Machine learning-based physical layer channel authentication method
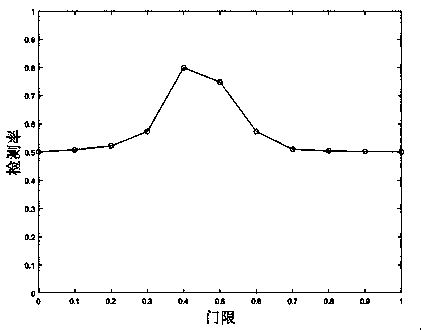
A physical layer channel and machine learning technology, which is applied in the direction of instruments, computer components, character and pattern recognition, etc., can solve the problems that affect the authentication accuracy and the threshold value is difficult to determine
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the following description.
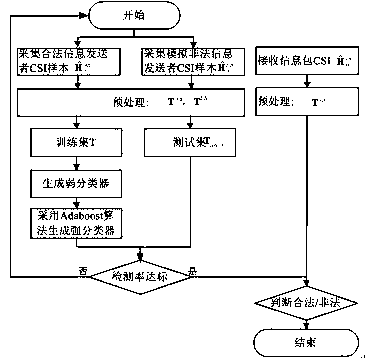
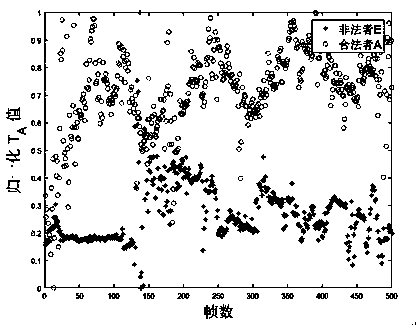
[0064] The present invention is implemented in an actual environment with a plurality of illegal nodes and legal nodes. First, the receiver B collects channel information (CSI) of information packets from the legal information sender A and the simulated illegal information sender E, so as to ensure the The maximum time difference between is within the coherence time, and the generated classifier takes the AdaBoost classifier as an example.
[0065] Such as figure 1 Shown, a kind of physical layer channel authentication method based on machine learning comprises the following steps:
[0066] S1. Receiver B carries out channel information (CSI) collection of information packet to legal information sender A and simulation illegal information ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com