Patents
Literature
88 results about "Trusted hardware" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
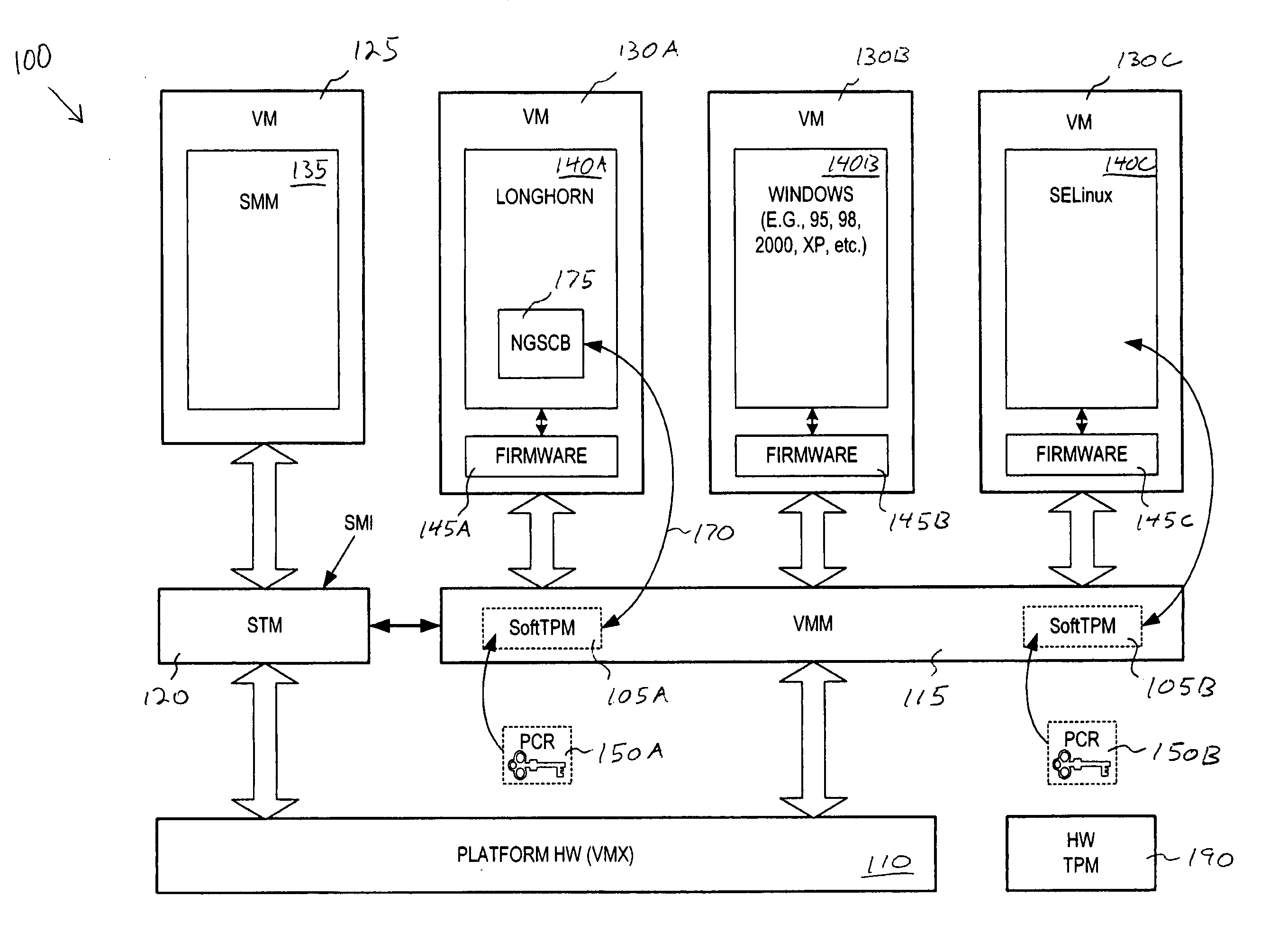
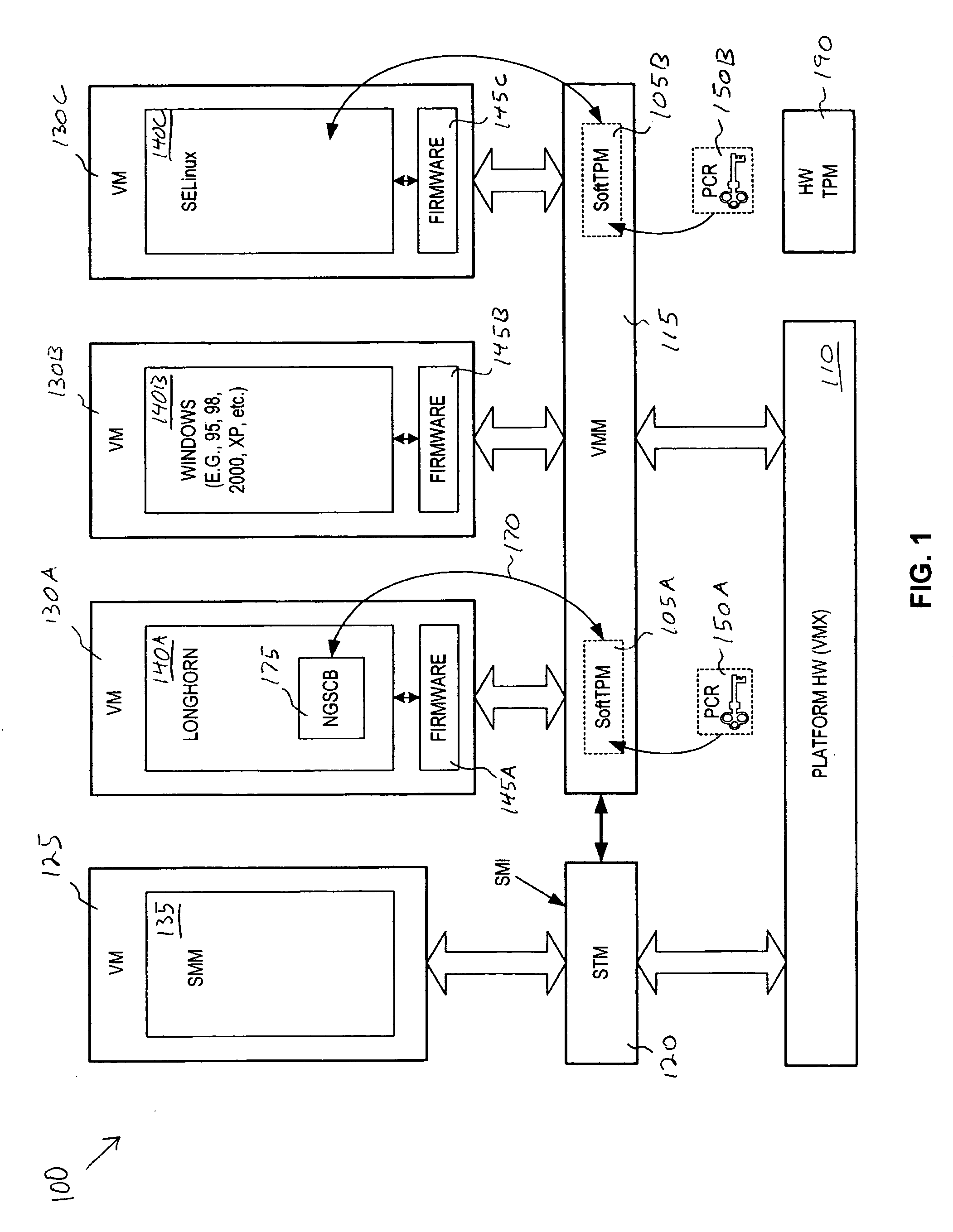
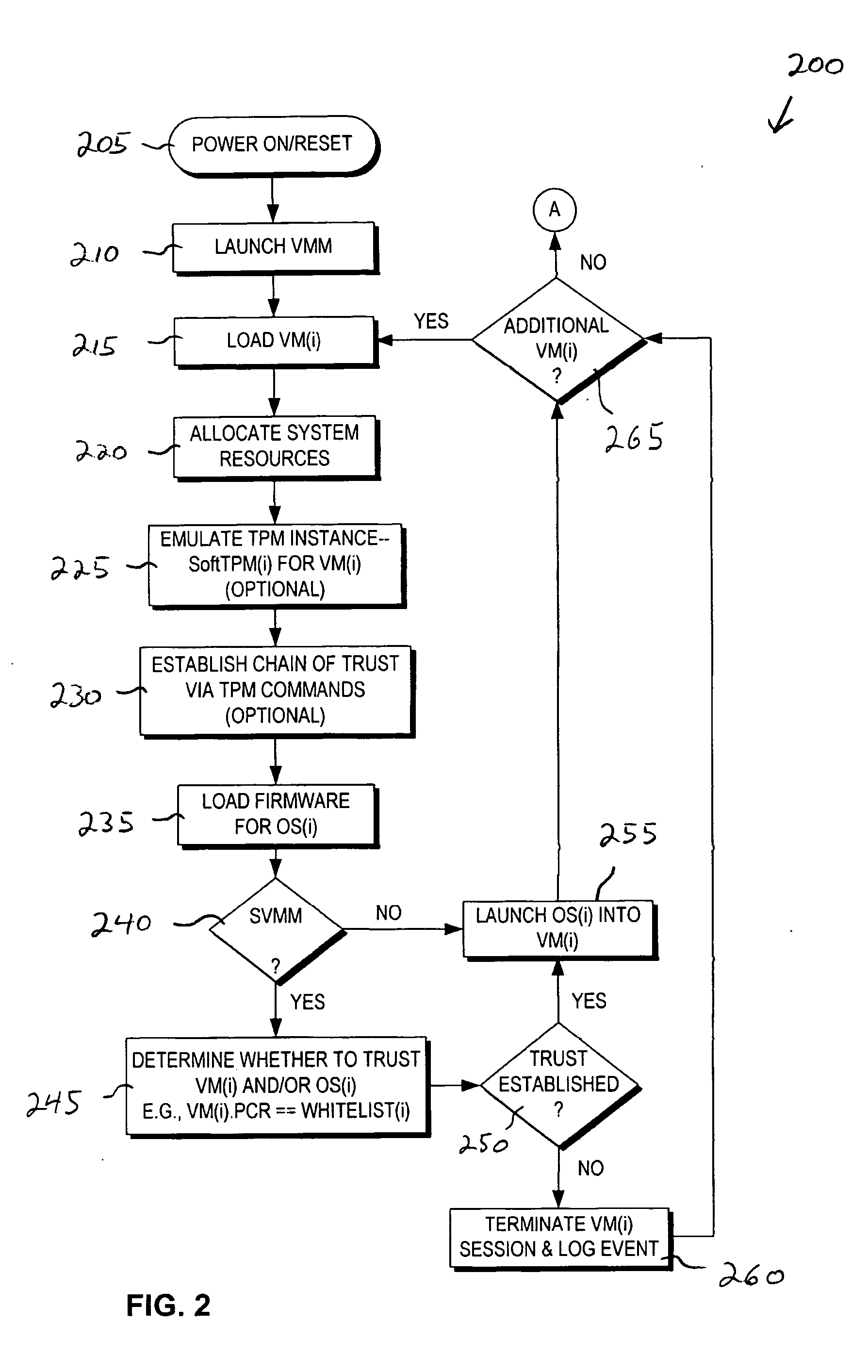
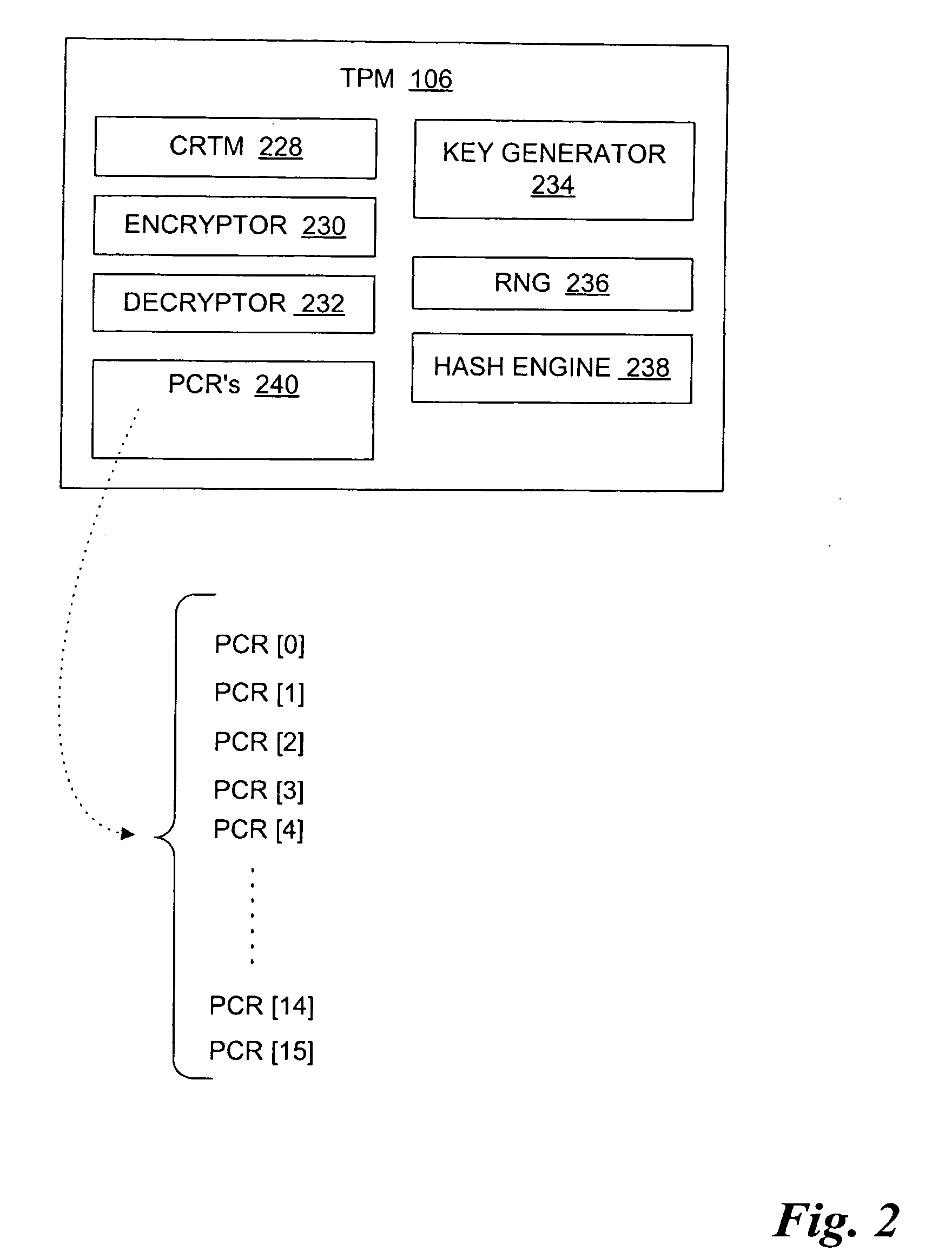
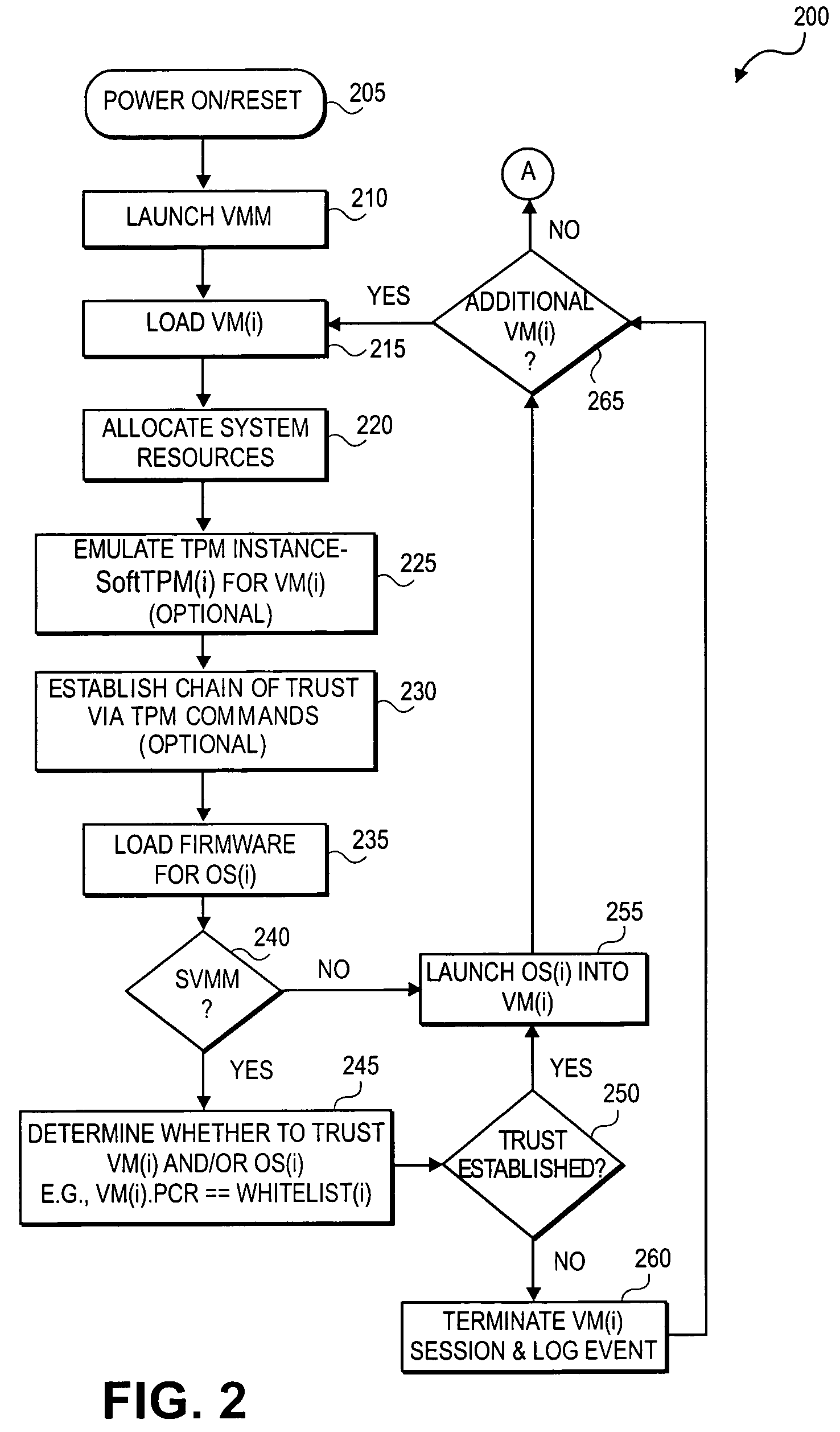
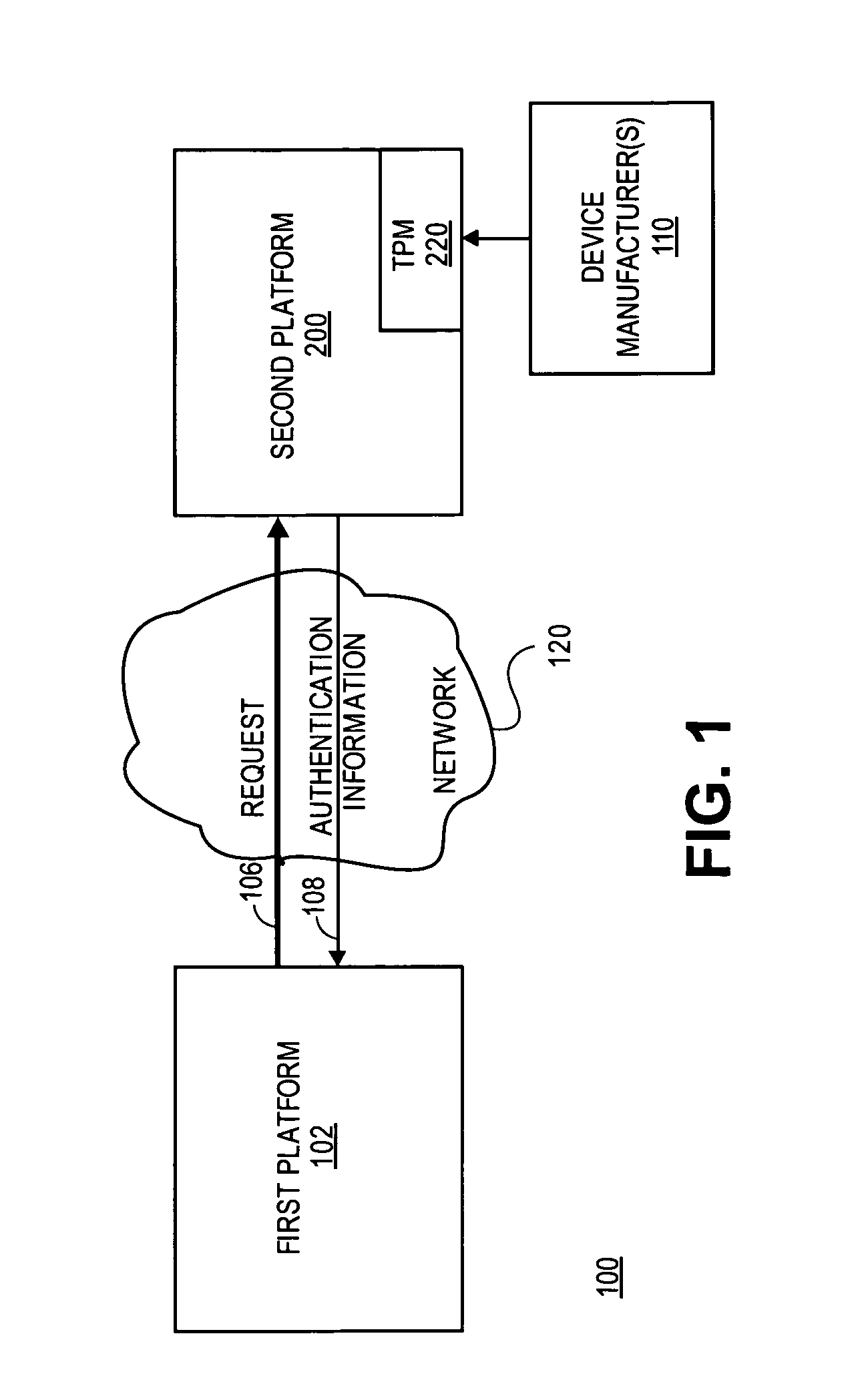
Method and system to support a trusted set of operational environments using emulated trusted hardware
InactiveUS20050138370A1Key distribution for secure communicationUnauthorized memory use protectionComputer hardwareOperational system
A method and system to emulate a trusted platform module to execute trusted operations. A virtual machine monitor is executed to support a virtual machine session. An operating system is loaded into the virtual machine session. The trusted platform module is emulated to hold a key associated with the virtual session and to execute trusted operations.
Owner:INTEL CORP
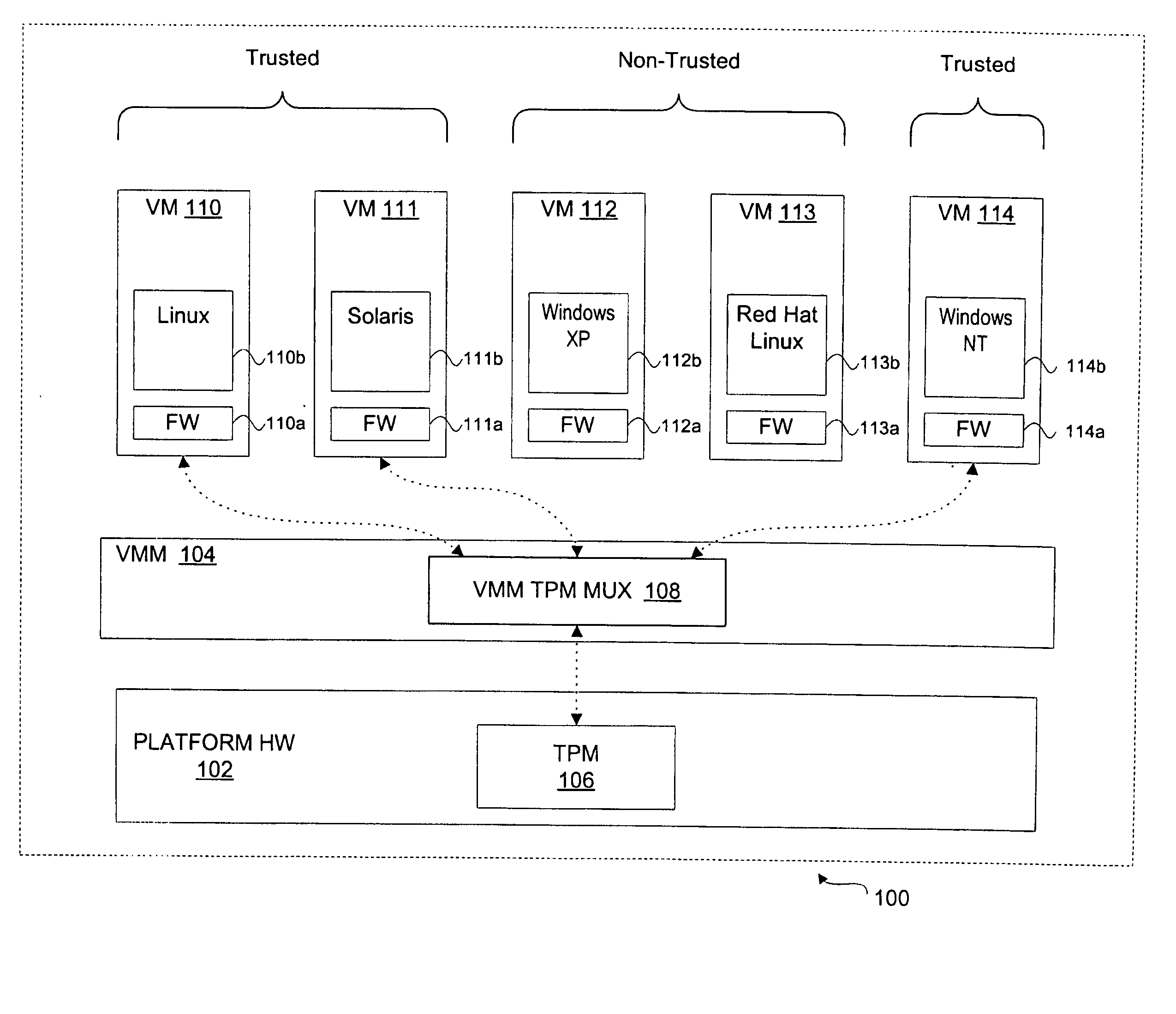
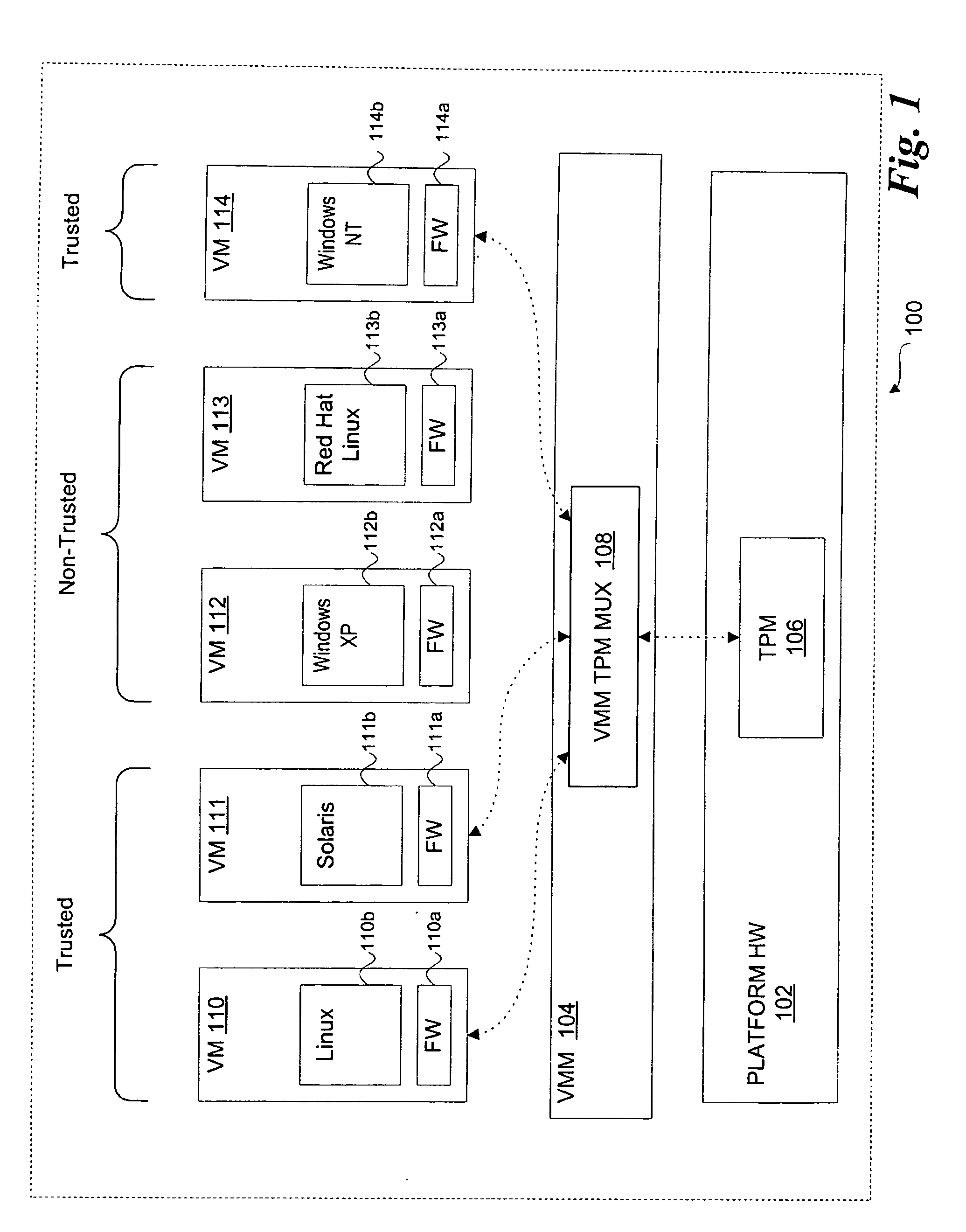
Sharing trusted hardware across multiple operational environments
InactiveUS20050210467A1Platform integrity maintainanceSoftware simulation/interpretation/emulationTrusted hardwareMultiplexer
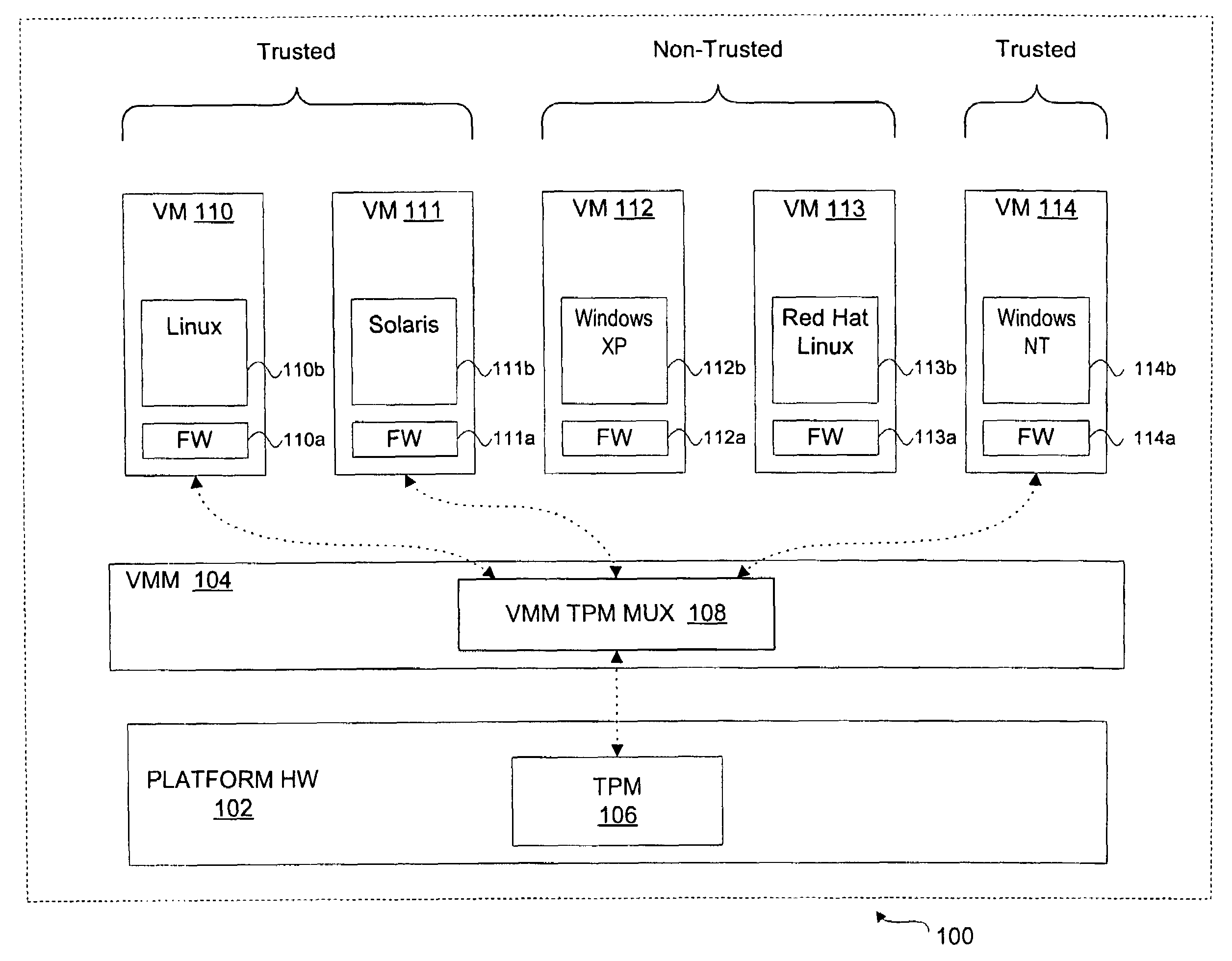
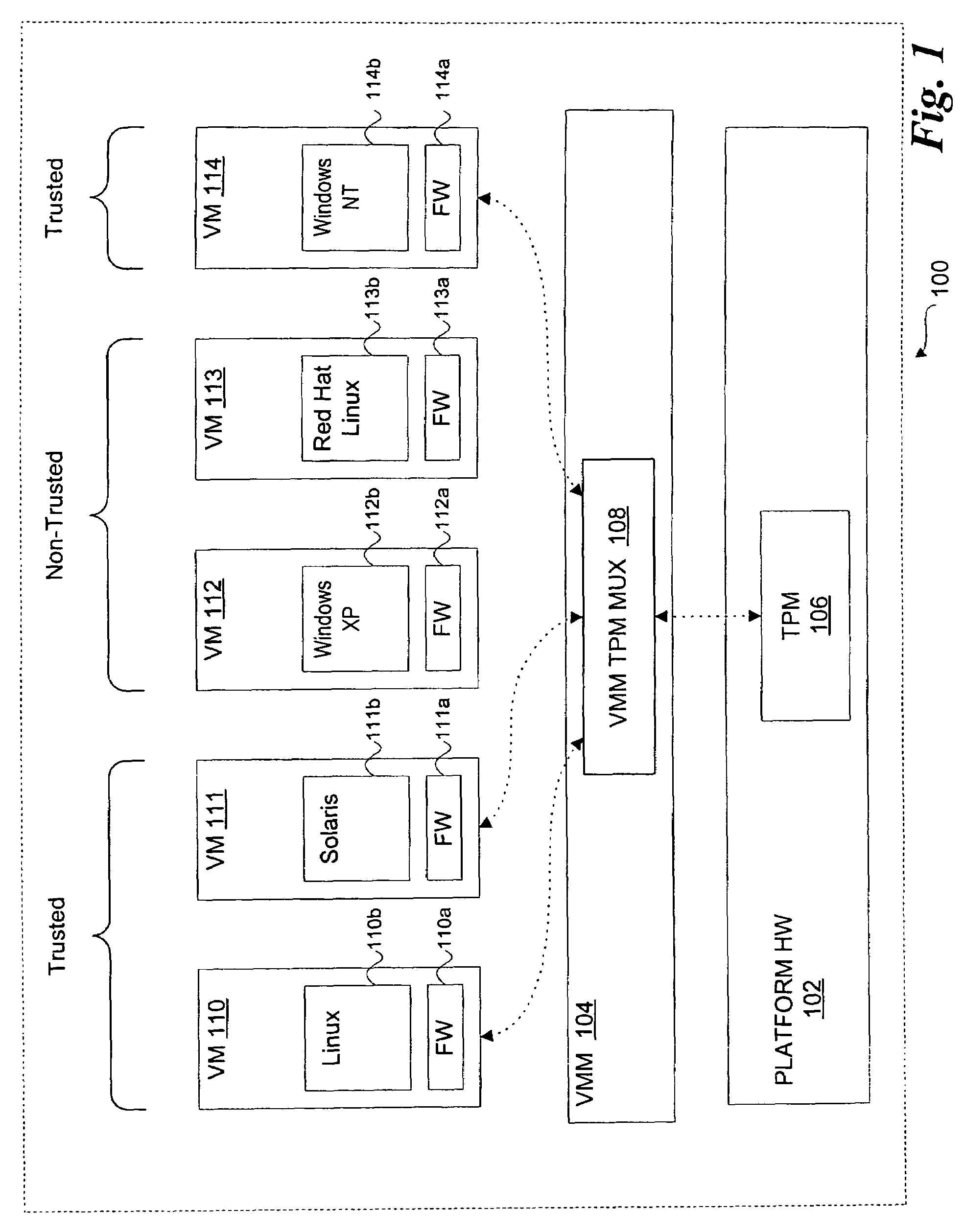
A method, system, and article of manufacture to share trusted hardware across multiple operational environments. A virtual machine monitor (VMM) is loaded to support a plurality of virtual machines in a computer system, the VMM including a VMM multiplexer. A first and a second virtual machine (VM) are loaded. A trusted hardware device is shared between the first VM and the second VM using the VMM multiplexer. In one embodiment, the trusted hardware device includes a trusted platform module (TPM).
Owner:INTEL CORP
Method and system to support a trusted set of operational environments using emulated trusted hardware
InactiveUS7222062B2Key distribution for secure communicationUnauthorized memory use protectionComputer hardwareTrusted hardware
A method and system to emulate a trusted platform module to execute trusted operations. A virtual machine monitor is executed to support a virtual machine session. An operating system is loaded into the virtual machine session. The trusted platform module is emulated to hold a key associated with the virtual session and to execute trusted operations.
Owner:INTEL CORP
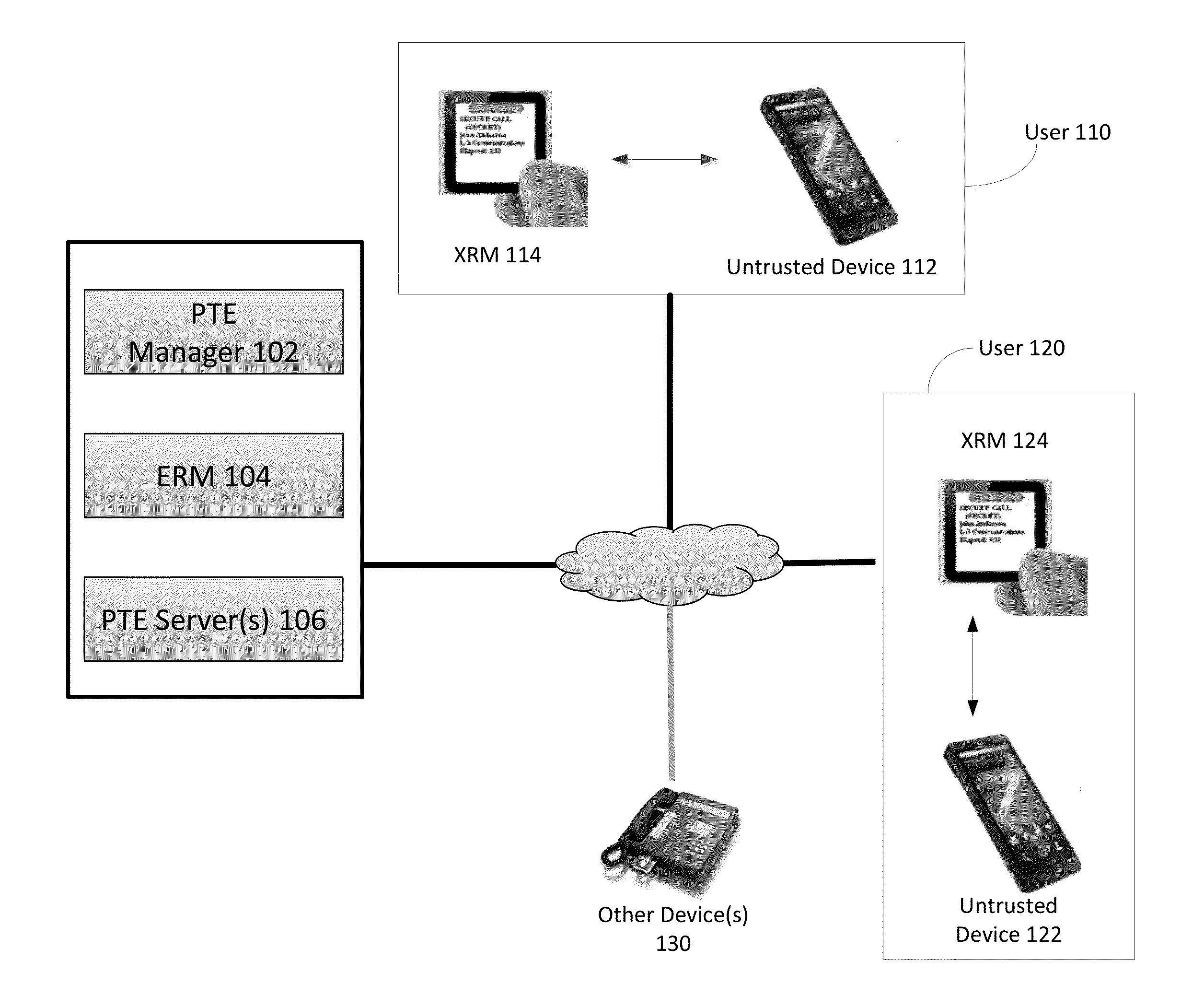
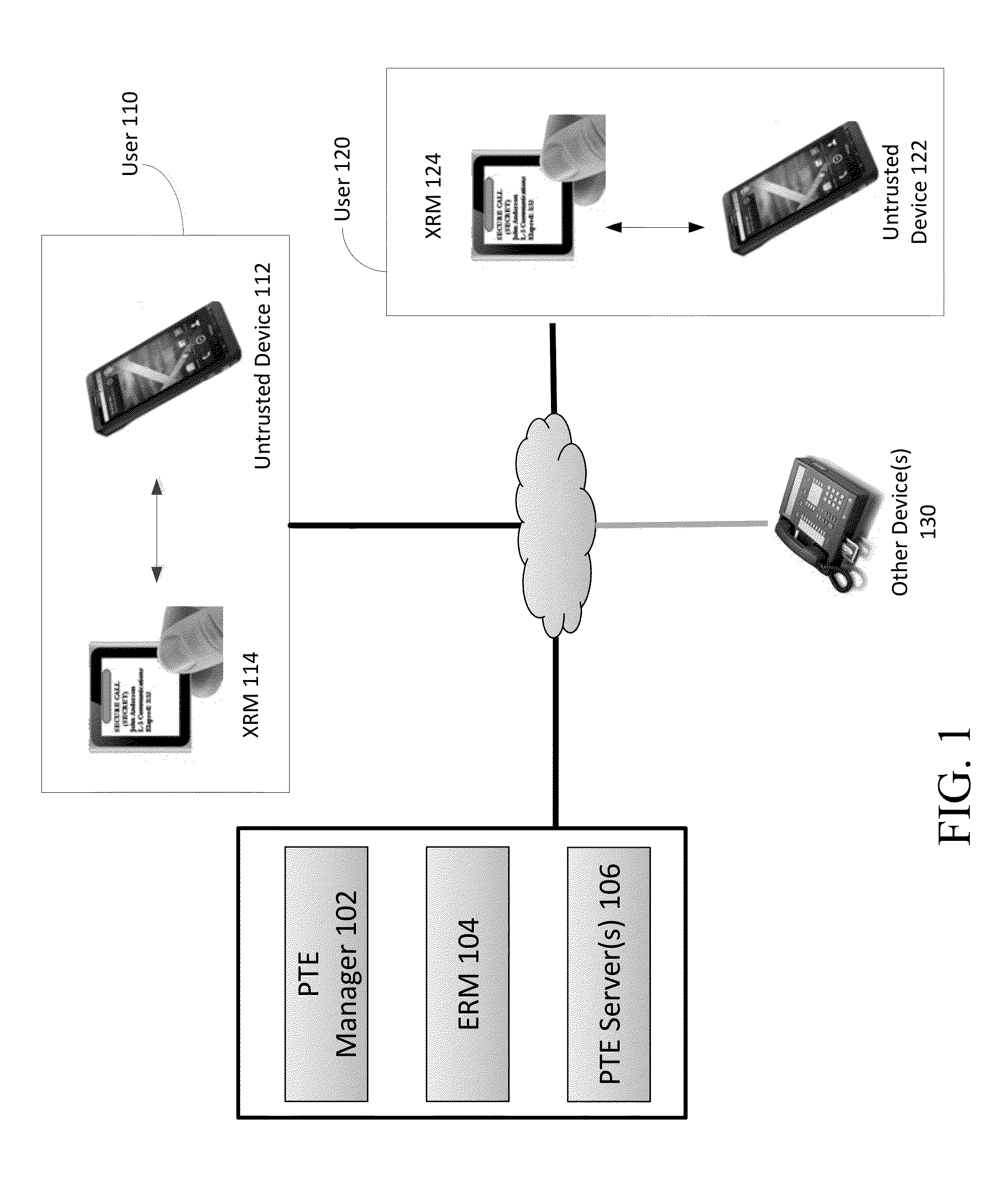
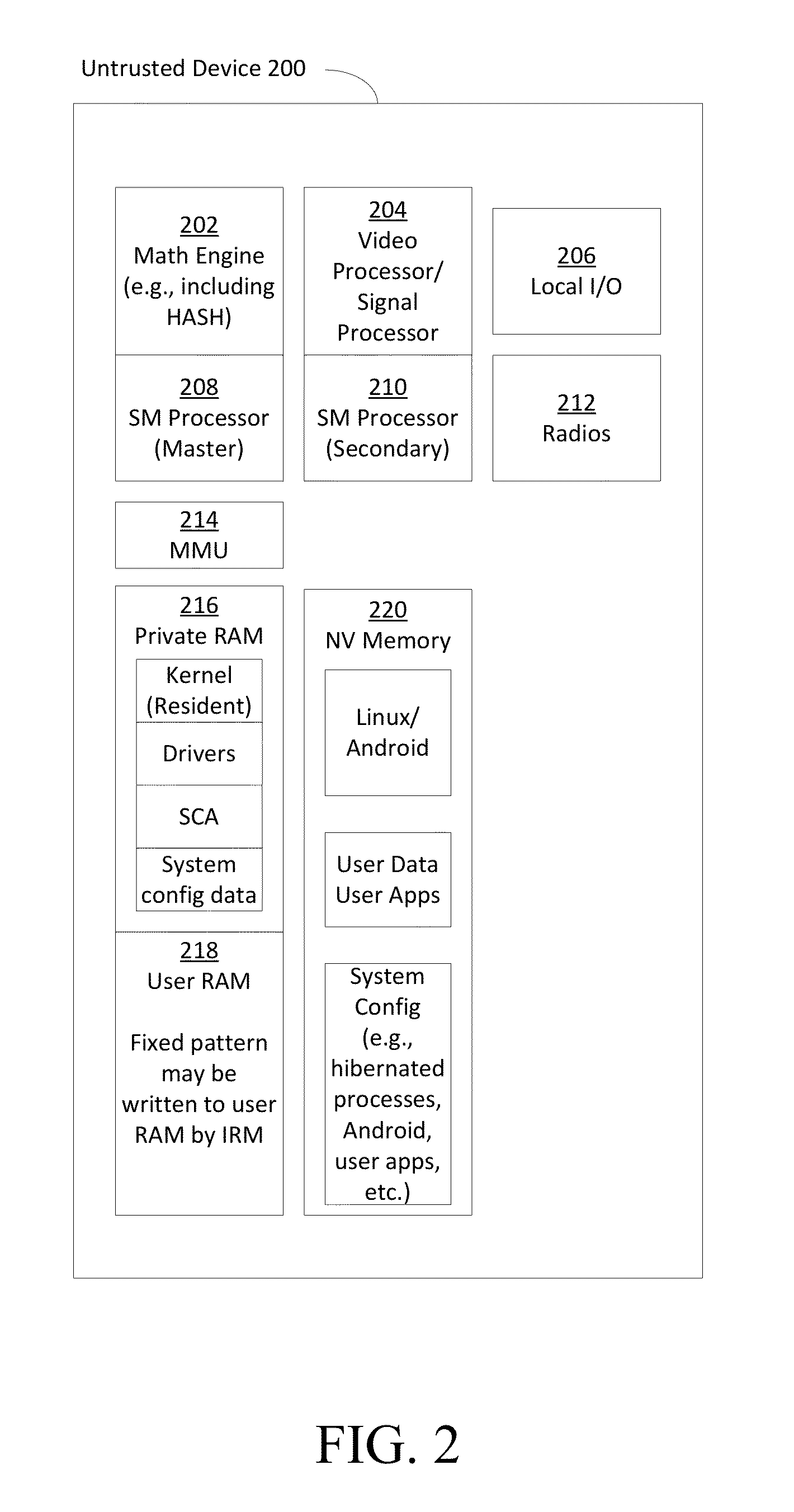
External Reference Monitor
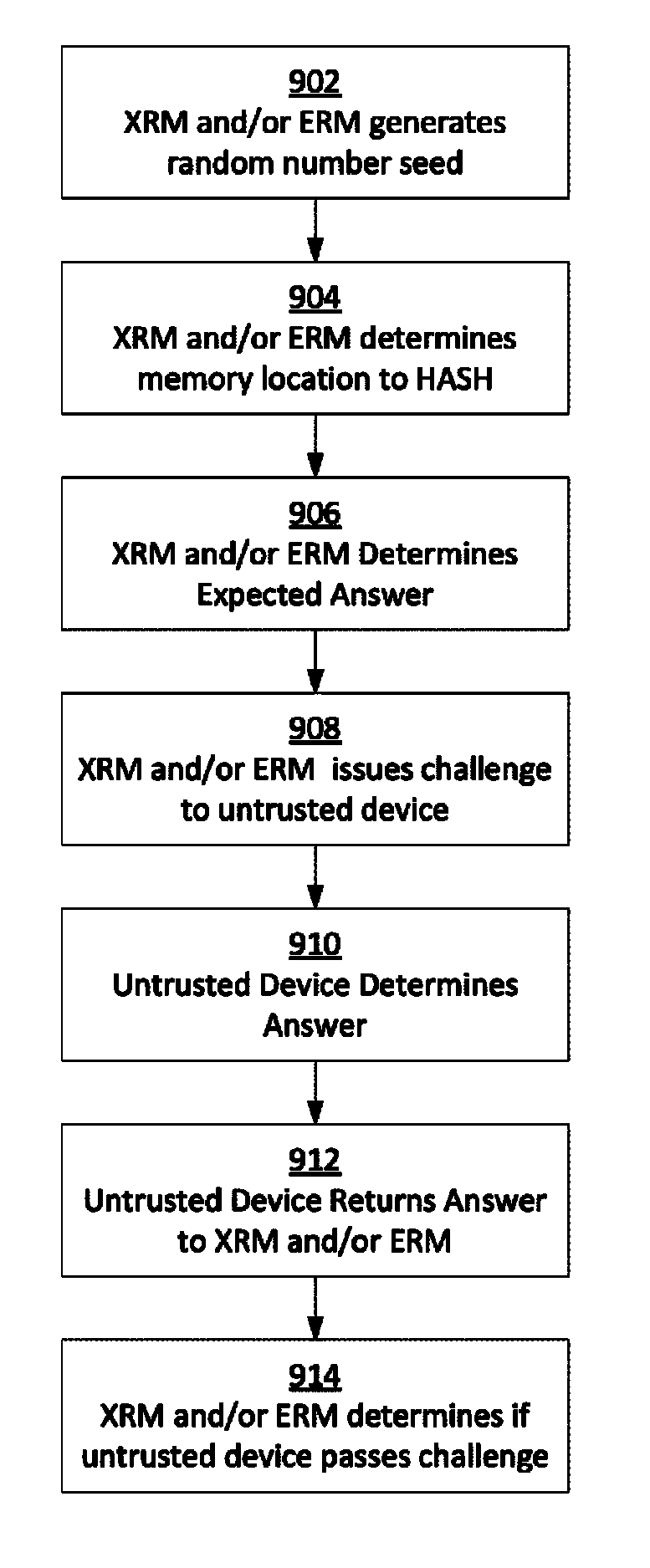
ActiveUS20130111211A1Improve trustPrevent cheatingDigital data processing detailsUser identity/authority verificationComputer hardwareTrusted hardware
Methods and systems for increasing the security or trust associated with an untrusted device are provided. For example, a trusted hardware component may send a request to the untrusted device. The request may indicate one or more challenges to be performed by a secure application executing on the untrusted device. The trusted hardware component may determine an expected response to the one or more challenges. The expected response may be determined at the secure hardware component based on an expected configuration of the untrusted device. The trusted hardware component may receive a response to the request from the untrusted device. The trusted hardware component may determine a security status of the untrusted device based on the expected response and the received response
Owner:LIONRA TECH LTD
Method and apparatus for tamper-proof wirte-once-read-many computer storage
InactiveUS20100088528A1Minimize overheadAvoids malicious actDigital data information retrievalUnauthorized memory use protectionTamper resistanceTrusted hardware
Disclosed is a method for storing digital information for storage in an adversarial setting in which trusted hardware enforces digital information compliance with data storage mandates. Secure storage overhead is minimized by identifying sparsely accessing the trusted hardware based on data retention cycles. Data retention assurances are provided for information stored by a Write-Once Read-Many (WORM) storage system.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Communications between modules of a computing apparatus
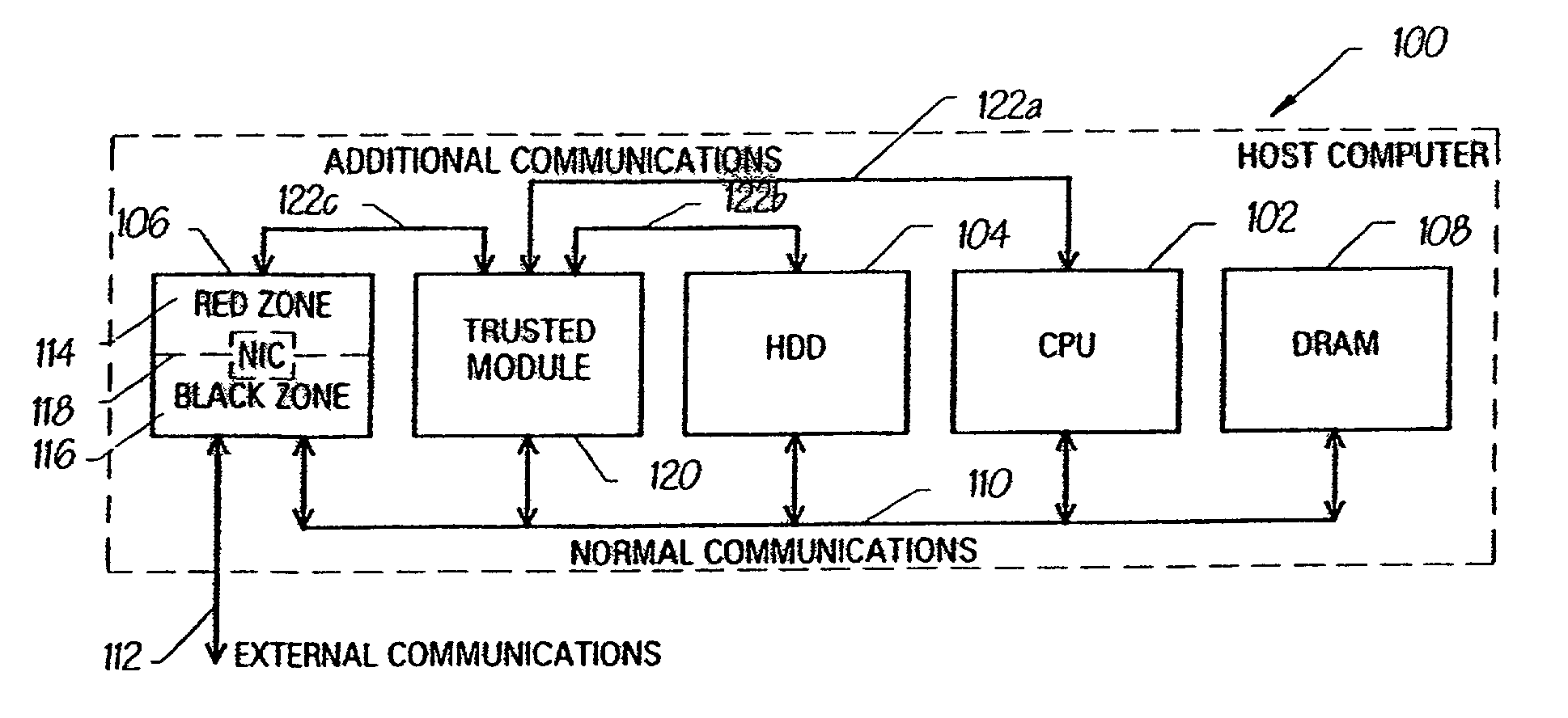
InactiveUS7236455B1Improve trustError preventionProgram control using stored programsSecure communicationTrusted hardware
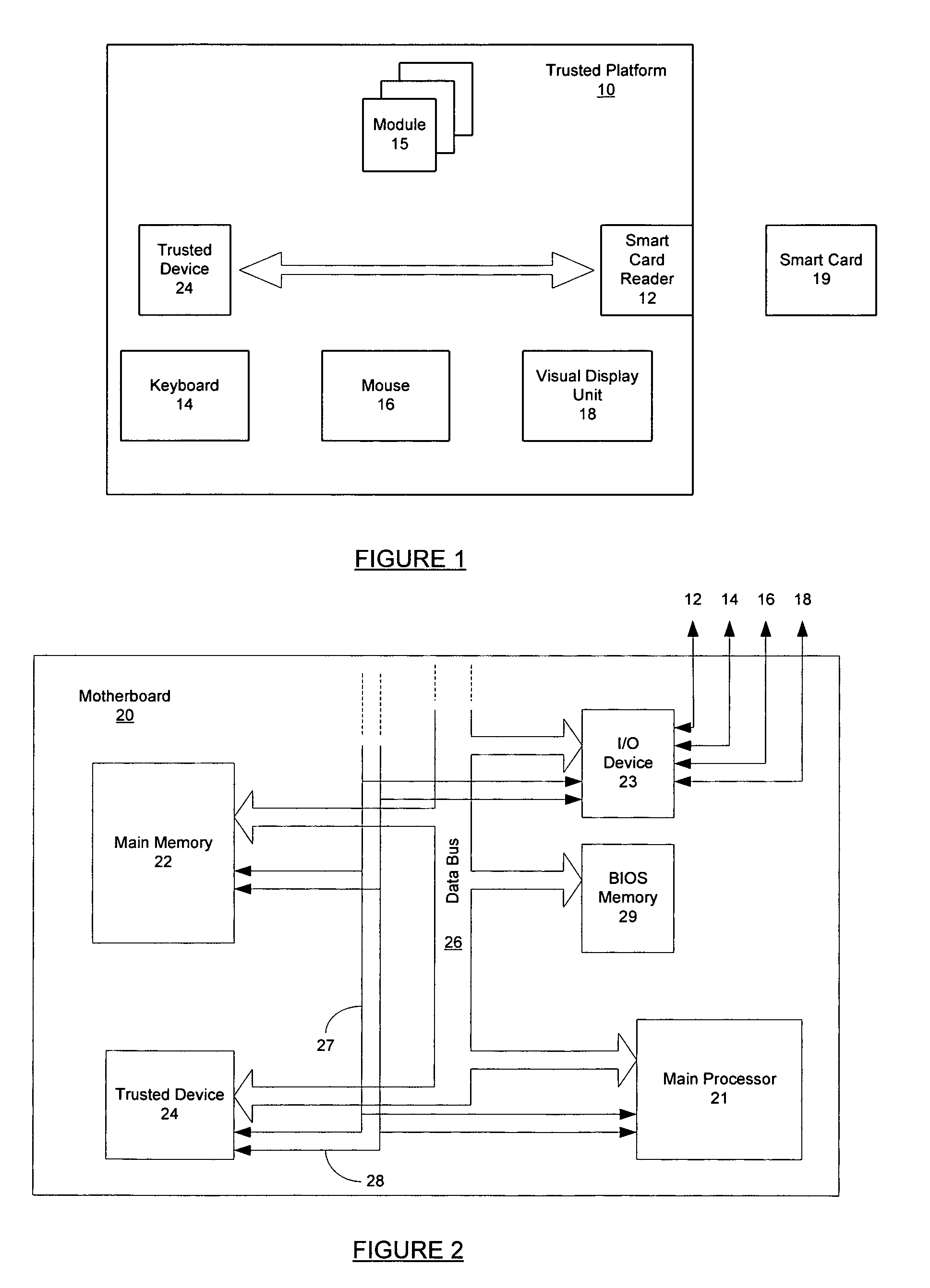
A computing apparatus comprises a plurality of hardware modules (102,104,106) and a shared communication infrastructure (110) by which the modules can communicate with each other in the usual way. In order to increase the level of trust and security in the apparatus, a trusted hardware module (120) is also provided and is connected to the other modules by respective communication paths (122a;122b;122c), distinct from the communication infrastructure, by which each of those modules can communicate directly with the trusted module but cannot communicate directly with any other of the modules. The trusted module can therefore have secure communications, for example of “unsafe” data, with each of the other modules without any of the remaining modules eavesdropping, and the trusted module can route unsafe data between any pair of the other modules, or decline to provide such routing, for example in dependence on policy stored in the trusted module.
Owner:HEWLETT PACKARD DEV CO LP
Sharing trusted hardware across multiple operational environments
InactiveUS7552419B2Platform integrity maintainanceSoftware simulation/interpretation/emulationTrusted hardwareMultiplexer
A method, system, and article of manufacture to share trusted hardware across multiple operational environments. A virtual machine monitor (VMM) is loaded to support a plurality of virtual machines in a computer system, the VMM including a VMM multiplexer. A first and a second virtual machine (VM) are loaded. A trusted hardware device is shared between the first VM and the second VM using the VMM multiplexer. In one embodiment, the trusted hardware device includes a trusted platform module (TPM).
Owner:INTEL CORP
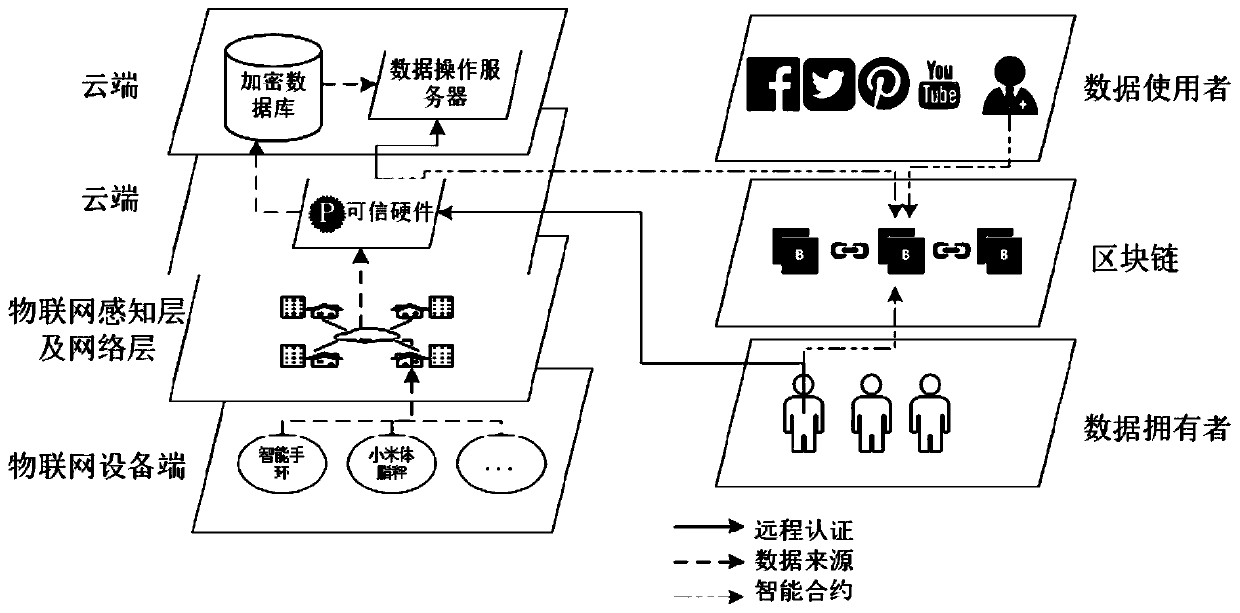
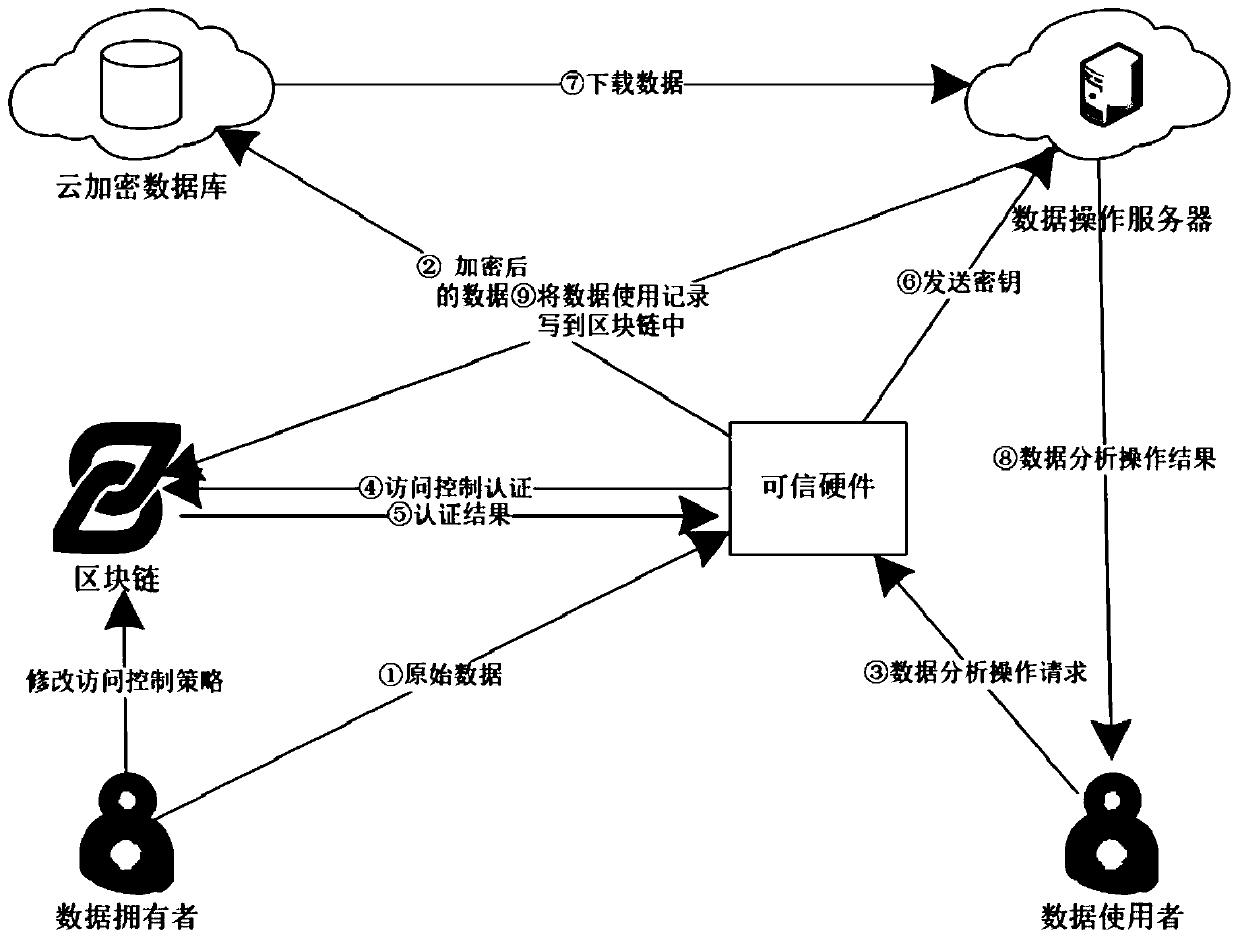
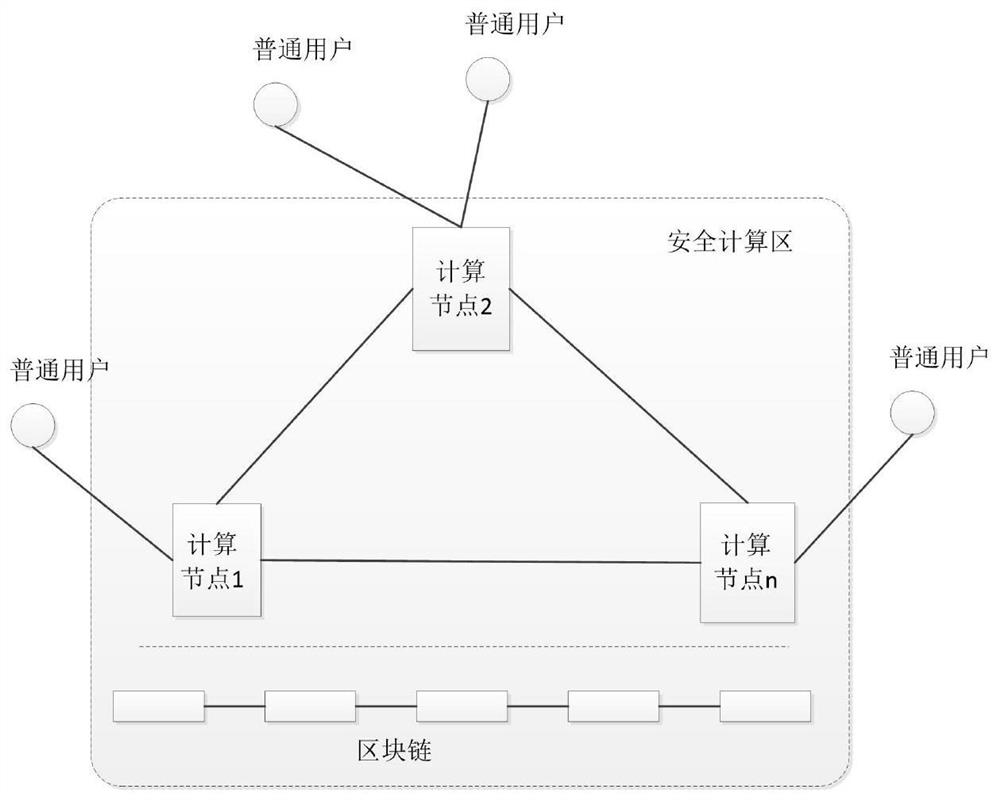
Internet of Things data privacy protection method based on block chain and trusted hardware
ActiveCN110086804AEnsure safetyGuaranteed reliabilityUser identity/authority verificationDigital data protectionData privacy protectionTrusted hardware
The invention relates to an Internet of Things data privacy protection method based on a block chain and the trusted hardware. The method comprises three stages of secret key management and data generation, data access control strategy definition and intelligent contract deployment and data access and intelligent contract execution, and Internet of Things data is encrypted by a hardware trusted entity IDA and uploaded to a cloud for storage; when there is an operation request, the trusted entity calls an access control authentication interface of the smart contract to carry out authority authentication; after the authority authentication passes, the trusted entity carries out security authentication on the operation execution server and sends the secret key to the data operation executionserver through a security channel; and the server downloads the data from the cloud, then decrypts the data and executes the operation, and writes the data use record into the block chain after the data analysis operation is completed. According to the scheme, the block chain is combined with the trusted entity, the data is effectively operated under the condition that the original data privacy isnot leaked, and the integrity and the safety of the data use records are guaranteed.
Owner:GUANGZHOU UNIVERSITY
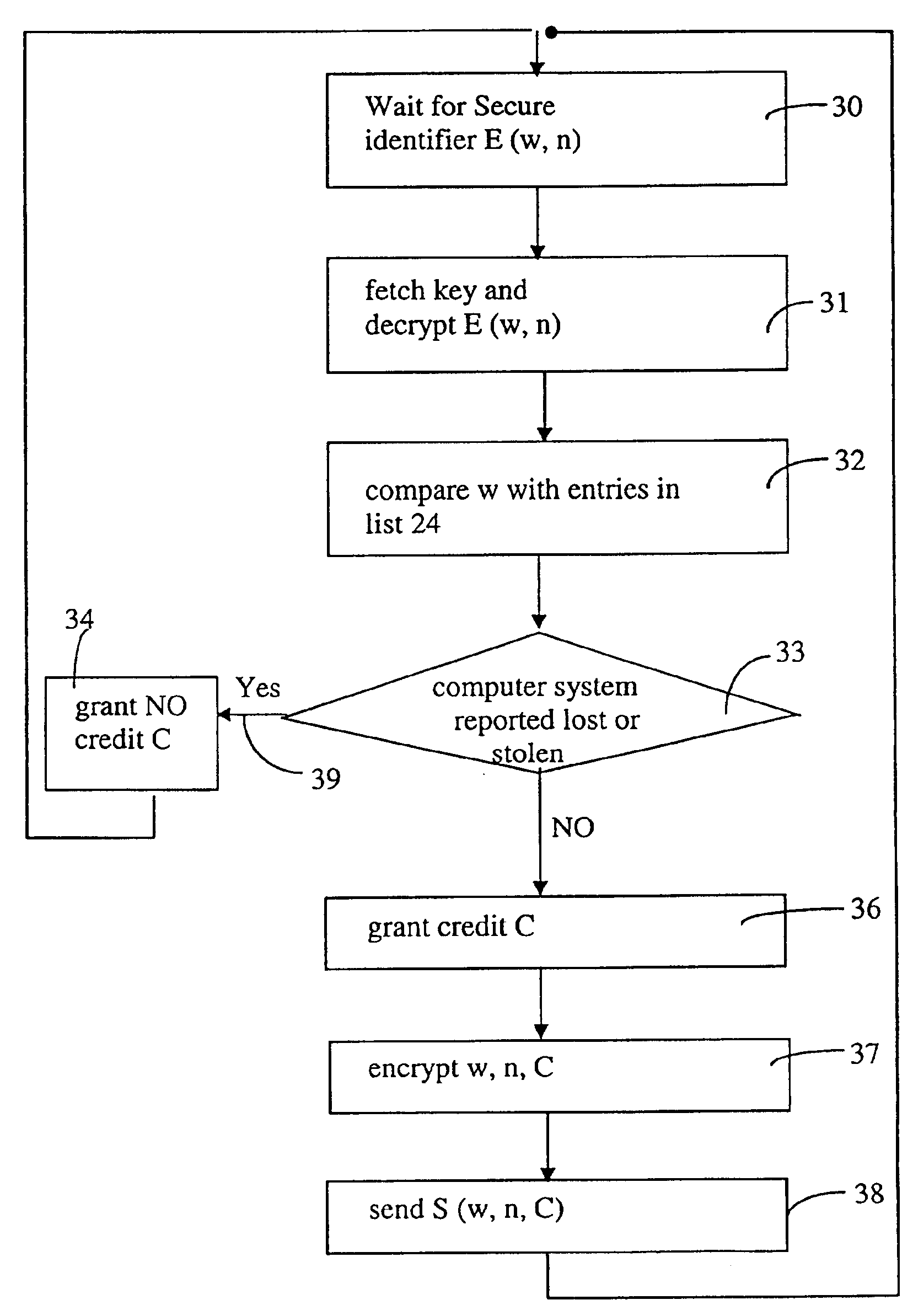
Scheme for blocking the use of lost or stolen network-connectable computer systems
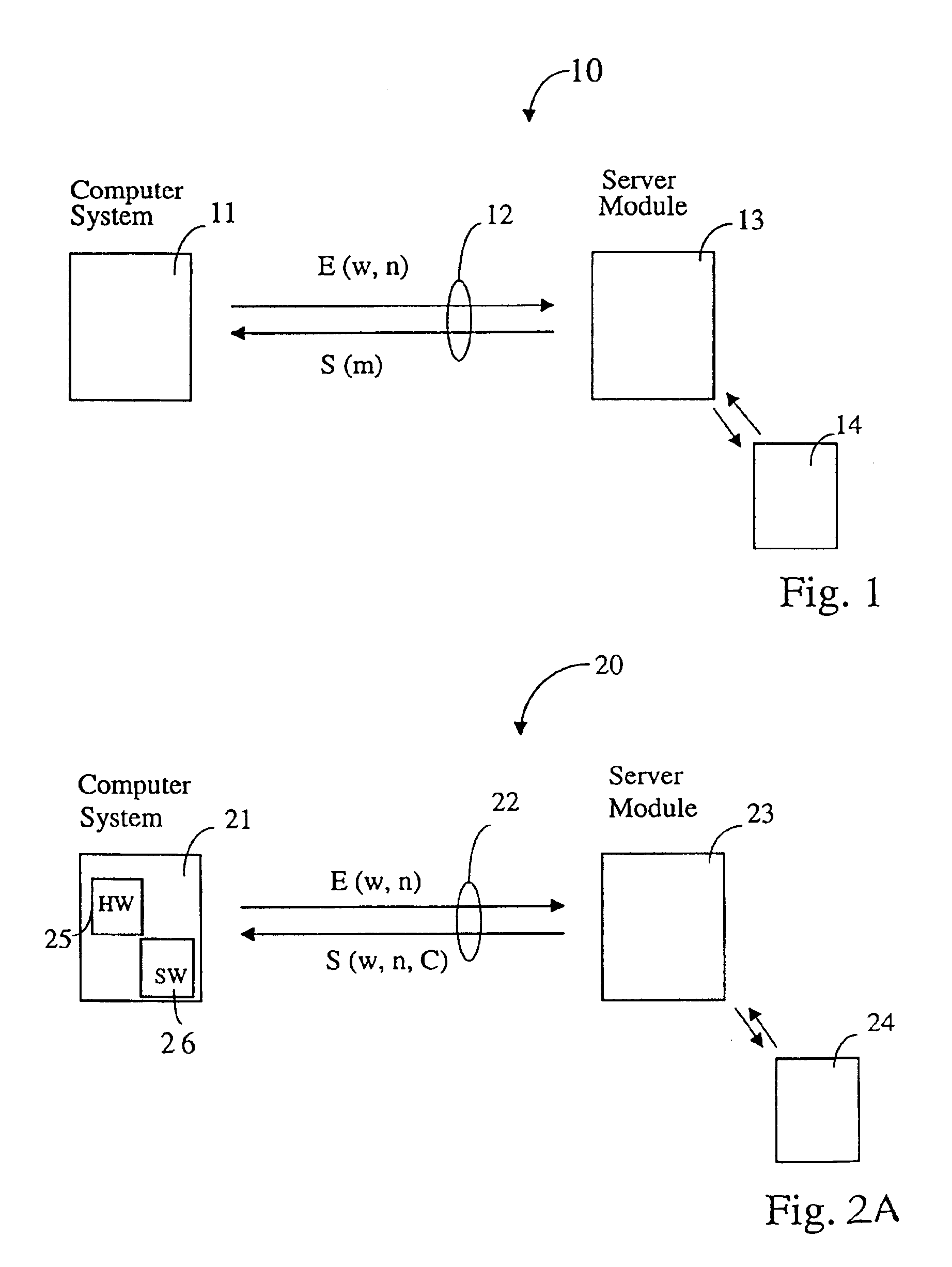
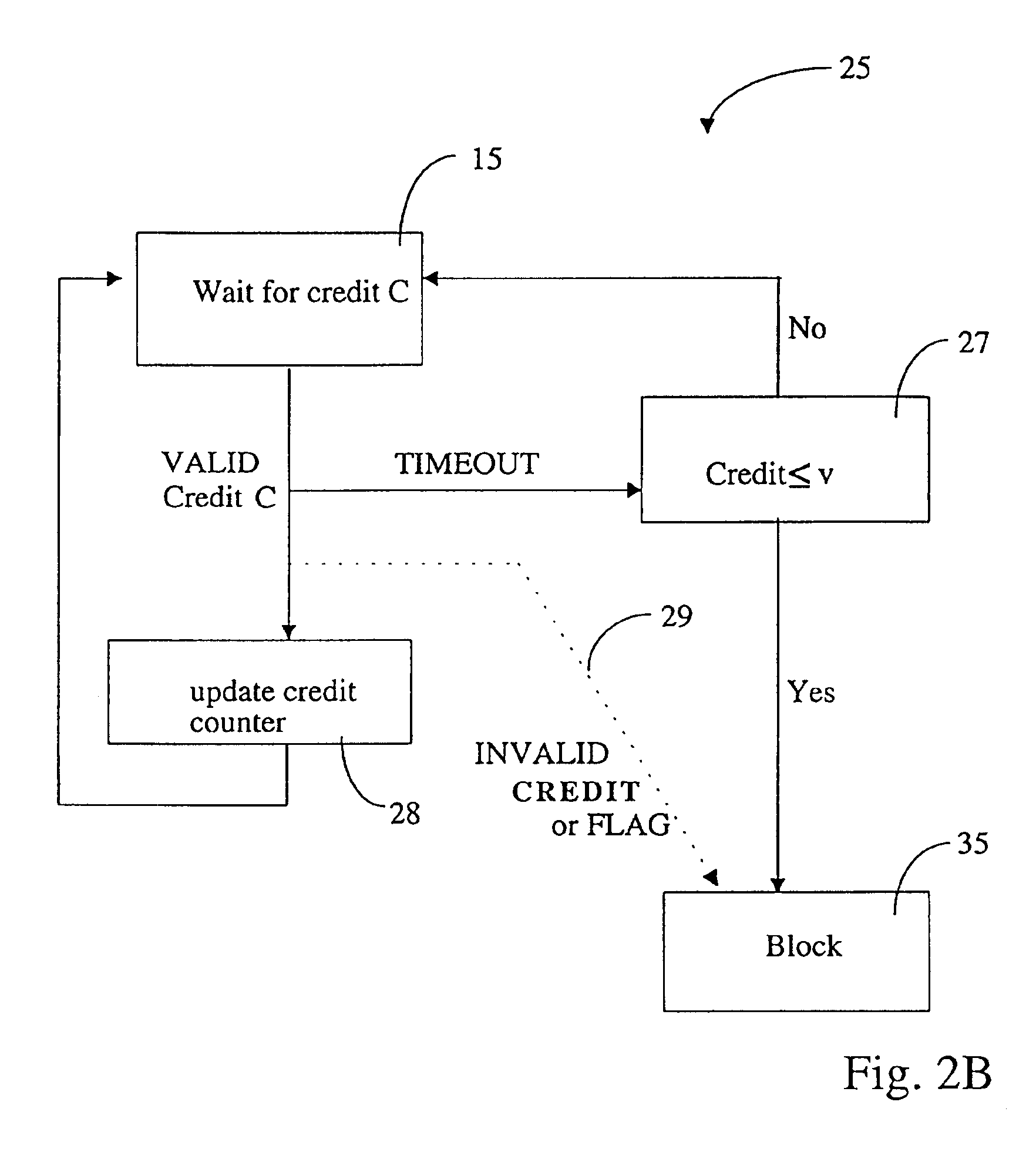
ActiveUS6925562B2Easy to tamper withMaximum flexibilityDigital data processing detailsUser identity/authority verificationCommunication interfaceTrusted hardware
Scheme for switching a computer system (21), which is connectable via a communication interface and a network (22) to a server module (23), into a special mode of operation. The computer system (21) comprises a software component (26) for sending an identifier (w) assigned to the computer system (21) via the communication interface and the network (22) to the server module (23). In response, the software component (26) receives a token (S), issued by the server module (23), whereby the token (S) comprises a credit (C). In addition, the computer system (21) comprises a trusted hardware component (25) storing the identifier (w) and comprising a credit counter (44) with a credit which is automatically exhaustible step-by-step, and which is updateable with the credit (C) received from the server module (23). The computer system (21) has a trigger unit for switching the computer system (21) into the special mode of operation, e.g. a mode where the computer system (21) is of limited use to a user, if the credit of the credit counter is exhausted.
Owner:TREND MICRO INC
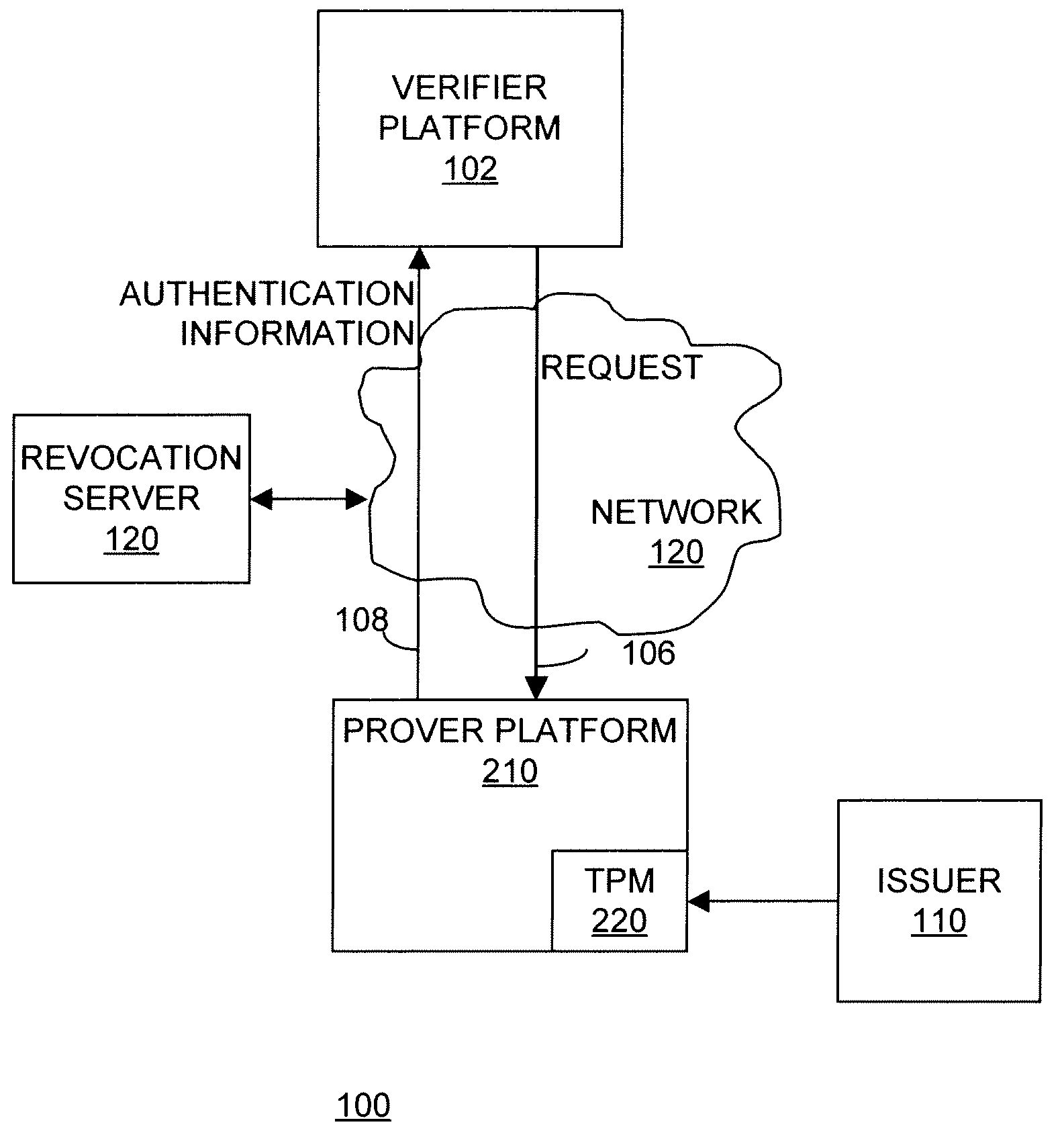
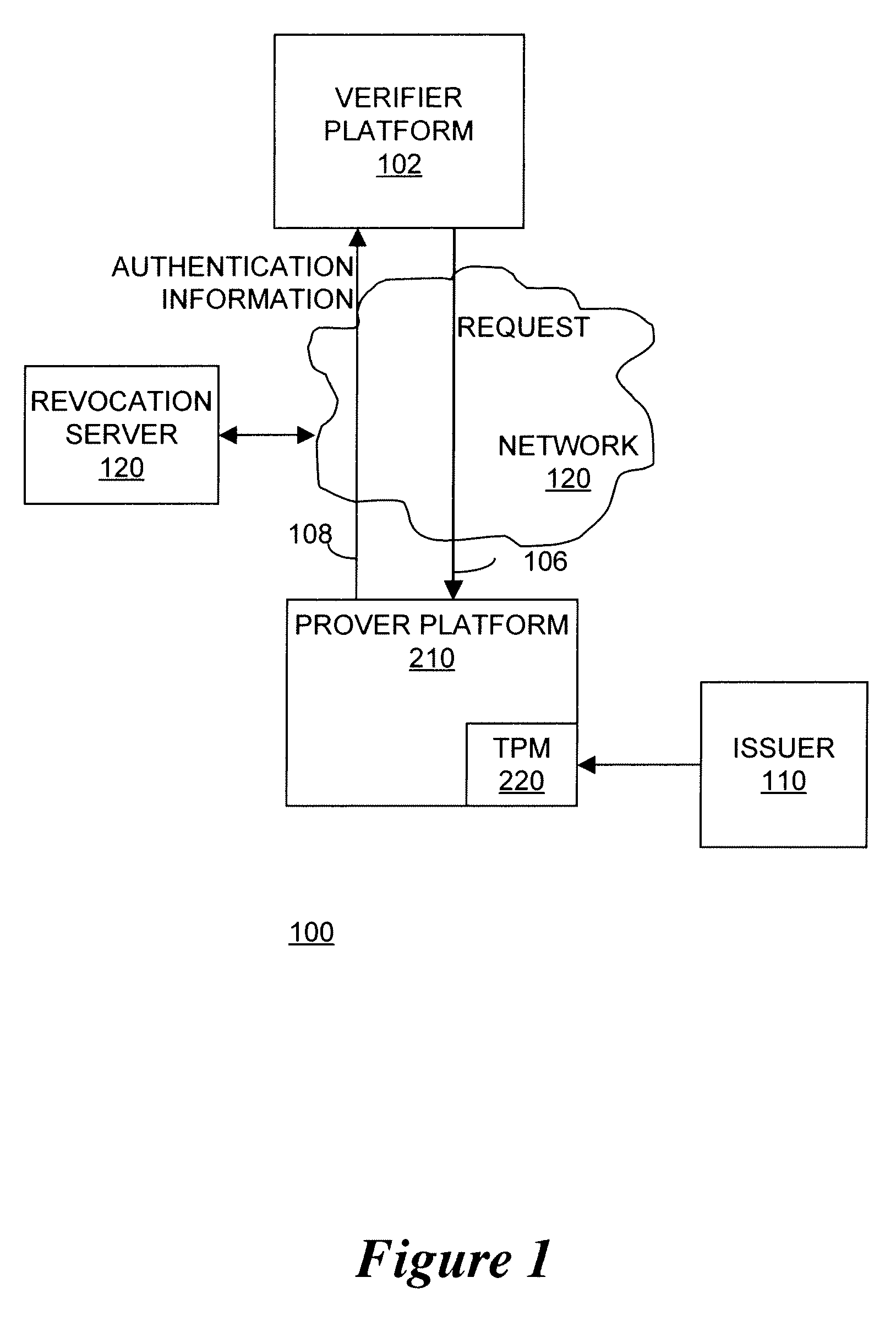
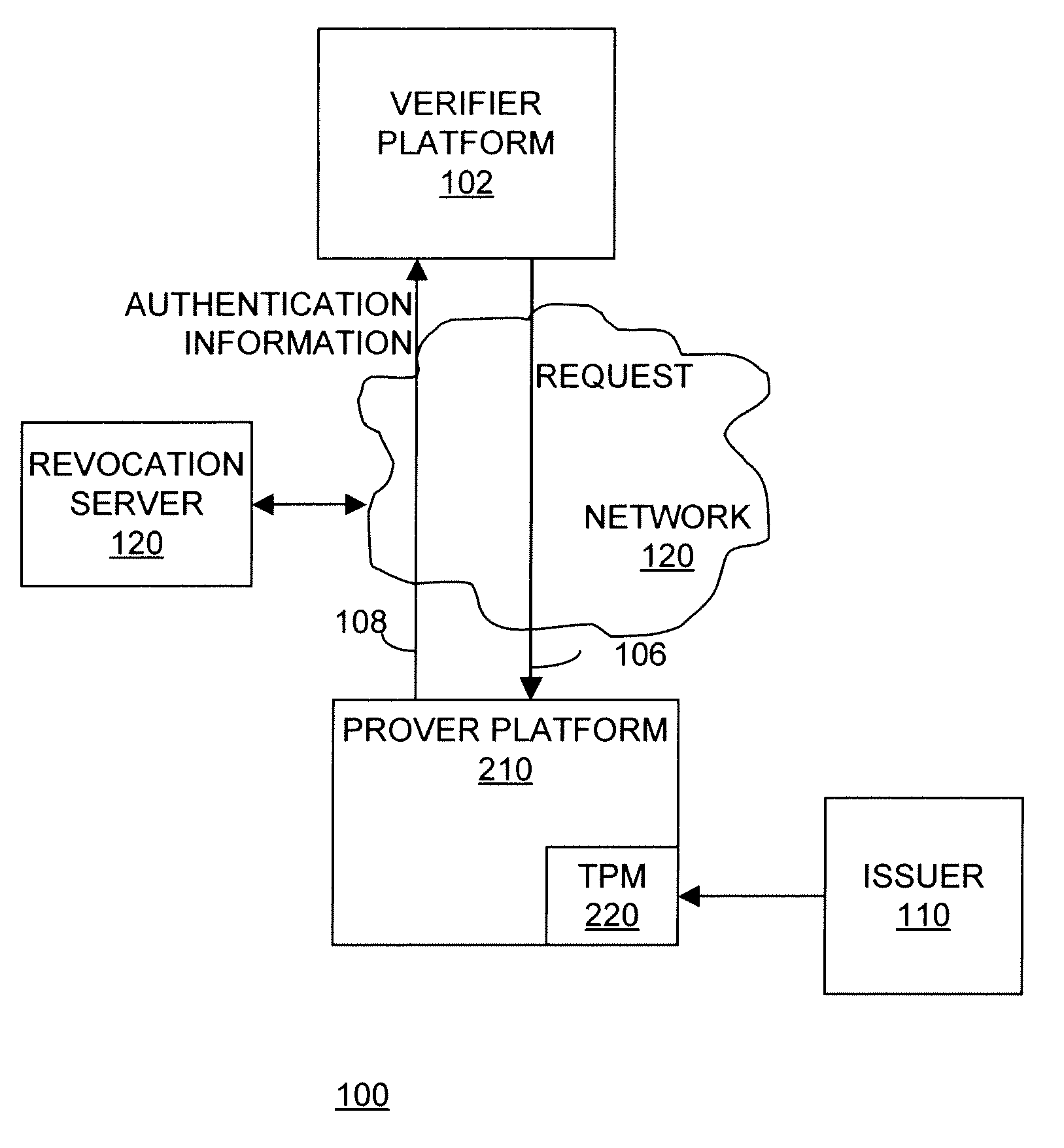
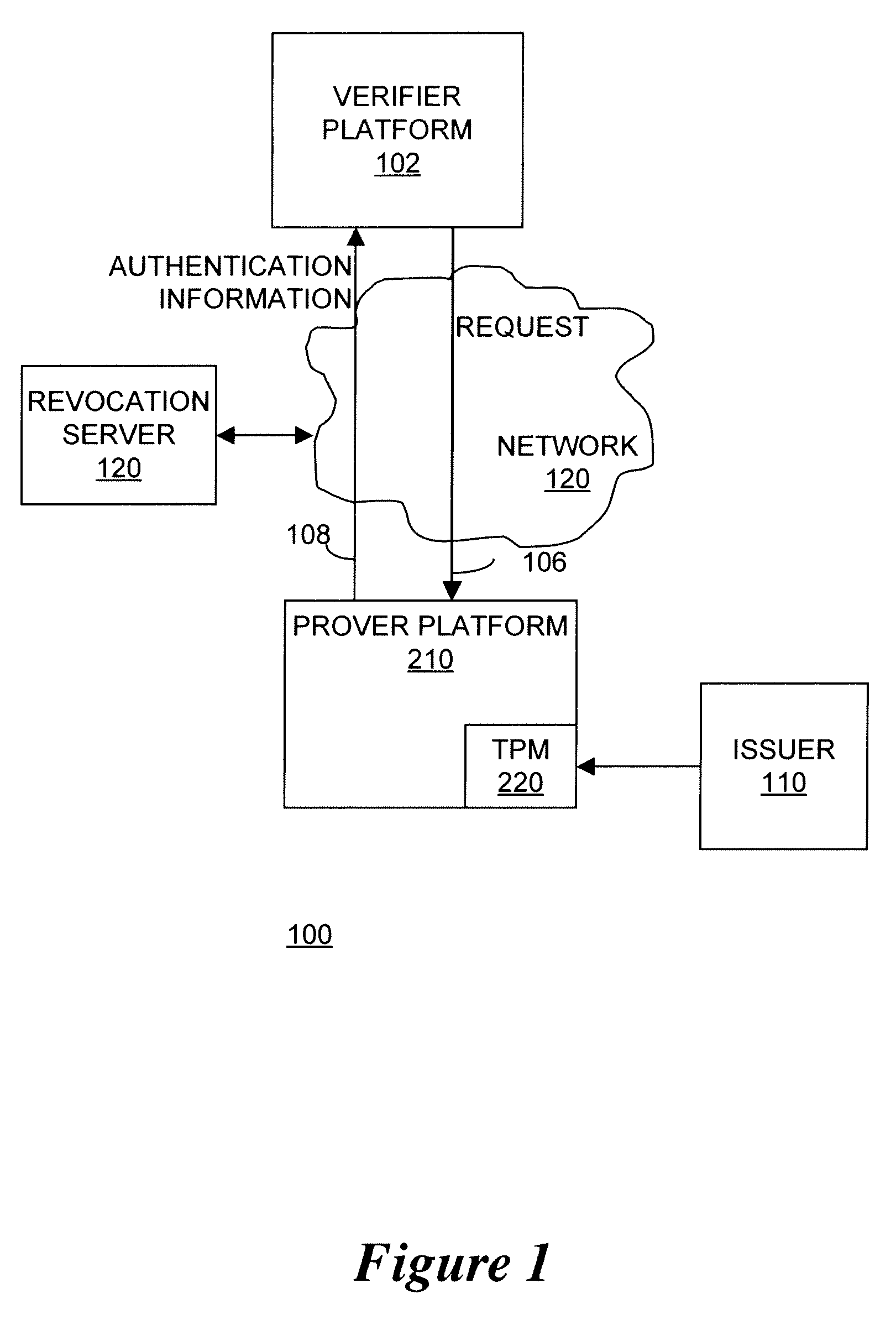
Apparatus and method for enhanced revocation of direct proof and direct anonymous attestation
InactiveUS20080270790A1Digital data processing detailsPublic key for secure communicationTrusted hardwareDigital signature
In some embodiments, a method and apparatus for enhanced revocation of direct proof and direct anonymous attestation are described. In one embodiment a trusted hardware device verifies that membership of the device within a trusted membership group is not revoked according to a revocation list received with a challenge request from a verifier. Once such verification is performed, the device convinces the verifier of possessing cryptographic information without revealing unique, device identification information of the trusted hardware device or the cryptographic information. In one embodiment, the trusted hardware device computes a digital signature on a message received with the challenge request to the verifier if membership of the anonymous hardware device within a trusted membership group is verified. In one embodiment, the verifier authenticates the digital signature according to a public key of the trusted membership group to enable a trusted member device to remain anonymous to the verifier. Other embodiments are described and claimed.
Owner:INTEL CORP
Hardened event counters for anomaly detection
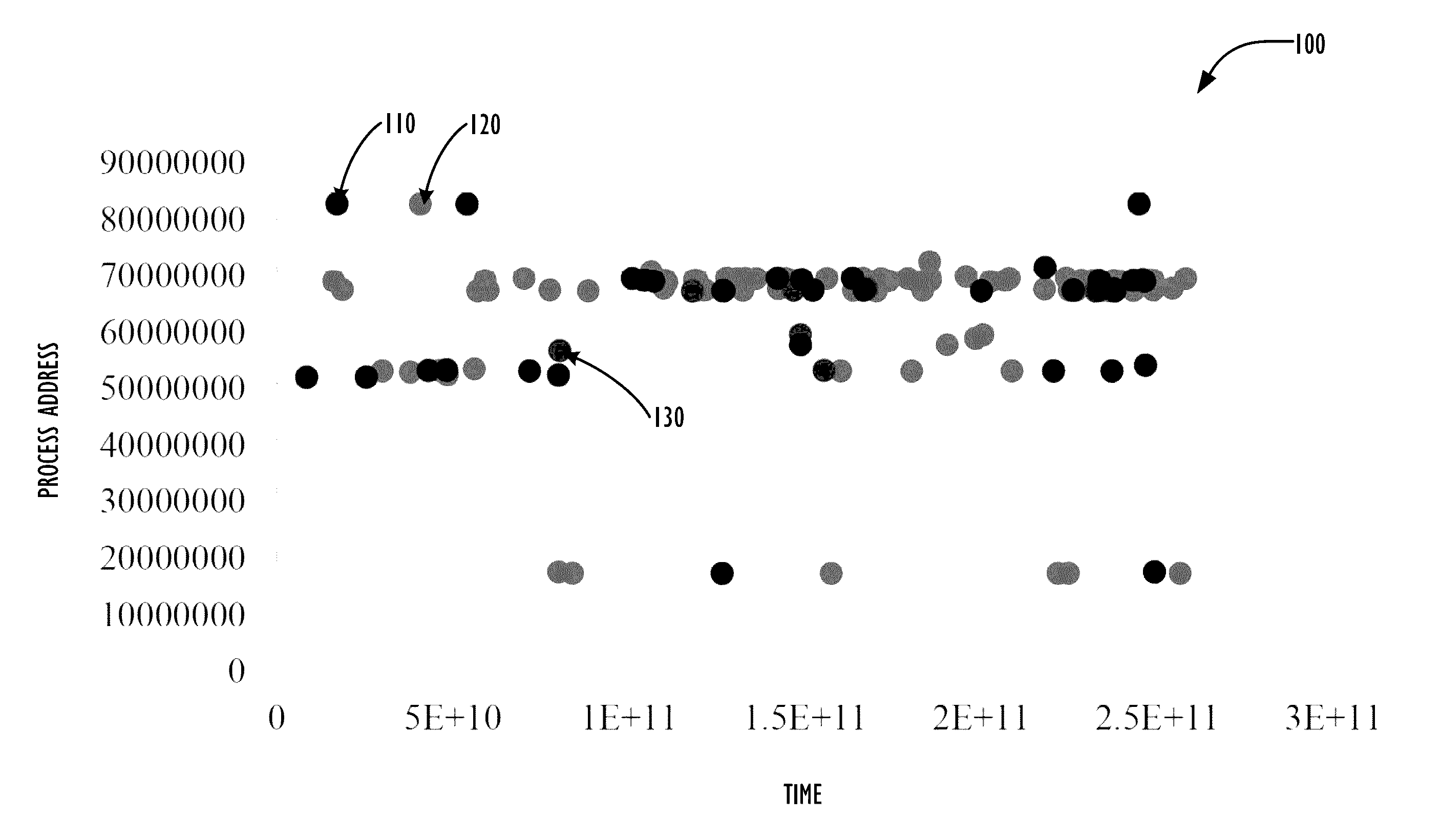
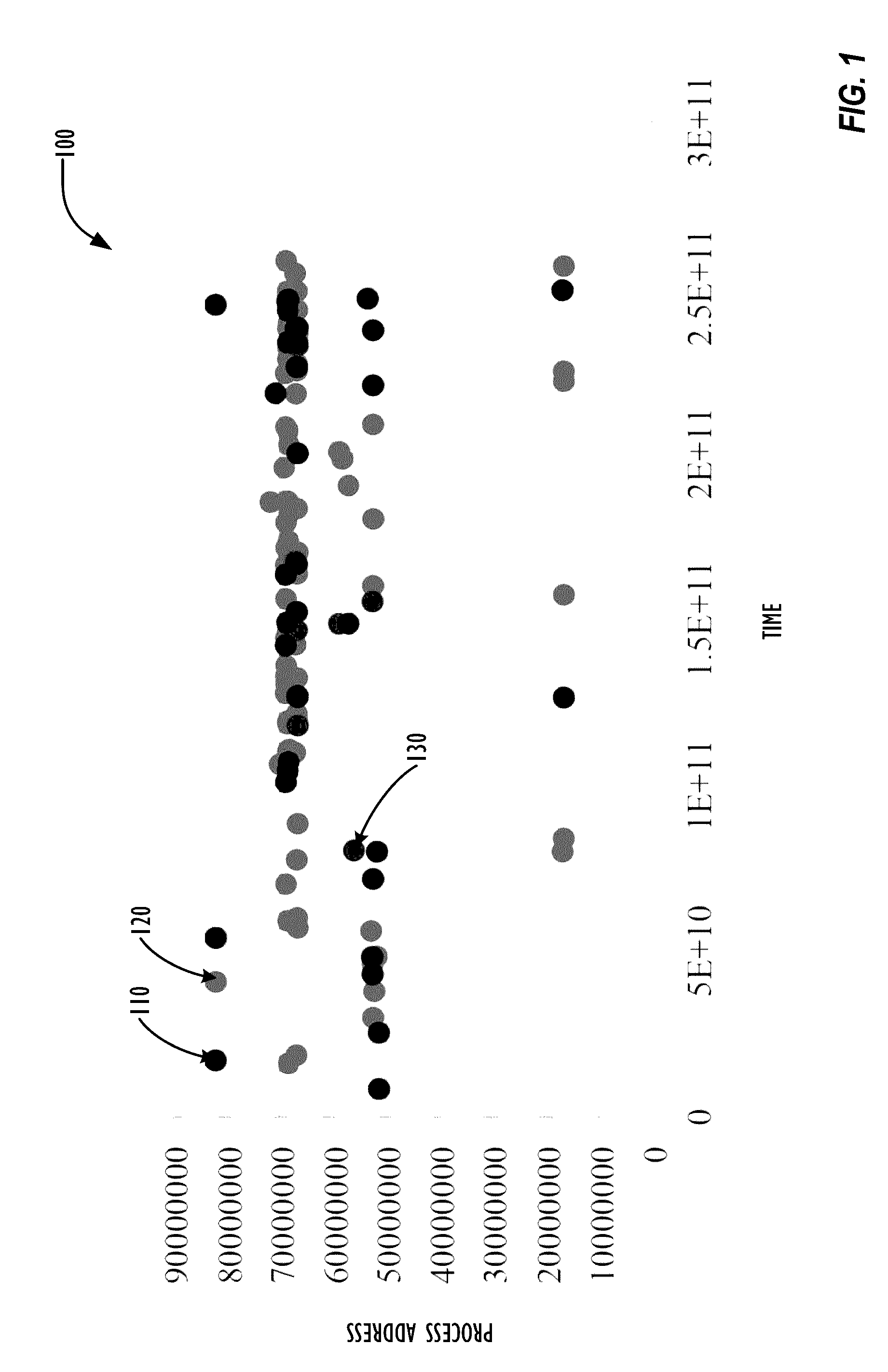
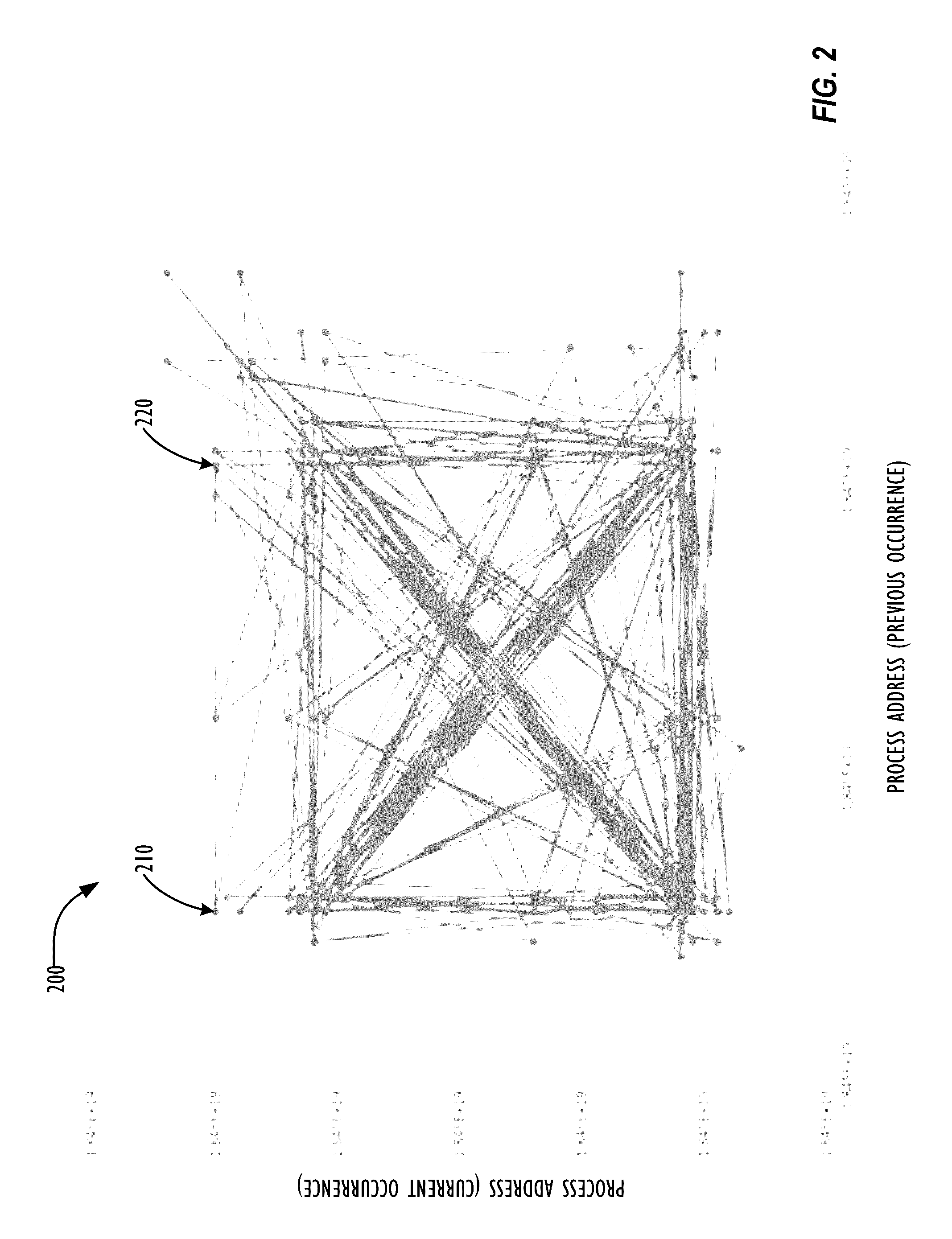
A collection of techniques allow for the detection of covert malware that attempts to hide its existence on a system by leveraging both trusted hardware event counters and the particular memory addresses (as well as the sequences of such addresses) of the instructions that are generating the suspected malicious activity. By monitoring the address distribution's specific patterns over time, one can build a behavioral model (i.e., “fingerprint”) of a particular process—and later attempt to match suspected malicious processes to the stored behavioral models. Whenever the actual measured behavior of a suspected malicious process fails to match said stored behavioral models, the system or system administrator may attempt to perform rehabilitative actions on the computer system to locate and remove the malware hiding on the system.
Owner:MCAFEE LLC
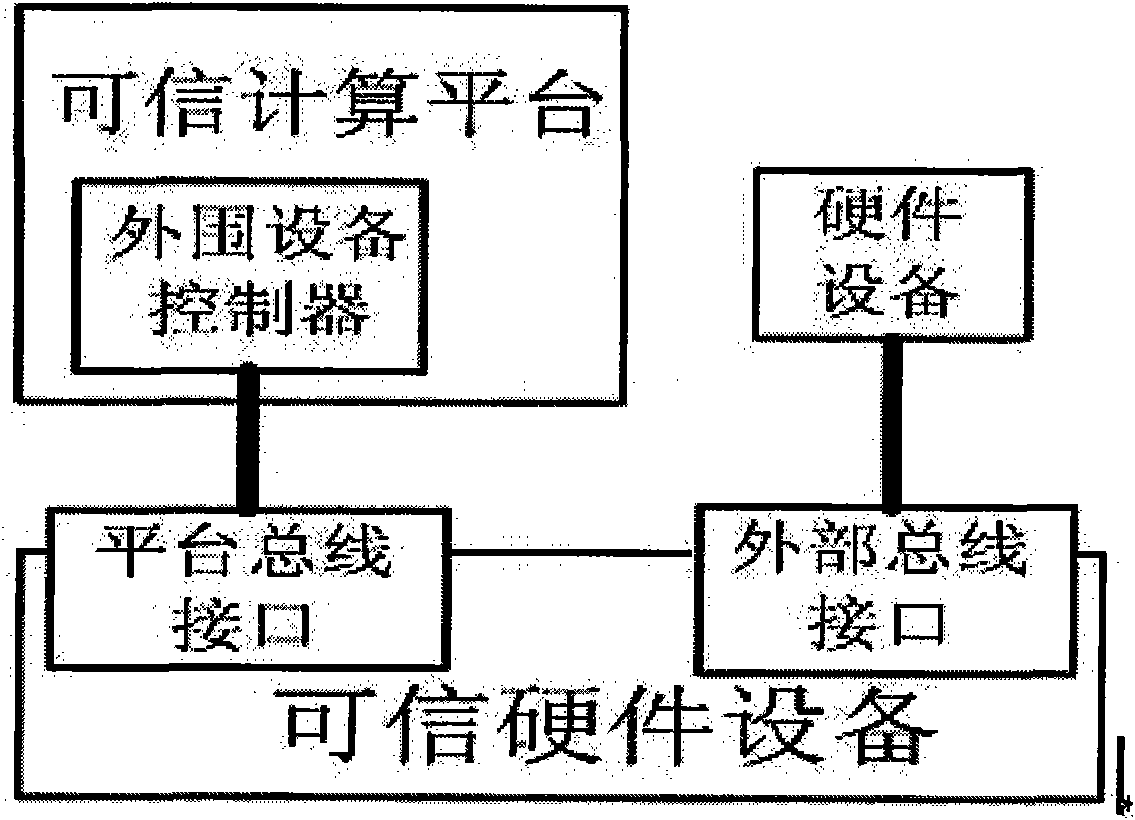
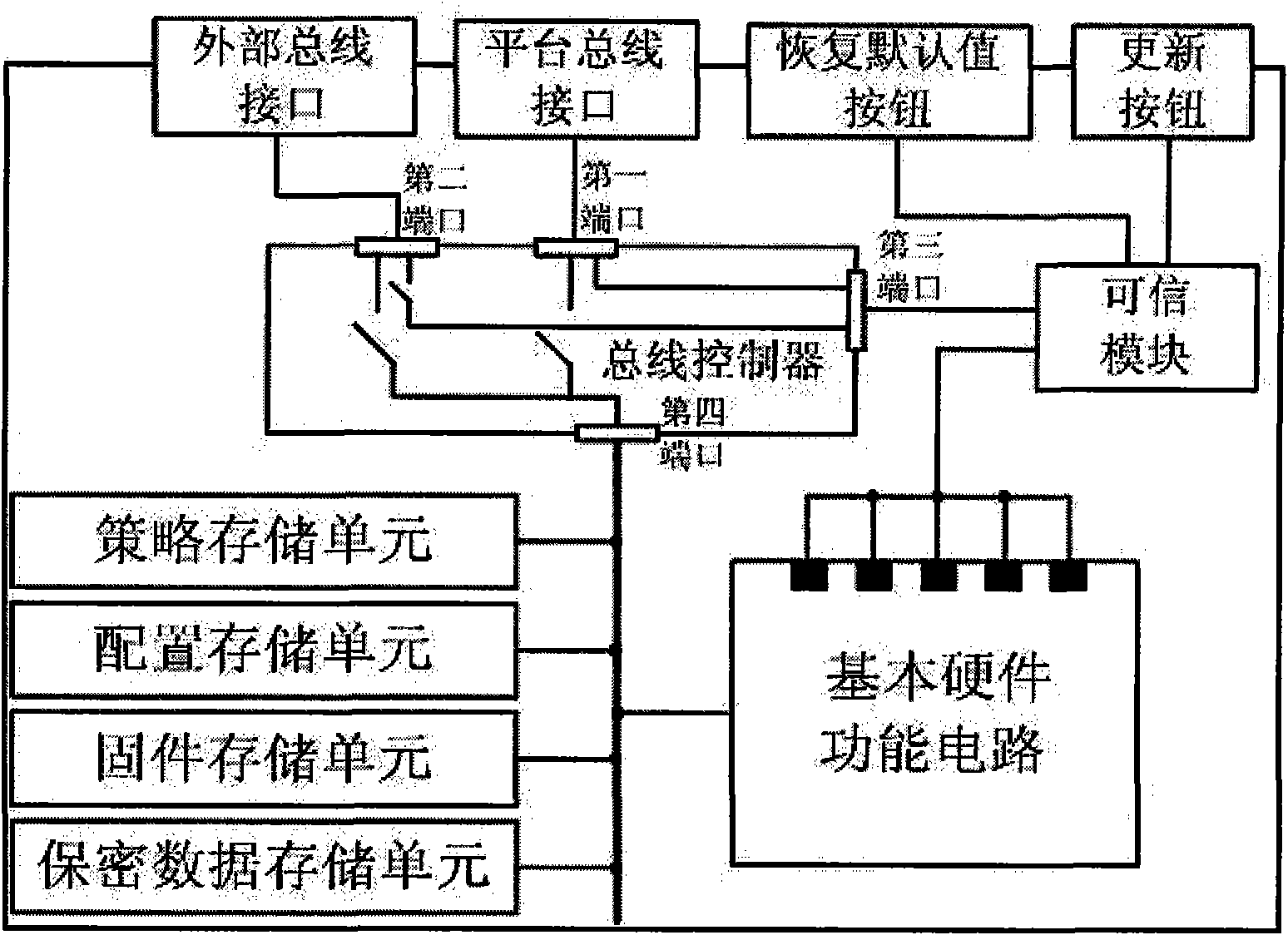
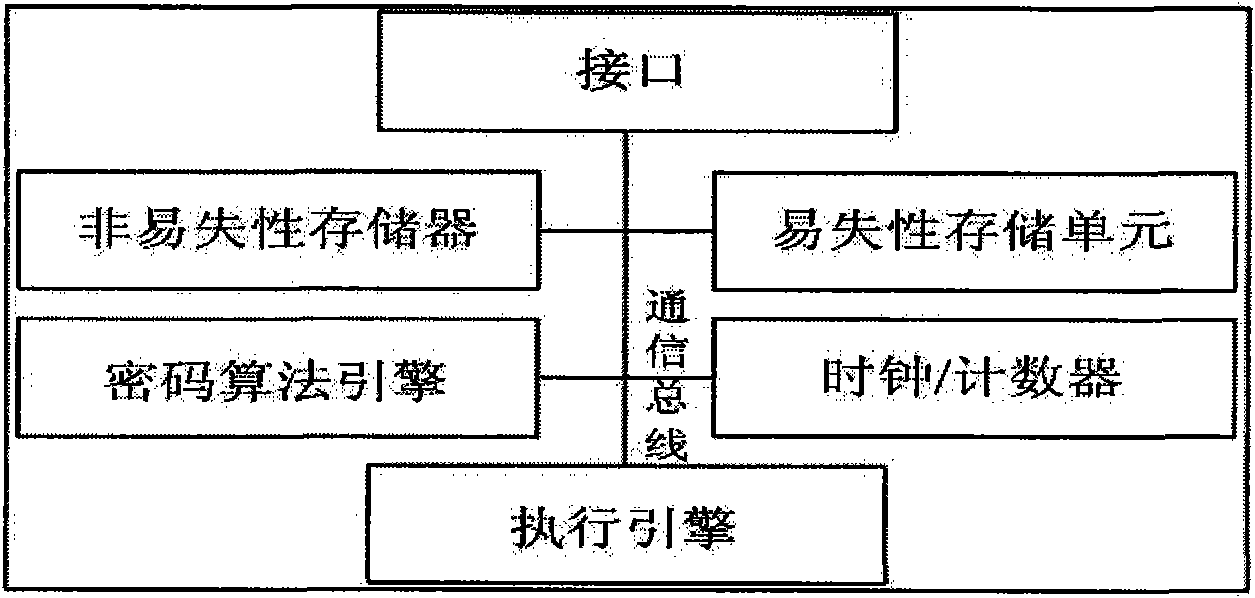
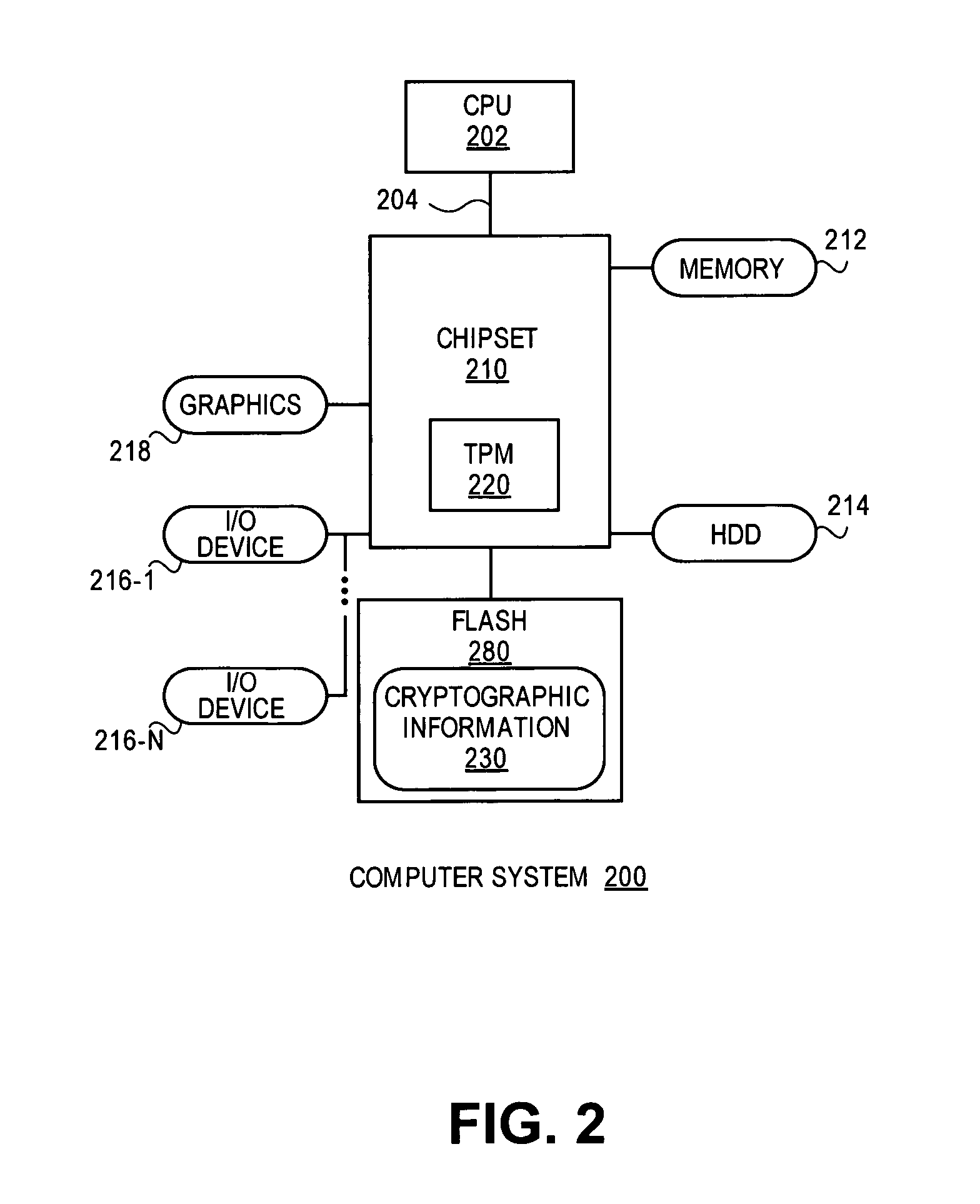
Trusted hardware equipment and using method thereof
ActiveCN101901318AReal-time integrity self-test functionIntegrity controlPlatform integrity maintainanceTrusted hardwareNetwork packet
The invention discloses trusted hardware equipment and a using method thereof, which belong to the field of trusted computing. A trusted module with control function in the trusted hardware equipment is used for checking operating state and completeness of the trusted hardware equipment. The checking contents include but are not limited to a firmware code of a basic hardware functional circuit, operating mode configuration information, control strategy configuration information, a session key, an equipment certificate, trusted interaction-based controlled function, operating state of the basic hardware functional circuit and the like. The trusted module can verify a trusted computing platform digital signature or encrypted data packet including the firmware code, the operating mode configuration information, the control strategy configuration information, the session key and the equipment certificate and store the verified data packet into the firmware memory unit, the configuration memory unit, the strategy memory unit and the private data memory unit of the trusted hardware equipment. The equipment and the method provide a judgment means for judging the creditability and trustiness of the hardware equipment for a trusted computing platform.
Owner:BEIJING UNIV OF TECH
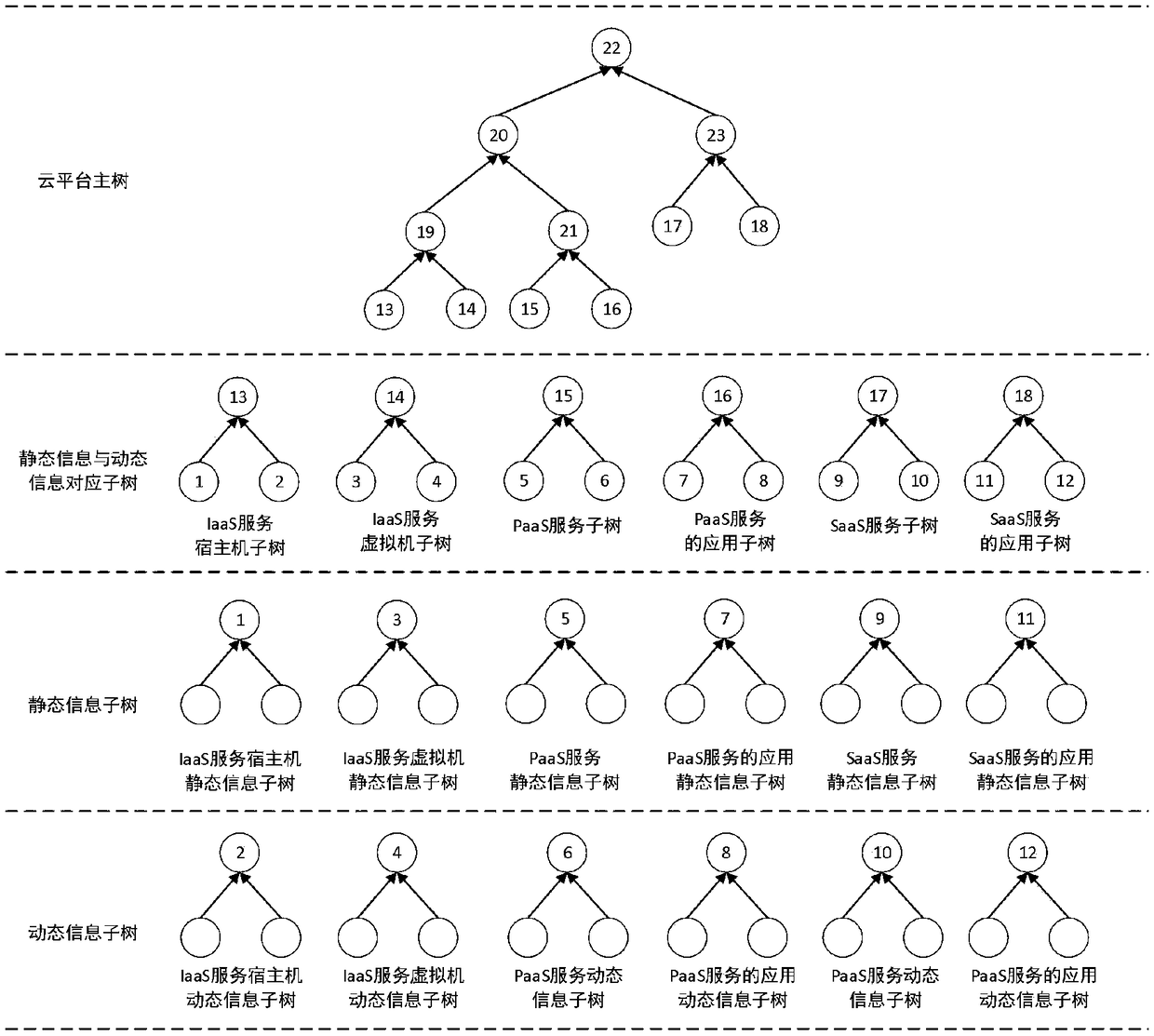
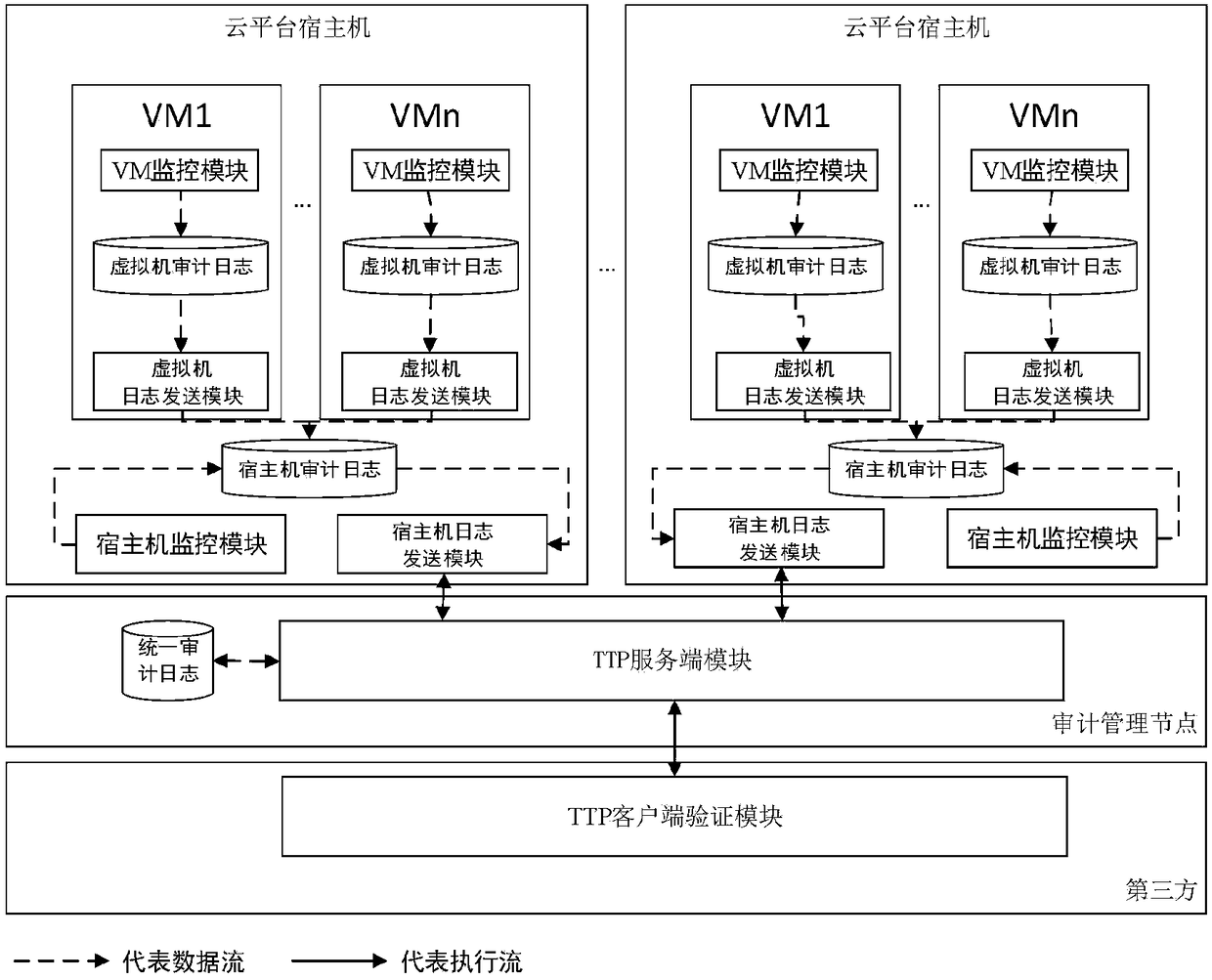
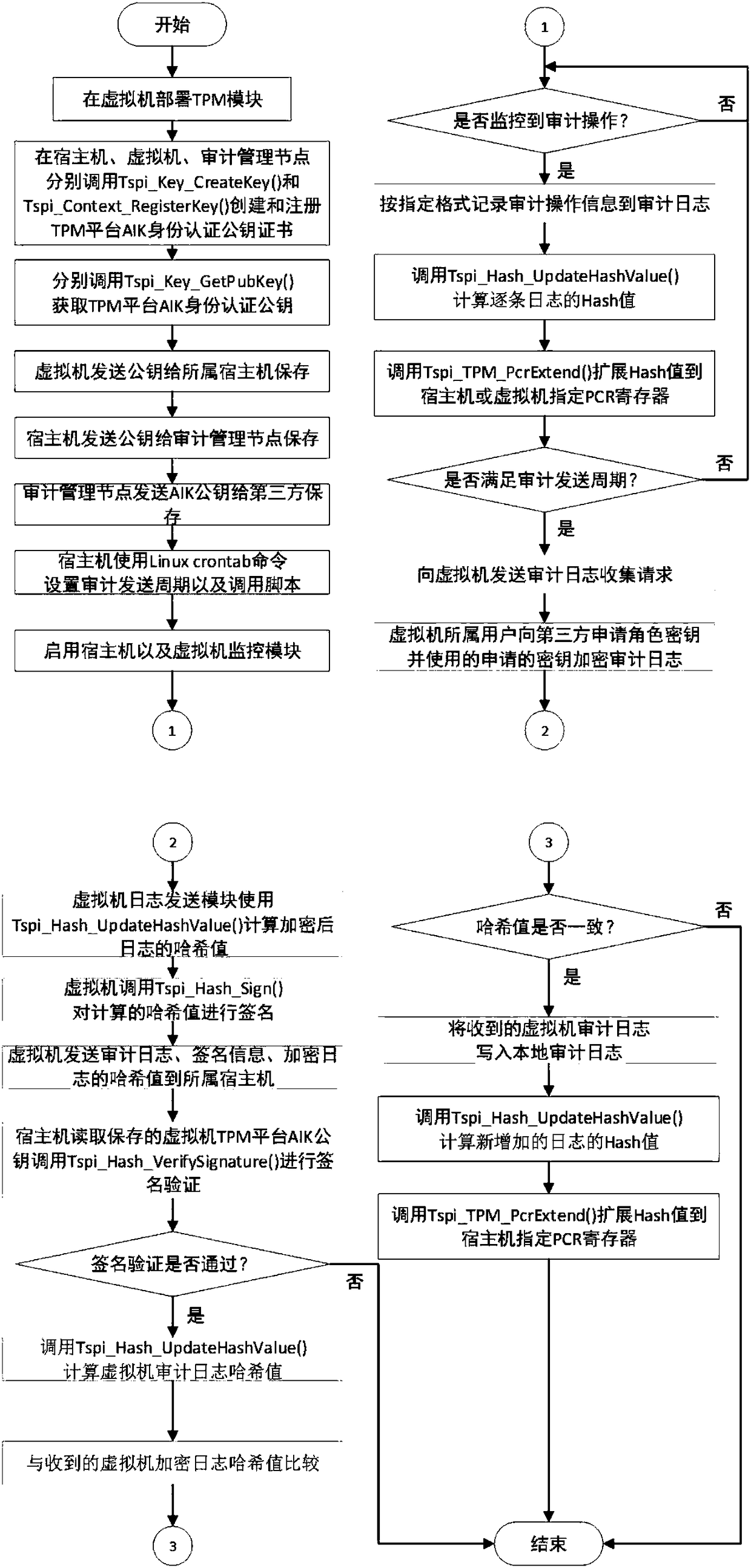
Cloud platform trusted log auditing method for privacy protection based on trusted third party
ActiveCN108322306ARealize the collectionGuarantee authenticityKey distribution for secure communicationUser identity/authority verificationThird partyCloud user
The invention discloses a cloud platform trusted log auditing method for privacy protection based on a trusted third party, and belongs to the field of cloud computing. The method comprises the following steps: step 1: collecting a cloud platform auditing log; step 2: securely transmitting the auditing log; step 3: generating and publishing a verification data structure of a third party auditing log; and step 4 verifying the auditing logs of a cloud service provider and the cloud user. Auditing responsibility association objects are added in the auditing events of different cloud service modes(IaaS, PaaS, SaaS), reliable collection and transmission of the auditing logs are provided based on trusted hardware, auditing log verification supporting privacy protection is provided based on a hierarchical random Merkle hash tree, and the cloud auditing responsibility chasing of cloud service providers and cloud users is supported.
Owner:BEIJING UNIV OF TECH
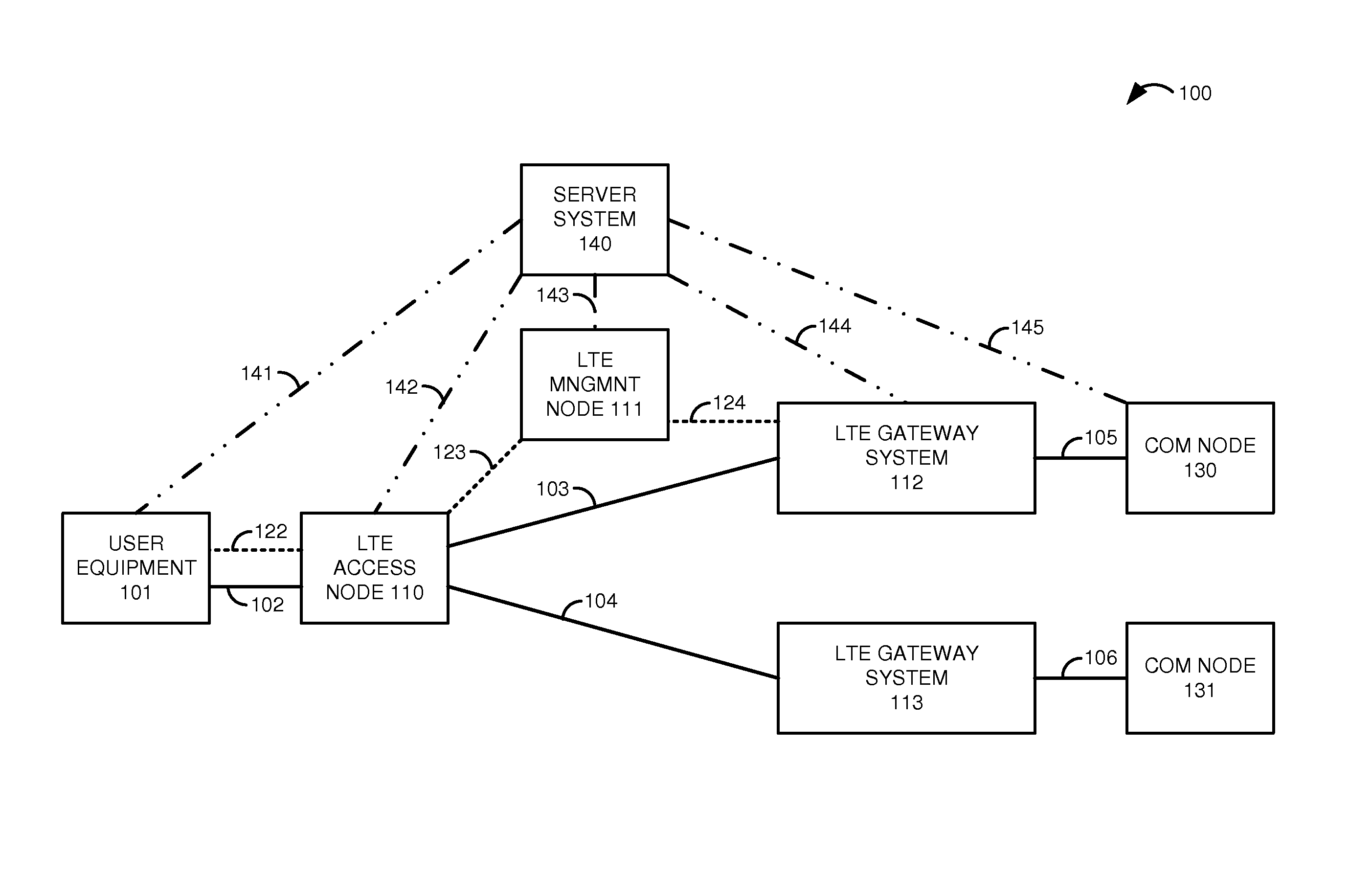
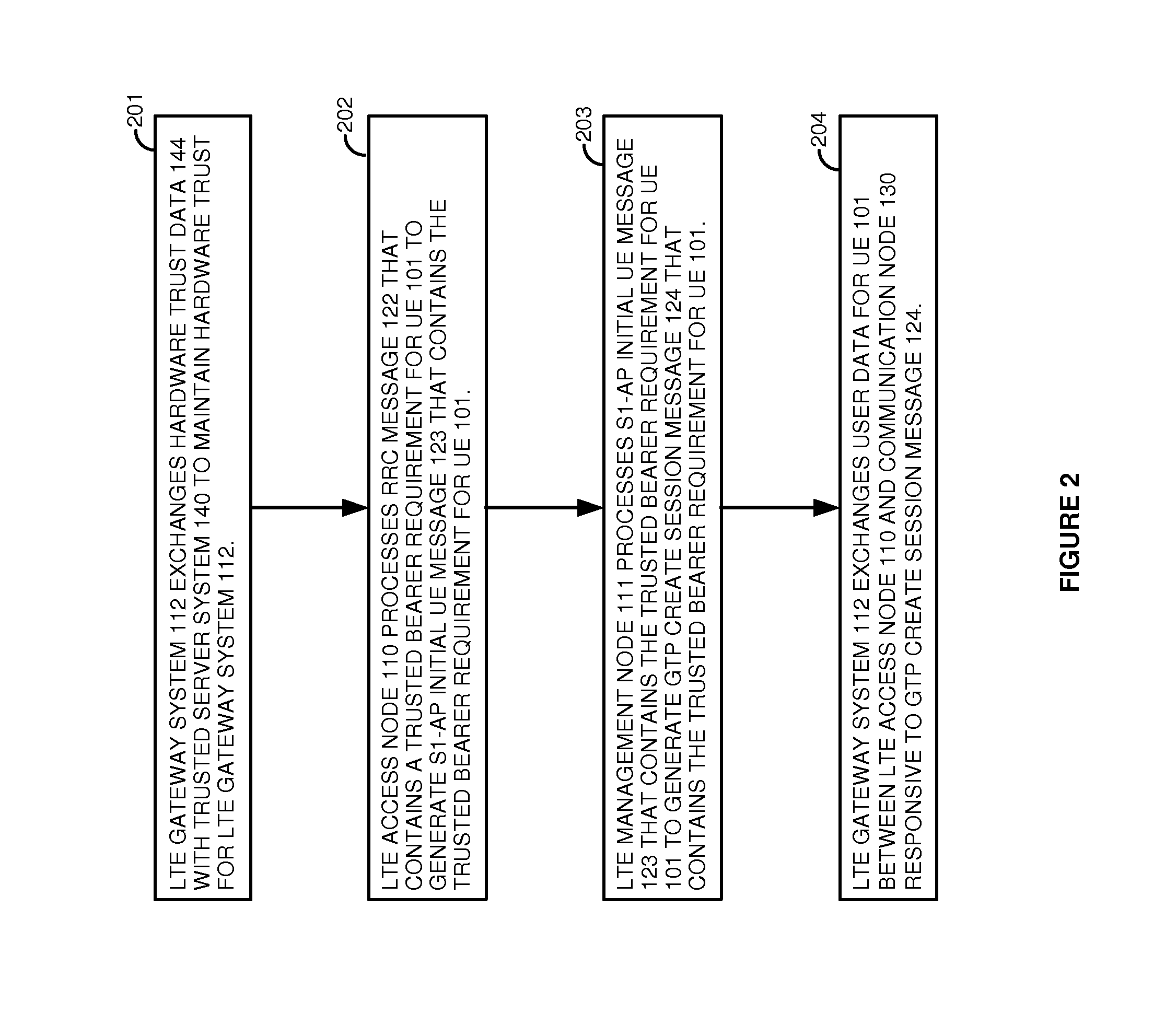
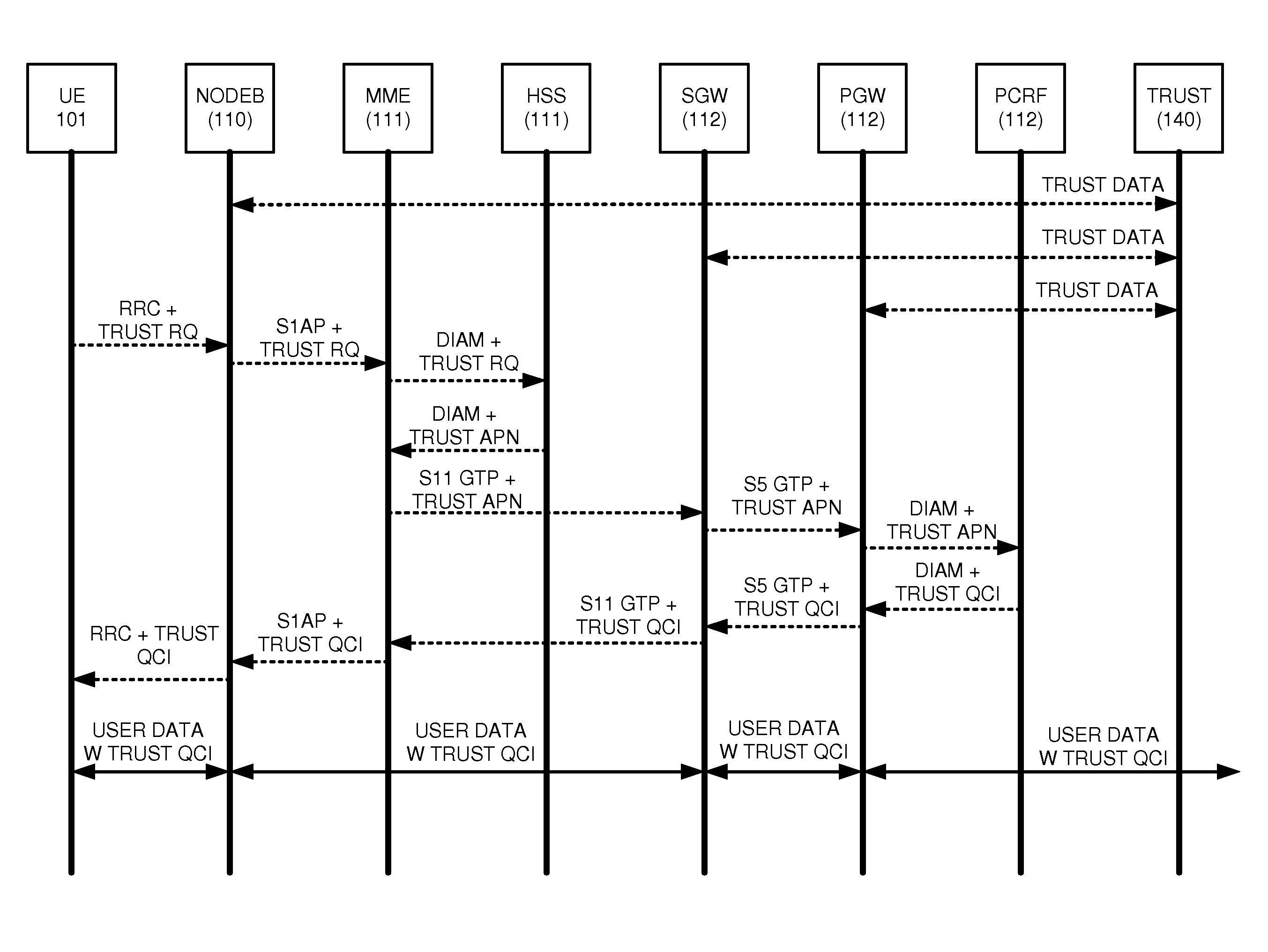
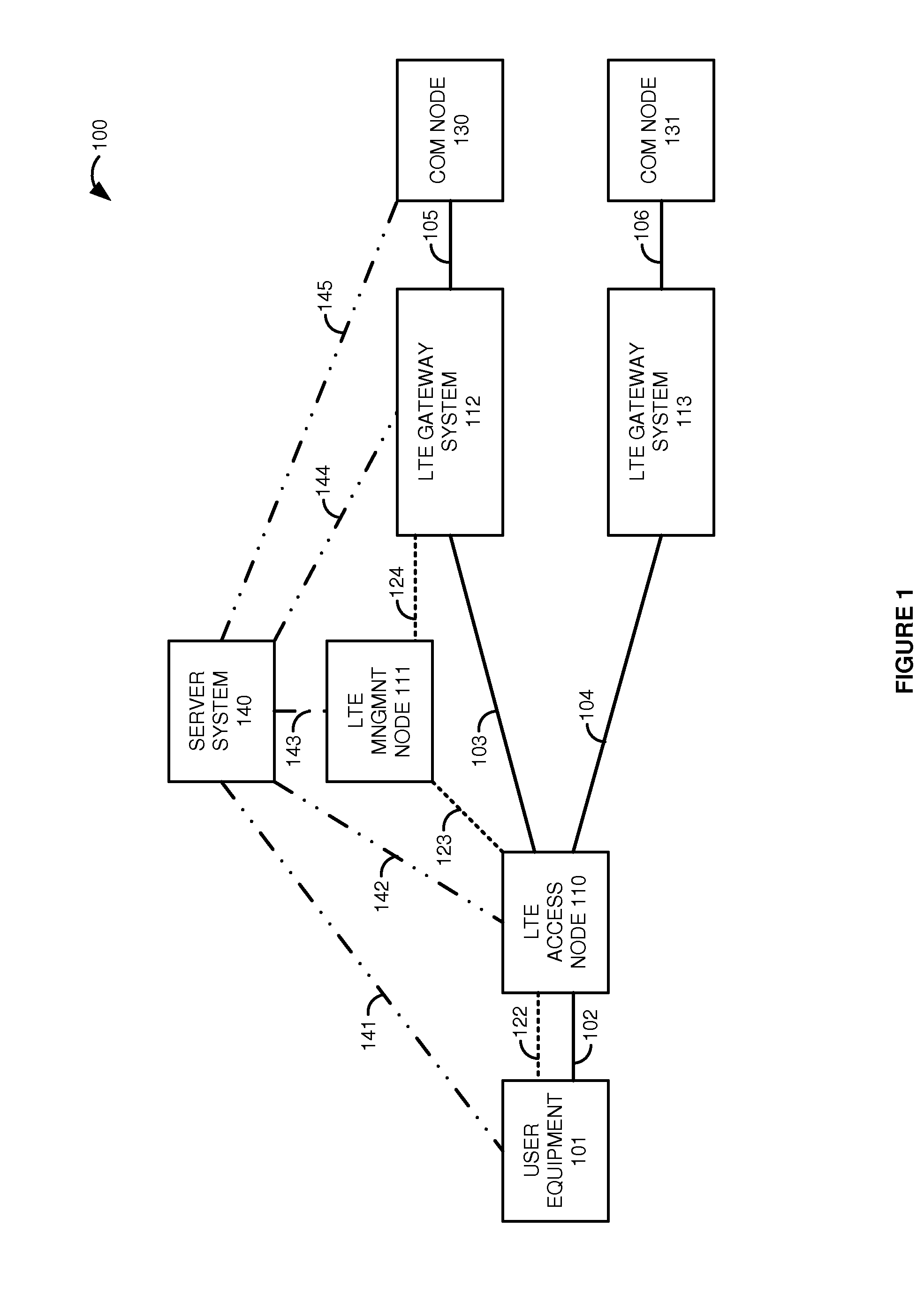
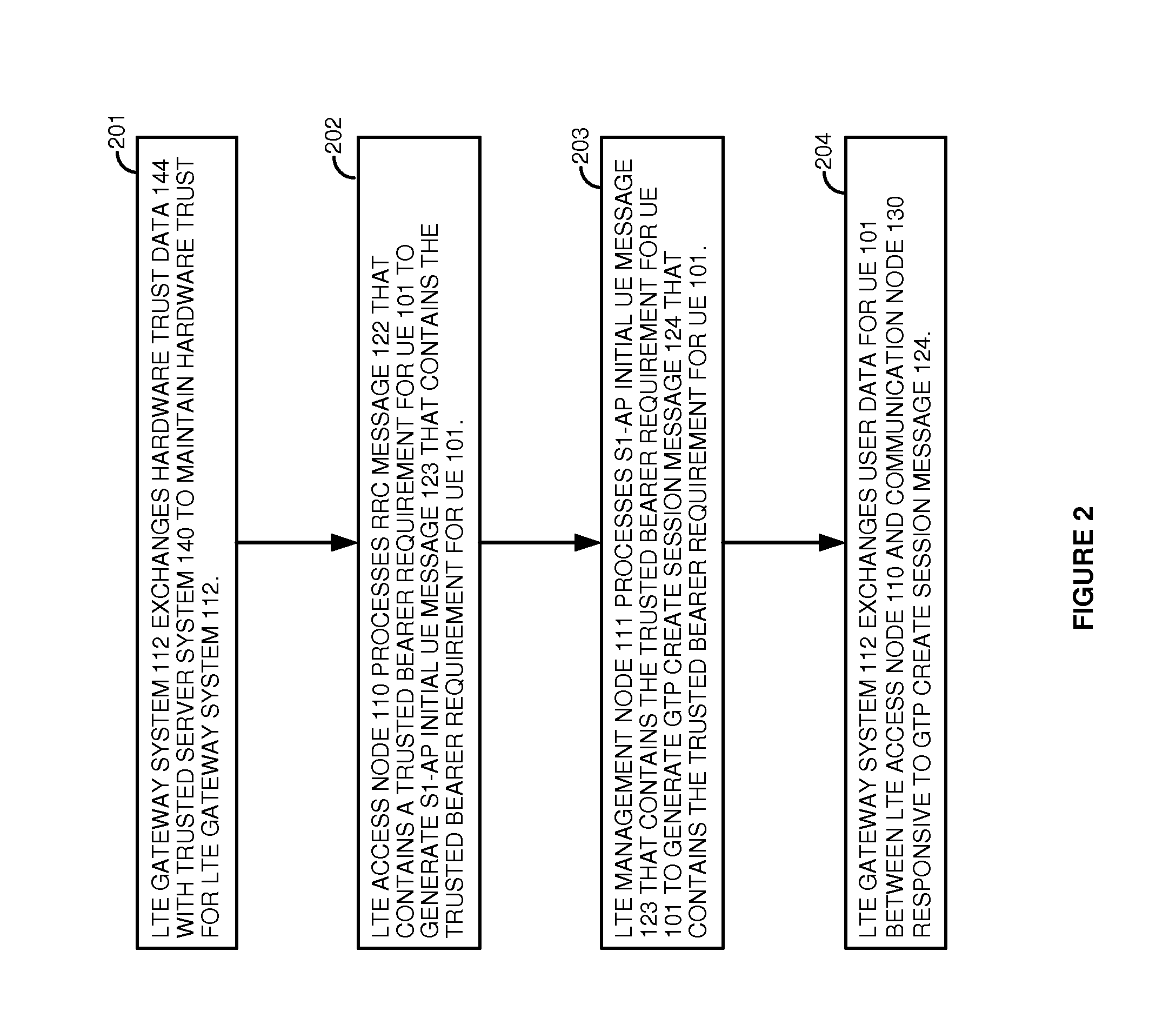
Long term evolution (LTE) communications over trusted hardware
A Long Term Evolution (LTE) communication network transfers data communications for User Equipment (UE). An LTE gateway system exchanges hardware trust data with a server system to maintain hardware trust for the LTE gateway system. An LTE access node processes a Radio Resource Control (RRC) message that contains a trusted bearer requirement for the UE to generate an S1 Application Protocol (S1-AP) initial UE message that contains the trusted bearer requirement for the UE. An LTE management node processes the S1-AP initial UE message to generate a General Packet Radio Service Transfer Protocol (GTP) create session message that contains the trusted bearer requirement for the UE. The LTE gateway system exchanges user data for the UE between the LTE access node and a communication node responsive to the GTP create session message.
Owner:T MOBILE INNOVATIONS LLC
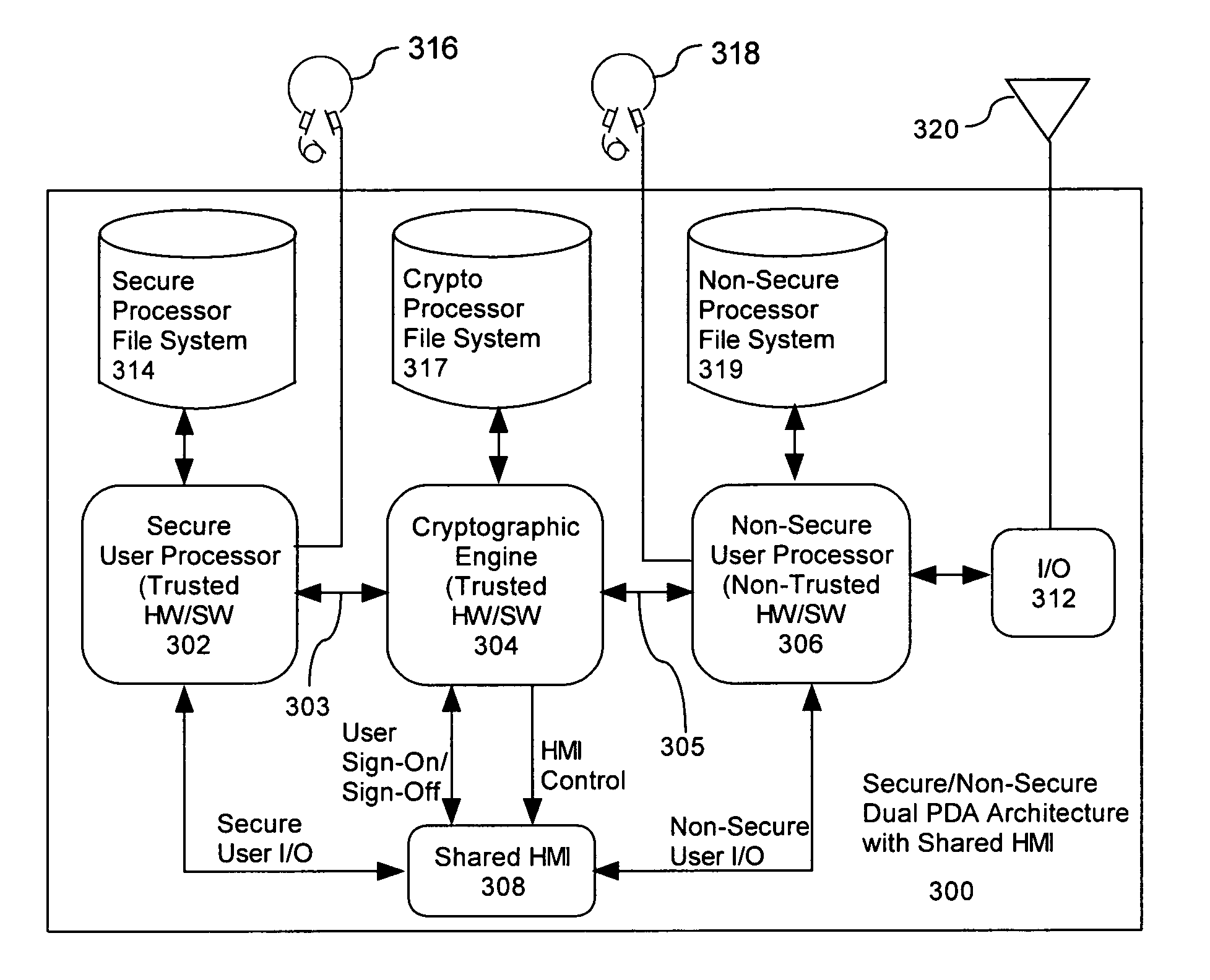
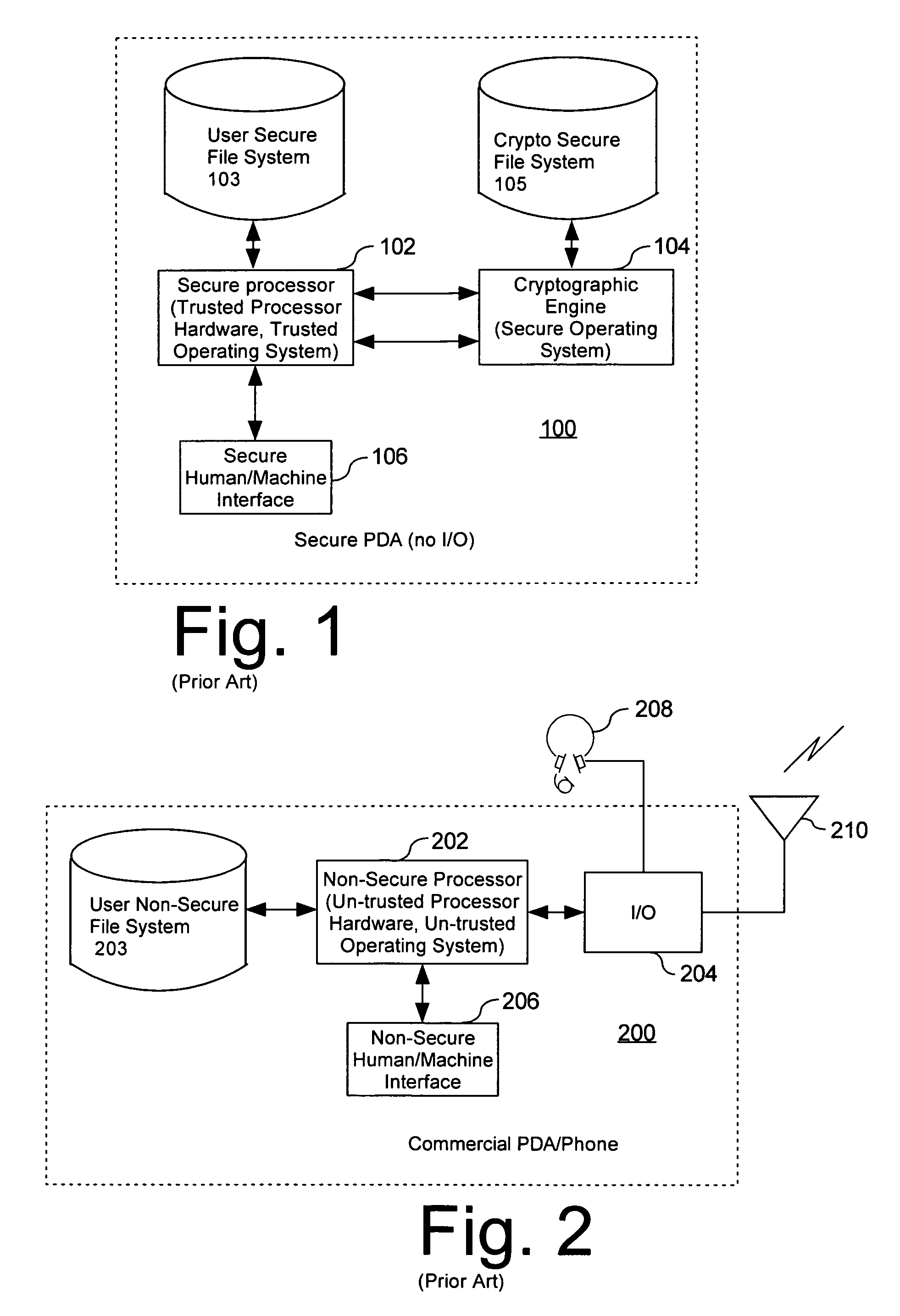
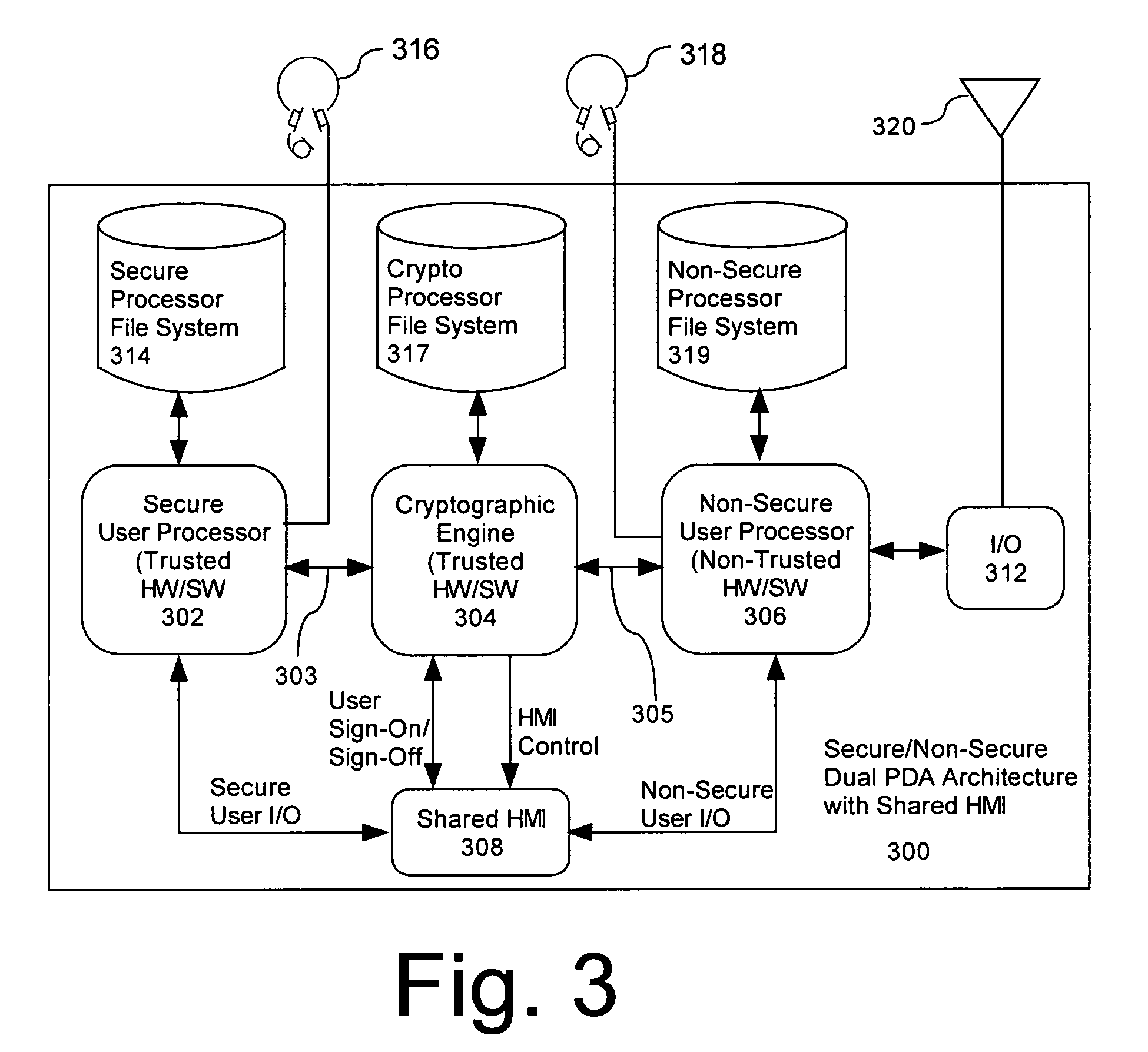
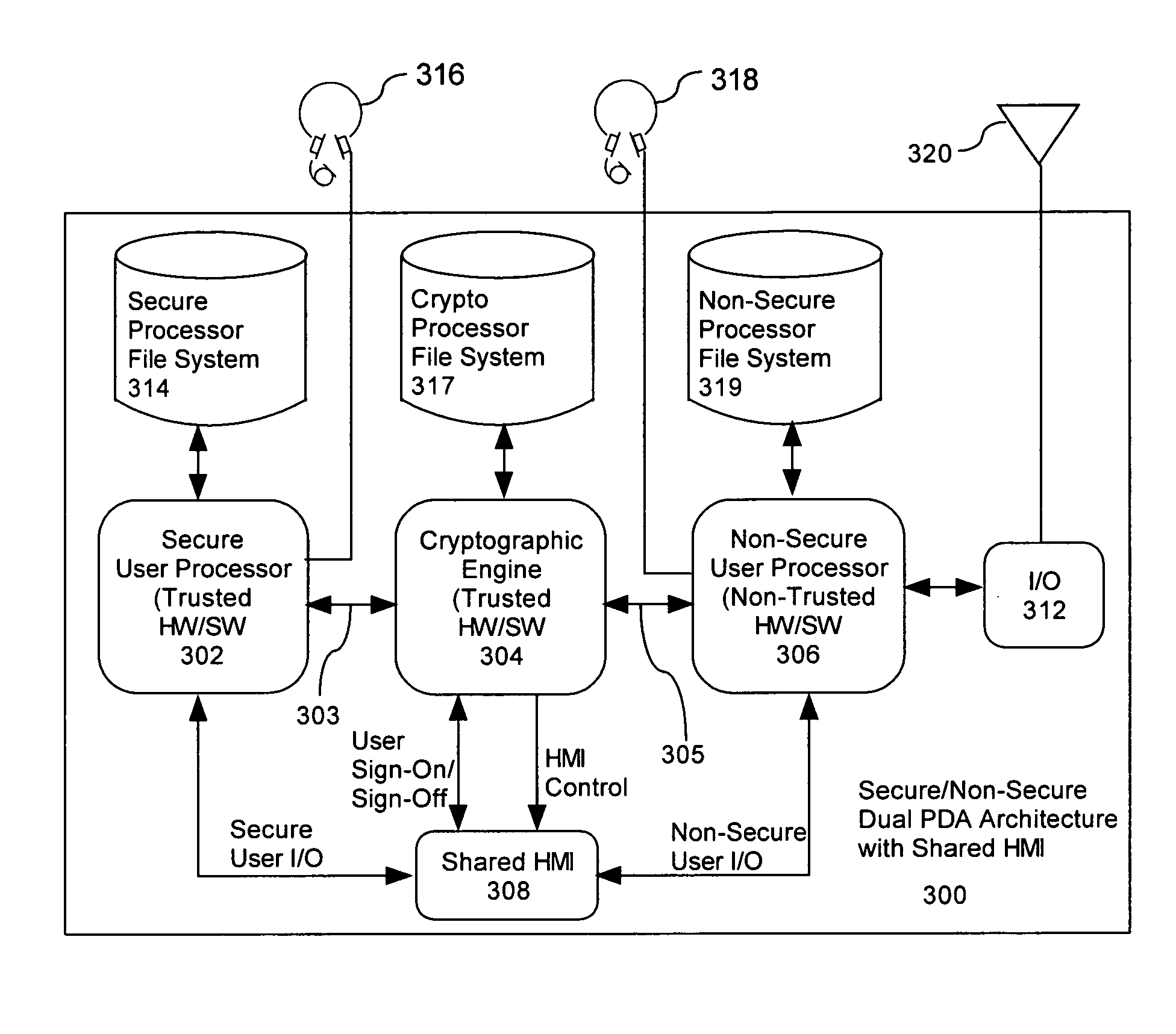
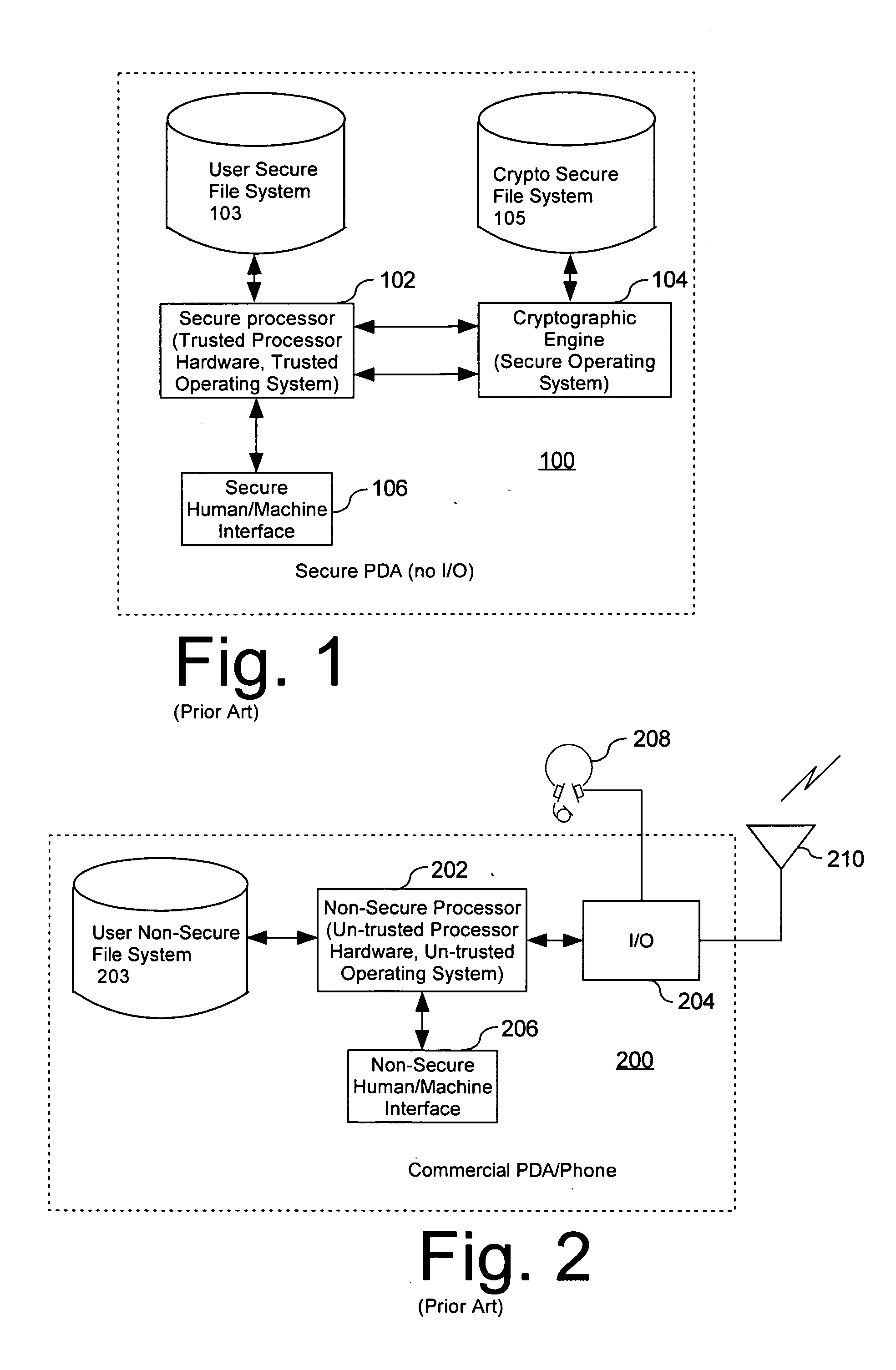
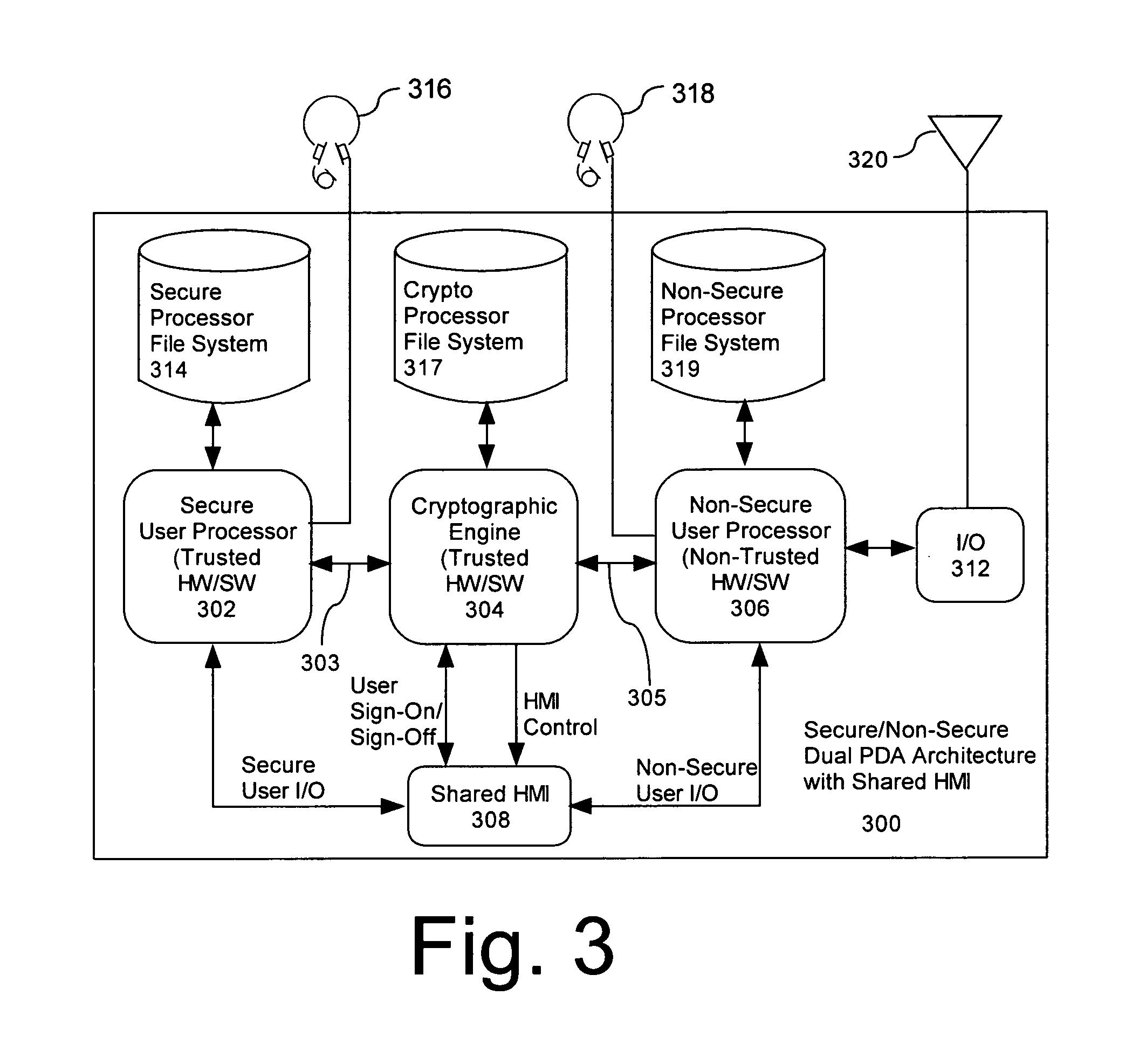
Computer architecture for a handheld electronic device with a shared human-machine interface
ActiveUS7779252B2Public key for secure communicationDigital data processing detailsTelecommunications linkOperational system
Mobile PDA computer system (300) includes a secure user processor (302), a non-secure user processor (306), a cryptographic engine (304), and a shared human / machine interface (HMI) (308). The secure user processor (302) can be comprised of a first trusted microprocessor and a first trusted operating system executing on the first trusted microprocessor. The non-secure user processor (306) can be comprised of a second non-trusted microprocessor and a second non-trusted operating system executing on the second non-trusted microprocessor. A cryptographic engine (304) can be comprised of a third trusted cryptographic processor and a third trusted operating system executing on the third trusted cryptographic processor. The cryptographic engine can be configured for encrypting and decrypting data. A first data communication link (303) communicates data between the secure user processor and the cryptographic engine. A second data communication link (305) communicates data between the cryptographic engine and the non-secure user processor. In this way, the cryptographic engine forms a bridge between the secure user processor and the non-secure user processor. An HMI (308) comprised of trusted hardware for user input and output is time-multiplex-shared among the secure user processor (302), the non-secure user processor (304), and the cryptographic engine (306) in a secure fashion.
Owner:SPEIR TECH LTD
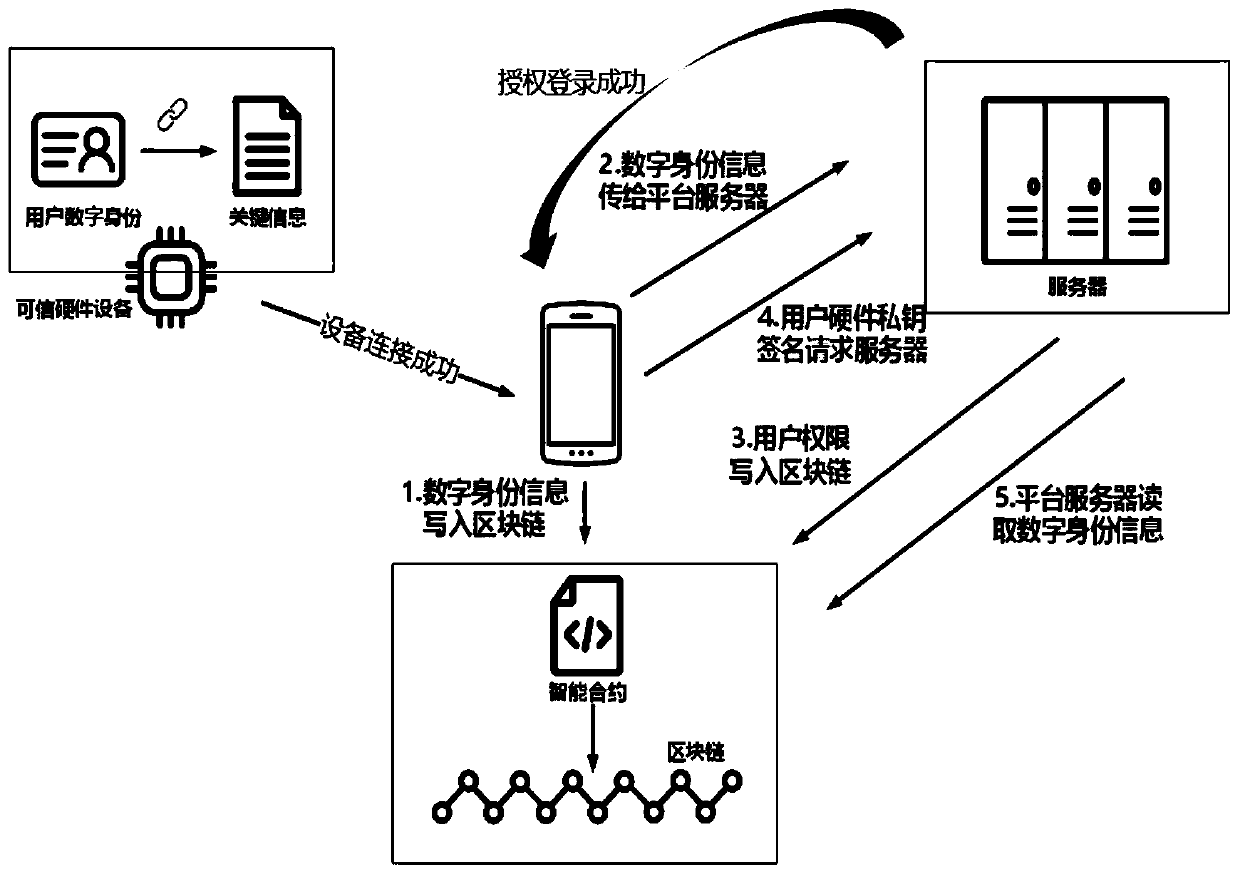
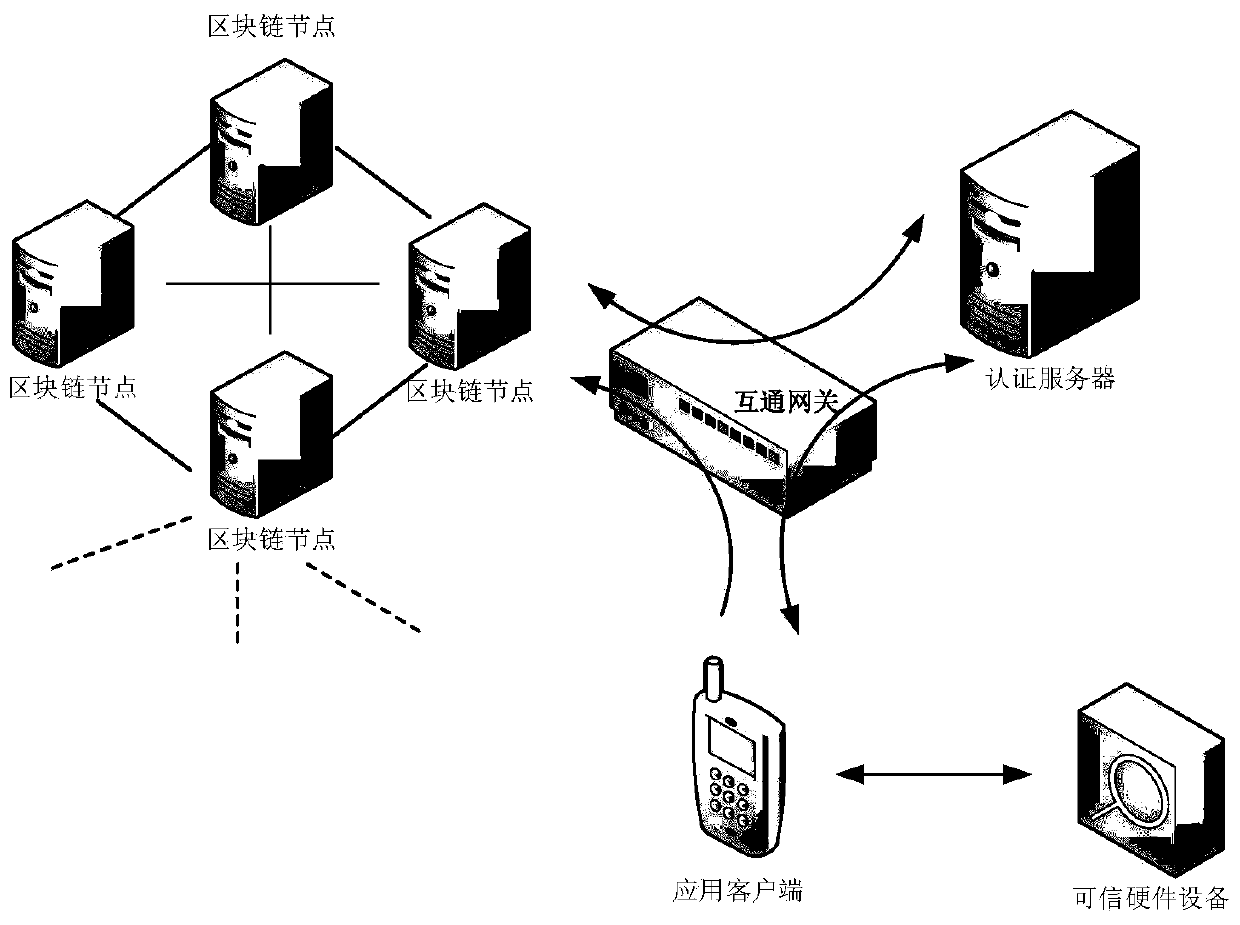
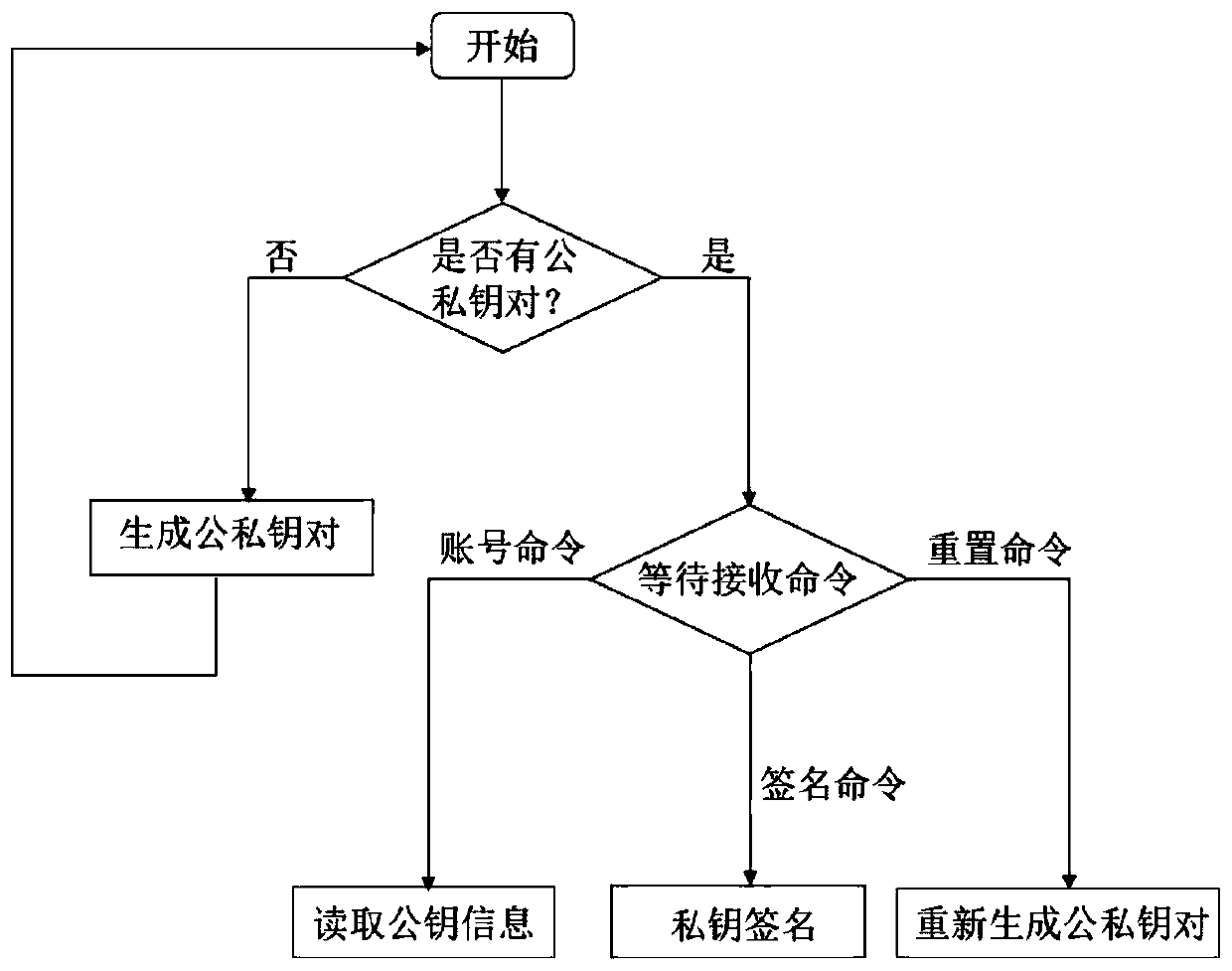
Distributed trusted identity storage method and system based on block chain
The invention discloses a distributed credible identity storage method and system based on a block chain. The method mainly comprises the steps that identity information is packaged and stored by means of tamper-proofing and decentralization characteristics of block chain storage; identity information capitalization is completed through trusted hardware, personal information is stored in a block chain, a private key is archived in a user terminal, and a third-party platform achieves identity authority authentication by calling hardware equipment. The method has the advantages of high security,strong privacy, wide universality and the like, and can provide a more efficient and credible identity authentication environment.
Owner:NANJING UNIV OF SCI & TECH
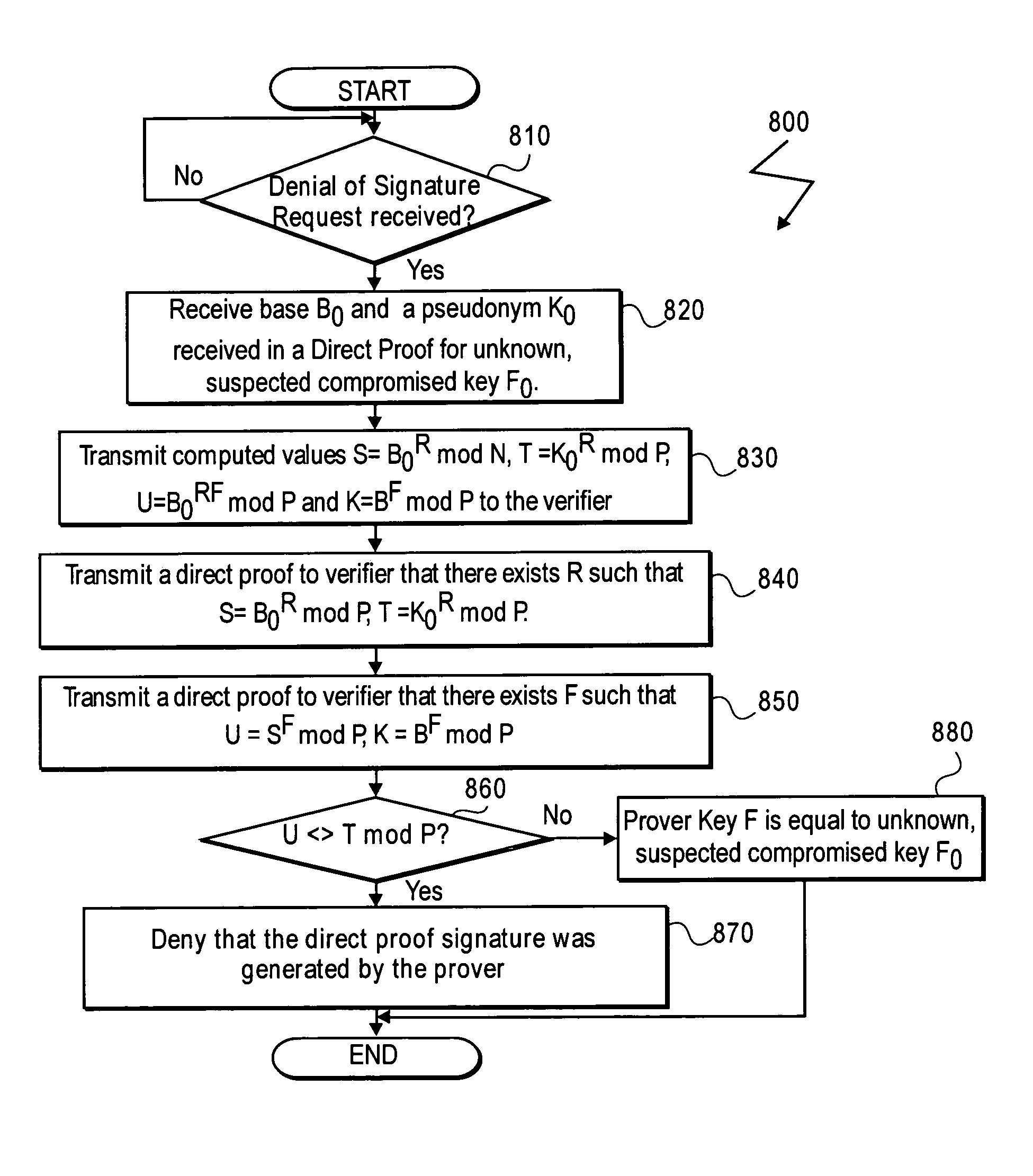
Apparatus and method for proving the denial of a direct proof signature
ActiveUS7490070B2User identity/authority verificationComputer security arrangementsTrusted hardwareInternet privacy
In some embodiments, a method and apparatus for proving the denial of a direct proof signature are described. In one embodiment, a trusted hardware device convinces a verifier that the trusted hardware device possesses cryptographic information without revealing unique, device identification information of the trusted hardware device or the cryptographic information. Once the verifier is convinced that the hardware device possesses the cryptographic information, the verifier may issue a denial of signature request to the trusted hardware device, including at least one compromised direct proof signature. In response, the trusted hardware device issues a denial of the compromised direct proof signature by proving to the verifier that a cryptographic key held by the trusted hardware device was not used to form the at least one compromised direct proof signature. Other embodiments are described and claims.
Owner:INTEL CORP
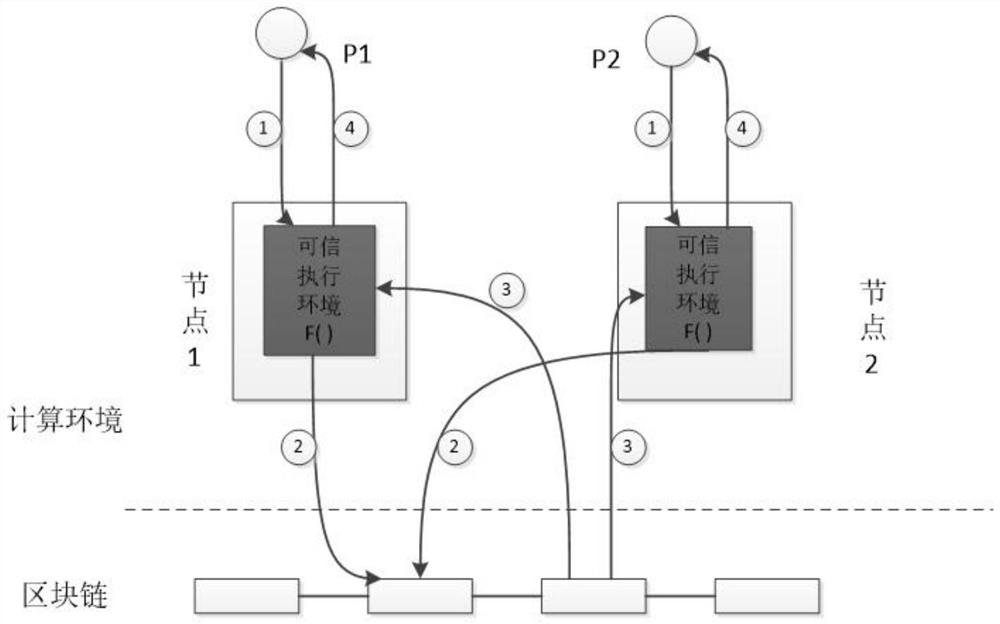
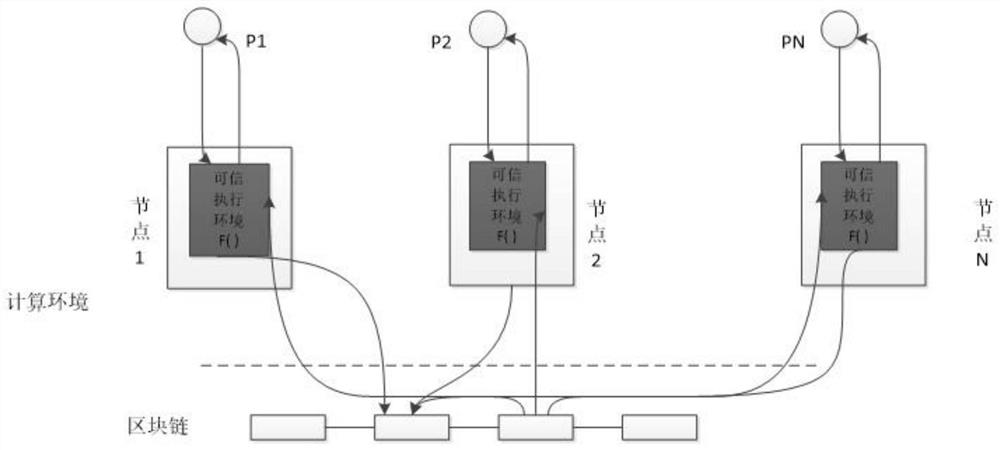
Secure multi-party computing method based on trusted hardware and block chain
PendingCN112380565AImplement secure multi-party computationImprove execution efficiencyDigital data protectionPlatform integrity maintainanceComputer hardwareTrusted hardware
The invention discloses a secure multi-party computing method based on trusted hardware and a block chain, which comprises the following steps that: a user encrypts input parameters and inputs the encrypted input parameters into a trusted execution environment, the trusted execution environment exchanges data with other participants through the block chain, executes a computing function in the trusted execution environment after collecting all the inputs, and outputs a result; based on the scheme, a plurality of participants can complete data sharing of security privacy under the condition ofprotecting respective data privacy, and finally, a distributed arbitrary multi-party joint computing task is realized. A fair data exchange process of multi-party participants is realized by utilizinga block chain, meanwhile, privacy protection is carried out on data exchange by utilizing an encryption algorithm, and the obtained encrypted data is decrypted and calculated in a trusted computing environment, so that an efficient and safe multi-party computing process is realized.
Owner:TIANYI ELECTRONICS COMMERCE
Computer architecture for a handheld electronic device with a shared human-machine interface
ActiveUS20070223689A1Digital data processing detailsPublic key for secure communicationHuman–machine interfaceTrusted hardware
Mobile PDA computer system (300) includes a secure user processor (302), a non-secure user processor (306), a cryptographic engine (304), and a shared human / machine interface (HMI) (308). The secure user processor (302) can be comprised of a first trusted microprocessor and a first trusted operating system executing on the first trusted microprocessor. The non-secure user processor (306) can be comprised of a second non-trusted microprocessor and a second non-trusted operating system executing on the second non-trusted microprocessor. A cryptographic engine (304) can be comprised of a third trusted cryptographic processor and a third trusted operating system executing on the third trusted cryptographic processor. The cryptographic engine can be configured for encrypting and decrypting data. A first data communication link (303) communicates data between the secure user processor and the cryptographic engine. A second data communication link (305) communicates data between the cryptographic engine and the non-secure user processor. In this way, the cryptographic engine forms a bridge between the secure user processor and the non-secure user processor. An HMI (308) comprised of trusted hardware for user input and output is time-multiplex-shared among the secure user processor (302), the non-secure user processor (304), and the cryptographic engine (306) in a secure fashion.
Owner:SPEIR TECH LTD
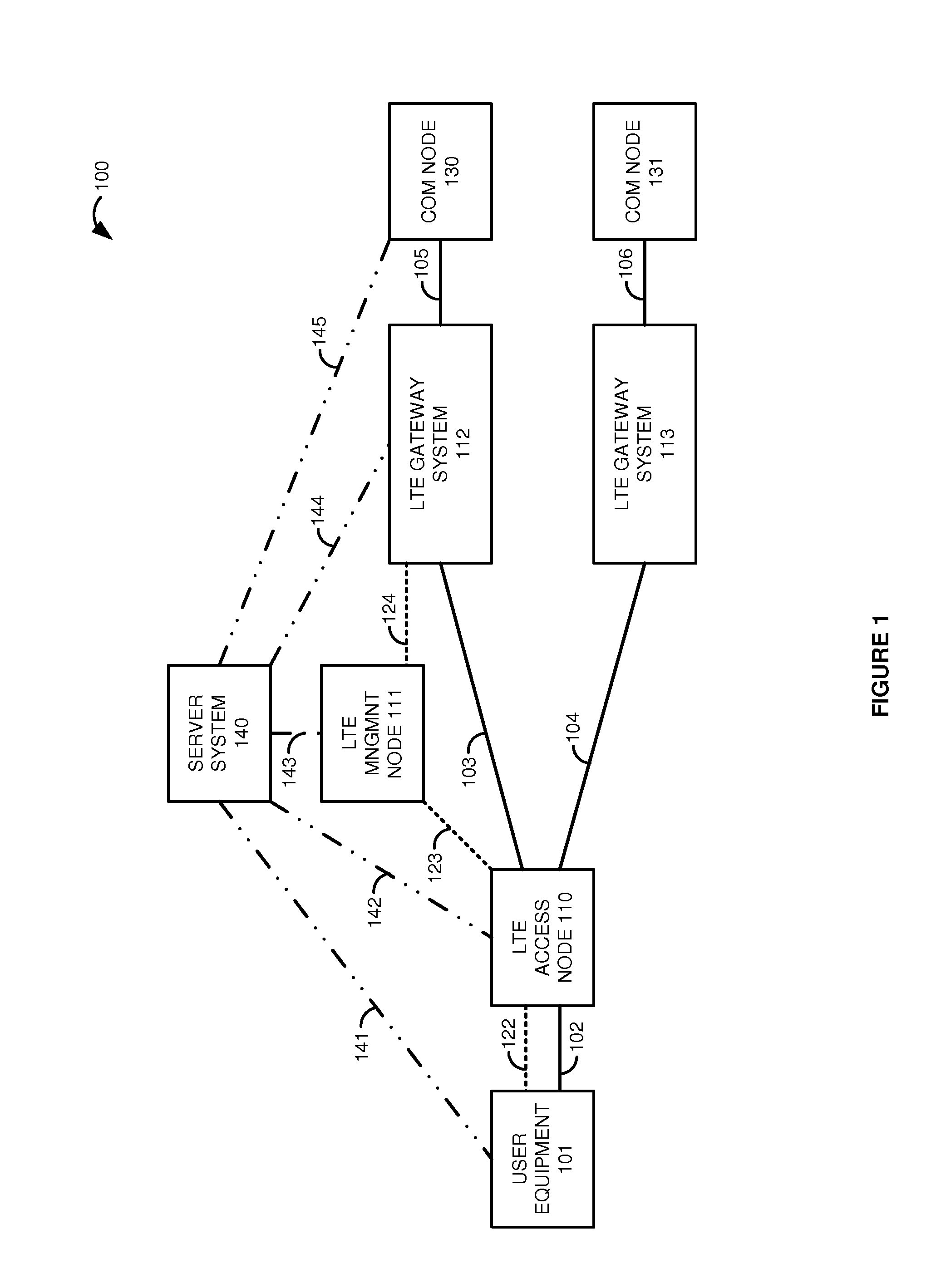
Long term evolution (LTE) communications over trusted hardware
A Long Term Evolution (LTE) communication network transfers data communications for User Equipment (UE). An LTE gateway system exchanges hardware trust data with a server system to maintain hardware trust for the LTE gateway system. An LTE access node processes a Radio Resource Control (RRC) message that contains a trusted bearer requirement for the UE to generate an S1 Application Protocol (S1-AP) initial UE message that contains the trusted bearer requirement for the UE. An LTE management node processes the S1-AP initial UE message to generate a General Packet Radio Service Transfer Protocol (GTP) create session message that contains the trusted bearer requirement for the UE. The LTE gateway system exchanges user data for the UE between the LTE access node and a communication node responsive to the GTP create session message.
Owner:T MOBILE INNOVATIONS LLC
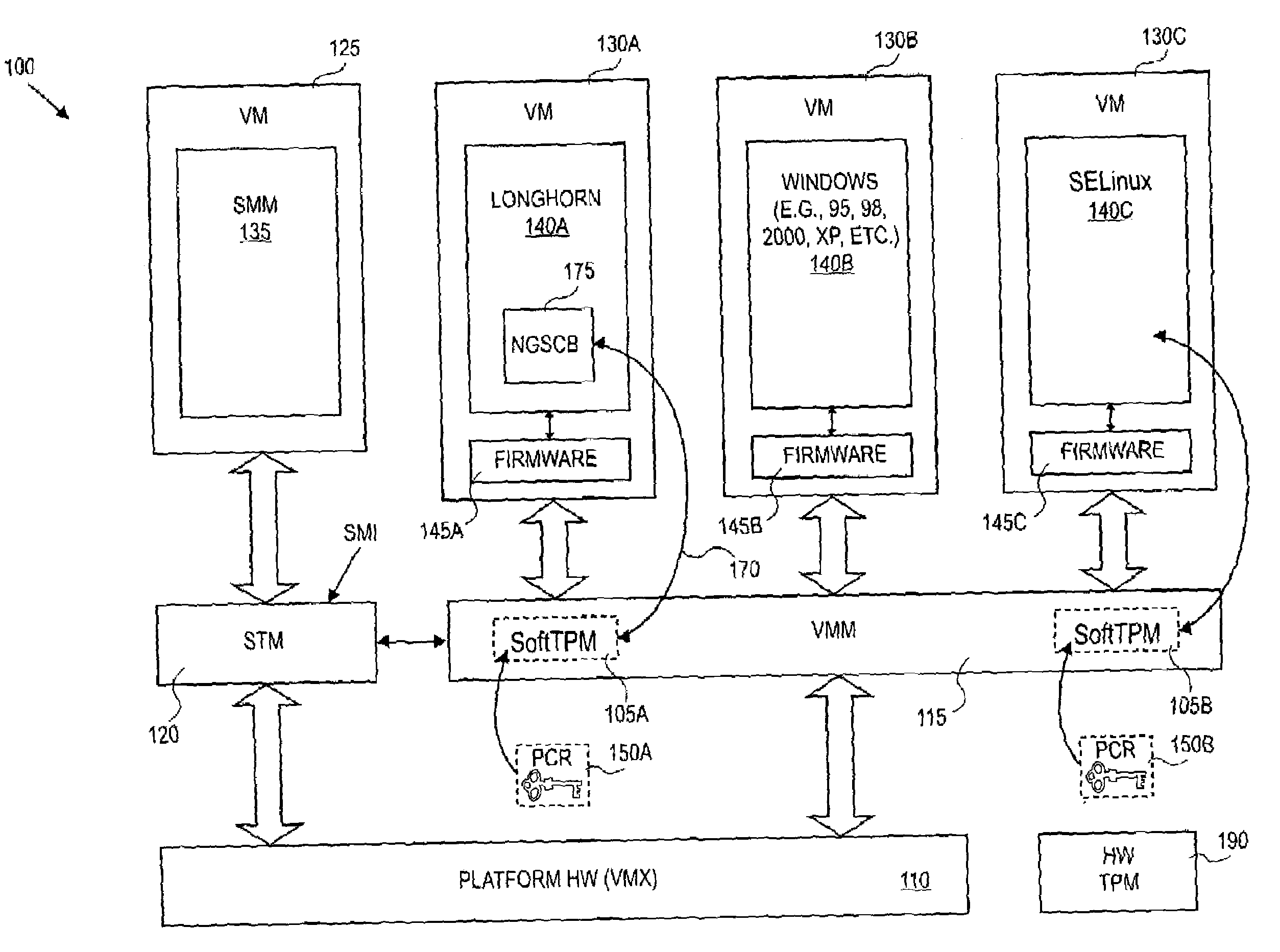
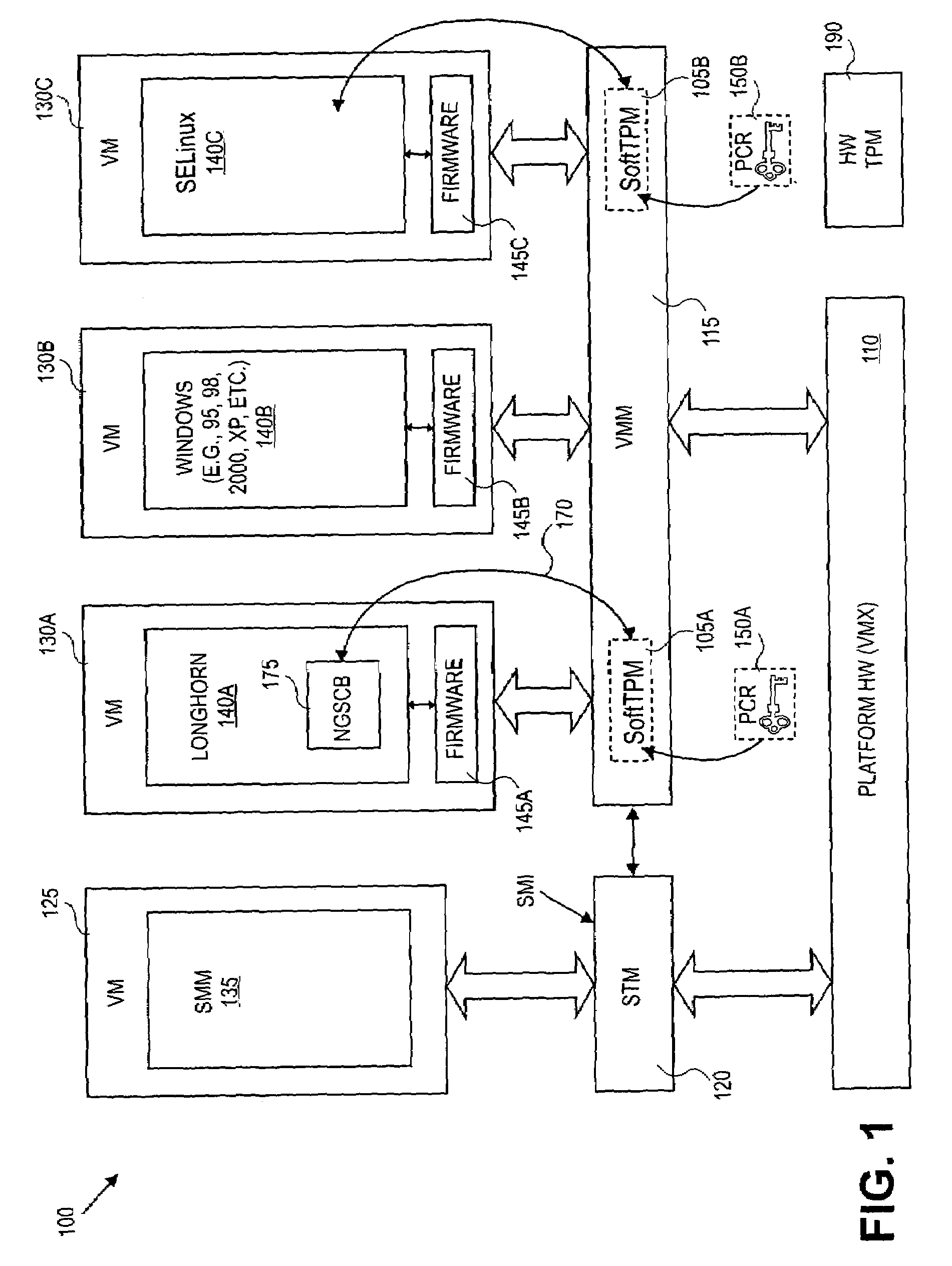
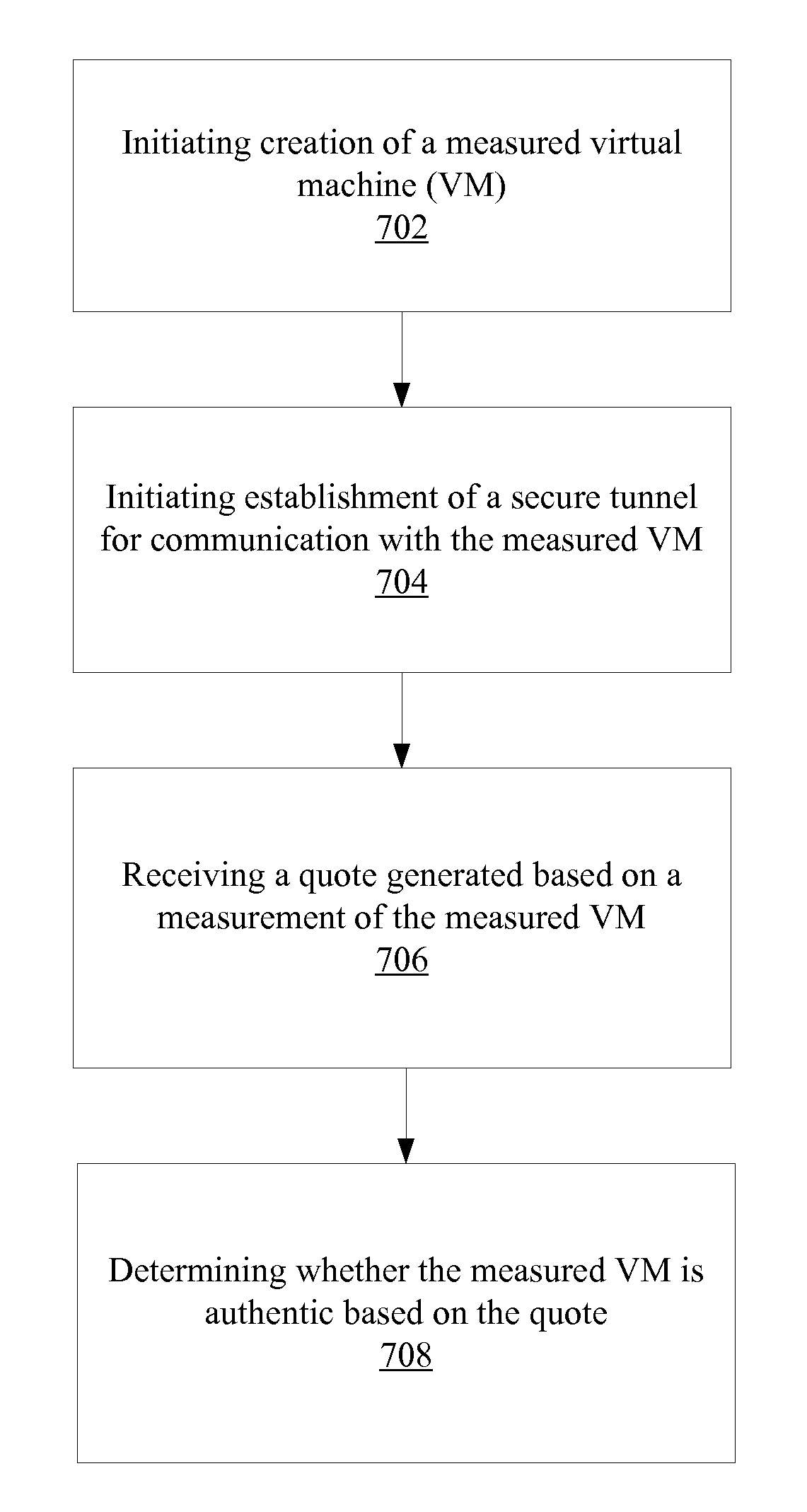
Trusted hardware for attesting to authenticity in a cloud environment
ActiveUS20120266213A1Digital data processing detailsMultiple digital computer combinationsVirtualizationTrusted hardware
Apparatuses, computer readable media, methods, and systems are described for storing a first measurement of a virtualization platform, storing a second measurement of a measured virtual machine, generating a quote using a key, wherein the quote is based on the first measurement and the second measurement, and providing the quote for attesting to authenticity of the virtualization platform and of the measured virtual machine. In a further example, the quote may be generated based on a third measurement of a secure tunnel.
Owner:BANK OF AMERICA CORP
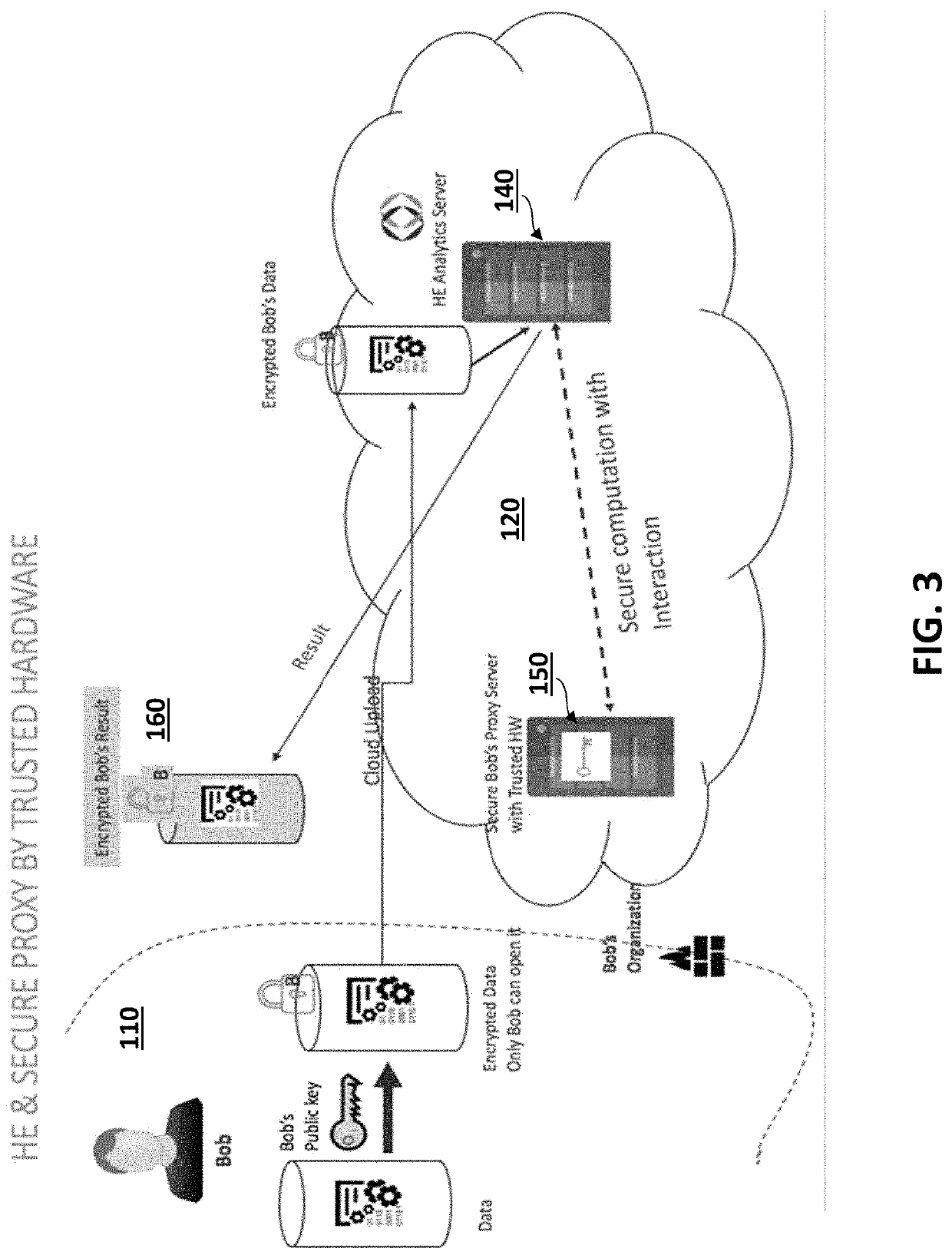
Hybrid system and method for secure collaboration using homomorphic encryption and trusted hardware
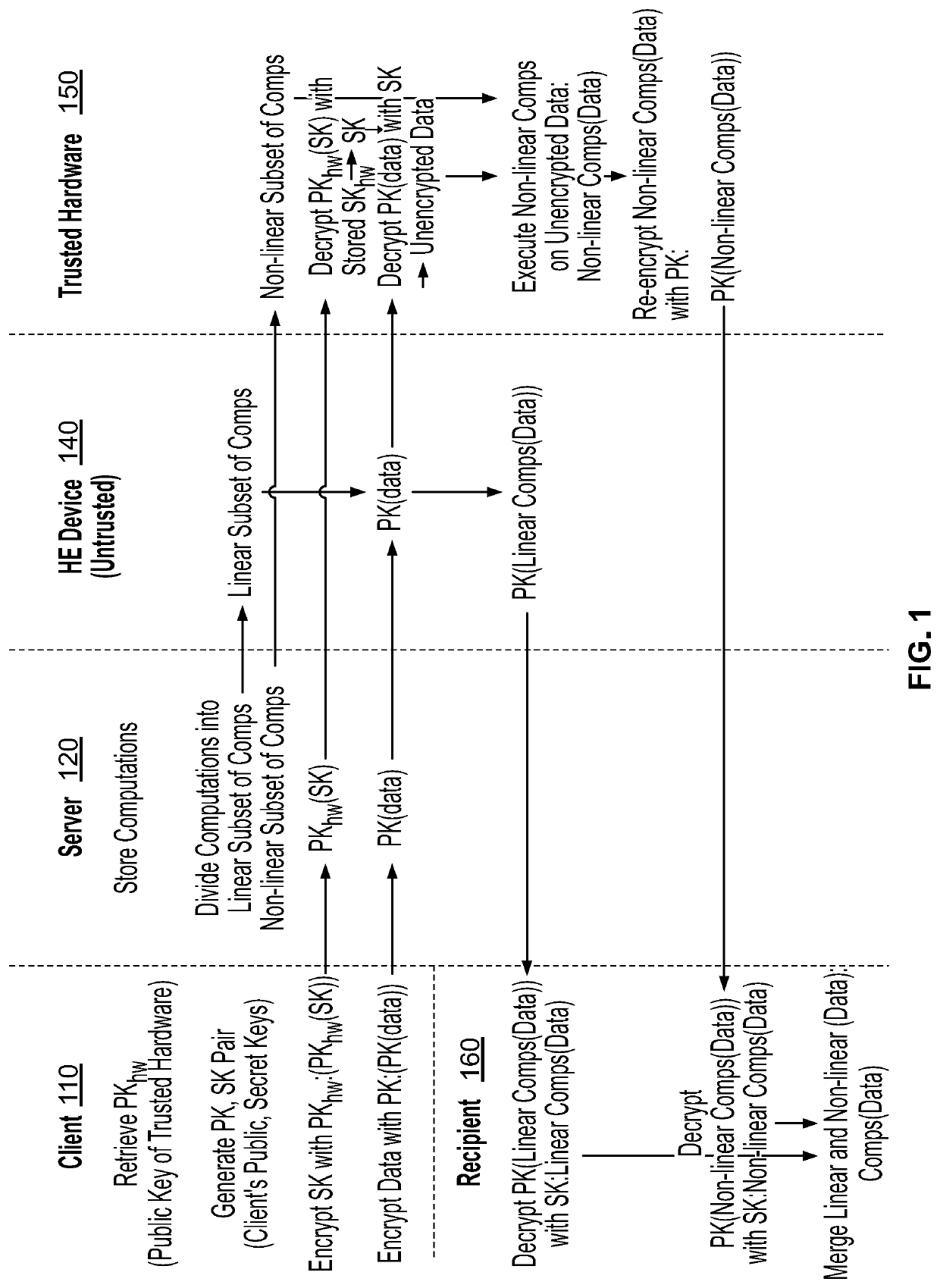
ActiveUS20200036512A1Fast and efficientFast and efficient performanceDigital data protectionInternal/peripheral component protectionTrusted hardwareHybrid system
A device, system and method for secure collaborations on encrypted data in a hybrid environment of a homomorphic encryption (HE) enabled device and trusted hardware. A set of computations may be divided into a subset of linear computations and a subset of non-linear computations. The linear computations on the encrypted data may be executed using homomorphic encryption (HE) in the homomorphic encryption (HE) enabled device. The non-linear computations on the unencrypted data may be executed in the trusted hardware in an unencrypted domain and encrypting the result. The results of the linear and non-linear computations may be decrypted and merged to generate a result equivalent to executing the set of linear and non-linear computations on the unencrypted data.
Owner:DUALITY TECH INC
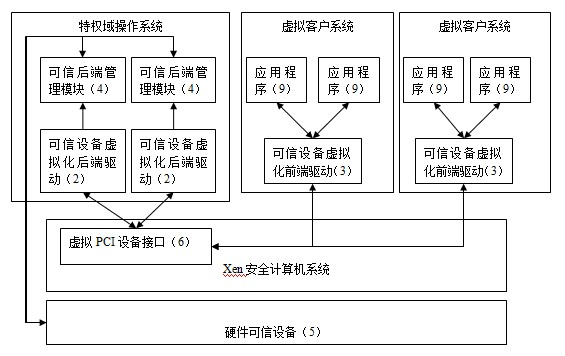
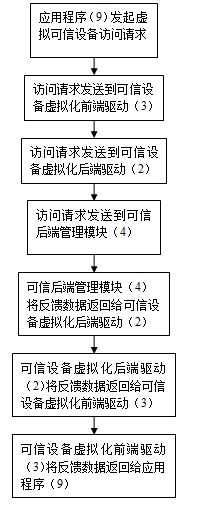
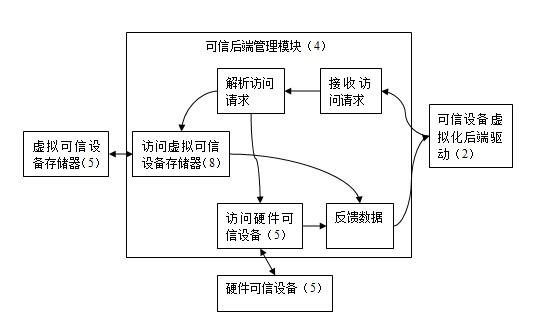
A virtualization system and method based on xen secure computer trusted device
InactiveCN102289620AEasy accessEnsure crediblePlatform integrity maintainanceVirtualizationTrusted hardware
The invention belongs to the application field of virtualization technology, and in particular relates to a virtualization system and method based on a Xen secure computer trusted device. The system includes a virtual trusted device, and the virtual trusted device includes a trusted device virtualization back-end driver, a trusted device virtualization front-end driver and a trusted back-end management module; the trusted device virtualization front-end driver is set in the virtual client system In the virtual client system, there is also an application program, and the application program is connected to the trusted device virtualization back-end driver set in the privileged domain operating system through the trusted device virtualization front-end driver; the trusted back-end management module is set in the privileged domain In the domain operating system, it is connected with the trusted device virtualization back-end driver and the hardware trusted device. The invention provides trusted device services for the virtual client system under the condition of ensuring the credibility of the virtual client operating system, relieves the dependence of the original trusted device virtualization technology on the trusted device simulation tool, and realizes the domestic trusted device virtualization.
Owner:SOUTH CHINA UNIV OF TECH
System and realization method for trusted authentication of user login in operating system
ActiveCN106127016AIdentity information protectionOvercome the defects of the login authentication methodDigital data protectionDigital data authenticationTrusted hardwareOperational system
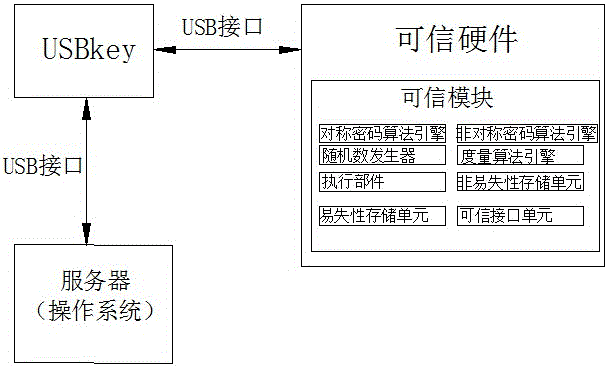
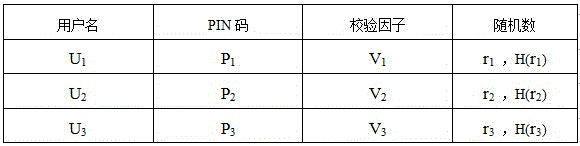
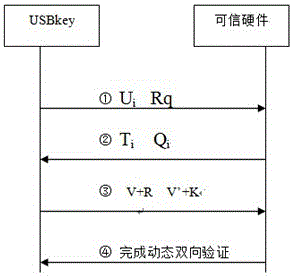
The invention discloses a system and realization method for trusted authentication of user login in an operating system, pertaining to the computer security field. The technical problem to be solved is that a host of insecurity factors are caused by the method of utilizing simple passwords to verity users' identities by a traditional mainstream operation system. The adopted technical scheme is characterized in that the system comprises a USBkey and trusted hardware. The USBkey is connected with the trusted hardware through a USBkey interface and used for connecting with a server through the USBkey interface so that mutual authentication between the operation system and a user is achieved. The trusted hardware is used for storing information on users' identities and private information on related keys. The invention further comprises the operation system and the realization method for mutual authentication.
Owner:SHANDONG INSPUR SCI RES INST CO LTD
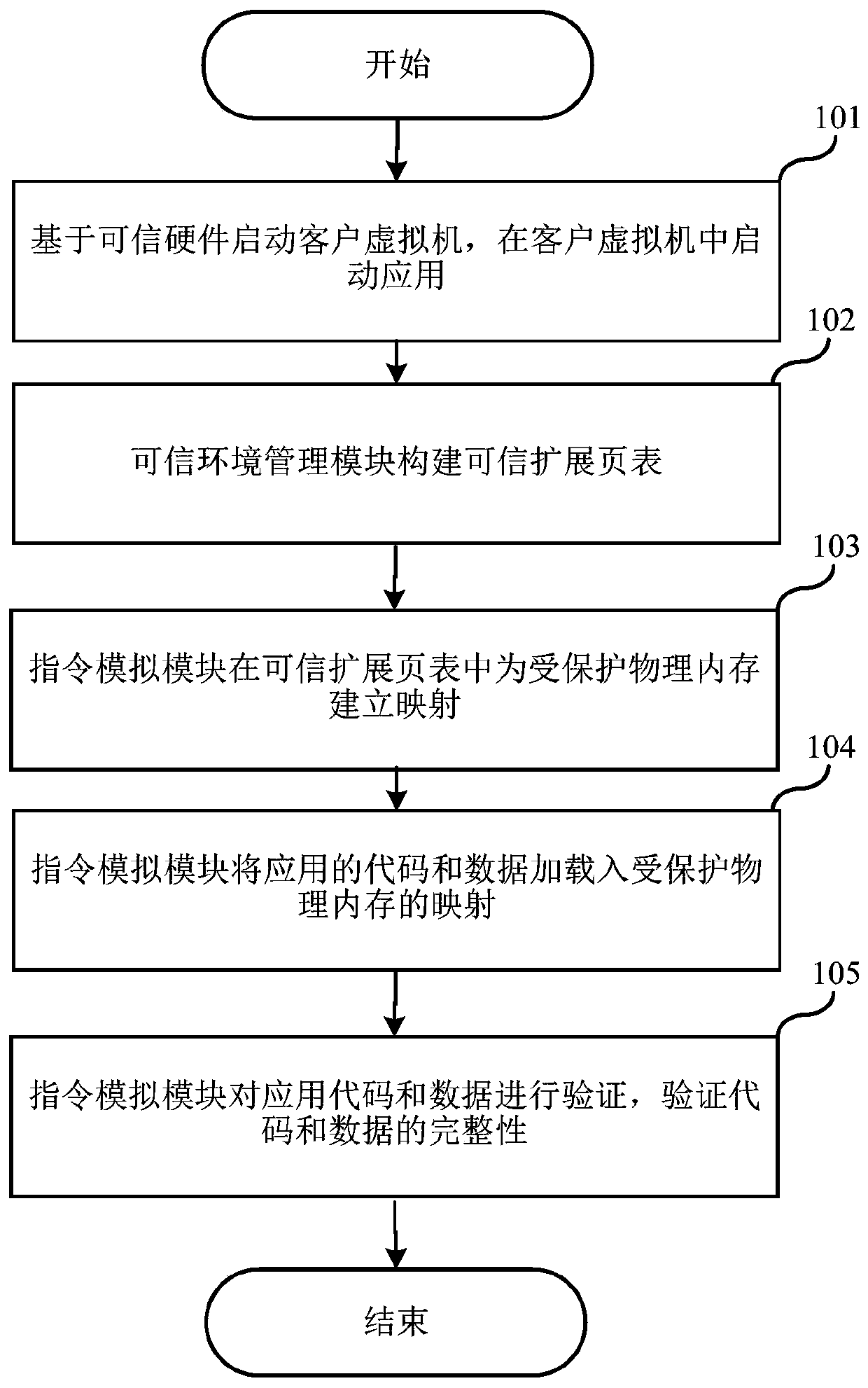
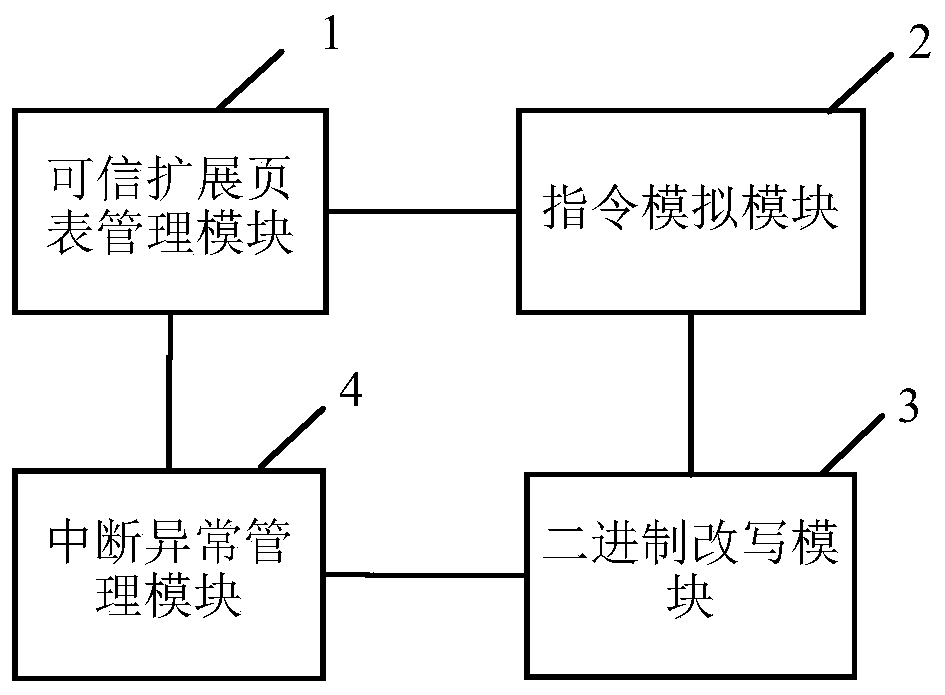
Virtual machine monitor and virtual trusted execution environment construction method
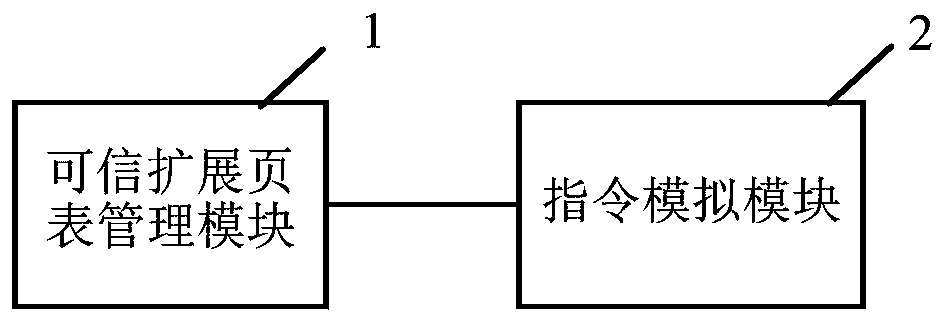
PendingCN110119302AWidely deployedAvoid difficultySoftware simulation/interpretation/emulationEnergy efficient computingTrusted hardwareComputer module
The embodiment of the invention relates to the technical field of software, and discloses a virtual machine monitor and a virtual trusted execution environment construction method. The invention provides a virtual machine monitor which starts a client virtual machine based on trusted hardware and starts an application in the client virtual machine. The virtual machine monitor comprises a trusted extension page table management module and an instruction simulation module, the trusted extension page table management module used for establishing a trusted extension page table when the applicationis started, and the instruction simulation module used for establishing mapping for the protected physical memory in the trusted extension page table, loading codes and data of an application into the protected physical memory, and verifying the integrity of the codes and the data; the instruction simulation module completes the construction of the virtual trusted execution environment when the verification is passed. Therefore, a trusted execution environment is realized without using an SGX technology, the difficulty brought to wide deployment of security applications due to the fact that only a few servers support the SGX technology is avoided, and wide deployment of the security applications is realized.
Owner:上海隔镜信息科技有限公司
Migration of credentials and/or domains between trusted hardware subscription modules
Owner:INTERDIGITAL PATENT HLDG INC
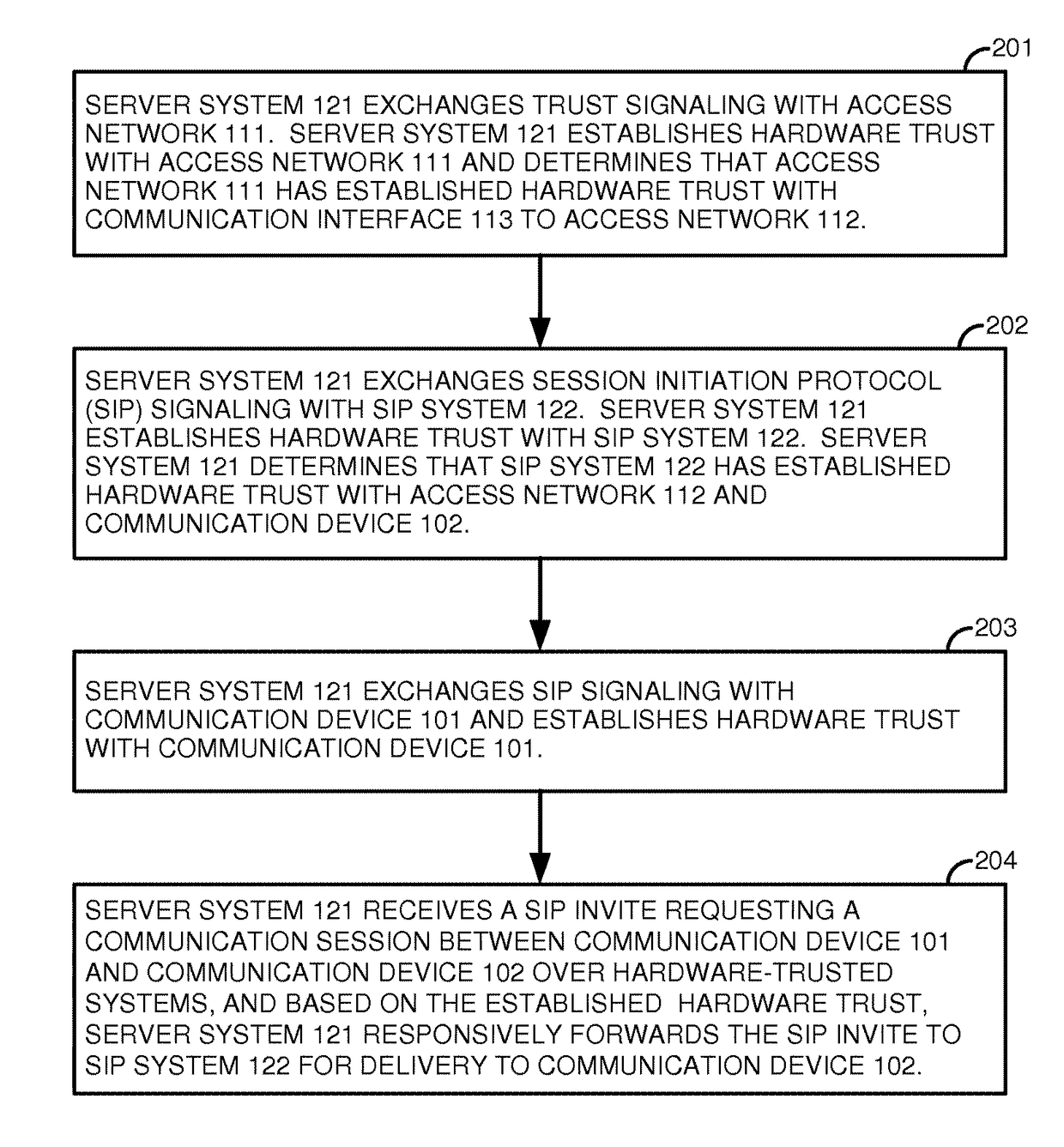
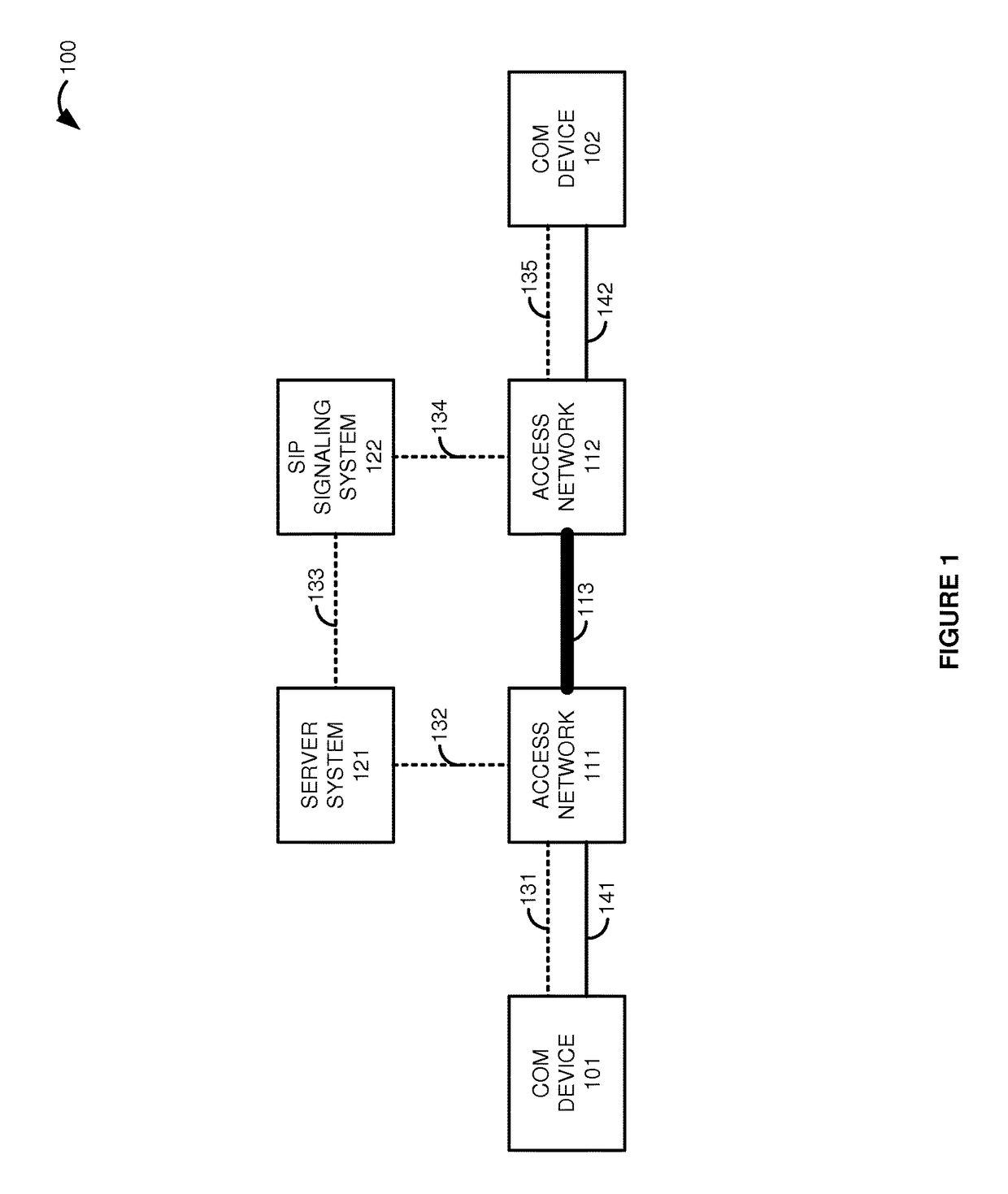
Session initiation protocol (SIP) communications over trusted hardware
ActiveUS9667665B1Network traffic/resource managementMultiple digital computer combinationsAccess networkCommunication interface
A server system exchanges trust signaling with a first access network, establishes hardware trust with the first access network, and determines that the first access network has established hardware trust with a communication interface to a second access network. The server system exchanges Session Initiation Protocol (SIP) signaling with a SIP system, establishes hardware trust with the SIP system, and determines that the SIP system has established hardware trust with the second access network and a second communication device. The server system exchanges SIP signaling with a first communication device and establishes hardware trust with the first communication device. The server system receives a SIP Invite requesting a communication session between the first communication device and the second communication device over hardware-trusted systems, and based on the established hardware trust, the server system responsively forwards the SIP Invite to the SIP system for delivery to the second communication device.
Owner:T MOBILE INNOVATIONS LLC
External reference monitor
ActiveUS8909930B2Digital data processing detailsUser identity/authority verificationTrusted hardwareExternal reference
Owner:LIONRA TECH LTD
Apparatus and method for enhanced revocation of direct proof and direct anonymous attestation
InactiveUS7844614B2Digital data processing detailsUser identity/authority verificationTrusted hardwareDigital signature
In some embodiments, a method and apparatus for enhanced revocation of direct proof and direct anonymous attestation are described. In one embodiment a trusted hardware device verifies that membership of the device within a trusted membership group is not revoked according to a revocation list received with a challenge request from a verifier. Once such verification is performed, the device convinces the verifier of possessing cryptographic information without revealing unique, device identification information of the trusted hardware device or the cryptographic information. In one embodiment, the trusted hardware device computes a digital signature on a message received with the challenge request to the verifier if membership of the anonymous hardware device within a trusted membership group is verified. In one embodiment, the verifier authenticates the digital signature according to a public key of the trusted membership group to enable a trusted member device to remain anonymous to the verifier. Other embodiments are described and claimed.
Owner:INTEL CORP
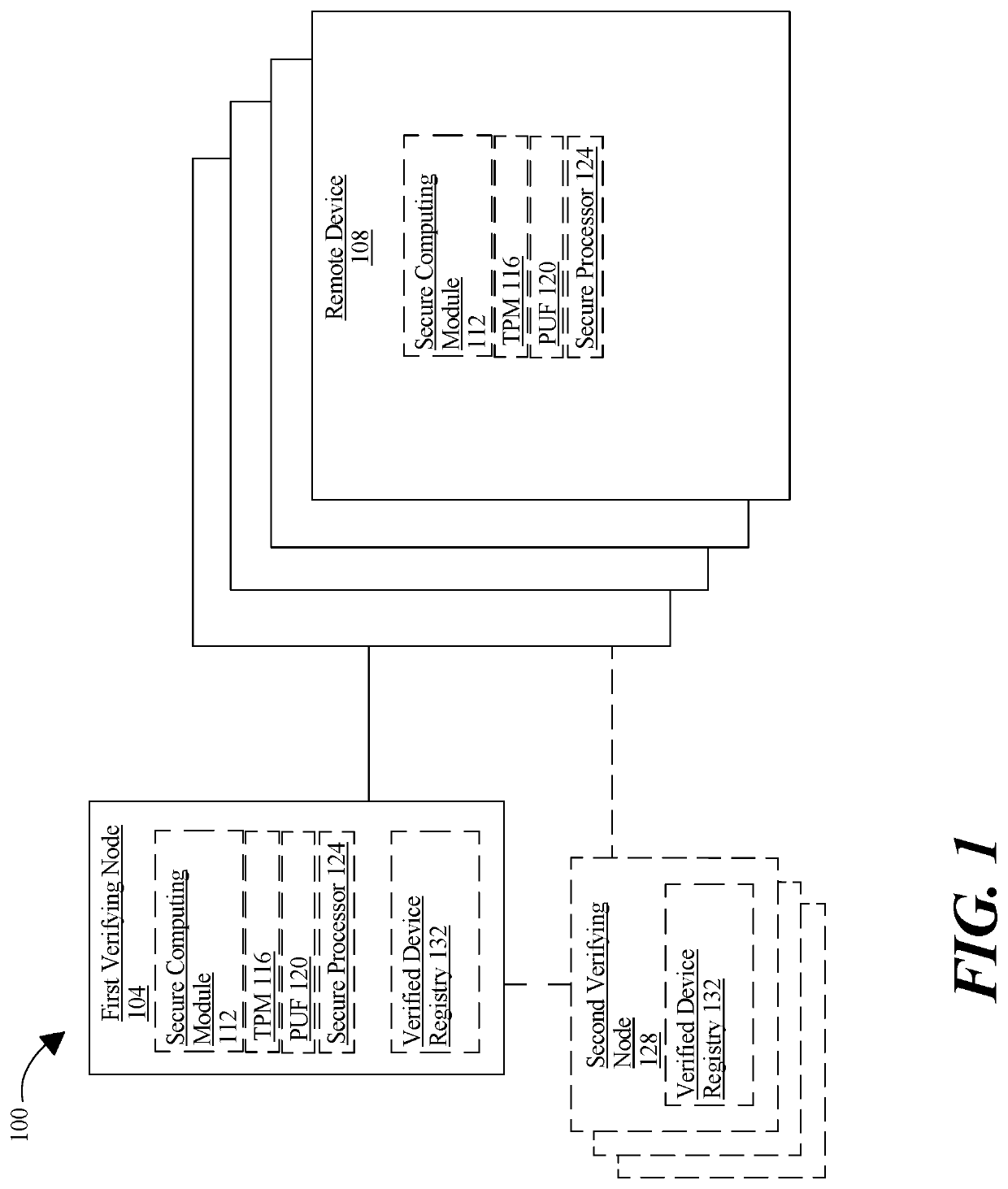
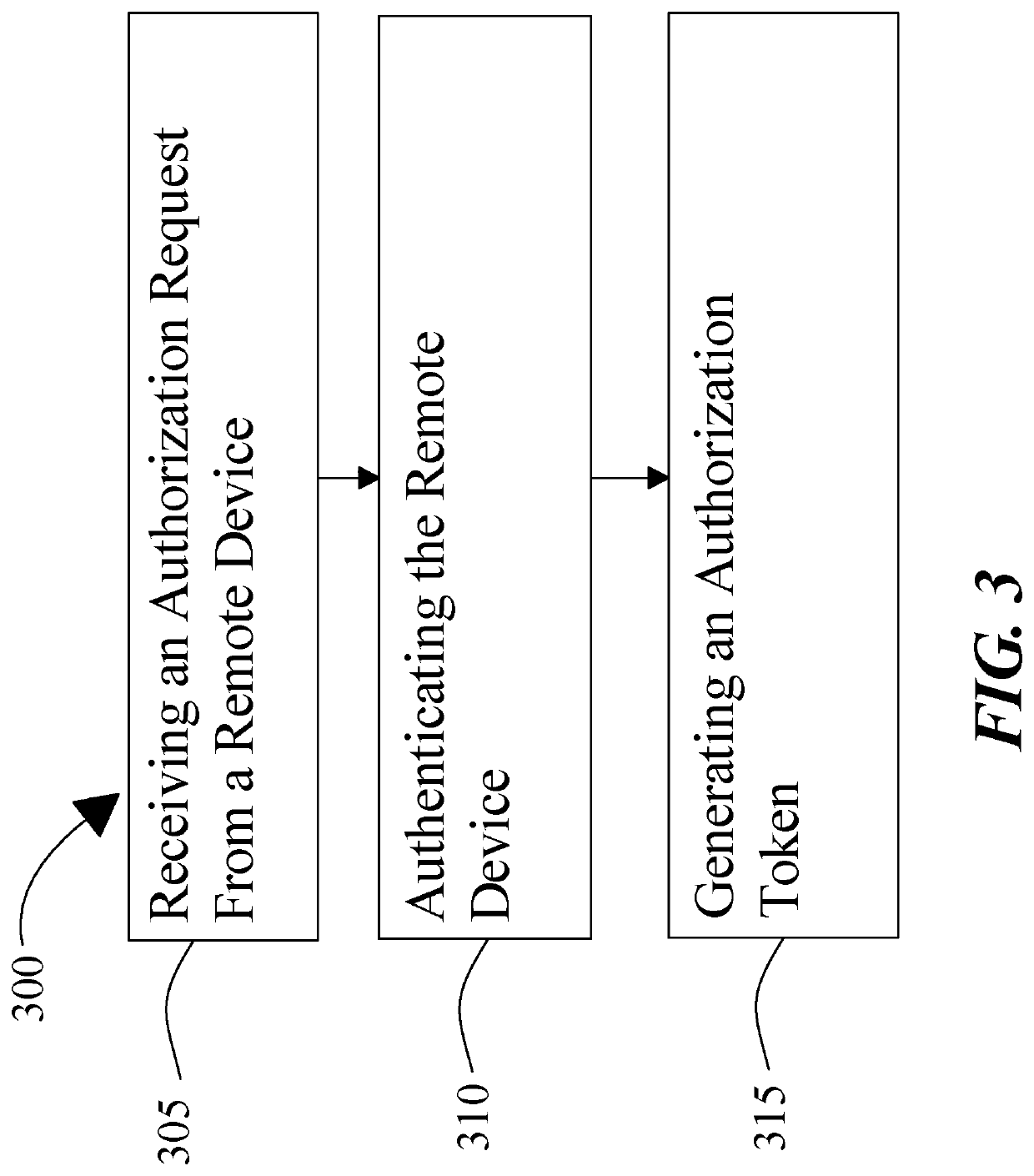
Methods and systems for a distributed certificate authority
A system for implementing a distributed certificate authority using trusted hardware includes a first verifying node communicatively coupled to a plurality of remote devices, the verifying node designed and configured to receive an authorization request from a remote device, wherein receiving the authorization request further comprises receiving an identifier of the remote device, authenticate the remote device, and generate an authorization token, wherein generating the authorization token further includes associating the identifier of the remote device with at least an authorization datum, associating the identifier of the remote device with at least a temporal attribute, and digitally signing the authorization datum, and generating the authorization token containing the digitally signed authorization datum.
Owner:ARES TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com