A certificate issuer anonymity entity identification method and system
A credential and entity technology, applied in the authentication method and system field of anonymity of the credential issuer, can solve the problems of malicious collection of data, differentiated treatment of users, destruction of cloud environment location independence, transparency, etc., to achieve increased anonymity and strong privacy Effects on sex and flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] Example 1. Issuer's Anonymous Authentication Algorithm
specific example
[0041] System establishment: let G 1 ,G 2 ,GT It is a prime number order cyclic group of p (the present invention needs to set three different prime number order cyclic groups, and use subscripts 1, 2 and T to distinguish two different prime number order cyclic groups), P 1 ,P 2 G respectively 1 ,G 2 generator of . ψ is G 2 to G 1 The isomorphic map of , satisfying ψ(P 2 ) = P 1 , e:G 1 ×G 2 →G T is a bilinear map, that is, the input of the bilinear map e belongs to the group G 1 and G 2 The two elements in , the output is the group G T in an element. Choose a hash function and P 0 ∈ G 2 ,in is an integer multiplicative group of order p. Then the public parameters generated by the system are params={G 1 ,G 2 ,G T ,p,e,ψ,P 1 ,P 2 ,P 0 ,h,H}, where e is a bilinear map as described above.
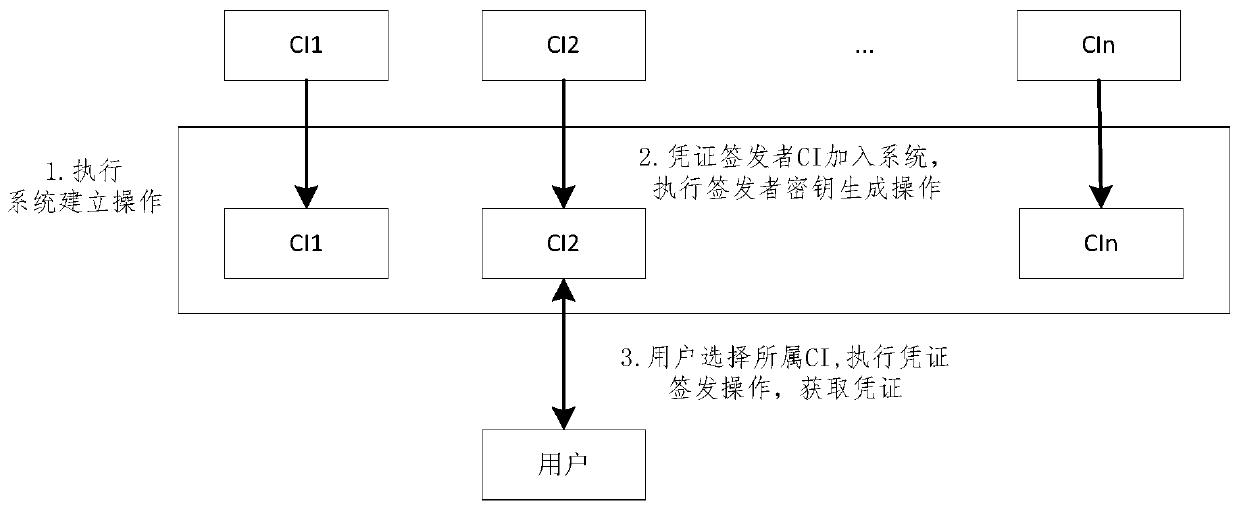
[0042] Issuer key generation: When the issuer of the certificate whose issuer ID is I needs to generate its own key, the following operations are performed: first...
Embodiment 2
[0055] Example 2. Anonymous authentication system with issuer anonymity
[0056] This embodiment aims to provide a specific example of the attribute-based anonymous authentication system of the present invention.
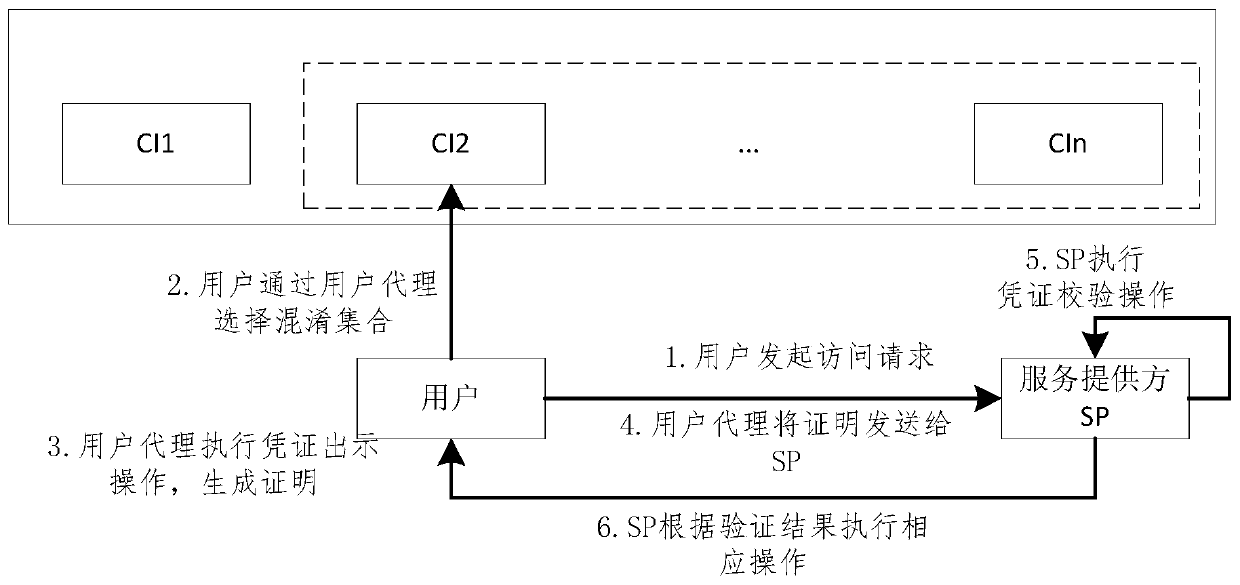
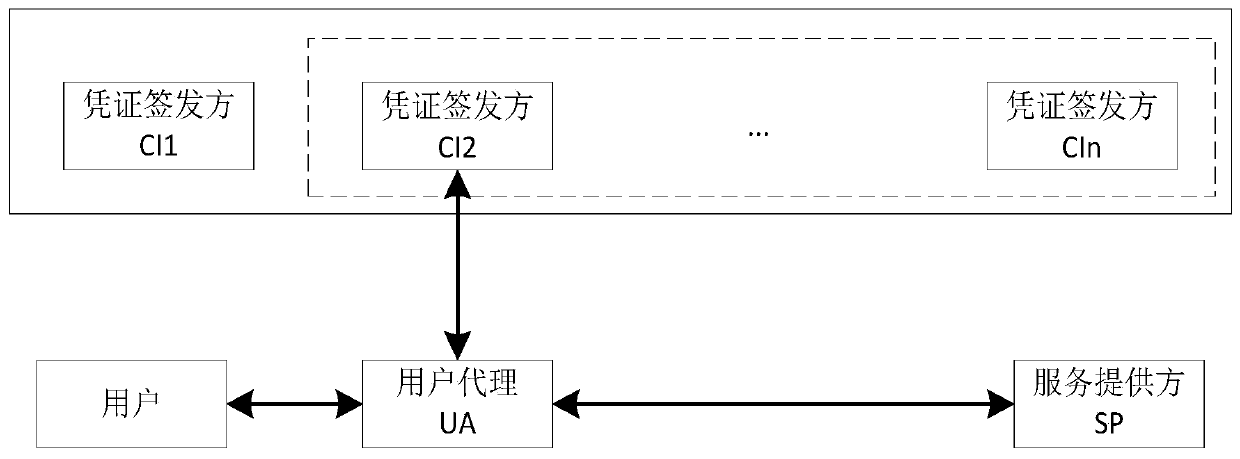
[0057] The system includes three types of subjects: credential issuer (Crendential Issuer, CI), user agent (UserAgent, UA), and service provider (Service Provider, SP). The three parts are connected through the network, and the certificate issuer is responsible for verifying the validity of the user's identity and issuing attribute certificates for the user. The main work of the user side is done by the user agent, mainly public parameter storage, credential reception, storage, query, and generation of identity certificates. Users need to apply for attribute certificates from the certificate issuer before requesting services. The service provider verifies the certificate presented by the user, and provides corresponding services or data if the verification is pass...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com