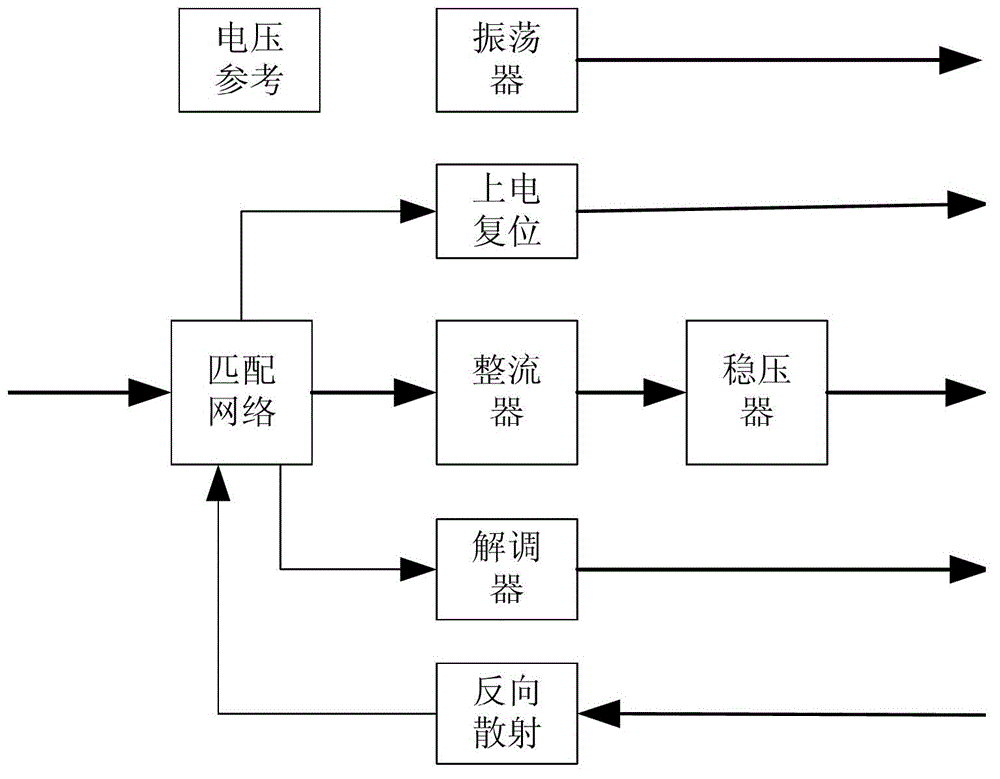
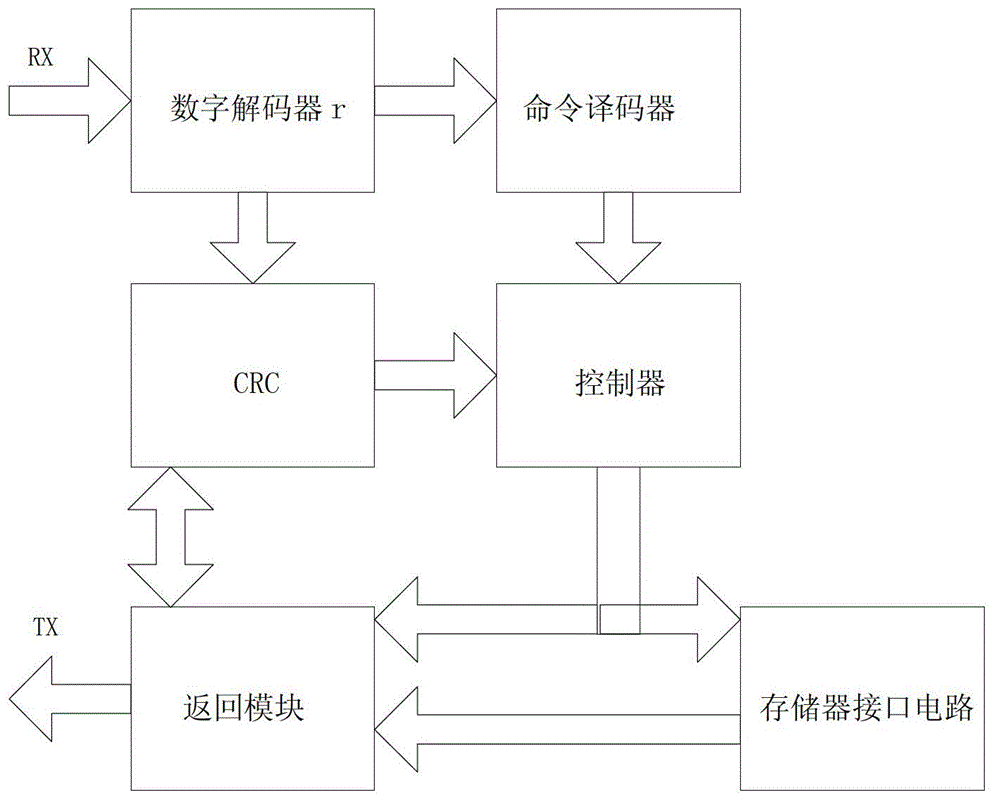
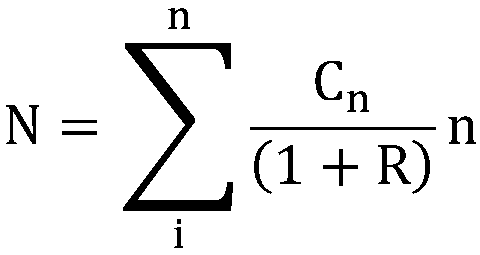Patents
Literature
83results about How to "Tamper-proof" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Electronic evidence preservation system and method based on block chain technology
InactiveCN107888375ASolve pain pointsFix bugsEncryption apparatus with shift registers/memoriesDigital data protectionOriginal dataComputer module
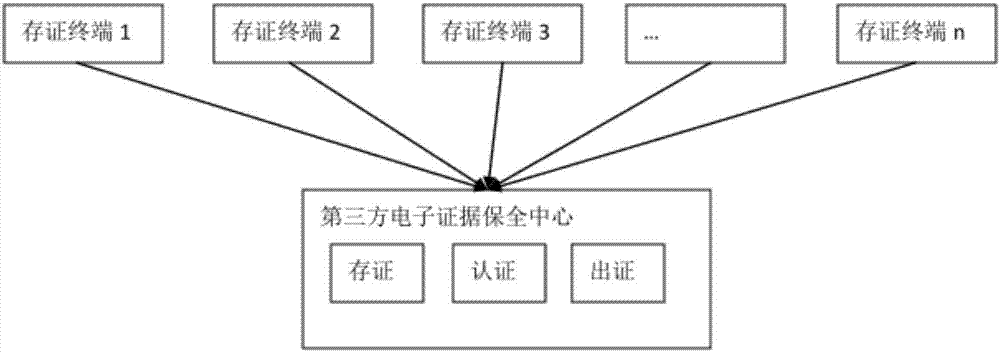
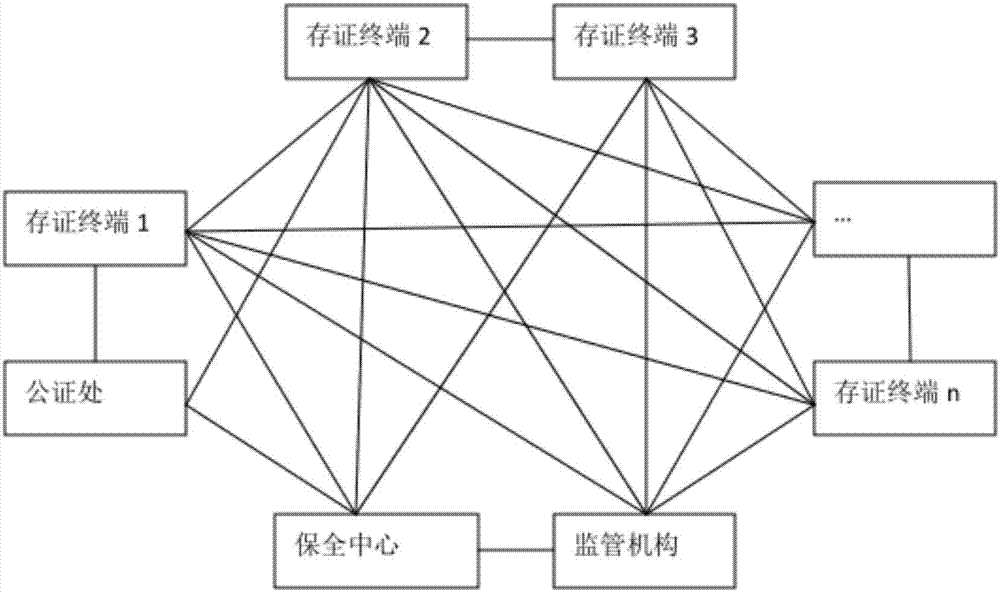
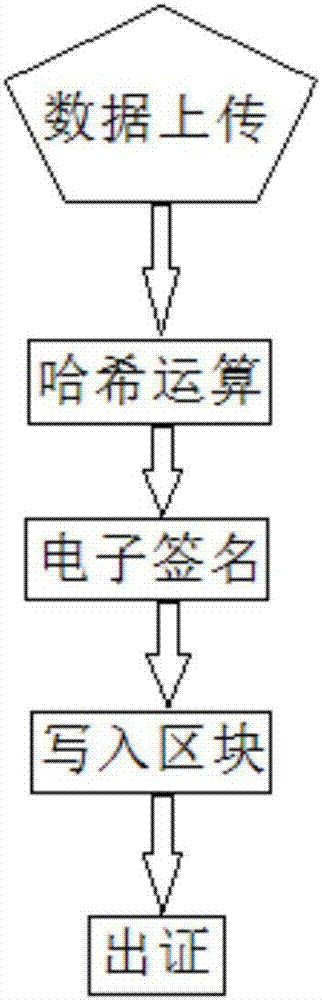
The invention discloses an electronic evidence preservation system and method based on the block chain technology. The preservation system comprises an evidence storage terminal and a block chain network. The evidence storage terminal comprises a hash operation module and an electronic signature module. The electronic data are uploaded to the evidence storage terminal, the evidence storage terminal performs hash operation on the uploaded electronic data to generate unique feature data of a fixed length of original data; then private key signature is performed on the generated data by using theasymmetric encryption technology, and the generated data are sent to the block chain network; and the block chain network performs primary consensus on the uploaded data and packs the uploaded data into blocks, and synchronously sends the blocks to nodes in the network for distributed storage. By establishing an evidence storage alliance by using the block chain technology, the electronic evidence preservation system has the characteristics of digitalized encryption, centralized grading, anti-tampering, data zero loss and so on. Each node in the block chain can preserve a complete block chaindata copy and witness the chain status of the blocks, so that the centralization risk can be effectively avoided.
Owner:SHENZHEN XIEWANG TECH CO LTD
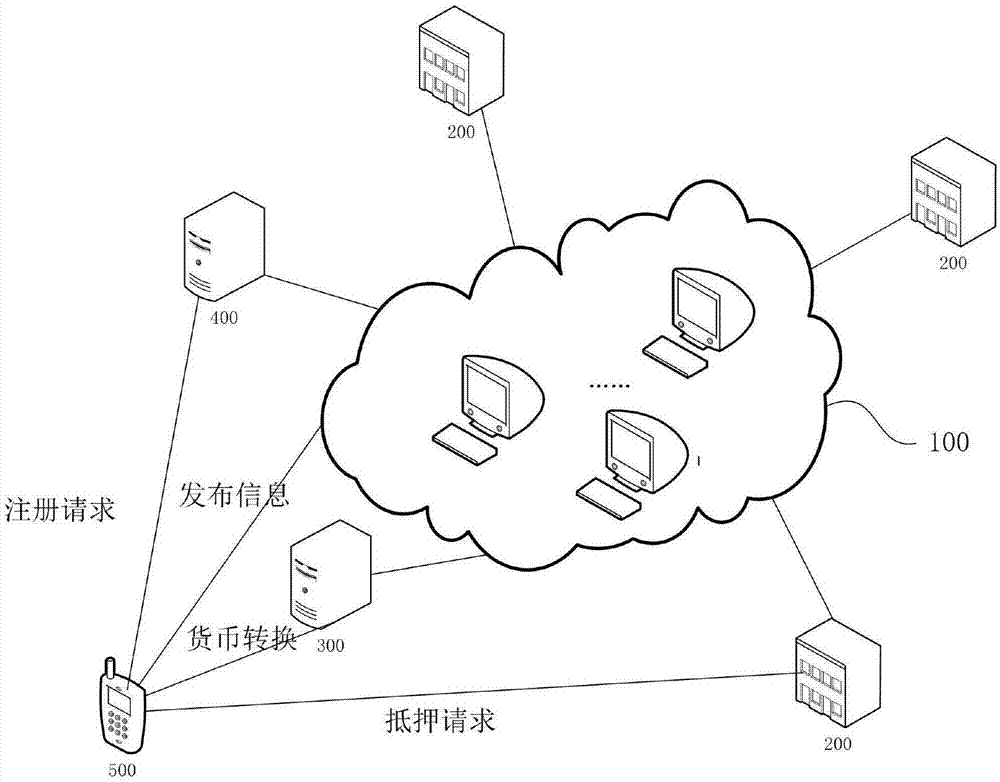
Mortgage financing method and system based on block chain technology
InactiveCN107292735AReduce redemption riskProtect transparencyFinanceUser identity/authority verificationComputer networkEngineering
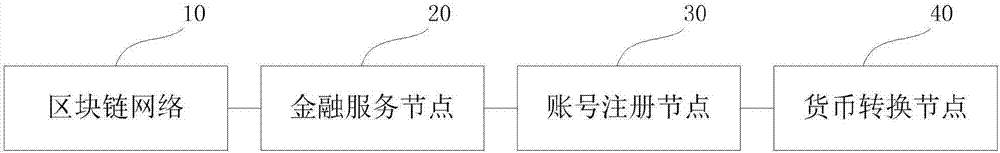
The invention discloses a mortgage financing method and system based on a block chain technology; the system comprises a block chain network, a finance service node, an account registering mode, and a currency transition gateway; the block chain network is used for receiving an exchange currency and redemption intelligent contract sent by a borrower client end and an exchange currency and transaction intelligent contract sent by an investor client end; the redemption intelligent contract and the transaction intelligent contract are broadcasted in the block chain network common recognition nodes for transactions, and the transaction data are broadcasted to other common recognition nodes when the transaction is complete. The method and system can hyalinize the finance mortgage field, can prevent information tampering, are convenient and reliable, efficient, have no intermediary cost, are transparent in risk control, have no region limitation, and need no compliance cost.
Owner:唐盛物联技术有限公司
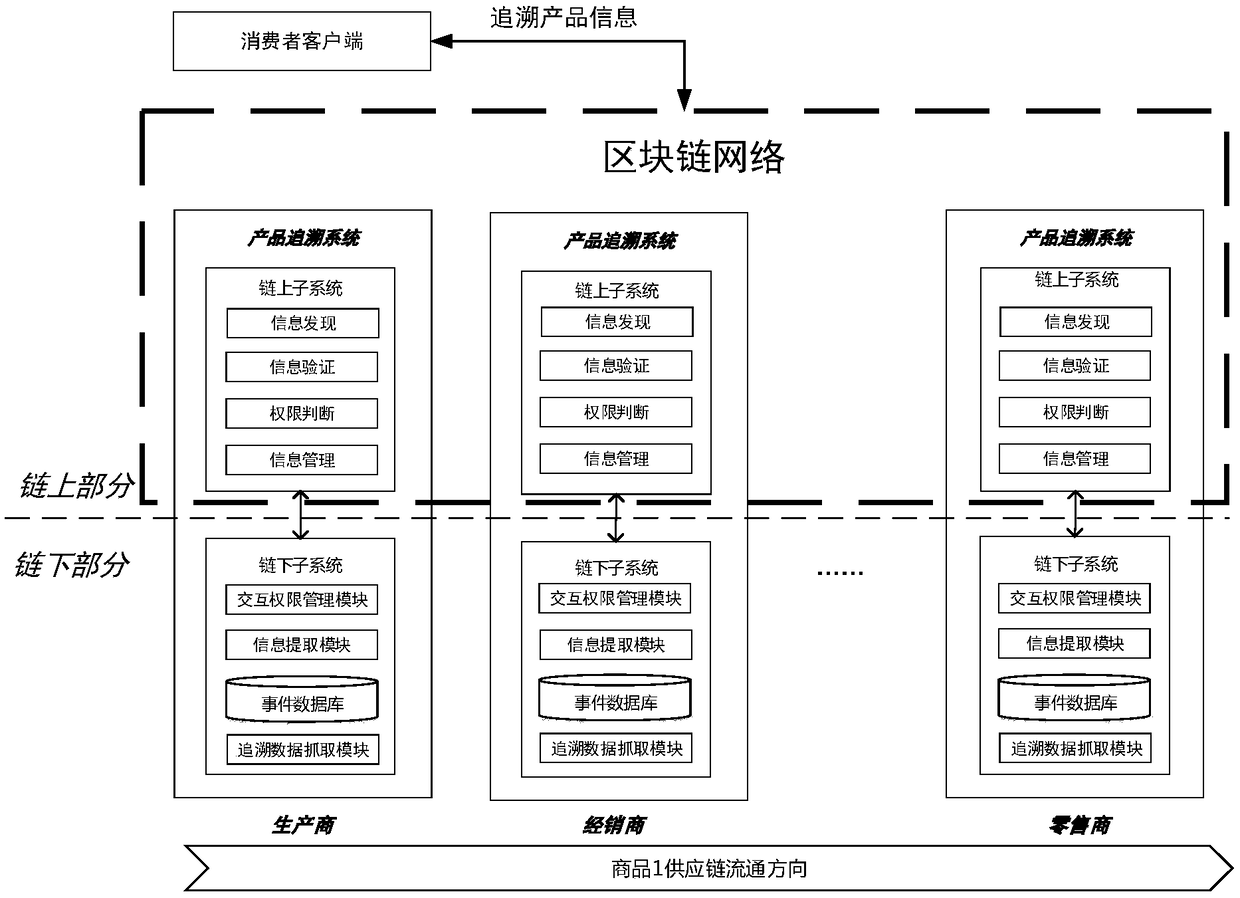
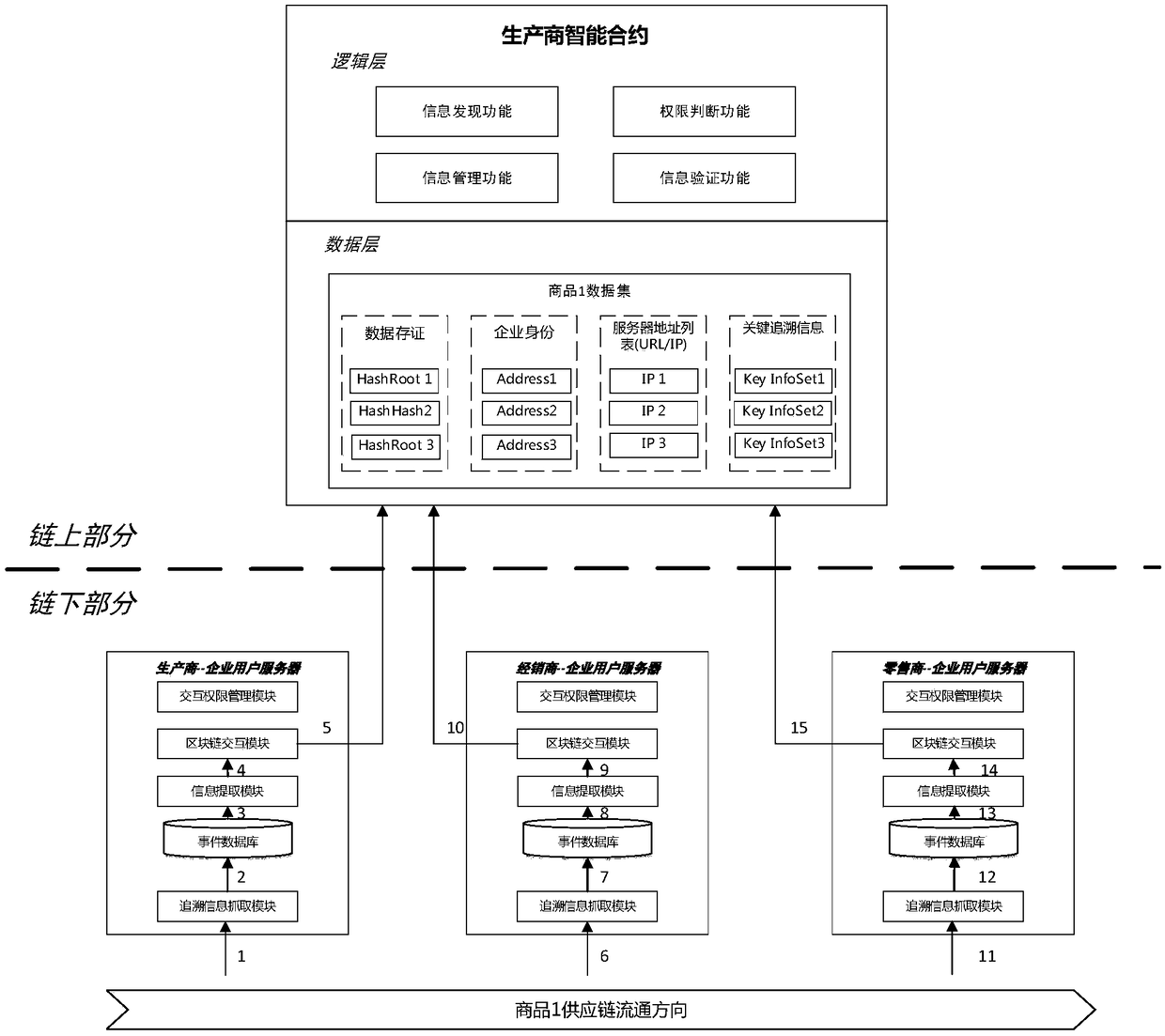
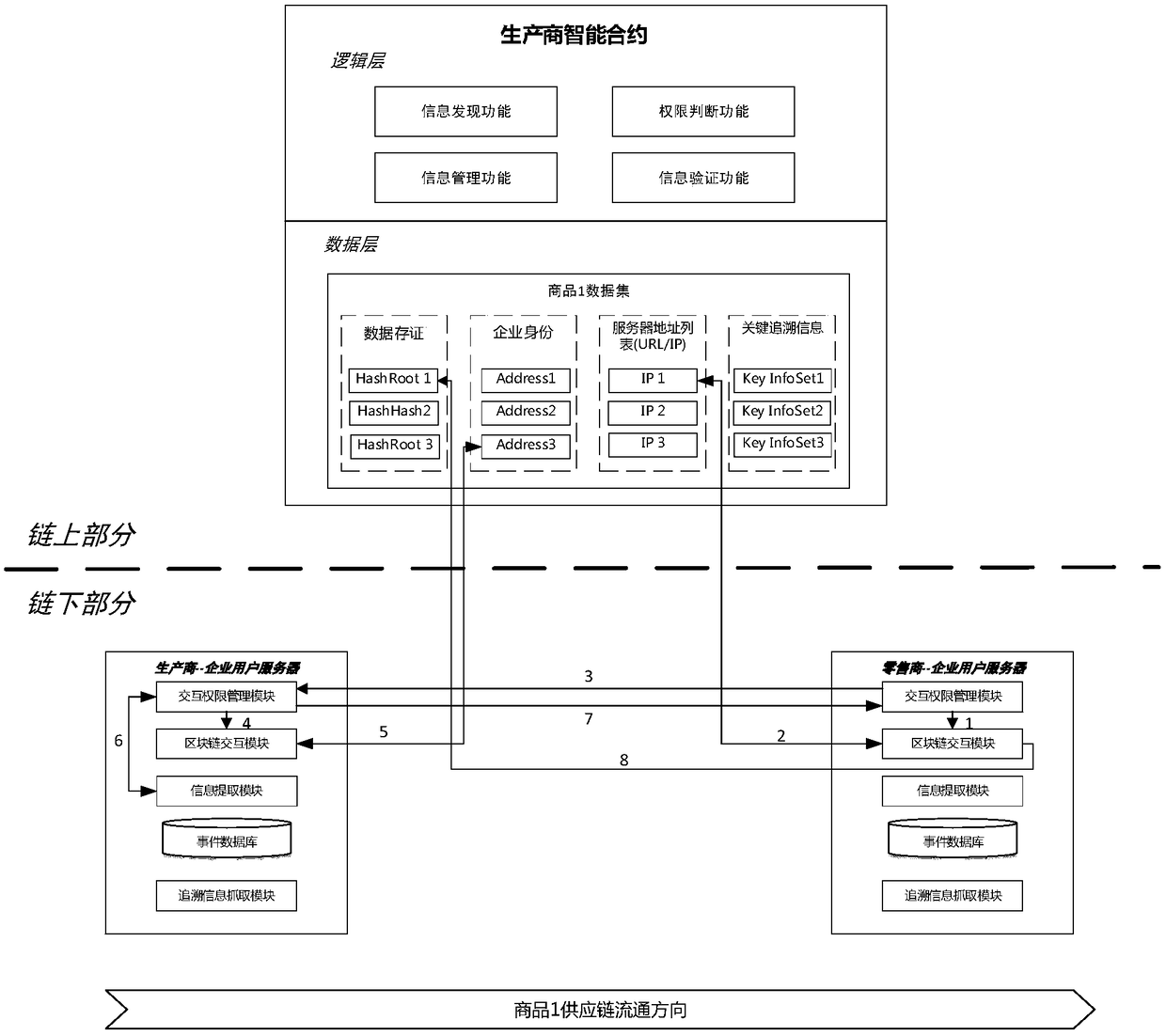
A product traceability information management system and method based on a block chain
ActiveCN109034833AParticipate in operationalParticipate in maintenanceTransmissionCommerceChain of trustProduct traceability
The invention belongs to the technical field of Internet of things, in particular to a product traceability information management system and method. The system adopts an up-chain and down-chain coordination mechanism to manage supply chain information: the manufacturer of a product supply chain collects, stores and manages the product information or the event information produced in the process of supply chain through the sub-system under the chain, and uploads the key traceability information with anti-tamper requirements, such as information storage certificate, information location, identity authentication evidence, etc. to the sub-system on the chain based on the block chain for storage and management; each link in the same supply chain is found through the functional modules of the subsystems on the chain to verify and share the data of the subsystems under each link in the supply chain to ensure the safety of the whole process. The invention solves the unauthorized tampering problem and the trust chain transmission problem faced by the traditional tracing system, improves the credibility of the product tracing system, and ensures the flexibility and scalability of the system.
Owner:FUDAN UNIV
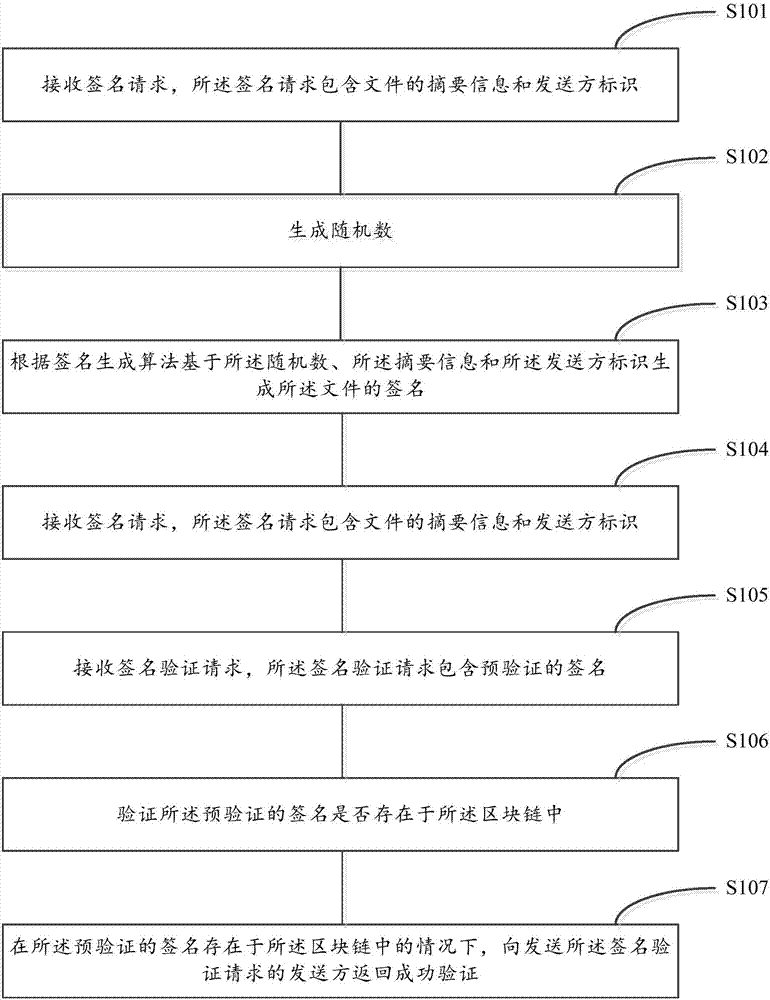
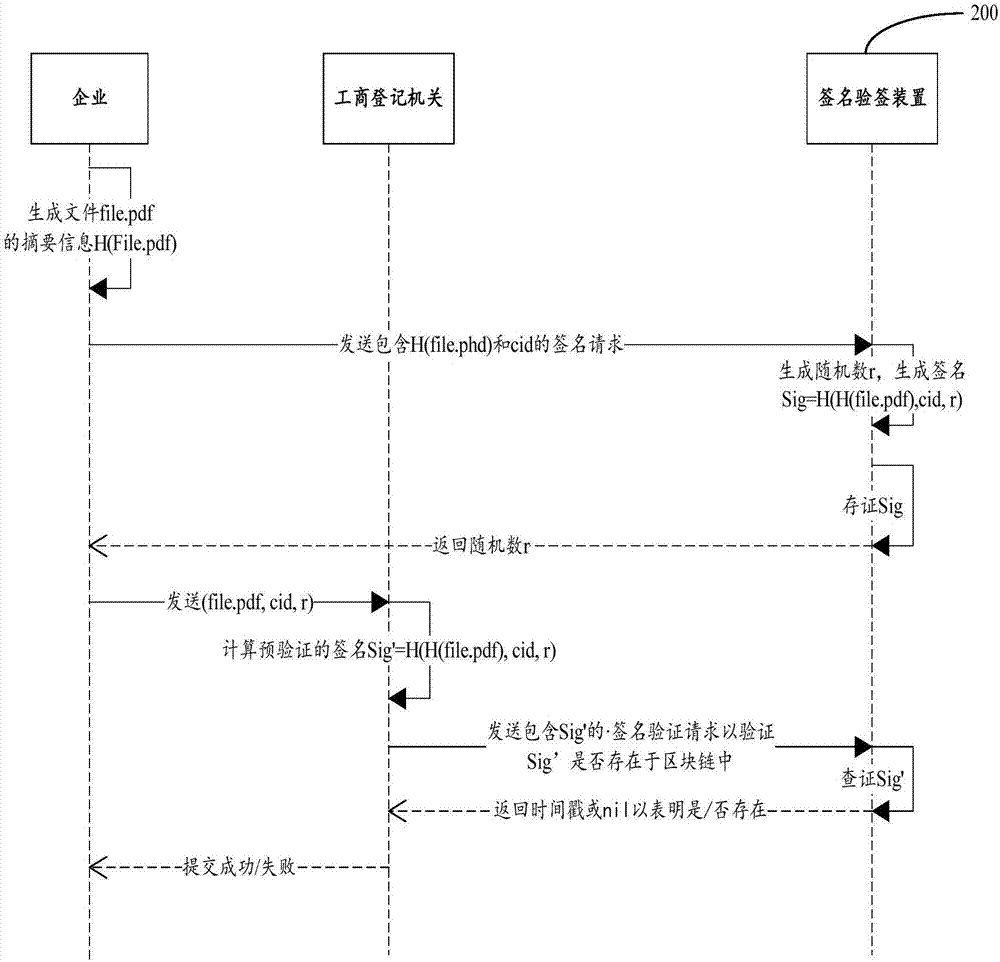
Signature verification method and device
ActiveCN107342867ALow costTamper proofKey distribution for secure communicationEncryption apparatus with shift registers/memoriesUSBComputer science
The invention discloses a signature verification method and a device. The signature verification method can include the following steps: receiving a signature request, wherein the signature request contains abstract information of a file and a sender identifier; generating a random number; generating a signature of the file according to a signature generation algorithm and based on the random number, the abstract information and the sender identifier; and saving the signature to a block chain, and returning the random number to a sender sending the signature request. Through the technical scheme of the invention, an electronic signature can be realized without a USB key.
Owner:深圳和信中欧科技有限公司
Data processing method and device, medium and electronic equipment
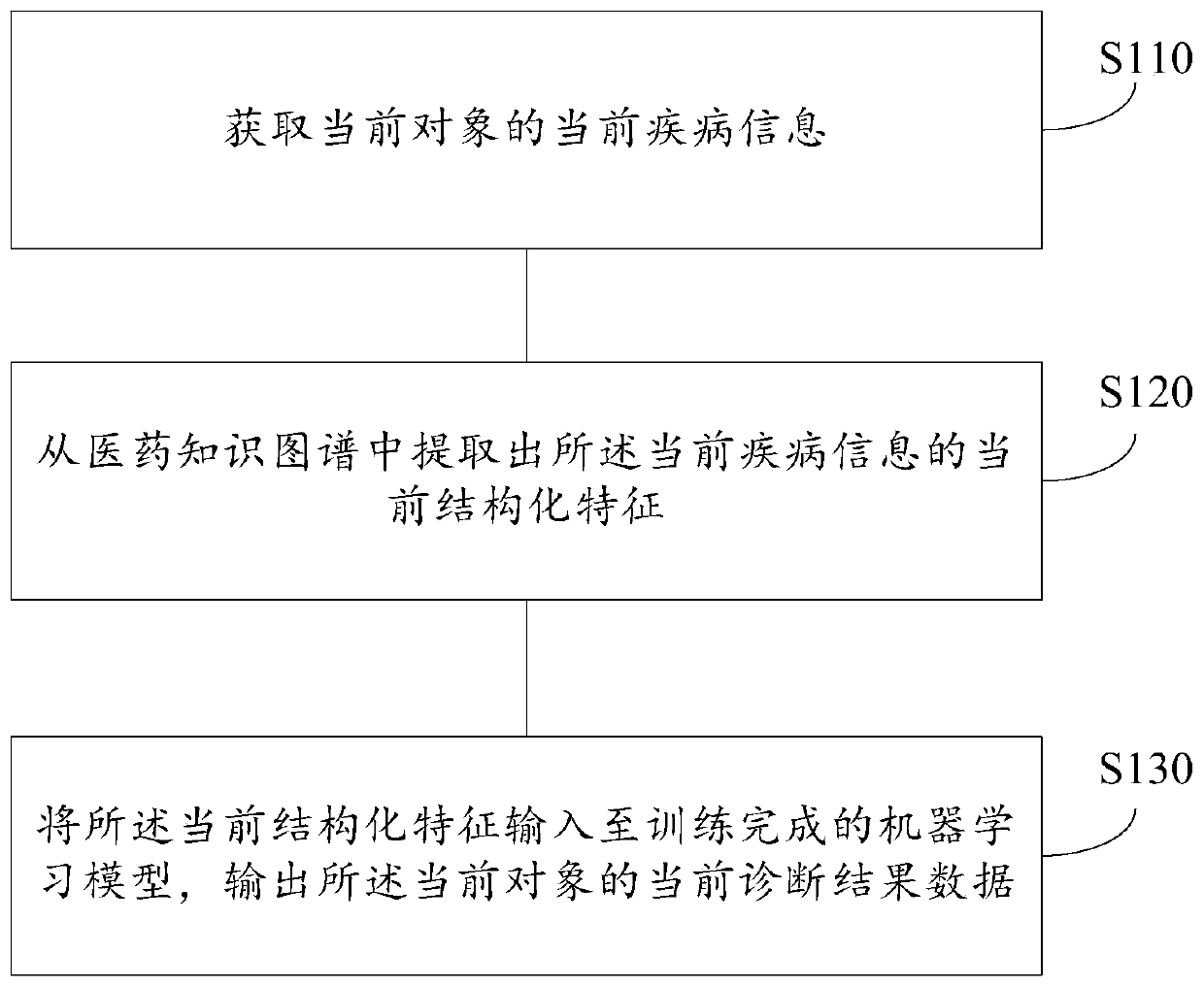
InactiveCN110335676ARealize automation and intelligenceImprove accuracy and diagnostic efficiencyMedical communicationMedical data miningMachine learningDisease
Owner:TAIKANG LIFE INSURANCE CO LTD
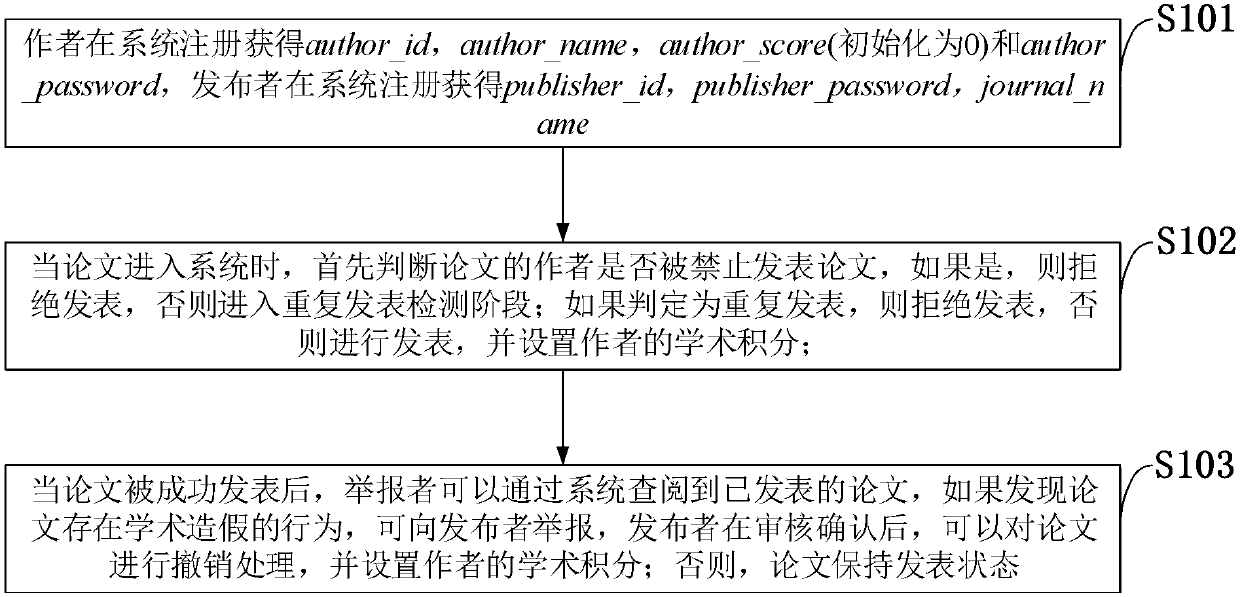
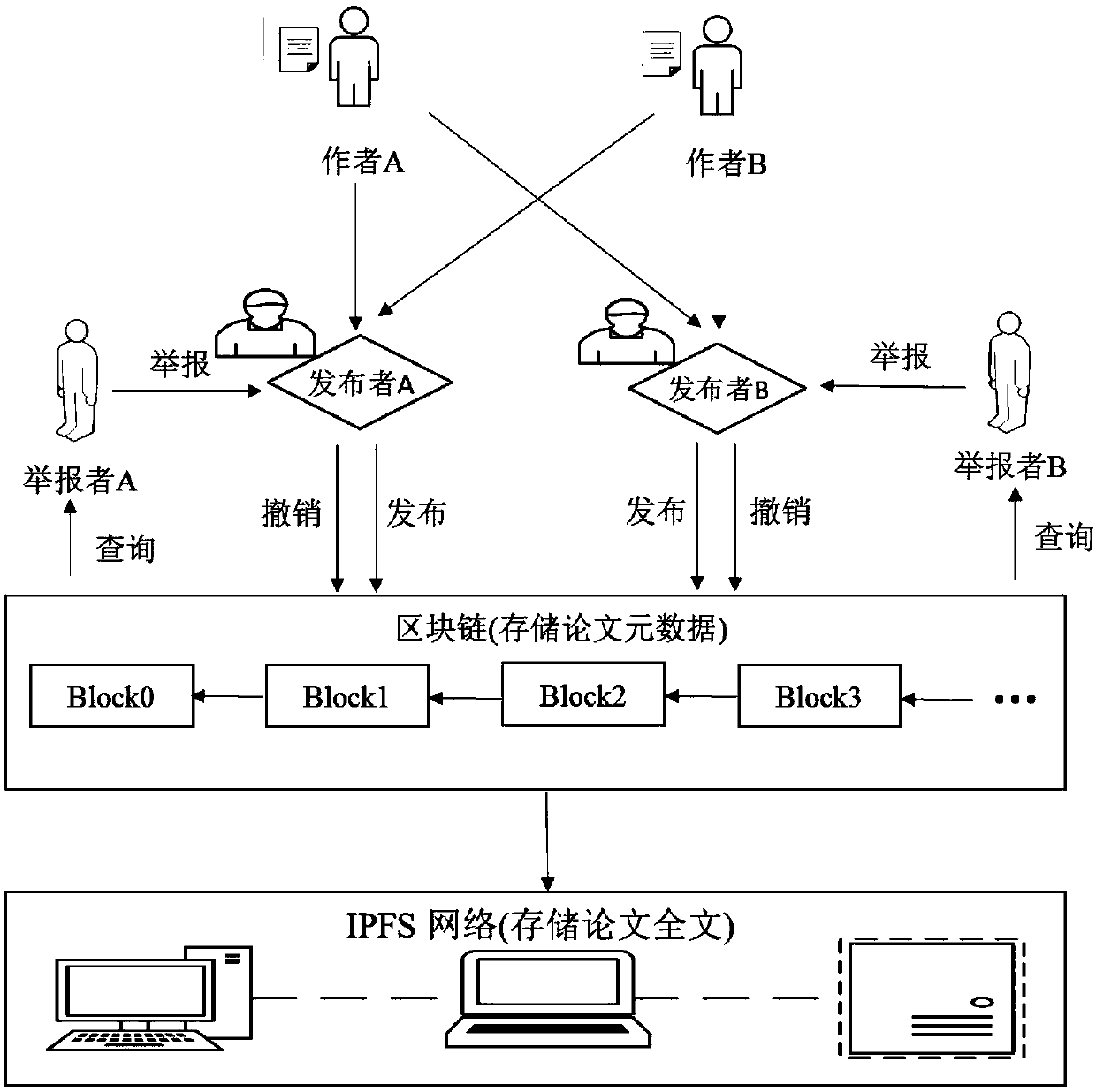
Blockchain-based academic platform service system and establishing method
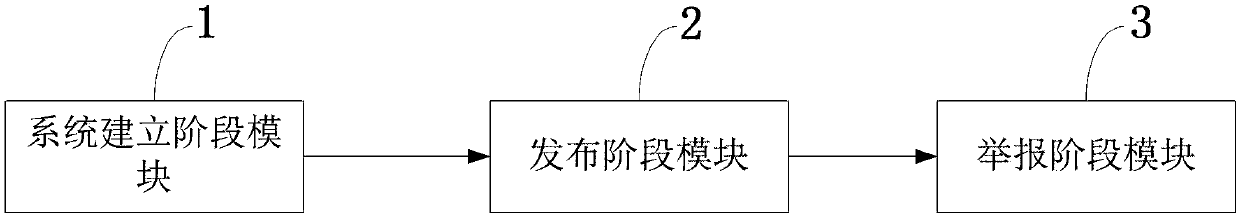
InactiveCN107563905AAgainst Academic CorruptionTamper proofData processing applicationsProgram/content distribution protectionSmart contractLibrary science
The invention discloses a blockchain-based academic platform service system and establishing method, which belongs to the technical field of database. The blockchain-based academic platform service system comprises a system establishing phase module for the registration of authors and publishers, a publishing phase module for determining whether the easy author is forbidden to publish essays and for detecting repetitive publication, and a reporting phase module for reporting essays having academic cheating to the publisher. The invention is advantageous in that decentralization is provided, academic data can be prevented from being tampered or lost, and safety in opposing and rejecting service attack can be guaranteed; the academic integration mechanism can be disclosed, and repetitive publication and academic cheating can be dealt with in a transparent manner; the system scheme can be realized based on Ethereum testing network, and interaction between visualized Web interface and intelligent contract can be conducted, and design demand can be met.
Owner:XIDIAN UNIV
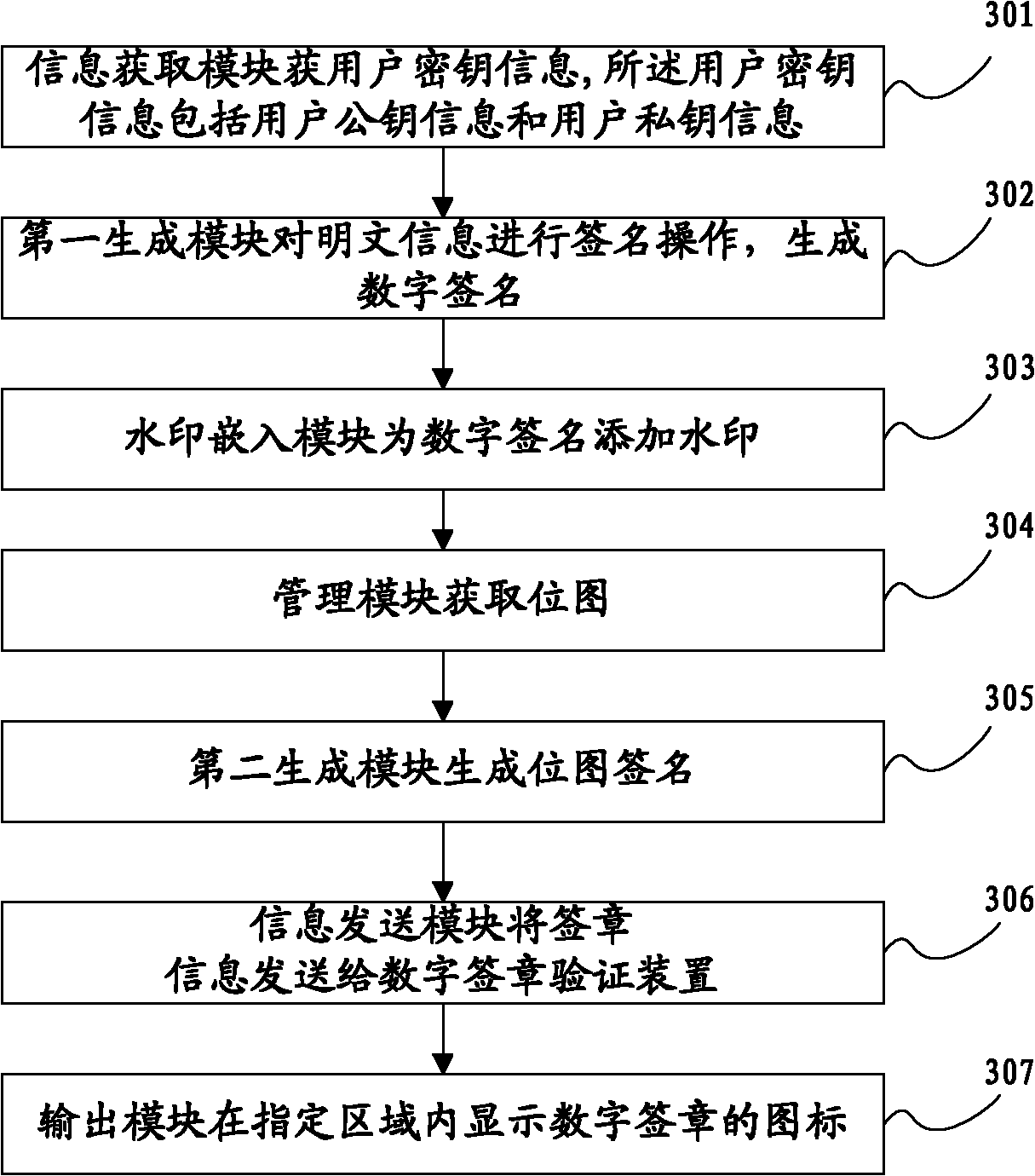
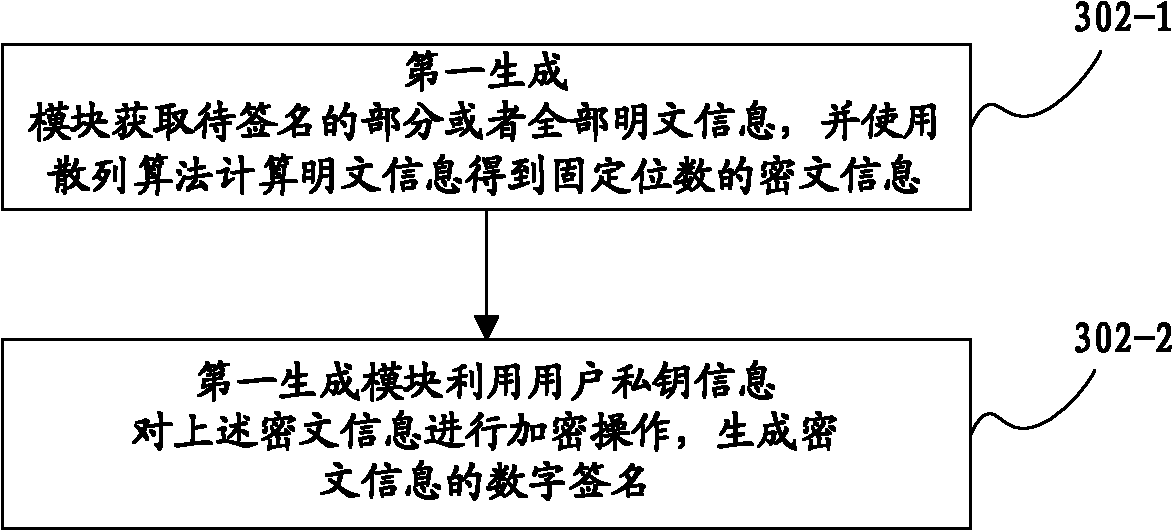
Digital signing system and method
ActiveCN102164037AEnsure safetyGuarantee authenticityUser identity/authority verificationTamper resistancePlaintext
The invention provides a digital signing method which comprises the following steps: acquiring the secret key information of a user; carrying out signing operation on plaintext information so as to generate a digital signature; changing the digital signature by using a watermark algorithm so as to form watermark information with the digital signature; acquiring a bitmap; processing the watermark information and the bitmap and carrying out signing on the bitmap so as to generate a bitmap signature; sending the digital signing information and the public key information of the user; showing the icon of the digital signature; acquiring the digital signing information and the public key information of the user; and verifying the bitmap signature and the digital signature; reporting the verification results of the bitmap signature and the digital signature; and verifying the effectiveness of the digital signature. The invention also provides a digital signing system. In the invention, through respectively carrying out signing on the plaintext information and the bitmap, the safety of a document is ensured; and through respectively verifying the bitmap signature and the digital signature, the authenticity of the document is ensured, and a tamper-proof effect is achieved.
Owner:FEITIAN TECHNOLOGIES
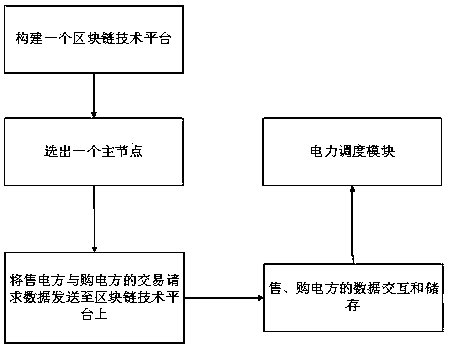
A power transaction method based on a block chain
PendingCN109785131AEfficient and reliable electricity tradingTamper-proofFinancePayment protocolsElectricity pricePower dispatch
The invention relates to a power transaction method based on a block chain, and belongs to the field of energy internet. According to the method, a power seller and a power purchaser are respectivelyused as a node, and N nodes jointly construct a block chain technical platform; an acknowledged master node is selected according to the voting system of the block chain, wherein the master node automatically formulates a power unit price according to the requirements of a power seller and a power purchaser; Transaction request data of the electricity seller and the electricity purchaser are sentto the block chain platform, and the data are stored in the block chain. Data interaction and storage of the electricity selling party and the electricity purchasing party pass through the block chainplatform, and after a transaction occurs, a result is stored in each node; And the transaction result notifies the power dispatching module to dispatch the electricity seller to the electricity purchaser, and the transaction is finished. According to the invention, the energy power transaction is more effective and reliable, the transaction is transparent, and the transaction information can be prevented from being tampered.
Owner:KUNMING UNIV OF SCI & TECH
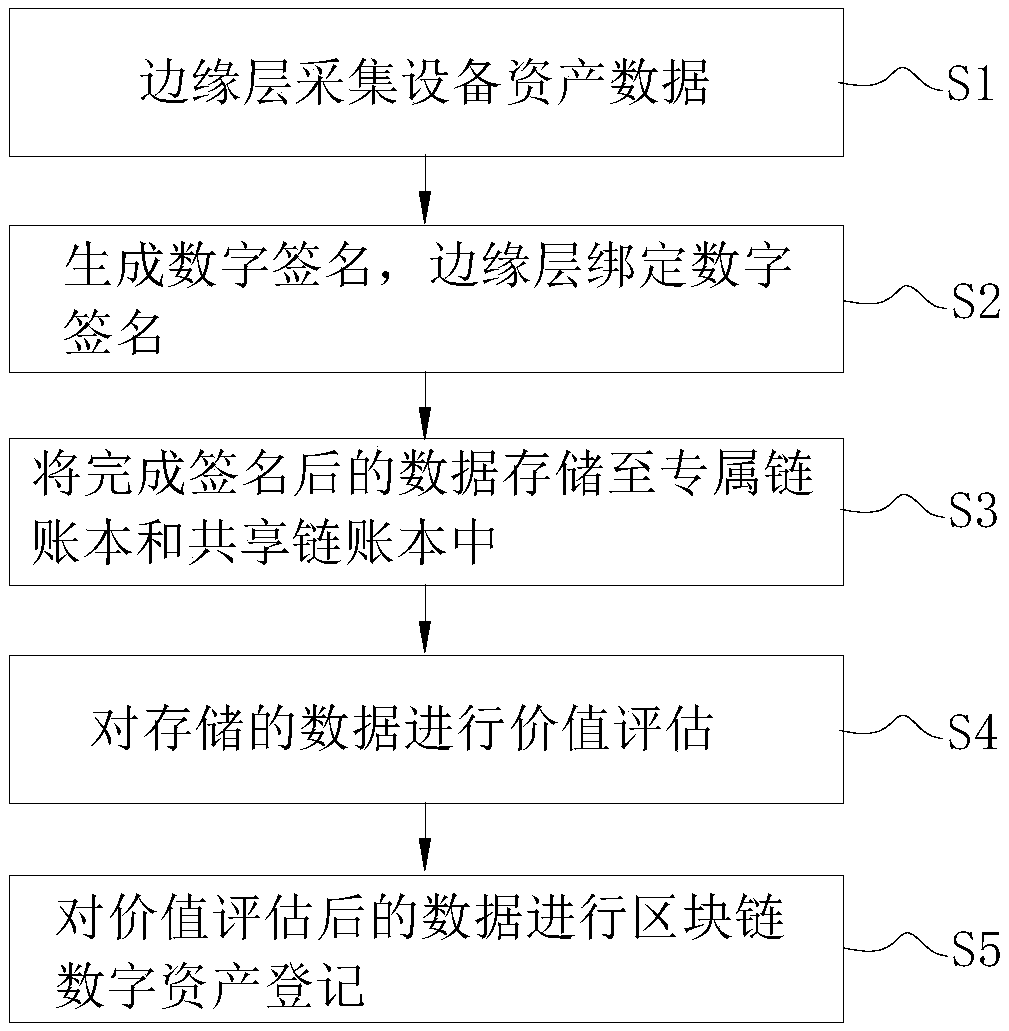
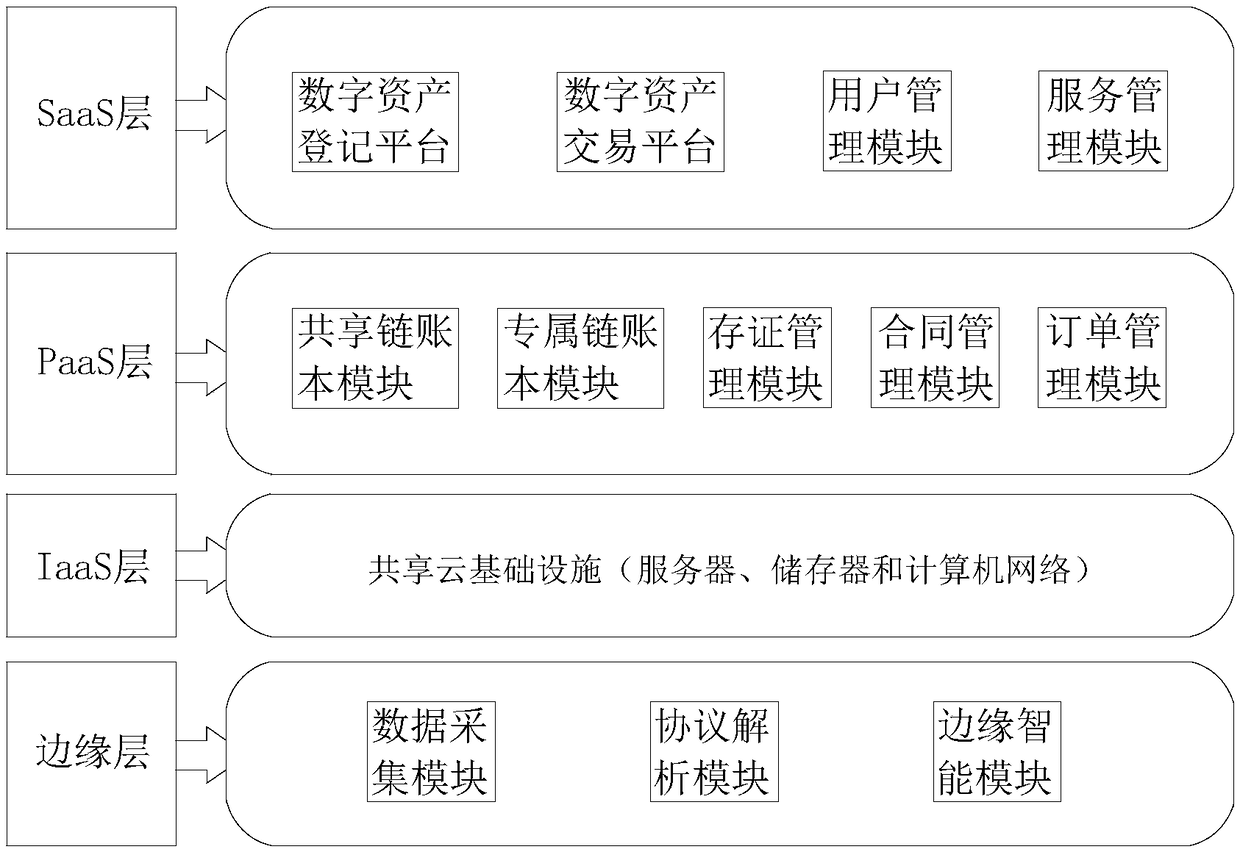
An enterprise digital assets management method and a system based on a block chain
InactiveCN109472605AIncrease production capacityTamper proofFinancePayment protocolsDigital signatureEnterprise data management
The invention discloses an enterprise digital assets management method based on block chain, which comprises the following steps: S1 edge layer collects equipment assets data; S2, generate a digital signature, and binding that digital signature to the edge lay; S3, storing the completed signature data in the exclusive chain account book and the shared chain account book; S4 assessing the value ofthe stored data; S5 Register the block chain digital assets on the valued data. The invention also discloses an enterprise digital assets management system based on a block chain. The invention provides an enterprise digital assets management method and a system, Through block chain technology to achieve intelligent production and intelligent operation, such as proprietary chain account book, shared chain account book and distributed service market, and through block chain to achieve decentralized distributed account book technology, so that the digital assets of enterprises with transparent,trustworthy, anti-tamper, traceability and high reliability characteristics.
Owner:成都航天科工大数据研究院有限公司
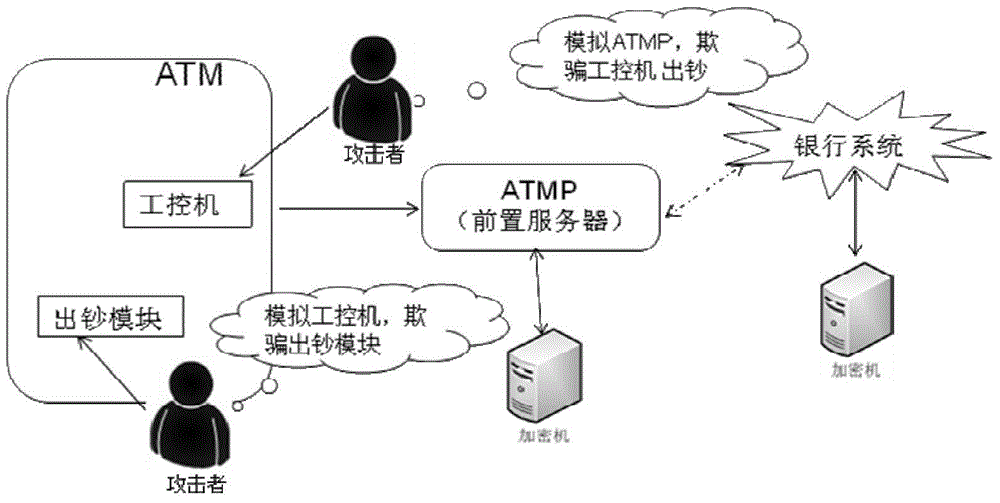
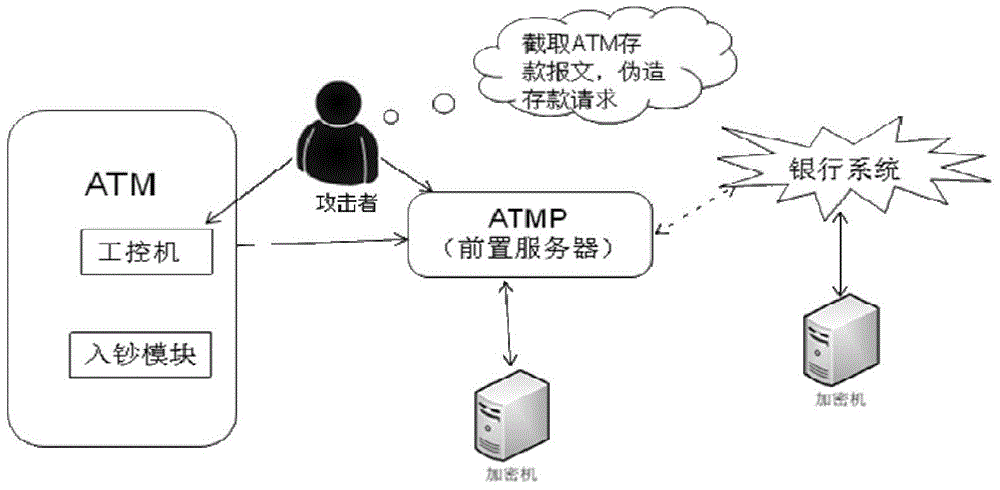
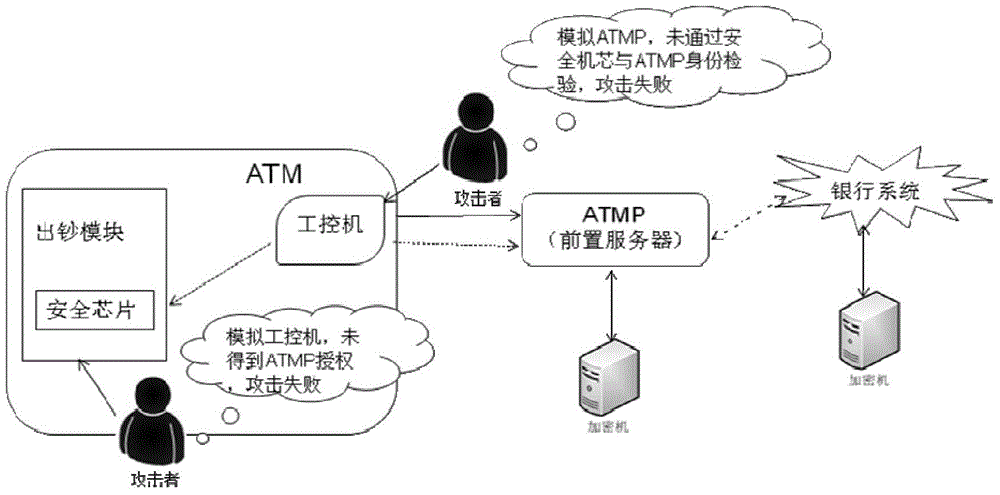
Method and system for controlling depositing and withdrawing safety based on safety core
The invention discloses a method and a system for controlling depositing and withdrawing security based on a security core. A security chip is arranged in a depositing and withdrawing core and put in the safe case of an automatic teller machine. The core safety chip is called the security core for short; the security core communicates with an automatic teller machine pre-system (ATMP); the safe communication of the security core with the ATMP is realized by virtue of certificate issuing and key exchange; the ATMP authorizes the core to dispense cashes, and meanwhile, checks the amount deposited. According to the method and the system for controlling the depositing and withdrawing security based on the security core, due to the safe communication of the security core and the ATMP, the identity is authenticated, an instruction sent out is verified legally and a message sent out is encrypted, and then the ATMP authorizes the core to dispense cashes and checks the amount deposited; the method and the system have the advantages that authentication and encryption / decryption can be effectively authenticated to achieve integrity protection, prevent tampering and prevent replay attack protection, and therefore, the security of the ATM is improved.
Owner:HUNAN GREATWALL INFORMATION FINANCIAL EQUIP
Decentralized image copyright protection system and method with infringement real-time detection
ActiveCN110110500AMeet the needs of copyright protectionGuaranteed to be authenticUser identity/authority verificationProgram/content distribution protectionTransmission protocolData set
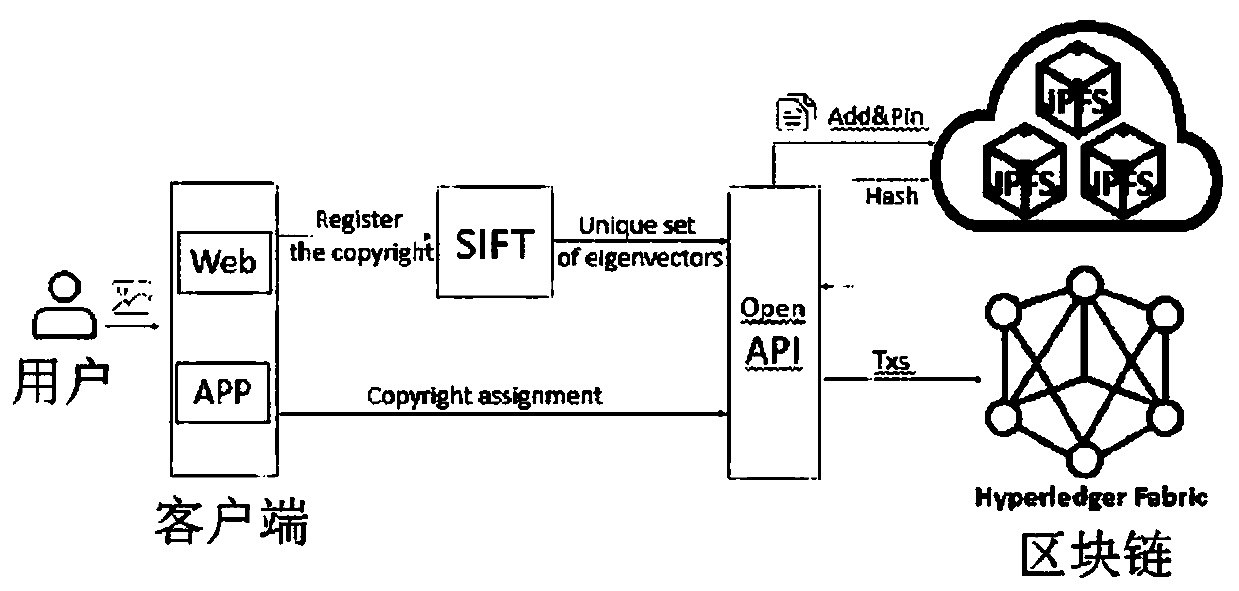
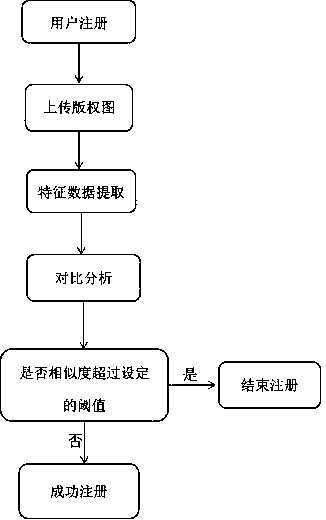
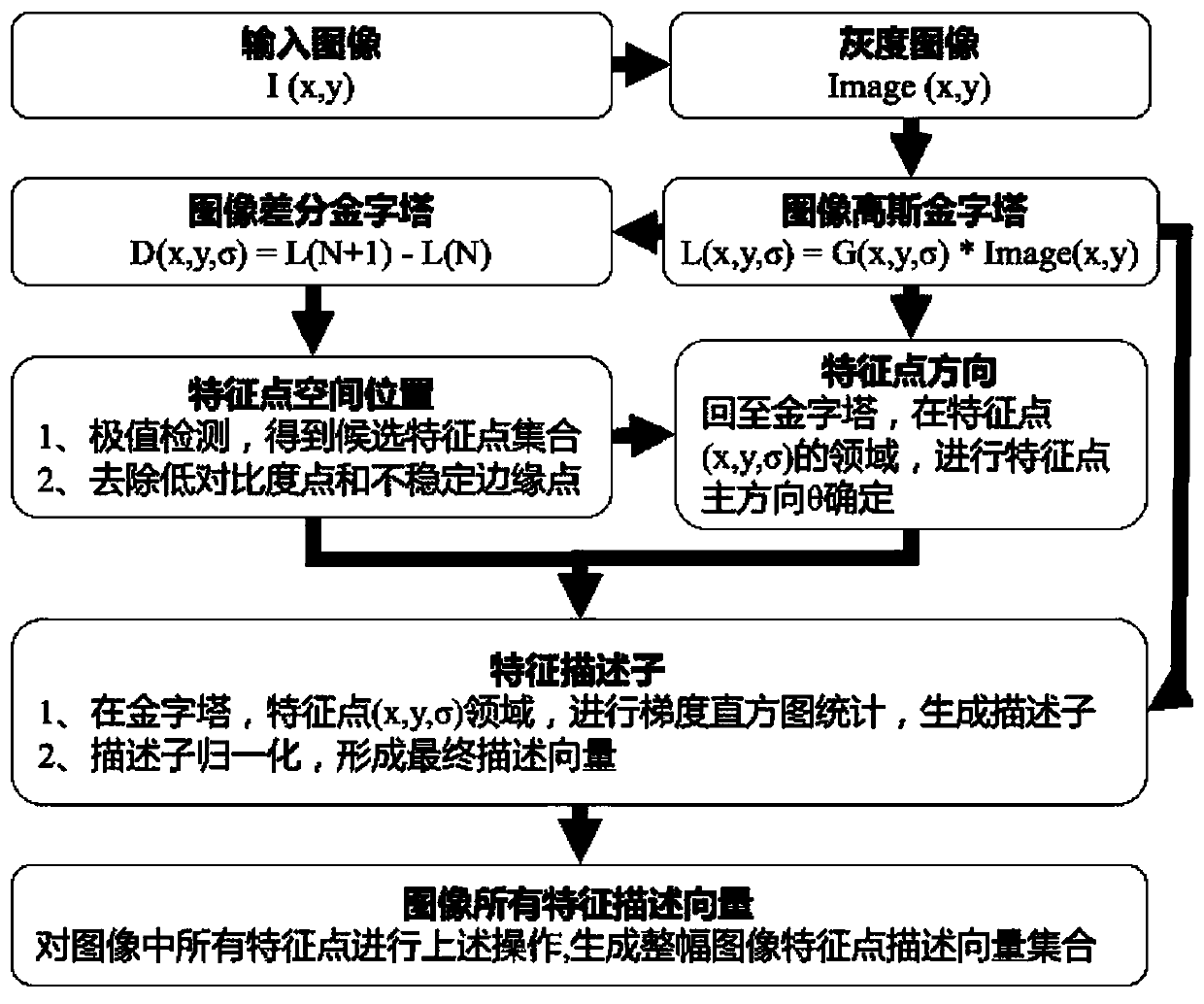
The invention relates to the technical field of copyright image protection, and provides a decentralized image copyright protection system and method with infringement real-time detection, and the method comprises the following steps of (1), enabling a registered user to upload an image through a client, and enabling an SIFT image feature extraction algorithm in the system to carry out the featuredata collection on the uploaded image; (2) extracting the invariant characteristics, such as visual angle, translation, affine, brightness, rotation, etc., of an existing copyright image by a user through an SIFT algorithm to form a local feature vector set of the image, and taking the local feature vector set as a registered image feature data set; (3) carrying out distributed storage on the feature data sets in the steps (1) and (2) by utilizing an IPFS (Internet Protocol File System), and constructing a network transmission protocol for persistent and distributed storage and file sharing;and (4) performing comparative analysis and calculation, and judging that the image does not accord with the condition of forming a new work. The system and the method provided by the invention have the characteristics of being tamper-proofing, realizing the high safety, permanent preservation and decentralization, being able to trace, being low in cost, etc.
Owner:施建锋
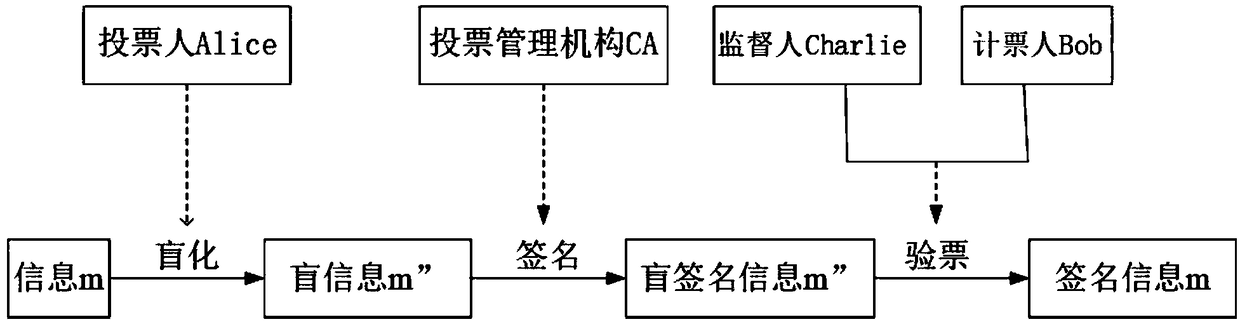
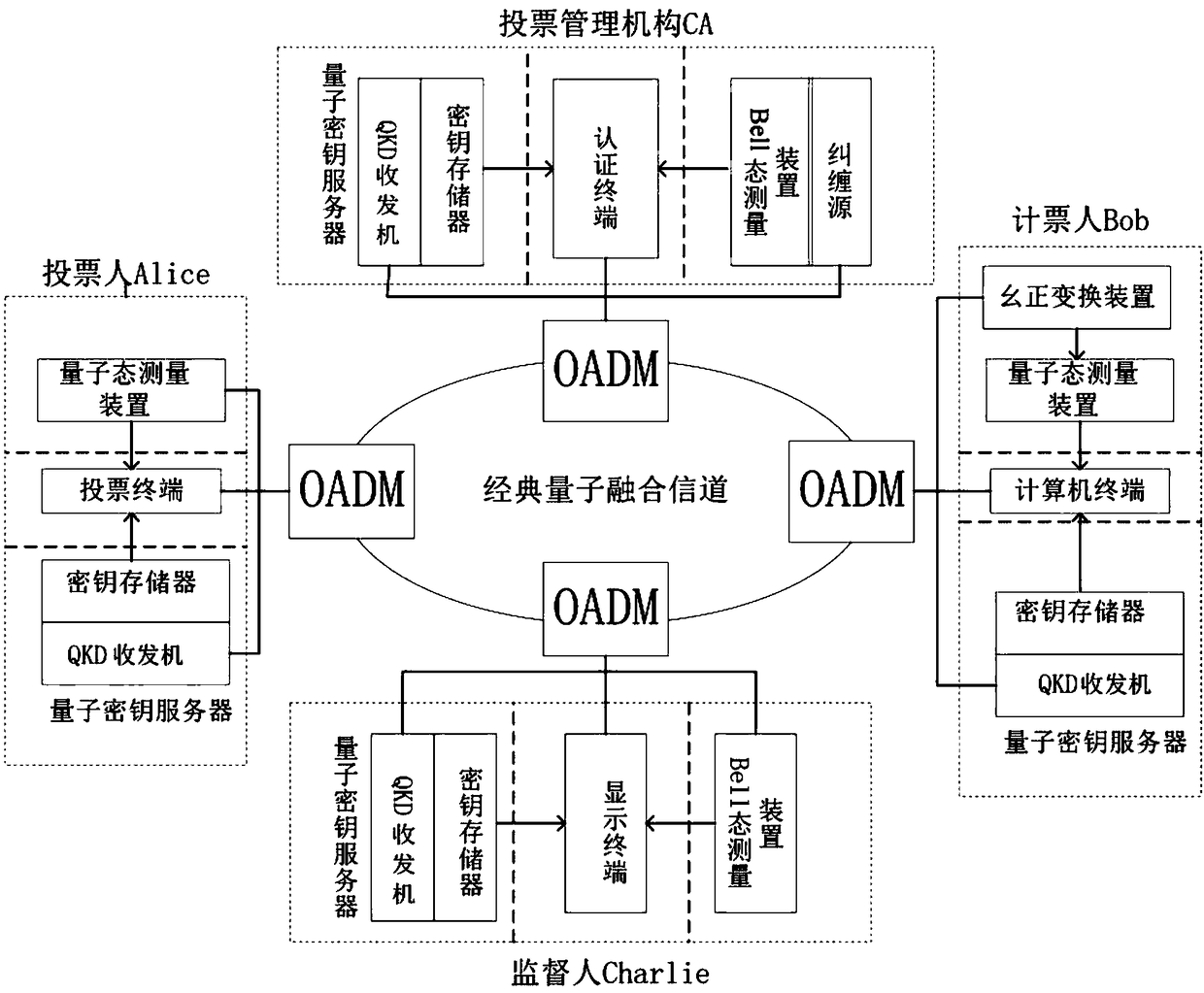
Quantum voting system and method based on quantum teleportation
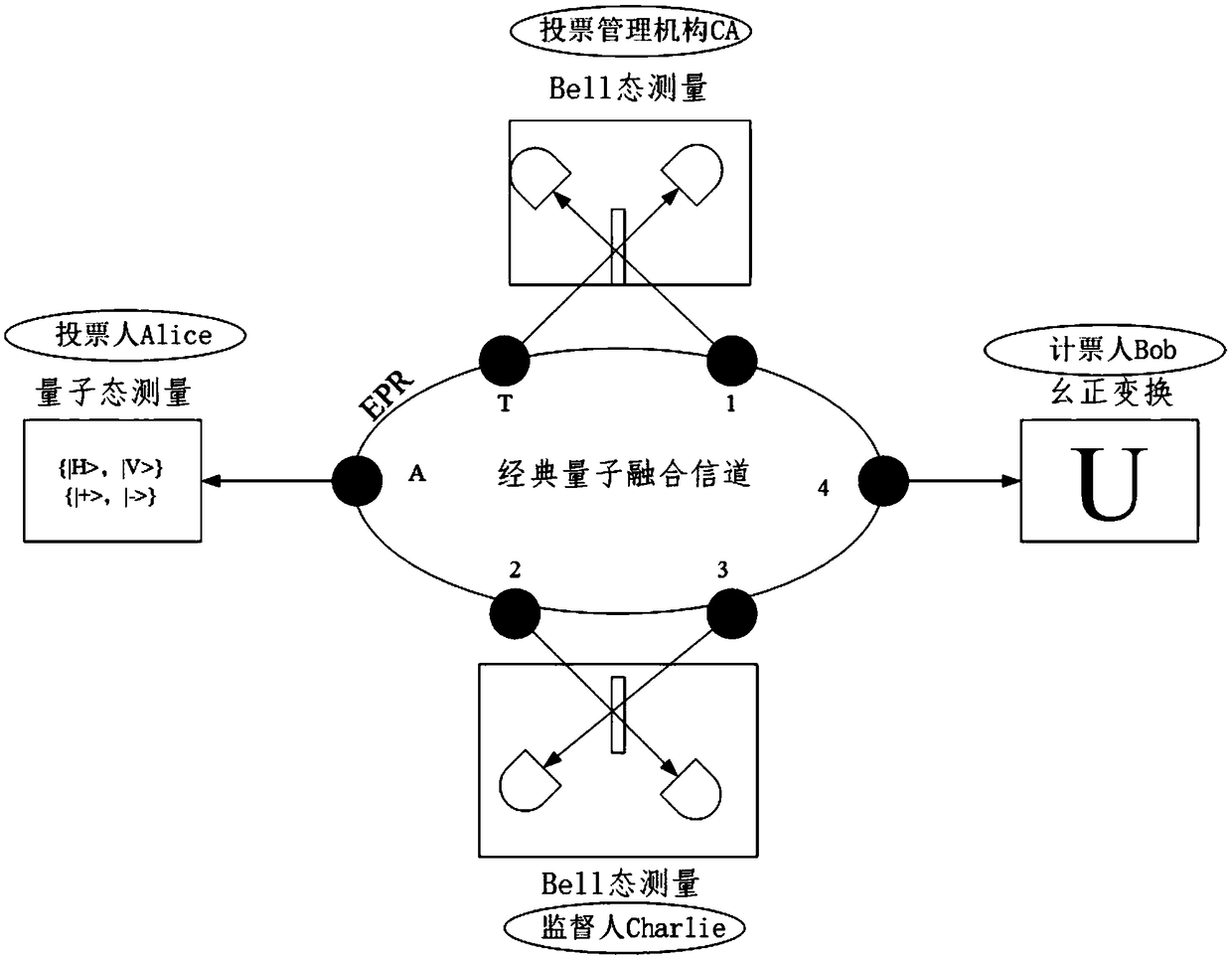
PendingCN108880790AGuaranteed legalityEnsure safetyKey distribution for secure communicationUser identity/authority verificationBell stateMeasurement device
The invention discloses a quantum voting system and method based on quantum teleportation. The quantum voting system comprises a voter Alice, a voting management organization CA, a supervisor Charlie,a teller Bob and four OADMs, wherein the voter Alice comprises a first a quantum key server, a voting terminal and a first quantum state measurement device; the voting management organization CA comprises a second quantum key server, an authentication terminal, an entanglement source and a first Bell state measurement device; the supervisor Charlie comprises a third quantum key server, a displayterminal and a second Bell state measurement device; and the teller Bob comprises a fourth quantum key server, a computer terminal, a unitary transformation device and a second quantum state measurement device. The quantum voting system disclosed by the invention ensures the security of the whole voting process by the coherence of entangled particles, a QKD protocol, a one-time-one-encryption encryption algorithm and quantum channel eavesdropping detection. In addition, the quantum voting system disclosed by the invention transmits the classical and quantum information through different wavelengths in the same optical fiber, so that the cost of an application can be greatly reduced, and the practicability is improved
Owner:GUANGDONG INCUBATOR TECH DEV CO LTD
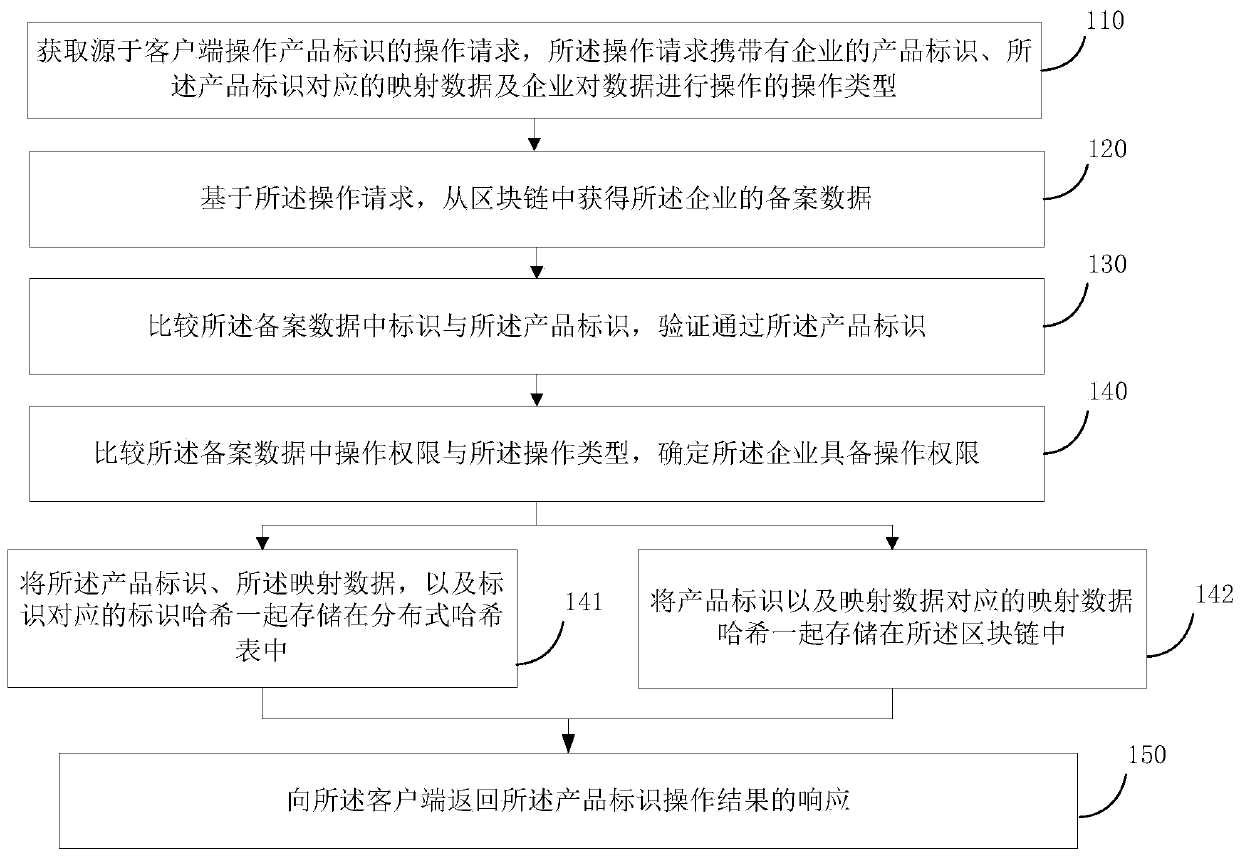
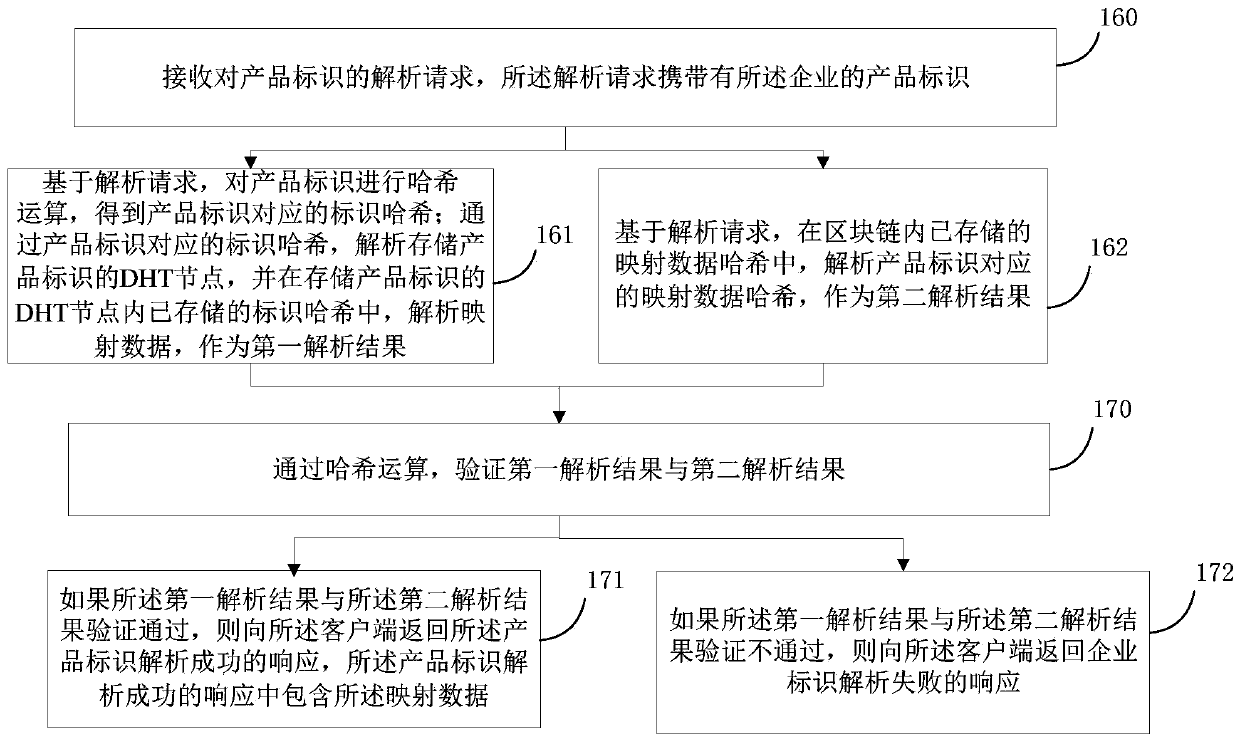
Industrial Internet identifier processing method and device based on block chain
PendingCN111368230ATamper proofGuaranteed reliabilityEncryption apparatus with shift registers/memoriesWebsite content managementThe InternetIndustrial Internet
The embodiment of the invention provides an industrial Internet identifier processing method and device based on a block chain, and the method comprises the steps: obtaining an operation request froma client for operating a product identifier, the operation request carrying the product identifier of an enterprise, the mapping data corresponding to the product identifier, and the operation type ofthe enterprise for the operation of the data; based on the operation request, obtaining record data of the enterprise from the block chain; comparing the identification in the record data with the product identification, and verifying that the product identification is passed; comparing the operation authority and the operation type in the record data, and determining that the enterprise has theoperation authority; and returning a response of the product identification operation result to the client. In this way, the block chain has the tamper-proof characteristic, the reliability of storedinformation can be guaranteed, and safe operation service is provided; through the verification identifier and the verification operation authority, the data security can also be improved through multiple verification, so that the security of the industrial Internet is ensured.
Owner:BEIJING UNIV OF POSTS & TELECOMM
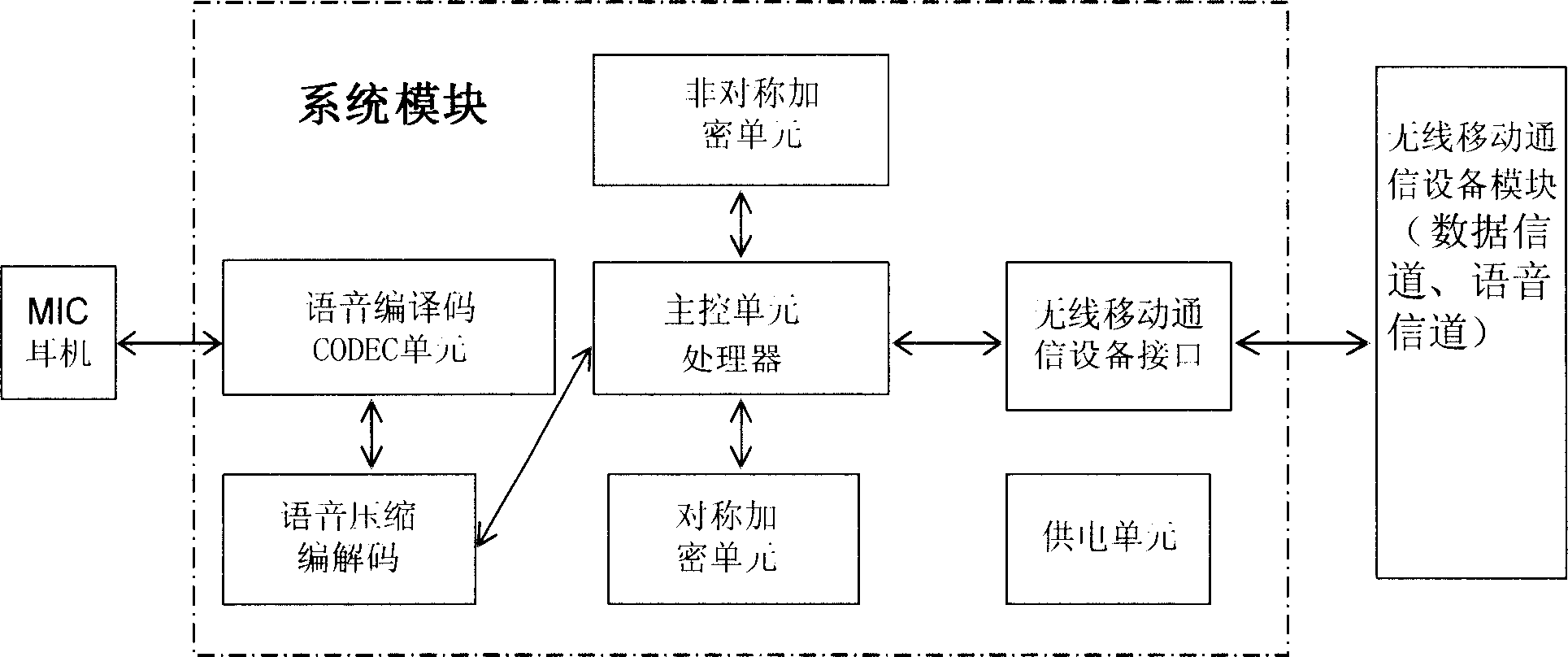
Apparatus and method for implementing data safety transmission of mobile communication apparatus
ActiveCN1688171AFlexible and convenient to useWill not affect the useUser identity/authority verificationRadio/inductive link selection arrangementsCircuit Switched DataData compression
This invention discloses a safety transmitting device and a method for mobile communication devices. Said device can be connected on radio mobile communication devices of GSM or CDMA network detachably via their interface units including seven parts: a master control unit, a CODEC unit, a data compression code / decode unit, an asymmetrical ciphering unit, a symmetrical ciphering unit, a power supply unit and an interface unit. Said device utilizes the current GSM or CDMA network to carry out identity certification and session cryptographic key transfered by the improved PK1 asymmetric ciphered code system without CA and ciphers the data by session cryptographic key to be transmitted by the circuit exchange data service supported by network and carries out inverse process at the receive end to realize end-to end cipher communication function.
Owner:GUANGZHOU SPACEFLIGHT HAITE SYST ENG
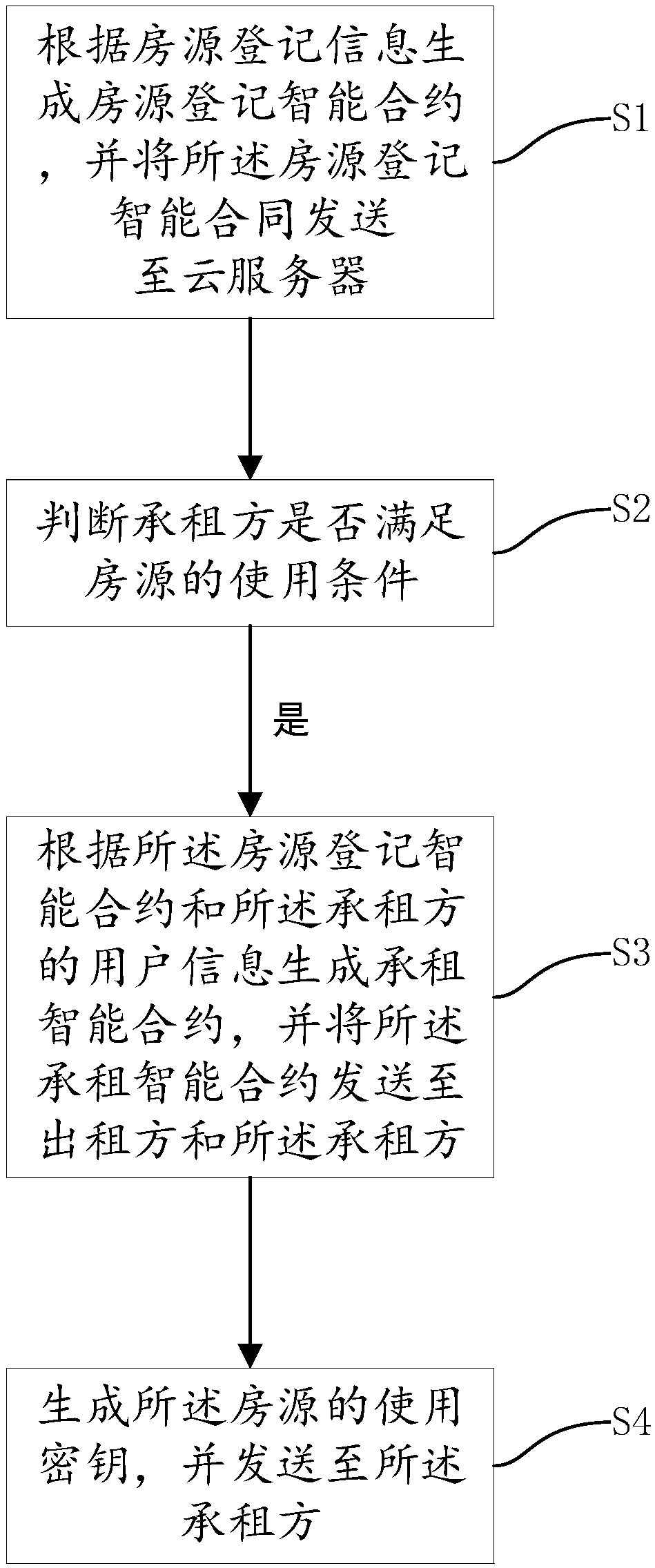
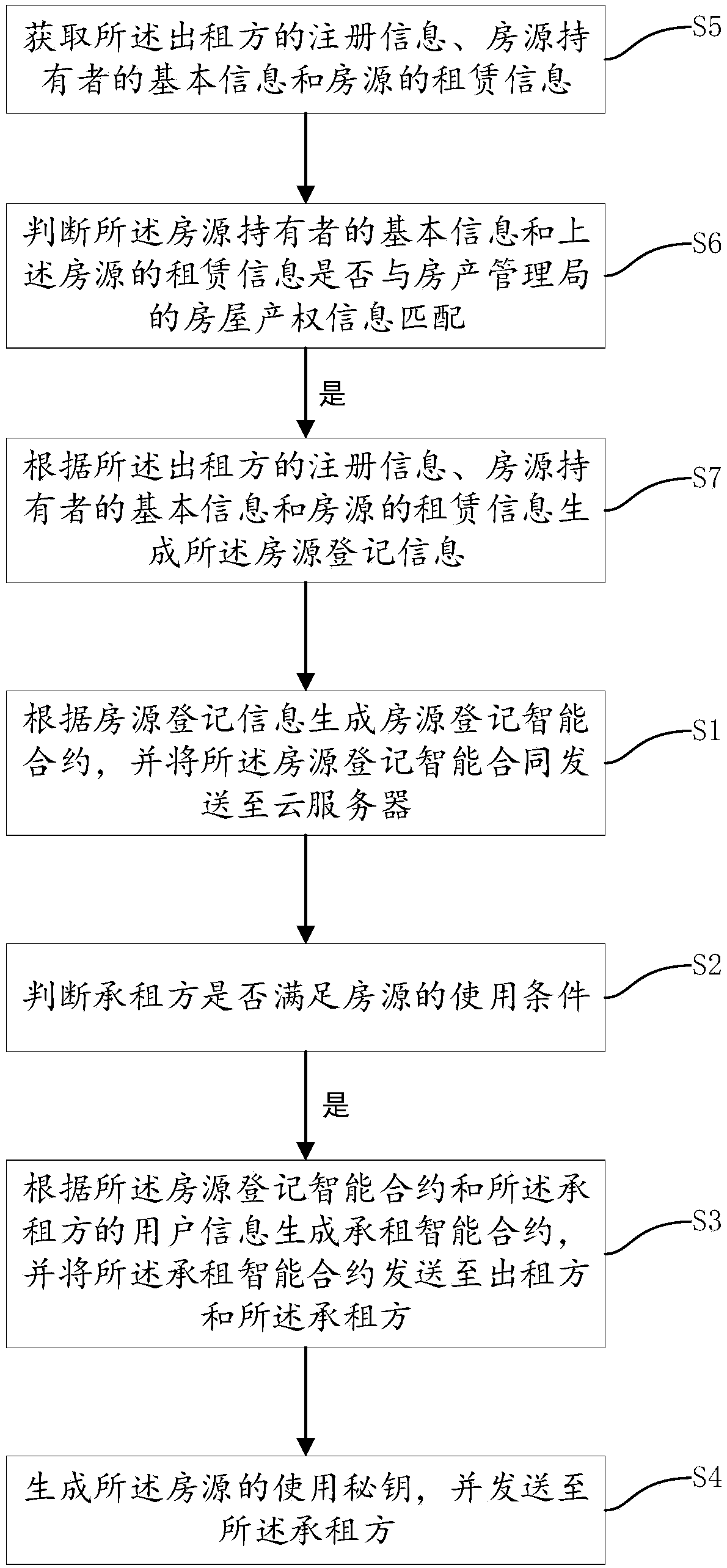
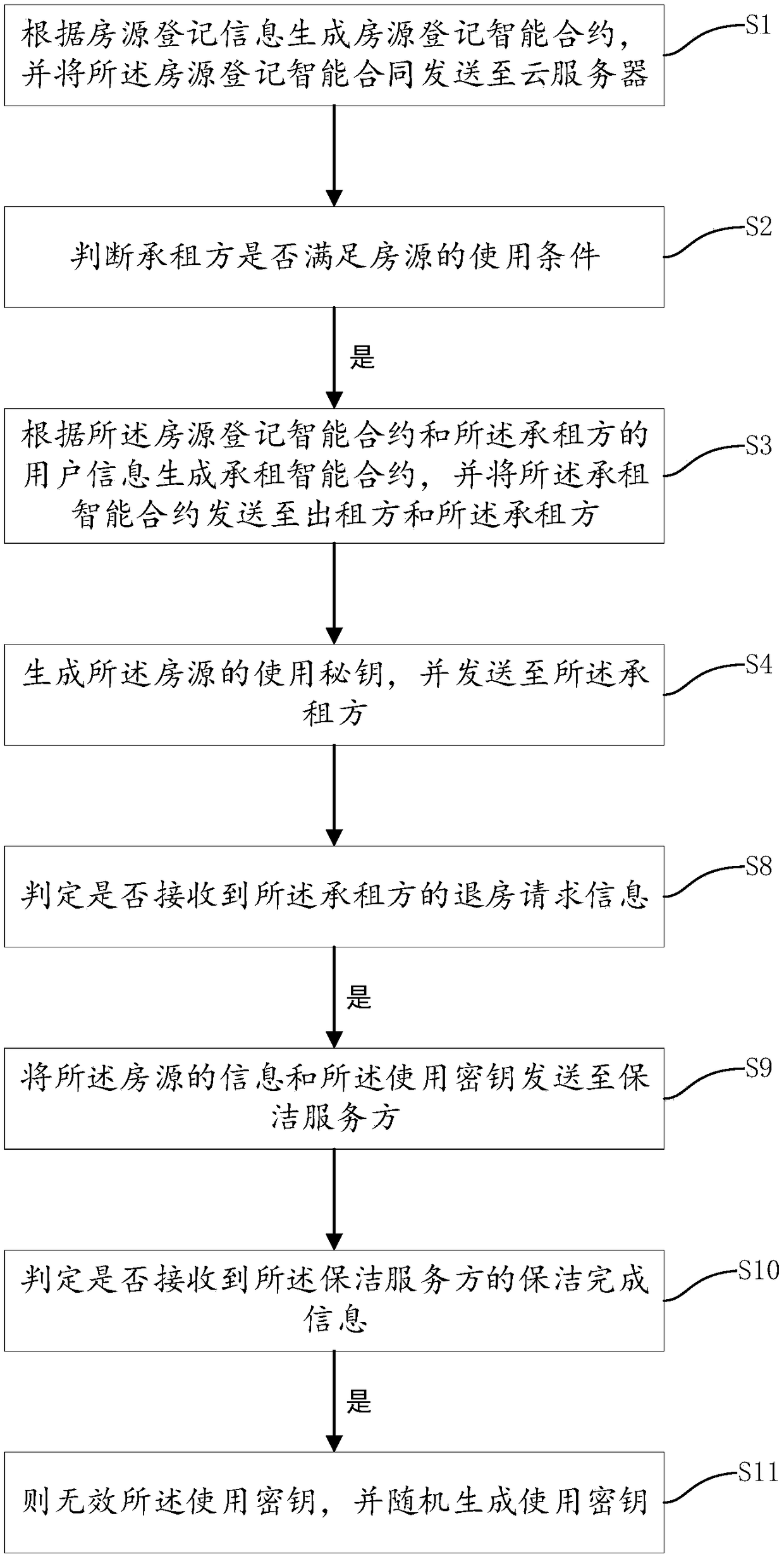
Leasing method and system based on block chain technology, device and storage medium
ActiveCN108764901AImprove convenienceGuarantee authenticityPayment protocolsBuying/selling/leasing transactionsOperating systemSmart contract
The invention discloses a leasing method and system based on block chain technology, a device and a storage medium, the method comprising the steps of: generating a house source registration intelligent contract according to the house source registration information and sending the house source registration intelligent contract to a cloud server; judging whether the lessee meets the conditions ofusing the source of the house; if yes, generating a lease intelligent contract according to the house source registration intelligent contract and the user information of the lessee, and sending the lease intelligent contract to the lesser and the lessee; and generating a usage key for the source of the house and sending it to the lessee. The leasing method and system based on the block chain technology, the device and the storage medium have the beneficial effects that: by automatically generating an intelligent lease contract and a use key, the steps of checking identity information, performing registering and obtaining the door key of the house source from the lesser are reduced, and the convenience of the lessee to check in the house source is improved.
Owner:POPULIFE TECH LLC
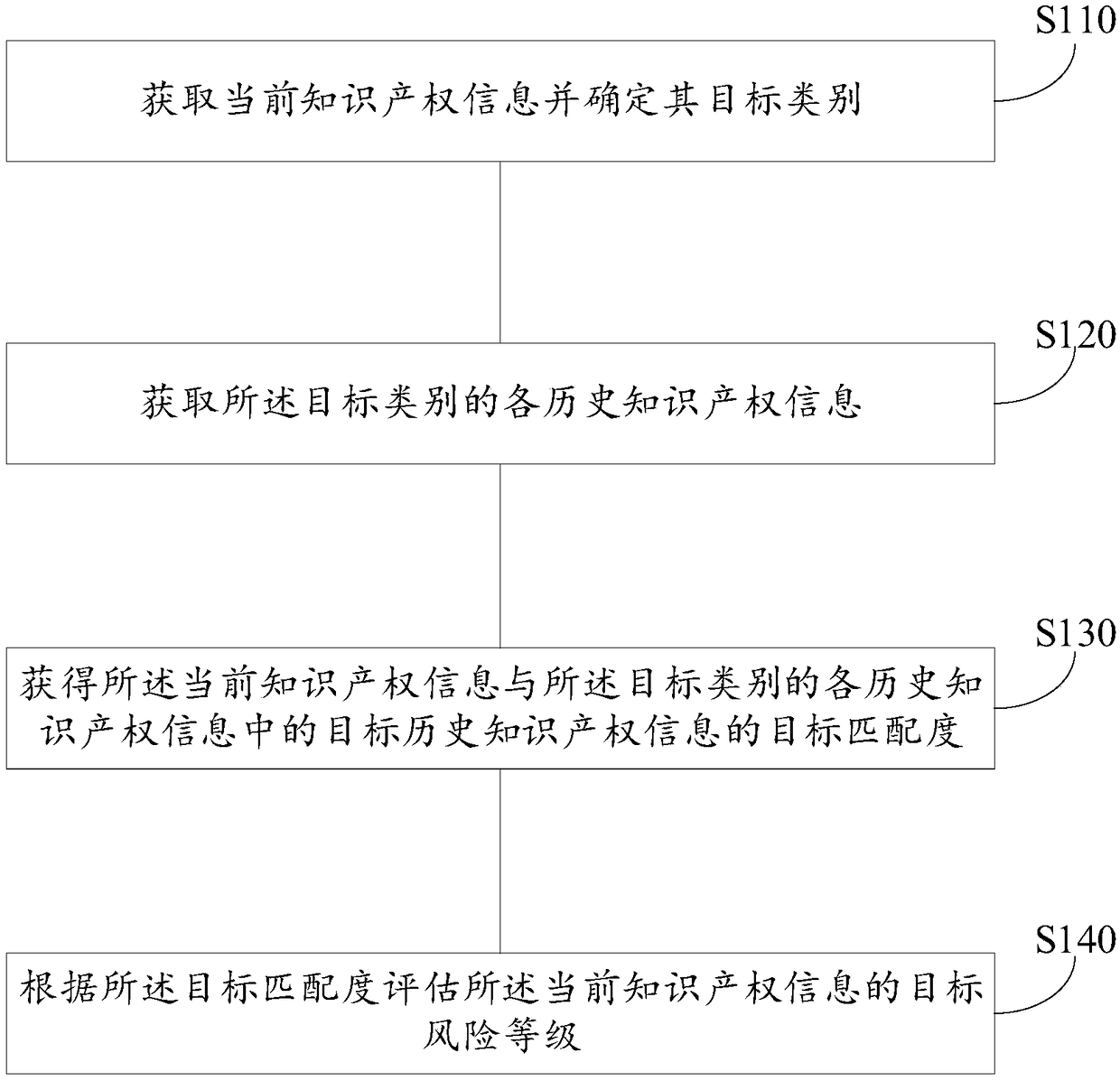
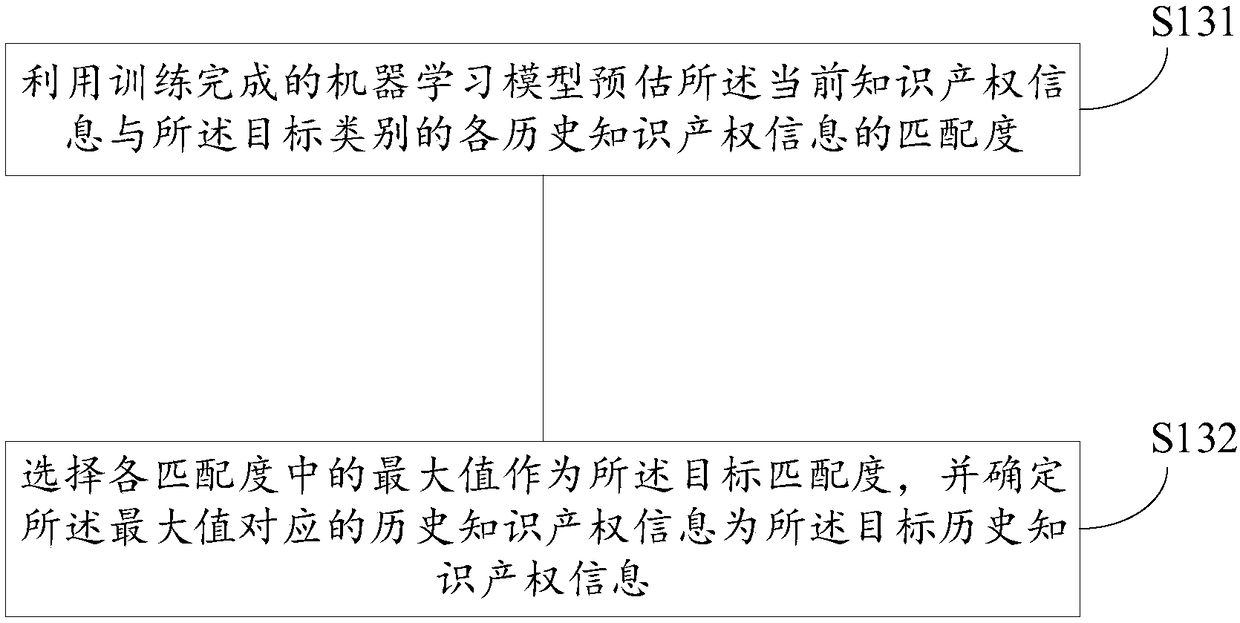
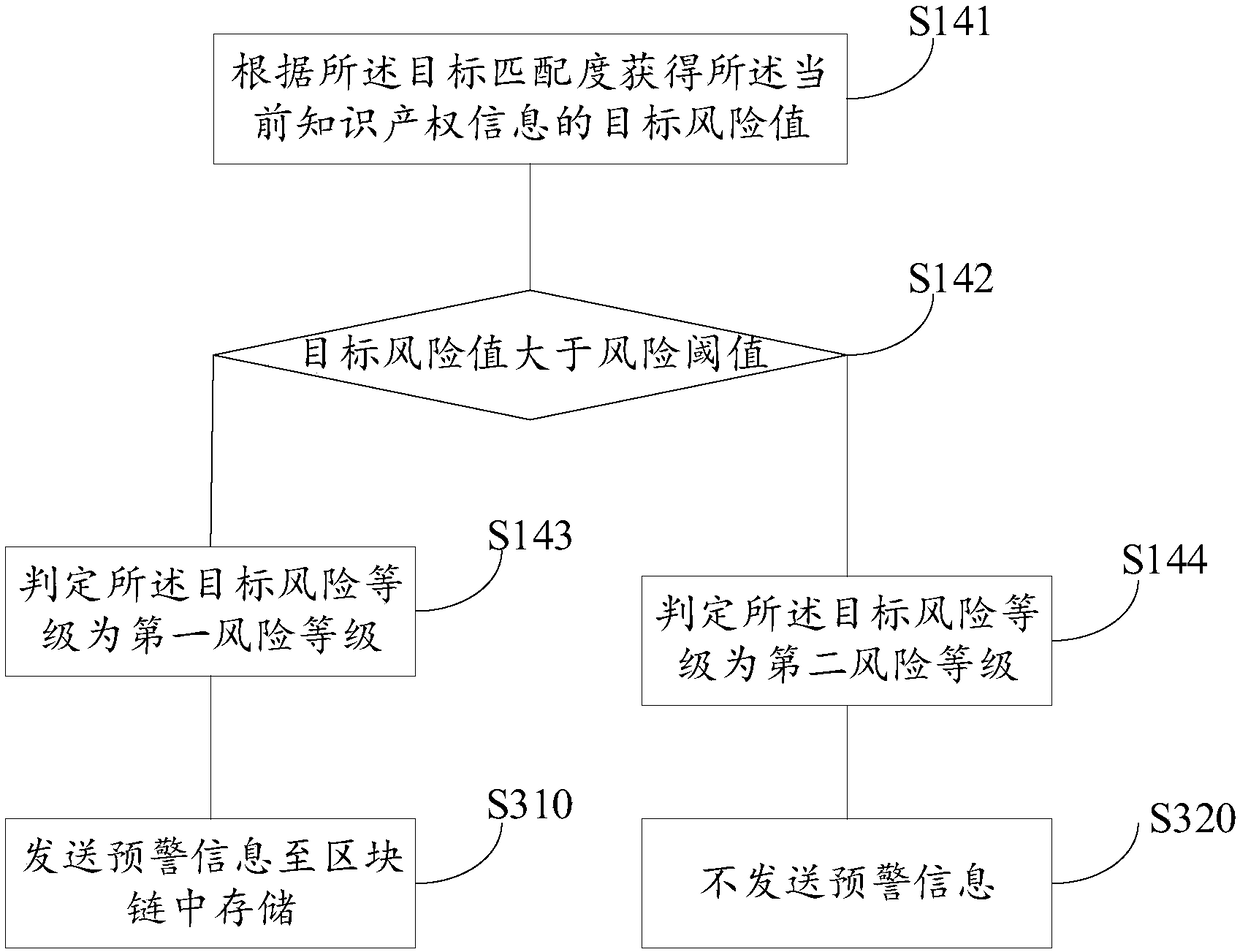
Data processing method, device, medium and electronic device
The embodiment of the invention provides a data processing method, a device, a medium and an electronic device. Acquiring each historical intellectual property information of the target category; Obtaining a target matching degree of the current intellectual property information and the target historical intellectual property information in each historical intellectual property information of thetarget category; Evaluating a target risk level of the current intellectual property information according to the target matching degree. The technical proposal of the embodiment of the invention canautomatically predict the target risk level of the current intellectual property information, so that early warning can be carried out according to the target risk level.
Owner:TAIKANG LIFE INSURANCE CO LTD
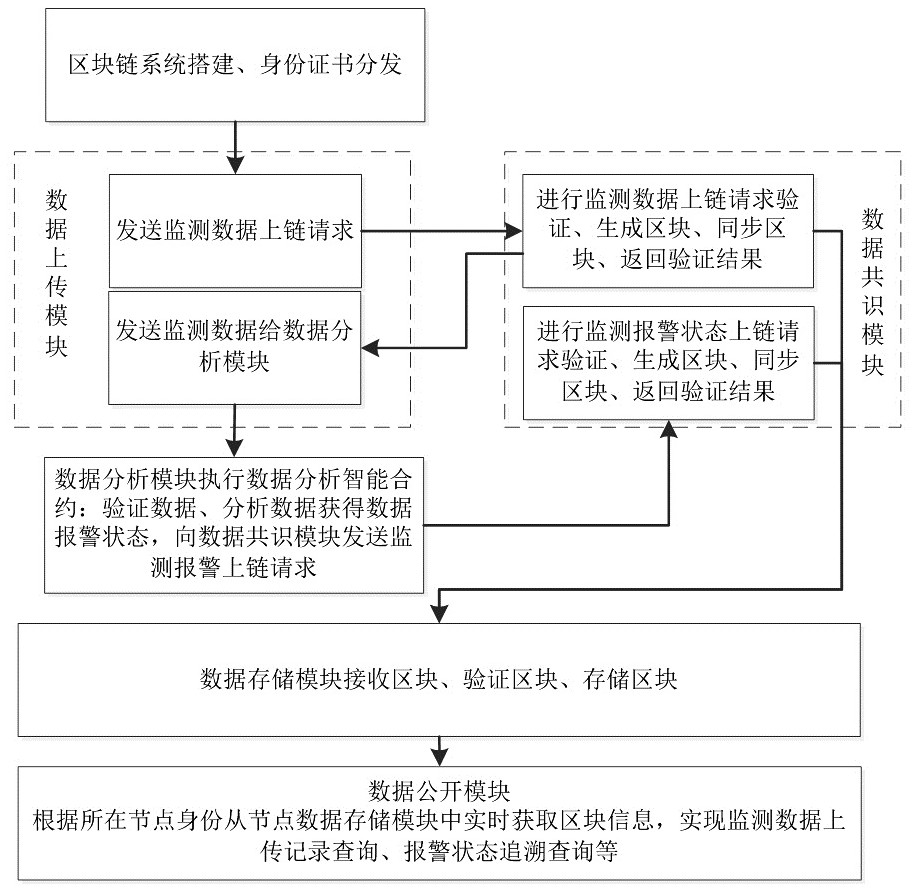
Engineering monitoring data management system based on block chain and working method thereof
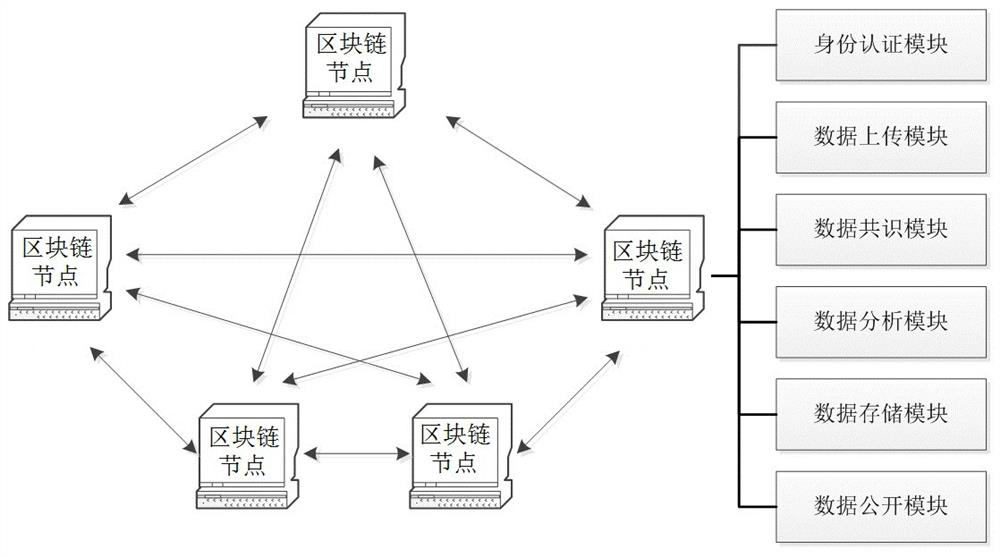
PendingCN112016133AUpload records can be tracedRealize uploading and depositing certificatesDigital data protectionDigital data authenticationAlarm stateData store
The invention discloses an engineering monitoring data management system based on a block chain and a working method thereof. The engineering monitoring data management system comprises a block chainnetwork and at least one block chain node distributed in the block chain network, wherein each block chain node is provided with one or more combinations of an identity authentication module, a data uploading module, a data consensus module, a data analysis module, a data storage module and a data disclosure module. According to the method, uploaded monitoring data are encrypted, identity certificates are added, and traceability of the monitoring data is achieved; the authenticity of the data is verified before the monitoring data is analyzed, so that the reliability of a data alarm state is improved; and the data alarm state is stored in a block chain to realize real-time update of the alarm state of the monitoring data and tracing of state change information.
Owner:SHANGHAI GEOTECHN INVESTIGATIONS & DESIGN INST
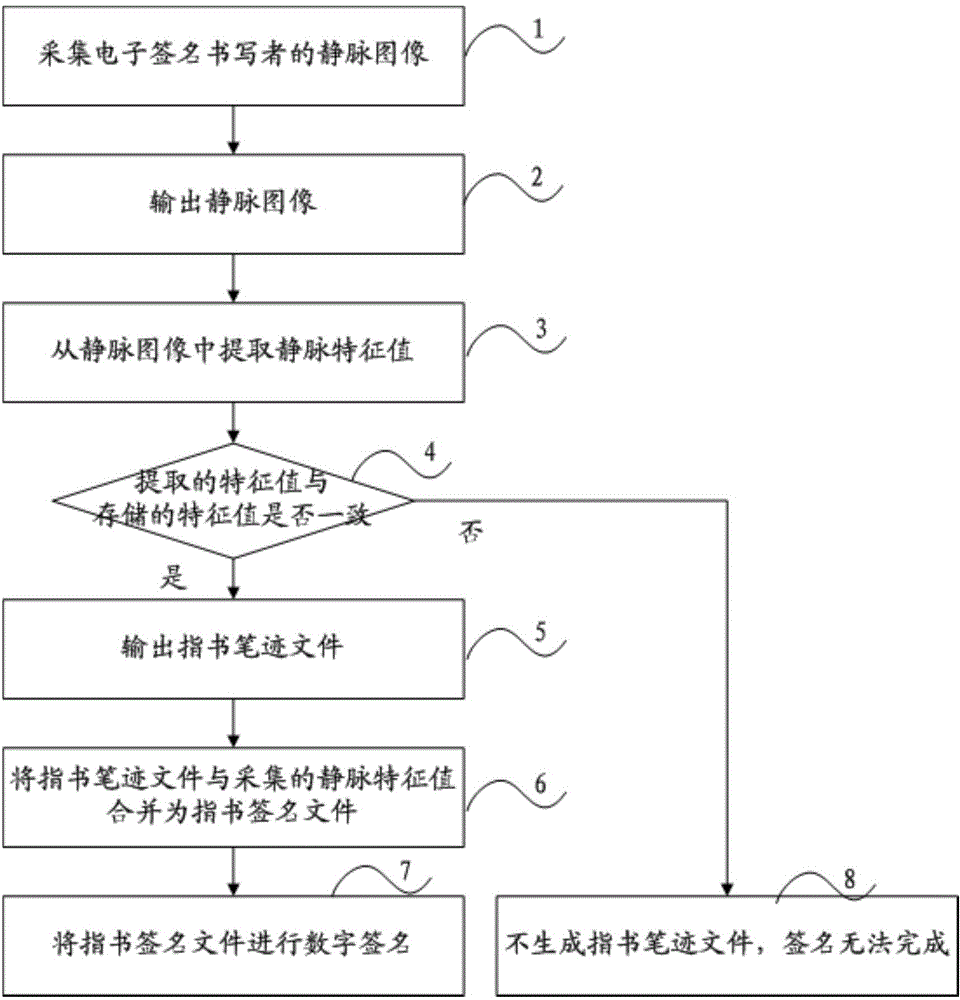
Method and system for finger-writing signatures on touch screen
ActiveCN104462908AImprove accuracyAnti-counterfeitingDigital data authenticationHandwritingPattern recognition
The invention discloses a method and a system for finger-writing signatures on a touch screen. The method includes: a vein image of a writer of an electronic signature; outputting the vein image; extracting vein feature values from the vein image; comparing the extracted vein feature values to stored vein feature values; if consistence is confirmed, outputting finger writing files, and combing the finger writing files and the extracted vein feature values into a finger-written signature file. The method and the system have the advantages that authentication is more accurate and faking and tampering is prevented.
Owner:CHINA TELECOM CORP LTD
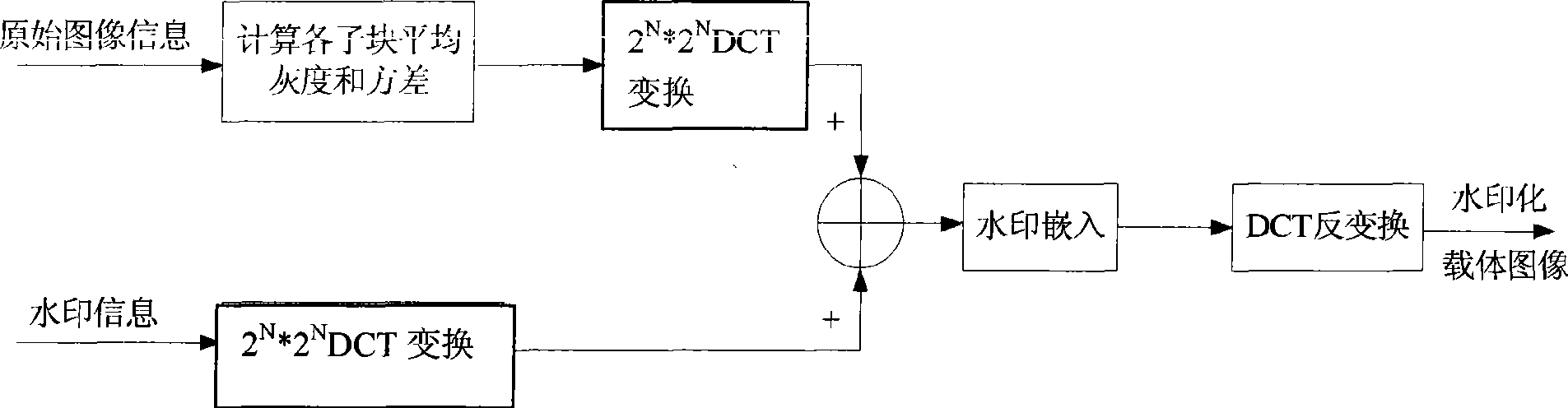
Digital image watermark imbedding method based on DCT algorithm
InactiveCN101504758AAnti-counterfeitingTamper proofImage codingImage data processing detailsComputer visionDigital image watermarking
The invention discloses a DCT algorithm-based method for digital image watermark embedment, which comprises: a first step of reading an original public image and a light and shade watermark image into two-dimensional arrays I and W respectively; a step two of dividing the original public image I and the watermark image W into 2*2 image blocks which do not cover each other respectively, computing the average gray m and a variance sigma of the sub blocks, and performing the DCT conversion of the sub blocks of the public image; a step three of embedding one element W(p,q) in the light and shade watermark in a sub block with a complex texture; a step four of performing the inverse DCT conversion of image blocks embedded with watermark information; and a step five of combining image the image blocks to obtain an image embedded with the light and shade watermark. The method is characterized by counterfeit prevention, falsification prevention, verification, and data security and integrity guarantee.
Owner:SHAANXI UNIV OF SCI & TECH
Anti-channel conflict code-spurting printing ink and its preparation method
The invention relates to an anti-channel conflict code-spurting printing ink and its preparation method. The invention firstly provides a code-spurting printing ink. Weighed according to the gross weight of the code-spurting printing ink, it is composed of the following raw materials of: by weight, 0.1-0.8% of a colorless organic fluorescent coloring agent, 2-10% of an organic solvent soluble dye, 1-10% of polymer resin and 80-90% of an organic solvent. The invention also provides a preparation method of the above code-spurting printing ink. The code-spurting printing ink provided by the invention remains properties and functions of a common printing ink, and is also endowed with a certain anti-channel conflict, anti-tamper and anti-counterfeit hiding performance, thus effectively hitting counterfeiters, increasing difficulty in counterfeiting to a large extent and avoiding further forgery. Simultaneously, according to the code-spurting printing ink, plain code and secret code jet printing can be realized only with an inkjet printing machine. Therefore, it is not necessary for manufacturers to increase new inkjet printing machines for secret code jet printing, thus greatly simplifying production process and saving production cost.
Owner:北京赛腾标识系统股份公司
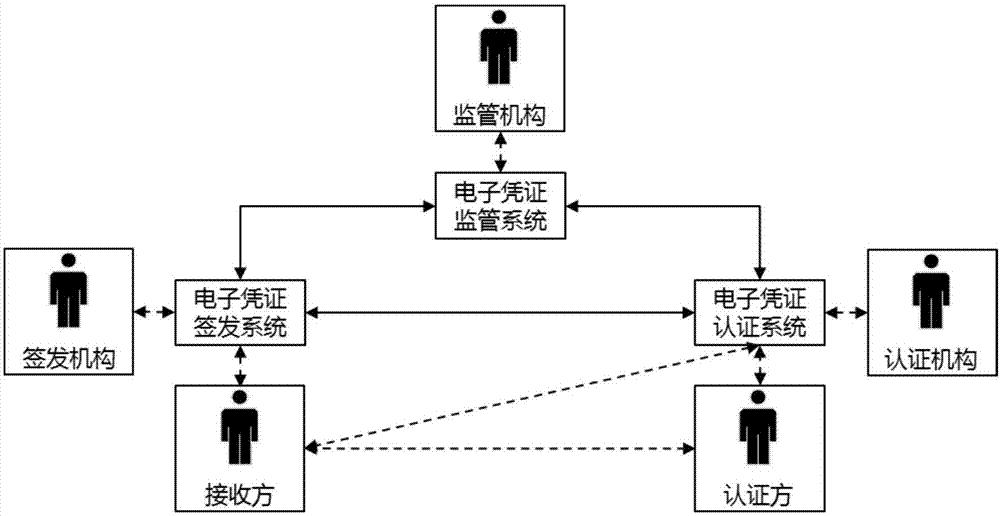
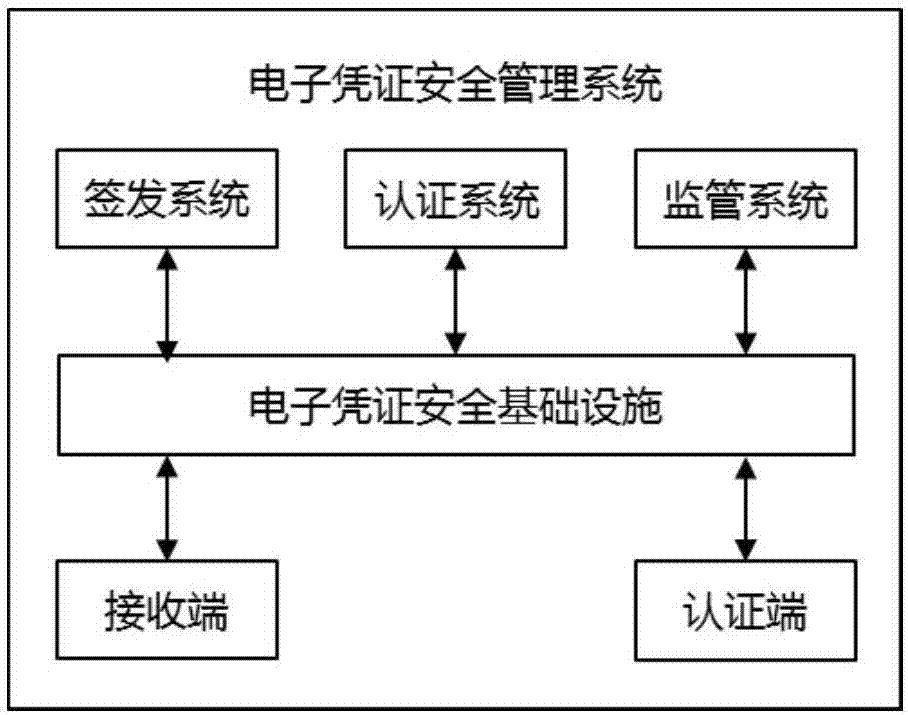
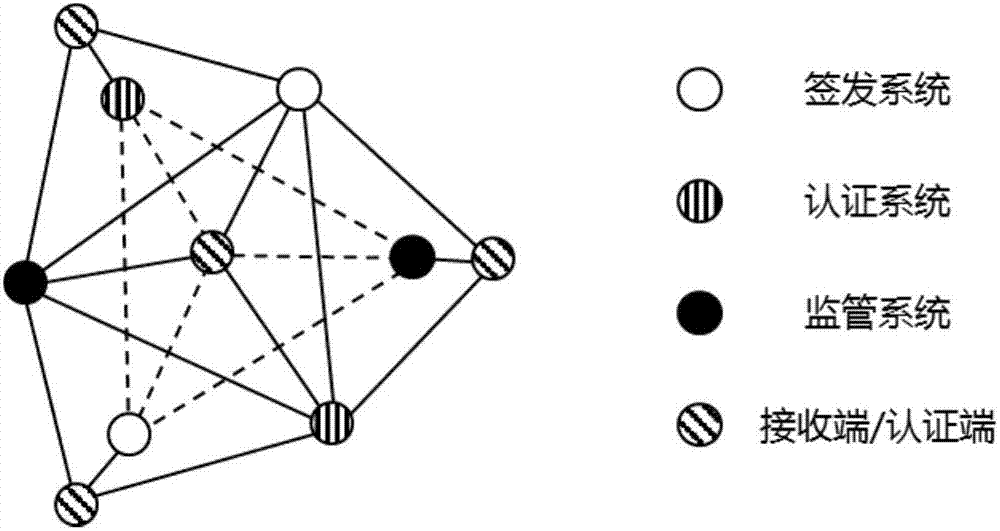
Electronic certificate security management method and system
ActiveCN107277000ASolve the costFix security issuesTransmissionMarketingSecurity managementAuthentication
The invention discloses an electronic certificate security management method and system. The electronic certificate security management method comprises the following steps: issuing electronic certificate signing and issuing application; authenticating the receiving end, generating the electronic certificate, and issuing the electronic certificate and the signing and issuing information to the security basic module of electronic certificate; obtaining the electronic certificate and the electronic certificate signing and issuing results from the electronic certificate security basic module; issuing the electronic certificate authentication application to the electronic certificate security basic module; authenticating the receiving end by means of the electronic certificate security basic module, issuing the authentication confirmation information to the electronic certificate security basic module, and waiting for the receiver to confirm; confirming the authentication confirmation information by the receiving end; and obtaining the authentication results of the electronic certificate from the electronic certificate security basic module. By means of the scheme disclosed by the invention, the defects of the electronic certificate issuing, authentication and supervision platform in the prior art in the aspects of cost, safety and convenience can be solved.
Owner:北京明朝万达科技股份有限公司
Face recognition method and device, medium and electronic device
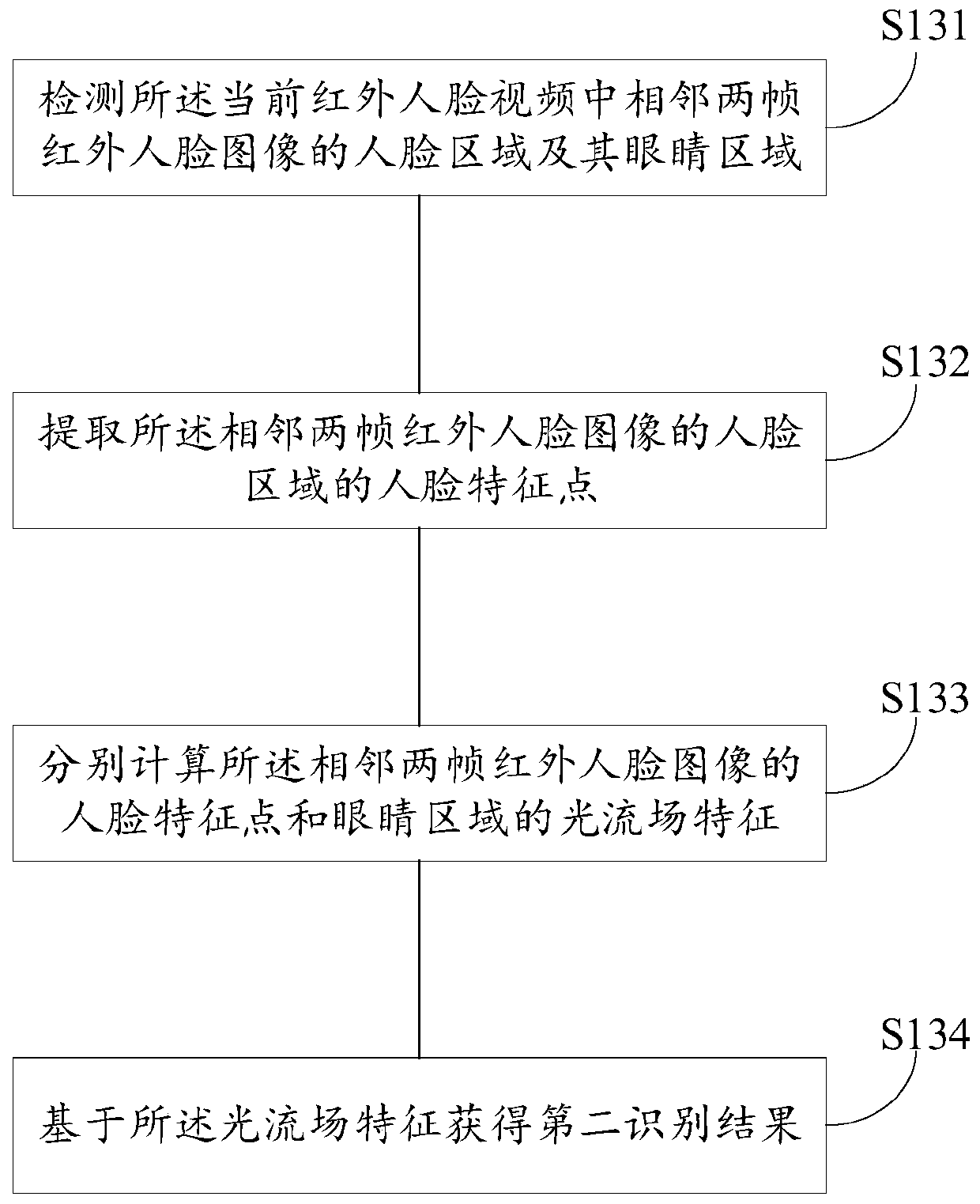
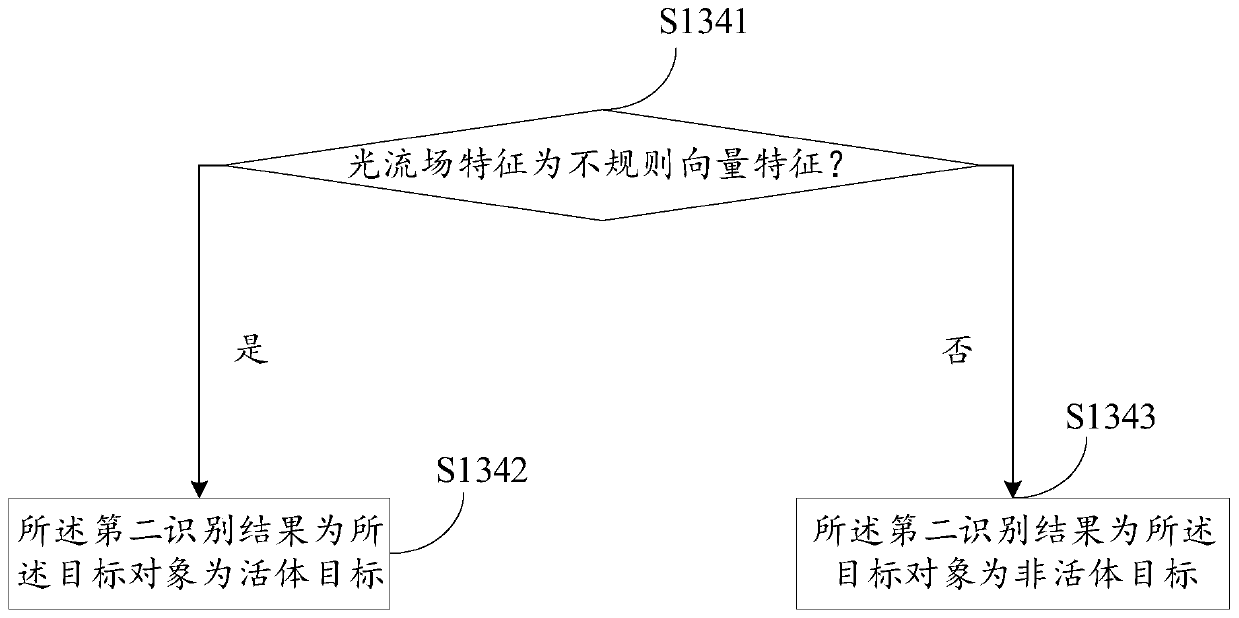
InactiveCN110276301AImprove intelligenceImprove recognition efficiencyDigital data protectionSpoof detectionComputer scienceConvolutional neural network
The embodiment of the invention provides a face recognition method and device, a medium and an electronic device, and belongs to the technical field of computers. The method comprises the steps of obtaining a current visible light face image and a current infrared face video of a target object; inputting the current visible light face image into a trained convolutional neural network model based on deep learning, and outputting a first recognition result; obtaining a second recognition result according to the current infrared face video; and obtaining a face recognition result of the target object according to the first recognition result and the second recognition result. According to the technical scheme provided by the embodiment of the invention, the final face recognition result can be obtained by integrating the recognition result of the visible light face image and the recognition result of the infrared face video, and the face recognition accuracy is improved.
Owner:TAIKANG LIFE INSURANCE CO LTD
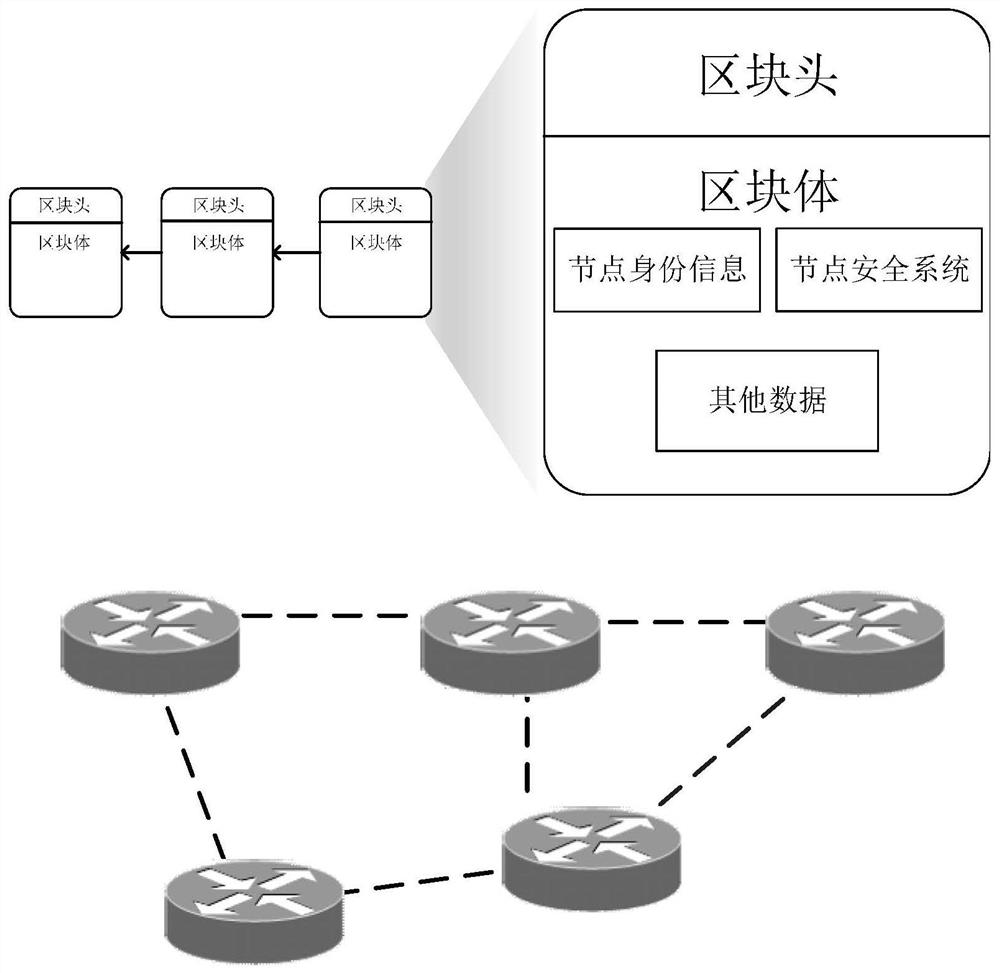
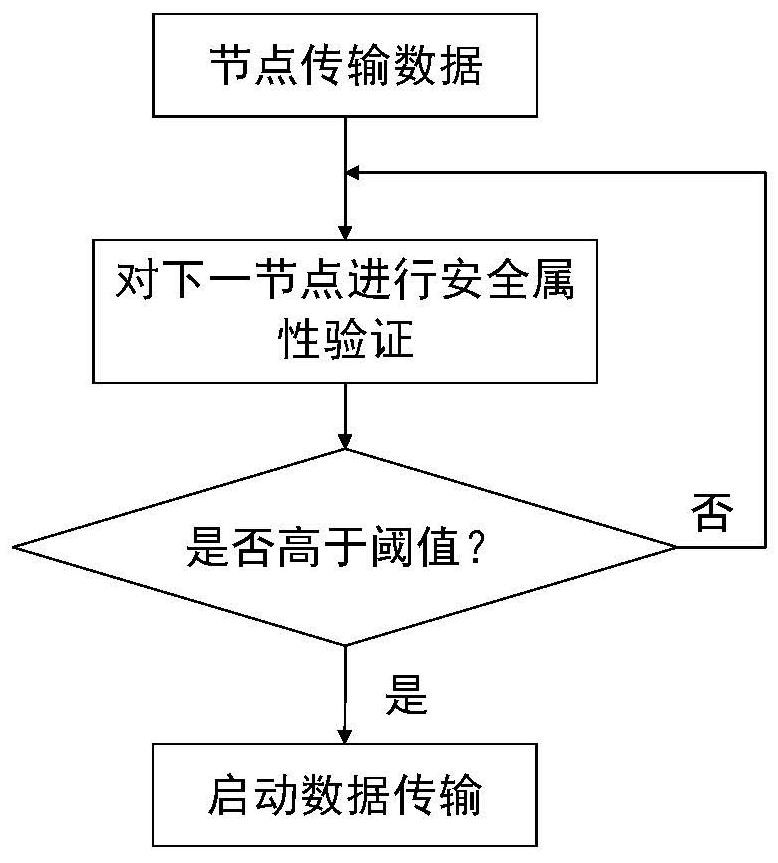
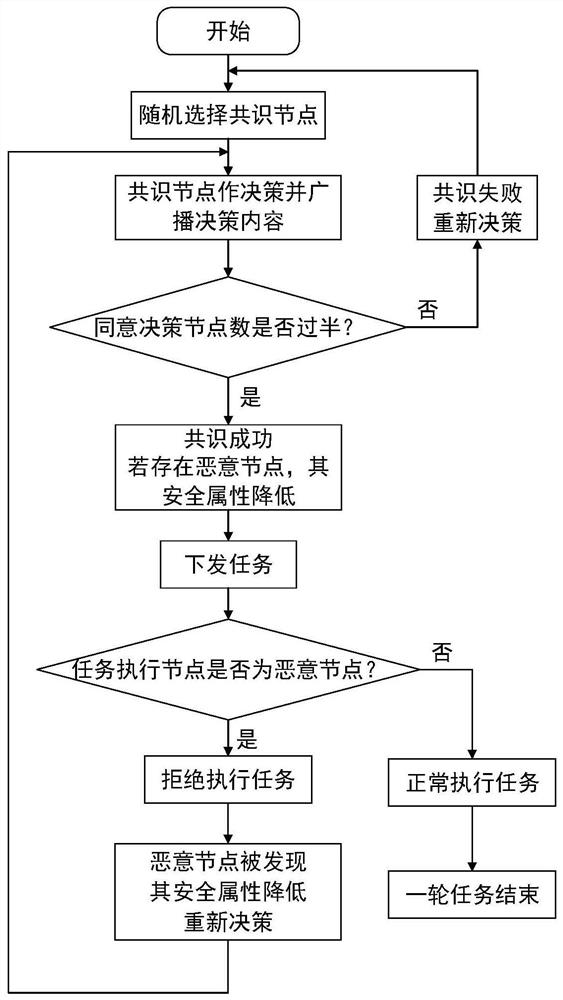
Network node security attribute evaluation method based on blockchain consensus result feedback
ActiveCN111770103AIncrease credibilityEnable secure communicationDatabase distribution/replicationDigital data protectionSecure communicationComputer network
The invention discloses a network node security attribute evaluation method based on blockchain consensus result feedback, which enhances the credibility between network nodes by combining a consensusmechanism of a blockchain, and has the characteristics of tamper resistance, traceability, decentration and the like. By establishing a security attribute evaluation mechanism based on a trust mechanism, security attribute evaluation is carried out to judge the security of each network node, and secure communication between the nodes is realized.
Owner:UNIV OF SCI & TECH OF CHINA
Client, server, block chain-based transaction method and storage medium
The invention relates to a block chain technology, and discloses a client, a server, a block chain-based transaction method and a computer-readable storage medium. The client end of the invention receives the transaction request with betting data sent by the user, verifyies the transaction request; generates the first transaction information according to the betting data, stors the first transaction information in the block chain and determines the storage location information of the first transaction information in the block chain when the verification is passed; according to the storage location information of the first transaction information in the block chain, the second transaction information is generated, and a transaction request carrying the second transaction information is sentto a server, so that the server acquires the first transaction information according to the second transaction information, and executes the transaction request according to the first transaction information. Compared with the prior art, the invention can prevent the transaction information from being tampered with maliciously, and improves the safety of the lottery transaction data.
Owner:PING AN TECH (SHENZHEN) CO LTD
Method and system for ordering business
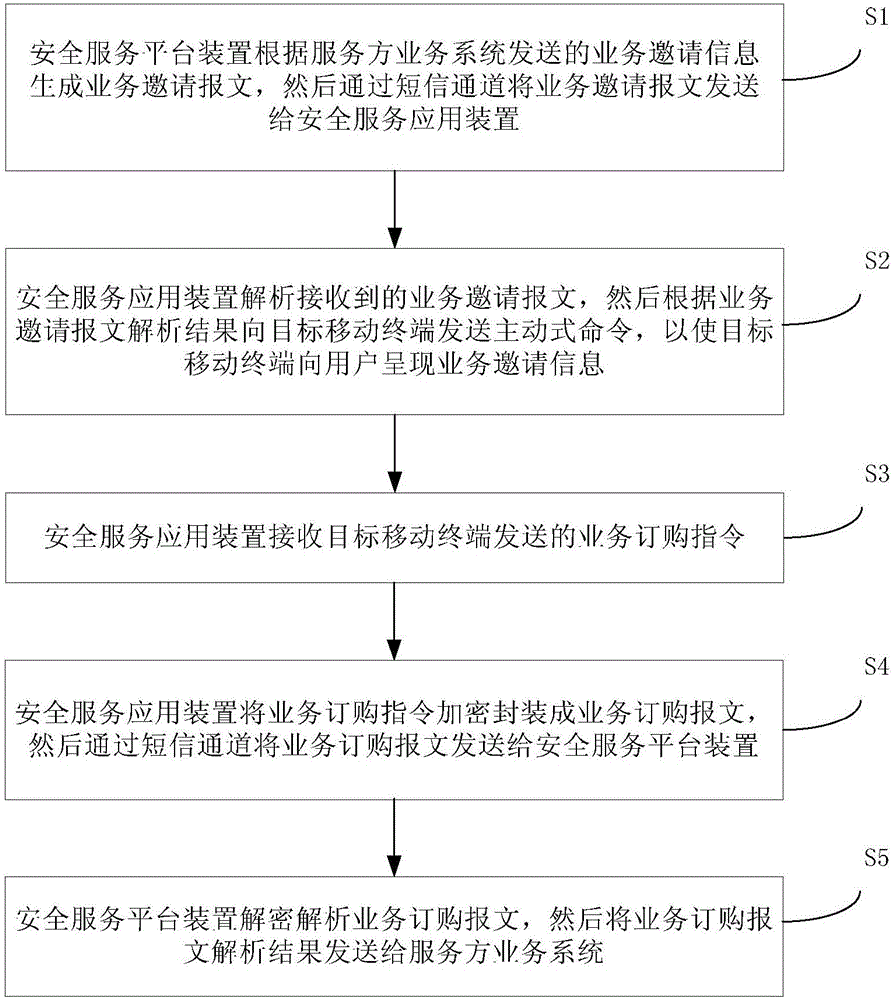
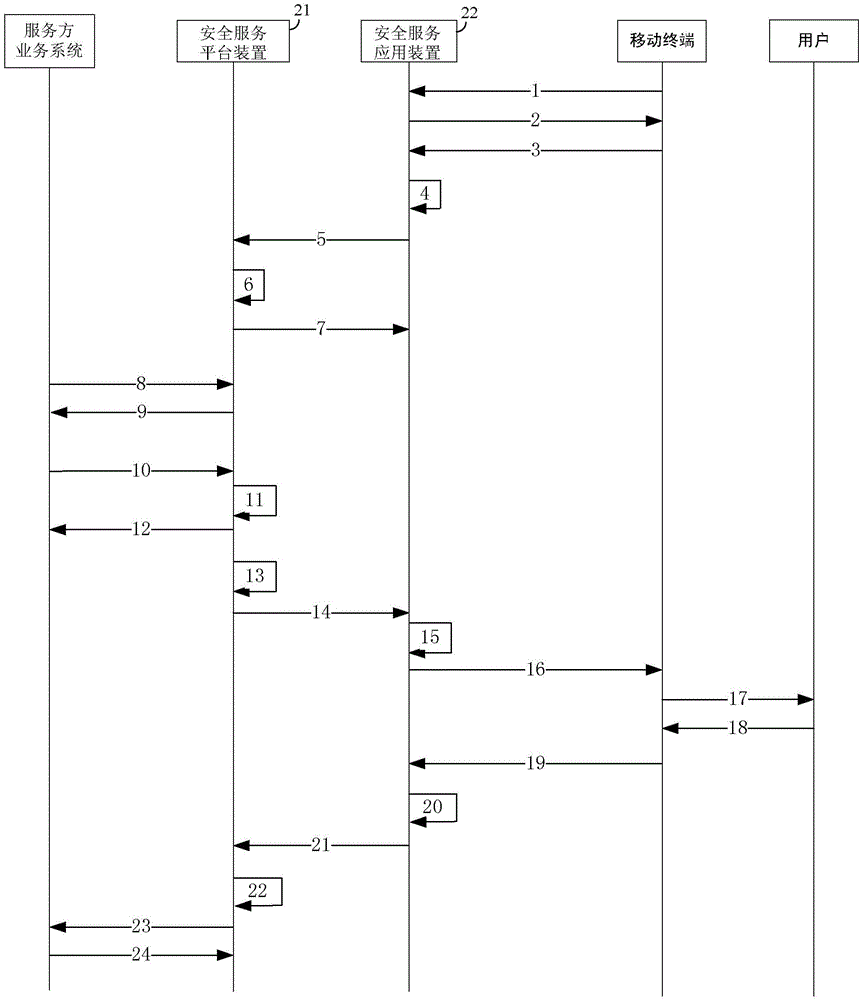
ActiveCN106302698AEasy to implement two-way authenticationEliminate the possibility of sending informationMessaging/mailboxes/announcementsTransmissionThird partyComputer terminal
The invention provides a method and a system for ordering business, which have the advantages of preventing the third party software from intercepting, and preventing users from being replied by personators. The method comprises the following steps that: a security service platform device generates a business invitation message according to business invitation information sent by a business system of a service supplier, and then sends the business invitation message to a security service application device through an SMS channel; the security service application device parses the received business invitation message, and then sends an active command to a target mobile terminal according to parsing results so that the target mobile terminal presents the business invitation message to the users, and the security service application device receives a business ordering instruction sent by the target mobile terminal; the security service application device encrypts and encapsulates the business ordering instruction into a business ordering message, and then sends the business ordering message to the security service platform device through the SMS channel, and the security service platform device decrypts and parses the business ordering message, and then sends the parsing result of the business ordering message to the business system of the service supplier.
Owner:尹子栋
Edge intelligent calculation method based on block chain and edge intelligent system
ActiveCN112333187ATraceableTamper proofUser identity/authority verificationDatabase distribution/replicationSmart systemIntelligent computing
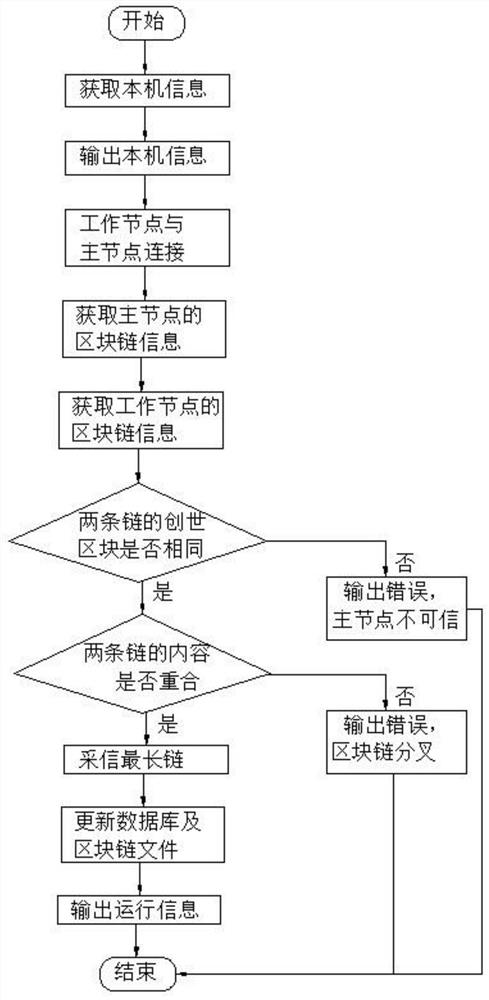
The invention discloses an edge intelligent calculation method based on a block chain and an edge intelligent system, belongs to edge intelligence, and aims to solve the technical problem of how to apply a block chain technology to edge intelligent calculation to ensure that data is correct and complete and ensure the legality of transmitted data. The calculation method comprises the following steps: configuring connection between a gateway and a main node and connection between the main node and a working node through the gateway; the main node generating a key pair, adding the block information to a locally stored block chain of the main node and publishing the block information to the outside, and each working node adding the verified block information to the locally stored block chain;and the main node sending the instruction data and the specified private key to a related working node, and the working node calling an artificial intelligence module to analyze the equipment acquisition data to obtain an analysis report and returning the analysis report to the gateway through the working node. The system comprises at least one gateway and at least one edge device, and the edge device comprises a main node and at least one working node.
Owner:QILU UNIV OF TECH
Digital watermark physical-electronic integrated stamp processing system
PendingCN108171023AStrong anti-counterfeiting traceability functionHighly consistentImage watermarkingProgram/content distribution protectionElectricityElectronic document
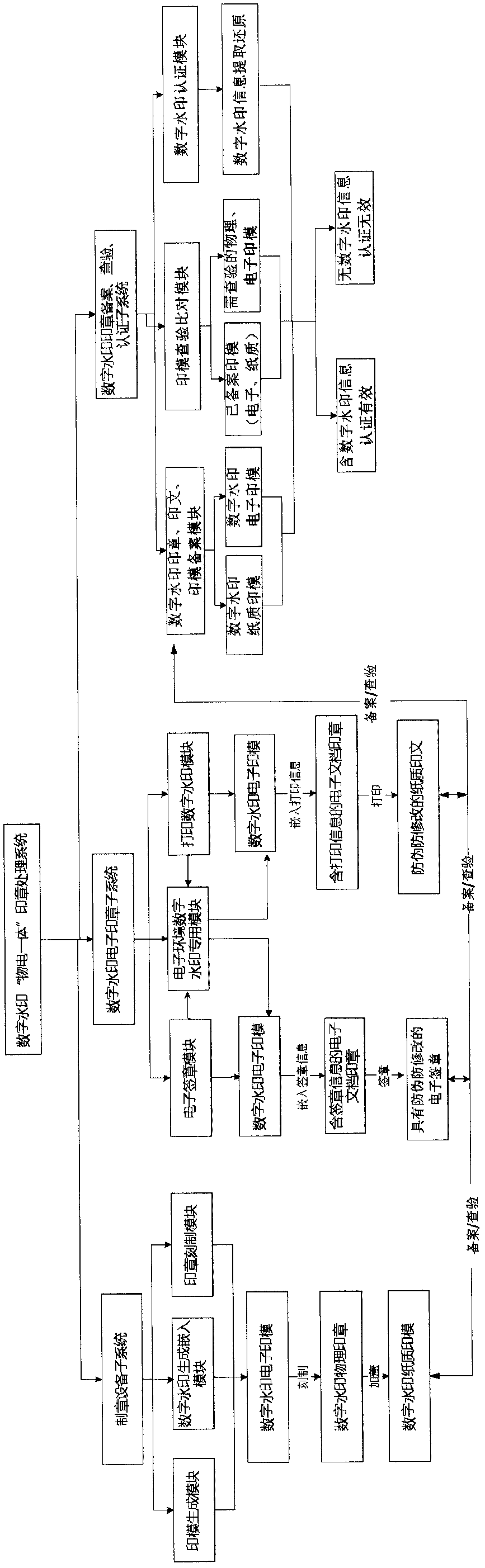
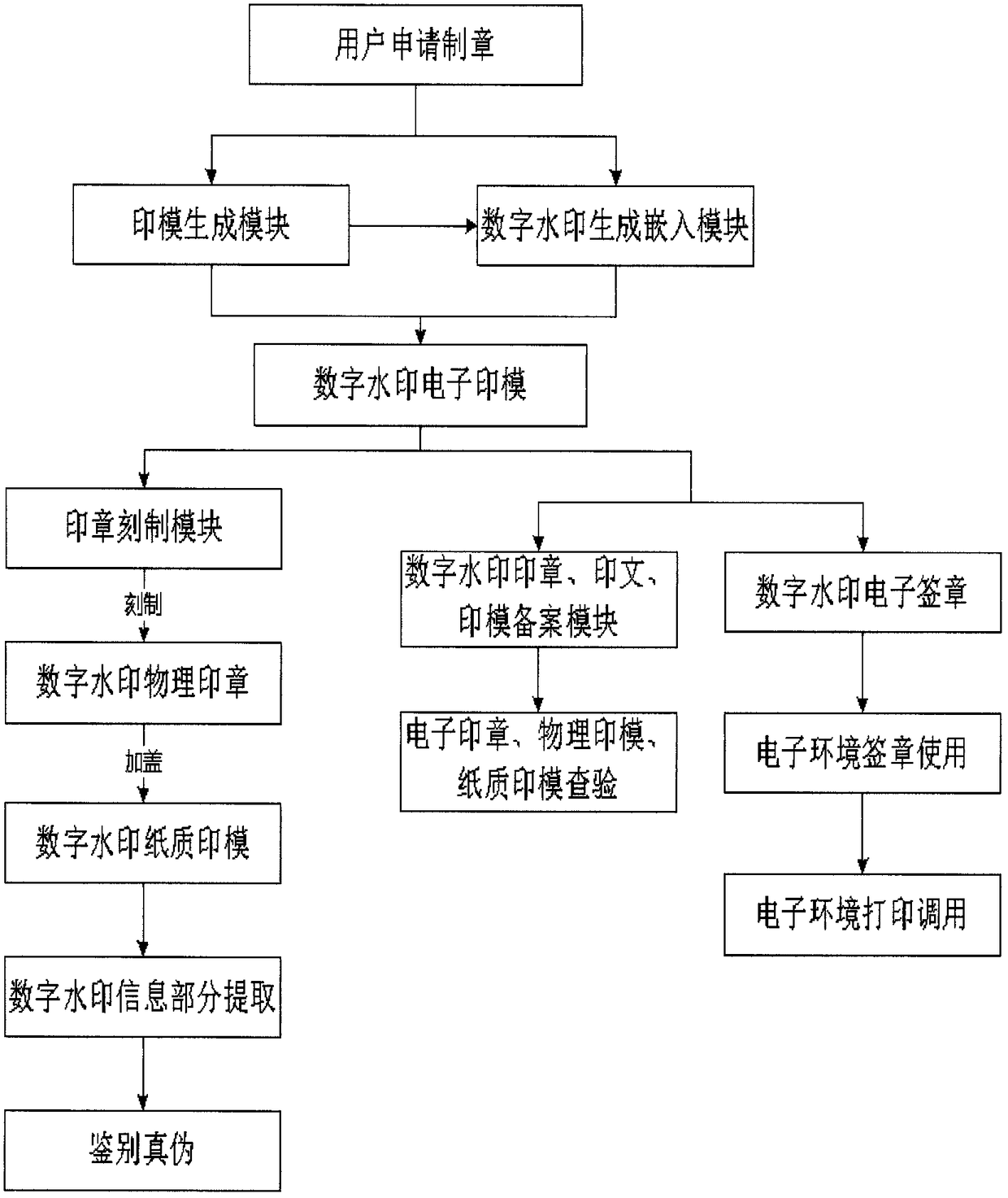
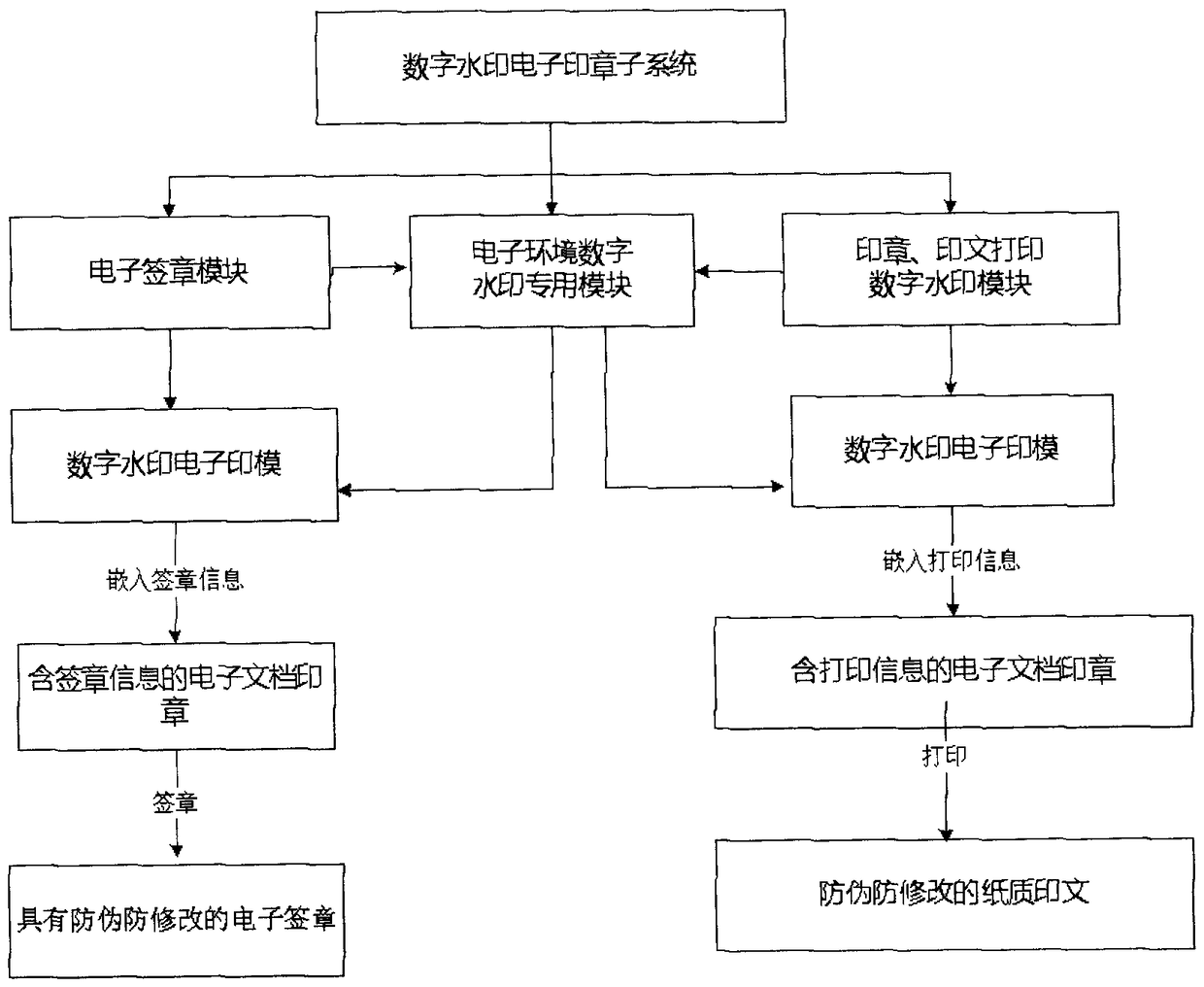
The invention discloses a digital watermark physical-electronic integrated stamp processing system which comprises a stamp making equipment subsystem, a digital watermark electronic stamp subsystem and a digital watermark stamp recording checking authentication subsystem, wherein the stamp making equipment subsystem consists of an impression generation module, a digital watermark generation embedding module and a stamp engraving module arranged in stamp engraving equipment; the digital watermark electronic stamp subsystem is arranged in a background server and consists of an electronic stamp module, a special module for an electronic environment digital watermark and a digital watermark printing module; and the digital watermark stamp recording checking authentication subsystem consists ofa stamp imprint impression recording module, an impression checking comparison module and a digital watermark authentication module. By operation, the system can implement digital watermark system control on the whole process of engraving and stamping of a physical stamp, electronic signature, printing and network access, storage and checking of physical and electronic stamps and an imprint, andidentifies true or false by determining whether the stamp, the imprint and the impression contain digital watermark information. Problems of identifying true or false of information, identity determination and responsibility confirmation in the online transaction and information exchange can be solved. Double counterfeiting prevention of an electronic document and a paper document (printed) can beimplemented.
Owner:CHENGDU YUFEI INFORMATION ENG
Equipment and method for authenticating block chain data by utilizing spatio-temporal information
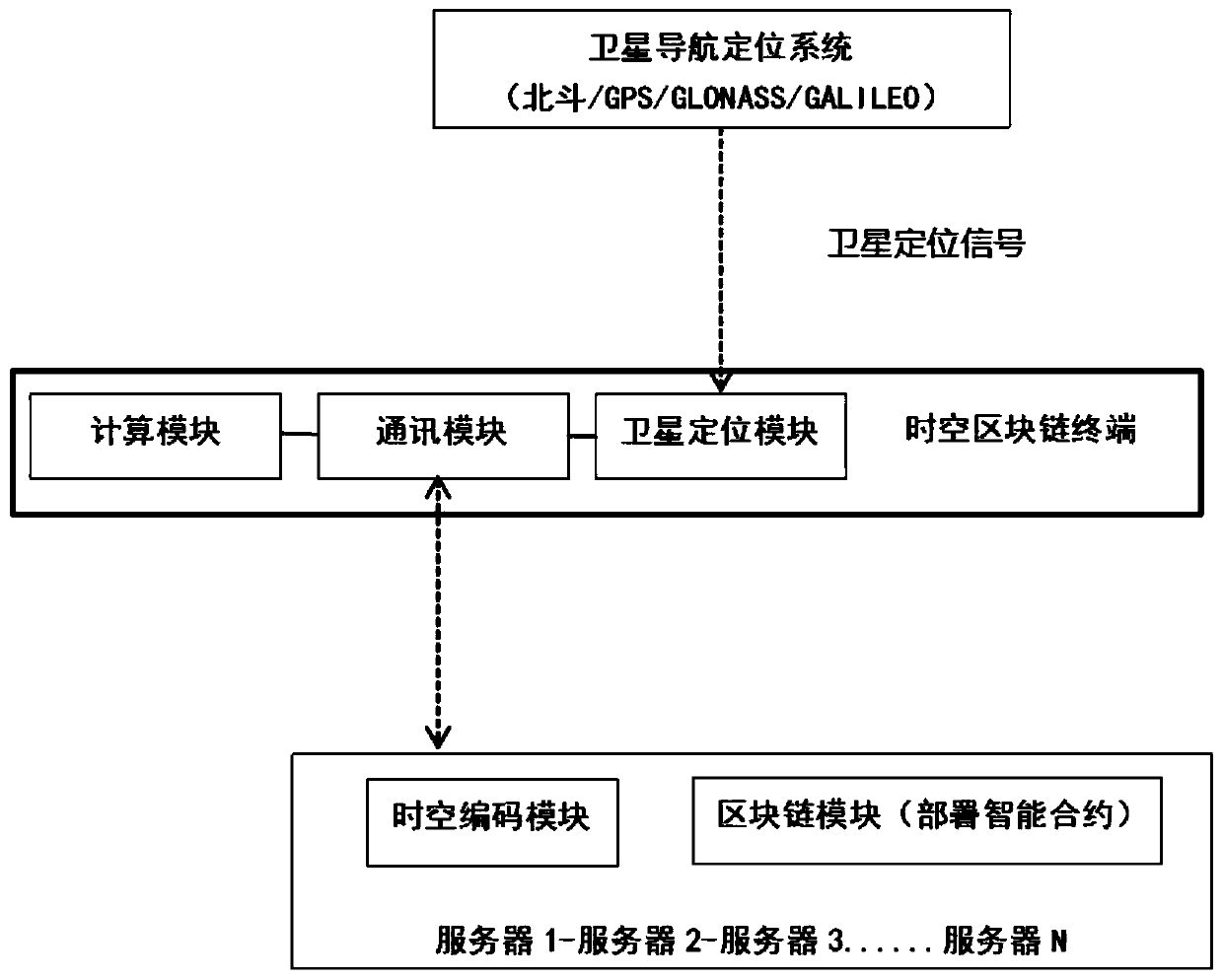
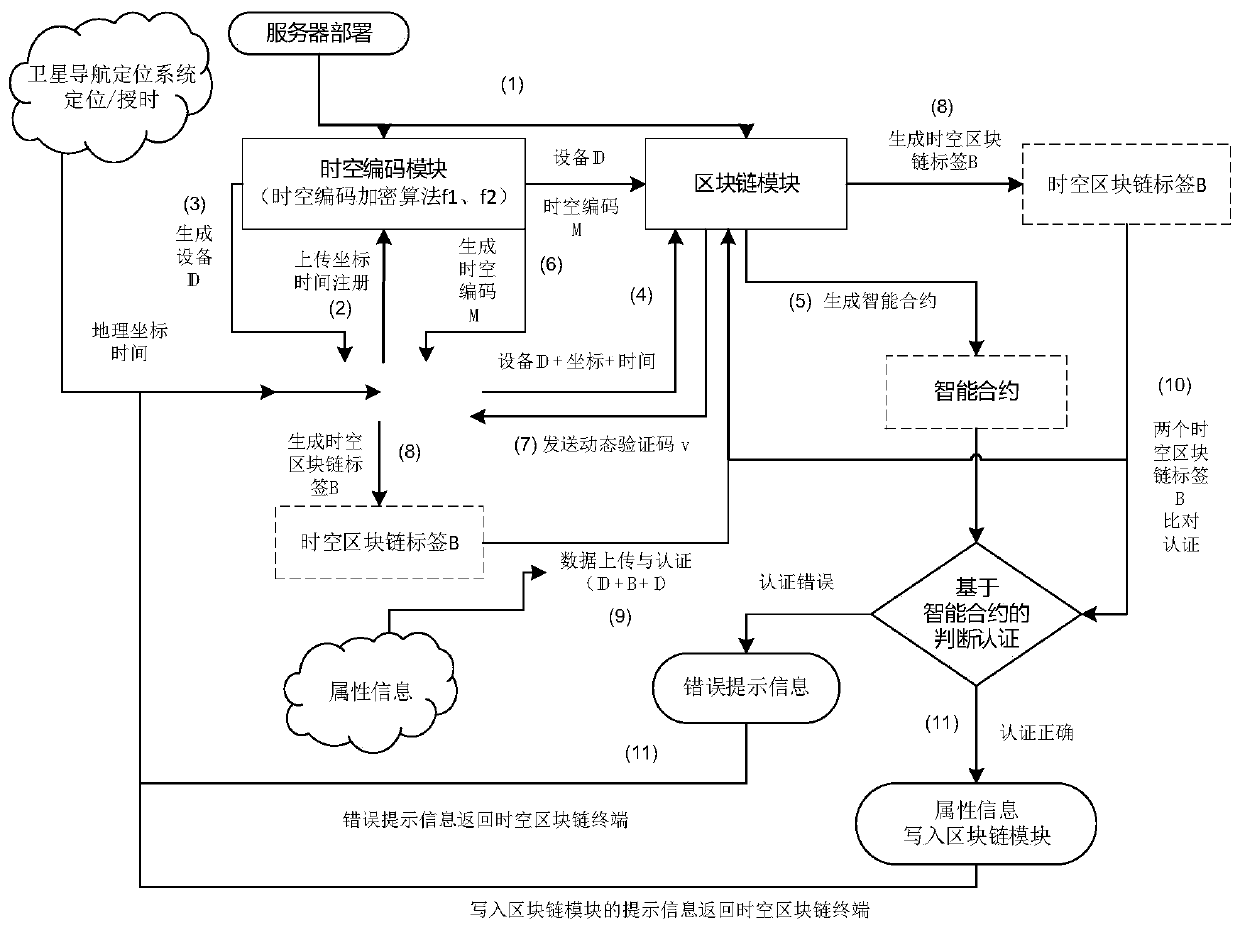
ActiveCN111586029AGuarantee authenticityEliminate the possibility of transferring dataSecuring communicationPoint dataServer
The invention discloses equipment and a method for authenticating block chain data by utilizing space-time information. The equipment comprises a space-time block chain terminal, a space-time coding module, a block chain module and a server, according to the invention, it is ensured that only if the data generated in the specified time of the specified position is correct and effective, the data can be uploaded to the block chain system; the possibility that a counterfeit terminal transmits data to the block chain system is avoided; the possibility that fake satellite positioning data generates space-time codes and a space-time block chain label transmits data to a block chain system is avoided, so that the data source transmitted to the block chain is reliable; the time of the equipment is difficult to tamper; a block chain intelligent contract is adopted, the characteristic that the block chain intelligent contract cannot be tampered is achieved, distributed storage is achieved, andit is guaranteed that the system can still operate normally even if part of server node data is lost or damaged.
Owner:北京数码汇博科技有限公司 +1
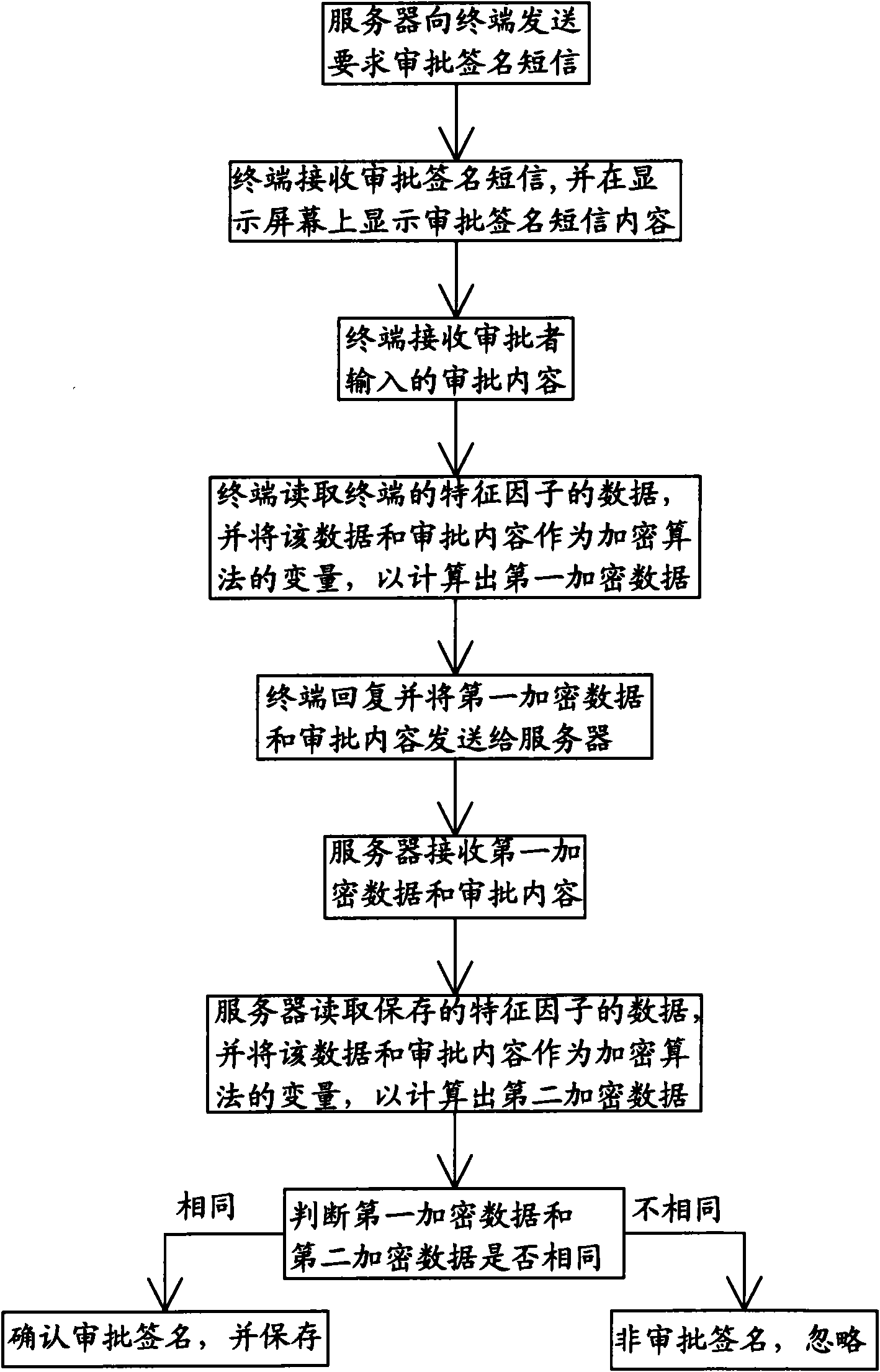
Method for mobile electronic signature
InactiveCN101605310AImprove securityAvoid confusionUser identity/authority verificationMessaging/mailboxes/announcementsMobile electronicsEncryption
The invention discloses a method for a mobile electronic signature. The method comprises the following steps that: a server sends a short message requesting an approval signature to a terminal; the terminal receives the approval signature short message and displays the content of the approval signature short message on a display screen; the terminal receives the approving content inputted by an approver; the terminal reads the data of the characteristic factor of the terminal, and works out the first encrypted data by taking the data and the approving content as variables of an encryption algorithm; the terminal answers and sends the first encrypted data and the approving content to the server; the server receives the first encrypted data and the approving content; the server reads the stored data of the characteristic factor, and works out the second encrypted data by taking the data and the approving content as variables of the encryption algorithm; and whether the first encrypted data and the second encrypted data are the same is judged, if so, the approval signature is confirmed and stored, otherwise the signature is the unapproved signature and neglected. The method has the advantages that the signature approver can give particular written instructions or assessments and examine the correctness of the approving content according to the content to be approved.
Owner:XIAMEN STELCOM INFORMATION & TECH
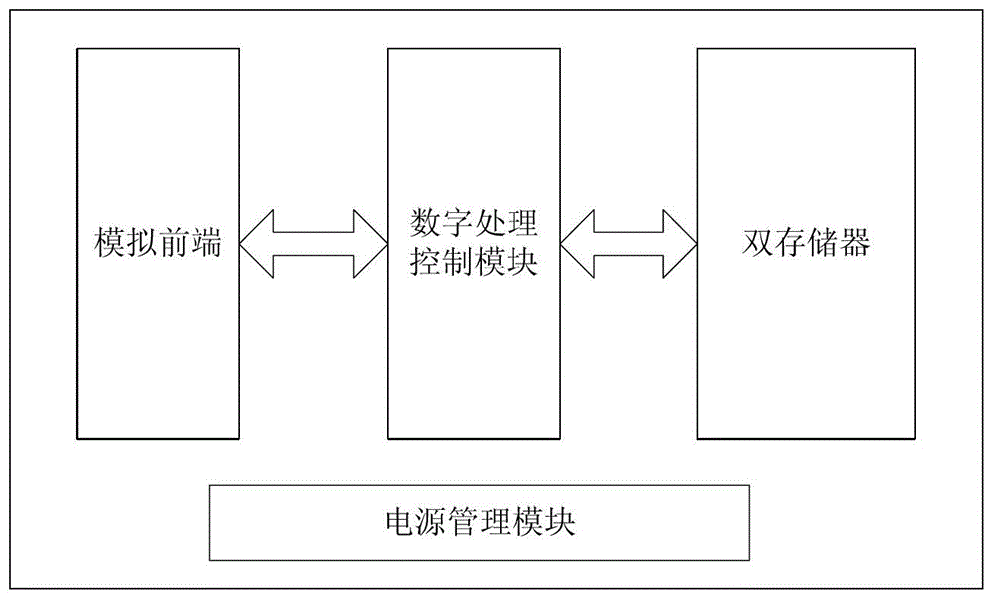
Electronic vehicle license plate with double-memory chip
InactiveCN103915116AMeet the needs of flexible applicationsLow costRead-only memoriesVehicle componentsMemory chipComputer module
The invention discloses an electronic vehicle license plate with a double-memory chip, and relates to electronic technology. The electronic vehicle license plate comprises a simulation front-end module, a memory module and a digit processing control module connected with the simulation front-end module and the memory module; and the memory module comprises a permanent memory cell and an erasable memory cell, and the permanent memory cell is used for storing vehicle registration information. The electronic vehicle license plate overcomes the disadvantages that conventional electronic vehicle license plate is bad in safety and short in storage time.
Owner:CHENGDU KILOWAY ELECTRONICS CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com