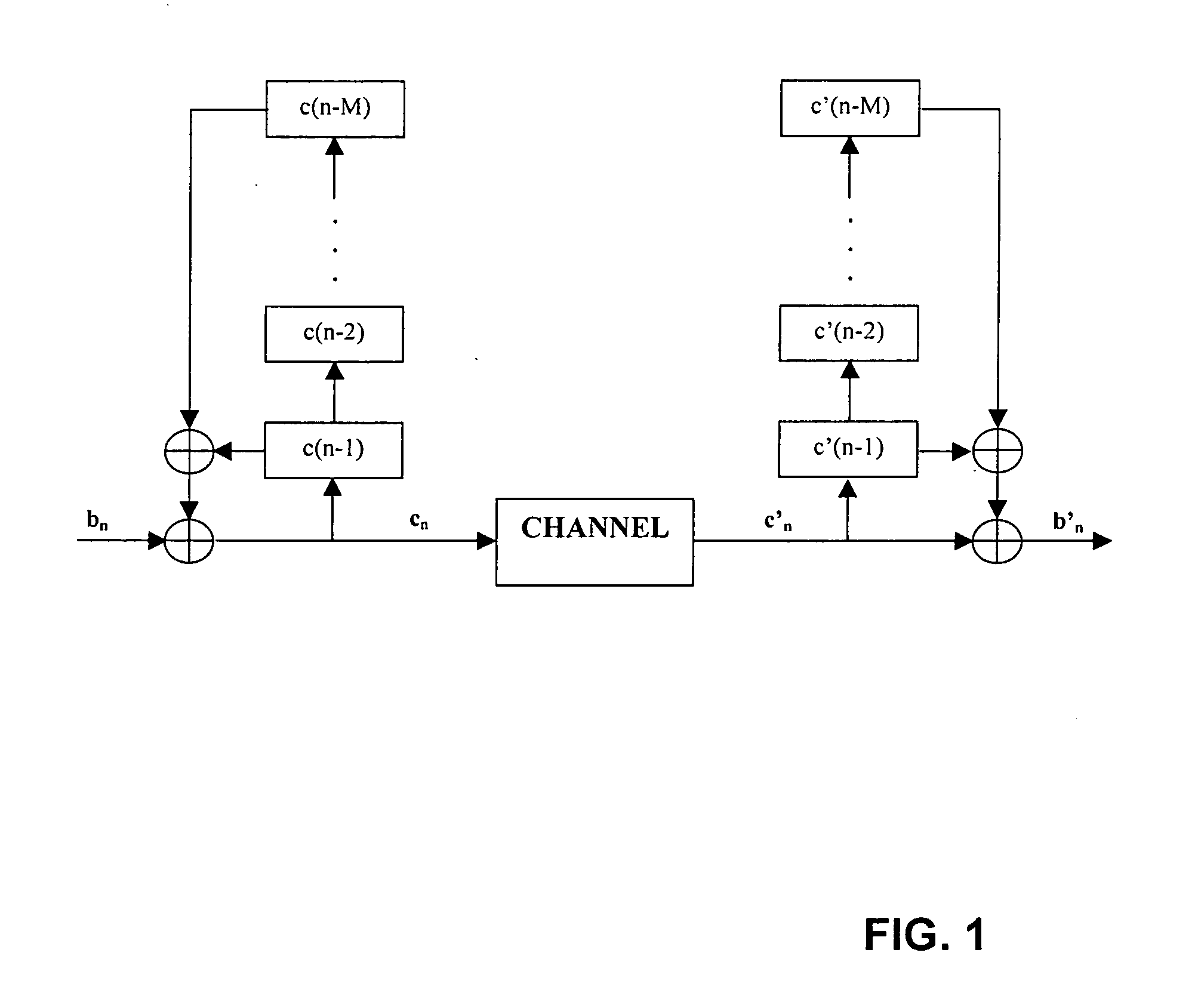
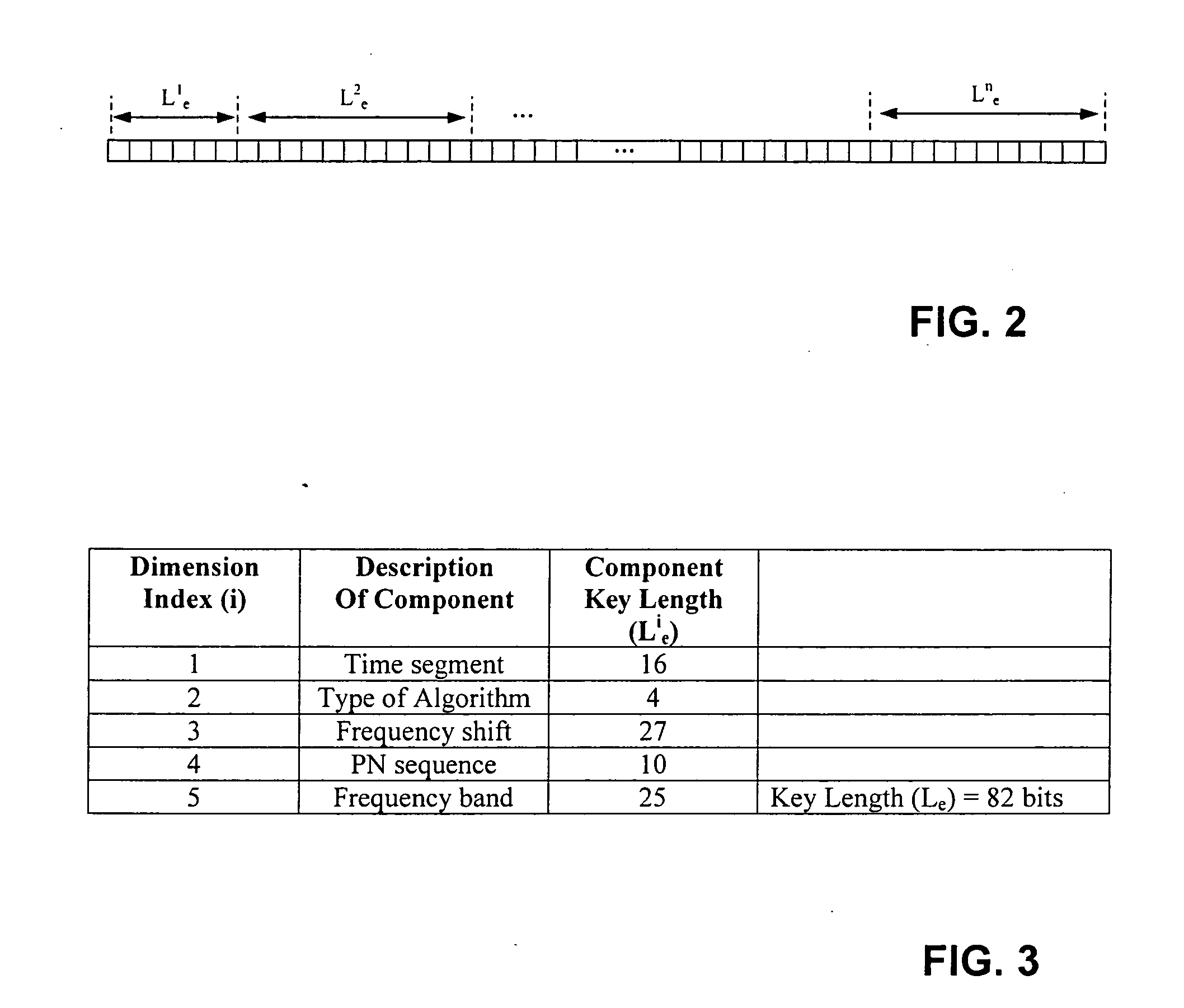
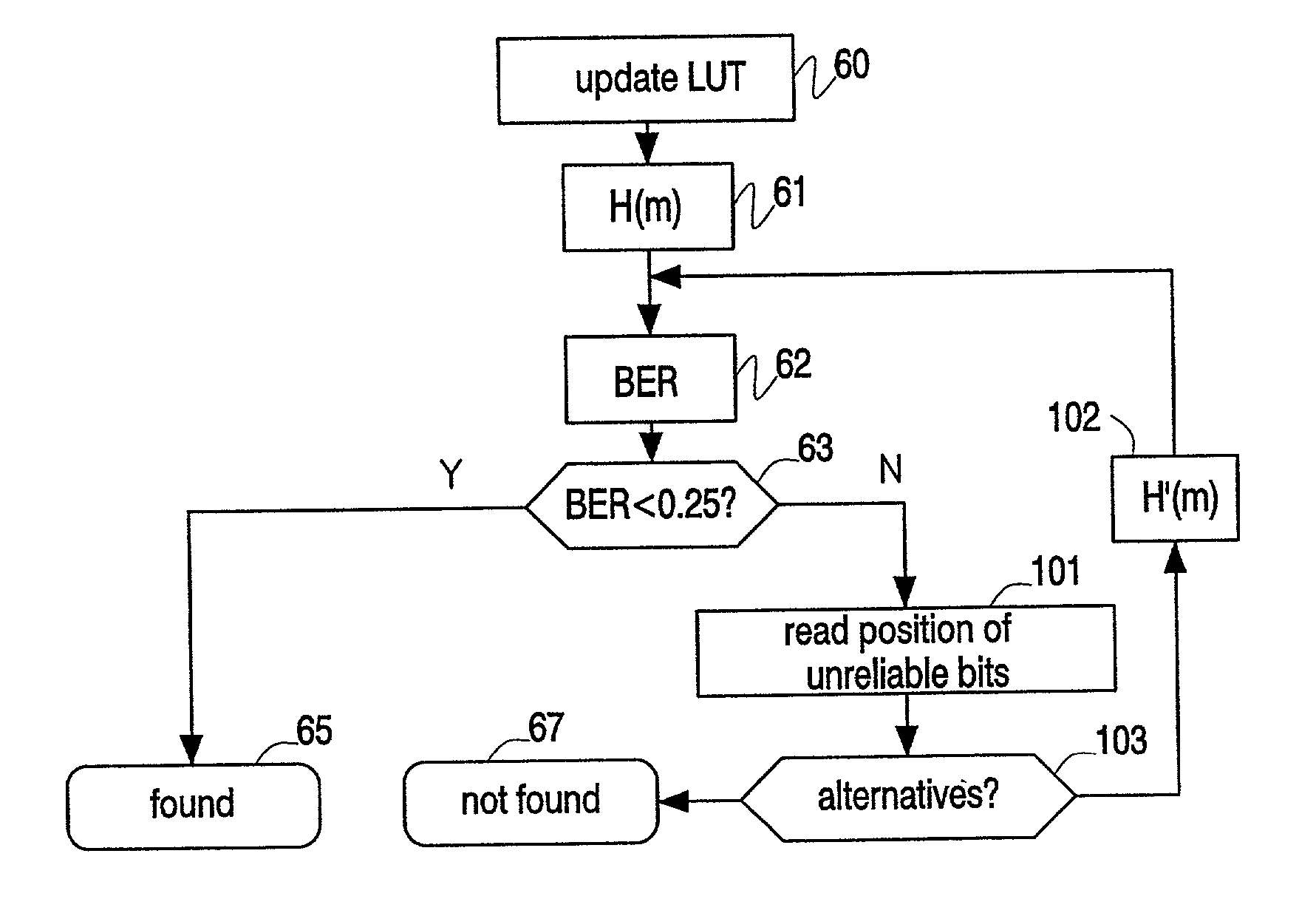
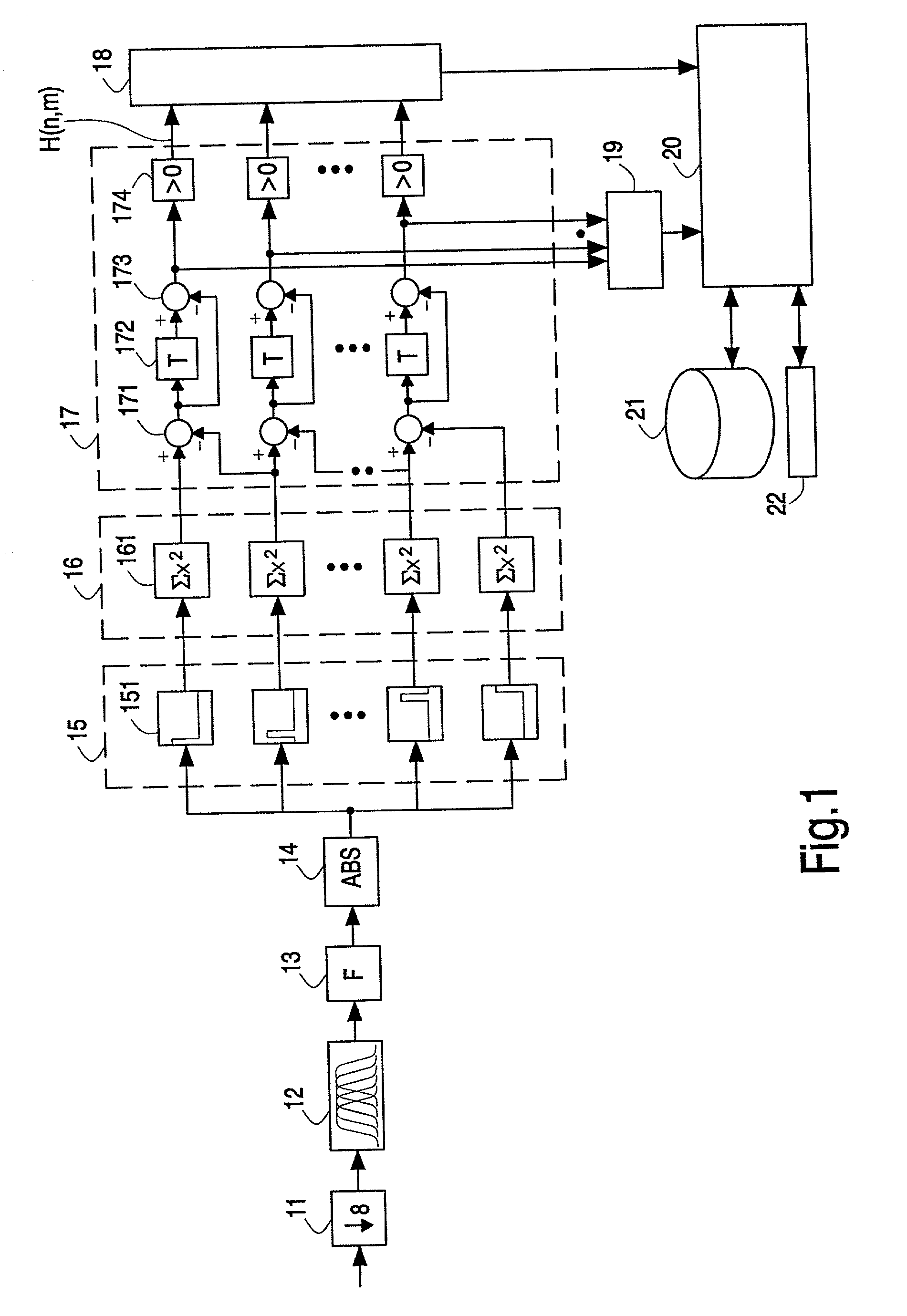
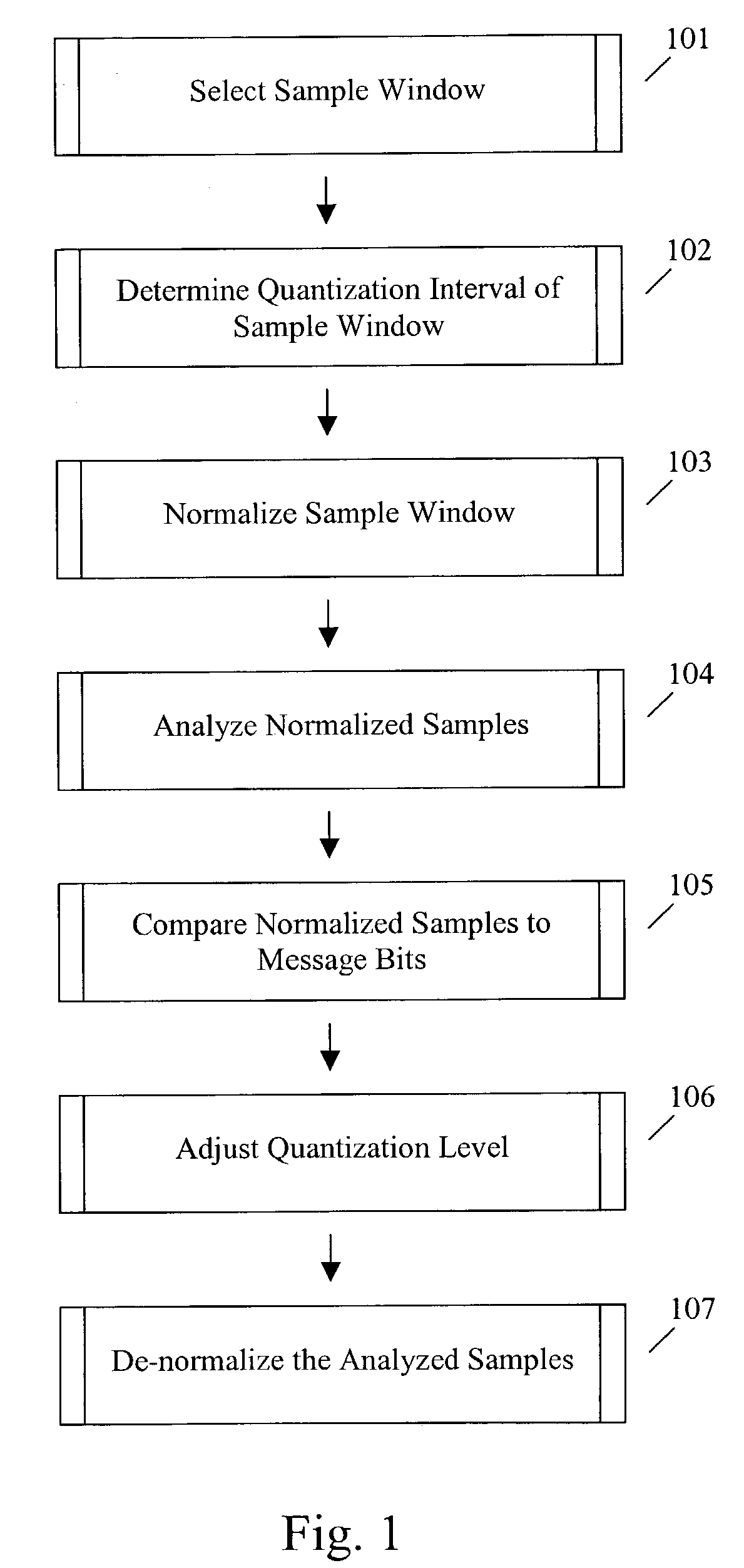
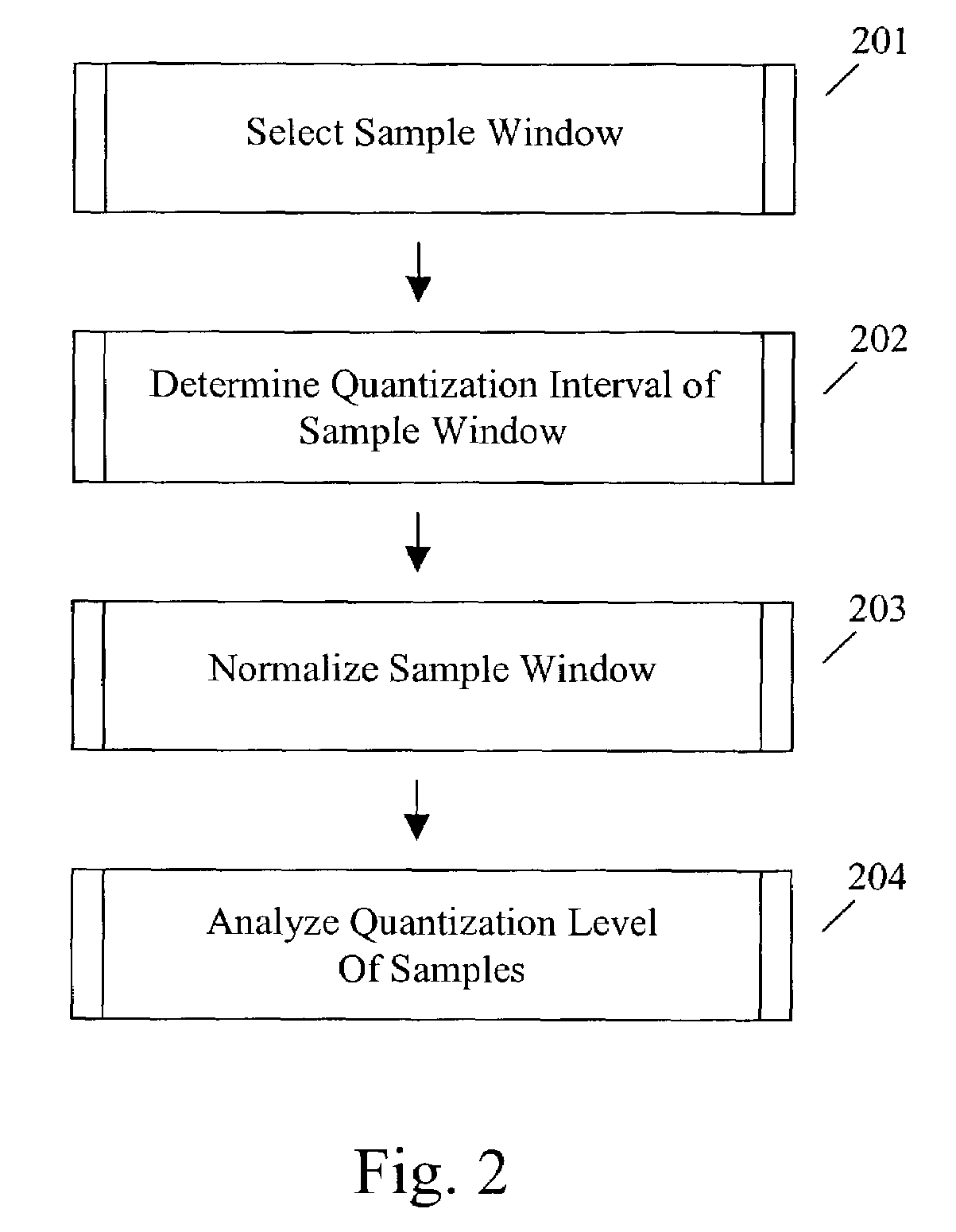
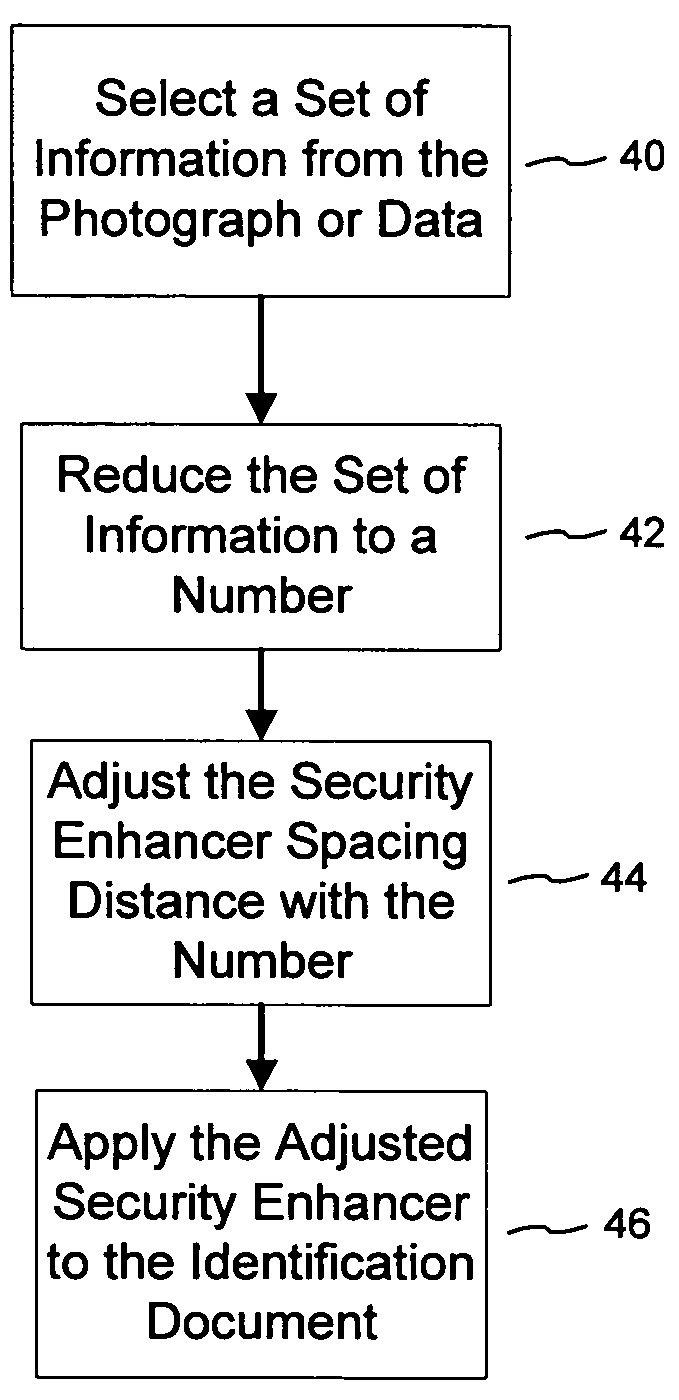
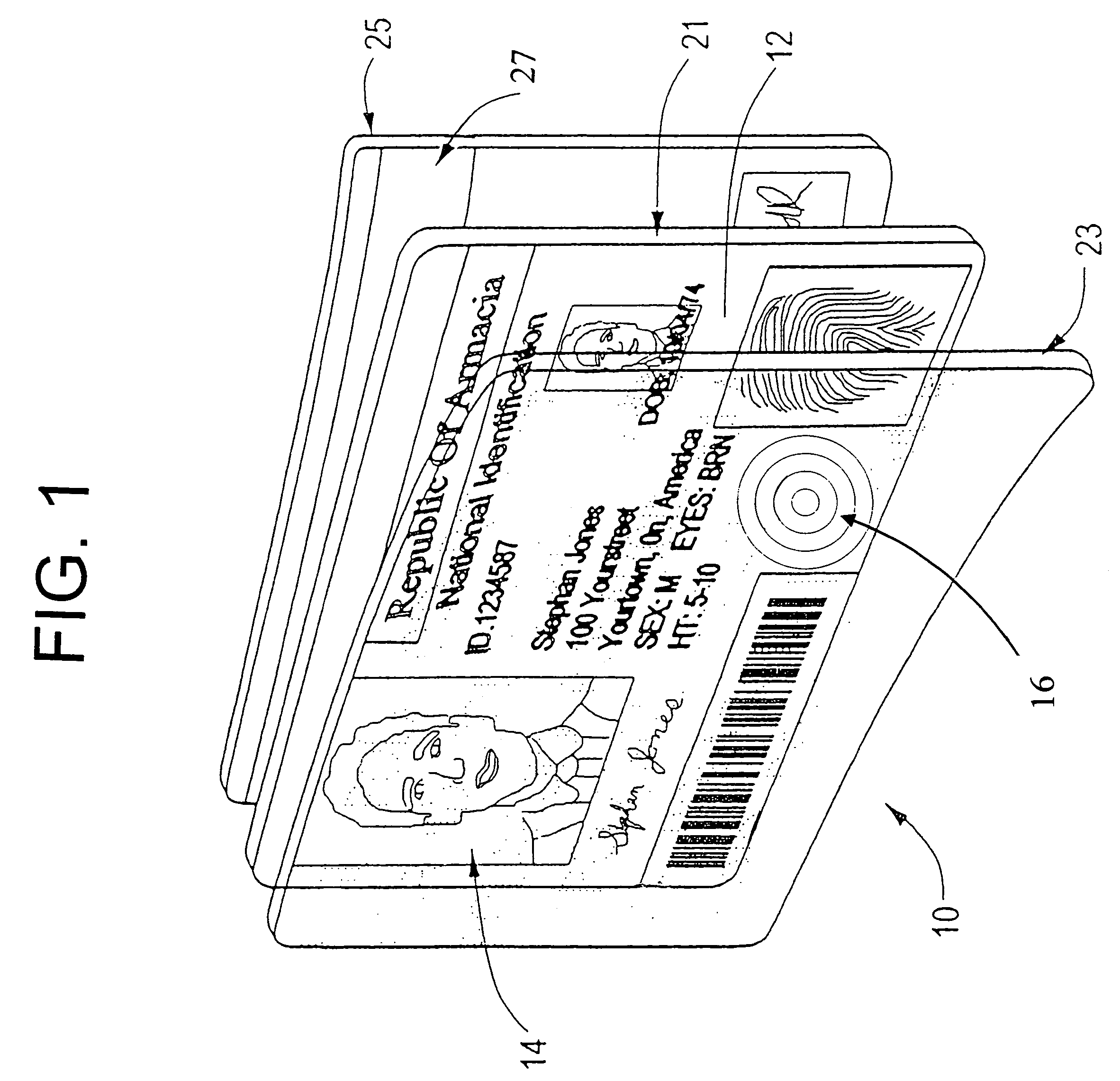
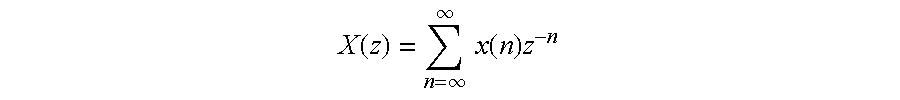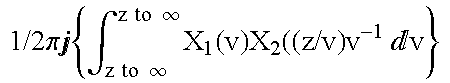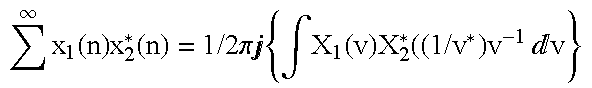Patents
Literature
1027results about "Image watermarking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
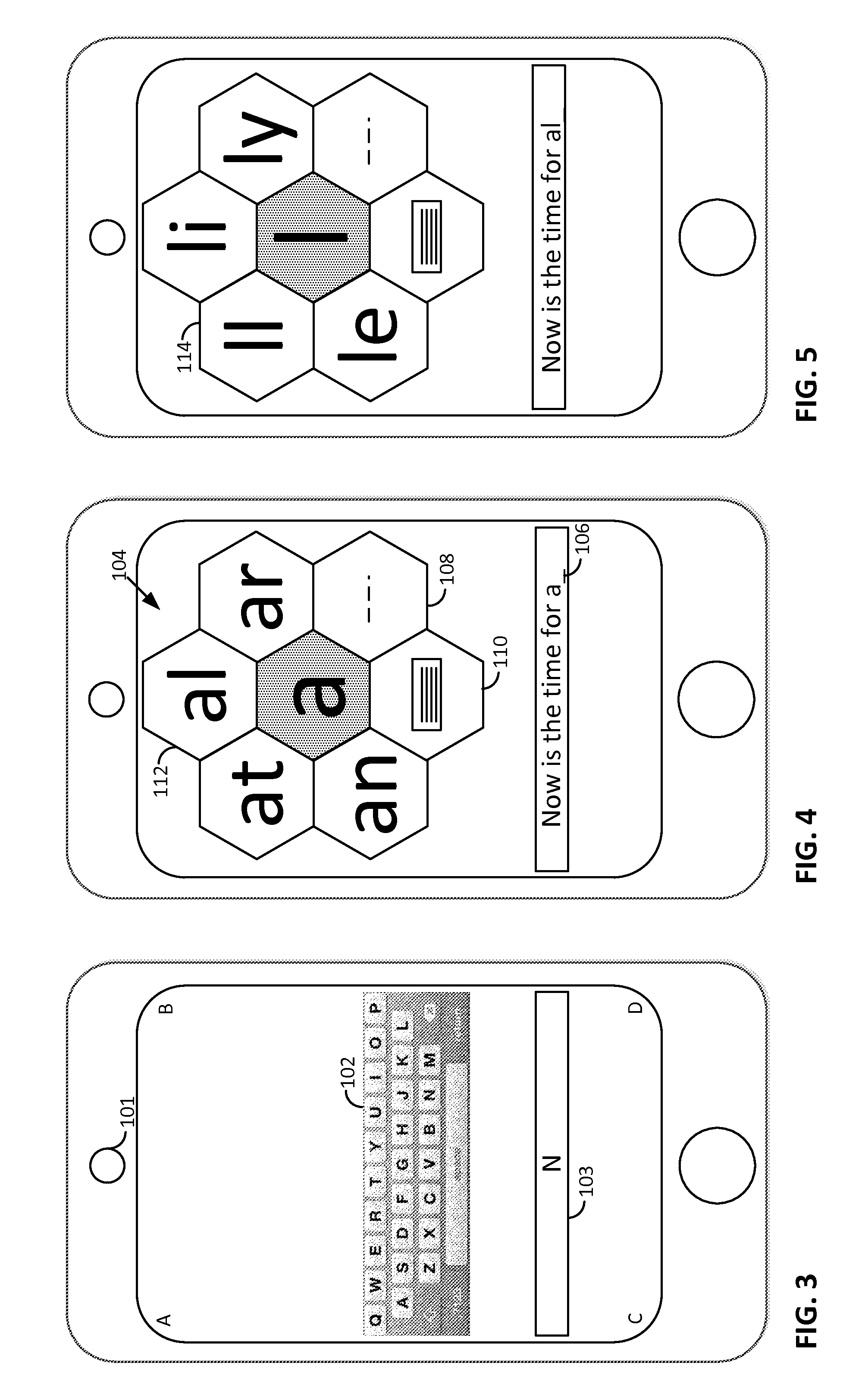
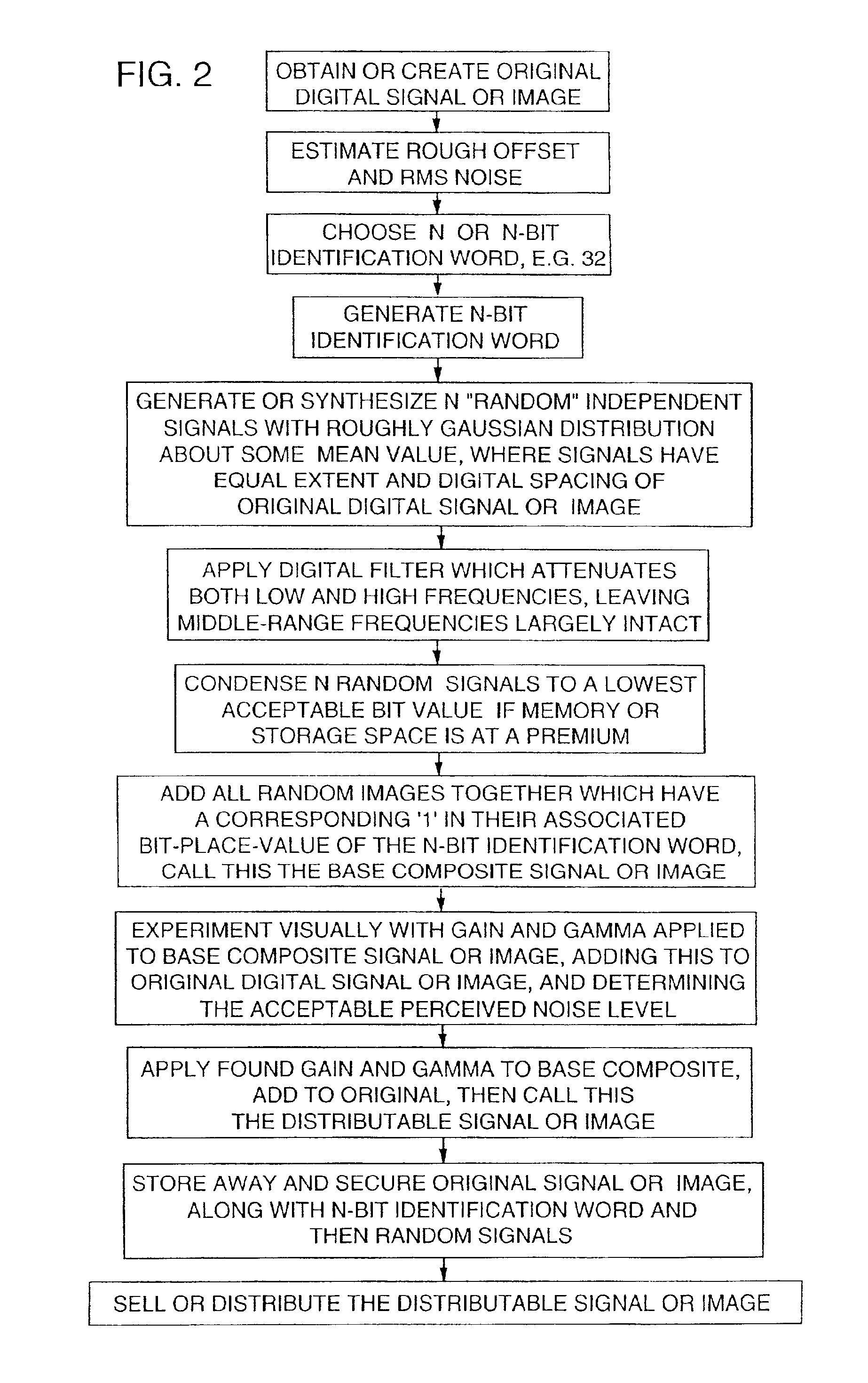
Method and apparatus for embedding data, including watermarks, in human perceptible images
InactiveUS6031914AGood autocorrelationPromote generationElectric signal transmission systemsCharacter and pattern recognitionPattern recognitionFrequency spectrum
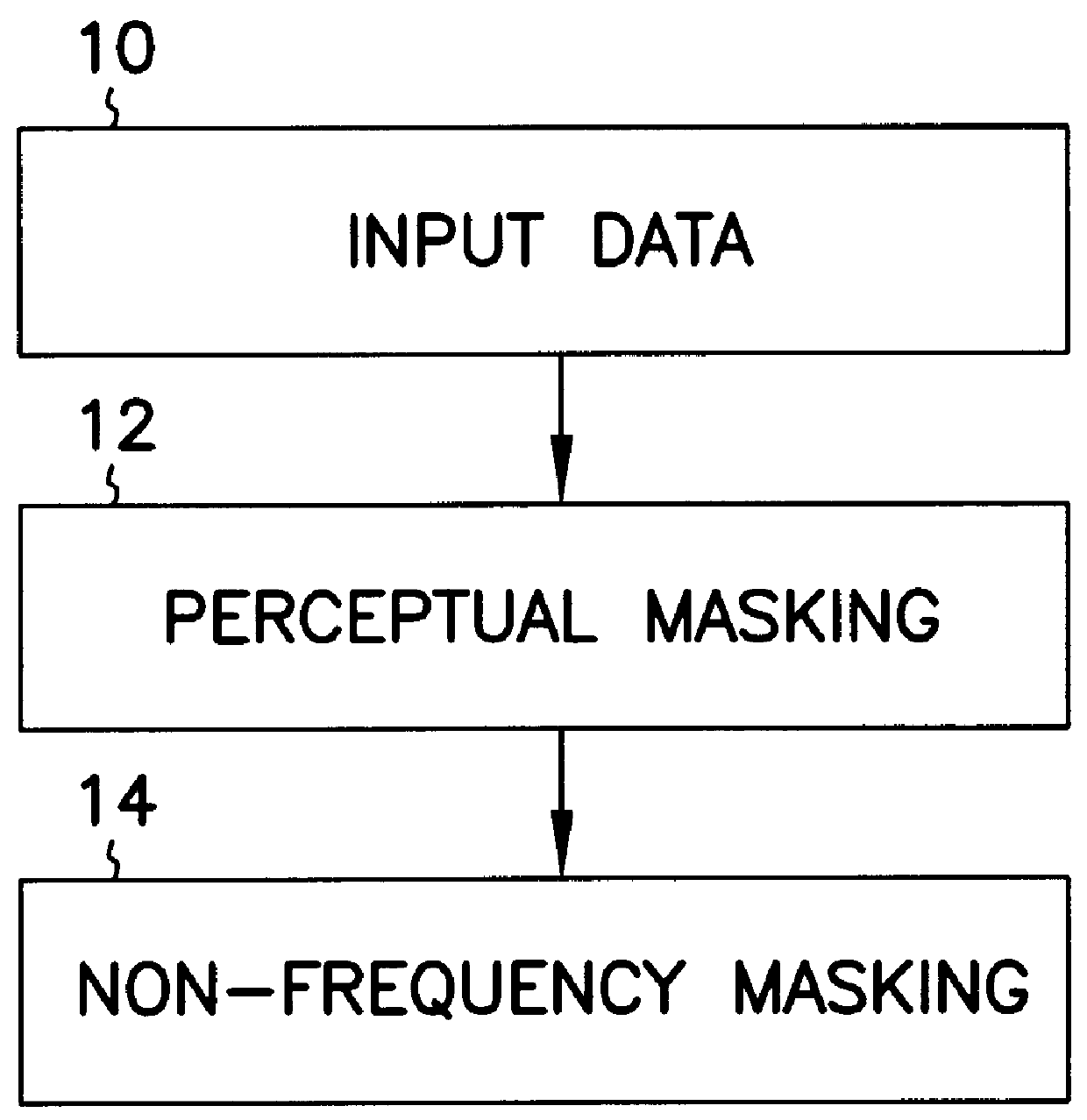
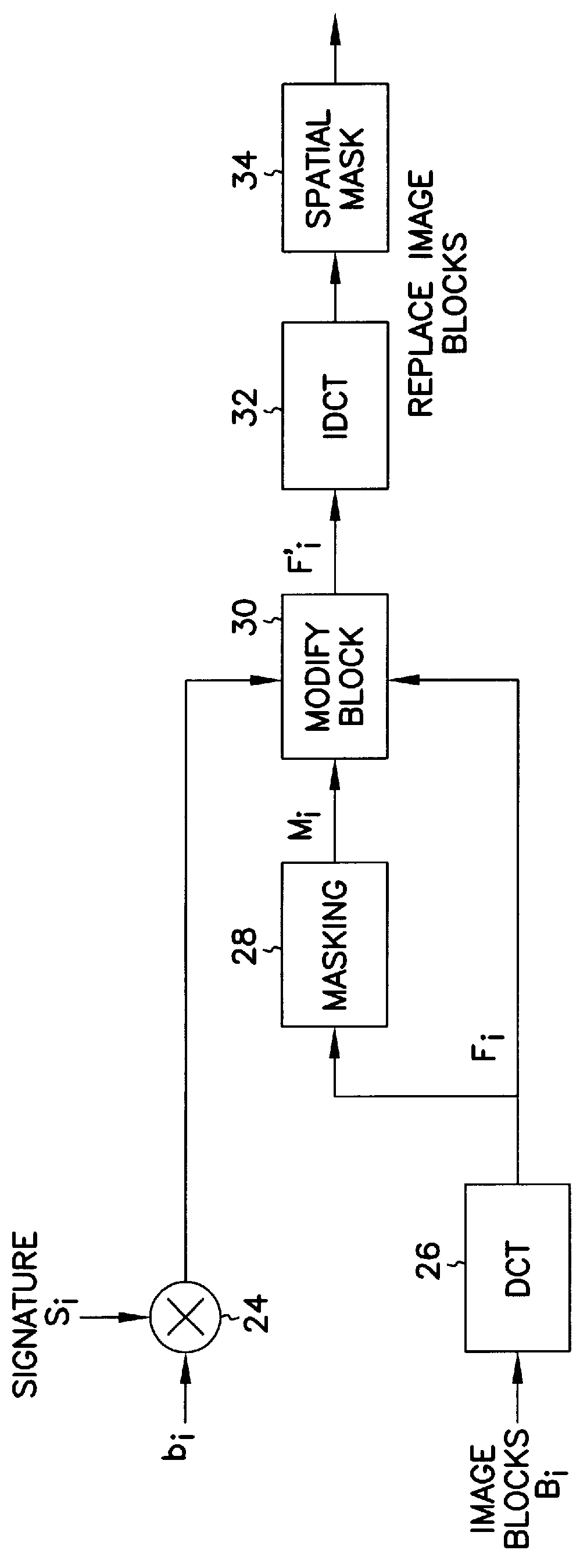
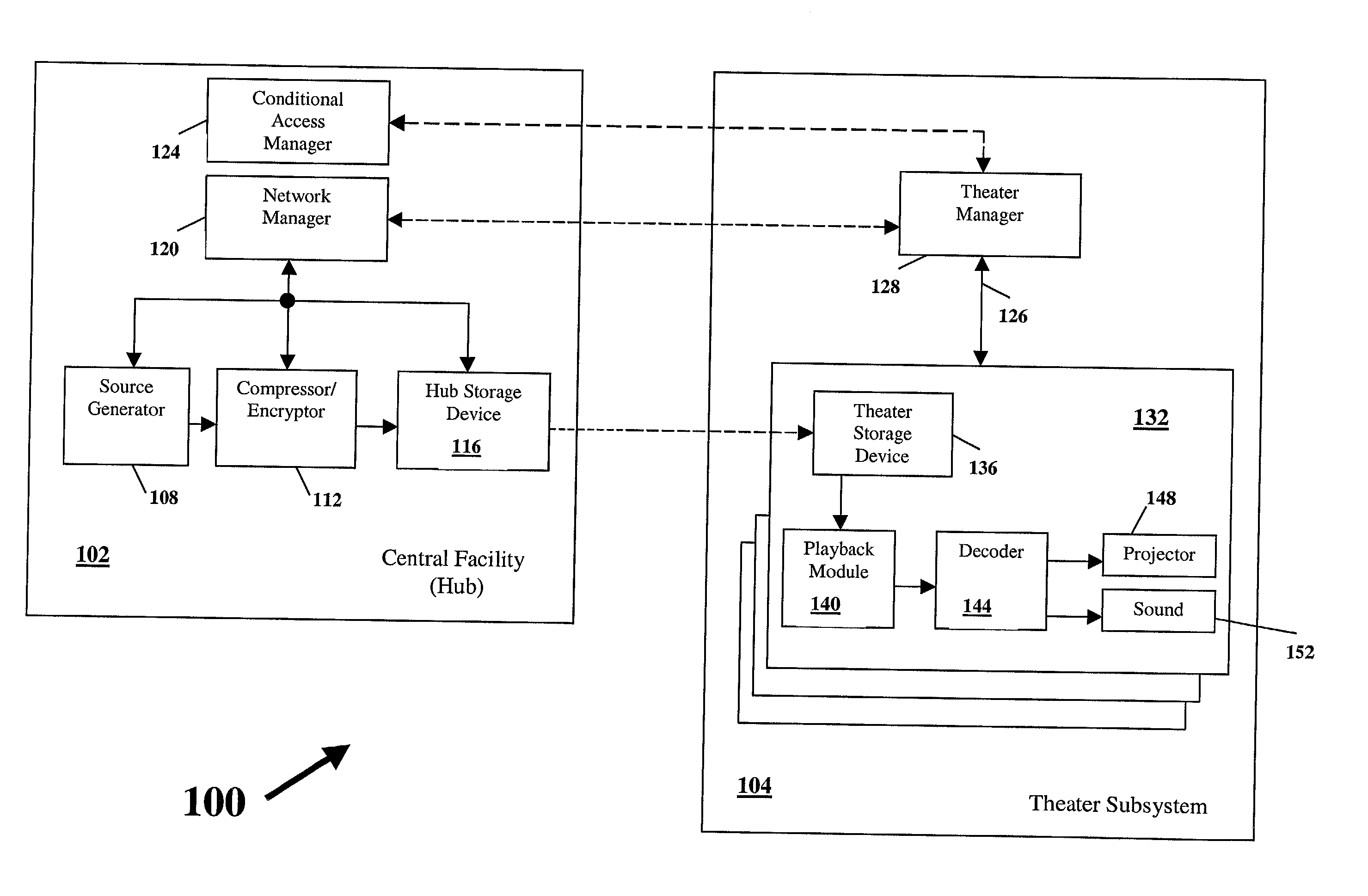
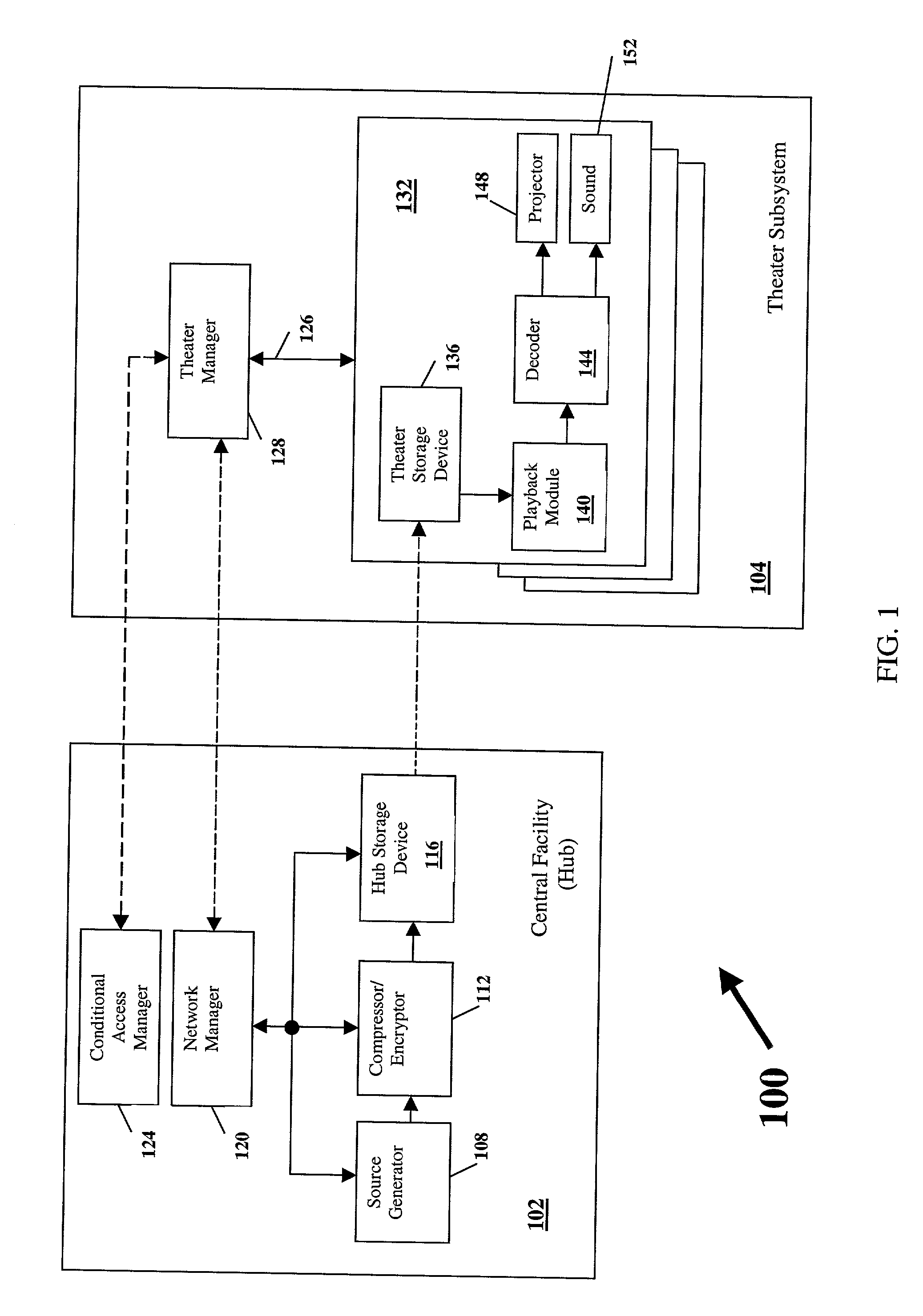
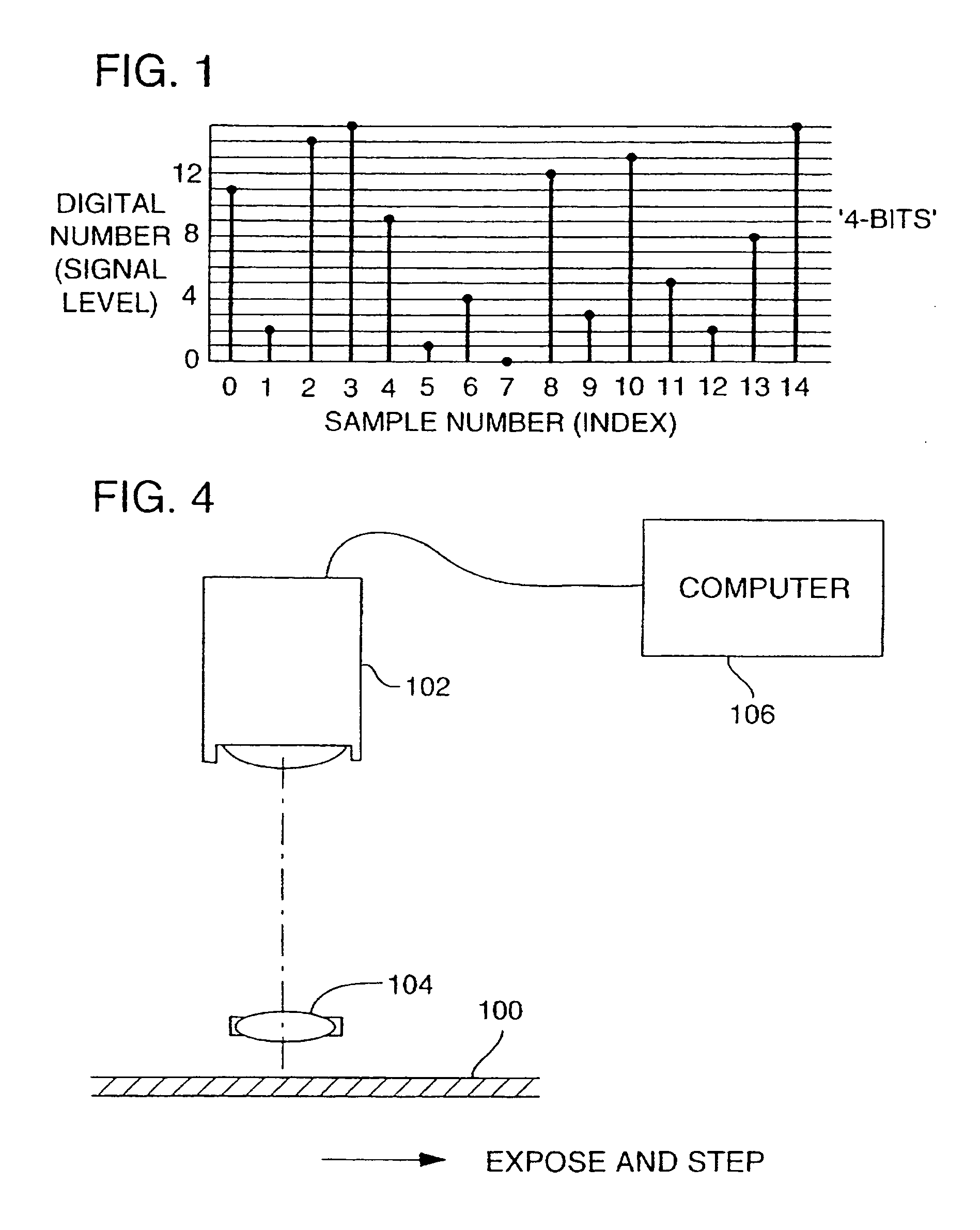
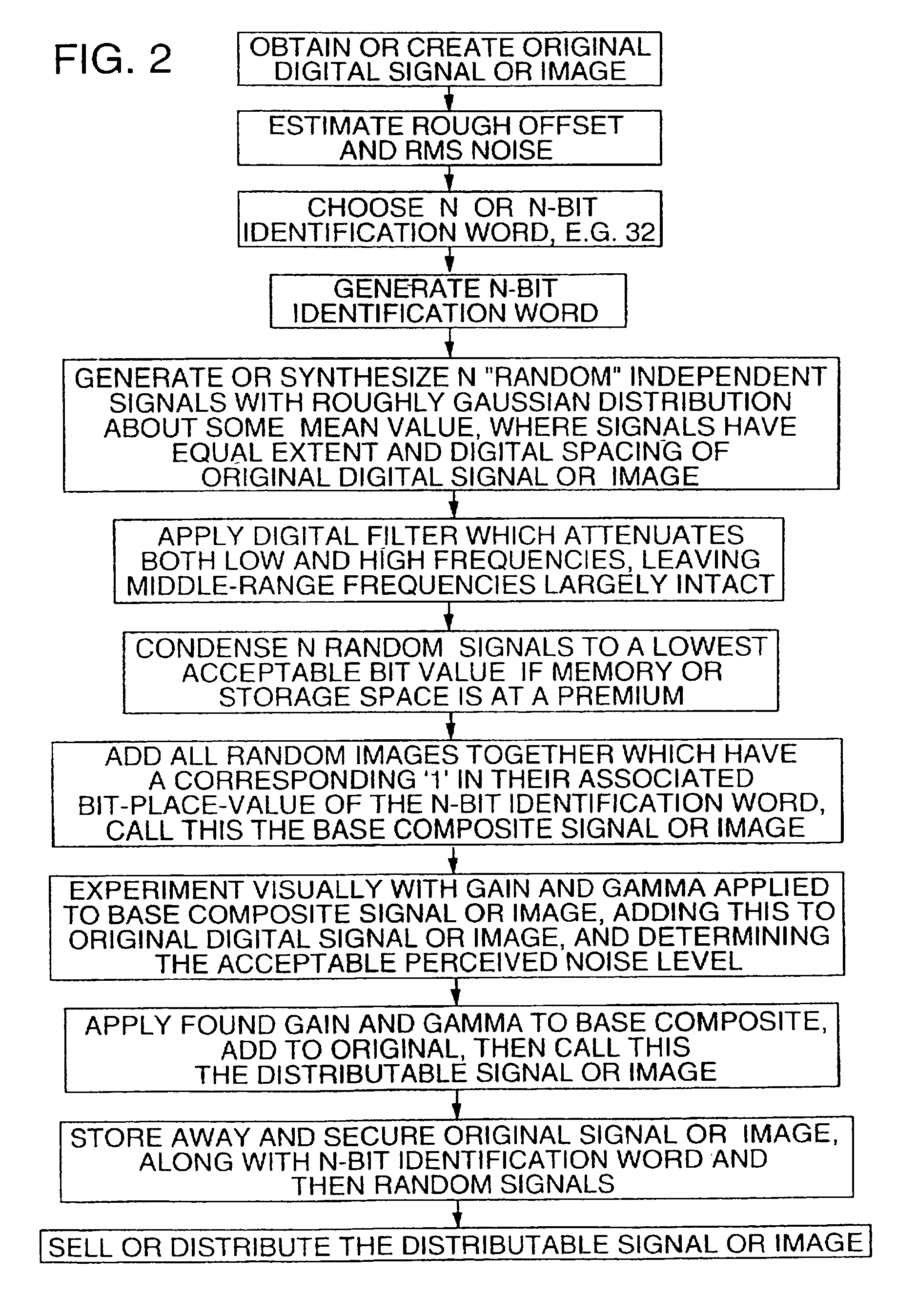
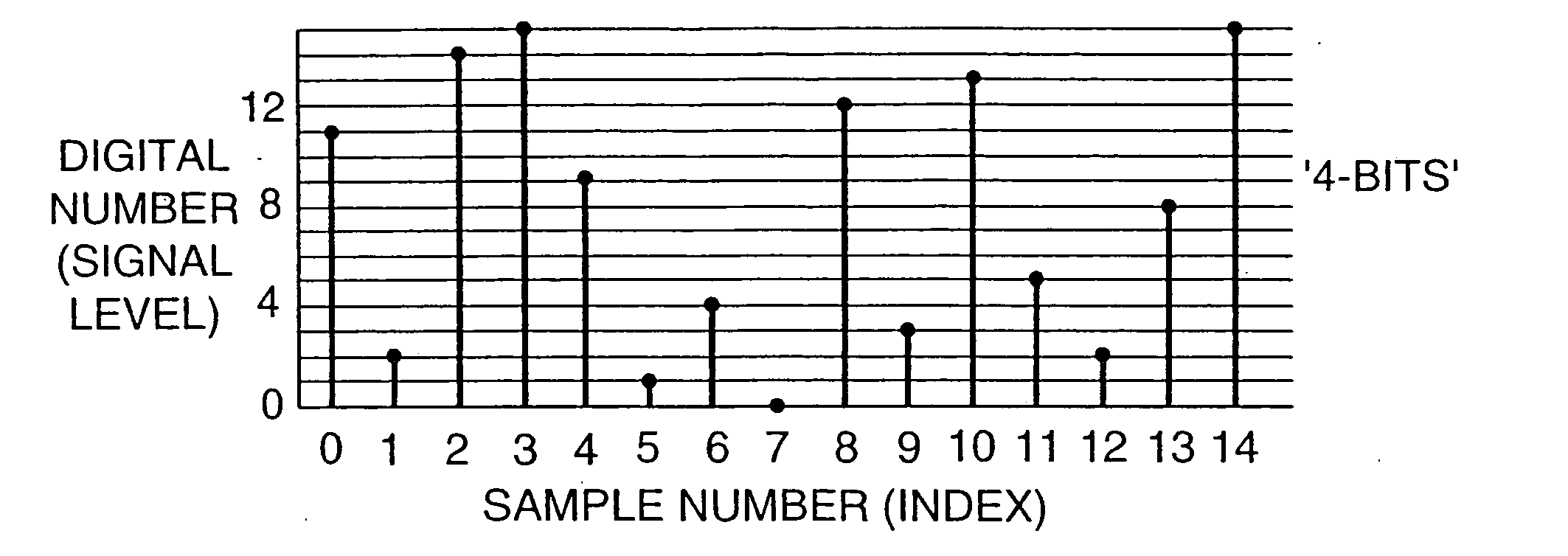
A technique for hiding of data, including watermarks, in human-perceptible images, that is, image host data, is disclosed. In one embodiment a method comprises three steps. In the first step, data to be embedded is inputted. In the case of a watermark, this data is a unique signature, and may be a pseudo-noise (PN) code. In the case of hidden data to be embedded in the host data, this data is the hidden data itself, or the hidden data as spread against the frequency spectrum by a pseudo-noise (PN) code. In the second step, the inputted data is embedded within the host data, in accordance with a perceptual mask of the host data. The perceptual mask determines the optimal locations within the host data to insert the inputted data. In the case of images, these optimal locations are determined by reference to the human visual system. In the third step, the host data, with the embedded data, is further masked by a non-frequency mask. In the case of image data, the non-frequency mask is a spatial mask.
Owner:MINNESOTA RGT UNIV OF A CORP OF MN
Security enhancements of digital watermarks for multi-media content
InactiveUS20060239501A1Reliable methodLow costUser identity/authority verificationSpeech analysisTheoretical computer scienceSecurity enhancement
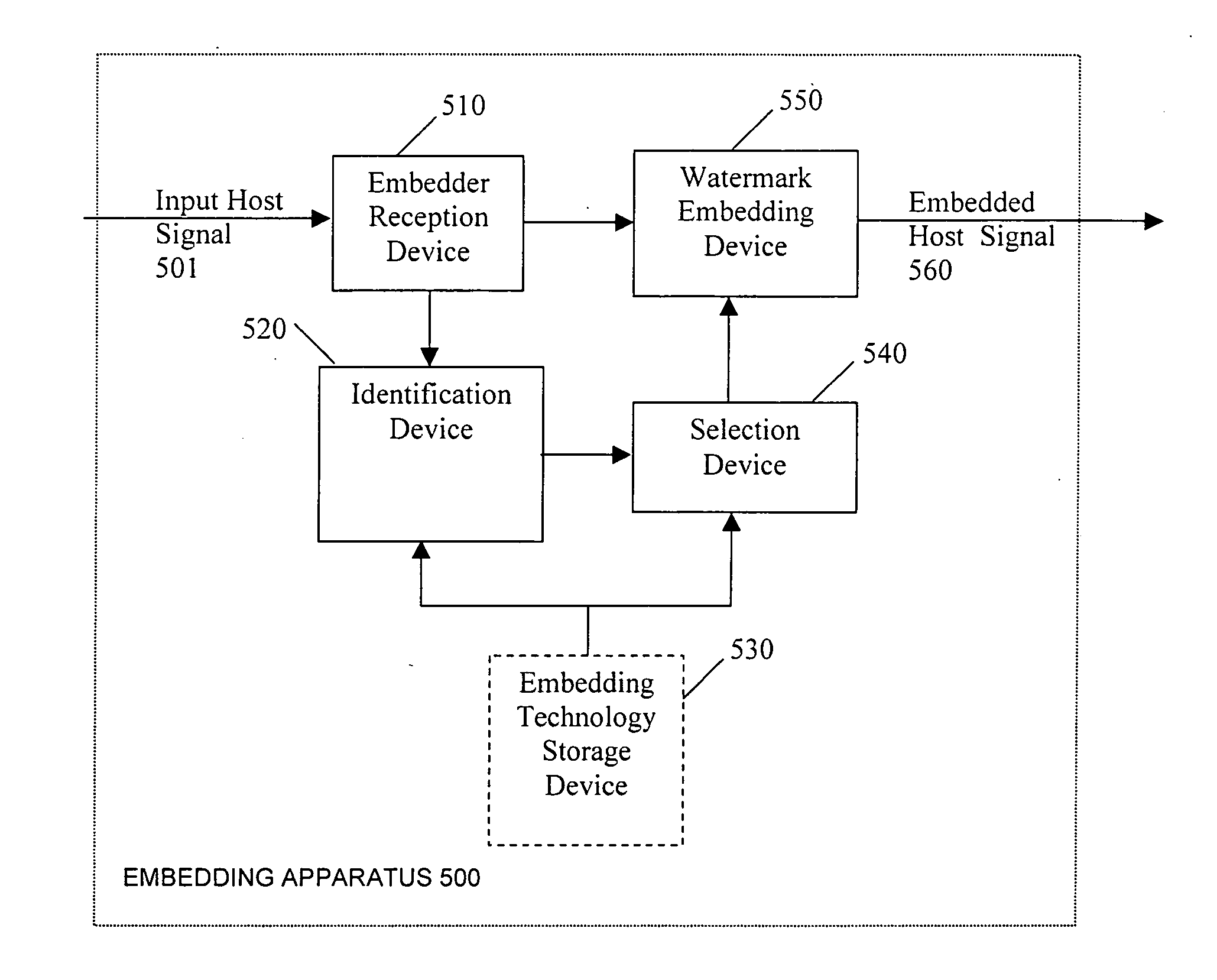
Methods and apparatus for embedding digital watermarks into a digital host content are provided. A digital host content is received, e.g., at a receiver or other device incorporating a receiver. One or more watermark embedding technologies is selected. Multiple embedding opportunities are identified within the host content. A subset of the identified embedding opportunities is selected. A multiplicity of digital watermarks are then embedded into the host content in accordance with the selected subset of embedding opportunities utilizing the one or more selected watermark embedding technologies. The selecting of the subset of embedding opportunities may be adapted to provide a desired tradeoff between levels of robustness, security, and transparency of the watermark. A plurality of watermarking embedding technologies may be selected and used in the embedding step.
Owner:VERANCE
Generating and matching hashes of multimedia content
ActiveUS20020178410A1RobustRobust hashingElectrophonic musical instrumentsCode conversionFrequency spectrumAlgorithm
Hashes are short summaries or signatures of data files which can be used to identify the file. Hashing multimedia content (audio, video, images) is difficult because the hash of original content and processed (e.g. compressed) content may differ significantly. The disclosed method generates robust hashes for multimedia content, for example, audio clips. The audio clip is divided (12) into successive (preferably overlapping) frames. For each frame, the frequency spectrum is divided (15) into bands. A robust property of each band (e.g. energy) is computed (16) and represented (17) by a respective hash bit. An audio clip is thus represented by a concatenation of binary hash words, one for each frame. To identify a possibly compressed audio signal, a block of hash words derived therefrom is matched by a computer (20) with a large database (21). Such matching strategies are also disclosed. In an advantageous embodiment, the extraction process also provides information (19) as to which of the hash bits are the least reliable. Flipping these bits considerably improves the speed and performance of the matching process.
Owner:GRACENOTE
Method and apparatus for image authentication
InactiveUS6532541B1User identity/authority verificationImage watermarkingDigital signatureDiscrete cosine transform
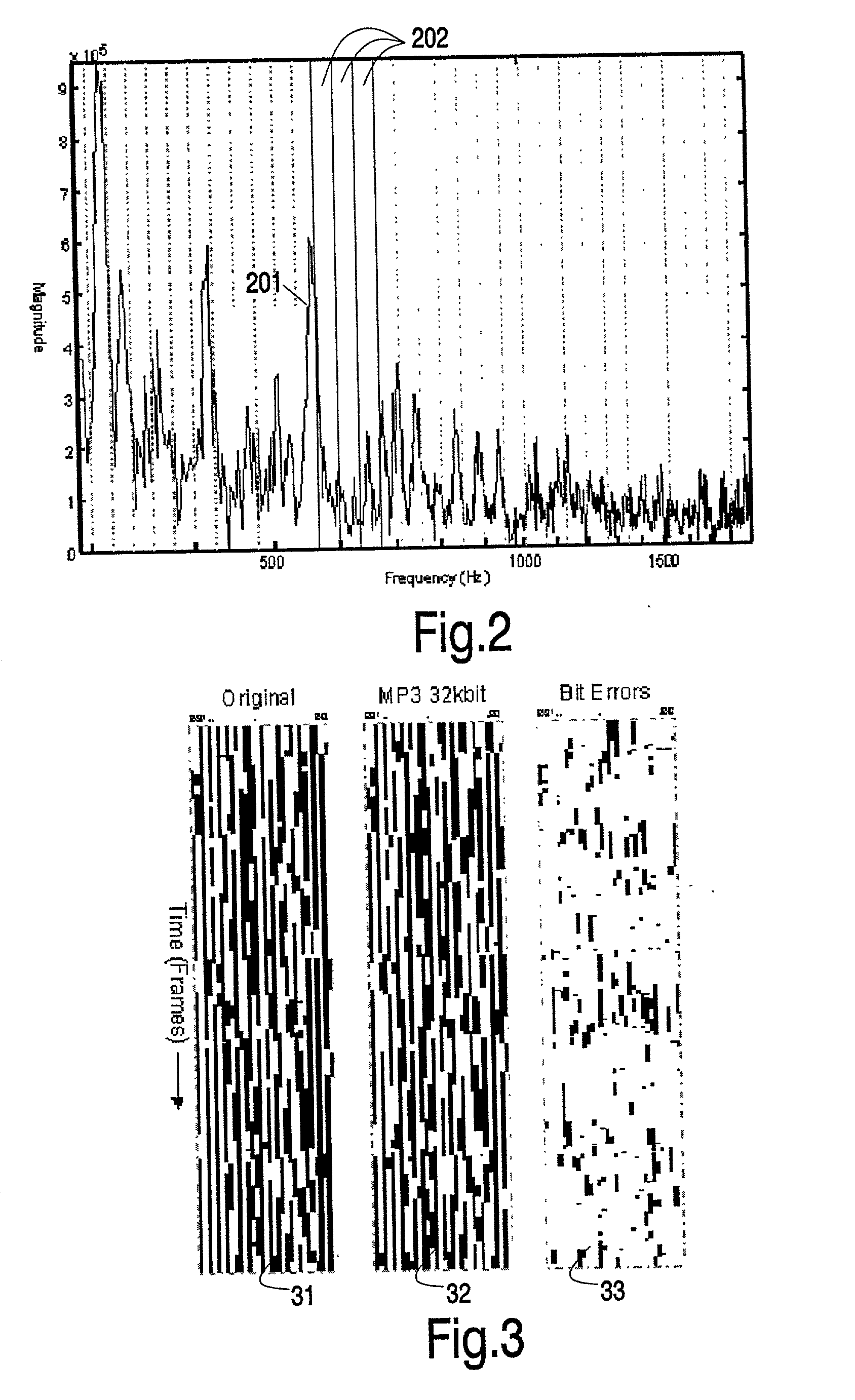
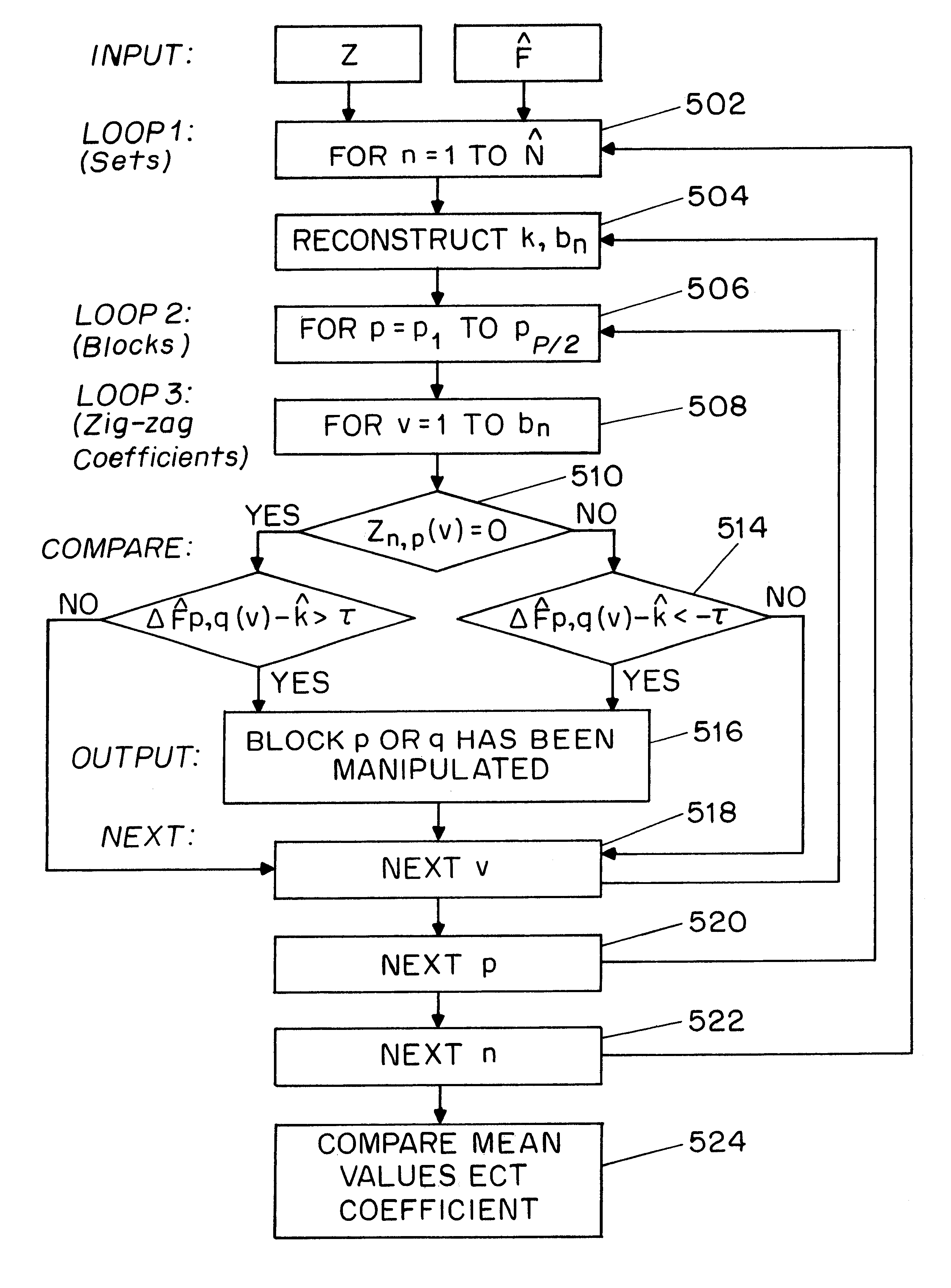
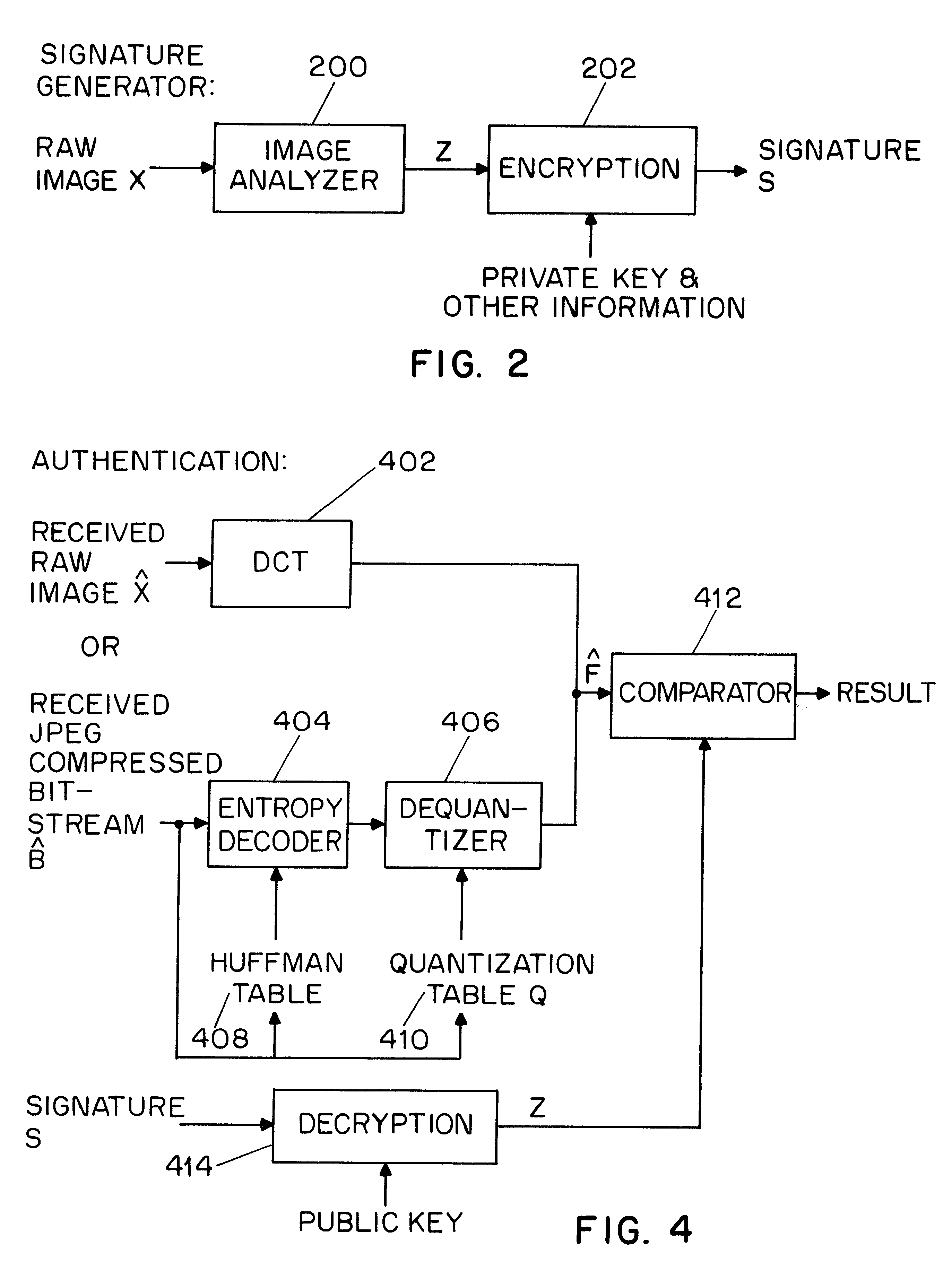
A system for authentication of a digital image includes a signature generator for creating a robust digital signature for an original image based on instrument features of the image. An authentication processor extracts a set of invariant features for the original image from the digital signature, generates a corresponding set of invariant features for the present image to be authenticated and compares the two sets of invariant features to determine whether the image has been subjected to malicious manipulation. The invariant features include the polarity and magnitude of the difference between discrete cosine transform coefficients at corresponding coefficient locations in selected image block pairs. The intensity of the original image is also authenticated by comparing a mean value of coefficient of the original image to the mean value of the coefficient of the present image.
Owner:NAT SCI FOUND NSF
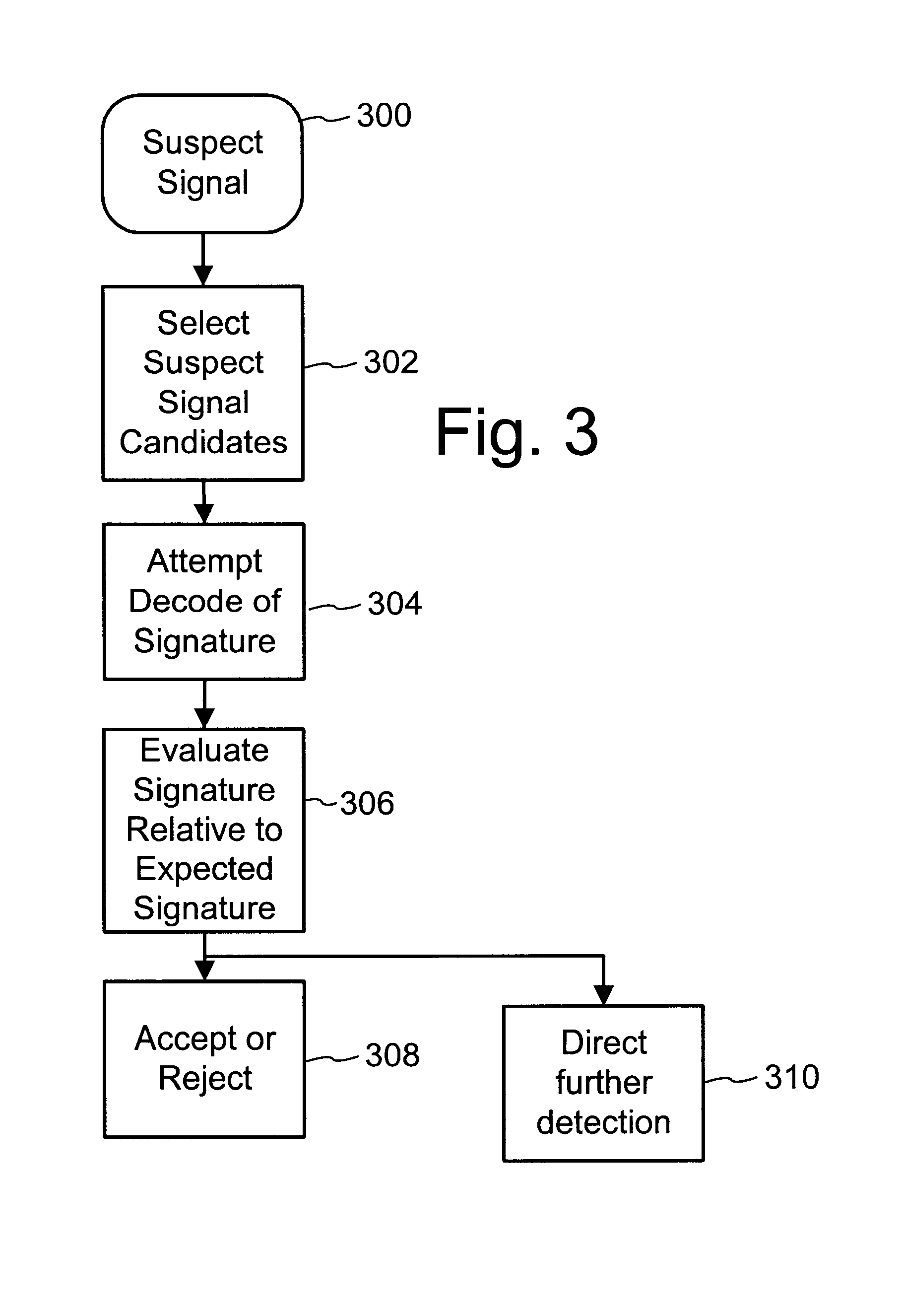
Digital watermark screening and detecting strategies
InactiveUS6516079B1Increase likelihoodPromote recoveryTelevision system detailsAnalogue secracy/subscription systemsDigital watermarkingPhysics
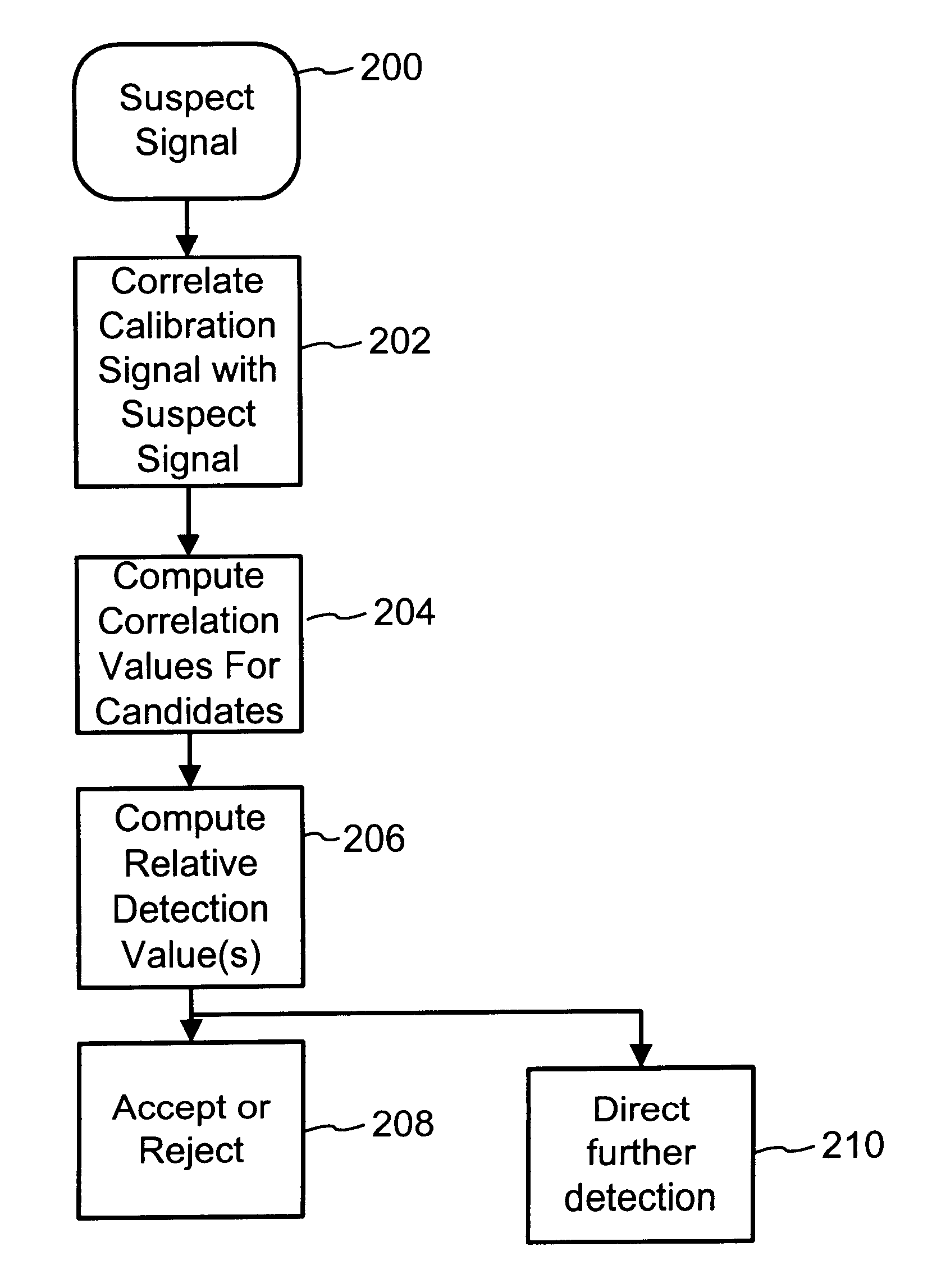
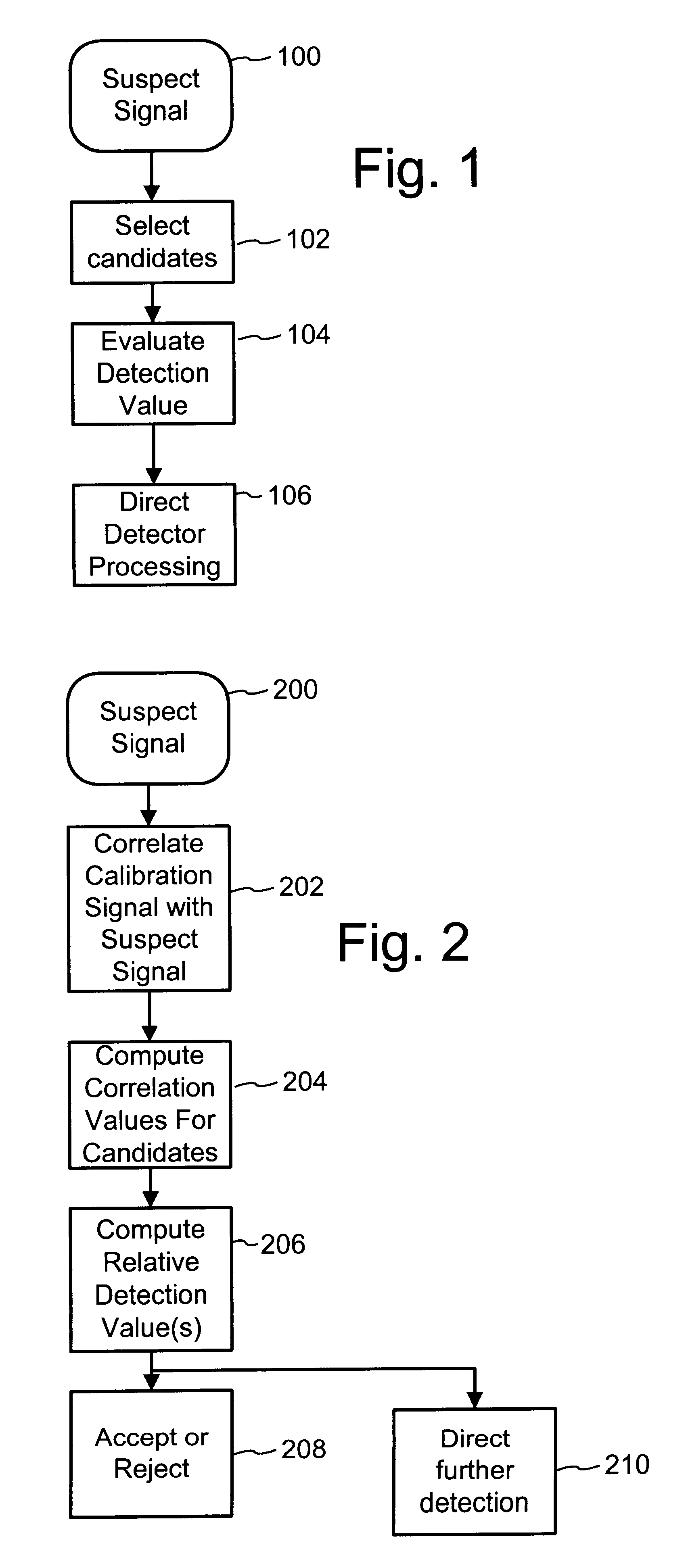
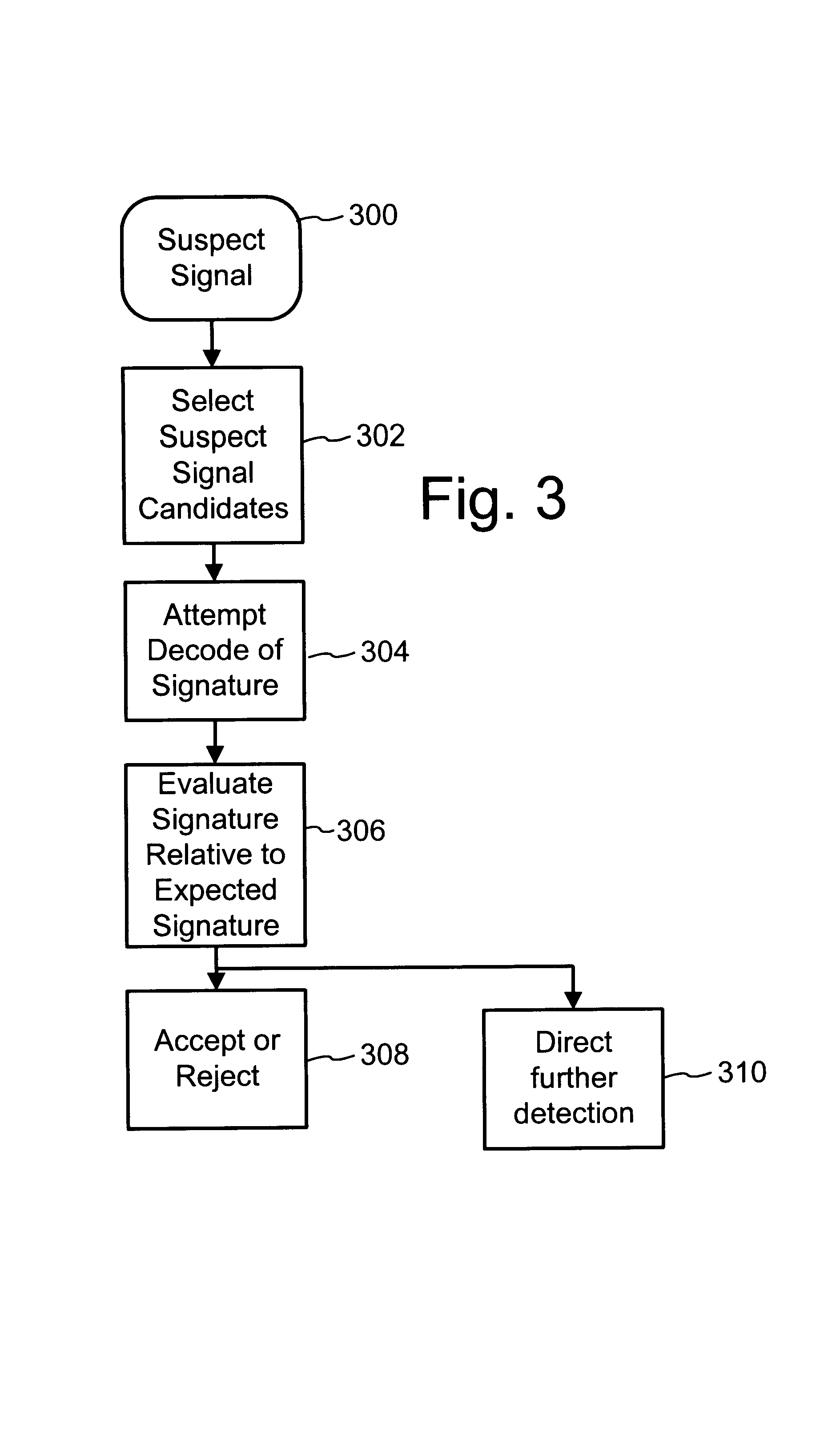
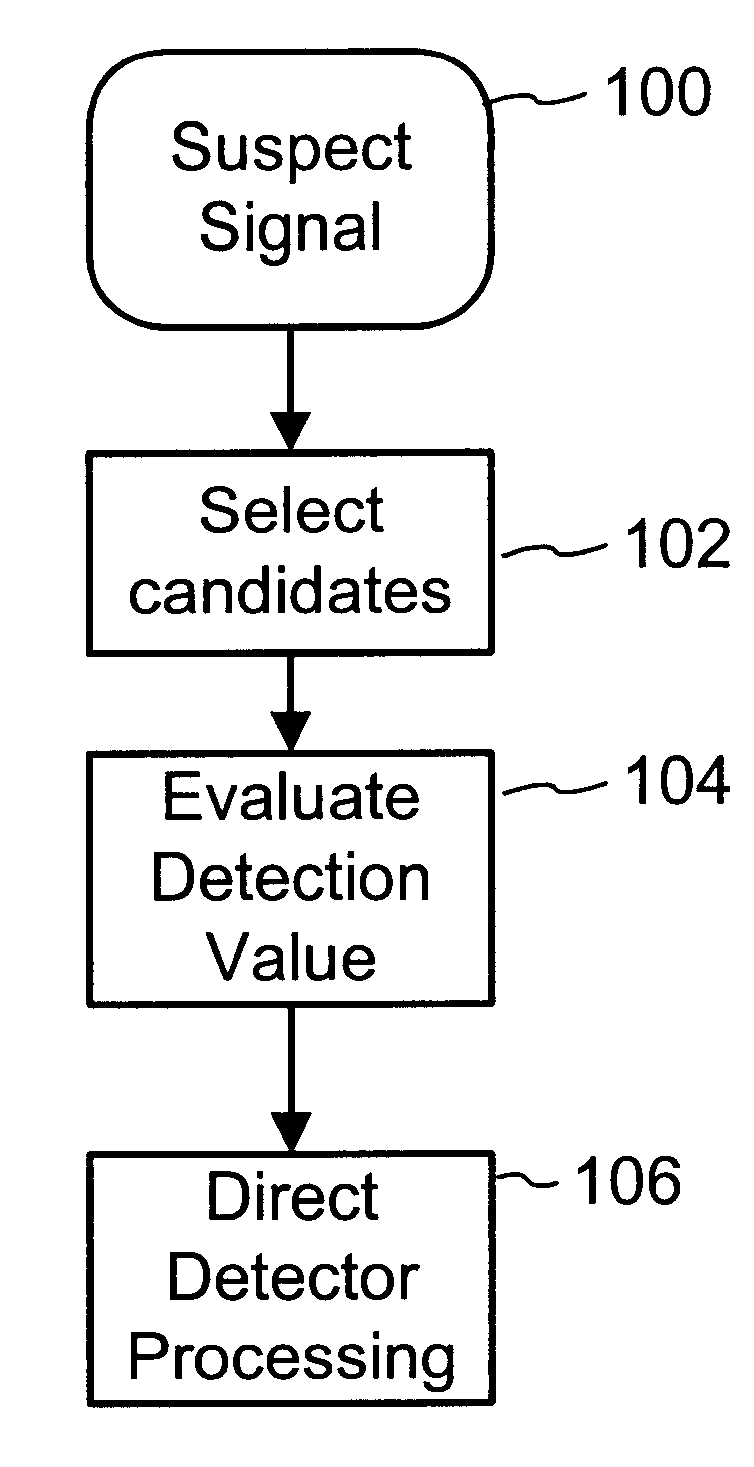
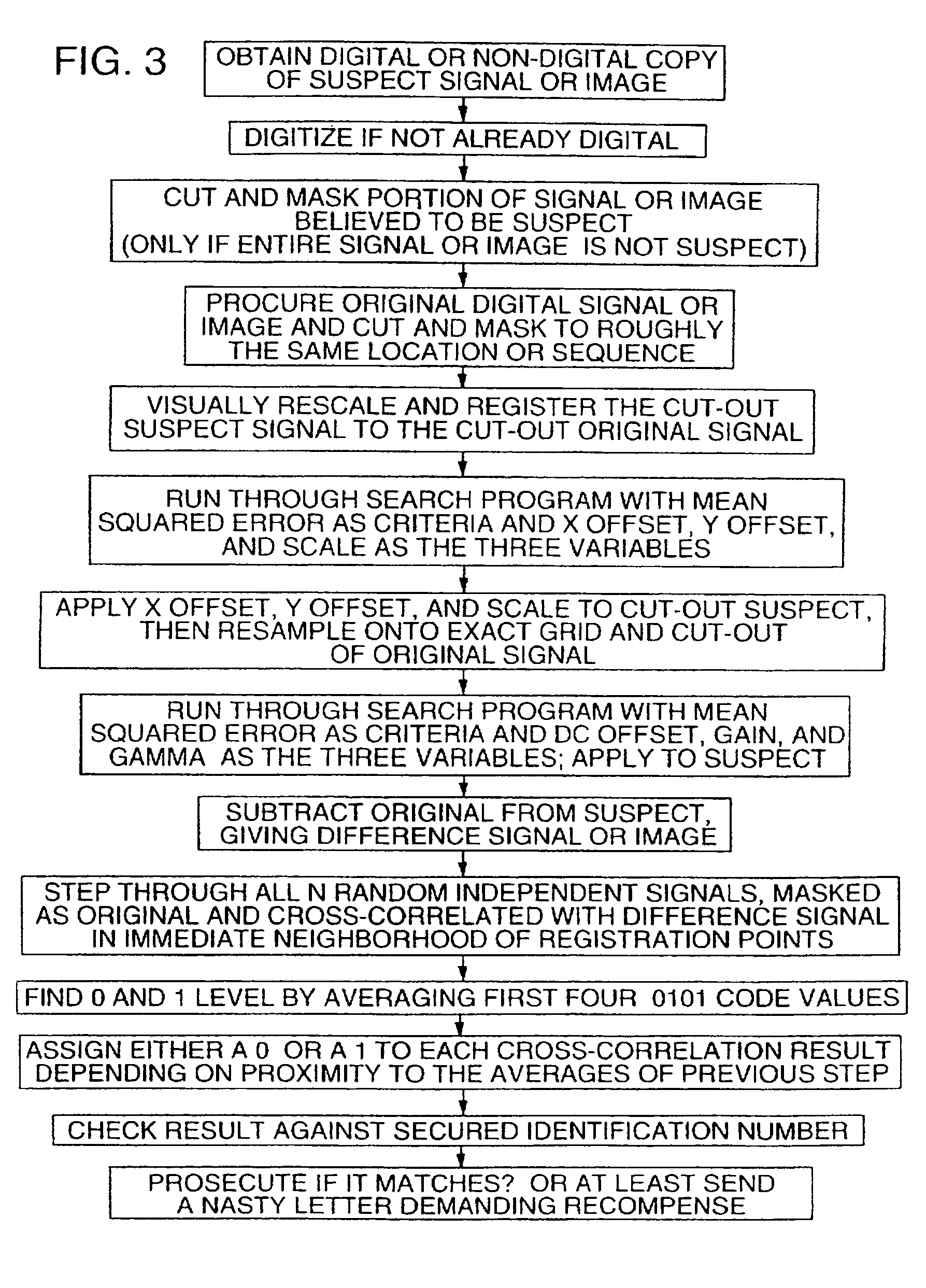
To enhance decoding of signals suspected of containing a watermark, a suspect signal is screened to compute detection values evincing presence and strength of a watermark. Screening strategies control detector actions, such as rejecting un-marked signals and improving synchronization of watermarks in suspect signals.
Owner:DIGIMARC CORP
Forensic communication apparatus and method
InactiveUS6996251B2Key distribution for secure communicationMultiple keys/algorithms usageTransmitterReal-time computing
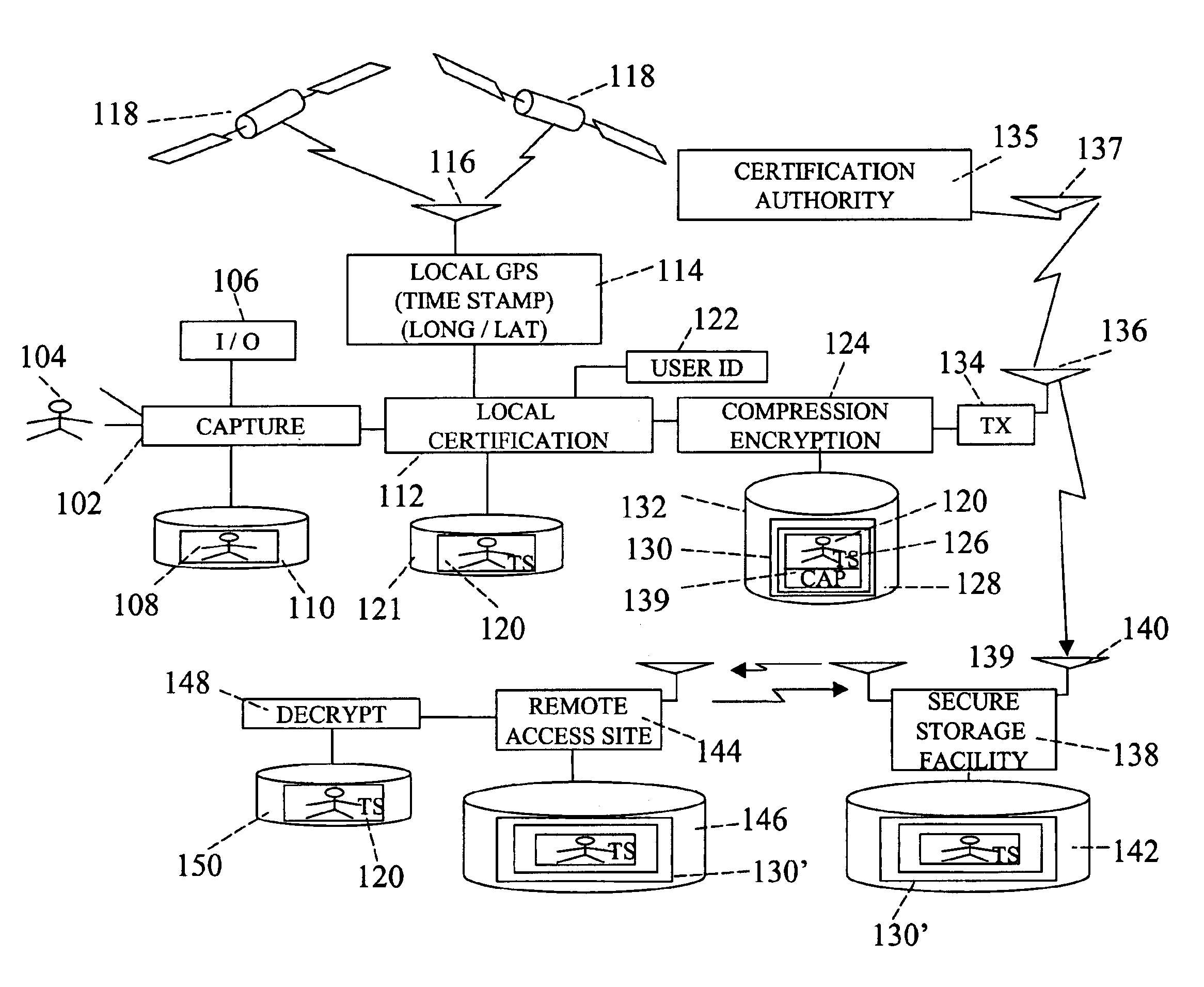
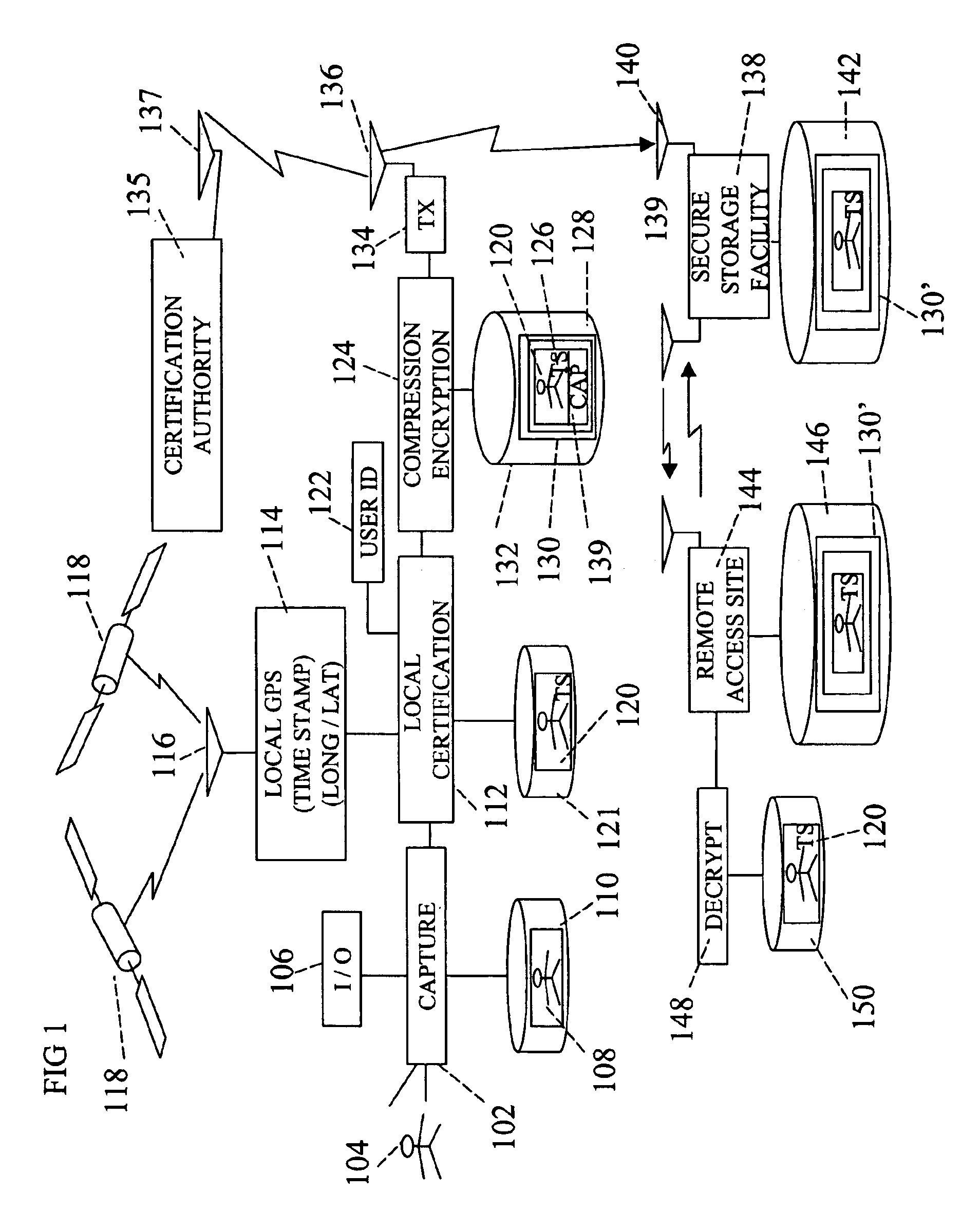
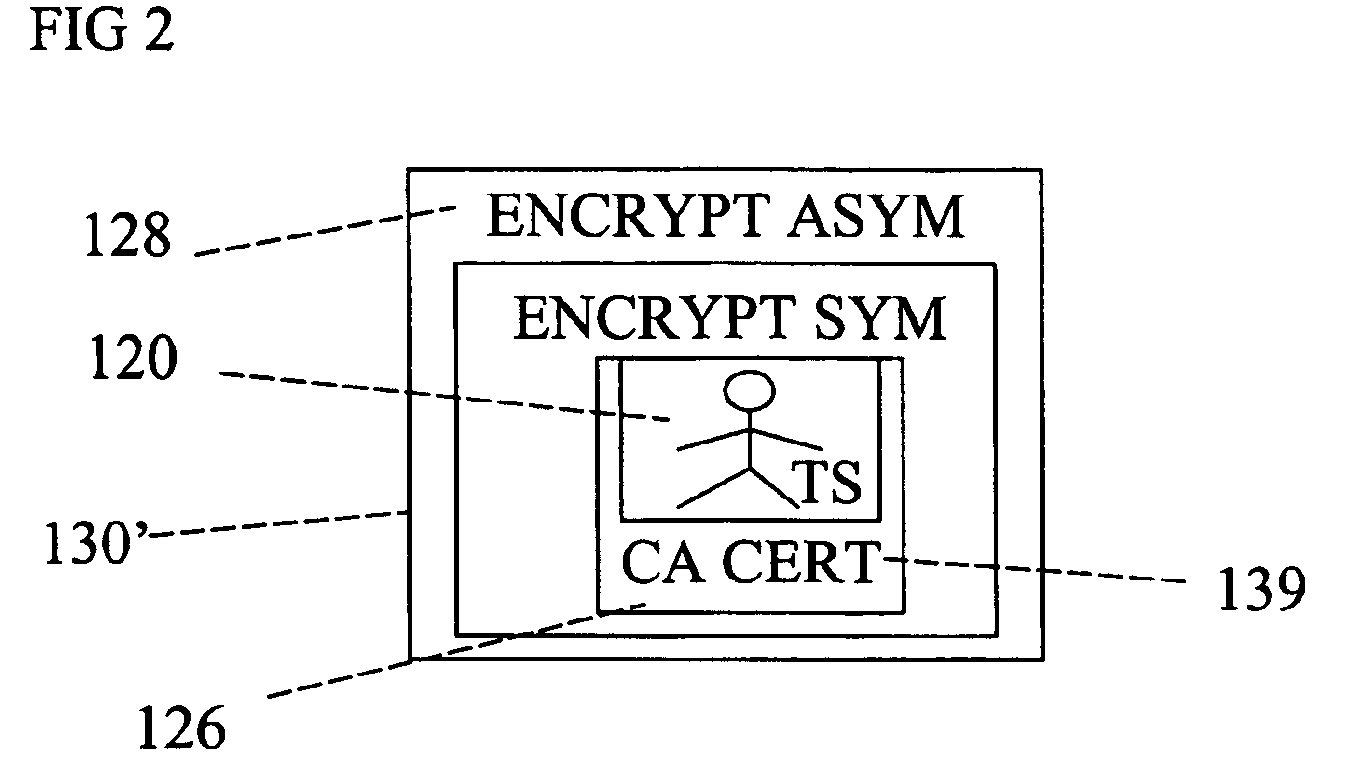
Forensic communication apparatus and method. An apparatus is disclosed for recording image or other data in real time. The apparatus includes a capture device for capturing the image or other information. Once captured, a local verification device is operable to indelibly mark the captured image or other information with the date, time, location and information identifying the creator of the data. A transmitter is provided for transmitting the locally verified captured image or other information in real time to a secure storage facility. The capture device is operable, after the locally verified captured image or other information is transmitted to the secure storage facility, to receive and verify acknowledgment of the receipt of the transmitted locally verified captured image or other information to the storage facility.
Owner:MYPORT IP
Digital watermark screening and detection strategies
InactiveUS6768809B2Avoid unnecessary processingPreventing copying, playing or recordingTelevision system detailsAnalogue secracy/subscription systemsComputer scienceDigital watermarking
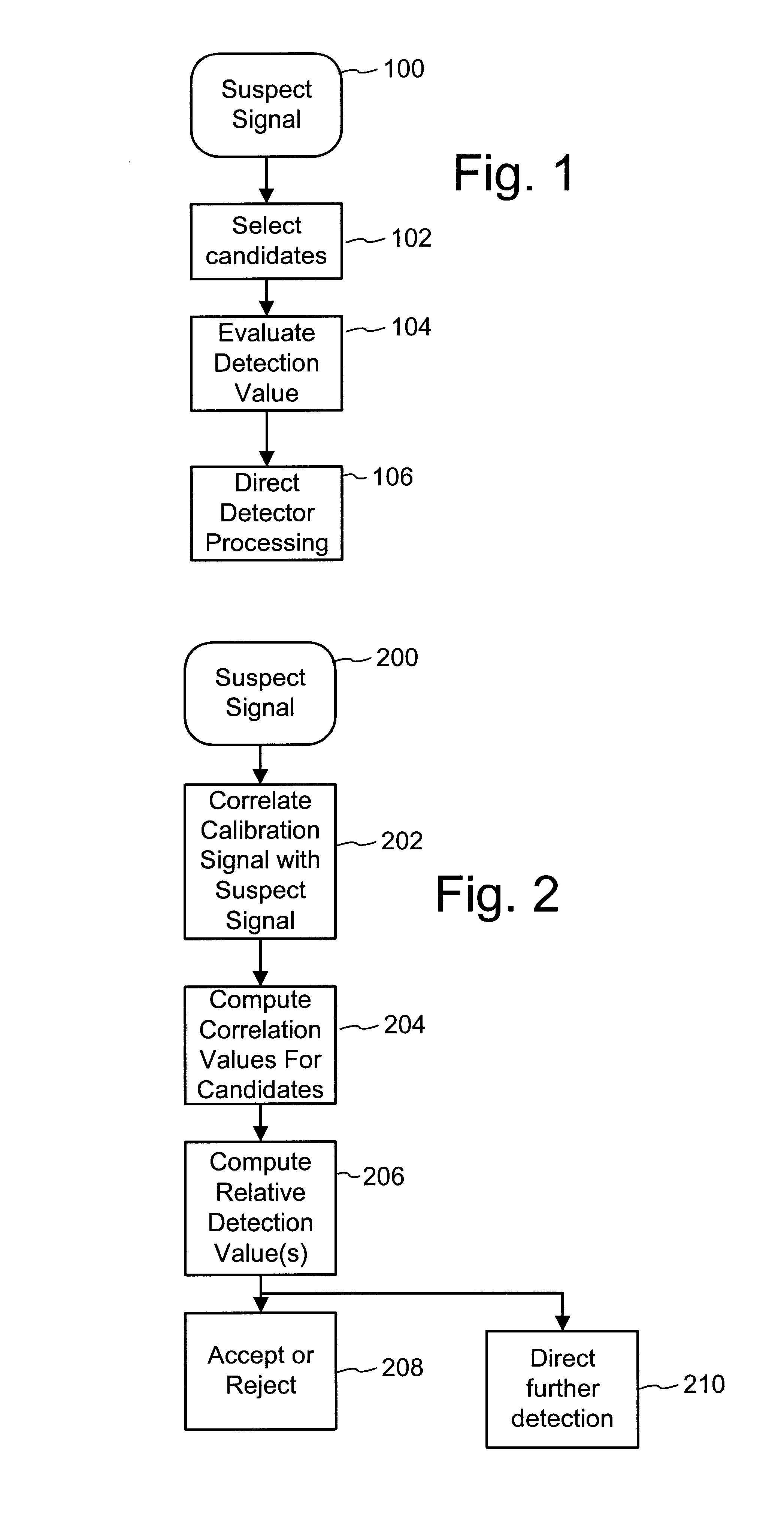
To enhance decoding of signals suspected of containing an embedded auxiliary signal, a suspect signal is screened to compute detection values evincing presence and strength of the embedded signal. Screening strategies control detector actions, such as rejecting un-marked signals, improving synchronization of a reader used to extract hidden messages in suspect signals, determining authenticity of signals, and controlling use of the signals.
Owner:DIGIMARC CORP
Methods and arrangements for identifying objects
InactiveUS20150310601A1Increase check-out speedImprove accuracyImage enhancementImage analysisPerspective transformationComputer science
Owner:DIGIMARC CORP
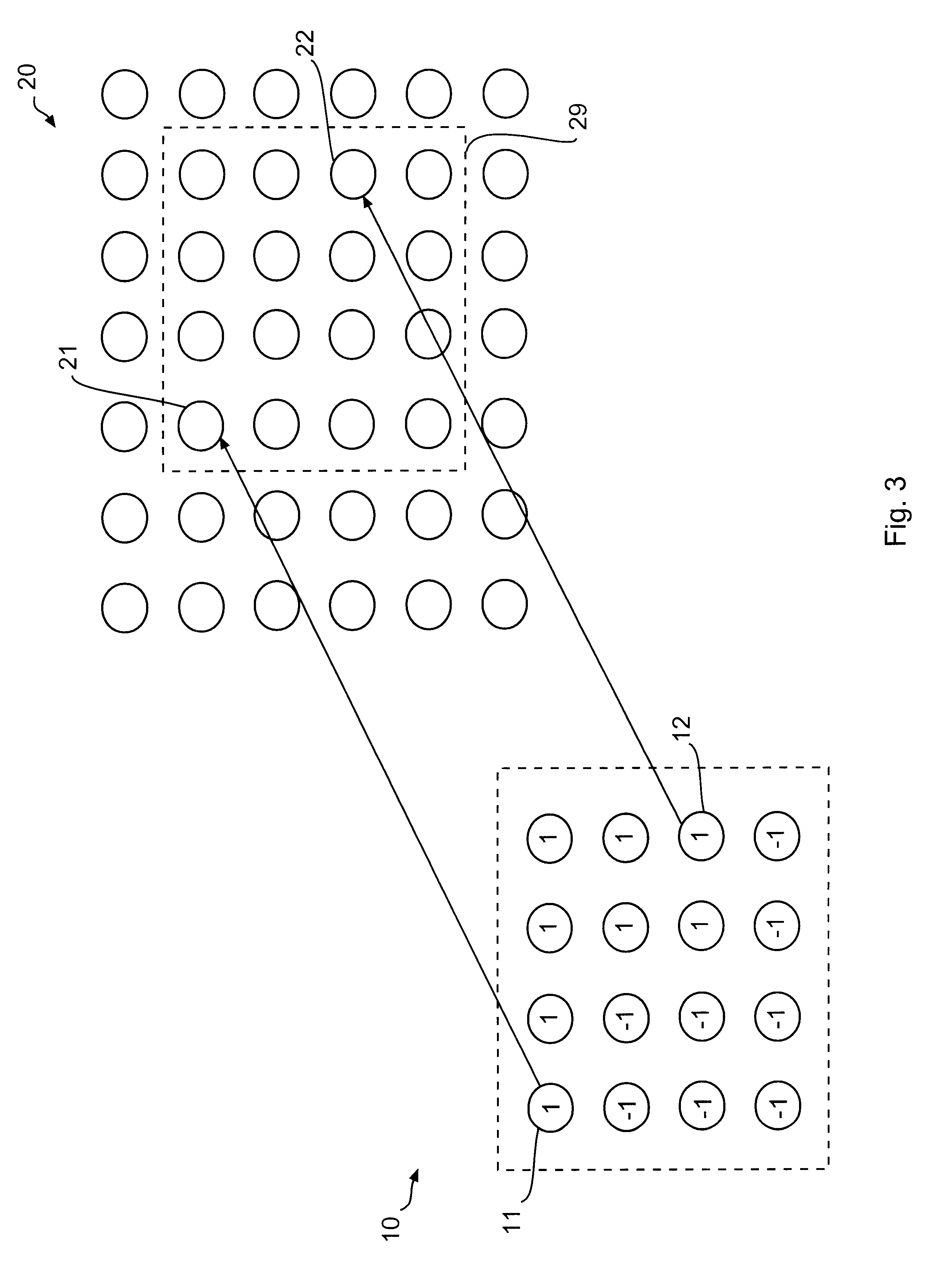
Watermarking with random zero-mean patches for printer tracking
InactiveUS6556688B1Efficient detectionUser identity/authority verificationCharacter and pattern recognitionVirtual cellControl signal
A steganographic method embeds hidden information like digital watermarks and digital fingerprints into an image by applying one or more zero-mean patches to a digital signal that conveys the image. Each zero-mean patch comprises elements having an average value substantially equal to zero. A printer tracking system is implemented by selecting a plurality of zero-mean patches according to a string of bits representing a printer serial number, and modifying printer control signals to embed the plurality of patches in each of a number of virtual cells within the image to be printed. The offset of the virtual cells with respect to the boundaries of the image and the location of the patches within each virtual cell are established in pseudo-random fashion. The printer tracking system further includes a technique for subsequently detecting the printer serial number by scanning the printed image and running a detection algorithm on the scanned data to recover the string of bits embedded in the zero-mean patches.
Owner:SEIKO EPSON CORP
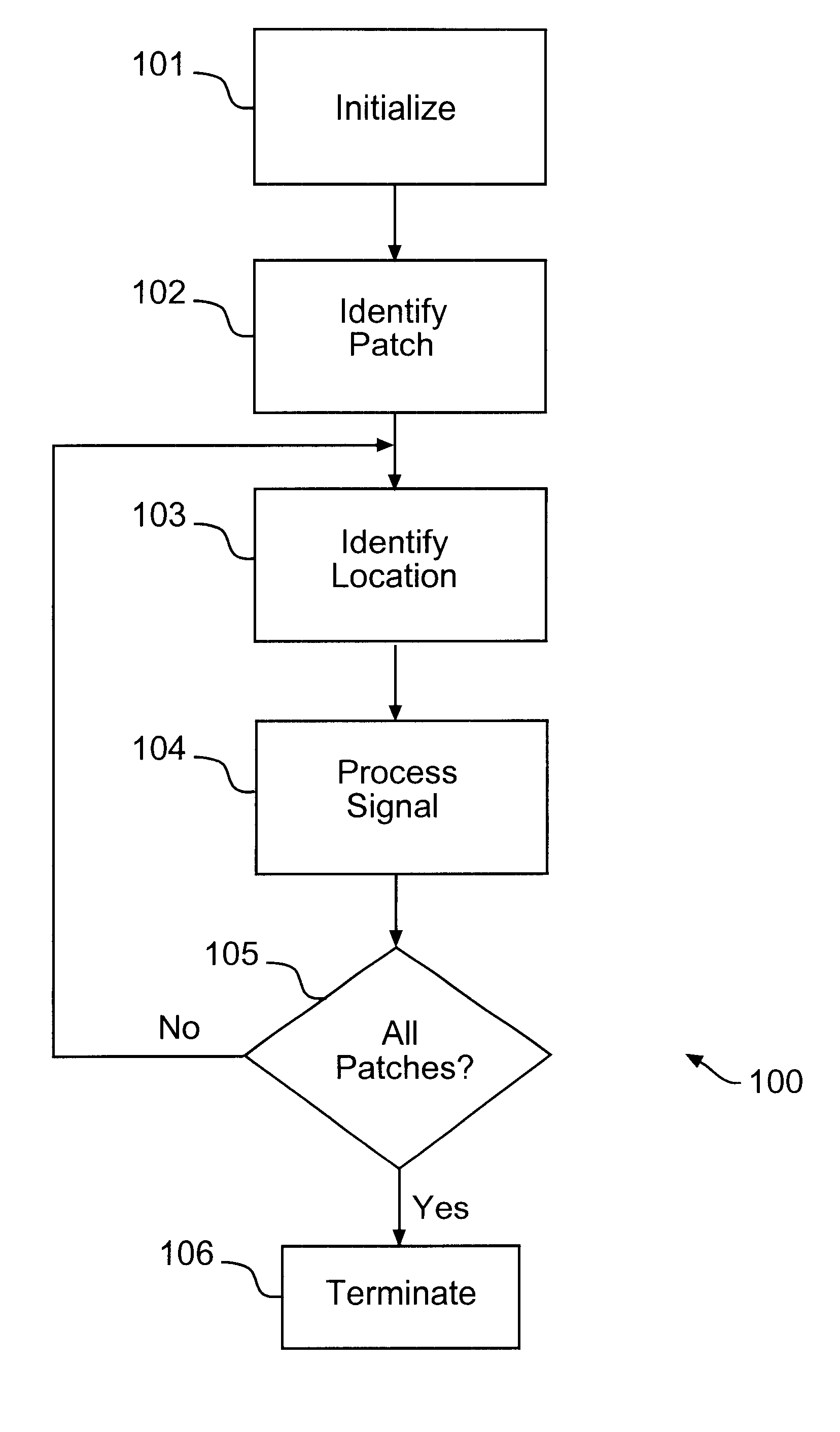
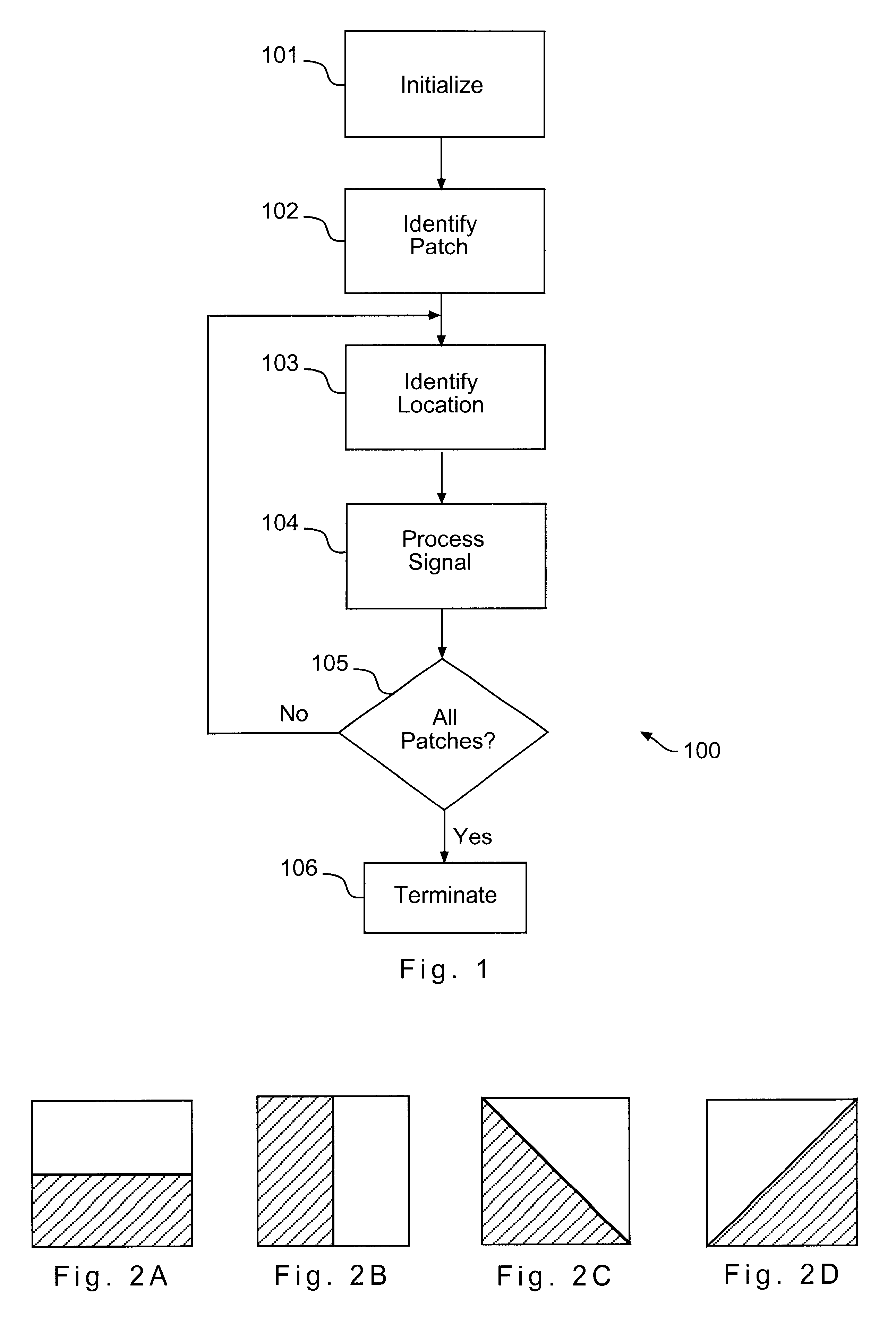
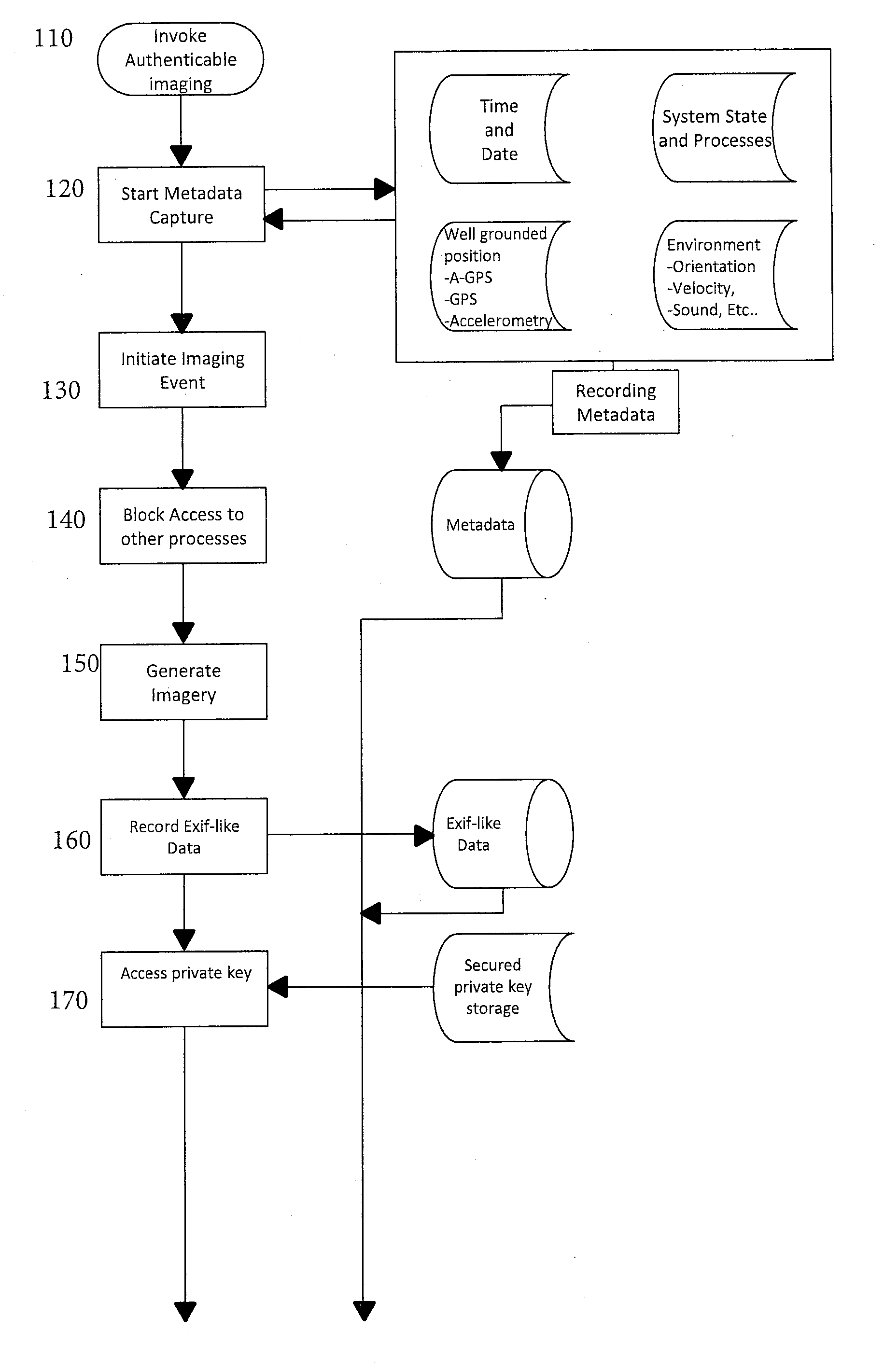
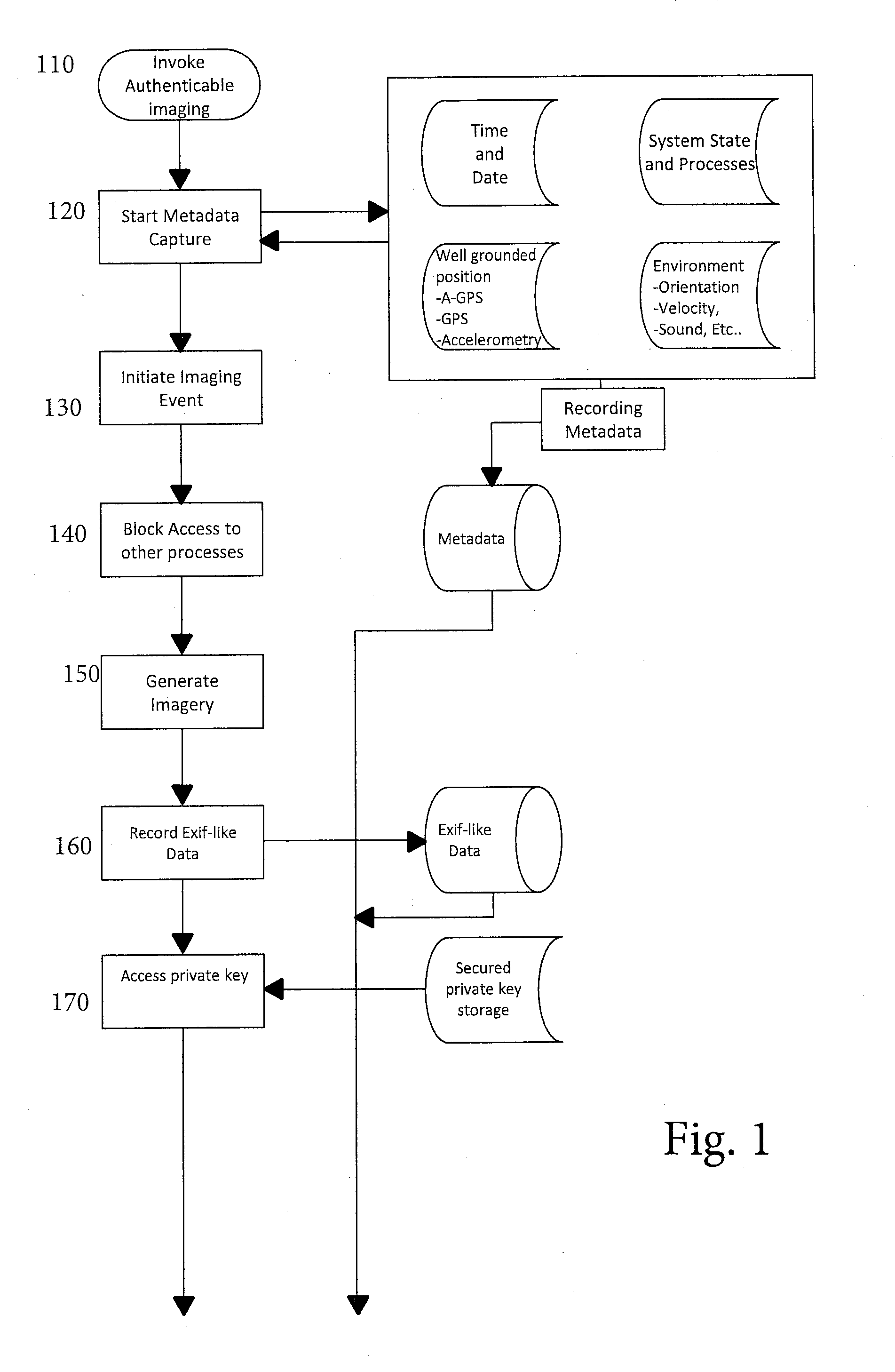
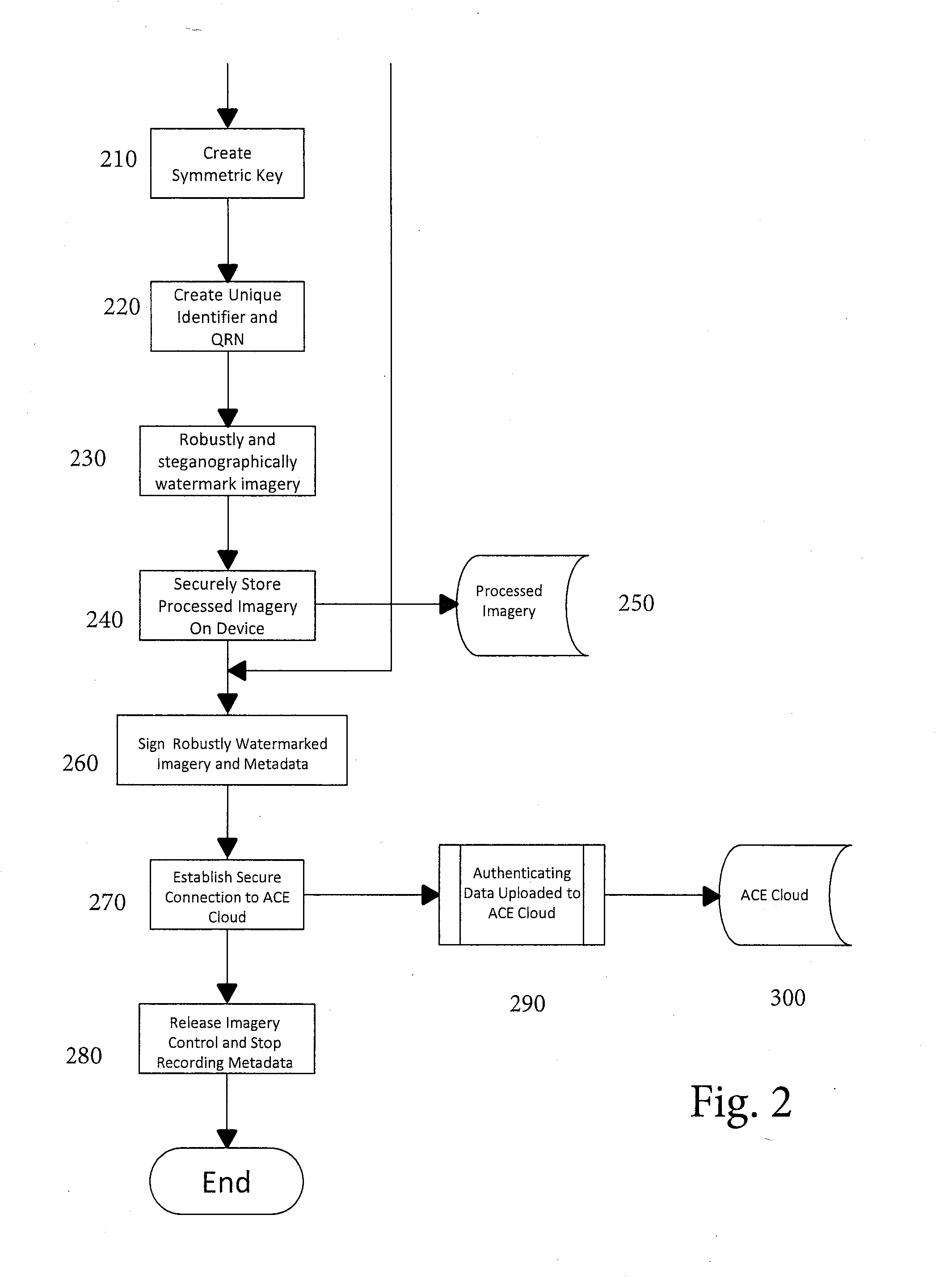
Authentication and Validation of Smartphone Imagery
A method, system, and processor-executable software for processing images or video captured by a smartphone or other digital image capture device for subsequent validation and authentication captures not only the image, but also metadata relevant to the authenticity of validity of the image, such as position, time, camera movement and orientation, image parameters, and so forth. The image is watermarked and both the watermarked image and the metadata, as well as a symmetric key used in the watermarking, are digitally signed and transmitted or uploaded to a web server or authentication centric entity for authentication and storage. When a third party submits an image to the web server or authentication centric entity, the submitted image is compared with the stored watermarked image for authentication and validation of the submitted image, and the metadata is then retrieved to enable analysis of the contents of authenticated and validated image.
Owner:TAUTACHROME INC
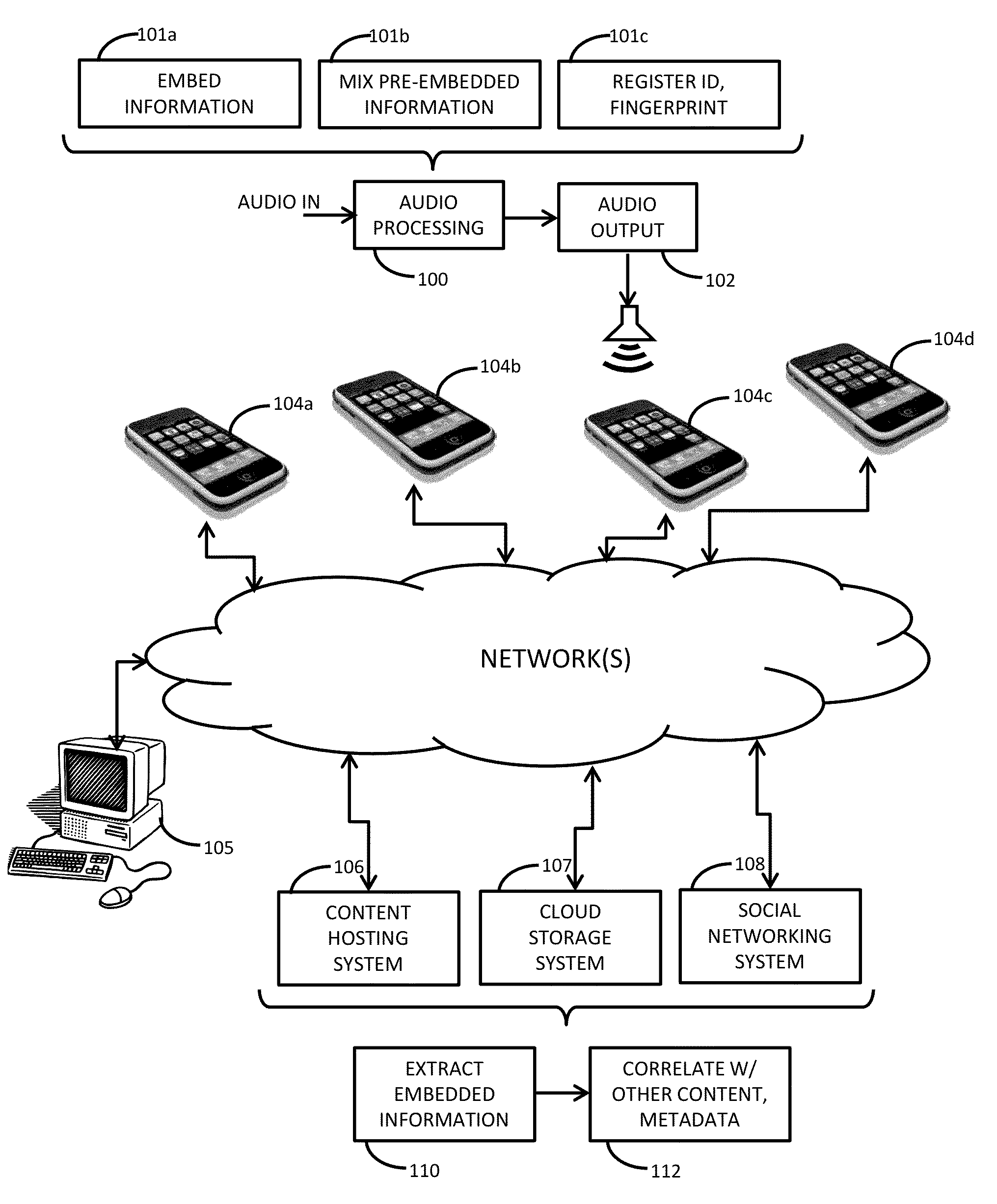
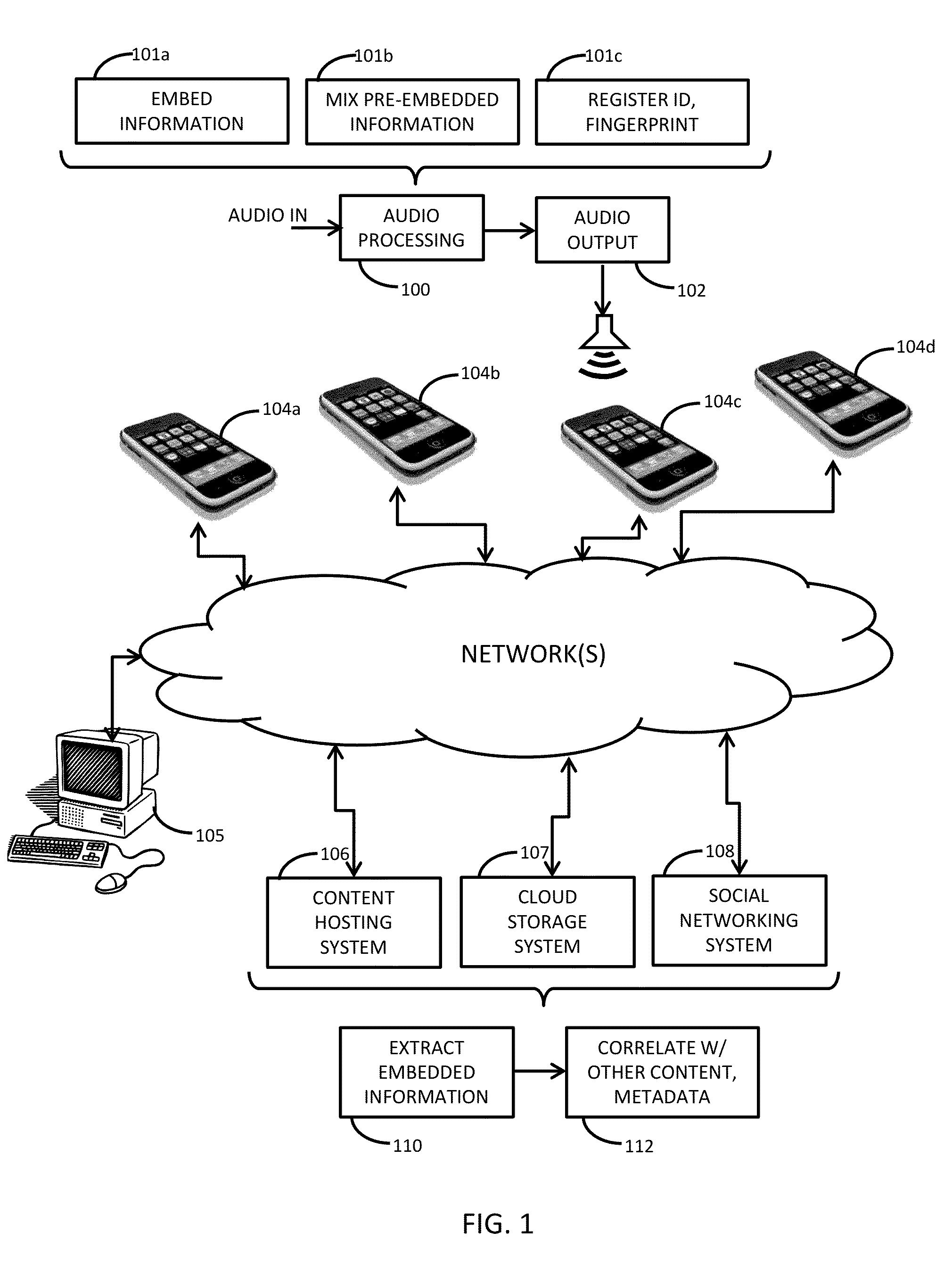
Watermarking and signal recognition for managing and sharing captured content, metadata discovery and related arrangements
ActiveUS20150016661A1Improve abilitiesIncrease influenceSpeech analysisCharacter and pattern recognitionMetadata discoveryMultimedia
Owner:DIGIMARC CORP
Method and apparatus for content-based image copy detection
InactiveUS7167574B2Digital data information retrievalCharacter and pattern recognitionComputerized systemCopy detection
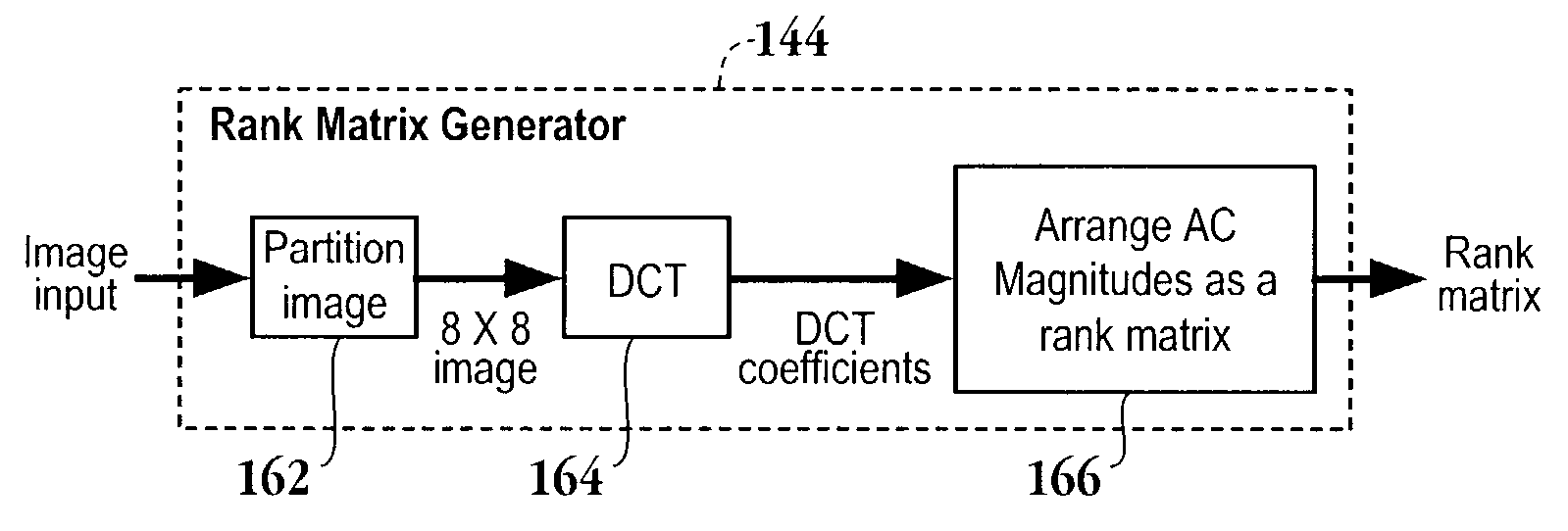
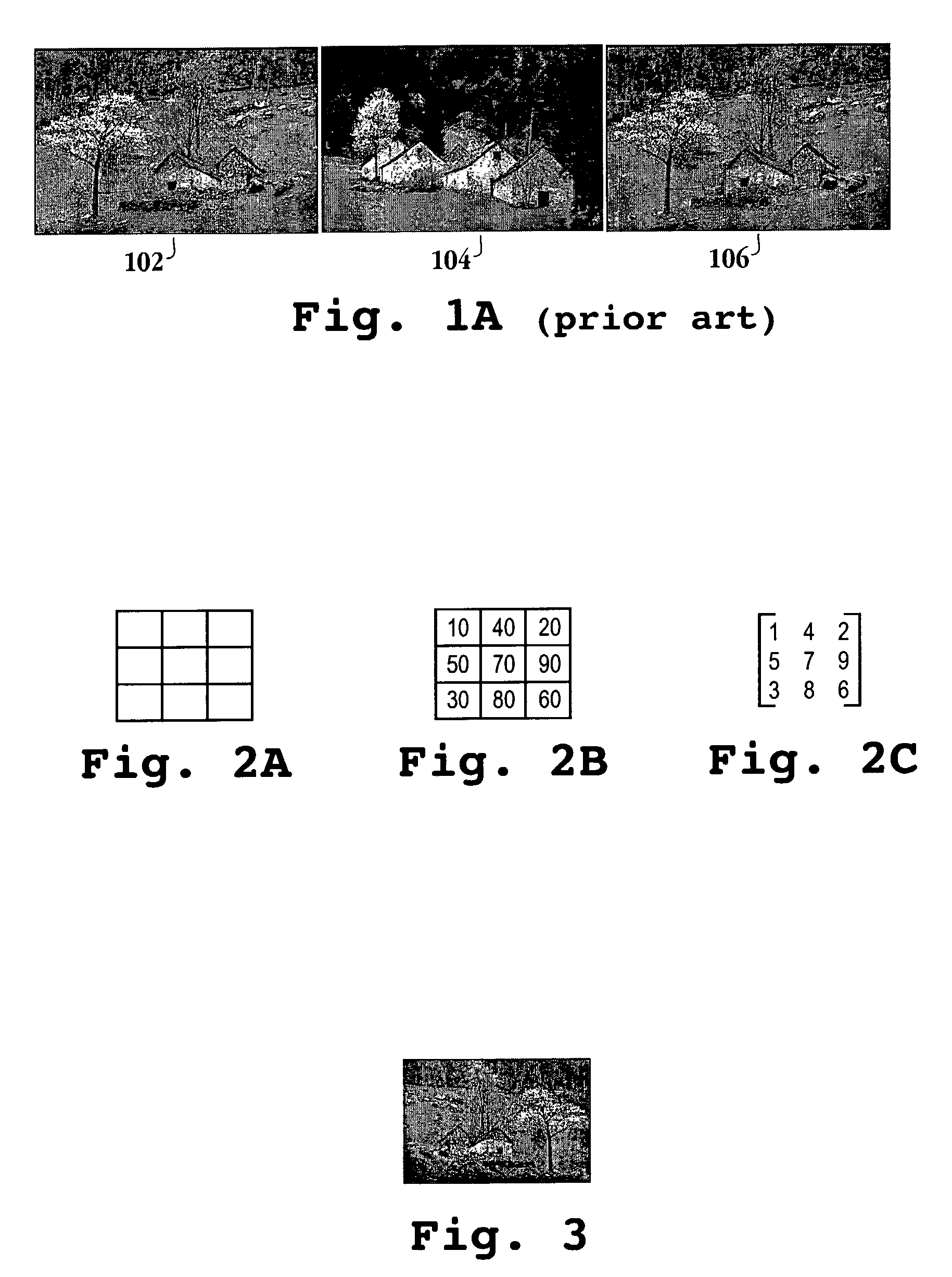
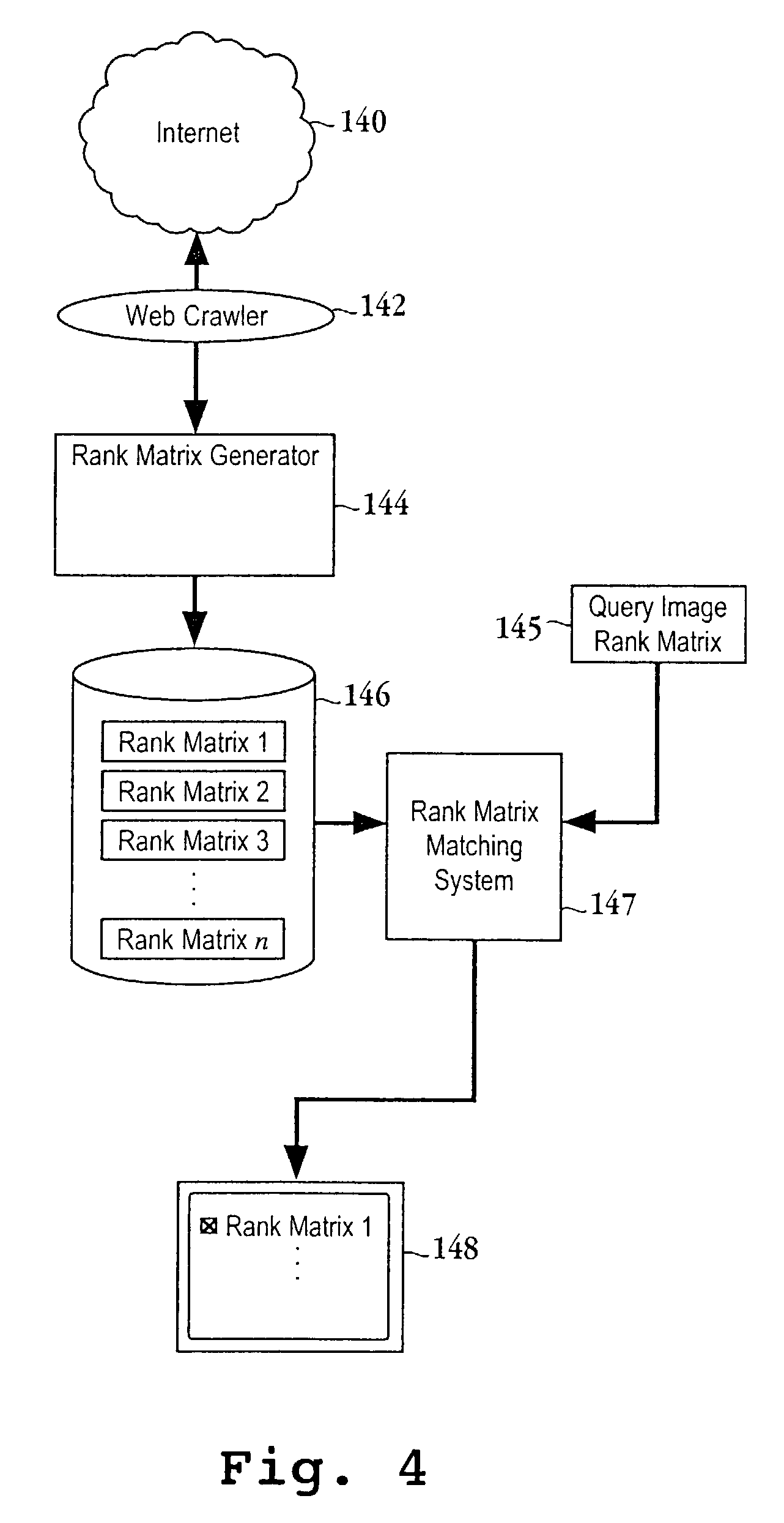
A method for detecting a copy of a digital image initiates with dividing a suspected copy of a digital image into sub-images. Then, the average intensities associated with each of the sub-images is determined. Next, the average intensities are transformed into a series of coefficients. Then, a rank matrix from the series of coefficients is defined. Next, the rank matrix from the series of coefficients is compared to a rank matrix of a query image to determine if the suspected copy is an actual copy of the digital image. A computer readable media, a computer system and computer code configured to be executed on a computer system are also provided.
Owner:SEIKO EPSON CORP
Embedding hidden auxiliary code signals in media
InactiveUS7003132B2Better pinpointEfficient and reliableTelevision system detailsRecord information storageGray levelImage signal
Methods for embedding and reading auxiliary messages from image signals use embedded code signals modulated with the auxiliary message. These embedded ode signals may be used to convey hidden tracking codes in images, video and printed objects. The embedded code signals are embedded by varying characteristics of the image signal, including, for example, gray-level, reflective properties, photo-reactive properties, etc.
Owner:DIGIMARC CORP
Apparatus and methods for improving detection of watermarks in content that has undergone a lossy transformation
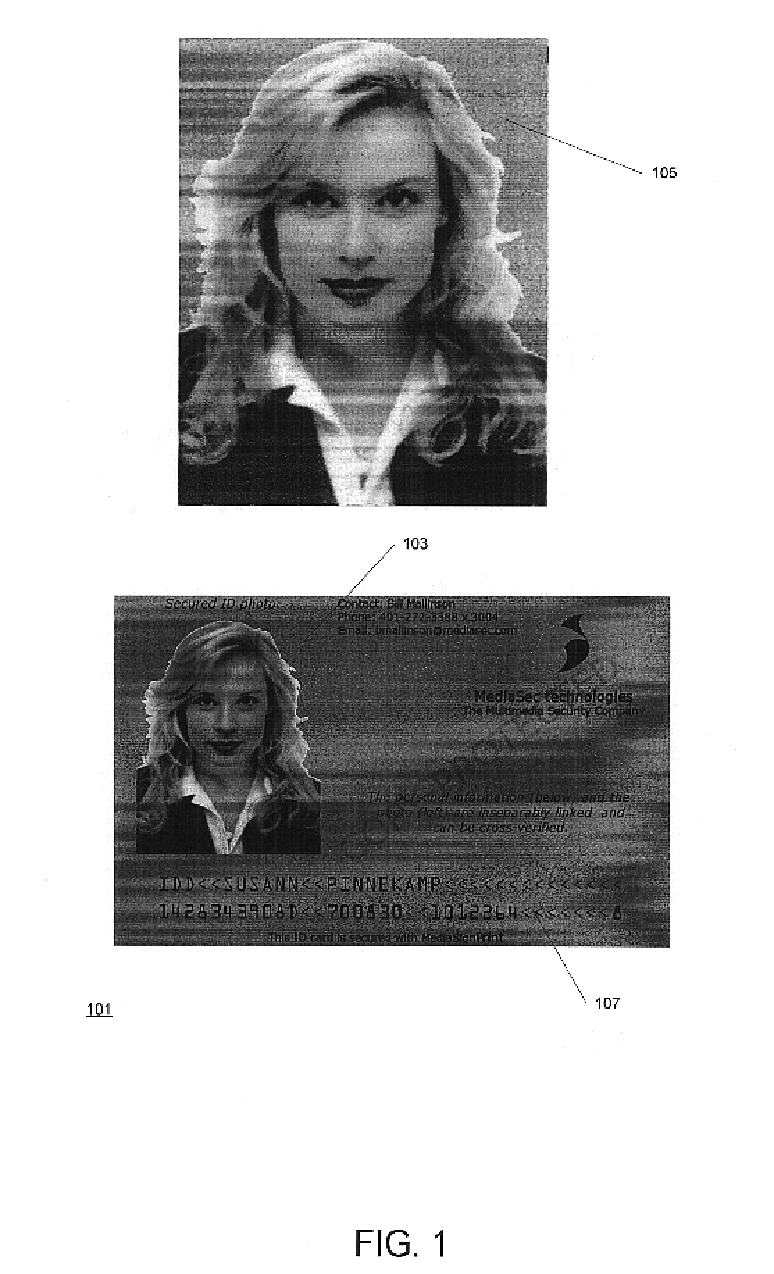
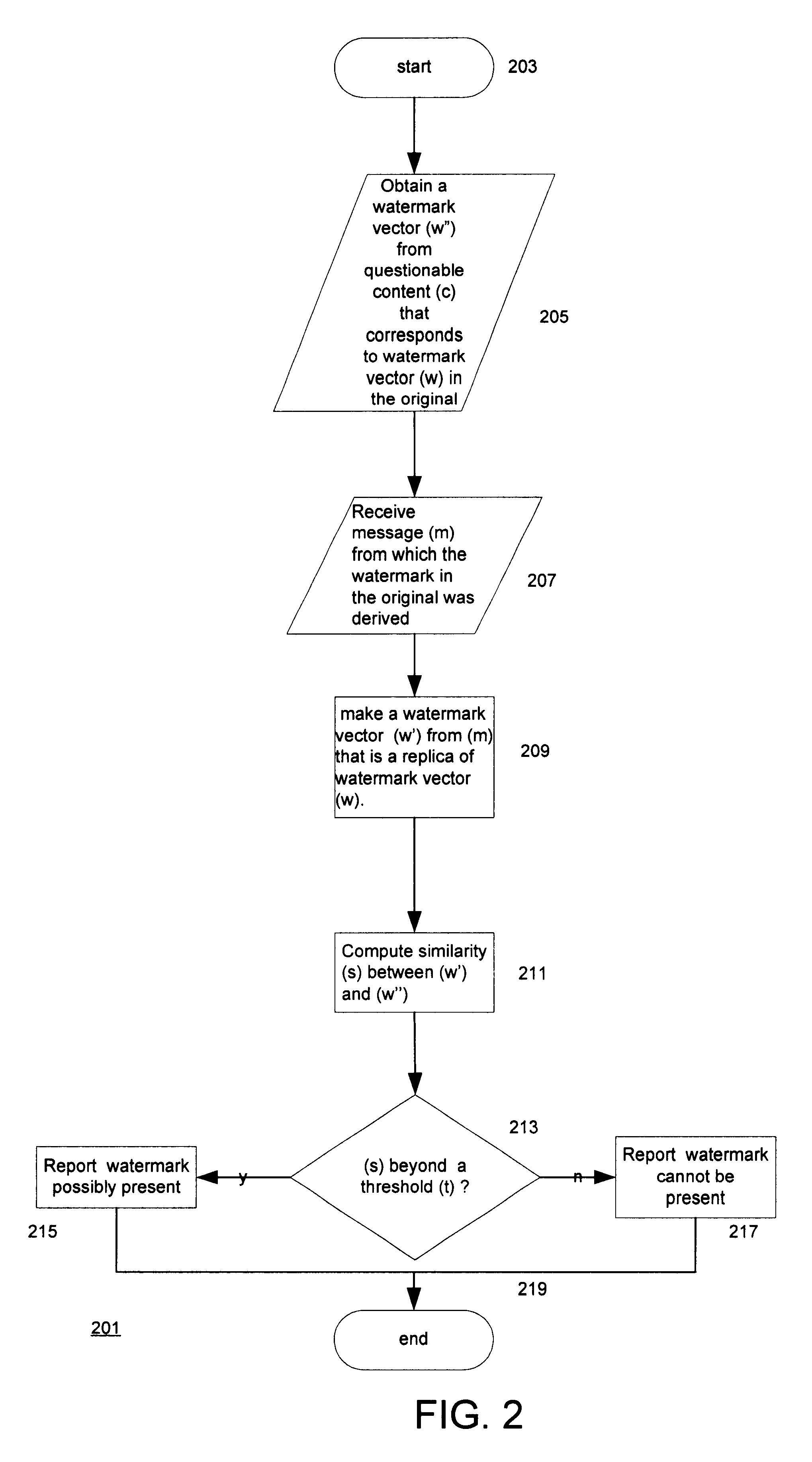
Techniques for improving detection of watermarks in content that has undergone a lossy transformation. One of the techniques is used when the message that is contained in a watermark belonging to a digital representation that is derived from an original watermarked digital representation cannot be decoded. The technique obtains information about the watermark by comparing the watermark vector for the watermark that cannot be decoded with a replica of the watermark vector from the original watermarked digital representation. The replica is made using the message. Depending on the degree of similarity, the watermark's presence and some of its characteristics may be determined. Another technique improves the robustness of watermarks that are used for authentication by employing a short (even single-bit) watermark vector to make the watermark and using the message needed for the authentication to determine where the watermark is located in the digital representation. Authentication of a digital representation is done by determining whether the watermark is present in the digital representation. In another technique, detection of the presence of a watermark is used to determine what areas of a digital representation have been subject to alteration. Techniques for synchronizing digital representations for watermark detection and other purposes include adding marks whose locations can be automatically detected only with the help of information that is external to the digital representation, such as a key, and adding marks to a sequence of digital representations and detecting the marks by summing the sequence.
Owner:THOMSON LICENSING SA
Salient Point-Based Arrangements
ActiveUS20120275642A1Increase operating spaceSimple processImage enhancementImage analysisTablet computerComputer graphics (images)
A variety of methods and systems involving sensor-equipped portable devices, such as smartphones and tablet computers, are described. One particular embodiment decodes a digital watermark from imagery captured by the device and, by reference to watermark payload data, obtains salient point data corresponding to an object depicted in the imagery. Other embodiments obtain salient point data for an object through use of other technologies (e.g., NFC chips). The salient point data enables the device to interact with the object in a spatially-dependent manner. Many other features and arrangements are also detailed.
Owner:DIGIMARC CORP
Method and system for digital watermarking
InactiveUS20060101269A1Improve fitMaximizing signal encoding levelUser identity/authority verificationSecret communicationComputer hardwareDigital watermarking
A method for applying a digital watermark to a content signal is disclosed. In accordance with such a method, a watermarking key is identified. The watermarking key includes a binary sequence and information describing application of that binary sequence to the content signal. The digital watermark is then encoded within the content signal at one or more locations determined by the watermarking key.
Owner:WISTARIA TRADING INC
Optimization methods for the insertion, protection, and detection of digital watermarks in digitized data
InactiveUS7095874B2User identity/authority verificationCharacter and pattern recognitionMaximum levelWaveform shaping
The implementations of digital watermarks can be optimally suited to particular transmission, distribution and storage mediums given the nature of digitally-sampled audio, video and other multimedia works. Watermark application parameters can be adapted to the individual characteristics of a given digital sample stream. Watermark information can be either carried in individual samples or in relationships between multiple samples, such as in a waveform shape. More optimal models may be obtained to design watermark systems that are tamper-resistant given the number and breadth of existent digitized sample options with different frequency and time components. The highest quality of a given content signal may be maintained as it is mastered, with the watermark suitably hidden, taking into account usage of digital filters and error correction. The quality of the underlying content signals can be used to identify and highlight advantageous locations for the insertion of digital watermarks. The watermark is integrated as closely as possible to the content signal, at a maximum level to force degradation of the content signal when attempts are made to remove the watermarks.
Owner:WISTARIA TRADING INC
Authentication of identification documents and banknotes
InactiveUS7239734B2Electric signal transmission systemsDigital data processing detailsElectronic documentDocumentation procedure
The present invention provides methods and systems that are helpful authentication of physical and electronic documents like financial documents and identification documents. Steganographic indicia plays a role in some of our implementations. In other implementations we bind design features to a user or to a document. In still other implementations we provide authentication methods to evaluate security documents.
Owner:DIGIMARC CORP
Watermark encoding using arbitrary features
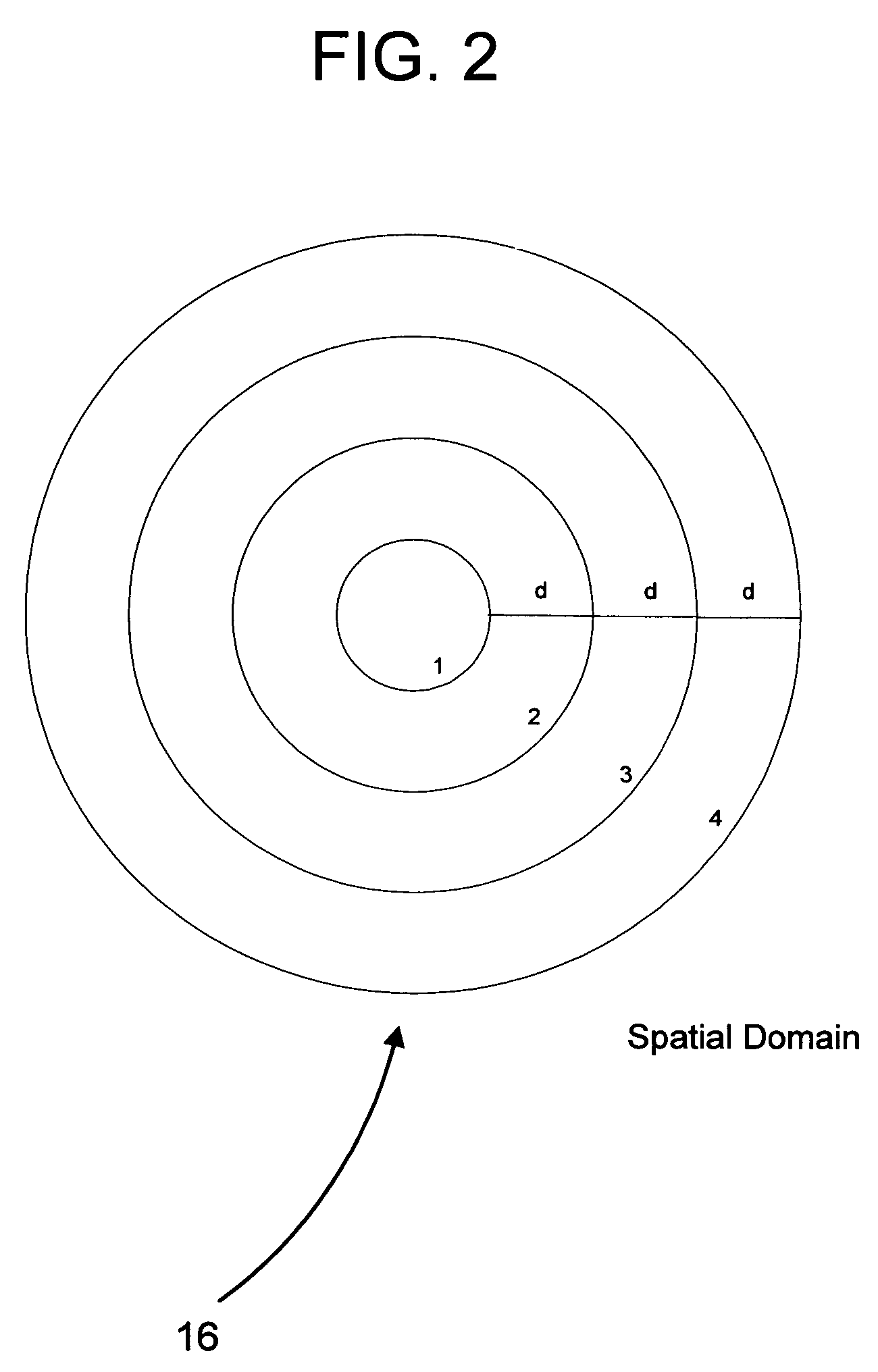
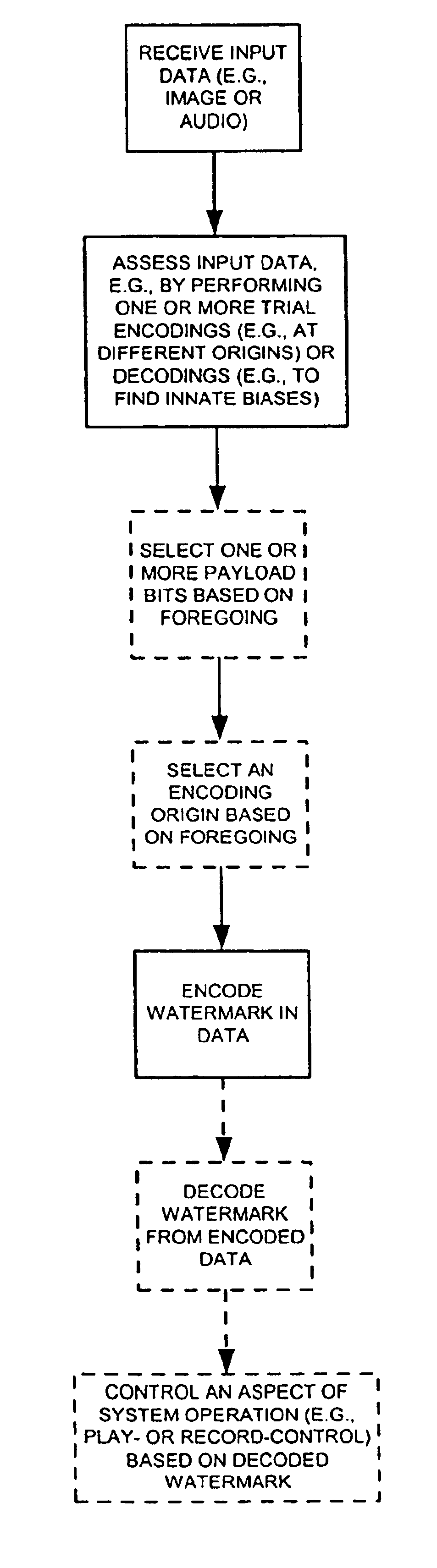
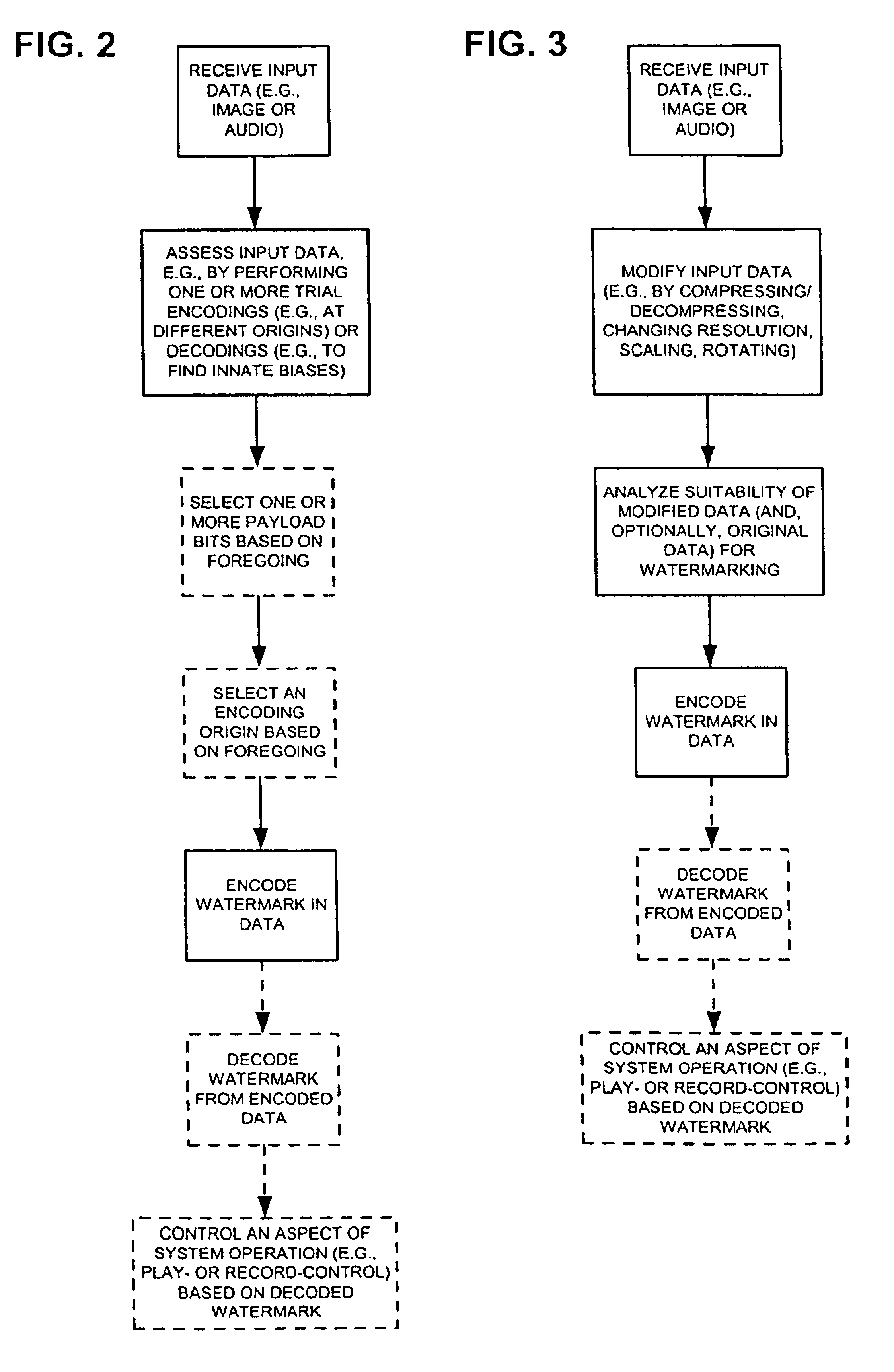
Watermark detection in an image or the like is optimized by exploiting the innate biases in the image to emphasize the watermark signal. The watermark signal can be trial-located with different origins in the image to find one that yields improved results. Similarly, the image can be processed (e.g., by changing resolution, rotation, or compression) so as to change the innate biases to better reinforce the watermark signal. Compression of an image can be done in accordance with a desired watermark signal, with the compressor deciding which image components to retain and which to discard based, in part, on a watermark signal that is to be encoded (or maintained) in the image.
Owner:DIGIMARC CORP
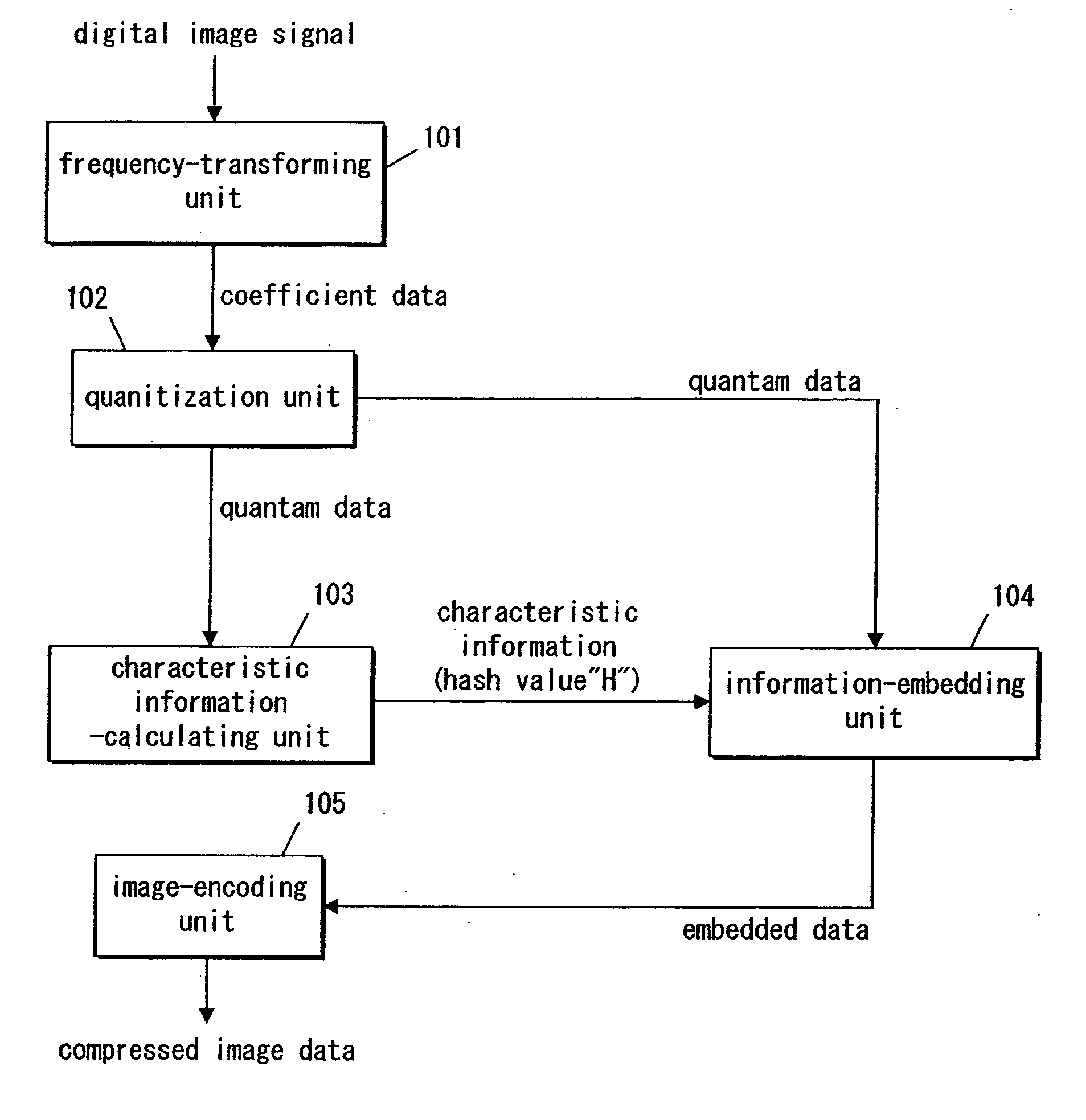
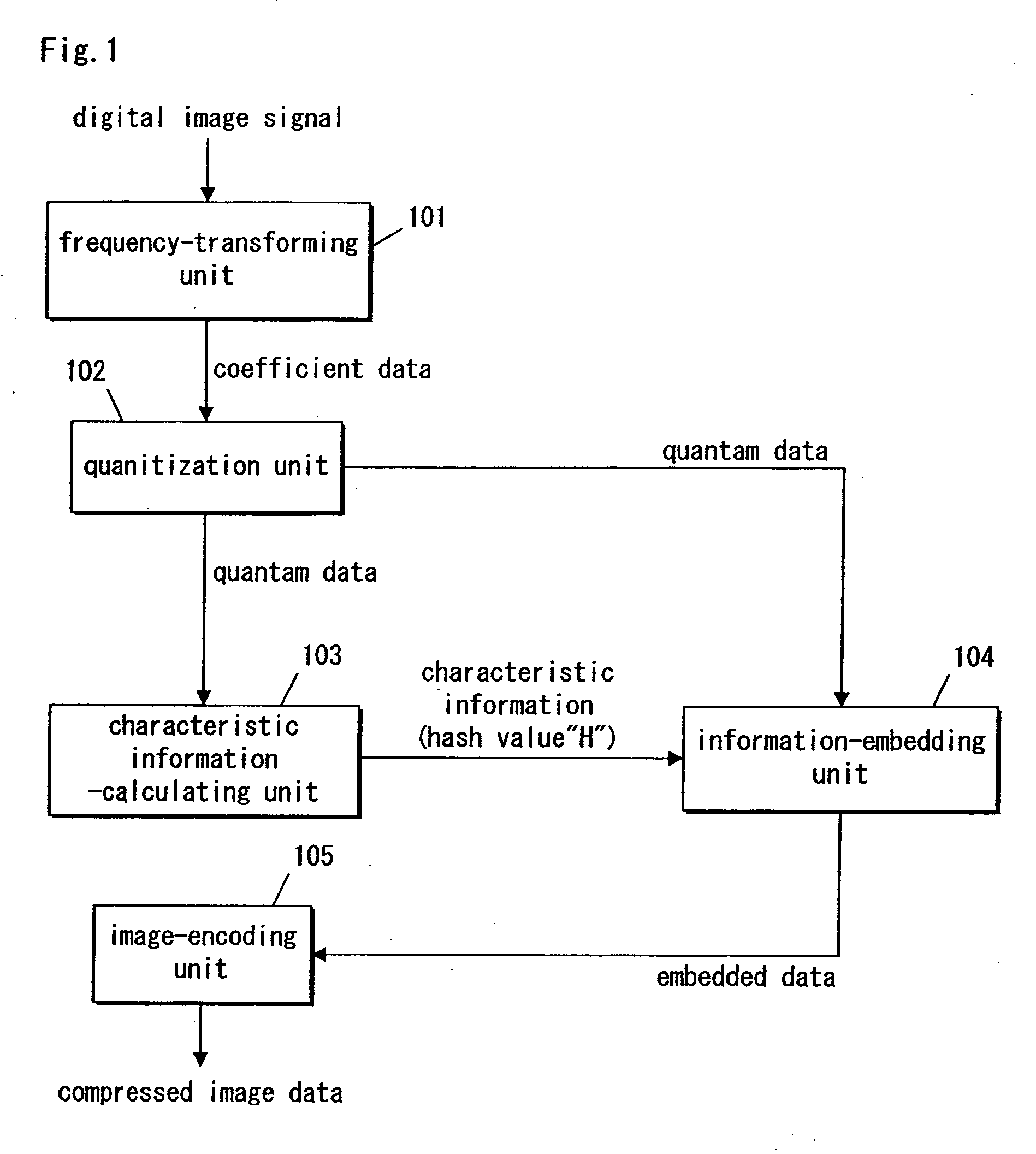
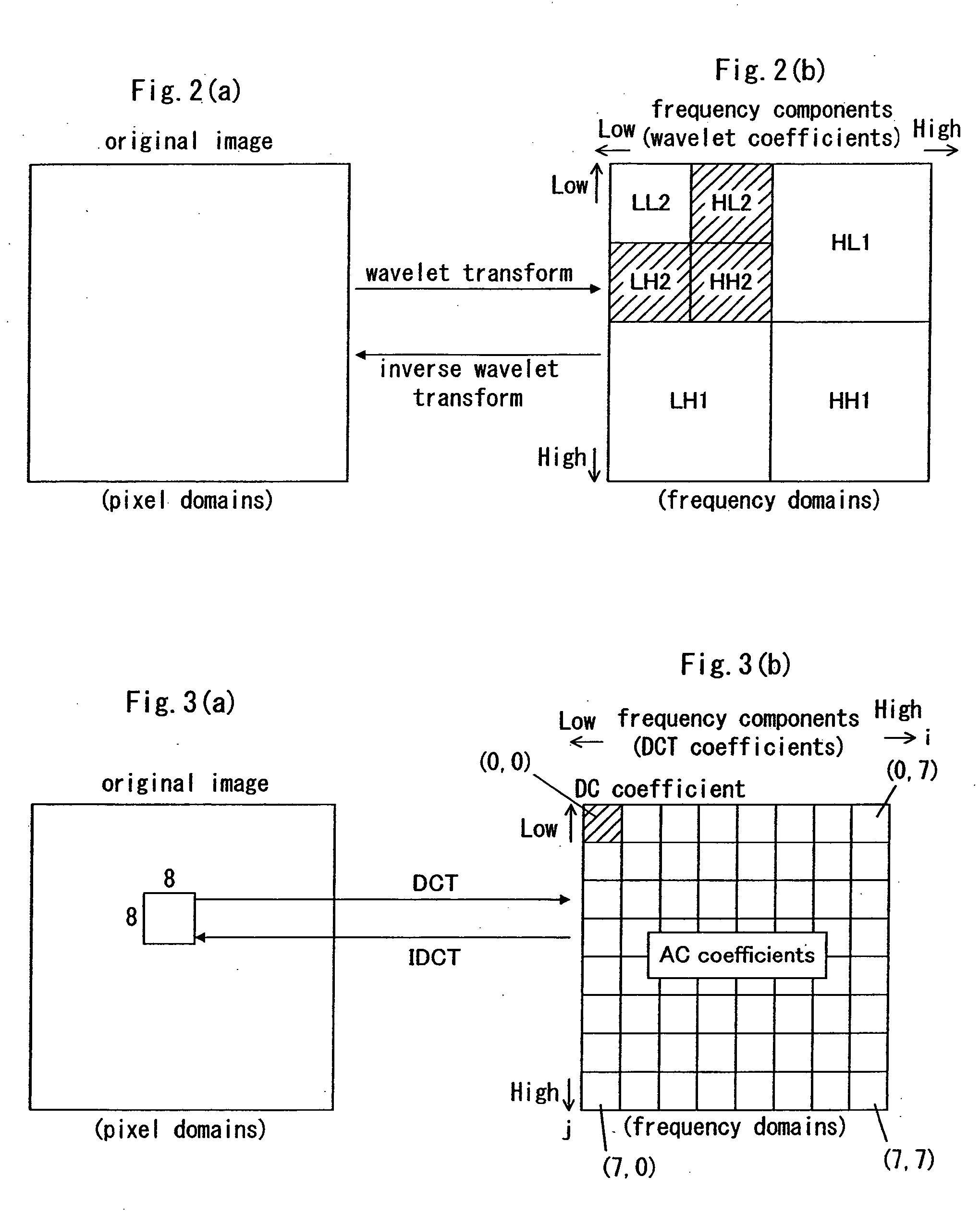
Information-embedding apparatus, encoder, tamper-detecting apparatus, information-embedding method, tamper-detecting method, and recording medium having program recorded therein for executing both of the methods
InactiveUS20060013488A1Possible to detectEliminate needCharacter and pattern recognitionImage watermarkingInformation embeddingDigital image
A digital image signal is transformed in frequency, thereby providing partitioned frequency components. Characteristic information is calculated in accordance with a coefficient at a first frequency domain that is selected from among the partitioned frequency components. A coefficient at a second frequency domain is handled in accordance with predetermined rules, thereby embedding the characteristic information into the coefficient at the second frequency domain. The second frequency domain is selected from among areas that differ from the first frequency domain. The frequency coefficients that exhibit several frequency components are encoded in a predetermined manner, thereby producing compressed image data.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Z-transform implementation of digital watermarks
InactiveUS6853726B1Public key for secure communicationUser identity/authority verificationCarrier signalData encoding
Z-transform calculations may be used to encode (and / or decode) carrier signal independent data (e.g., digital watermarks) to a digital sample stream. Deterministic and non-deterministic components of a digital sample stream signal may be analyzed for the purposes of encoding carrier signal independent data to the digital sample stream. The carrier signal independent data may be encoded in a manner such that it is restricted or concentrated primarily in the non-deterministic signal components of the carrier signal. The signal components can include a discrete series of digital samples and / or a discreet series of carrier frequency sub-bands of the carrier signal. Z-transform calculations may be used to measure a desirability of particular locations and a sample stream in which to encode the carrier signal independent data.
Owner:WISTARIA TRADING INC
Apparatus and method for watermarking a digital image
InactiveUS20020191810A1Minimizing introductionTelevision system detailsUser identity/authority verificationComputer hardwareDigital image
An apparatus for adding a watermark to a moving image as it is displayed comprises a watermark generator in which data representing a watermark is generated. The watermark contains at least one of location data and time data pertaining to the displaying of the moving image. The location and time data is protected by forward error encoding. The watermark also contains at least one of program data identifying the moving image and frame data unique in identifying each frame of the moving image. The program and time data is protected by scrambling. A watermark applicator applies the watermark data to image data representing substantially all of the moving image depending on a characteristic, such as amplitude, of the data.
Owner:QUALCOMM INC
Character and vector graphics watermark for structured electronic documents security
ActiveUS20060075241A1Reasonable data-hiding rateIncrease chanceUser identity/authority verificationDigital data protectionDocumentation procedurePaper document
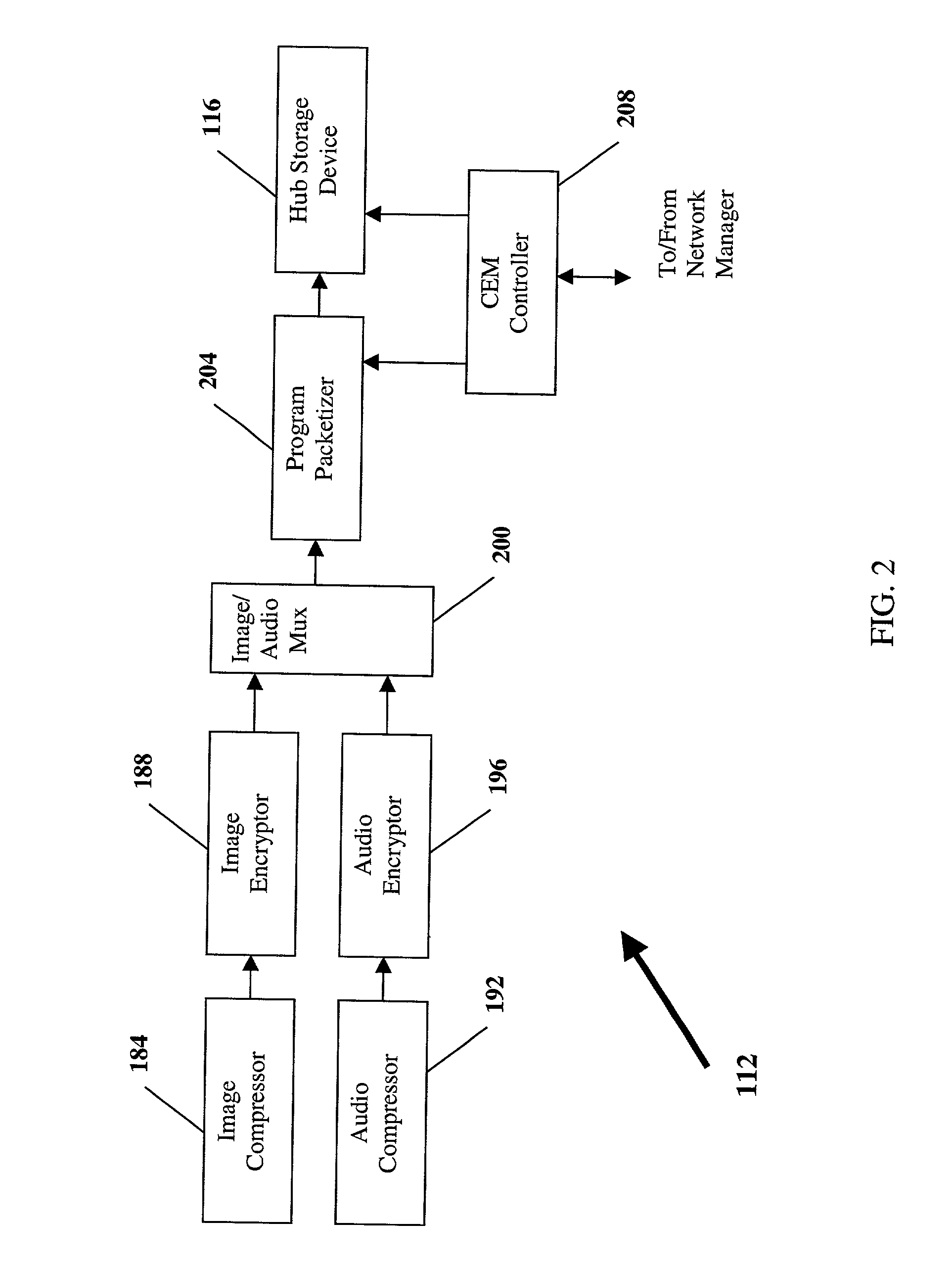
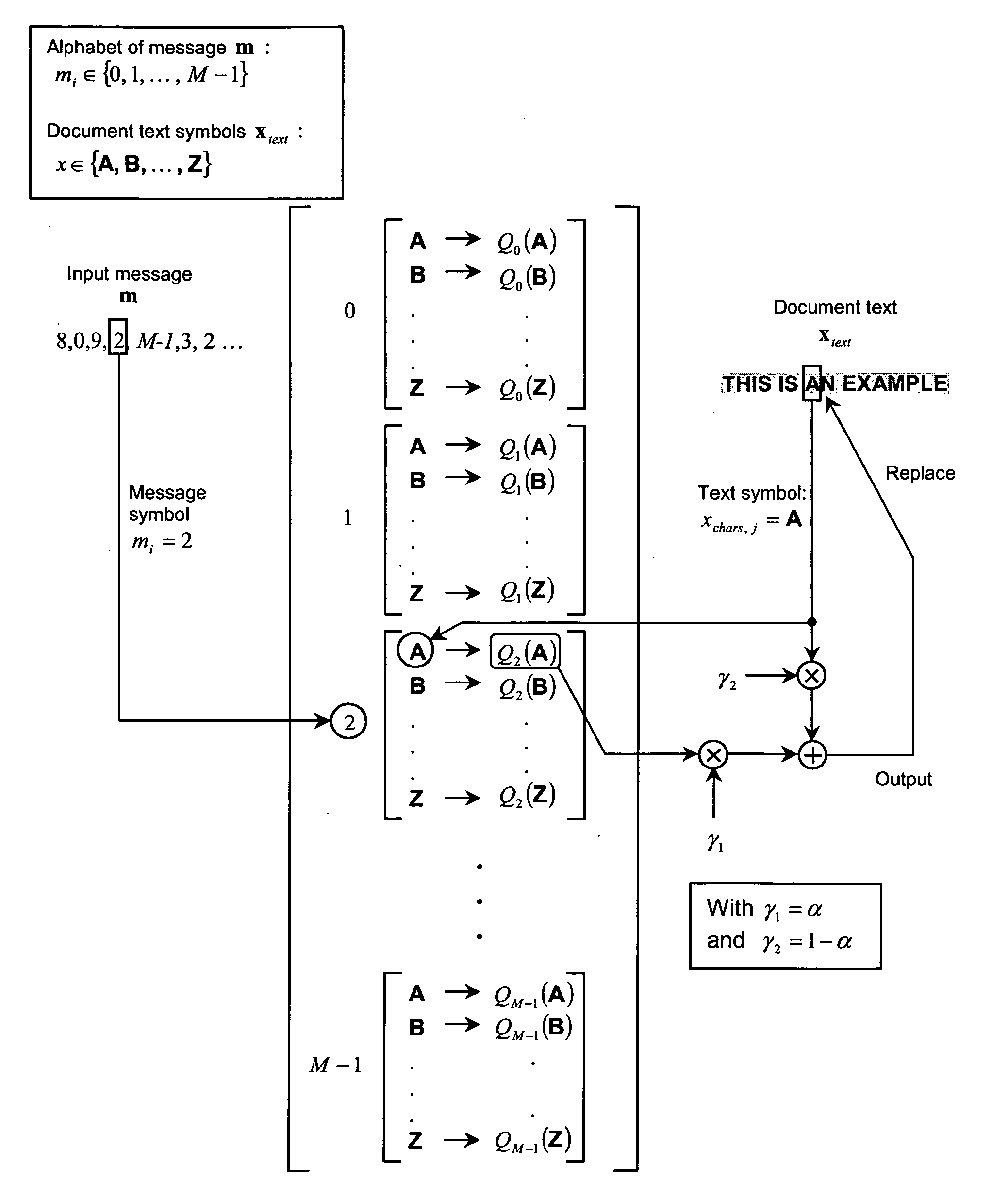
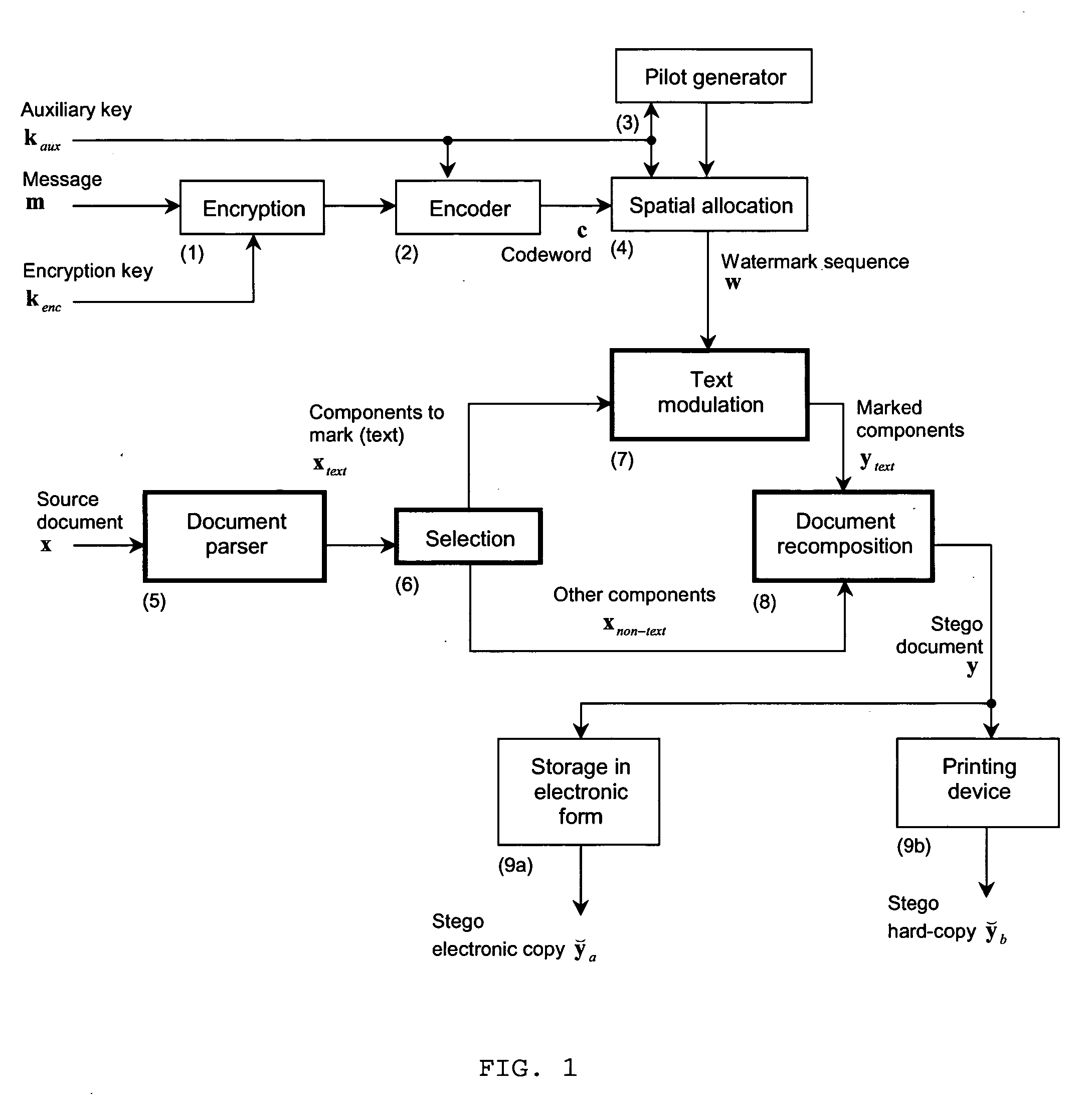
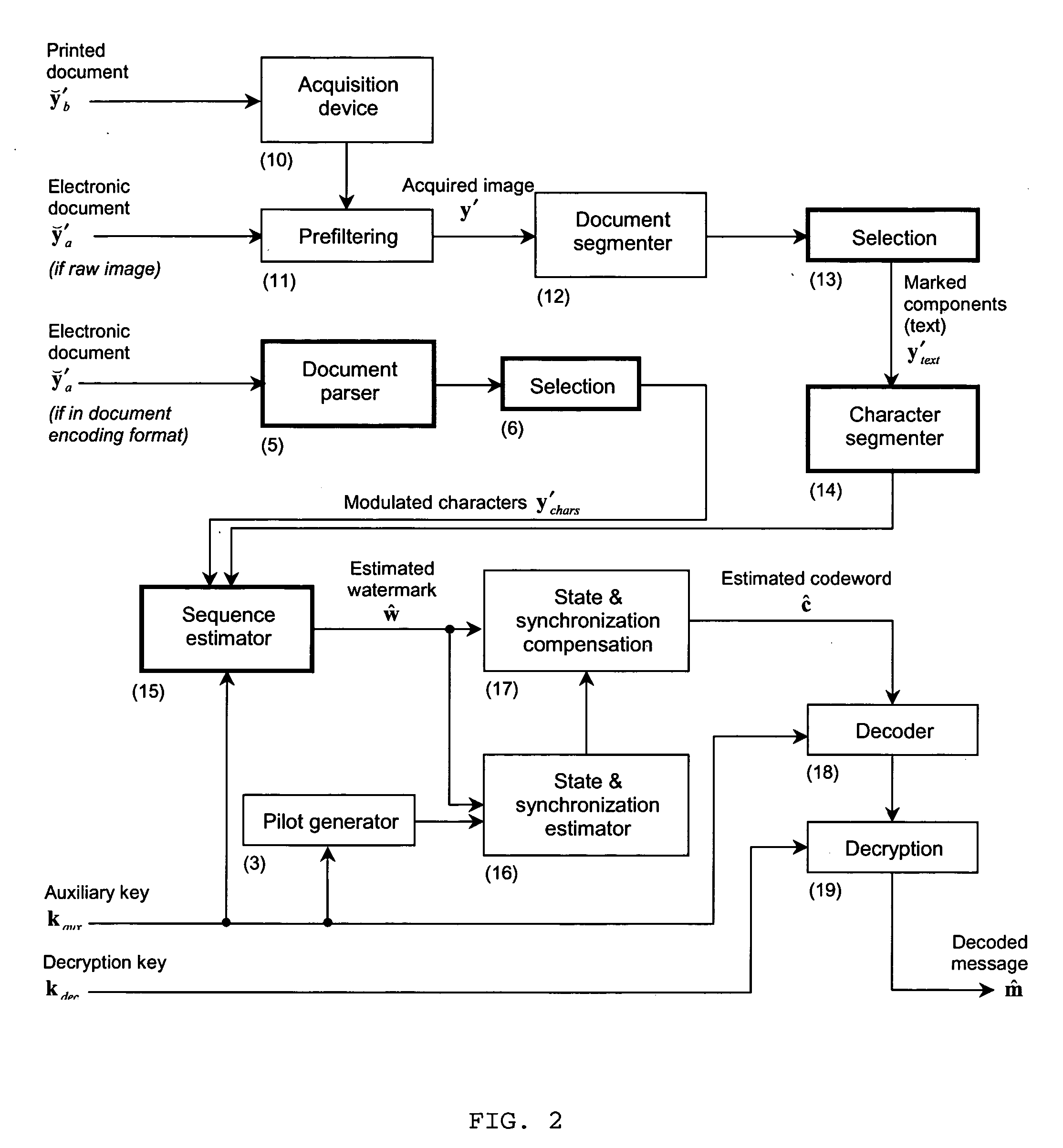
The present invention is a method and apparatus for watermarking text or vector graphics documents. It is based on character-wise or vector graphics element-wise grayscale or color modulation. At high resolution, halftone or dither modulation can also be used in addition or in place of grayscale / color modulation, for printed representation of electronic document. For the detection, the document is acquired through an acquisition device, document segmentation is performed, characters / elements are segmented, the watermark signal is estimated and the information is decoded. Although the proposed scheme mostly addresses the watermarking of hard-copy documents, it can easily be integrated into electronic document editing and acquisition tools, and the watermark is attached to the document electronic version. The invention is applicable either using expensive high- resolution printing and acquisition devices, either using common cheap low-resolution devices, depending on the application needs. The proposed scheme is suitable for example to the protection of security documents, contracts, technical and commercial documentation; it can use any physical support like paper, cellulose, or plastic; it can be used for copy protection, authentication, or tamper proofing; finally it can also be applied to other non security-related applications, such as document tracking, as well as document embedded annotation and watermarked-assisted automatic processing.
Owner:UNIVERSITY OF GENEVA +1
Methods and systems for steganographic processing
InactiveUS7184570B2Easy to recordEfficient and reliableTelevision system detailsUser identity/authority verificationAuthorizationElectronic content
Electronic content data that is copied without authorization can be traced back to its source using steganographically encoded information. Such arrangements are useful, e.g., where electronic content is rendered to an audience—one of whom may be making an illicit recording. In such embodiments, the encoding may be performed as the content is made available to the consumer, e.g., allowing data identifying time and place of rendering to be encoded. The specification details a variety of other steganographic techniques and applications, including conveying different messages using different parts of an image, and conveying record control information with electronic content.
Owner:DIGIMARC CORP
Steganographic encoding and decoding of auxiliary codes in media signals
InactiveUS20060062386A1Accurate recoveryTelevision system detailsPaper-money testing devicesVIT signalsAudio signal
Owner:DIGIMARC CORP
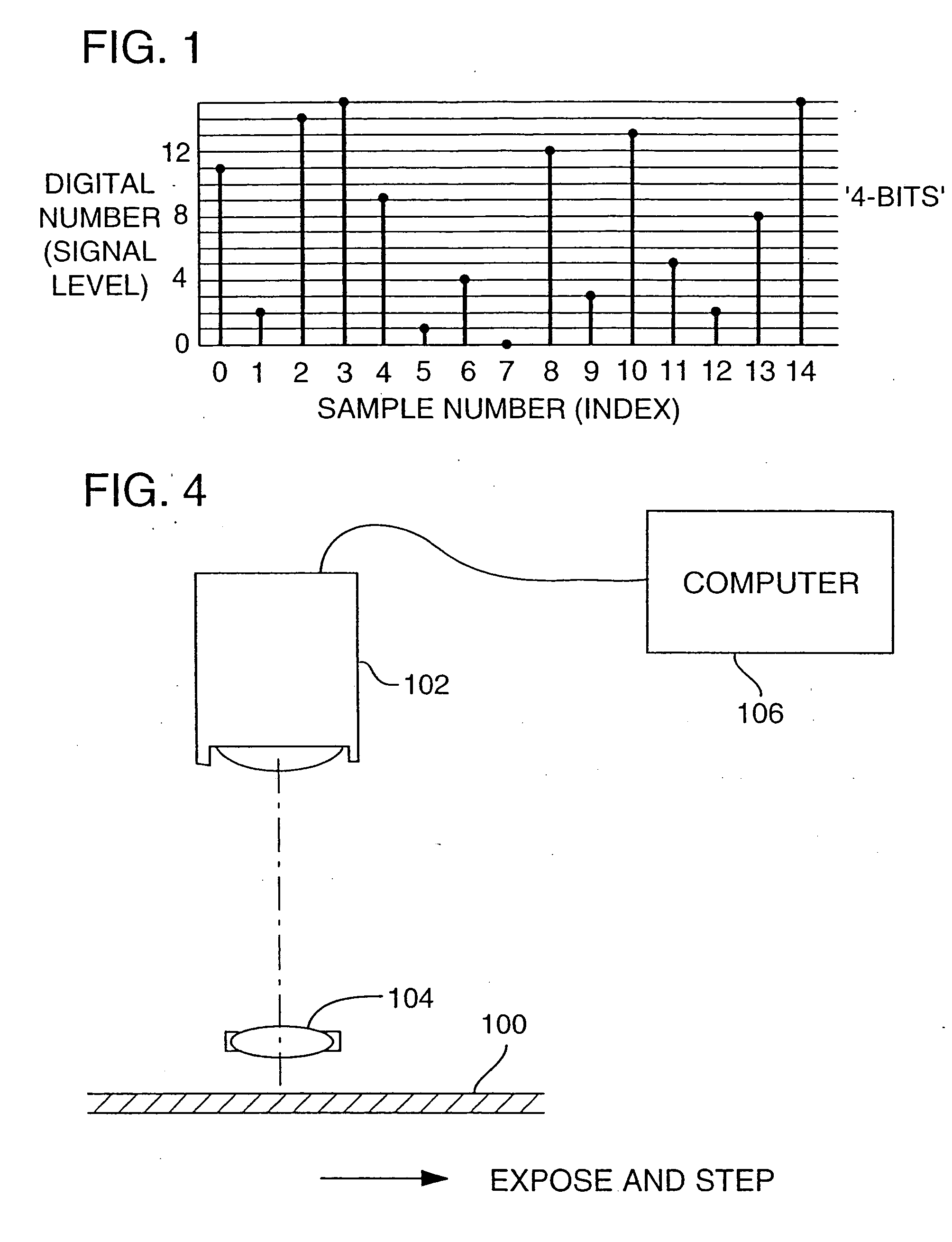
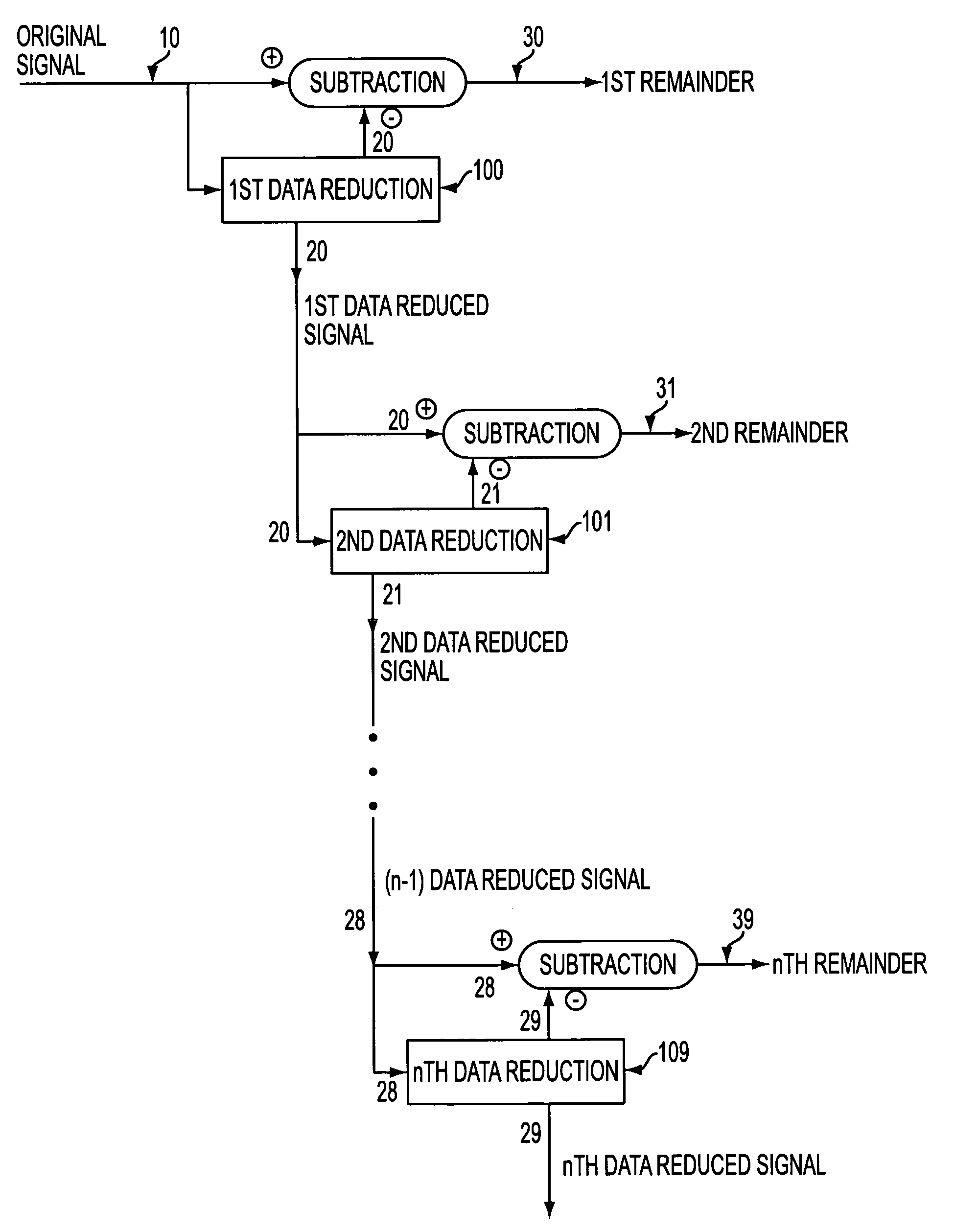
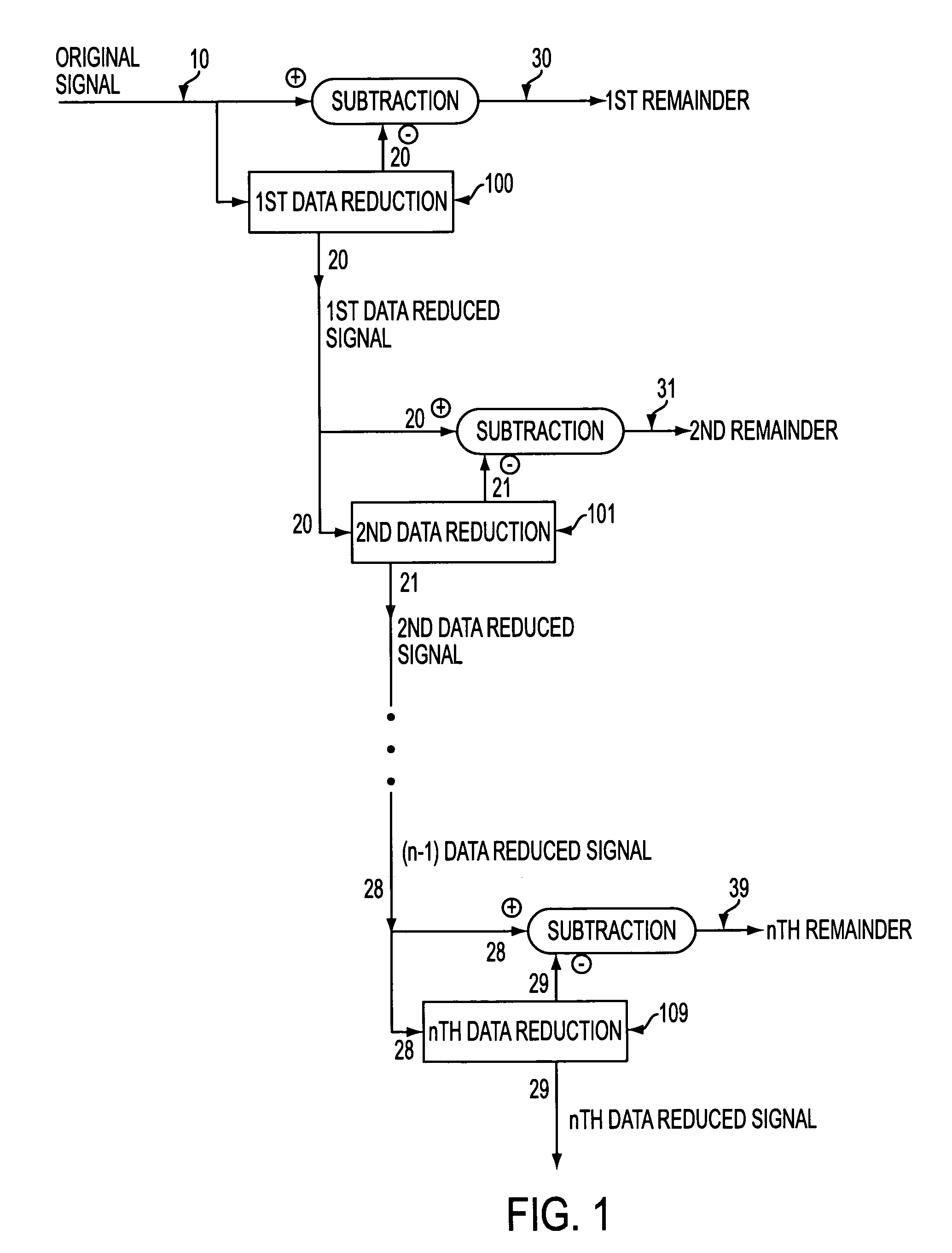
Utilizing data reduction in stegnographic and cryptographic systems
ActiveUS7123718B1Improve securitySafe formMultiple keys/algorithms usageUser identity/authority verificationSecret codeData signal
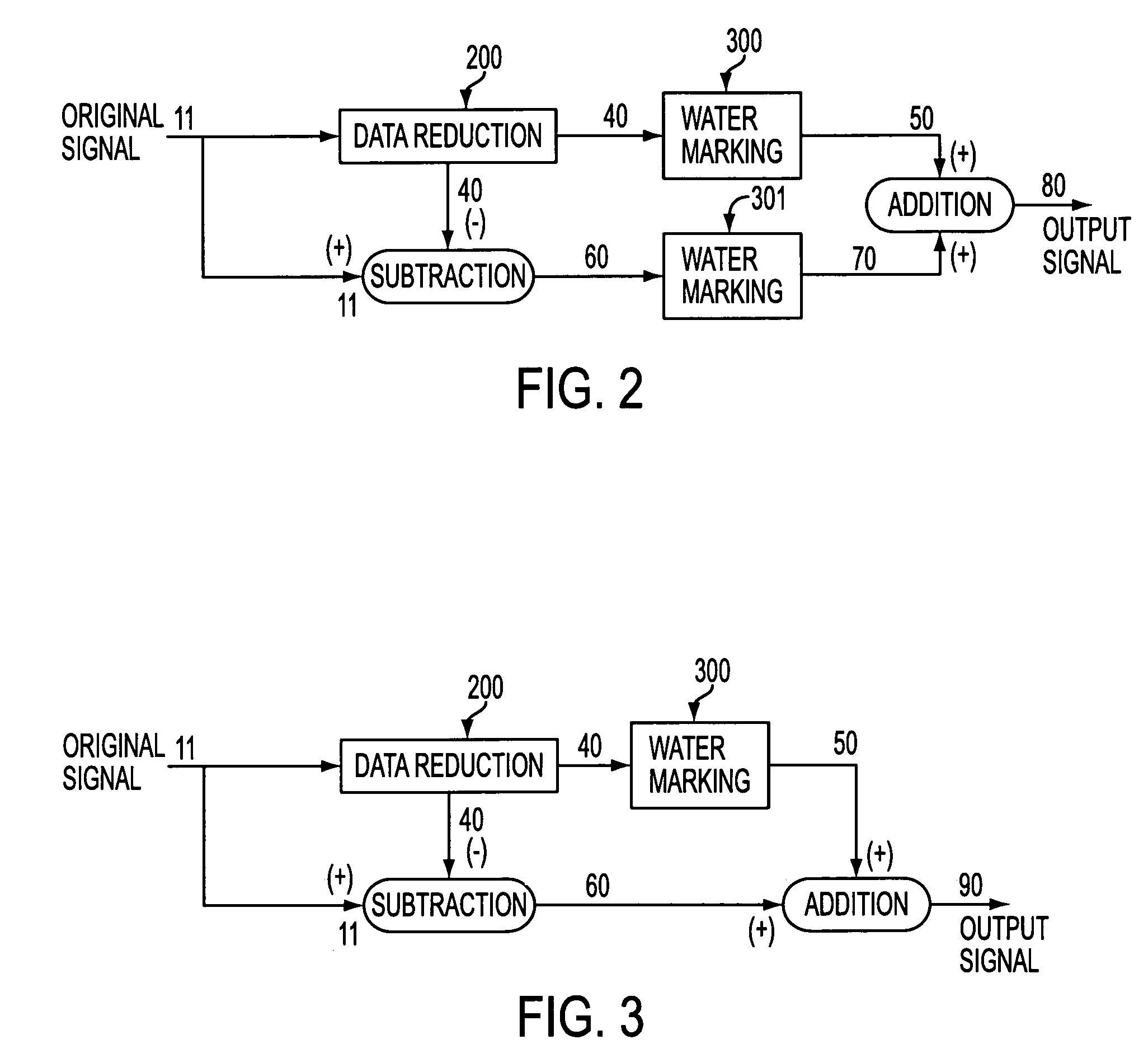
The present invention relates to methods for protecting a data signal using the following techniques: applying a data reduction technique to reduce the data signal into a reduced data signal; subtracting the reduced data signal from the data signal to produce a remainder signal; embedding a first watermark into the reduced data signal to produce a watermarked, reduced data signal; and adding the watermarked, reduced data signal to the remainder signal to produce an output signal. A second watermark may be embedded into the remainder signal before the final addition step. Further, cryptographic techniques may be used to encrypt the reduced data signals and to encrypt the remainder signals before the final addition step. The present invention also relates to systems for securing a data signal. Such systems may include computer devices for applying a data reduction technique to reduce the data signal into a reduced data signal and means to subtract the reduced data signal from the data signal to produce a remainder signal. Such systems may include means to apply a first cryptographic technique to encrypt the reduced data signal to produce an encrypted, reduced data signal and means to apply a second cryptographic technique to encrypt the remainder signal to produce an encrypted remainder signal; and means to add the encrypted, reduced data signal to the encrypted remainder signal to produce an output signal.
Owner:WISTARIA TRADING INC
Systems and methods for embedding media forensic identification markings
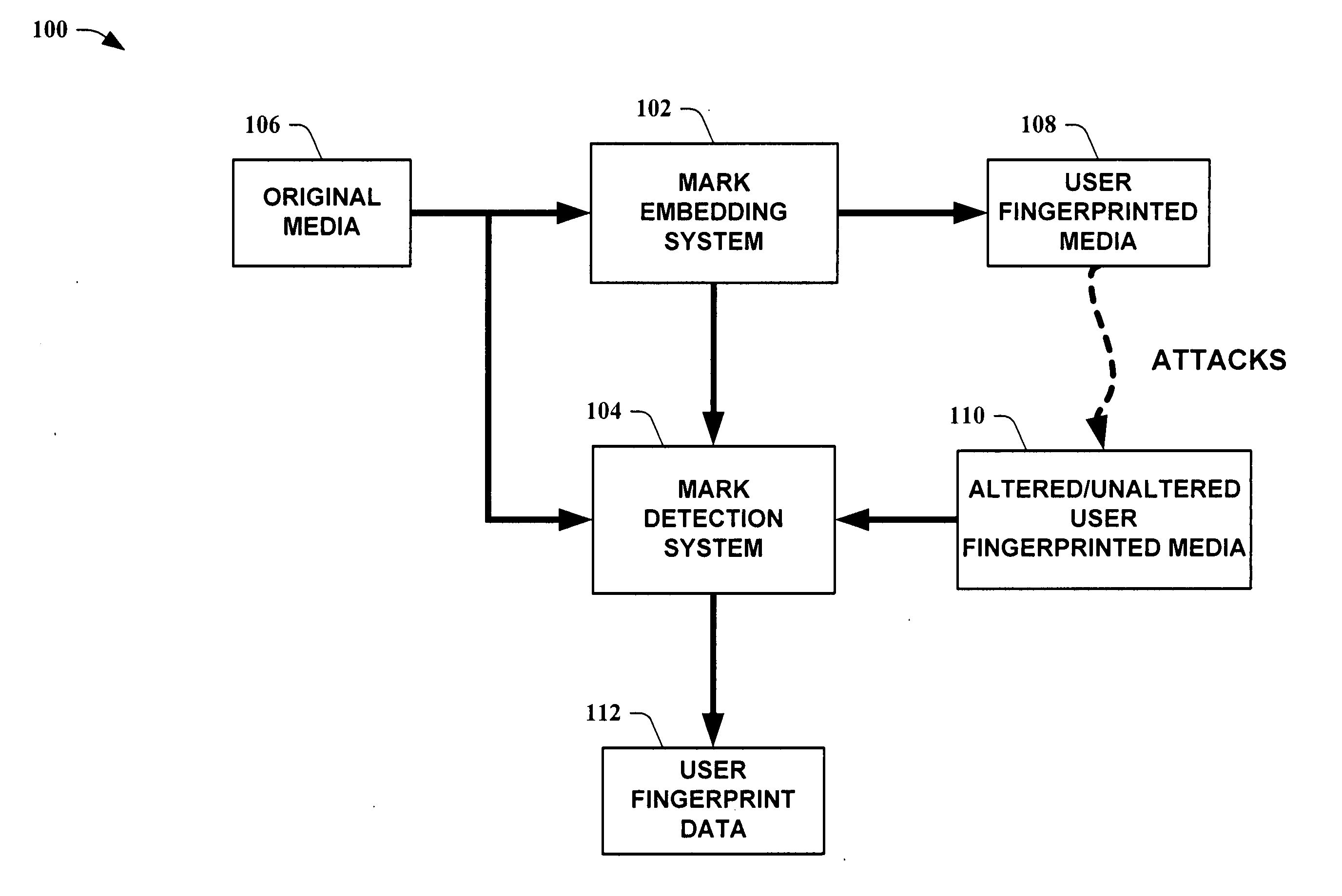
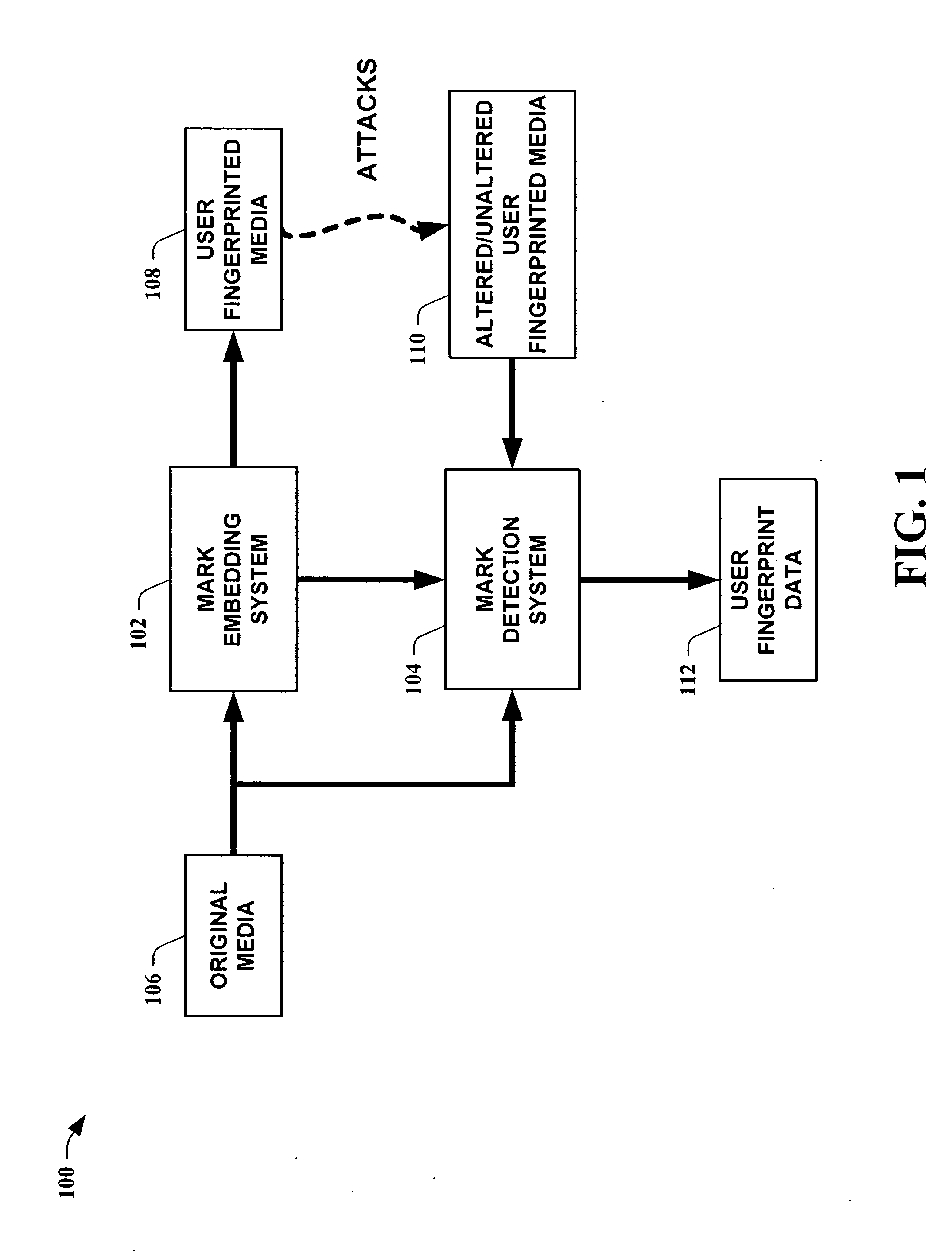
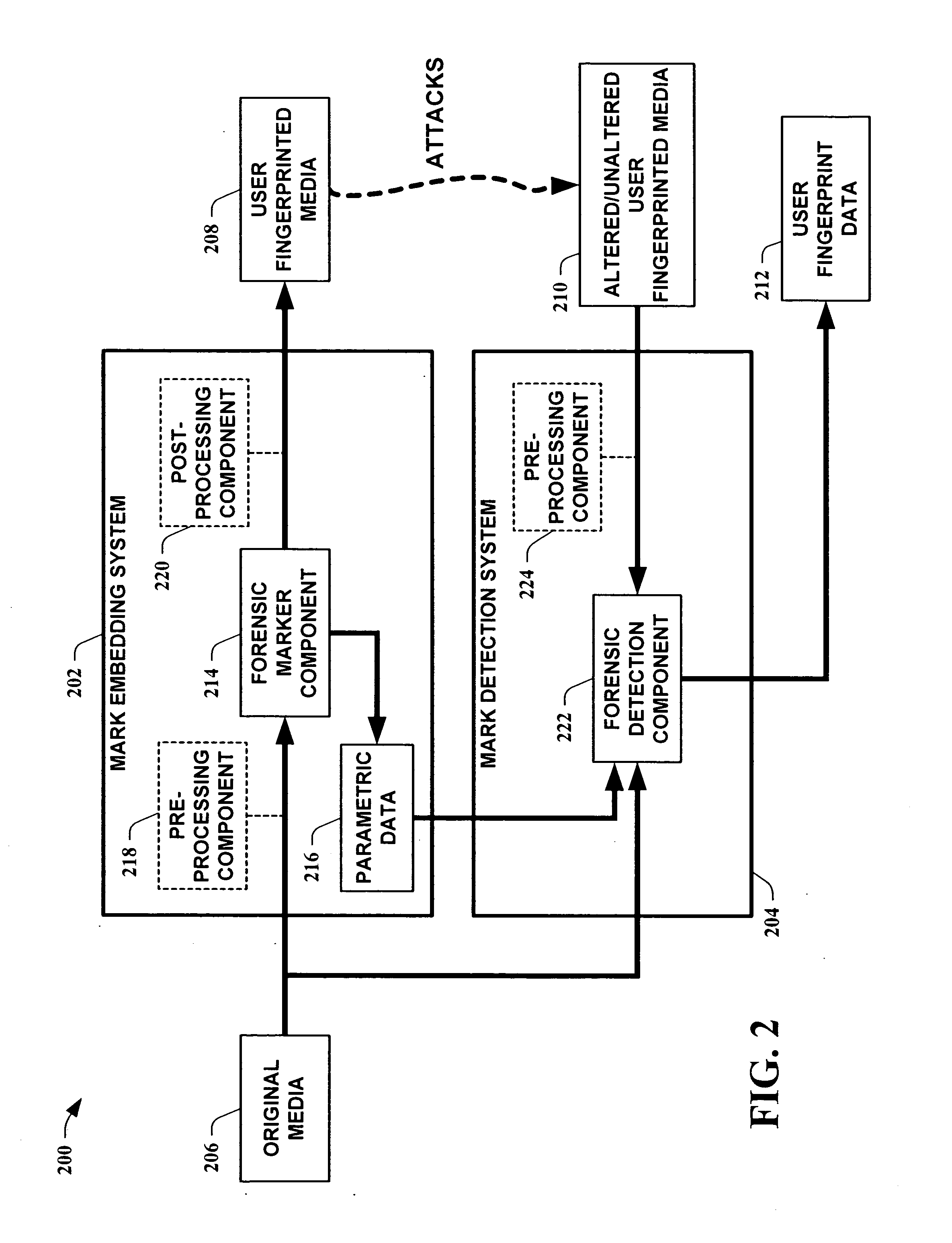
InactiveUS20050154892A1Improve certaintySimilar quantized statisticsUser identity/authority verificationCharacter and pattern recognitionDegree of certaintyForensic identification
The present invention leverages a series of media watermark locations to provide information relating to media ownership and / or distribution source. This provides a forensic means to establish a source of media with a high degree of certainty despite malicious and / or non-malicious attacks. By providing embedded user unique identification, a source of copied media can be determined without the embedded information substantially interfering with the intended purpose of the media itself. In one instance of the present invention, digital media is transformed into an N-dimensional media signal. User unique keys are then utilized along with a master key to determine locations for embedding a watermark signal that possesses substantially similar quantized statistics as the transformed media signal. The watermark signal is then embedded into the media signal, fingerprinting the media.
Owner:MICROSOFT TECH LICENSING LLC
Variable message coding protocols for encoding auxiliary data in media signals
InactiveUS7412072B2Character and pattern recognitionImage watermarkingComputer hardwareCODE protocol
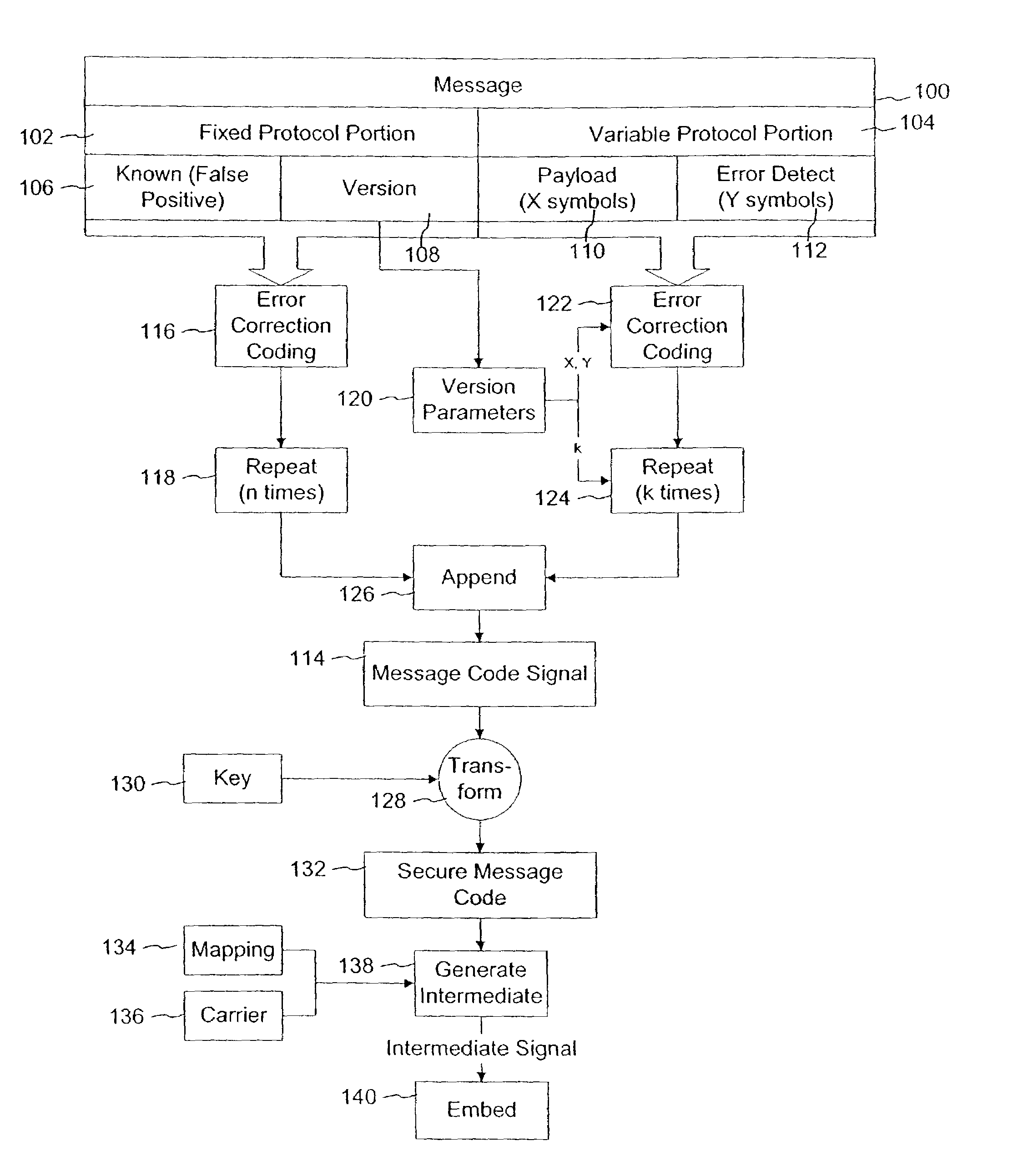
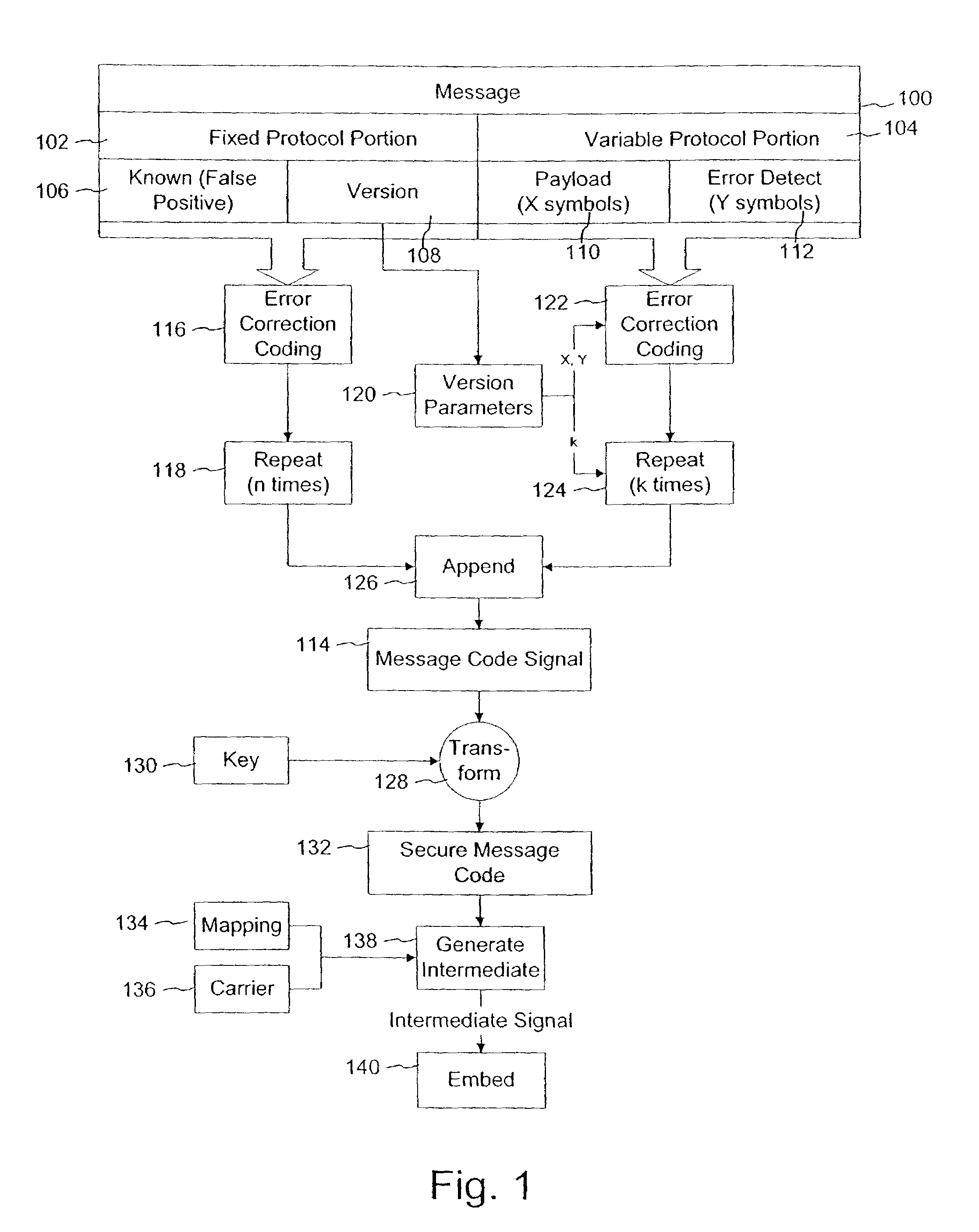
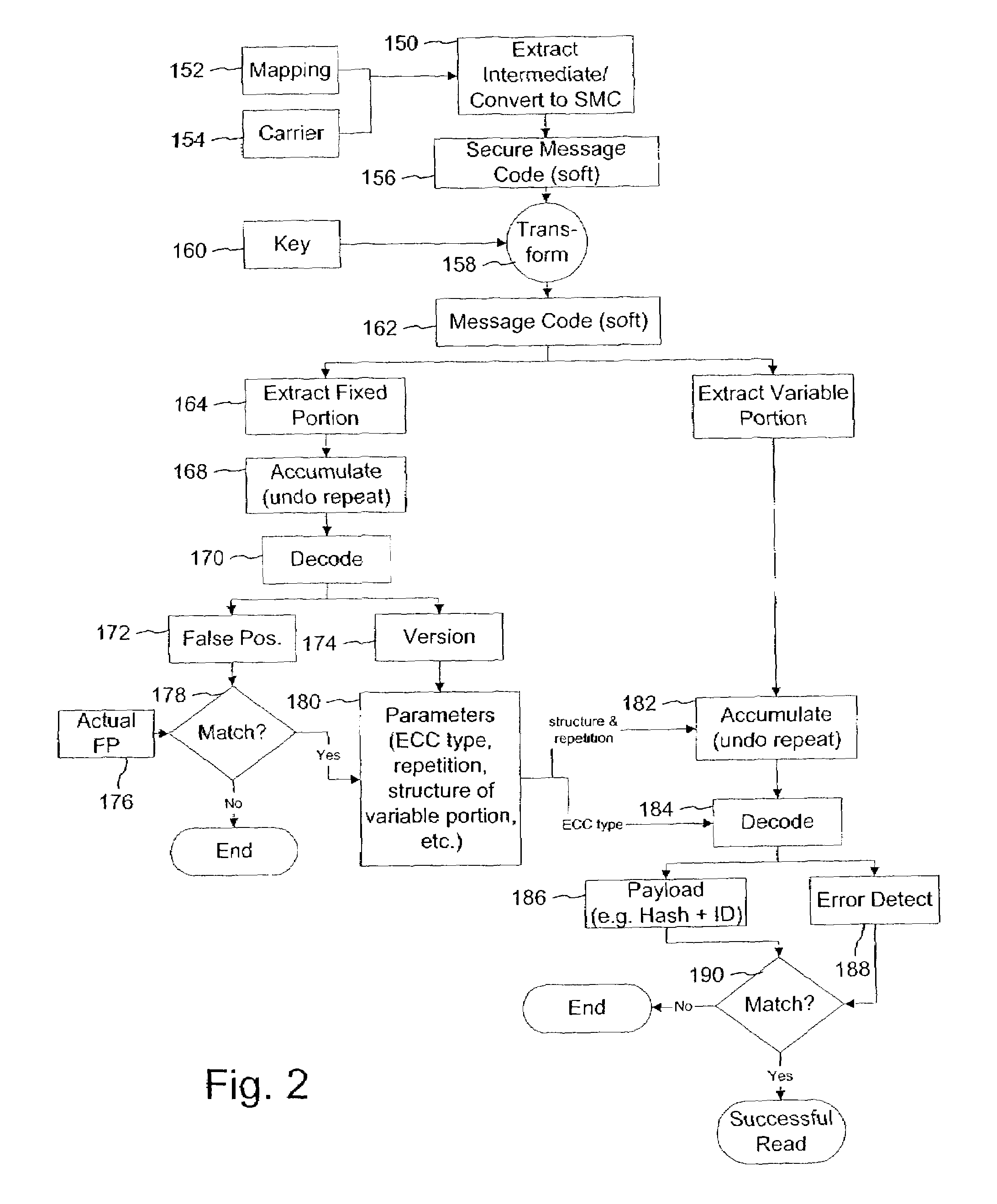
Variable message coding protocols enable greater flexibility in encoding auxiliary data in media signals. One such protocol employs a version identifier that indicates the type of coding used to process an auxiliary data message before it is embedded in a host media signal. This version identifier specifies the type of error robustness coding applied to a variable message. The error robustness coding may be varied to alter the message payload capacity for different versions of auxiliary data embedding and reading systems. Another protocol uses control symbols to specify the format and variable length of the variable message.
Owner:DIGIMARC CORP
Copy protection for digital motion picture image data
InactiveUS7043019B2Television system detailsUser identity/authority verificationComputer graphics (images)Copy protection
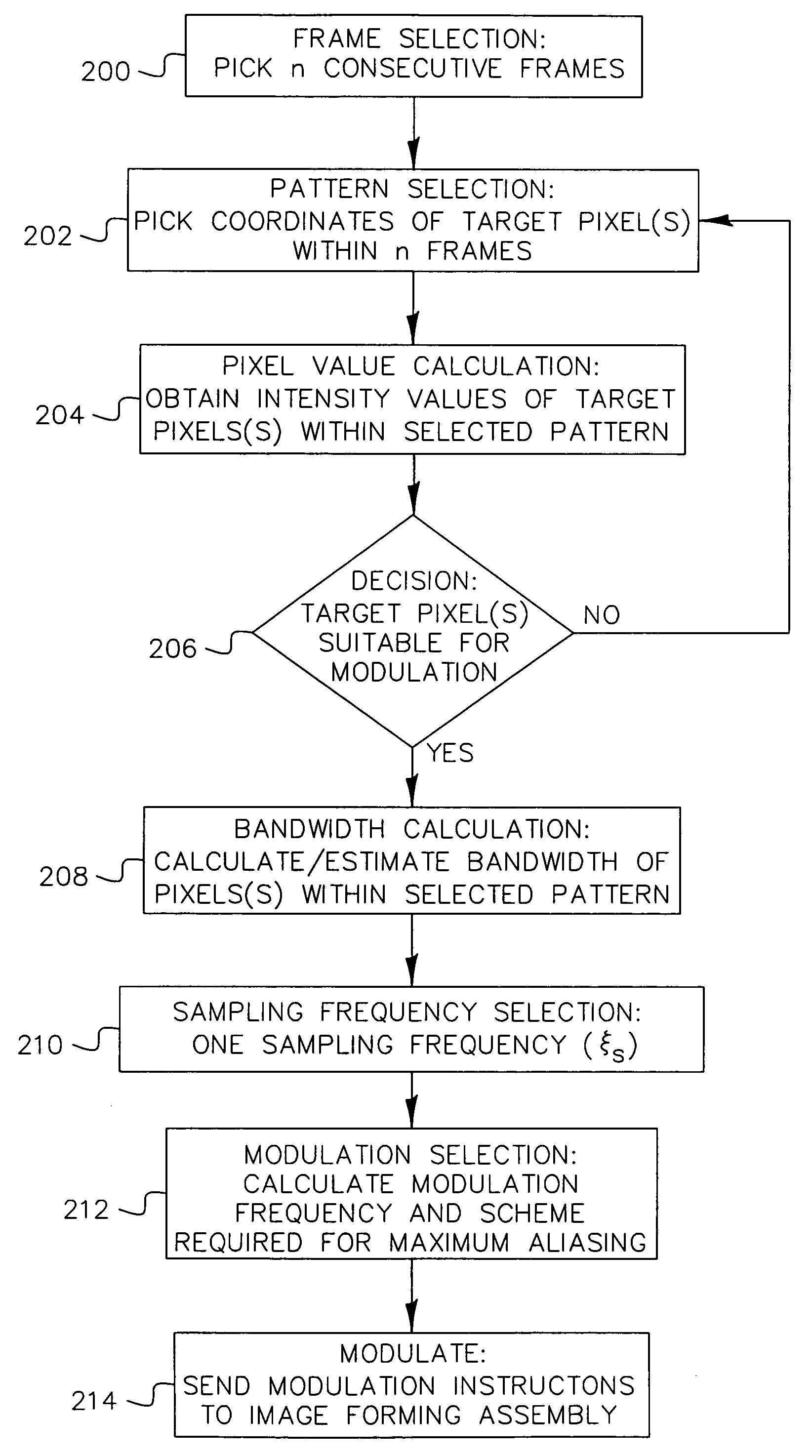
An apparatus and method for displaying a copy-deterrent pattern (104) within a digital motion picture in order to discourage recording of the motion picture using a video camera or other sampling recording device. A copy-deterrent pattern (104) could be, for example, one or more symbols, a random pattern, a digital watermark or a text message (106). The copy-deterrent pattern (104) comprises a plurality of pixels within each frame of the digital motion picture, and the displayed pixel intensities are modulated at a temporal frequency using modulation characteristics deliberately selected to be imperceptible to human observers while simultaneously producing objectionable aliasing in any copy made using a video camera.
Owner:EASTMAN KODAK CO
Steganographic encoding and decoding of auxiliary codes in media signals
InactiveUS6944298B1Accurate recoveryTelevision system detailsData representation error detection/correctionAudio frequencyAudio signal
One aspect of the invention is a method of decoding an auxiliary code embedded in an audio signal. The method performs a statistical decoding of a multibit auxiliary code embedded in an audio signal. The auxiliary code has been repetitively embedded in the audio signal. The method decodes code values of the auxiliary code from two or more different portions of the audio signal, each having the multibit auxiliary code. It then uses the code values decoded from two or more different portions to determine statistically the code values of the auxiliary code. Another aspect of the invention is another method of decoding an auxiliary code embedded in an audio signal. The method receives an audio signal suspected of being embedded with an auxiliary code. It evaluates a statistical feature of a portion of the audio signal to decode code values of the auxiliary code from the audio signal. It then determines a code value in the auxiliary code based on the statistical feature. The statistical feature may comprise, for example, the power of the audio signal. The statistical feature may be analyzed over different portions of the audio signal to decode two or more values of the auxiliary code.
Owner:DIGIMARC CORP
Popular searches
Television systems Analogue-digital converters Digital video signal modification Coding/ciphering apparatus Selective content distribution Pictoral communication Broadcast components for monitoring/identification/recognition Broadcast information monitoring Coding details Broadcast characteristics identification/recognition
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com