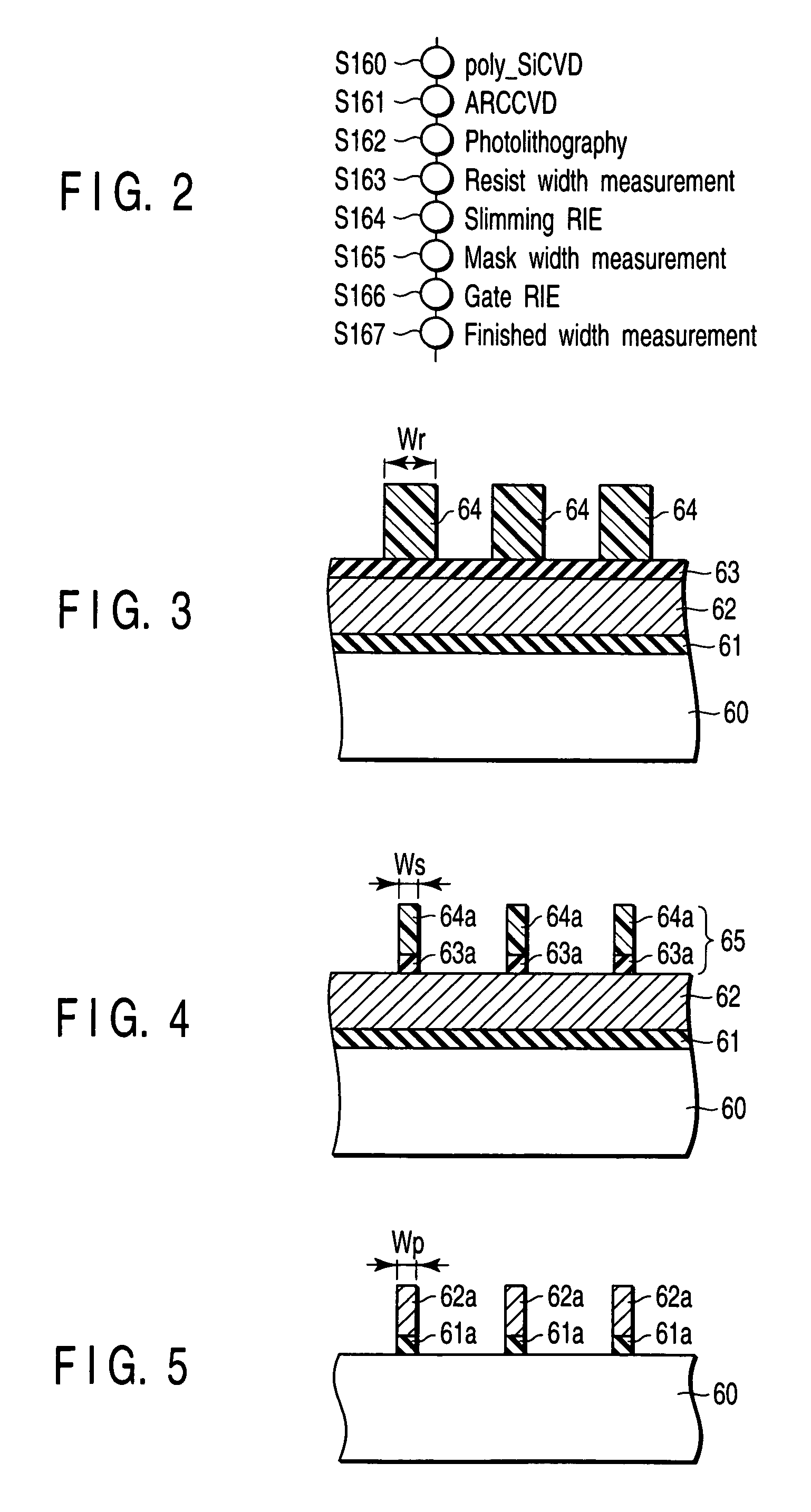
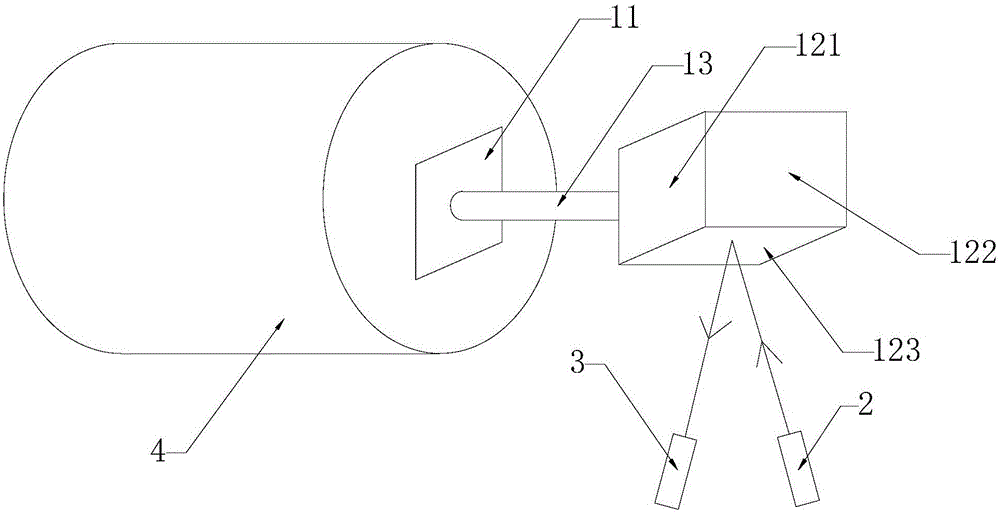Patents
Literature
43 results about "Reference monitor" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
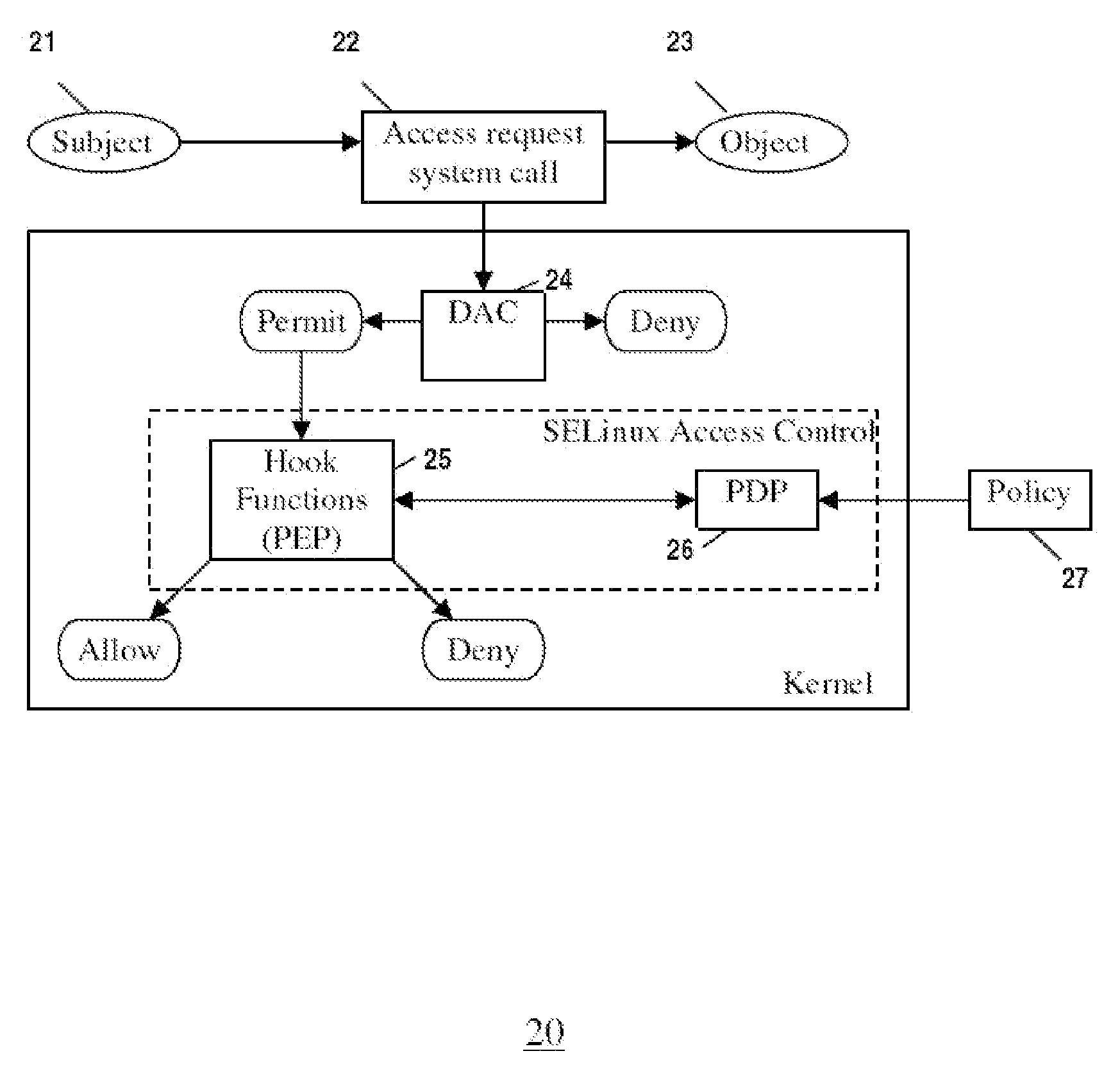
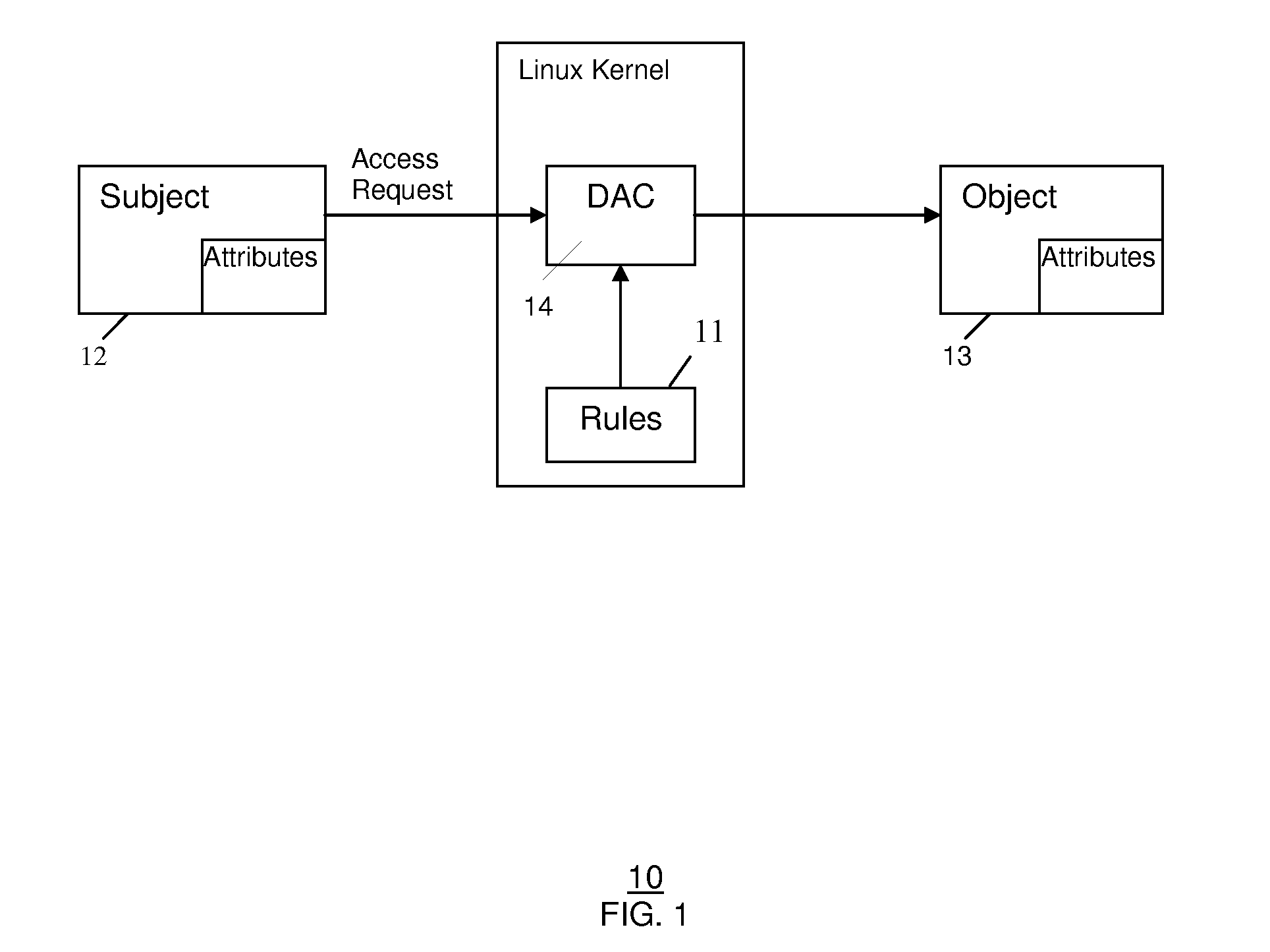
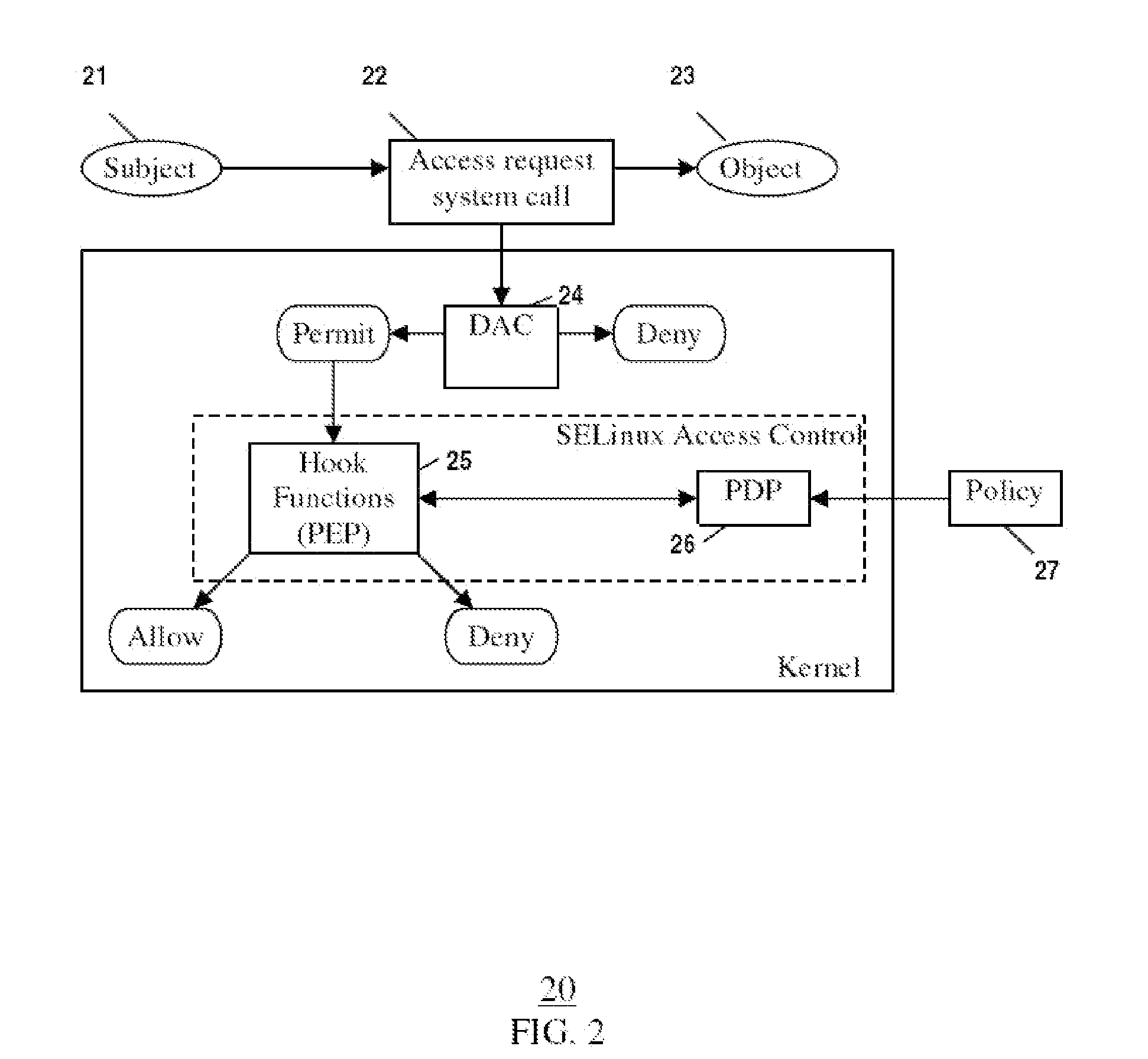
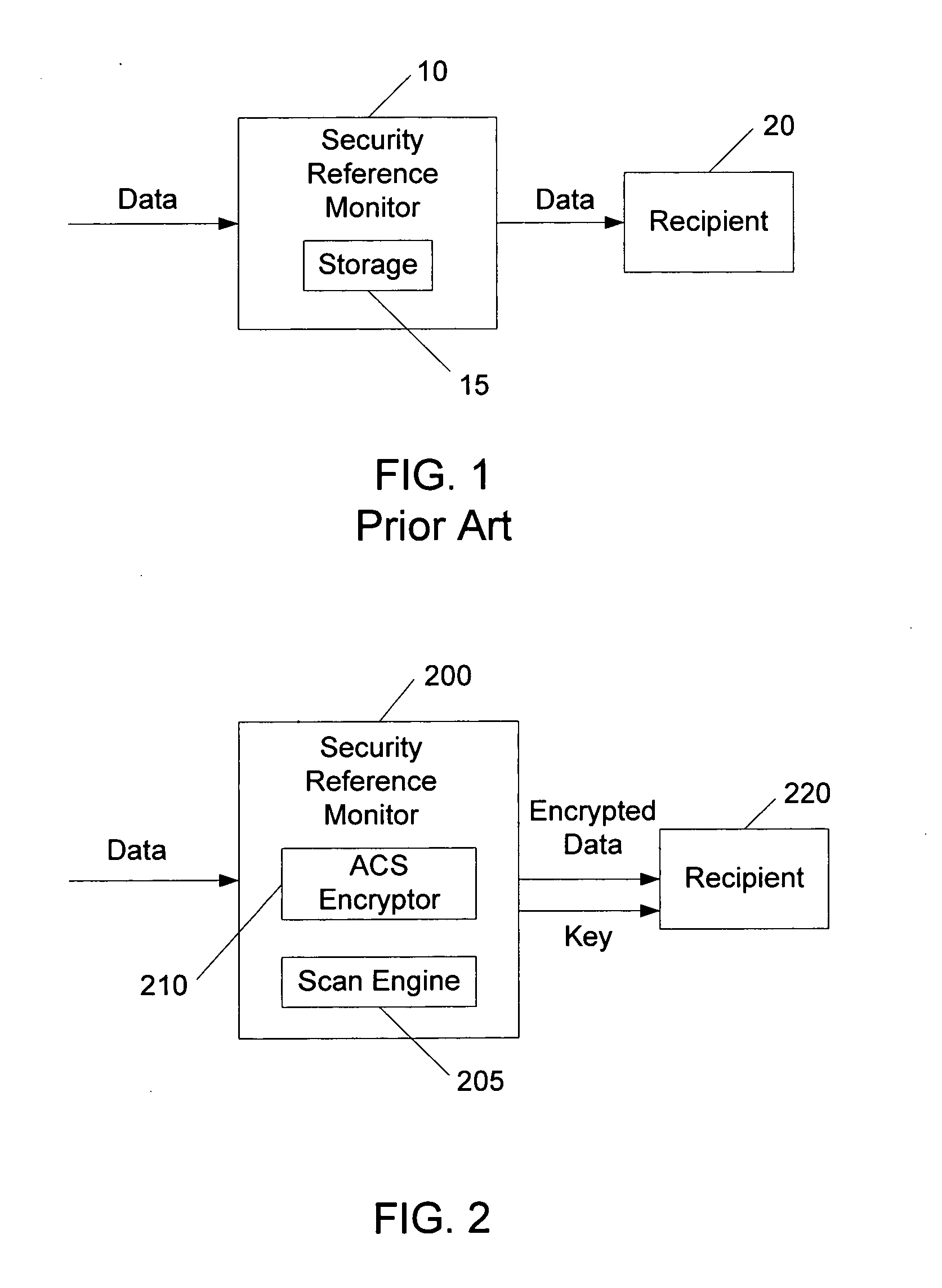
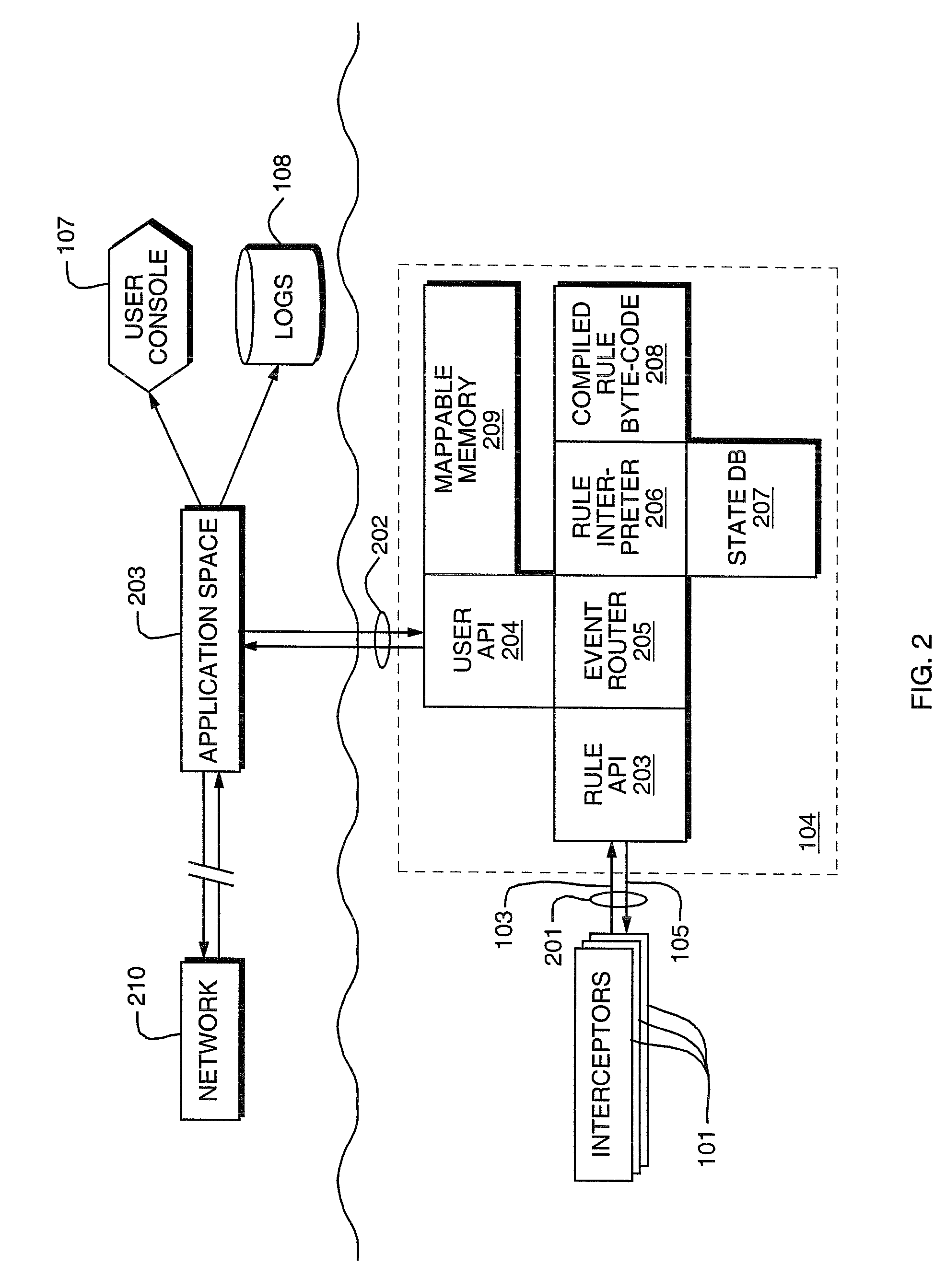
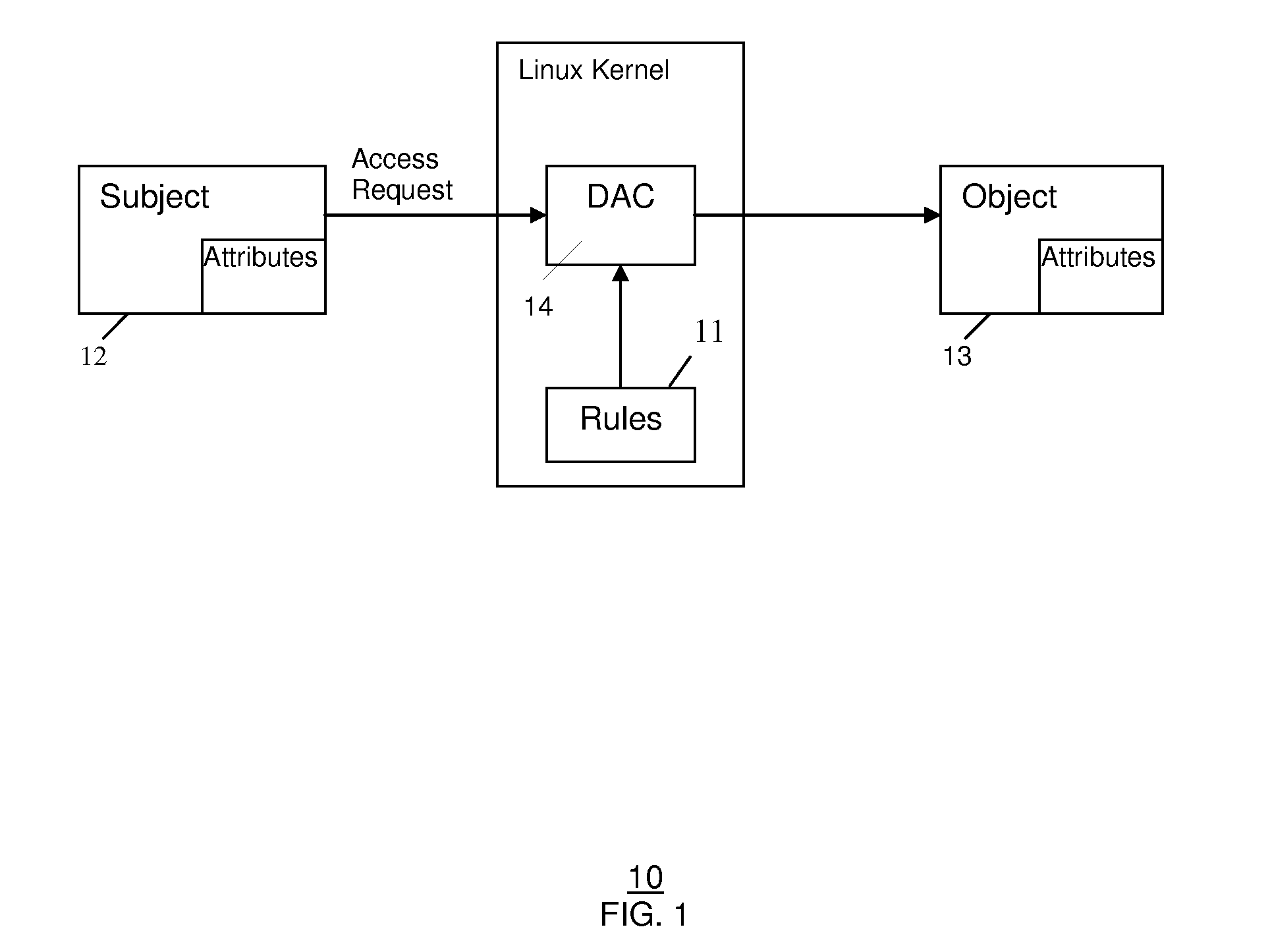
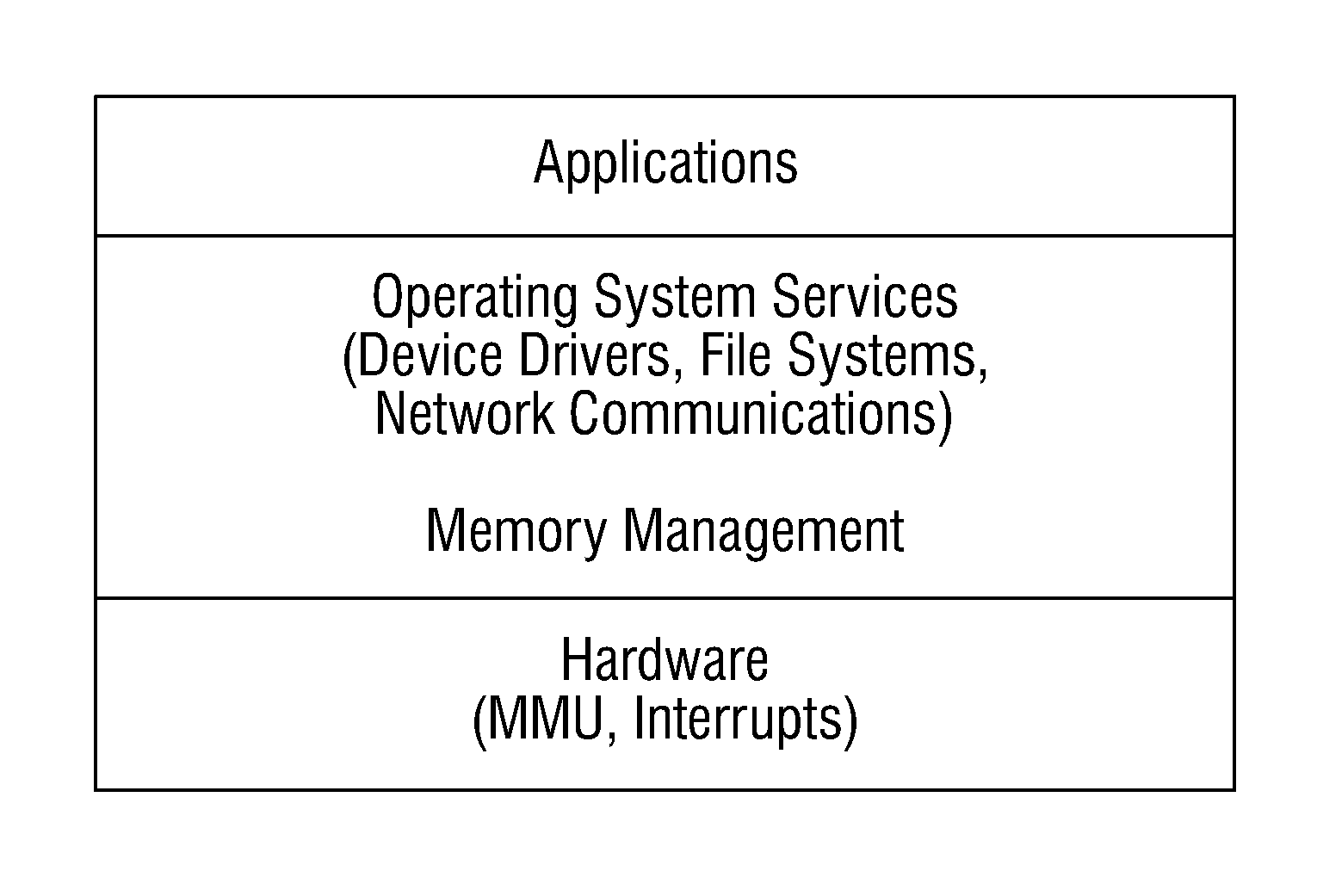
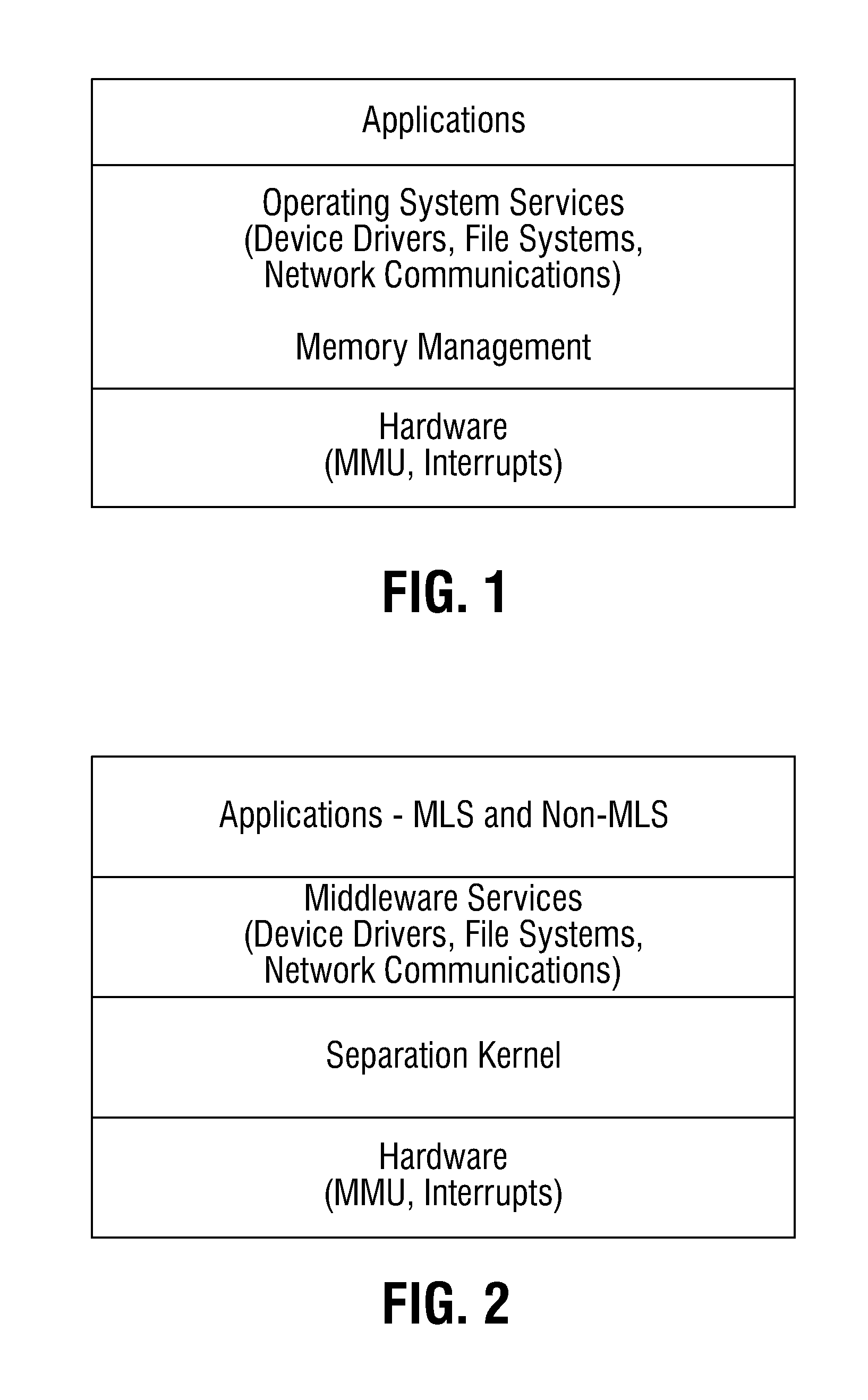
In operating systems architecture a reference monitor concept defines a set of design requirements on a reference validation mechanism, which enforces an access control policy over subjects' (e.g., processes and users) ability to perform operations (e.g., read and write) on objects (e.g., files and sockets) on a system. The properties of a reference monitor are captured by the acronym NEAT, which means...
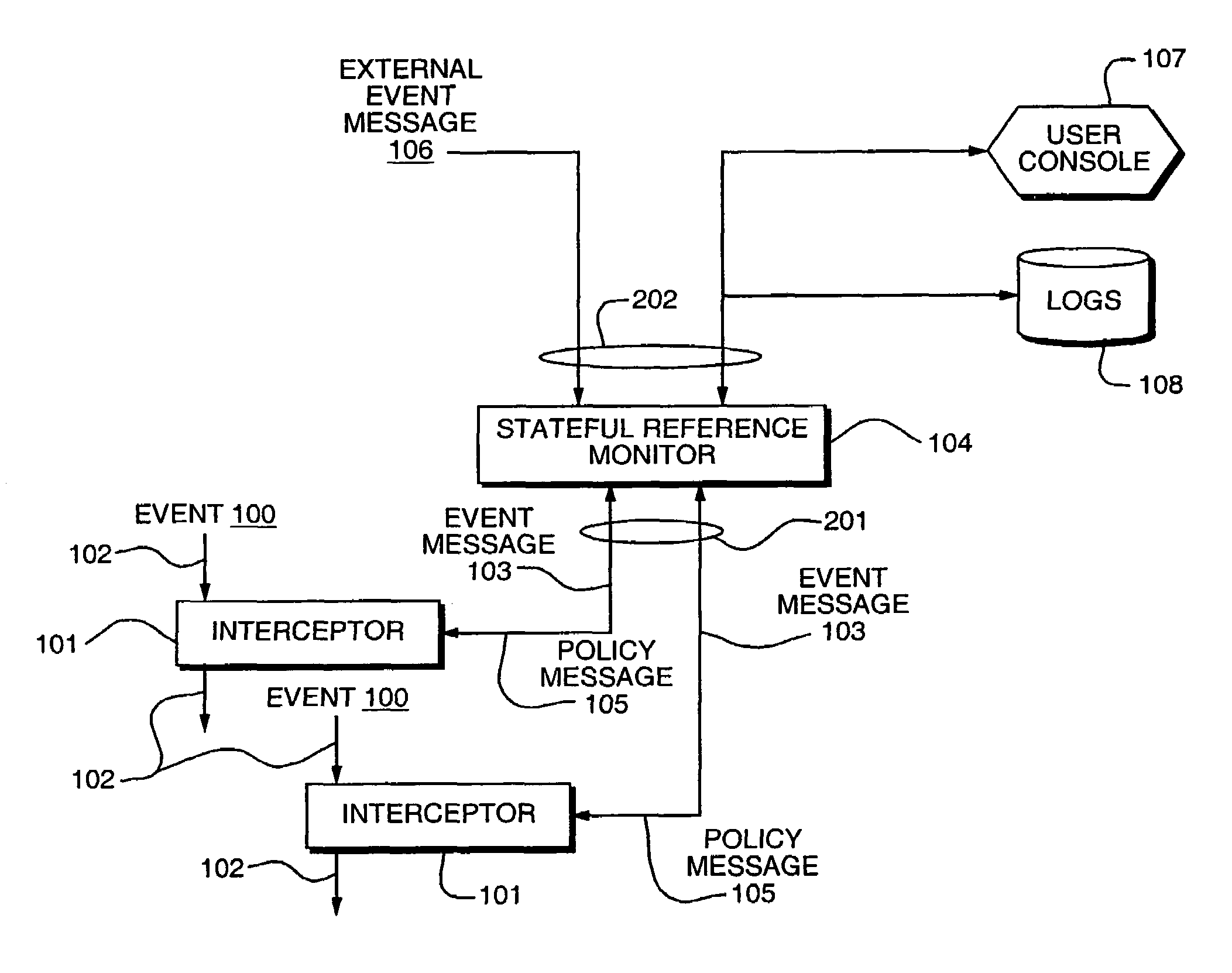
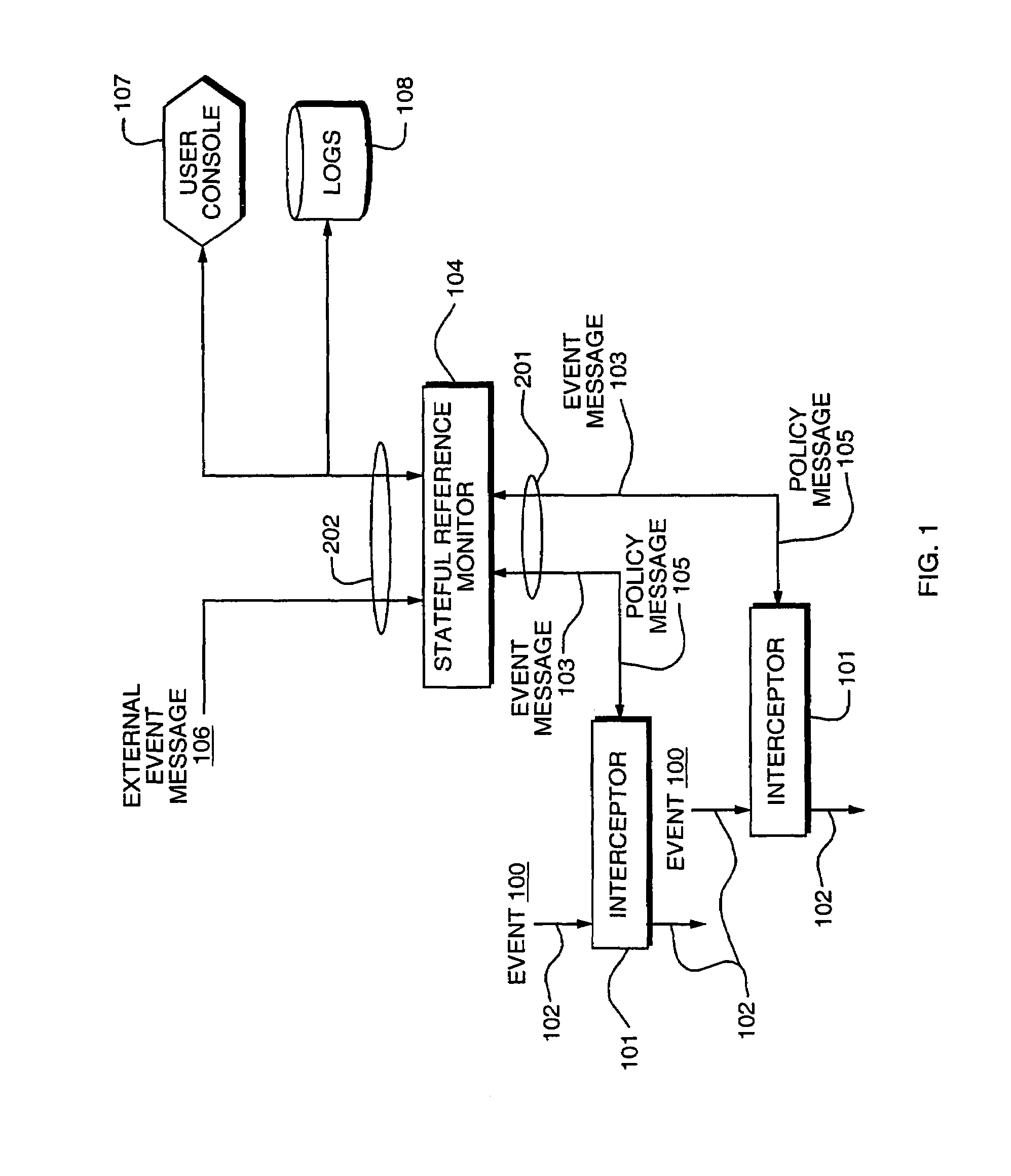
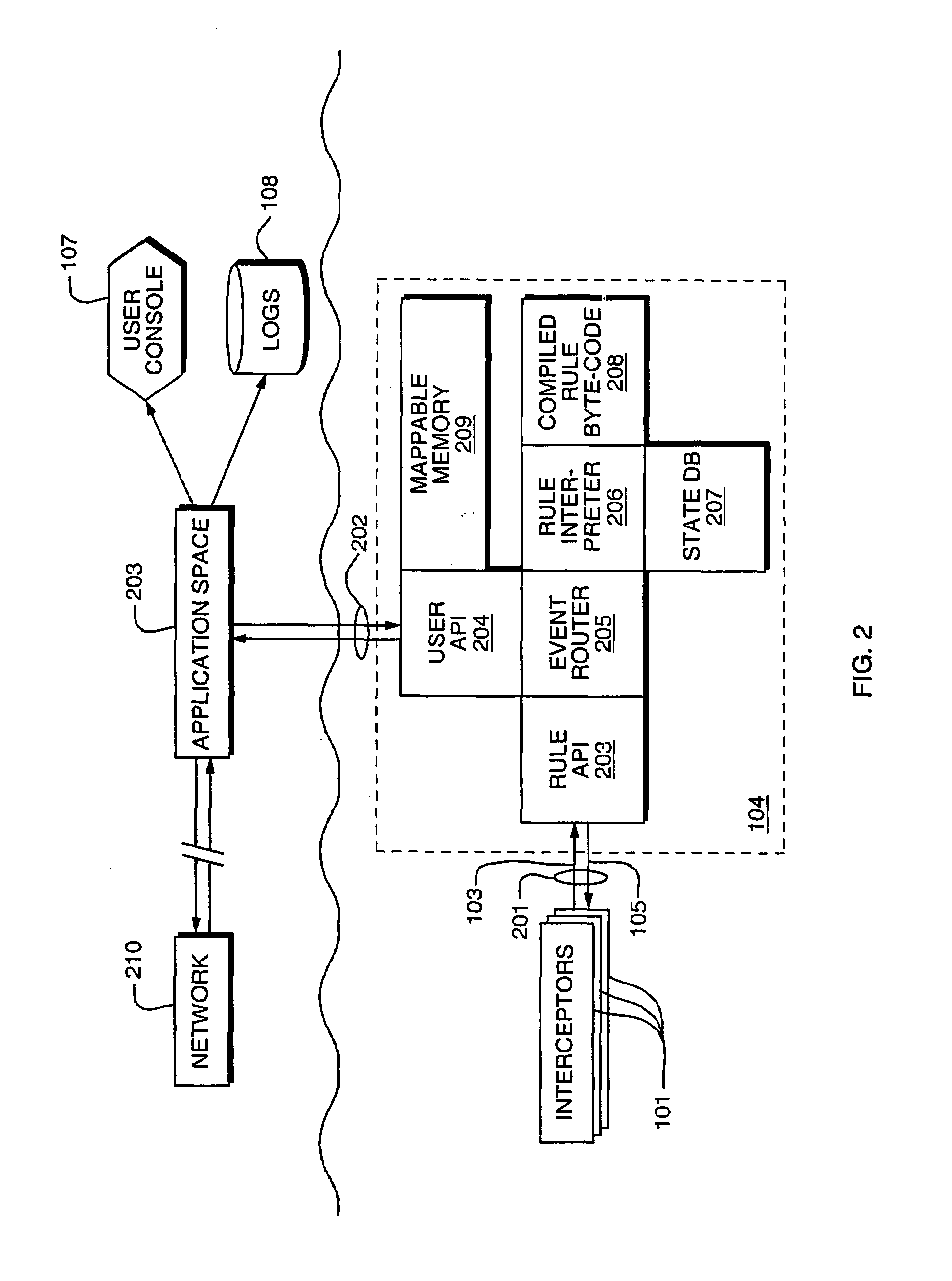
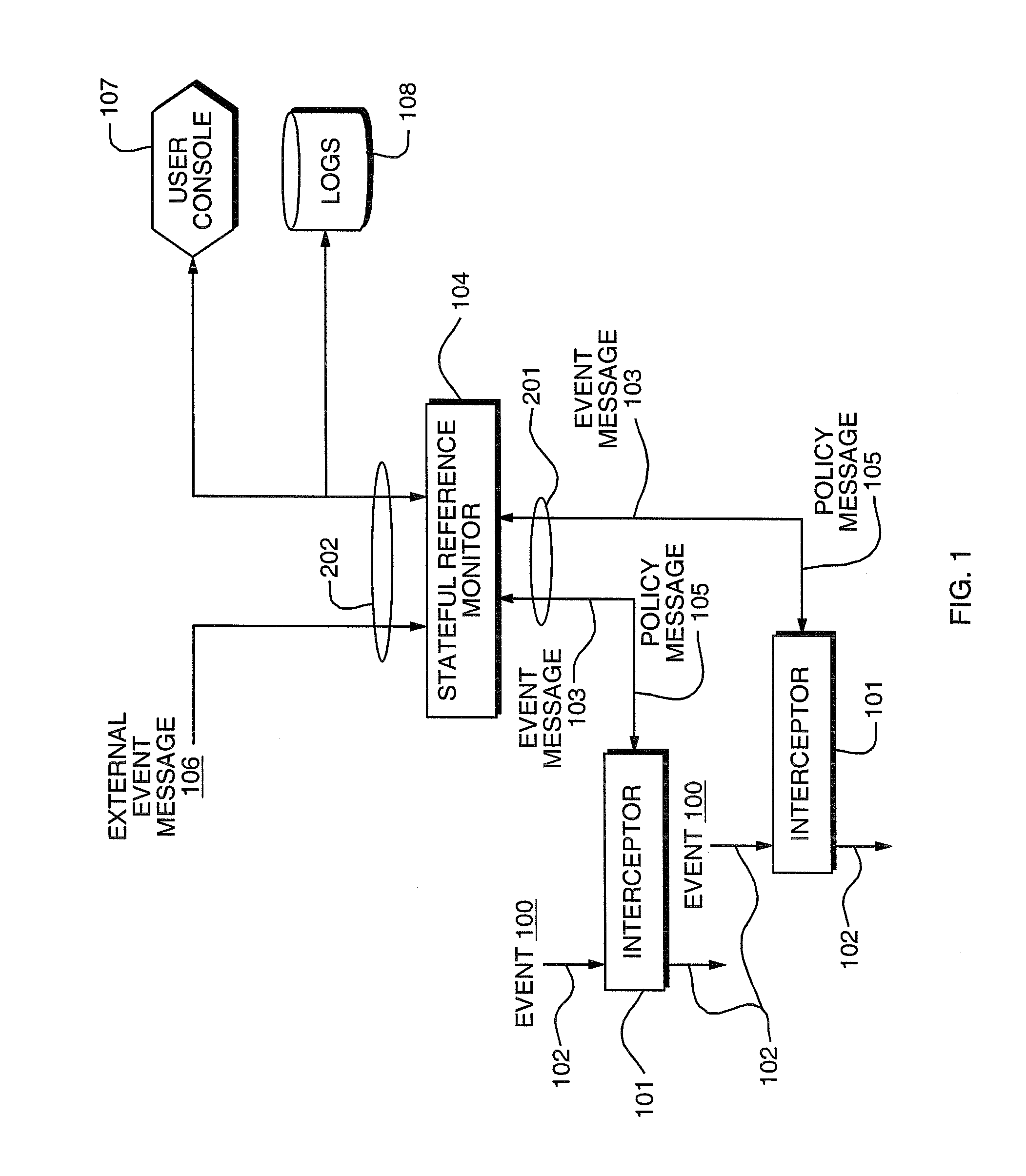
Access control by a real-time stateful reference monitor with a state collection training mode and a lockdown mode for detecting predetermined patterns of events indicative of requests for operating system resources resulting in a decision to allow or block activity identified in a sequence of events based on a rule set defining a processing policy
ActiveUS7290266B2Access control difficultSpecific access rightsDigital data processing detailsOperational systemRule sets
A Stateful Reference Monitor can be loaded into an existing commercial operating system, and then can regulate access to many different types of resources. The reference monitor maintains an updateable storage area whose contents can be used to affect access decisions, and access decisions can be based on arbitrary properties of the request.
Owner:CISCO TECH INC
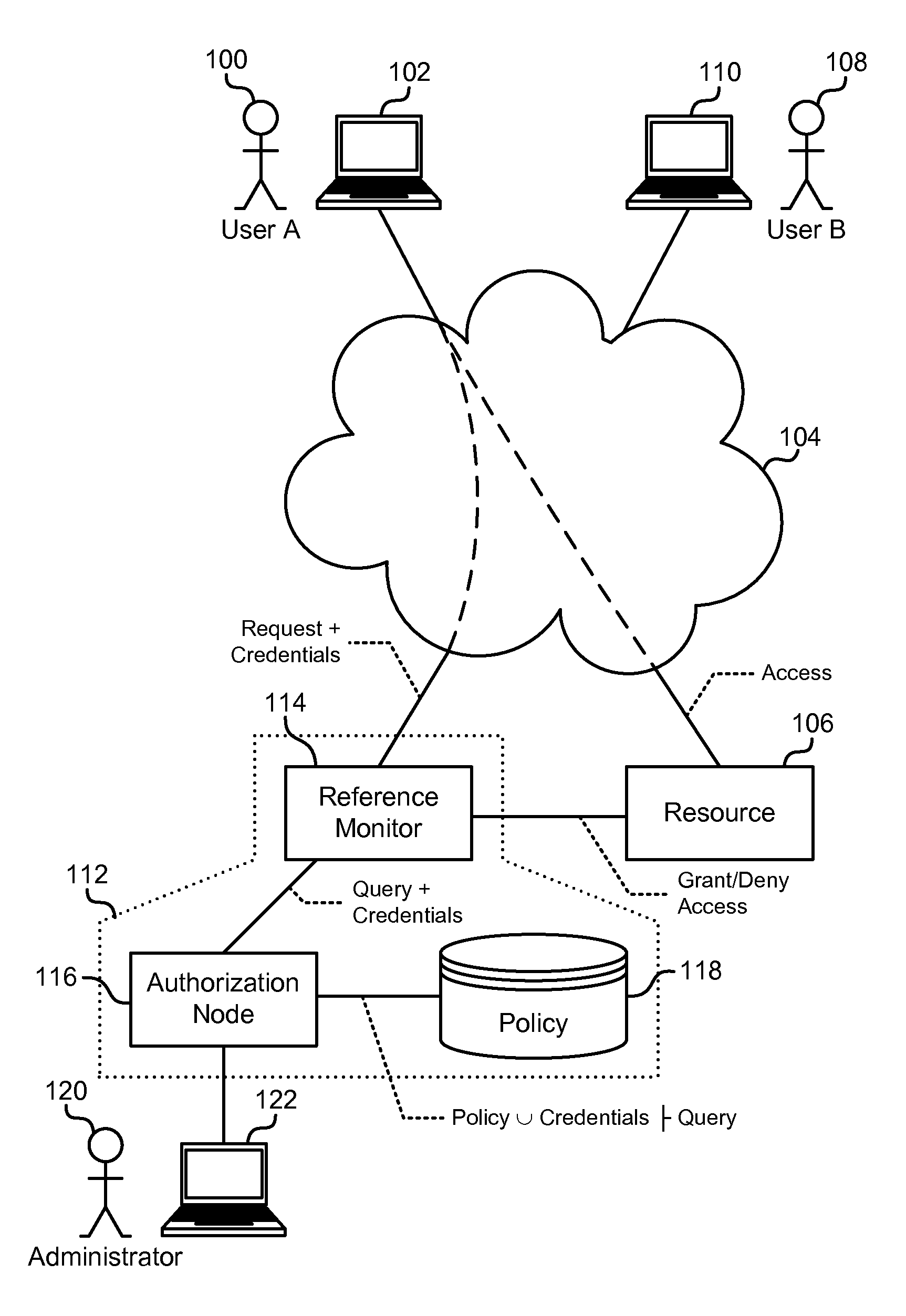
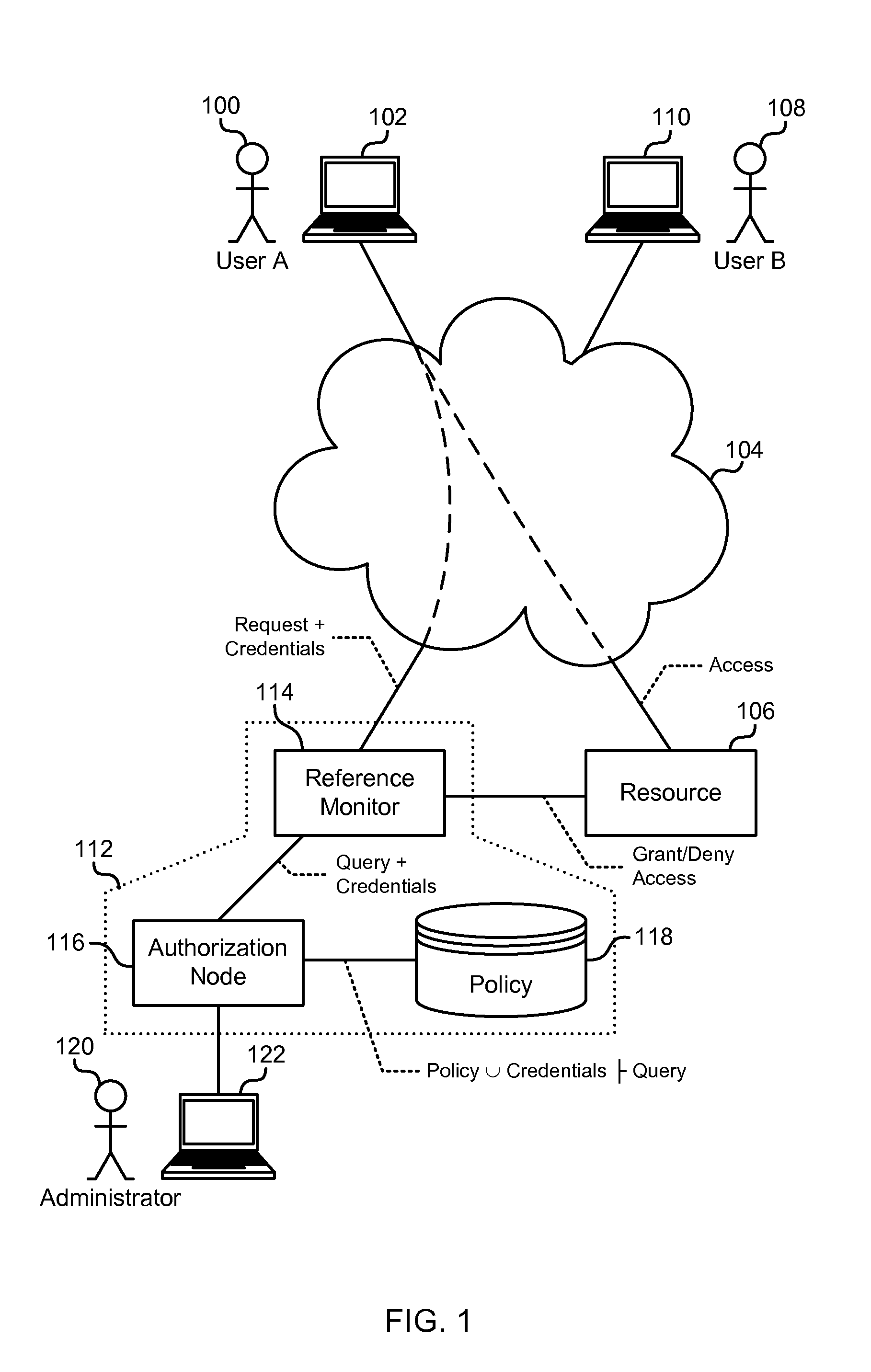
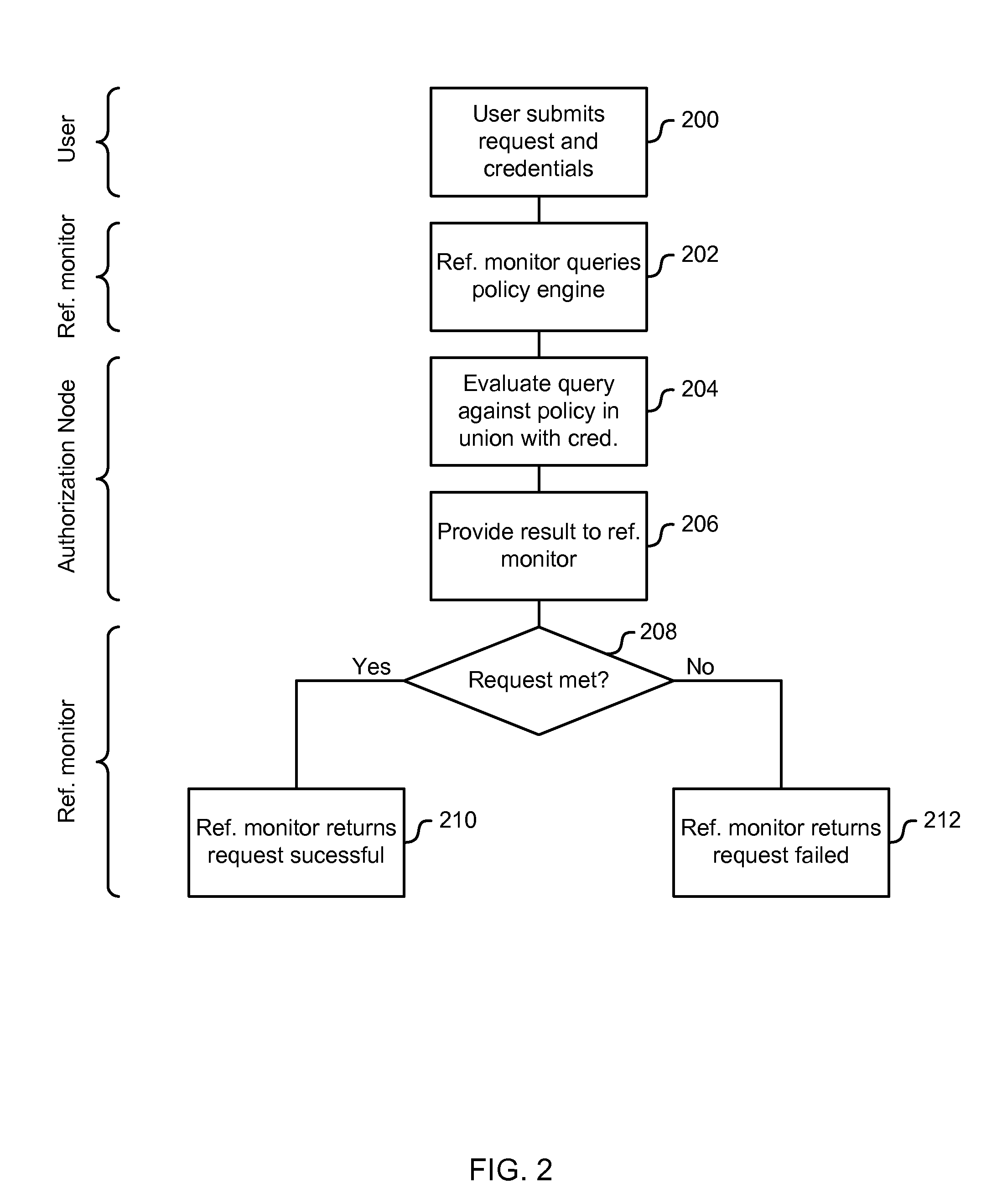
Delegation-Based Authorization
ActiveUS20110296497A1Digital data processing detailsMultiple digital computer combinationsAuthorizationReference monitor
Delegation-based authorization is described. In one example, a reference monitor receives from a first entity a request and a credential statement comprising a delegation of authority over a fact to a further entity. An authorization node then determines whether the further entity consents to provide the fact to the first entity and evaluates the request in accordance with an authorization policy and the credential statement. In another example, an assertion comprising a statement delegating authority over a fact to a further entity is received at an authorization node from a first entity. An authorization policy is then used to determine that the first entity vouches for the fact if each of these conditions are met: i) the first entity consents to import the fact from the further entity, ii) the further entity consents to export the fact to the first entity, and iii) the further entity asserts the fact.
Owner:MICROSOFT TECH LICENSING LLC
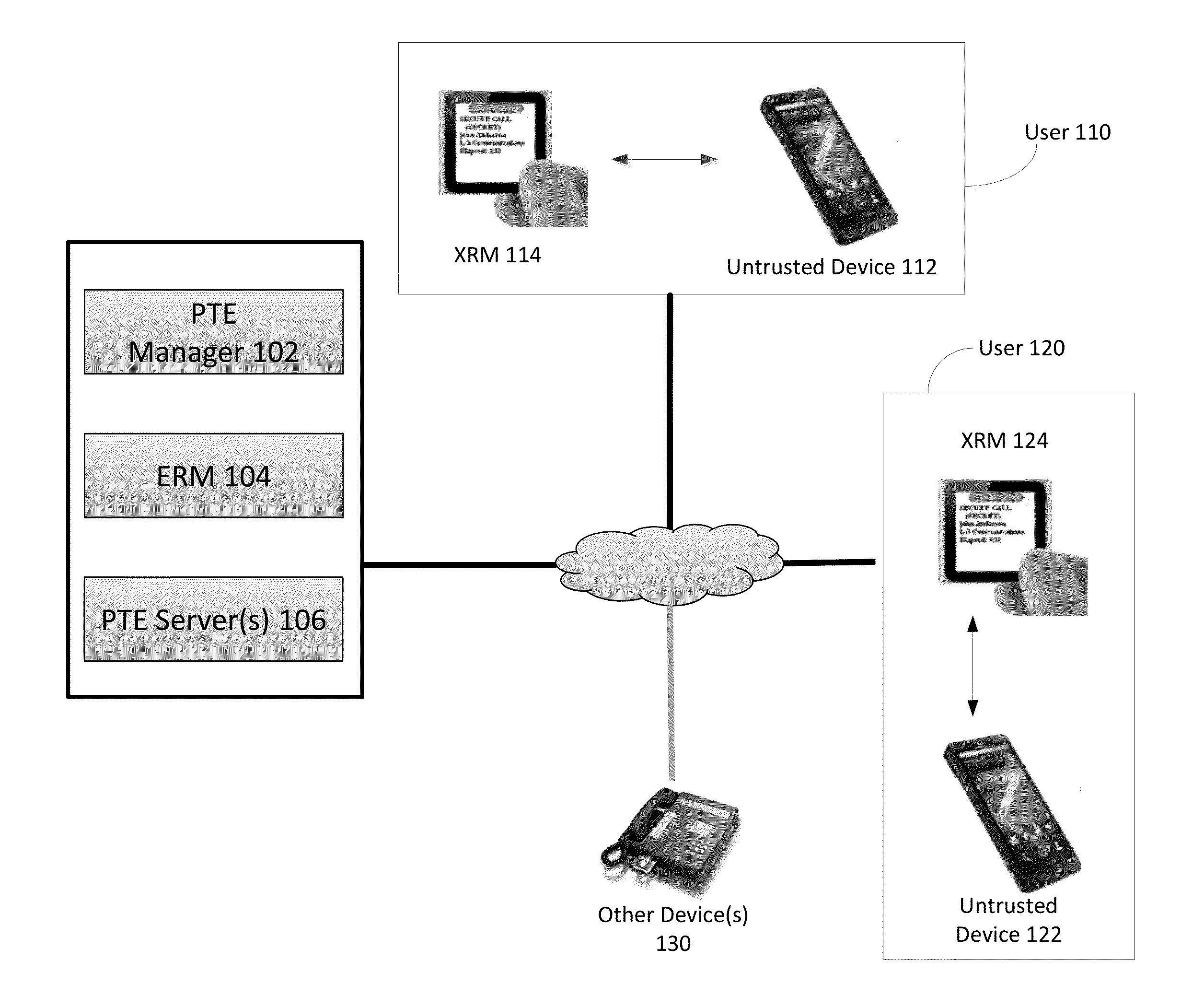
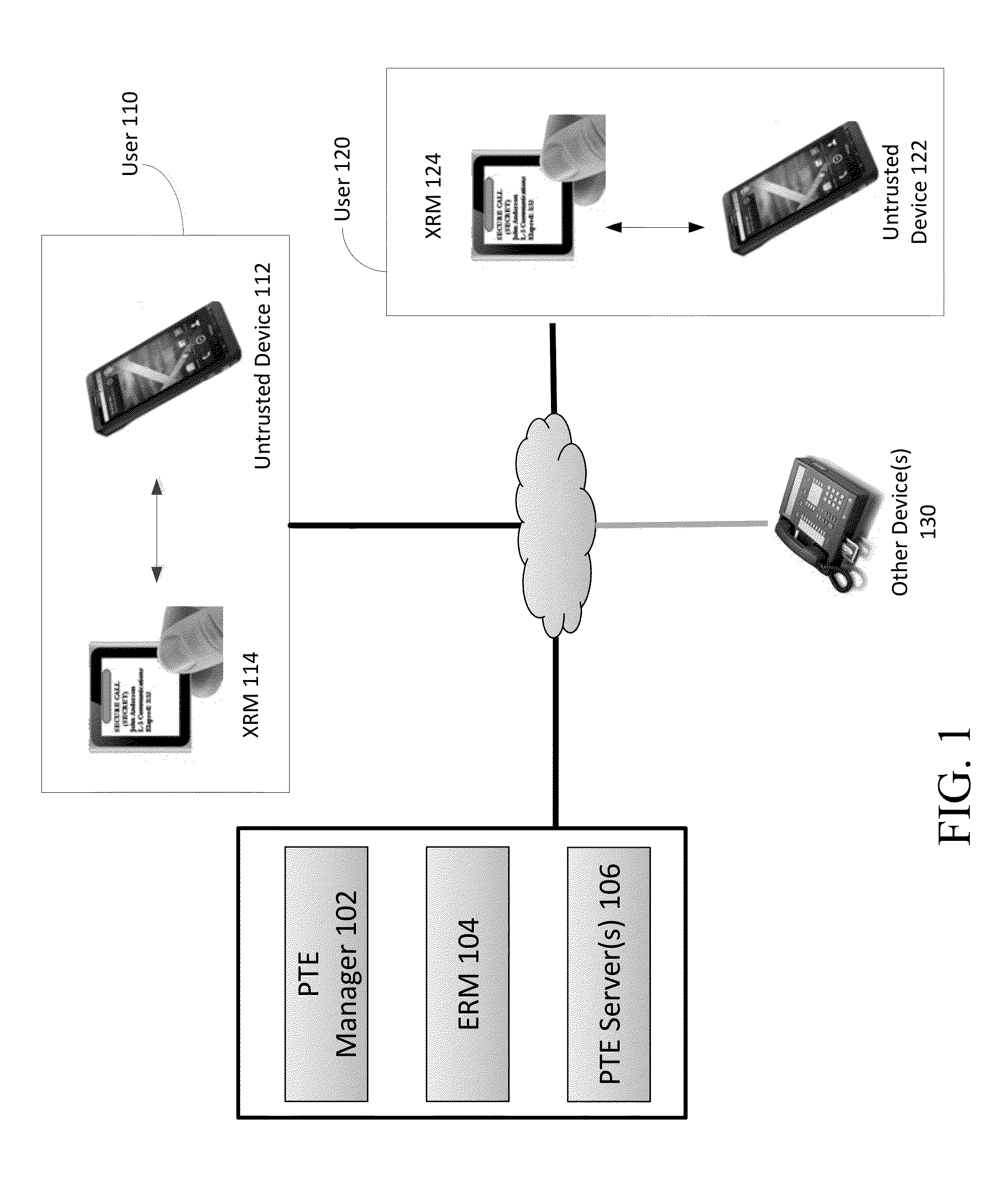
External Reference Monitor
ActiveUS20130111211A1Improve trustPrevent cheatingDigital data processing detailsUser identity/authority verificationComputer hardwareTrusted hardware
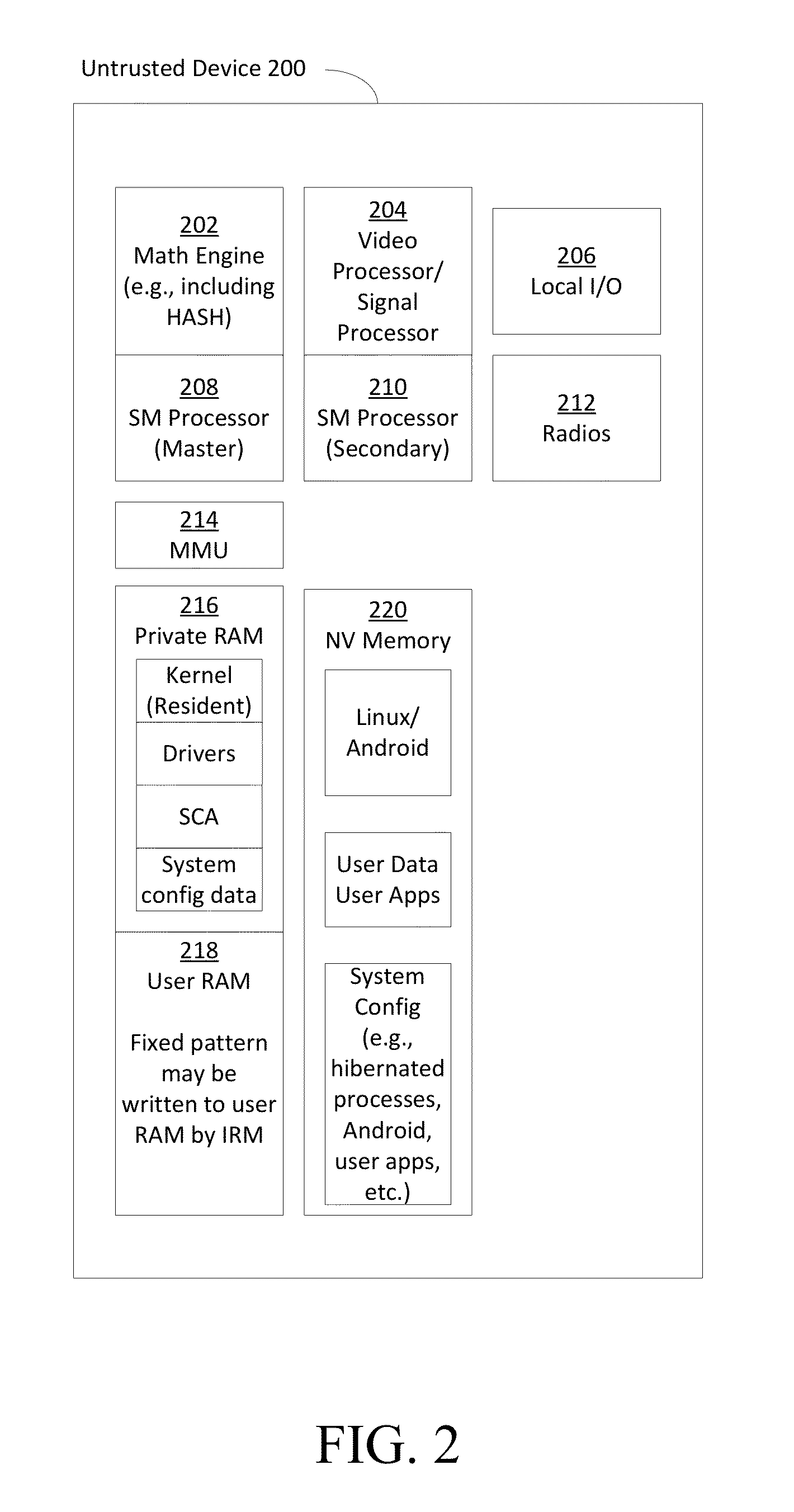
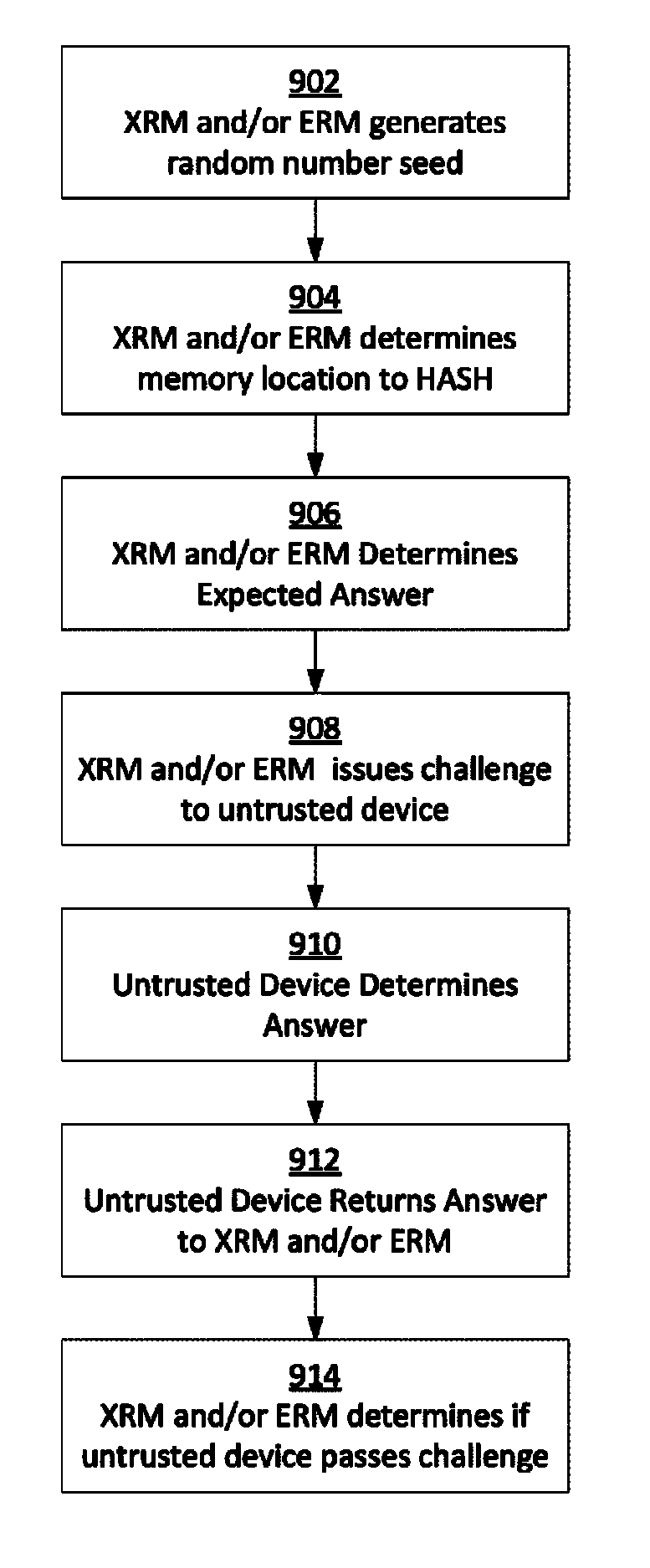
Methods and systems for increasing the security or trust associated with an untrusted device are provided. For example, a trusted hardware component may send a request to the untrusted device. The request may indicate one or more challenges to be performed by a secure application executing on the untrusted device. The trusted hardware component may determine an expected response to the one or more challenges. The expected response may be determined at the secure hardware component based on an expected configuration of the untrusted device. The trusted hardware component may receive a response to the request from the untrusted device. The trusted hardware component may determine a security status of the untrusted device based on the expected response and the received response
Owner:LIONRA TECH LTD
Method and System for Access Control in Distributed Object-Oriented Systems
InactiveUS20070233883A1Reduce probabilityMultiple digital computer combinationsTransmissionEntity linkingLimited access
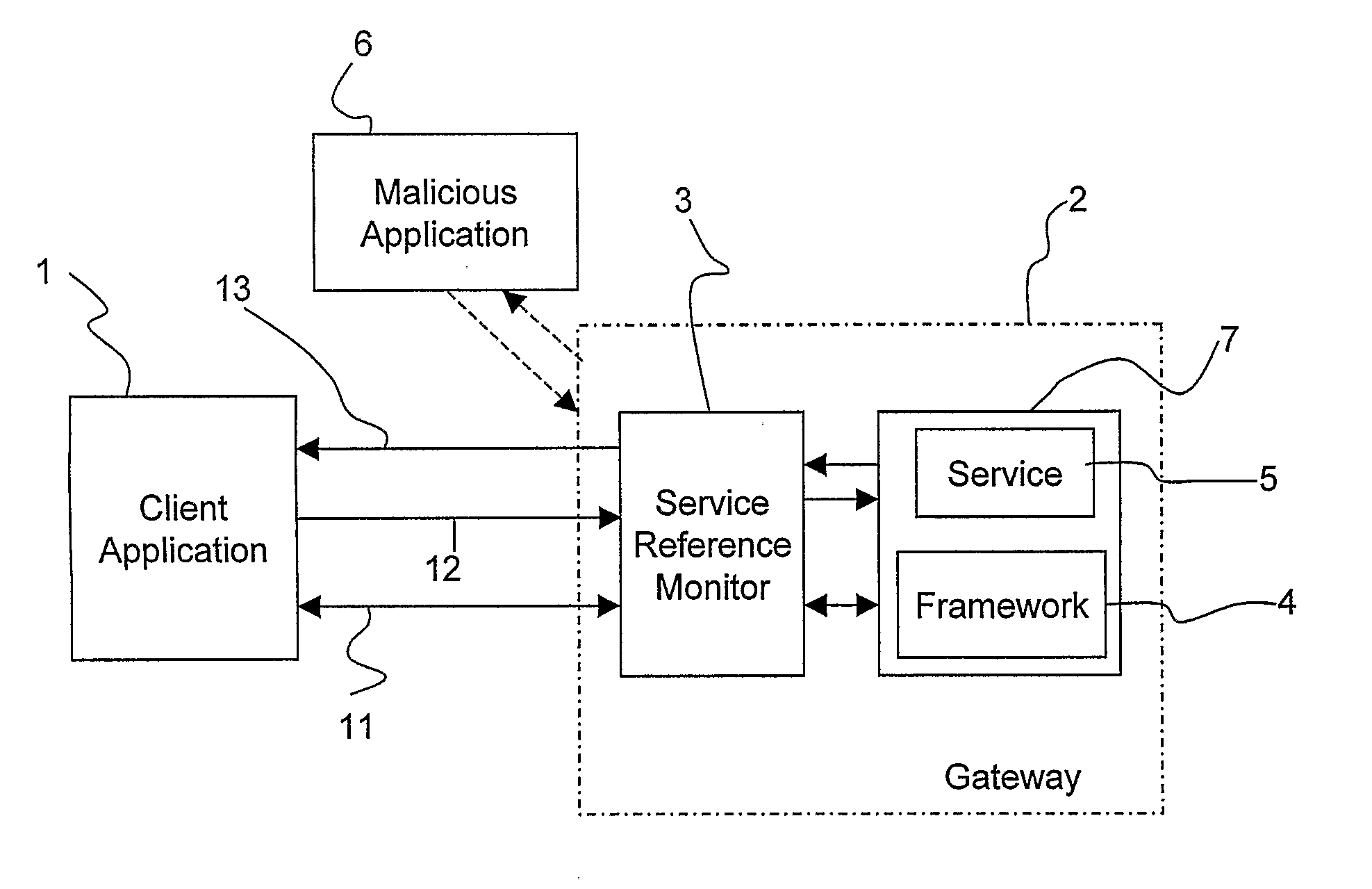
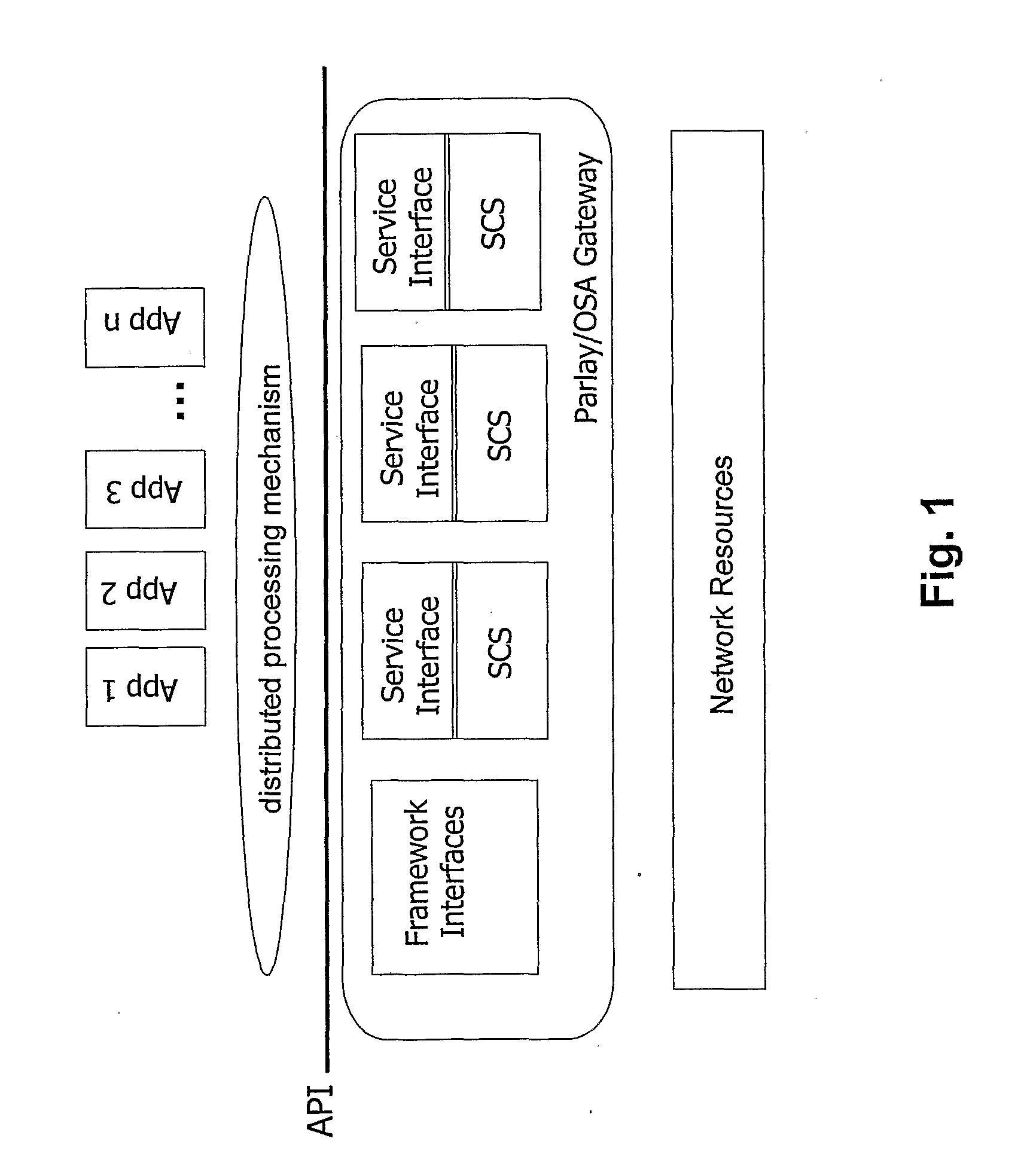
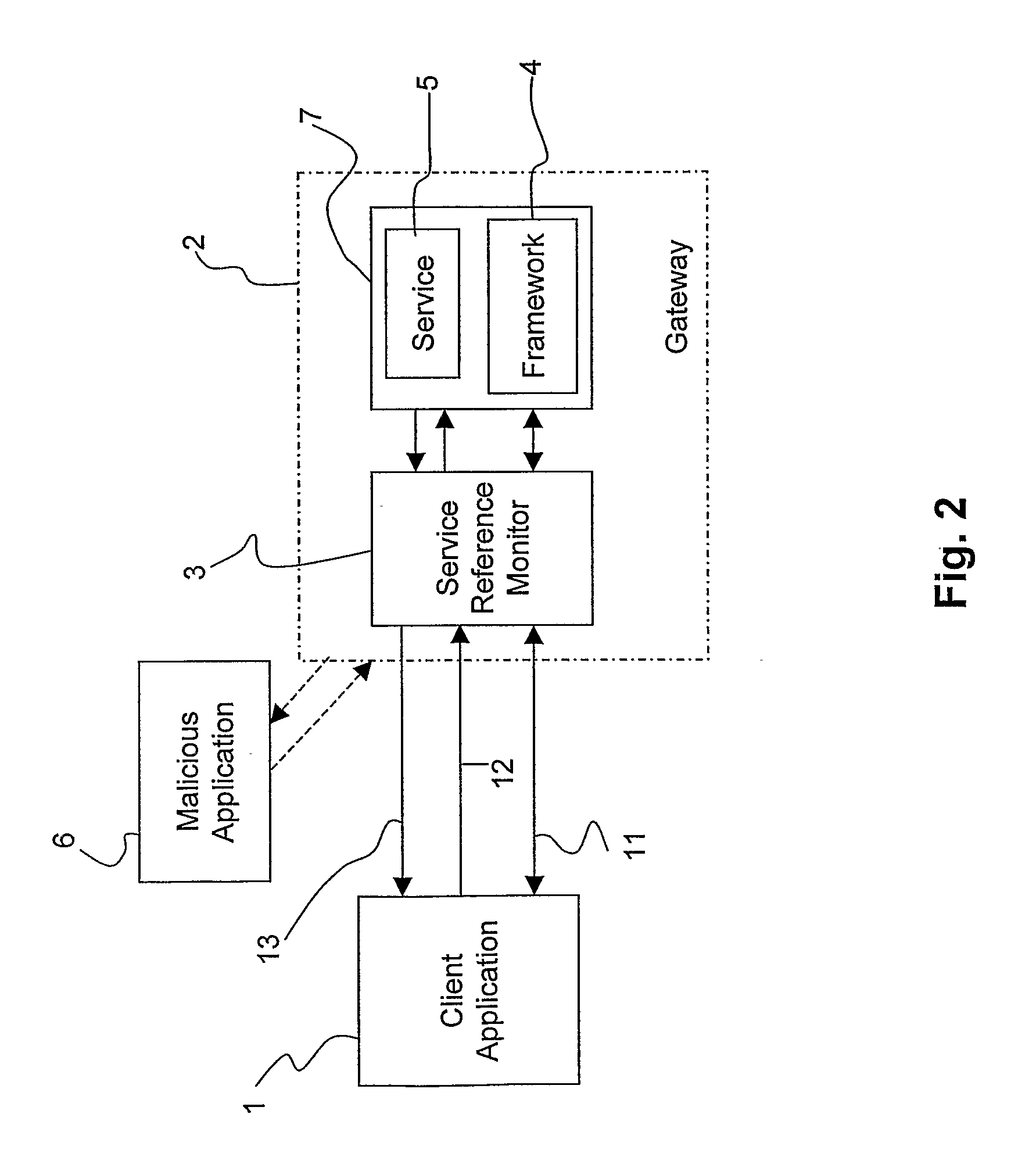
A method and a system for accessing services provided by network resources in communication networks. Access to service capabilities is controlled at the application level by controlling the access through a gateway wherein an object-oriented service architecture based on abstracted application programming interfaces is implemented. Preferably, the service architecture is defined in OSA / Parlay standards. Access control is carried out by means of a logical entity, the service reference monitor, which is linked to the gateway and configured so that it intercepts all the communications passing between the client applications and the gateway. The service reference monitor captures the object reference to the service capability and assigns to the object reference a lifetime. At the expiration of the lifetime, the service reference monitor destroys the service capability. The probability of a malicious attack is lowered by limiting the time window of the life of access to a service.
Owner:TELECOM ITALIA SPA
Systems and methods for securing multimedia transmissions over the internet
InactiveUS8024560B1Communication securityUser identity/authority verificationUnauthorized memory use protectionSecure communicationThe Internet
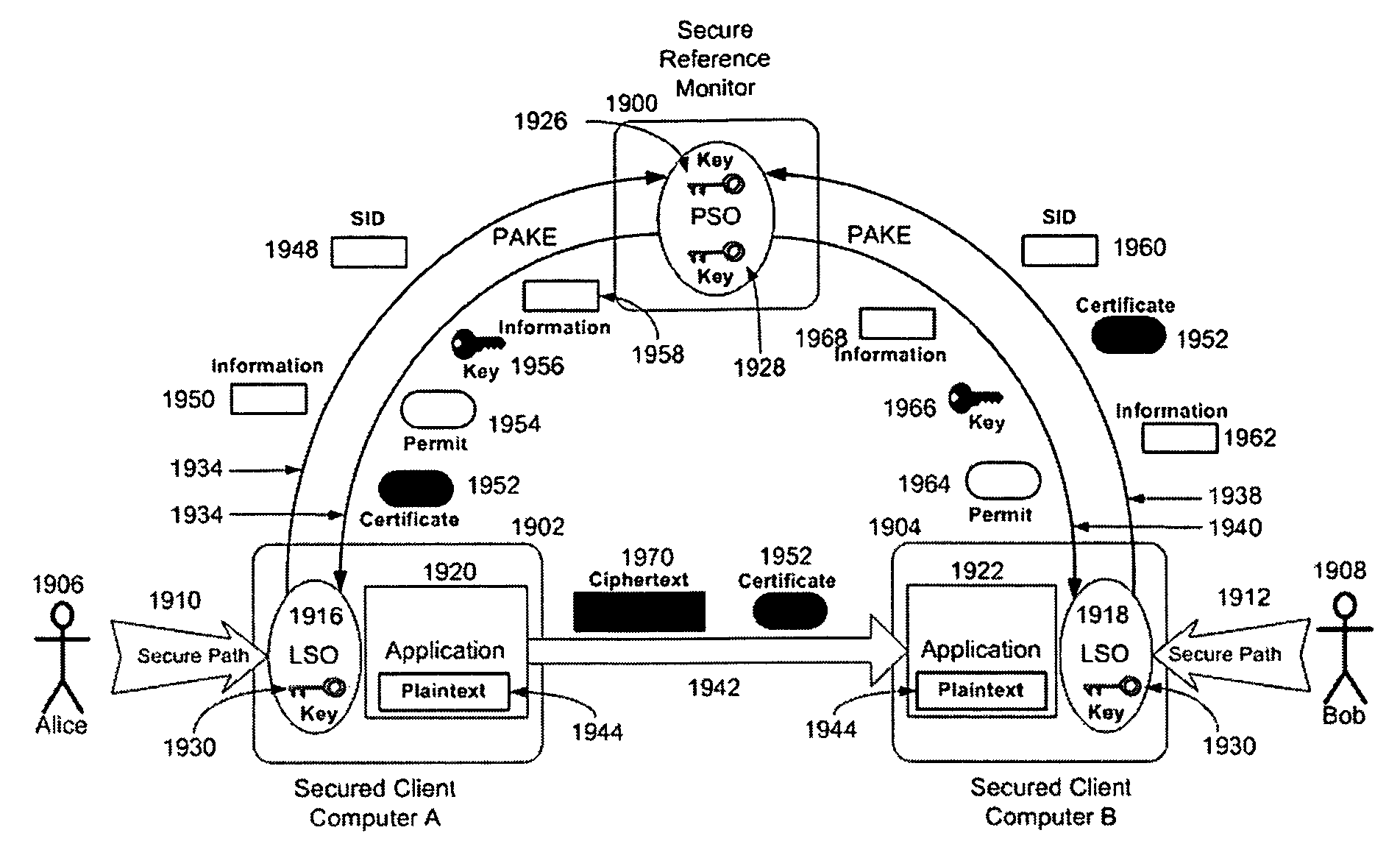
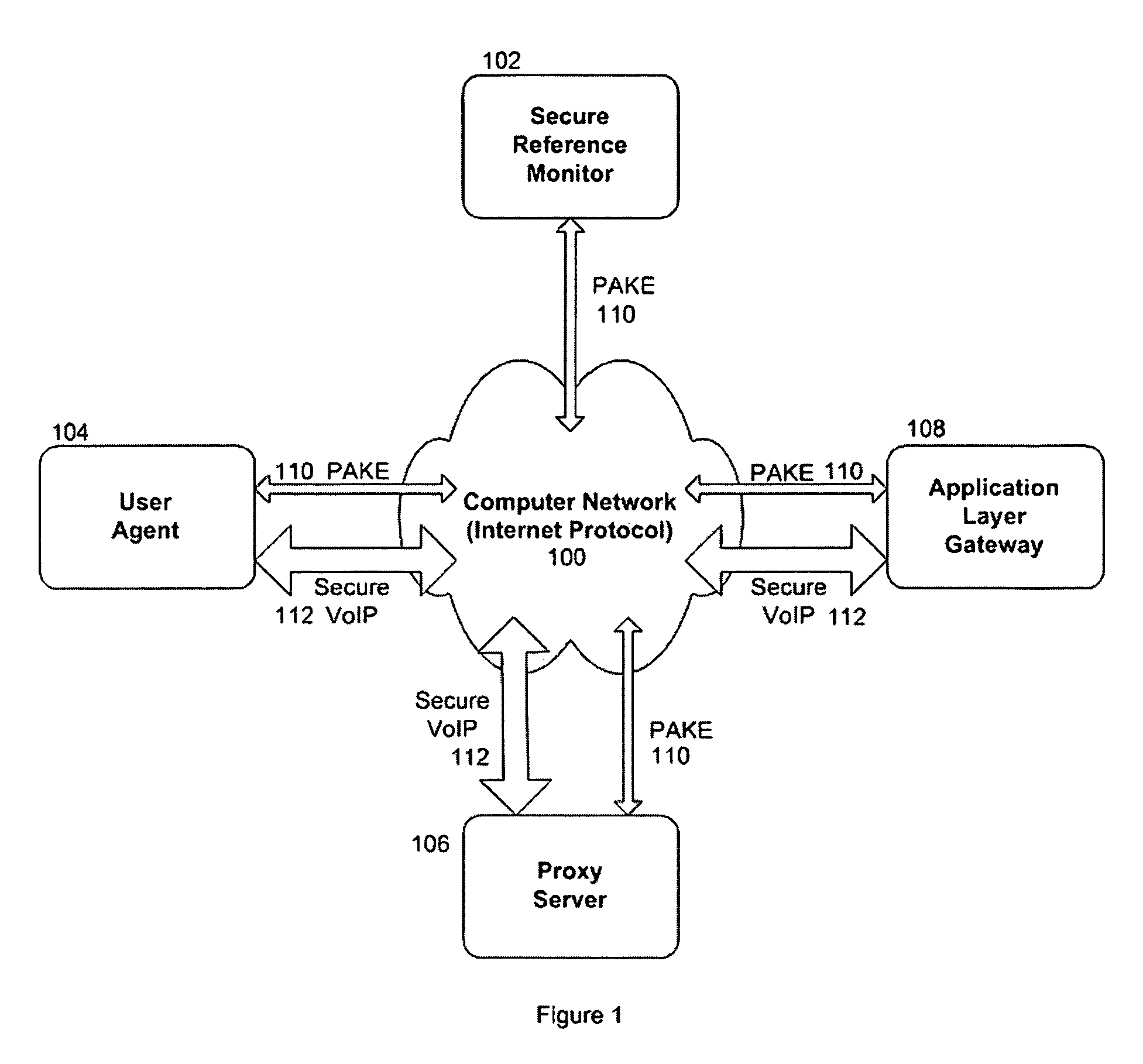
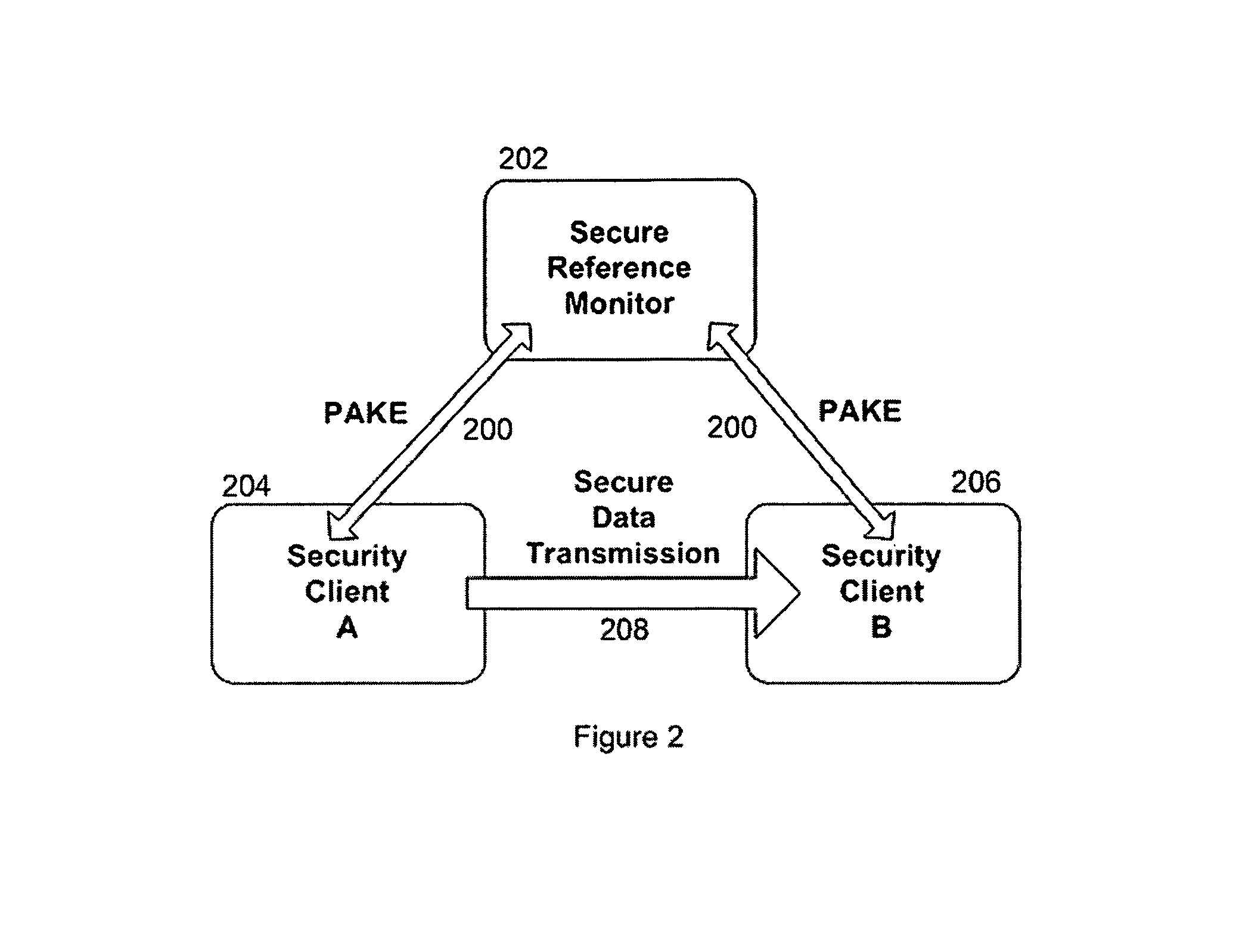
In one embodiment, the systems and methods utilizes an enciphered permit identification number, called a session certificate, to reference the policy attribute values and session key that are stored in a secured, online reference monitor (SRM). The session key is used to encipher confidential communications, such as voice and audio communications over the Internet (VoIP), between computers. Each computer uses a unique key with a cryptographic transaction protocol for authentication and key agreement (PAKE) to securely communicate with the SRM. A sender computer uses PAKE to get a session certificate and a session key from the SRM. It sends the session certificate to a receiver computer. The receiver computer sends the session certificate to the SRM and gets back the session key. The sender computer encrypts its VoIP message with the session key and transmits it to the receiver computer. The receiver computer decrypts the VoIP message.
Owner:ALTEN ALEX I
Mechanism to trap obsolete web page references and auto-correct invalid web page references
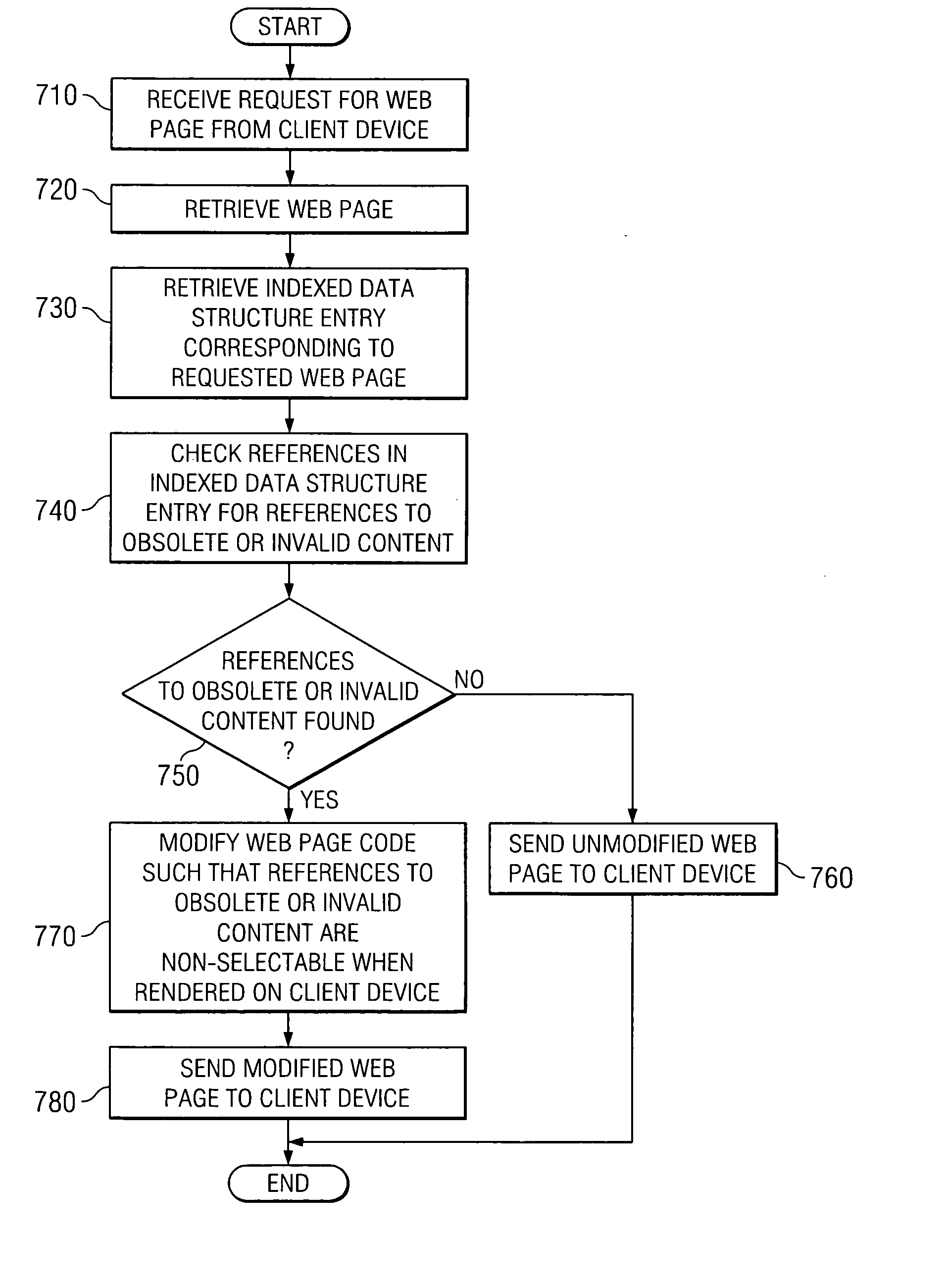
InactiveUS20070174324A1For easy referenceReduce network trafficDigital data processing detailsWebsite content managementClient-sideReference monitor
A mechanism to trap obsolete web page references and auto-correct invalid Web page references is provided. With the mechanism, Web pages of a Web site are indexed in an indexed data structure having entries that list the references contained in the Web page. A Website reference monitor monitors changes to the Web pages and content referenced by these Web pages. If a change to the Web pages or referenced content is detected, other Web pages in the Web site that reference the modified content or Web pages are identified using the indexed data structure. The identified other Web pages may then be automatically updated. In addition, when a client device requests a Web page, the references in the Web page are checked to determine if they reference obsolete or invalid content and such references are modified to be non-selectable before providing the Web page to the client device.
Owner:IBM CORP
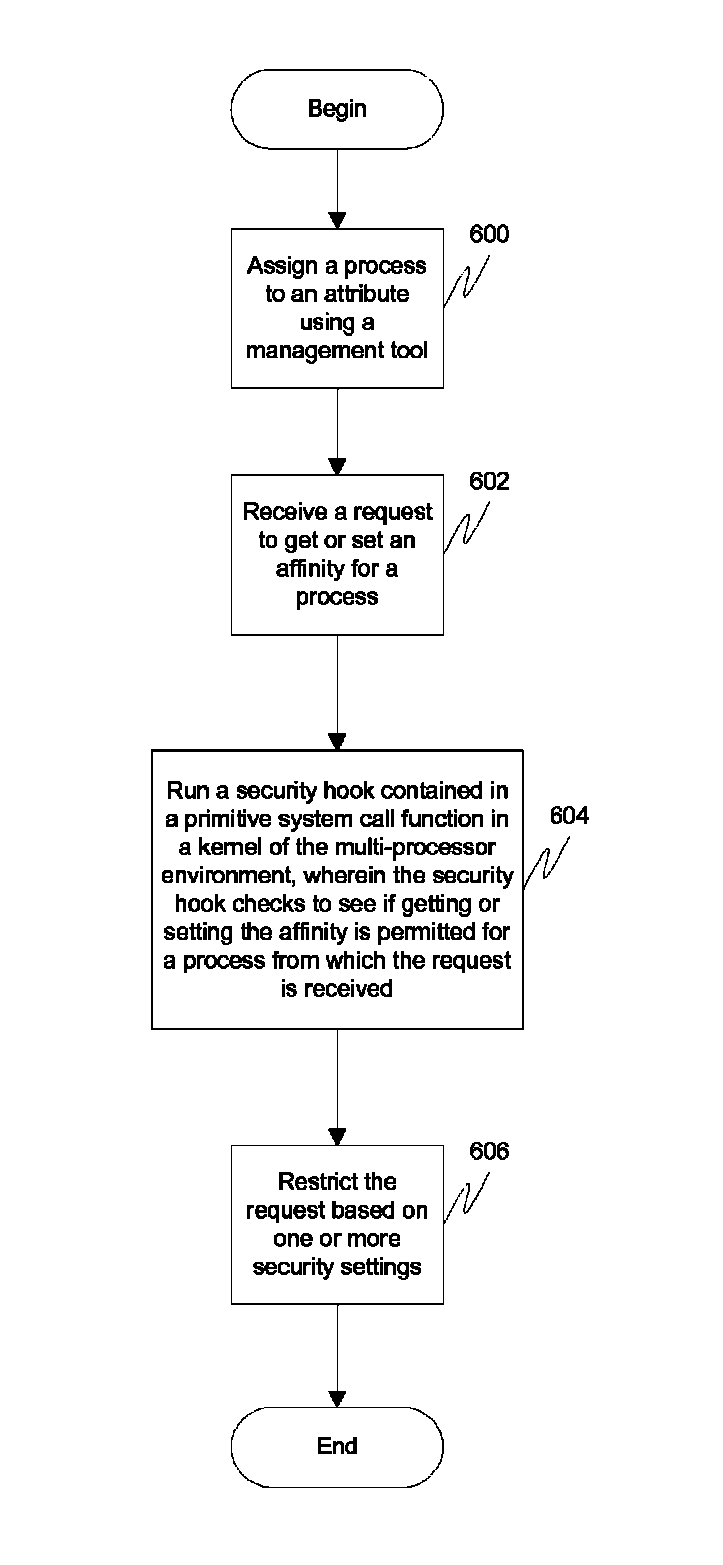
Securing CPU affinity in multiprocessor architectures
InactiveUS20090126006A1Limited abilityDigital data processing detailsUnauthorized memory use protectionMulti processorMultiprocessor architecture
In an embodiment of the present invention, the ability for a user or process to set or modify affinities is restricted in order to method for control a multi-processor environment. This may be accomplished by using a reference monitor that controls a process' capability to retrieve and set its or another process' affinity. This aids in the prevention of security breaches.
Owner:SAMSUNG ELECTRONICS CO LTD
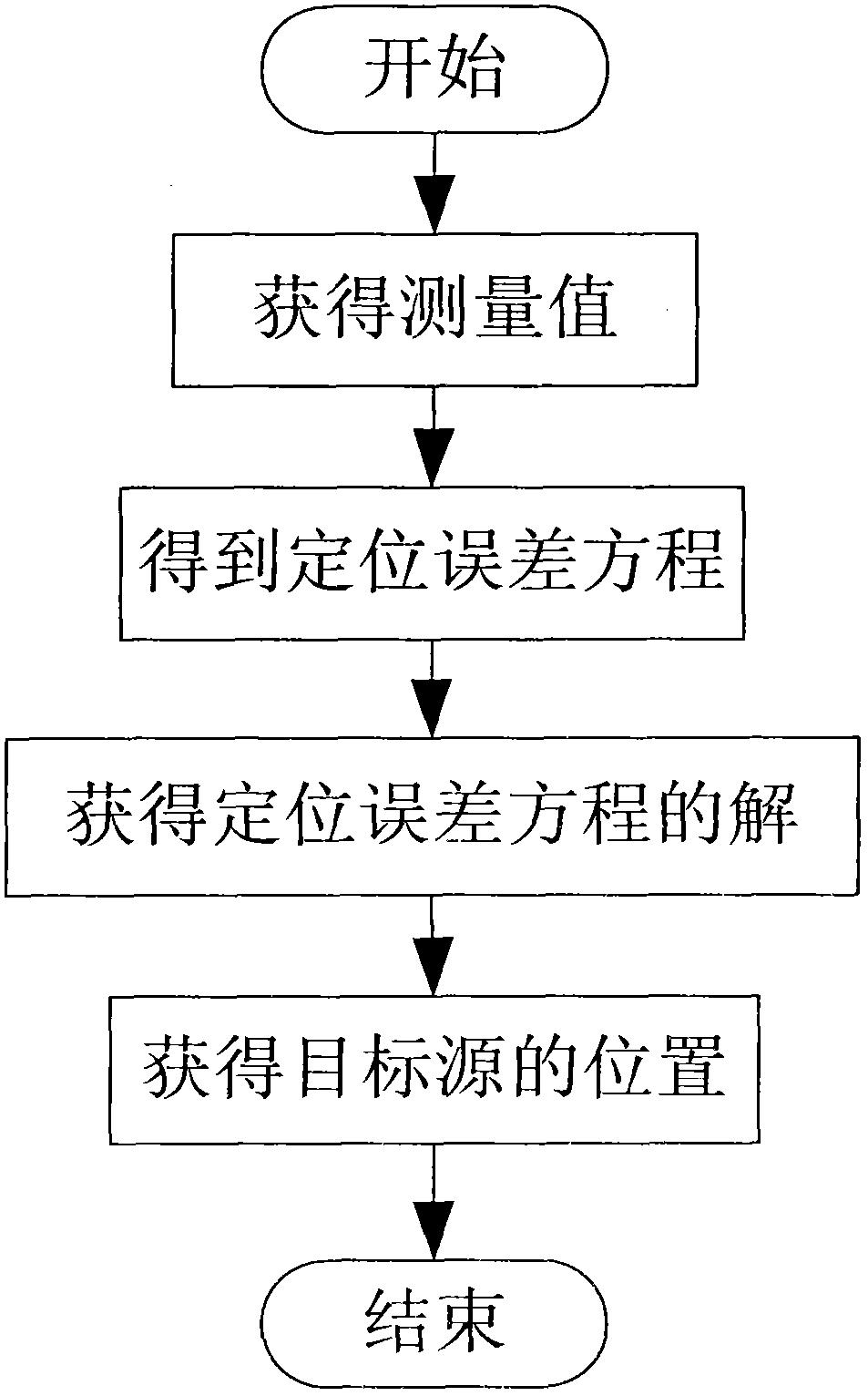
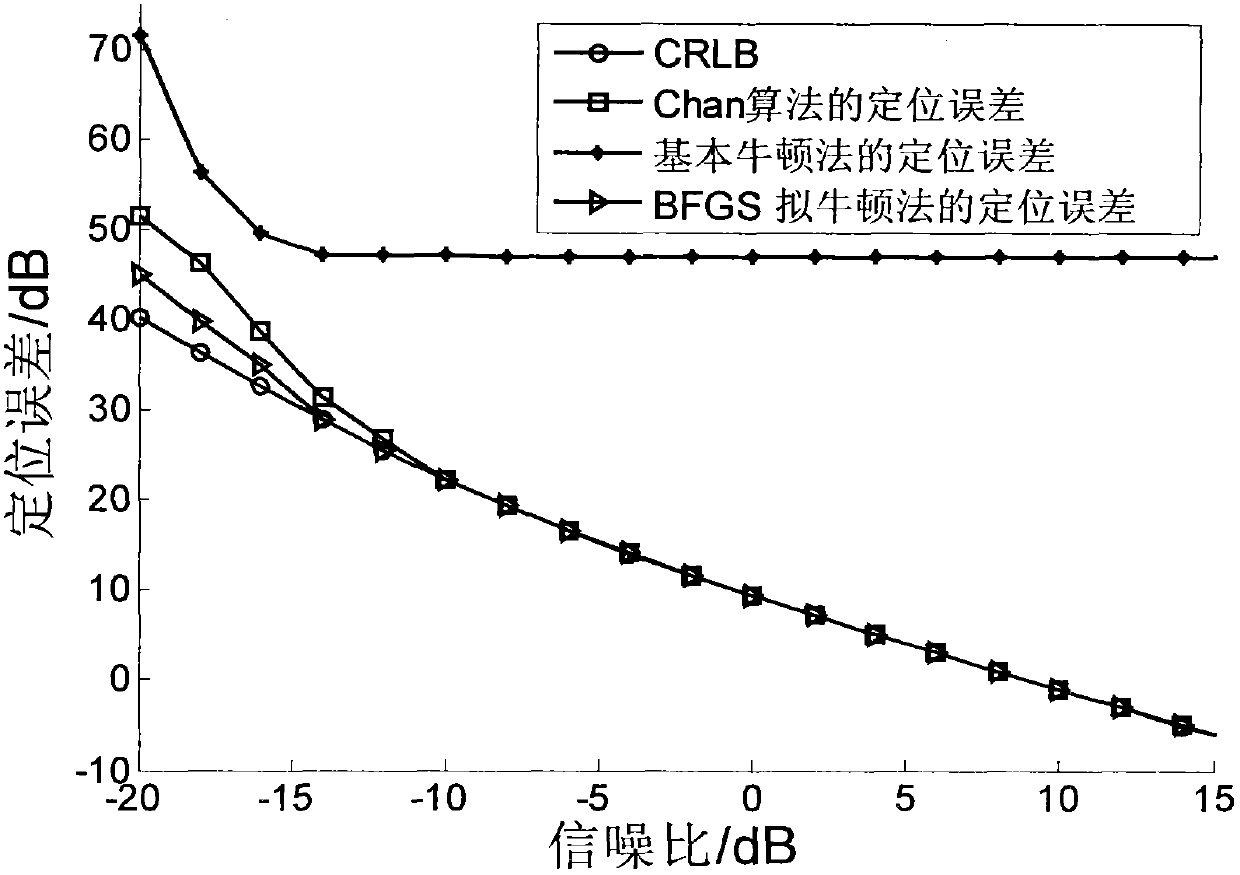
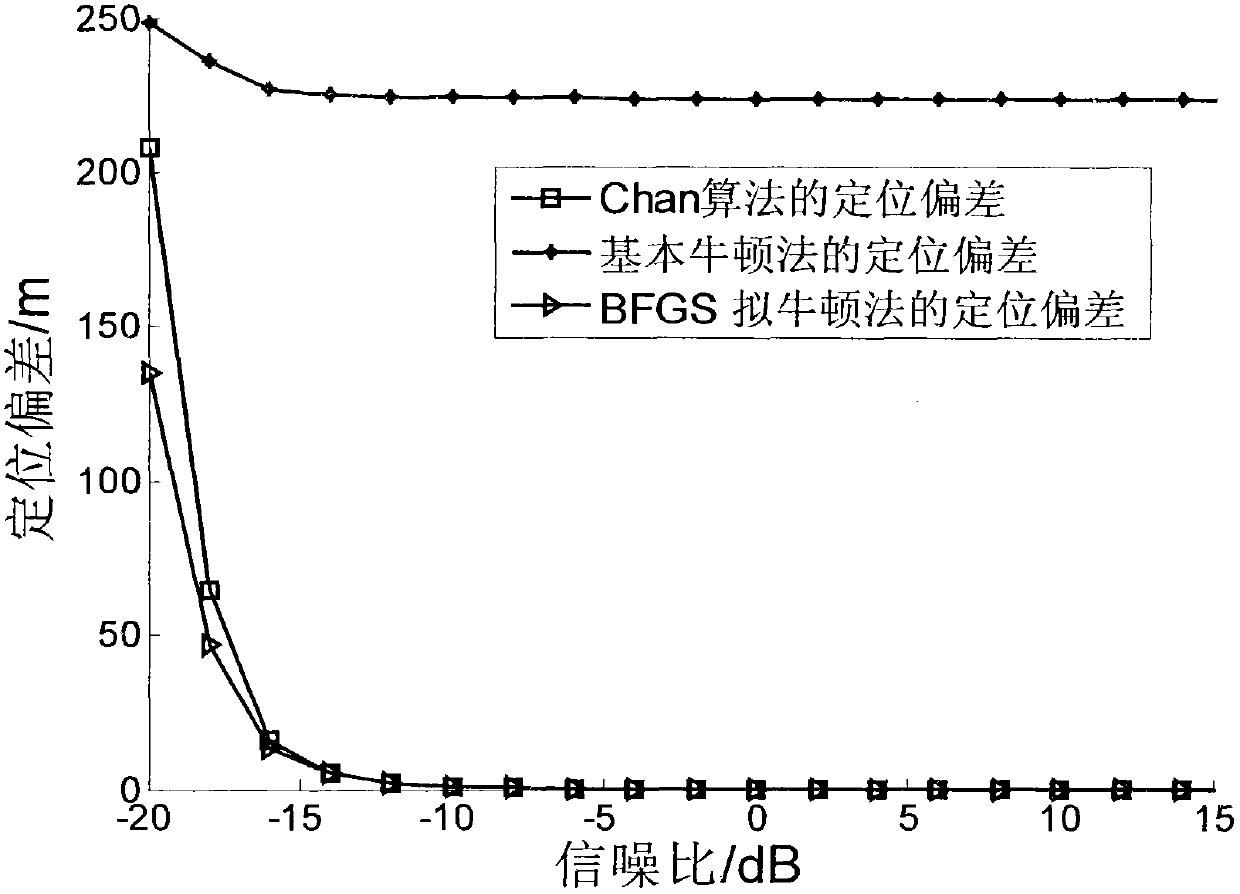
Signal source positioning method based on BFGS quasi-Newton method
InactiveCN103135094AOvercome errorHigh positioning accuracyPosition fixationObservational errorMultilateration
The invention discloses a signal source positioning method based on a BFGS quasi-Newton method and mainly aims to solve the problems that median error is introduced in an existing positioning method, positioning results are fuzzy, practicality is not strong, calculation amount is large, positioning results are not stable and the like. The signal source positioning method based on the BFGS quasi-Newton method comprises the following steps of obtaining a measured value reaching time difference and a measured value reaching gain ratio; setting joint positioning error equations through the relationship that the measured valve minus measured error is a real value; obtaining solution of the positioning error equations through the BFGS quasi-Newton method; and obtaining position coordinate values of a target source through the fact that the solution of the positioning error equations plus position coordinate values of a reference monitor node. According to the signal source positioning method based on the BFGS quasi-Newton method, stable and high precision positioning is achieved. The signal source positioning method based on the BFGS quasi-Newton method is suitable for the environment with low signal-noise rate and strong in practicability.
Owner:XIDIAN UNIV
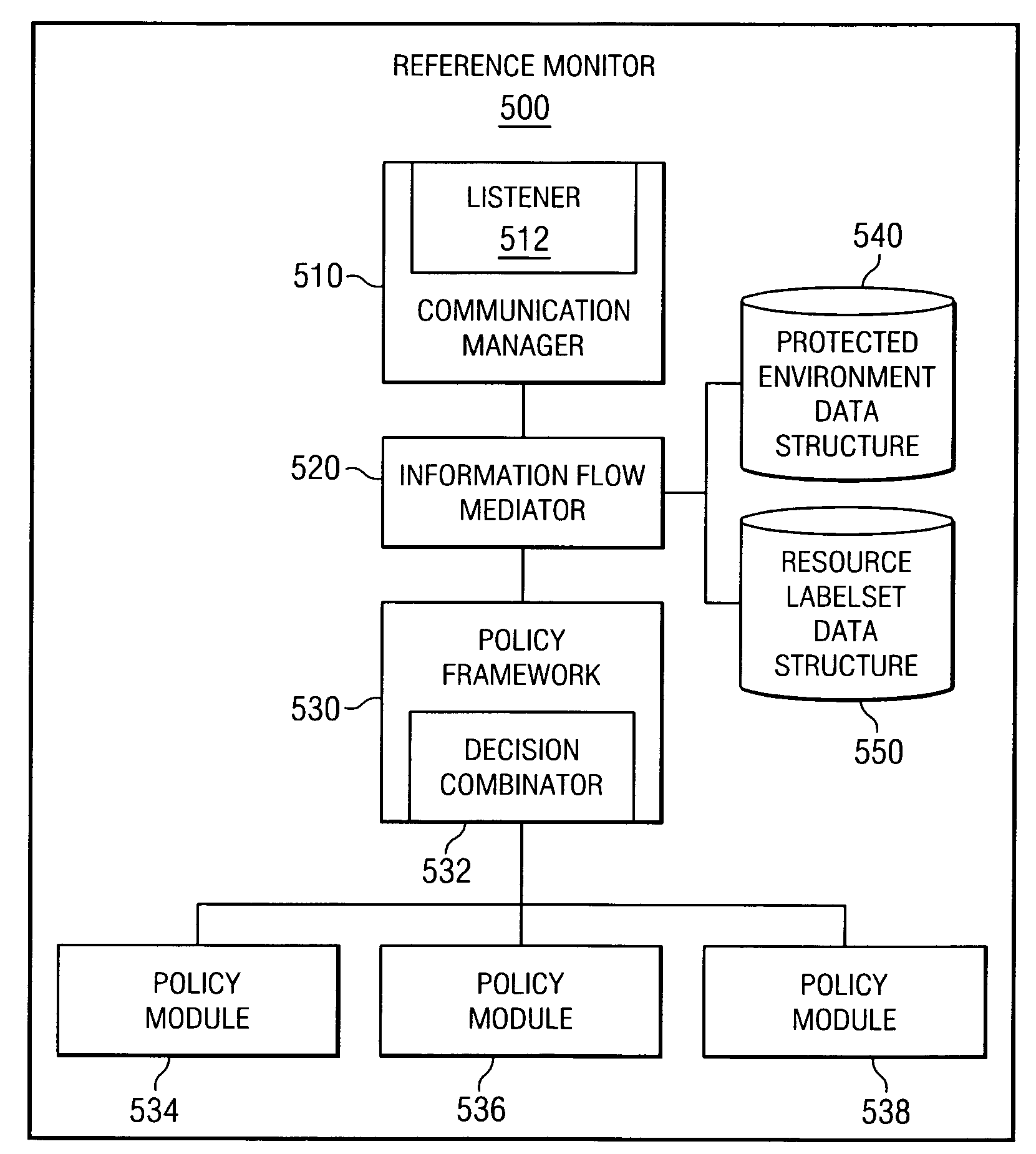
Reference monitor method for enforcing information flow policies
InactiveUS7512792B2Digital data processing detailsUnauthorized memory use protectionData processing systemSecurity policy
A reference monitor system, apparatus, computer program product and method are provided. In one illustrative embodiment, elements of the data processing system are associated with security data structures in a reference monitor. An information flow request is received from a first element to authorize an information flow from the first element to a second element. A first security data structure associated with the first element and a second security data structure associated with the second element are retrieved. At least one set theory operation is then performed on the first security data structure and the second security data structure to determine if the information flow from the first element to the second element is to be authorized. The security data structures may be labelsets having one or more labels identifying security policies to be applied to information flows involving the associated element.
Owner:IBM CORP
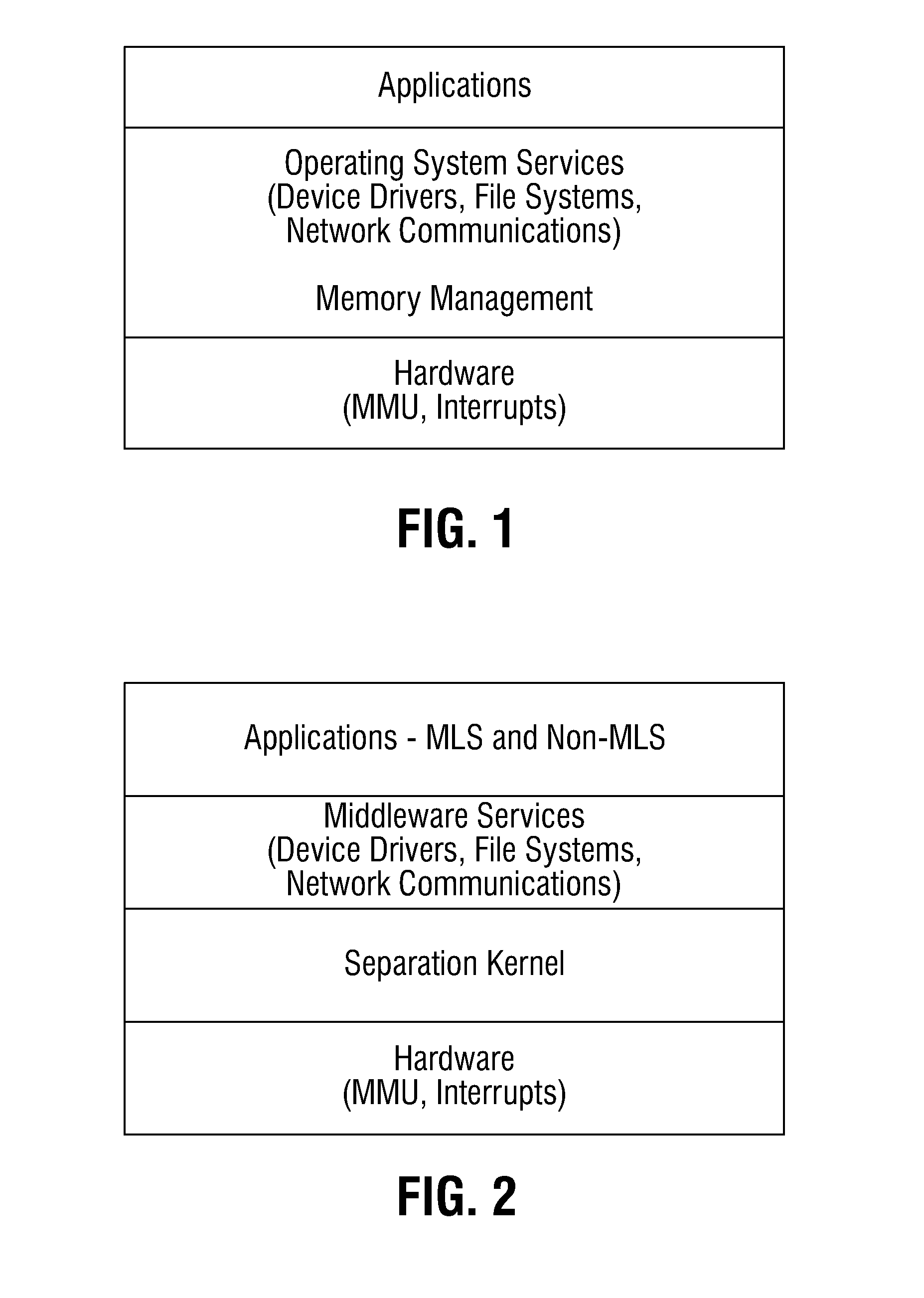
Multi-level security system for enabling secure file sharing across multiple security levels and method thereof
ActiveUS20160117519A1Maintaining data separation of the informationDigital data information retrievalDigital data protectionFile systemSecurity level
A multi-level security system includes a storage medium partitionable into a plurality of partitions, a file system coupleable to the plurality of partitions, and a plurality of enclaves. Each enclave is assigned a security classification level. Each enclave resides in a different storage partition of the storage medium. Data stored on the storage medium is cryptographically separated at rest on a per-enclave basis. Cryptographic separation occurs at the disk block level, allowing individual blocks to be read and decrypted. The system also includes a reference monitor that enforces a system security policy that governs access to information between the enclaves. The reference monitor allows an enclave having a first classification level to securely read-down to an enclave having a second classification level lower than the first classification level and to write to another enclave having the first classification level.
Owner:NORTHROP GRUMMAN SYST CORP
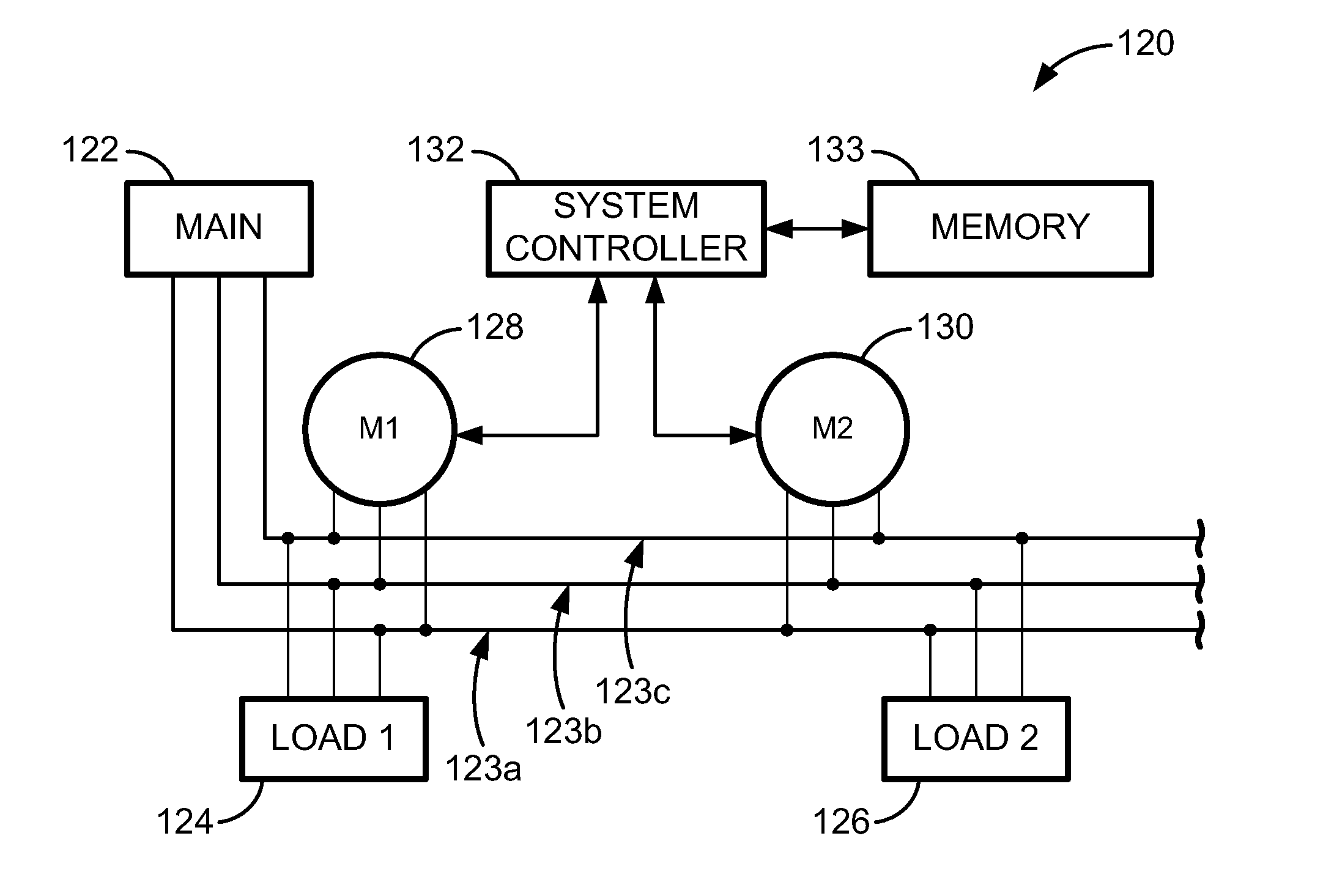
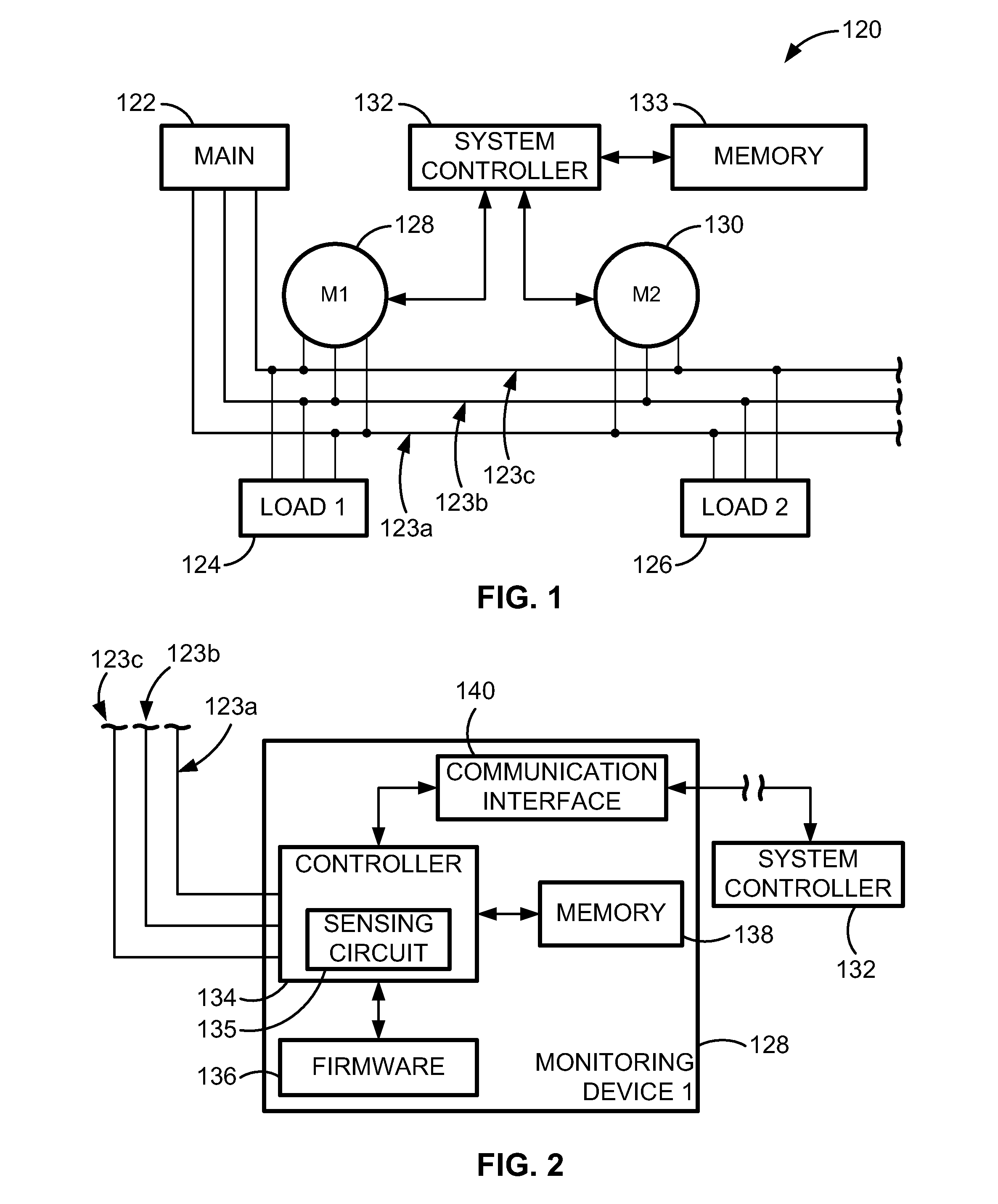
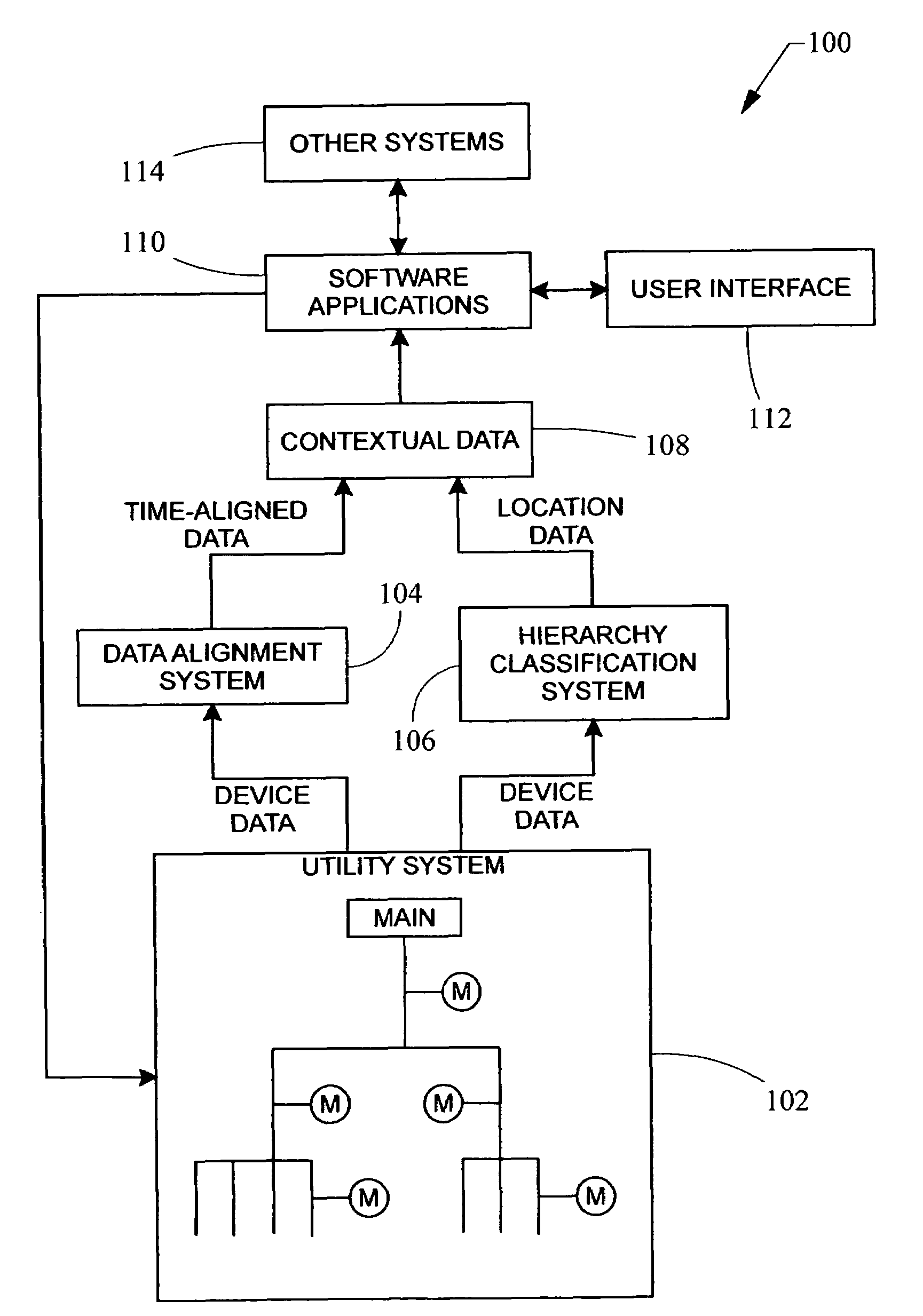
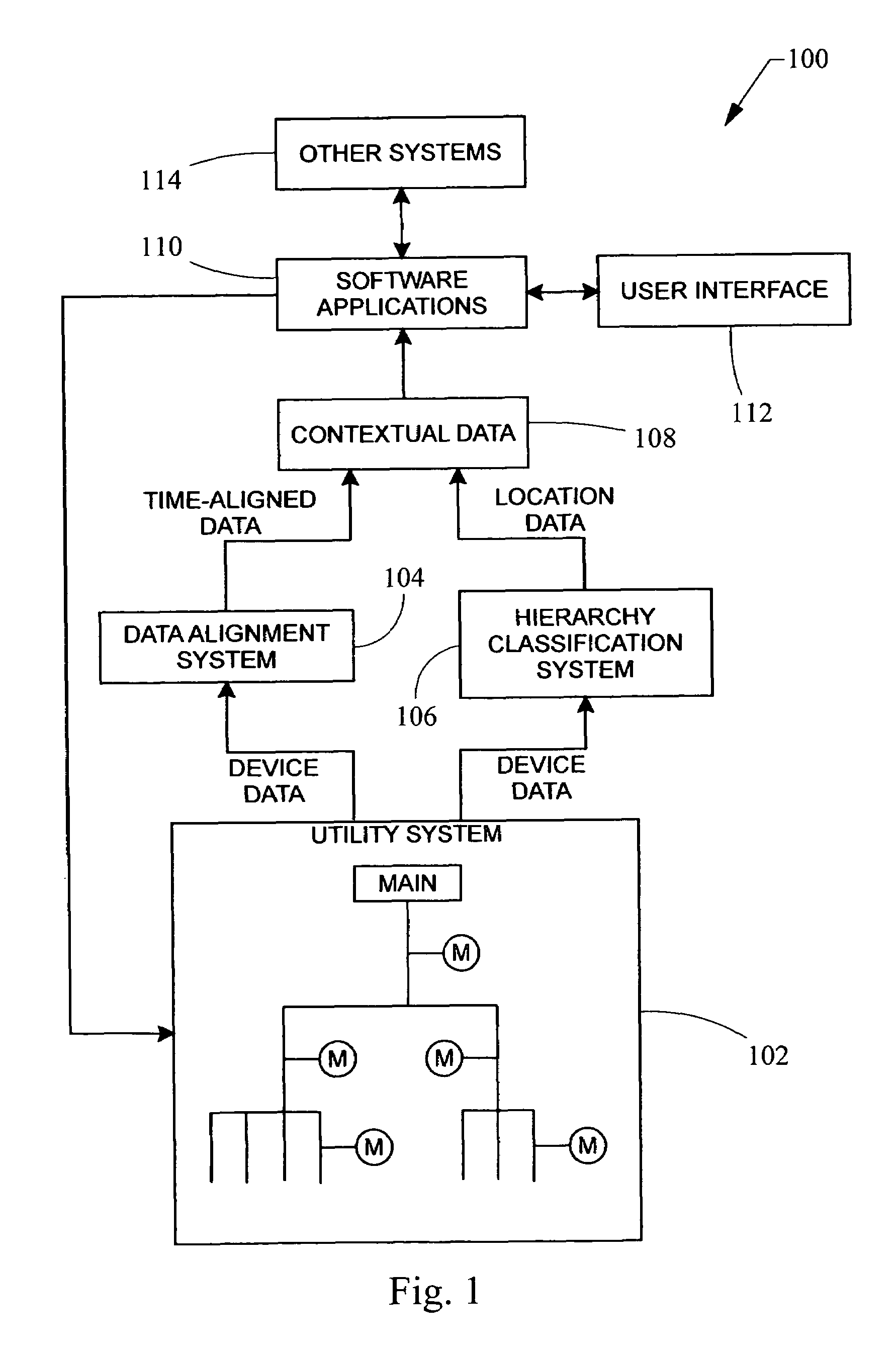
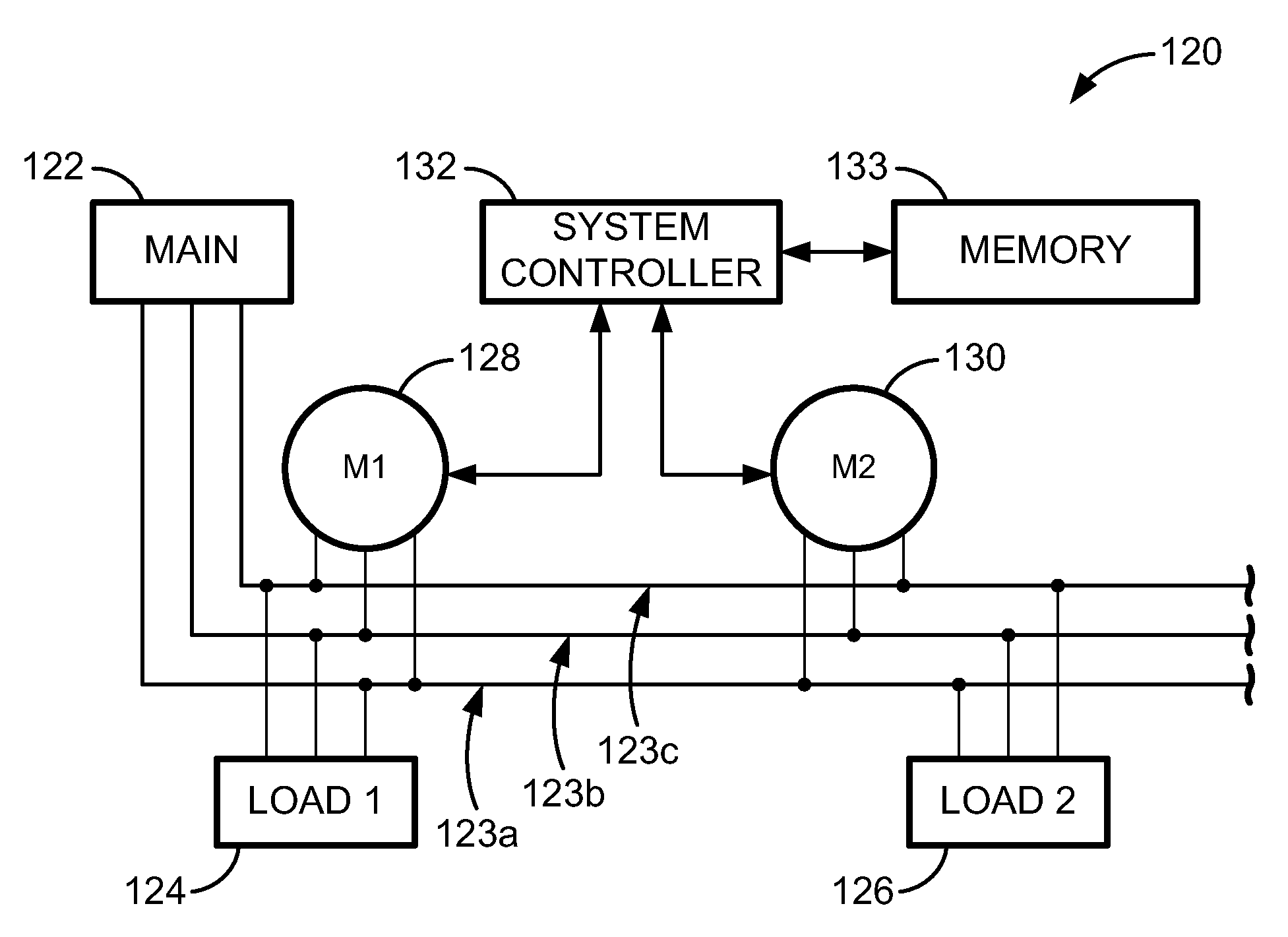
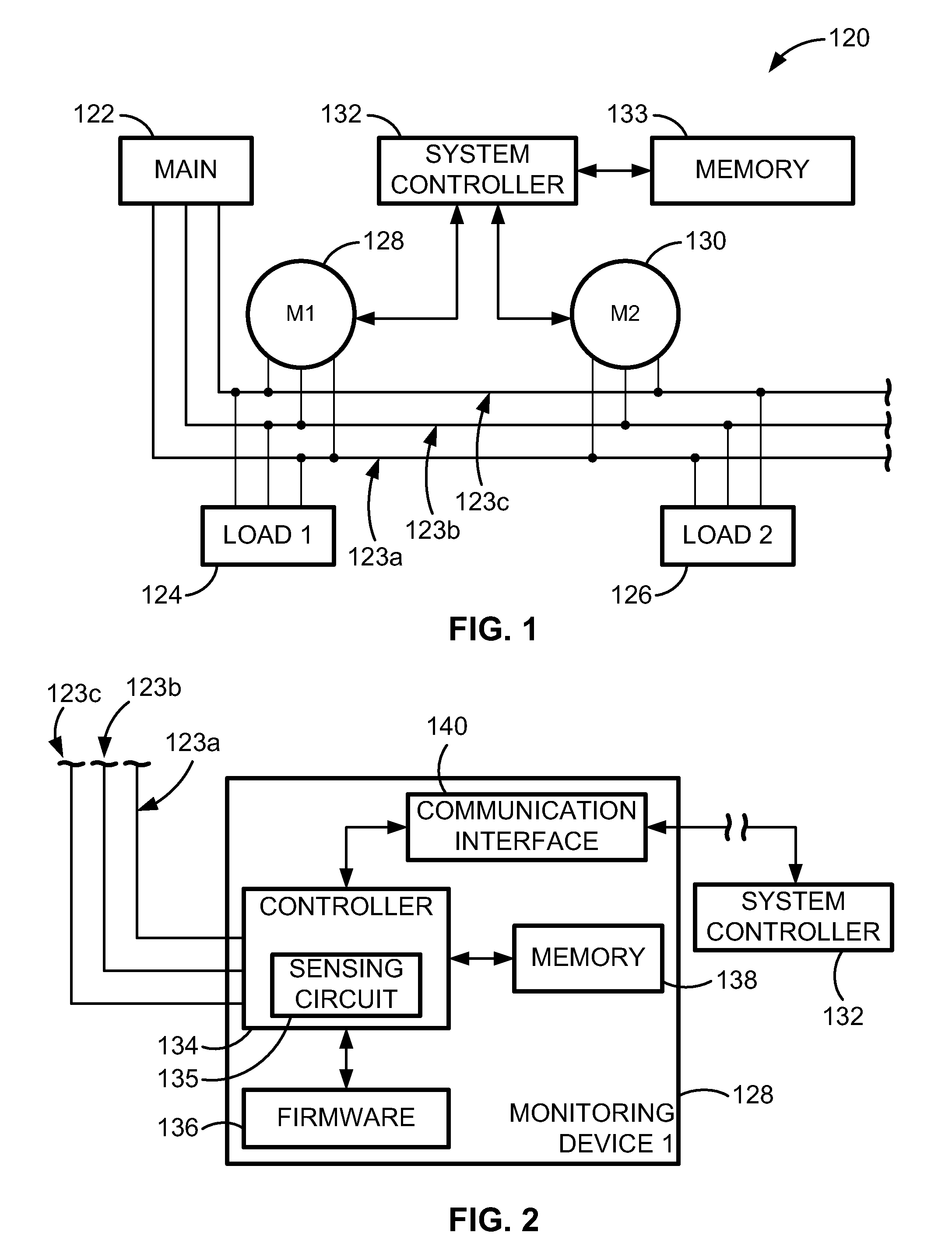
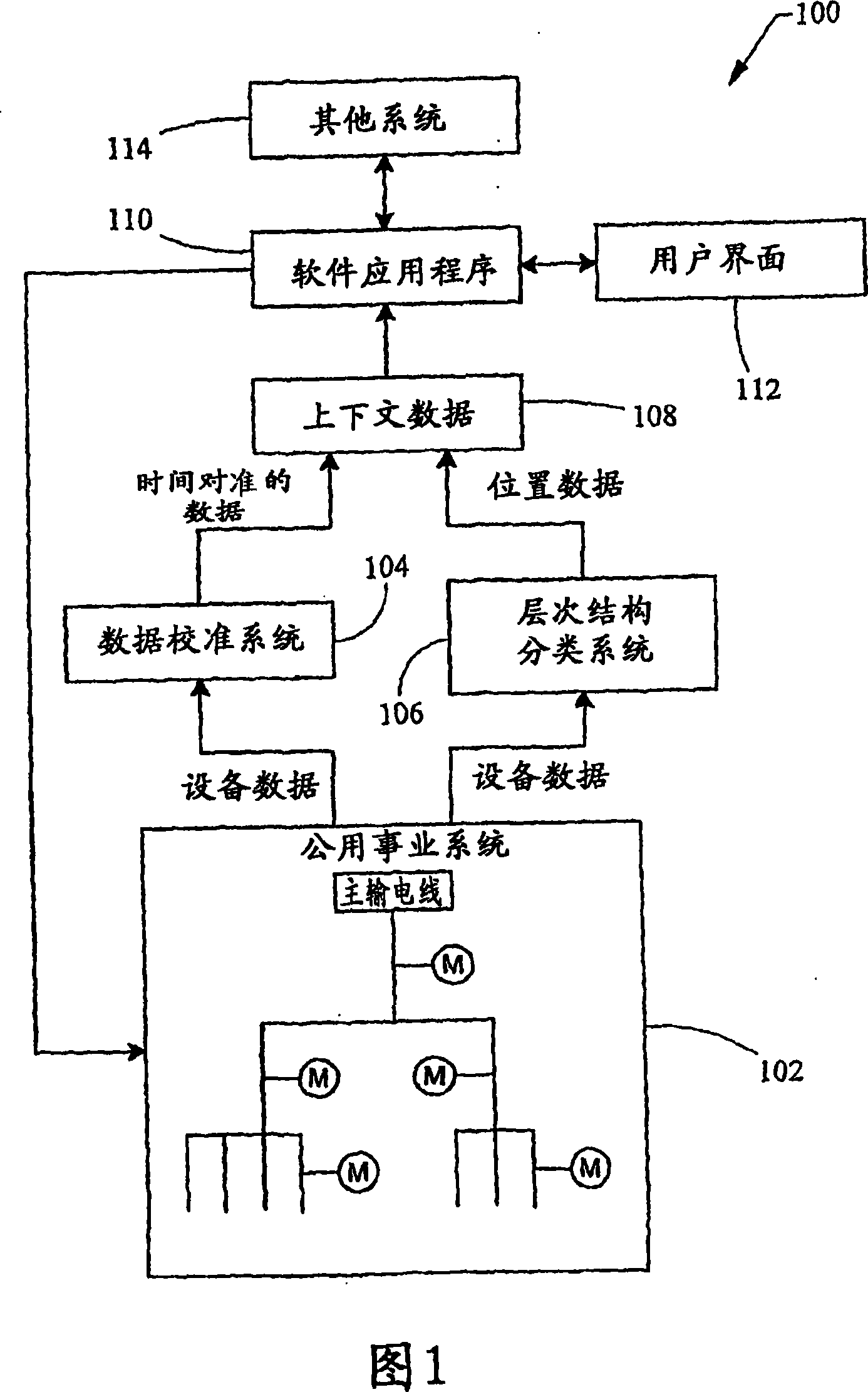
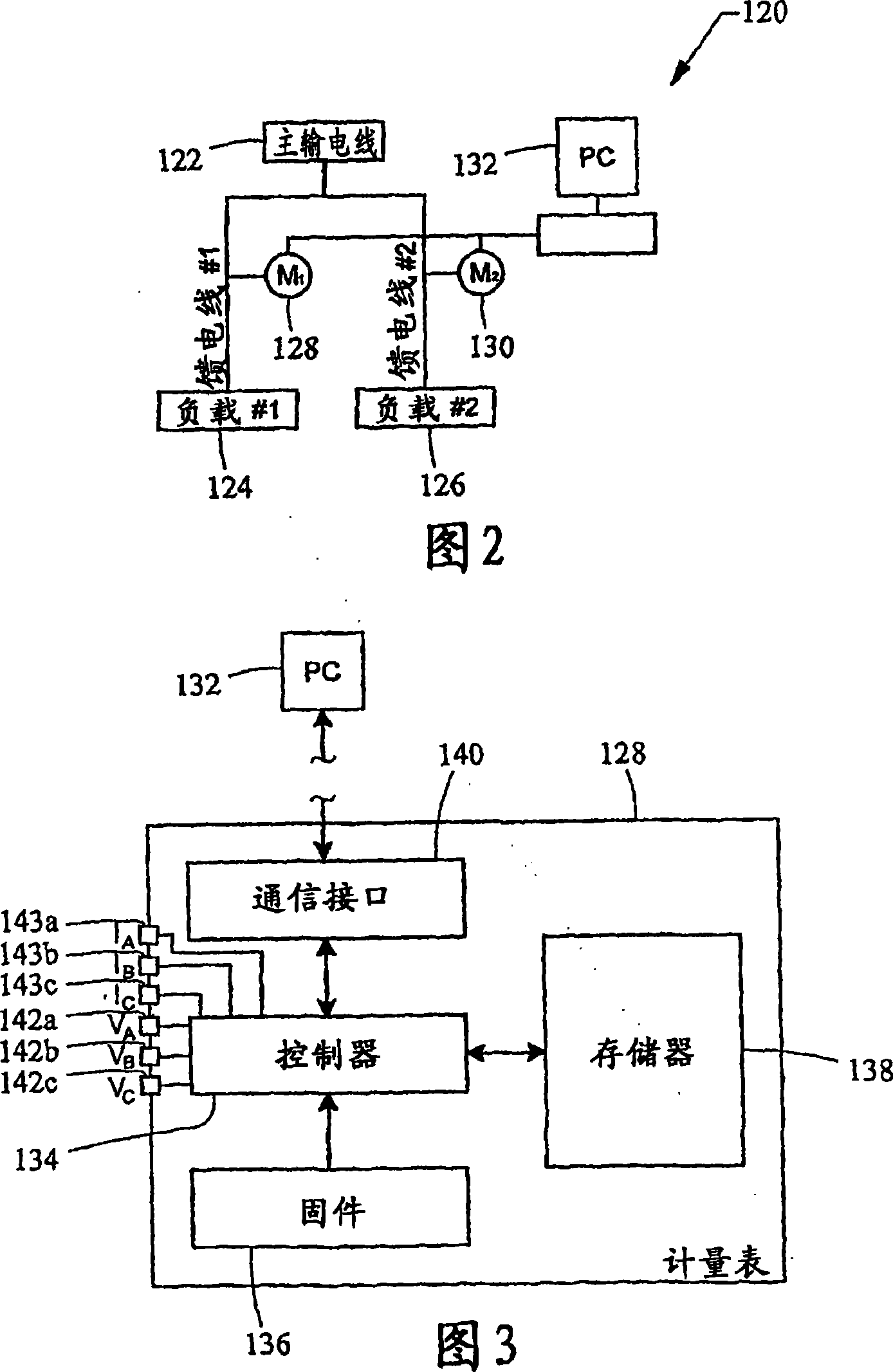
Data alignment in large scale electrical system applications
ActiveUS20120130656A1Improve approachReduce in quantityElectric devicesCircuit arrangementsPhase shiftedElectrical conductor
A method for automatically aligning measured power-related data in a power monitoring system to a common reference point. A conductor in a power delivery system is modeled according to an equivalent pi model of a transmission line that is characterized by model parameters. The conductor is monitored on both ends by a reference monitoring device and a second monitoring device. The voltage and current are measured in either the reference monitoring device or the second monitoring device and a phase shift offset between the voltages or currents at the two devices is calculated. The calculated phase shift offset corresponds to a temporal delay between events observed at the pair of devices, and calculating and storing the phase shift offset allows a power monitoring system controller to more accurately align data received from monitoring devices.
Owner:SCHNEIDER ELECTRIC USA INC
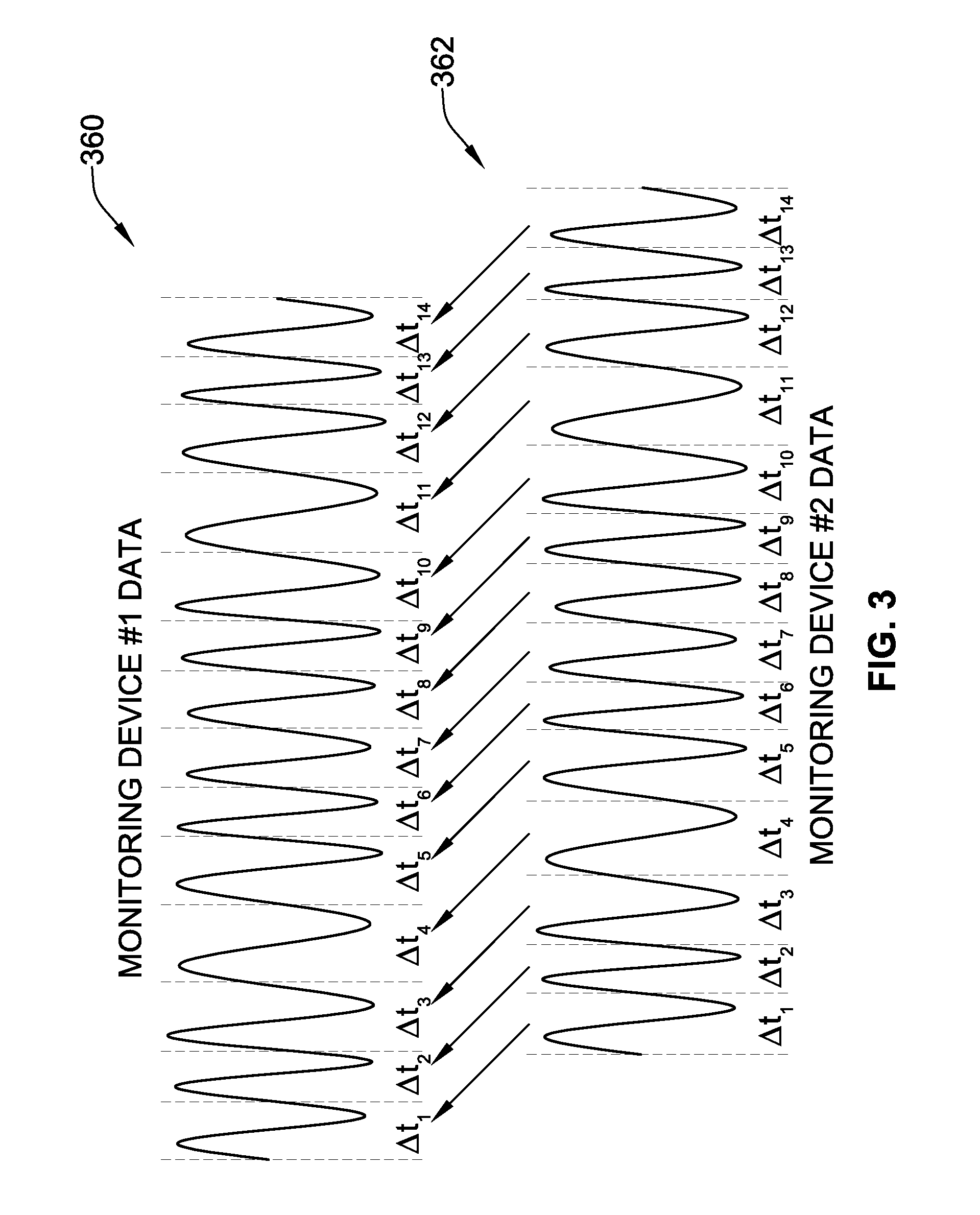
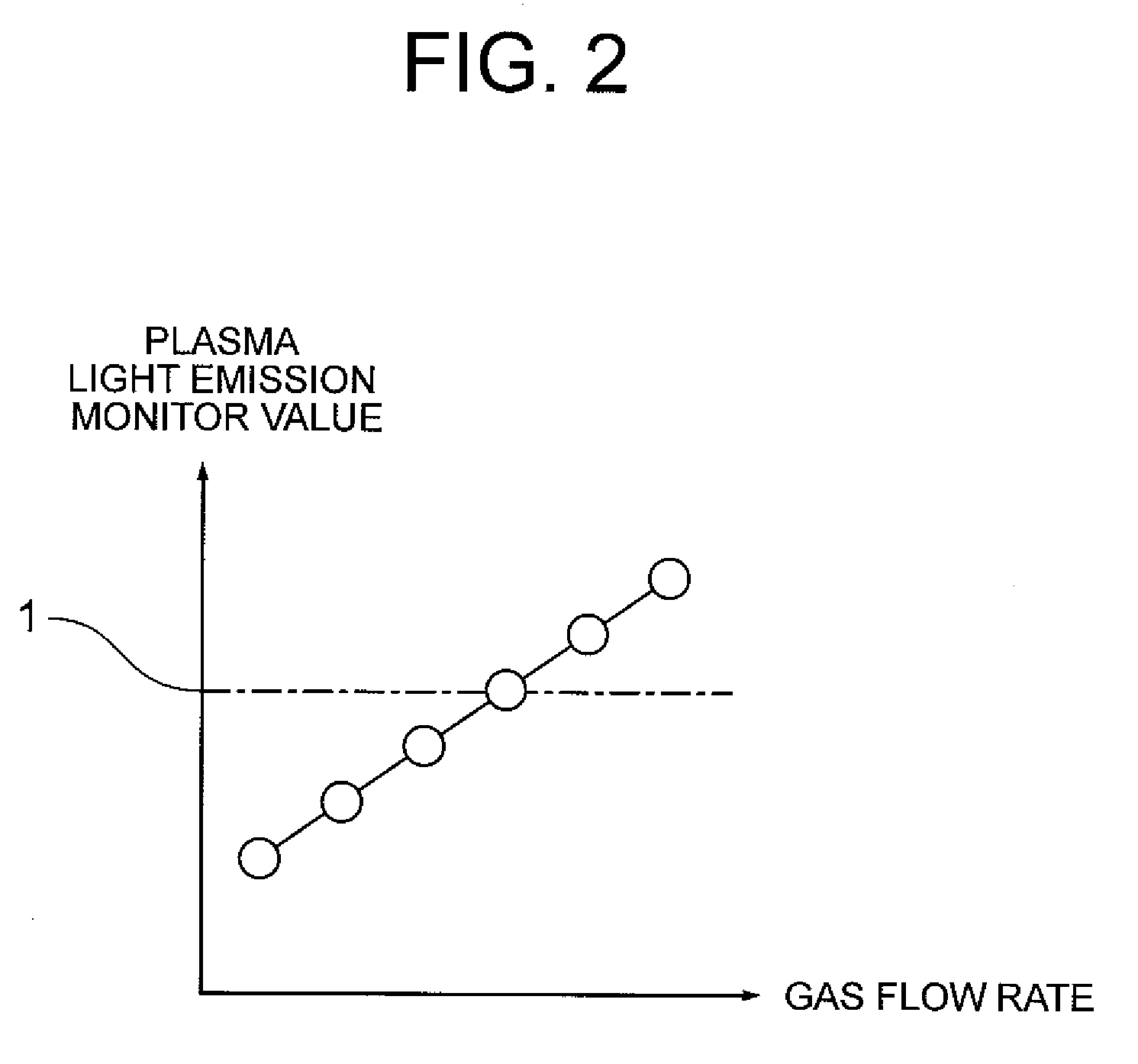
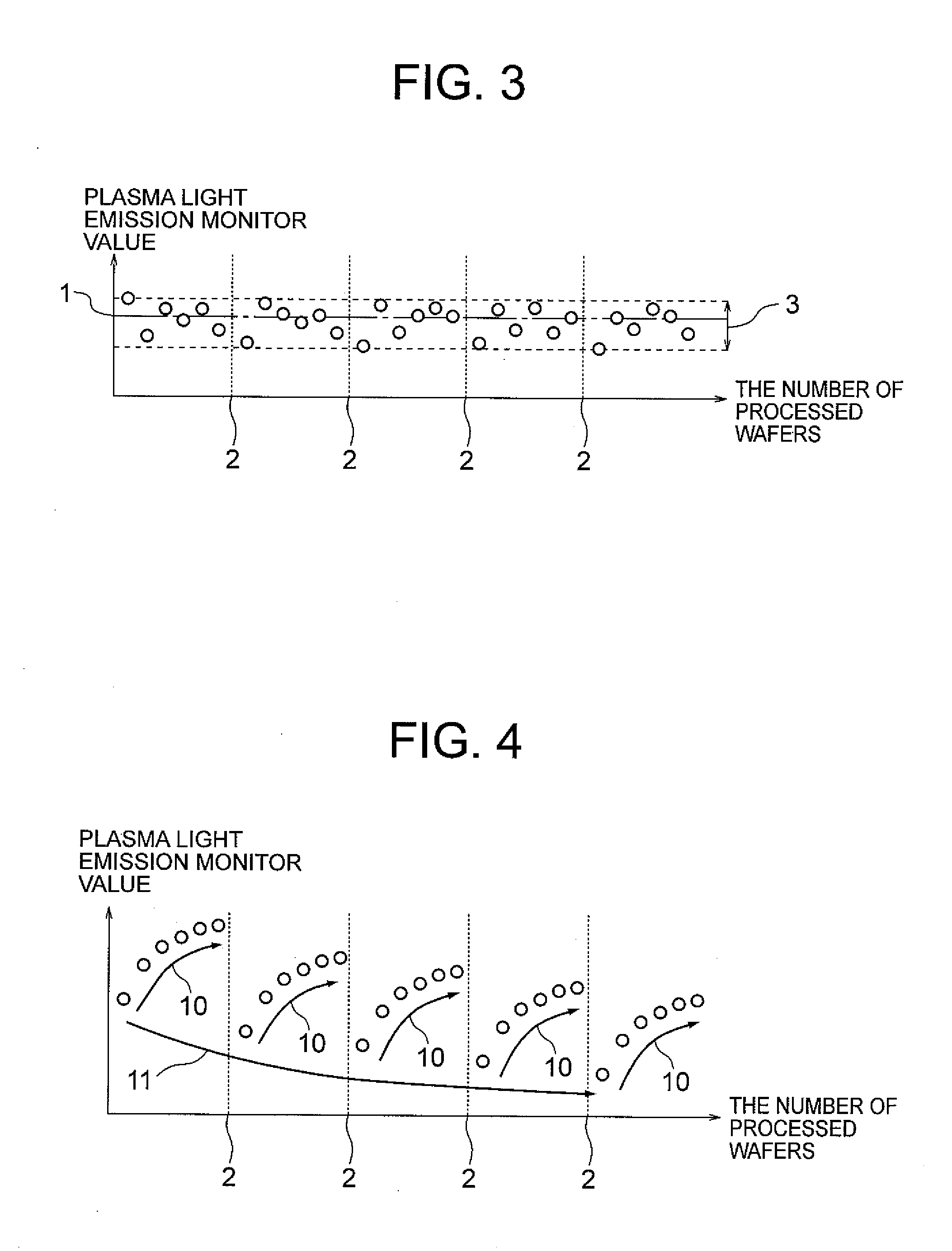
Plasma processing apparatus
ActiveUS20110083808A1The result is stableProgramme controlElectric discharge tubesProcess engineeringProcess conditions
A plasma processing apparatus including: a monitor device which monitors a process quantity generated at plasma processing; a monitor value estimation unit which has monitor quantity variation models for storing change of a monitor value of the process quantity in accordance with the number of processed specimens and which estimates a monitor value for a process of a next specimen by referring to the monitor quantity variation models; and a control quantity calculation unit which stores a relation between a control quantity for controlling the process quantity of the vacuum processing device and a monitor value and which calculates the control quantity based on a deviation of the estimated monitor value from a target value to thereby control the process quantity for the process of the next specimen. Thus, a process model indicating variation of the state of a process processing apparatus can be added to a control loop in such run-to-run control that process conditions are changed according to each wafer process, so that stable processed results can be obtained even when variation occurs in processes.
Owner:HITACHI HIGH-TECH CORP
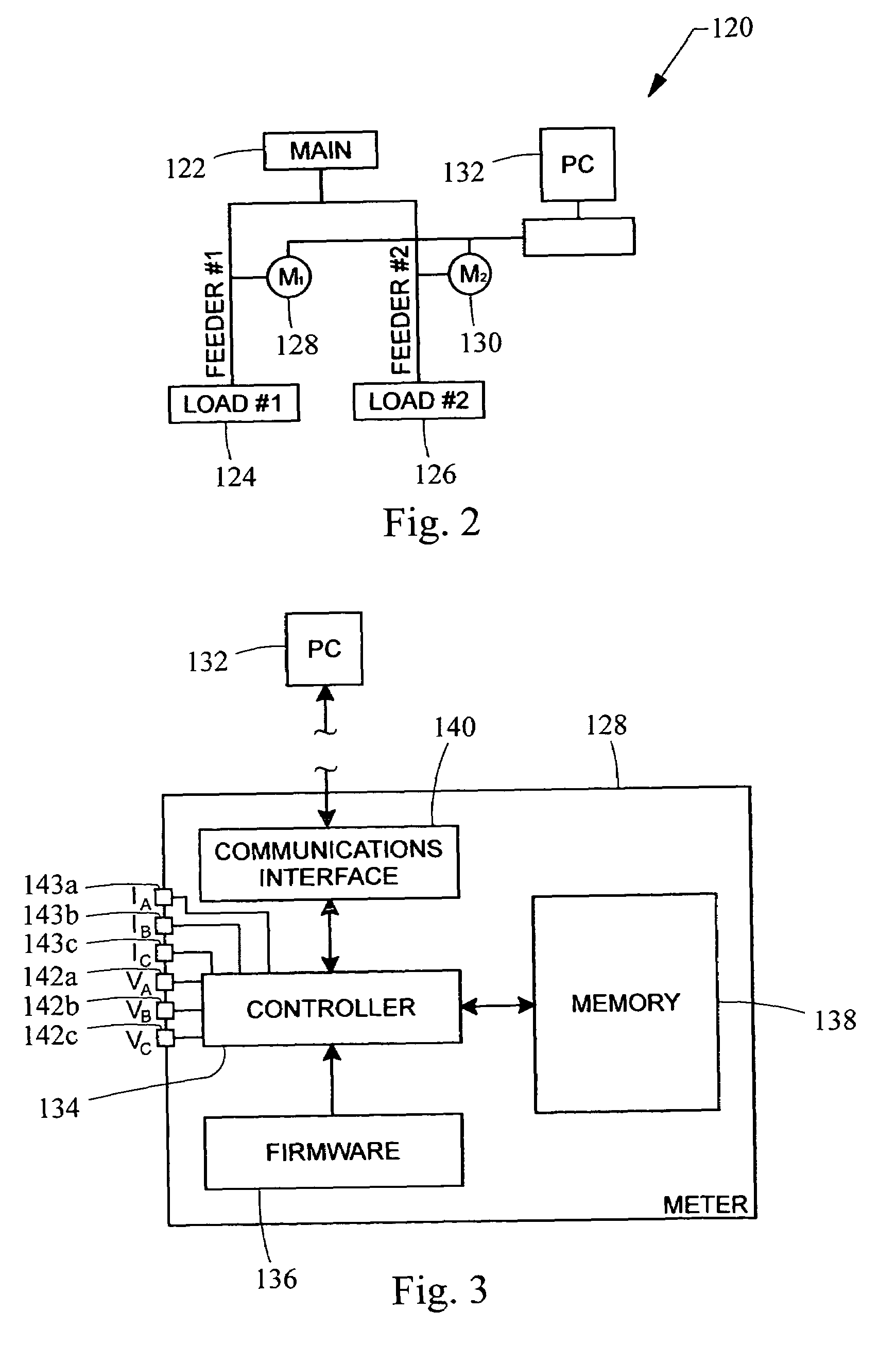
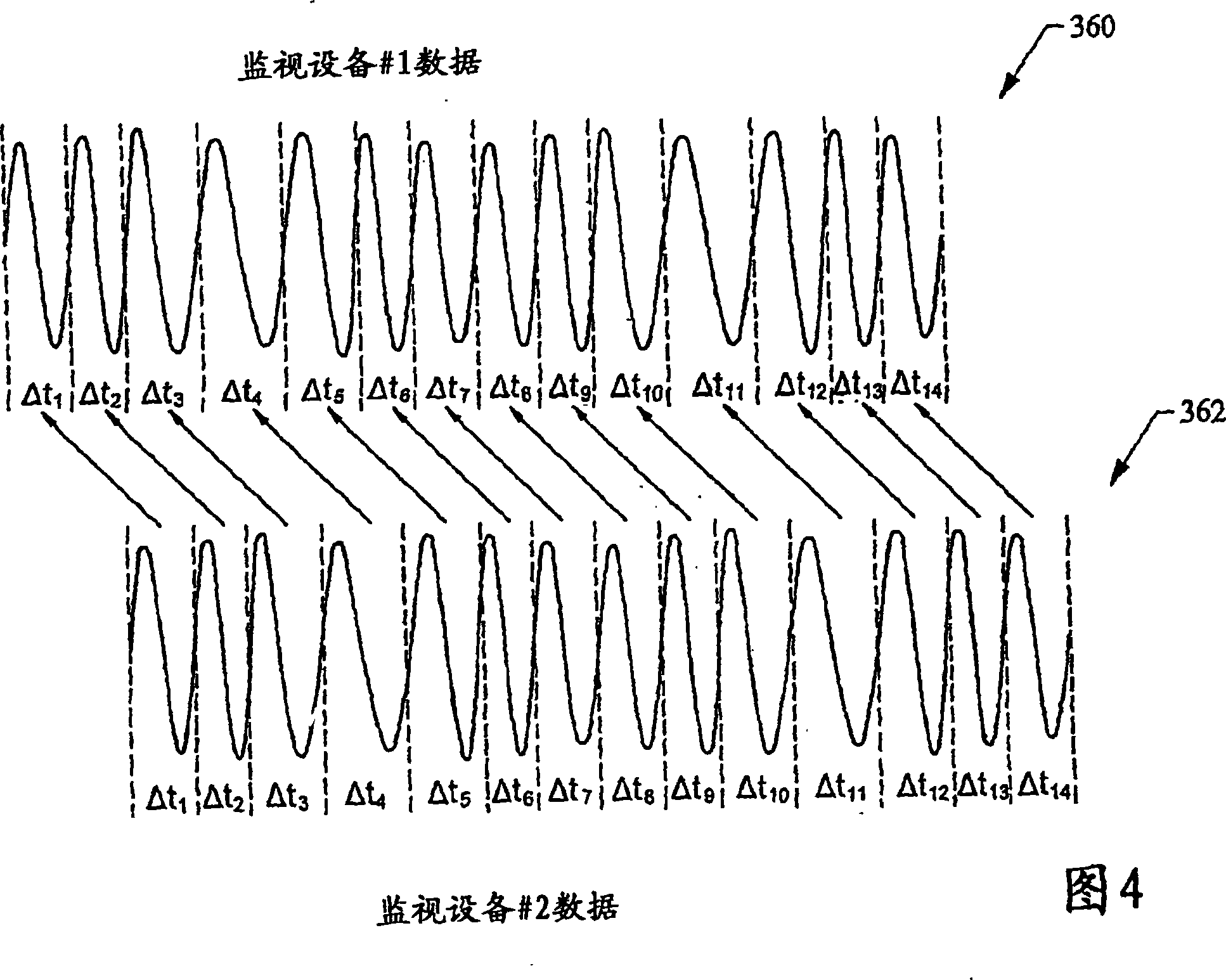
Automated precision alignment of data in a utility monitoring system
ActiveUS7684441B2Electric devicesNoise figure or signal-to-noise ratio measurementCorrelation coefficientMonitoring system
A data alignment algorithm that automatically aligns data from multiple monitoring devices to the same zero-crossings at the same point in time. Cycle-by-cycle frequency data is received from each monitoring device and a cross-correlation algorithm is performed to determine a correlation coefficient between a reference monitoring device and another monitoring device. The data of the other monitoring device is shifted by one cycle and another correlation coefficient is calculated by the cross-correlation algorithm. The data of the two monitoring devices is aligned at the point at which the maximum correlation coefficient is calculated or the point at which the correlation coefficient exceeds a threshold value. The clocks of the monitoring devices can also be synchronized at the same point of alignment.
Owner:SQUARE D CO
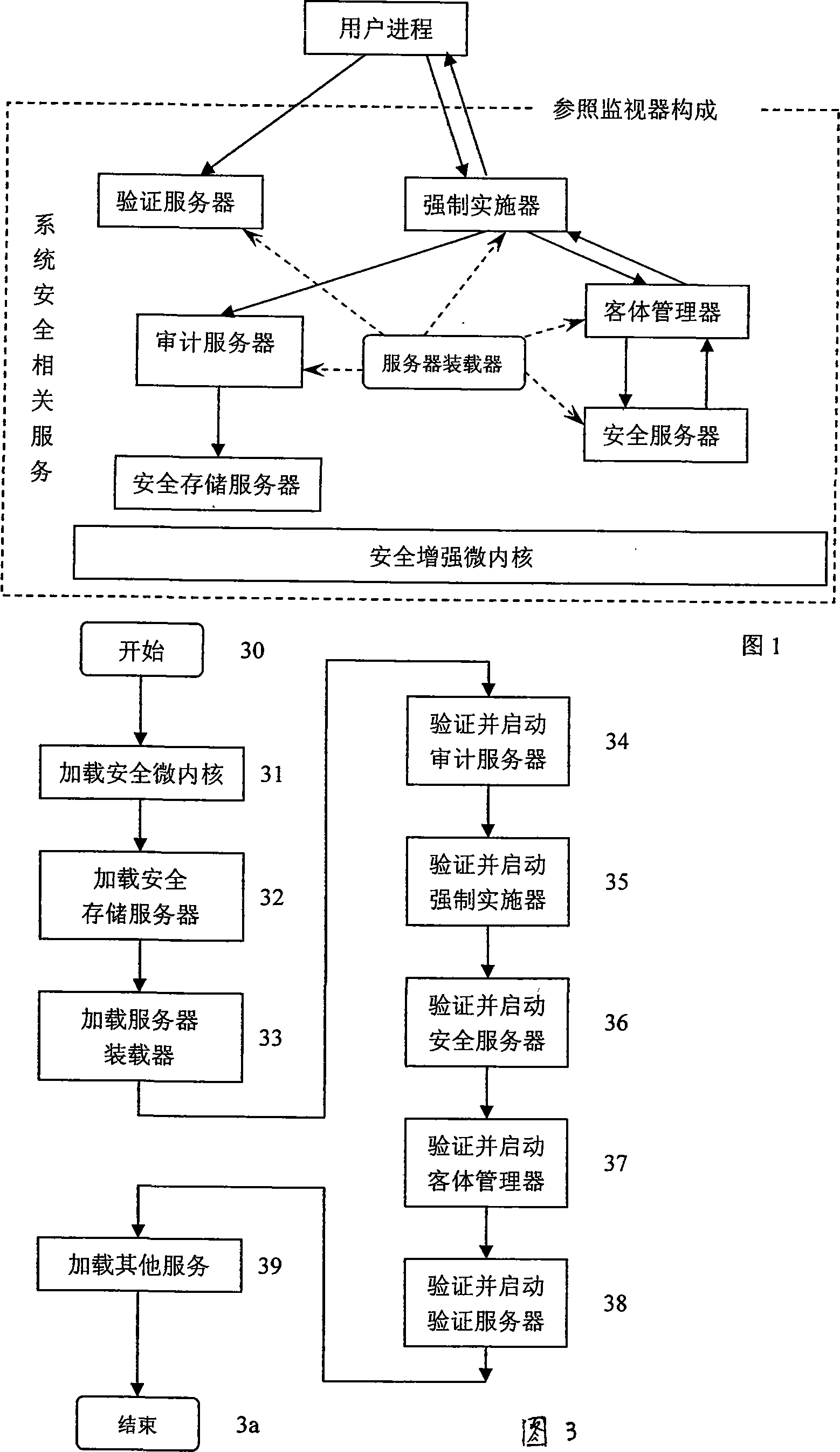
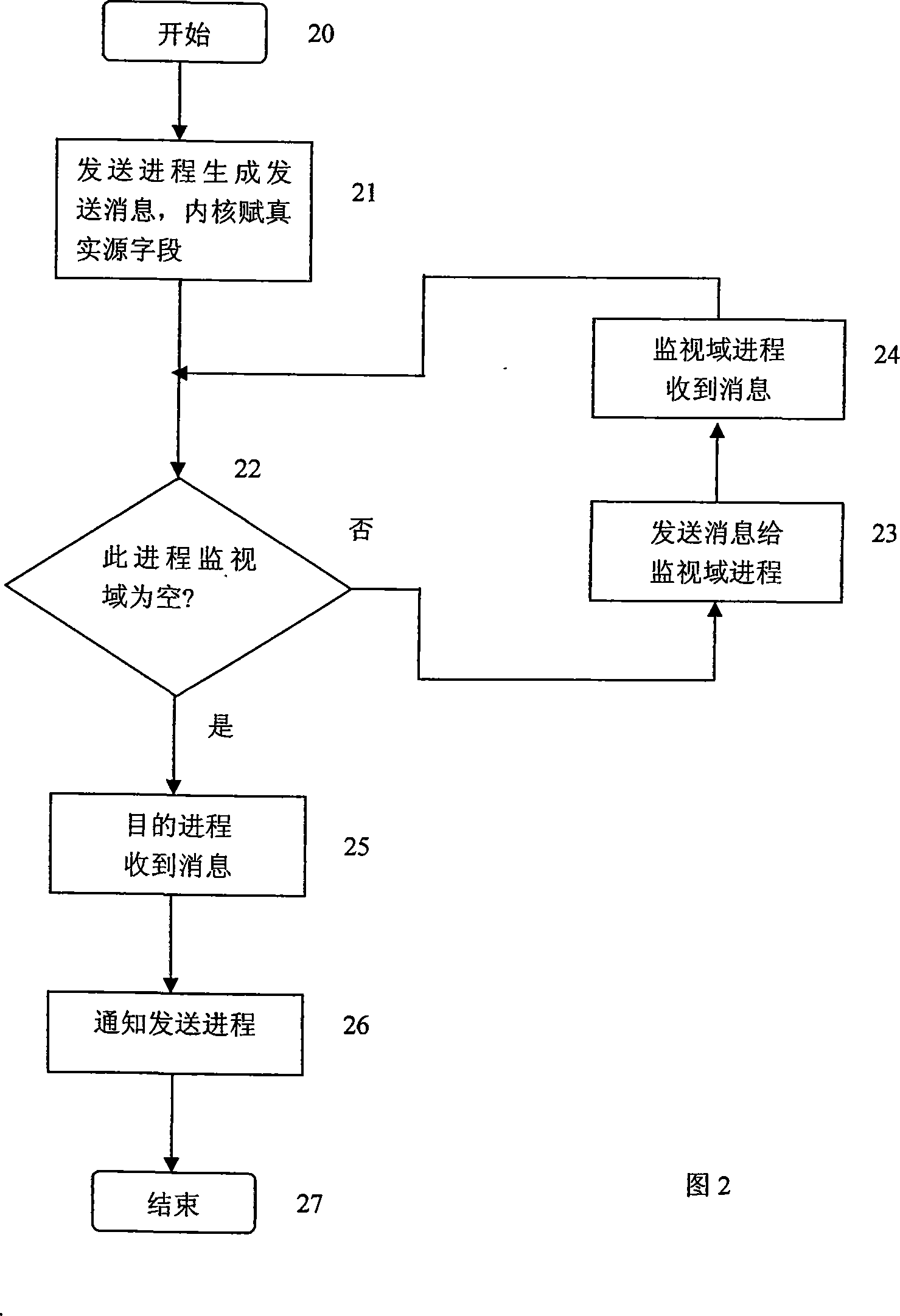
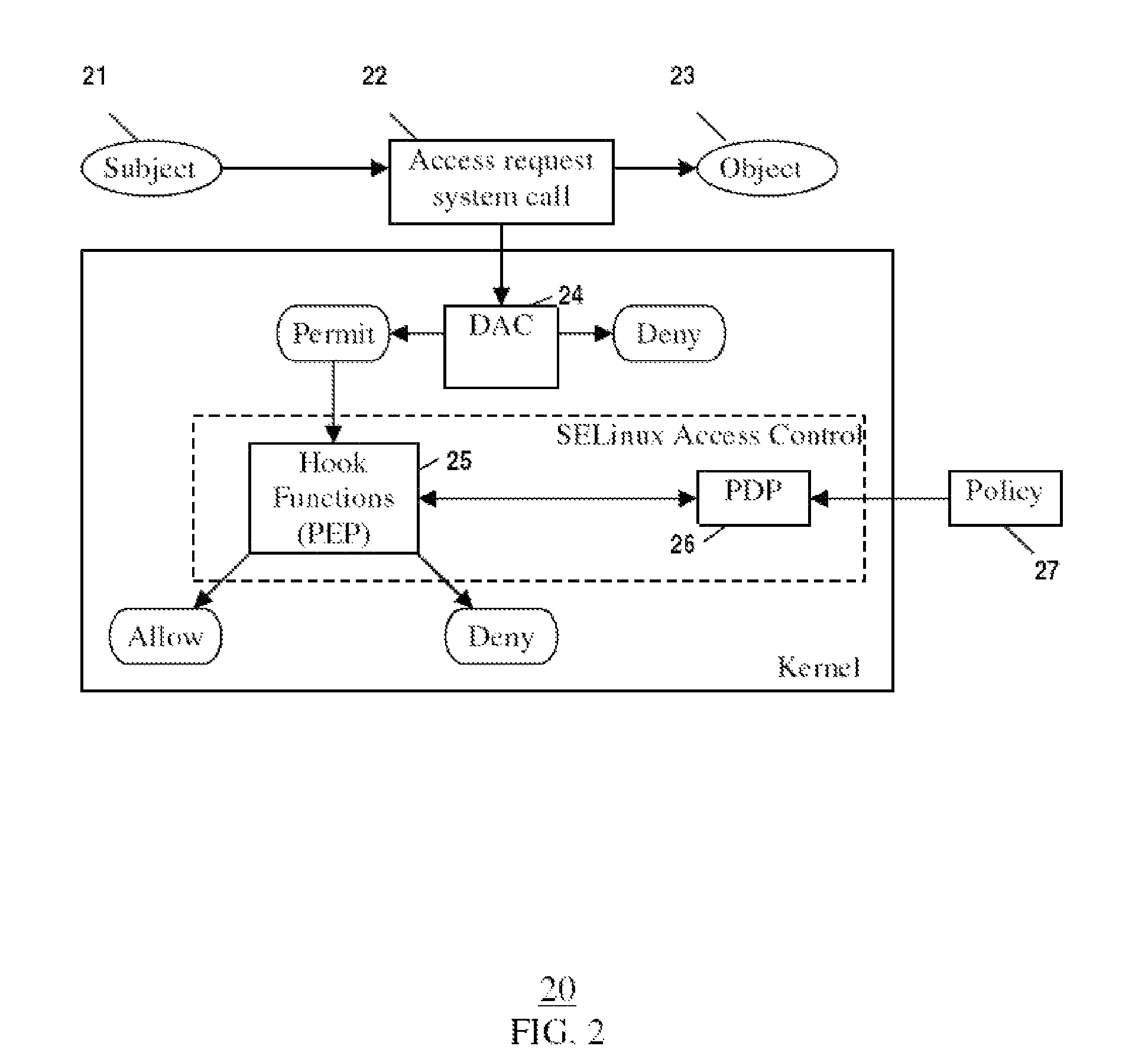
Reference monitor implementing method of high safety grade operating system
InactiveCN101174293AAvoid bypassMeet safety requirementsDigital data protectionOperational systemInter-process communication
The invention relates a method which can realize reference monitors of high level secure operating system, mainly comprising: (1) the structure of a reference monitor; (2) the realization of the controlling of microkernel IPC communications; (3) the initiated process according to the security services needed by the reference monitor. The structure of the reference monitor comprises that the structure reference monitor bases on a microkernel with enhanced security while all service procedures and user applications are out of the microkernel; the inter-process communication (IPC) is the only way for applications to acquire service and access resources and for the interactions between servers. Making use of the structure of the reference monitor to limit the communications between users and acquire system service, the invention enforces of the security verification strategy of access control to avoid authentification bypass, having guaranteed the validity of the utilization and protection of the system resources by the reference monitor and thus improved the safety and service ability of the system. The invention satisfies the security requirements of high-level operating system.
Owner:NANJING UNIV
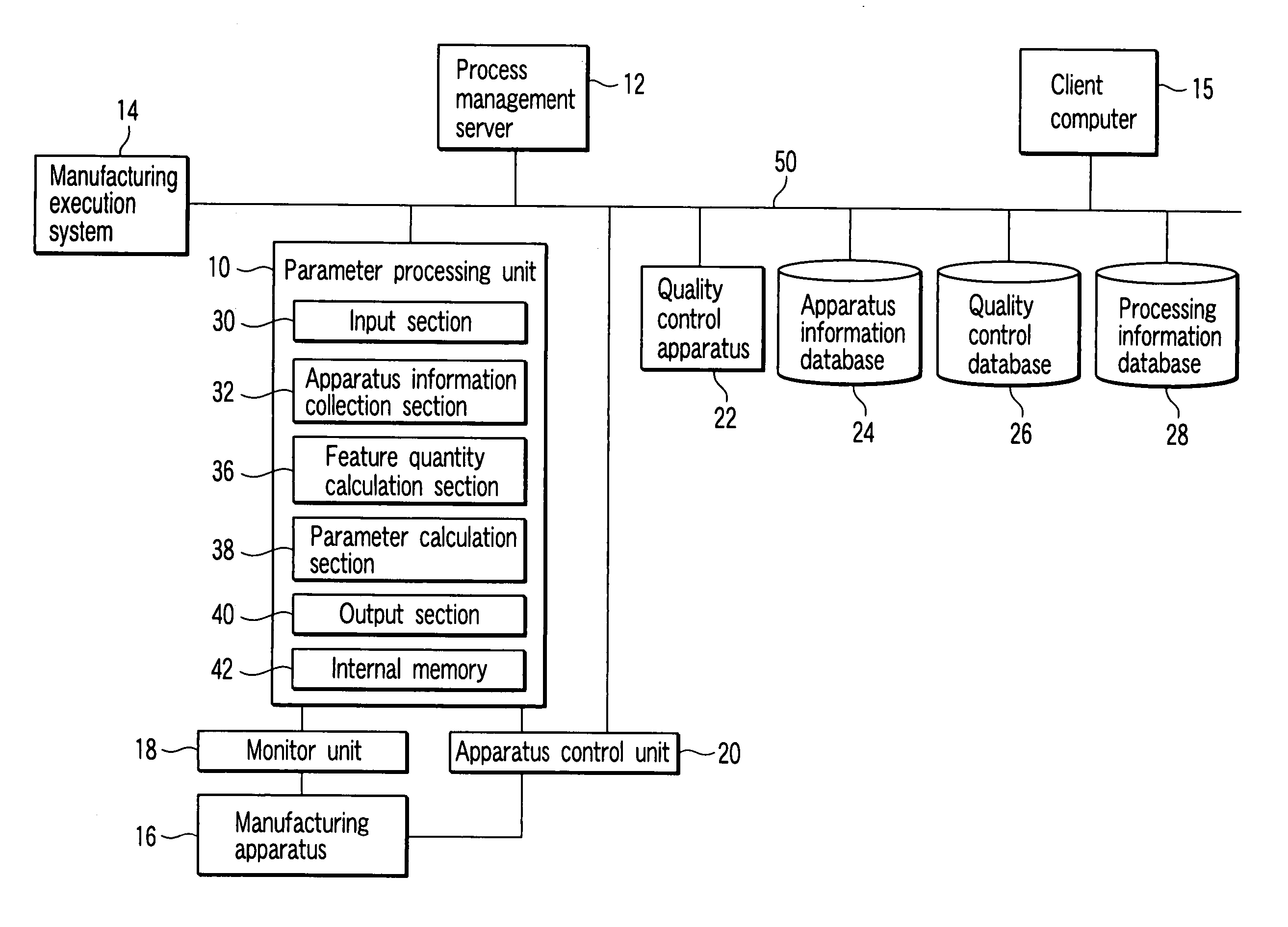
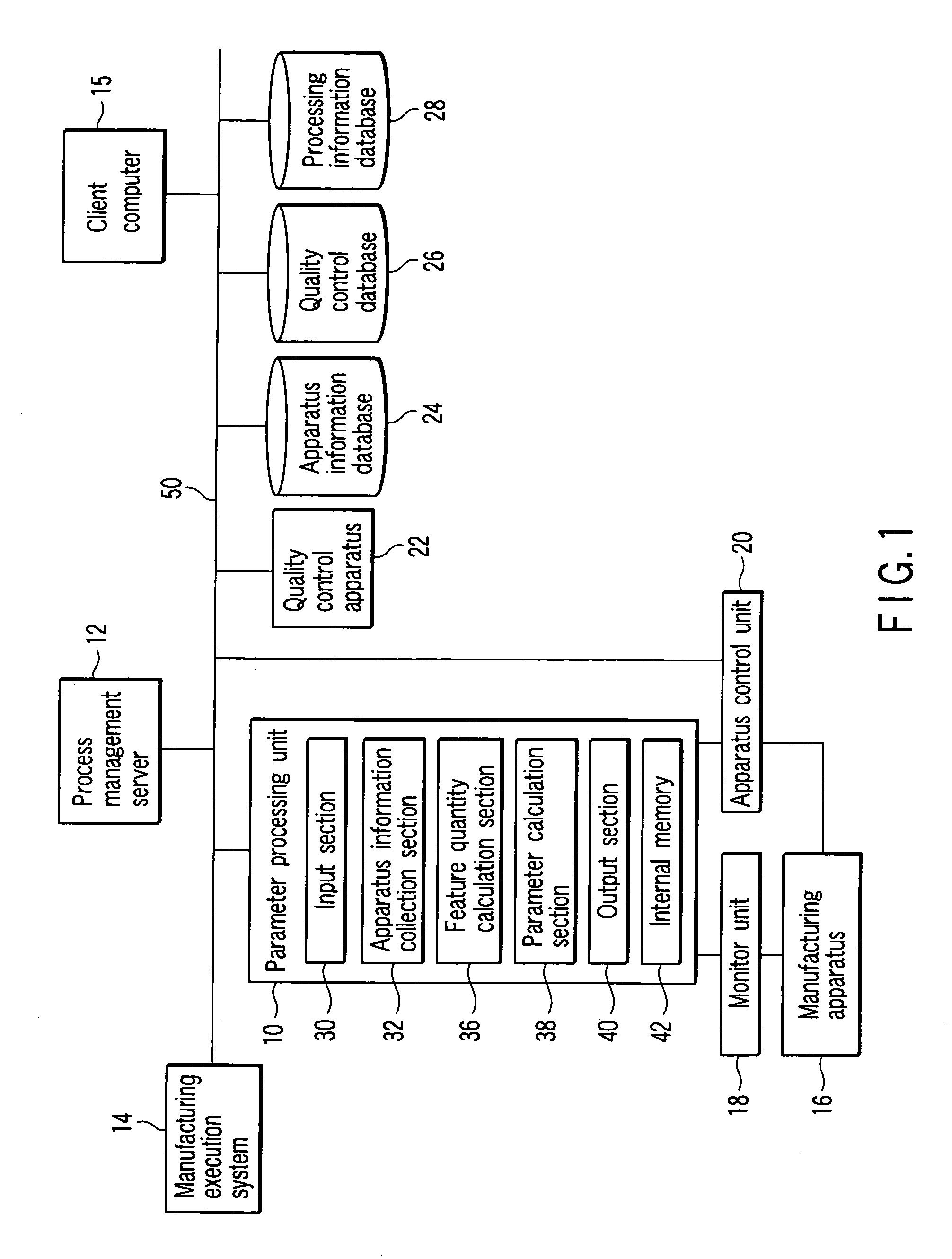
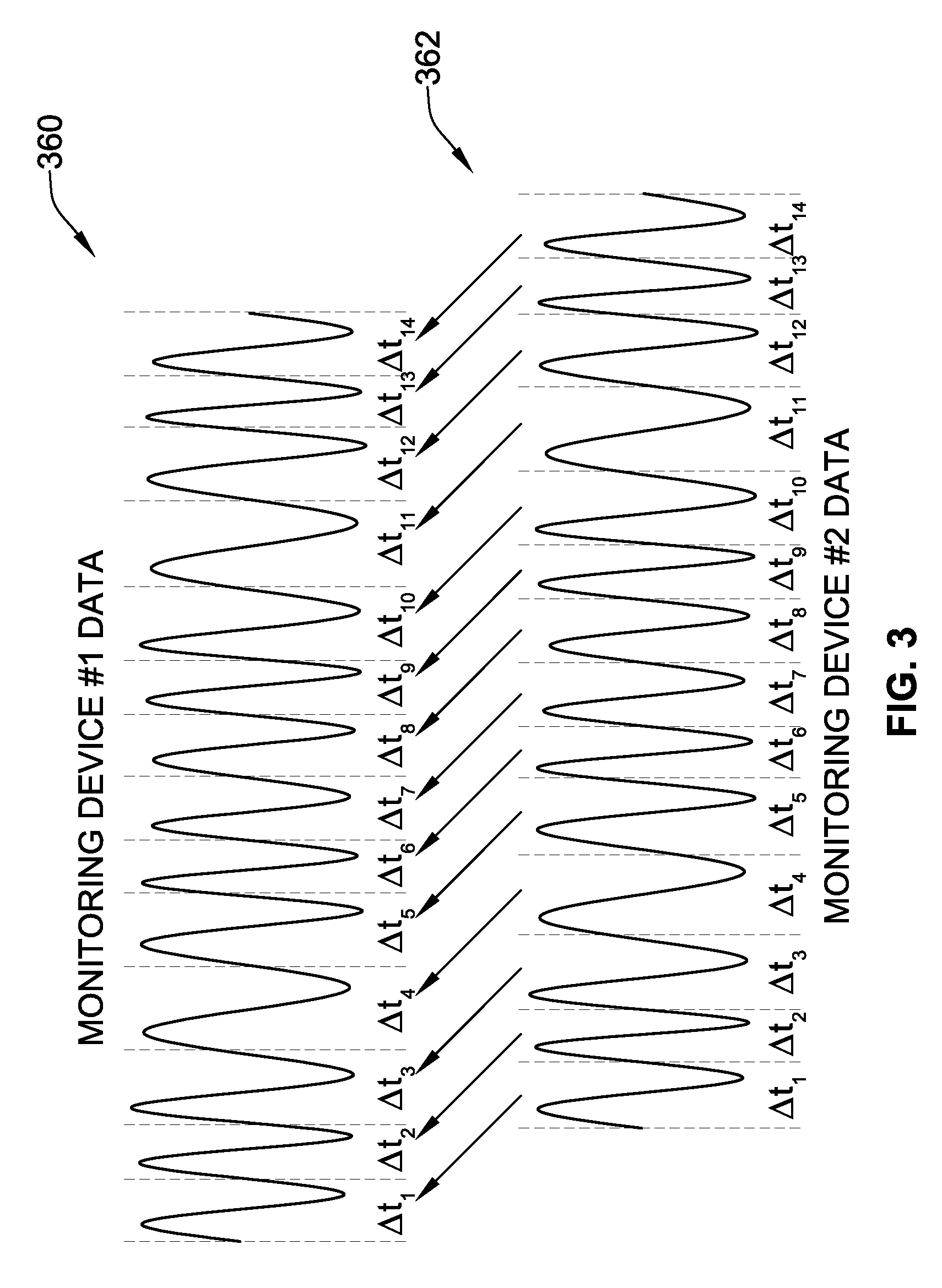
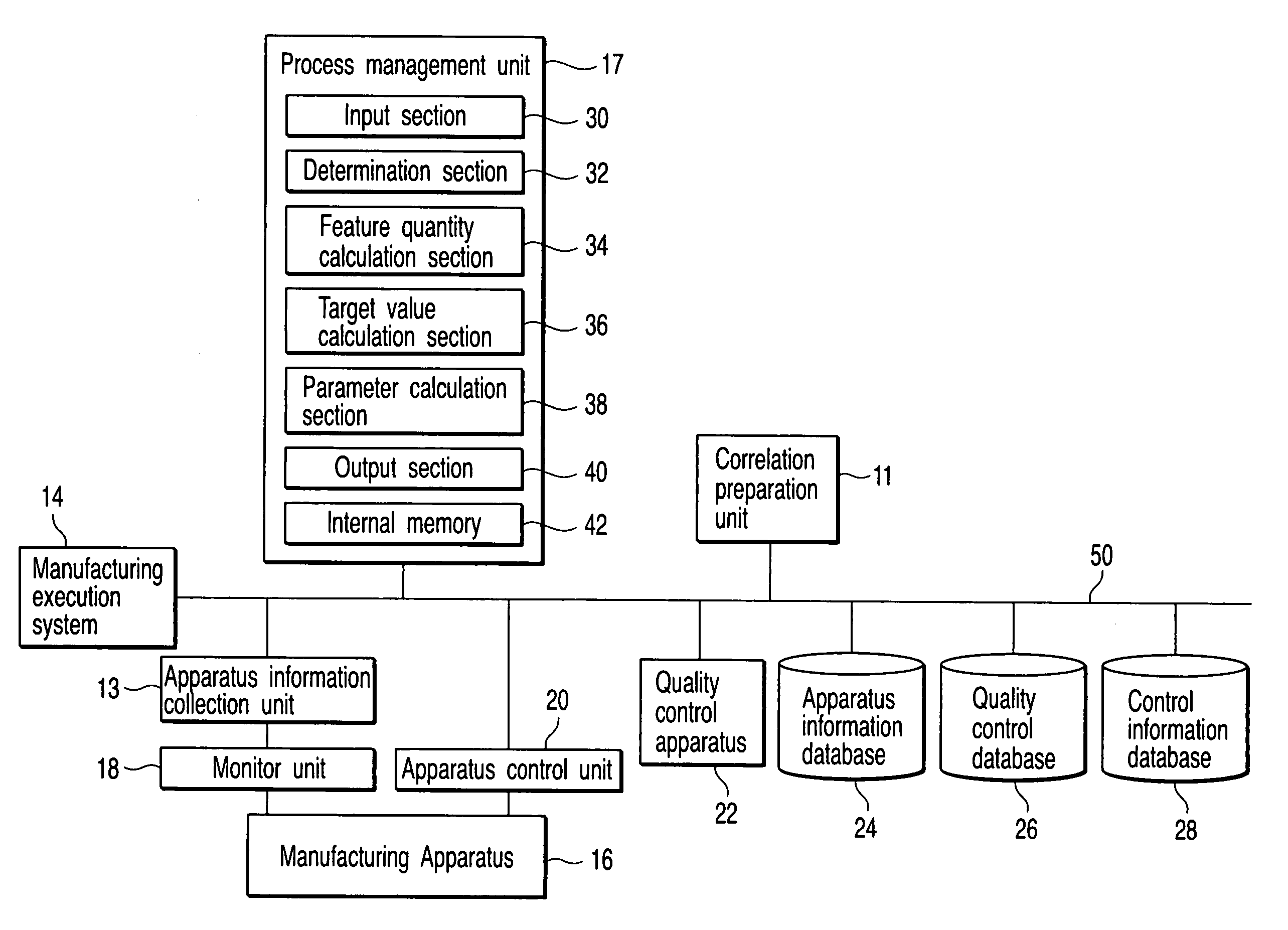
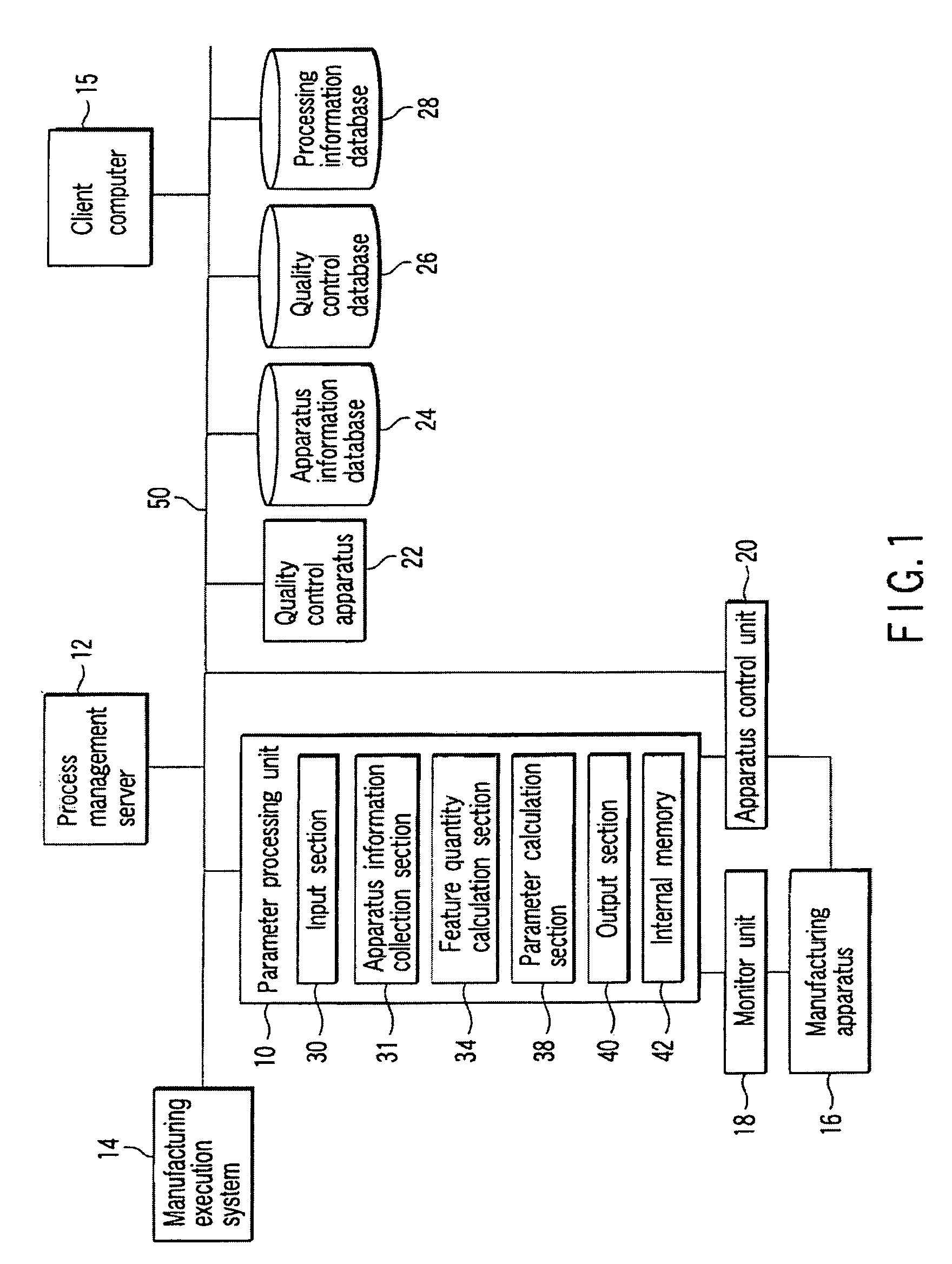
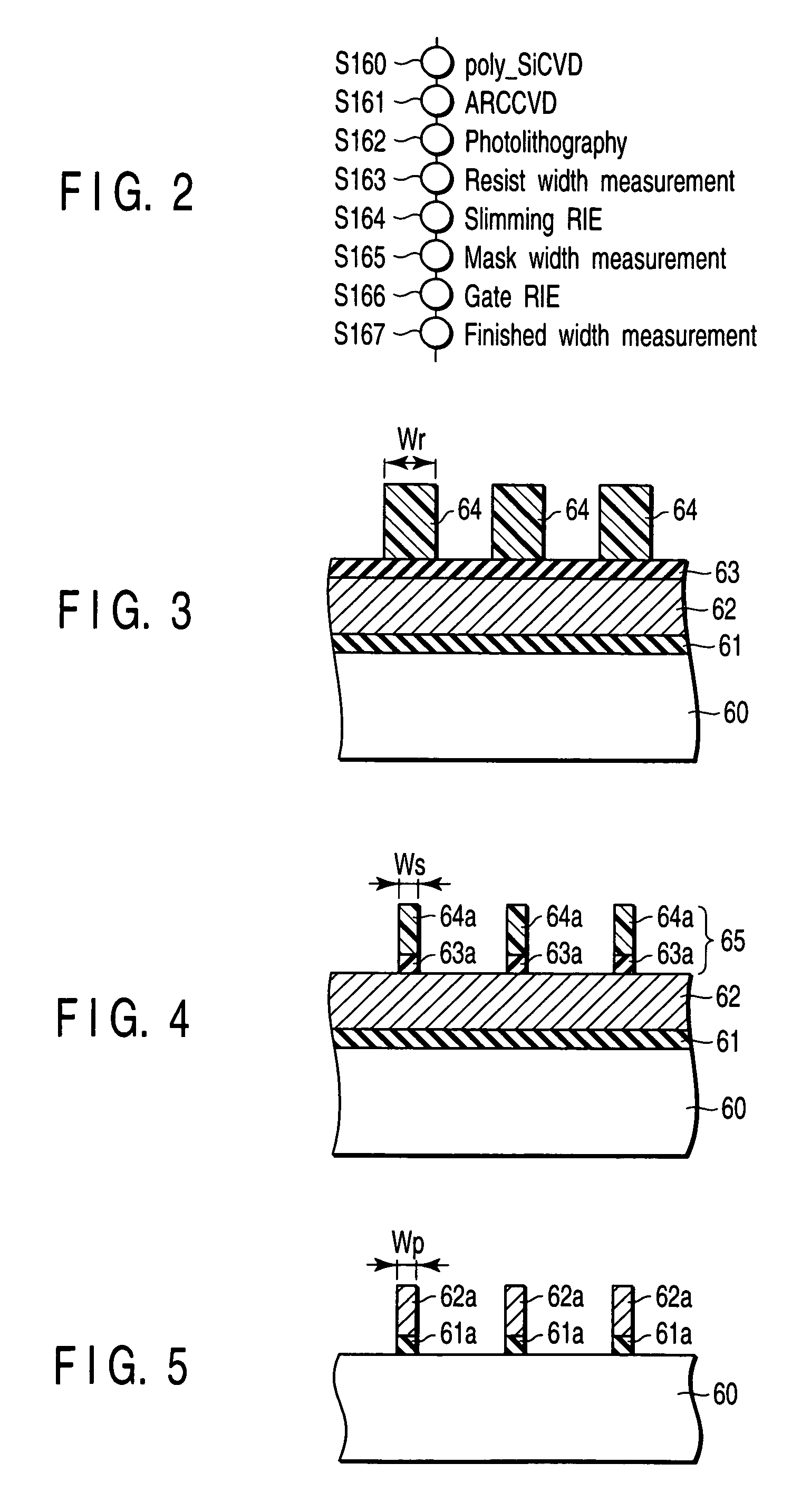
Process control system, process control method, and method of manufacturing electronic apparatus
ActiveUS20060287754A1Programme controlTotal factory controlControl systemManufacturing execution system
A process control system includes a client computer which prepares a correlation between a reference monitored value of apparatus information and a feature quantity, a manufacturing execution system which prepares a processing recipe describing, as a first setting value in an actual manufacturing process, a value of the control parameter, an apparatus information collection section which collects an objective monitored value of the apparatus information in operation of the actual manufacturing process with the first setting value, a feature quantity calculation section which calculates a value of a feature quantity corresponding to the objective monitored value based on the correlation, a parameter calculation section which calculates a second setting value in the actual manufacturing process on the basis of the value of the feature quantity, and an apparatus control unit which changes the processing recipe with the second setting value being as a setting value of the second step.
Owner:KIOXIA CORP
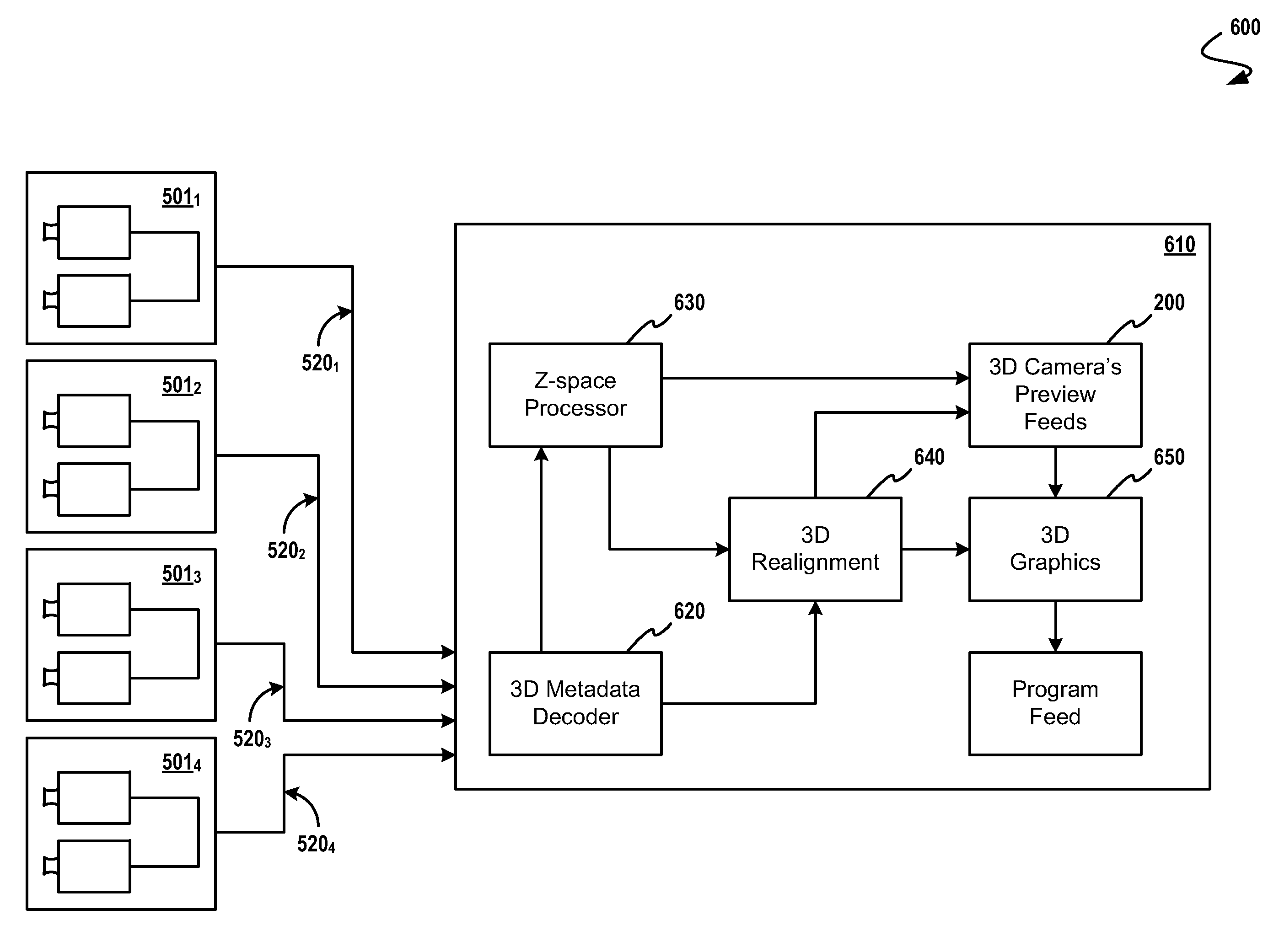
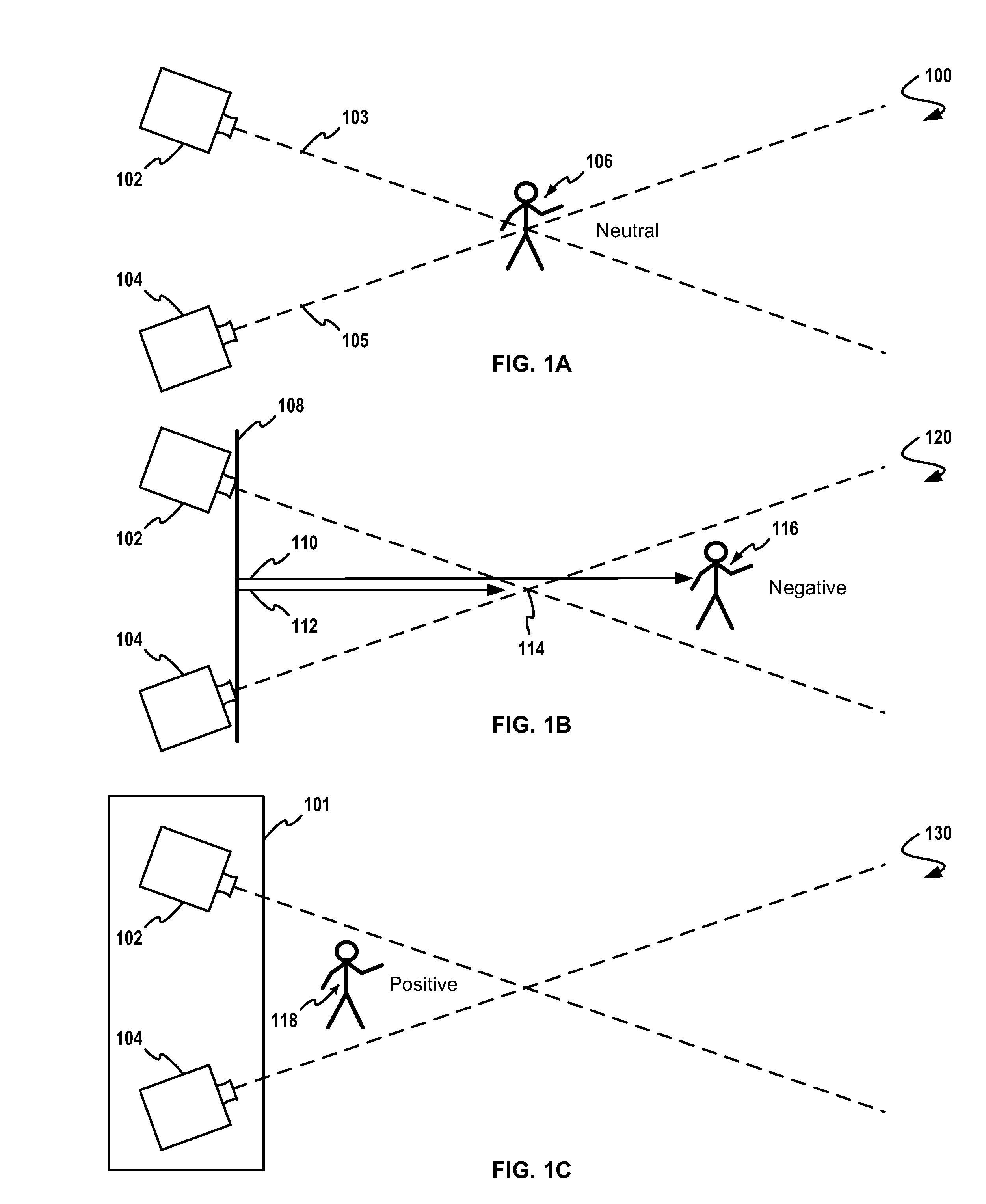
Flagging of Z-Space for a Multi-Camera 3D Event
InactiveUS20100245545A1Electronic editing digitised analogue information signalsCharacter and pattern recognitionMulti cameraComputer graphics (images)
A method for selecting one from among a plurality of three-dimensional (3D) cameras comprising calculating, in a computer, a plurality of z-space cut zone flag values corresponding to the plurality of 3D cameras, then comparing the z-space cut zone flag corresponding to a reference monitor image to a plurality of candidate z-space cut zone flags corresponding to candidate monitor images. In response to the results of the calculations and comparisons, a safe / not-safe indication is prepared for displaying on any of a variety of visual displays, at least one aspect of the safe / not-safe indication, the at least one aspect determined in response to said comparing. The method uses 3D camera image data, 3D camera positional data and 3D camera stage data (e.g. interaxial data, convergence data, lens data) for encoding the 3D camera data into an encoded data frame which is then transmitted to a processor for producing a visual safe / not-safe indication.
Owner:VISUAL 3D IMPRESSIONS
External reference monitor
ActiveUS8909930B2Digital data processing detailsUser identity/authority verificationTrusted hardwareExternal reference
Owner:LIONRA TECH LTD
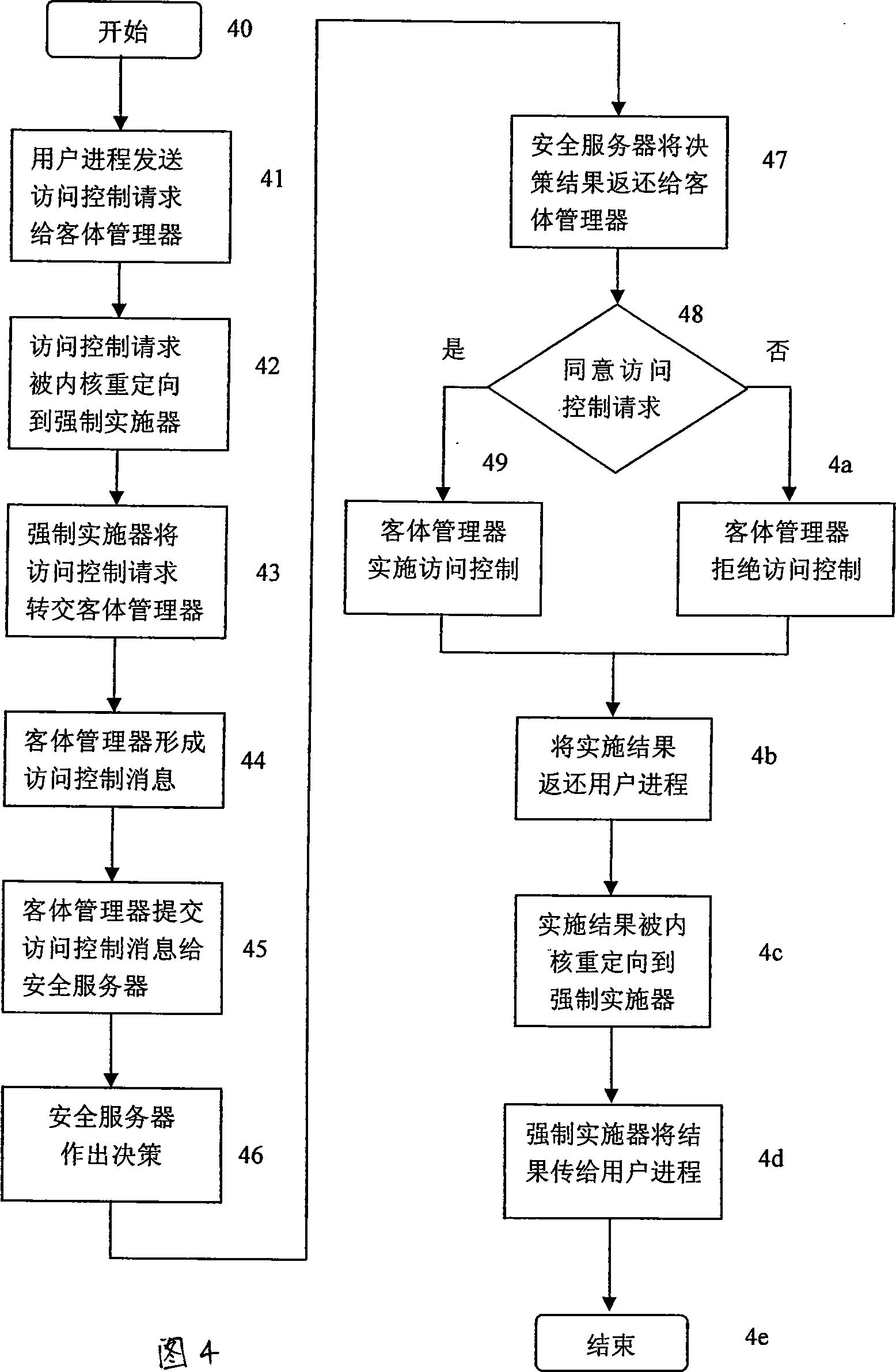
On-the-fly contents-based access control system
ActiveUS20070061896A1Digital data processing detailsUnauthorized memory use protectionOperational systemControl system
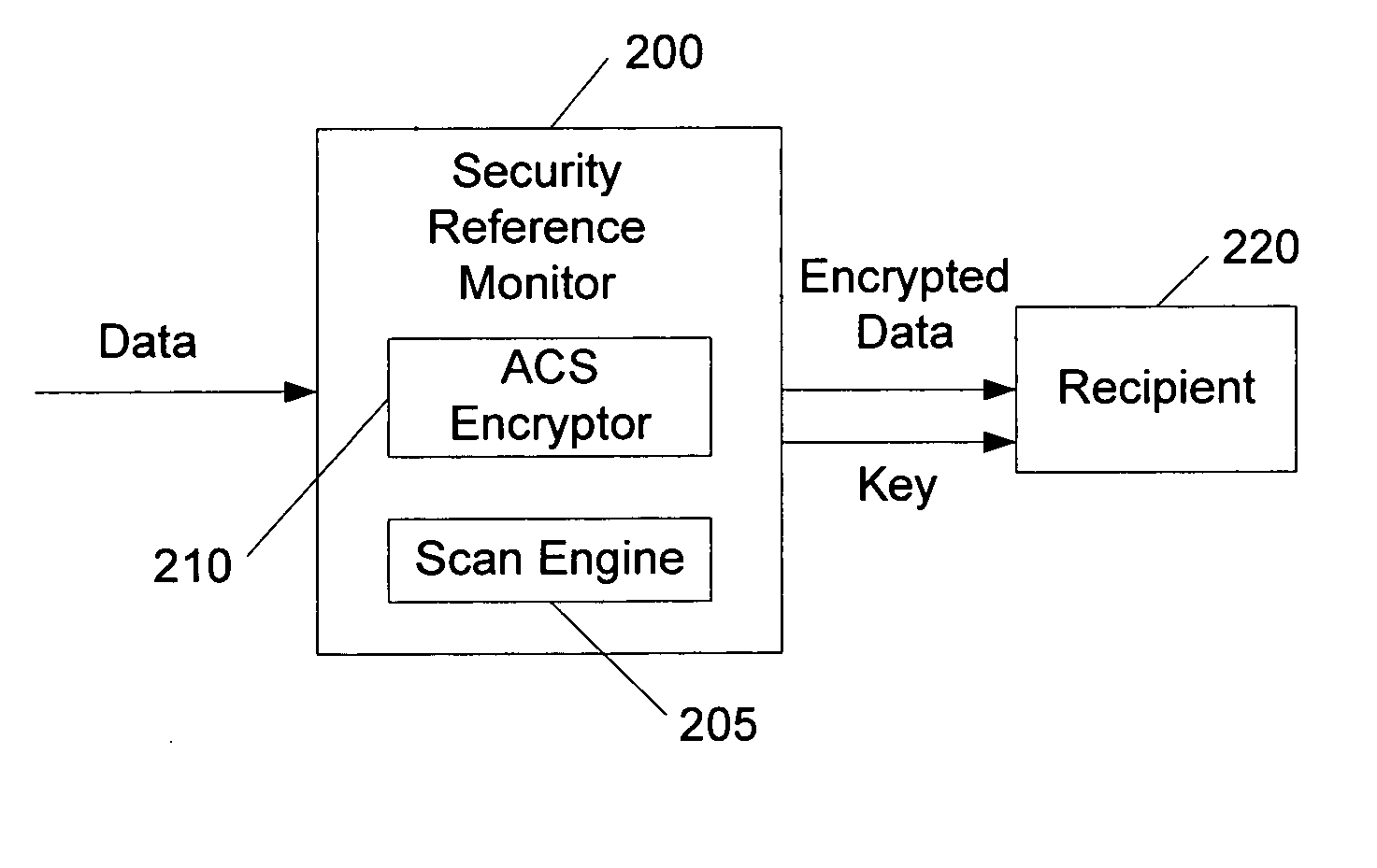
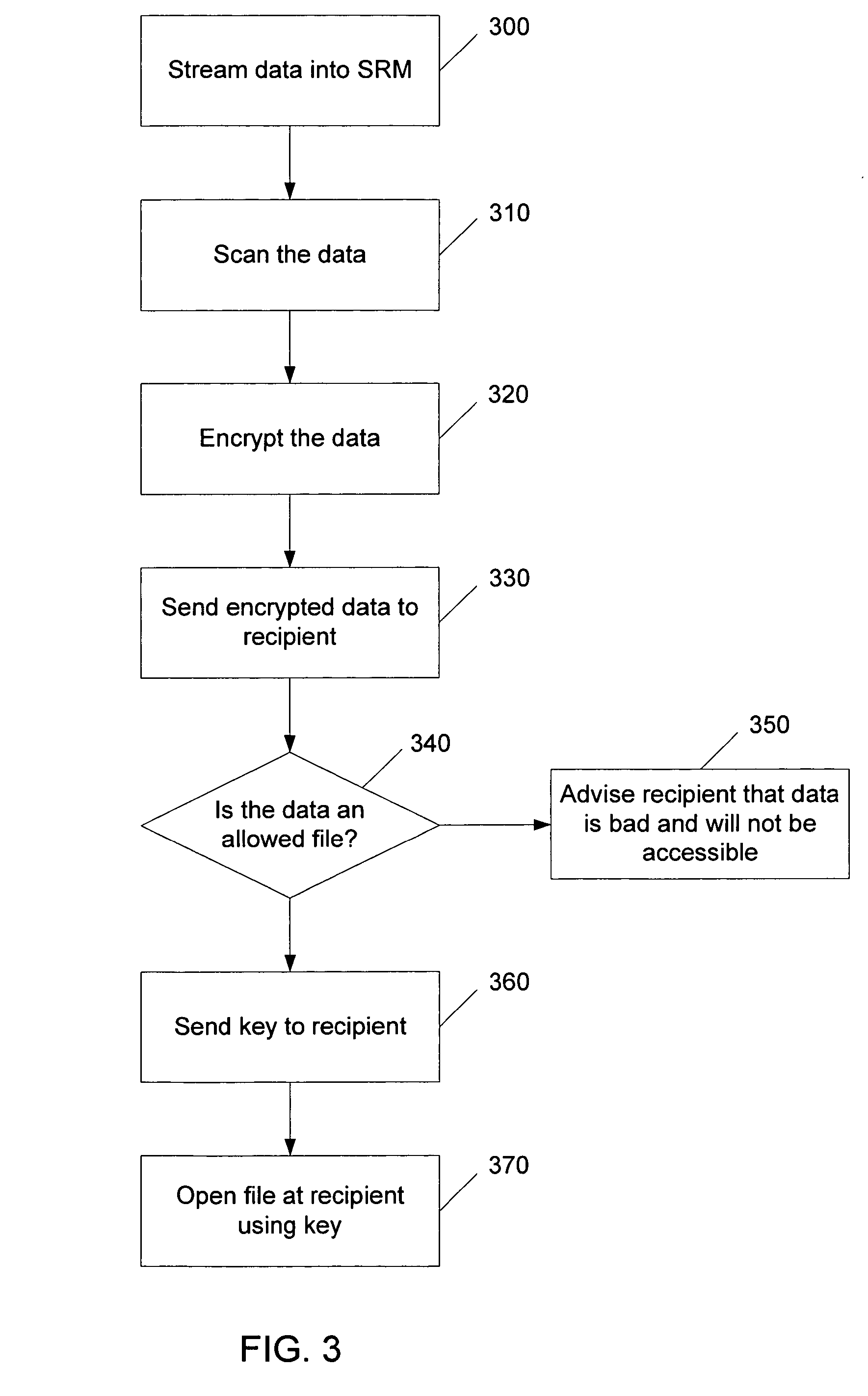
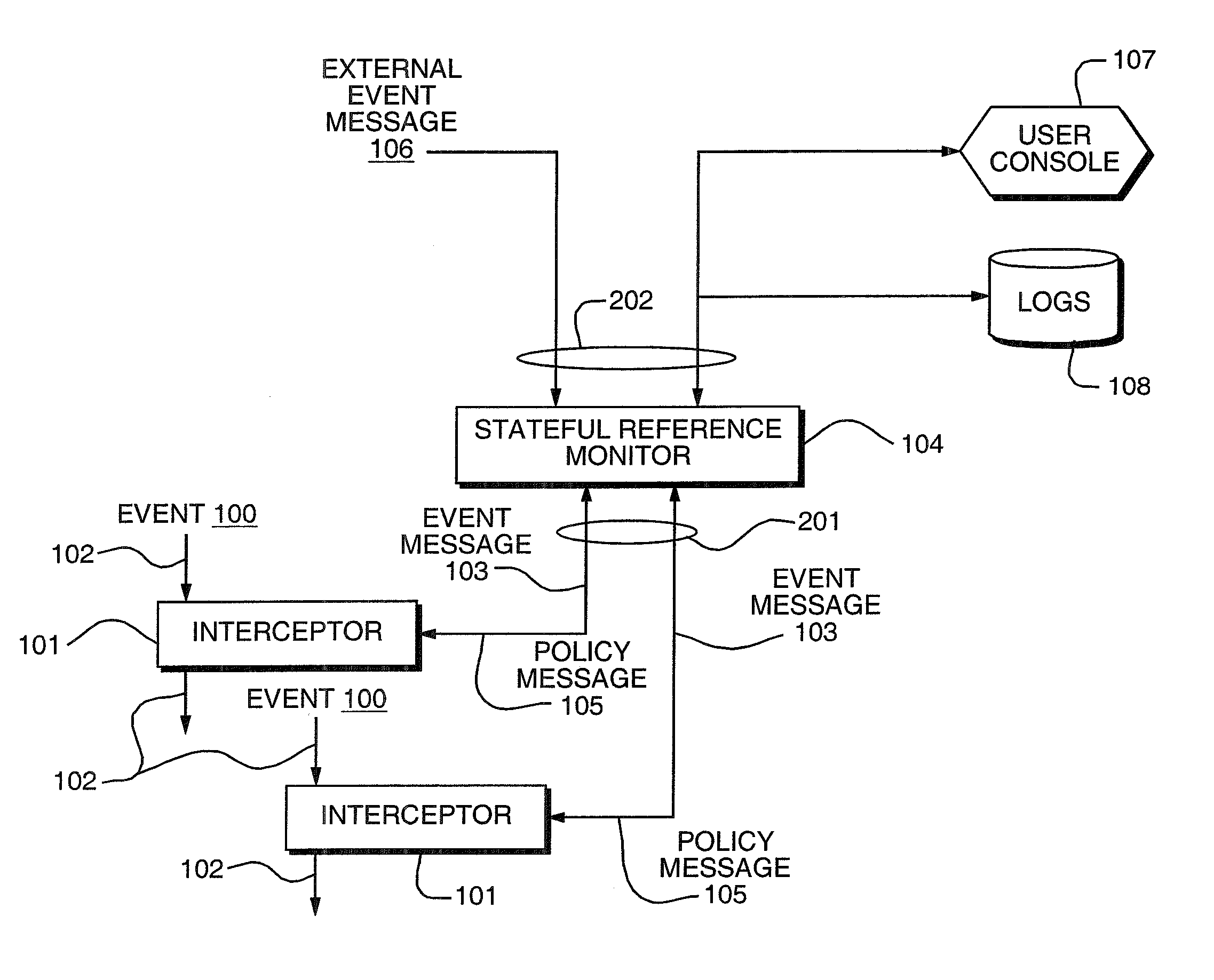
An access control system applies contents-based policies to data that is being transferred. This transfer can be between different computers, different operating systems on a single computer, different applications within on the same operating system, or different parts of the same operating system, for example. Data is scanned at a scan engine associated with a security reference monitor (SRM) as the data is being transmitted, on-the-fly. The data is forwarded directly to the recipient, so the data is not stored at the SRM. The data is encrypted at the SRM as it comes by, and the key is revealed to the recipient if it is subsequently determined that the transfer is allowed.
Owner:MICROSOFT TECH LICENSING LLC
Stateful reference monitor
ActiveUS20080022359A1Specific access rightsDigital data processing detailsOperational systemDecision taking
A Stateful Reference Monitor can be loaded into an existing commercial operating system, and then can regulate access to many different types of resources. The reference monitor maintains an updateable storage area whose contents can be used to affect access decisions, and access decisions can be based on arbitrary properties of the request.
Owner:CISCO TECH INC
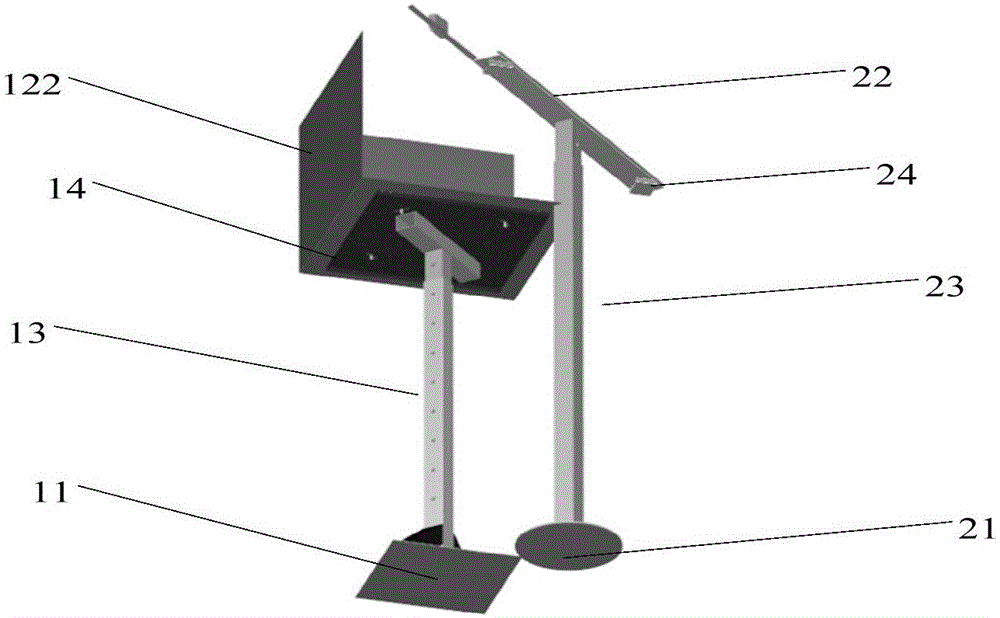
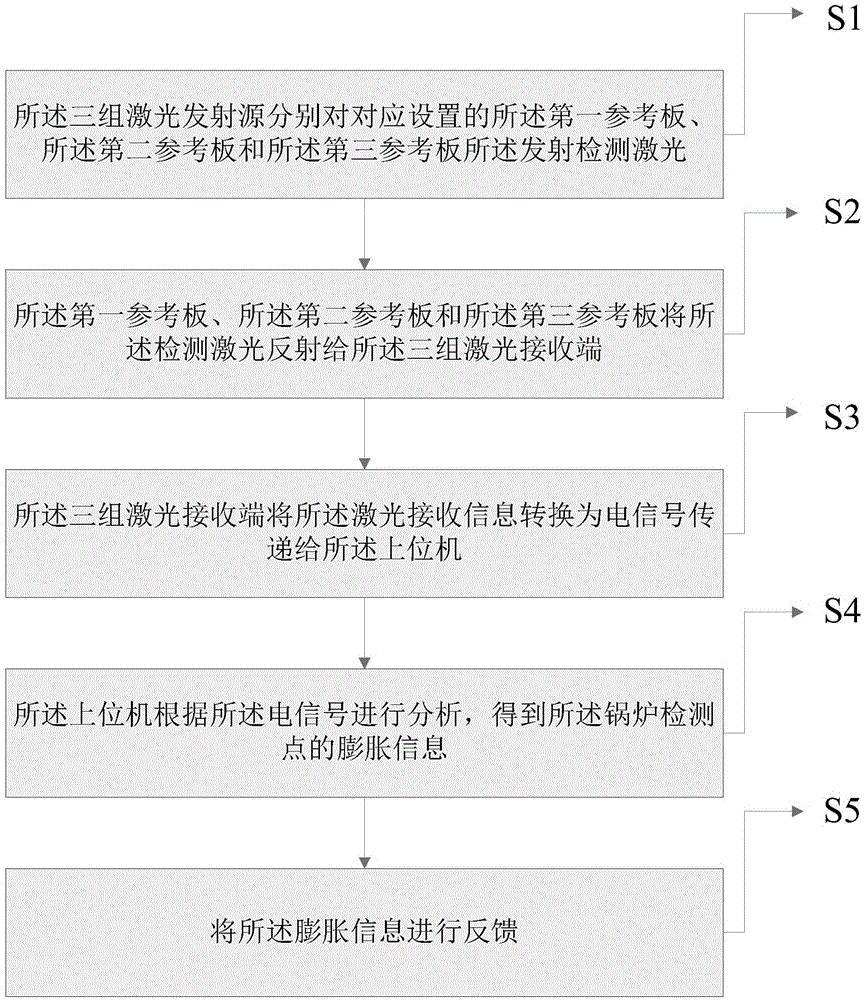
Boiler expansion monitoring system and monitoring method
The invention discloses a boiler expansion monitoring system and a monitoring method. The boiler expansion monitoring system comprises a reference monitoring device, a laser emission device, a laser receiving device, and an upper computer. The reference monitoring device comprises three reference plates, which are vertical to each other, and are used to form a three-dimensional coordinate. The laser emission device comprises three laser emission sources, which are used to emit monitoring laser. The laser receiving device comprises three laser receiving ends, which are used to receive the reflected laser. The upper computer is used for analysis and feedback according to laser receiving information transmitted by three laser receiving ends. The boiler expansion monitoring system and the monitoring method are advantageous in that a boiler monitoring point is fixedly connected with a reference monitoring device, and the laser monitoring is carried out by the three reference plates, which are disposed on the reference monitoring device, are vertical to each other, and are used to form the three-dimensional coordinate; after the boiler monitoring point is expanded, the three reference plates on the reference monitoring device is deviated, and then the reflected laser received by the laser receiving device is deviated, and by calculating deviation amounts, the expansion information of the boiler monitoring point is acquired.
Owner:BEIJING YUANSHEN ENERGY SAVING TECH
Processing method for video monitor image
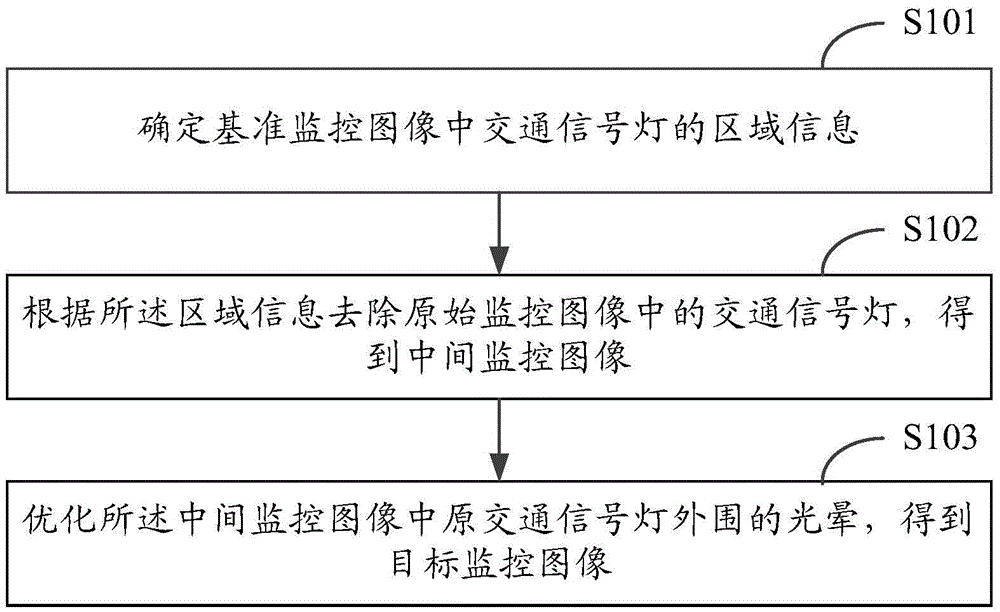
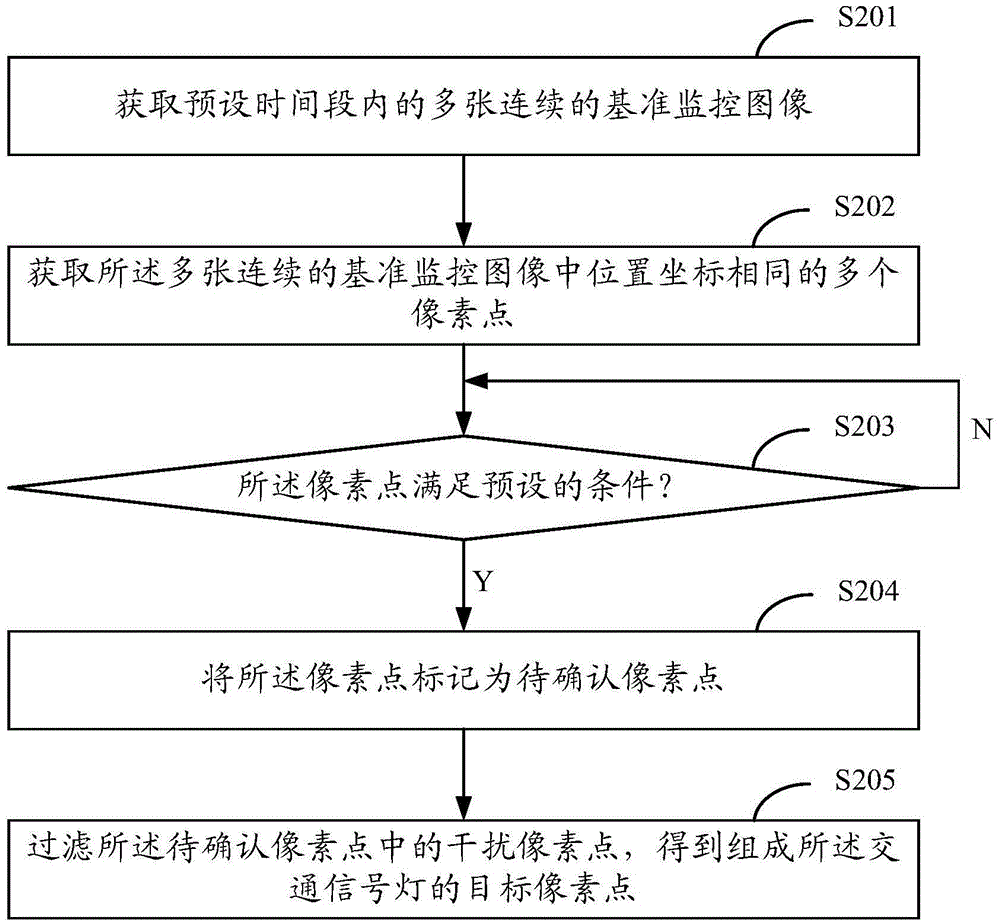
ActiveCN105430352AClear outlineResolve unresolved issuesDetection of traffic movementClosed circuit television systemsVideo monitoringTraffic signal
The invention provides a processing method for a video monitor image. The method comprises the steps of determining area information of a traffic light in a reference monitor image; removing the traffic light in an original monitor image according to the area information to obtain an intermediate monitor image; and optimizing halo around the original traffic light part in the intermediate monitor image to obtain a target monitor image. According to the processing method for the video monitor image, the problem that the outline of the traffic light in a night monitor image cannot be distinguished can be solved, so that a user can clearly distinguish the indication direction of the traffic light, and thereby efficiency and accuracy for identifying traffic violations in later are improved.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
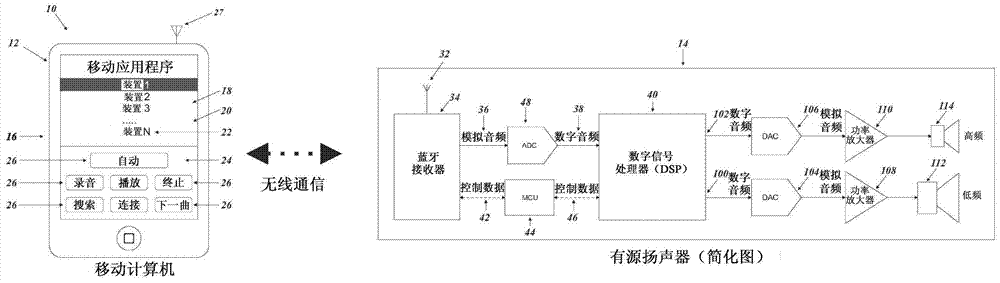
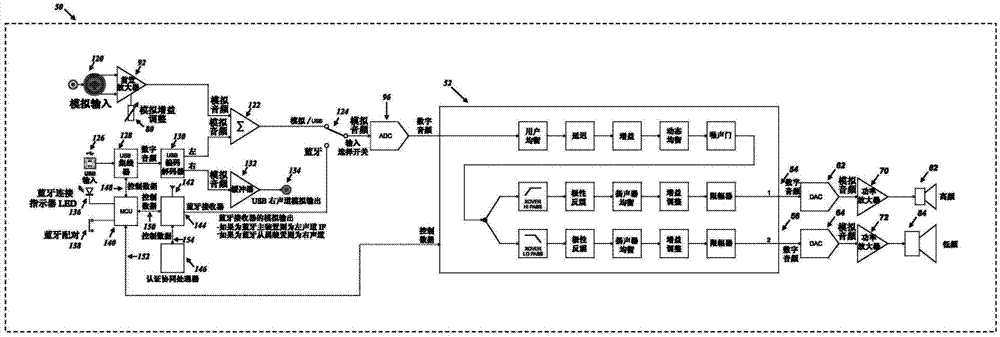
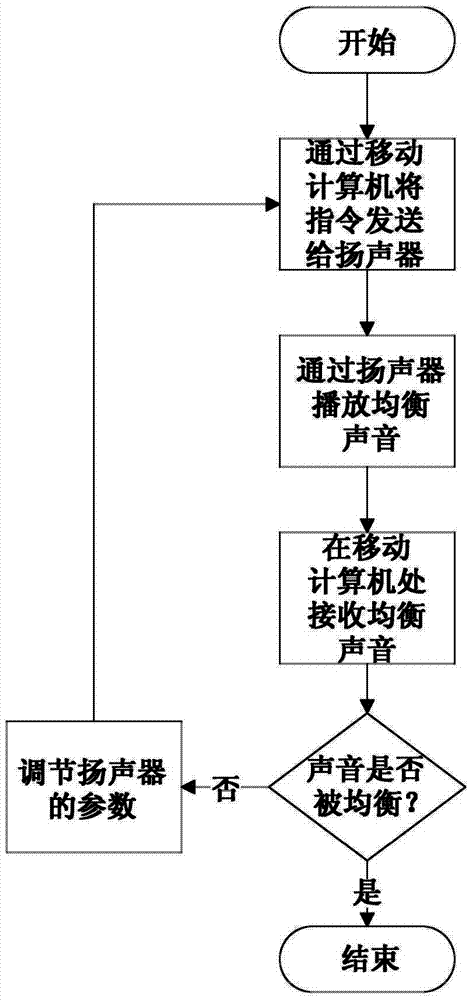
System and method for remotely controlling audio equipment
InactiveCN103676827AUltrasonic/sonic/infrasonic diagnosticsGain controlApplication softwareEqualization
Owner:MUSIC GROUP IP
Securing CPU affinity in multiprocessor architectures
InactiveUS8136153B2Limited abilityDigital data processing detailsUnauthorized memory use protectionMulti processorMultiprocessor architecture
In an embodiment of the present invention, the ability for a user or process to set or modify affinities is restricted in order to method for control a multi-processor environment. This may be accomplished by using a reference monitor that controls a process' capability to retrieve and set its or another process' affinity. This aids in the prevention of security breaches.
Owner:SAMSUNG ELECTRONICS CO LTD
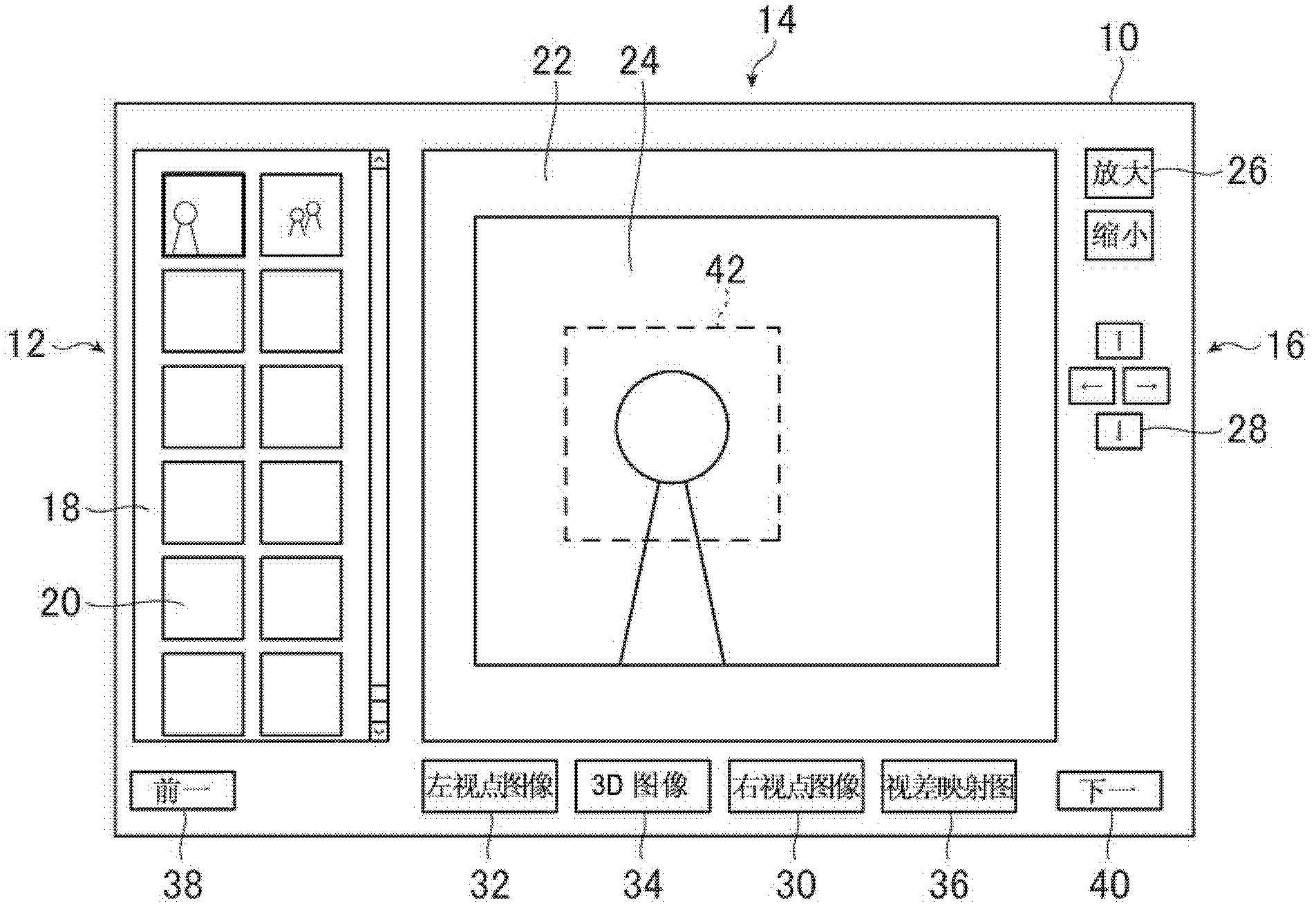
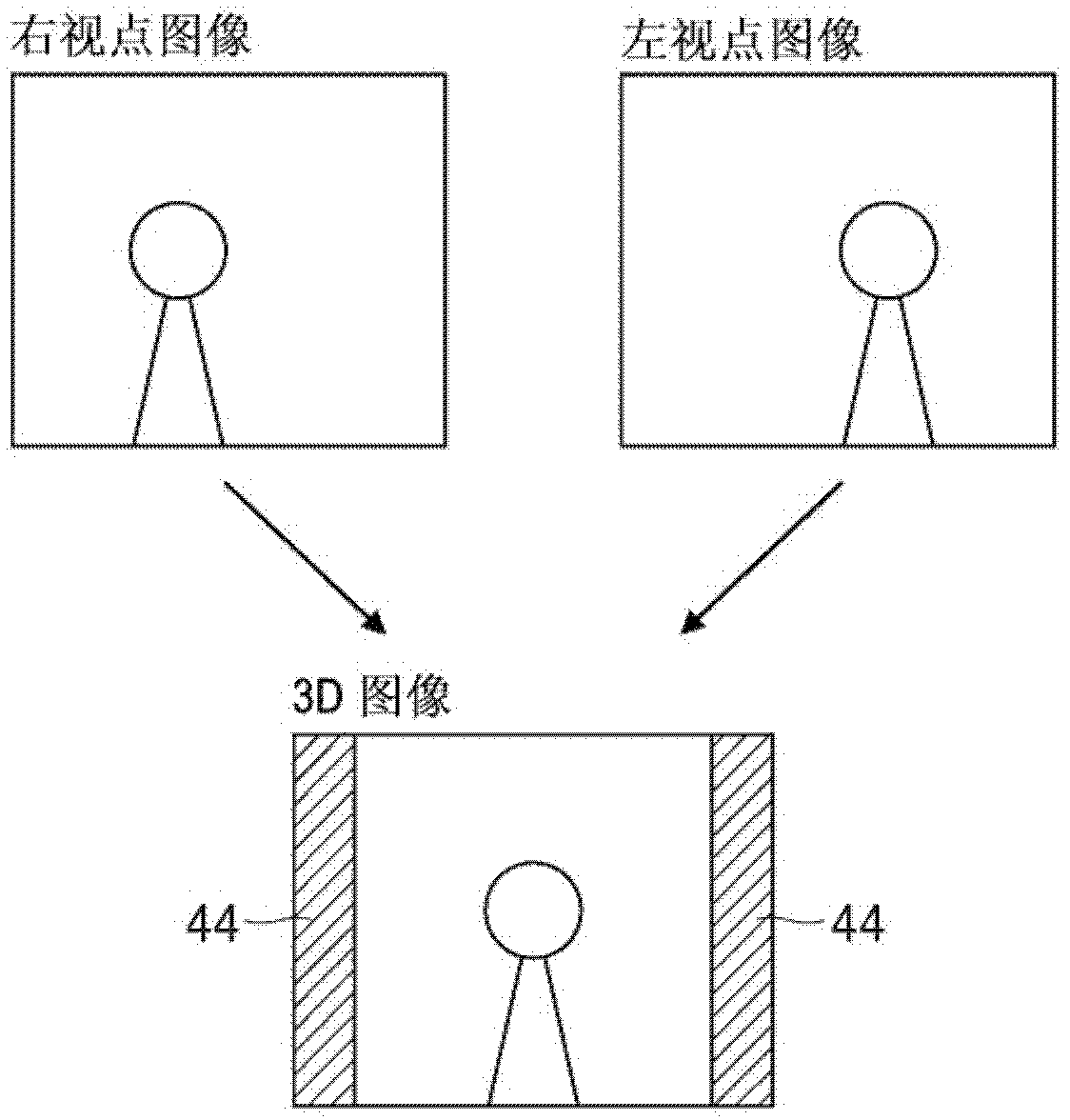
Image processing apparatus and image processing method as well as image processing system
The invention discloses an image processing apparatus and an image processing method as well as an image processing system. The image processing apparatus includes a monitor for displaying an image based on a right viewpoint image and left viewpoint image, or multi-viewpoint images, with the displayed image being used by a user for specifying an indispensable output area which the user wants to be included in a 3D image synthesized by merging the right viewpoint image and left viewpoint image, or multi-viewpoint images, together, and outputted; an input device for inputting information on the indispensable output area as specified by the user referring to the image as displayed on the monitor; a control unit for causing the indispensable output area to be indicated in the image as displayed on the monitor; and an output device for outputting the right viewpoint image and left viewpoint image, or multi-viewpoint images, and information on the indispensable output area.
Owner:FUJIFILM CORP
Multi-level security system for enabling secure file sharing across multiple security levels and method thereof
ActiveUS9489534B2Maintaining data separation of the informationDigital data information retrievalDigital data protectionFile systemSecurity level
A multi-level security system includes a storage medium partitionable into a plurality of partitions, a file system coupleable to the plurality of partitions, and a plurality of enclaves. Each enclave is assigned a security classification level. Each enclave resides in a different storage partition of the storage medium. Data stored on the storage medium is cryptographically separated at rest on a per-enclave basis. Cryptographic separation occurs at the disk block level, allowing individual blocks to be read and decrypted. The system also includes a reference monitor that enforces a system security policy that governs access to information between the enclaves. The reference monitor allows an enclave having a first classification level to securely read-down to an enclave having a second classification level lower than the first classification level and to write to another enclave having the first classification level.
Owner:NORTHROP GRUMMAN SYST CORP
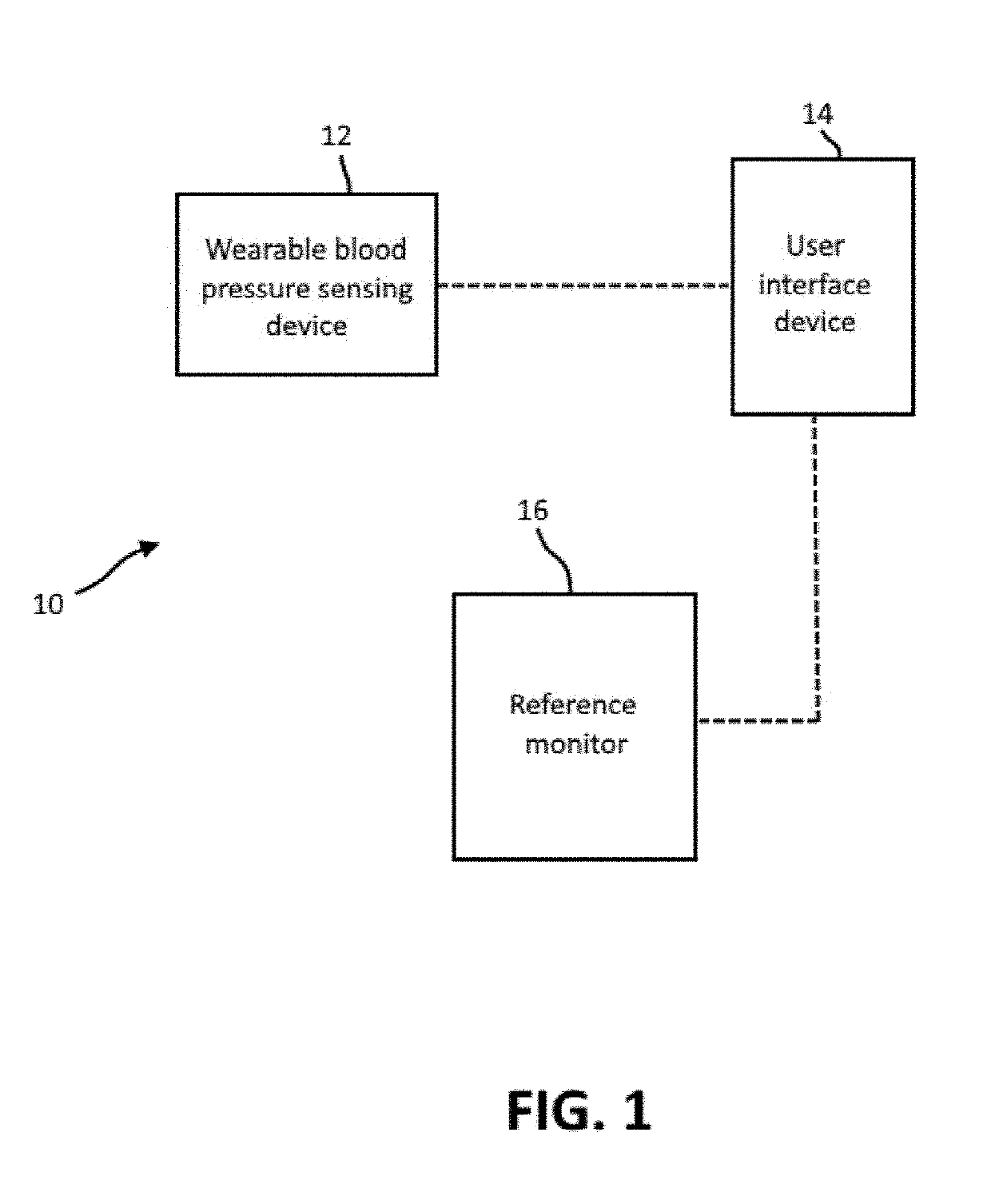
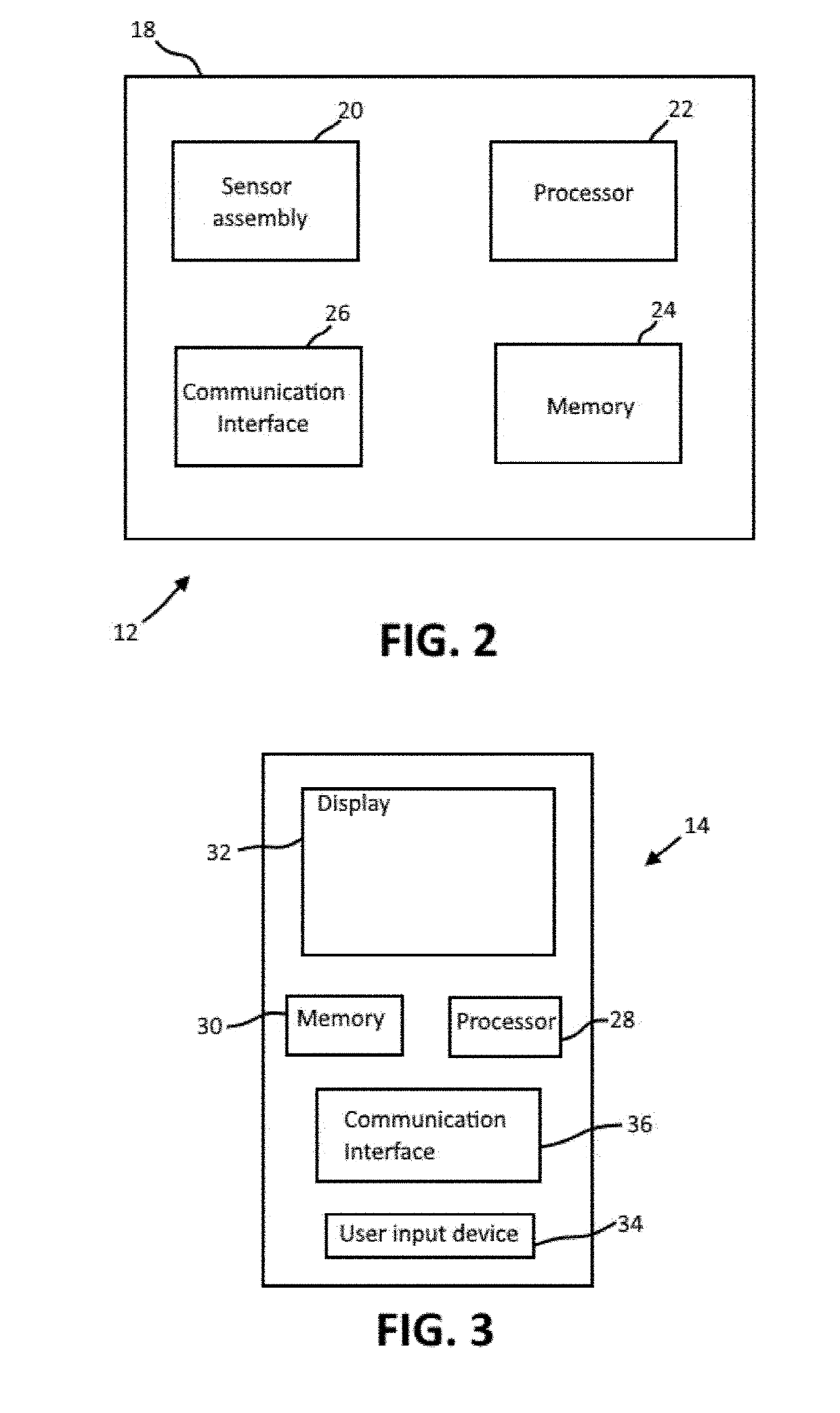
Calibration methods for blood pressure devices
ActiveUS20190274553A1Accurate estimateInertial sensorsEvaluation of blood vesselsCorrelation factorsBlood pressure device
A method for calibrating a blood pressure monitoring system includes activating a reference monitor to perform a reference measurement of the blood pressure of a user as part of a calibration process. A wearable sensing device is activated to detect a parameter of user that is correlatable to the user's blood pressure. A processor of the user interface device processes the at least one parameter detected by the wearable blood pressure sensing device with reference to the reference measurement to determine a correlation factor that correlates the at least one parameter detected by the wearable blood pressure sensing device to the blood pressure of the user. The reference measurement includes an inflation phase, a measurement phase and a deflation phase. The processor is configured to only use the at least one parameter detected by the wearable blood pressure sensing device during the measurement phase in determining the correlation factor.
Owner:ROBERT BOSCH GMBH
Data alignment in large scale electrical system applications
ActiveUS9176171B2Reduce in quantityImprove approachElectric devicesCircuit arrangementsElectrical conductorPhase shifted
A method for automatically aligning measured power-related data in a power monitoring system to a common reference point. A conductor in a power delivery system is modeled according to an equivalent pi model of a transmission line that is characterized by model parameters. The conductor is monitored on both ends by a reference monitoring device and a second monitoring device. The voltage and current are measured in either the reference monitoring device or the second monitoring device and a phase shift offset between the voltages or currents at the two devices is calculated. The calculated phase shift offset corresponds to a temporal delay between events observed at the pair of devices, and calculating and storing the phase shift offset allows a power monitoring system controller to more accurately align data received from monitoring devices.
Owner:SCHNEIDER ELECTRIC USA INC
Process control system, process control method, and method of manufacturing electronic apparatus
A process control system includes a client computer which prepares a correlation between a reference monitored value of apparatus information and a feature quantity, a manufacturing execution system which prepares a processing recipe describing, as a first setting value in an actual manufacturing process, a value of the control parameter, an apparatus information collection section which collects an objective monitored value of the apparatus information in operation of the actual manufacturing process with the first setting value, a feature quantity calculation section which calculates a value of a feature quantity corresponding to the objective monitored value based on the correlation, a parameter calculation section which calculates a second setting value in the actual manufacturing process on the basis of the value of the feature quantity, and an apparatus control unit which changes the processing recipe with the second setting value being as a setting value of the second step.
Owner:KIOXIA CORP
Automated precision alignment of data in utility monitoring system
ActiveCN101213718ACurrent/voltage measurementInformation technology support systemCorrelation coefficientAlgorithm
Algorithms that automatically align data from multiple monitoring devices to the same zero crossing at the same point in time. Frequency change data per cycle is received from each monitoring device, and a cross-correlation algorithm is performed to determine a correlation coefficient between the reference monitoring device and another monitoring device. The data of another monitoring device is shifted by one cycle, and another correlation coefficient is calculated by a cross-correlation algorithm. The data of the two monitoring devices are aligned at the point where the maximum correlation coefficient is calculated or at the point where the correlation coefficient exceeds a threshold value. It is also possible to synchronize the clocks of the monitoring devices at the same alignment point.
Owner:SQUARE D CO
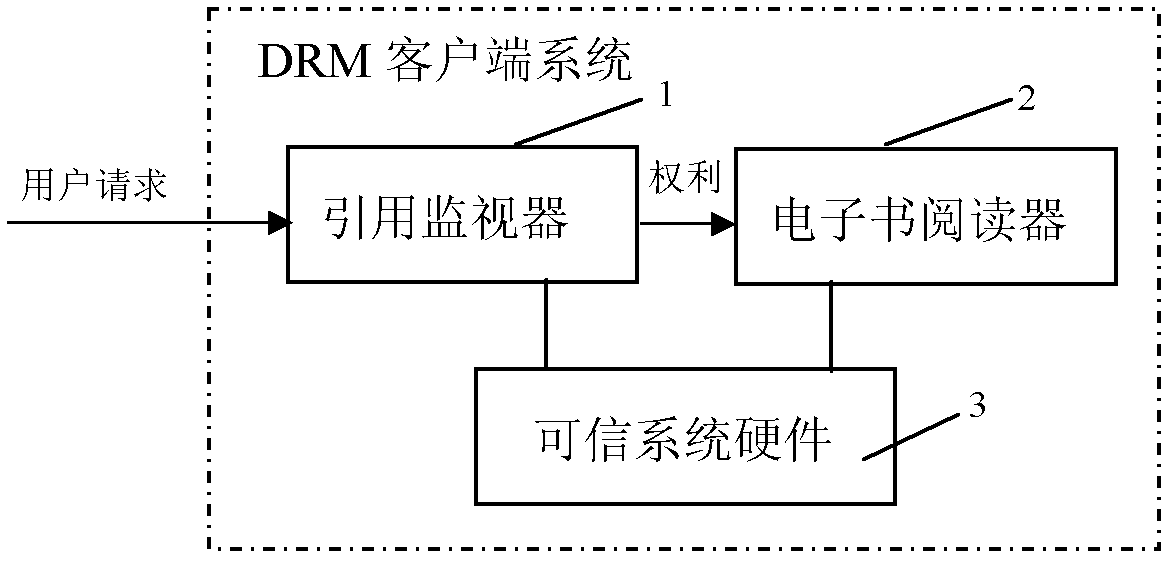
Real-time-control-oriented client-side system for protecting digital copyright of electronic book and implementation method thereof
InactiveCN102222186AMeet the needs of flexible controlStrong real-time authorization control capabilityProgram/content distribution protectionElectrical appliancesExtensibilityElectronic book
The invention discloses a real-time-control-oriented client-side system for protecting the digital copyright of an electronic book and an implementation method thereof. The client-side system comprises a reference monitor, an electronic book reader and trusted system hardware, wherein the reference monitor is used for providing permit protection, decision making and updating; the electronic book reader is used for operating digital contents; the trusted system hardware is used for providing security protection for the reference monitor and the electronic book reader; and the reference monitor is used for carrying out decryption and decision making on a permit, and granting the right of the electronic reader so that the electronic book reader carries out corresponding operations. In the client-side system disclosed by the invention, a UCON ABC model is adopted as a decision-making model, while a nontraditional access control model can carry out positive auditing on the right use condition instantaneously, and an effective real-time control function can be achieved. In addition, UCON REL is designed based on XML (Extensive Makeup Language), so that the system has good openness and expandability and enriches the use of control function for a client side.
Owner:SOUTH CHINA NORMAL UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com