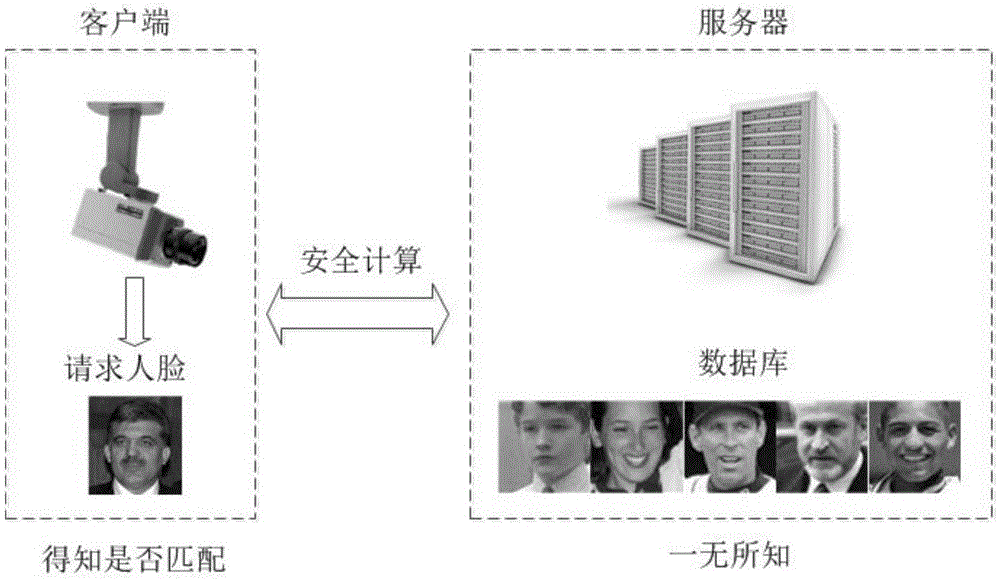
Design method of safety face verification system based on CNN (convolutional neural network) feature extractor
A feature extraction and authentication system technology, which is applied in the Paillier algorithm and inadvertent transmission protocol for encryption, biometric authentication and encryption fields, can solve the problems of low authentication rate, limited accuracy of authentication algorithm, attacks, etc., to achieve the removal of noise influence, authentication The effect of high accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] In order to achieve the above problems, the present invention provides a method for designing a security authentication system based on deep facial features. The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
[0044] The method specifically includes:
[0045] Preparatory stage
[0046] 1. Design a CNN network structure
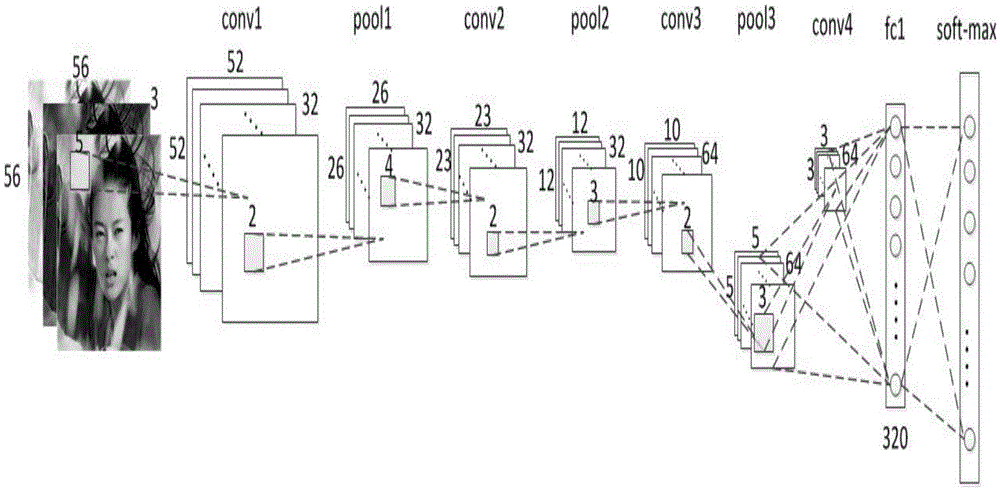
[0047] The CNN structure that the present invention adopts is as figure 2 shown. The network consists of 4 convolutional layers, 1 fully connected layer, and a softmax layer. The first three convolutional layers are followed by a pooling layer, and the activation function of neurons uses the ReLU function. The input is an RGB color image set to 56*56. The side length of the rectangle in the figure indicates the size of the featuremap and the filter, and the number of rectangles indicates the number of featuremaps. Since the higher the number of convolutional layers, the m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com