Network safety isolation file transmission control method
A network security and data transmission method technology, which is applied in the field of file transmission control between taxation network security isolation systems, can solve problems such as slowing down access speed, hidden dangers of product security, and long switching time, so as to ensure network security, content security, and high-speed The effect of safety information exchange
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention is described in further detail below in conjunction with accompanying drawing:
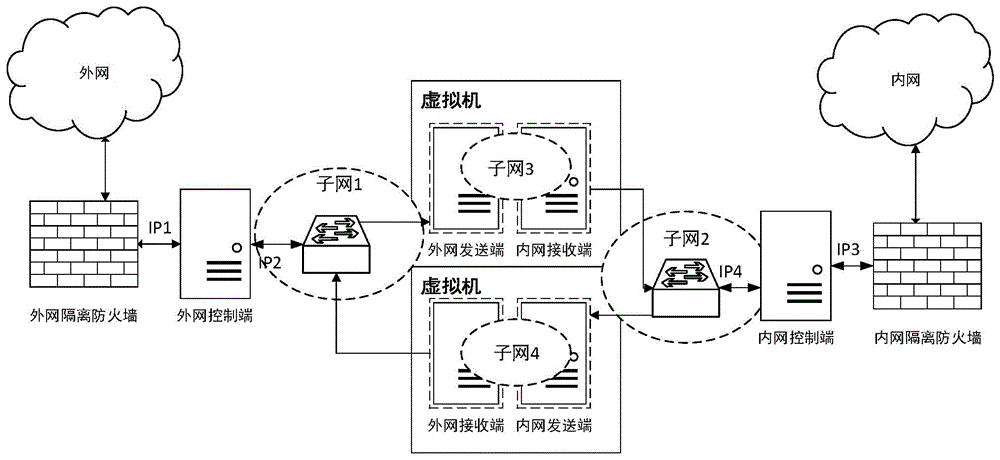
[0030] figure 1 It is a network architecture diagram of the present invention, including an external network control terminal, an external network sending terminal, an external network receiving terminal, an internal network receiving terminal, an internal network transmitting terminal, an internal network control terminal, an external network isolation firewall and an internal network isolation firewall.
[0031] The external network control terminal and the internal network control terminal work in an industrial computer with multiple network ports. As the core server, it is specifically responsible for the analysis and execution of the entire transmission control protocol, and undertakes the storage and forwarding of shared files, making file interaction more efficient. Controllable and efficient.
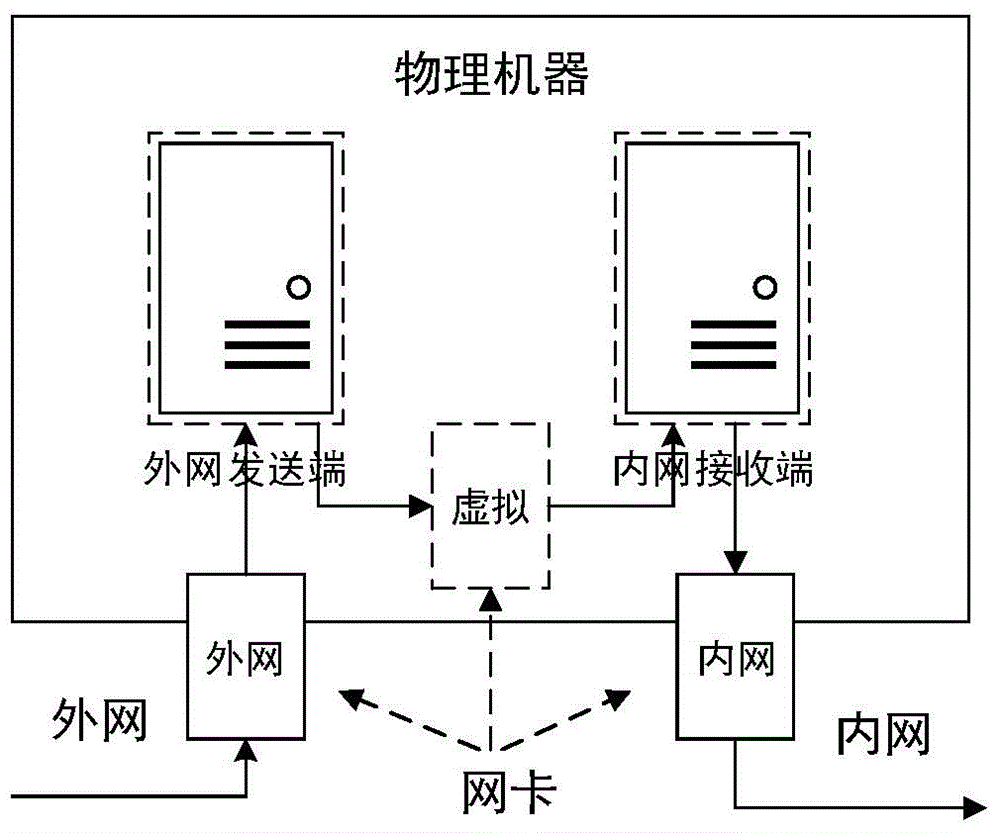
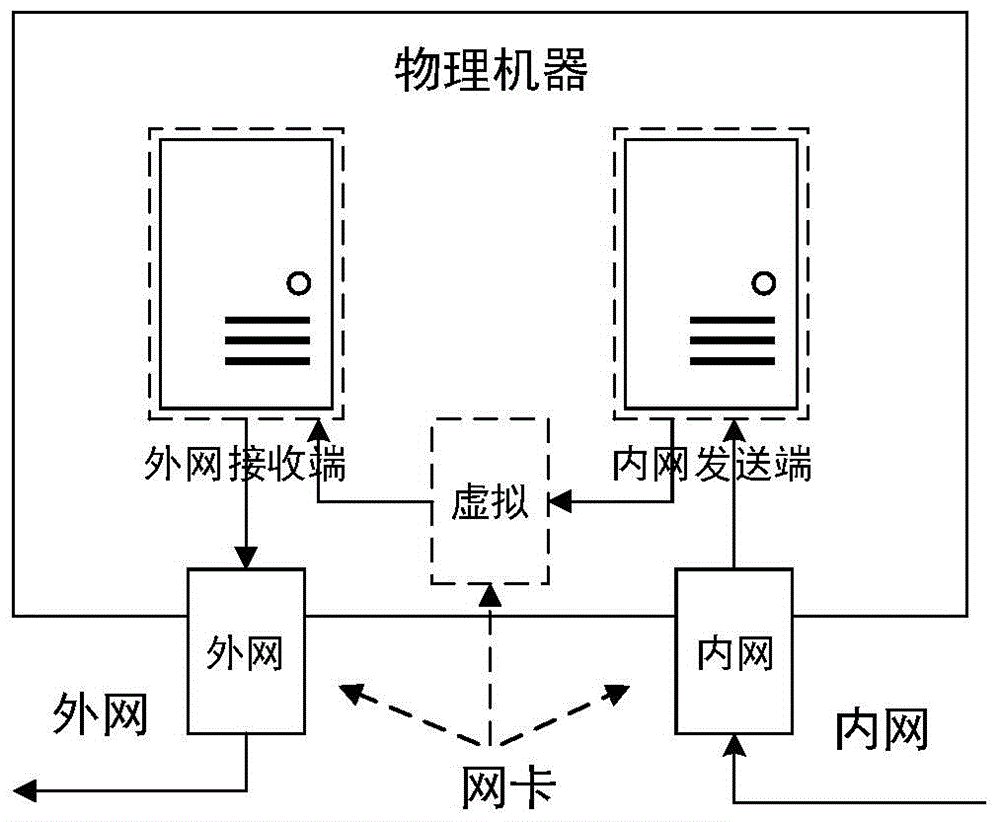
[0032] figure 2 It is the network architecture of the sending en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com