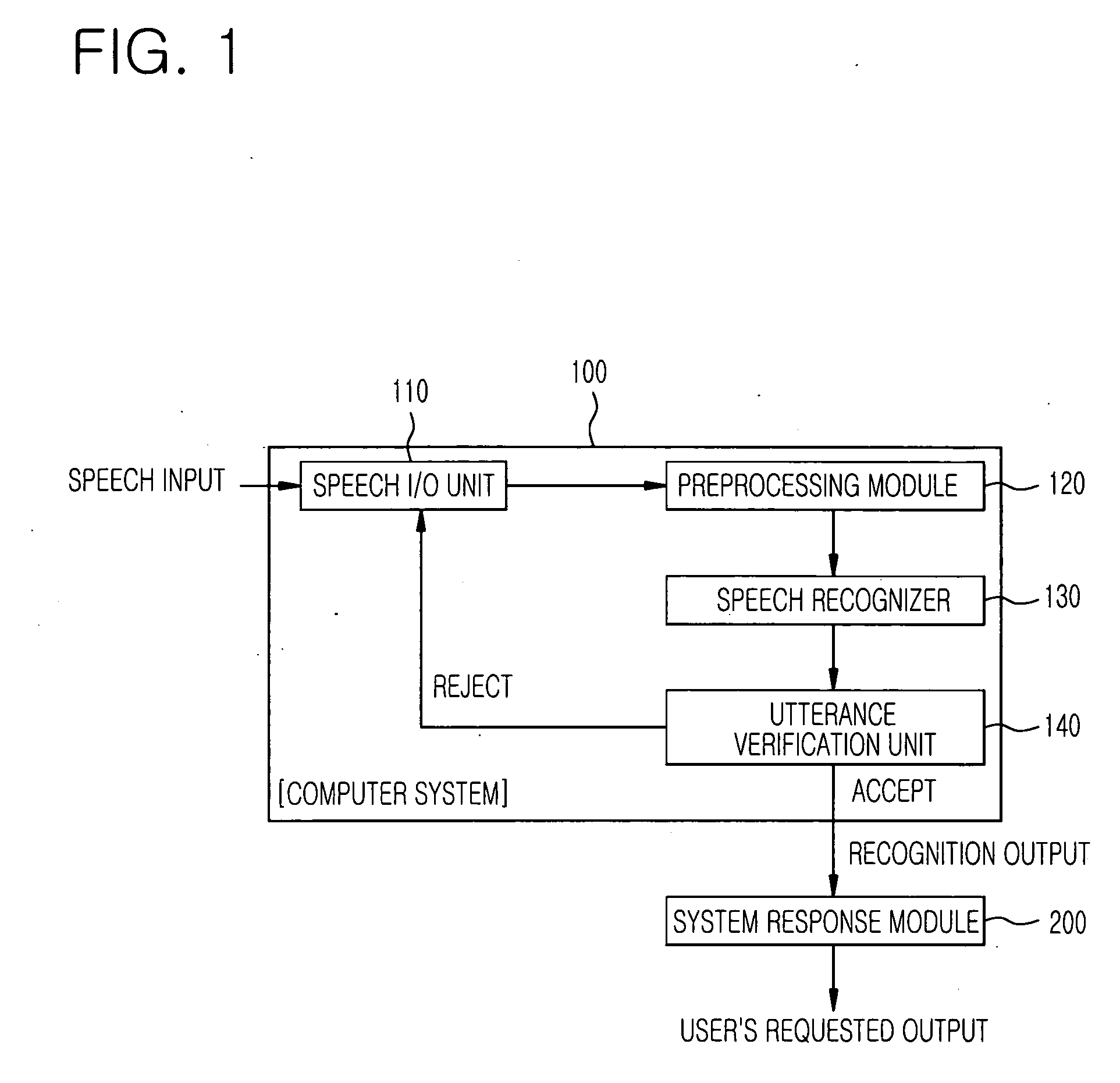
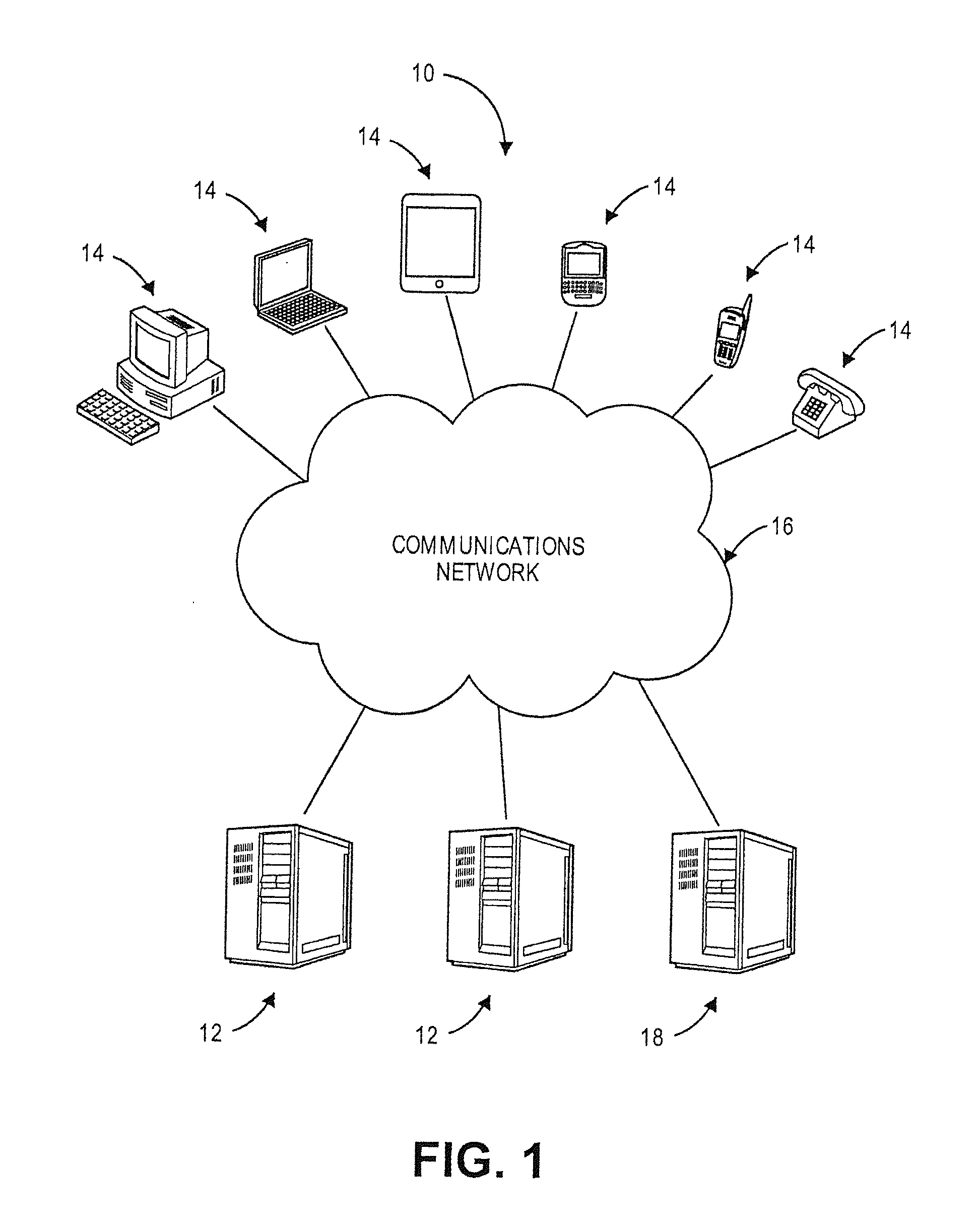
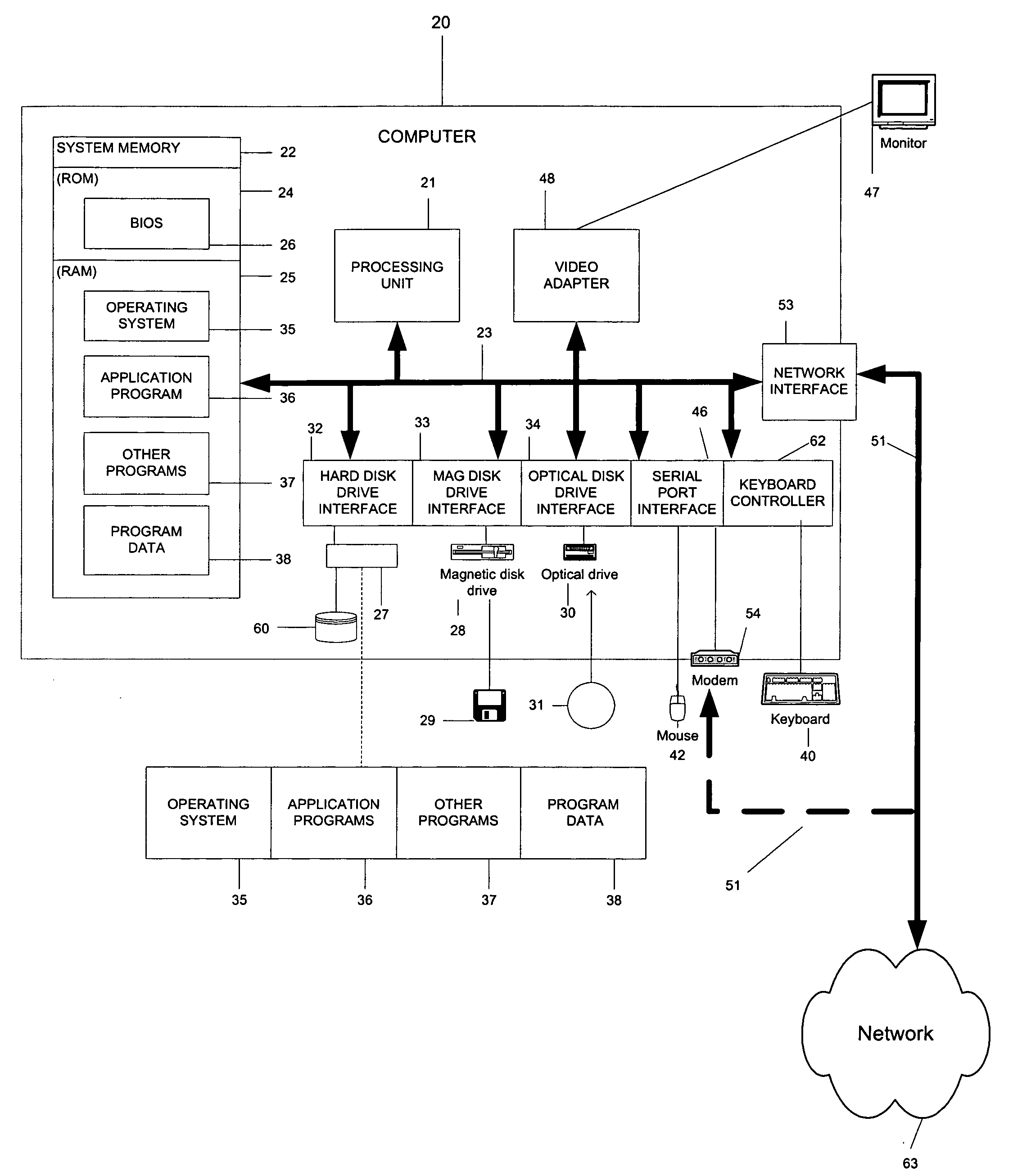
Patents
Literature
134 results about "Speech verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
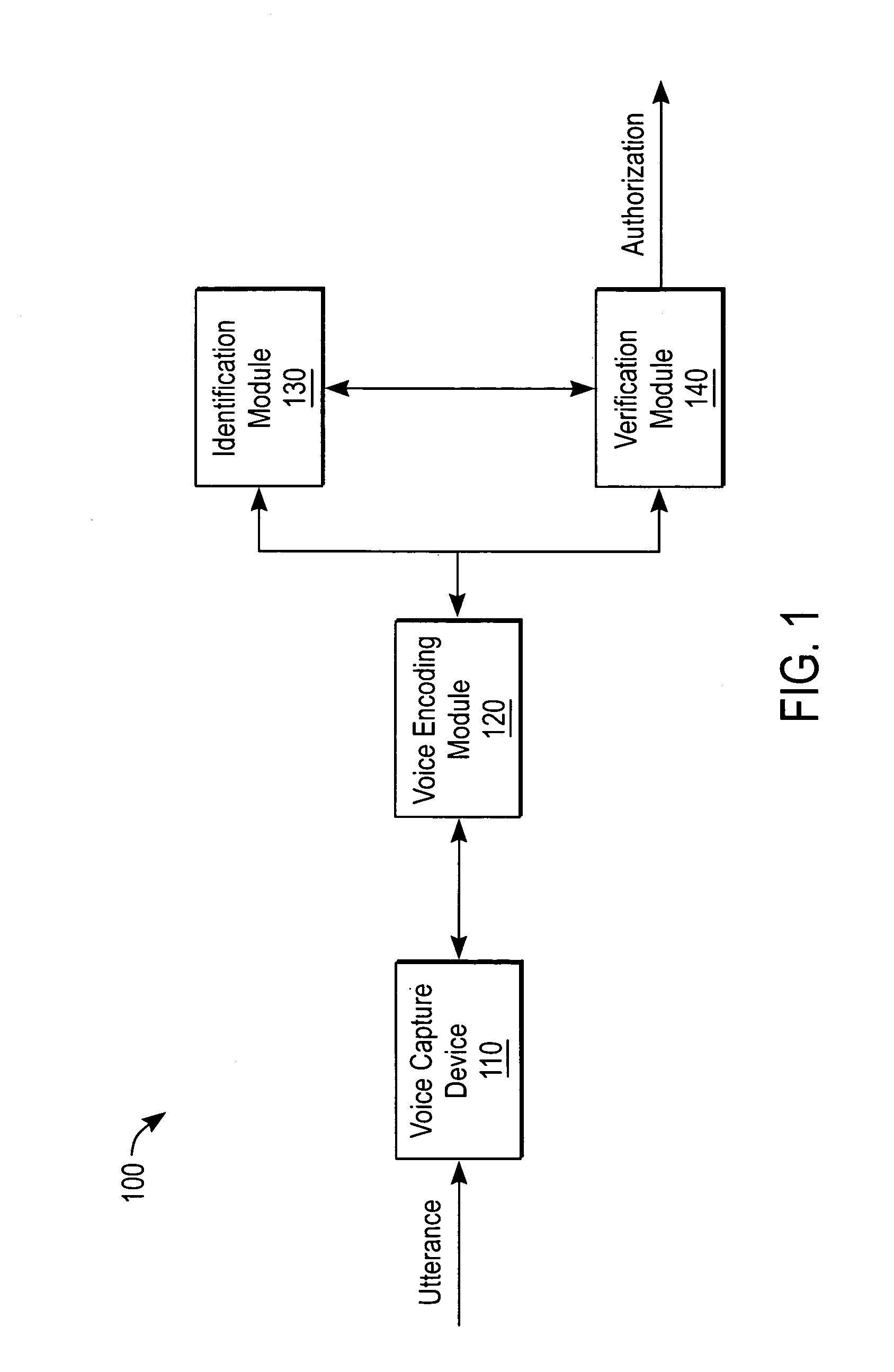
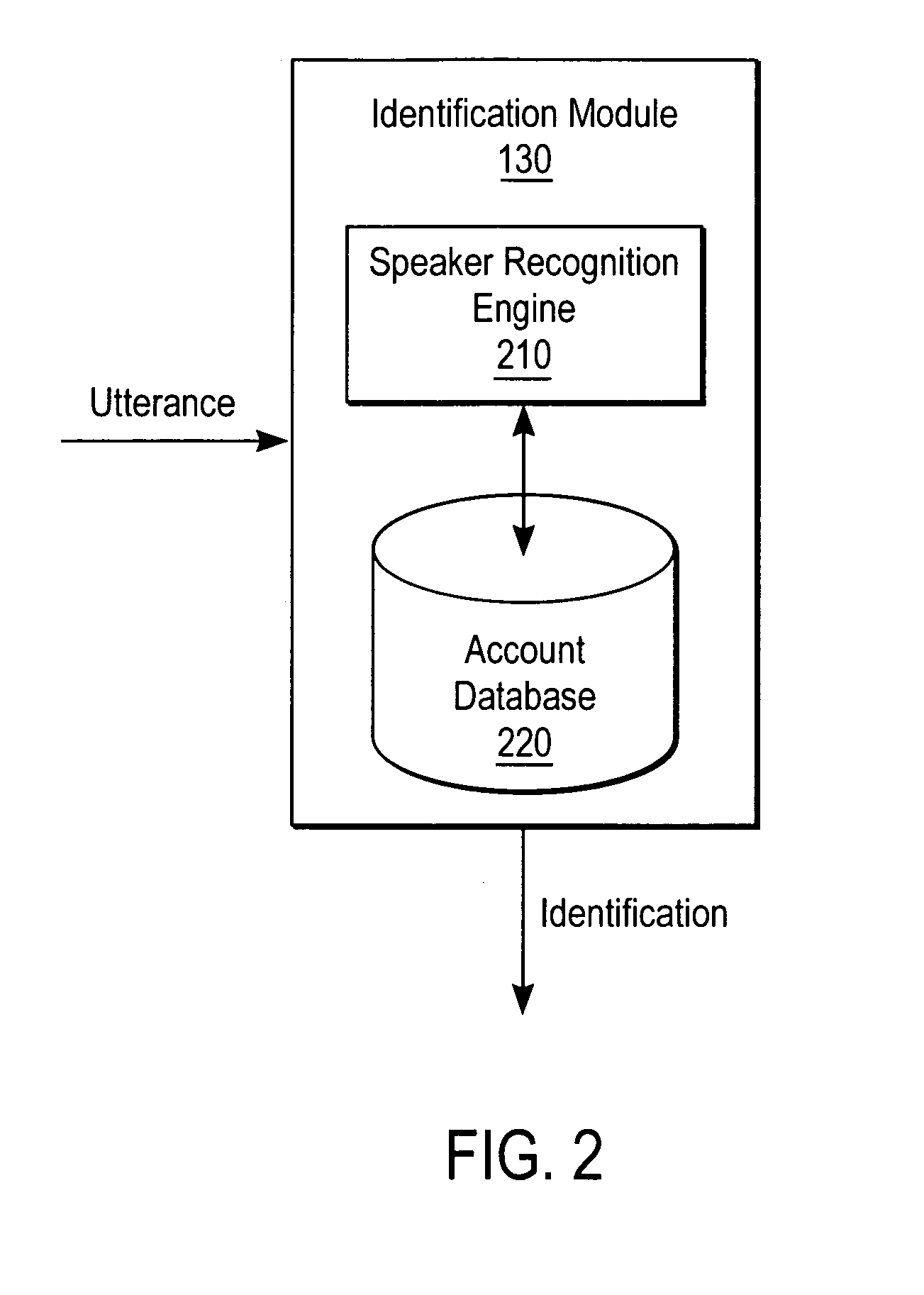
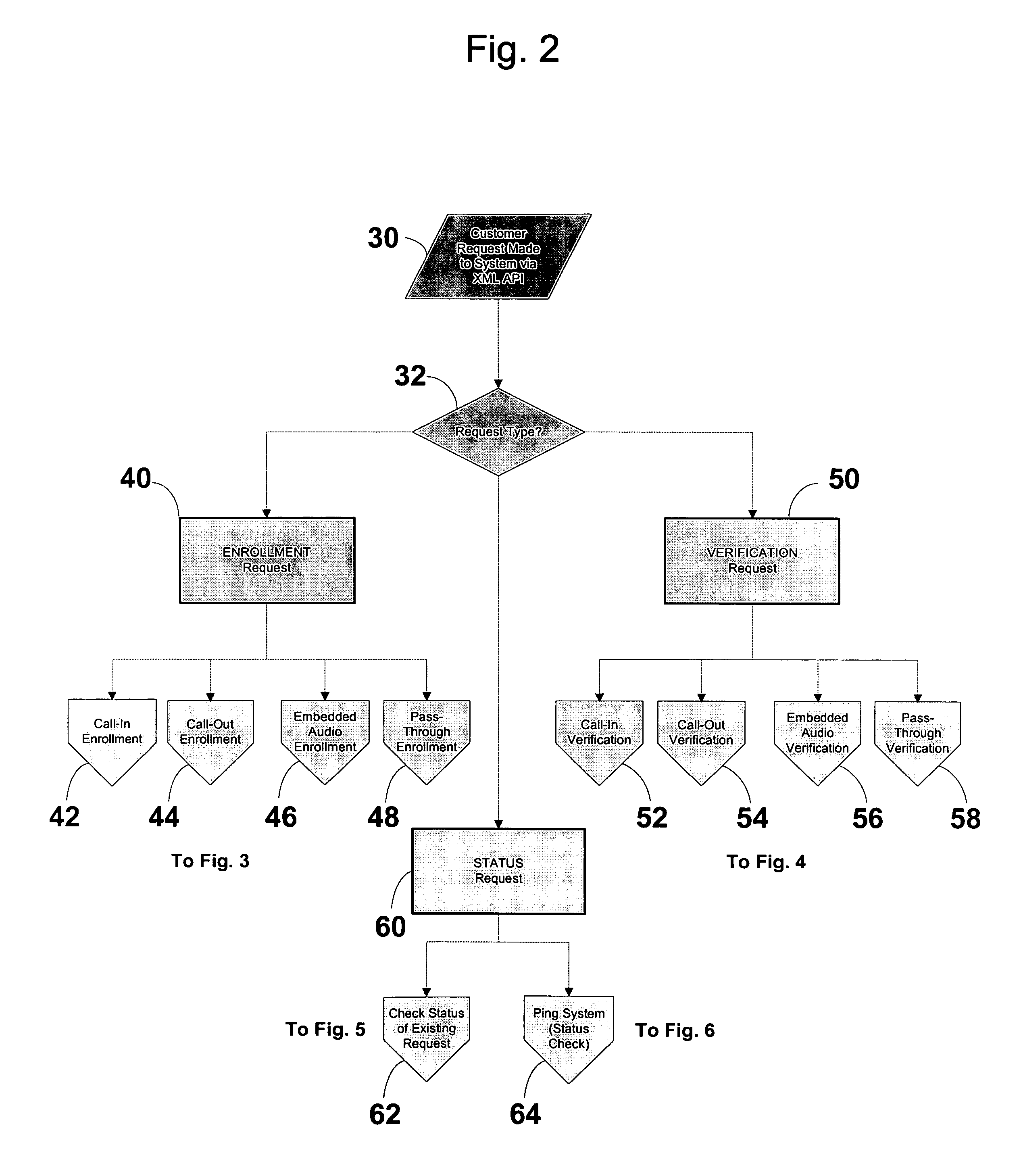
Speech verification uses speech recognition to verify the correctness of the pronounced speech. Speech verification does not try to decode unknown speech from a huge search space, but instead, knowing the expected speech to be pronounced, it attempts to verify the correctness of the utterance's pronunciation, cadence, pitch, and stress. Pronunciation assessment is the main application of this technology, which is sometimes called computer-aided pronunciation teaching.
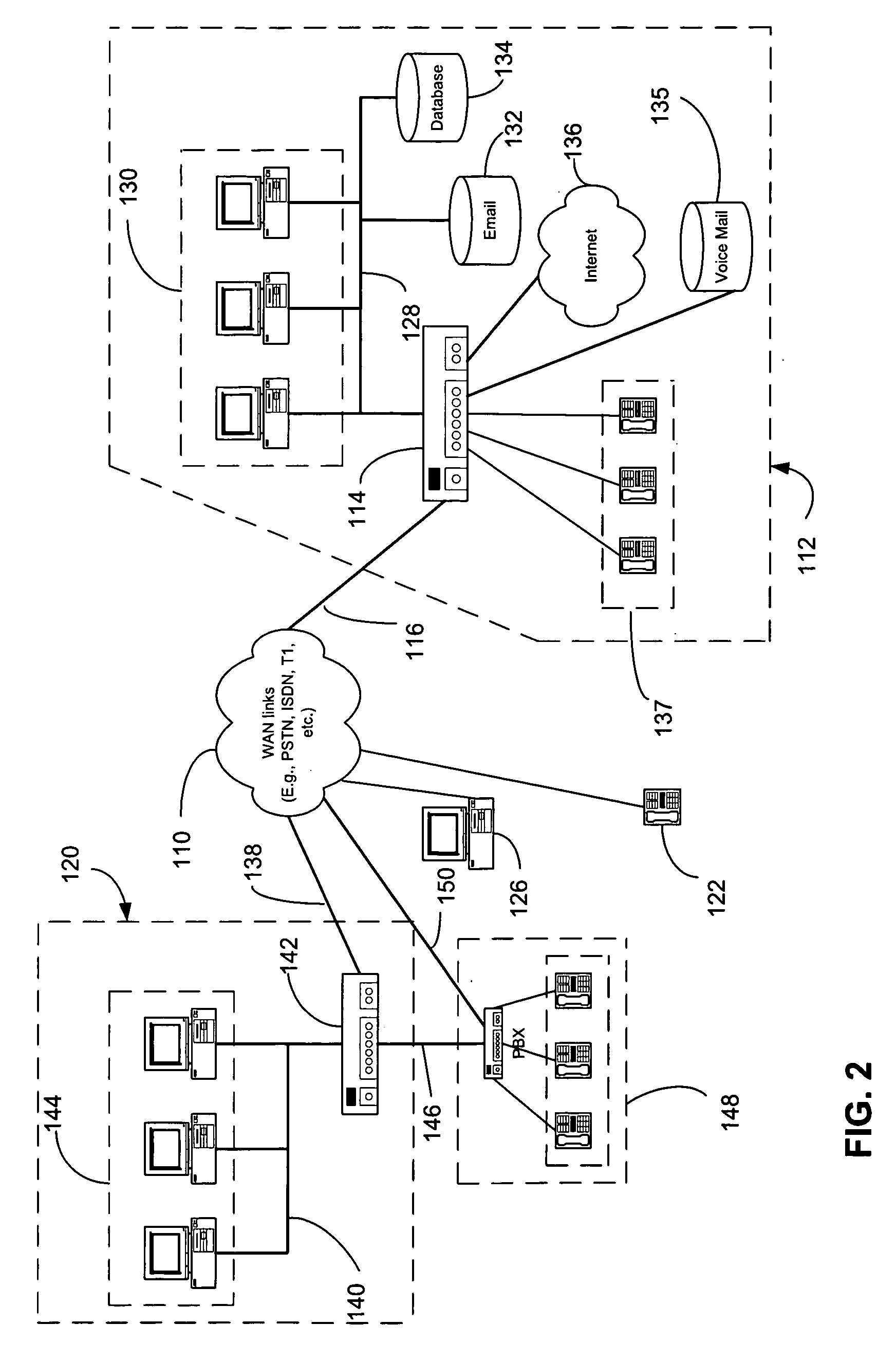
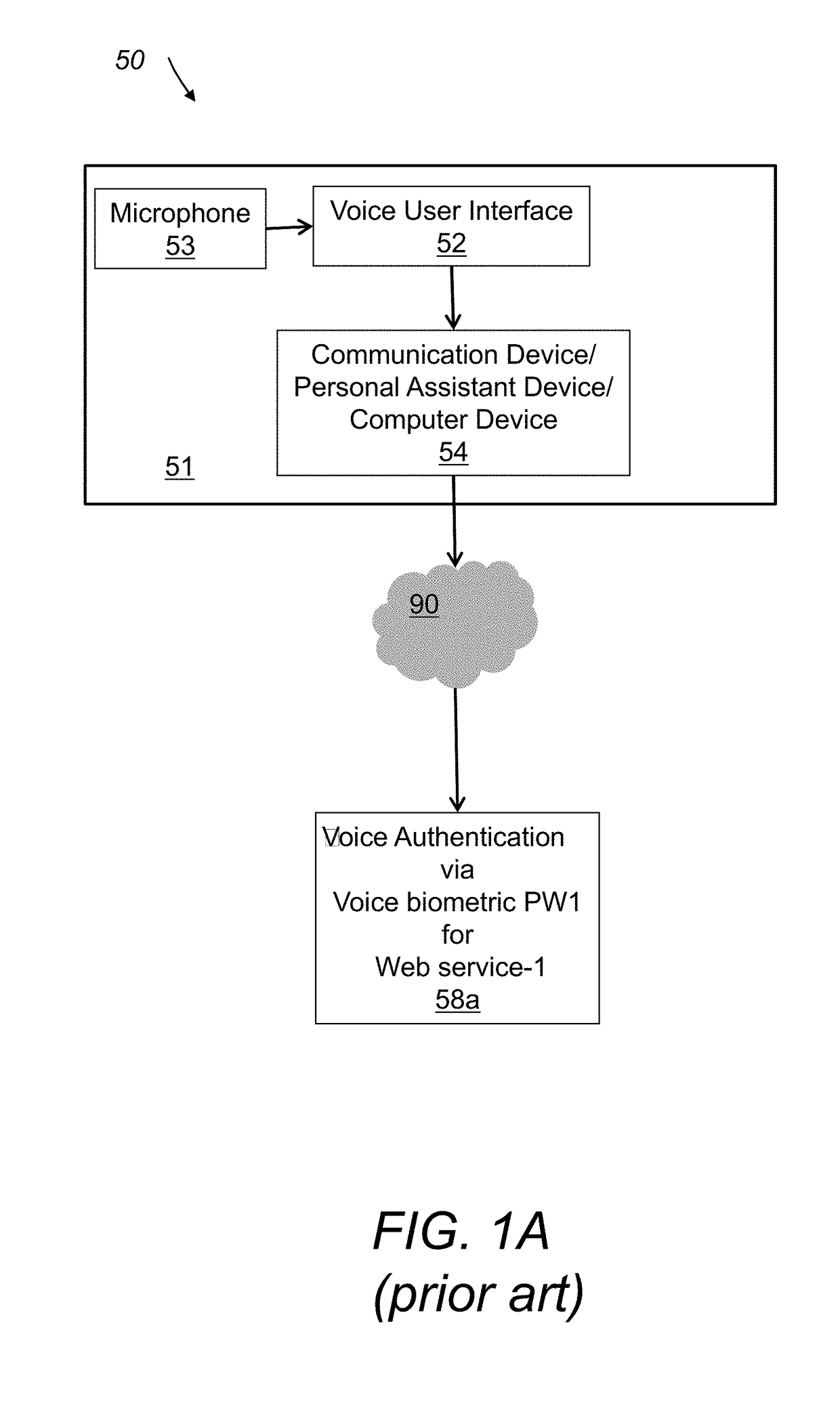
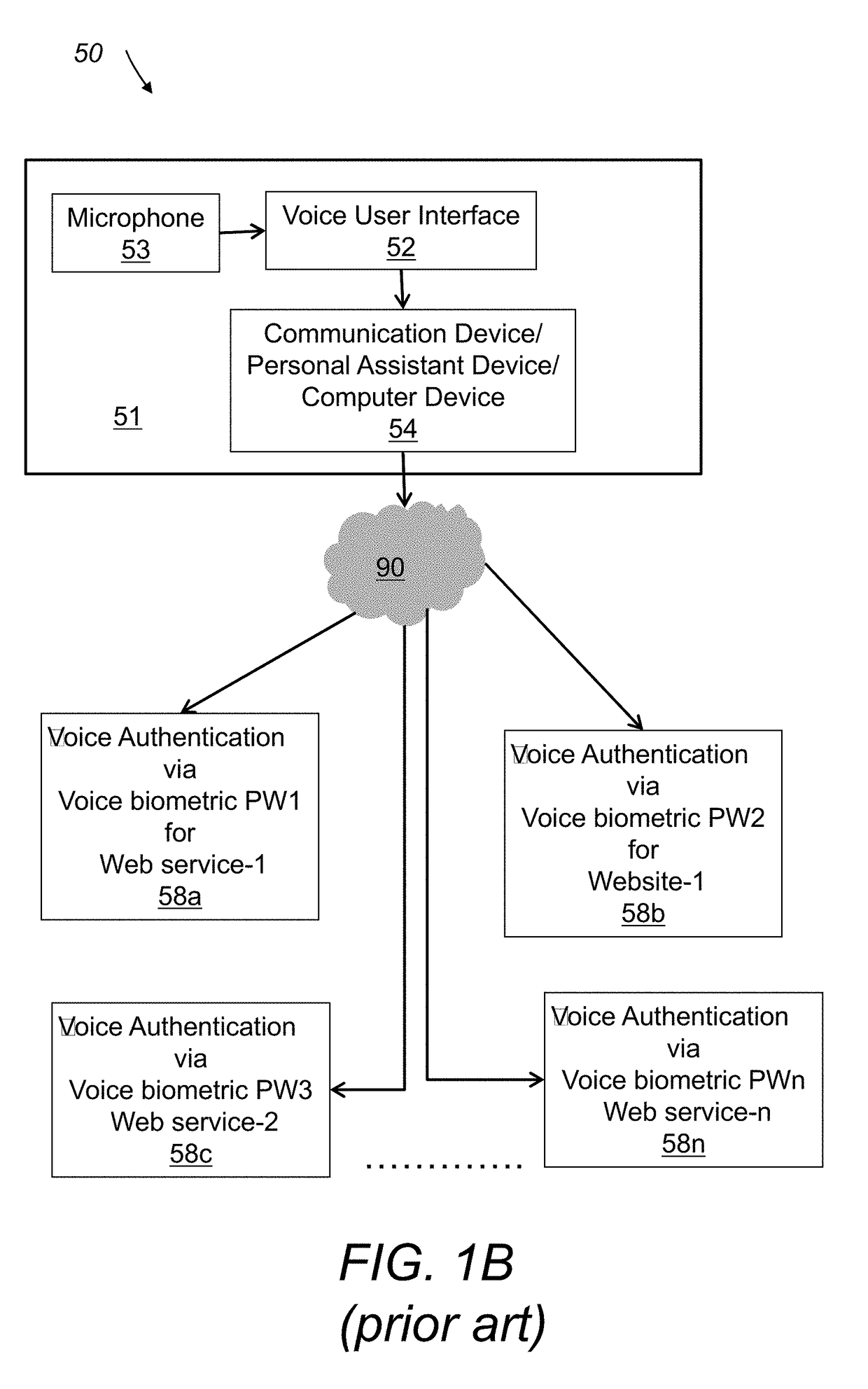
Voice authentication method and system utilizing same
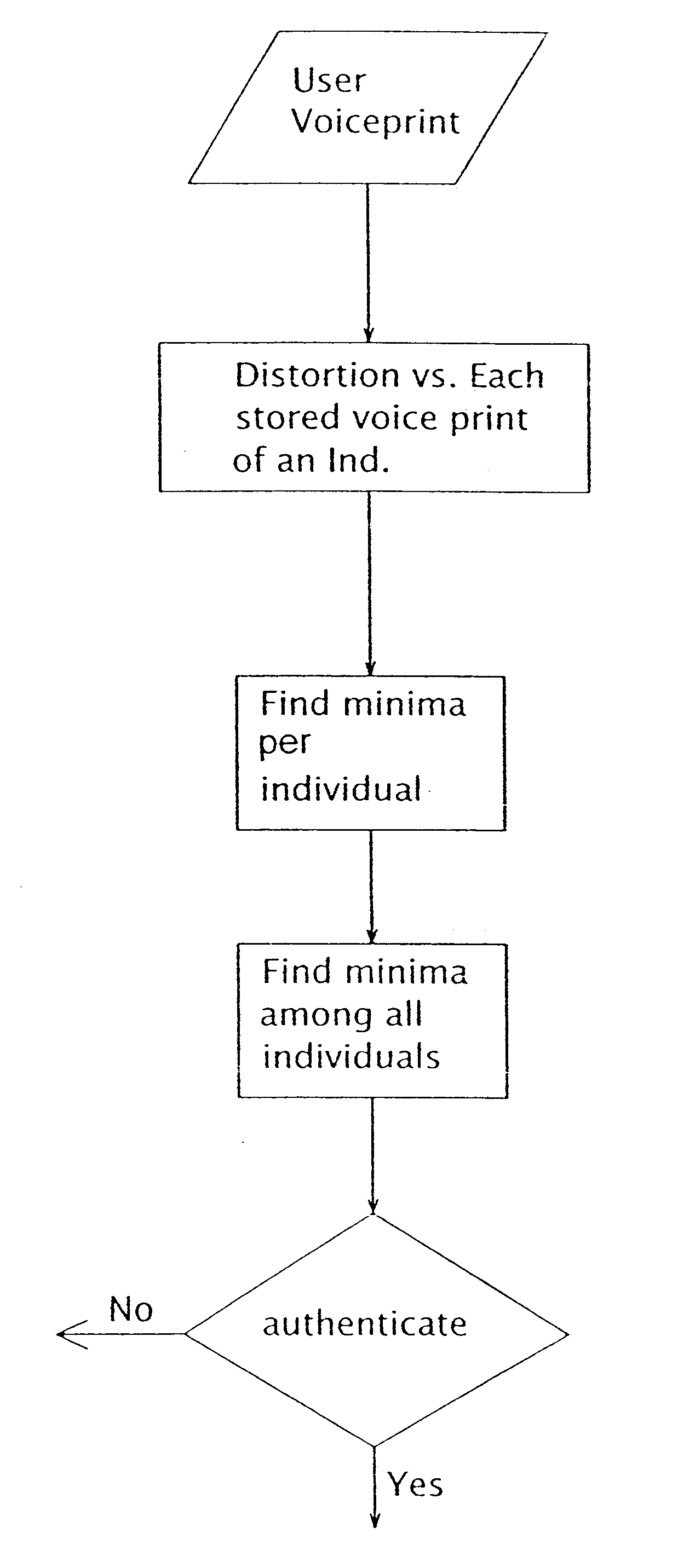
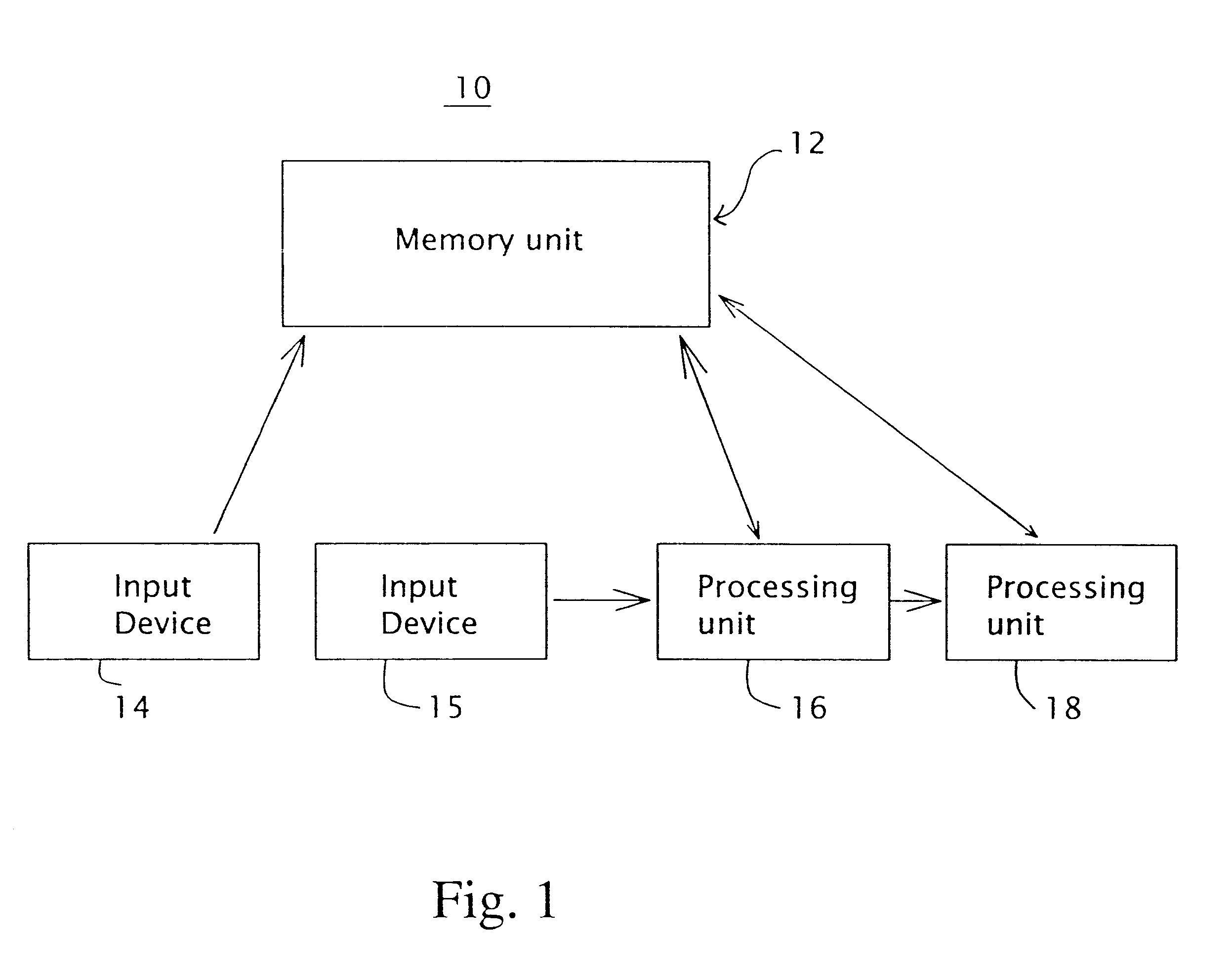
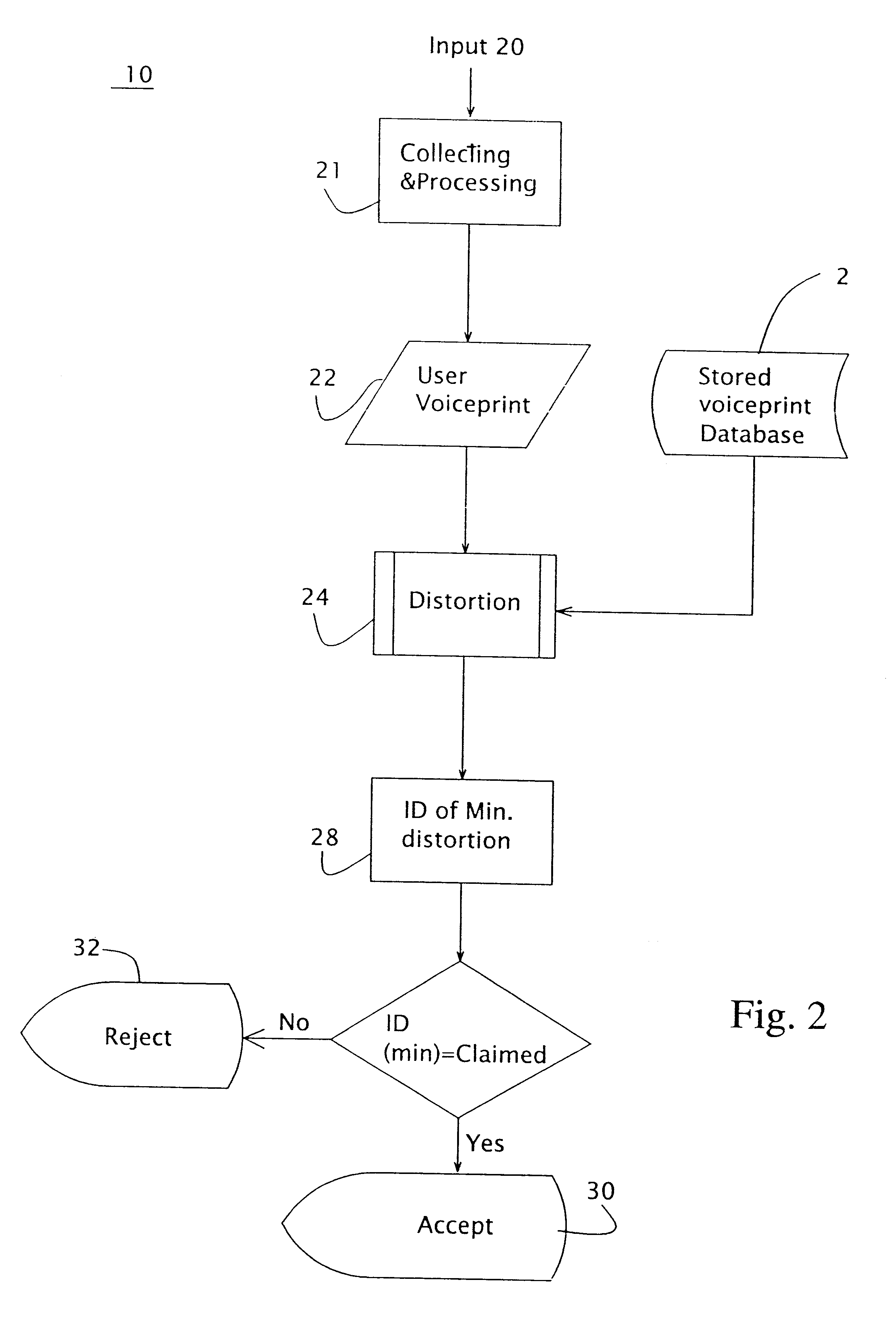
A system for authorizing user access to a secure site includes a memory unit, first and second input devices, and first and second processing devices. The memory unit stores voice prints and identities of the set of individuals that have access to the secure site. The first input device is for inputting information that identifies the user as a member of the set. The second input device is for inputting temporary user voice data. The first processing device is for generating a temporary voice print from the temporary data. The second processing device is for comparing the temporary voice print to the stored voice prints. Access is granted only if the temporary voice print is most similar to the voice print of the individual that the user claims to be.
Owner:SENTRYCOM
Biometric voice authentication
ActiveUS7386448B1Reducing user complexityReduce complexityAutomatic call-answering/message-recording/conversation-recordingAutomatic exchangesBiometric dataPersonal identification number
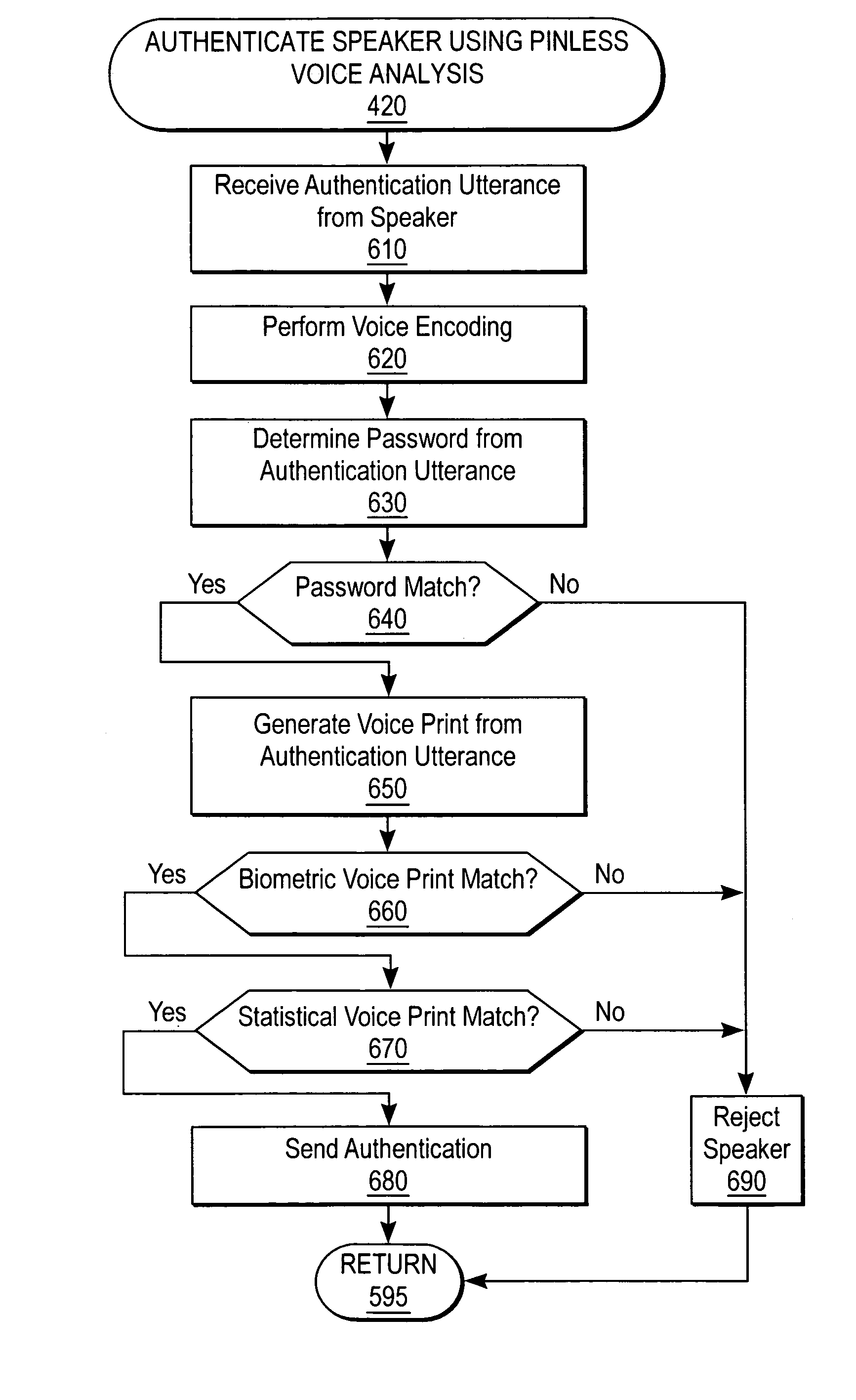
A system and method enrolls a speaker with an enrollment utterance and authenticates a user with a biometric analysis of an authentication utterance, without the need for a PIN (Personal Identification Number). During authentication, the system uses the same authentication utterance to identify who a speaker claims to be with speaker recognition, and verify whether is the speaker is actually the claimed person. Thus, it is not necessary for the speaker to identify biometric data using a PIN. The biometric analysis includes a neural tree network to determine unique aspects of the authentication utterances for comparison to the enrollment authentication. The biometric analysis leverages a statistical analysis using Hidden Markov Models to before authorizing the speaker.
Owner:SECURUS TECH LLC
Method and system for verifying and enabling user access based on voice parameters
InactiveUS7054811B2Improve securityAutomatic exchangesBuying/selling/leasing transactionsSpeech verificationSpeech sound
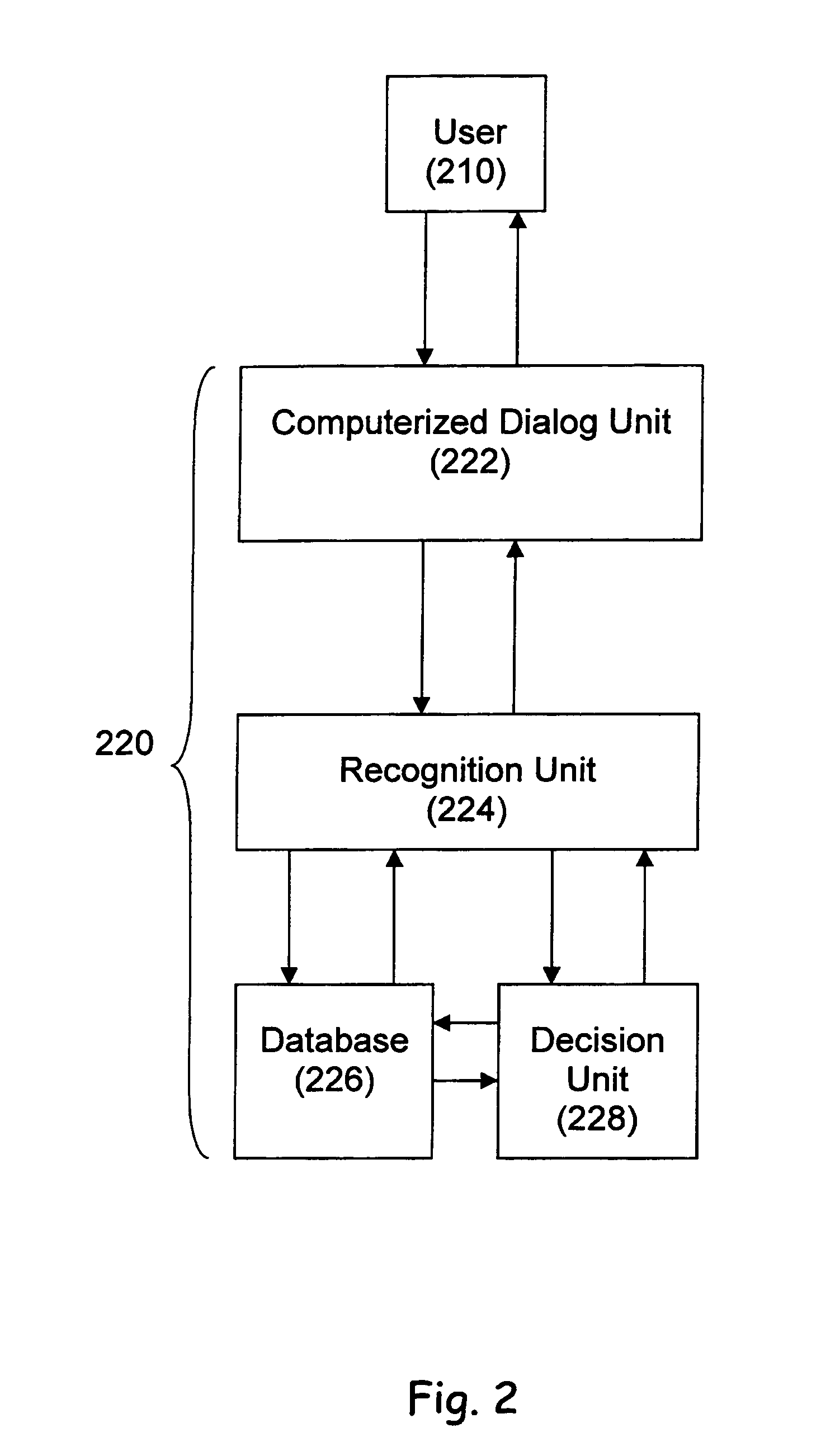
A system for verifying and enabling user access, which includes a voice registration unit for providing a substantially unique and initial identification of each of a plurality of the speaker / users by finding the speaker / user's voice parameters in a voice registration sample and storing same in a database. The system also includes a voice authenticating unit for substantially absolute verification of an identity of one of said plurality of users. The voice authenticating unit includes a recognition unit for providing a voice authentication sample, and being operative with the database. The voice authenticating unit also includes a decision unit operative with the recognition unit and the database to decide whether the user is the same as the person of the same identity registered with the system, such that the identity of one of the plurality of users is substantially absolutely verified.
Owner:CELLMAX SYST
Voice authentication system and methods therefor
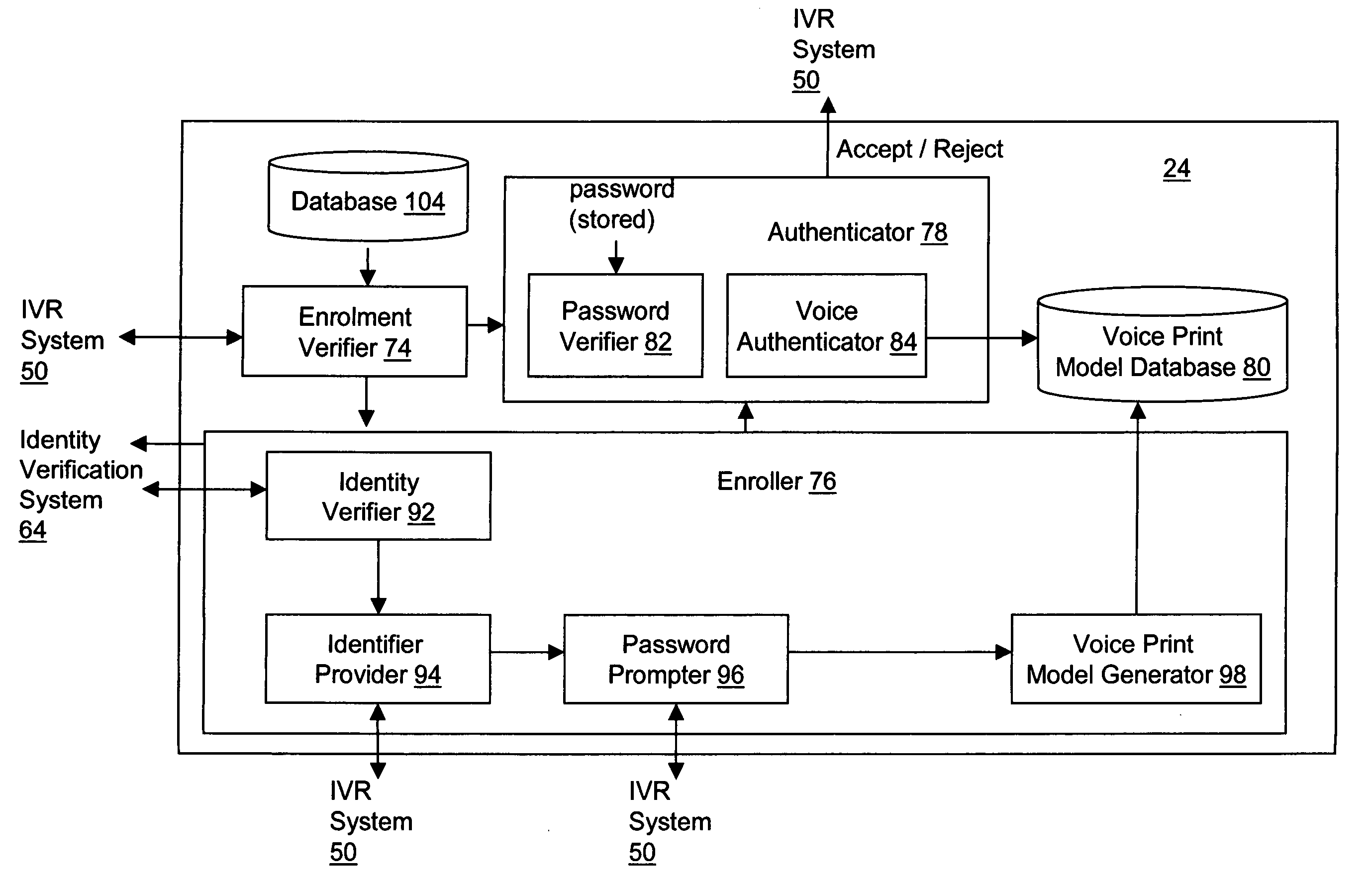
The present invention relates to methods and systems for enrolling a user for voice authentication and for performing voice authentication on a user of a network. The method of enrolling a user for voice authentication includes verifying the identity of the user and assigning an enrolment identifier to the user, if the identity of the user is verified. The enrolment identifier is then presented to the user. Subsequently, the user is prompted to utter a personal voice authentication password. The personal password uttered by the user is received and stored. A voice print model for the user is generated from the previously stored voice print. The method further includes storing the voice print model and associating the voice print model and the personal password with the enrolment identifier assigned to the user to facilitate retrieval thereof during voice authentication of the user. A method for performing voice authentication on a user of a network is also provided. The method includes determining whether the user is enrolled for voice authentication based on an available attribute of the logical address of the user on the network. Upon determining that the user is enrolled for voice authentication, a personal password and stored voice print model for the user is retrieved. The stored voice print model includes a voice print of a personal password previously uttered by the user. The method further includes prompting the user to utter the personal password and receiving a spoken response from the user. The spoken response is verified to determine whether it contains the personal password and whether it matches the stored voice print model. If the spoken response contains the personal password and matches the stored voice print model for the user, the identity of the user is authenticated.
Owner:TOMES EDWARD +1
Voice authentication system
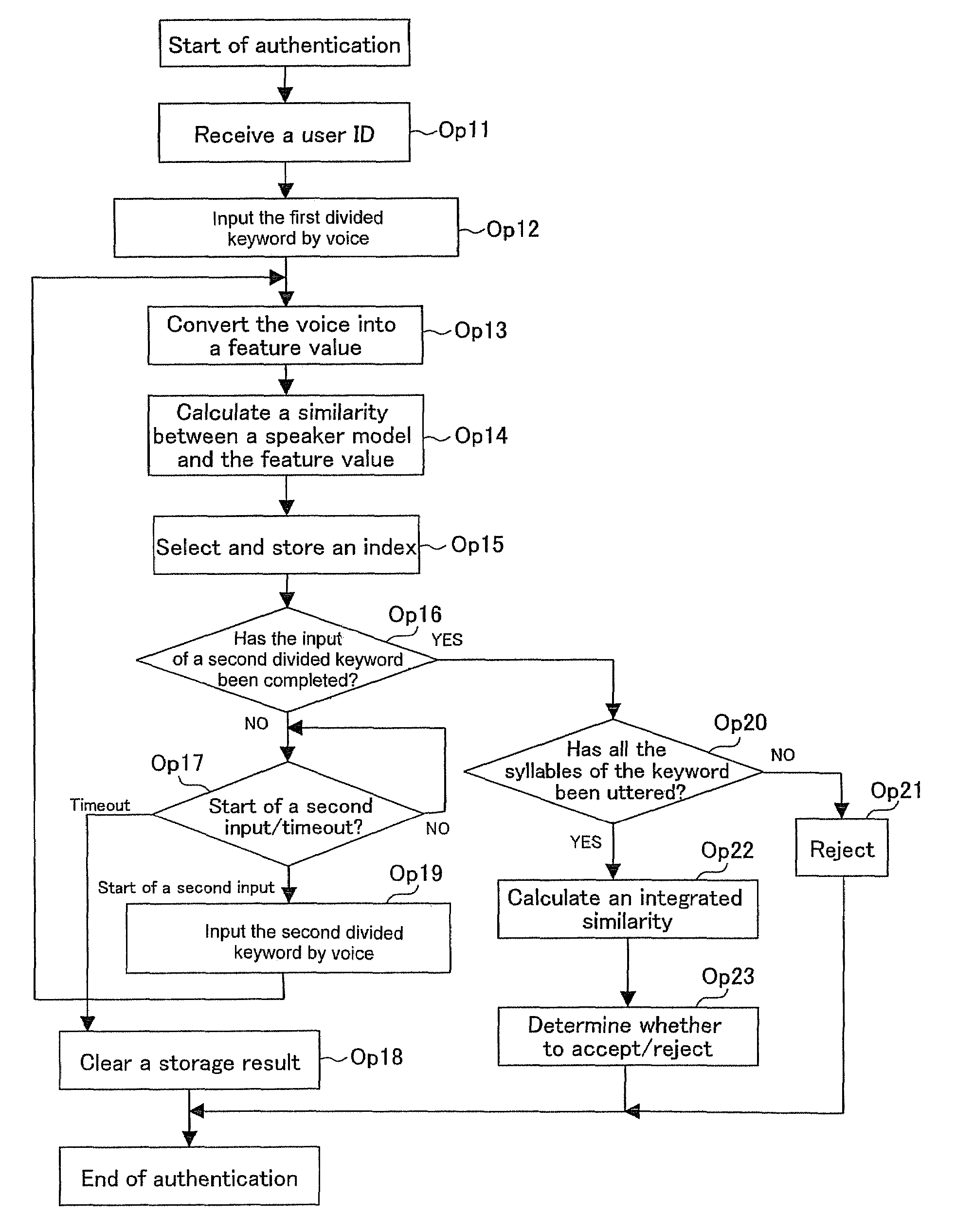
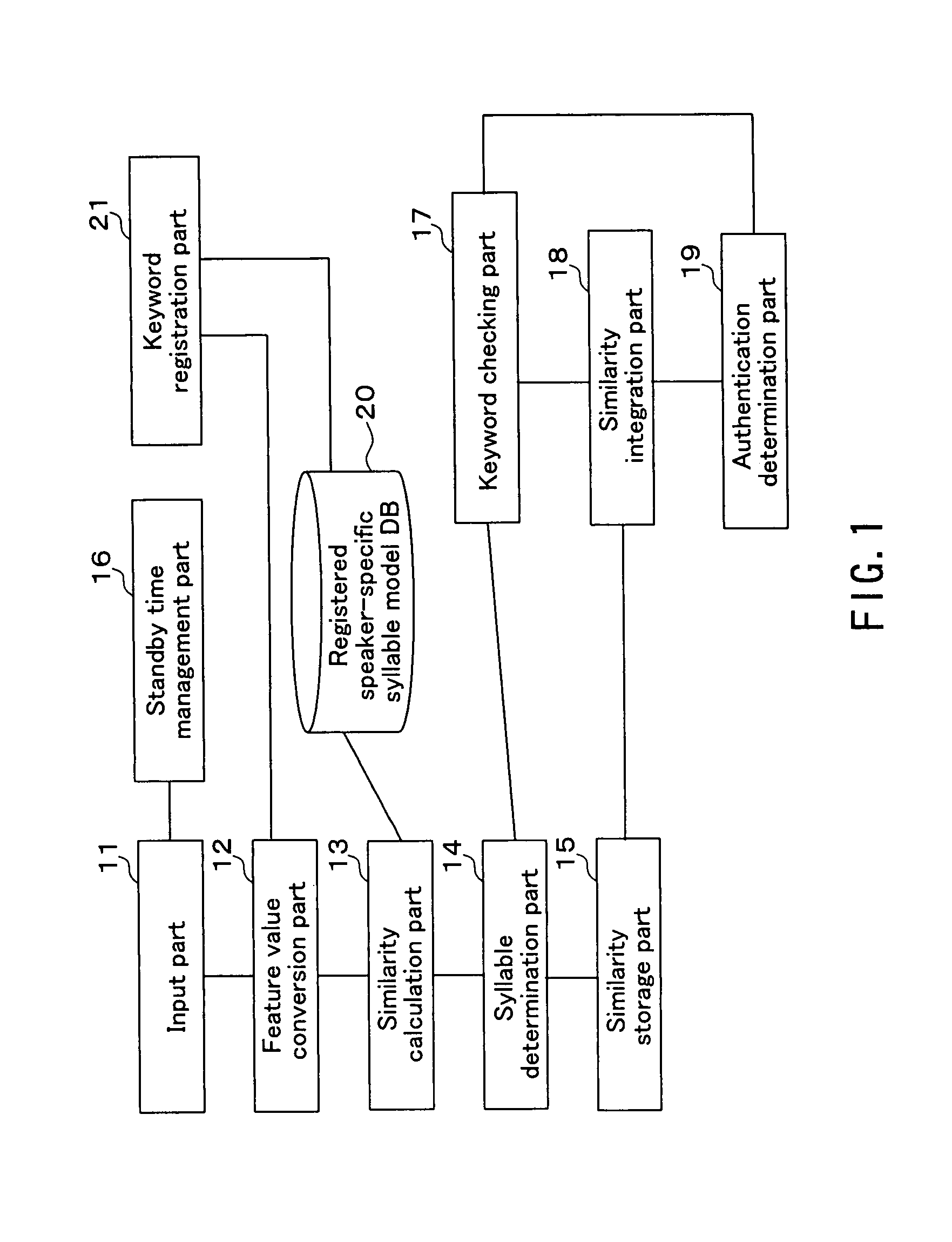
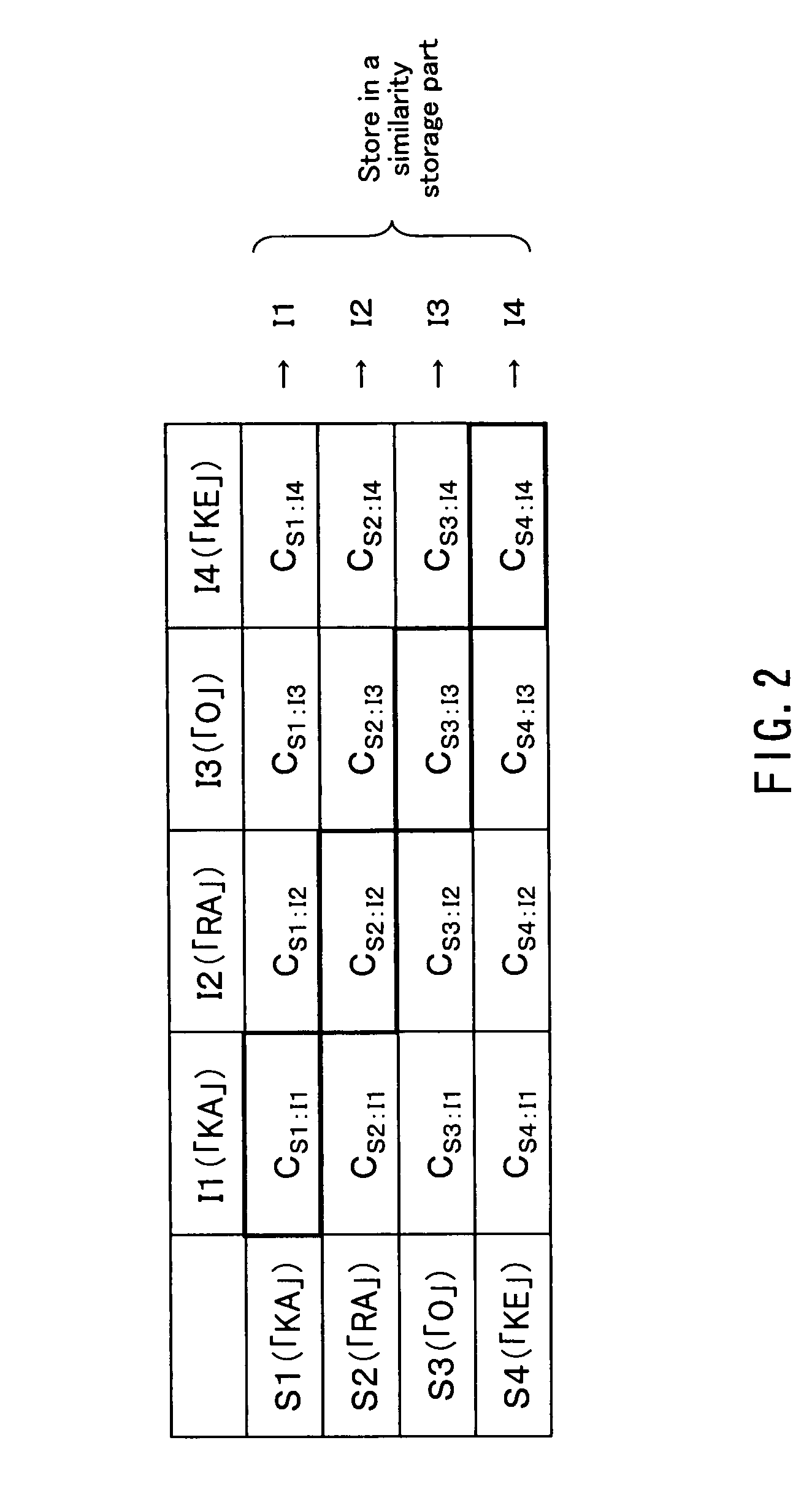
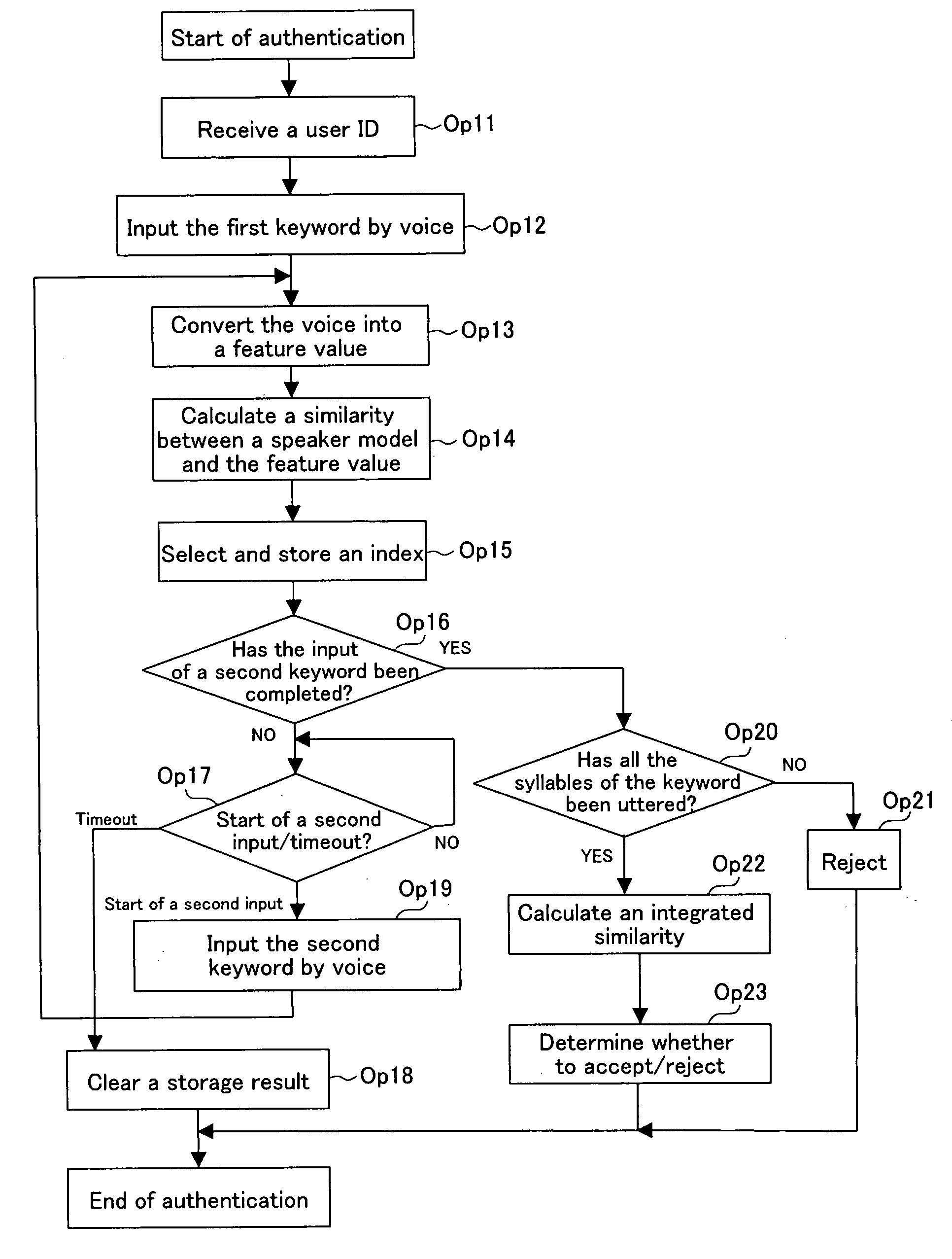
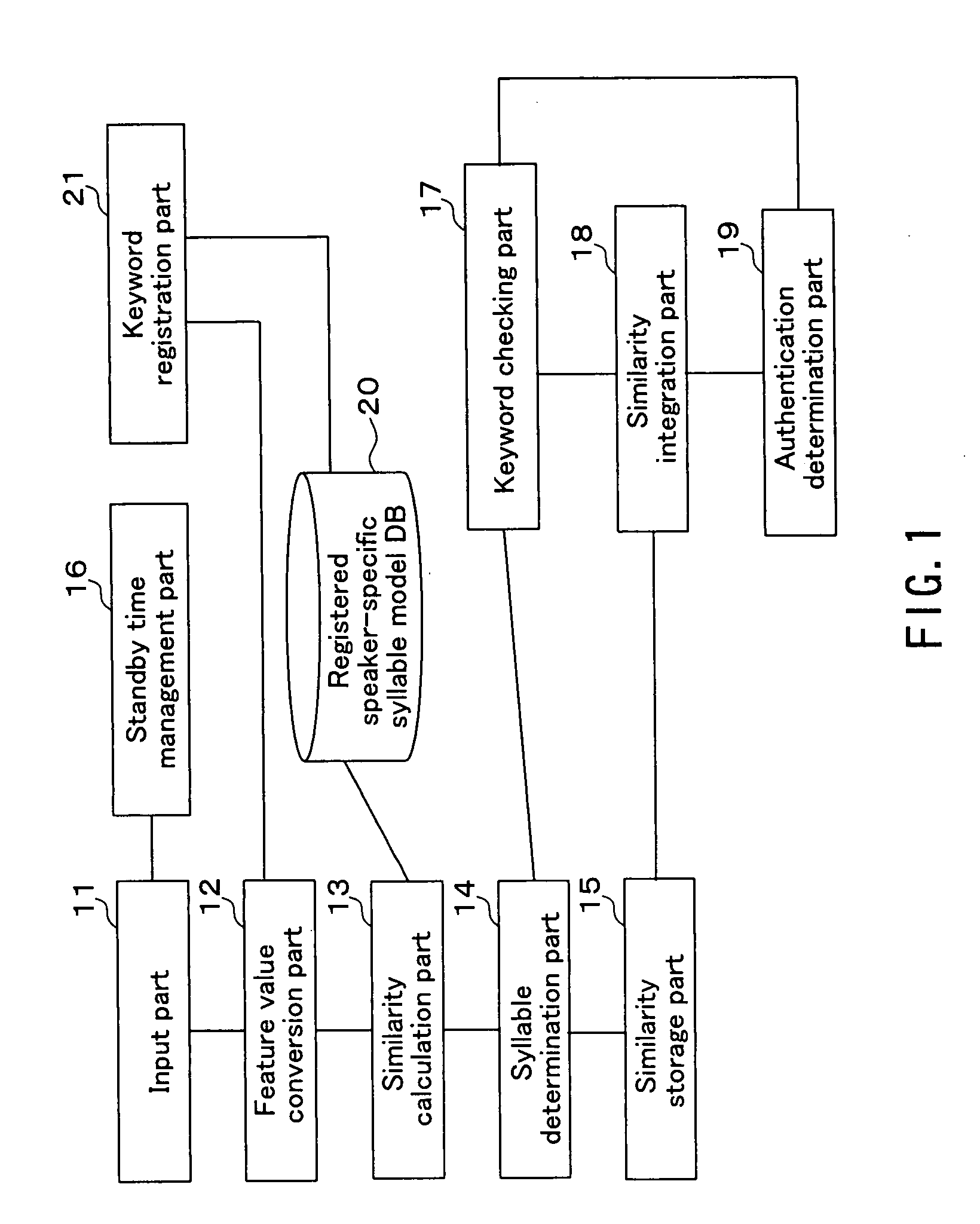
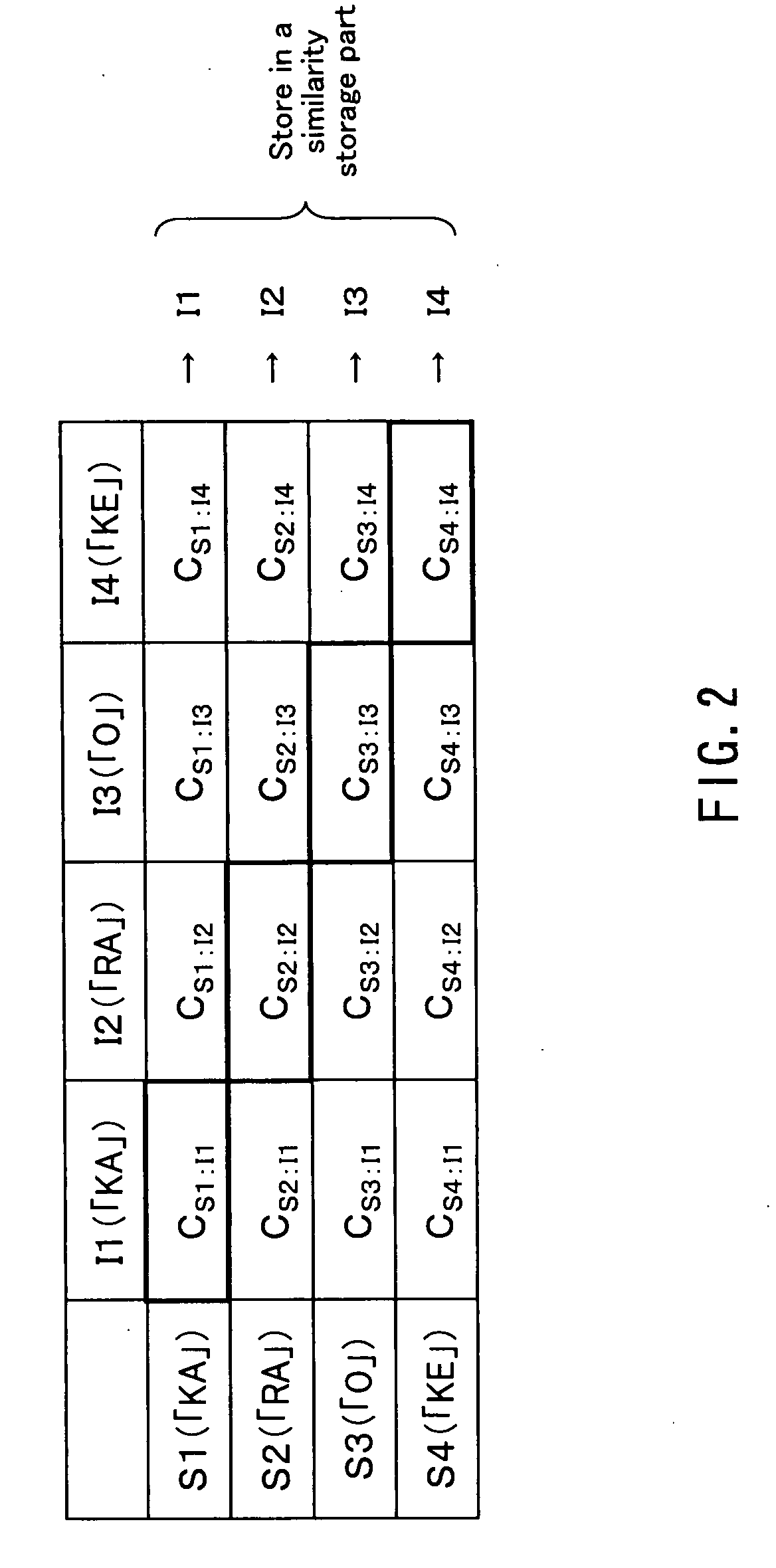
A text-dependent voice authentication system that performs authentication by urging a user to input a keyword by voice includes: an input part (11) that receives a voice input of a keyword divided into a plurality of portions with an utterable unit being a minimum unit over a plurality of times at a time interval for each of the portions; registered speaker-specific syllable model DB (20) that previously stores a registered keyword of a user as a speaker model created in the utterable unit; a feature value conversion part (12) that obtains a feature value of a voice contained in a portion of the keyword received by each voice input in the input part (11) from the portion; a similarity calculation part (13) that obtains a similarity between the feature value and the speaker model; a keyword checking part (17) that determines whether or not voice inputs of all the syllables or phonemes configuring an entire registered keyword by the plurality of times of voice inputs, based on the similarity obtained in the similarity calculation part; and an authentication determination part (19) that determines whether to accept or reject authentication, based on a determination result in the keyword checking part and the similarity obtained in the similarity calculation part.
Owner:FUJITSU LTD
System and method of subscription identity authentication utilizing multiple factors
ActiveUS7340042B2Low costRaise security concernsAutomatic call-answering/message-recording/conversation-recordingSpeech recognitionSpeech verificationSpeech sound
Owner:CSIDENTITY CORP
Electronic device and voice recognition method thereof
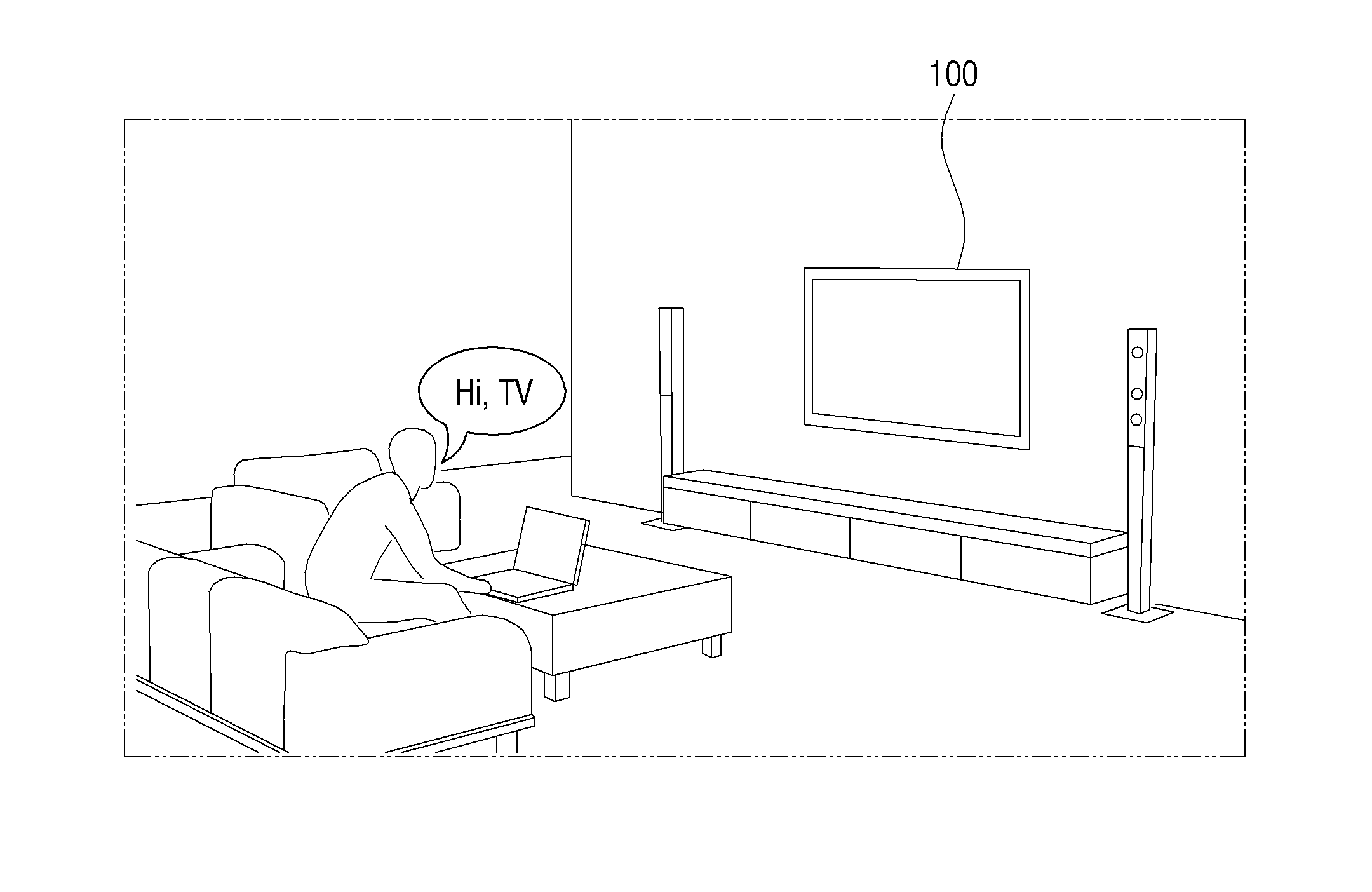
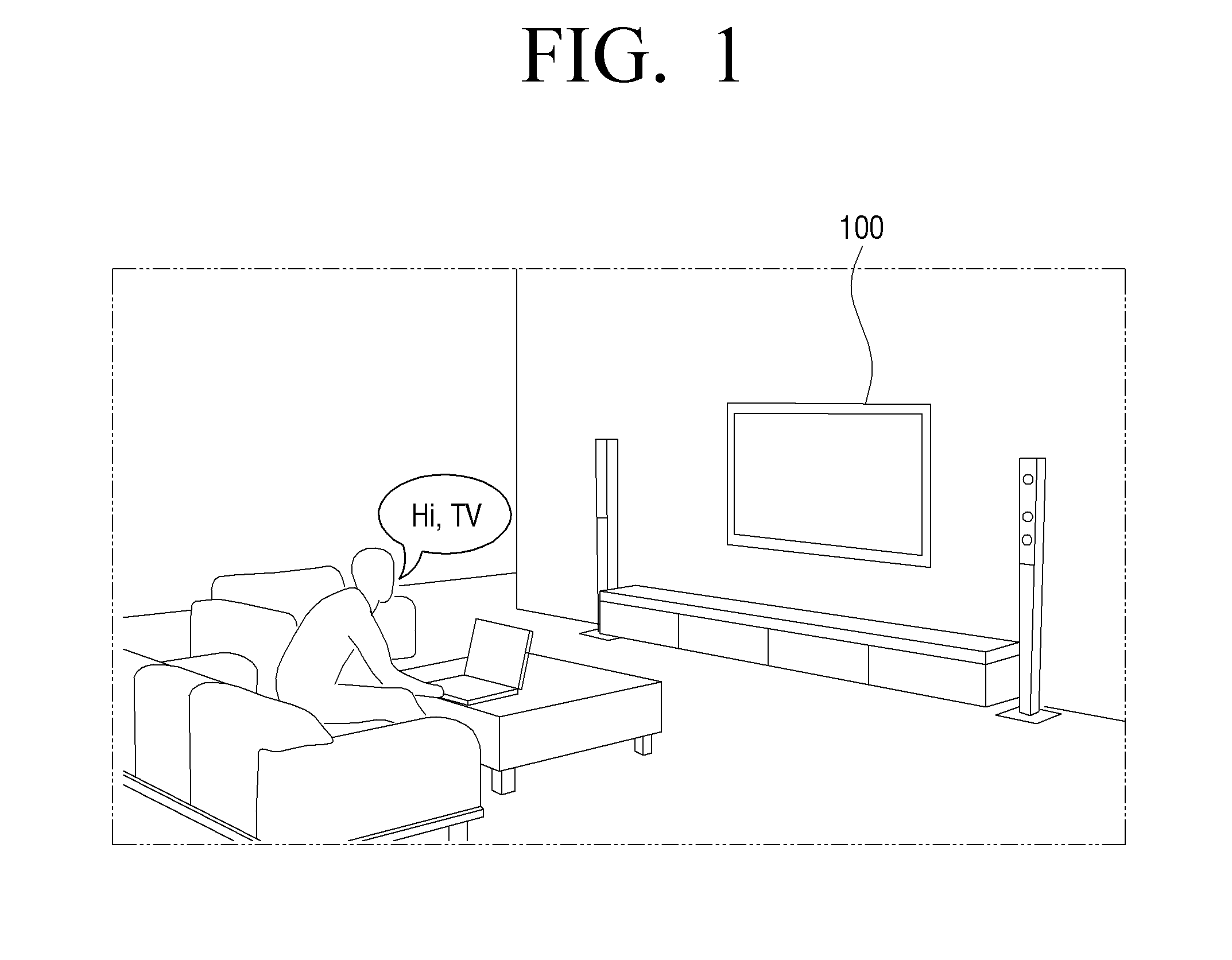
An electronic device and a voice recognition method thereof are provided. A voice recognition method of an electronic device includes receiving trigger voice, storing a characteristic of the trigger voice for voice verification by analyzing the trigger voice. When a user issues a voice command, determining whether the user voice command comprises the characteristic belonging to the trigger voice, and performing function of the electronic device corresponding to the user voice command based on the determination. Accordingly, users may easily use the voice recognition function of the electronic device.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method of subscription identity authentication utilizing multiple factors
ActiveUS20070106517A1Low costRaise security concernsAutomatic call-answering/message-recording/conversation-recordingSpeech recognitionSpeech verificationSpeech sound
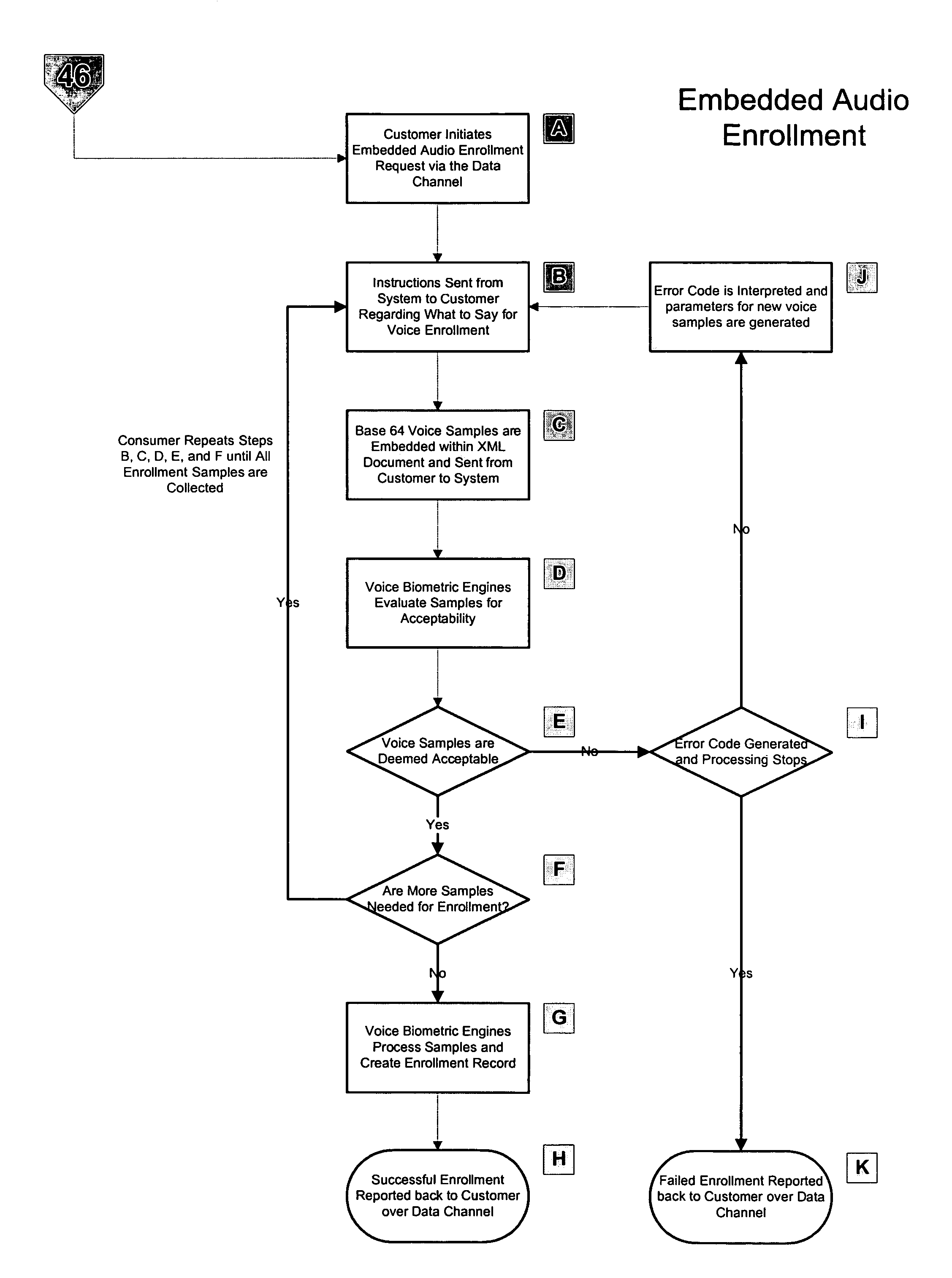
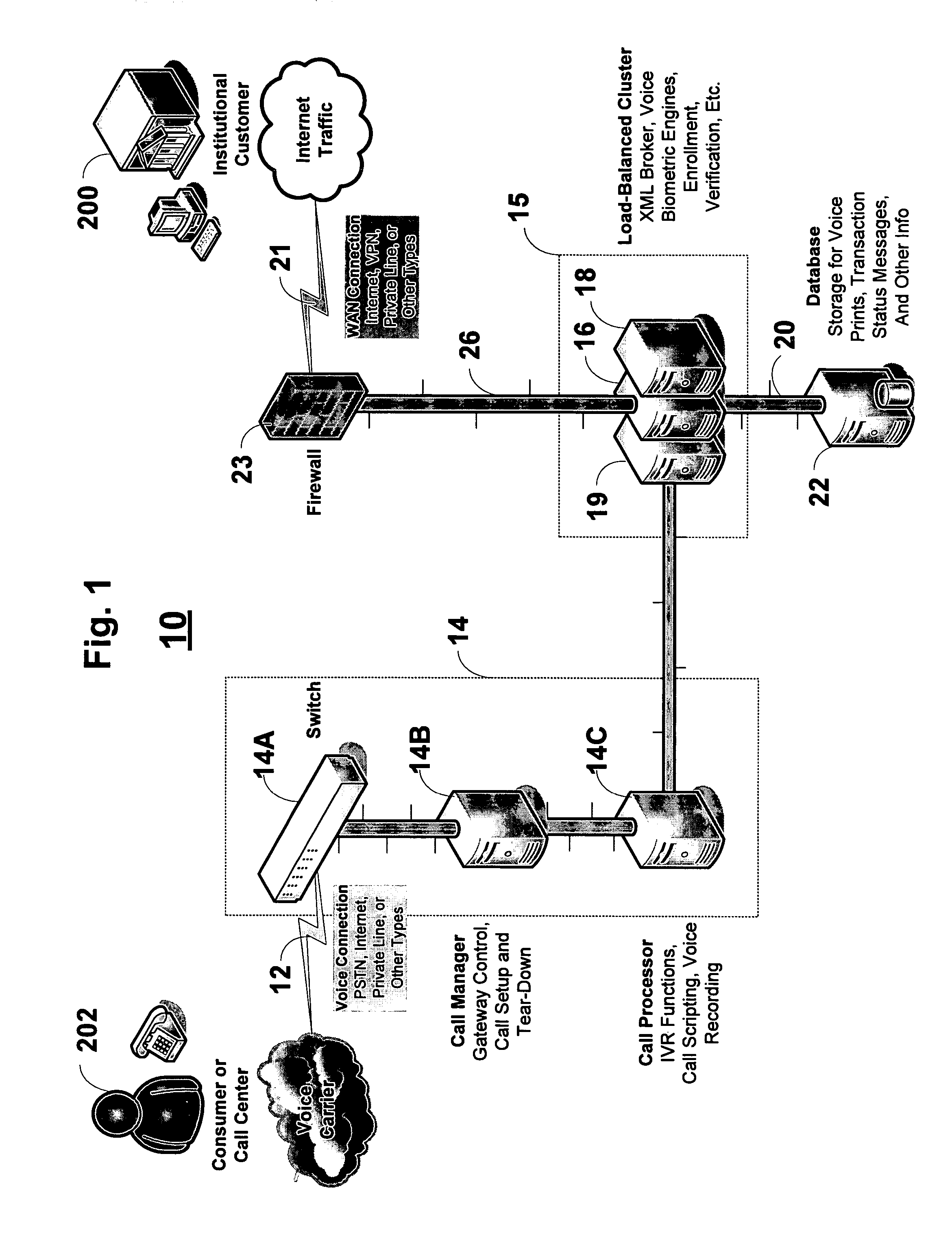
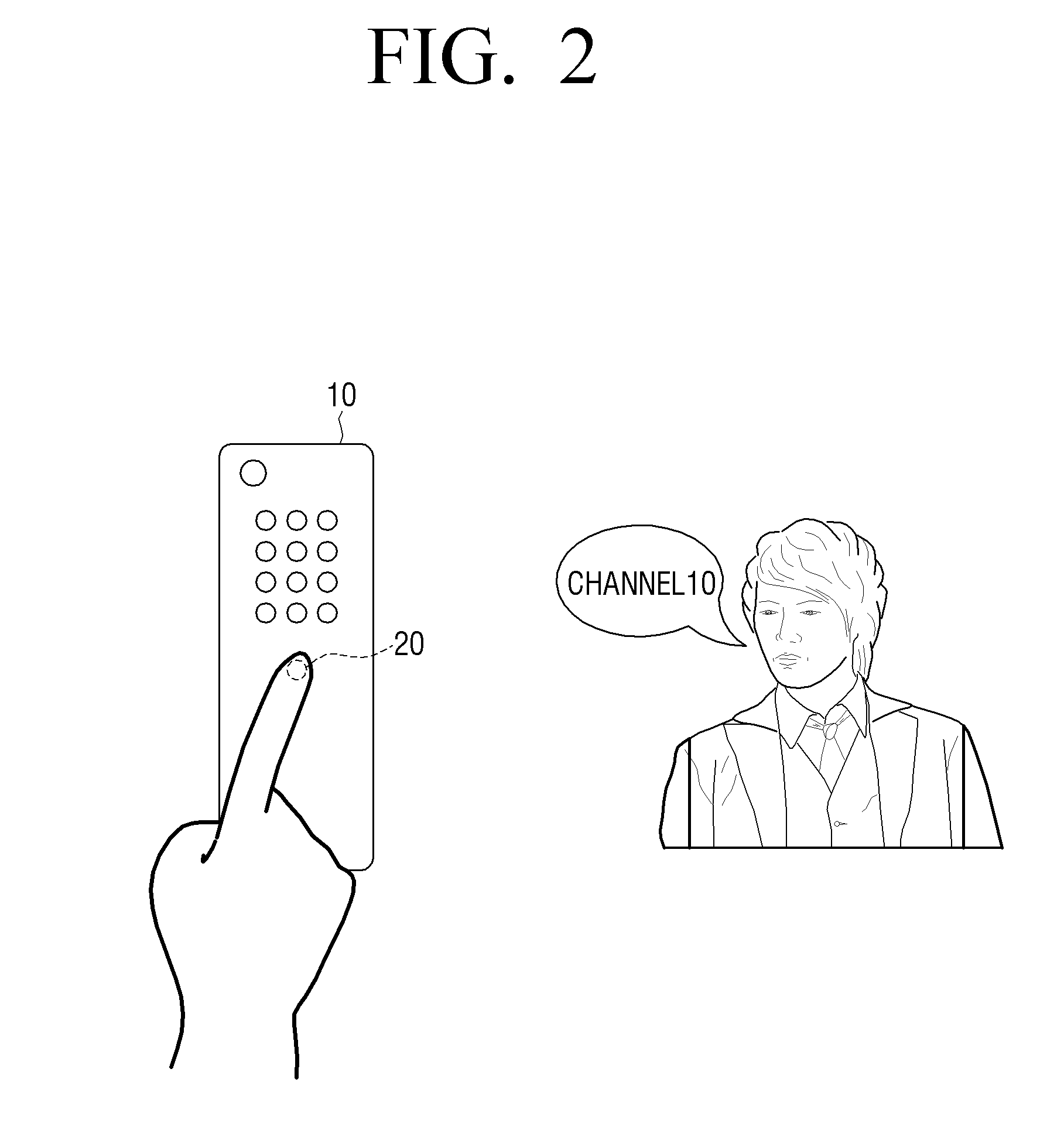
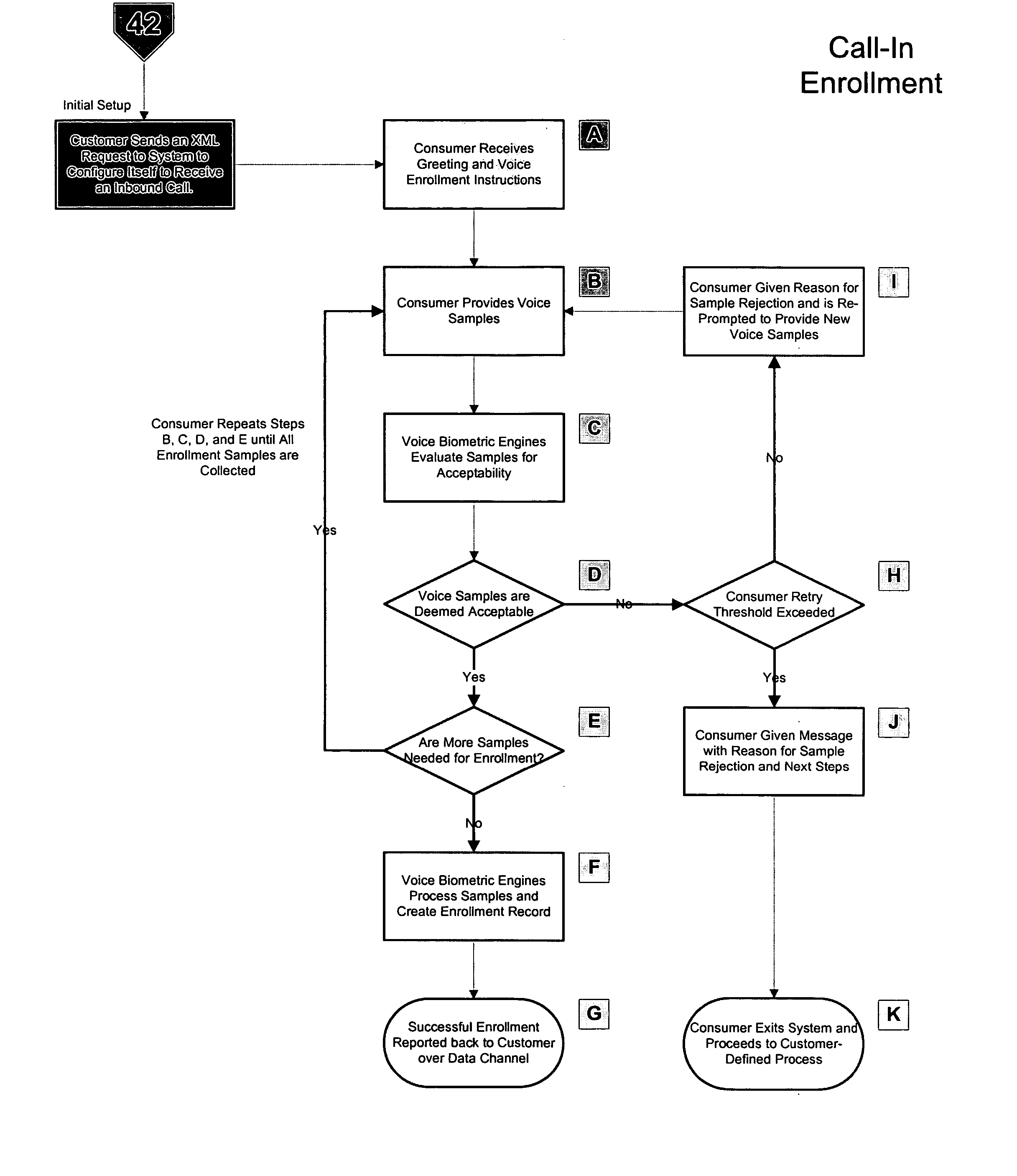
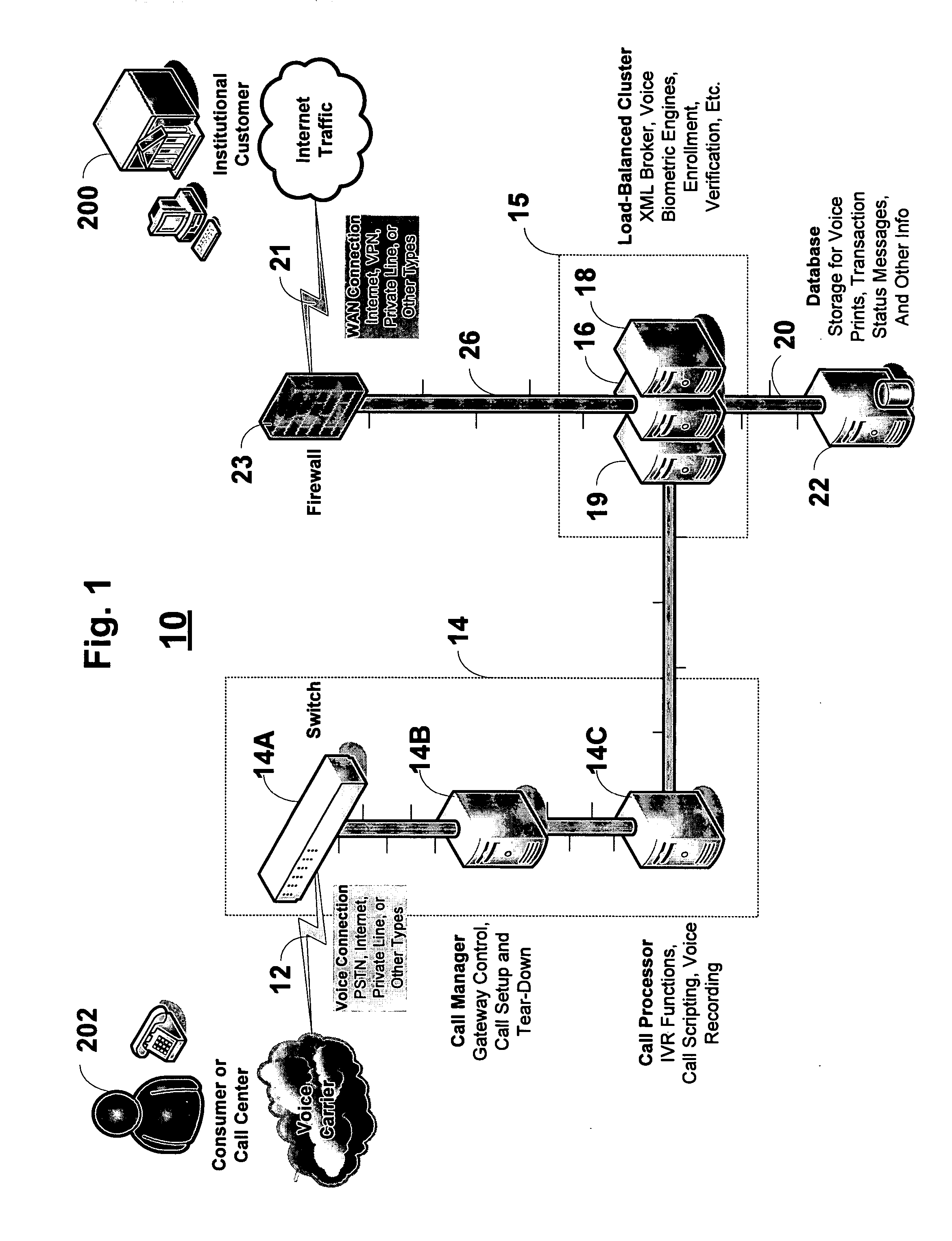
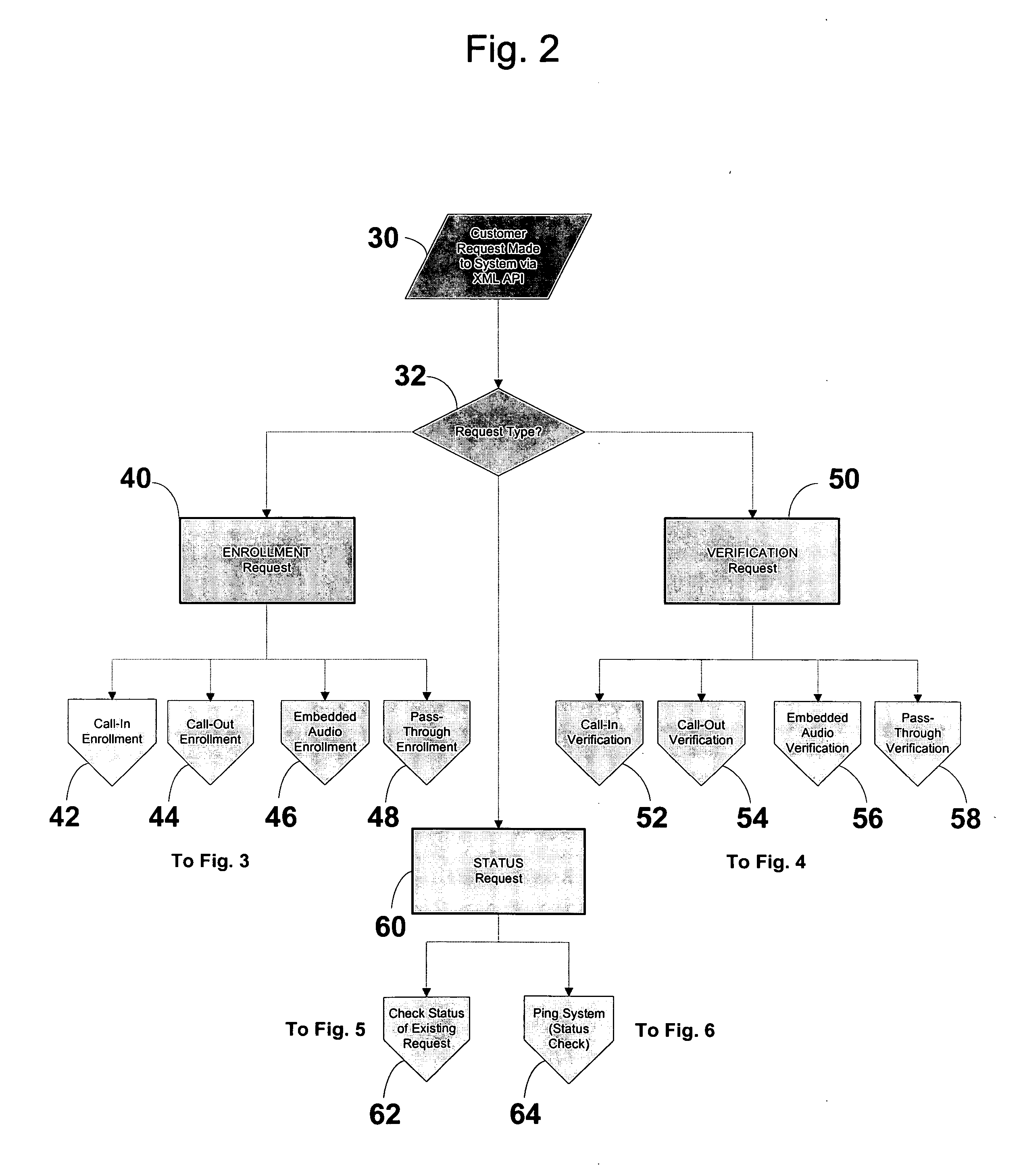
A system and method of providing voice authentication to institutional customers having consumers or users. The system includes an enrollment module, a verification module, and a database. Each institutional customer has an authentication profile on the system that includes both i) instructions indicating which one or more of the voice biometric engines are to be used for a given consumer's enrollment and / or authentication, and ii) variables for implementing those instructions. A given institutional customer may have more than one set of instructions or variables for different classes of users. Vocal information is received from a user, and a baseline voiceprint is constructed therefrom for enrollment. Subsequently, more vocal information is received from the user to construct a temporary voiceprint. The temporary voiceprint is compared to a corresponding baseline voiceprint in accordance with the institutional customer's authentication profile. The profile is preferably remotely configurable by the institutional customer.
Owner:CSIDENTITY CORP
Method for verifying the identity of a speaker and related computer readable medium and computer
InactiveUS20150112682A1Improve securityPrevent fraudSpeech recognitionSpeech verificationSpeech sound
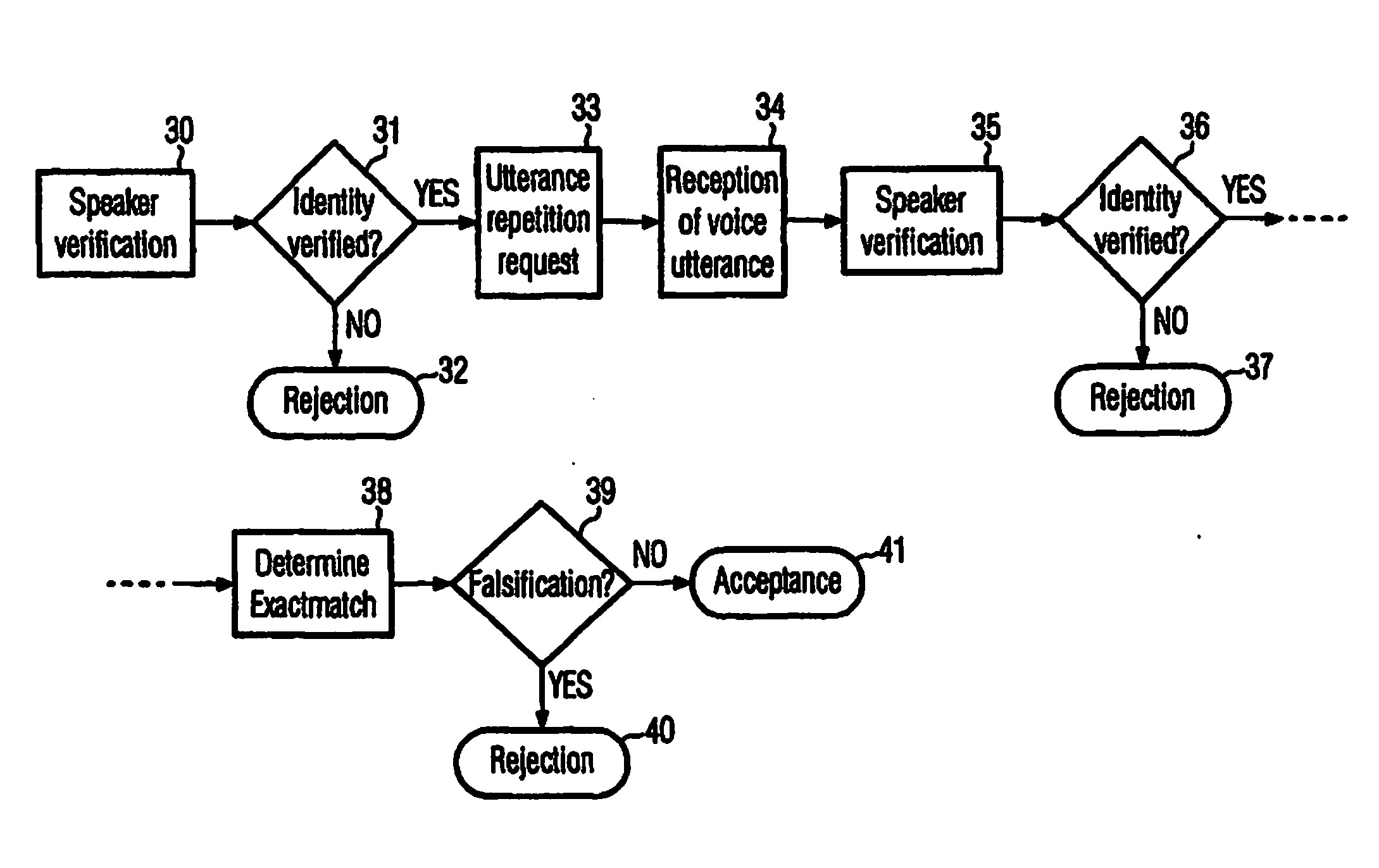
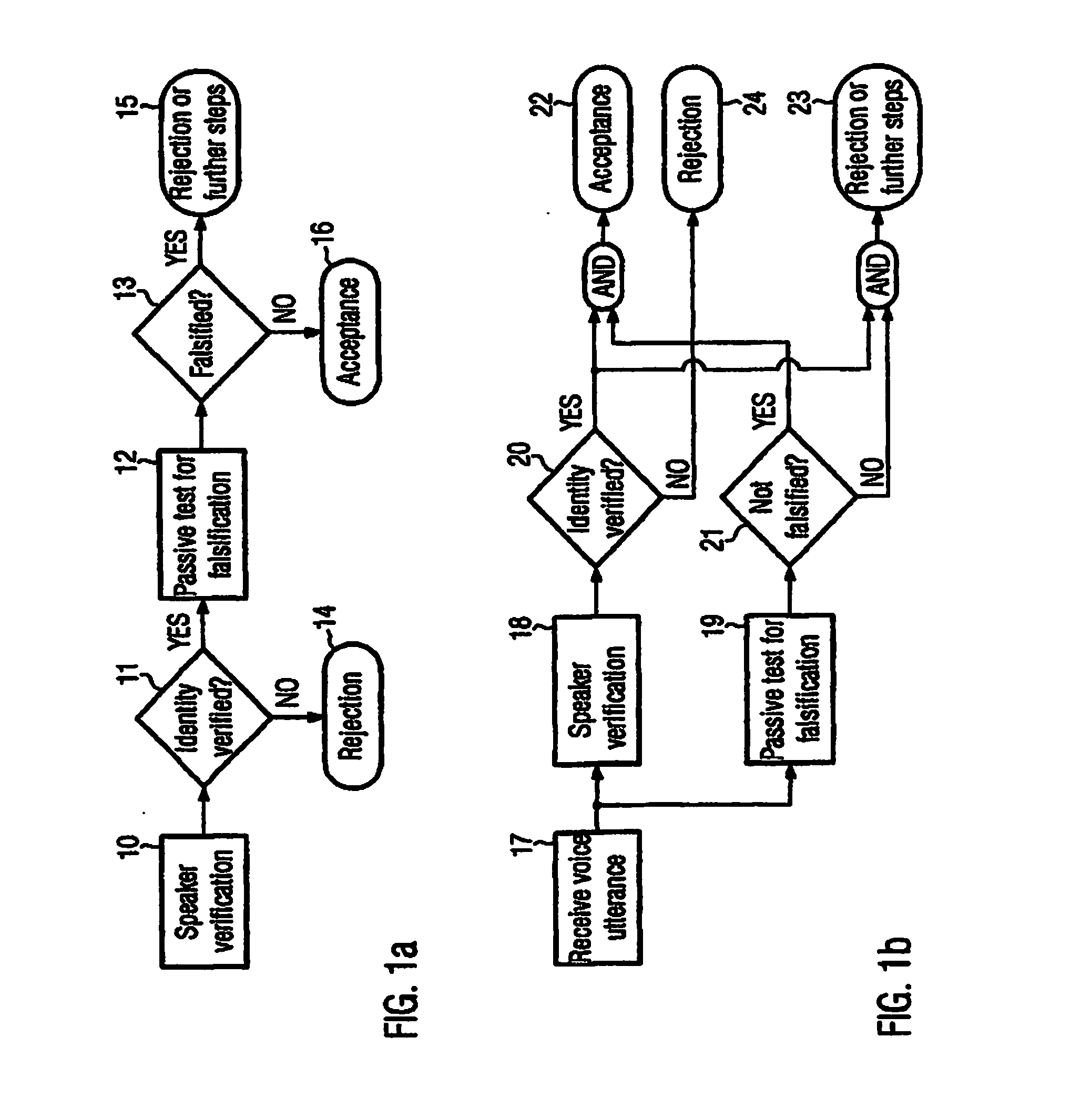
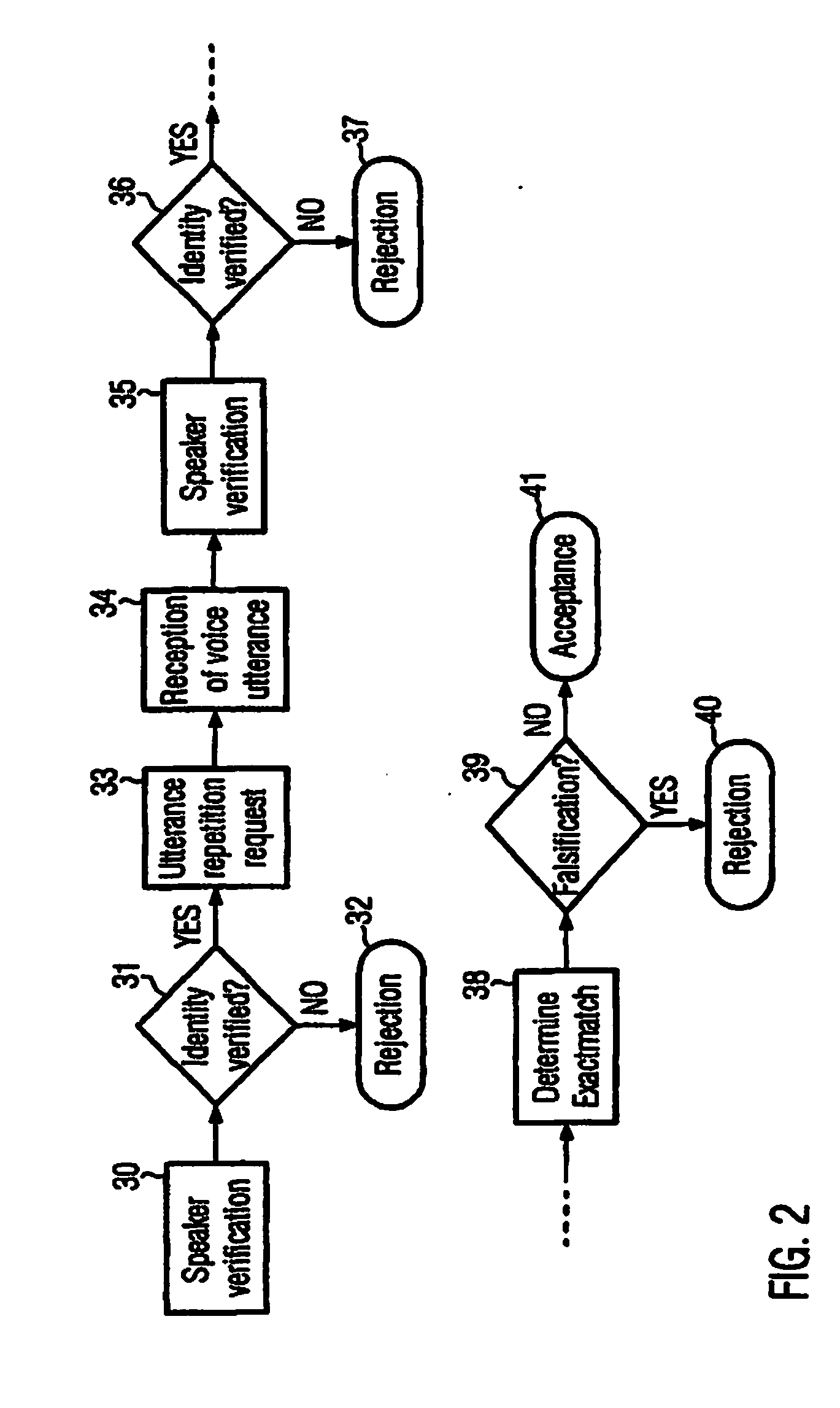
The present invention refers to a method for verifying the identity of a speaker based on the speaker's voice comprising the steps of: a) receiving a voice utterance; b) using biometric voice data to verify that the speakers voice corresponds to the speaker the identity of which is to be verified based on the received voice utterance; and c) verifying that the received voice utterance is not falsified, preferably after having verified the speakers voice; d) accepting the speaker's identity to be verified in case that both verification steps give a positive result and not accepting the speaker's identity to be verified if any of the verification steps give a negative result. The invention further refers to a corresponding computer readable medium and a computer.
Owner:AGNITIO
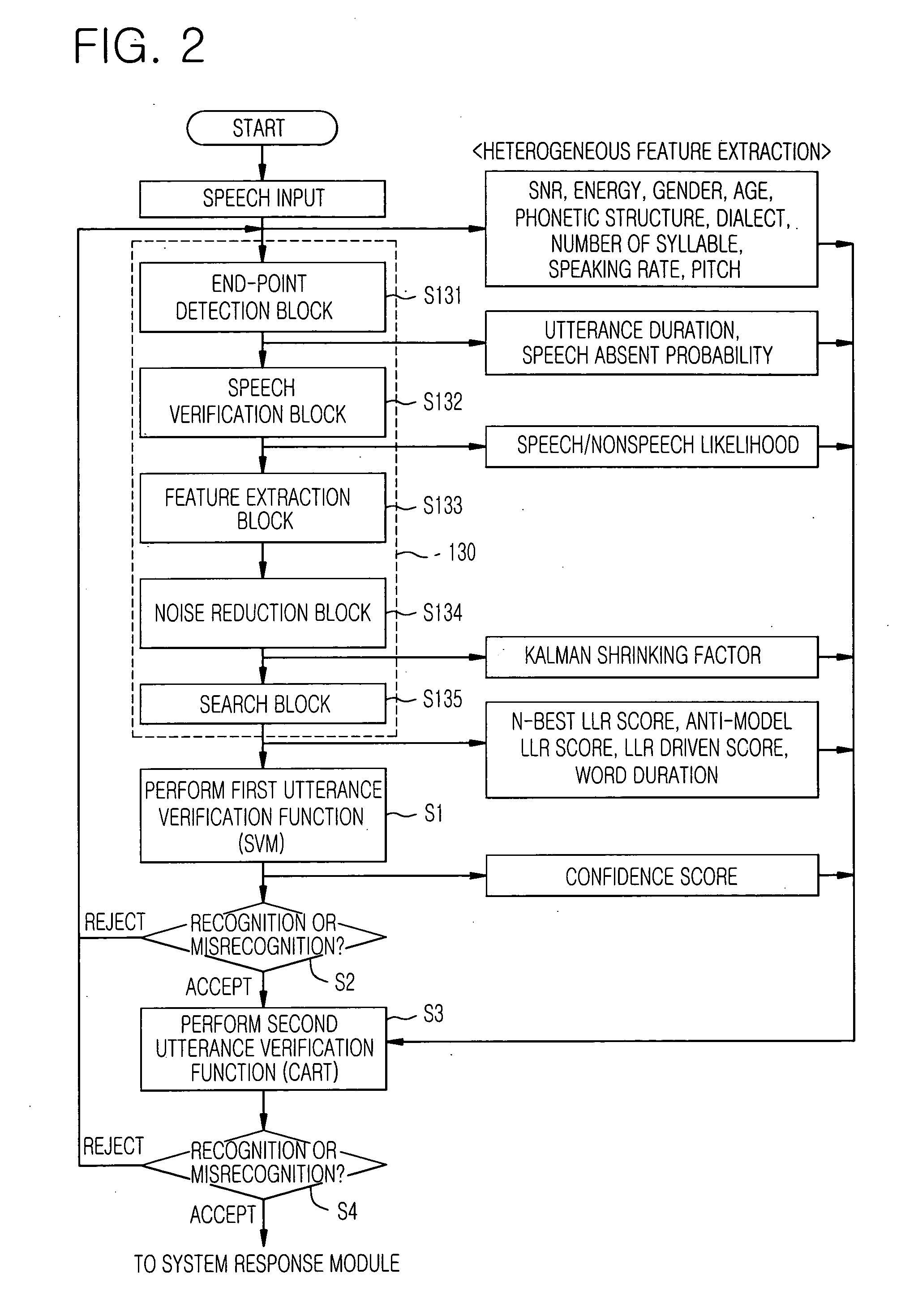
Two stage utterance verification device and method thereof in speech recognition system
InactiveUS20060136207A1Improve reliabilityQuality improvementSpeech recognitionClassification methodsFeature data
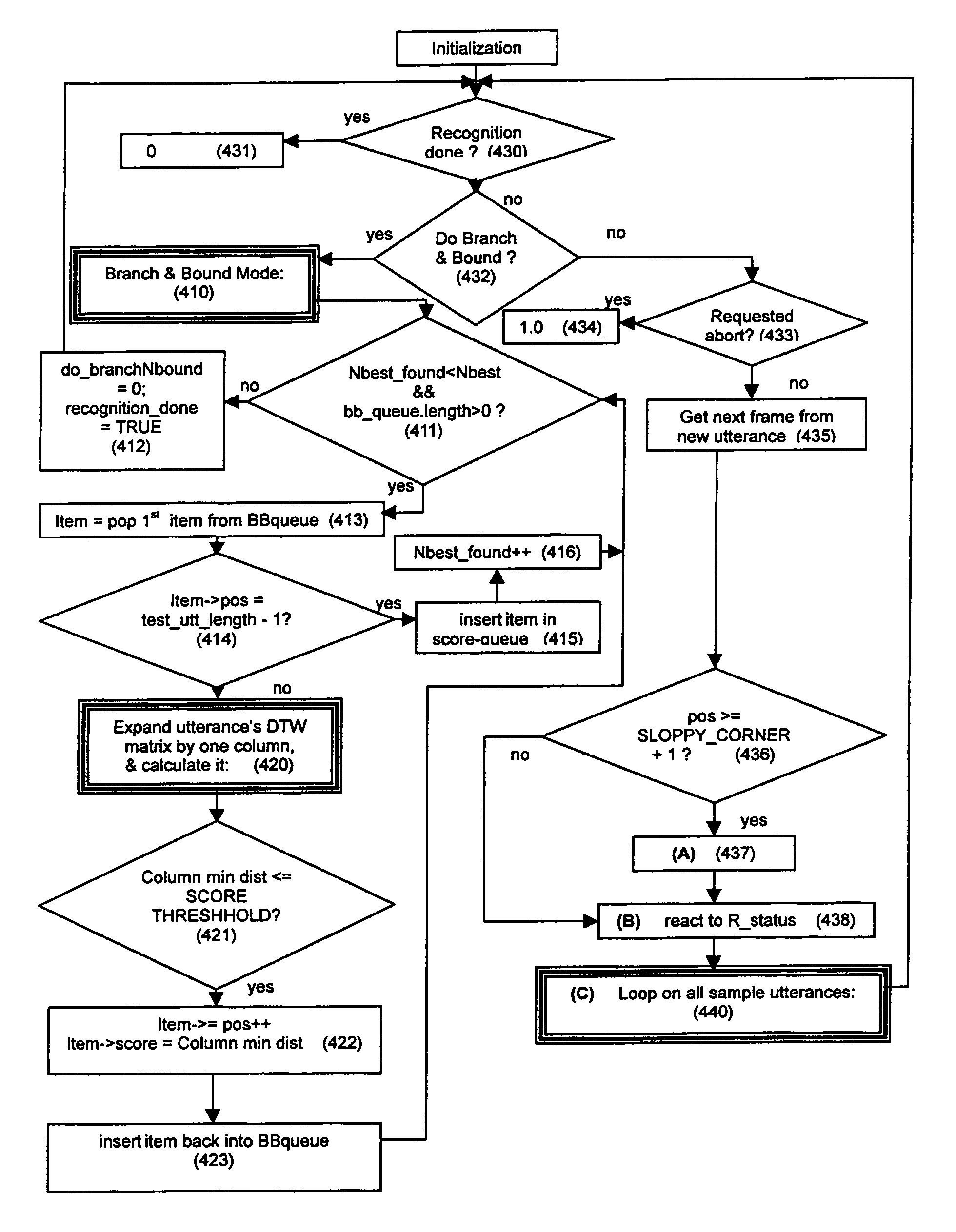
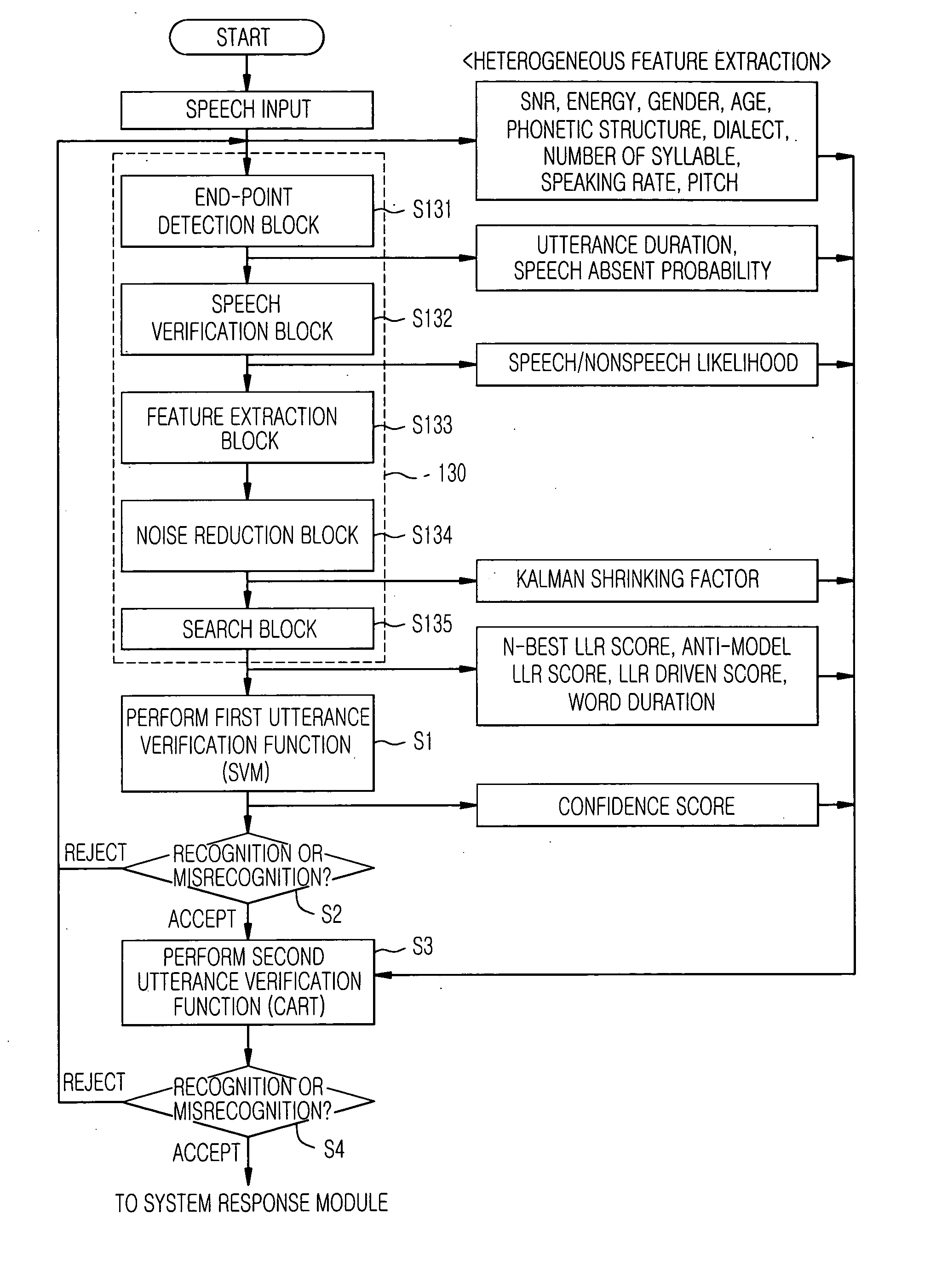
A two stage utterance verification device and a method thereof are provided. The two stage utterance verification method includes performing a first utterance verification function based on a SVM pattern classification method by using feature data inputted from a search block of a speech recognizer and performing a second utterance verification function based on a CART pattern classification method by using heterogeneity feature data including meta data extracted from a preprocessing module, intermediate results from function blocks of the speech recognizer and the result of the first utterance verification function. Therefore, the two state utterance verification device and the method thereof provide a high quality speech recognition service to a user.
Owner:ELECTRONICS & TELECOMM RES INST
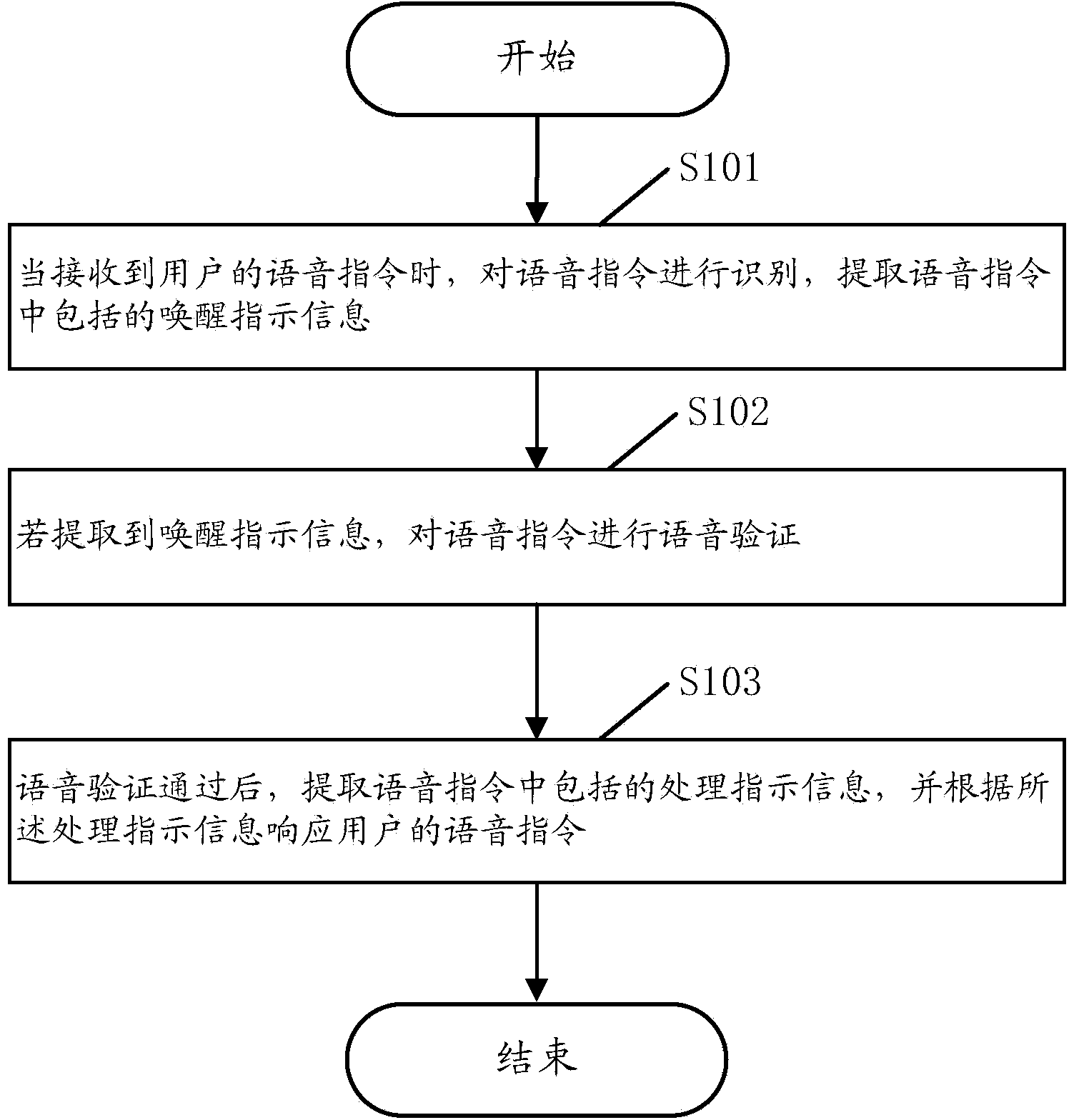
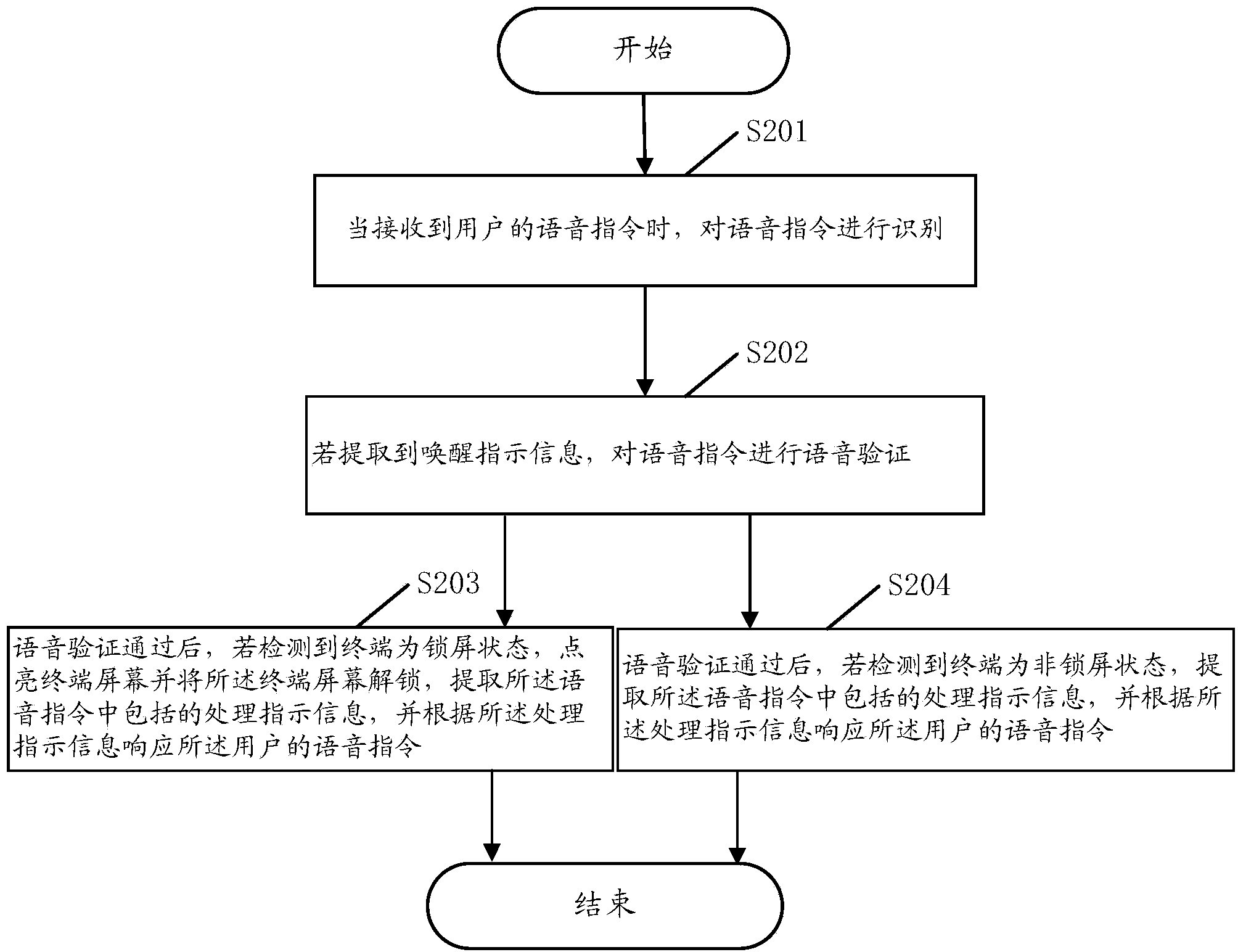
Terminal voice control method and device and terminal
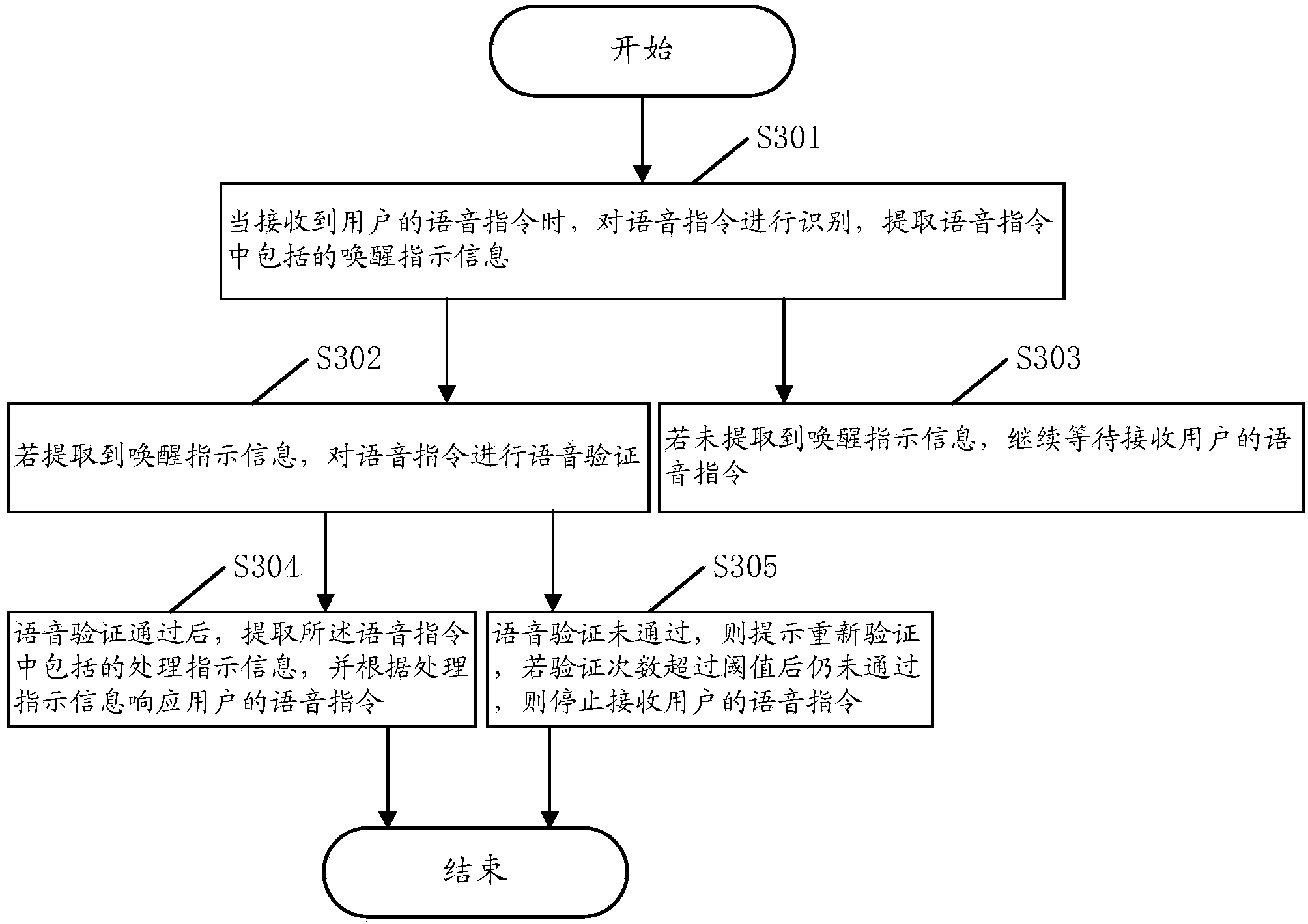
InactiveCN103595869AEasy to useImprove securityUnauthorised/fraudulent call preventionDevices with voice recognitionProcessing InstructionSpeech verification
The embodiment of the invention discloses a terminal voice control method. The terminal voice control method includes the steps that when a voice command of a user is received, the voice command is recognized, and rouse instruction information contained in the voice command is extracted; if the rouse instruction information is extracted, the voice command undergoes voice verification; after the voice command passes the voice verification, processing instruction information contained in the voice command is extracted, and the voice command of the user is responded to according to the processing instruction information. With the terminal voice control method, the user can control a terminal to finish multiple tasks through one voice command, voice interaction does not need to be carried out many times, and the method is easy to use and high in safety performance.
Owner:HUAWEI DEVICE CO LTD
Voice based caller identification and screening
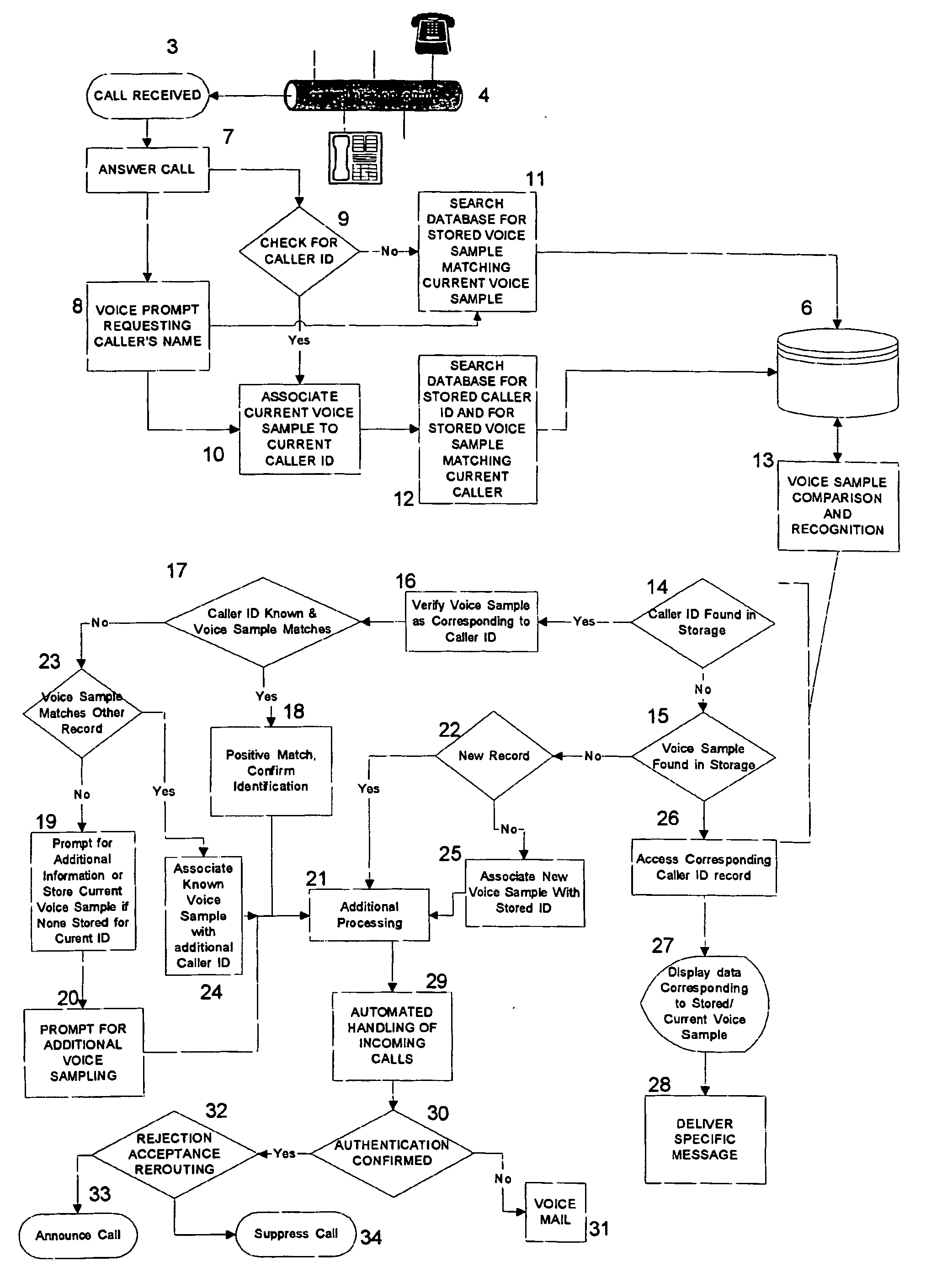
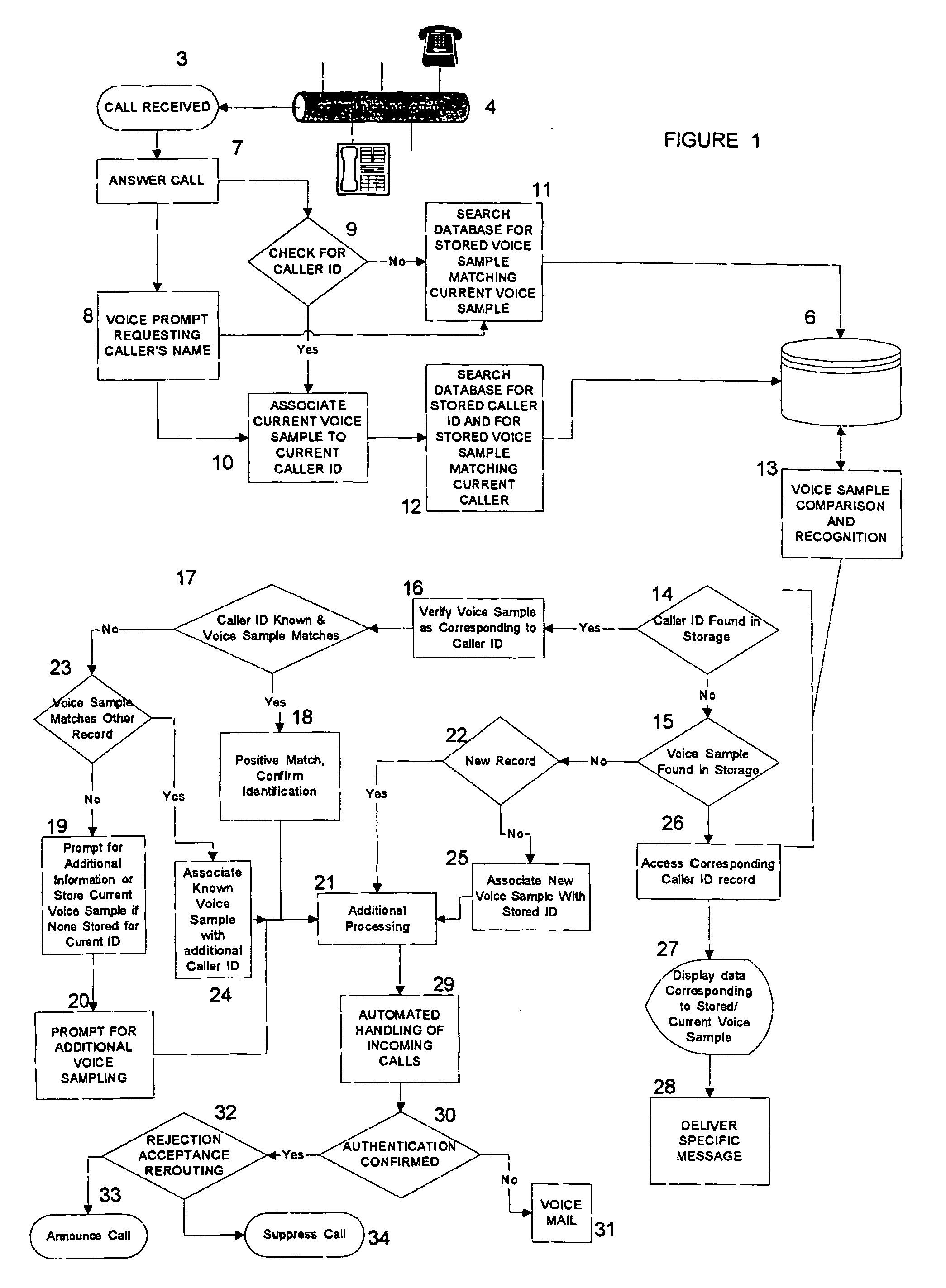
InactiveUS20080159488A1Improve accuracyReduce rejectionAutomatic call-answering/message-recording/conversation-recordingSpeech analysisThe InternetSpeech verification
Verification of Caller identification, used independently of caller ID or as an adjunct to caller ID for caller verification by matching caller voice samples to voice samples previously stored. Verification algorithms can be implemented as a stand alone device connected to the telephone line or the interne, in software which can be a resident on a PSTN phone, mobile phone or an IP phone or resident on a computer. Voice samples of the current caller are recorded and compared a database of previously recorded voice samples. When a call is received for the first time, the caller records the caller's name which is stored into a database and correlated with the received caller ID information of the present caller, if such information was received. If no caller ID information is received, the voice sample is stored in the database with an indication of a lack of caller ID information. The collection and storage of voice samples allows the use of such samples for voice authentication if the caller calls again. When a caller calls again, the caller records the caller's name as the current caller's voice sample which is compared to the stored database. The enhanced accuracy will aid in acceptance and rejection decisions as well as decisions regarding the handling of incoming telephone calls and will aid in the retrieval of additional information regarding the caller if available.
Owner:TEXAS INSTR INC
Payment method and system of voice recognition terminal
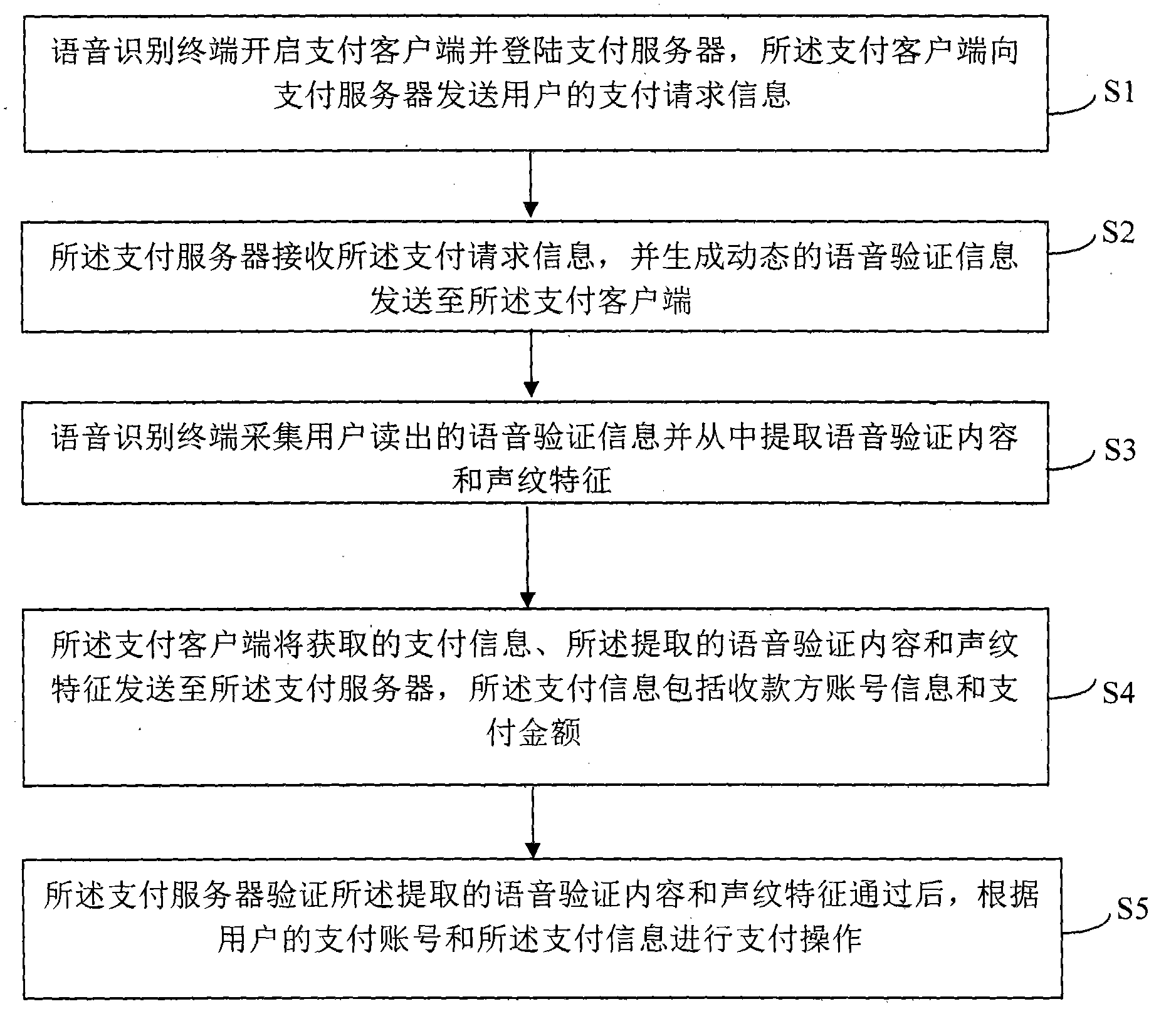
InactiveCN104392353AImprove securityImprove reliabilityDigital data authenticationSpeech recognitionUser verificationPayment
The invention relates to a payment method and system of a voice recognition terminal. According to the method, a voice recognition terminal logs in a payment server and sends a payment request of a user; the payment server generates dynamic voice verification information and carries out returning; the voice recognition terminal collects the voice verification information read out by the user and extracts a voice verification content and a voice print feature from the information; a payment client sends the obtained payment information, voice verification content, and voice print feature to the payment server; and after verifying the voice verification content and the voice print feature successfully, the payment server carries out payment operation according to the payment account number and payment information of the user. According to the technical scheme of the invention, the legal identity of the user is verified based on the voice print verification and identification; and because the voice verification content is generated dynamically and is changed randomly, a phenomenon that the user verification voice is intercepted and copied can be prevented, thereby improving security and reliability of the voice identity authentication.
Owner:WUXI BIOKEE BIOMETRICS TECH
Telephonic certification of electronic death registration
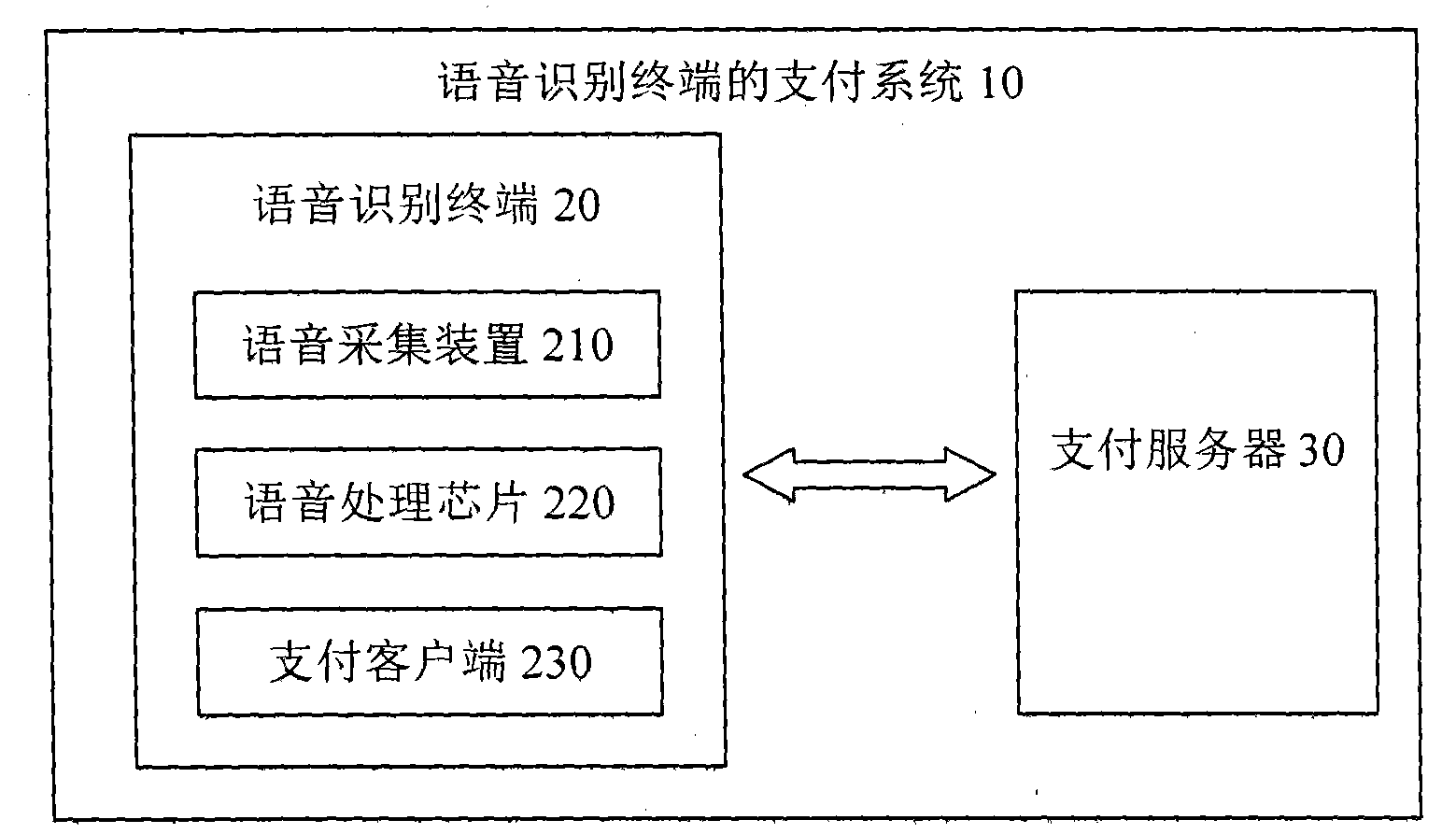
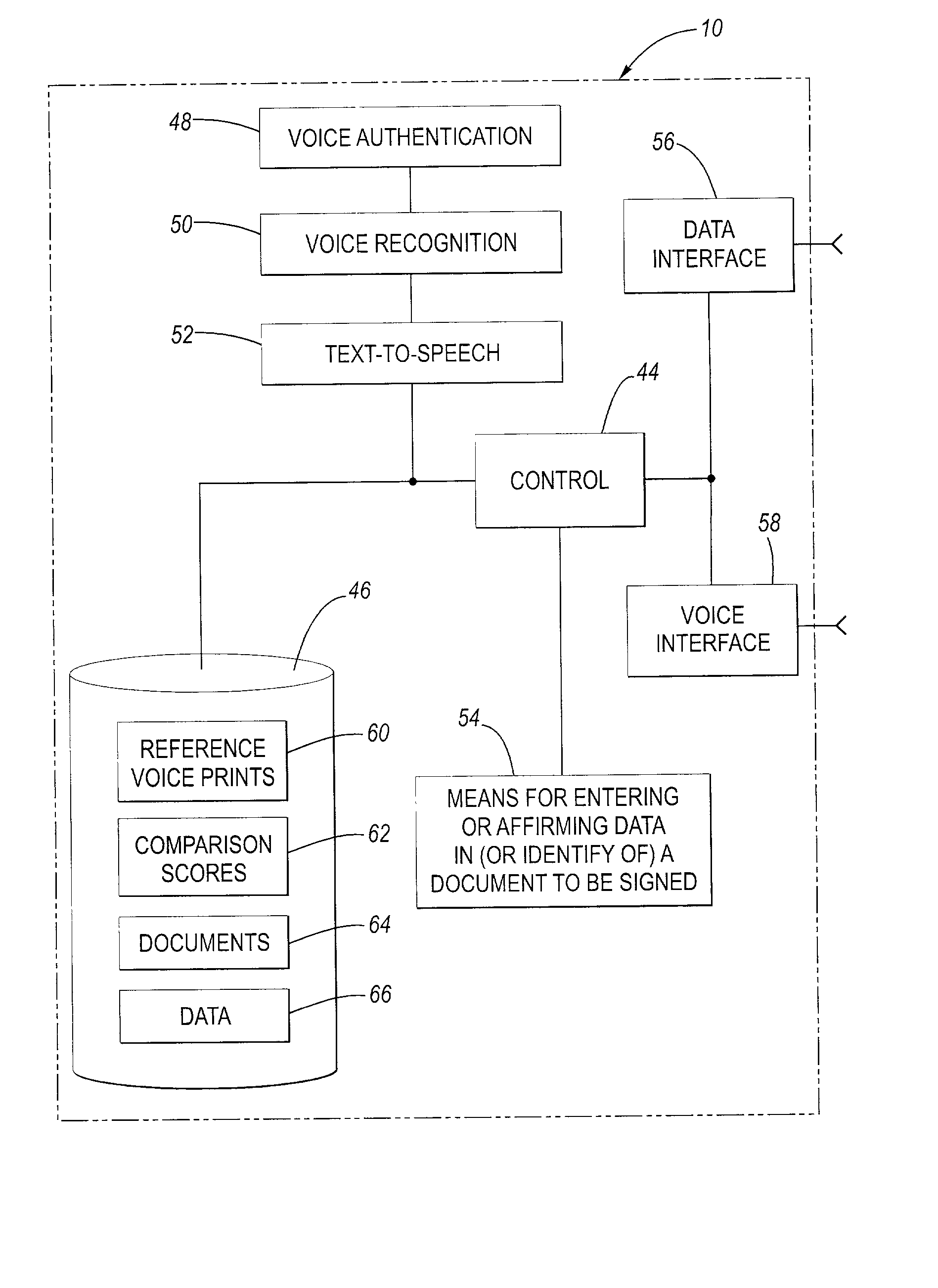
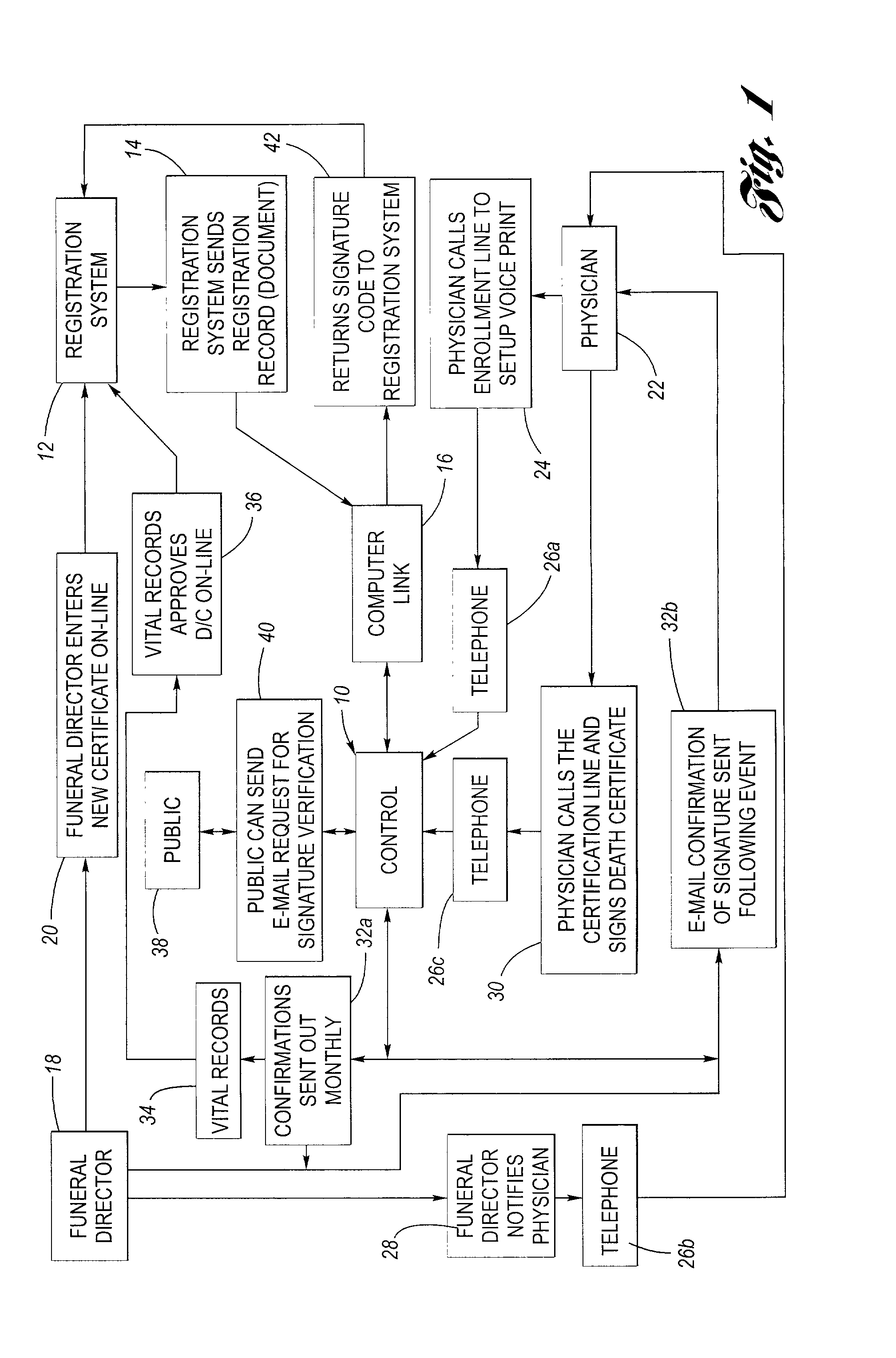
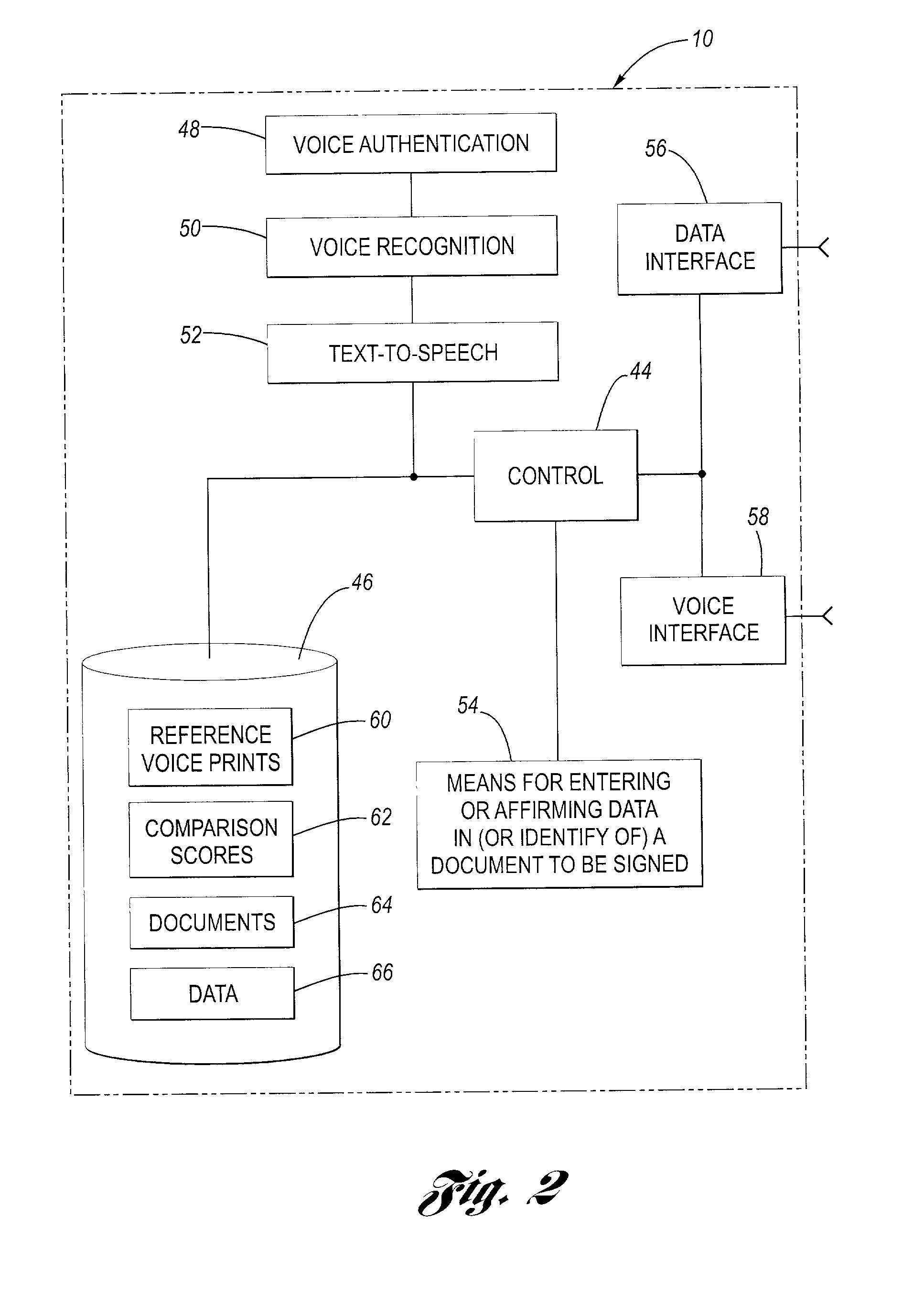
InactiveUS20020128844A1Use and accurate and secure and rapidFacilitate entering or affirming dataUser identity/authority verificationSpeech analysisUsabilitySpeech verification
A system for facilitating an electronic signature of a document such as a death certificate includes a voice authentication unit, a voice recognition and a database for storing information relating to the electronic signature ceremony. The system includes an enrollment interface to telephonically receive a reference voiceprint from a future signer of the death certificate, for example a physician. The system is further configured to receive an authentication voiceprint from the enrolled physician wherein the voice authentication unit compares the reference voiceprint and the authentication voiceprint to confirm identity. The system employs the voice recognition unit to allow the physician to telephonically perform at least one of the functions selected from the group including (i) identifying the death certificate, (ii) entering data into the death certificate, or (iii) affirming data that is in the death certificate. The system provides improved ease of use, more rapid and accurate signing of death certificates and is more secure than prior systems.
Owner:TELEPHONIC SIGNATURES
Voice authentication system
InactiveUS20080172230A1Improve authentication accuracyImprove accuracySpeech recognitionSyllableSpeech verification
A text-dependent voice authentication system that performs authentication by urging a user to input a keyword by voice includes: an input part (11) that receives a voice input of a keyword divided into a plurality of portions with an utterable unit being a minimum unit over a plurality of times at a time interval for each of the portions; registered speaker-specific syllable model DB (20) that previously stores a registered keyword of a user as a speaker model created in the utterable unit; a feature value conversion part (12) that obtains a feature value of a voice contained in a portion of the keyword received by the first voice input in the input part (11) from the portion; a similarity calculation part (13) that obtains a similarity between the feature value and the speaker model; a keyword checking part (17) that determines whether or not voice inputs of all the syllables or phonemes configuring an entire registered keyword by the plurality of times of voice inputs, based on the similarity obtained in the similarity calculation part; and an authentication determination part (19) that determines whether to accept or reject authentication, based on a determination result in the keyword checking part and the similarity obtained in the similarity calculation part.
Owner:FUJITSU LTD
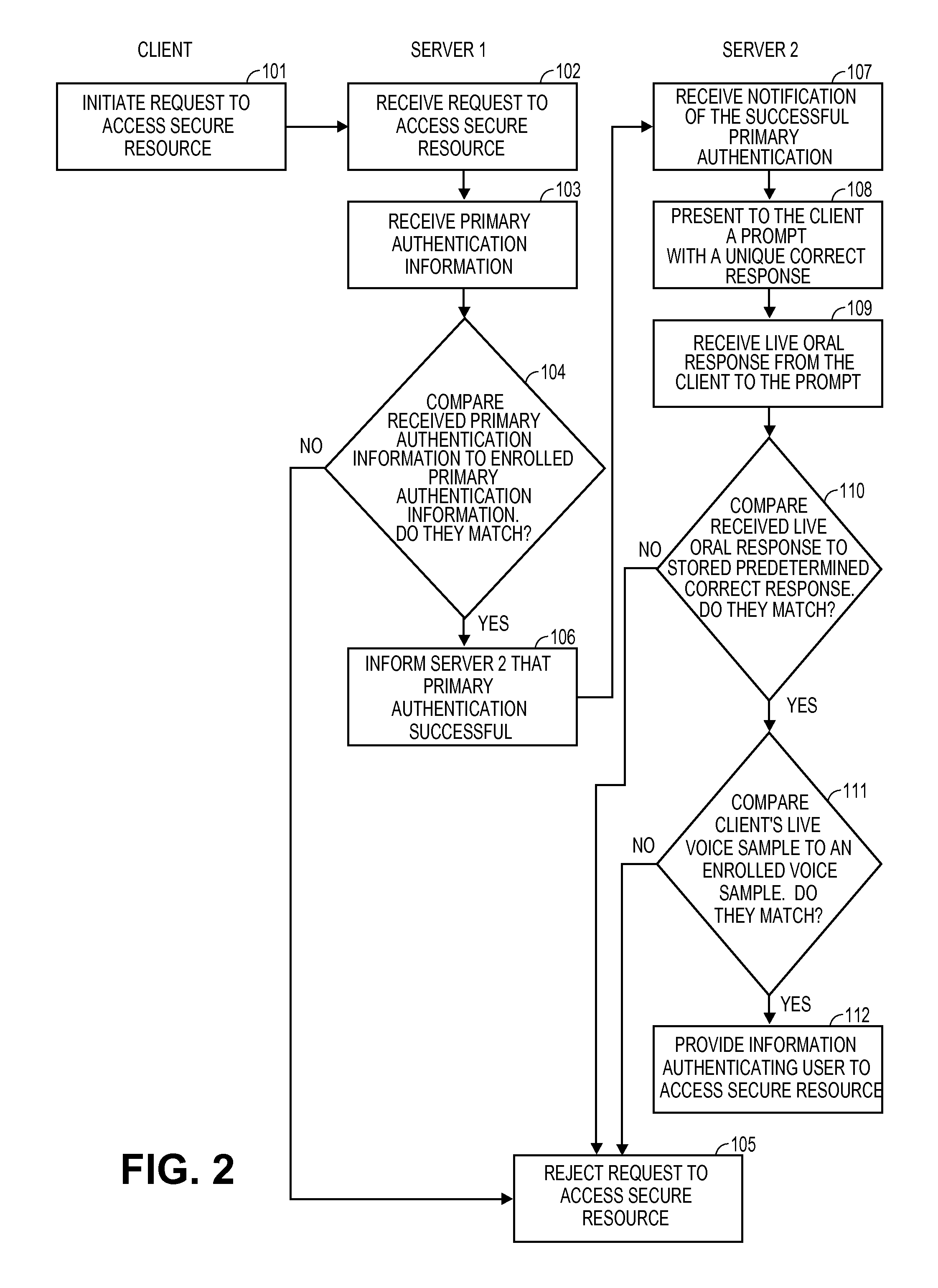
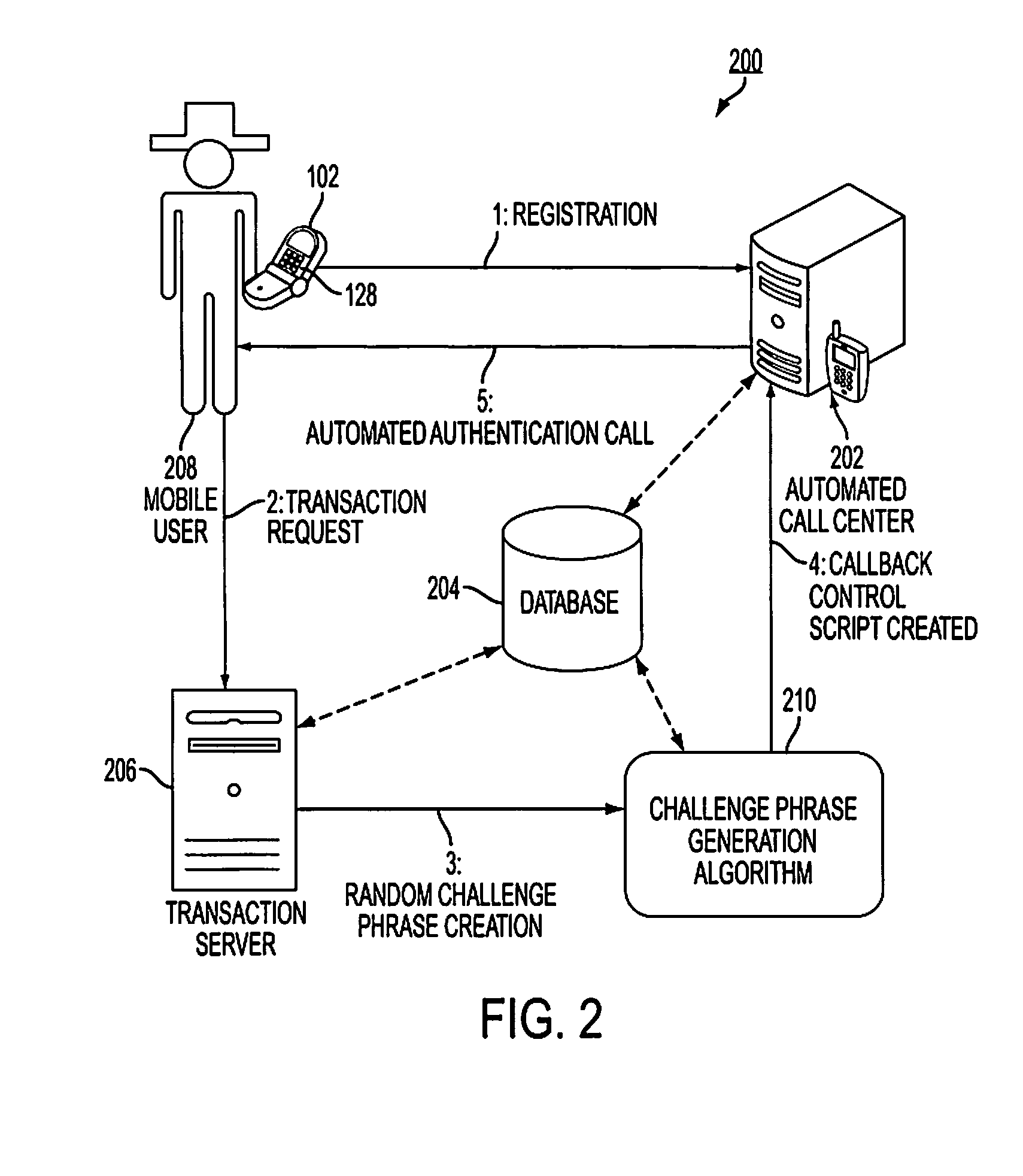
Computer program, method, and system for voice authentication of a user to access a secure resource
InactiveUS20120253810A1Prevent imitationDigital data authenticationSpeech recognitionLive voiceCorrect response
Authenticating a purported user attempting to access a secure resource includes enrolling a user's voice sample by requiring the user to orally speak preselected enrollment utterances, generating prompts and respective predetermined correct responses where each question has only one correct response, presenting a prompt to the user in real time, and analyzing the user's real time live response to determine if the live response matches the predetermined correct response and if voice characteristics of the user's live voice sample match characteristics of the enrolled voice sample.
Owner:PHONEFACTOR
Distributed conference bridge and voice authentication for access to networked computer resources
InactiveUS20080253549A1Digital data information retrievalMultiplex communicationComputer resourcesVocal response
Owner:MICROSOFT TECH LICENSING LLC
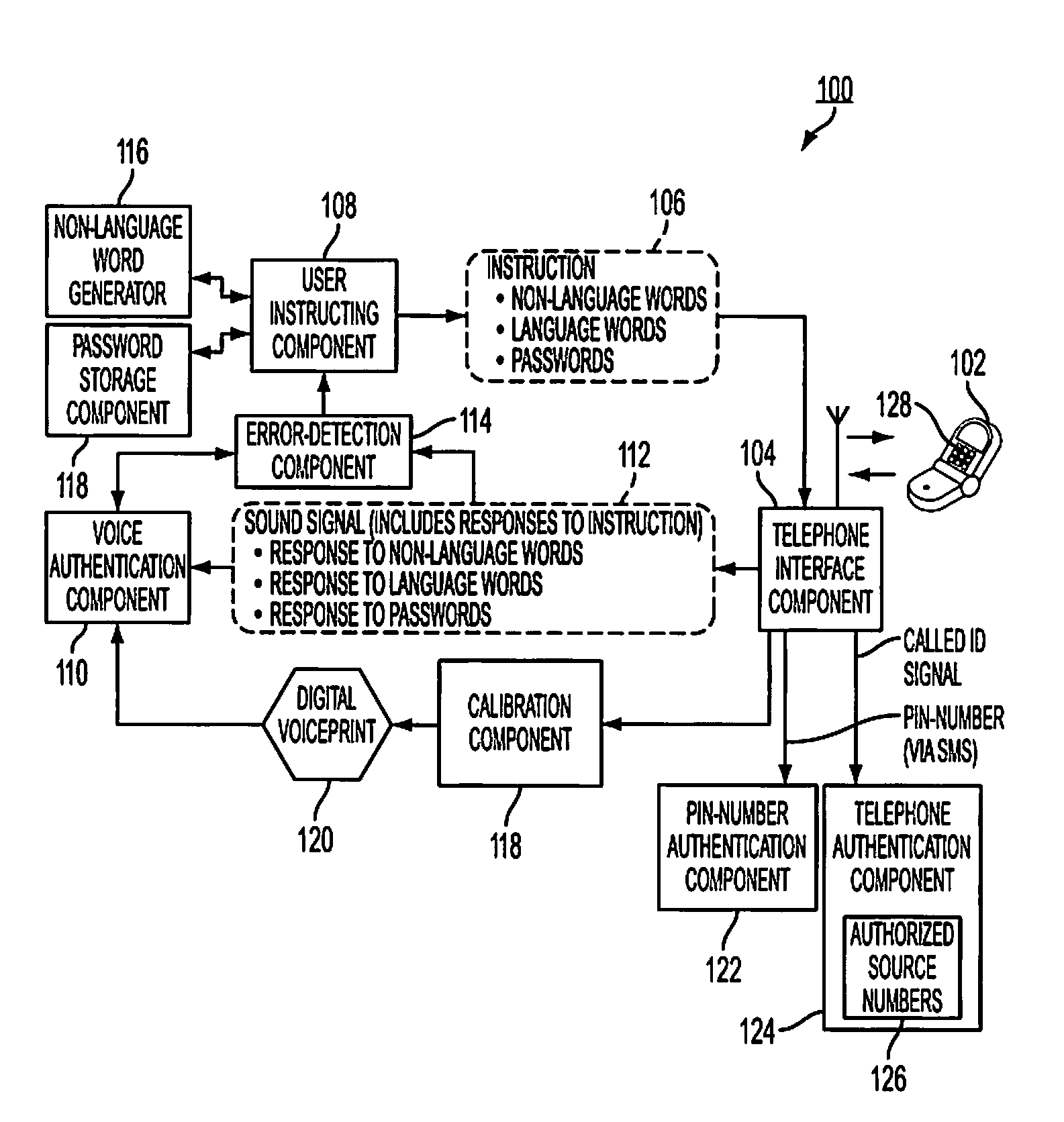
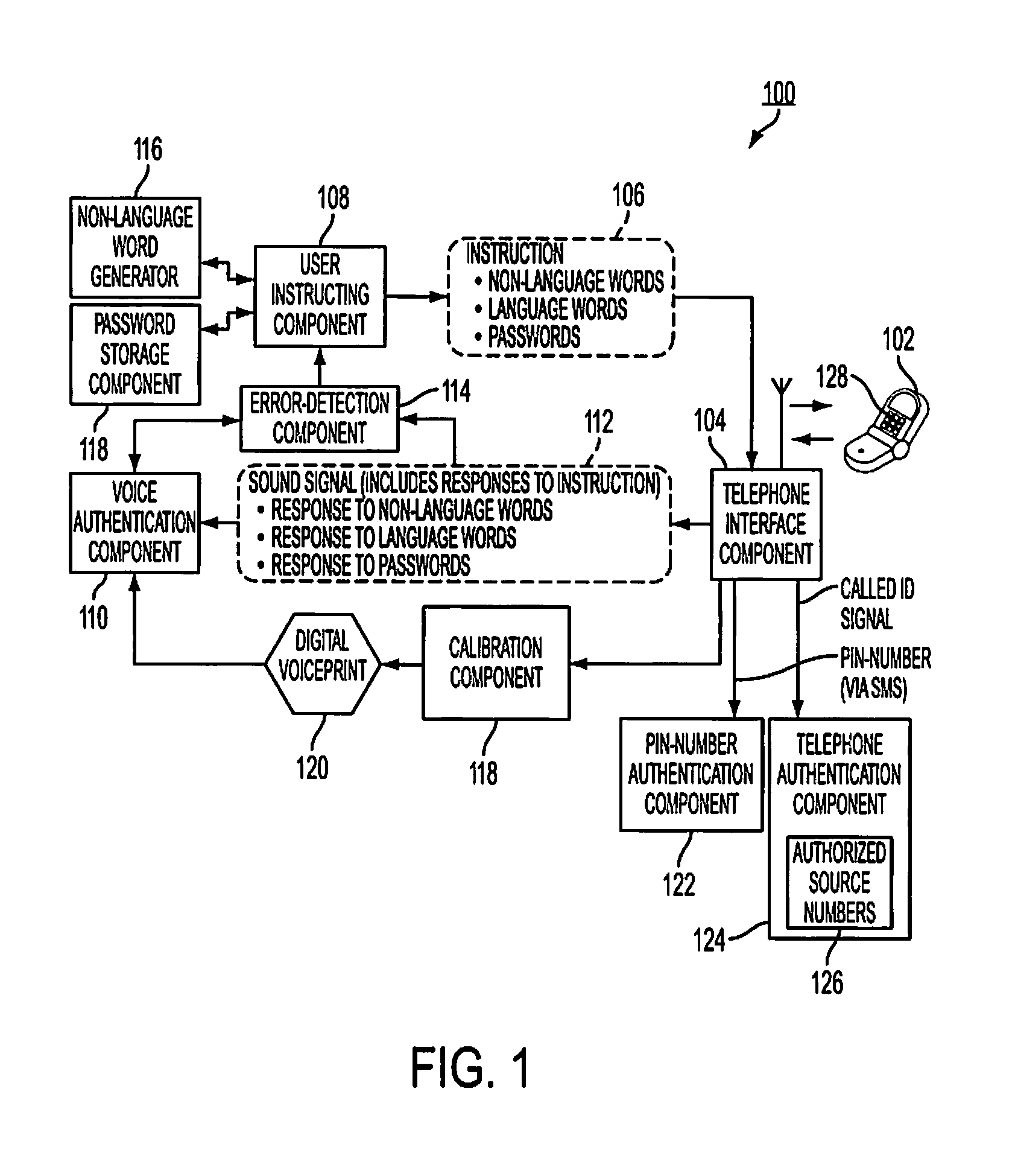
System and method for user authentification using non-language words
ActiveUS20100106975A1Digital data processing detailsUser identity/authority verificationUser authenticationSpeech verification
A system and method for user authentication include a user instructing component and a voice authentication component. The user instructing component generates an instruction for authenticating a voice of a user. The instruction includes a first instruction to recite one or more non-language words. The voice authentication component analyzes a sound signal which includes a response to the instruction. The voice authentication component can authenticate the voice of the user using the response to the instruction including a response to the first instruction to recite the one or more non-language words.
Owner:XEROX CORP
Methods and systems for voice authentication service leveraging networking
ActiveUS20150082404A1Digital data information retrievalDigital data processing detailsInternet Authentication ServiceDatabase services
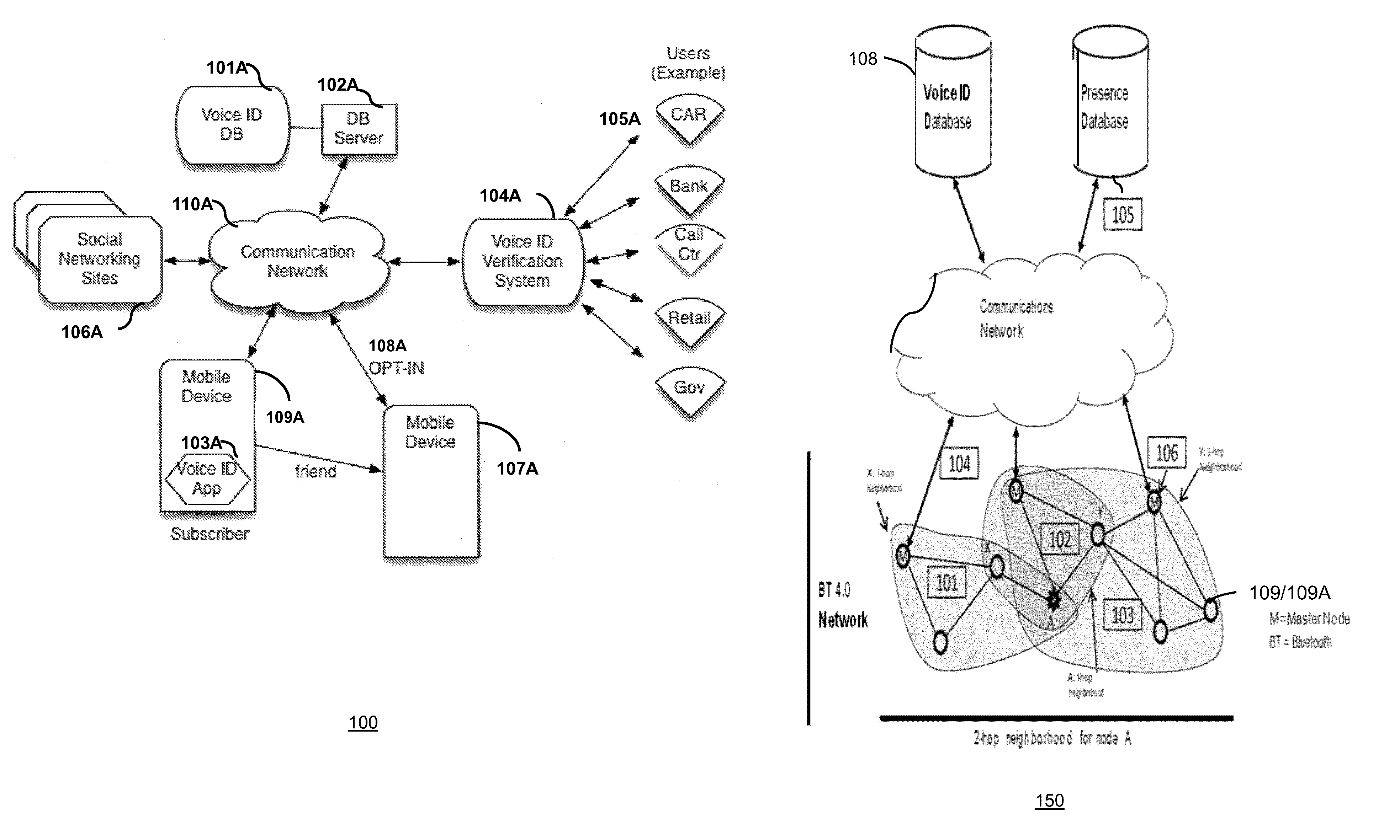
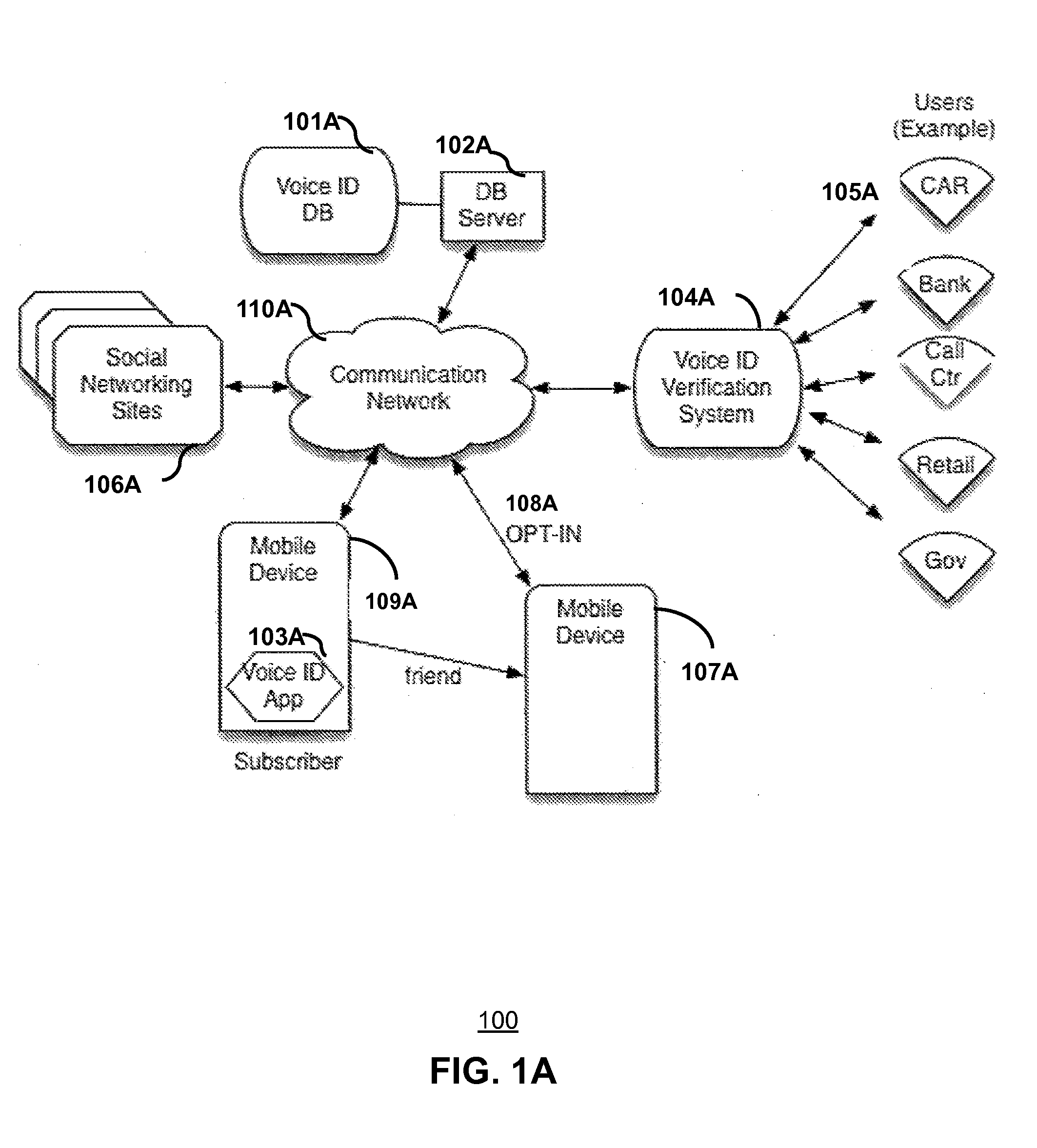
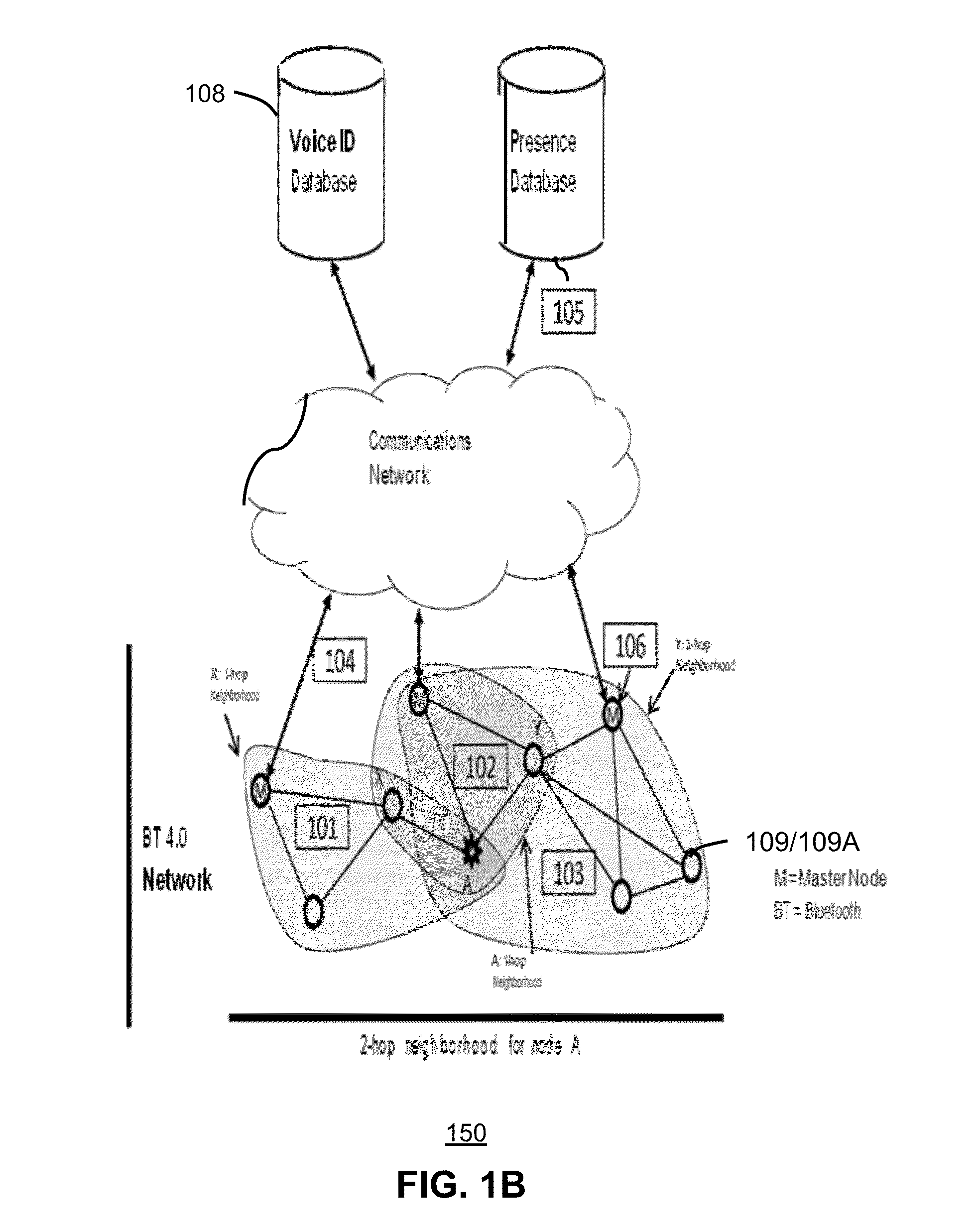
A method and system for persona authentication includes obtaining from a server a presence list of devices at a location, refining the presence list according to a user profile of the devices thereby forming a dynamic presence list, capturing at least one biometric input from at least one of the devices, authenticating a persona of an individual at the location according to the biometric input and the user profiles in the dynamic presence list, and presenting at least one descriptor of the persona of the individual. In one embodiment, voice authentication uses a centralized voice id database service in conjunction with a Bluetooth 4.0 UUID service to obtain multi-modal biometric user data. Other embodiments are disclosed
Owner:STATON TECHIYA LLC
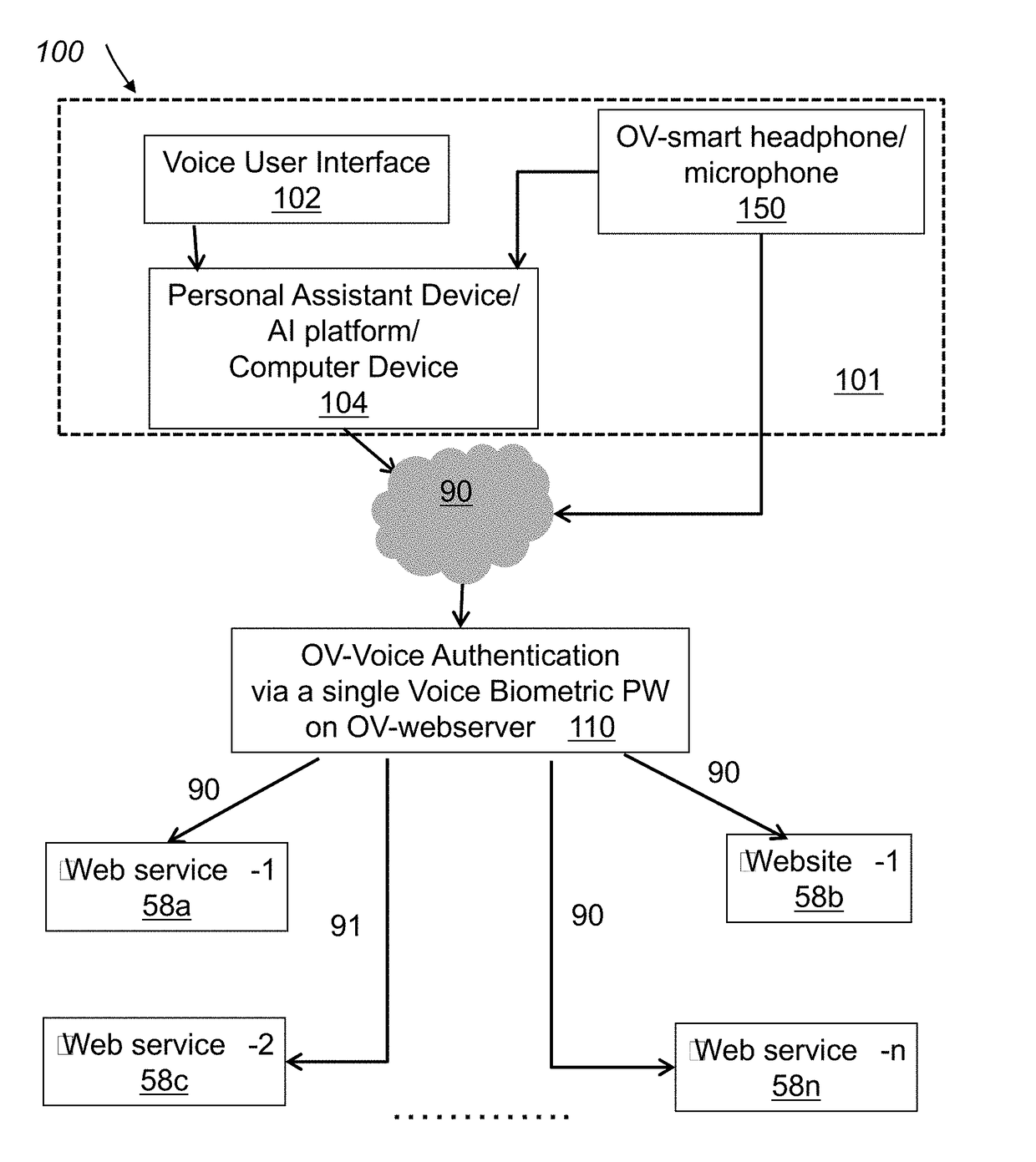
System and method for voice authentication
A system and a method for single sign-on voice authentication that provides access to multiple voice recognition and artificial intelligence platforms, to multiple devices and to multiple third party web service systems.
Owner:OV LOOP INC
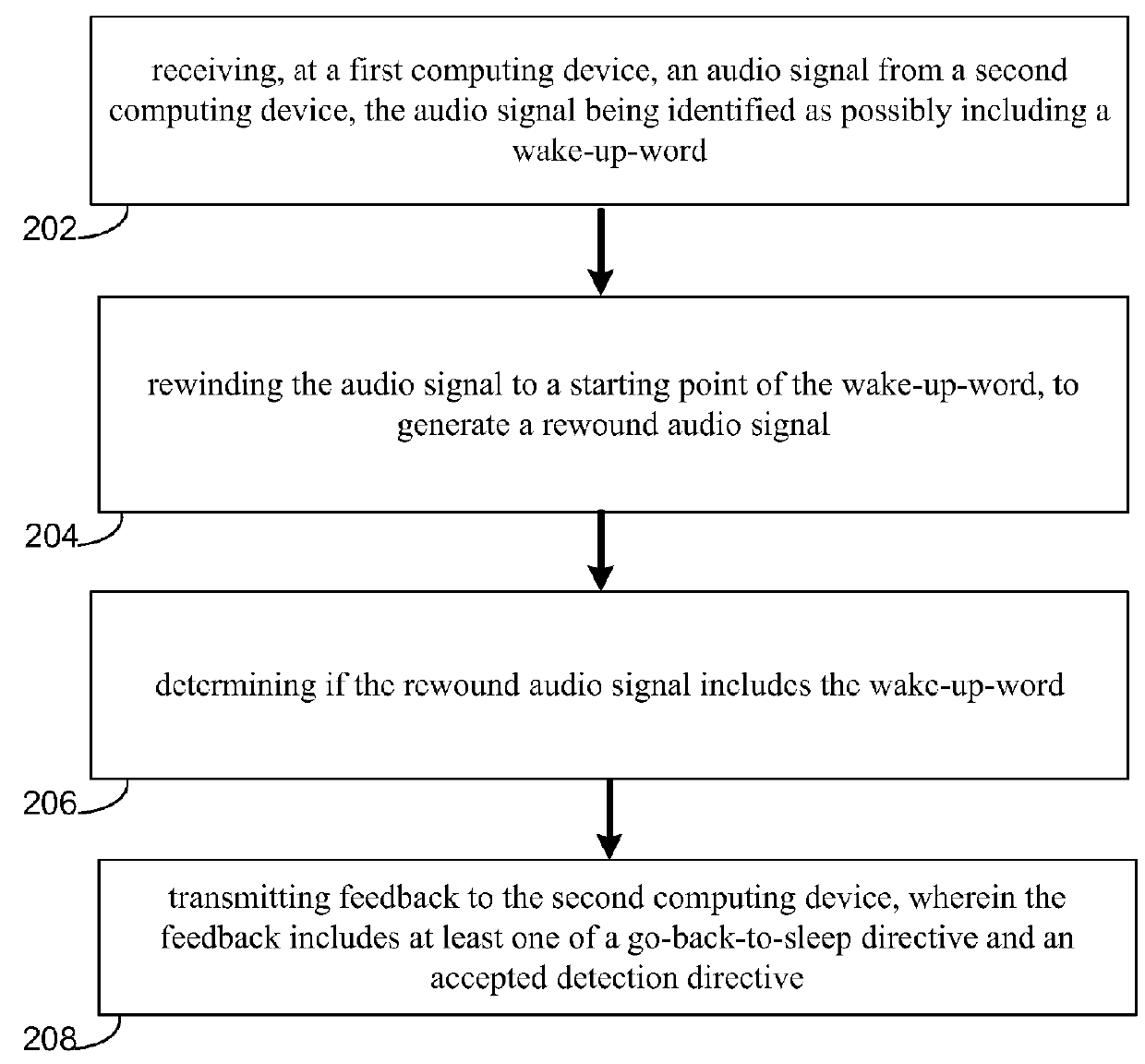
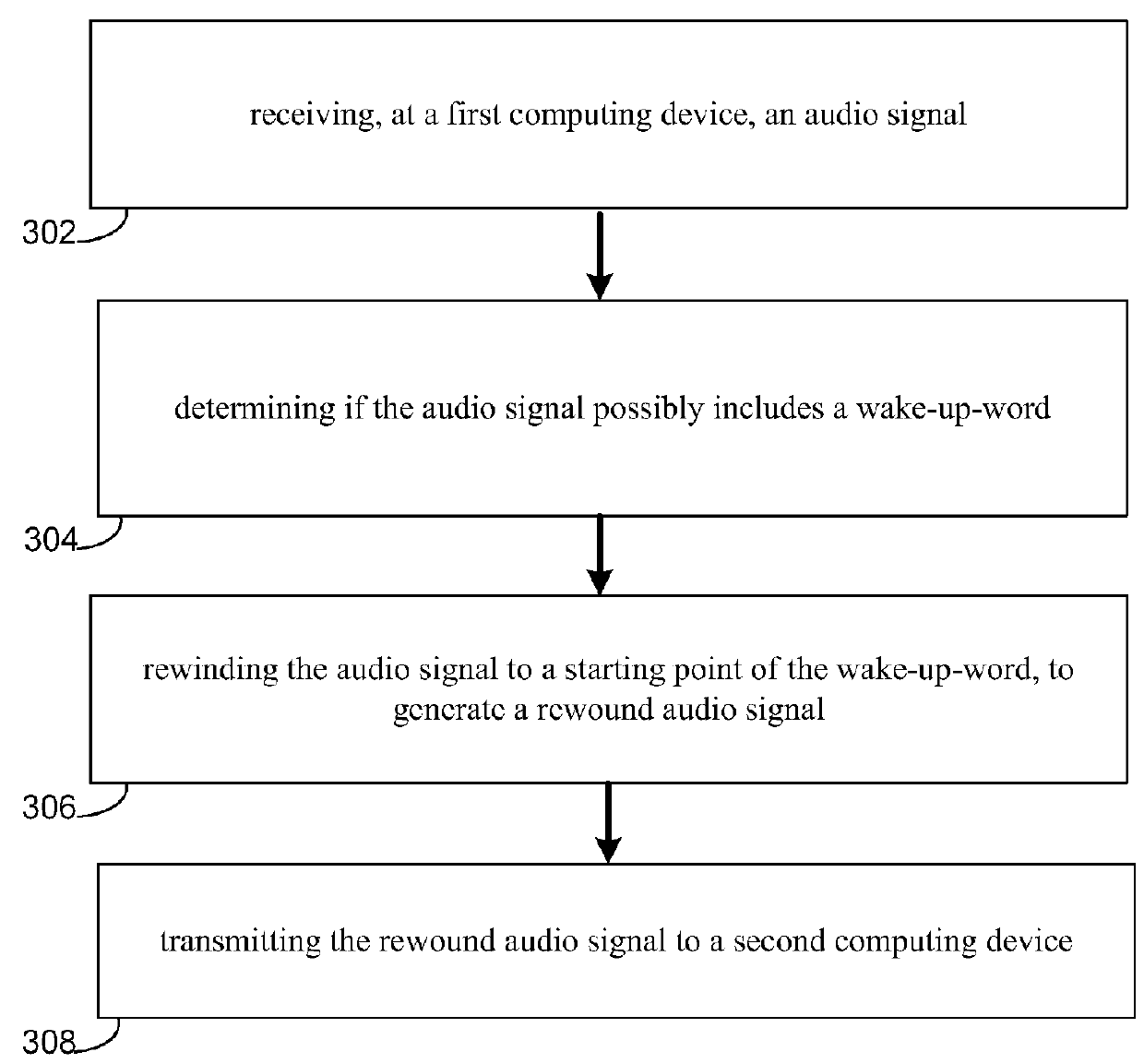
System and method for speech validation
InactiveUS20160055847A1Improve pronunciationSound input/outputSpeech recognitionSpeech verificationSpeech sound
A system and method for validating a wake-up-word. Embodiments of the present disclosure may include receiving, at a first computing device, an audio signal from a second computing device, the audio signal being identified as possibly including a wake-up-word. Embodiments may further include rewinding the audio signal to a starting point of the wake-up-word, to generate a rewound audio signal. Embodiments may also include determining if the rewound audio signal includes the wake-up-word. Embodiments may further include transmitting feedback to the second computing device, wherein the feedback includes at least one of a go-back-to-sleep directive and an accepted detection directive.
Owner:NUANCE COMM INC
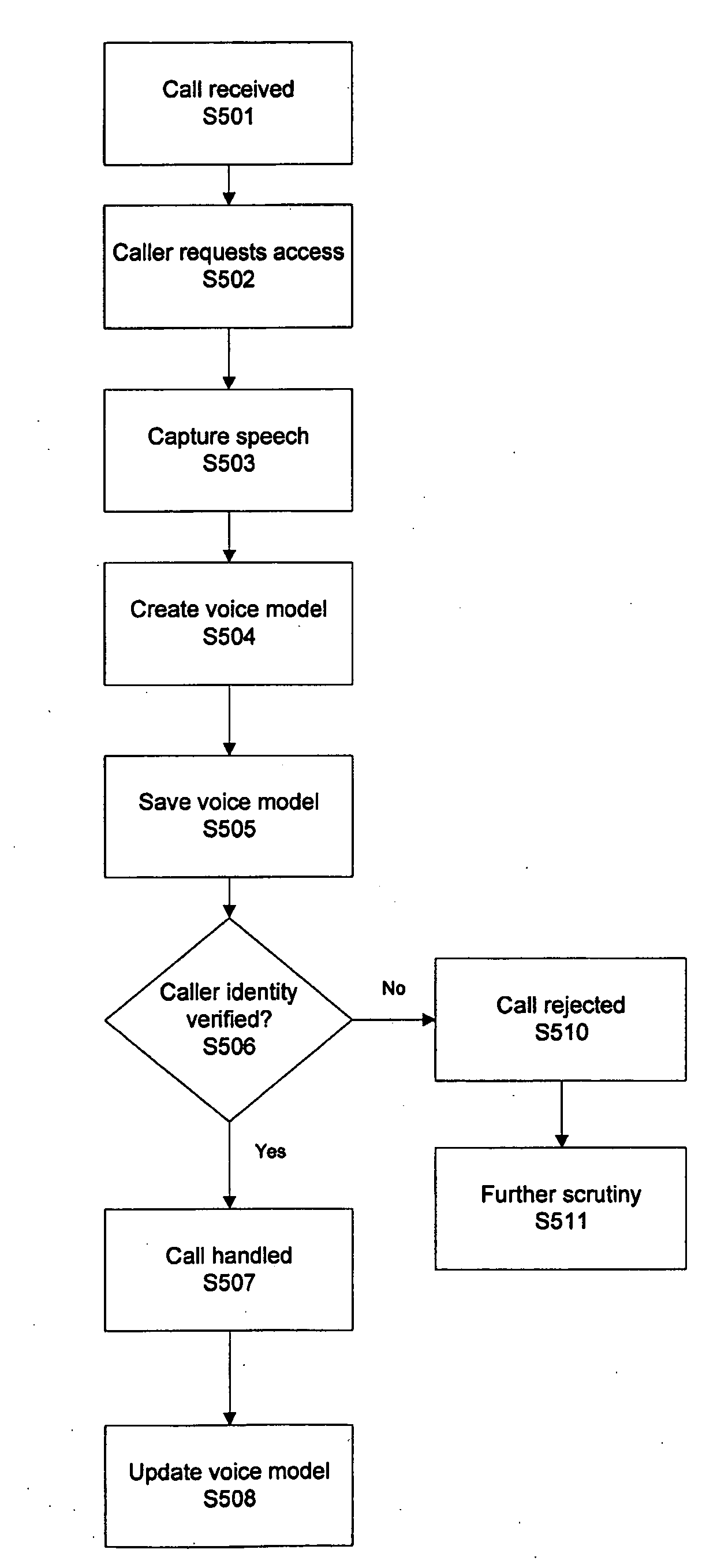
Transparent voice registration and verification method and system
ActiveUS20100027767A1Automatic call-answering/message-recording/conversation-recordingSpecial service for subscribersValidation methodsSpeech verification
Transparent voice registration of a party is provided in order to provide voice verification for communications with a service center. Verbal communication spoken by a party during interaction between the party and an agent of the service center is captured. A voice model associated with the captured communication is created and stored in order to provide voice verification during a subsequent call to the service center. When a requester contacts the service center, a comparison of the voice of the requester and a voice model of the person that the requester claims to be is performed, in order to verify the identity of the requester. Additionally, a voice model associated with a party is automatically updated after a subsequent communication between the party and the service center.
Owner:INTERACTIONS LLC (US)
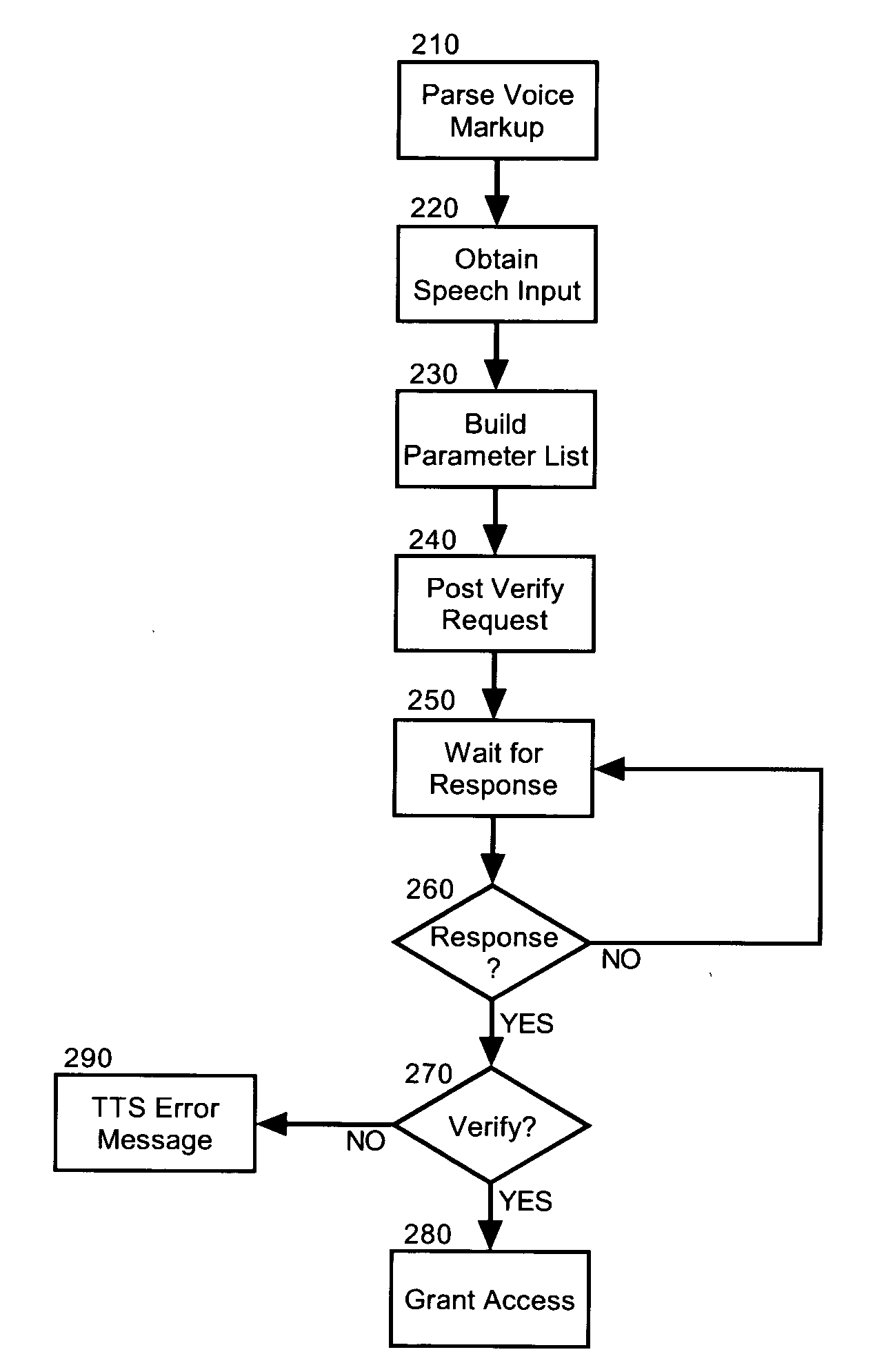
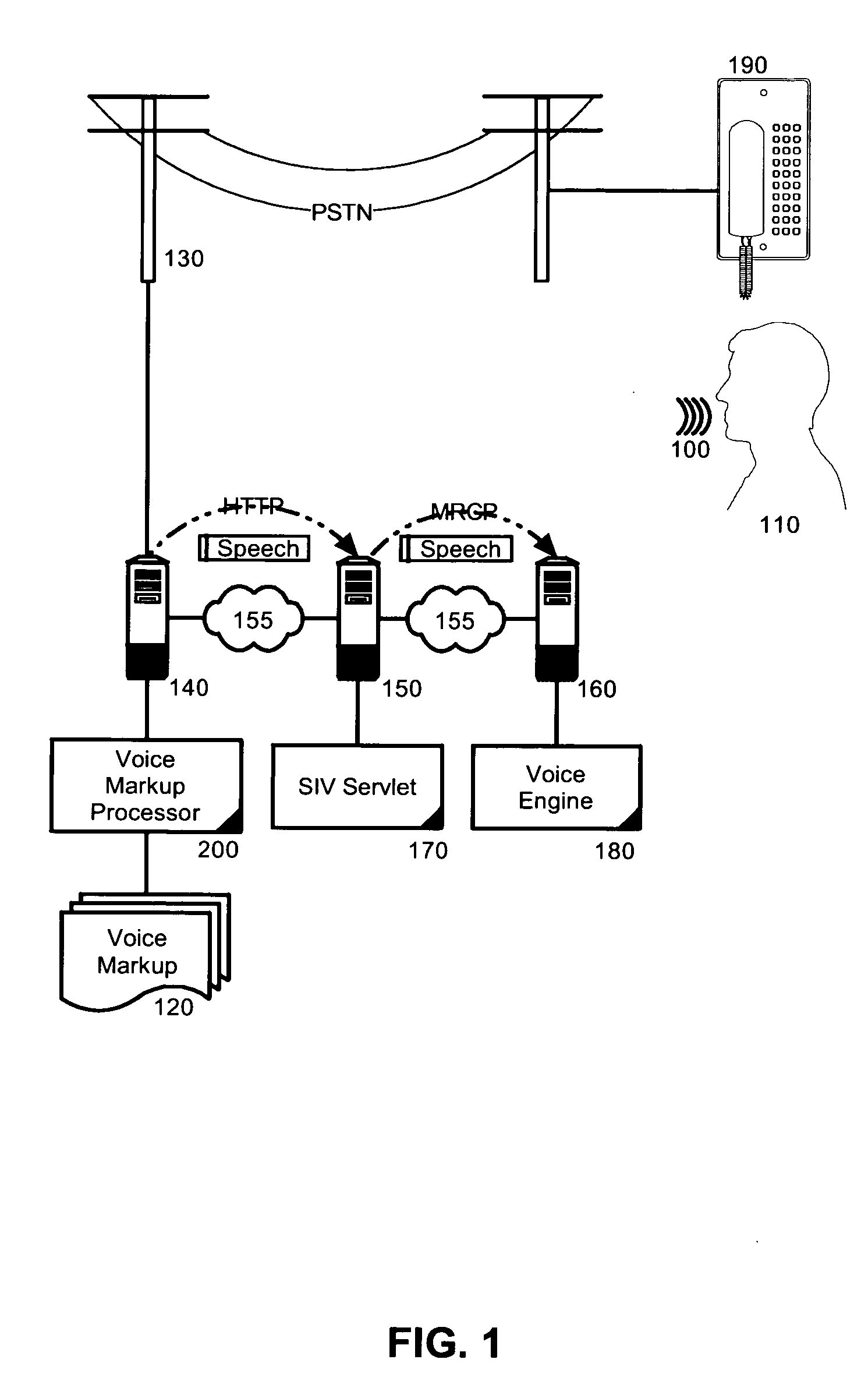
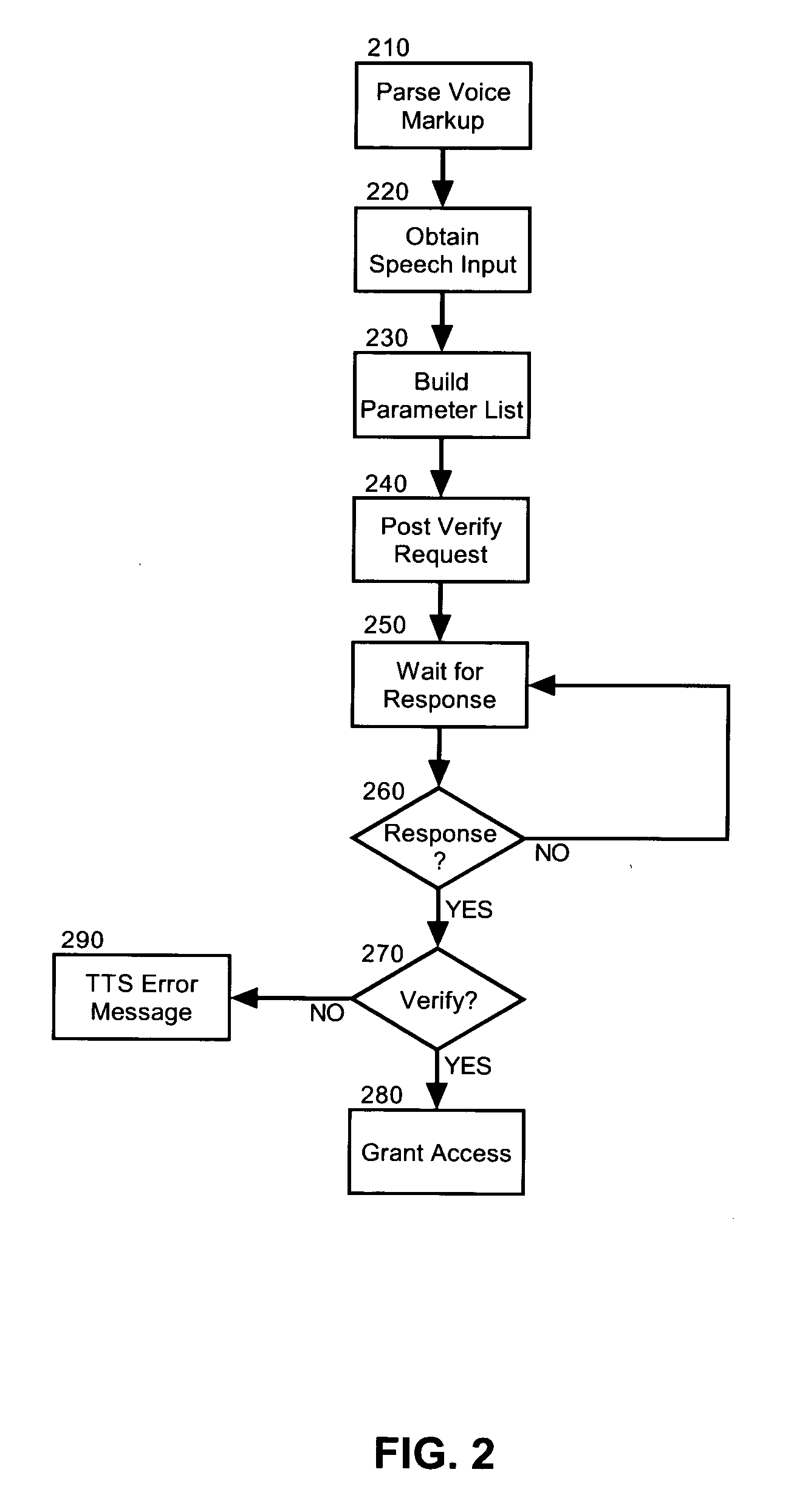
Speaker identification and voice verification for voice applications
Embodiments of the present invention address deficiencies of the art in respect to voice markup processing and provide a method, system and computer program product for speaker identification and voice verification in a voice processing system. In one embodiment, a speaker identification and voice verification data processing system can include a voice markup processor configured to process voice markup defining a voice application and server side logic enabled to be communicatively coupled to the voice markup processor and to a voice engine programmed for speaker identification and voice verification. For example, the voice engine can be programmed to provide speaker identification and voice verification using speaker identification verification (SIV) technology.
Owner:NUANCE COMM INC
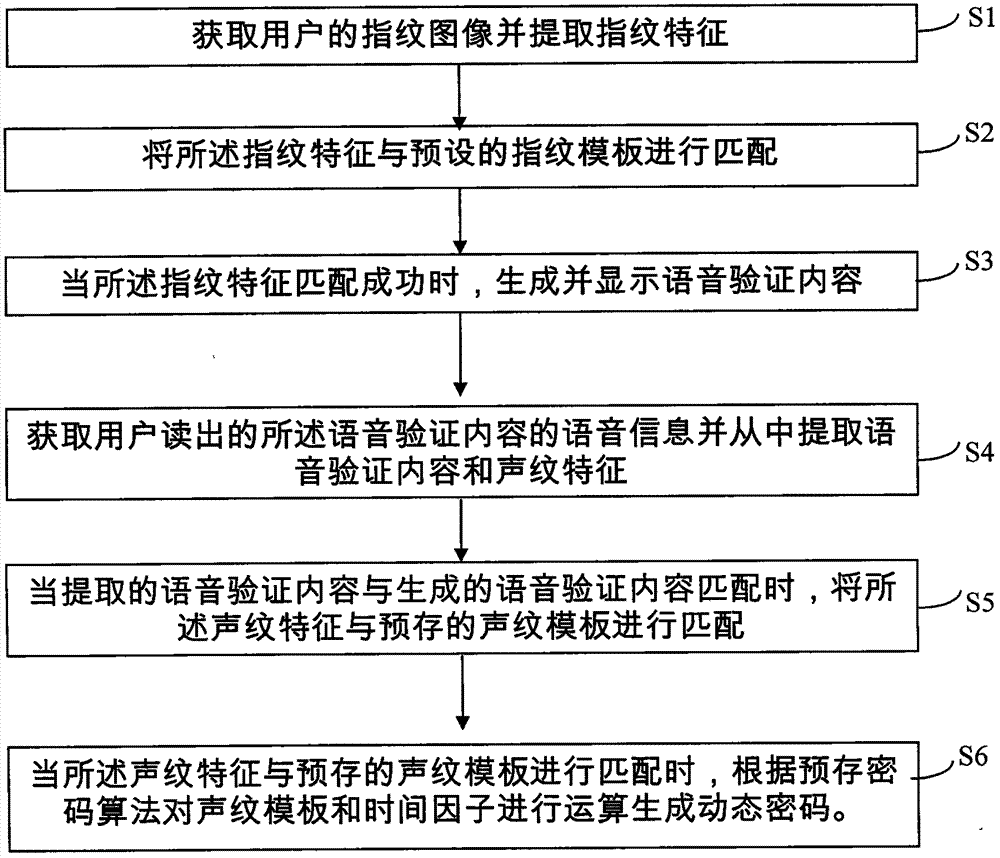
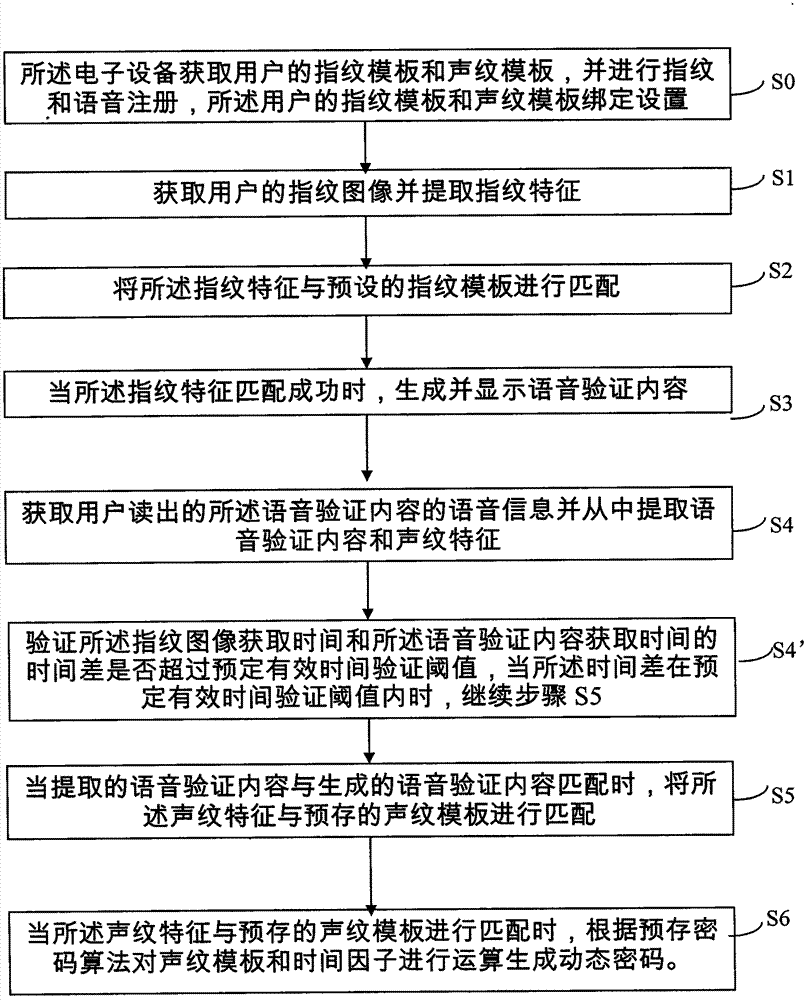
Dynamic cipher generation method for electronic equipment for fingerprint and voice recognition
InactiveCN104331652AAddresses vulnerabilities that are vulnerable to crackingImprove securityDigital data authenticationUser authenticationDependability
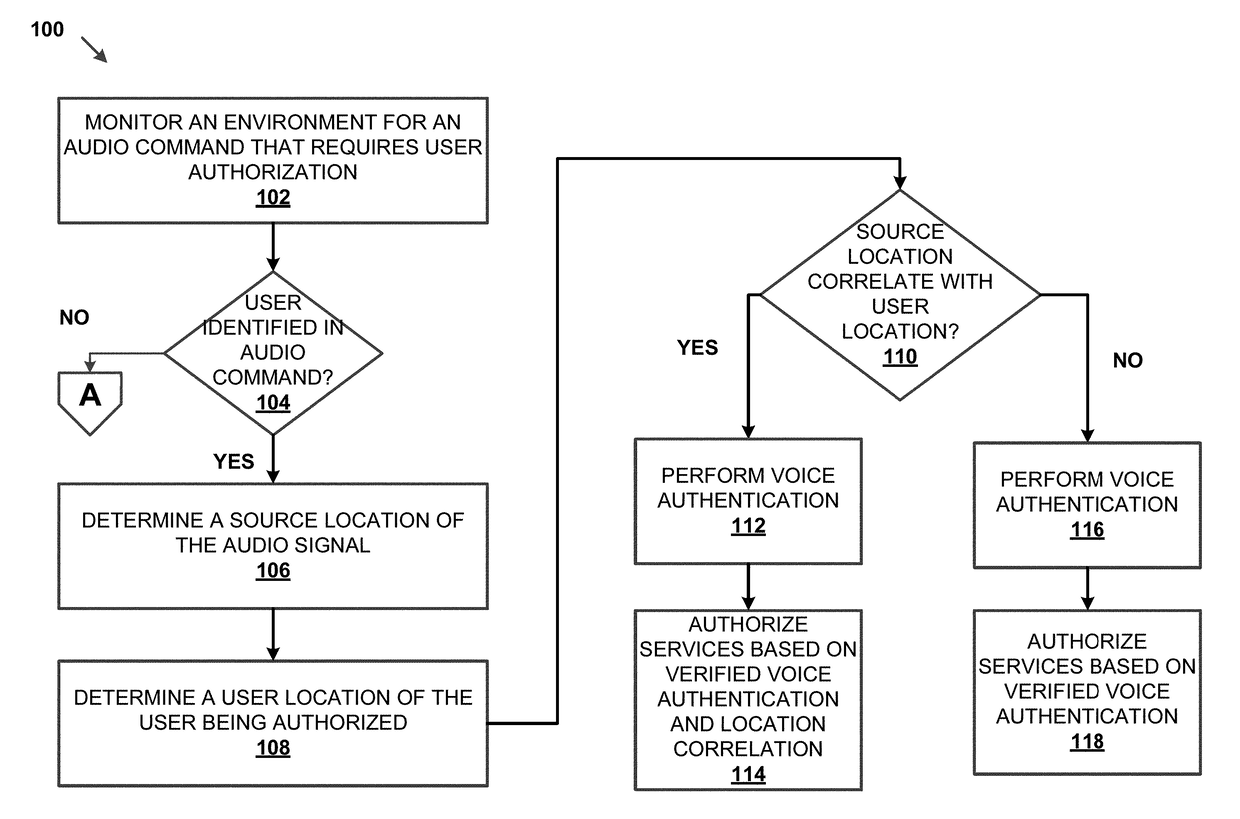
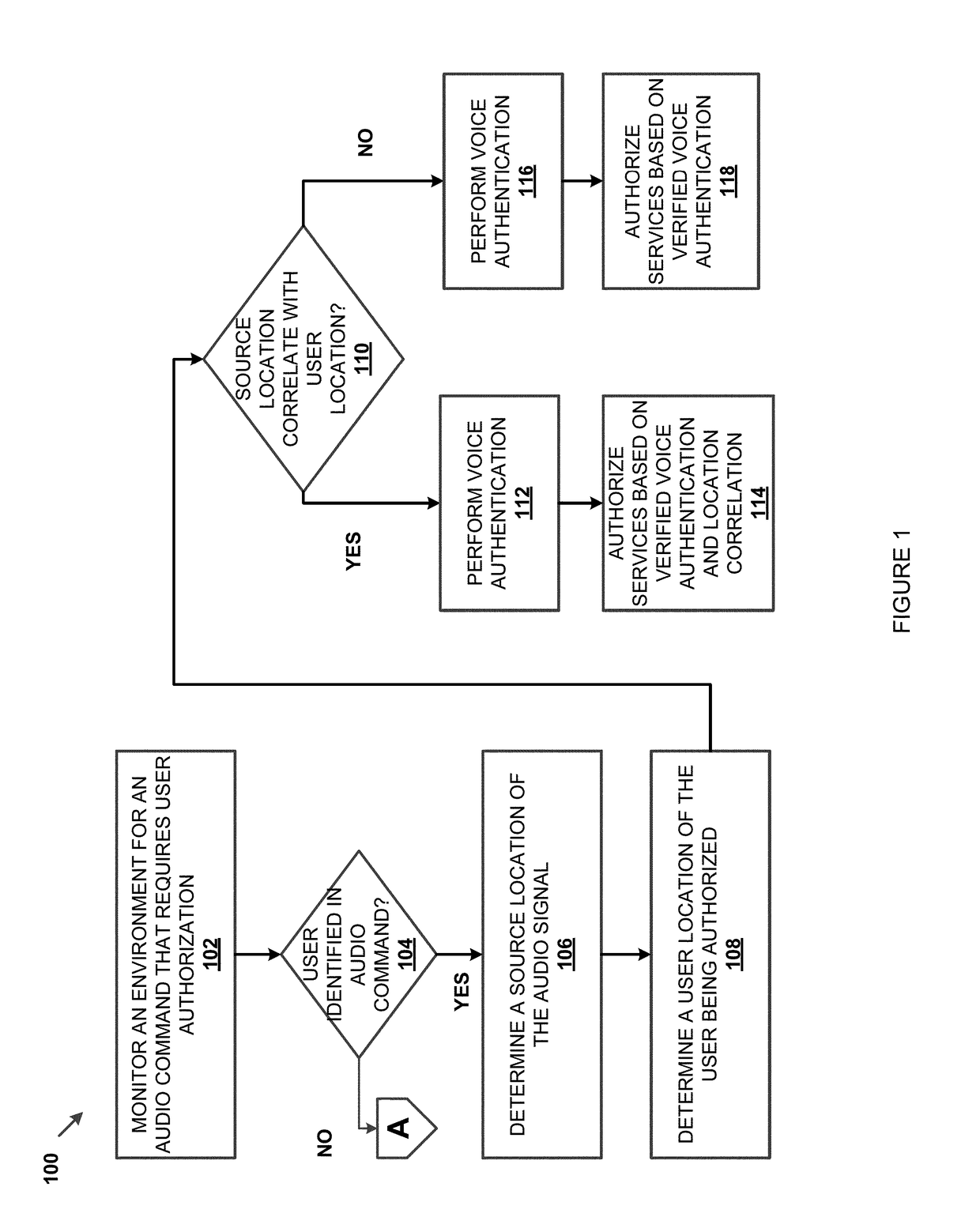
The invention discloses a dynamic cipher generation method for electronic equipment for fingerprint and voice recognition. The dynamic cipher generation method comprises the following steps: acquiring a fingerprint image of a user and extracting fingerprint features; performing matching the fingerprint features and a fingerprint template; when the fingerprint features are matched successfully, generating and displaying voice verification content; acquiring the voice message of the voice verification content read by the user and extracting the voice verification content and voiceprint features from the voice message; when the extracted voice verification content is matched with the generated voice verification content, performing matching on the voiceprint features and a voiceprint template; when matching is performed on voiceprint features and the voiceprint template, performing operation on the voiceprint template and a time factor according to a pre-stored cipher algorithm to generate a dynamic cipher. According to the dynamic cipher generation method disclosed by the invention, user authentication is performed by closely combining the fingerprint and voice recognition technology, so that the safety and the reliability of the electronic equipment and dynamic cipher generation are improved.
Owner:WUXI BIOKEE BIOMETRICS TECH
Voice authentication system
InactiveUS7447632B2High precisionReduce rejection rateSpeech recognitionComputer hardwareSpeech verification
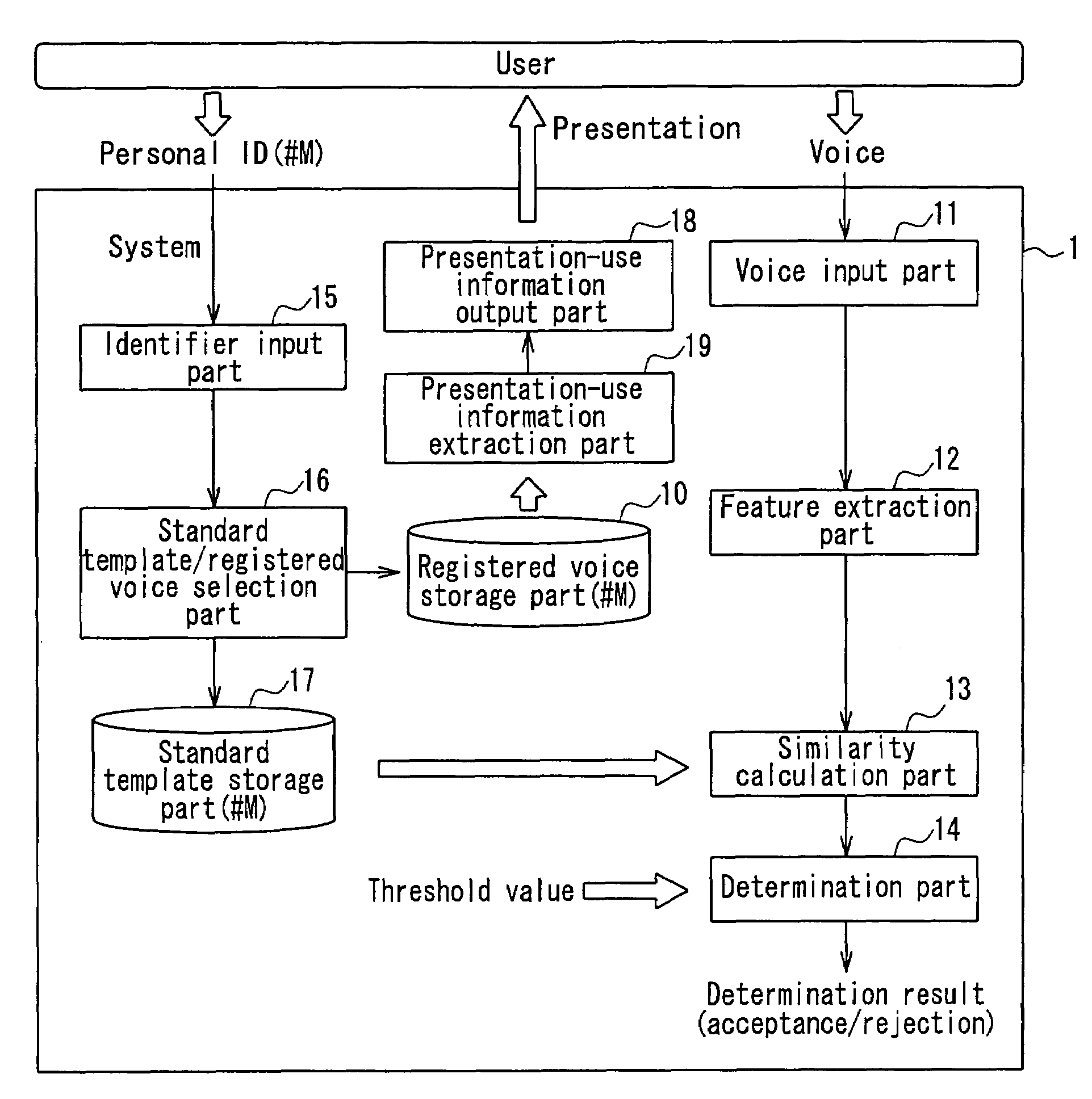
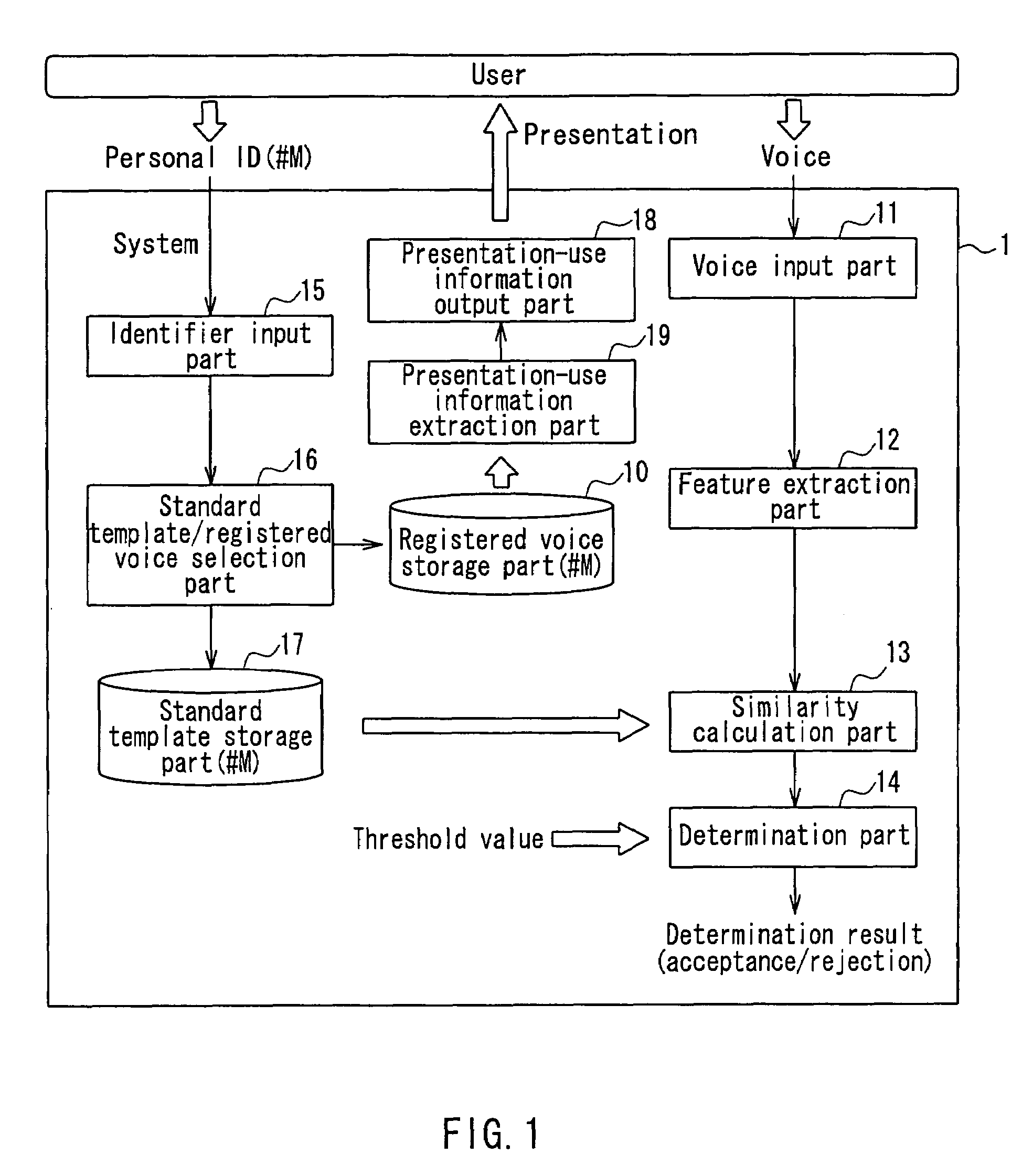
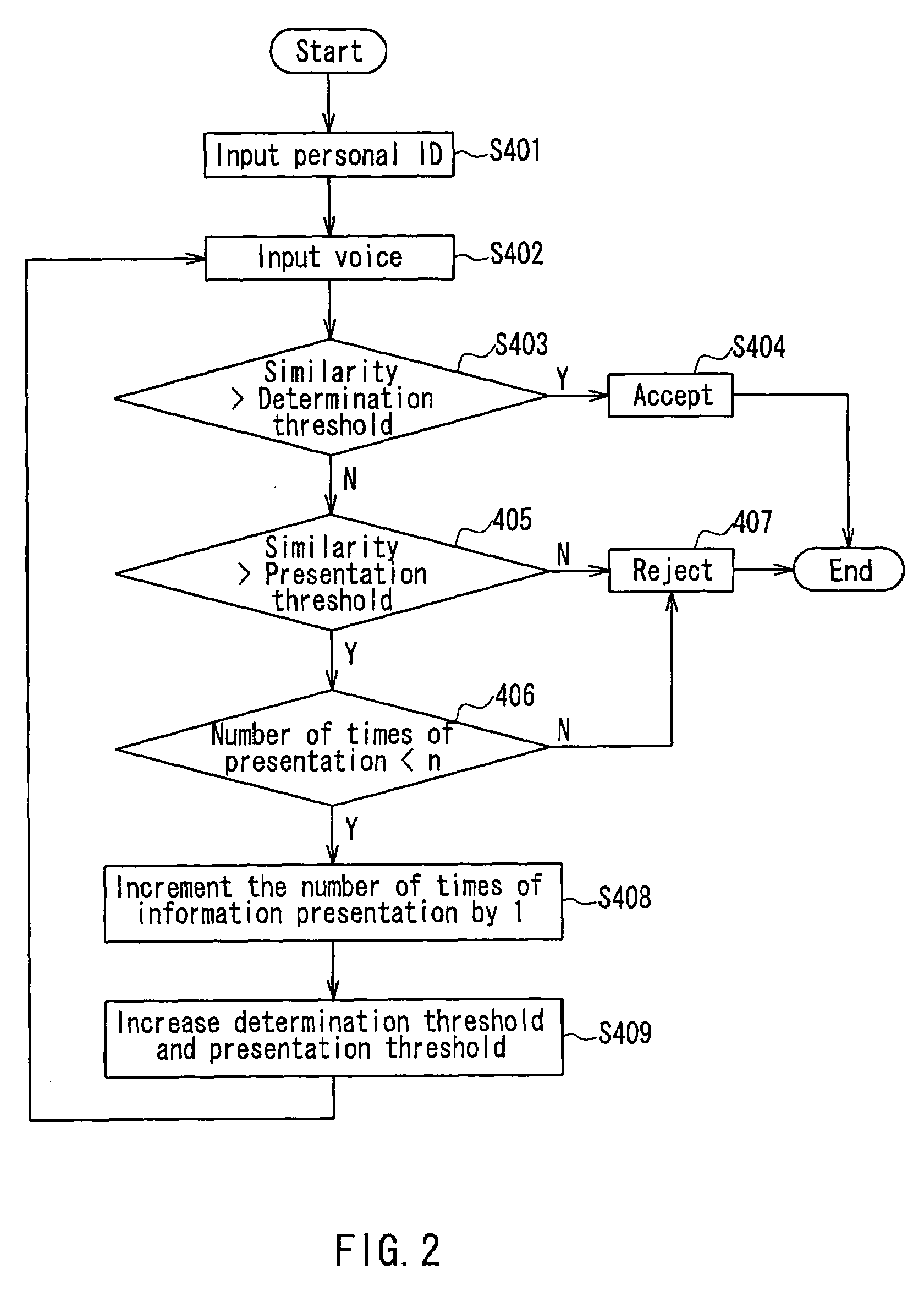
A voice authentication system includes: a standard template storage part 17 in which a standard template that is generated from a registered voice of an authorized user and featured with a voice characteristic of the registered voice is stored preliminarily in a state of being associated with a personal ID of the authorized user; an identifier input part 15 that allows a user who intends to be authenticated to input a personal ID; a voice input part 11 that allows the user to input a voice; a standard template / registered voice selection part 16 that selects a standard template and a registered voice corresponding to the inputted identifier; a determination part 14 that refers to the selected standard template and determines whether or not the inputted voice is a voice of the authorized user him / herself and whether or not presentation-use information is to be outputted by referring to a predetermined determination reference; a presentation-use information extraction part 19 that extracts information regarding the registered voice of the authorized user corresponding to the inputted identifier; and a presentation-use information output part 18 that presents the presentation-use information to the user in the case where it is determined by the determination part that the presentation-use information is to be outputted to the user.
Owner:FUJITSU LTD
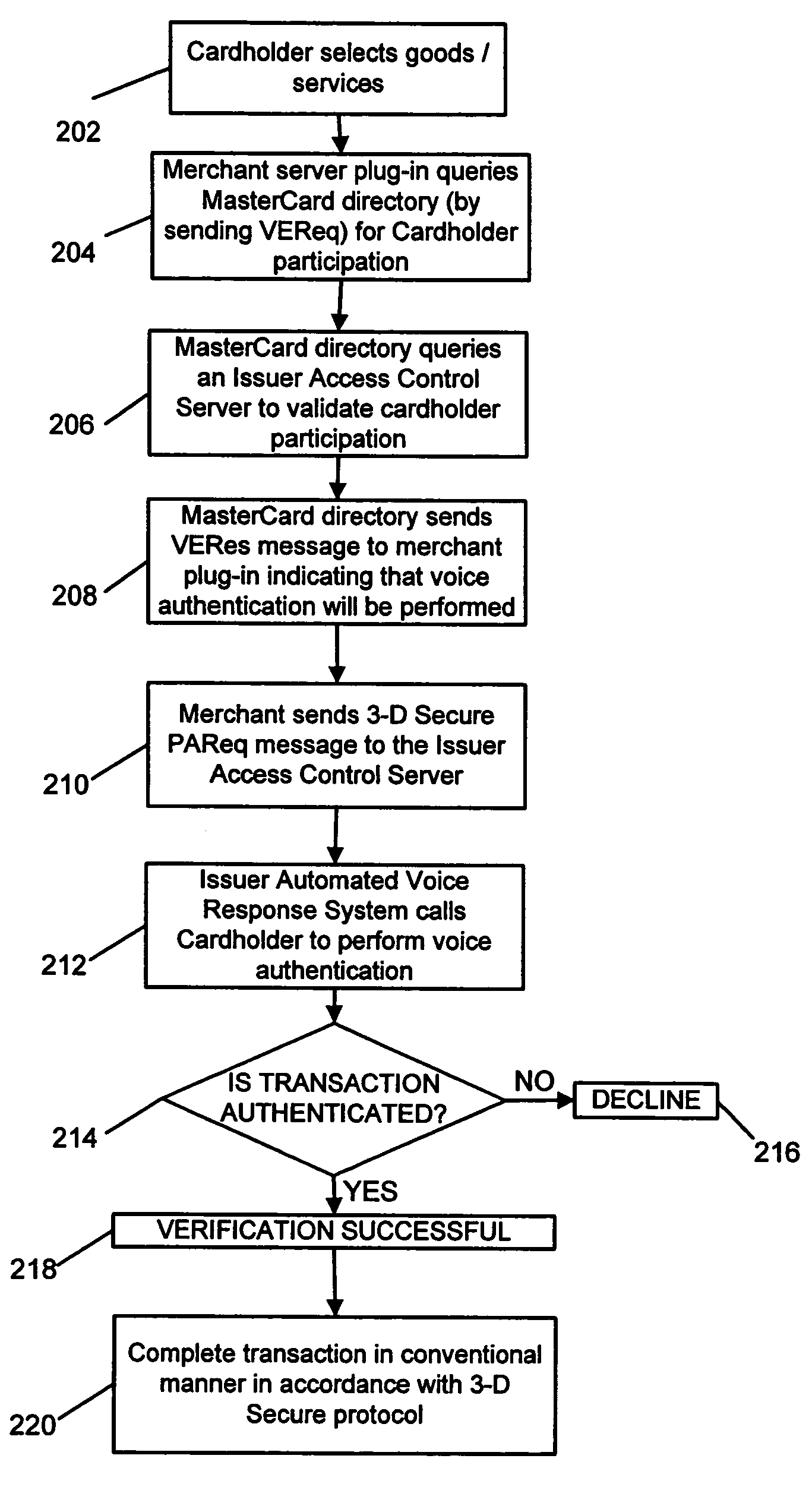
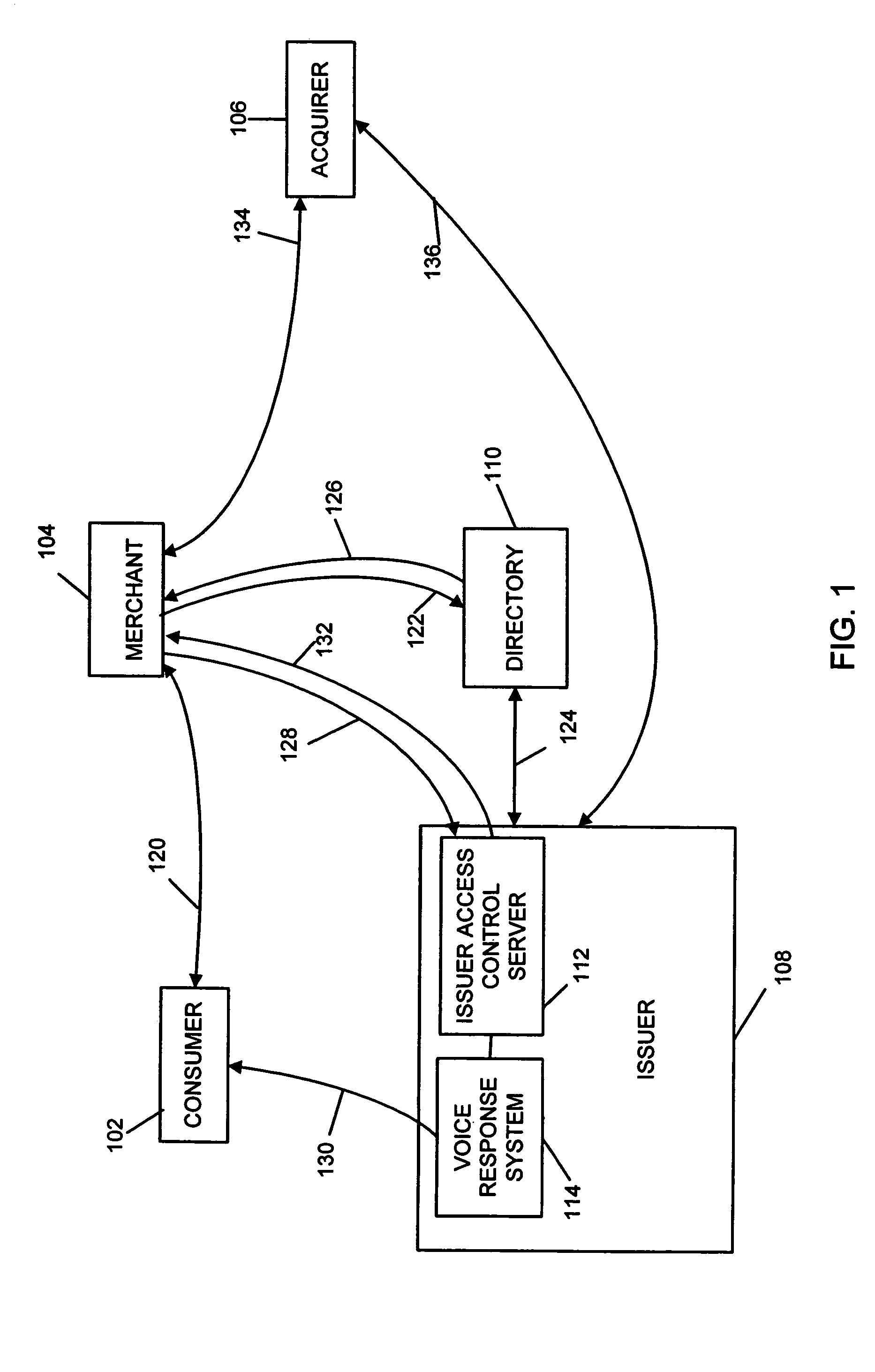
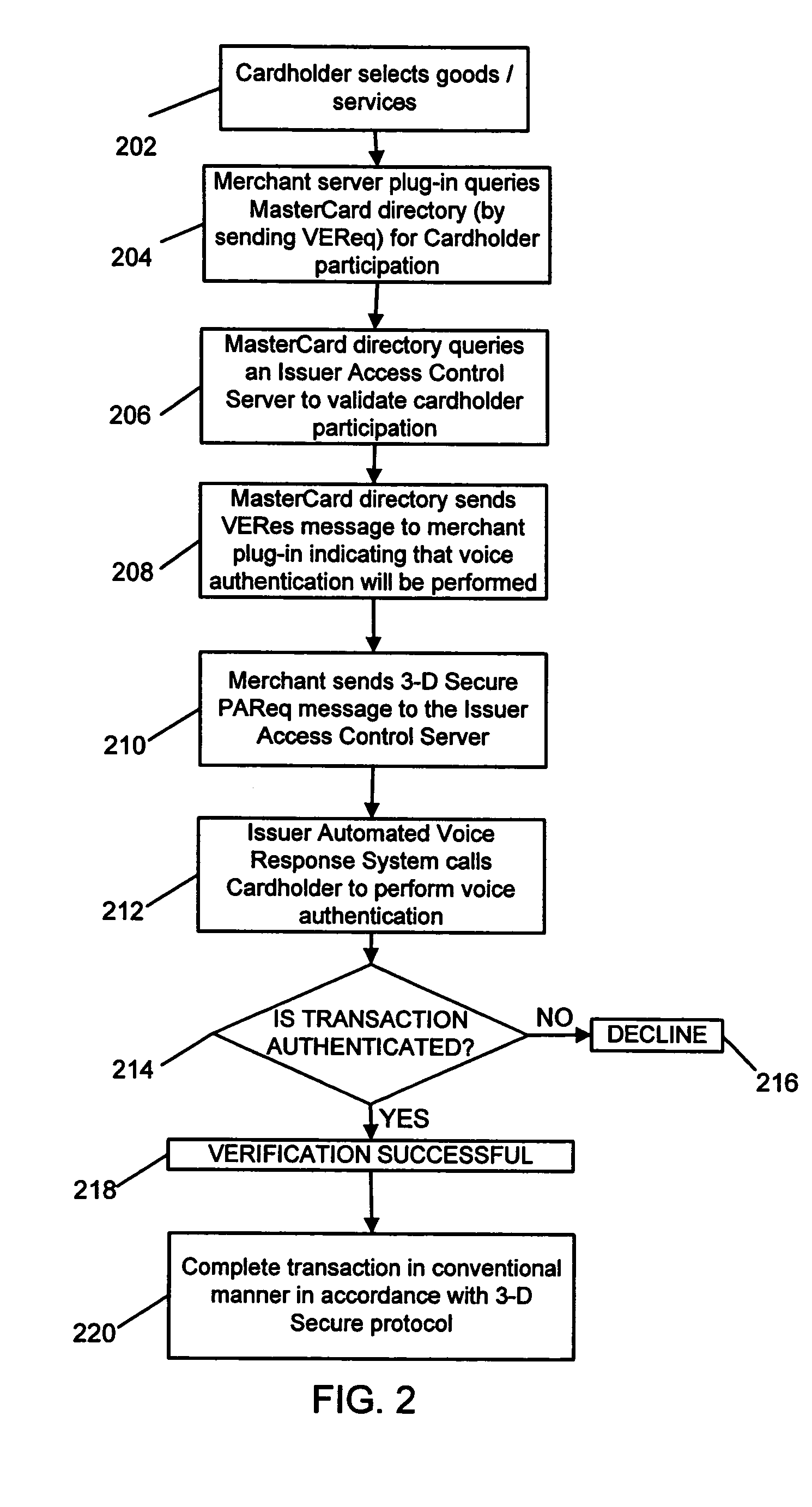
System and method for secure telephone and computer transactions using voice authentication
A secure electronic payment system and method for conducting a secure transaction using voice authentication is provided. A merchant's computer transmits an authorization request to an access control server. The access control server places a telephone call to the purchaser and performs voice authentication to confirm the identity of the purchaser. The access control server then transmits a response to the merchant's computer. If the purchaser is authorized to access the account, payment is processed by the merchant and the transaction is completed.
Owner:MASTERCARD INT INC
Voice phone-based method and system to authenticate users
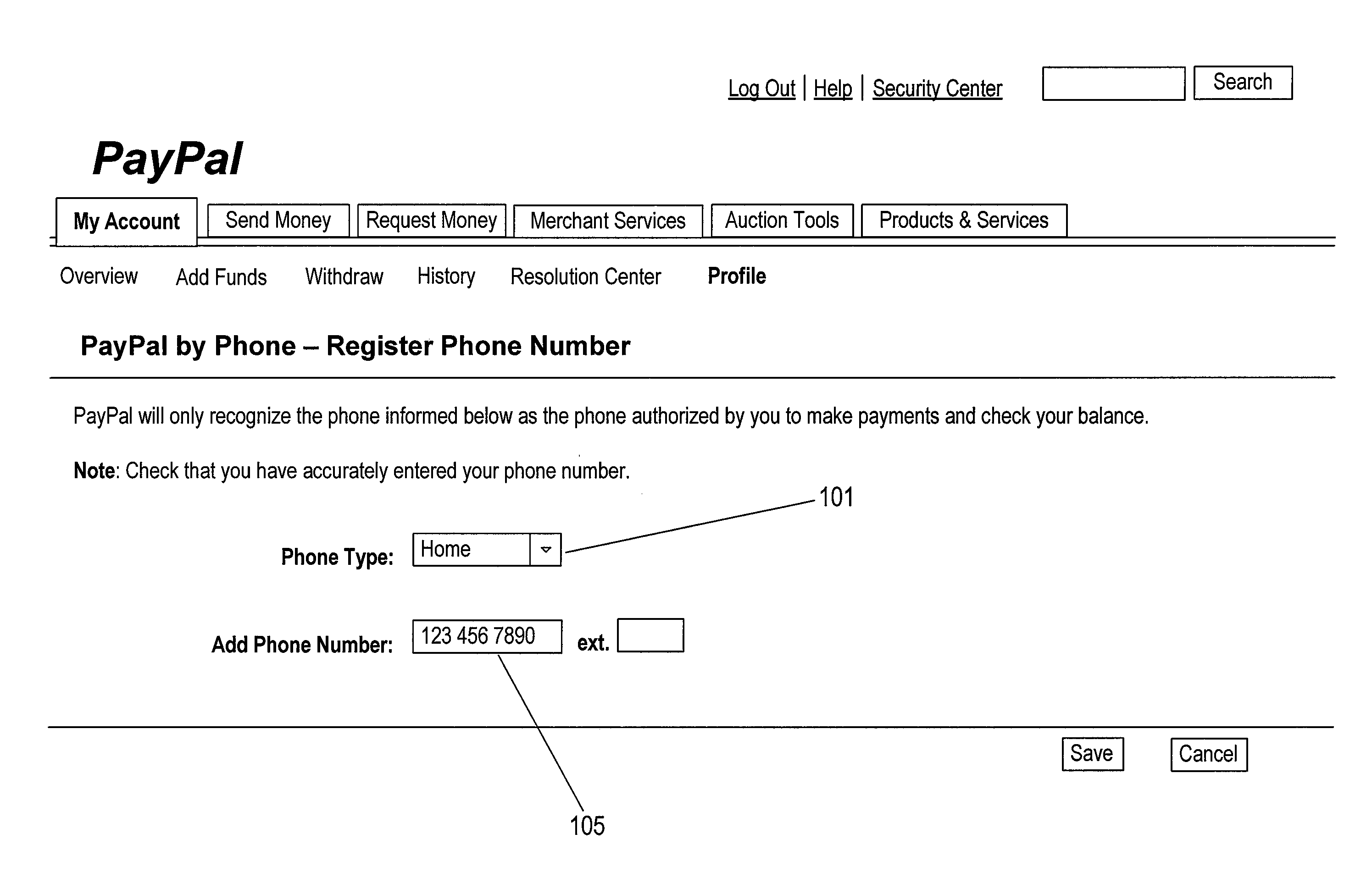
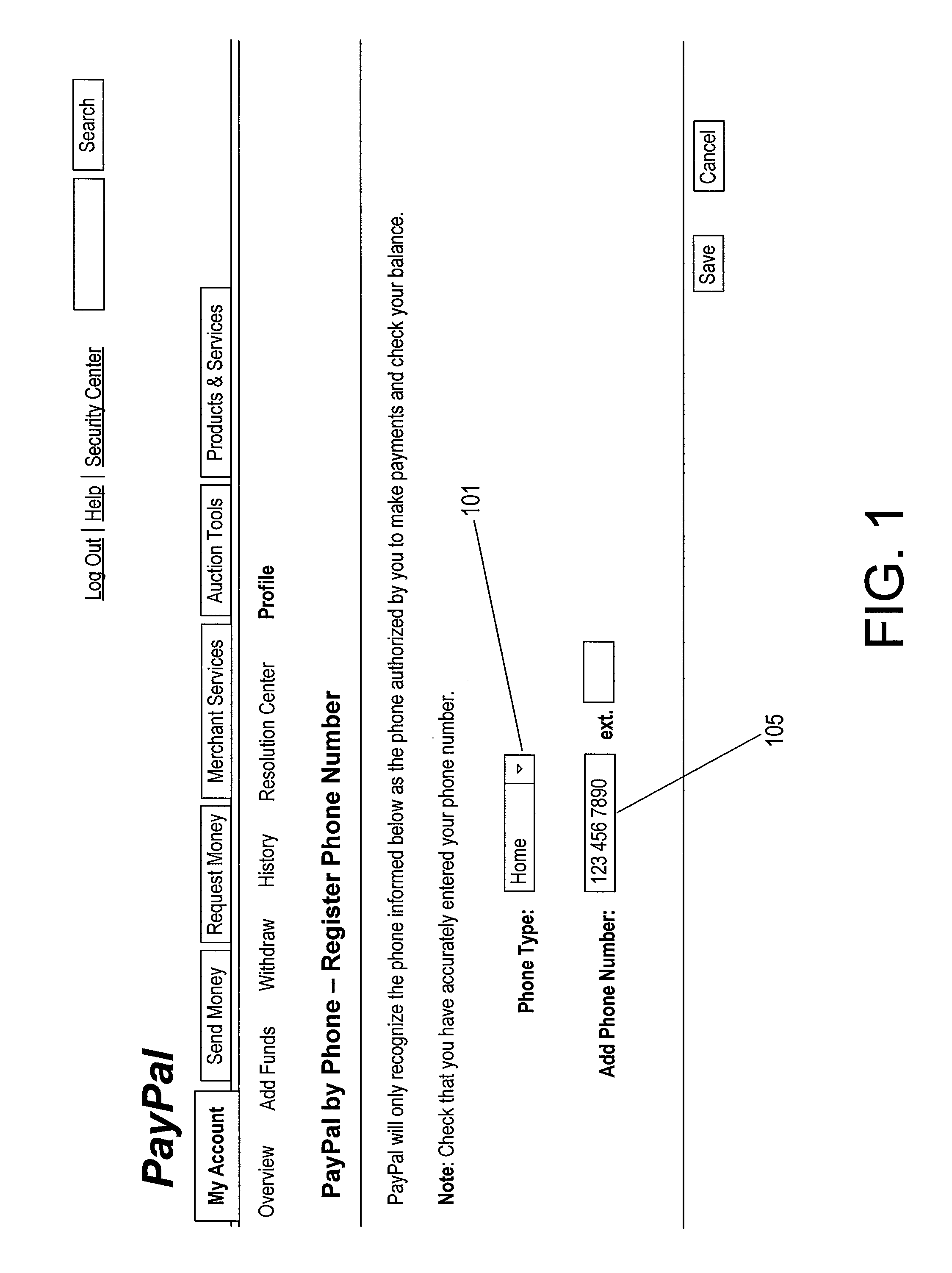
ActiveUS20100054429A1Safely and securely conduct transactionFinanceDigital data processing detailsThe InternetFinancial transaction
Provided is a method and a telephone-based system with voice-verification capabilities that enable a user to safely and securely conduct transactions with his or her online financial transaction program account over the phone in a convenient and user-friendly fashion, without having to depend on an internet connection.
Owner:PAYPAL INC
Methods and apparatus for performing speaker independent recognition of commands in parallel with speaker dependent recognition of names, words or phrases
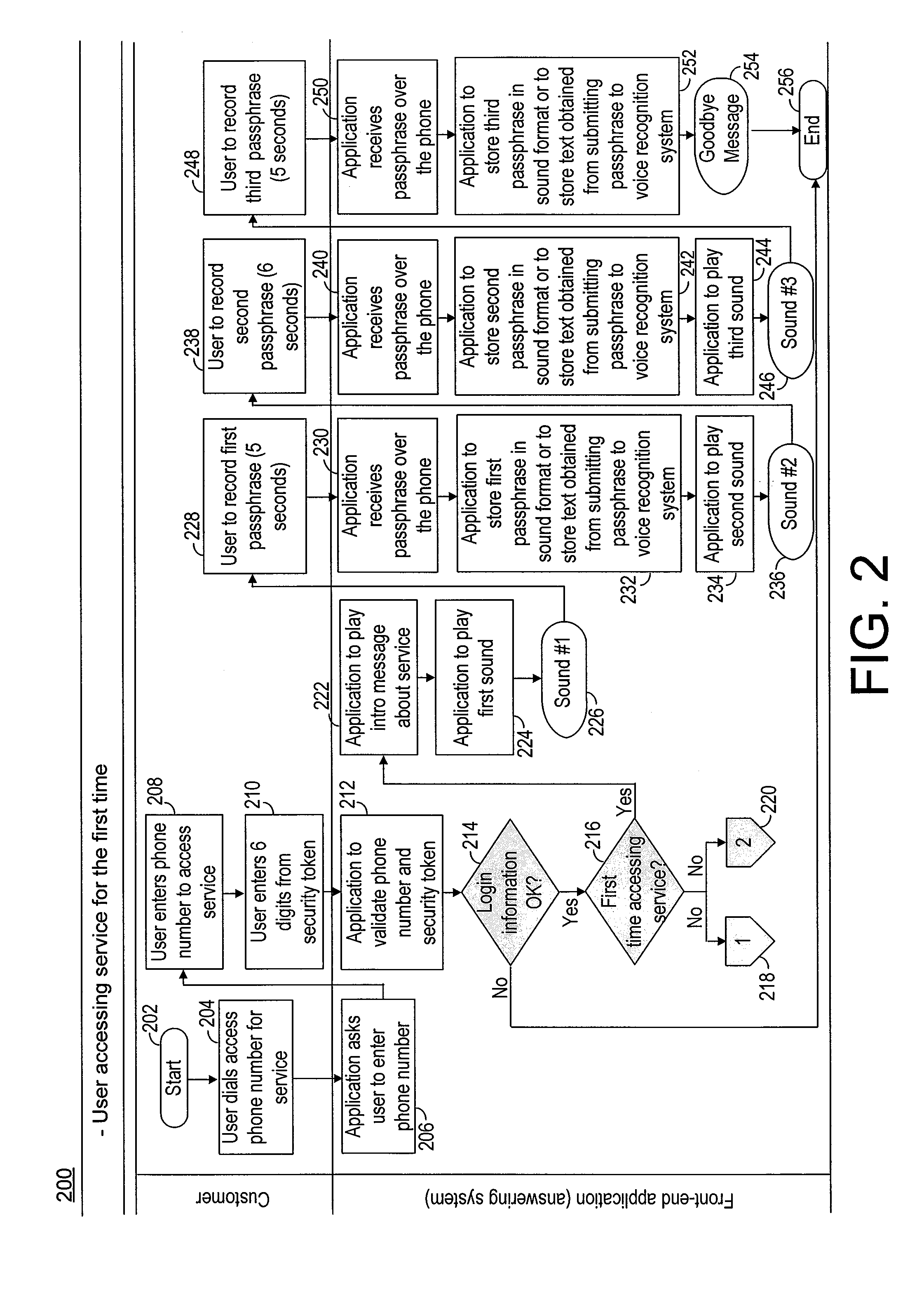
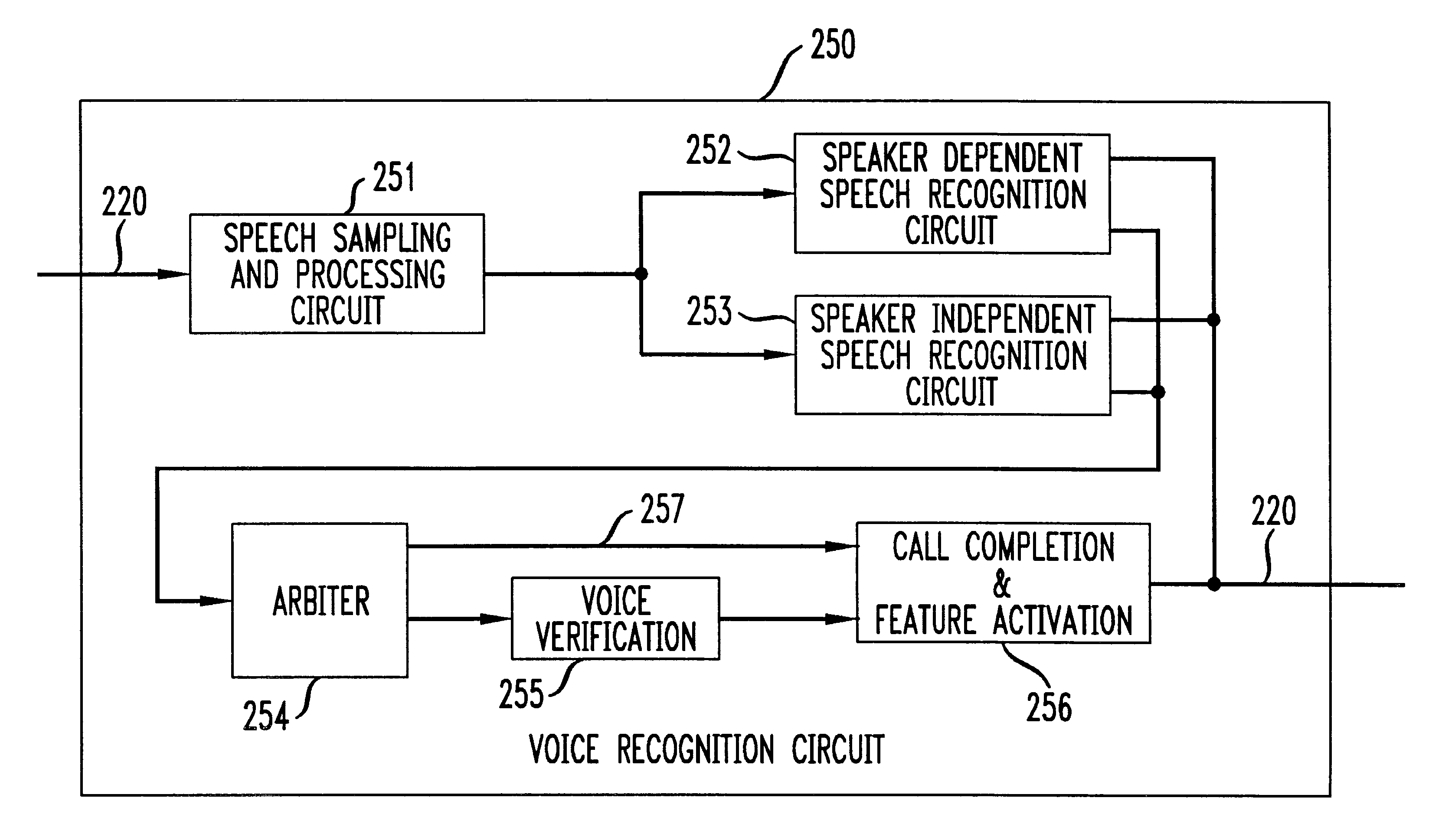
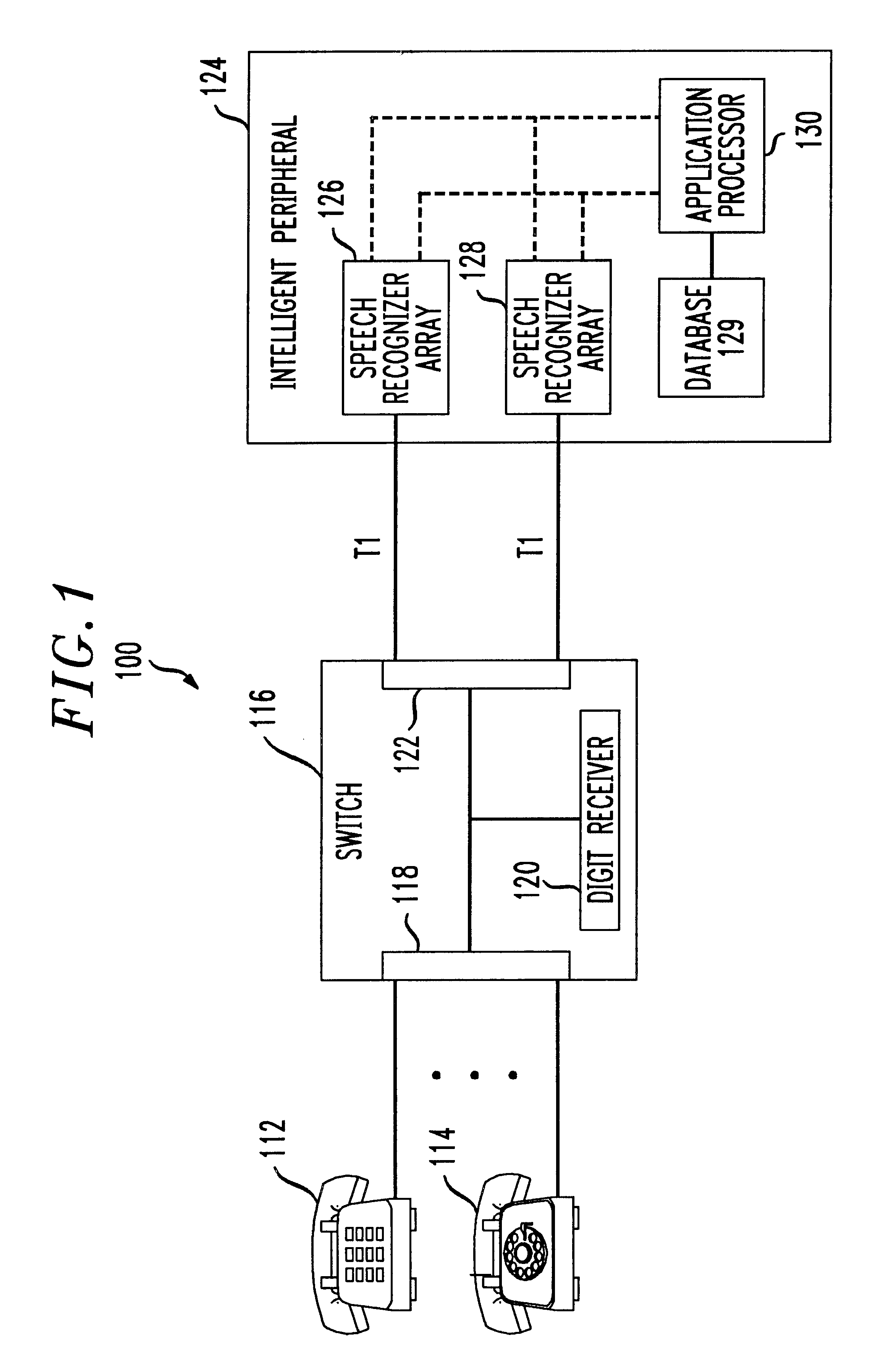
InactiveUSRE38101E1Provide securityUnauthorised/fraudulent call preventionAutomatic call-answering/message-recording/conversation-recordingSpeech identificationSpeech verification
Methods and apparatus for activating telephone services in response to speech are described. A directory including names is maintained for each customer. A speaker dependent speech template and a telephone number for each name, is maintained as part of each customer's directory. Speaker independent speech templates are used for recognizing commands. The present invention has the advantage of permitting a customer to place a call by speaking a person's name which serves as a destination identifier without having to speak an additional command or steering word to place the call. This is achieved by treating the receipt of a spoken name in the absence of a command as an implicit command to place a call. Explicit speaker independent commands are used to invoke features or services other than call placement. Speaker independent and speaker dependent speech recognition are performed on a customer's speech in parallel. An arbiter is used to decide which function or service should be performed when an apparent conflict arises as a result of both the speaker dependent and speaker independent speech recognition step outputs. Stochastic grammars, word spotting and / or out-of-vocabulary rejection are used as part of the speech recognition process to provide a user friendly interface which permits the use of spontaneous speech. Voice verification is performed on a selective basis where security is of concern.
Owner:GOOGLE LLC
Apparatus and method for generating and verifying a voice signature of a message and computer readable medium thereof
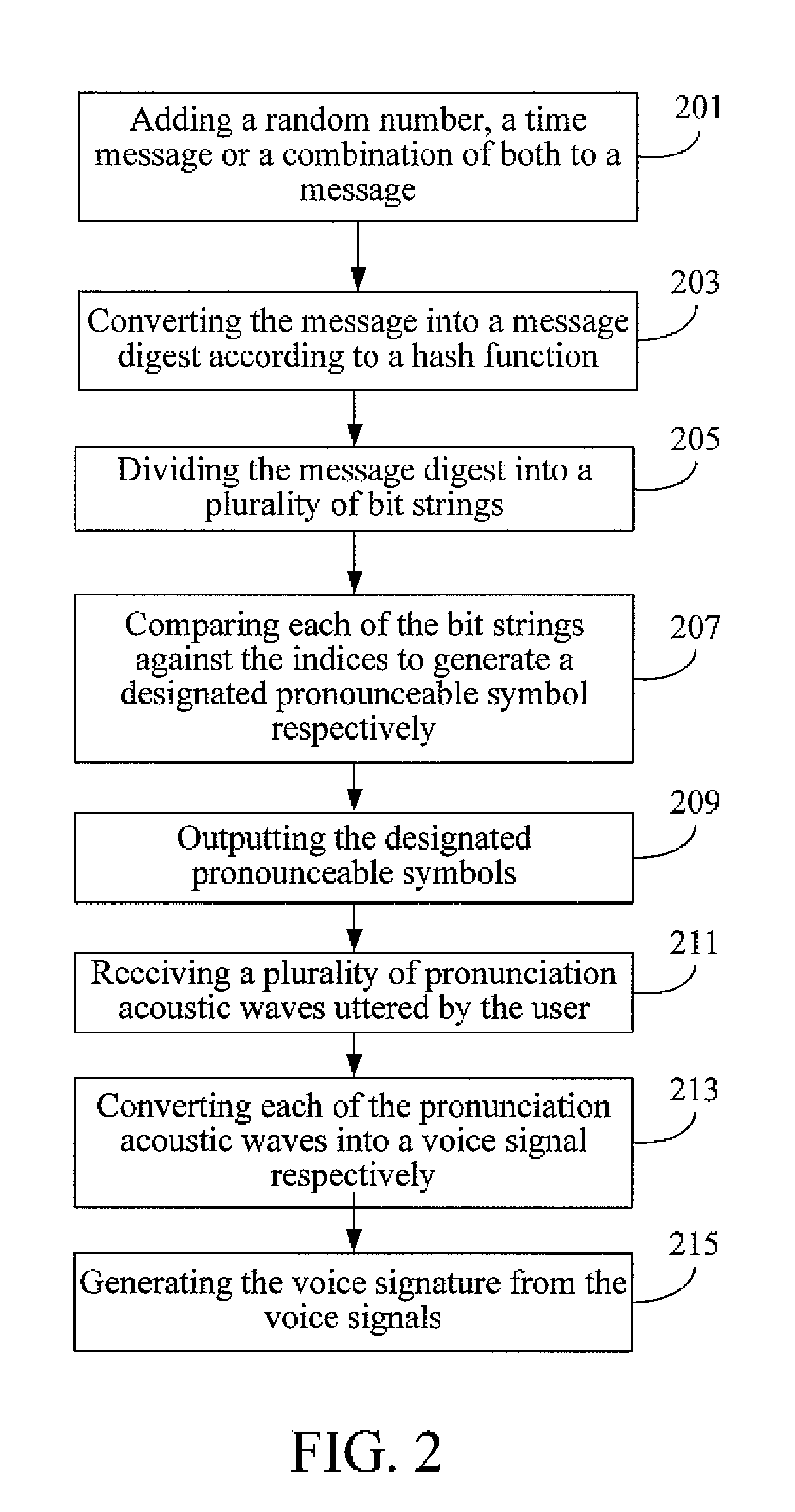
InactiveUS20100131272A1Shorten the lengthReduce riskUser identity/authority verificationNatural language data processingHash functionSpeech verification
Apparatuses and methods for generating and verifying a voice signature of a message and computer readable medium thereof are provided. The generation and verification ends both use the same set of pronounceable symbols. The set of pronounceable symbols comprises a plurality of pronounceable units, and each of the pronounceable units comprises an index and a pronounceable symbol. The generation end converts the message into a message digest by a hash function and generates a plurality of designated pronounceable symbols according to the message digest. A user utters the designated pronounceable symbols to generate the voice signature. After receiving the message and the voice signature, the verification end performs voice authentication to determine a user identity of the voice signature, performs speech recognition to determine the relation between the message and the voice signature, and determines whether the user generates the voice signature for the message.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
Location based voice recognition system
ActiveUS9892732B1Direction finders using ultrasonic/sonic/infrasonic wavesPosition fixationSpeech identificationSpeech verification
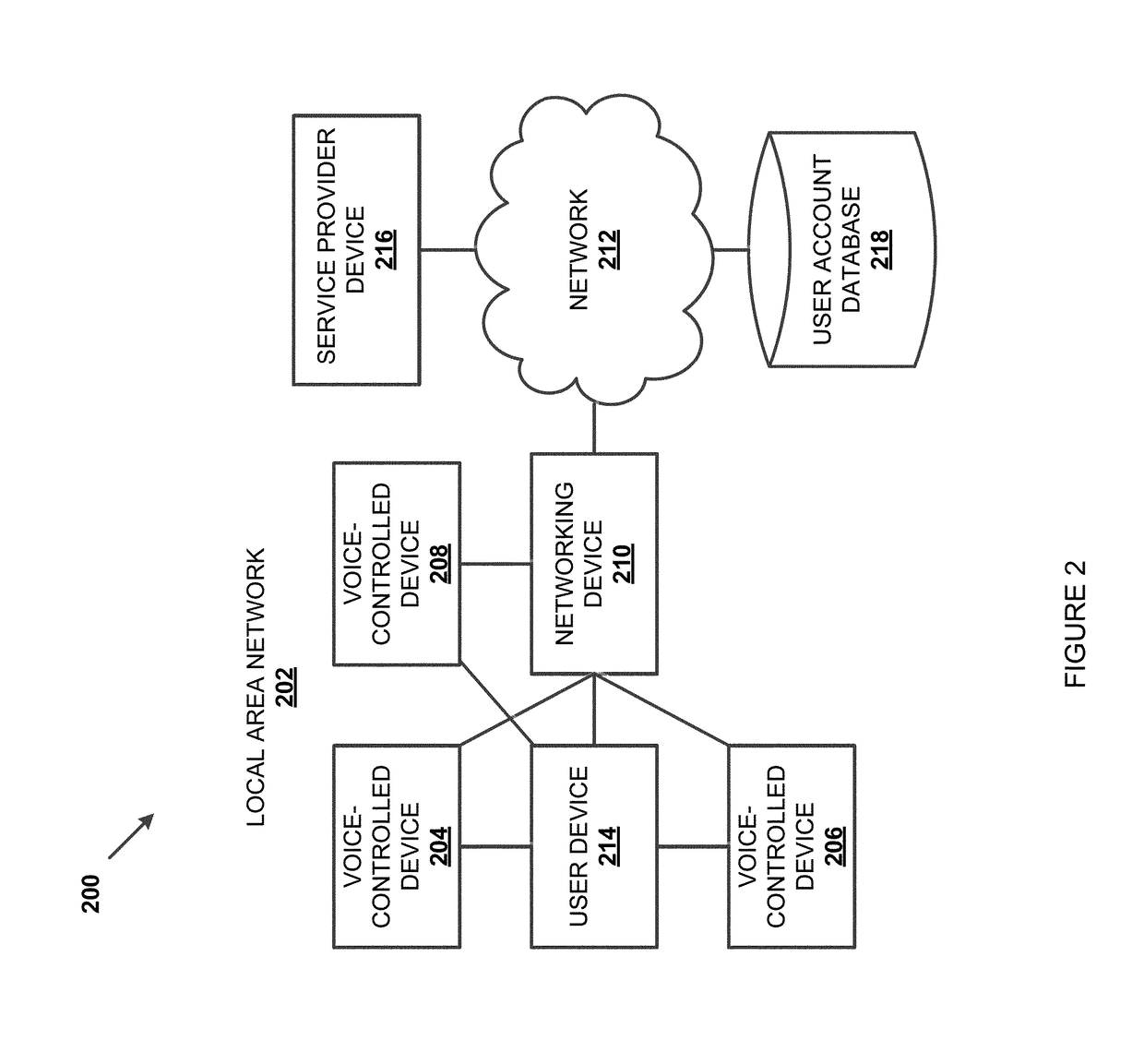
Systems and methods for providing location based voice recognition include receiving, through a first microphone, an audio signal from a first user that includes an audio command requesting a service that requires user authorization before access to at least a portion of the service is granted. The user authorization is based on voice recognition (e.g., voice authentication and / or voice identification) of the audio signal. The source location of the audio signal is determined and a user location of the first user is determined. If the source location of the audio signal correlates with the user location, voice recognition on the audio signal may be performed. The first user may be authorized to access the service based on the voice recognition performed on the audio signal.
Owner:PAYPAL INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com