Patents
Literature
47results about How to "Keep Content Safe" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
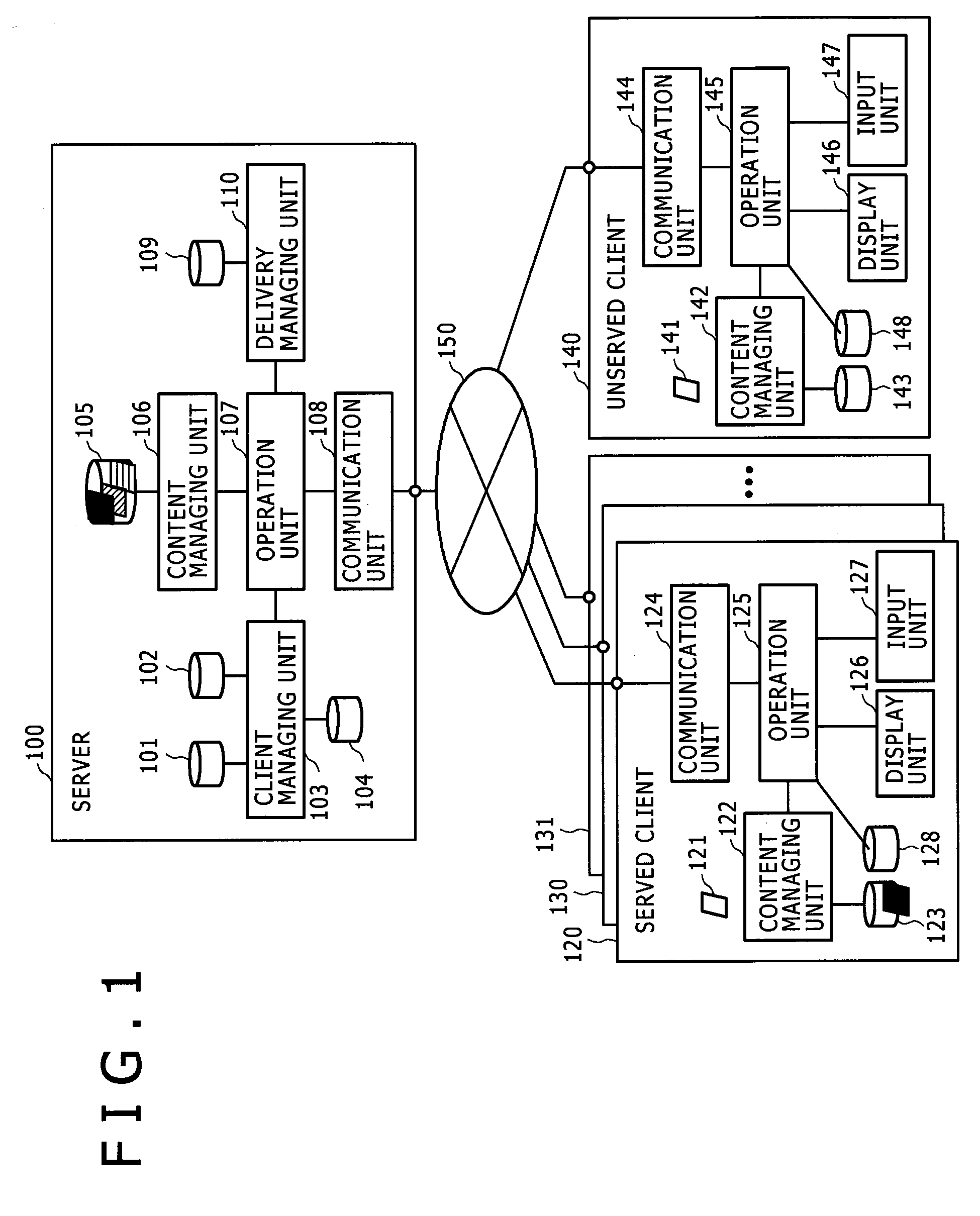
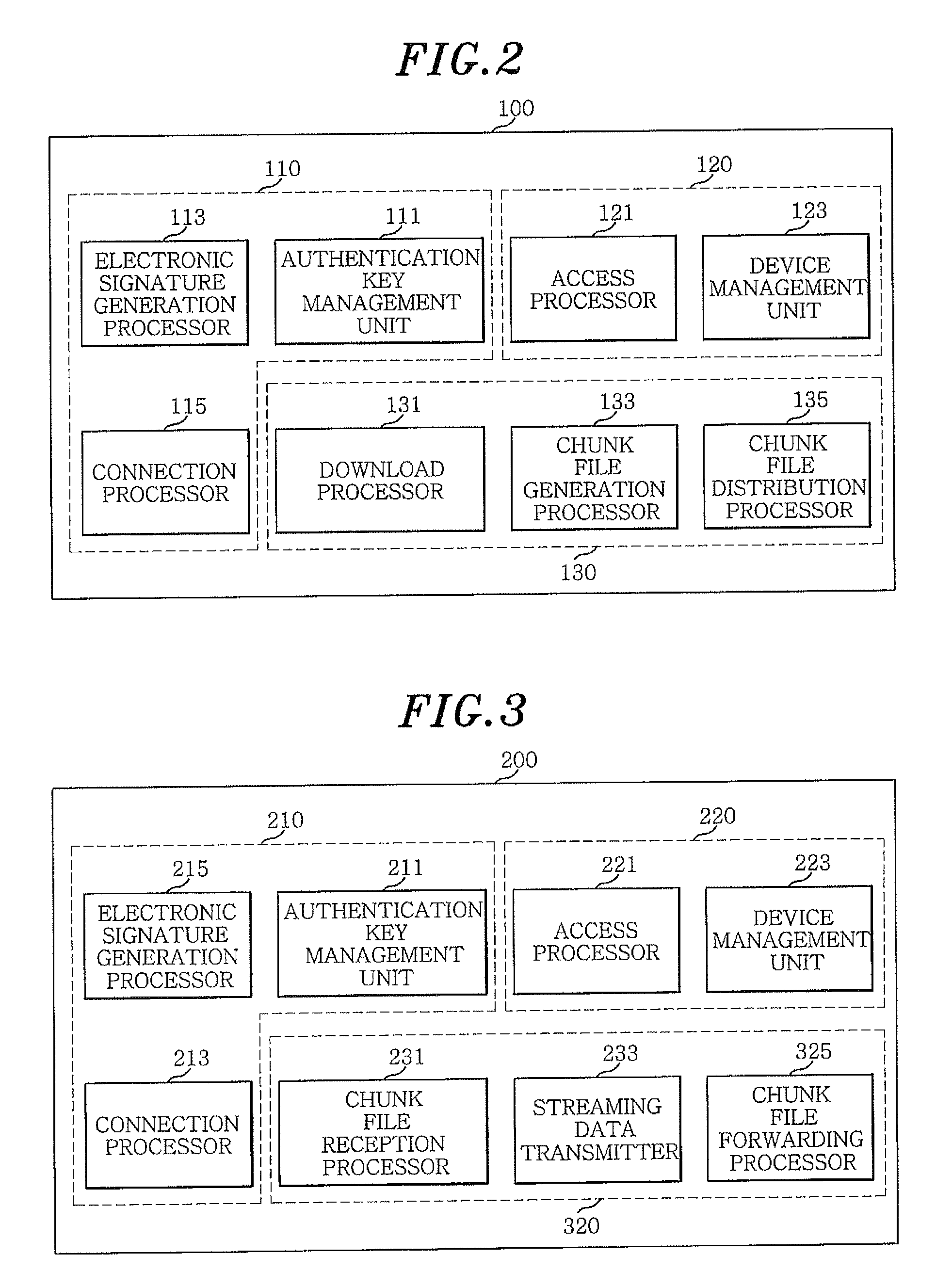
System and method for securing an enterprise computing environment
InactiveUS20180027006A1Process safetyKeep Content SafeMultiprogramming arrangementsComputer security arrangementsInternet privacyEnterprise computing
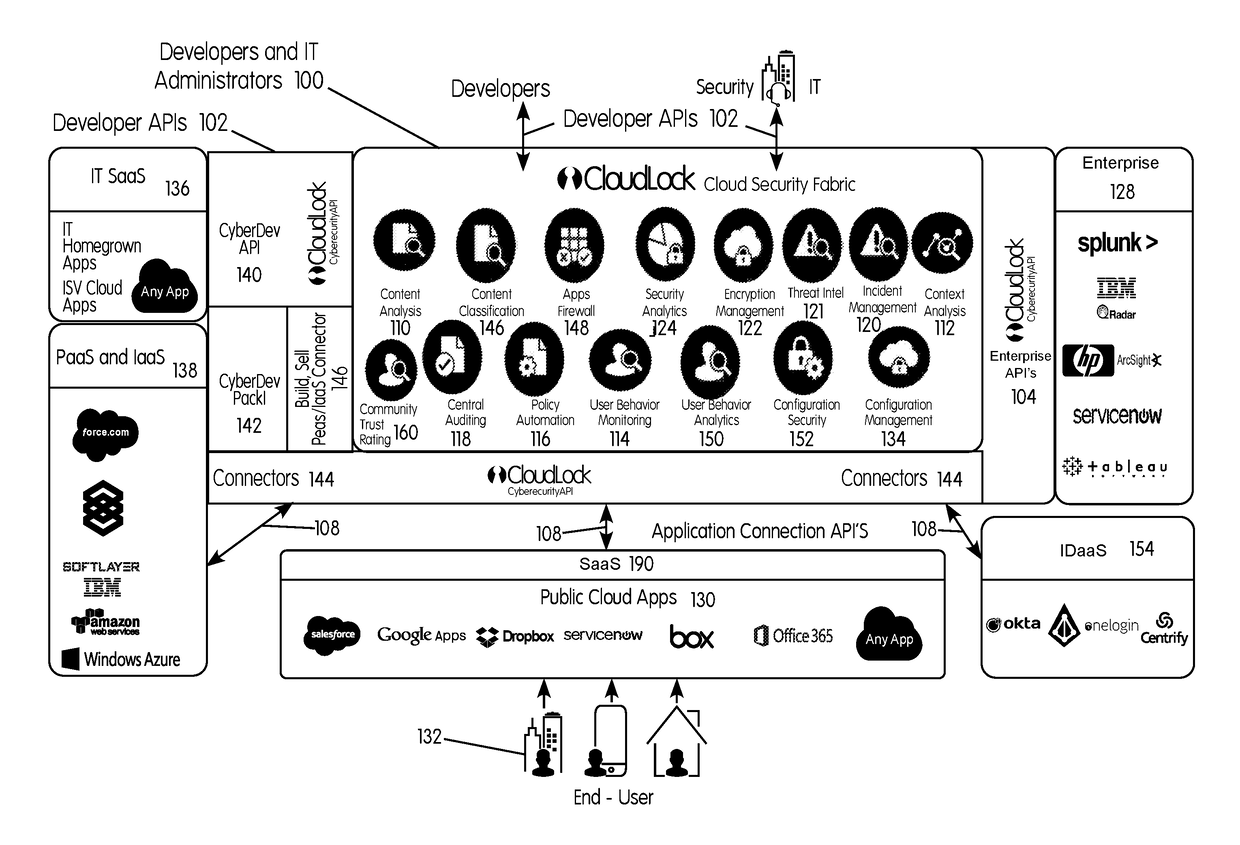
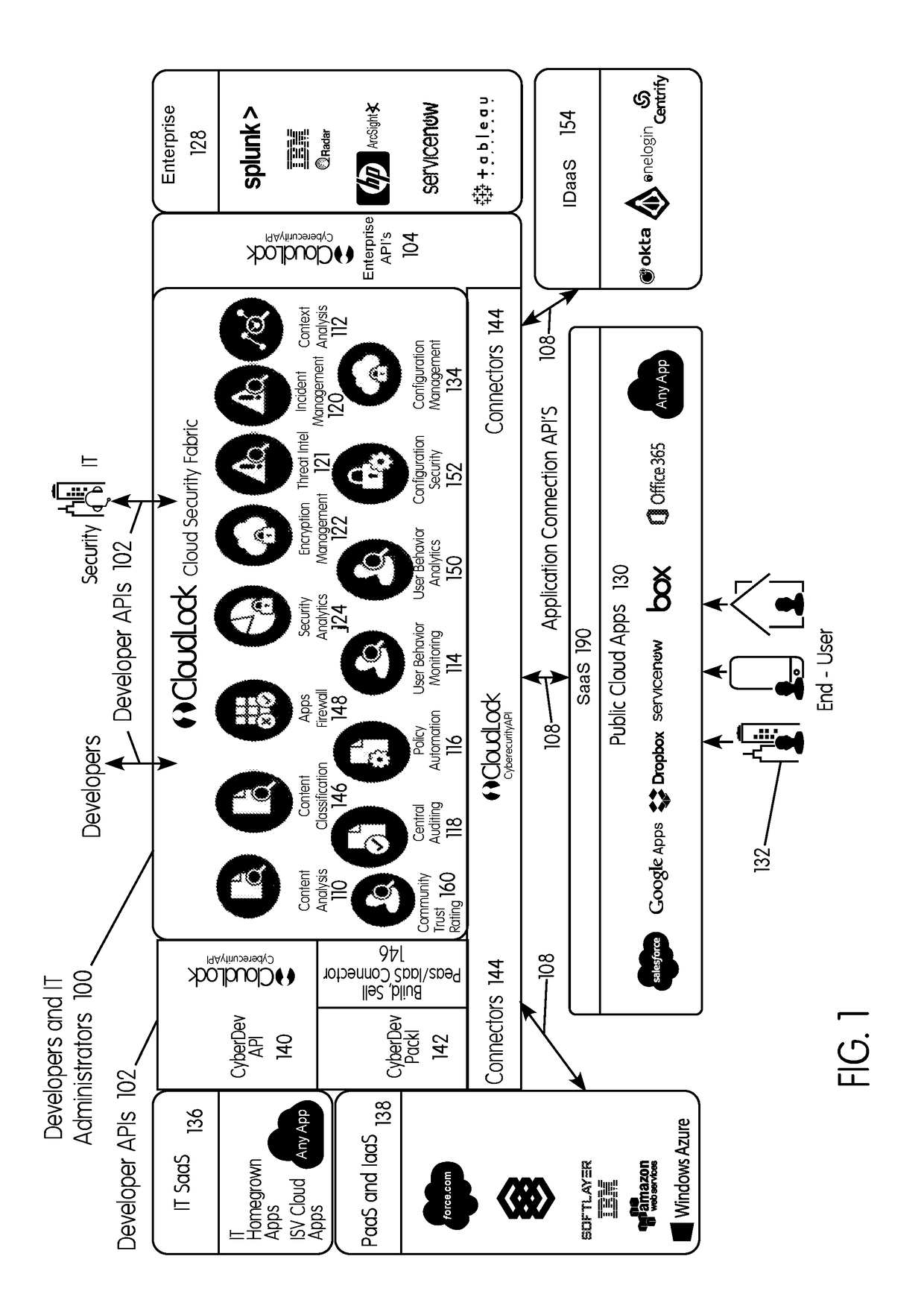
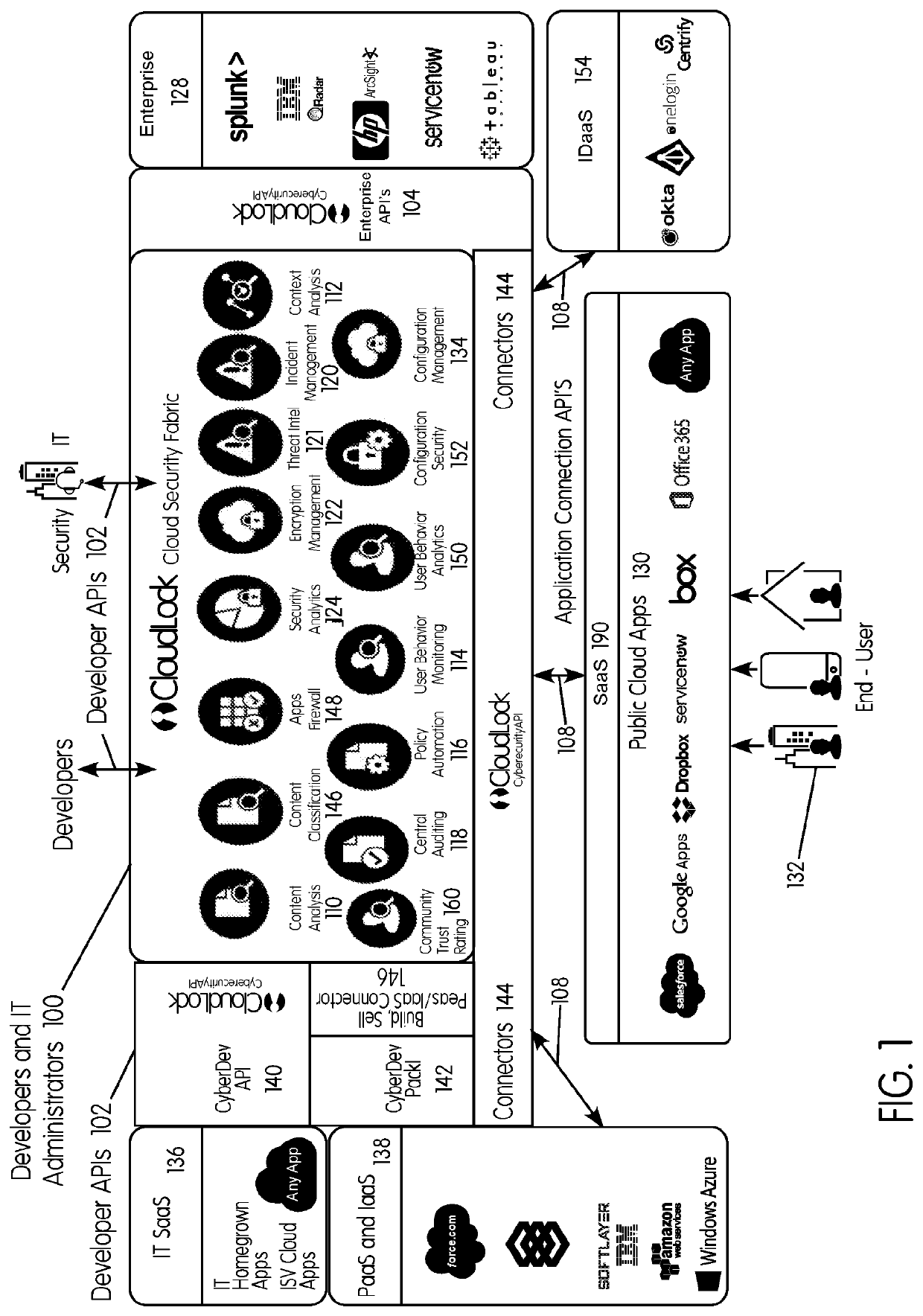
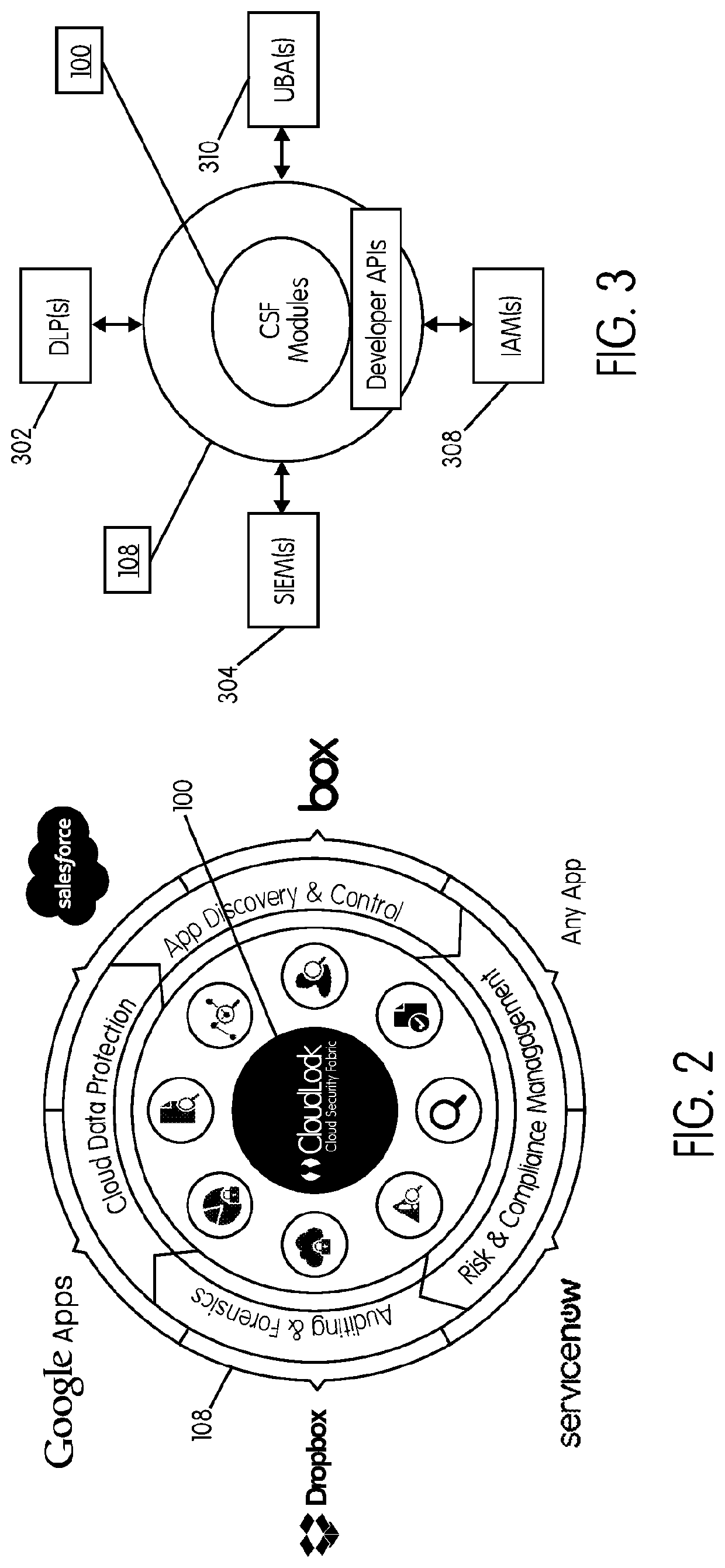
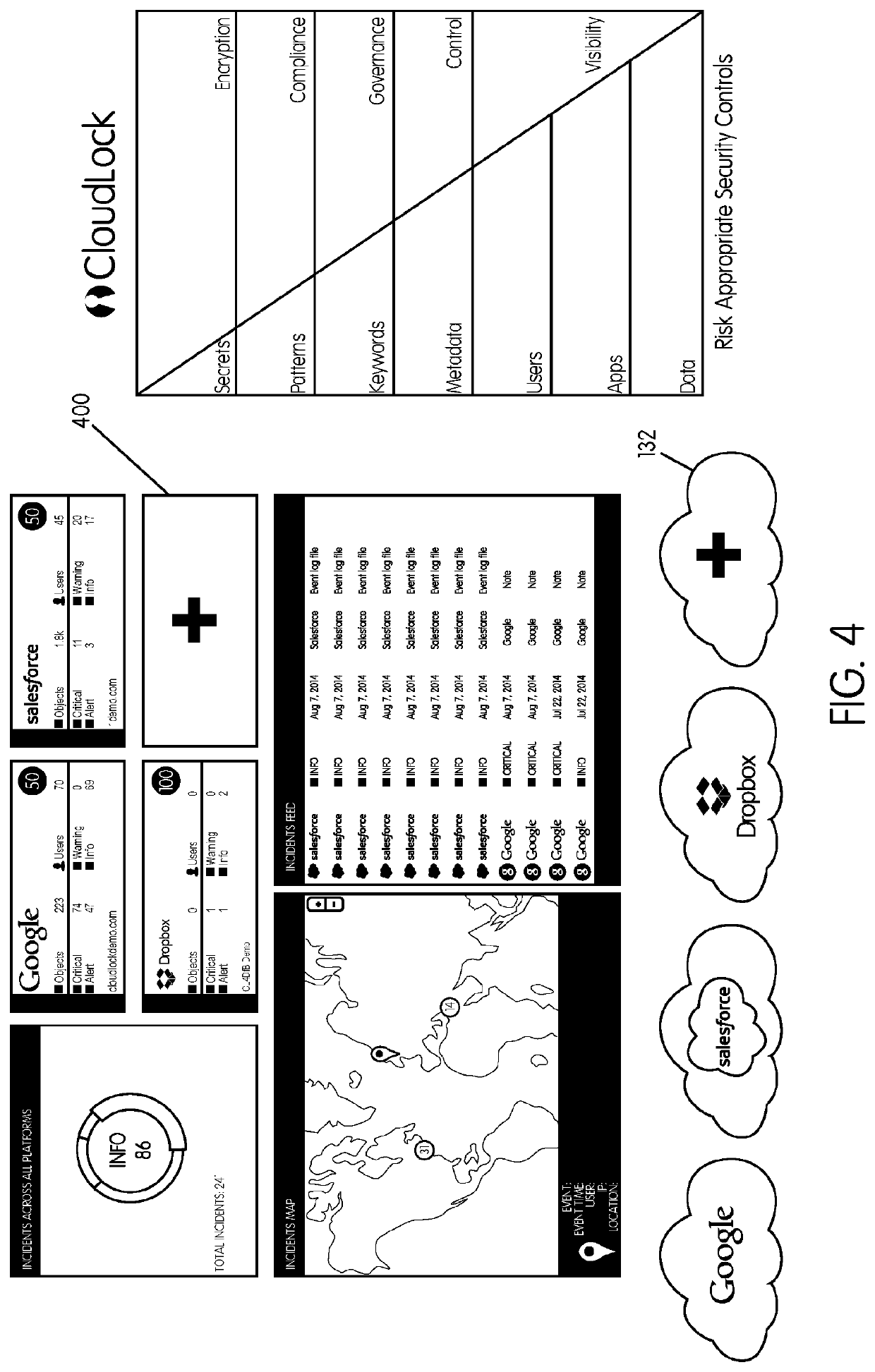
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CLOUDLOCK
System and method for securing an enterprise computing environment
InactiveUS20200137097A1Process safetyKeep Content SafeMultiprogramming arrangementsDigital data protectionBusiness enterpriseEnterprise computing
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CISCO TECH INC
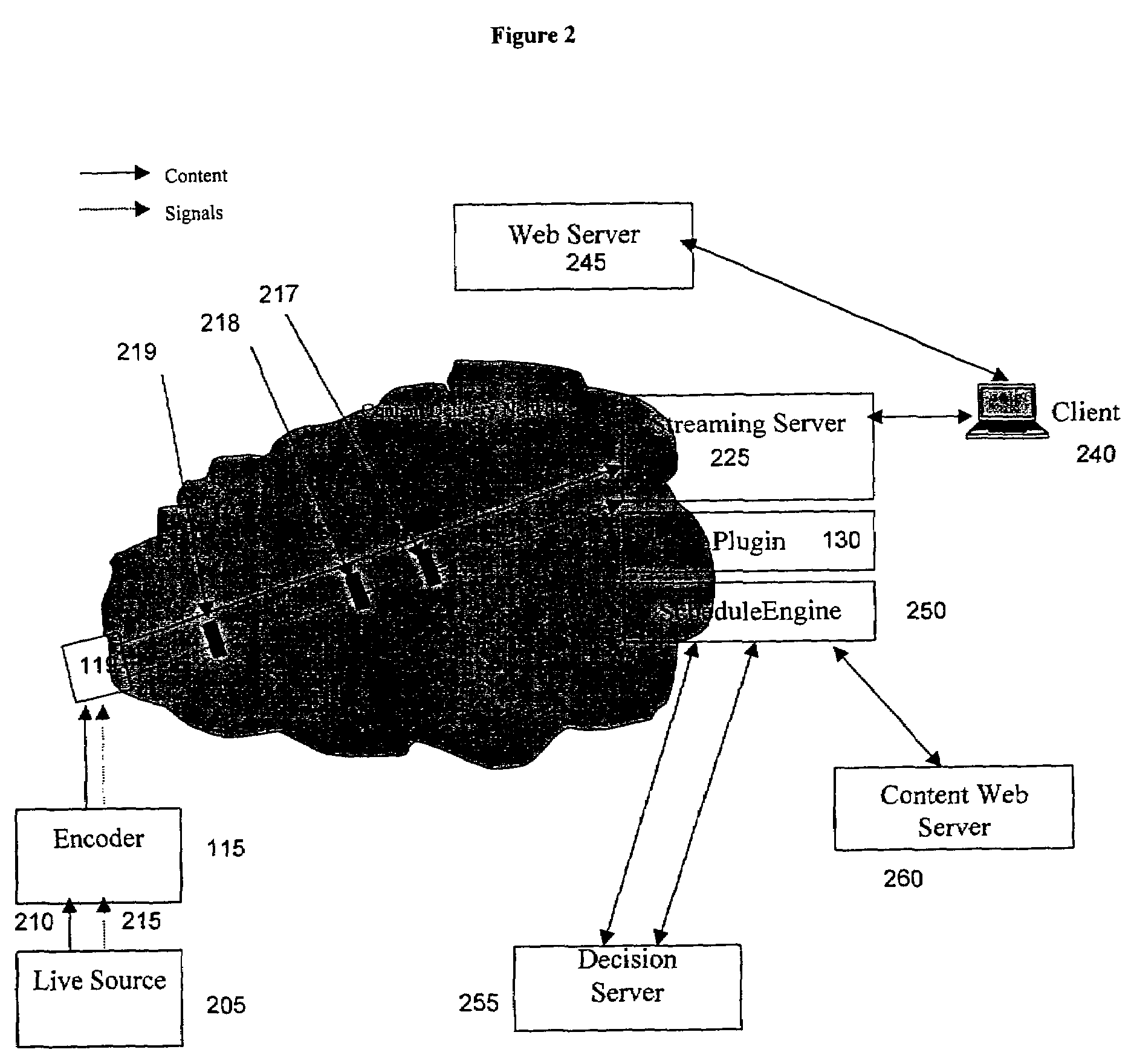
System and method for selective insertion of content into streaming media
ActiveUS7203758B2Targeted optimizationMinimize effortPulse modulation television signal transmissionAnalogue secracy/subscription systemsSystem usageOn demand
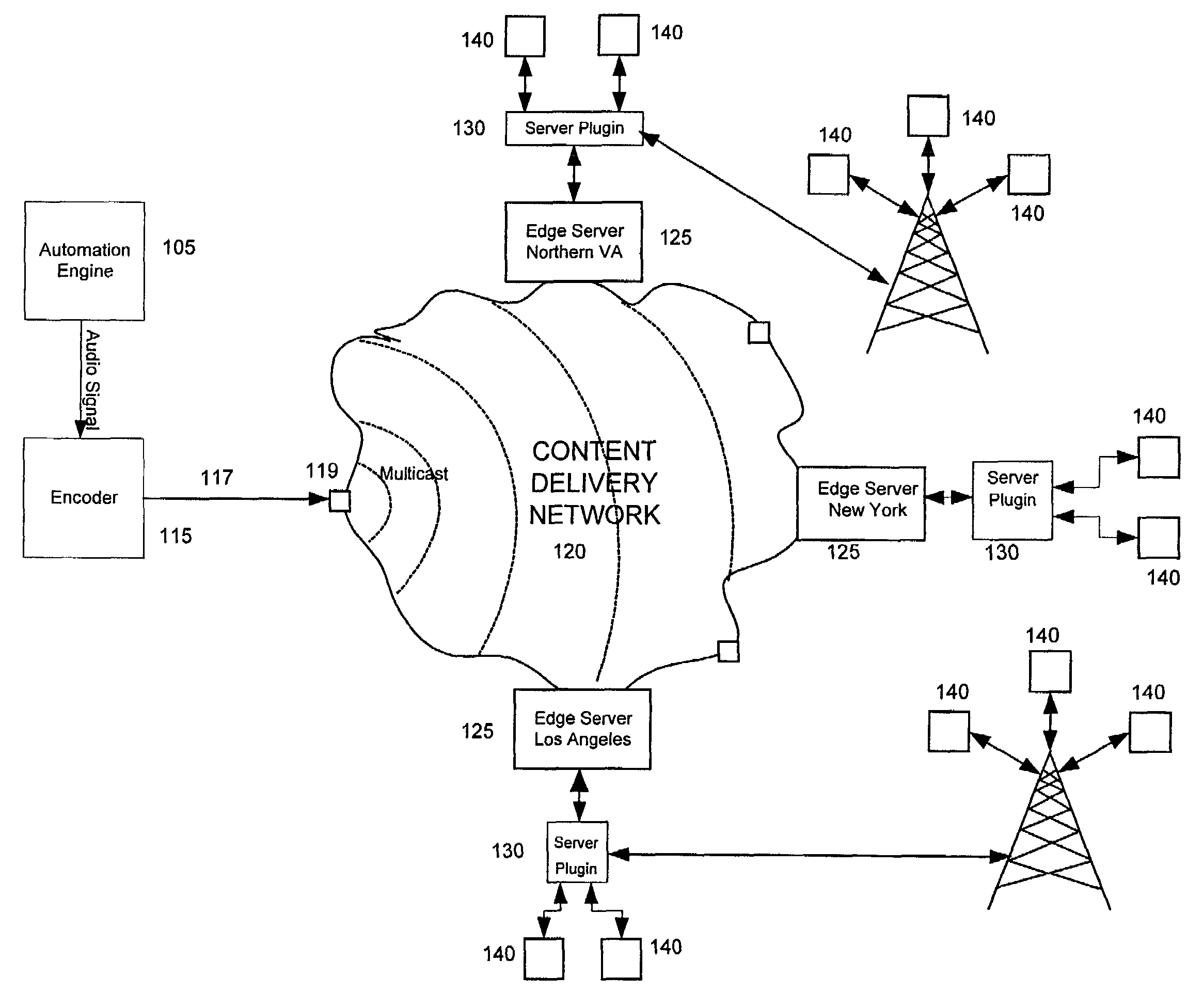
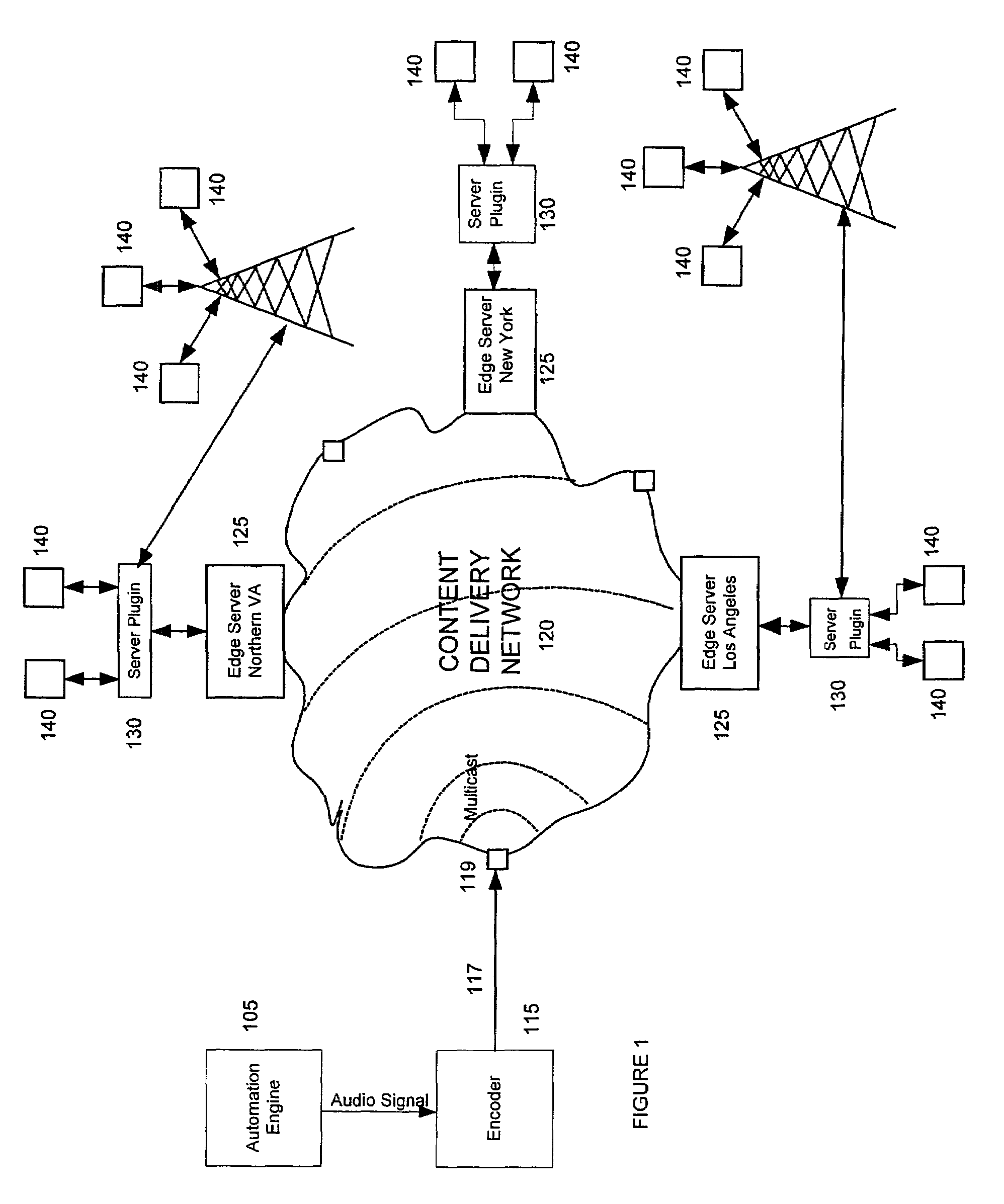
Method and system for server side insertion of rich content into a media stream uses an insertion plugin to redirect users' requests for streaming media through a server, and operates on either live broadcasts or on demand playlists. The live broadcast identifies impending local interrupt breaks and seamlessly inserts content chosen to match user attributes. The on demand implementation broadcasts a playlist of encoded content including predetermined file content and additional rich content inserted based on user attributes as selected by a decision engine. The insertion of content can be performed on already encoded media. In one embodiment, time matching is performed to avoid rebuffering.
Owner:RPX CORP
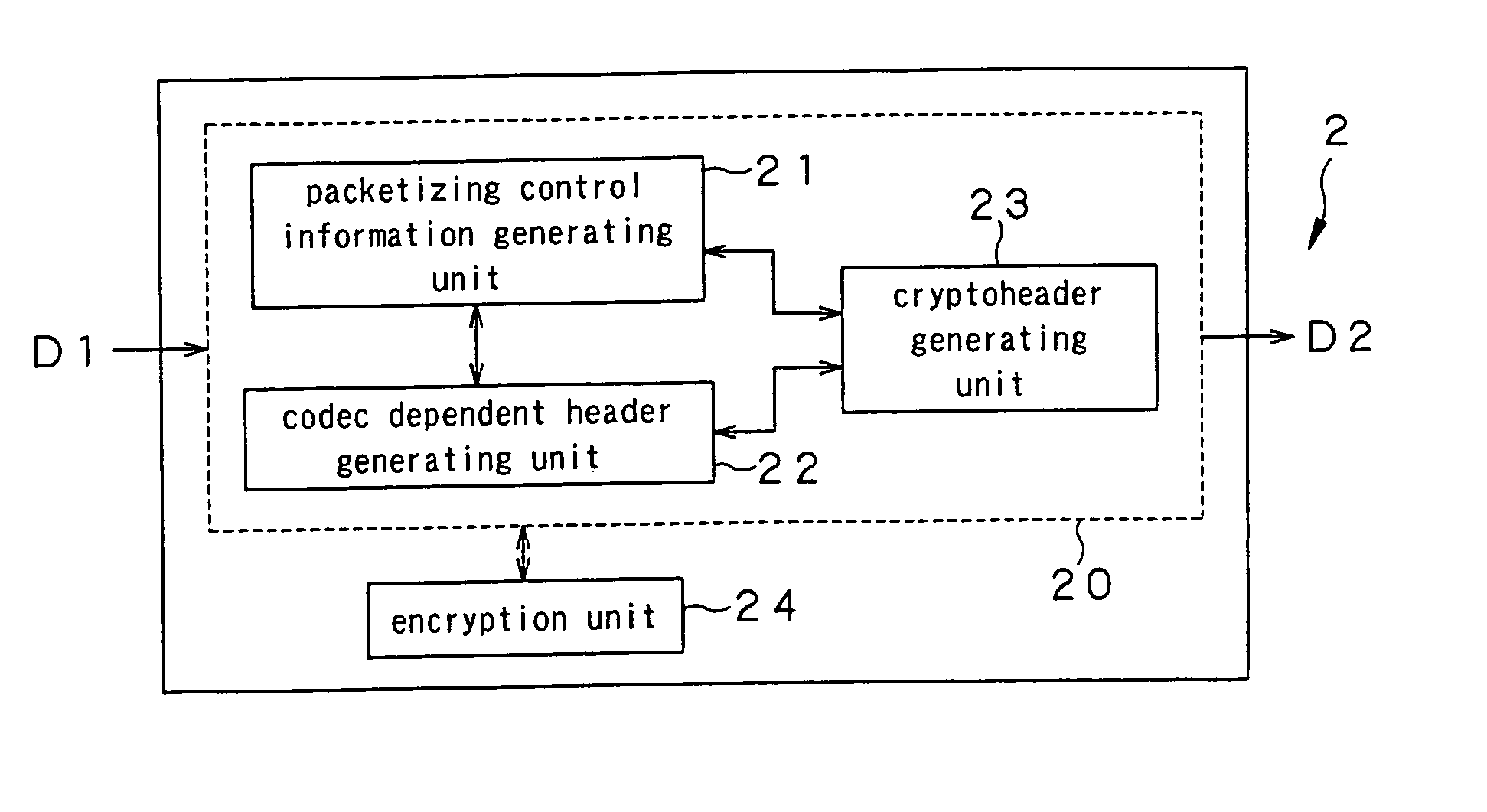
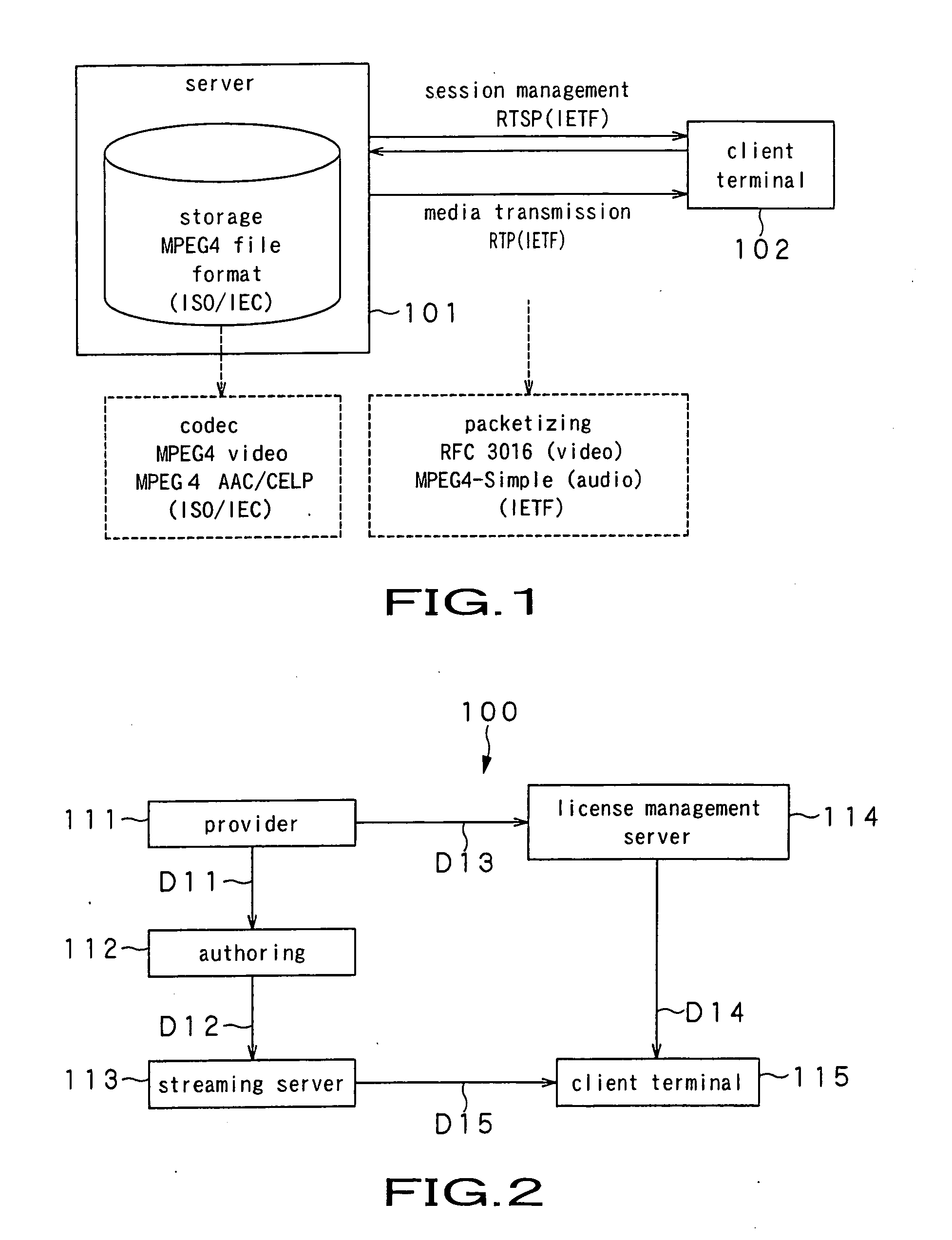
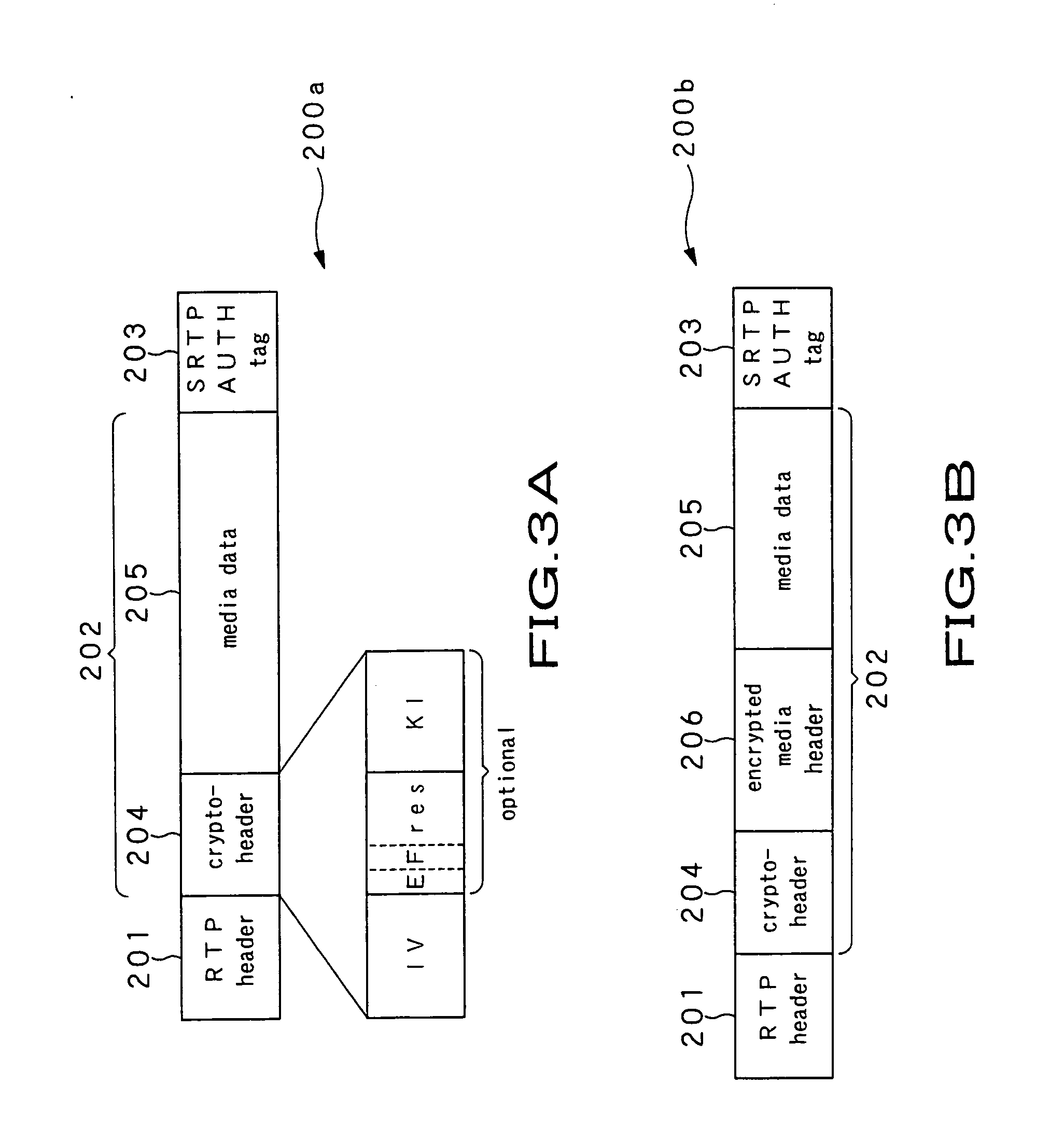
Streaming system and streaming method
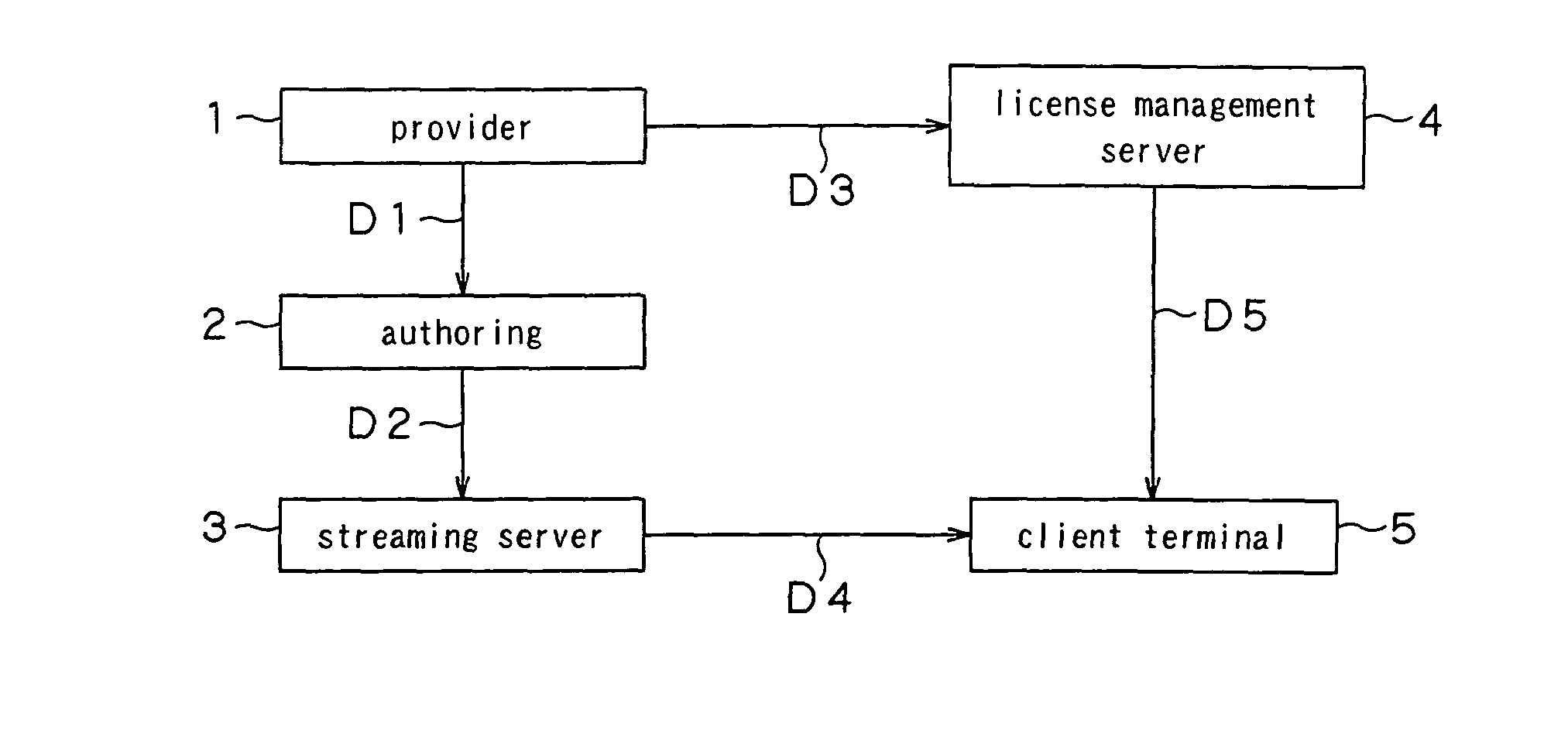
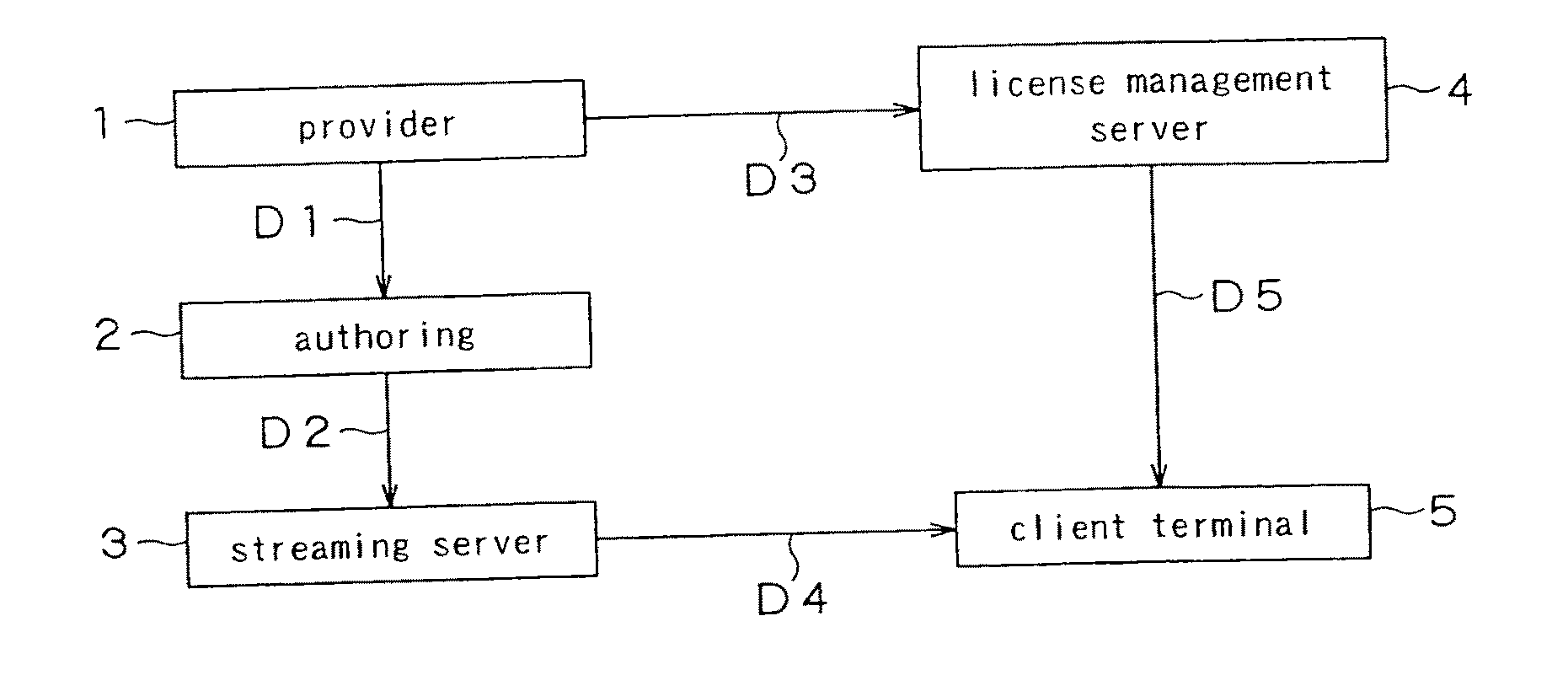
ActiveUS20050108746A1Low production costKeep Content SafeKey distribution for secure communicationUser identity/authority verificationComputer scienceEncryption
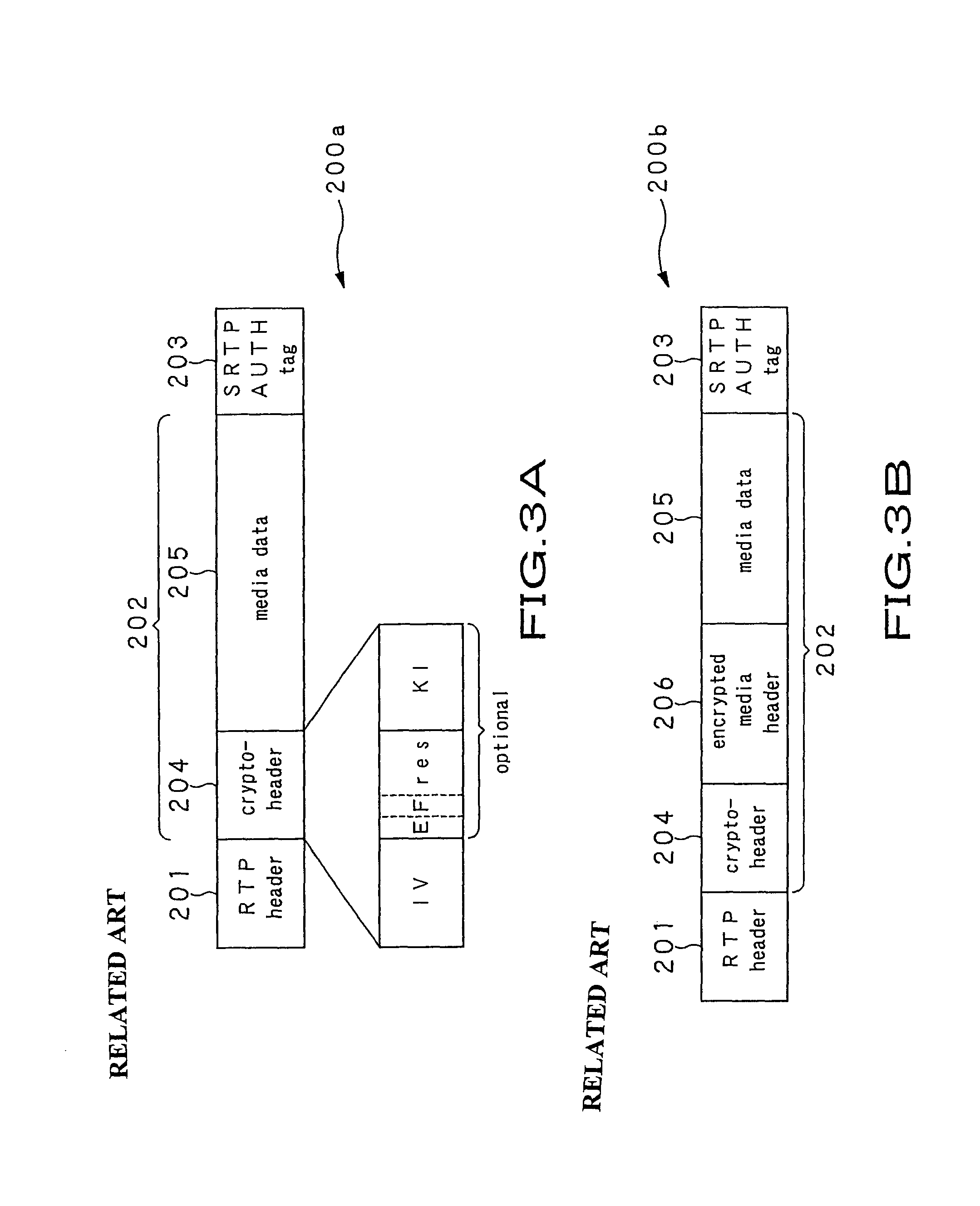
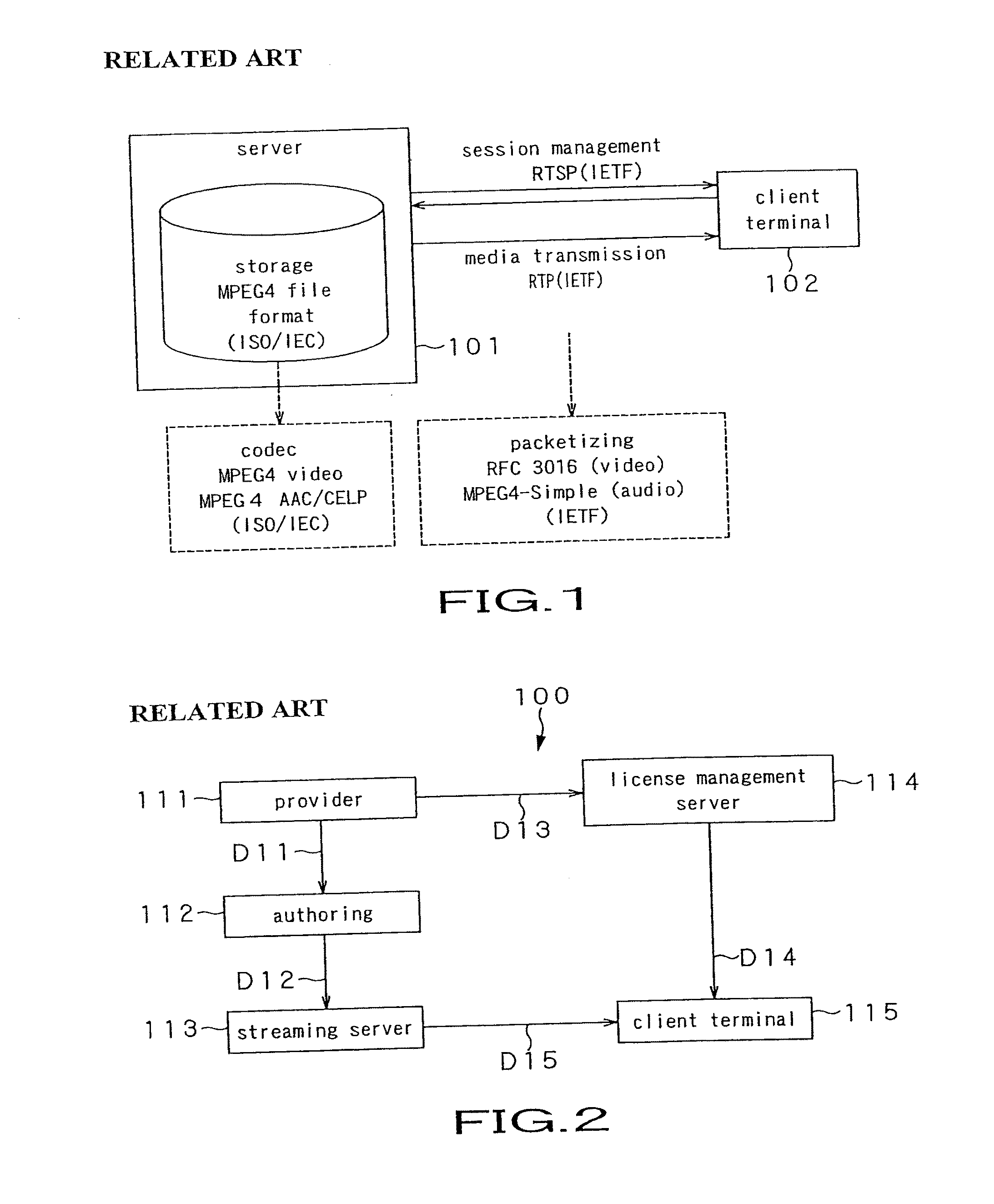
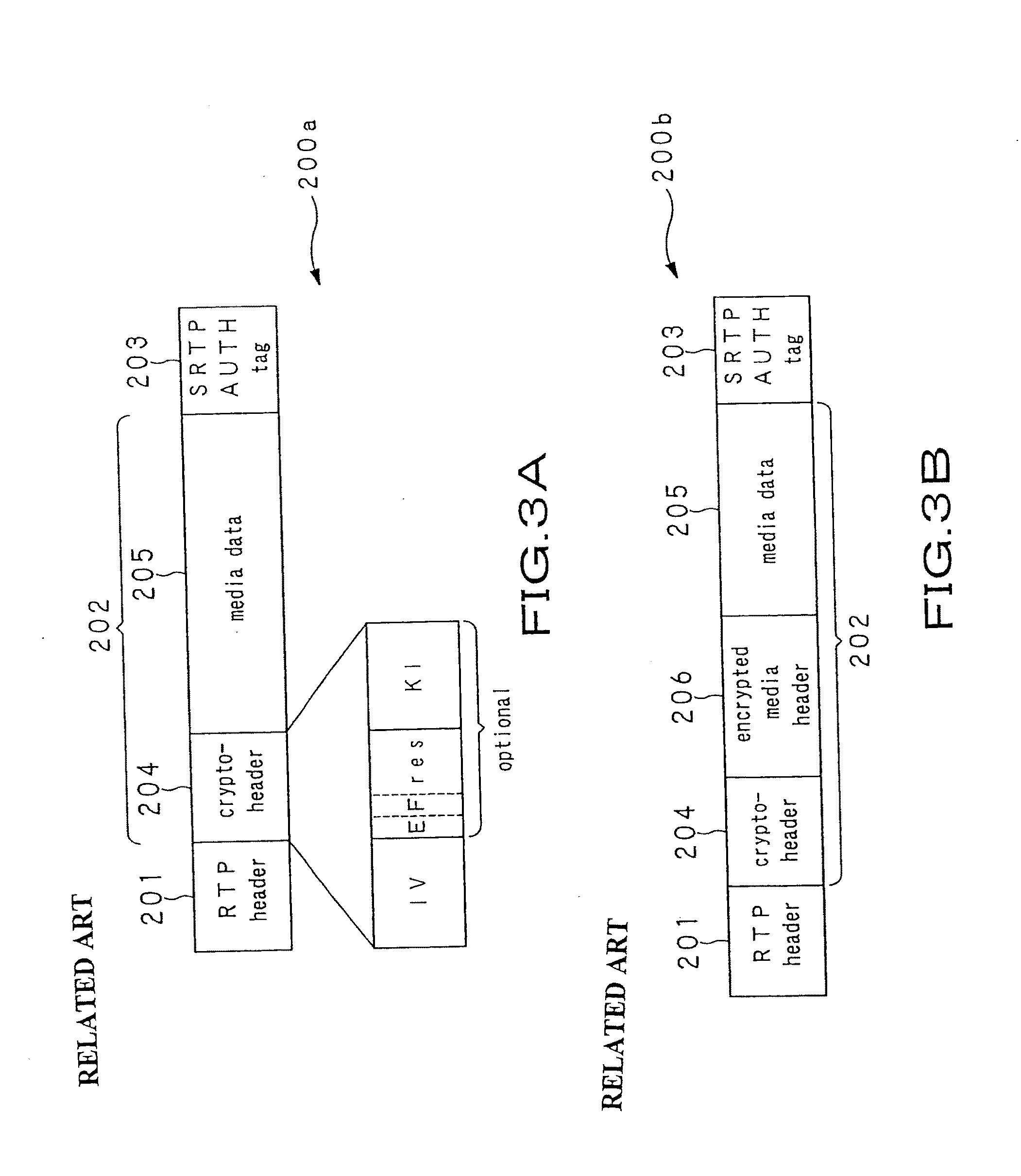
A streaming system includes an authoring unit (2), a stream server (3) and a client terminal (5). The authoring unit generates a file composed of encrypted contents data and the ancillary information at least containing the packetizing control information for generating an RTP packet, a non-encrypted codec dependent header made up of the information pertinent to encoded contents data, and the encryption information for decrypting the encrypted contents data form packet to packet. The streaming server packetizes the encrypted contents data along with at least the codec dependent header and distributes the resulting data as a stream. The client terminal refers to the codec dependent header of the received packet, re-assembles the packet, and decrypts the encrypted contents data of the re-assembled packet to generate contents data.
Owner:SONY CORP
Method and computer system for managing data exchanges among a plurality of network nodes in a managed packet network
InactiveUS6938080B1Security bandwidthSecurity content deliveredMetering/charging/biilling arrangementsMultiple digital computer combinationsHigh-definition televisionHigh bandwidth
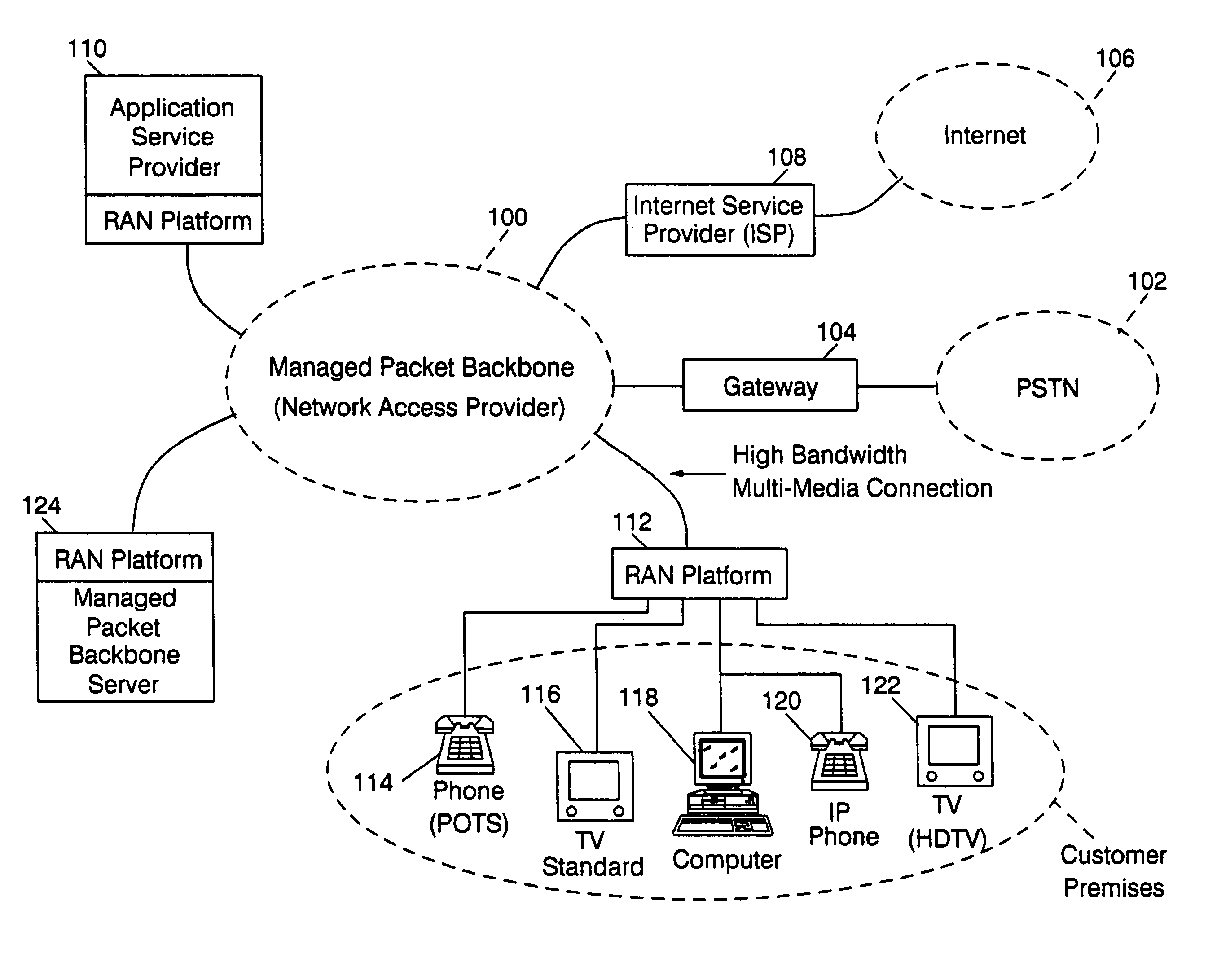
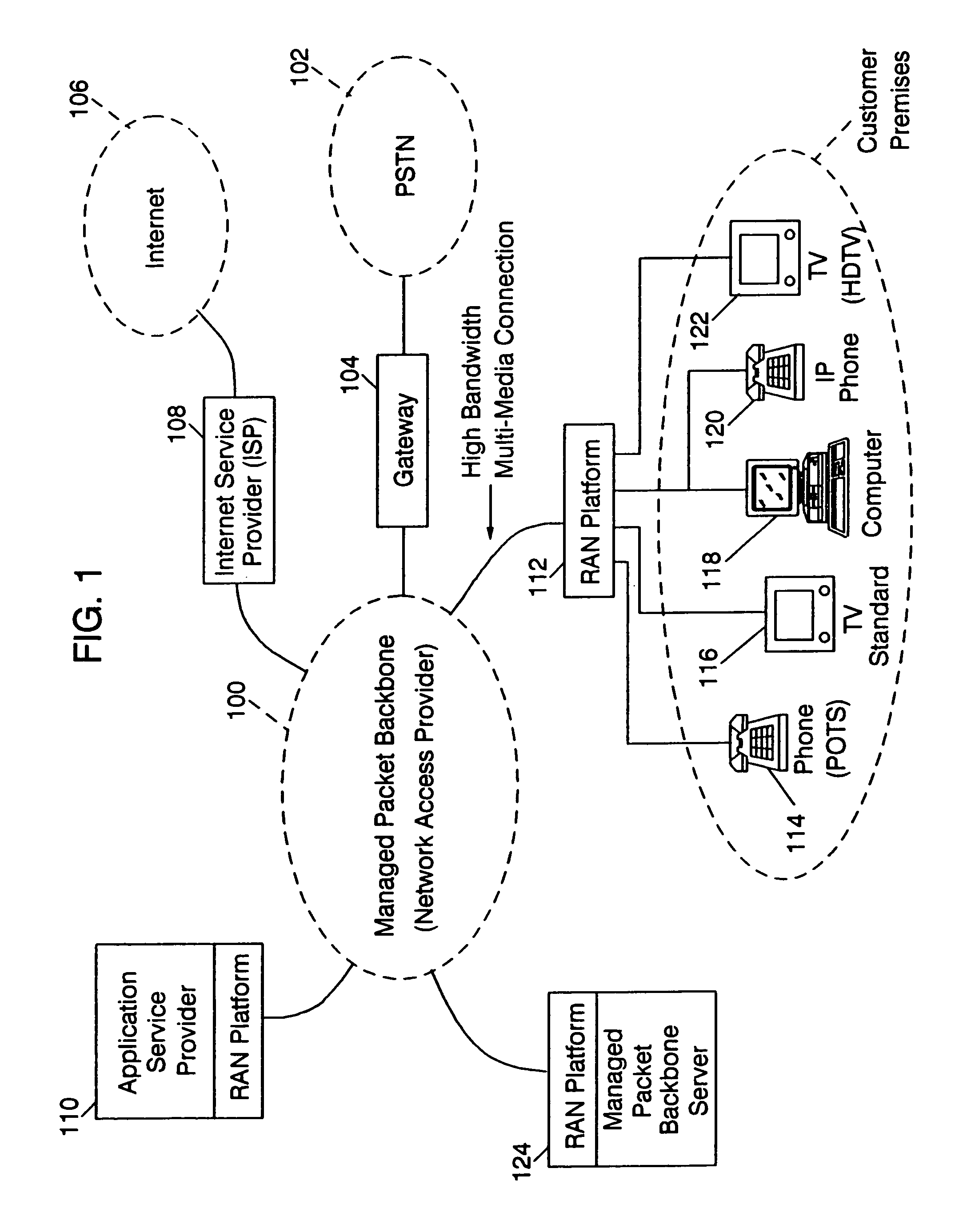
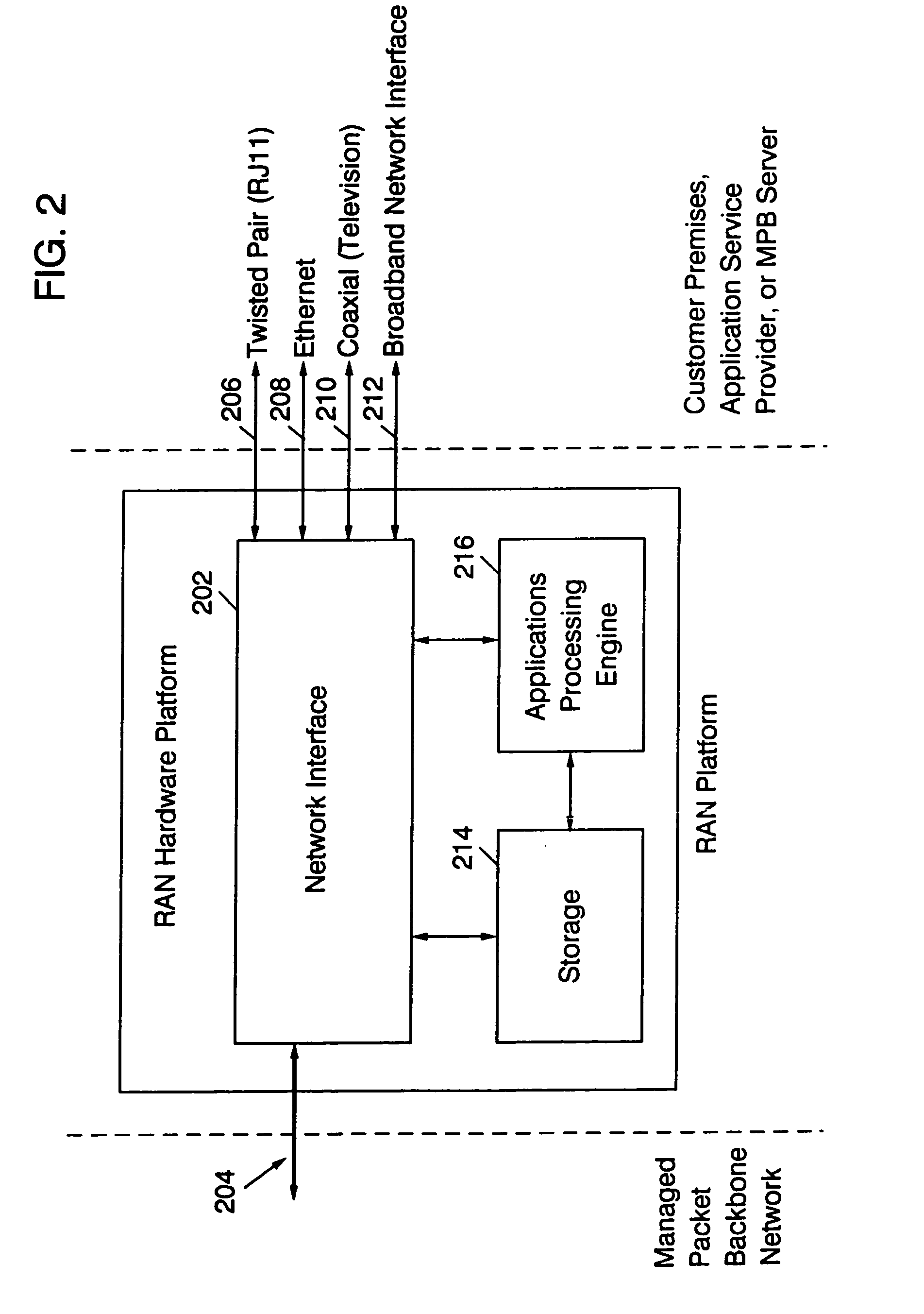
A residential access node (RAN) running a RAN platform 112 which includes means for interfacing a plurality of peripheral equipment such as analog (POTS) phones 114, standard televisions 116, computers 118, IP telephones 120, and high definition televisions 122 to a packet data network 100. The Network Access Provider RAN platform 124 manages sessions among Customer Premises RAN platforms 112 and Application Service Provider RAN platforms 110 over high bandwidth connections. The Customer Premises RAN platform 112 also determines the number and type of data packets entering or departing via the packet data network 100. Such an architecture allows for the efficient transfer of services (data content) from Application Service Providers to individual network access subscribers by seamlessly accommodating various data types and providing an integrated metering and billing mechanism managed by the Network Access Provider.
Owner:RPX CLEARINGHOUSE
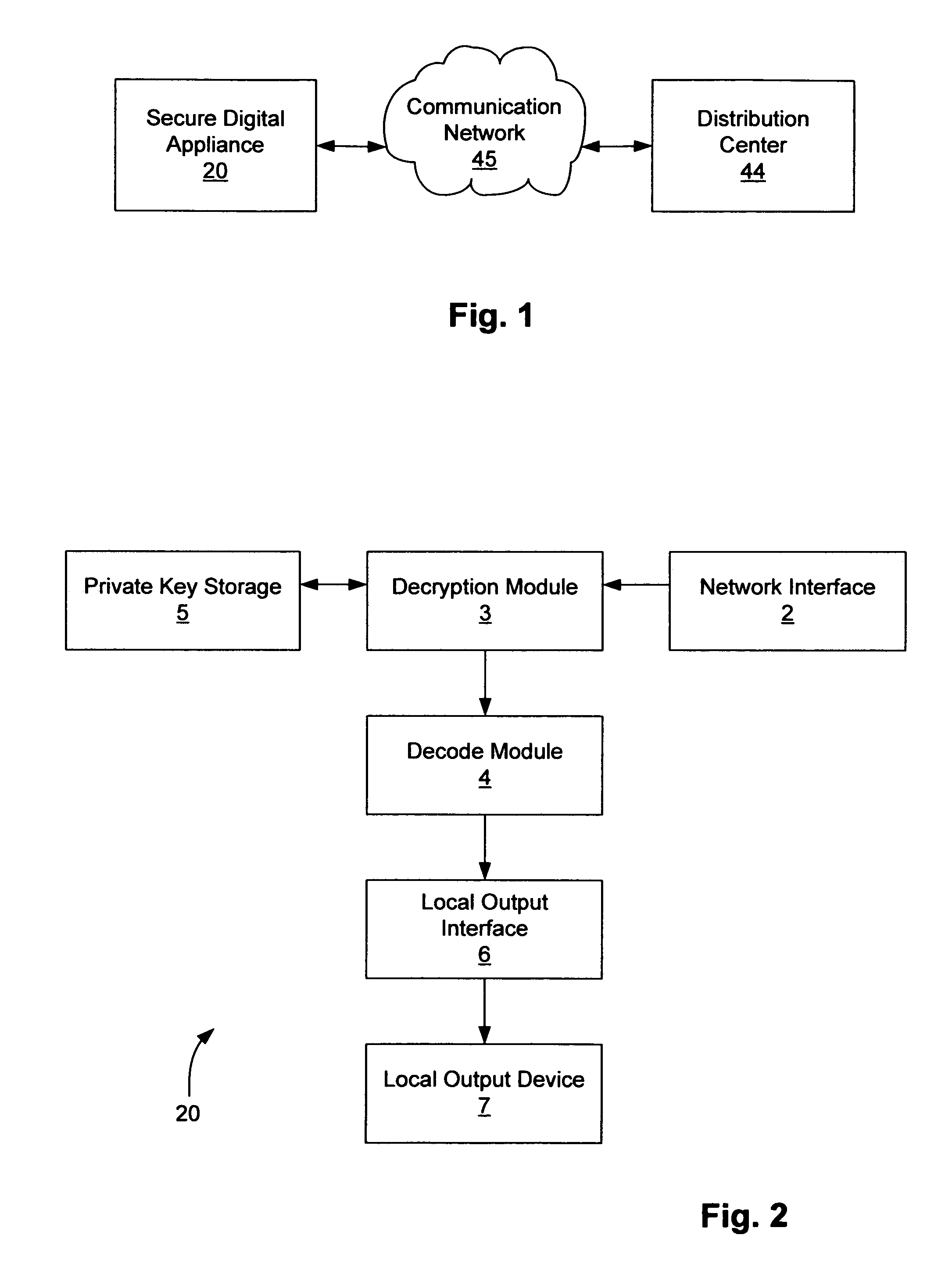
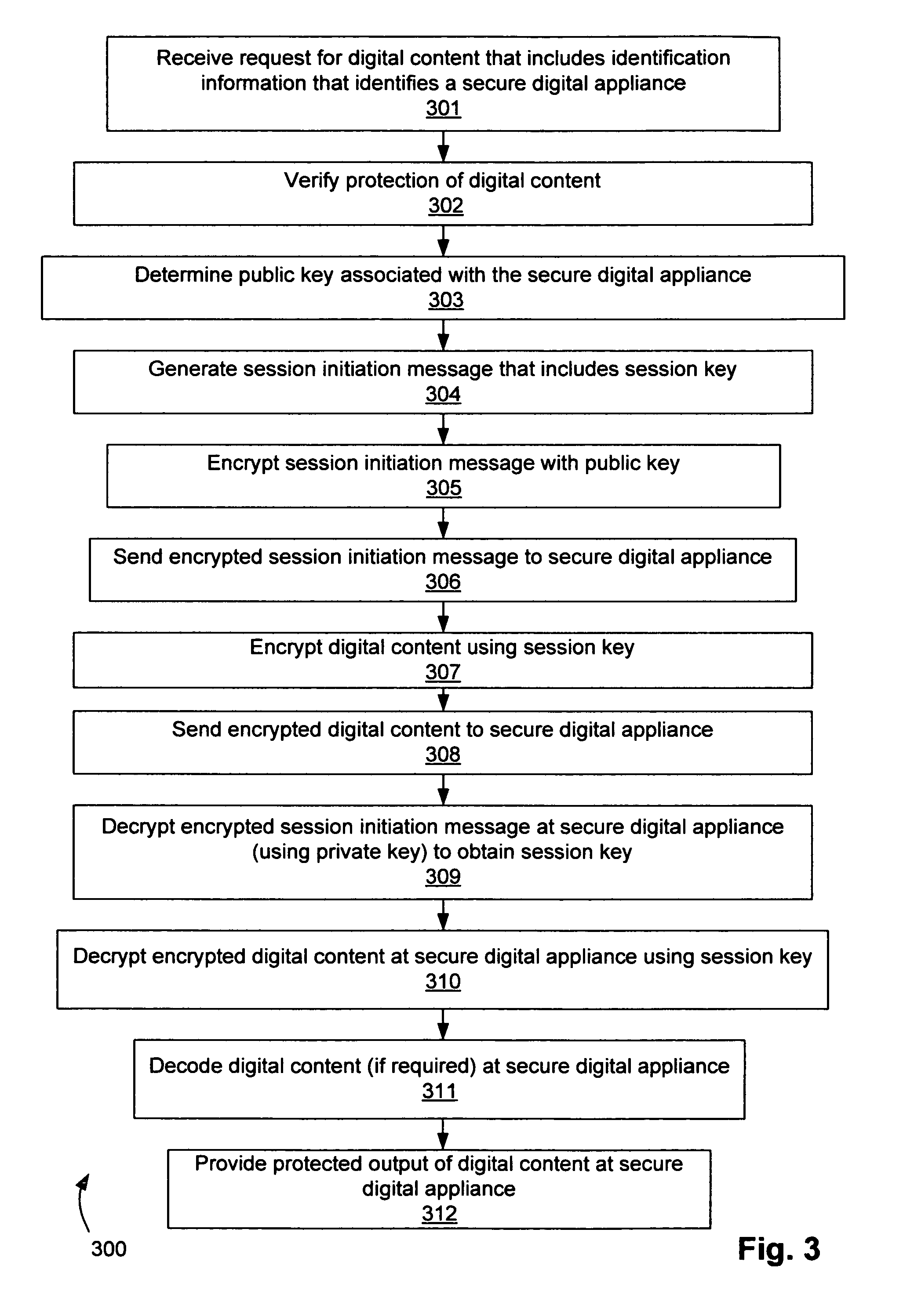
Secure digital appliance and method for protecting digital content
InactiveUS7062658B1Quality improvementSure easyData processing applicationsUnauthorized memory use protectionDigital contentDigital copy
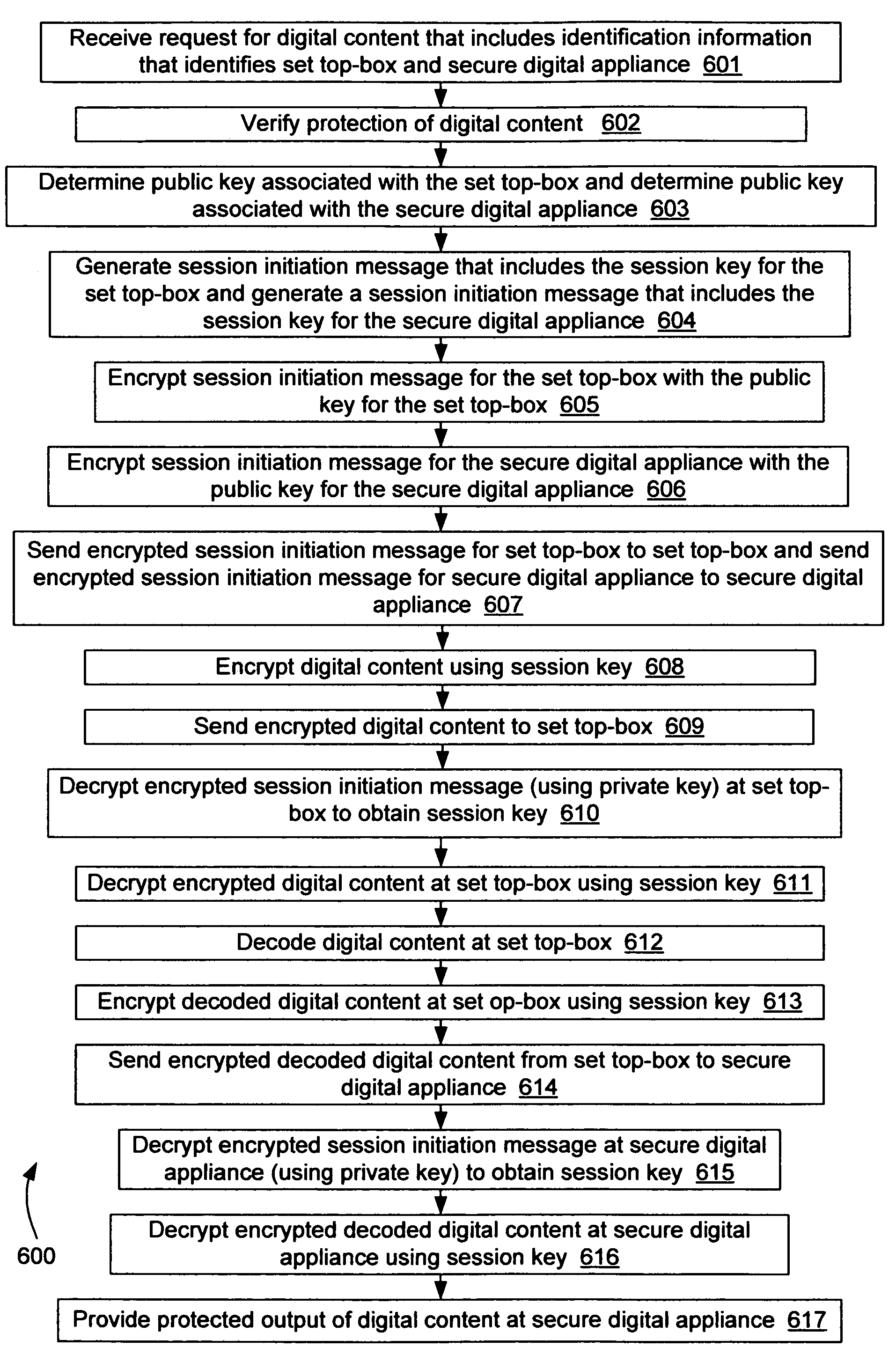
A method and apparatus for protecting digital content. A secure digital appliance is disclosed for receiving communications coupled over a communication network. A private key of a private key and public key pair is stored in the secure digital appliance in such a way that the stored private key cannot be obtained by tampering with the secure digital appliance. Upon receipt of a session initiation message that is encrypted using the public key (of the private key and public key pair) the secure digital appliance decrypts the session initiation message using the stored private key to obtain a session key. The session key is then used to decrypt communications that include encrypted digital content. The secure digital appliance includes a local output device (e.g., a TV screen and / or speakers) that is operable to provide protected output of the digital content. The secure digital appliance does not contain any provision for output other than the protected output of digital content. Because the secure digital appliance does not allow for any output of the digital content other than the protected output, the end user cannot obtain a high quality digital copy of the digital content. Therefore, there is little chance that the security of digital content will be compromised.
Owner:CISCO TECH INC
Stable thermos multi-cup
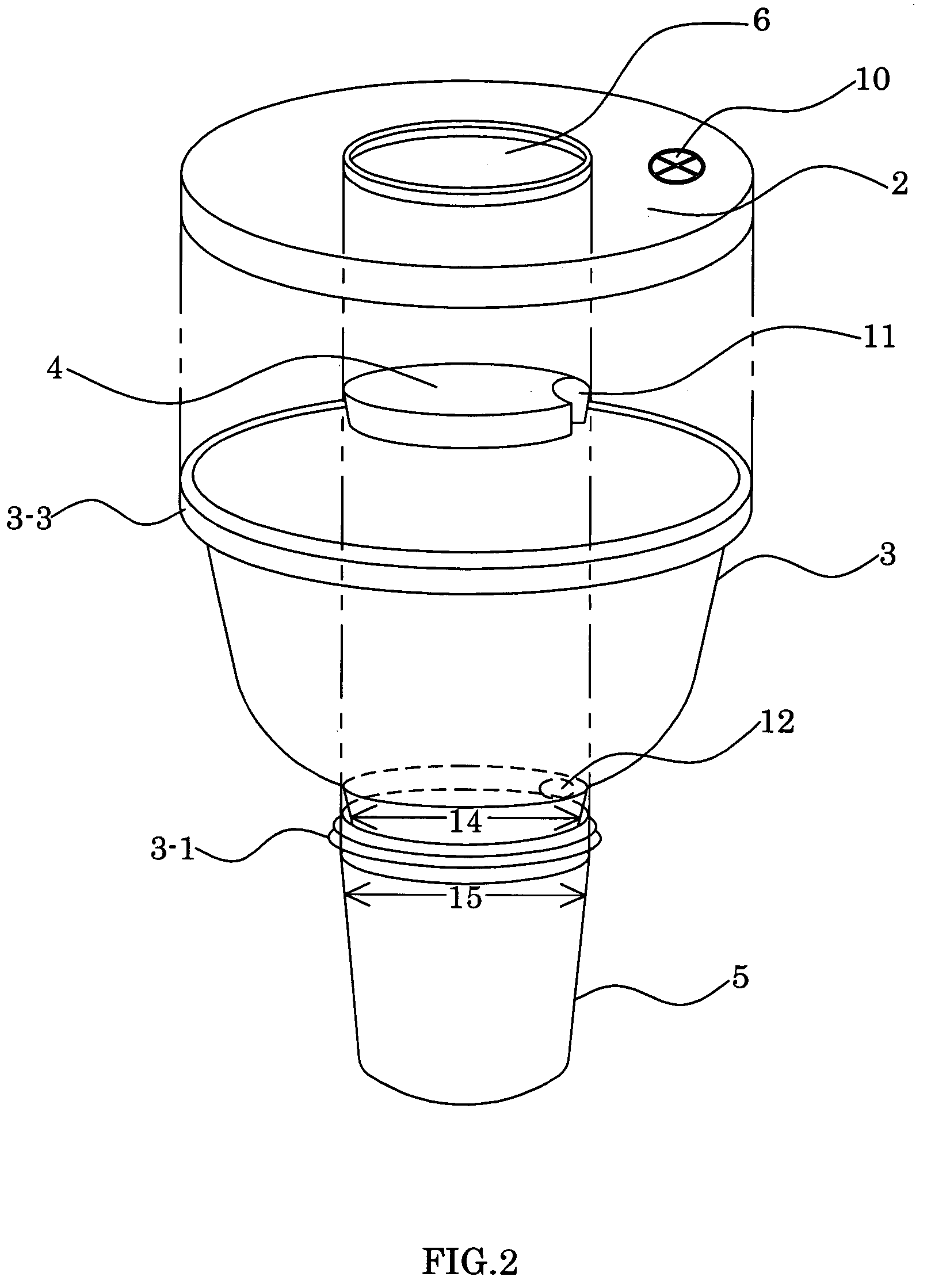
A novel combination cup for carrying soft drinks and snacks within one cup structure is comprised of: 1) an upper cup body, 2) a lid cover for the upper cup body, 3) an insulating plate 4) a ring, and, 5) a lower cup body jointed together. The upper cup body lid cover may be used as cup holder to prevent the cup from falling over and spilling its contents. The lower cup body may be used to contain liquid drinks while the upper cup body may be used to contain solid snacks. The convenient combination of this invention enables a user to eat and drink using only one hand, and also to enjoy the cool or hot temperature of the drinks longer and safer.
Owner:CHA WON IL
Semiconductor memory card
InactiveUS20070101143A1Increase storage capacityMaximum flexibilityInput/output to record carriersUser identity/authority verificationCommunication unitMemory cards
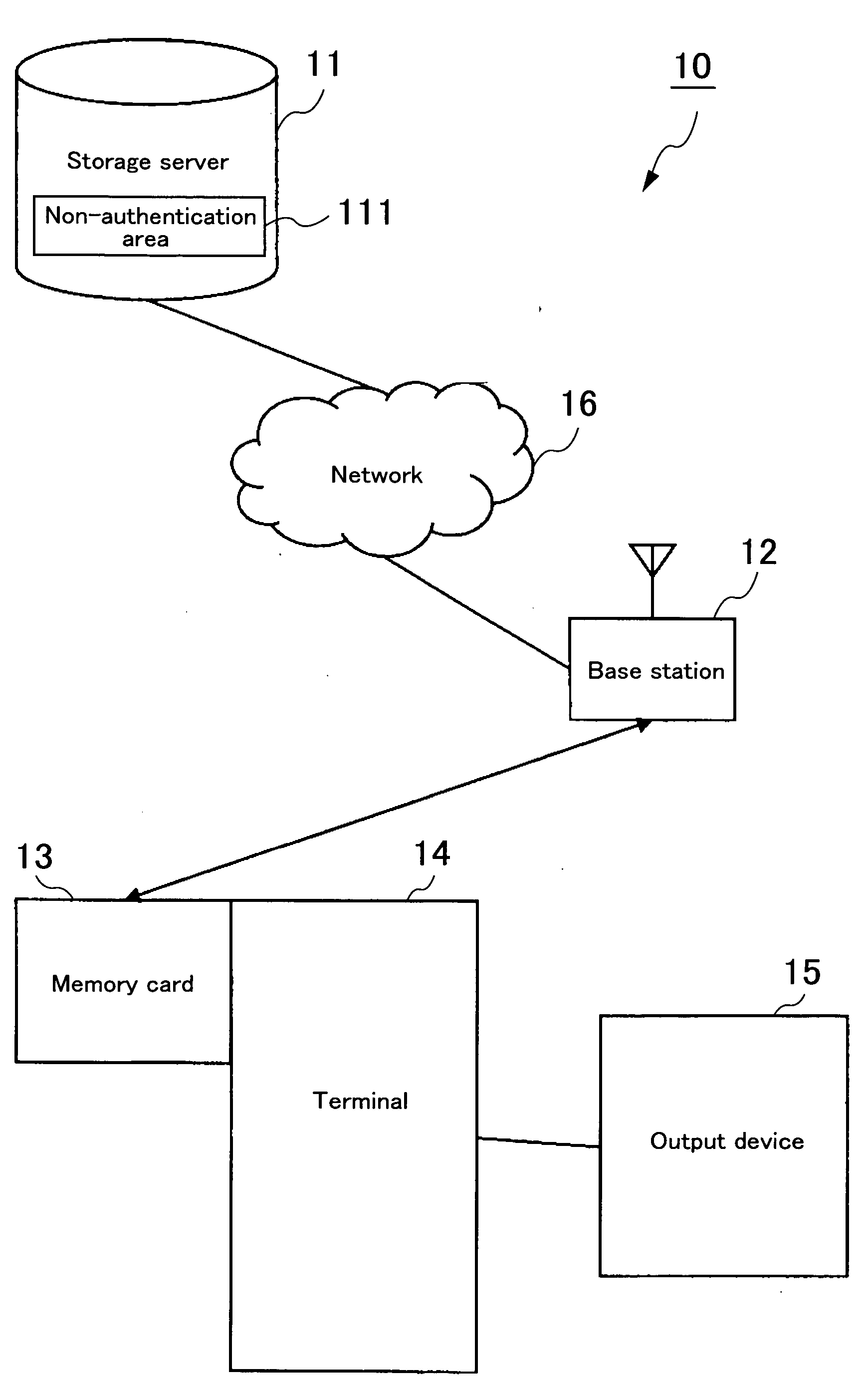
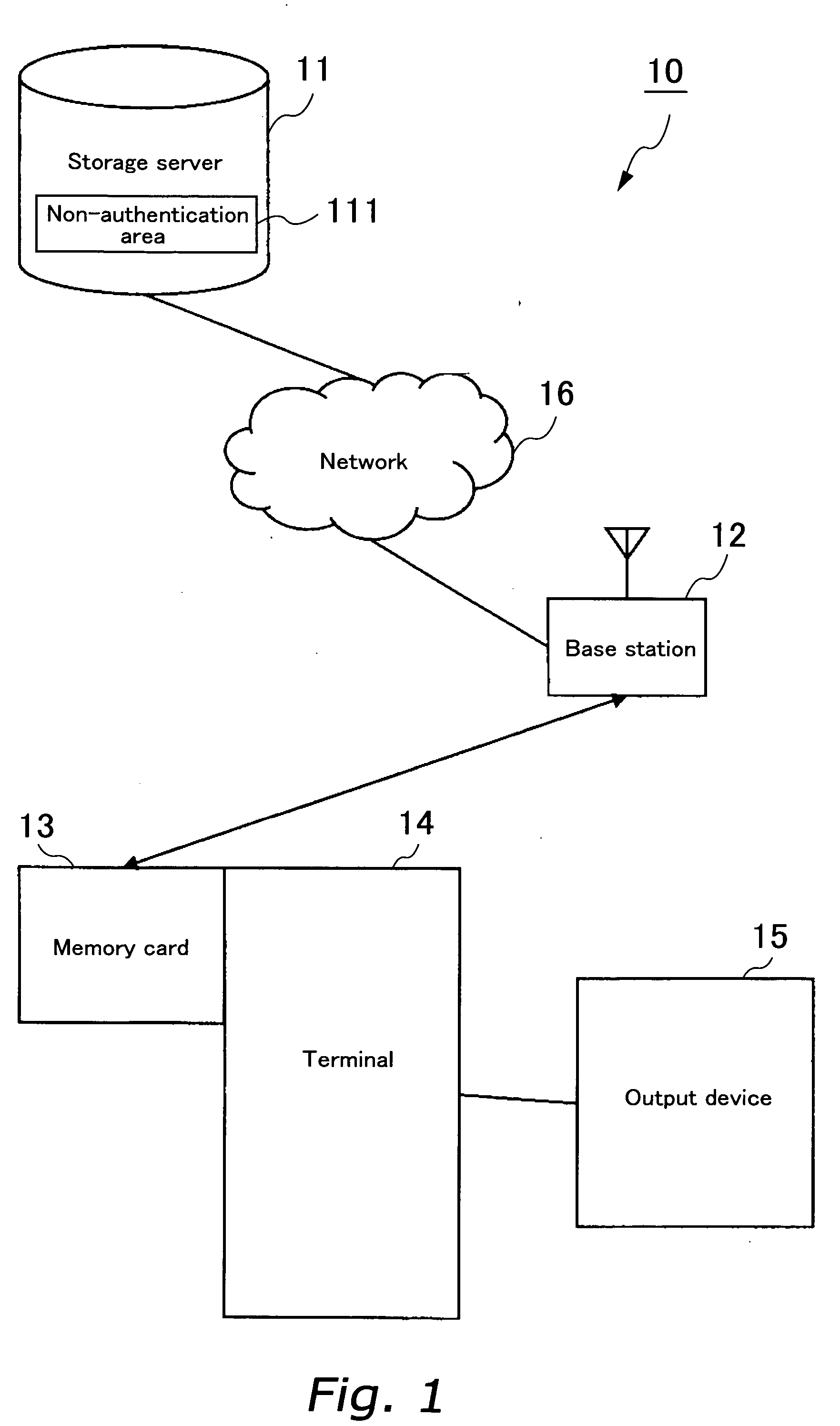
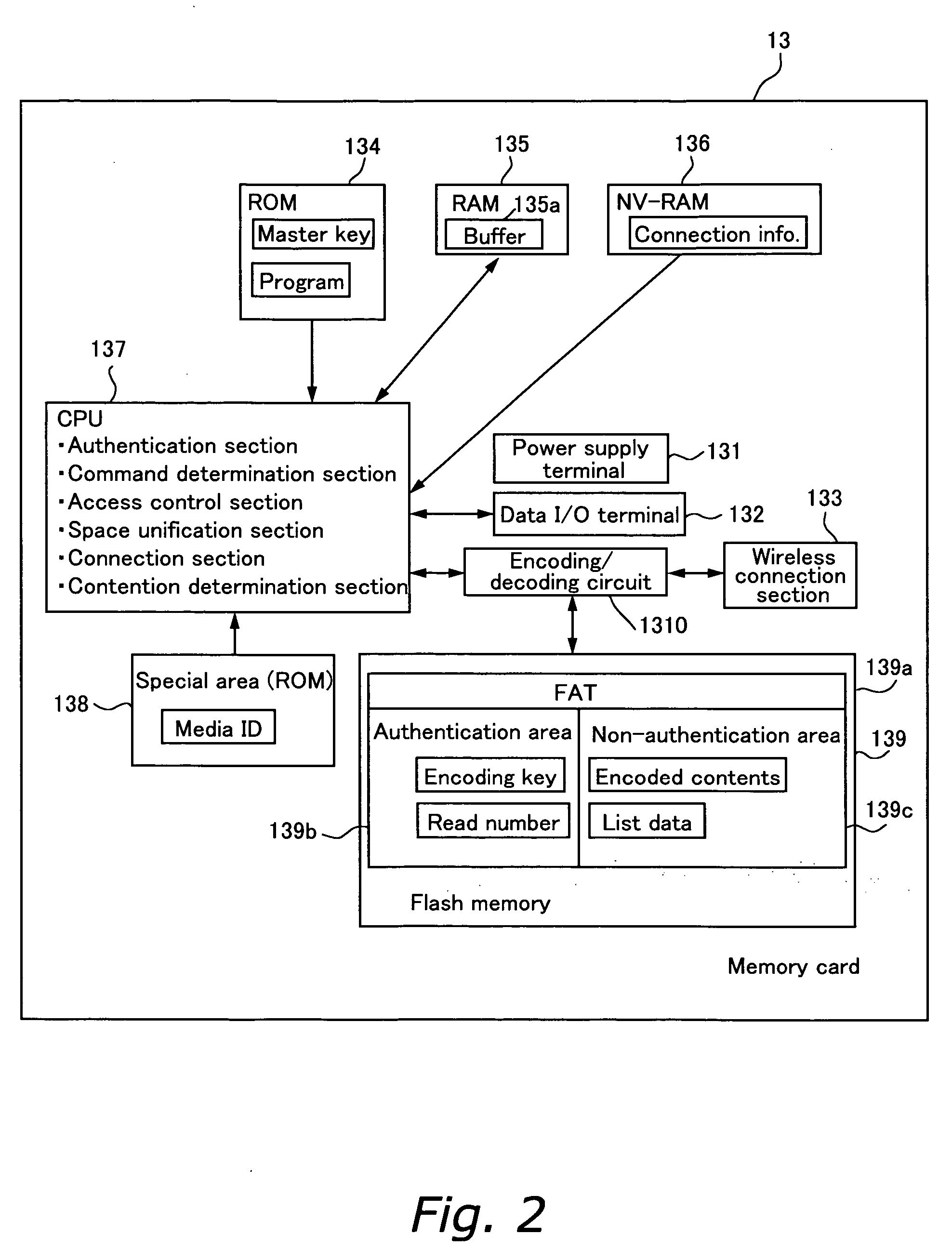
A memory card 13 includes wireless network communication unit for having electronic equipment to access a storage server 11 on a network. The storage server 11 includes at least a non-authentication area 111. Data such as contents is written into a non-authentication area of the memory card 13 or the non-authentication area 111 of the storage server 11. In other words, an area of a storage area to which data can be written is expanded by the non-authentication area 111 of the storage server 11. Thus, the non-authentication area of the memory card 13 increases apparently. Encoding key used for encoding and decoding contents protected by copyrights is written to an authentication area on the memory card 13. Anyone can access content data in the non-authentication area 111 of the storage server 11, but an encoding key required for decoding the content is in the memory card 13. Thus, only a person who has the memory card 13 and valid electronic equipment can decode, reproduce and output the content using the encoding key. In this way, the storage capacity of the memory card 13 can be increased apparently while security of data protected by copyrights is guaranteed.
Owner:PANASONIC CORP
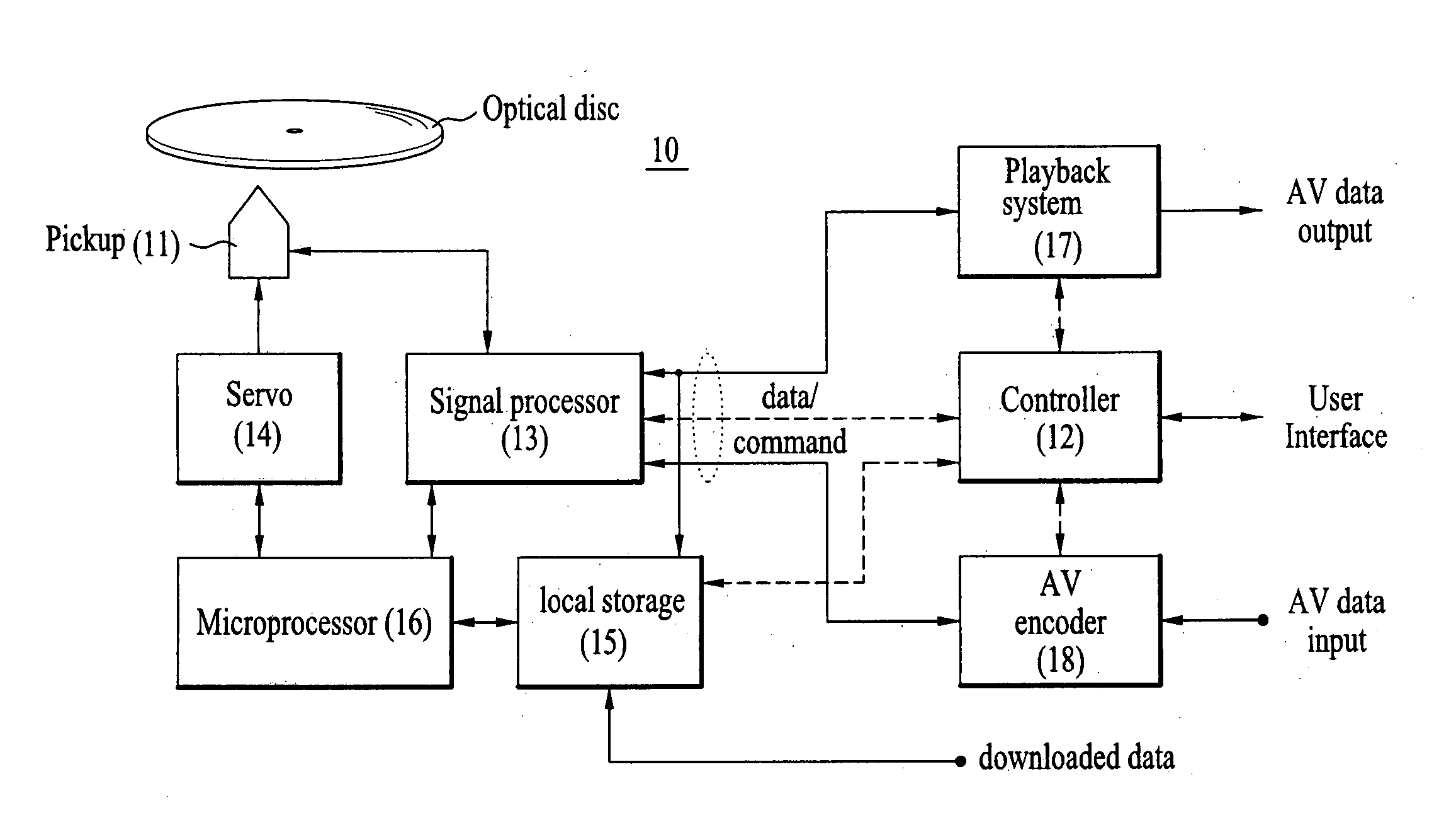
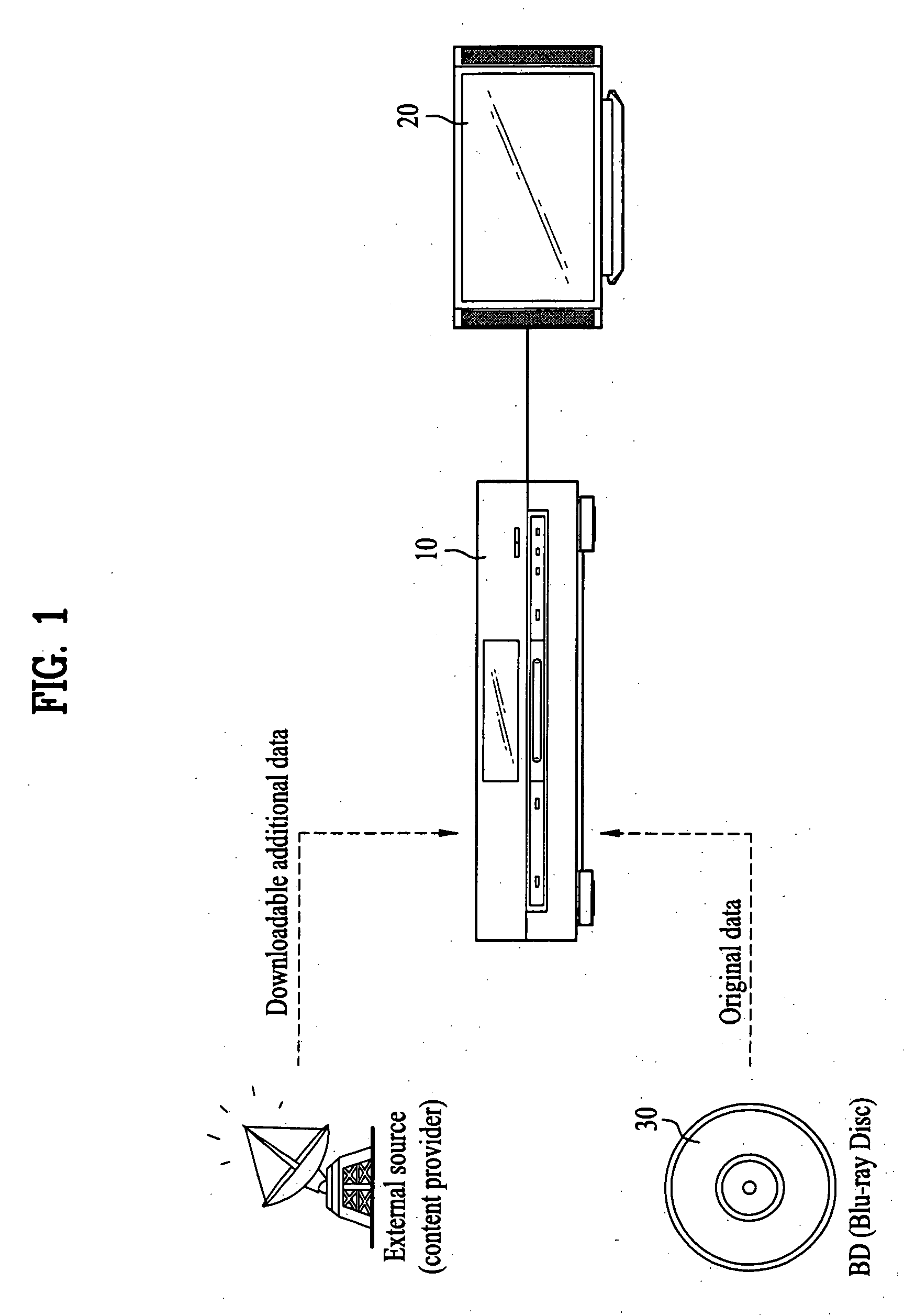
Method and apparatus for protecting shared data and method and apparatus for reproducing data from recording medium using local storage
InactiveUS20060153017A1Function increaseKeep Content SafeElectronic editing digitised analogue information signalsUsing non-detectable carrier informationComputer hardwareApplication software
A method and apparatus for protecting shared data and method and apparatus for reproducing data from a recording medium using a local storage are disclosed. The present invention includes downloading the shared data associated with a recording medium to a local storage and permitting an application having valid access information for the shared data to access the shared data. The present invention includes downloading encrypted shared data associated with the recording medium to the local storage, constructing a virtual package including the shared data by binding data within the local storage to data within the recording medium, decrypting the shared data using the virtual package, and reproducing the decrypted shared data. Accordingly, the contents provided by an authentic content provider and the non-transmuted contents can be reproduced, whereby the shared data can be protected. And, the shared data can be protected against a malicious function caused by an unauthorized application.
Owner:LG ELECTRONICS INC
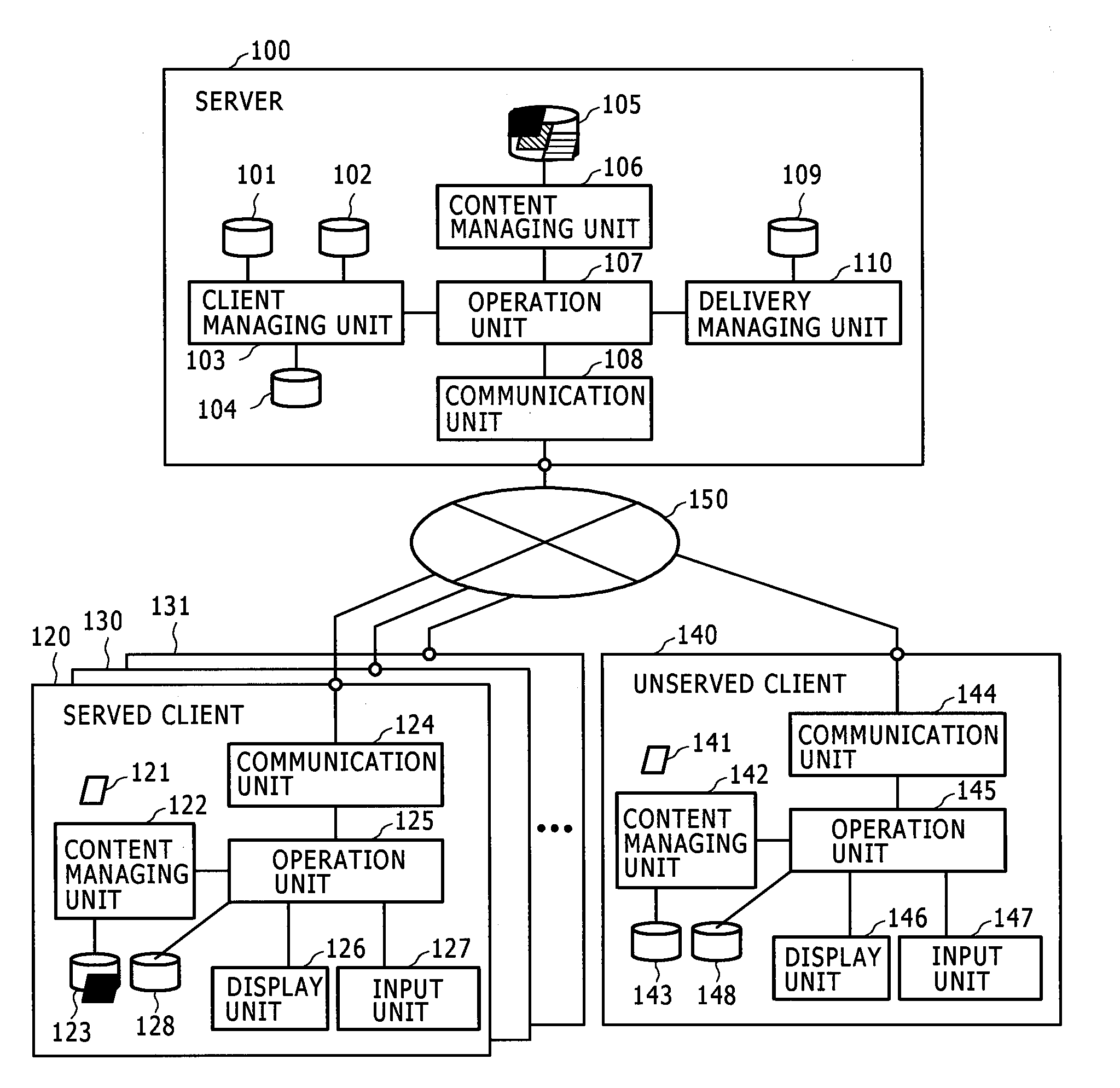
Content delivery method, server, and terminal
ActiveUS20090138576A1Safer content deliveryReduce riskDigital data protectionMultiple digital computer combinationsClient-sidePeer-to-peer
In hybrid peer-to-peer type content delivery, a server confirms user's intension as to content disclosure, guarantees content delivery by mutual authentication between a client to which content has been delivered and a client to which content has not been delivered, and guarantees the integrity of content having been delivered. Further, the server configures delivery connection based on the network relationship between the clients and priority factors taking account of a reservation status.
Owner:HITACHI LTD
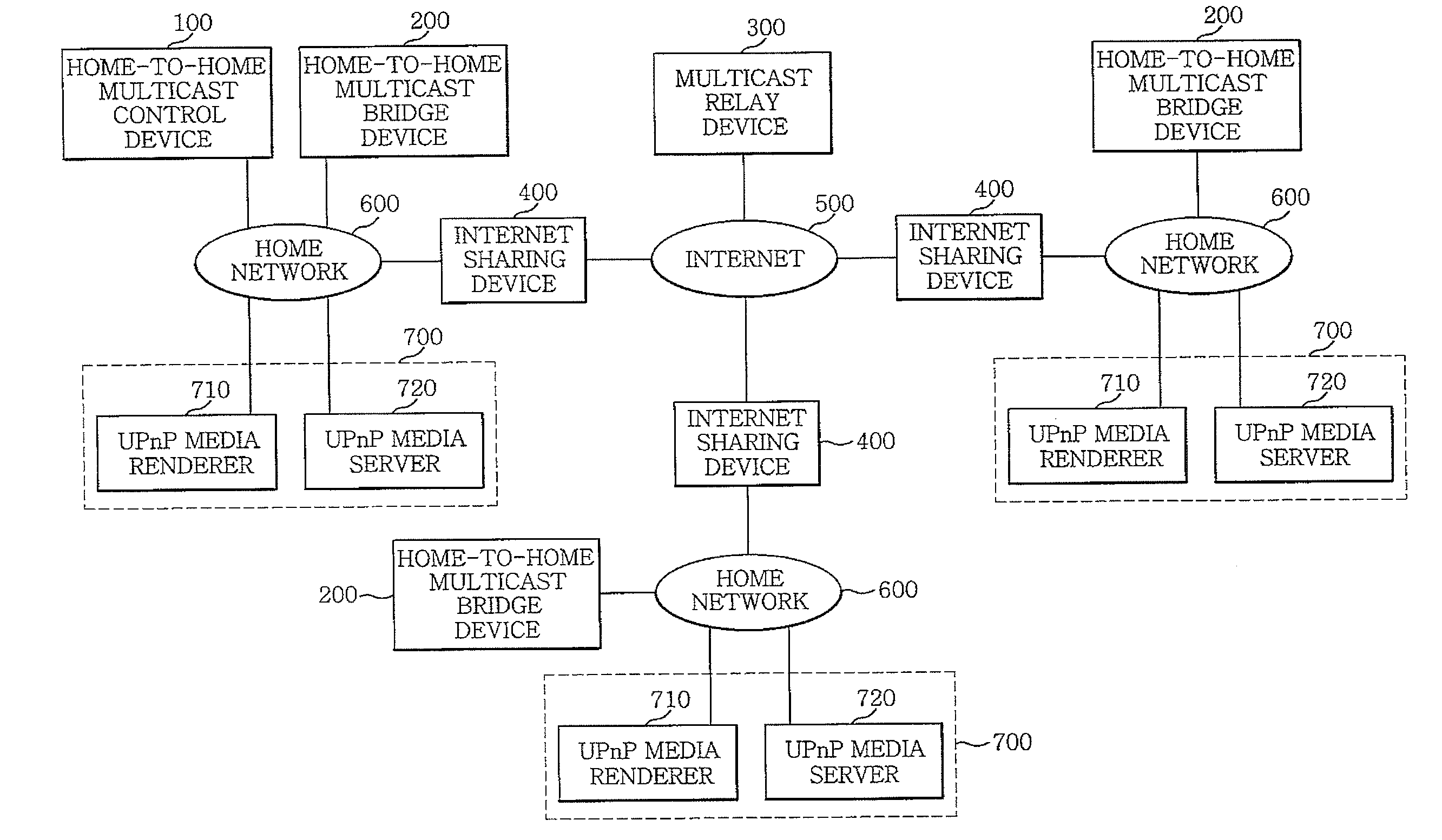
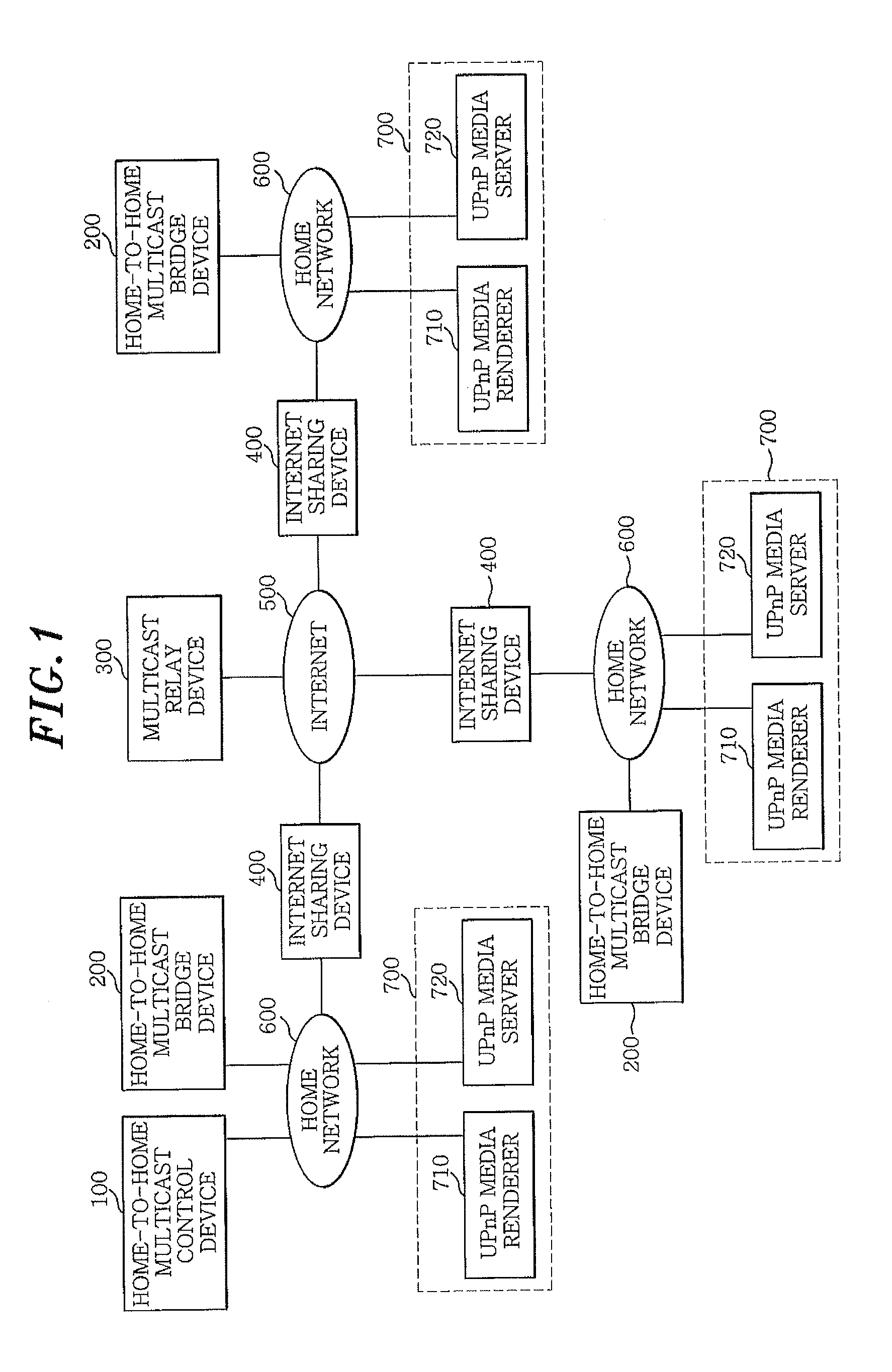
Method and apparatus for multicasting contents between devices in networks
ActiveUS20100135296A1Less network resourceKeep Content SafeError preventionTransmission systemsComputer networkRelay
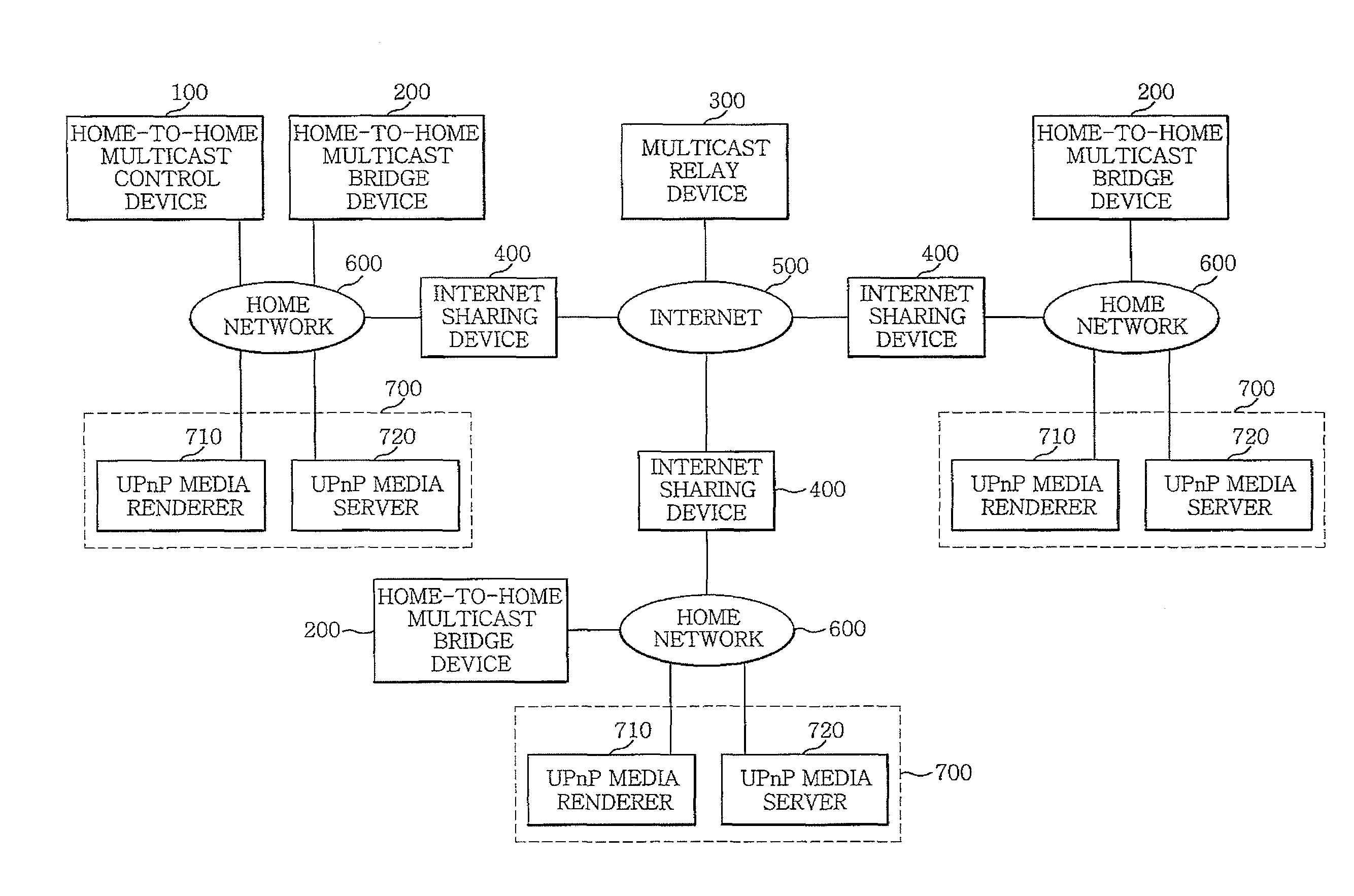
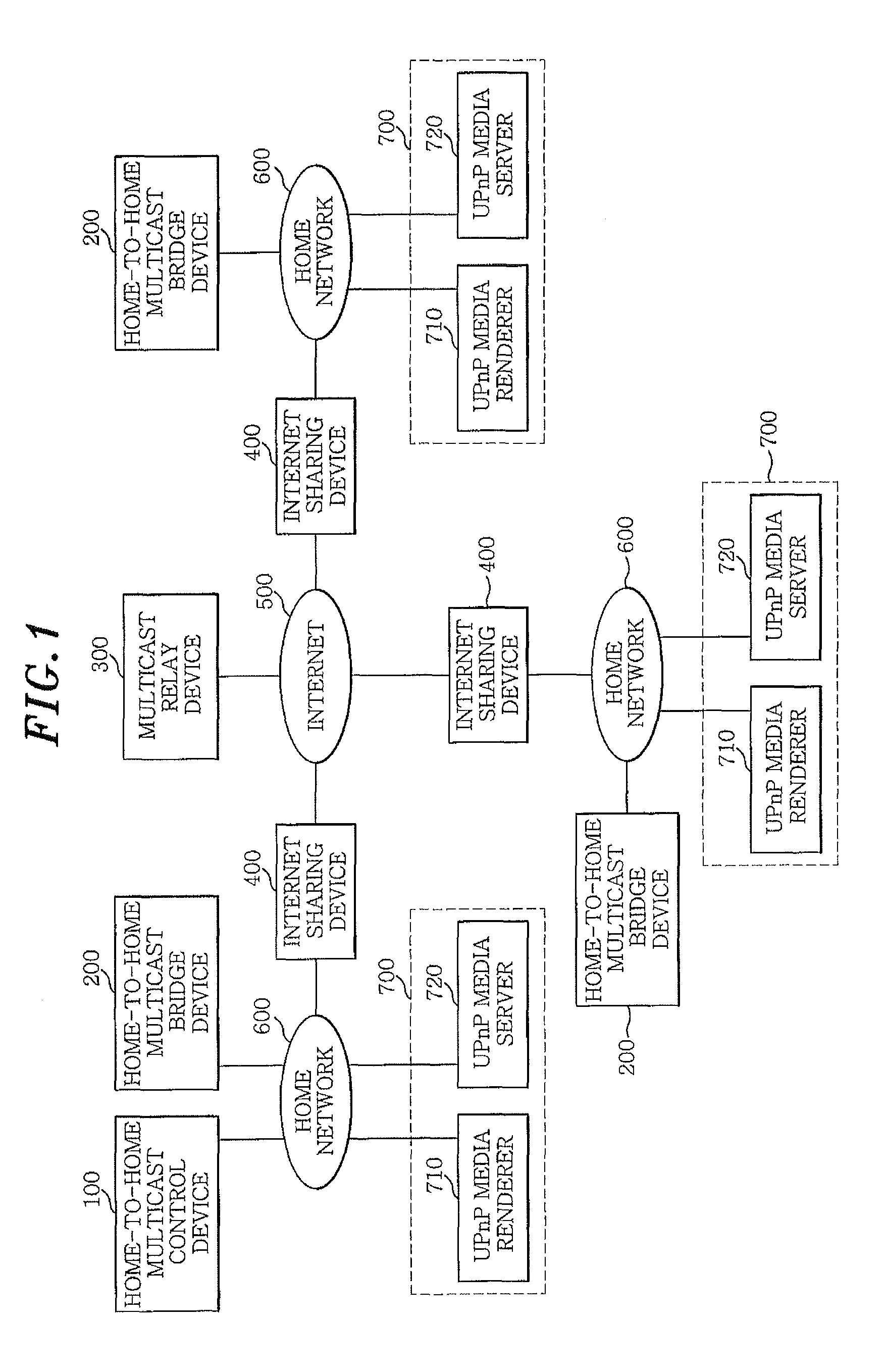
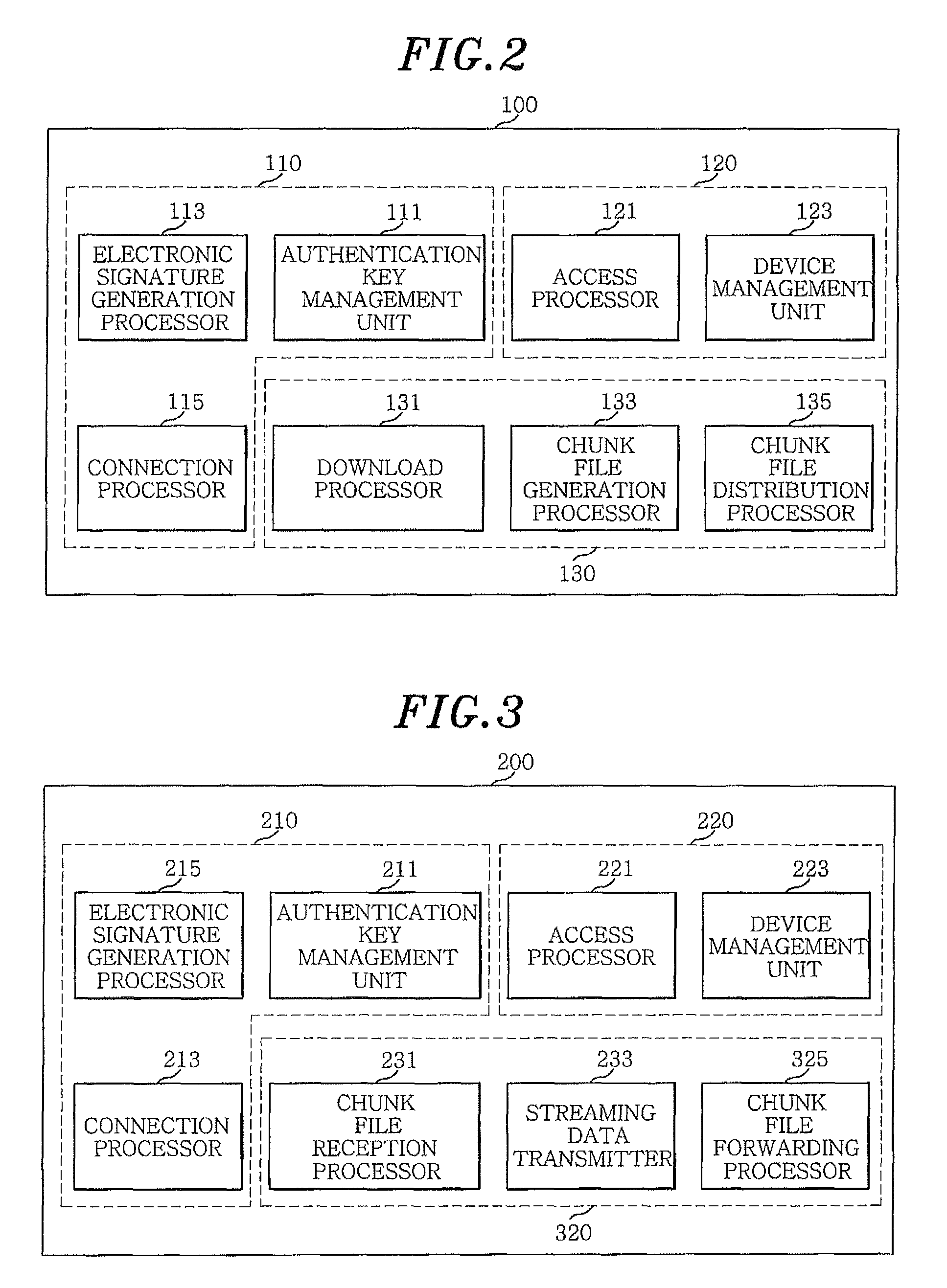
An apparatus for multicasting contents between devices in different networks includes: a home-to-home multicast control device for finding the devices in the networks, downloading contents from a device in a network to which the home-to-home multicast control device belongs, processing the contents to generate file blocks, each file block having chunk files, and multicasting the processed contents to the devices in the networks; and at least one home-to-home multicast bridge device for receiving the contents transmitted from the home-to-home multicast control device and streaming the contents to one or more devices in a network to which the home-to-home multicast bridge device belongs. The apparatus further includes a multicast relay device for relaying the contents between the home-to-home multicast control device and the home-to-home multicast bridge device.
Owner:ELECTRONICS & TELECOMM RES INST
Method for implementing multimedia information content protection
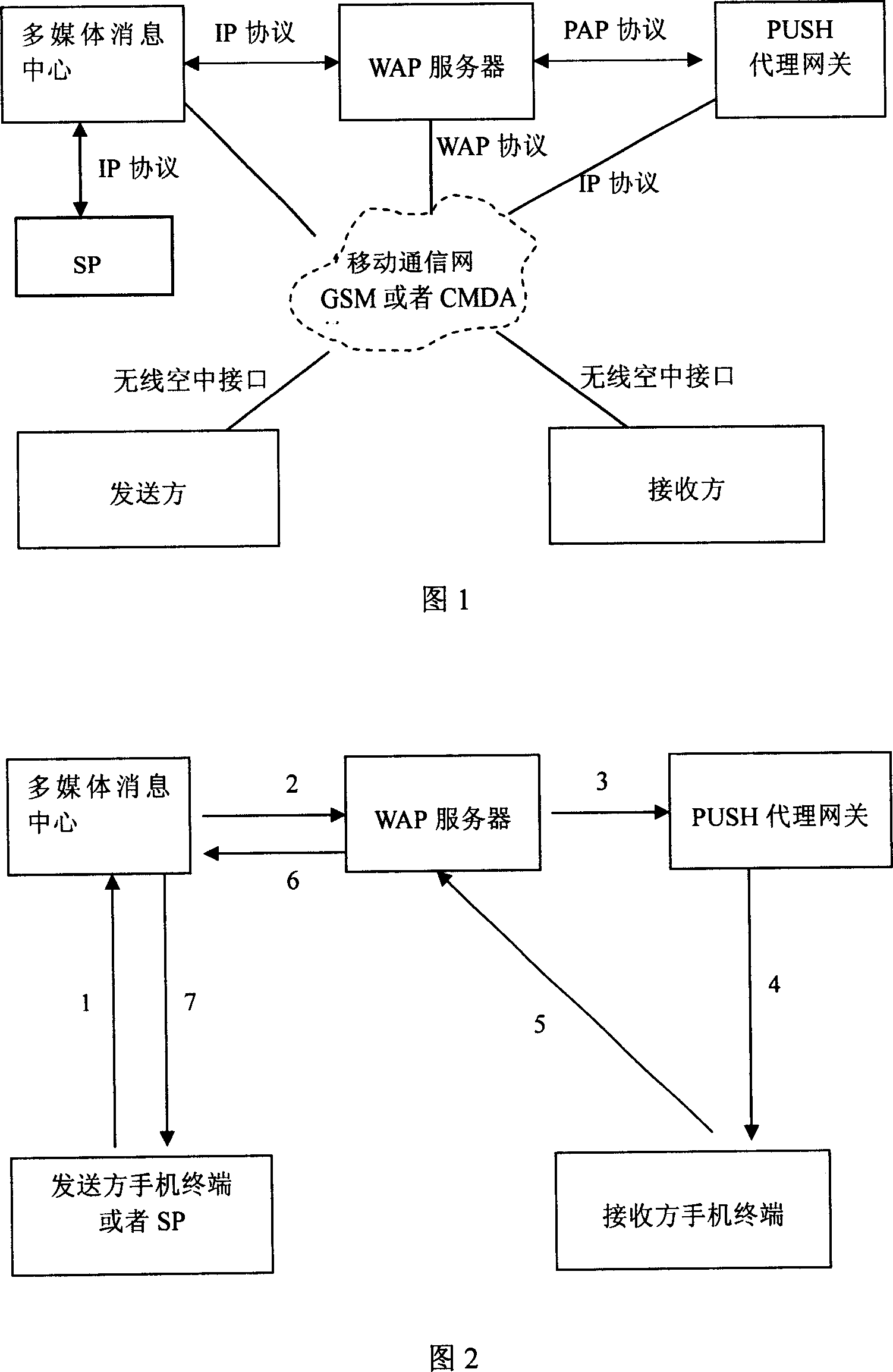
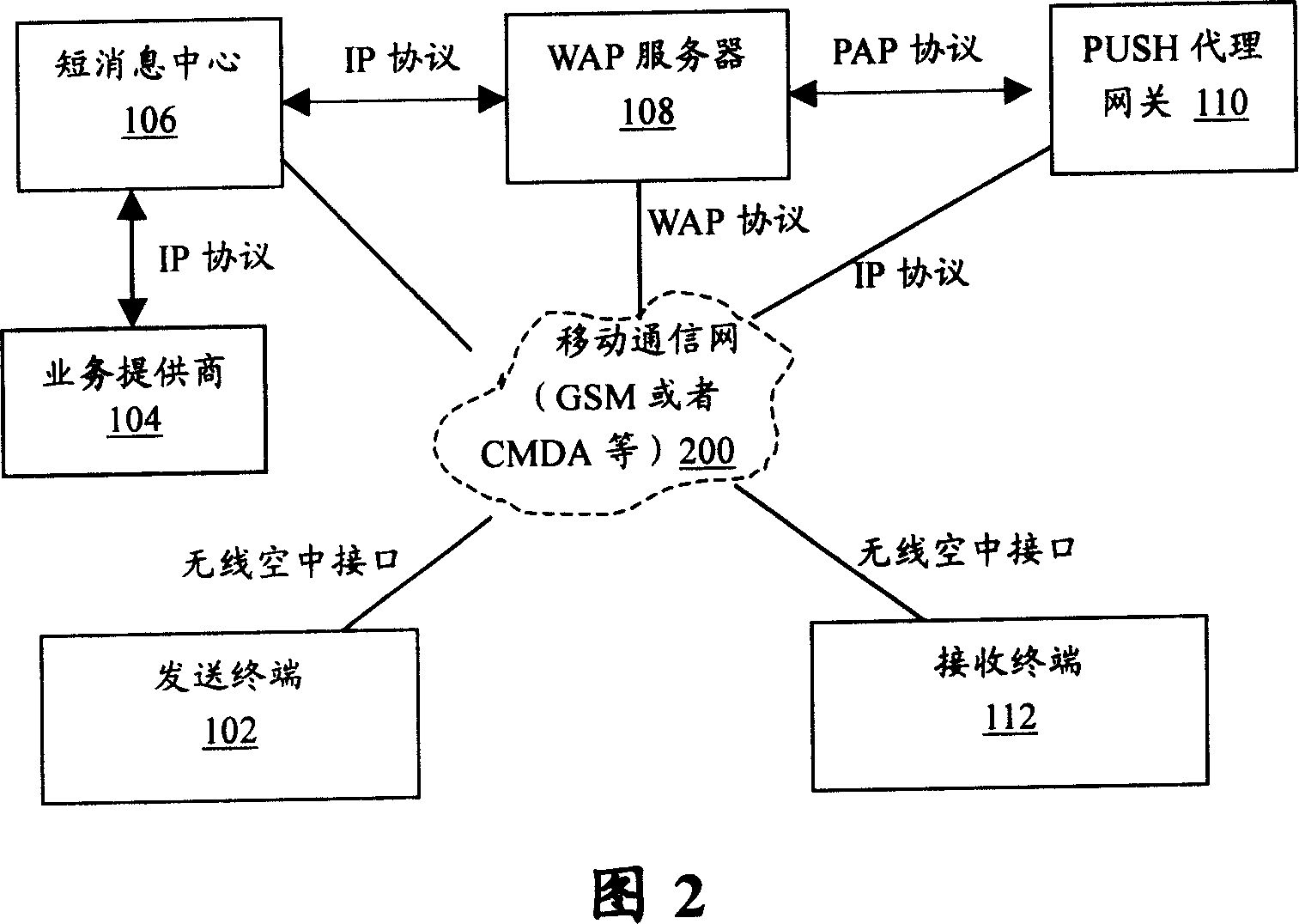
InactiveCN101098338AKeep Content SafeSpecial service provision for substationUser identity/authority verificationComputer compatibilityComputer terminal
The invention relates to a multimedia message content protecting technique of mobile communication network, in particular to a method for protecting multimedia message content. The invention adds a WAP server in a mobile communication network, stores and generates a WAP webpage of protected multimedia message content, sends the URL linkage of the WAP webpage via PUSH message to a PUSH proxy network gate. The invention can effectively protect the content safety of multimedia message, and holds the control priority of multimedia message content in sender or SP. Therefore, multimedia message receiver is limited to access multimedia message, without storage, edit, and transfer abilities, to protect the safety of multimedia message content. And the invention is not based on DRM function of mobile phone, with better compatibility.
Owner:ZTE CORP
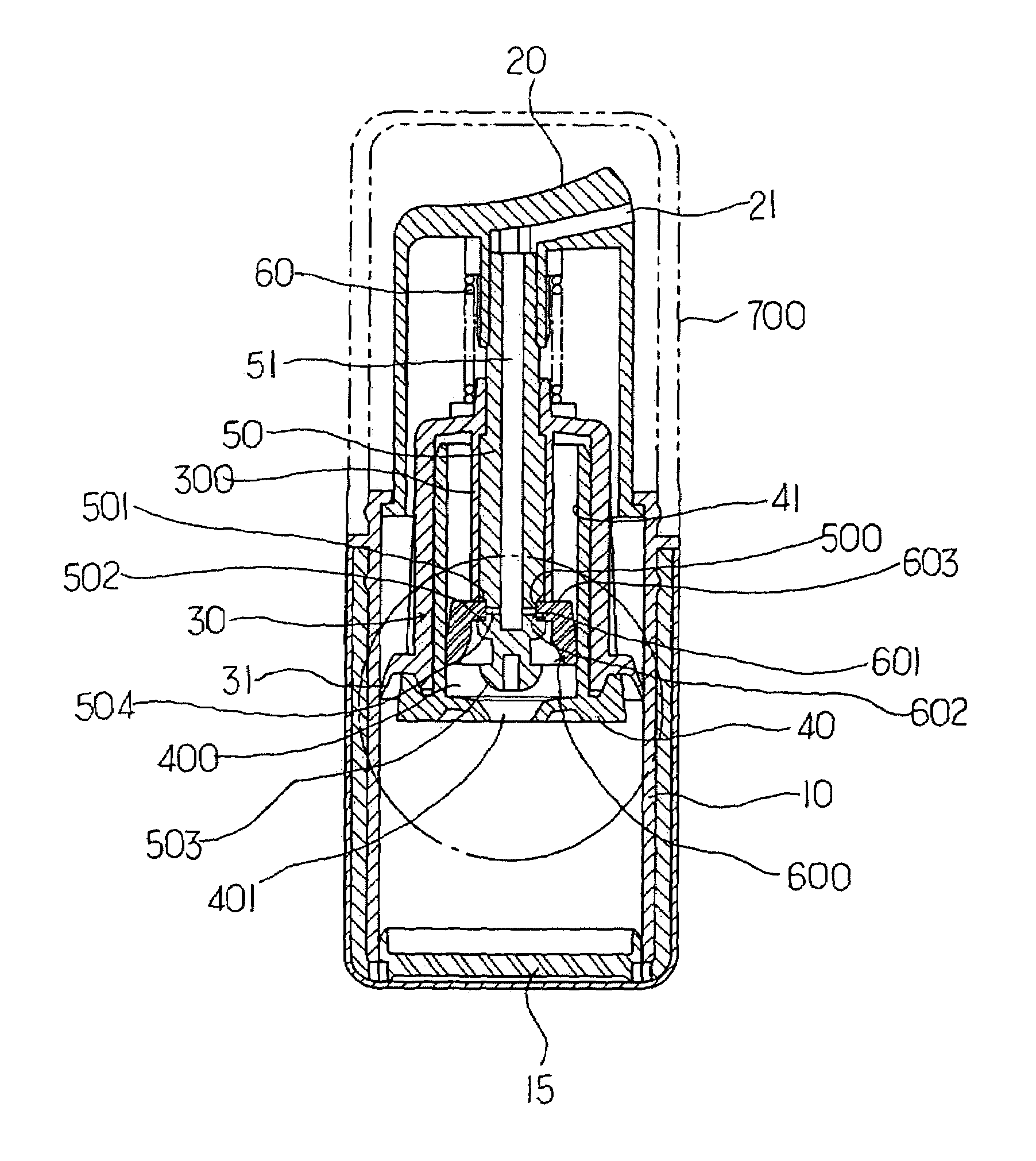
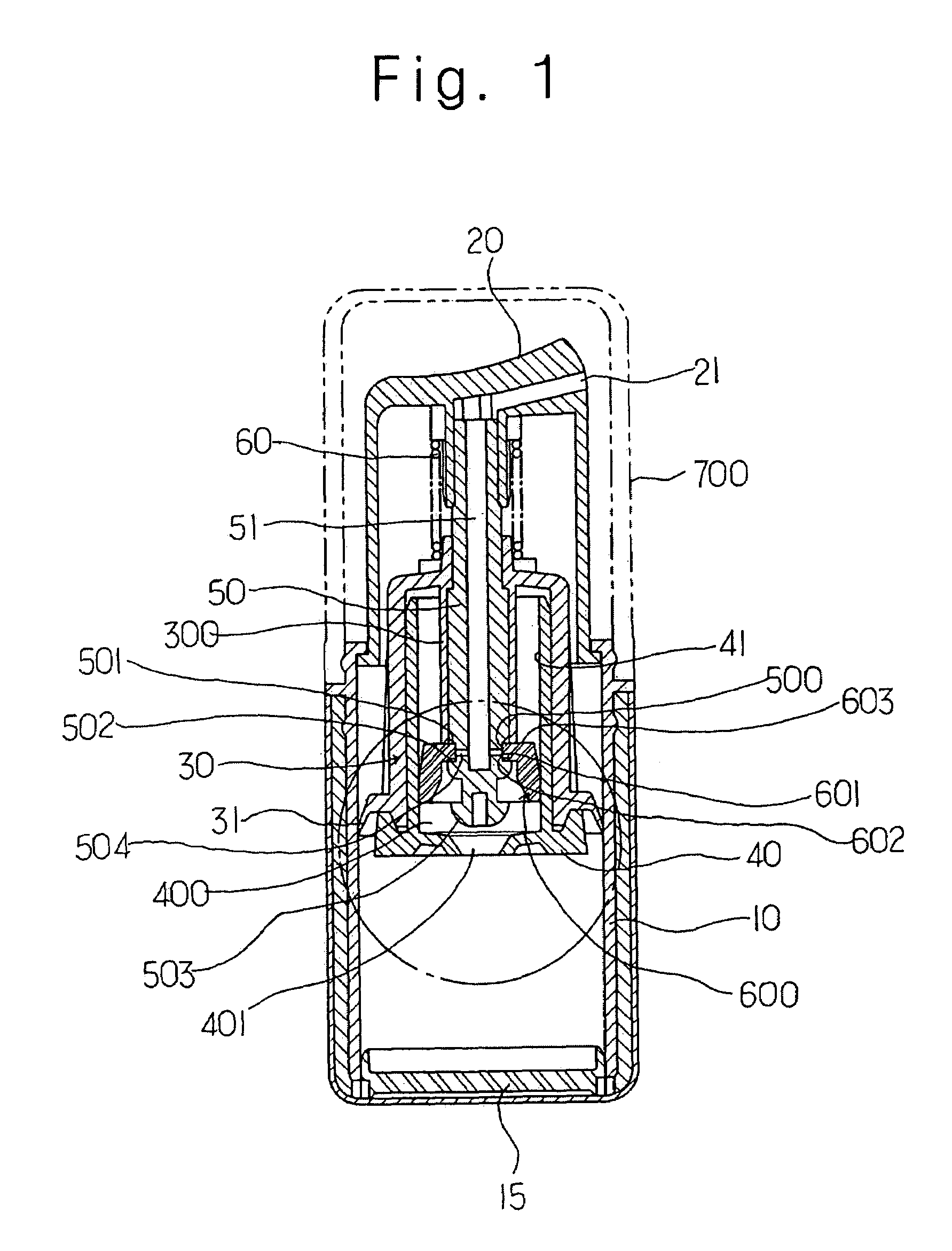
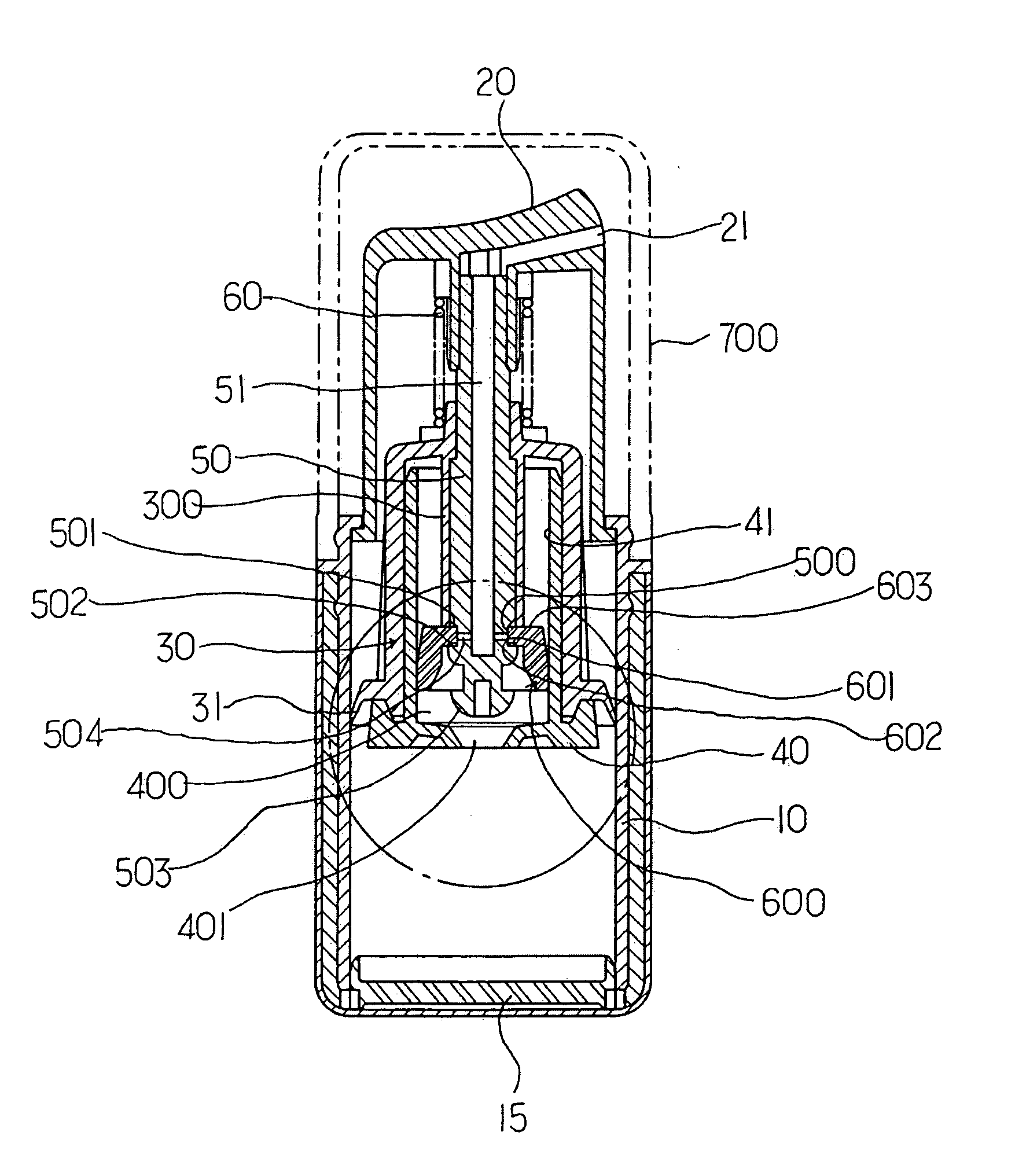
Constant discharge structure for nozzle head lowering type vacuum cosmetic container
Disclosed is a constant discharge structure for a nozzle head lowering type vacuum cosmetics container for containing high functional cosmetics. The constant discharge structure includes a liquid collecting chamber having a liquid inflow hole in the lower portion of a piston support member mounted in the container, a groove having an inclined short jaw, a support jaw and a liquid inlet hole and an open / close unit for opening / closing the liquid inflow hole in the lower portion of a central shaft, an elastic pumping member being inserted into the groove of the shaft and including a hole having an inner wall for opening / closing the liquid inlet hole on a flat surface unit, and a cylinder incorporated inside a piston for supporting the central shaft.
Owner:CDR
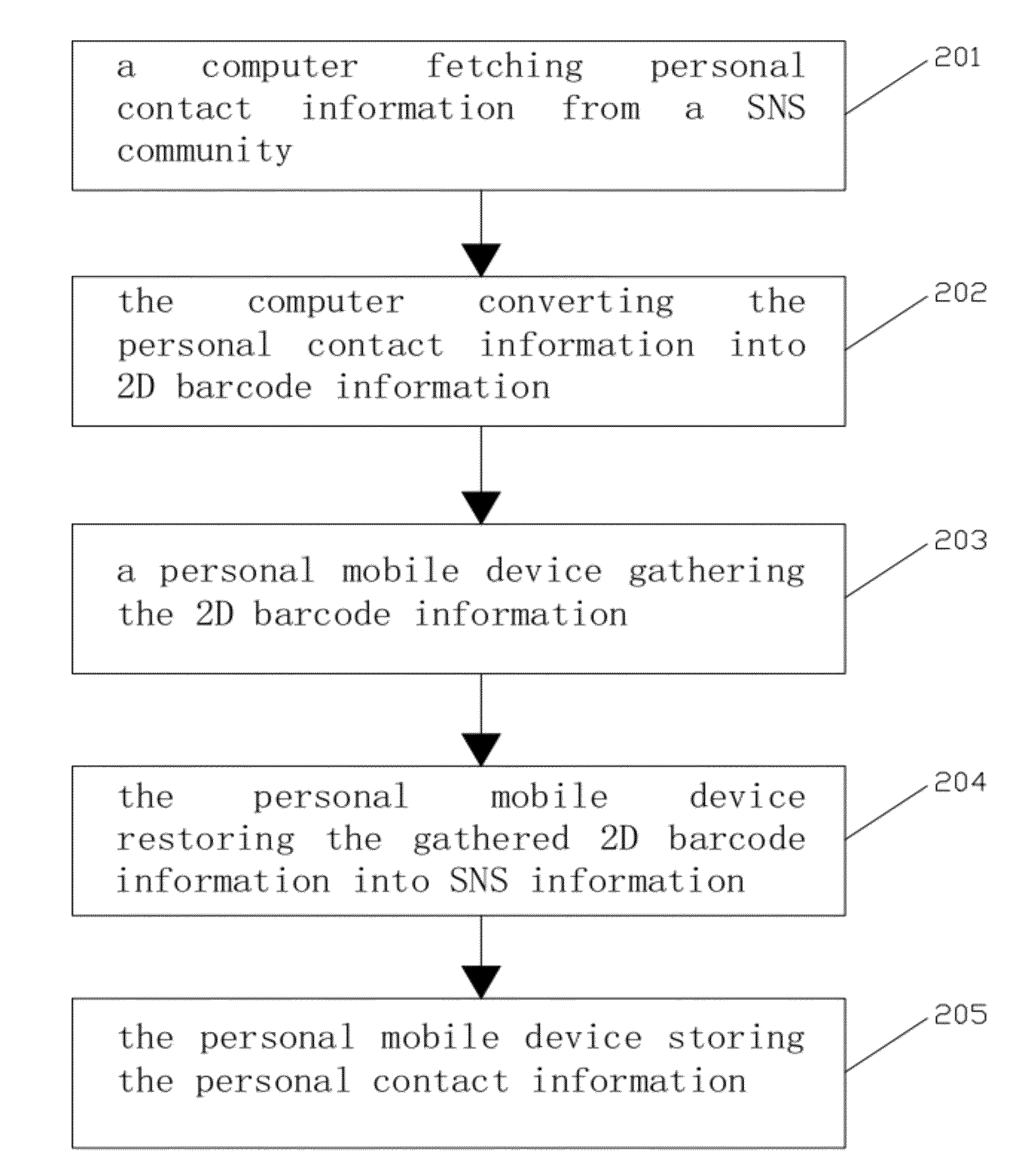
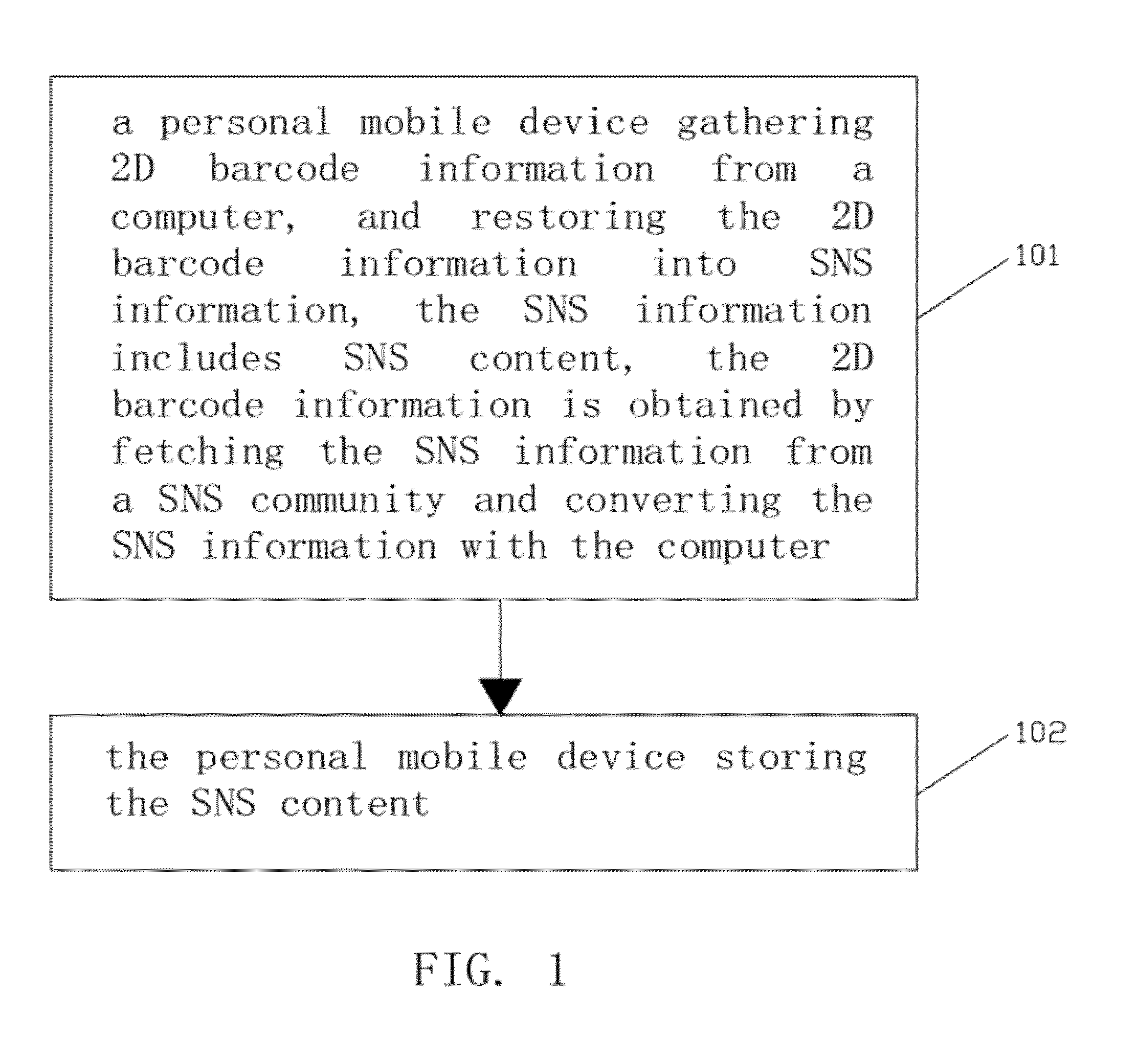
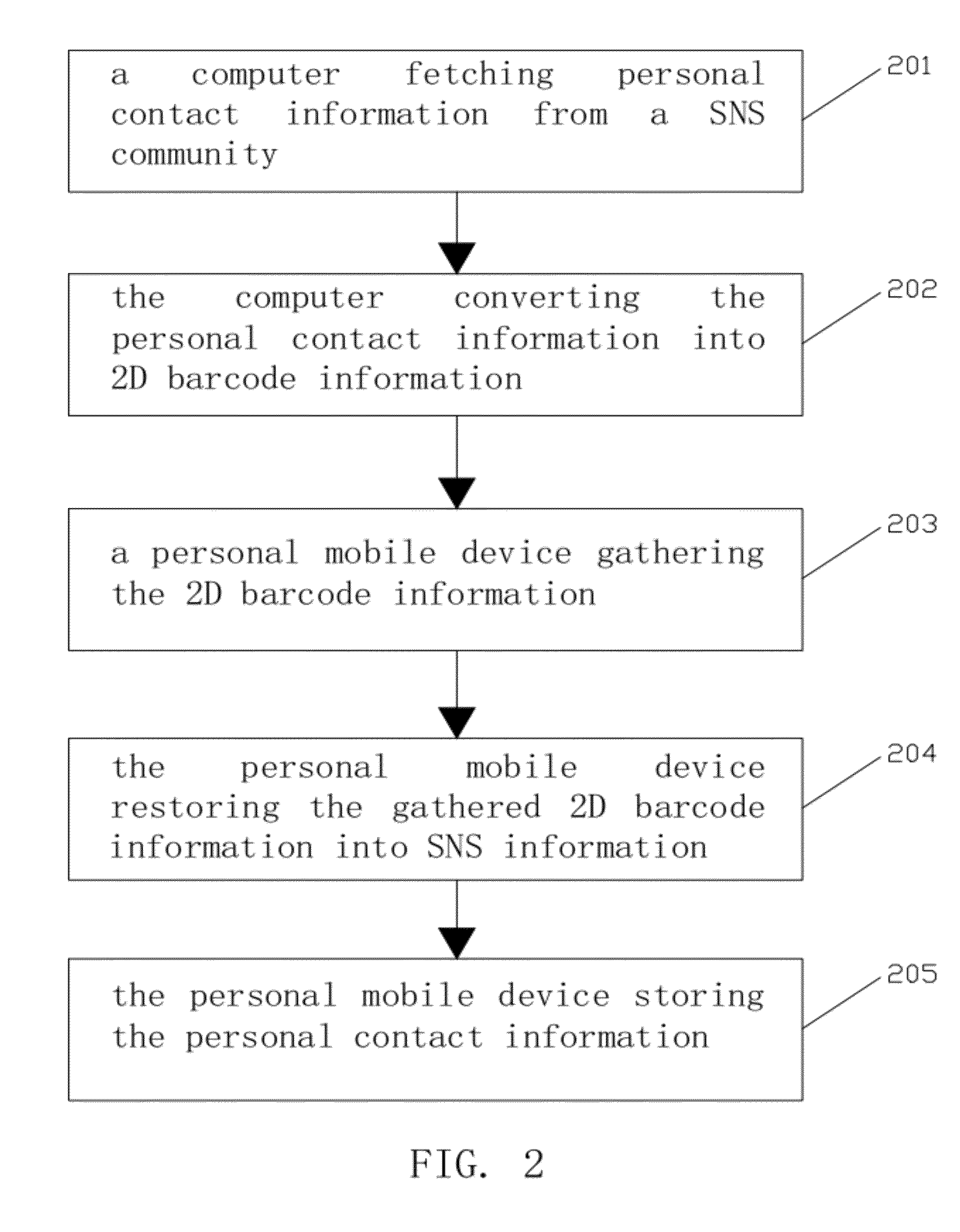
Method, device and system for storing social networking services content
InactiveUS20120273565A1Keep Content SafeImprove accuracyServices signallingData acquisition and loggingBarcodeSocial network service
The present invention publishes a method, a device and a system for storing SNS content. The method includes the following steps. A personal mobile device gathers two-dimensional barcode information from a computer and restores it into SNS information, wherein the SNS information includes SNS content, and the two-dimensional barcode information is obtained by converting the SNS information fetched from a SNS community with the computer. The personal mobile device stores the SNS content. The present invention improves the efficiency an accuracy of storing SNS content, and can further store the SNS content in a corresponding space according to the SNS type of the SNS content such that user can directly use the SNS content. For example, the user may directly dial the phone number in a contact list, or click a URL. The operation is simple and convenient, and the user's using experience is good.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and apparatus for multicasting contents between devices in networks
ActiveUS8126001B2Less resourcesKeep Content SafeError preventionTransmission systemsComputer networkControl equipment
An apparatus for multicasting contents between devices in different networks includes: a home-to-home multicast control device for finding the devices in the networks, downloading contents from a device in a network to which the home-to-home multicast control device belongs, processing the contents to generate file blocks, each file block having chunk files, and multicasting the processed contents to the devices in the networks; and at least one home-to-home multicast bridge device for receiving the contents transmitted from the home-to-home multicast control device and streaming the contents to one or more devices in a network to which the home-to-home multicast bridge device belongs. The apparatus further includes a multicast relay device for relaying the contents between the home-to-home multicast control device and the home-to-home multicast bridge device.
Owner:ELECTRONICS & TELECOMM RES INST
Short message content protection system and method
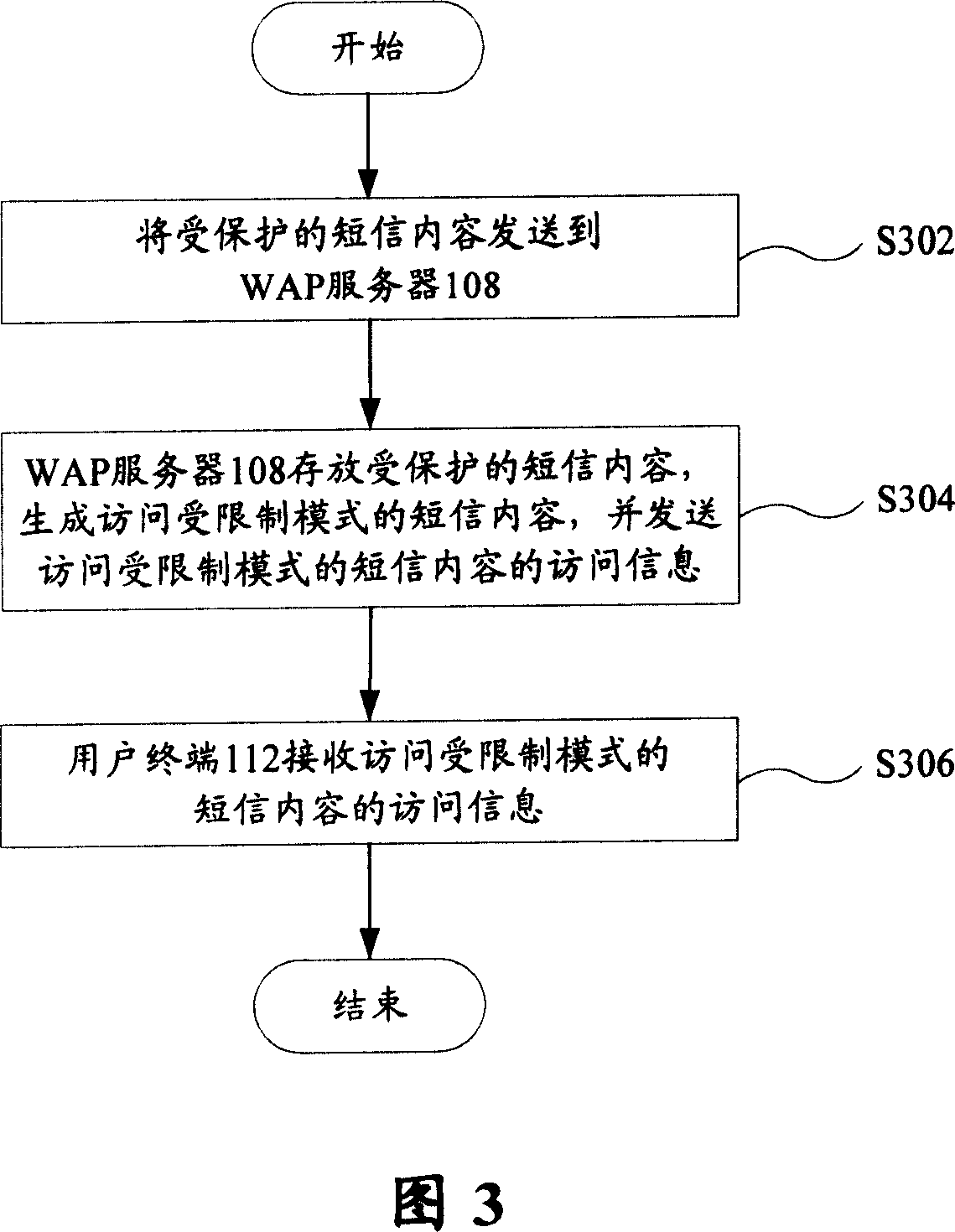
InactiveCN101072093ALimit viewingKeep Content SafeSpecial service for subscribersRadio/inductive link selection arrangementsWireless Application ProtocolContent security
The method includes following steps: (1) sending protected content of short message to server in wireless application protocol (WAP); (2) server in WAP stores the protected content of short message, and generates content of short message in access limited mode, and sends the access information of content of short message in access limited mode; (3) user terminal receives the access information of content of short message in access limited mode. Since protected contents of short messages are stores in server in WAP, receiving party can only look protected content of short message in mode of browsing web page in WAP, is unable to save, edit and forwards short message. The invention can protect security of content of short message effectively.
Owner:ZTE CORP
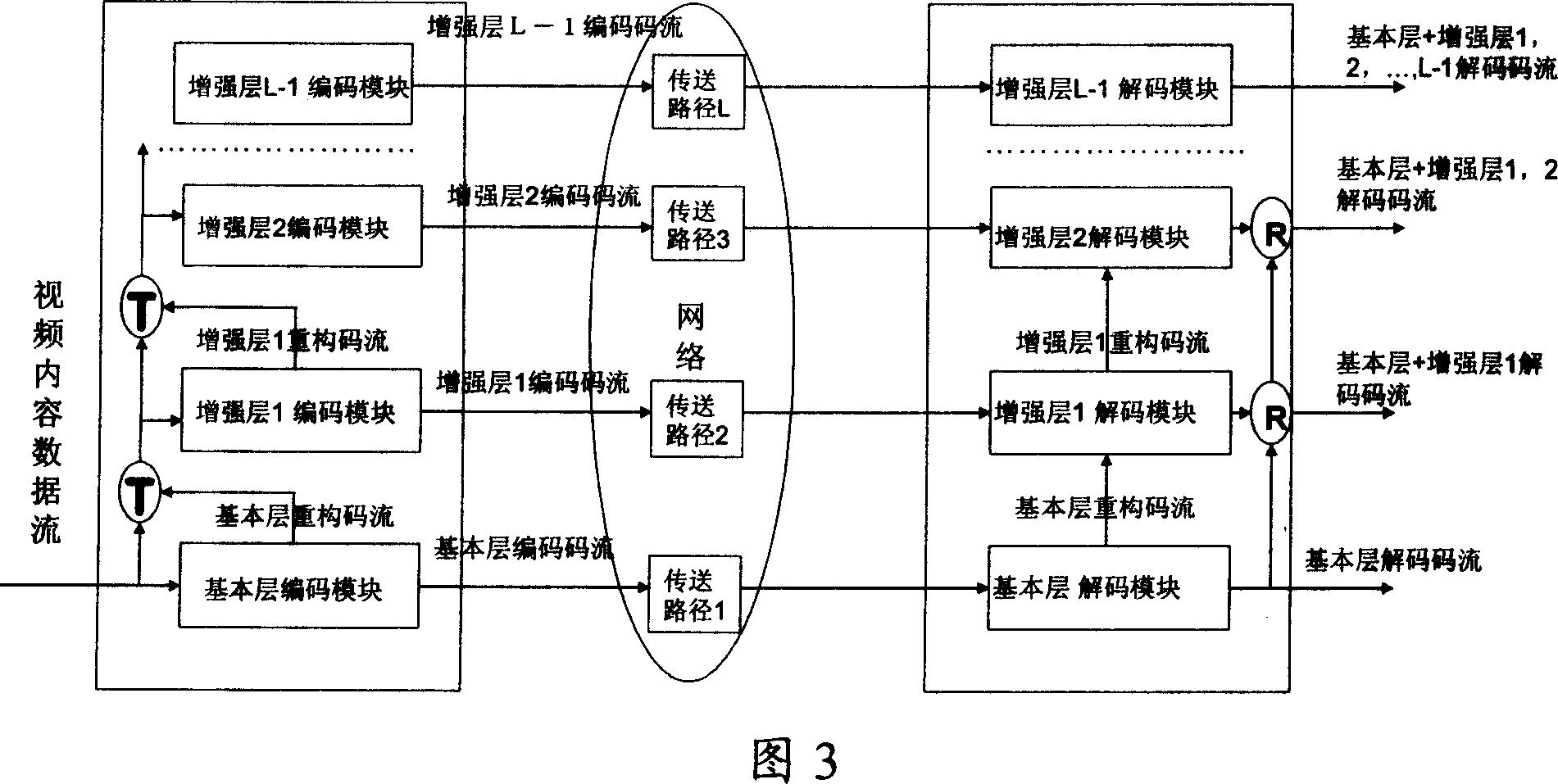
Video code stream checking method, system and device
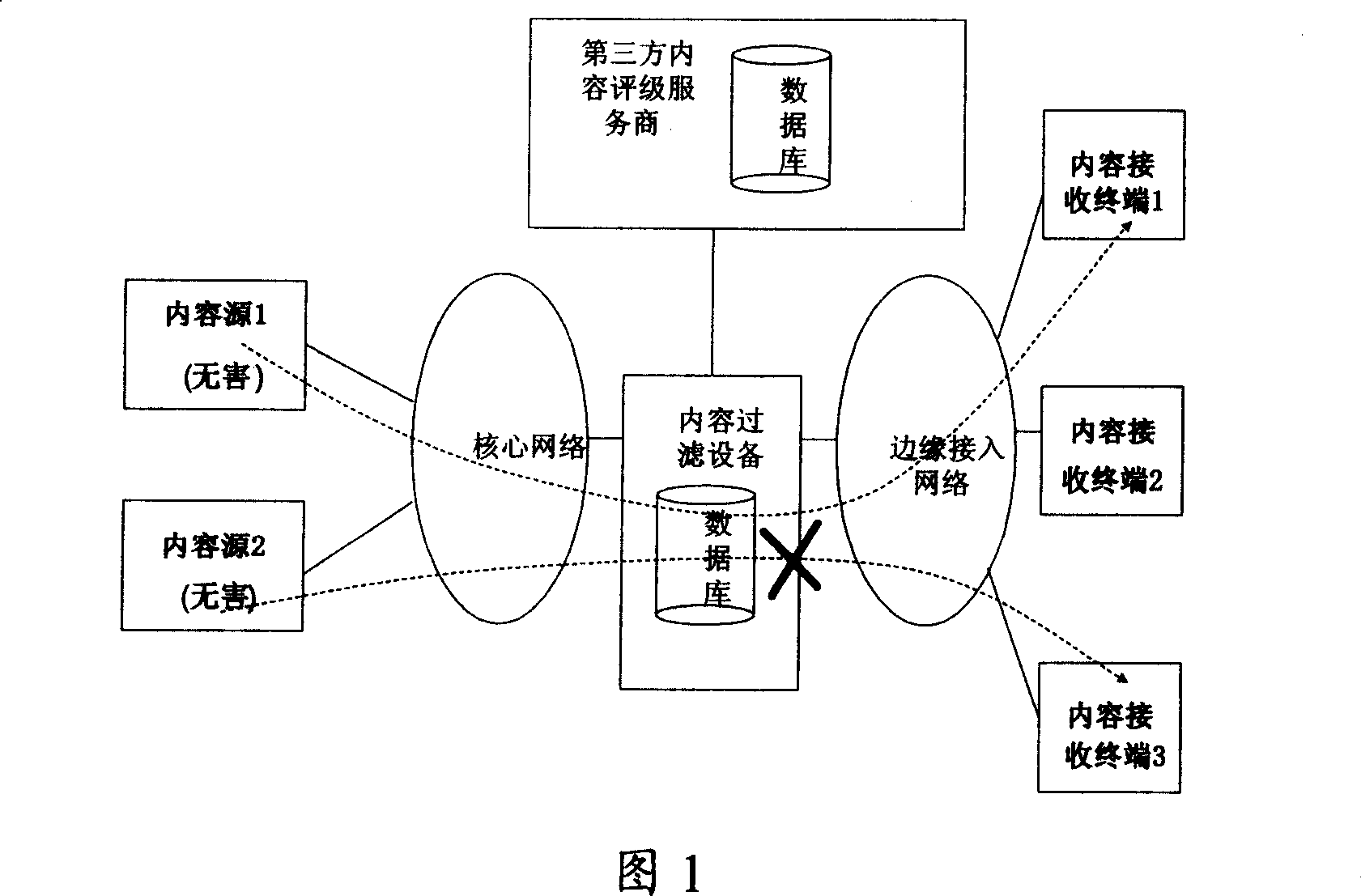
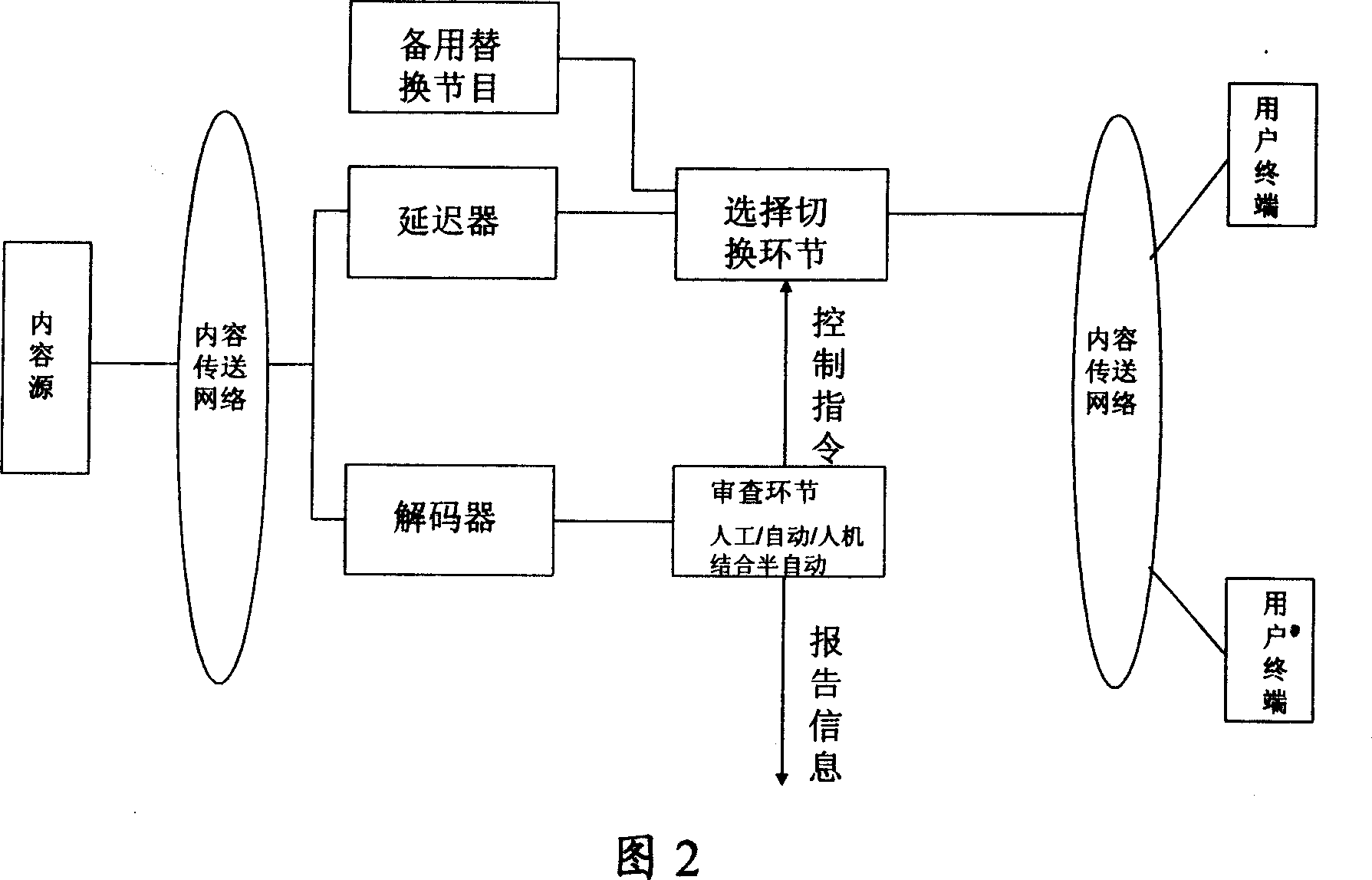
InactiveCN1968250AReduce the burden onKeep Content SafePulse modulation television signal transmissionAnalogue secracy/subscription systemsParallel computing
The invention relates to a video flow inquiring method, system and relative devices, wherein said invention utilizes the relationship between basic layer and strengthen layer of code flow multilayer structure of interlayer code mechanism, to generate inquire code flow; the inquire code flow comprises basic layer code flow, and / or strengthen layer code flow; using special inquirer to inquire and transfer inquire code flow; when the special inquirer inquires out the harmful content in code flow, it will cut off the inquire code flow transmission to the user; user can not decode and rebuild original video flow, to control the transmission of harmful content. The invention can be used to in live broadcast mode and store content play mode.
Owner:HUAWEI TECH CO LTD
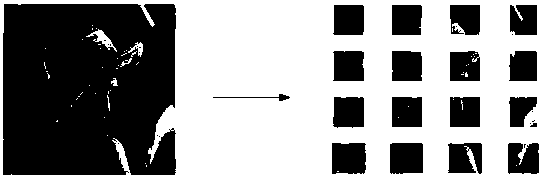
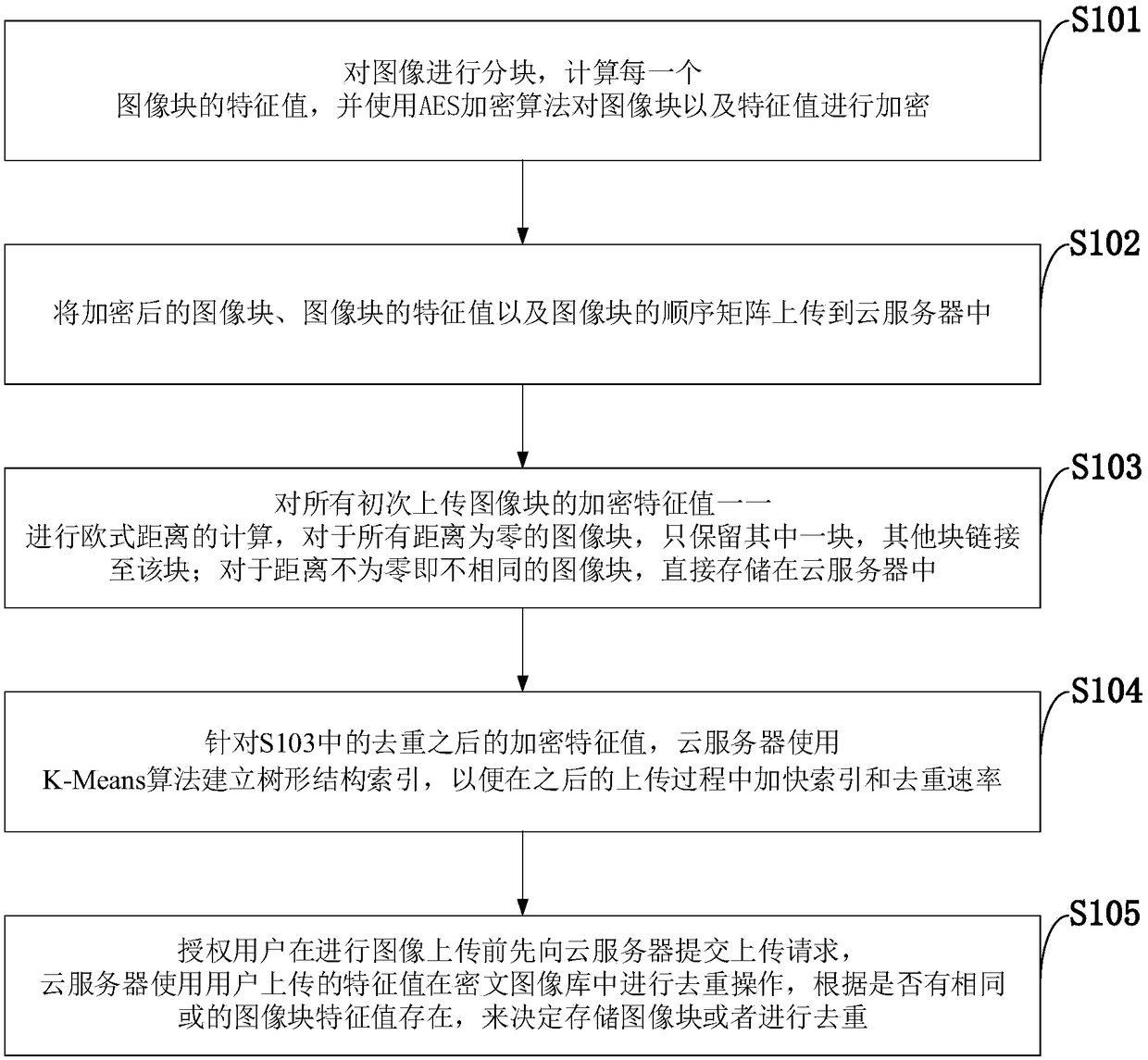
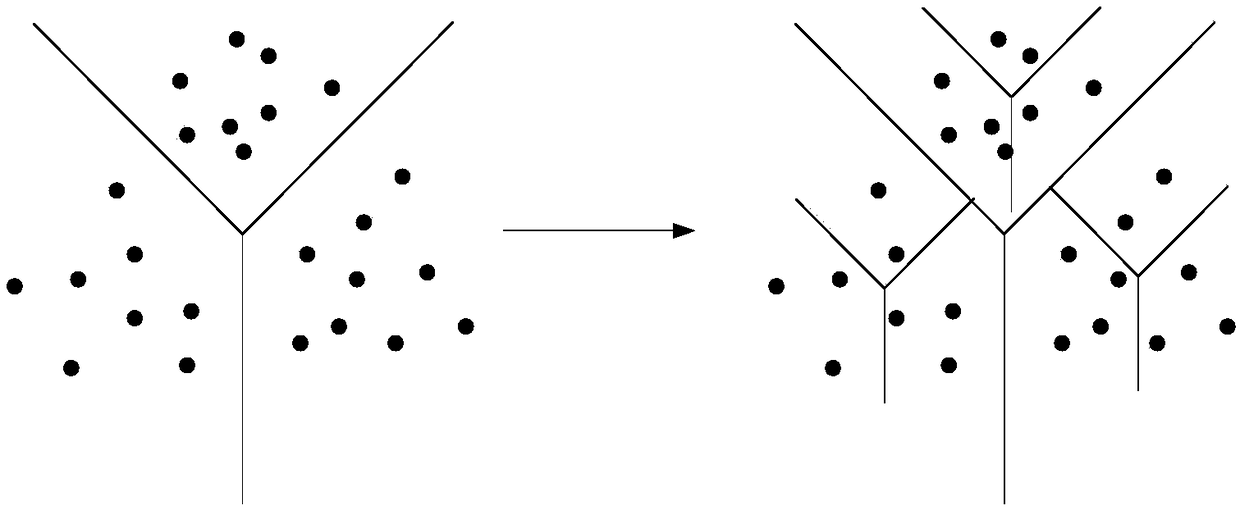
Ciphertext image deduplication method used in cloud environment and cloud server
ActiveCN108334593AReduce image storageKeep Content SafeStill image data retrievalTransmissionStorage efficiencyCiphertext
The invention belongs to the technical field of image deduplication and discloses a ciphertext image deduplication method used in the cloud environment and a cloud server. An image in a database is partitioned, characteristic values of image blocks are calculated, and the image blocks and the characteristic values are encrypted with any one rapid symmetrical encryption algorithm; the encrypted image blocks, a sequence matrix of the image blocks and the encrypted characteristic values are uploaded to the cloud server, and ciphertext image deduplication operation is executed by the server; if other authorized users upload the image again, the encrypted image blocks and the encrypted characteristic values are required to be sent to the cloud server, the cloud server performs retrieval operation in an encrypted image library, and storage of the image blocks or deduplication is decided according to the fact that whether the same characteristic values of the image blocks or the characteristic values of the image blocks in a set threshold value range exist. On the basis of conventional image deduplication, safe deduplication of ciphertext images is realized, deduplication of different images is realized, the expected safety purpose is achieved, and besides, the storage efficiency is improved under the condition that the accuracy is guaranteed.
Owner:XIDIAN UNIV
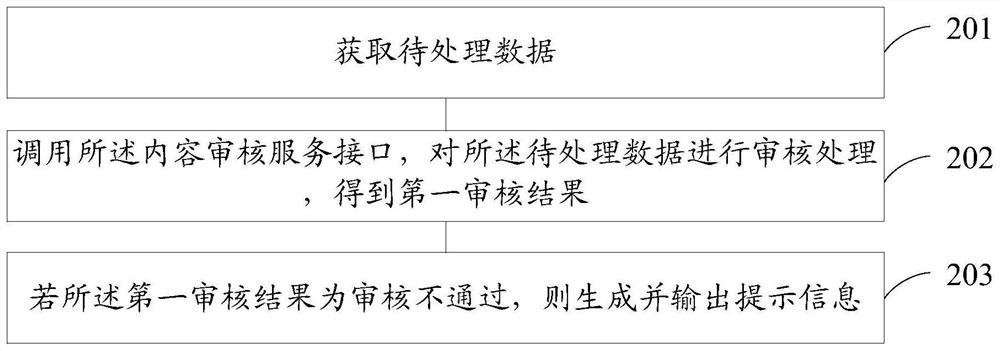
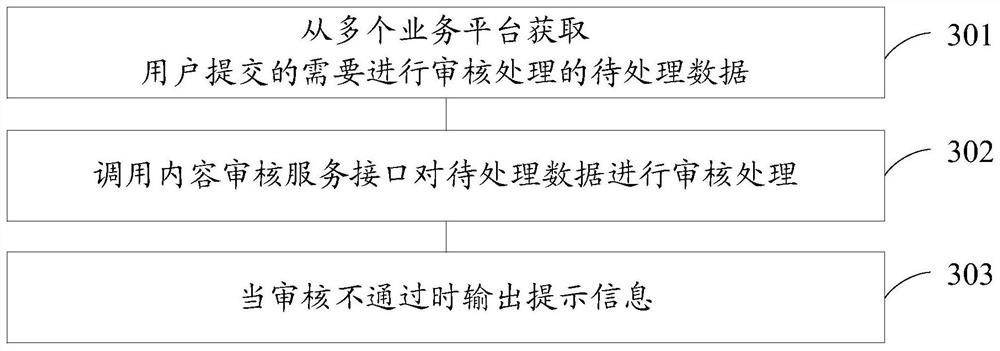
Content auditing method and device
PendingCN112287270AKeep Content SafeWebsite content managementSpecial data processing applicationsEngineeringContent security
The embodiment of the invention provides a content auditing method and device, the content auditing method and device are applied to an operation center, the operation center is integrated in an urbanportal system, the urban portal system further comprises a content security management platform, the content security management platform is used for providing a content auditing service interface, and the method comprises the following steps: obtaining to-be-processed data; calling the content auditing service interface, and auditing the to-be-processed data to obtain a first auditing result; and if the first auditing result is that auditing is not passed, generating and outputting prompt information. In the urban portal system, the content auditing service interface provided by the contentsecurity management platform is called through the operation center for processing, so that the operation center of the urban portal system can conveniently perform content auditing on to-be-processeddata in other business platforms to ensure the content security of the data of the other business platforms; and the influence of non-compliance and non-real content on platform users is reduced.
Owner:ZHUHAI DAHENGQIN TECH DEV CO LTD
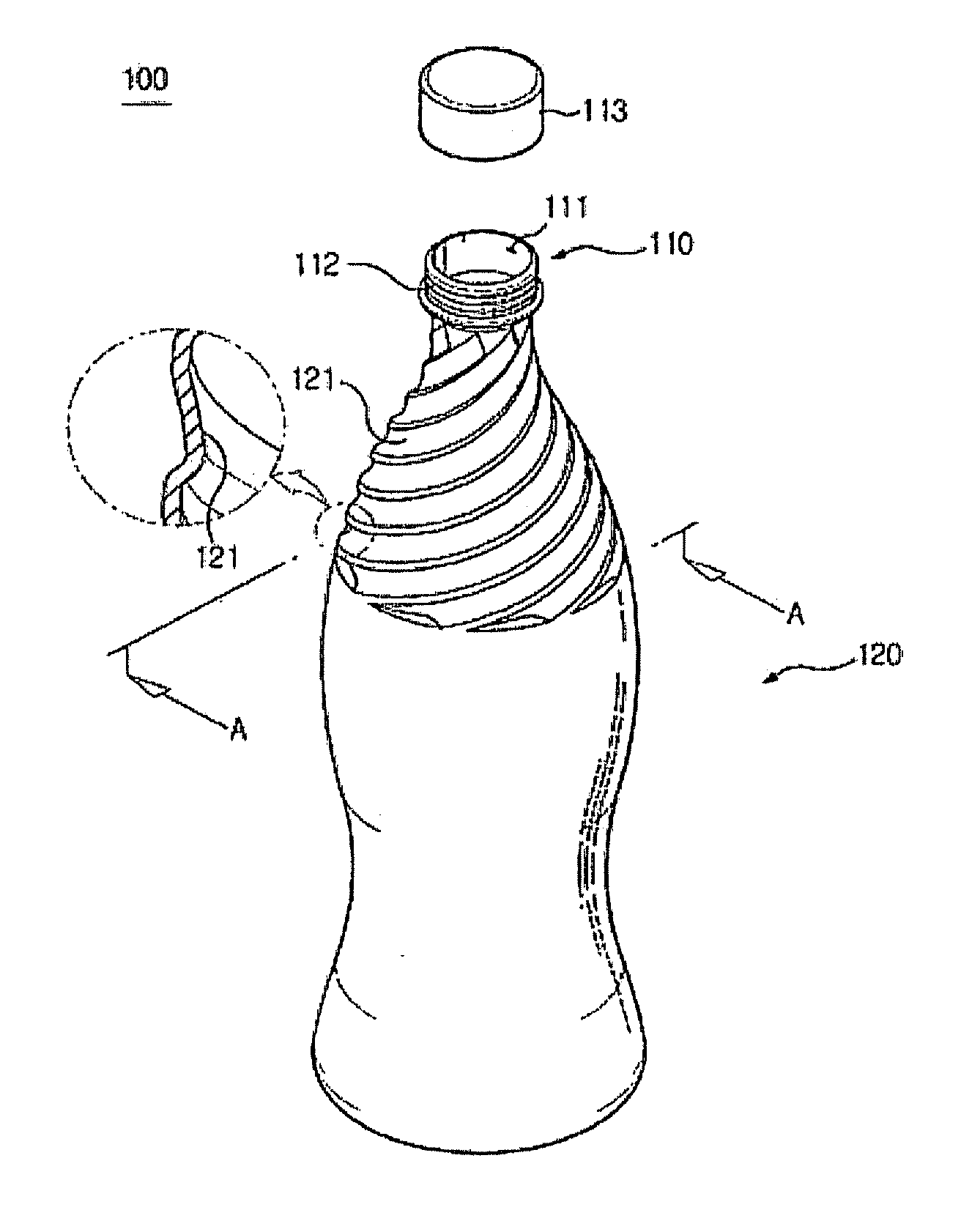
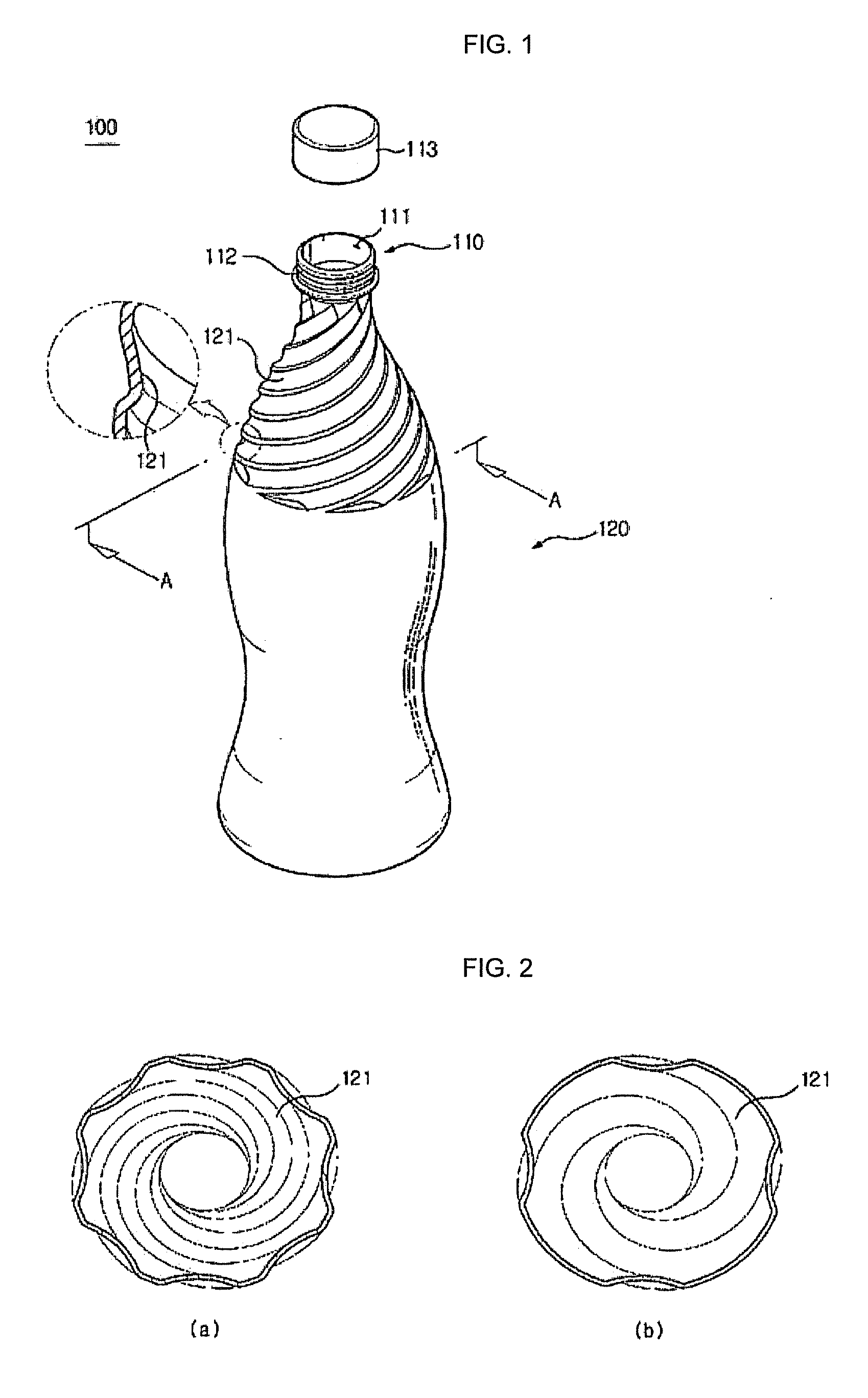
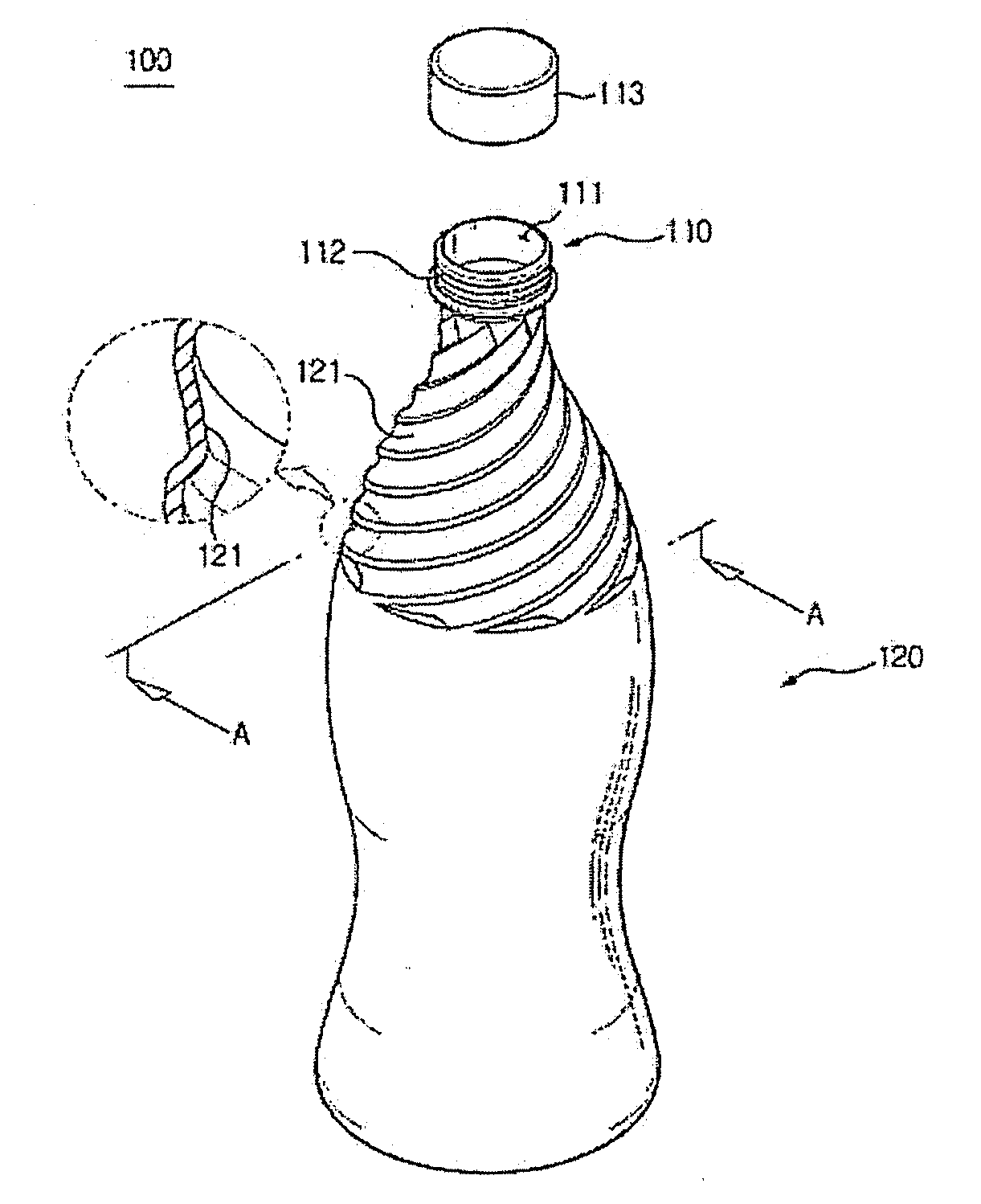
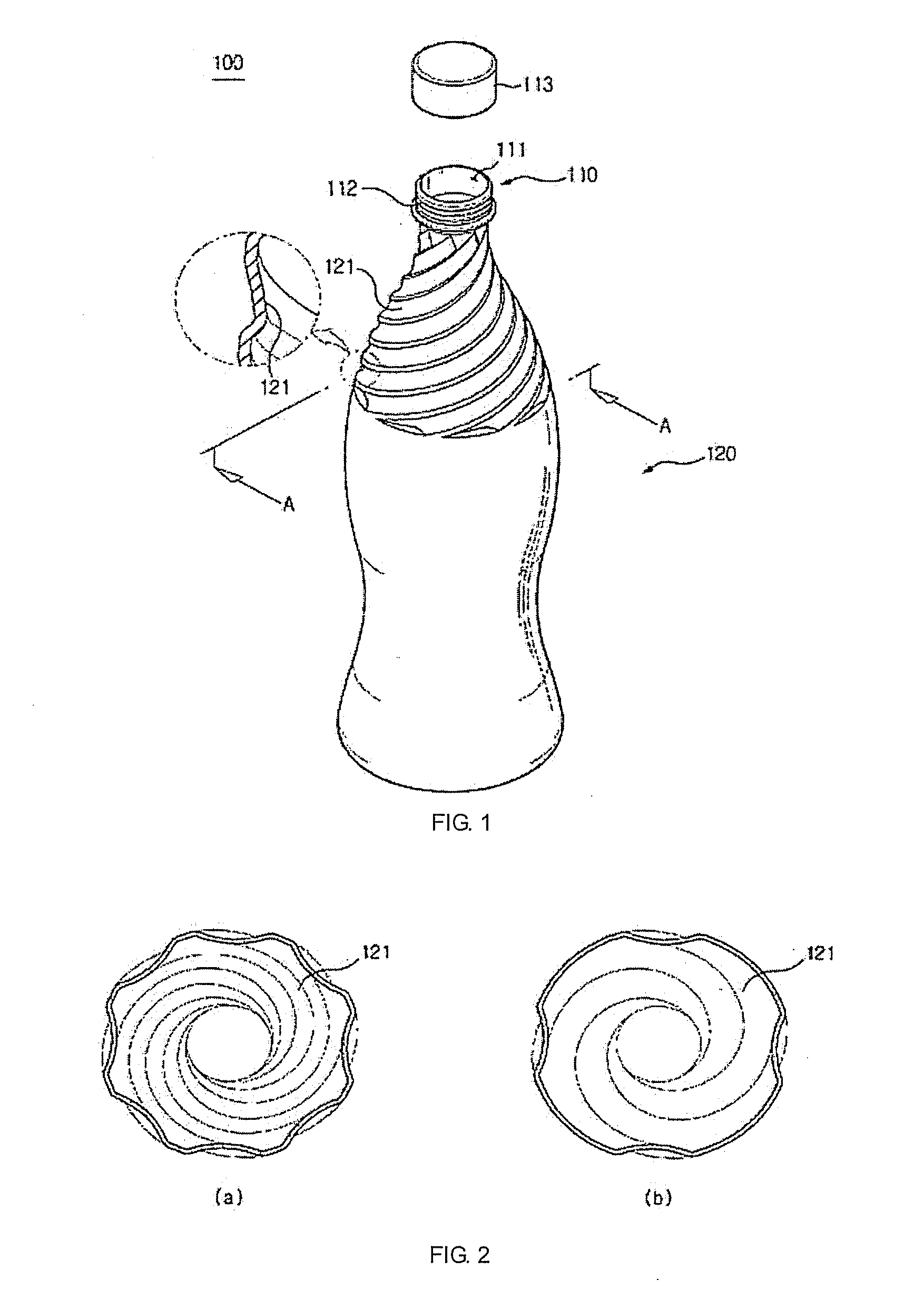
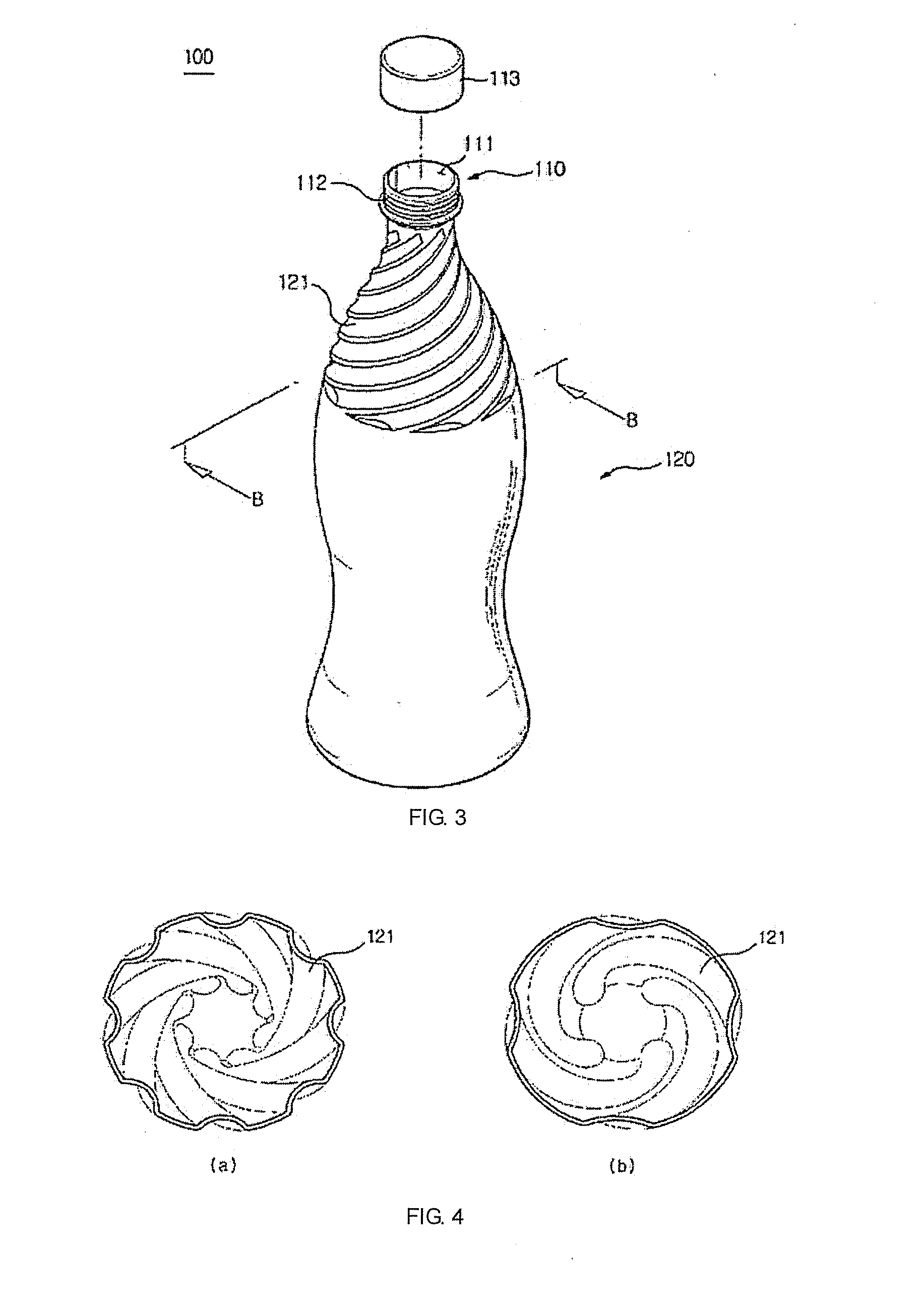
Discharging contents from a container while filling the same with gas
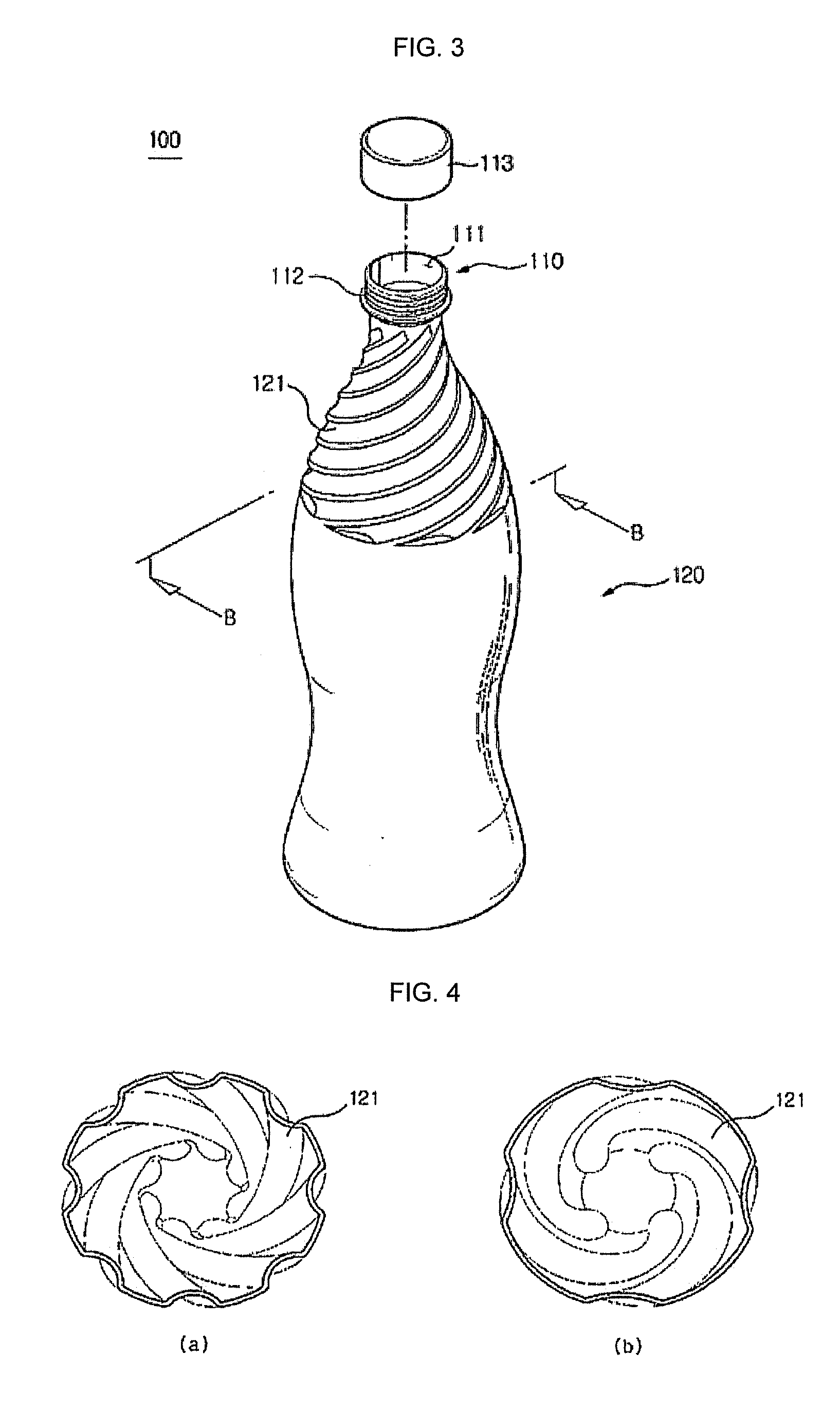
InactiveUS20130048593A1Prevent of liquid contentAvoid accidentsBottlesLarge containersBottleLiquid content
Disclosed is a bottle for containing liquid content including a body portion, at least part or the entire portion of an upper portion of which is provided with a plurality of guides which protrudes inward from an inside surface thereof and is in a spiral pattern so that the liquid content can be guided towards an opening of a neck portion of the bottle while spirally revolving inside the bottle.
Owner:LEE JONATHAN
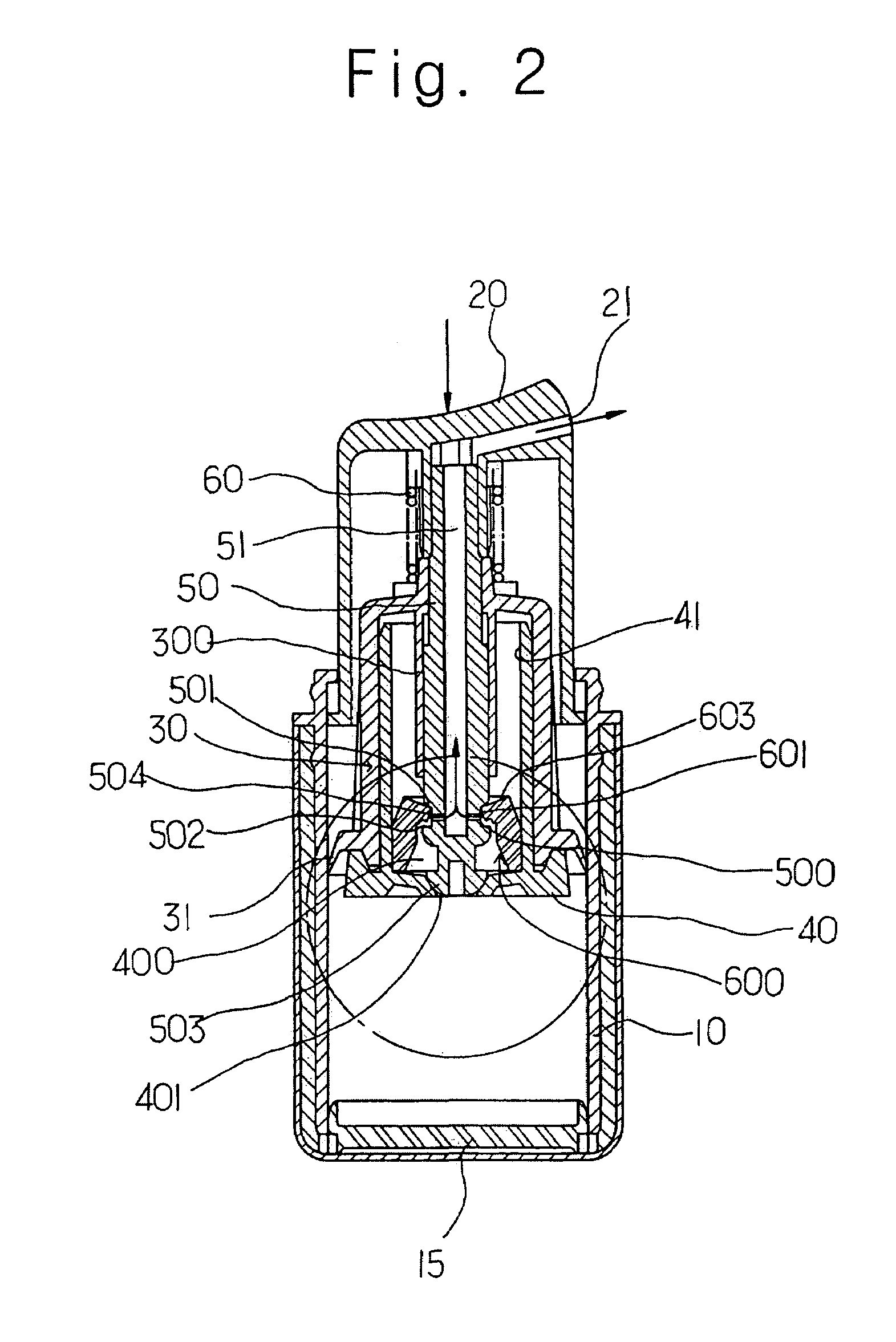
Constant discharge structure for nozzle head lowering type vacuum cosmetic container
InactiveUS20050109797A1Safely protect contentKeep Content SafeLarge containersLiquid transferring devicesEngineeringPiston
Disclosed is a constant discharge structure for a nozzle head lowering type vacuum cosmetics container for containing high functional cosmetics. The constant discharge structure includes a liquid collecting chamber having a liquid inflow hole in the lower portion of a piston support member mounted in the container, a groove having an inclined short jaw, a support jaw and a liquid inlet hole and an open / close unit for opening / closing the liquid inflow hole in the lower portion of a central shaft, an elastic pumping member being inserted into the groove of the shaft and including a hole having an inner wall for opening / closing the liquid inlet hole on a flat surface unit, and a cylinder incorporated inside a piston for supporting the central shaft.
Owner:CDR
Discharging contents from a container while filling the same with gas
InactiveUS20130082025A1Prevent of liquid contentAvoid accidentsBottlesLarge containersEngineeringBottle
Disclosed is a bottle for containing liquid content including a body portion, at least part or the entire portion of an upper portion of which is provided with a plurality of guides which protrudes inward from an inside surface thereof and is in a spiral pattern so that the liquid content can be guided towards an opening of a neck portion of the bottle while spirally revolving inside the bottle.
Owner:LEE JONATHAN
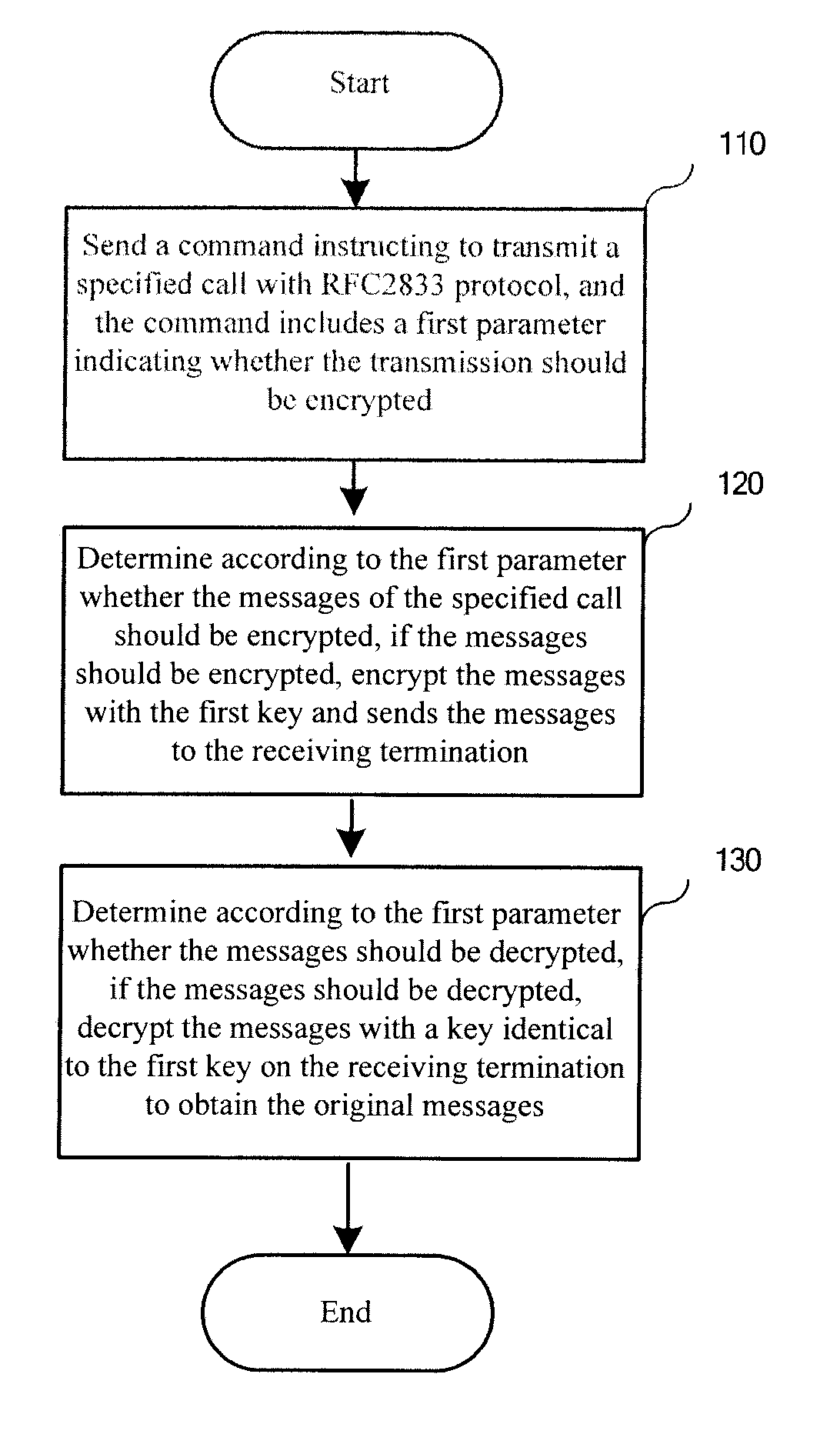
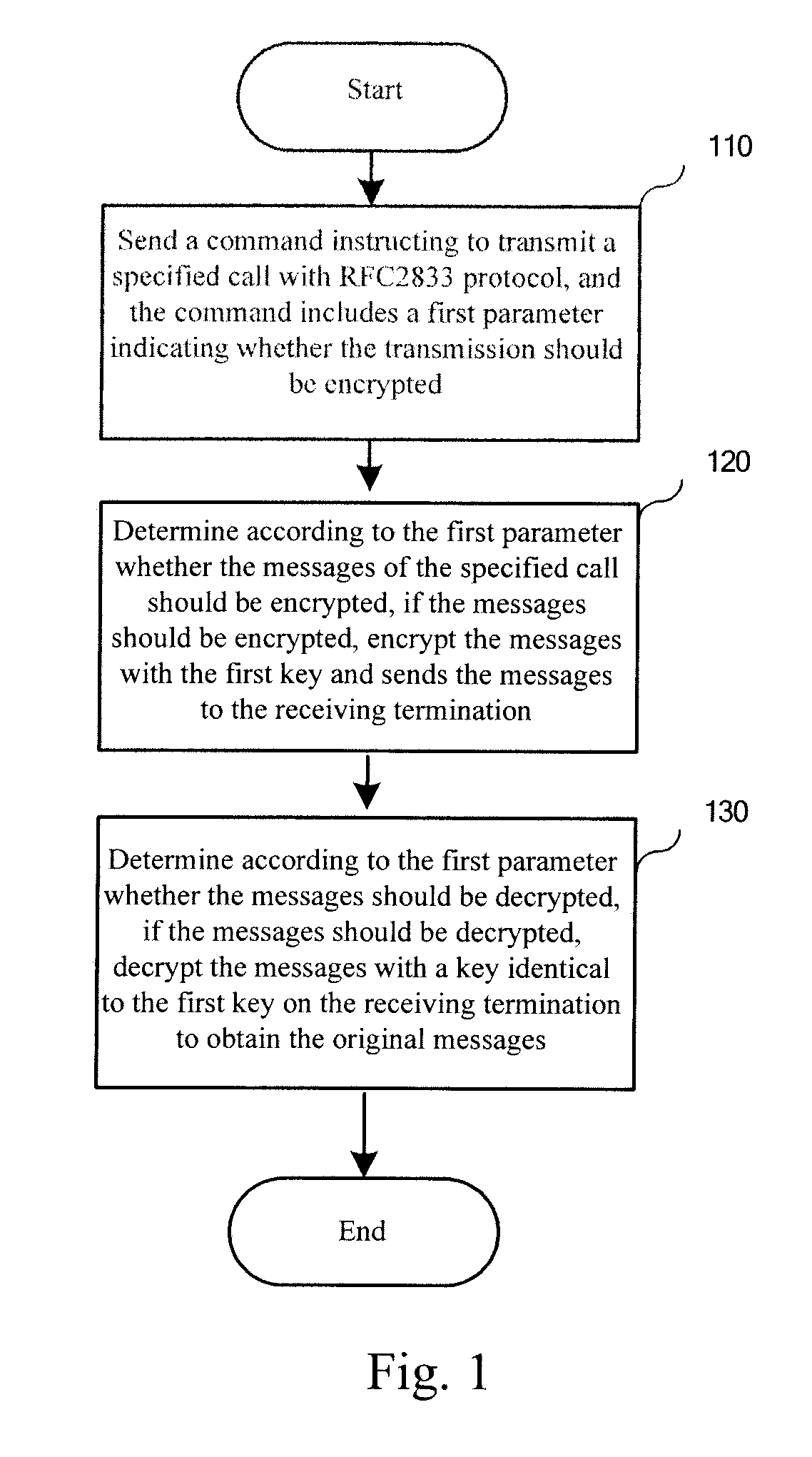
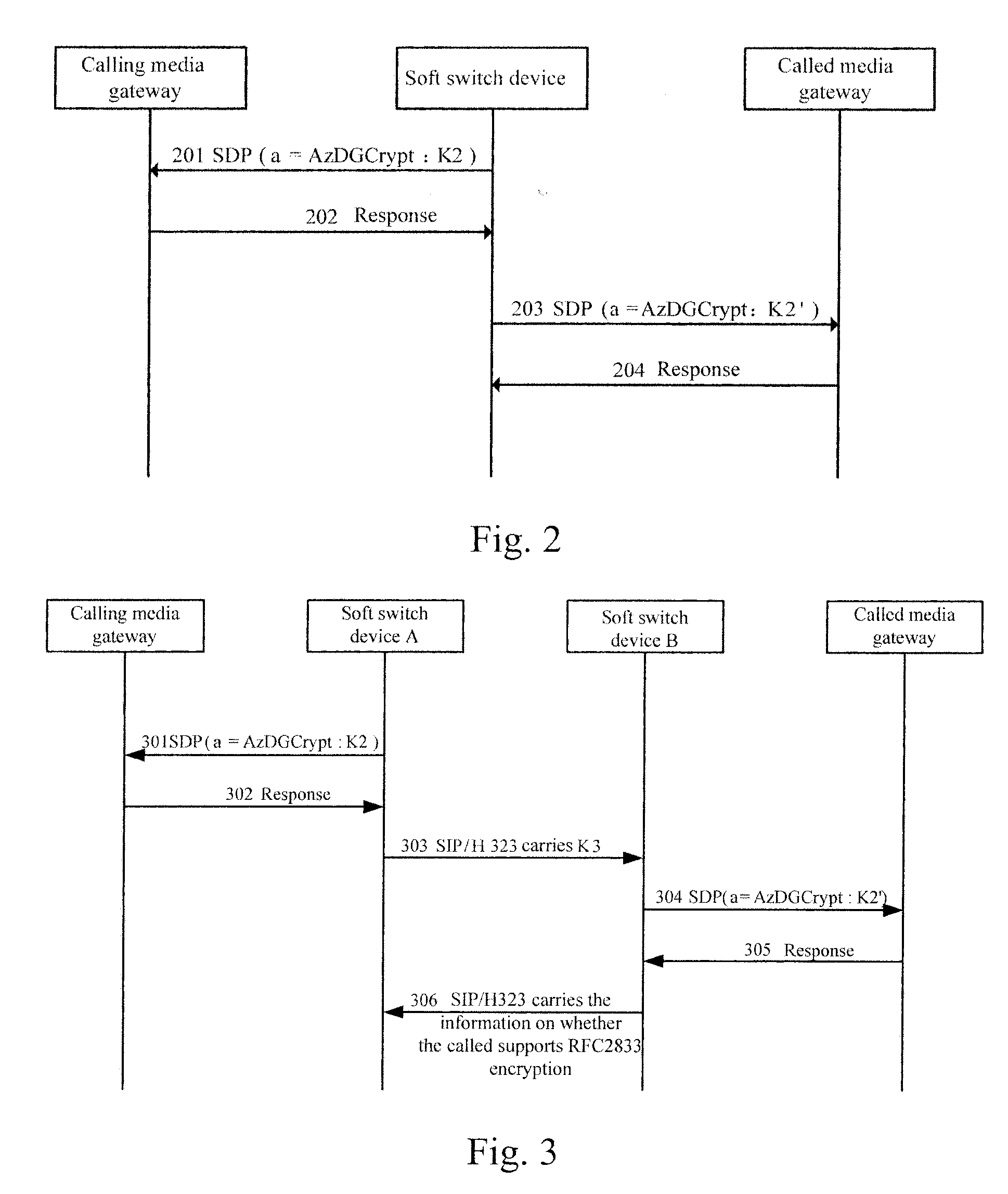
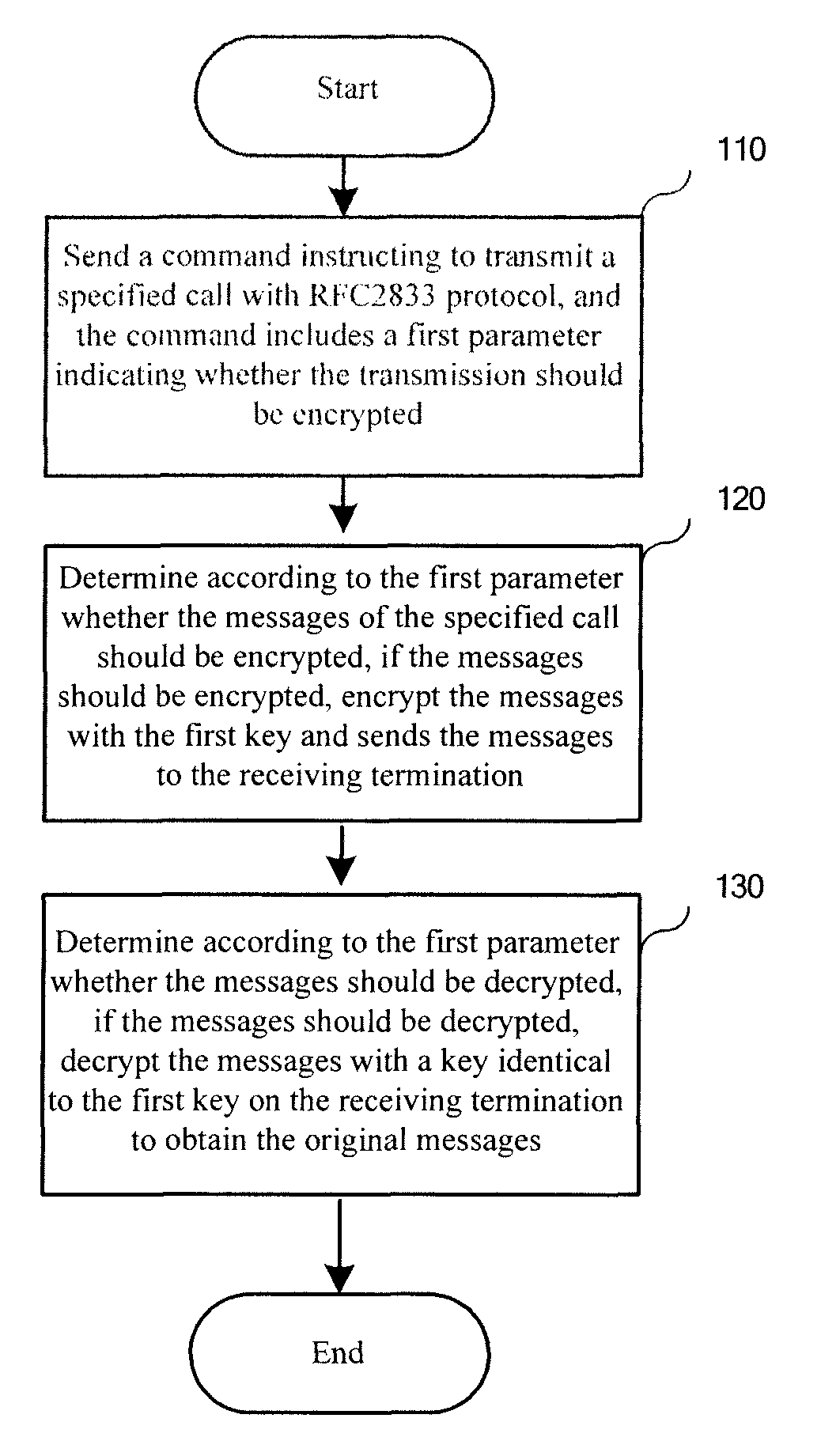
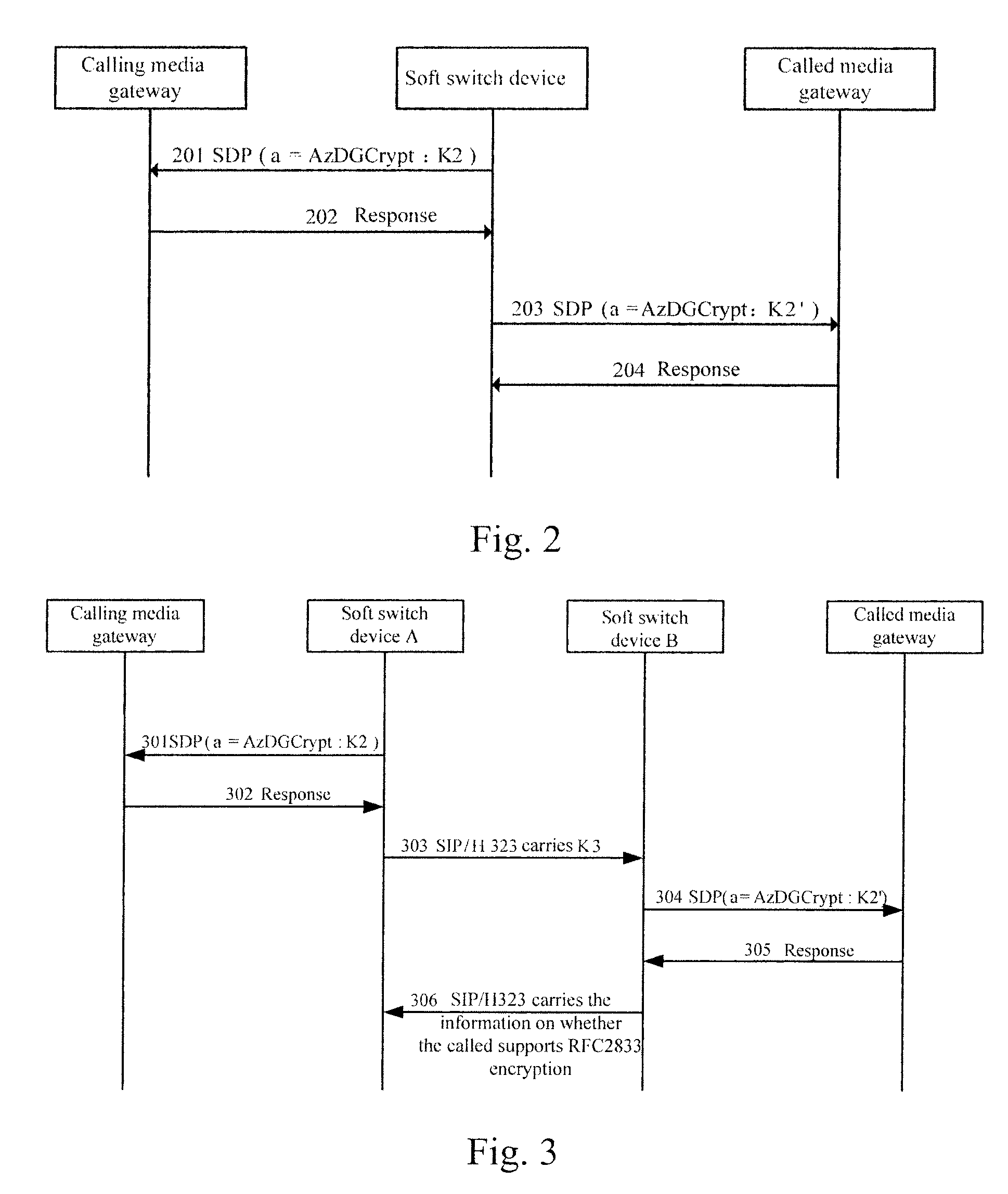
Method, media gateway and system for transmitting content in call established via media gateway control protocol
ActiveUS20080109652A1Improve securityDifficult to interceptSecuring communicationSelection arrangementsSoft switchMediaFLO
A method for transmitting content in a call established via media gateway control protocol includes: encrypting an RFC, Request for Comment, 2833 message with a first key; and sending out the encrypted RFC2833 message. The key used for encryption and decryption may be configured in advance on a calling and a called media gateways, or be sent from a soft switch device once and for all, or be sent from the soft switch device every time when a call is initiated. The key sent from the soft switch device may be in clear text or be encrypted. The technical scheme of the present invention greatly improves the security of the content in the RFC2833 protocol transmission.
Owner:HUAWEI TECH CO LTD
Streaming system and streaming method
ActiveUS8572380B2Keep Content SafeImprove securityKey distribution for secure communicationUser identity/authority verificationEncryption
Owner:SONY CORP
Method of providing information via a communication network and information providing system
ActiveUS7219232B2Improve securityFair performanceFinanceUser identity/authority verificationData matchingFinancial transaction
An information providing system for highly secure transactions includes an information providing apparatus that provides content data and provided information describing data, which describes the content of the content data, and an information receiving apparatus that is connected to the information providing apparatus via a communication network, receives the content data and the provided information describing data, and transmits a receipt for the received content data to the information providing apparatus. The information receiving apparatus confirms whether the content data is authentic based on the content data and the provided information describing data, and transmits the receipt to the information providing apparatus only when the content of the content data matches the provided information describing data.
Owner:PANASONIC CORP
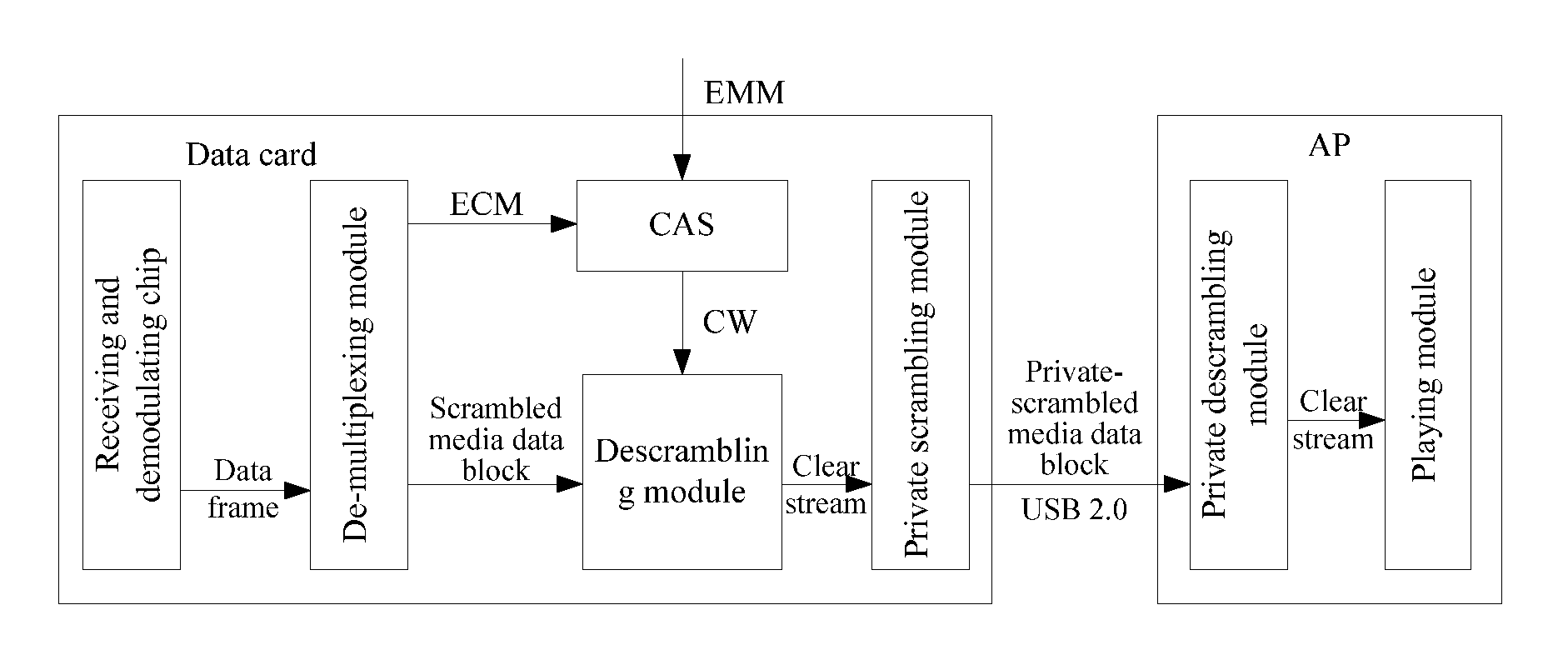
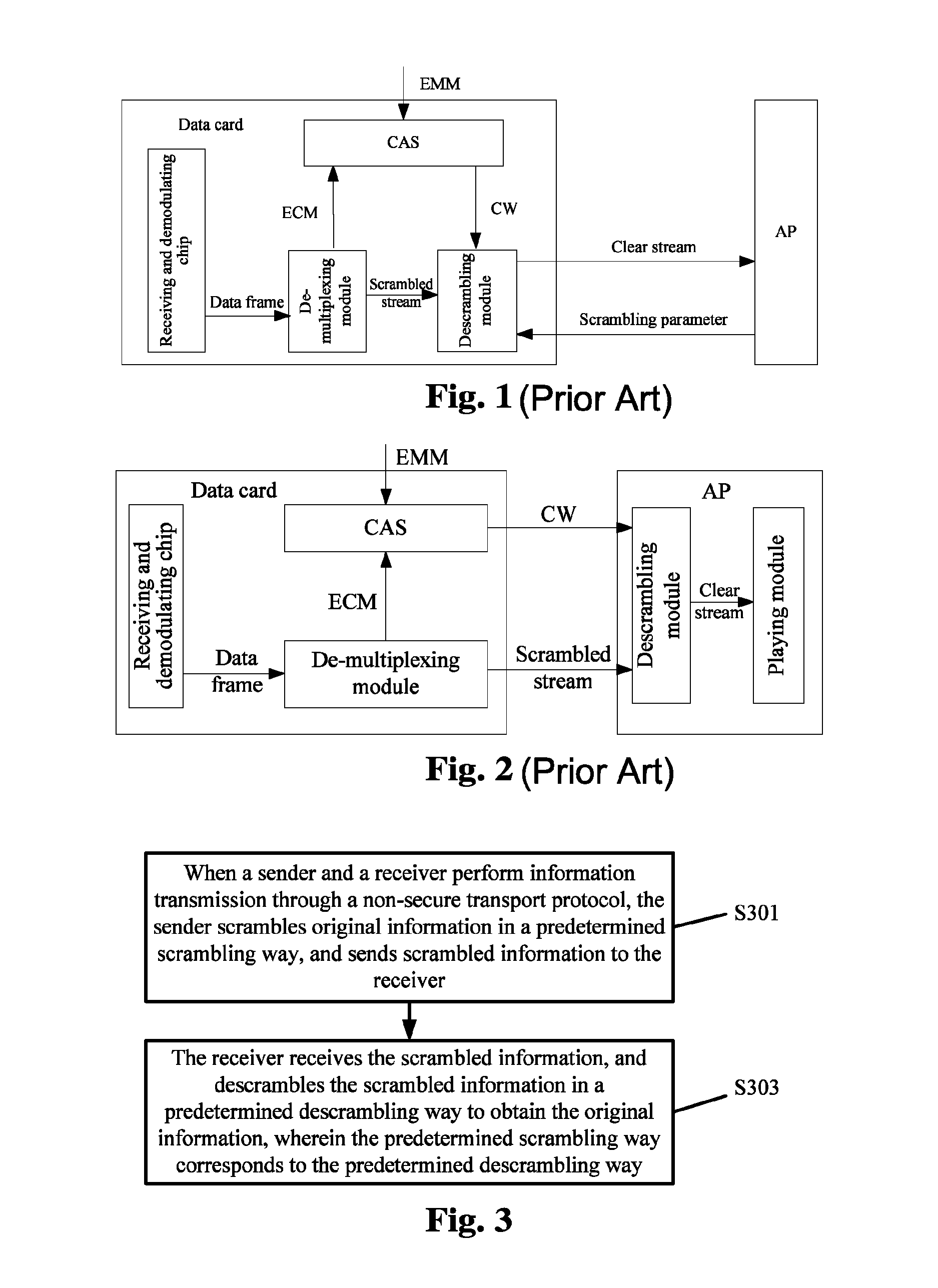
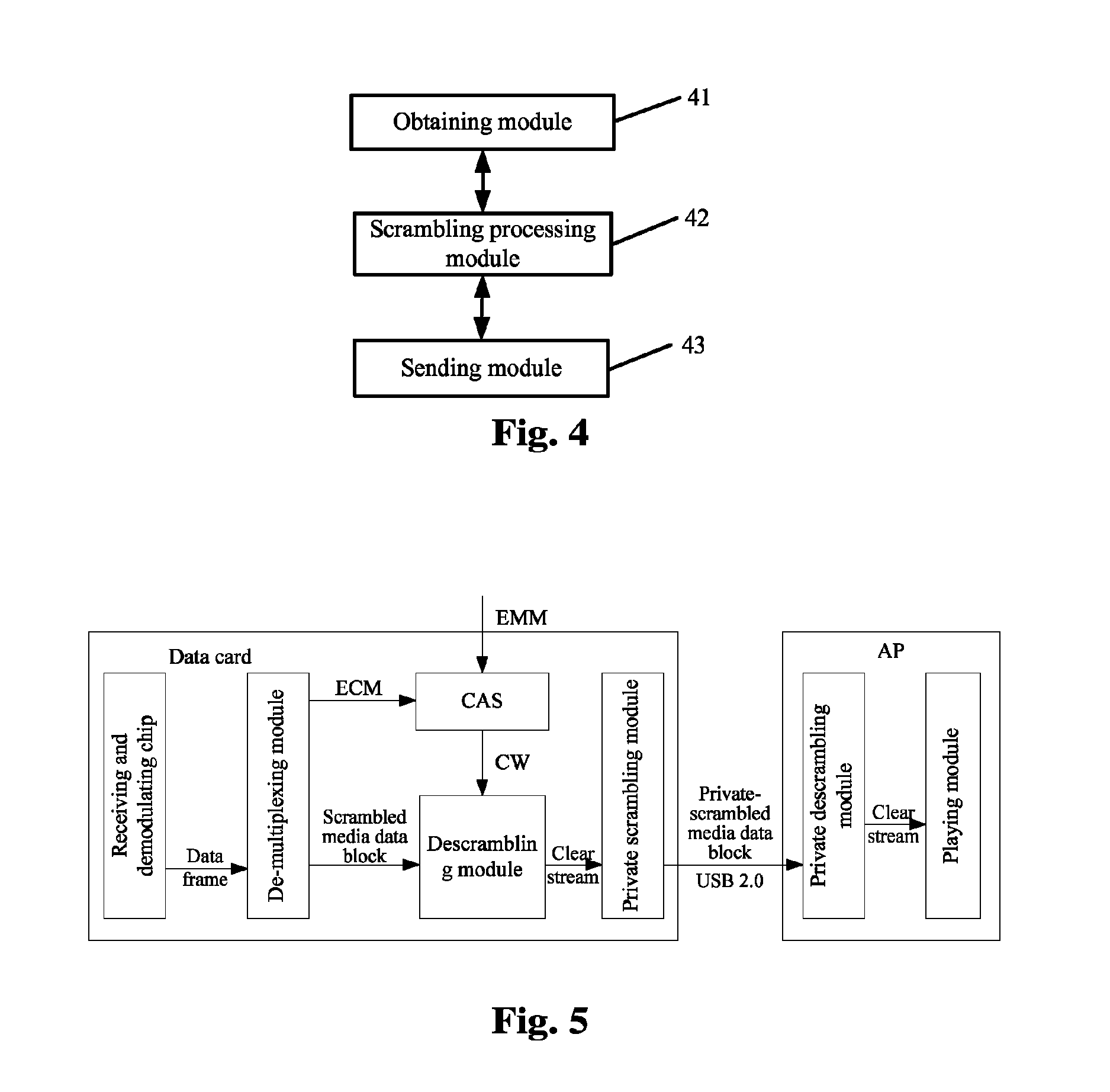
Information transmission method, system and data card
ActiveUS8843954B2Reduce loss rateKeys are prevented from being stolenUser identity/authority verificationGHz frequency transmissionInformation transmissionComputer science
The disclosure provides an information transmission method, system and data card, wherein the method comprises: a sender scrambling original information in a predetermined scrambling way, and sending scrambled information to a receiver; the receiver receiving the scrambled information, and descrambling the scrambled information in a predetermined descrambling way to obtain the original information, wherein the predetermined scrambling way corresponds to the predetermined descrambling way. In accordance with the disclosure, contents to be transmitted are scrambled and the scrambled contents are sent to the receiver, and the receiver can restore the transmitted contents by performing descrambling according to the scrambling way used by the sender. The disclosure can avoid the transmitted contents from being monitored, as well as avoid the keys from being stolen; therefore, the security of the transmitted contents is effectively improved.
Owner:EIGHT DEER VENTURES LLC
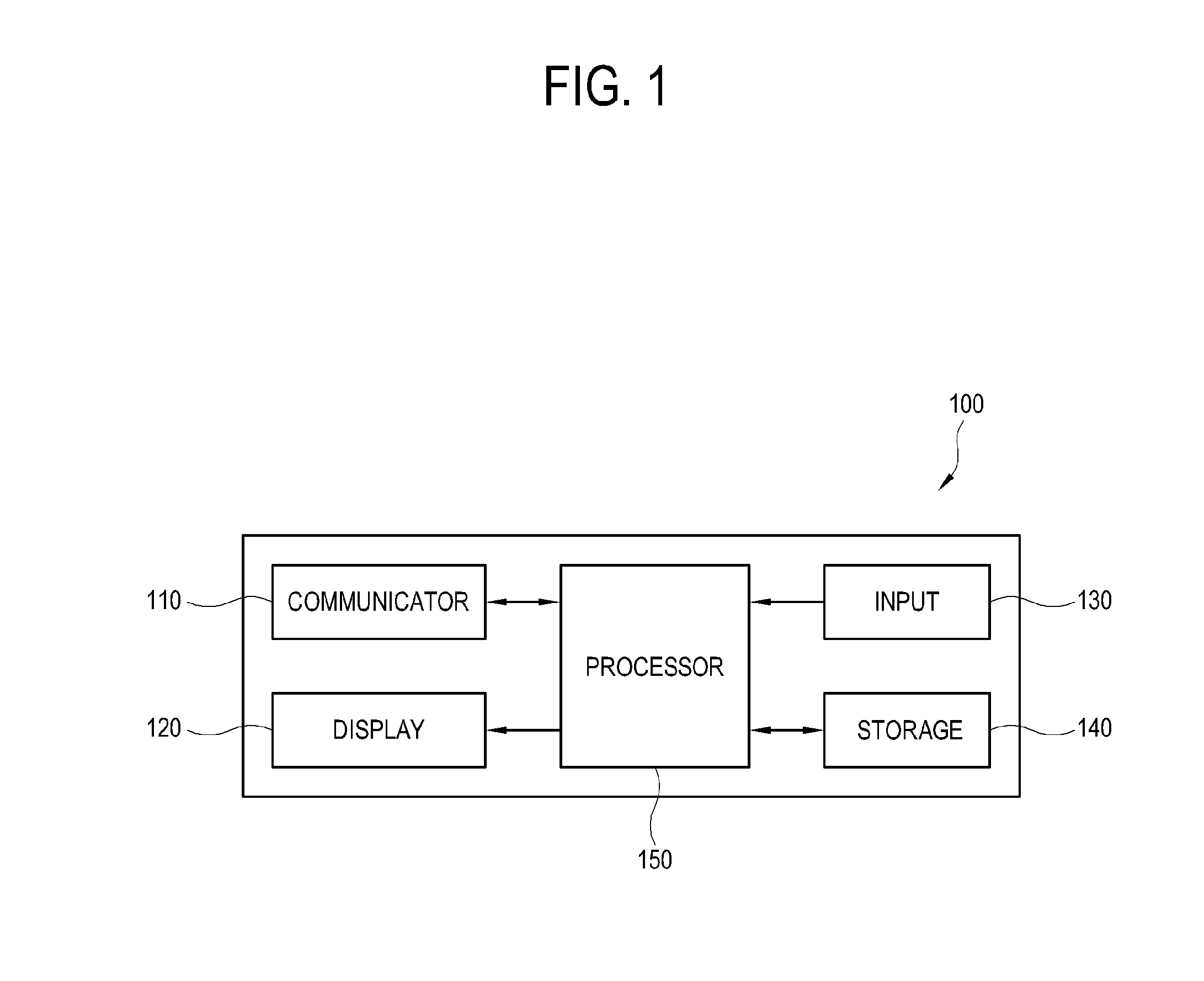
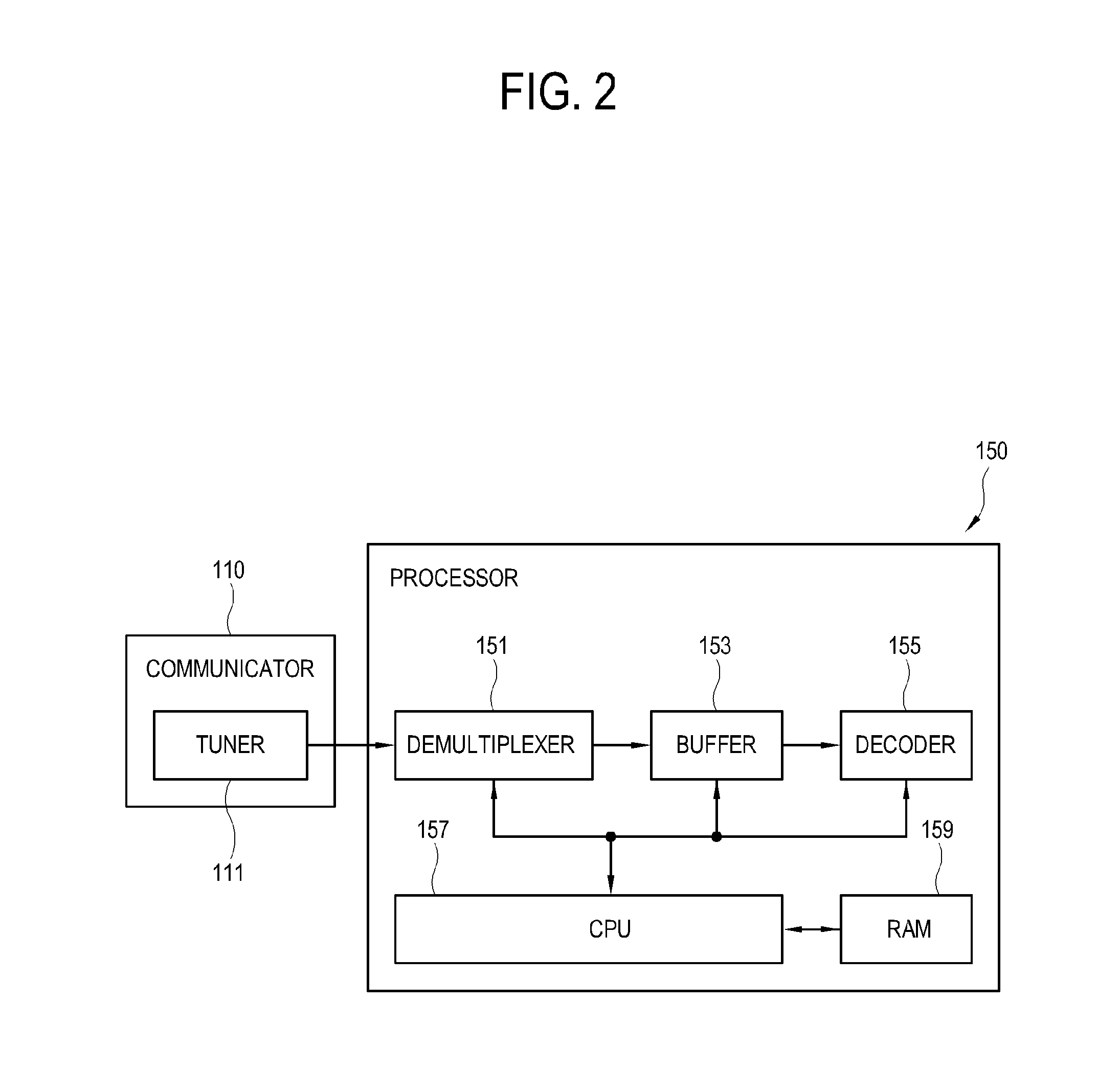
Image processing apparatus and control method thereof
ActiveUS20160098544A1Tightening content securityKeep Content SafeTelevision systemsImage acquisitionComputer hardwareImaging processing
An image processing apparatus includes: a signal receiver configured to receive an encrypted image signal; a storage configured to temporarily store the encrypted image signal received in the signal receiver; a signal decryptor configured to convert the encrypted image signal into a decrypted image signal by decrypting the encrypted image signal output from the storage with a preset first secret key; and a decoder configured to decode the decrypted image signal output from the signal decryptor to be displayed an image.
Owner:SAMSUNG ELECTRONICS CO LTD
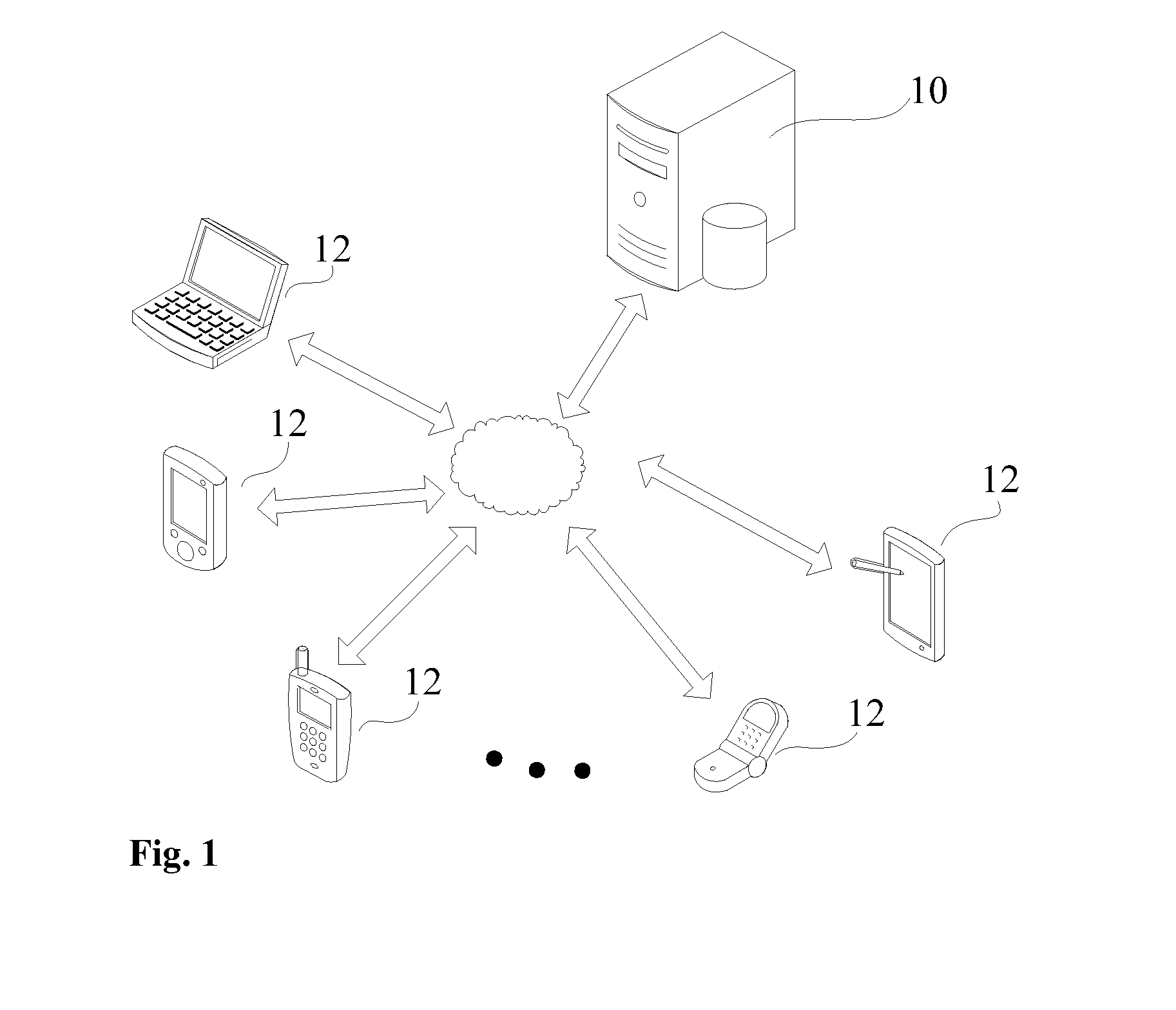
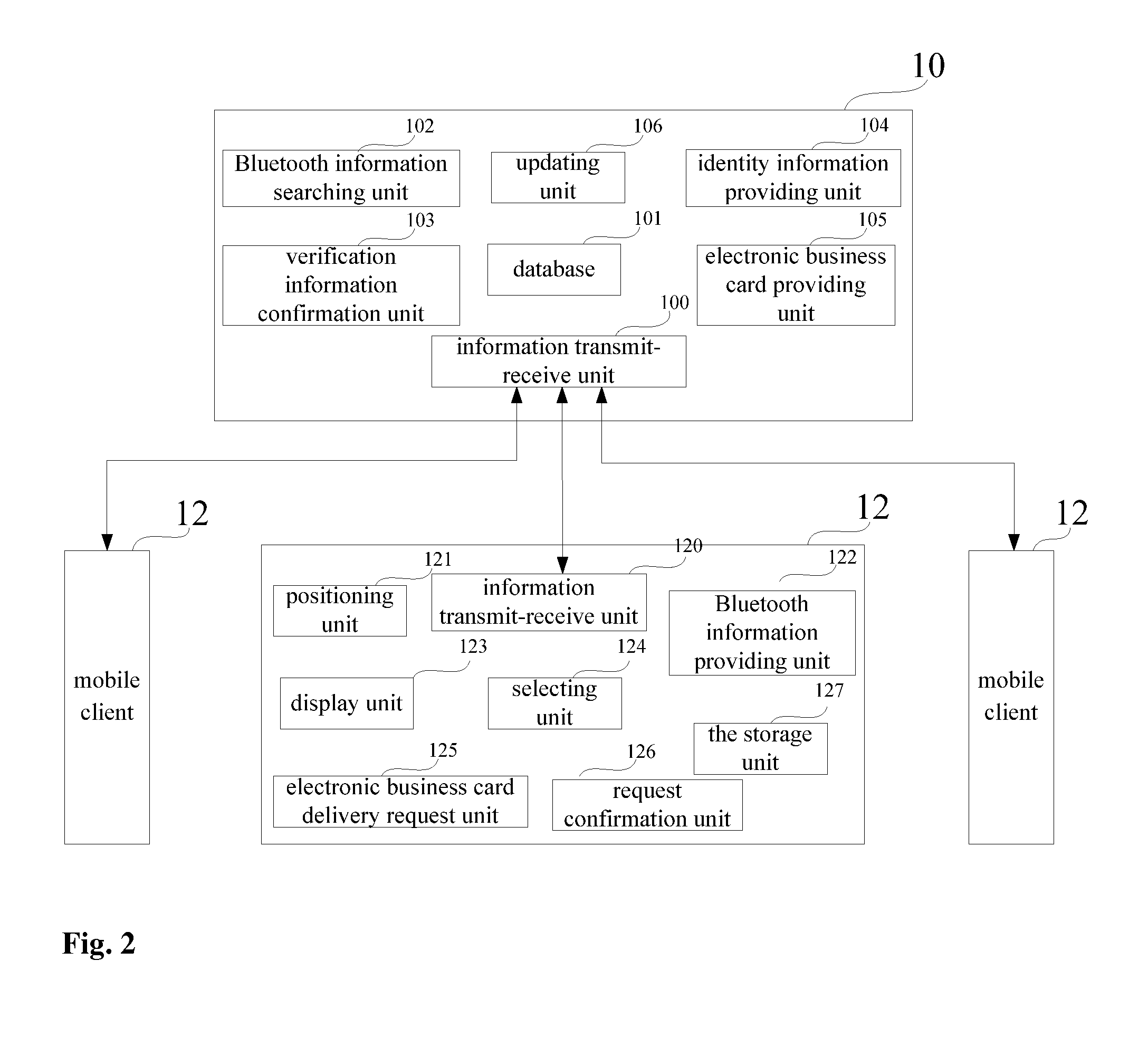
Method and system integrating geographical location information and bluetooth technology for relaying electronic business card
ActiveUS9008652B2Easy to operateAccuracy safetySubstation equipmentOffice automationBusiness cardGeolocation
Provided in the present invention are method and system for delivering an electronic business card by combining geographical location information and Bluetooth technology. The method comprises: a requesting user submitting the current geographical location information, the name of a Bluetooth communication device, and a list of the names of other detected Bluetooth communication devices to an electronic business card delivery server by using a mobile client, acquiring a list of users corresponding to neighboring mobile clients as well as the user's condensed identity information, the neighboring mobile clients being located within a predetermined distance range and located within a detection range of the Bluetooth communication device; selecting a user from the user list, sending an electronic business card delivery request to the electronic business card delivery server; the electronic business card delivery server transmitting the request to the mobile client corresponding to the selected user, and when receiving corresponding confirmation information, responding to the request so as to deliver the electronic business card. Compared with the prior art, the present invention allows for the delivery of large quantity of electronic business cards, simplified operations, and ensured accuracy and security of electronic business card contents.
Owner:SHANGHAI HEHE INFORMATION TECH DEV
Method, media gateway and system for transmitting content in call established via media gateway control protocol
ActiveUS8181013B2Keep Content SafeImprove securitySecuring communicationSelection arrangementsPlaintextSoftswitch
Owner:HUAWEI TECH CO LTD
Streaming System and Streaming Method
InactiveUS20120016958A1Keep Content SafeImprove securityKey distribution for secure communicationUser identity/authority verificationEncryption
A streaming system includes an authoring unit (2), a stream server (3) and a client terminal (5). The authoring unit generates a file composed of encrypted contents data and the ancillary information at least containing the packetizing control information for generating an RTP packet, a non-encrypted codec dependent header made up of the information pertinent to encoded contents data, and the encryption information for decrypting the encrypted contents data form packet to packet. The streaming server packetizes the encrypted contents data along with at least the codec dependent header and distributes the resulting data as a stream. The client terminal refers to the codec dependent header of the received packet, re-assembles the packet, and decrypts the encrypted contents data of the re-assembled packet to generate contents data.
Owner:SONY CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com