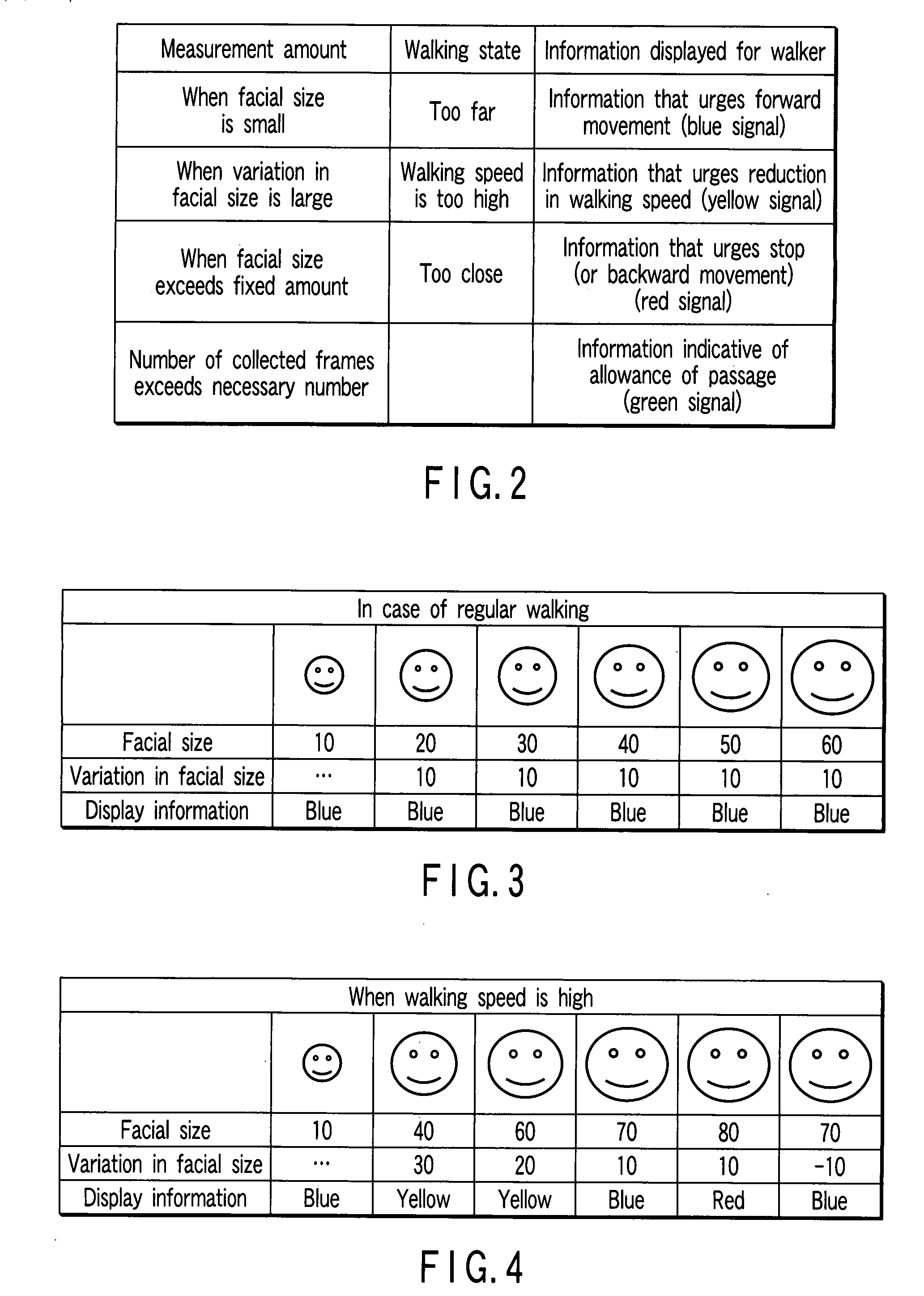
Patents
Literature
199results about How to "Improve authentication accuracy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
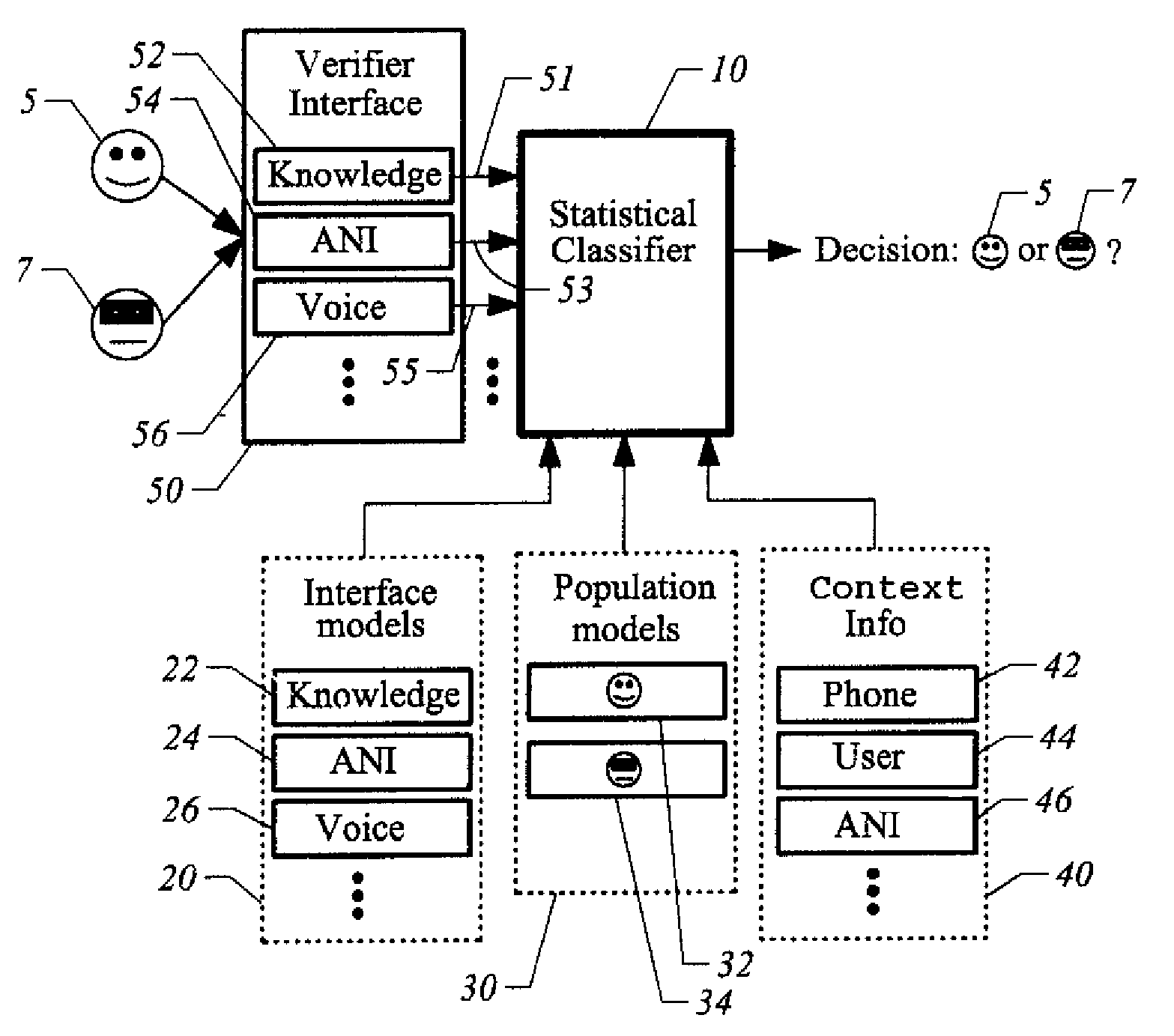
System and method for providing improved claimant authentication
ActiveUS7404087B2Improve accuracy“tuned” (manipulated or optimized) more easilyDigital data processing detailsUser identity/authority verificationAlgorithmAuthentication
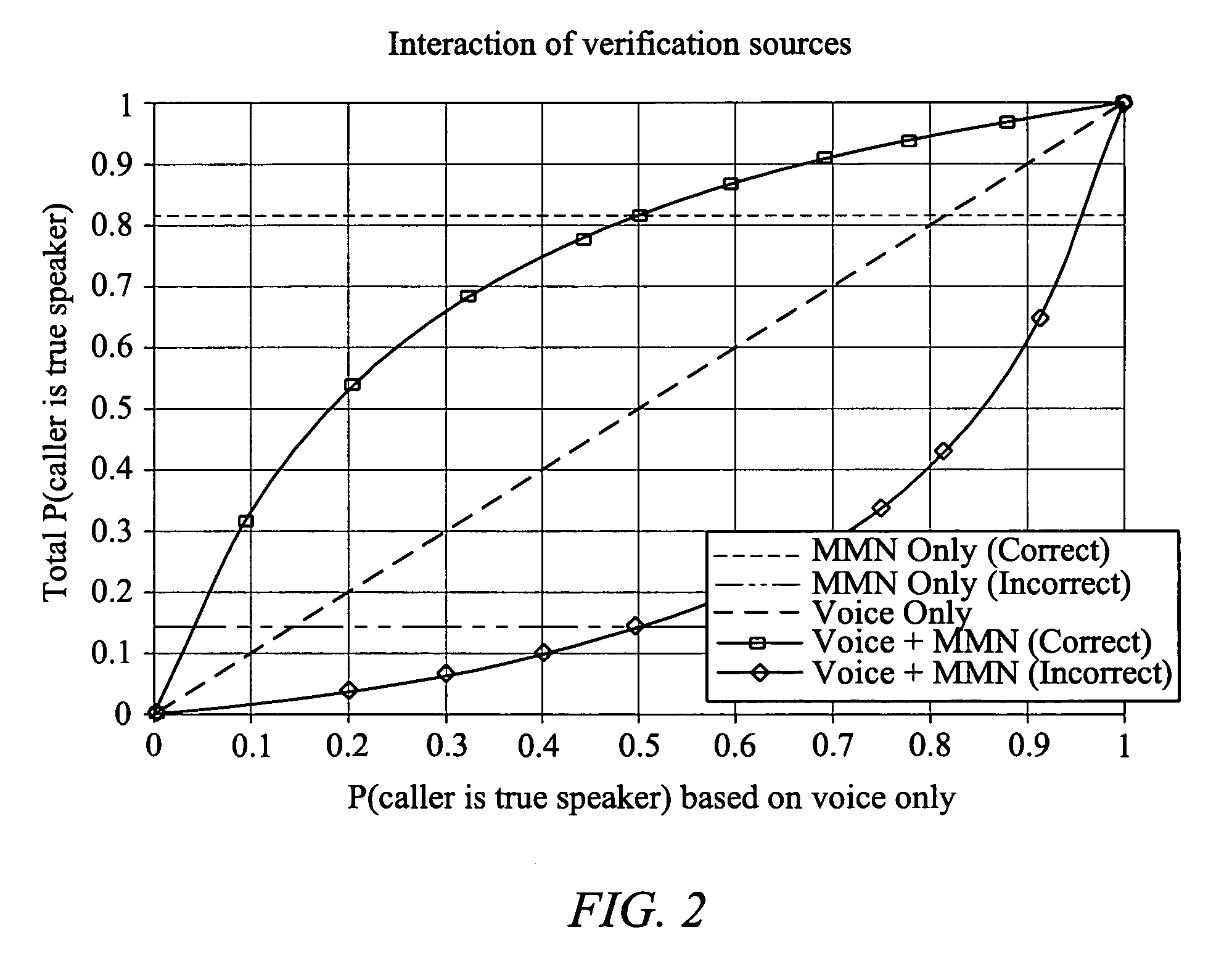
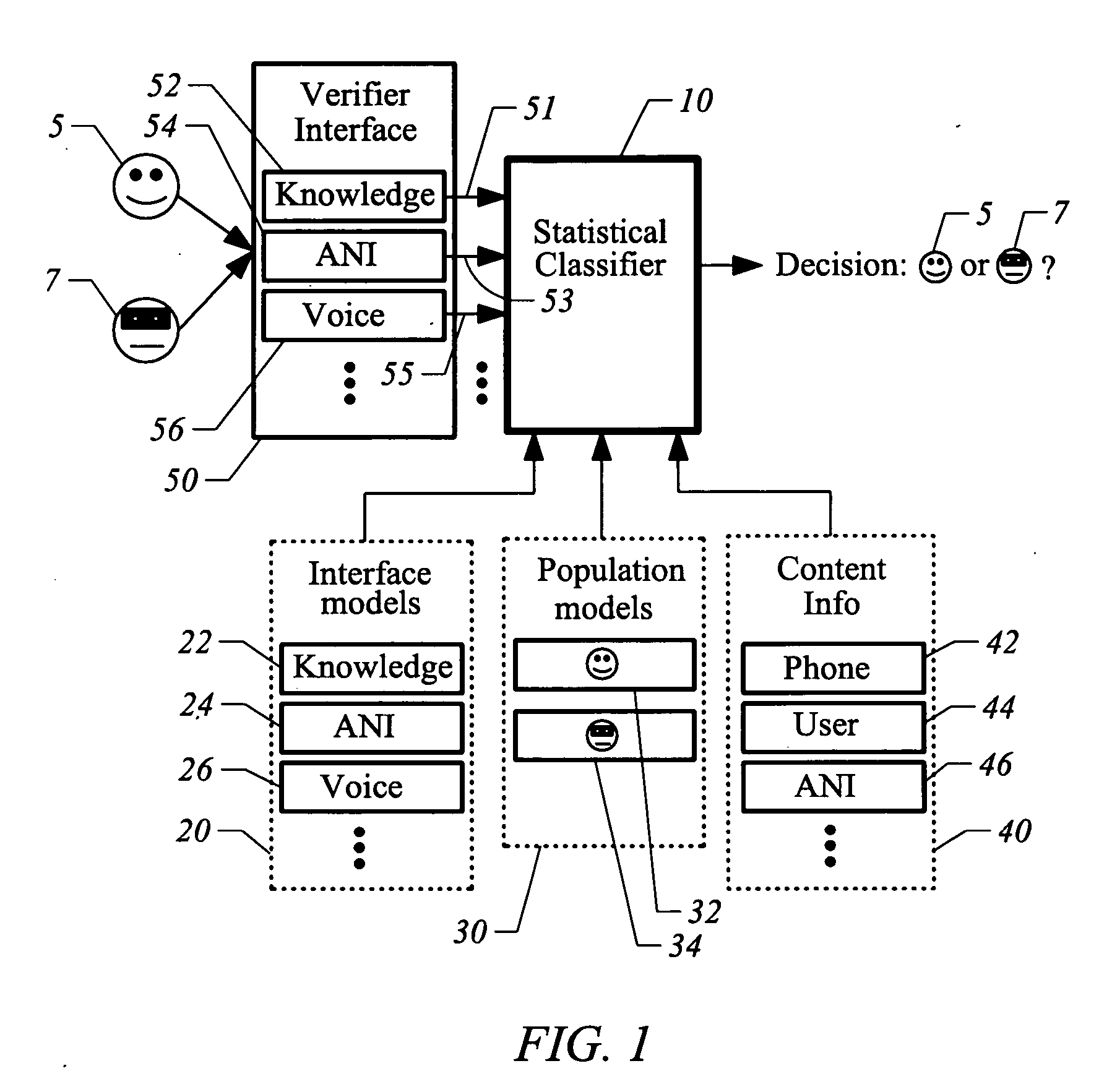
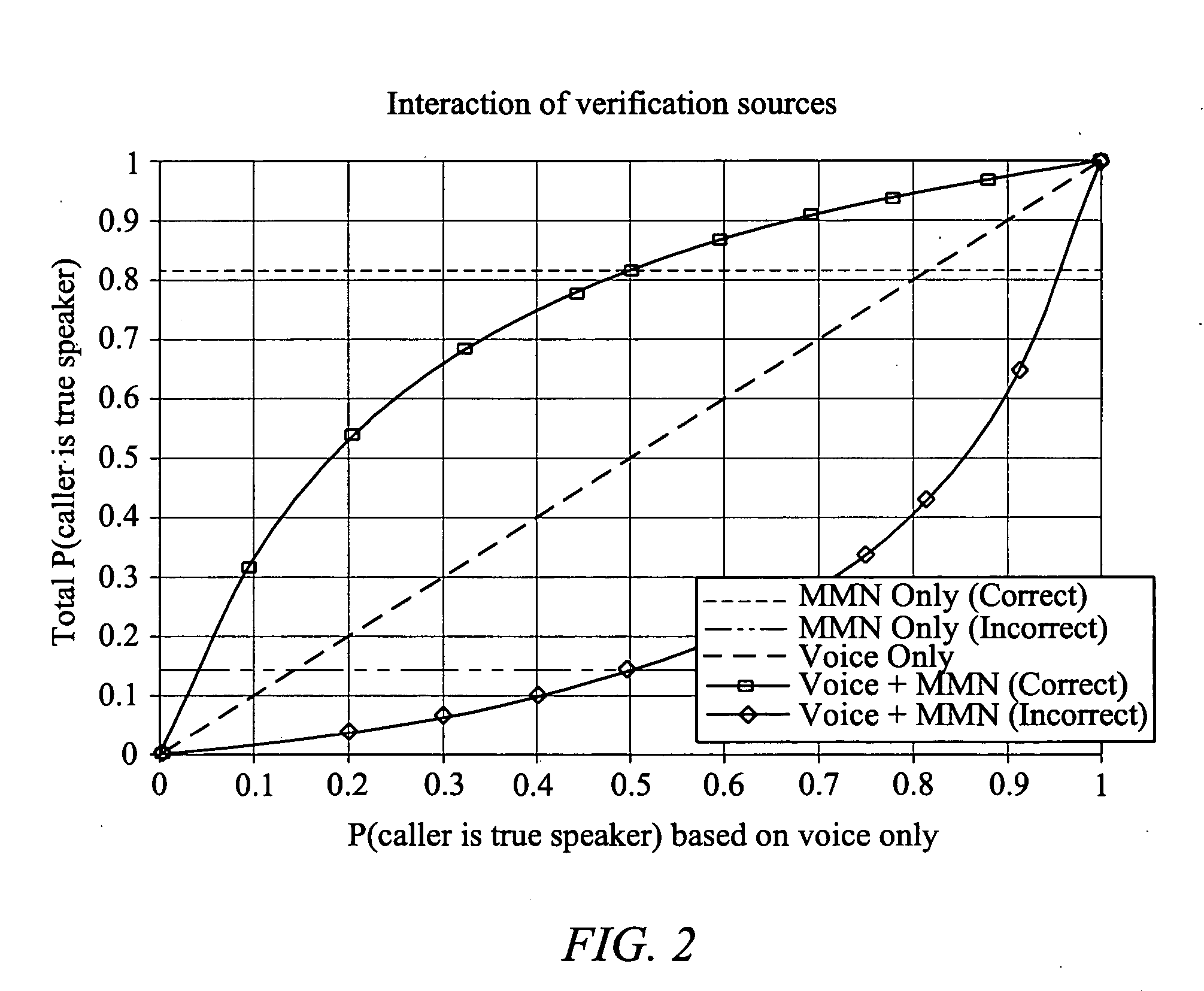
A system and method are provided for improving the accuracy of speaker authentication by combining the results of multiple verification sources using statistical modeling. A statistical classifier is built on top of the underlying verification sources. The classifier combines the multiple verification inputs with associated models of the respective verification technologies underlying the verification inputs. The classifier functions to classify a claimant as a true speaker or impostor based upon the verification inputs, the model or models and, potentially, additional information related to the context in which the classifier is being used.
Owner:EMC IP HLDG CO LLC
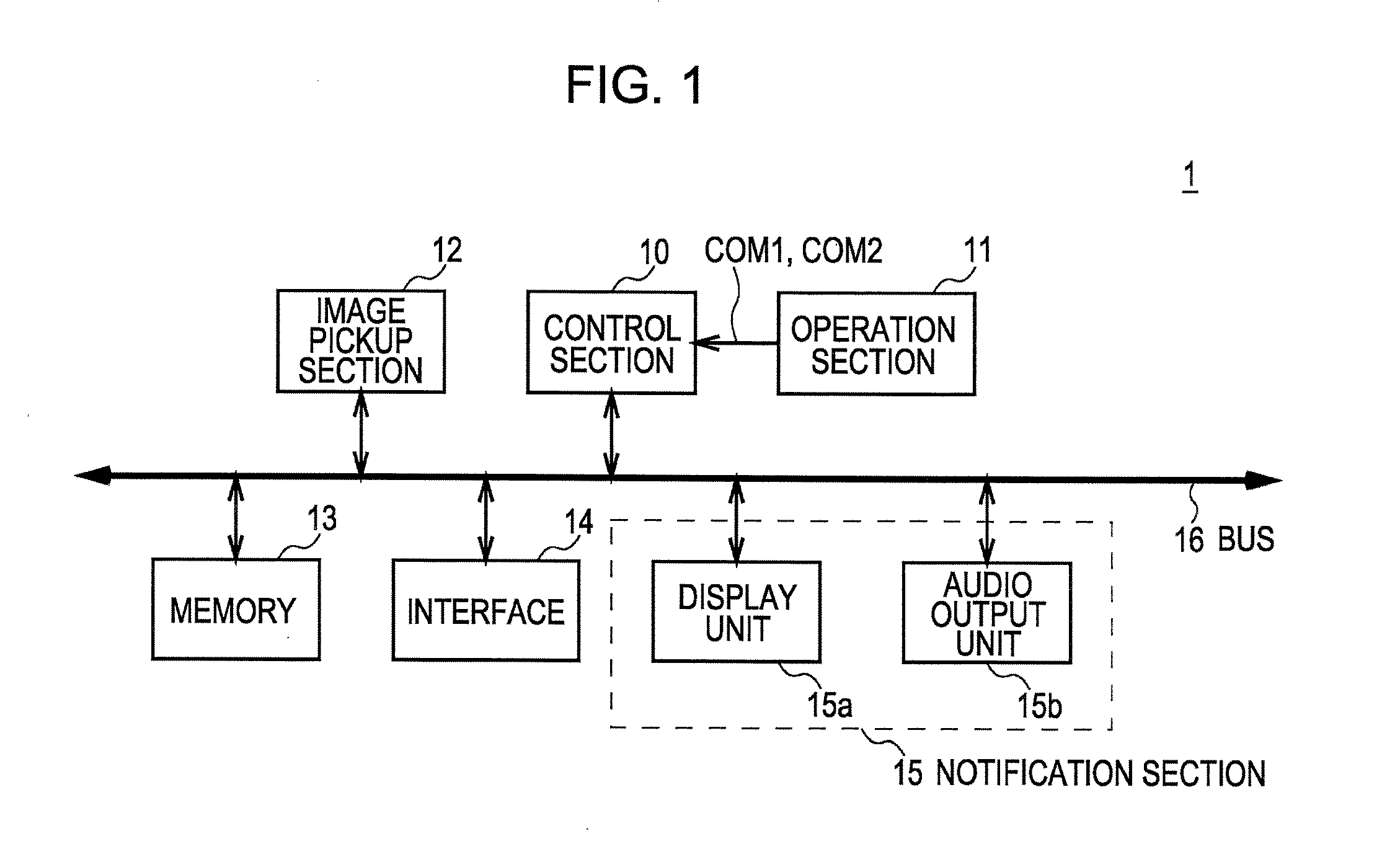
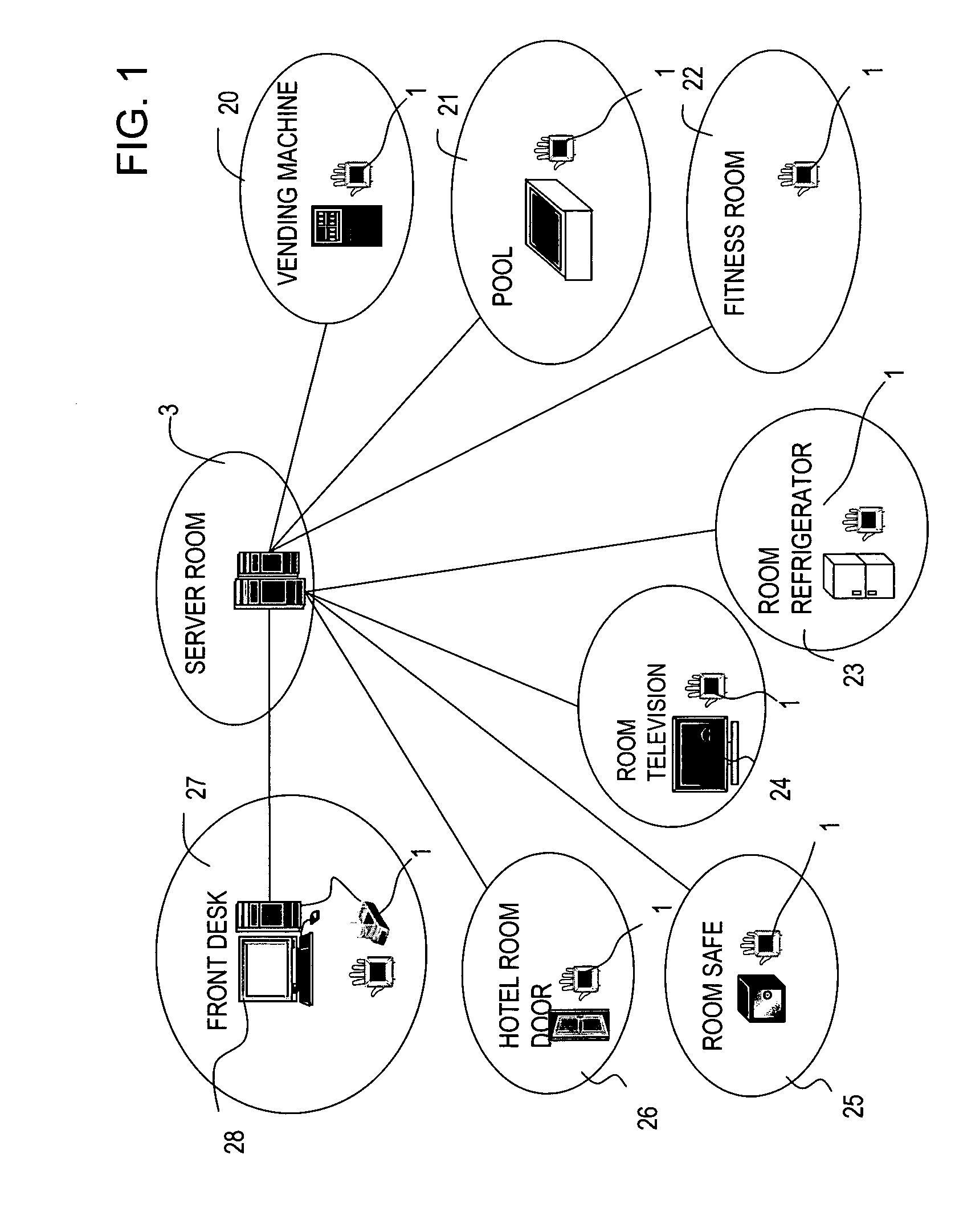
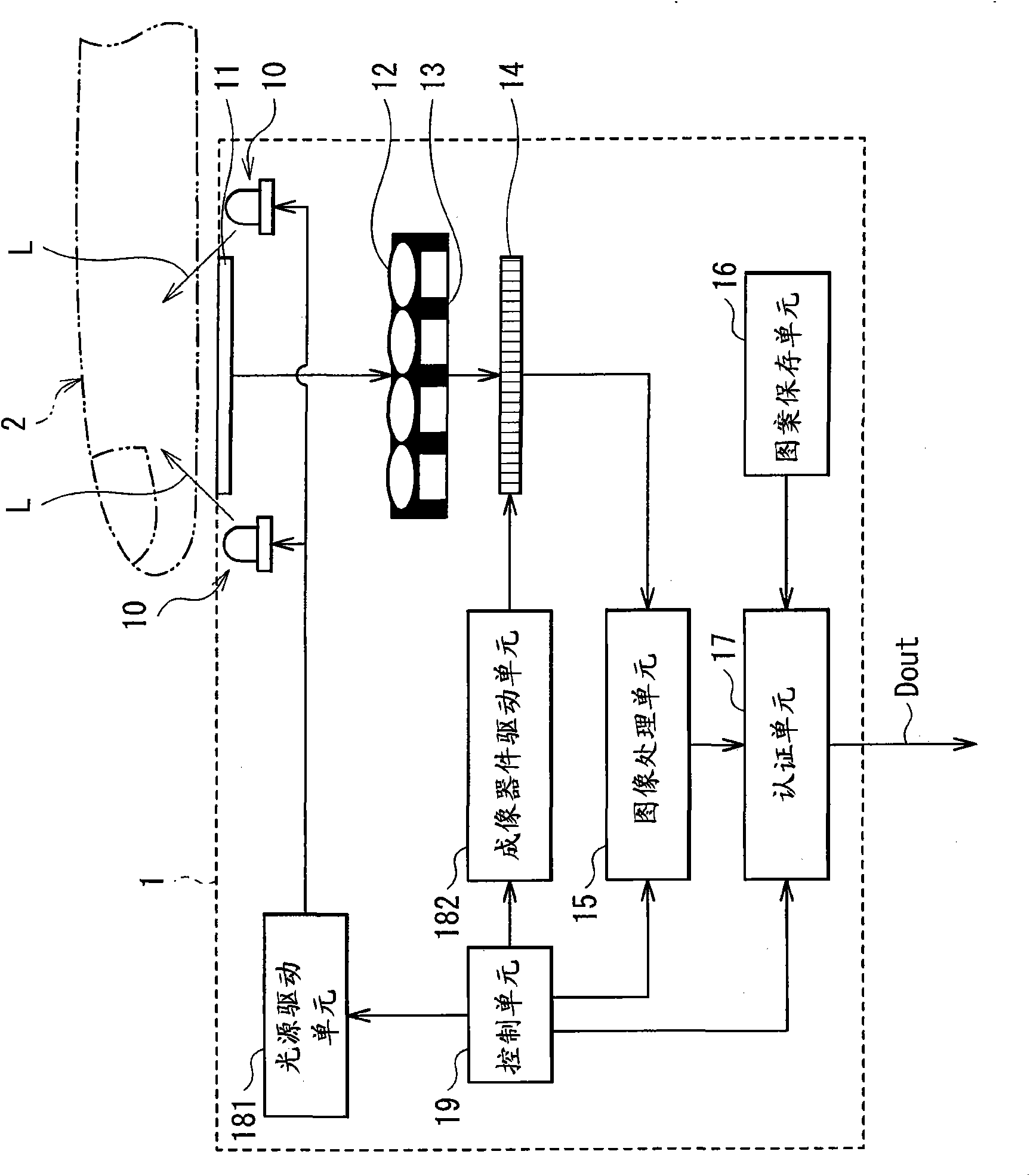
Biometrics authentication device and portable terminal
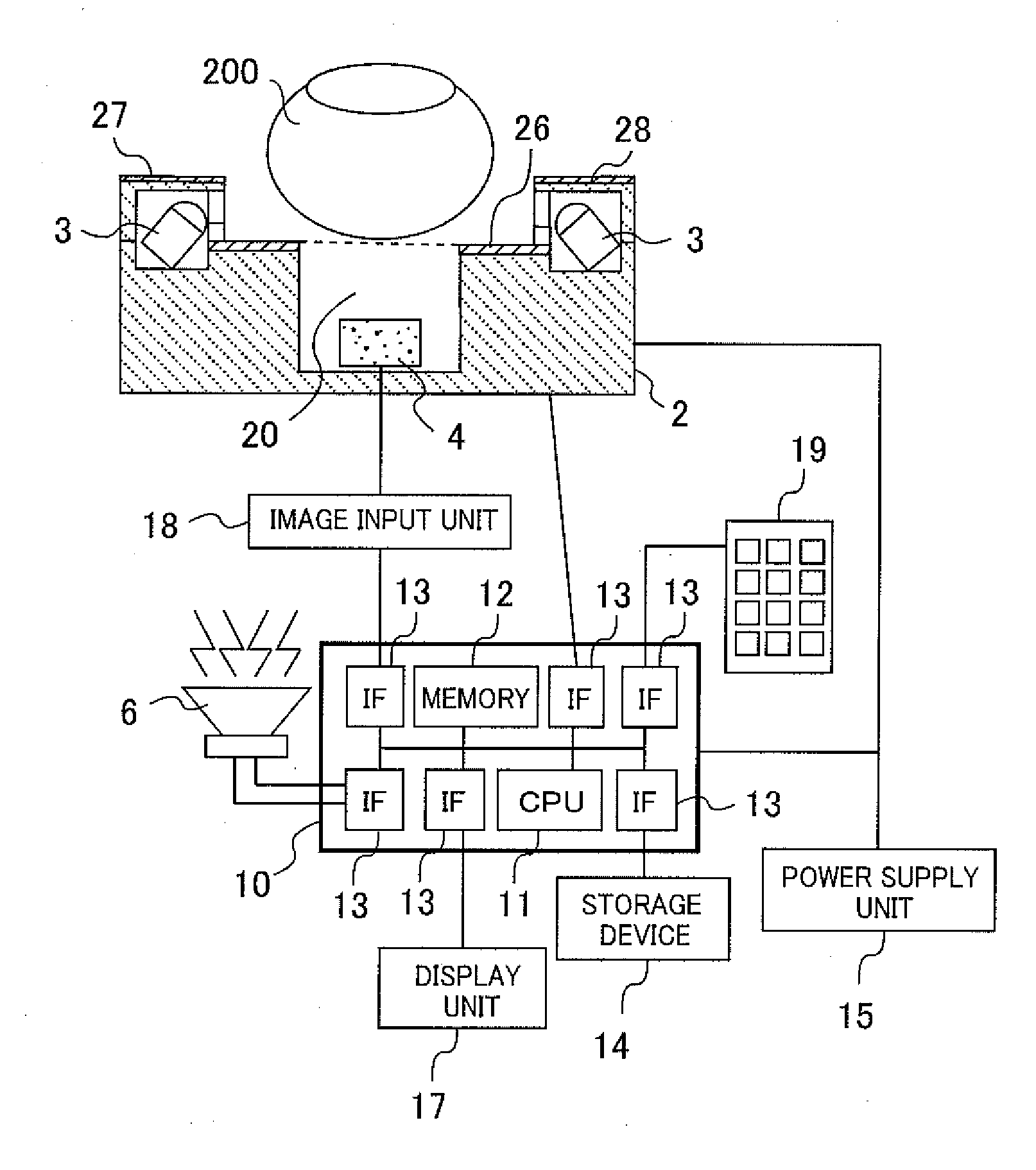
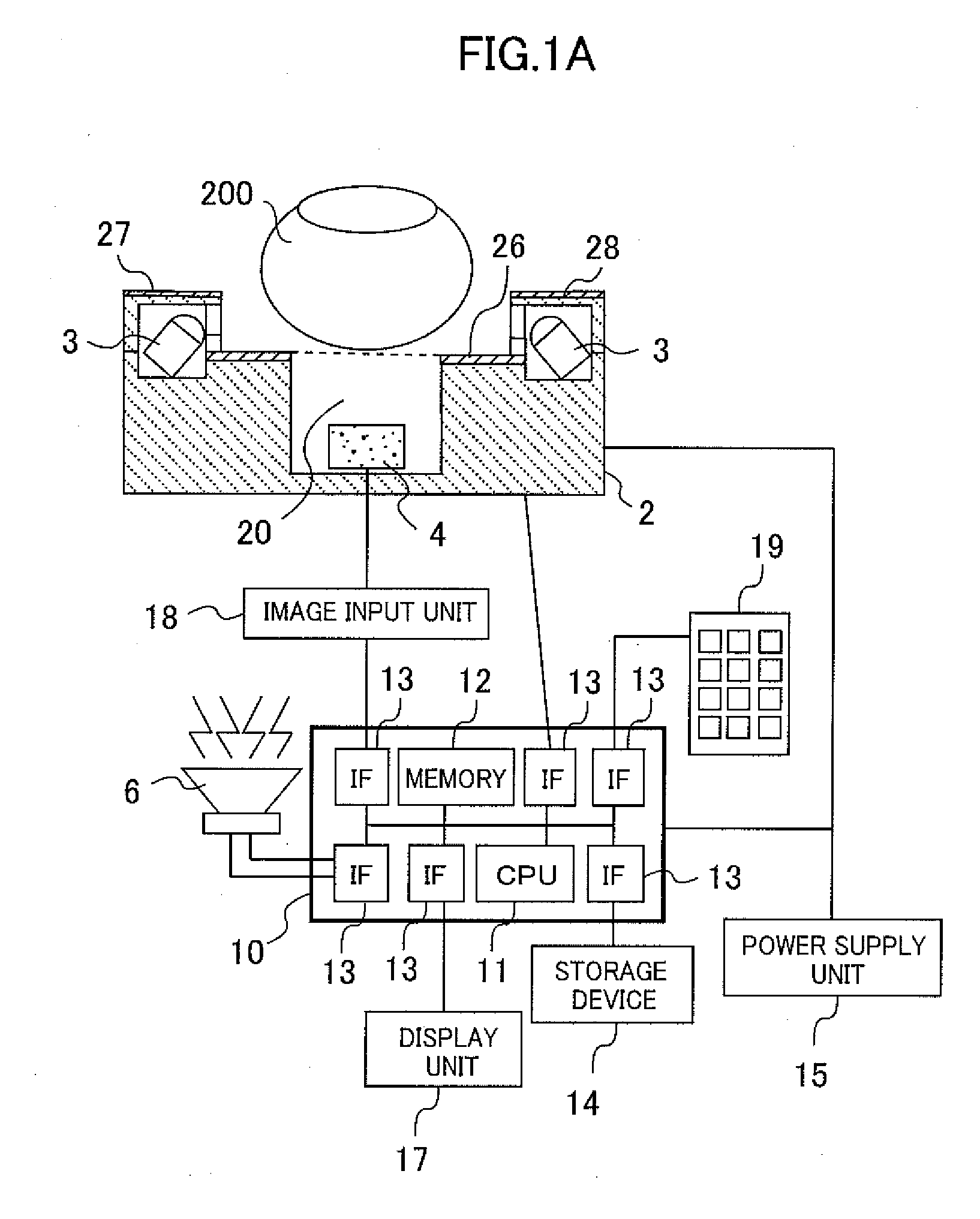
ActiveUS20100008545A1Improve authentication accuracyPrecise positioningSubstation equipmentTransmissionLiquid-crystal displayLight guide
Provided is a biometric authentication device for identifying an individual based on a biometric pattern of the subject included in a picked up image, comprising: a light guiding unit for outputting light from a surface thereof; a liquid crystal display (LCD) unit for adjusting, on a display pixel basis, an intensity of light output from the surface of the light guiding unit; an image pickup unit for picking up an image of the subject; a display light source for emitting light used as a backlight of the LCD unit; a detection light source for emitting light for irradiating the subject; and a control unit for controlling processing of the biometric authentication device The control unit turns on the detection light when the image pickup unit picks up a first image, which is used for authentication, and turns on the display light source when the LCD unit displays information.
Owner:HITACHI LTD
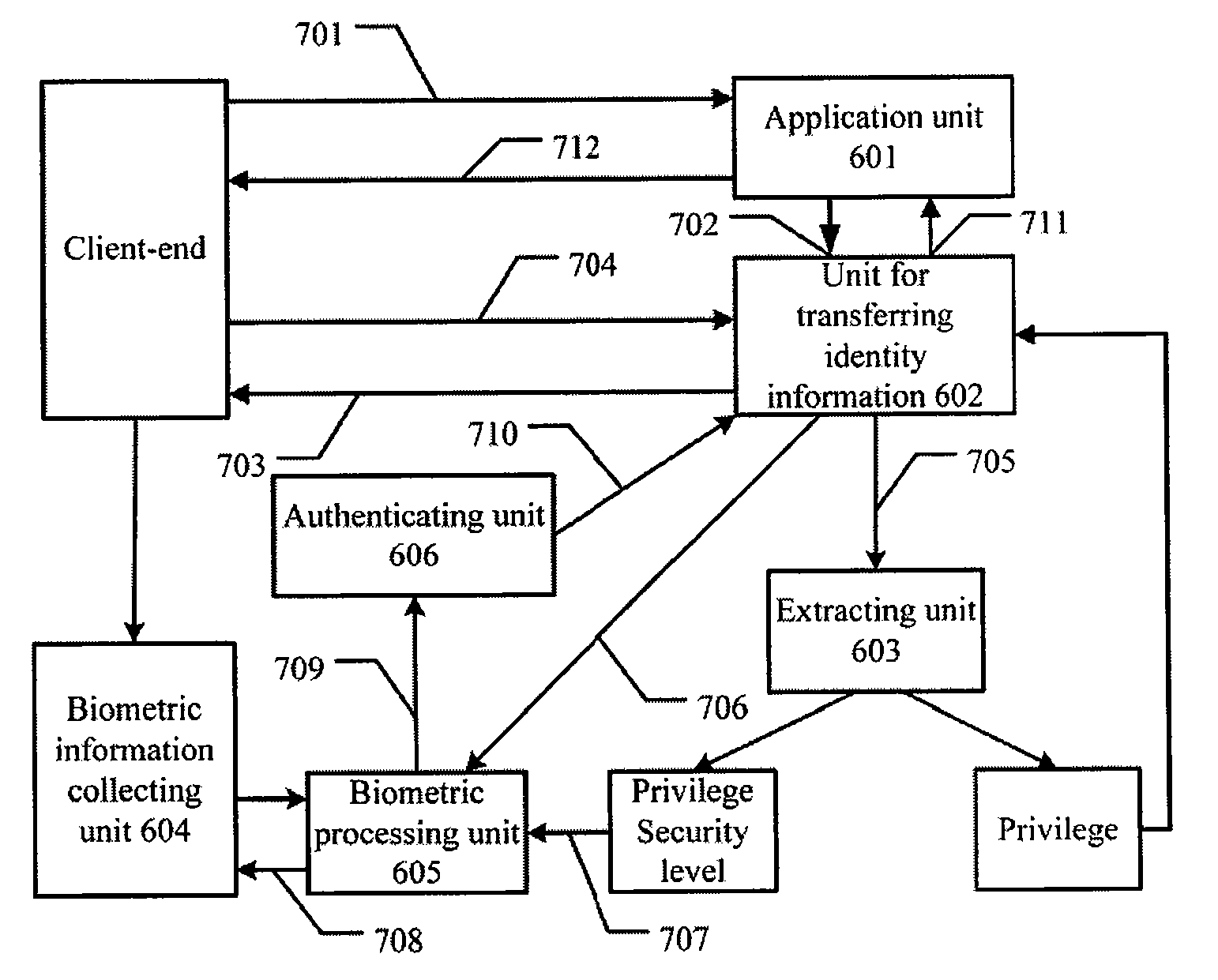
Methods and systems for authentication
InactiveUS20090271635A1Increased processing flexibilityIncrease flexibilityAcutation objectsMultiple keys/algorithms usageClient-sideSecurity level
The present invention discloses a method and system for authentication. The method for authentication includes: acquiring the privilege security level corresponding to a client-end; inquiring the identity security level corresponding to the privilege security level according to an established relation of association between privilege security level and identity security level; determining the authentication parameters for identity authentication according to the identity security level; performing identity authentication on the client-end using the authentication parameters; and obtaining an authentication result. The identity authentication and privilege authentication are combined, and identity authentication is performed according to the identity security level in accord with the privilege security level so that rules of identity authentication can be adjusted, and the flexibility of the process of authentication may be improved.
Owner:HUAWEI TECH CO LTD
Authentication techniques in a monitoring system
InactiveUS6844816B1Improve abilitiesReduce the possibilityElectric signal transmission systemsMultiple keys/algorithms usageMonitoring systemTransmitter
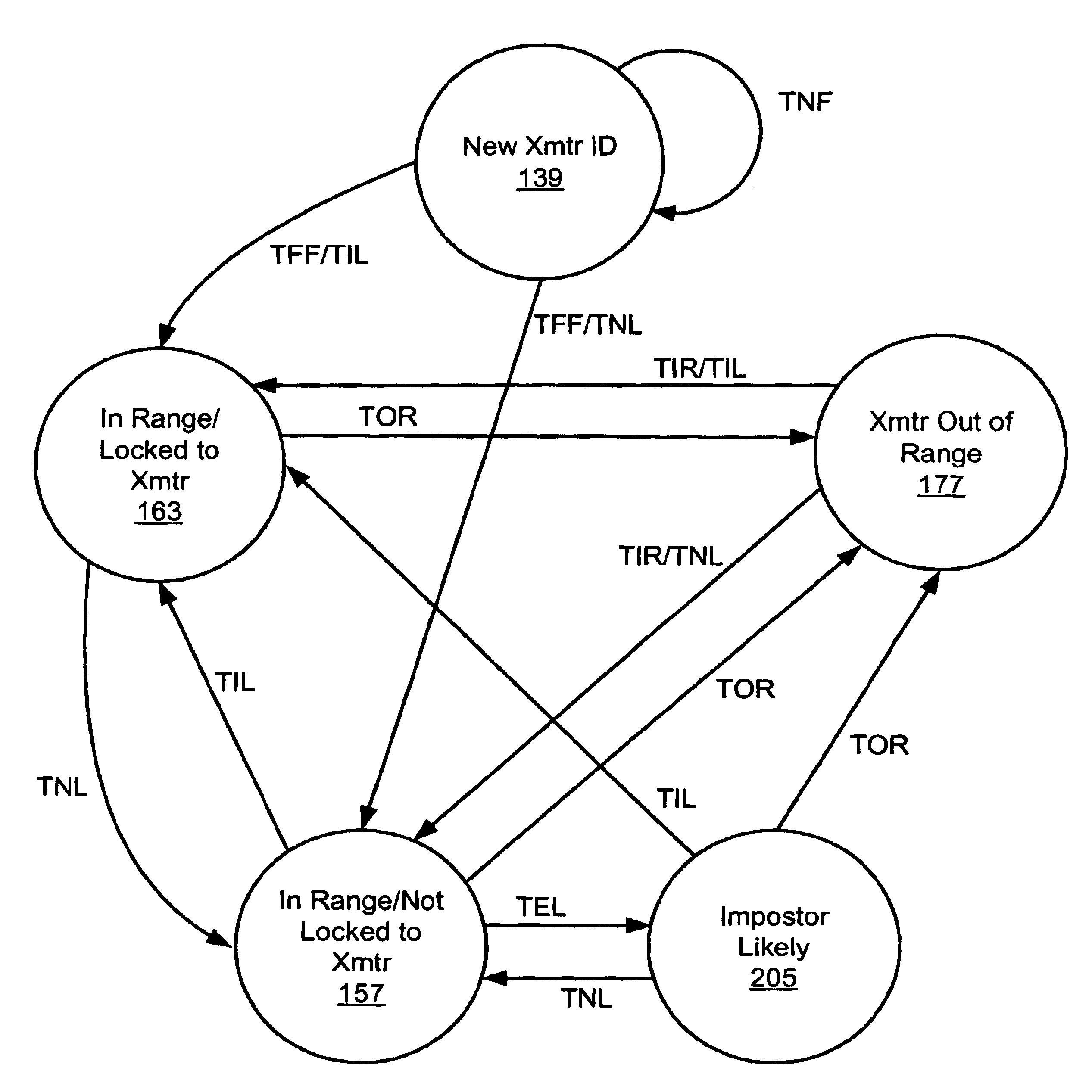
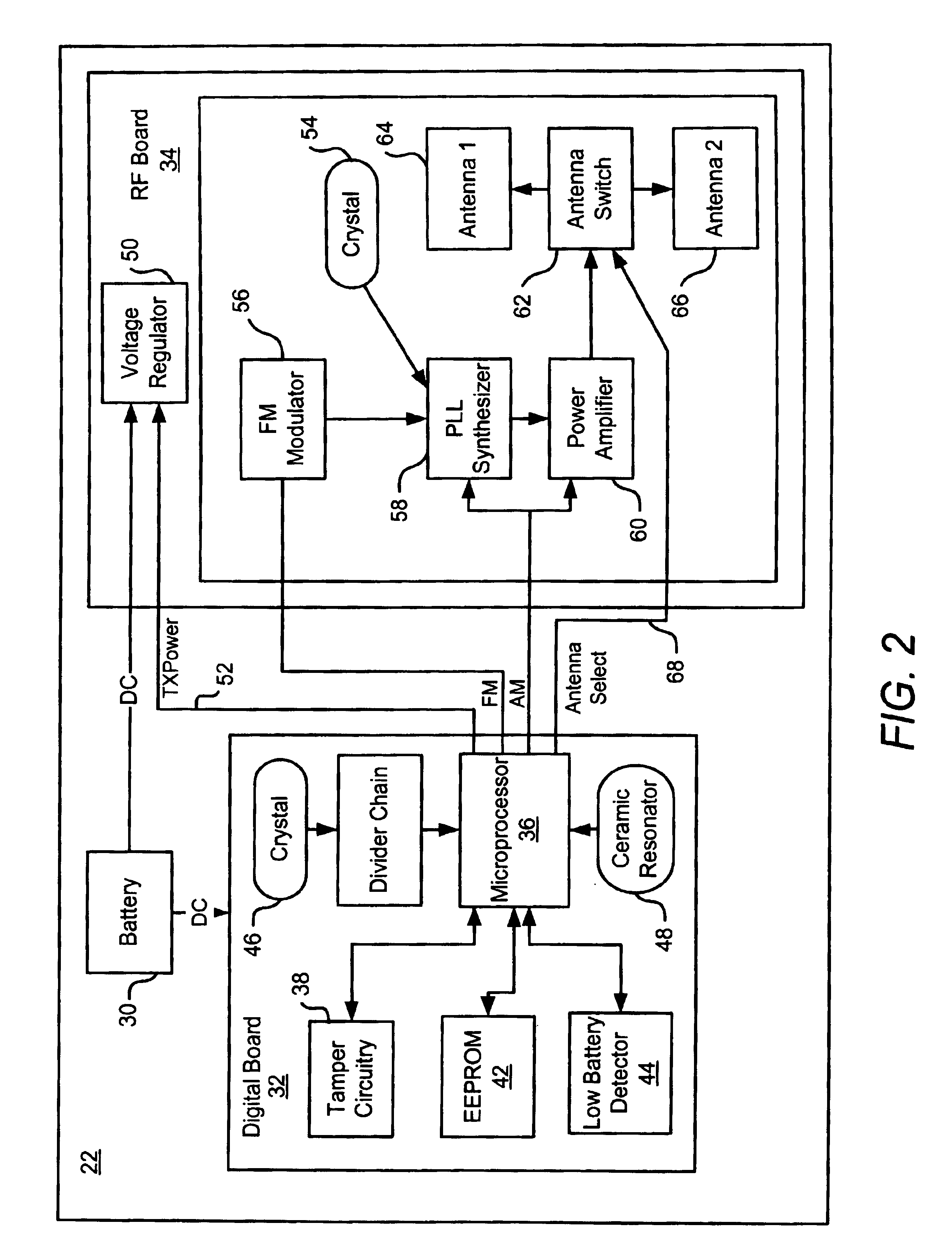
An Electronic House Arrest Monitoring (EHAM) system of the present invention includes a transmitter attached to a monitored offender and a receiver positioned in the vicinity of the desired monitoring location. The transmitter and the receiver each have a pattern stored or generated therein for determining the interval of time between signal transmissions and receptions. The pattern is pseudo-random to offer improved protection against imposter transmitters, in other words the time intervals are selected to be unequal and randomly varying but the pattern is repeated or cycled to allow continuing signal transmission by the transmitter. The transmitter transmits signals at varying time intervals according to this pattern, and the receiver authenticates signals it receives as coming from the monitored transmitter based on the expected time intervals from the pattern. The pattern may include any number of time intervals and, in one embodiment, includes more than one subpattern to extend the length of the repeat cycle to increase the difficulty of defeating the monitoring system. As further protection against imposter devices, the receiver may verify the signals based on information unique to the transmitter included in each signal. The receiver may further use the received signals and unique time interval patterns to determine a number of operating states, including New Transmitter ID Received, Transmitter In Range and Locked to Transmitter, Transmitter In Range and Not Locked, Transmitter Out of Range, and Imposter Likely. The monitoring system may also include a remote host computer linked to the receiver or receivers to enable these operating states to be monitored remotely by enforcement personnel.
Owner:BI
Internet of things terminal secure access method and system based on edge computing
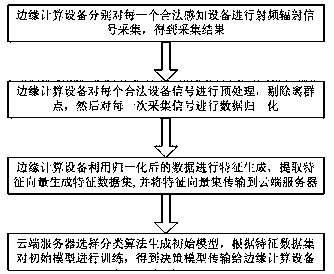
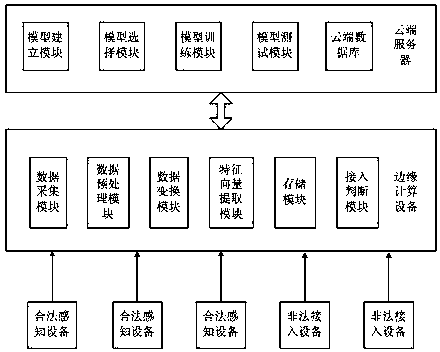
ActiveCN107770263AReduce computational complexityReduce latencyTransmission monitoringSecurity arrangementComputation complexityData set
The invention discloses an Internet of things terminal secure access method and system based on edge computing. The method comprises the steps that an edge computing device carries out radio frequencyradiation signal collection on each legal sensing device, thereby obtaining collection results; the edge computing device preprocesses each legal device signal, removes outliers and carries out datanormalization on collected signals of each time; the edge computing device generates features through utilization of the normalized data, extracts feature vectors to generate feature data sets and transmits the feature vector sets to a cloud server; and the cloud server selects a classification algorithm to generate a data model, trains the data model according to the feature data sets and transmits an obtained decision-making model to the edge computing device. According to the method and the system, the data processing and access judgment are carried out at the edge computing side, and the method and the system are applicable to an Internet of things device interconnection scheme with limited resources and have the advantages of low computing complexity and high authentication accuracy.
Owner:CERTUS NETWORK TECHNANJING
Information Extraction Method, Information Extraction Device, Program, Registration Device, and Verification Device
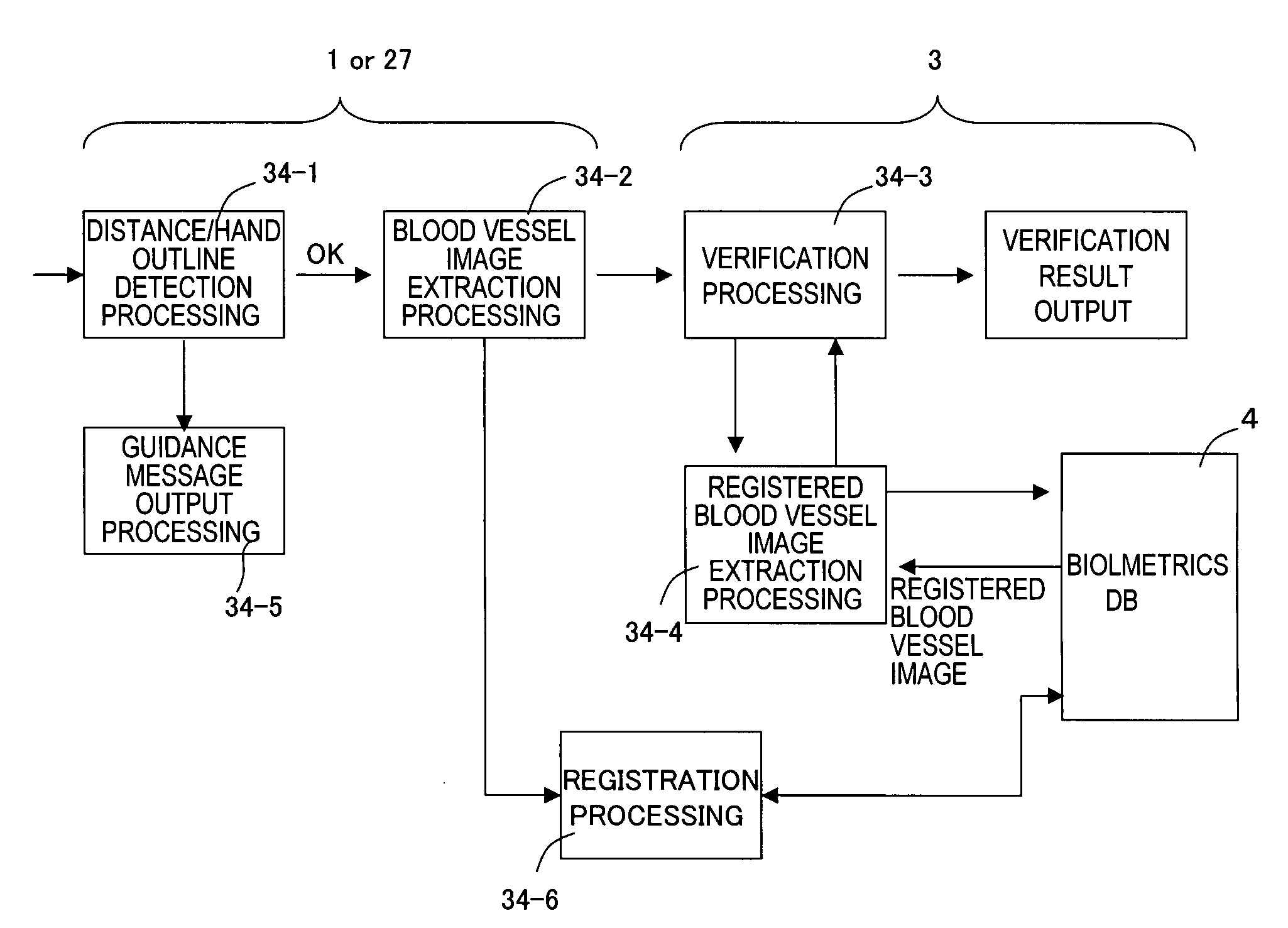
InactiveUS20100098299A1Reduce the amount of informationImprove authentication accuracyImage enhancementImage analysisImage extractionComputer graphics (images)
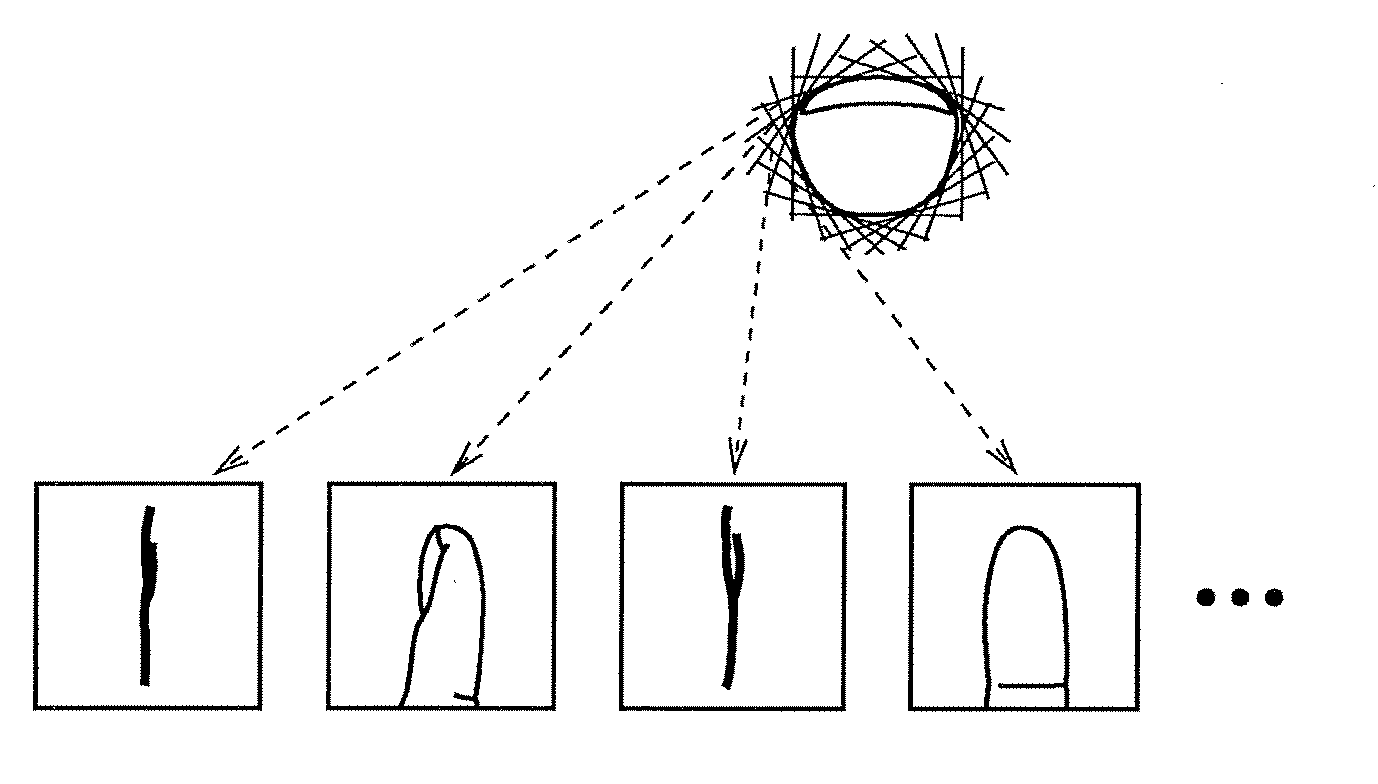
An information extraction method, an information extraction device, a program, a registration device, and a verification device that improve authentication accuracy simultaneously with reduction of the amount of information concerning an identification target are proposed. From a plurality of first images obtained from viewpoints in surroundings of a living body portion, common portions of silhouettes of the living body portion that is shown in the images are generated as a first stereoscopic image in a target space. From a plurality of second images obtained from the viewpoints in the surroundings of the living body portion, common portions of silhouettes of an inner surface image of the living body portion that is shown in the images are generated as a second stereoscopic image in the target space. A value representing a shape of a cross section of the second stereoscopic image that has a predetermined positional relationship with respect to a reference position of the first stereoscopic image is extracted as an identification information item.
Owner:SONY CORP
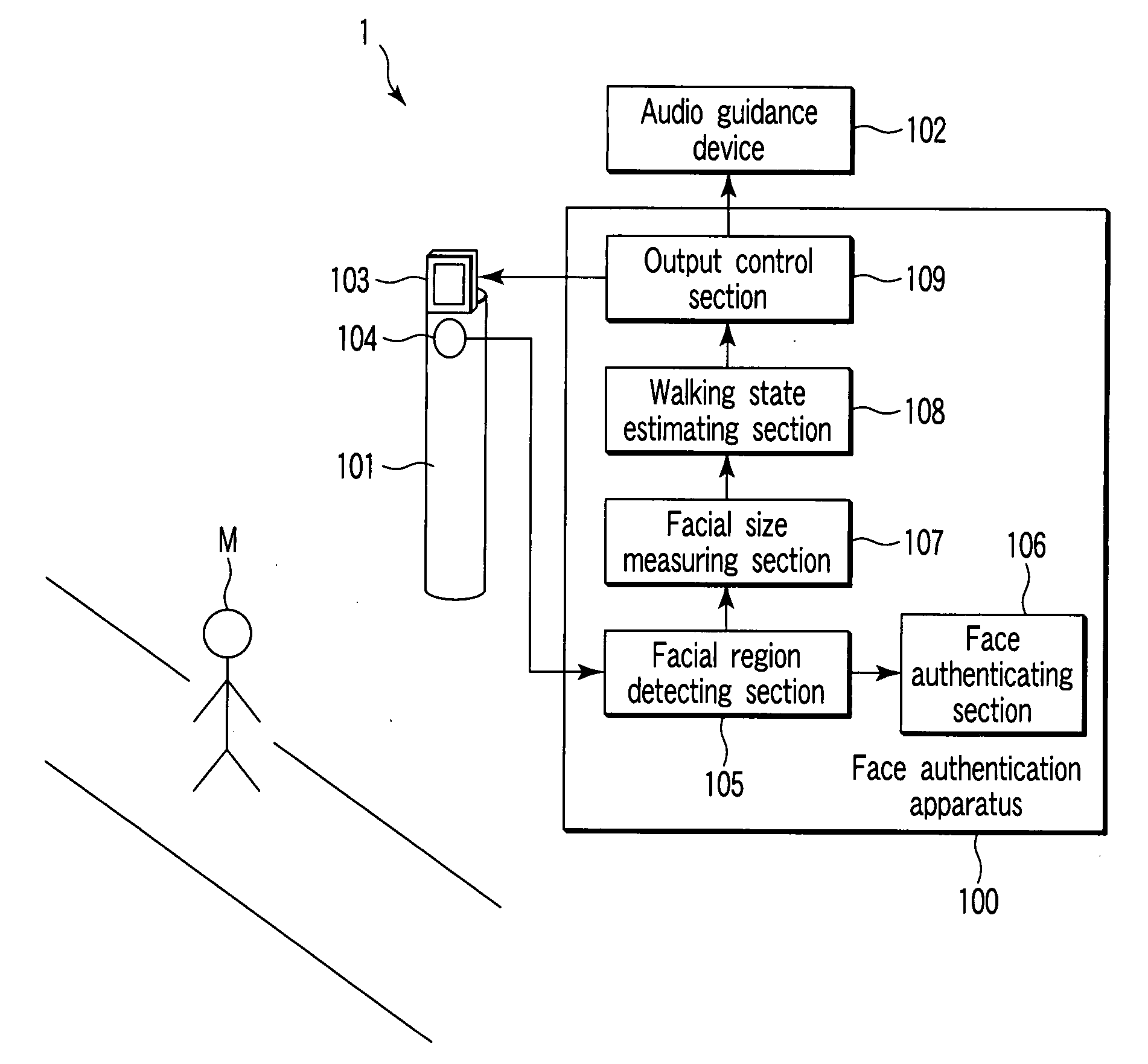
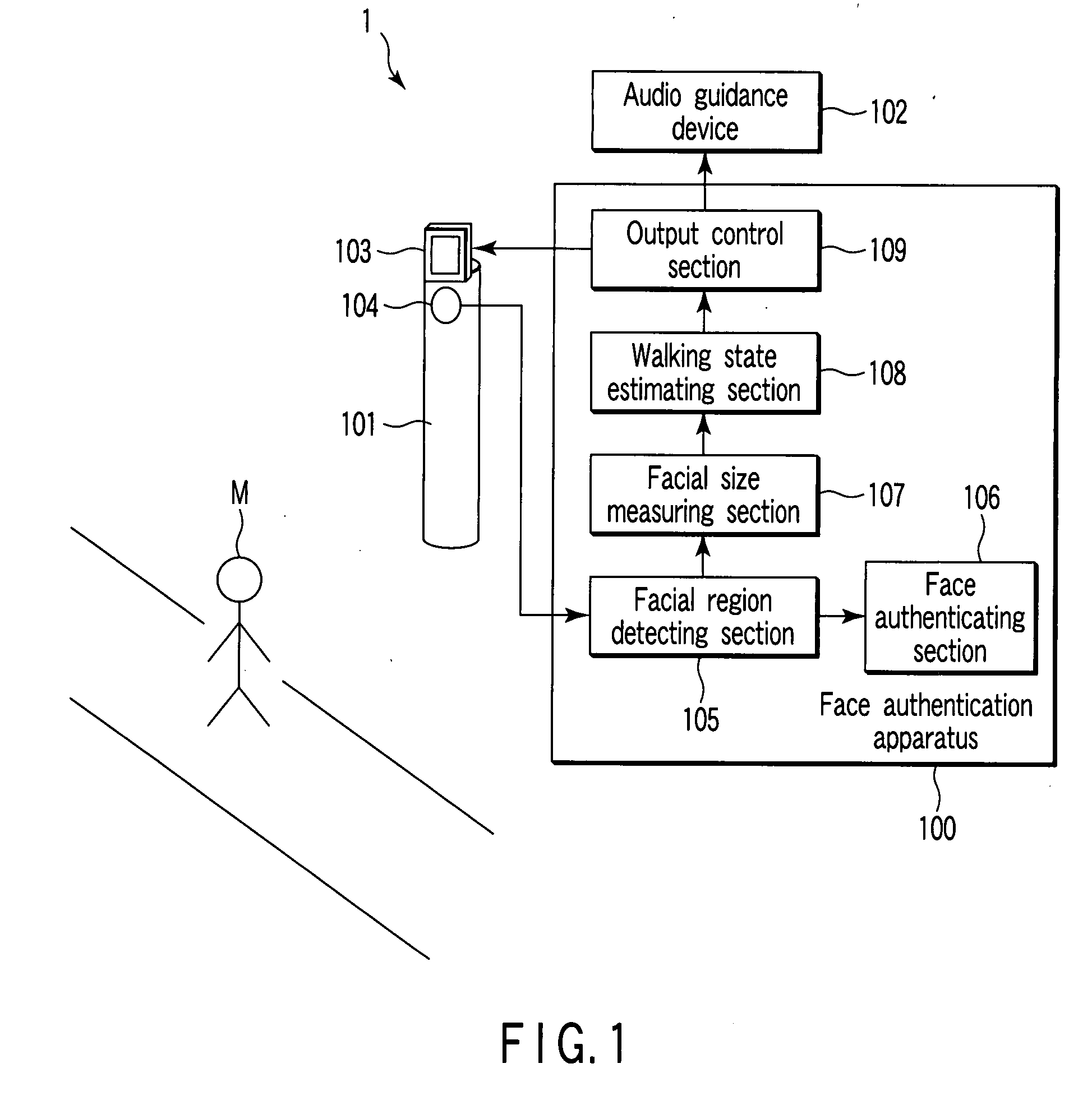
Face authentication apparatus and face authentication method
InactiveUS20070211925A1Improve authentication accuracyCharacter and pattern recognitionDigital data authenticationPattern recognitionComputer graphics (images)
A face authentication apparatus uses a facial region detecting section to detect an image of a facial region of an authentication target person based on each of a plurality of images supplied from a camera that continuously shoots a predetermined target range, uses an authenticating section to authenticate the authentication target person based on a facial image detected from each image captured by the camera, uses a state estimating section to estimate a state of the authentication target person based on the facial image detected from each image captured by the camera, determines a guidance in accordance with the estimated state of the authentication target person, and outputs the guidance to a display device or an audio guidance device from an output section.
Owner:KK TOSHIBA
Iris authentication apparatus
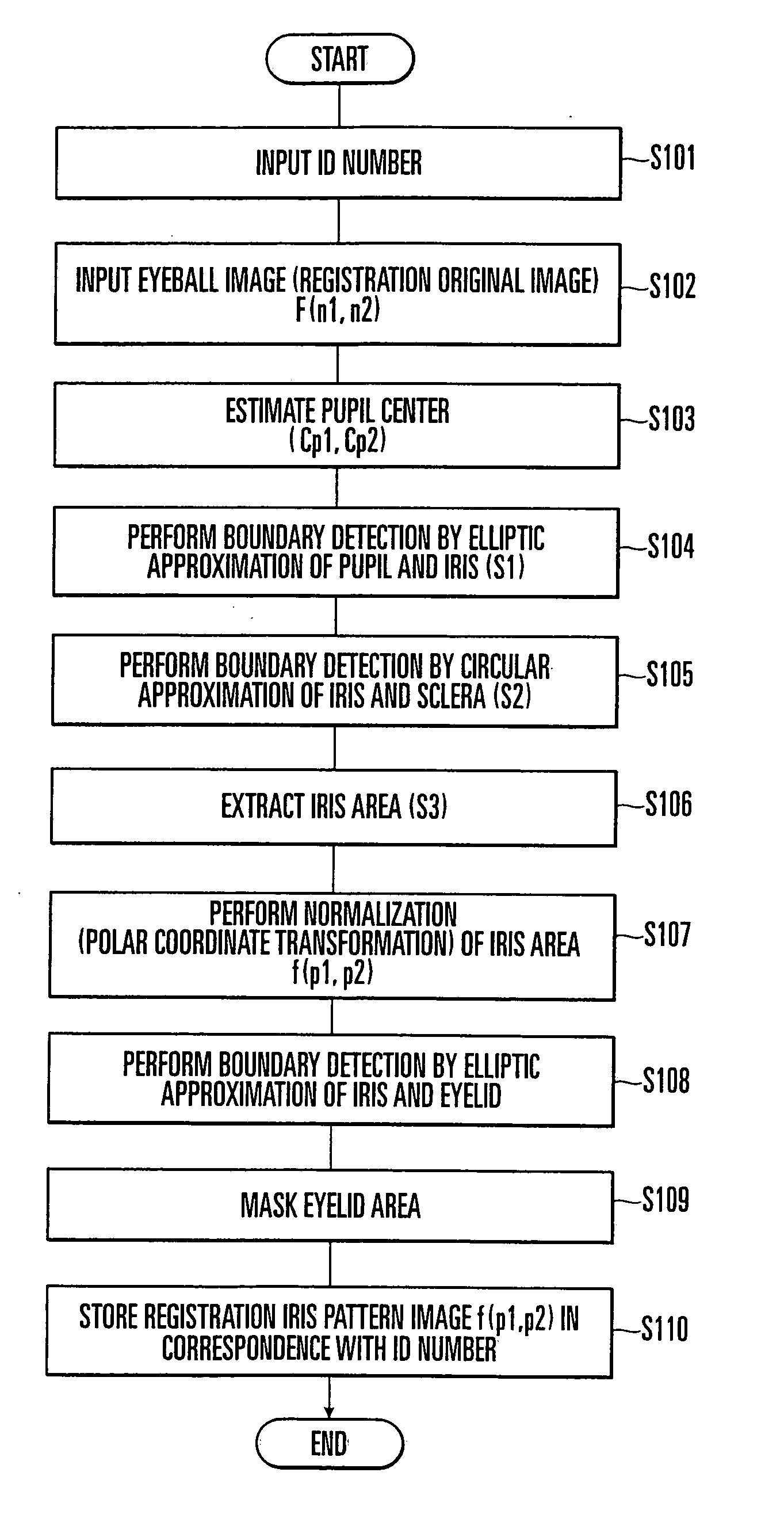
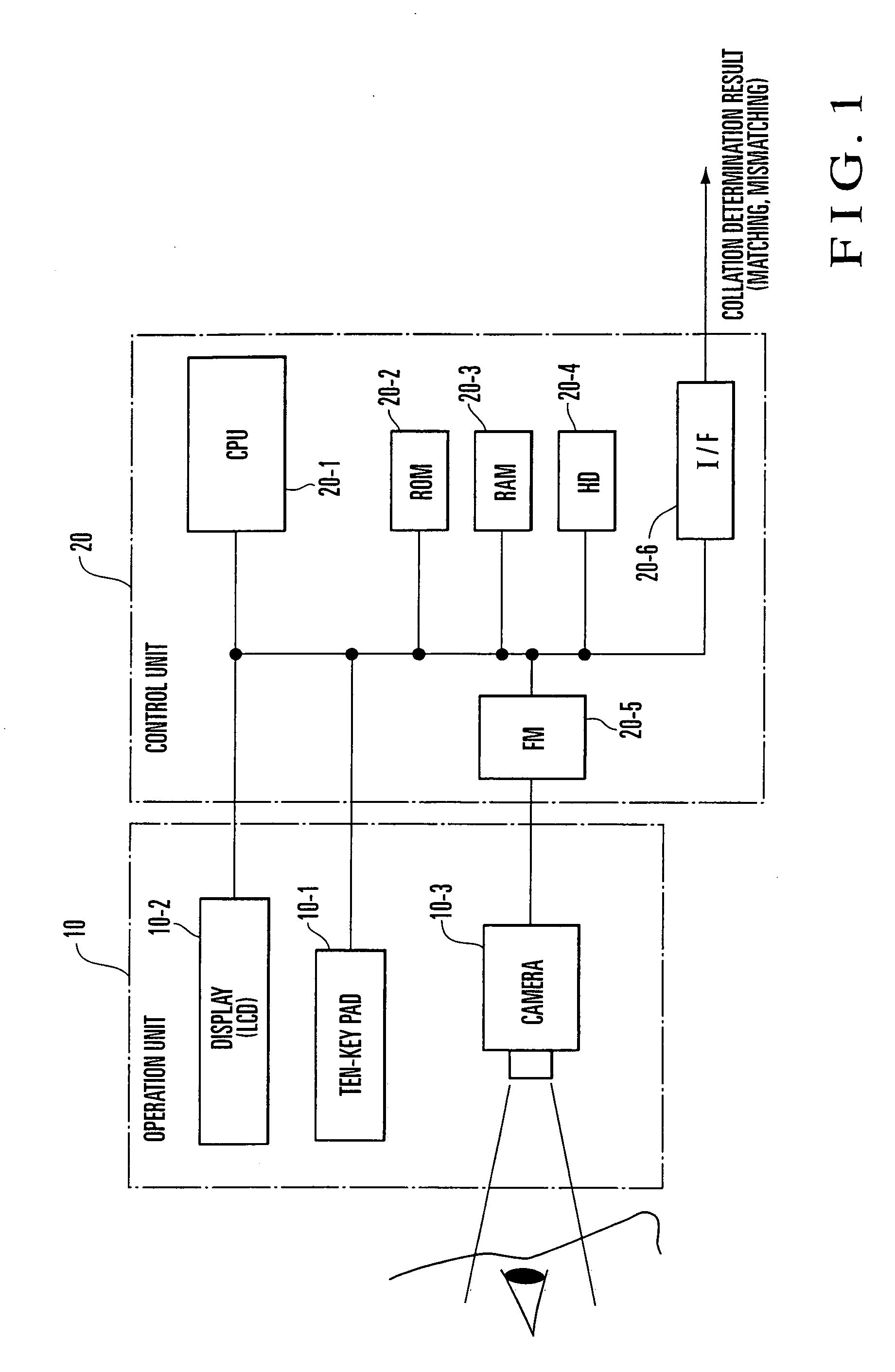
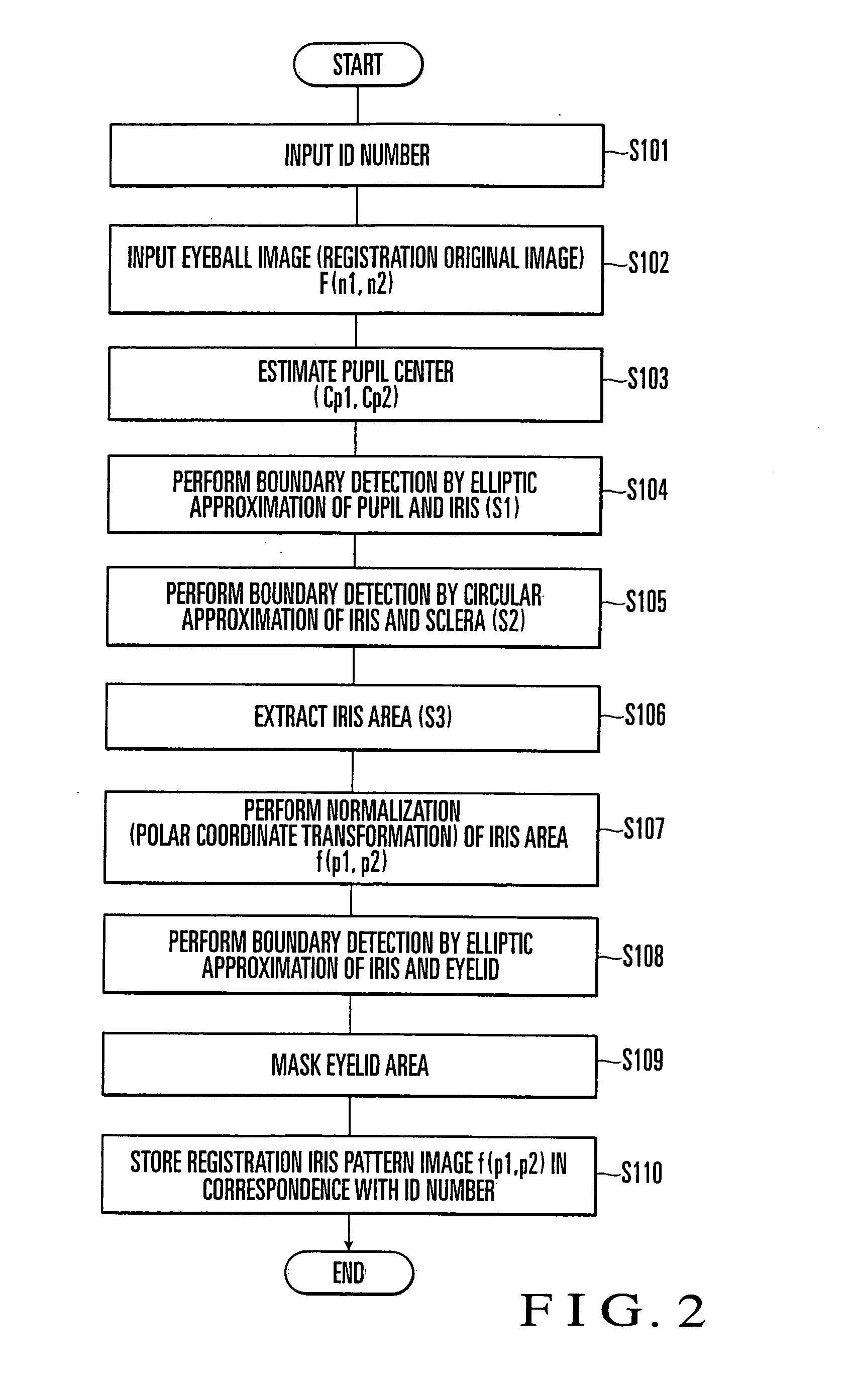
InactiveUS20070025598A1Accurately perform authenticationImprove authentication accuracyAcquiring/recognising eyesPerson identificationPattern generationComputer vision
An iris authentication apparatus includes an iris area extraction unit, registration pattern generating unit, collation pattern generating unit, and collation unit. The iris area extraction unit extracts iris areas from a sensed registration eyeball image and a sensed collation eyeball image. When the iris area extraction unit extracts an iris area from the registration eyeball image, the registration pattern generating unit generates a registration iris pattern image by performing polar coordinate transformation of an image in the extracted iris area. When the iris area extraction unit extracts an iris area from the collation eyeball image, the collation pattern generating unit generates a collation iris pattern image by performing polar coordinate transformation of an image in the extracted iris area. The collation unit collates the registration iris pattern image output from the registration pattern generating unit and the collation iris pattern image output from the collation pattern generating unit on the basis of a correlation therebetween.
Owner:YAMATAKE HONEYWELL CO LTD +1
Voice authentication system
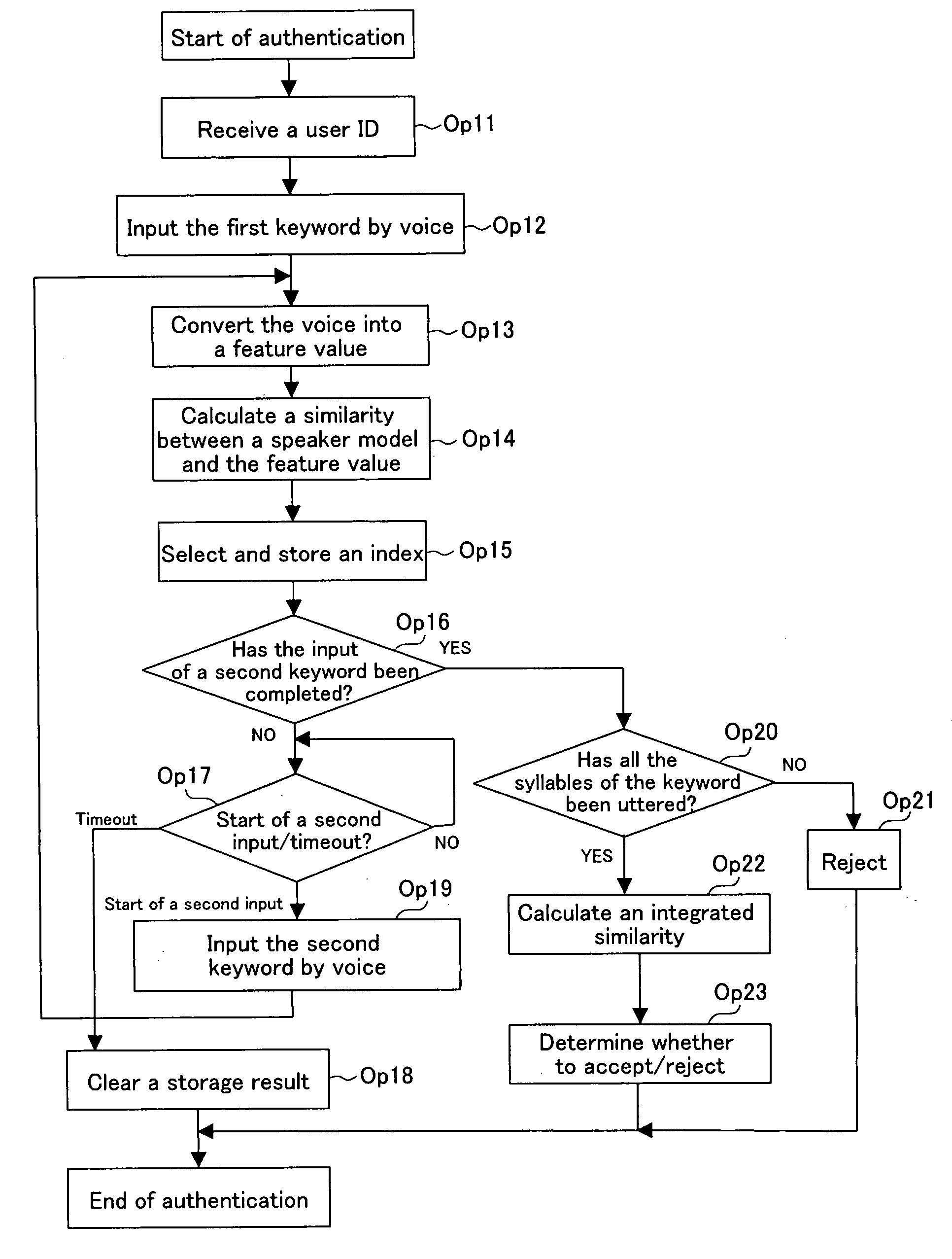
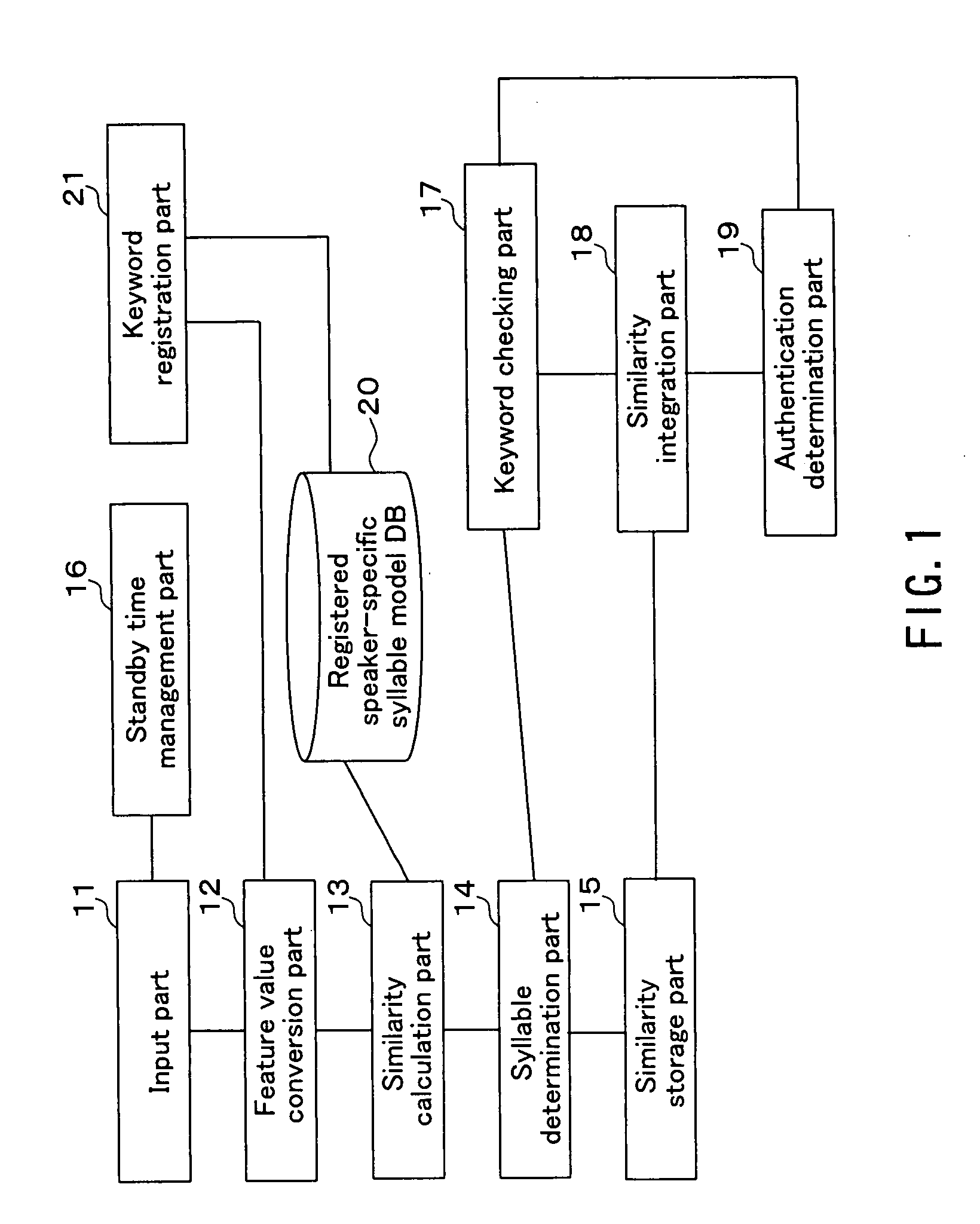
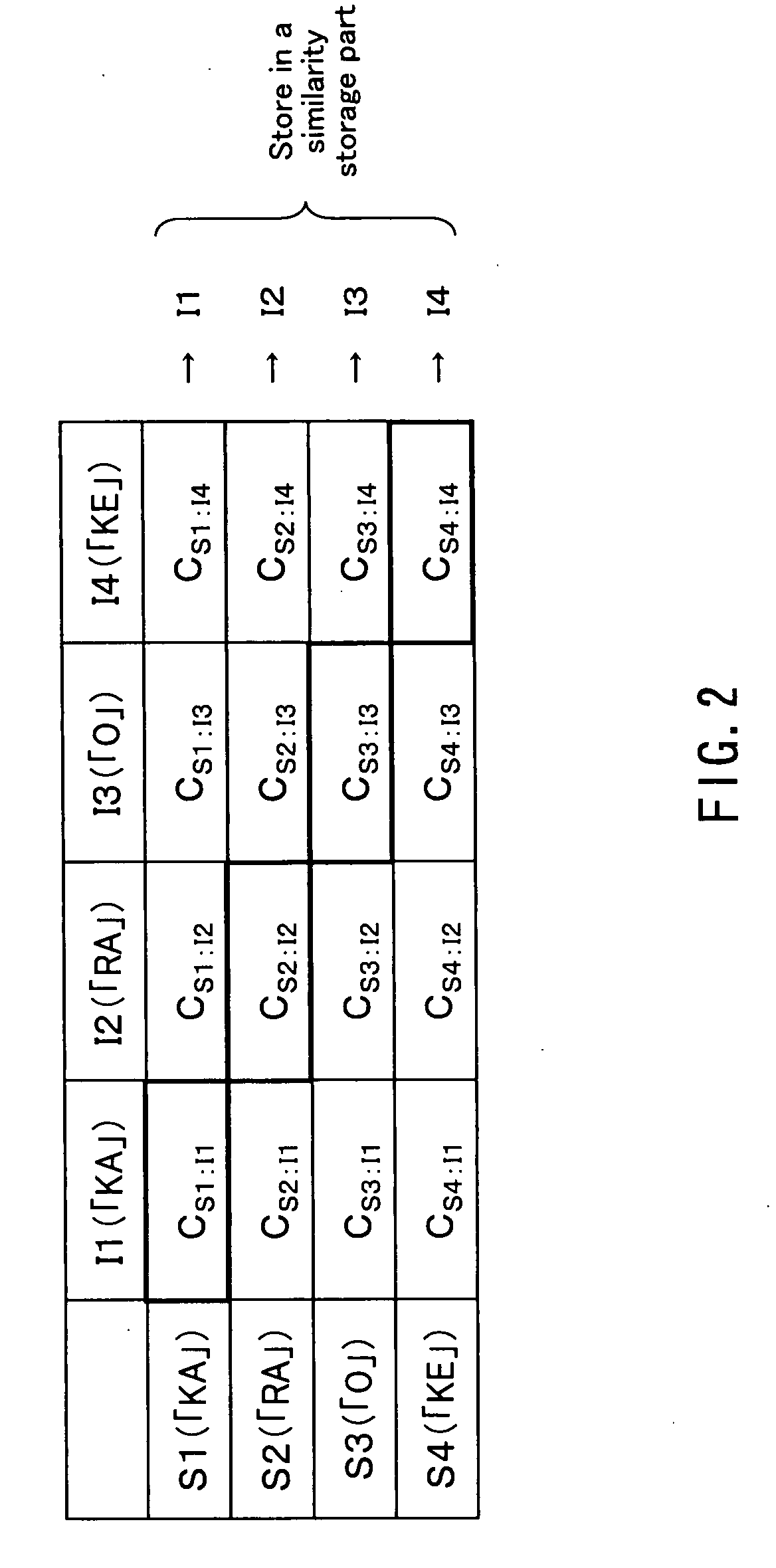
InactiveUS20080172230A1Improve authentication accuracyImprove accuracySpeech recognitionSyllableSpeech verification
A text-dependent voice authentication system that performs authentication by urging a user to input a keyword by voice includes: an input part (11) that receives a voice input of a keyword divided into a plurality of portions with an utterable unit being a minimum unit over a plurality of times at a time interval for each of the portions; registered speaker-specific syllable model DB (20) that previously stores a registered keyword of a user as a speaker model created in the utterable unit; a feature value conversion part (12) that obtains a feature value of a voice contained in a portion of the keyword received by the first voice input in the input part (11) from the portion; a similarity calculation part (13) that obtains a similarity between the feature value and the speaker model; a keyword checking part (17) that determines whether or not voice inputs of all the syllables or phonemes configuring an entire registered keyword by the plurality of times of voice inputs, based on the similarity obtained in the similarity calculation part; and an authentication determination part (19) that determines whether to accept or reject authentication, based on a determination result in the keyword checking part and the similarity obtained in the similarity calculation part.
Owner:FUJITSU LTD
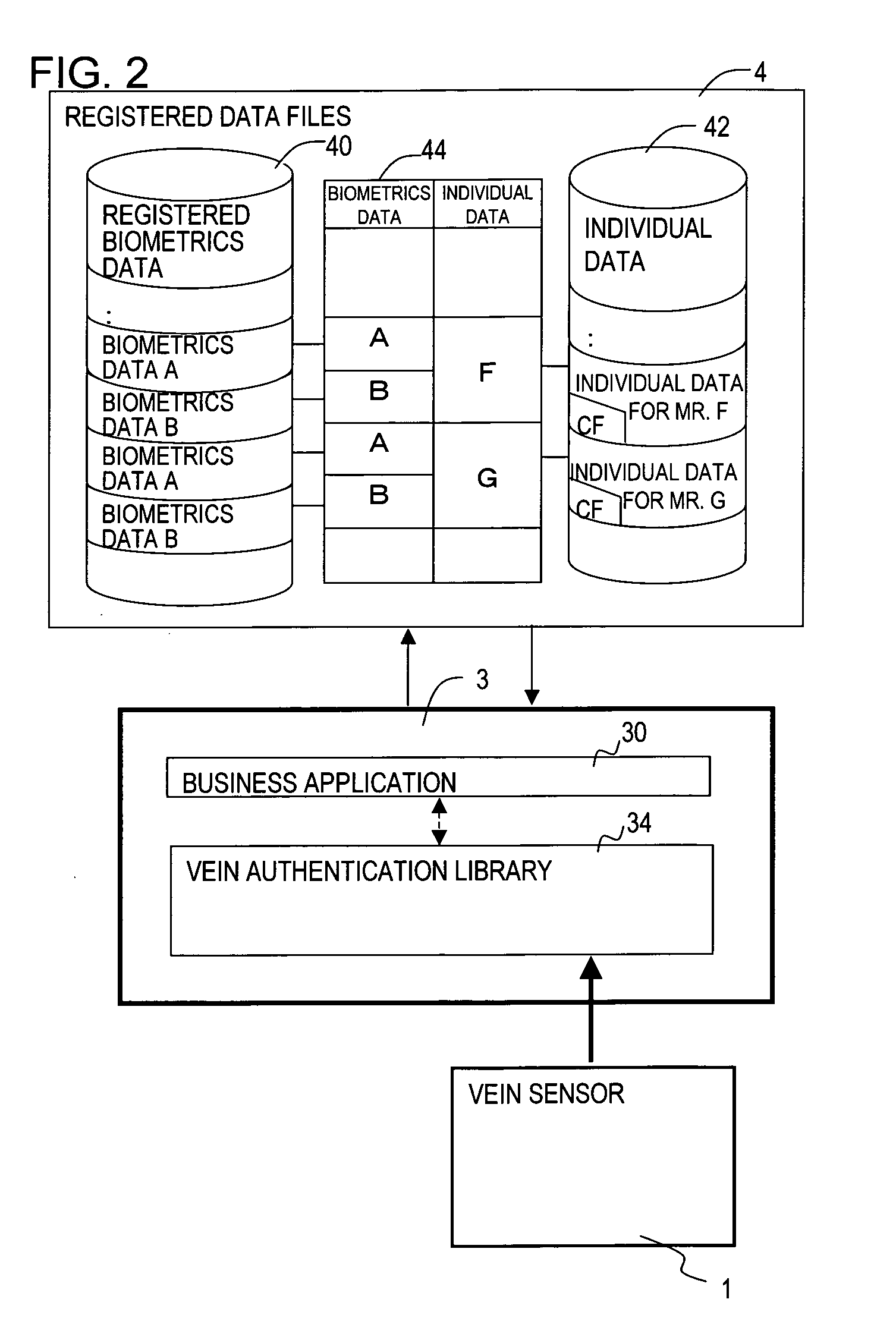
Biometrics authentication method and biometrics authentication system
ActiveUS20080002861A1Accurate authenticationLow reliabilityPerson identificationCharacter and pattern recognitionData setBiometric data
A biometrics authentication system detect body characteristics, verify the characteristics against registered biometrics data to perform individual authentication. In 1:n authentication, a plurality of different type biometrics database sets of a user are registered in a database, and at the time of verification of one type biometrics data set with one type registered biometrics data set, the control unit judges whether similar biometrics data sets of other person are registered, and if other person's similar biometrics data sets are registered, performs verification of each of the another type biometrics data sets of the plurality of similar biometrics data sets with the detected another type biometrics data set, and identifies the individual in question.
Owner:FUJITSU LTD
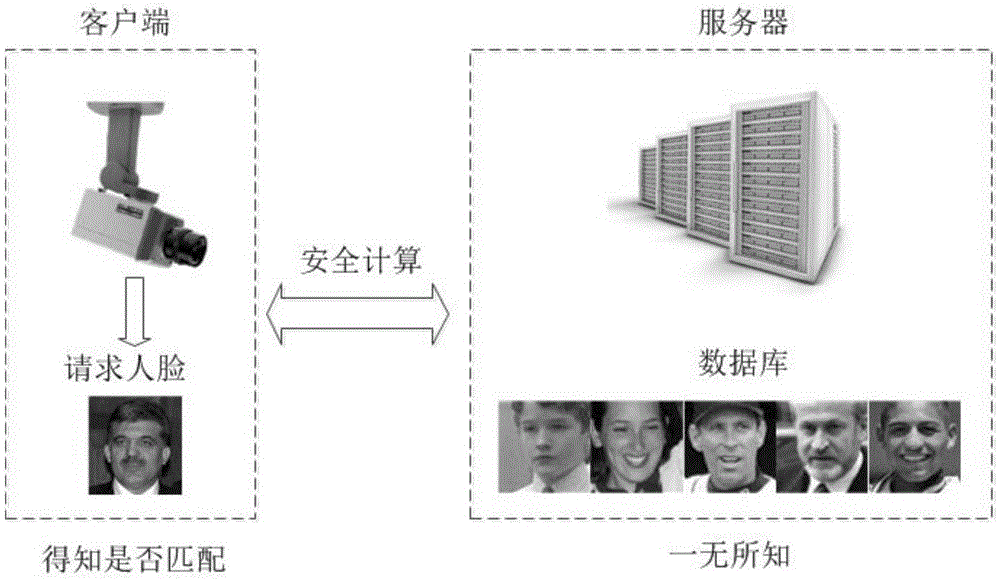
Design method of safety face verification system based on CNN (convolutional neural network) feature extractor
ActiveCN105631296AImprove authentication accuracyImprove securityUser identity/authority verificationCharacter and pattern recognitionCiphertextOblivious transfer
The invention provides a design method of a safety face verification system based on a CNN (convolutional neural network) feature extractor, belongs to the field of biological feature identification, and particularly relates to a method of utilizing the CNN to extract face features and using a Paillier algorithm and an oblivious transfer technique to encrypt. Compared with the SCiFi (secure computation of face identification) system, the method has the advantages that the manually extracted feature is converted into the CNN self-learning feature, and the CNN self-learning feature is performed with binarization to remove the noise effect, so that the identification accuracy is higher; the testing identification rate is 91.48% on a view 2 of an LFW (labeled face wild) base; in the whole identification process, a server will not obtain any feature information of a requester, and only receive the feature ciphertext information, but not decrypt; a client only obtains whether the identification is passed or not, and does not know the other information, including hamming distance; one face picture is expressed by the 320bit feature, and compared with the SCiFi system, the feature data volume is decreased by 2 / 3, so that the consumption time of encrypting and identification is low, and the real-time performance is high.
Owner:BEIJING UNIV OF TECH
Personal authentication using heart sound waveform and/or breathing waveform pattern
InactiveUS20060293606A1Improve authentication accuracyIncrease speedPerson identificationAuscultation instrumentsMedicineHeart sounds
We provide quite a novel personal authentication system using heart sound waveform and / or breathing waveform pattern which promptly judges personal authentication of a person to be authenticated with a very high degree of accuracy. The personal authentication system is comprised of a waveform detection means which detects a heart sound waveform pattern and a means which compares a heart sound waveform pattern detected by the waveform detection means with a previously registered heart sound waveform pattern. If the detected heart sound waveform pattern coincides with the registered heart sound waveform pattern, the system authenticates the person to be identical. In such constitution, the system can check the autonomic heart sound which cannot be controlled by a personal will based on the previously registered heart sound waveform pattern in real time, and performs personal authentication of the person to be authenticated with very high accuracy promptly.
Owner:TOMITA SEIJIRO
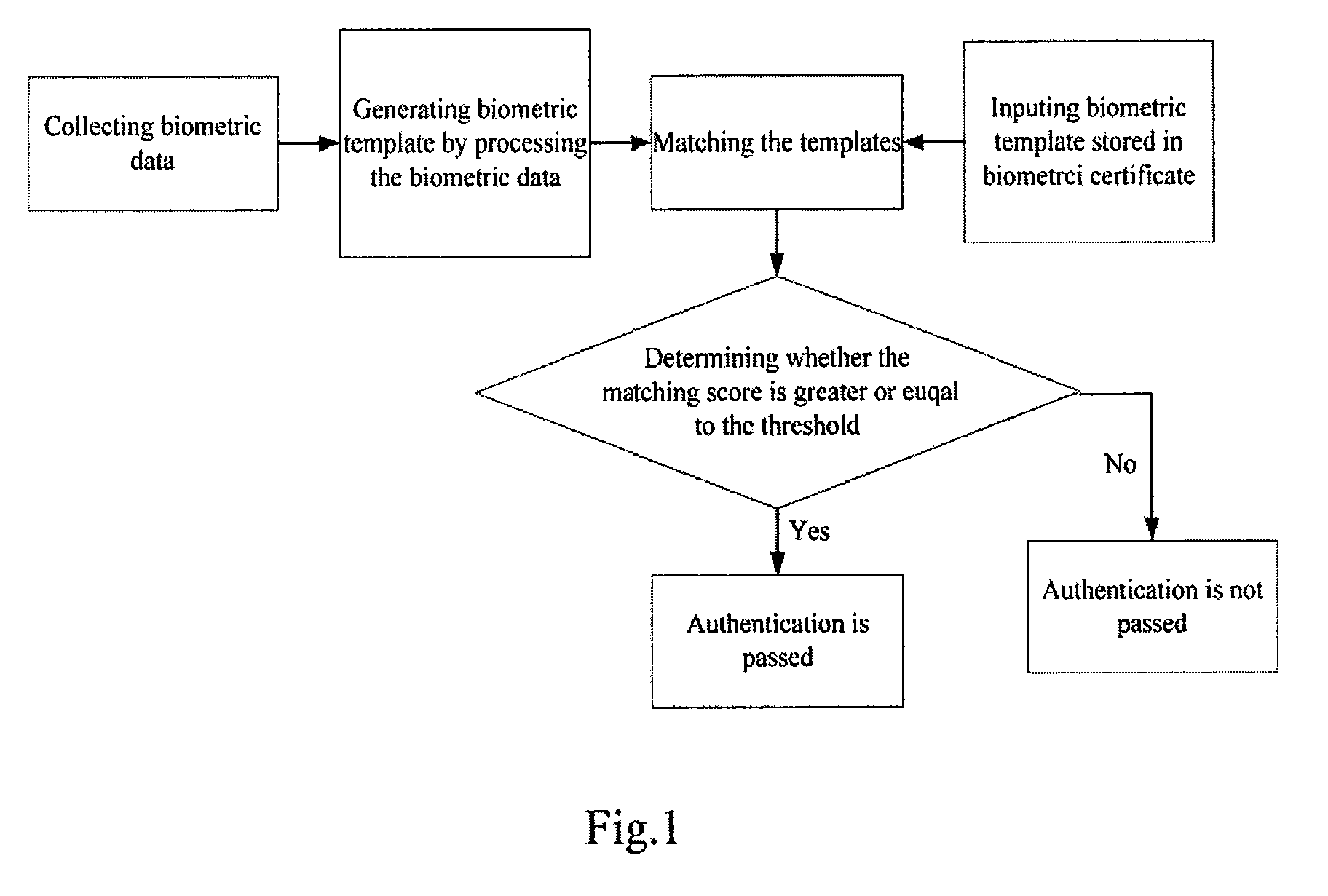
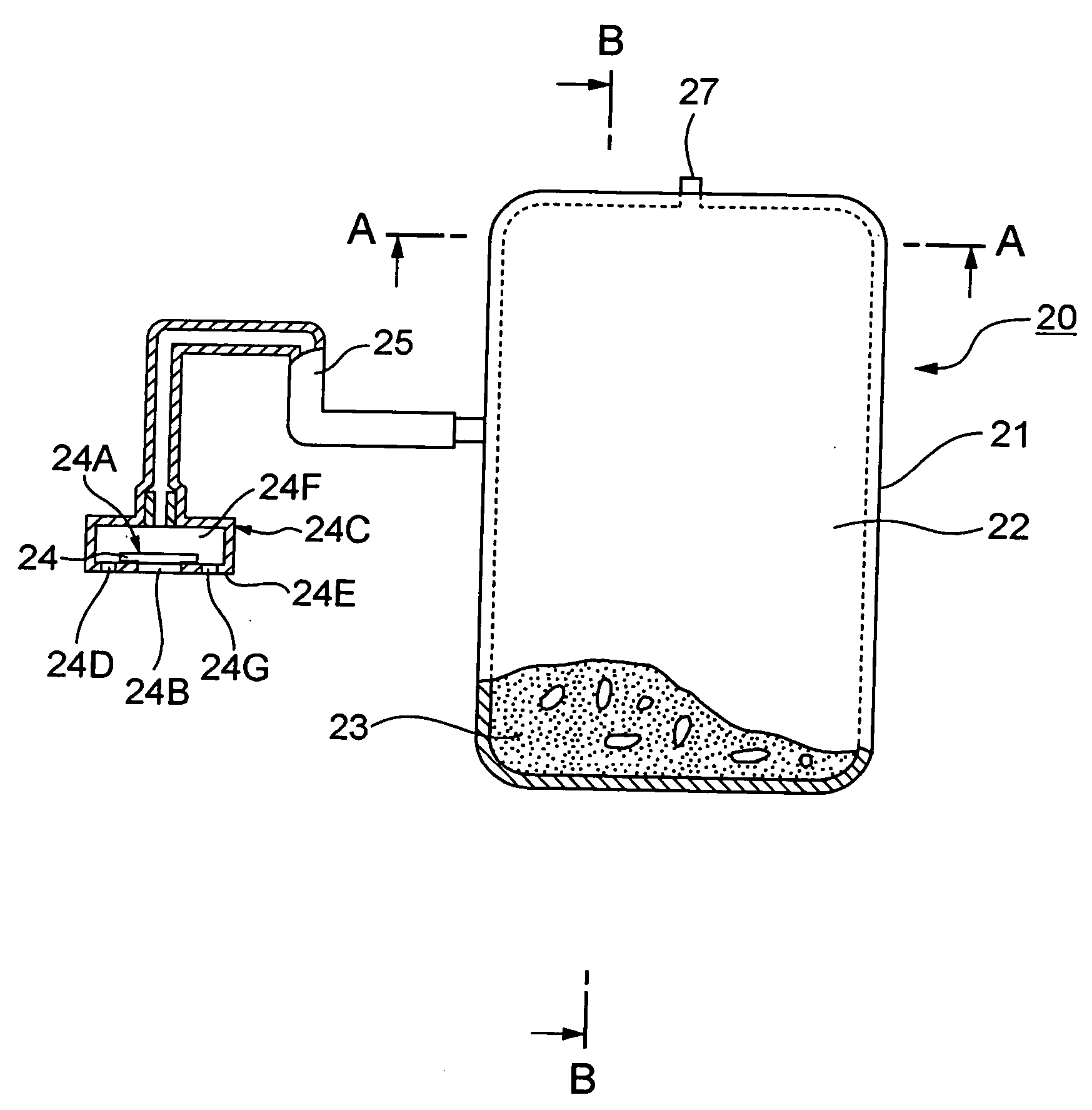
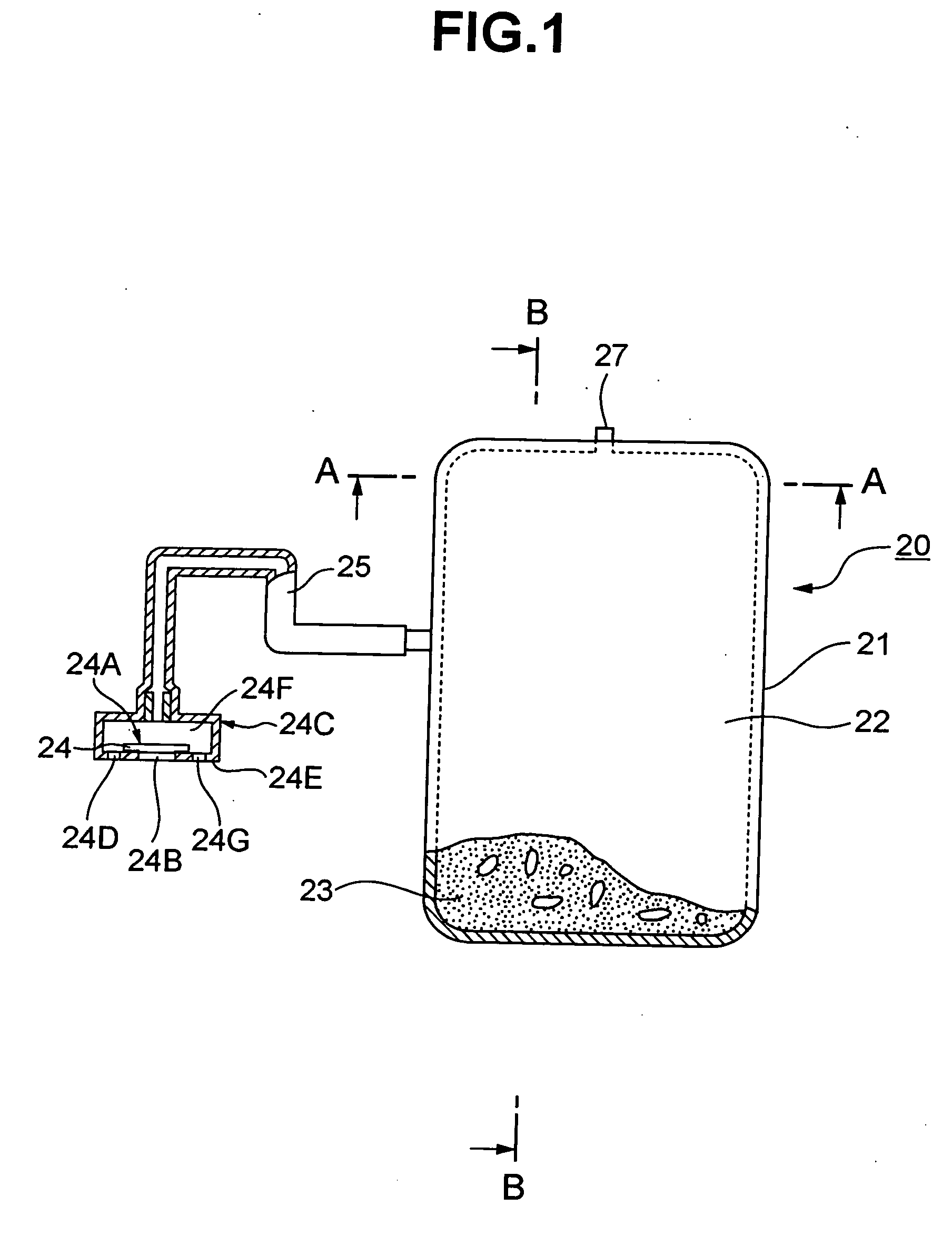
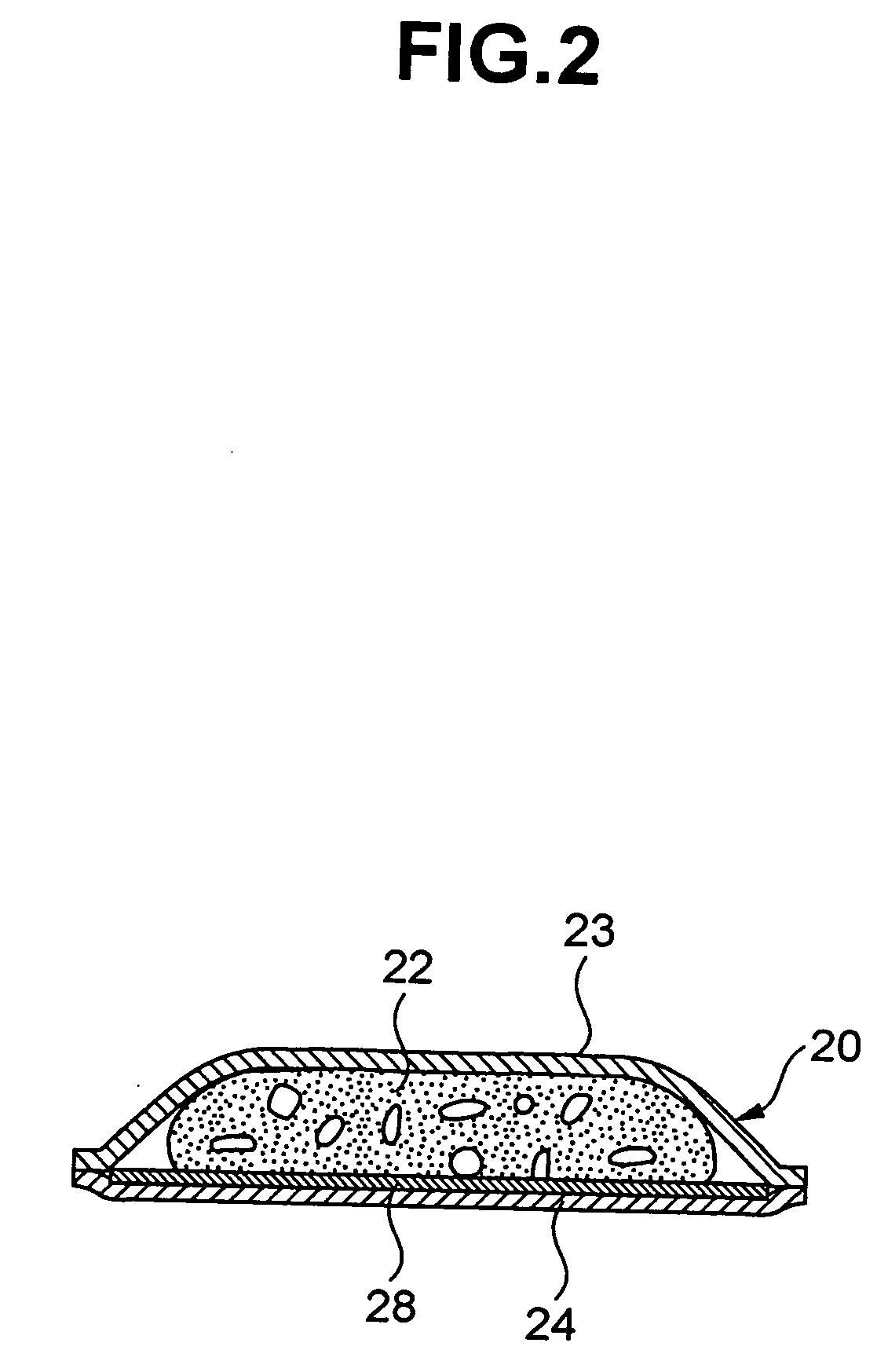
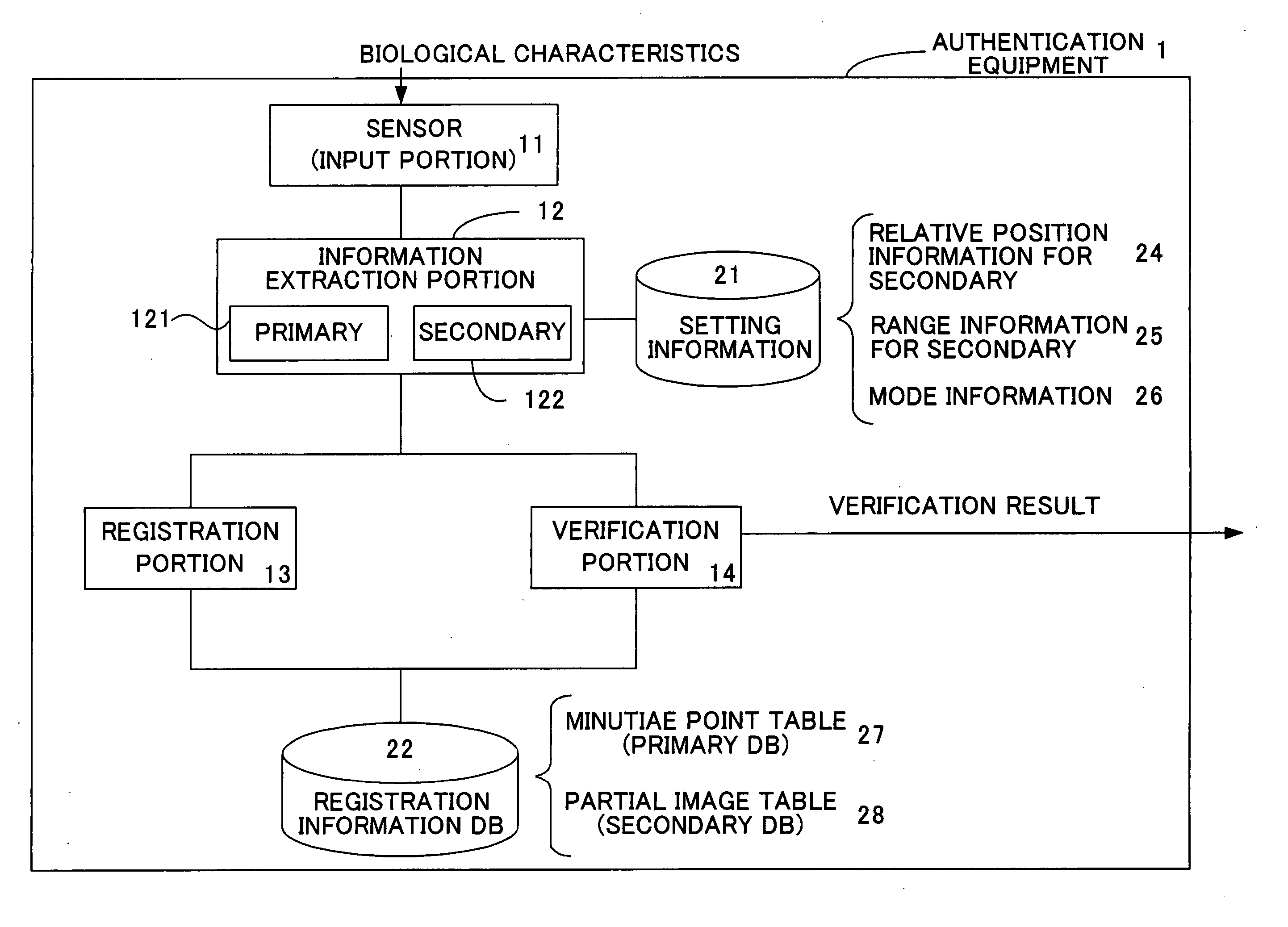
Authentication method based on biological characteristic information
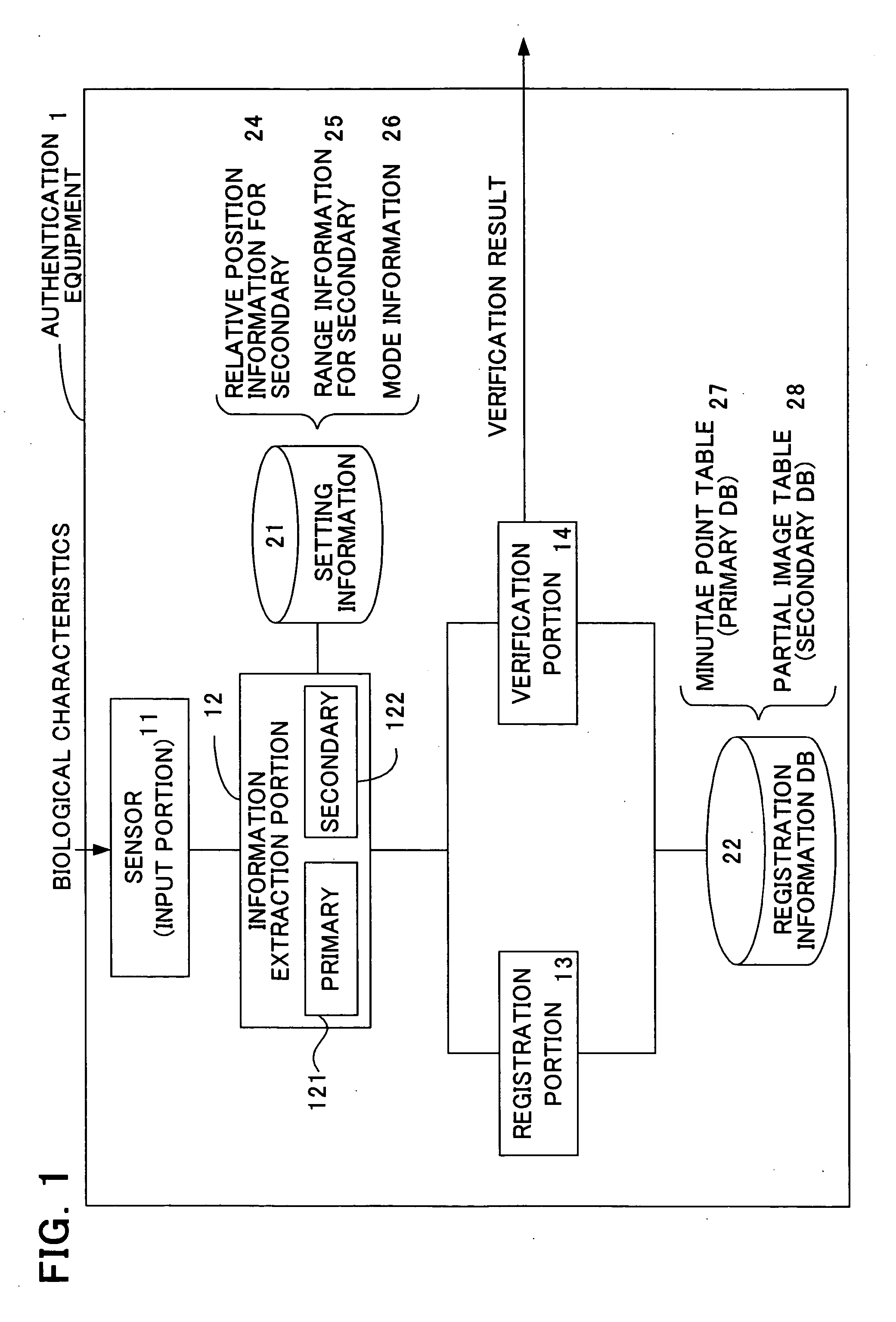
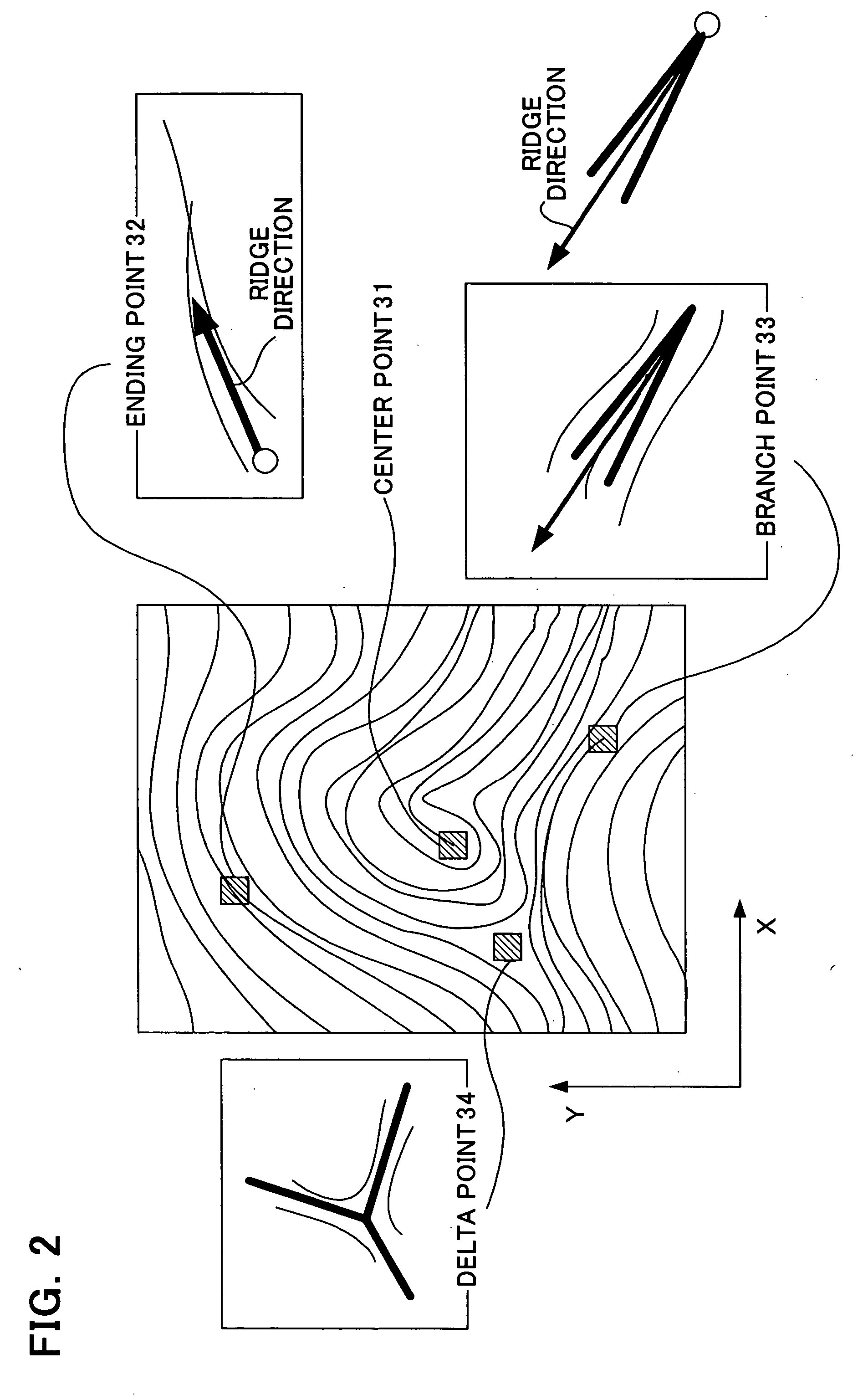
InactiveUS20060047970A1Reduce the burden onImprove authentication accuracyDigital data authenticationSecret communicationBiometricsAuthentication
The present invention provides authentication equipment having functions for prevention of erroneous authentication using biometrics data, and which can reduce the burden of registration placed on users. The authentication equipment is characterized in comprising an input portion, which generates primitive-format information of biological characteristics based on biological characteristics specific to individuals; a primary information extraction portion, which extracts primary information identifying the biological characteristics from the primitive-format information; a secondary information extraction portion, which extracts, as secondary information, a part of the primitive-format information using the primary information; a registration portion, which stores in a storage portion the secondary information extracted by the secondary information extraction portion; and a verification portion, which compares the secondary information extracted by the secondary information extraction portion with secondary information stored in the storage portion, and judges whether authentication has been successful.
Owner:FUJITSU LTD
Registration determination device, control method and control program therefor, and electronic apparatus
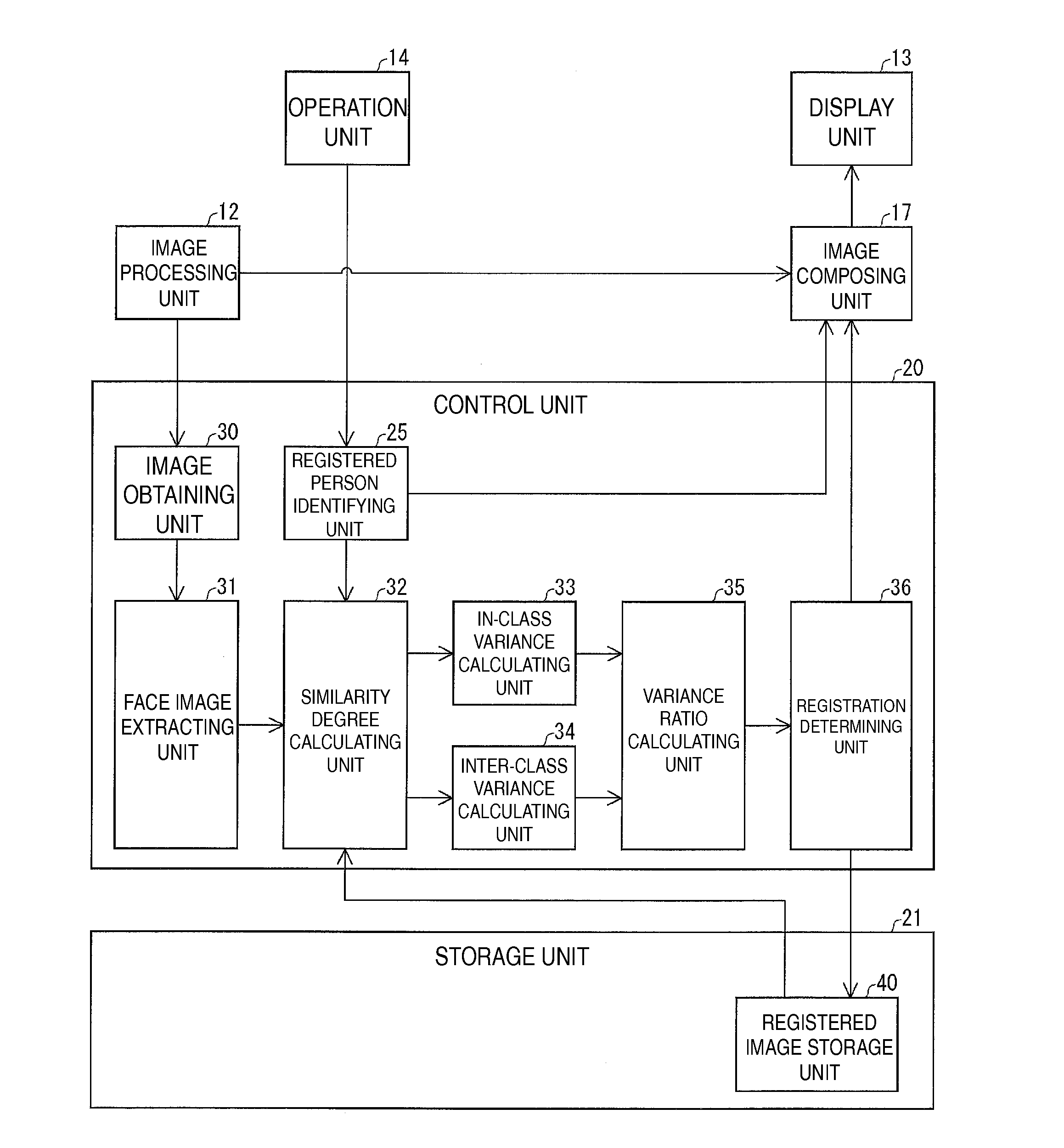
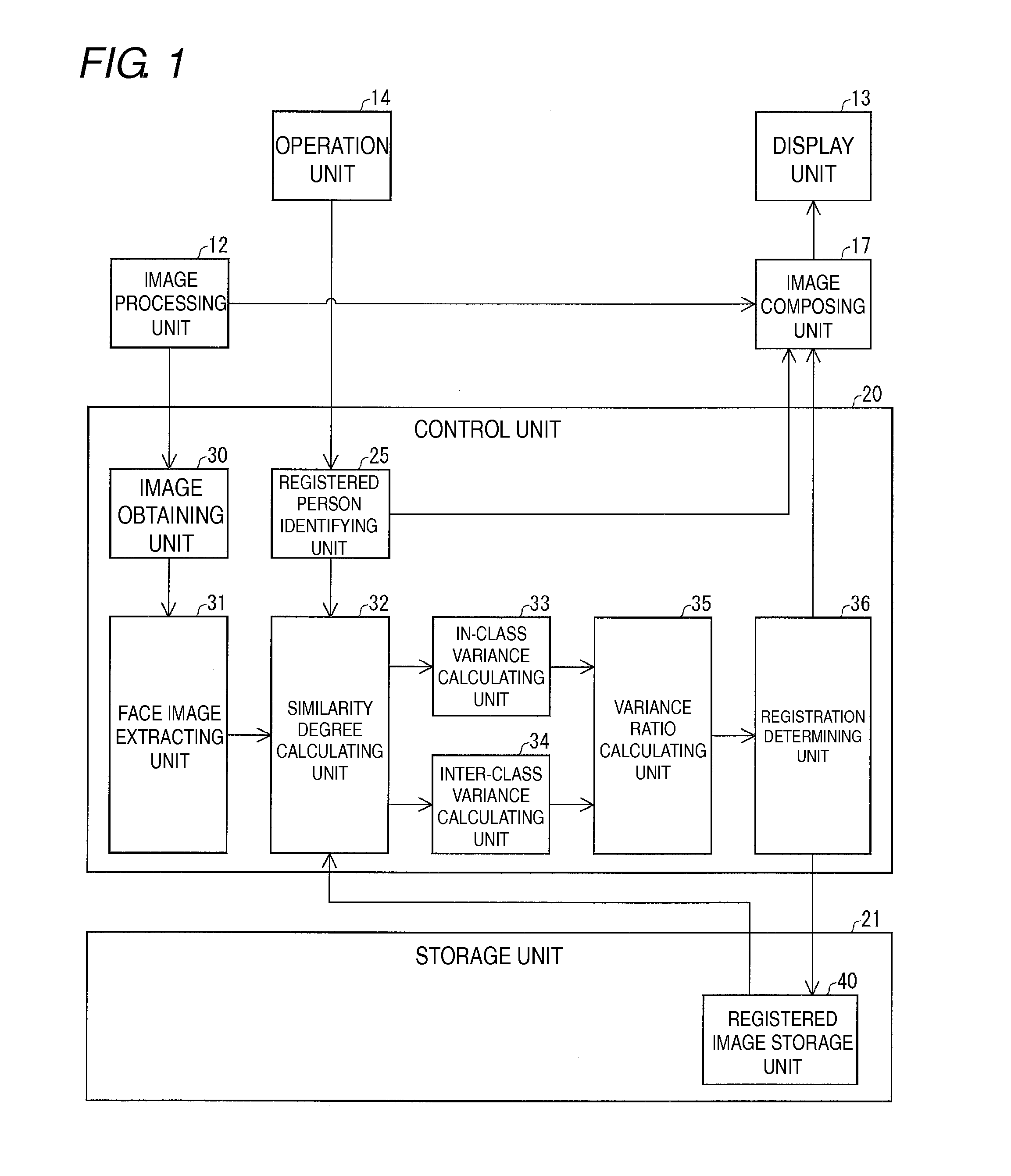
ActiveUS20130243328A1Improve convenienceAvoid wastingImage analysisCharacter and pattern recognitionPattern recognitionDegree of similarity
Whether an obtained candidate face image is registered or not is appropriately determined. A similarity degree calculating unit calculates the degree of similarity between a candidate face image extracted by a face image extracting unit and a registration face image registered in a storage unit. An in-class variance calculating unit calculates an in-class variance of the degree of similarity of the registered person identified by a registered person identifying unit, and an inter-class variance calculating unit calculates an inter-class variance of the degree of similarity of each registered person registered in the storage unit. A variance ratio calculating unit calculates a variance ratio between the inter-class variance and the in-class variance, and on the basis of the calculated variance ratio, a registration determining unit determines whether a target face image is to be registered or not.
Owner:ORMON CORP
System and method for providing improved claimant authentication
ActiveUS20050132235A1Improve accuracy“tuned” (manipulated or optimized) more easilyDigital data processing detailsUser identity/authority verificationAlgorithmAuthentication
A system and method are provided for improving the accuracy of speaker authentication by combining the results of multiple verification sources using statistical modeling. A statistical classifier is built on top of the underlying verification sources. The classifier combines the multiple verification inputs with associated models of the respective verification technologies underlying the verification inputs. The classifier functions to classify a claimant as a true speaker or impostor based upon the verification inputs, the model or models and, potentially, additional information related to the context in which the classifier is being used.
Owner:EMC IP HLDG CO LLC
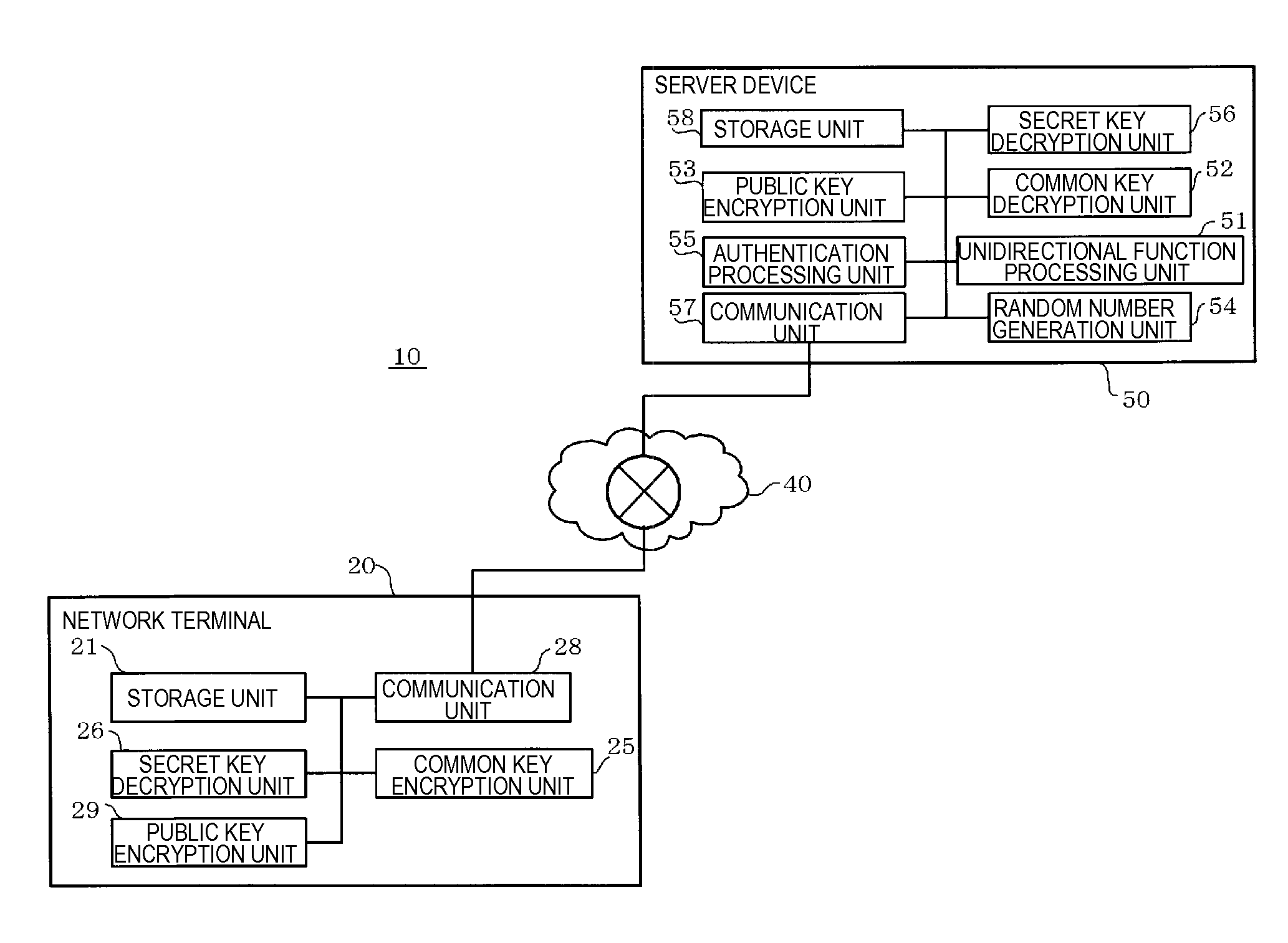
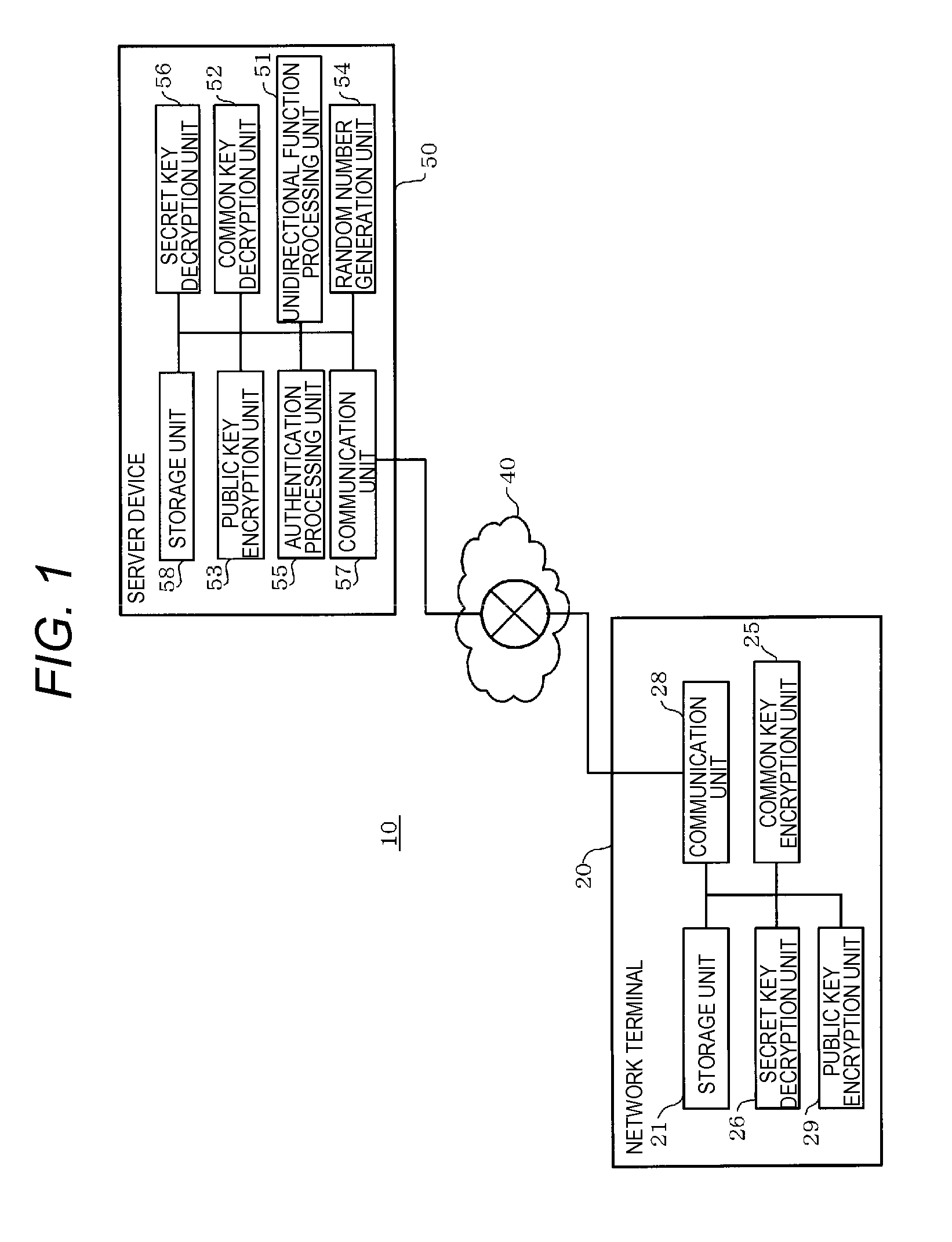
Terminal authentication system, server device, and terminal authentication method
ActiveUS20150350196A1Improve terminal authentication accuracyImproving terminal authentication accuracyTransmissionClient-sideAuthentication system
Provided is a terminal authentication system including a client terminal and a server device. The client terminal transmits first information based on secret information different for each client terminal and a client certificate including a hash value of the secret information which is derived from the secret information, to a server device. The server device receives the first information and the client certificate, derives a hash value from the secret information based on the first information using a unidirectional function, and authenticates the client terminal on the basis of the derived hash value and the hash value of the secret information which is included in the client certificate.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
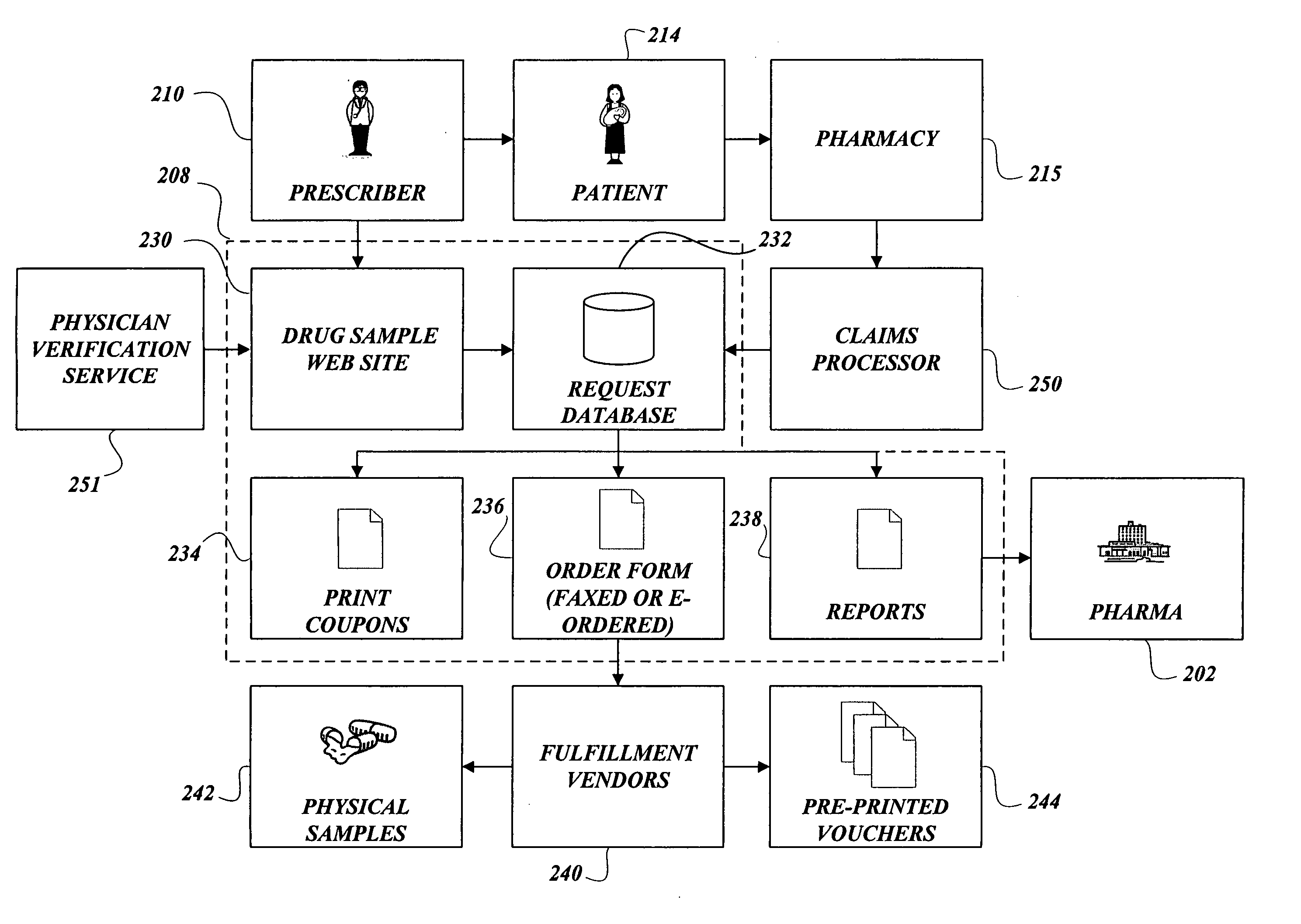
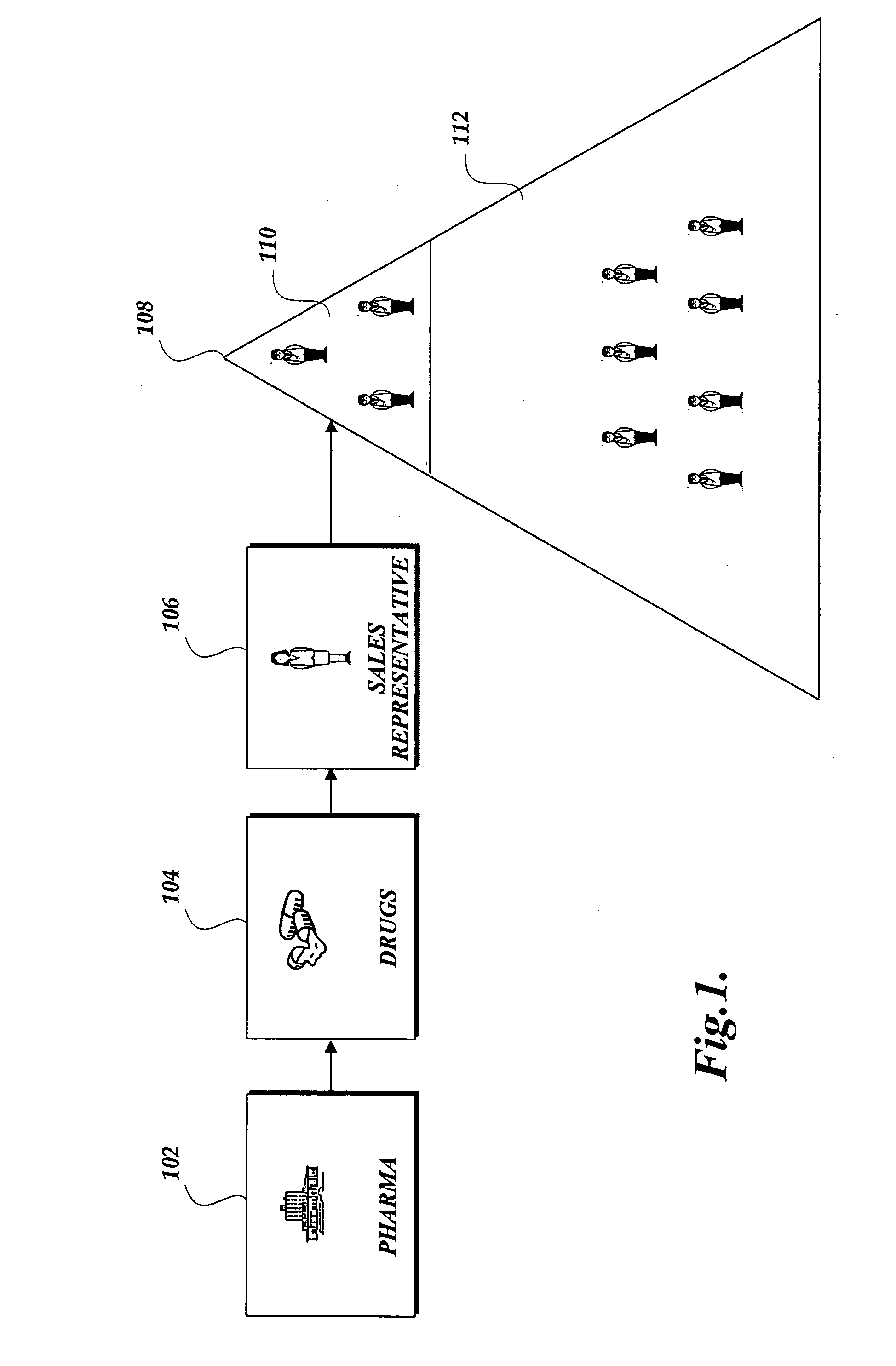
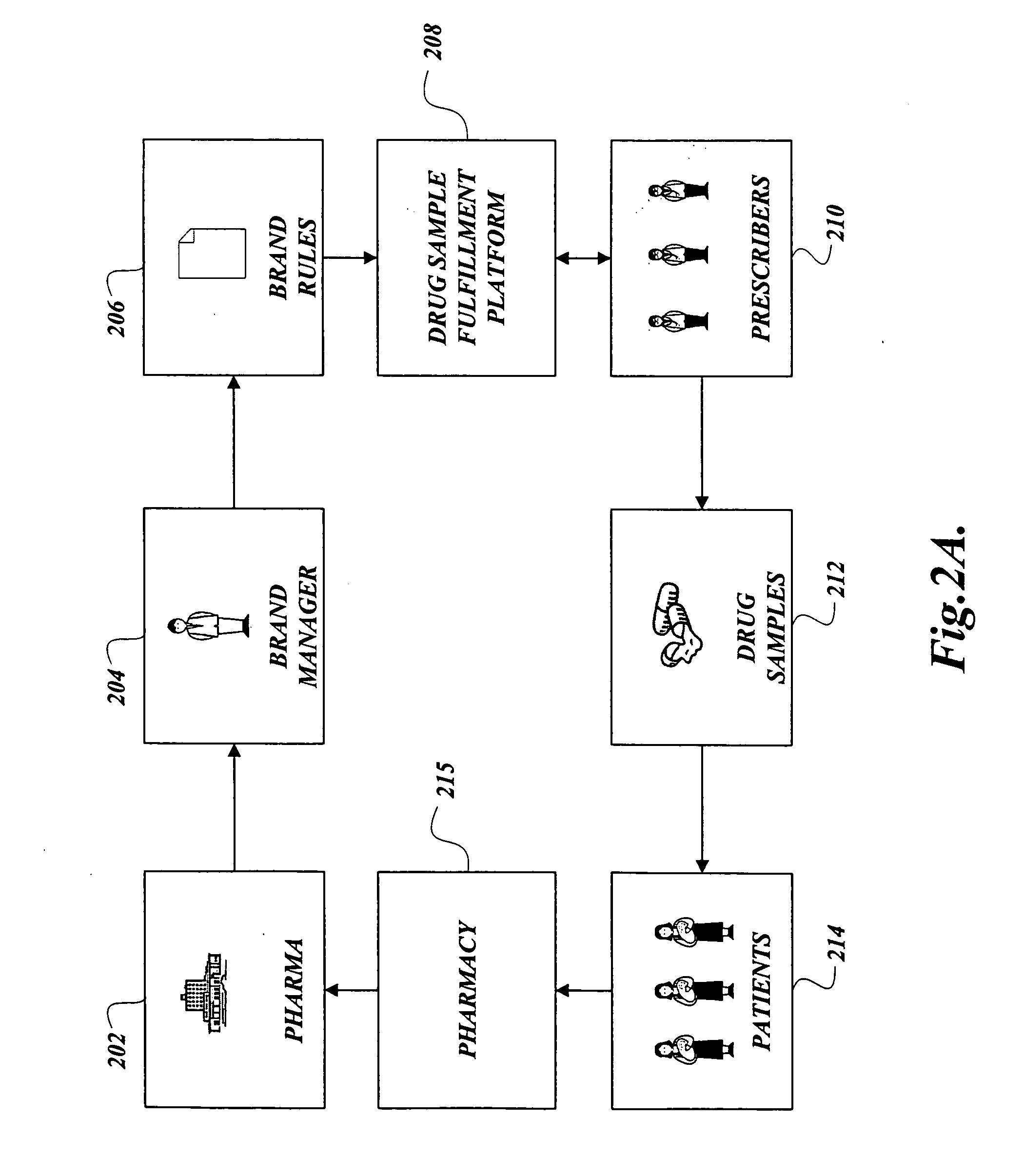
Authenticating prescriber identity to enable electronically ordering drug samples from a drug sample fulfillment platform
ActiveUS20060161453A1Improve authentication accuracyIncrease the number ofMultiple digital computer combinationsMarketingMedical prescriptionDrug Sample
An fully online process to facilitate the fulfillment of drug samples to prescribers is described. With the present invention, a prescriber may order physical drug samples online by undergoing an authentication process that is in lieu of requiring a signature match. In the invention, the ordering of drug samples is made over a communication network without requiring a handwritten signature.
Owner:SYMMETRYRX LLC
Smart identification terminal system and method based radio-frequency identification and biological characteristic
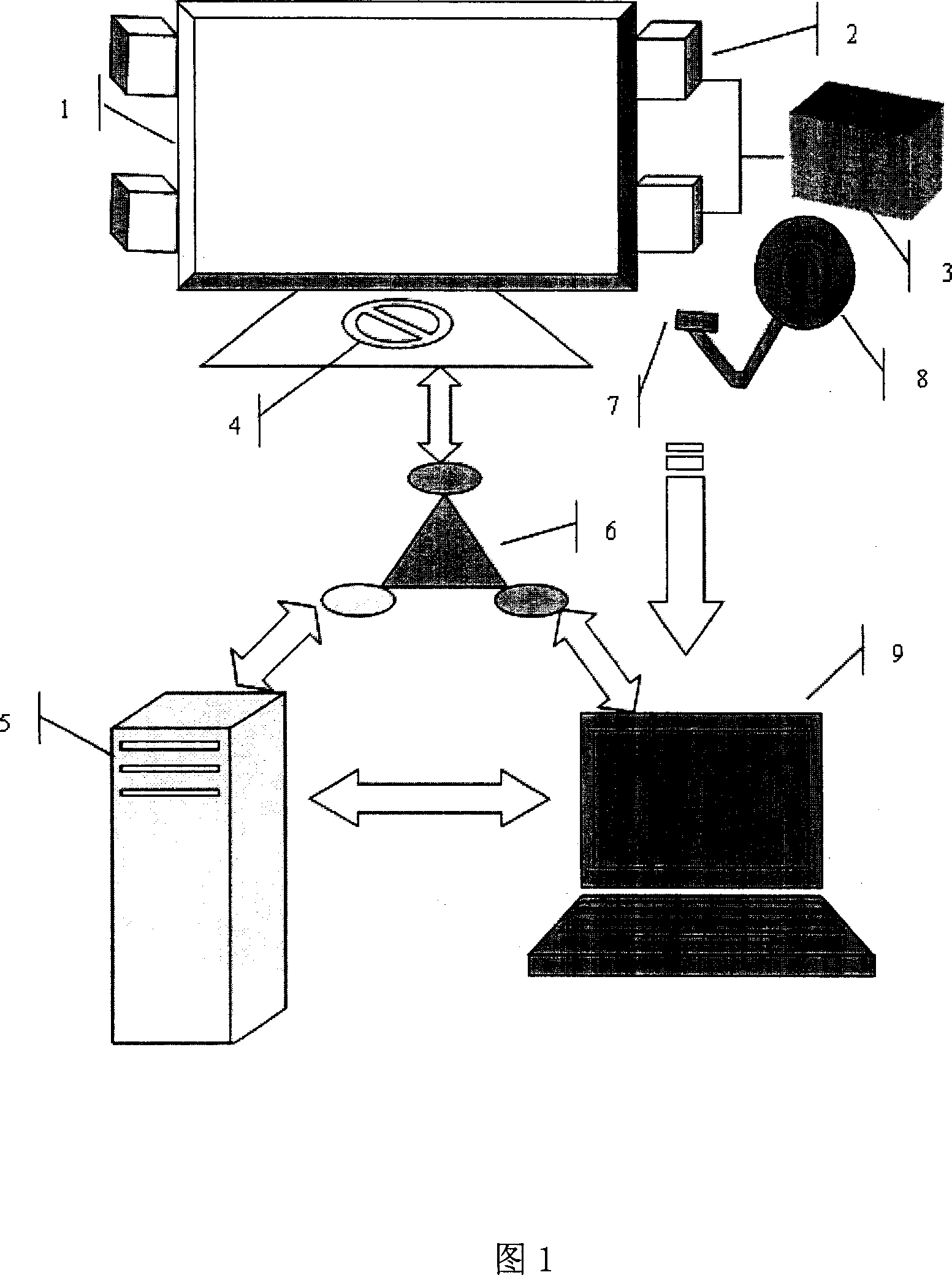
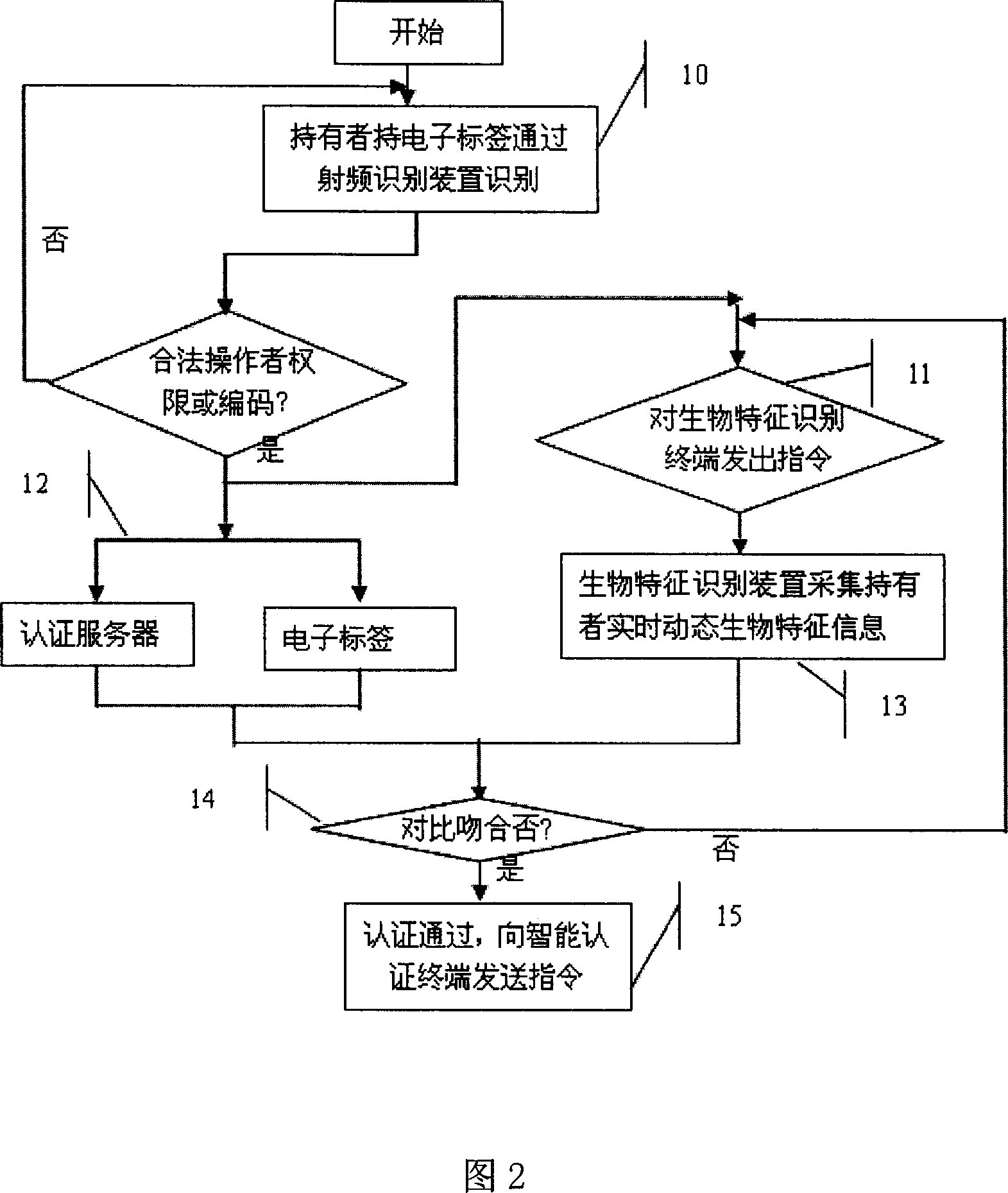
InactiveCN1979518AAccurate authenticationShorten the timeUser identity/authority verificationCharacter and pattern recognitionOperating instructionData acquisition
The invention belongs to information electronic field, integrating RFID technique with bio-character recognition technique to implement two authentication mode-complementary intelligent authentication terminal systems and besides, implementing reliable instruction executing operation by the RFID technique and bio-character recognition technique. When an operator holding an electronic tag with right information sends operating instructions to intelligent terminal, a RFID system finds out the right information and bio-character information corresponding to the electronic tag, and makes bio-character recognition on the operator by bio-character recognition data collector, and executes the instruction the operator sends after authentication passes. Thus, the operators with different rights can execute different operations in different read regions by electronic tag, and the authentication course and operation are united in a terminal.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Method for obtaining biometric information using light source corresponding to biometric information and electronic device thereof
ActiveUS20190065717A1Improve authentication accuracyDiagnostics using lightDigital data processing detailsComputer scienceLight source
Owner:SAMSUNG ELECTRONICS CO LTD
Intelligent vein authentication method and system having autonomous learning capability
ActiveCN107832684AAbility to learn independentlyImprove authentication accuracyNeural architecturesSubcutaneous biometric featuresFeature extractionAutodidacticism
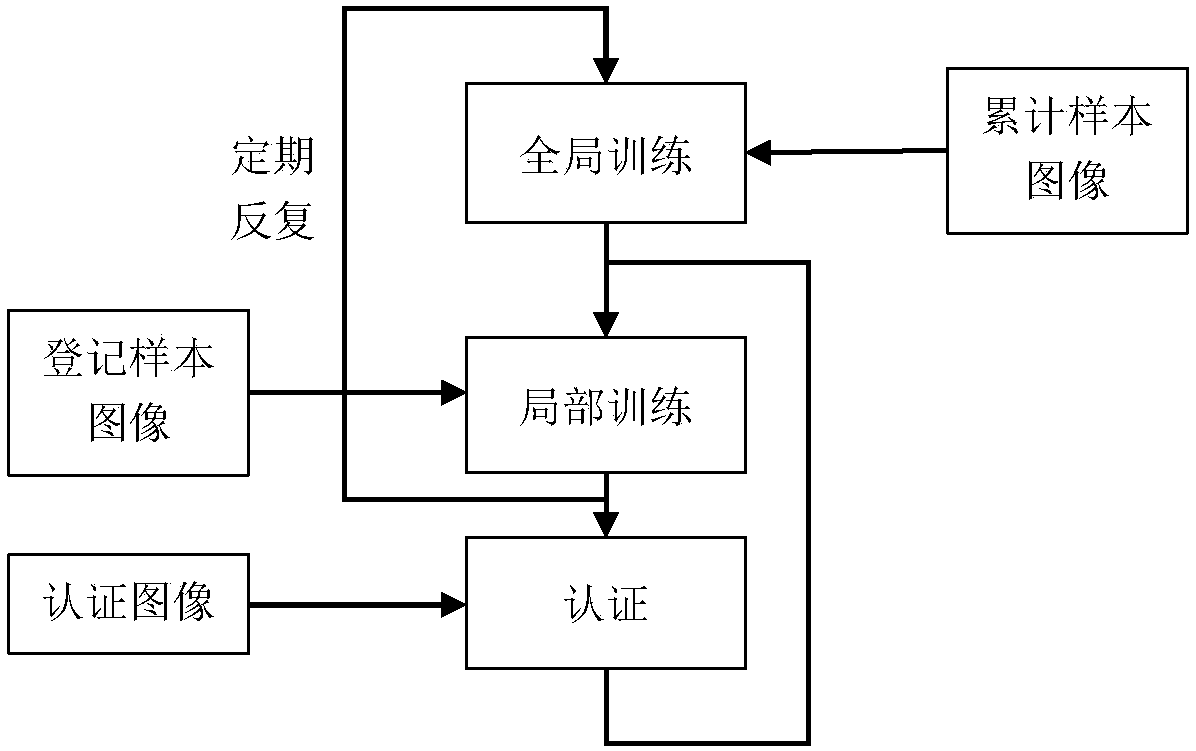
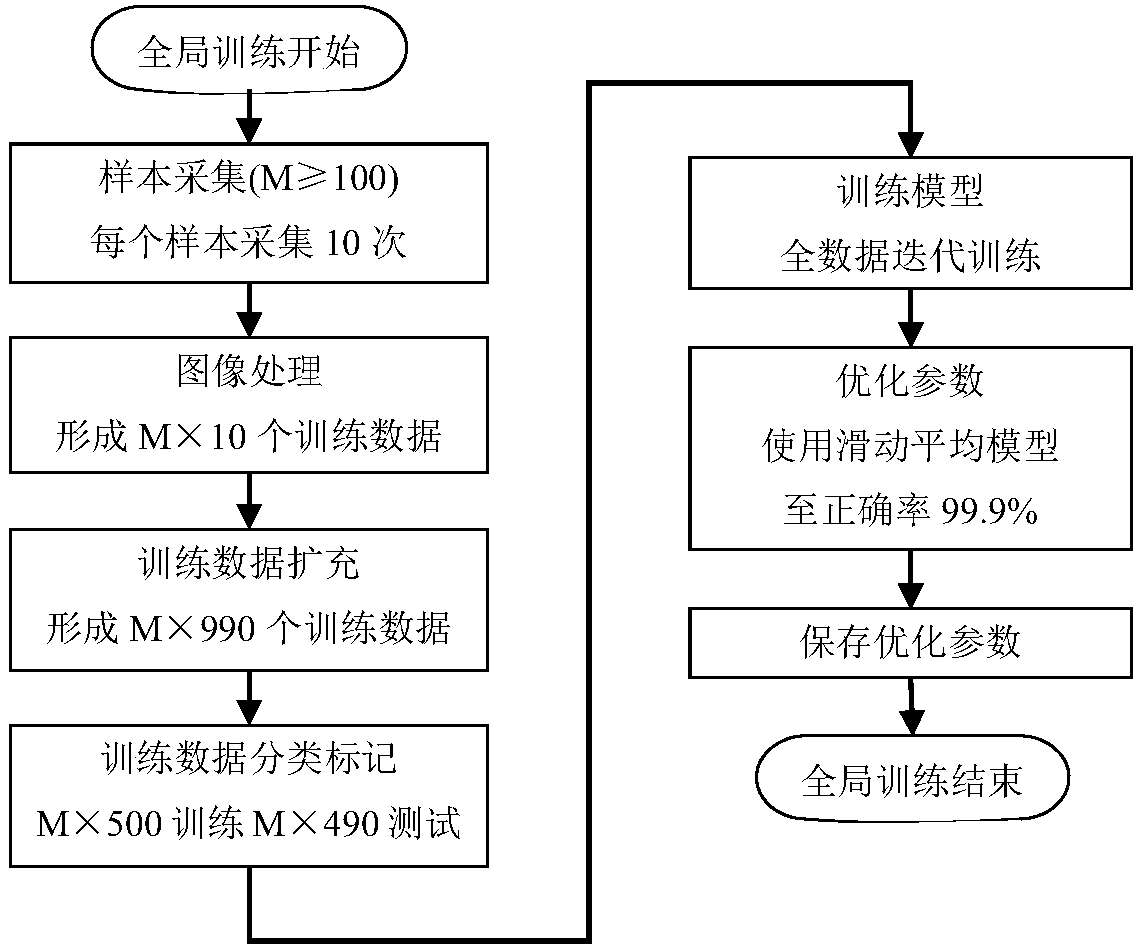
The invention discloses an intelligent vein authentication method and system having autonomous learning capability. The method comprises steps that model training of the full convolutional neural network depth learning model in repeated and regular global training and irregular local training modes is carried out, before online operation of the full convolutional neural network depth learning model, one global training is carried out through utilizing accumulated samples, and optimized characteristic extraction, characteristic identification and characteristic classification parameters are stored; after online operation of the model, newly-registered samples are utilized to carry out irregular local training of the model, and characteristic classification parameter optimization is completed; under the specific condition, the newly-accumulated samples are utilized to carry out regular global training of the model, and the characteristic extraction, characteristic identification and characteristic classification parameters are optimized for another time, the model is guaranteed to be the intelligent authentication system having the autonomous learning capability, and vein authentication precision is further enhanced.
Owner:通华科技(大连)有限公司
Machine learning-based physical layer channel authentication method
ActiveCN108304877AReduce computational complexityImprove authentication accuracyCharacter and pattern recognitionTransmissionLearning basedLimited resources
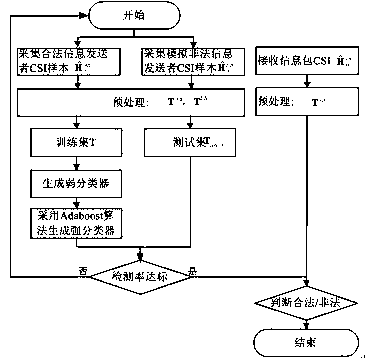
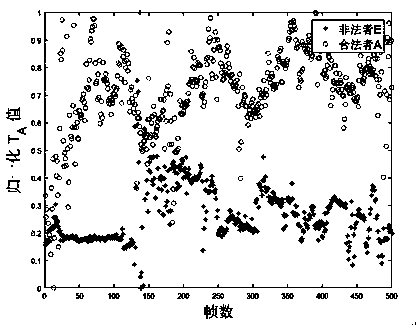
The invention discloses a physical layer channel authentication method based on machine learning. The method comprises the steps of S1, collecting the information packet channel information (CSI) of alegal information sender A and a simulated illegal information sender E by means of a receiver B; S2, pre-processing the information packet channel information of the legal information sender A and the simulated illegal information sender E by the receiver B; S3, generating a binary training data set by the receiver B; S4, based on the classification algorithm in the machine learning algorithm, carrying out the training by the receiver B according to the binary training data set to generate a classifier; S5, judging whether a received information packet is legal or not by the receiver B by utilizing the classifier, and realizing the authentication of the information packet. The invention provides the physical layer channel authentication method based on machine learning. The method is suitable for authentication equipment and authentication scenes with limited resources. The method has the advantages of low calculation complexity and high authentication accuracy.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Biometric data acquisition device, biometric data acquisition method and biometric authentication device
ActiveUS20070253602A1Quality improvementReduced dynamic rangeDiagnostic recording/measuringSensorsBiological bodyBiometric data
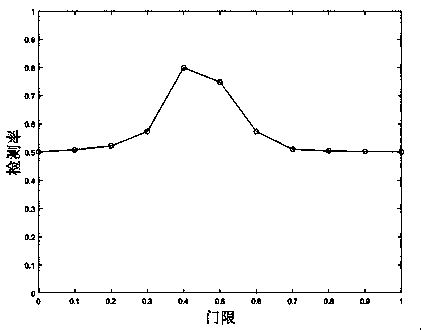
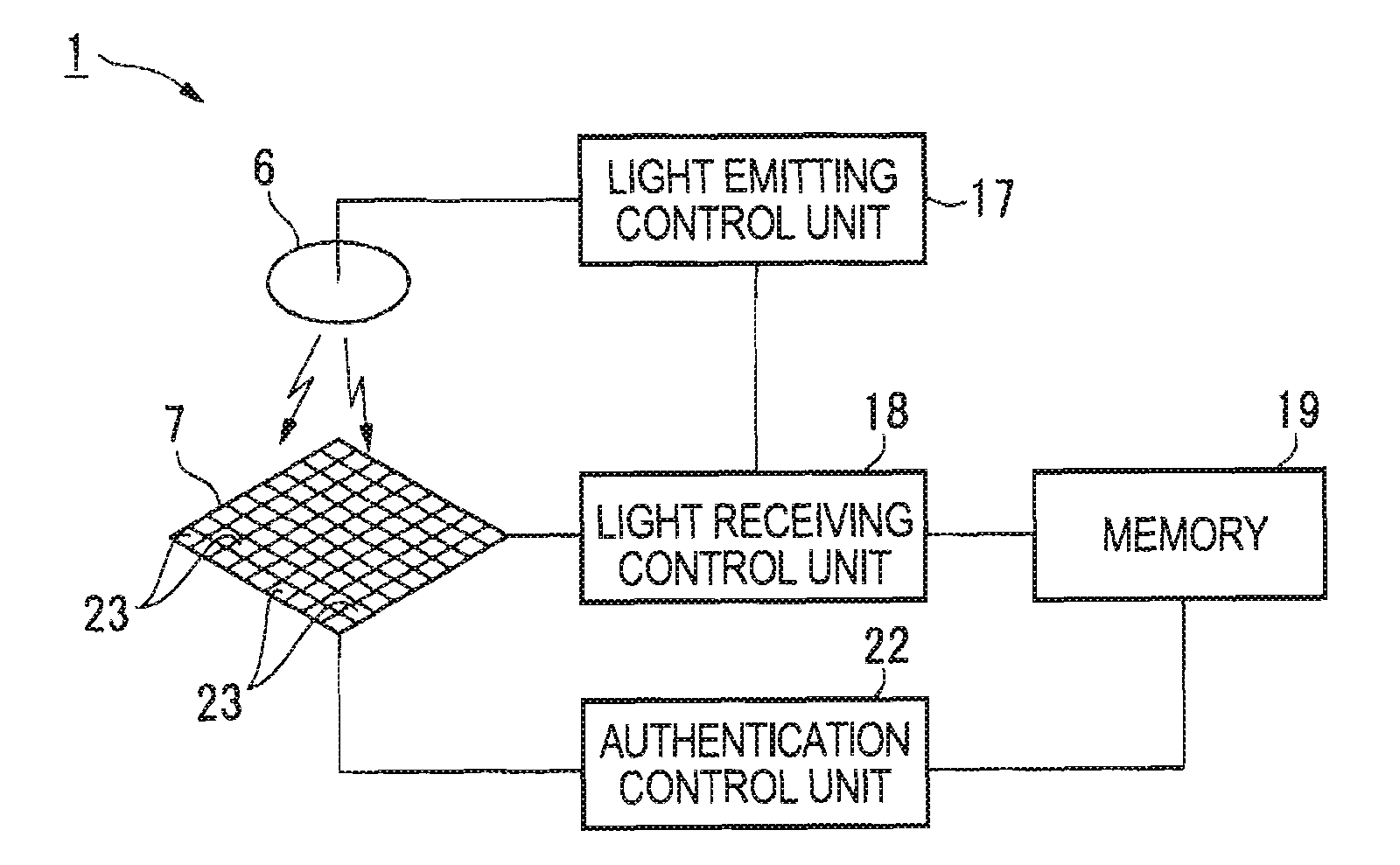
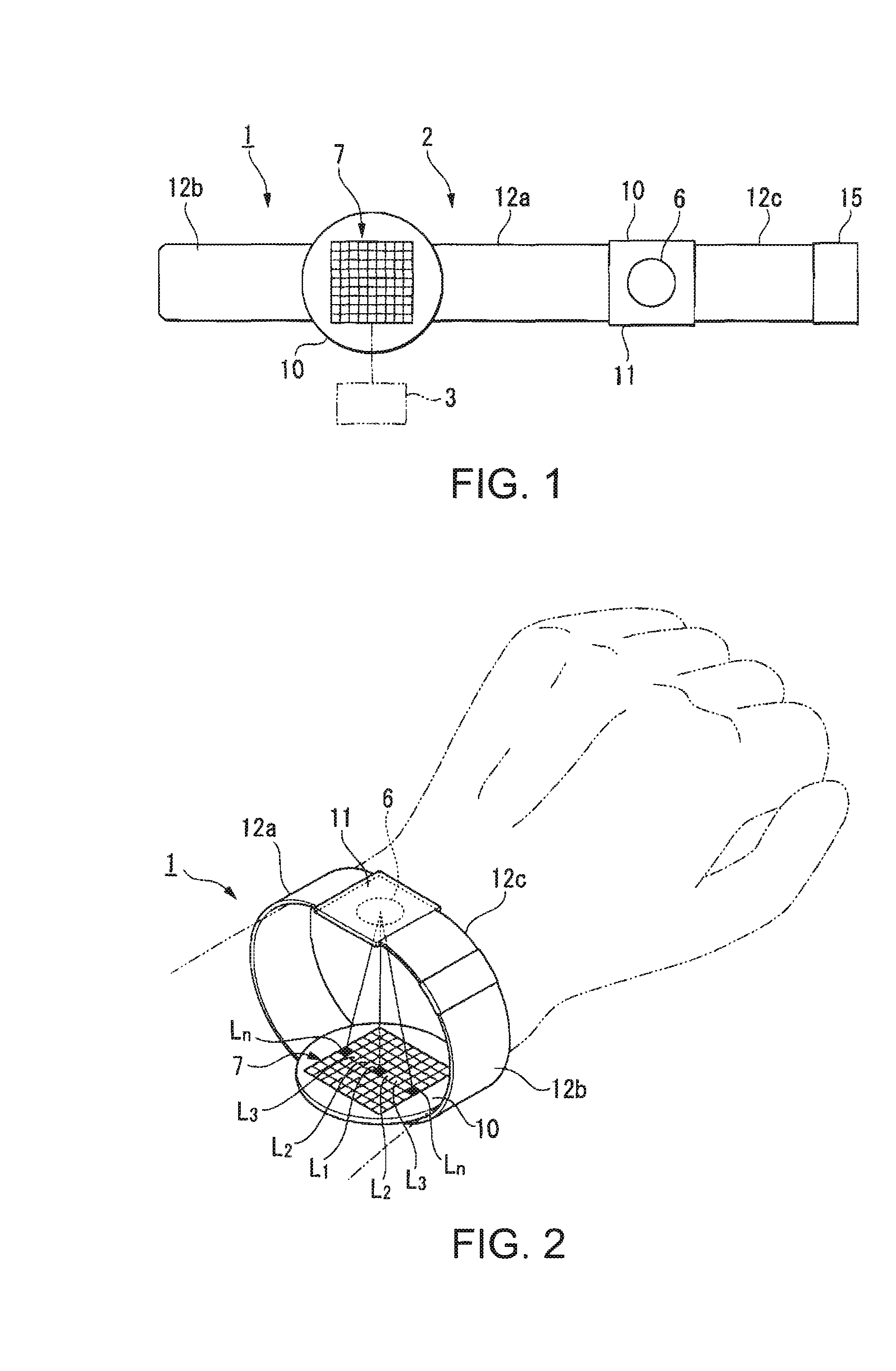
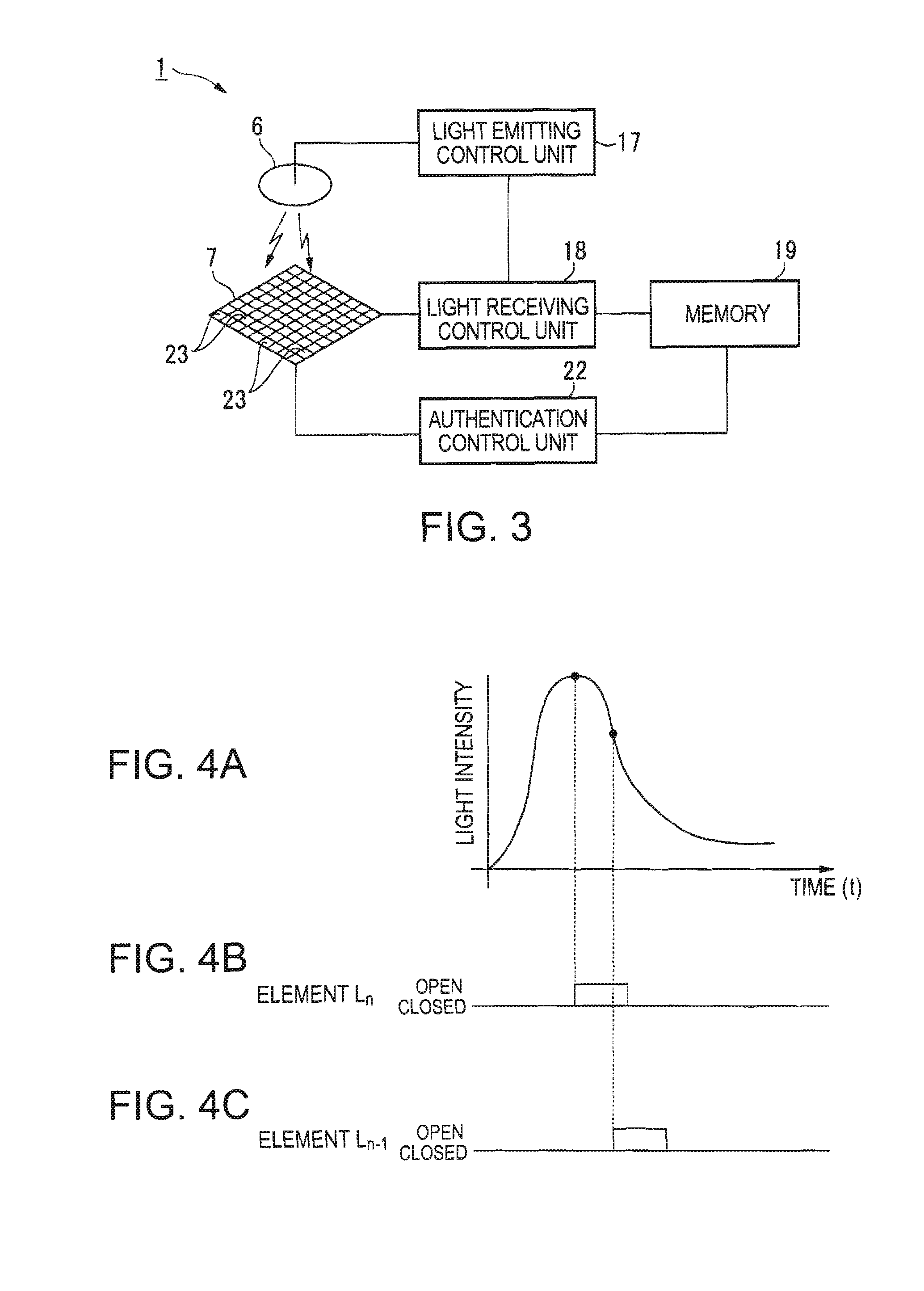
A biometric data acquisition device for acquiring data of a living body by irradiating the living body with light includes: a light source unit that emits light to the living body; a plurality of light receiving elements that receive transmitted light or reflected light, which is transmitted through the living body or reflects from the living body, respectively, by irradiating the living body with the light from the light source unit; an openable and closable gate provided for each of the plurality of light receiving elements; and an opening and closing control unit that controls opening and closing of the gate so as to make uniform intensities of light received by the plurality of light receiving elements.
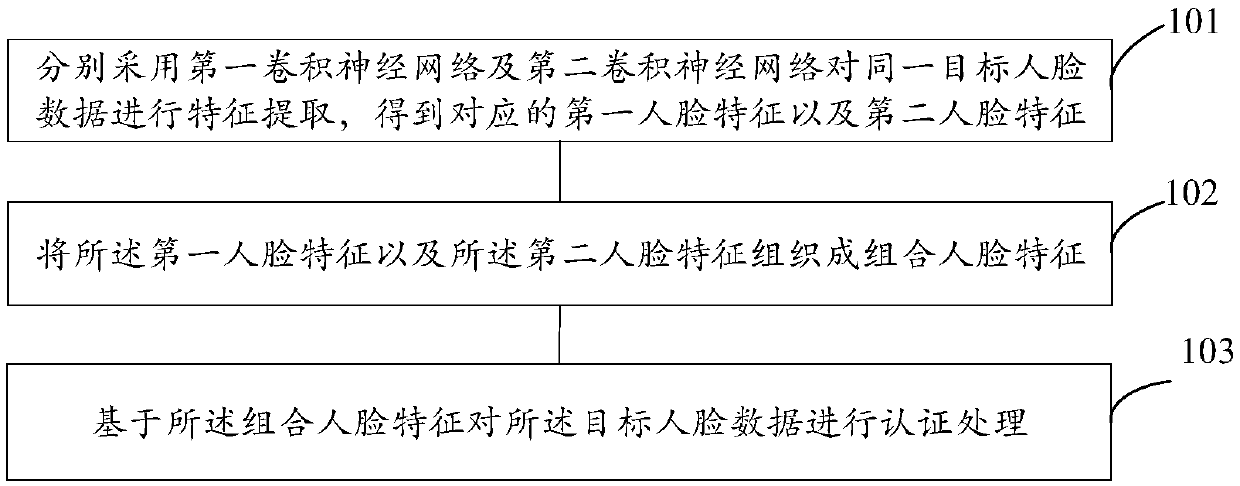
Owner:SEIKO EPSON CORP
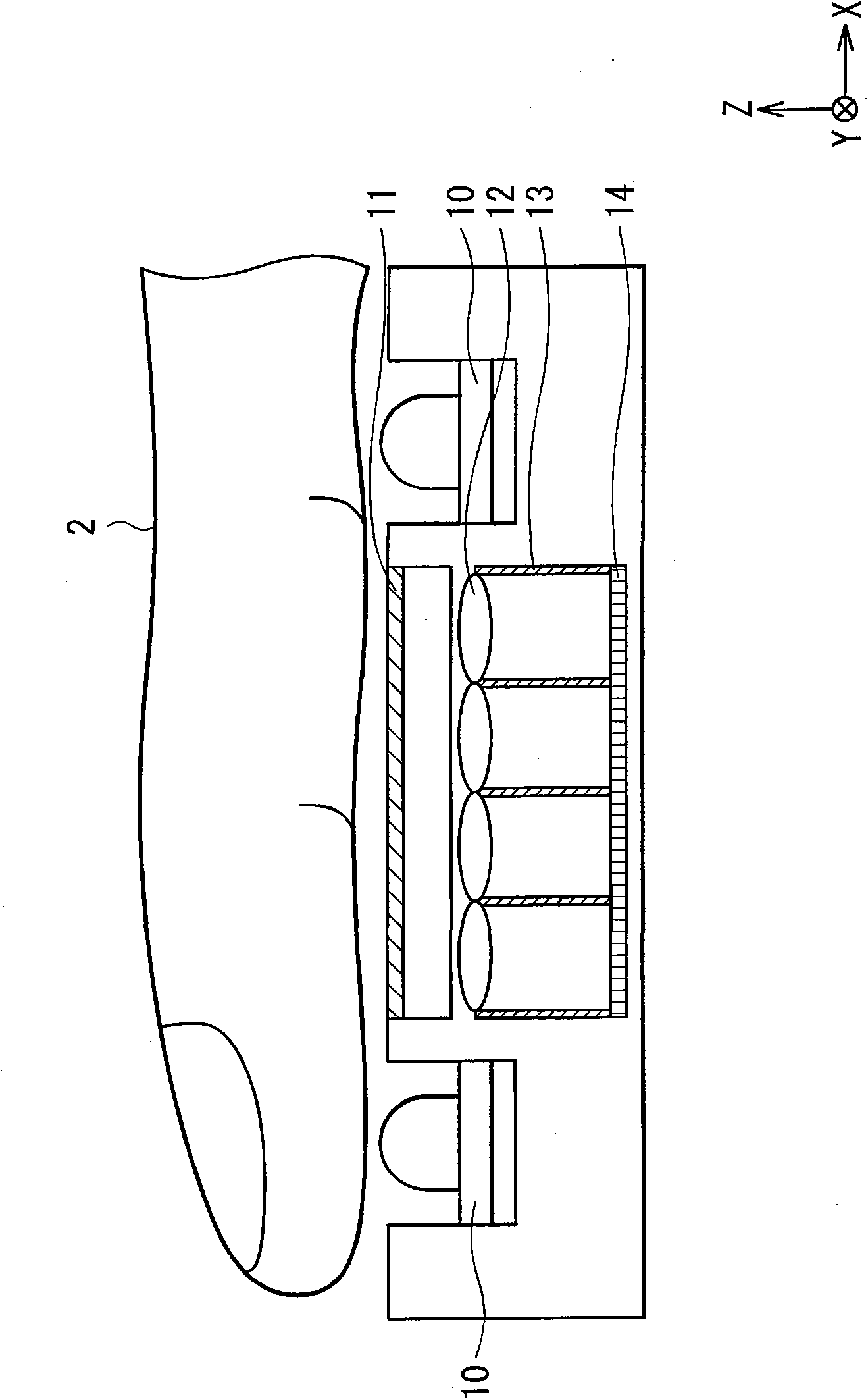
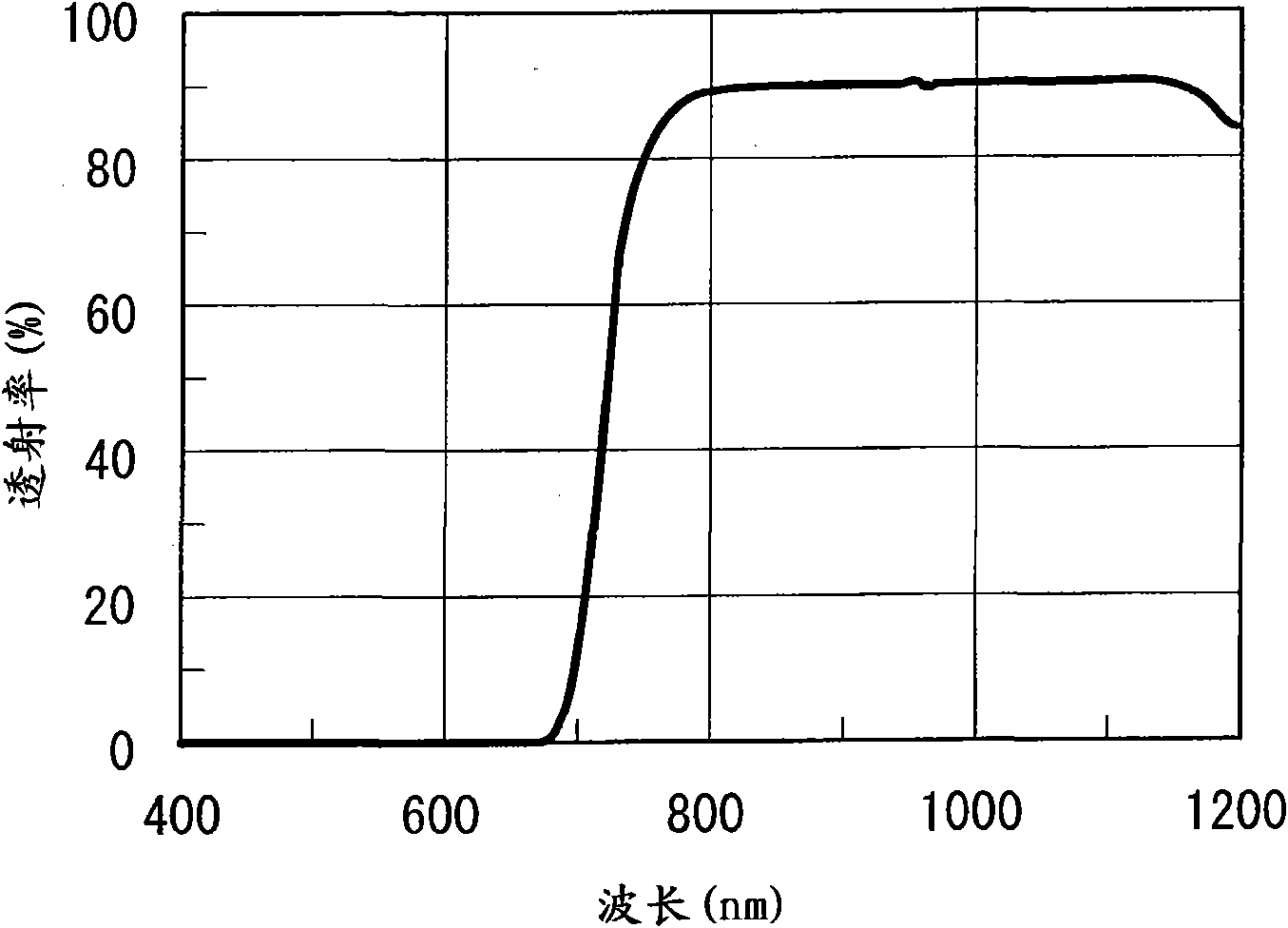
Biometric authentication apparatus
InactiveCN101953689AWith light gathering functionWith wavelength selective transmission functionSolid-state devicesPerson identificationLiving bodyMicro lens array
The present invention provides a biometric authentication apparatus realizing reduction in thickness while holding high authentication precision. The biometric authentication apparatus includes: a light source emitting light in a wavelength range including a wavelength range for authentication toward a living body; a microlens array condensing light from the living body and selectively transmitting light in the wavelength range for authentication; an imaging device obtaining image data of the living body on the basis of the light condensed by the microlens array; and an authentication unit authenticating the living body on the basis of the image data obtained by the imaging device. The microlens array includes: a first resin layer made of thermoplastic transparent resin material as a base material of the microlens array; and an opaque material included in the first resin layer and used for blocking the light with the wavelength range different from that for authentication.
Owner:SONY CORP
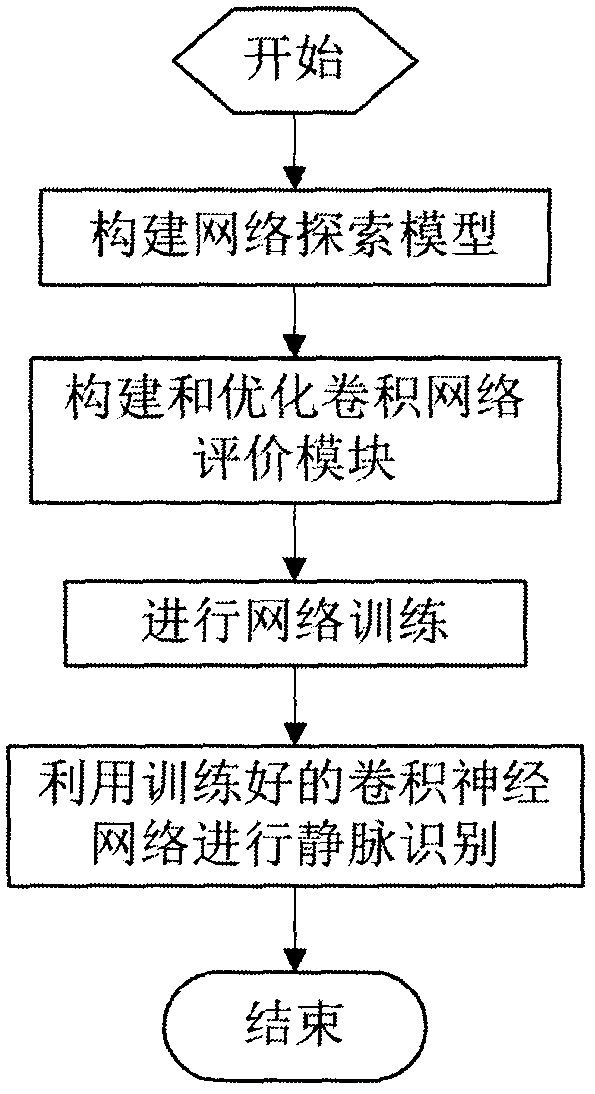
A vein recognition method based on a reinforcement learning algorithm optimized convolution neural network
InactiveCN109034034AImprove authentication accuracyImprove characterization efficiencyBiometric pattern recognitionNeural architecturesVeinReinforcement learning algorithm
The invention discloses a vein recognition method based on a reinforcement learning algorithm optimized convolution neural network, which utilizes the reinforcement learning algorithm to optimize theconvolution neural network to construct a vein recognition model. The vein recognition model includes a network exploration model based on reinforcement learning algorithm and a multi-layer convolution network evaluation model. The network exploration model includes an encoder, a linear layer, a nonlinear layer, a Softmax classification layer, a decoder and a reward evaluation module. The convolution network evaluation model includes a data input preprocessing layer, multiple normal convolution module layers and multiple compression convolution module layers spaced apart, a global pooling layer and a full connection layer, and finally outputs vein eigenvector. The vein recognition method based on a reinforcement learning algorithm optimized convolution neural network can get the highest evaluation model, so as to obtain a higher recognition accuracy.
Owner:MELUX TECH CO LTD
Finger vein authentication device
ActiveUS20100098304A1Good reproducibilityImprove accuracyIndividual entry/exit registersSubcutaneous biometric featuresVeinEngineering
A compact and highly accurate downward irradiation type finger vein authentication device achieved by providing a structure that stabilizes the finger and also prevents adverse effects caused by the left and right fingers. The finger vein authentication device comprises a center finger stand for mounting the finger for authentication; a light source for irradiating infrared light onto the finger; an image capture unit for capturing an image of the finger veins by way of light from a light source; an aperture to open in the image capture direction of the image capture unit; a storage device to store the finger biological information; an authentication processor unit to extract the features from the image captured by the image capture unit and match the features with the biological information stored in the storage device; and a left and right finger stand for the fingers on the left and right of the finger for authentication. This left and right finger stand is installed at a position somewhat higher than the center finger stand. This left and right finger stand is also made from a light blocking member and a light source is installed in the lower section.
Owner:HITACHI INFORMATION & CONTROL SOLUTIONS LTD
Hand-wirte signature recognition program, method and device
InactiveCN1445723AAvoid the authentication processAvoid false rejectionsImage analysisSpecial data processing applicationsHandwritingPattern recognition
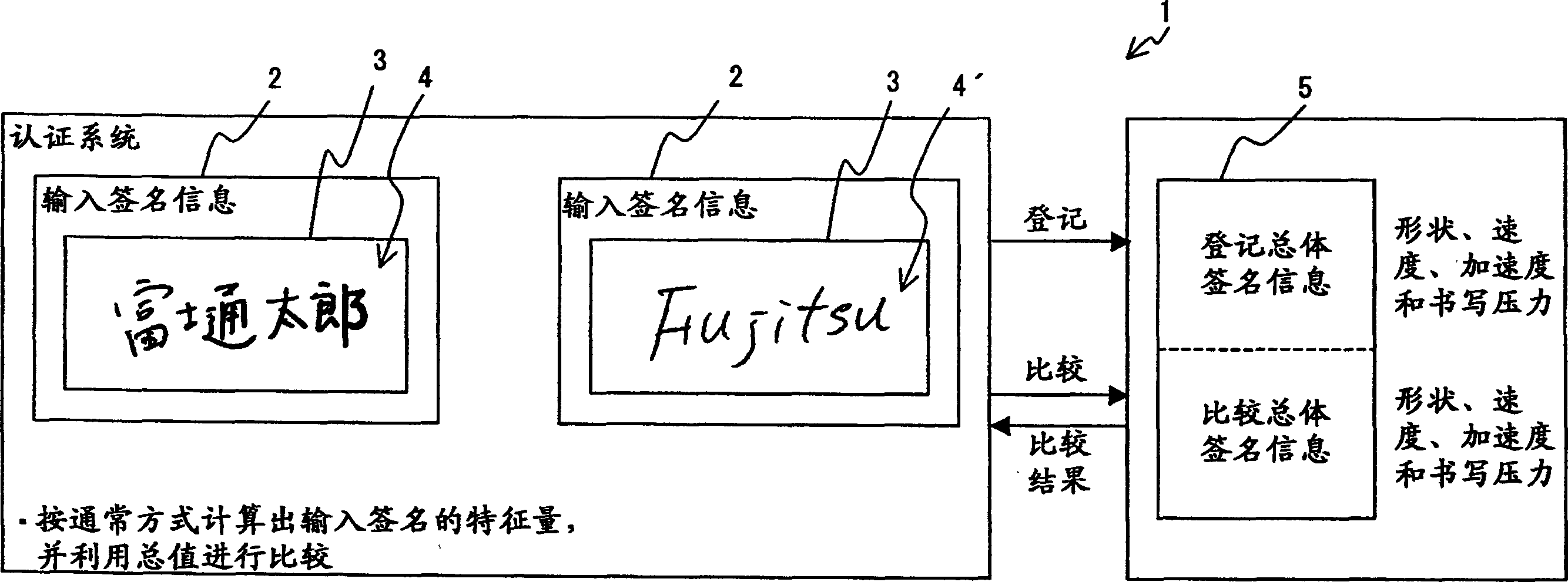
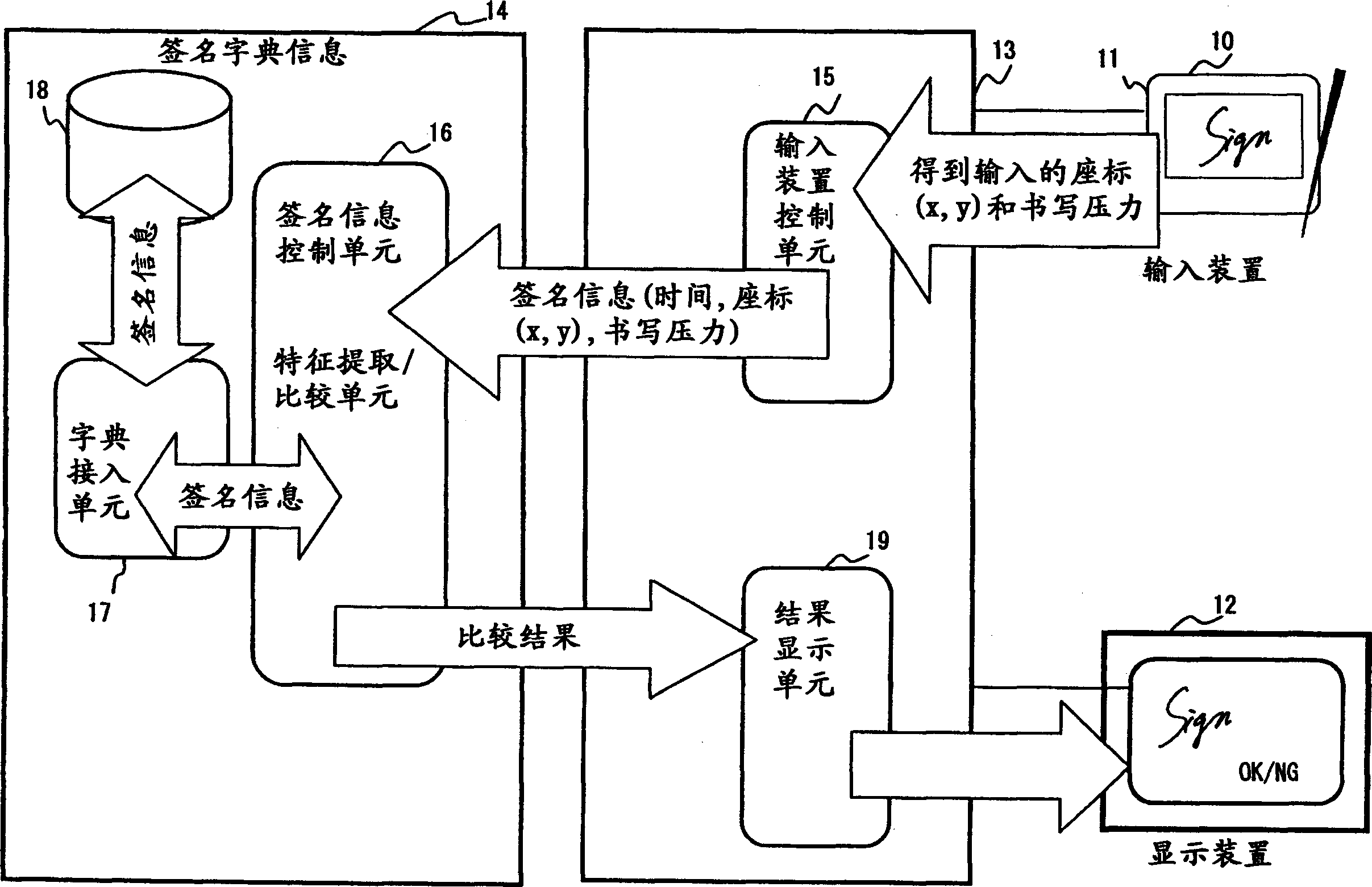
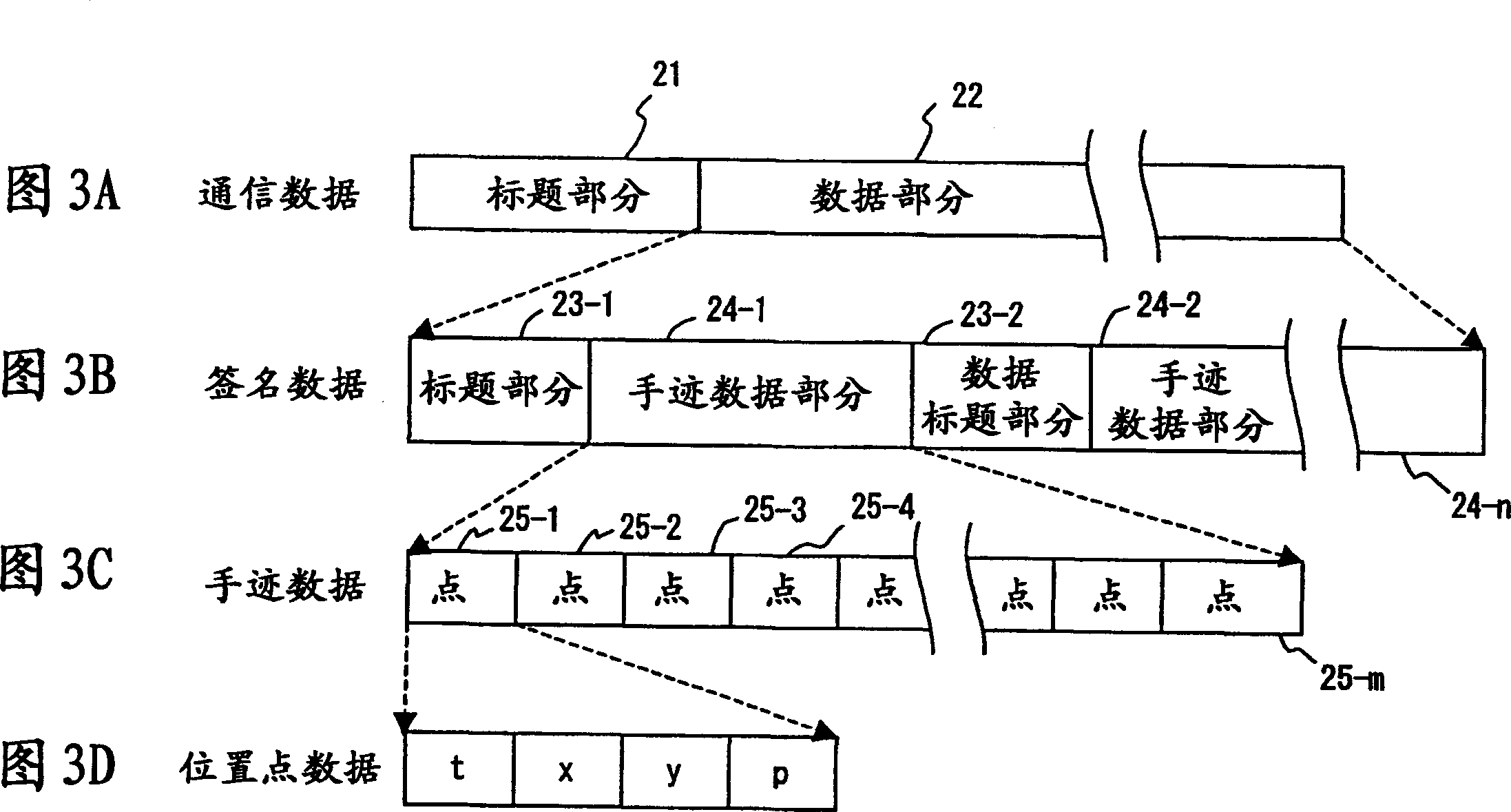
The invention provides a handwritten signature authentication program, method and device. When registering a signature, input a Japanese signature such as "Fujitsu" ("Fujitsu") or an English signature such as "Fujitsu" n times through the input device of the input device of a signature authentication system, and calculate handwriting shape, writing speed, and writing acceleration and elements of writing pressure. Set the combination of nC2 for each element of the input data n times, get the inverse of each similarity, calculate the average value of the similarity of each element, determine the weight of each similarity according to the average value, and calculate the four elements and define it as the total similarity of the registered signatures. During the authentication process, the signature data to be compared is input / output m times. The total similarity of the signatures to be compared can be obtained in the same way.
Owner:FUJITSU LTD
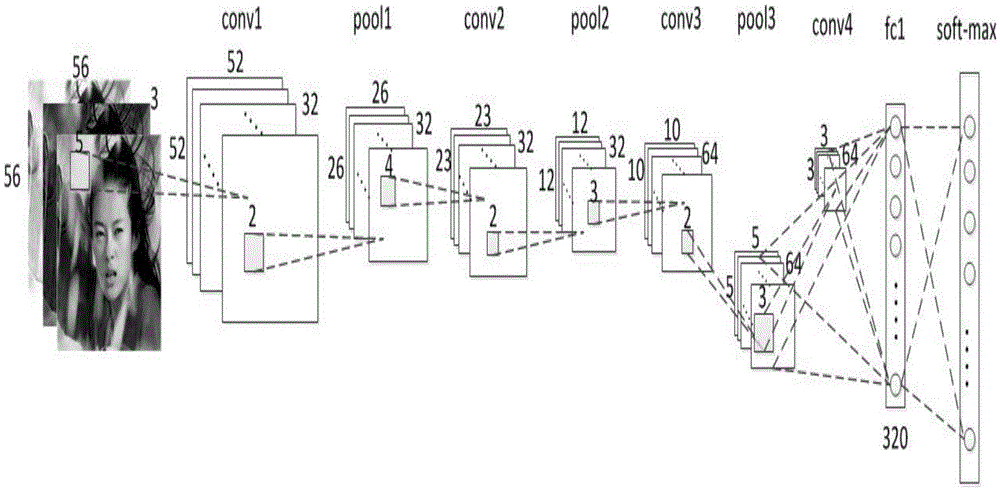
Face authentication method and device
ActiveCN107871105AImprove authentication accuracyCharacter and pattern recognitionConvolutionFeature extraction
The embodiment of the invention provides a face authentication method and a face authentication device. The method comprises the following steps of conducting the feature extraction on the data of a same target face through a first convolution neural network and a second convolution neural network respectively so as to obtain a corresponding first face feature and a corresponding second face feature, wherein the first convolution neural network and the second convolution neural network are trained through different loss functions; combining the first face feature and the second face feature into combined face features; and conducting authentication treatment on the data of the target face based on the combined face features. According to the embodiment of the invention, the accuracy of face authentication can be improved.
Owner:BEIJING EYECOOL TECH CO LTD
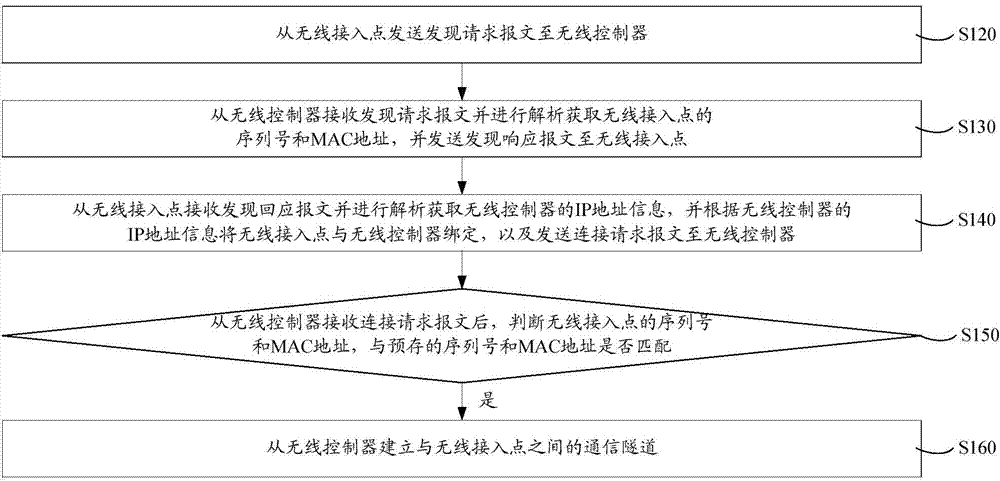
Wireless access point safe authentication method and system
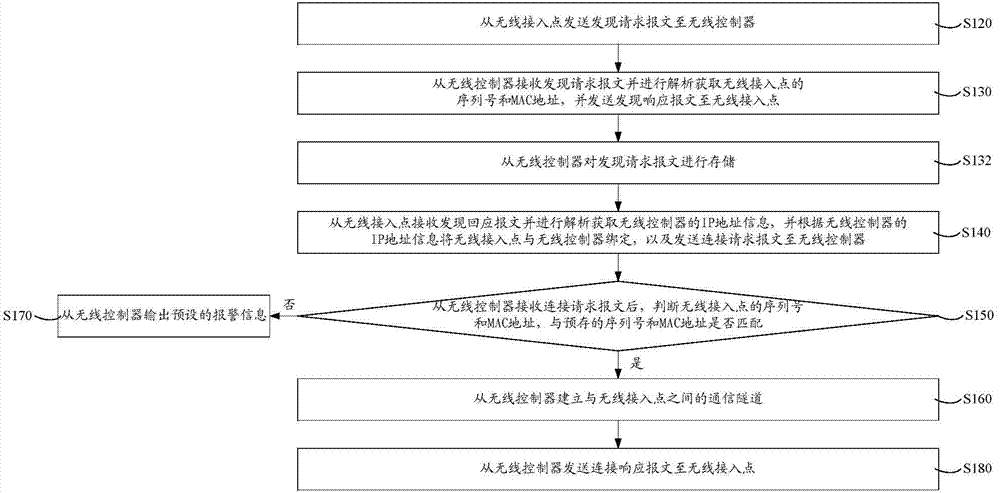
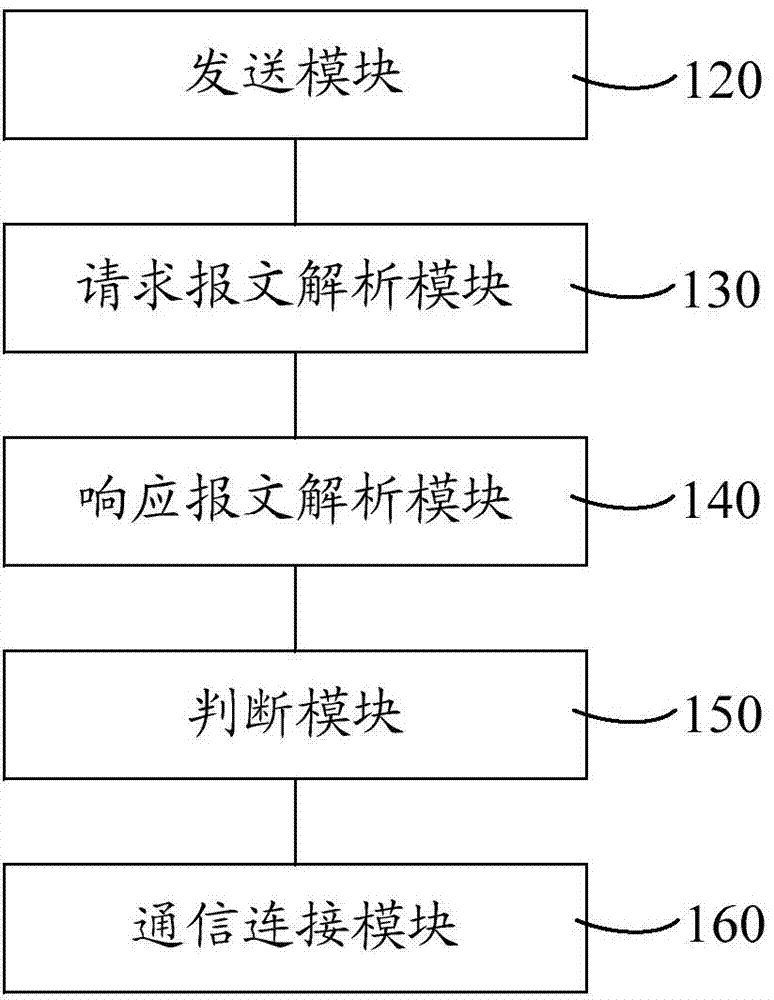
ActiveCN104125568AAvoid the authentication processImprove authentication accuracyConnection managementSecurity arrangementTelecommunicationsWireless control
Disclosed is a wireless access point safe authentication method and system. The method comprises transmitting a discovery request message from a wireless access point to a wireless controller; receiving the discovery request message from the wireless controller, analyzing the discovery request message to obtain the serial number and the MAC (media access control) address of the wireless access point, and transmitting a discovery responding message to the wireless access point; receiving the discovery responding message from the wireless access point and analyzing the discovery responding message to obtain the IP (Internet protocol) address information of the wireless controller, binding the IP address information with the wireless controller, and transmitting a connection request message to the wireless controller; after receiving the connection request message from the wireless controller, determining whether the serial number and the MAC address of the wireless access point are matched with a prestored serial number and a prestored MAC address; if so, establishing a communication channel between the wireless controller and the wireless access point. By taking that whether the serial number and the MAC address of the wireless access point are matched as the access basis, the wireless access point safe authentication method and system prevents unallowed wireless access points from access to the wireless controller, thereby improving the authentication accuracy.
Owner:湖南恒茂信息技术有限公司
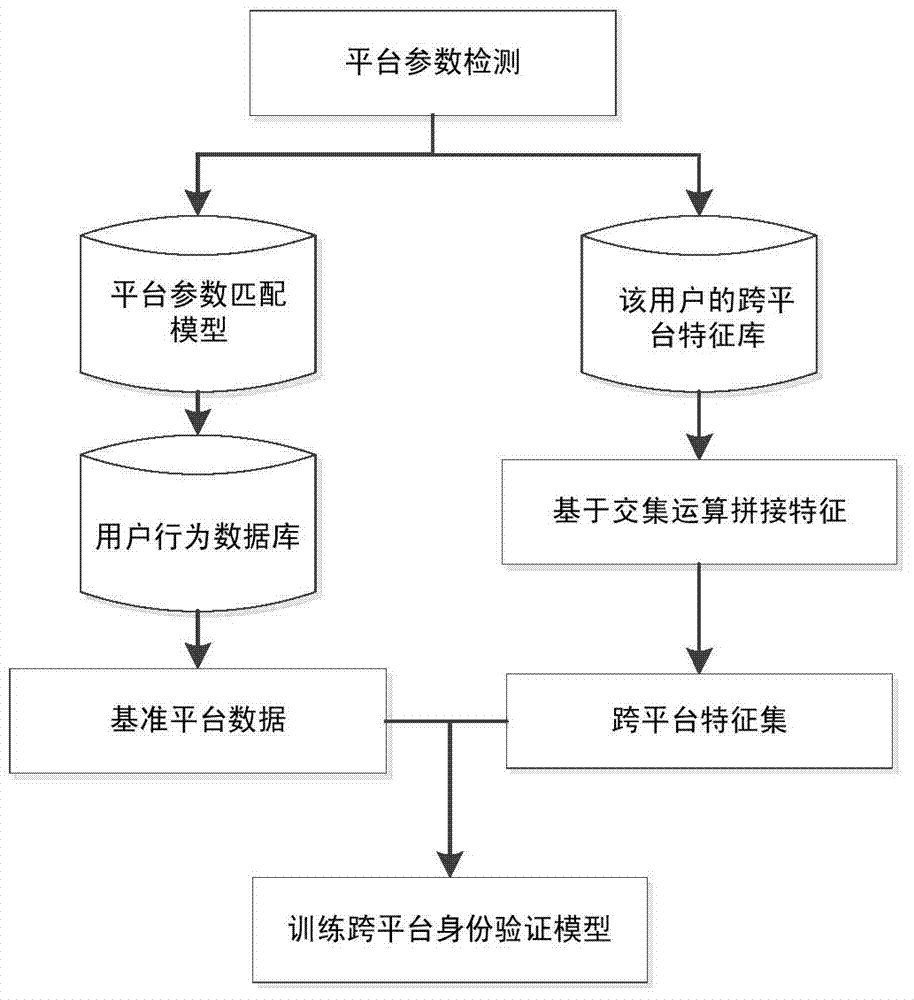
Cross-platform identity authentication system and method based on human-computer interaction behaviors
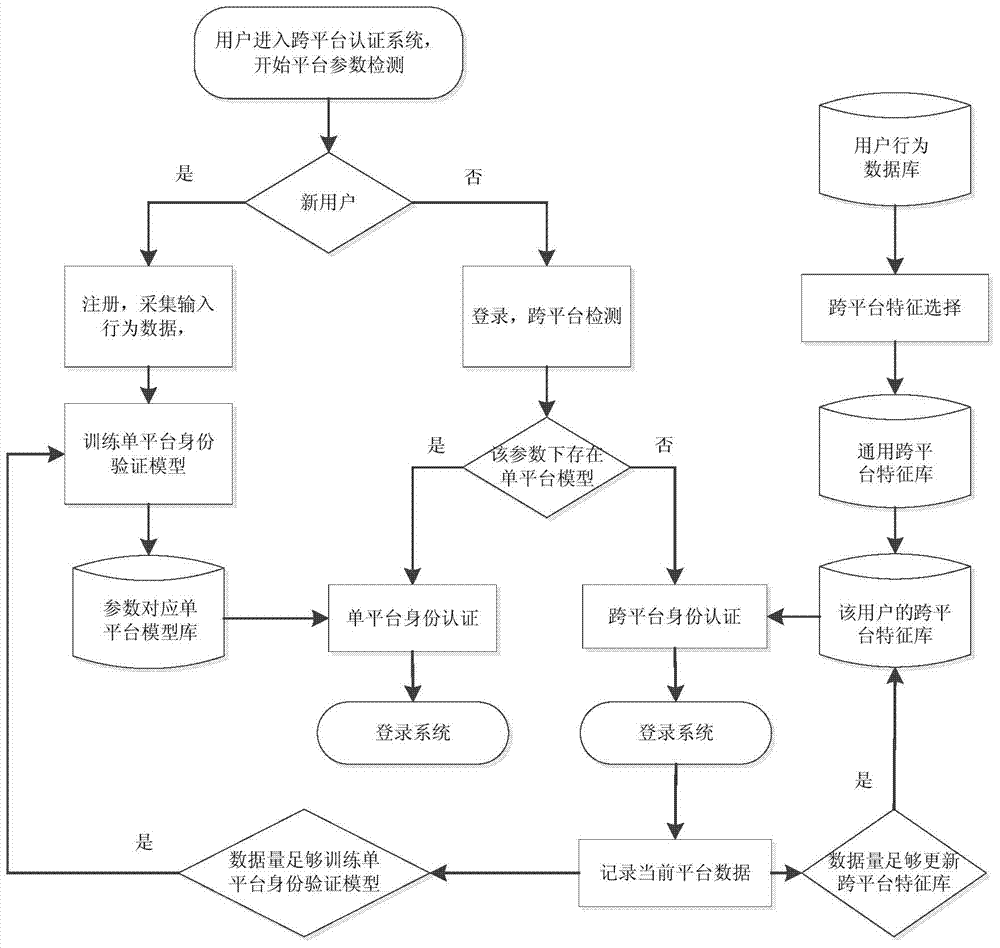
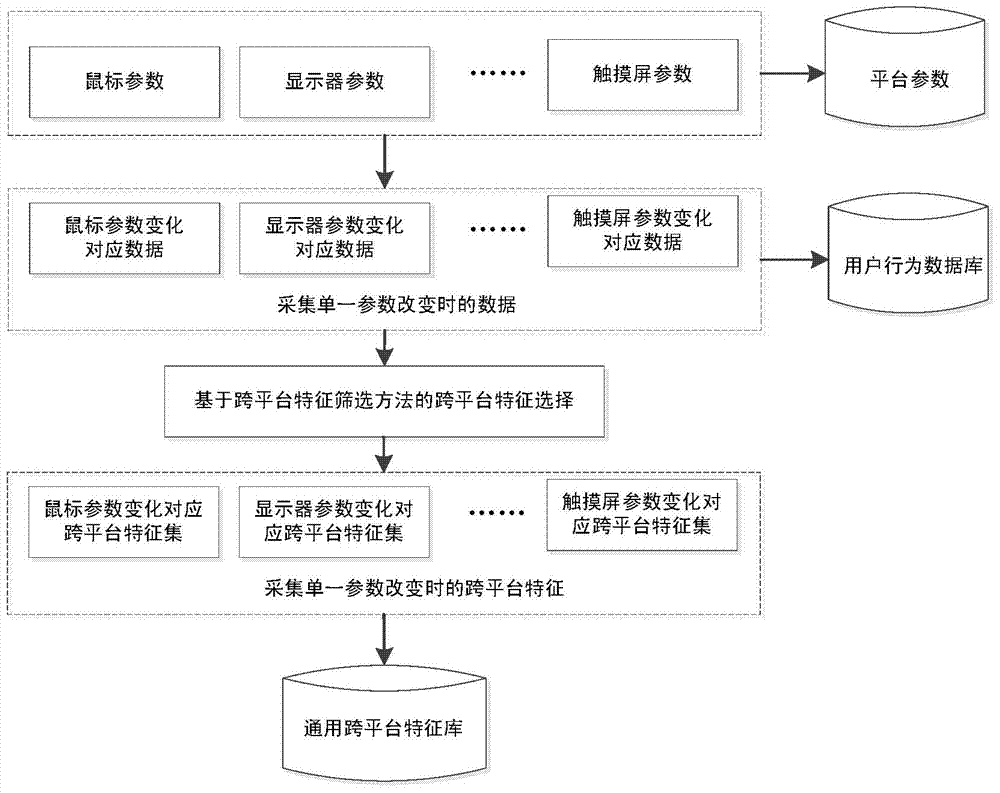
ActiveCN104778387ASolve the problem of reduced authentication accuracyImprove authentication accuracyDigital data authenticationAuthentication systemHuman system interaction
The invention discloses a cross-platform identity authentication system and method based on human-computer interaction behaviors. The cross-platform identify authentication method comprises the following steps that (1) a user enters a behavior authentication system, wherein the behavior authentication system judges whether the user is a new user, and if so, a step (2) is carried out for registration, and if the user is a registered user, a step (3) is carried out for cross-platform detection; (2) the new user carries out registration; (3) cross-platform detection is carried out, and if the user crosses platforms, a step (5) is carried out for cross-platform identity authentication; (4) single-platform identity authentication is carried out; (5) cross-platform identity authentication is carried out, a cross-platform feature library of the user is updated, and a single-platform identity authentication model is established. Under an existing internet environment, the user can often access the same network account by using different terminal equipment, and the accuracy of a traditional identity authentication technology based on the human-computer interaction behaviors is greatly reduced by different hardware environments. The problems can be effectively solved by the cross-platform authentication method based on a cross-platform identity verification model.
Owner:XI AN JIAOTONG UNIV
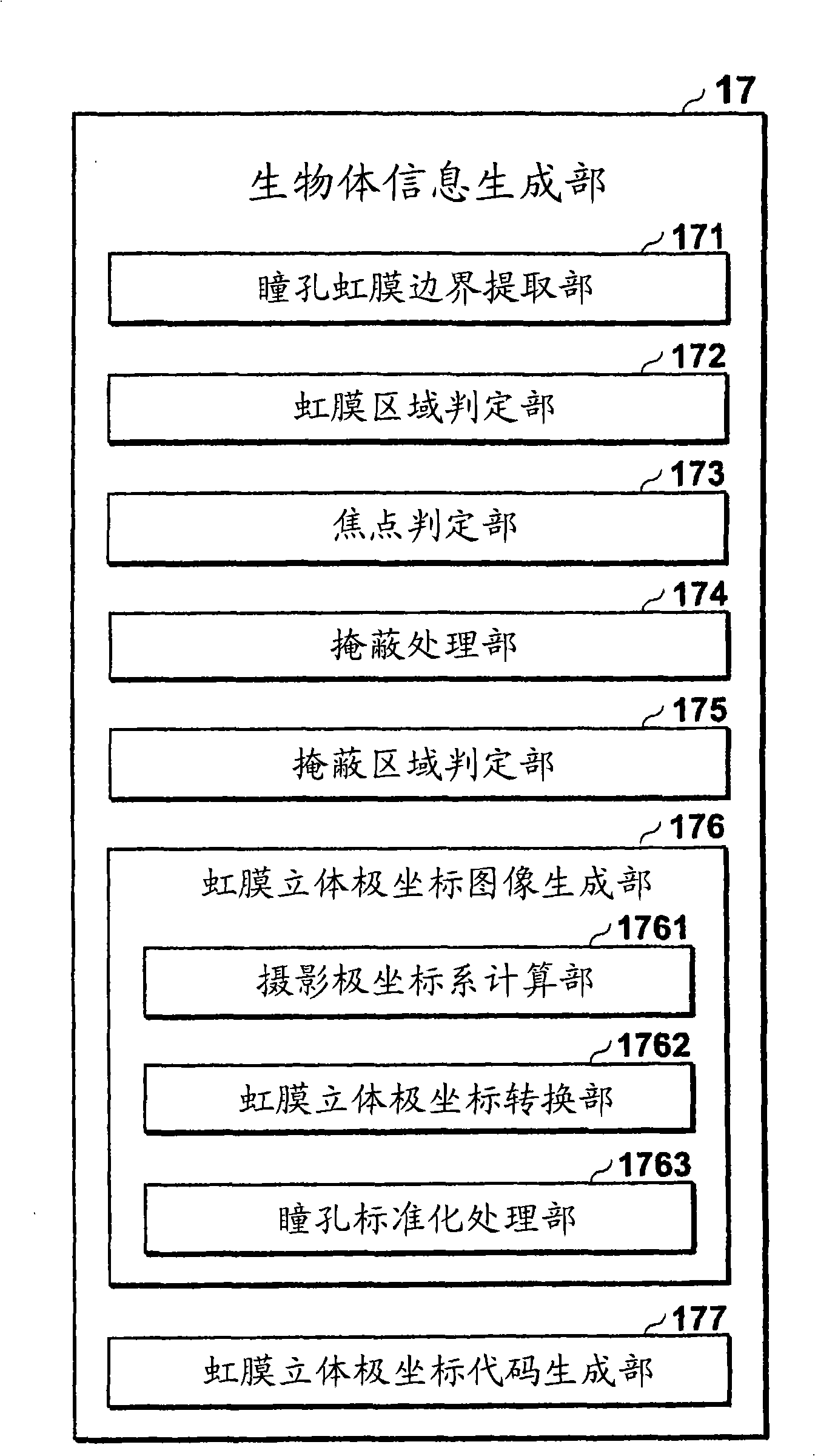
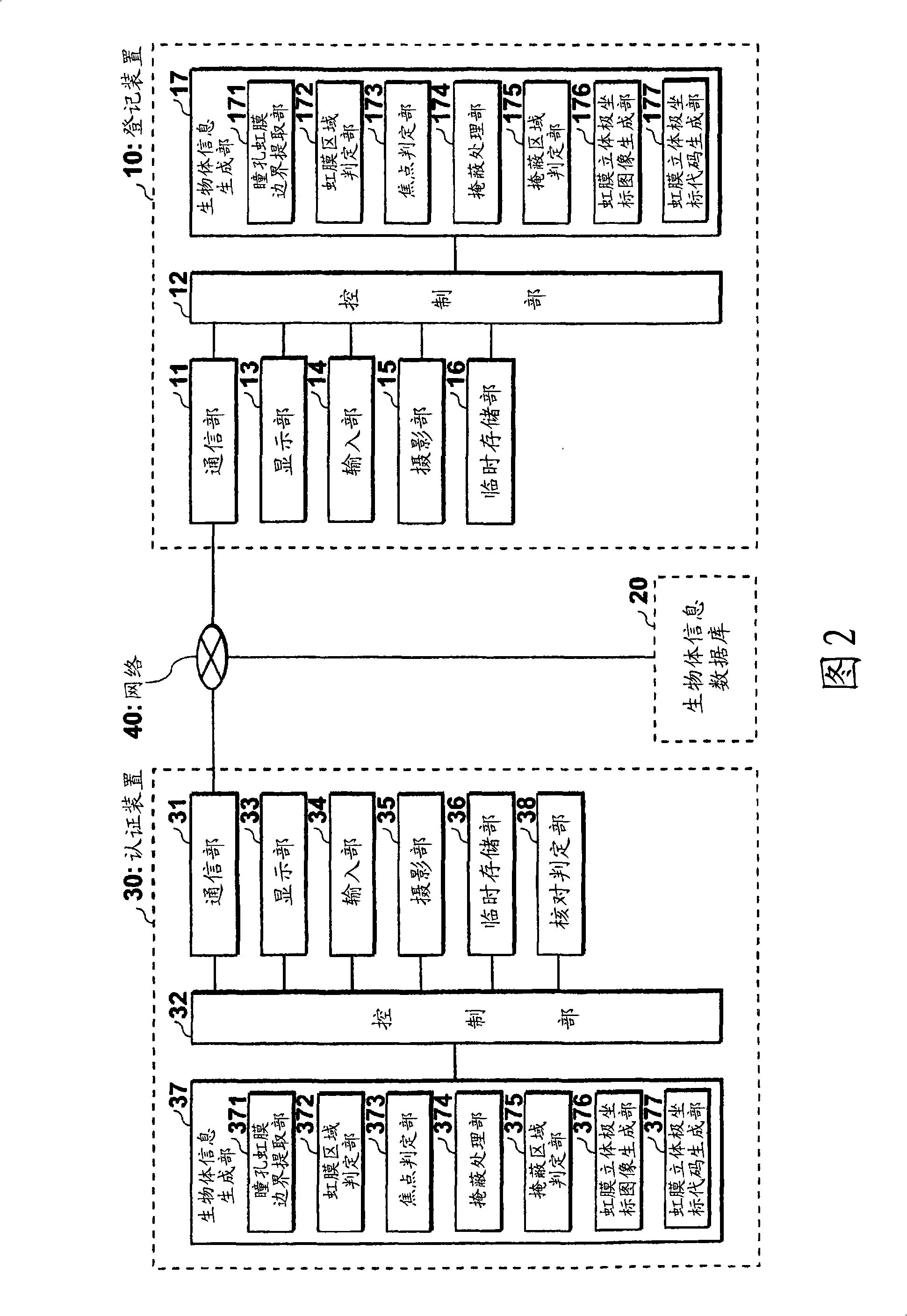
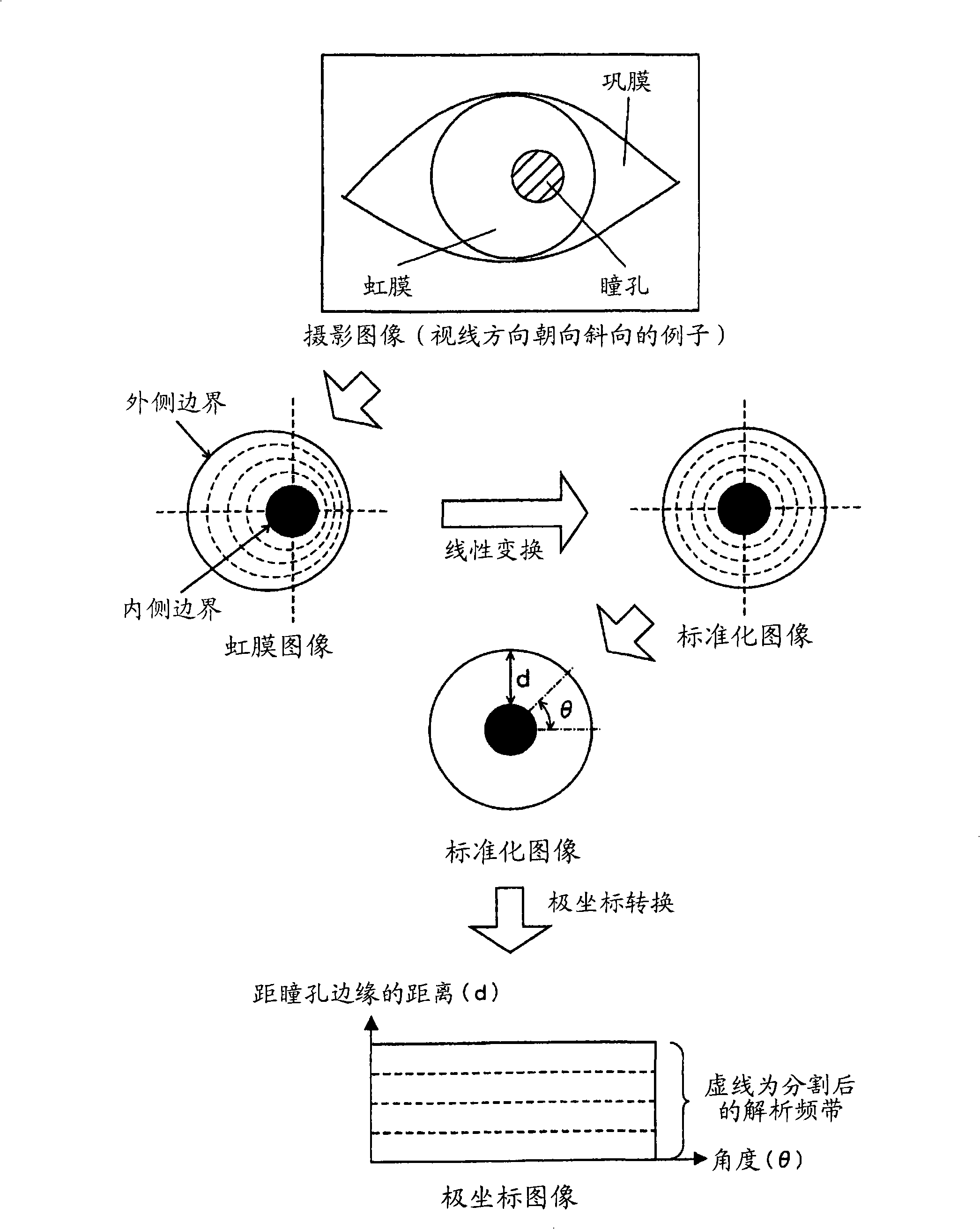
Personal authentication system and personal authentication method
InactiveCN101517615AImprove authentication accuracyImage analysisAcquiring/recognising eyesAuthentication systemImage code
A personal authentication system comprises an imaging section for capturing an image of a user's eye including the iris; pupil / iris region extraction section for extracting a pupil region and an iris region from the captured image; a three-dimensional polar coordinate image creation section for estimating the three-dimensional center position of the eyeball based on the extracted pupil region and iris region and for creating a three-dimensional polar coordinate image by converting the iris region into three-dimensional coordinates with reference to the center position of the eyeball; and a three-dimensional polar coordinate image coding section for creating a three-dimensional polar coordinate image code formed by extracting and coding a characteristic of the created three-dimensional polar coordinate image. The personal authentication system can create iris information highly accurately representing characteristics of a user's iris independent of the direction of line of sight of the user.
Owner:OKI ELECTRIC IND CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com