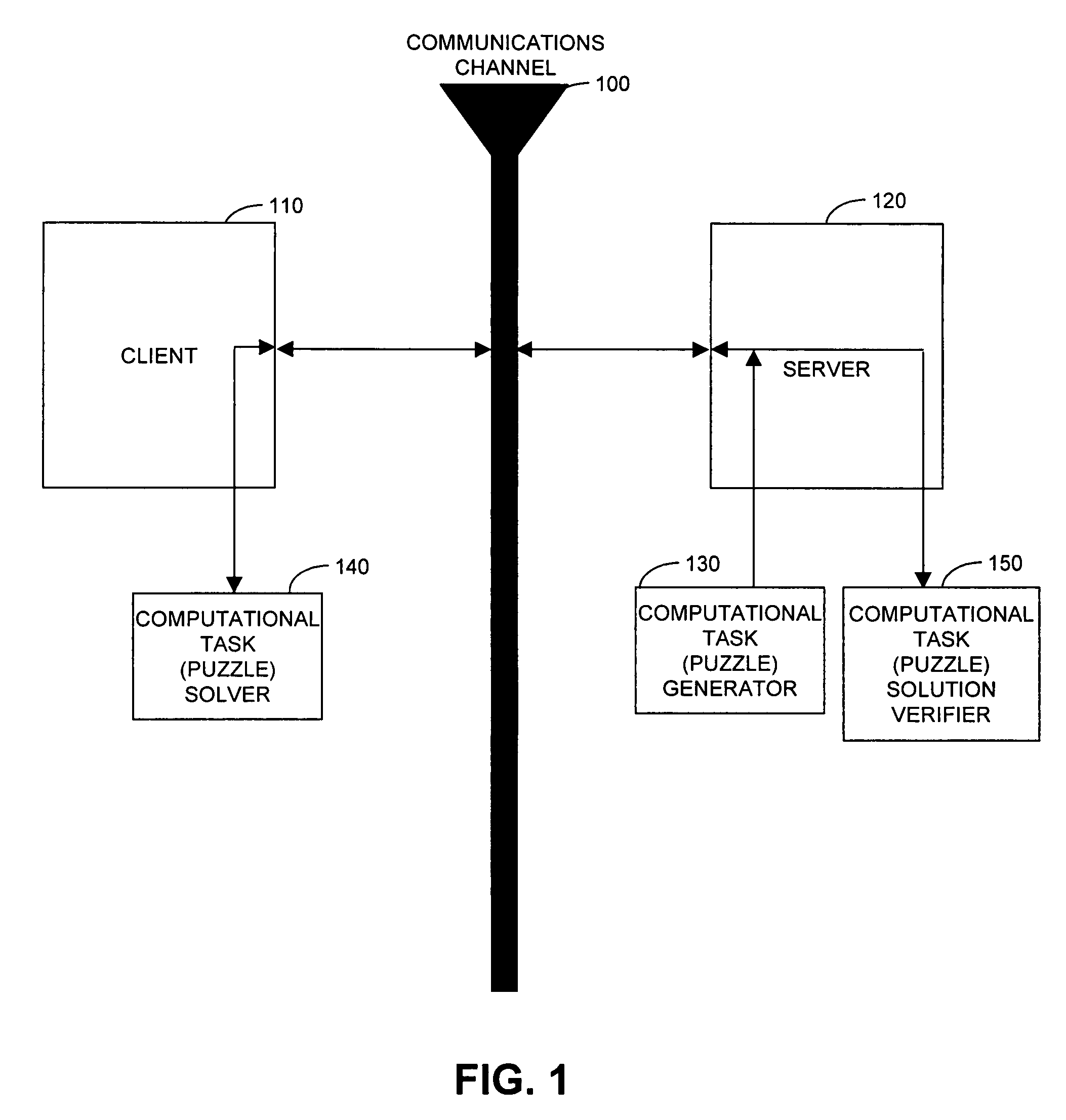
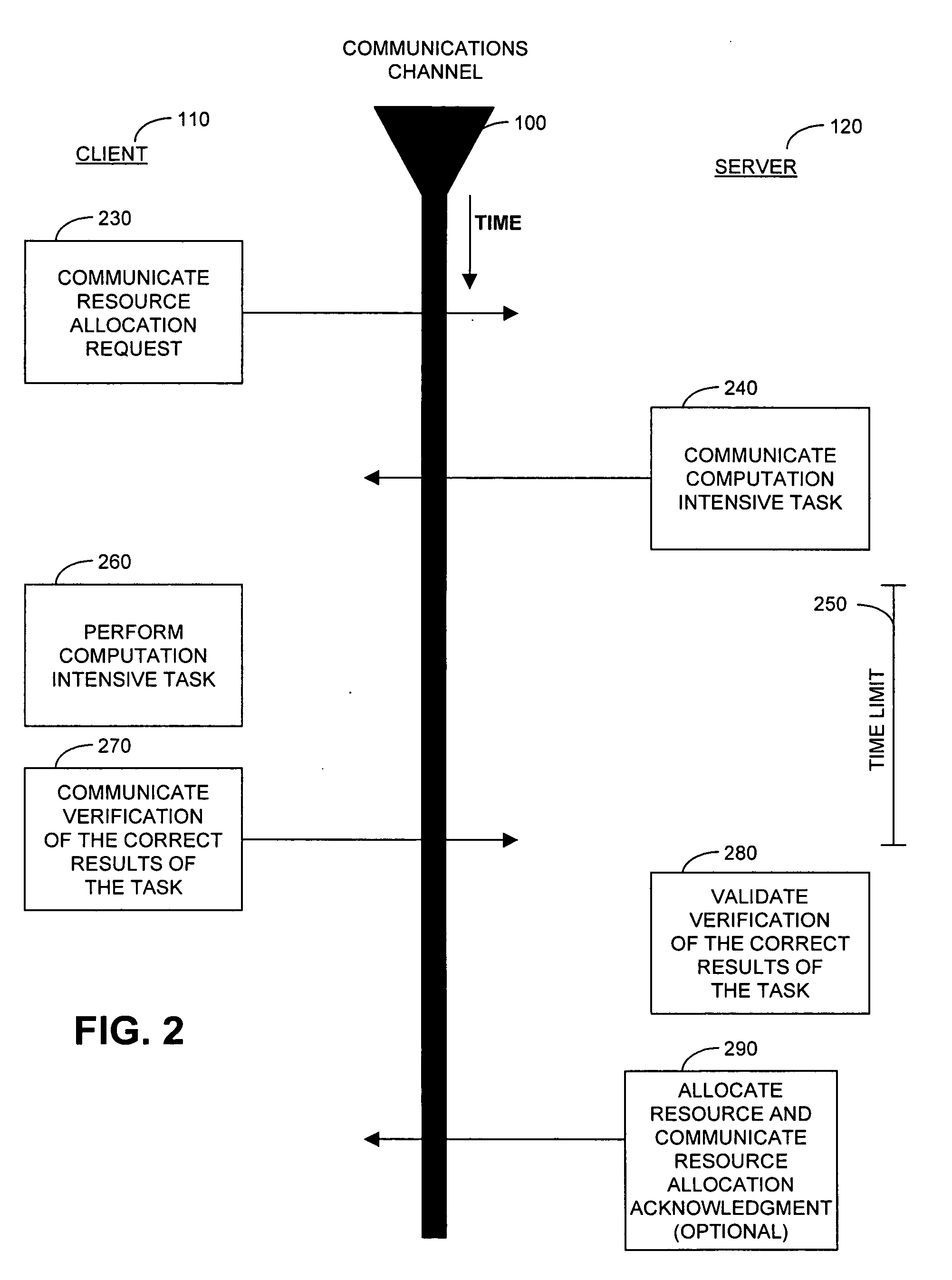
Cryptographic countermeasures against connection depletion attacks
InactiveUS7197639B1Ensure correct executionDigital data processing detailsUser identity/authority verificationCountermeasureTime limit
This invention relates to cryptographic communications methods and systems that protect a server from a connection depletion attack. Specifically, the invention presents a method for allocating a resource comprising the steps of receiving a resource allocation request from a client, imposing a computational task and a time limit for correct completion of the task upon the client, verifying that the task was performed correctly within the time limit, and allocating the resource if the task was correctly performed within the time limit.
Owner:EMC IP HLDG CO LLC
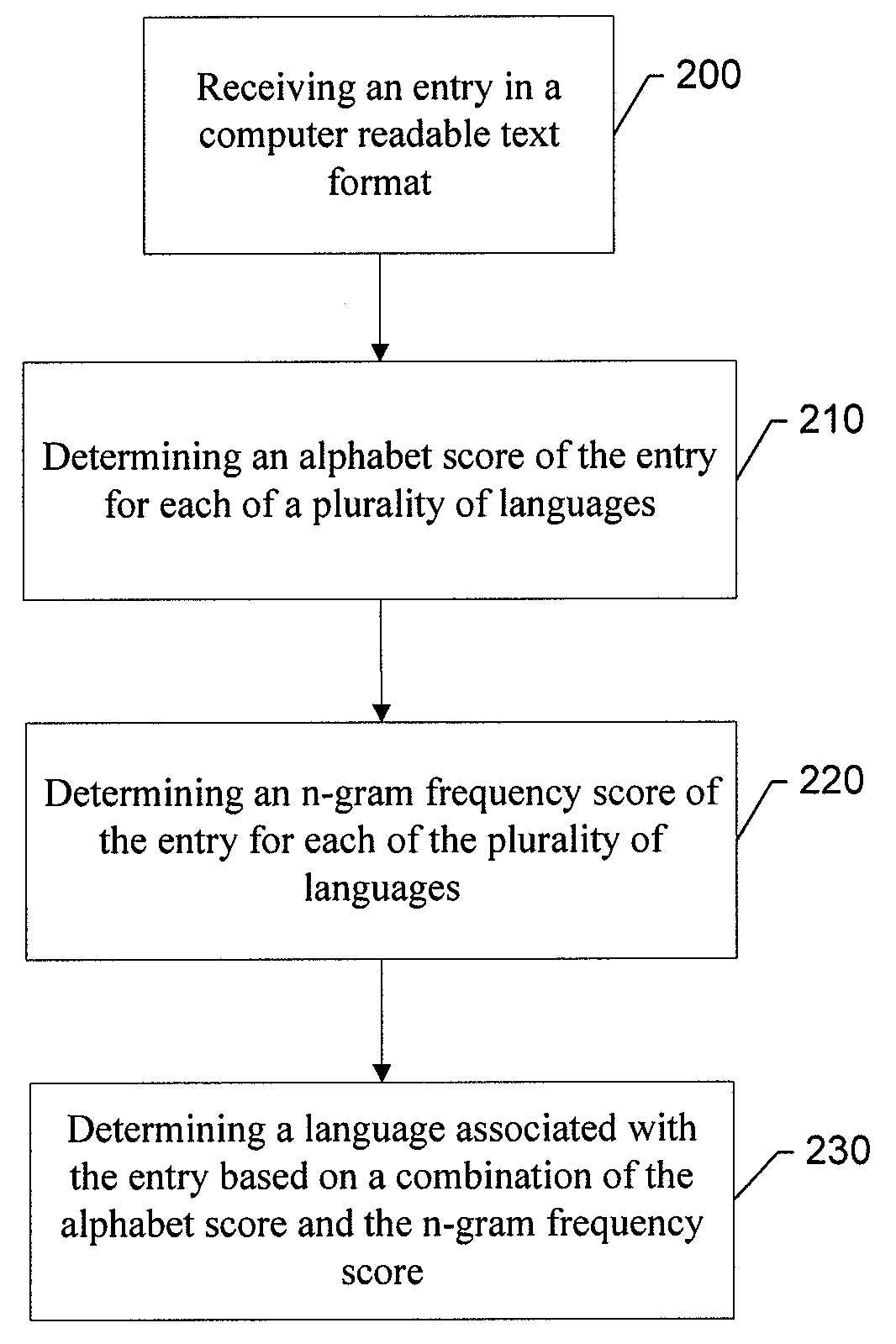
Method, apparatus and computer program product for providing flexible text based language identification
ActiveUS7552045B2Accurate analysisHighly configurable multilingualSpeech analysisNatural language data processingProcessing elementHuman language
An apparatus for providing flexible text based language identification includes an alphabet scoring element, an n-gram frequency element and a processing element. The alphabet scoring element may be configured to receive an entry in a computer readable text format and to calculate an alphabet score of the entry for each of a plurality of languages. The n-gram frequency element may be configured to calculate an n-gram frequency score of the entry for each of the plurality of languages. The processing element may be in communication with the n-gram frequency element and the alphabet scoring element. The processing element may also be configured to determine a language associated with the entry based on a combination of the alphabet score and the n-gram frequency score.
Owner:NOKIA TECH OY
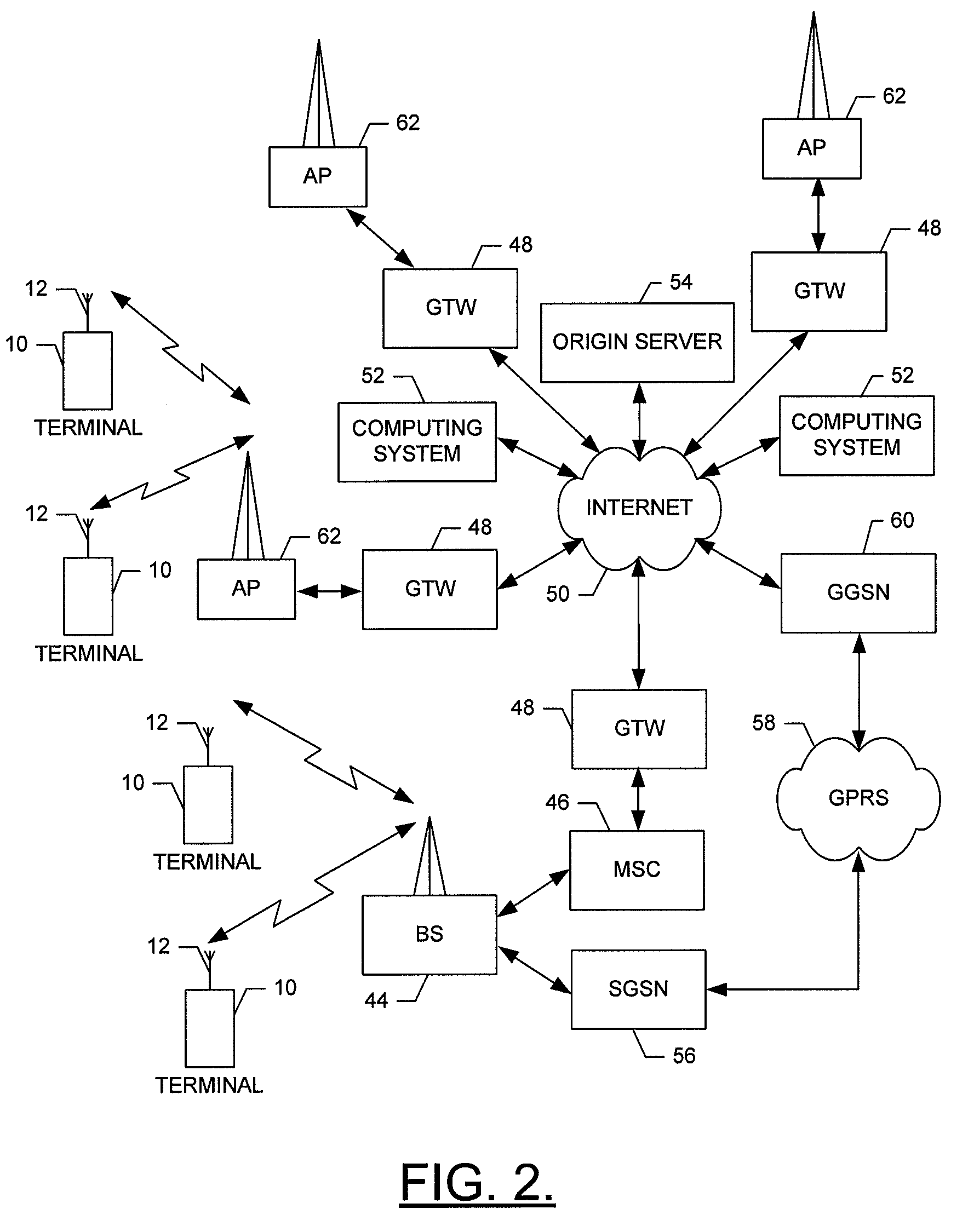
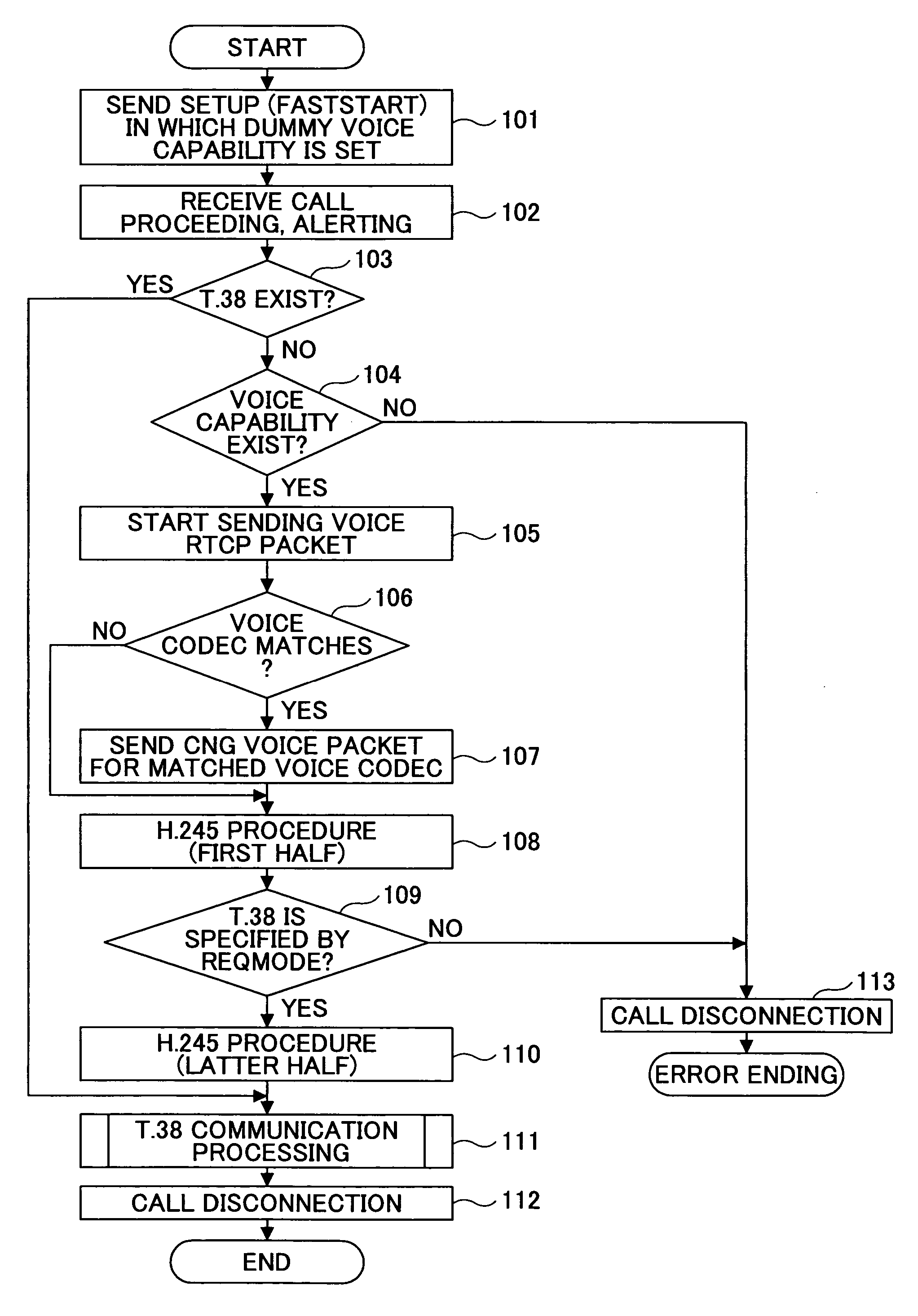
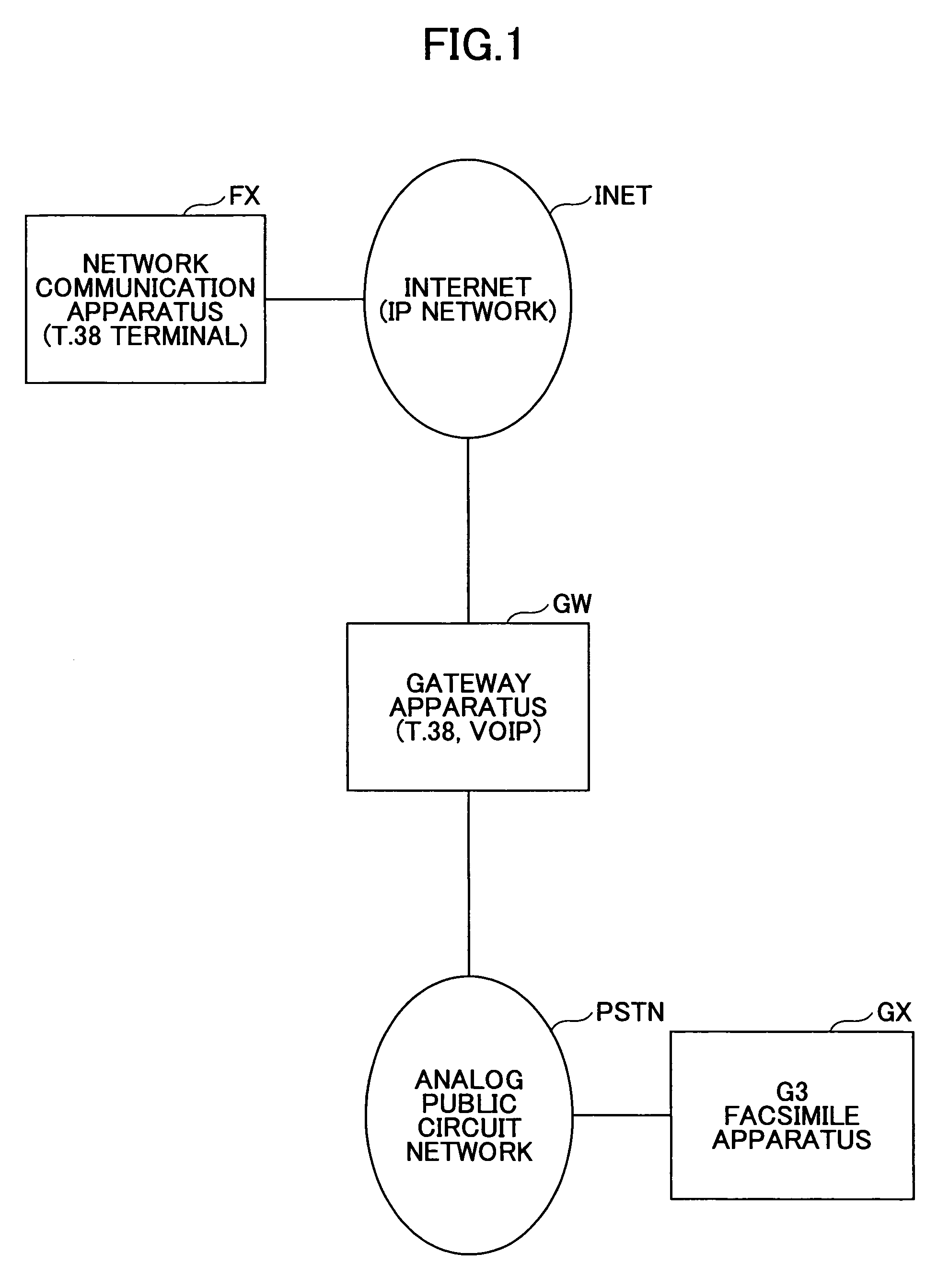
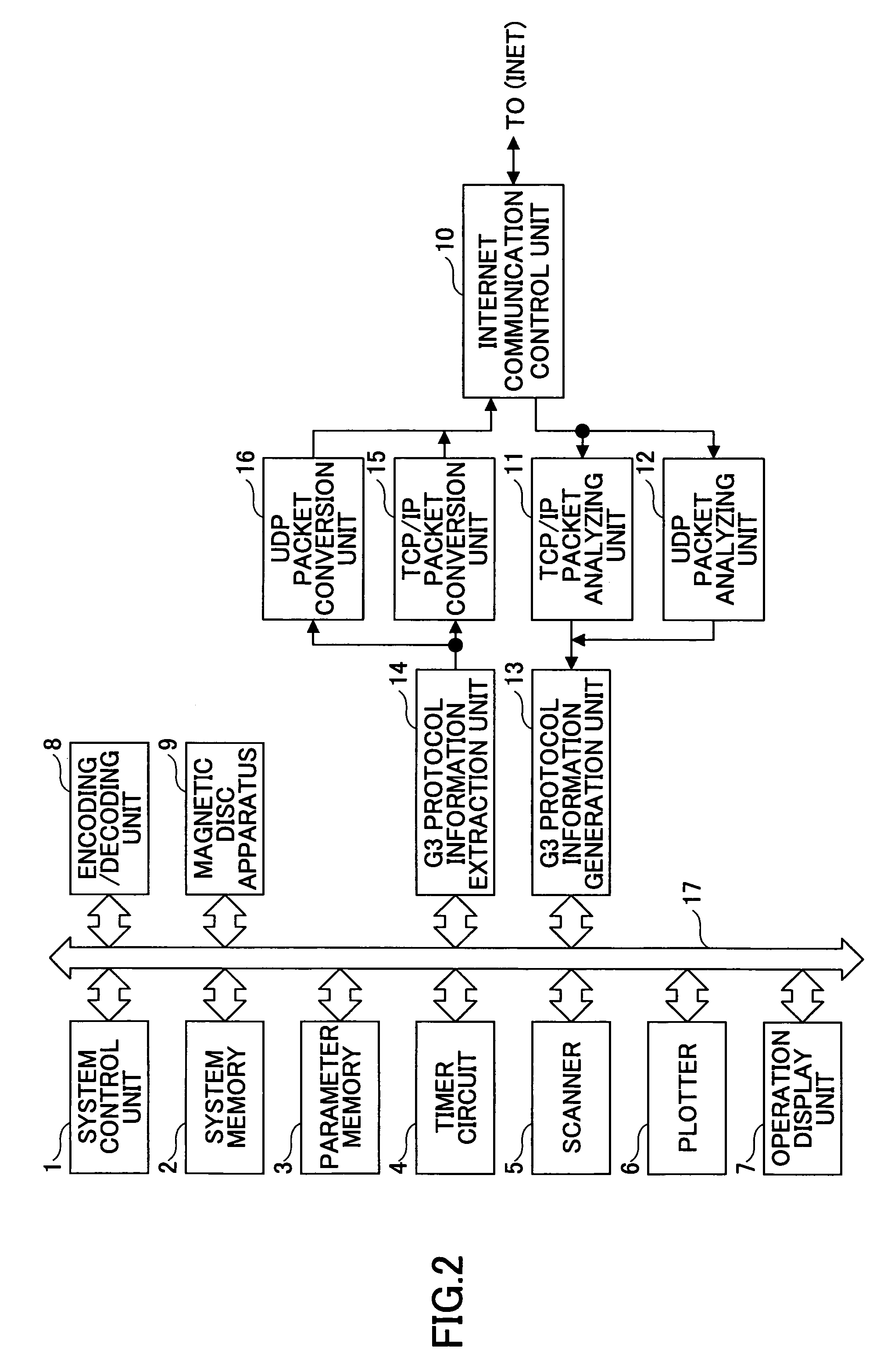
Network communication apparatus and method for performing a T.38 communication function using a voice capability of a gateway apparatus
InactiveUS7701931B2Ensure correct executionTelephonic communicationMultiple digital computer combinationsVoice communicationNetwork communication
A network communication apparatus that includes a function for performing communications via an IP network and that includes an ITU-T standard T.38 communication function but does not include a voice communication function is disclosed. The network communication apparatus includes: a unit configured to generate a call connection signal including T.38 communication capability and dummy voice capability to start call connection operation; and a unit configured to perform T.38 communication operation after sending a dummy CNG packet when detecting that a second network communication apparatus at the other end does not include the T.38 communication function based on a call connection signal received from the second network communication apparatus.
Owner:RICOH KK
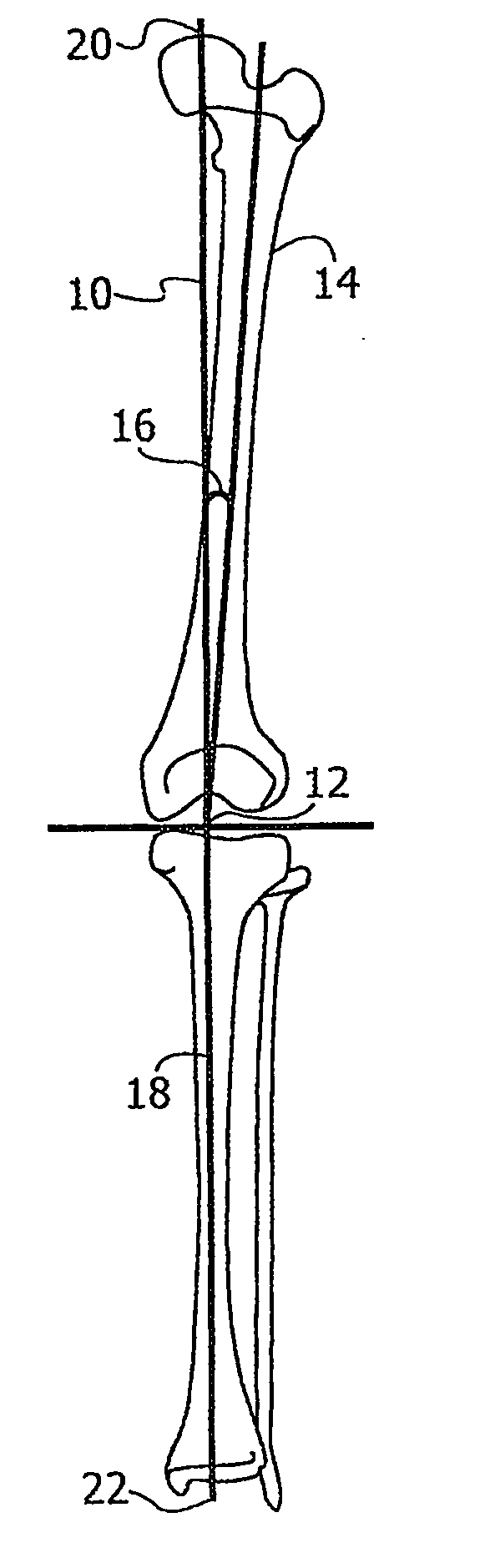
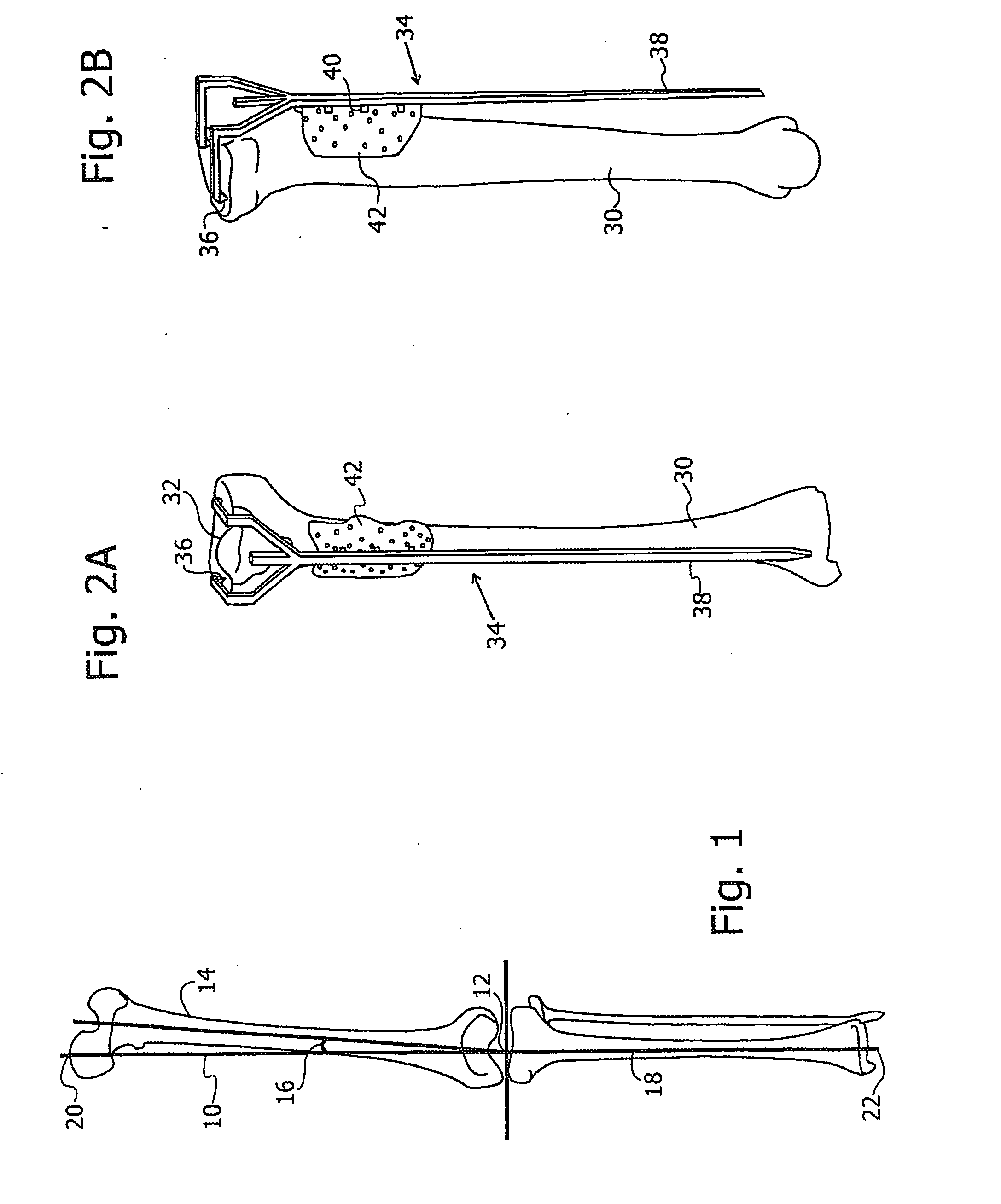
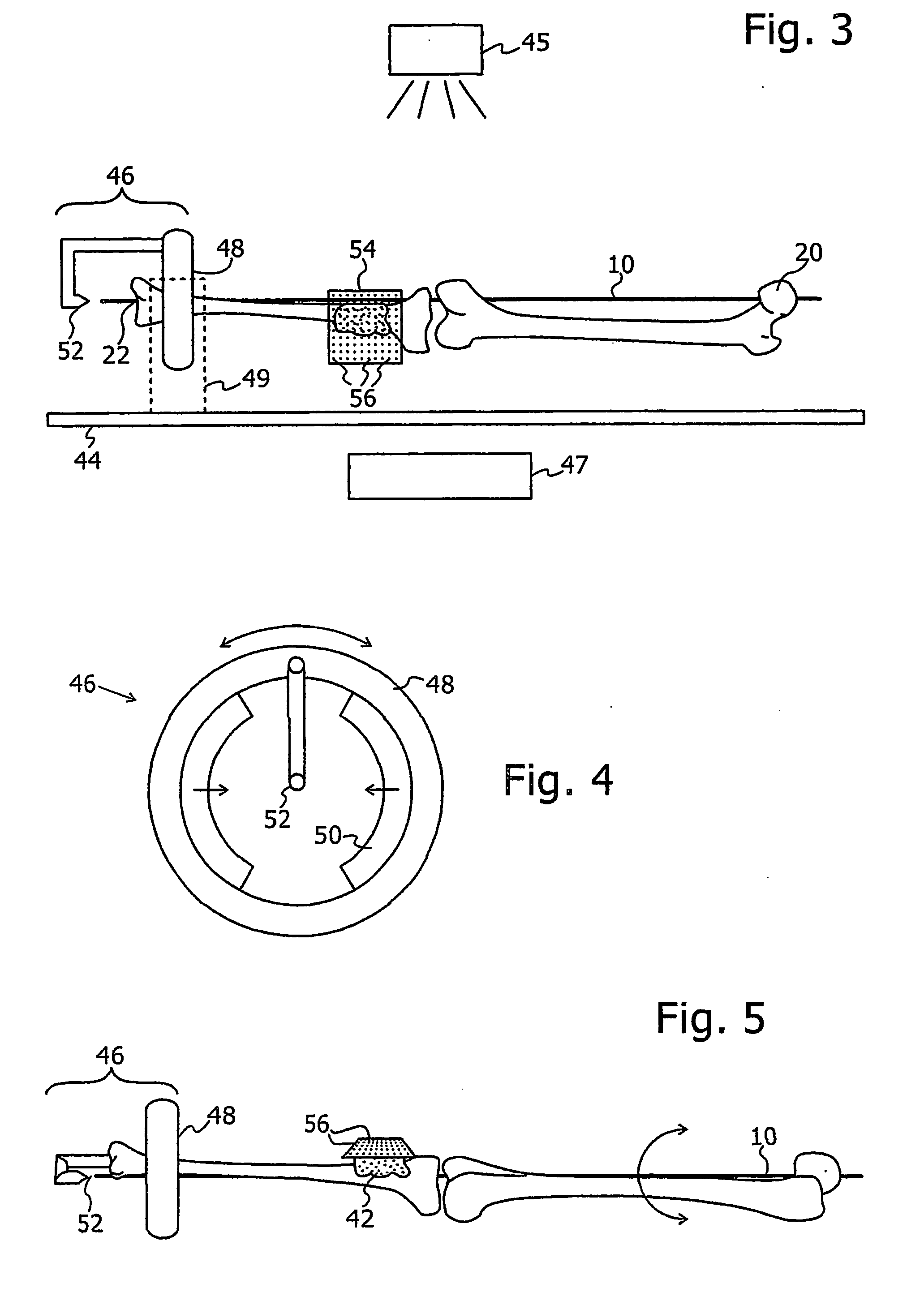
Robotic total/partial knee arthroplastics
ActiveUS20070100258A1Improve accuracyReduce responsibilityPerson identificationMaterial analysis by optical meansTibiaSurgical robot
A system and method for knee arthroplasty procedures, using a novel leg rotation fixture to enable the leg mechanical axis, the tibia and the femur to be mutually disposed such that the load bearing, mechanical axis of the leg runs through the center of the knee joint. A measurement gauge is provided for mounting on the tibia and for aligning a baseplate in a known position on the tibia. This baseplate supports an X-ray target plate in a known position relative to the tibia, used in determining the mechanical axis, and an optional surgical robot, used to perform tibial and femoral cuts. The position of the femur relative to the robot may be determined from X-ray imaging of the pelvic region after attachment to the baseplate of an additional target extending to the pelvic region. The system enables improvement in the accuracy of knee arthroplasty procedures.
Owner:MAZOR ROBOTICS
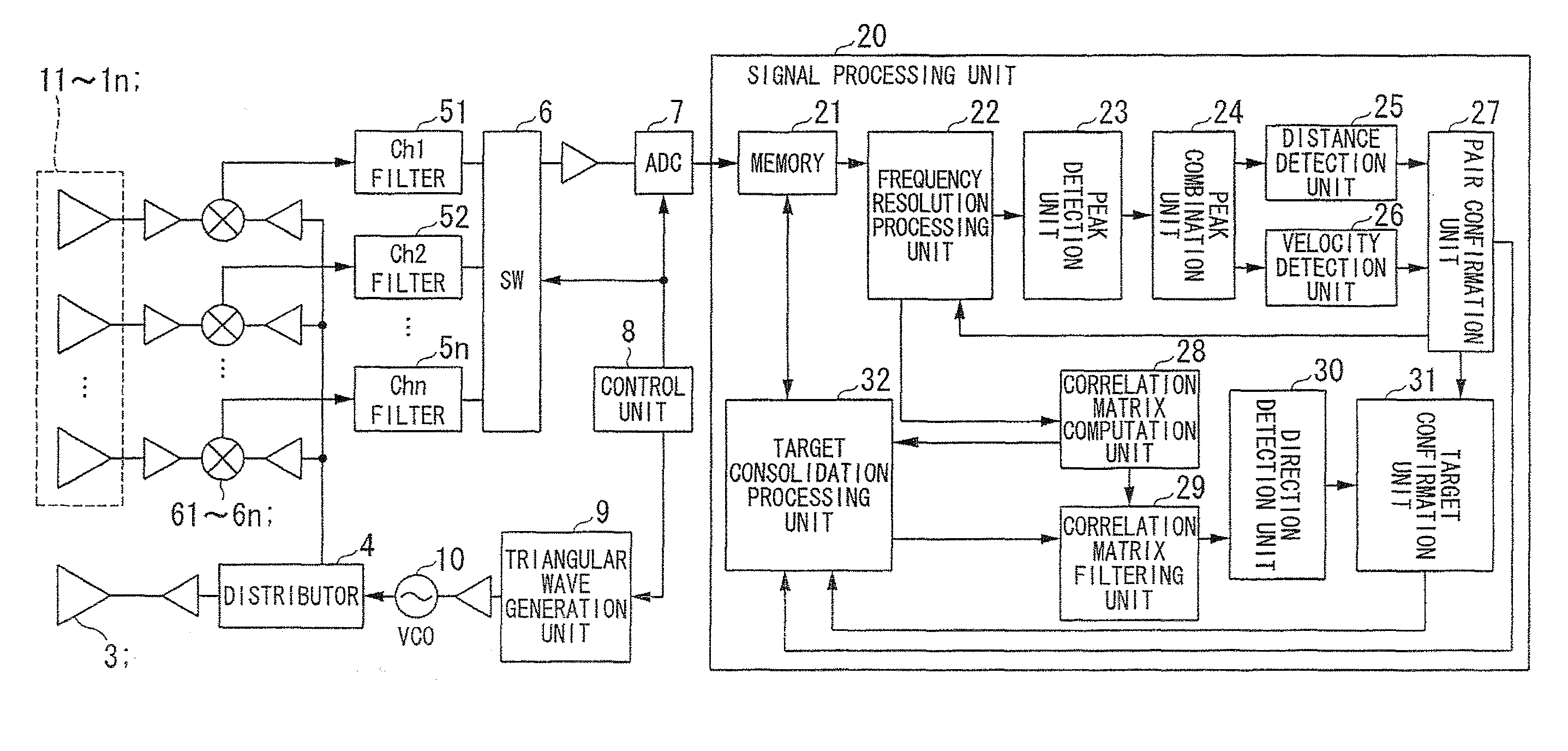
Electronic scanning type radar device, estimation method of direction of reception wave, and program estimating direction of reception wave
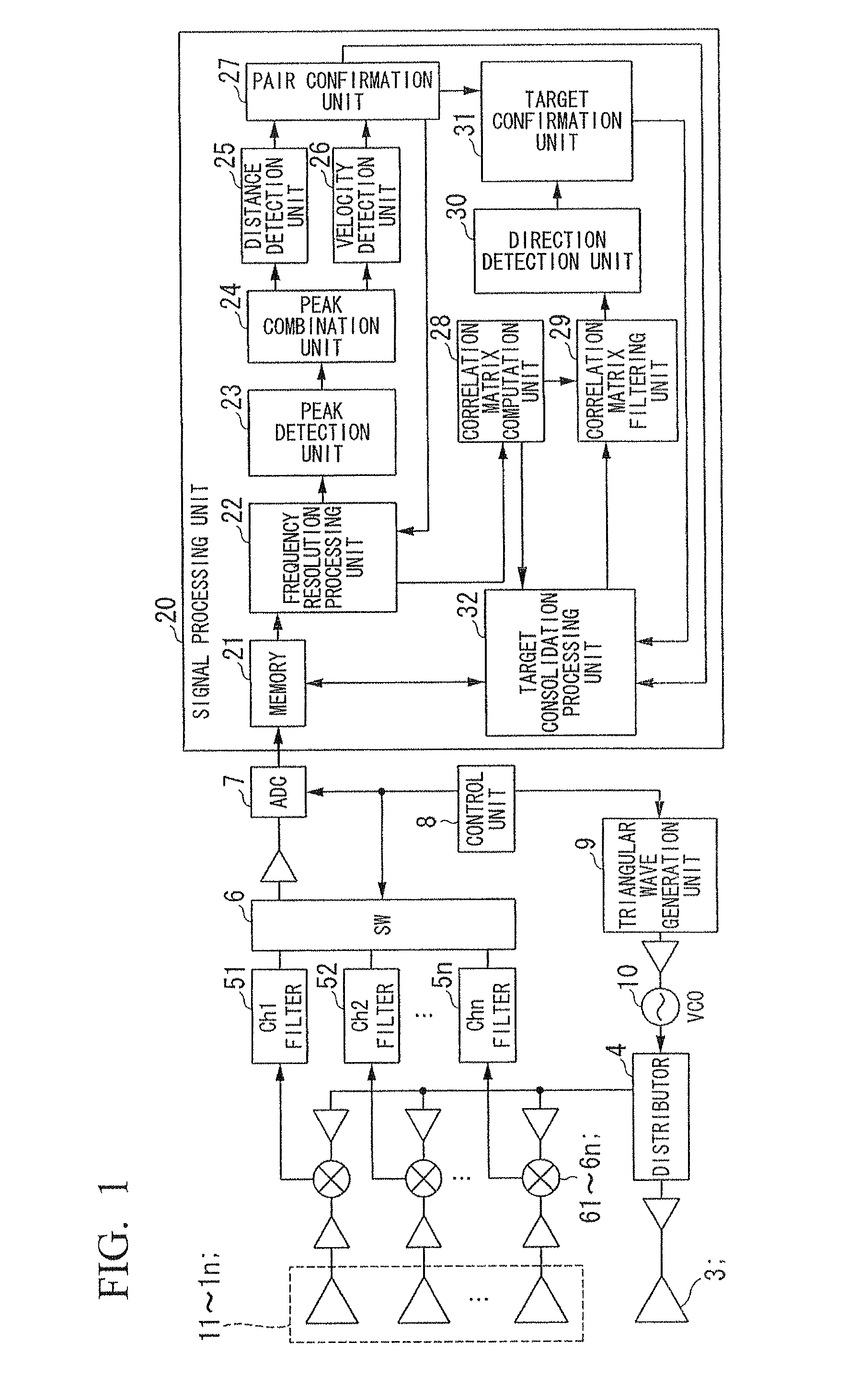
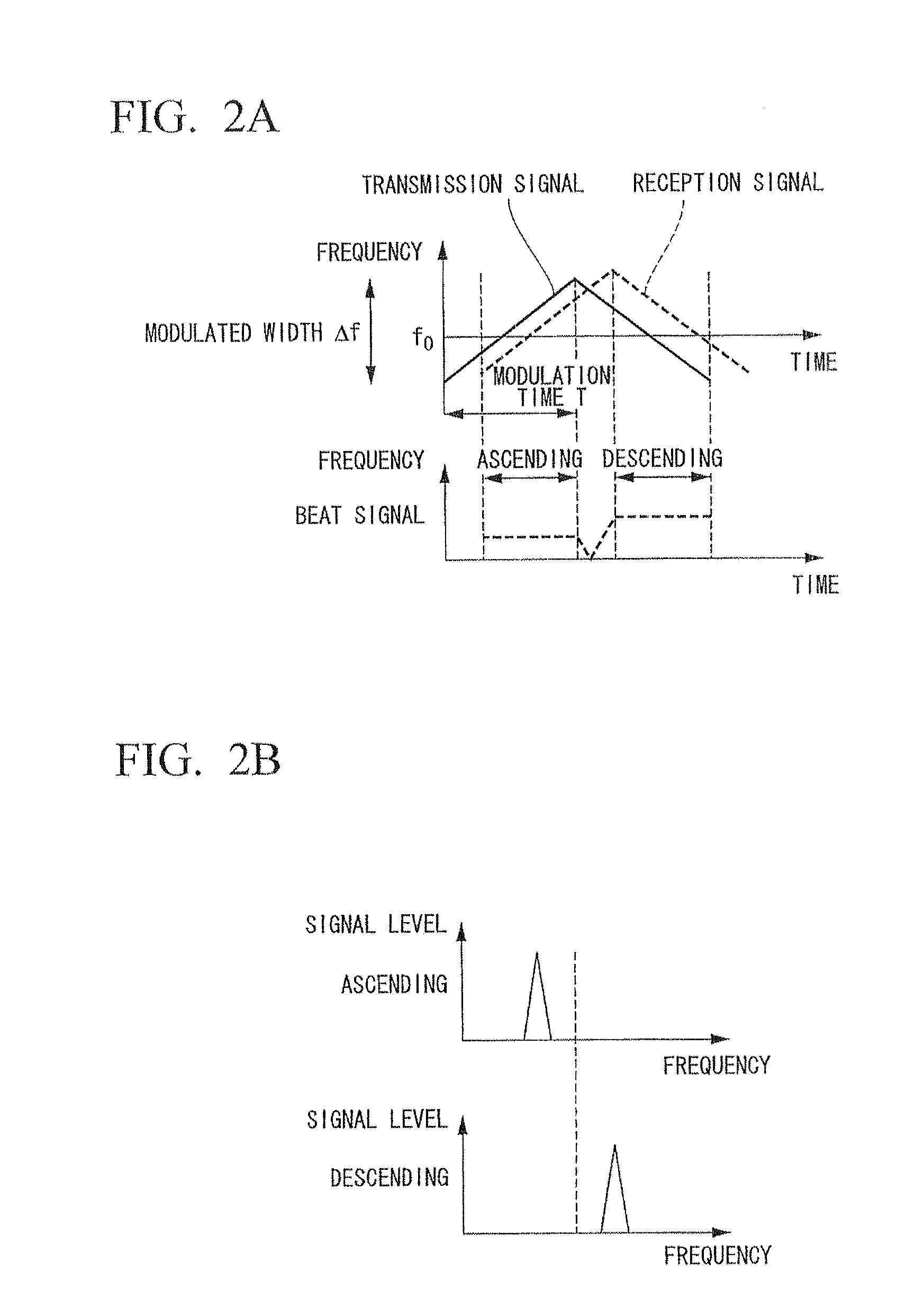
ActiveUS8446312B2Easy to identifyEnsure correct executionMulti-channel direction-finding systems using radio wavesRadio wave reradiation/reflectionRadarImage resolution
An electronic scanning type radar device mounted on a moving body includes: a transmission unit transmitting a transmission wave; a reception unit comprising a plurality of antennas receiving a reflection wave of the transmission wave from a target; a beat signal generation unit generating a beat signal from the transmission wave and the reflection wave; a frequency resolution processing unit frequency computing a complex number data; a target detection unit detecting an existence of the target; a correlation matrix computation unit computing a correlation matrix from each of a complex number data of a detected beat frequency; a target consolidation processing unit linking the target in a present detection cycle and a past detection cycle; a correlation matrix filtering unit generating an averaged correlation matrix by weighted averaging a correlation matrix of a target in the present detection cycle and a correlation matrix of a related target in the past detection cycle; and a direction detection unit computing an arrival direction of the reflection wave based on the averaged correlation matrix.
Owner:HONDA ELESYS OF YBP HI TECH CENT
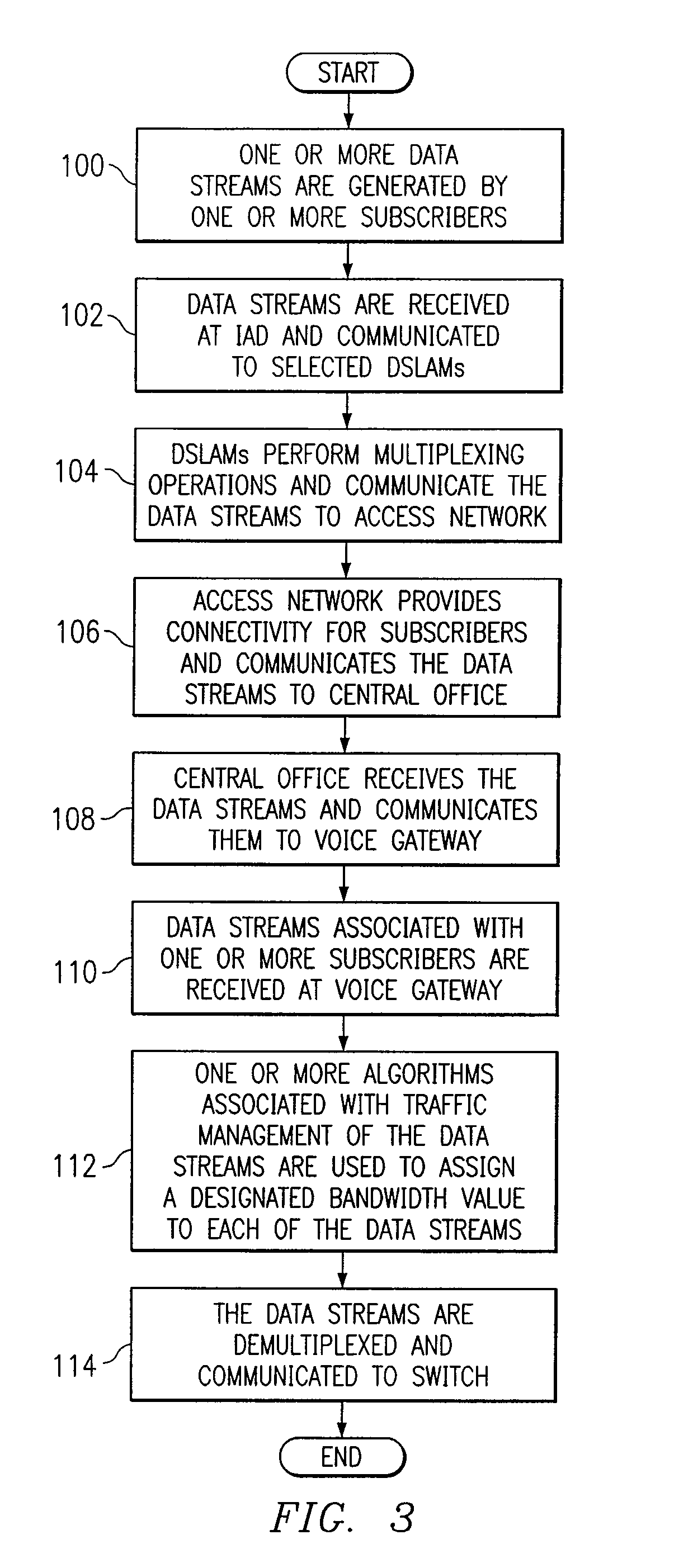
System and method for allocating bandwidth in a communications environment
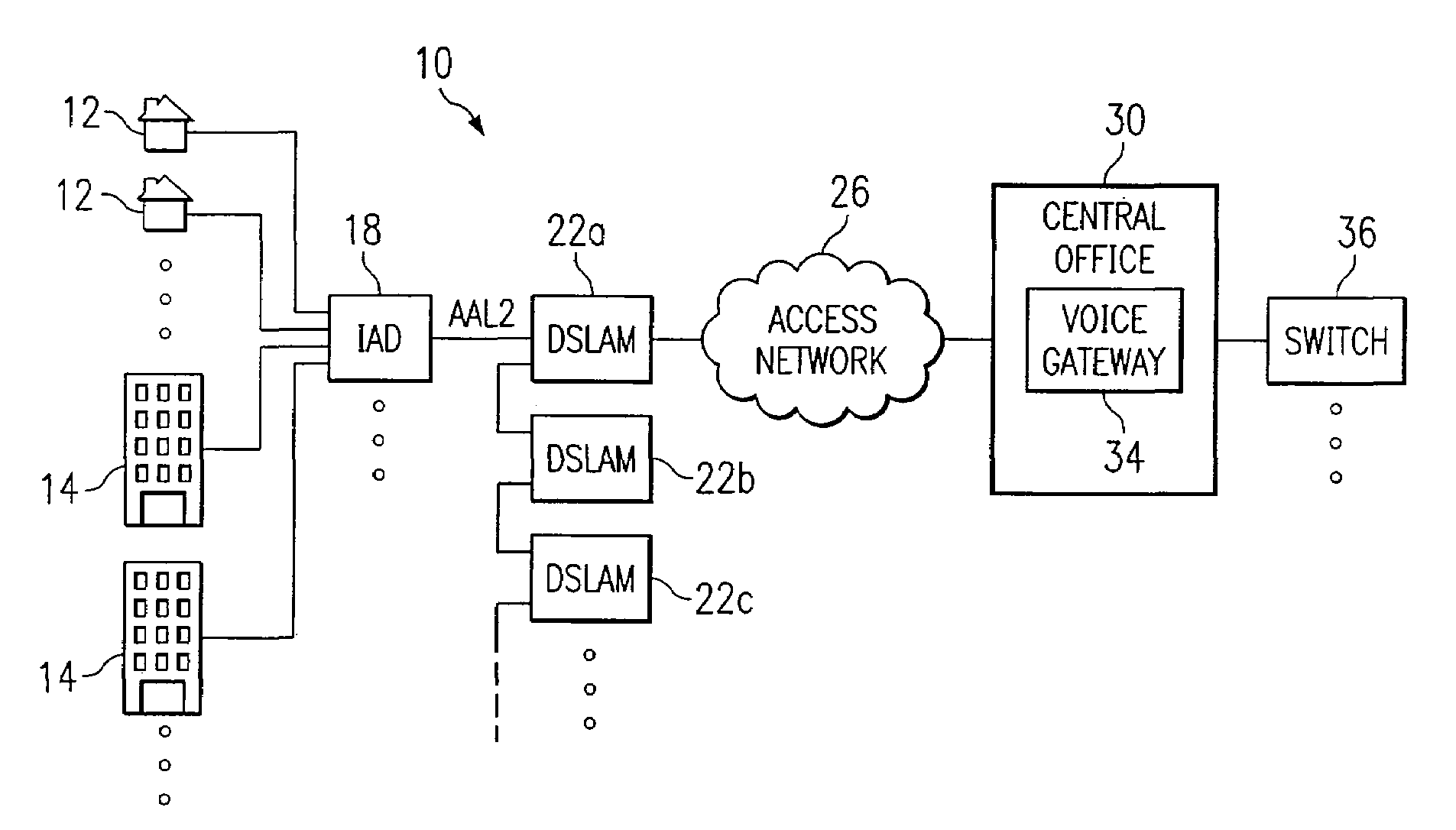
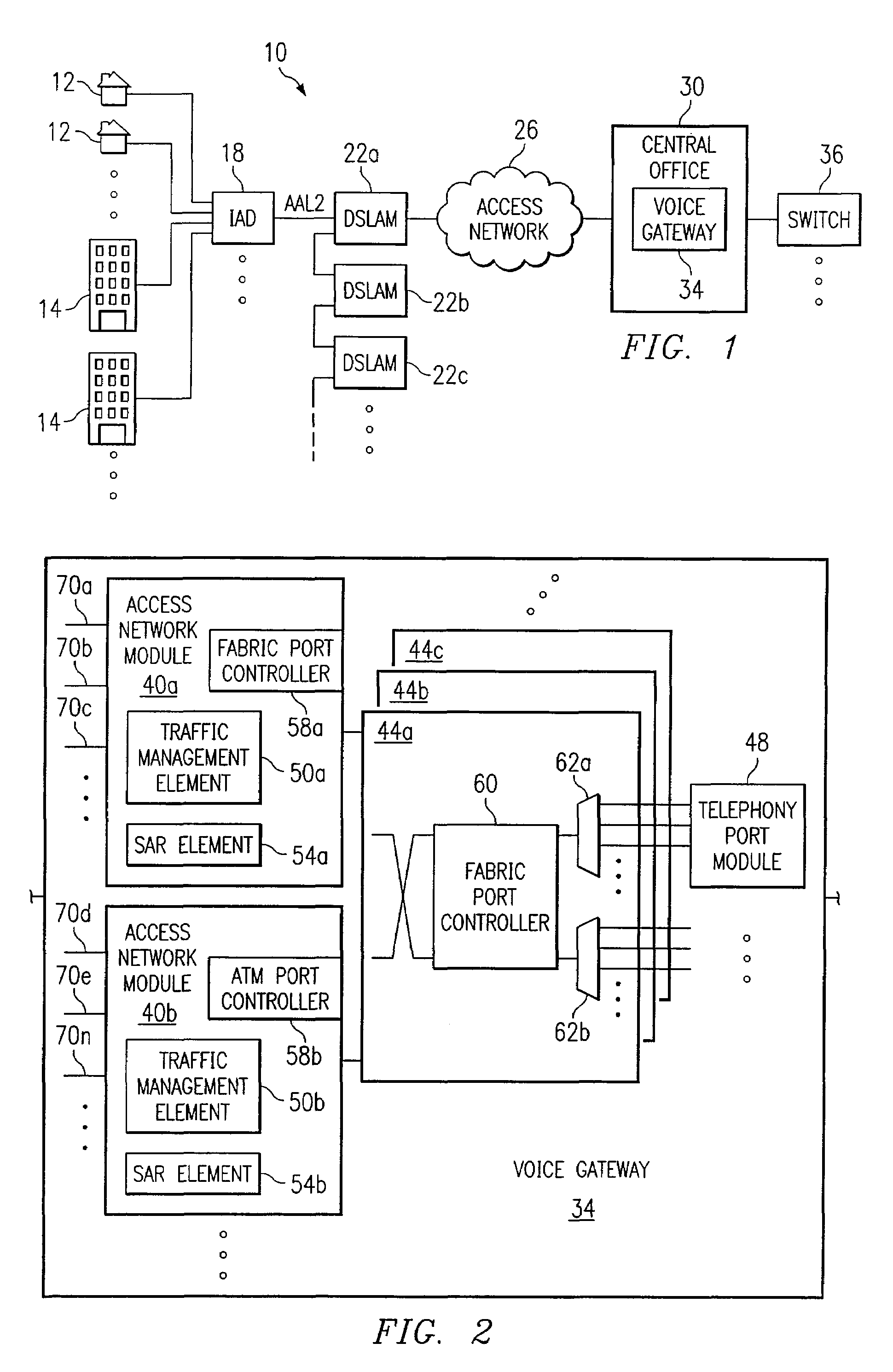
ActiveUS7266122B1Increase flexibilityEnsure correct executionTelephonic communicationData switching by path configurationData streamDistributed computing
A method for allocating bandwidth in a communications environment is provided that includes receiving one or more data streams associated with one or more subscribers at a voice gateway. One or more algorithms included in the voice gateway are executed that are associated with traffic management of the data streams in order to generate a designated bandwidth value associated with one or more of the data streams. The designated bandwidth value is assigned to one or more of the data streams based on one or more of the algorithms that use an aggregation of one or more activity characteristics associated with a selected one or more of the subscribers.
Owner:GENBAND US LLC
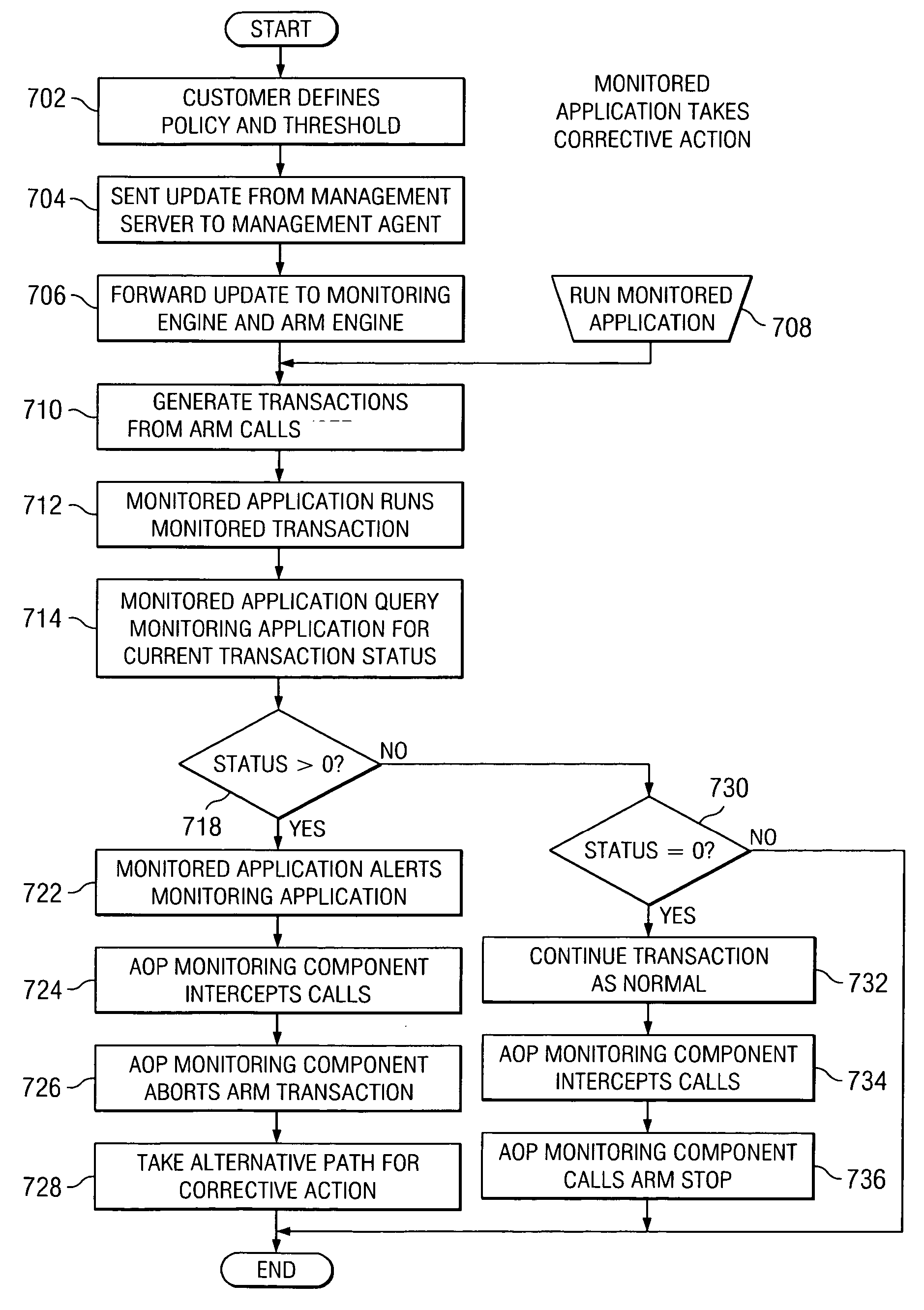
Method and apparatus for exposing monitoring violations to the monitored application
InactiveUS20060168199A1Ensure correct executionDigital computer detailsOffice automationComputer scienceReal-time computing
A method and system for exposing monitoring violations to monitored applications is provided. A monitored application may detect that a monitoring application has been applied to monitor a transaction. Based on a defined policy or a threshold within policy, the monitored application may determine if the transaction is in a violation state. If the transaction is in a violation state, the mechanism of the present invention enables the monitoring application to notify the monitored application, such that the monitored application may take corrective action to correct the violation.
Owner:IBM CORP
Game apparatus having general-purpose remote control function
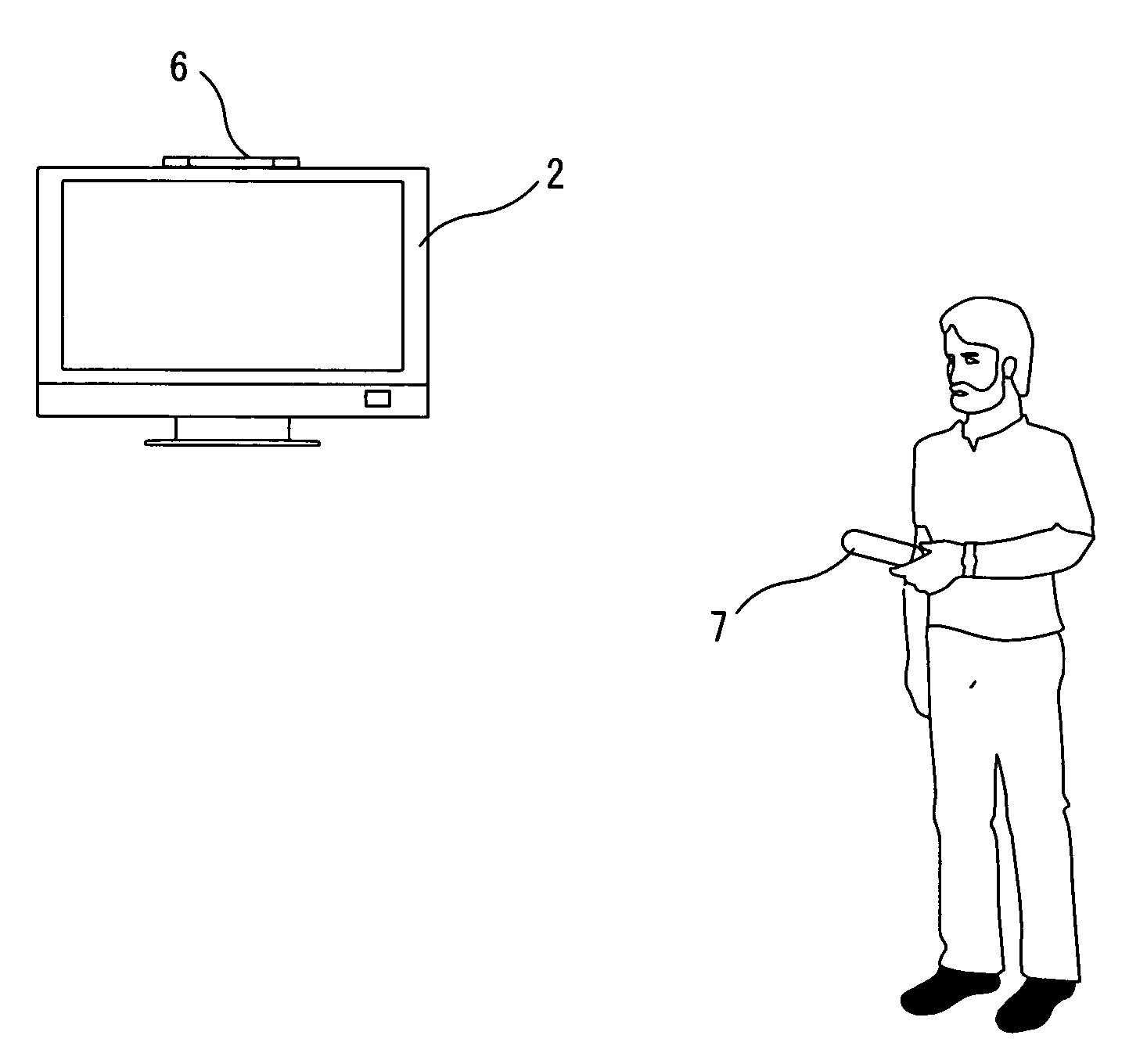
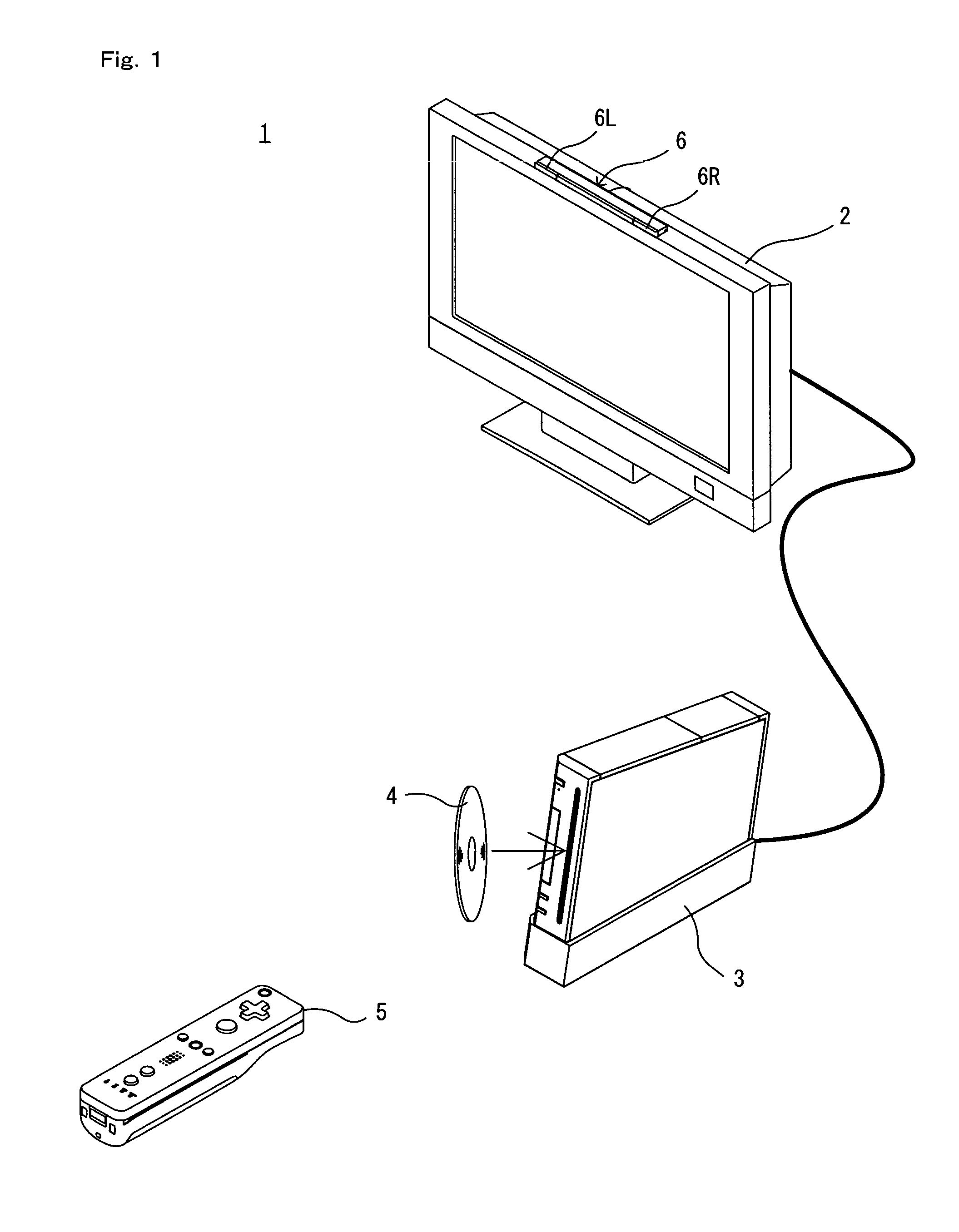
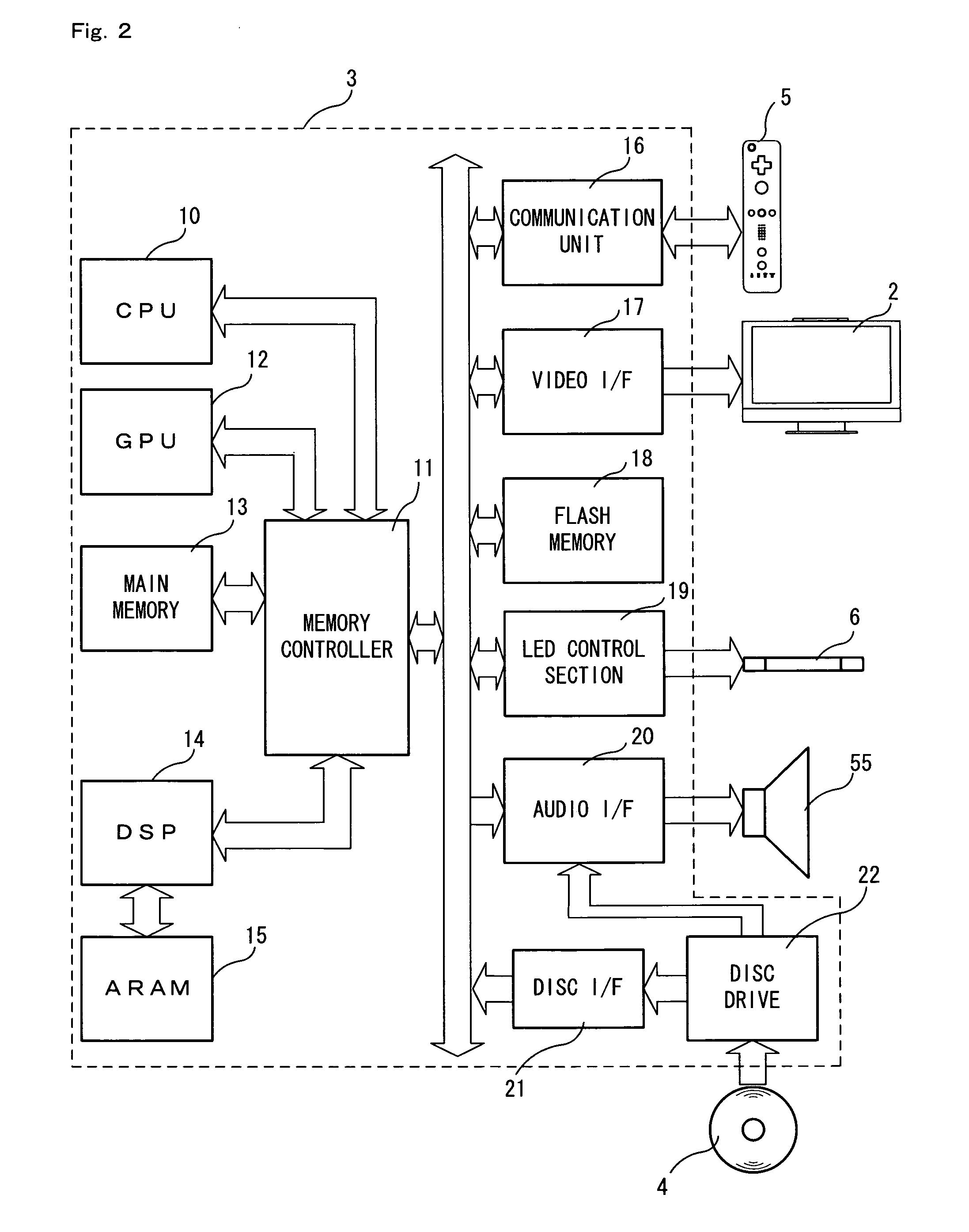
ActiveUS20080039202A1Image information is accurateEnsure correct executionCosmonautic condition simulationsBall sportsGeneral purposeInfrared
A game apparatus is capable of controlling infrared radiation means for radiating infrared light. The game apparatus executes game processing using imaging information on the infrared light obtained from an input device. The input device takes an image of the infrared light radiated by the infrared radiation means, and also receives an input from a user. The game apparatus comprises pattern storage means; selection means; and radiation control means. The pattern storage means stores at least one signal pattern of an infrared signal usable by a control target device. The selection means selects at least one of the at least one signal pattern stored by the pattern storage means, using the input received by the input device. The radiation control means causes the infrared radiation means to output an infrared signal of the signal pattern selected by the selection means.
Owner:NINTENDO CO LTD
Charged particle beam irradiation system and charged particle beam extraction method
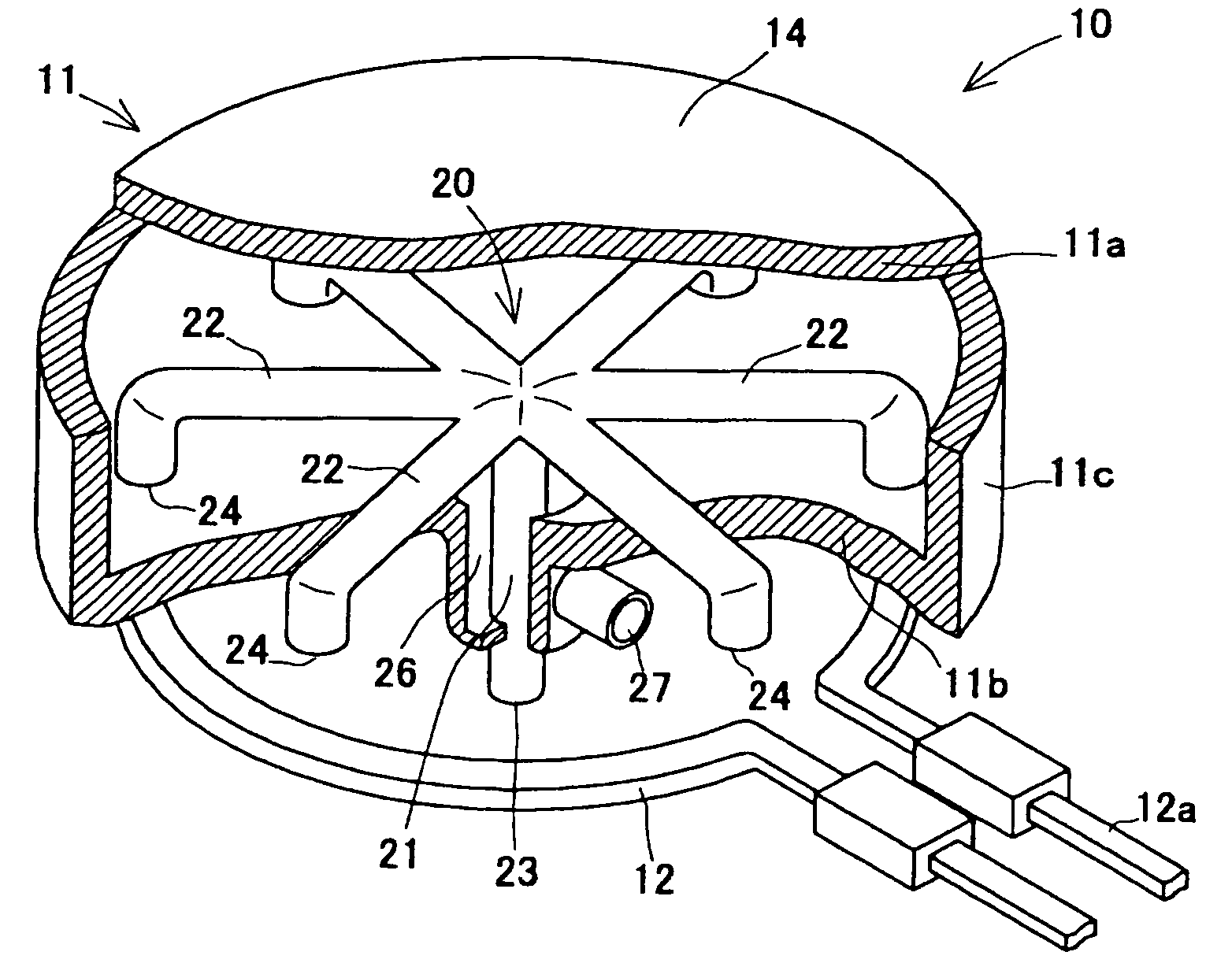
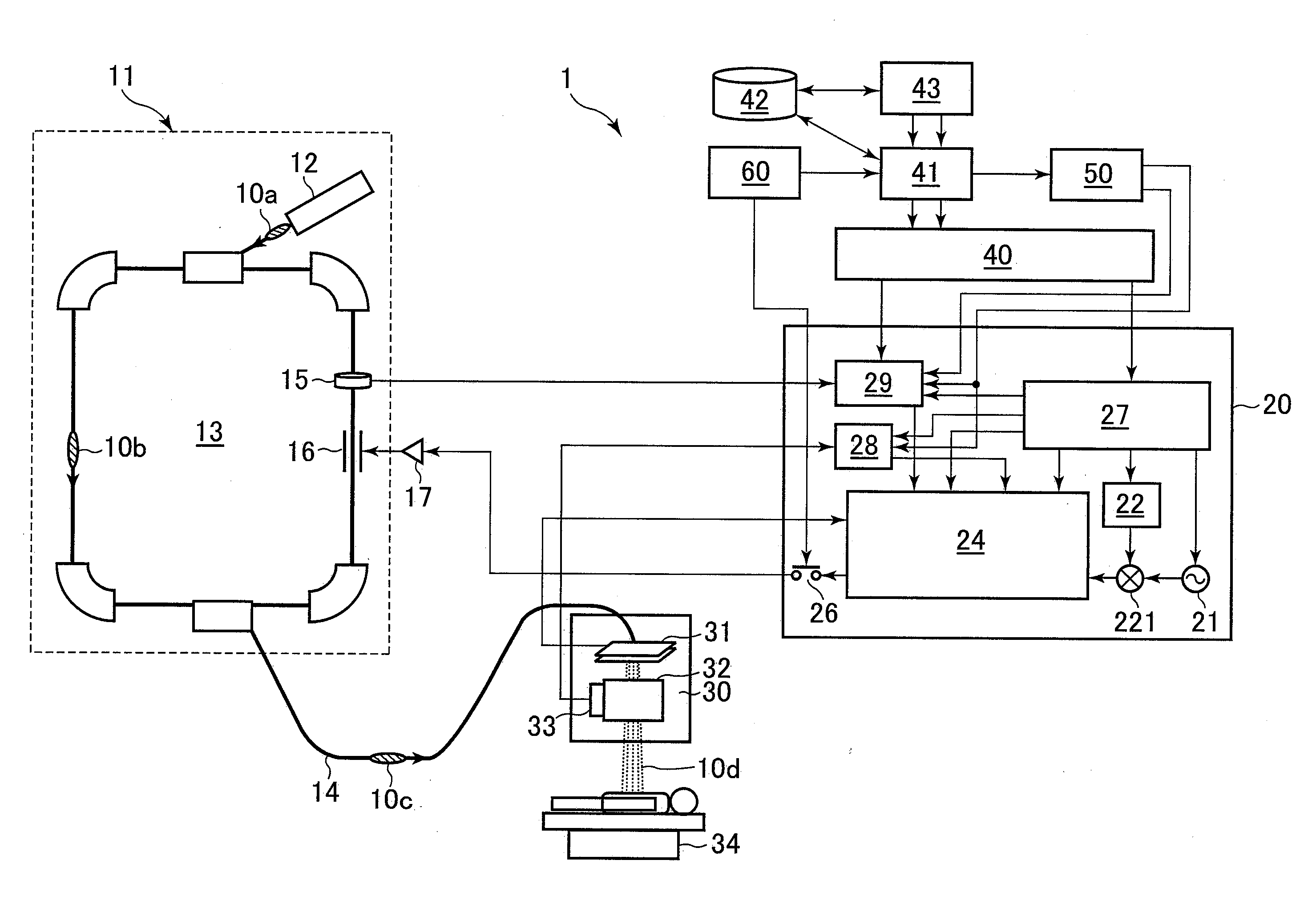
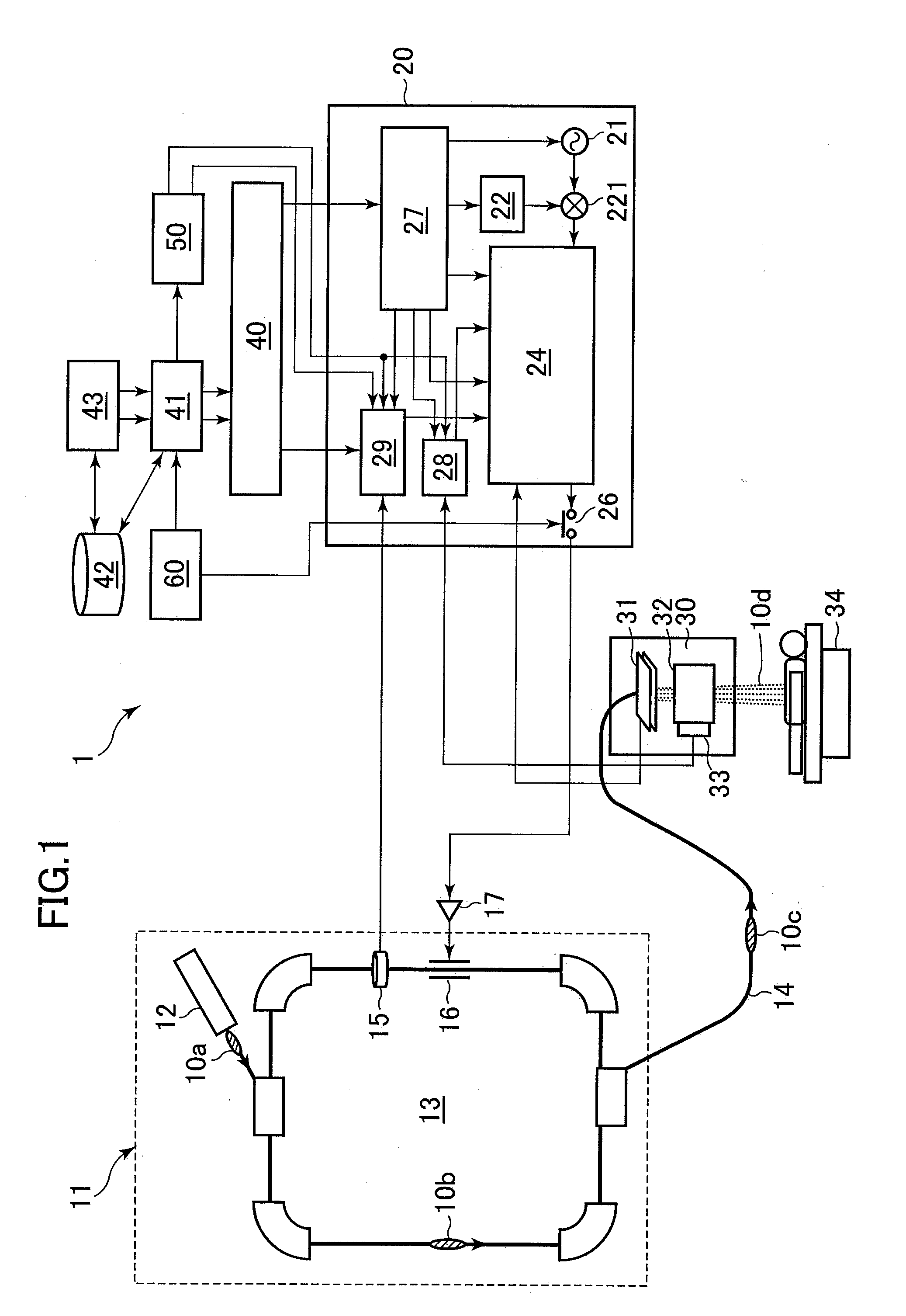
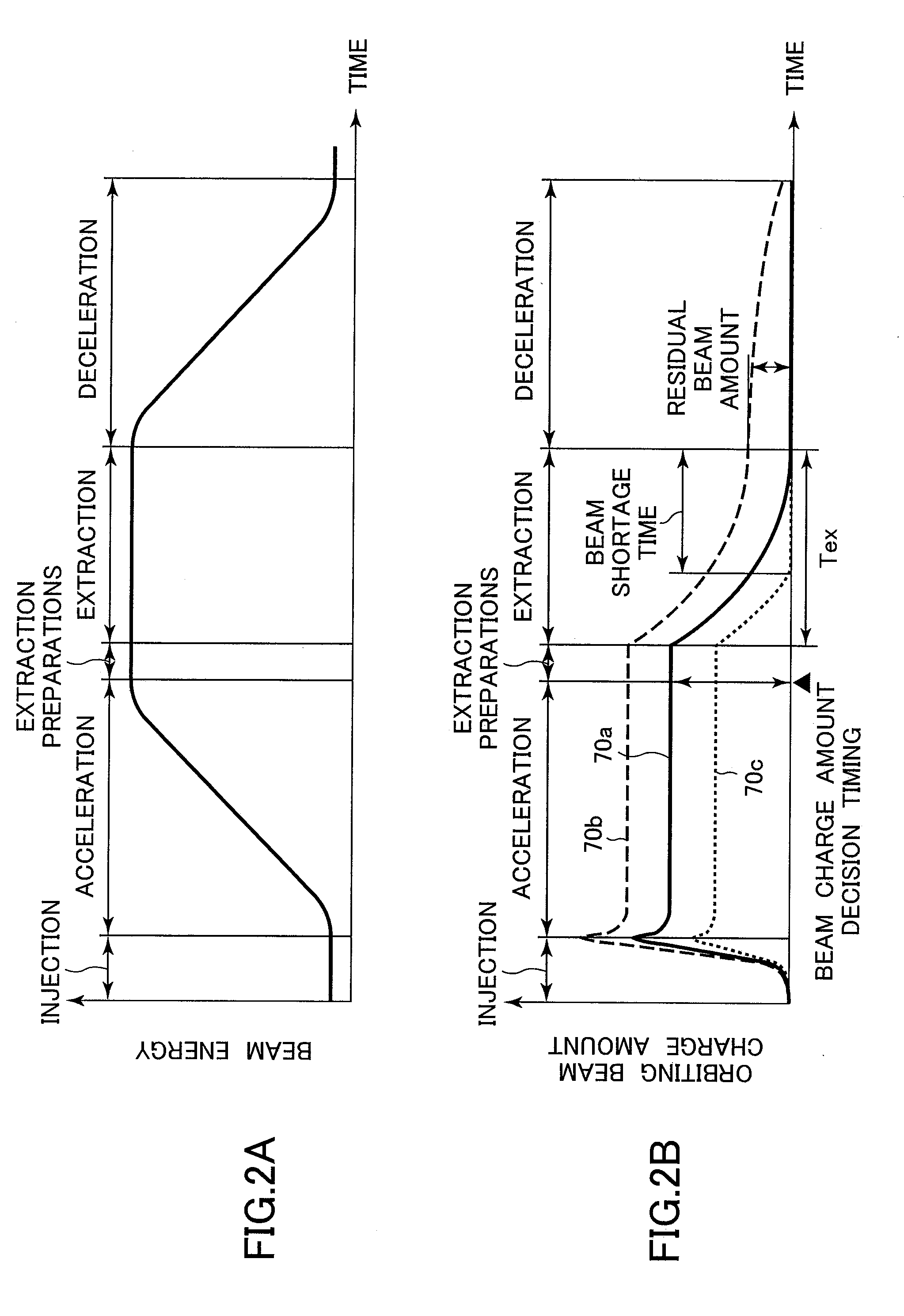
ActiveUS20100001212A1Ensure correct executionEfficient extractionThermometer detailsBeam/ray focussing/reflecting arrangementsControl periodVoltage
A charged particle beam irradiation system includes measurement means 15 for measuring an accumulated beam charge amount Qm0, the ion beams orbiting in a synchrotron 13, immediately before an extraction control period in an operating cycle of the synchrotron 13; and beam extraction control means 20, 24, 28, 29 for controlling extraction of the ion beams so that extraction of a total of the ion beams is to be completed in time with expiration of an extraction control time Tex which is set in advance based on the measurement Qm0 of the accumulated beam charge amount. When an irradiation apparatus includes an RMW 32, an amplitude of an extraction radiofrequency voltage is controlled according to a ratio Qm0 / Qs0 of the measurement to a reference value of the accumulated beam charge amount and a ratio Tb / Ta of an actual beam extraction time to the extraction control time Tex.
Owner:HITACHI LTD
Automated bulk configuration of network devices
InactiveUS7013331B2Ensure correct executionMultiple digital computer combinationsProgram controlComputer hardwareData transformation
Owner:NOKIA TECHNOLOGLES OY
Exposure apparatus and device manufacturing method
InactiveUS20070242247A1Ensure correct executionSemiconductor/solid-state device manufacturingPhotomechanical exposure apparatusProjection opticsEngineering
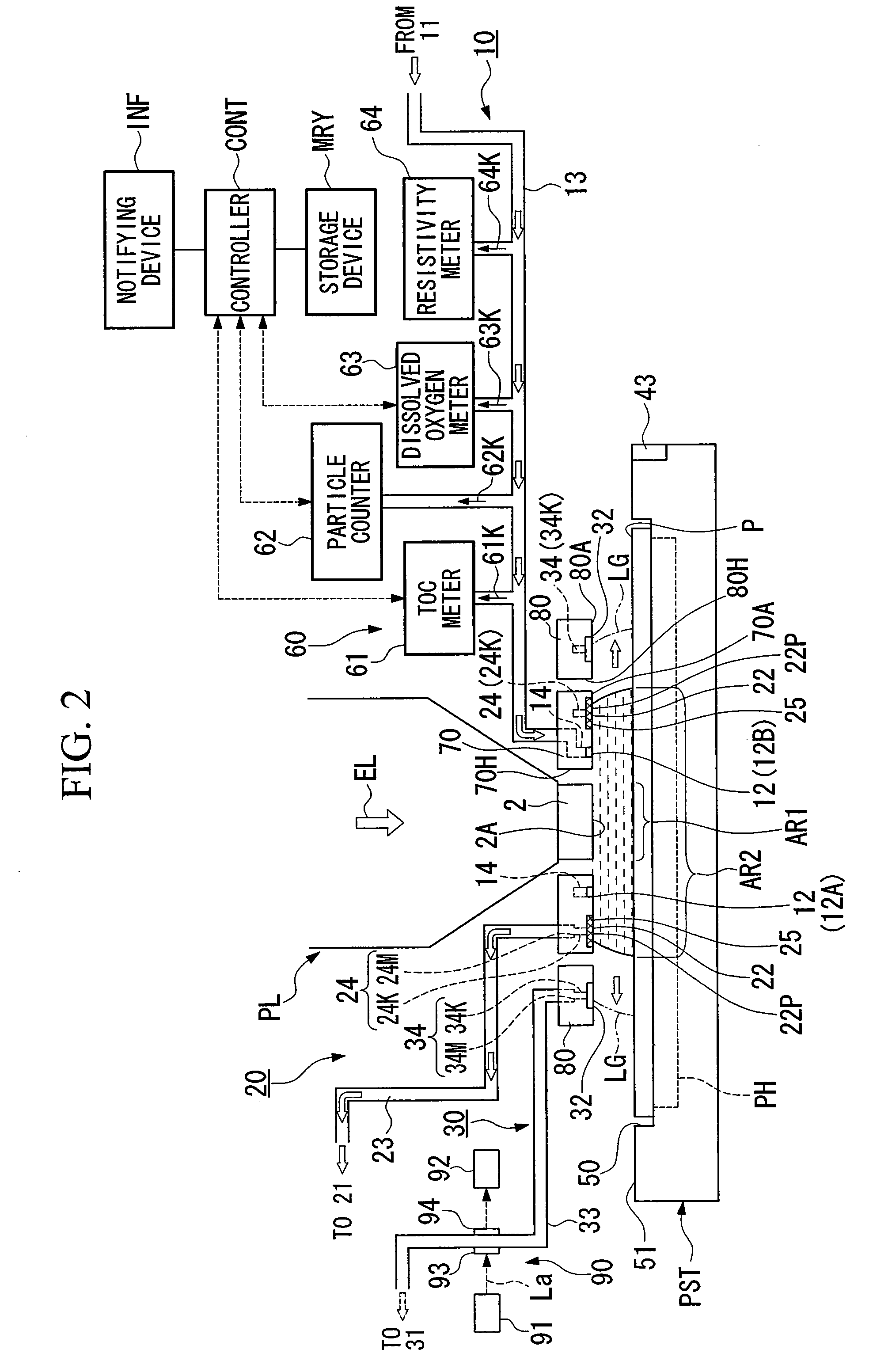
There is provided an exposure apparatus capable of accurately performing an exposure process and a measurement process based on a liquid immersion method. The exposure apparatus (EX), which forms a liquid immersion area (AR2) of a liquid (LQ) on an image surface side of a projection optical system (PL), and exposes a substrate (P) via the projection optical system (PL) and the liquid (LQ) of the immersion area (AR2), is provided with a measuring device (60) which measures at least one of a property and composition of the liquid (LQ) for forming the liquid immersion area (AR2).
Owner:NIKON CORP
Transceiver apparatus and transceiving method
InactiveUS20050163238A1Accurate detectionResidual carrier-frequency error is not negligibleTransmission path divisionTime-division multiplexTransceiverCarrier signal
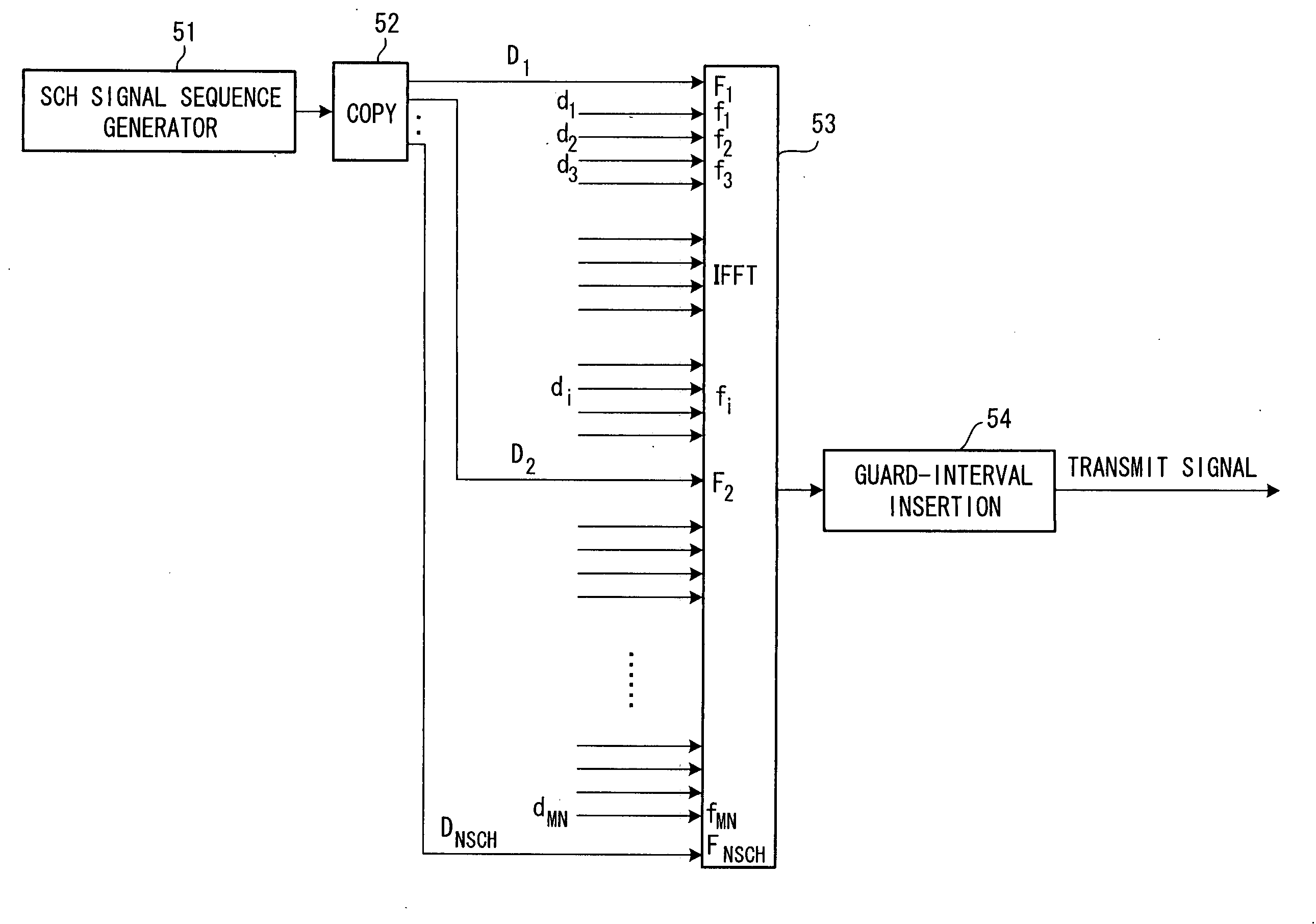
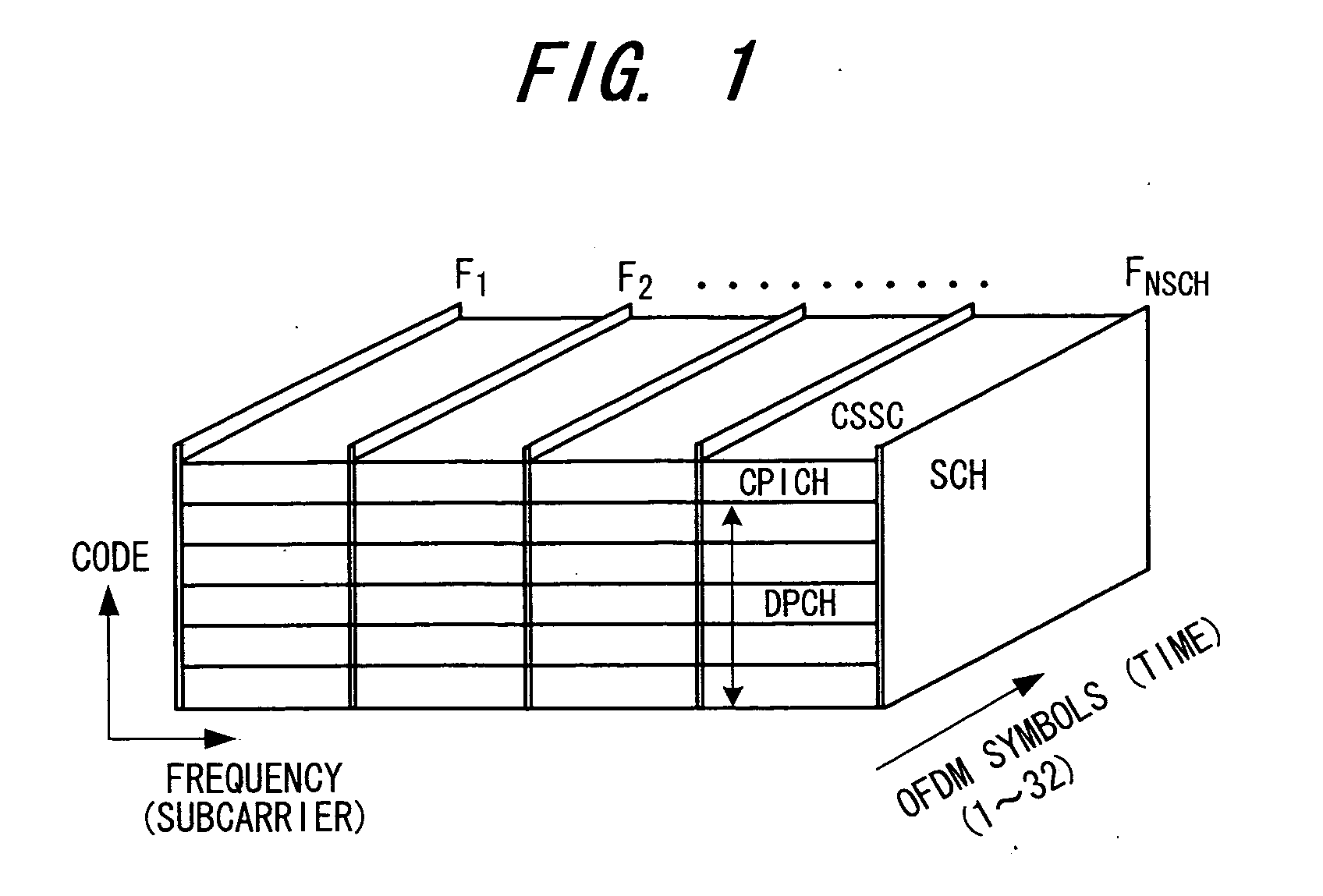
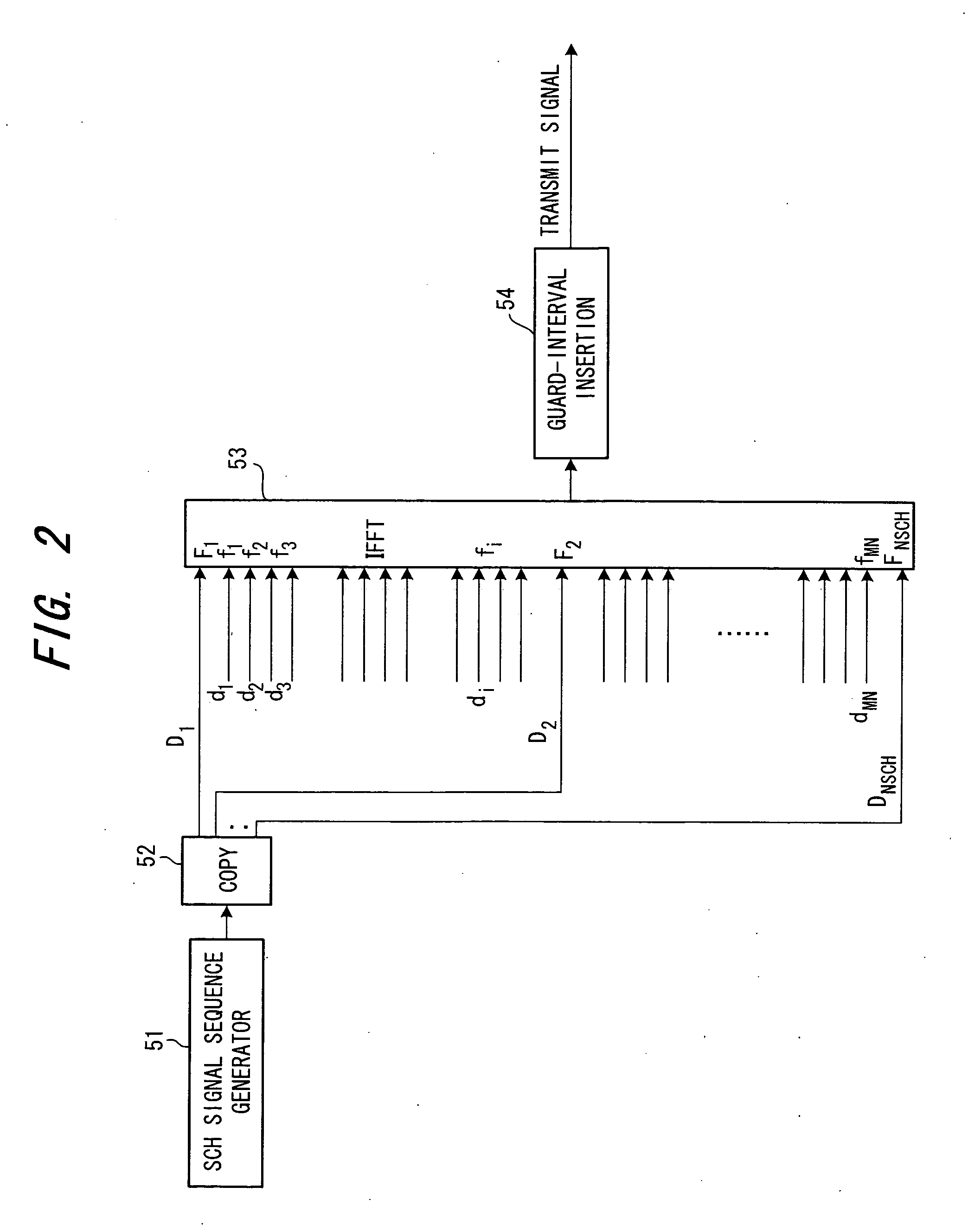
In a transmitting method for transmitting a transmit signal sequence by a number of subcarriers, a plurality of subcarriers F1, F2, . . . FNSCH exclusively for a synchronization channel are provided, a signal sequence of synchronization channel SCH is transmitted by the plurality of exclusive subcarriers, and a common pilot CPICH or dedicated signal DPCH is transmitted on the other subcarriers. In this case, the signal sequence of the synchronization channel is subjected to differential encoding processing and the differentially encoded signal sequence is transmitted by the exclusive subcarriers.
Owner:FUJITSU LTD
Monitoring function-equipped dispensing system and method of monitoring dispensing device
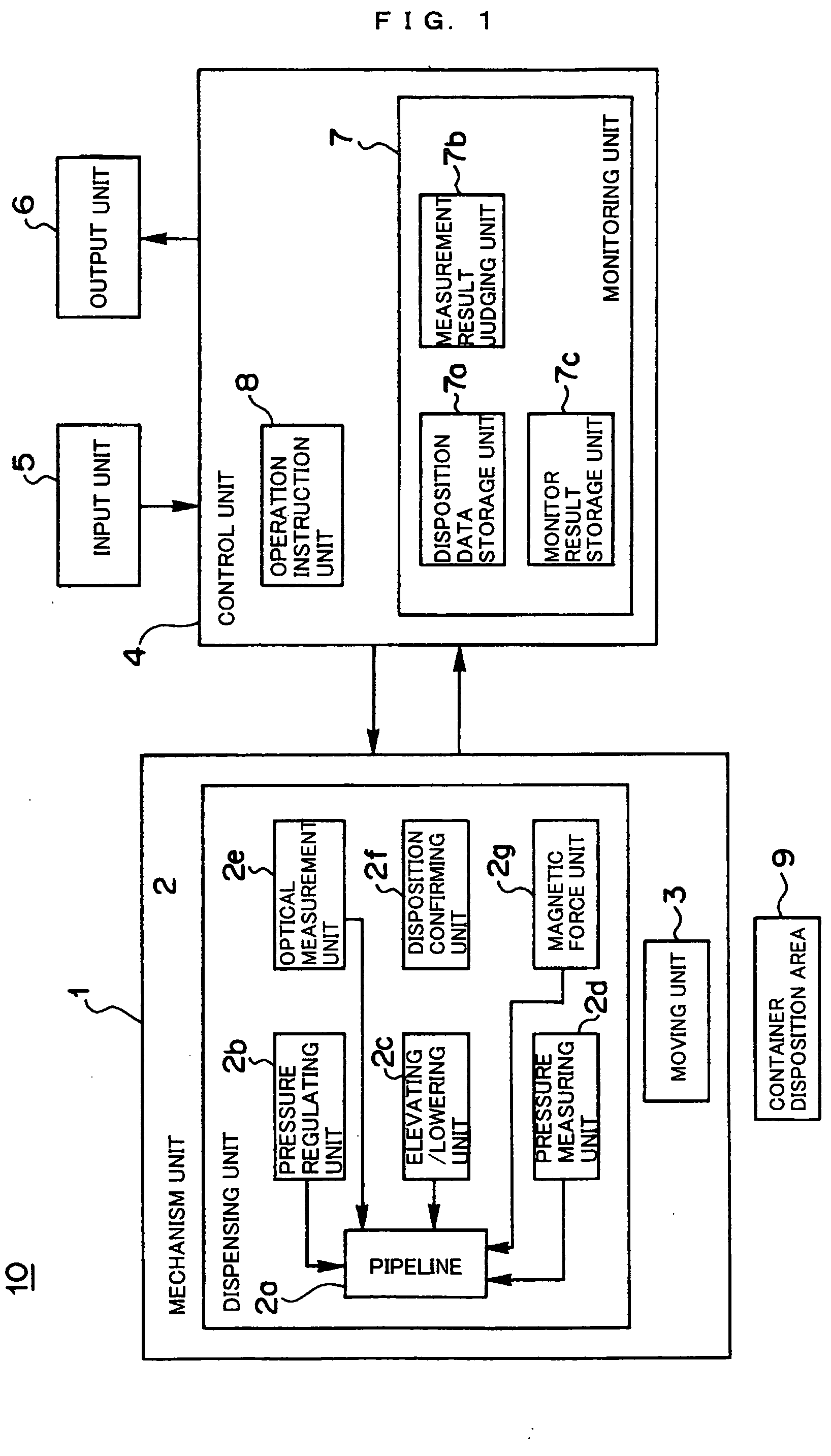
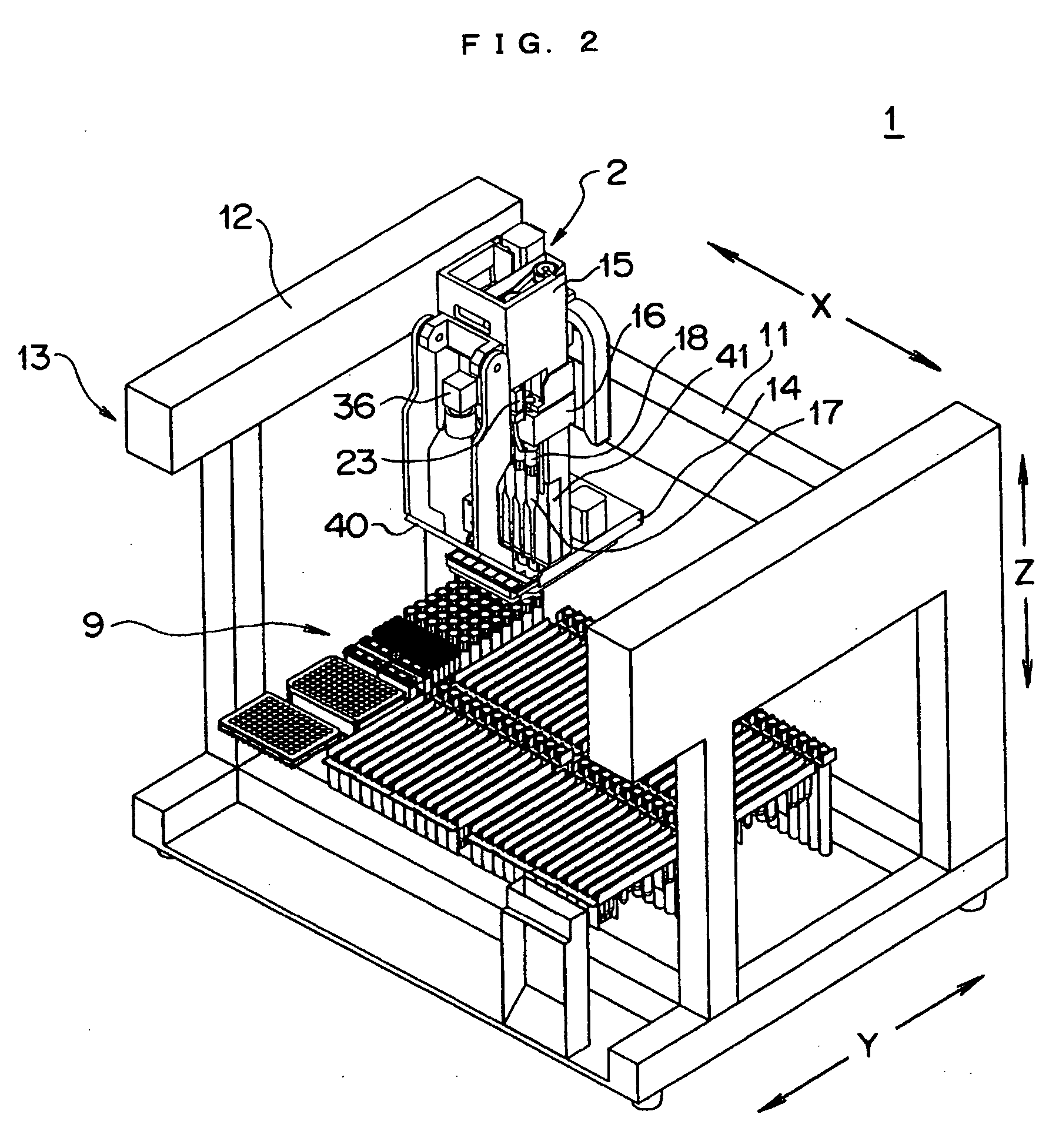
InactiveUS20060133965A1Ensure correct executionEfficient executionAnalysis using chemical indicatorsLaboratory glasswaresOptical measurementsMonitoring features
A monitoring function-equipped dispensing system and a method of monitoring the dispensing system wherein conditions in a pipeline can be identified accurately and precisely by not only optically measuring conditions in the pipeline, but performing other measurements reinforcing the former. The system comprises: one or more translucent or semi-translucent pipelines; one or more pressure regulating units which respectively regulate the pressures in the pipelines; an elevating / lowering unit which enables the pipelines to be elevated / lowered; a pressure measuring unit which measures the pressures in the respective pipelines when operation instructions are given to the pressure regulating unit; an optical measurement unit which optically measures the conditions of the pipelines above the container disposition area, when operations based on operation instructions including operation instructions to the pressure regulating unit are completed; and a monitoring unit which judges the conditions in the pipelines based on the operation instructions and measurement results of the pressure measuring unit and the optical measurement unit so as to obtain monitoring results that associate the judged results with respective pipelines and the operation instructions.
Owner:UNIVERSAL BIO RESEARCH CO LTD
Fail judging method for analysis and analyzer
InactiveUS7083712B2Eliminating and lesseningEnsure correct executionImmobilised enzymesBioreactor/fermenter combinationsClassical mechanicsPhysical quantity
Owner:ARKRAY INC +1
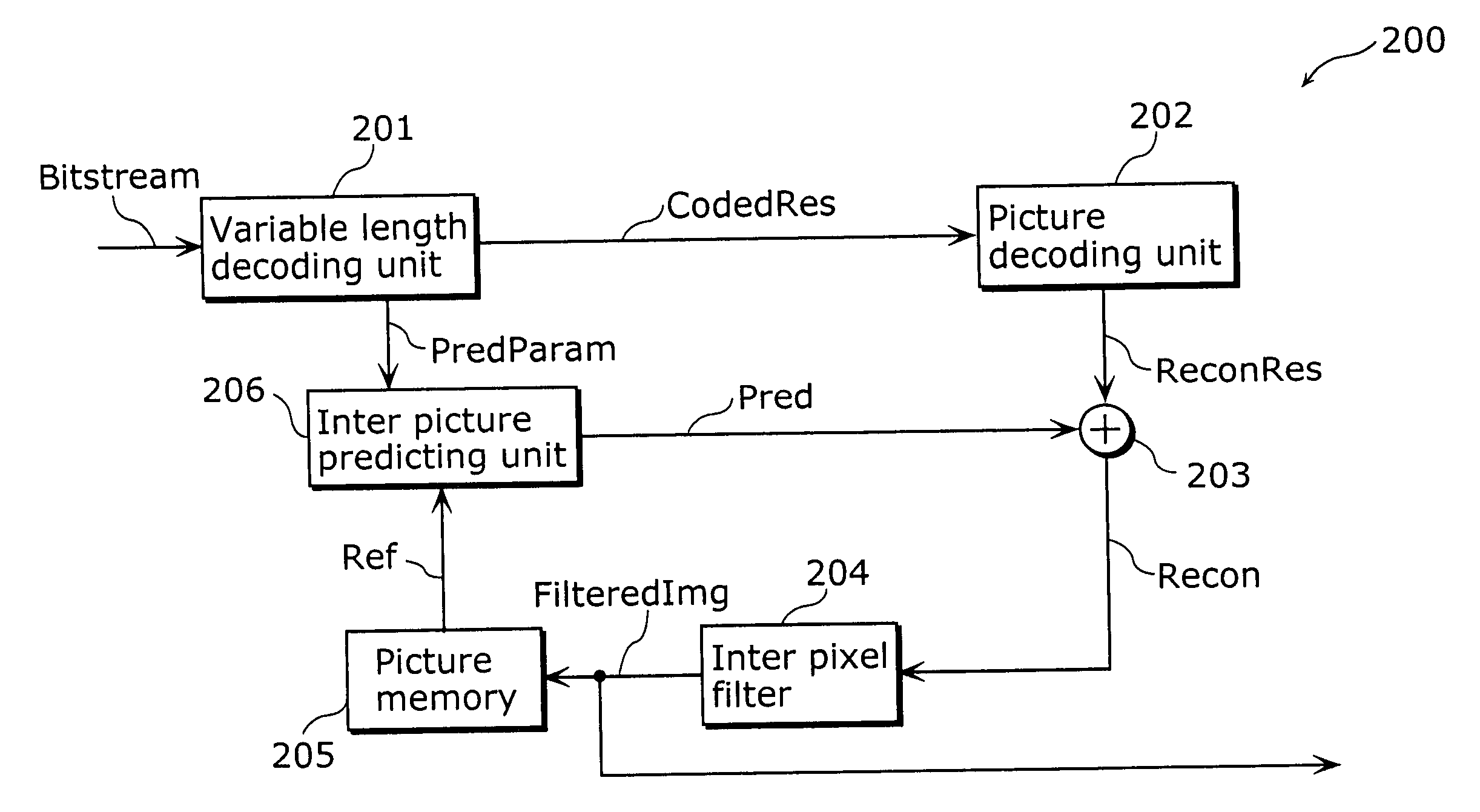
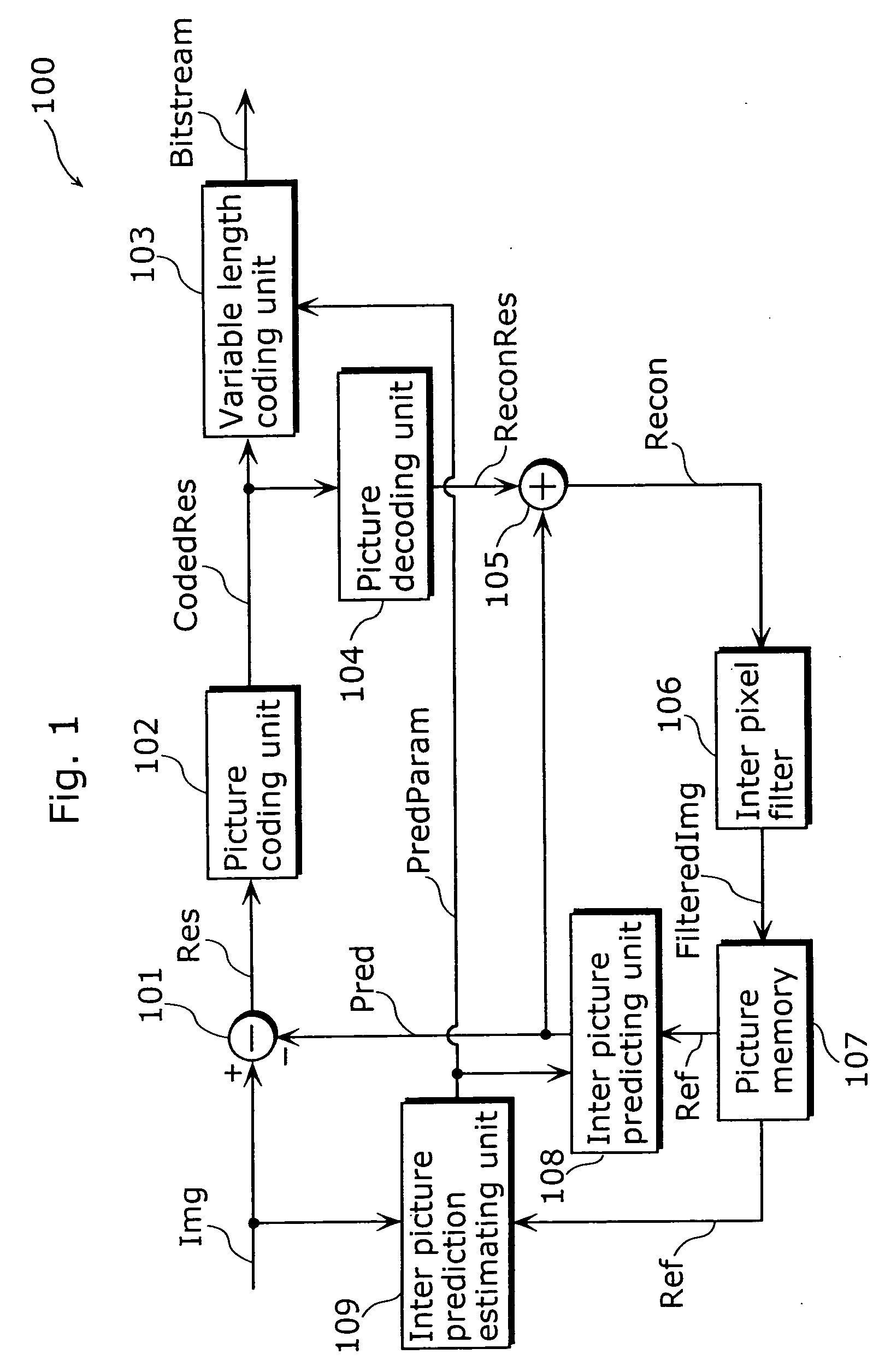
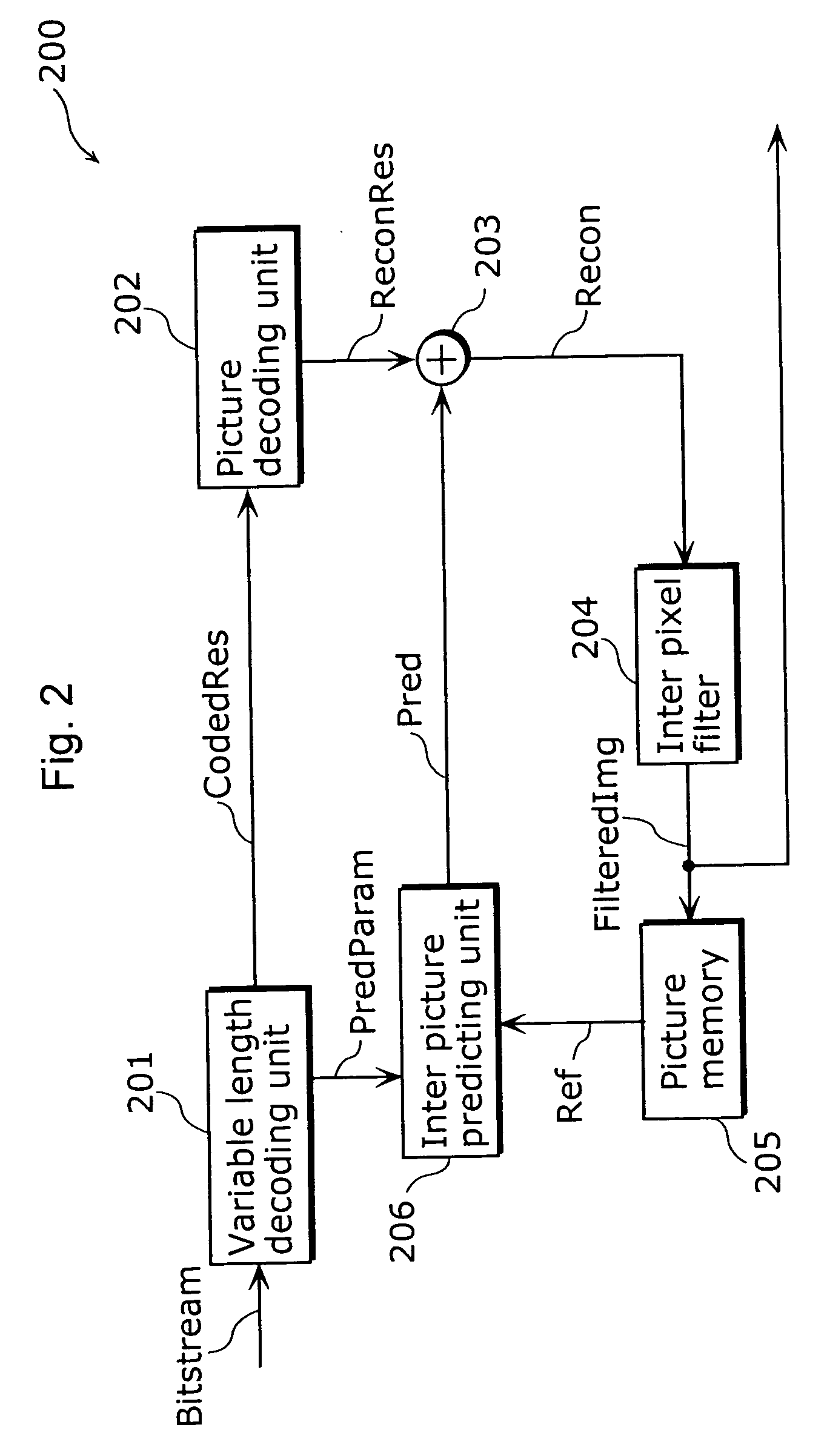
Image coding method and image decoding method
InactiveUS20040032908A1Improve efficiencyImprove picture qualityPicture reproducers using cathode ray tubesCode conversionDecoding methodsComputer graphics (images)
A picture coding apparatus (300) is a picture coding apparatus that codes a difference between picture data (Img) representing an input picture and predictive picture data (Pred) representing a predictive picture for the input picture and generates coded picture data, and includes a picture decoding unit (104) for decoding coded picture data (Img) after the picture data (Img) is coded; inter pixel filters A and B (303 and 304) for performing inter pixel filter operation for decoded picture data (Recon) obtained by the picture decoding unit (104); switches (301 and 302) for selecting one of the inter pixel filters; and an inter picture predicting unit (108) for generating the predictive picture data (Pred) for the input picture data (Img) using filtered decoded picture data (FilteredImg1), as reference picture data (Ref), obtained by the selected inter pixel filter.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Apparatus and method for a scanning probe microscope
InactiveUS7022985B2Easy to modifyImprove measurement stabilityNanotechMaterial analysis using wave/particle radiationScanning electron microscopeScanning probe microscopy
The invention relates to an apparatus and a method for a scanning probe microscope, comprising a measuring assembly which includes a lateral shifting unit to displace a probe in a plane, a vertical shifting unit to displace the probe in a direction perpendicular to the plane, and a specimen support to receive a specimen. A condenser light path is formed through the measuring assembly so that the specimen support is located in the area of an end of the condenser light path.
Owner:JPK INSTR
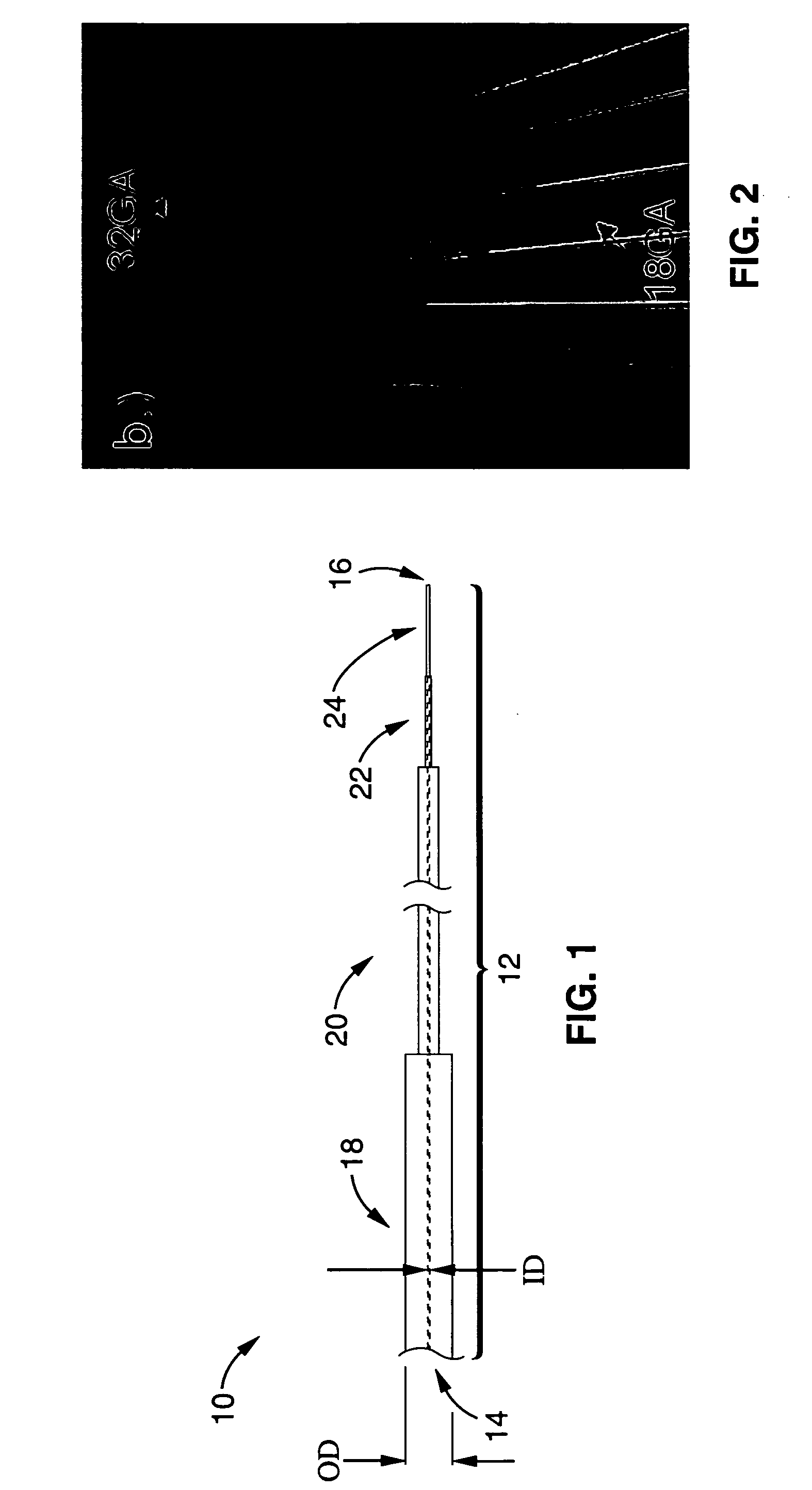
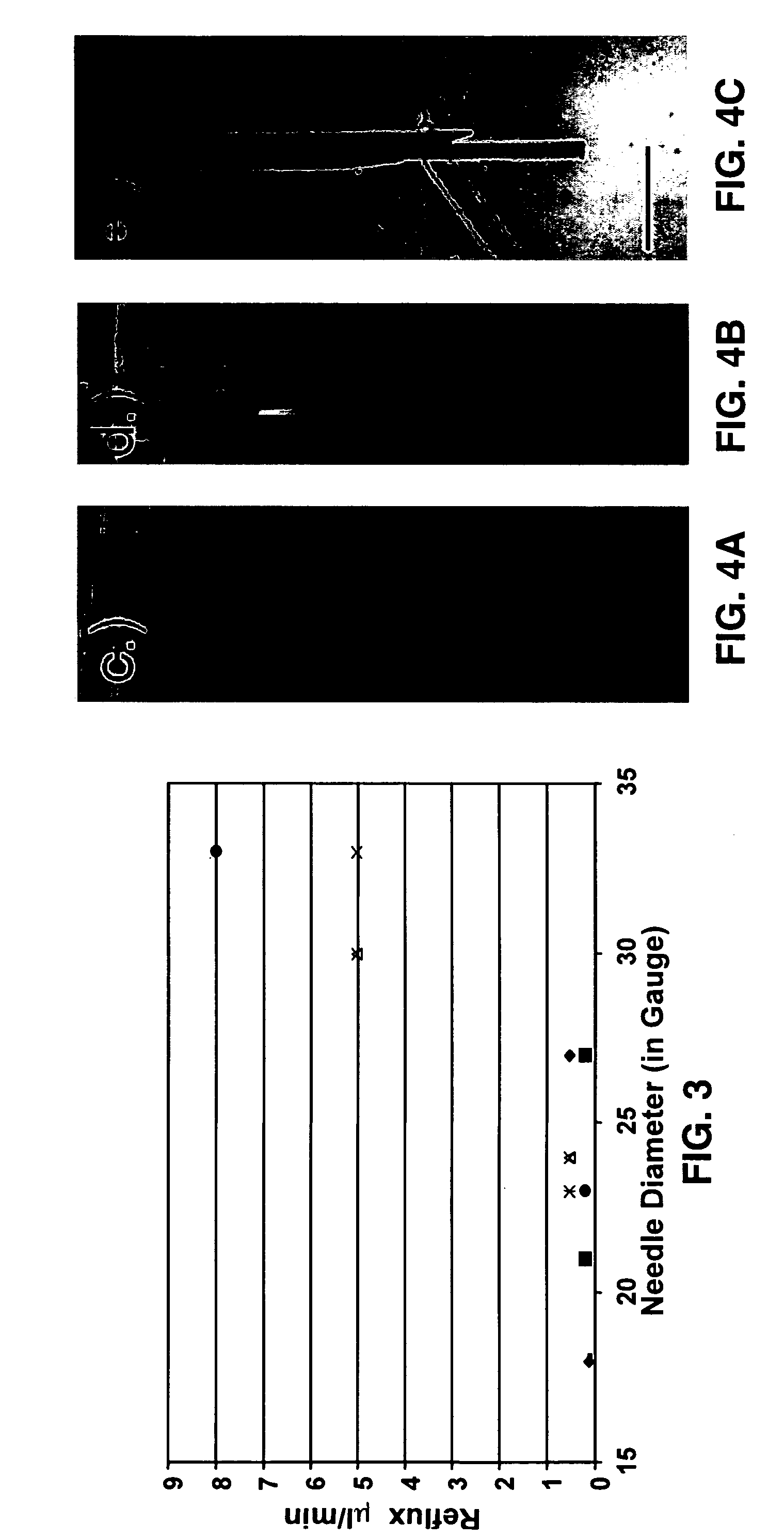
Reflux resistant cannula and system for chronic delivery of therapeutic agents using convection-enhanced delivery
ActiveUS20070088295A1Increase flow rateOvercome limitationsGuide needlesCannulasRefluxTherapeutic effect
A step-design cannula and delivery system for chronic delivery of therapeutic substances into the brain using convention-enhanced delivery of therapeutic substances and which effectively prevents reflux in vivo and maximizes distribution in the brain.
Owner:RGT UNIV OF CALIFORNIA
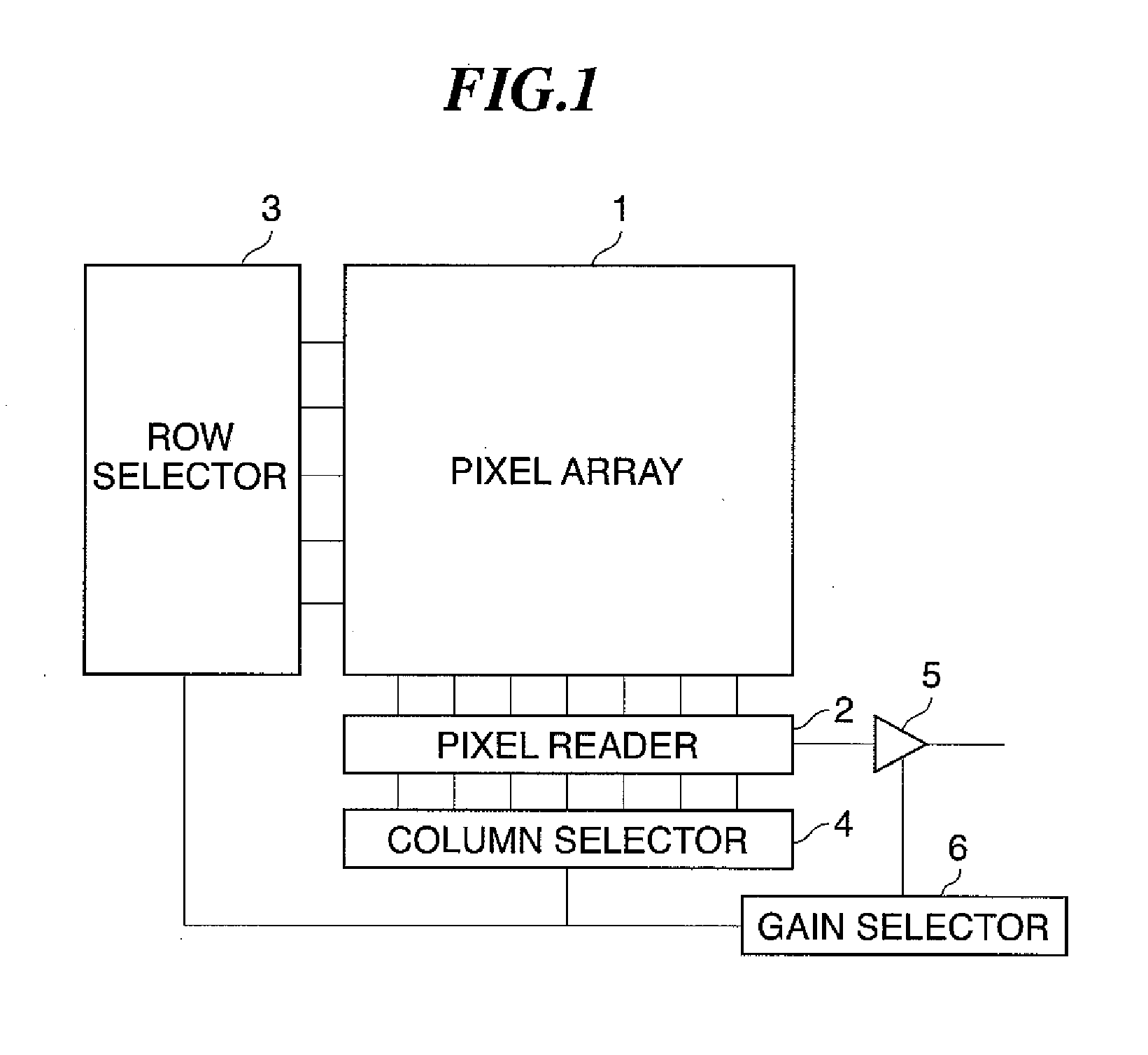
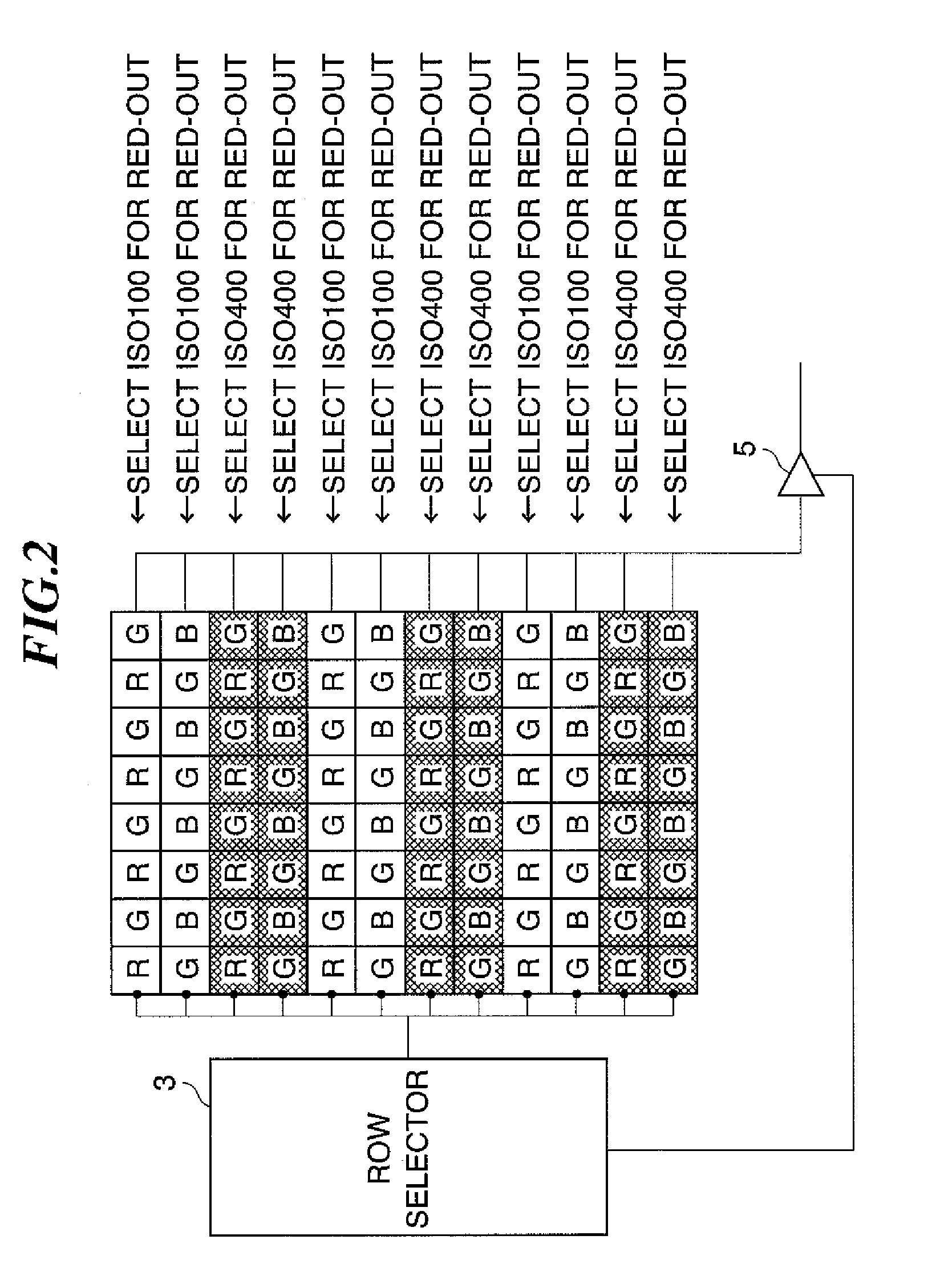
Image pickup device, image pickup apparatus, control method, and program
InactiveUS20080180547A1Improve dynamic rangeEnsure correct executionTelevision system detailsTelevision system scanning detailsPhotoelectric conversionComputer science
An image pickup device which makes it possible to expand the dynamic range of photometry. The image pickup device comprises a pixel array, a pixel reader, a row selector, a column selector, a gain circuit, a gain selector. The pixel array comprises a plurality of pixels including photoelectric conversion elements and arranged in the horizontal direction and in the vertical direction. The pixel reader reads out selected pixel signals from the pixel array. The gain circuit is capable of having at least two gains set therein, and amplifies and outputs the pixel signals read out from the pixel array by the pixel reader. The gain selector sets different gains in the gain circuit such that pixel signals amplified by the different gains can be obtained for one-time read-out from the pixel array by the pixel reader.
Owner:CANON KK
Telemetric orthopaedic implant
ActiveUS8486070B2Accurate predictionAccurately prescribeInternal osteosythesisBone implantPlastic surgeryElectronic component
An instrumented orthopaedic implant, such as an intramedullary (IM) nail, is disclosed. The implant has the capacity to provide an accurate measurement of the applied mechanical load across the implant. The implant includes sensors and associated electronic components located in recesses on the outer surface of the implant. The implant houses the sensing apparatus, the interface circuitry, the data transmitter, and the power receiver. The hermetically sealed housing is adapted for implantation in the body of a patient. The implant is used with a controller which communicates with it by telemetry, and there is an acting unit connected to the electronic components which is adapted to carry out a function based upon a condition detected by the sensors.
Owner:SMITH & NEPHEW INC
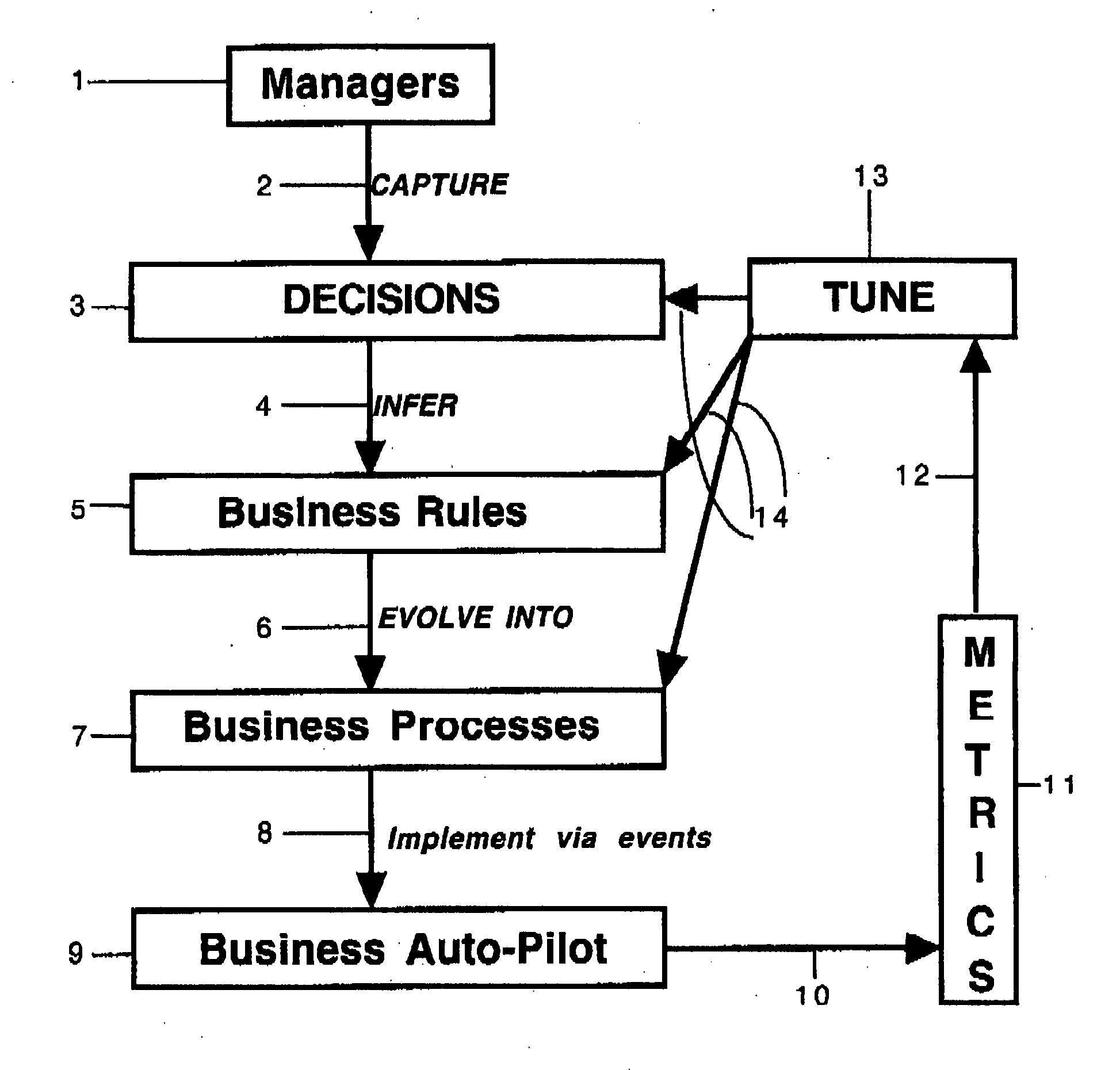
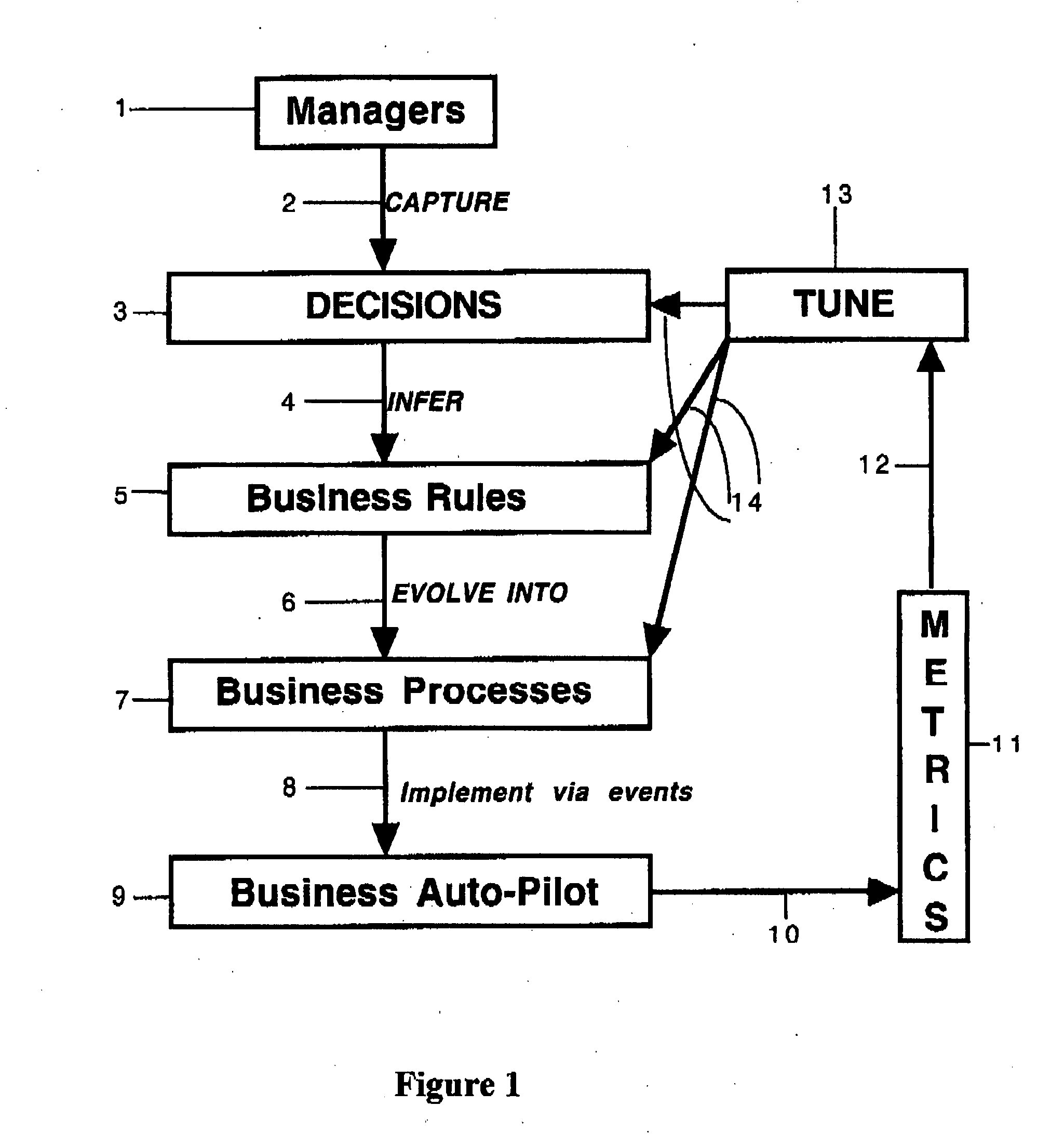
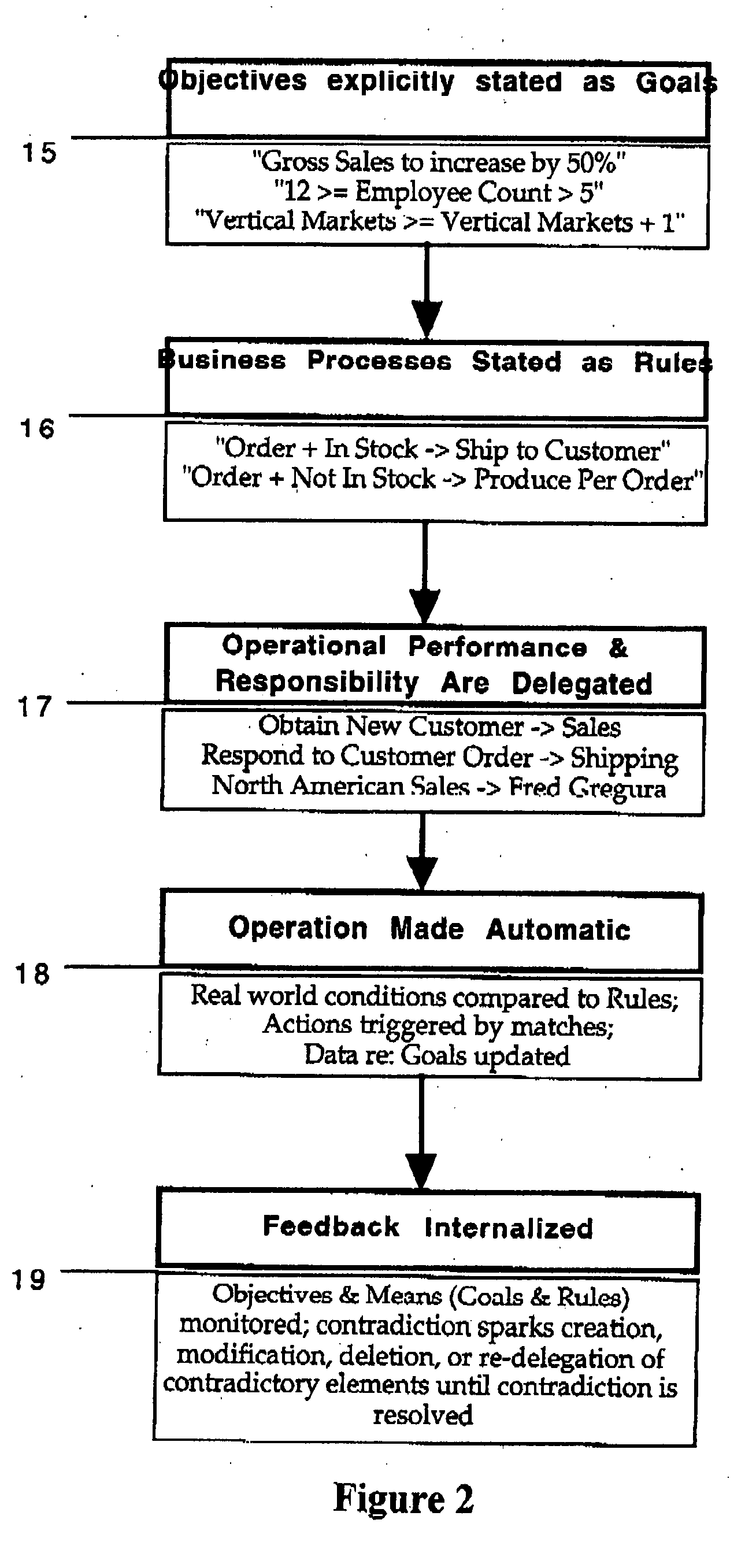
Rules-based method and system for managing emergent and dynamic processes
InactiveUS20070150330A1Reduce riskReduce the amount requiredFinanceResourcesKnowledge managementBusiness process
This invention details a method, and a device incorporating the same, for managing and controlling dynamic and emergent processes, including multi-entity business processes and enterprise workflow. The method is declarative, goal-driven, enables continuous modification in response to real-world events and measures, and capable of adaptation through self-modification.
Owner:MCGOVERAN DAVID
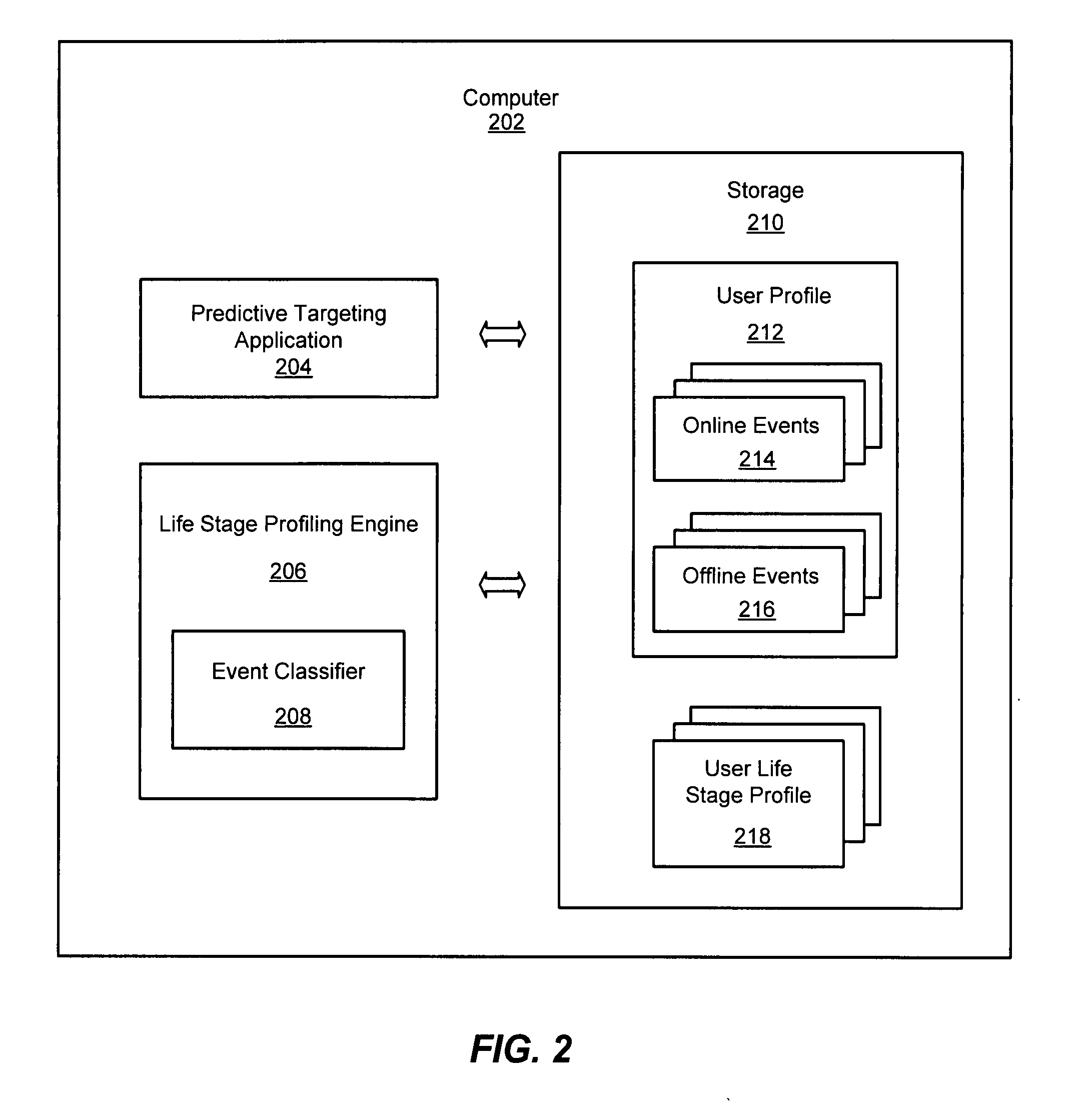
System and method for predictive targeting in online advertising using life stage profiling
An improved system and method for predictive targeting in online advertising using life stage profiling is provided. A life stage profiling engine may be provided in an embodiment for generating a life stage profile for a user. A life stage profile may include a collection of events or a distribution of characteristics that may represent a life stage of a taxonomy of life stages that may be generated from online or offline events. The events and attributes may be categorized and assigned a probability that a user may belong to a particular life stage, and the life stage of a user may be determined using the assigned probabilities, for instance, by applying naïve Bayesian techniques. Predictive targeting may be applied, either online or offline, using life stage profiles to target users for receiving advertising, content, ecommerce offers or other electronic communications.
Owner:OATH INC
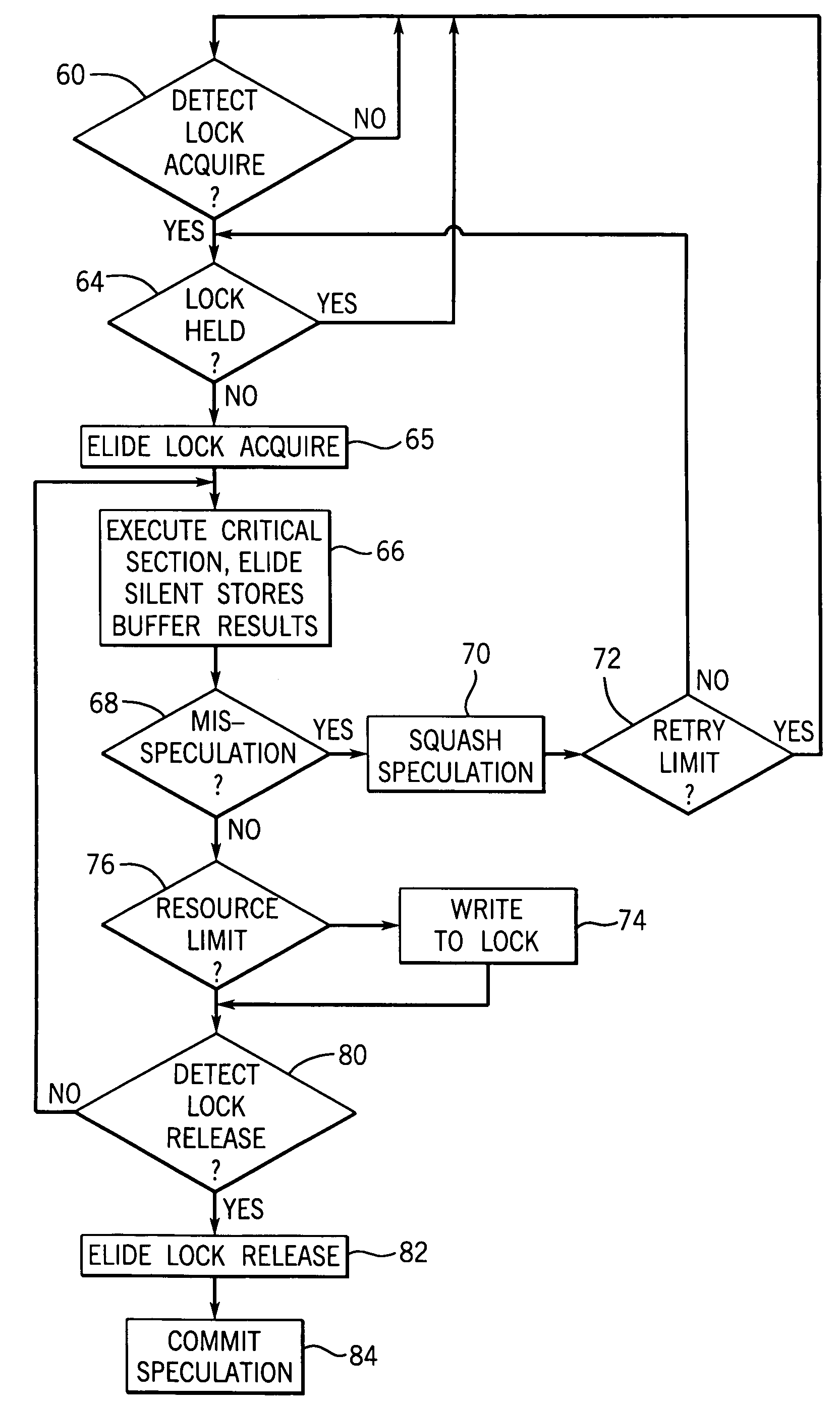
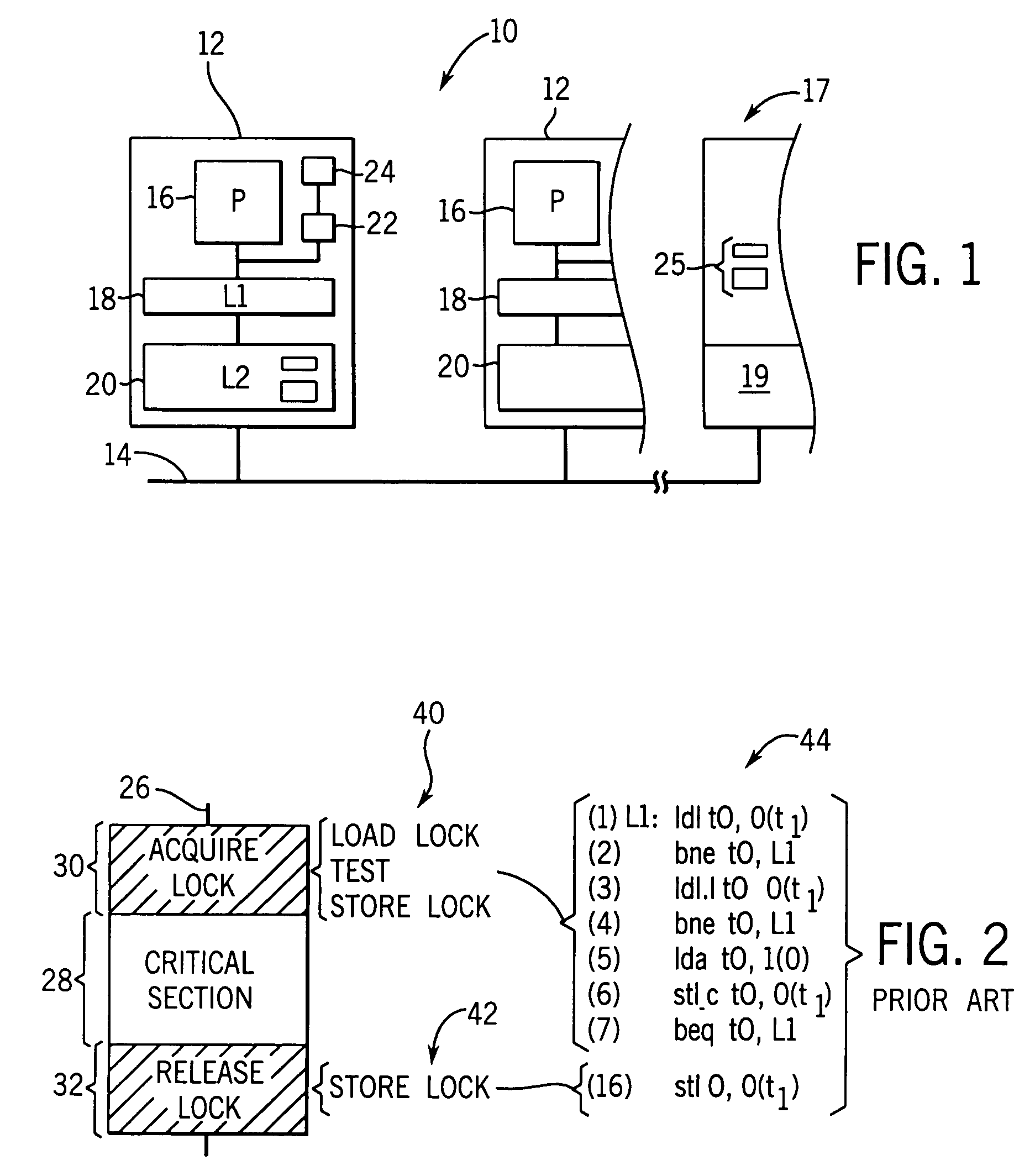
Concurrent execution of critical sections by eliding ownership of locks
ActiveUS7120762B2Ensure correct executionEfficient executionMemory architecture accessing/allocationProgram synchronisationSpeculative executionCritical section
Critical sections of multi-threaded programs, normally protected by locks providing access by only one thread, are speculatively executed concurrently by multiple threads with elision of the lock acquisition and release. Upon a completion of the speculative execution without actual conflict as may be identified using standard cache protocols, the speculative execution is committed, otherwise the speculative execution is squashed. Speculative execution with elision of the lock acquisition, allows a greater degree of parallel execution in multi-threaded programs with aggressive lock usage.
Owner:WISCONSIN ALUMNI RES FOUND
Autonomous citation indexing and literature browsing using citation context
InactiveUS6738780B2Ensure correct executionData processing applicationsWeb data indexingNatural language processingElectronic form
An autonomous citation indexing system which can be used as an assistant agent automates and enhances the task of finding publications in electronic form, including publications located on the world wide web. The system parses citations from papers and identifies citations to the same paper that may differ in syntax. The system also extracts and provides the context of citations to a given paper, allowing a researcher to determine what is published in other papers about a given paper. Common citations and word or string vector distance similarity are used to find related articles in a search.
Owner:NEC CORP
Driving apparatus
InactiveUS20070109412A1Improve responseImprove cooling effectTelevision system detailsOpticsEllipseImage stabilization
In an auto image stabilization system, a driving member formed as a wire of shape memory alloy (SMA) is retained by a projection of an image capturing unit. A distance Lb from the rotation center of an elastic deforming part to center of gravity (point of application) of the image capturing unit is longer than a distance La from the rotation center of the elastic deforming part to the projection (power point). In the configuration, equivalent mass (apparent mass) of the image capturing unit becomes (Lb / La) times, and it causes deterioration in response. Consequently, the driving member having an ellipse-shaped section in which a value obtained by dividing the width in the longer direction of the section by the width in the shorter direction is 1.3 or larger is employed. As a result, heat dissipation of the driving member increases, so that response in the SMA actuator can be properly improved.
Owner:KONICA MINOLTA INC
Method and Apparatus for Measuring Fluid Properties
InactiveUS20060010973A1Simple methodEnsure correct executionSurveyConstructionsThermal energyEngineering
A method of measuring fluid properties such as flow velocity, flow rate, and fluid composition comprises positioning a heat exchange element with a temperature sensor, such as an optical fiber temperature sensor, arranged centrally inside the element in thermal contact with a fluid of interest, heating or cooling the heat exchange element to cause a temperature difference and exchange of thermal energy between the element and the fluid, using the temperature sensor to measure the temperature of the heat exchange element during the exchange of thermal energy, and determining properties of the fluid from the temperature measurement. A second temperature sensor can be provided offset from the first sensor to provide additional measurements to improve accuracy, and a plurality of heat exchange elements with temperature sensors can be used together to determine fluid properties over a large region.
Owner:SCHLUMBERGER TECH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com