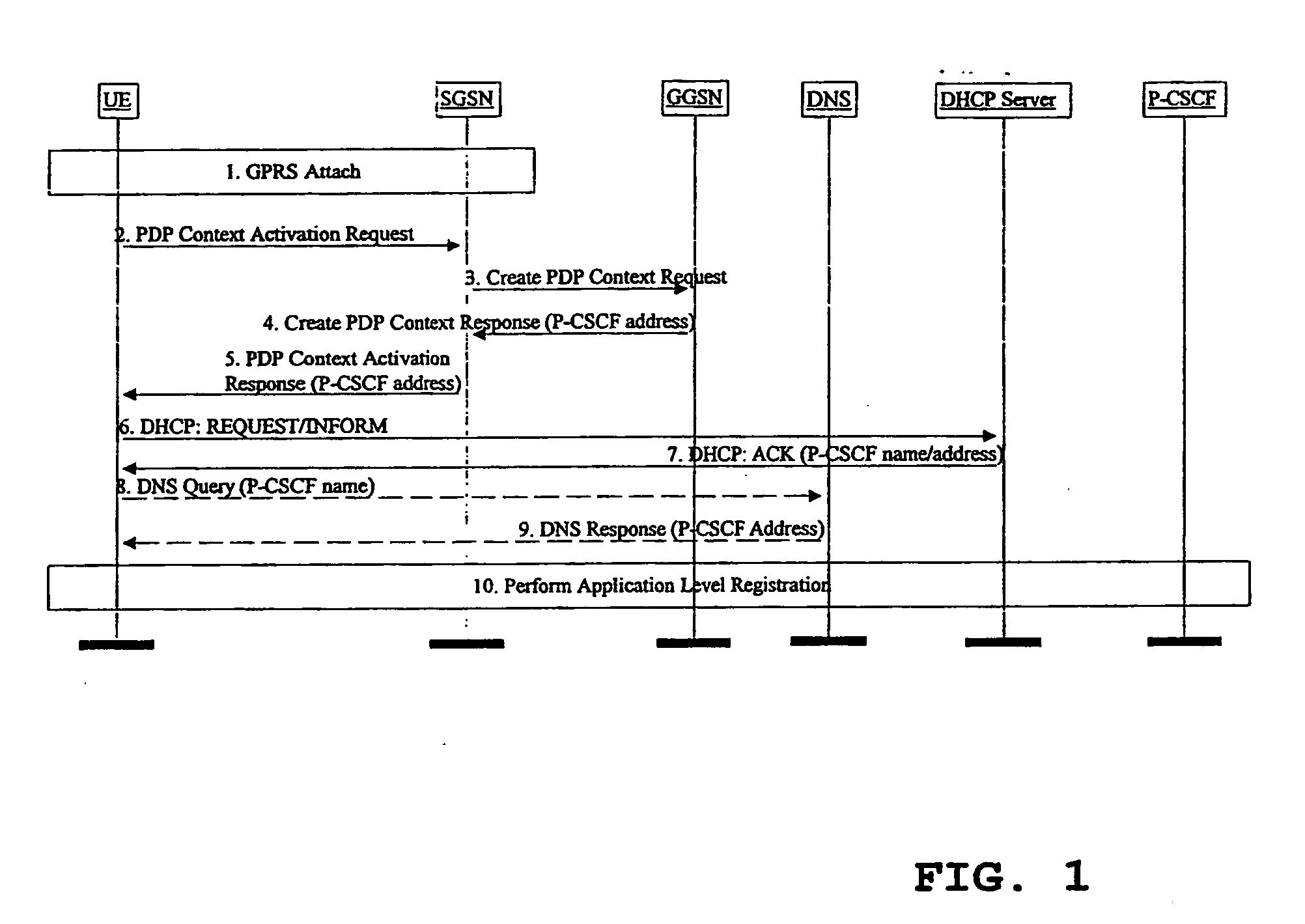
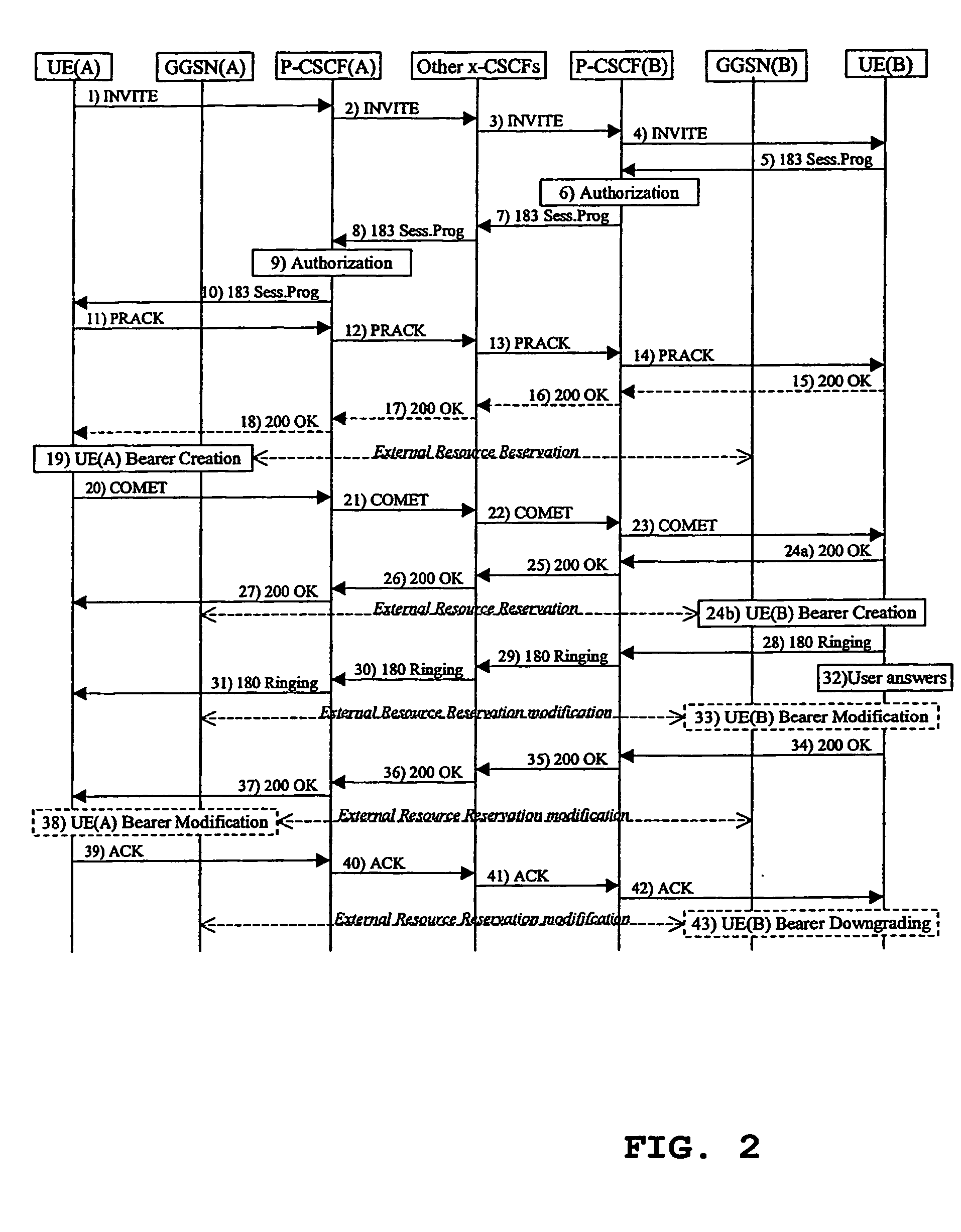
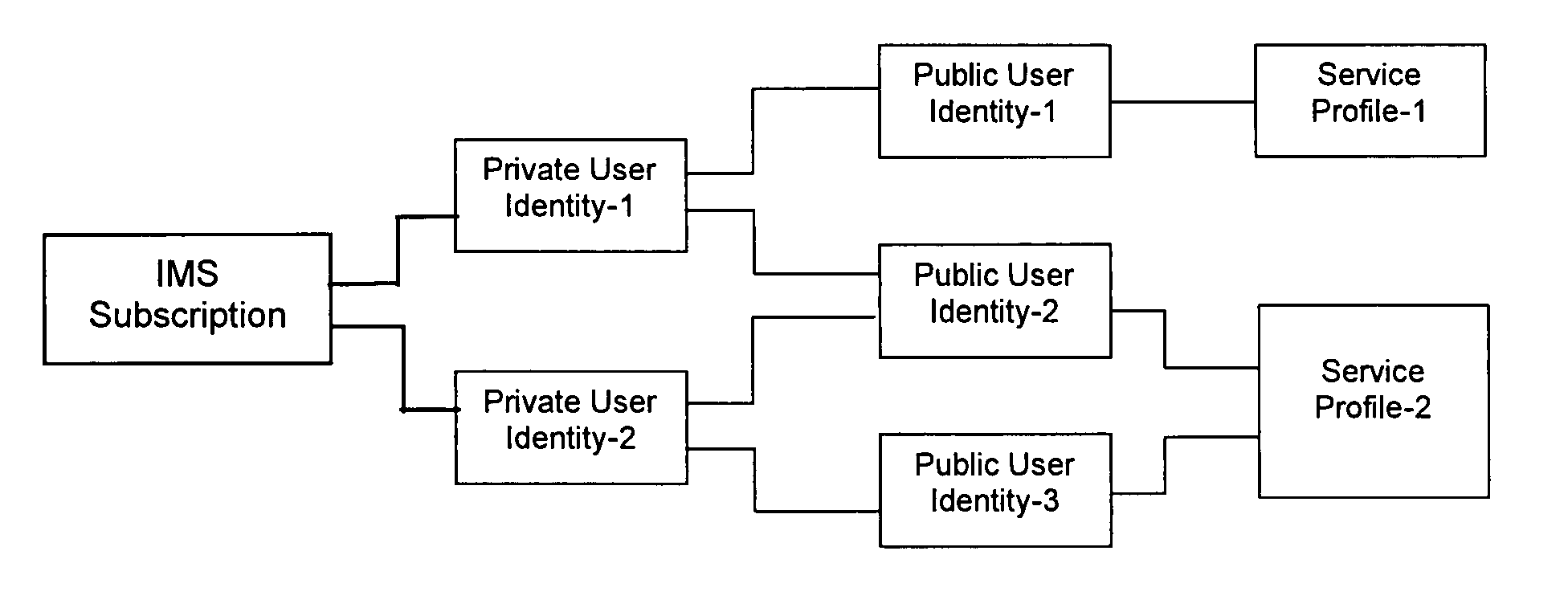
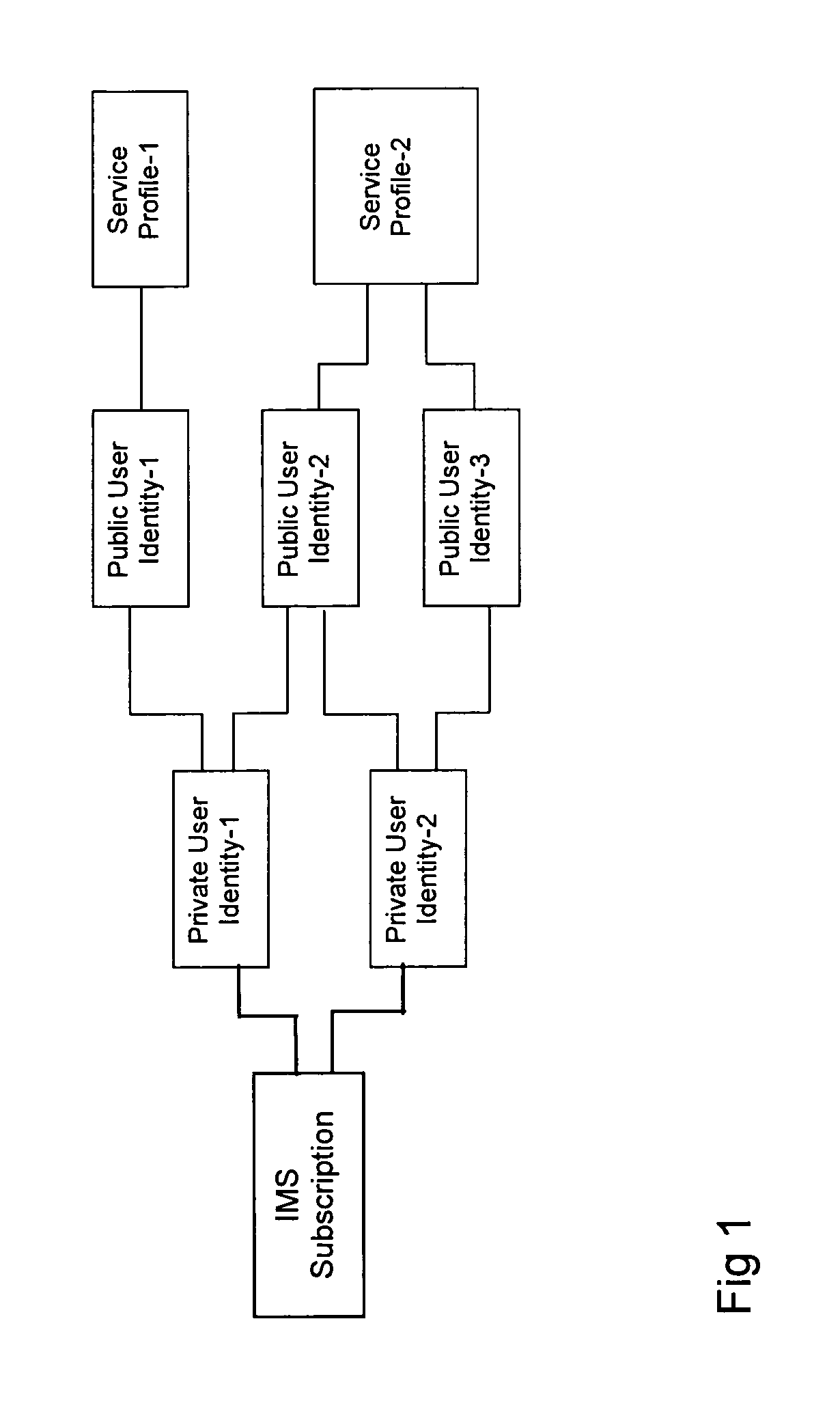
Patents
Literature
273 results about "Registration procedure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
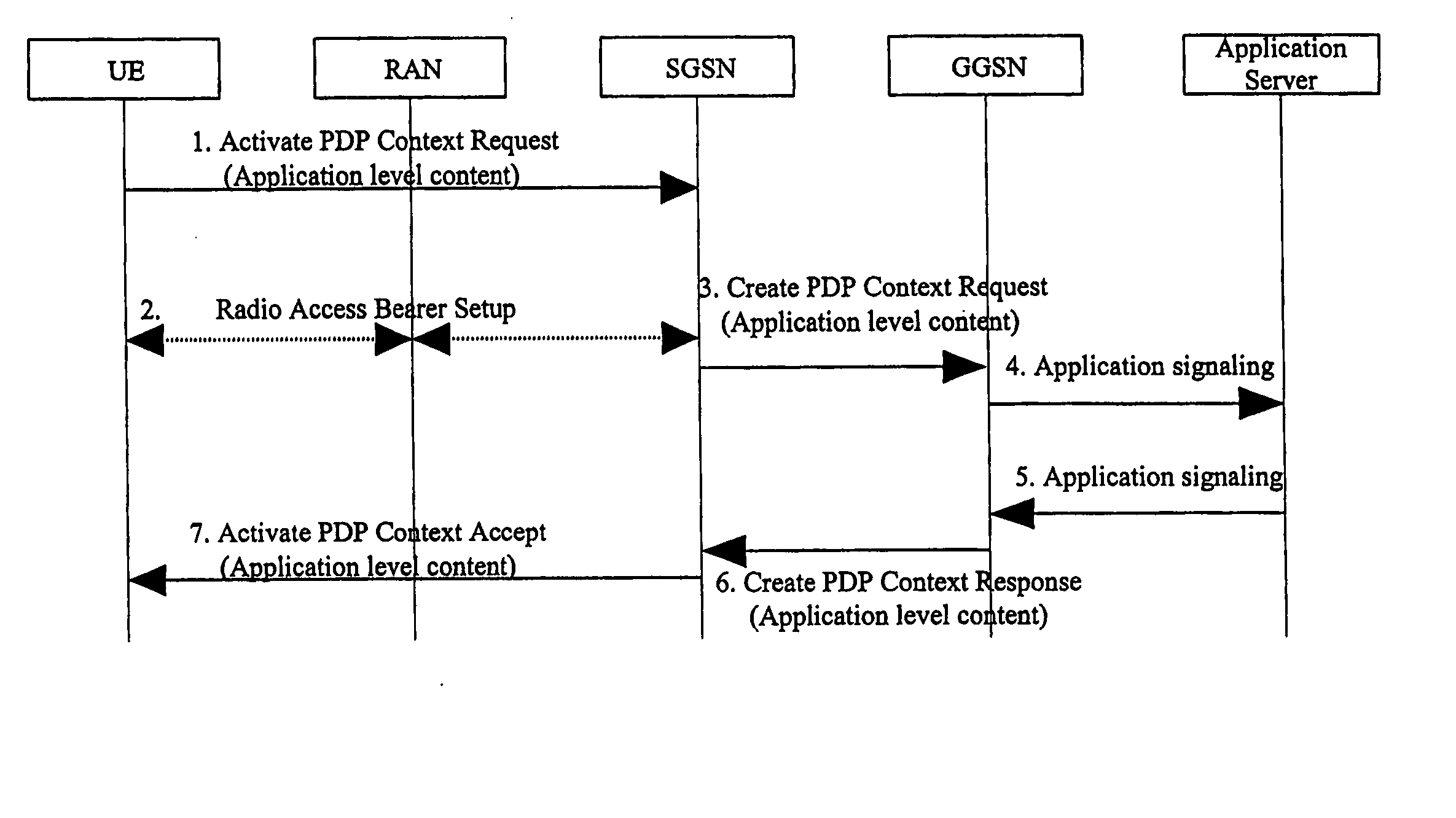
Method for programming a mobile station using a permanent mobile station identifier
InactiveUS6879825B1Reduce the possibilityAvoid disturbanceRadio/inductive link selection arrangementsAutomatic exchangesTelecommunications networkMobile station
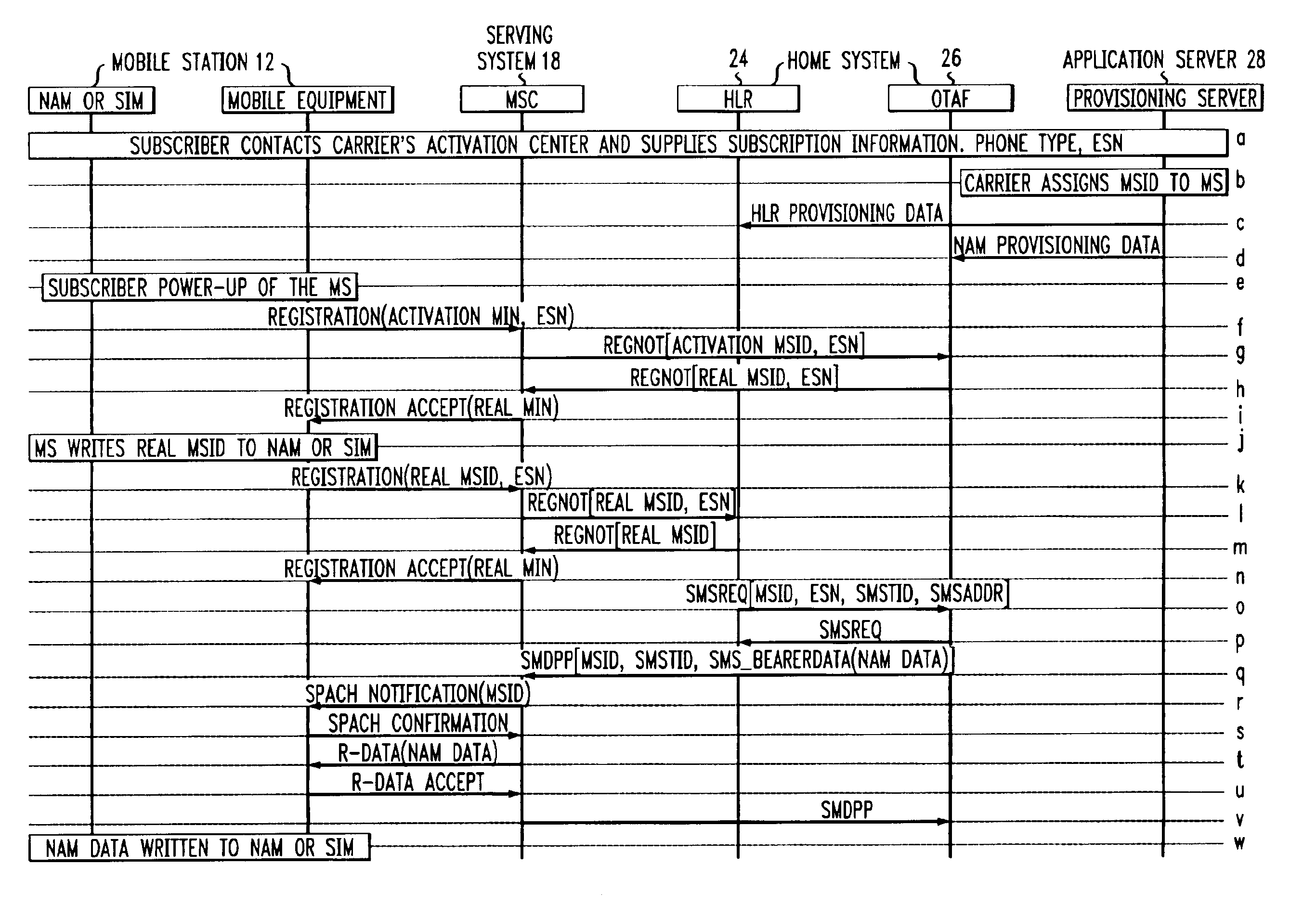
A method of activating a mobile station for communicating with a telecommunications network, the method encompassing a two-stage registration procedure whereby in the first registration procedure, a permanent mobile station ID is obtained by the mobile station and in the second registration procedure, the permanent mobile station ID is used to identify the mobile station when downloading programming data from the telecommunications network. The invention allows for programming the mobile station with a permanent MSID of either a MIN or IMSI format, without requiring a TIA / EIA-136 SPACH notification process to notify the MS of incoming programming data. In particular, the steps of the method comprise: receiving at the telecommunications network a temporary activation ID from a mobile station; the network verifying the temporary activation ID; the network communicating a permanent MSID to the mobile station; the network receiving a permanent MSID from the mobile station; the network verifying the permanent MSID and then downloading programming data to the MS.
Owner:AT&T WIRELESS SERVICES
Generic activation and registration framework for wireless devices
InactiveUS20060030306A1Easy to installReadily make themselves compatibleSubstation equipmentAutomatic exchangesService provisionPersonal computer
Owner:QUALCOMM INC
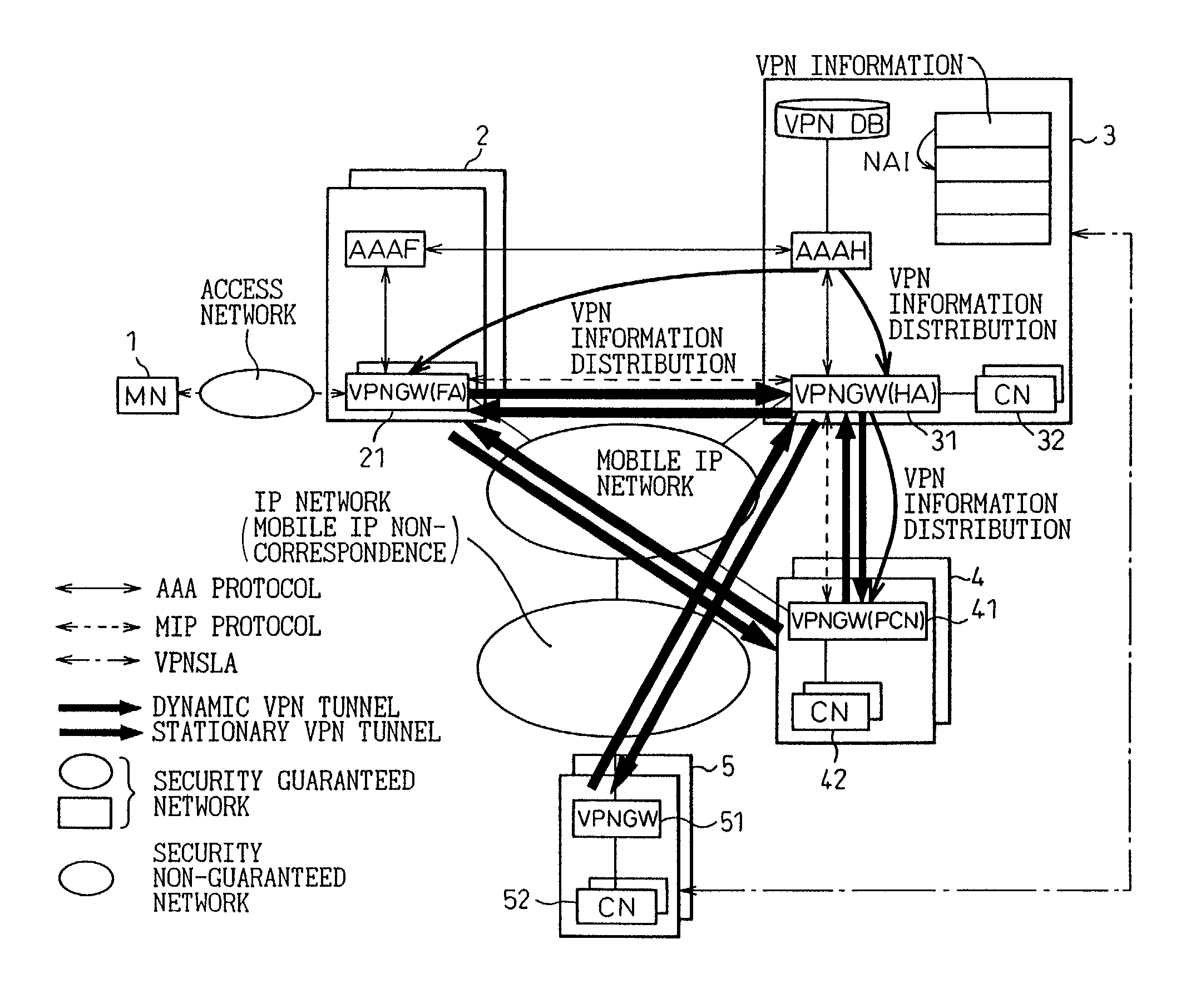
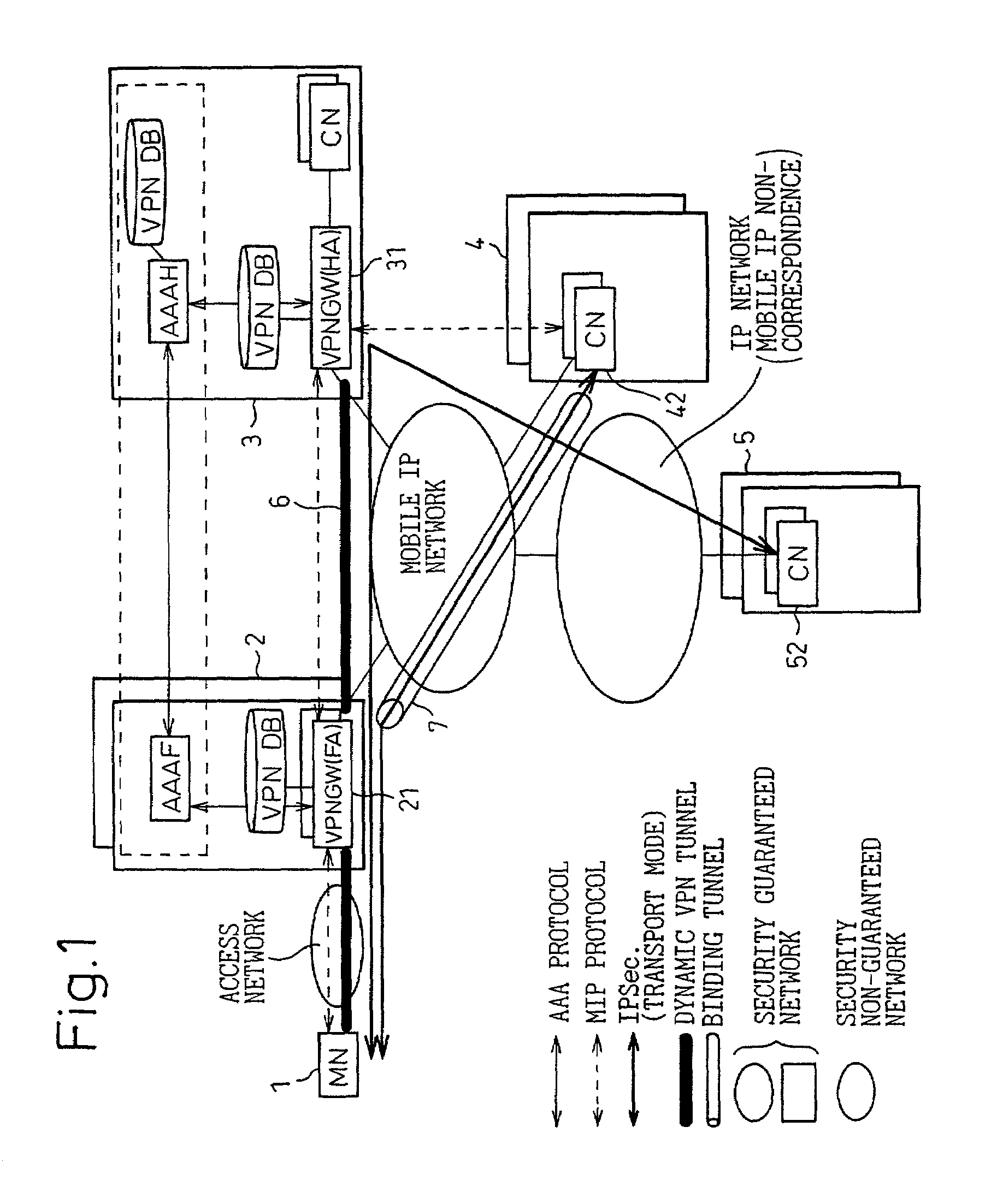
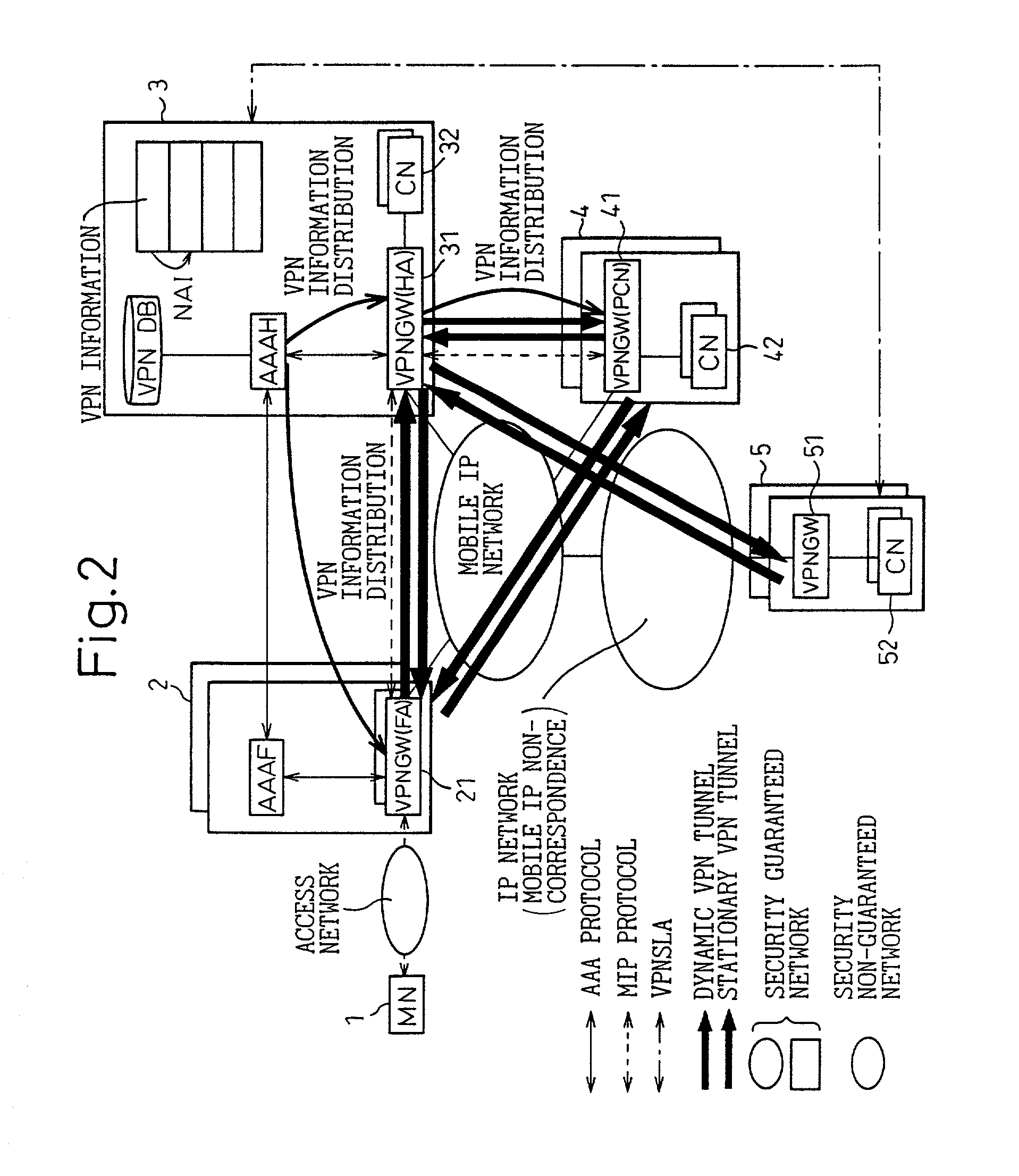
VPN system in mobile IP network, and method of setting VPN
InactiveUS7068640B2Improve user convenienceData taking preventionTime-division multiplexAuthentication serverMobile IP
Linked with a position registration procedure in a mobile IP, the invention provides a VPN setting service using an IP Sec. tunnel between optional terminals without requiring these terminals to have a specific VPN function. This service is provided by a mobile terminal, authentication servers, a VPN database, and network apparatuses. A home authentication server extracts from the VPN database the VPN information of a user who has requested the authentication at the time of making a position registration request from the mobile terminal. The home authentication server then posts the VPN information to each network apparatus using a predetermined position registration message and an authentication response message. Based on the posted VPN information, the network apparatuses set a VPN path by the IP Sec. to between a home network apparatus and an external network apparatus, between the home network apparatus and a predetermined network apparatus, and / or the external network apparatus and the predetermined network apparatus, respectively.
Owner:FUJITSU LTD
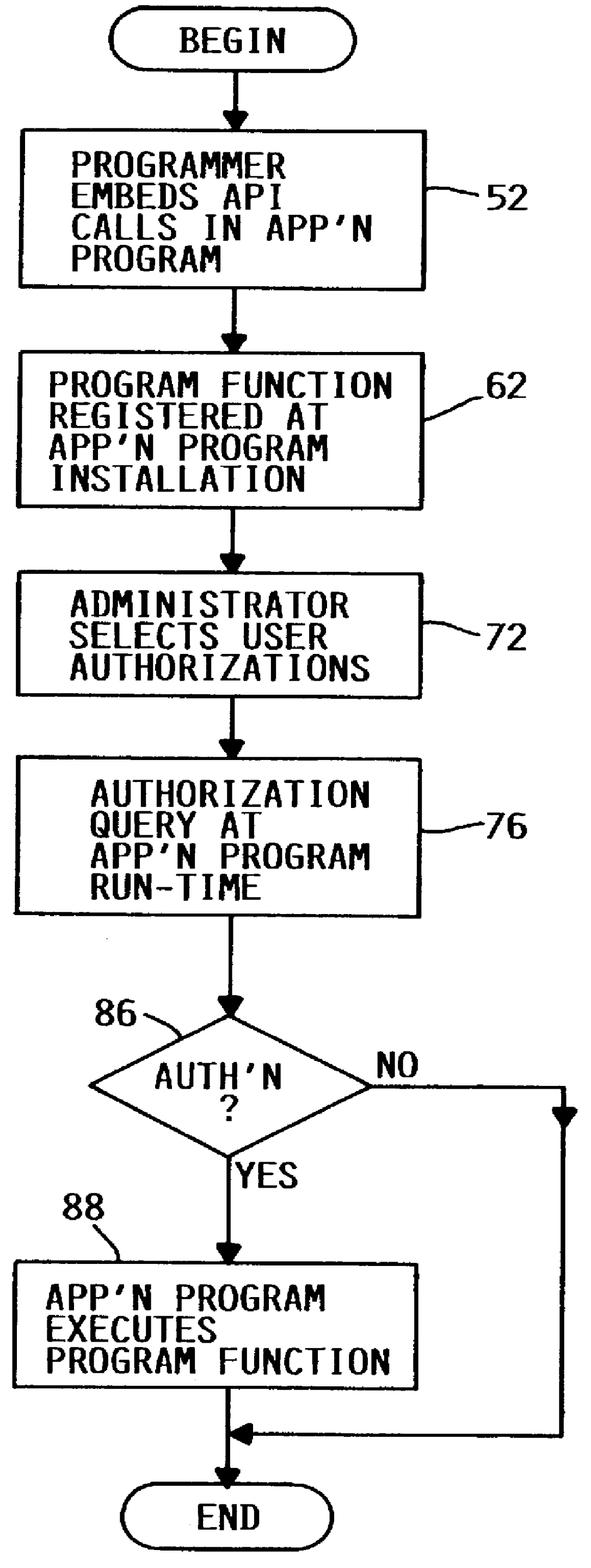
Limit access to program function
InactiveUS6101607ASpecific access rightsDigital data processing detailsOperational systemApplication programming interface
A method, system and computer program product for selectively restricting access to a program function in a computer system having an operating system security mechanism operates via an application programming interface (API) that includes a program function registration API function, an authorization selection API function, and an authorization query API function. In response to a call to the API registration function, the program function is registered in a repository in the computer system. After the program function has been registered, a system administrator can select user authorizations using a software tool that includes calls to the authorization selection API function. The system administrator may select whether a particular user or group of users is authorized to access each registered program function. A programmer can embed a call to the authorization query API function in an application program, which includes or calls the program function. When the application program reaches the call to the authorization query API function, the function is executed and returns an indicator or value indicating whether or not that user is allowed to access the program function.
Owner:IBM CORP
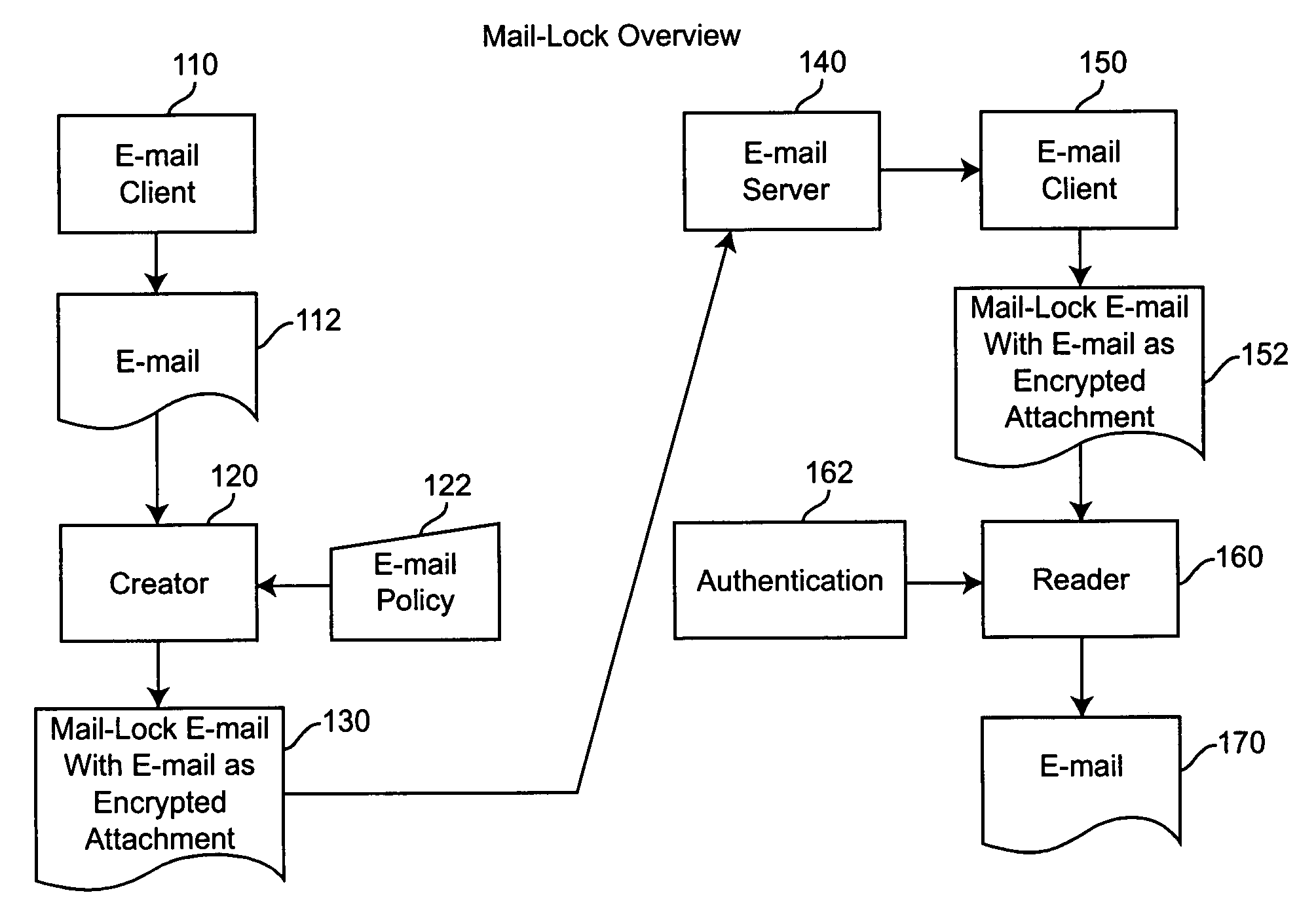
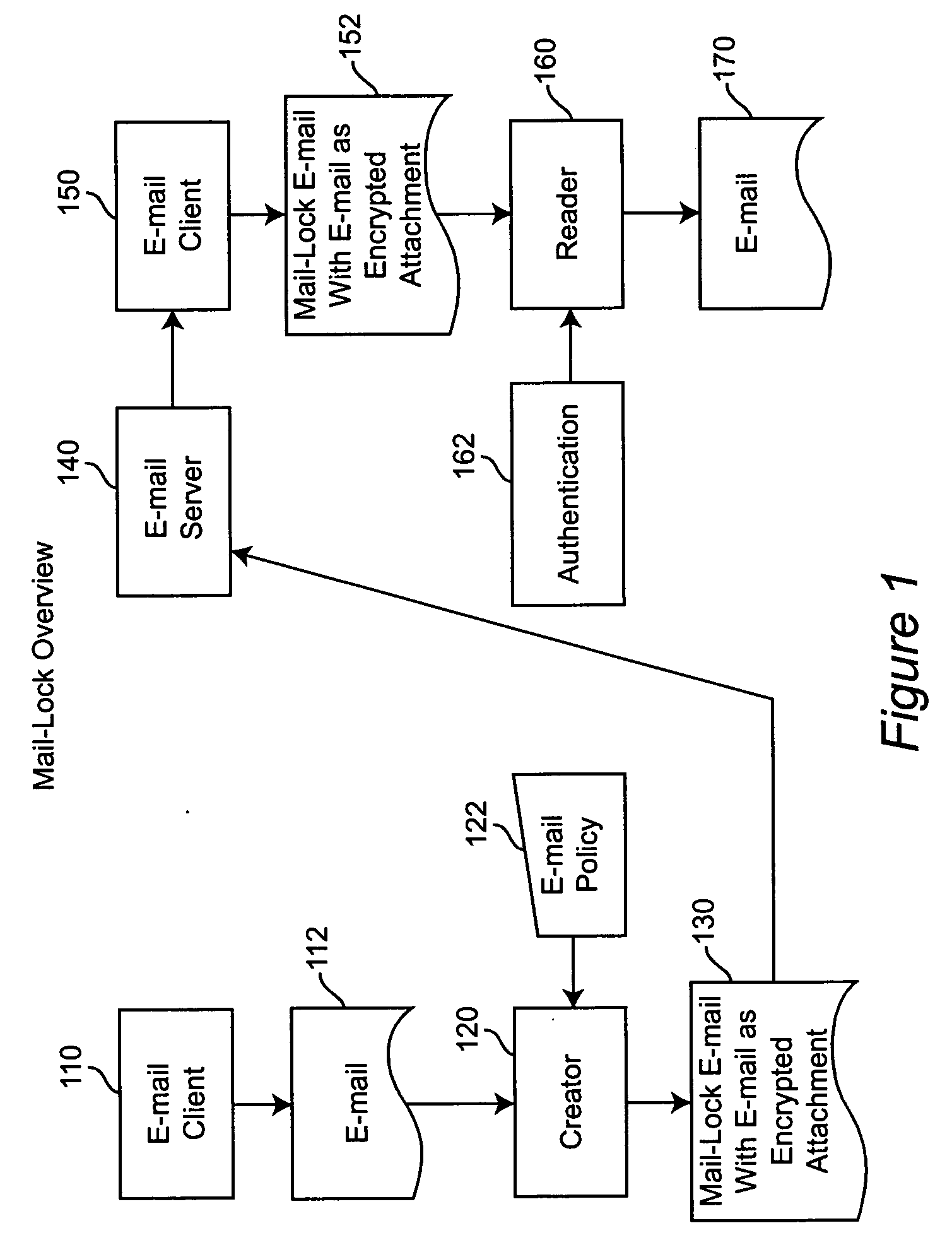
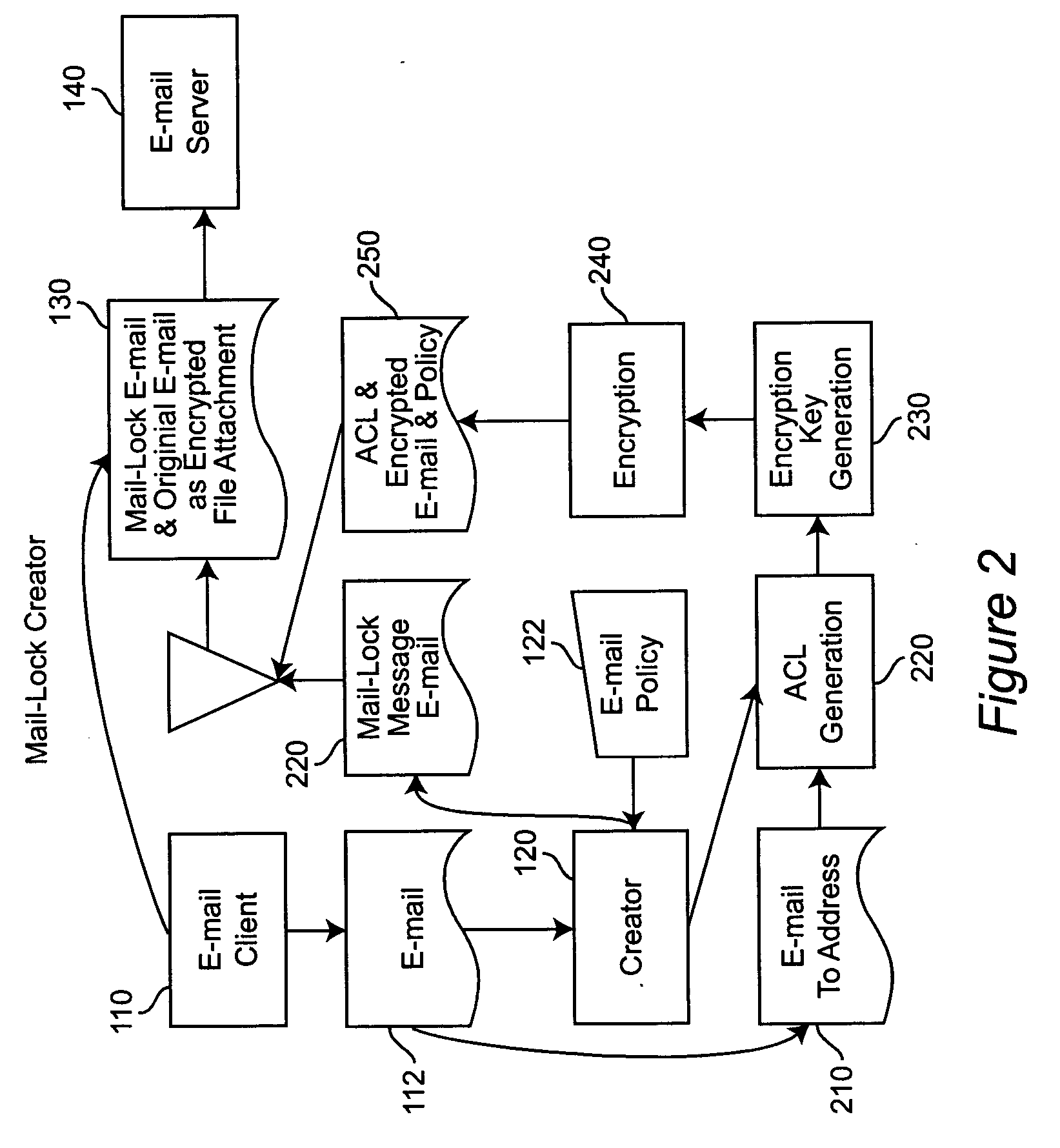
System and method for controlling the downstream preservation and destruction of electronic mail
InactiveUS20050204008A1Simple interfaceMultiple digital computer combinationsData switching networksEmail addressPassword
A system and method for controlling the downstream preservation and destruction of electronic mail by encrypting the electronic mail and limiting access to the encrypted file based on registration of recipient e-mail addresses, and detection and restriction of output functionality available to the recipient. The registration procedure limits access to recipients included on an access control list, who receive a pre-configured reader and then authenticate their e-mail address to the reader via a known SMTP Server. The sender of an e-mail is provided with a dialog for determining the limitations on access to the e-mail by the recipient: whether the e-mail is to be inaccessible after a certain period of time, whether a recipient may copy or print the e-mail and / or its attachments, or whether a password is required to read the e-mail. These limitations comprise an access control policy applicable to the e-mail, the pre-configured reader being adapted to decrypt the e-mail and apply the policy.
Owner:GRPWARE SOFTWARE SOLUTIONS
System and method for managing resource in communication system
ActiveUS20120195269A1Easy to useWireless commuication servicesNetwork planningCommunications systemFrequency sharing
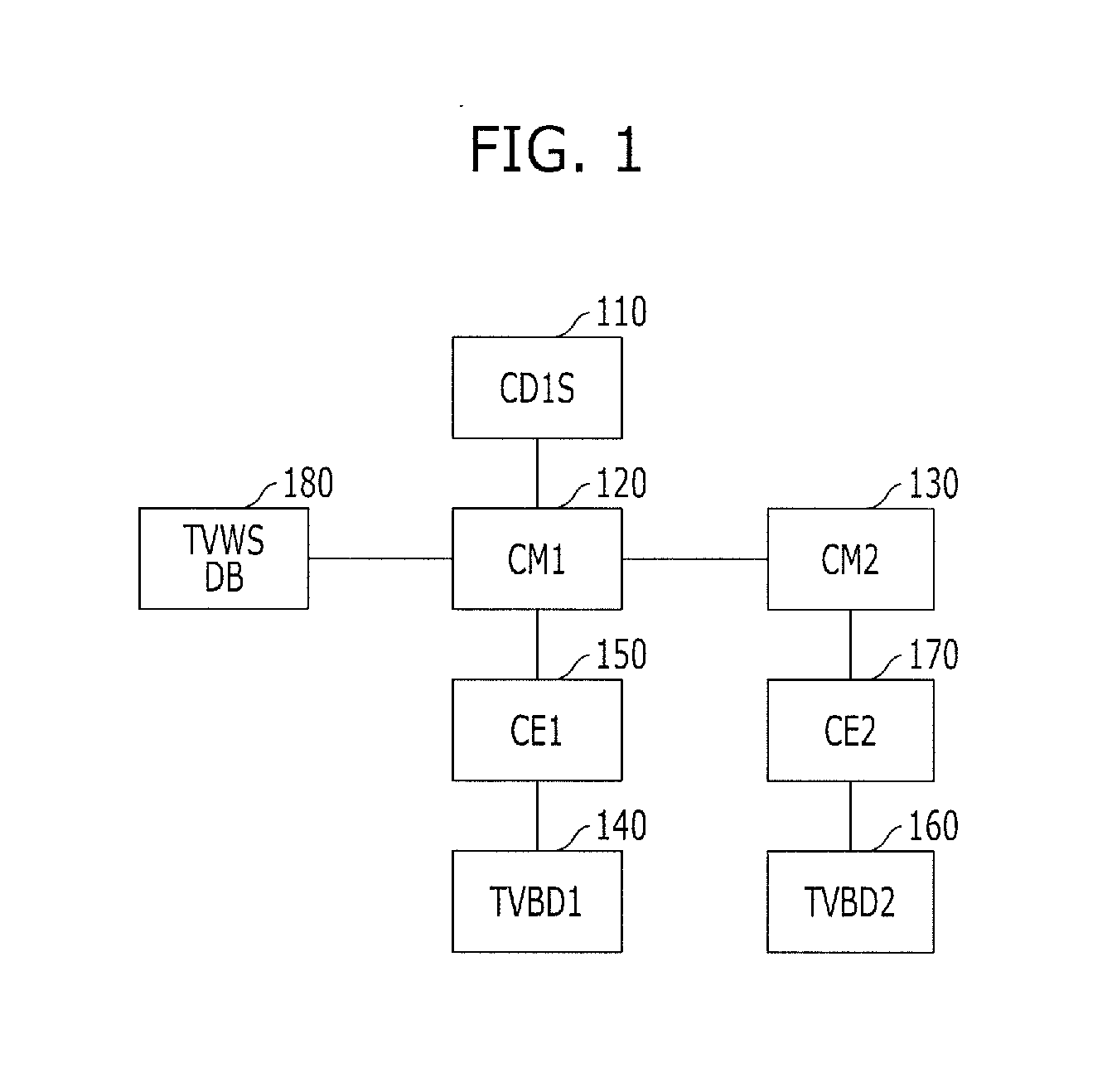
A system for managing resources in a communication system including systems, which do not have a permission for a first frequency band, includes coexistence managers configured to, when a frequency band available for the systems is searched from the first frequency band, manage the systems for coexistence and frequency sharing of the systems in the available frequency band; a coexistence enabler configured to transmit and receive information of the systems and information of the coexistence managers; and a coexistence discovery and information server configured to support control of the coexistence managers over the systems, wherein predetermined messages are transmitted and received among the coexistence discovery and information server, the coexistence managers and the coexistence enabler to perform a registration procedure, a coexistence information gathering procedure, a coexistence decision making procedure, a reconfiguration procedure, a management procedure and an event procedure, for the coexistence and frequency sharing of the systems.
Owner:ELECTRONICS & TELECOMM RES INST
Generic activation and registration framework for wireless devices
InactiveUS6961567B1Easy to installReadily make themselves compatibleInterconnection arrangementsSpecial service for subscribersService provisionPersonal computer
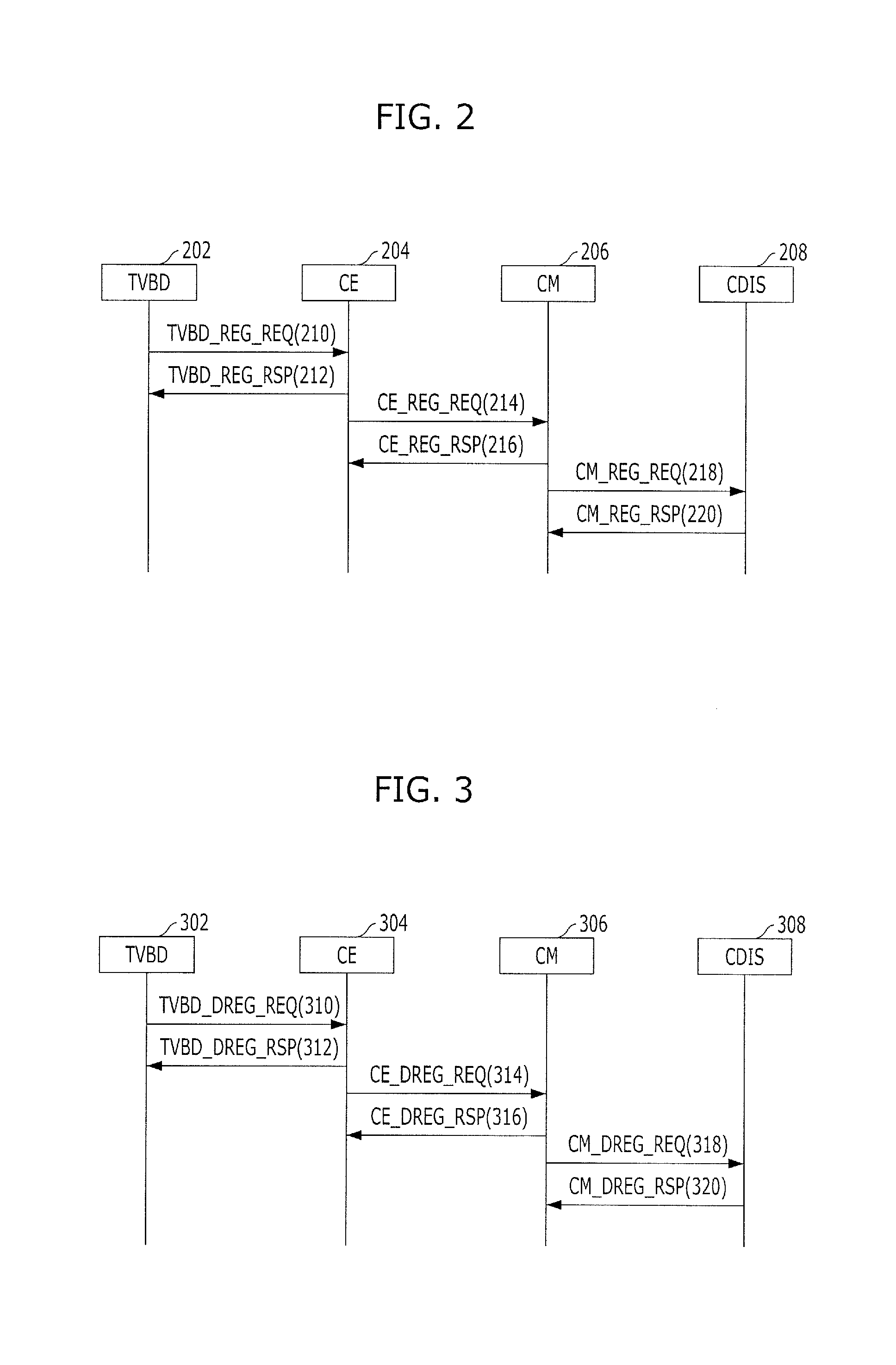
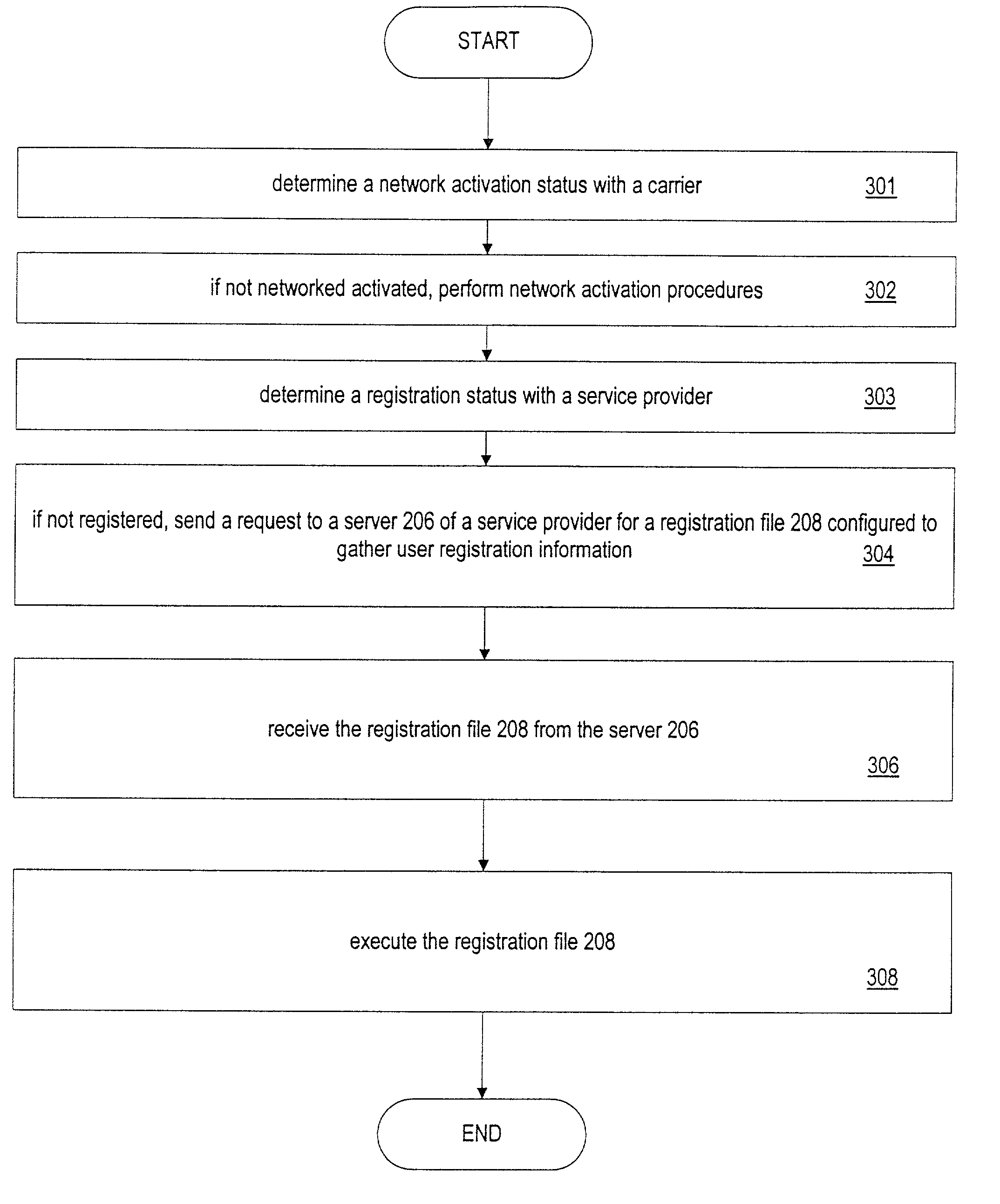
A system and a method are provided for managing network activation with a carrier and registration with a service provider. In one example, the method determines a network activation status. If the network is not activated, a utility is used to perform the activation. Further, the status of registration with a provider is determined. If not registered, a request is sent to a server of the service provider for a registration file configured to gather user registration information. The registration file is then received from the server. The registration file is executed on the personal computer. Data gathered by the registration file is then returned to the service provider's server to complete the registration procedures.
Owner:QUALCOMM INC
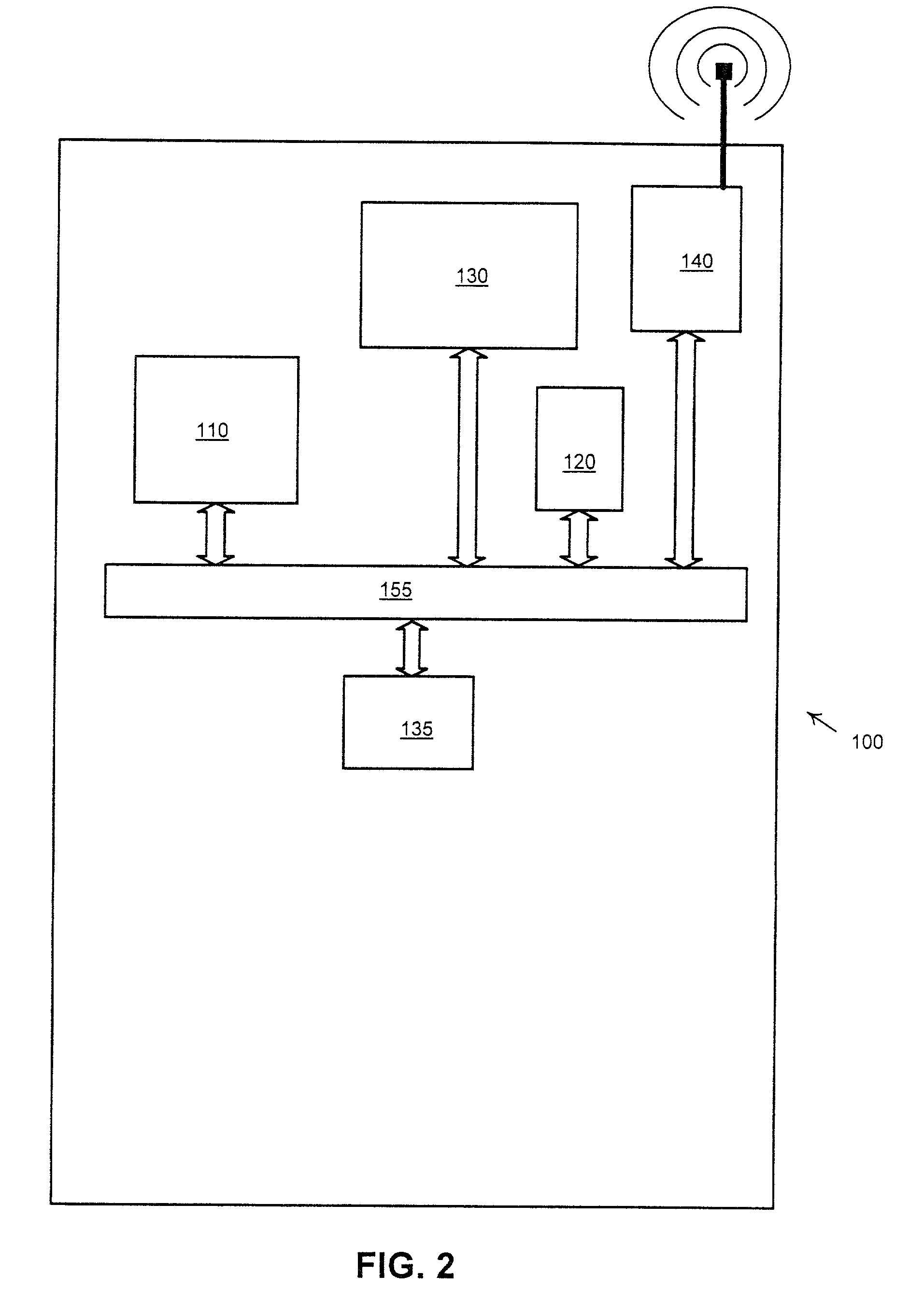
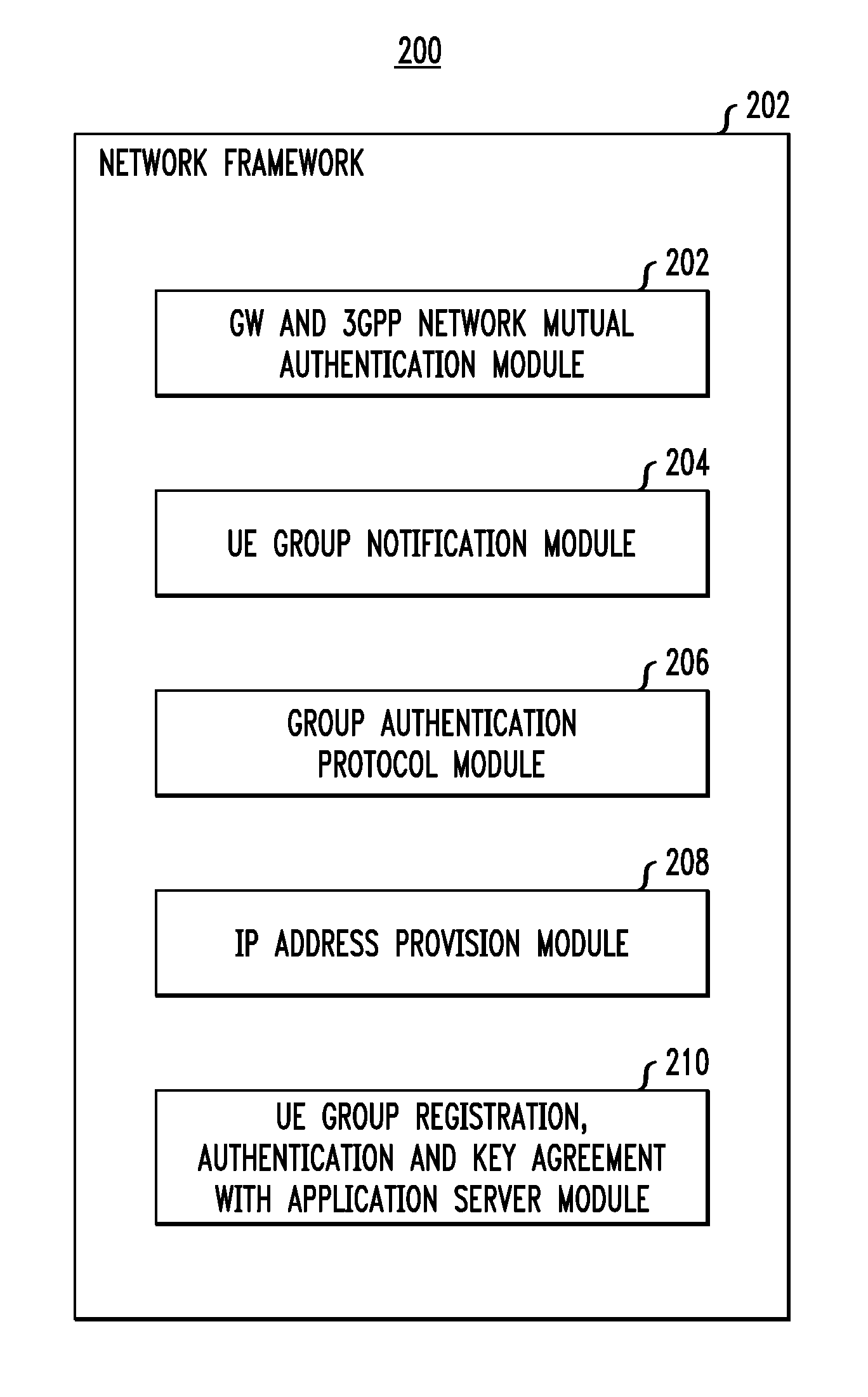
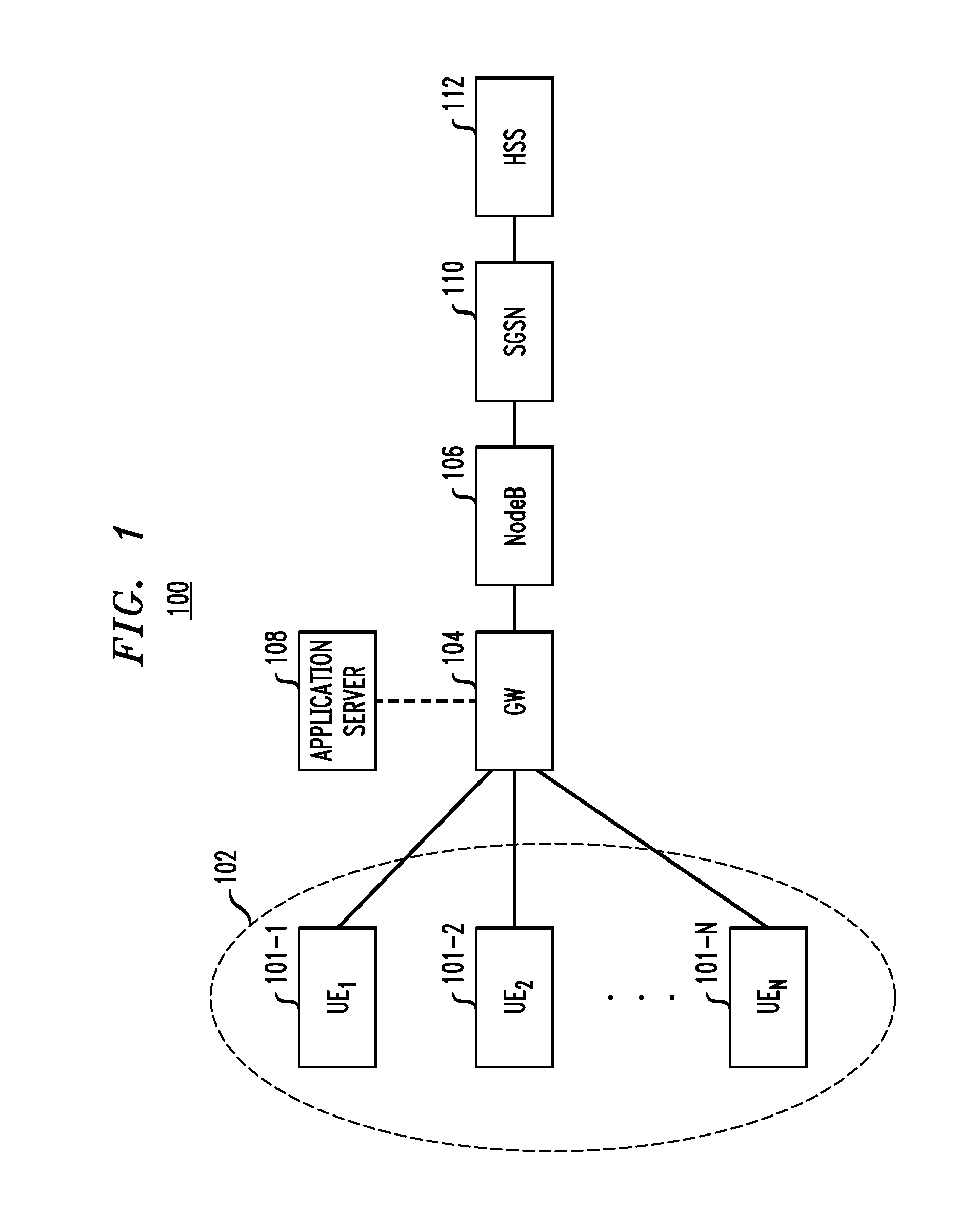
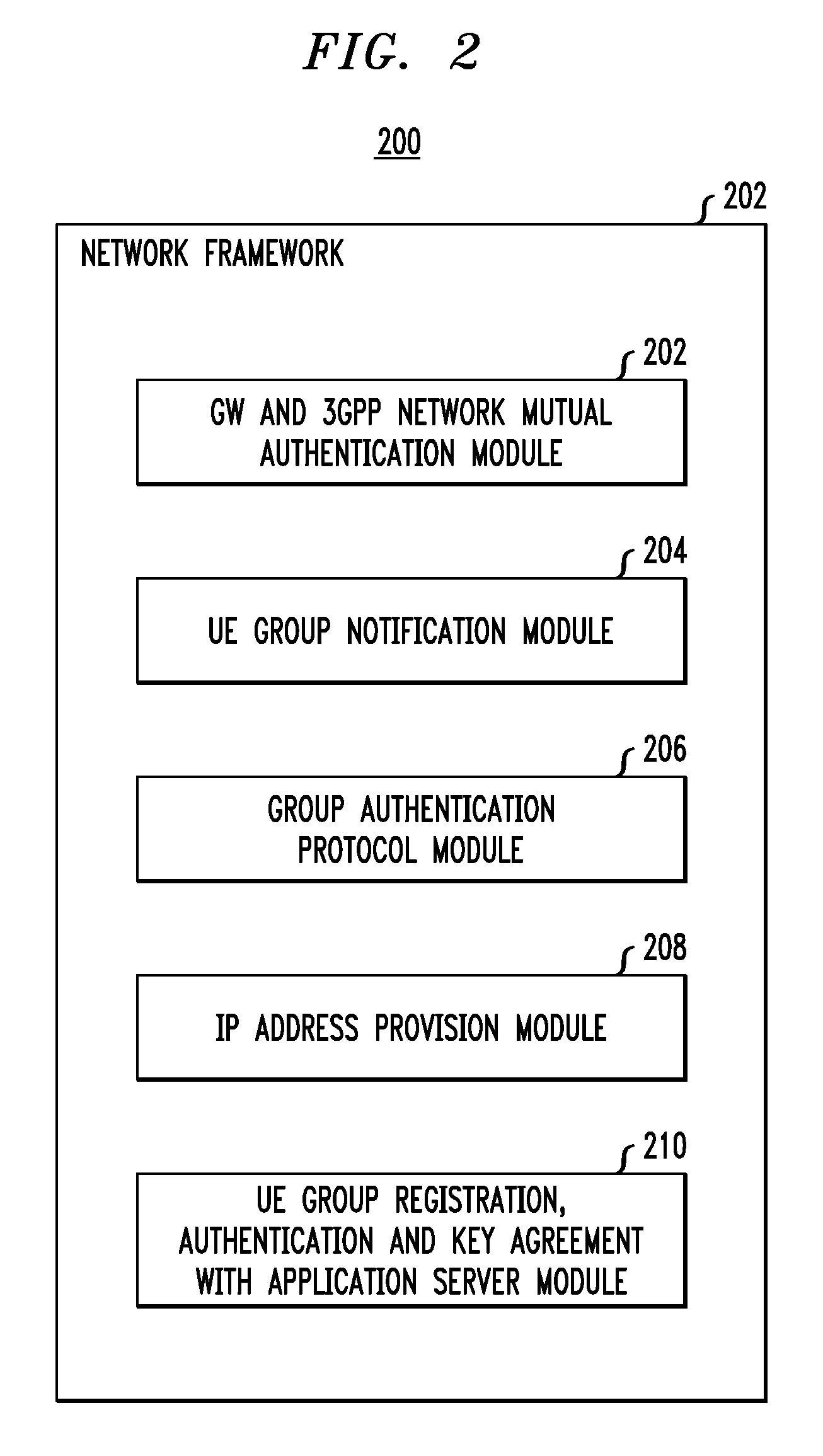
Secure Registration of Group of Clients Using Single Registration Procedure
ActiveUS20110307694A1Compromising privacyReduce signalingDigital data processing detailsUser identity/authority verificationCommunication deviceSingle sign-on
Automated secure registration techniques for communication devices are provided which address the problem of allowing multiple clients to gain access to one system, and thus provide a solution to the “reverse single sign-on” problem. For example, a method for registering a group of two or more communication devices in a communication network comprises the following steps. A group challenge message is sent from a network device to the group of two or more communication devices. The network device receives one or more response messages to the group challenge respectively from one or more of the group of two or more communication devices, wherein the response message from each of the responding communication devices in the group comprises a group credential corresponding to the group.
Owner:THALES DIS FRANCE SA
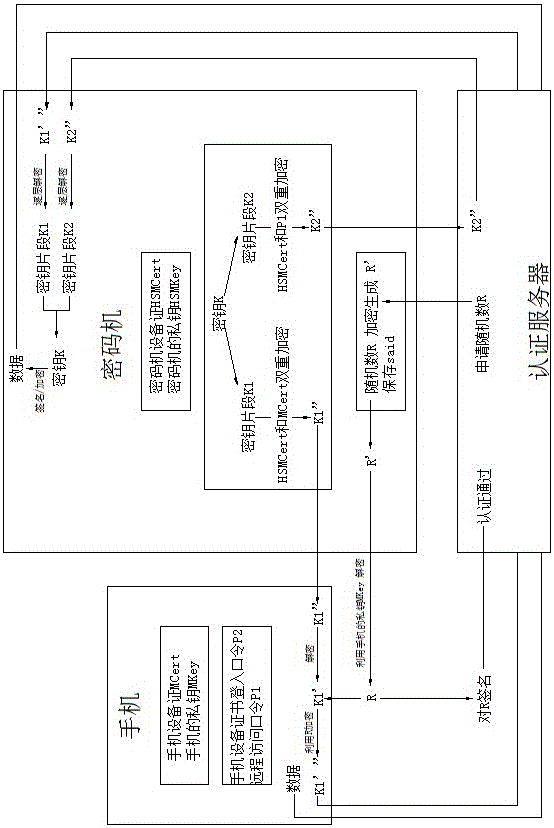
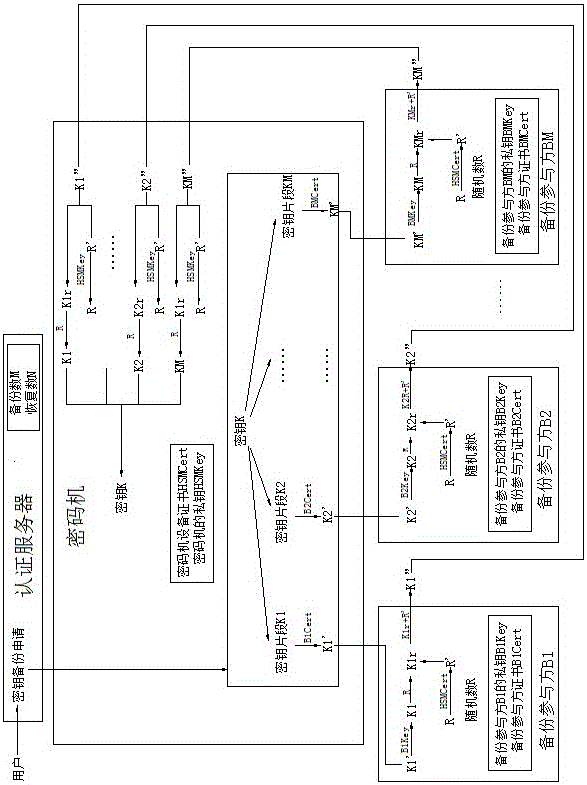
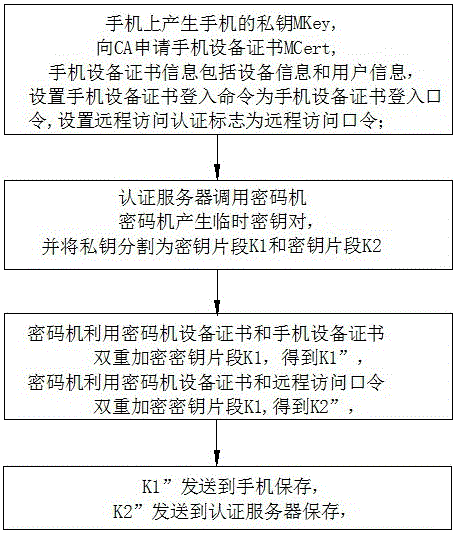
Method and system for realizing block chain private key protection based on key segmentation
ActiveCN106548345AImprove securityAvoid Permission RisksKey distribution for secure communicationPayment protocolsPasswordStructure of Management Information
The invention discloses a method and a system for realizing block chain private key protection based on key segmentation, and aims to solve a technical problem that a private key of a block chain is lack of security and cannot be retrieved. The method for realizing block chain private key protection based on key segmentation comprises that hard encryption for a block chain private key supporting mobile phone equipment certificate authentication and password authentication is realized by taking a mobile phone as a terminal carrier and using a cipher machine and an authentication server of the cloud; and the block chain private key is segmented by using a threshold algorithm, and multi-party participating key backup and key recovery / retrieval is realized. The method comprises (1) a registration procedure, (2) a private key utilization procedure, (3) a private key backup procedure, and (4) a private key recovery / retrieval procedure. The system structurally comprises a cipher machine and an authentication server of the cloud and a mobile phone acting as the terminal carrier. The method and the system disclosed by the invention can realize safe storage, safe utilization, multi-party participating backup and multi-party participating retrieval of the block chain private key.
Owner:北京信任度科技有限公司
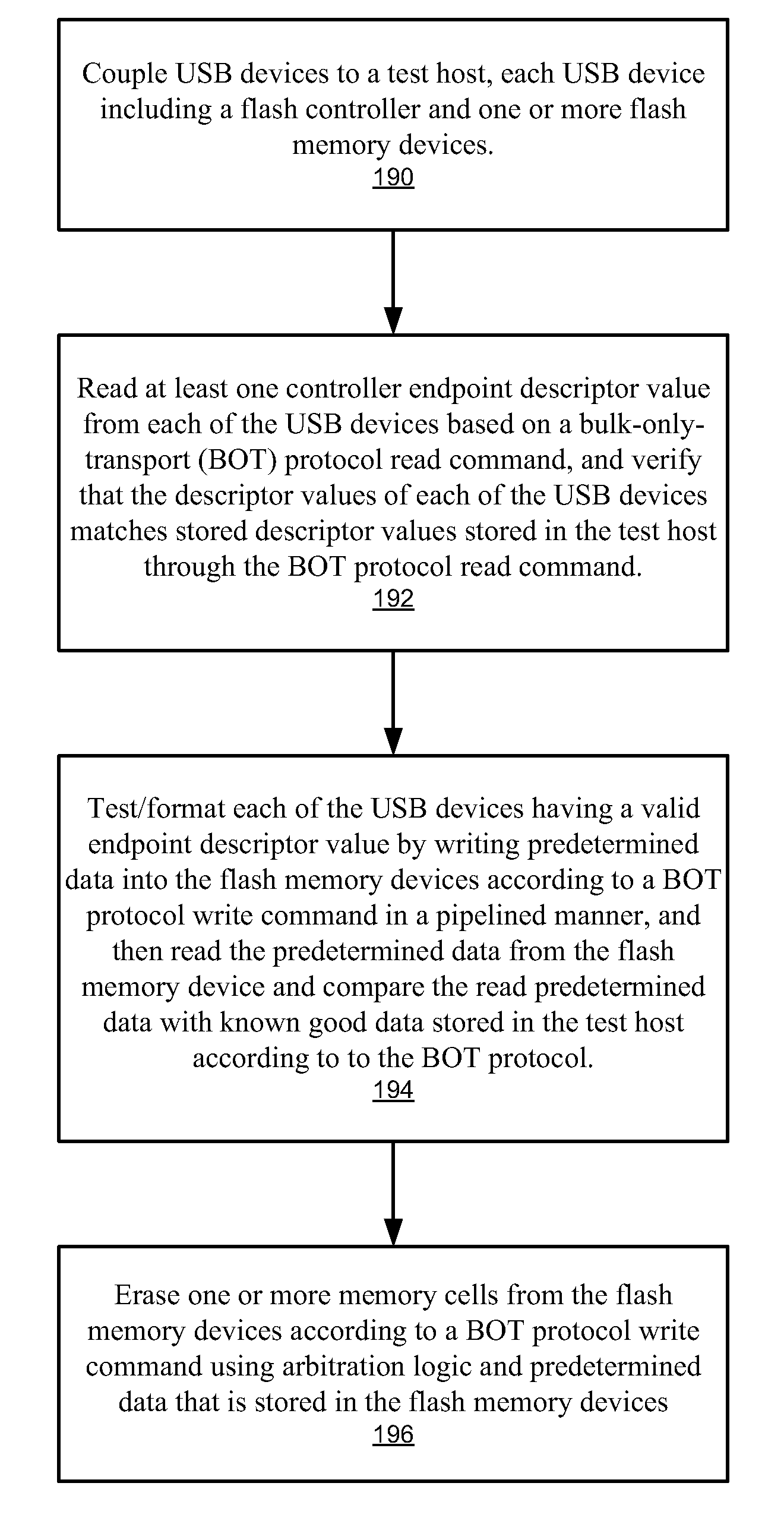
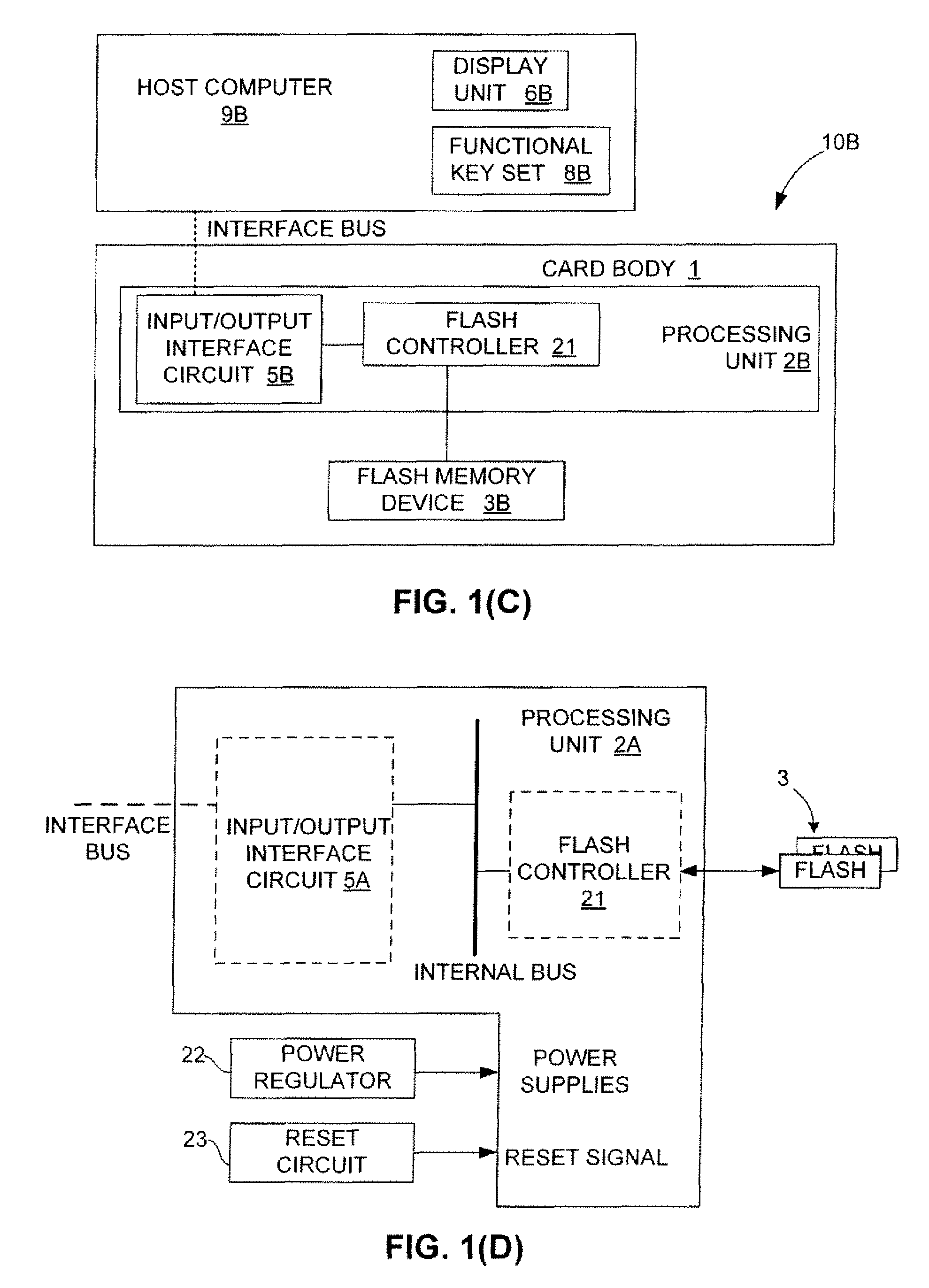
Mass production testing of USB flash cards with various flash memory cells
InactiveUS20080177922A1Improve efficiencyFacilitates high volume testing/formattingElectronic circuit testingError detection/correctionCard readerUSB
A high volume testing / formatting process is provided for Universal Serial Bus-based (USB-based) electronic data flash cards (USB devices) that meets the increasing demand for USB electronic data flash cards (USB devices). A test host is simultaneously coupled to the multiple USB devices (e.g., using a multi-port card reader or a probe fixture), a controller endpoint value is read from each of the USB devices and verified with a known good value, and then testing / formatting is performed on each of the USB devices by writing predetermined data into each USB device in a pipelined manner, then reading out and testing the predetermined data. In one embodiment, the test host implements a special USB driver that blocks standard USB registration procedures upon detecting the plurality of USB devices. Control and / or boot code data are written onto the flash memory device (i.e., instead of being provided on a controller ROM).
Owner:SUPER TALENT TECH CORP
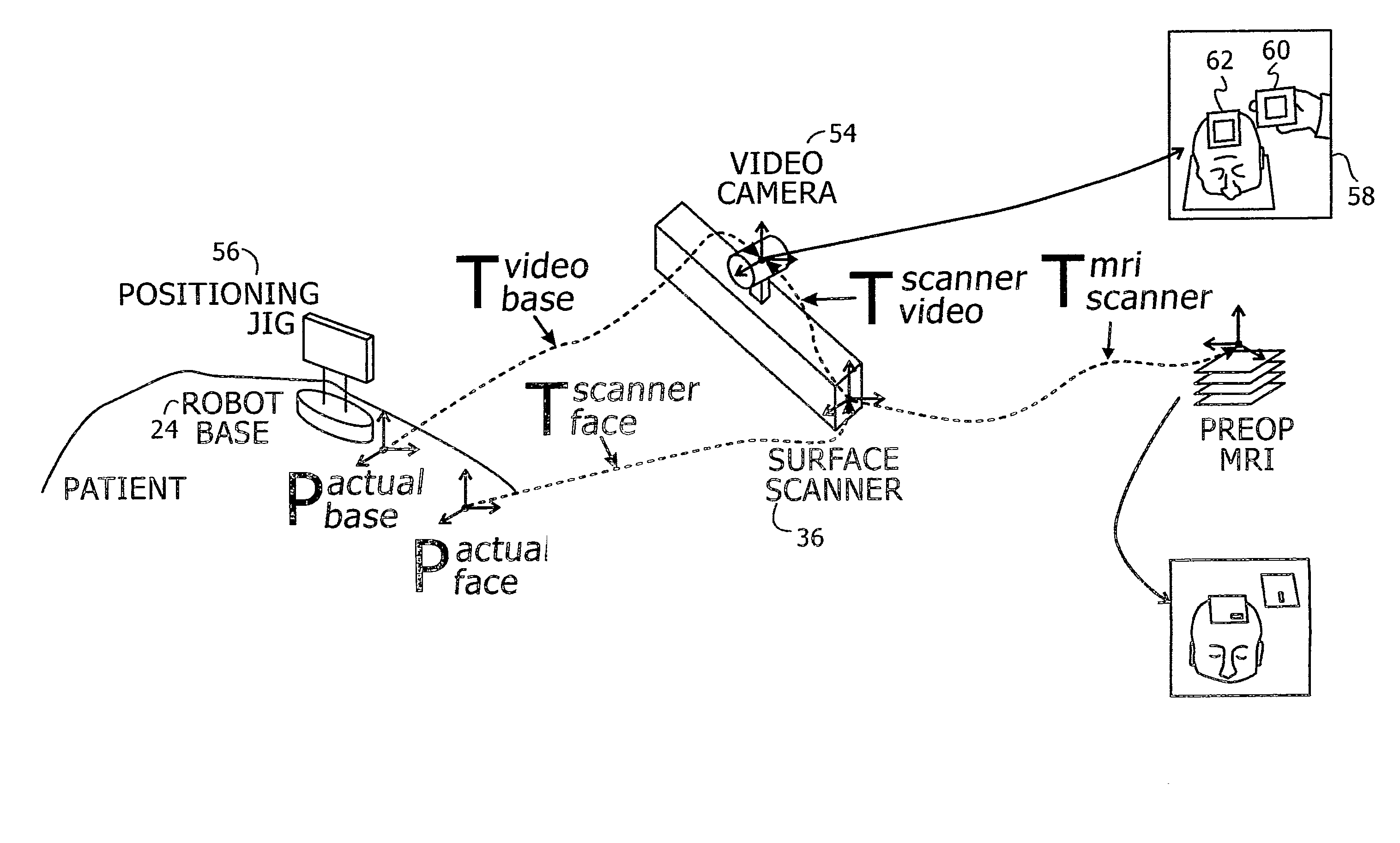
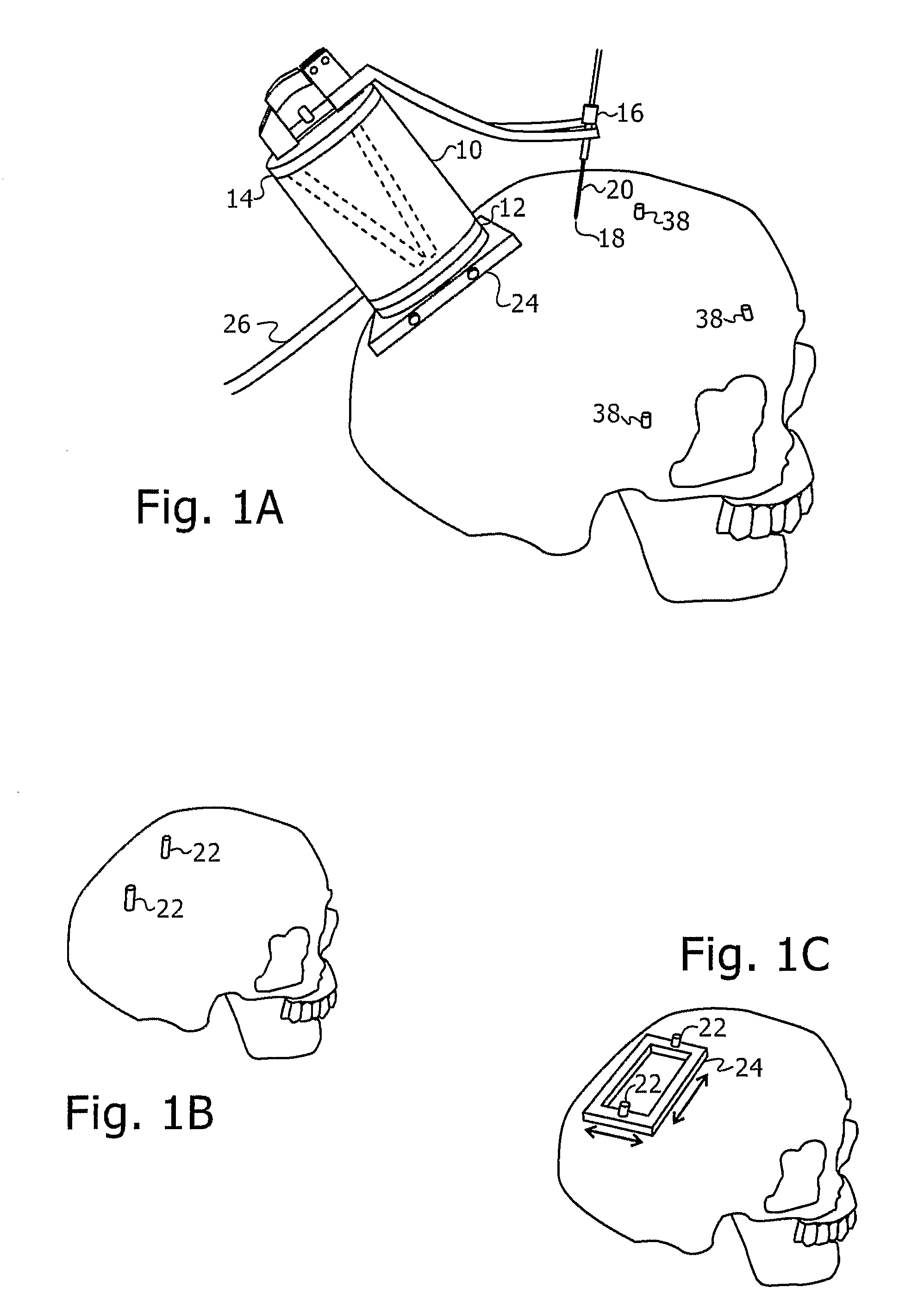
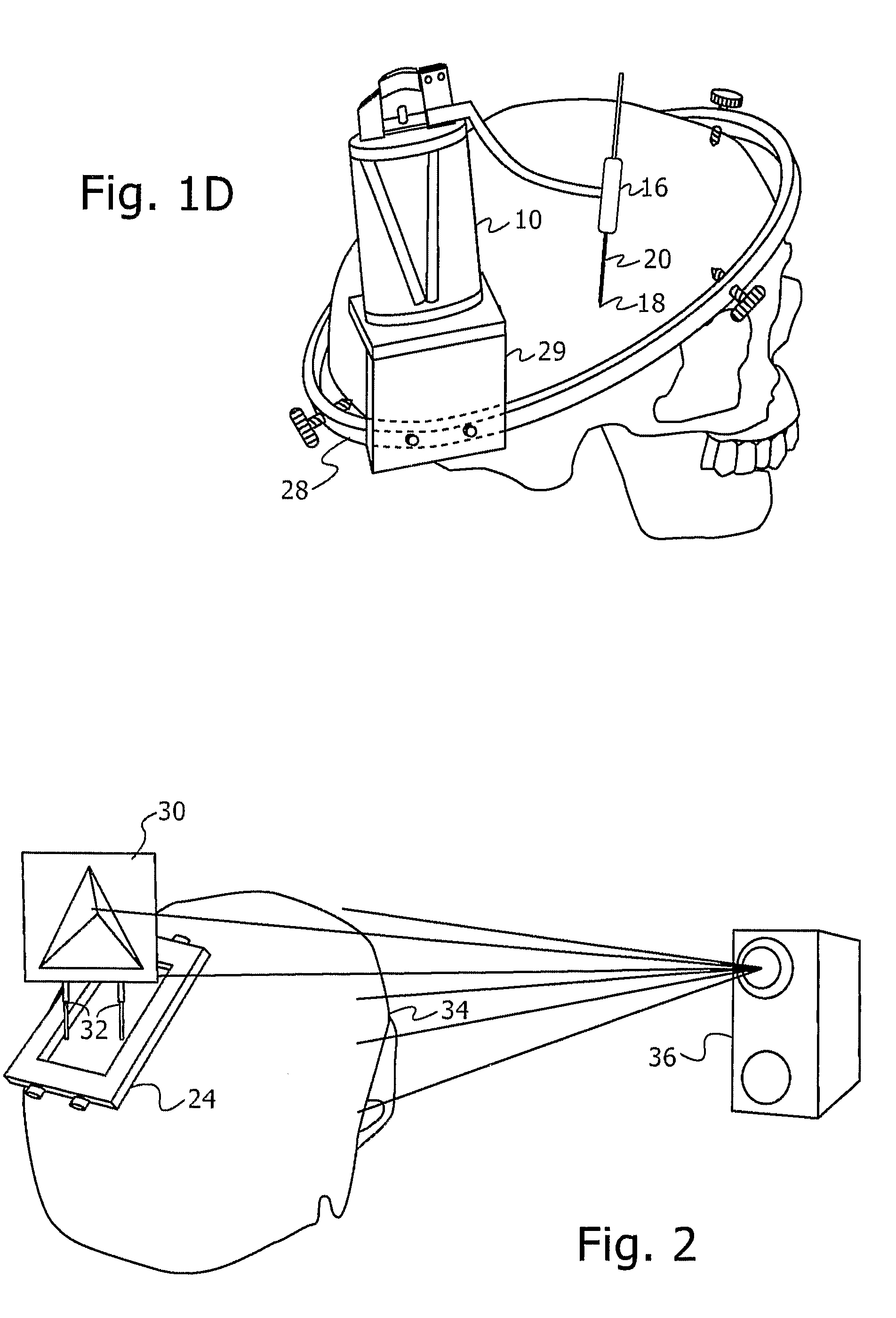
Image guided robotic system for keyhole neurosurgery
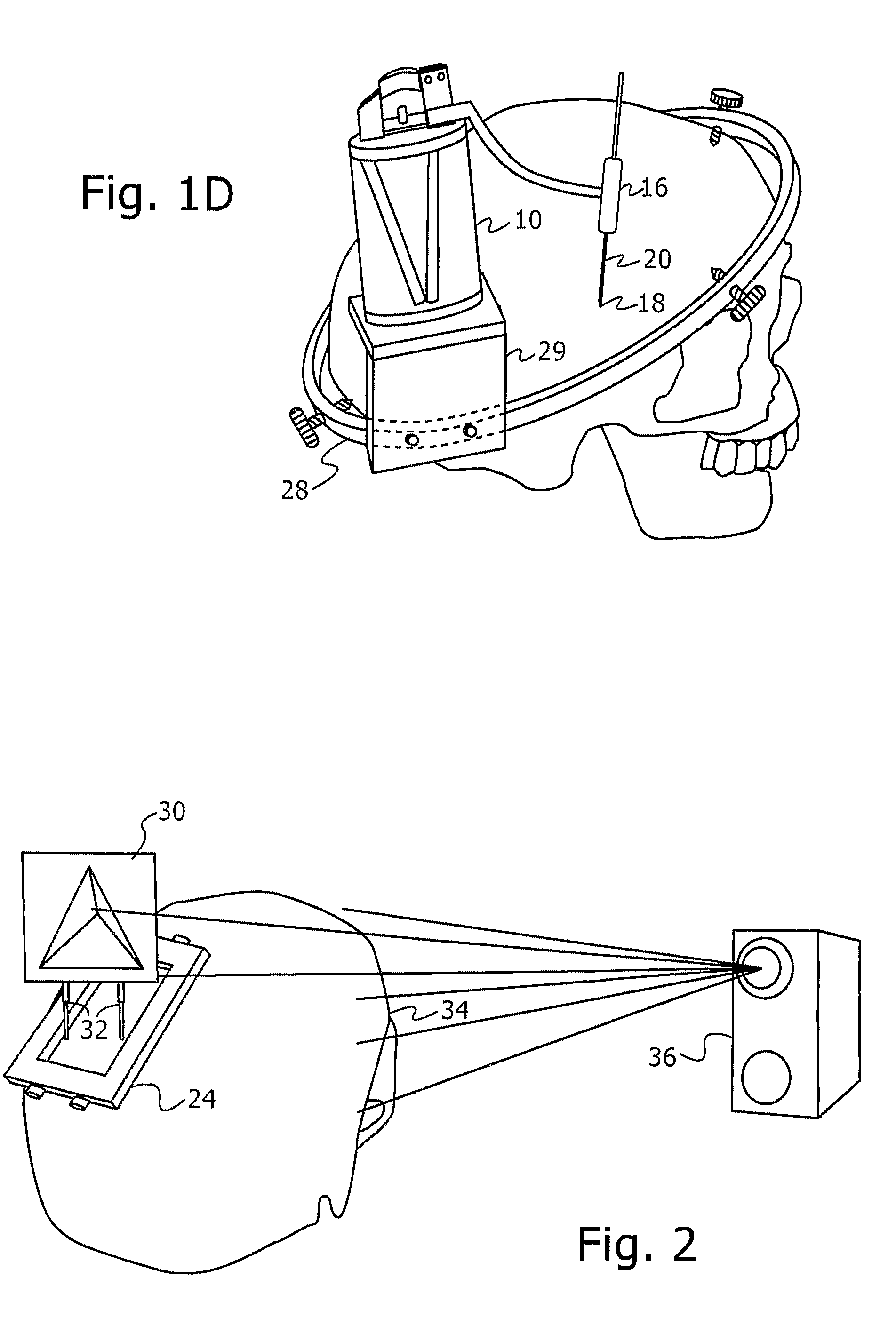
ActiveUS20090177081A1Scan accuratelyPotentially accurateSurgical needlesSurgical navigation systemsEntry point3d surfaces
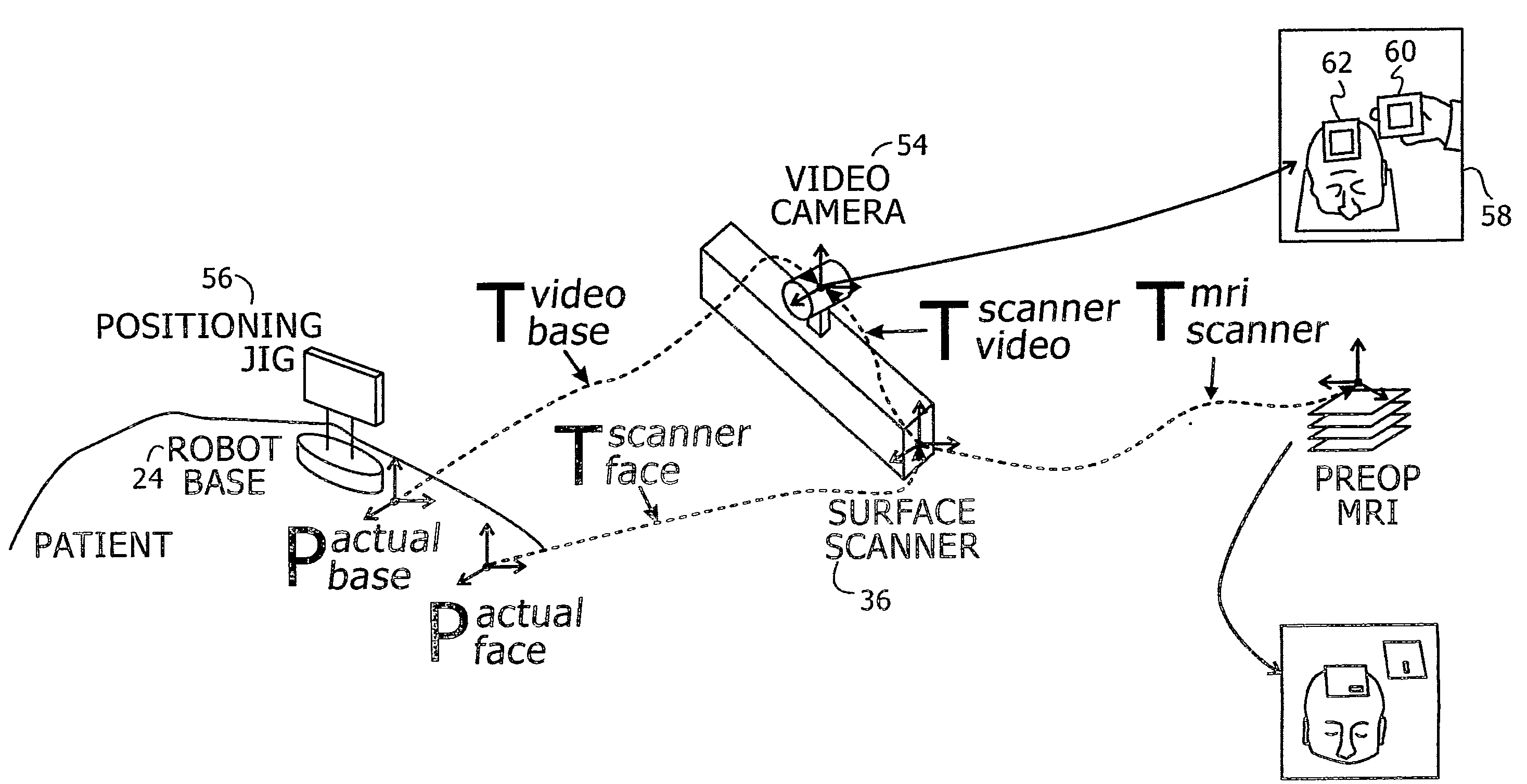
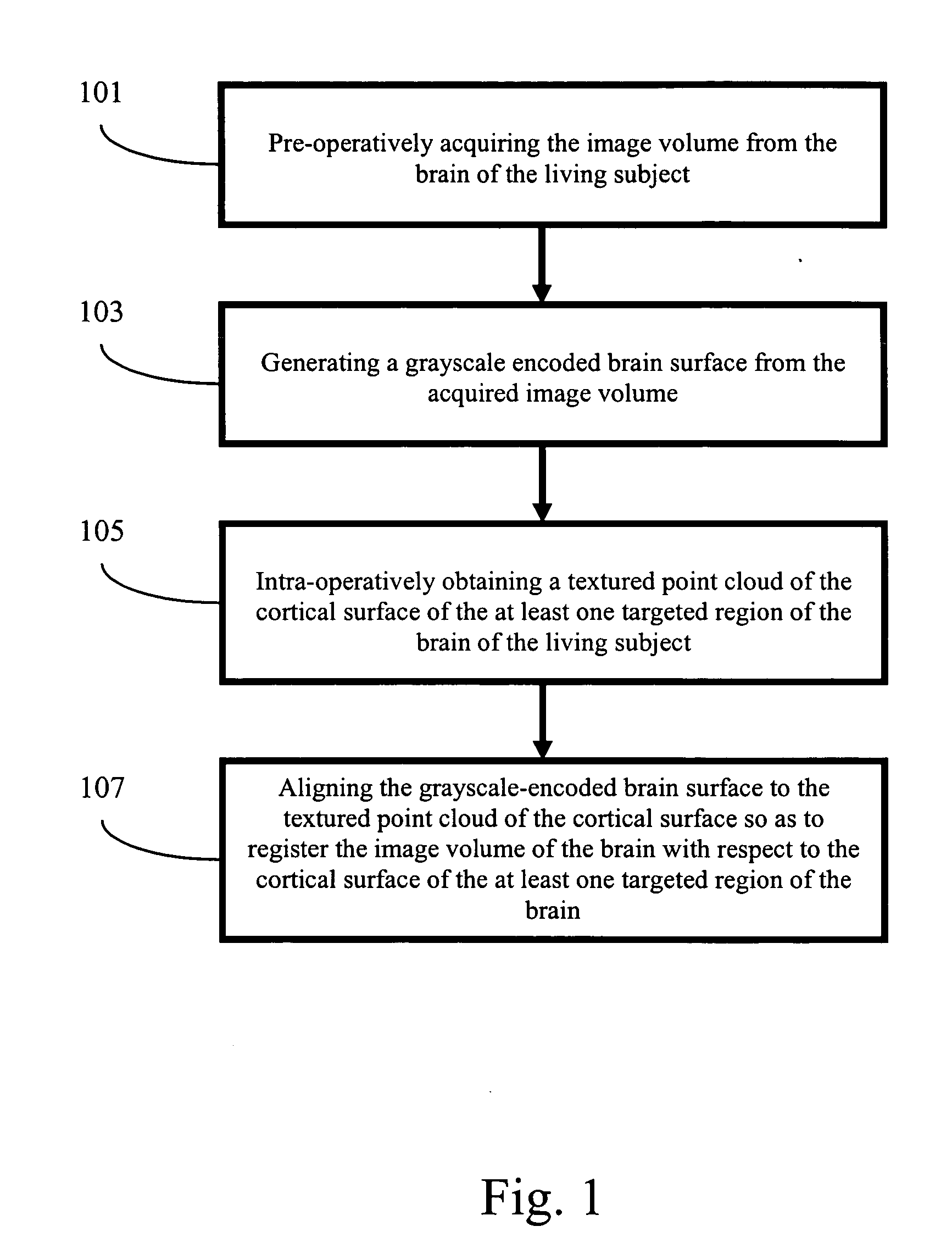
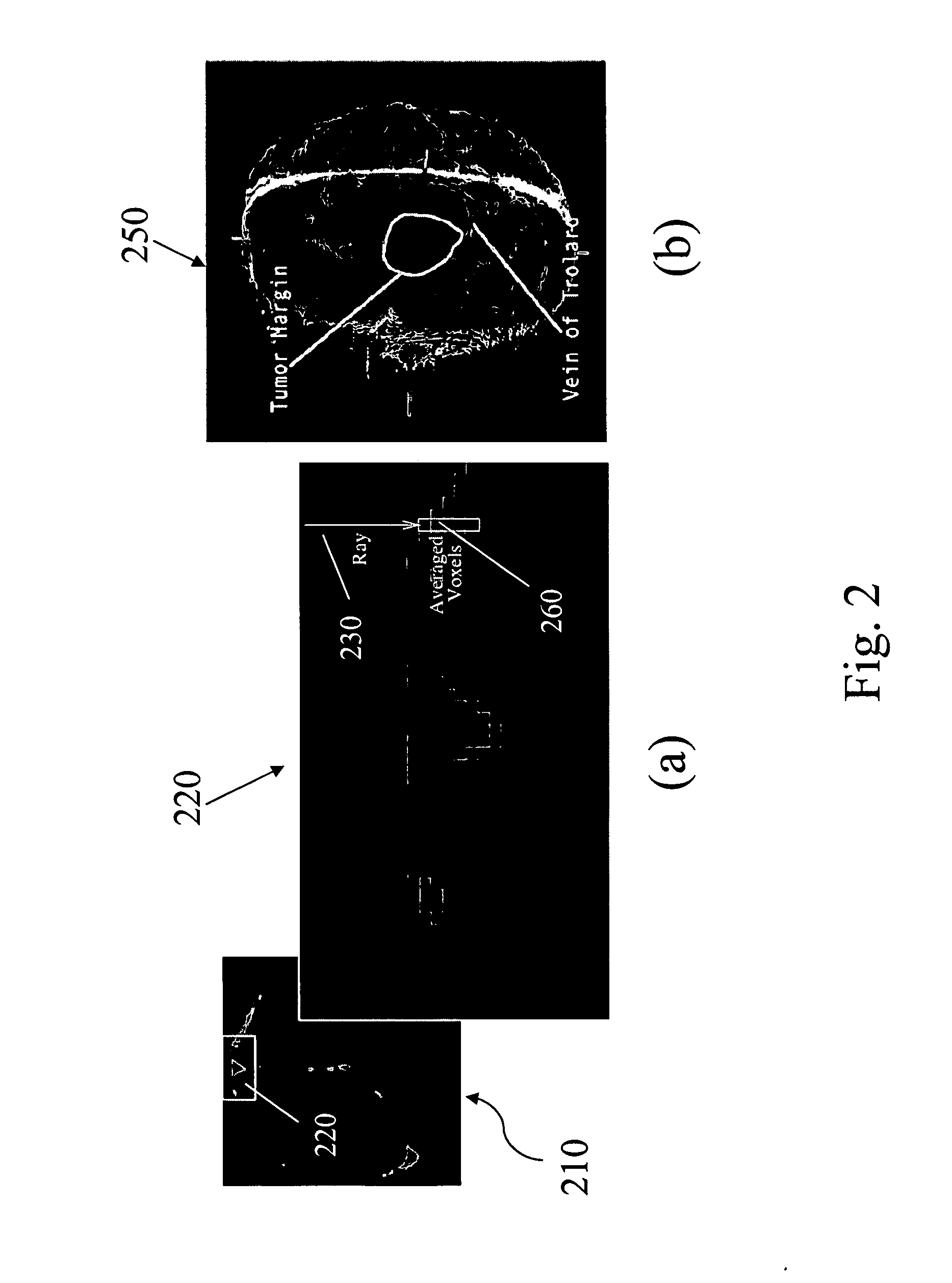
A novel image-guided system for precise automatic targeting in minimally invasive keyhole neurosurgery. The system consists of a miniature robot fitted with a mechanical guide for needle, probe, or catheter insertion. Intraoperative, the robot is directly affixed to a head clamp or to the patient skull. It automatically positions itself with respect to predefined entry points and targets in a preoperative CT / MRI image following an anatomical registration with an intraoperative 3D surface scan of the patient facial features and a registration jig. The registration procedure is a novel three-way scheme, in which the intraoperative surface scan including the registration jig is matched to a model generated from the preoperative CT / MRI image, the robot position is known in relation to the registration jig, and the entry and target points are known from the preoperative CT / MRI image, such that the robot position can be related to the entry and target points.
Owner:MAZOR ROBOTICS
Method for managing registration in wireless communication system and device for same
A method for managing registration in a wireless communication system and a device for the same are disclosed. More specifically, the method for managing registration performed by a User Equipment (UE), that cannot be paged by a network and does not perform a periodic registration area update, in the wireless communication system, may include receiving a timer value for managing a Deregistered state of the UE from the network during a registration procedure, starting a timer if the UE enters an Idle state, and allowing the UE to enter the Deregistered state if the timer expires.
Owner:LG ELECTRONICS INC
Data communication method and apparatus via interlock between heterogeneous networks in radio access system supporting multi radio access technology
InactiveUS20120178448A1Reduce power consumptionReduce distractionsSynchronisation arrangementAssess restrictionRadio access technologyBeacon frame
The present invention relates to a method for transmitting and receiving data via a first base station supporting a first radio access technology (RAT) and a second base station supporting a second RAT in a radio access system supporting a multi-radio access technology, and the method may include allowing the first base station to perform a registration procedure with the second base station; and allowing the first base station to transmit control information required for accessing the second base station to a terminal supporting multi-RAT (multi-RAT terminal), wherein the control information comprises beacon frame transmission timing information of the second base station, and the beacon frame transmission timing is maintained in transmission timing of a downlink frame or downlink sub-frame of the first base station with relative timing offset interval.
Owner:LG ELECTRONICS INC
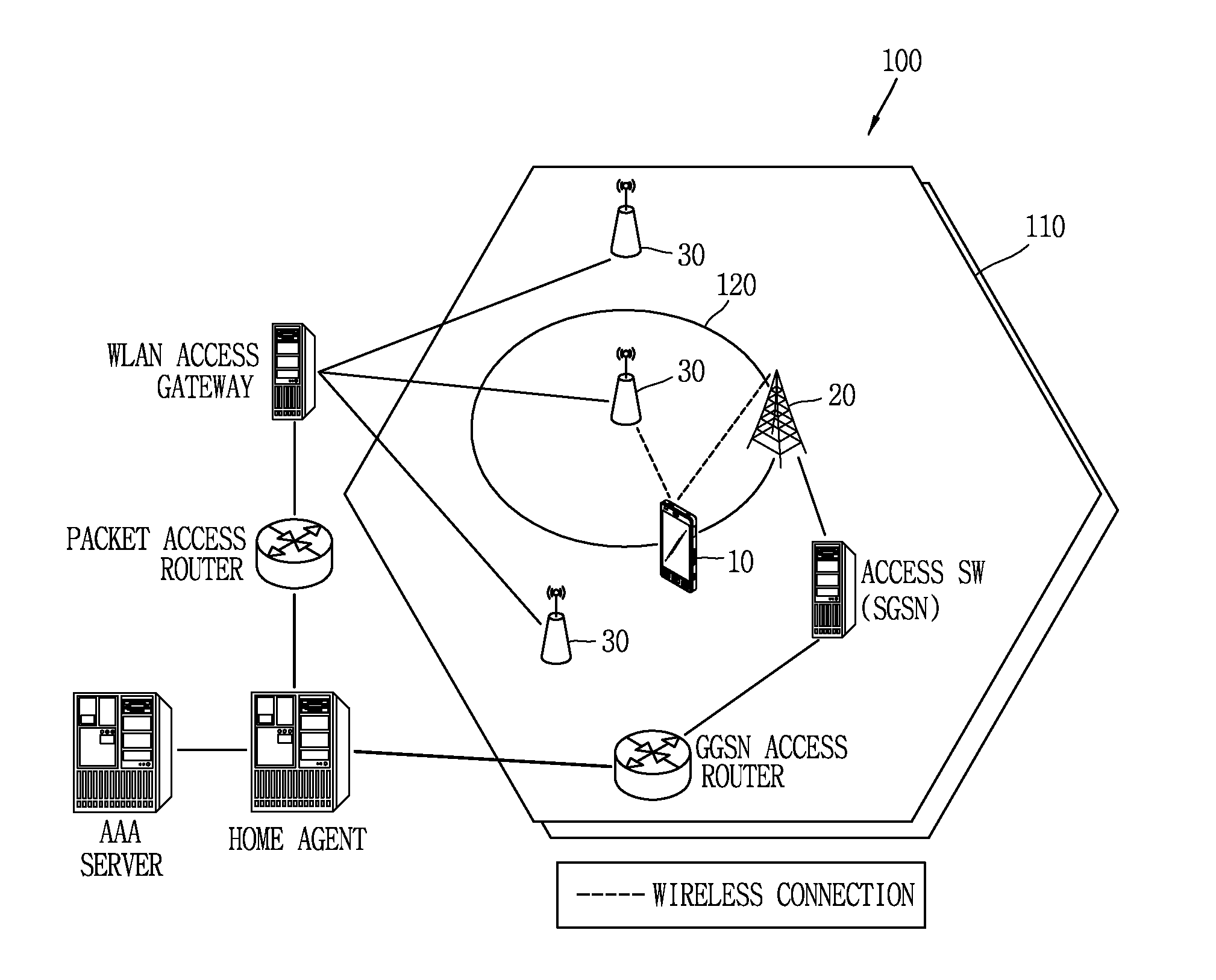
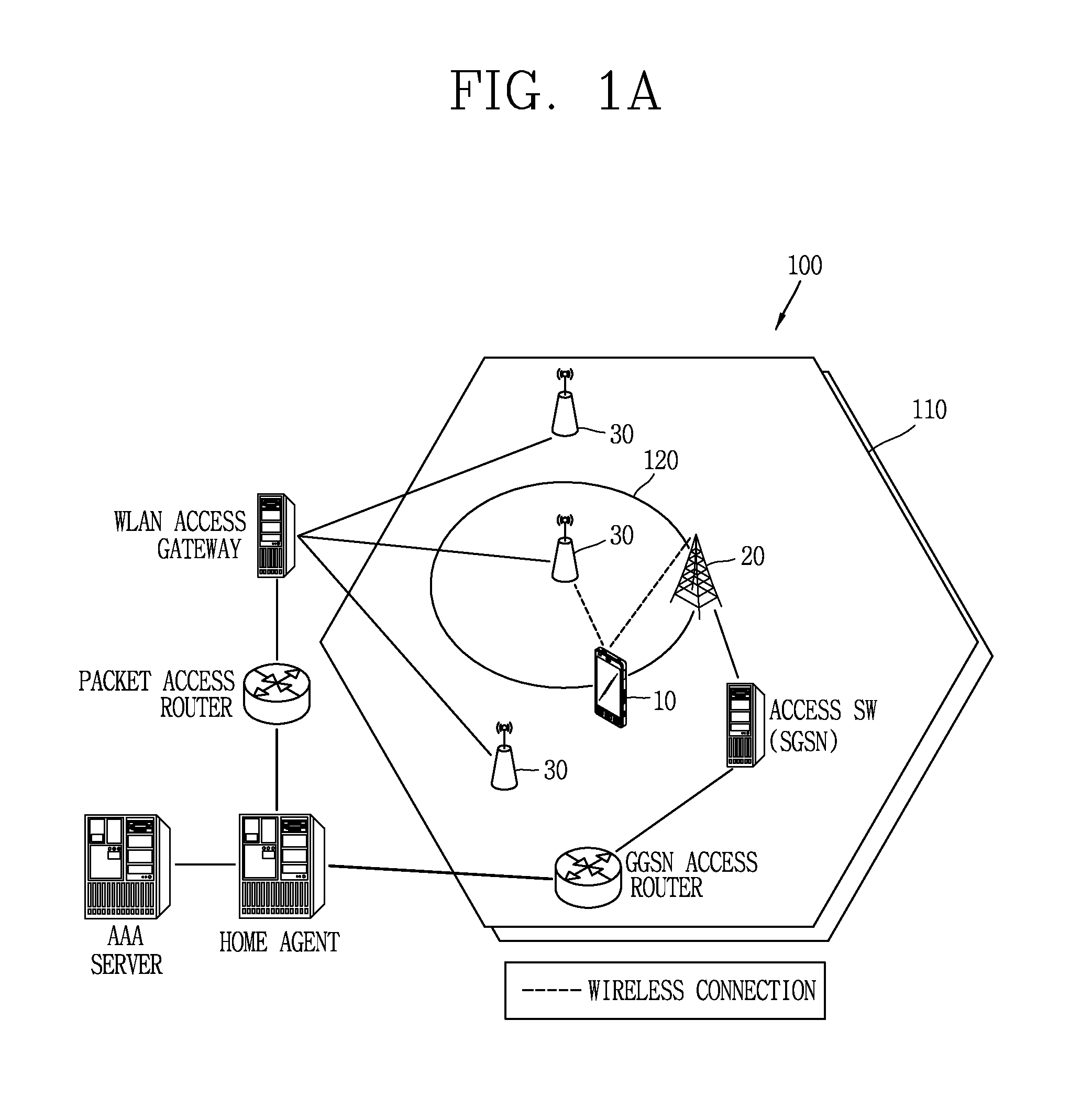
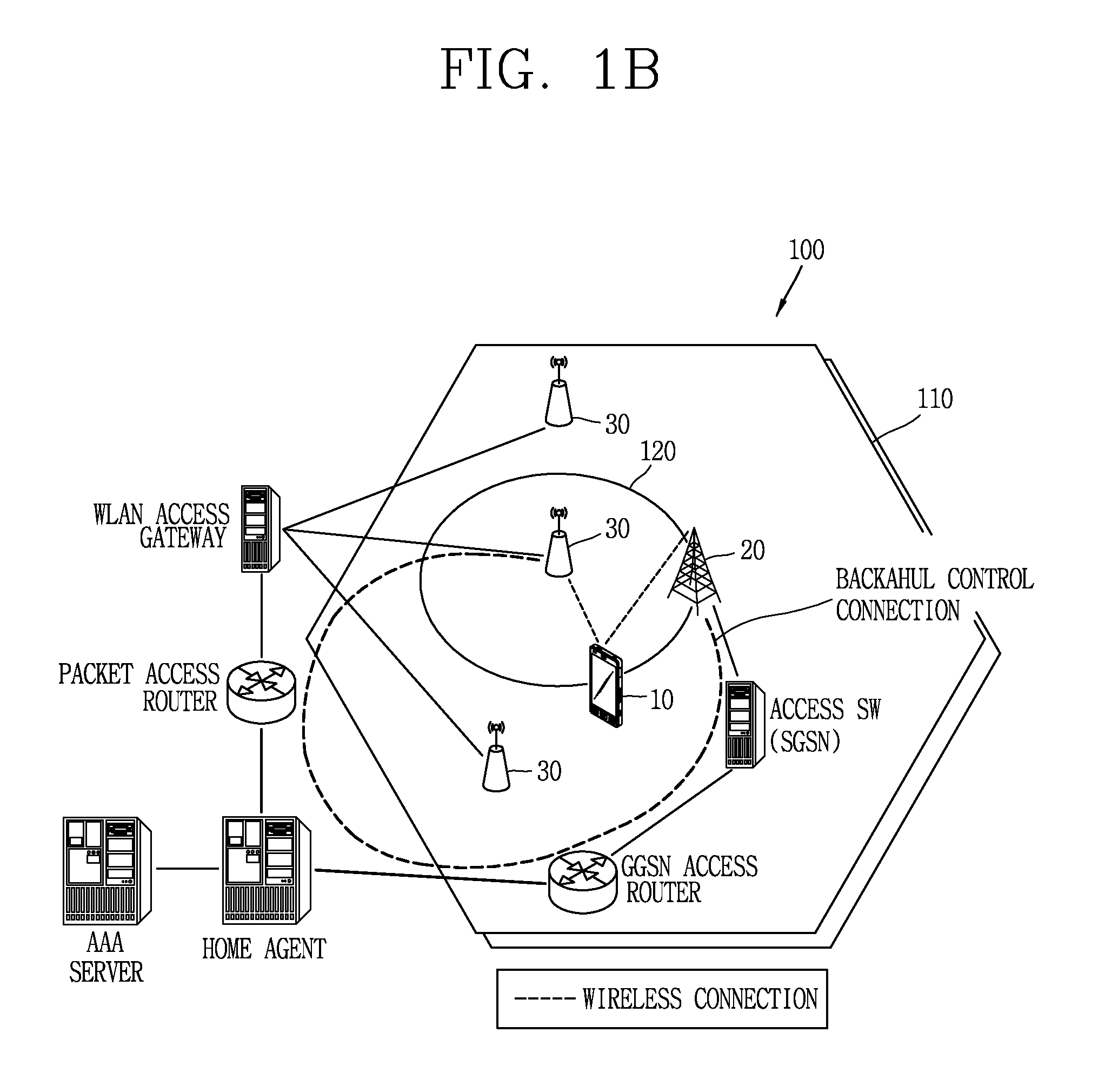
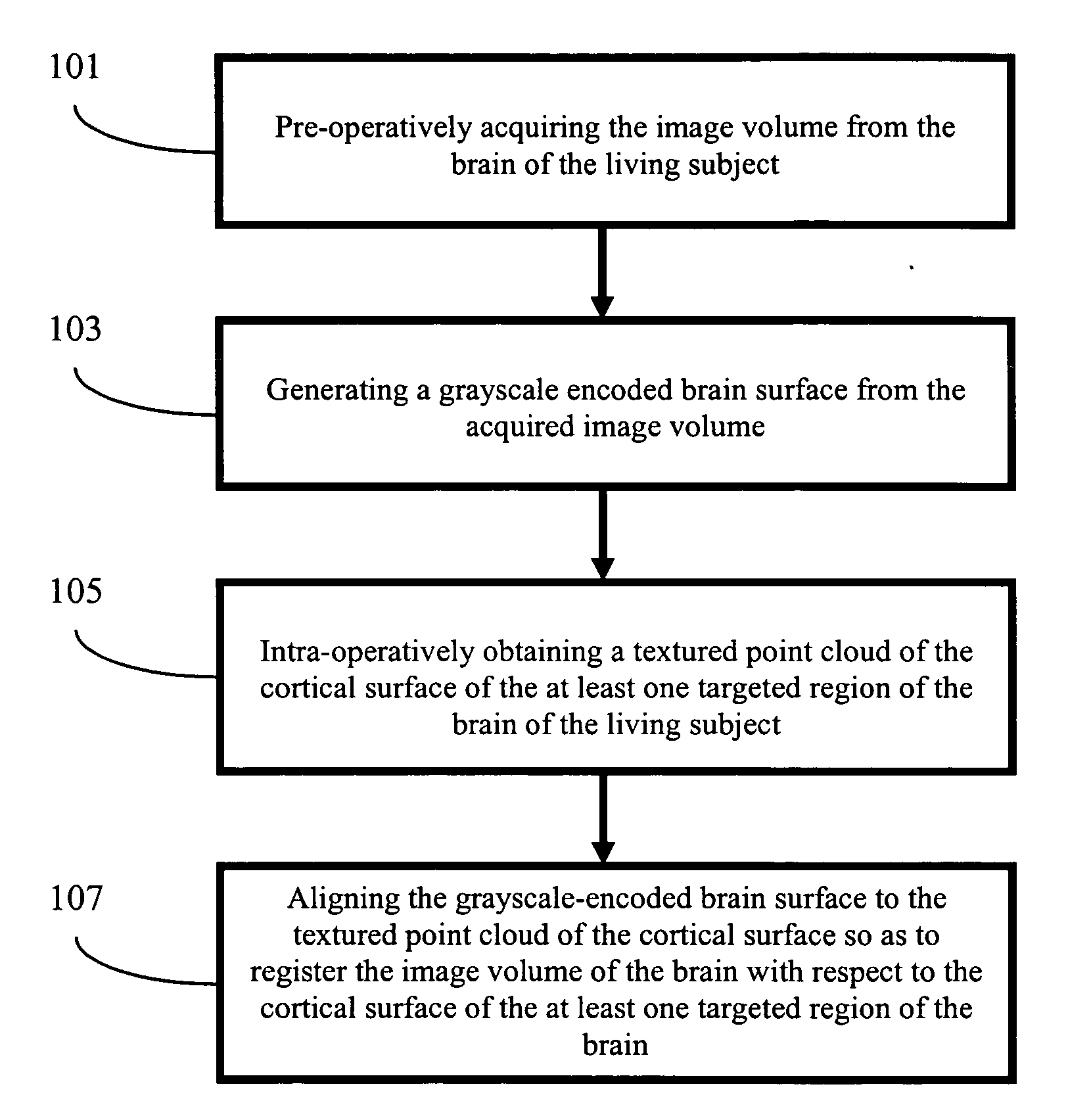
Apparatus and methods of cortical surface registration and deformation tracking for patient-to-image alignment in relation to image-guided surgery
ActiveUS20050148859A1Facilitate surgical procedureImage analysisSurgical navigation systemsPoint cloudMedicine
Owner:VANDERBILT UNIV
System and method for register mark recognition
InactiveUS20040163562A1Minimize timeReduce material wastePlaten pressesInvestigating moving sheetsOperator interfacePunching
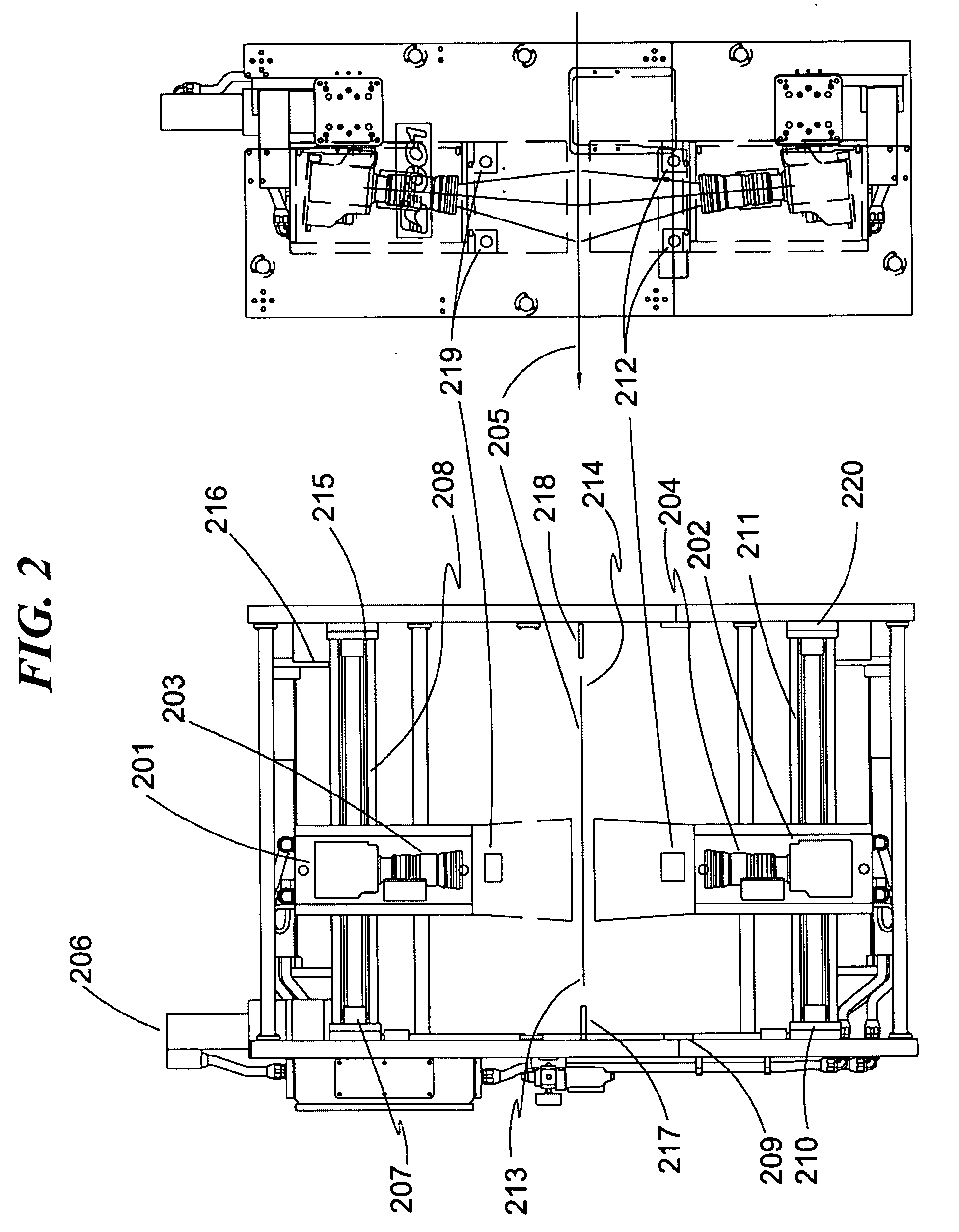
A system, method, and process that determine and automatically correct registration errors between printed objects and mechanically produced objects using advanced image processing techniques is disclosed. Means are also presented for maintaining all registered functions to within very close tolerances during normal running, with other means for rapidly obtaining initial registration with substantial savings in material waste. The disclosed system and method / process are compatible with the printing and converting industry in which rolls of material are processed by printing a number of colors that require close registration especially in pictorial representation. These roll-fed printing machines are quite versatile and in addition to the printing of any number of colors on both front and back can perform any number of additional operations on the printed web at the same time. Some of these additional operations can be the punching of line holes, scoring, perforation and die cutting all of which impart a specific shape mechanically on the printed web. All of these functions must be initially registered to each other and maintained within close tolerances during normal running conditions. The presently disclosed registration system permits these initial registration procedures to be performed with high accuracy, speed, and across a wide variety of web materials and colors. The system generally applies to any web material (5701) on which register marks (5702) are applied, wherein images of the web are obtained (5703) and image processed (5704) under optional control of an operator interface display (5705), resulting in web press motor control (5706) to affect improved print registration on the web material (5701).
Owner:CC1
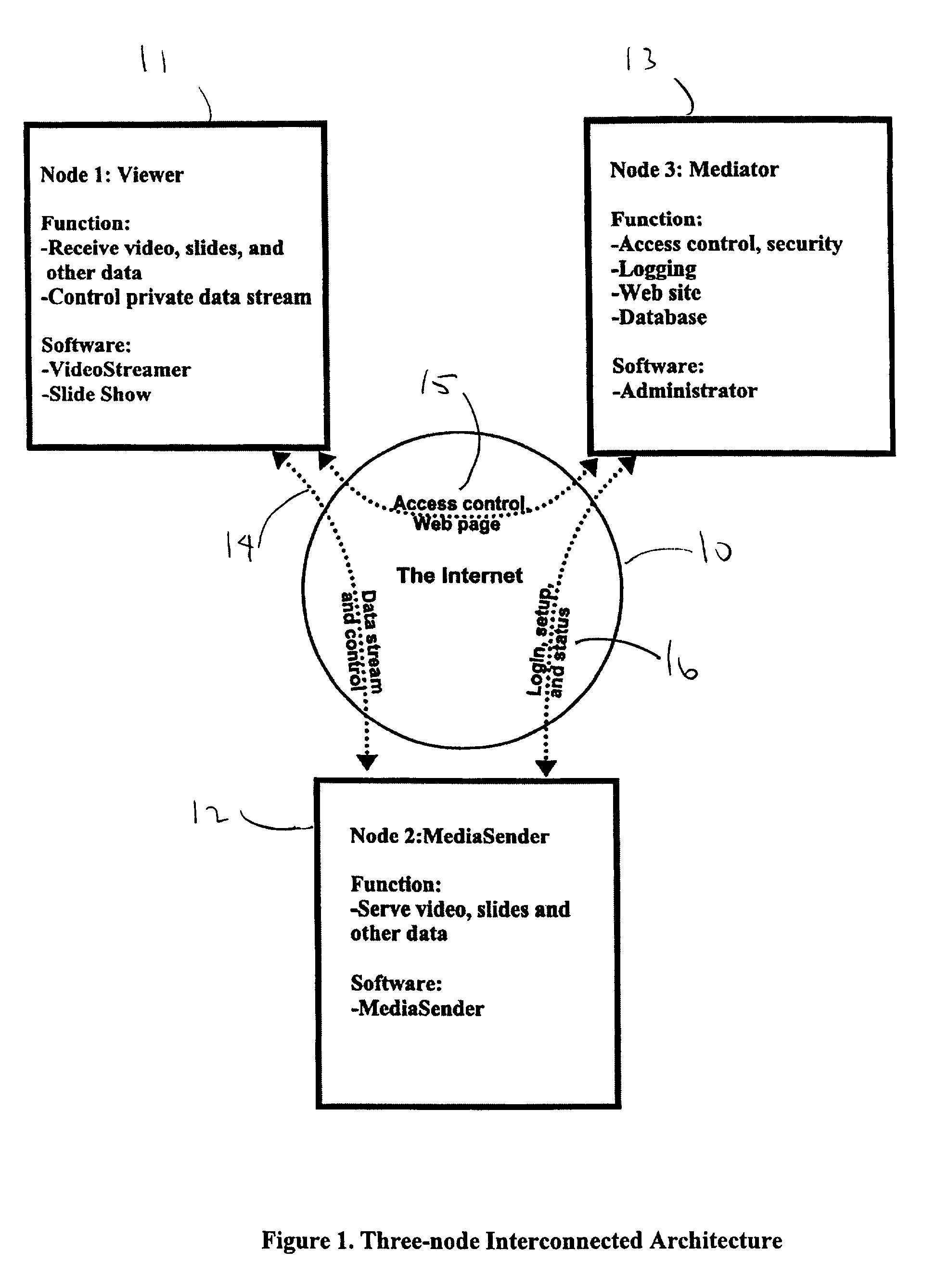
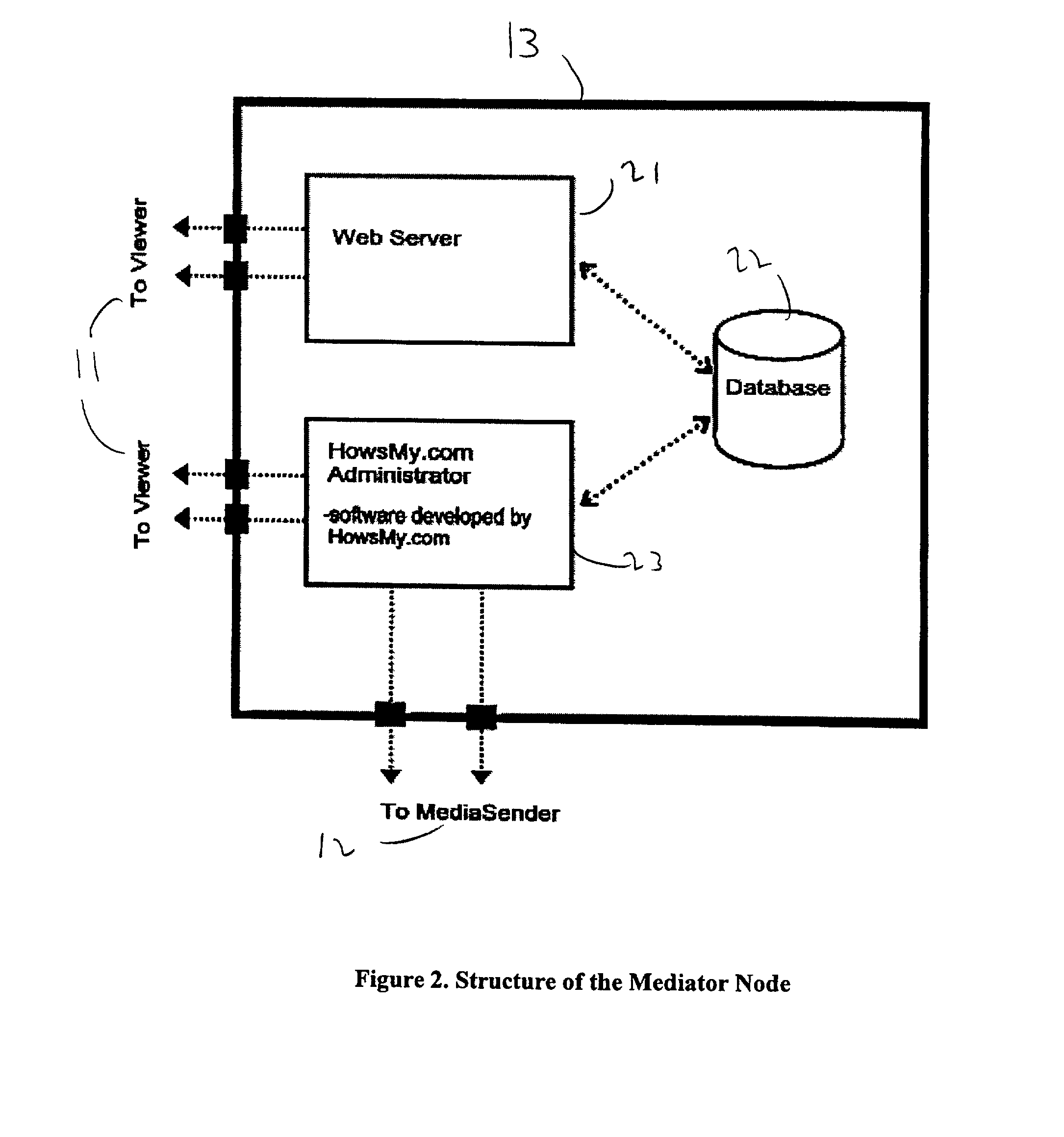
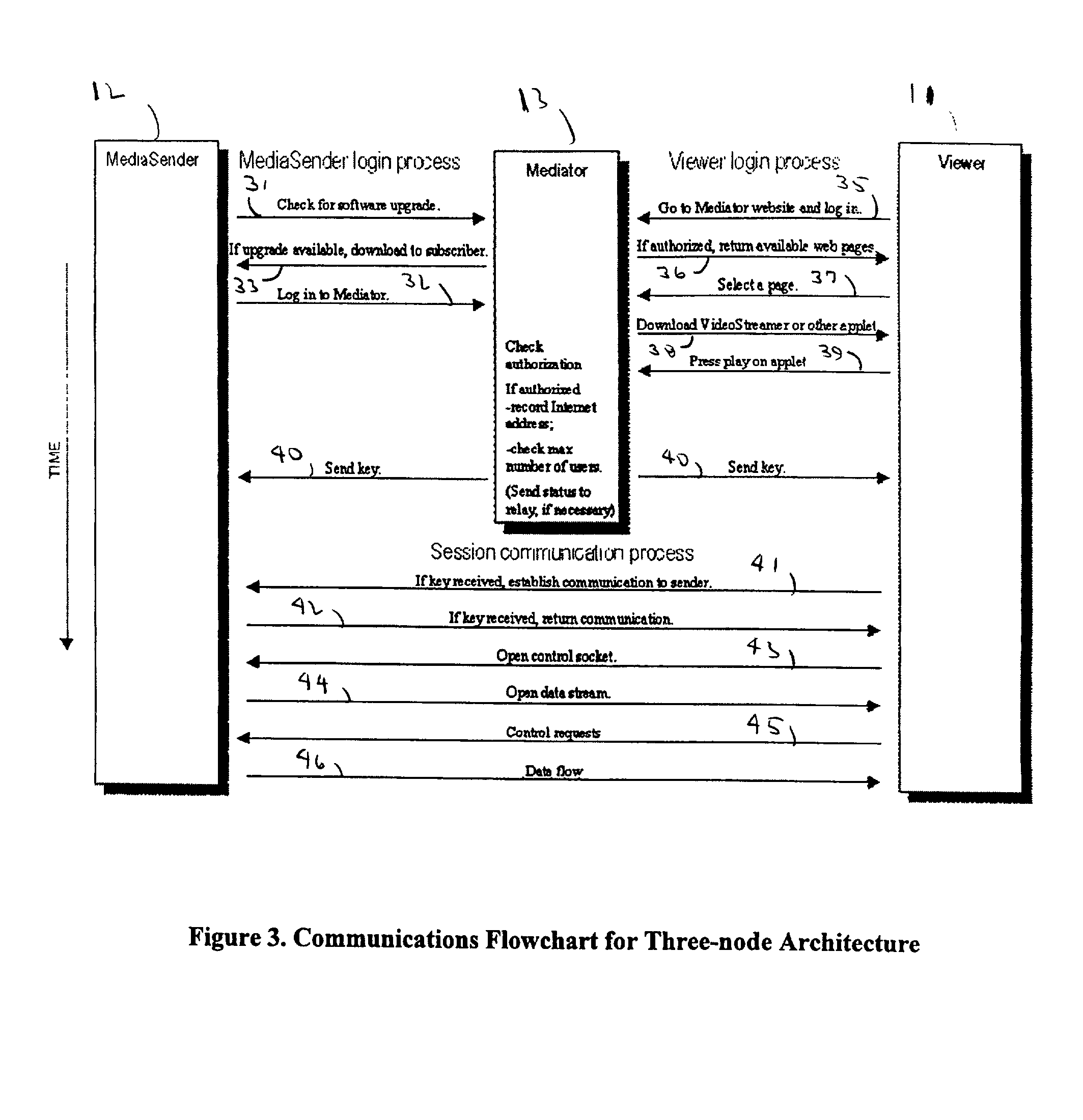
Point-to-point data streaming using a mediator node for administration and security
InactiveUS7103770B2Digital data processing detailsUser identity/authority verificationData streamWeb service
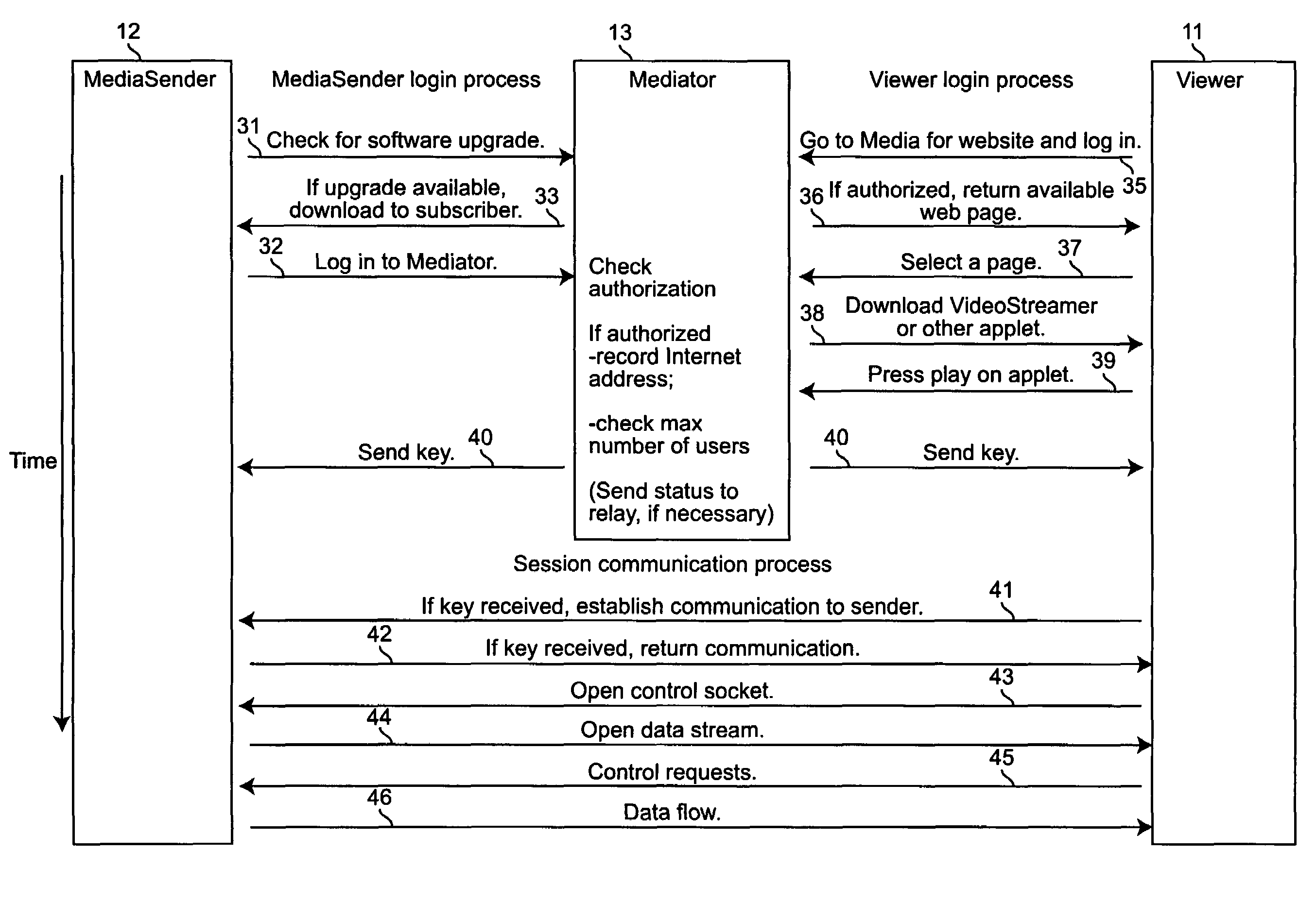
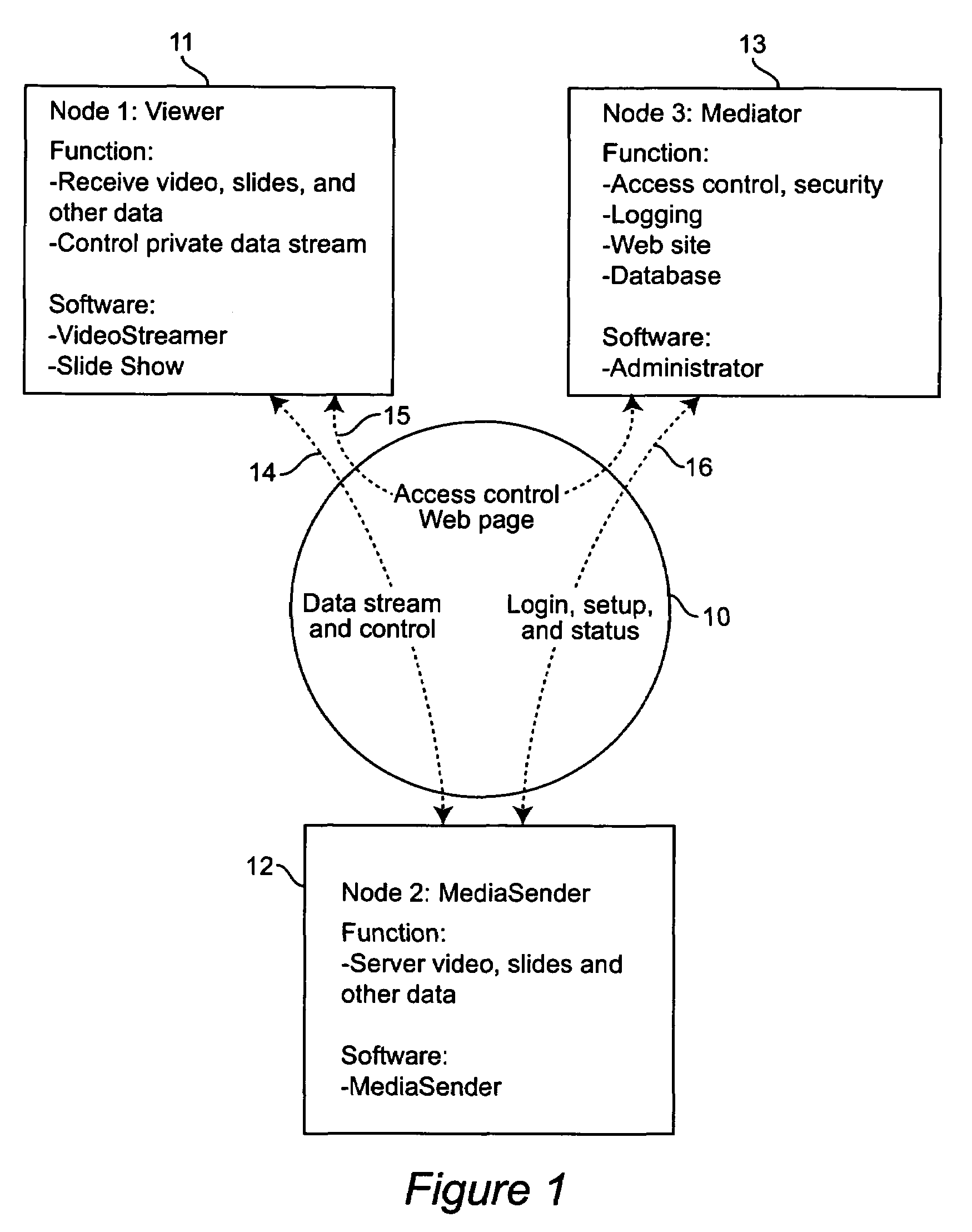
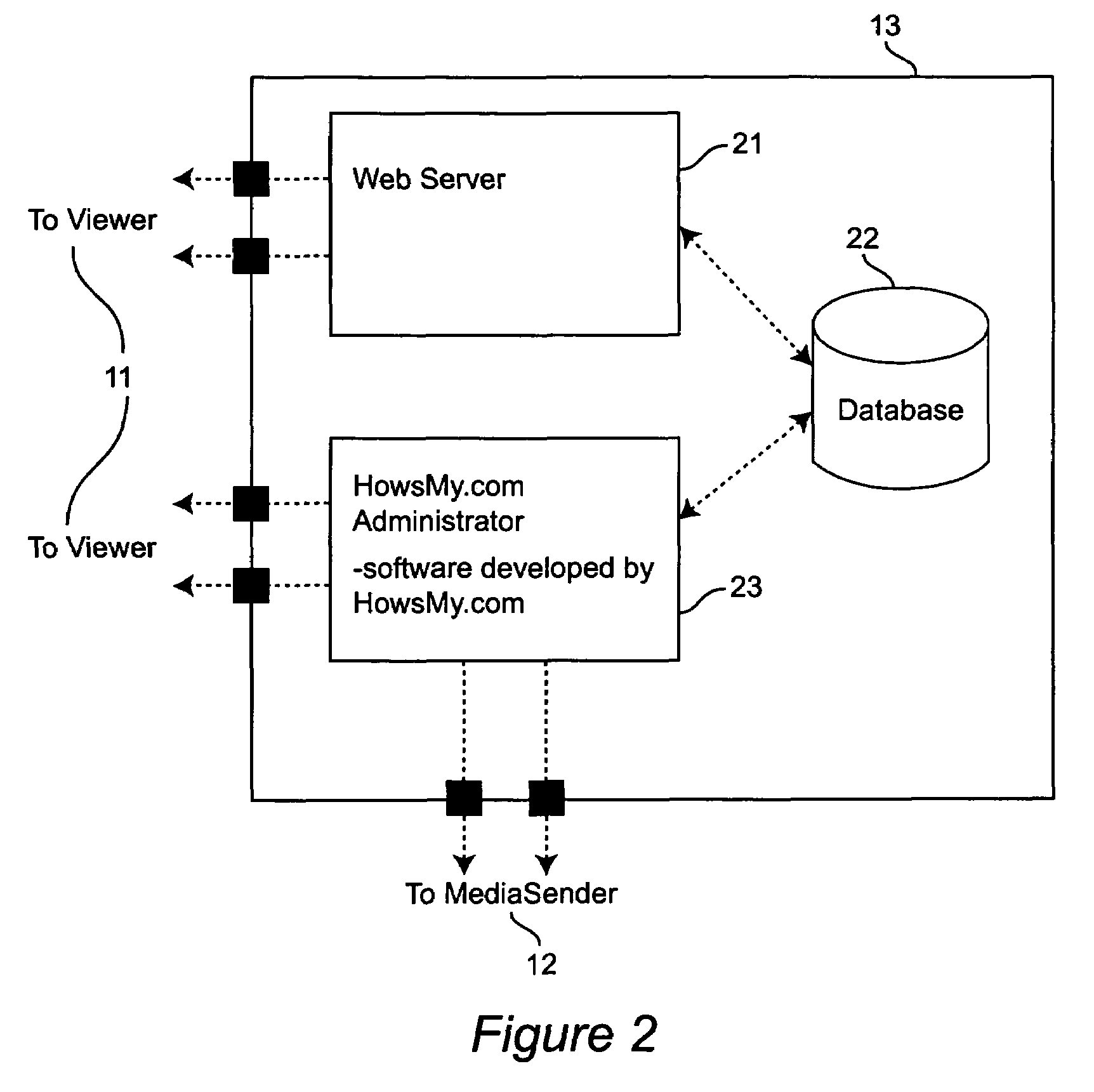
A system and method for point-to-point data streaming over a TCP / IP network. A Sender node serves data to the network, with one or more Viewer nodes receiving the data. A Mediator node provides administration and security and a static Internet location for accessing the system. As a result of the administration and security provided by the Mediator node, the data are communicated directly between the Sender and Viewer thereby minimizing resources and costs required for the Mediator. The Mediator node comprises a web server, an administrator and a database. An optional fourth MediaRelay node is provided to which the data are sent by the Sender and from which the data are received by multiple Viewers. The MediaRelay node permits a Sender having low bandwidth to service multiple Viewers.The Mediator uses versioning control to upgrade MediaSender software at the Sender node, and stores in a database information provided by a Sender during a registration procedure. At login by the Sender, the Sender is authenticated and the Mediator unlocks the MediaSender software. At login by the Viewer, the Viewer is authenticated and the Mediator downloads viewing software to the Viewer. Authentication is based upon information in the database provided by the Sender at registration. Upon authentication of both Sender and Viewer, the Mediator sends both nodes a key enabling bi-directional communication between Sender and Viewer using respective sockets which are maintained until the communication is terminated by the Sender or the Viewer.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for changing a subscription
ActiveUS20050065801A1Special service for subscribersDigital computer detailsConfigfsTerminal equipment
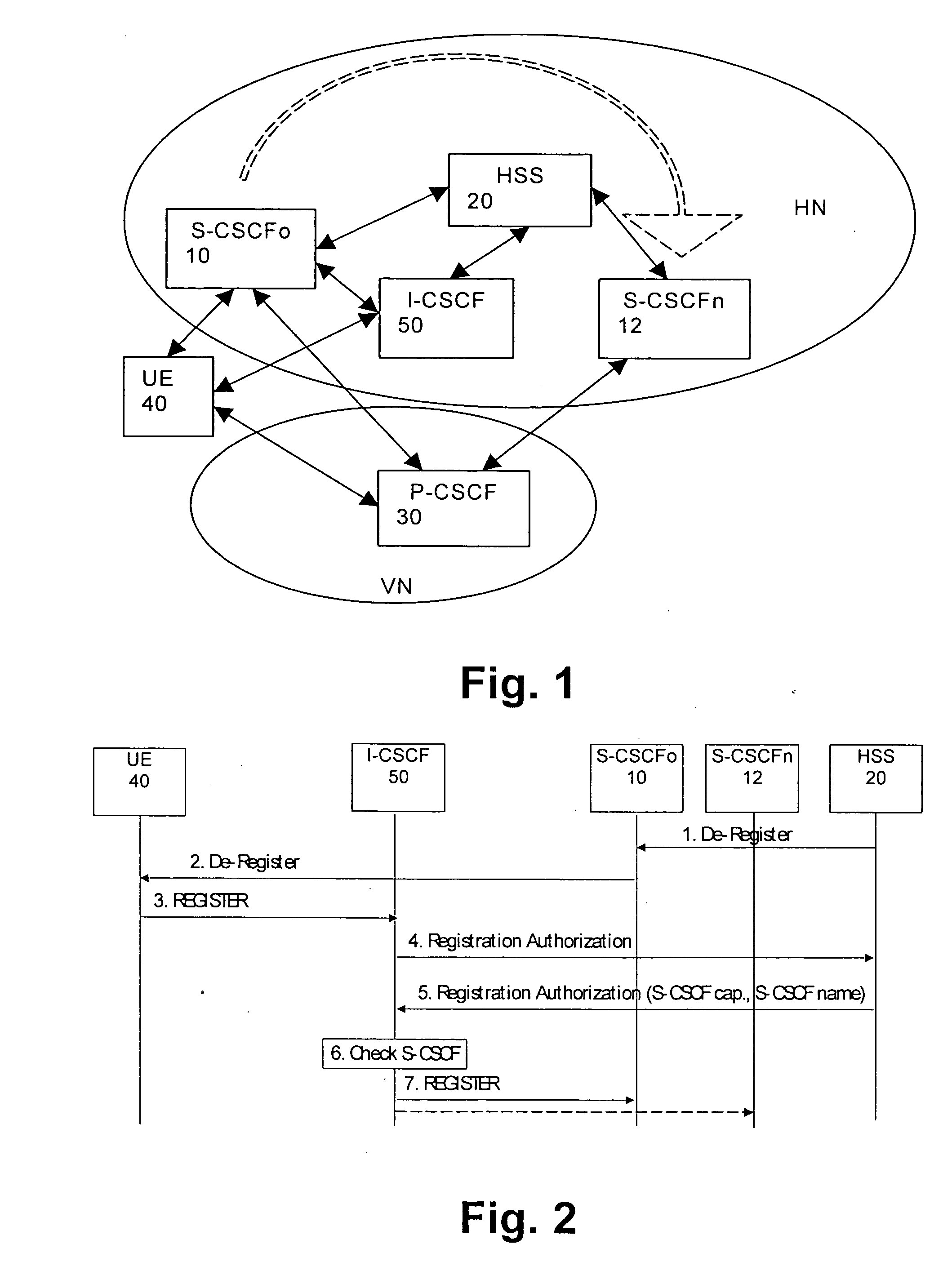
The present invention relates to a method and system for changing a subscription information of a subscriber in a data network. When a subscriber profile or subscription information is changed or updated, this is detected and a registration procedure for registering a terminal device (40) of the subscriber to a new serving network element (12) is initiated in response to the result of a checking step for checking whether a capability of a network element (10) serving a terminal device (40) of said subscriber is still in accordance with said changed subscription information. Thereby, an automatic or semi-automatic adaptation of the serving entity to the changed subscription can be achieved.
Owner:SISVEL INT +1
Method and apparatus for protection switching in passive optical network
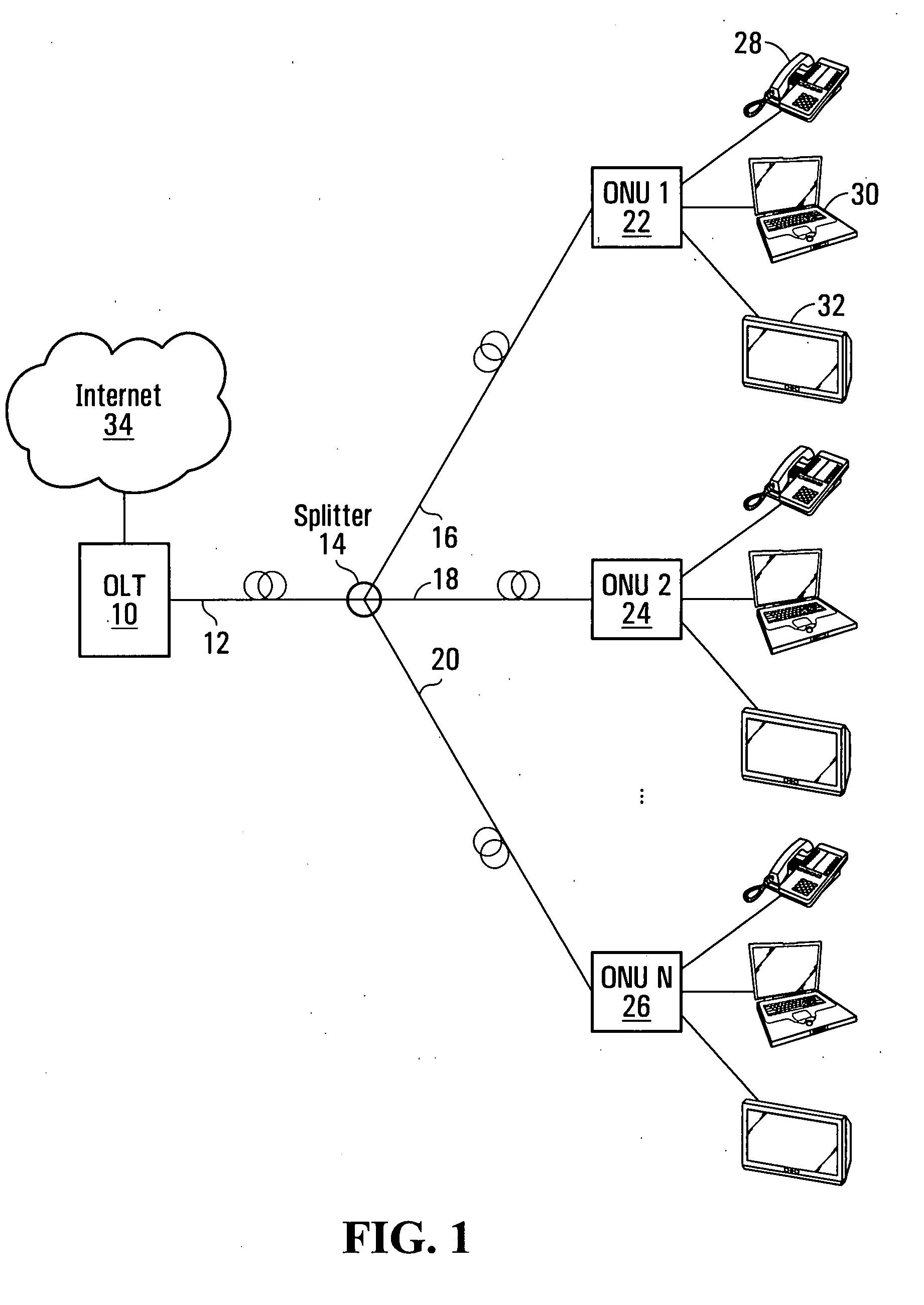
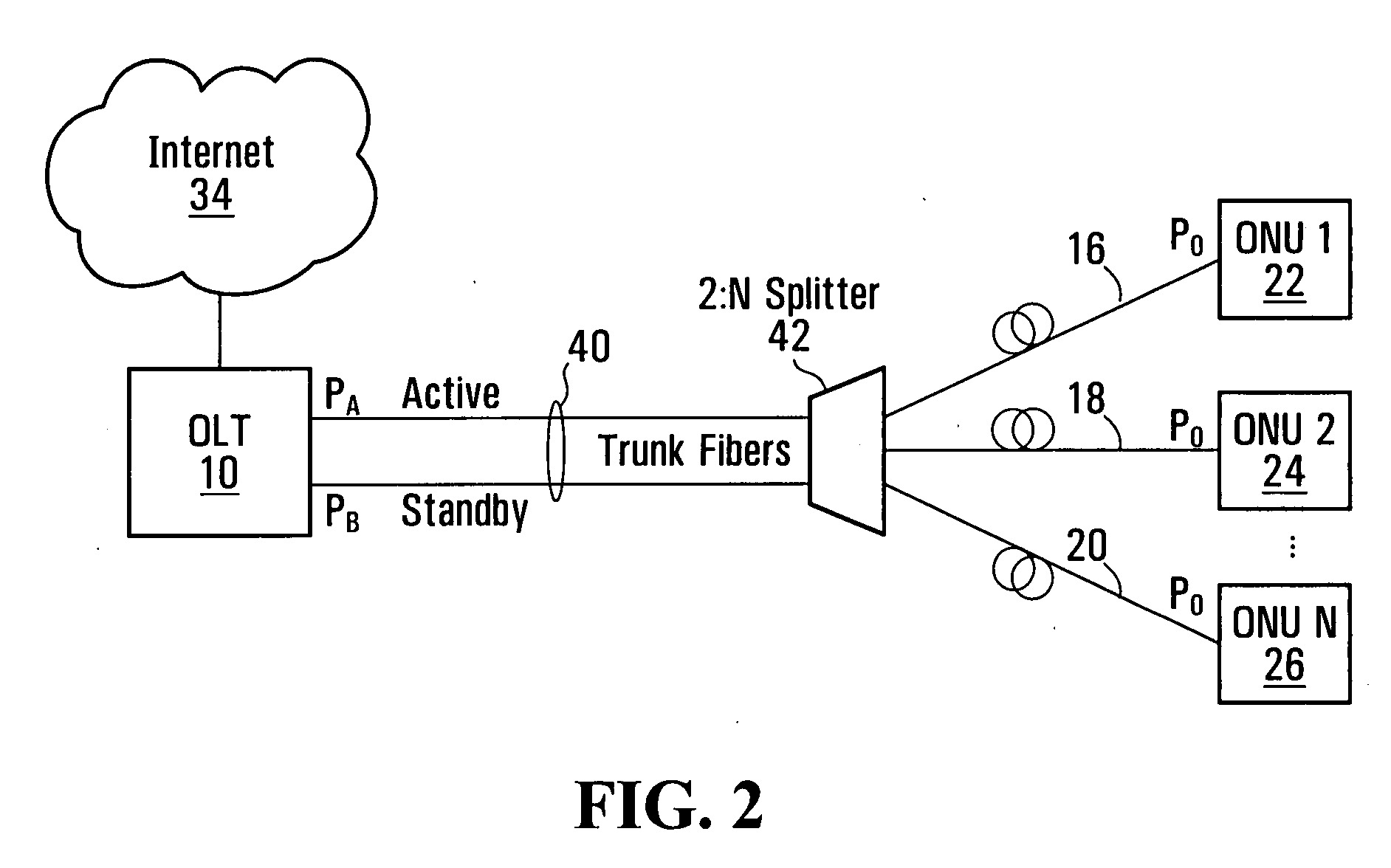
ActiveUS20090067835A1Quick checkImprove protectionMultiplex system selection arrangementsLaser detailsFiberEngineering
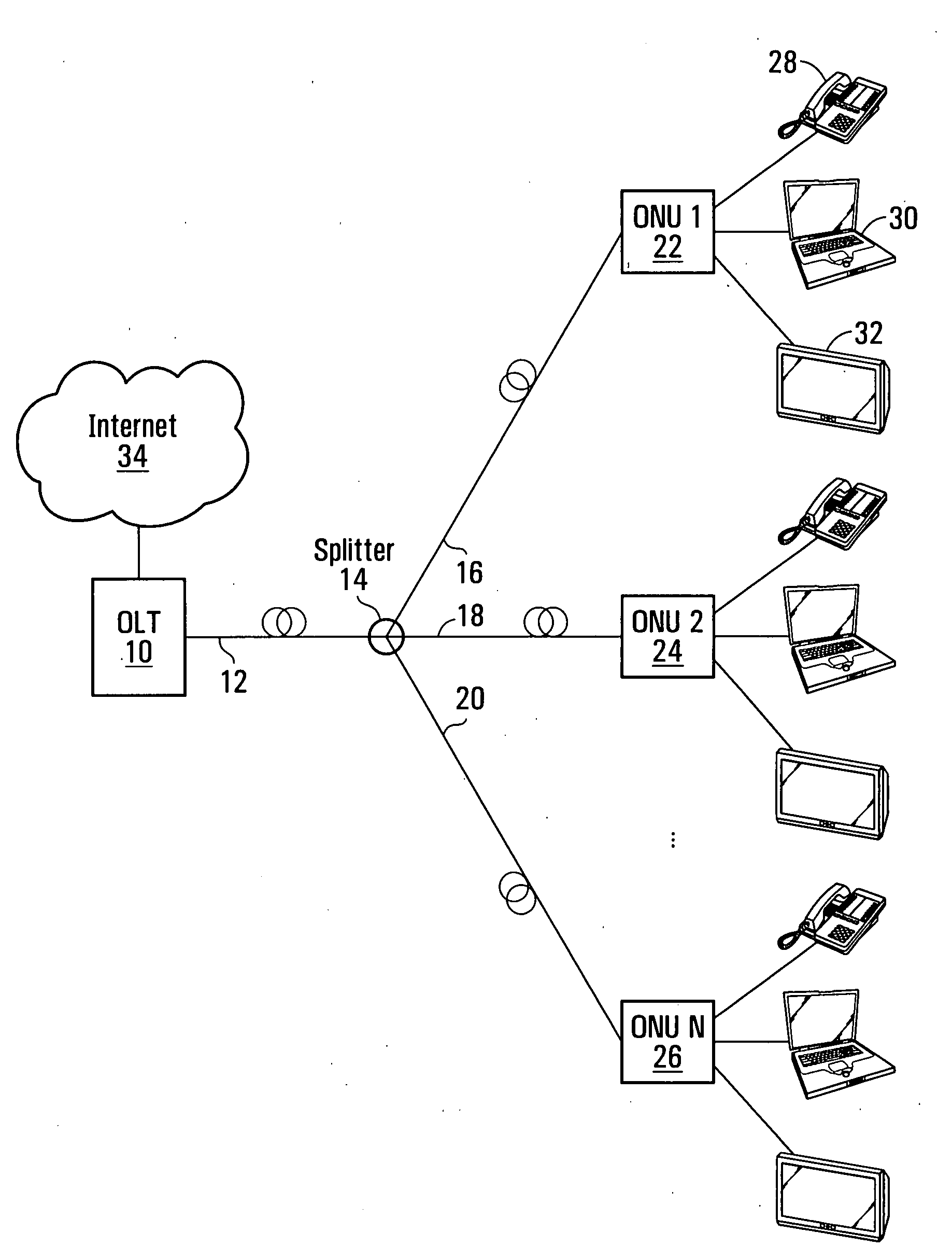
Systems and methods for performing protection switching in a passive optical network are provided. When a fiber cut is detected, control and management plane applications are not immediately informed. A rapid re-registration procedure is instigated upon detection of a fiber cut event. This allows multiple optical network units to re-register quickly without restarting control and management applications.
Owner:REALTEK SINGAPORE PTE LTD
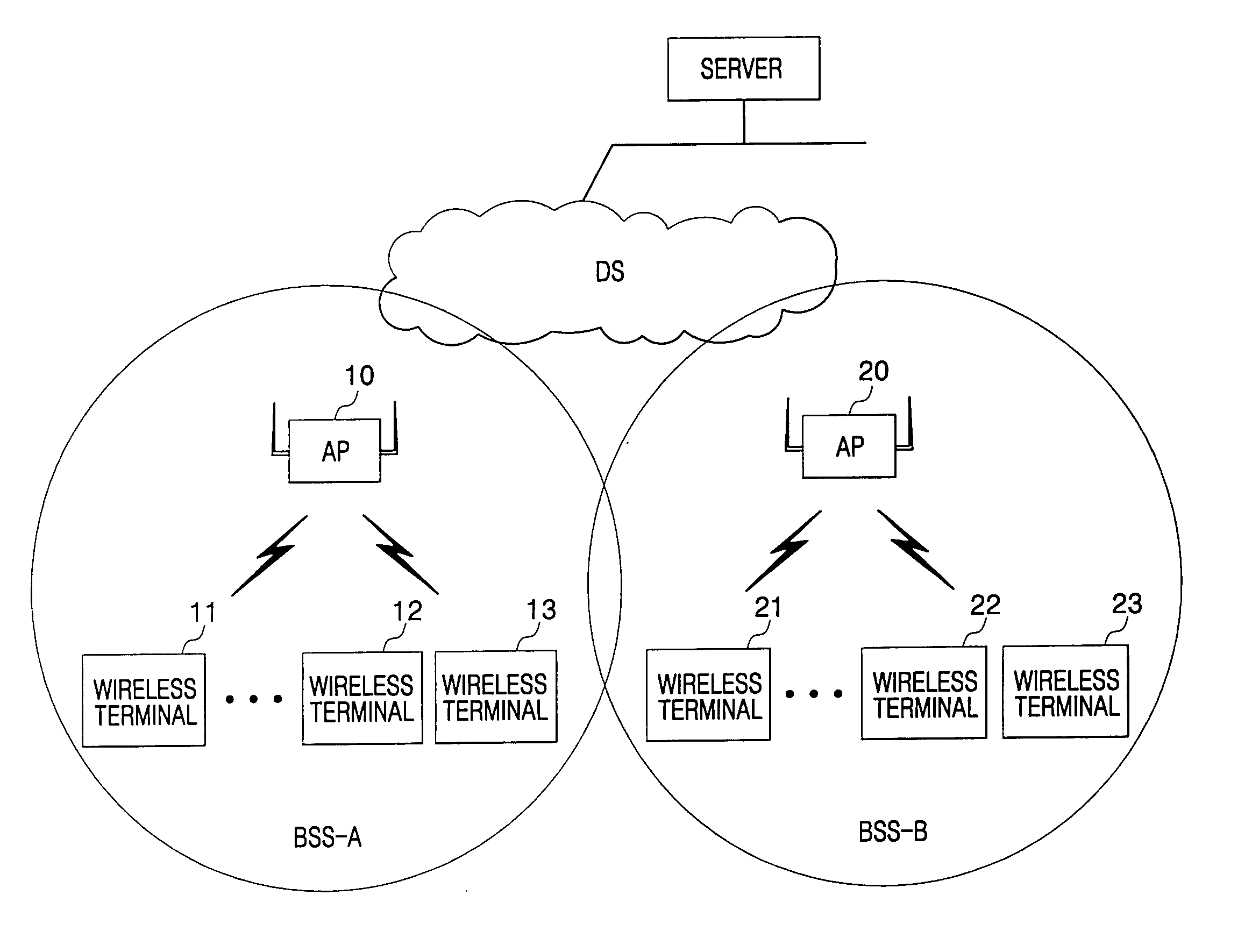
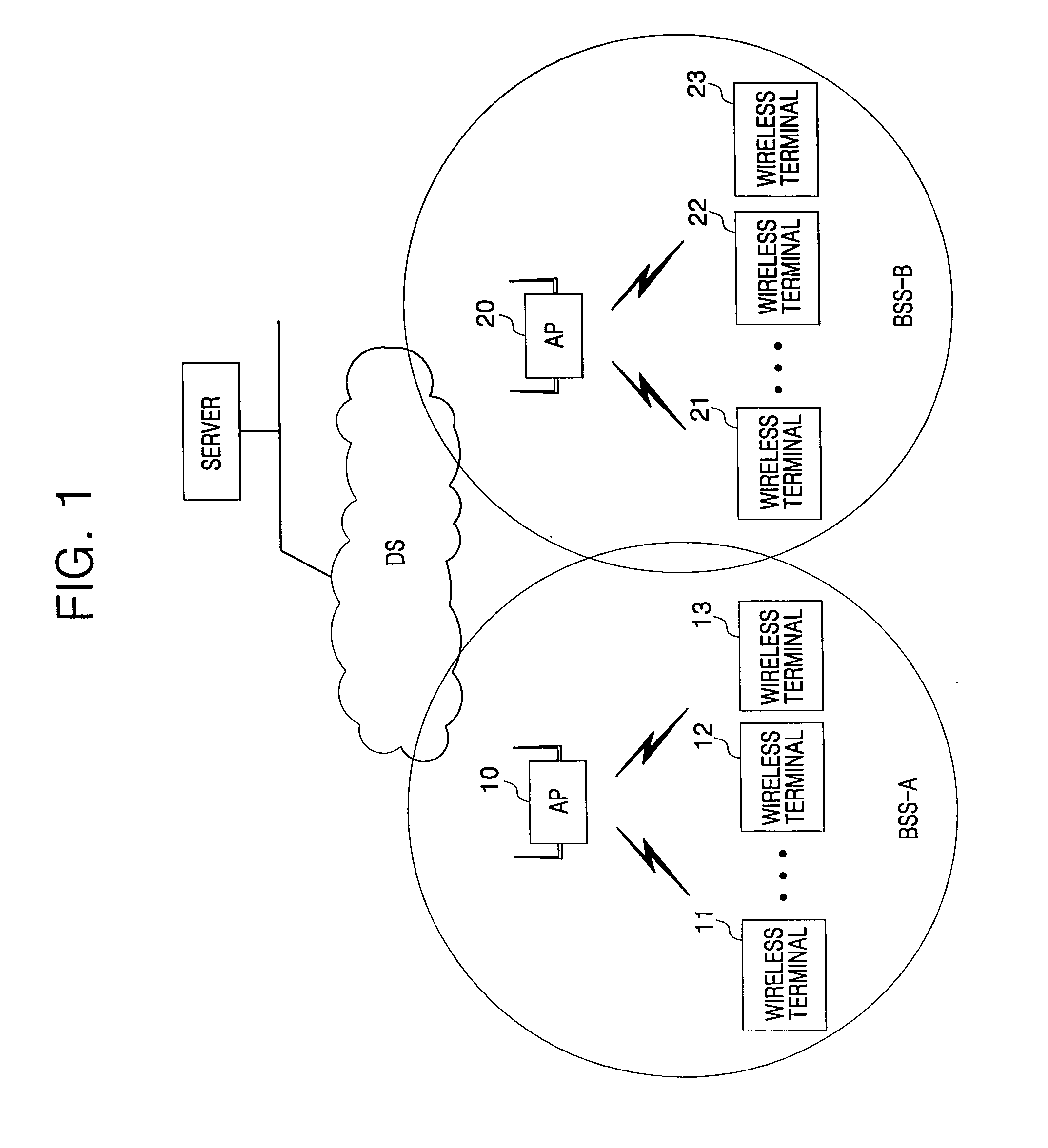
Apparatus and method for registering wireless terminals with access point through wireless network
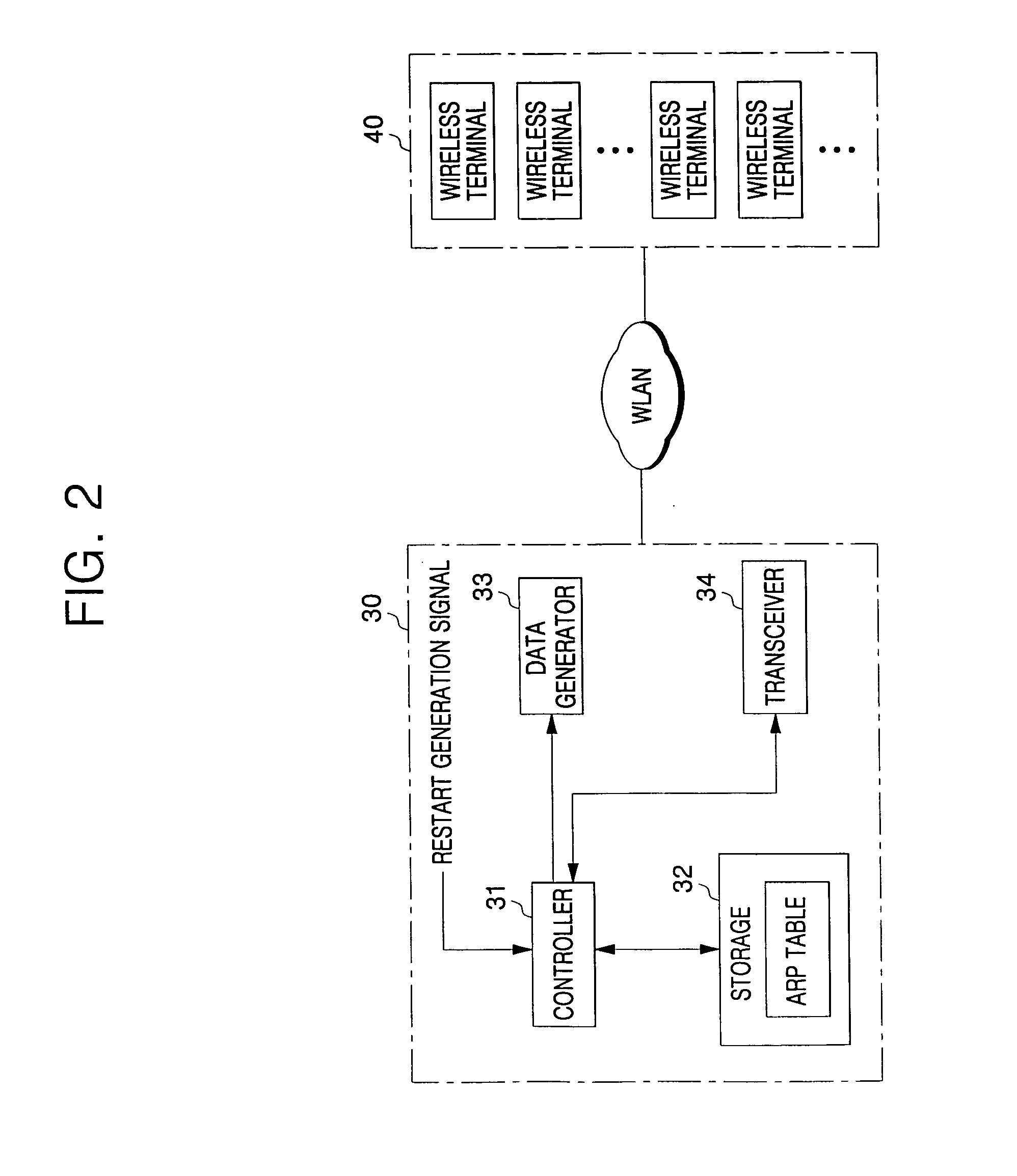
ActiveUS20050122921A1Errors such as connection failure or the like can be preventedAssess restrictionNetwork topologiesAddress Resolution ProtocolBroadcast data
In the method and apparatus for registering wireless terminals with an access point (AP) through a wireless network according to the present invention, there is no need for a re-registration procedure for terminals because, when the AP is restarted, the AP informs wireless terminals registered in its service area of the restart of the AP so as to allow each of the terminals to perform its own location registration. In addition, total update is possible, this method being in contrast to methods in which notification of a restart of the AP is carried out in a one-to-one manner using the broadcast data. As a result, efficiency in time and in the overall network is achieved by the invention. The AP can easily restore the address resolution protocol (ARP) table that has been cleared by the restart process because the terminals send the ARP table themselves, thereby providing for stabilized service.
Owner:SAMSUNG ELECTRONICS CO LTD
Technologies to authorize user equipment use of local area data network features and control the size of local area data network information in access and mobility management function
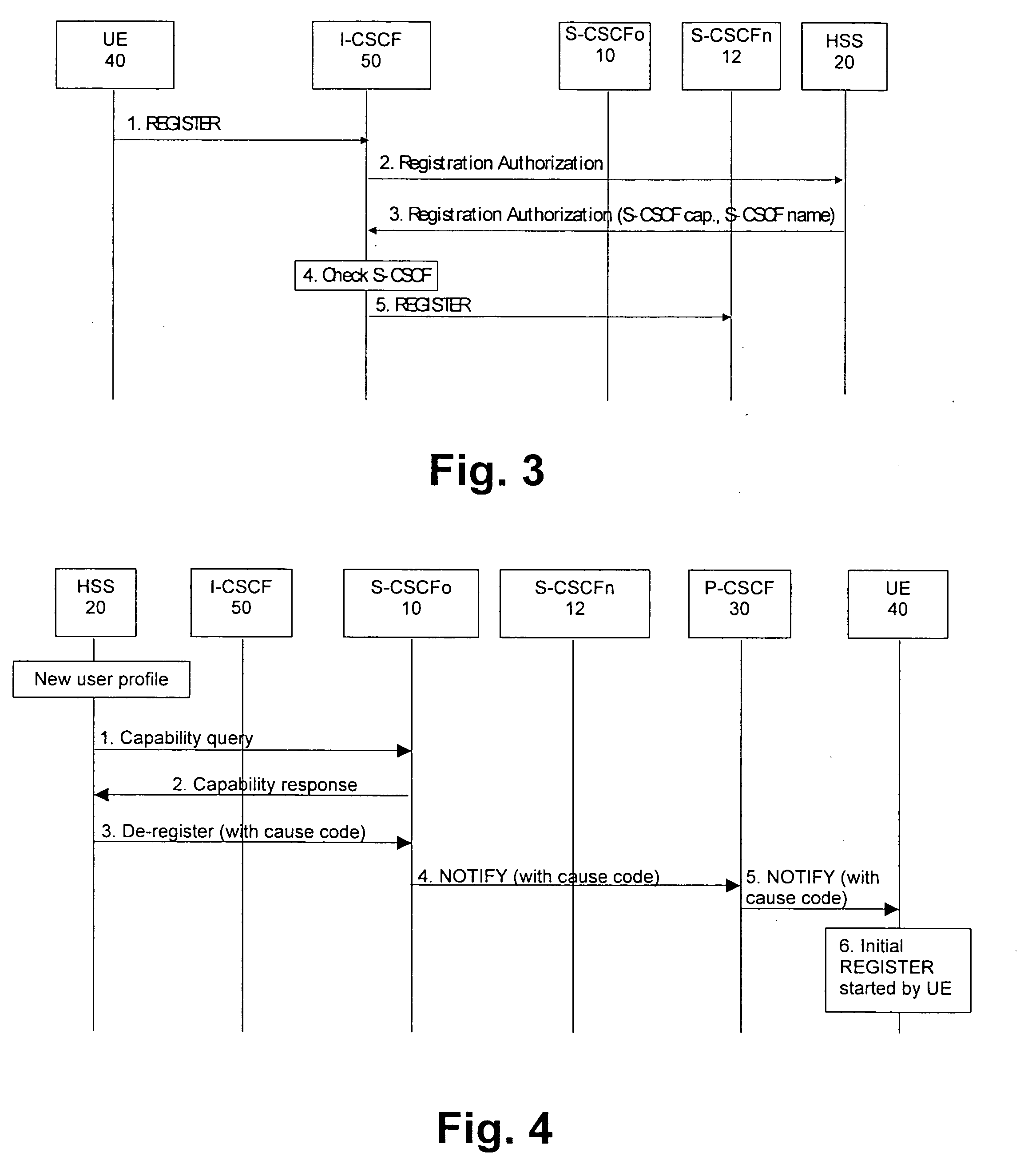
Systems, apparatuses, methods, and computer-readable media are provided for indicating local area data network (LADN) data network names (DNNs). In embodiments, a user equipment (UE) provides a list of configured LADN DNNs in a registration request message during a registration procedure. An Access and Mobility Management Function (AMF) determines LADN information for the UE by looking into configured LADN DNNs in the AMF and / or retrieved LADN authorization / subscription information. The LADN information includes a list of LADN DNNs and corresponding LADN service area(s) that the UE can use, including LADN DNNs that the UE can use in a current registration area. The AMF sends the LADN information to the UE in a registration accept message. Other embodiments may be described and / or claimed.
Owner:INTEL CORP
Mass production testing of USB flash cards with various flash memory cells
InactiveUS7788553B2Facilitates efficient and high volume testing/formattingFacilitates high volume formatting/testingElectronic circuit testingError detection/correctionCard readerUSB
A high volume testing / formatting process is provided for Universal Serial Bus-based (USB-based) electronic data flash cards (USB devices) that meets the increasing demand for USB electronic data flash cards (USB devices). A test host is simultaneously coupled to the multiple USB devices (e.g., using a multi-port card reader or a probe fixture), a controller endpoint value is read from each of the USB devices and verified with a known good value, and then testing / formatting is performed on each of the USB devices by writing predetermined data into each USB device in a pipelined manner, then reading out and testing the predetermined data. In one embodiment, the test host implements a special USB driver that blocks standard USB registration procedures upon detecting the plurality of USB devices. Control and / or boot code data are written onto the flash memory device (i.e., instead of being provided on a controller ROM).
Owner:SUPER TALENT TECH CORP
Point-to-point data streaming using a mediator node for administration and security
InactiveUS20010037461A1Complex procedureMinimal technological skillDigital data processing detailsAnalogue secracy/subscription systemsData streamWeb service
A system and method for point-to-point data streaming over a TCP / IP network. A Sender node serves data to the network, with one or more Viewer nodes receiving the data. A Mediator node provides administration and security and a static Internet location for accessing the system. As a result of the administration and security provided by the Mediator node, the data are communicated directly between the Sender and Viewer thereby minimizing resources and costs required for the Mediator. The Mediator node comprises a web server, an administrator and a database. An optional fourth MediaRelay node is provided to which the data are sent by the Sender and from which the data are received by multiple Viewers. The MediaRelay node permits a Sender having low bandwidth to service multiple Viewers. The Mediator uses versioning control to upgrade MediaSender software at the Sender node, and stores in a database information provided by a Sender during a registration procedure. At login by the Sender, the Sender is authenticated and the Mediator unlocks the MediaSender software. At login by the Viewer, the Viewer is authenticated and the Mediator downloads viewing software to the Viewer. Authentication is based upon information in the database provided by the Sender at registration. Upon authentication of both Sender and Viewer, the Mediator sends both nodes a key enabling bi-directional communication between Sender and Viewer using respective sockets which are maintained until the communication is terminated by the Sender or the Viewer.
Owner:MICROSOFT TECH LICENSING LLC
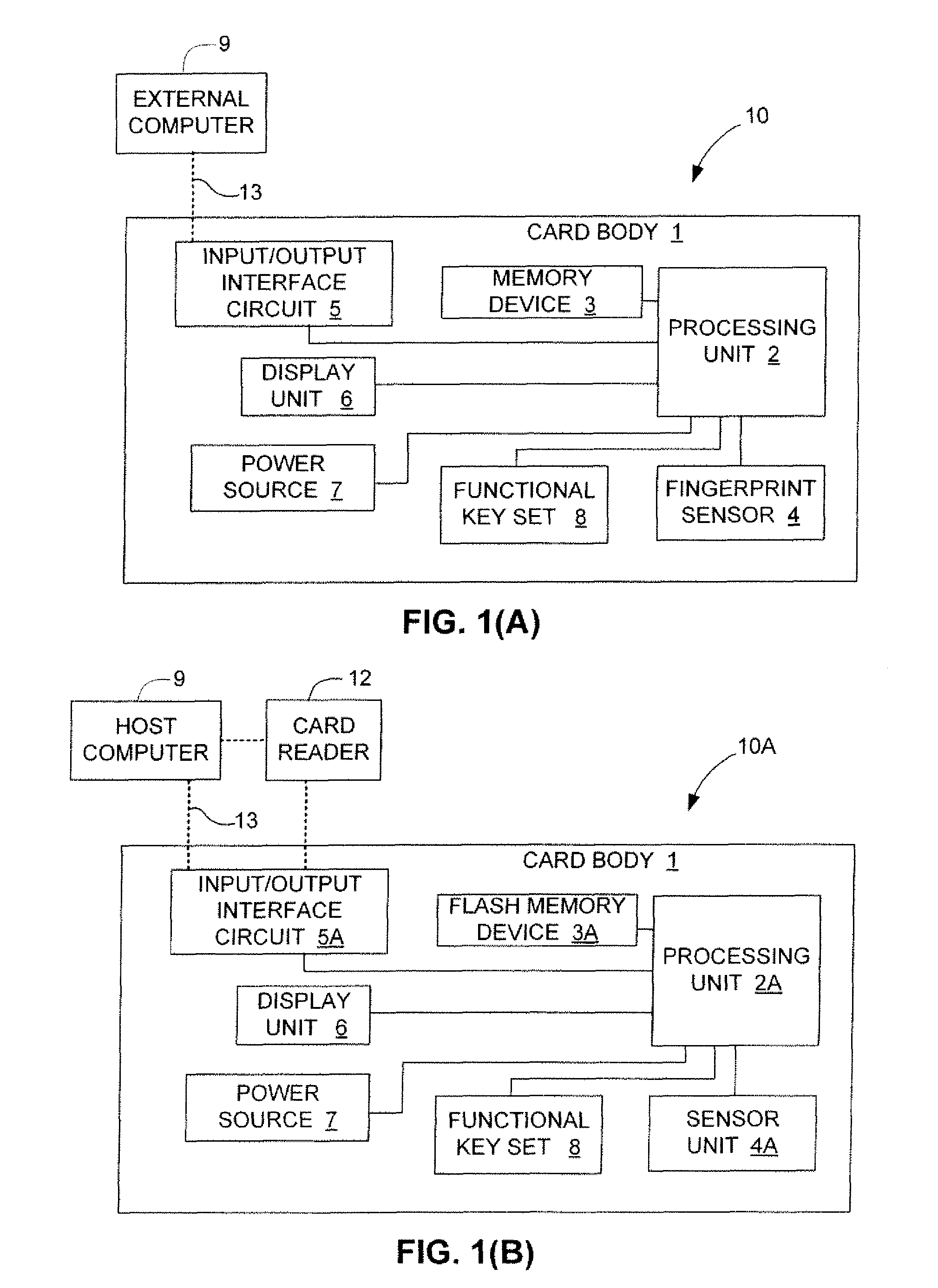
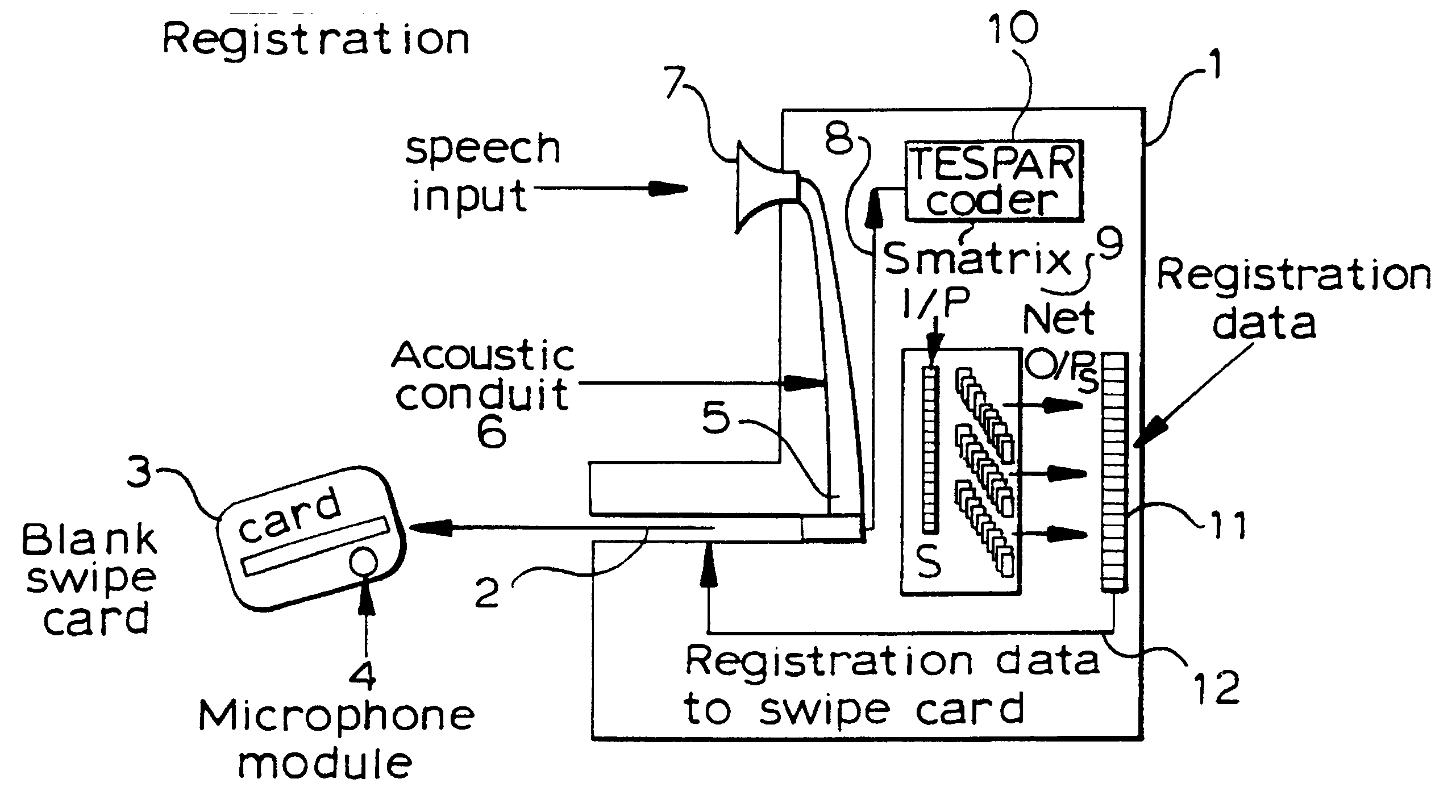
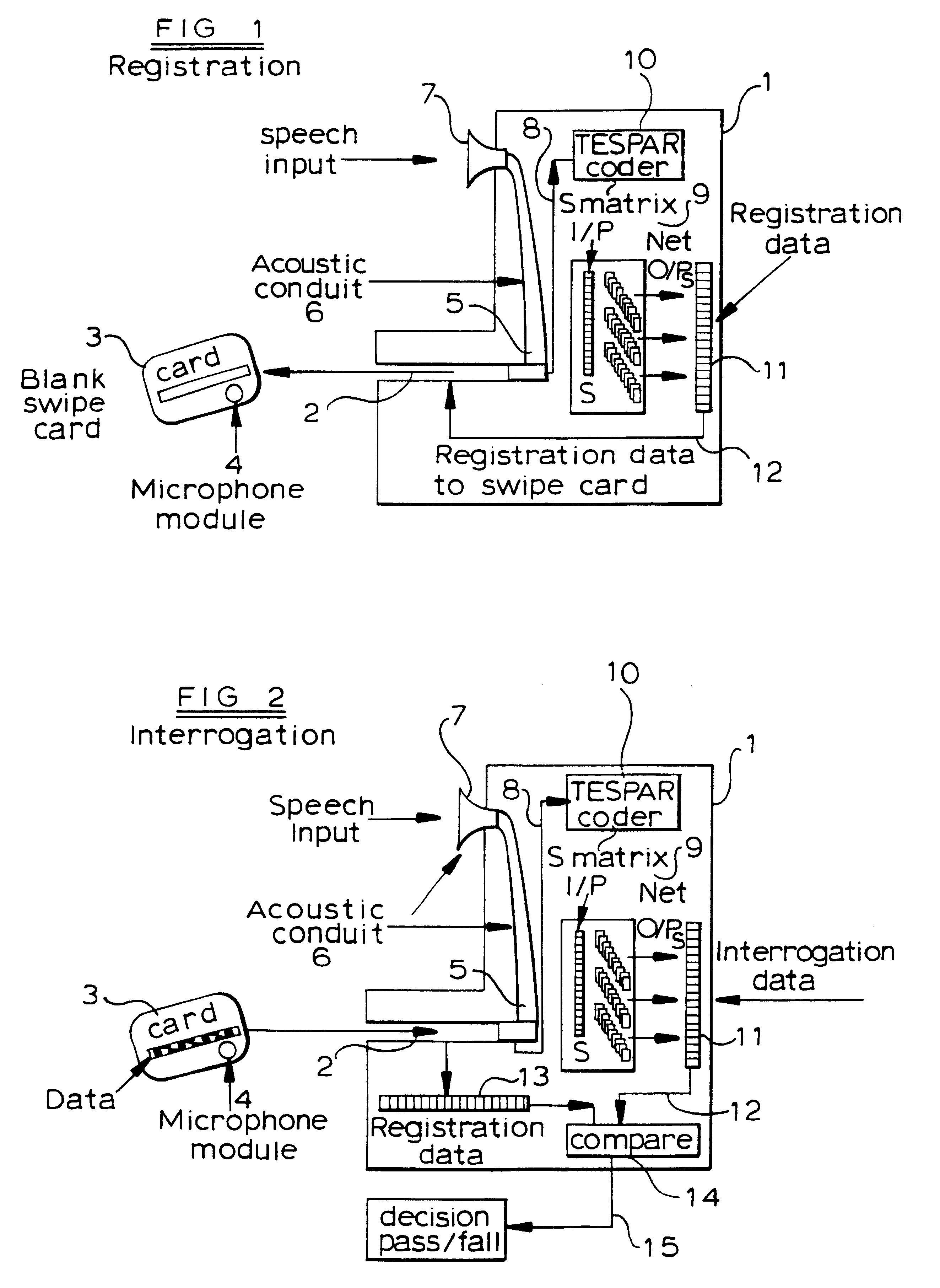
Security system including a portable secure medium having a microphone therein
InactiveUS6382516B1Conveying record carriersCo-operative working arrangementsComputer hardwareBiometrics
A security device and a security system incorporating such a device comprises a portable secure object which includes a unit for storing information, a unit for storing a voice biometric signal or a signal indicative thereof, and an integral microphone. The microphone generates the voice biometric signal during a registration procedure, and subsequently derives a further voice biometric signal for comparison with the generated voice biometric signal for subsequent interrogation purposes.
Owner:DOMAIN DYNAMICS
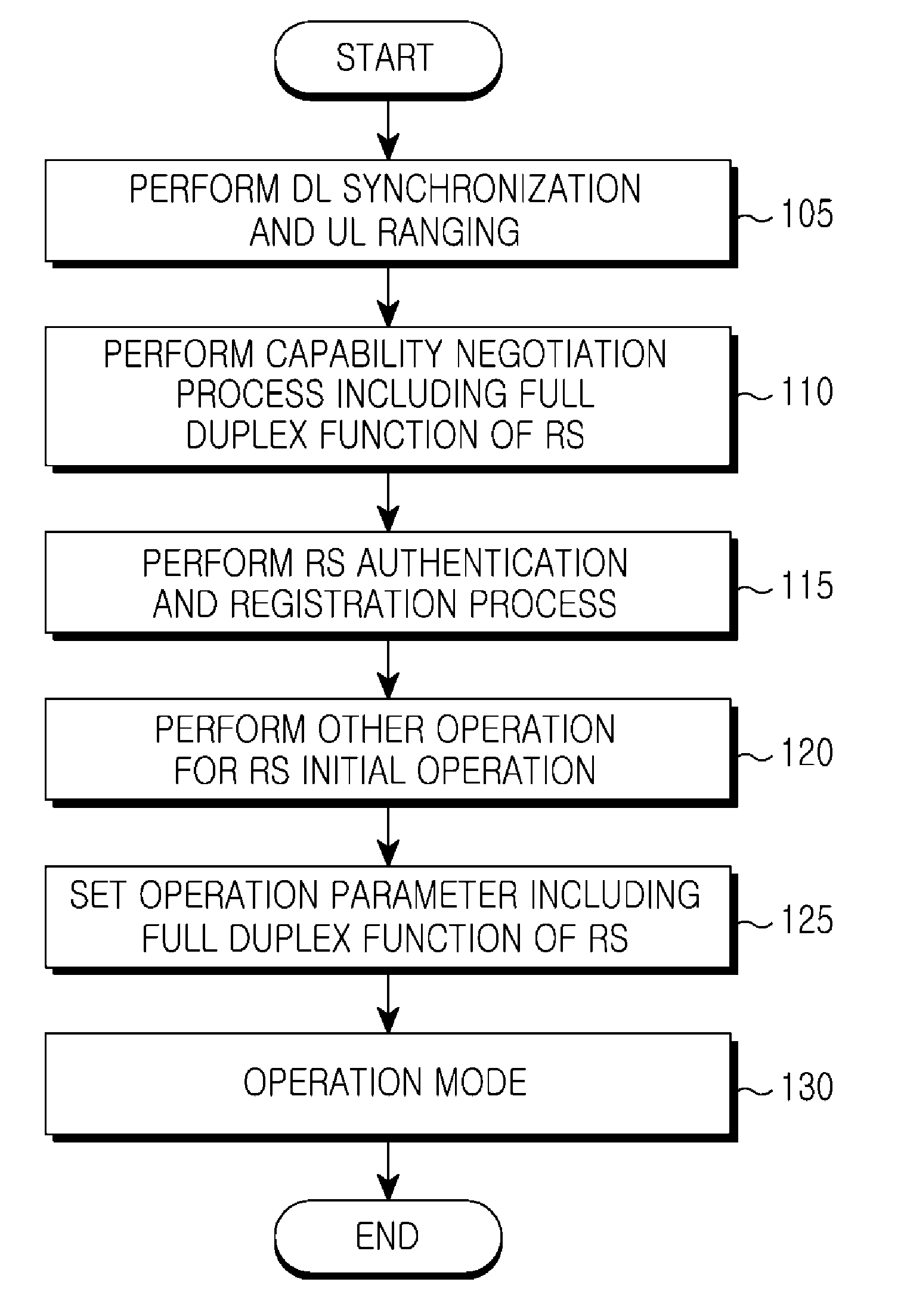
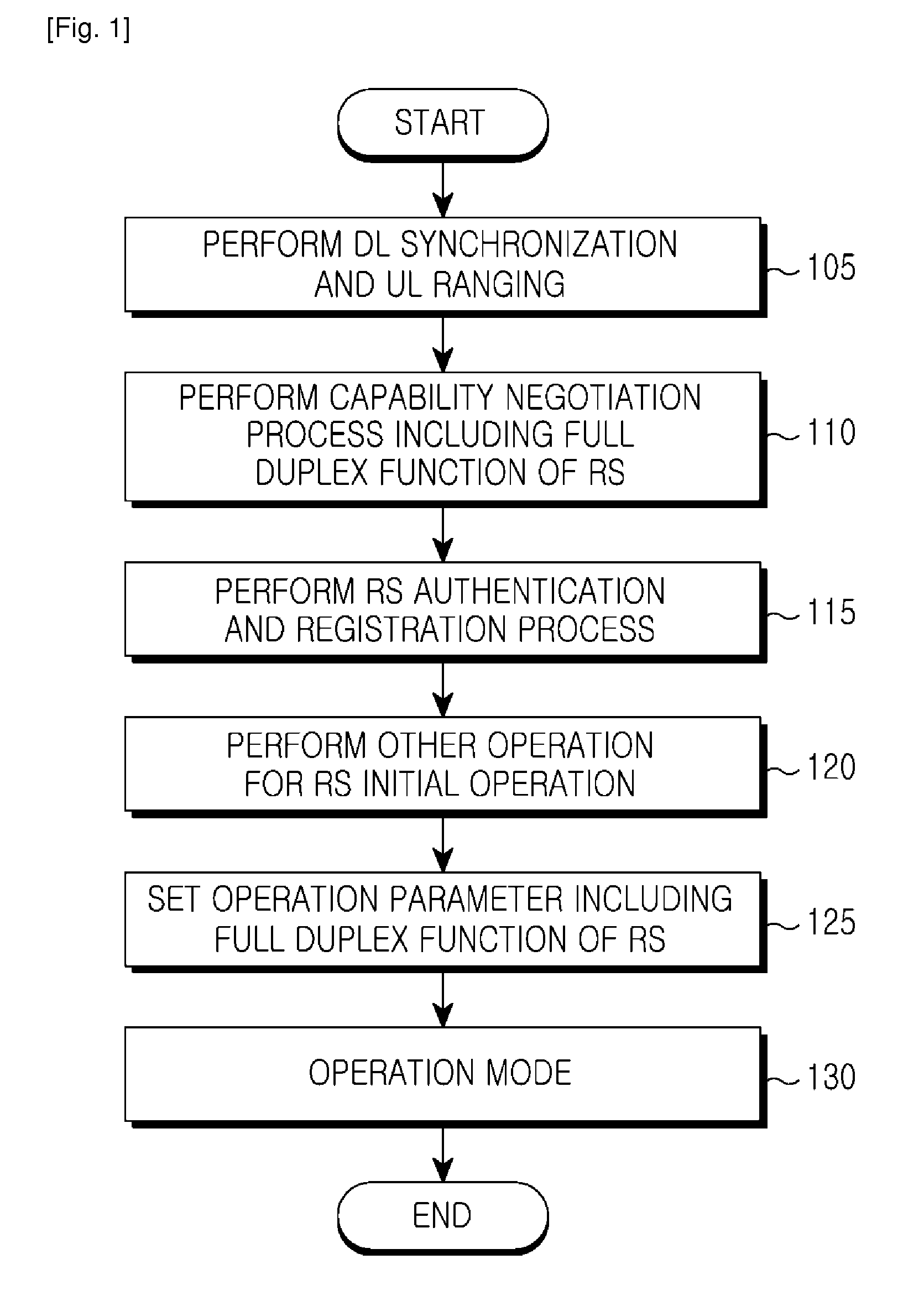
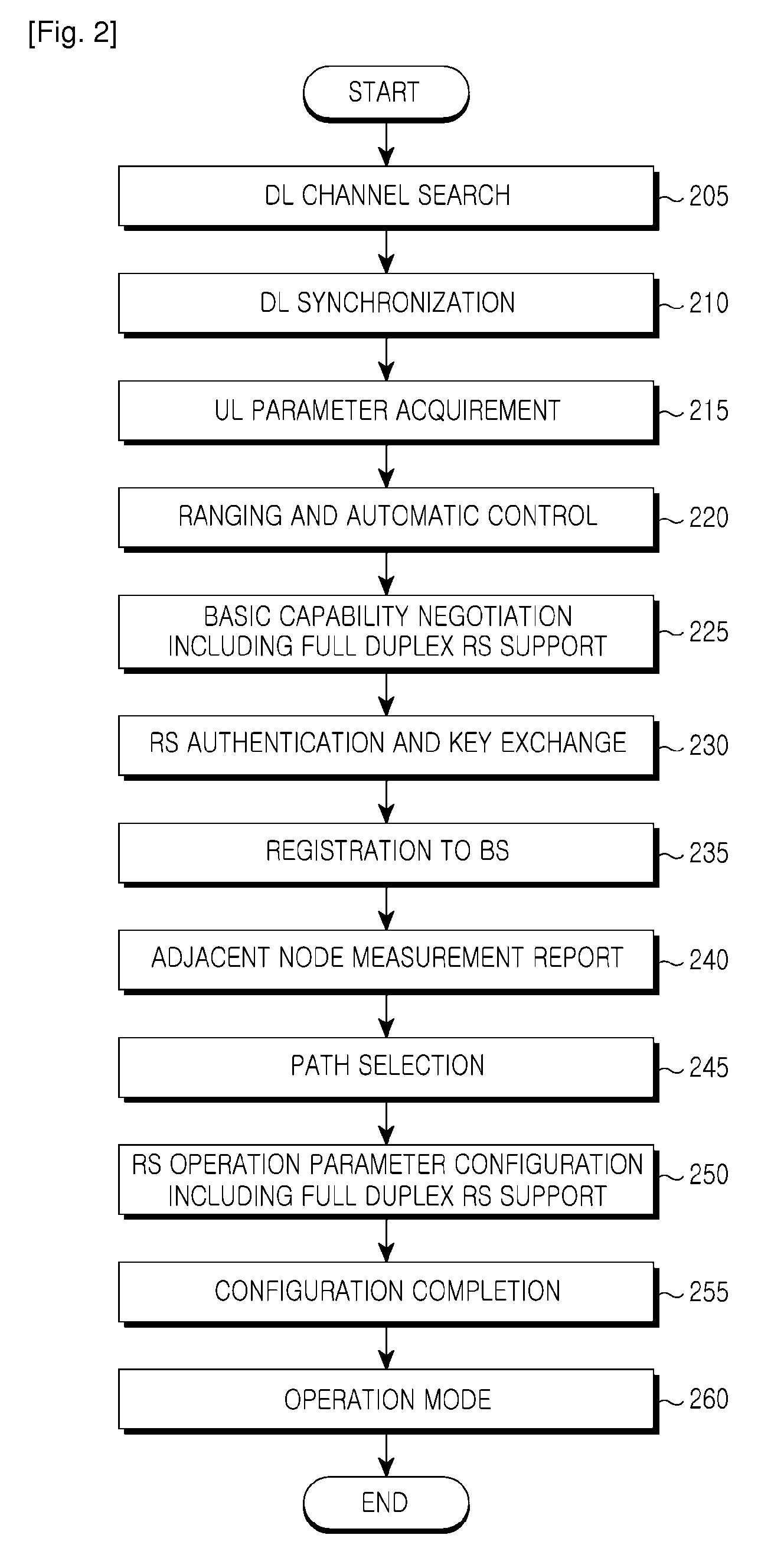
Network entry apparatus and method for relay station using full duplex in mobile communication system
ActiveUS20110038283A1Effective supportEliminating Error Vector MagnitudeNetwork traffic/resource managementTransmission path divisionEngineeringMobile communication systems
A network entry apparatus and method for a Radio Station (RS) using full duplex in a mobile communication system are provided. The method includes performing a capability negotiation procedure including a full duplex function with a BS, performing an authentication and registration procedure with the BS, and performing an operation parameter configuration procedure including a full duplex function with the BS.
Owner:SAMSUNG ELECTRONICS CO LTD
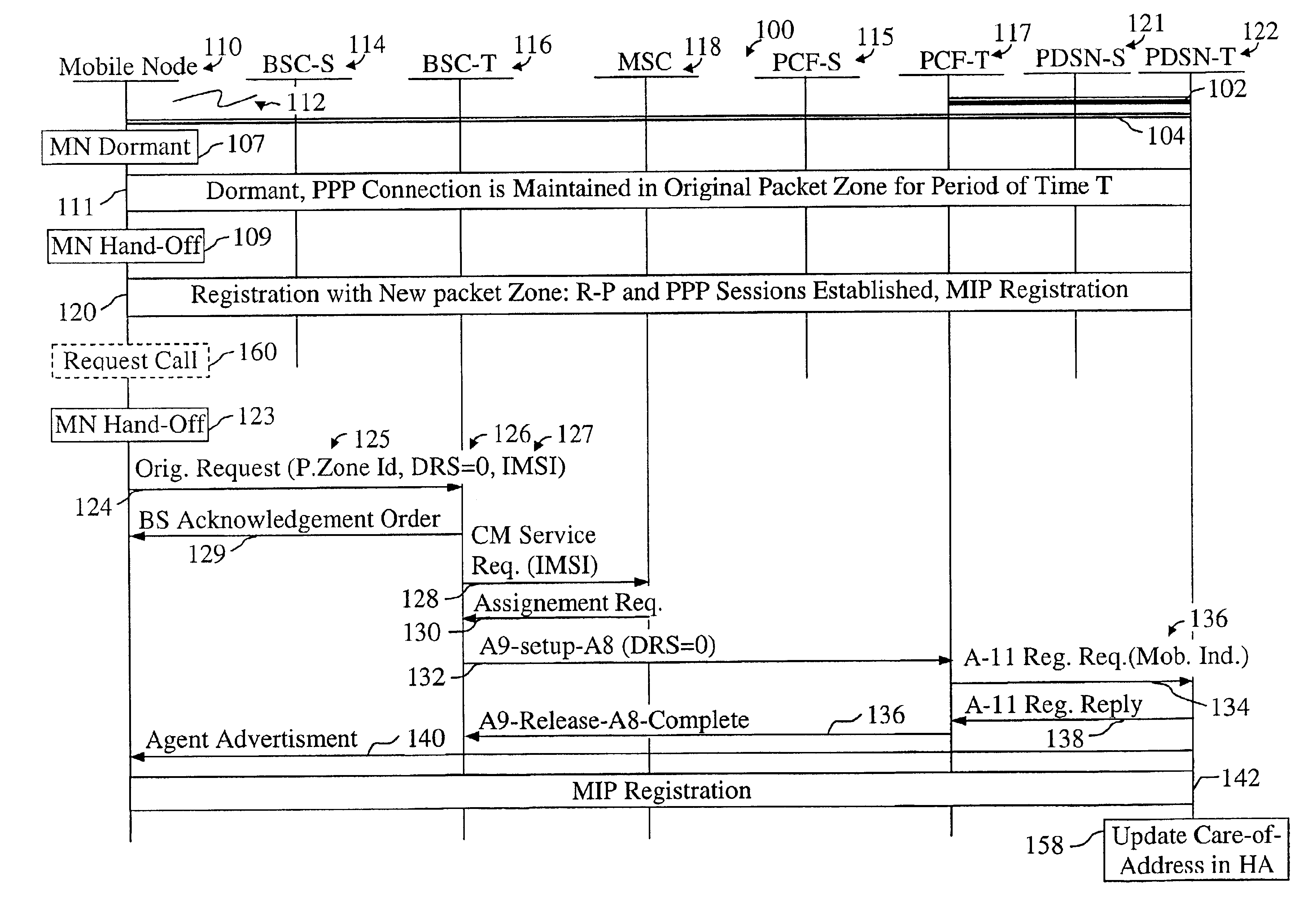
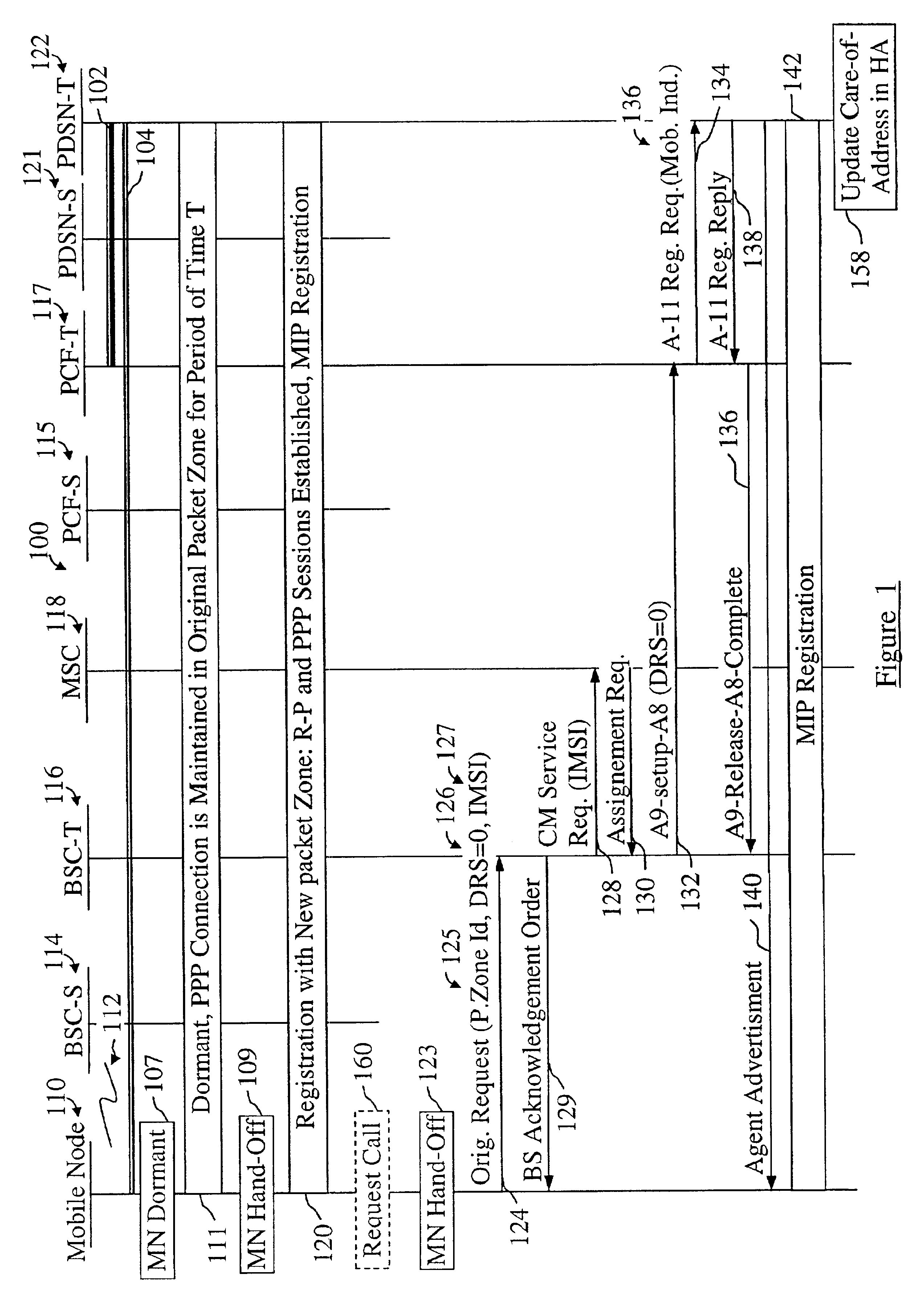
Mobile IP registration in selected inter-PDSN dormant hand-off cases in a CDMA2000-based cellular telecommunications network
InactiveUS6907016B2Time-division multiplexRadio/inductive link selection arrangementsPacket data serving nodeTelecommunications network
In a cellular telecommunications network, a method and system for performing dormant hand-off for a dormant Mobile Node (MN) between a source packet zone an a target packet zone, when the MN still has an active A10 and Point-to Point Protocol (PPP) connection in the target packet zone. According to the method, when handed-off, the MN issues an origination request with a Data Ready to Sent (DRS) parameter set to zero for the target Base Station Controller (BSC-T) which responsive to the request further sends an A9-setup-A8 registration request to a target Packet Control Function (PCF-T). The PCF-T then sends an A-11 Registration Request message to a Packet Data Service Node (PDSN-T) of the target packet zone. Responsive to the receipt of the Registration request, the PDSN-T sends an agent advertisement message to the MN and initiates the Mobile IP (MIP) registration procedure, and the MN can register the care-of-address information relating to the new serving PDSN, the PDSN-T, with its Home Agent (HA). According to another embodiment, the same method is to be used for performing a hand-off of the dormant MN to the target packet zone, when the MN, before issuing the origination request, demands the activation of a packet data session.
Owner:TELEFON AB LM ERICSSON (PUBL)
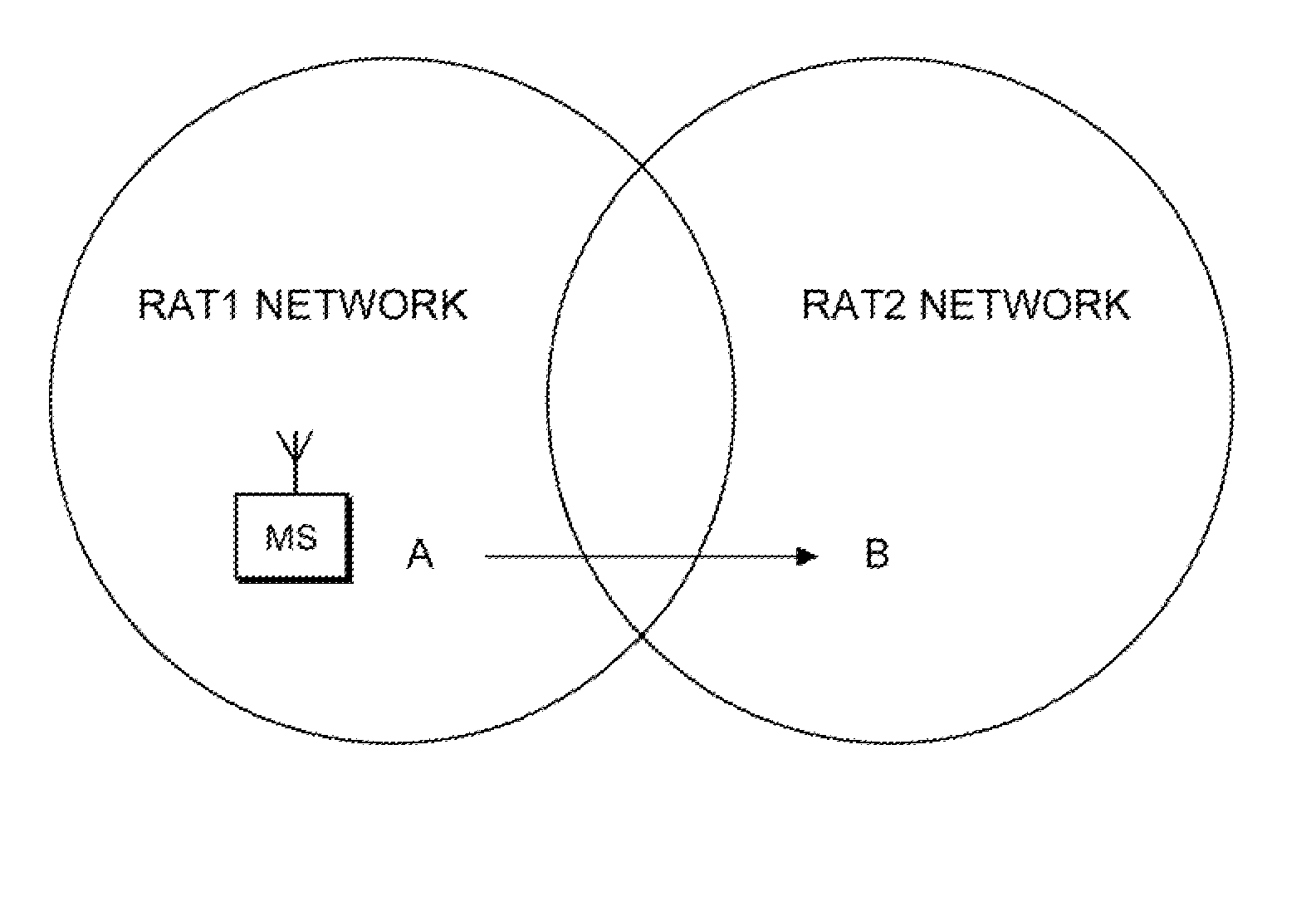
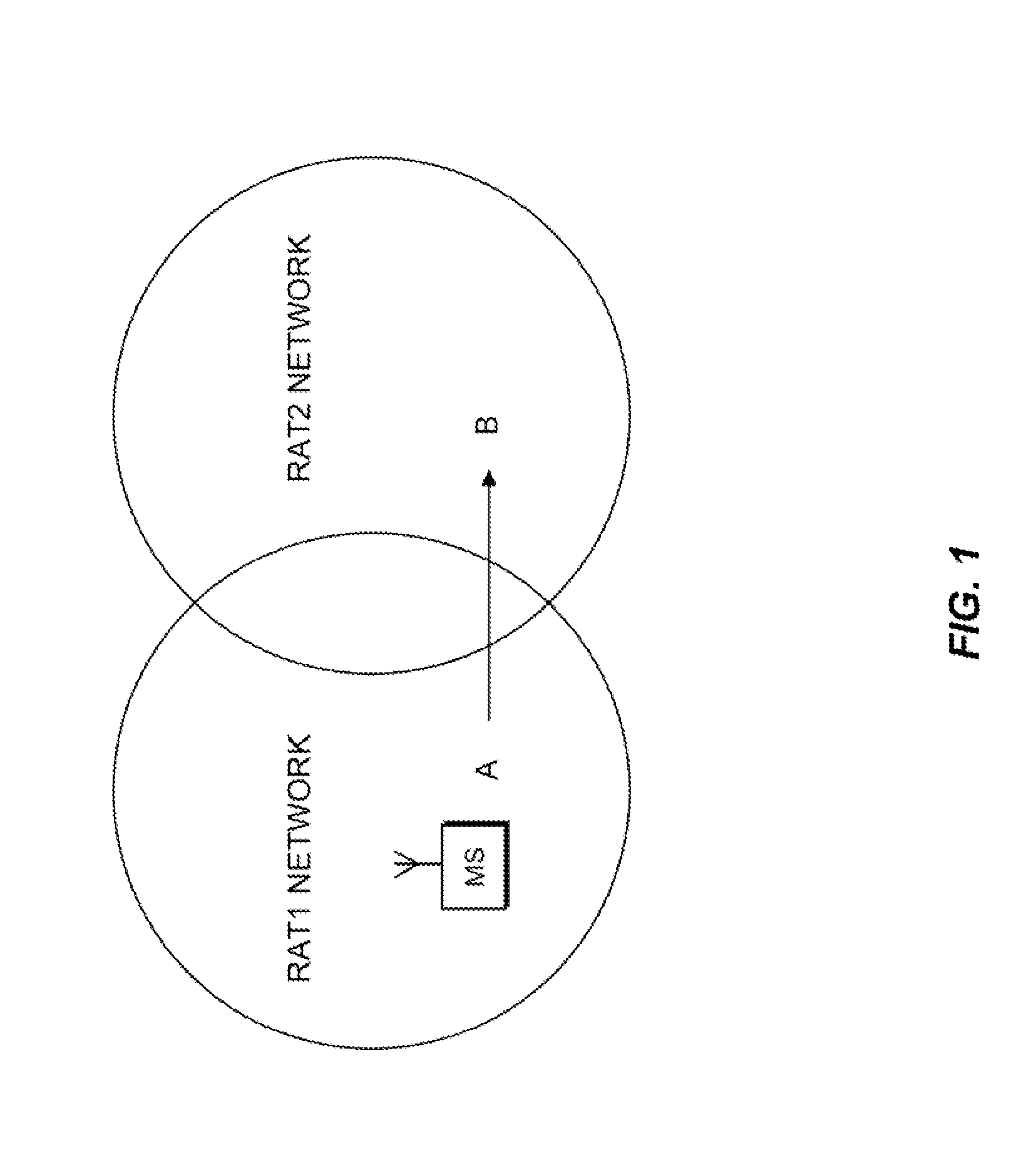
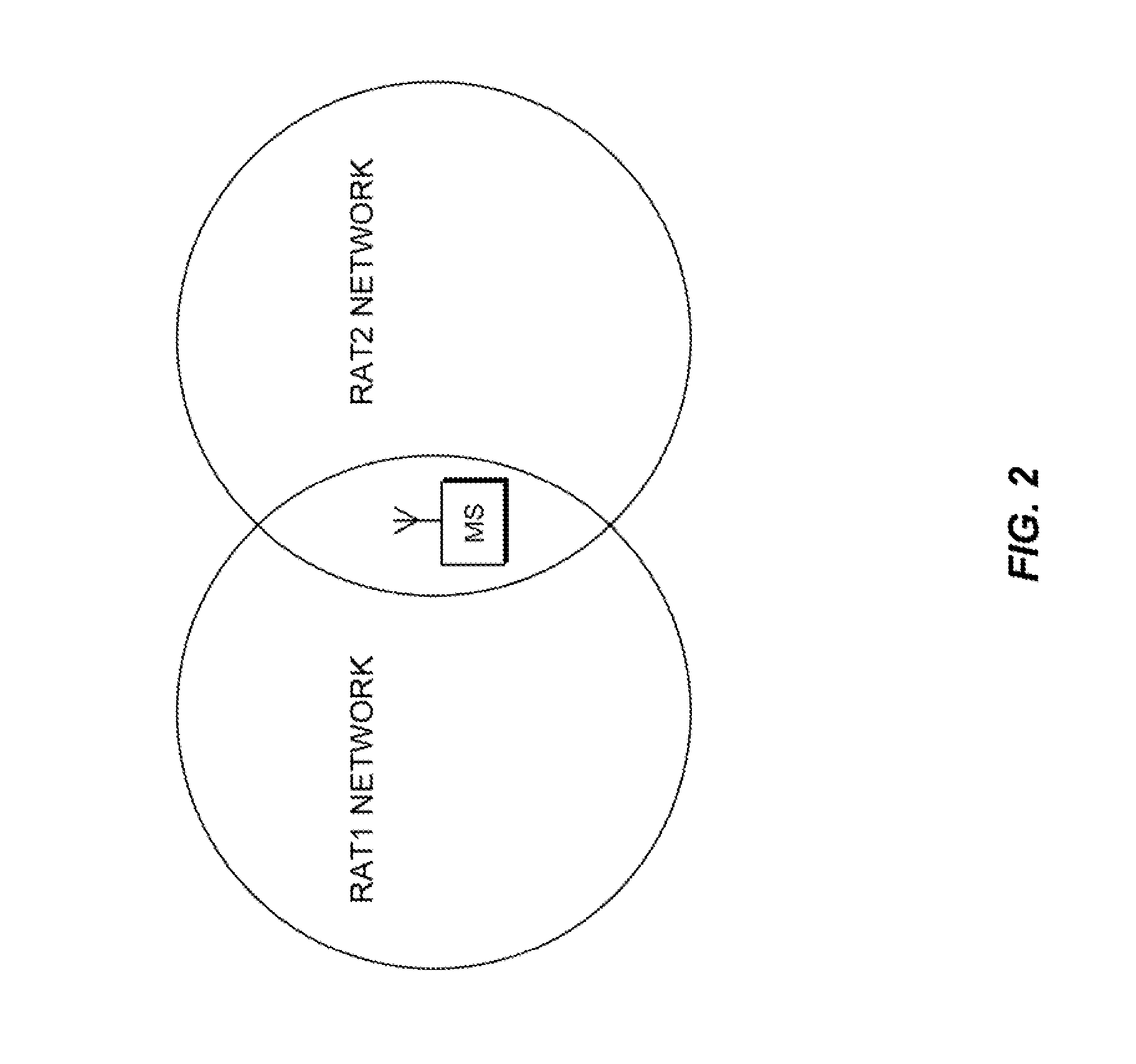
Reducing resource allocations for inter-technology handover between wireless communication networks
InactiveUS20110176511A1Reduce resource allocationAvoid switching failuresNetwork topologiesConnection managementMobile stationHandover
Disclosed is a method for reducing resource allocations for inter-technology handover between heterogeneous wireless communication networks. The method includes a first step of completing network entry and new session registration procedures for a mobile station with a handover target technology network. A next step includes defining an activity mode of the new session. A next step includes waiting for the expiration of a resource timer at the target network. A next step includes assigning the resources for the new session upon the expiration of the timer.
Owner:MOTOROLA MOBILITY LLC
Image guided robotic system for keyhole neurosurgery
ActiveUS9492241B2Precise structureSmall heightSurgical needlesSurgical navigation systemsRobotic systemsEntry point
Owner:MAZOR ROBOTICS
Method of speeding up the registration procedure in a cellular network
ActiveUS20050249238A1Speeding up registration procedureSpeed up the procedureTime-division multiplexConnection managementAccess networkSignaling process
A method of carrying an application level message encapsulated inside a signaling message of an access network, said method comprising the steps of: receiving (1) an application level message from a sender application process to an access network signaling process; adapting (3) said application level message and encapsulating it in a signaling message of an access network; and delivering (1, 3, 4) said encapsulated application level message to a receiver application process by transmitting said signaling message, wherein said encapsulated application level message is transparent to the means of said access network transmitting said signaling message.
Owner:NOKIA TECHNOLOGLES OY
Correlating communication sessions
ActiveUS20110270995A1Avoid forksMultiple digital computer combinationsTransmissionApplication serverCommunications system
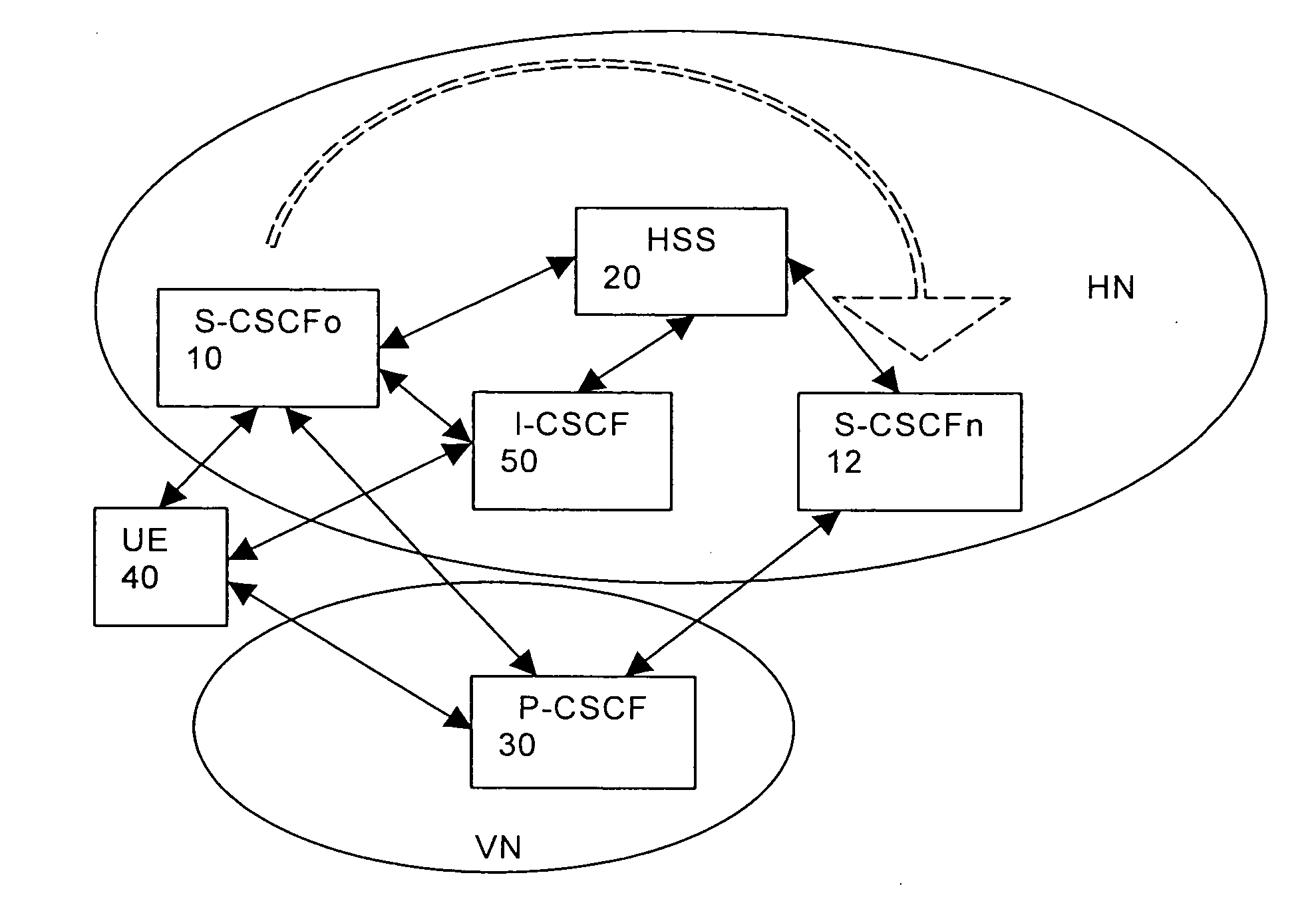
The present invention relates to a session handling entity and an application server (AS) in a communication system, the session handling entity (S-CSCF) is obtaining, from a register entity, a correlation identity for a registering private user identity of a user, transmitting the correlation identity as part of a registration procedure to the application server, and the application server initiates, based on a received session request associated with the user, at least one session request towards corresponding number of devices of the user wherein the application server is configured to check the correlation identity to ensure that not more than one session request is initiated for each device of the user.
Owner:NOKIA TECHNOLOGLES OY
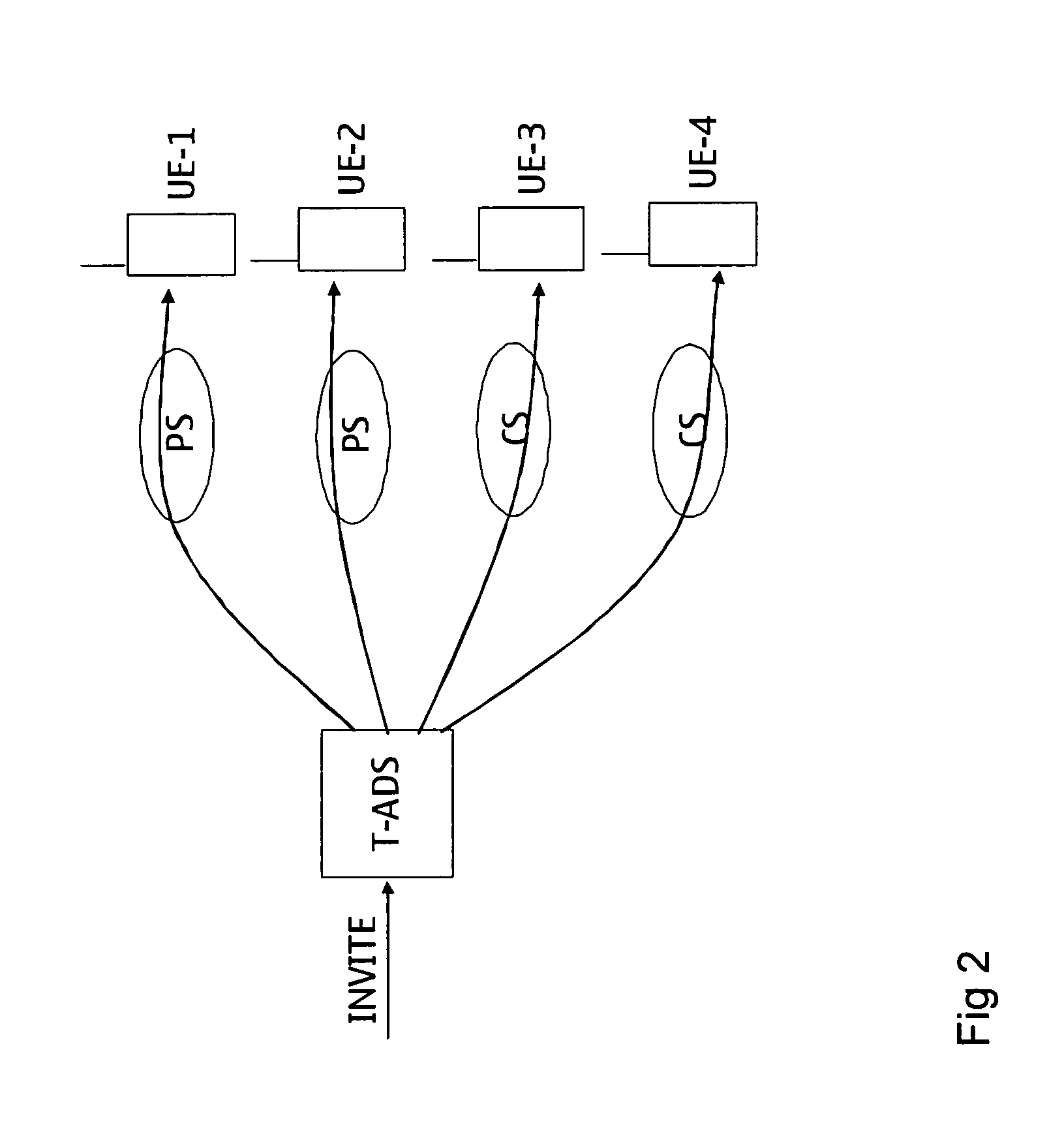
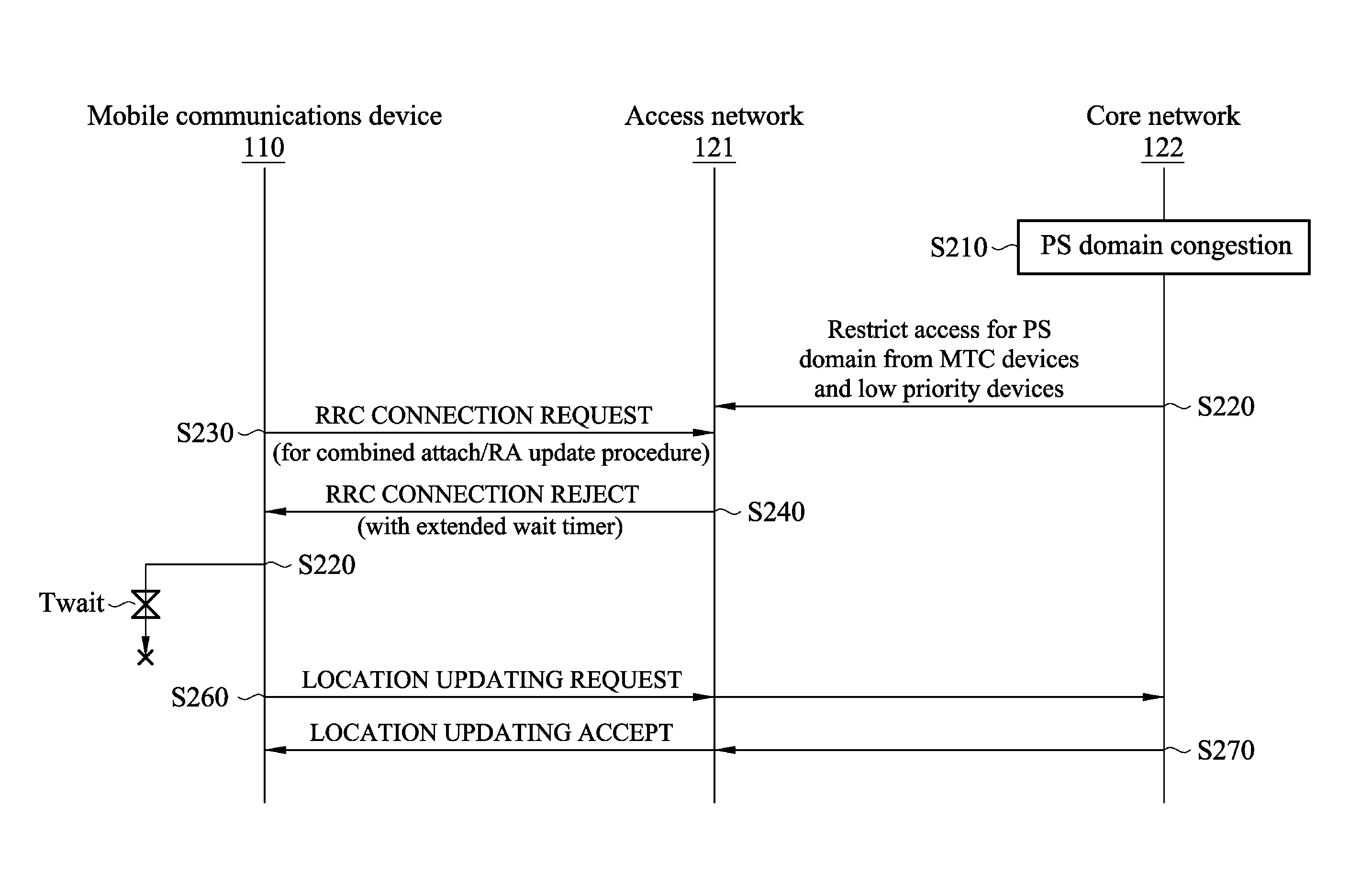
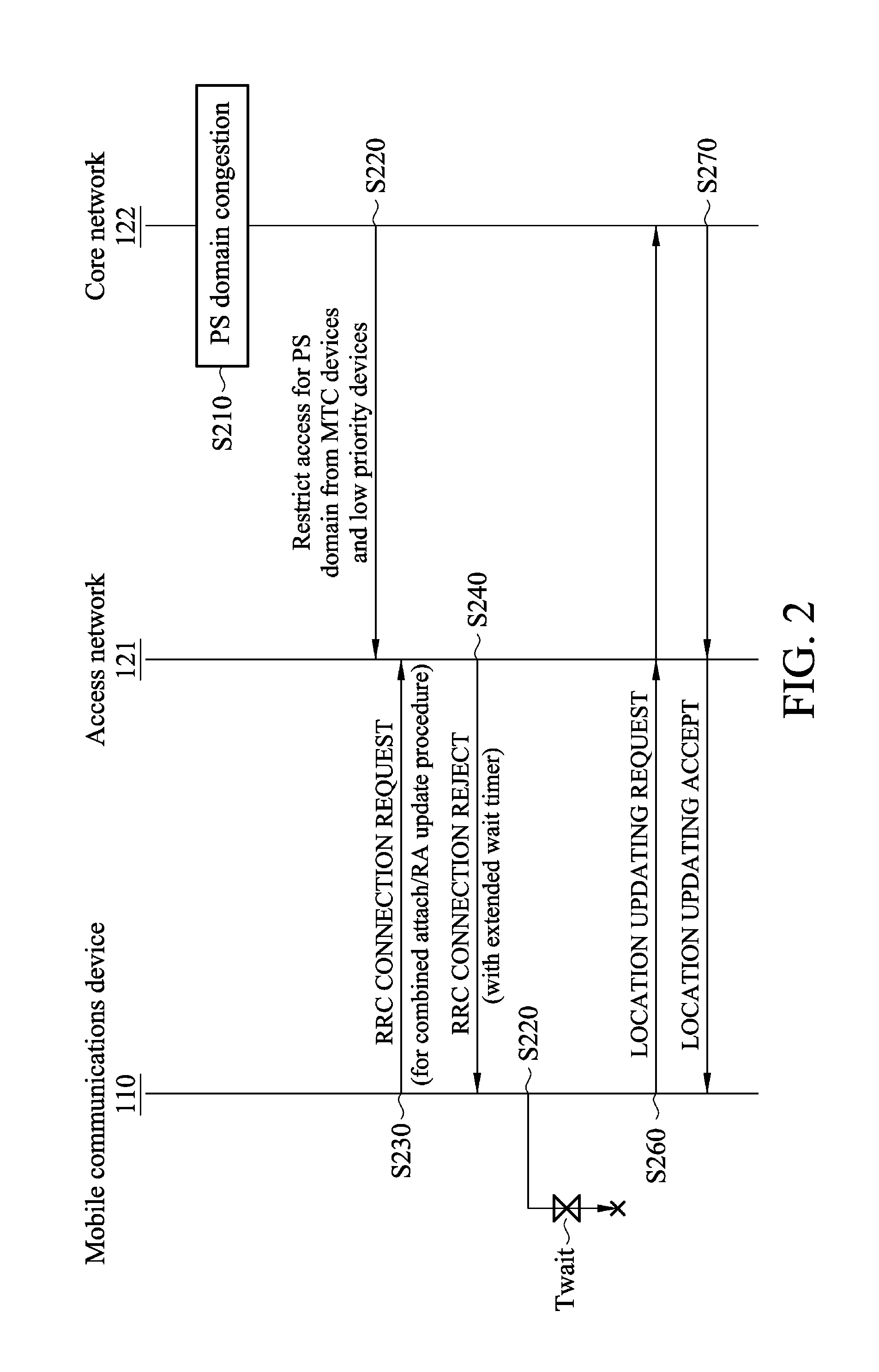
Methods for congestion control for machine type communication (MTC) devices or low priority devices, and apparatuses using the same
ActiveUS20120155257A1Limited accessError preventionFrequency-division multiplex detailsWireless transmissionPacket switched
A mobile communication device configured for Machine Type Communication (MTC) or configured as a low priority device is provided. In the mobile communication device, a wireless module performs wireless transmissions and receptions to and from a service network, and a controller module transmits a connection request message to the service network via the wireless module in response to initiating a combined attachment procedure or a combined routing area update procedure for both Packet-Switched (PS) and Circuit-Switched (CS) domains, and receives a connection rejection message with an indication of an extended wait timer from the service network via the wireless module. Also, the controller module initiates a location registration procedure for the CS domain or enters a substate in which initiation of the location registration procedure for the CS domain is allowed, in response to the connection rejection message for the PS domain.
Owner:HTC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com