Network node security attribute evaluation method based on blockchain consensus result feedback
A security attribute and network node technology, which is applied in the field of network node security attribute evaluation based on blockchain consensus result feedback, can solve the problems of subjectivity, different ability to obtain evaluation data, and different data recognition, so as to enhance credibility , to achieve the effect of secure communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
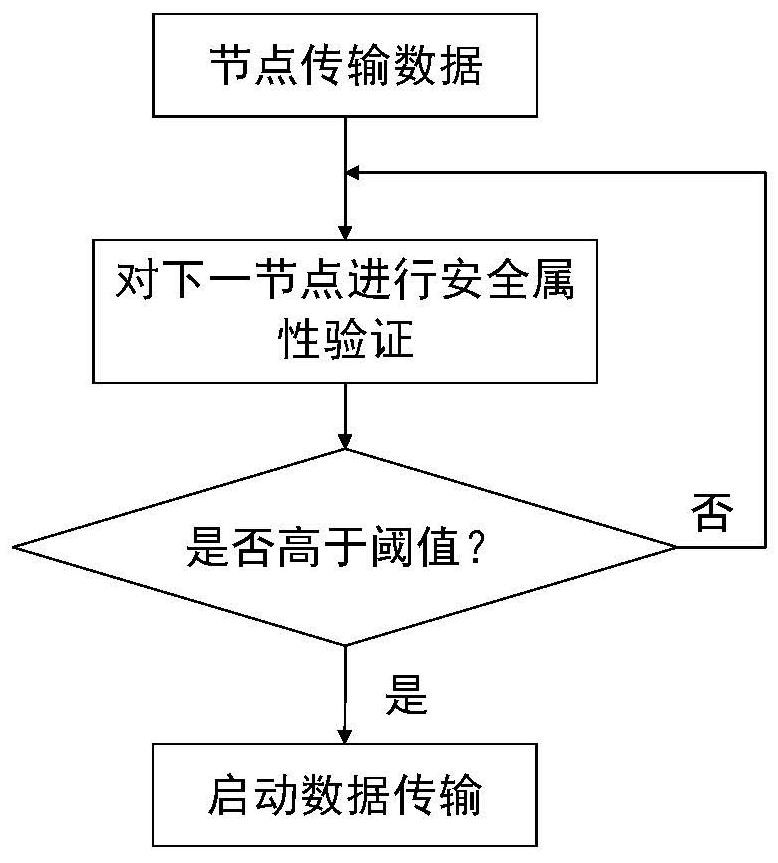
[0048] Such as figure 2 As shown, the node needs to verify the security attributes of the next-hop node drone before transmitting data. Only when the security attributes of the next-hop node of the transmission are higher than the security attribute threshold, the content hop-by-hop transmission is started, which is based on The hop-by-hop transmission method transmits data between network nodes. Before forwarding, the node stores the received data in the memory, and then periodically checks the security attribute value of the next hop node. When it detects that the security attribute value of the next hop node is updated above the threshold, the stored data is forwarded, otherwise Send temporarily. When the node receives the data sent by the previous hop routing node, it immediately sends confirmation information to the next hop routing node. The last hop routing node deletes the stored data corresponding to the confirmation message after receiving the confirmation message s...
example 2
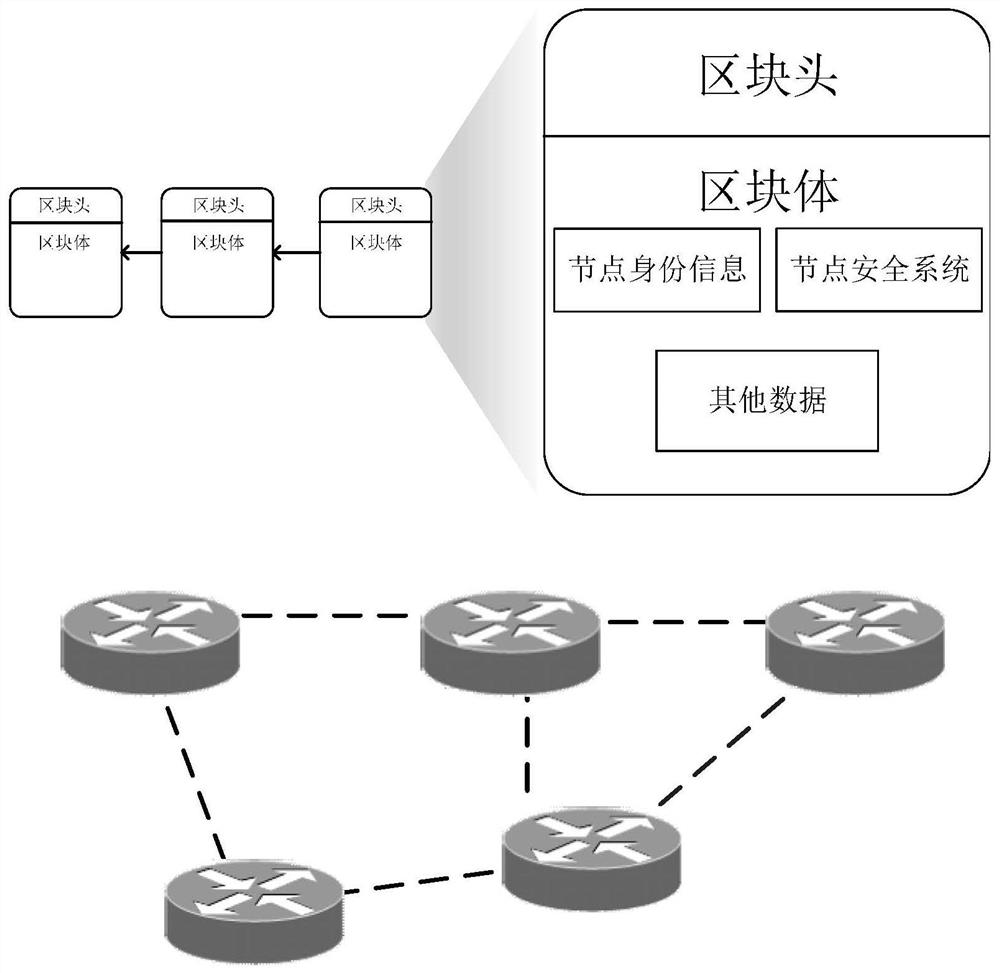
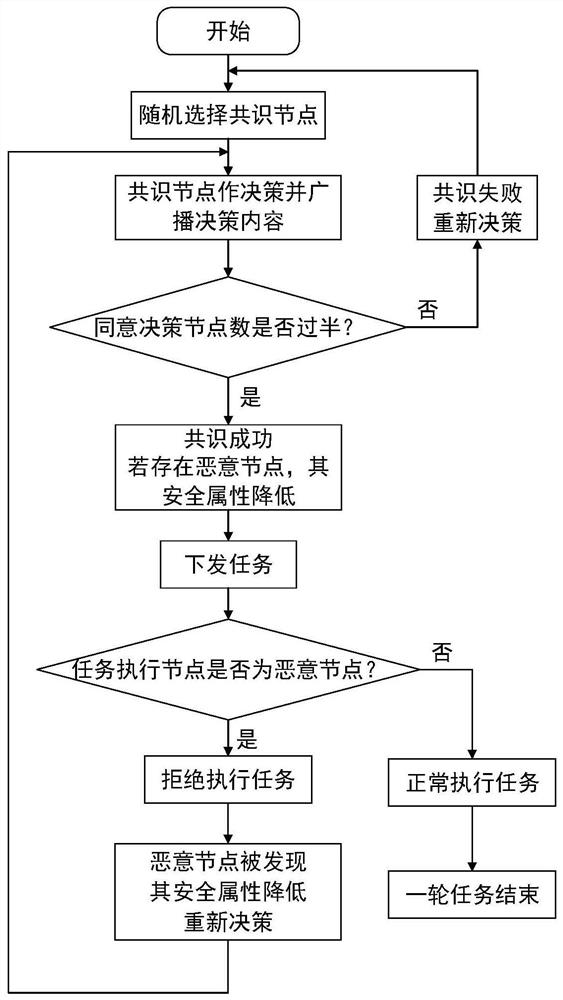
[0050] In the drone swarm, the drone node needs to take on the two roles of task execution and data communication at the same time. Among them, task execution means that the nodes in the network judge who will perform the task through a certain mechanism. Data communication means the drone node. Data packets can be transmitted to each other. Due to constraints such as low computing power, small storage space, and less spare energy in the drone swarm, it is difficult to deploy complex security defense function modules in the nodes. Moreover, the wireless channel of the UAV network is open, and the information in the network may be transmitted to any node, and the attacker can eavesdrop on the wireless channel to obtain the information in the network. When the UAV network is under attack, malicious nodes can be identified through the security attribute evaluation mechanism.
[0051] Such as image 3 As shown, in a drone swarm with a built-in blockchain, a number of drone nodes wil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com