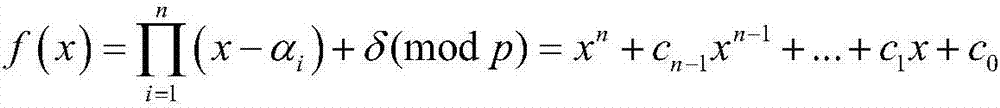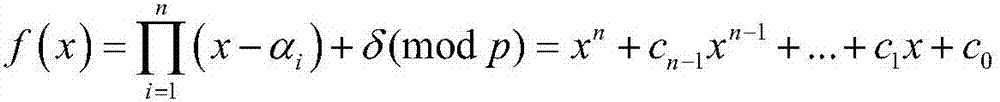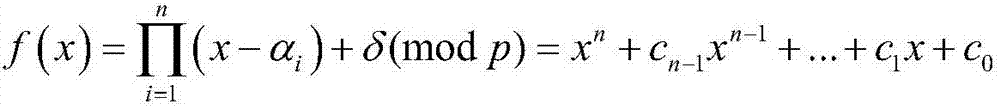Elliptic curve-based efficient and anonymous certificateless multi-receiver signcryption method
An elliptic curve and multi-receiver technology, which is applied to the public key of secure communication, user identity/authority verification, digital transmission system, etc., can solve the problem of low computing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0106] Glossary:
[0107] PKG (Private Key Generator): private key generation center;
[0108] η: system security parameters;
[0109] p: large prime number;
[0110] f p : A finite field whose order is a large prime number p;
[0111] G p : additive cyclic group;
[0112] E(F p ): safe elliptic curve;
[0113] P: additive cyclic group G p Generators on
[0114] s: system master key;
[0115] P pub : system public key;
[0116] ∈: limited domain symbol, such as A∈B, means that A belongs to B;
[0117] h i : Anti-collision hash function, where i=0,1,2,3,4;
[0118] A→B: mapping from domain A to value domain B;
[0119] S: sender;
[0120] L i : the i-th recipient, i=1,2,...,n;
[0121] n: the number of recipients randomly selected by the sender S;
[0122] ID: user's identity information;
[0123] ID S : the identity information of the sender S;
[0124] ID i : the i-th receiver L i Identity information of , i=1,2,...,n;
[0125] lambda 1 : the length ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com