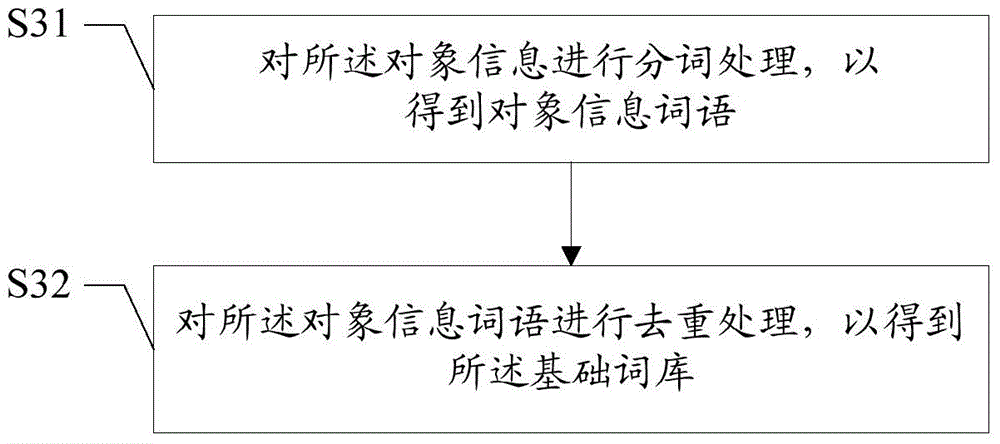
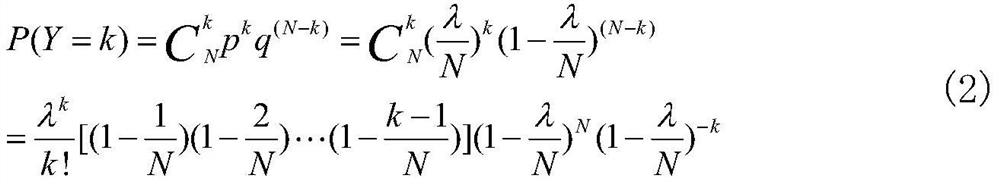Patents
Literature
43results about How to "Extensive sources of data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Path planning method for avoiding of traffic hotspots
InactiveCN103278168AExtensive sources of dataIncrease credibilityInstruments for road network navigationFast pathMinimum time
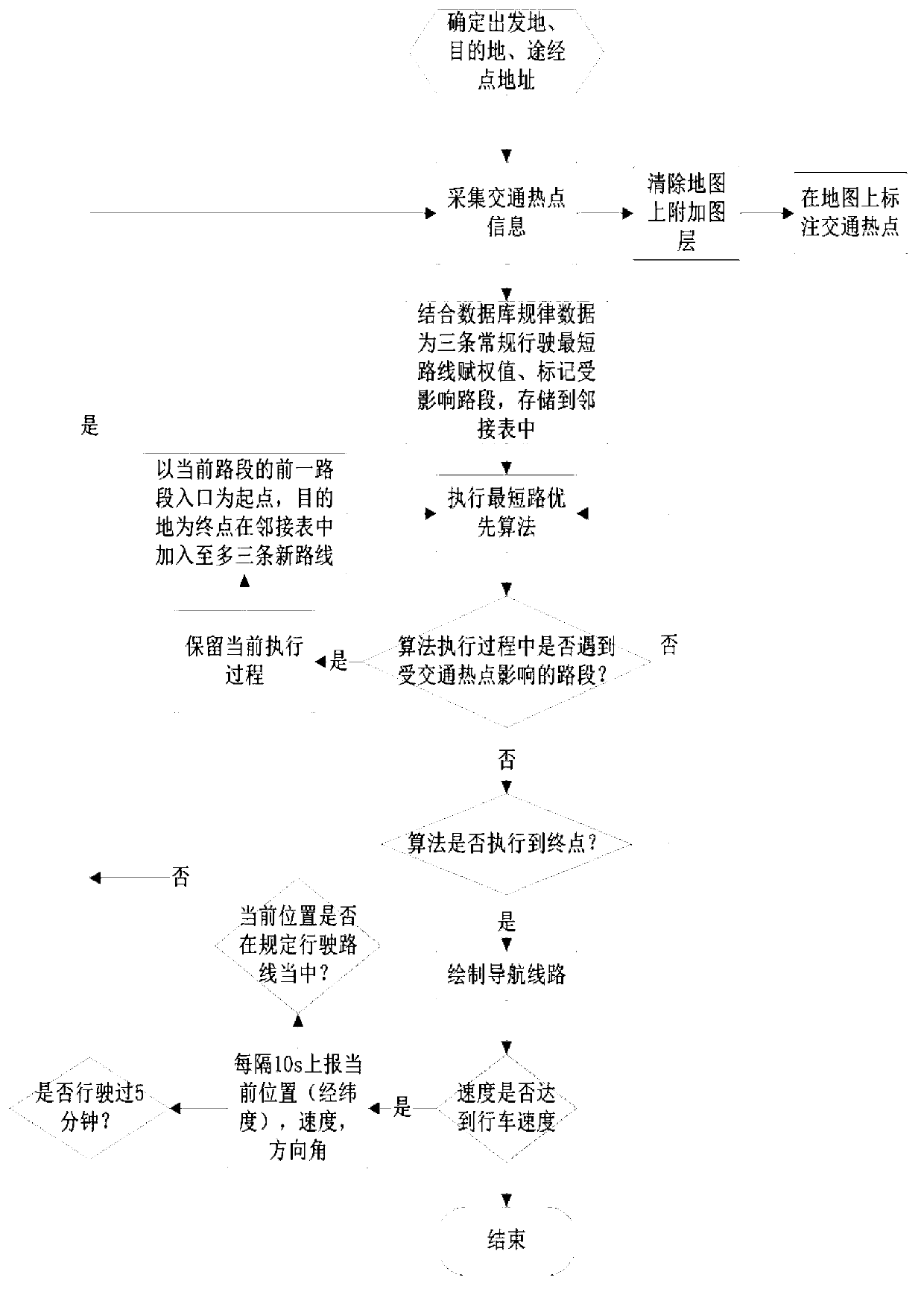
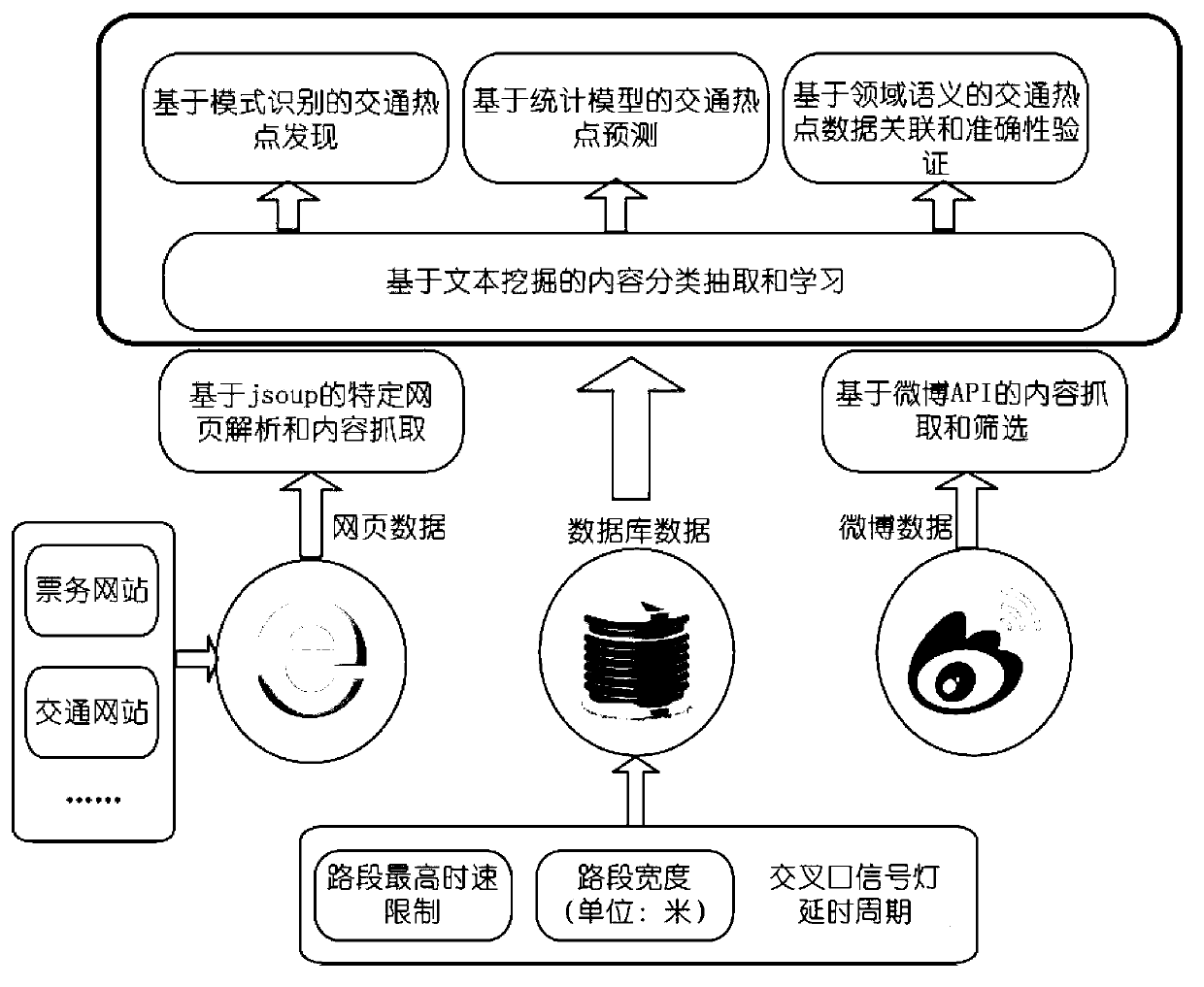
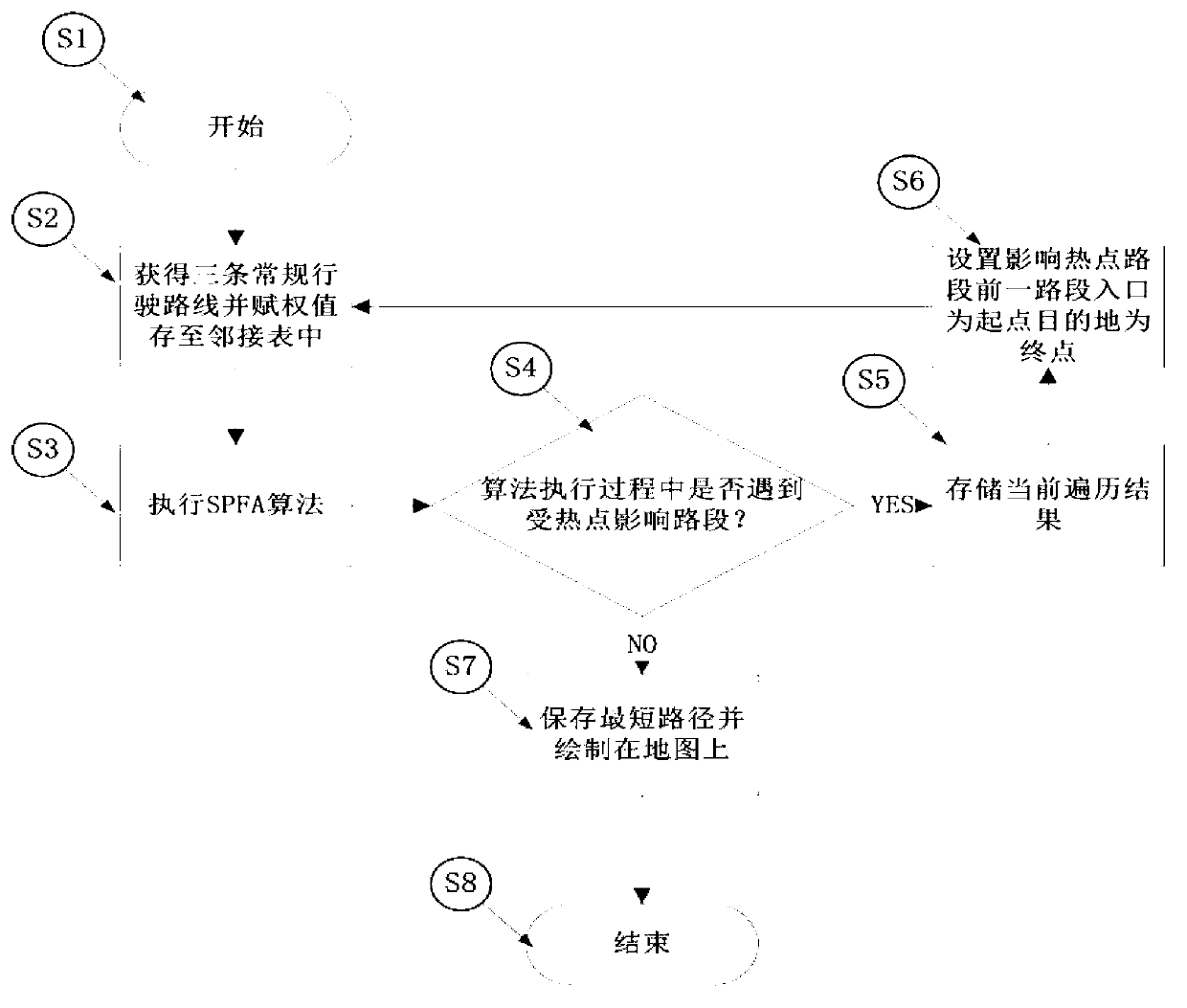
A path planning method for avoiding of traffic hotspots helps to realize an intelligent path planning method with a purpose of the shortest journey time, by dynamical planning of paths with an avoiding property, based on a destination where a driving user goes. The traffic hotspot information, such as large-scale activities, traffic accidents, traffic-peak block roads, school time or commuter time of large-scale units, weather information and the like, are mined continually from a plurality of data sources comprising webpages, microblogs, real-time reported traffic information, historical regularity information and the like. By acquisition of the traffic hotspot information in real time, and combination with influences of a road maximum speed limit, road width and traffic light delay at intersections to driving as well as whether a main road containing a non-motor vehicle zone, a rapid navigation route with an avoiding function is planed, and also a dynamic path planning can be carried out in real time base on a current position. The method helps to provide a fastest path to the destination for drivers and alleviate city traffic jam in certain degree.
Owner:BEIHANG UNIV
Vehicle running track reconstruction method based on multiple probability matching under sparse sampling
ActiveCN103162702ALow data requirementsExtensive sources of dataInstruments for road network navigationReconstruction methodAlgorithm
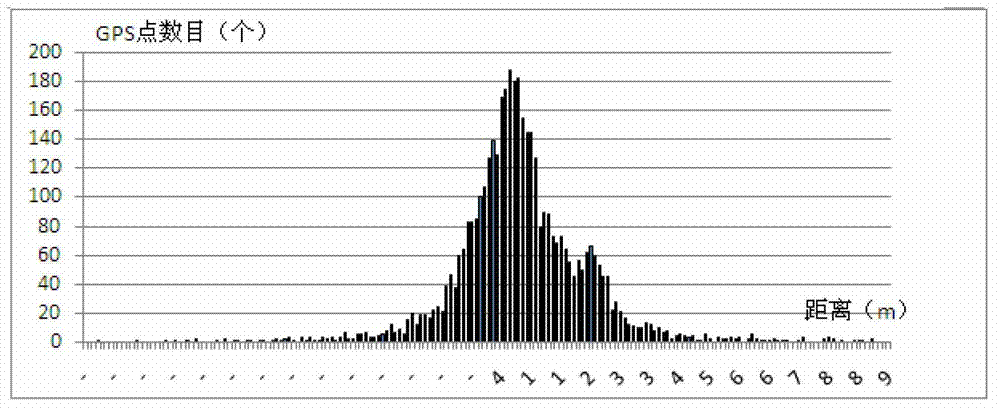
The invention provides a vehicle running track reconstruction method based on multiple probability matching under sparse sampling, which is characterized in that a historical data statistics sparse sampling point tolerance distribution is used, and a search area is determined; then a candidate match object (road section or intersection) is searched in a region of search, and can be divided into various types according to the characteristics of the candidate object, if no match object is in the search area, the sampling point is not considerate, if only one object is in the search area, then the sampling point couples to the only object, if various candidate objects is in the search area, a double layer probability matching model is used for further processing; the double layer probability matching model can calculate the coupling probability of each possible track according to matching probability of the sampling point and the selection probability of the reasonable path, and the track with utmost possible probability can be selected for being taken as a reconstruction track of the sparse sampling point. The vehicle running track reconstruction method can reduce the matching error of the sparse sampling data, and can effectively increase the precision and speed of reconstructed vehicle running track in a complex road net.
Owner:SUN YAT SEN UNIV
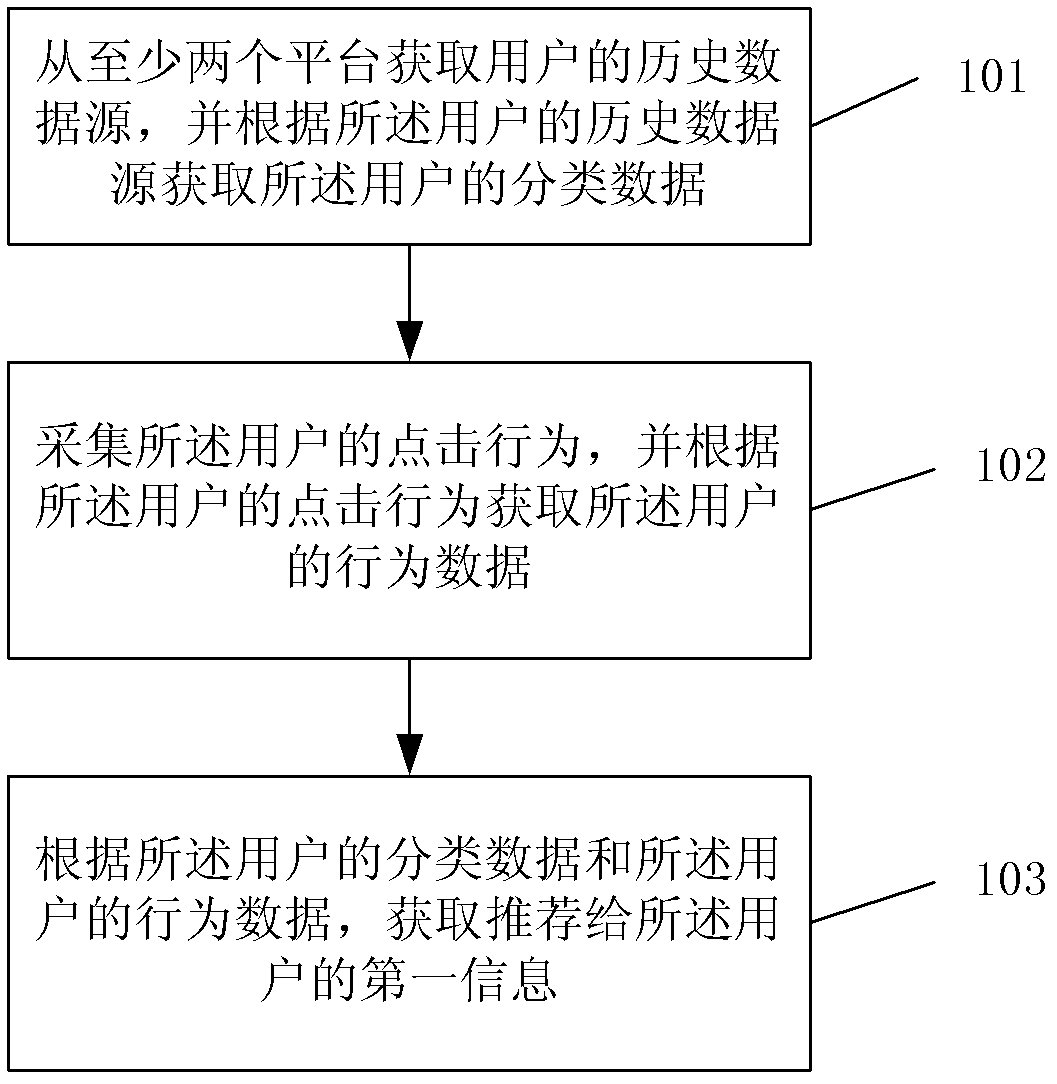
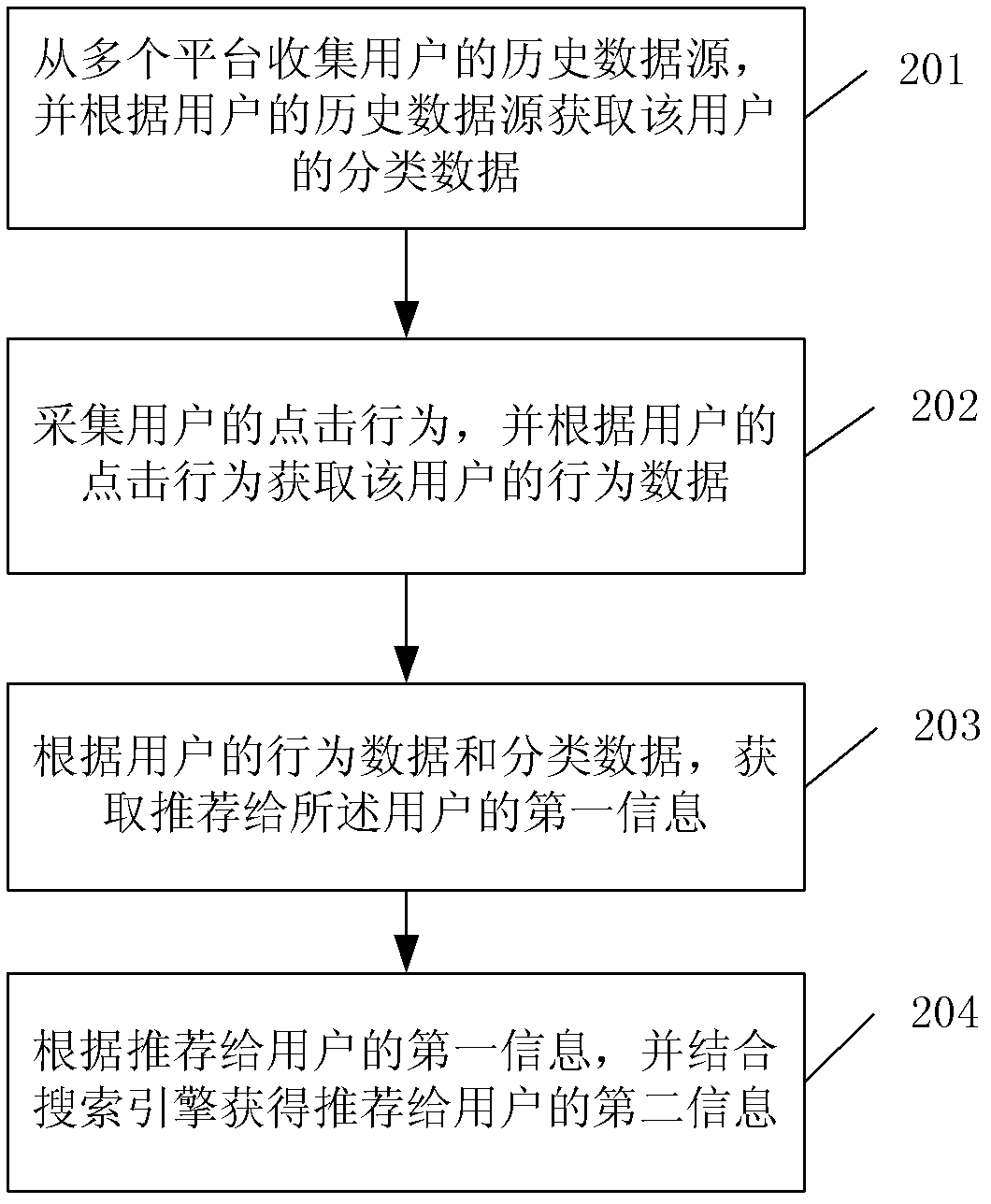
Method and device of acquiring information
InactiveCN103136253AImprove experienceMeeting the Need for Integrated Recommended ContentSpecial data processing applicationsData sourceThe Internet
Owner:TENCENT TECH (SHENZHEN) CO LTD
Oil-water distribution recognition method based on well-ground potential method
InactiveCN105822302AAccurate identificationNo damageBorehole/well accessoriesPotential methodOil water
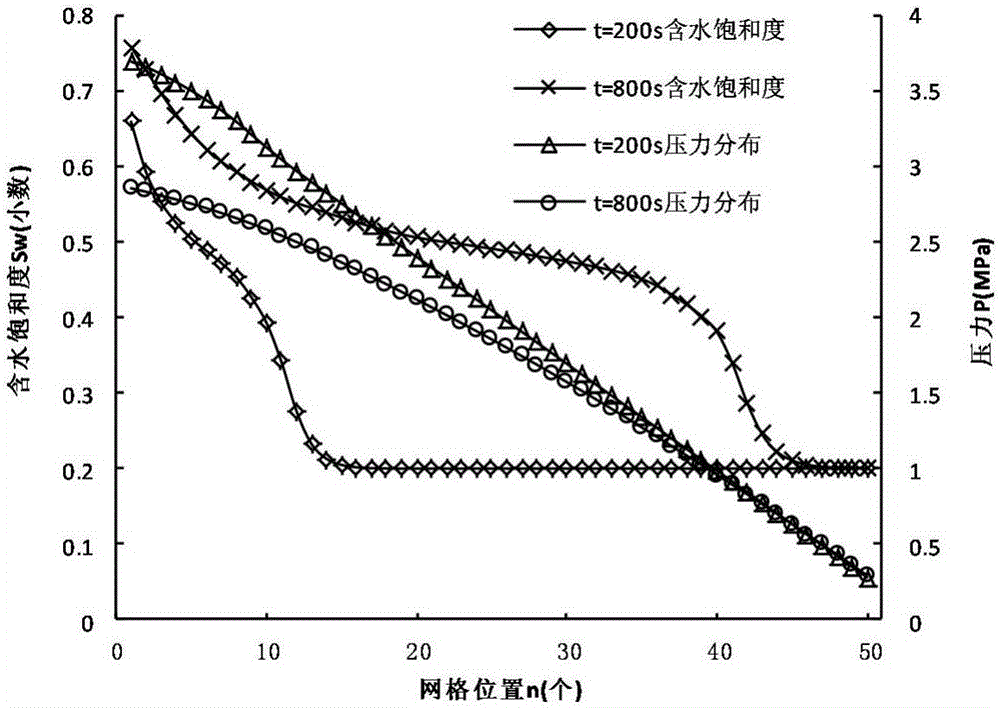
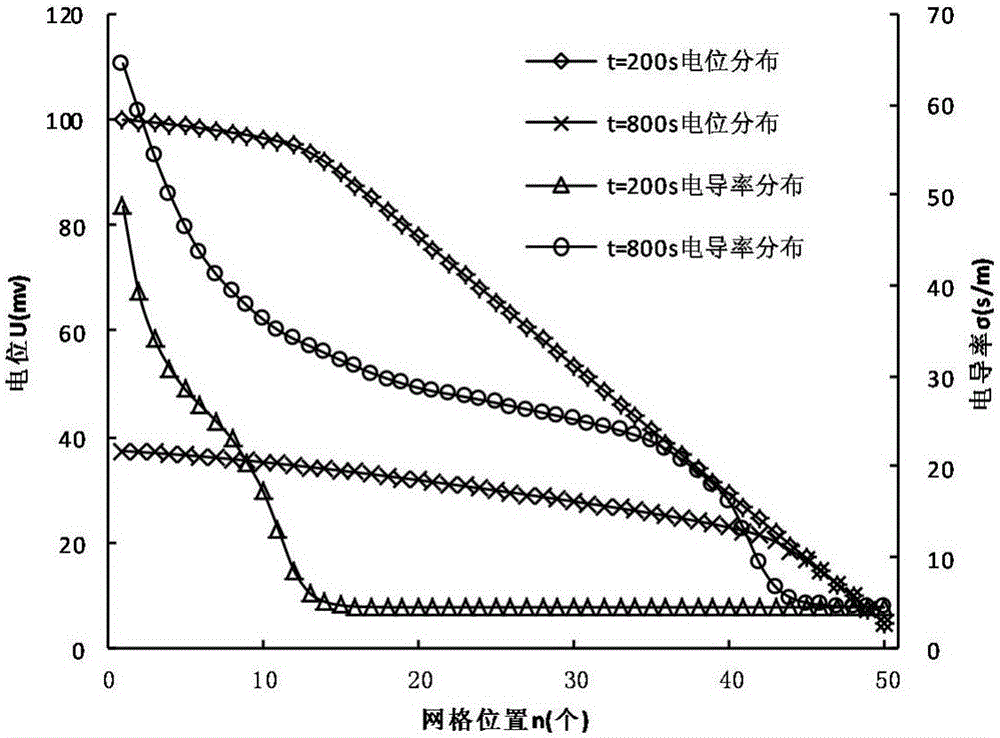
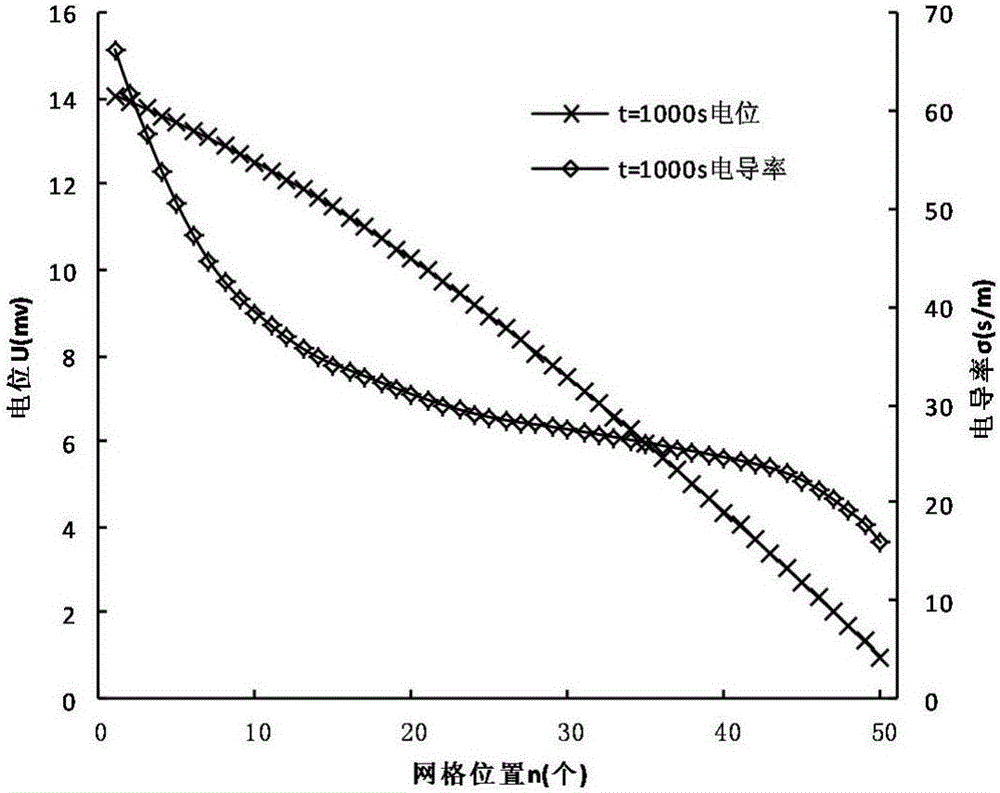
The invention discloses an oil-water distribution recognition method based on a well-ground potential method. The oil-water distribution recognition method comprises the following steps: firstly, establishing an oil-water two-phase seepage equation; based on a potential and water saturation model, coupling the seepage equation with a potential differential equation to form a well-ground potential model; adopting a finite difference method and solving the pressure of the model by adopting an implicit expression and solving the saturation degree of the model by adopting an explicit expression; establishing a difference potential differential equation by utilizing a relation between the water saturation and conductivity, and solving the potential by adopting the implicit expression; establishing a computer solving model on the basis; carrying out analog computation on a one-dimensional water displacement oil process; simulating the whole water displacement oil process through numerical solution to obtain a correlational relation between potential distribution and resistivity of an underground target layer; after solving the resistivity of the target layer, inversing the water saturation of a reservoir stratum by utilizing an Archie equation. The method can be used for quantitatively describing the water saturation and oil saturation in the reservoir stratum by utilizing the potential determined on the ground, and oil-water distribution can be more rapidly and accurately recognized.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
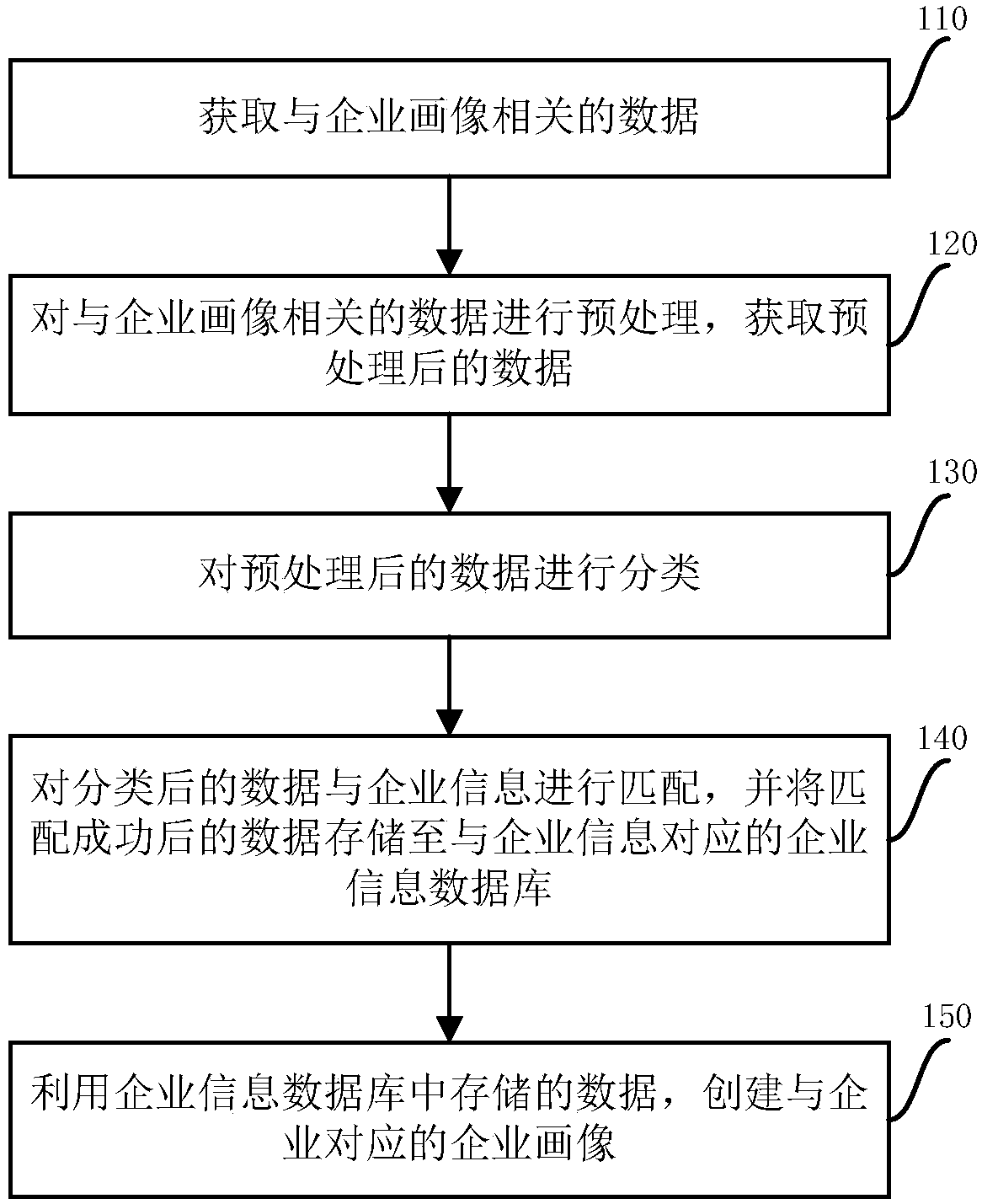
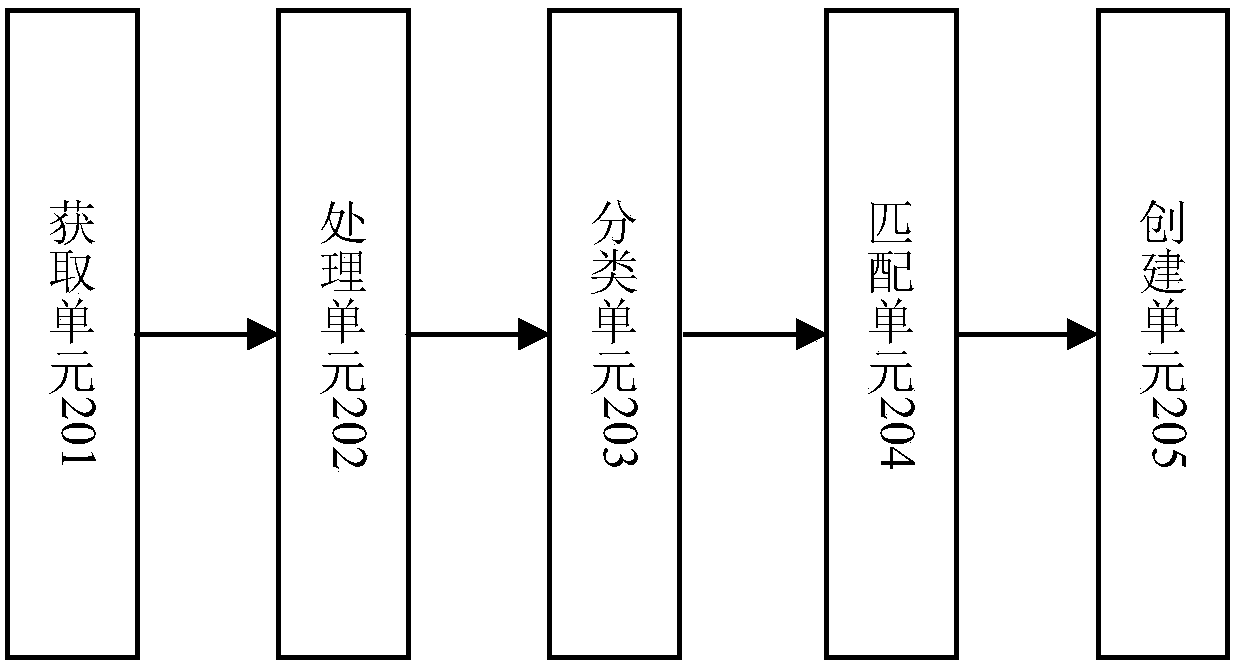
Method and device for establishing enterprise image
ActiveCN108572967AEasy to sort and storeExtensive sources of dataSpecial data processing applicationsData miningData library
The invention relates to a method and device for establishing an enterprise image. The method includes the steps that data related to the enterprise image is obtained; the data related to the enterprise image is preprocessed, and preprocessed data is obtained; the preprocessed data is classified; the classified data is matched with an enterprise, and data after being successfully matched is storedin an enterprise information database corresponding to the enterprise; through data stored in the enterprise information database, the enterprise image corresponding to the enterprise is established.The data related to the enterprise image is obtained to be correspondingly preprocessed, and some useless data or repeated data or the like can be removed; then the data is classified to be matched with enterprise information so that the matched data can also be separately stored; the enterprise image is established according to the classified data, enterprise all-dimensional information is integrally depicted, and the established enterprise image is more comprehensive and objective.
Owner:DIGITAL CHINA SYST INTEGRATION SERVICE
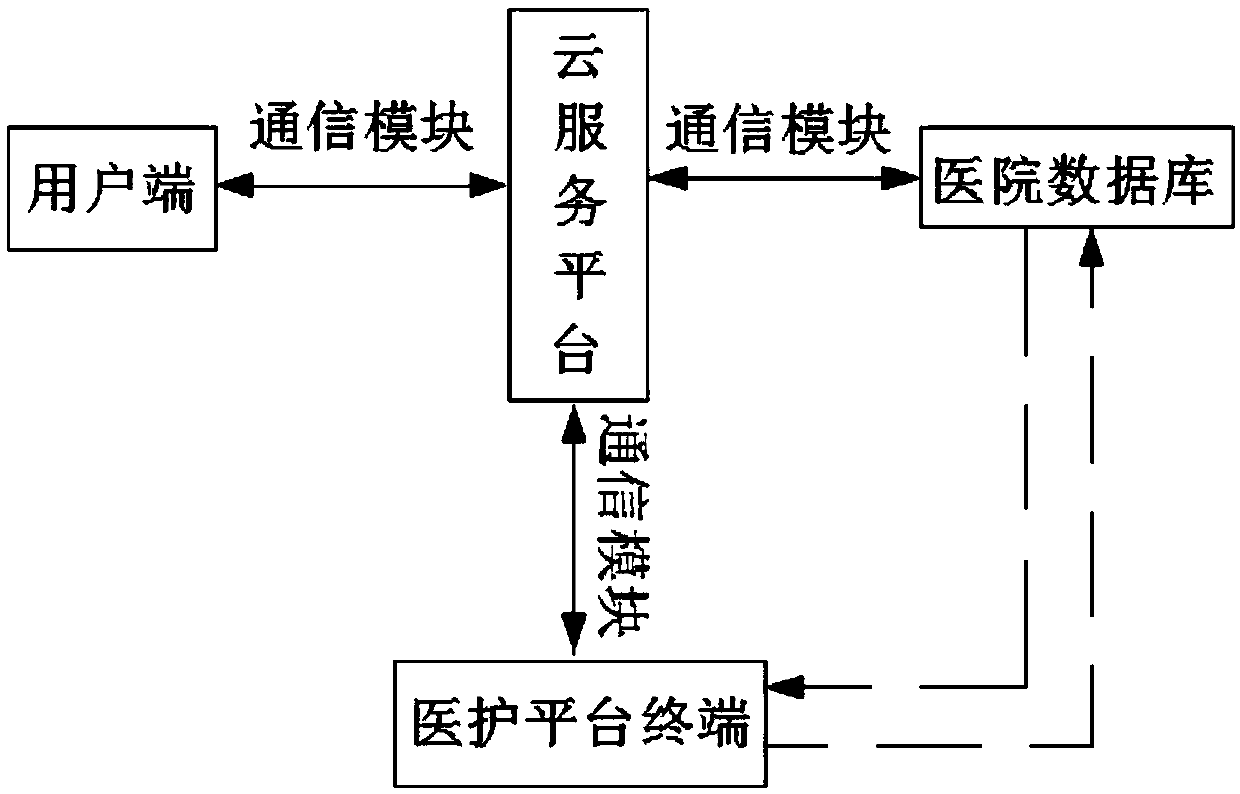
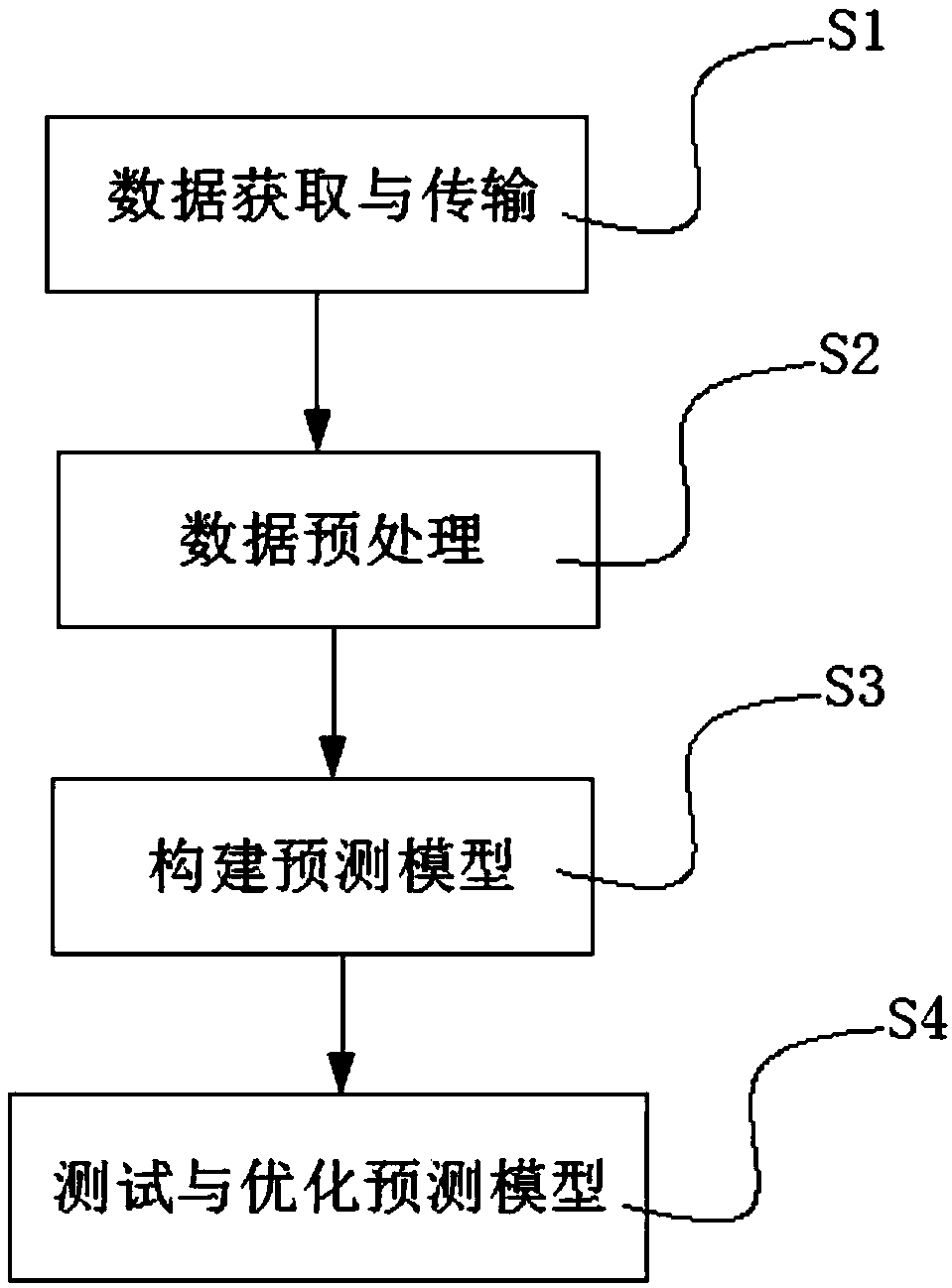
Medical big-data analysis and processing system and method based on IOT (Internet of Things)
PendingCN109545385AExtensive sources of dataEasy way to getMedical data miningNeural architecturesData informationData acquisition
The invention discloses a medical big-data analysis and processing system and method based on the IOT (Internet of Things), and belongs to the technical field of data processing. The big-data analysisand processing system mainly comprises a cloud service platform, a user terminal, a hospital database and a medical platform terminal. The medical big-data analysis and processing method of the invention comprises the steps: data acquisition and transmission, data preprocessing, prediction model constructing, and testing and optimizing of a prediction model. Therefore, the prediction model for indicating the probability of a disease of a predicted object or the probability that the predicted object has a certain disease is obtained, and the IOT transmission of the data information is achievedthrough a communication module. Moreover, the prediction model is obtained based on the convolutional neural network The data source with many correlations and wide influences is inputted, and the data has been preprocessed, which greatly improves the accurate reference value of the prediction results.
Owner:周立广
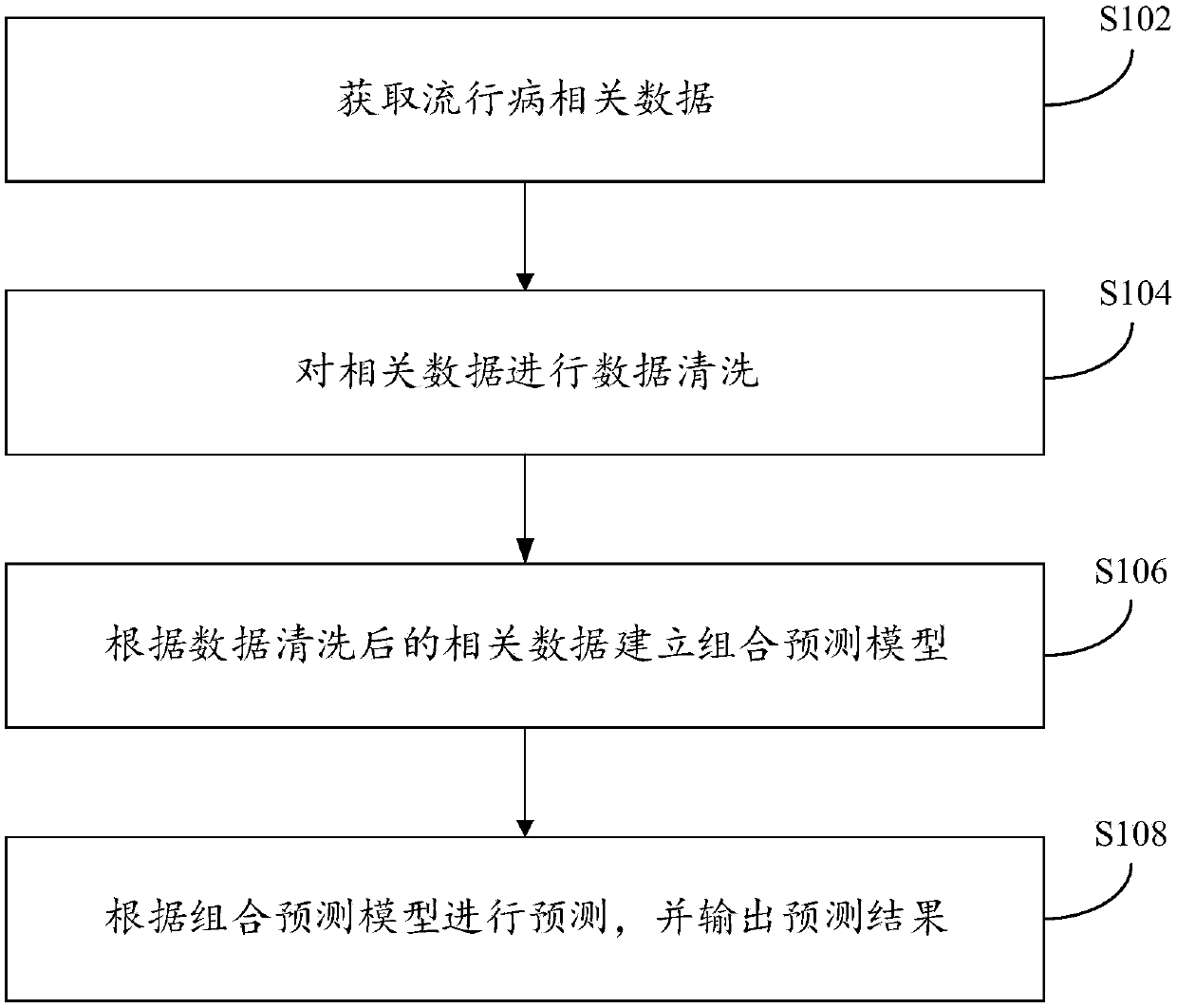
Epidemic disease forecasting method, system and equipment
InactiveCN108417274AExtensive sources of dataGood forecastEpidemiological alert systemsThe InternetBusiness forecasting
The invention provides an epidemic disease forecasting method, system and equipment, and relates to the technical field of epidemic disease forecasting. The method comprises the steps that the epidemic disease relevant data are acquired, wherein the relevant data include the internet data, the weather data and the biological information data acquired by the intelligent terminal, and the internet data include the search data and the social network data; the data cleaning is performed on the relevant data; an integrated forecasting model is established according to the relevant data after data cleaning; and forecasting is performed according to the integrated forecasting model and the forecasting result is outputted. According to the epidemic disease forecasting method, system and equipment,the data sources are wider, the forecasting effect is better, the forecasting accuracy is higher, the cost is lower and the effectiveness is higher and the possible epidemic disease outbreak can be forecasted earlier.
Owner:SOUTHEAST UNIV +1
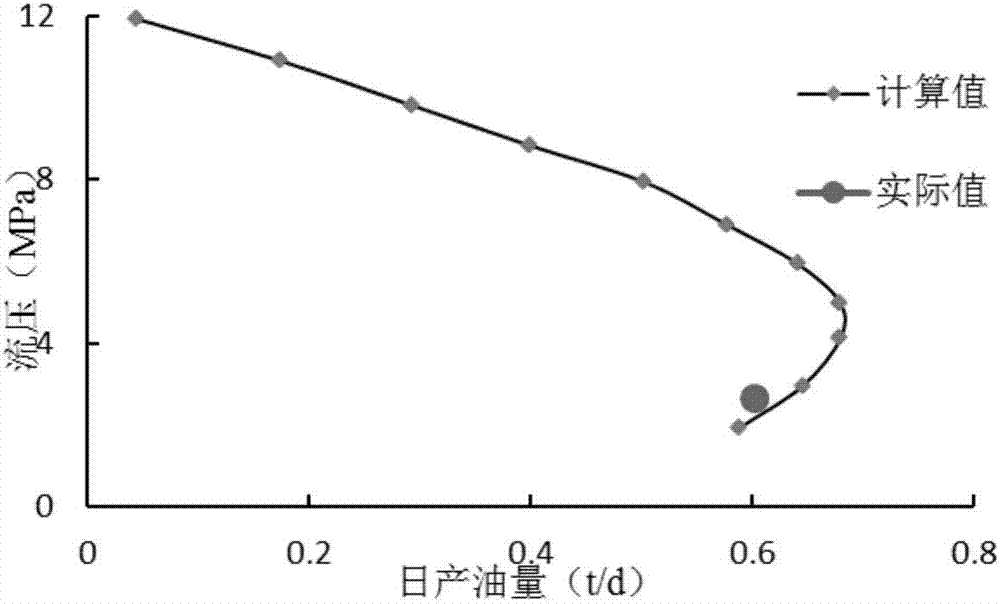
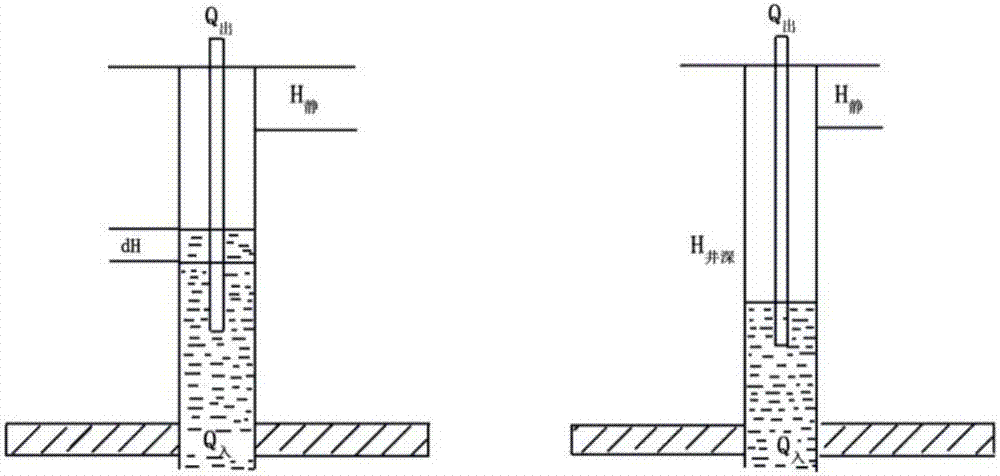
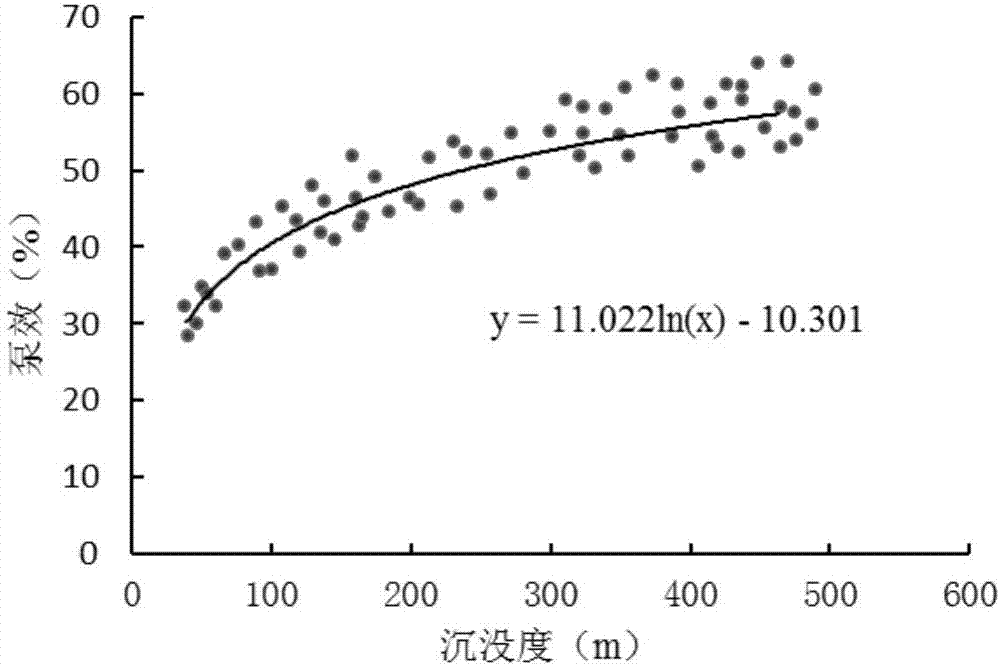
Method for optimizing low-permeability reservoir intermittent mining working system based on model coupling exhaustion method
ActiveCN107578342ATruly reflect the law of seepageQuantitative precisionData processing applicationsSpecial data processing applicationsDynamic modelsEngineering
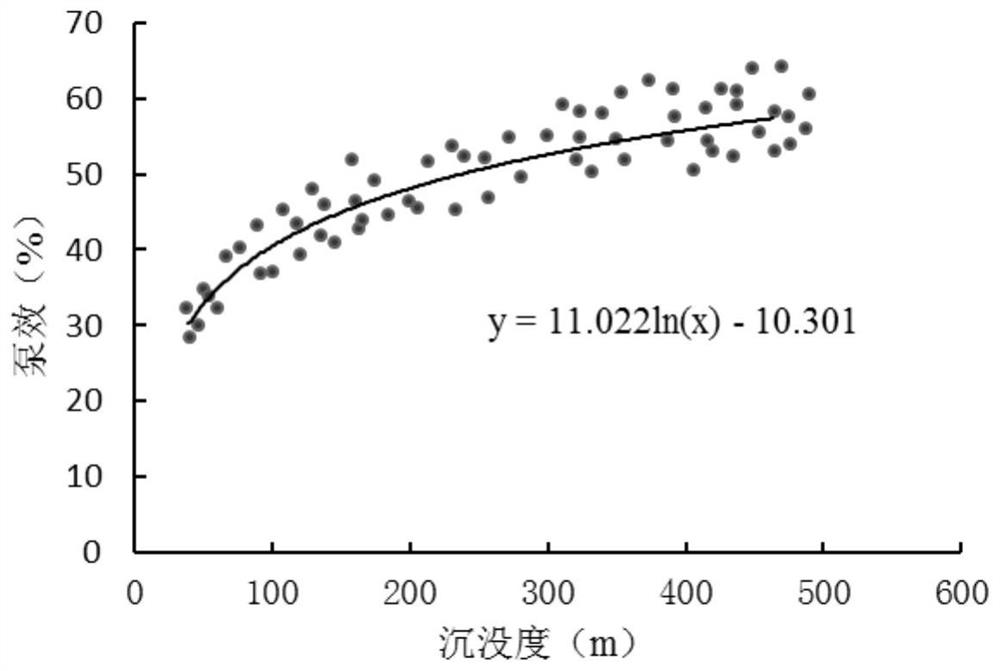
The invention discloses a method for optimizing a low-permeability reservoir intermittent mining working system based on a model coupling exhaustion method. Aiming at the input and output characteristics of a low-permeability and low-yield well, through the combination of the flow-in dynamic characteristics of the low-permeability reservoir, the liquid level change rule of an intermittent mining well shaft and the pump efficiency analysis, and based on the relation between the stratum liquid supply capacity and the pumping and suction capacity, a stratum flow-in dynamic model and a well shaftoutflow dynamic model are established, a coupling model is established through the coupling parameters of the bottom flow pressure and the pump efficiency, a computer solution model is established onthis basis, and the optimization of the low-permeability reservoir intermittent mining working system determination method is carried out by means of an exhaustion method. The method can accurately describe the low-permeability reservoir seepage law, realizes the real-time dynamic changes of the bottom flow pressure and the pump efficiency during the intermittent mining, and realizes the accuratequantified intermittent mining limit. The exhaustion method has better optimization precision, and the program calculation efficiency is high.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
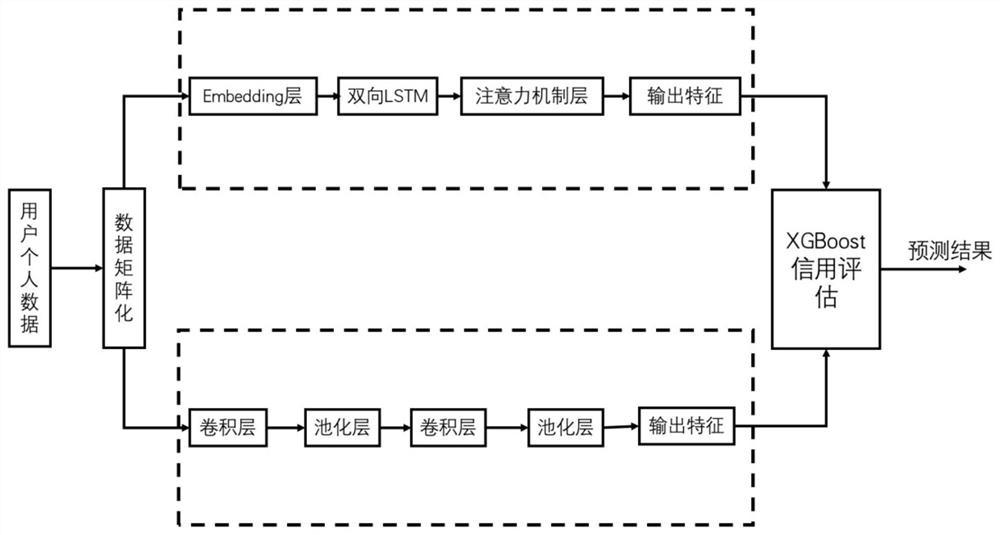
Personal credit assessment method and system based on fusion neural network feature mining
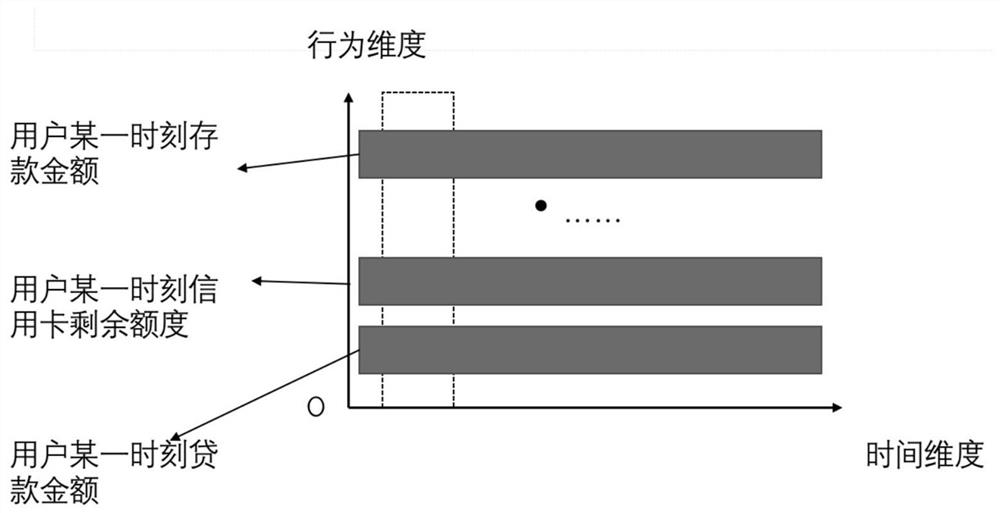
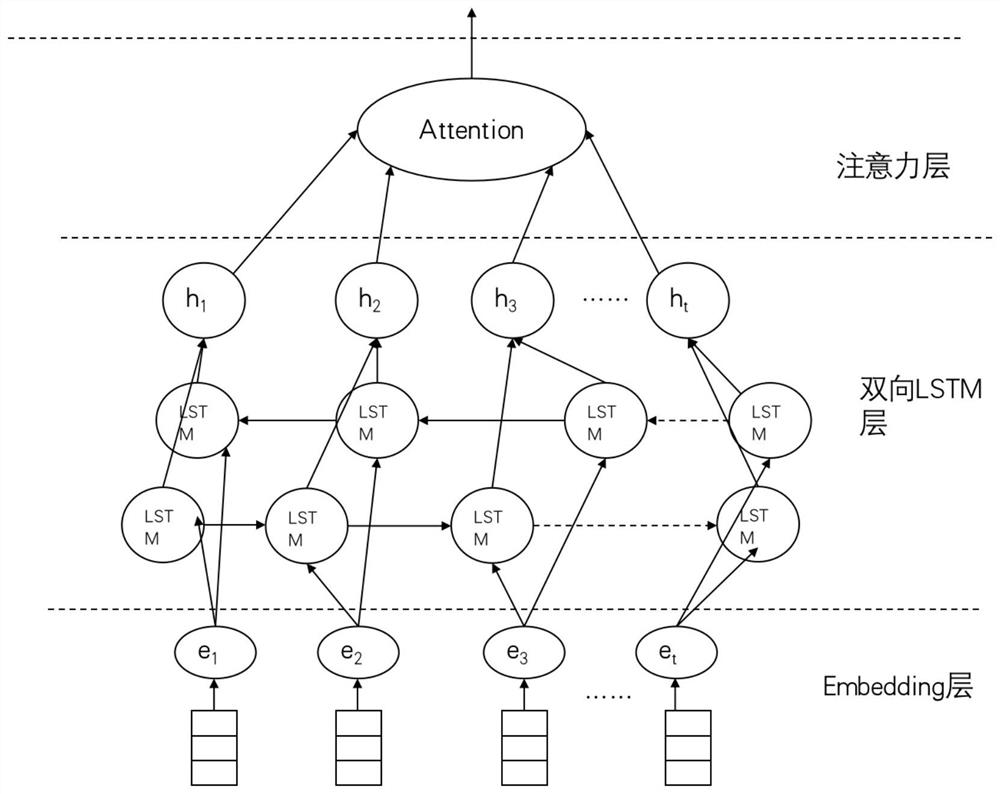
PendingCN112819604AComprehensive coverage of indicatorsComprehensive Indicator CoverageFinanceCharacter and pattern recognitionFeature miningFeature vector
The invention relates to a credit assessment technology, and aims to provide a personal credit assessment method and system based on fusion neural network feature mining. The method comprises the steps that behavior data of an individual user are preprocessed and checked and then subjected to matrix processing, and the obtained data serve as input of an LSTM model and a CNN model at the same time; in the LSTM model, sequentially processing by an embedding layer, a bidirectional long short-term memory neural network and an attention mechanism layer, and outputting a time sequence behavior feature vector extracted from the data; in the convolutional neural network model, processing is carried out through a convolutional layer and a pooling layer in sequence, and local behavior feature vectors extracted from the data are output; and carrying out vector splicing on the two types of feature vectors, taking the spliced feature vectors as input of an XGBoost classifier, and carrying out training to finally obtain a personal credit evaluation result. Compared with the prior art, the method has the characteristics of comprehensive index coverage, wide processing index source, advanced modeling mode, flexible model expansion, complete and effective feature extraction and accurate result.
Owner:浙江农村商业联合银行股份有限公司
Relational network construction method, device and electronic equipment
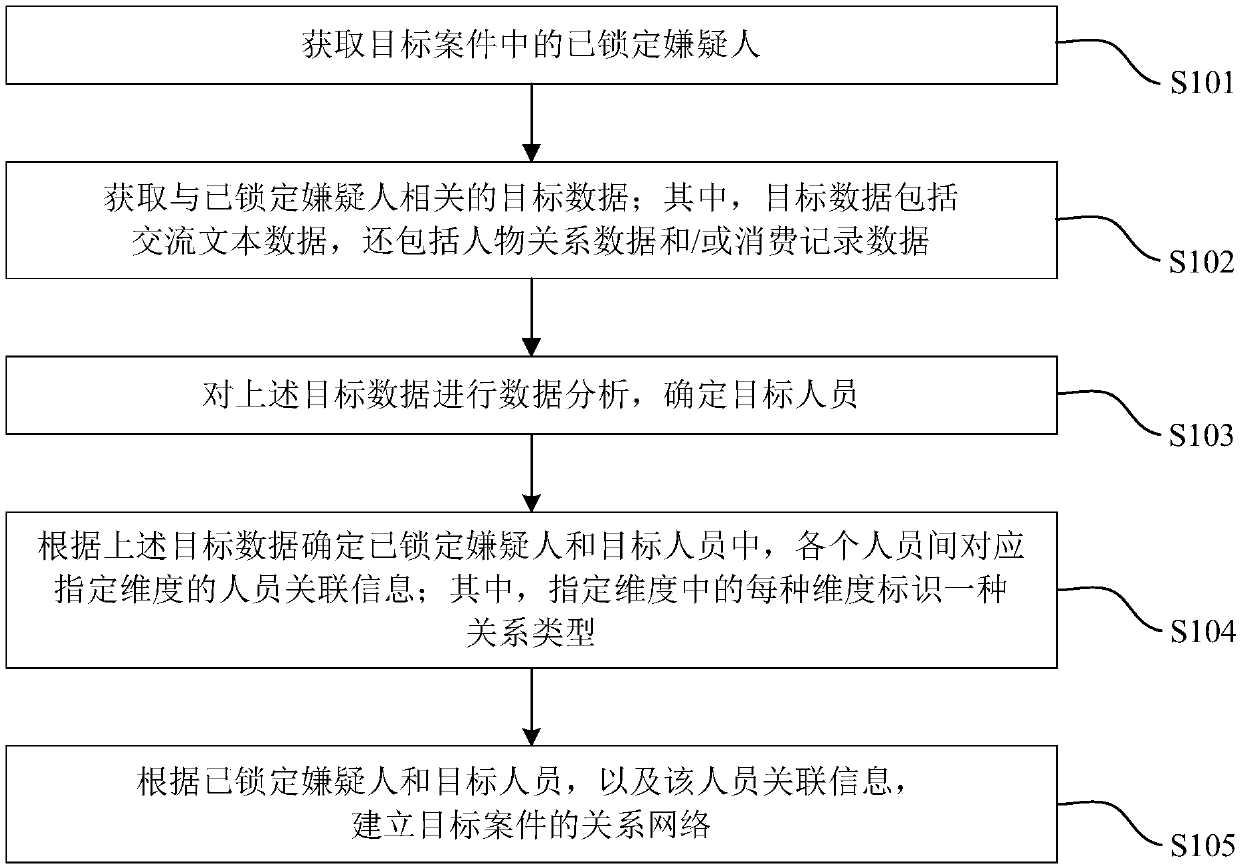
ActiveCN107729466AComprehensive coverageImprove reliabilityData processing applicationsSpecial data processing applicationsNetwork constructionData science
The invention provides a relational network construction method, a device and electronic equipment. The method includes the steps of acquiring locked suspects in a target case; acquiring target data related to the locked suspects, wherein the target data include communication text data and also include person relationship data and / or consumption record data; carrying out data analysis of the target data and determining target persons; determining person association information corresponding to a specified dimension among the locked suspects and the target persons according to the target data;and establishing the relational network of the target case according to the locked suspects and the target persons as well as the person association information. Data sources in the relational networkconstruction method, the device and the electronic equipment are extensive and are not limited to the communication text data, and also relate to the person relationship data and / or the consumption record data. Based on these data, the relational network is constructed, a single data source problem is solved, and the reliability and practicality of the relationship network are improved.
Owner:杭州中奥科技有限公司
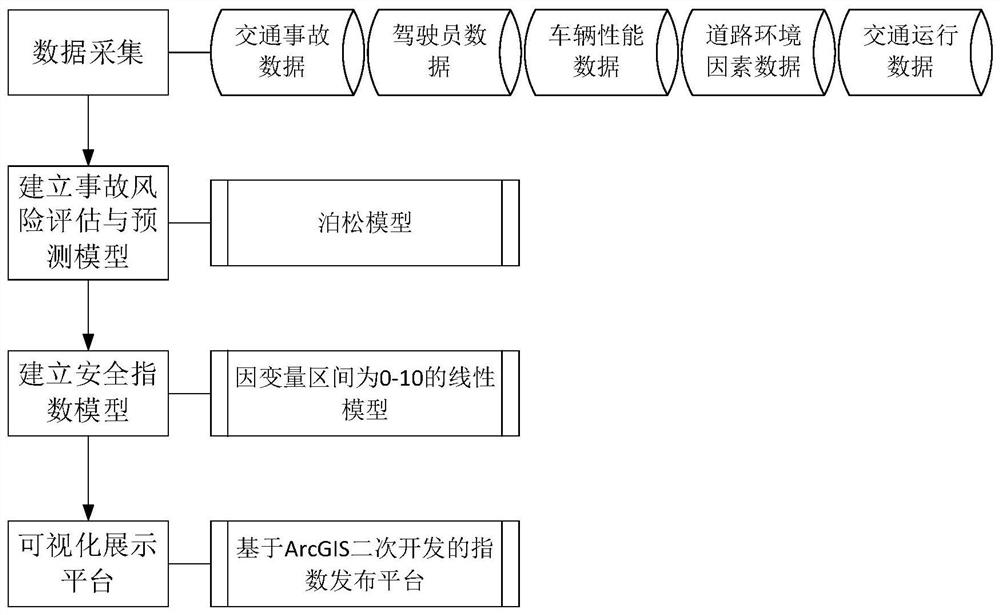
Real-time traffic safety index dynamic comprehensive evaluation system and construction method thereof
PendingCN112037513AImprove accuracyExtensive sources of dataDetection of traffic movementCharacter and pattern recognitionDriving safetyRoad traffic safety
The invention relates to a real-time traffic safety index dynamic comprehensive evaluation system and a construction method thereof. The construction method is characterized by comprising the following steps: step 1, collecting related data influencing traffic accidents and extracting characteristics of various data; step 2, establishing an accident risk assessment and prediction model by taking the characteristics of the collected related data as independent variables and taking a traffic safety index formed by the number and the grade of historical traffic accidents as dependent variables, and solving model parameters; step 3, according to the accident risk assessment and prediction model obtained in the step 2, calculating expectation of the number of traffic accidents occurring in different areas in combination with real-time road conditions, road structure attributes and driving safety coefficients, and obtaining real-time traffic safety indexes of the different areas through calculation according to a pre-established safety index model; and step 4, establishing a visual display platform for displaying the real-time traffic safety indexes of different areas. The system and method can be widely applied to the field of traffic safety evaluation.
Owner:TSINGHUA UNIV
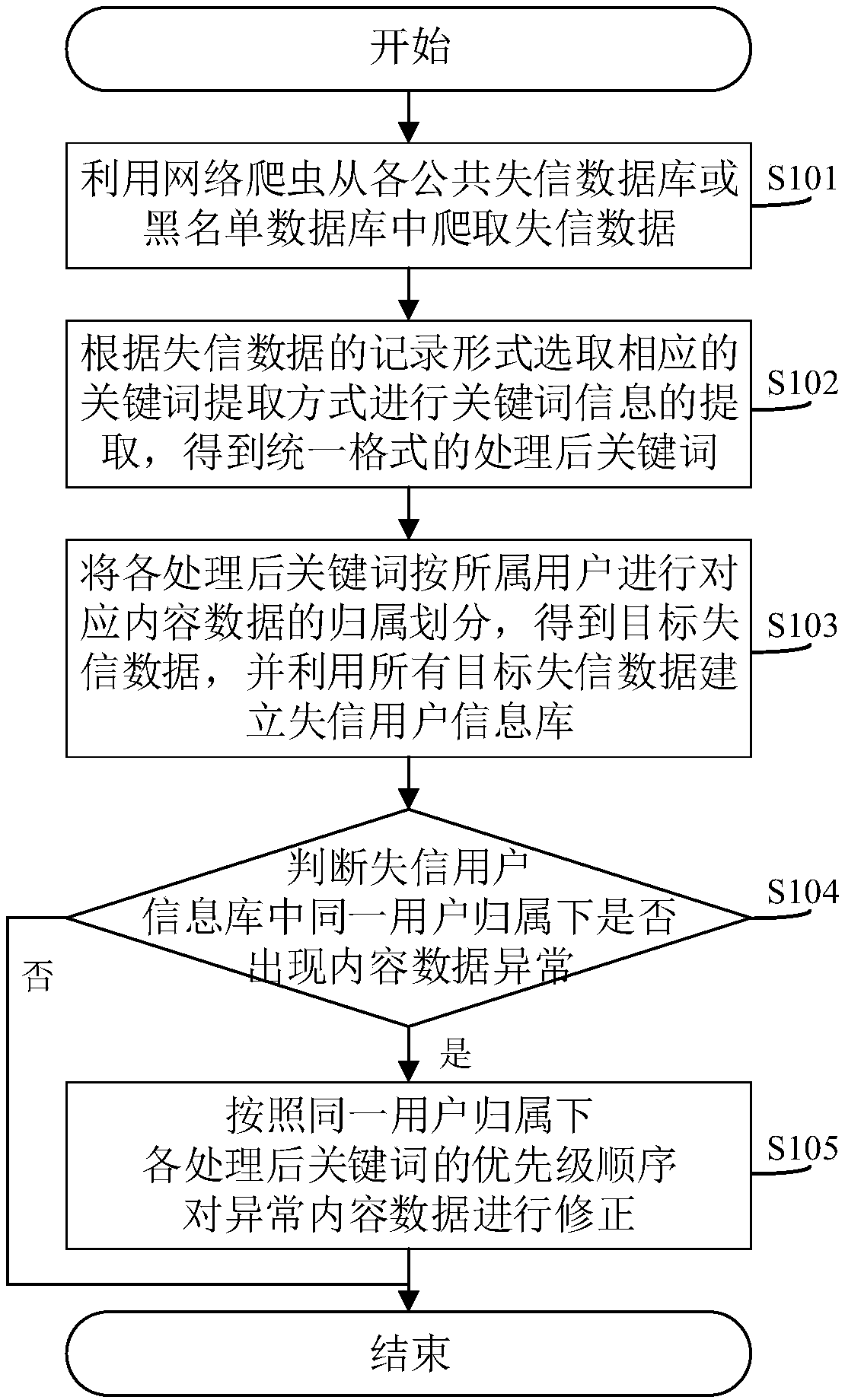
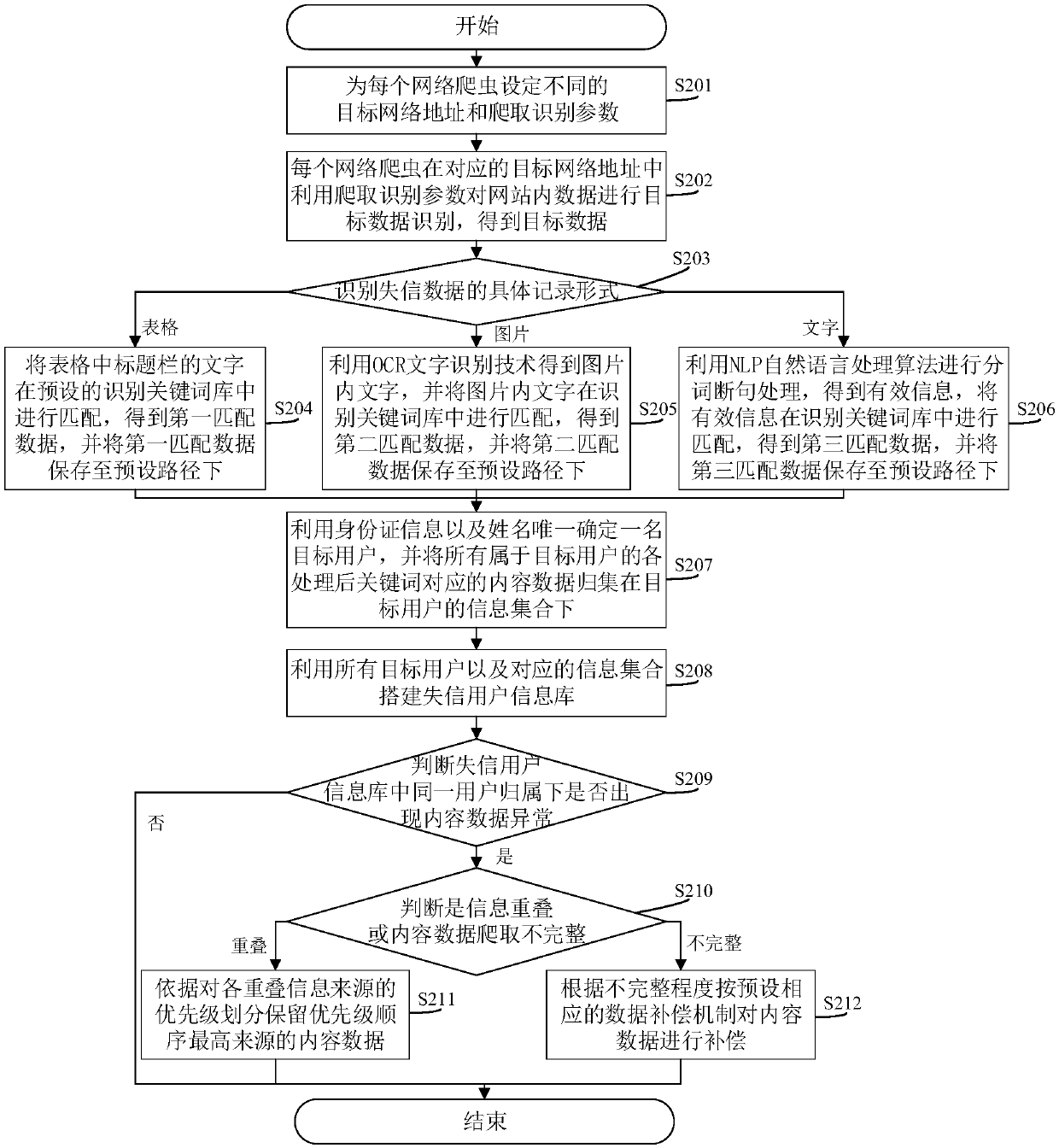
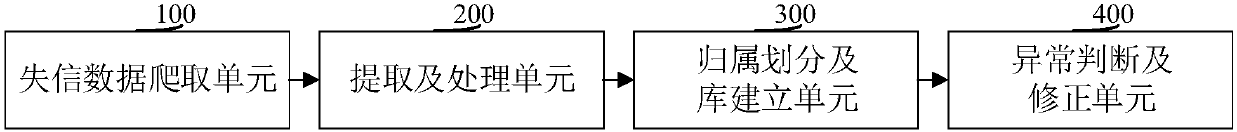
Untrusted user data processing method, system and related apparatus
InactiveCN107798068AImprove data qualityExtensive sources of dataSpecial data processing applicationsData processing systemInformation repository
The invention discloses an untrusted user data processing method. The method comprises the steps of crawling untrusted data from public untrusted databases or blacklist databases by utilizing a network crawler; according to a recording form of the untrusted data, selecting a corresponding mode for performing keyword information extraction to obtain processed keywords; performing attribution division of corresponding content data on the processed keywords according to users which the processed keywords belong to, thereby obtaining target untrusted data, and establishing an untrusted user information library by utilizing the target untrusted data; and judging whether abnormal content data occurs in the untrusted user information library or not, and if the abnormal content data occurs, correcting the abnormal content data according to a priority sequence of the processed keywords. The related data can be crawled through multiple channels; the data processing mode is more reasonable, moreconvenient and quicker; and the data is compared and processed, so that the untrusted user data quality is higher. Meanwhile, the invention furthermore discloses an untrusted user data processing system and apparatus, and a computer readable storage medium, which have the abovementioned beneficial effects.
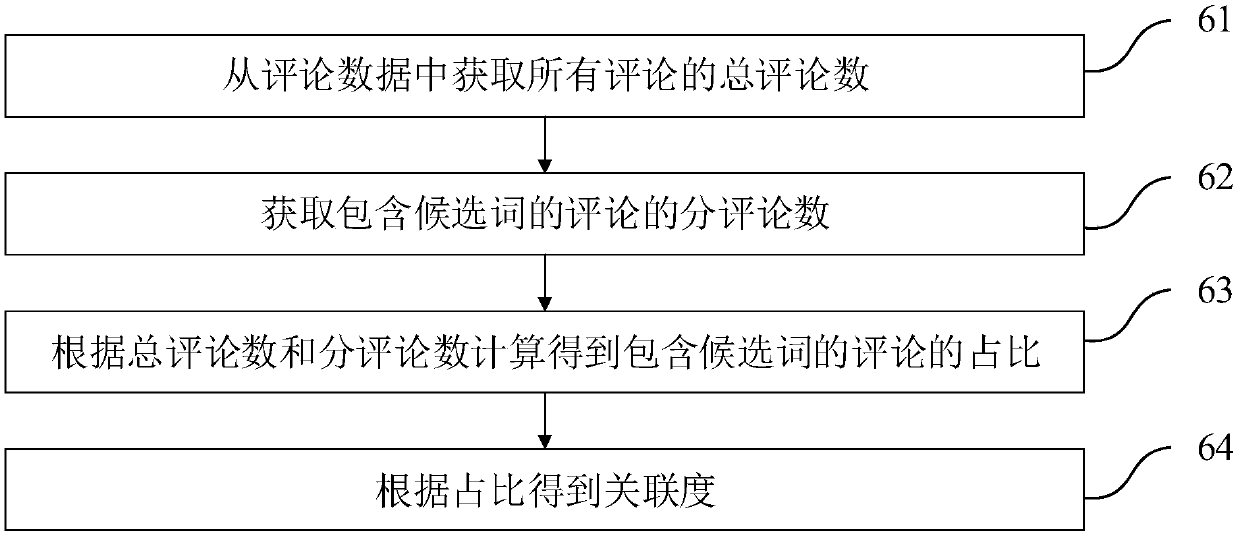
Owner:浙江极赢信息技术有限公司
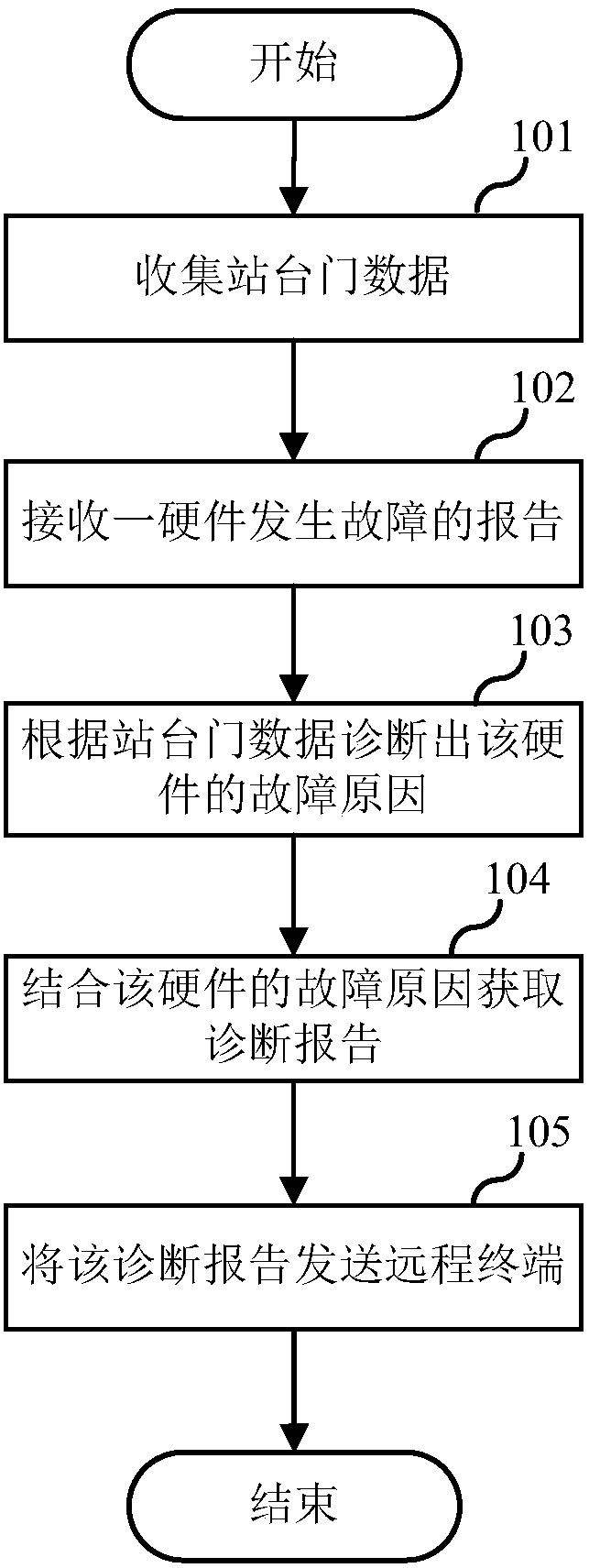
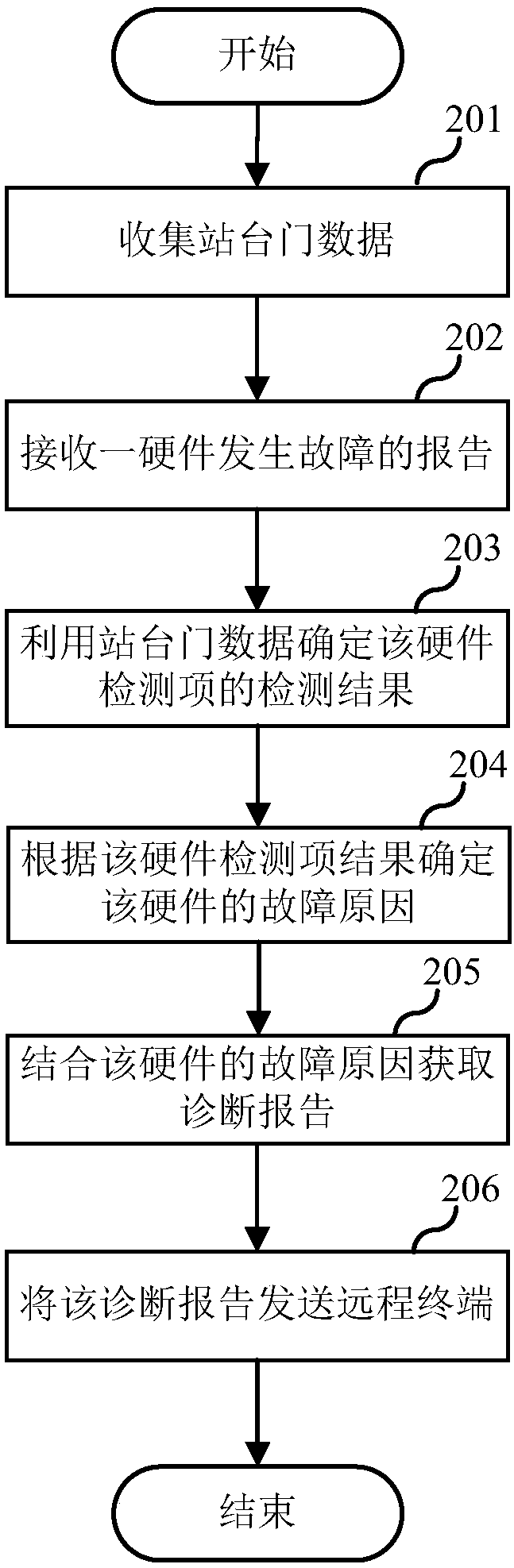
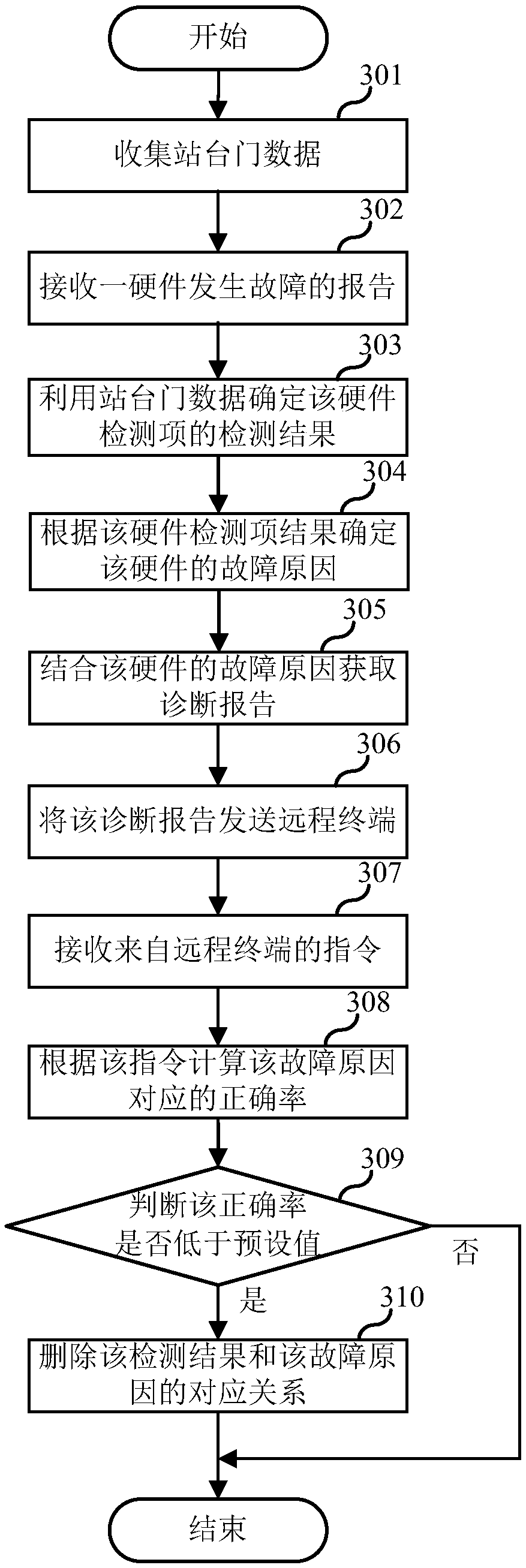
Rail transit platform door remote fault diagnosis method and system
ActiveCN108268023AExtensive sources of dataAccurate judgmentElectric testing/monitoringInformation technologyDiagnosis methods
The invention relates to the technical field of information, and discloses a rail transit platform door remote fault diagnosis method and system. The method comprises the steps that the platform doordata are collected, the platform door data are from at least two platforms, and the platform door data include the state parameters of each device; when a hardware fault report is received, the faultcause of the hardware is diagnosed according to the platform door data; the feature parameters, the purchasing information and the logistics information of the hardware are extracted, and the diagnosis report is acquired through combination of the fault cause of the hardware; and the diagnosis report is transmitted to a remote terminal. The diagnostic basis of the remote fault diagnosis technologyis abundant and the feedback is rapid so that the common maintenance personnel can remotely determine the fault and eliminate the fault through the remote terminal with no requirement for the manufacturer to send professional research and development technicians for field maintenance when the fault of the platform door occurs, and thus the fault maintenance speed can be enhanced and the labor cost can be reduced.
Owner:SHANGHAI JIACHENG RAILWAY TRANSPORTATION SAFETY SYST
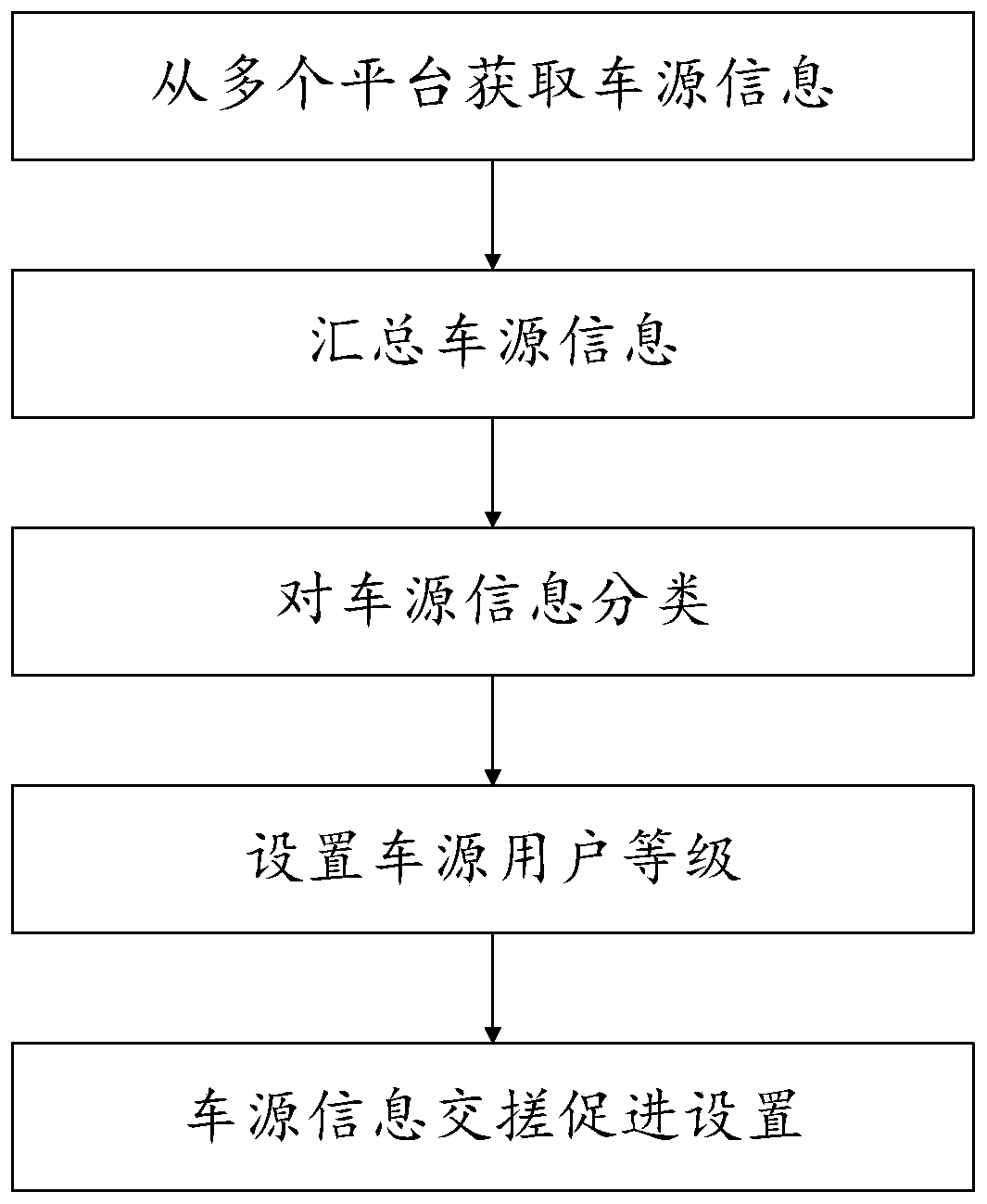
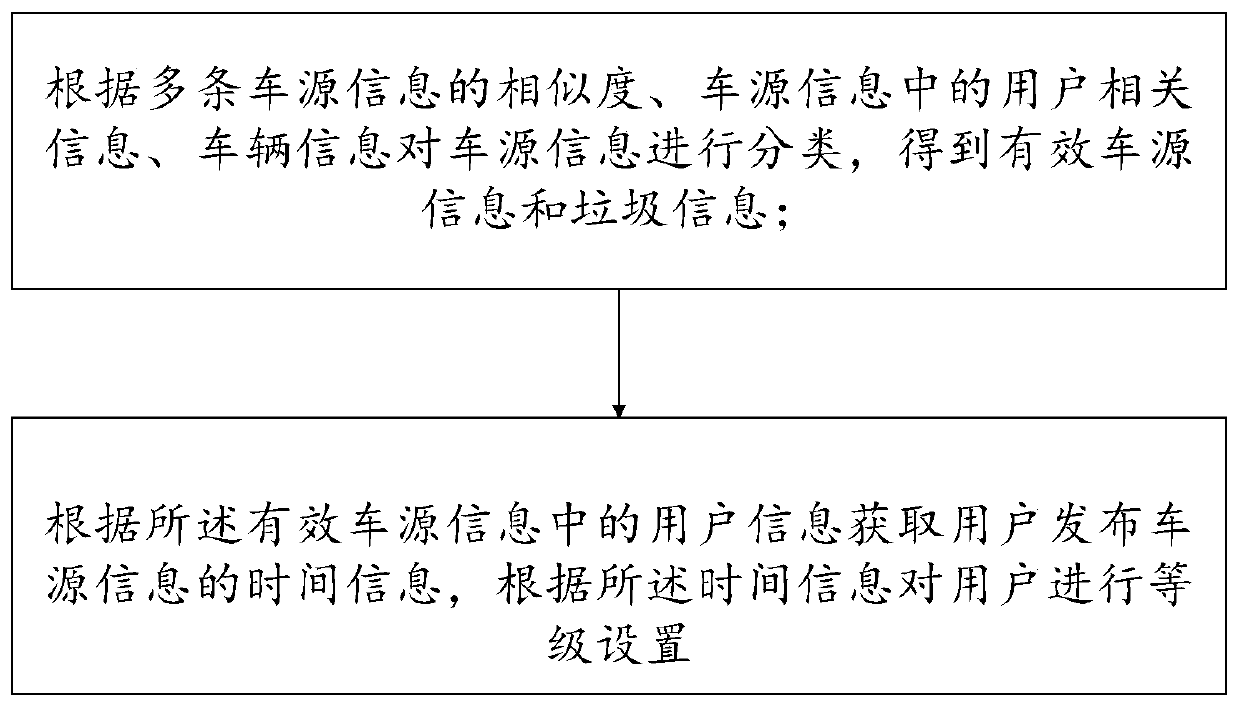
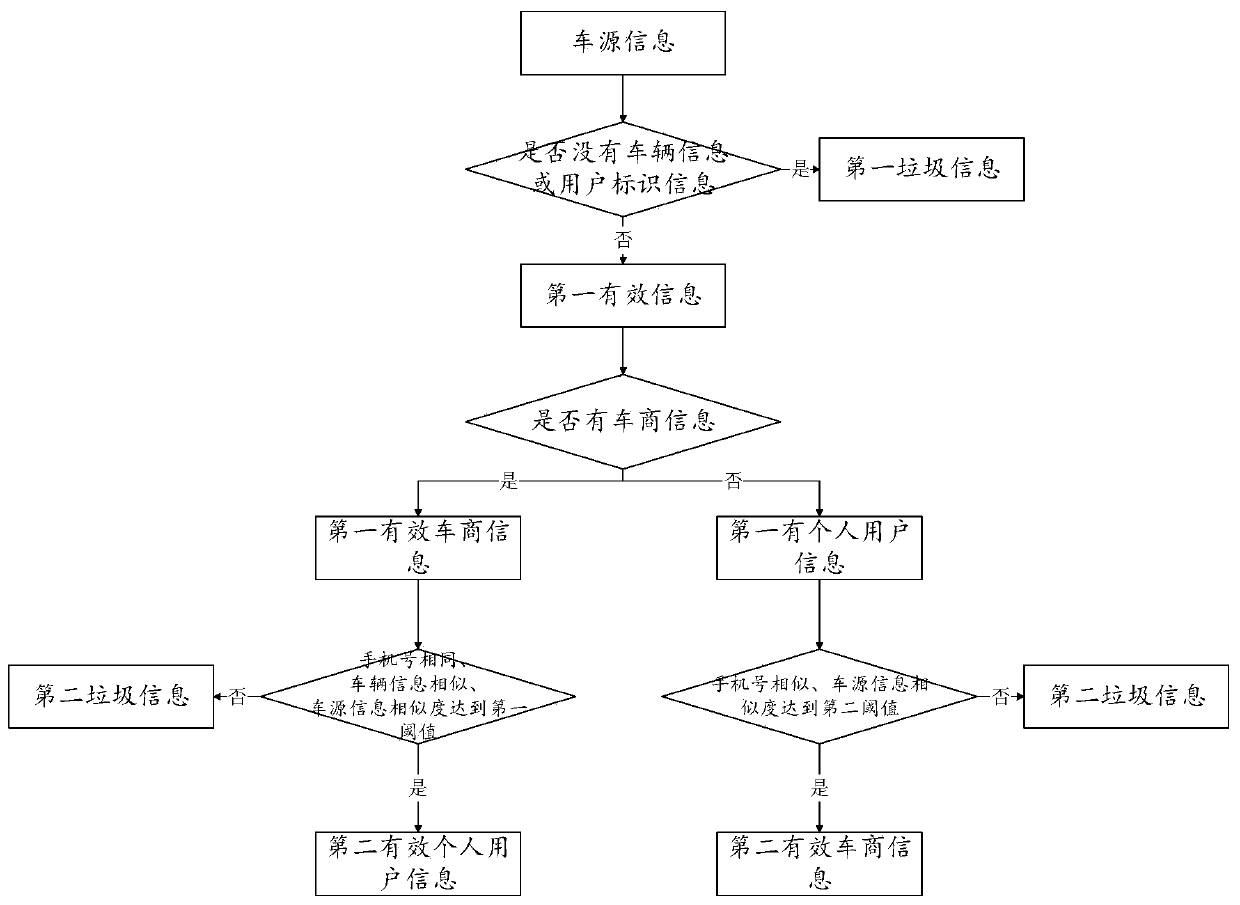
Vehicle source information processing method, system and device
InactiveCN110427963AImprove accuracyImprove reliabilityDigital data information retrievalCharacter and pattern recognitionTemporal informationInformation processing
The invention provides a vehicle source information processing method, system and device, and the method comprises the steps: carrying out the classification of vehicle source information according tothe similarity of a plurality of pieces of vehicle source information, user related information in the vehicle source information, and vehicle information, and obtaining effective vehicle source information and junk information; and according to the user information in the effective vehicle source information, obtaining time information of the vehicle source information published by the user; andaccording to the time information, carrying out grade setting on the user. The data is classified and graded through similarity calculation according to the characteristics of Internet vehicle selling information in combination with the user related information of the vehicle source information, so that effective and high-quality vehicle source information can be efficiently and accurately extracted.
Owner:YOUXINPAI BEIJING INFORMATION TECH CO LTD
Suspicious threat index active validation method and system based on source-opening information
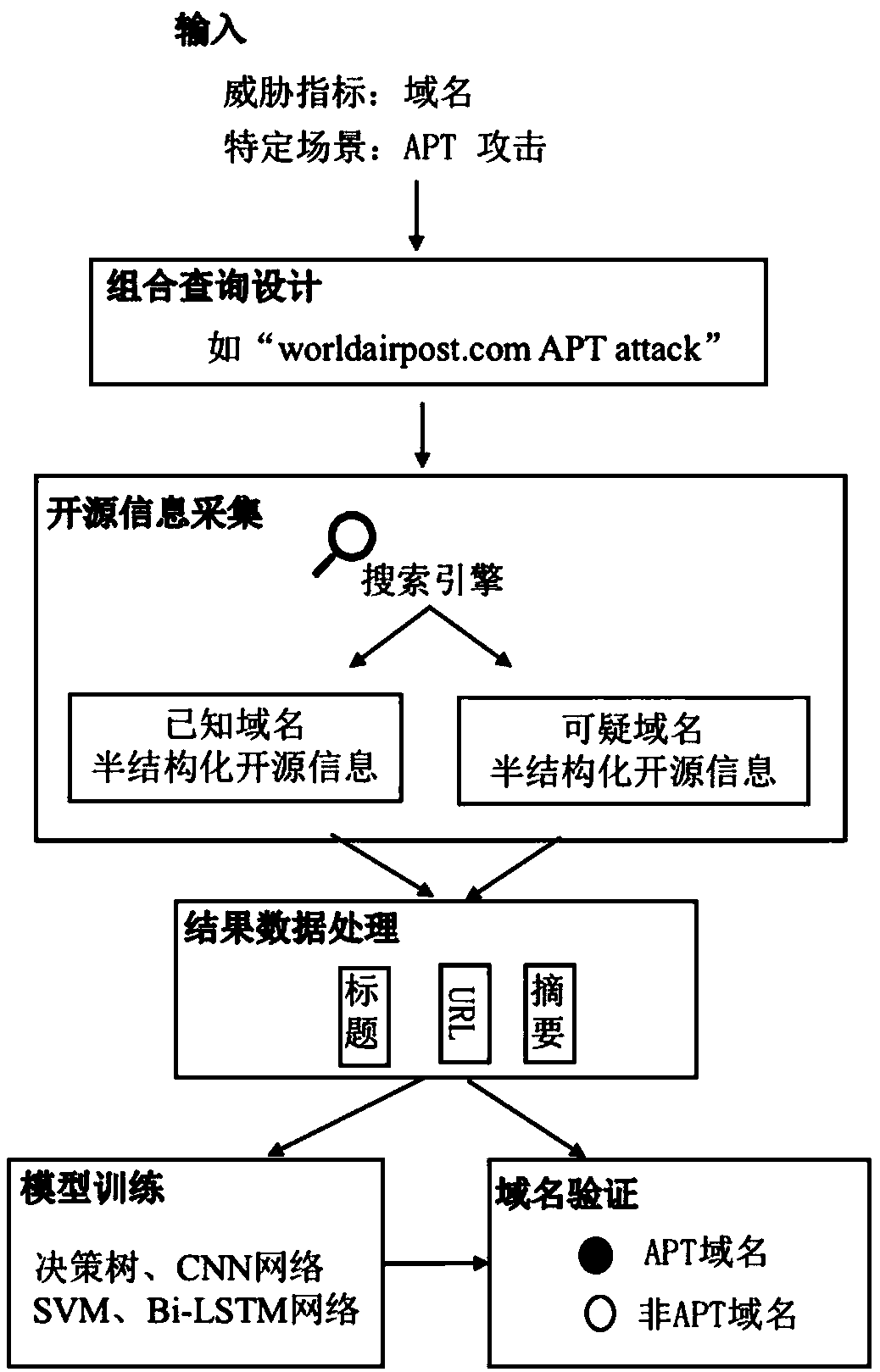
ActiveCN109194605ALow costAvoid the Problem of Low Intelligence CoverageTransmissionValidation methodsThe Internet
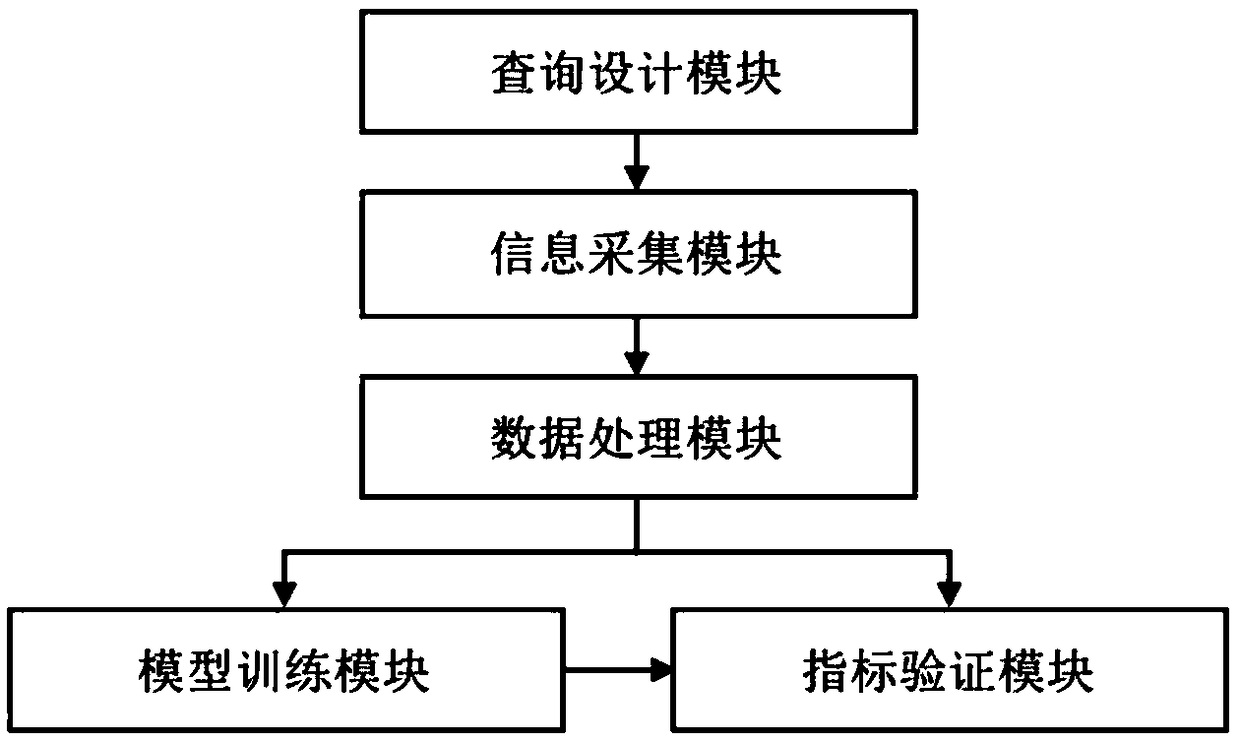
The present invention relates to a suspicious threat index active validation method and system based on source-opening information. The method comprises the following steps of: 1) designing a specialquery statement, wherein the special query statement is combination of suspicious threat indexes and special scenes; 2) collecting and crawling result information obtained through retrieval on the internet according to the special query statement; 3) performing structuring processing of the related source-opening information in the result information to obtain structural data; 4) employing the structural data to fully learn the hidden features and train a corresponding classification model; and 5) employing the classification model to verify the malevolence of the suspicious threat indexes inthe special scenes so as to identify the network threat. The system comprises a query design module, an information collection module, a data processing module, a model training module and an index verification module. The suspicious threat index active validation method and system based on source-opening information can efficiently and accurately complete the verification of the suspicious threatindexes to help users with identification of high-class threat attack so as to ensure network safety.
Owner:INST OF INFORMATION ENG CAS
Classification method and device
InactiveCN105740389AExtensive sources of dataWeb data indexingSemantic analysisWeb siteCategorical models
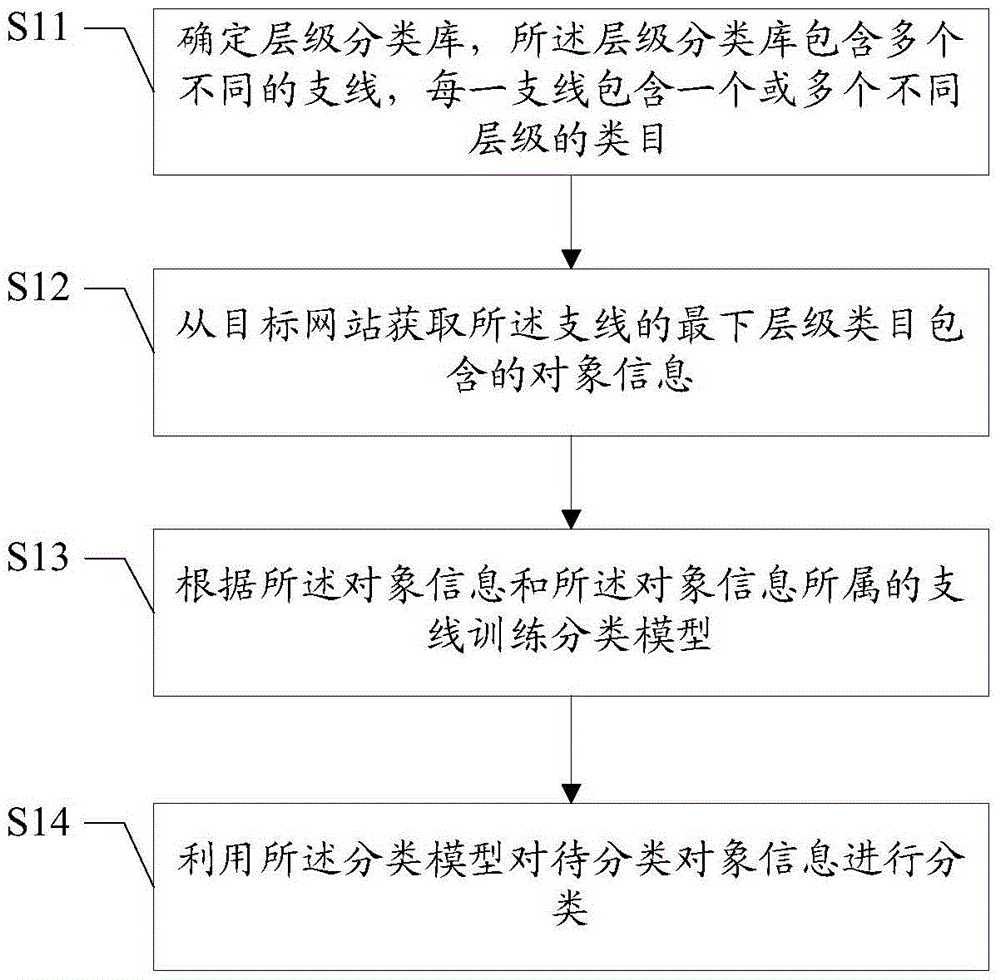
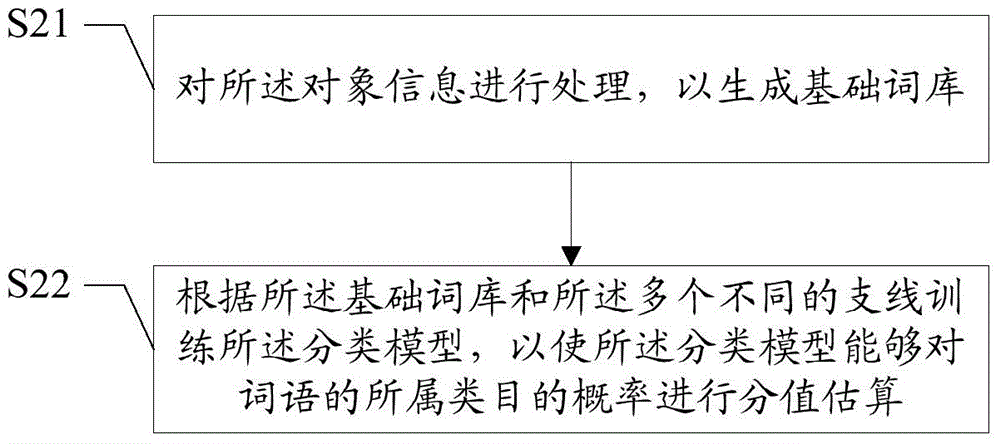
The invention discloses a classification method and device. The classification method comprises the following steps: determining a hierarchical classification library, wherein the hierarchical classification library comprises a plurality of different branches and each branch comprises one or more categories at different hierarchies; obtaining object information contained in the categories, at the lowest hierarchy, of the branches from a target website; and training a classification model according to the object information and branches, to which the object information belong. The classification method and device are higher in classification correctness.
Owner:上海晶赞企业管理咨询有限公司
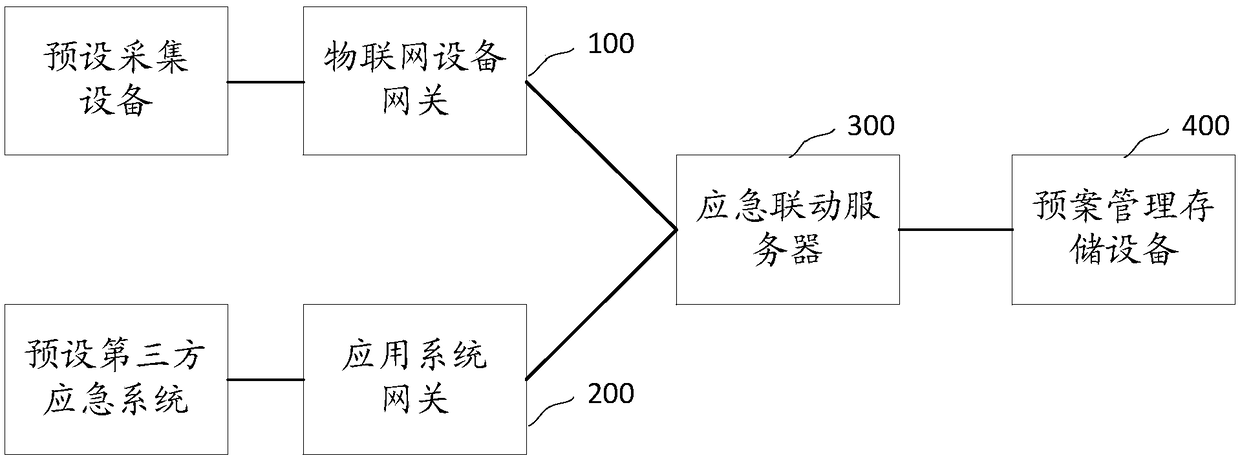
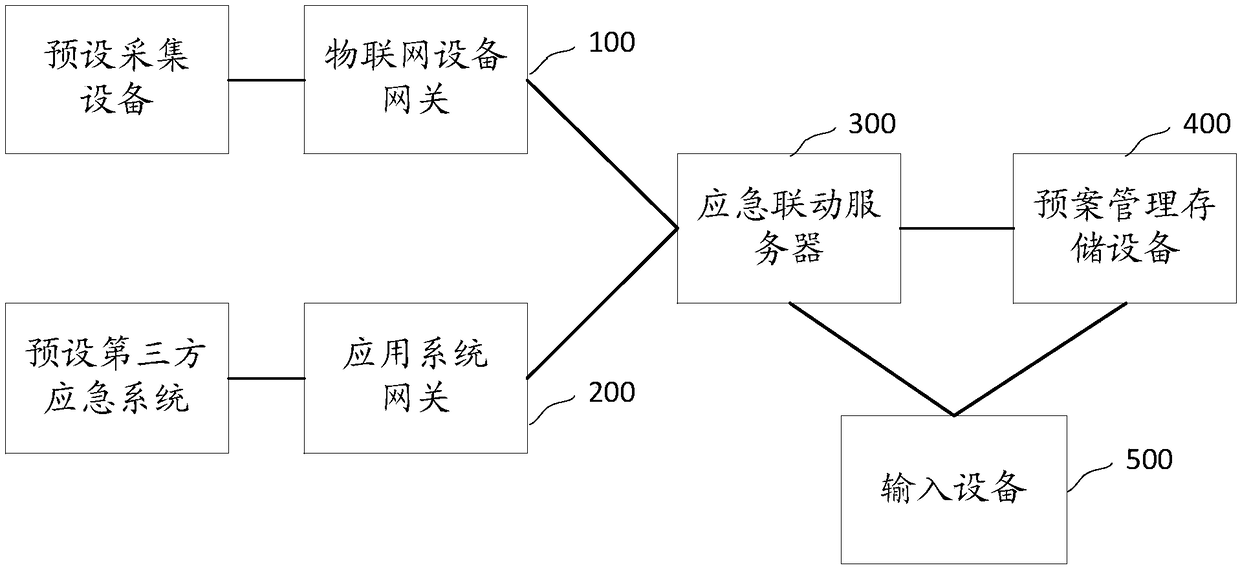
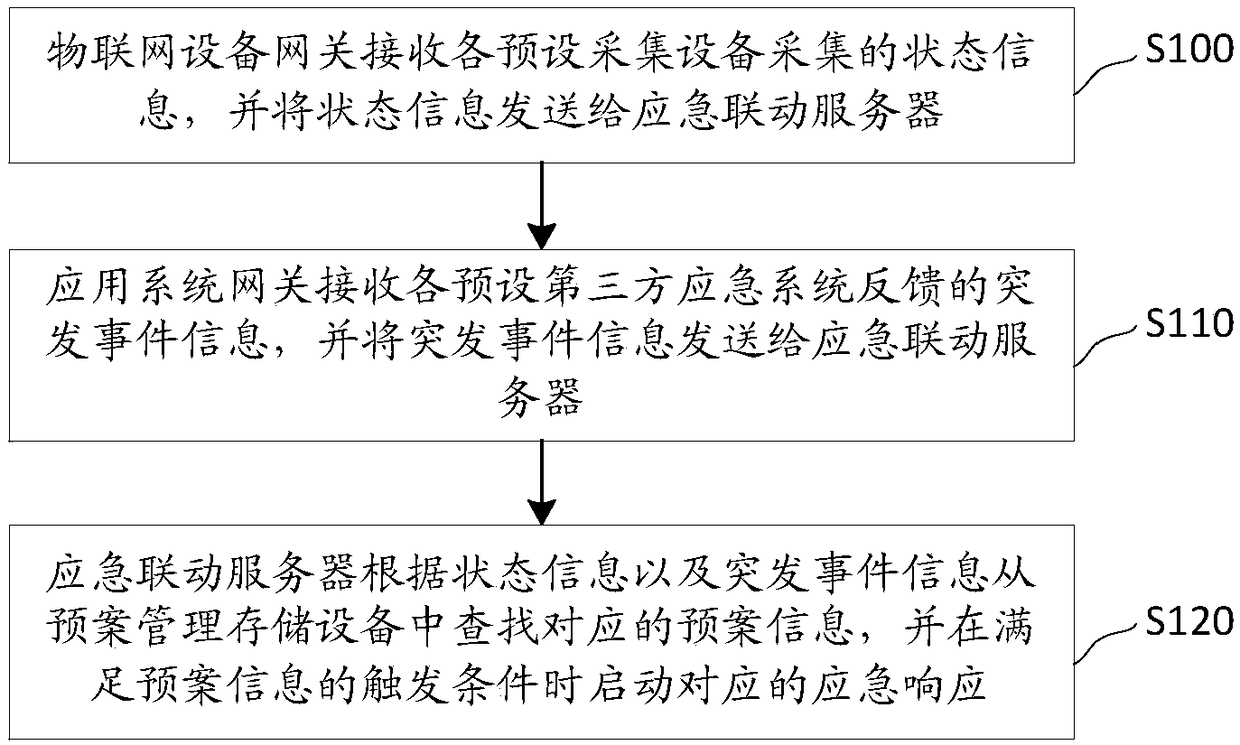
Emergency linkage system and method, and computer readable storage medium
InactiveCN108921756AImprove reliabilityExtensive sources of dataData processing applicationsNetwork connectionsThird partyUnexpected events
The invention relates to the technical field of data processing, and discloses an emergency linkage system. The emergency linkage system comprises the following steps that: an Internet of Things equipment gateway receives state information collected by each piece of preset collection equipment, and sends the state information to an emergency linkage server; an application system gateway receives emergency information fed back from each preset third-party emergency system, and sends the emergency information to the emergency linkage server; the emergency linkage server searches corresponding plan information from plan management and storage equipment according to the state information and the emergency information, and a corresponding emergency response is started when a plan information trigger condition is met; and the plan management and storage equipment stores each piece of plan information. By use of the system, the problems in the prior art that an existing emergency linkage system can not accurately perceive field situations due to a data island phenomenon are avoided, and therefore, each type of emergency forms intercommunication to obtain a scientific commanding decision.The invention also provides an emergency linkage method and a computer readable storage medium and also has the above beneficial effects.
Owner:ZHEJIANG UHOPE COMM TECH
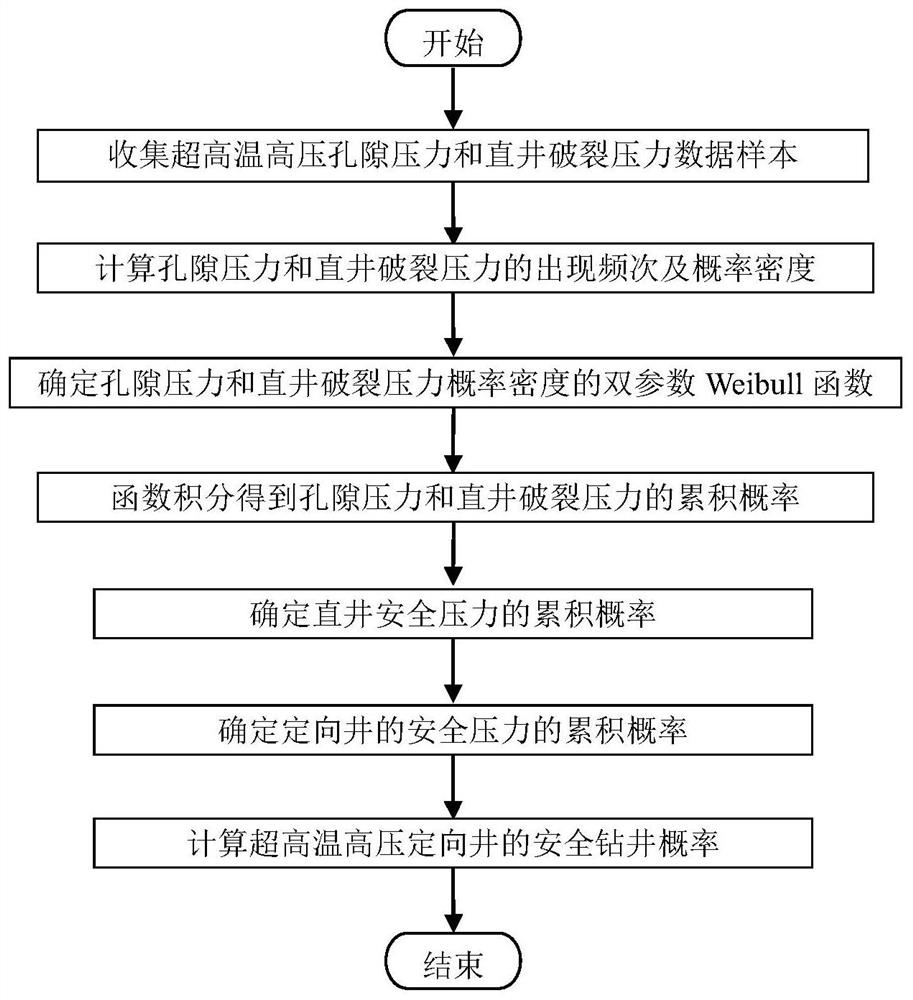
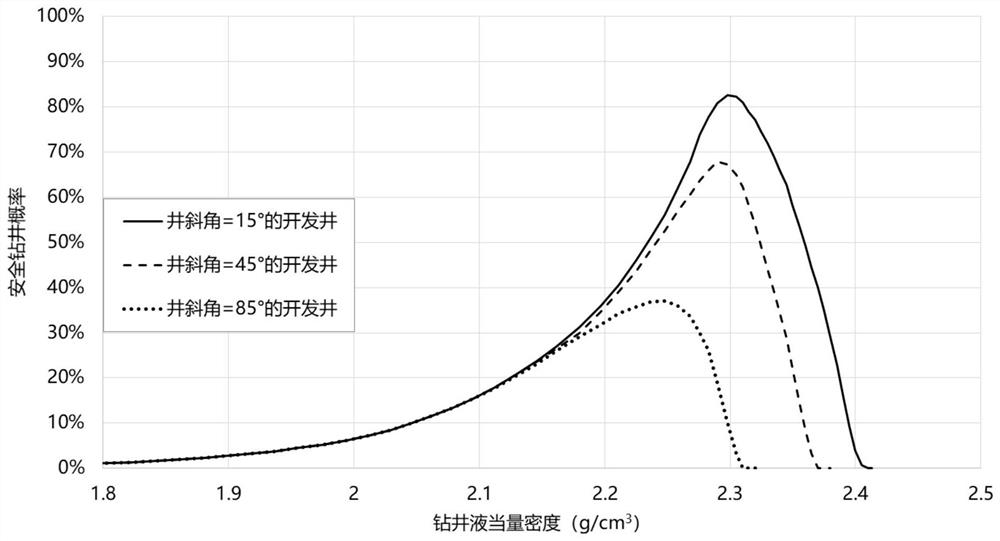
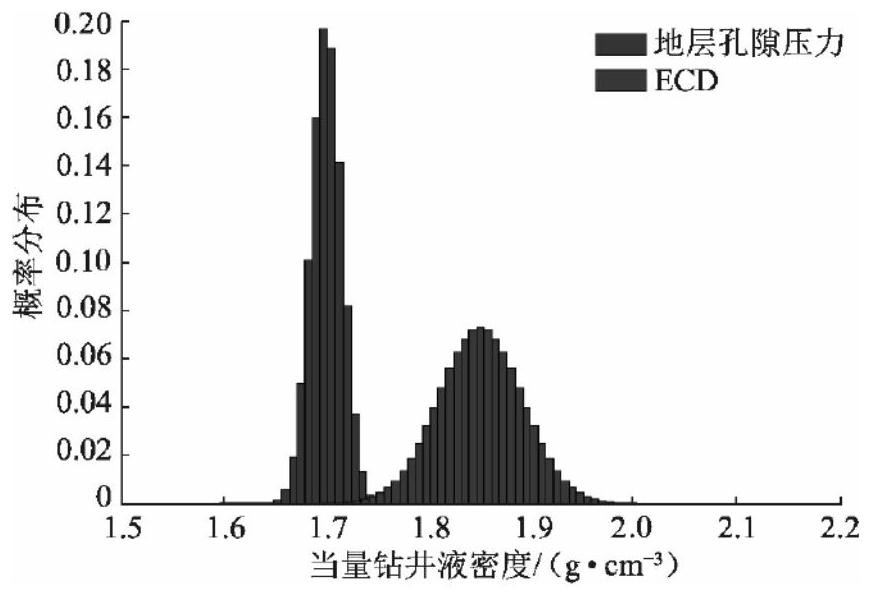
Method for evaluating safety drilling probability of ultra-high temperature and high pressure development based on Weibull function
PendingCN112347424AAvoid High Risk JobsLow costResourcesComplex mathematical operationsThermodynamicsDirectional well
The invention discloses a method for evaluating the safety drilling probability of ultra-high temperature and high pressure development based on a Weibull function. The method comprises the followingsteps: collecting a pore pressure data sample of an ultrahigh-temperature high-pressure stratum and a vertical well fracture pressure data sample; obtaining probability density distribution of the pore pressure of each section and the fracture pressure of a vertical well according to the occurrence frequency of the pore pressure of each section and the fracture pressure of the vertical well; determining a dual-parameter Weibull function expression of pore pressure and vertical well fracture pressure probability density; integrating to obtain a cumulative probability function expression of thepore pressure and the vertical well fracture pressure; determining a cumulative probability expression of the vertical well safety pressure; determining a cumulative probability expression of the safety pressure of a directional well; and calculating a safe drilling probability value of the ultrahigh-temperature and high-pressure directional well. By means of the method, the safe drilling probability can be evaluated before drilling of a development well, high-risk operation is avoided, cost and safety accidents are reduced, and the method has important significance in development of an ultra-high-temperature and high-pressure oil and gas field.
Owner:CHINA NATIONAL OFFSHORE OIL (CHINA) CO LTD +1
Personnel efficient physical examination risk management and control system
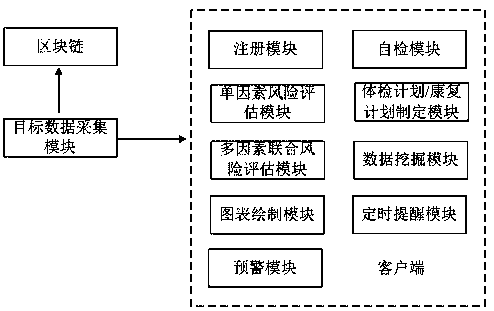
PendingCN110534200ARisk of timely physical examinationExtensive sources of dataHealth-index calculationDiseaseControl system
The invention discloses a personnel efficient physical examination risk management and control system, and the system comprises a target data acquisition module used for acquiring target data throughmultiple ports and sending the acquired data to a block chain for storage; a client which communicates with the blockchain in a mobile phone APP form, and is internally provided with a single-factor risk assessment module used for realizing independent risk assessment of each physical examination index; a multi-factor joint risk assessment module which is used for mining corresponding physical examination indexes in the received target data according to the factor composition corresponding to each disease so as to realize multi-factor joint risk assessment; and a chart drawing module which isused for filling the result of the single-factor risk assessment, the result of the multi-factor joint risk assessment and the dynamic change curve of each assessment result into a prefabricated latextemplate, and performing compiling to generate a pdf report. According to the invention, the efficient monitoring and comprehensive evaluation of the user physical examination indexes are realized, so that the physical examination risk can be found in time.
Owner:吉林大学中日联谊医院
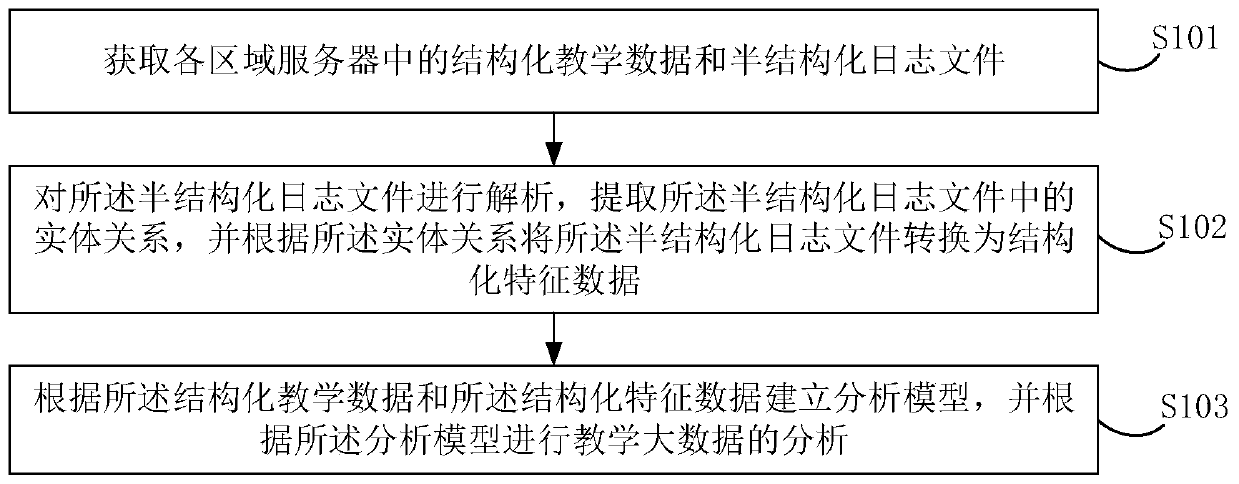
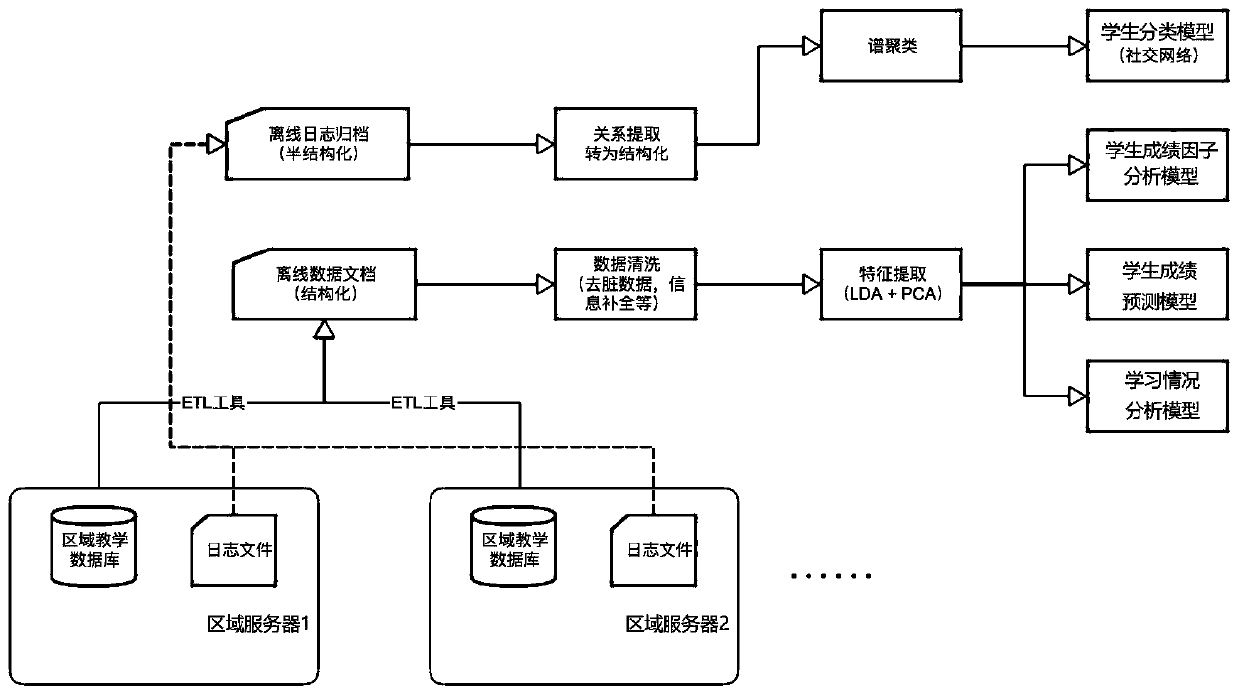
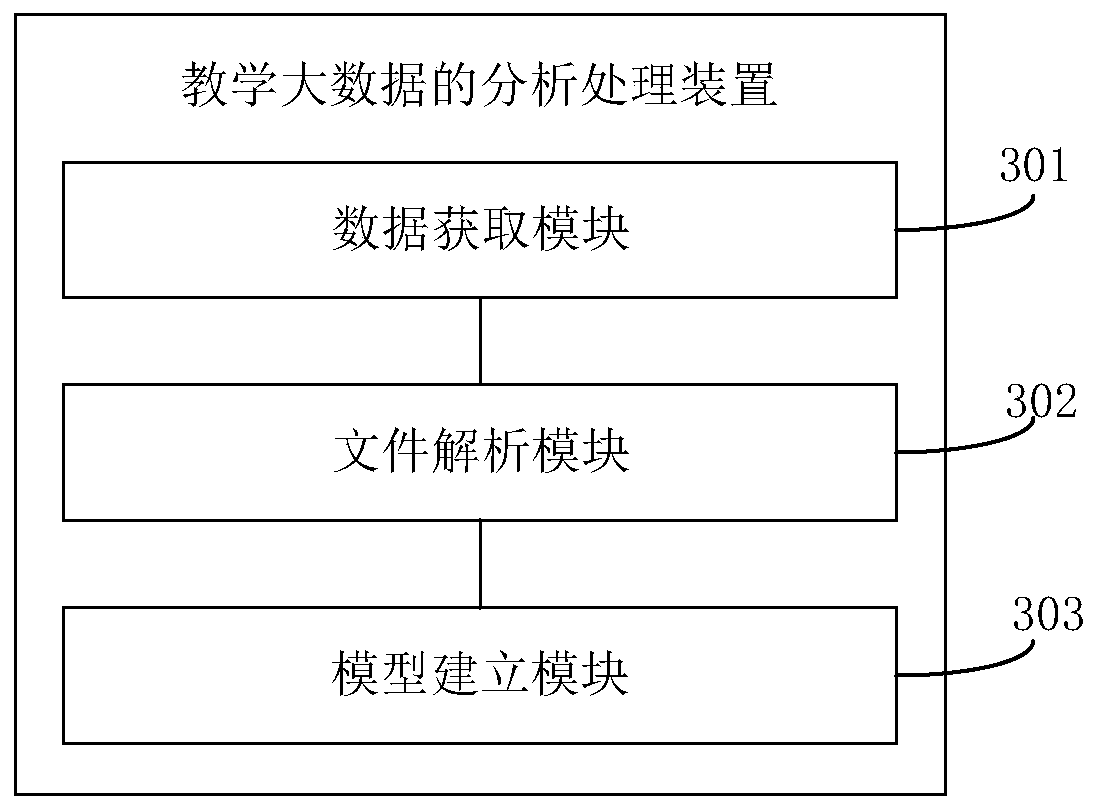
Analysis processing method and device for teaching big data
InactiveCN110059117AEasy to set upRealize scientific modelingData processing applicationsDatabase management systemsData sourceFeature data
The embodiment of the invention discloses an analysis processing method and device for teaching big data. The method comprises the steps of acquiring structured teaching data and semi-structured log files in all regional servers; analyzing the semi-structured log file, extracting an entity relationship in the semi-structured log file, and converting the semi-structured log file into structured feature data according to the entity relationship; and establishing an analysis model according to the structured teaching data and the structured feature data, and analyzing teaching big data accordingto the analysis model. Structured teaching data and semi-structured log files in all regional servers are acquired, so that the data source is relatively wide; by analyzing the semi-structured log file into structured feature data, the data structure is consistent, an analysis model is conveniently established, scientific modeling and analysis of teaching big data are achieved, monitoring, evaluation and diagnosis can be conducted on all aspects of student learning, and a teacher is guided to be continuously adjusted into a better teaching mode.
Owner:北京那镁克科技有限公司
Driving behavior data acquisition and analysis method and system
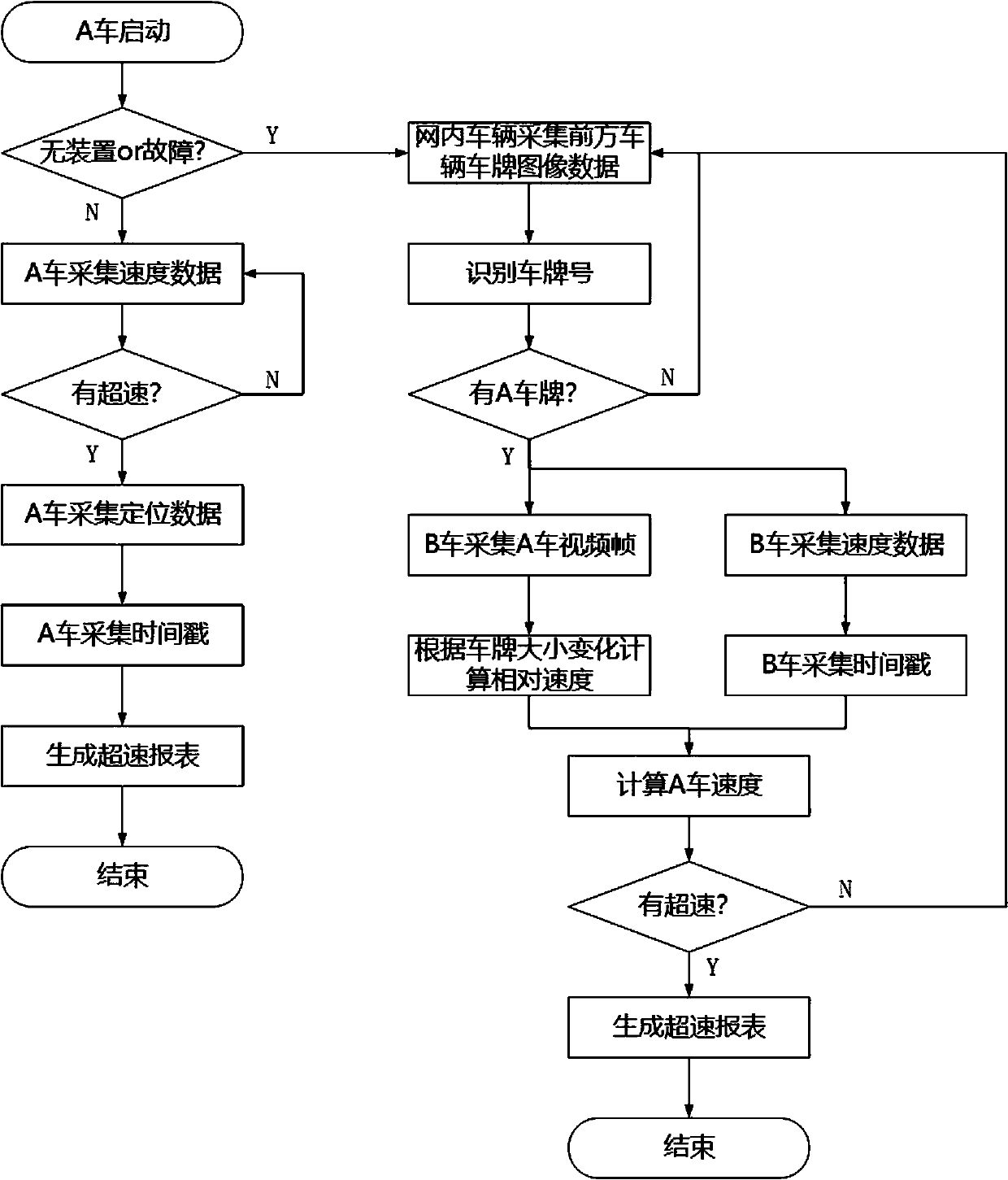
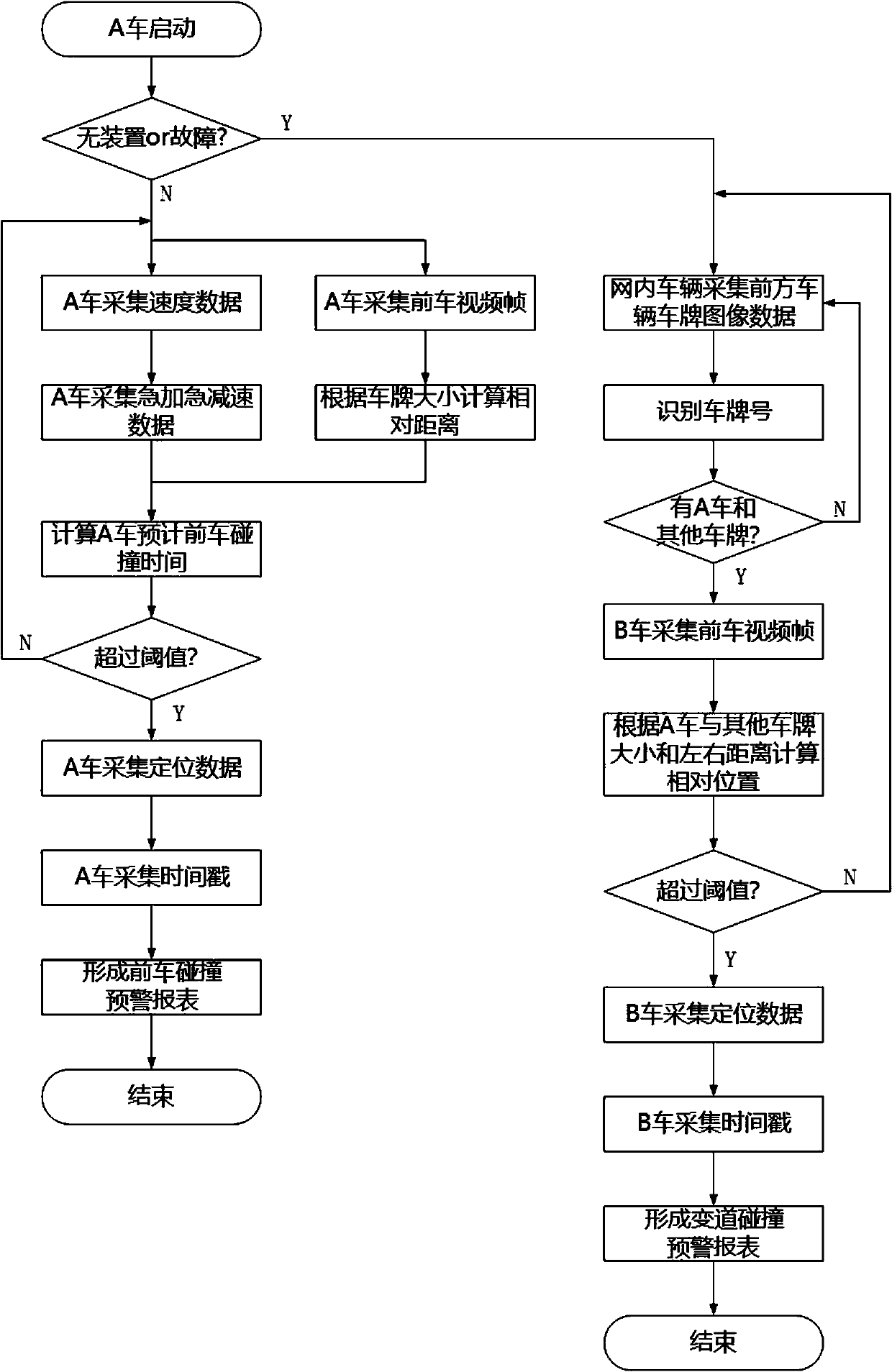
ActiveCN111243290ALower performance requirementsExtensive sources of dataRegistering/indicating working of vehiclesRoad vehicles traffic controlData OriginSimulation
The invention discloses a driving behavior data acquisition and analysis method and system. The invention relates to the technical field of traffic big data analysis, and solves the problem of high data acquisition and analysis cost caused by a traditional driving behavior data acquisition mode. According to the invention, data contents are selected as positioning data, speed data, urgent acceleration and deceleration data, lane departure data, license plate image data and front road video data, the data source can be an automobile data recorder or a vehicle-mounted mobile phone of any vehicleon the road. More than 90% of road vehicles can be basically covered on the premise of not increasing extra construction cost. The method has the advantages of wide data source, simple data acquisition, simple analysis method and low analysis equipment performance requirement, greatly reduces the construction, operation and maintenance cost on the whole, and is more beneficial to the realization,popularization and promotion of driving behavior analysis.
Owner:JIANGSU HOSKI NETWORK TECH CO LTD NANJING
Urban disaster prediction system
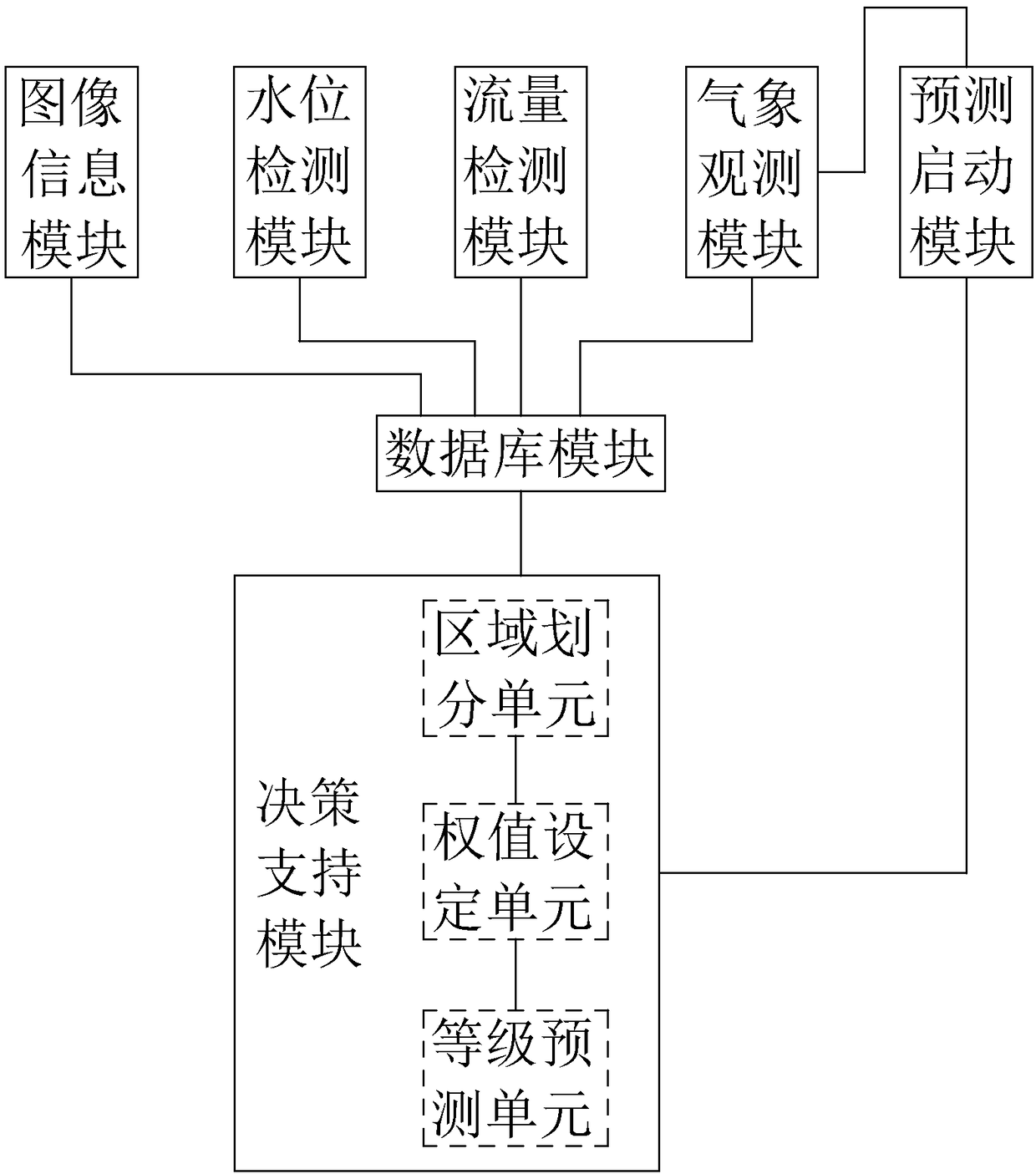
InactiveCN108564190AExtensive sources of dataImprove forecast accuracyMeasurement devicesForecastingDecision takingPrediction system
The invention discloses an urban disaster prediction system. The system comprises an image information module, a water level detection module, a flow detection module, a meteorological observation module, a database module and a detection support module, wherein the decision support module is used for judging the occurrence grade of a flood disaster according to data collected by the image information module, the water level detection module, the flow detection module and the meteorological observation module, and the higher the occurrence grade, the higher the probability of flood disaster occurrence. According to the system, multiple pieces of data causing flood disaster occurrence are collected through the image information module, the water level detection module, the flow detection module and the meteorological observation module, data sources are comprehensive and wide, multiple factors causing the flood disaster are comprehensively considered, and prediction accuracy is high. The system is used for predicting the probability of occurrence of the urban flood disaster.
Owner:FOSHAN UNIVERSITY
Big data-oriented potential adverse drug reaction data mining system and method
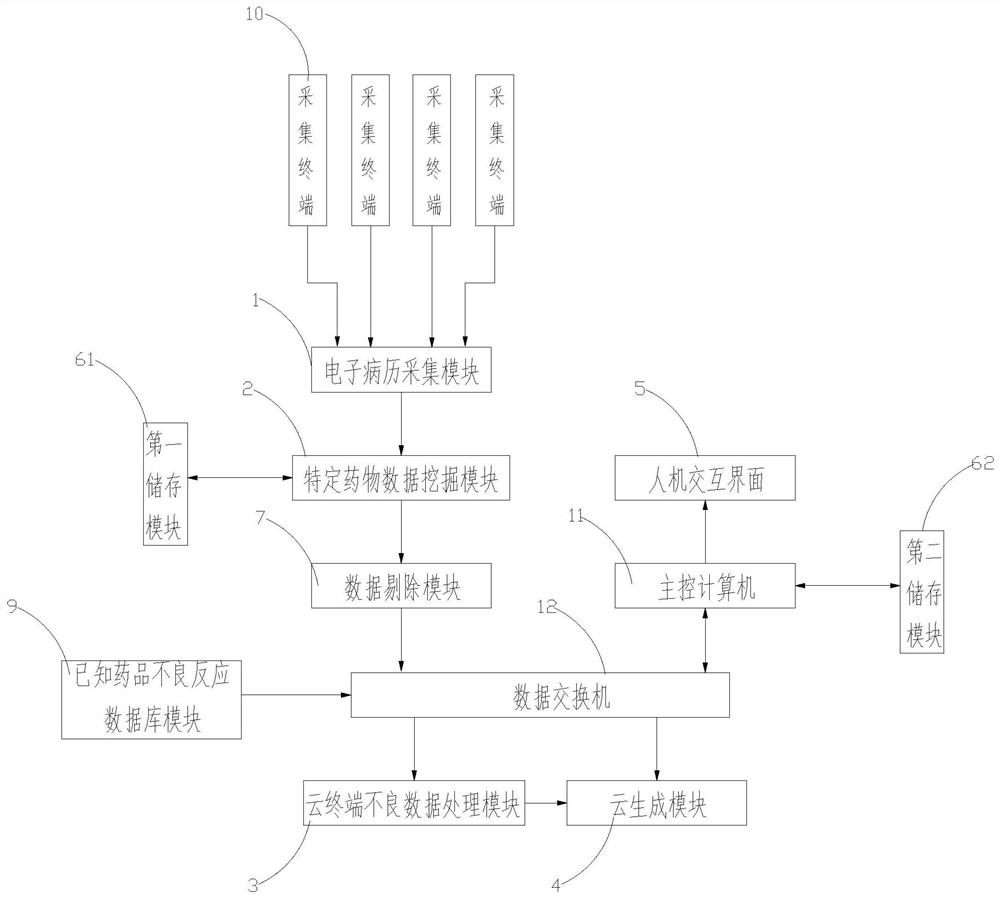
PendingCN112289458AReduce analysis workloadHigh precisionMedical data miningDrug referencesMedical recordInteraction interface
The invention discloses a big data-oriented potential adverse drug reaction data mining system and method. The system comprises a plurality of acquisition terminals, an electronic medical record acquisition module, a specific drug data mining module, a cloud terminal adverse event data processing module, a cloud generation module, a main control computer, a human-computer interaction interface anda data switch, the method comprises the following steps: S1, networking electronic medical record systems of hospitals; S2, capturing a patient who takes the specific medicine in the electronic medical record system; S3, establishing a database of related drugs and adverse reactions after the drugs are used; S4, screening data; and S5, performing feature classification. According to the invention, adverse reactions of specific drugs are analyzed by integrating electronic medical records of various hospitals, the data source is wider, various populations exist, and the analysis of reactions ofdrugs relative to various populations is facilitated. Useless data can be eliminated in the analysis process, analysis is facilitated, the data analysis workload is reduced, and the sample accuracy is improved.
Owner:WENZHOU PEOPLES HOSPITAL
Non-contact respiration detection method and device
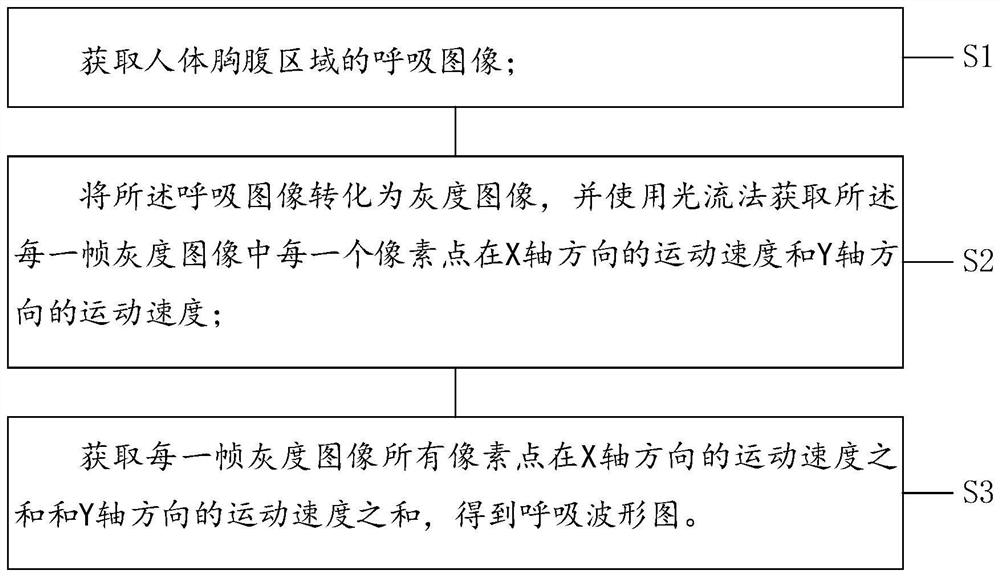
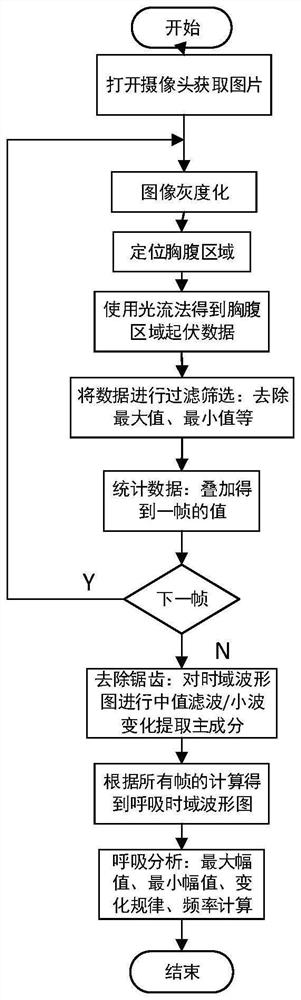
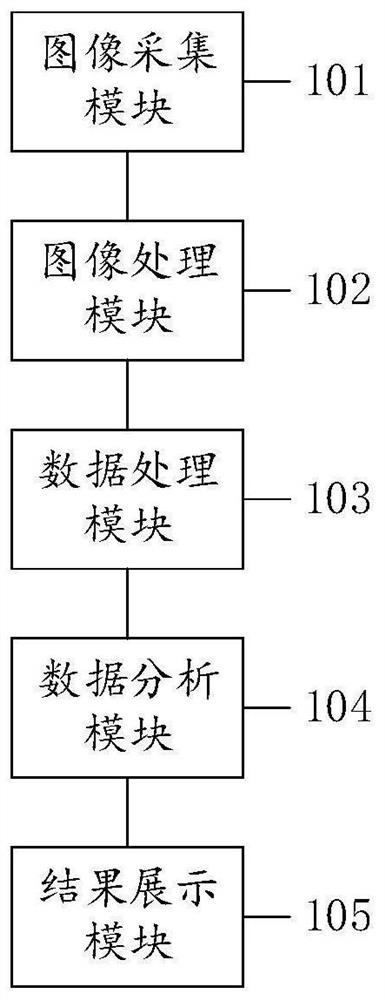
PendingCN114140496AExtensive sources of dataSimple methodImage enhancementImage analysisHuman bodyMachine vision
The invention belongs to the technical field of machine vision, and discloses a non-contact respiration detection method and device. The detection method comprises the following steps: acquiring a breathing image of a chest and abdomen area of a human body; the breathing image is converted into a gray level image, and the movement speed of each pixel point in each frame of gray level image in the X-axis direction and the movement speed of each pixel point in the Y-axis direction are obtained through an optical flow method; and obtaining the sum of the movement speeds of all the pixel points in the X-axis direction and the sum of the movement speeds in the Y-axis direction of each frame of gray level image to obtain a breathing oscillogram. The method has the advantages that the breathing oscillogram is obtained through the breathing image of the chest and abdomen area of the human body, the breathing image can be collected through the camera, and therefore data sources are wide, and the method can adapt to breathing detection in more application scenes.
Owner:国家海洋局南海调查技术中心
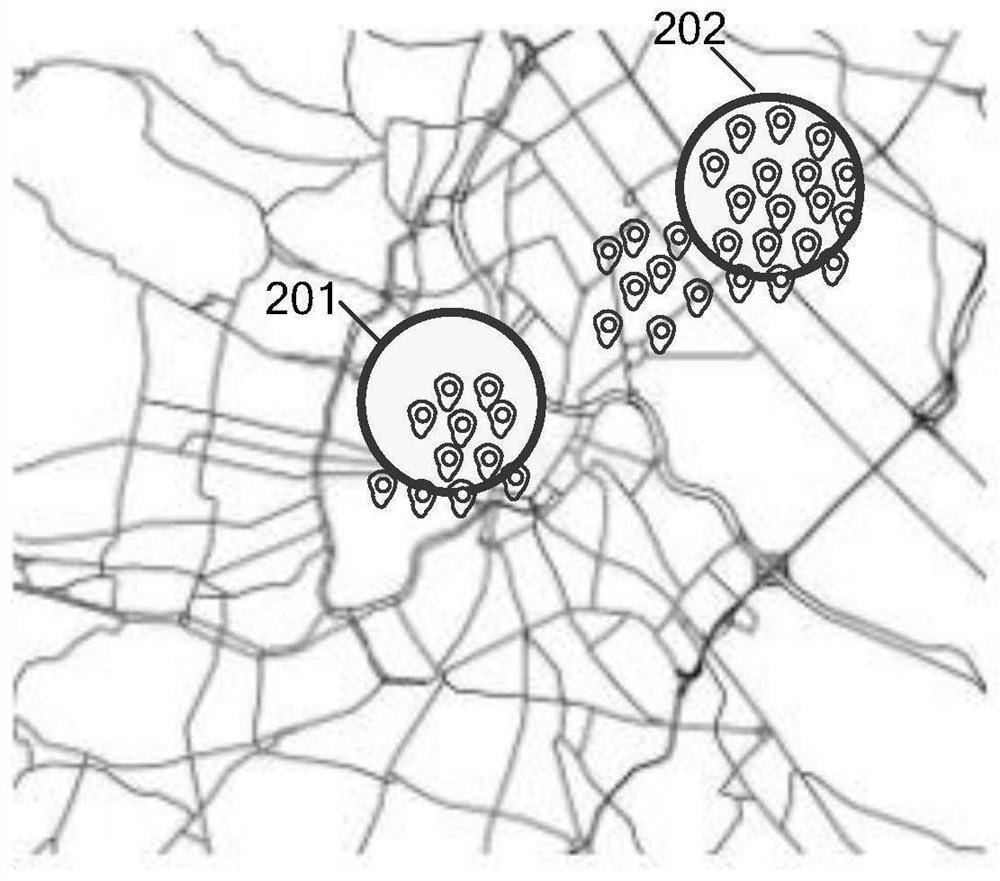
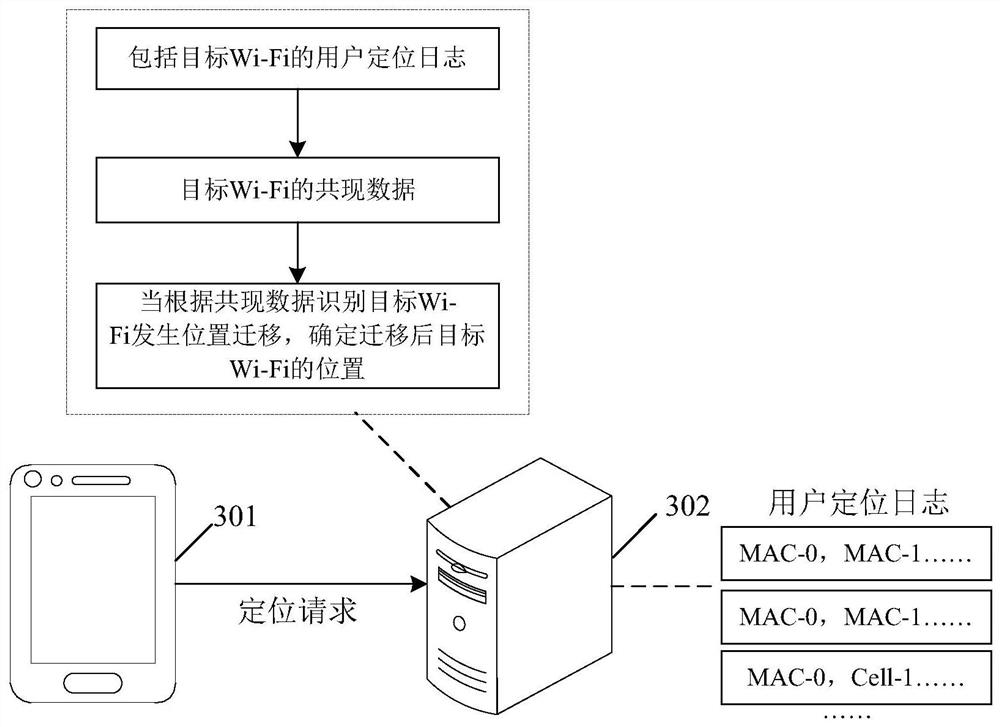
A method and related device for identifying wi-fi location migration
ActiveCN112261705BPromote accumulationQuick discoveryAssess restrictionNetwork topologiesData OriginData mining
The embodiment of the present application discloses a method and a related device for identifying Wi-Fi location migration, obtains user location logs including target Wi-Fi, determines co-occurrence access points of target Wi-Fi according to user location logs, and obtains target Wi-Fi For the co-occurrence data of Fi, the co-occurrence access point and the target Wi‑Fi appear in the same user location log at the same time. The co-occurrence access point reflects the actual location of the target Wi-Fi, and identifies whether the location of the target Wi-Fi has migrated based on the co-occurrence data. When it is recognized that its location has migrated, the location of the target Wi-Fi after migration is determined, and the location of the target Wi-Fi in the location database is updated, thereby providing more accurate positioning services. Co-occurrence data has a wide range of data sources and rapid data accumulation, which greatly shortens the time for finding location migration, and updates the location database by determining the new location in time, which greatly improves the reliability of location services provided by map-based applications.
Owner:TENCENT TECH (SHENZHEN) CO LTD
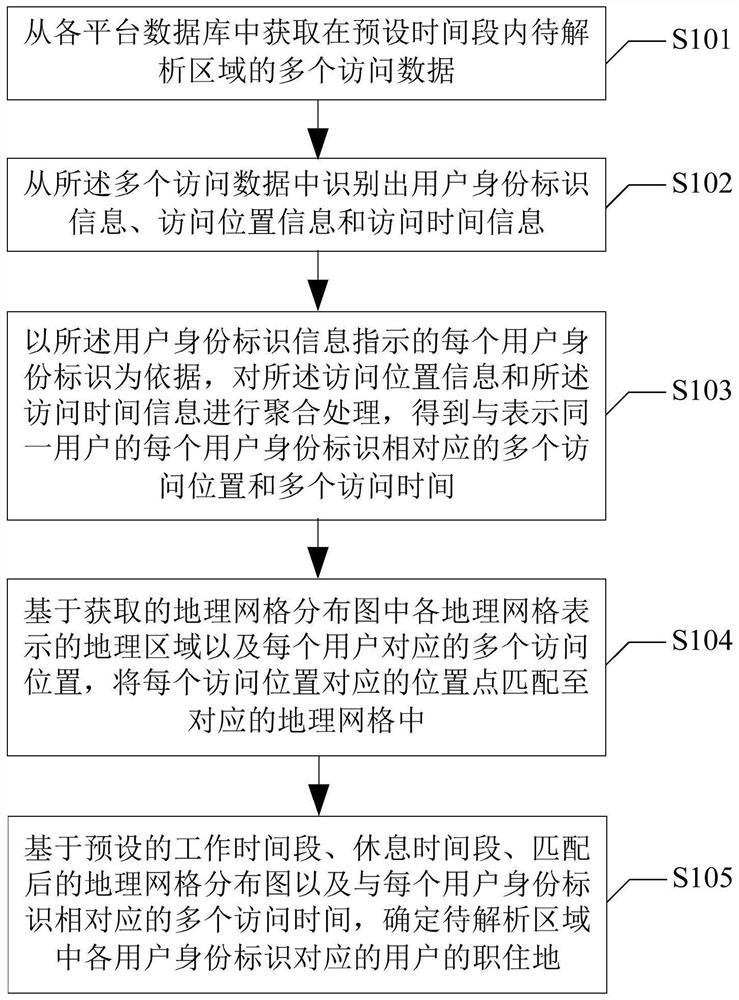
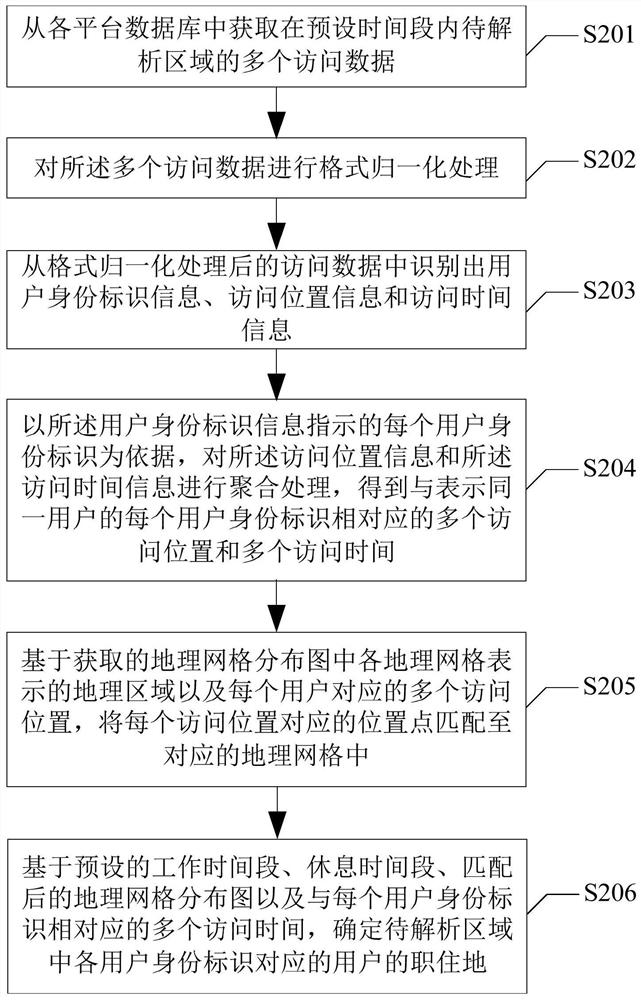
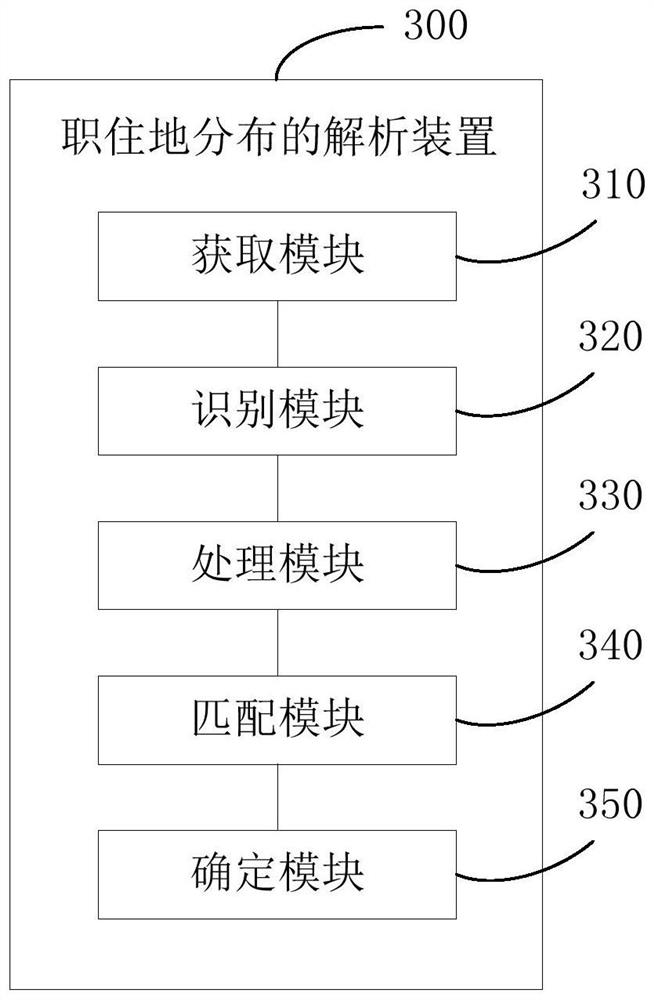
A kind of analysis method, analysis device and readable storage medium of job and residence distribution
ActiveCN110659320BDiversity guaranteedGuaranteed accuracyDatabase management systemsSpecial data processing applicationsAnalysis dataGeoweb
The present application provides an analysis method, an analysis device and a readable storage medium for the distribution of jobs and residences. By acquiring a plurality of access data of the area to be analyzed within a preset time period from each platform database, the user identity information, the identification information, Access location information and access time information; based on each user ID, aggregate the access location information and access time information to obtain multiple access locations and multiple access locations corresponding to each user ID representing the same user. Access time; match the location points corresponding to each access location to the corresponding geographic grid; based on the preset working time period, rest time period, the matched geographic grid distribution map and corresponding to each user ID The multiple access times of the user IDs in the to-be-analyzed area are determined to determine the jobs and residences of the users corresponding to the user IDs in the to-be-analyzed area. In this way, the diversity and accuracy of the analysis data can be ensured, and the accuracy of the user's job and residence analysis result can be improved.
Owner:恩亿科(北京)数据科技有限公司
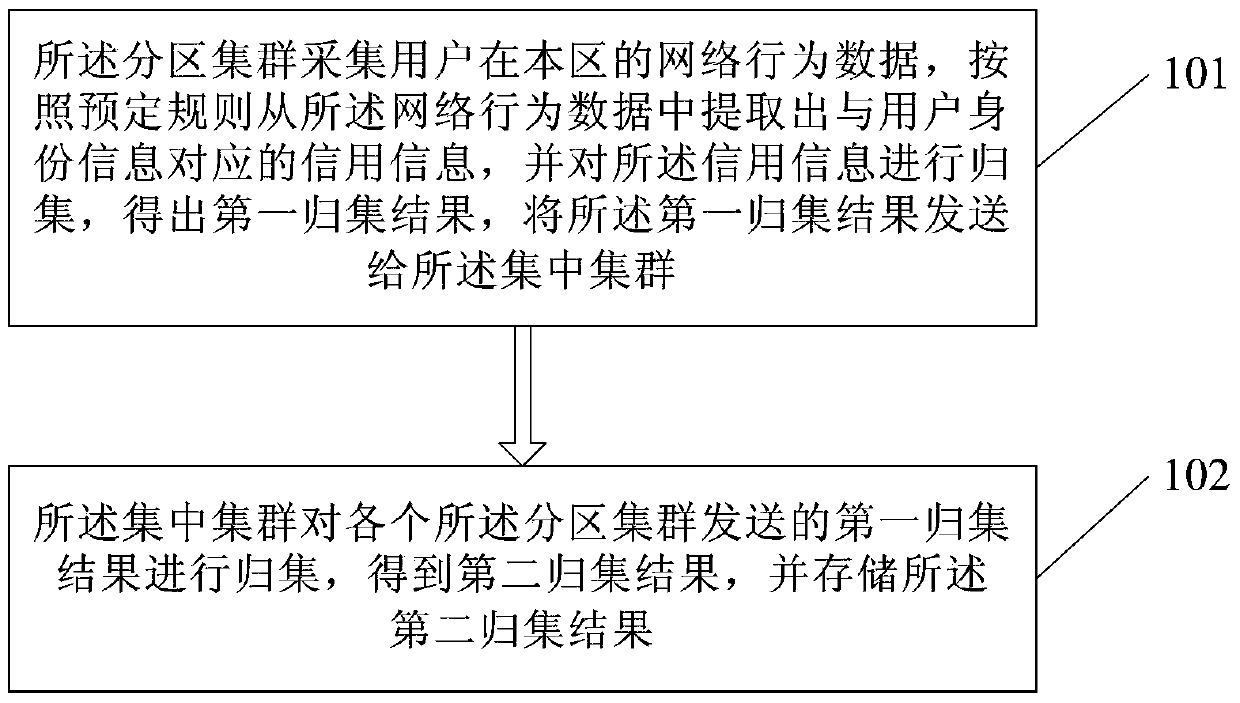
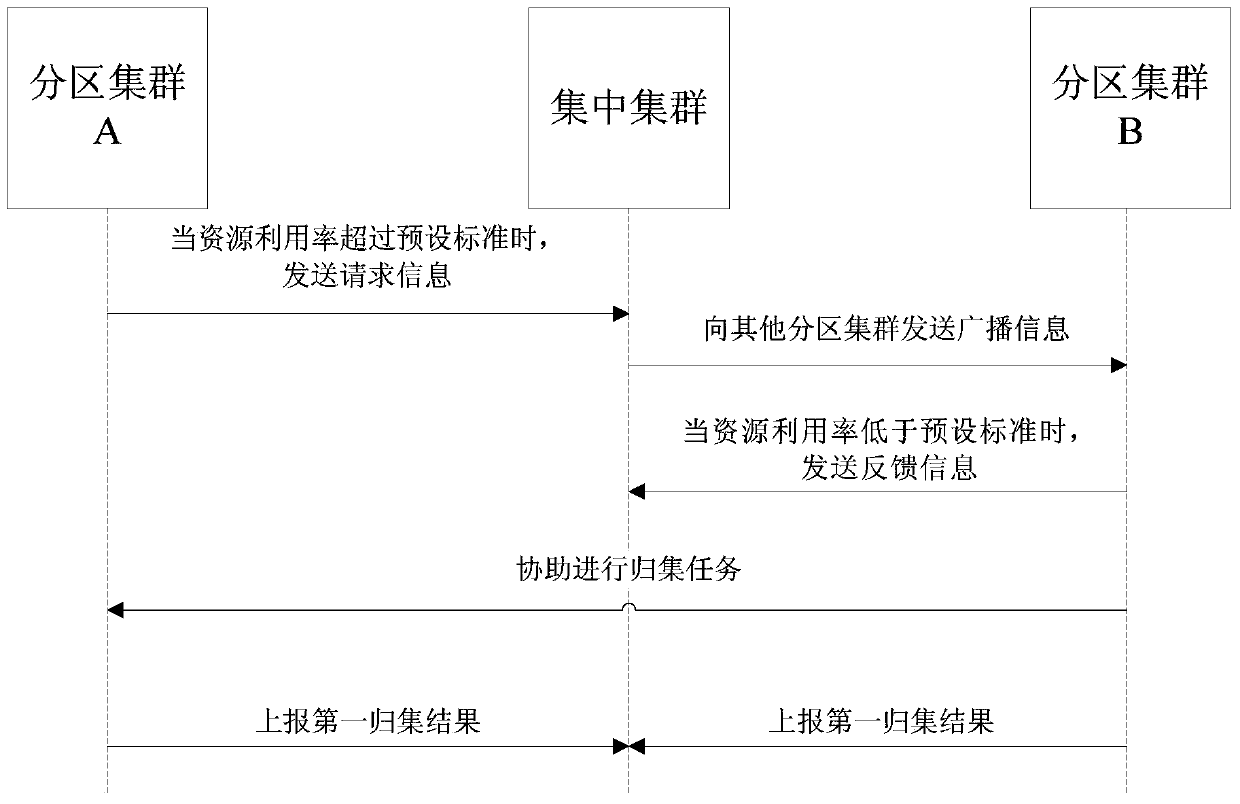
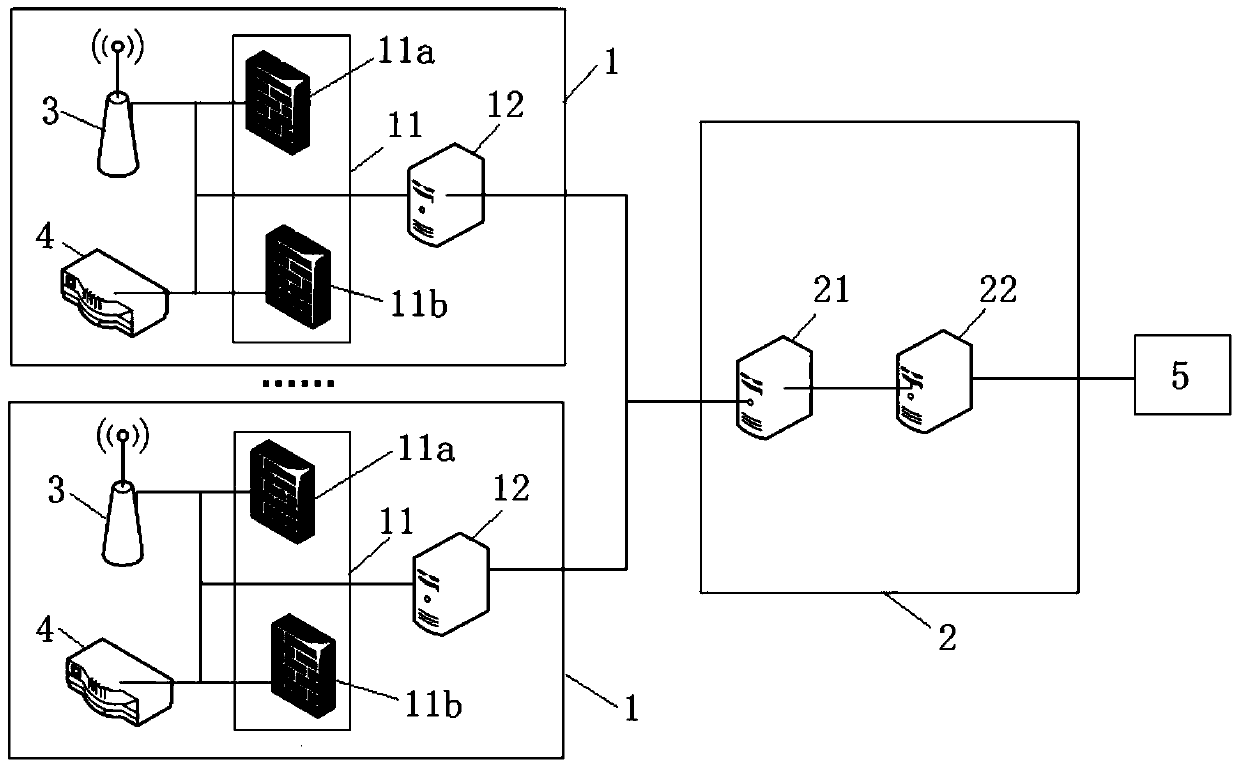
User information processing method and system
ActiveCN105306213BImprove efficiencyImprove accuracyUser identity/authority verificationData OriginInformation processing
The invention discloses a user information processing method and system. The user information processing method is based on the user information processing system, the system comprises a plurality of partition clusters and a centralized cluster, the method comprises the steps that: each partition cluster collects network behavior data of a user in the partition, and extracts credit information corresponding to user identity information from the network behavior data according to a preset rule to obtain a first collection result; the centralized cluster trims the first collection results obtained by the partition clusters to obtain a second collection result; and when needing to verify the credit information of the user, data within a preset period are extracted from the second collection result in real time, and the extracted data are evaluated according to a self-defined evaluation rule. According to the user information processing method and system disclosed by the invention, the data source is wide, and the credit information of the user in various fields can be comprehensively associated and are collected in real time to be extracted and verified subsequently, so that the efficiency and accuracy of collecting and verifying the user identity and credit information are improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
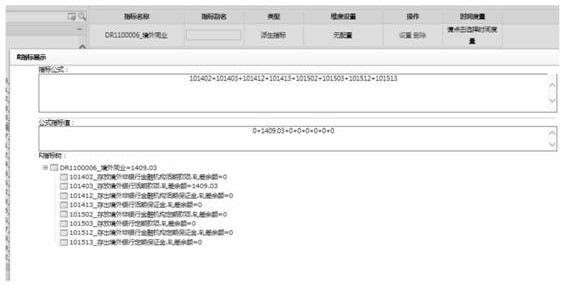
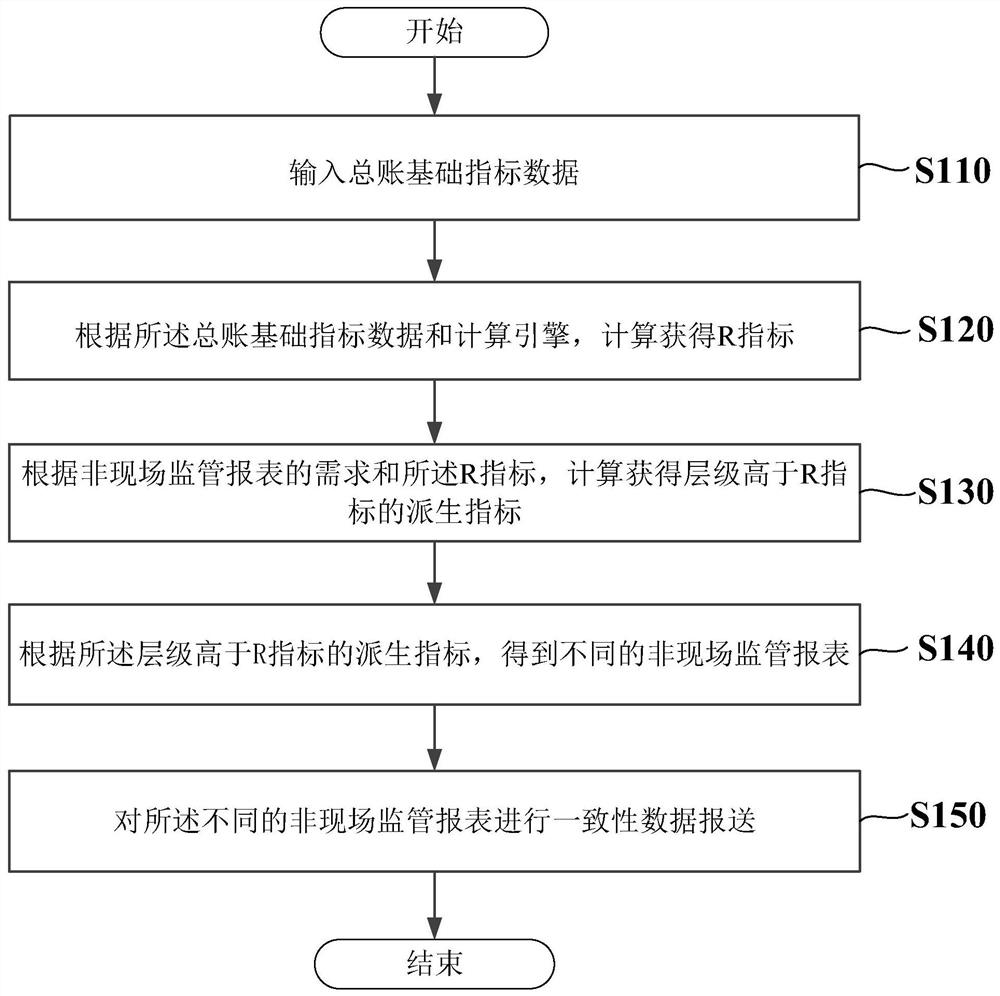
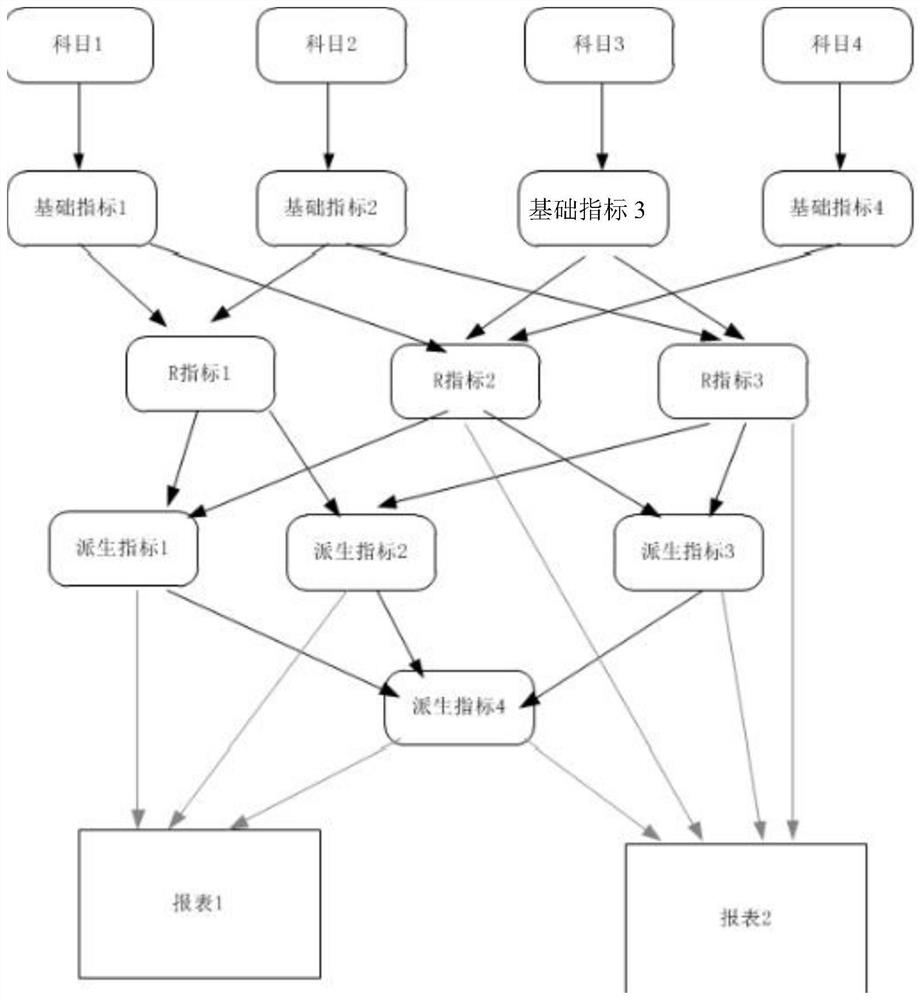
A general ledger-based supervision index configuration implementation method and device, a medium and equipment
The invention provides a general ledger-based supervision index configuration implementation method and device, a medium and equipment. The method comprises the steps of inputting general ledger basic index data; calculating to obtain an R index according to the general ledger basic index data and a calculation engine; according to the demand of the off-site supervision report and the R index, calculating to obtain a derived index of which the hierarchy is higher than the R index; obtaining different off-site supervision reports according to derived indexes of which the levels are higher than the R index; and performing consistent data submission on different off-site supervision reports. On the basis of the basic indexes, a set of R indexes is configured and generated according to 1104 off-site supervision requirements, and report filling is performed on the basis of the R indexes to meet the requirements of consistent submission calibers and high accuracy requirements. And when the index caliber changes, the effect can be taken in all related reports only by modifying the configuration, so that the submission pressure is greatly reduced.
Owner:CHINA CONSTRUCTION BANK
Article alias mining method and system, electronic equipment and readable storage medium
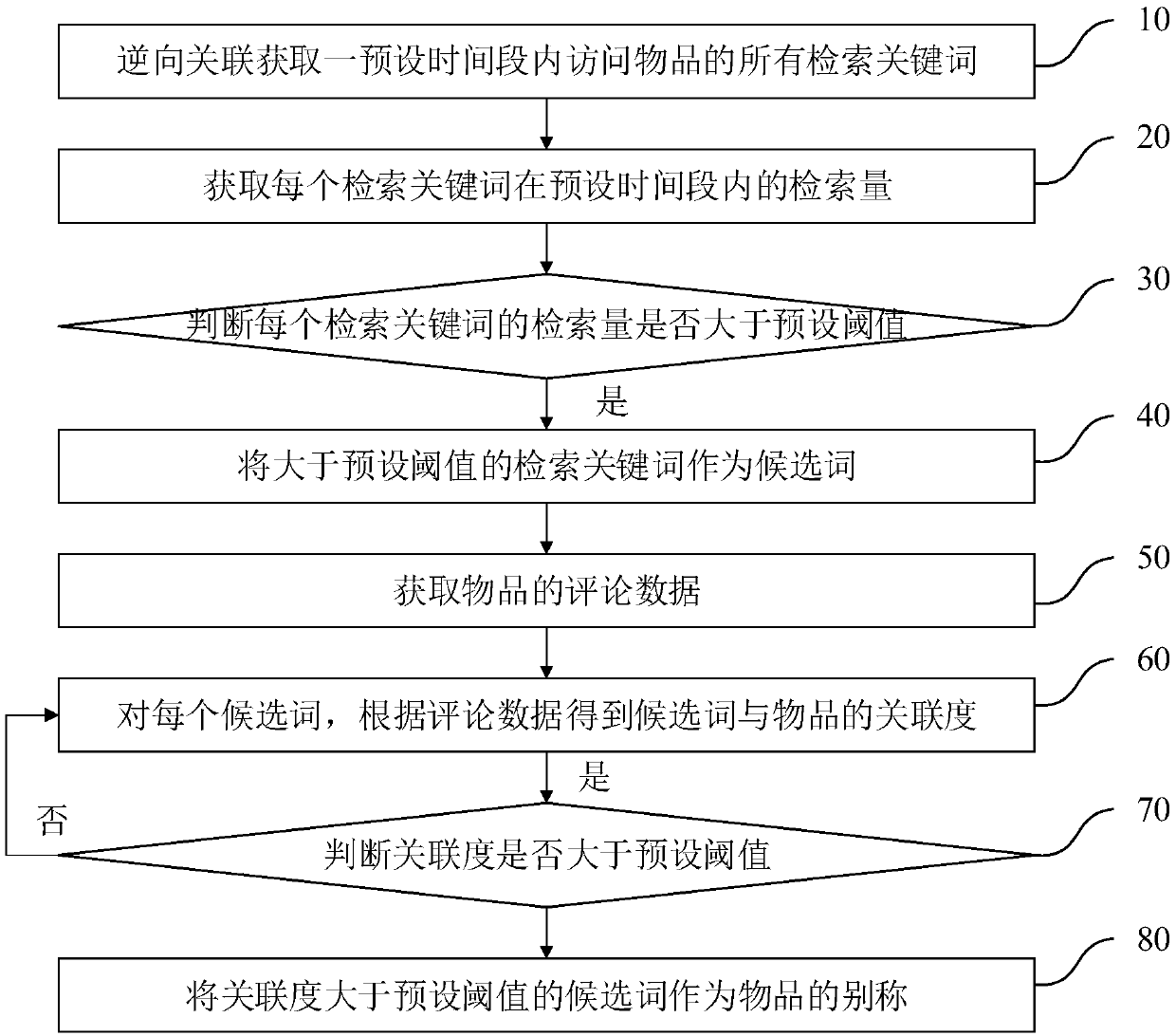
PendingCN110727851AImprove experienceLow data costDigital data information retrievalSpecial data processing applicationsData OriginData source
The invention discloses an article alias mining method and system, electronic equipment and a readable storage medium. The article alias mining method comprises the steps of performing reverse association to obtain all retrieval keywords of an accessed article in a preset time period; obtaining the retrieval amount of each retrieval keyword in the preset time period; judging whether the retrievalamount of each retrieval keyword is larger than a preset threshold value, and if so, taking the retrieval keywords larger than the preset threshold value as the candidate words; obtaining comment dataof the article; for each candidate word, obtaining the association degree of the candidate word and the article according to the comment data; and judging whether the association degree is greater than a preset threshold, and if so, taking the candidate words of which the association degree is greater than the preset threshold as another name of the article. According to the article alias miningmethod, the user comments and the user retrieval data are used as mining data sources, and the data cost is low, and the data sources are wide, meanwhile, the data comes from users, and the mining precision is higher, and the user experience is better.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
A method based on model-coupling exhaustive method to realize low-permeability reservoir inter-operating system optimization method
ActiveCN107578342BQuantitative precisionAccurate and efficient quantificationData processing applicationsDesign optimisation/simulationDynamic modelsIndustrial engineering
The invention discloses a method for optimizing a low-permeability reservoir intermittent mining working system based on a model coupling exhaustion method. Aiming at the input and output characteristics of a low-permeability and low-yield well, through the combination of the flow-in dynamic characteristics of the low-permeability reservoir, the liquid level change rule of an intermittent mining well shaft and the pump efficiency analysis, and based on the relation between the stratum liquid supply capacity and the pumping and suction capacity, a stratum flow-in dynamic model and a well shaftoutflow dynamic model are established, a coupling model is established through the coupling parameters of the bottom flow pressure and the pump efficiency, a computer solution model is established onthis basis, and the optimization of the low-permeability reservoir intermittent mining working system determination method is carried out by means of an exhaustion method. The method can accurately describe the low-permeability reservoir seepage law, realizes the real-time dynamic changes of the bottom flow pressure and the pump efficiency during the intermittent mining, and realizes the accuratequantified intermittent mining limit. The exhaustion method has better optimization precision, and the program calculation efficiency is high.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com