Personal authentication system and personal authentication method
An authentication system and authentication method technology, which are applied in the fields of digital data authentication, character and pattern recognition, image data processing, etc., can solve the problems of low authentication accuracy, and achieve the effect of improving authentication accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0062]
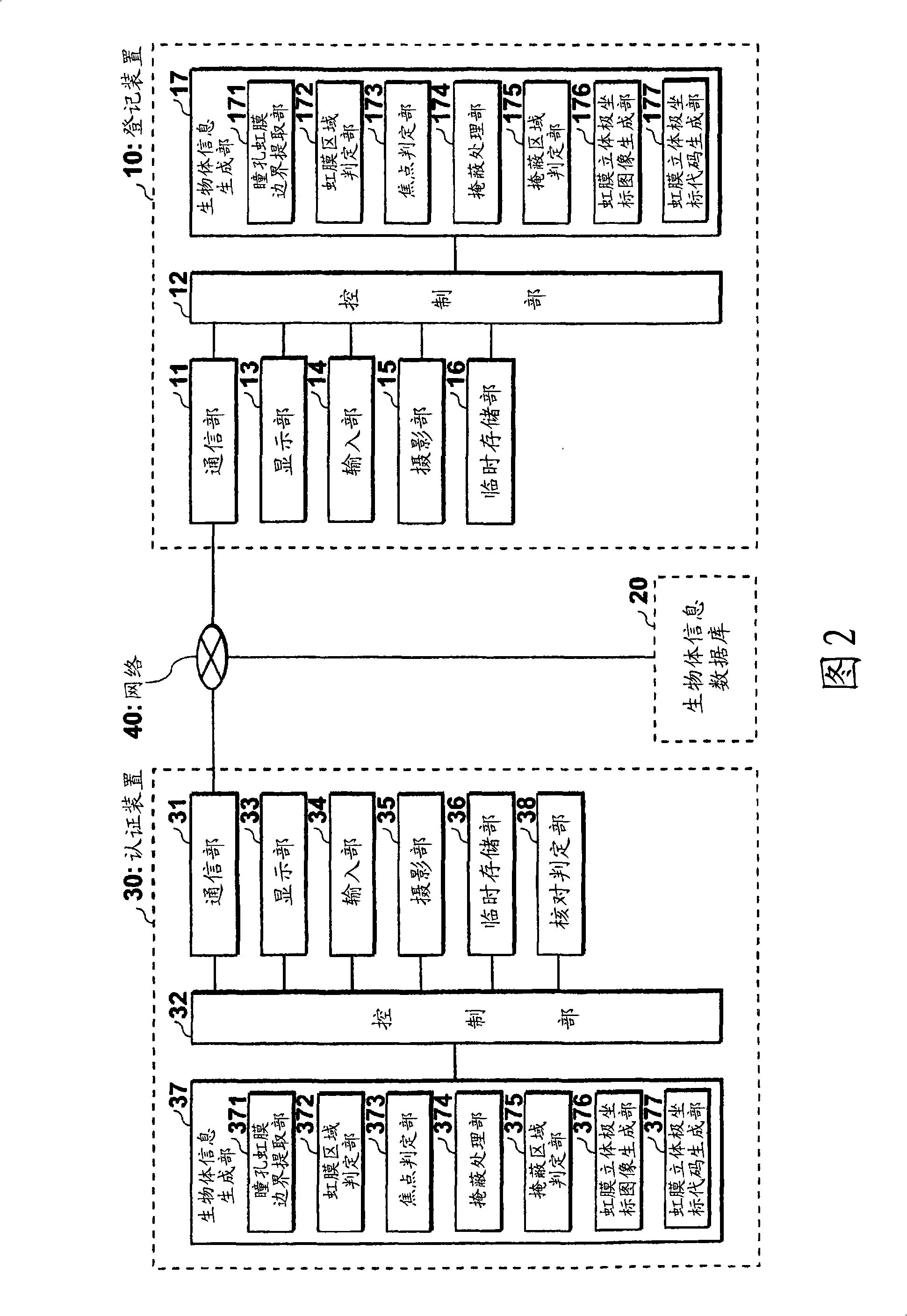
[0063] Such as figure 2 As shown, the personal authentication system according to the embodiment of the present invention is composed of a registration device 10 , a biometric information database (DB) 20 connected to the registration device 10 via a network 40 , and an authentication device 30 . Here, the personal authentication system of the present invention is used, for example, in an electronic door unlocking system of a building of a company or a research facility.
[0064] Here, to simplify the description, figure 2 Only one authentication device 30 is shown, but a plurality of authentication devices 30 having the same functions as the authentication device 30 are connected to the network 40 .
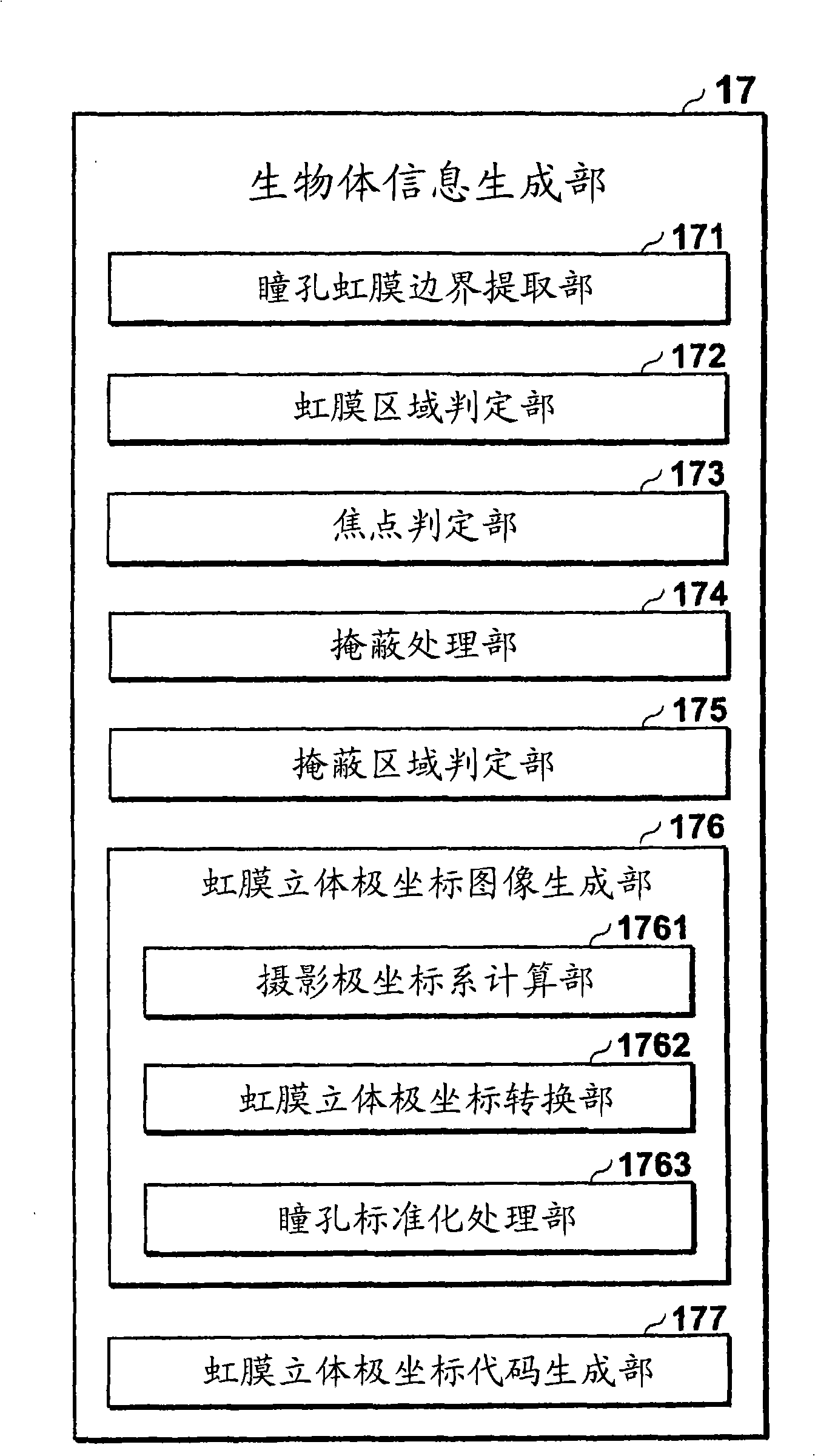
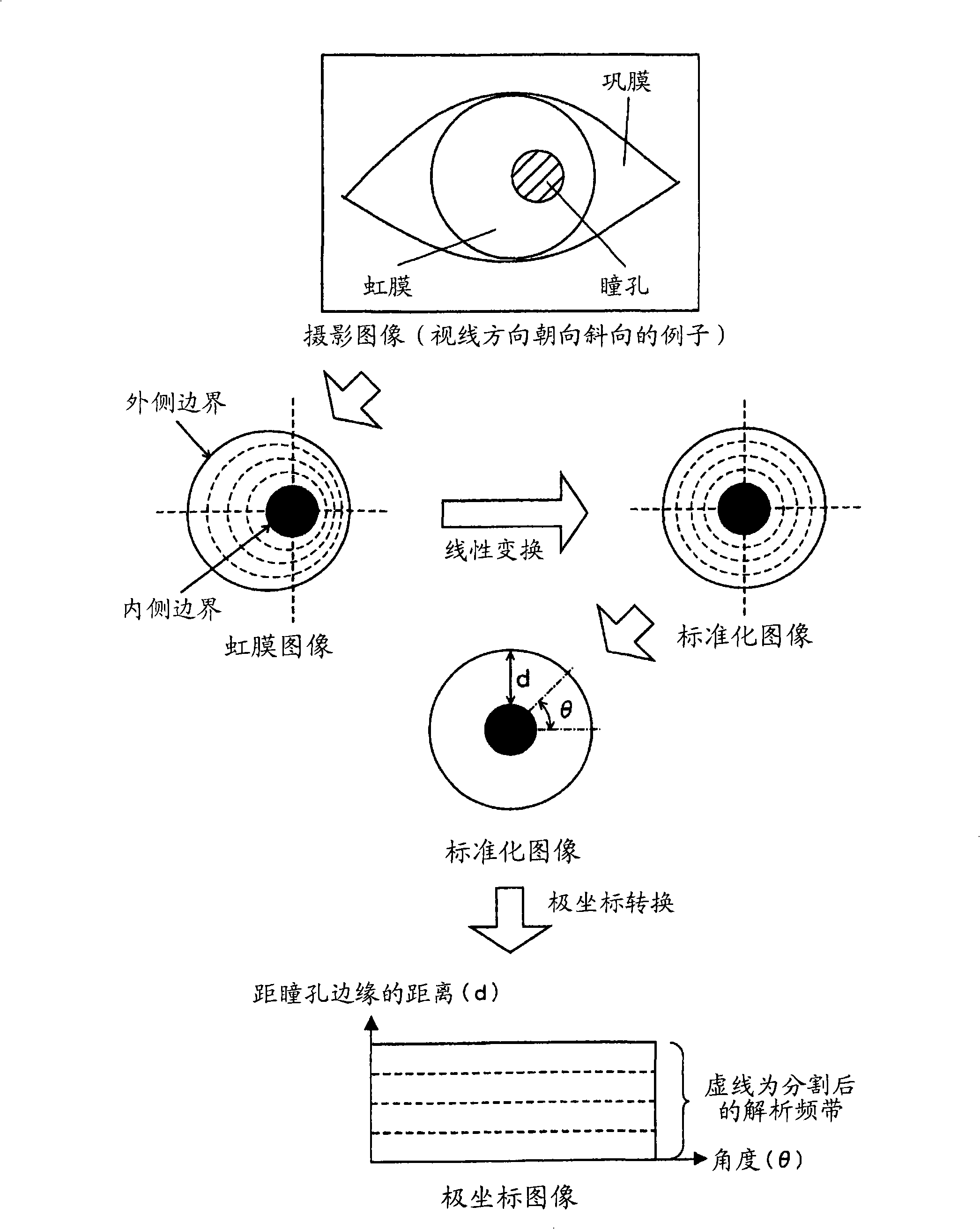
[0065] The registration device 10 is a device operated by a registration applicant in order to perform a registration procedure as a user of the personal authentication system, and the registration device 10 has a communication unit 11 connected to the network 40, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com