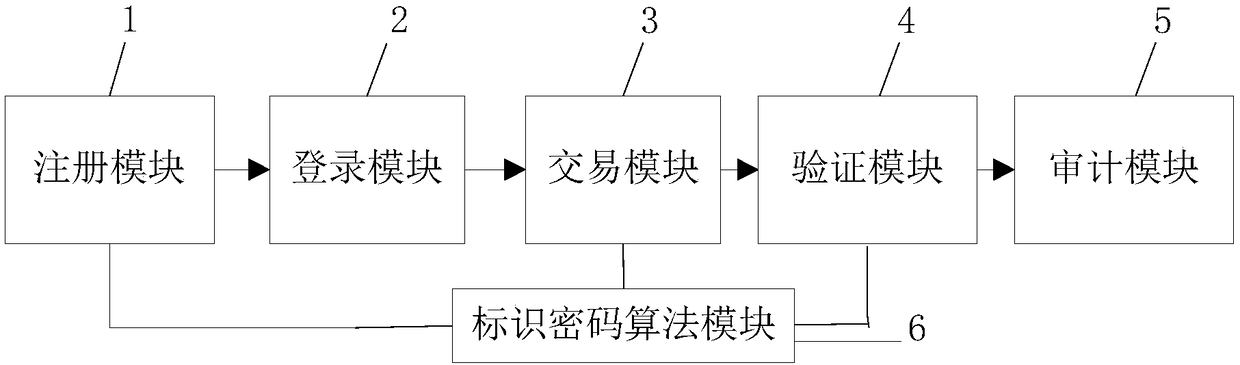
Patents
Literature
224results about How to "Guaranteed non-repudiation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
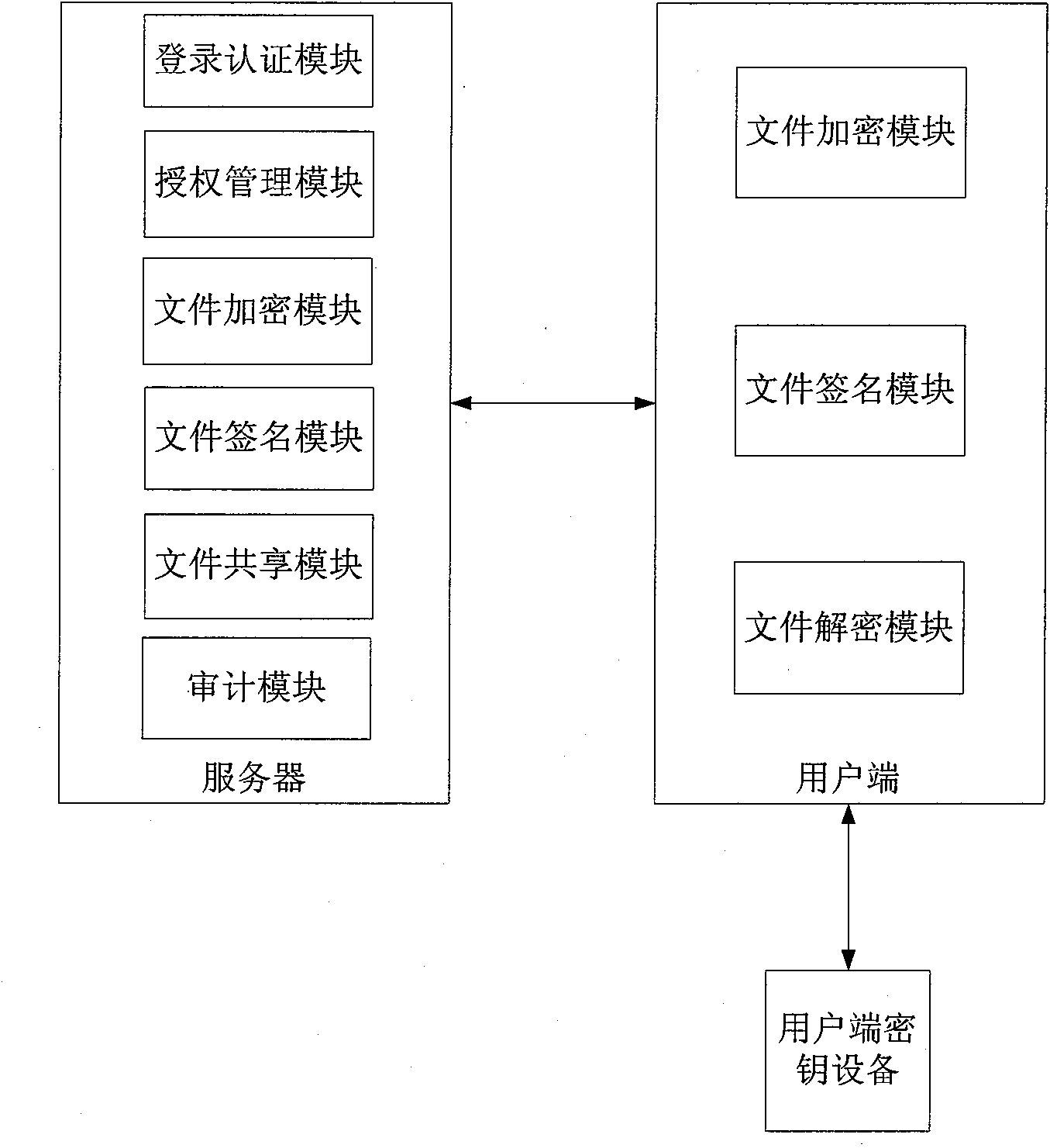
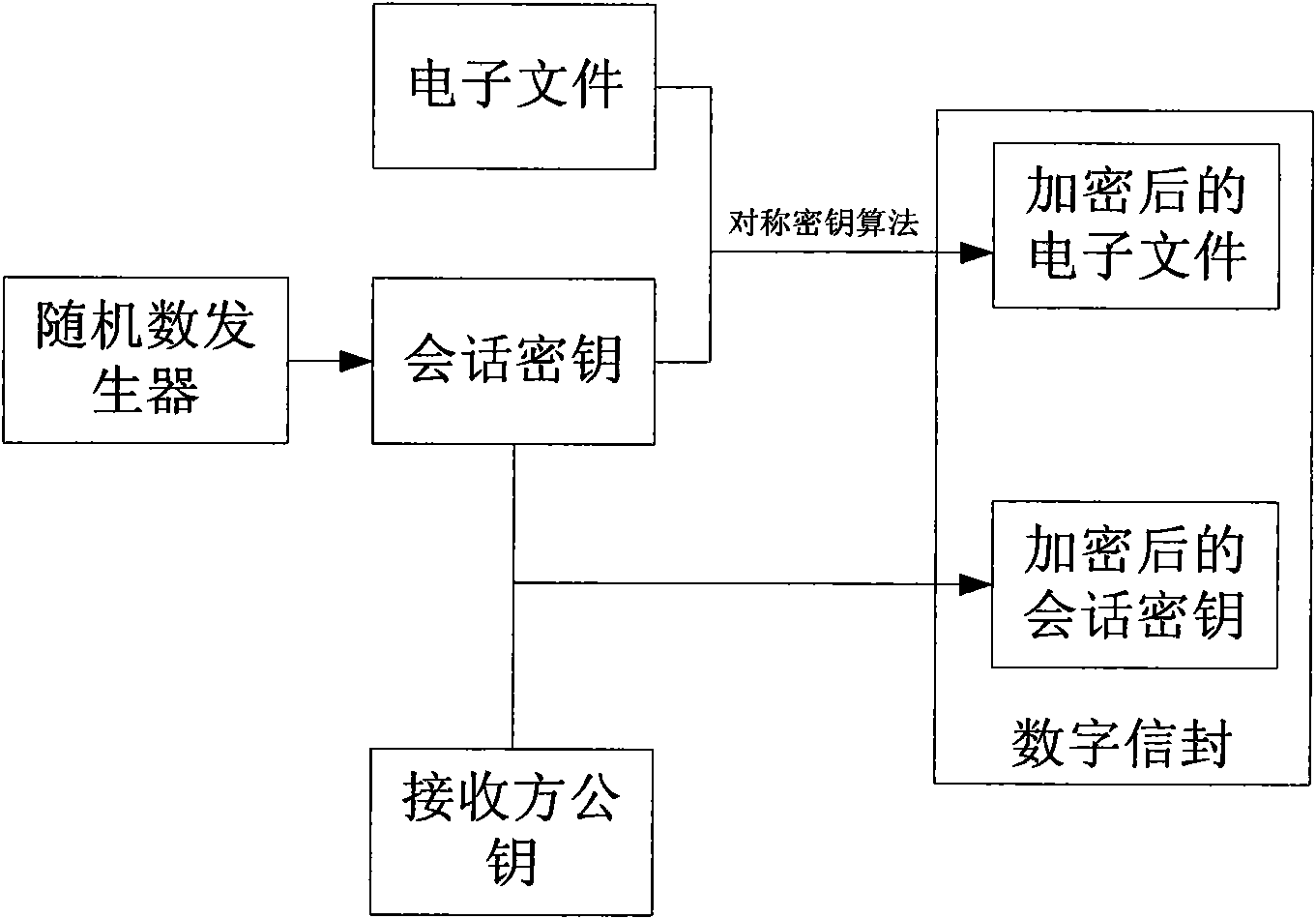
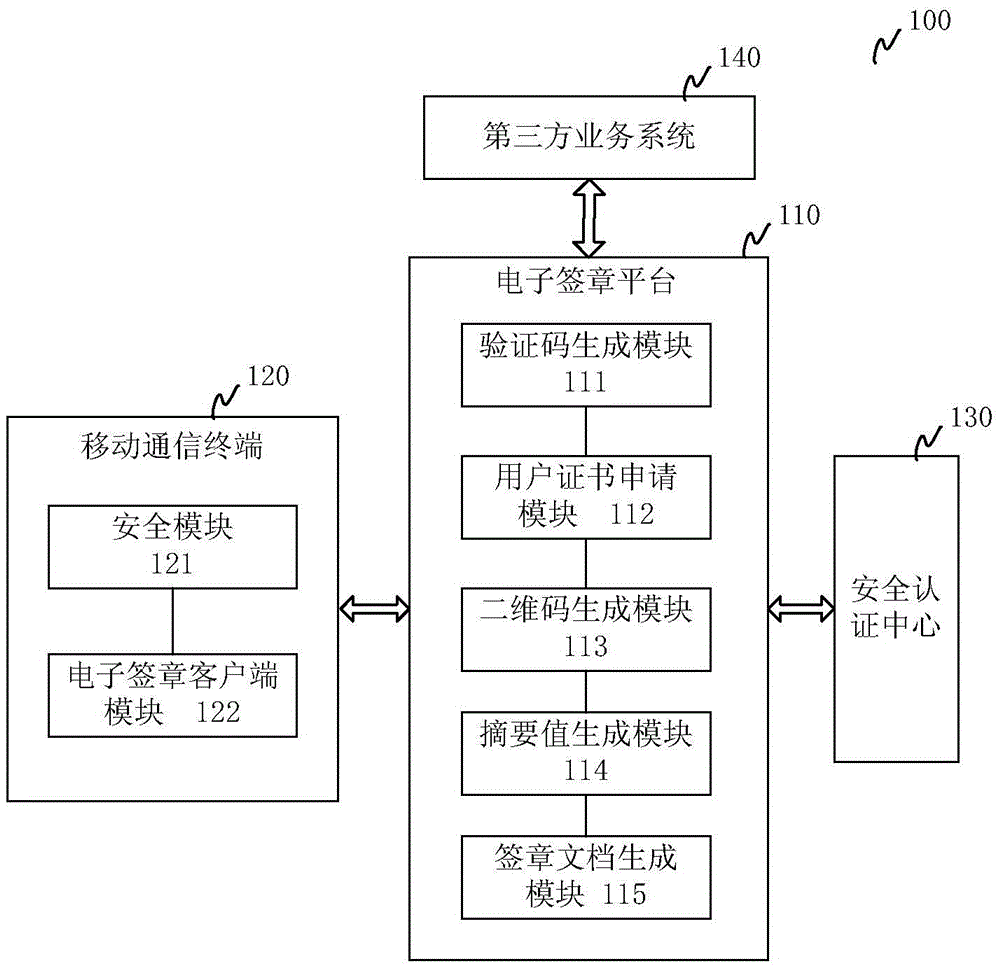
Electronic document safe sharing system and method thereof
InactiveCN101989984AGuarantee authenticitySafe storagePublic key for secure communicationUser identity/authority verificationClient-sideSafe storage
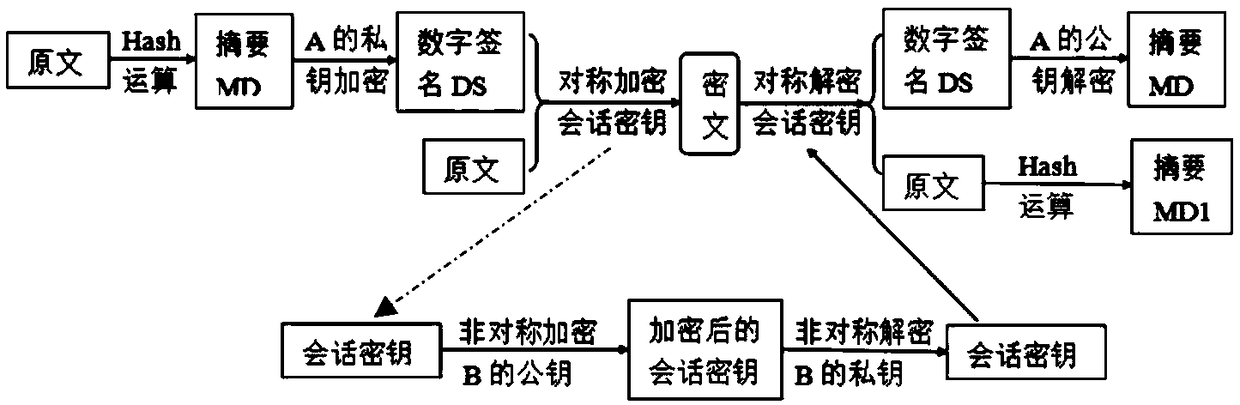
The invention discloses an electronic document safe sharing system which can realize safe storage and fully sharing of secret document. The electronic document safe sharing system comprises a document encrypting module and a document decrypting module; wherein the document encrypting module utilizes a session key to symmetrically encrypt electronic document data, receiver identification (public key) is utilized to asymmetrically encrypt the session key, and finally the encrypted symmetric key and encrypted electronic document data are packed into a digital envelop; and the document decrypting module utilizes an own private key to decrypt the digital envelop. The electronic document safe sharing method of the invention takes CPK combined public key or CPK compound public key technology as the basis, flexible digital signature and secret key exchange capacity thereof are utilized, and a confidential document management system which is from a server to a client, contains information storage and transmission to each use link and is integrated with document data encryption, access control, authorization management, dynamic key exchange and process audit trail into a whole is constructed.
Owner:BEIJING E HENXEN AUTHENTICATION TECH +1
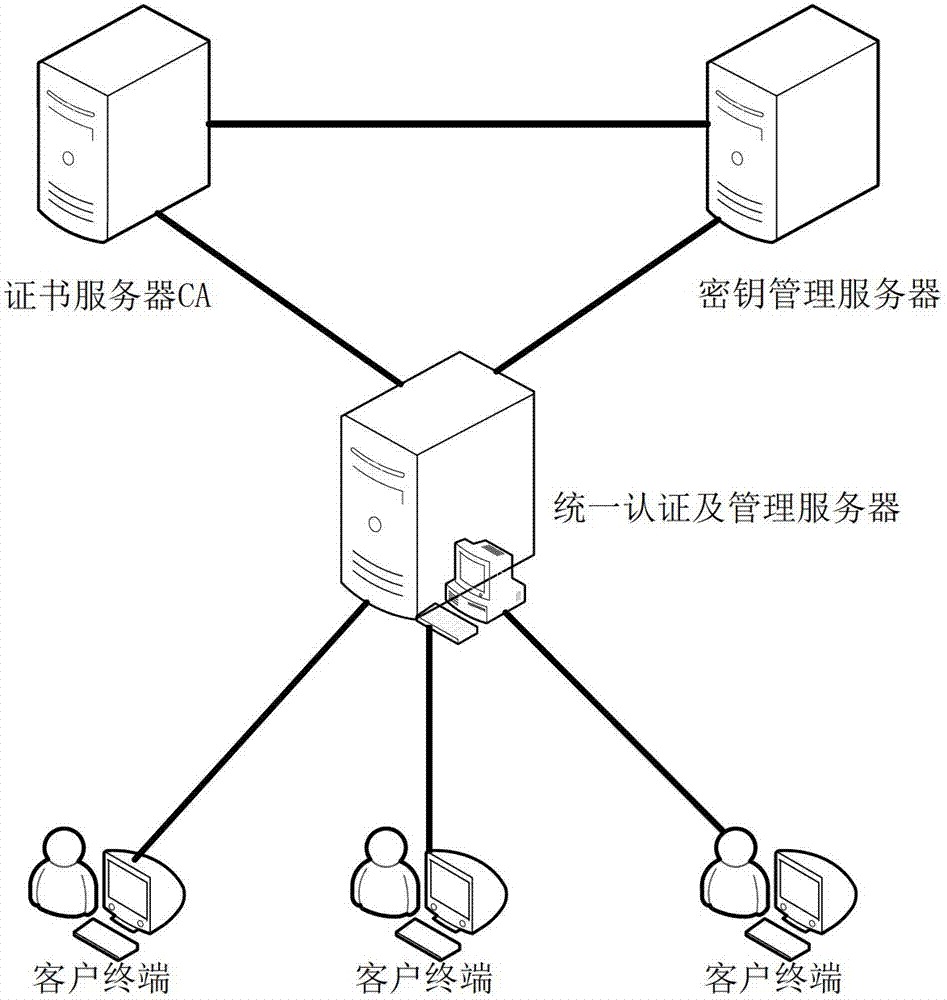
File safe protection system and method thereof
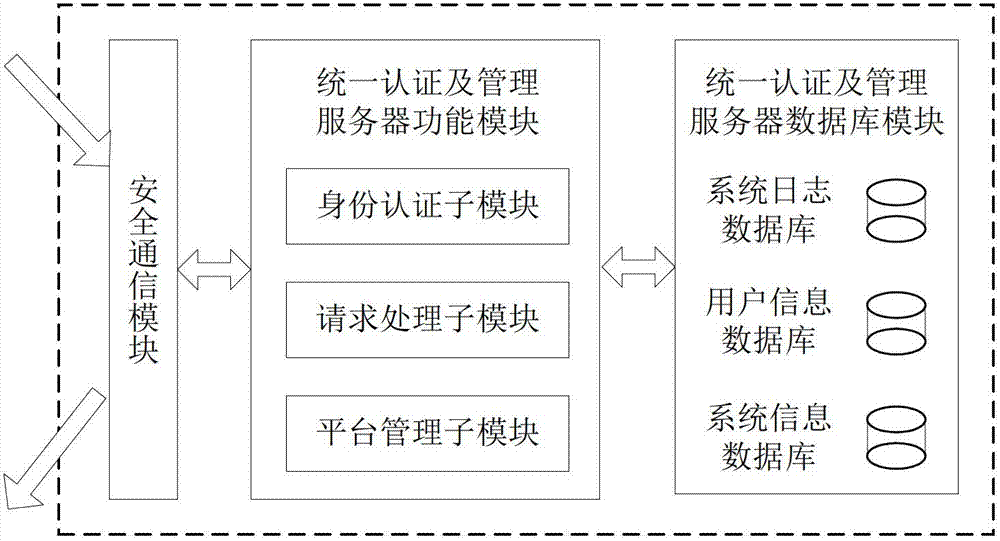
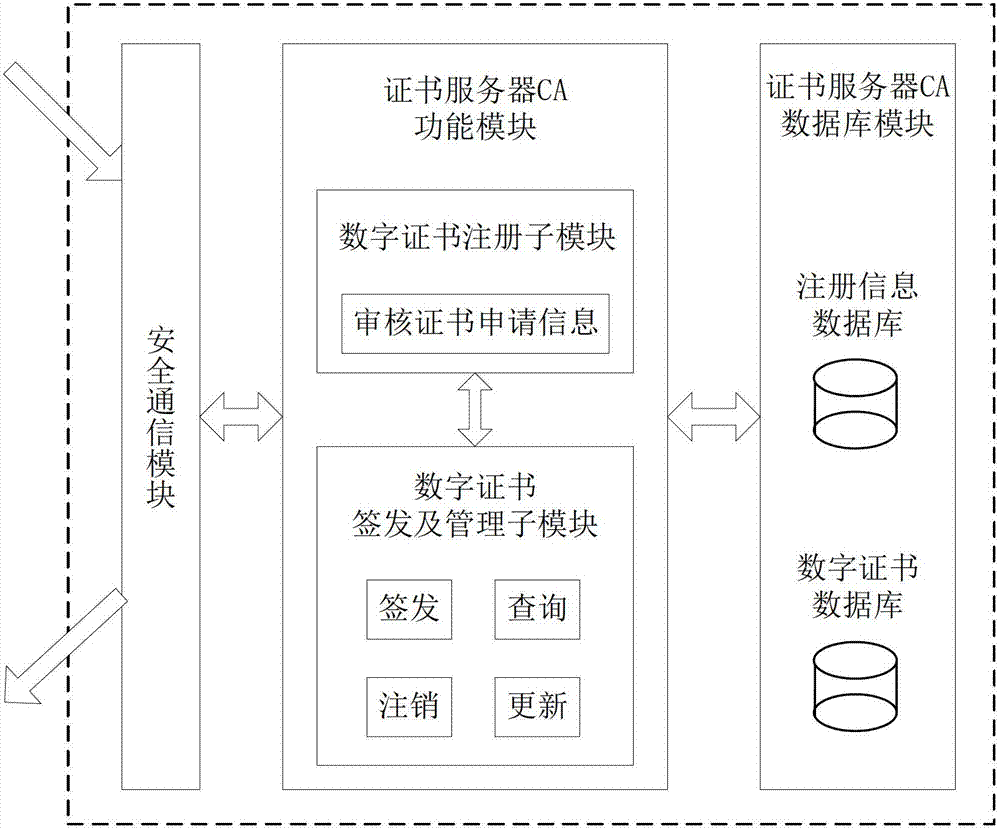
ActiveCN102970299ASimple structureEasy to buildKey distribution for secure communicationUser identity/authority verificationConfidentialityComputer terminal
The invention discloses a file safe protection system and a method, which mainly solves the problems of network illegal invasion, information stealing and tamping, impersonation and weak deny resistance in the conventional information system. The file safe protection system consists of a unified authentication and management server, a certificate server CA, a secret key management server and a client terminal; the unified authentication and management server is used as a middle node and is used for processing or transmitting a service request sent by the client terminal; the certificate server CA processes a certificate service request of the client terminal and provides basic support for identification; and the secret key management server processes the secrete key service requests of the client terminal and the certificate server CA, and is used for encrypting and decrypting a file for the client terminal and providing parameter support for a digital certificate signed by the certificate server CA. With the adoption of the file safe protection system and method provided by the invention, identification, confidentiality, integration and non-repudiation services can be provided; and the file can be safely protected in transmission, storage, sharing and access processes.
Owner:XIDIAN UNIV
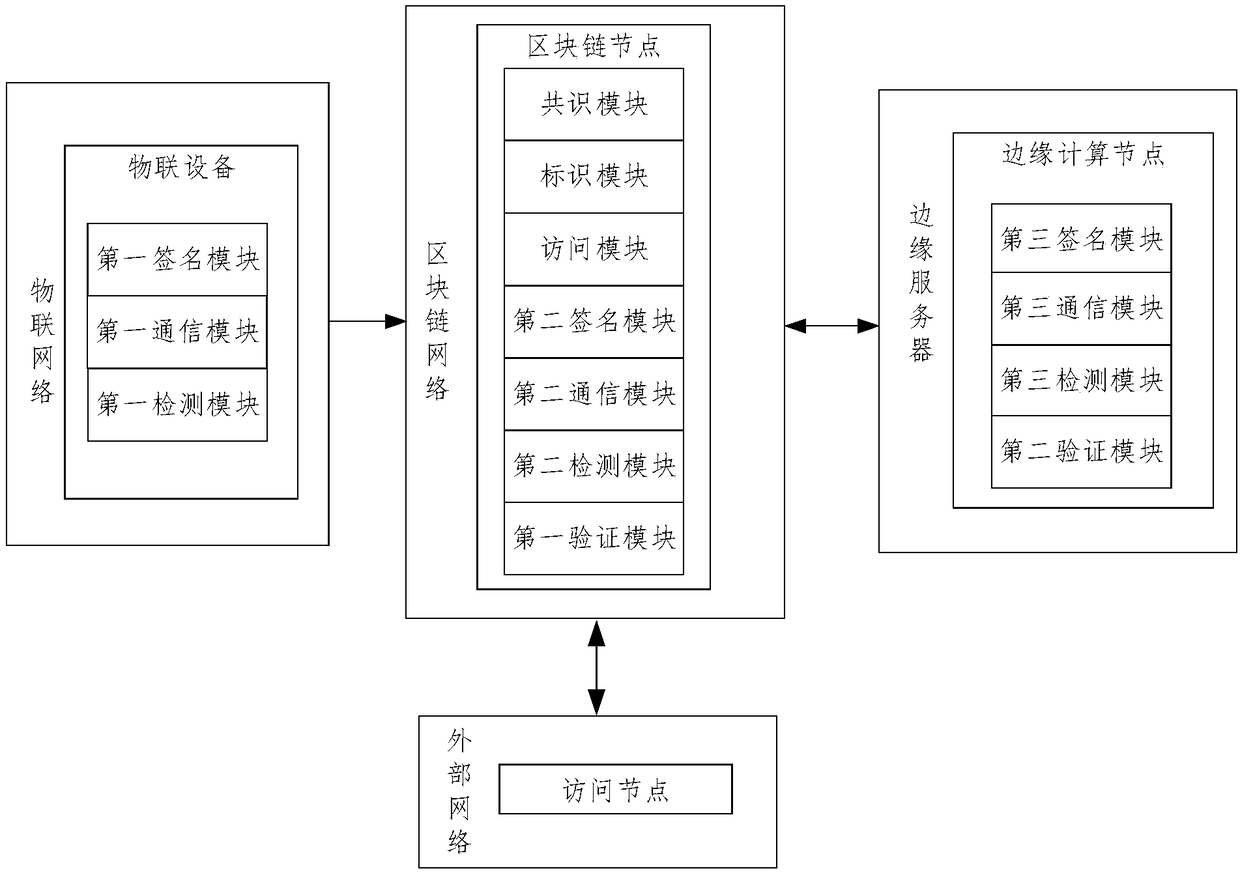
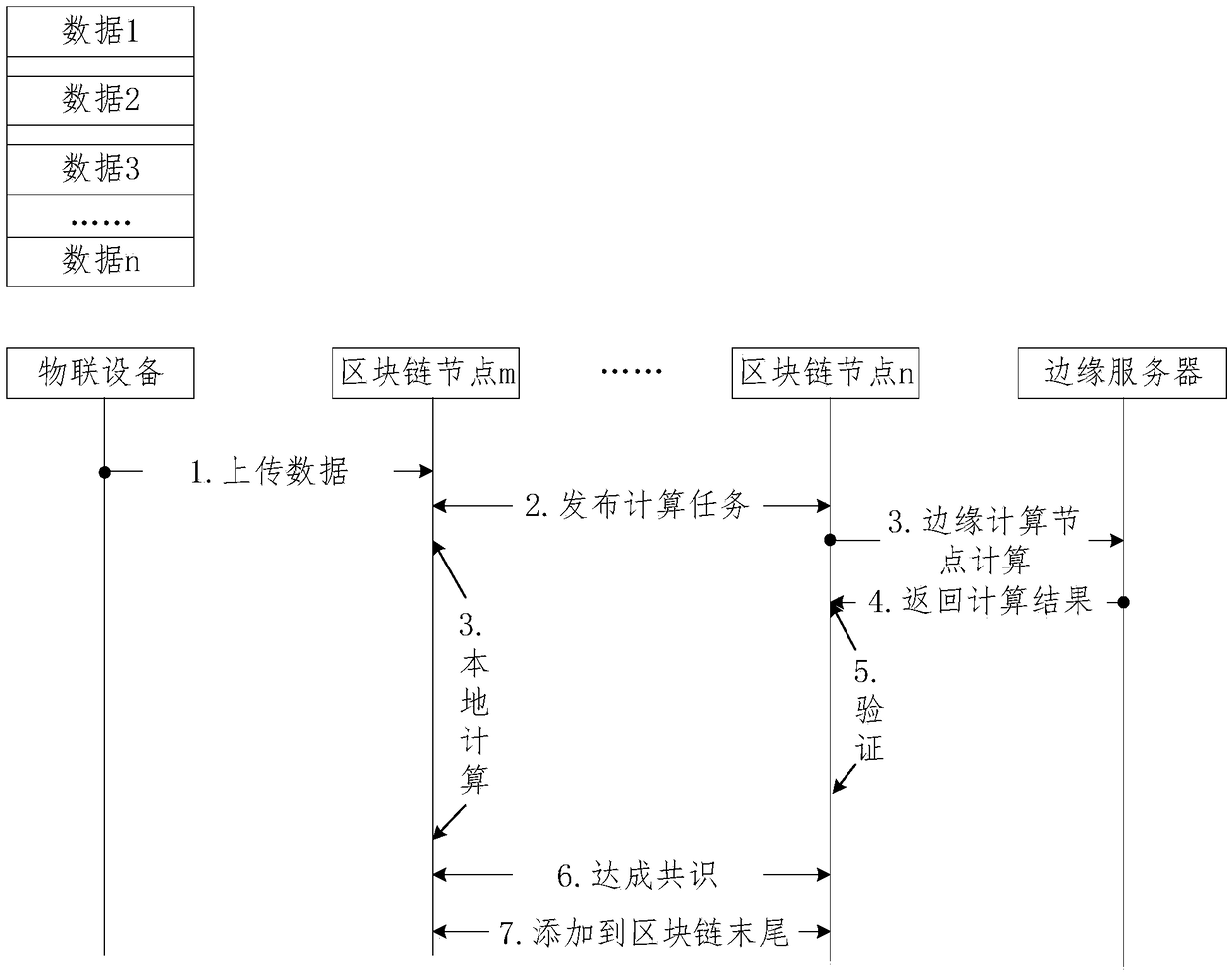
Industrial data detection block chain network architecture based on edge computing and detection method
ActiveCN109302405ARealize open and transparent managementPrevent leakageEncryption apparatus with shift registers/memoriesUser identity/authority verificationEdge serverEdge computing
The invention discloses industrial data detection block chain network architecture based on edge computing and a detection method, and belongs to the field of industrial data detection. The block chain network architecture comprises Internet of things, a block chain network, an edge server and an external network. A public chain is introduced, so that every citizen can join the public chain as a block chain node to maintain the block chain network, and access the block chain network as an access node at the same time. Meanwhile, edge computing is introduced, and services are provided for the block chain nodes by means of the computing power of the edge server to solve the problem of incapability of detecting acquired data due to inadequate computing power of certain block chain nodes, thereby detecting the authenticity and reliability of the acquired data, and preventing bad manufacturers from tampering with data and harming social interests. At the same time, an intelligent contract access mode is introduced, thereby enabling enterprises to automatically execute intelligent contracts, preventing bad enterprises from defaulting fines, and improving the enforcement of supervision after out-of-standard emission.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Identity authentication server and identity authentication token
ActiveCN108092776APrevent replay attacksAddressing leaked passwordsUser identity/authority verificationClient-sideNon-repudiation
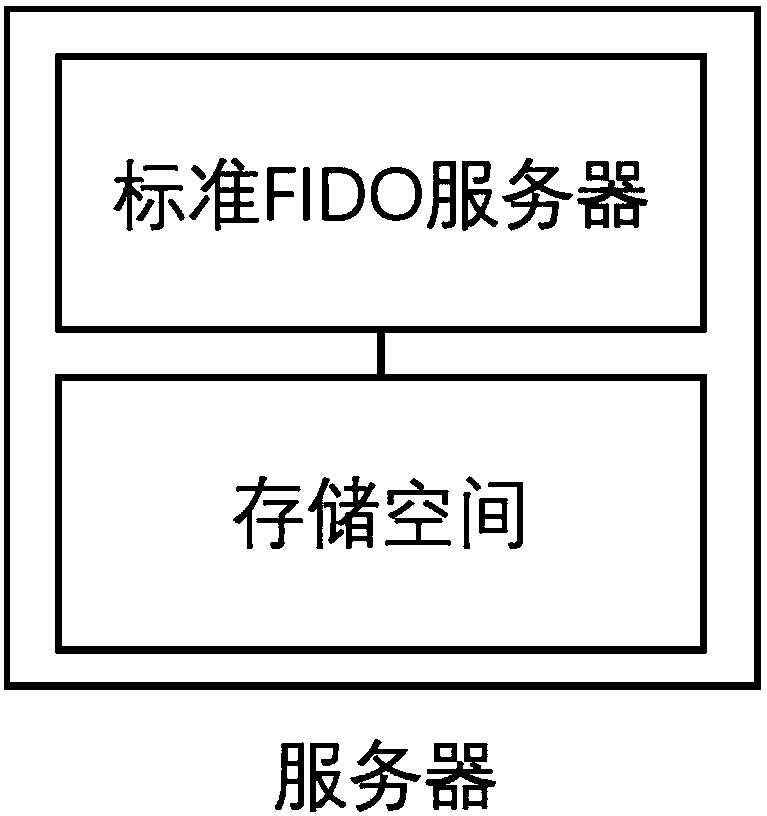
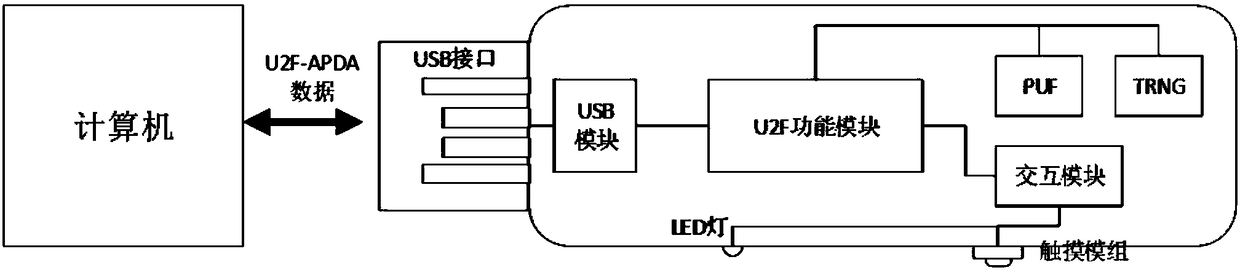
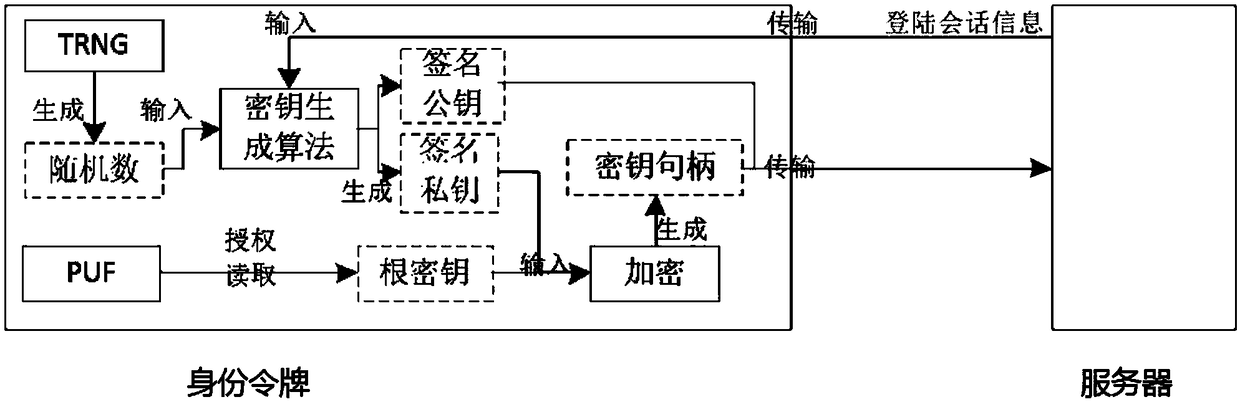
The invention discloses an identity authentication server and an identity authentication token, wherein the identity authentication server comprises a standard FIDO server and a storage space for storing keys, namely, a database, which are connected with each other; the identity authentication token is based on physical unclonable and the FIDO U2F protocol and comprises a U2F module, and a PUF module,a TRNG module, a USB module and an interaction module, which are connected with the U2F module, and a touch module connected with the interaction module; and an identity token interacts with a client browser, and the client browser in turn interacts with an FIDO server in the authentication server. According to the identity authentication server disclosed by the invention, the physical unclonable function is combined with the FIDO, the uniqueness and non-replicability of the token are ensured by the physical unclonable function, and the accuracy of the user identity and the non-defective modification and non-repudiation of the operation are ensured by the FIDO.
Owner:NARI INFORMATION & COMM TECH
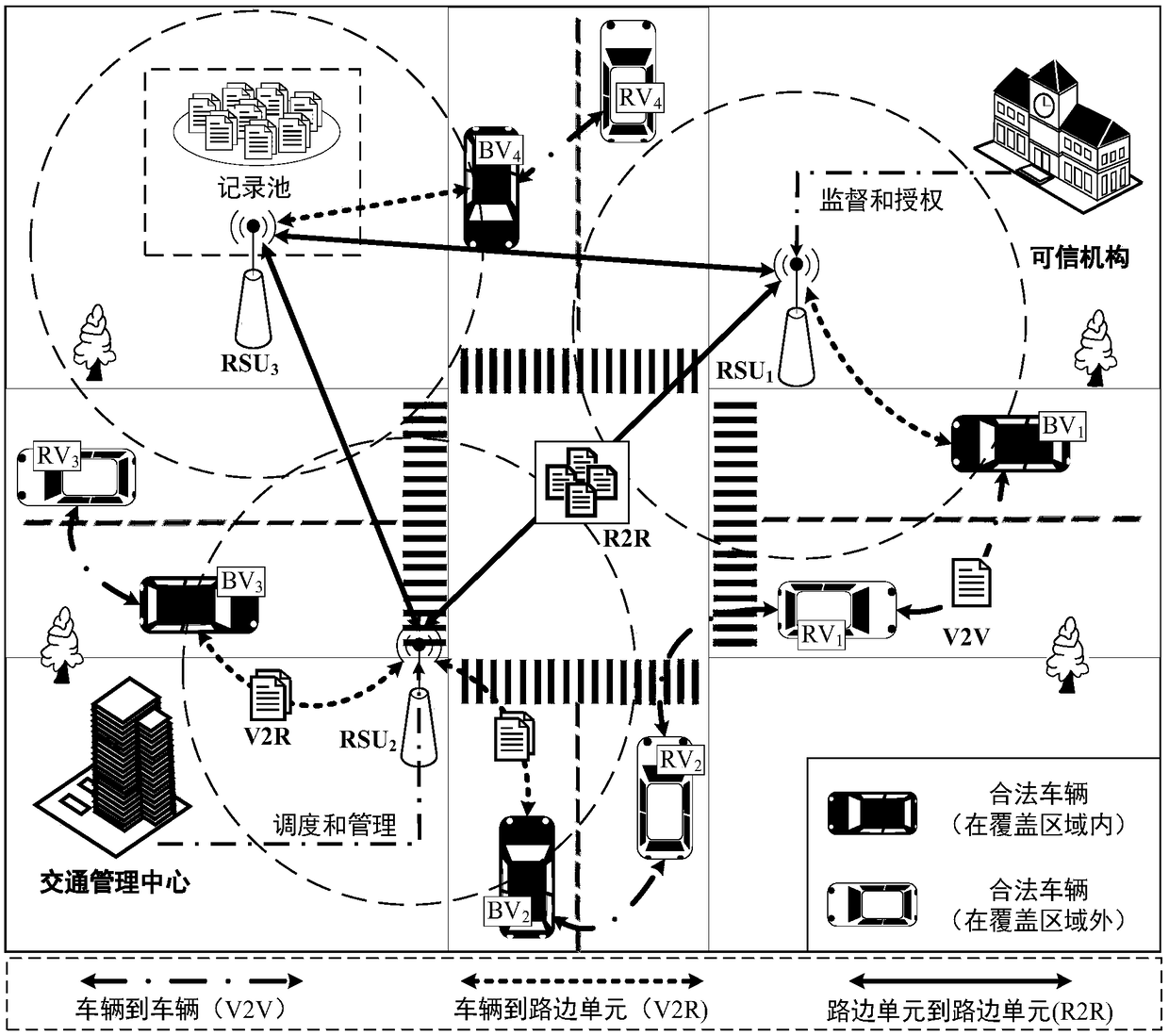
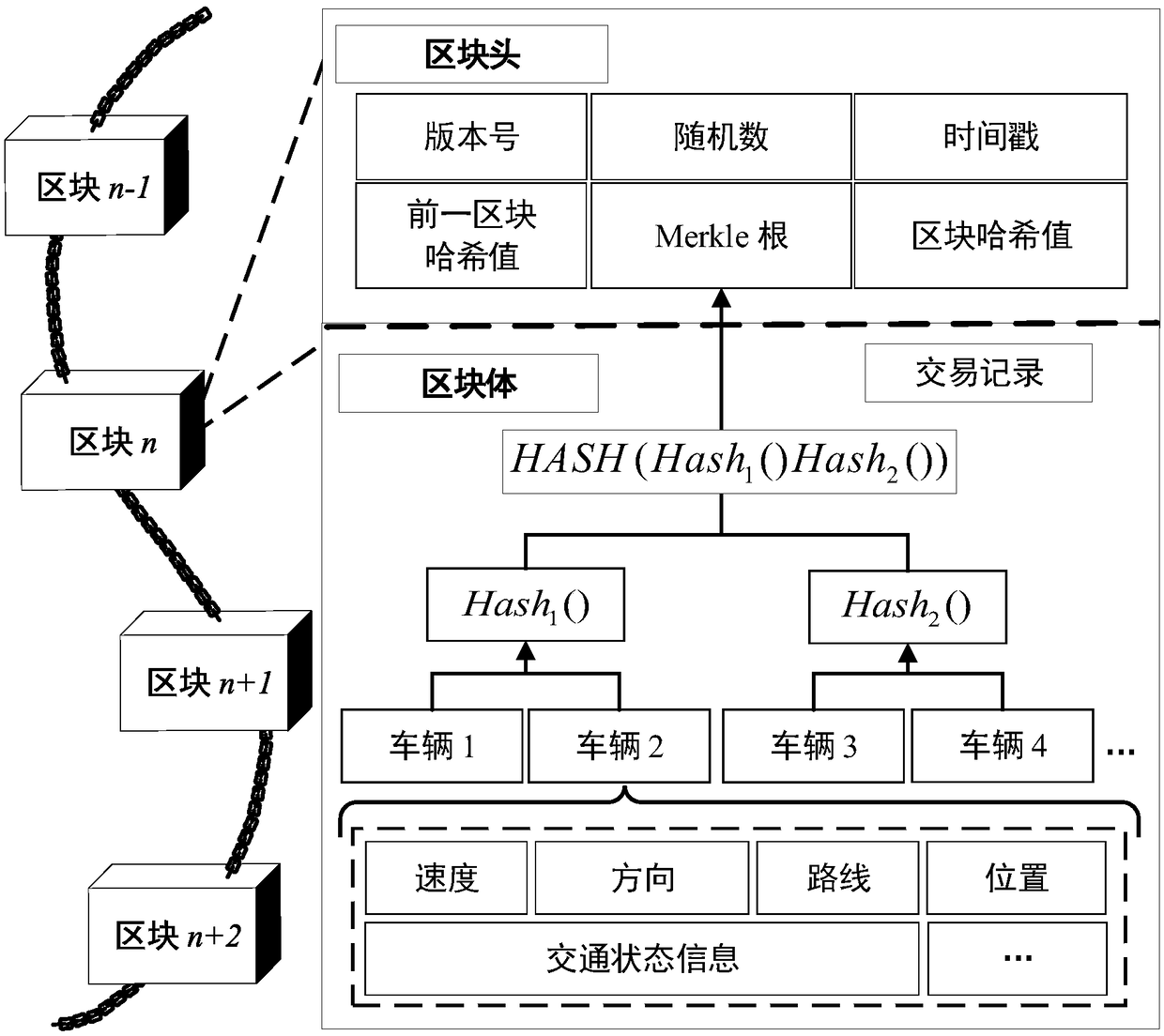
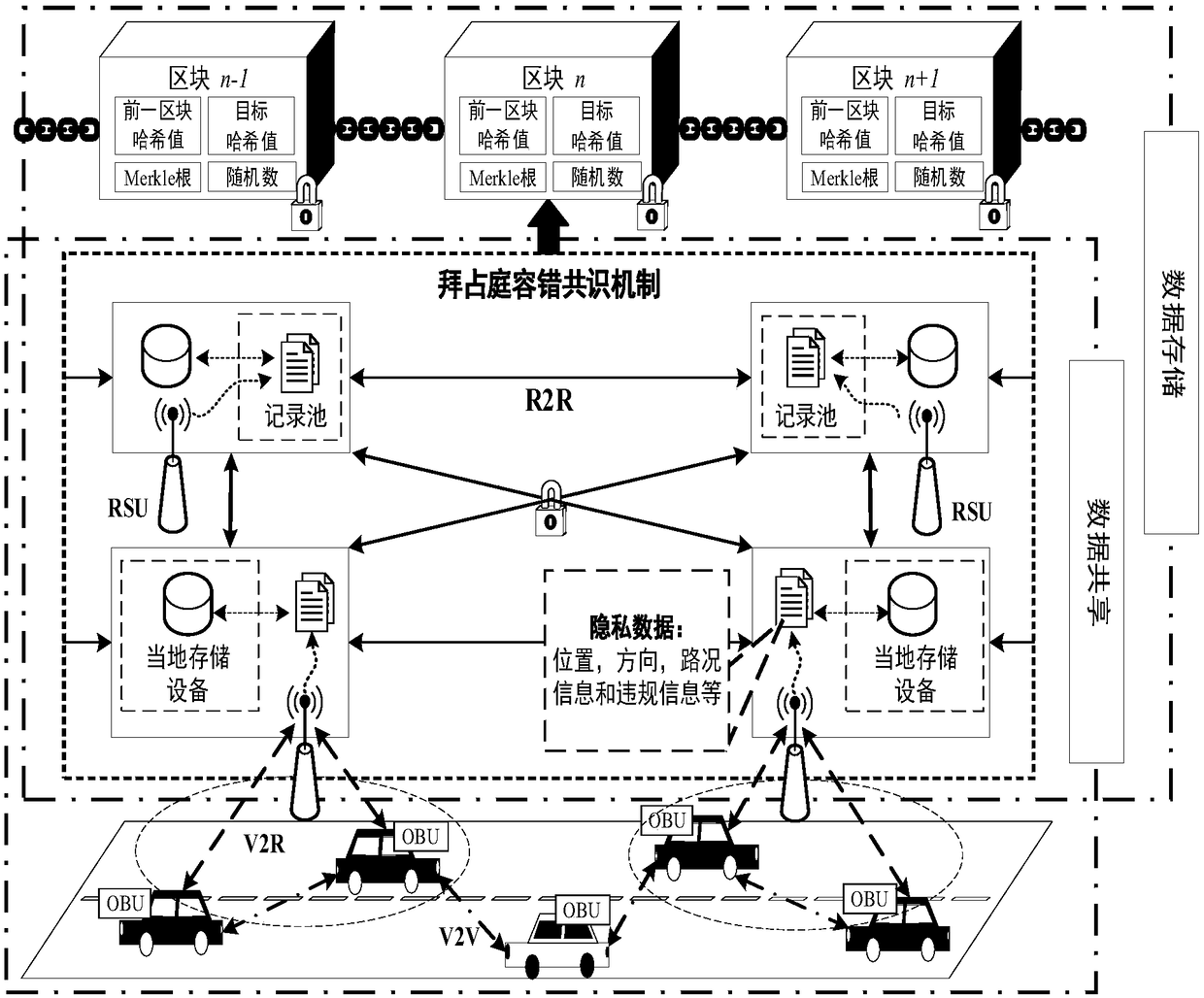
Vehicular ad-hoc network data security sharing and storage system based on blockchain technology
ActiveCN109451467AImprove efficiencyPrevent leakageParticular environment based servicesUser identity/authority verificationByzantine fault toleranceDigital signature
The invention discloses a vehicular ad-hoc network data security sharing and storage system based on a blockchain technology. The vehicular ad-hoc network data security sharing and storage system based on the blockchain technology comprises a vehicle, a roadside unit, and a trusted institution. When data shared by the roadside unit, the vehicle performs digital signature on interactive informationby using a bilinear algorithm based on an elliptic curve to ensure the non-repudiation and integrity of the data; the roadside unit packs the collected data into a block, and uses the Byzantine fault-tolerant consensus mechanism to make the data block reach a coherent protocol across the network, thereby improving the fault tolerance of the system and making system more stable; after reaching theconsensus, the block is sorted by a smart contract in the roadside unit and stored in the blockchain, and other consensus nodes save the data synchronously; and the system rewards a corresponding number of data coins to the roadside unit, and then the data coins are assigned to the vehicle contributing the data by the smart contract, so as to keep the entire system active and stable.
Owner:JIANGXI UNIV OF SCI & TECH
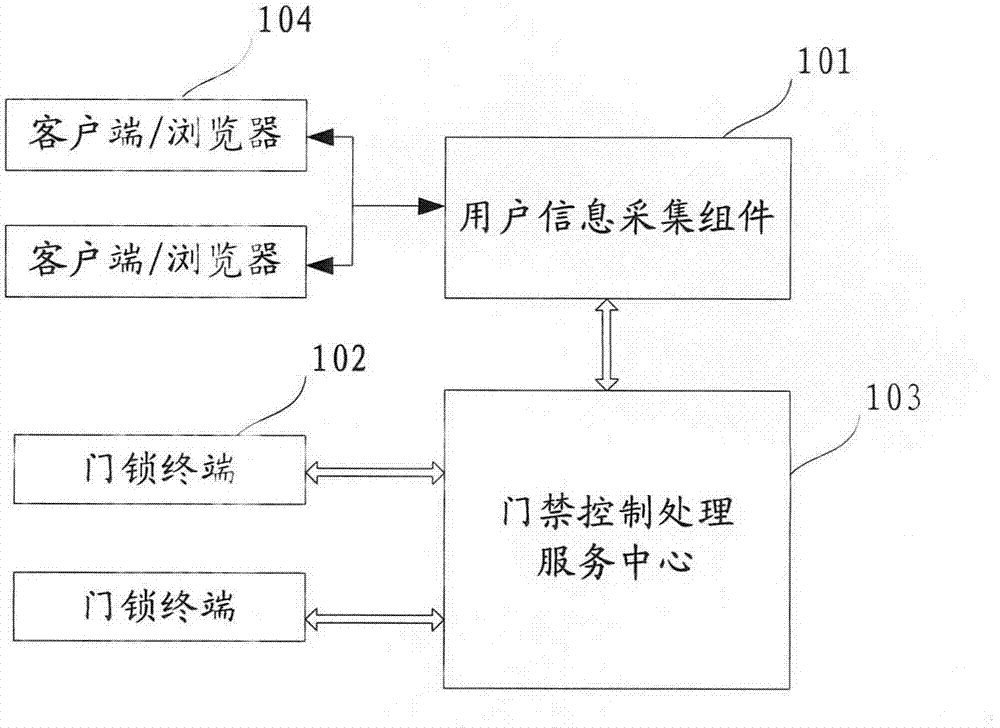
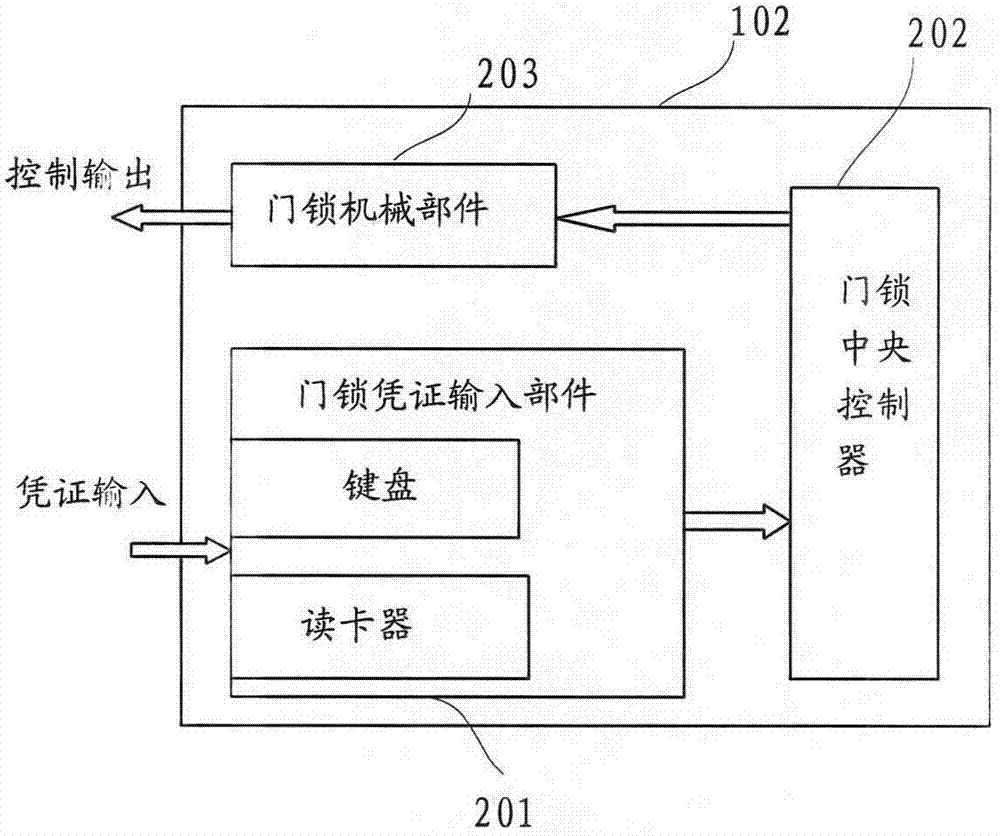
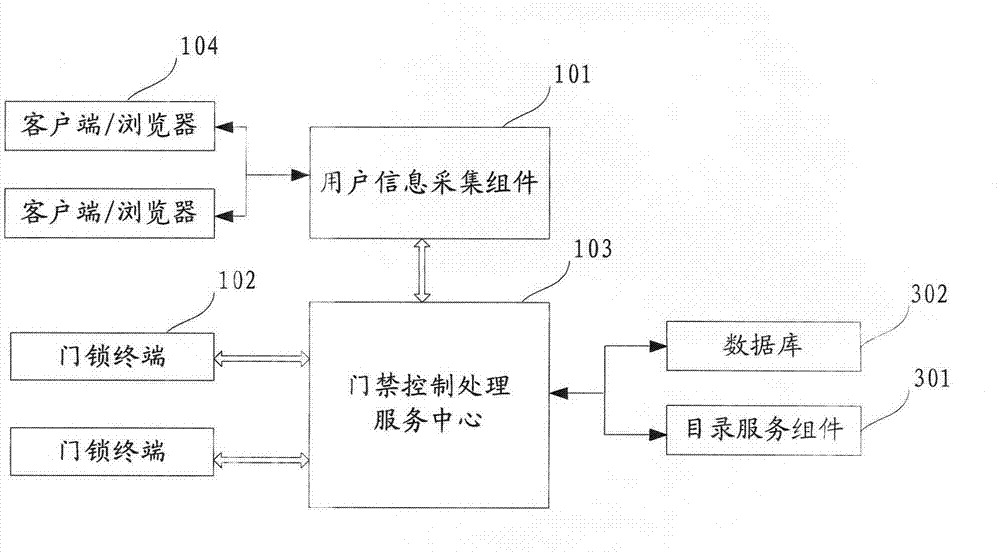
Door access control system and method
ActiveCN103248484AHigh degree of intelligenceGuaranteed non-repudiationUser identity/authority verificationIndividual entry/exit registersManagement efficiencyAuthorization
The invention relates to the technical field of door access control, and discloses a door access control system and method. The system comprises a user information acquisition assembly, a door lock terminal and a door access control and processing service center. The system can identify a user through unified account number management, authenticate the door lock terminal through unified authentication management, and authorize a room resource through unified authorization management, so that intelligentization, safety and management efficiency of a door access control process can be improved.
Owner:BEIJING GUO JIA INTELLIGENT TECH CO LTD
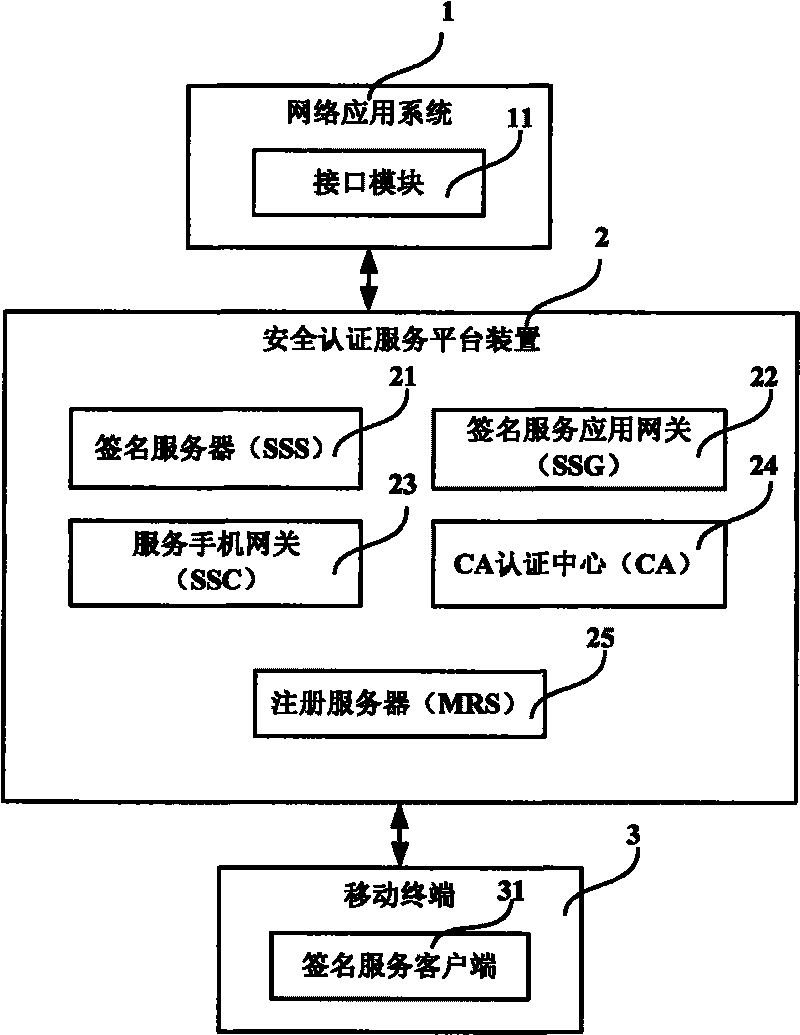
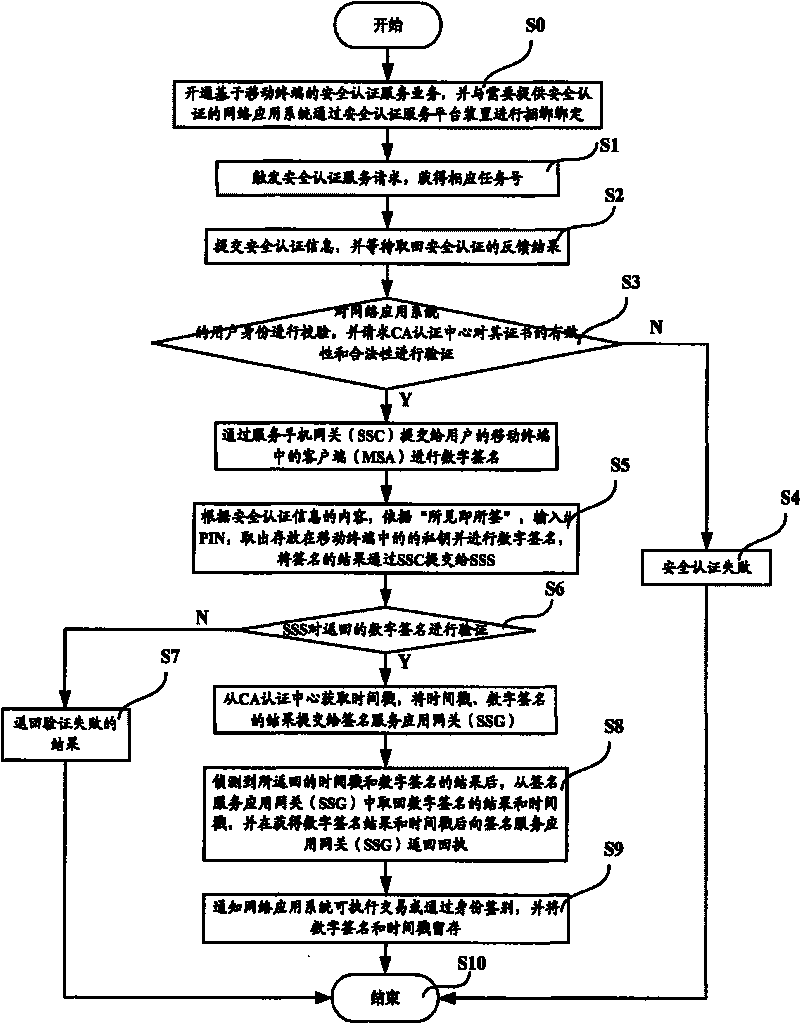
Safety certification service platform system, device and method based on mobile terminal
ActiveCN101765108AReduce overheadEliminate potential safety hazardsUser identity/authority verificationSecurity arrangementTimestampDigital signature
The invention discloses a safety certification service platform system based on mobile terminal, a device and a method thereof. The system comprises a mobile terminal and a network application system, as well as a safety certification service platform device for receiving a safety certification request coming from the network application system, verifying the identity of a requestor for safety certification and checking contents of safety certification; after passing verification and check, the safety certification request is submitted to the mobile terminal for digital signature and the digital signature of the mobile terminal is verified; after passing the verification, the digital signature result and timestamp are returned to the network application system. The safety certification system and method disclosed in the invention are brand-new, convenient, rapid, low in cost and high in safety and efficiency.
Owner:BEIJING TEAMSUN TECH
Two-dimension code-based mobile terminal transaction encryption method
ActiveCN103714458ANot burdenedEnsure safetyUser identity/authority verificationBuying/selling/leasing transactionsPaymentRelevant information
The invention discloses a two-dimension code-based mobile terminal transaction encryption method and belongs to the network technical field. According to the two-dimension code-based mobile terminal transaction encryption method of the invention, based on the combination of a two-dimensional code technology and an existing mobile transaction protocol, related information can be encrypted through two-dimension codes in identity authentication of two transaction parties, order confirmation and payment, such that transaction security can be ensured. With the two-dimension code-based mobile terminal transaction encryption method of the invention adopted, safer and more reliable online transactions can be realized without too much burden brought to a mobile terminal device, and the safety, confidentiality and non-repudiation performance of the online transactions of the mobile terminal can be ensured.
Owner:JIANGSU UNIV
Information security control system
InactiveCN101043335AImplement encrypted transmissionAvoid illegal acquisitionUser identity/authority verificationError processingConfidentiality
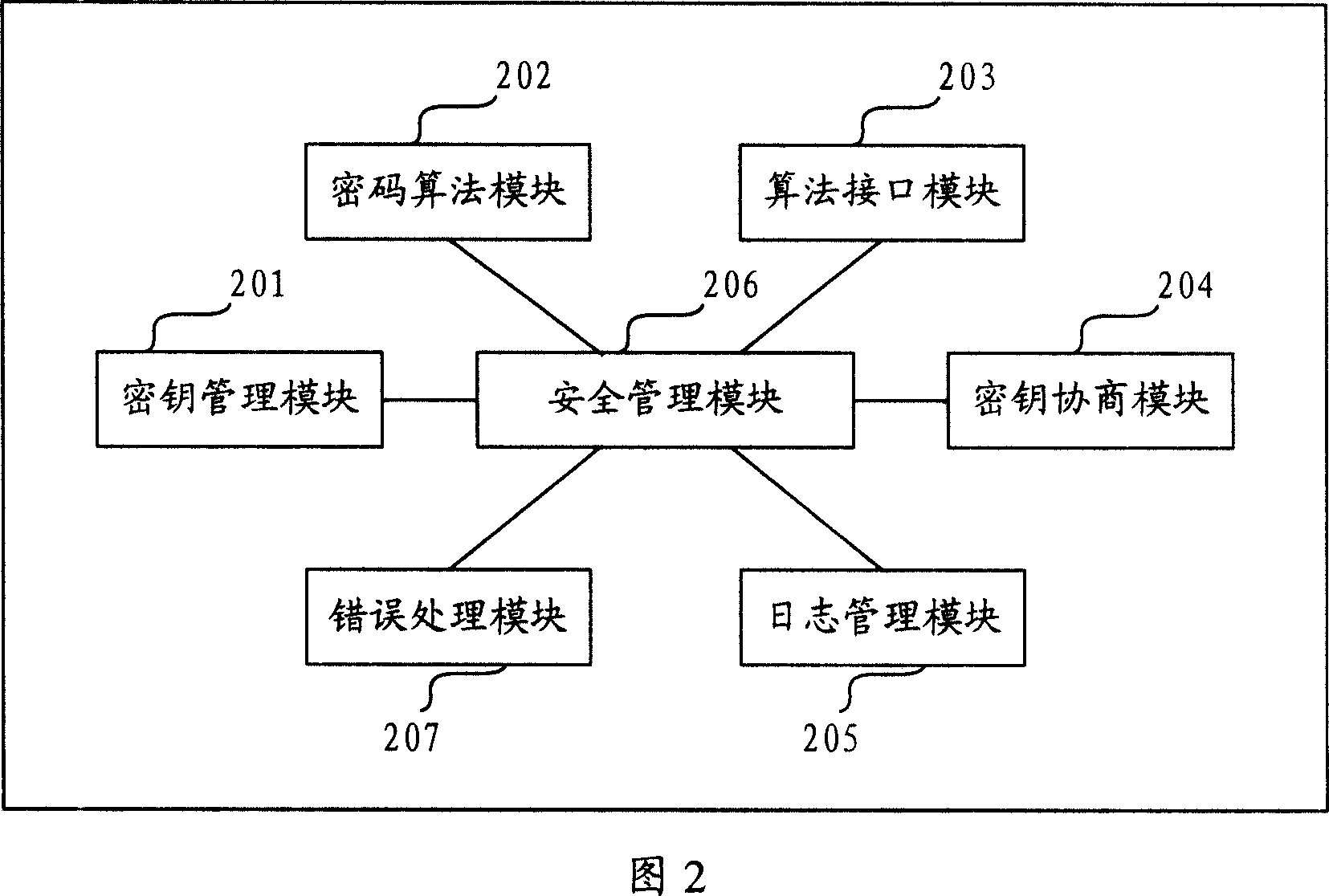
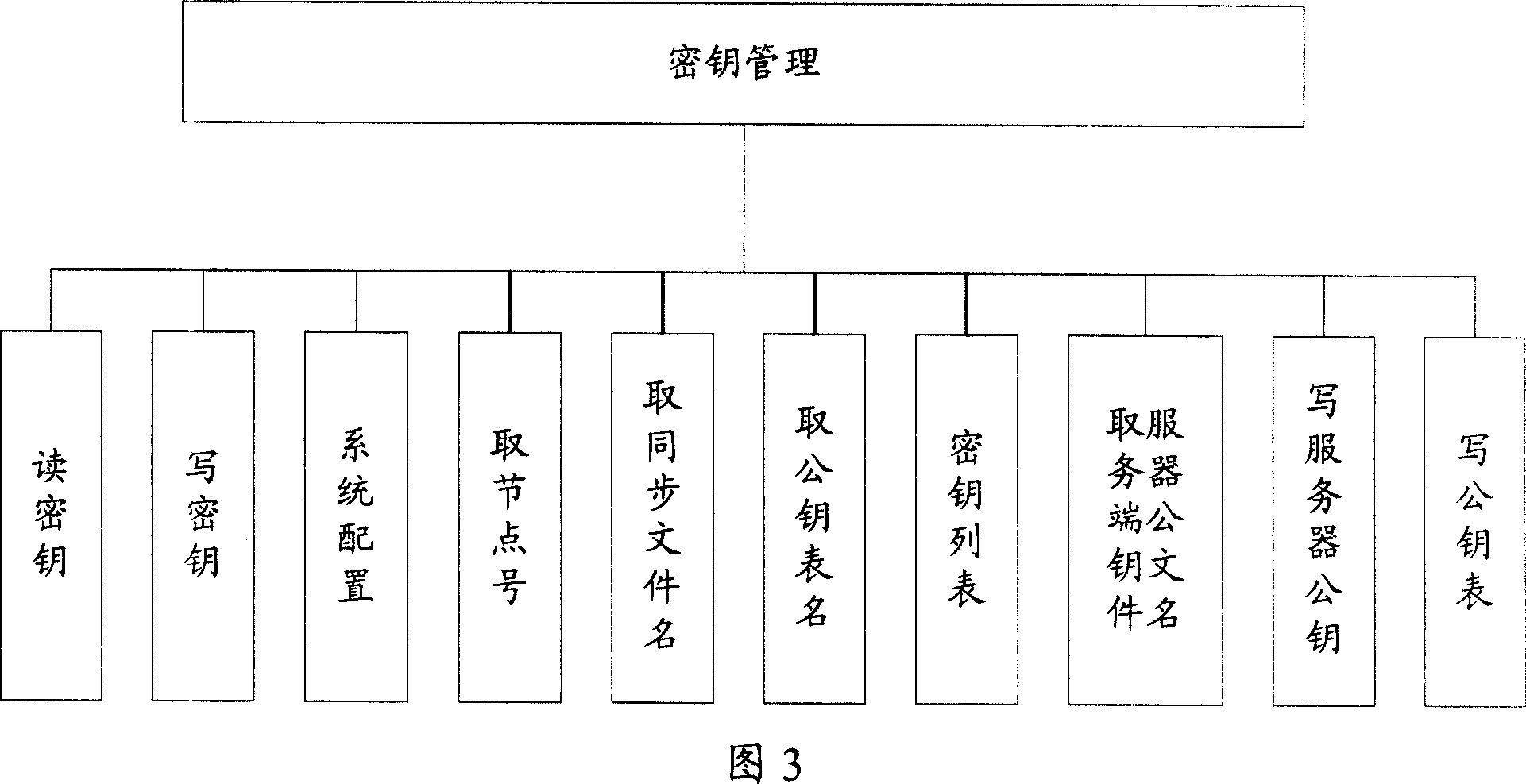
The invention provides a control system for the information safety to solve the safe problems existed in the business system, and prevent the important data from leakage and illegal interpolation. The system includes: key management module, key negotiation module, code interface module, log management module, security management module and mistake processing module. The control system for the information safety provided by the invention can combine with the business system closely, and it is classified following the business system on the structure design, the business logic of every hierarchy has the corresponding security control to protect the every aspects of business, and the business safety technical measures cover the every aspect of business system that includes data transmission, data storage, database, files, logs and operation certification and so on, and it can assure the confidentiality, integrality, anti-aggression, usability, anti-repudiation, ID identify and authority control of business system.
Owner:CHINA CONSTRUCTION BANK
Remote identity authentication method and system and remote account opening method and system
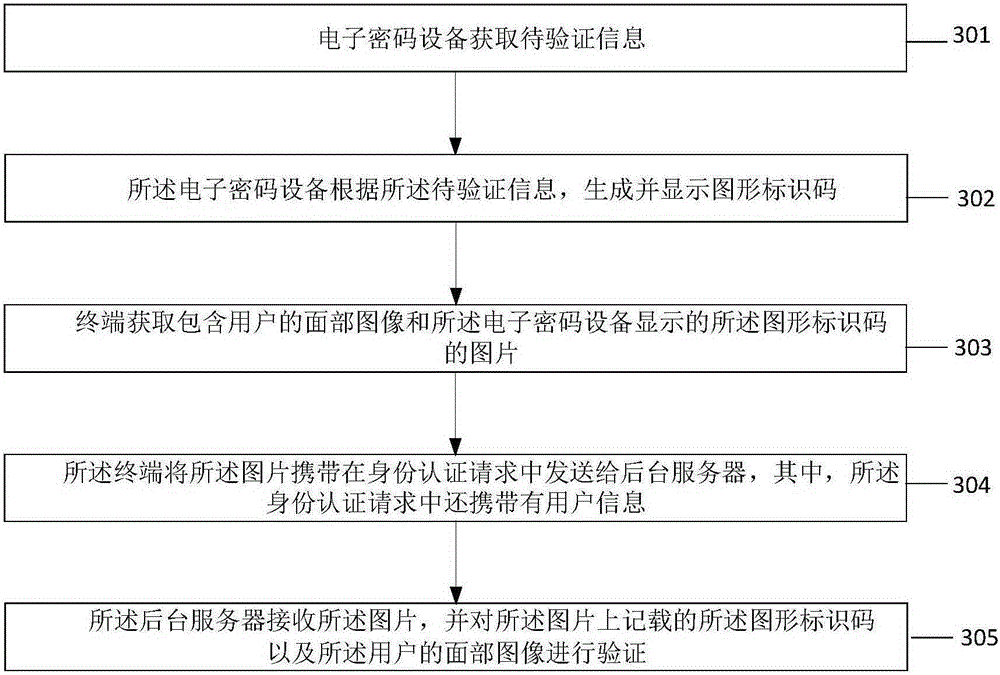
ActiveCN105245341AGuaranteed non-repudiationWill not be tampered withUser identity/authority verificationDigital data authenticationGraphicsComputer terminal
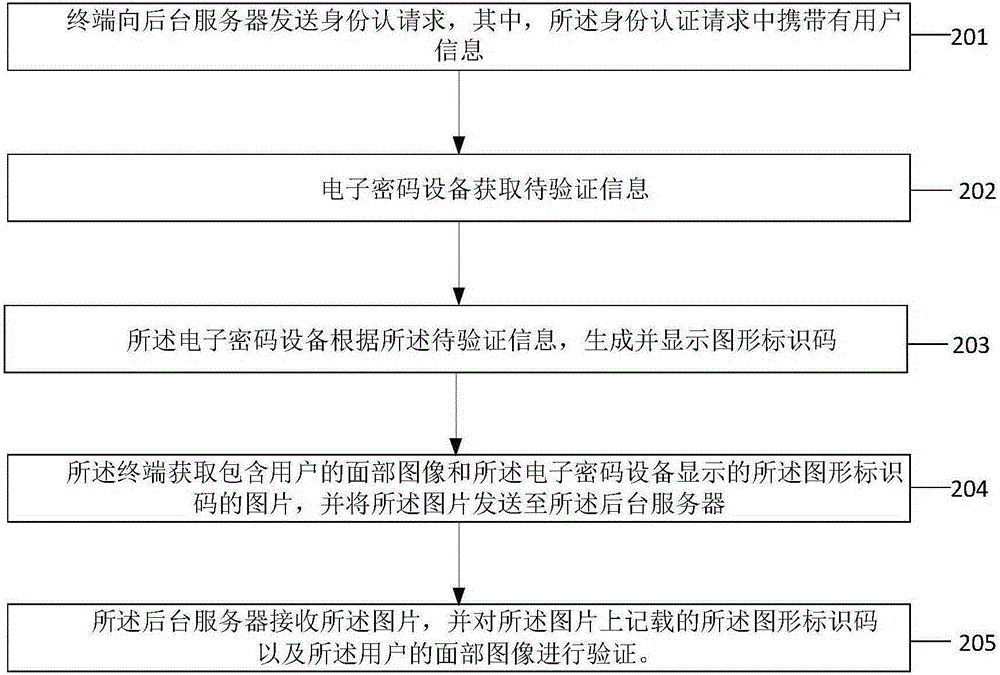
The invention provides a remote identity authentication method and a system and a remote account opening method and a system. The remote identity authentication method comprises steps: electronic cipher equipment acquires to-be-authenticated information, a graph marking code is generated and displayed according to the to-be-authenticated information, a terminal acquires a picture comprising a facial image of the user and the graph marking code displayed by the electronic cipher equipment, the picture is sent to a backstage server, the backstage server receives the picture, and the graph marking code and the facial image of the user recorded on the picture are authenticated.
Owner:TENDYRON CORP
Electronic health record management system and method
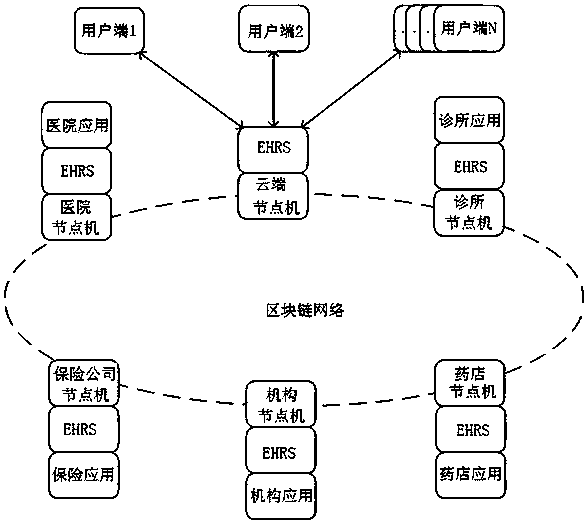
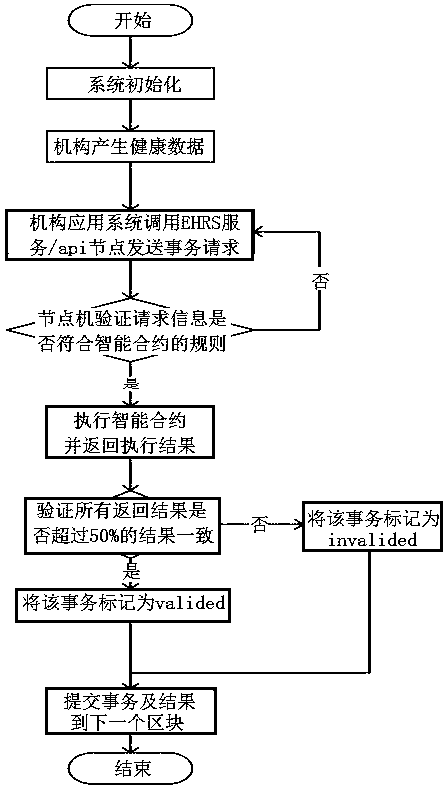
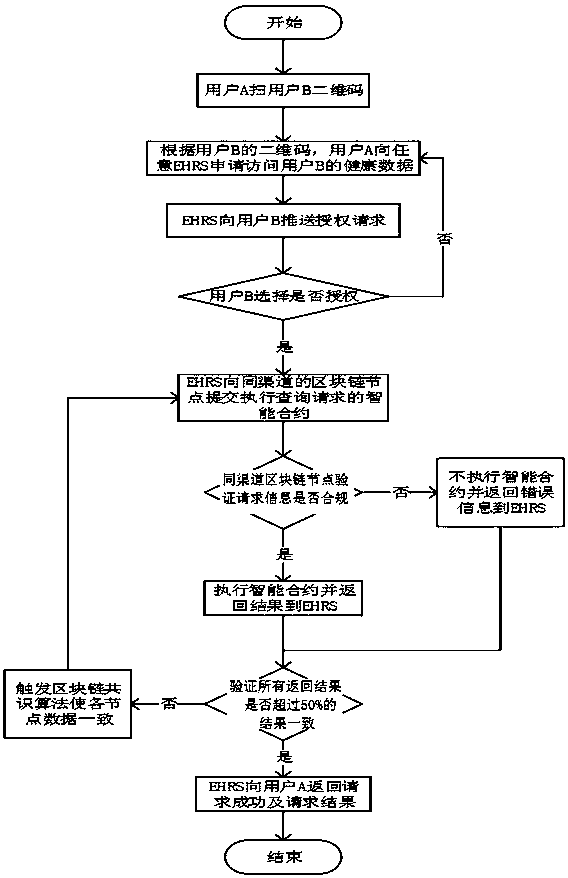
InactiveCN108460290AGuaranteed originalityKeep storage safeDigital data protectionPayment protocolsBlockchainManagement system
The present invention relates to an electronic health record management system and method, which solves the technical problem of low confidentiality. The method is characterized in that: by taking a blockchain as a storage underlying layer of a health record system, de-intermediated trust of all nodes is achieved; all data cannot be tampered with, and traceability and consistency of all the data are achieved; and open transparency of non-sensitive data and confidentiality of sensitive and private data are achieved. The technical scheme of the present invention has the following beneficial effects that: the originality and authenticity of health data and operational data are ensured, and the health data and the operational data cannot be tampered with; the storage security of the health data and of the operational data of the health data is ensured; it is ensured that personal privacy and sensitive information cannot be leaked; and the technical scheme for fast sharing of health data and operational data better solve the problem and can be used in medical electronic applications.
Owner:江苏省卫生统计信息中心
Near field communication payment method authenticated by both sides of deal
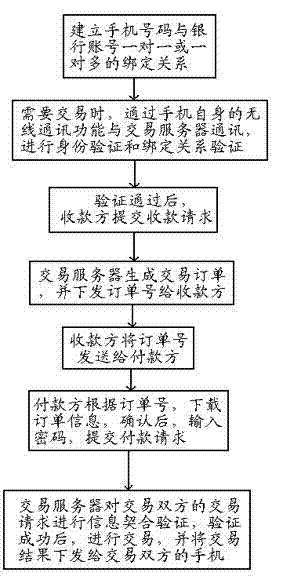
InactiveCN103116844ARealize identificationAvoid card swipingUser identity/authority verificationPayment architectureBank accountComputer science
The invention discloses a near field communication payment method authenticated by both sides of the deal. The method includes steps that 1, a binding relationship of one-to-one and one-to-many of a cell phone number and a bank account is established; 2, identity authentication on both sides of the deal through a cell phone is performed when a near field communication deal is needed; 3, after authenticating, the payee inputs amount collected to the cell phone, submits a collection request to a deal server, and the deal server generates a trade order and sends the order number to the payee; 4, the payee chooses a payer to trade, and sends the order number to the payer by means of near field communication; 5, the payer downloads the order information from the deal server, identifies the order information, inputs a payment code to the cell phone, and submitting a payment request; 6, information verification is performed, the trade is carried on when the verification is successful, otherwise, the trade is not carried on. The method of identity authentication is high in safety and reliability and easy to achieve based on the uniqueness of the cell phone number and background server.
Owner:李锦风 +2
Wireless Mesh network identity authentication method based on blockchain
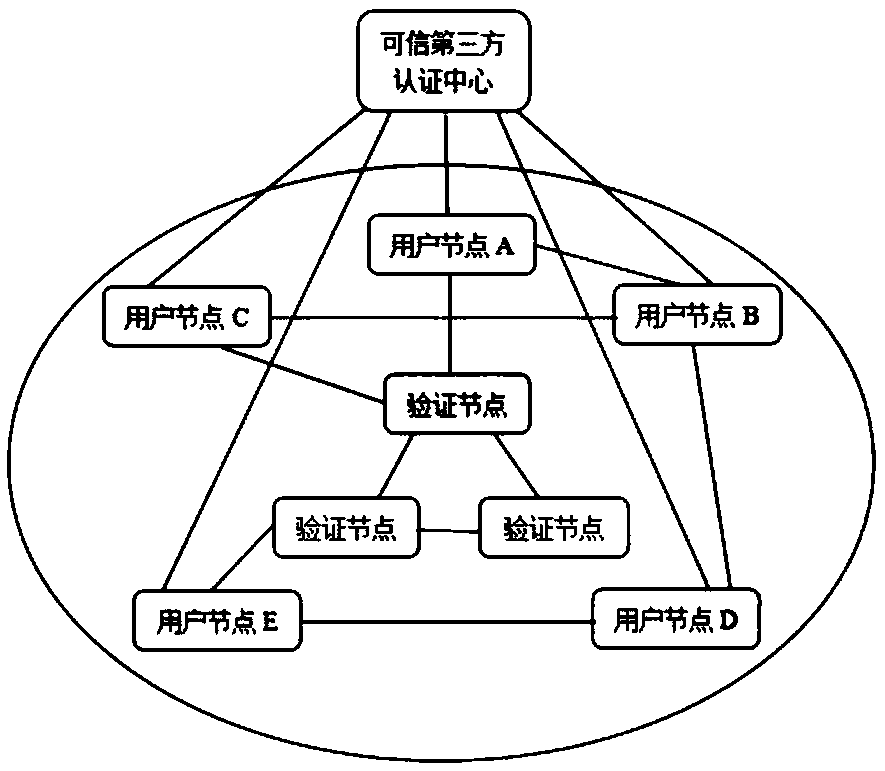
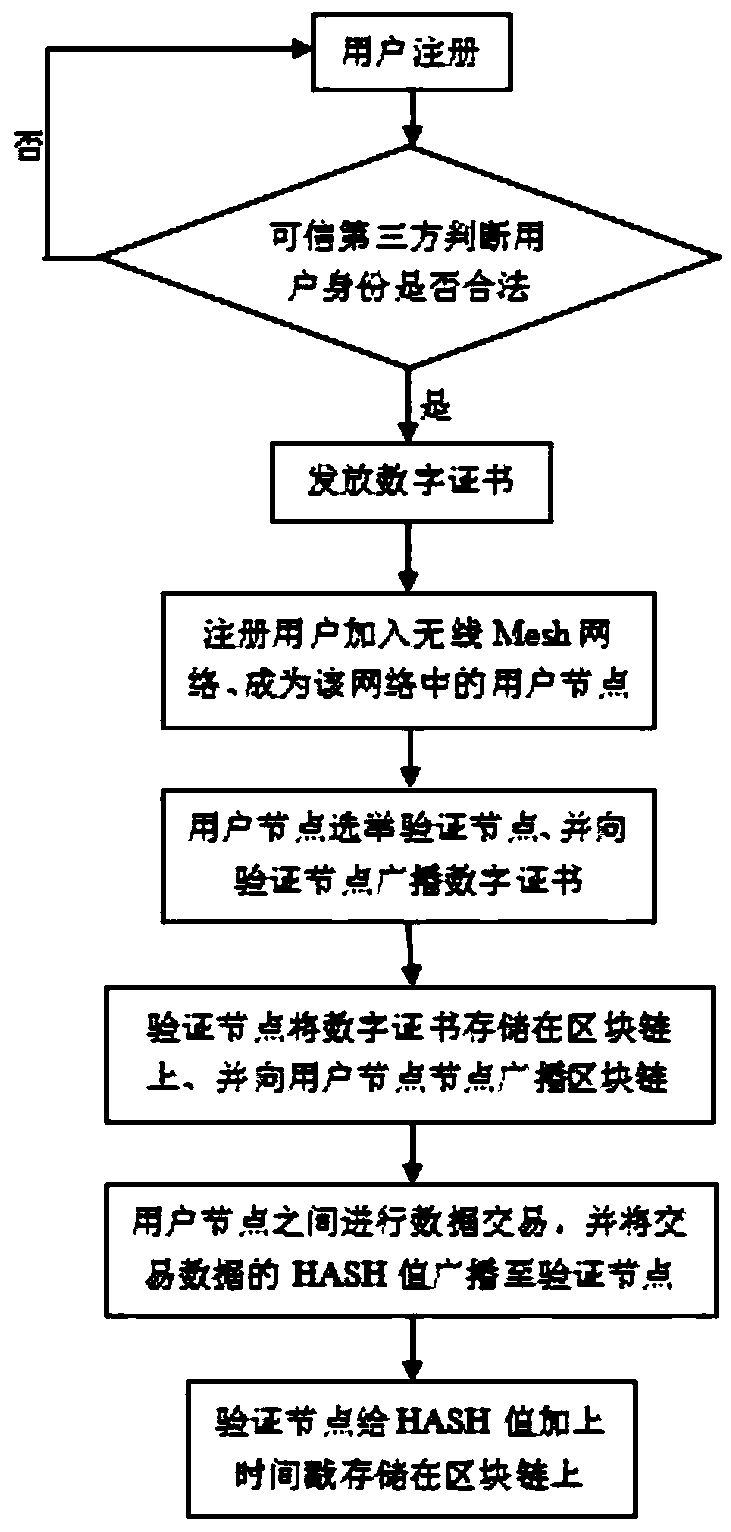
ActiveCN108810895AUniqueness guaranteedNot easily tampered withUser identity/authority verificationSecurity arrangementBlockchainTimestamp
The invention proposes a wireless Mesh network identity authentication method based on blockchain. The method comprises the following steps: registering with a trusted third party certification authority by a user and obtaining a digital certificate; adding a registered user to a wireless Mesh network as a user node, selecting a certain number of distributed verification nodes, broadcasting the digital certificate to the verification nodes and storing the digital certificate on the blockchain of the verification nodes; broadcasting information stored on the own blockchain of each verificationnode to all user nodes; encrypting and transmitting information between the user nodes through a public key system; after the transaction is completed, broadcasting HASH values of transaction data tothe distributed verification nodes by the user nodes; adding timestamps to the HASH values by each distributed verification node, obtaining transaction information, and saving the transaction information on the blockchain of each distributed verification node. According to the wireless Mesh network identity authentication method based on the blockchain provided by the invention, the digital certificate and the transaction information are stored on the blockchain, so that information leakage and Internet fraud are effectively solved, and the data security is guaranteed.
Owner:XIDIAN UNIV
Credible extraction method for digital evidence of Android
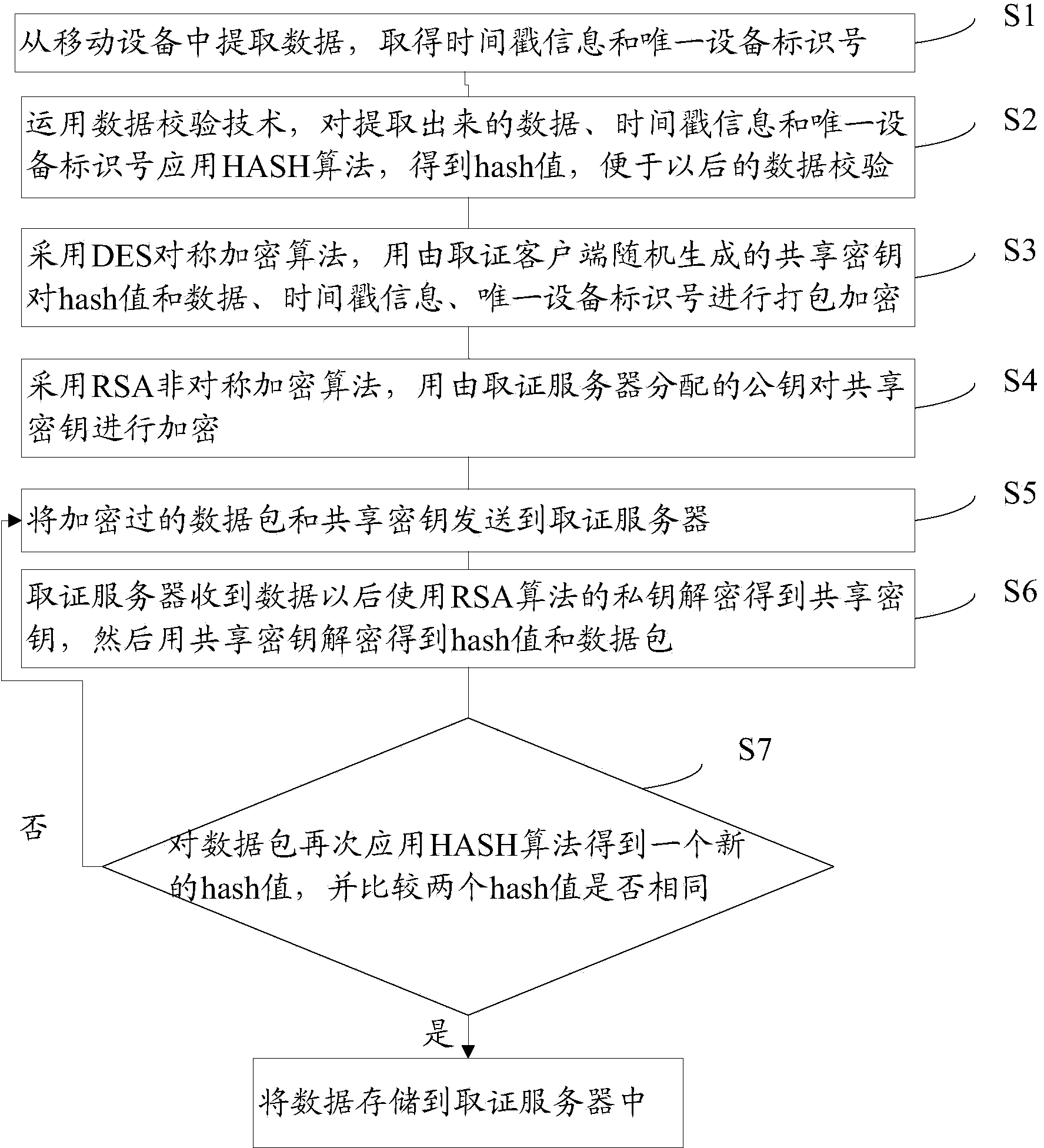
ActiveCN103475664AGuaranteed originalityGuaranteed non-repudiationMultiple keys/algorithms usageSubstation equipmentData verificationClient-side
The invention provides a credible extraction method for digital evidence of Android. The credible extraction method comprises the following steps: step 1, data are extracted from a mobile device, and timestamp information and a unique device identification number are obtained; a data verification technology is used for acquiring a hash value of a result of the step 1; a DES symmetric encryption algorithm is adopted for packaging and encrypting the hash value, the data, the timestamp information and the unique device identification number through a shared key generated randomly by an evidence obtaining client-side; an RSA asymmetric cryptographic algorithm is adopted for encrypting the shared key through a public key distributed by an evidence obtaining server, and the encrypted shared key is sent to the evidence obtaining server; after the evidence obtaining server receives the data, a private key of an RSA algorithm is used for decryption to obtain the shared key, and the shared key is used for decryption to obtain the hash value and a data package; a HASH algorithm is applied to the data package to obtain a new hash value, and whether the two hash values are the same is judged through comparison. The credible extraction method for the digital evidence of Android can improve the originality and false accusation forbiddingness of the data.
Owner:山东政信大数据科技有限责任公司
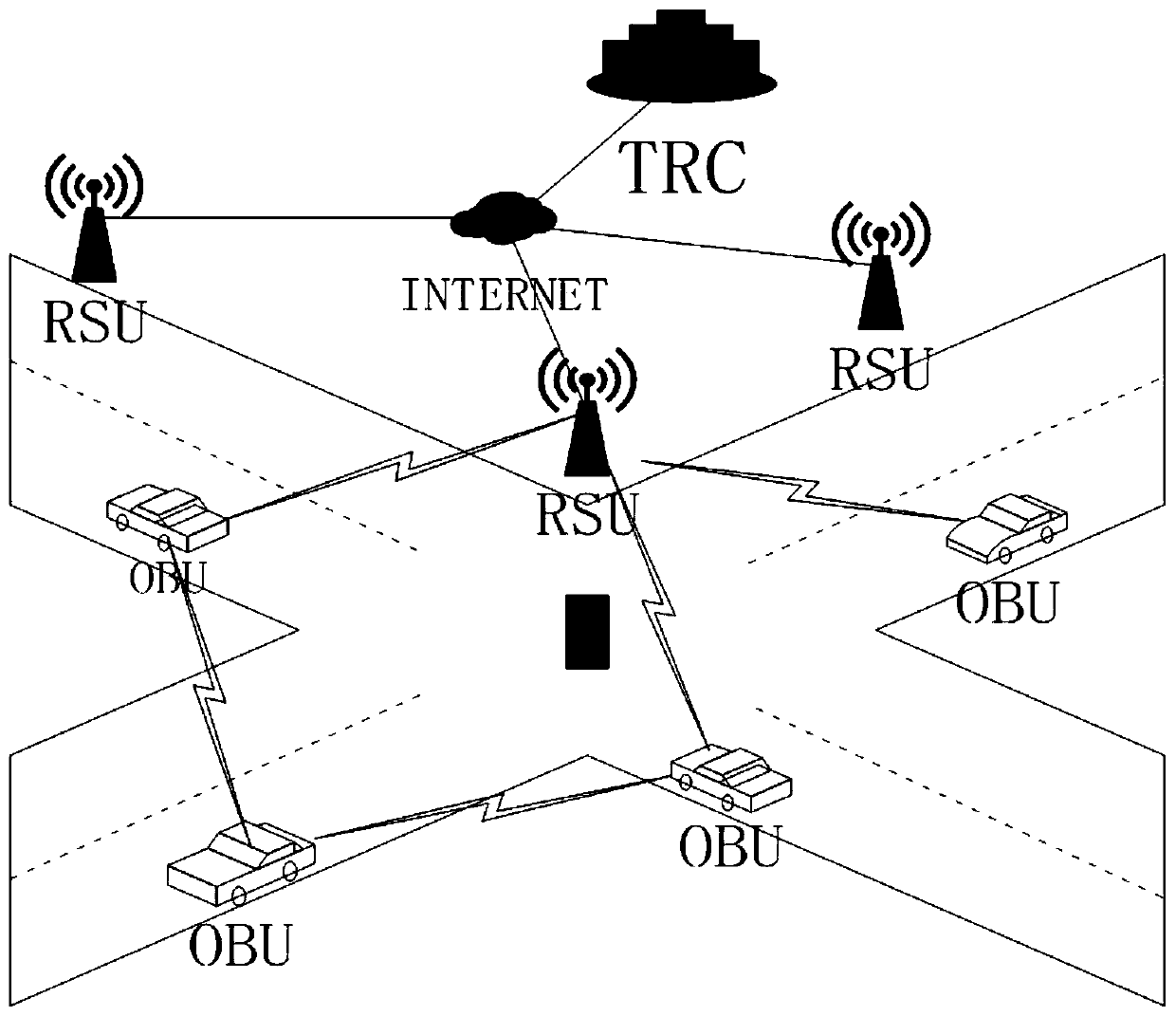
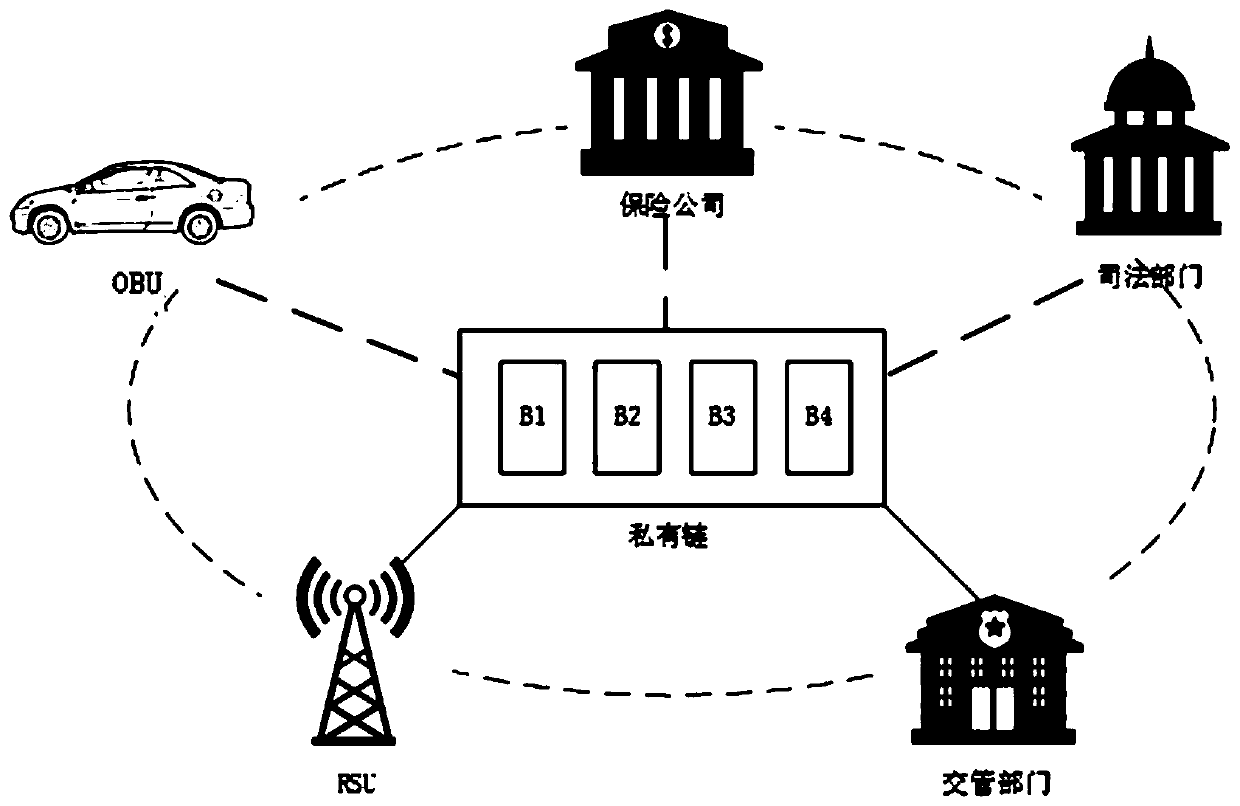
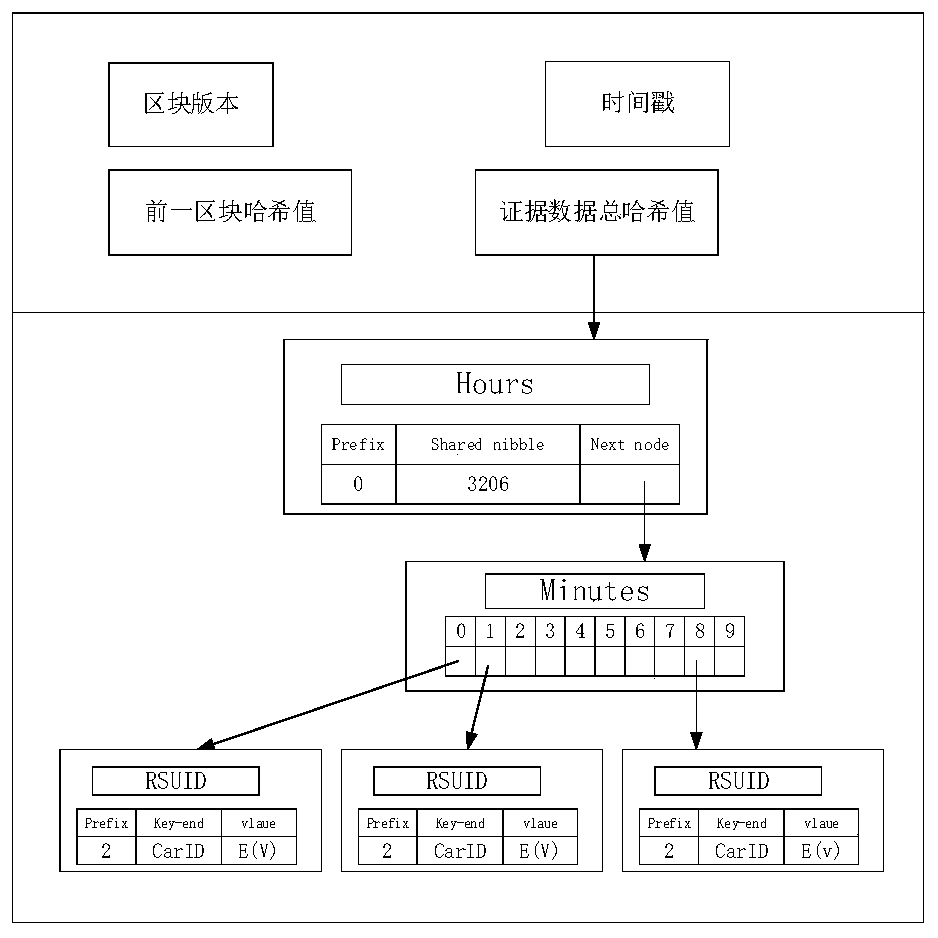
Electronic evidence obtaining device and method based on block chain in Internet-of-Vehicles environment
ActiveCN111464980AProtection against the risk of tamperingImprove access efficiencyData processing applicationsParticular environment based servicesComputer networkTraffic crash
The invention provides an electronic evidence obtaining device and method based on a block chain in an Internet-of-Vehicles environment. The method comprises the following steps of S10, offline registration, S20, vehicle online identity registration, S30, real-time evidence storage and S40, query and evidence obtaining. According to the electronic evidence obtaining device and method based on theblock chain in the Internet-of-Vehicles environment, the block chain technology is used for traffic accident electronic evidence obtaining, the integrity, non-repudiation and permanence of evidence are guaranteed through the characteristics of block chain distributed data storage and the like, many problems of traditional traffic accident evidence obtaining are solved, and the evidence obtaining efficiency is high.
Owner:NANTONG UNIVERSITY
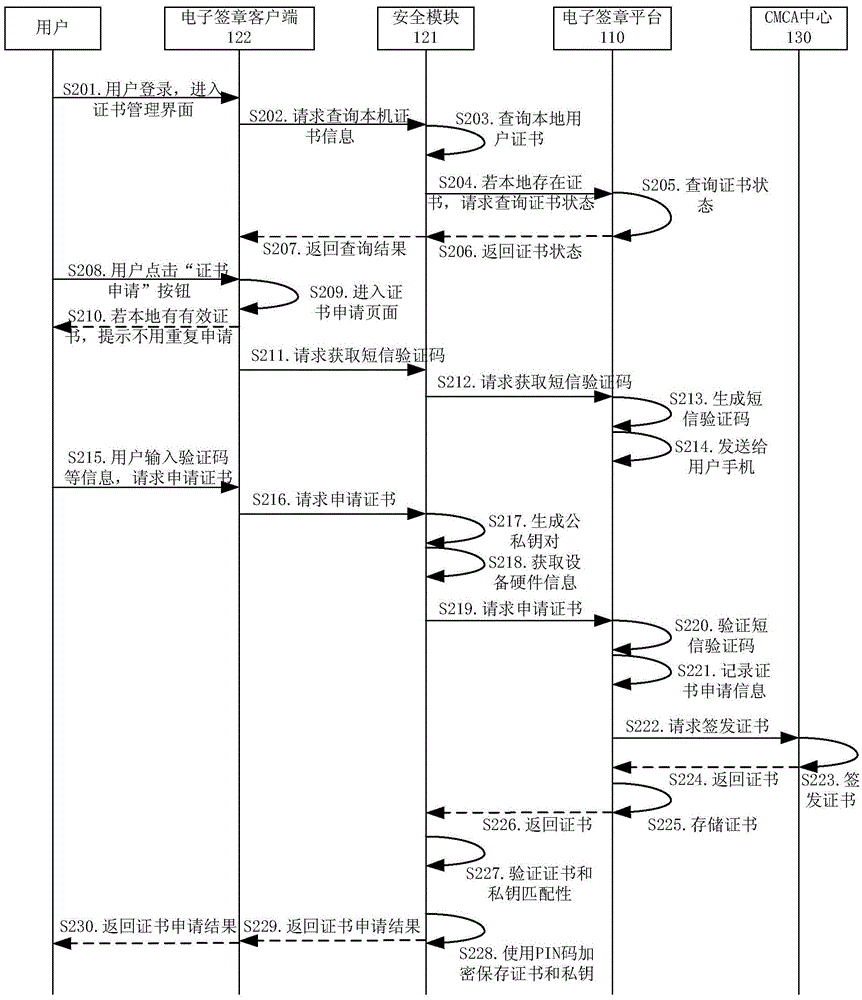
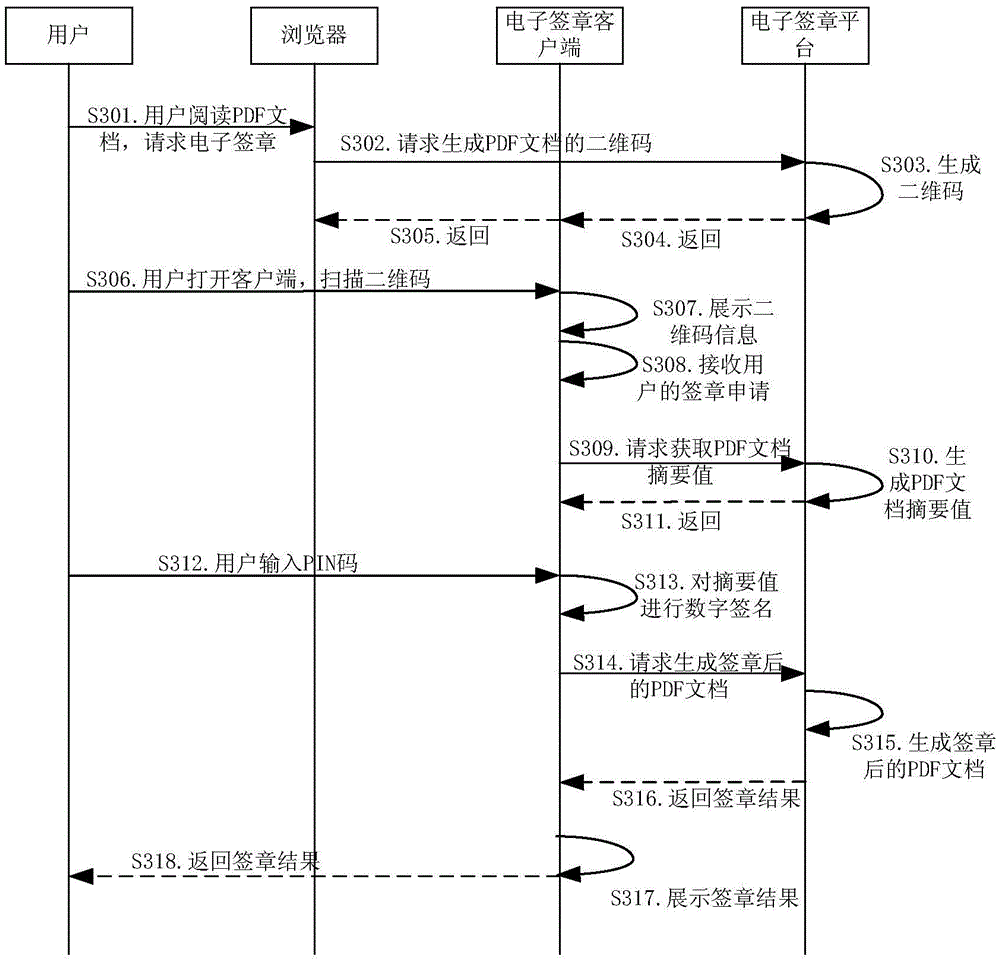
Method and system for electronic signature and mobile communication terminal used for electronic signature
ActiveCN106888089AProtection securityChen BenlowUser identity/authority verificationDigital signatureElectronic signature
The invention relates to a method and system for electronic signature and a mobile communication terminal used for electronic signature. The method includes the following steps: an electronic signature platform generates a two-dimensional code of a document to be signed based on a first electronic signature request sent by a user, and sends the two-dimensional code to a mobile communication terminal of the user; the mobile communication terminal scans the two-dimensional code and displays two-dimensional code information to the user, and requests the electronic signature platform for abstract values of the document to be signed based on a second electronic signature request of the user; the electronic signature platform generates abstract values and returns to the mobile communication terminal; the mobile communication terminal uses a user certificate stored therein to perform digital signature on the abstract values, and sends the digitally signed abstract values to the electronic signature platform to request for a document with a generated signature; and the electronic signature platform embedded the digitally signed abstract values into the document to be signed, and returns the document with the generated signature to the user. The electronic signature method provided by the invention is relatively safe, simple and rapid, and is low in cost.
Owner:卓望数码技术(深圳)有限公司
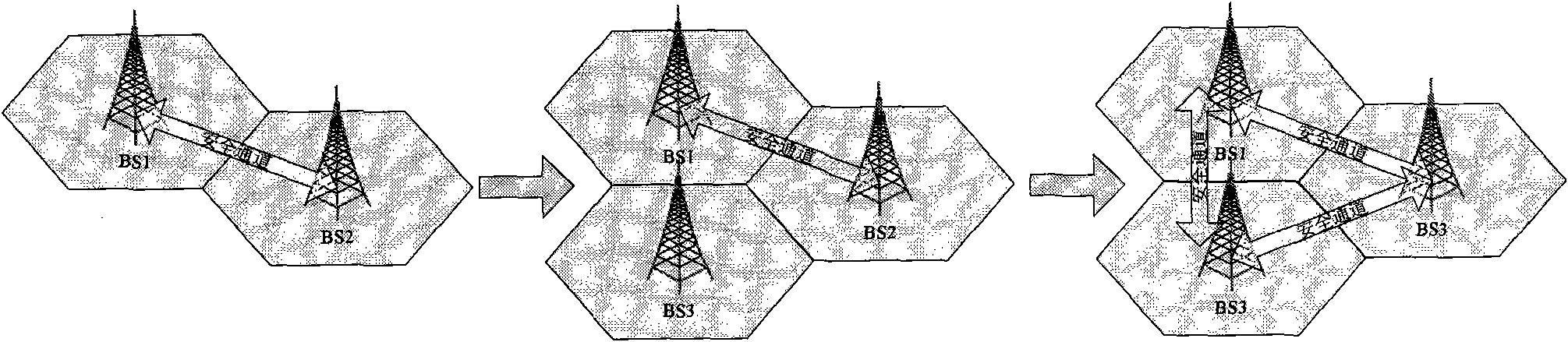
Base station secure accessing method of mobile communication system
InactiveCN101552984AIntegrity guaranteedGuaranteed non-repudiationNetwork traffic/resource managementAssess restrictionMobile communication systemsComputer science
Base station secure accessing method of mobile communication system, including steps: a first base station sends negotiate request message of security capability; a neighbor base station judging the security capability matches whether or not with security capability of the first base station, if matching, then sending response message; the first base station accomplishes access identity identification with the neighbor base station and consulting exit passageway identification cipher key; the base station and the neighbor base station respectively identifying encryption key of cipher key derivation generating passageway via the exit passageway and passageway integrality cipher key thereby establishing exit passageway of the first base station and the neighbor base station via passageway encryption key, passageway integrality cipher key. The passageway encryption key accomplishes encrypt to data, passageway integrality cipher key assures integrality of data and non-repudiation of the information senders so that assuring safety between the first base station and the neighbor base station, improving security gradation of mobile communication system.
Owner:GCI SCI & TECH
Operation request processing method and system
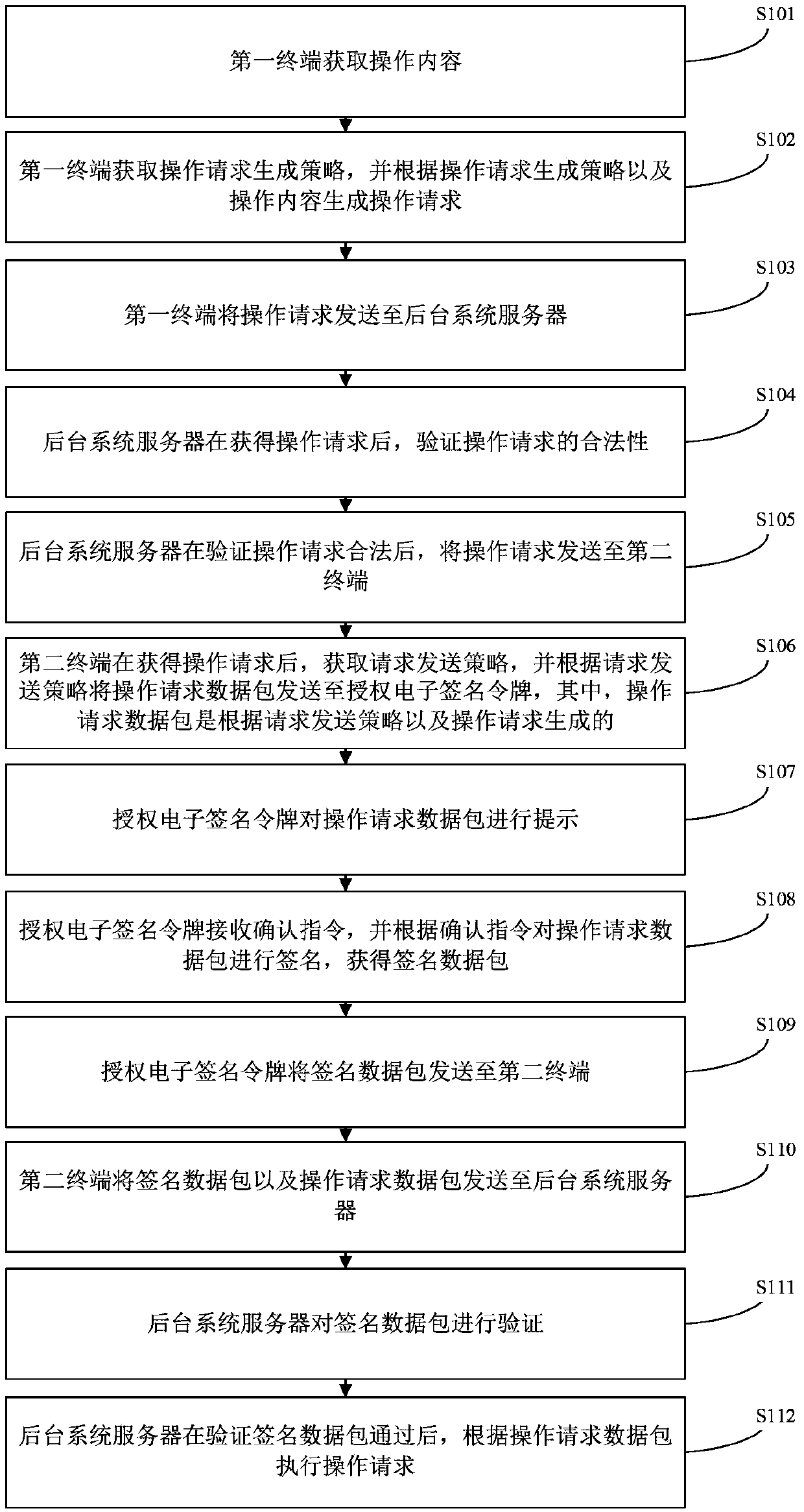
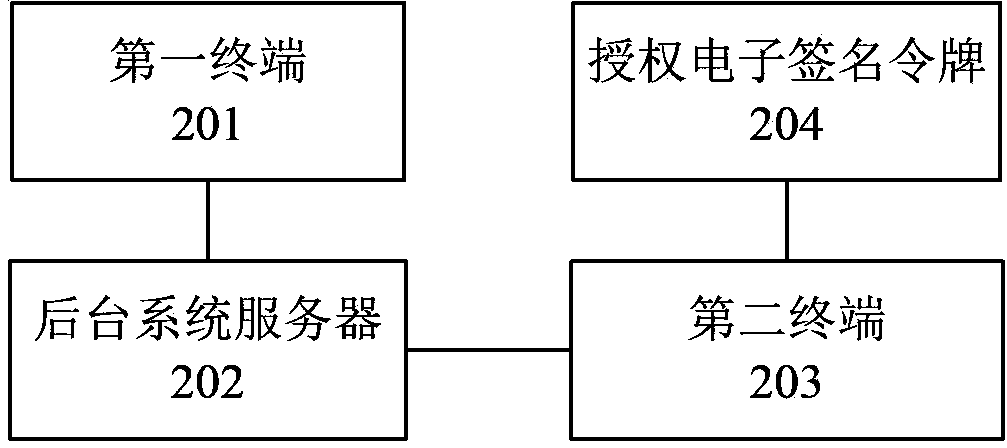
ActiveCN103401844AEasy to useEnsure safetyFinanceUser identity/authority verificationNetwork packetElectronic form
The invention provides an operation request processing method and an operation request processing system, wherein the method comprises the following steps that a first terminal generates operation requests and sends the operation requests to a background system server; the background system server sends the operation requests to a second terminal after verifying that the operation requests are legal; a second terminal sends the operation request data packet to an authorization electronic signature token, the authorization electronic signature token carries out prompt on the operation request data packet, confirming instructions are received, the signing is carried out, and the signed data packet is obtained; the authorization electronic signature token sends the signed data packet to the second terminal; the second terminal sends the signed data packet and the operation request data packet to a background system server; and after the background system server verifies that the data packet is passed, the operation requests are executed according to the operation request data packet. When the operation request processing method and the operation request processing system are adopted, the electronic form can be adopted for examination and approval, the use is convenient, and meanwhile, the safety and the non-repudiation of the examination and approval are also ensured.
Owner:TENDYRON CORP
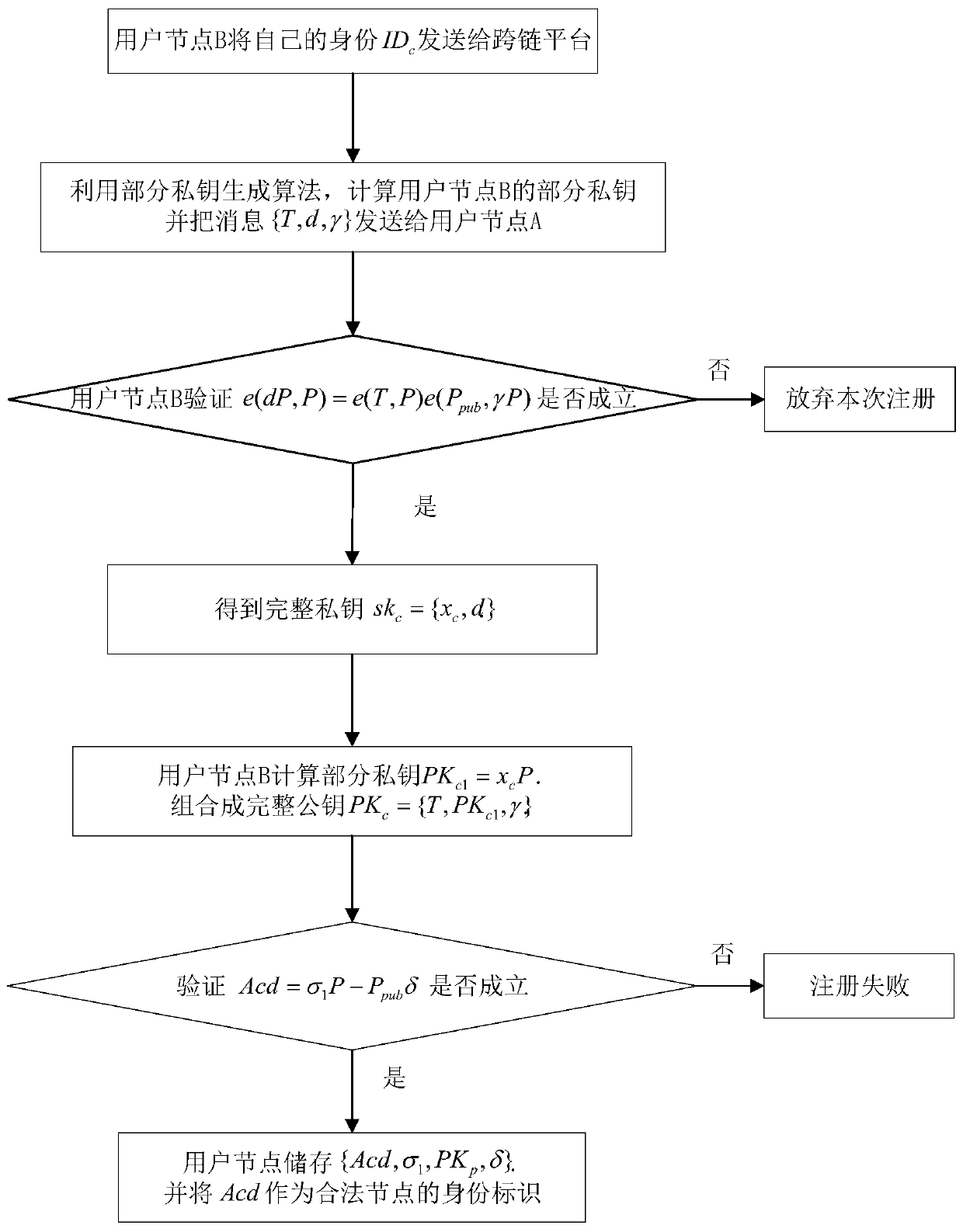
Identity authentication method for heterogeneous blockchain in cross-chain scene
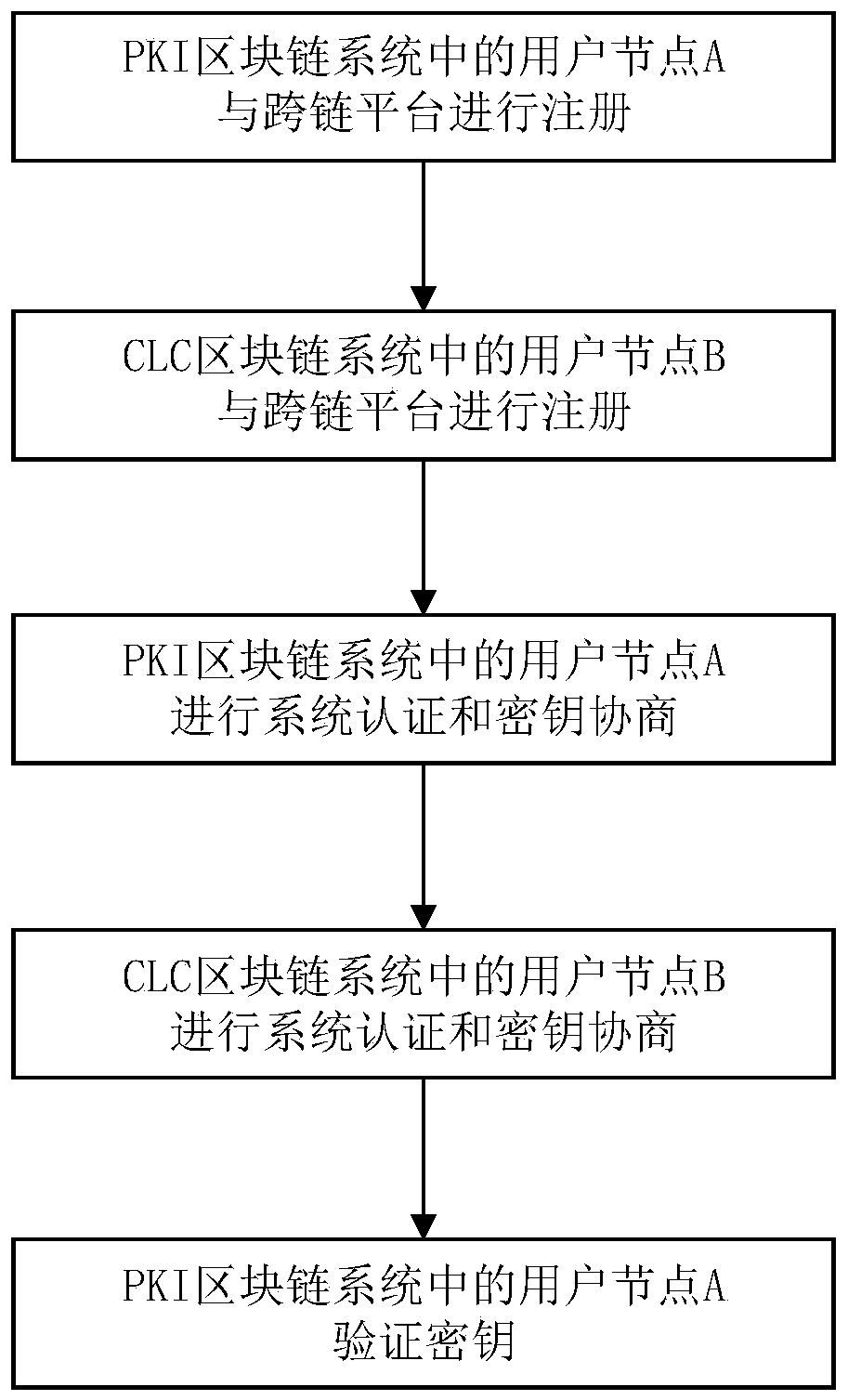
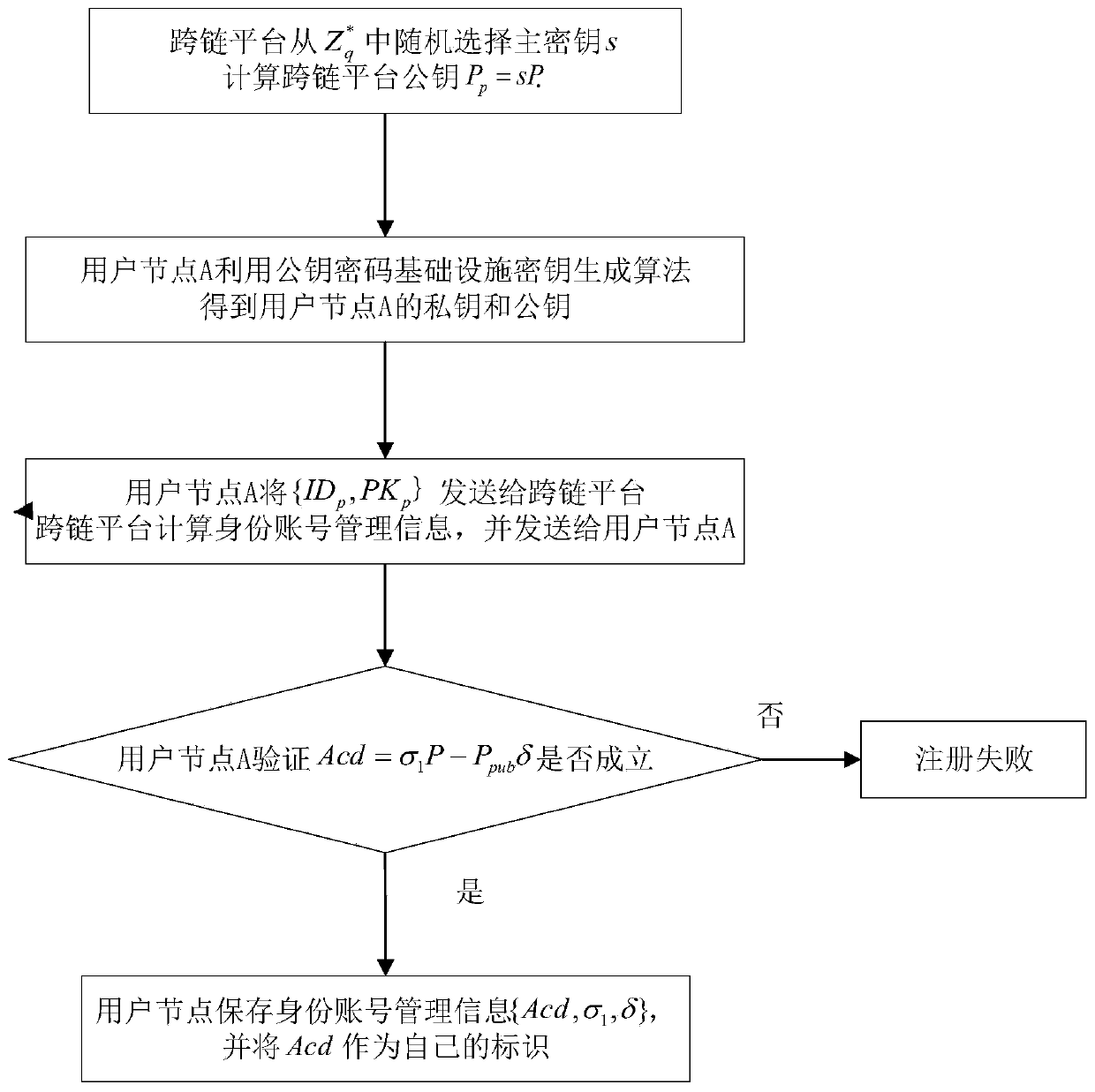
ActiveCN110505058AImprove the efficiency of authentication methodsEnsure safetyKey distribution for secure communicationMultiple keys/algorithms usageComputation complexityProcess efficiency
The invention discloses an identity authentication method for a heterogeneous blockchain in a cross-chain scene. The method comprises the following steps: 1) registering a user node A of a PKI blockchain system with a cross-chain platform; 2) registering a user node B of the CLC block chain system with a cross-chain platform; 3) enabling the user node A of the PKI block chain system to perform system authentication and key negotiation; 4) enabling the CLC block chain system user node B to perform system authentication and key agreement; and 5) enabling the user node A of the PKI block chain system to verify the key. Identity authentication between the block chain systems adopting different public key cryptography systems in the architecture in a cross-chain scene is realized, then the twoheterogeneous block chain systems can communicate safely, and the method has the advantages of high process efficiency, low computation complexity and low communication overhead.
Owner:XIDIAN UNIV
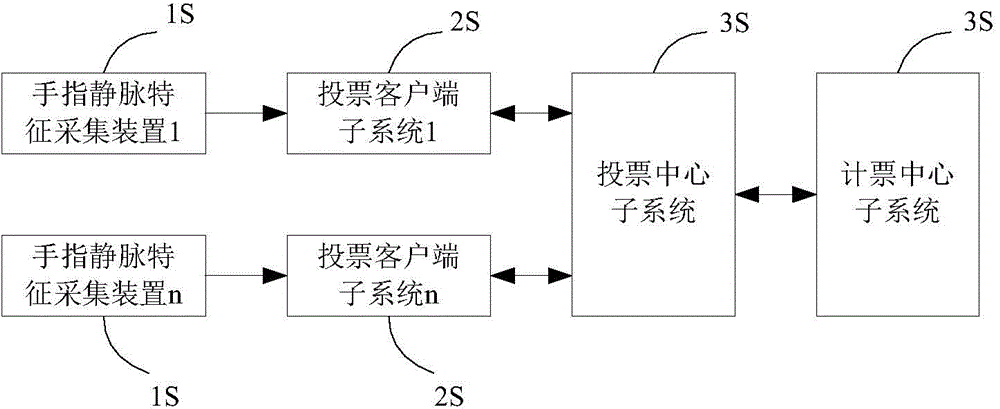
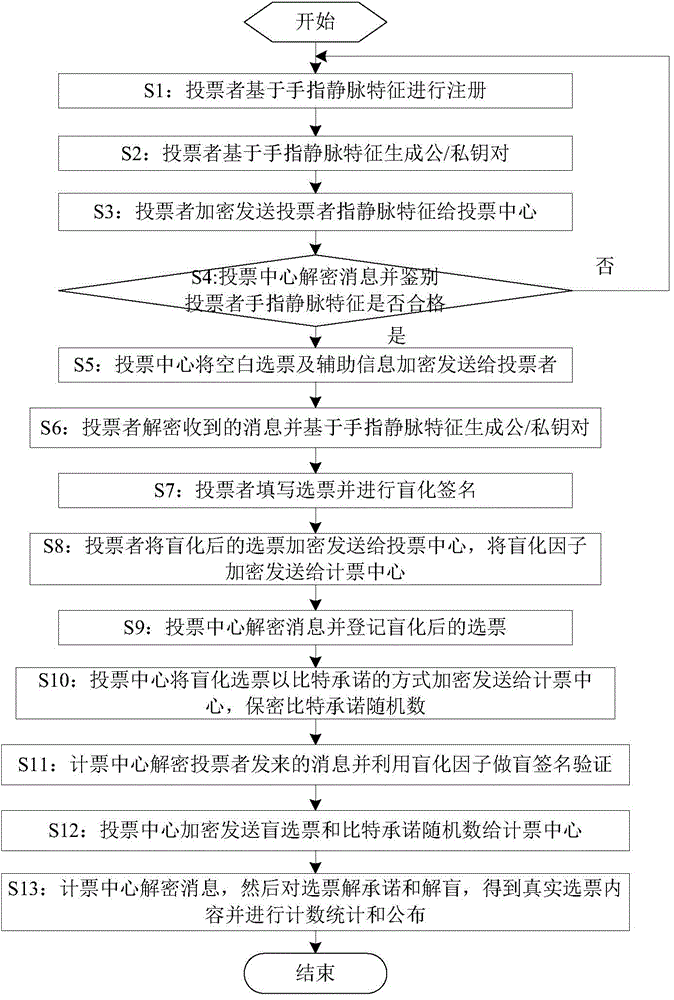
Electronic voting system based on finger vein feature recognition
ActiveCN104392534ASafe Finger Vein AuthenticationImprove ease of useVoting apparatusCharacter and pattern recognitionSystem verificationEngineering
The invention discloses an electronic voting system based on finger vein feature recognition. The system comprises a finger vein feature acquisition device, a voting client sub-system, a voting center sub-system and a vote counting center sub-system. The finger vein image of a voter is acquired by the finger vein feature acquisition device, the voter is registered in the voting center sub-system by the finger vein feature, the legality of the voter is verified by the voting center sub-system, and the vote is issued to the voter if the voter is qualified. A biological characteristic public / private key pair of the voter can be generated by software of the voting client sub-system, and the voting process is realized by the interaction of security protocols such as certificate signing among the voting client sub-system, the voting center sub-system and the vote counting center sub-system. Compared with other electronic voting systems, the system enables a finger vein feature recognition technology to be introduced, and the finger vein feature recognition technology replaces ways such as passwords and digital certificates and takes part in the network identity authentication and the voting process, so that the safety and use convenience of the system are improved; the electronic voting system based on finger vein feature recognition also has anonymity, transparency and openness.
Owner:SOUTHWEST JIAOTONG UNIV
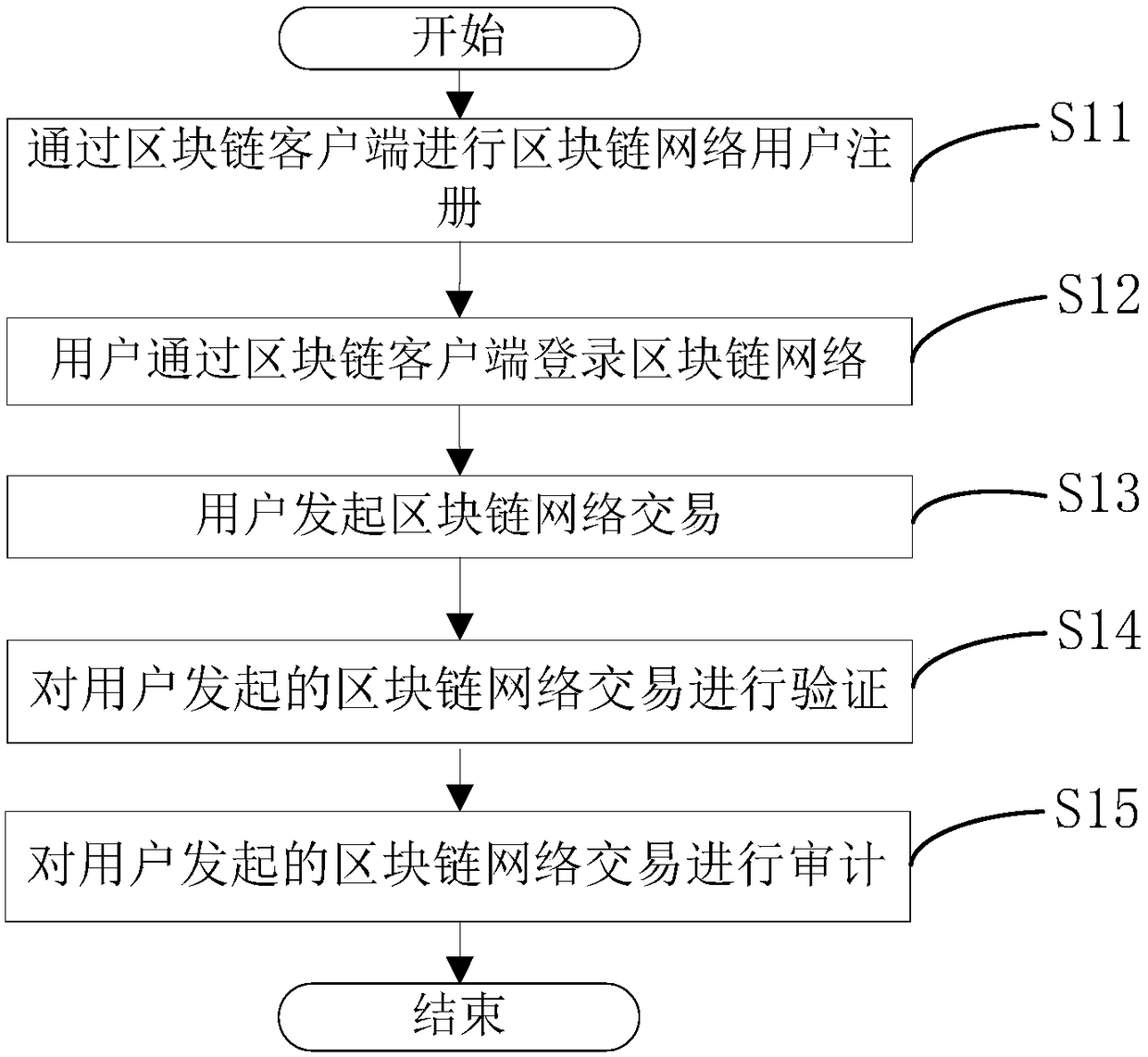
A block chain member management method and system based on an identification cryptographic algorithm
ActiveCN109005036AReduce complexityGuaranteed unforgeabilityKey distribution for secure communicationUser identity/authority verificationChain networkBlockchain
The invention relates to a block chain member management method and system based on an identification cryptographic algorithm. The method of the invention comprises the following steps: (1) registering a user of a block chain network through a block chain client, and generating a signature private key according to the user identity information by using an identification cryptographic algorithm; (2) loging in the block chain network through the block chain client by a user; 3) initiating a block chain network transaction by the user, and using an identification cryptographic algorithm to sign adigital summary of the transaction calculated by the user's block chain client end to generate signature information; (4) verifying the block chain network transaction initiated by the user, and verifying the correctness of the signature of the block chain network transaction by using the identification cryptography algorithm. The method and the system of the invention can reduce the complexityof the management of the members in the block chain network and facilitate the audit of the transaction.
Owner:WATCHDATA SYST
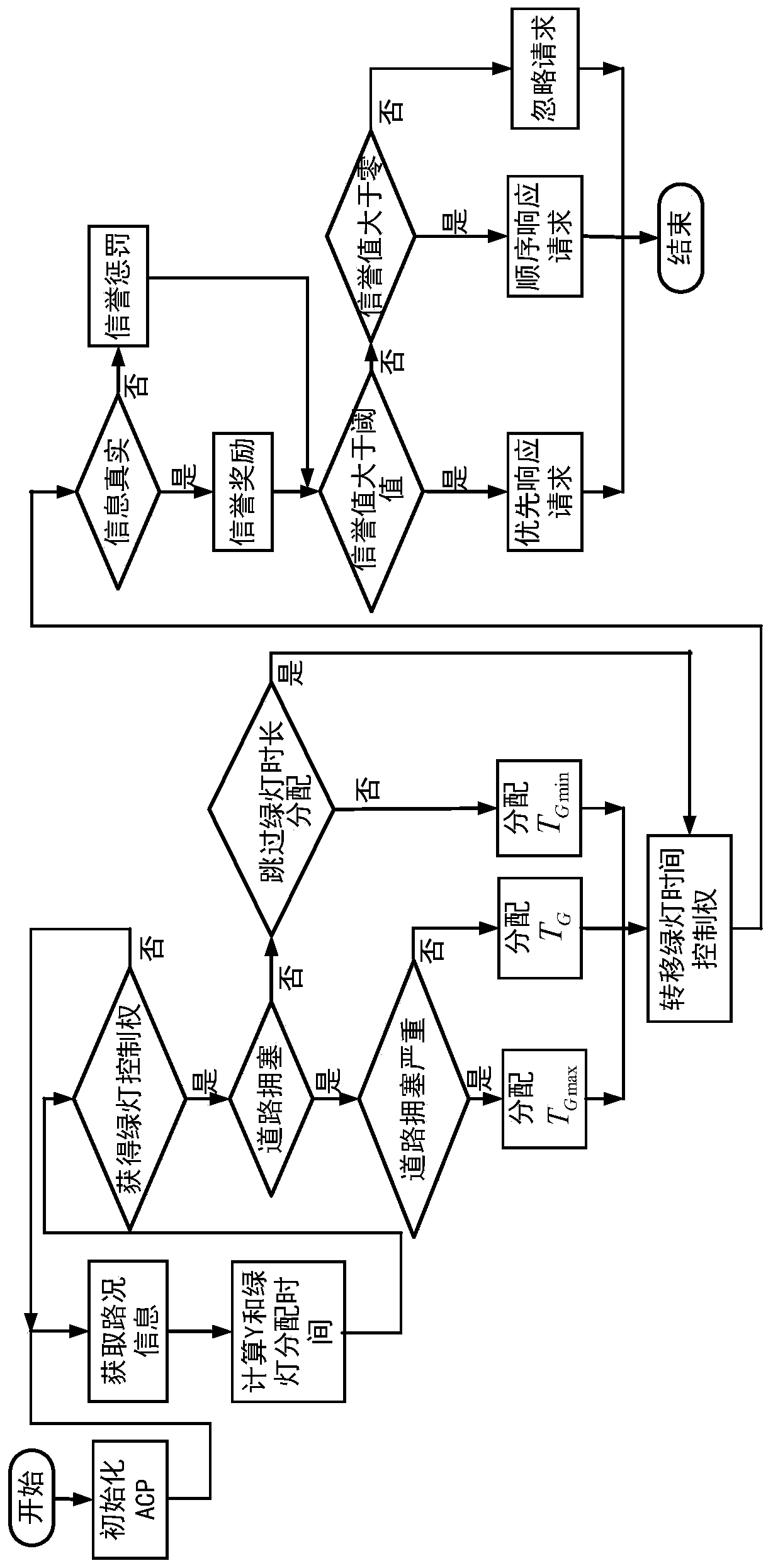
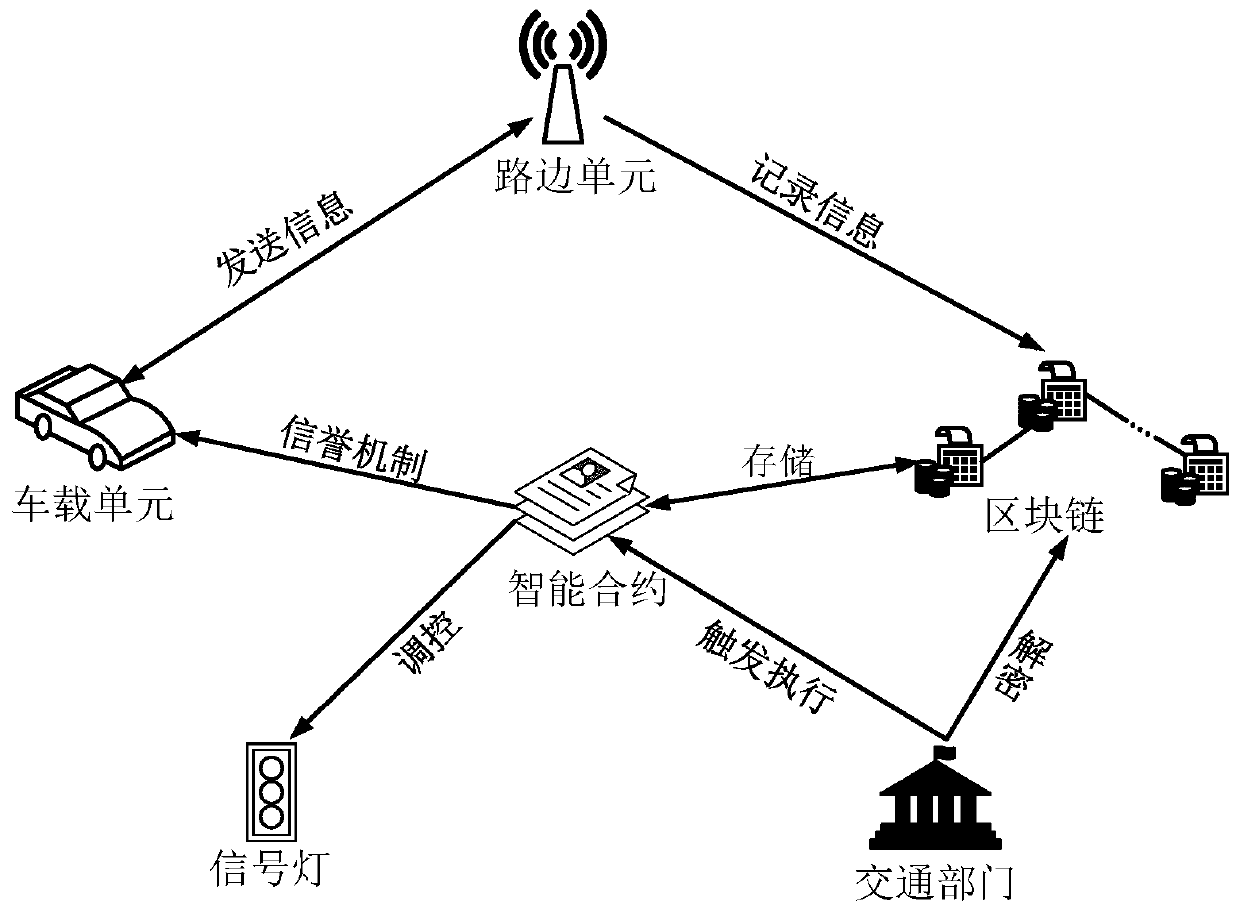
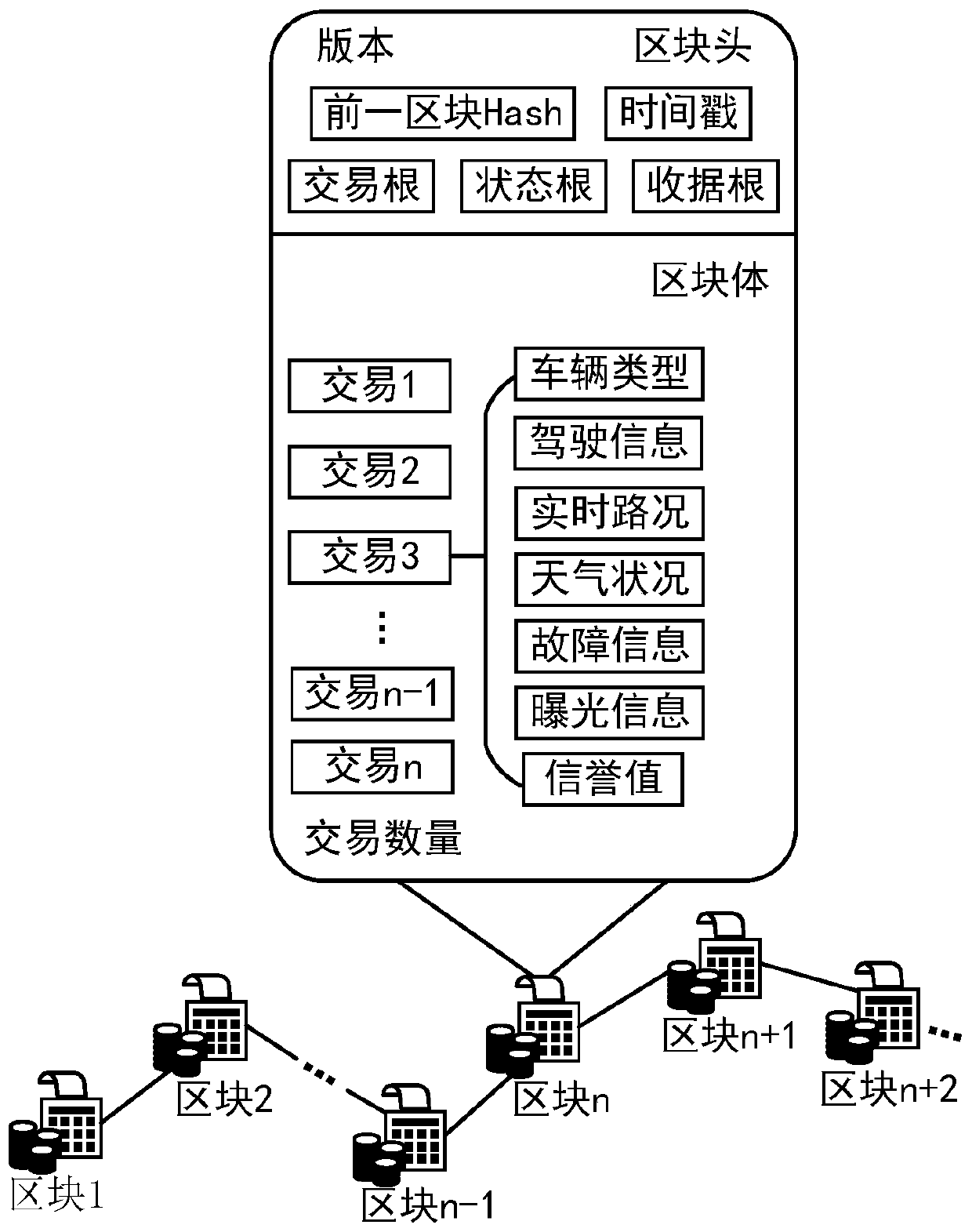
Intelligent traffic light safety dynamic regulating and controlling method based on alliance block chain technology
InactiveCN109816995AGuaranteed confidentialityGuaranteed privacyControlling traffic signalsKey distribution for secure communicationTraffic signalConfidentiality
The invention provides an intelligent traffic light safety dynamic regulating and controlling method based on the alliance block chain technology. A vehicle-mounted unit, a roadside unit, a transportagency and an ACP system are included. The vehicle-mounted unit sends real-time road condition information to the roadside unit, the information is recorded in blocks through pre-selected bookkeepingroadside unit nodes, the transport agency decodes and acquires the road condition information from block chains, an intelligent contract is triggered to be automatically executed, and the duration oftraffic lights is dynamically regulated and controlled by the ACP system through the acquired road condition information. After the traffic lights are regulated and controlled, the reputation value ofthe vehicle-mounted unit is evaluated through the transport agency, and the real-time road condition information and other services can be enjoyed by paying the reputation value. The problem of centralization of traffic light control is solved, high human intervention in the traffic light management and coordination processes is reduced, and financial resources and material resources are saved. Coordination optimization of traffic light management and control is achieved, and the safe and credible communication environment is provided for a vehicle-mounted Ad-Hoc network. Meanwhile, the confidentiality, privacy and non-repudiation of the information are guaranteed.
Owner:徐州虹智智能科技有限公司
Intelligent medical service method based on undistinguishable confusion
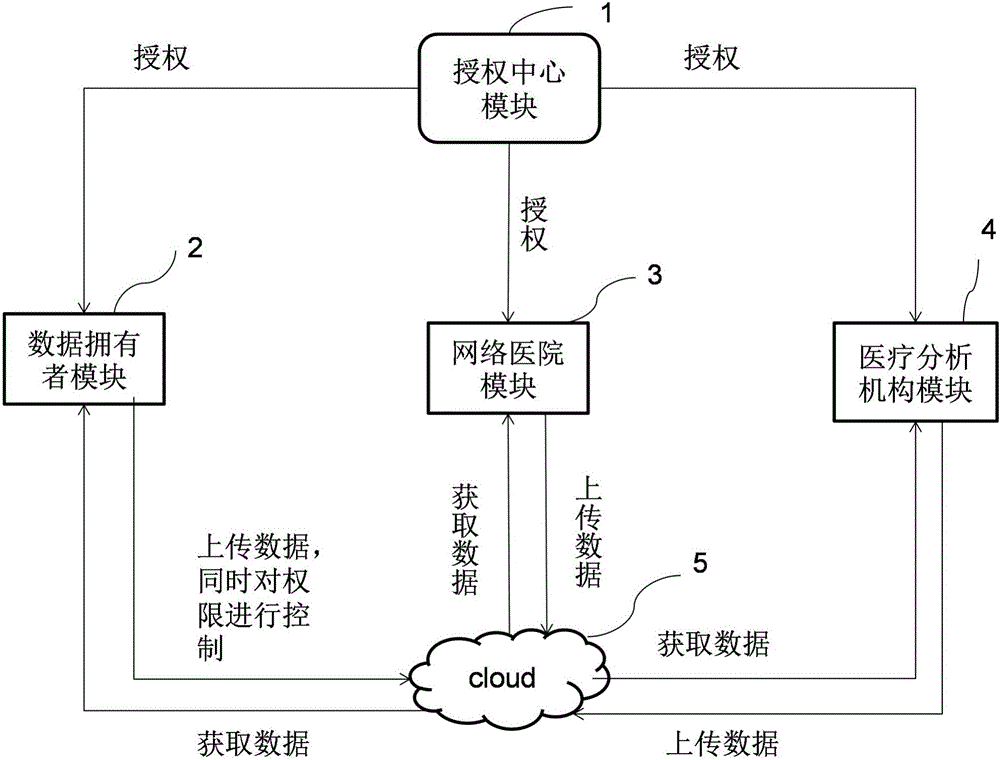
ActiveCN105978854AFlexible Control AllocationAssignment Convenience ControlKey distribution for secure communicationData processing applicationsCiphertextData access
The invention discloses an intelligent medical service method based on undistinguishable confusion, which is characterized in that a data owner independently decides allocation for the medical data access authority through carrying out security symmetric encryption on medical information uploaded to a cloud server; a medical data analysis mechanism carries out confusion on a medical data analysis program by using an undistinguishable confusion technology, the confused program is deployed to the cloud server, and security analysis is carried out on the medical data by using a confusion program so as to acquire a correct medical analysis result; and the access authority of other related mechanisms for a ciphertext can be controlled conveniently without changing the ciphertext structure by using a key sharing scheme. According to the invention, the privacy of data is realized, interaction of keys is reduced, and storage and management of a great number of keys are avoided; the integrity and the effectiveness of data can be verified; and the access type of medical data is decided by the user, the overall structure of an algorithm is not change at the same time, and the expansibility of the scheme is enhanced.
Owner:XIDIAN UNIV
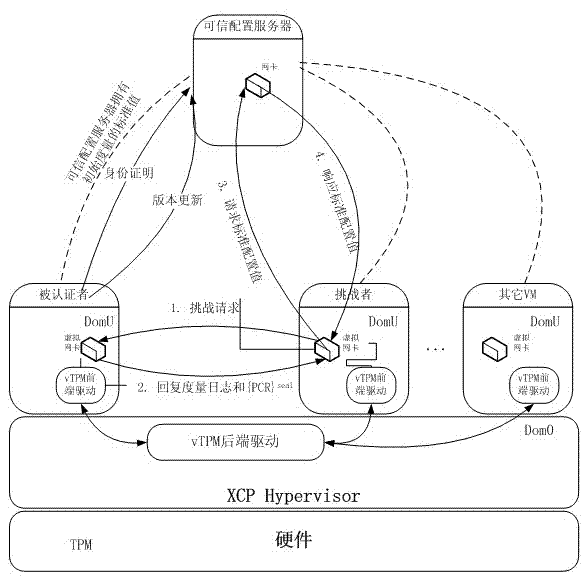
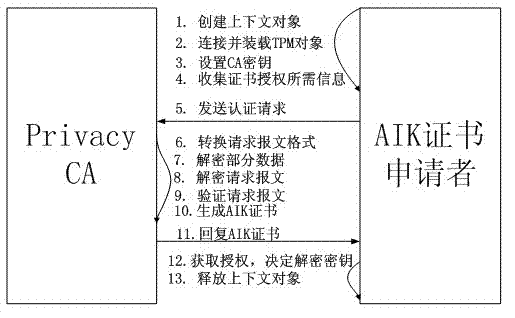
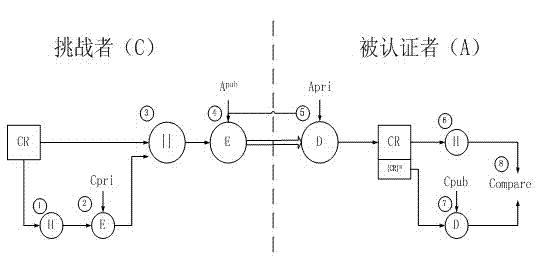
Remote attestation method based on cloud computing infrastructure as a service (IaaS) environment
ActiveCN103179129AIntegrity guaranteedGuaranteed non-repudiationTransmissionApplication moduleCloud computing
The invention discloses a remote attestation method based on a cloud computing infrastructure as a service (IaaS) environment. The remote attestation method is realized by an identity authentication module, a remote attestation module and a credible platform standard metric version updating module, wherein the identity authentication module comprises an attestation identity key (AIK) certificate application module, a Privacy CA certificate issuing module and an AIK request process verifying module; and the remote attestation module comprises a communication module for a challenger and an authenticated party, and a communication module for the challenger and a credible configuration server. The remote attestation method disclosed by the invention has the beneficial effects that a connection is permitted to be established only if virtual machines (VM) to be communicated are credible through a remote attestation by adding a remote attestation process before a normal communication channel is established between the virtual machines. On one hand, the remote attestation method disclosed by the invention can implement identity authentication and remote attestation on the authenticated party, and on the other hand, the authenticated party can update version under a situation that platform varies, so as to finally realize actually feasible remote attestation of the cloud computing IaaS environment.
Owner:SOUTH CHINA UNIV OF TECH
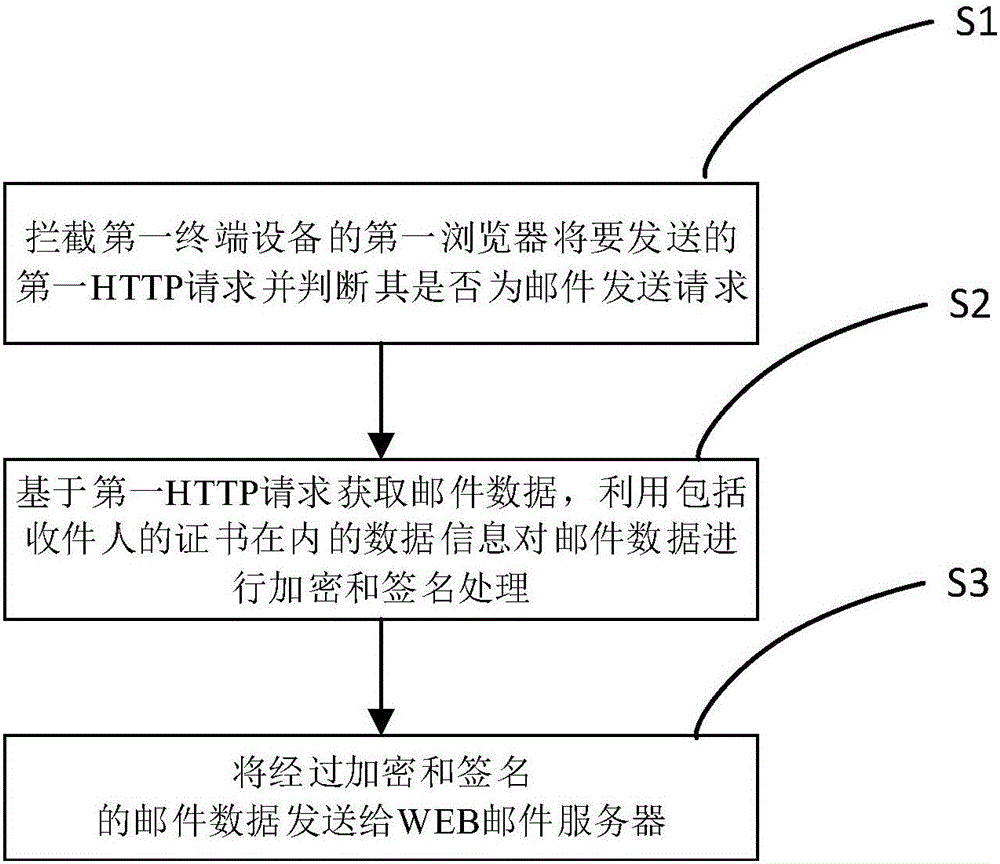
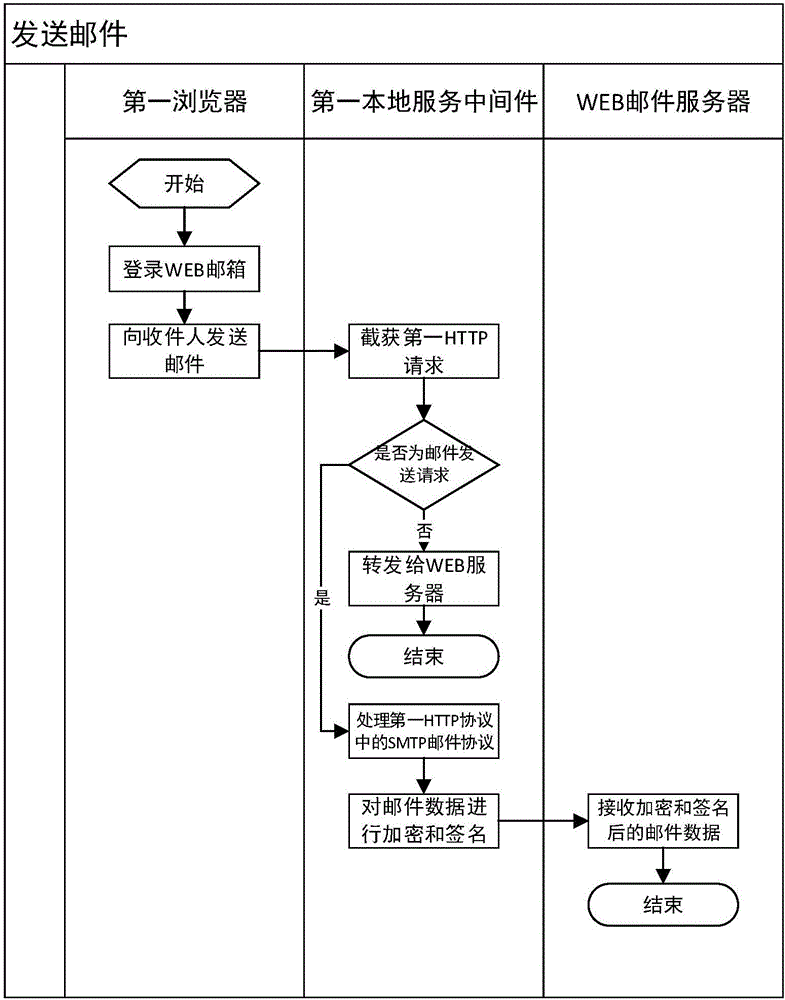
Method for using WEB emails safely, and terminal and system
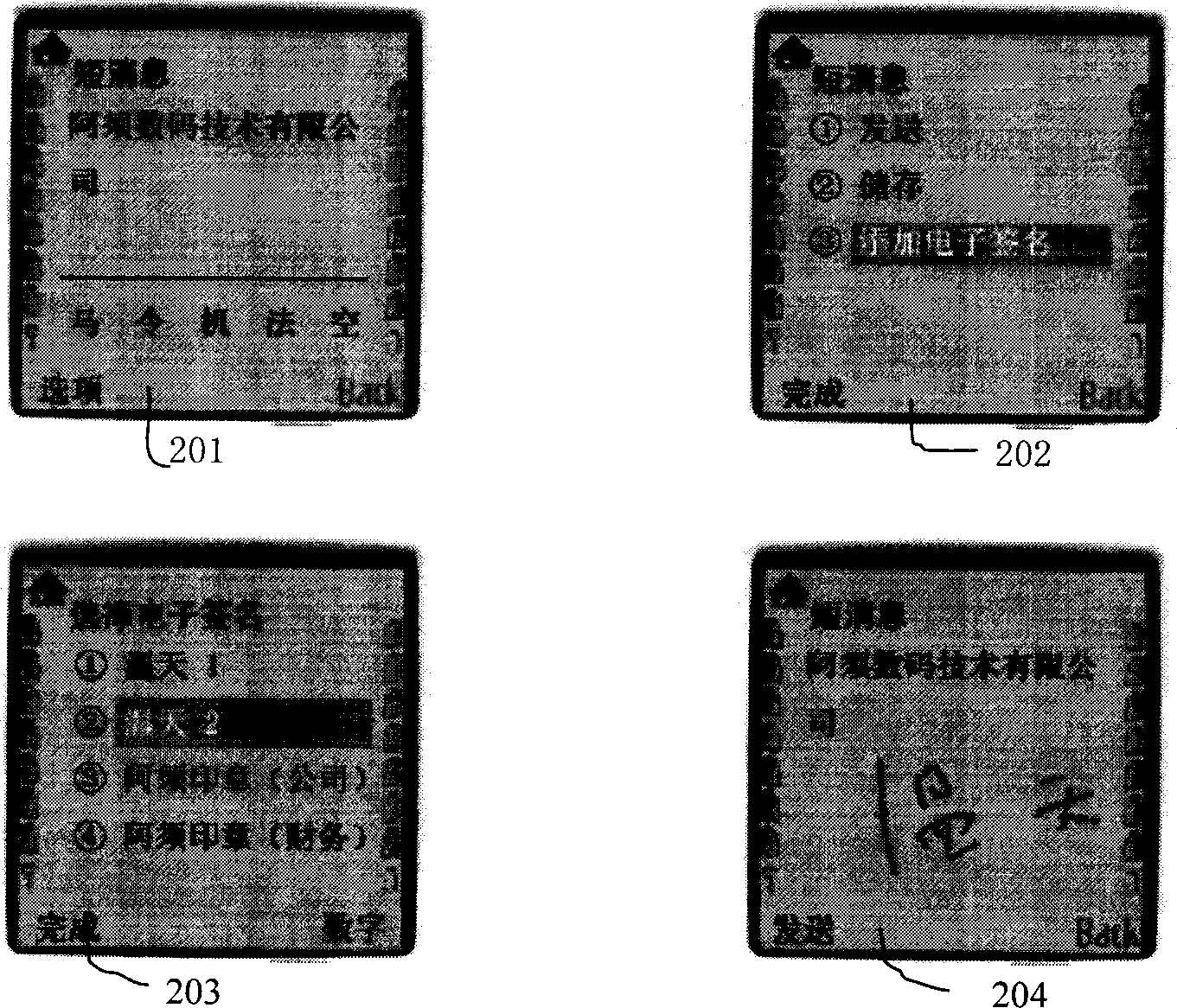
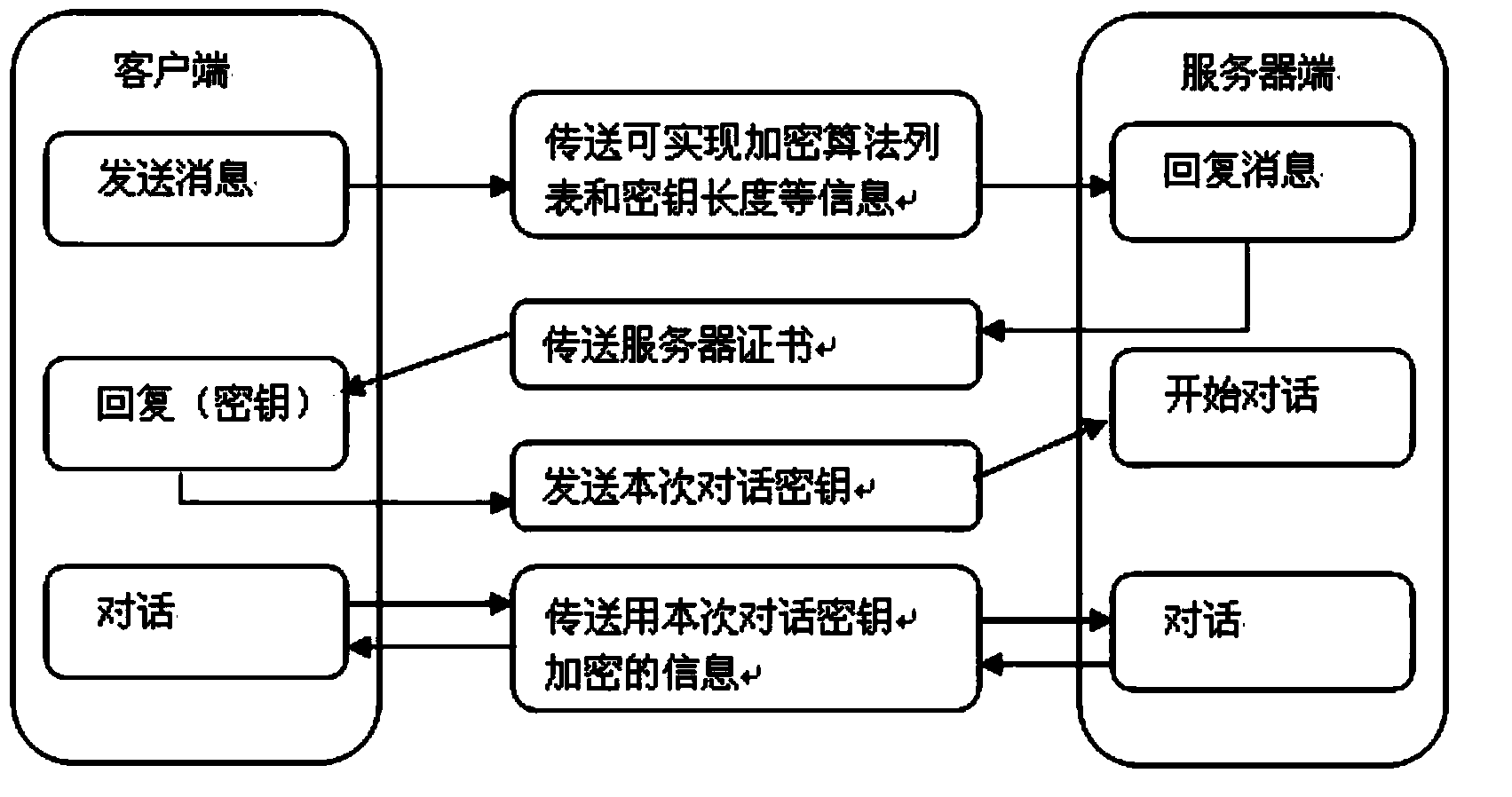
ActiveCN106209606AEnsure safetyGuaranteed non-repudiationData switching networksWeb serviceData information
This invention discloses a method for using WEB emails safely, and a terminal and a system. The method comprises the steps of: S1, intercepting a first HTTP (Hyper Text Transport Protocol) request that is to be sent by a first browser of a first terminal device, and judging whether the first HTTP request is an email sending request or not; if so, executing step S2; if not, forwarding the first HTTP request to a WEB server; S2, based on the first HTTP request, acquiring email data; encrypting and signing email data by using data information containing a certificate of a receiver; and S3, sending the encrypted and signed email data to a WEB email server. The method provided by the invention has the following beneficial effects: the browser can be effectively operated in the email service based on the Word-Wide-Web; and according to the corresponding HTTP request, the email can be encrypted, decrypted, signed, verified, and so on. The safety and the non-repudiation of the email can be ensured by multiple means of encryption in the sending and receiving processes.
Owner:BEIJING SENSESHIELD TECH
Cell phone seal verifying method and its system
InactiveCN1859092AIncrease authenticityAchieving unforgeable changeabilityUser identity/authority verificationHandwritingTelecommunications
This invention provides a cell phone seal system, which signs electronic names to short messages to be transmitted, inserts the electronic stamps with the signing information into the short meaasges to be transmitted to certify the identity of a sending party, the complete content of a short message, the orthority of the receiving party based on the property of the electronic seals to guarantee the duty and right of the two parties and the mode of the seal can be handwriting or a seal containing the special information of the sending party, such as SIM seal with the SIM card information, a cipher seal with the cipher of the sending party and E-KEY with its information or even seals based on the bio-character of a sending party such as fingerprint, iris, face, handwritings and voice.
Owner:刘瑞祯
Electronically signing method and system
ActiveCN103326862AGuarantee authenticityEnsure safetyUser identity/authority verificationDigital data authenticationNetwork packetComputer terminal
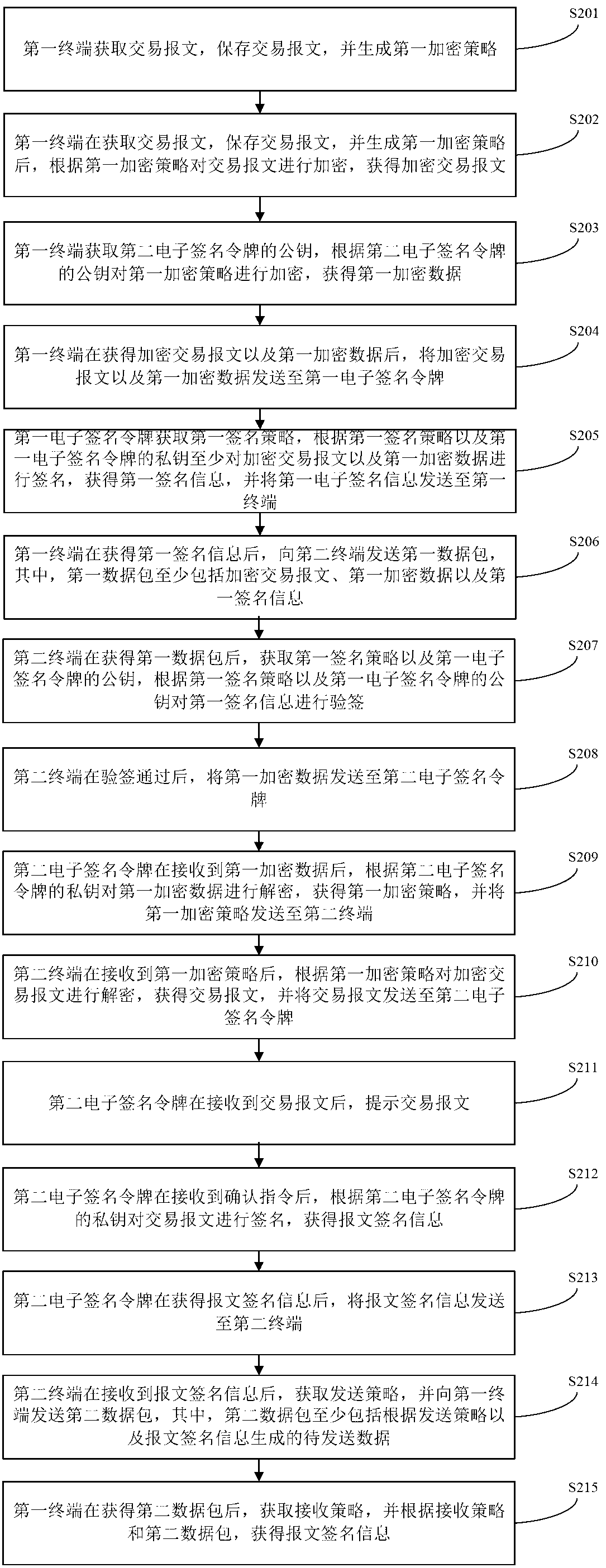
The invention provides an electronically signing method and system, wherein the method includes the steps that a first terminal obtains an encrypted transaction message and first encrypted data, sends the encrypted transaction message and the first encrypted data to a first electronic signature token to conduct signing and obtains first signature information, the first terminal sends a first data package to a second terminal, the second terminal conducts signing verification on the first signature information and sends the first encrypted data to a second electronic signature token after the first signature information passes the verification, the second electronic signature token conducts decryption on the first encrypted data to obtain a first encryption strategy and sends the first encryption strategy to the second terminal, the second terminal conducts decryption on the encrypted transaction message to obtain the transaction message according to the first encryption strategy and sends the transaction message to the second electronic signature token to conduct signing to obtain message signature information, the second terminal sends a second data package to the first terminal, and the first terminal obtains the message signature information. Through the electronically signing method and system, the problem that potential safety hazards are caused and the use is inconvenient due to the uniqueness of the electronic signature token is solved.
Owner:TENDYRON CORP
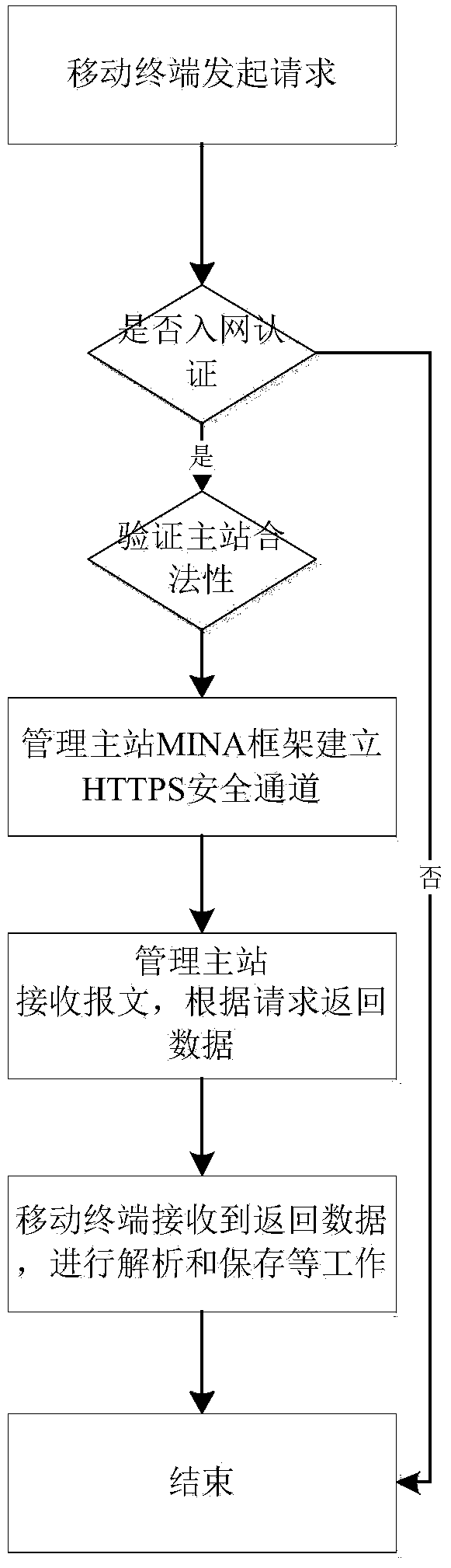
Communication method of power asset management master station system and RFID (radio frequency identification device) terminal
The invention relates to a communication method of a power asset management master station system and an RFID terminal. The method guarantees the identity legitimacy of a client by providing bidirectional authentication for the RFID terminal and the management master station system and encrypting private data and through digital signatures; a terminal layer is mainly composed of the RFID mobile terminal and an RFID reading and writing module and mainly achieves the operations such as field installation, label information inquiry and equipment checking of power grid equipment labels. The communication method of the power asset management master station system and the RFID terminal can guarantee the communication safety between the power asset management master station system and the RFID terminal; two communicating parties can establish safe communication channels therebetween for data transmission only by holding key certificates and being authorized.
Owner:STATE GRID CORP OF CHINA +3
Virtual power plant security scheduling and trading method based on dual blockchain technology
PendingCN112434343ASafe storageEnsure normal communicationFinanceDigital data protectionID-based encryptionCurrent electric
A virtual power plant security scheduling and transaction method based on a dual blockchain technology comprises a scheduling private chain for scheduling and a transaction alliance chain for transaction, adopts a hybrid proxy re-encryption algorithm based on a ciphertext strategy, and is formed by combining an identity-based encryption algorithm and an attribute proxy re-encryption algorithm based on the ciphertext strategy. The agent converts the ciphertext based on attribute encryption into the ciphertext based on identity encryption, so that the decryption cost of the data accessor is reduced, and the non-repudiation and reliability of production information are ensured. In the transaction process, a continuous bilateral auction mechanism based on reputation is adopted, participants can continuously adjust their own quotation according to the current electric quantity transaction price, benefit maximization is achieved, transaction information and a reputation value are recorded inan alliance chain, and tamper resistance and transparency of the information are guaranteed. A low-cost, open and transparent information and transaction platform is provided for a virtual power plant, and the safety, tamper resistance, non-repudiation, integrity and the like of data are guaranteed.
Owner:JIANGXI UNIV OF SCI & TECH
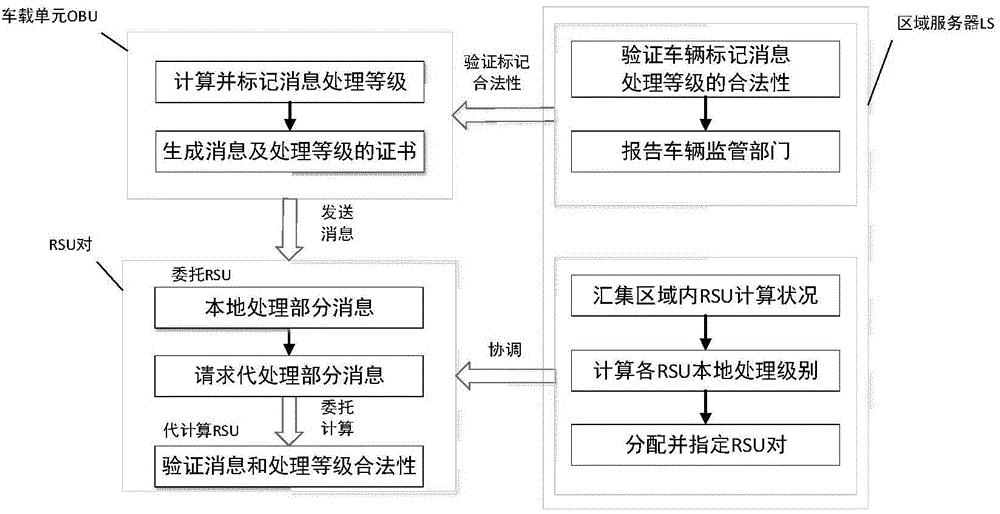
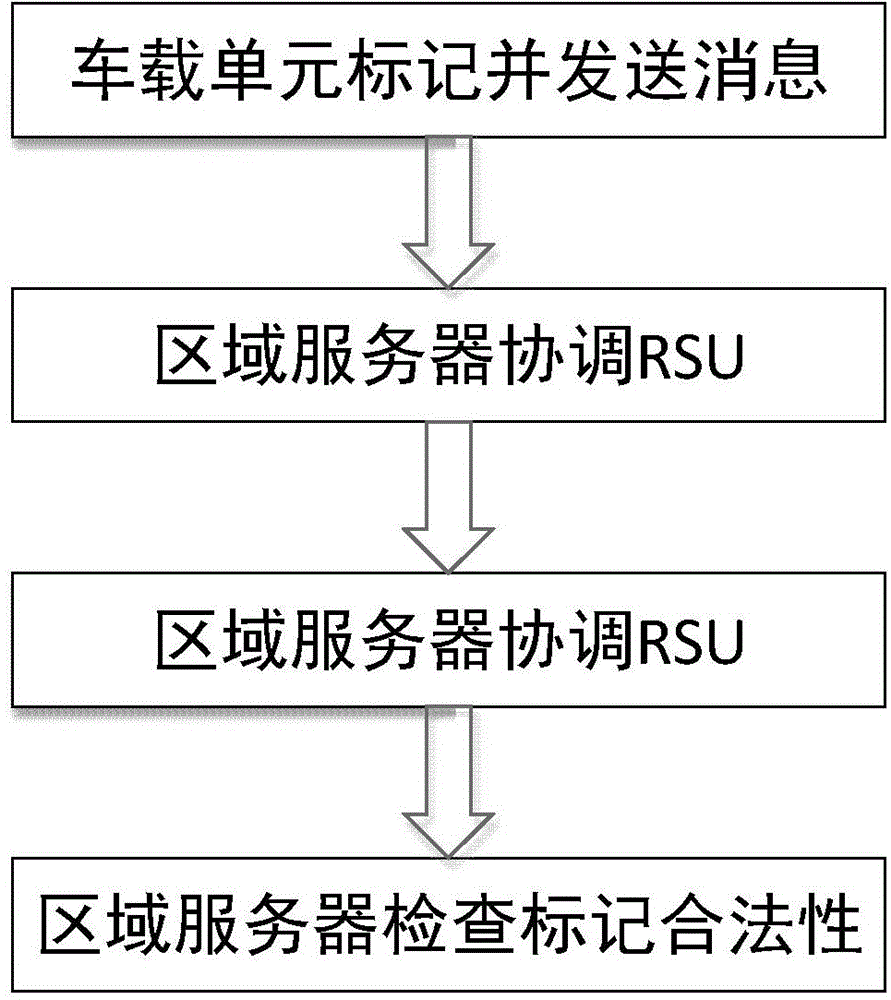
Vehicle identity authentication method capable of evenly sharing RSU calculated amount
ActiveCN104702418AEnhance response service capabilitiesImprove service qualityUser identity/authority verificationWork periodMessage processing
The invention discloses a vehicle identity authentication method capable of evenly sharing the RSU calculated amount. The method comprises the following steps that a vehicle is marked and a message is sent, wherein the step comprises message processing level calculating, message signature generating and processing level signature generating; a region server coordinates RSU, wherein the step comprises a coordinating period and a working period; calculation replacing RSU assist delegation RSU to perform identity authentication on the vehicle message; the region server verifies a message processing level of the vehicle.
Owner:JIANGSU UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com