Computer network security early warning system
A security early warning system and computer network technology, applied in computer security devices, calculations, instruments, etc., can solve the problems that information security cannot be guaranteed, computers are easy to be illegally started by others, and documents are easy to be illegally tampered or stolen by others. safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
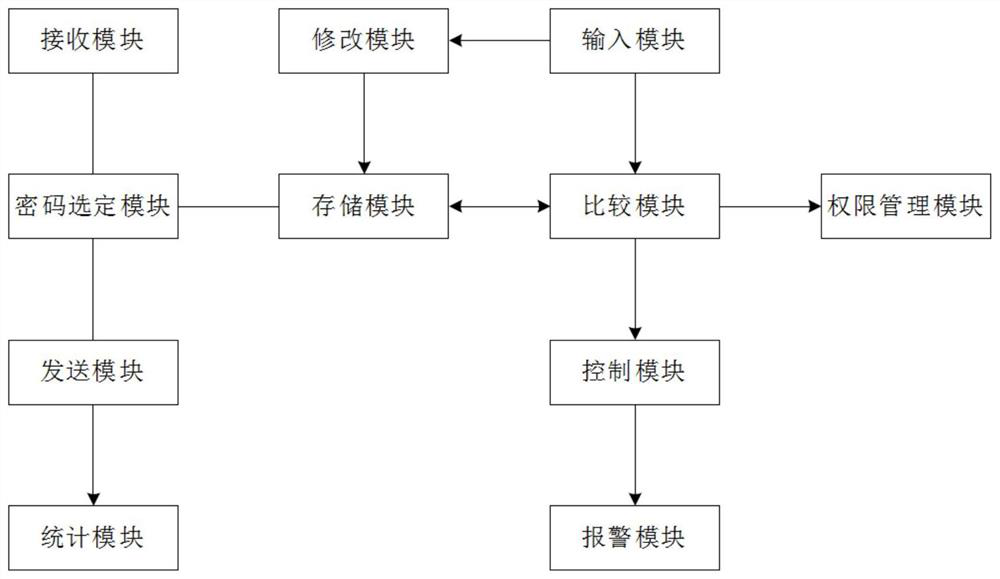
[0029] Basic as attached figure 1 Shown: computer network security early warning system, including storage module, is used for storing multiple sets of standard password information, and standard password information includes sequence number and password plaintext, and ten sets of standard password information are stored in this embodiment, then the sequence number is set There are ten numerical values, and the ten numerical values of the serial numbers are set to be 0-9 in this embodiment. If the plain text of the password is set to four characters, then a group of standard password information includes five characters, then the standard password information of the first group can be expressed as 0****, and * is any character set.
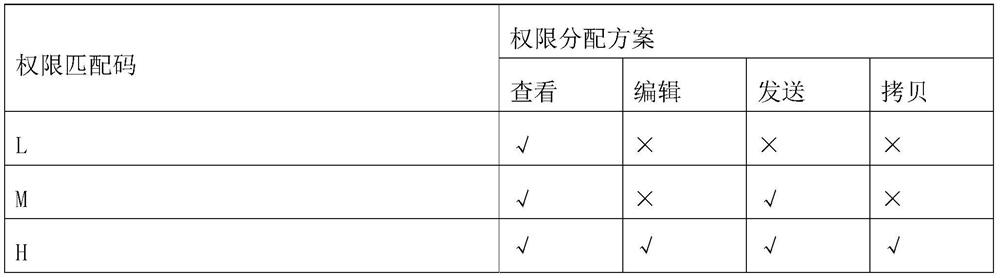
[0030] The storage module includes an ordinary storage area for storing ordinary files and an encrypted storage area for storing confidential files. The storage module also stores the number of thresholds and the authority allocation table. The ...
Embodiment 2
[0056] The difference with Embodiment 1 is that in this embodiment, when the comparison module fails to compare, the comparison module sends prompt information, and the alarm module prompts according to the prompt information, and the statistical module is also used to count the number of failures of comparison failure; the storage module stores The failure threshold, the comparison module also compares the number of failures and the failure threshold, and when the number of failures is equal to the failure threshold, the comparison module sends an alarm message; when the comparison module sends startup information or alarm information, the statistics module clears the number of failures.
[0057] Considering that when inputting the verification information, wrong verification information may be entered due to manual mistakes, so in this embodiment, when the comparison module fails to compare, the comparison module will first send a prompt message, such as "Verification failed, ...
Embodiment 3
[0061] The difference from Embodiment 1 and Embodiment 2 is that the authority allocation table in this embodiment also includes the operation time limit corresponding to the authority matching code, the authority matching code includes the temporary authority code, and the authority allocation scheme corresponding to the temporary authority code also includes Permission allocation duration; it also includes a timing module. When the comparison module compares the temporary permission code that matches the permission code from the permission distribution table, the timing module starts timing and obtains the operation duration. The comparison module is also used to match the corresponding The duration of authority distribution is compared with the duration of operation, and when it is compared that the duration of operation is equal to the duration of authority, the control module controls the computer to freeze the current access operation.
[0062] Considering that when askin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com