Distributed trusted identity storage method and system based on block chain
A blockchain and distributed technology, applied in the transmission system, electrical components, etc., can solve the problems of identity information redundant key management security and privacy, and achieve the effect of strong versatility of the method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
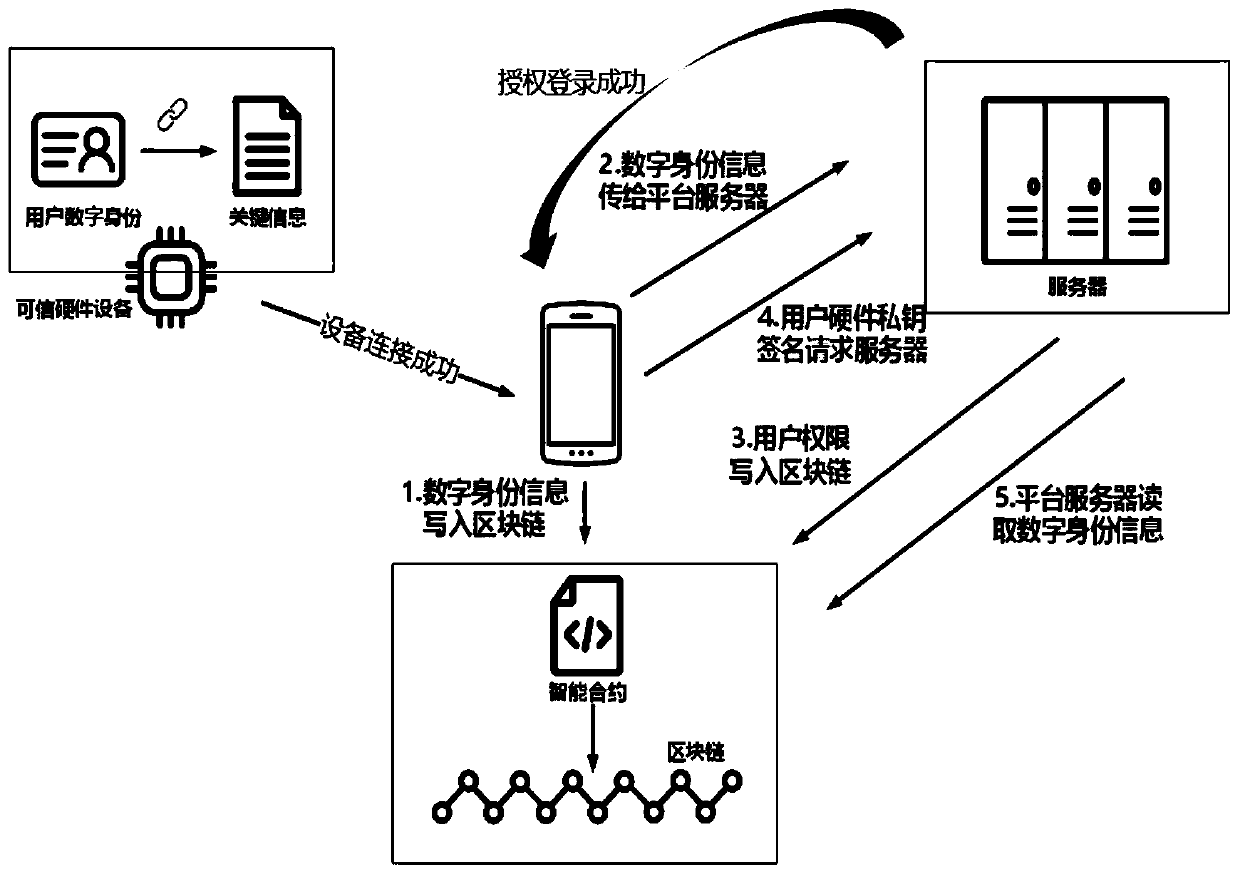
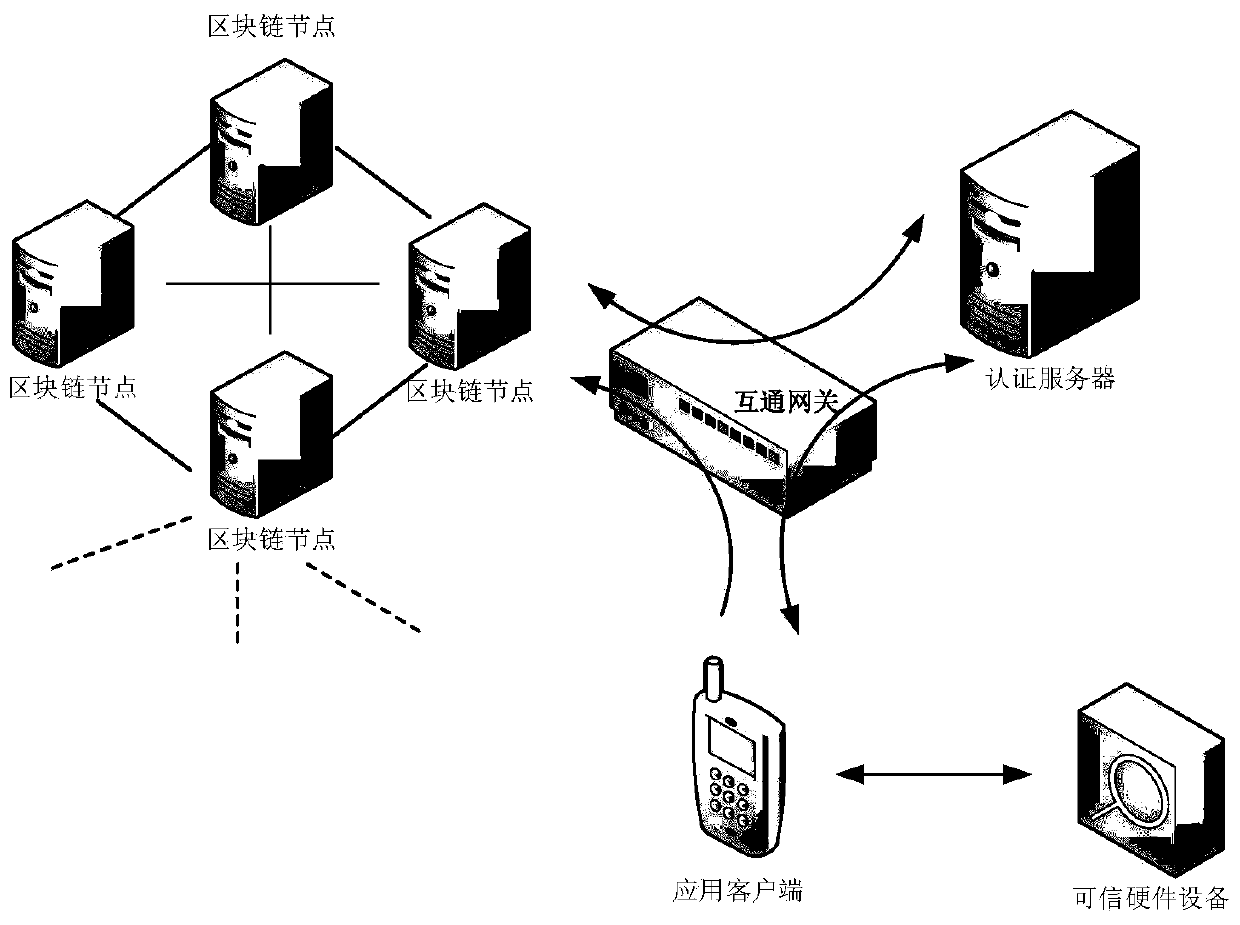
[0022] Such as figure 1 , 2 As shown, a blockchain-based distributed trusted identity storage method, the specific steps are:
[0023] Step 1. Connect the trusted hardware with the smart terminal, write the user's digital identity information in the trusted hardware into the blockchain through the smart terminal, and upload the user's digital identity information to the server of the third-party platform for registration through the smart terminal.
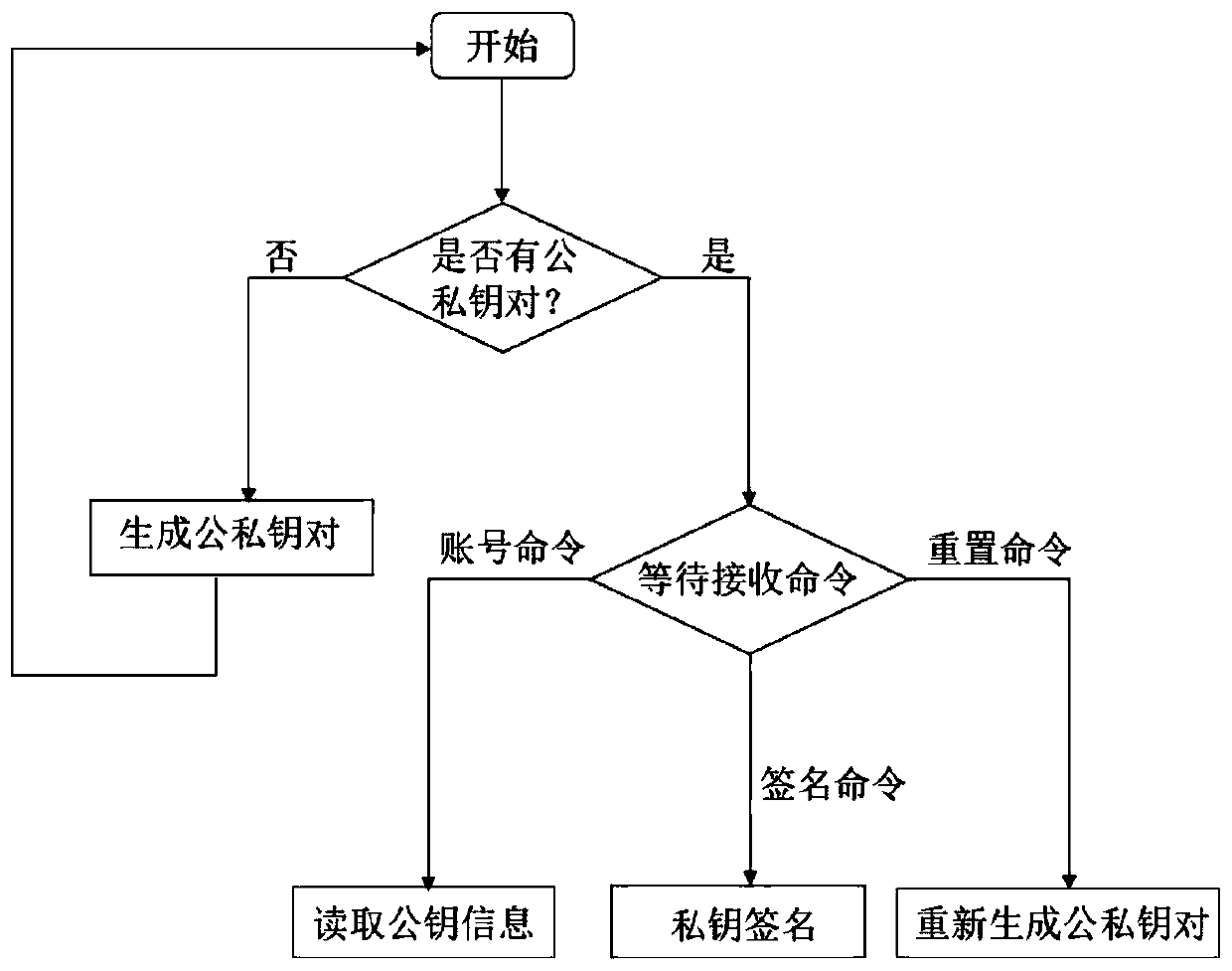
[0024] Among them, the trusted hardware stores the user's private key separately in a chip through mnemonic words, isolating from the Internet, and realizes plug-and-play through the USB interface. Such as image 3 As shown, the specific workflow of trusted hardware is as follows:
[0025] 1. After the trusted hardware is started, it is first necessary to determine whether the user’s public ke...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com