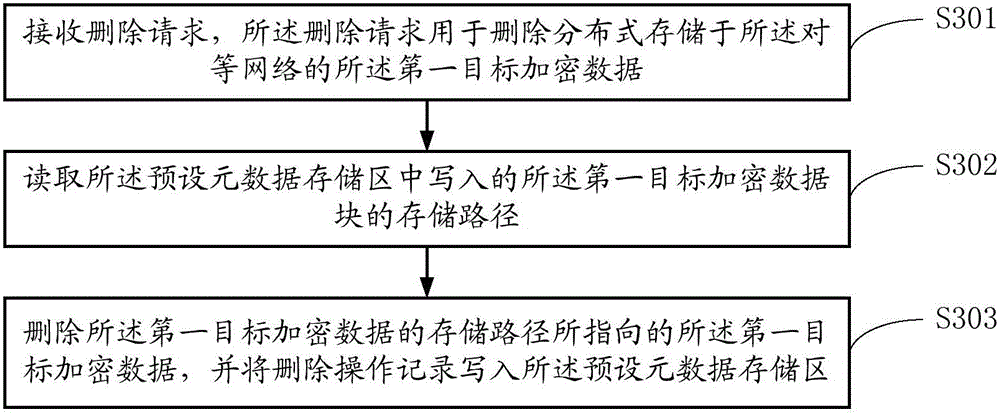
Patents
Literature
57results about How to "Keep storage safe" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
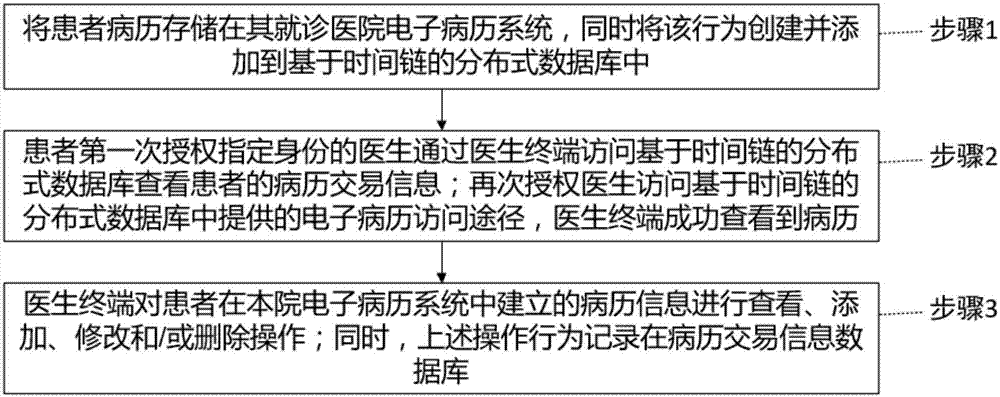
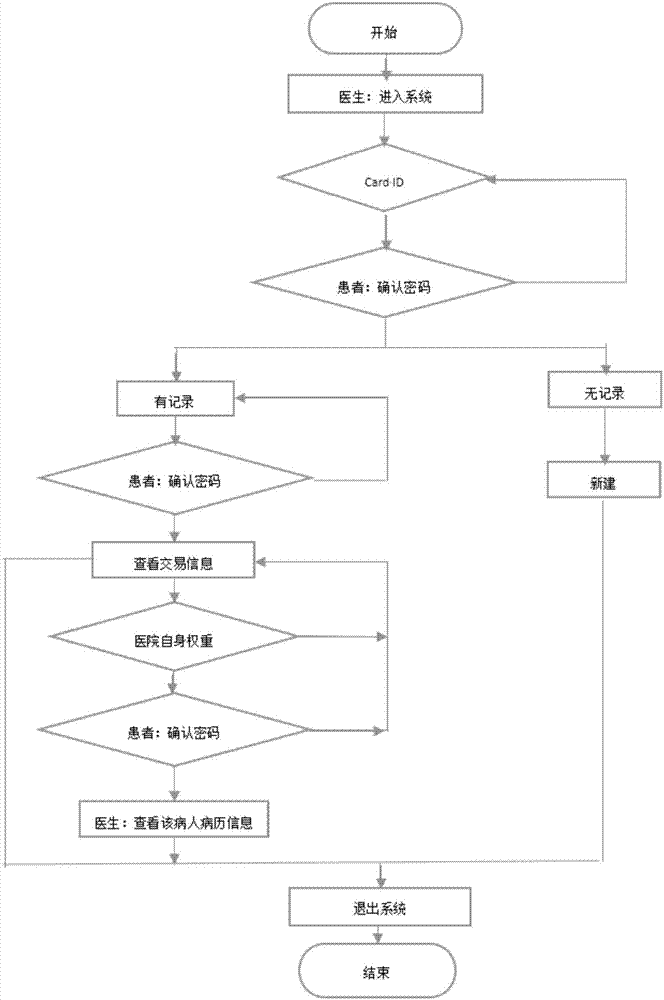
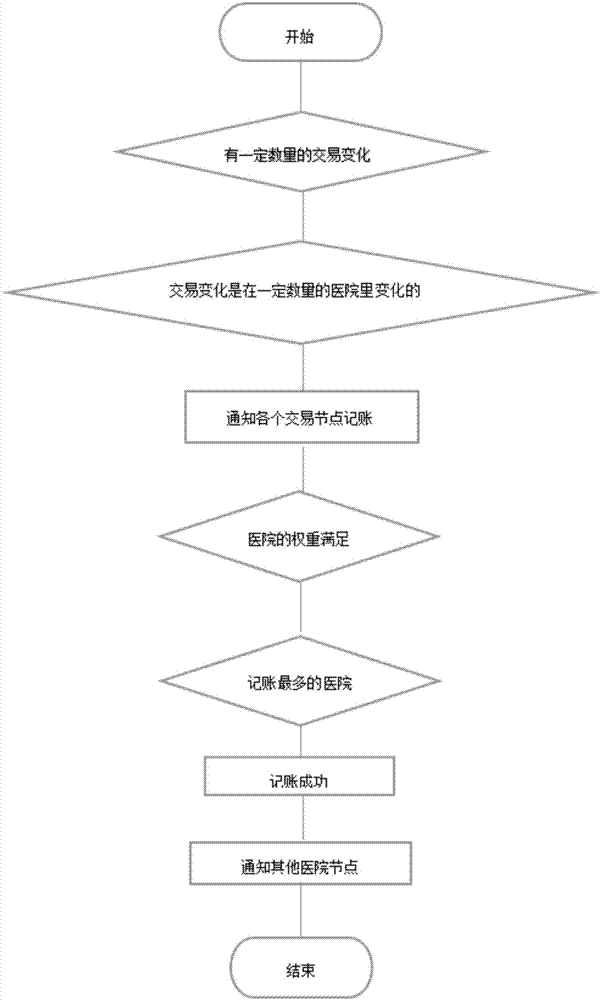
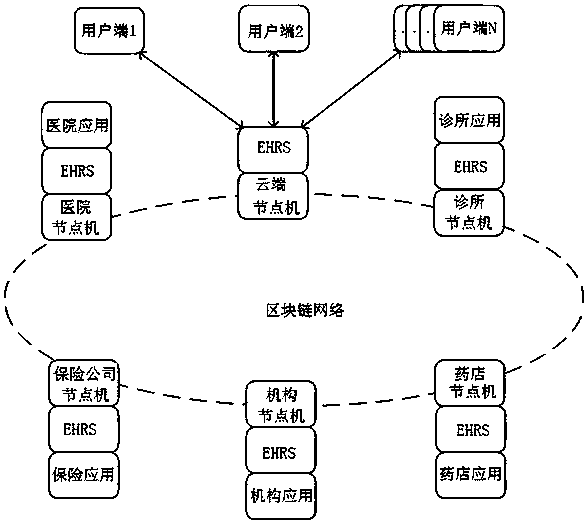
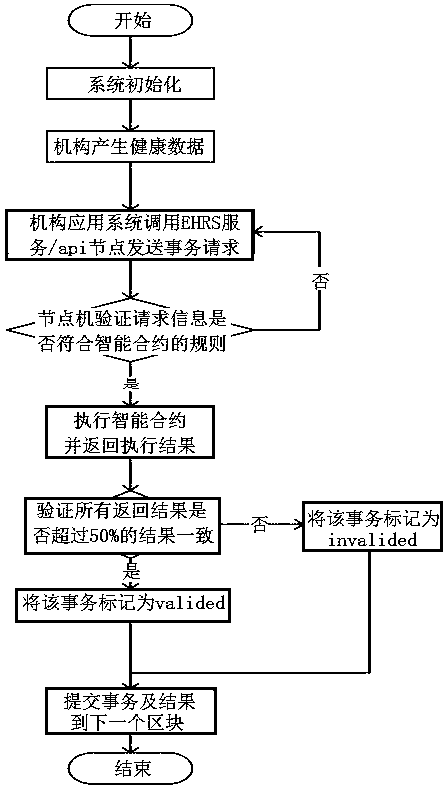
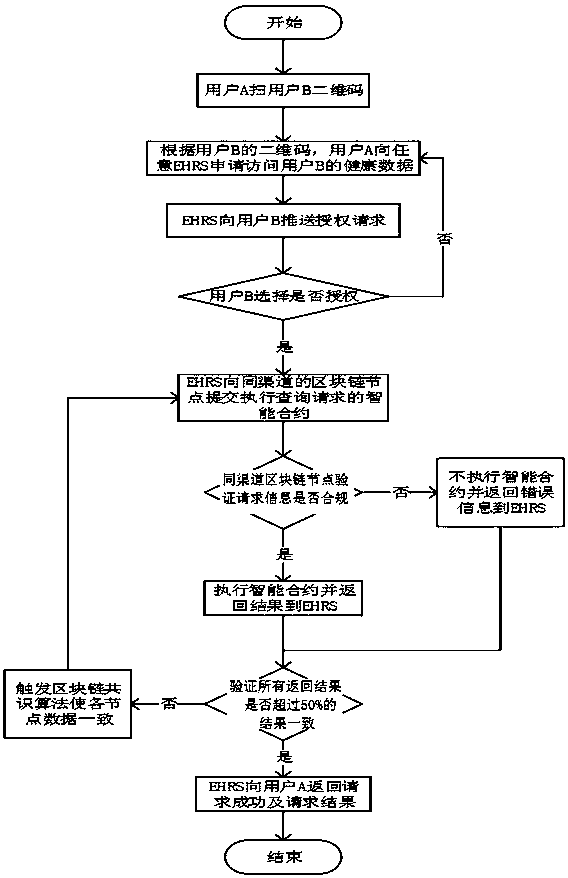
Electronic medical record management method and system
InactiveCN106934243AGuaranteed originalityGuarantee authenticitySpecial data processing applicationsPatient-specific dataMedical recordStorage security
The present invention provides an electronic medical record management method and system. According to the method and system provided by the present invention, the block chain idea is used in the electronic medical record system, the time chain based distributed database is used to keep patient historical medical record information original, and the source for each record can be traced. The method and system provided by the present invention have the following beneficial effects that: 1. medical record information and medical record operation information are ensured to be original and authentic; 2. data storage security of medical record information and medical record operation information is ensured; 3. personal privacy of the patient can be ensured not to be exposed; and 4. rapid sharing of medical record information and medical record operation information is realized.
Owner:北京医拍智能科技有限公司
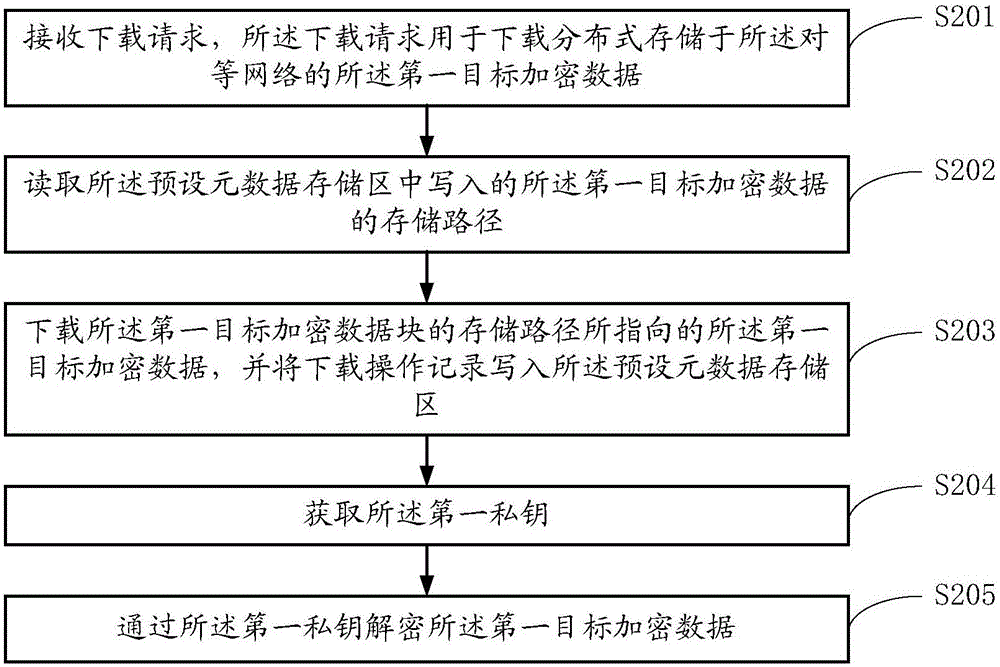
Distributed cloud data management method and system based on peer-to-peer network
ActiveCN106612285AKeep storage safeIncrease storage spaceTransmissionCloud data managementStorage security
The invention belongs to the technical field of electronics, and provides a distributed cloud data management method and system based on a peer-to-peer network. The peer-to-peer network comprises a plurality of user nodes, and each user node in the peer-to-peer network can encrypt data via a private key of a user of the node and then upload the data to the peer-to-peer network to store the encrypted data to other user nodes of the peer-to-peer network in a distributed manner. By encrypting data and storing the data to the user nodes of the peer-to-peer network in the distributed manner, mass data can be stored, so that the storage security of data is effectively guaranteed while the existing storage space is expanded.
Owner:TCL CORPORATION
Distributed storage system
ActiveCN106843750AImprove reliabilityImprove usabilityInput/output to record carriersTransmissionMaster controllerClient-side
The invention discloses a distributed storage system. The system comprises multiple storage layers, a main controller and a storage monitor, wherein the multiple storage layers are used for conducting classification storage on data with different security levels, the main controller is used for receiving a data storage request sent from a client side to the main controller and establishing a storage log, and the storage monitor is used for seeking a storage layer with the same security level according to the security level of data which the main controller requests to store and performing data storage, then storing a storage path in a block chain in a form of a link, wherein the link is correlated to the storage log established on the main controller. According to the distributed storage system, secure classification storage of the data can be achieved; meanwhile, due to the existence of a data interaction and backup mechanism among storage devices in the multiple storage layers, automatic renew and backup storage of the data can be achieved, even if fault occurs in one of the storage devices, it still can be guaranteed that duplicate backups of the data are reserved in the storage device all the time, thus the permanent storage of the storage data is achieved, and not too many storage resources are occupied at the same time.
Owner:SUZHOU INST OF BIOMEDICAL ENG & TECH CHINESE ACADEMY OF SCI
Electronic health record management system and method
InactiveCN108460290AGuaranteed originalityKeep storage safeDigital data protectionPayment protocolsBlockchainManagement system
The present invention relates to an electronic health record management system and method, which solves the technical problem of low confidentiality. The method is characterized in that: by taking a blockchain as a storage underlying layer of a health record system, de-intermediated trust of all nodes is achieved; all data cannot be tampered with, and traceability and consistency of all the data are achieved; and open transparency of non-sensitive data and confidentiality of sensitive and private data are achieved. The technical scheme of the present invention has the following beneficial effects that: the originality and authenticity of health data and operational data are ensured, and the health data and the operational data cannot be tampered with; the storage security of the health data and of the operational data of the health data is ensured; it is ensured that personal privacy and sensitive information cannot be leaked; and the technical scheme for fast sharing of health data and operational data better solve the problem and can be used in medical electronic applications.
Owner:江苏省卫生统计信息中心
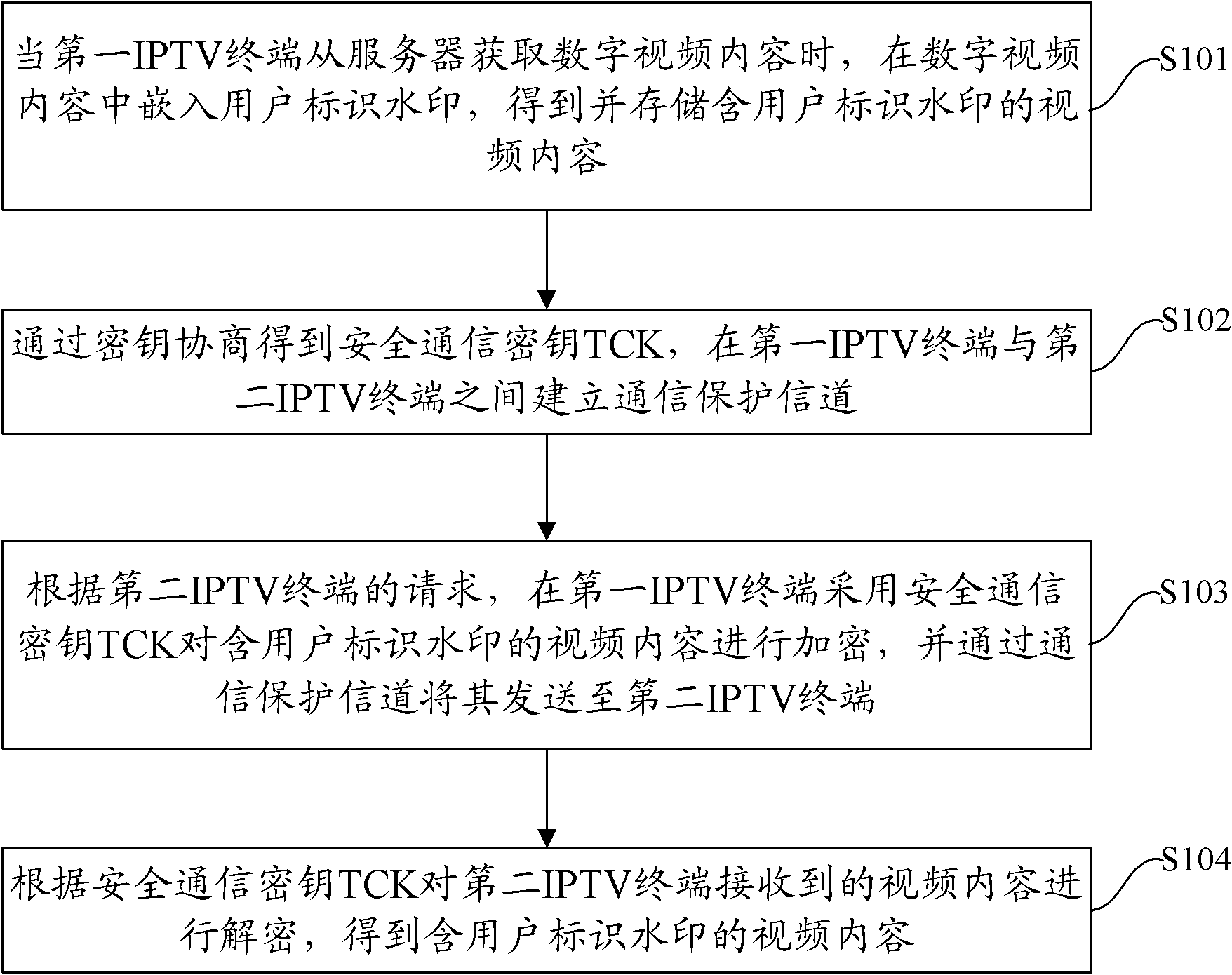
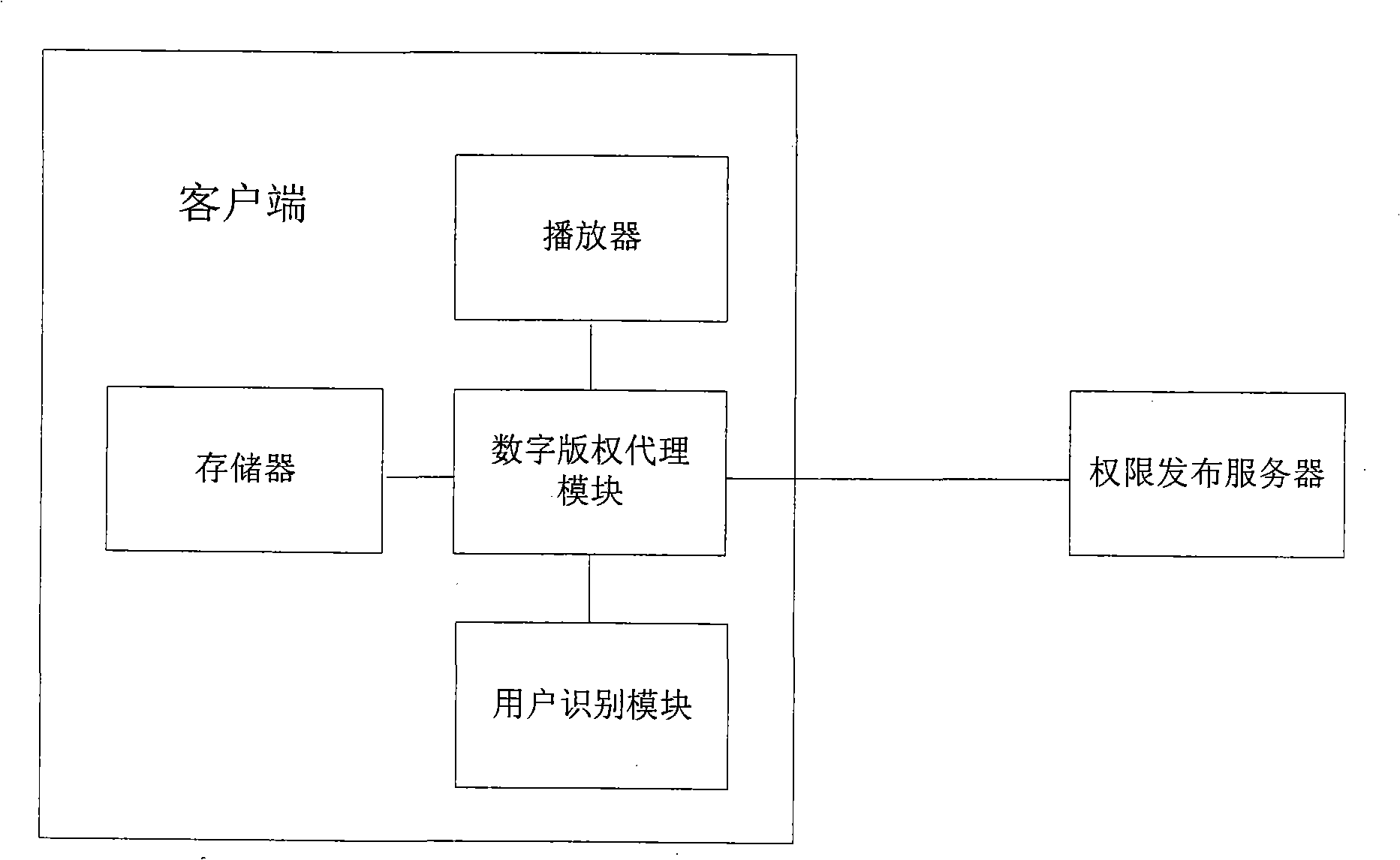
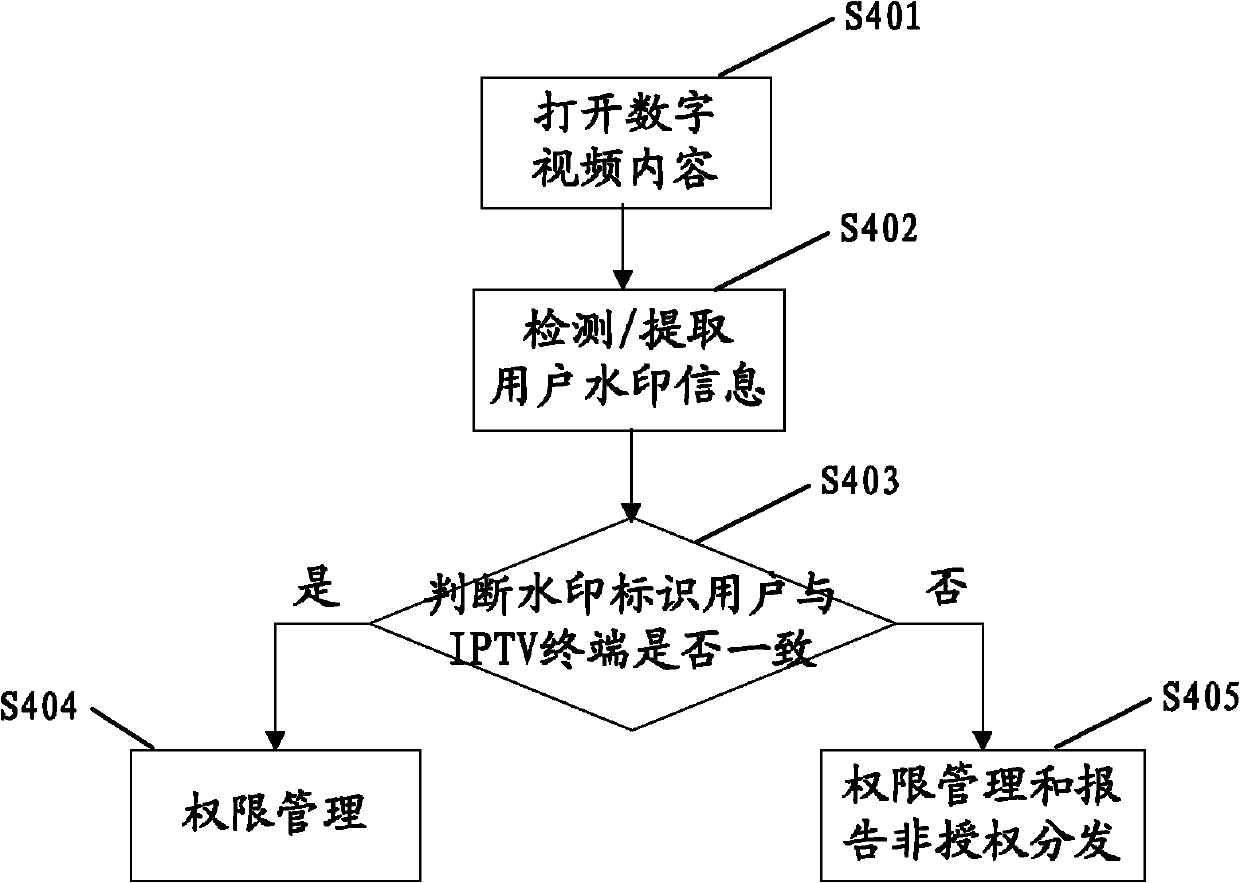
Digital-watermark-based digital copyright management method and device for IPTV terminals
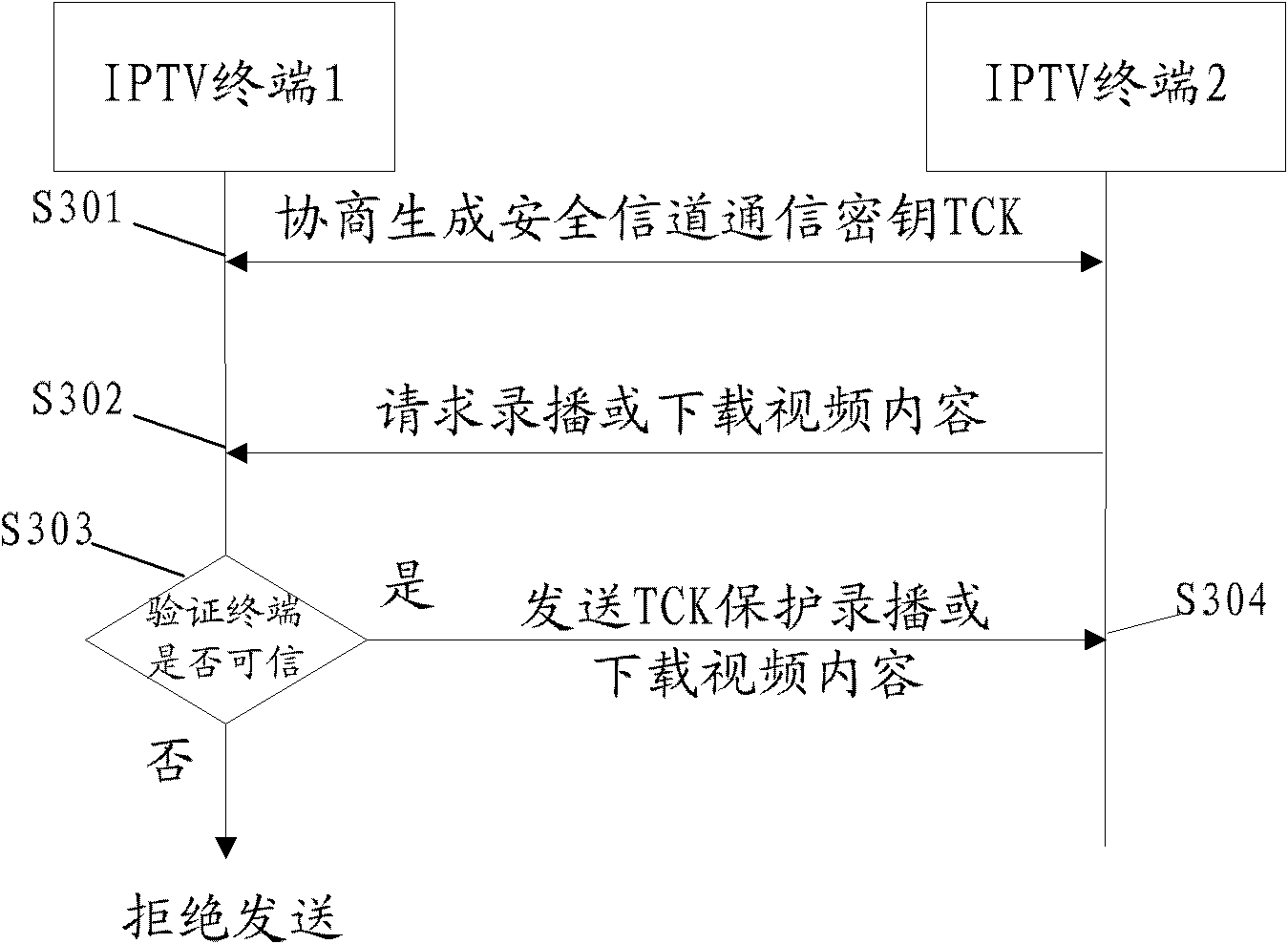
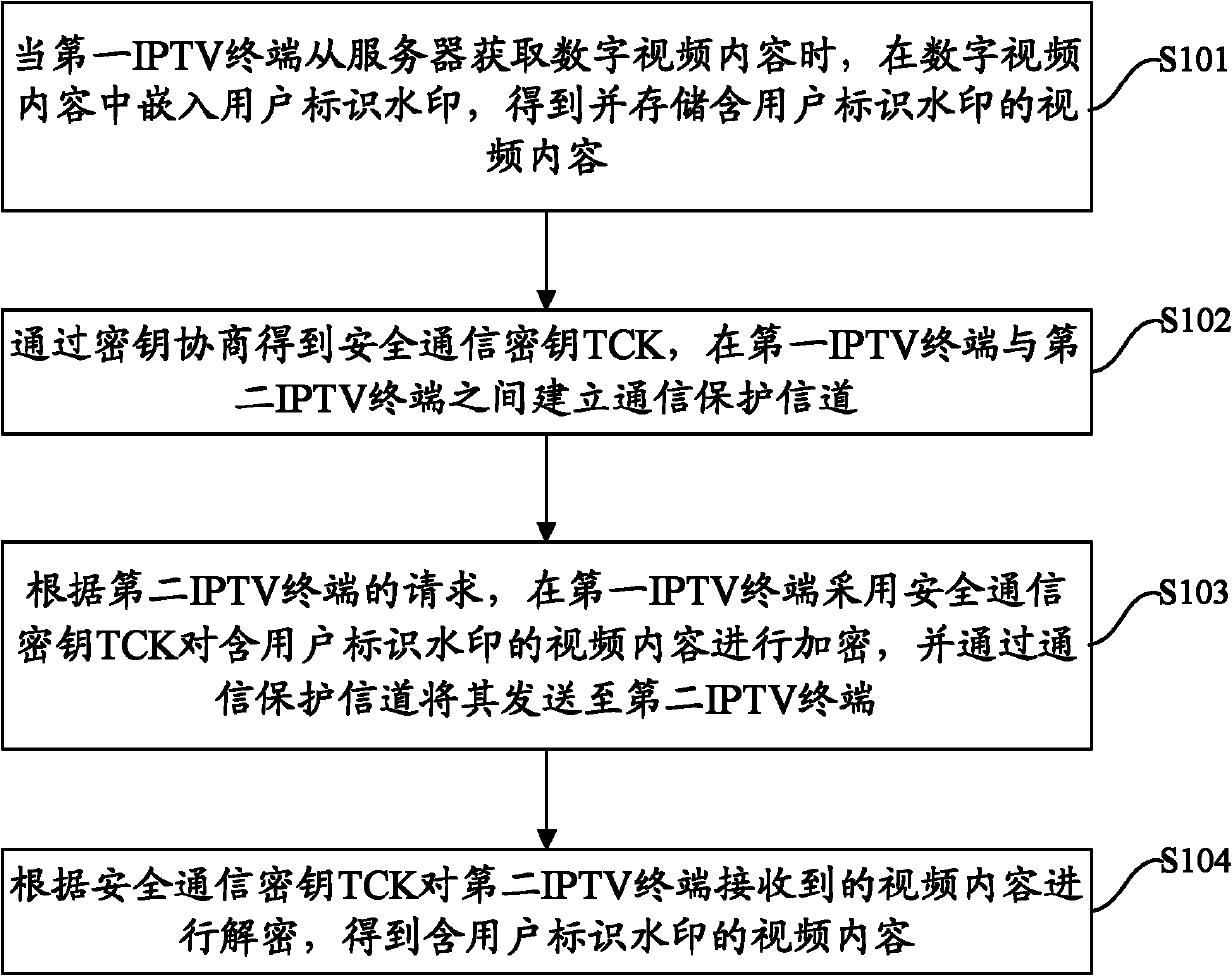
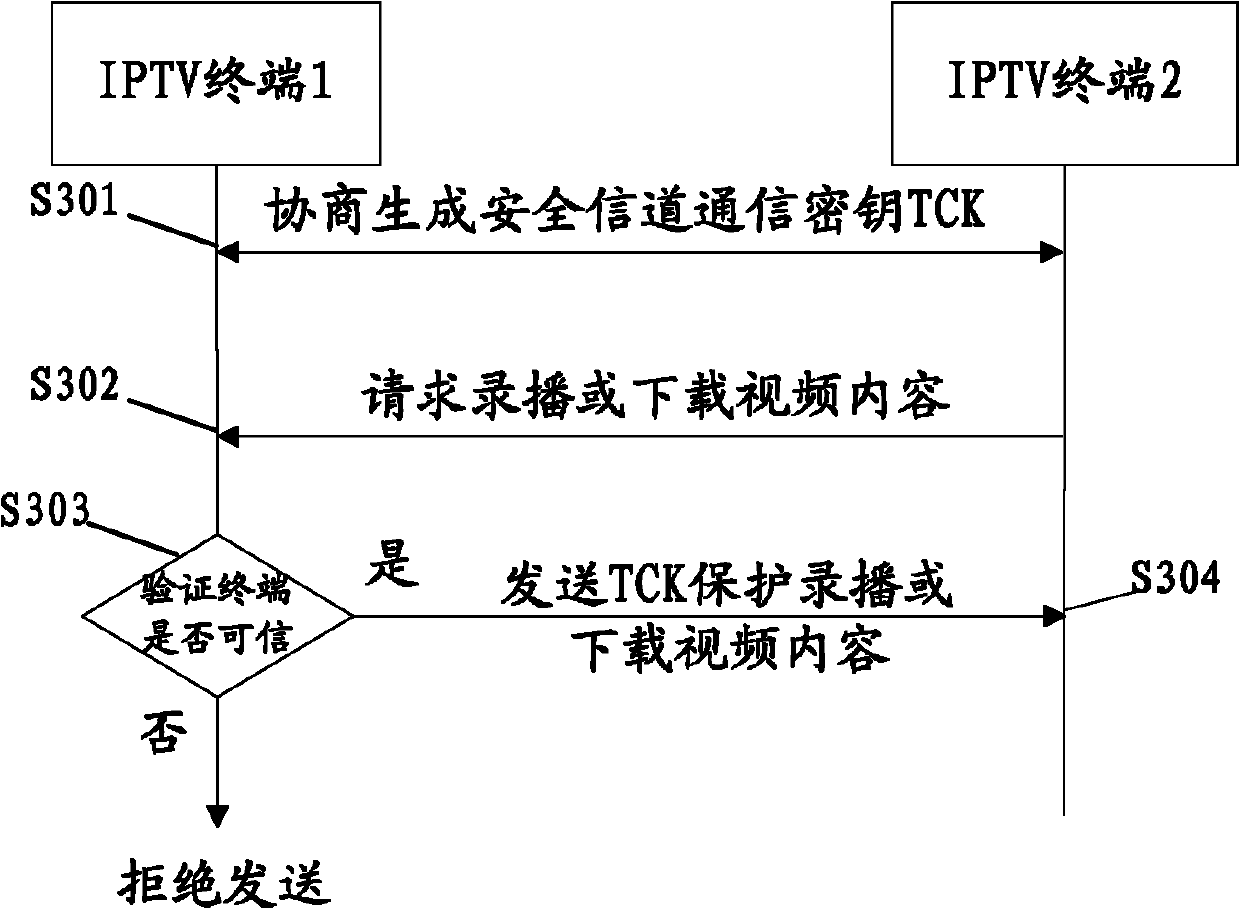
The invention discloses a digital-watermark-based digital copyright management method and a device for IPTV (Internet Protocol Television) terminals, wherein the method comprises the steps as follows: embedding a user identity watermark in a digital video content when a first IPTV terminal obtains the digital video content from a server, thereby obtaining and storing the video content with the user identity watermark; obtaining a security communication key TCK (Technology Compatibility Kit) through key agreement, and establishing a communication protection channel between the first IPTV terminal and a second IPTV terminal; adopting the security communication key TCK to encrypt the video content with the user identity watermark at the first IPTV terminal according to the request of the second IPTV terminal, and sending the encrypted video content to the second IPTV terminal through the communication protection channel; and decoding the video content received by the second IPTV terminal according to the secure communication key TCK, thereby obtaining the video content with the user identity watermark.
Owner:AEROSPACE INFORMATION
Addition key segmentation-based SM2 signature method
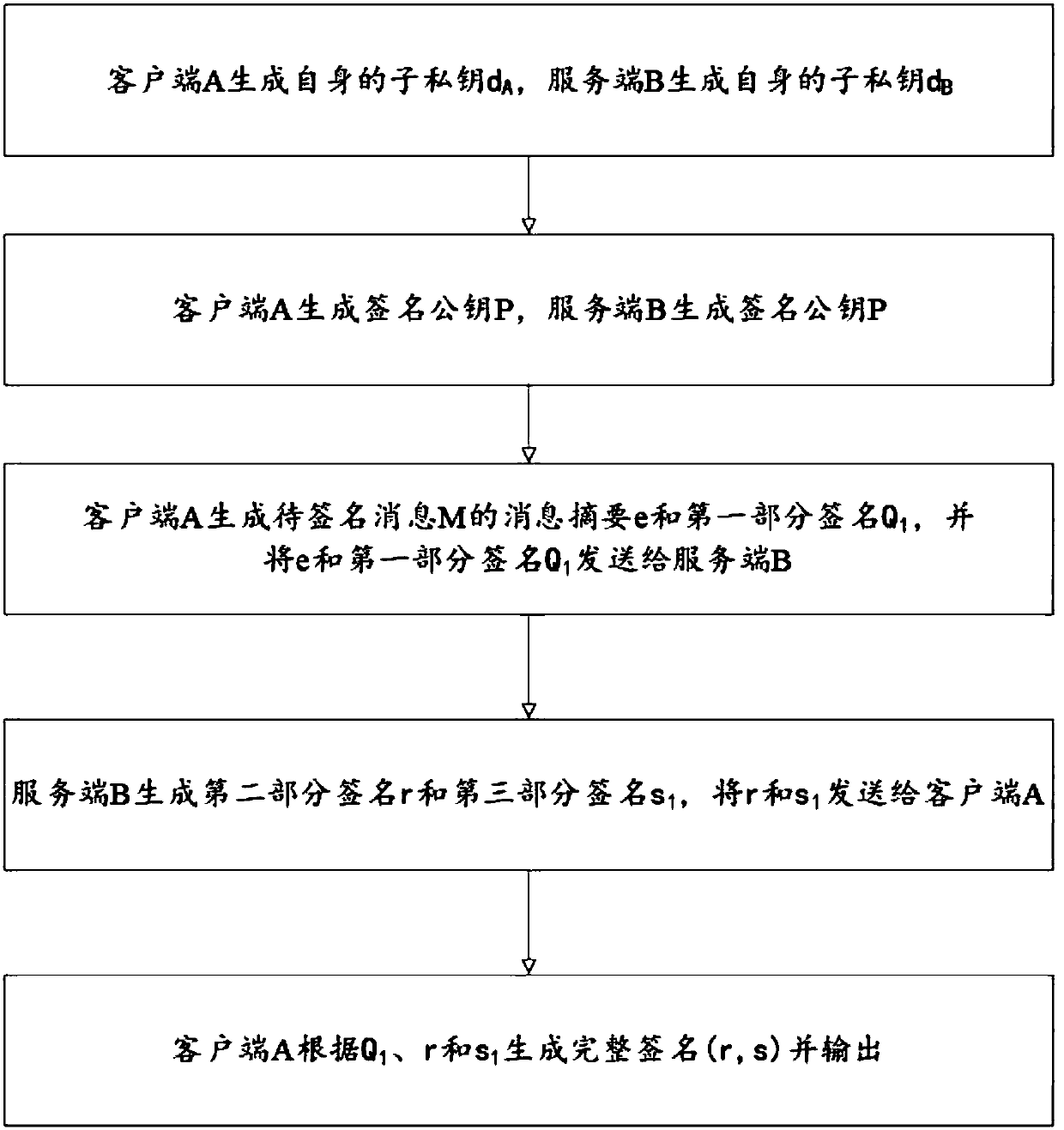
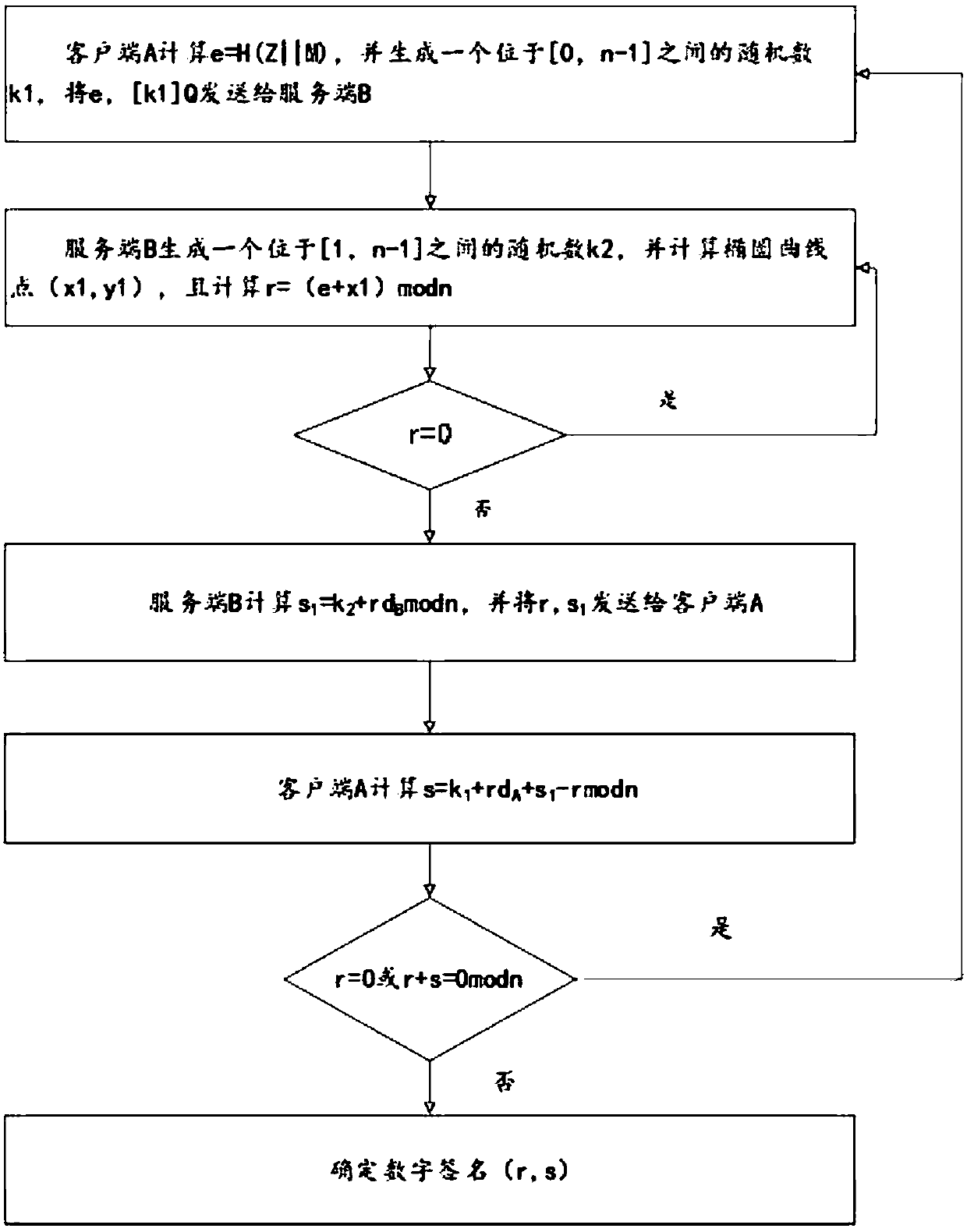
ActiveCN107623570AKeep storage safeEnsure safetyKey distribution for secure communicationPublic key for secure communicationStorage securityComputer security
The invention relates to an addition key segmentation-based SM2 signature method. According to the method, a private key is split into two private key components, wherein one private key component islocated at a server end and the other private key component is located at a client end. Therefore, each of two communication parties cannot obtain the complete private key, so that the storage security of the private key is ensured. Both the server end and the client end need to participate in the signature operation process, while any one of the server end and the client end cannot independentlycomplete the signature of the private key. As a result, the usage safety of the private key is ensured.
Owner:北京无字天书科技有限公司
Method for protecting copyright of video content using user recognizing module
ActiveCN101350909AEnsure safetyKeep storage safePulse modulation television signal transmissionAnalogue secracy/subscription systemsVideo playerDigital rights management system
The invention relates to a video content copyright protection method which uses the subscriber identity module, belonging to the technical field of digital copyright protection. A video player advances the requests and a DRM Agent receives the requests to access a corresponding RO and requests an SIM card for decoding the RO; the SIM card returns a key to the DRM Agent for decoding the RO; the DRM Agent receives the key and adopts the AES algorithm to decode the RO and extract a video content key and permission information; the content key is used for decoding the video content which is protected; the DRM Agent and SIM card separately upgrade the permission information after playing. The method of the invention has the advantages that by introducing the subscriber identity module, the storage safety of the permission limit in the digital copyright management system; even after the subscriber replaces the mobile terminal, the digital content with the purchased copyright could be also protected; therefore, the invention could be widely used.
Owner:TSINGHUA UNIV
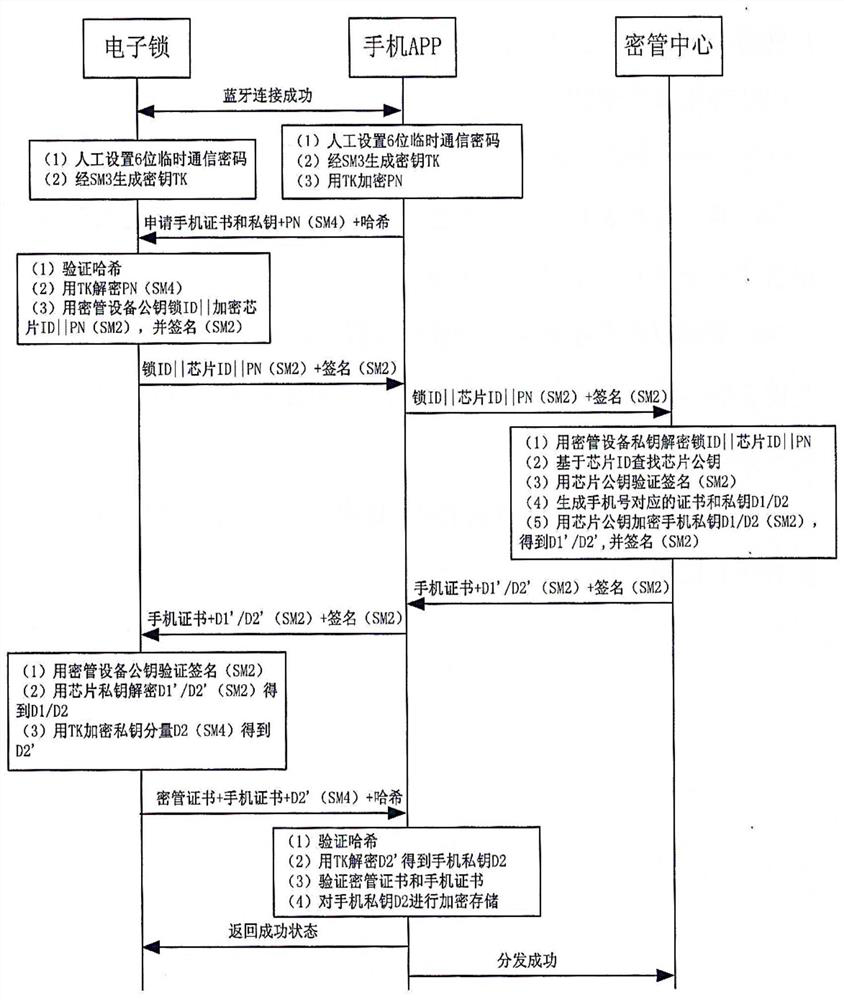
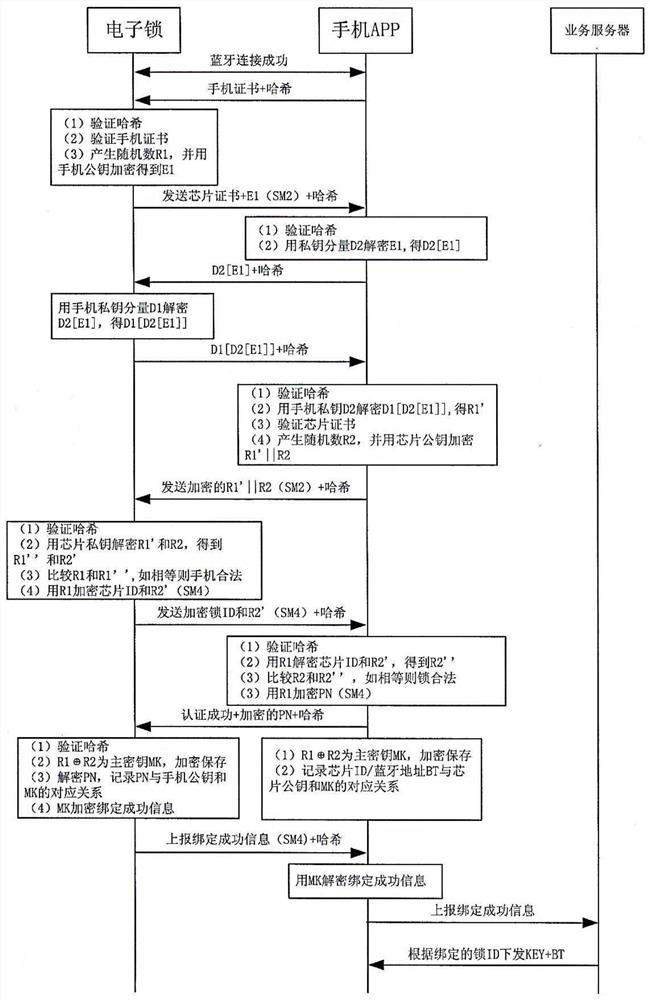
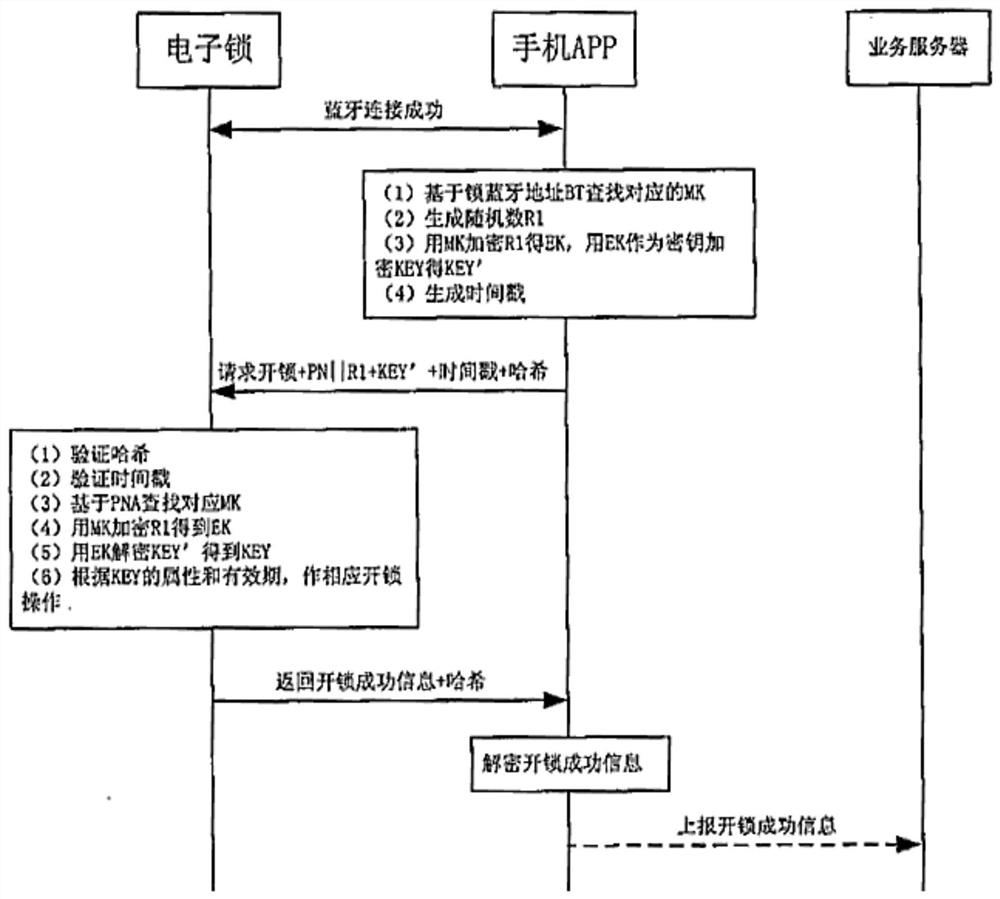
Electronic lock safety system and key distribution method thereof
ActiveCN111815816AAchieve distributionEnsure safetySubstation equipmentIndividual entry/exit registersInternet privacyMobile end
The invention discloses an electronic lock safety system and a key distribution method thereof. A electronic lock terminal and a mobile communication terminal generate a temporary communication key according to temporary data, and the electronic lock terminal encrypts the ID of an electronic lock security chip and the ID of an electronic lock by using a temporary communication key and a public keyof a key management center, and decrypts an encrypted private key of the mobile communication terminal to obtain a first component of the private key; and the mobile communication terminal encrypts the number of the mobile communication terminal by using the temporary communication key, sends a request for applying for the certificate and the private key of the mobile communication terminal to the electronic lock terminal, realizes forwarding between the electronic lock terminal and the key management center terminal, obtains, encrypts and stores a second component of the private key of the mobile communication terminal, and verifies the certificate of the key management center and the certificate of the mobile communication terminal. The key management center terminal generates a certificate and a private key corresponding to the number of the mobile communication end by using the private key of the key management center based on a public key of the electronic lock security chip, andsends the certificate and the encrypted private key of the mobile communication terminal to the mobile communication terminal after encryption. Secure issuing of the certificate and the private key of the mobile terminal is realized, and the security of the key is ensured.
Owner:合肥智辉空间科技有限责任公司
Private data-based network security sharing method and communication terminal
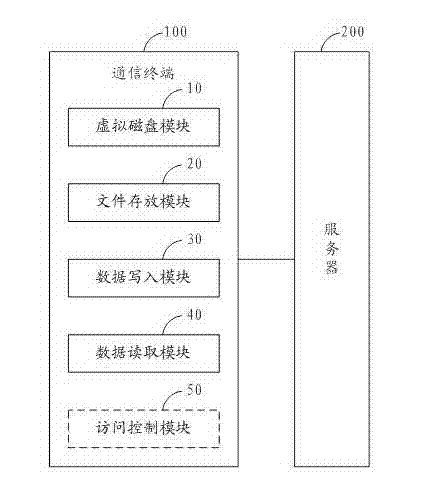
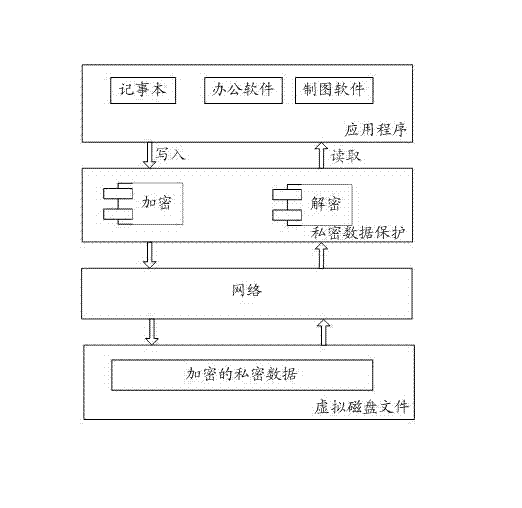
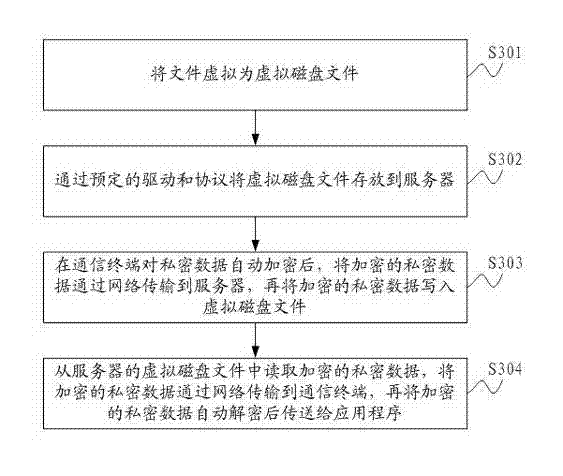
ActiveCN102761559AKeep storage safeAchieve real-time synchronizationUser identity/authority verificationData switching networksNetworked Transport of RTCM via Internet ProtocolPrivate network
The invention is suitable for the technical field of computer network safety, and provides a private data-based network security sharing method and a communication terminal. The private data-based network security sharing method comprises the following steps of: virtualizing a document to a virtual disk document; storing the virtual disk document to a server through a preset drive and a protocol; transmitting encrypted private data to the server through a network after the private data is automatically encrypted on the communication terminal, and then writing the encrypted private data into the virtual disk document; reading the encrypted private data from the virtual disk document of the server, and transmitting the encrypted private data to the communication terminal through a network, and then transmitting the decrypted private data to an application after automatically decrypted. Therefore, the invention realizes a private data network sharing three-dimensional protection system, ensures storage safety and network transmission safety of private data during network sharing, is convenient and easy, comprehensive and efficient, and realizes real-time synchronization of shared data.
Owner:SUNINFO INFORMATION TECH
Communication terminal and communication information processing method thereof
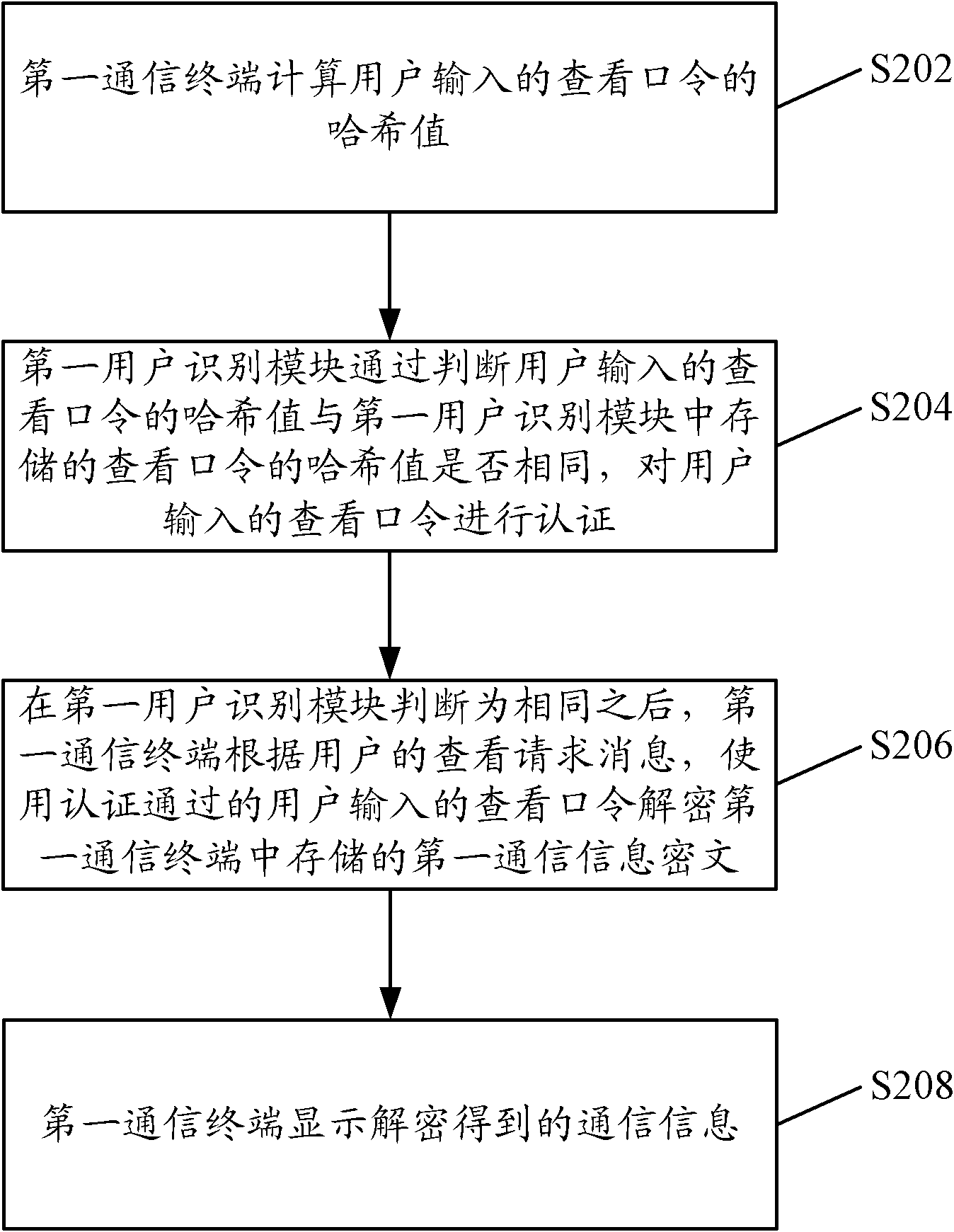
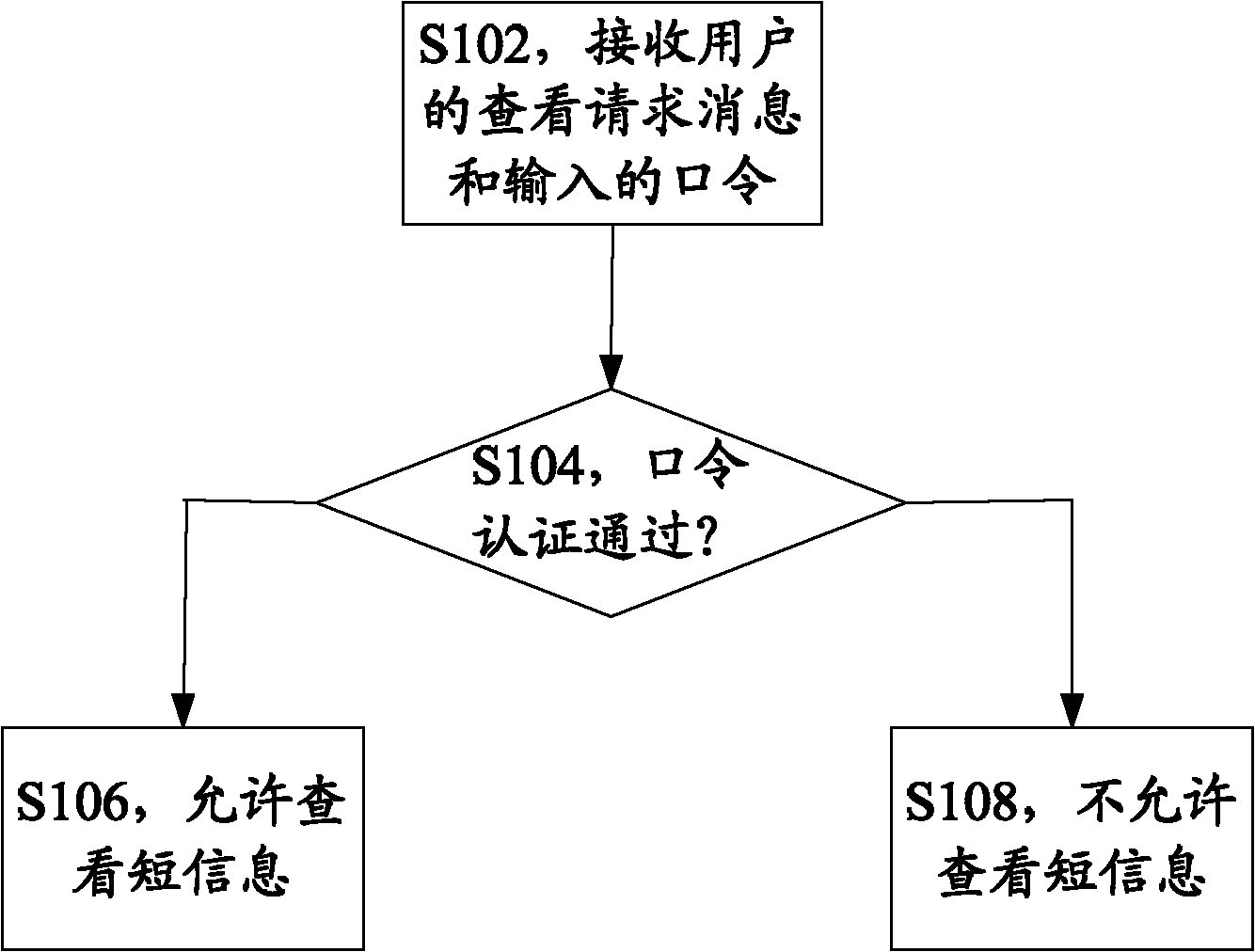
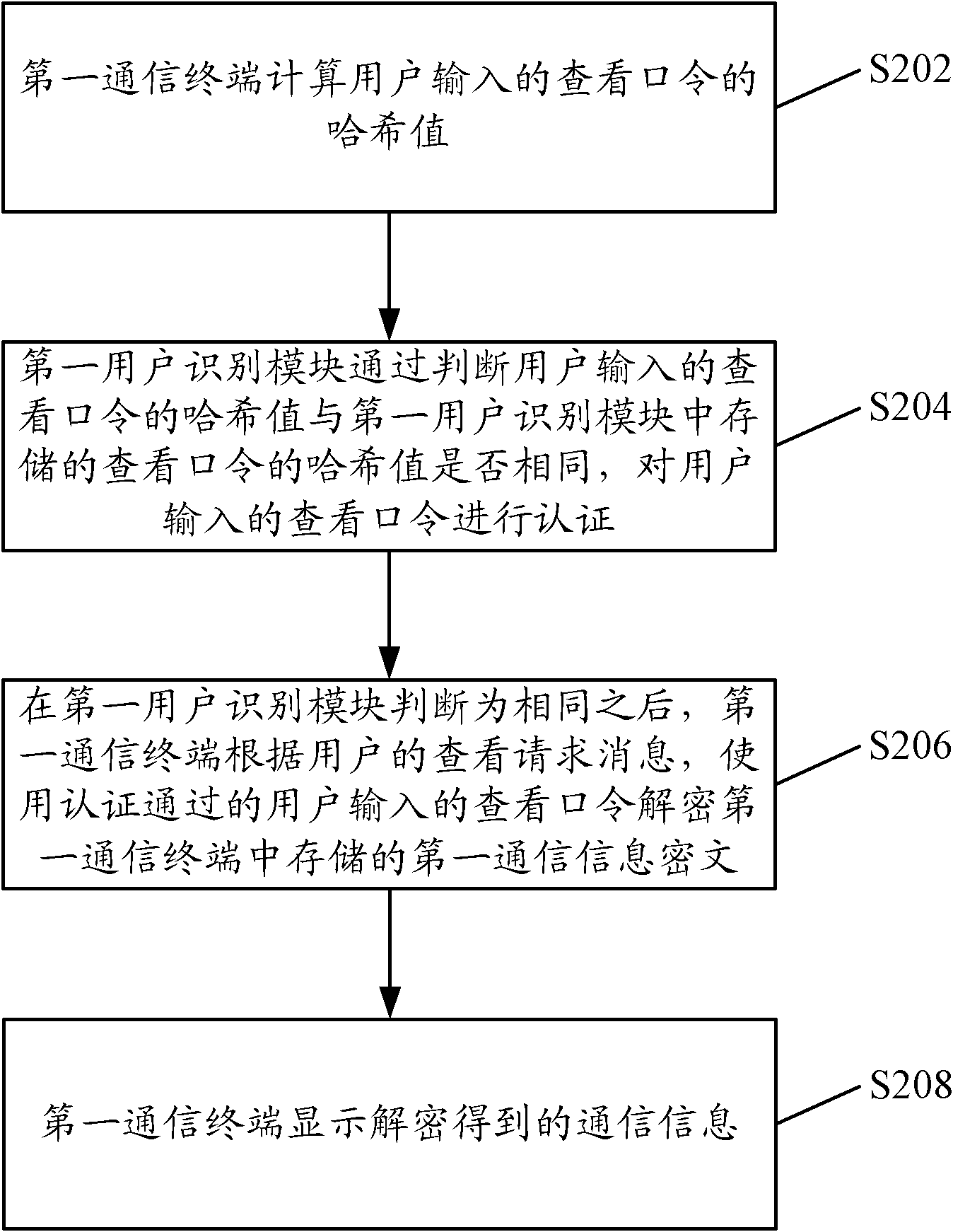
ActiveCN102098391AImprove securityKeep storage safeDigital data protectionSubstation equipmentHash tableCiphertext
The embodiment of the invention provides a communication terminal and a communication information processing method thereof, being applicable to the field of a communication technology. The communication information processing method of the communication terminal comprises the steps: a first communication terminal computes a hash value of a view password inputted by a user; a first user identification module arranged on the first communication terminal identifies the view password inputted by the user by judging whether the hash value of the view password inputted by the user is as the same as a hash value of a view password stored in the first user identification module; after the first user identification module judges that the hash value of the view password inputted by the user is as the same as the hash value of the view password stored in the first user identification module, the first communication terminal decrypts a first communication information ciphertext stored in the first communication terminal by the successfully-identified view password inputted by the user according to a view request message of the user after the first user identification module judges that the hash value of the view password inputted by the user is as the same as the hash value of the view password stored in the first user identification module; and the first communication terminal displays the deciphered communication information.
Owner:CHENGDU HUAWEI TECH
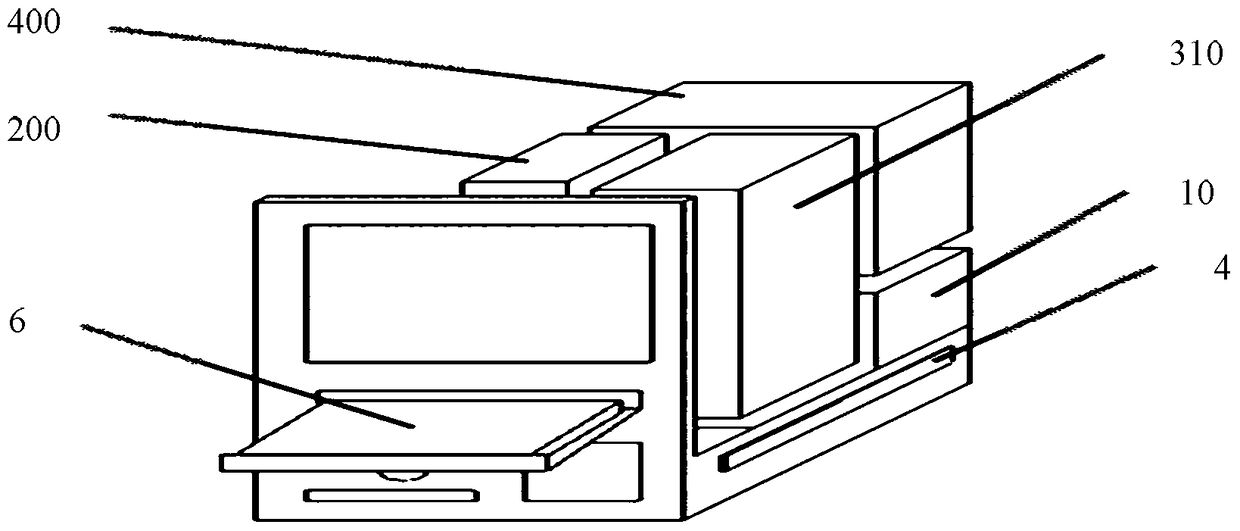
Smart item management cabinet and item receiving management system
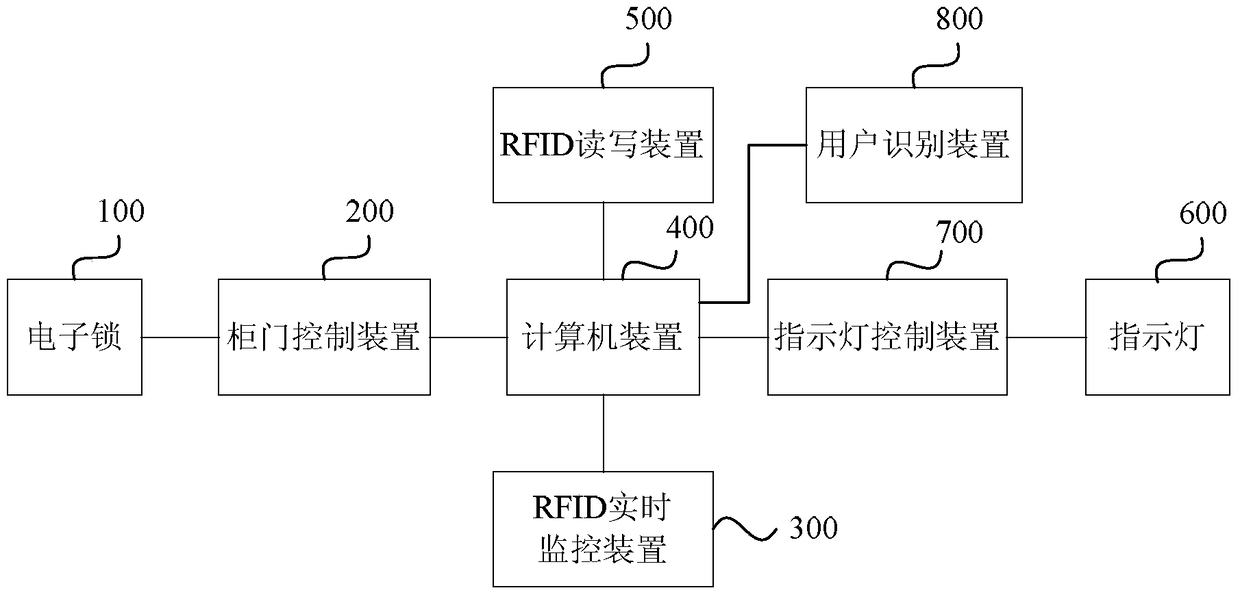
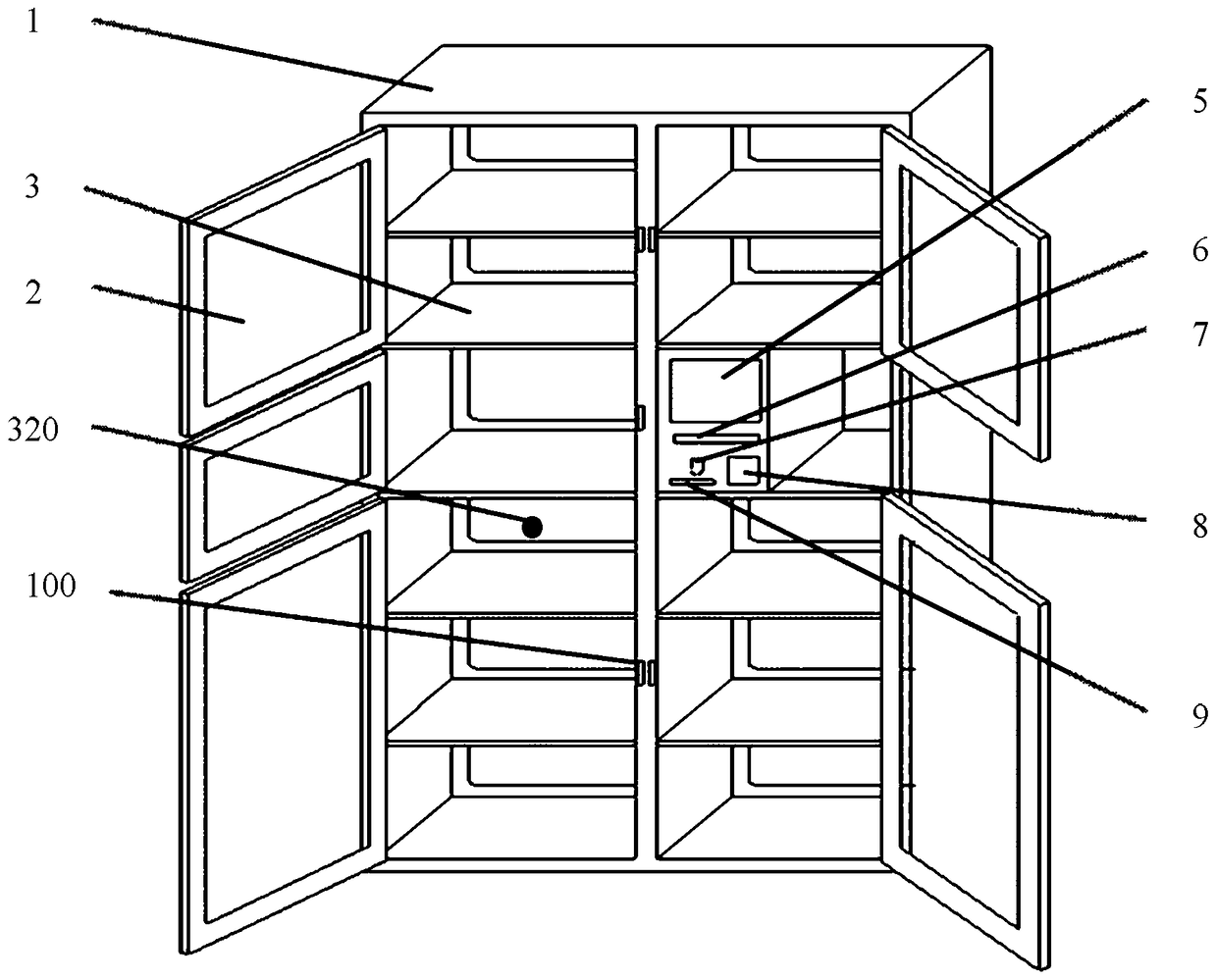
ActiveCN105006073BKeep storage safeReal-time monitoring storageCo-operative working arrangementsApparatus for meter-controlled dispensingCollection managementEmbedded system
The invention provides an intelligent item management cabinet and an item receiving management system. The intelligent item management cabinet includes a cabinet body, an electronic lock, a cabinet door control device, an RFID real-time monitoring device, and a computer device; the cabinet door control device and the RFID real-time monitoring The devices are respectively connected with the computer device; the cabinet body is provided with a cabinet door, and the cabinet door and the cabinet body form at least one closed storage cavity; the RFID real-time monitoring device is arranged inside the cabinet body, and collects the RFID tags located in the storage cavity. The information of the tagged items is fed back to the computer device to realize the monitoring of the whole process of depositing, taking out and storing the items in the storage cavity. The intelligent item management cabinet and the item receiving management system provided by the present invention realize the whole-process monitoring of the items during storage, fetching and storage, and effectively ensure the storage safety of the items.
Owner:霍智勇
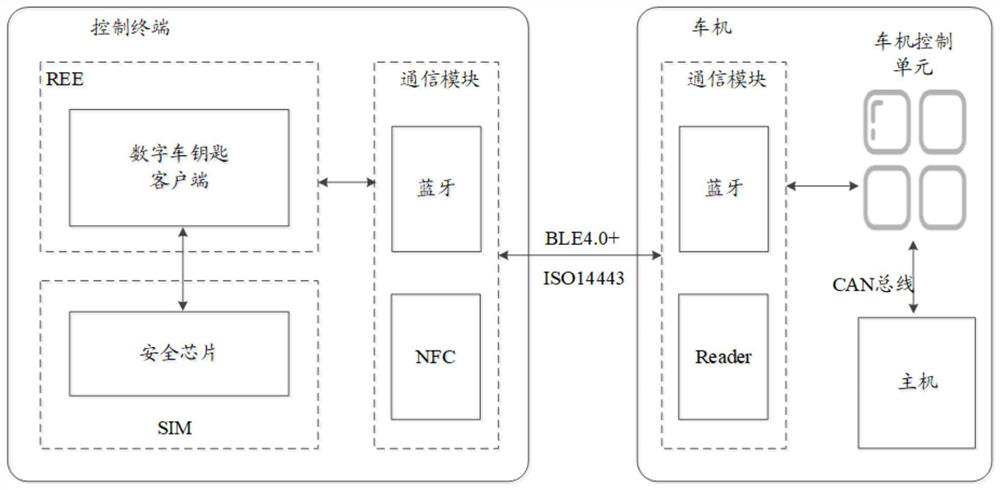
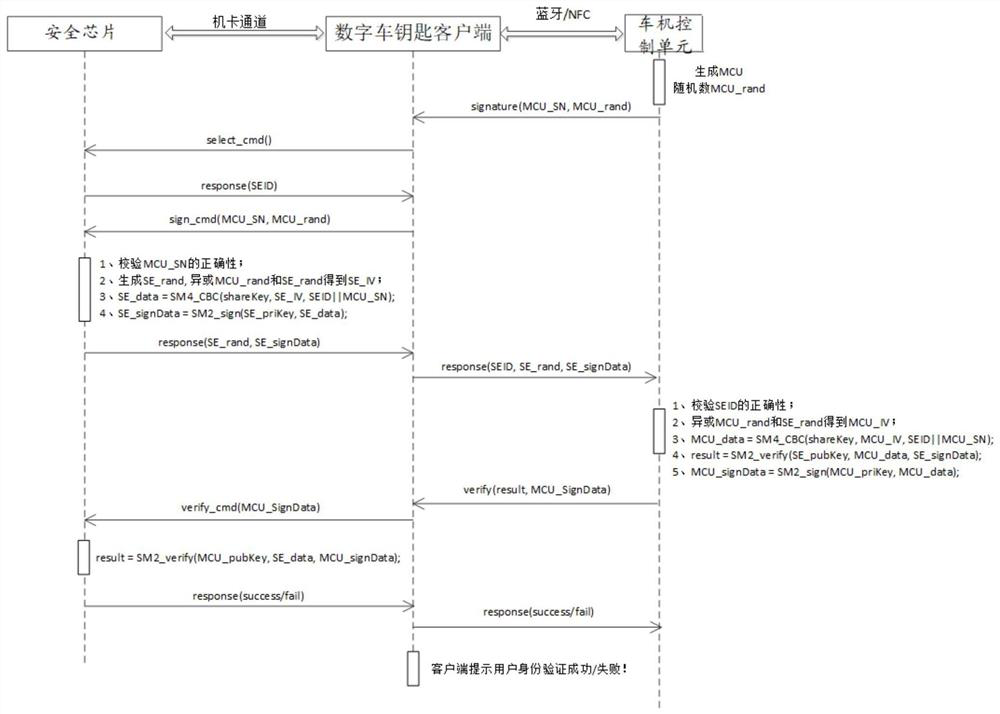
Vehicle control method based on digital vehicle key
ActiveCN111923863AKeep storage safeSecure transmissionAnti-theft devicesStorage securityMachine control
The invention discloses a vehicle control method based on a digital vehicle key. The method is applied to a vehicle control system, the vehicle control system comprises a control terminal and a vehicle machine control unit, a client and a security chip are installed on the control terminal, and all encryption, decryption and signature verification operations of the method are performed in the security chip, so that the storage security of sensitive data such as a secret key is ensured; the data is also transmitted after being encrypted by the security chip; therefore, the data transmission security is ensured, the advantages of highsecurity, high convenience, high universality and the like are realized; therefore, the technical problems that when an existing digital vehicle key achieves the functions of data encryption and decryption, signature verification and the like on the basis of a digital vehicle key client, sensitive data such as a secret key and a password stored on the clientare easily stolen by lawbreakers, the identity security of the digital vehicle key cannot be guaranteed, and then hidden danger exists during vehicle control are solved.
Owner:EASTCOMPEACE TECH
Household intelligent medicine dispensing device and medicine dispensing method
PendingCN111361864AKeep storage safeEasy accessSmall article dispensingSpecial dispensing meansPharmacy medicineControl system
The invention discloses a household intelligent medicine dispensing device and a medicine dispensing method. The device comprises a medicine containing mechanism, a medicine dispensing mechanism and amedicine storage mechanism which are located above the medicine containing mechanism, and further comprises a control system arranged on the medicine storage mechanism; a two-dimensional code moduleis used for scanning a bar code outside a medicine box to read the name, number, dosage and other parameters of medicine, the medicine is sorted according to the time periods and required dosages every day and categories through the medicine dispensing device, a main control board controls a motor to rotate, a rotating medicine cabin enables the medicine to fall into a medicine dispensing pipelinefrom the rotating medicine cabin, a medicine dispensing mechanical arm controls the dosage of the medicine falling into the medicine dispensing pipeline, and the medicine containing mechanism controls a medicine rotating disc of the medicine containing cabin to enable the medicine to sequentially fall into a medicine containing cabin. The device provides functions of detection alarm of temperature and humidity inside the medicine cabin and medicine taking reminding, and is convenient for a patient to take on time and carry outside.
Owner:XIAN UNVERSITY OF ARTS & SCI
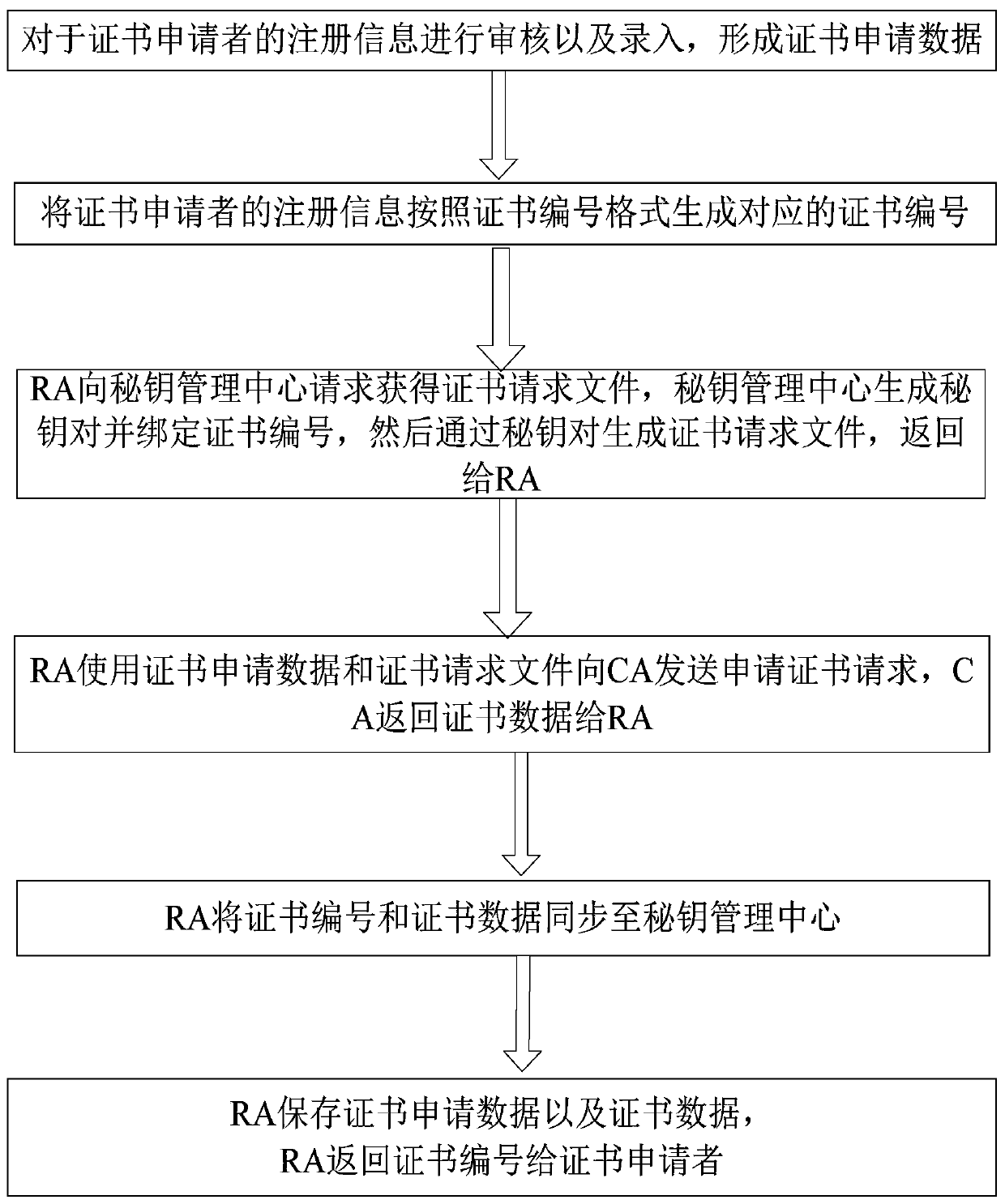
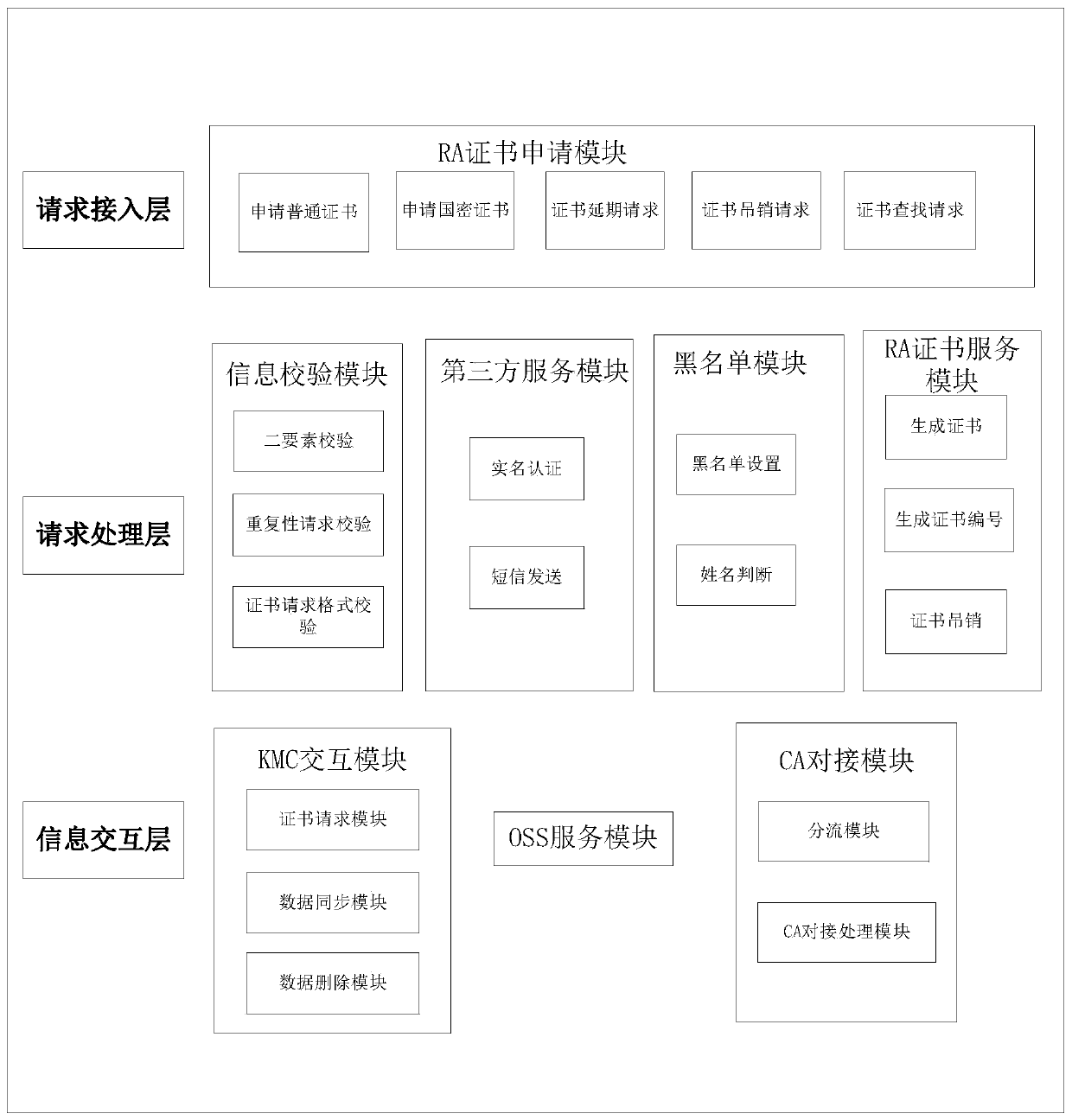
High-concurrency digital certificate registration management method based on multiple CAs
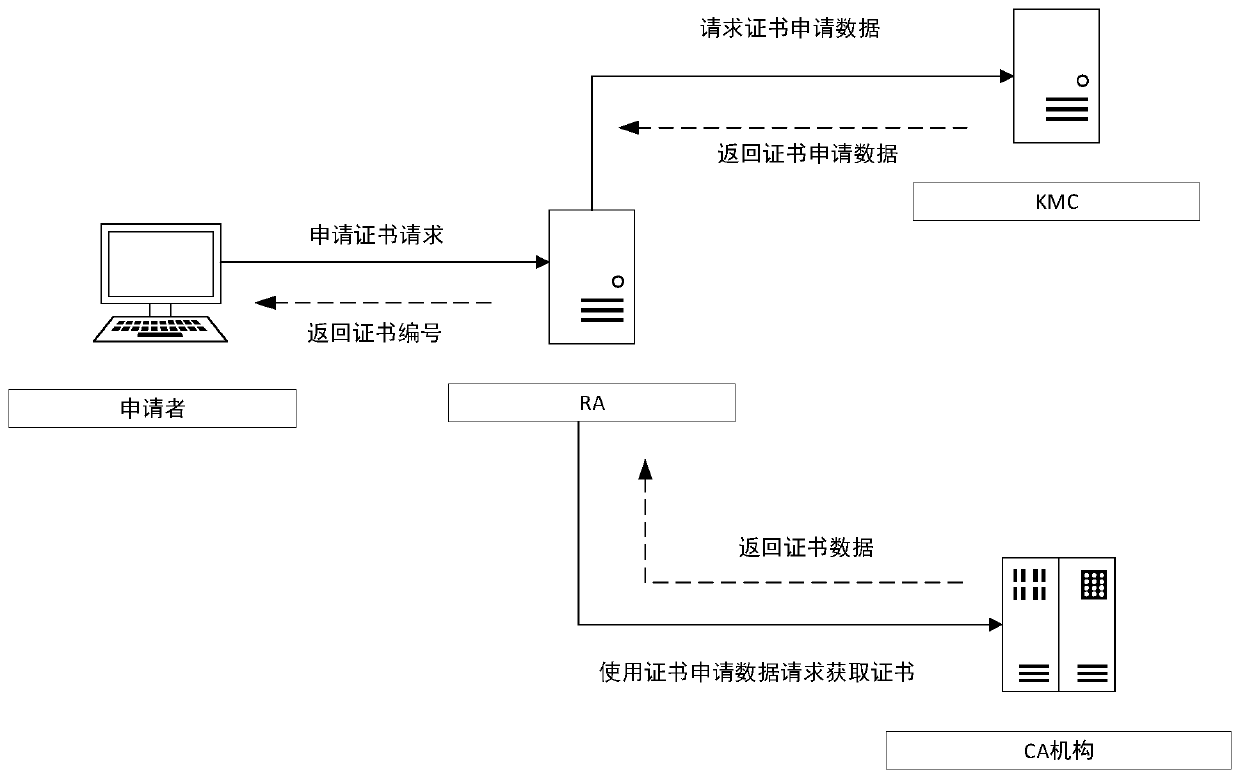
ActiveCN110635915AEfficient accessImprove throughputUser identity/authority verificationDependabilityKey management
The invention discloses a high-concurrency digital certificate registration management method based on multiple CAs, and the method comprises the following steps: registration information is checked and input, and then certificate application data is formed; the secret key management center generates a secret key pair, binds a certificate number, generates a certificate request file through the secret key pair, and returns the certificate request file to the RA; the RA sends a certificate application request to the CA by using the certificate application data and the certificate request file,and the CA returns the certificate data to the RA; the RA synchronizes the certificate number and the certificate data to a secret key management center; and the RA stores the certificate applicationdata and the certificate data, and returns a certificate number to the certificate applicant. According to the invention, a user can acquire the certificate more conveniently according to his / her name, the certificate storage reliability is improved, and the digital certificate is effectively managed; and meanwhile, a unified interface can be provided for different CA mechanisms to complete certificate application.
Owner:杭州尚尚签网络科技有限公司
Network security data sharing and control method and system
PendingCN112784230AEnsure safetyKeep storage safeDigital data protectionDigital data authenticationData operationsData access
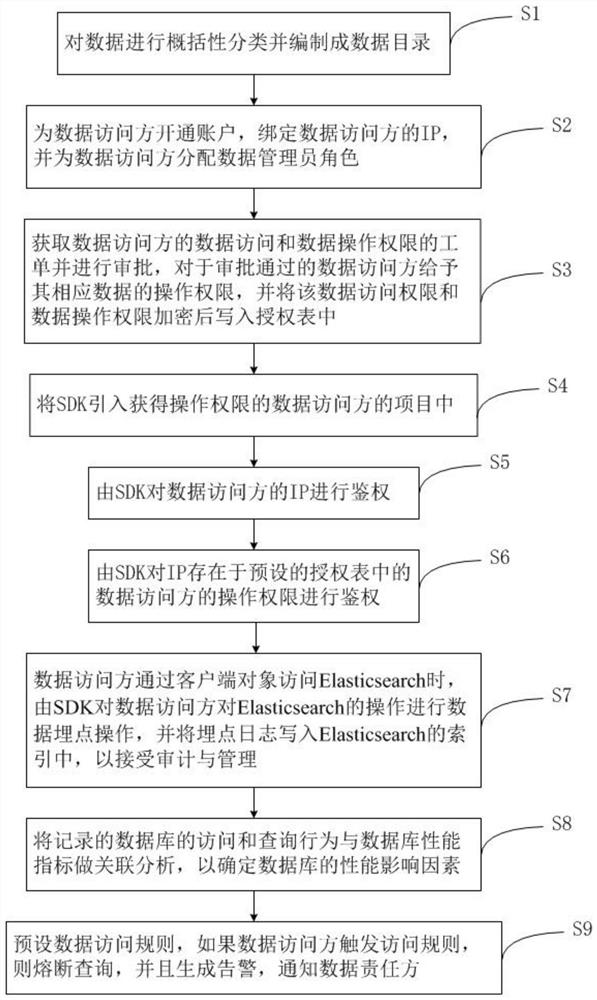
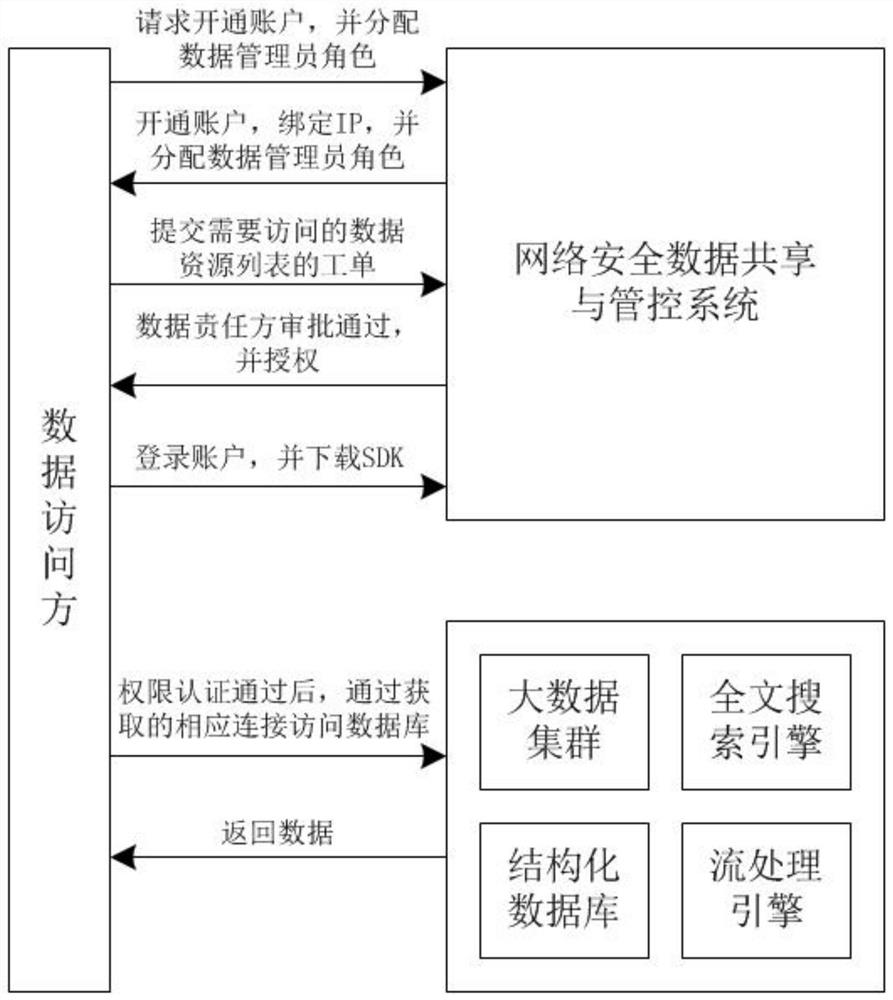
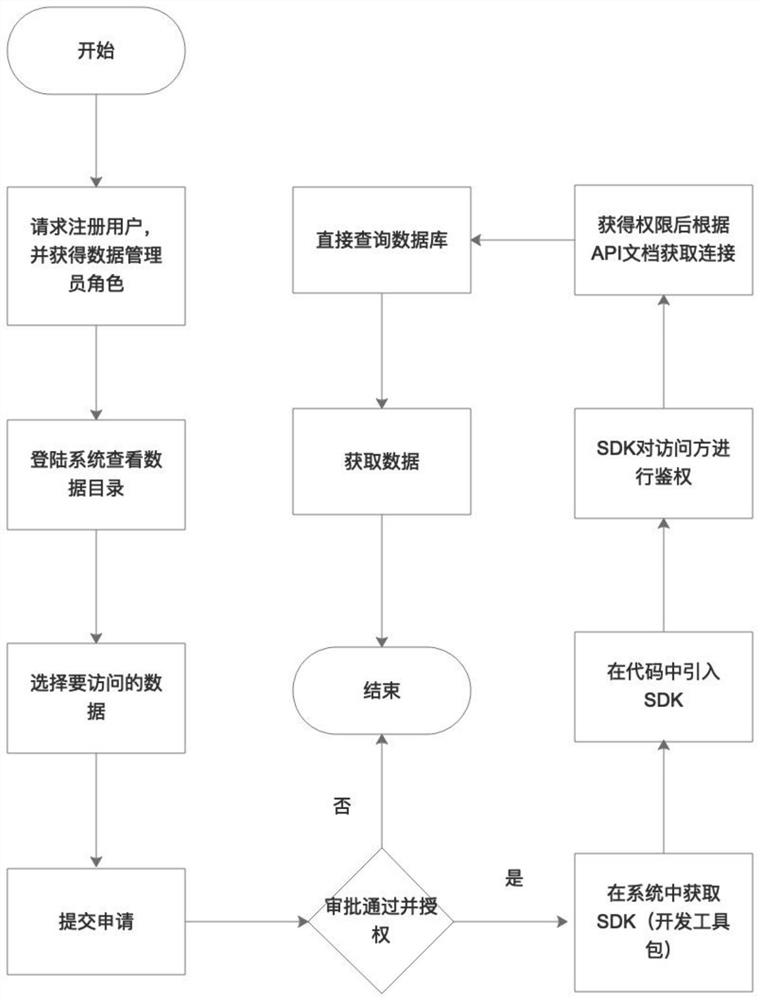
The invention provides a network security data sharing and control method and system. The sharing and control method comprises: classifying data and compiling the data into a data directory; opening an account for a data access party, binding an IP, and allocating a data administrator role; obtaining work orders of data access and data operation authority of a data access party, examined and approved the work orders of the data access and the data operation authority of the data access party, giving operation authority of corresponding data to the approved work orders, and encrypting the access and operation authority to be written into an authorization table; introducing the SDK into a project of the data access party obtaining the operation authority; authenticating the IP of the data access party by the SDK; authenticating, by the SDK, the operation authority of the data access party of which the IP is stored in a preset authorization table; performing association analysis on the access and query behaviors of the database and the database performance indexes; and presetting a data access rule, and if a data access party triggers the access rule, fusing query and giving an alarm. According to the application, auditing, monitoring and alarming of the data sharing process can be ensured.
Owner:BEIJING VENUS INFORMATION SECURITY TECH +1
Offline physical isolation authentication method and authentication system thereof
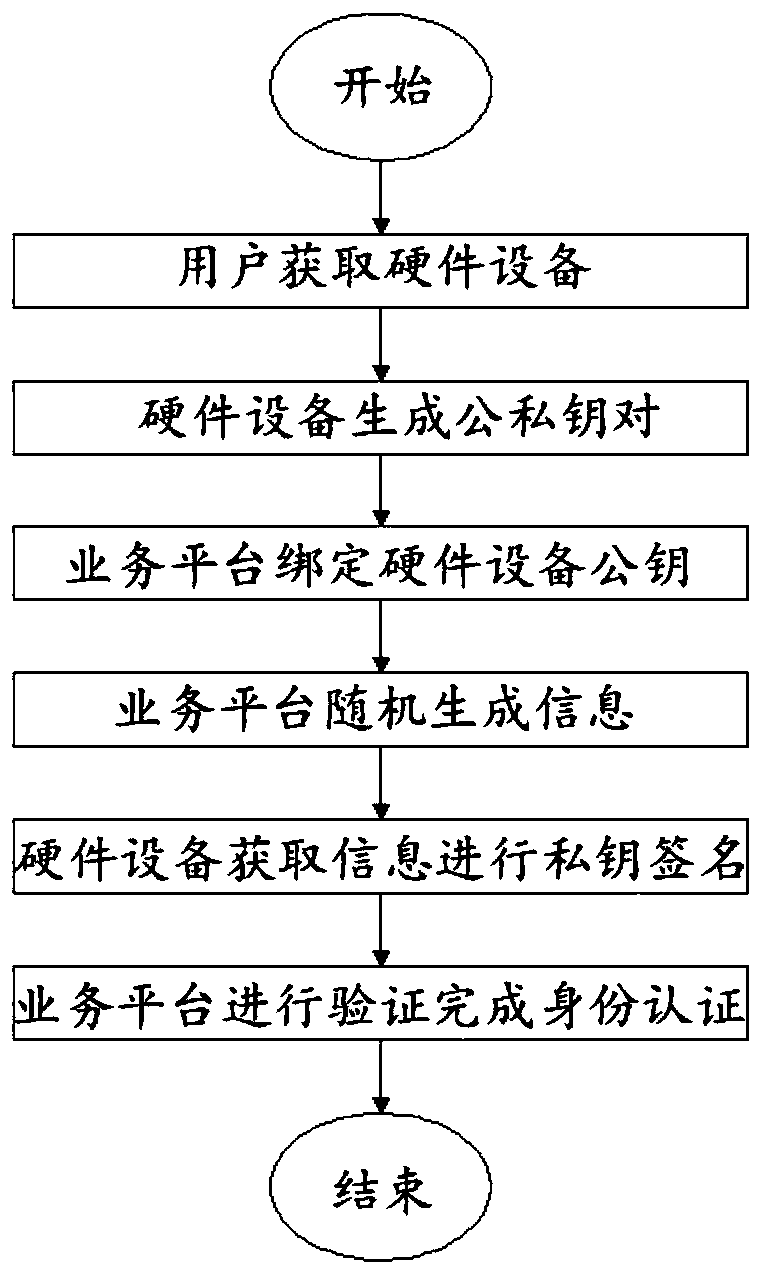
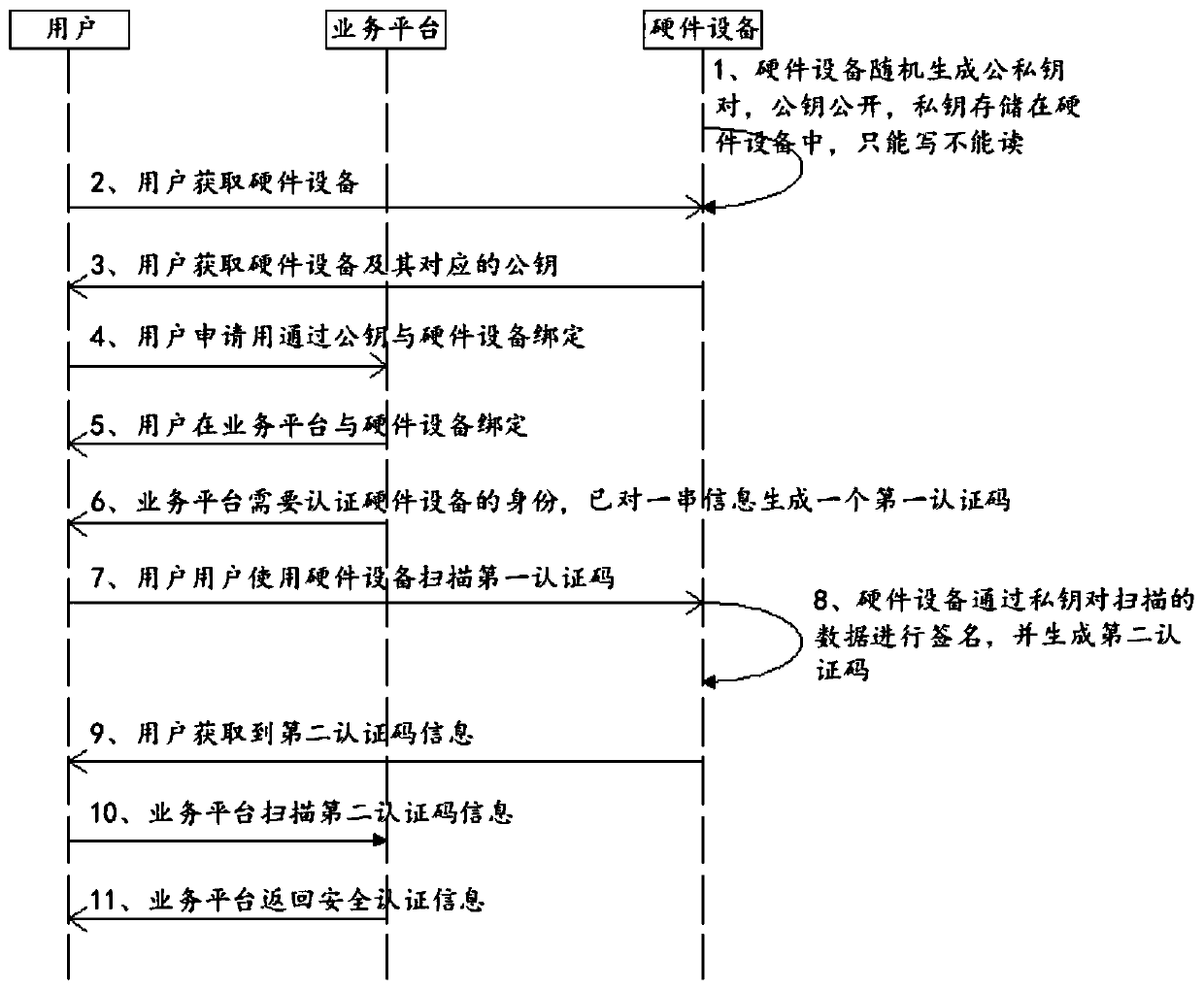
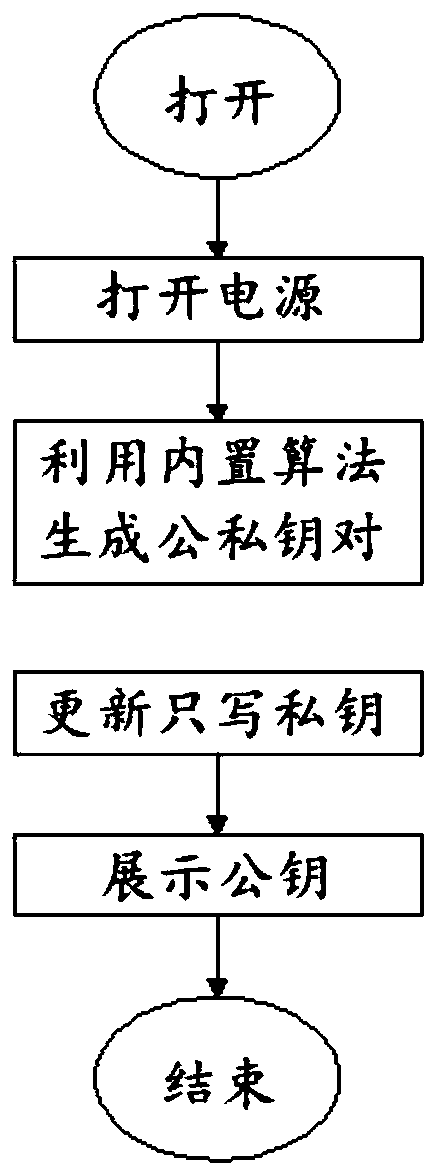
ActiveCN110659470AKeep storage safeEnsure safetyDigital data authenticationPublic key infrastructure trust modelsEngineeringAuthentication system
The invention discloses an off-line physical isolation authentication method, which comprises hardware equipment and a service platform, and comprises the following steps that: the hardware equipmentrandomly generates a pair of public key and private key, the private key is only written and stored, and the public key is displayed; the user acquires hardware equipment and a corresponding public key; the user applies for binding to the service platform through a public key, wherein the public key is used for verifying the identity of the user; the user is bound with the hardware equipment in the service platform; when the service platform needs to verify the identity of the user, a first authentication code is generated for a string of random information; the user scans the first authentication code by using the hardware device; the hardware equipment signs the scanned first authentication code data through a private key, and generates a second authentication code from signed information; and the service platform scans the second authentication code and then carries out verification by using the public key of the user so as to authenticate the user identity and return authenticationinformation. The invention further discloses an authentication system for offline physical isolation. The authentication process is offline and physically isolated.
Owner:SICHUAN PANOVASIC TECH
Computer network security early warning system
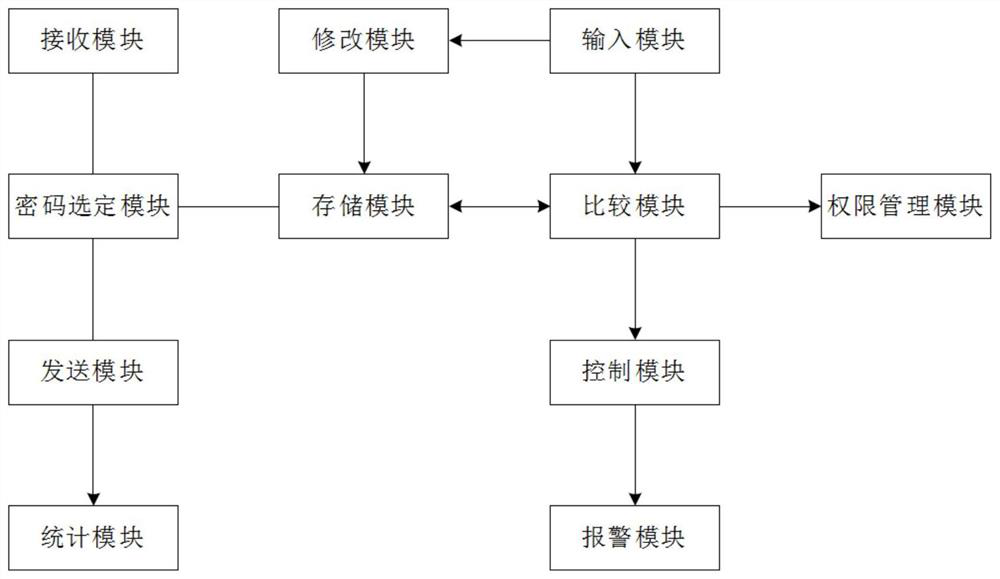
ActiveCN112214754AImprove securityPrevent theftDigital data protectionDigital data authenticationPlaintextEarly warning system
The invention relates to the technical field of computer security management, and provides a computer network security early warning system so as to solve the problem of low security of a computer dueto password leakage in the prior art. The system comprises an input module for inputting verification information, a storage module which is used for storing standard password information, sending starting information when comparison succeeds, and sending alarm information when comparison fails, and a control module which is used for controlling the computer to be normally started according to the received starting information, wherein the standard password information comprises a sequence number and a password plaintext; the system further comprises a receiving module which is used for acquiring verification request information of a request terminal, a password selection module which is used for randomly selecting a group of standard password information from the storage module, and a sending module which is used for sending the sequence number of the selected standard password information to the request terminal; the input module inputs verification information according to the sequence number, and the comparison module compares the verification information with the password plaintext of the selected standard password information during comparison.
Owner:CHONGQING RADIO & TV UNIV
Multi-chain isomerizing method
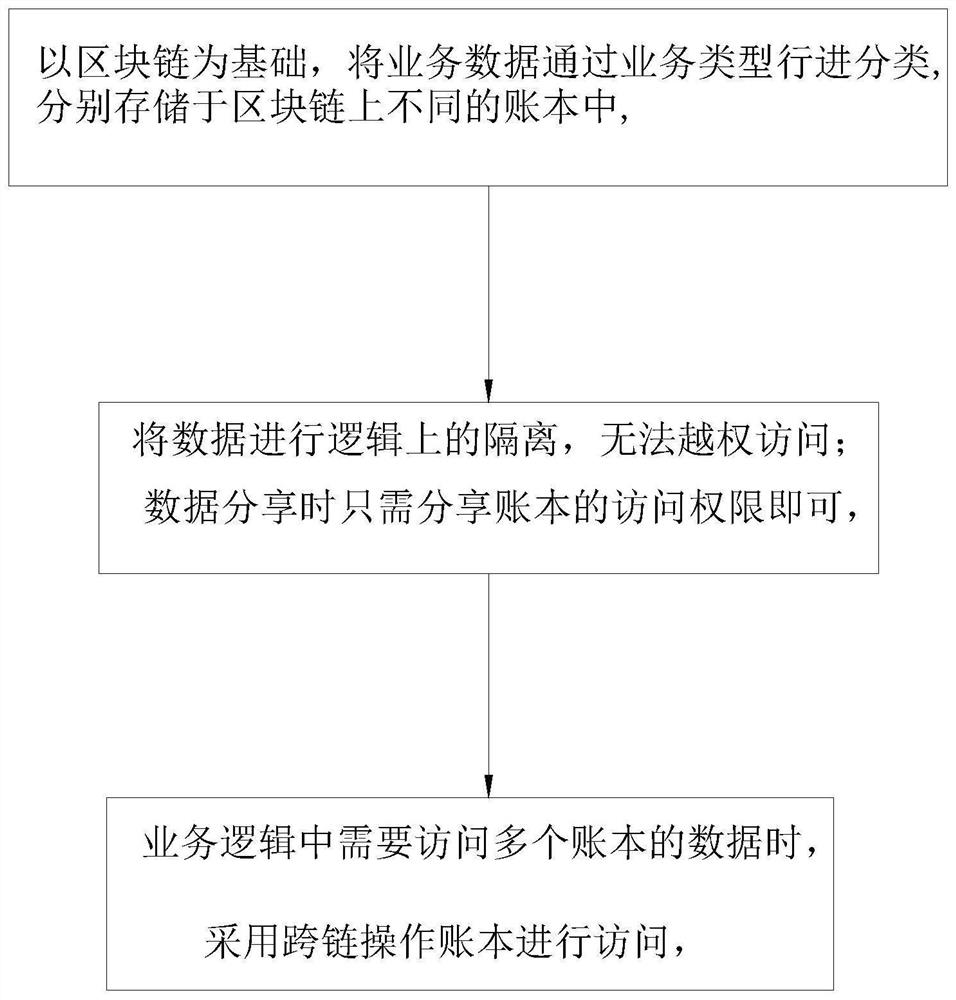
PendingCN112507025ANo unauthorized accessKeep storage safeDatabase distribution/replicationRelational databasesStorage securityConfidentiality
The invention discloses a multi-chain isomerizing method, which comprises the following steps of: classifying service data through service types on the basis of a block chain, respectively storing theservice data in different account books on the block chain, and logically isolating the data without unauthorized access. During data sharing, only the access permission of the account book needs tobe shared, and when the data of multiple account books needs to be accessed in the service logic, the account books are operated in a cross-chain mode for access; the data storage security is ensured,unauthorized access cannot be performed, and only the access authority of the account book needs to be shared during data sharing, so that the data sharing is very convenient and safe, a great promptis given to the performance of a block chain system, and the data of a plurality of account books needs to be accessed in service logic and is completed by adopting a cross-chain operation account book mode, and therefore, the security and confidentiality of the data are facilitated, and data classification and data sharing authorization are facilitated.
Owner:四川商通实业有限公司
Storage and utilization device for hydrogen produced by electrolysis
InactiveCN108642514AThe generation of solutionNo pollution in the processCellsElectrodesElectricityHydrogen
The invention relates to a storage and utilization device for hydrogen produced by electrolysis. By the storage and utilization device for hydrogen produced by electrolysis, water is decomposed by electric energy, and combustible hydrogen is prepared and is safely stored and utilized. According to the structure of the storage and utilization device for hydrogen produced by electrolysis, a divisionboard is placed in a tank body so that the tank body is divided into a water tank and a gas tank, the gas tank is positioned on one side of the bottom surface of the tank body, the upper plane of thegas tank is lower than the upper plane of the water tank, the bottom of the water tank communicates with the bottom of the gas tank via a channel, a gas tube which extends out of the water surface isarranged on the upper portion of the gas tank, the water tank and the gas tank contain water, the water in the water tank immerses the gas tank at least, and thus, the gas tank is sealed from the outside; and a positive electrode chip is arranged in the water tank, a negative electrode chip is arranged in the gas tank, the location of the positive electrode chip and the location of the negative electrode chip are higher than the channel which communicates the water tank with the gas tank, and the positive electrode chip and the negative electrode chip are connected with an external power supply via waterproof wires so as to obtain a structure for producing hydrogen by water electrolysis. The storage and utilization device for hydrogen produced by electrolysis is convenient to use, water is electrolyzed by electricity to generate hydrogen which serves as fuel gas for families, hotels and canteens, the hydrogen is stored safely, and environmental pollution is not caused.
Owner:王时豪
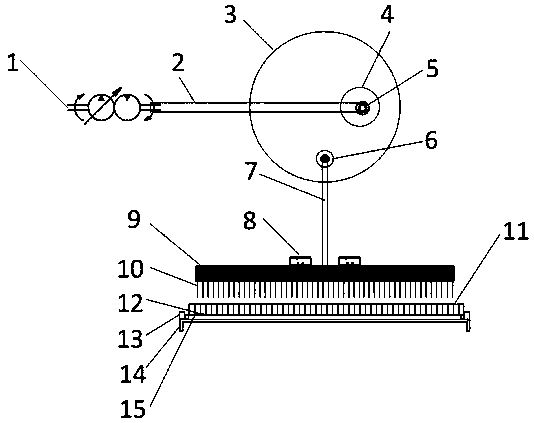
Tilting type paraffin scraping mechanism
The invention discloses a tilting type paraffin scraping mechanism which is located under a floating roof and distributed in an array way. The paraffin scraping mechanism comprises first scraper pieces distributed in an array way and second scraper pieces distributed in an array way, wherein the first scraper pieces comprise fixed pieces and support pieces; connecting pieces and right-angle rods are arranged between the fixed pieces and the support pieces; and sixth penetrating holes and seventh penetrating holes are formed in the connecting pieces. According to the tilting type paraffin scraping mechanism provided by the invention, the paraffin scraping mechanism is acted on the second scraper pieces and the first scraper pieces through balance weight, so that a paraffin scraping plate and the inner wall of an oil tank contact and extrude each other, the vertical-direction paraffin scraping areas of paraffin scraping plates of the second scraper pieces and the first scraper pieces areintersected, paraffin on the inner wall of the oil tank is seamlessly scraped, the occurrence of the phenomenon that the paraffin is remained on the inner wall of the oil tank so as to produce an oxidation layer and influence the service life of the oil tank is avoided, the safety in storing grease is ensured, the occurrence of the phenomenon that the paraffin is attached to the inner wall of theoil tank so as to go bad after being irradiated by an ultraviolet ray, and the quality of oil is ensured.
Owner:洛阳恒基石化科技有限公司
Digital-watermark-based digital copyright management method and device for IPTV terminals
ActiveCN102761790BKeep storage safeSpecial service provision for substationDigital data protectionDigital videoSecure communication
The invention discloses a digital-watermark-based digital copyright management method and a device for IPTV (Internet Protocol Television) terminals, wherein the method comprises the steps as follows: embedding a user identity watermark in a digital video content when a first IPTV terminal obtains the digital video content from a server, thereby obtaining and storing the video content with the user identity watermark; obtaining a security communication key TCK (Technology Compatibility Kit) through key agreement, and establishing a communication protection channel between the first IPTV terminal and a second IPTV terminal; adopting the security communication key TCK to encrypt the video content with the user identity watermark at the first IPTV terminal according to the request of the second IPTV terminal, and sending the encrypted video content to the second IPTV terminal through the communication protection channel; and decoding the video content received by the second IPTV terminal according to the secure communication key TCK, thereby obtaining the video content with the user identity watermark.
Owner:AEROSPACE INFORMATION
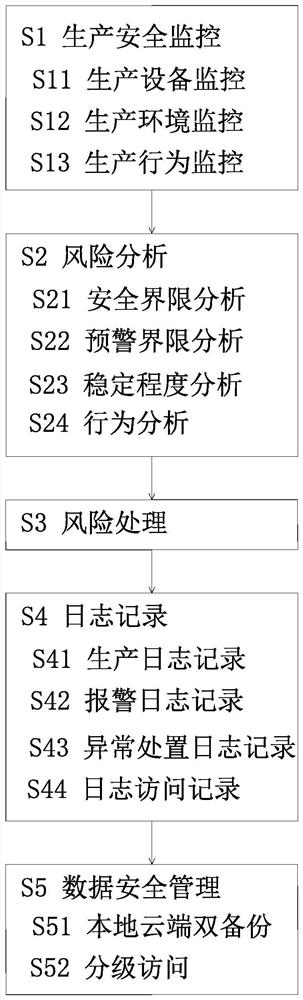
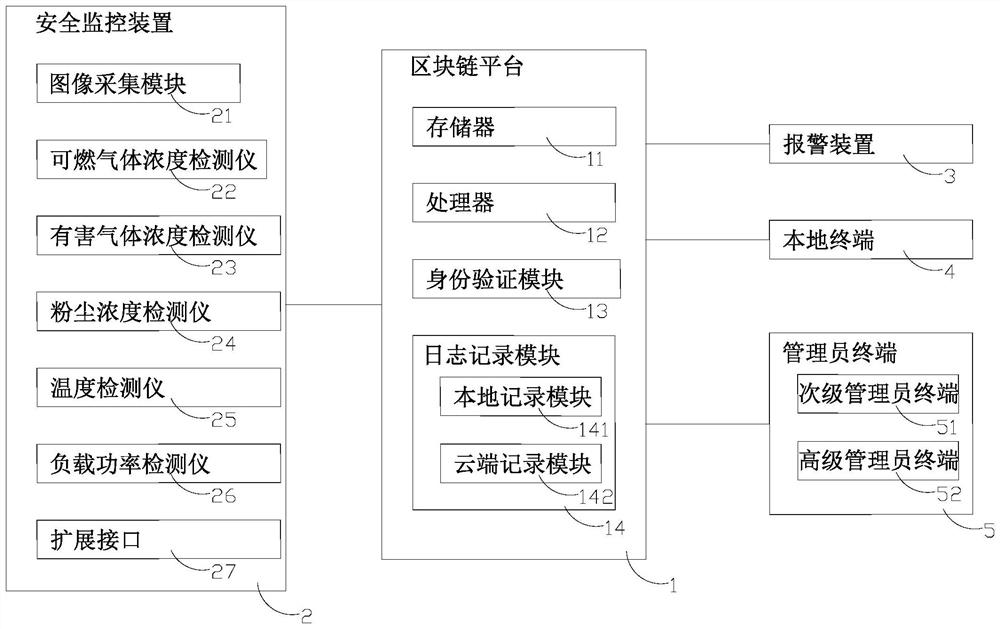
Intelligent industrial safety management method and system based on block chain
PendingCN114491605AImprove predictabilityEasy to identifyDigital data protectionResourcesData accessRisk awareness
The invention relates to an intelligent industrial safety management method based on a block chain. The method comprises the following steps: monitoring production safety; risk analysis; risk processing; log recording and data security management. According to the method, an early warning limit with a smaller range is set in a safety range, the trend of safety parameter change is judged, the predictability of safety risks is improved, and the industrial safety degree is enhanced; the fluctuation condition of safety parameters is analyzed, so that the identification capability of potential safety hazards is enhanced, and the risk awareness and the predictability of safety risks are improved; the production process is recorded comprehensively, malicious tampering of parameters is effectively prevented based on the security of the block chain technology, and the authenticity of data is ensured; a hierarchical access strategy is implemented for data access, and different levels of data are accessed according to different permissions, so that the privacy security of the data is improved.
Owner:顾春霞
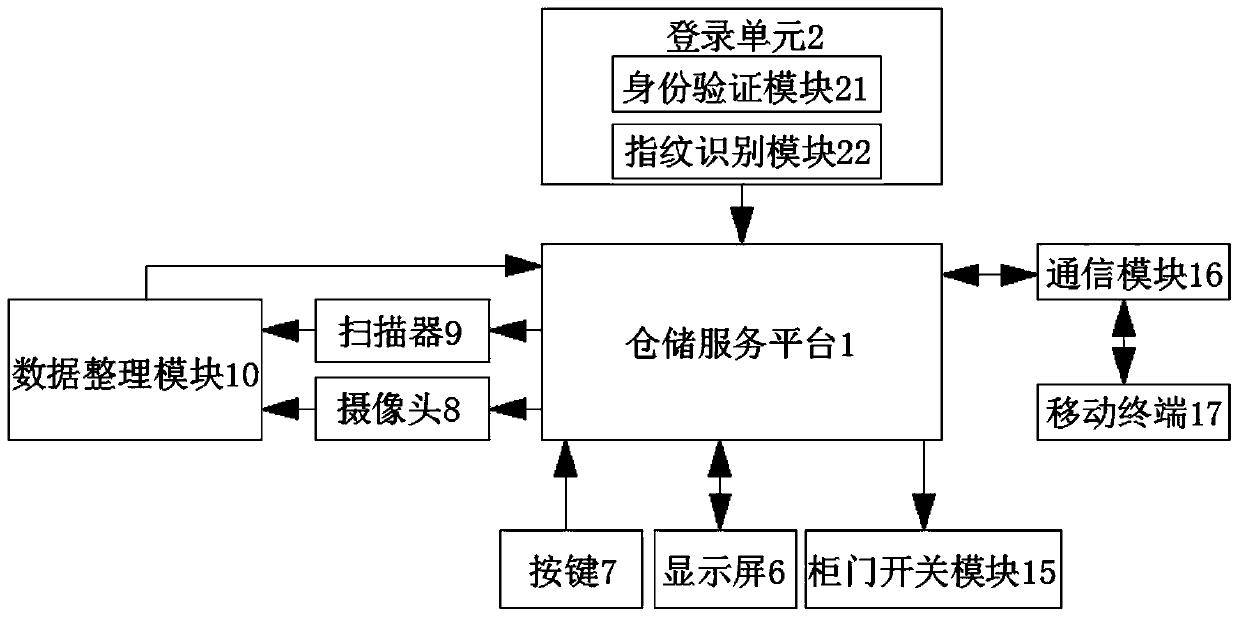
Online warehousing service platform and equipment
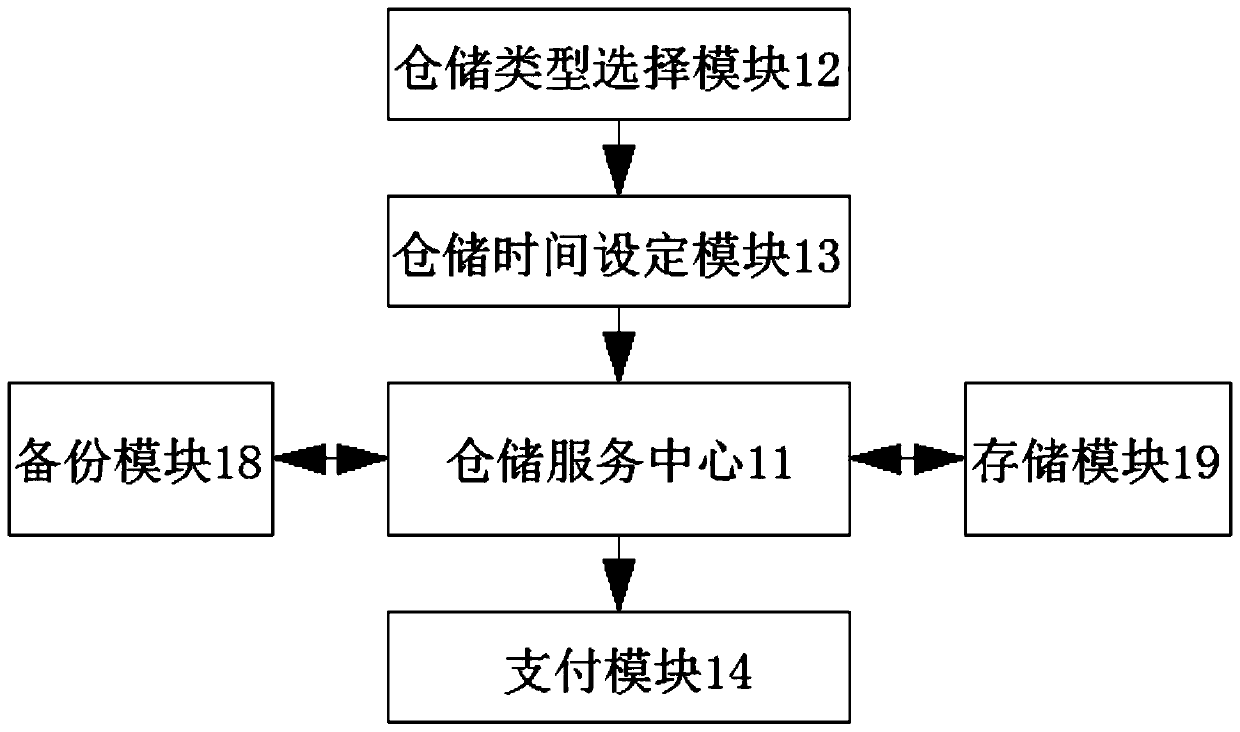
InactiveCN110728473AEasy to scanAvoid depositingApparatus for meter-controlled dispensingIndividual entry/exit registersStorage typeAuthentication
The invention discloses an online warehousing service platform and equipment. The warehousing service platform and equipment comprises a storage service platform, a login unit, a support frame and a storage cabinet body, the input end of the warehousing service platform is connected with the output end of the login unit. The interior of the supporting frame is fixedly connected with the surface ofthe storage cabinet body, the login unit comprises an identity verification module and a fingerprint verification module, and the storage service platform comprises a storage service center, a storage type selection module and a storage time setting module. The invention discloses an online warehousing service platform and equipment. To-be-stored articles of a client can be well scanned; according to the method, the client is prevented from storing flammable and explosive or prohibited articles, the potential safety hazard caused by the flammable and explosive articles is avoided, the storagesafety of other storage clients is ensured, the loss of a user is reduced to a certain extent, the overall storage quality is improved, the practicability is high, and the identity of the user can beauthenticated.
Owner:安徽融易供应链管理有限公司
Subscription method and system for library table resource of data sharing exchange platform
InactiveCN112836236AKeep storage safeGuaranteed independenceDatabase management systemsDigital data protectionData packStorage security
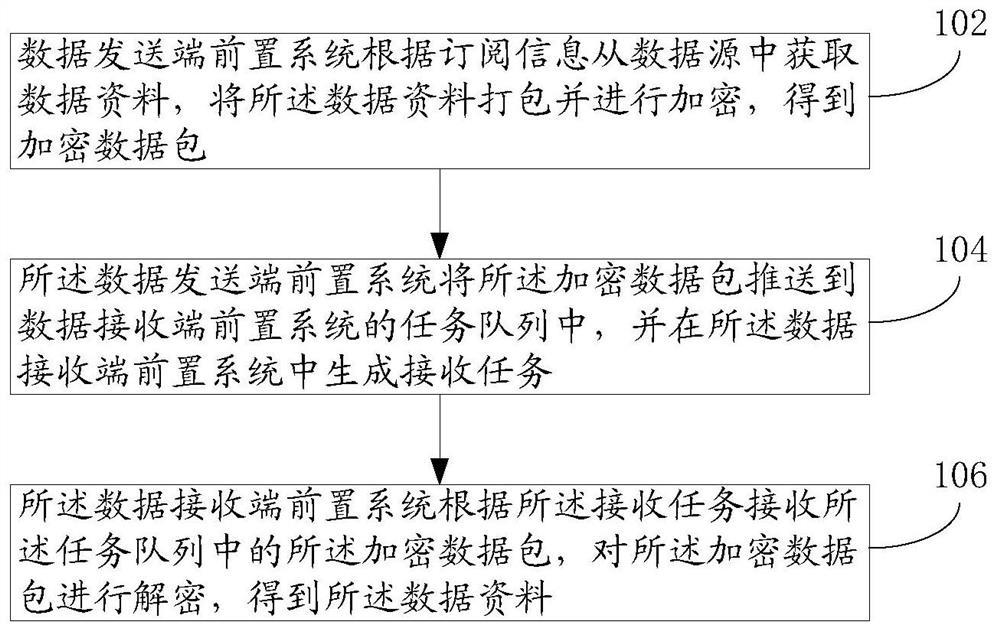
The invention discloses a subscription method and system for library table resources of a data sharing exchange platform. The method comprises the steps: a data transmitting end front-end system obtains data information, packages the data information, and encrypts the data information, thereby obtaining an encrypted data packet; the encrypted data packet is pushed to a task queue of a data receiving end front-end system, and a receiving task is generated; and the data receiving end front-end system receives the encrypted data packet in the task queue and decrypts the encrypted data packet to obtain data information. According to the embodiment of the invention, an end-to-end deployment mode is adopted, the exchange data is extracted to form a standardized data file, the standardized data file is encrypted and then sent to the data transmitting end front-end system in a subpackage form, then the data file is packaged, decrypted, analyzed and stored, and finally the data sharing service is completed. According to the application,all database ports do not need to be opened to the outside, the data storage security is guaranteed, and the subscription service is carried out by adopting a front-end system mode, so that databases of two parties are effectively isolated, and the independence of a service system and a databases is ensured.
Owner:航天广通科技(深圳)有限公司
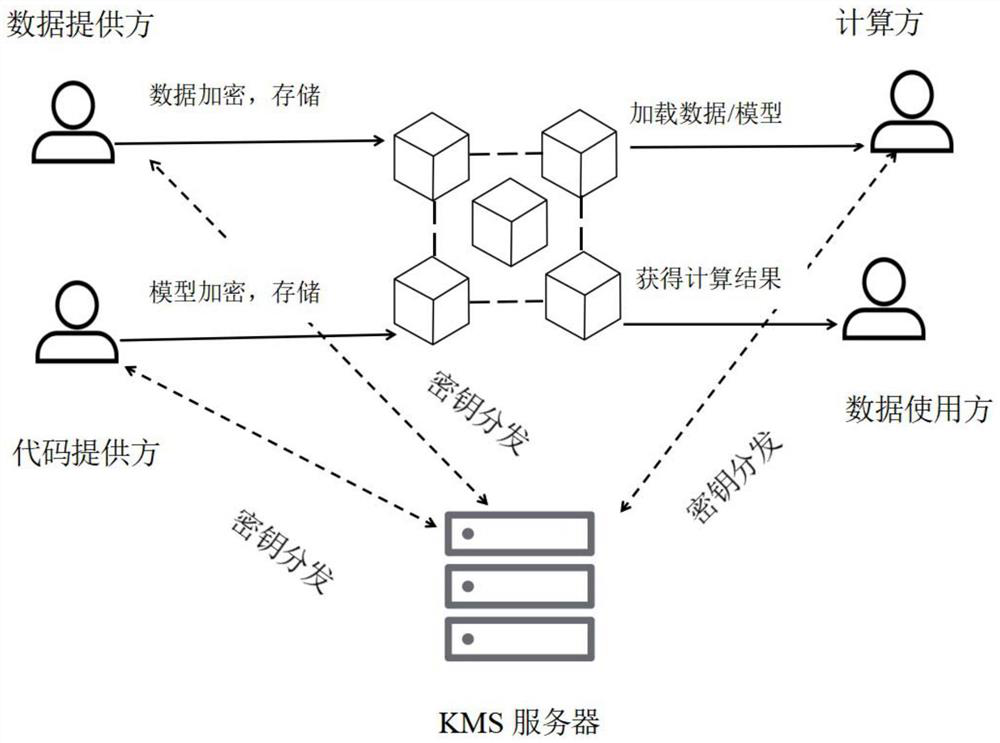
Privacy calculation method based on distributed storage
PendingCN114154181AKeep storage safePrevent tamperingEncryption apparatus with shift registers/memoriesDigital data protectionStorage securityAuthorization
The invention discloses a privacy computing method based on distributed storage, and the method comprises the steps: obtaining a secret key through a KMS server, encrypting data and a code, and then uploading the data and the code to a distributed storage block chain; a data requester requests the encrypted data and codes, and authorization information is recorded after the request is passed; the KMS server receives the task, the calculation party receiving the task confirms the authorization information again to the KMS server, the authorization information is ensured to be accurate, and the calculation party is arranged to prevent the data requester from directly contacting the code and the data and reduce the possibility of leakage of the code and the data; and the data is uploaded to the distributed storage block chain for encrypted storage, so that the storage security of the data and the codes can be ensured, and the data and the codes are prevented from being tampered.
Owner:HANGZHOU VASTCHAIN TECH CO LTD
Online writing method of product identification information and electronic product
ActiveCN102622190BAvoid erasureEasy to operateInput/output to record carriersProduction lineStorage security
The invention discloses a on-line write-in method for product identifying information and an electronic product, that is, an independent memorizer is used for keeping the product identifying information of the electronic product. When the product identifying information of the electronic product is written in, the memorizer is plugged in the electronic product, and the system program of the electronic product is used for reading the product identifying information in the memorizer and writing the product identifying information into an appointed position of the electronic product. According to the invention, through writing the identifying information of the electronic product into the independent memorizer, using the electronic product to read the product identifying information kept in the memorizer and accomplishing on-line write-in process, the write-in process of the product identifying information can be accomplished without the need of collocating auxiliary equipment such as computers on a product line, the operation is simple and quick, special training for workers on line is not required, the efficiency is high, the probability of errors is low, the product identifying information can be effectively prevented from being erased incorrectly during the upgrade of the system program, and the storage security can be ensured.
Owner:HISENSE VISUAL TECH CO LTD
Computer hard disk read-write device
InactiveCN110739007AAccurate reading and writingImprove qualityRecord information storageMounting heads on rotating supportEngineeringHeat sink
The invention discloses a computer hard disk read-write device. The device comprises a micro rotating wheel, a transmission rod, a balance wheel, a wobble plate, a positioning micro button, a bearing,a needle beam, a cooling fin, a read-write board, a read-write needle, a driving hard disk, a driving belt, a limiting block, a buckling plate and a disk sector, wherein the micro rotating wheel is fixedly connected with the transmission rod, the transmission rod is rotatably connected with the positioning micro button, the positioning micro button is fixedly connected with the wobble plate, thewobble plate is fixedly connected with the wobble wheel, the right side of the wobble wheel is fixedly connected with the bearing, and the bearing is rotatably connected with the needle beam. According to the computer hard disk read-write device, through the arrangement of the drive hard disk and the drive belt, reading and writing of sectors are accurate, the product quality is improved, meanwhile, one working process is circulated in a reciprocating mode, the reading and writing accuracy is further enhanced, the disk sectors facilitate big data storage, the storage safety of a computer is guaranteed, and the actual working requirement is met.
Owner:XIAN HUIFU RONGTONG INFORMATION TECH CO LTD
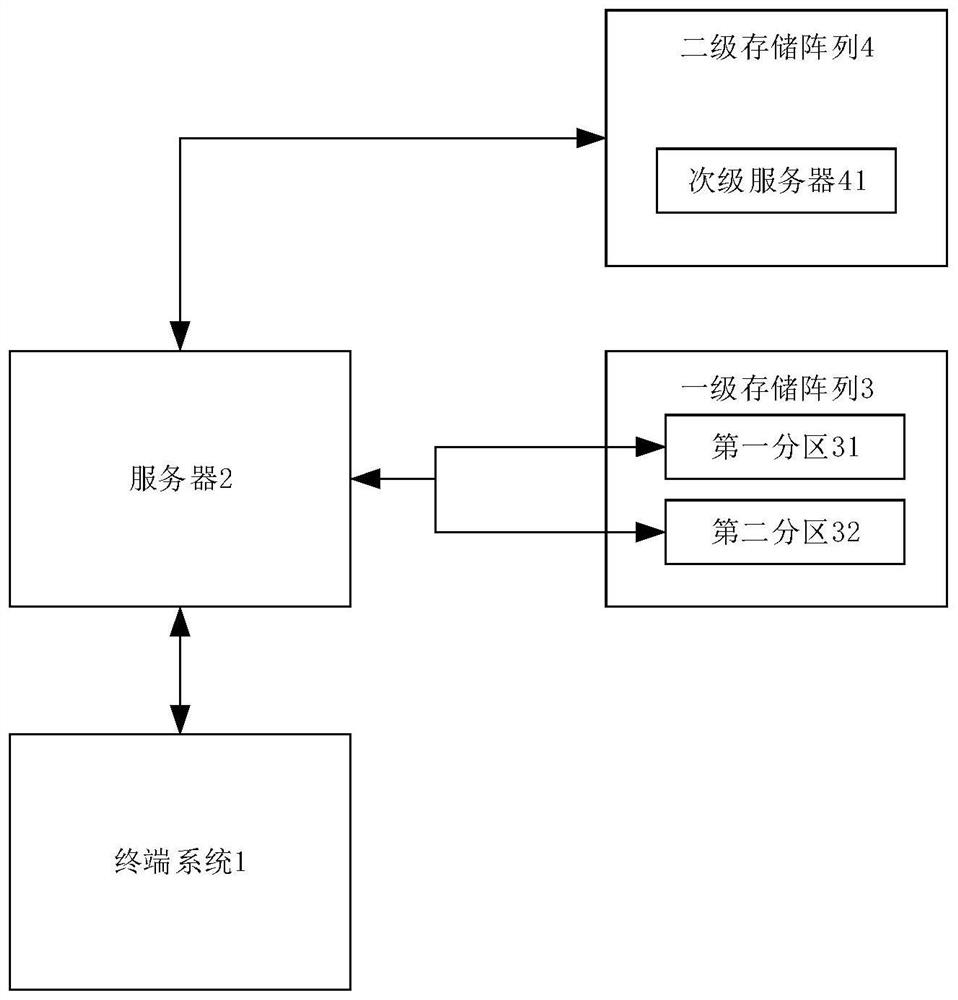
Hierarchical storage method and device of image data, electronic equipment and medium
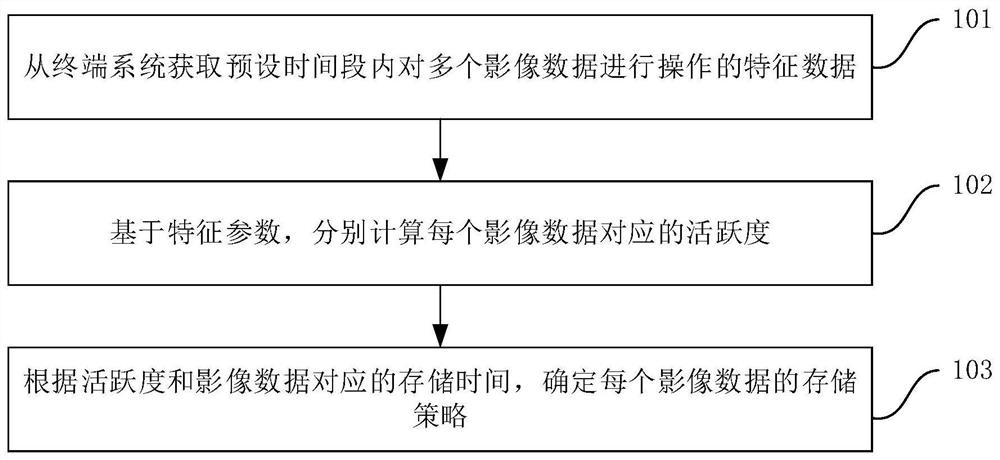
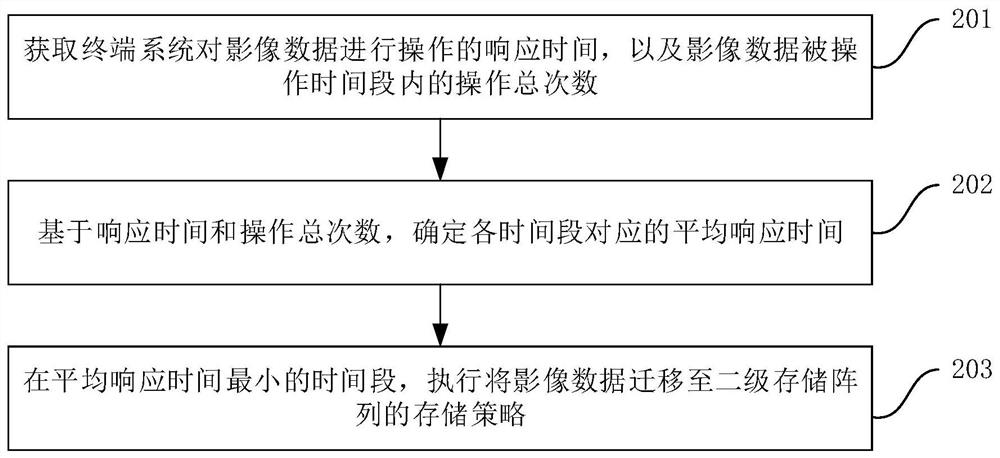
PendingCN114579512APrecise managementKeep storage safeInput/output to record carriersFile system administrationComputer graphics (images)Engineering
The invention discloses a hierarchical storage method and device for image data, electronic equipment and a medium. The method comprises the steps that feature parameters for operating multiple pieces of image data in a preset time period are obtained from a terminal system; on the basis of the feature parameters, respectively calculating the activeness corresponding to each piece of image data; according to the activeness and the storage time corresponding to the image data, the storage strategy of each piece of image data is determined, and the use efficiency of hierarchical storage of the image data can be effectively improved.
Owner:GENERAL HOSPITAL OF PLA
A method of electronic archives storage based on blockchain technology
ActiveCN112600898BRealize distributed storageReduce storageFinanceSecuring communicationEngineeringFinancial transaction
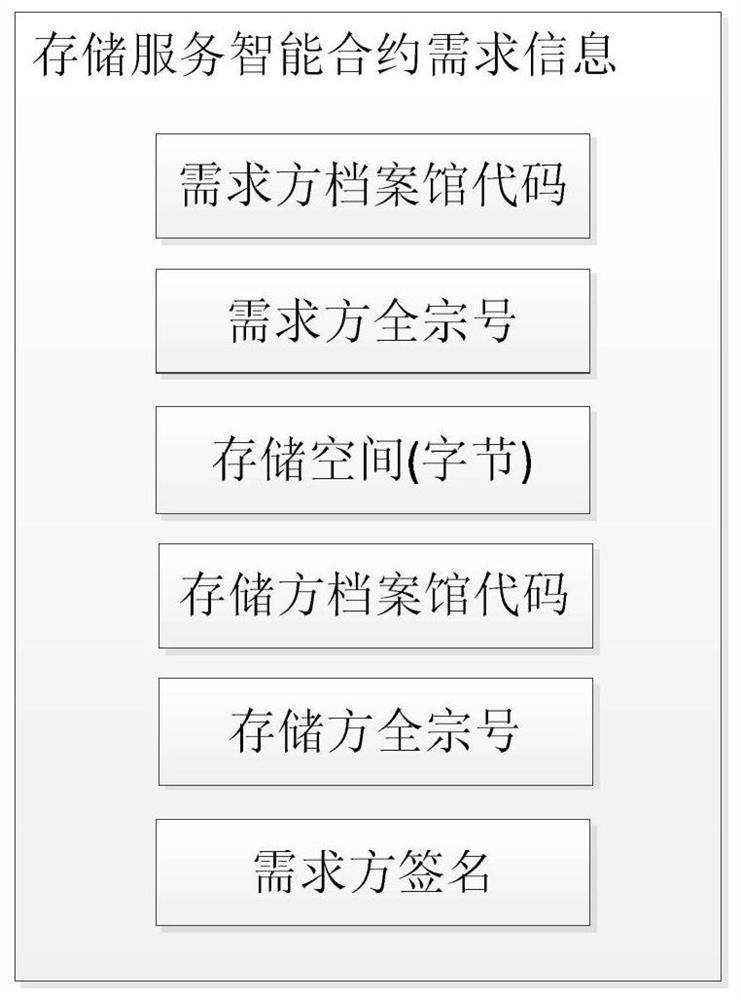
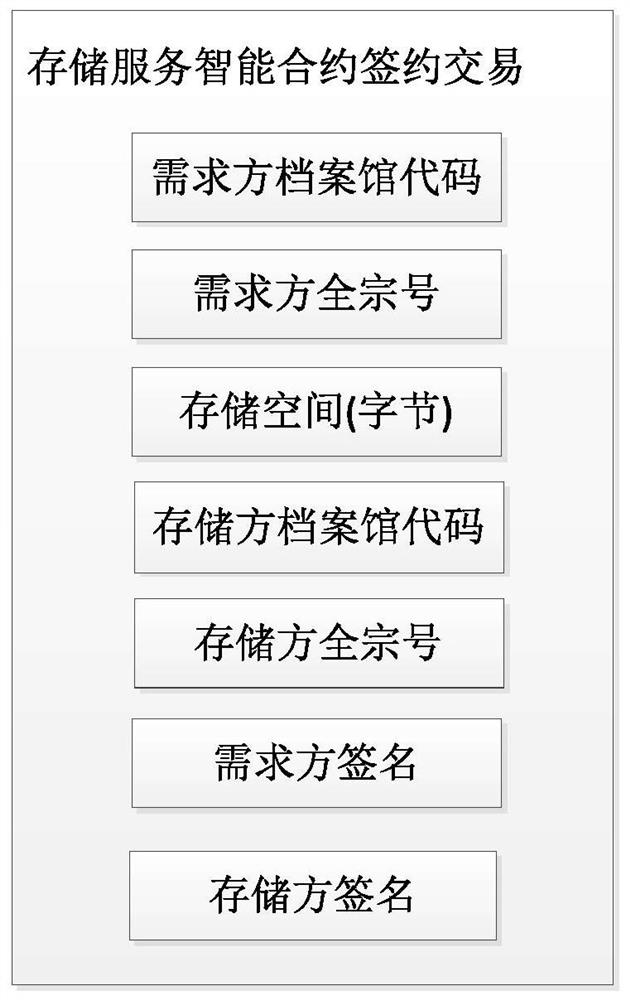
The invention discloses an electronic file storage method based on block chain technology, which includes: each demander signs a storage service smart contract with its corresponding storage party according to its own storage service requirements, and the storage service smart contract takes effect on the chain; The demander processes the electronic files to be stored into storage blocks, publishes the storage demand information to the corresponding storage party to trigger the storage service smart contract between the two, and the storage party stores the relevant storage blocks in its corresponding storage space to generate a storage transaction. The information is submitted to the blockchain; the storage block is only stored on the demand side and the storage side, and the storage service smart contract signing transaction, storage service smart contract contract cancellation transaction, storage transaction and storage block deletion transaction are defined as blockchain transaction information. Submitted to the blockchain according to the blockchain consensus mechanism and then stored in the blockchain, thus realizing the safe and efficient storage and daily management of archive data.
Owner:南京珥仁科技有限公司
Virtual asset storage method and device and virtual asset query method and device
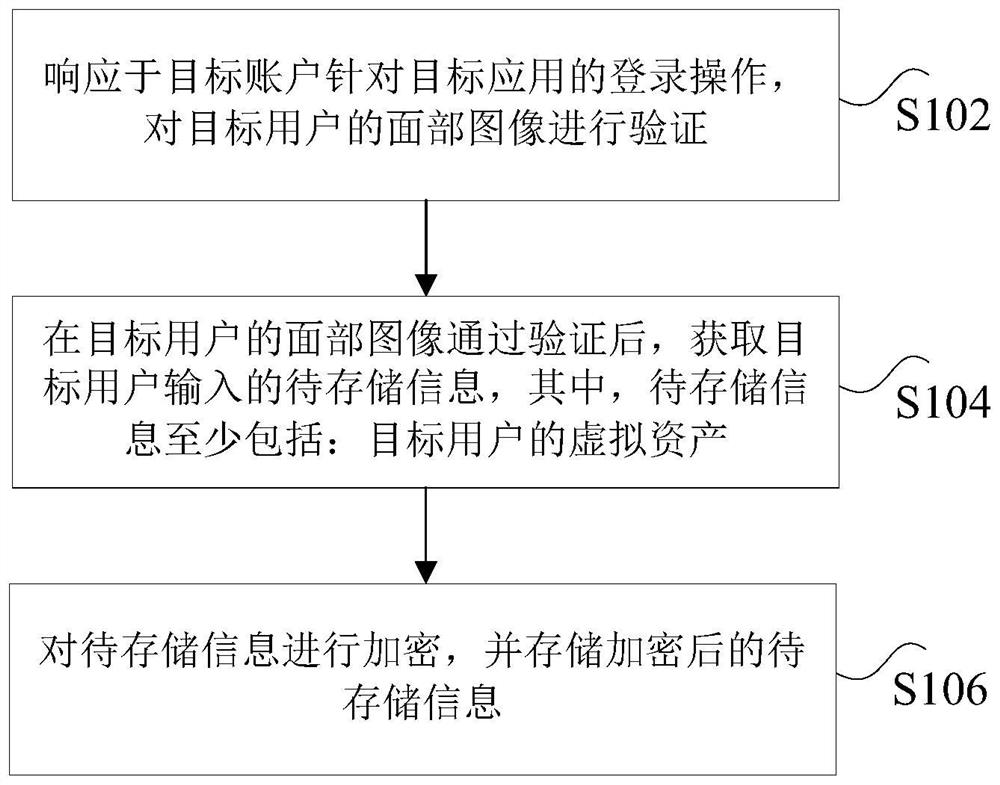
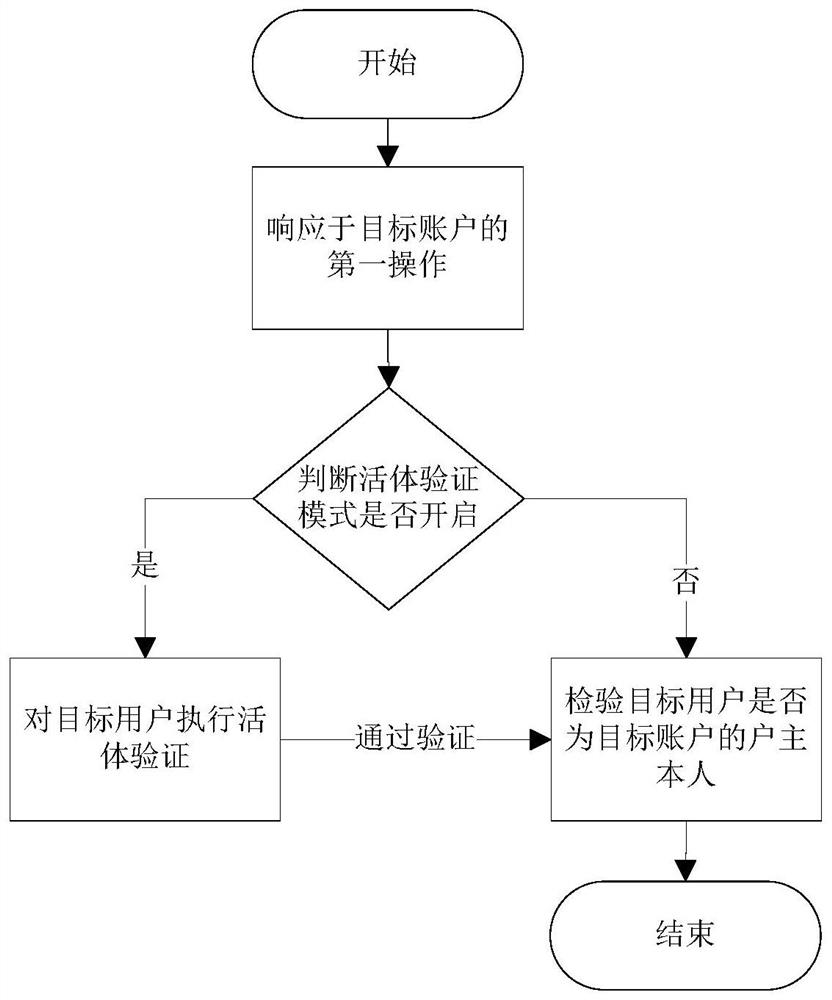
PendingCN114238909AEnsure safe entryKeep storage safeInput/output to record carriersDigital data protectionOperating systemDatabase
The invention discloses a virtual asset storage method and device and a virtual asset query method and device, and relates to the financial science and technology field, and the storage method comprises the steps: responding to a first operation of a target account for a target application, and verifying a face image of a target user; after the face image of the target user passes verification, to-be-stored information input by the target user is obtained, and the to-be-stored information at least comprises virtual assets of the target user; and encrypting the to-be-stored information, and storing the encrypted to-be-stored information. The technical problem that in the prior art, a user cannot store virtual assets is solved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com