Patents
Literature
37 results about "Death certificate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The phrase death certificate can refer either to a document issued by a medical practitioner certifying the deceased state of a person or, popularly, to a document issued by a person such as a registrar of vital statistics that declares the date, location and cause of a person's death as later entered in an official register of deaths.
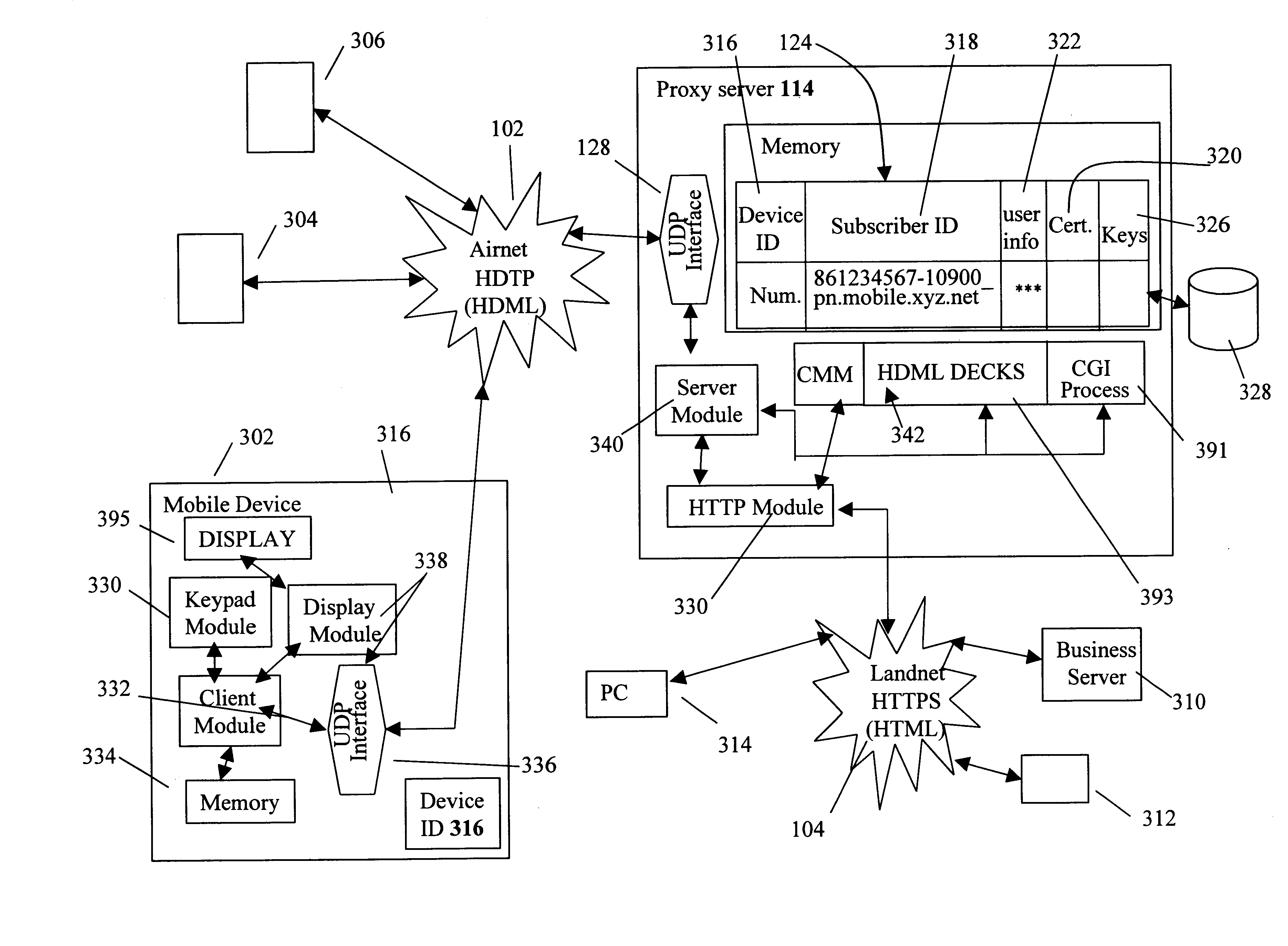
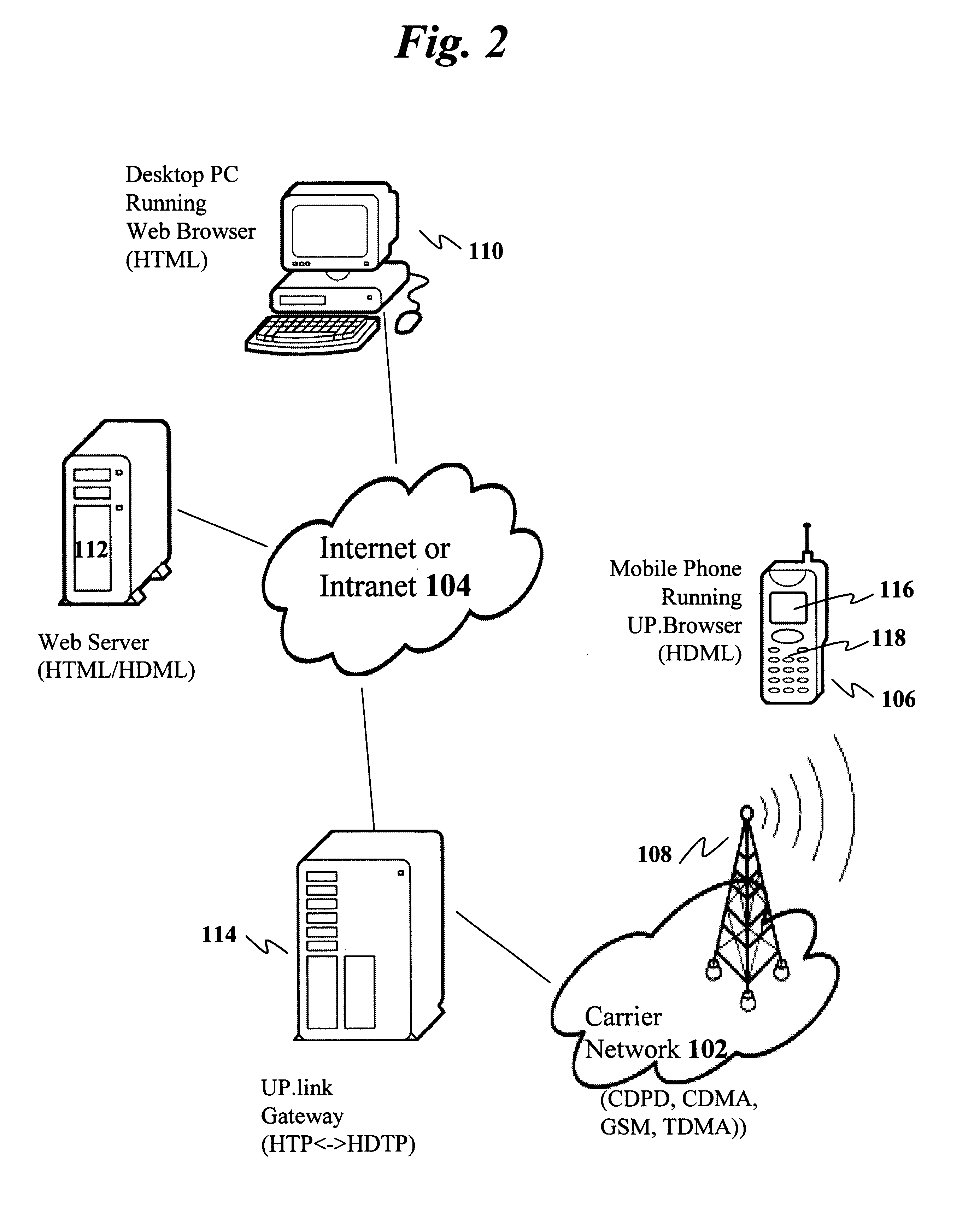
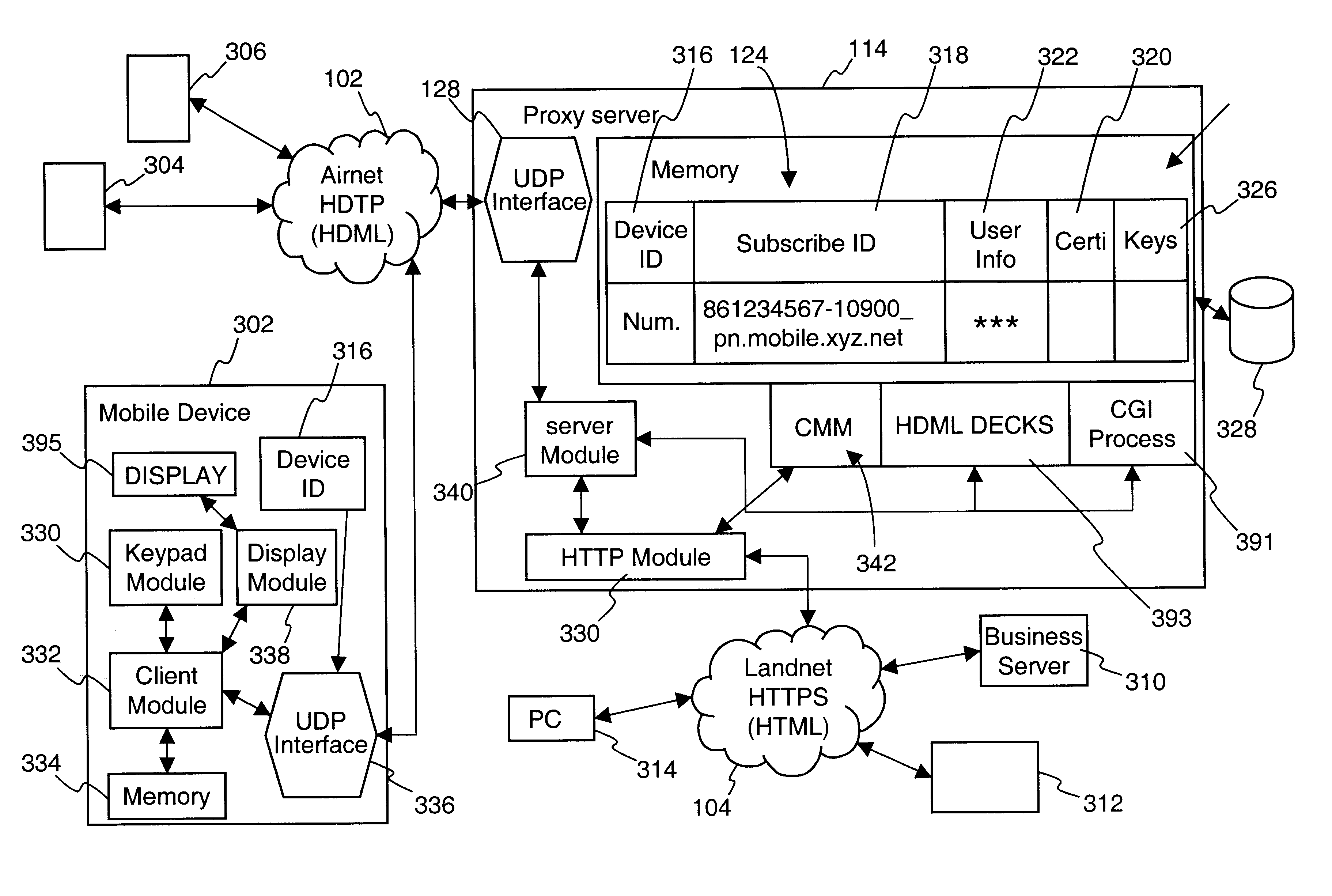
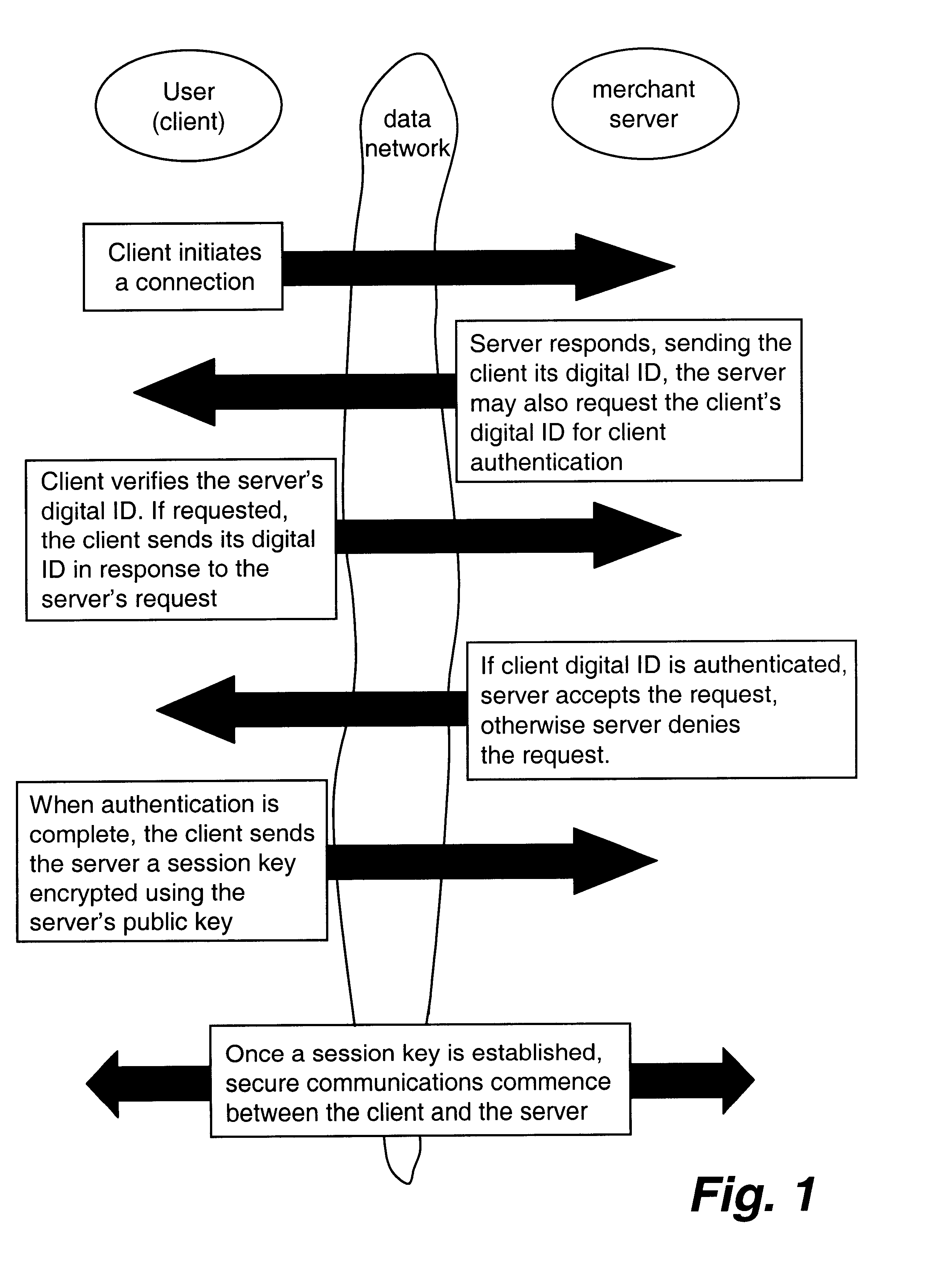
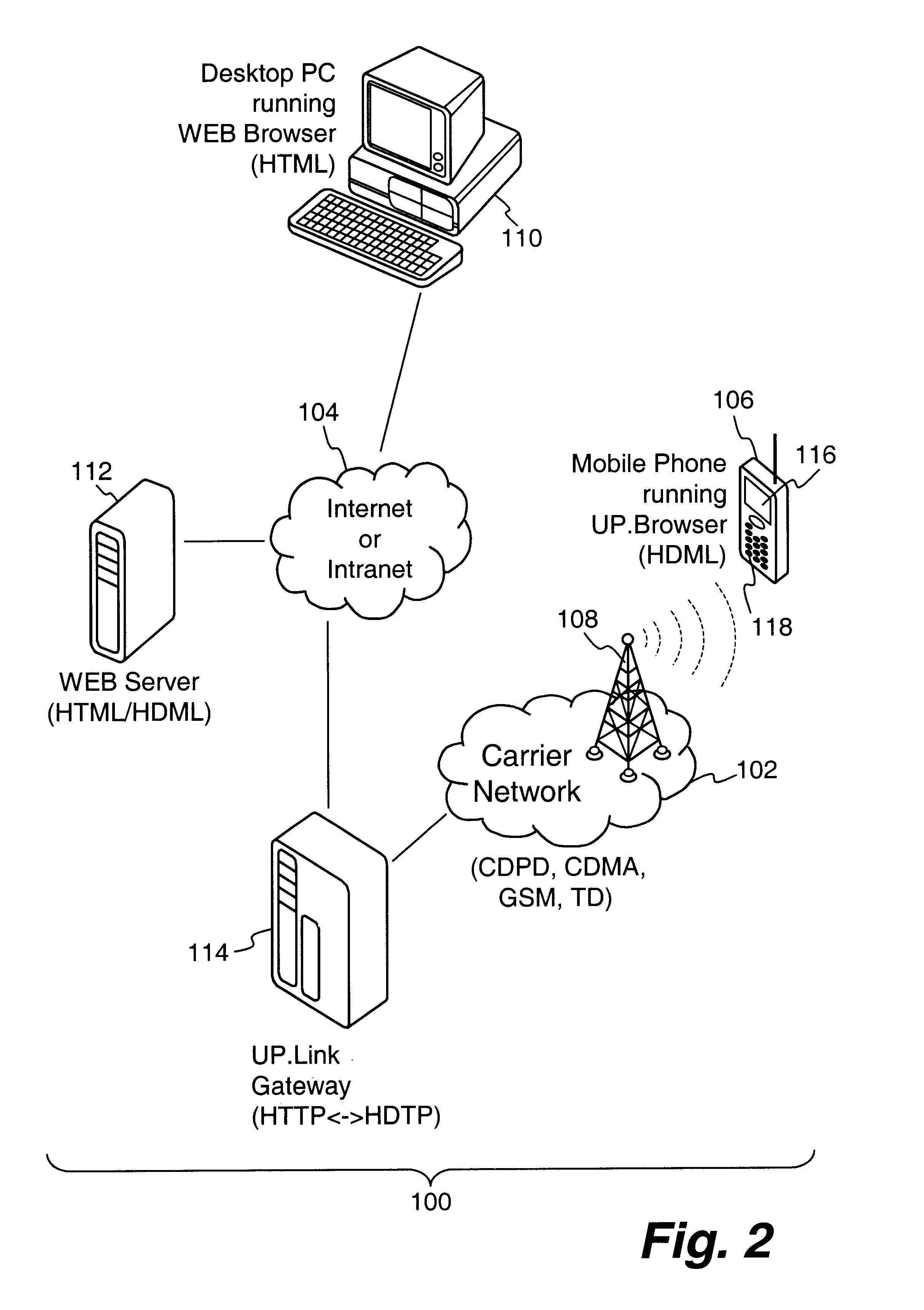
Centralized certificate management system for two-way interactive communication devices in data networks
InactiveUS6233577B1Key distribution for secure communicationData processing applicationsServer applianceCommunication device
The present invention discloses a central certificate management system for thin client devices in data networks and has particular applications to systems having a large number of the thin clients serviced by a proxy server through which the thin clients communicate with a plurality of secure server computers over a data network. According to one aspect, the present invention provides a certificate management module that causes the server device to manage digital certificates for each of the thin client devices. To minimize the latency of obtaining certificates for each of the thin client devices, the certificate management module reserves a fixed number of free certificates signed by a certificate authority and their respective private keys in a certificate database and frequently updates the free certificate according to a certificate updating message. Whenever a user account is created for a thin client device, the certificate management module fetches one or more free certificates from the certificate database and associate the fetched certificates to the created account and meanwhile the certificate management module creates new free certificates with the certificate authority to fill in the certificate database. Apart from the tradition of obtaining certificates locally in client devices that normally have sufficient computing power, the present invention uses the computing resources in a server device to carry out the task of obtaining and maintaining certificates asynchronously in the proxy server and further. These and other features in the present invention dramatically minimize the demands for computing power and memory in thin client devices like mobile devices, cellular phones, landline telephones or Internet appliance controllers.
Owner:UNWIRED PLANET
Centralized certificate management system for two-way interactive communication devices in data networks
InactiveUS6516316B1Key distribution for secure communicationData processing applicationsServer applianceCommunication device
The present invention discloses a centralized certificate management system for thin client devices in data networks and has particular applications to systems having a large number of the thin clients serviced by a proxy server through which the thin clients communicate with a plurality of secure server computers over a data network. According to one aspect, the present invention comprises a certificate management module that causes the server device to manage digital certificates for each of the thin client devices. To minimize the latency of obtaining certificates for each of the thin client devices, the certificate management module reserves a fixed number of free certificates signed by a certificate authority and their respective private keys in a certificate database and frequently updates the free certificate according to a certificate updating message. Whenever a user account is created for a thin client device, the certificate management module fetches one or more free certificates from the certificate database and associate the fetched certificates to the created account and meanwhile the certificate management module creates new free certificates with the certificate authority to fill in the certificate database. Apart from the tradition of obtaining certificates locally in client devices that normally have sufficient computing power, the present invention uses the computing resources in a server device to carry out the task of obtaining and maintaining certificates asynchronously in the proxy server and further. These and other features in the present invention dramatically minimize the demands for computing power and memory in thin client devices like mobile devices, cellular phones, landline telephones or Internet appliance controllers.
Owner:UNWIRED PLANET
Foam security substrate
InactiveUS20050104365A1Deter counterfeitingImprove melt strengthOther printing matterDuplicating/marking methodsPolymer sciencePaper document
Owner:3M INNOVATIVE PROPERTIES CO
Foam security substrate
InactiveUS7820282B2Deter counterfeitingIncreased durabilitySynthetic resin layered productsPaper articlesPolymer sciencePaper document
Owner:3M INNOVATIVE PROPERTIES CO
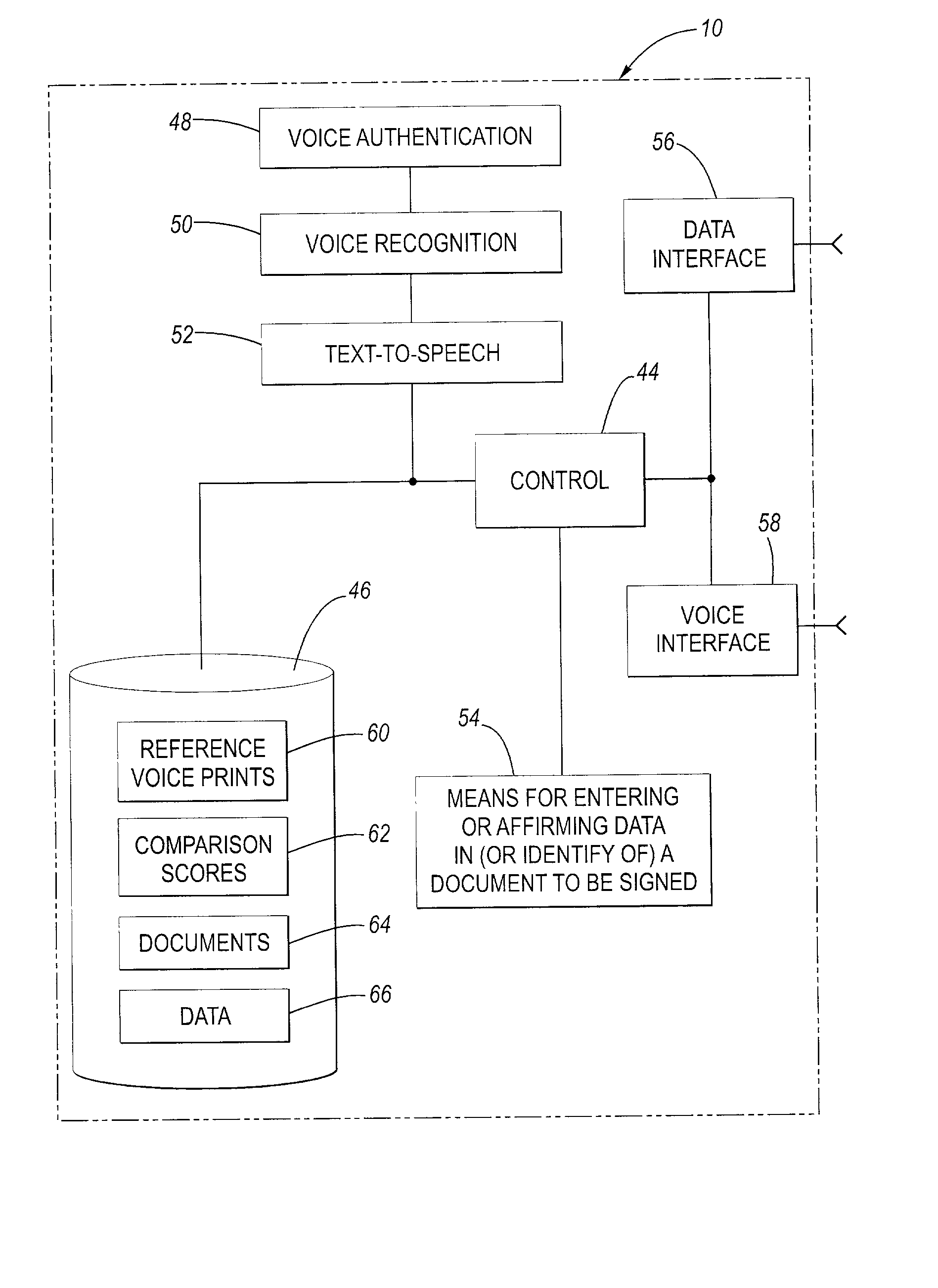
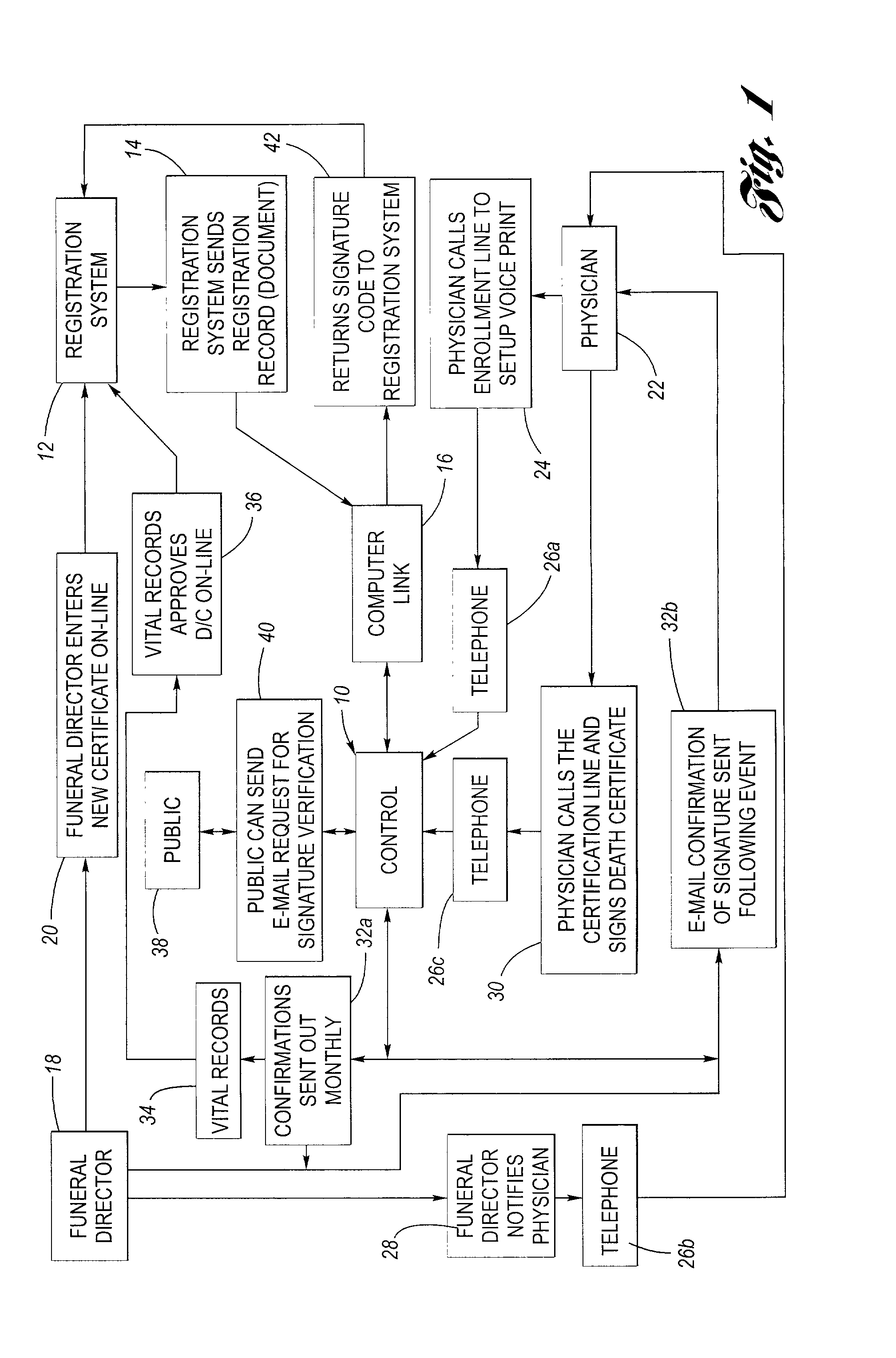
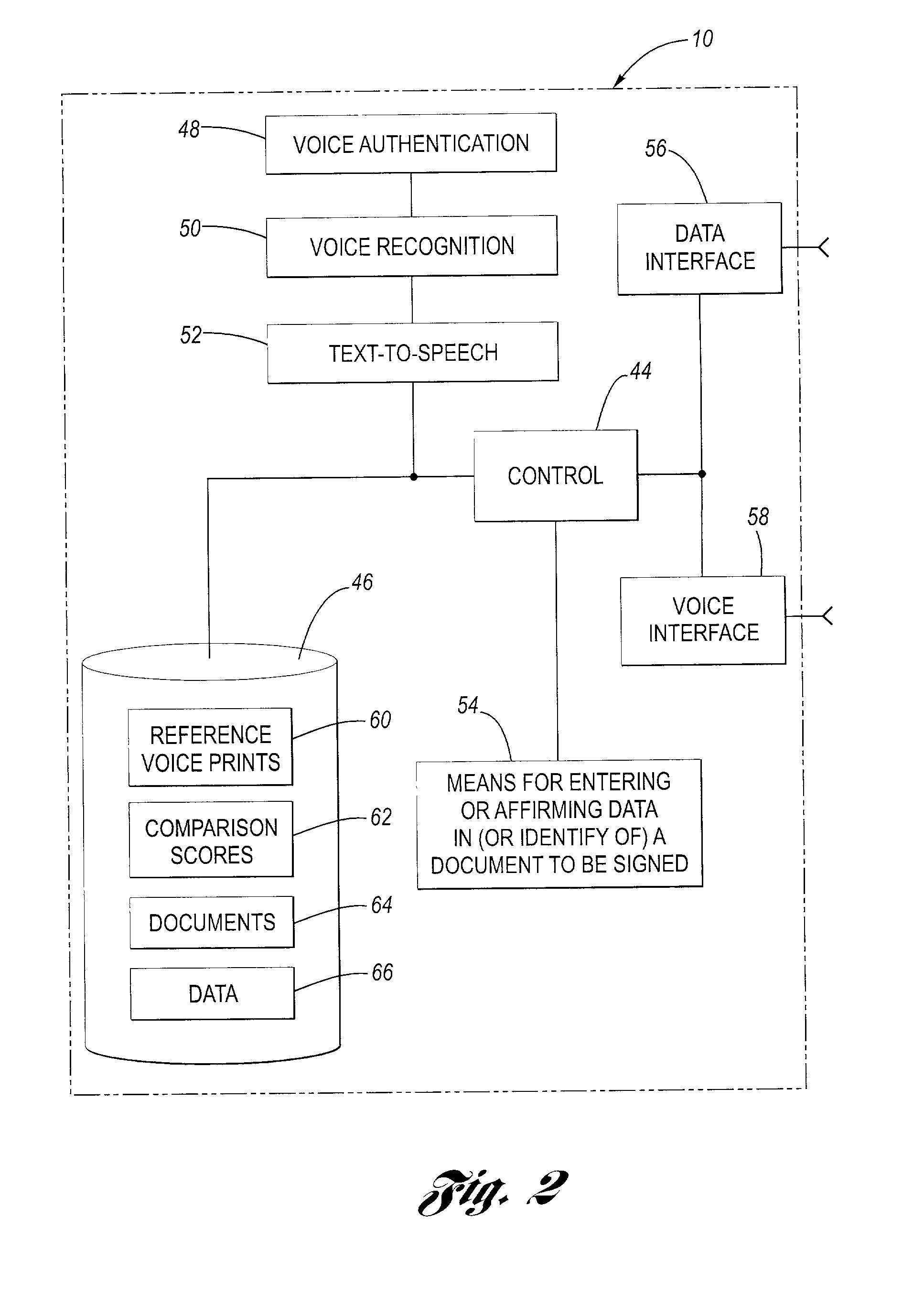
Telephonic certification of electronic death registration
InactiveUS20020128844A1Use and accurate and secure and rapidFacilitate entering or affirming dataUser identity/authority verificationSpeech analysisUsabilitySpeech verification
A system for facilitating an electronic signature of a document such as a death certificate includes a voice authentication unit, a voice recognition and a database for storing information relating to the electronic signature ceremony. The system includes an enrollment interface to telephonically receive a reference voiceprint from a future signer of the death certificate, for example a physician. The system is further configured to receive an authentication voiceprint from the enrolled physician wherein the voice authentication unit compares the reference voiceprint and the authentication voiceprint to confirm identity. The system employs the voice recognition unit to allow the physician to telephonically perform at least one of the functions selected from the group including (i) identifying the death certificate, (ii) entering data into the death certificate, or (iii) affirming data that is in the death certificate. The system provides improved ease of use, more rapid and accurate signing of death certificates and is more secure than prior systems.
Owner:TELEPHONIC SIGNATURES
PKI (Public Key Infrastructure) implementation method based on safety certificate
InactiveCN102664739AKeep storage safeEnsure credibleUser identity/authority verificationCiphertextCryptographic protocol
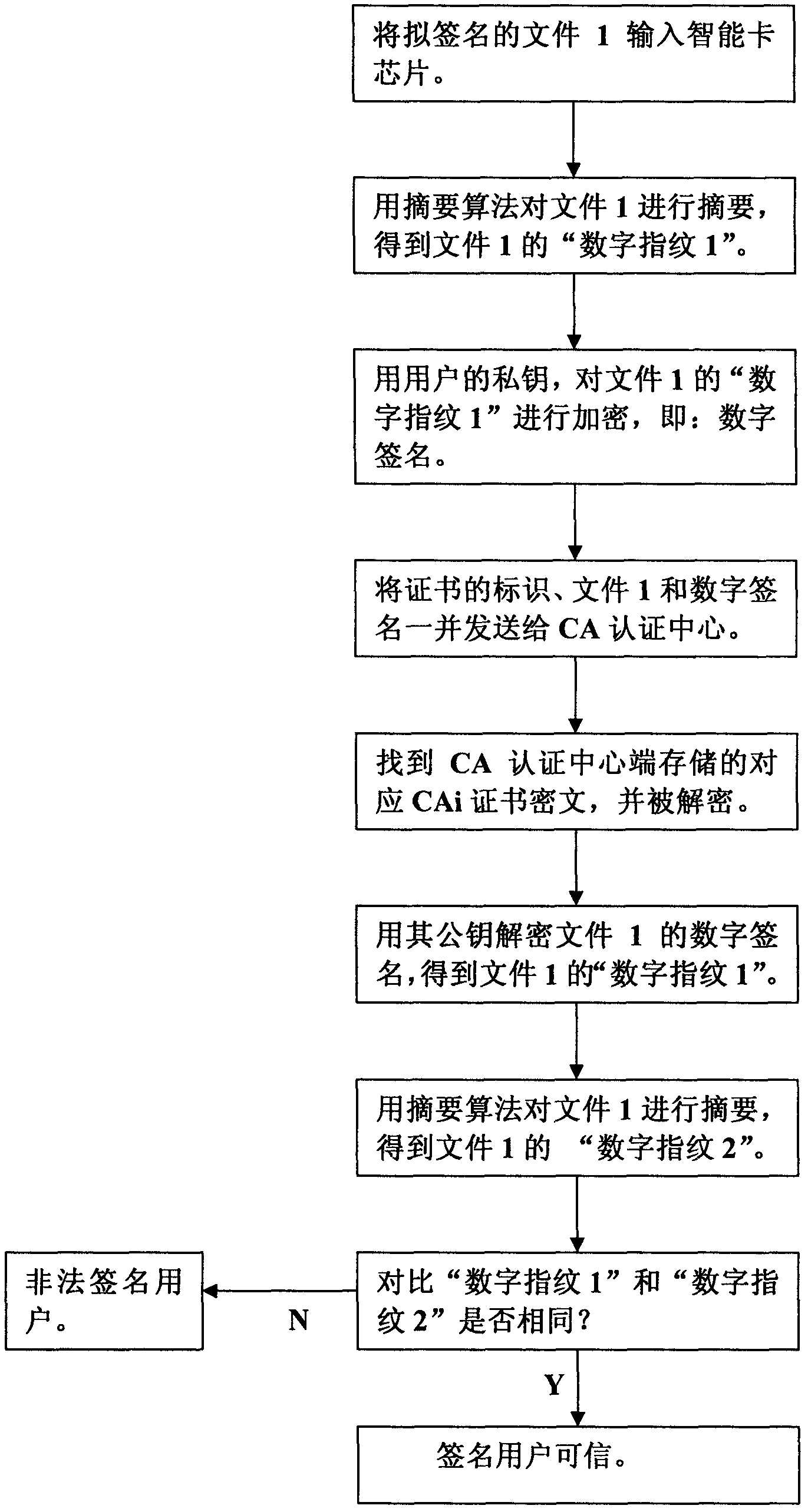
The invention discloses a PKI (Public Key Infrastructure) implementation method based on a safety certificate. The method comprises the following steps of: deploying an encryption card or encryption equipment hardware equipment on the end part of a CA (Certificate Authority); encrypting all final entity CA certificates in the CA into a cipher text for storing; storing each middle-class CA certificate and root CA certificate in a CA encryption card or a chip of the encryption equipment; generating a key in a safety protocol of the PKI and calling the key to encrypt or decrypt the certificate in the chip; establishing a 'chip-class' PKI safety protocol between a user terminal and a CA terminal; establishing a certificate safety detection protocol in the CA; and detecting the CA certificate in a full trusted link in the CA timely to prevent an attacker from tampering the CA certificate to establish a PKI system based on the safety certificate.
Owner:杜丽萍 +1
Method and system for managing certificates
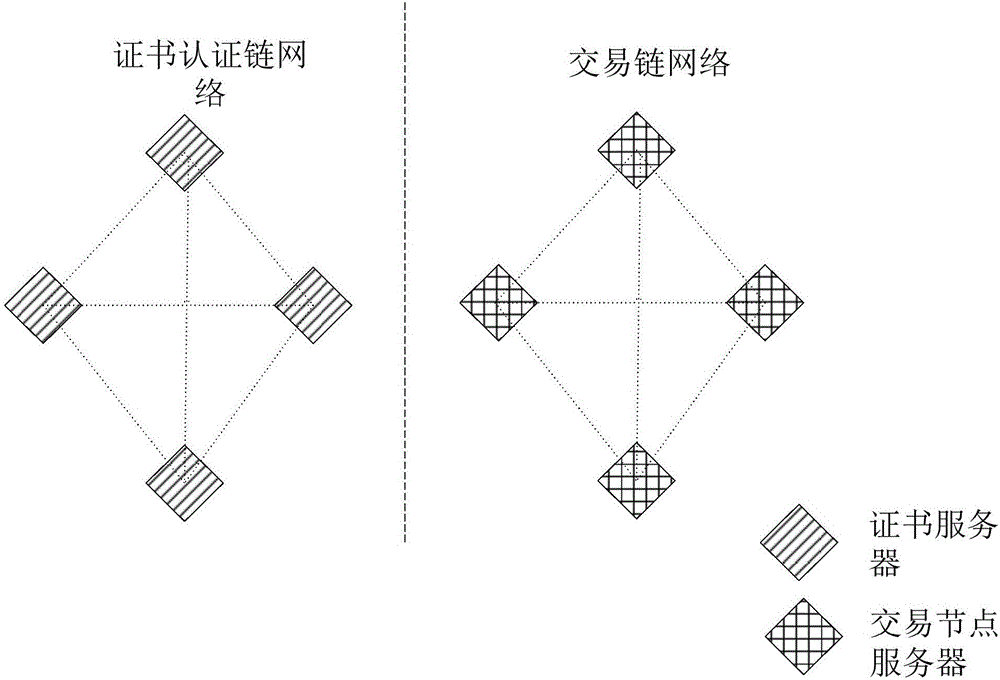
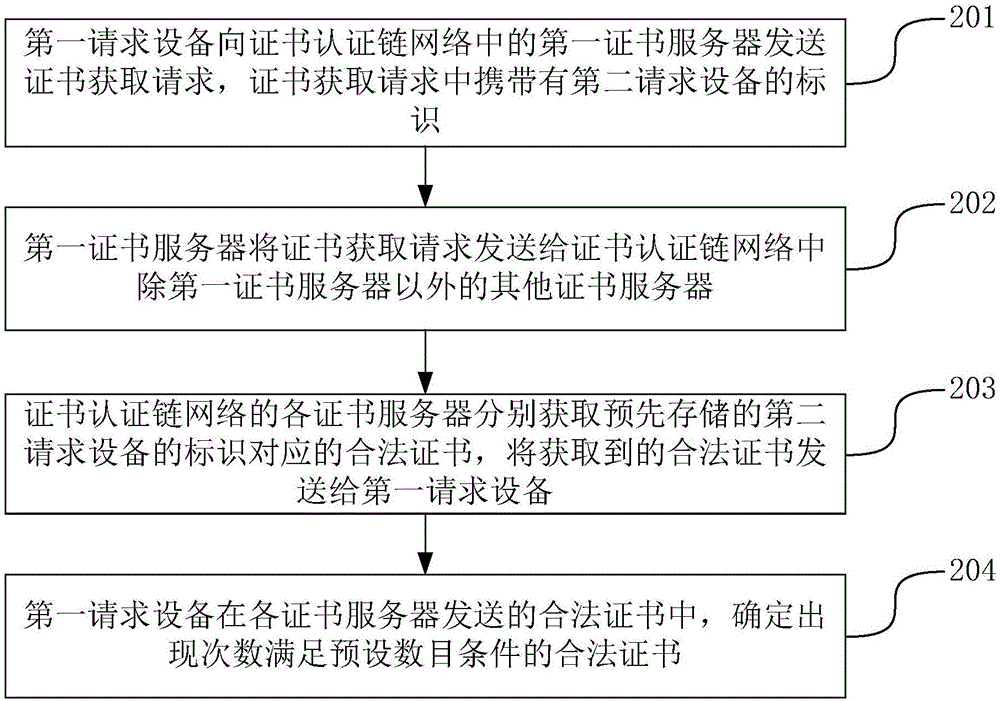
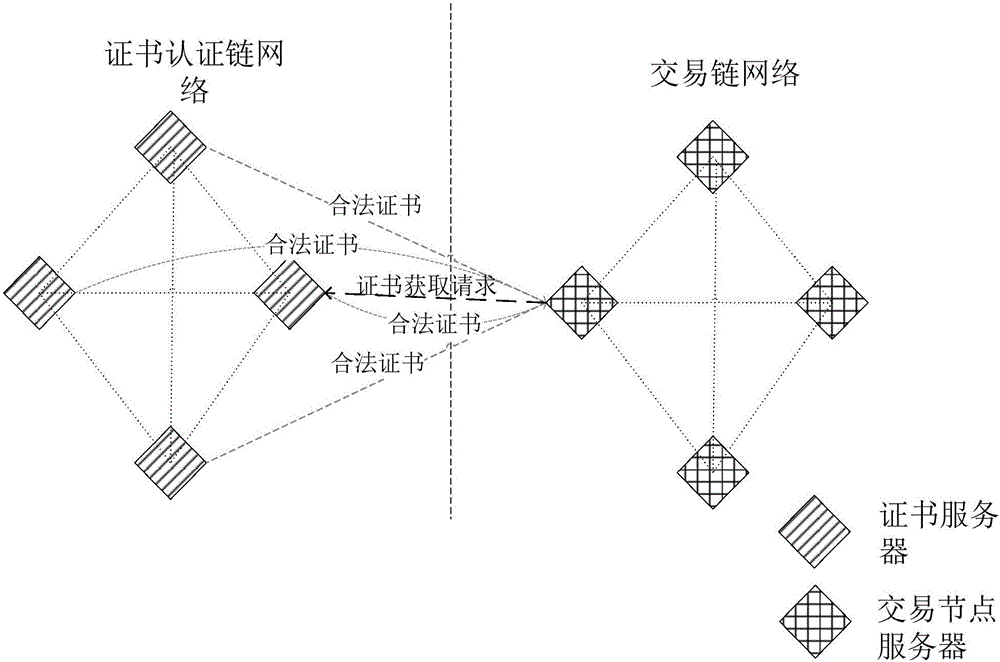
ActiveCN106789089ANormal transactionUser identity/authority verificationChain networkCertificate server
The invention discloses a method and system for managing certificates, and belongs to the technical field of computers. The method comprises the following steps that a certificate obtaining request sent by first requesting equipment is received, wherein the certificate obtaining request carries with an identifier of second requesting equipment; the certificate obtaining request is sent to other certificate servers in a certificate authentication chain network, a legal certificate corresponding to the prestored identifier of the second requesting equipment is obtained, the obtained legal certificate is sent to the first requesting equipment, and the first requesting equipment determines the legal certificates of which the occurrence numbers meet the preset number conditions in the legal certificates sent by the certificate servers. By adopting the method and system for managing the certificates, transactions in a block chain can be normally operated.
Owner:TENCENT TECH (SHENZHEN) CO LTD
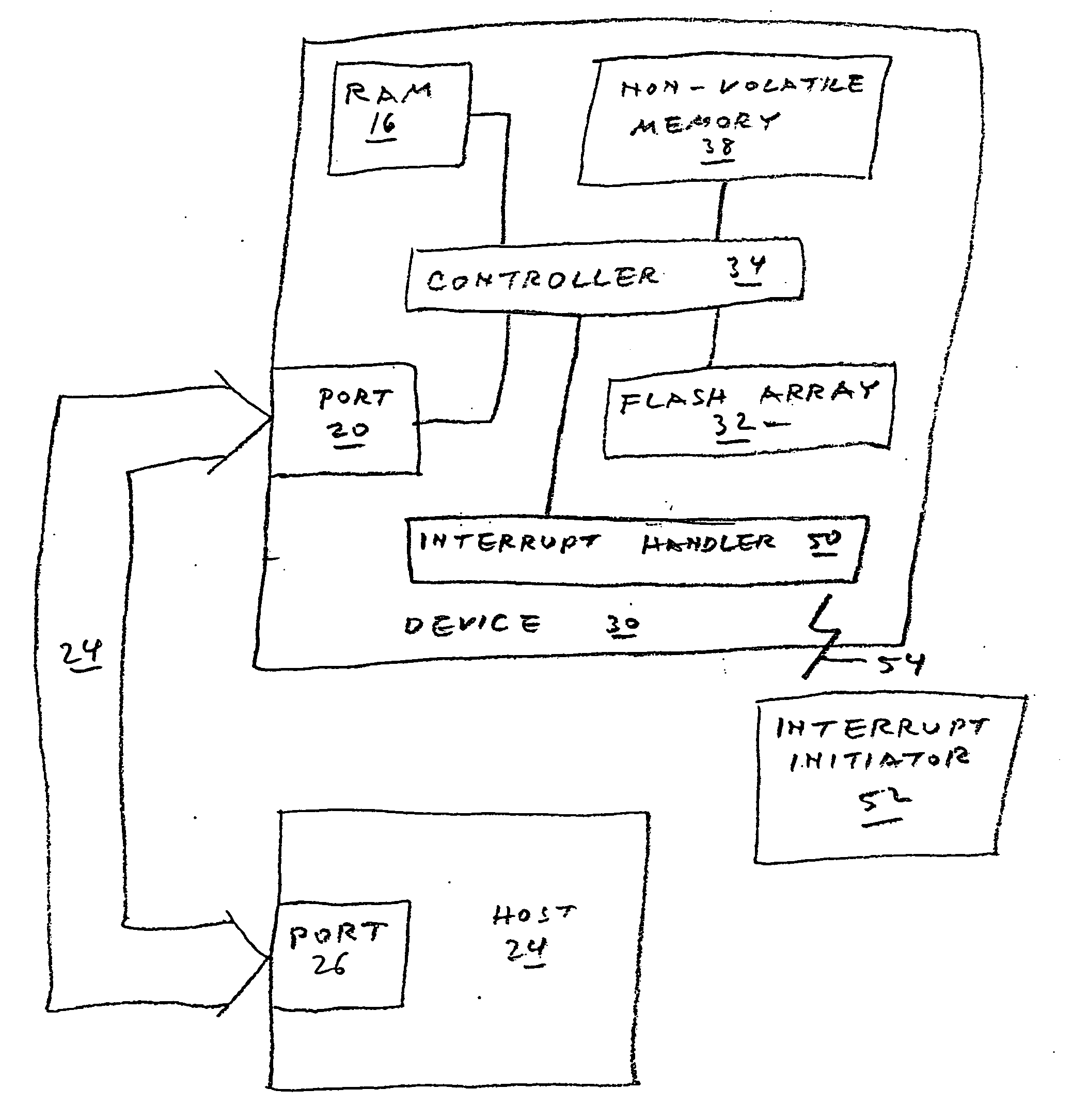
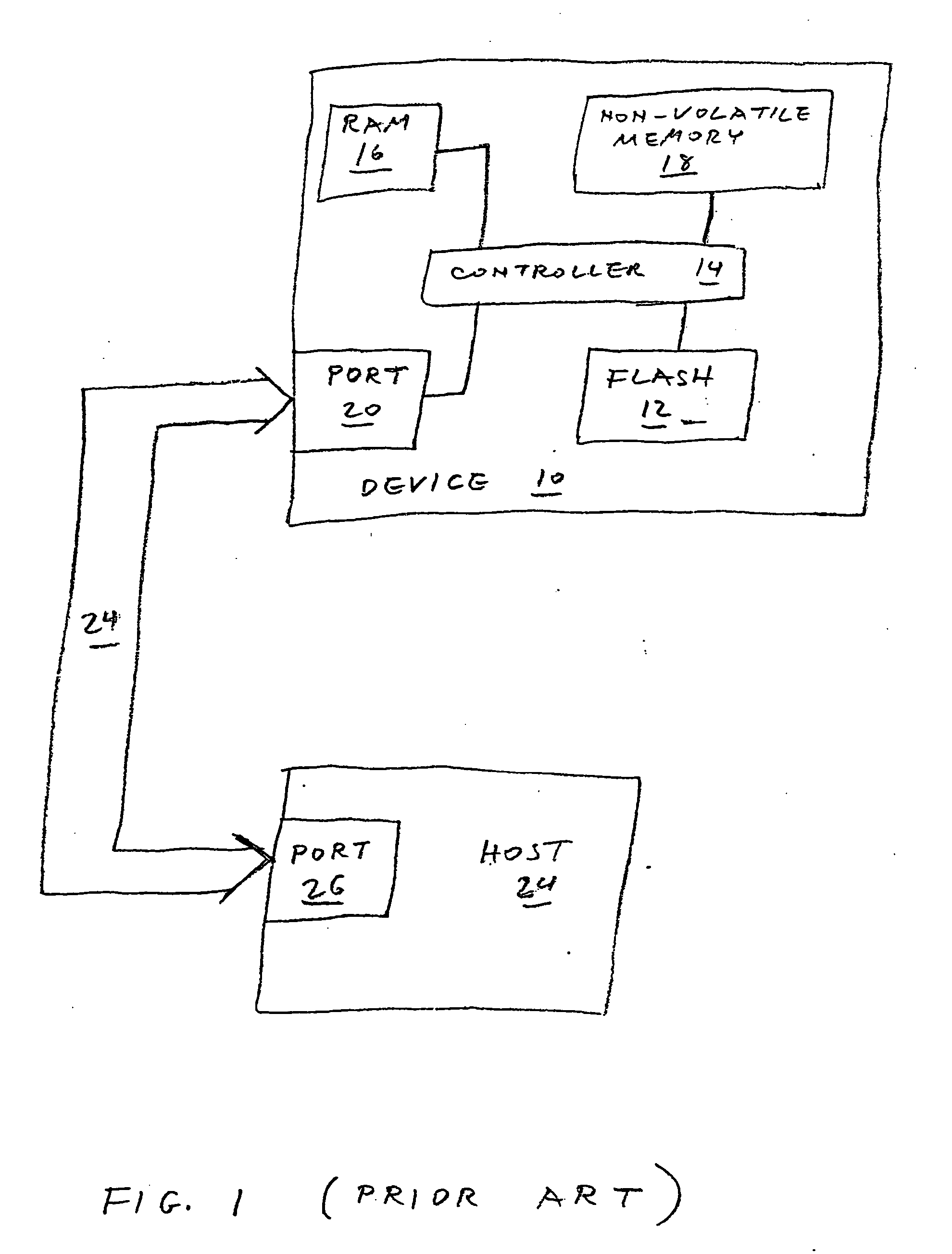
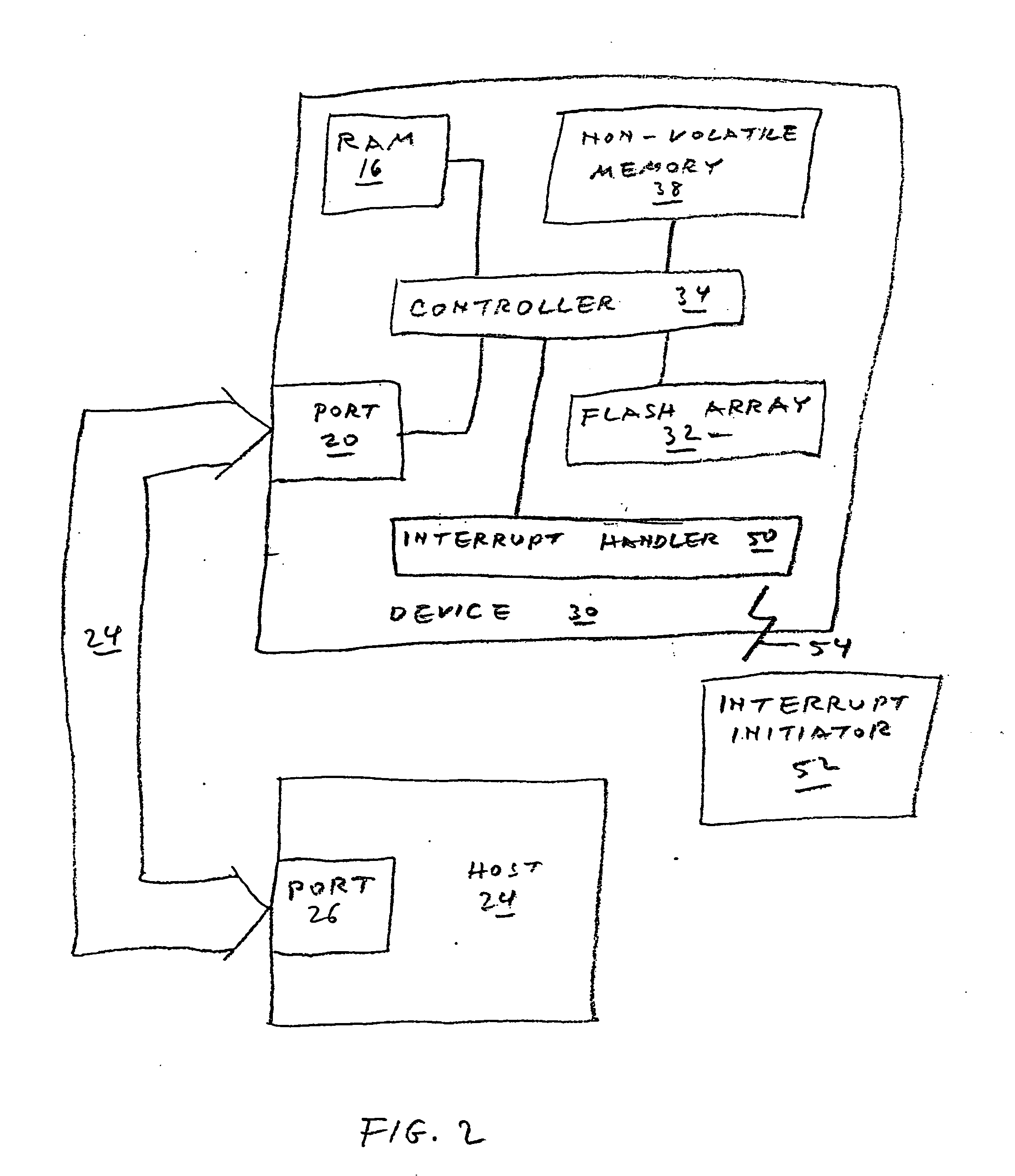
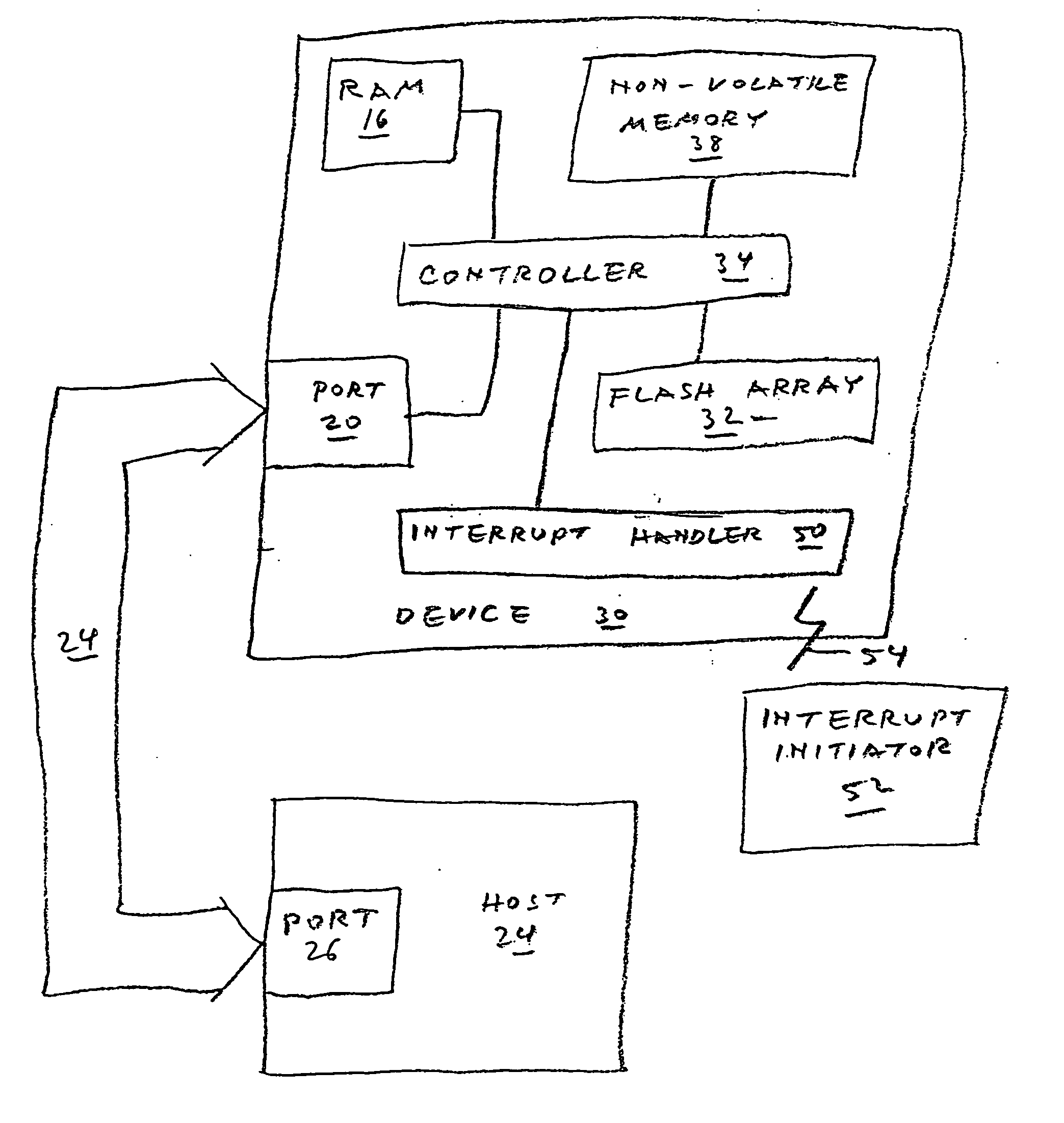
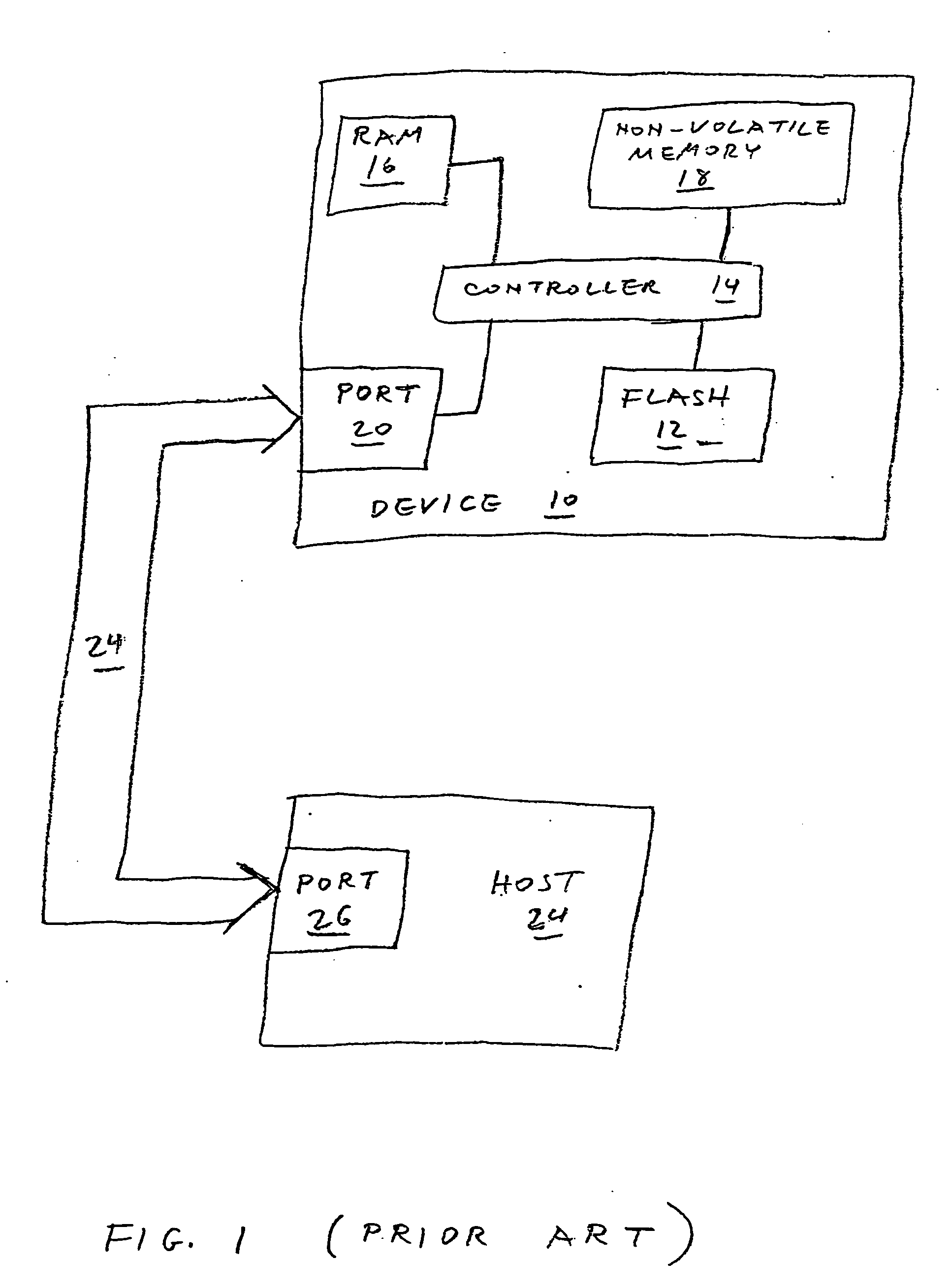
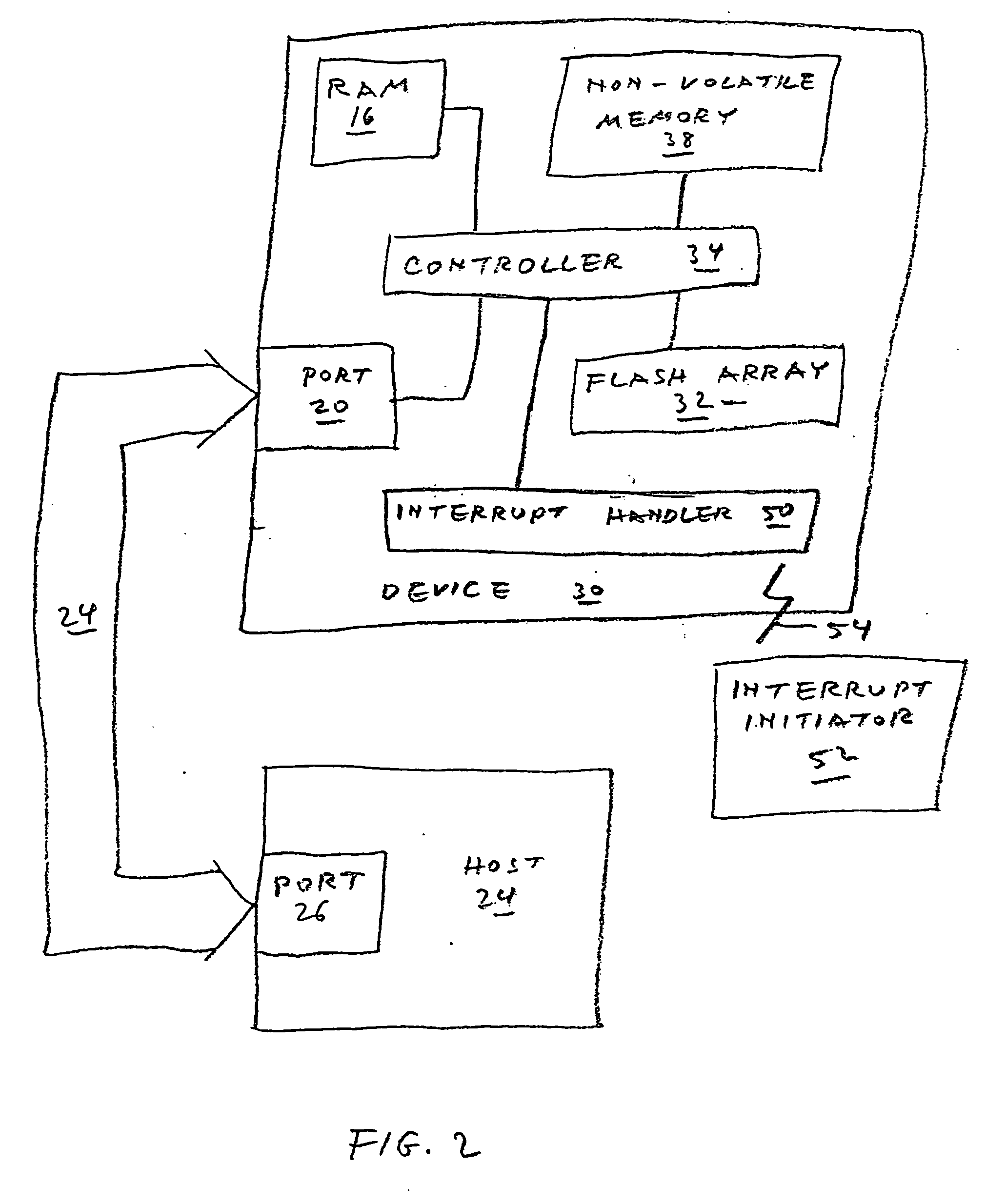
Methods of sanitizing a flash-based data storage device
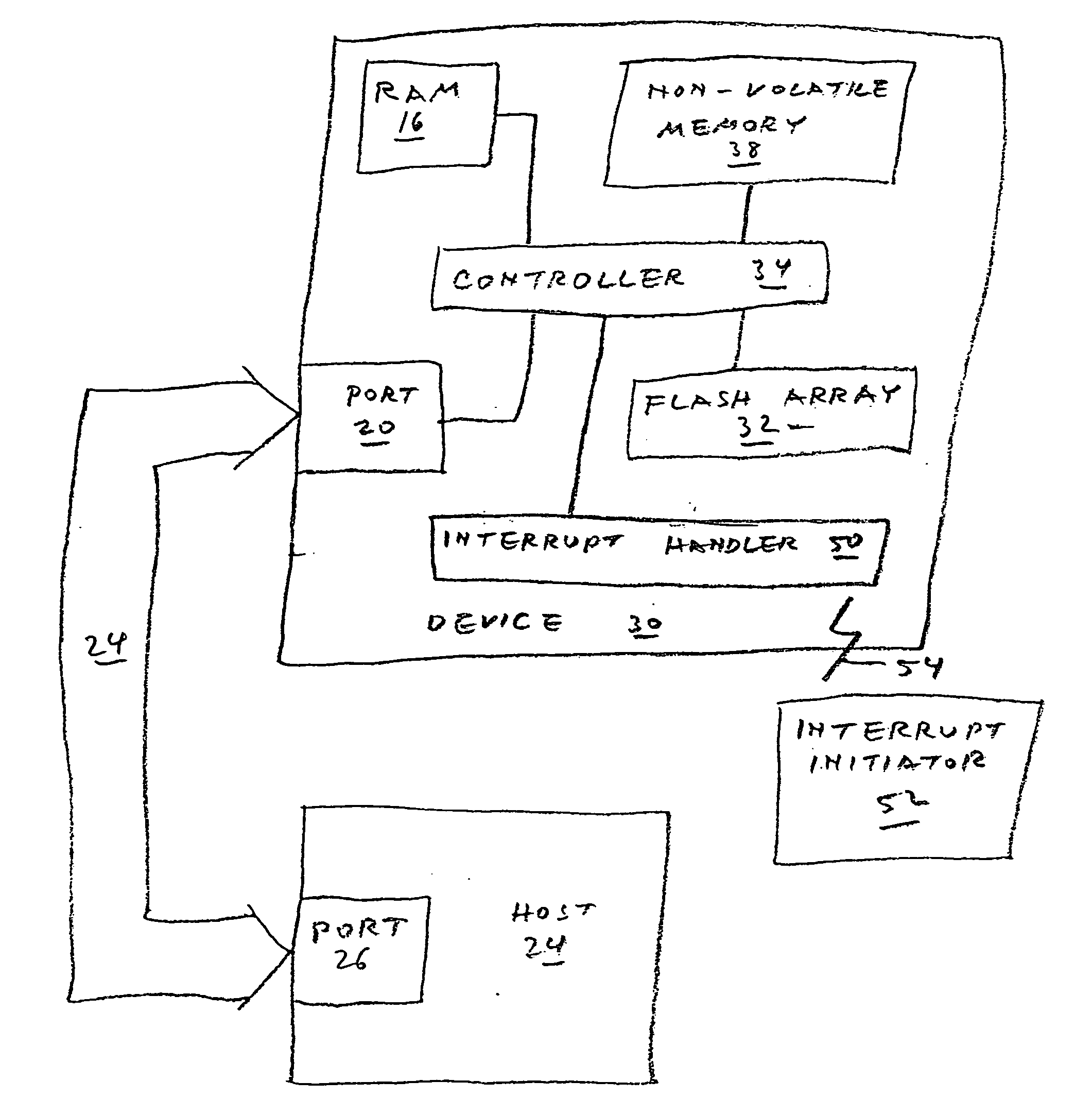
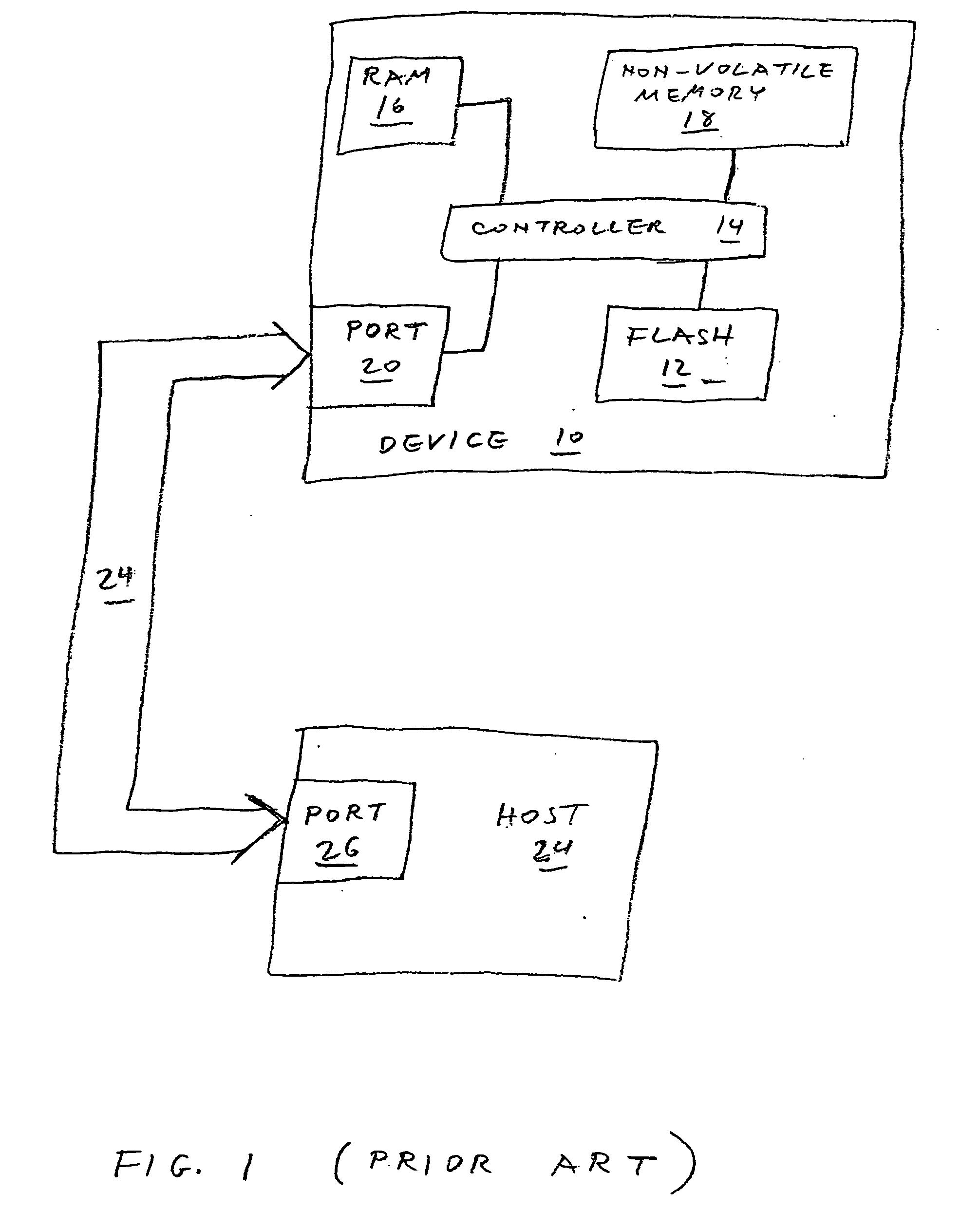
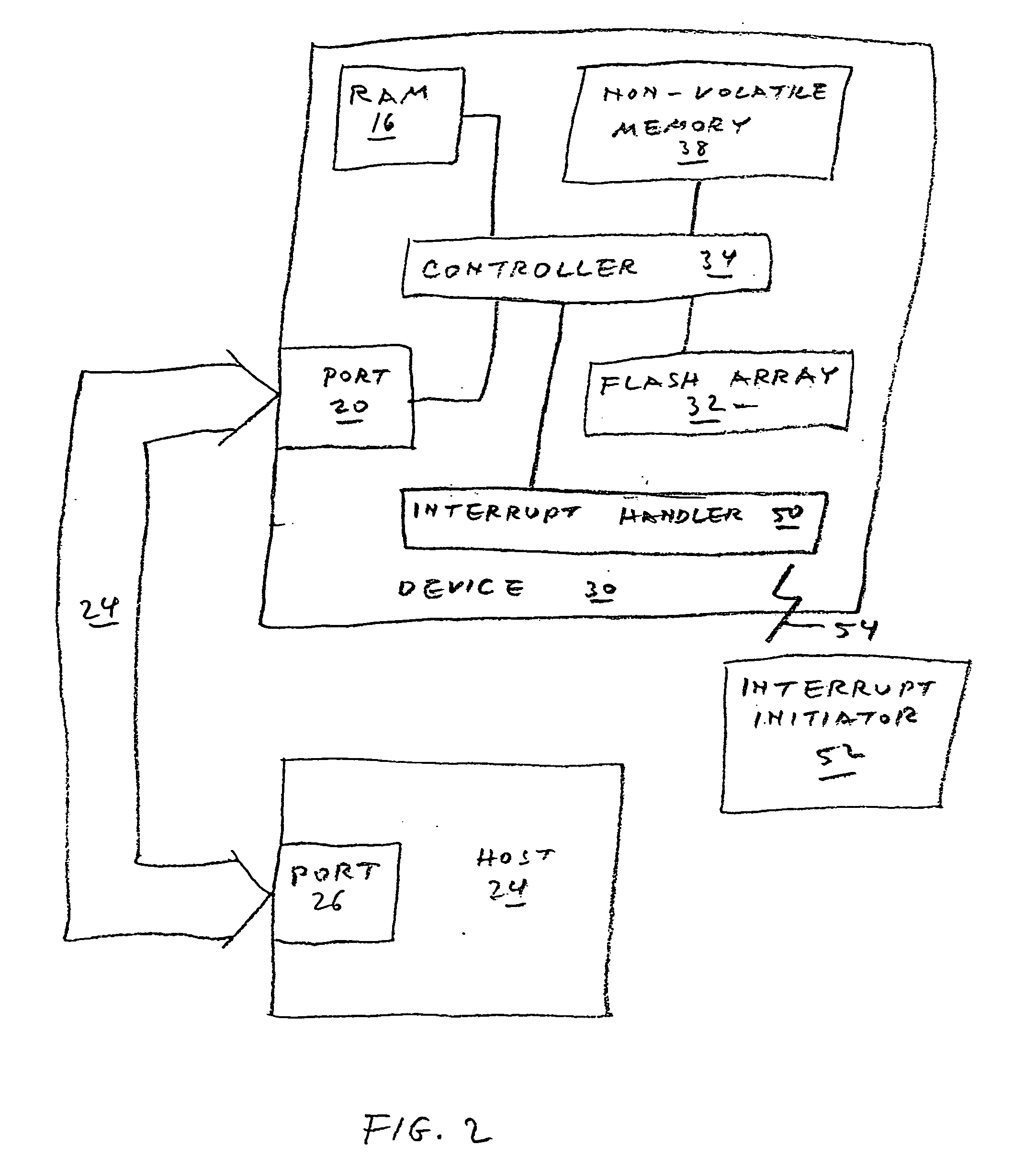
A data storage device includes one or more non-volatile, blockwise erasable data storage media and a mechanism for sanitizing the media in response to a single external stimulus or in response to a predetermined physical or logical condition. Optionally, only part of the media is sanitized, at a granularity finer than the blocks of the medium. Setting a flag in an auxiliary nonvolatile memory enables an interrupted sanitize to be detected and restarted. Optionally, a “death certificate” verifying the sanitizing is issued. Preferably, the media are configured in a manner that allows atomic operations of the sanitizing to be effected in parallel.
Owner:WESTERN DIGITAL ISRAEL LTD
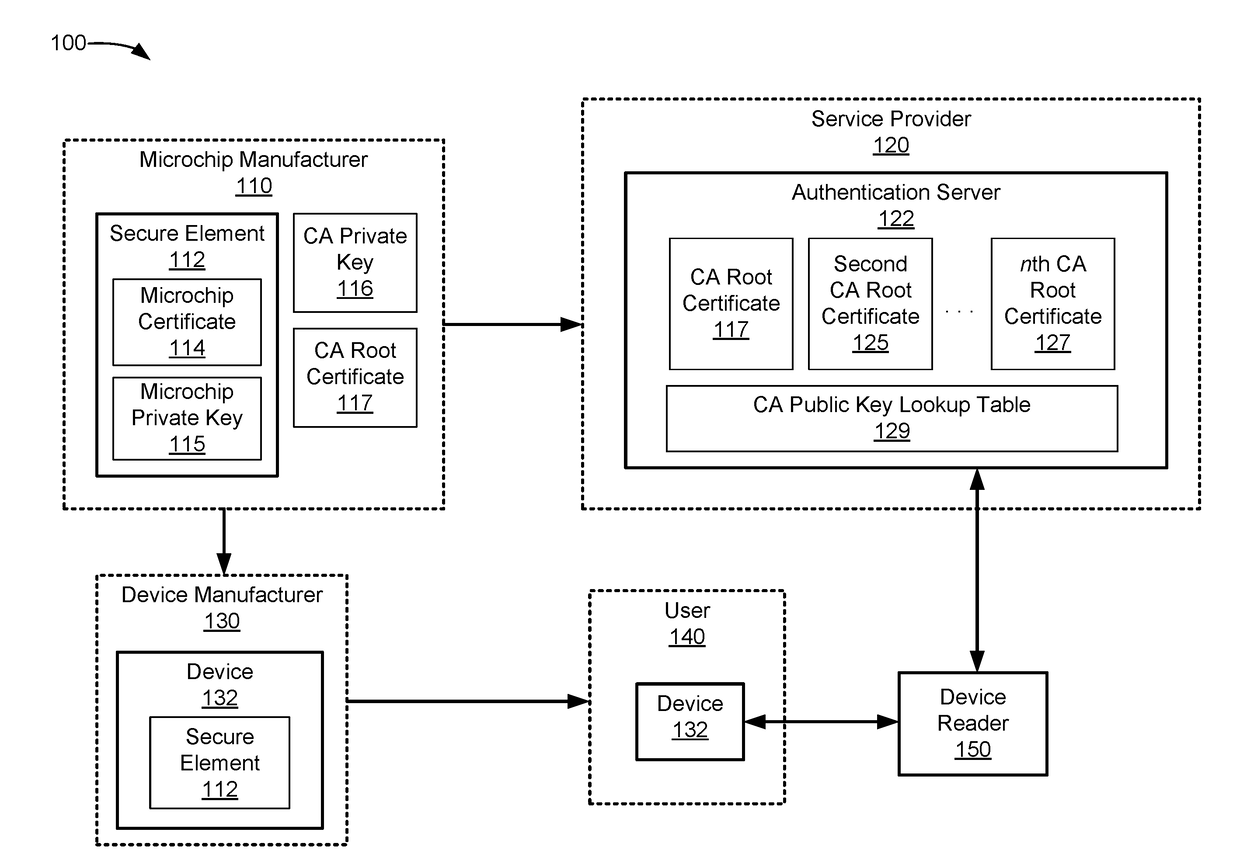
Systems and methods for certificate chain validation of secure elements
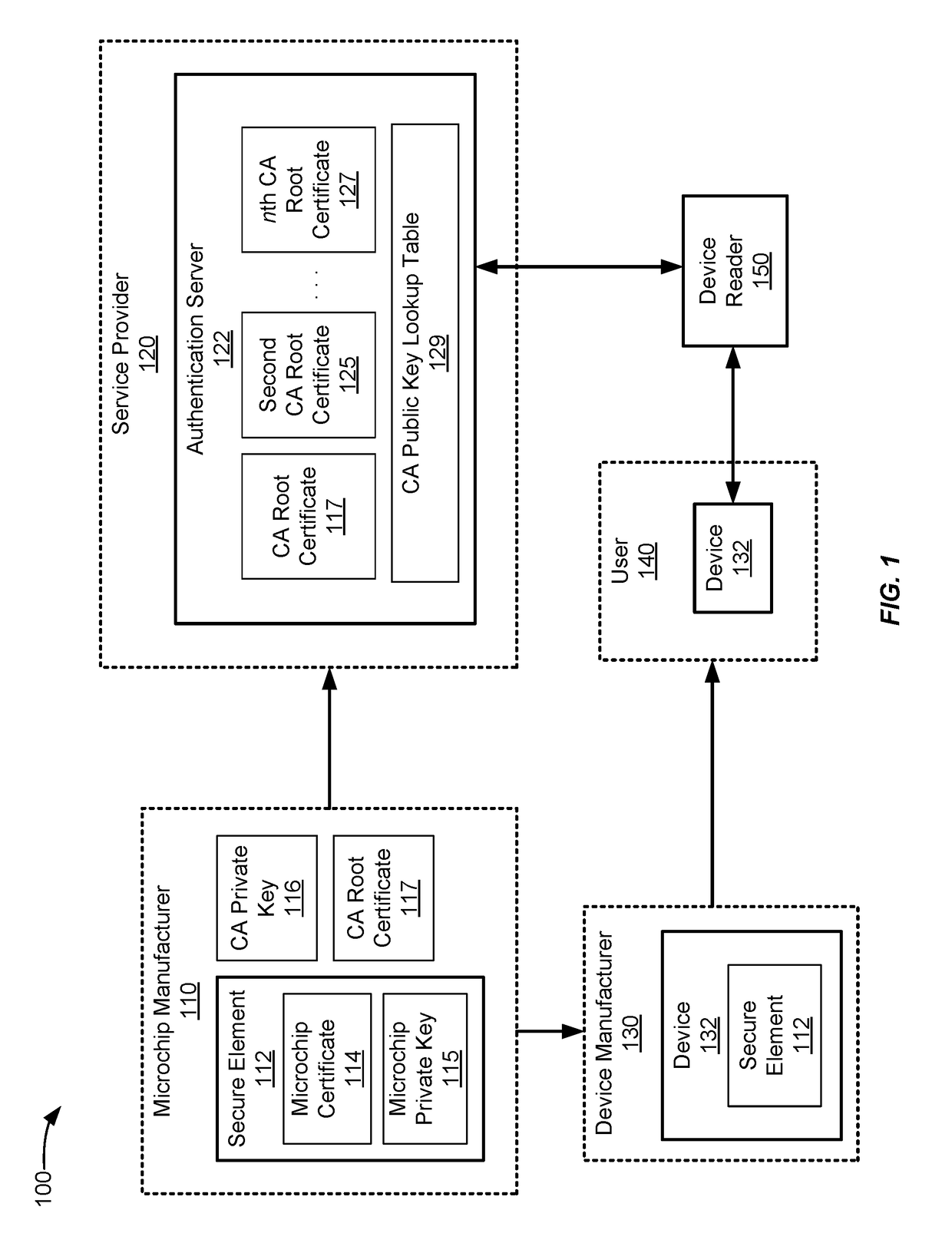
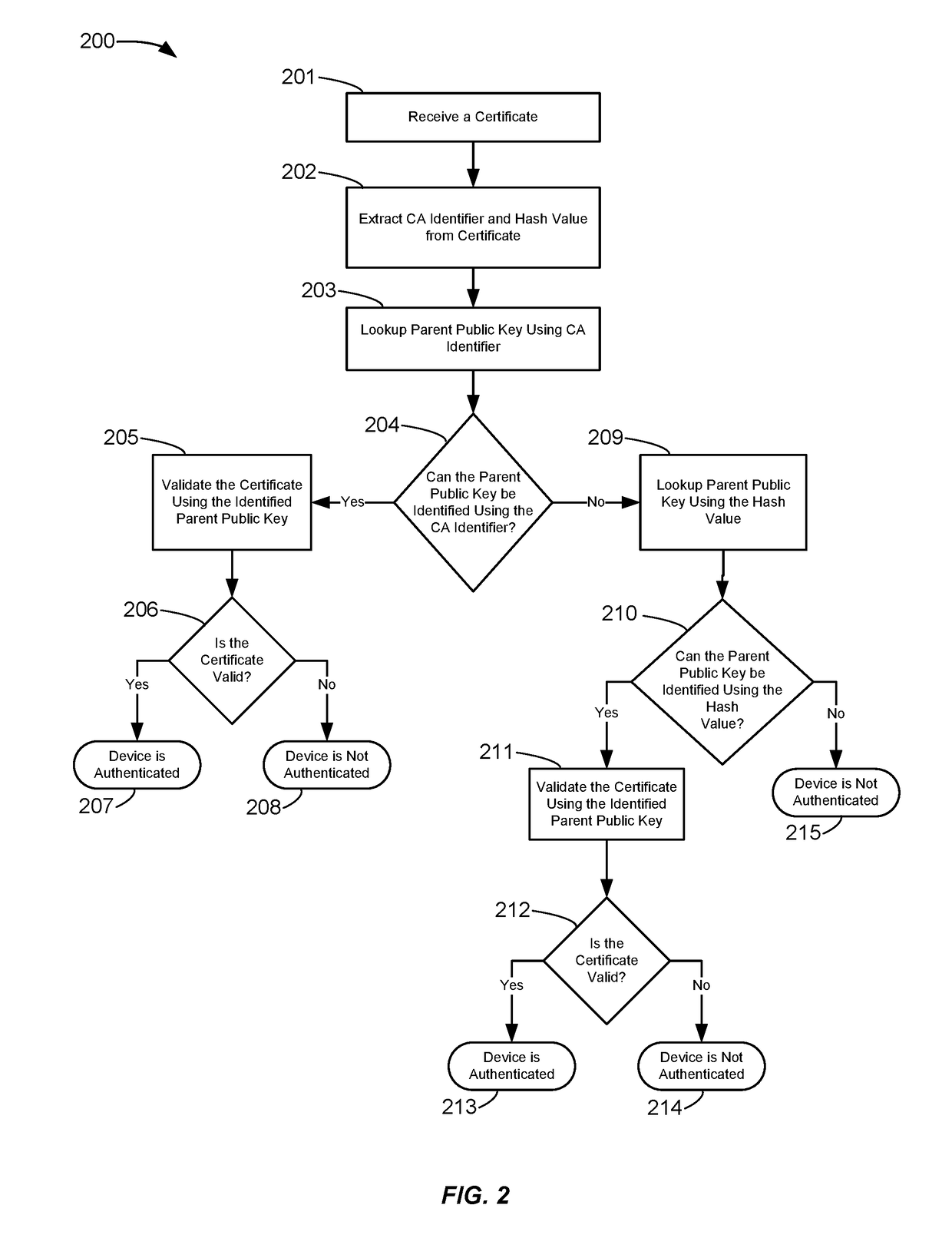
In certificate chain validation, a parent certificate is used to validate a child certificate. The child certificate can indicate which parent certificate can be used to validate it. In some situations, a child certificate may not contain a certificate authority identifier that can be used to identify the parent certificate. Instead, the child certificate can contain a hash value of a modulus of the parent public key that can be used to identify the parent certificate. The hash value of the modulus of the parent public key can be associated with the parent public key. As such, the parent public key used in certificate chain validation of the child certificate can be identified using the hash value of the modulus of the parent public key.
Owner:VISA INT SERVICE ASSOC
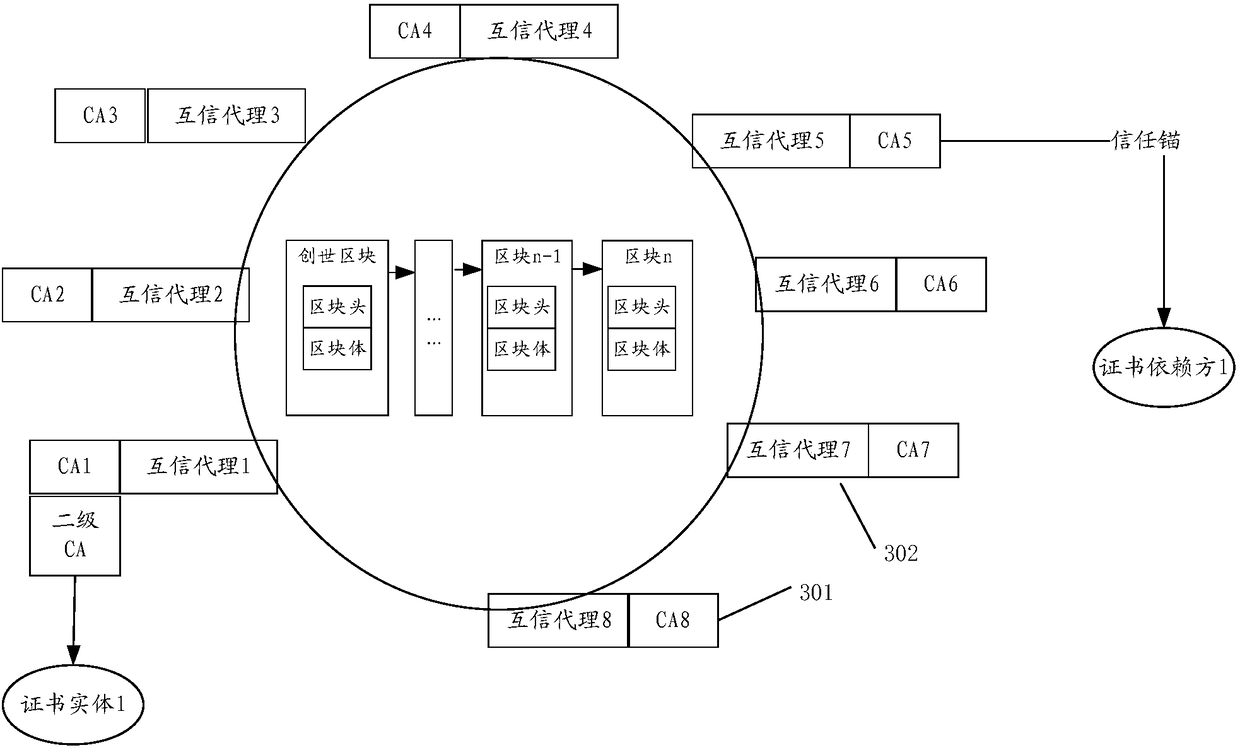
Method, apparatus and system for implementing CA mutual trust, and electronic device
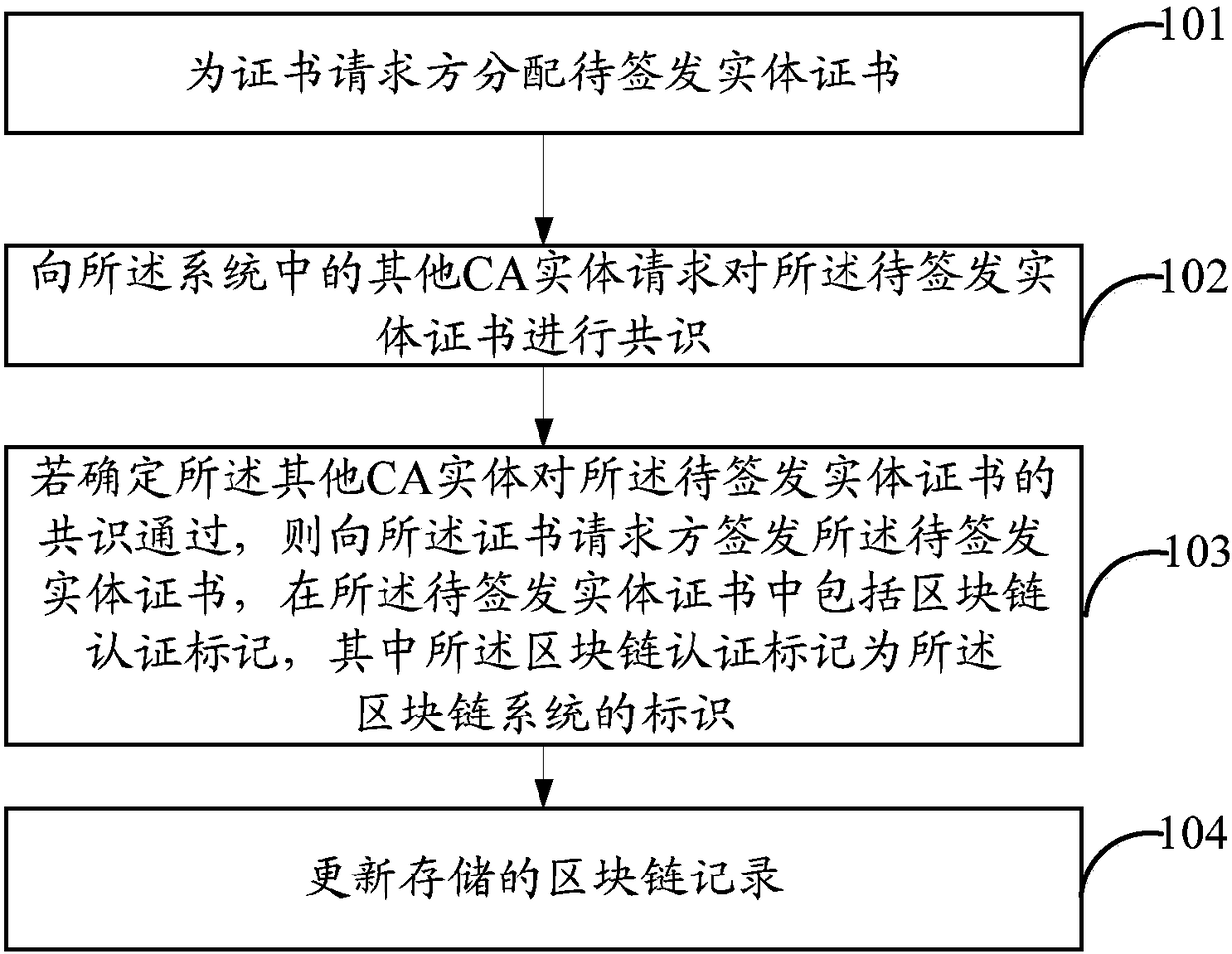
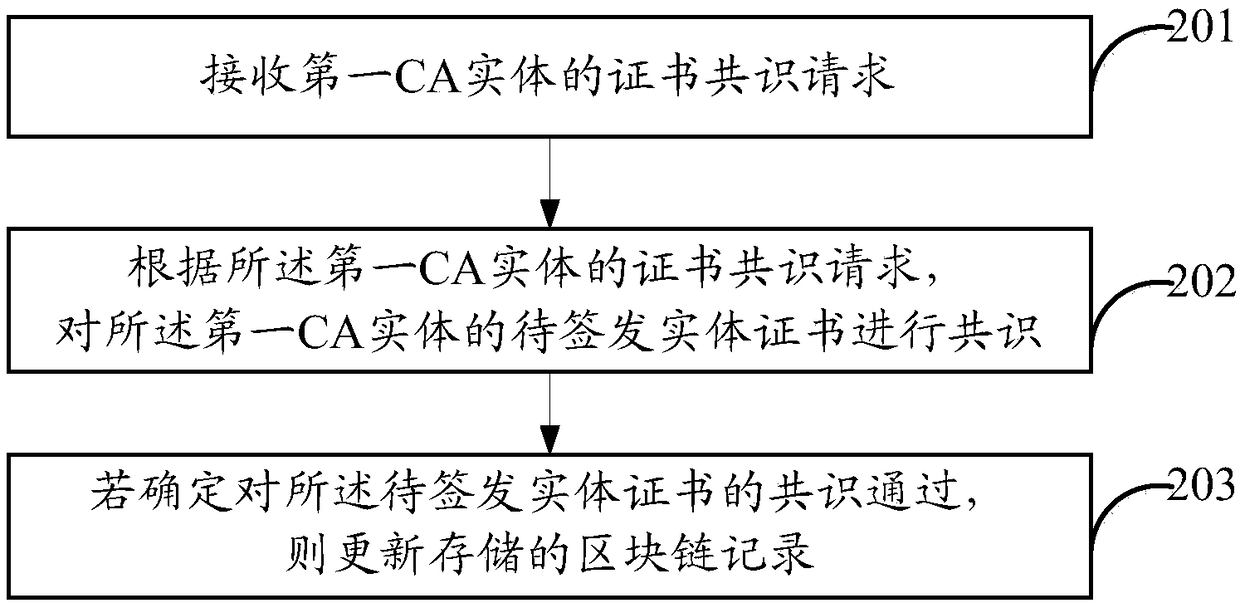
InactiveCN108696348AIncrease flexibilityKey distribution for secure communicationUser identity/authority verificationElectric equipmentAuthentication
The invention provides a method, apparatus and system for implementing CA mutual trust, and an electronic device, and relates to the technical field of communication. The flexibility of implementing the CA mutual trust is improved. The method for implementing the CA mutual trust provided by the invention comprises the following steps: allocating an entity certificate to be signed and issued to a certificate requester; requesting the other CA entities in the system to perform consensus on the entity certificate to be signed and issued; if it is determined that the authentication of the other CAentities on the entity certificate to be signed and issued is passed, signing and issuing the entity certificate to be signed and issued to the certificate requester, wherein the entity certificate to be signed and issued comprises a blockchain authentication mark, and the blockchain authentication mark is an identifier of a blockchain system; and updating a stored blockchain record. By adoptionof the scheme of the embodiment of the invention, the flexibility of implementing the CA mutual trust is improved.
Owner:CHINA MOBILE COMM LTD RES INST +1
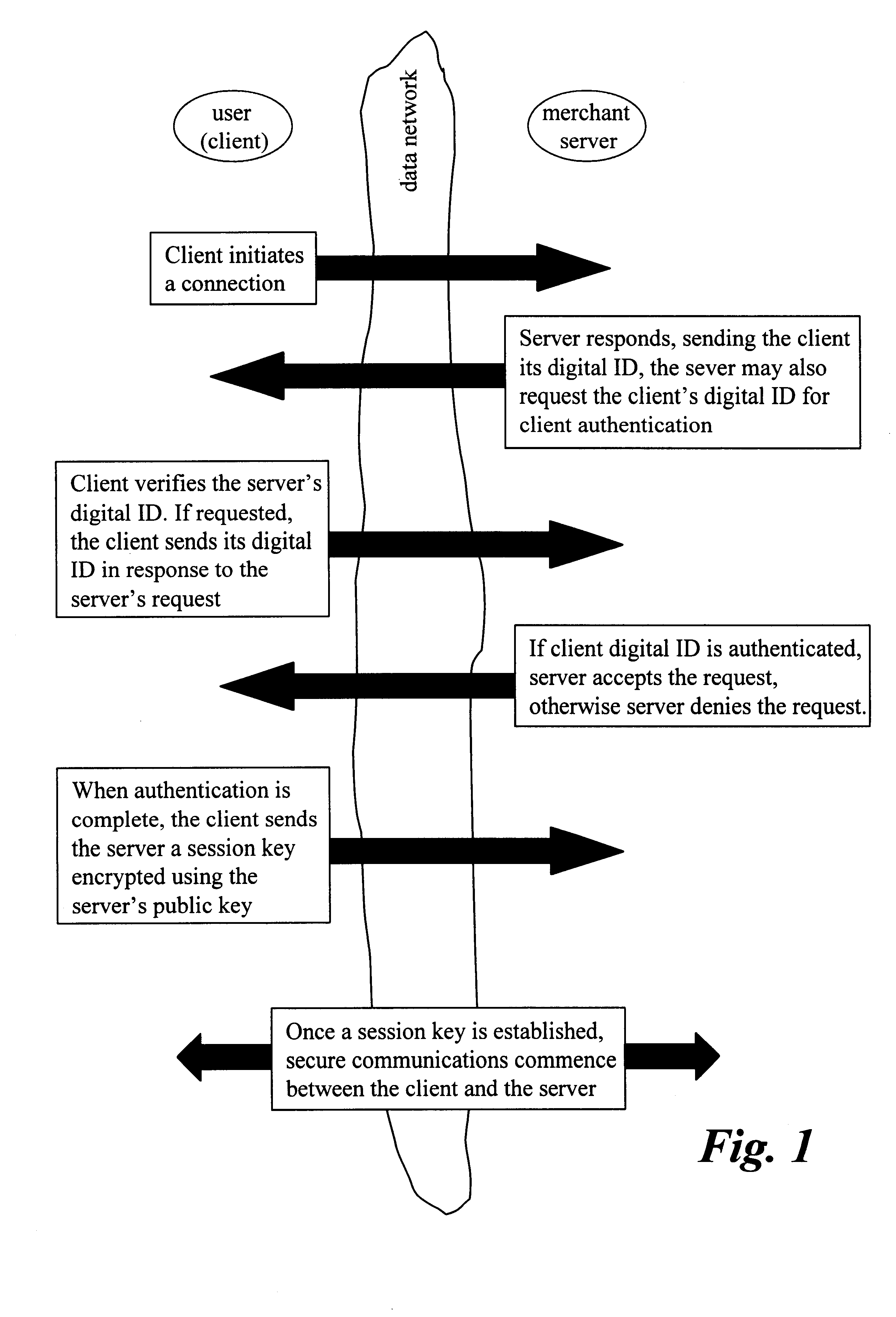
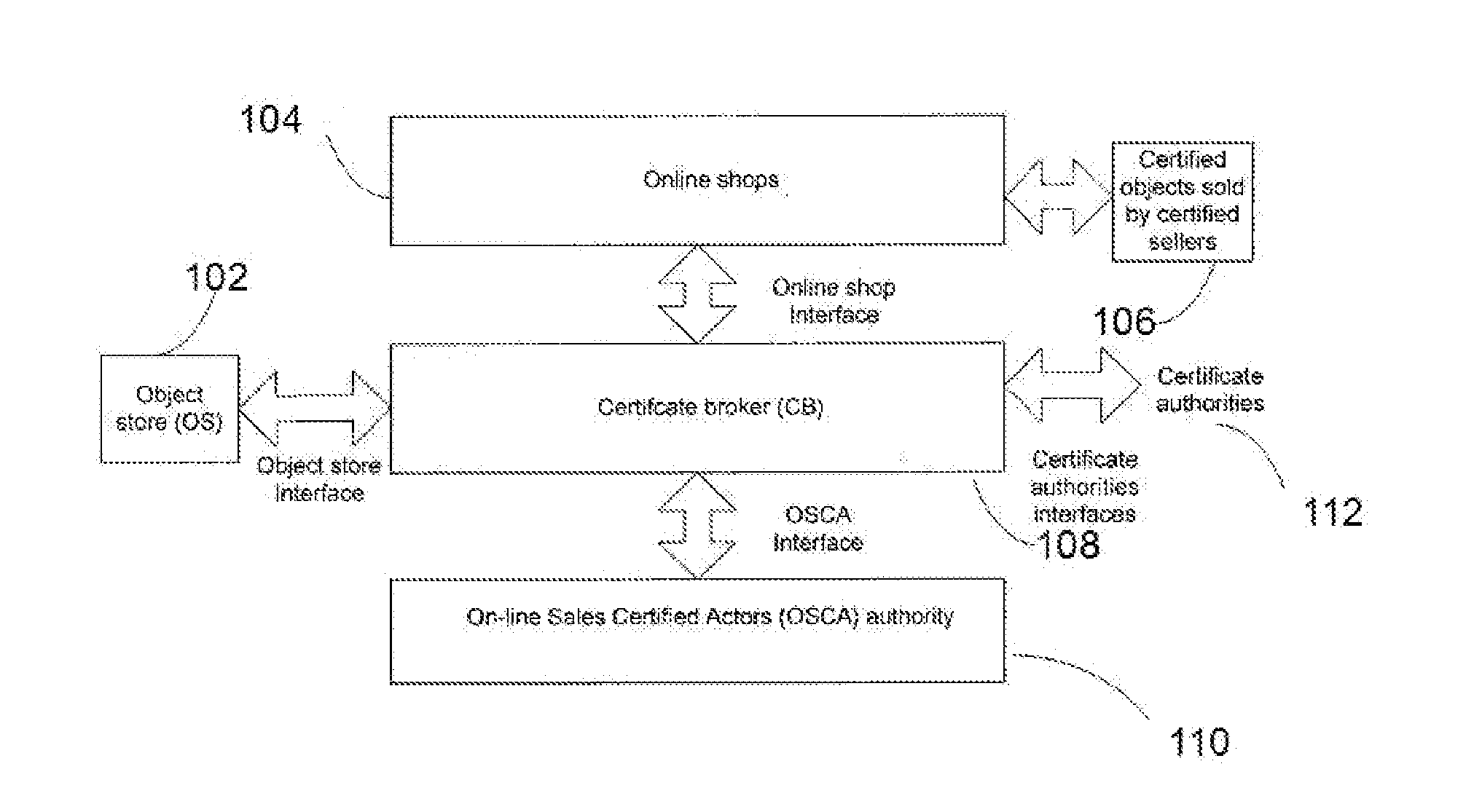
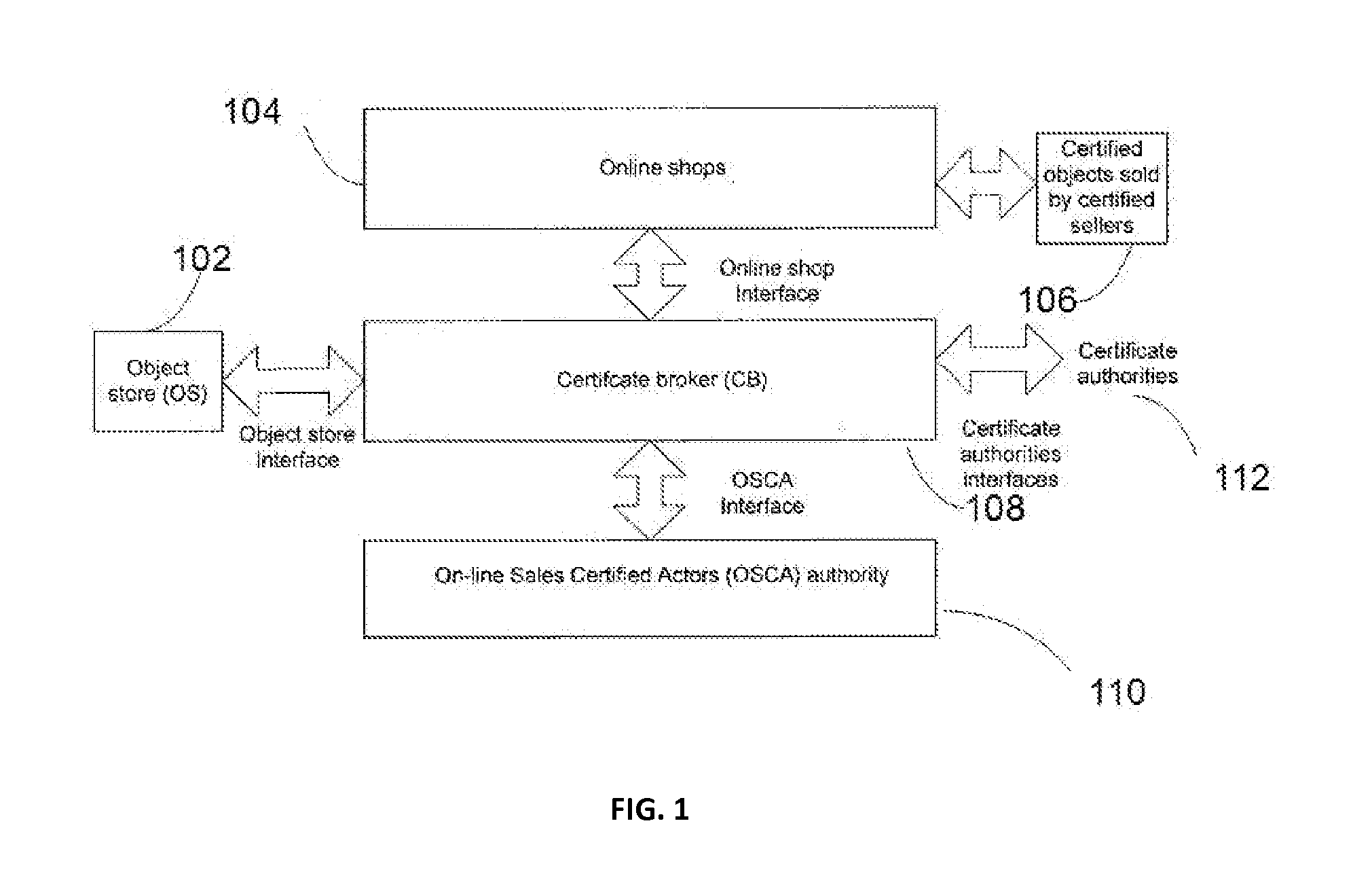
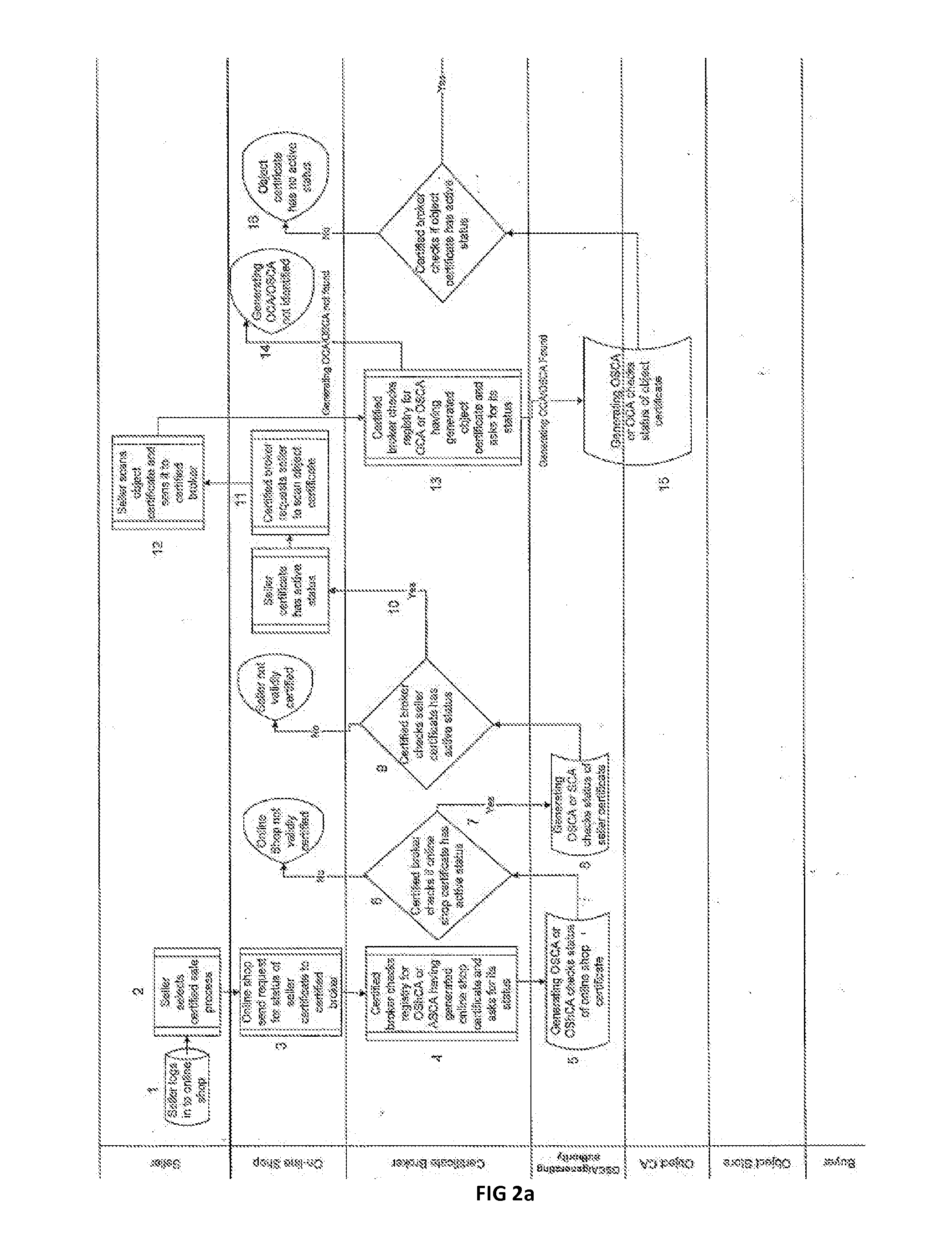
Method For Providing Secure E-Commerce Transactions
Method for providing e-Commerce secure transactions through a computer network comprising the steps of generating an encrypted digital object certificate for an object; generating an encrypted digital seller certificate for a seller of said object; assigning an active or a suspended or a revoked status to said object certificate according to first predetermined criteria; assigning an active or a suspended or a revoked status to said seller certificate according to second predetermined criteria. The method further comprises the steps of generating an encrypted digital sale certificate by means of aggregating elements comprising said object certificate and said seller certificate; assigning by said online sales certified actors authority a revoked status to said sale certificate if the status of said seller certificate and of said object certificate are not both active and an active status otherwise; publishing said sale certificate and / or its status in said online shop. Thanks to the invention, sale certificates in a plurality of online shops can be simultaneously revoked if a seller certificate or an object certificate is revoked
Owner:S A SELINKO
A method and a related device for issuing an identity certificate to a block chain node
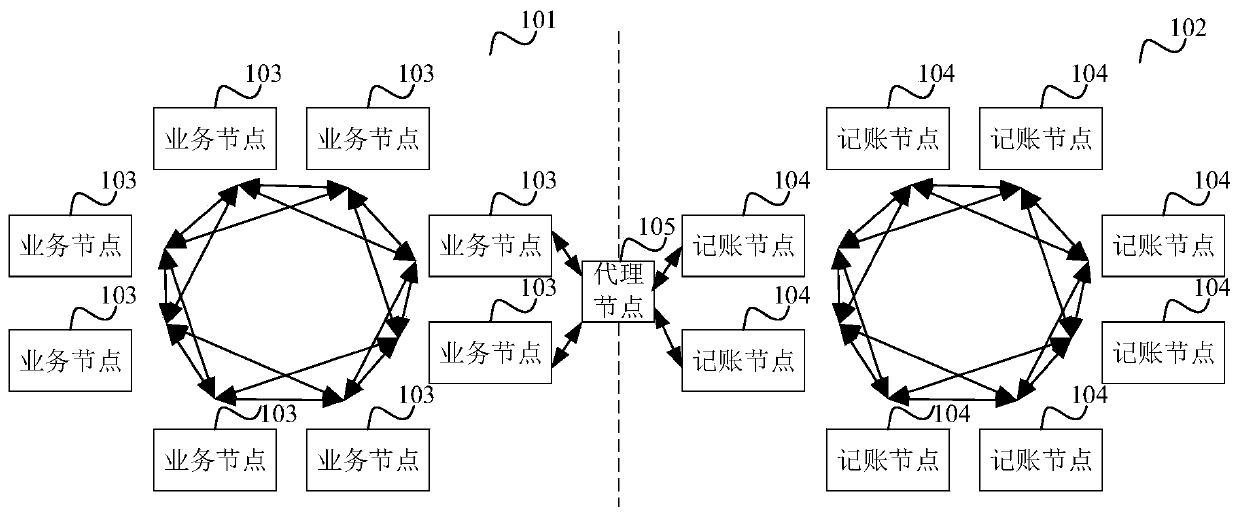
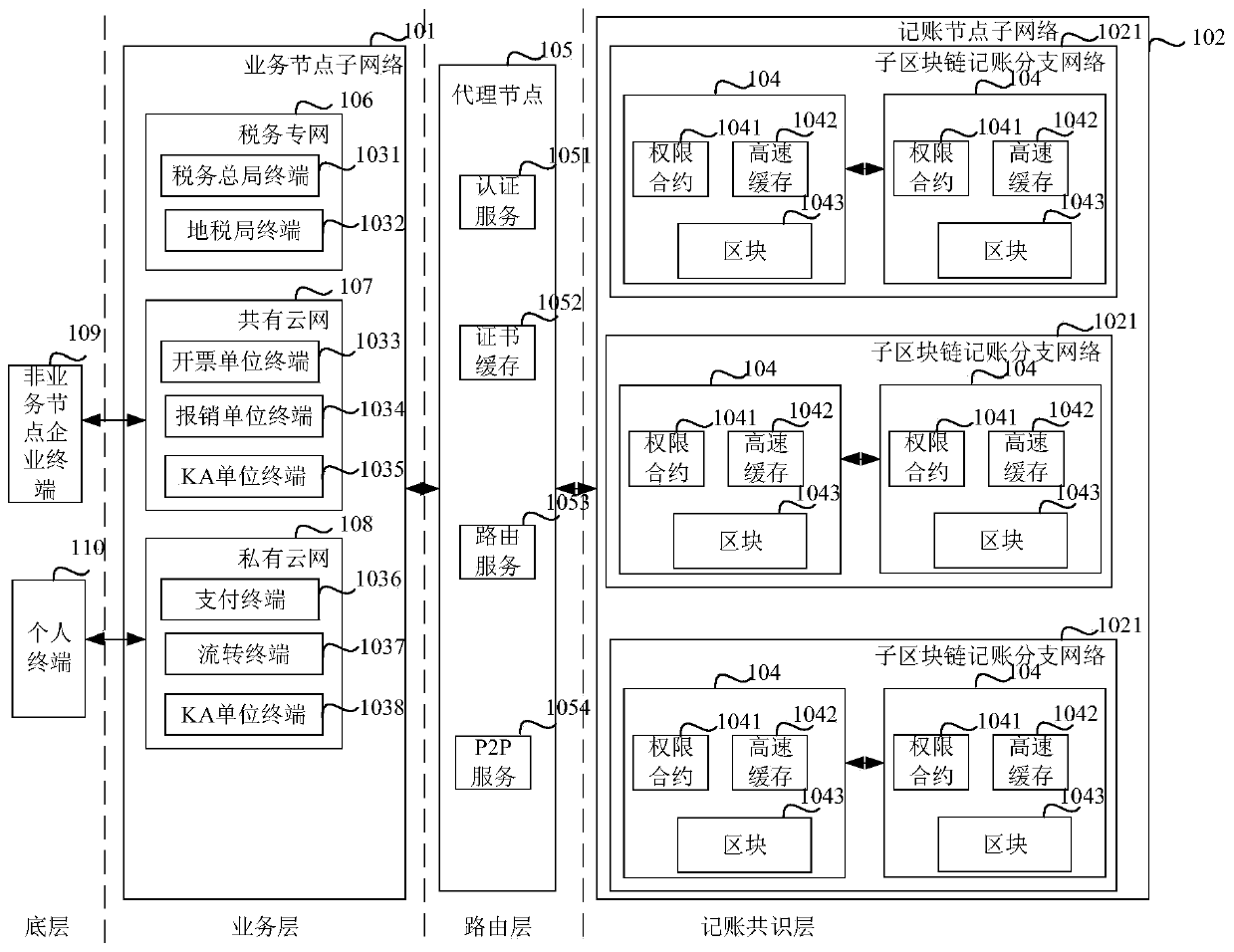
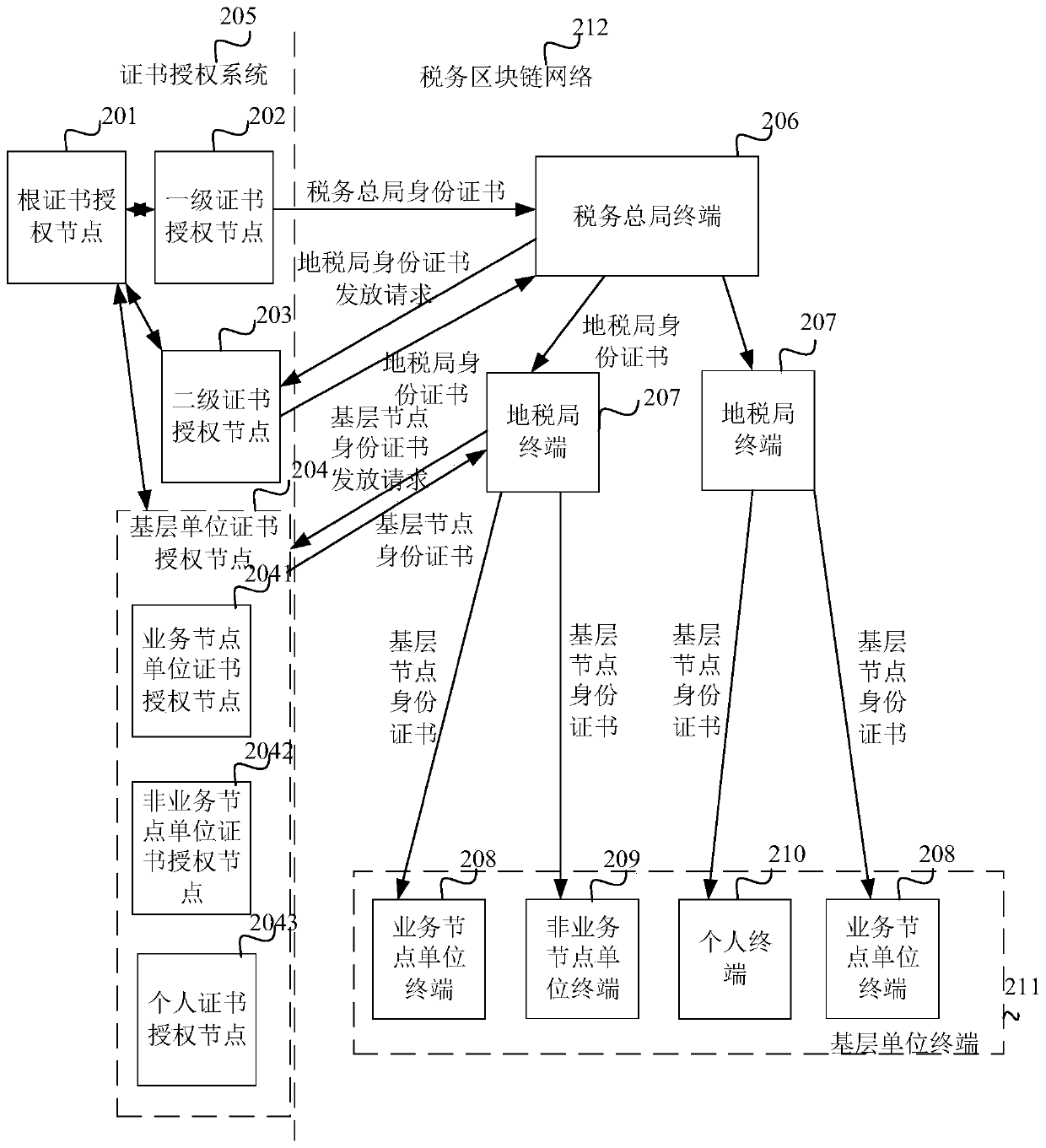
Owner:深圳市智税链科技有限公司
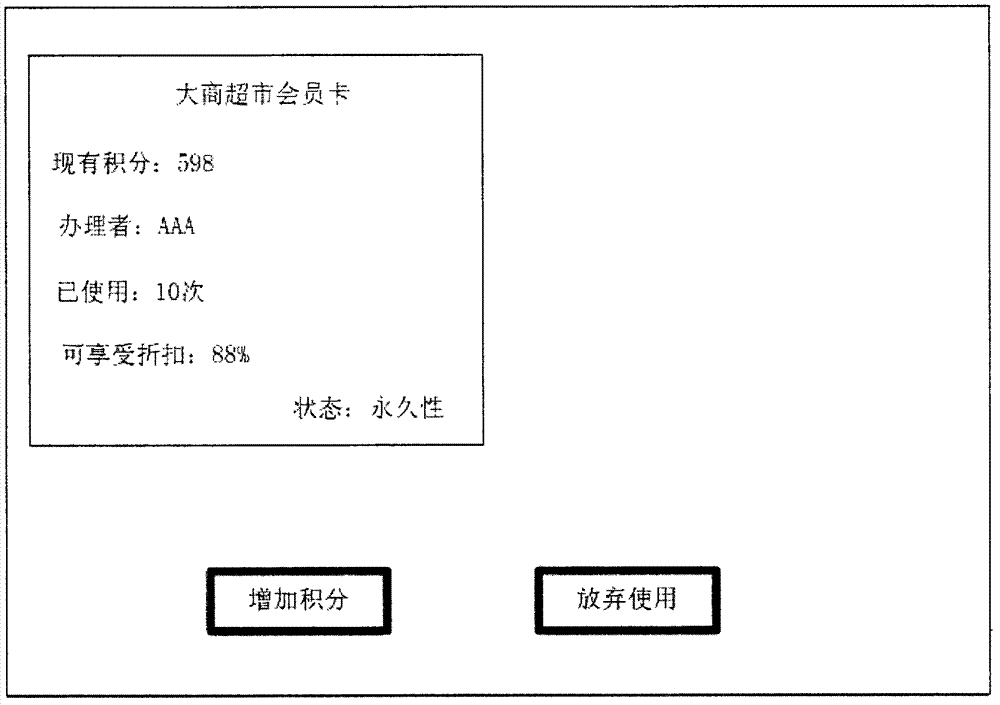
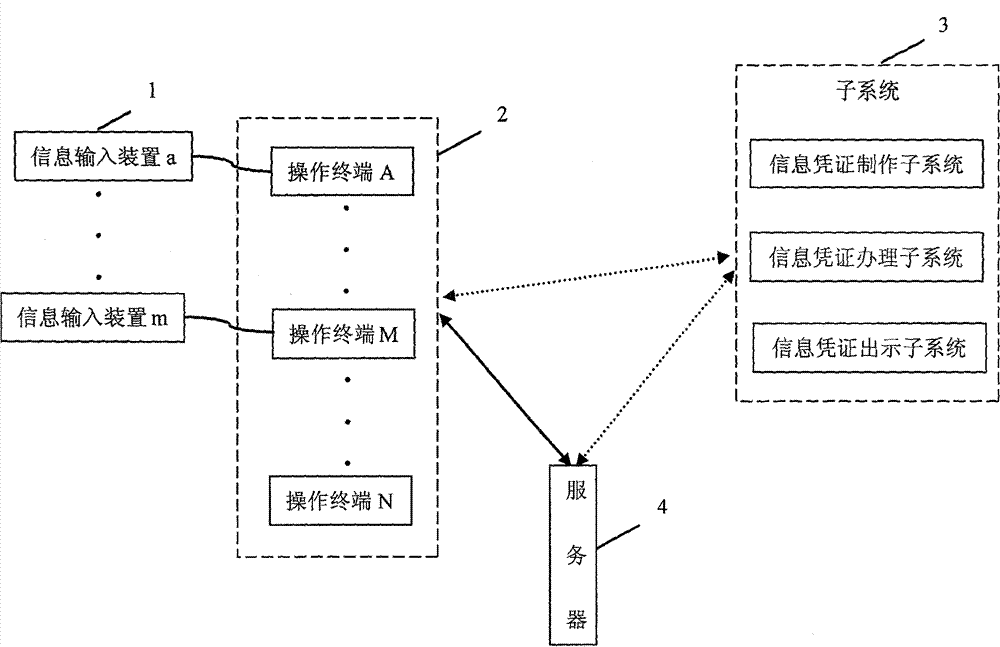
Information certificate system and related operation method thereof
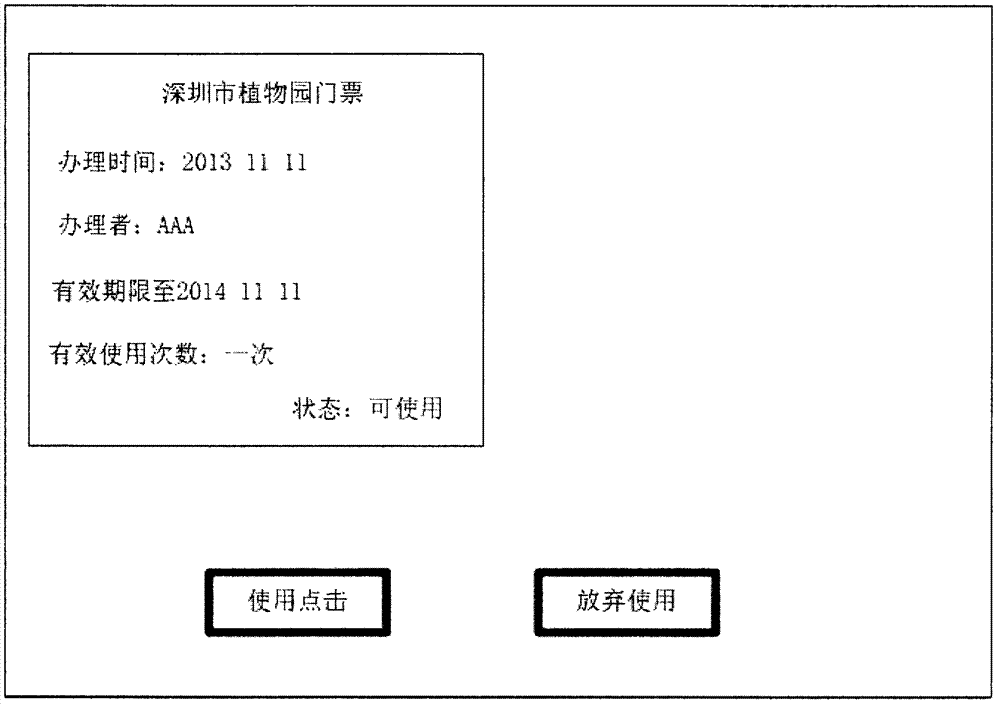
The invention provides an information certificate system and a related operation method thereof. A certificate can prove the identify of a user, comprises a card, a ticket, a voucher, a document and the like, and can be divided into two kinds, i.e., an object certificate and an information certificate. The system provided by the invention provides an information certificate which is opposite to the object certificate. The system comprises information certificate making subsystems operated at servers and certificate making terminals, information certificate handling subsystems operated at the servers and certificate handling terminals, and information certificate showing subsystems operated at the servers and certificate showing terminals. When the system is operated, a made information certificate is stored in the servers, a handled information certificate is associated with a system account of a certificate user and then is stored in the servers, when the information certificate is shown, the information certificate showing subsystems performs matching on external connection information obtained by the certificate showing terminals and obtains a corresponding system account, retrieval is carried out according to retrieval conditions, and an information certificate according with the retrieval conditions is outputted.
Owner:冯建中
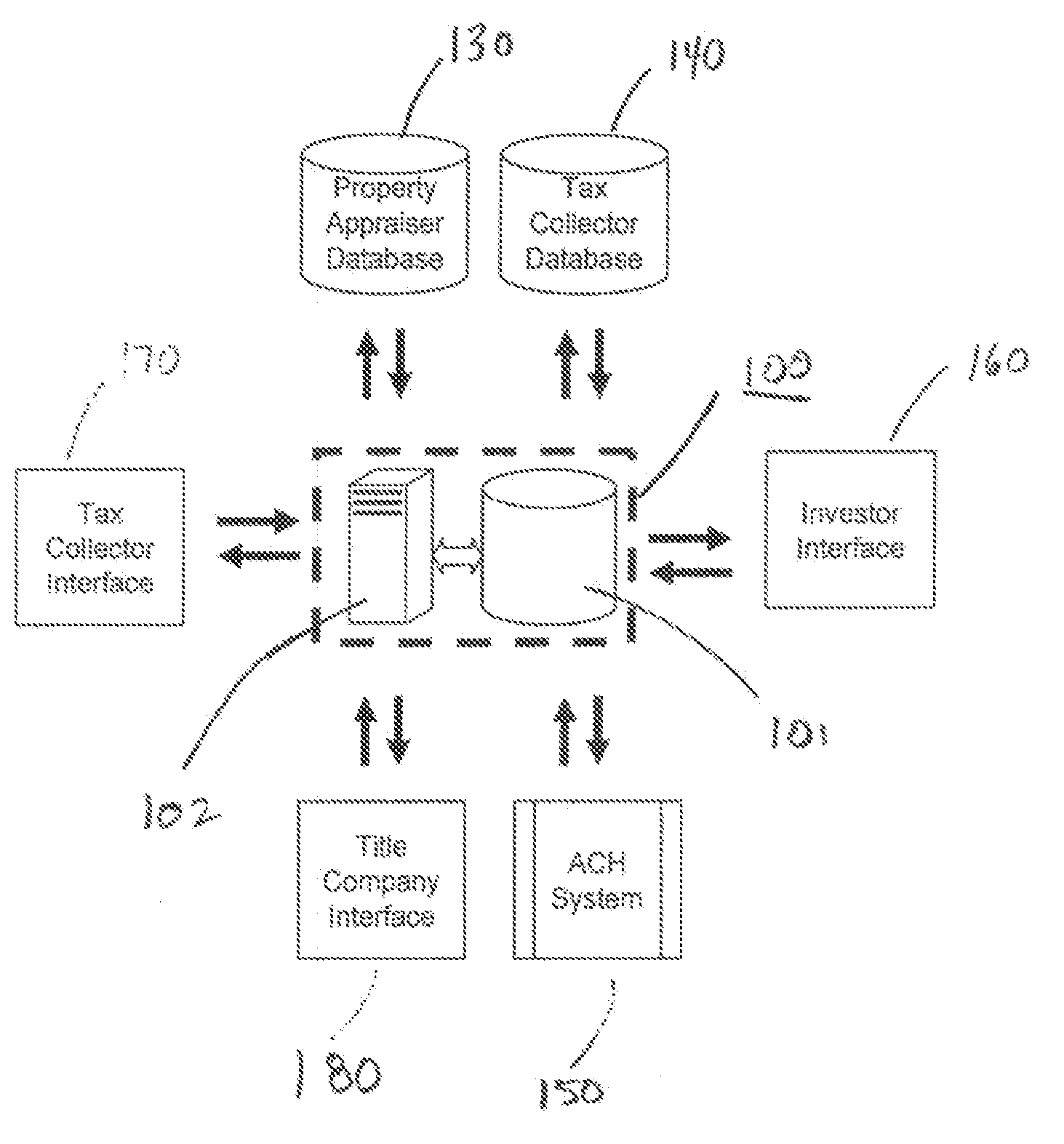
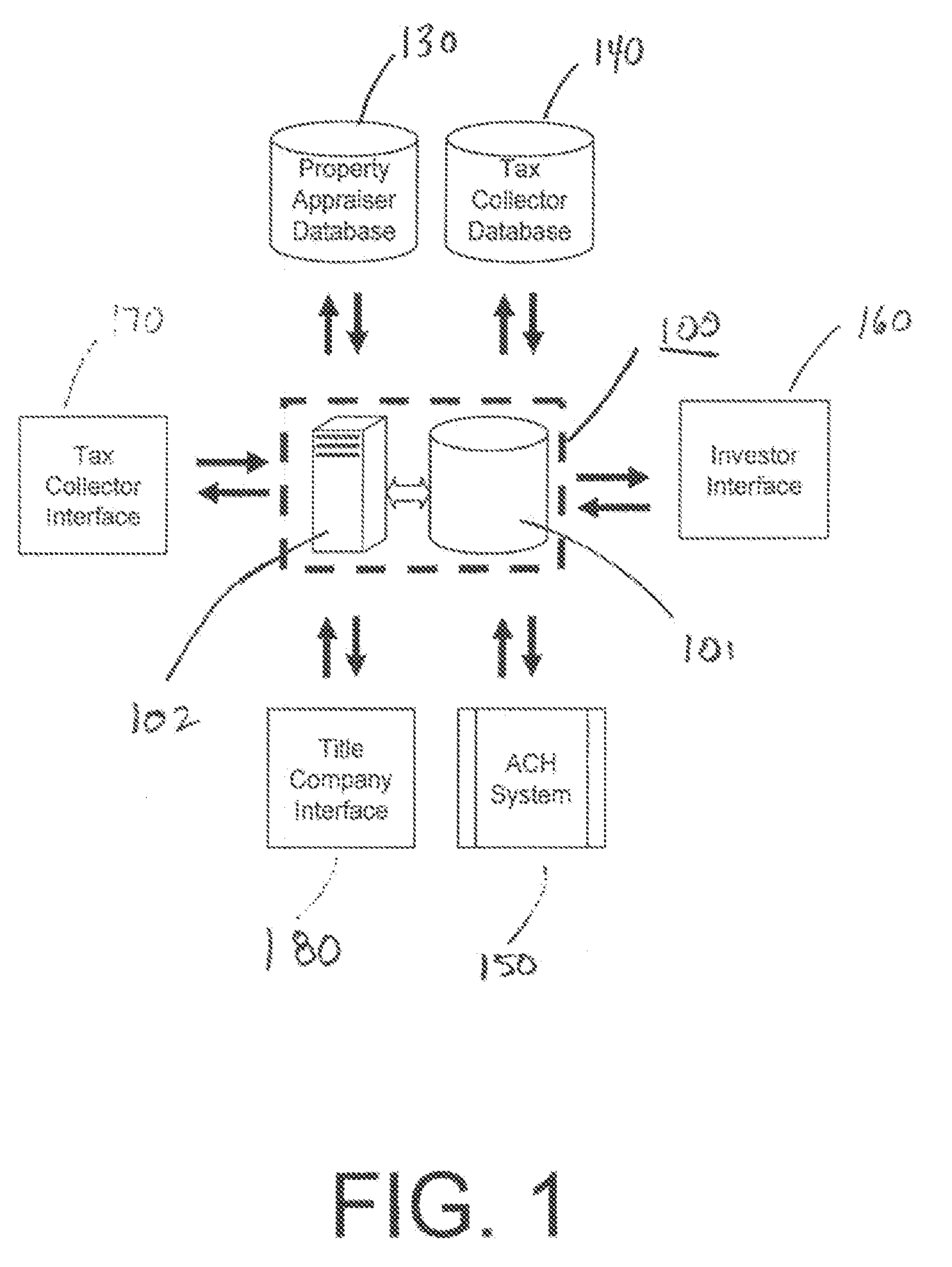
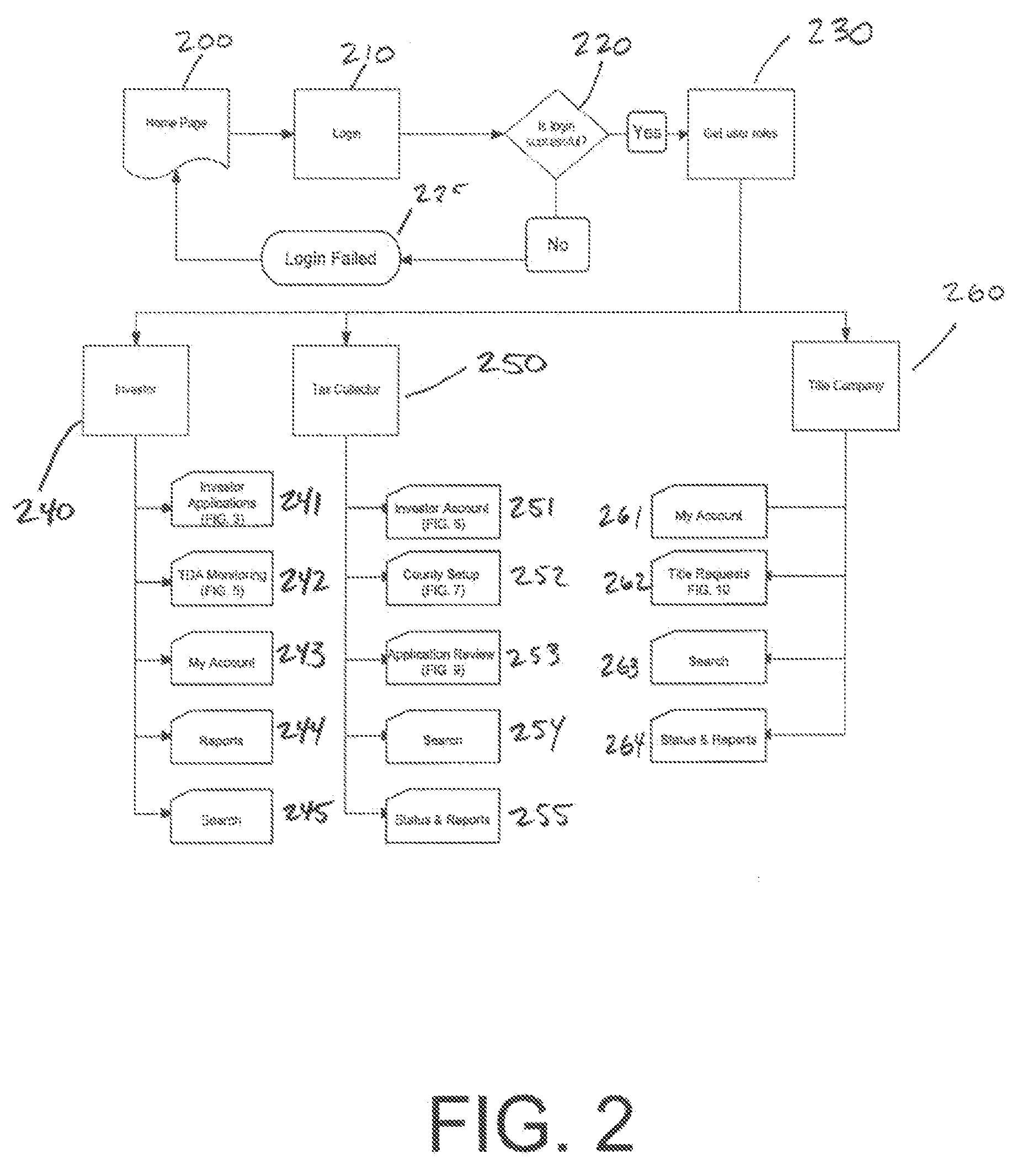
Property Sale Application and Tracking System
A property sate application system, such as for a tax deed, is provided that receives sale applications. The tax deed application can include information associated with a parcel, certificate information associated with a tax certificate associated with the parcel, and investor information associated with an investor associated with the at least one tax certificate. The system can enter data representative of the application into a database, transmit the application for review, and retrieve parcel information related to the identification information, the certificate information, or the investor information. The system may update the application data in the tax deed database based at least in part on the parcel information, receive a title search request based at least in part on the parcel information, transmit the title search request for processing, provide a status identifier representative of a current status of the tax deed application, and update the status identifier.
Owner:REALAUCTION COM
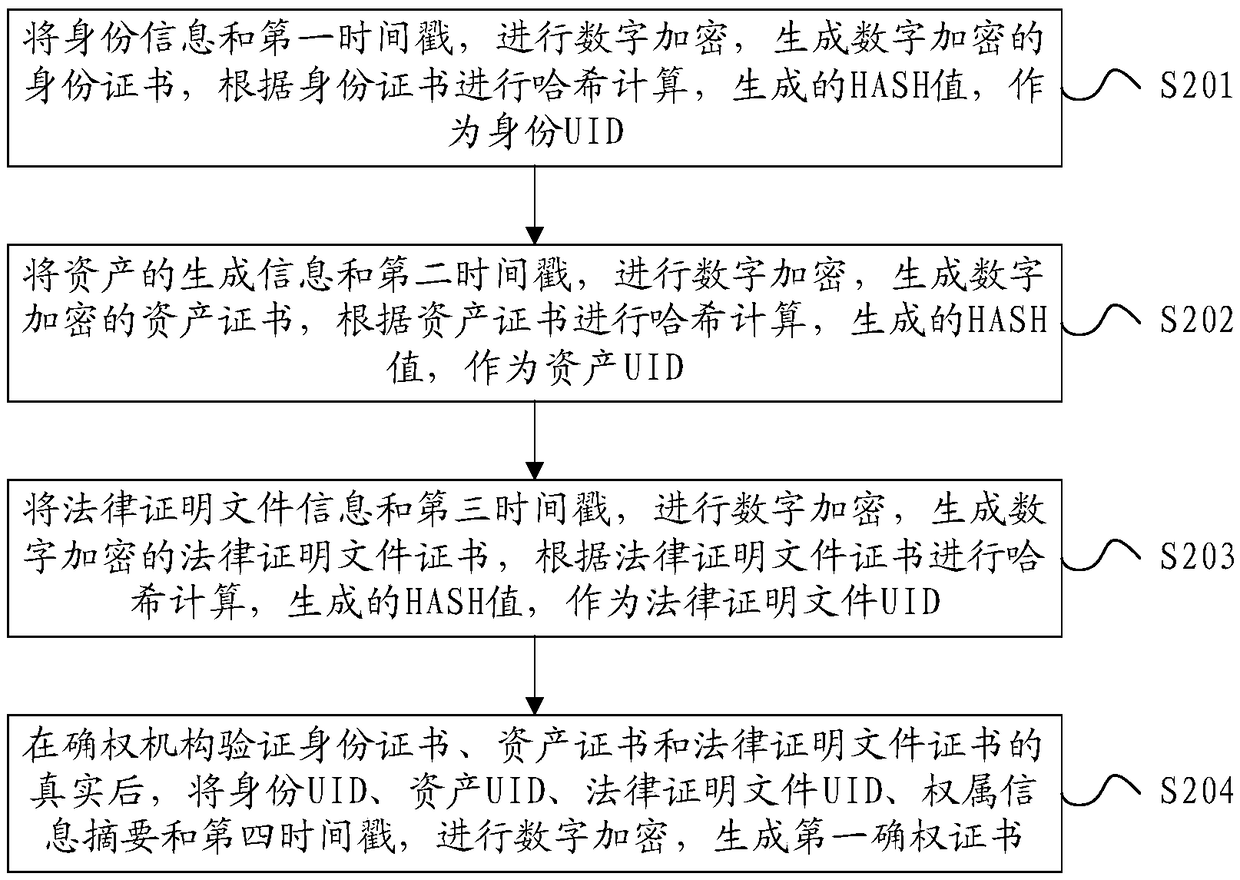
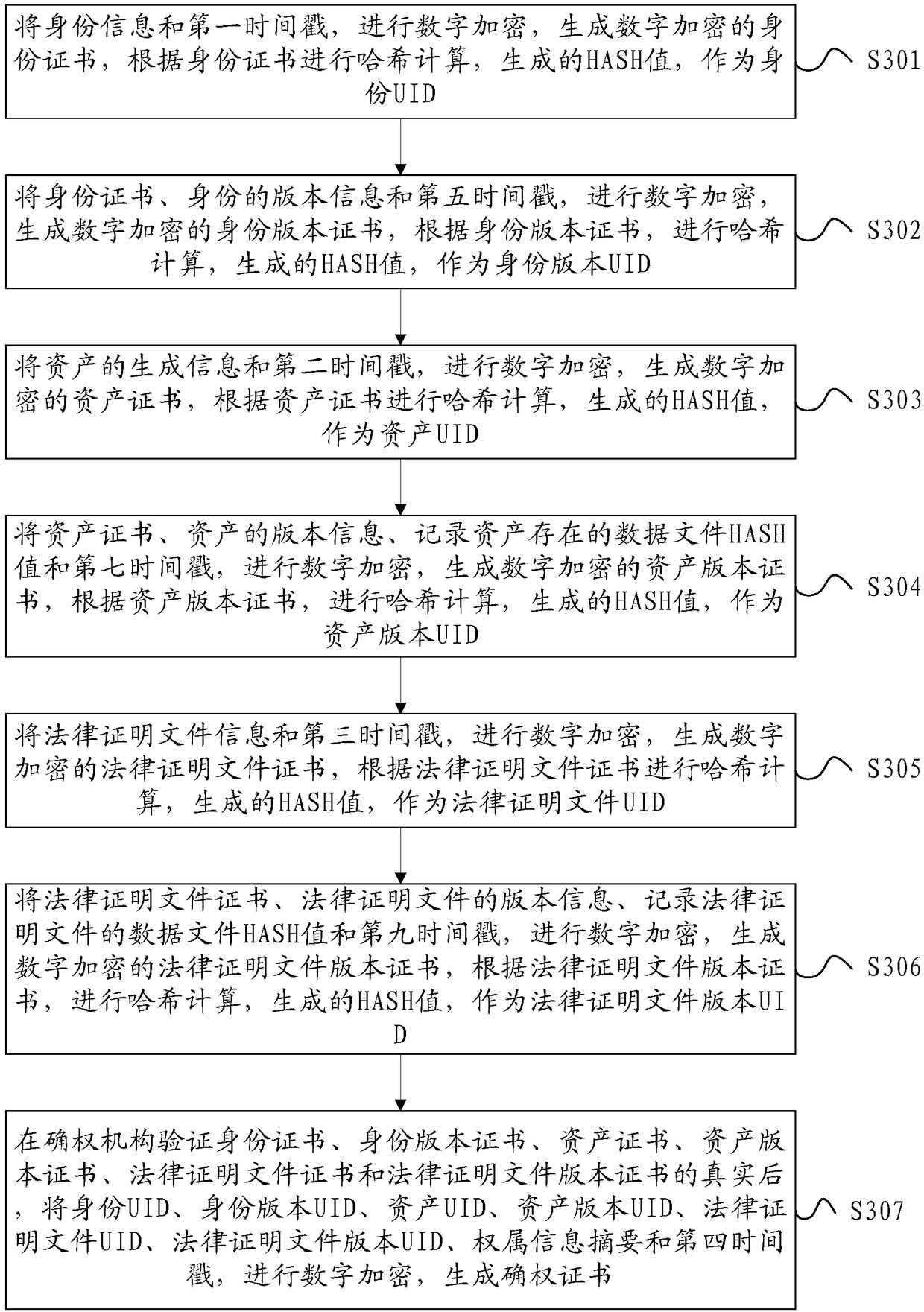
Method, device and system for generating right confirmation certificate
ActiveCN109033789AUniqueness guaranteedGuarantee authenticityDigital data authenticationDocument preparationClient certificate
The invention relates to a method, a device and a system for generating an authentication certificate, wherein, the method comprises the following steps: digitally encrypting identity information anda first time stamp to generate a digitally encrypted identity certificate; calculating a hash according to the identity certificate; and generating a HASH value as an identity uniqueness identifier UID; performing digital encryption on the generated information of the asset and the second timestamp to generate a digitally encrypted asset certificate, performing hashing calculation according to theasset certificate, and generating a HASH value as an asset UID; carrying out digital encryption on the legal proof document information and the third timestamp, generating a digital encrypted legal proof document certificate, calculating a hash according to the legal proof document certificate, and generating a HASH value as a UID of the legal proof document; after verifying the authenticity of the ID card, asset certificate and legal certificate, the confirming authority digitally encrypts the identity UID, asset UID, legal certificate UID, ownership information summary and fourth timestampto generate the first confirming certificate.
Owner:北京文创园投资管理有限公司
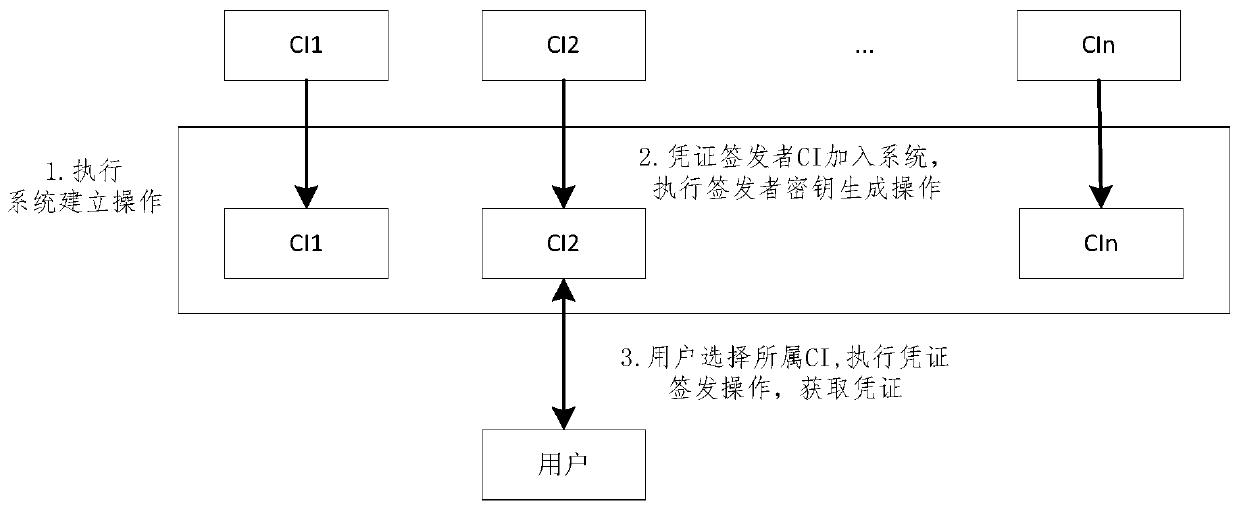
A certificate issuer anonymity entity identification method and system
InactiveCN109902508AEnhanced anonymityStrong privacyDigital data protectionRoot certificateConfusion
The invention discloses a certificate issuer anonymity entity identification method and system. The method comprises the following steps that: 1) each certificate issuer joining a system generates a private key and a public key of the certificate issuer according to system public parameters; 2) the certificate issuer I generates an identity certificate of the user according to the input user identity identifier, the private key of the certificate issuer I and the system public parameters and transmits the identity certificate to the user; 3) the user selects a plurality of certificate issuersto form a confusion set; an anonymous identity certificate of the user is generated according to the public parameters of the system, the public keys of all the selected certificate issuers and the identity certificate held by the user, and sending the anonymous identity certificate to an identity verifier; Wherein the confusion set comprises a certificate issuer I for issuing a user certificate to the user; And 4) the identity verifier verifies the received anonymous identity certificate according to the system public parameters and the public key of each certificate issuer in the confusion set, and determines whether the received anonymous identity certificate is valid or not.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Automated certificate management
ActiveCN102792632AUser identity/authority verificationDigital data authenticationRoot certificateCertificate policy
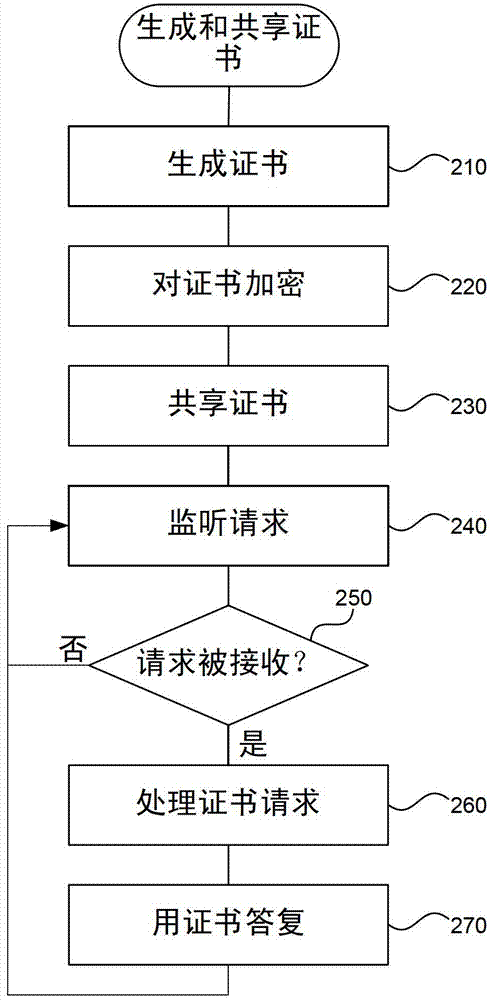
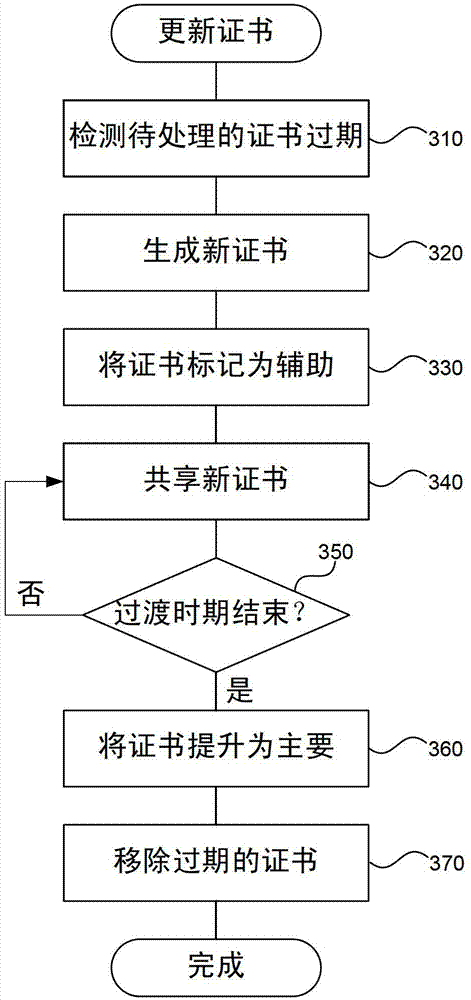
A certificate management system provides automated management of certificate lifecycles and certificate distribution. Rather than depend upon an administrator to manually distribute and manage certificates, the system self-generates certificates, distributes the certificates to appropriate servers or other parties, and transitions from old certificates to new certificates in a well-defined manner that avoids breaking functionality. After generating one or more certificates, the system securely shares certificates in a way that parties that use them can find the new certificates without an administrator manually distributing the certificates. When it is time to update certificates, the system generates new certificates and shares the new certificates in a similar way. During a transition period, the system provides a protocol by which both old and new certificates can be used to perform authenticated access to resources, so that the transition from an old to a new certificate does not break services.
Owner:MICROSOFT TECH LICENSING LLC
Using Trusted Platform Module To Build Real Time Indicators of Attack Information
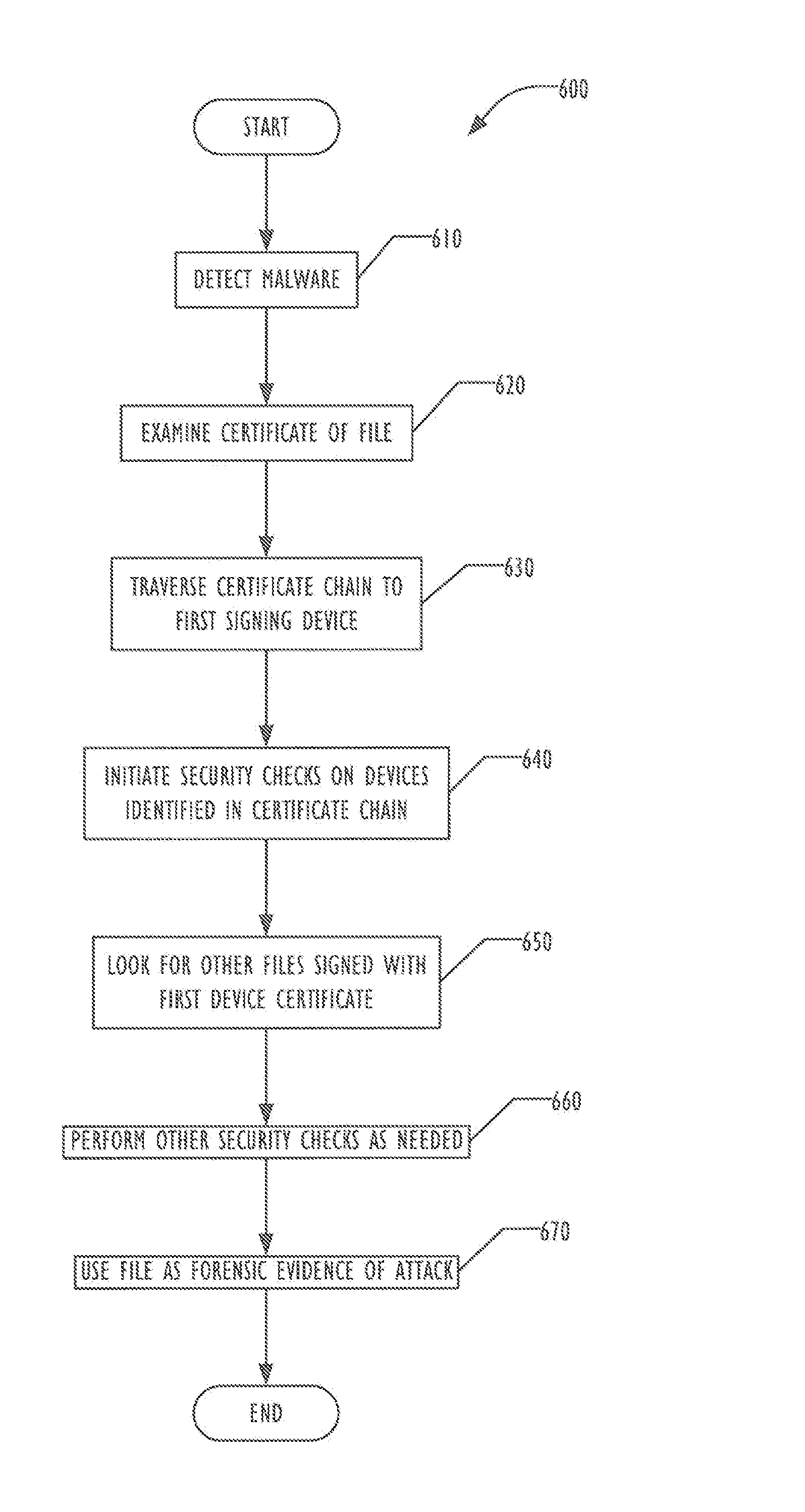
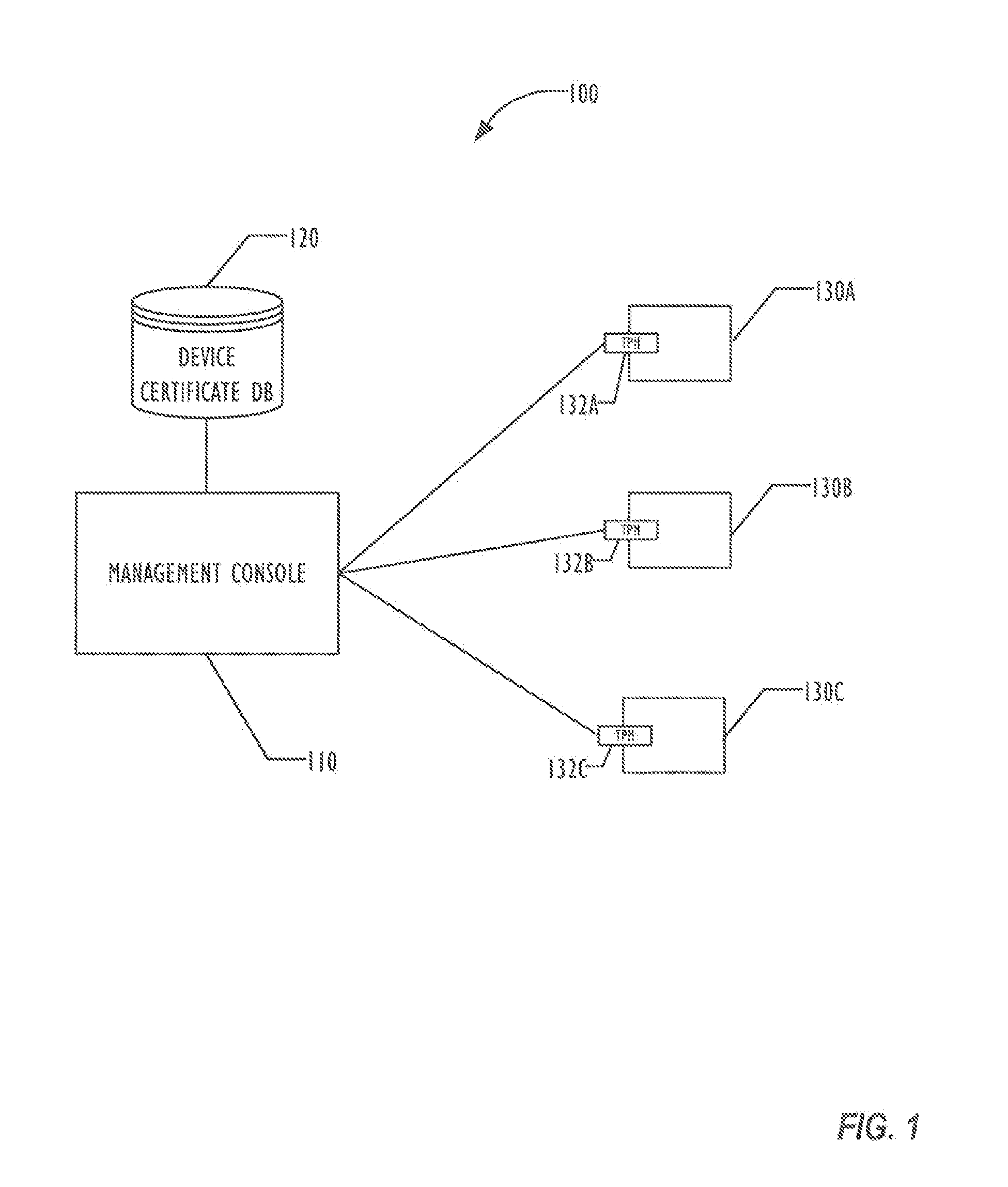
Managed devices containing a Trusted Platform Module (TPM) to provide a trusted environment generate a device certificate at initialization of the TPM and send the device certificate to a management console for storing in a certificate database. Upon detecting a file of interest, the TPM signs the file, adding to a signature list created by previous managed devices. The signature list can be used to analyze the spread of the file across the system of managed devices, including tracking the file to the first managed device to have had a copy, without requiring real-time access to the managed devices during the spread of the file. In some embodiments, additional security measures may be taken responsive to determining the first managed device and the path the file has taken across the system of managed devices.
Owner:MUSARUBRA US LLC
Methods of sanitizing a flash-based data storage device
A data storage device includes one or more non-volatile, blockwise erasable data storage media and a mechanism for sanitizing the media in response to a single external stimulus or in response to a predetermined physical or logical condition. Optionally, only part of the media is sanitized, at a granularity finer than the blocks of the medium. Setting a flag in an auxiliary nonvolatile memory enables an interrupted sanitize to be detected and restarted. Optionally, a “death certificate” verifying the sanitizing is issued. Preferably, the media are configured in a manner that allows atomic operations of the sanitizing to be effected in parallel.
Owner:SANDISK IL LTD
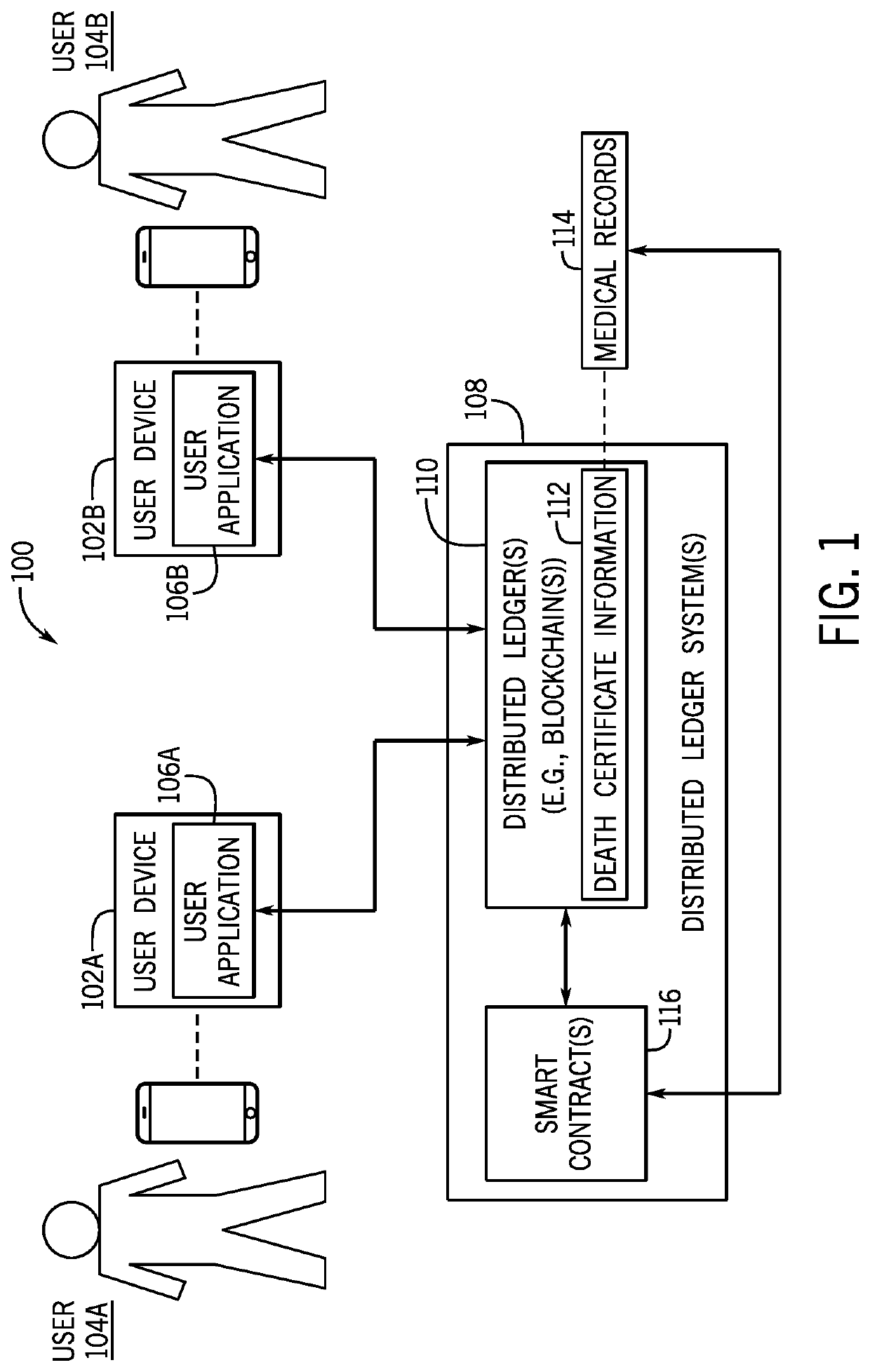
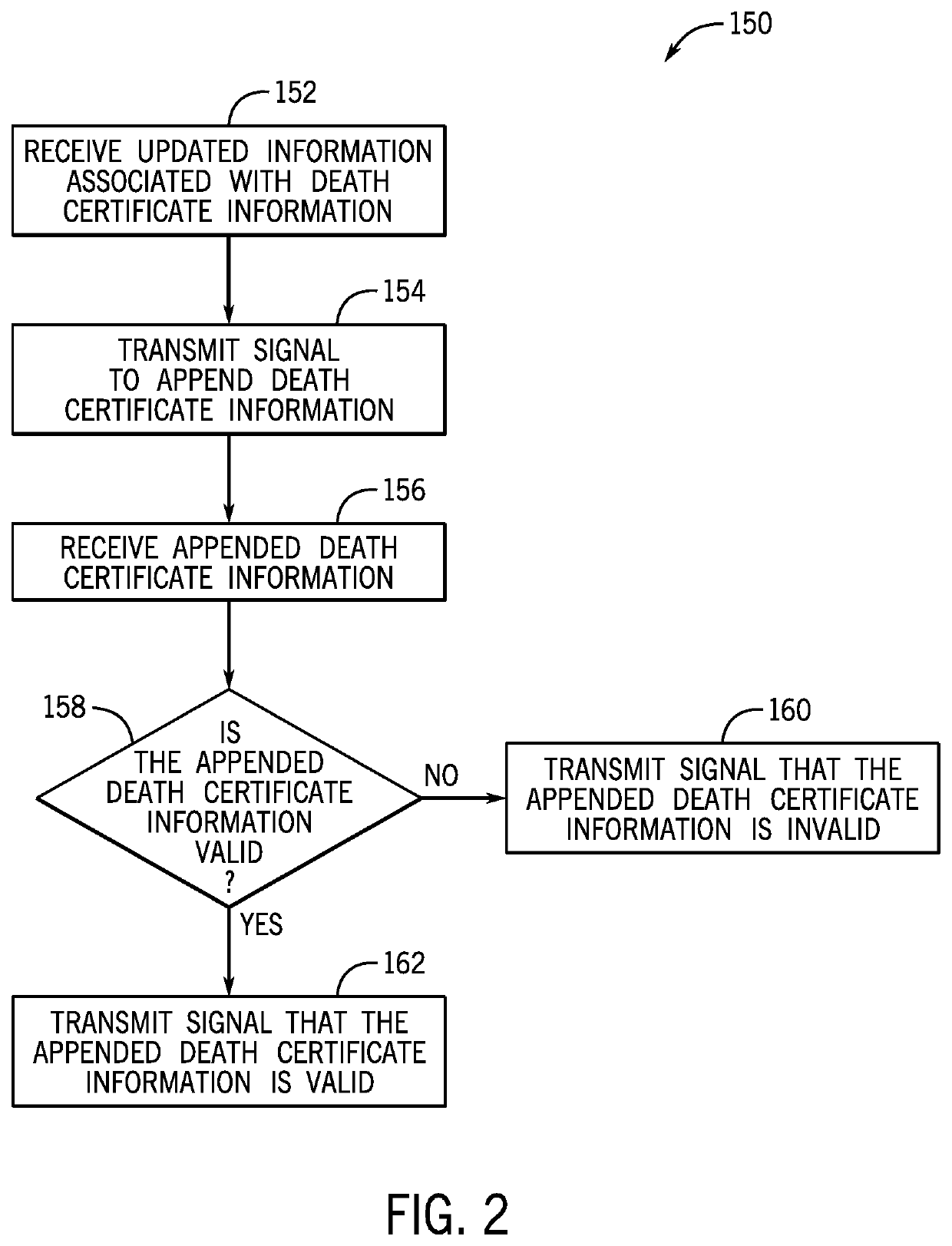
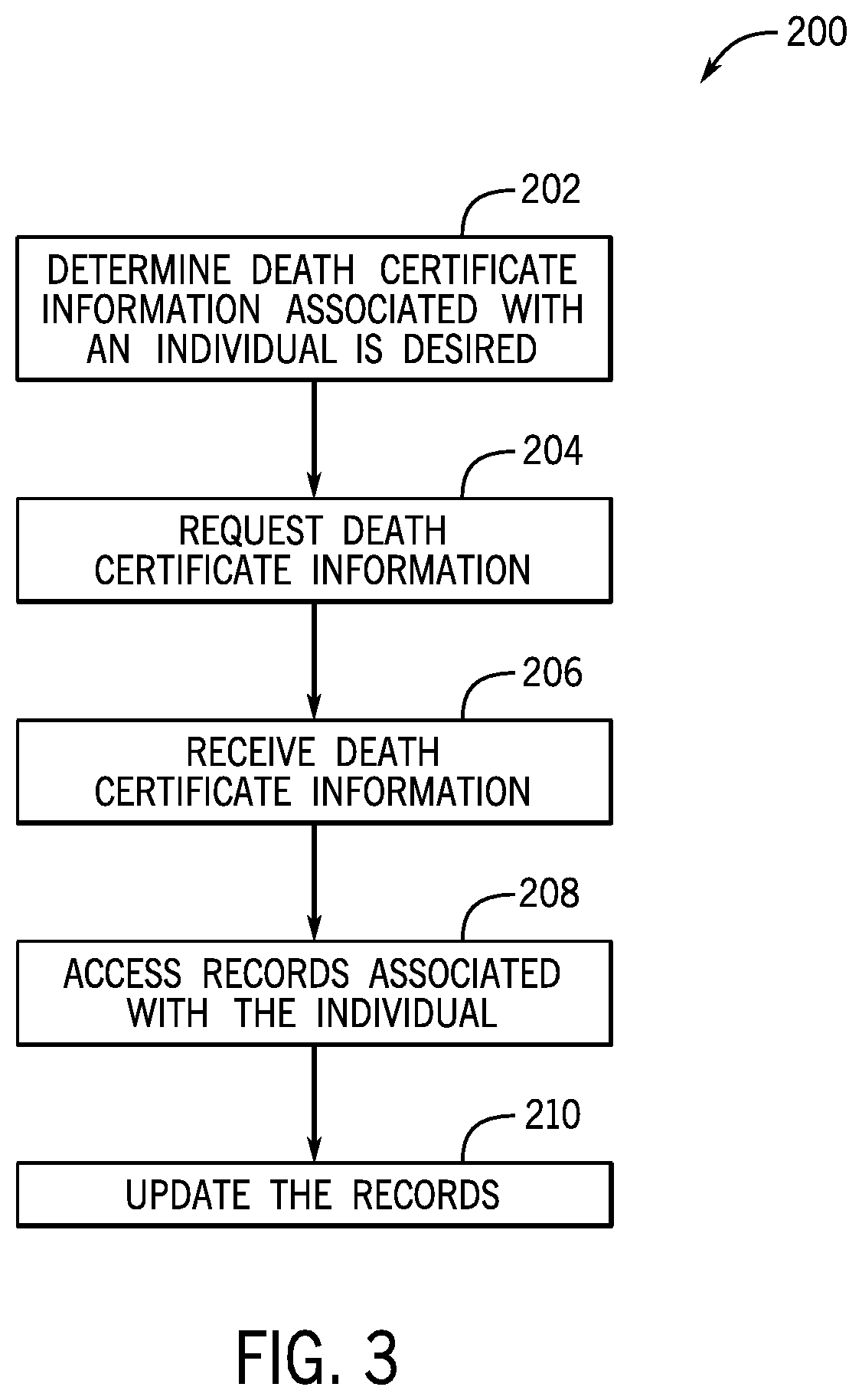
Death certificate information processing techniques
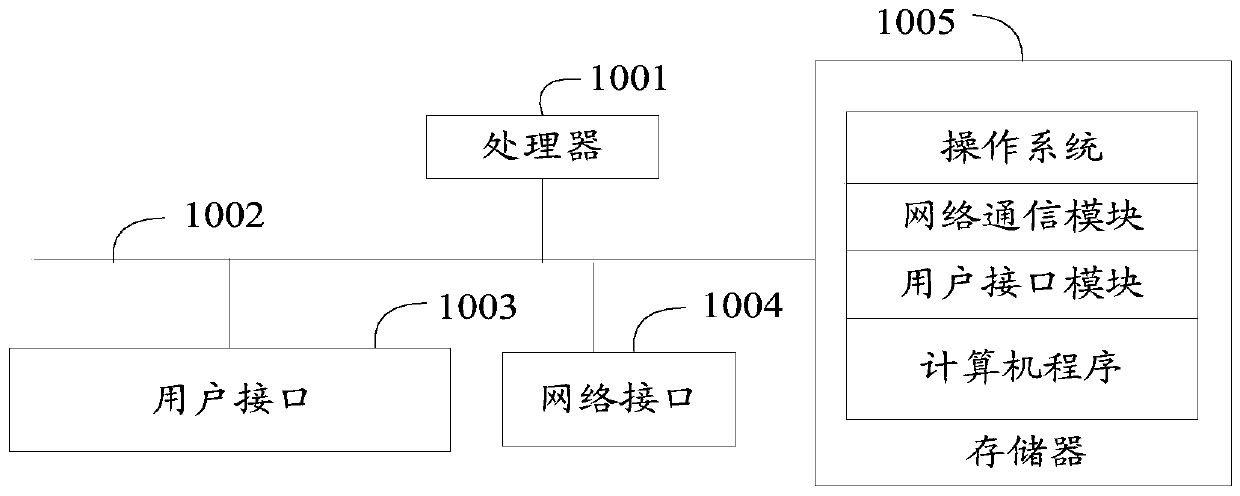
ActiveUS11341267B1Encryption apparatus with shift registers/memoriesUser identity/authority verificationInformation processingEngineering
A system includes at least one processor and at least one memory communicatively coupled to the at least one processor, where the at least one memory stores instructions. When executed by the at least one processor, the instructions are configured to receive death certificate information from a node of a distributed ledger system, determine, a record to be updated based at least in part on the death certificate information, and update the record. The death certificate information and the record are associated with an individual.
Owner:USAA
Secure single sign-on and conditional access for client applications
ActiveCN109558721ADigital data authenticationSecurity arrangementSecure communicationConditional access
Methods and systems for implementing single sign on (SSO) and / or conditional access for client applications are described herein. The system may comprise an identity provider gateway, and the system may authenticate a user of the client application using the identity provider gateway. In some aspects, a secure communication tunnel may be established between the client application and the identityprovider gateway, and the secure communication tunnel may use, for example, a client certificate. The identity provider gateway may grant or deny the client application access to one or more resourcesbased on information associated with the client certificate.
Owner:CITRIX SYST INC
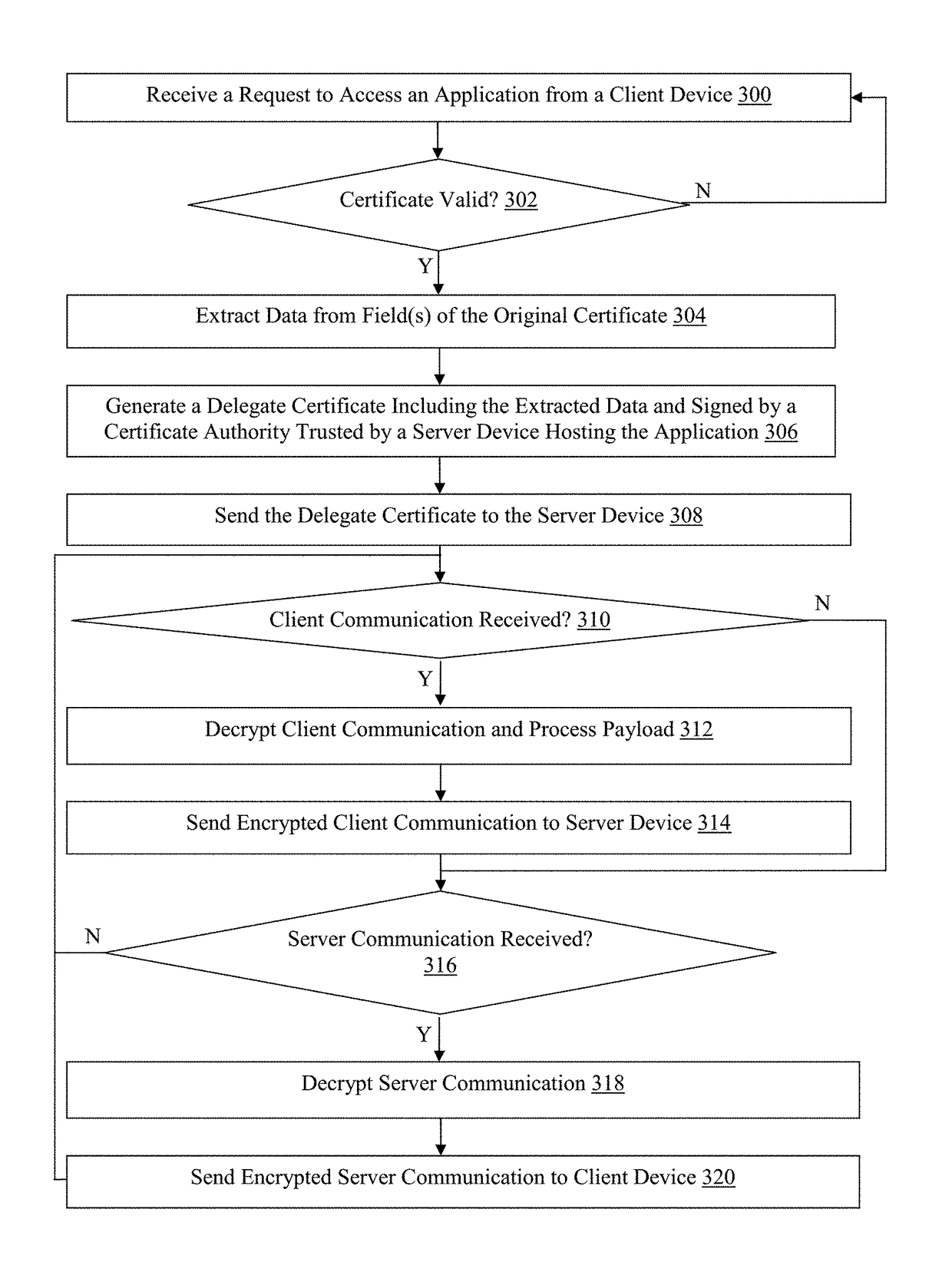
Methods for client certificate delegation and devices thereof
ActiveUS9800568B1Improve securityConnection securityTransmissionApplication softwareProxy certificate
Methods, non-transitory computer readable media, and network traffic management apparatuses that receive a request from a client device to access an application. The request comprises an original certificate. A determination is made when the certificate is valid. Data is extracted from one or more fields of the certificate, when the determining indicates that the user certificate is valid. A delegate certificate comprising the data and signed by a certificate authority trusted by a server device hosting the application is generated. The delegate certificate is sent to the server device. With this technology, network traffic management apparatuses can secure SSL connections using PFS-capable ciphers, while also inspecting payload data in network traffic exchanged between client and server devices in order to provide intelligent services in the network.
Owner:F5 NETWORKS INC
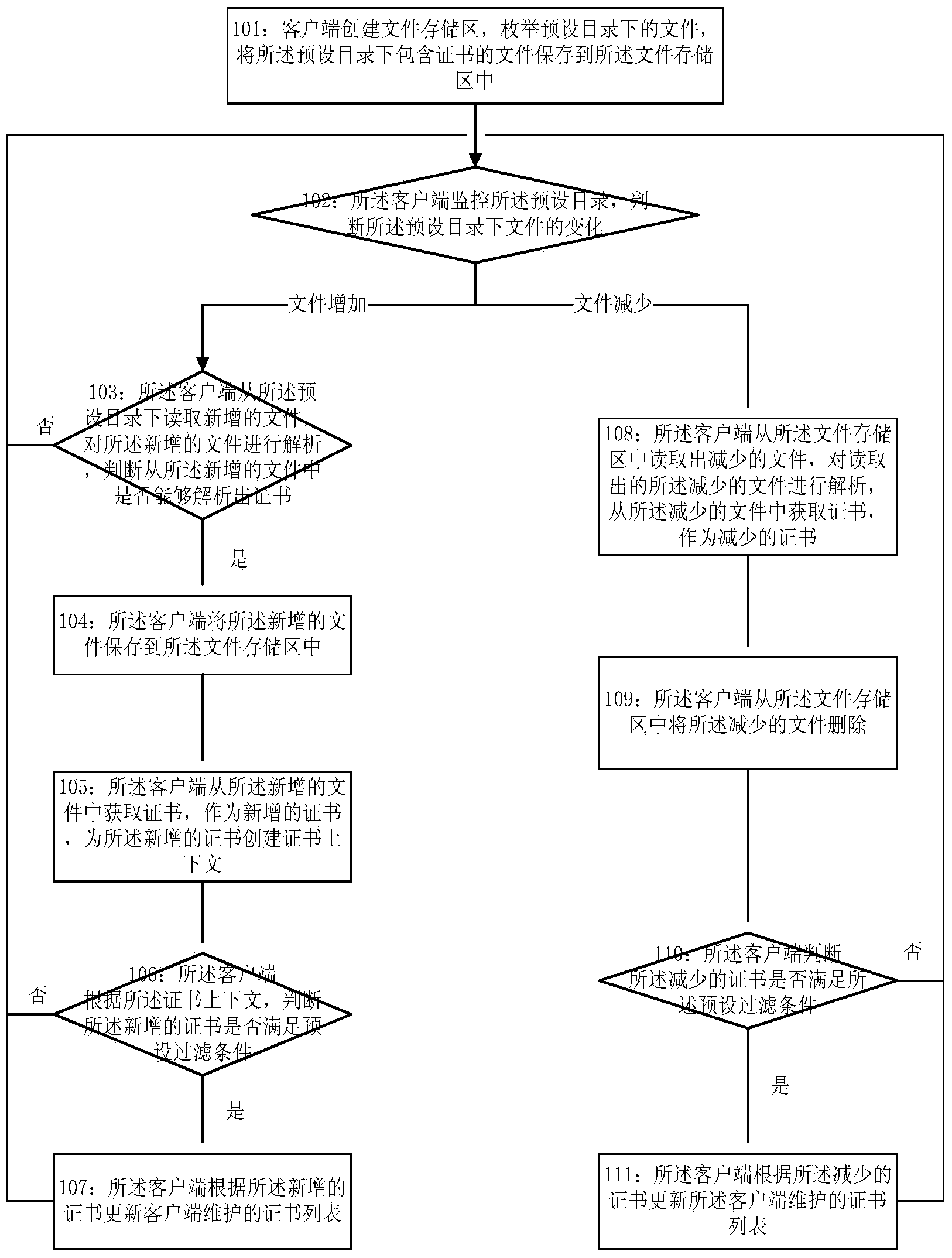
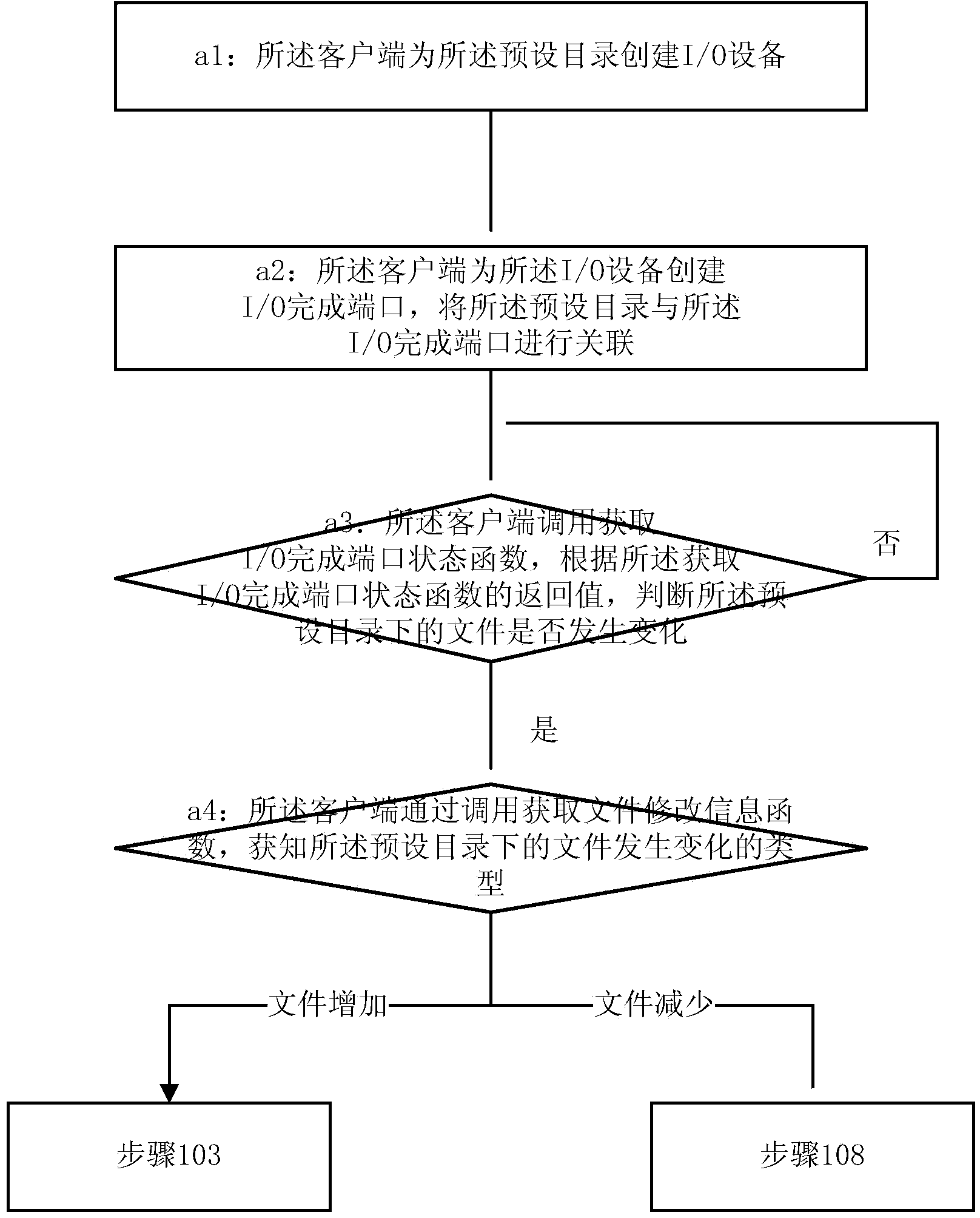
Method for monitoring certificates in real time
The invention discloses a method for monitoring certificates in real time and belongs to the field of information security. The method includes: allowing a client side to monitor a default directory, obtain new files which are added, analyze the new files to obtain new certificates, update a certificate list maintained in the client side according to the new certificates when the new certificate meet default filter conditions, and return to continue monitoring the default directory; if the files are decreased, reading the reduced files from a file storage area, analyzing and obtaining the reduced certificates from the reduced files, updating the certificate list of the client side according to the reduced files when the reduced certificates meet the default filter conditions, and returning to continue monitoring the default directory. By application of the method, certificate registration or cancellation events can be effectively monitored, so that the certificate registration or cancellation events can be processed in real time through the client side, and the certificates can be filtered at the same time.
Owner:FEITIAN TECHNOLOGIES
Account management
According to the present invention there is provided a method of managing access to at least one service account comprising storing identify verification details of at least one service account in a repository and releasing the identity verification details to a third party on production of proof of death of a service account holder. The invention also provides a method of managing access to at least one internet banking account comprising storing identify verification details of at least one internet banking account in a repository and releasing the identity verification details to a third party on production of proof of death of a service account holder.
Owner:BAKER KENNETH
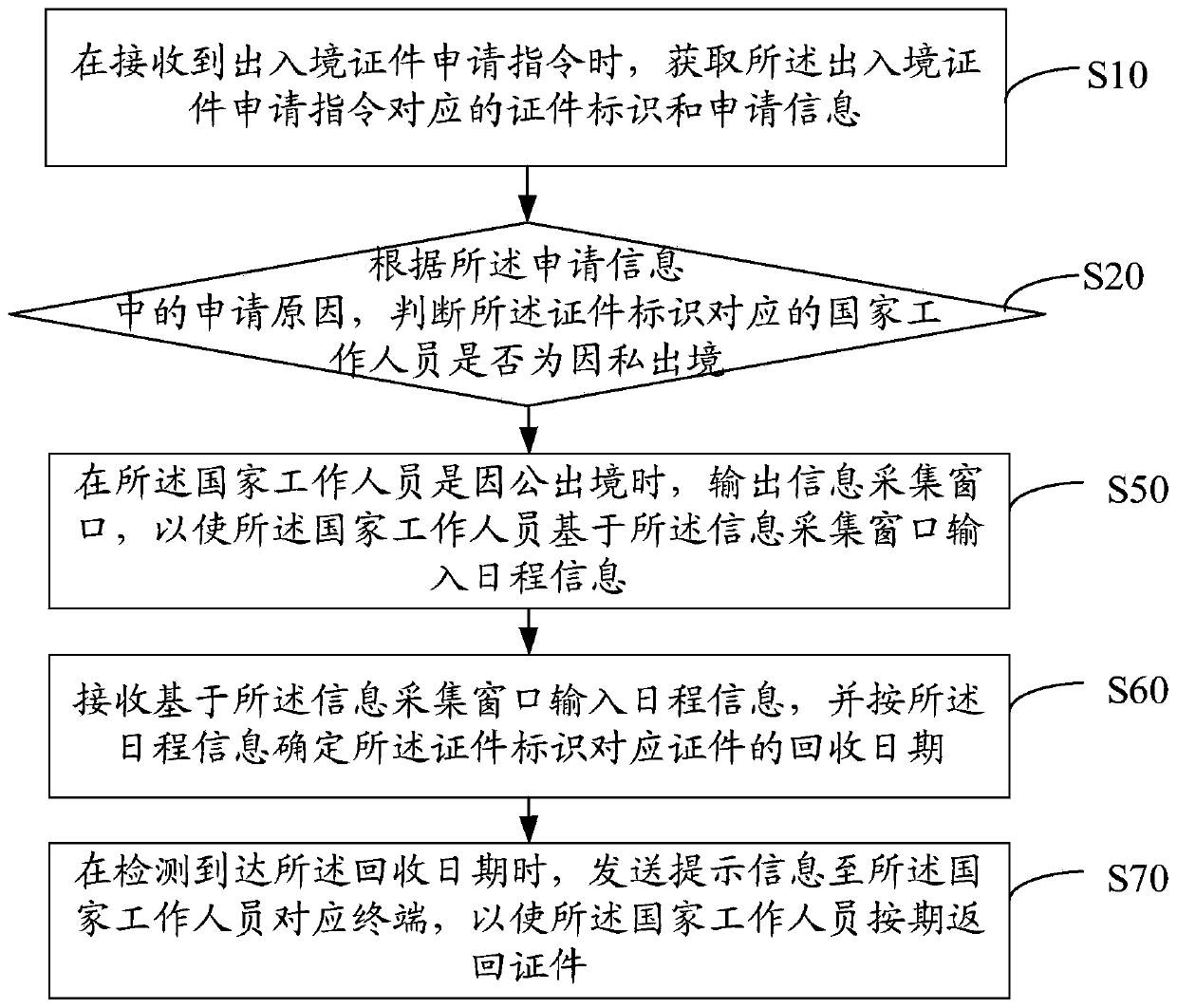
National staff entry and exit certificate management method and device, equipment and medium
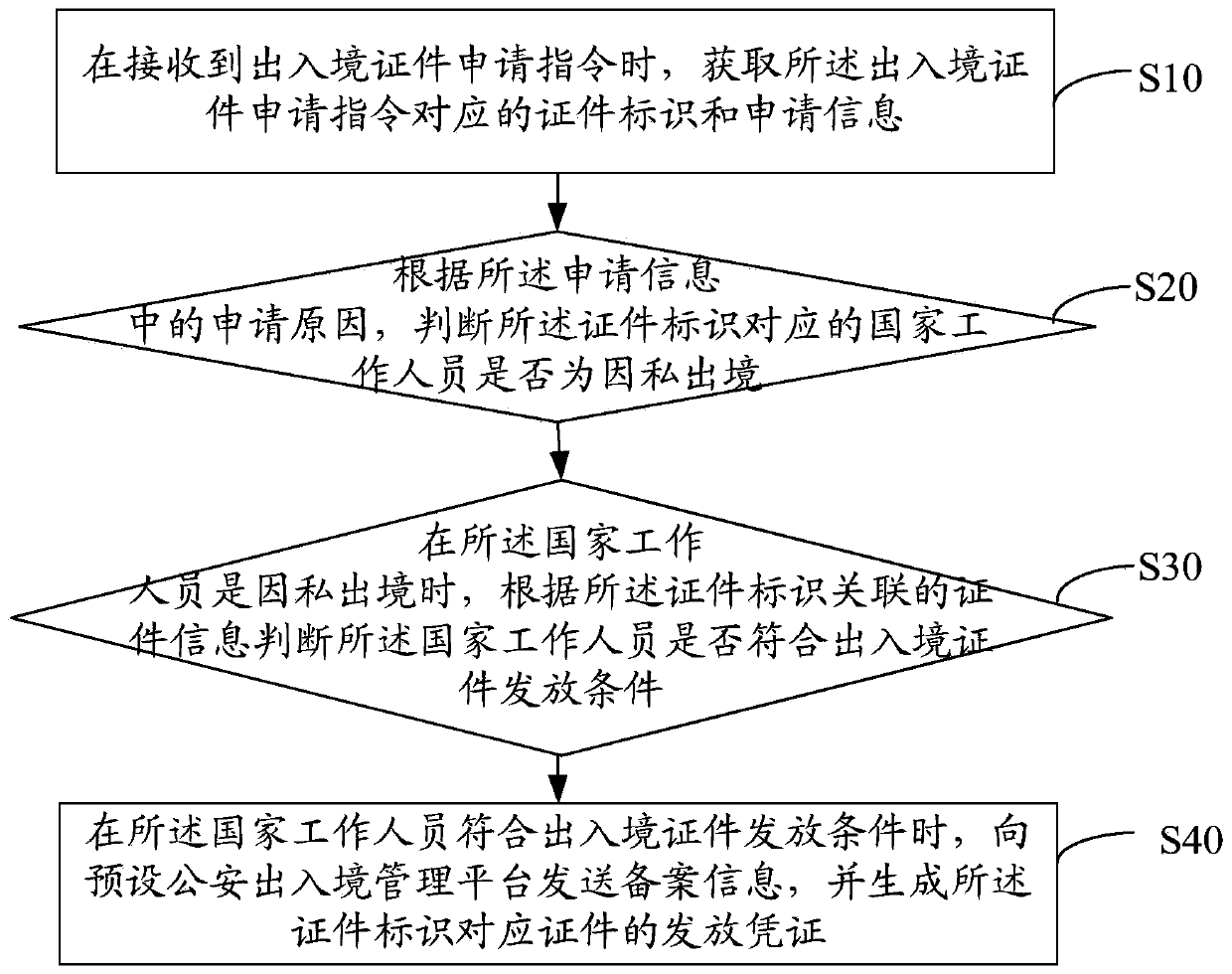
InactiveCN110322213AReasonable managementAvoid unreasonable issuesOffice automationApproaches of managementElectronic information
The invention belongs to the field of electronic information, and discloses a national worker entry and exit certificate management method, which comprises the steps of obtaining a certificate identifier and application information corresponding to an entry and exit certificate application instruction when the entry and exit certificate application instruction is received; according to an application reason in the application information, judging whether a country worker corresponding to the certificate identifier exits due to privacy or not; when the national staff exit due to privacy, judging whether the national worker meets an exit-entry certificate issuing condition or not according to certificate information associated with the certificate identifier; and when the national staff meets exit and entry certificate issuing conditions, sending record information to a preset public security exit and entry management platform, and generating an issuing certificate of a certificate corresponding to the certificate identifier. The invention also discloses a national staff entry and exit certificate management device, equipment and a medium. Reasonable management and issuing of entry and exit certificates of national workers are realized.
Owner:SHENZHEN LONGRISE SCI & TECH
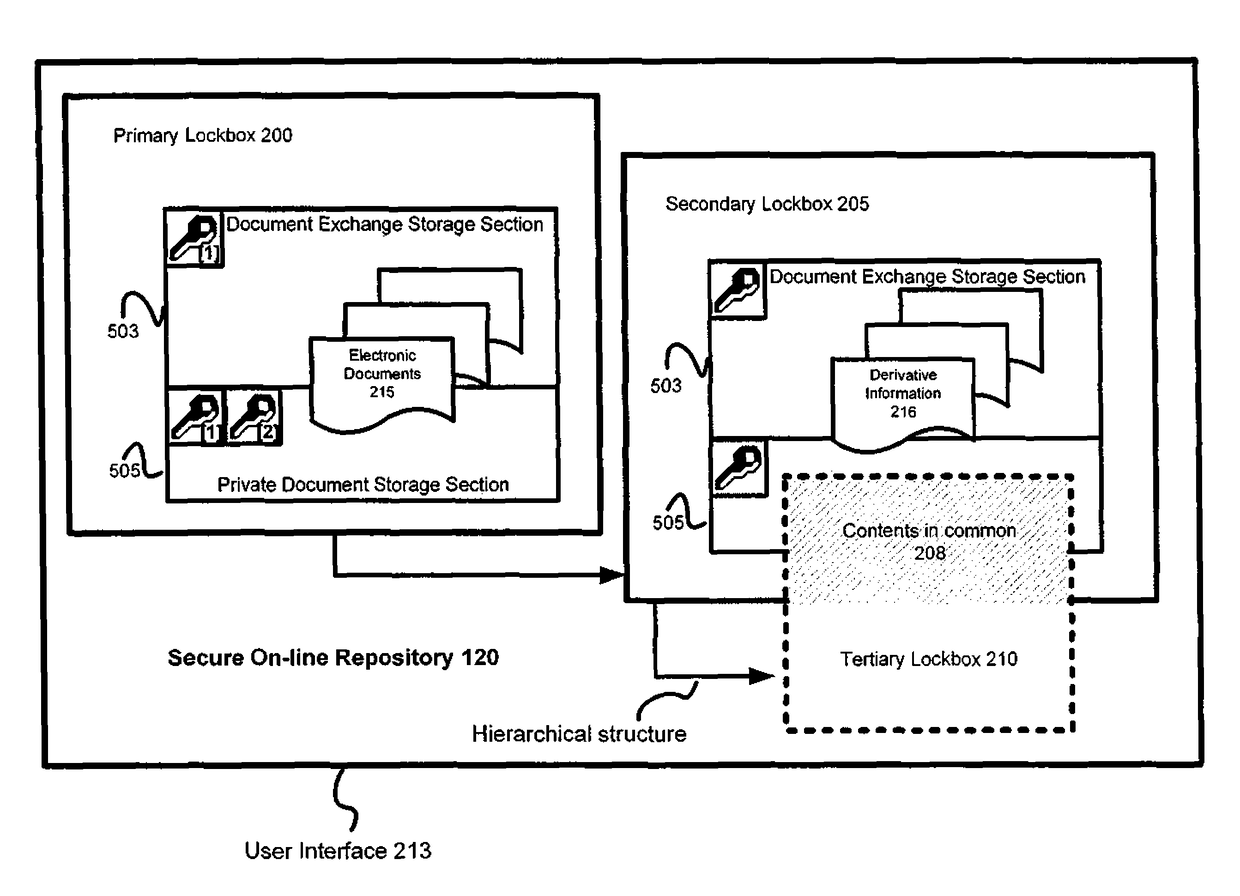
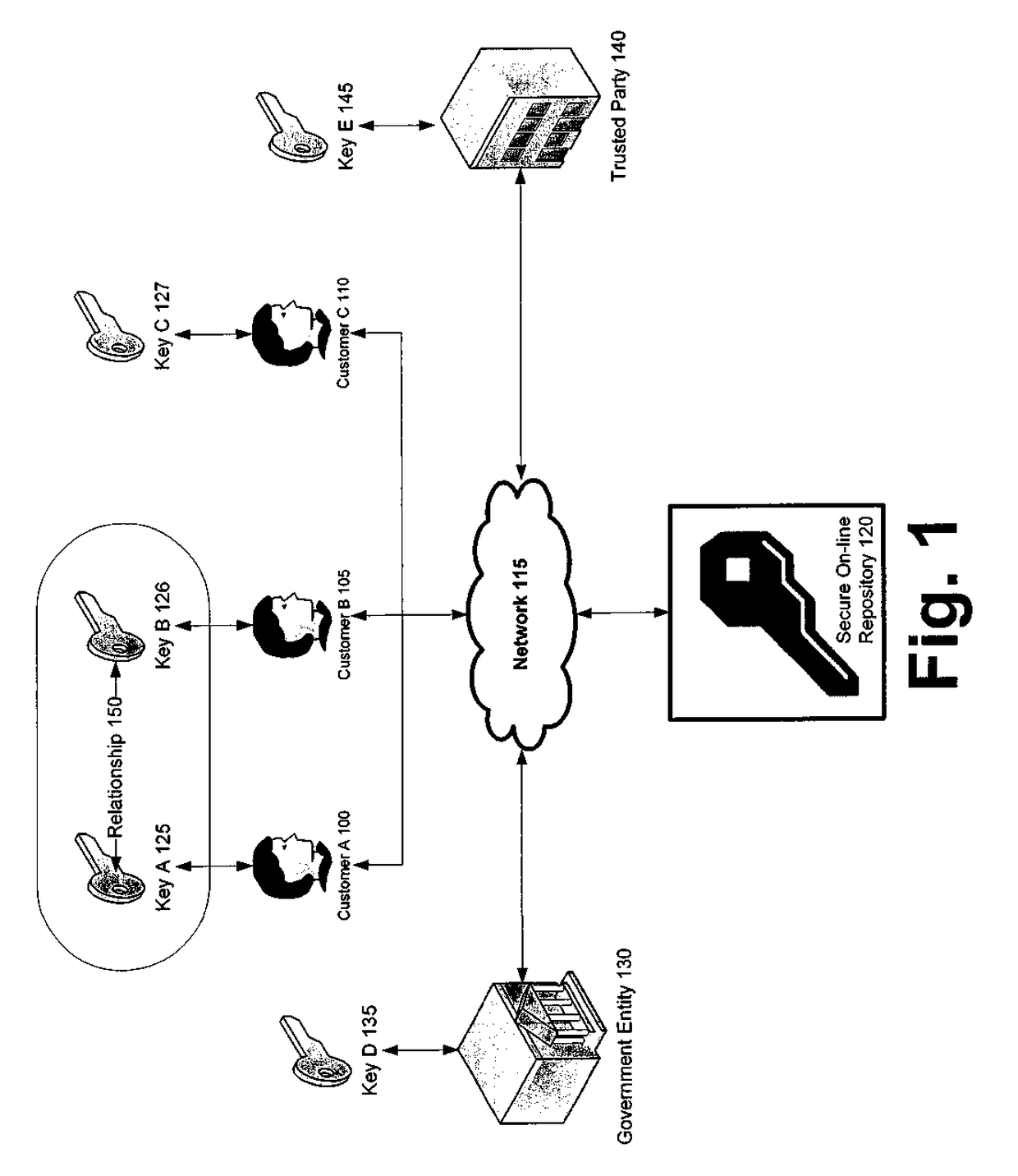
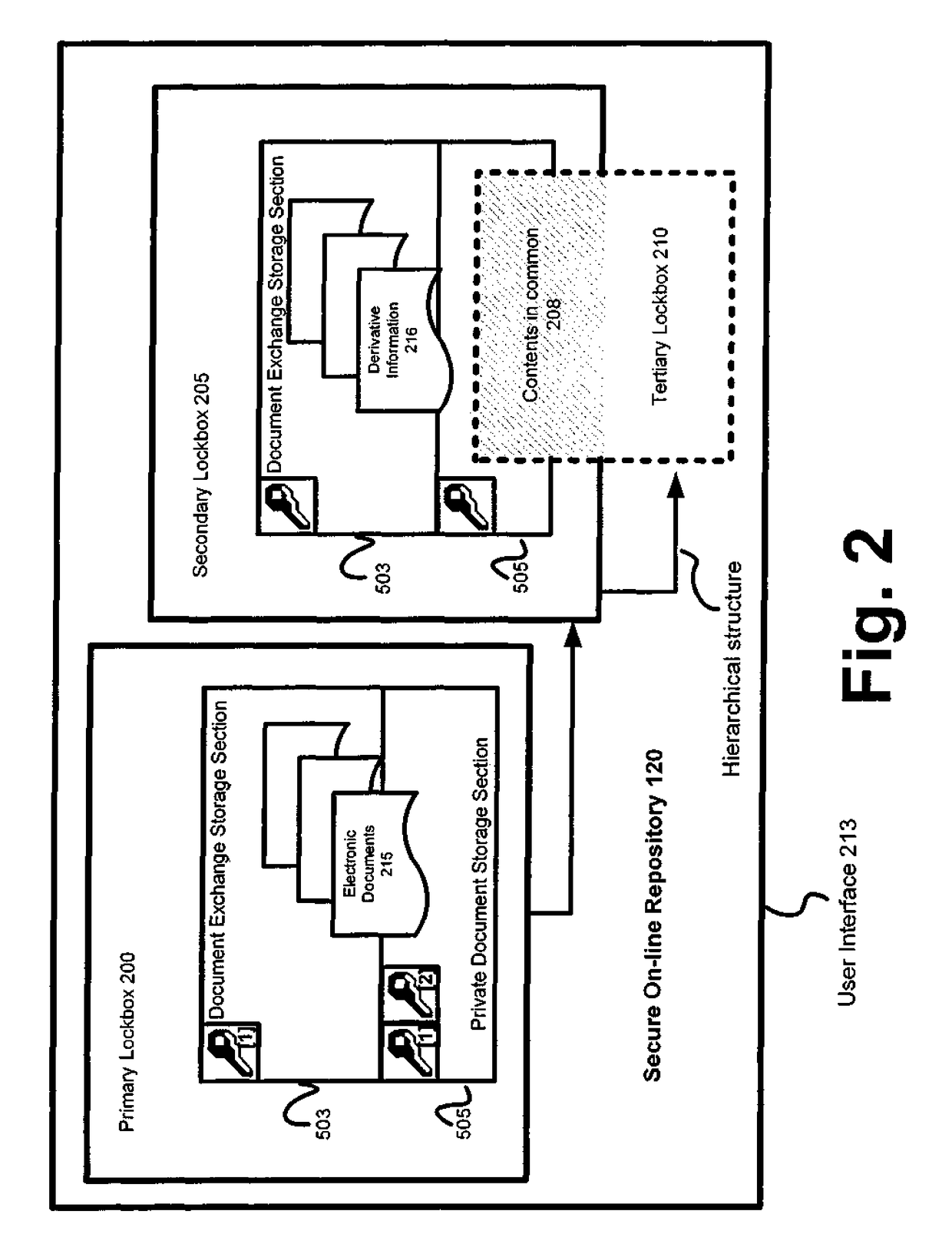
Systems and methods for secure online repositories
Mechanisms are disclosed herein for storing various records. Numerous keys and parties can access online repositories. These repositories contain a plurality of lockboxes, structured hierarchically and otherwise, providing public and private areas with varying levels of access. Some content of such lockboxes can be sharable. These lockboxes can be used not only to store diverse content, ranging from birth certificates to deeds and social security numbers, but they can also be accessed in a variety of ways. For example, keys to lockboxes can be made available by such events as the issuing of death certificates or birth certificates. Alternatively, keys can be issued according to various rules and heuristics stipulated by lockbox users. In either case, the plurality of lockboxes residing in repositories can be configured to provide centralized storage facilities that are secure and readily accessible from various computing devices.
Owner:USAA
Methods of sanitizing a flash-based data storage device
A data storage device includes one or more non-volatile, blockwise erasable data storage media and a mechanism for sanitizing the media in response to a single external stimulus or in response to a predetermined physical or logical condition. Optionally, only part of the media is sanitized, at a granularity finer than the blocks of the medium. Setting a flag in an auxiliary nonvolatile memory enables an interrupted sanitize to be detected and restarted. Optionally, a “death certificate” verifying the sanitizing is issued. Preferably, the media are configured in a manner that allows atomic operations of the sanitizing to be effected in parallel.
Owner:SANDISK IL LTD
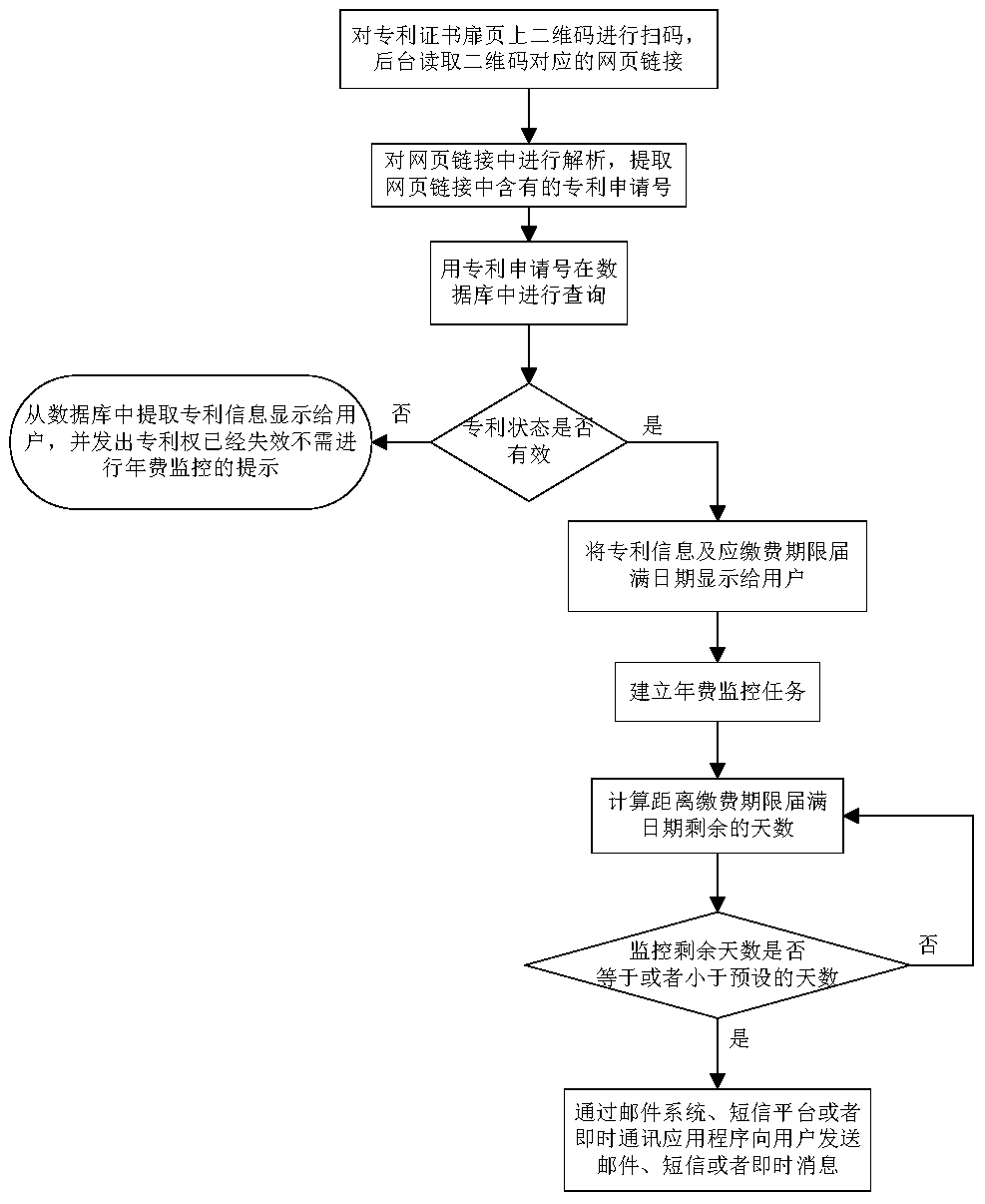
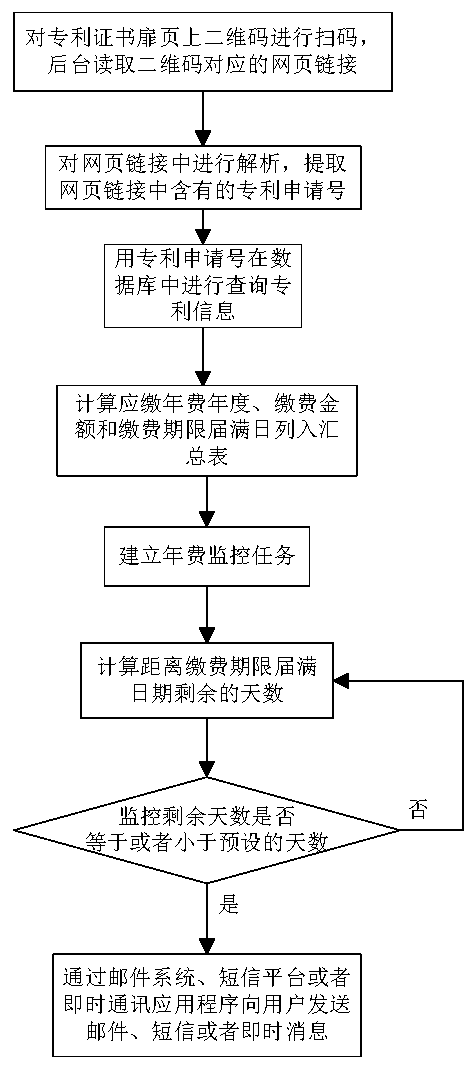
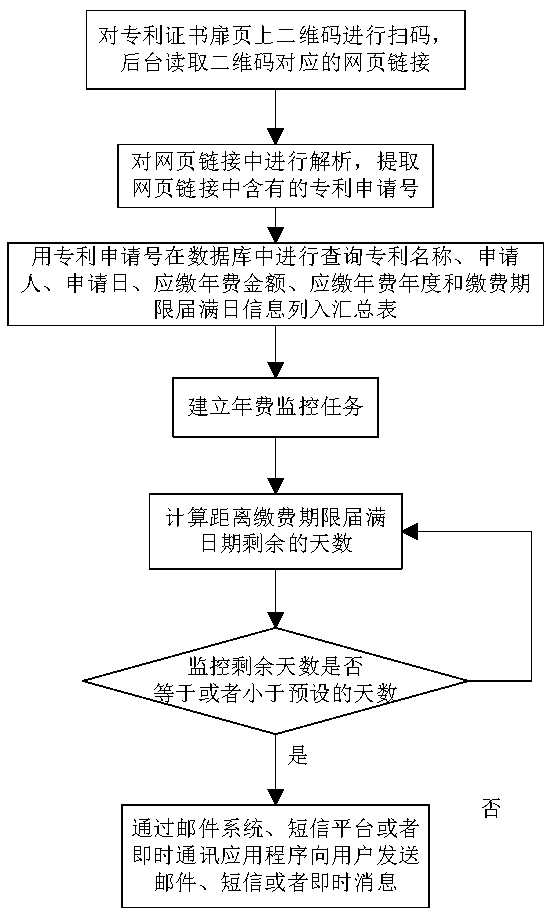
Annual fee monitoring method
InactiveCN108062345ASimple Automated LookupIntuitive monitoringOffice automationSpecial data processing applicationsPaymentIntellectual property
The invention discloses an annual fee monitoring method. The method comprises the following steps of: (1) scanning a two-dimensional code on the title page of a patent certificate by a user by using equipment with a code scanning function; (2) extracting patent information from a page or link obtained through scanning the two-dimensional code; (3) querying patent information by using an application number, and displaying the patent information to the user; and (4) every year, in a certain time before the fee payment deadline of the year, reminding the user. According to the annual fee monitoring method, users only need to scan two-dimensional codes on title pages of certificates by using mobile phones or other devices with code scanning functions without other multifarious jobs, all the patent authorization announcement texts can be looked up and downloaded from the State Intellectual Property Office, and the self-applied patents, agented patents and other's patents can be automatically looked up and monitored through simple scanning.
Owner:广州市知君信息科技有限公司
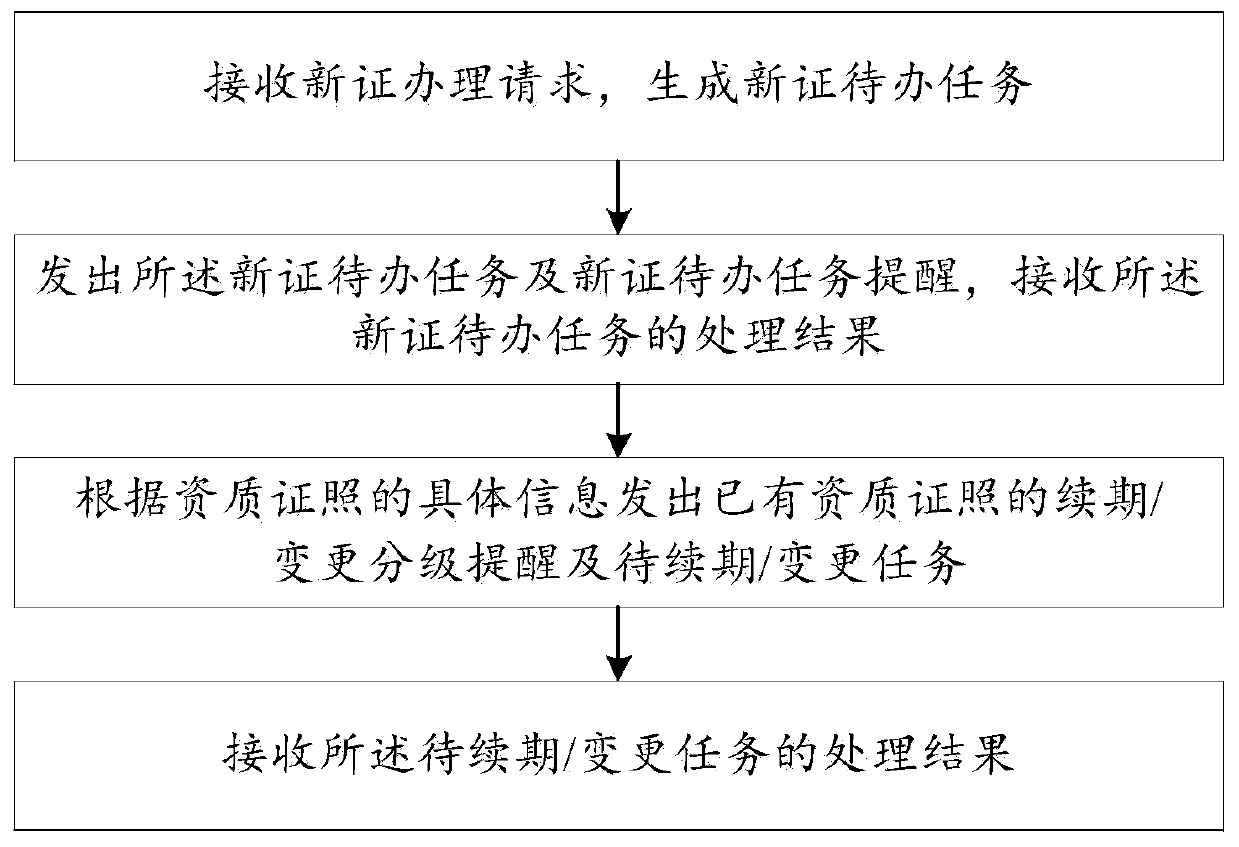
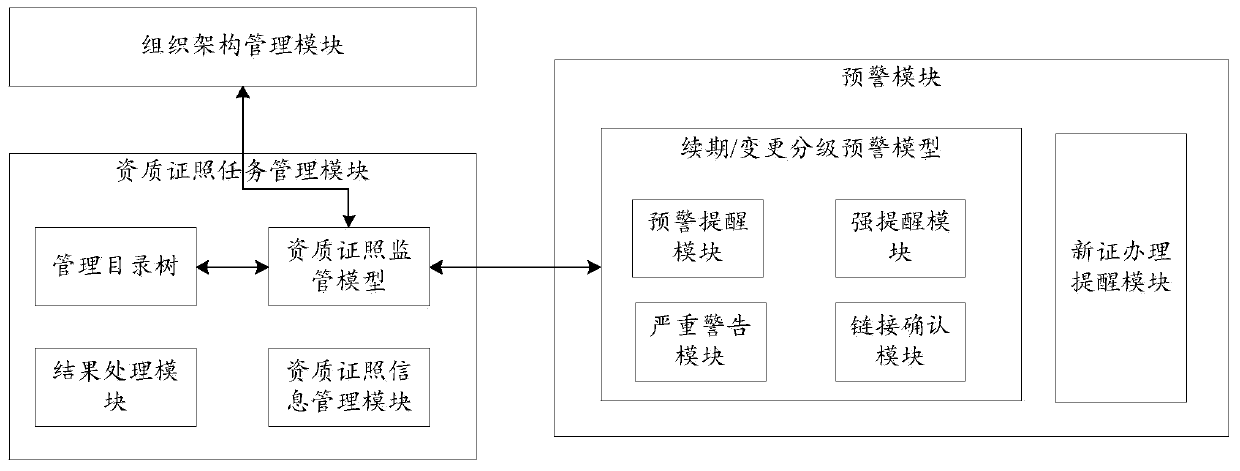
Qualification certificate management method and system
InactiveCN110310010ARealize the whole process managementRealize regulationForecastingOffice automationOperating systemDeath certificate
The invention discloses a qualification certificate management method and system. The qualification certificate management method comprises the steps: receiving a new certificate handling request, andgenerating a new certificate to-be-handled task, wherein the new certificate handling request comprises category information of a qualification certificate requested to be handled and enterprise organization architecture information to which the qualification certificate requested to be handled belongs; sending out the new certificate to-do task and a new certificate to-do task reminder, and receiving a processing result of the new certificate to-do task; sending renewal change grading reminding and to-be-renewal change tasks of existing qualification certificates according to the specific information; and receiving a processing result of the to-be-continued change task. According to the qualification certificate management method disclosed by the invention, two dimensions of supervisionand early warning are realized; and according to the invention, the management problems of new certificate handling and renewal change handling of existing qualification certificates are solved, and full-process management, supervision and early warning of the qualification certificates are realized, so that enterprise operation risks caused by poor qualification certificate management are avoided, and irreversible serious consequences brought to enterprises are avoided.
Owner:SUNING CLOUD COMPUTING CO LTD
Tax handling system and tax handling method
InactiveCN107093139AImprove handling efficiencyRealize self-service uploadFinanceSource Data VerificationHandling system
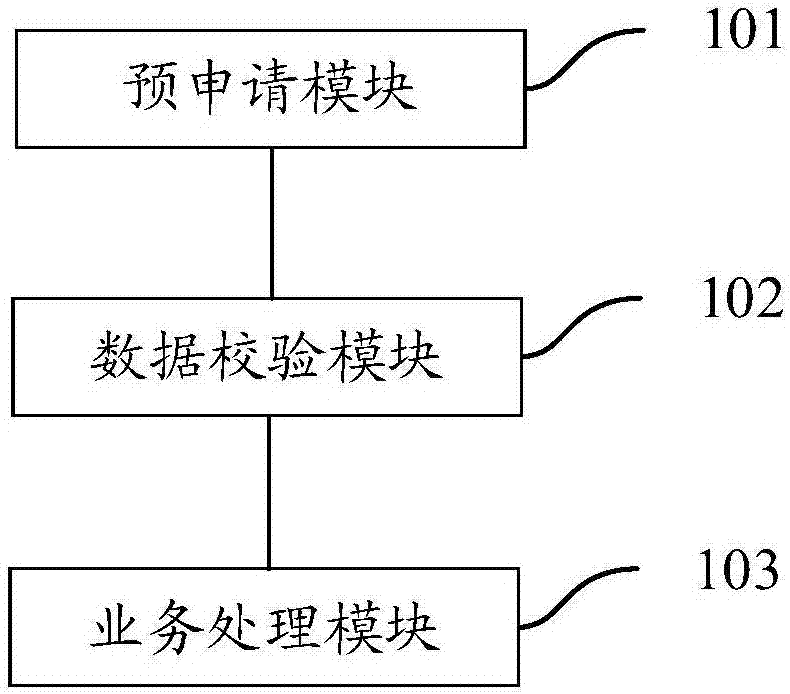
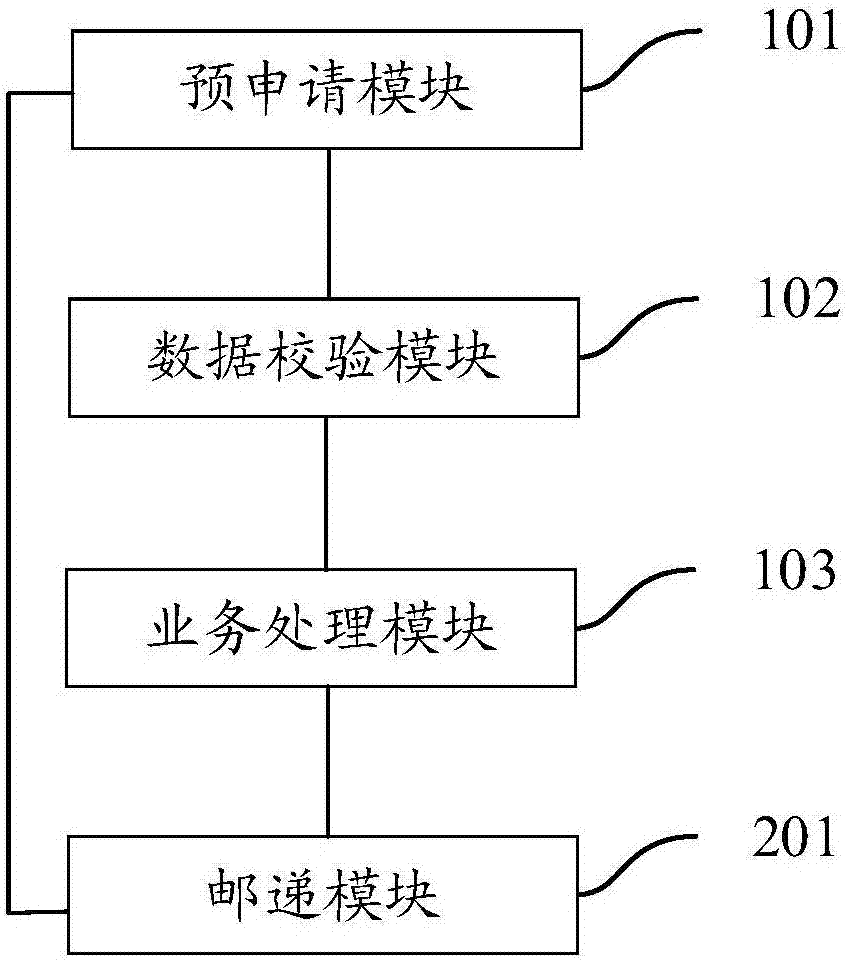
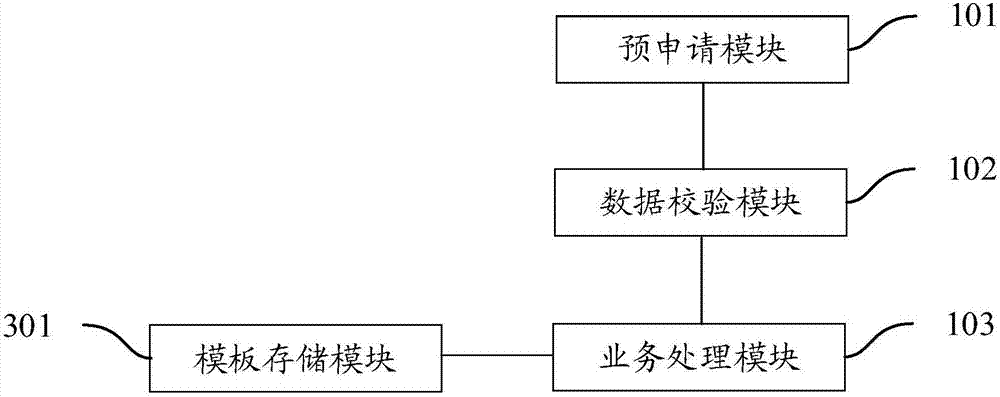
The invention provides a tax handling system and a tax handling method. The tax handling system comprises a pre-application module, a data verification module, and a service processing module. The pre-application module is used for receiving a tax handling request input by a user, wherein the tax handling request carries corresponding tax data. The data verification module is used for verifying the tax data according to pre-stored tax standard information, and triggering the service processing module when the tax data passes verification. The service processing module is used for processing the tax data and generating a corresponding tax certificate. The scheme can improve the efficiency of tax handling.
Owner:SHANDONG INSPUR COMML SYST CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com