Patents
Literature
1198 results about "Multiple factors" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
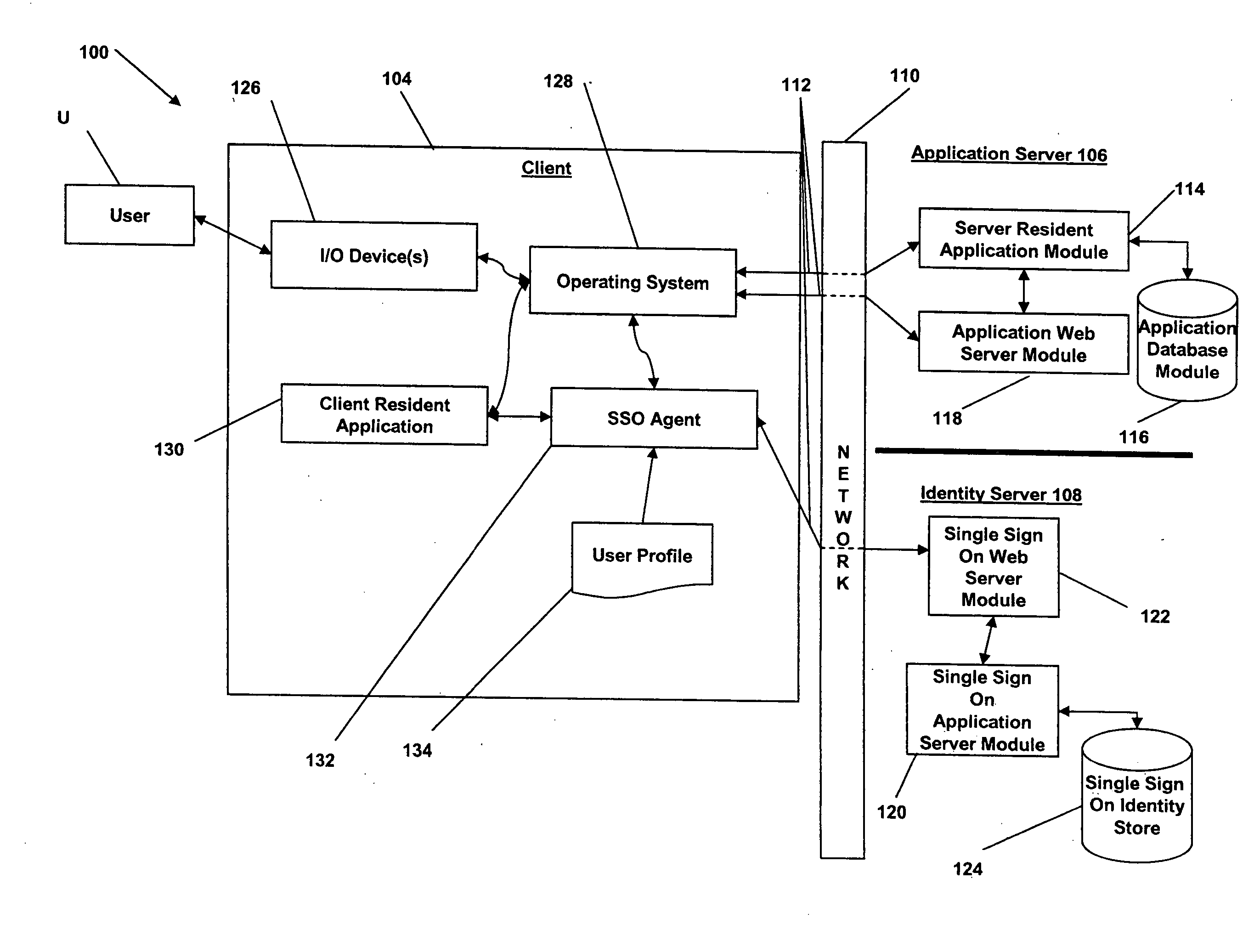
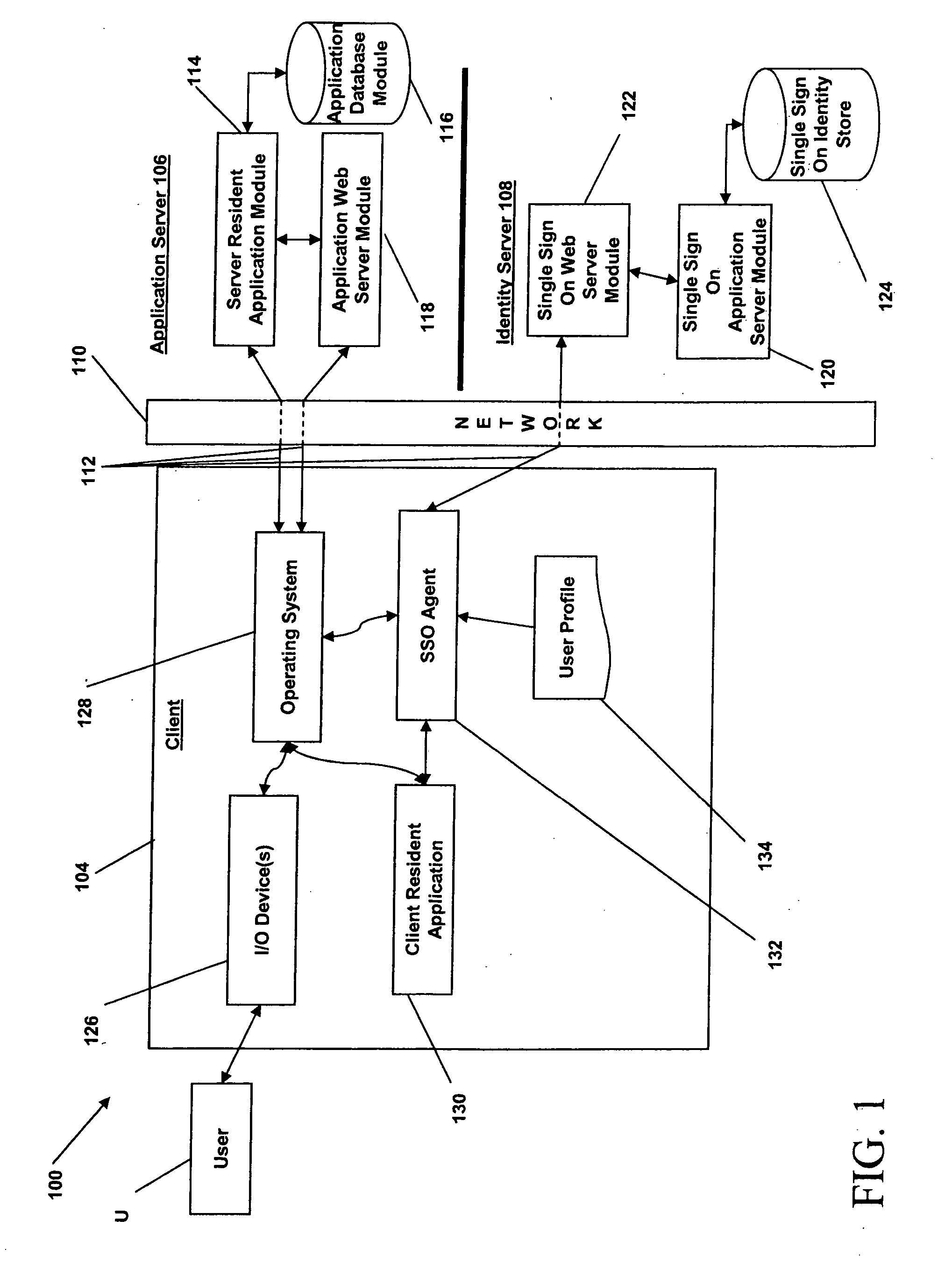
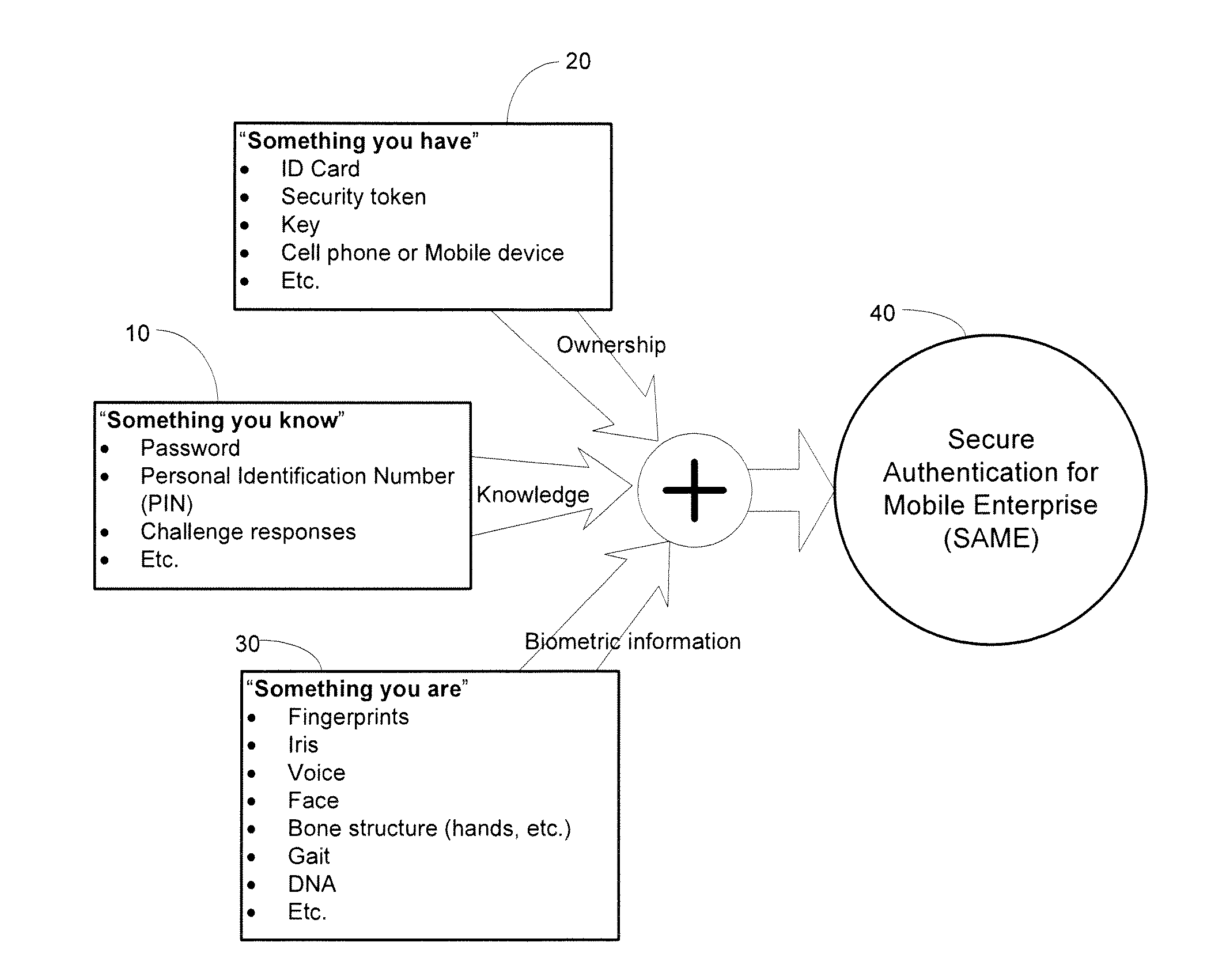
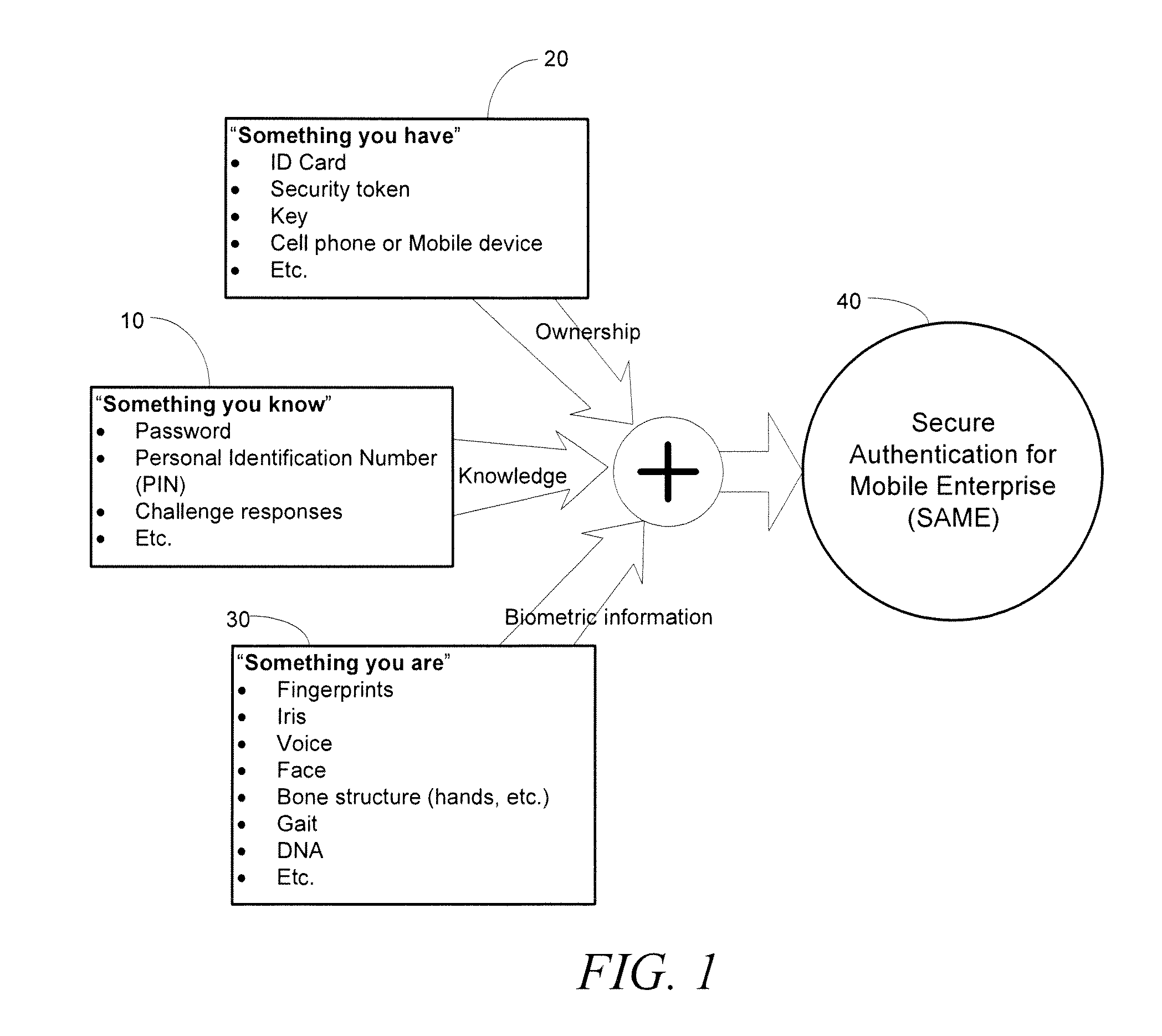
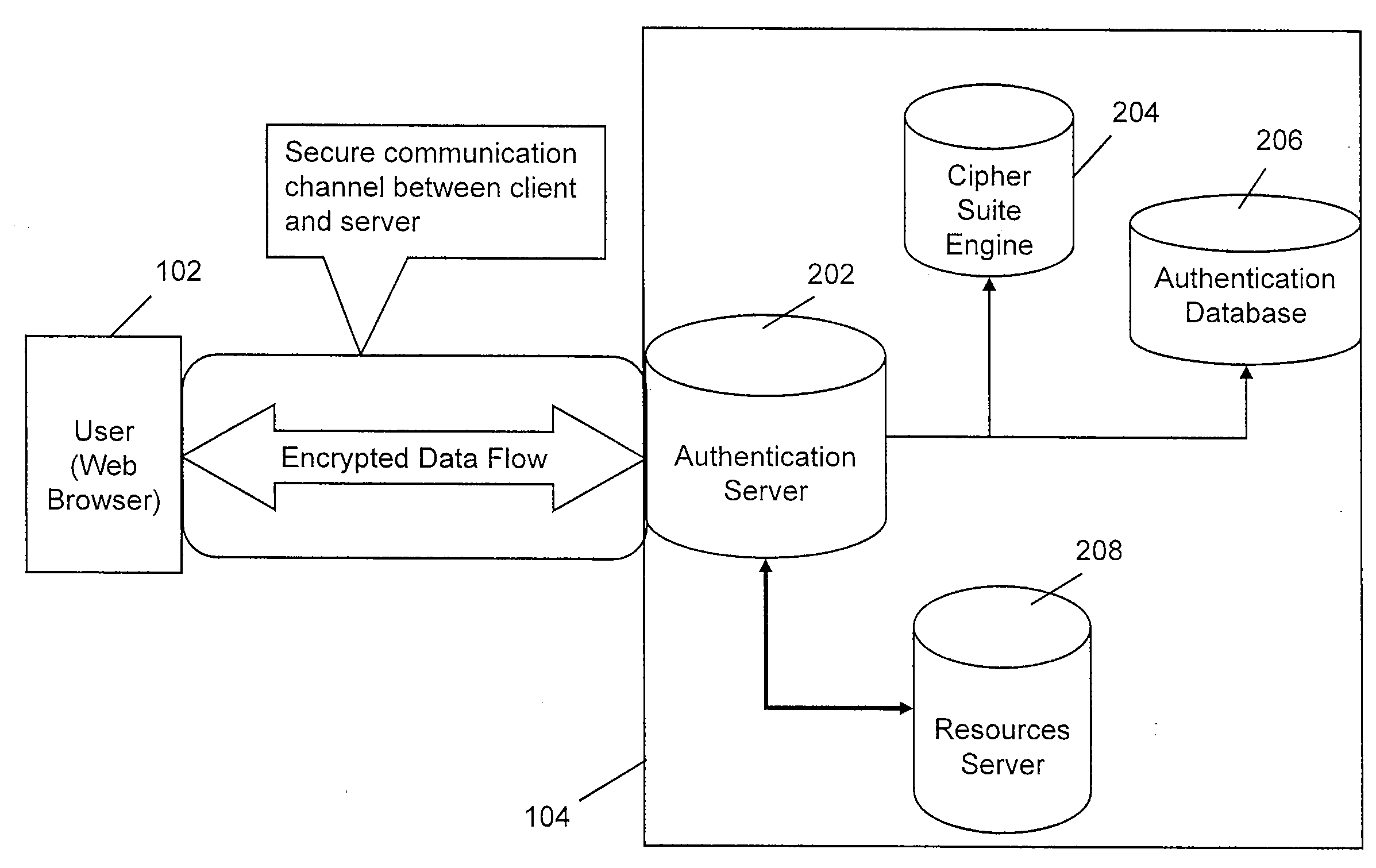
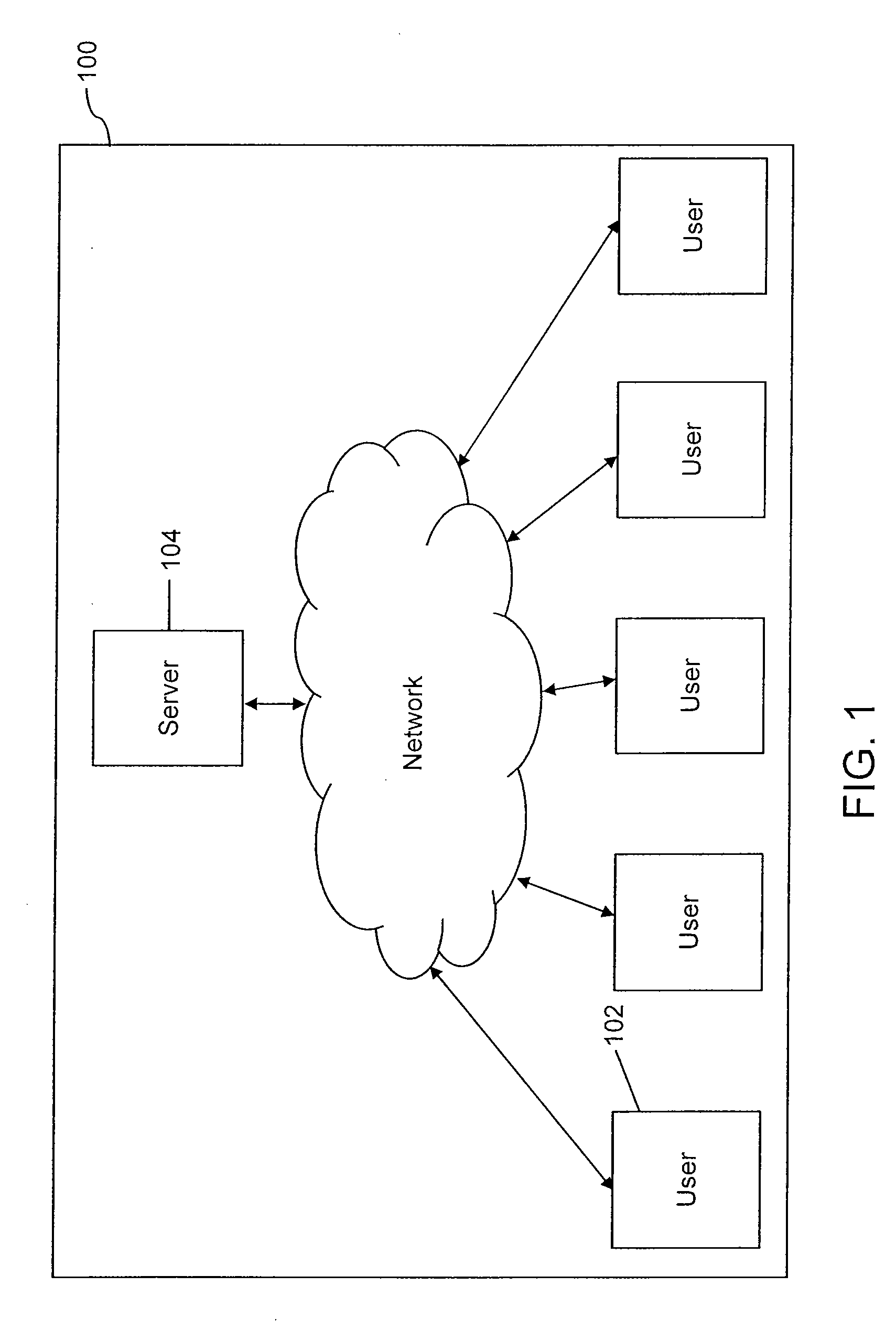
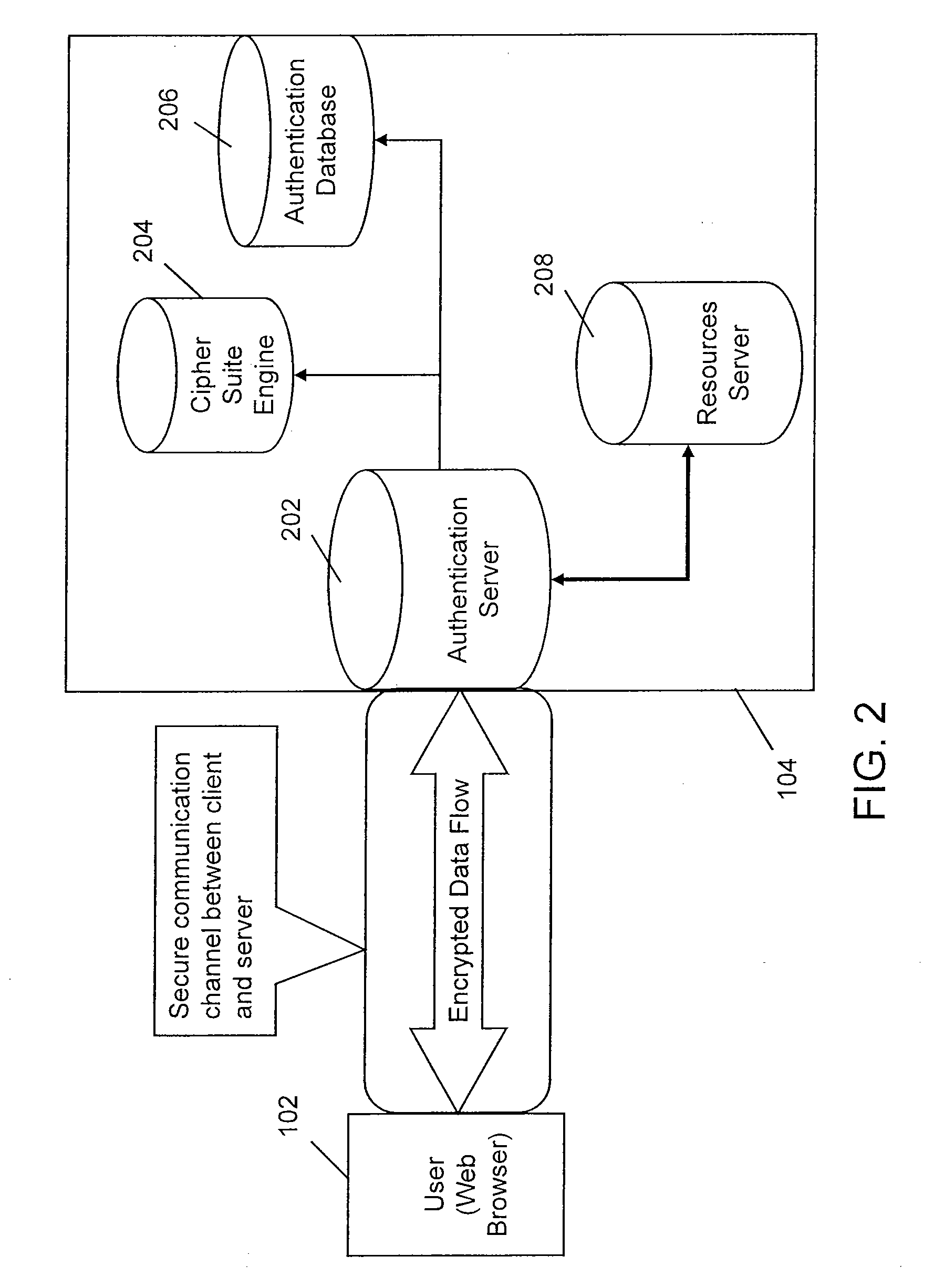
Systems and methods for multi-factor authentication
ActiveUS20070186106A1User identity/authority verificationElectric digital data processingInternet privacyControl system
Requests to gain access to secure resources are adjudicated according to authentication policies that include rules based on user-states derived from multiple heterogeneous access-control systems.
Owner:IMPRIVATA
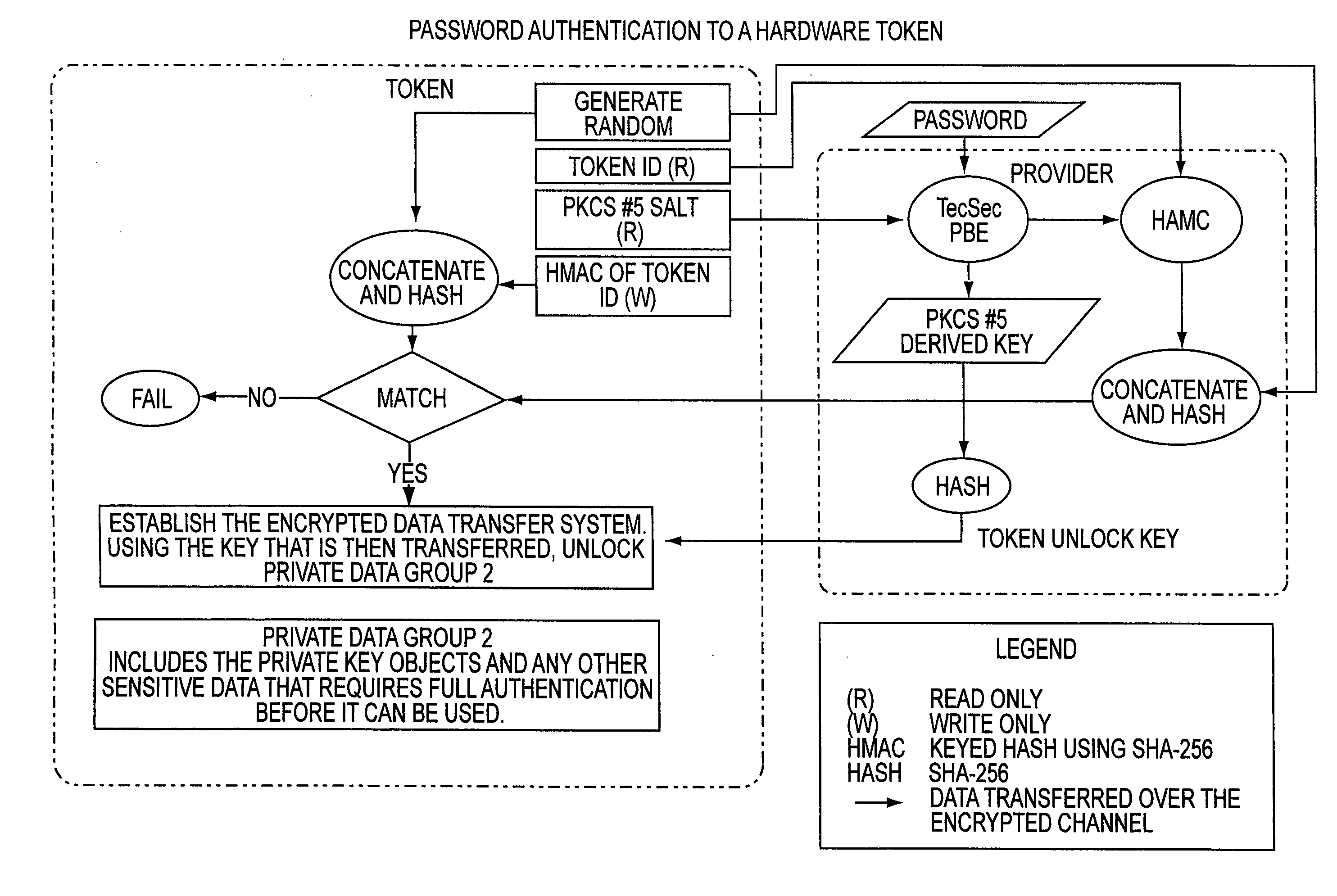
Access system utilizing multiple factor identification and authentication
InactiveUS20050235148A1Flexible approachEasy to useKey distribution for secure communicationPublic key for secure communicationTransfer systemPassword
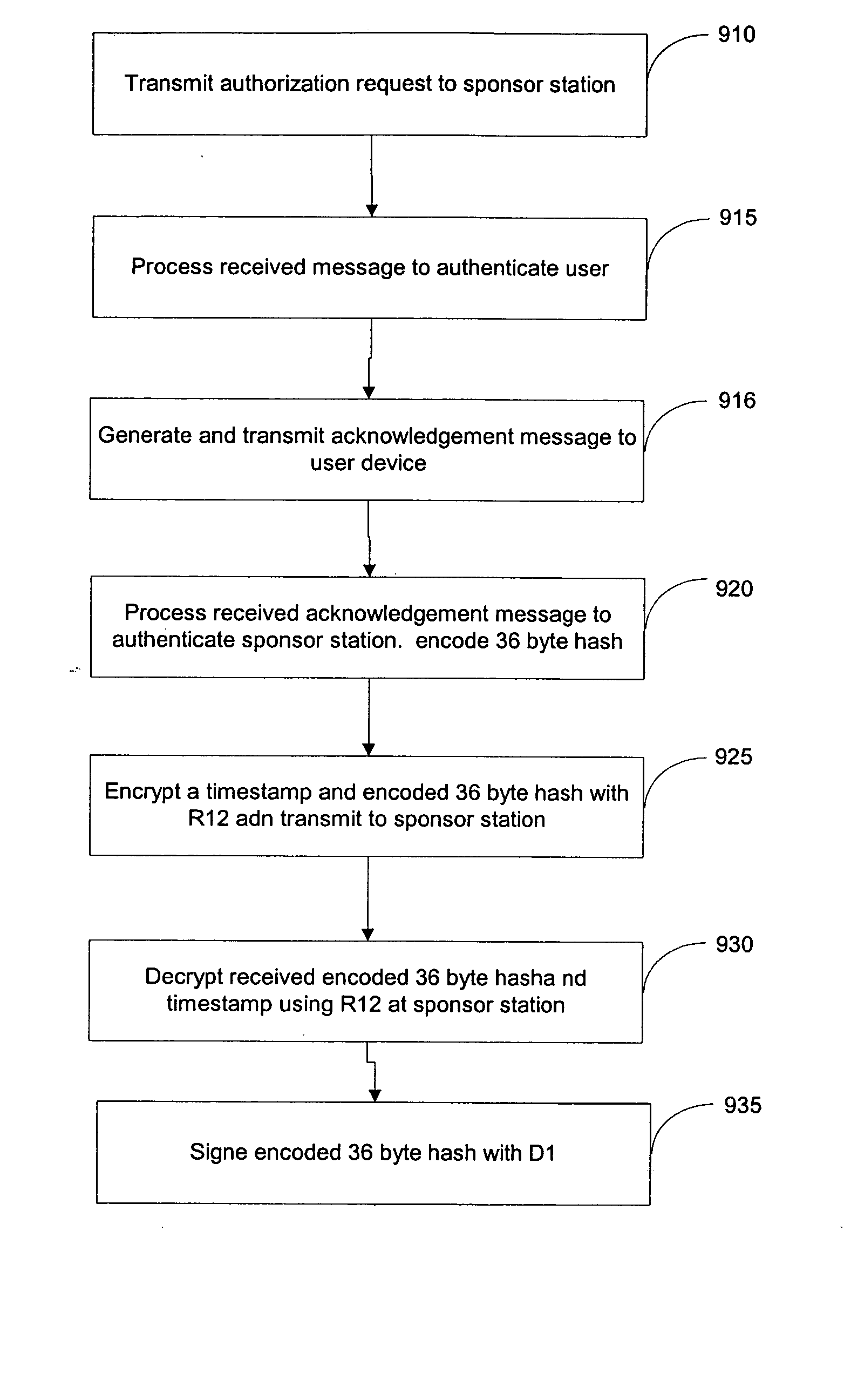
A method of authenticating a user to use a system includes using a provider token to generate a random value. The token generates a derived key based at least in part on a token-provided salt value and a user-provided password. The provider generates a token unlock key based at least in part on the derived key and sends it to the token. First and second challenge data instances are generated by the provider and the token, respectively, and the process is terminated if the challenge data instances are determined not to match. If the challenge data instances are determined to match, then an encrypted data transfer system is established between the token and the provider, and the token unlocks locked private data stored on the token. The user is authenticated for secured use of the system based at least in part on the unlocked private data.
Owner:TECSEC
Access system utilizing multiple factor identification and authentication
InactiveUS7178025B2Easy to useSelection of credentials can be automatedKey distribution for secure communicationDigital data processing detailsTransfer systemPassword
A method of authenticating a user to use a system includes using a provider token to generate a random value. The token generates a derived key based at least in part on a token-provided salt value and a user-provided password. The provider generates a token unlock key based at least in part on the derived key and sends it to the token. First and second challenge data instances are generated by the provider and the token, respectively, and the process is terminated if the challenge data instances are determined not to match. If the challenge data instances are determined to match, then an encrypted data transfer system is established between the token and the provider, and the token unlocks locked private data stored on the token. The user is authenticated for secured use of the system based at least in part on the unlocked private data.
Owner:TECSEC
Multi-Factor Authentication Using a Mobile Phone
InactiveUS20110142234A1Acutation objectsUnauthorised/fraudulent call preventionPaymentBiometric data
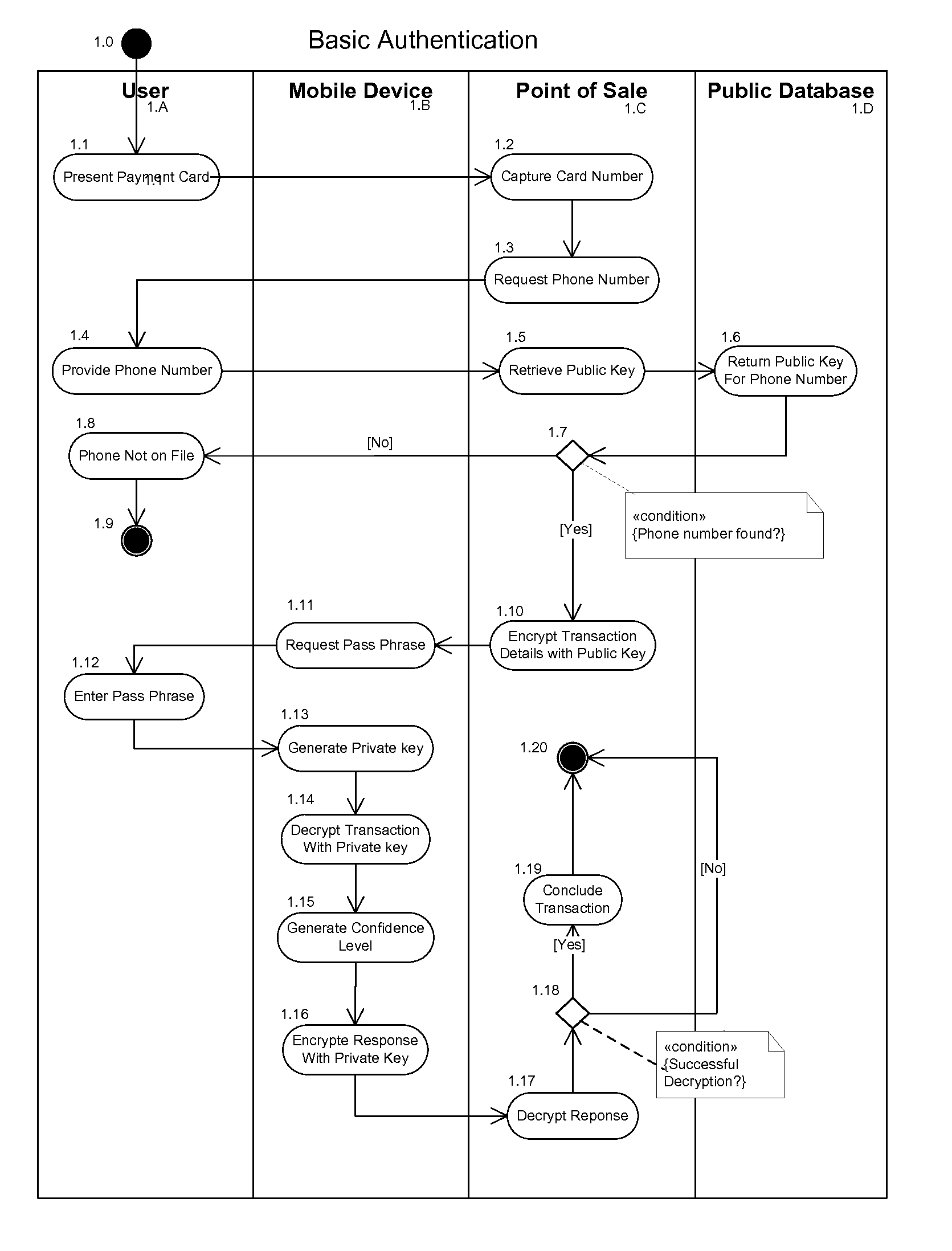
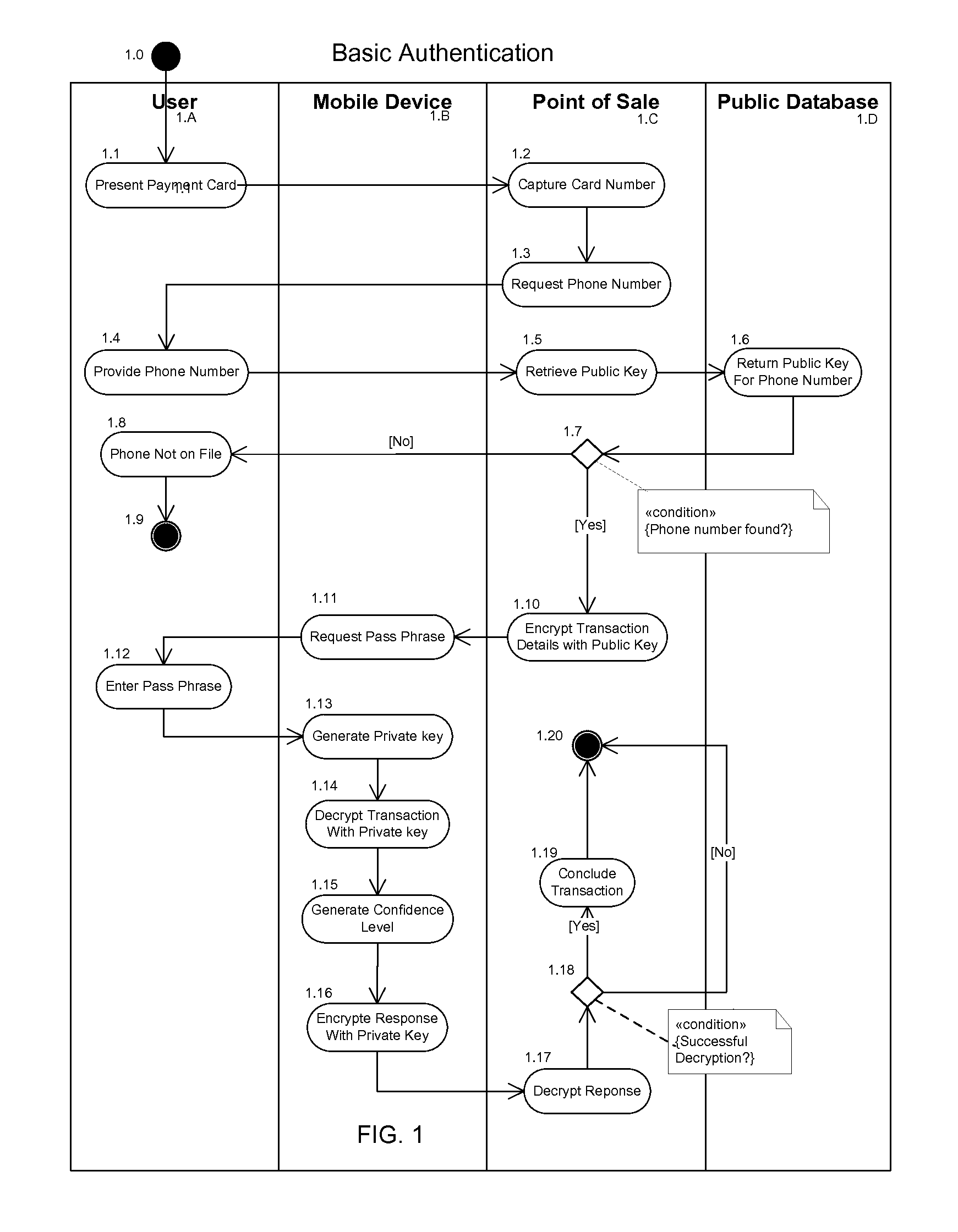
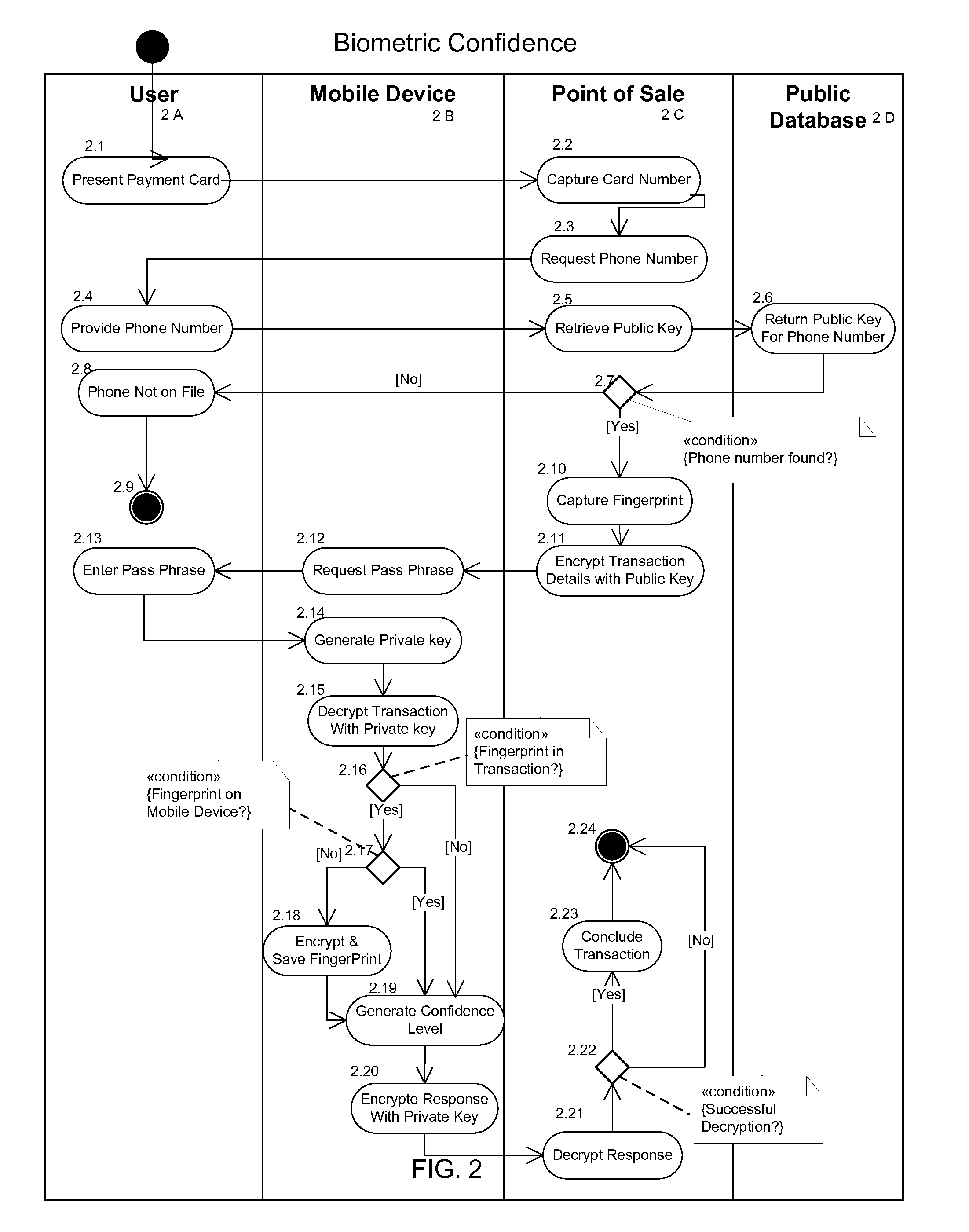
The invention described here provides a fully-distributed solution to the problem of confirming the identity of the presenter of a payment card or other credentials, using multiple factors to authenticate the presenter. The invention leverages the wide penetration of mobile phones in modern economies as the basis for the distributed multi-factor authentication. For additional confidence levels biometric data can be incrementally included as part of the multi-factor authentication. The loss of any one of the multiple authentication factors does not compromise the integrity of the system or the individual, and there is no single point of vulnerability for attack or theft. The invention is fully backwards compatible with current payment cards systems and can be extended to almost any situation where the identity of the presenter of credentials needs to be authenticated prior to allowing the individual access to the protected services, systems, or locations. This allows for incremental adoption across a wide range of current and future systems.
Owner:ROGERS MICHAEL LEONARD
Method and system for authenticating remote users
A user of a mobile device can be authenticated based on multiple factors including biometric data of the user. During an enrollment process of the user, an encryption key is sent to the mobile device via a message. The encryption key is recovered from the message and used to encrypt communications between the mobile device and a server. Biometric data is collected from the user and sent to the server for computing a biometric model (e.g., a voice model, etc.) of the user for later use in authentication. An encrypted biometric model is stored only in the mobile device and the encrypted biometric model is sent to the server for authentication of the user. For authentication, various information including an identification of the mobile device, responses to challenge questions, biometric data including the biometric model, etc. are used at the server.
Owner:CGI FEDERAL
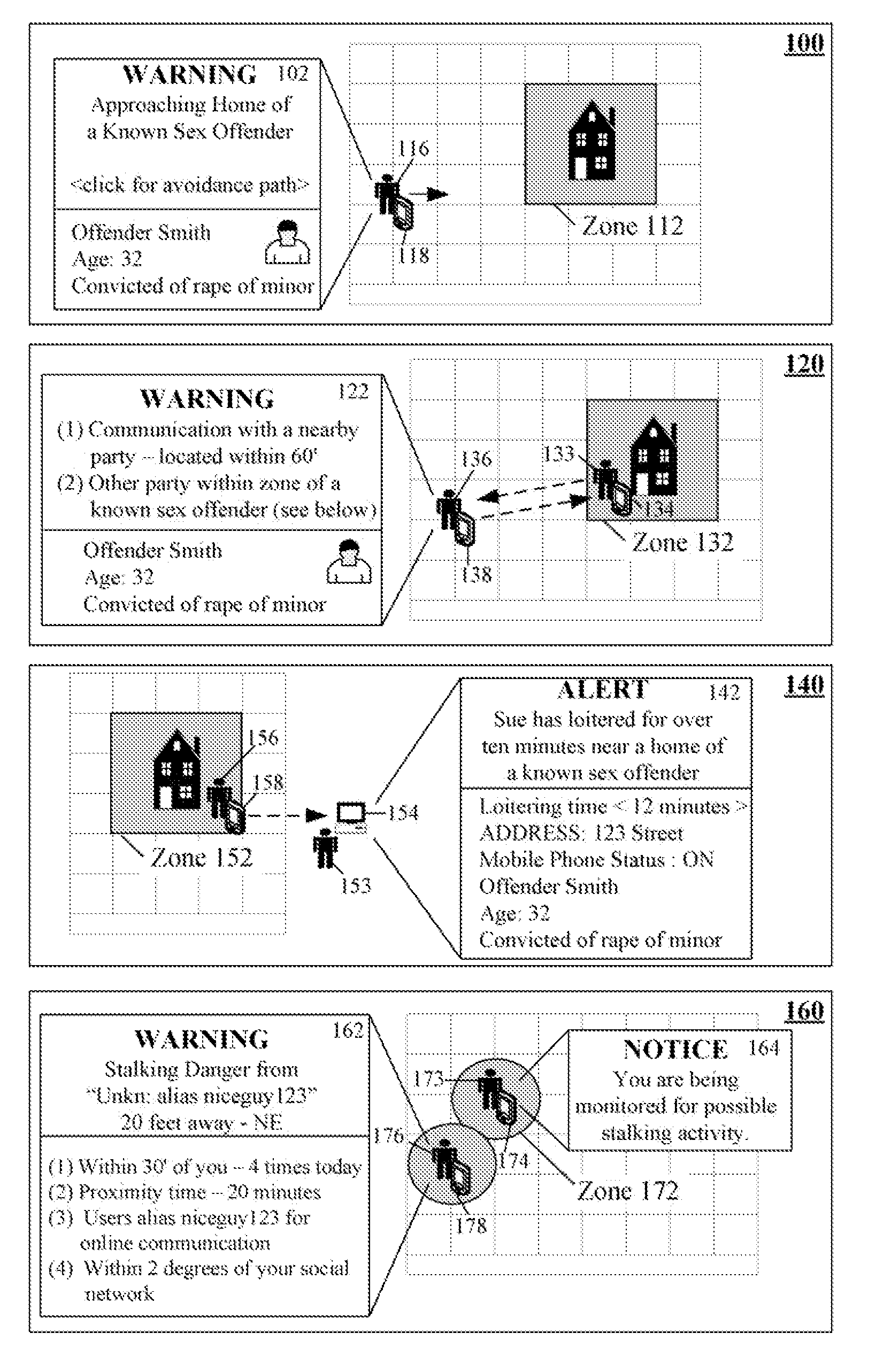
Using location capabilities of a mobile device to permit users to avoid potentially harmful interactions
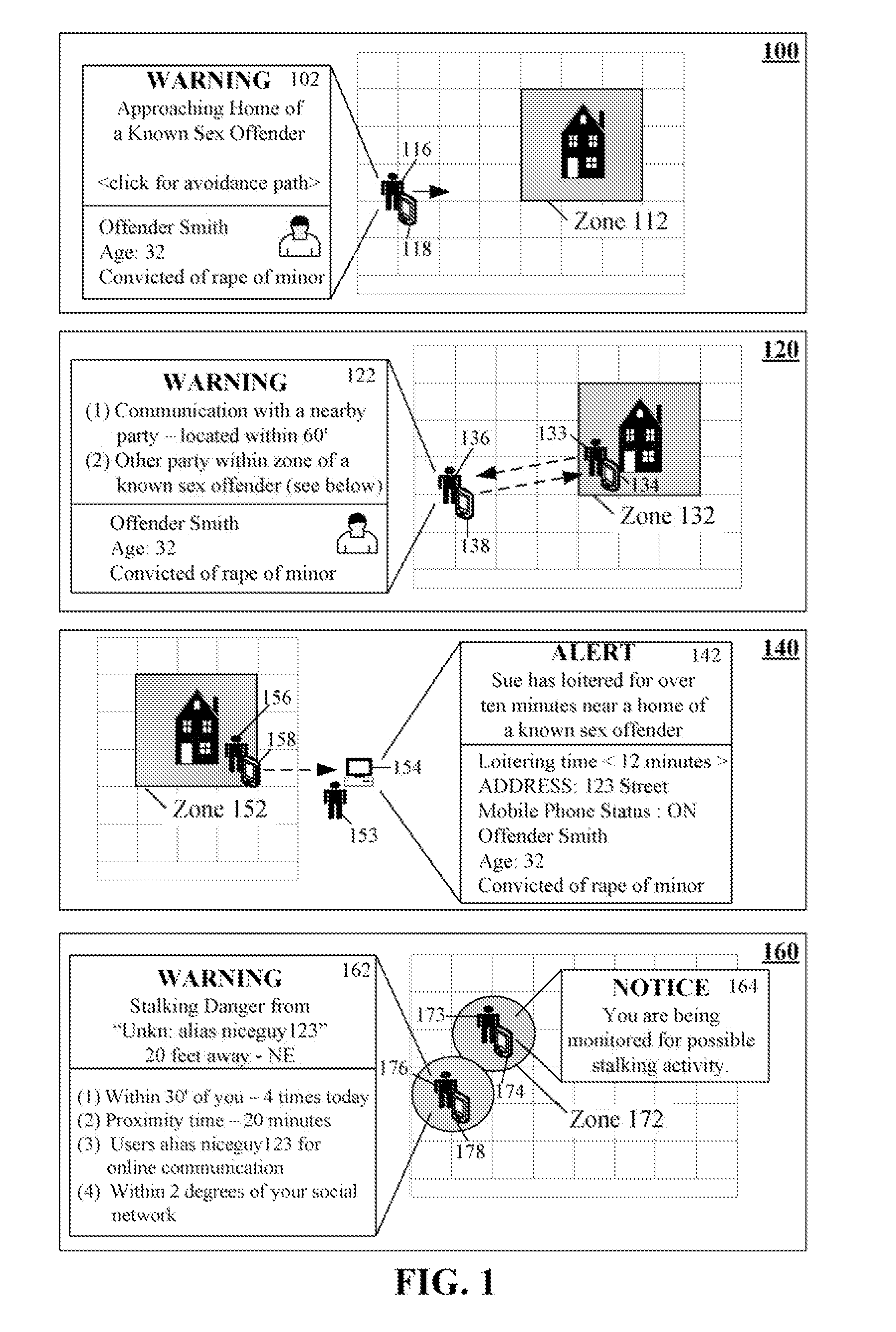
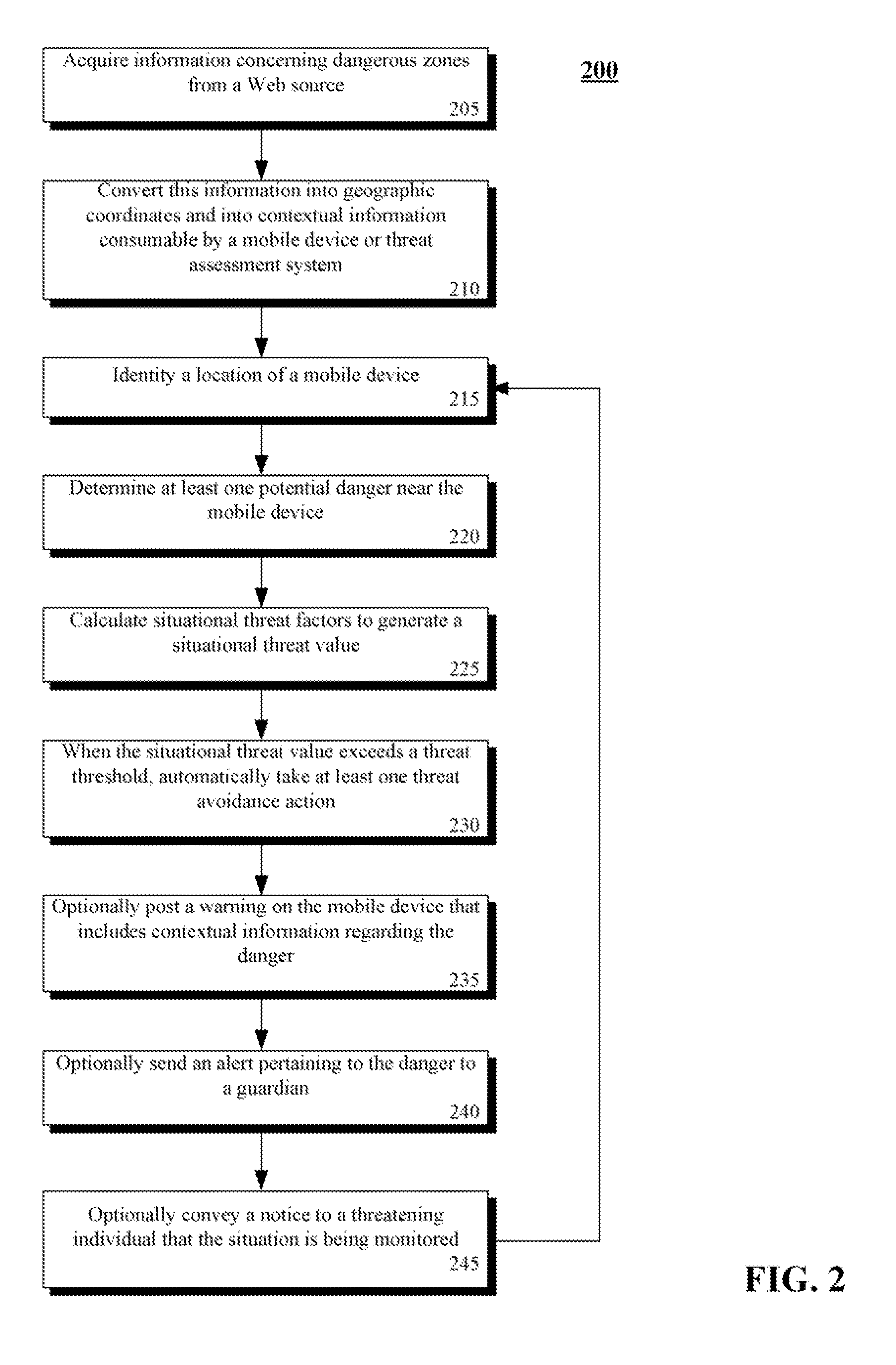
InactiveUS20080094230A1Enhanced Situational AwarenessAvoid harmAlarmsElectric signalling detailsProximateSimulation
The present invention automatically increases situational awareness relating to potential sexual predators, criminals, and / or stalkers located near a mobile device user. A location of the mobile device can be determined by device location electronics, such as a Global Positioning System (GPS). The location can be compared against at least one zone believed to be associated with a sexual predator, a criminal, and / or a stalker. Zones can be static or dynamic. A threat level associated with a zone can be computed from multiple factors, which are compared against one or more thresholds. When the threat level exceeds a thresholds, an associated threat avoidance action can be automatically initiated. One threat avoidance action is to present a warning upon a user's mobile device along with contextual information about a proximate danger.
Owner:MOTOROLA INC
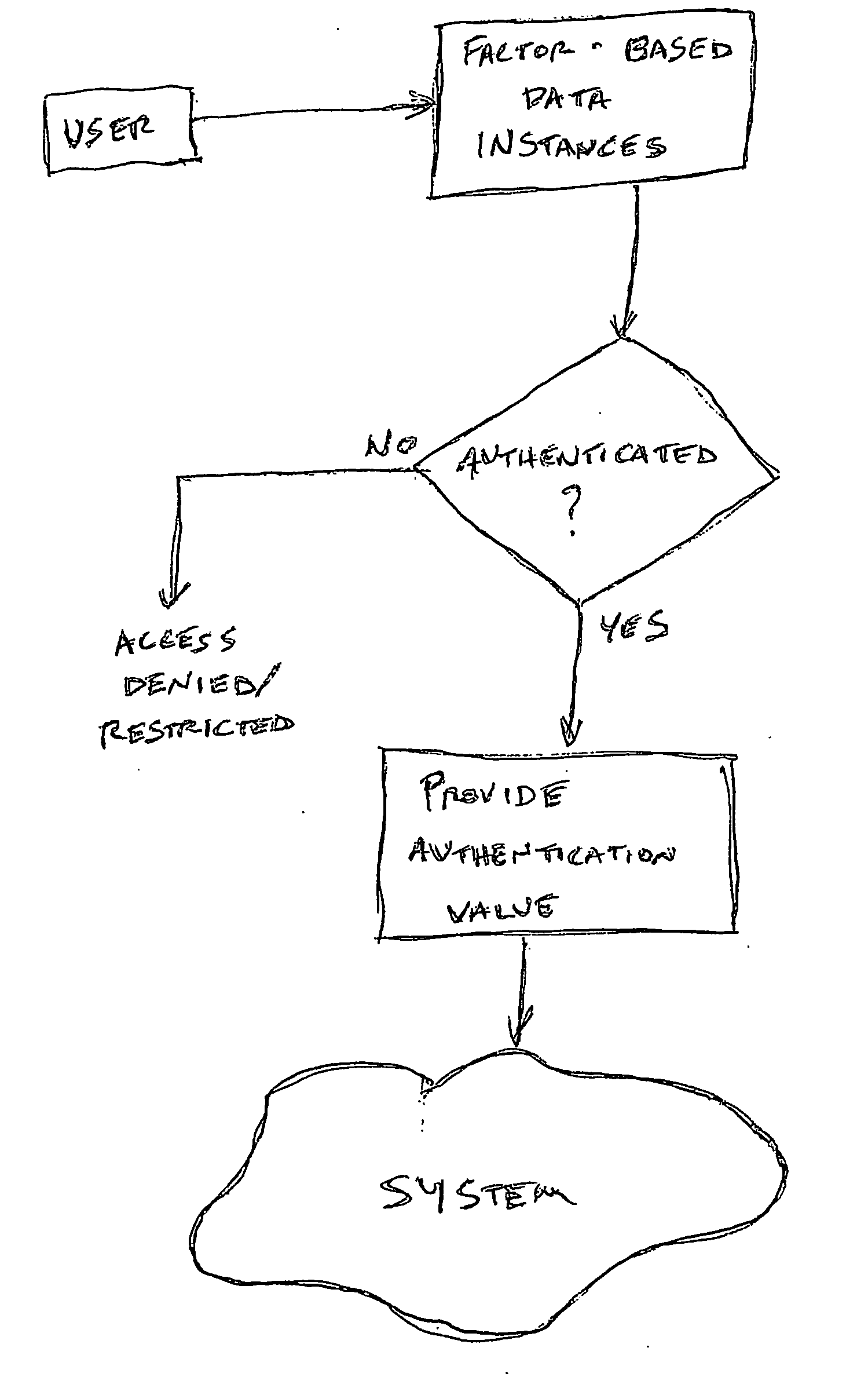
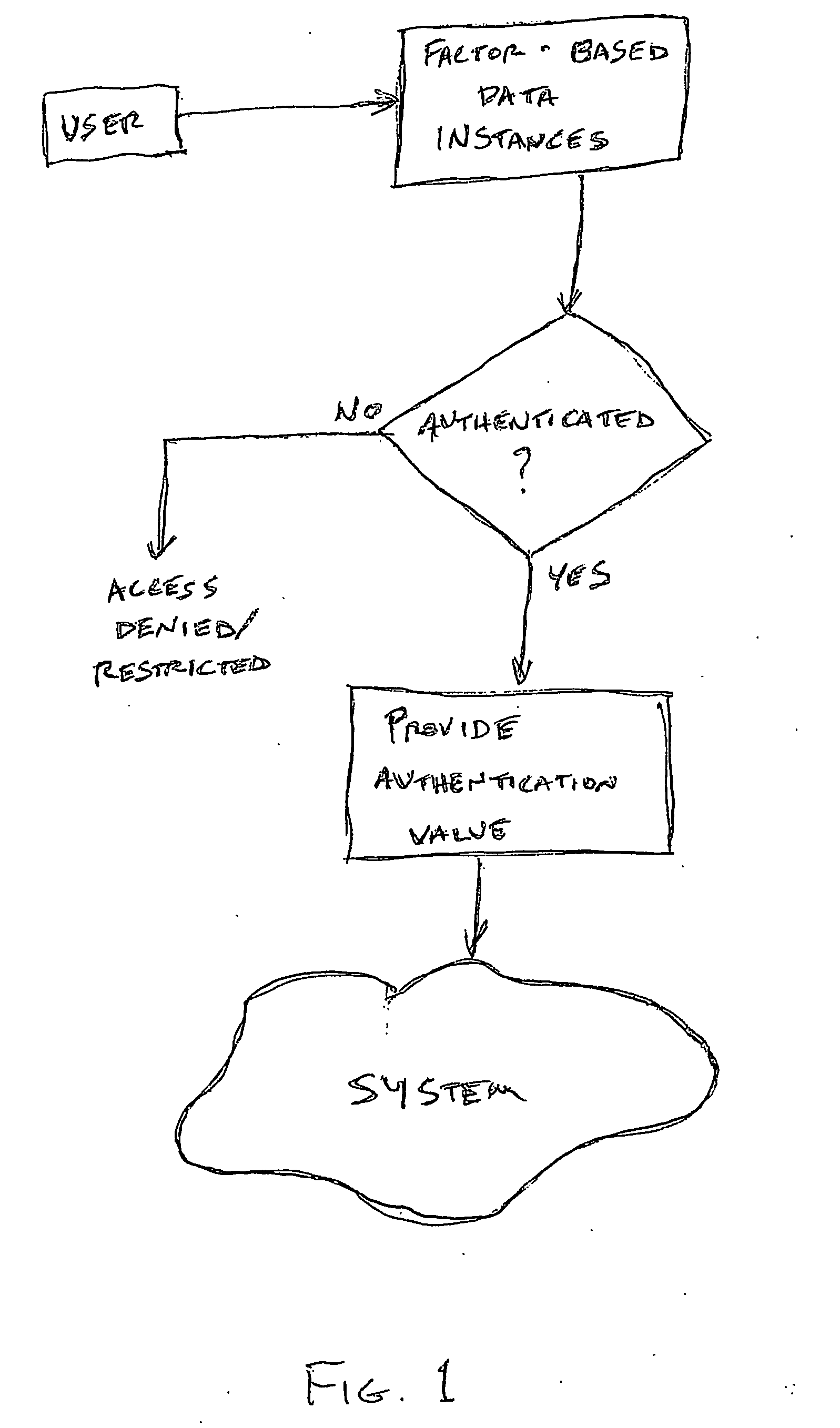
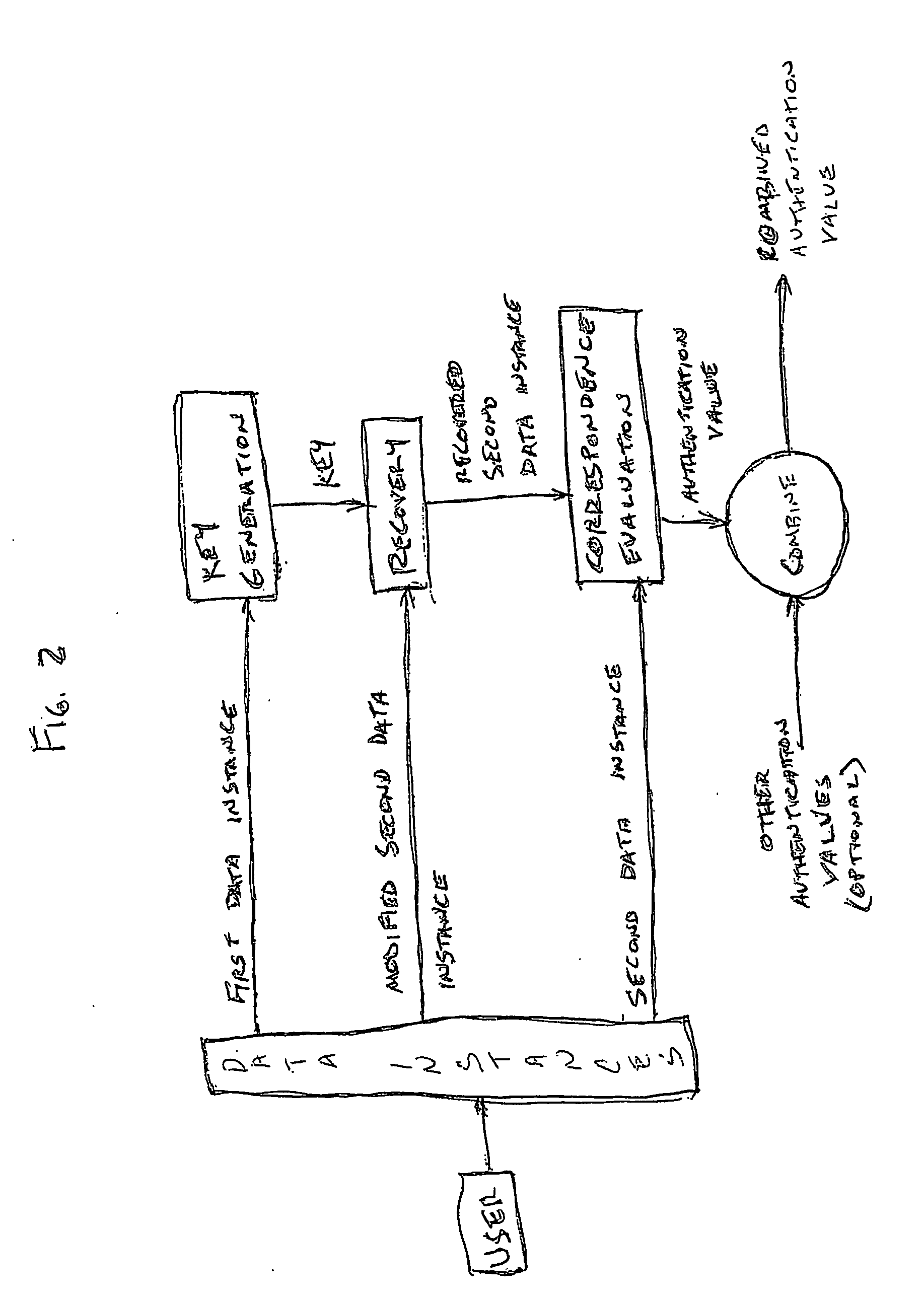
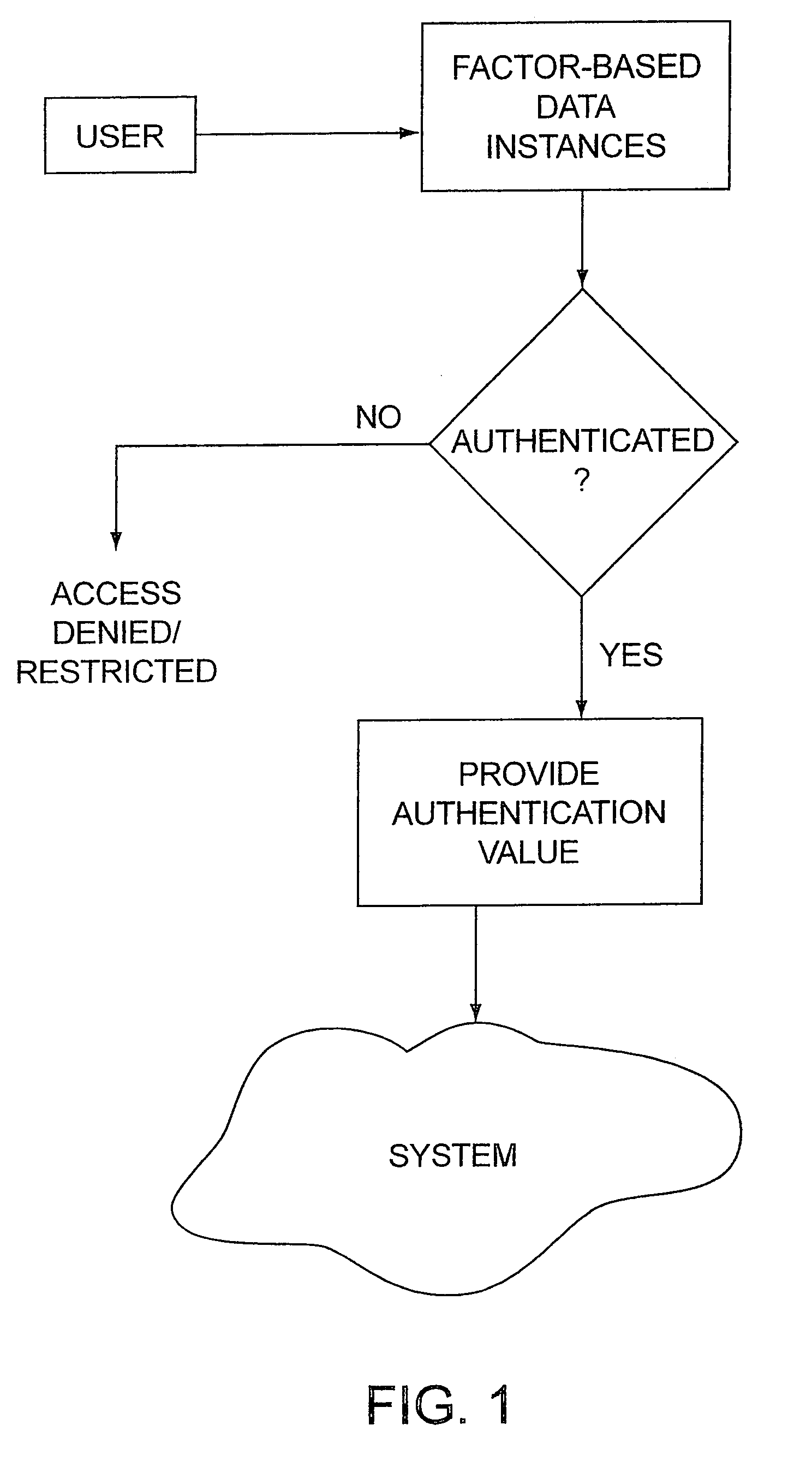
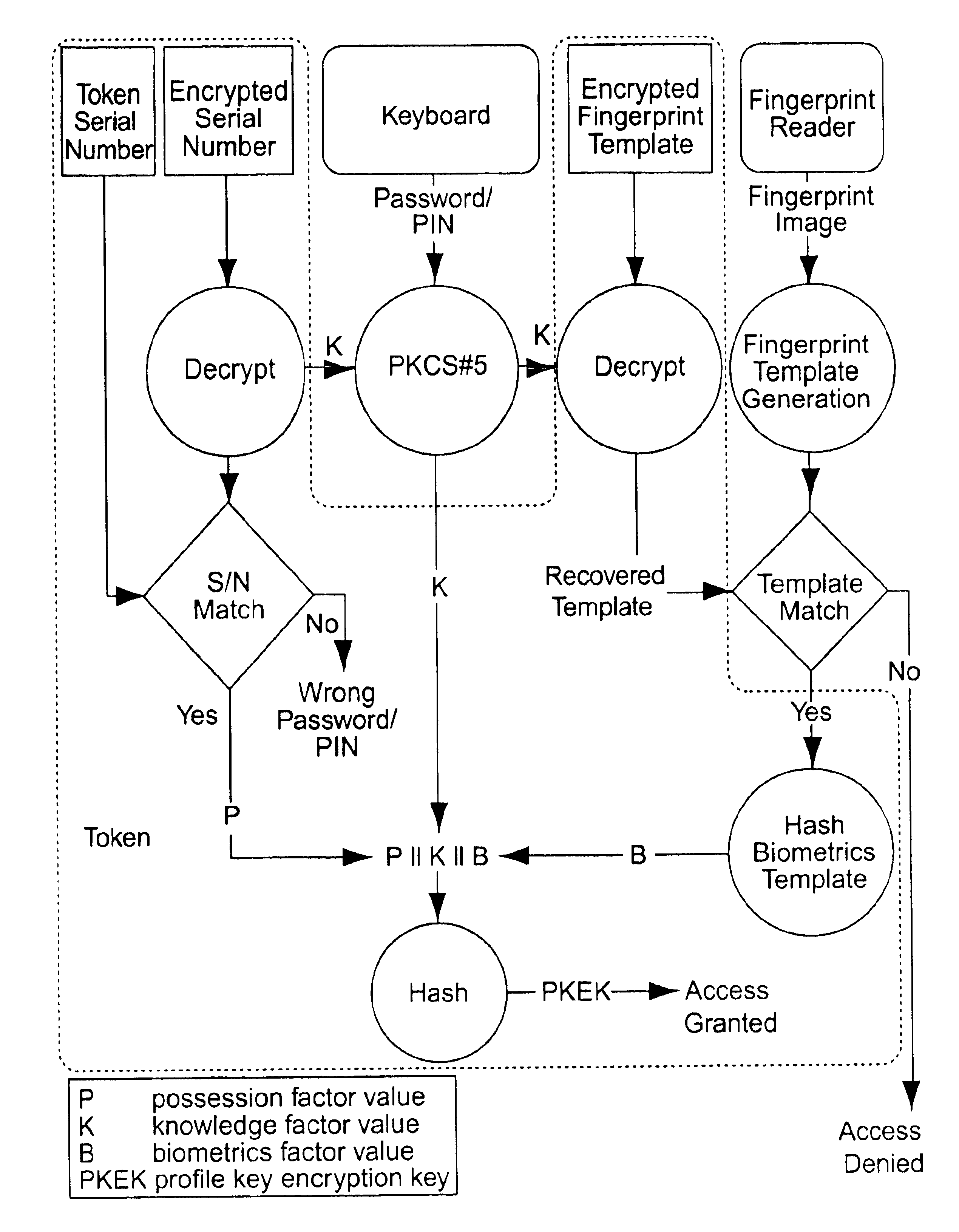
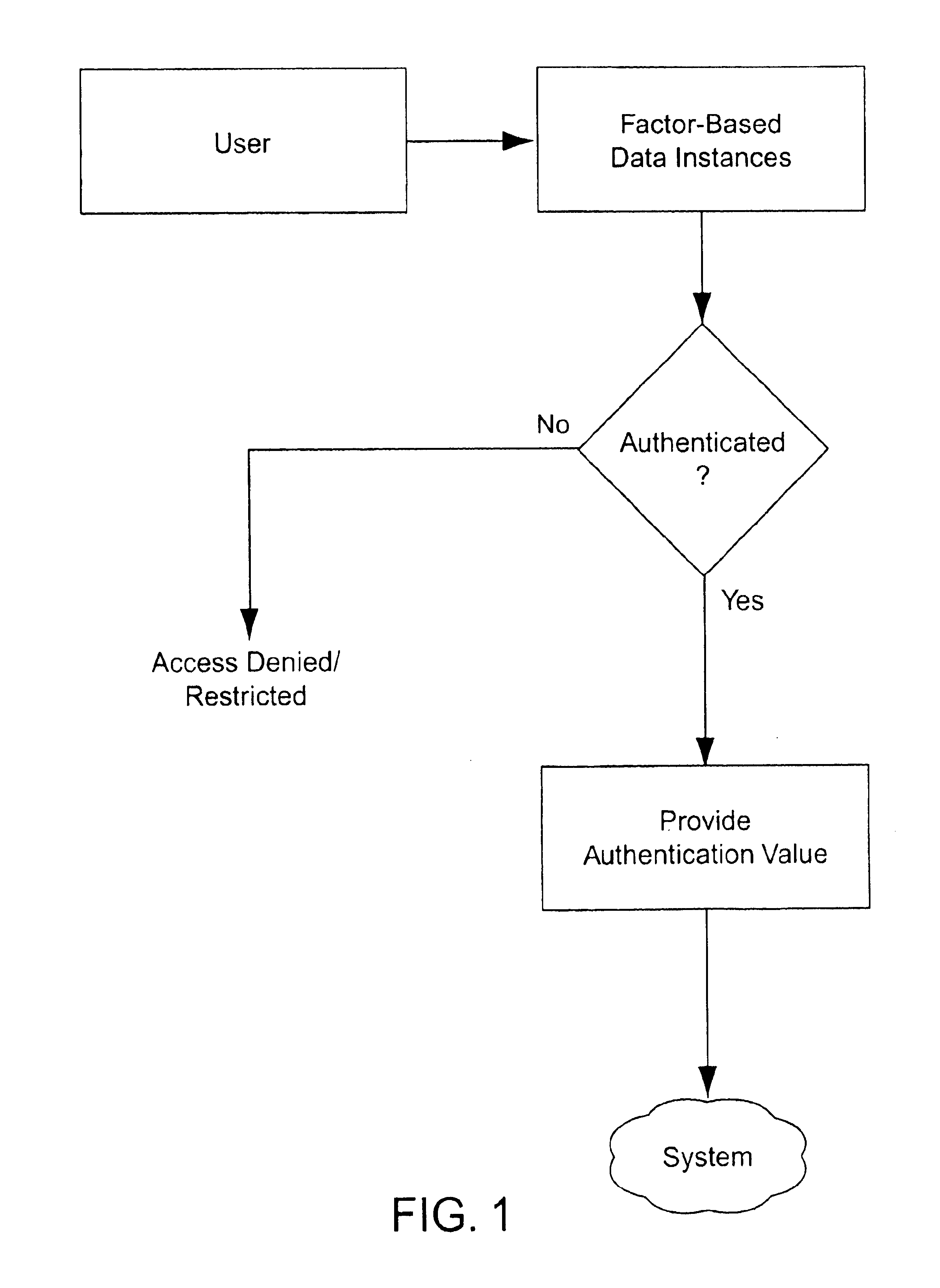
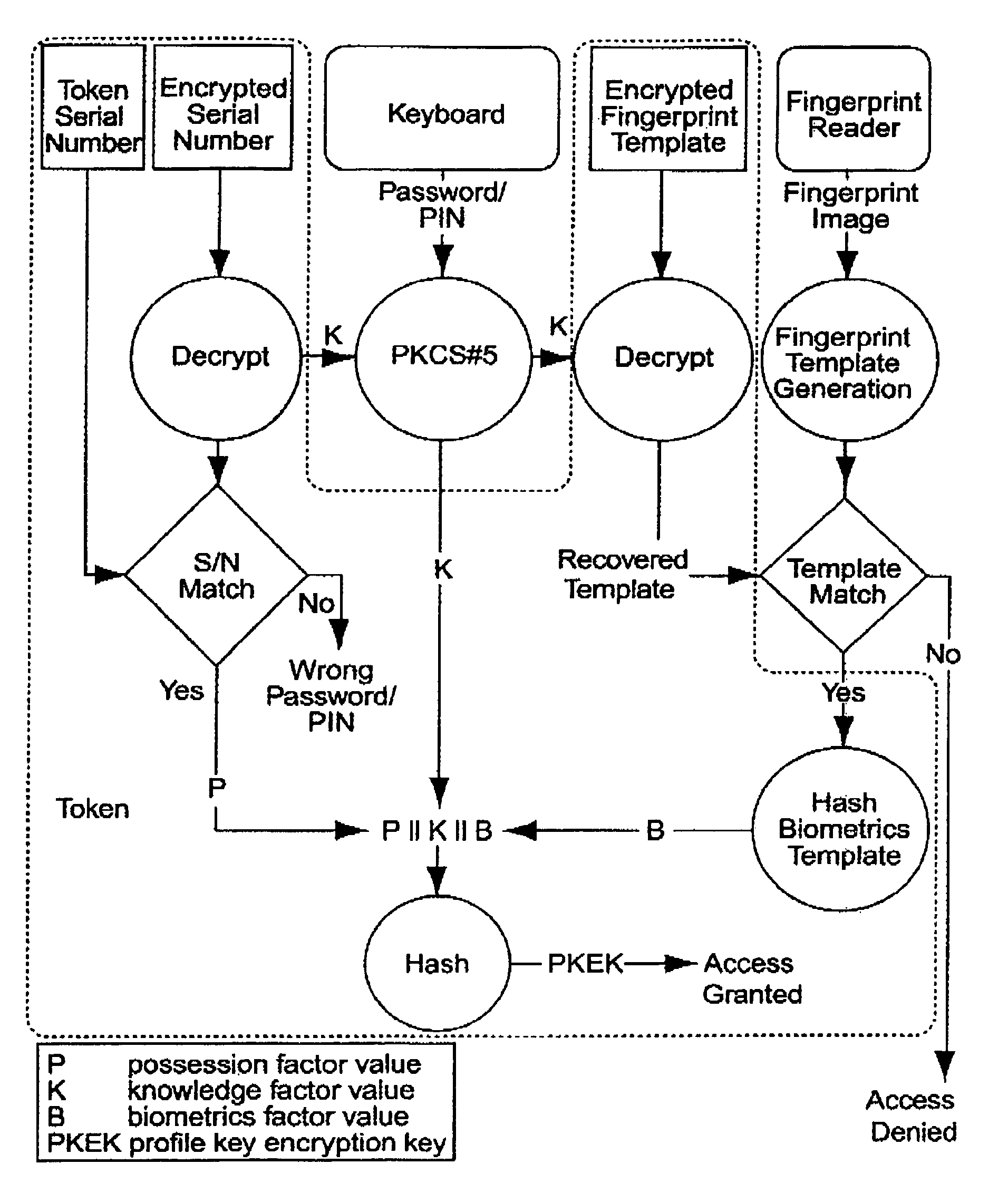
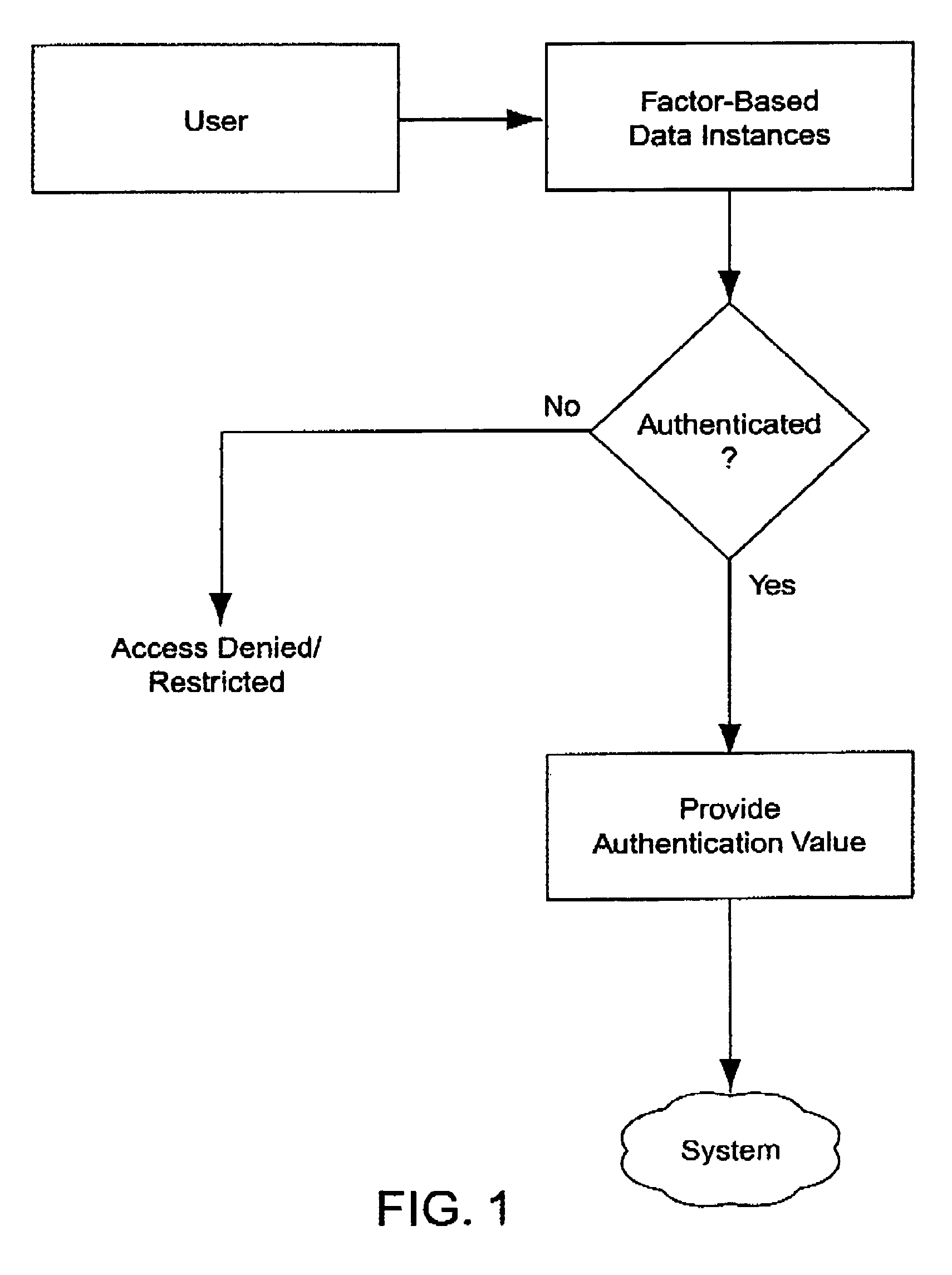
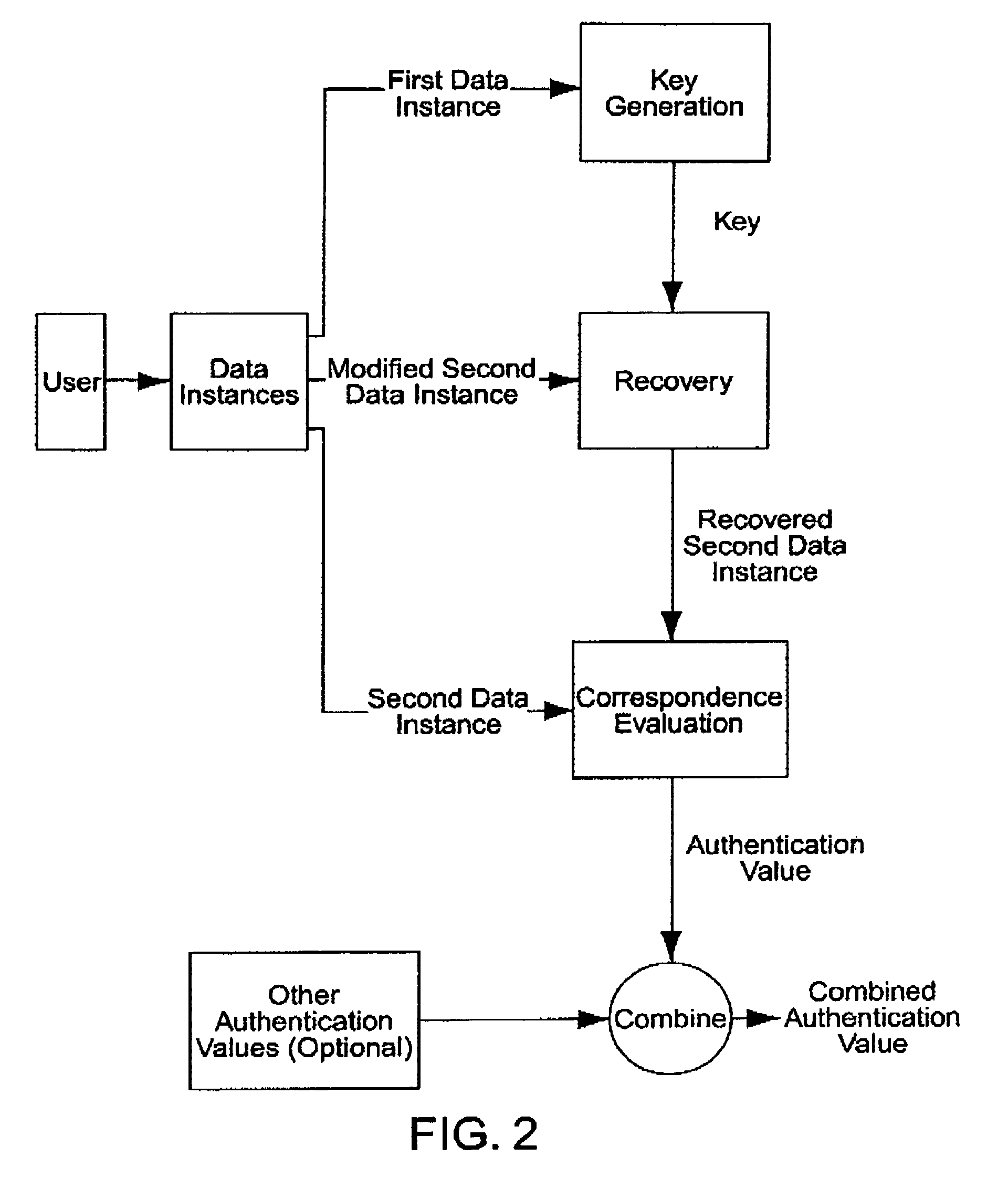
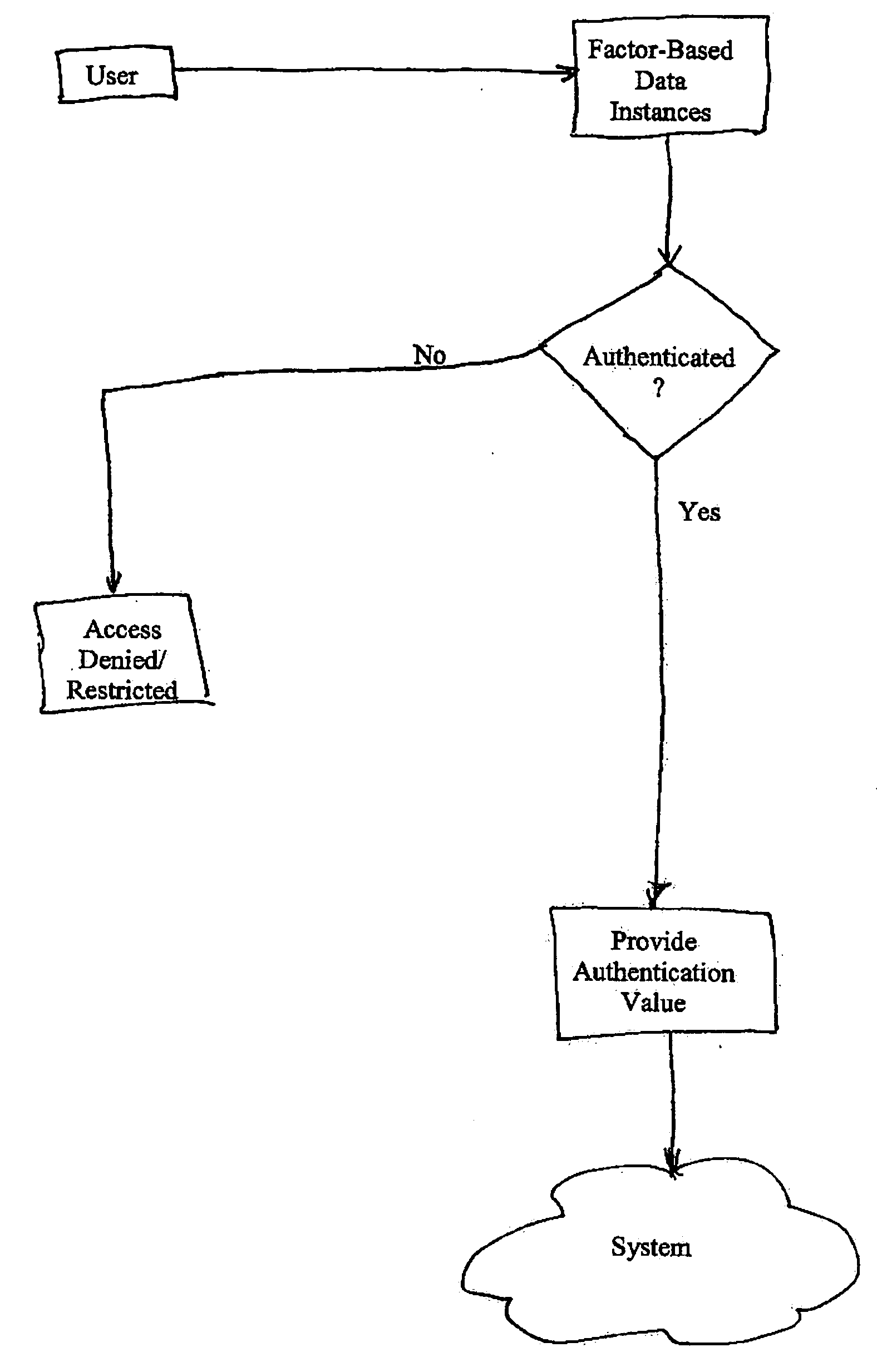
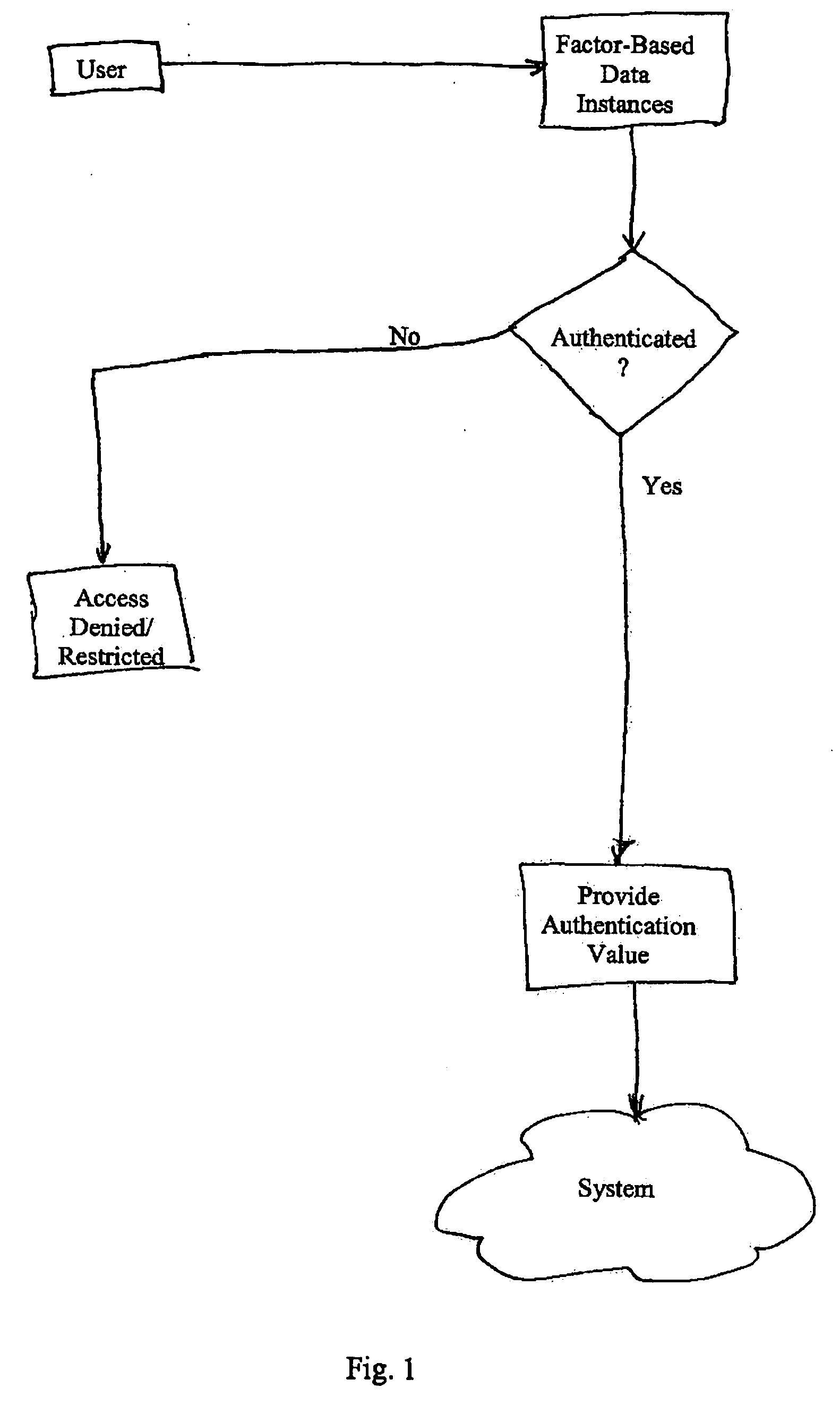
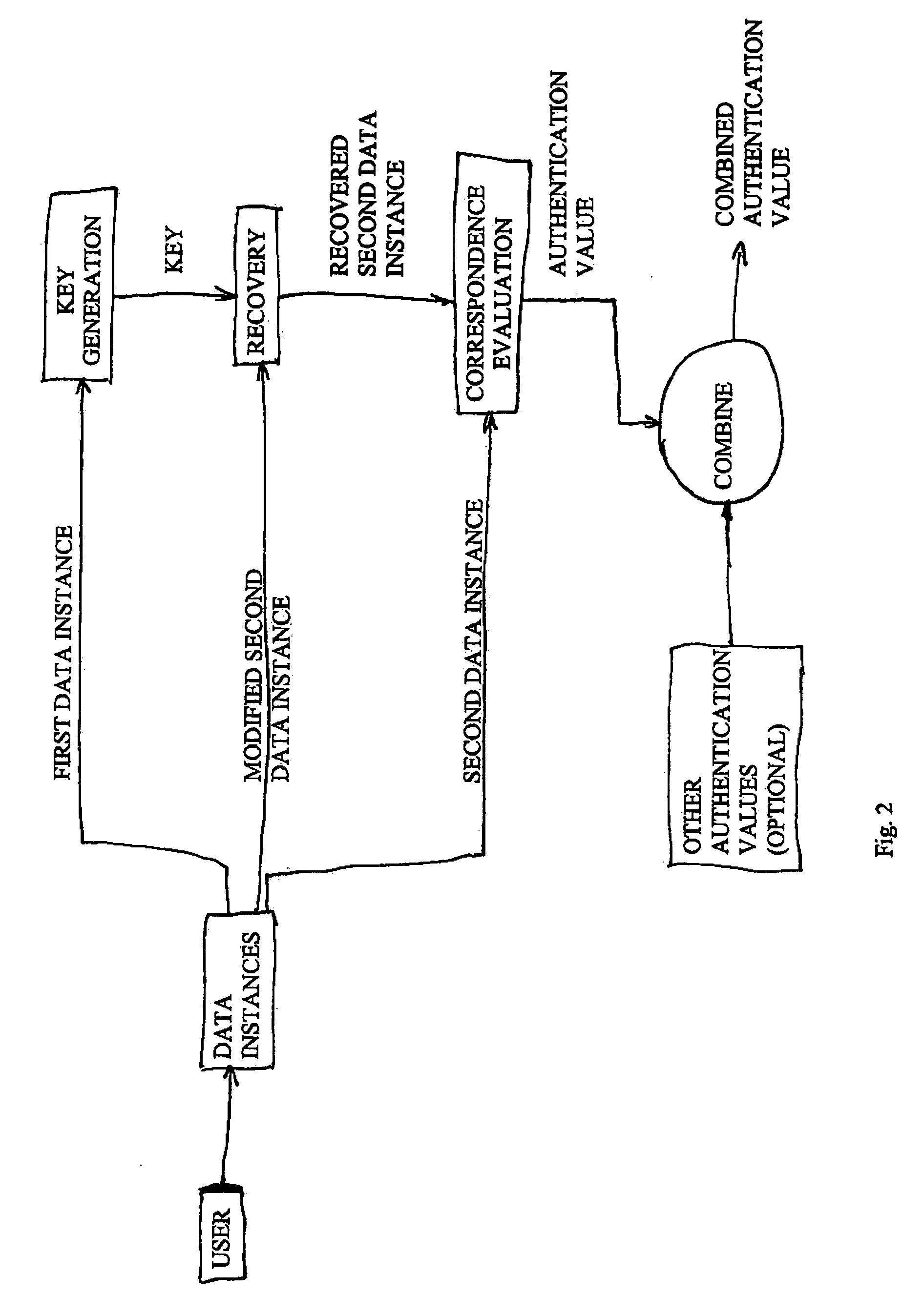
Multiple factor-based user identification and authentication
InactiveUS6845453B2Key distribution for secure communicationDigital data processing detailsInternet privacyMultiple factors
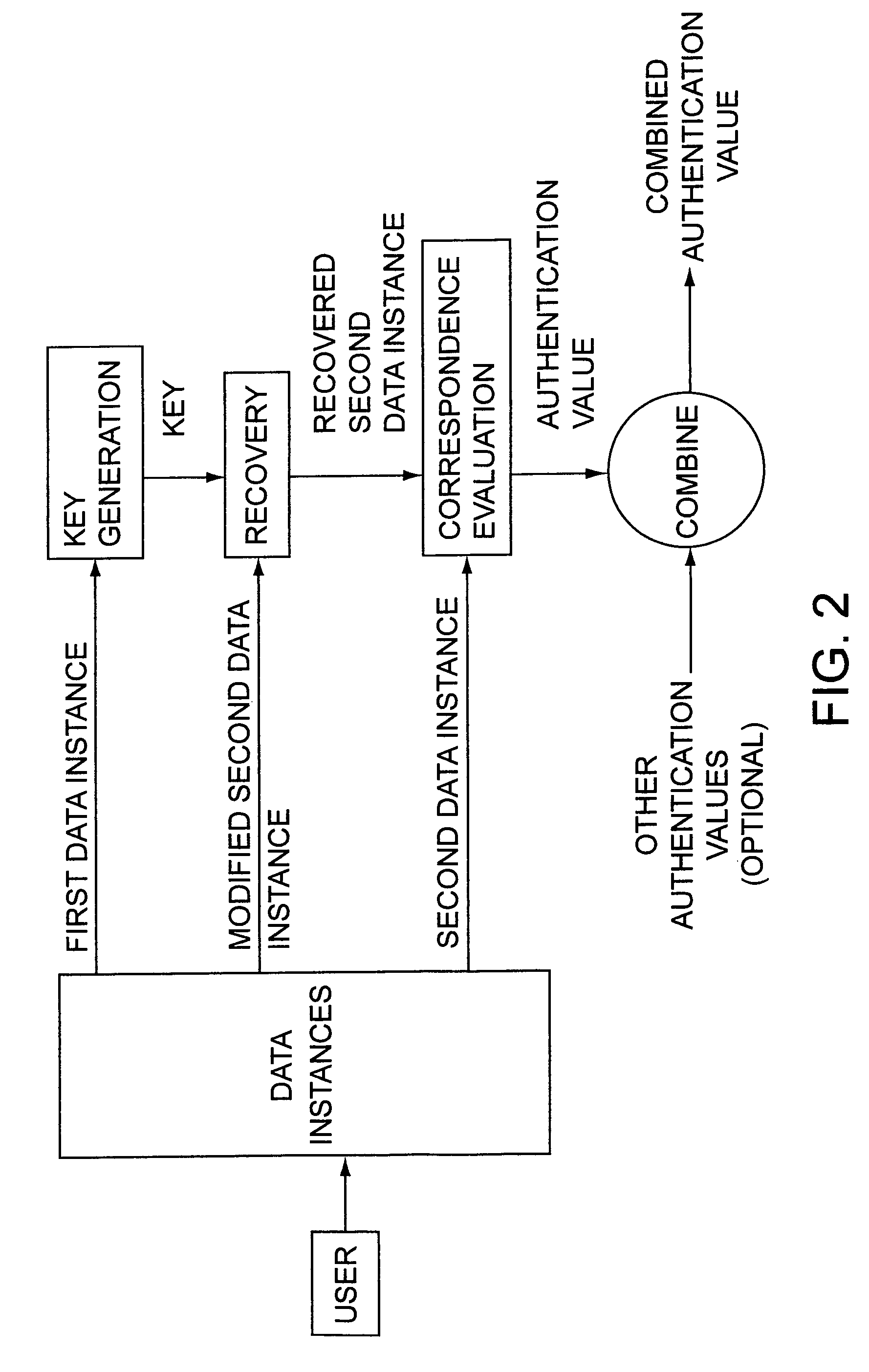
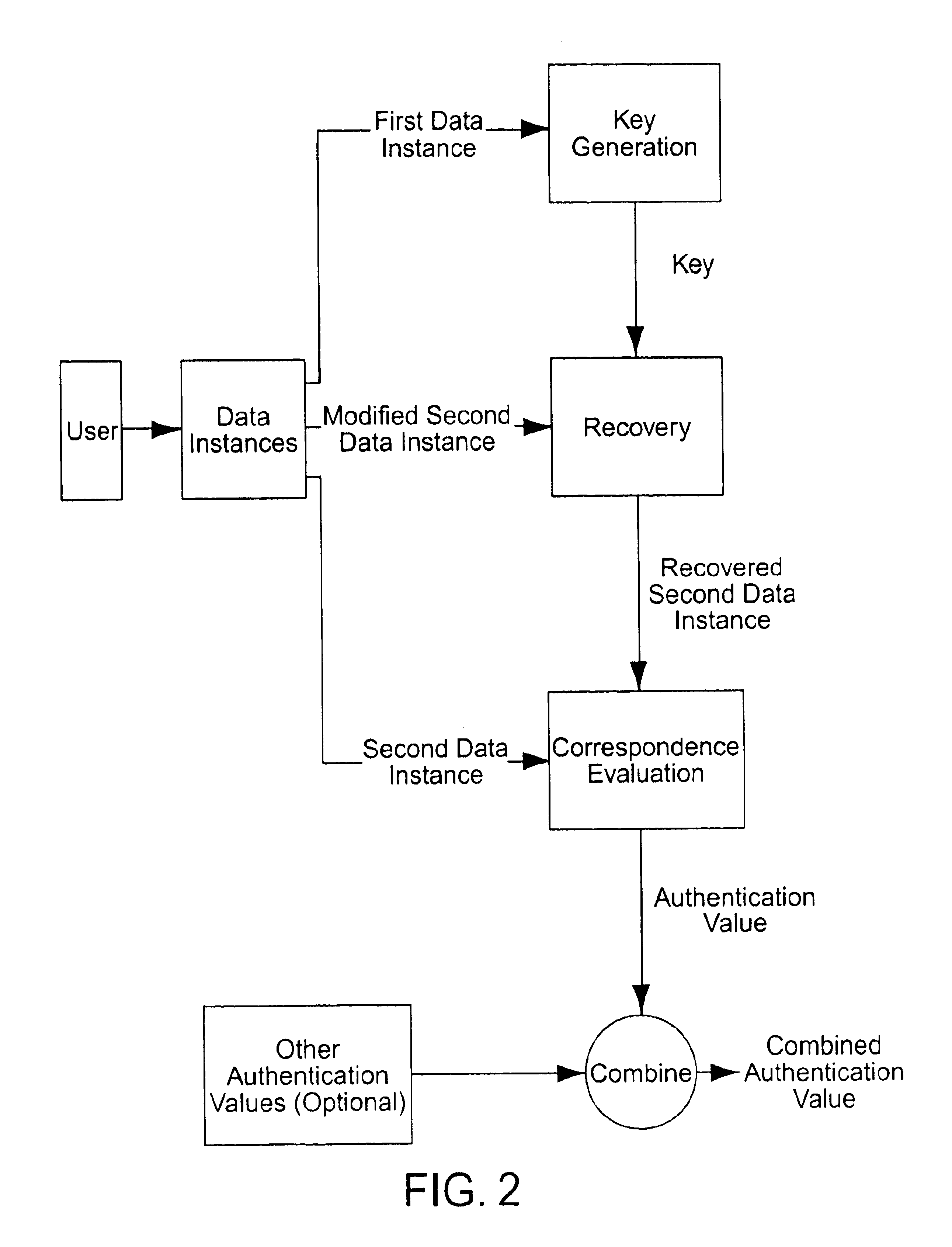
A method of authenticating the identity of a user to determine access to a system includes providing a plurality of factor-based data instances corresponding to a user, evaluating the factor-based data instances to determine if the user's identity is authenticated, and granting or restricting the user's access to the system if the user's identity is authenticated. More particularly, the method includes providing a modified data instance based on a second data instance, generating a key based on a first data instance, applying the key to the a modified data instance to generate a recovered data instance, interrogating the recovered data instance against the second data instance to generate an authentication value as a result of a correspondence evaluation, and granting or restricting the user's access to the system based at least in part on the validity of the authentication value.
Owner:TECSEC
Method and meeting scheduler for automated meeting insertion and rescheduling for busy calendars
A method and meeting scheduler are provided for automated meeting insertion and rescheduling for busy calendars. An electronic calendar meeting scheduling program stores meeting automation properties defined for each scheduled meeting. The electronic calendar meeting scheduling program stores meeting attendee automation properties defined for each attendee of each scheduled meeting. The electronic calendar meeting scheduling program utilizes the stored meeting automation properties and the stored meeting attendee automation properties to calculate a conflict score and action list for each potential time block for automated meeting insertion and rescheduling. The calculated conflict score and action list for each potential time block for rescheduling a meeting are based upon multiple factors including a move score, a leave early score, and a shorten meeting score. The action list includes an entry for each meeting altered for automated meeting insertion and rescheduling.
Owner:IBM CORP
System for testing physical model for large-scale landslides under action of multiple factors
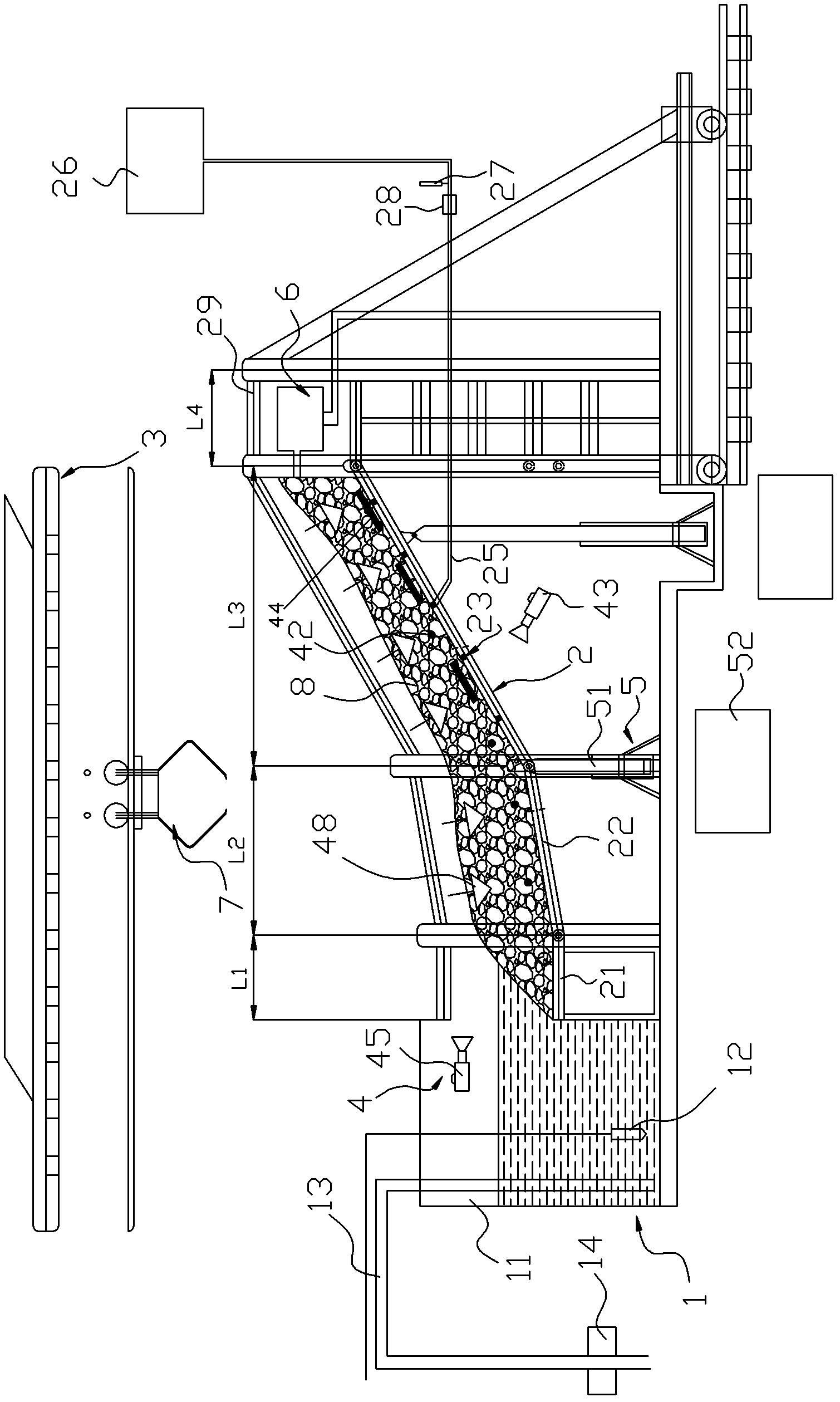
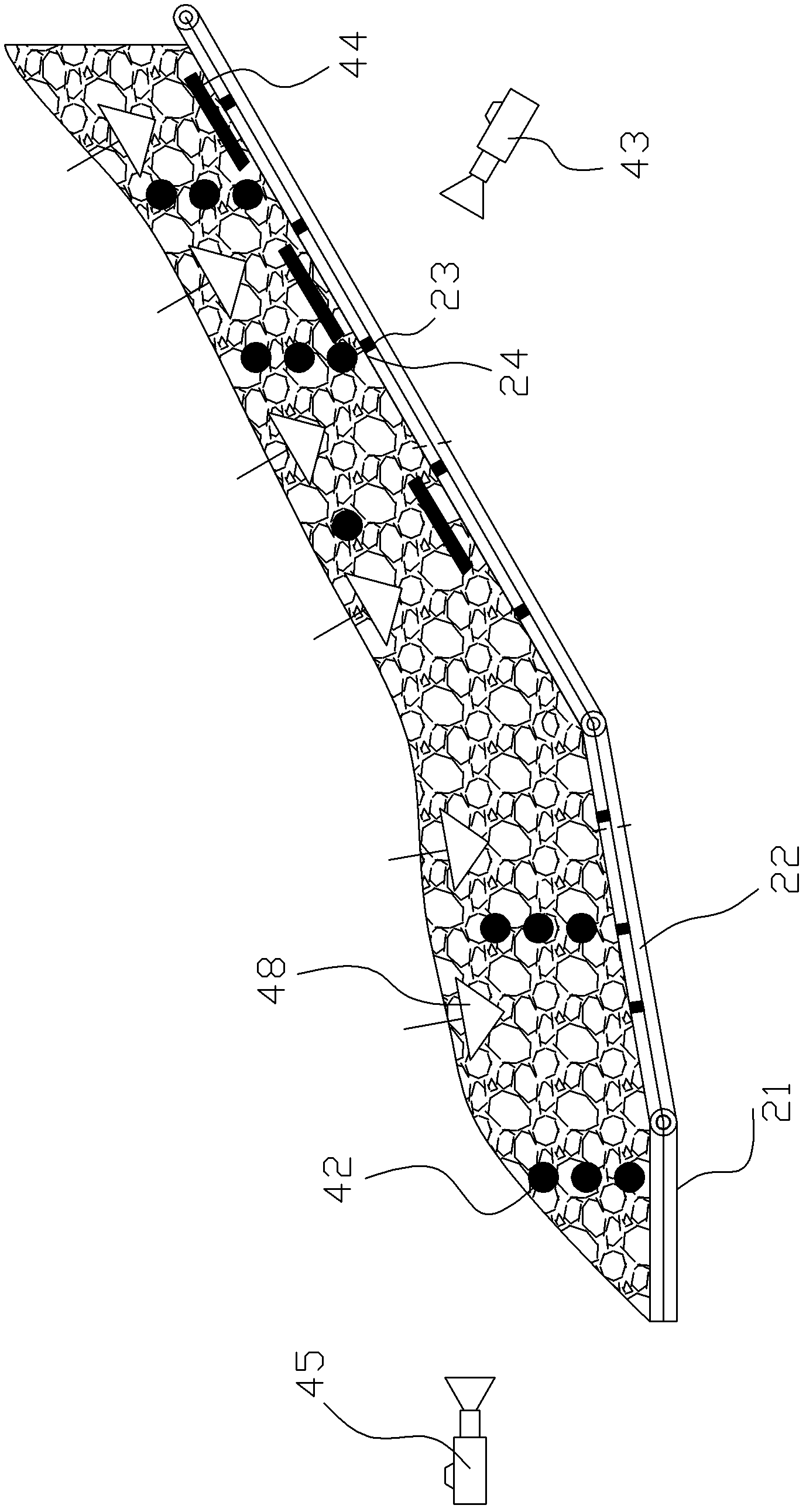
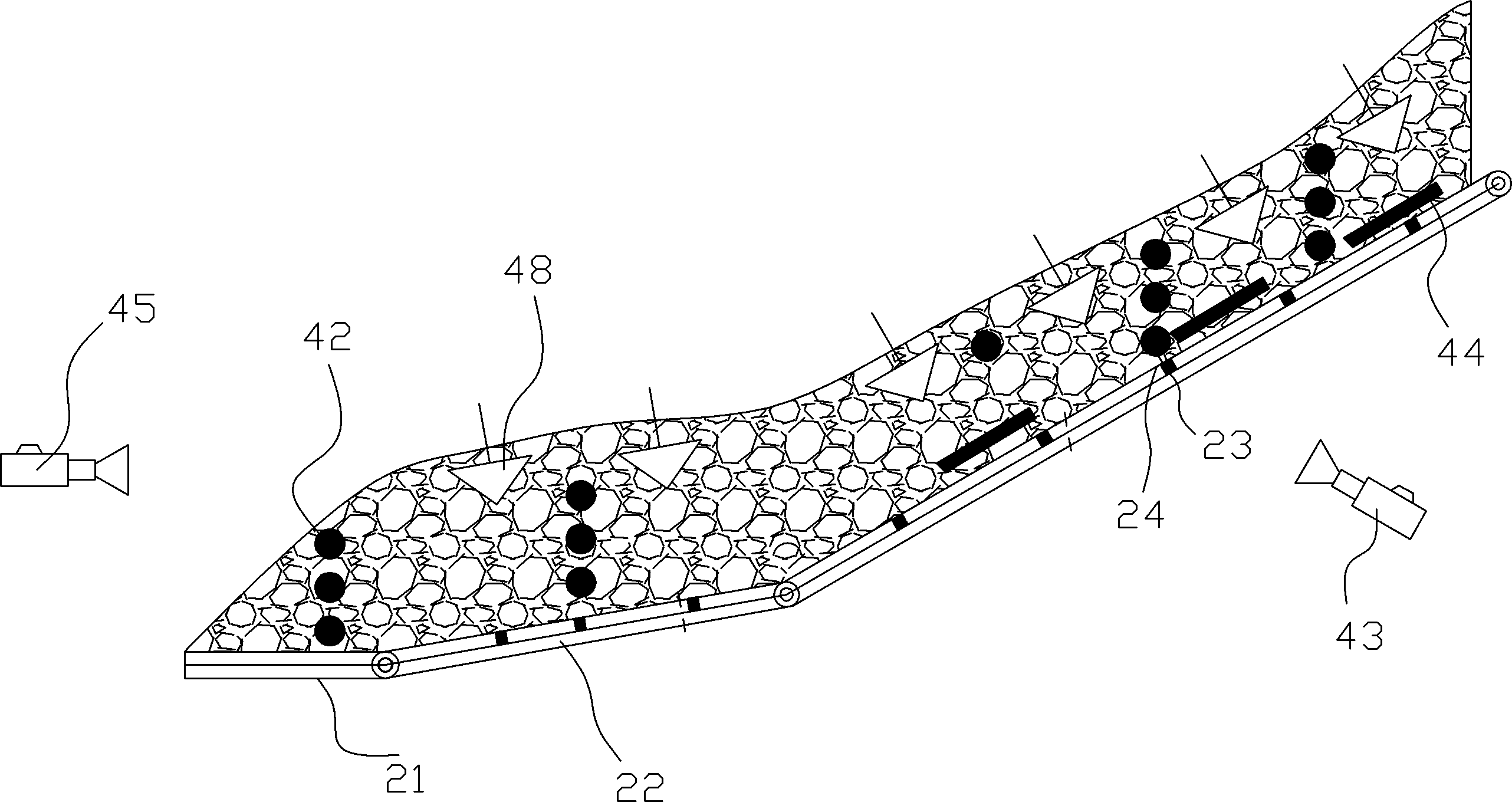
ActiveCN102331489ASmall sizeHigh precisionEarth material testingUsing optical meansRainfall simulationStress measures
The invention discloses a system for testing a physical model for large-scale landslides under the action of multiple factors, which comprises a reservoir level fluctuation simulation unit, a landslide experiment slot section, an artificial rainfall simulation unit and a measuring unit, wherein the landslide experiment slot section comprises a horizontal slot section and a slope slot section, the horizontal slot section and the slope slot section are respectively paved with a slope body consisting of sand-soil mixtures, and the rear end of the horizontal slot section is hinged with the front end of the slope slot section; the slope slot section is composed of more than two slot sections which are sequentially hinged end to end, and the bottom of each slot section is provided with a lifting unit which can adjust the dip angle of the slot section; the rear end of the slope slot section is provided with a Malpighian-tube rear-edge water-replenishing unit; and the measuring unit comprises a deformation measuring part and a stress measuring part, wherein the deformation measuring part is used for measuring the deformation process of the slope body, and the stress measuring part is used for measuring the water pressure and water content of a pore of the slope body. By using the system disclosed by the invention, the changing regularity of each measurable physical quantity of a landslide in different development stages can be grasped accurately, thereby providing a possibility for better developing the studies on key parameters of landslides in different evolution stages.
Owner:INST OF MECHANICS - CHINESE ACAD OF SCI
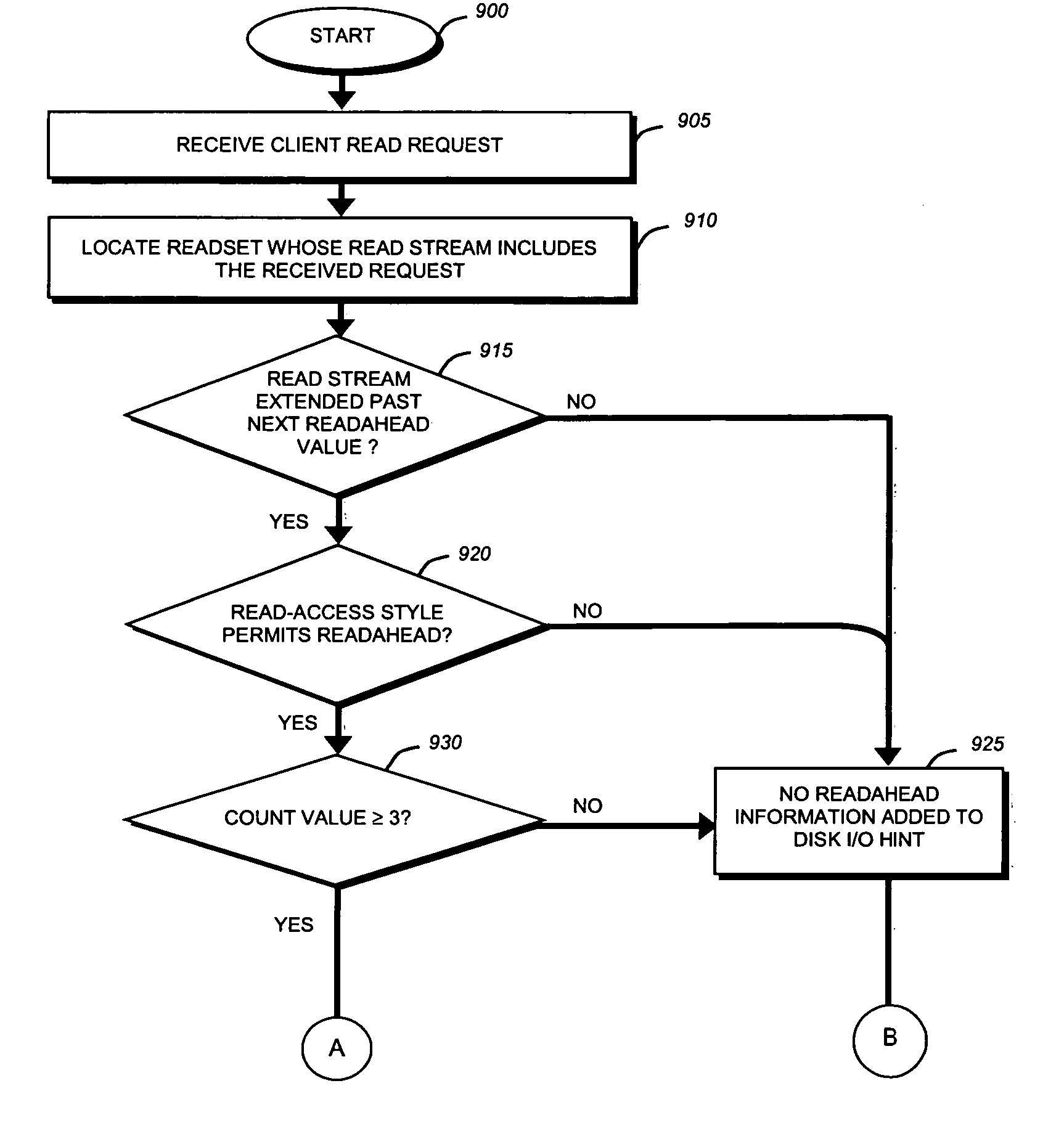
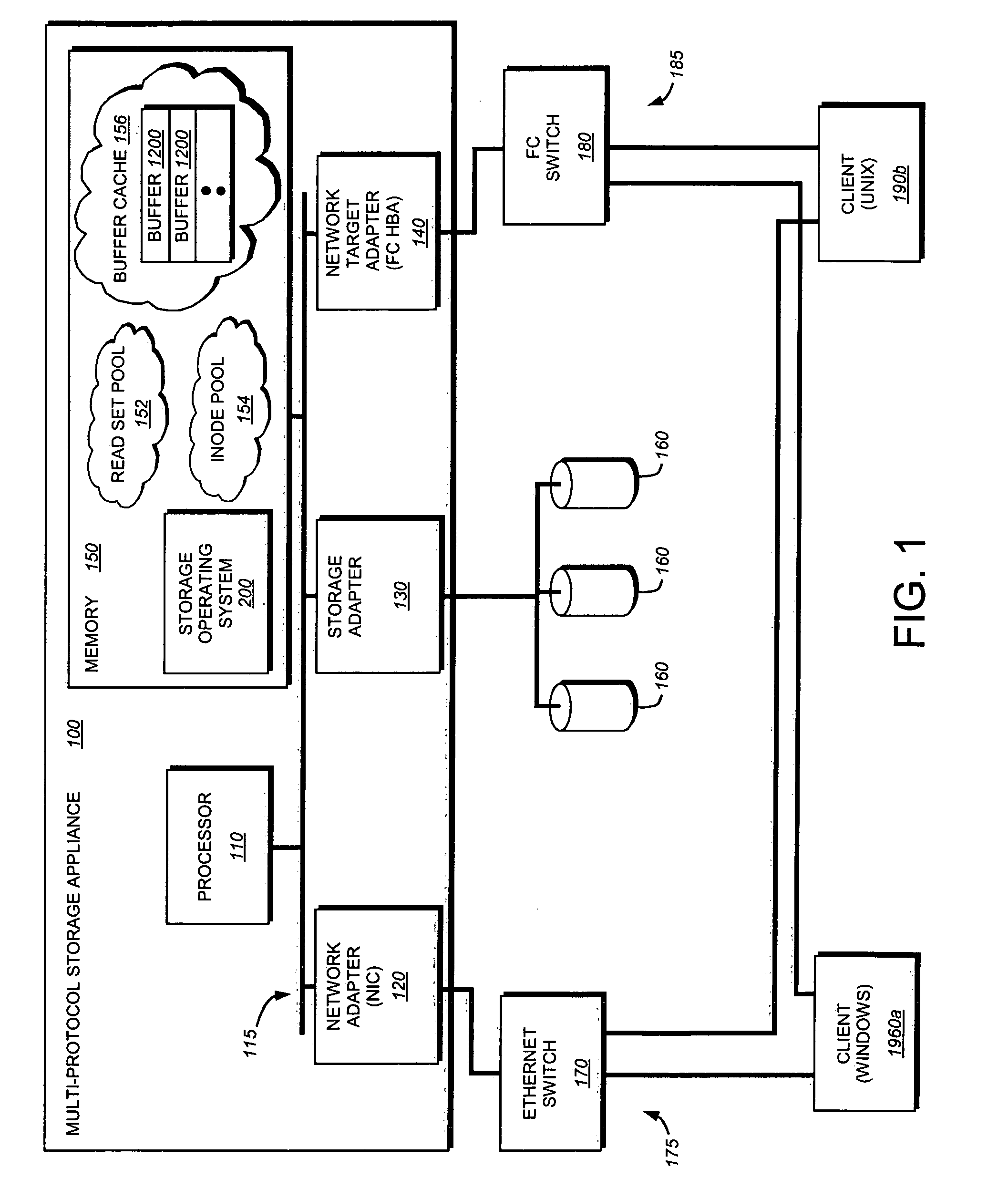
Adaptive file readahead based on multiple factors
ActiveUS20050154825A1Minimize cache pollutionConvenient amountInput/output to record carriersDigital data information retrievalClient-sideMultiple factors
A storage system is provided that implements a file system configured to optimize the amount of readahead data retrieved for each read stream managed by the file system. The file system relies on various factors to adaptively select an optimized readahead size for each read stream. Such factors may include the number of read requests processed in the read stream, an amount of client-requested data requested in the read stream, a read-access style associated with the read stream, and so forth. The file system is also configured to minimize cache pollution by adaptively selecting when readahead operations are performed for each read stream and determining how long each read stream's retrieved data is retained in memory.
Owner:NETWORK APPLIANCE INC
Critically/vulnerability/risk logic analysis methodology for business enterprise and cyber security
InactiveUS20100153156A1Reduce unacceptable riskFinanceOffice automationBusiness enterpriseAnalysis method
Method and apparatus for computer-aided assessment of risk, criticality, and vulnerability with respect to a site. The method and apparatus may use multiple factors to determine overall risk. In some embodiments, the method may assess or determine an impact if a site or asset is lost. The method and apparatus may identify and quantify what risks are acceptable and unacceptable. In an embodiment, a method and apparatus may incorporate mathematical evaluations and numeric assignments that result in a criticality vector and a vulnerability vector. In some embodiments, the criticality vector and vulnerability vector may be used to represent a site's overall risk and / or prioritization and ranking relative to other sites.
Owner:AZ-TECH INT INC
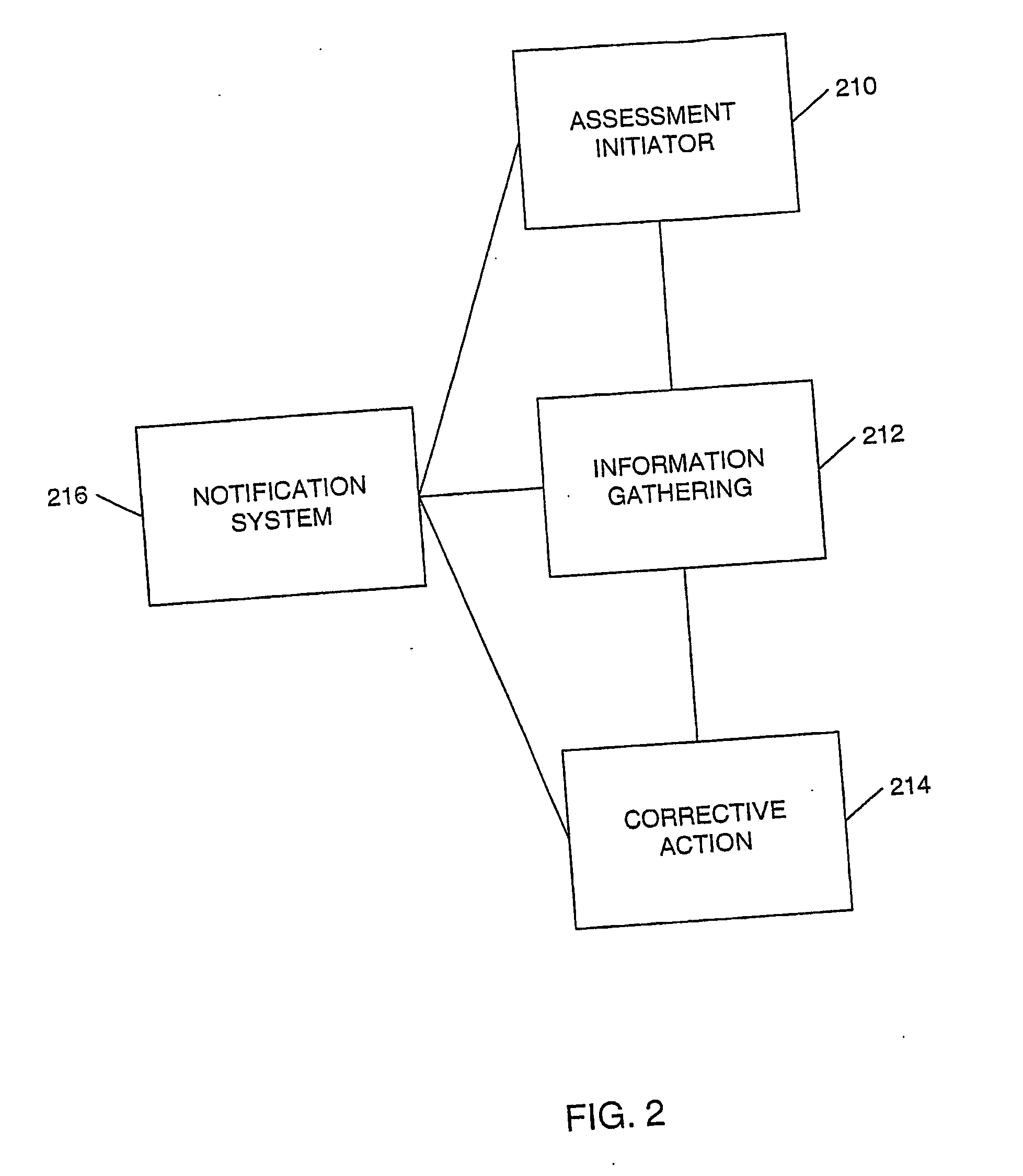
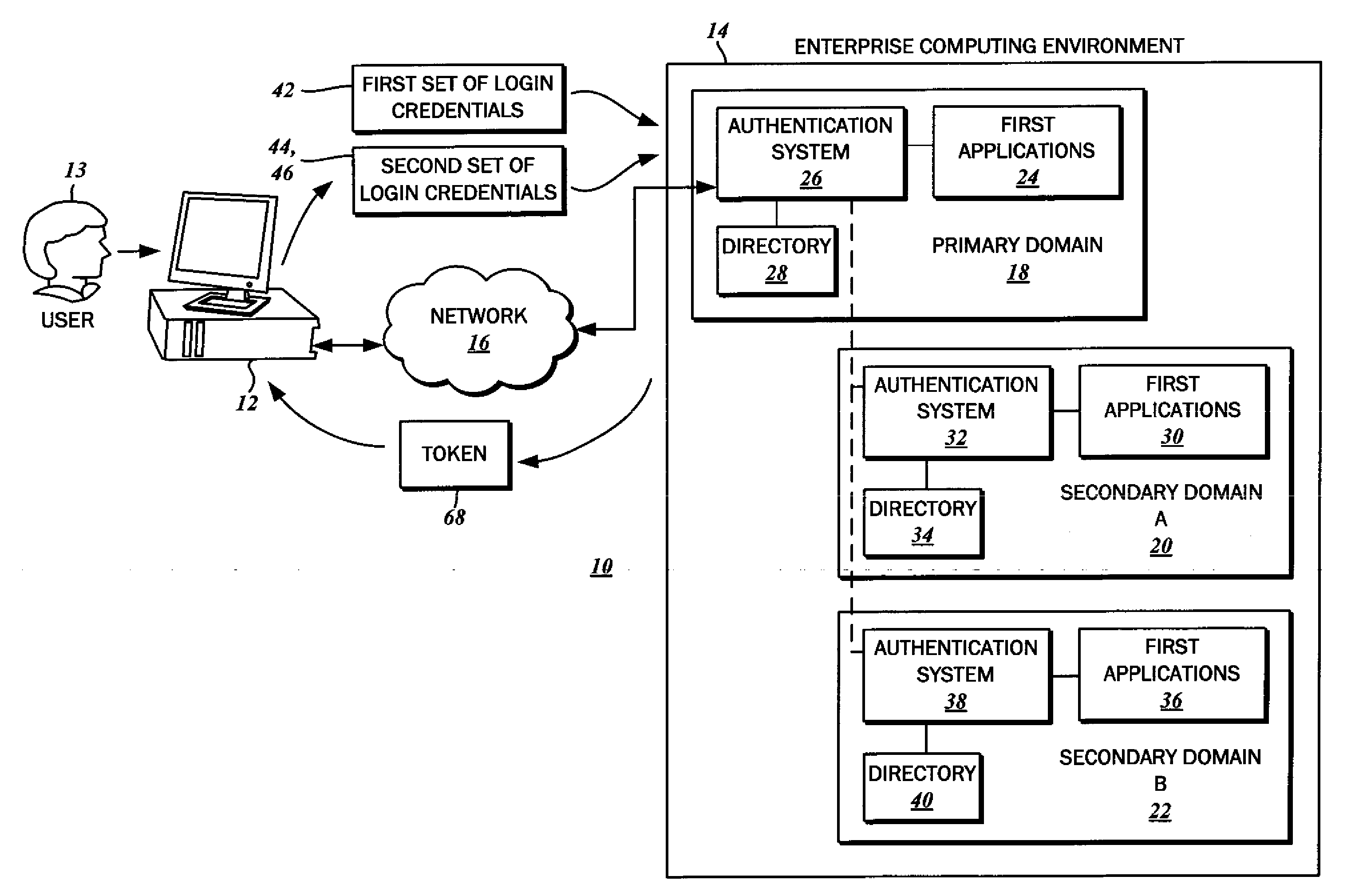
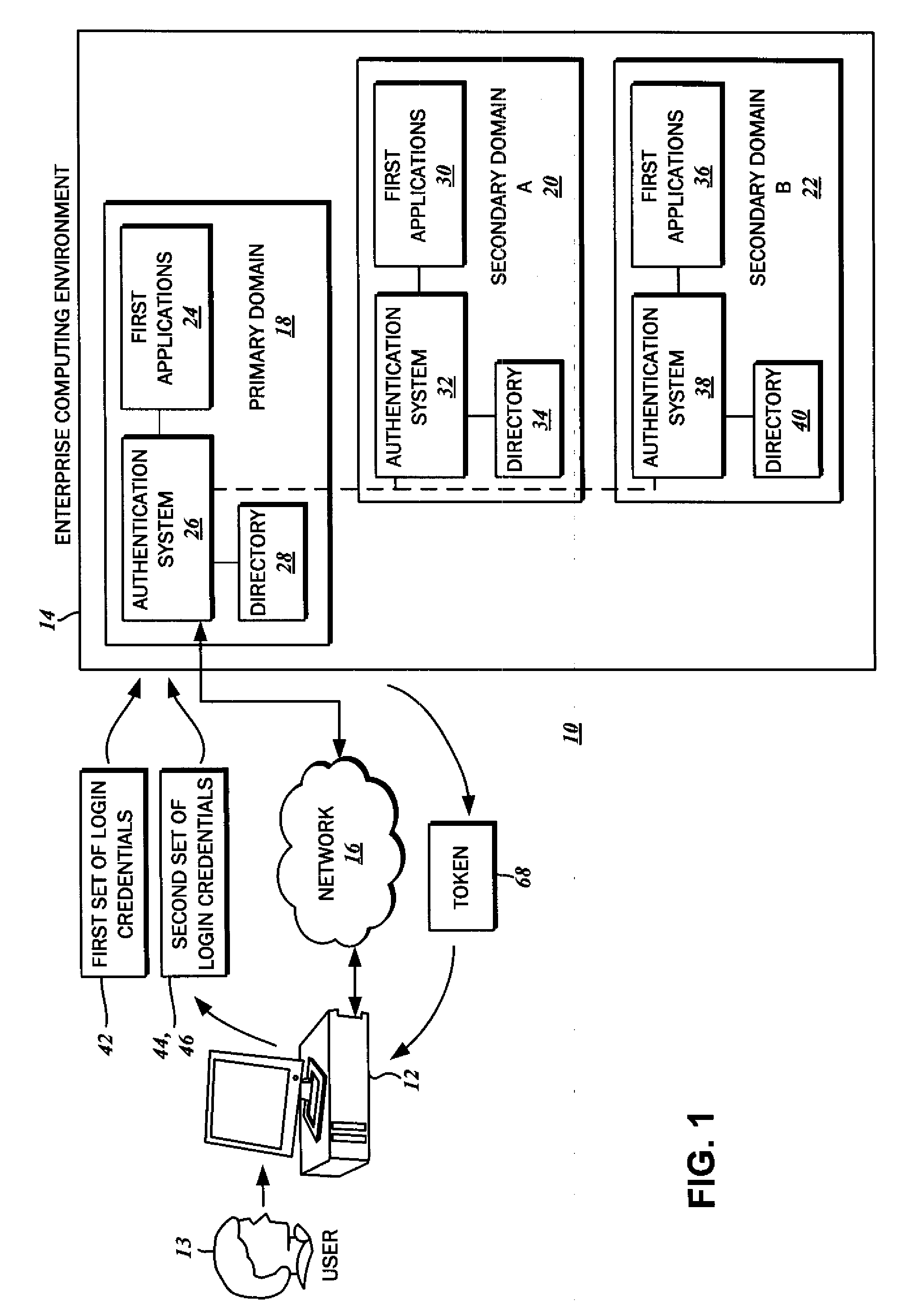
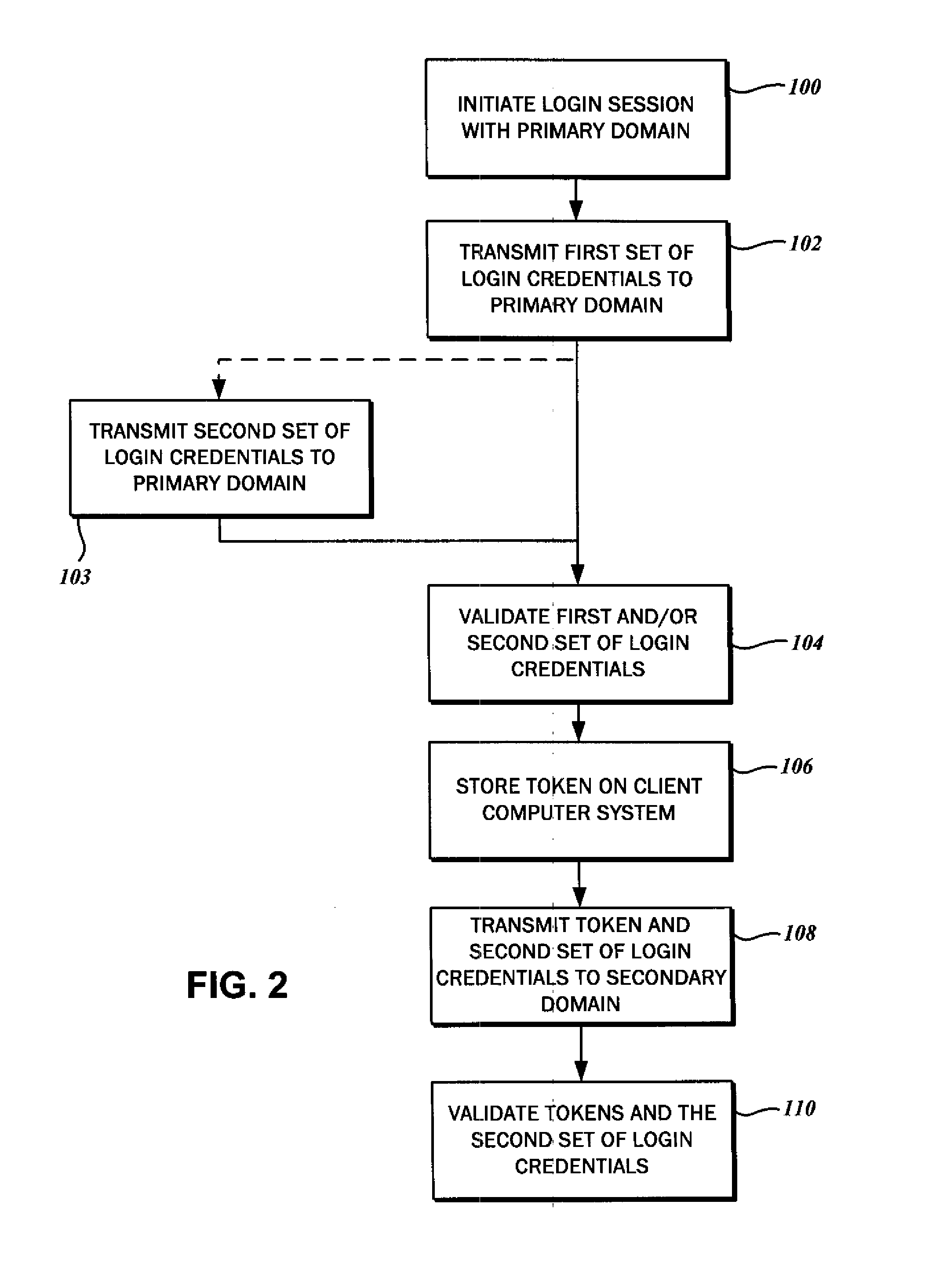
Single sign on with multiple authentication factors
ActiveUS20110119747A1Reduce decreaseMinimize the numberDigital data processing detailsUser identity/authority verificationClient-sideAuthentication system
The authentication of a client to multiple server resources with a single sign-on procedure using multiple factors is disclosed. One contemplated embodiment is a method in which a login session is initiated with the authentication system of a primary one of the multiple server resources. A first set of login credentials is transmitted thereto, and validated. A token is stored on the client indicating that the initial authentication was successful, which is then used to transition to a secondary one of the multiple resources. A second set of login credentials is also transmitted, and access to the secondary one of the multiple resources is granted on the basis of a validated token and second set of login credentials.
Owner:SECUREAUTH CORP
System and method of subscription identity authentication utilizing multiple factors
ActiveUS7340042B2Low costRaise security concernsAutomatic call-answering/message-recording/conversation-recordingSpeech recognitionSpeech verificationSpeech sound
Owner:CSIDENTITY CORP
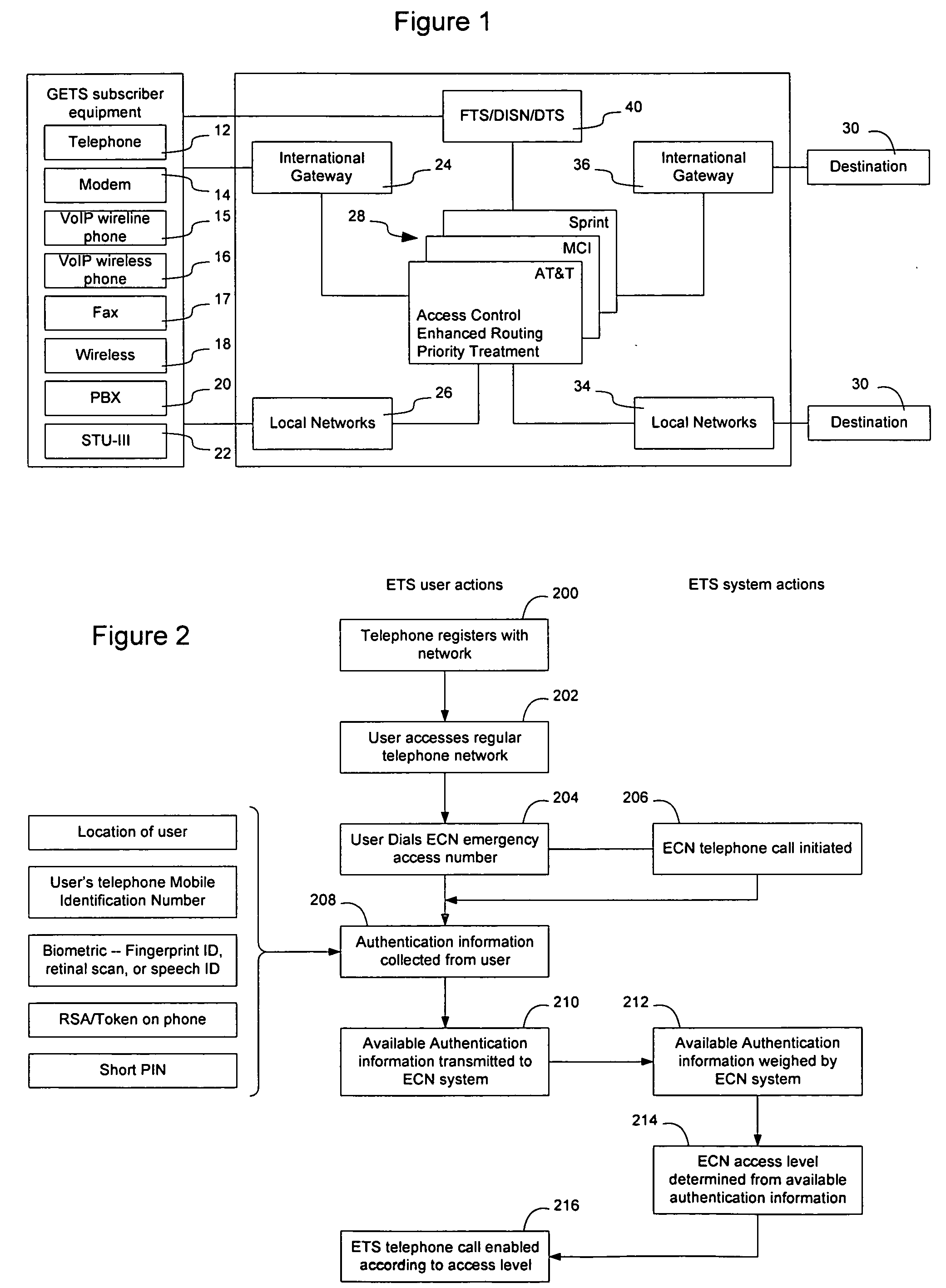
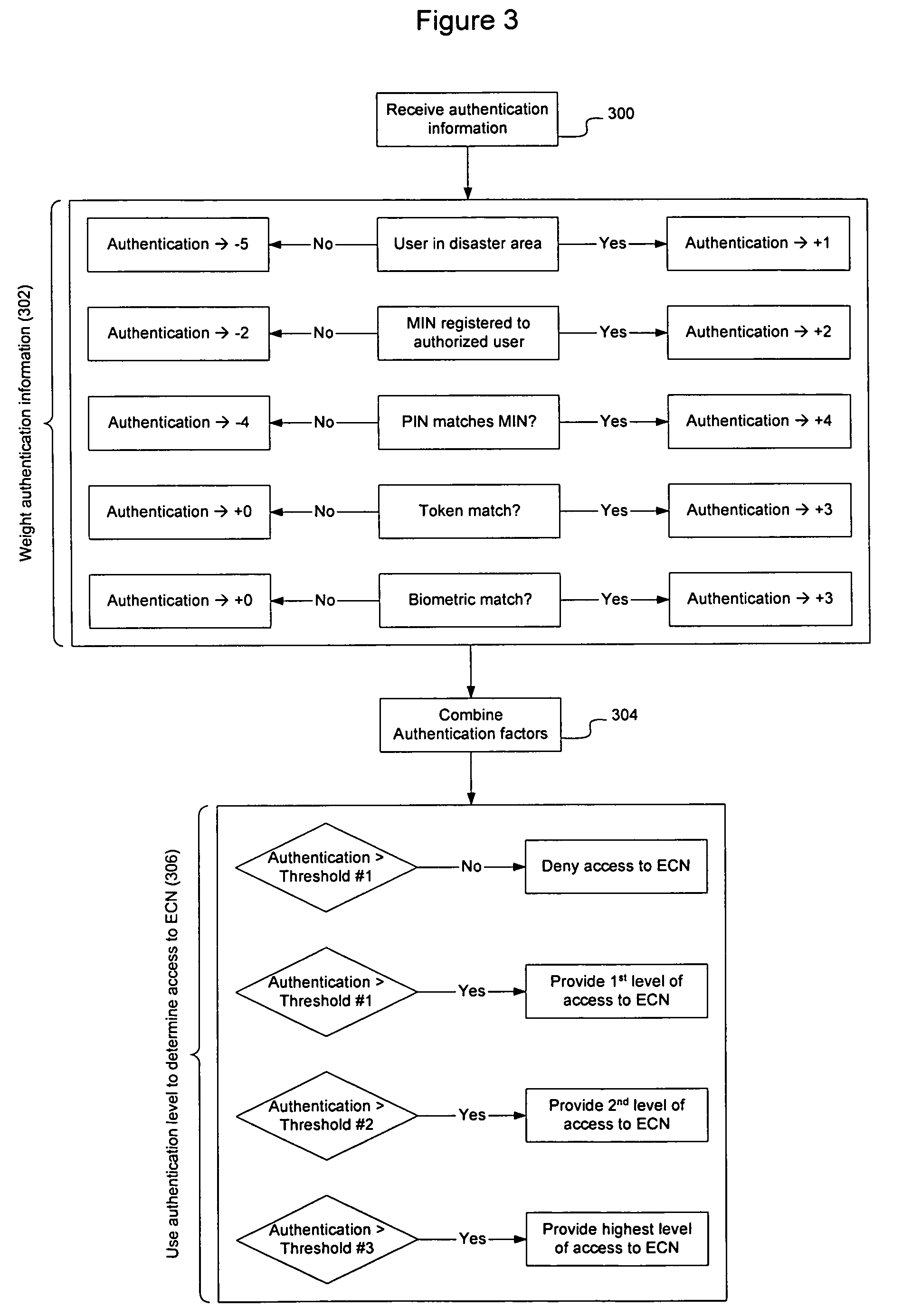
Method and apparatus for authenticating users of an emergency communication network
InactiveUS20080010674A1Lower requirementAuthentication requirements of group members may be reducedUnauthorised/fraudulent call preventionDigital data processing detailsPush-to-talkAuthentication system
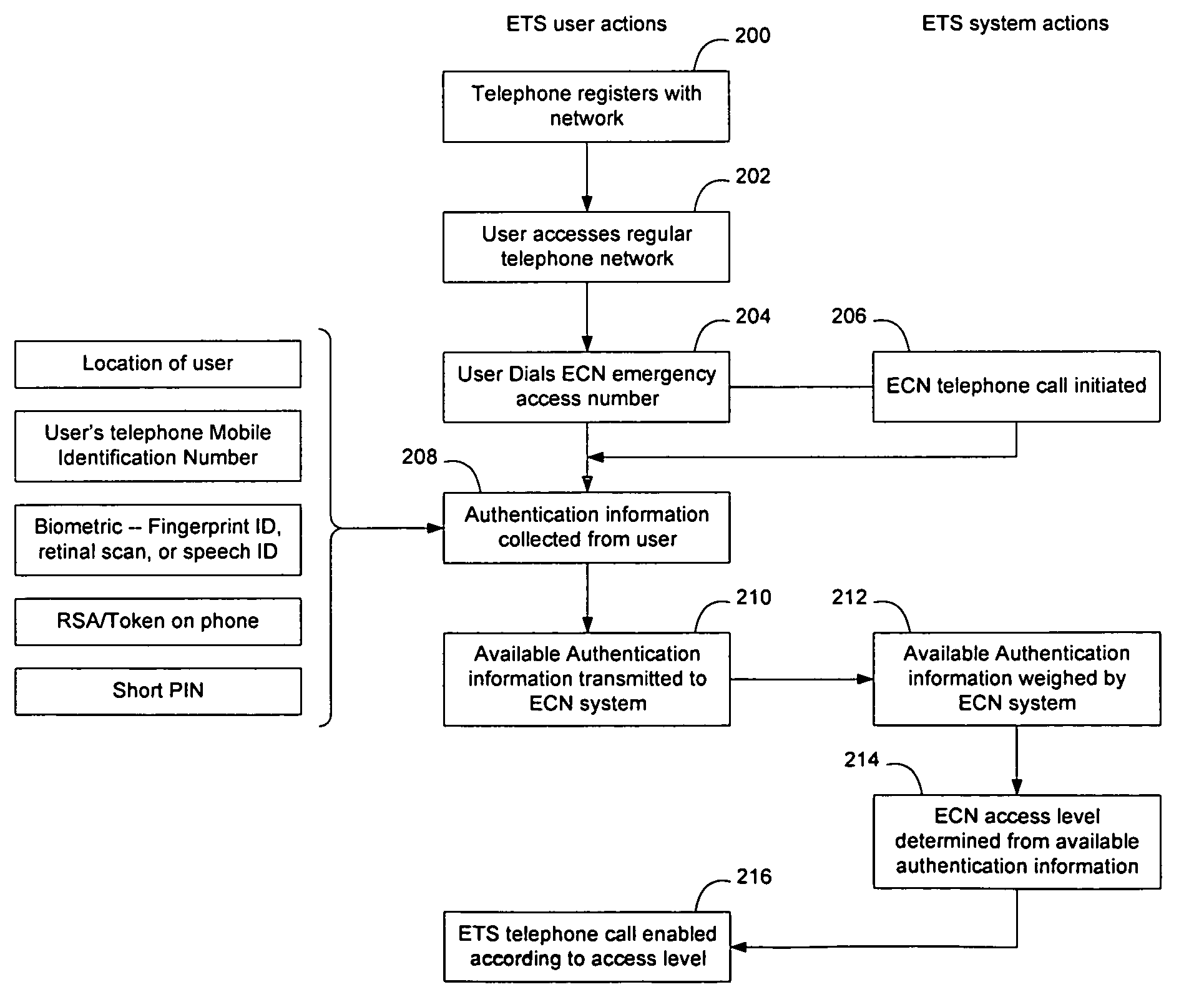
An authentication system is configured to weight multiple available network supplied and user supplied authentication factors to determine whether a user should be provided with access to an Emergency Communication Network (ECN). The multiple factors may include the location of the user, MIN, short PIN, token, biometric information, and other information. The level of access to be provided to the user may be tiered based on the authentication level achieved during the weighting process. Authentication information may be shared between groups of individuals, so that the authentication requirements for group members may be reduced as other members of the group supply authentication information to the ECN. Group authentication may be used to enable group services such as conferencing and push-to-talk to be set up automatically for the group.
Owner:RPX CLEARINGHOUSE
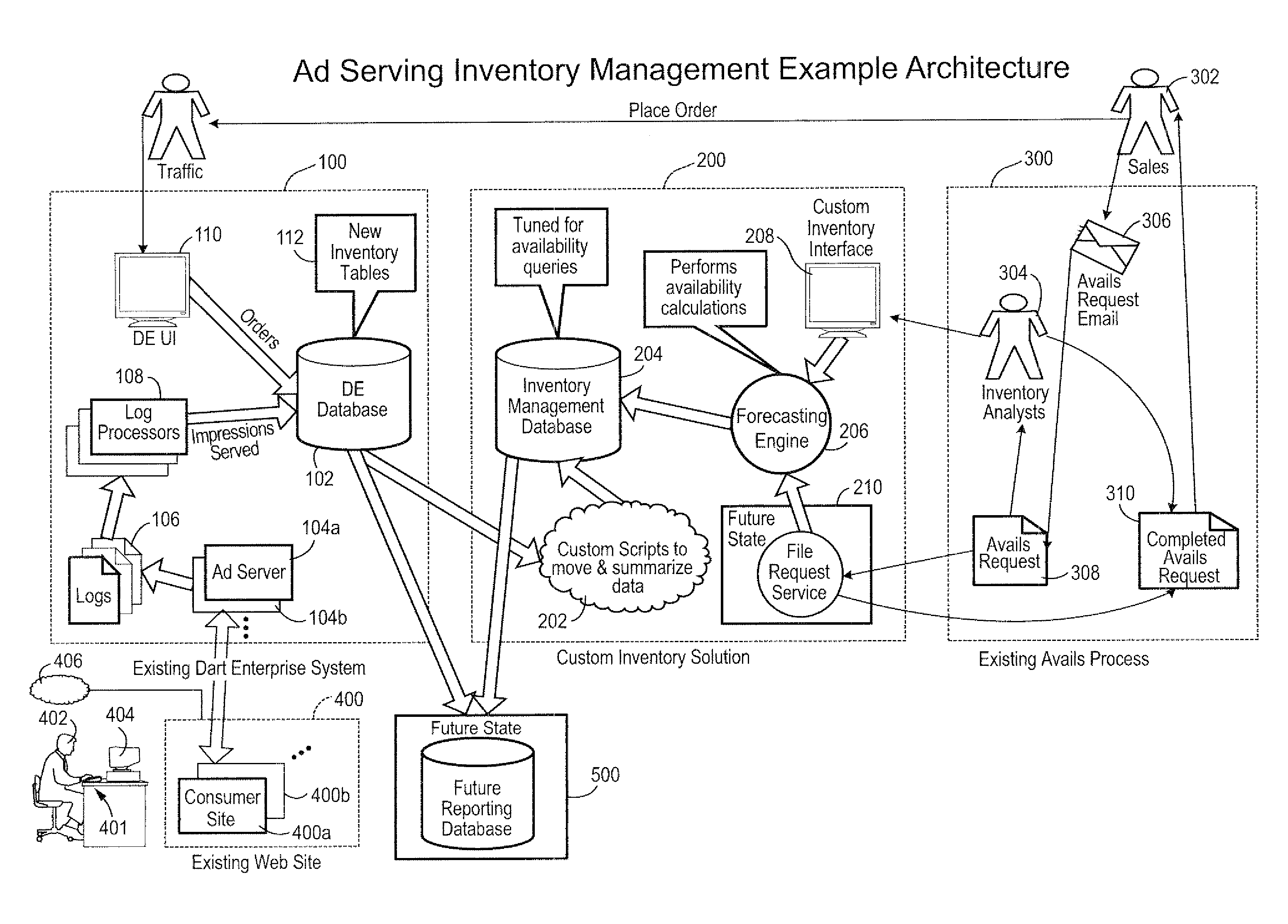
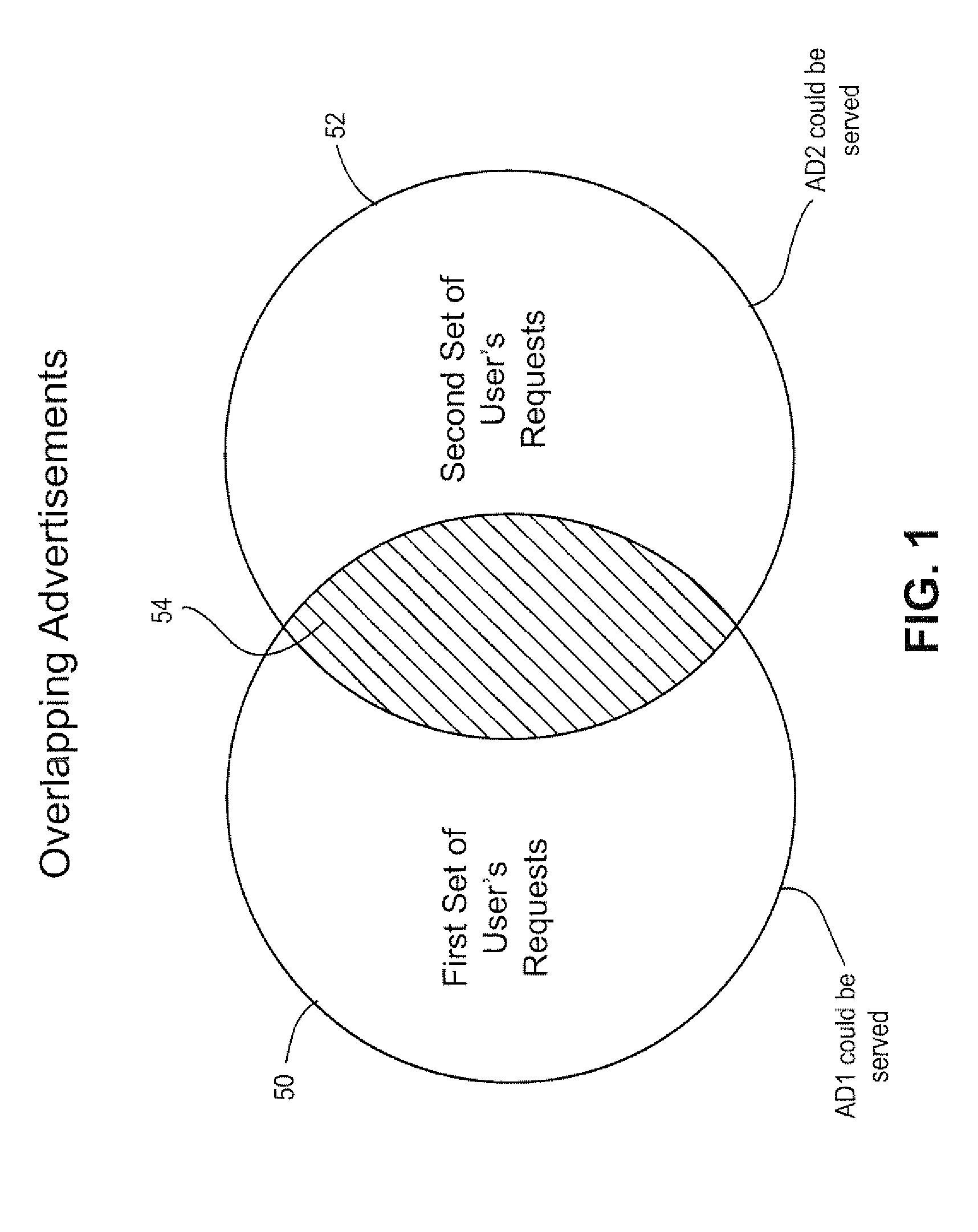
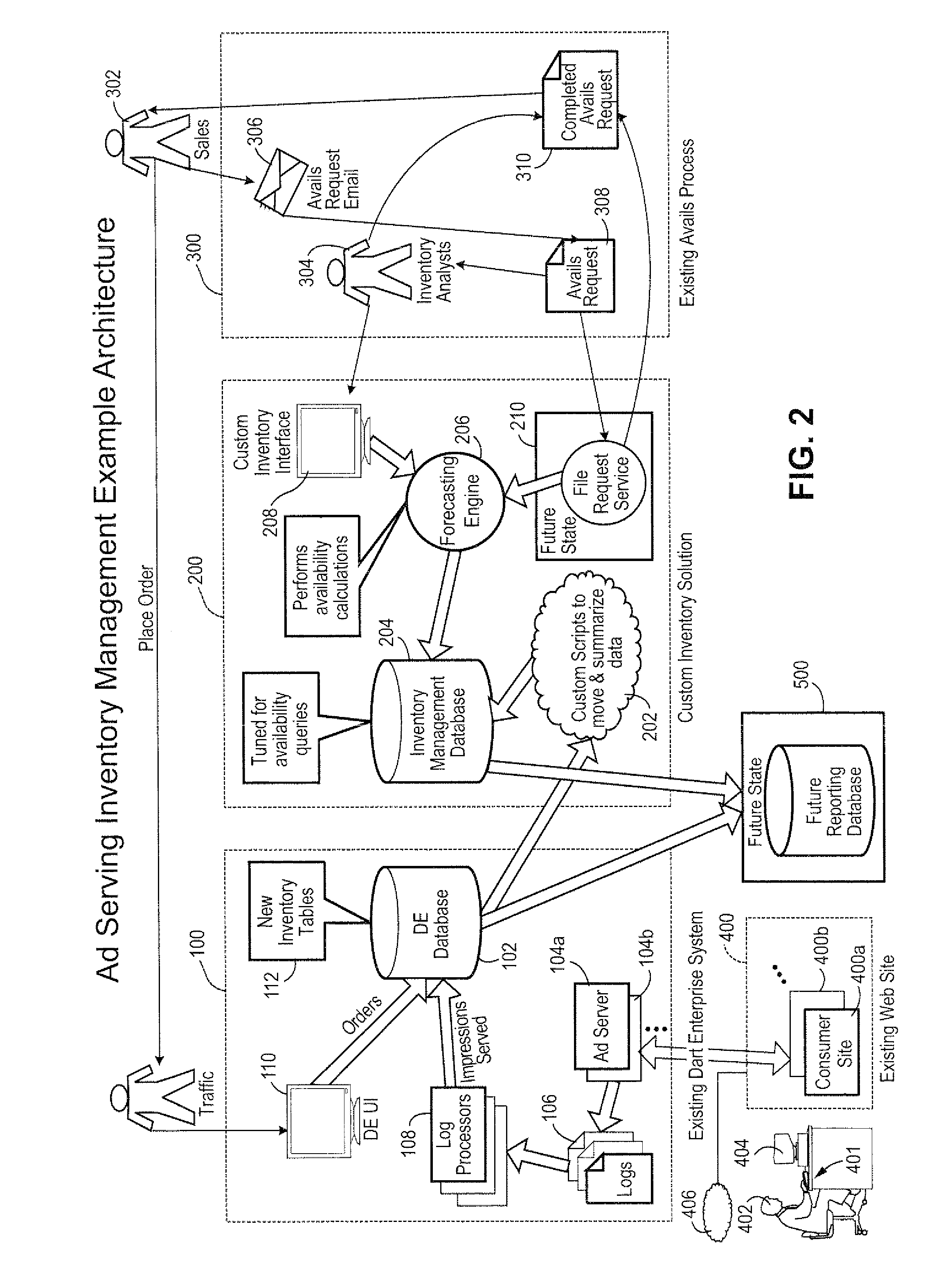
Computer based systems and methods for managing online display advertising inventory
A system and method for determining total capacity, amount reserved or sold and remaining availability of ad impressions for an online advertising publishing system. Calculations may be based on multiple factors including for example 1) actuals of historical data of ad impression delivery, 2) various delivery parameters including ad targeting overlap with other ads, timing, priority and impression goals, and 3) a mathematical algorithm and calculations of the above incorporating adjustments due to seasonality and market factors. The resulting calculations are used to reserve, schedule and target advertisements to be delivered over a network to be viewed by consumers.
Owner:AUTOTRADER COM
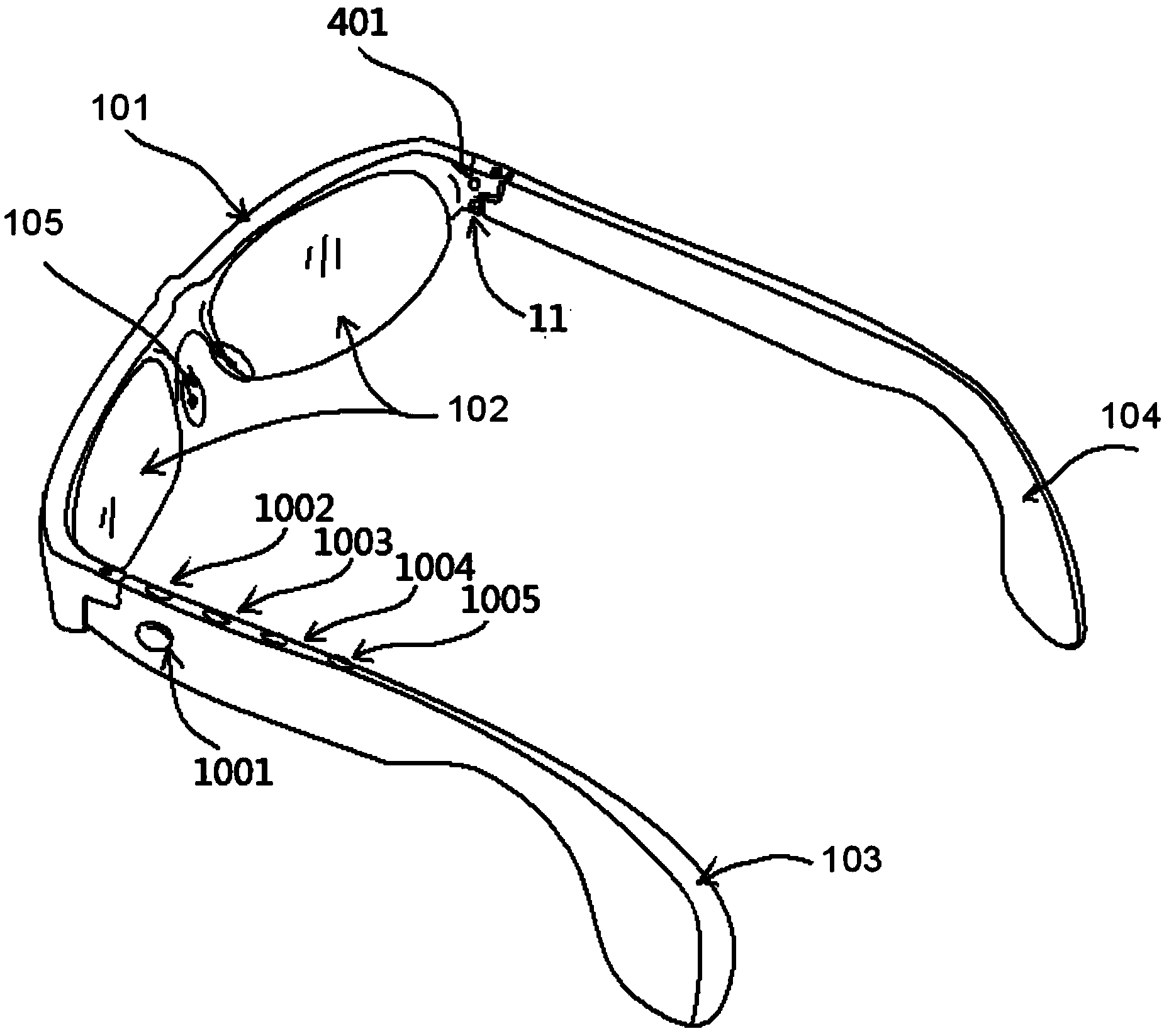
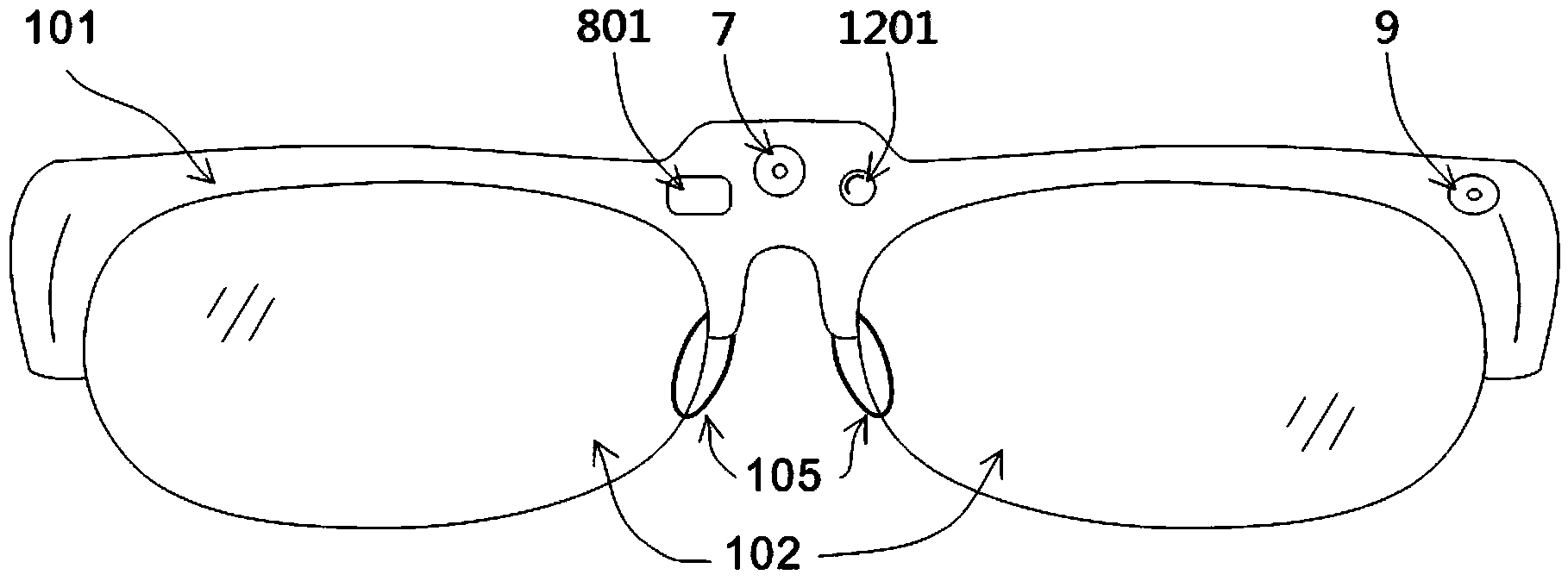
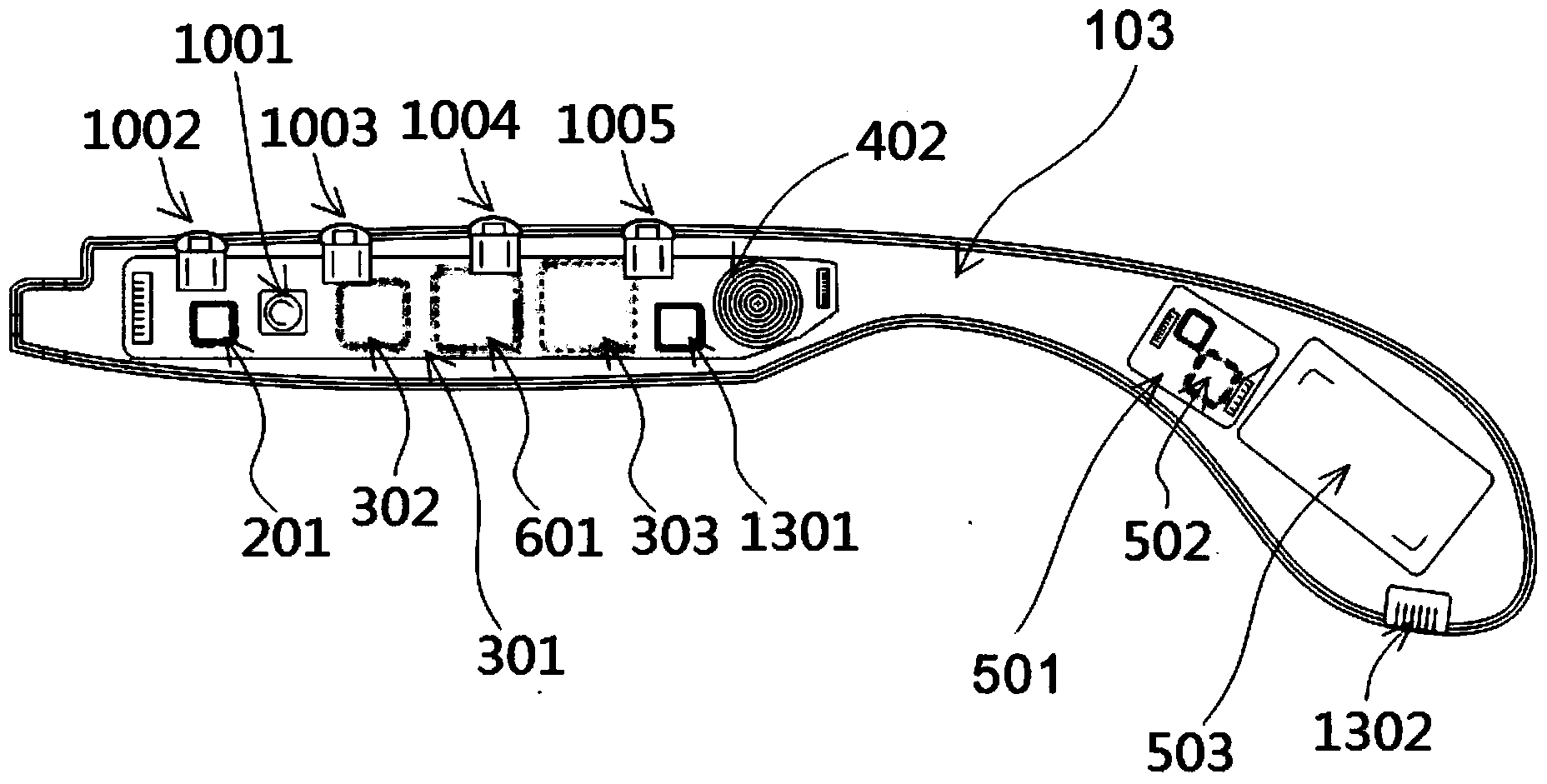
Intelligent glasses and method for monitoring movement, preventing shortsightedness and correcting sitting postures by utilizing same
ActiveCN103479361AEnsure healthy eyesFunctionally targetedNon-optical adjunctsDiagnostic recording/measuringAccelerometerAngular velocity
The invention discloses intelligent glasses and a method for monitoring movement, preventing shortsightedness and correcting sitting postures by utilizing the same. The intelligent glasses comprise a glasses frame, and an inertial sensor, a data processing module, an alarm display module and a power module which are arranged in the glasses frame; the inertial sensor, the alarm display module and the power module are all connected with the data processing module electrically; the inertial sensor adopts an accelerometer, or an angular velocity sensor, or an inertia measurement unit with single, double or three shaft combination of the accelerometer or the angular velocity sensor, or a navigation position reference system. The intelligent glasses are simple in structure, comprehensive in functions and good in ductility; by full-featured accurate detection on multiple factors influencing vision, including postures in two directions of the head of a user, viewing distance, viewing time and various lighting conditions, the eye health of the user under various conditions is ensured.
Owner:成都爱目视光科技有限公司
Multiple factor-based user identification and authentication
InactiveUS7131009B2Key distribution for secure communicationDigital data processing detailsFactor baseInternet privacy
A method of authenticating the identity of a user to determine access to a system includes providing a plurality of factor-based data instances corresponding to a user, evaluating the factor-based data instances to determine if the user's identity is authenticated, and granting or restricting the user's access to the system if the user's identity is authenticated. More particularly, the method includes providing a modified data instance based on a second data instance, generating a key based on a first data instance, applying the key to the a modified data instance to generate a recovered data instance, interrogating the recovered data instance against the second data instance to generate an authentication value as a result of a correspondence evaluation, and granting or restricting the user's access to the system based at least in part on the validity of the authentication value.
Owner:TECSEC
Multiple factor user authentication system
InactiveUS20090063850A1Avoid attackUser identity/authority verificationDigital data authenticationUser authenticationUser identifier
The present invention describes a method and a system for multi-level authentication of a user and a server. The user registration process in the invention enables user to personalize the web page of the server. Further, the user authentication takes place in a multi-step process including entering credentials such as user ID, subset of user's password, subset of shared secret and a One Time Password (OTP). The system of the present invention provides various means of entering the said credentials which prevents phishing attacks.
Owner:JORAM SHARWAN KUMAR +3
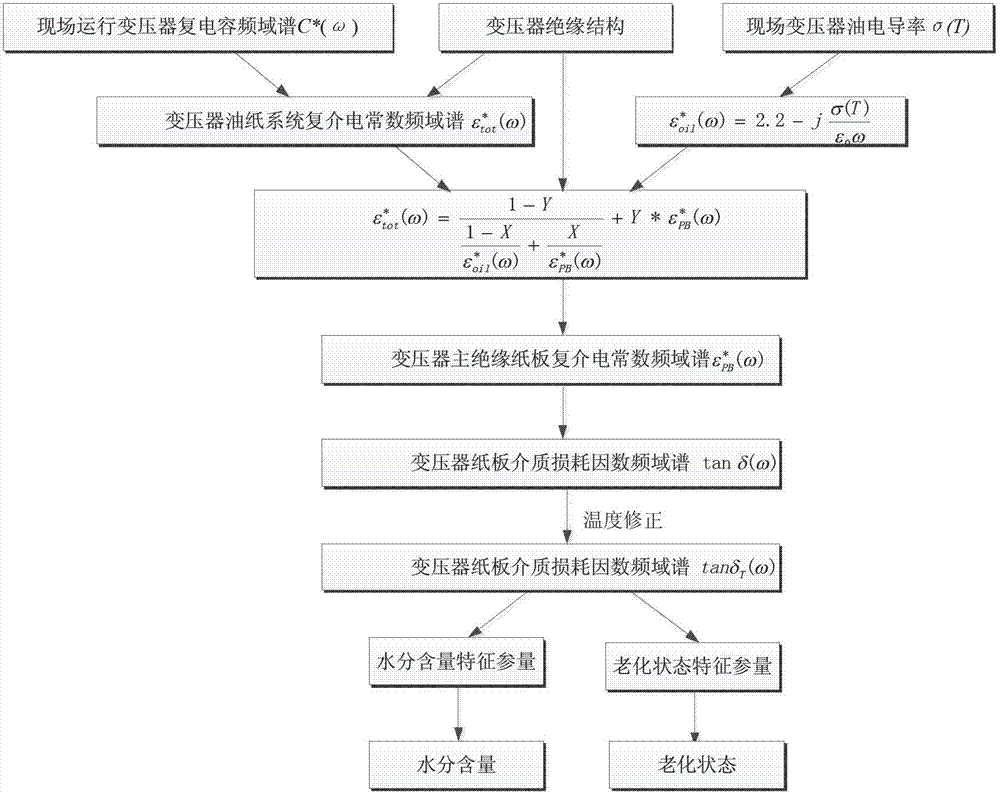
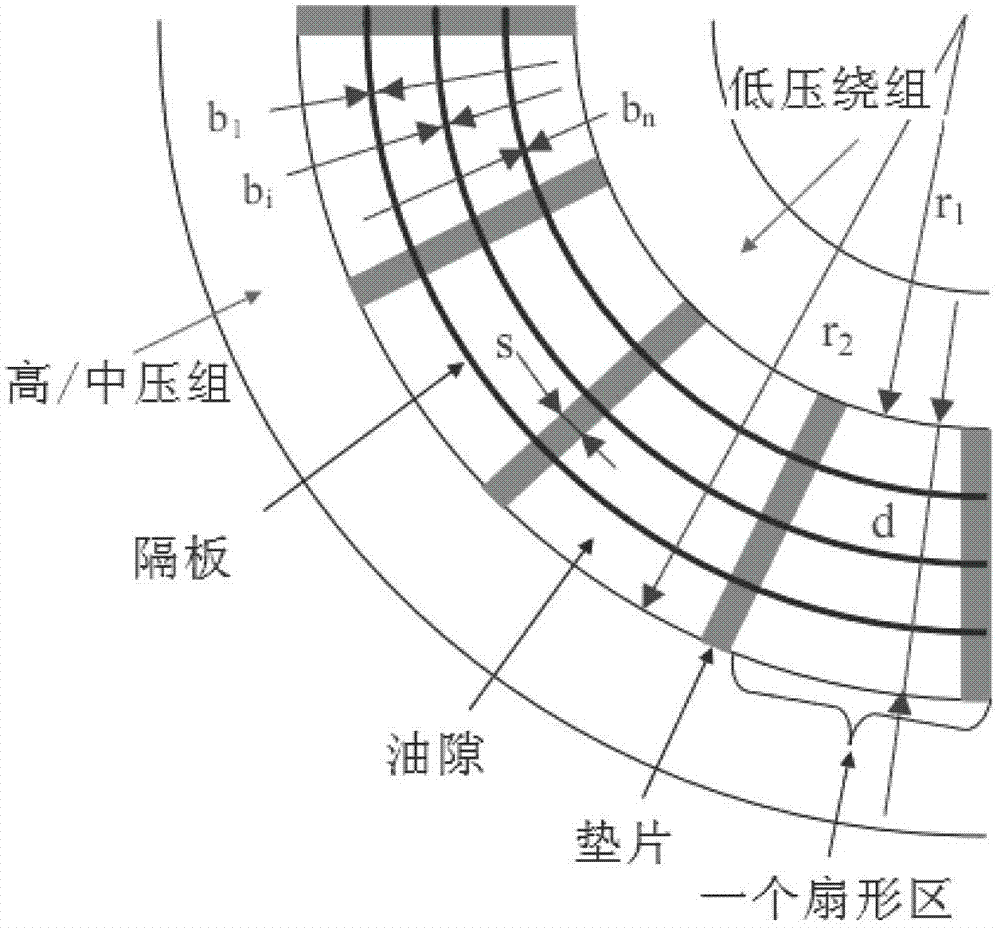
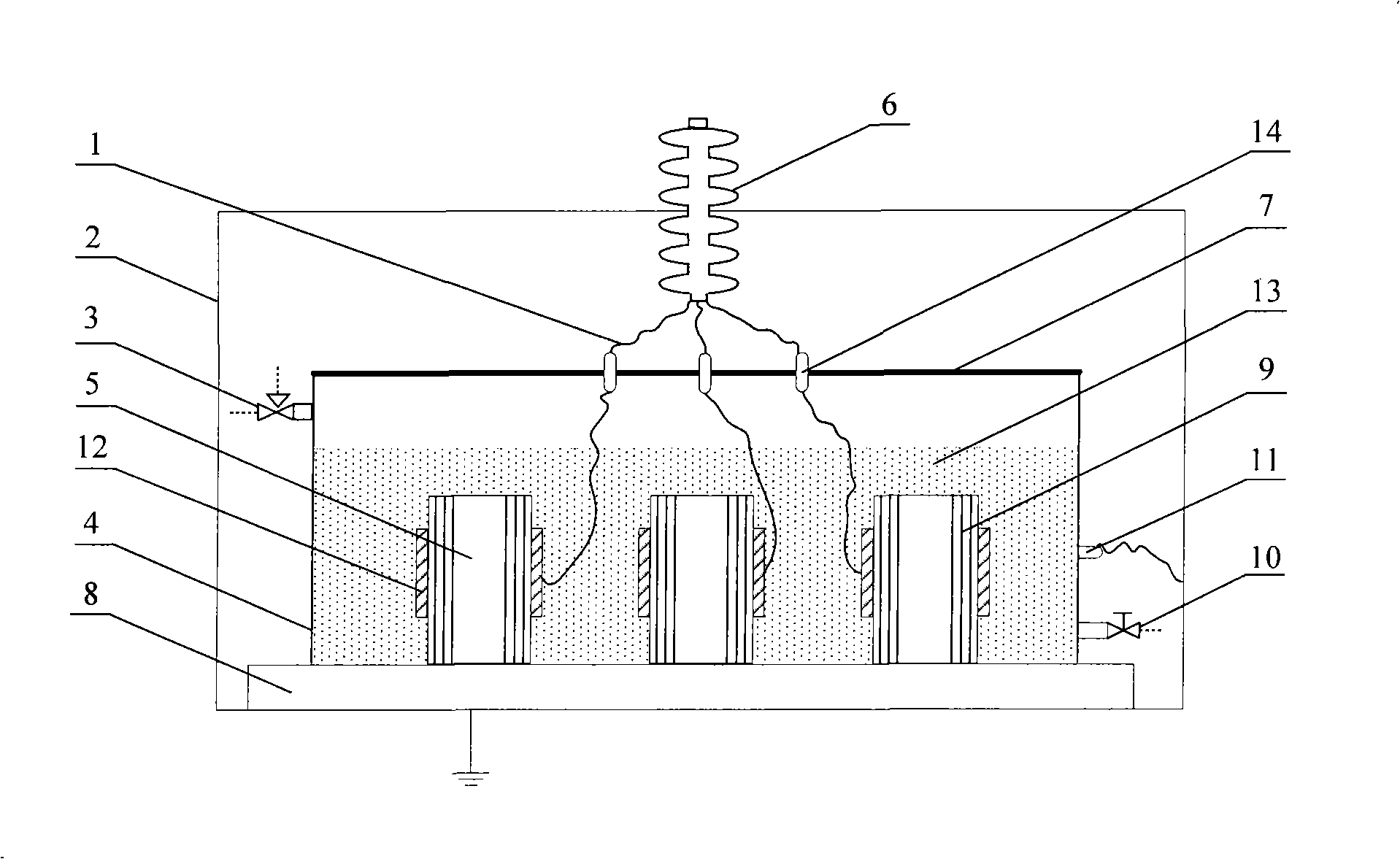
Method for evaluating aging degree of main insulation of transformer
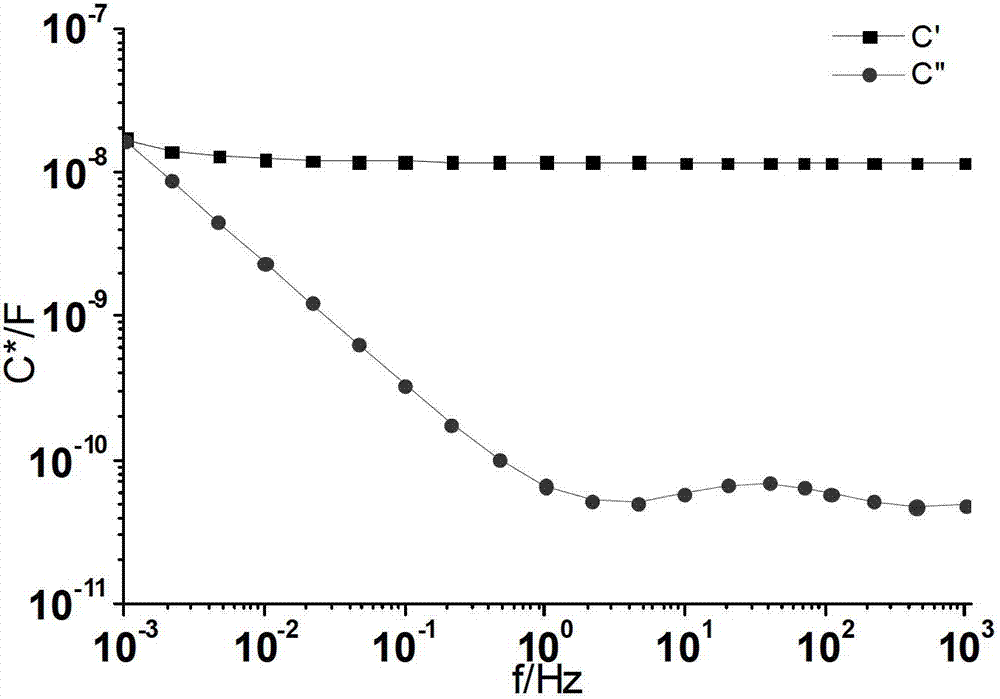
ActiveCN102818974AWide applicabilityEasy to moveTesting dielectric strengthResistance/reactance/impedenceCapacitanceElectricity
The invention discloses a method for evaluating the aging degree of main insulation of a transformer. The method comprises the following steps of: firstly measuring a complex capacitance frequency domain spectrum C*(ohm) and an oil conductivity sigma of the main insulation of the transformer on the scene, collecting structure parameters of the main insulation of the transformer and transmitting the structure parameters to a data processing device; subsequently calculating the complex capacitance frequency domain spectrum so as to obtain a medium loss factor frequency domain spectrum of a main insulation paper board of the transformer; and finally evaluating the state of the main insulation of the transformer by adopting frequency domain-based dielectric characteristic parameters. The method considers the influence of multiple factors such as measuring temperature, a main insulation structure, and oil conductivity, and has wide applicability to an oil-immersed transformer; the defects in a traditional chemical and electric method are compensated; the moisture content of the main insulation of the transformer can be diagnosed, and meanwhile the aging state of the insulation can be evaluated; and moreover the method can be used for on-site diagnosis directly, and has the advantages of lossless, convenience, transplantation and the like.
Owner:云南电力试验研究院(集团)有限公司
Methods and computer executable instructions for rapidly calculating simulated particle transport through geometrically modeled treatment volumes having uniform volume elements for use in radiotherapy
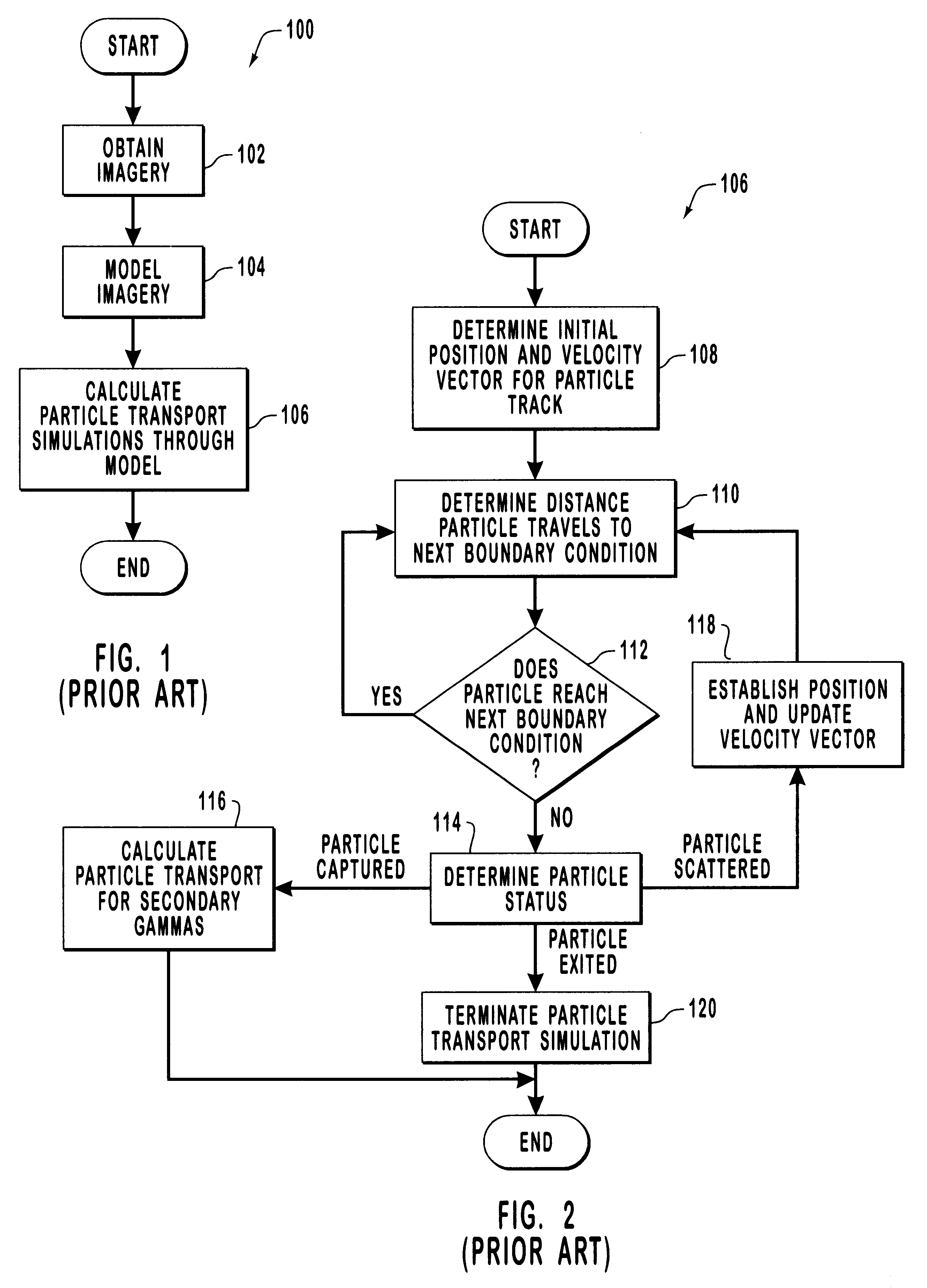
InactiveUS6175761B1Reduce computing timeImprove calculation accuracyData processing applicationsSurgeryPlan treatmentDosimetry radiation
Methods and computer executable instructions are disclosed for ultimately developing a dosimetry plan for a treatment volume targeted for irradiation during cancer therapy. The dosimetry plan is available in "real-time" which especially enhances clinical use for in vivo applications. The real-time is achieved because of the novel geometric model constructed for the planned treatment volume which, in turn, allows for rapid calculations to be performed for simulated movements of particles along particle tracks there through. The particles are exemplary representations of neutrons emanating from a neutron source during BNCT. In a preferred embodiment, a medical image having a plurality of pixels of information representative of a treatment volume is obtained. The pixels are: (i) converted into a plurality of substantially uniform volume elements having substantially the same shape and volume of the pixels; and (ii) arranged into a geometric model of the treatment volume. An anatomical material associated with each uniform volume element is defined and stored. Thereafter, a movement of a particle along a particle track is defined through the geometric model along a primary direction of movement that begins in a starting element of the uniform volume elements and traverses to a next element of the uniform volume elements. The particle movement along the particle track is effectuated in integer based increments along the primary direction of movement until a position of intersection occurs that represents a condition where the anatomical material of the next element is substantially different from the anatomical material of the starting element. This position of intersection is then useful for indicating whether a neutron has been captured, scattered or exited from the geometric model. From this intersection, a distribution of radiation doses can be computed for use in the cancer therapy. The foregoing represents an advance in computational times by multiple factors of time magnitudes.
Owner:BATTELLE ENERGY ALLIANCE LLC
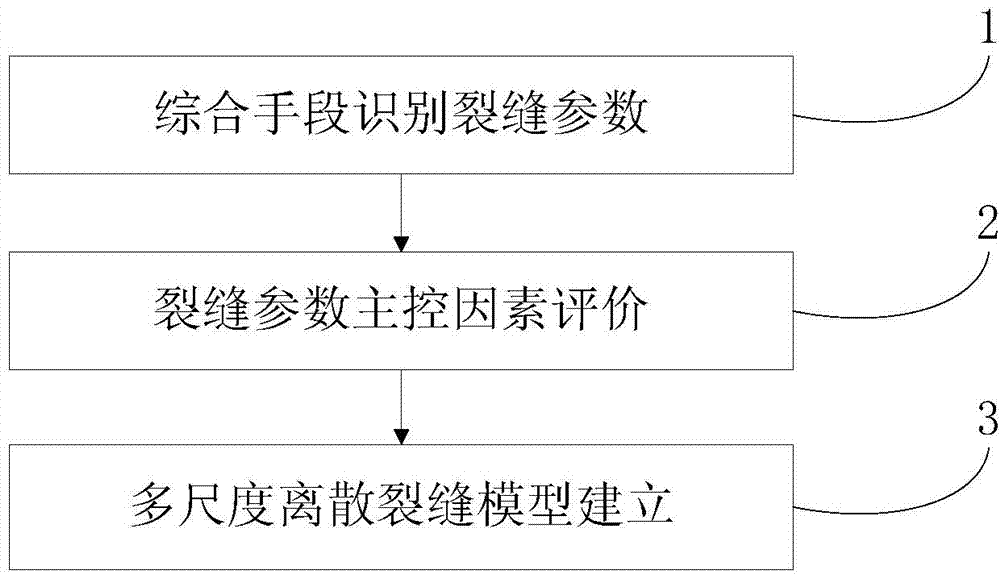
Discrete fracture modeling method based on multiscale factor restraint
InactiveCN104730596AReflect spatial heterogeneityAvoid complexityGeological measurementsTectonic stressWrinkle skin
The invention provides a discrete fracture modeling method based on multiscale factor restraint. The discrete fracture modeling method based on multiscale factor restraint comprises the following steps that the fracture parameter of a single well is recognized and described in details; a fault-wrinkle-fracture symbiosis evolution system is established based on the counted fracture parameters, and a key fracture making period is determined; the fracture parameter based on detailed tectonic stress field simulation is calculated in a quantitative mode; main controlling factors for fracture development are optimally selected; the weights of the main controlling factors of the fracture are optimally selected according to the entropy weight method; a multiscale fracture DFN model restrained by multiple factors is established; a double-hole and double-permeability geologic model is established. According to the discrete fracture modeling method based on multiscale factor restraint, the mutual control and influence between multiscale fractures are analyzed based on detailed description, obtained through CT scanning, of one single well, the multiple geological factors, such as the structure and deposition, controlling fracture development are analyzed, the main controlling factors for fracture development are optimally selected according to the entropy weight method, a large-scale discrete fracture model, a medium-scale discrete fracture model and a small-scale discrete fracture model are established, an idea and method for establishing a detailed fracture geologic model are formed, and an important basis is provided for efficient development of a fractured oil reservoir and scheme optimization.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
Multiple factors accelerated aging test apparatus and method for oil paper insulation of transformer
InactiveCN101408578AReveal the law of agingImprove reliabilityElectrical testingPaper testingHigh pressureVacuum drying
The invention provides a testing device and a testing method of electricity-heat-mechanical stress three-factor combined ageing for transformer paper oil insulation ageing study; the testing device comprises an electric heating ageing oven, in which a transformer paper oil insulation simulator, a shake unit and a temperature control device used for controlling the temperature of the electric heating ageing oven. The shake unit can drive the simulator to vibrate, the simulator is electrically connected with a high-voltage power supply; the testing method includes vacuum drying and oil impregnation of insulating paper, attaching the paper to the earth electrode in a stainless steel case of the testing device, winding coils as a high voltage electrode outside the insulating paper and the earth electrode and injecting insulating oil to the stainless steel case; connecting a high tension lead with the high-voltage power supply and starting the shake unit; sampling the insulating paper and the insulating oil alternately and measuring insulation ageing parameters.
Owner:CHONGQING UNIV
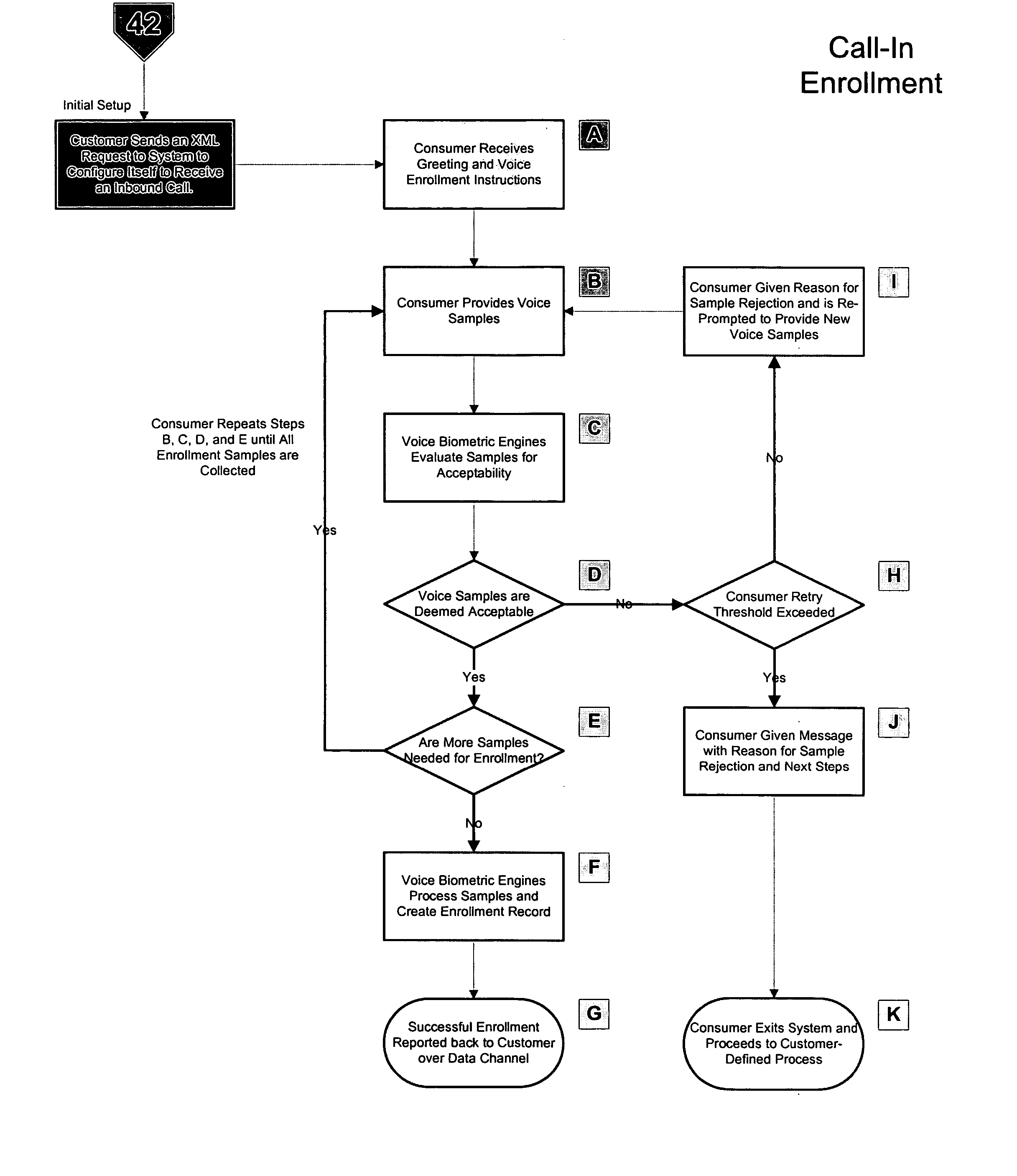
System and method of subscription identity authentication utilizing multiple factors
ActiveUS20070106517A1Low costRaise security concernsAutomatic call-answering/message-recording/conversation-recordingSpeech recognitionSpeech verificationSpeech sound
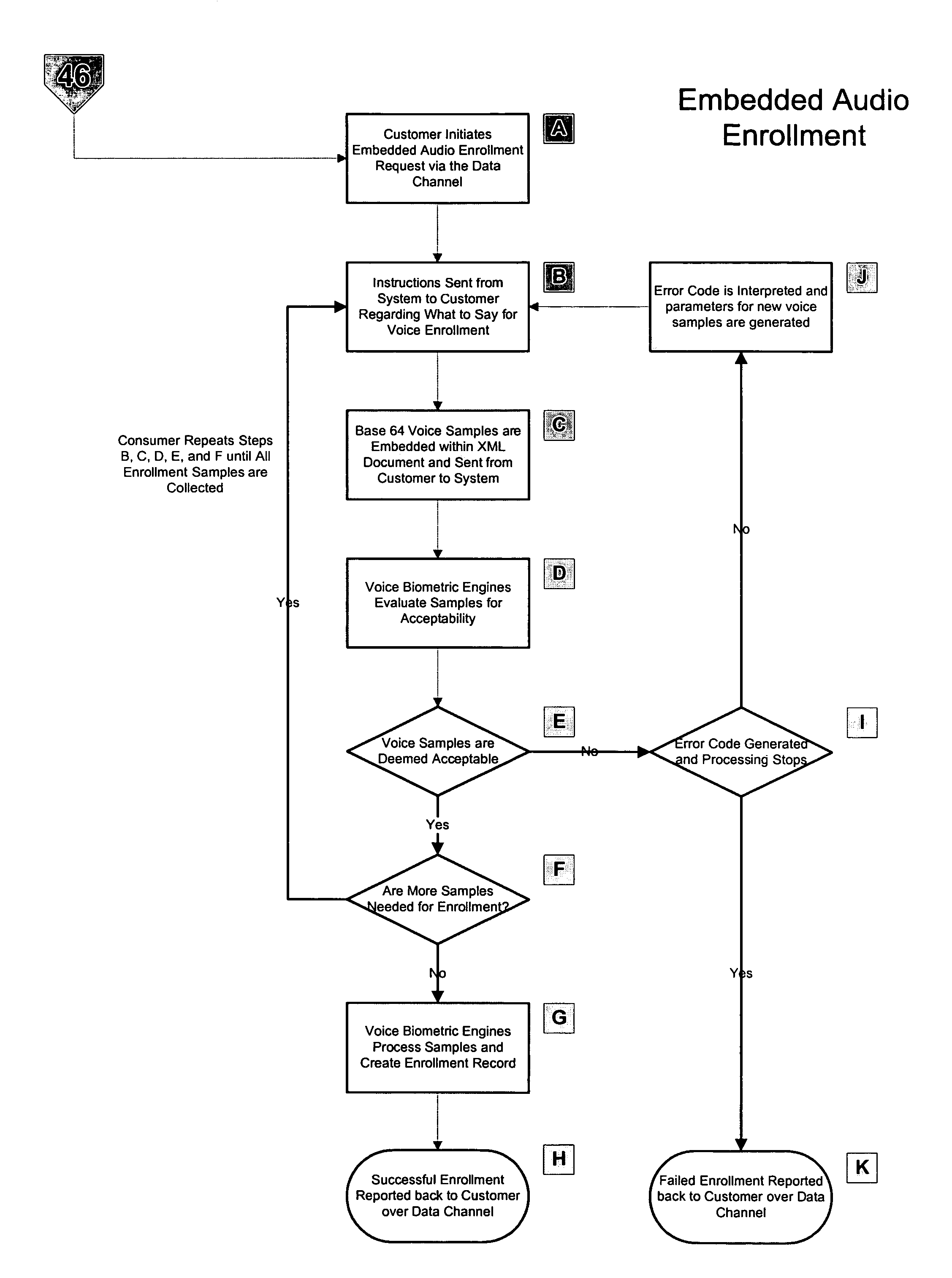
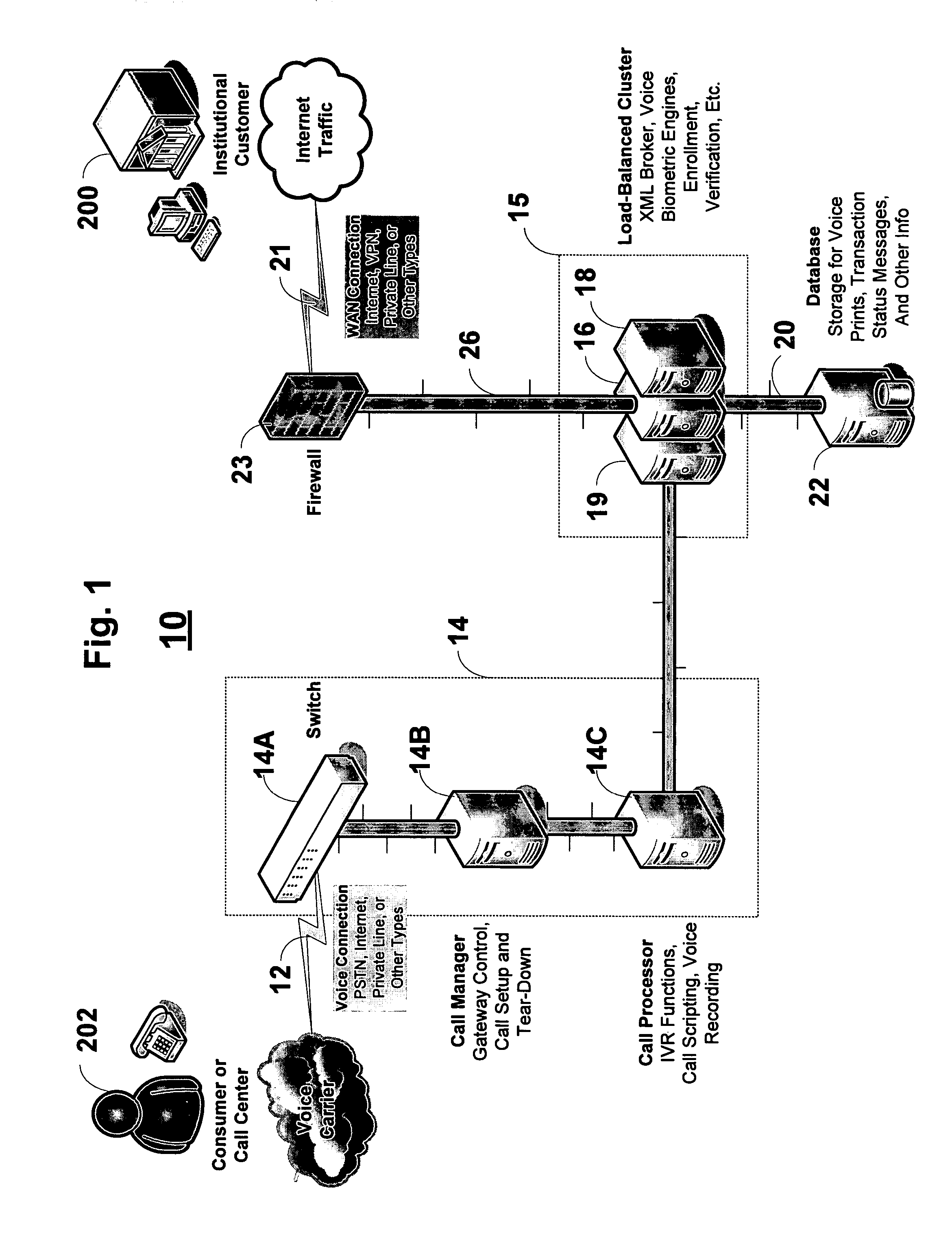
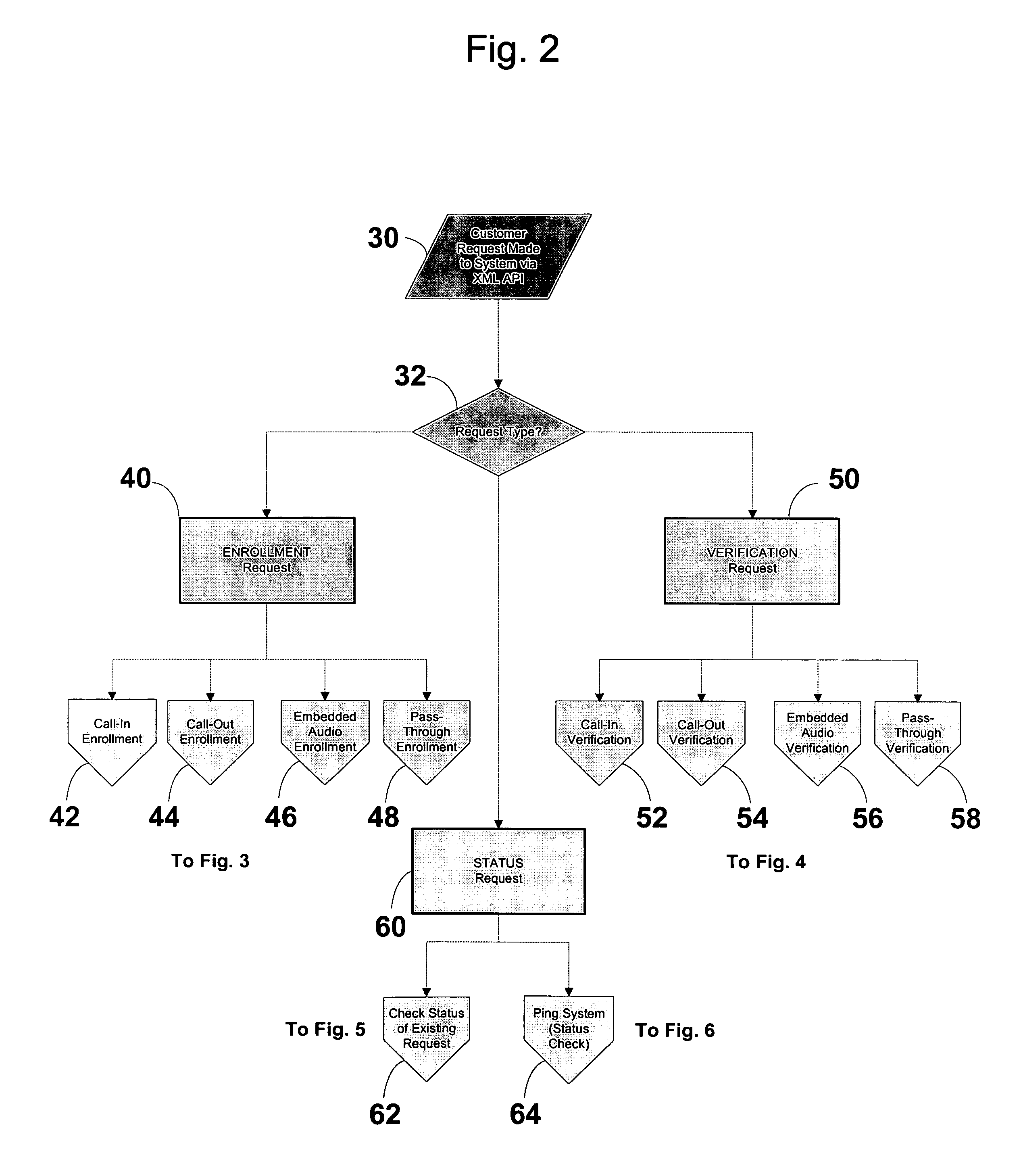
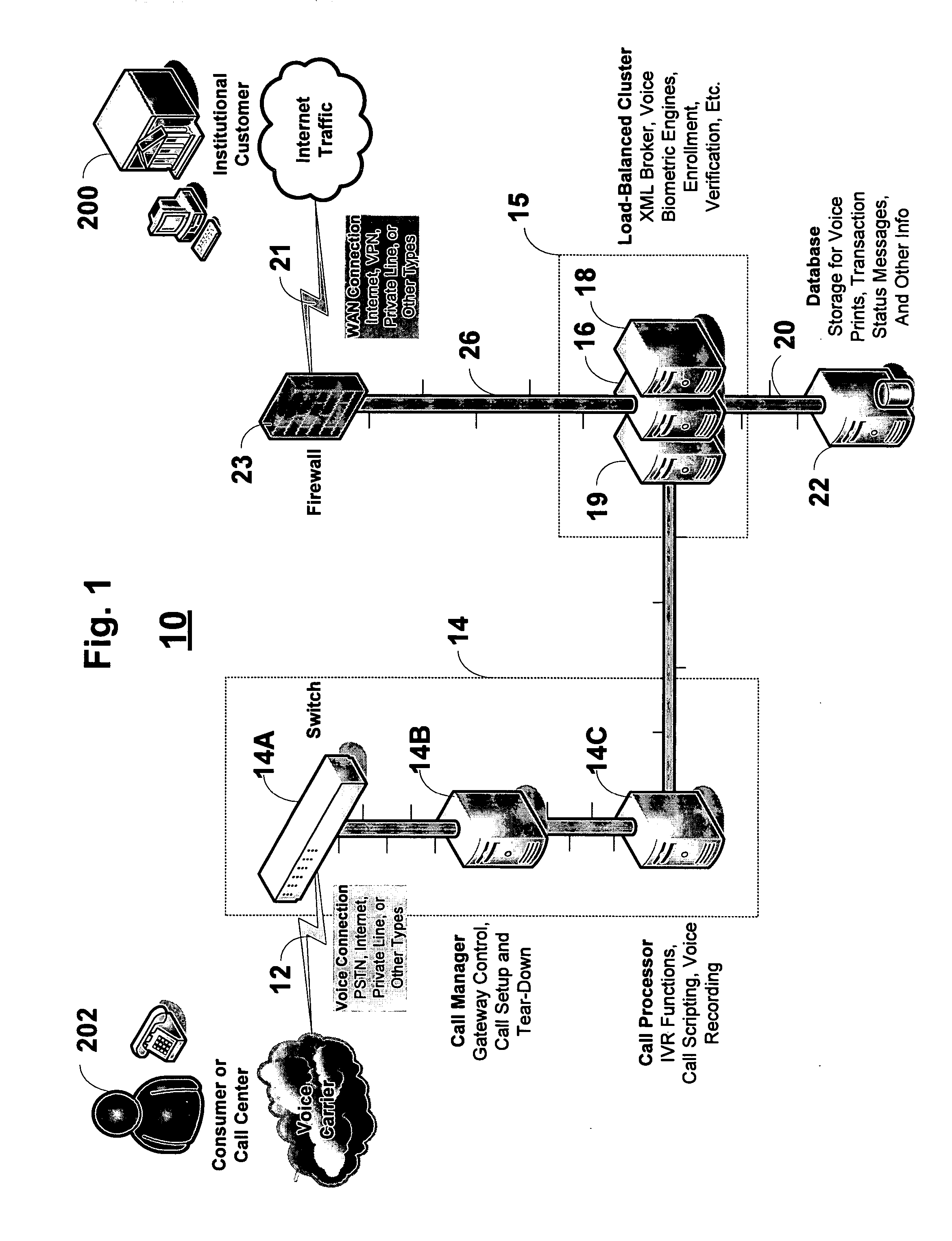
A system and method of providing voice authentication to institutional customers having consumers or users. The system includes an enrollment module, a verification module, and a database. Each institutional customer has an authentication profile on the system that includes both i) instructions indicating which one or more of the voice biometric engines are to be used for a given consumer's enrollment and / or authentication, and ii) variables for implementing those instructions. A given institutional customer may have more than one set of instructions or variables for different classes of users. Vocal information is received from a user, and a baseline voiceprint is constructed therefrom for enrollment. Subsequently, more vocal information is received from the user to construct a temporary voiceprint. The temporary voiceprint is compared to a corresponding baseline voiceprint in accordance with the institutional customer's authentication profile. The profile is preferably remotely configurable by the institutional customer.
Owner:CSIDENTITY CORP
Multiple factor private portion of an asymmetric key
ActiveUS20060184788A1Key distribution for secure communicationPublic key for secure communicationMultiple factorsComputer security
Techniques for generating a private portion of a split private key of an asymmetric key pair are provided. Multiple factors upon which the private portion of the split private key is based are received. Each of these multiple factors is under control of a user associated with the asymmetric key pair. Multiple cryptographic operations are then performed using the received multiple factors to generate the private portion.
Owner:VMWARE INC
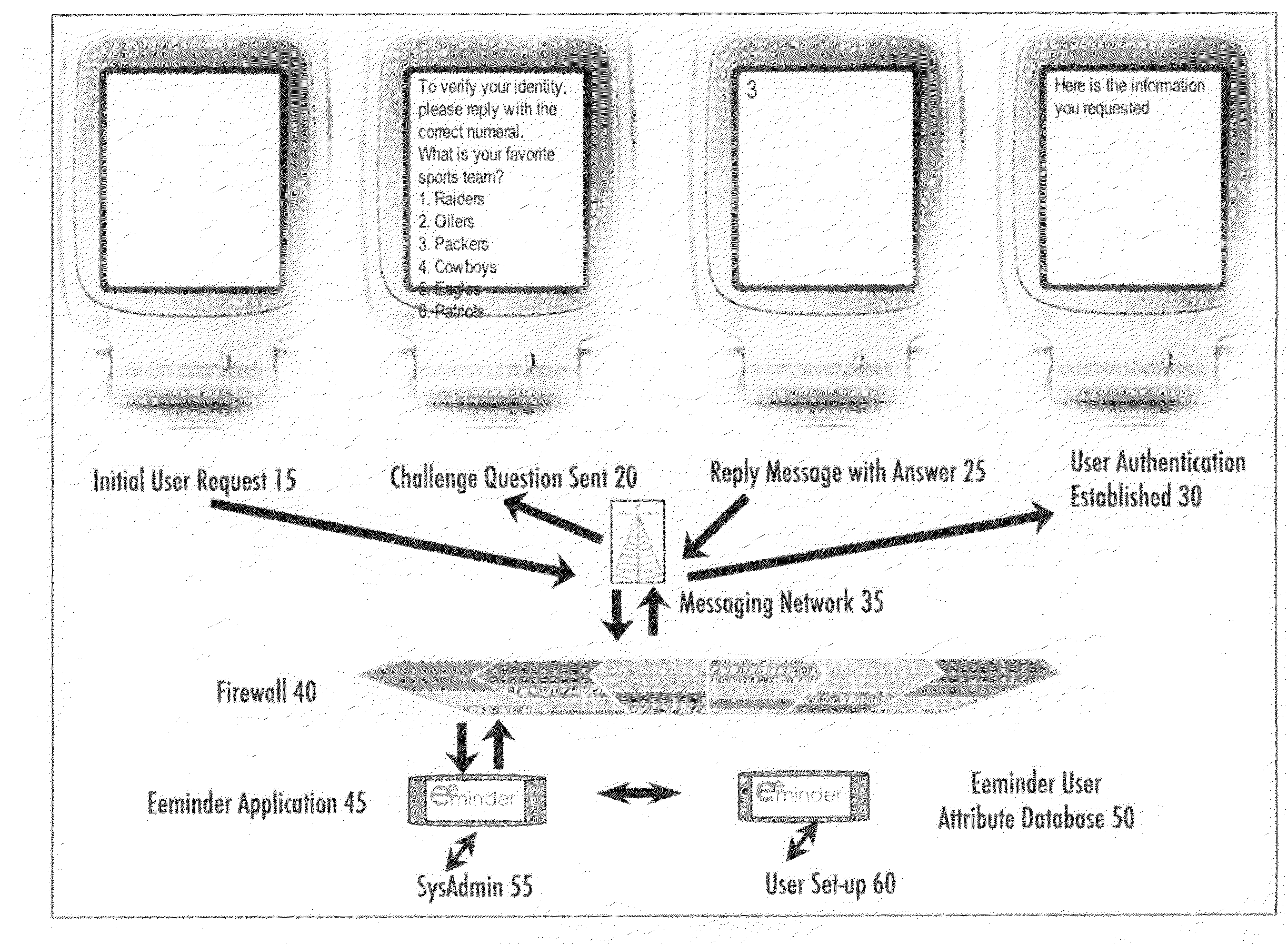
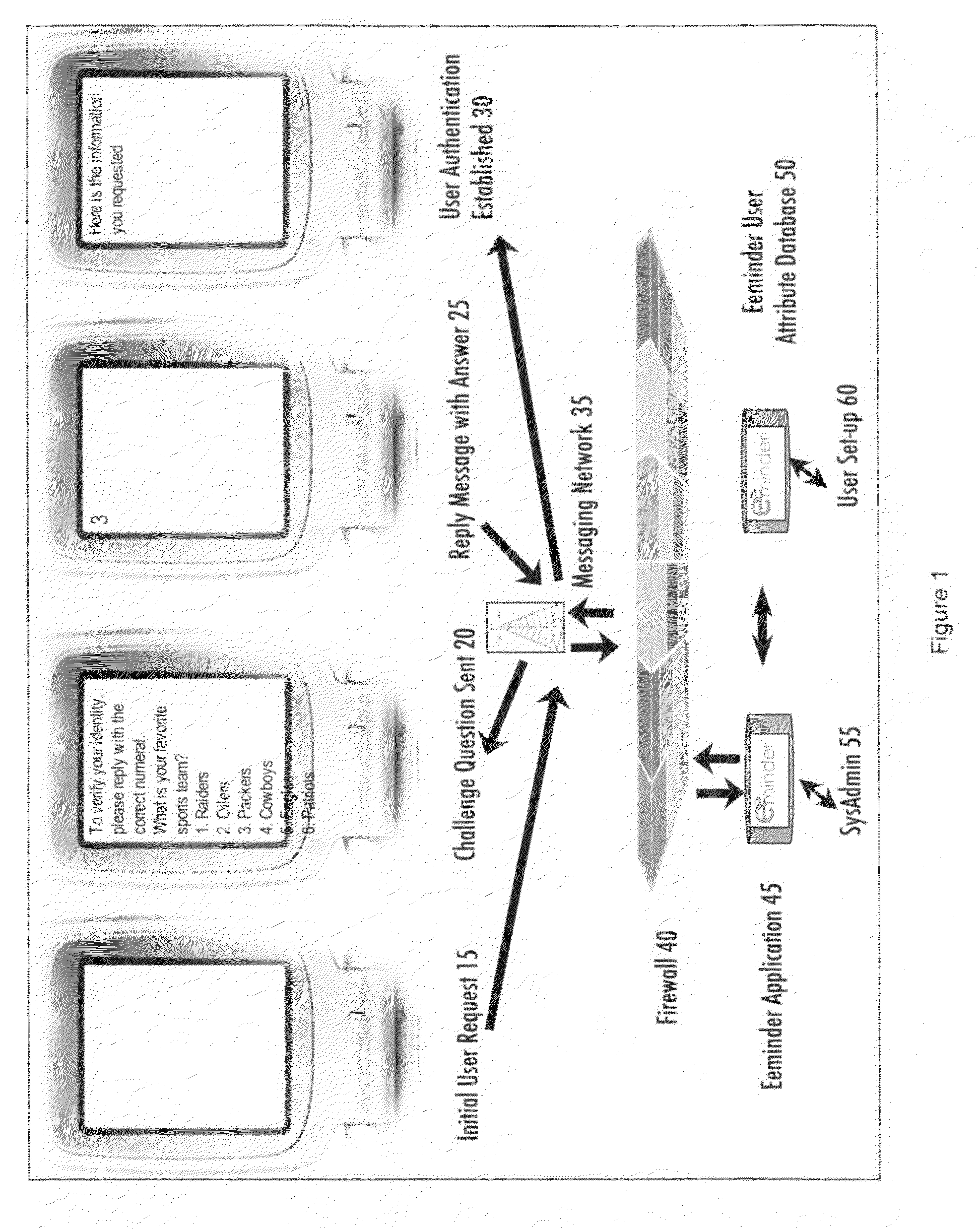
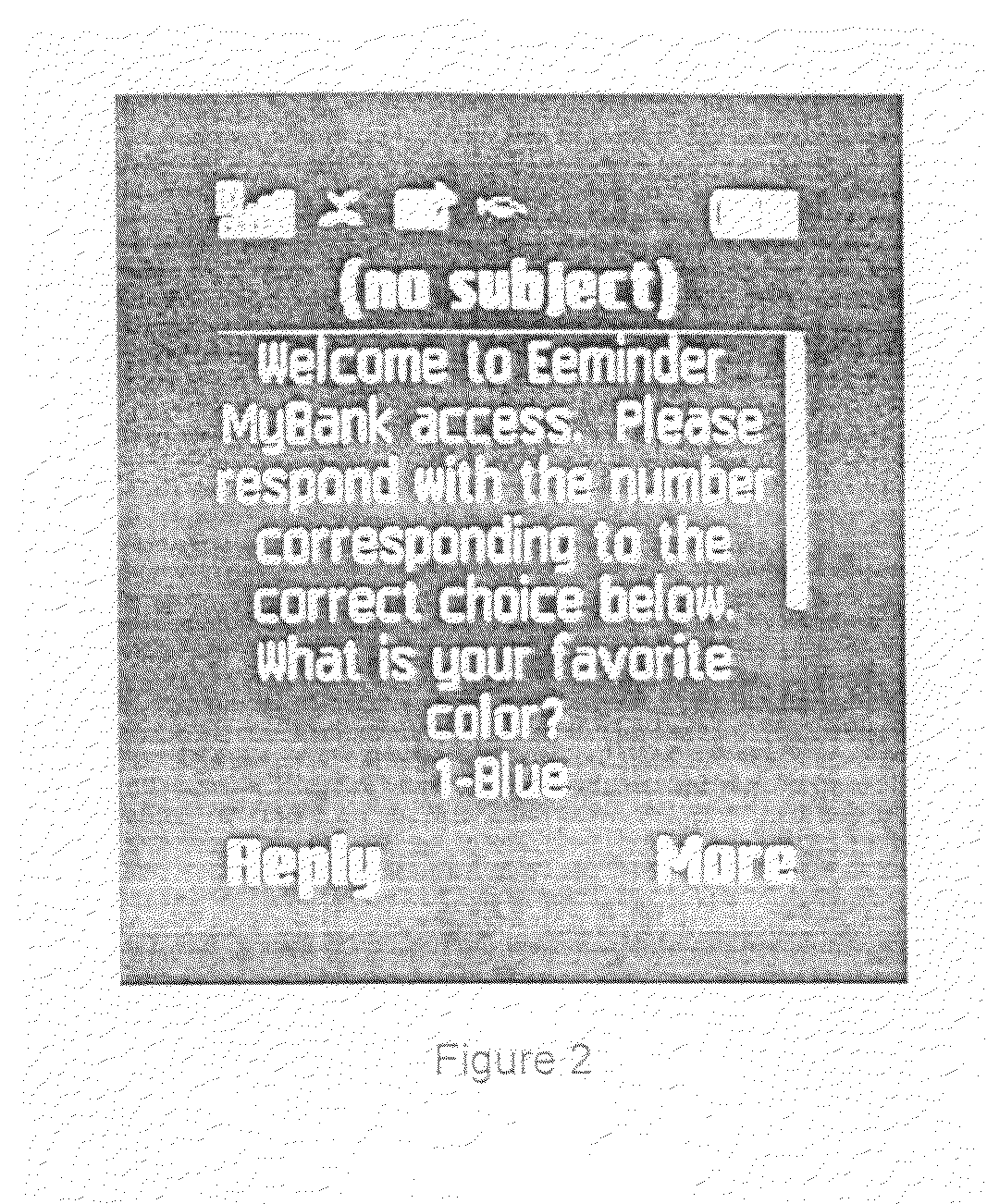
Method and system for using message based security challenge and response questions for multi-factor authentication in mobile access to electronic information
InactiveUS20090047928A1Improve usabilityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsInternet privacyElectronic information
A method for allowing an alleged user to establish using multiple factors of authentication that he or she is in fact the authorized user of an information source. The method uses multiple factor authentication using challenge and response messages containing personal choices of the user which are not known to people other than the authorized user, presenting the challenge questions as enumerated multiple choice questions for ease of use, and imposing time-out restrictions on a session.
Owner:UTSCH THOMAS F +1
Day-dimension regional traffic index prediction method considering influences of multiple factors
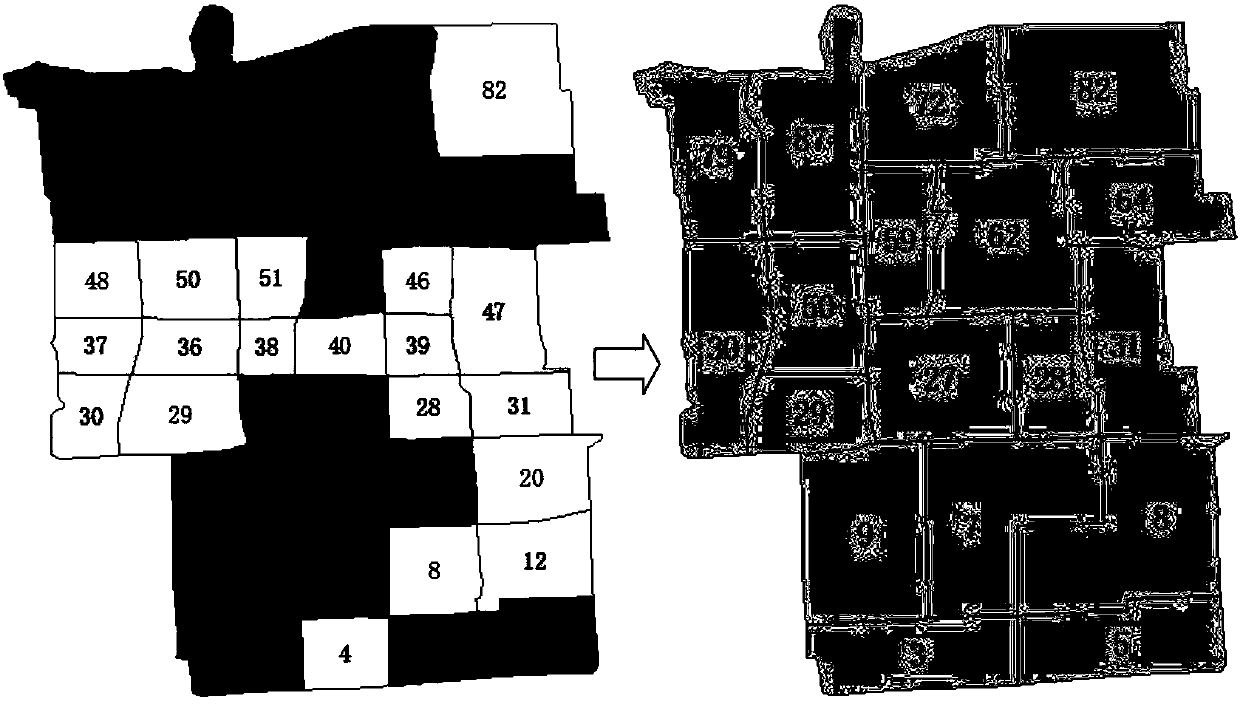
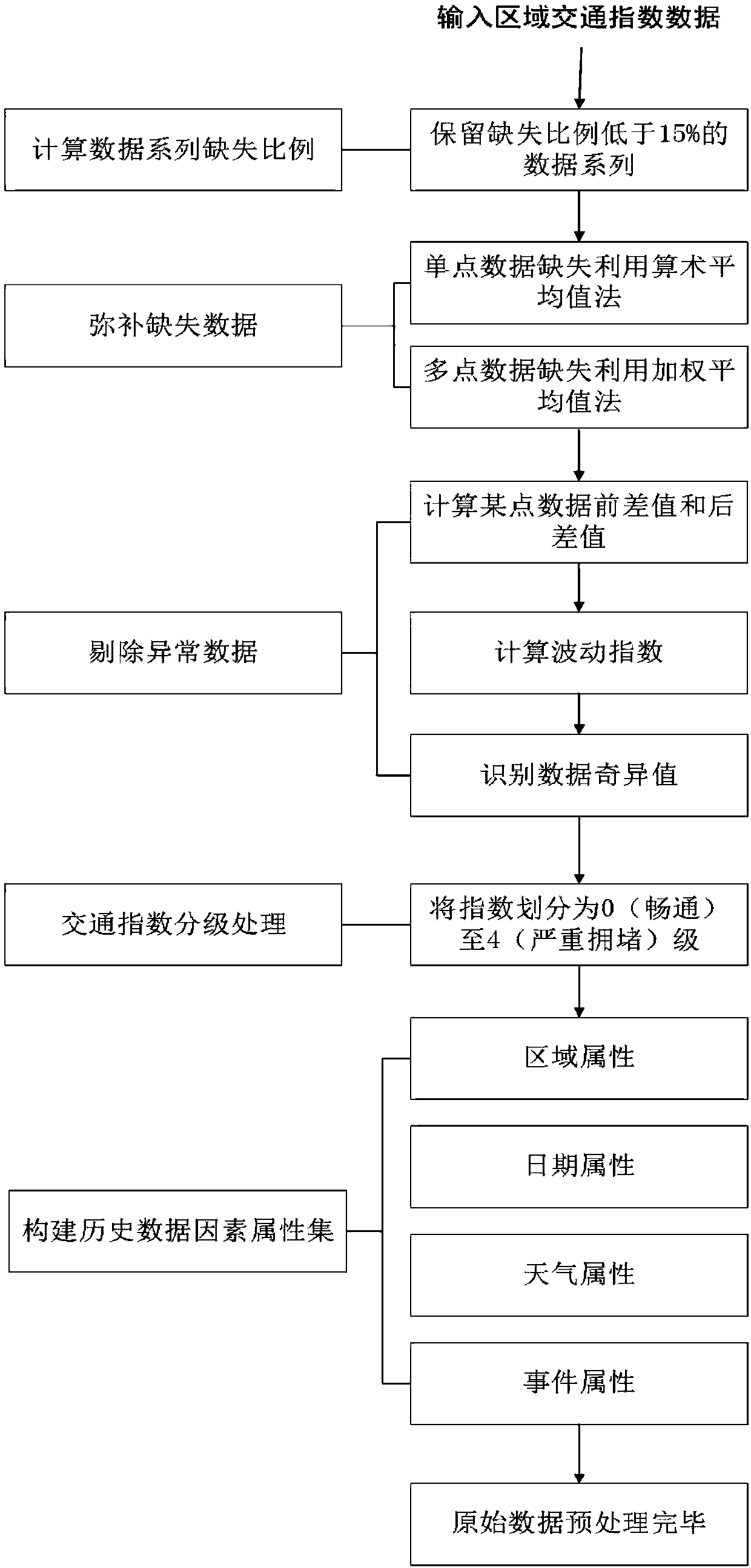
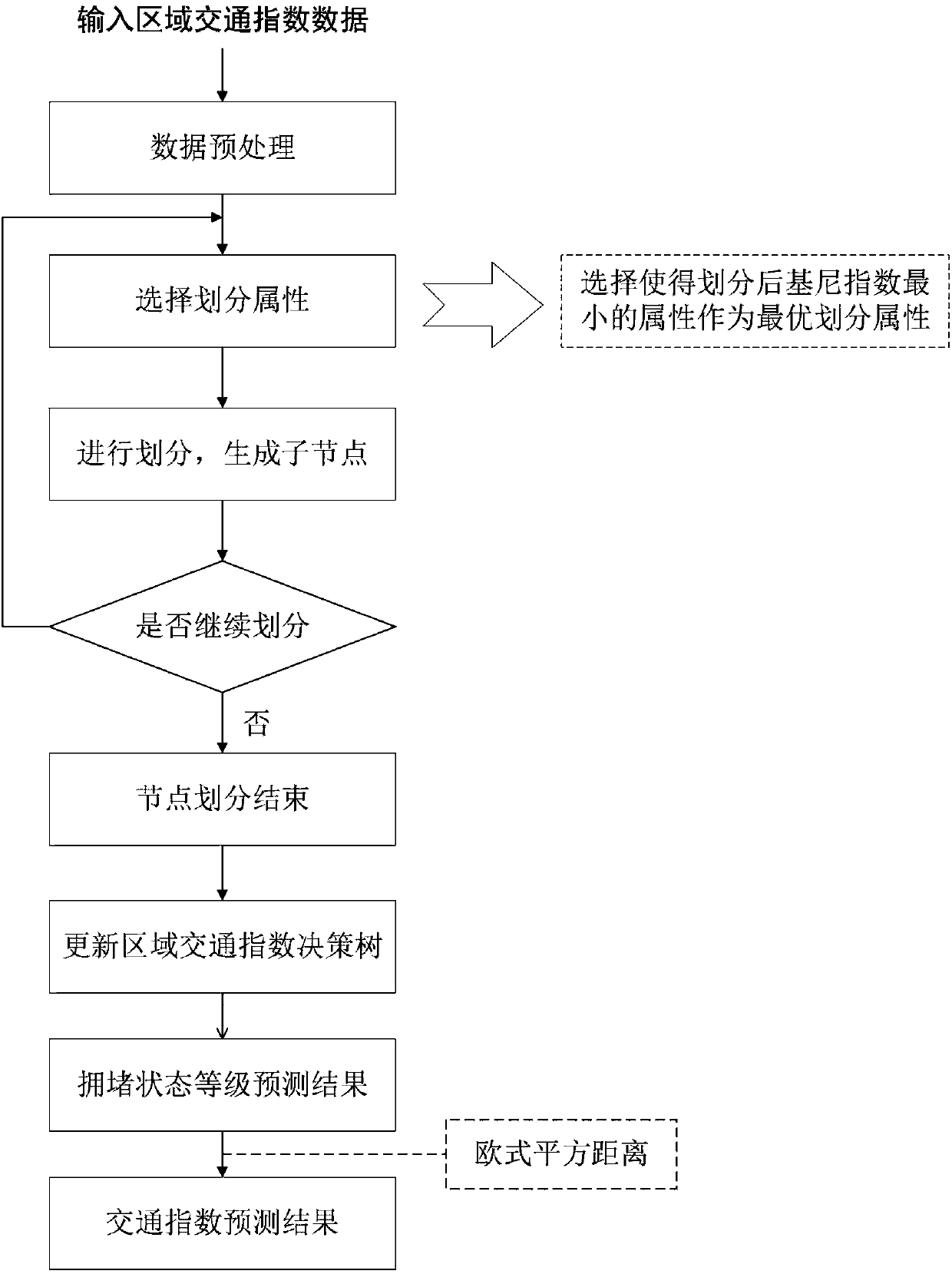
ActiveCN107610469AAccurate portrayalEasy to operateDetection of traffic movementForecastingState predictionOriginal data
The invention discloses a day-dimension regional traffic index prediction method considering influences of multiple factors. The method comprises the steps that regions are divided and aggregated; regional traffic index original data preprocessing is carried out; the influences of multiple factors are considered, and regional traffic index prediction under the day dimension is carried out. According to the specific technical scheme of the method, on the basis of traffic cell division, traffic cells with the same aggregation property are aggregated, and regional traffic indexes are calculated;on the basis of road network operation early warning requirements, a prediction time period and a prediction cycle are determined; regional traffic data is extracted, made up for and removed, and preprocessing such as comprehensive building of a historical data factor attribute set from different angles is conducted on the data; on the basis of a decision tree theory, regional road network operation congestion state prediction is carried out; a final prediction result of the regional traffic indexes is determined by means of the square euclidean distance. By means of the method, on the one hand, monitoring and application of the urban road network operation state is deepened, and on the other hand, technical support is provided for early warning and forecasting work of the road network operation state.
Owner:BEIJING UNIV OF TECH
Multi-waypoint navigation route planning method and system
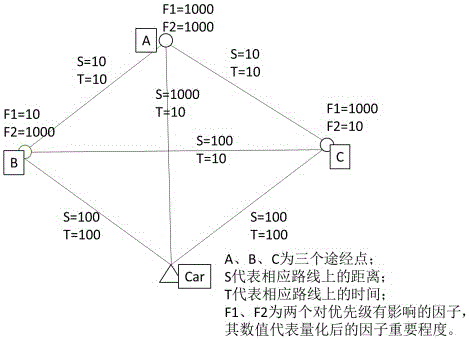
InactiveCN105675002AInstruments for road network navigationSatellite radio beaconingLearning basedWeight coefficient
The invention provides a multi-waypoint (destination) navigation route planning method and system in an actual demand situation that the multiple waypoints have different priority under multi-factor influence. The method adopts a weight scoring based optimum route determining model and a machine learning based multi-influence-factor weight coefficient determining method. Specifically, a multi-point road planning model oriented to multiple waypoints with different priority is designed firstly; the machine learning based influence factor weight coefficient determining method is provided for determining coefficients in the model; then the multi-point road planning system capable of being widely popularized to numerous fields is obtained. One new solution is provided for multi-influence-factor and multi-waypoint route navigation, and route planning is more intelligent, higher in efficiency, more dynamic and more automatic.
Owner:闫凯 +1
Authentication protocol using a multi-factor asymmetric key pair
ActiveUS7386720B2Key distribution for secure communicationDigital data processing detailsInternet privacyPassword
Techniques for user authentication based upon an asymmetric key pair having a public key and a split private key are provided. A first portion of the split private key is generated based upon multiple factors under control of the user. The factors include a password. A challenge is cryptographically combined with a first one of the multiple factors, but not the user password, to form a first message. The first message is transformed with the generated first portion to form a second message, which is then sent to an authentication entity. The sent second message is transformed to authenticate the user by proving direct verification of user control of the first factor.
Owner:VMWARE INC
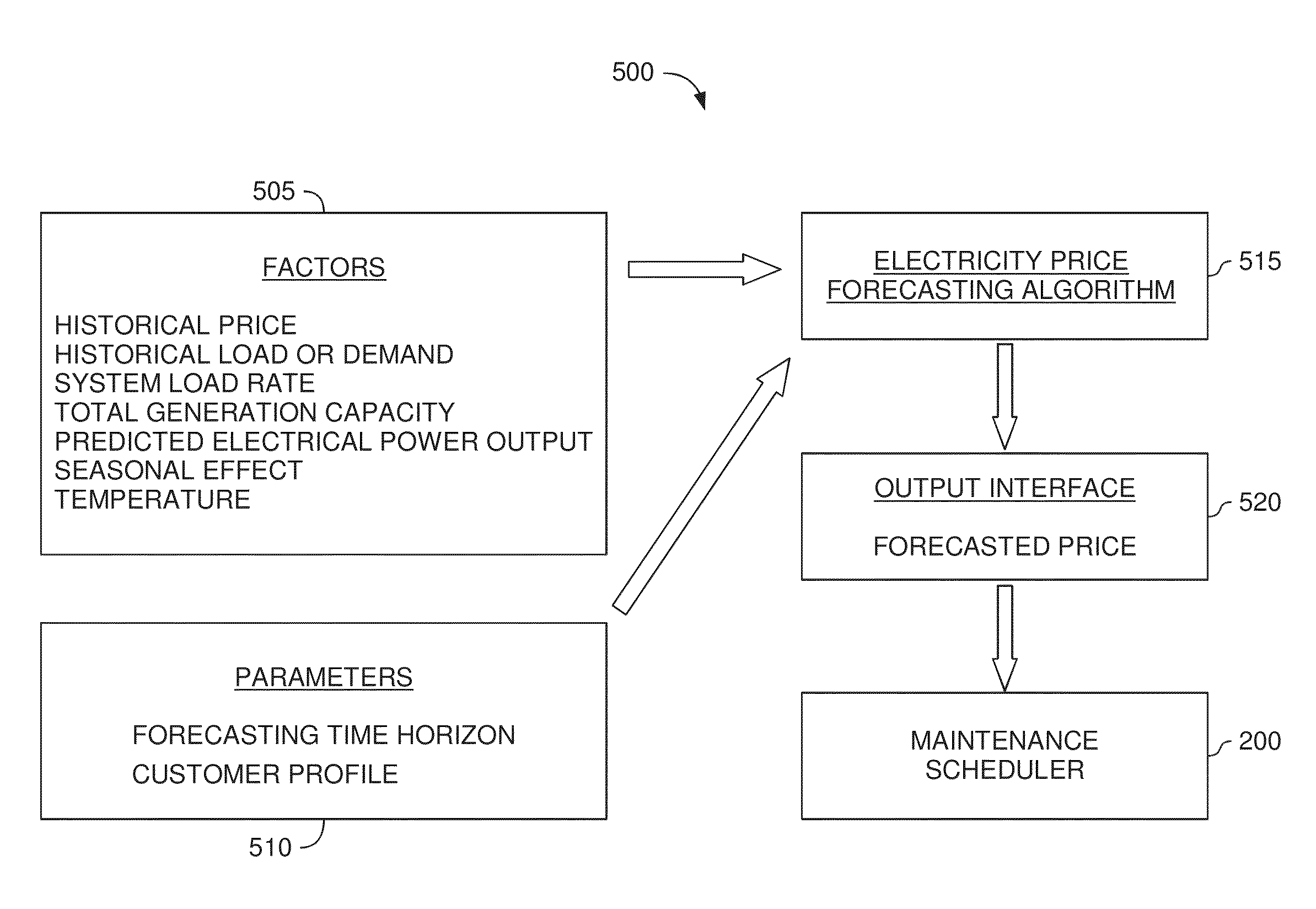
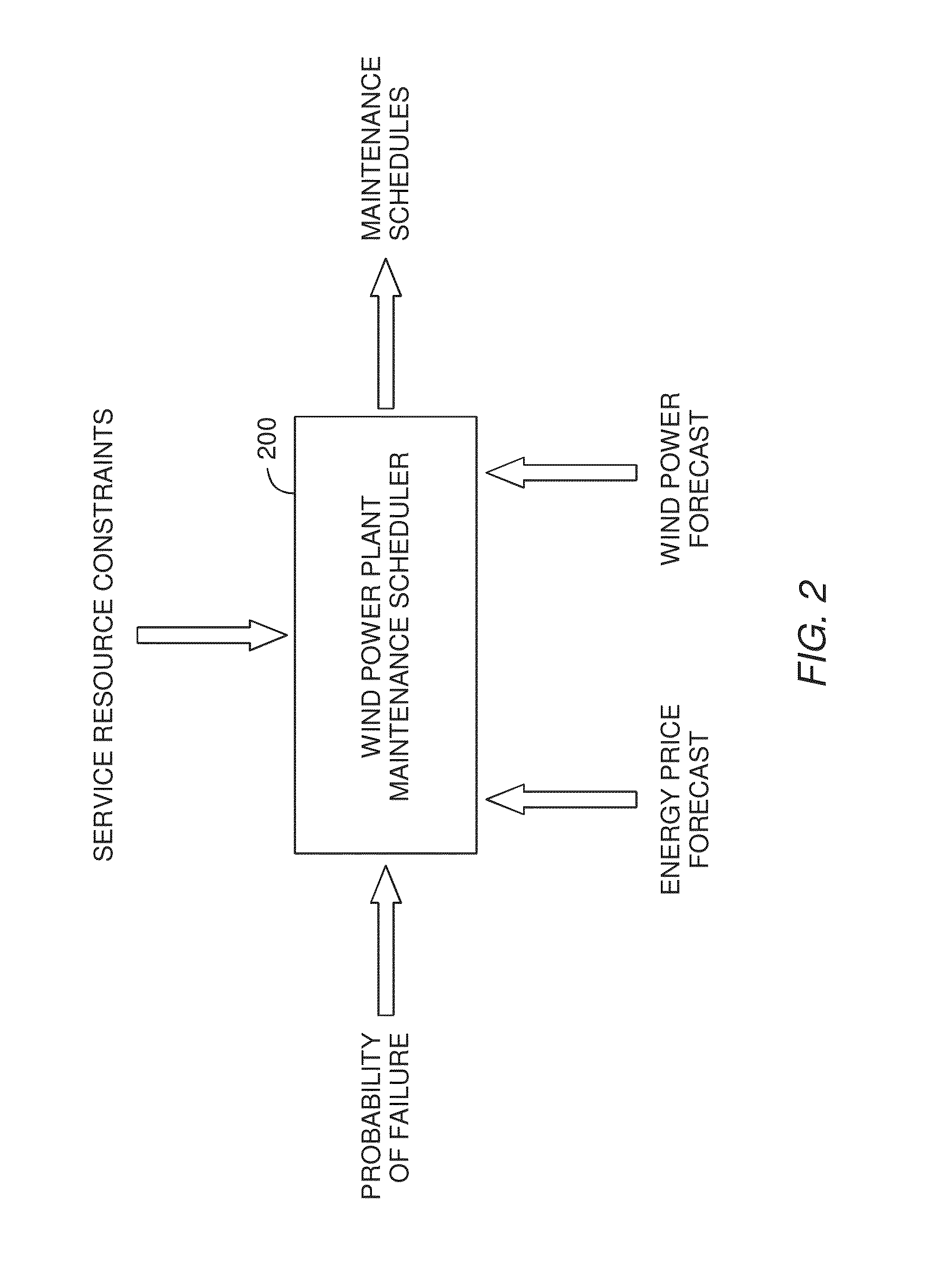
Wind turbine maintenance optimizer
Determining when to perform preventative maintenance is an important consideration for maximizing the revenue of a wind turbine. For example, performing preventative maintenance may be cheaper than replacing turbine components when they fail. When determining to perform preventative maintenance, a maintenance scheduler may consider multiple factors. These factors may include the probability of failure, the predicted price of energy, predicted wind power production, resource constraints, and the like. Specifically, the maintenance scheduler may predict the future values of these factors which are then integrated into a net present value (NPV) for each of the components. Based on the respective NPVs, the maintenance scheduler may determine which maintenance actions to perform and in what order.
Owner:VESTAS WIND SYST AS
Multiple factor-based user identification and authentication
InactiveUS20050154924A1Key distribution for secure communicationDigital data processing detailsInternet privacyMultiple factors
A method of authenticating the identity of a user to determine access to a system includes providing a plurality of factor-based data instances corresponding to a user, evaluating the factor-based data instances to determine if the user's identity is authenticated, and granting or restricting the user's access to the system if the user's identity is authenticated. More particularly, the method includes providing a modified data instance based on a second data instance, generating a key based on a first data instance, applying the key to the a modified data instance to generate a recovered data instance, interrogating the recovered data instance against the second data instance to generate an authentication value as a result of a correspondence evaluation, and granting or restricting the user's access to the system based at least in part on the validity of the authentication value.
Owner:TECSEC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com