Base station secure accessing method of mobile communication system
A mobile communication system and secure access technology, applied in the secure access field of base stations, can solve problems affecting security, information monitoring, affecting the security of base stations and base station content, etc., and achieve the effect of improving security levels and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
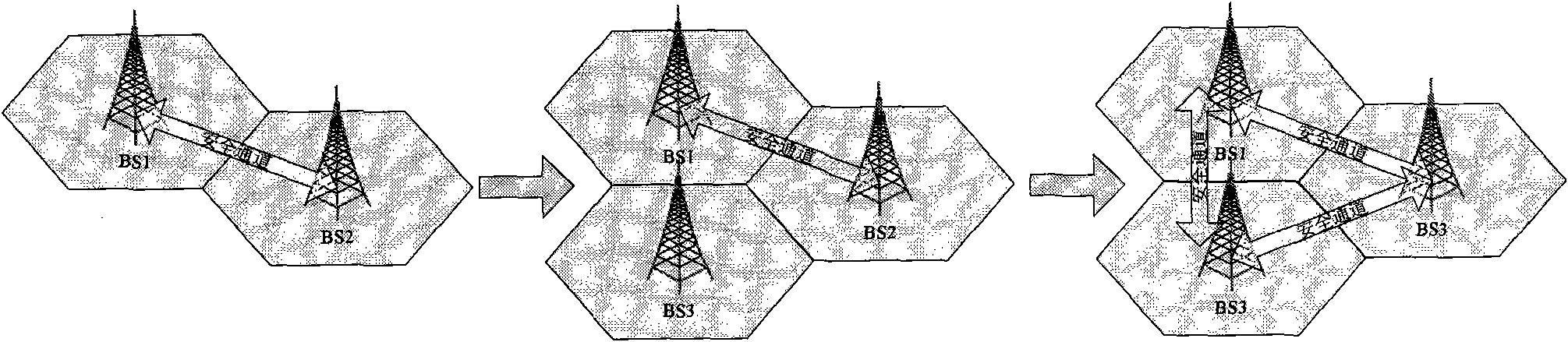
[0015] The secure access method of the base station of the mobile communication system in the present invention is to ensure the security of the information transmitted between the base stations when the information is transmitted between the base stations. In order to achieve this goal, the solution of the present invention is realized by establishing a mutual trust relationship and a safe channel between two base stations that need to communicate, wherein, since the networks of the current mobile communication systems all conform to the cellular structure, the base station usually only needs to Communicate with its adjacent neighbor base stations. Therefore, the base station only needs to establish mutual trust relationships and security channels with its neighbor base stations, and does not need to establish mutual trust relationships and security channels with all other base stations, so as to reduce the need to establish mutual trust relationships between base stations. an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com