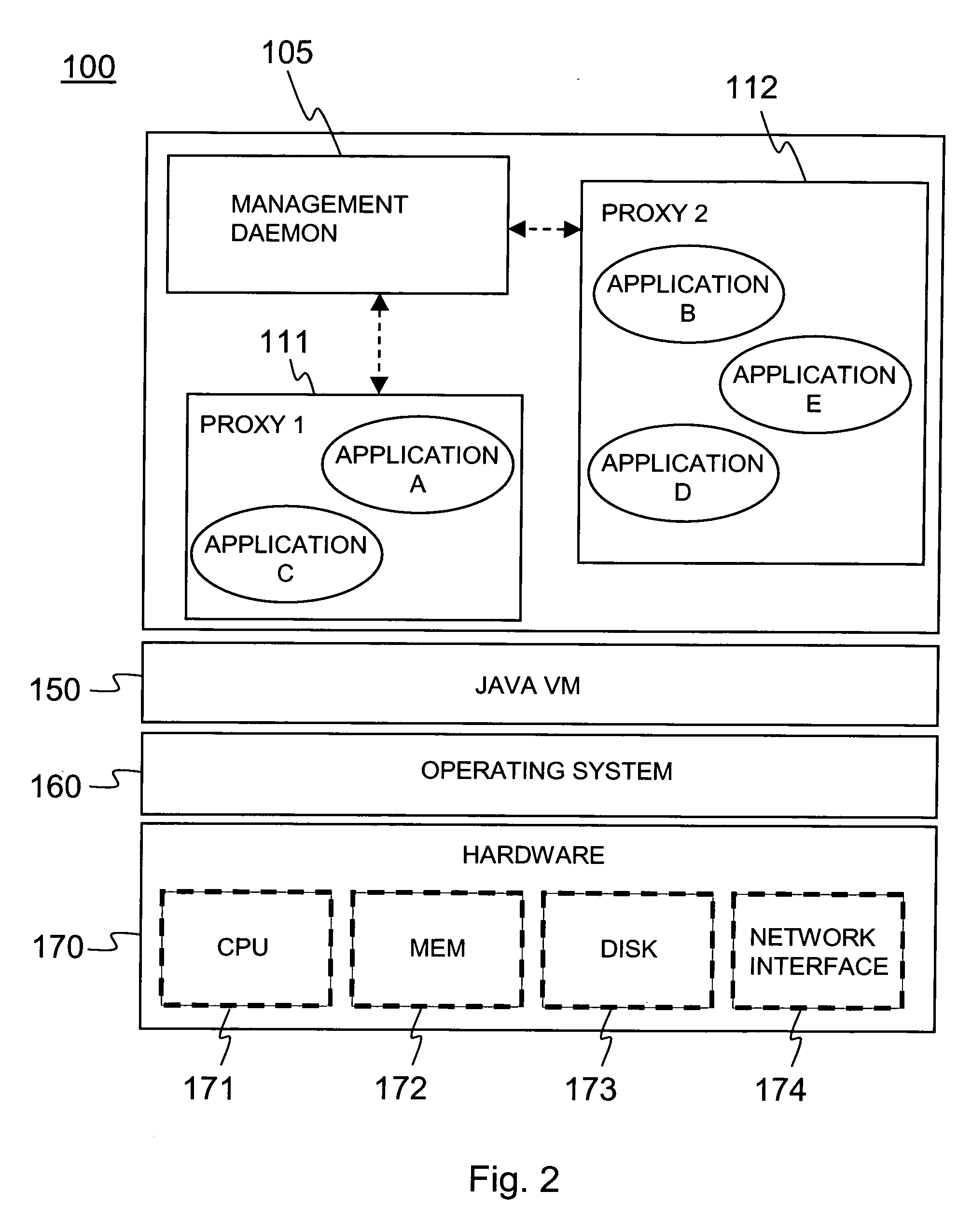
Patents
Literature
80 results about "Application firewall" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An application firewall is a form of firewall that controls input, output, and/or access from, to, or by an application or service. It operates by monitoring and potentially blocking the input, output, or system service calls that do not meet the configured policy of the firewall. The application firewall is typically built to control all network traffic on any OSI layer up to the application layer. It is able to control applications or services specifically, unlike a stateful network firewall, which is - without additional software - unable to control network traffic regarding a specific application. There are two primary categories of application firewalls, network-based application firewalls and host-based application firewalls.
System and method for securing an enterprise computing environment
InactiveUS20180027006A1Process safetyKeep Content SafeMultiprogramming arrangementsComputer security arrangementsInternet privacyEnterprise computing
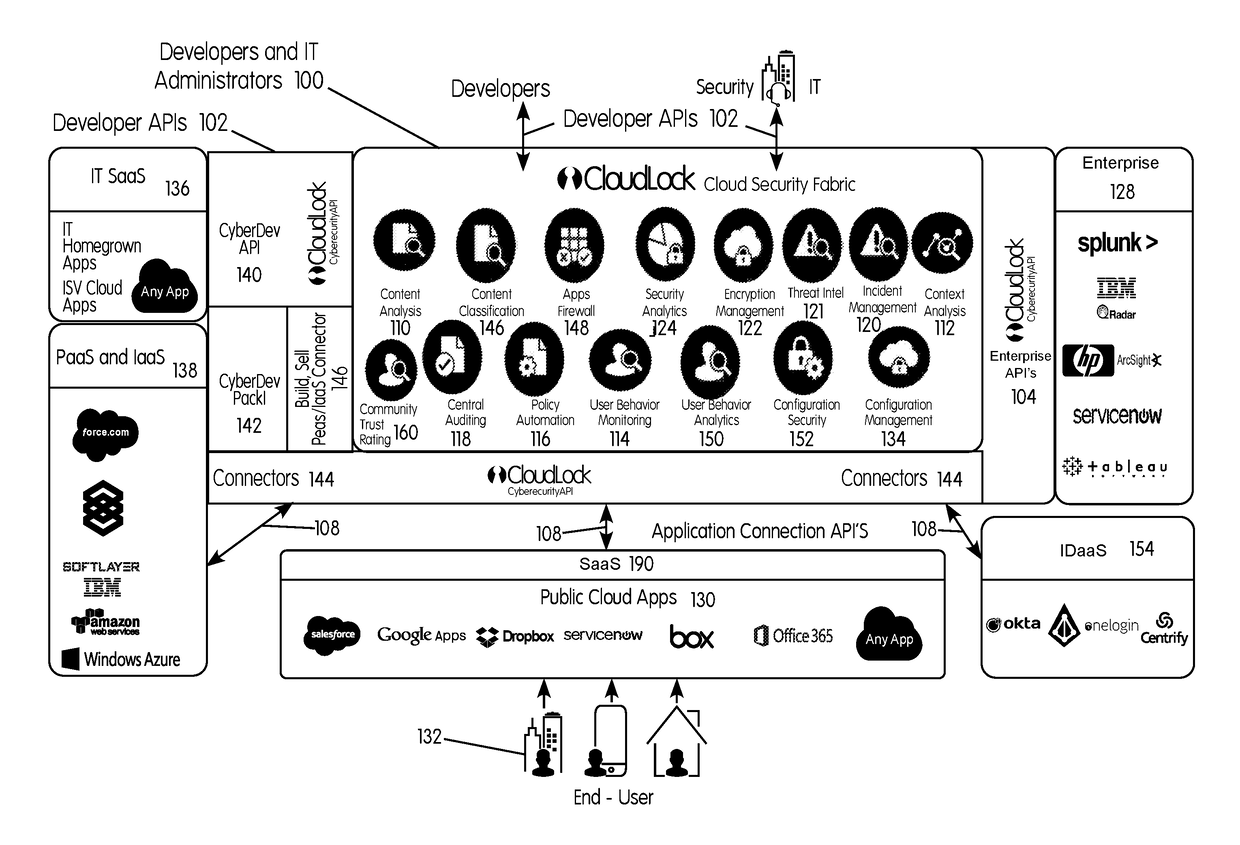
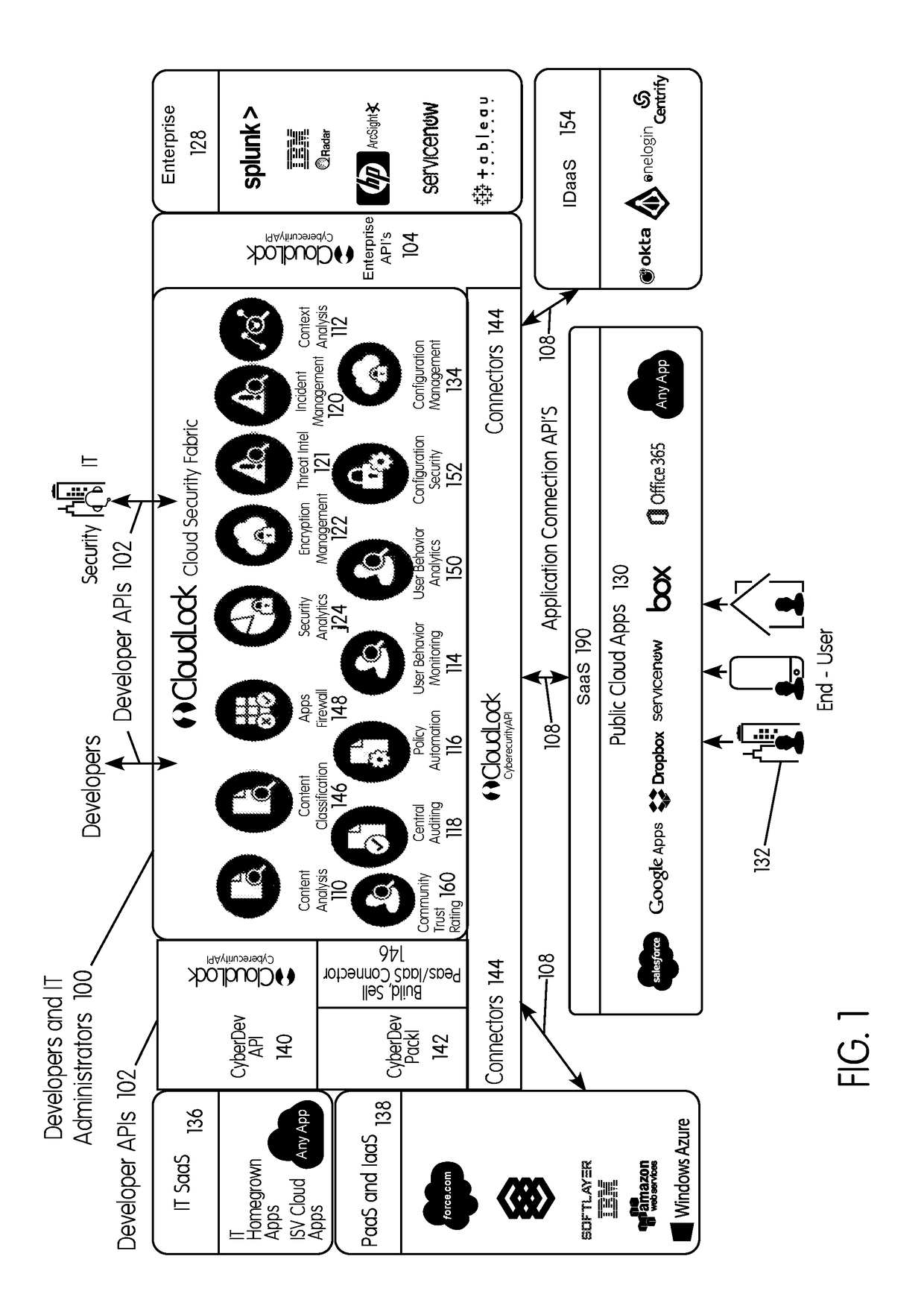
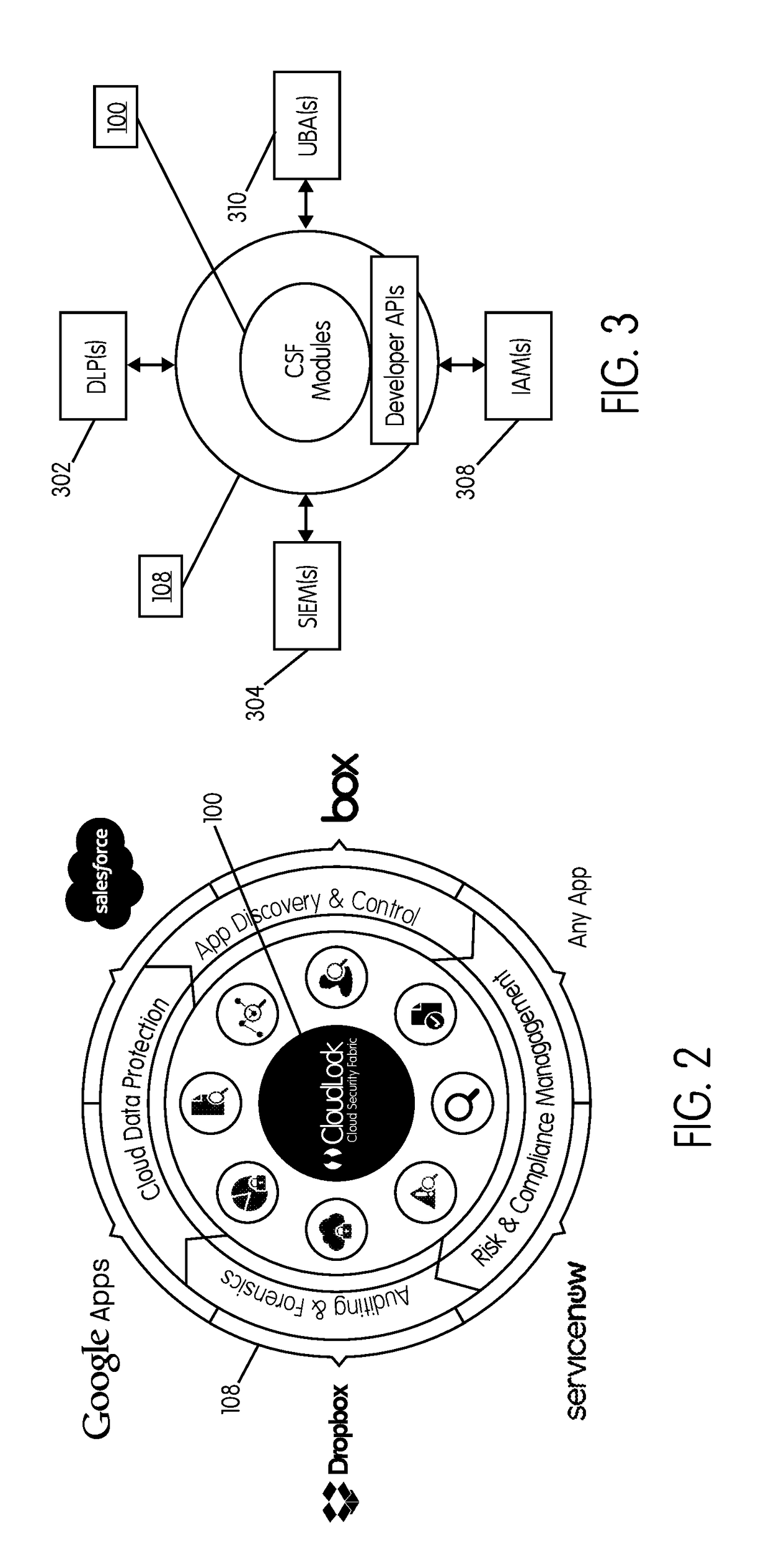
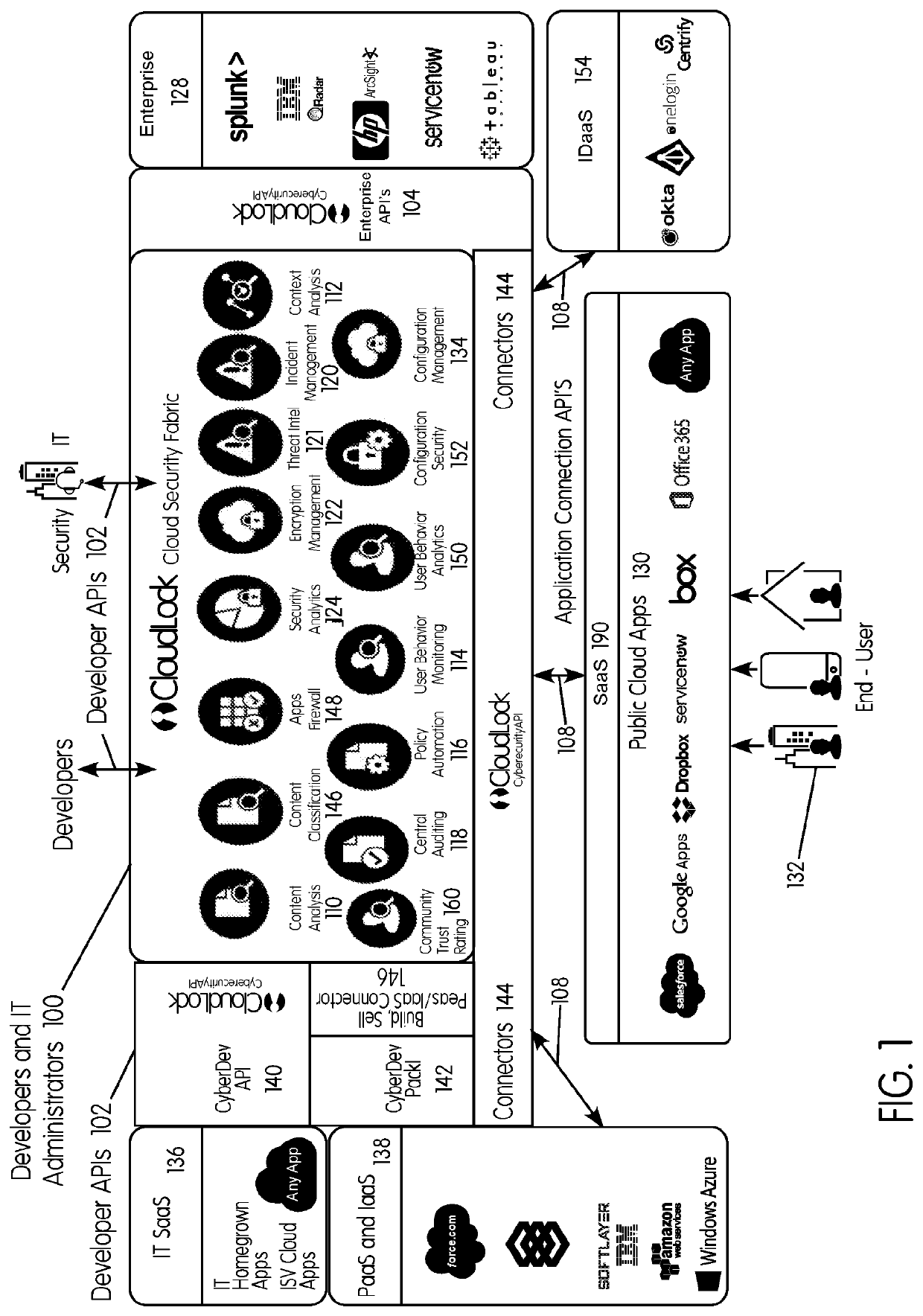
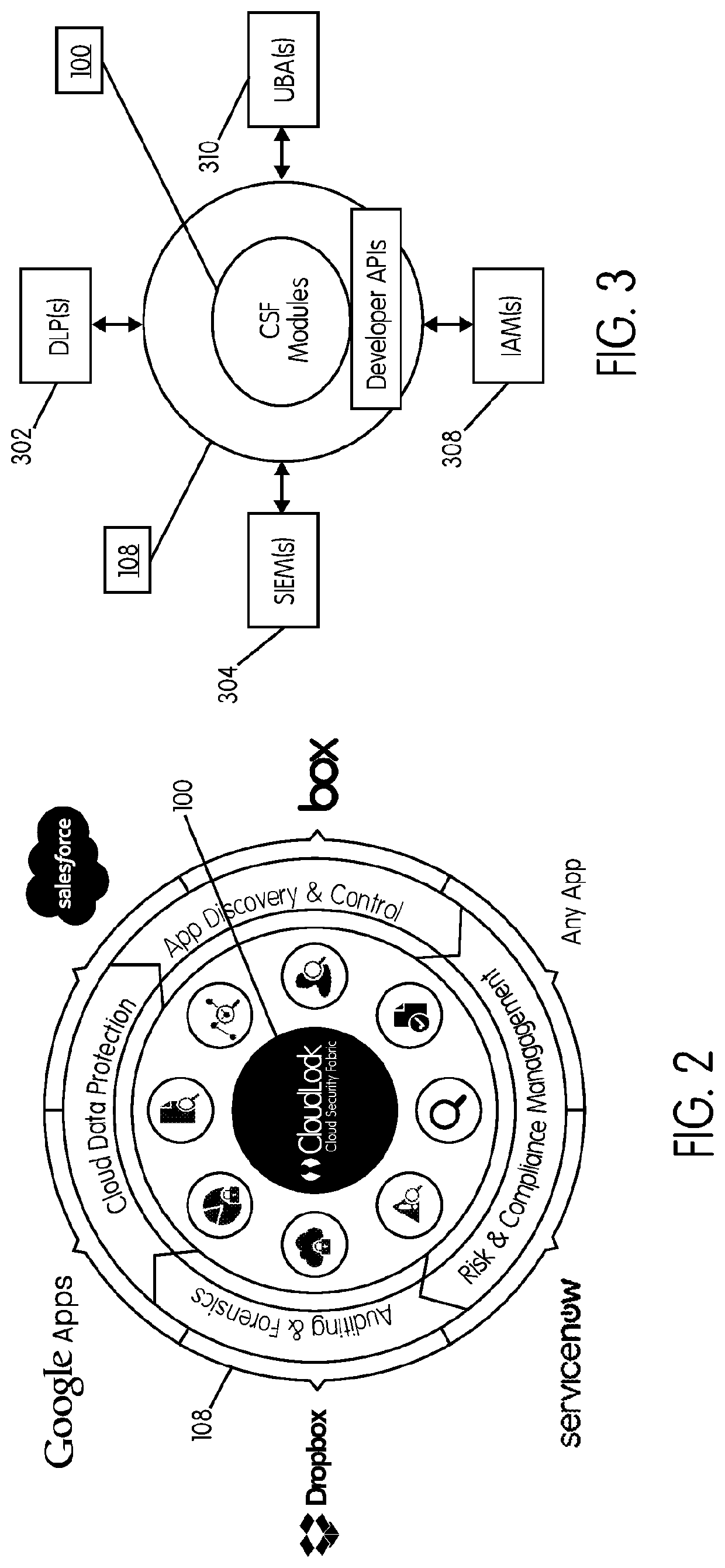
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CLOUDLOCK
System and method for securing an enterprise computing environment
InactiveUS20200137097A1Process safetyKeep Content SafeMultiprogramming arrangementsDigital data protectionBusiness enterpriseEnterprise computing
Methods and systems provided herein include a cyber intelligence system, a unified application firewall, and a cloud security fabric that has enterprise APIs for connecting to the information technology infrastructure of an enterprise, developer APIs 102 for enabling developers to access capabilities of the fabric and connector APIs by which the fabric may discover information about entities relevant to the information security of the enterprise (such as events involving users, applications, and data of the enterprise occurring on a plurality of cloud-enabled platforms, including PaaS / IaaS platforms), with various modules that comprise services deployed in the cloud security fabric, such as a selective encryption module, a policy creation and automation module, a content classification as a service module, and user and entity behavior analytics modules.
Owner:CISCO TECH INC
Distributed web application firewall
ActiveUS20090328187A1Computer security arrangementsMultiple digital computer combinationsWeb applicationWeb service
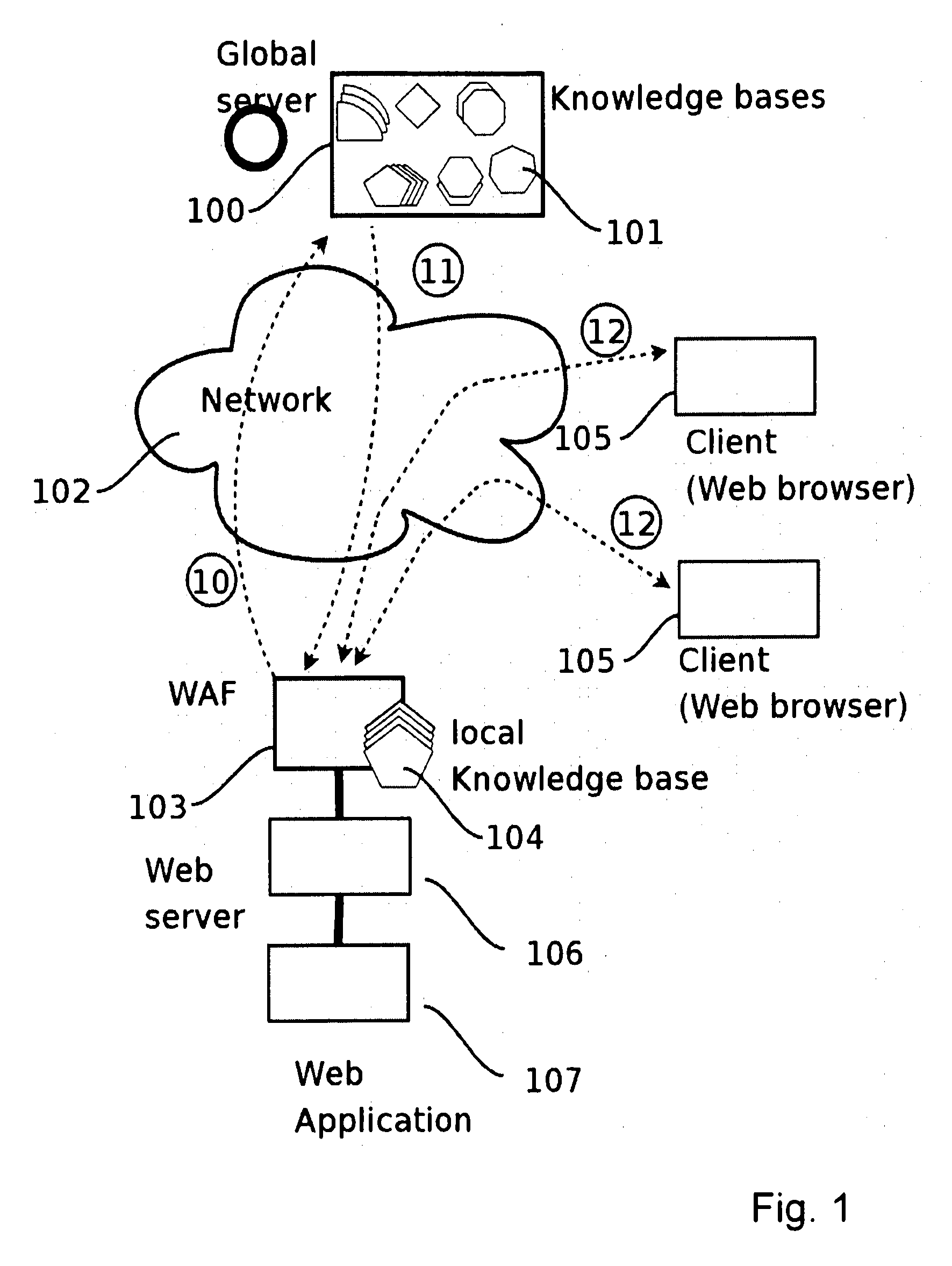
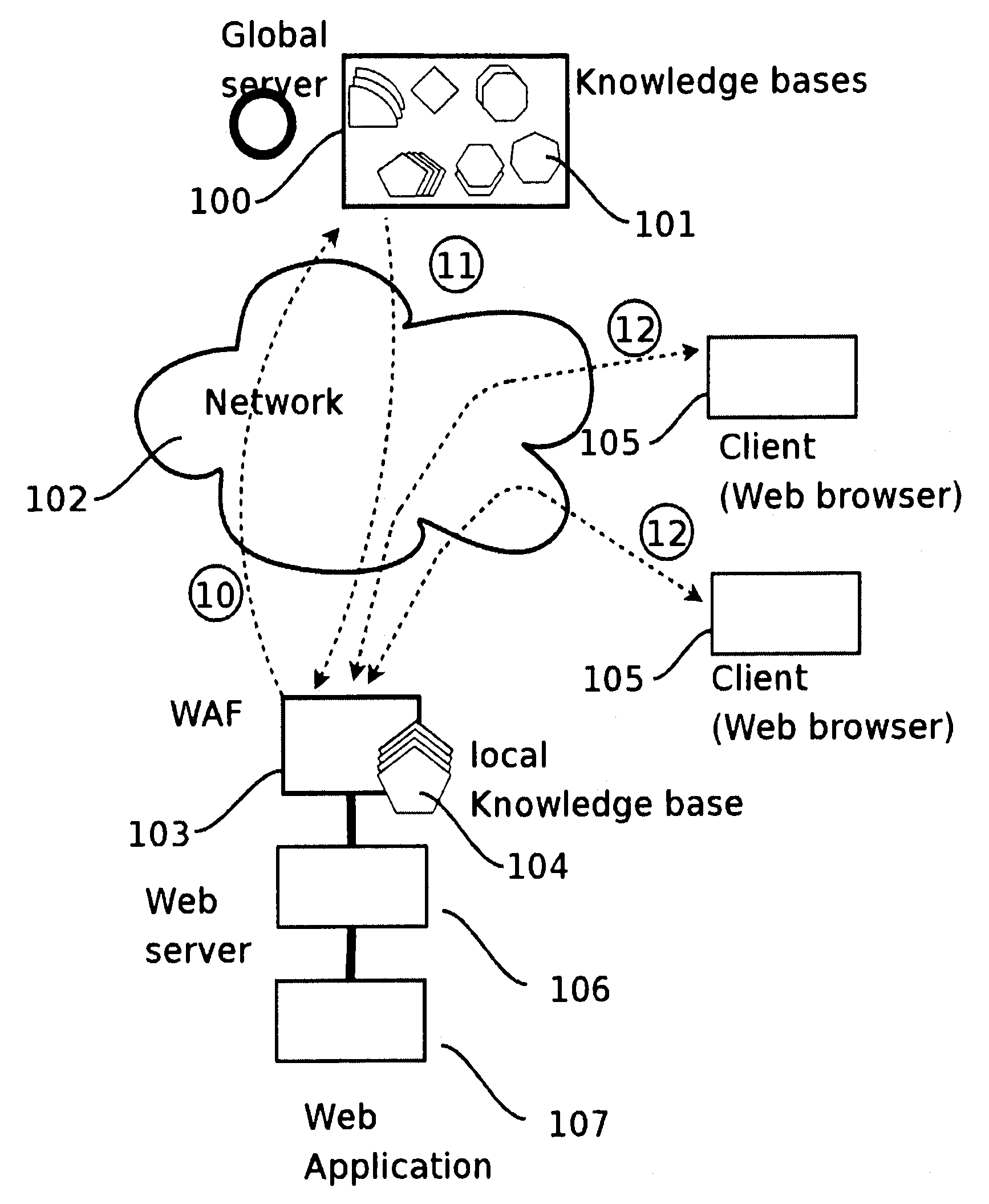
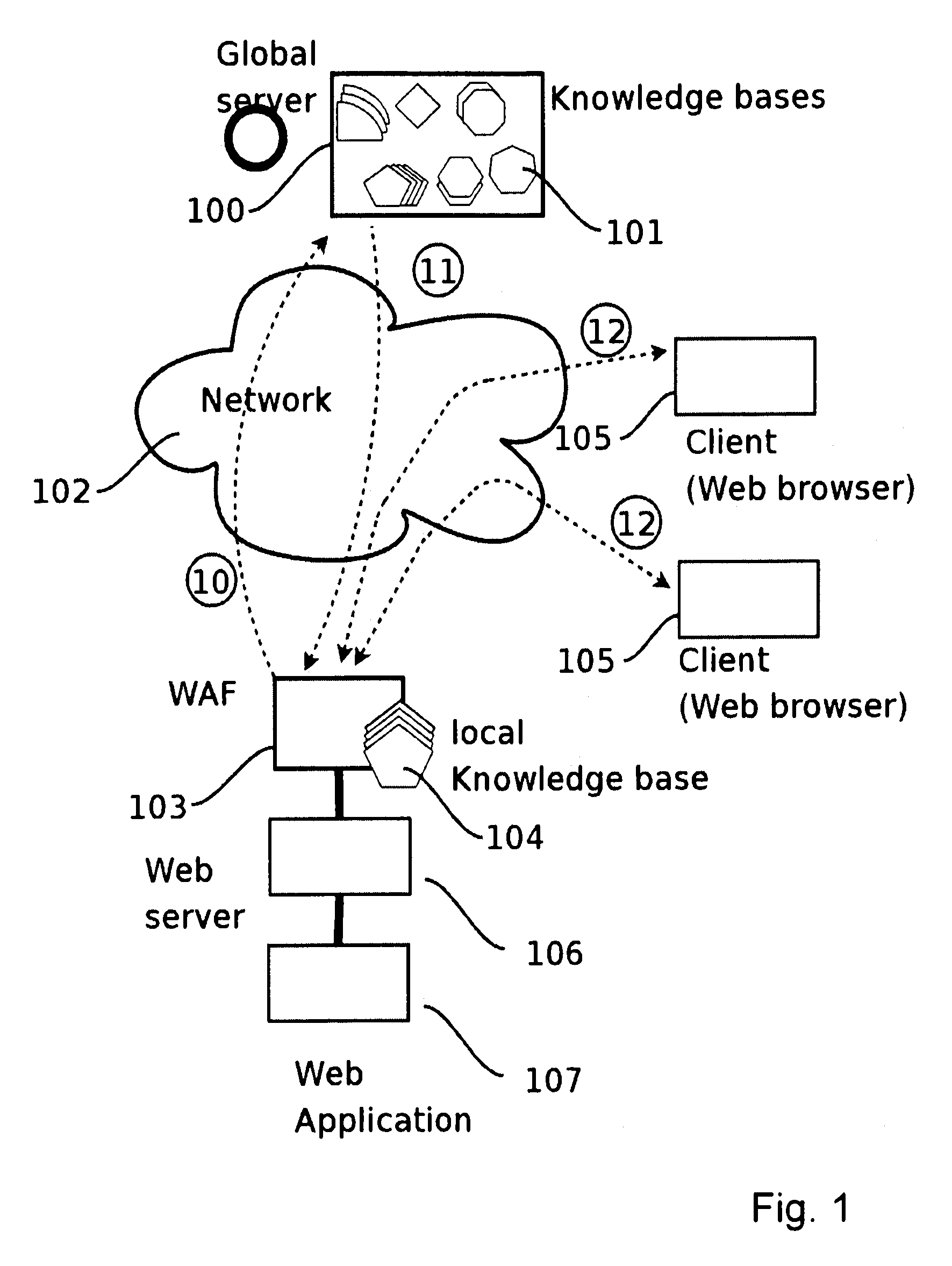
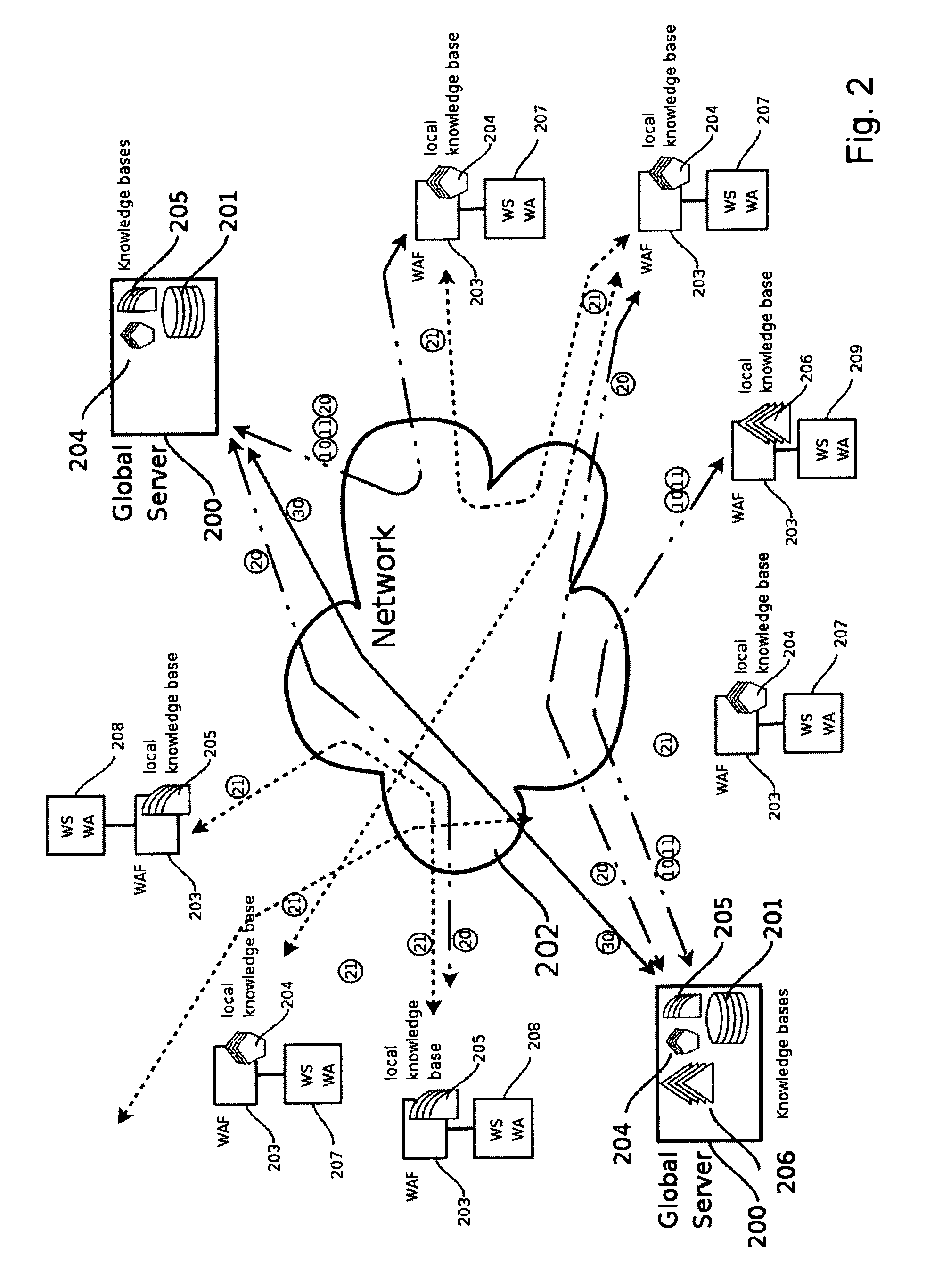
A method for protecting a Web application running on a first local Web Server bases from hacker attacks, said Web Server being connectable to at least one client, the method comprising the following steps: —providing a plurality of preset rules on said Server, which correspond to specific characteristics of HTTP requests; —receiving an HTTP request on said server from the client, said HTTP request comprising a plurality of characteristics; —analyzing said characteristics of said received HTTP request in accordance with said rules provided on said server; —rejecting said HTTP request, if said rules identify said HTTP request as harmful request; —accepting said HTTP request, if said rules identify said HTTP request as trustable request; —classifying said HTTP request as doubtful request, if said rules identify said request neither as harmful request nor as trustable request; —evaluating the characteristics of said doubtful local request; —generating a learned rule on basis of the edge base evaluation.
Owner:PULSE SECURE +1
Access control list checking
Method and system for dynamically checking an access control list during the data transfers between a client web browser and a web server. The method and system allow checking of access control list by an application firewall, independent from the web application. The rules, upon which the checking is based, can be easily updated without affecting the web application.
Owner:PALO ALTO NETWORKS INC
Web application security filtering
InactiveUS20100332837A1Simple and efficientLess sensitiveDigital data processing detailsUser identity/authority verificationWeb applicationApplication server
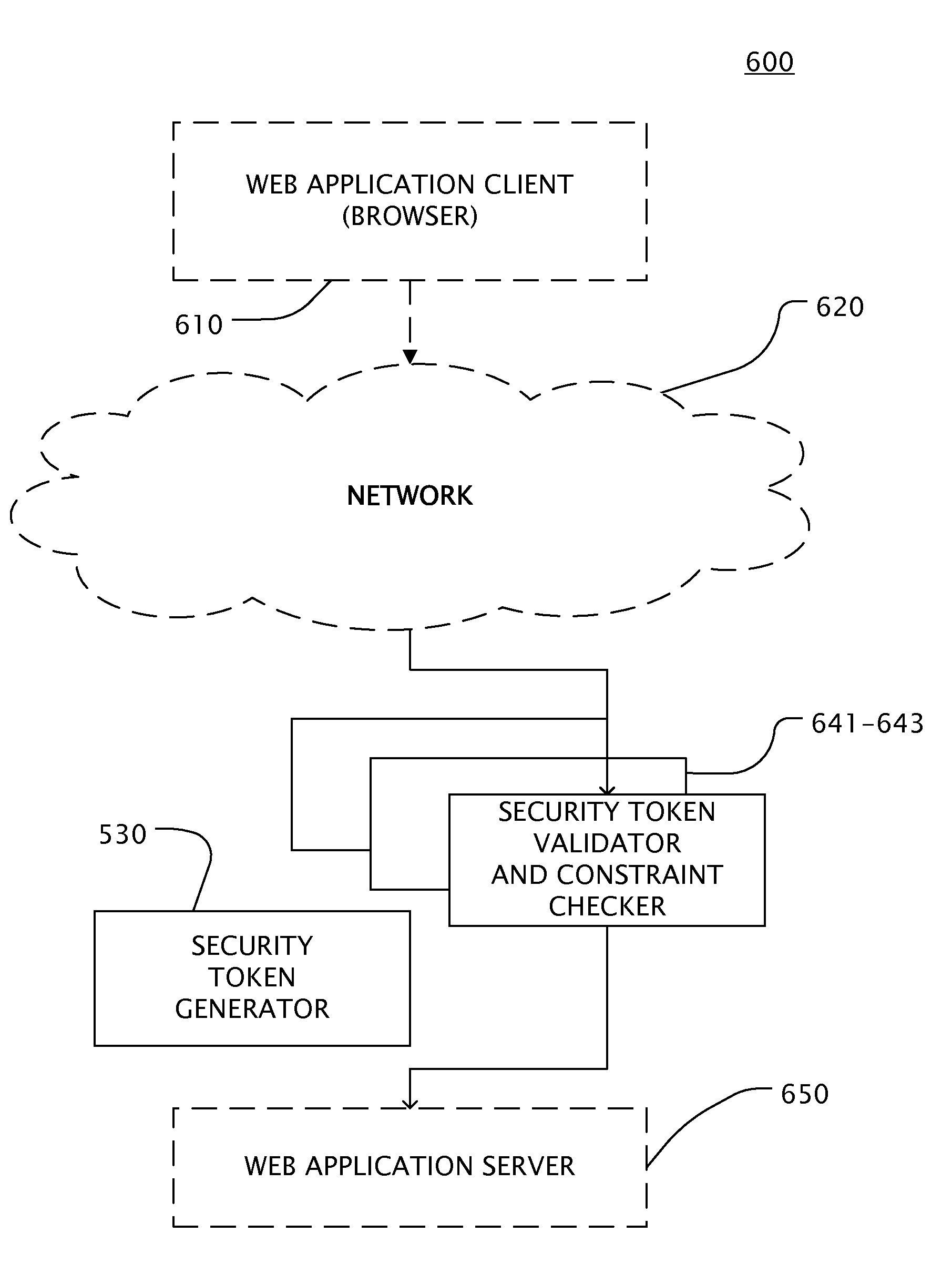
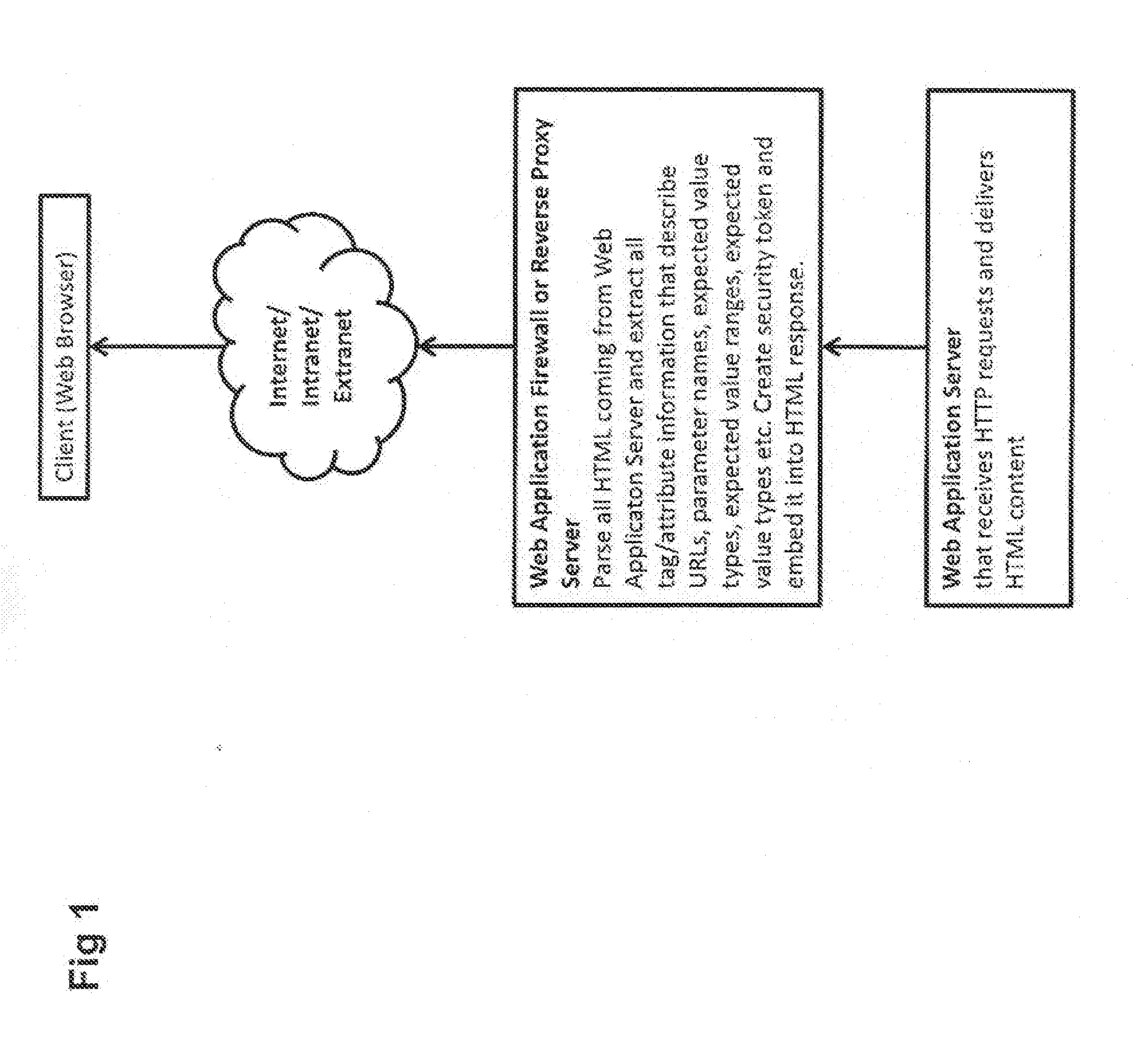
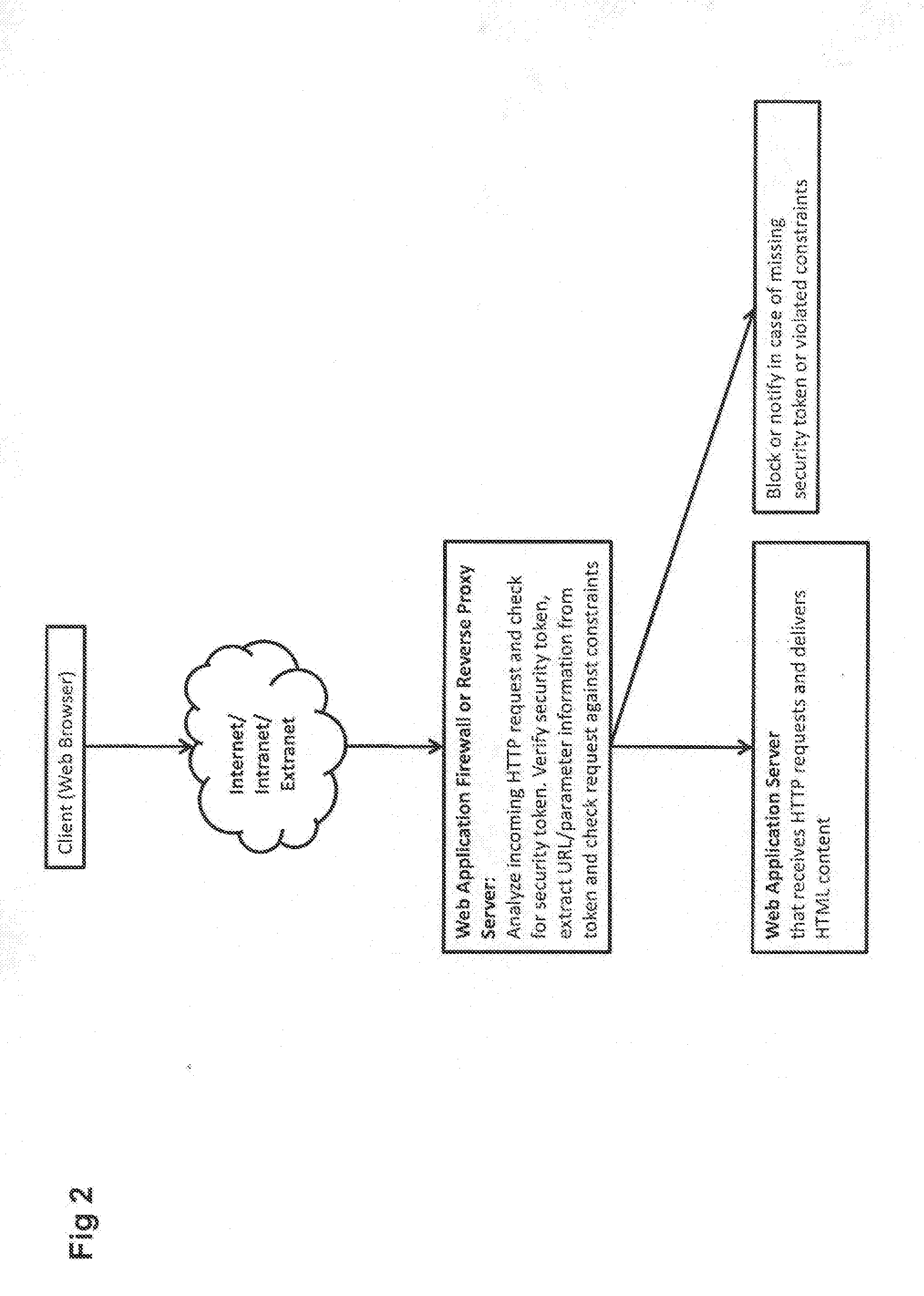
User inputs and / or Uniform Resource Identifier (URI), historically and popularly referred to as Universal Resource Locator (URL), requests in a content description language are passed through a security service (Web application firewall or a reverse Web proxy server) that is placed in front of Web application servers in order to protect the servers from hacking attempts. For validating Webform user inputs and / or URI requests and parameters the content description language is enriched by the security service with additional security tokens that are dynamically created based on the content being transferred. The user receives the information and returns input with the security tokens. The security service can then verify all provided user input data against the constraints described in the corresponding security token. As a result, the method may block the HTTP request or create log messages or notification events in reaction to violations of the user input data compared to the constraints in the security token.
Owner:PHION
Next-generation application firewall system and defense method
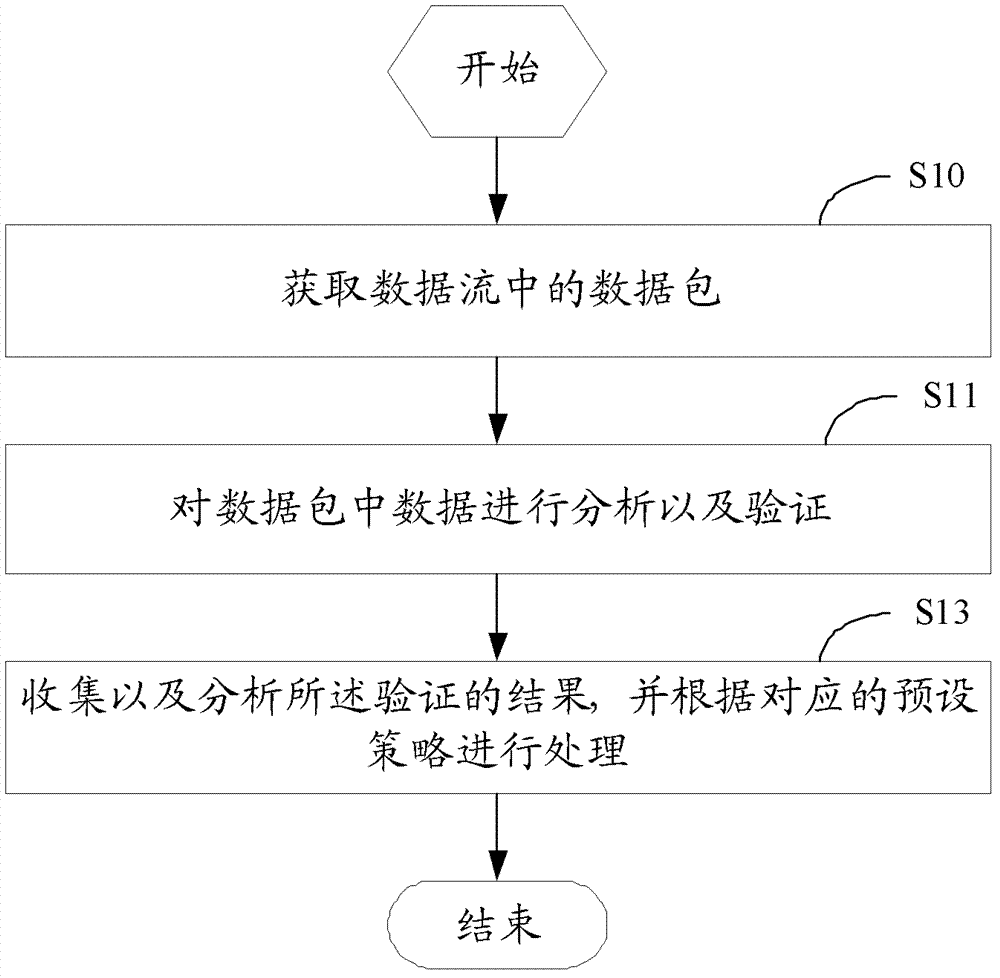
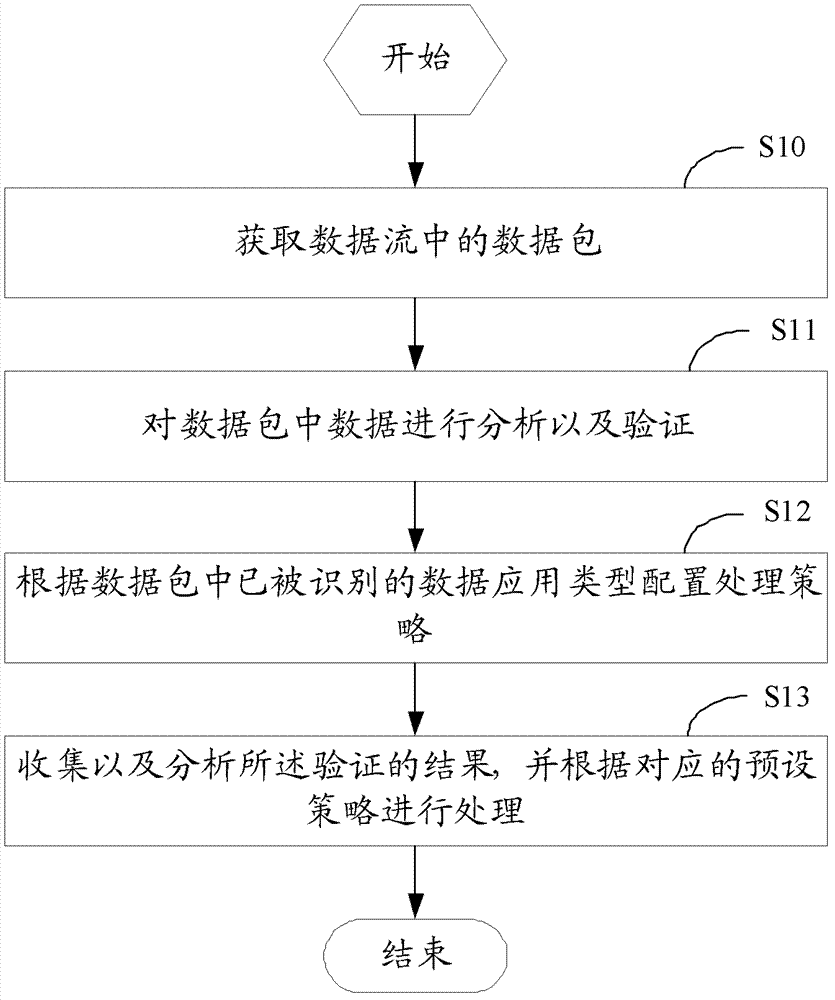
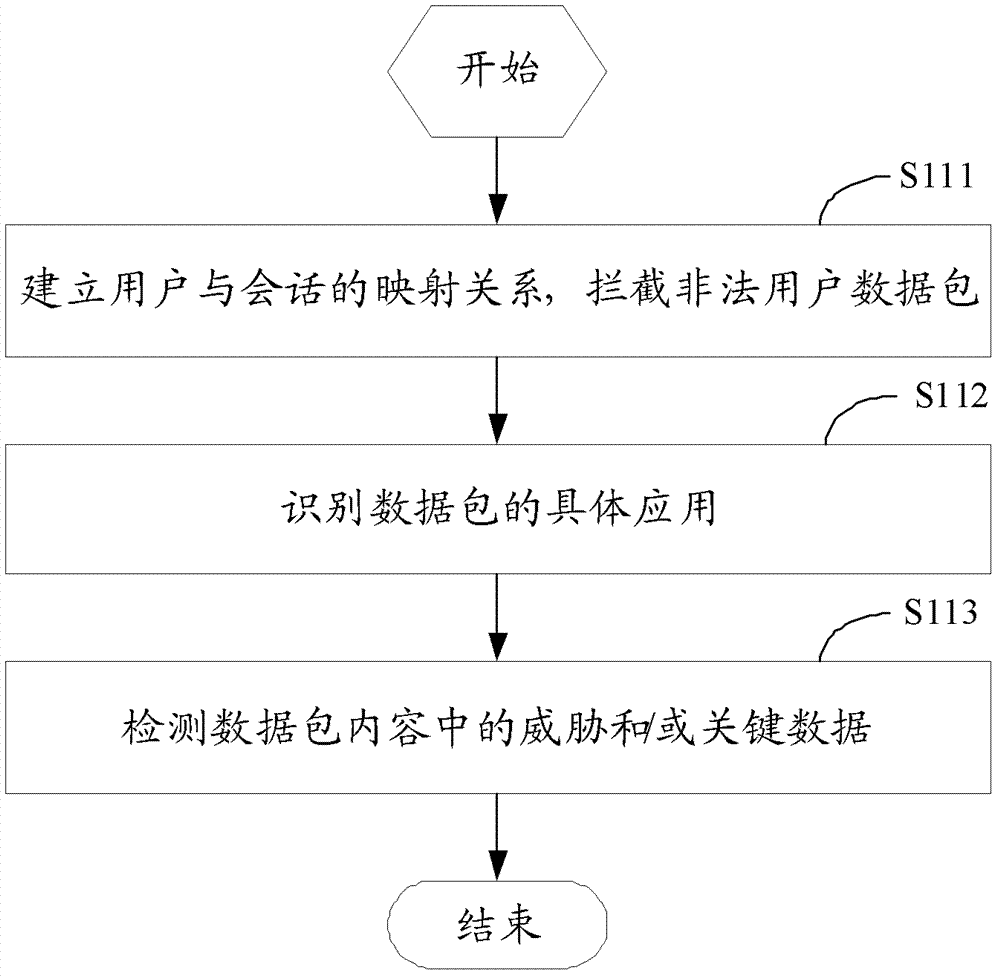
The invention discloses a next-generation application firewall system and a defense method. The defense method can comprise the following steps of: acquiring a data package in a data stream; carrying out analyzing and verifying on the data in the data package; and collecting and analyzing verified results, and carrying out processing according to a corresponding preset strategy. According to the next-generation application firewall system and the defense method, the shortages of traditional safety devices are holistically solved, and meanwhile, the performances of the devices can not degrade after all functions are started.
Owner:SANGFOR TECH INC
Security of virtual computing platforms
InactiveUS20070073858A1Process safetyDigital computer detailsSecuring communicationAnti virusComputer hardware
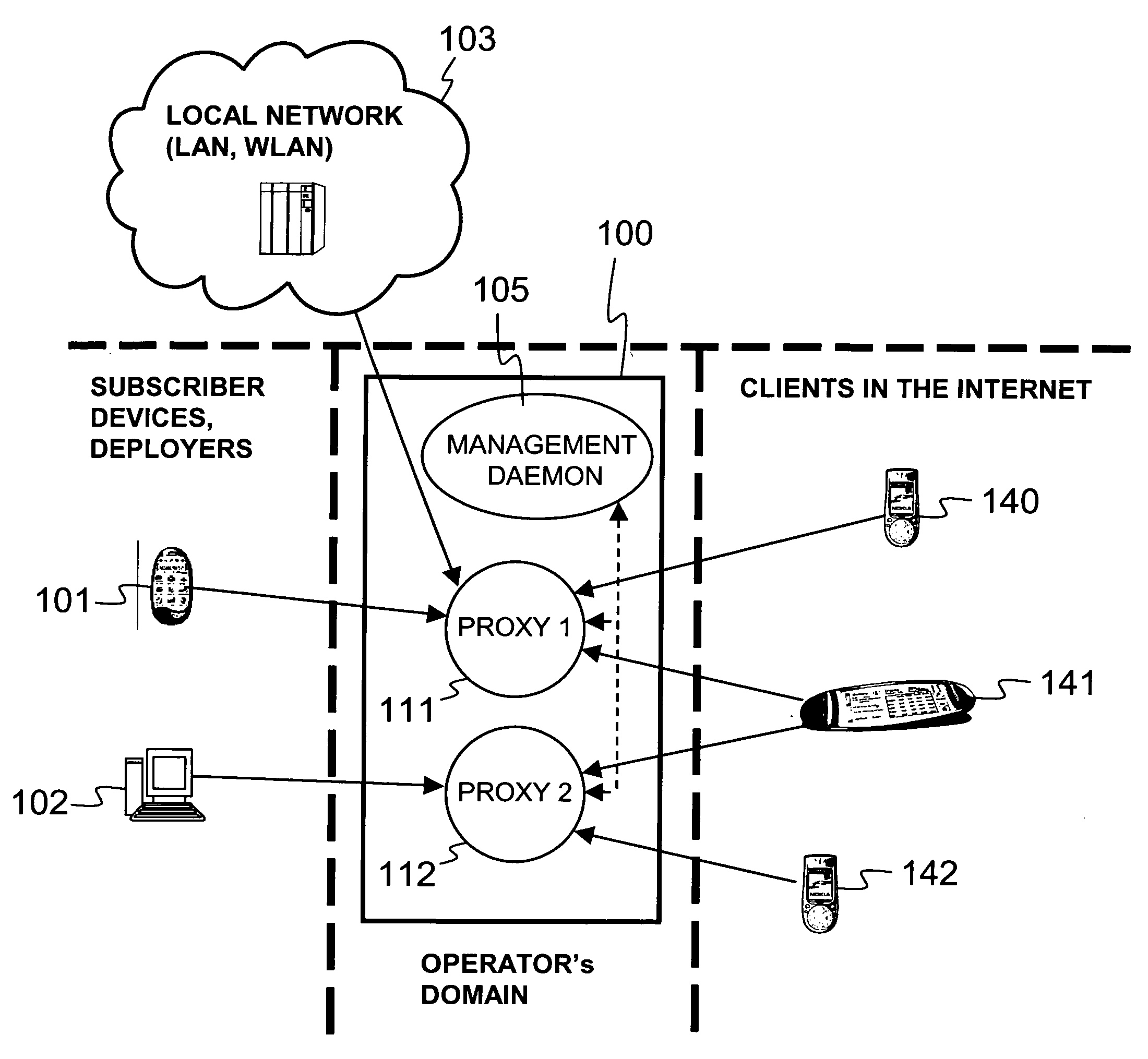
The invention relates to a virtual computing platform for providing subscribers of the virtual computing platform with means for running their applications on the platform instead of running the applications on their mobile devices. The virtual computing platform is adapted to route internal communication directed from a first application of the platform to a second application of the platform via a set of external security appliances. The set may include a firewall, a security gateway, an application layer firewall, a web shield, an anti-virus device and an anti-spam device.
Owner:NOKIA CORP
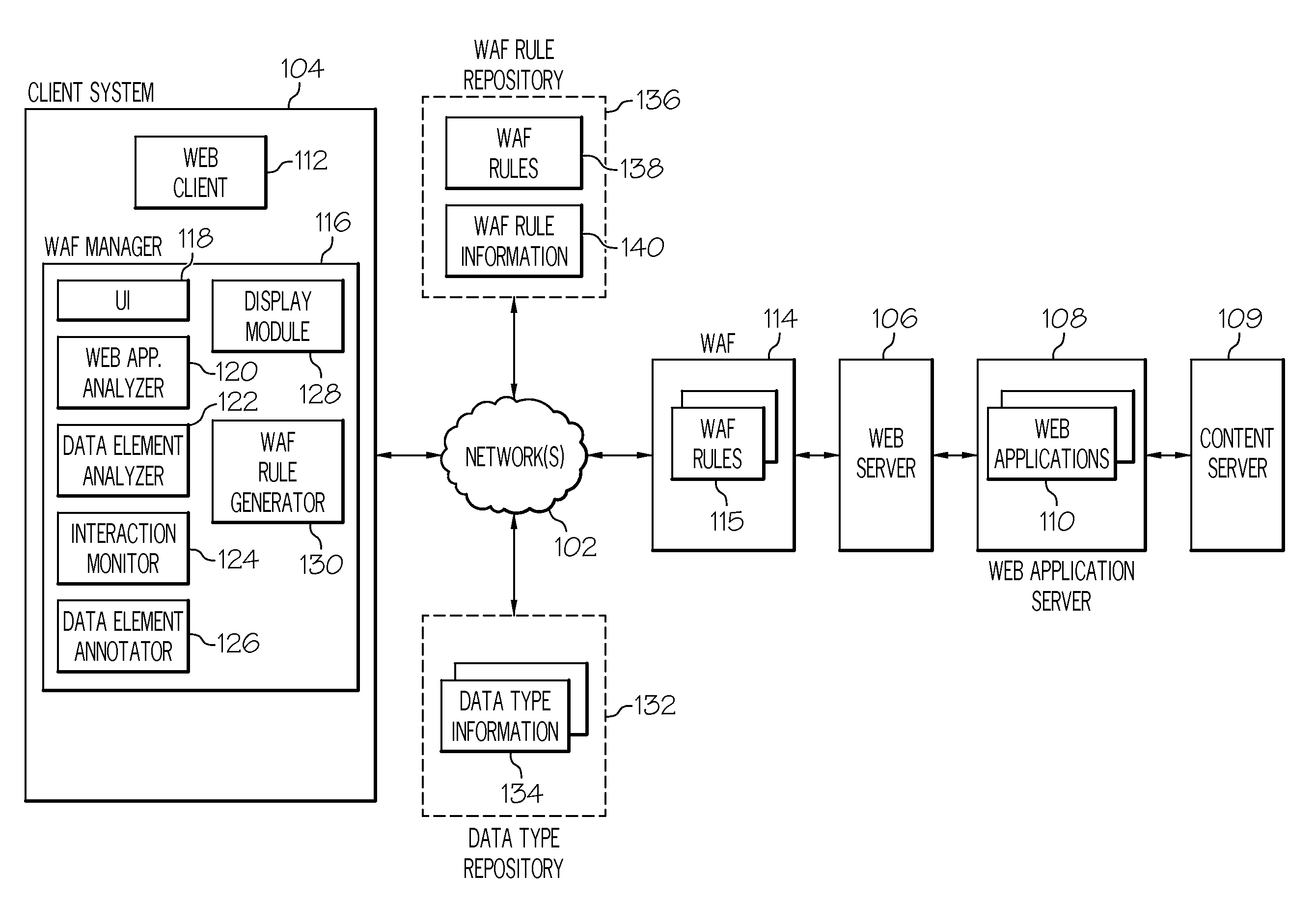
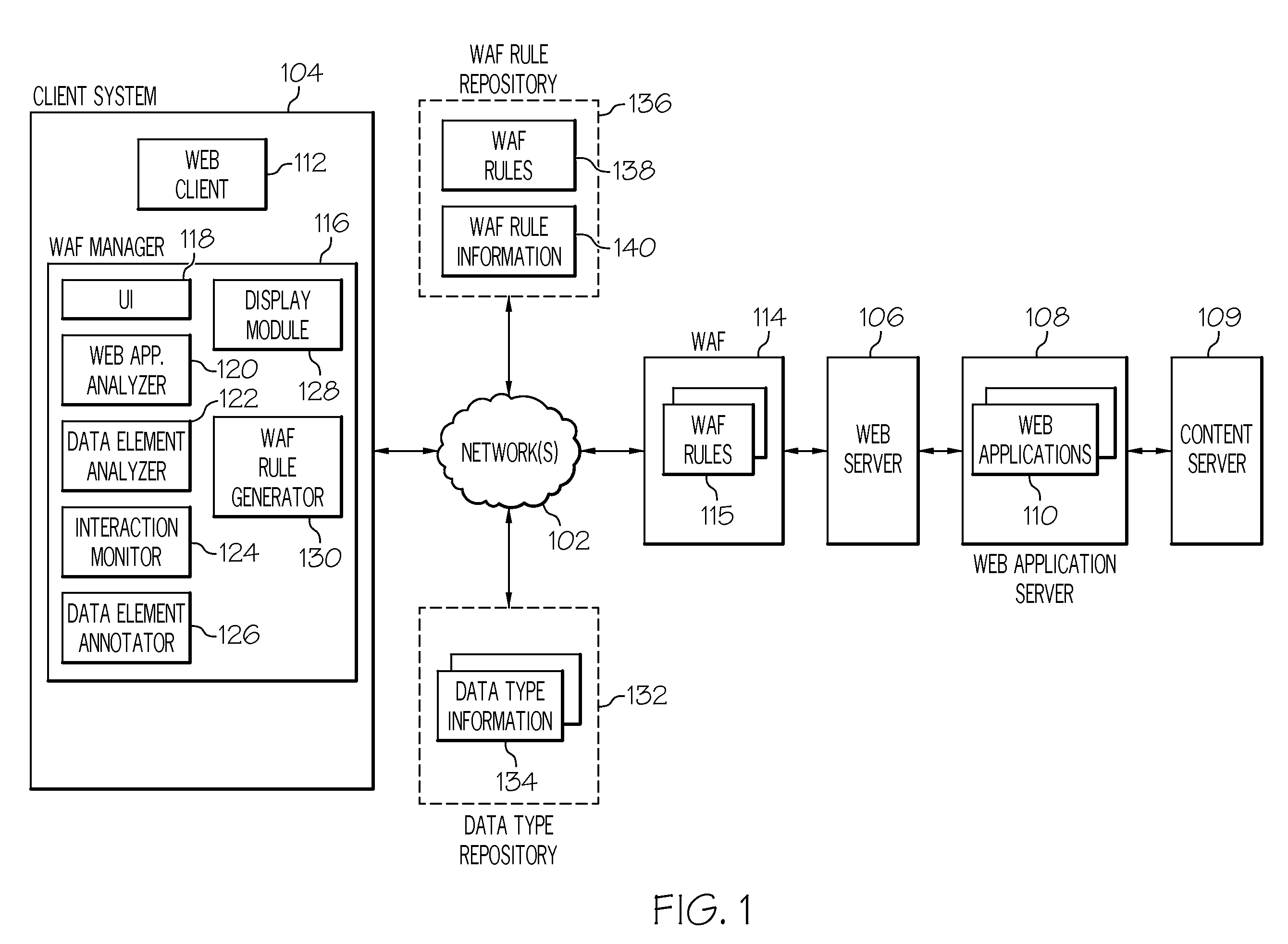
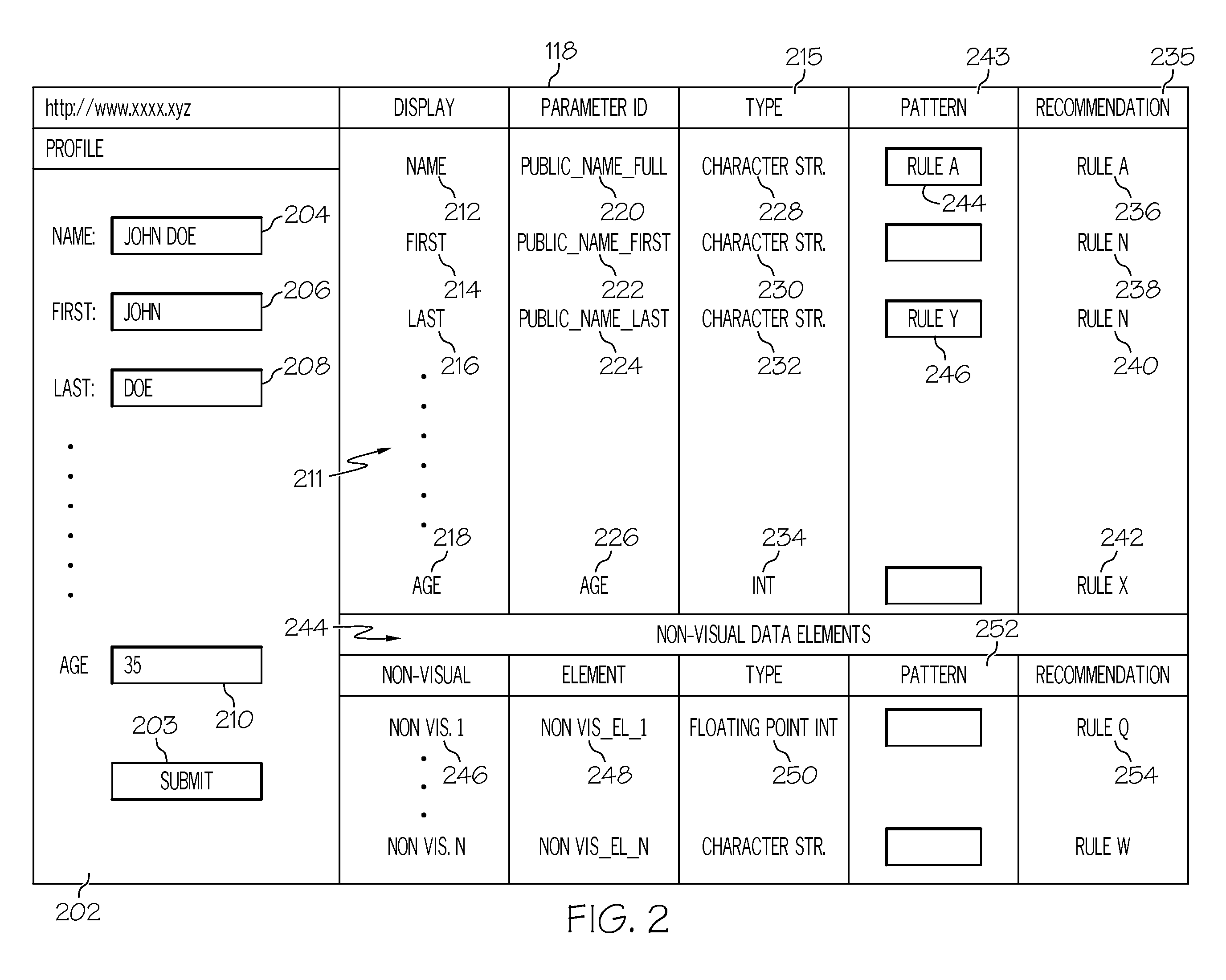
Interactive management of web application firewall rules
InactiveUS20110099482A1Computer security arrangementsMultiple digital computer combinationsInformation processingWeb service
A computer implemented method, information processing system, and computer program product manage web application firewall rule configuration. A web application is analyzed. A set of data elements within the web application is identified. Each data element in the set of data elements stores information that is sent from a web client to a web server. Each data element in the set of data elements is analyzed. A data type is associated with each data element in the set of data element. The data type describes a type of data stored by the data element. A web application firewall rule recommendation is automatically generated for each data element based at least on the data type associated therewith.
Owner:IBM CORP
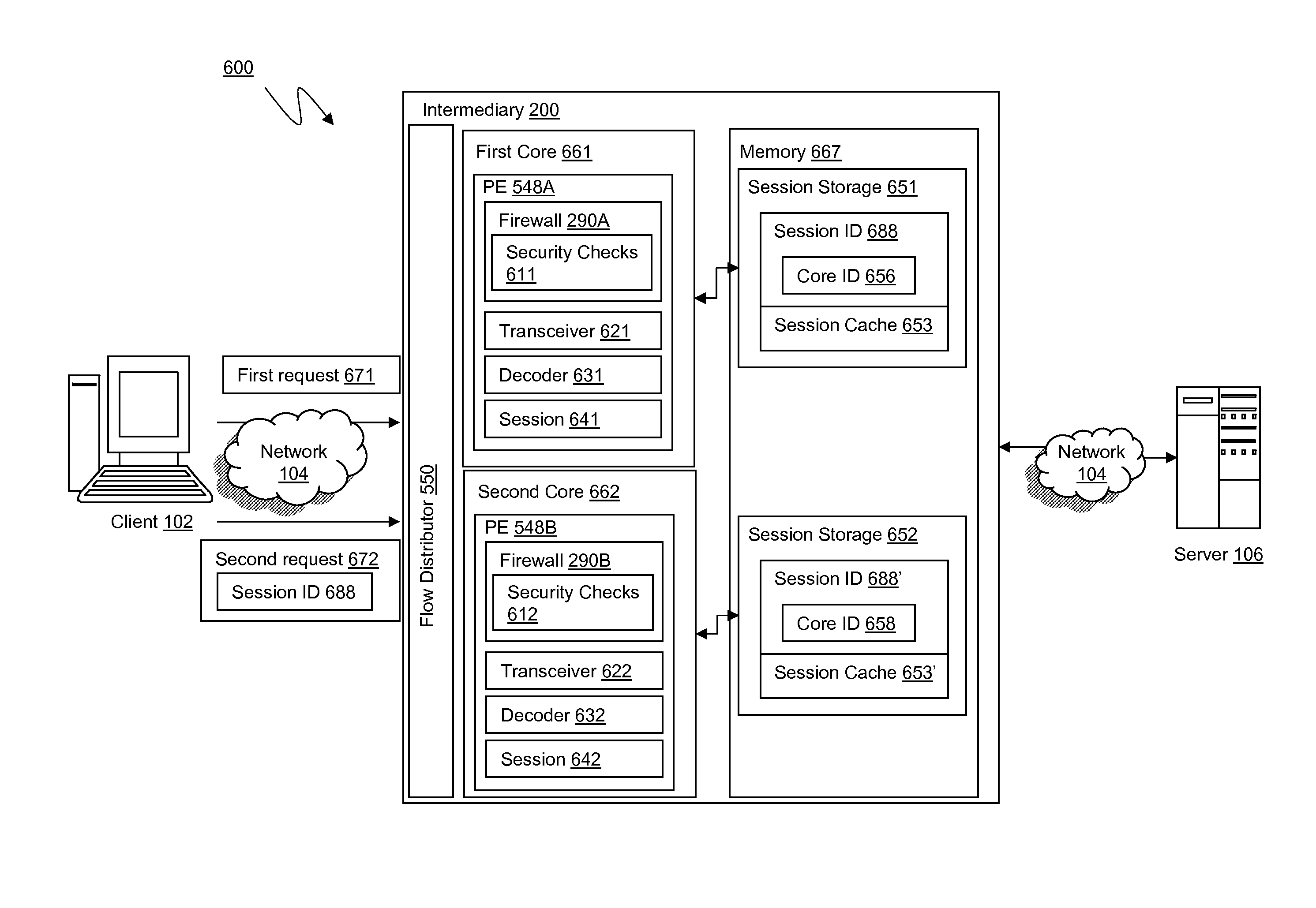
Systems and methods for management of common application firewall session data in a multiple core system
ActiveUS20110154461A1Efficient processingDigital data processing detailsComputer security arrangementsClient-sideUniform resource locator
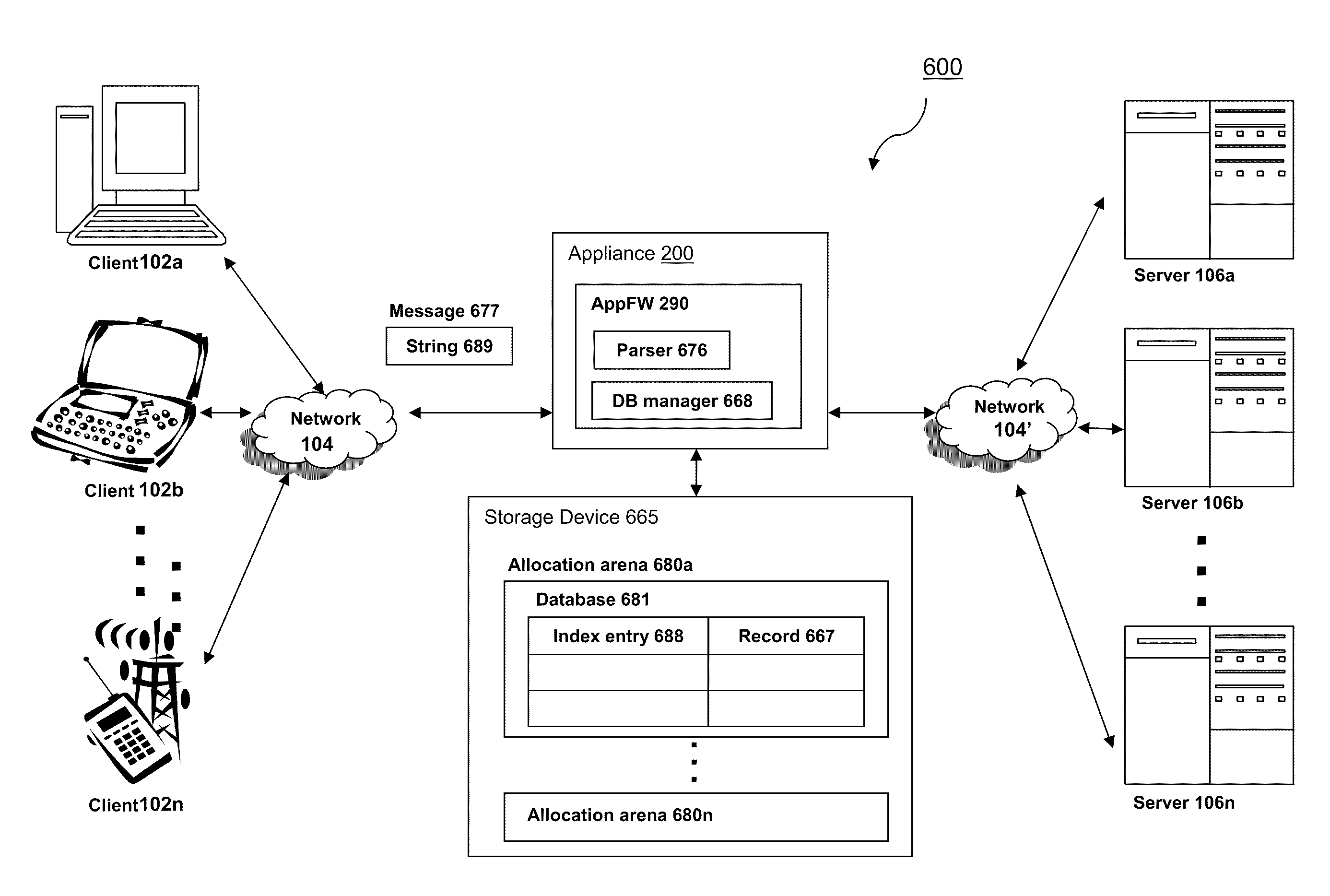
The present invention is directed towards systems and methods for efficiently an intermediary device processing strings in web pages across a plurality of user sessions. A device intermediary to a plurality of clients and a server identifies a plurality of strings in forms and uniform resource locators (URLs) of web pages traversing the device across a plurality of user sessions. The device stores each string of the plurality of strings to one or more allocation arenas shared among a plurality of user session. Each string is indexed using a hash key generated from the string. The device recognizes that a received string transmitted from a webpage of a session of a user is eligible to be shared among the plurality of user sessions. The device determines that a copy of the received string is stored in an allocation arena using a hash generated from the received string. The device uses the copy of the received string stored in the allocation arena in place of the string in the web page of the session of the user to process the web page.
Owner:CITRIX SYST INC
Systems and methods for processing application firewall session information on owner core in multiple core system
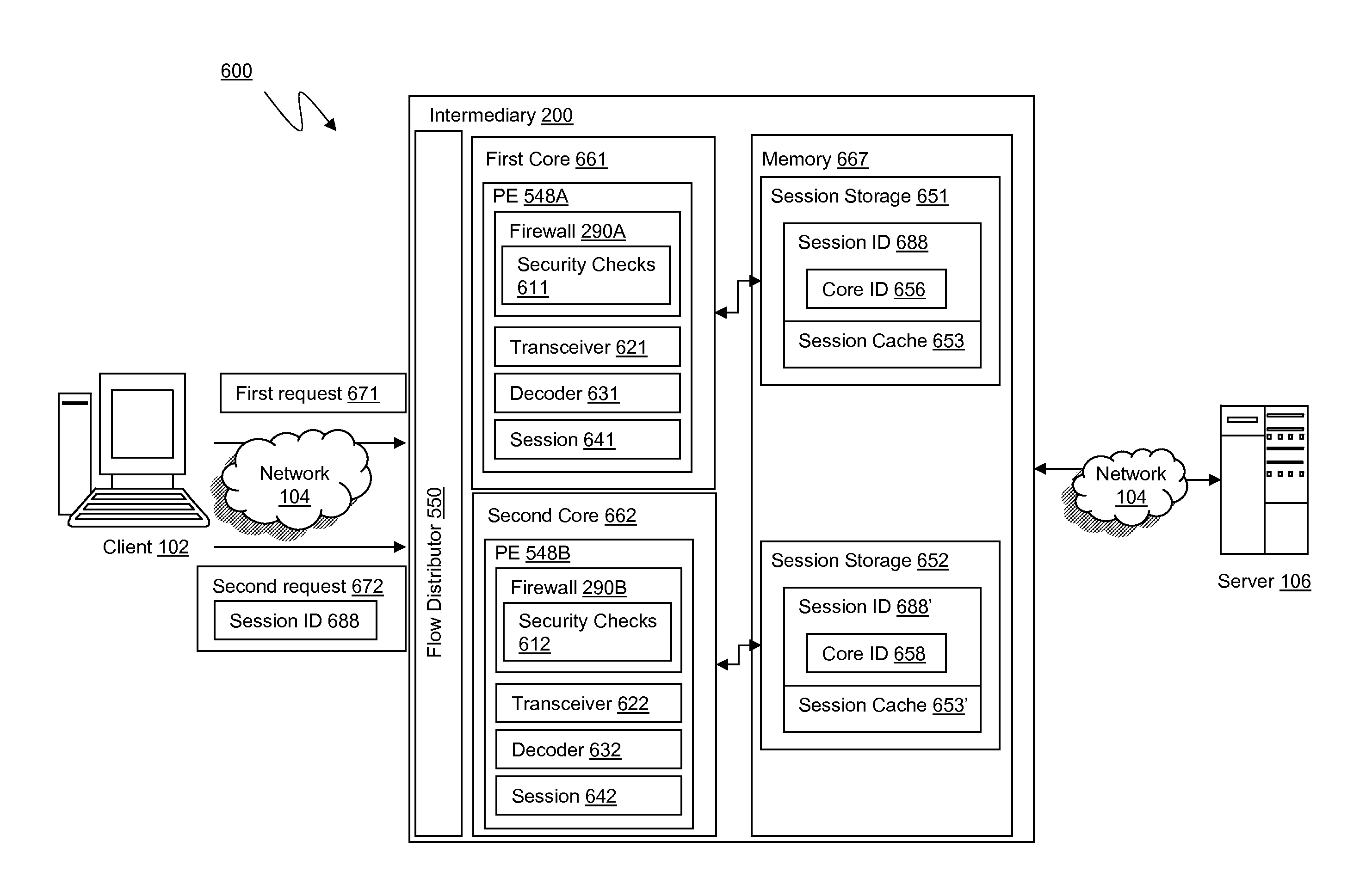
ActiveUS8438626B2Improve computing powerInterprogram communicationMultiple digital computer combinationsComputer networkSecurity check
The present invention is directed towards systems and methods for sharing session data among cores in a multi-core system. A first application firewall module executes on a core of a multi-core intermediary device which establishes a user session. The first application firewall module stores application firewall session data to memory accessible by the first core. A second application firewall module executes on a second core of the multi-core intermediary device. The second application firewall module receives a request from the user via the established user session. The request includes a session identifier identifying that the user session was established by the first core. The second application firewall module determines to perform one or more security checks on the request and communicates a portion of the request the first core. The second application firewall module receives and processes the security check results and instructions from the first core.
Owner:CITRIX SYST INC
Systems and methods for processing application firewall session information on owner core in multiple core system
ActiveUS20110154471A1Improve computing powerInterprogram communicationMultiple digital computer combinationsComputer networkSecurity check
The present invention is directed towards systems and methods for sharing session data among cores in a multi-core system. A first application firewall module executes on a core of a multi-core intermediary device which establishes a user session. The first application firewall module stores application firewall session data to memory accessible by the first core. A second application firewall module executes on a second core of the multi-core intermediary device. The second application firewall module receives a request from the user via the established user session. The request includes a session identifier identifying that the user session was established by the first core. The second application firewall module determines to perform one or more security checks on the request and communicates a portion of the request the first core. The second application firewall module receives and processes the security check results and instructions from the first core.
Owner:CITRIX SYST INC
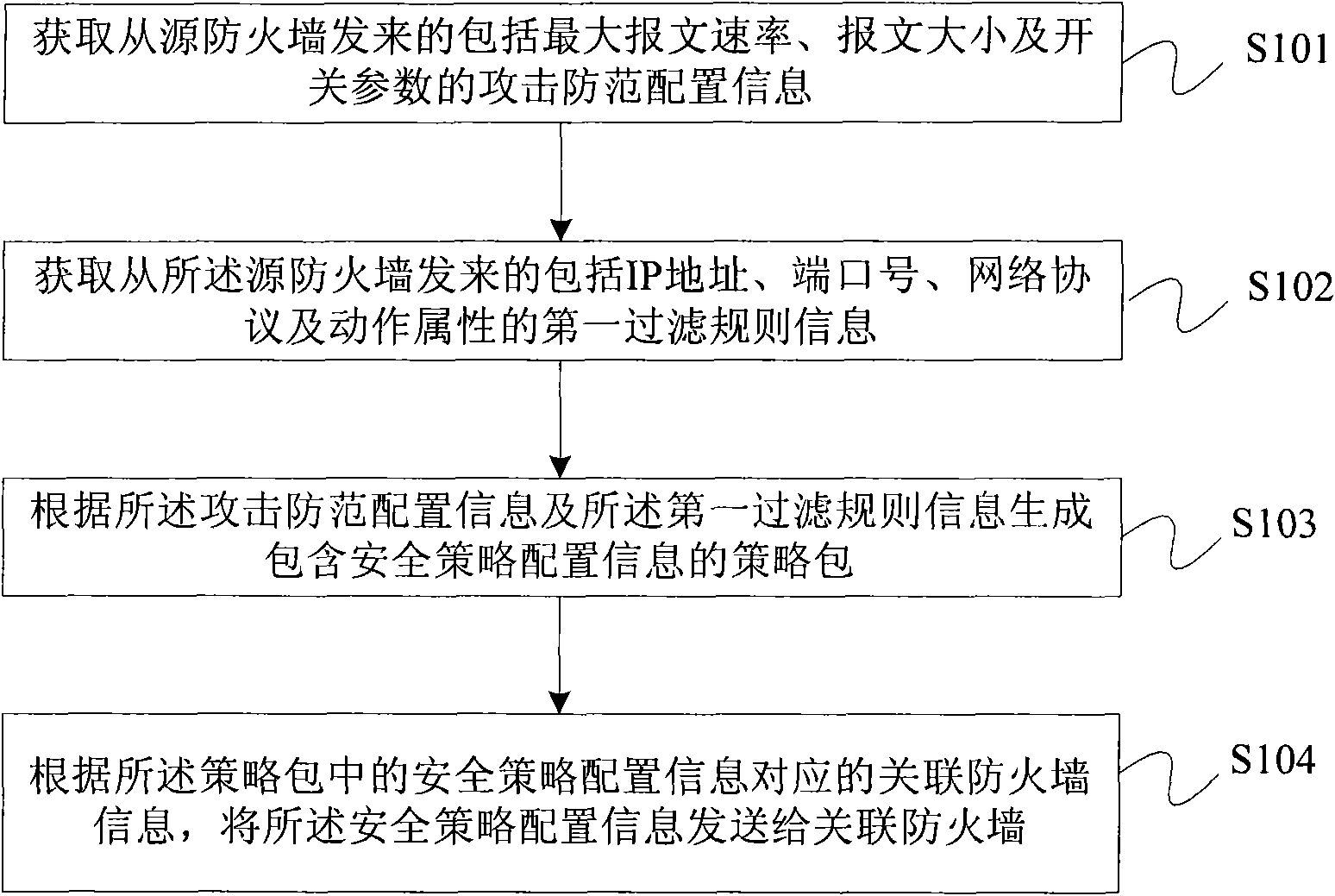
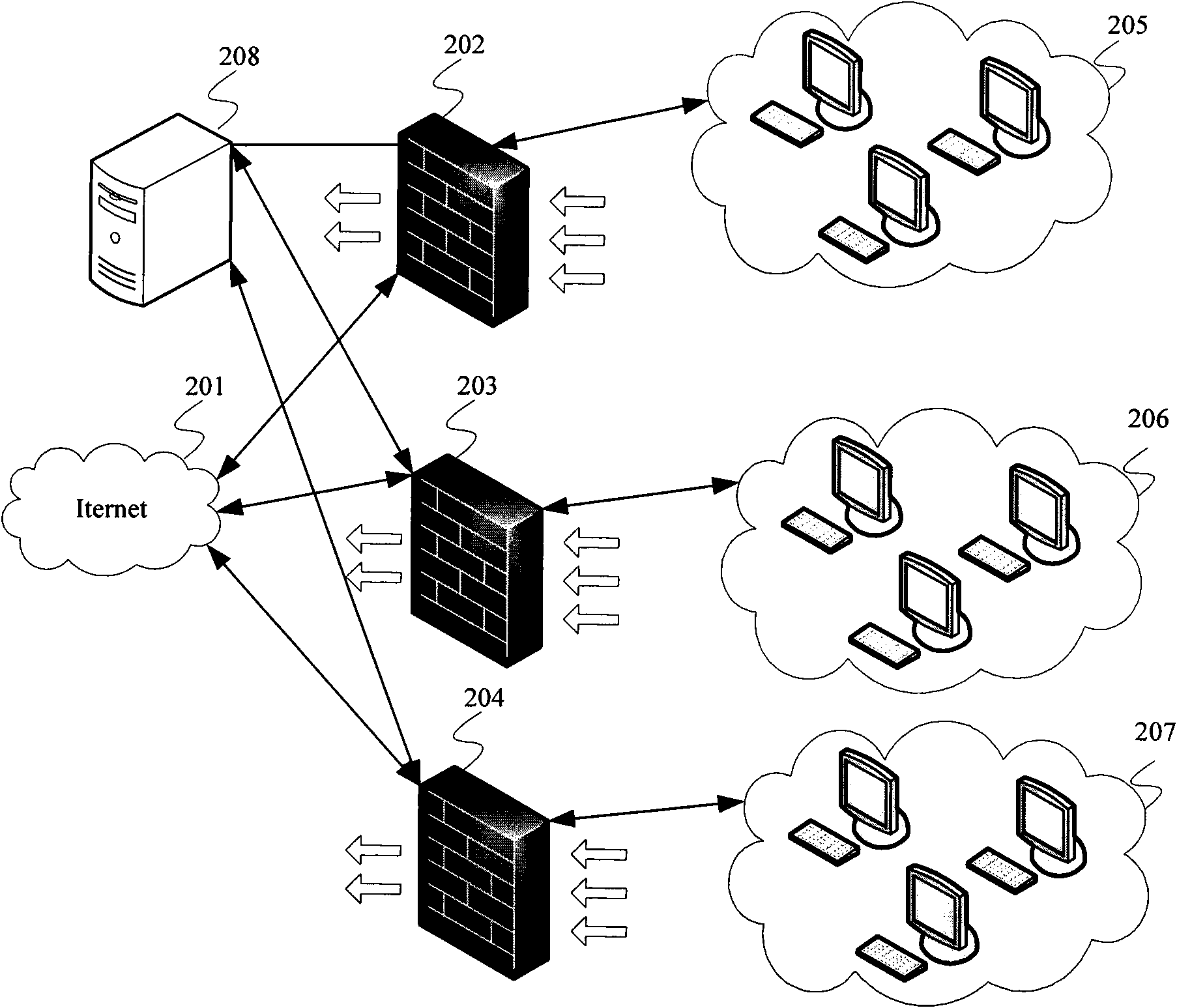
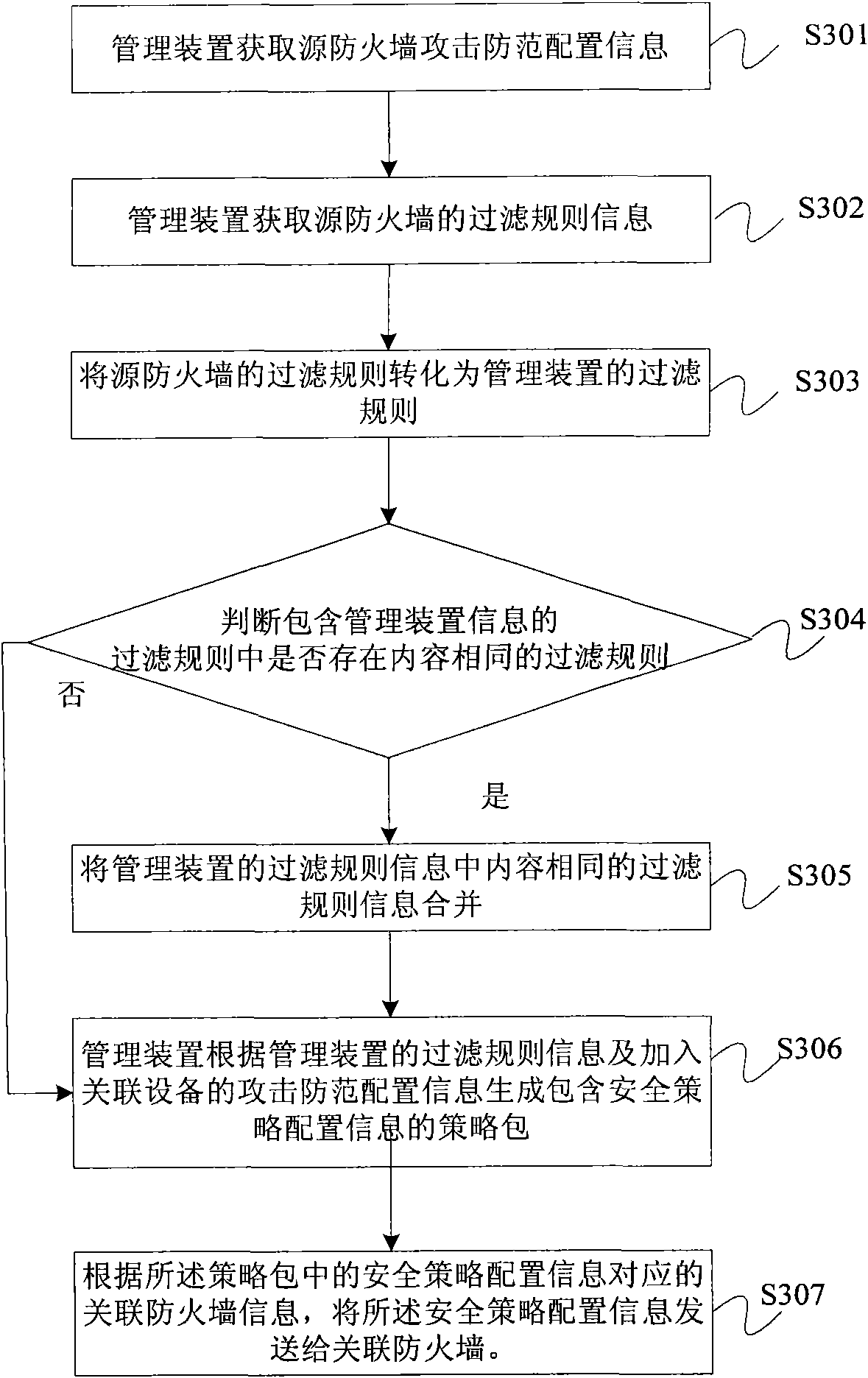
Firewall security policy configuration method and management unit
The invention provides a firewall security policy configuration method and a management unit. The method comprises the following steps of: obtaining attack prevention configuration information which includes maximum message rate, message size or an on-and-off parameter and is sent from the firewall; obtaining first filter rule information which includes an IP address, a port number, a network protocol and action attribute and is sent from the firewall; generating a policy package including security policy configuration information according to the attack prevention configuration information and the first filter rule information; and sending the security policy configuration information to the association firewall according to association firewall information corresponding to the security policy configuration information in the policy package. In the embodiment of the invention, the security policy of a single firewall is reversely reduced to the policy package, thus providing convenience for a user to conduct security policy configuration on the firewall.
Owner:CHENGDU HUAWEI TECH
Distributed web application firewall
ActiveUS8566919B2Multiple digital computer combinationsProgram controlWeb applicationComputer network
A method for protecting a Web application running on a first local Web Server bases from hacker attacks, said Web Server being connectable to at least one client, the method comprising the following steps: —providing a plurality of preset rules on said Server, which correspond to specific characteristics of HTTP requests; —receiving an HTTP request on said server from the client, said HTTP request comprising a plurality of characteristics; —analyzing said characteristics of said received HTTP request in accordance with said rules provided on said server; —rejecting said HTTP request, if said rules identify said HTTP request as harmful request; —accepting said HTTP request, if said rules identify said HTTP request as trustable request; —classifying said HTTP request as doubtful request, if said rules identify said request neither as harmful request nor as trustable request; —evaluating the characteristics of said doubtful local request; —generating a learned rule on basis of the edge base evaluation.
Owner:PULSE SECURE +1
Network security monitoring method and device, and cloud WEB application firewall
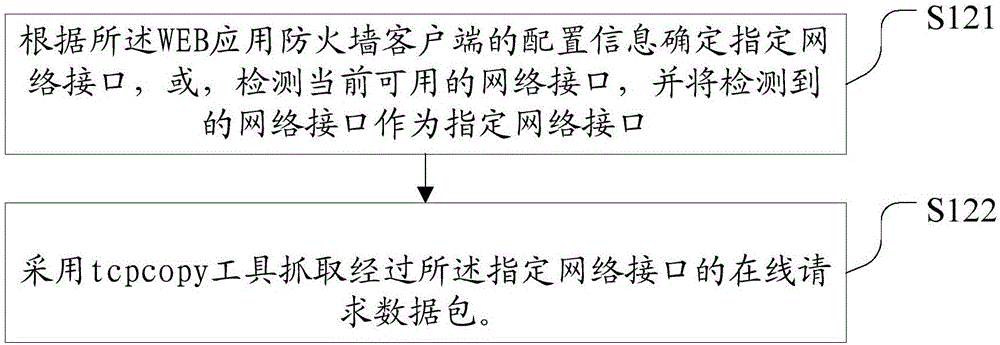
ActiveCN106453299APerformance is not affectedWill not affect the experienceTransmissionTraffic capacityWeb application
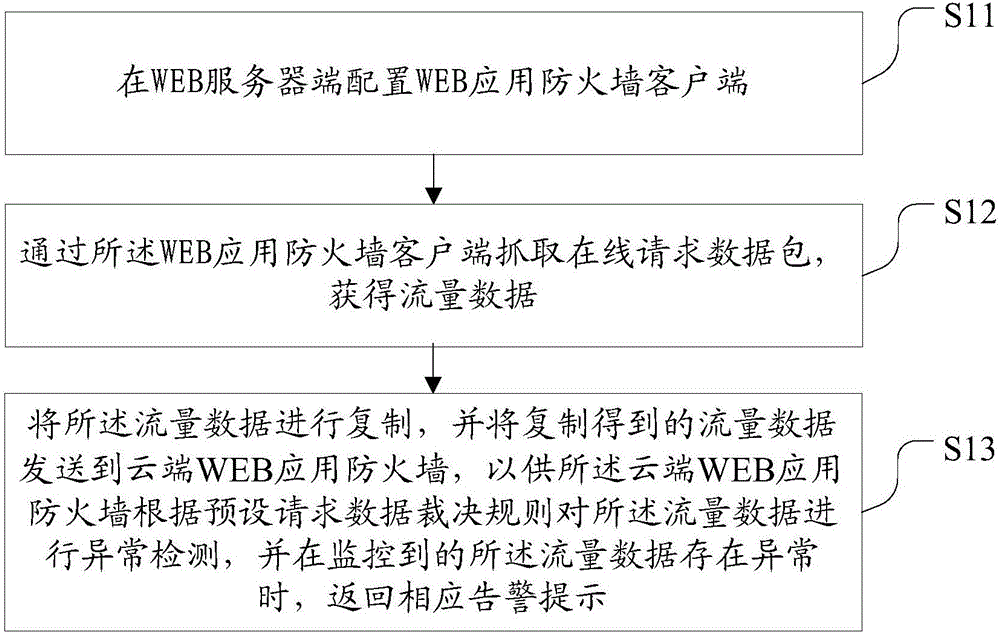
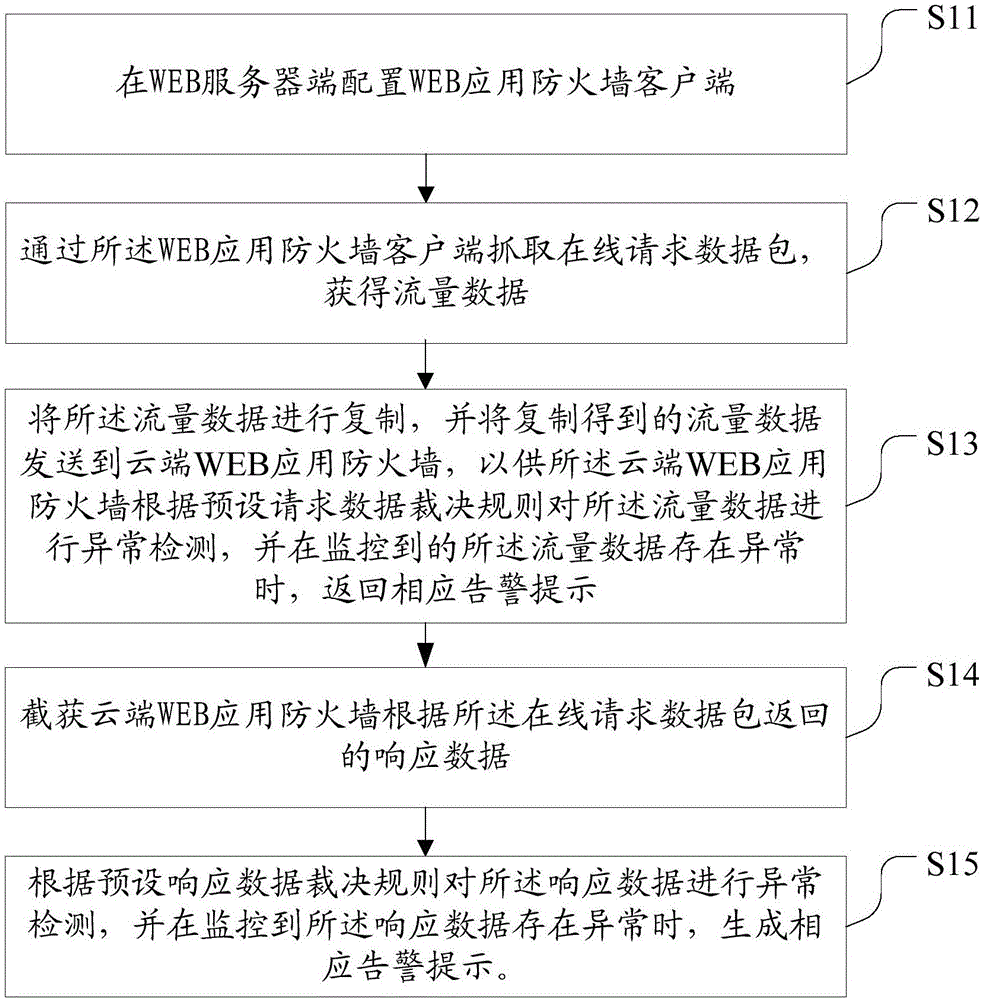
The invention discloses a network security monitoring method and device, and a cloud WEB application firewall. The network security monitoring method comprises the steps of configuration a WEB application firewall client side at a WEB server side; capturing online request data packets through the WEB application firewall client side, thereby obtaining traffic data; and copying the traffic data and sending the data traffic obtained through copying to the cloud WEB application firewall, thereby enabling the cloud WEB application firewall to carry out anomaly detection on the traffic data according to a preset request data judgment rule and returns a corresponding alarm prompt when it is monitored that an anomaly occurs in the data traffic. According to the method, the device and the firewall, a hardware device does not need to be added in the traffic collection process; the device deployment cost is low and the maintenance is convenient; the service is senseless and the configuration is flexibly; the performance of a WEB server is not influenced; and the service experience of a user is not influenced.
Owner:三六零数字安全科技集团有限公司
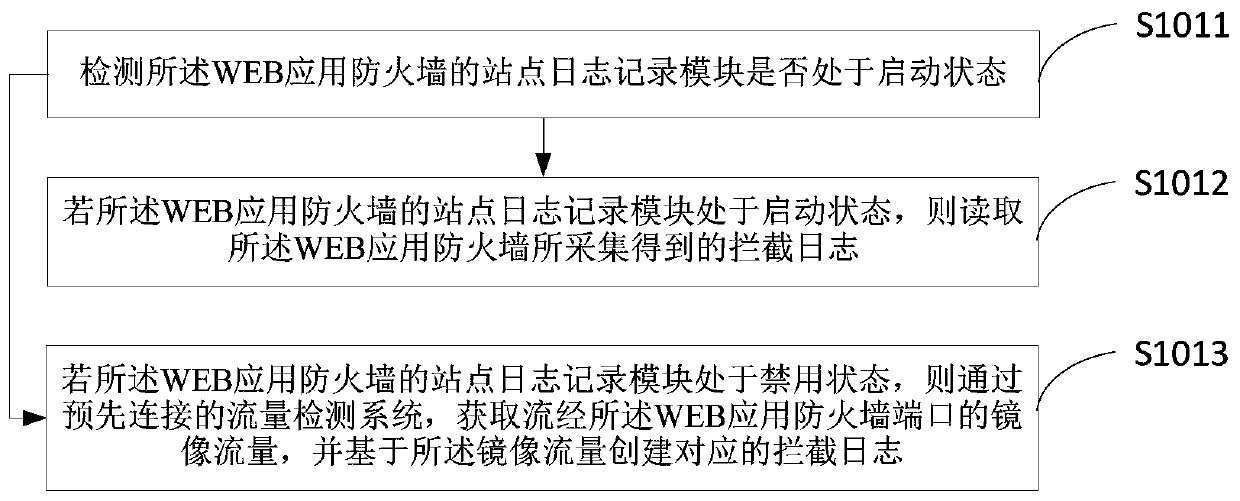
System vulnerability detection method, device, terminal equipment and medium
PendingCN110472414AAvoid manual analysis item by itemQuick fixPlatform integrity maintainanceObject basedTerminal equipment
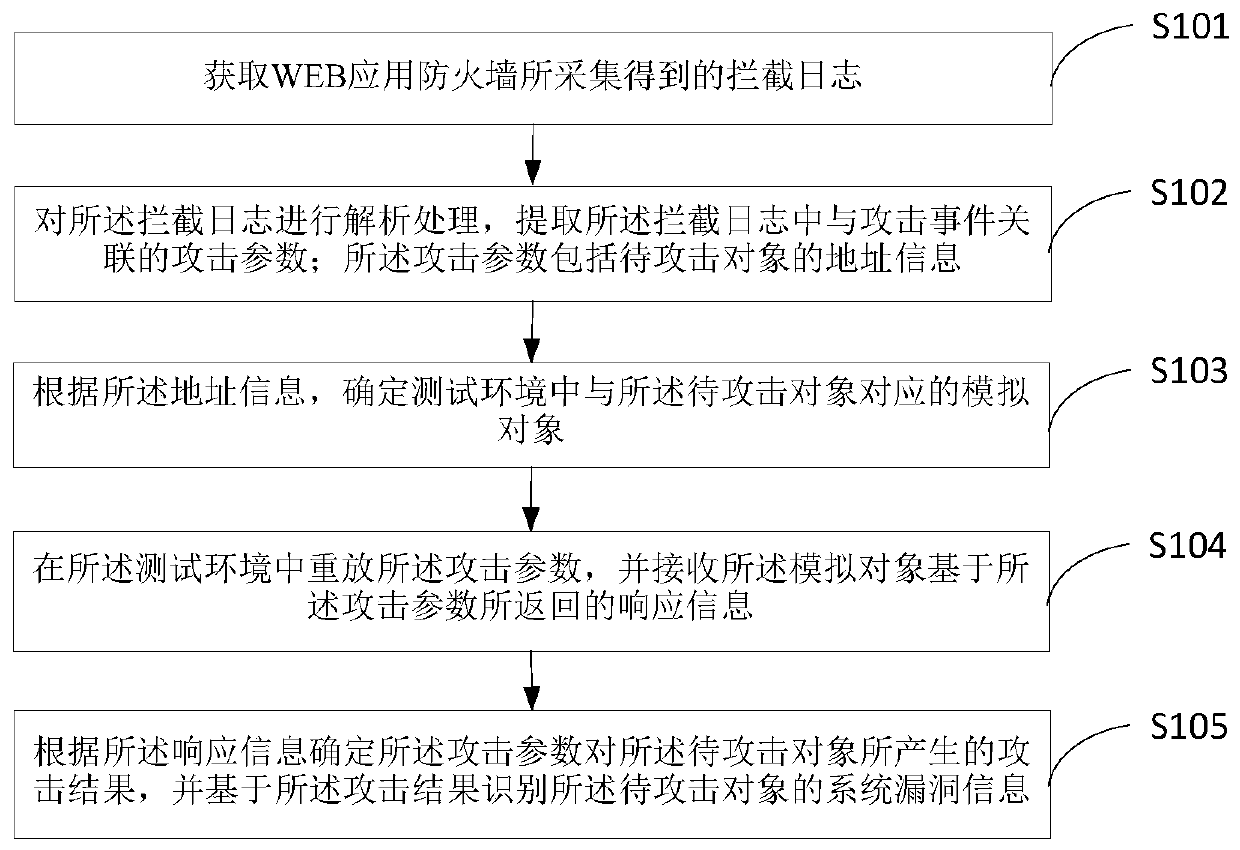
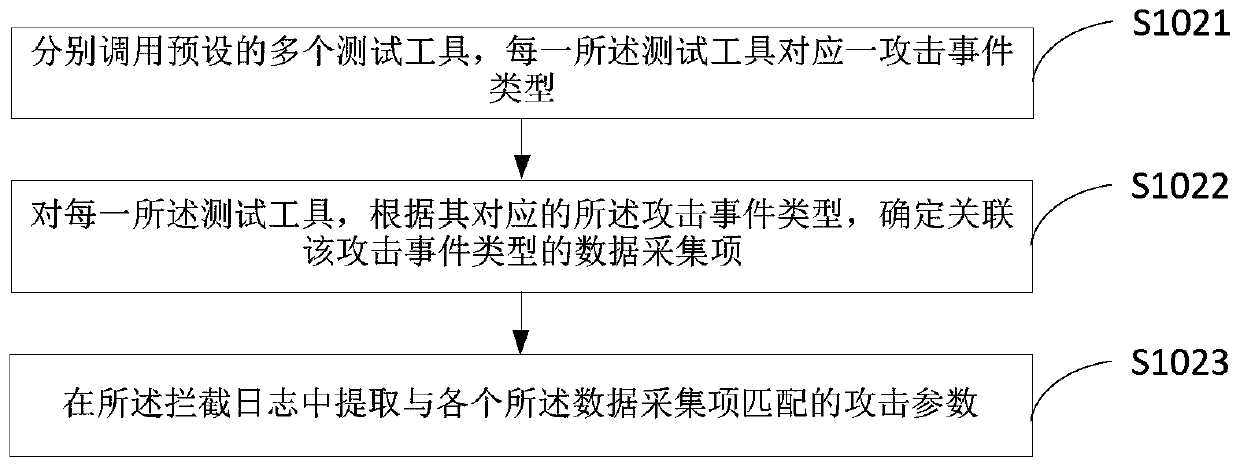
The invention provides a system vulnerability detection method, a system vulnerability detection device and terminal equipment, and belongs to the technical field of signal processing. The method comprises the steps of obtaining an interception log collected by an application firewall; analyzing the interception log, and extracting attack parameters associated with the attack event in the interception log; determining a simulation object corresponding to the to-be-attacked object in the test environment according to the address information; replaying the attack parameters in the test environment, and receiving response information returned by the simulation object based on the attack parameters; and determining an attack result generated by the attack parameter to the to-be-attacked objectaccording to the response information, and identifying system vulnerability information of the to-be-attacked object based on the attack result. According to the method, the simulation operation about the historical attack event of the production environment is executed in the test environment, and the attack result of the to-be-attacked object about the attack parameter is indirectly determined,so that whether the historical attack event succeeds or not is automatically verified, and the detection efficiency and the detection accuracy of the system vulnerability are improved.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
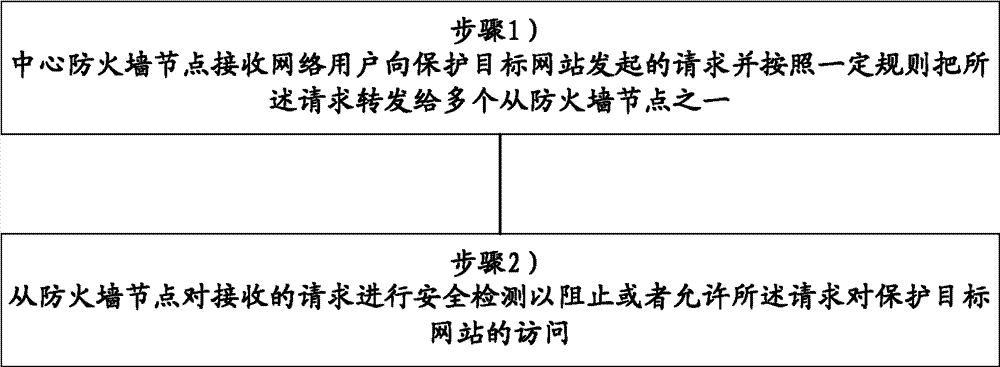
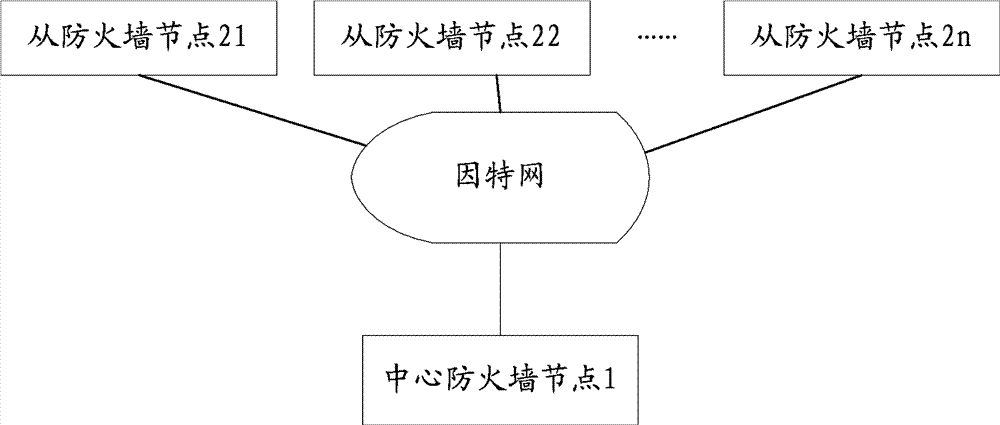
Web application firewall and web application safety protection method
InactiveCN103095778ATroubleshoot service outagesNo need to modify the erection methodTransmissionWeb applicationApplication firewall
The invention discloses a web application firewall and a web application safety protection method. The web application firewall comprises a center firewall node and a plurality of auxiliary firewall nodes, wherein the center firewall node receives a request sent by a network user to a protection target website and transmits the request to one of the plurality of the auxiliary firewall nodes according to a certain rule, and the auxiliary firewall nodes conduct safety detection to the received request to prevent or allow the visitation of the request to the protection target website. The web application safety protection method comprises that the center firewall node receives the request sent by the network user to the protection target website and transmits the request to one of the plurality of the auxiliary firewall nodes according to the certain rule, and the auxiliary firewall nodes conduct safety detection to the received request to prevent or allow the visitation of the request to the protection target website. According to the technical scheme, the problem of service interrupt caused by single node error can be prevented.
Owner:BEIJING KNOWNSEC INFORMATION TECH
Access control list checking
Owner:PALO ALTO NETWORKS INC
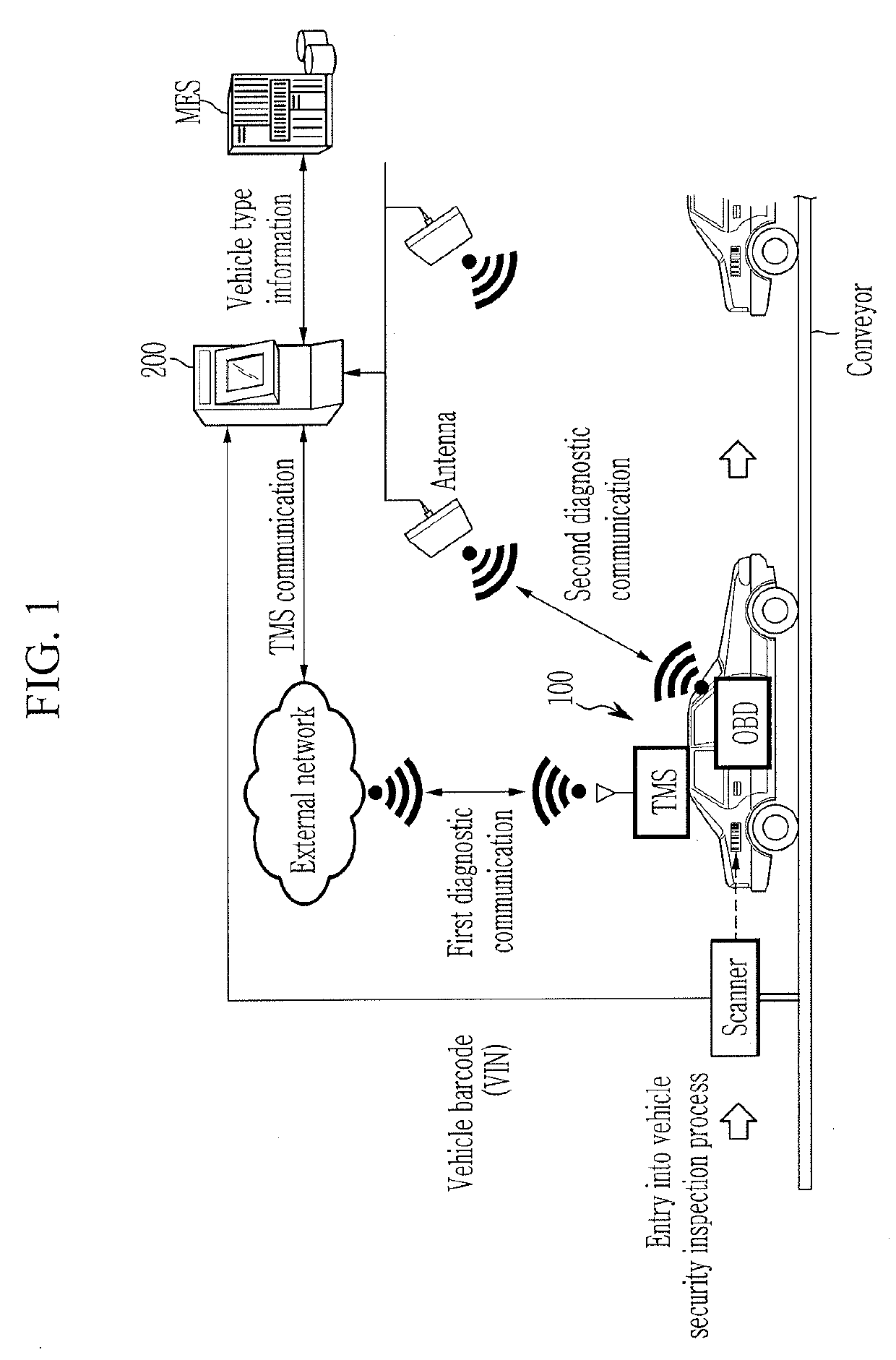
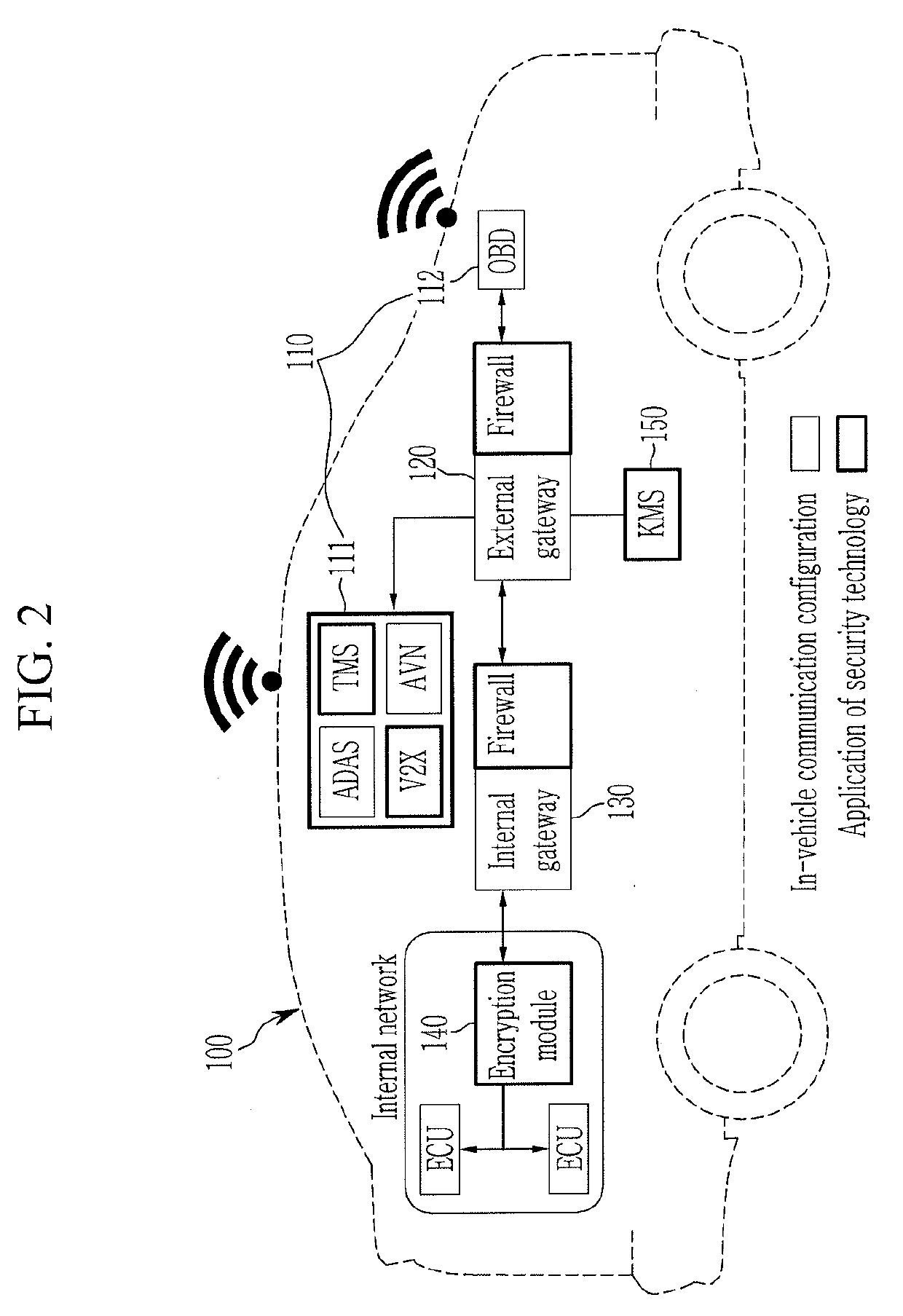
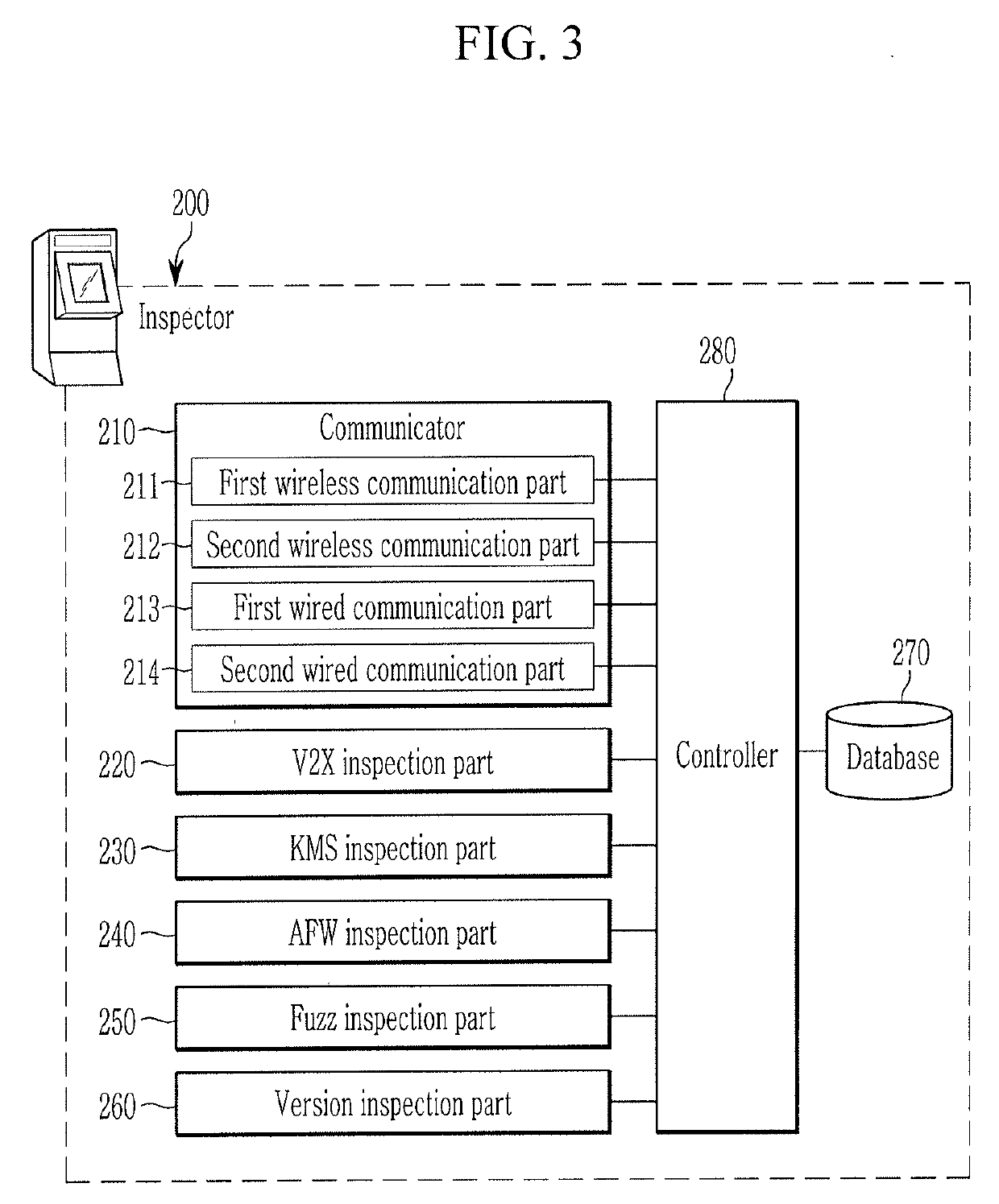
System and method for security inspection of electronic equipment
ActiveUS20190268376A1Improve reliabilityImprove securityKey distribution for secure communicationParticular environment based servicesProduction lineEngineering
A security inspection system verifying a security system of electronic equipment may include an inspector having: a communicator connecting wireless diagnostic communication with the electronic equipment entering a process line; a KMS inspection portion inspecting a management state of generation and destruction of encryption key of a key management system device included in the electronic equipment; an application firewall inspection portion inspecting security policy of an application firewall disposed in a gateway of the electronic equipment; a version inspection portion updating at least one of a patch program and a firmware of the security system included in the electronic equipment; a database storing a program and data for a security inspection of the electronic equipment; and a controller performing diagnostic test of a firewall installation state, an encryption key management state, a transmission / reception state of an encrypted message, or blocking of abnormal data of the security system.
Owner:HYUNDAI MOTOR CO LTD +1
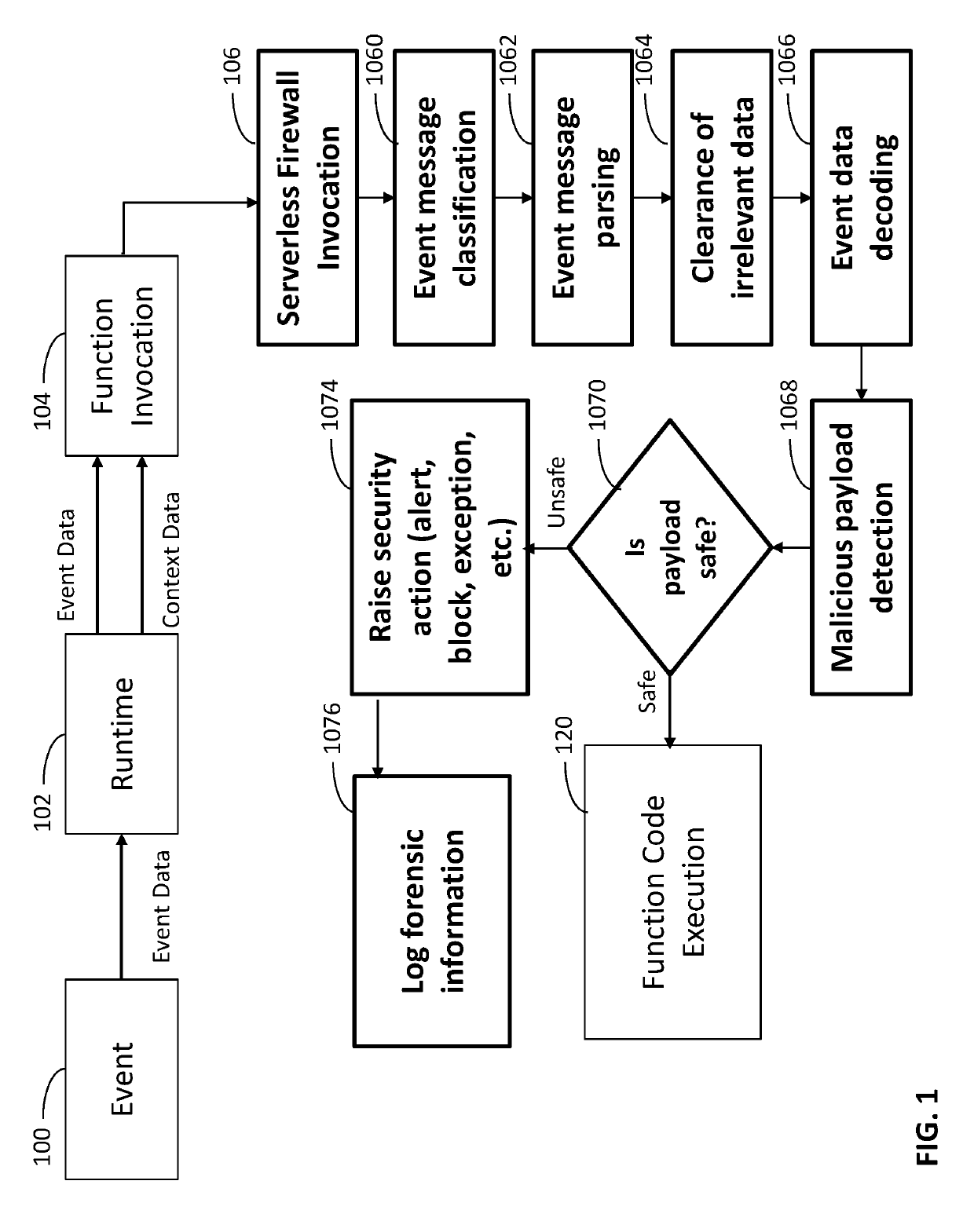
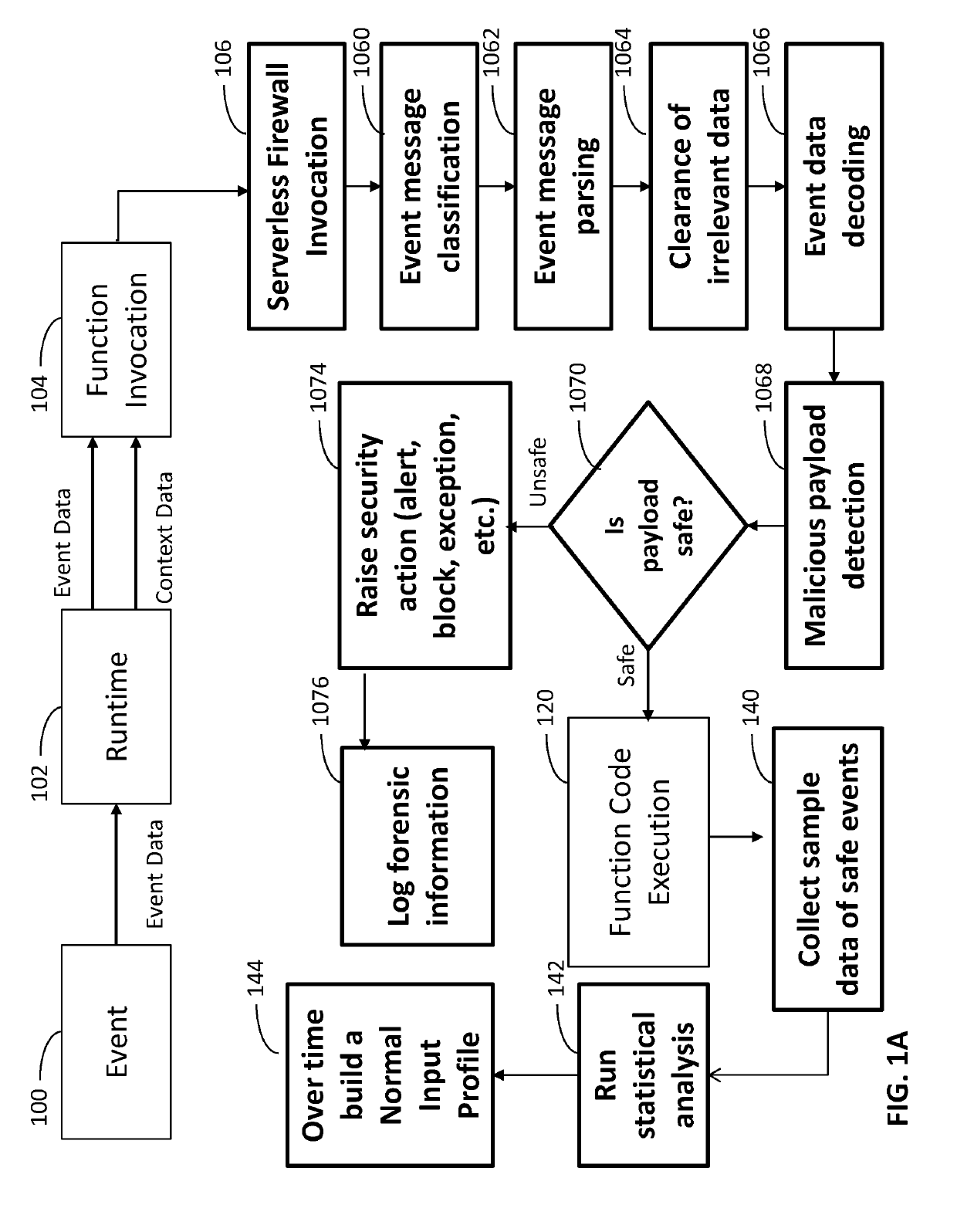
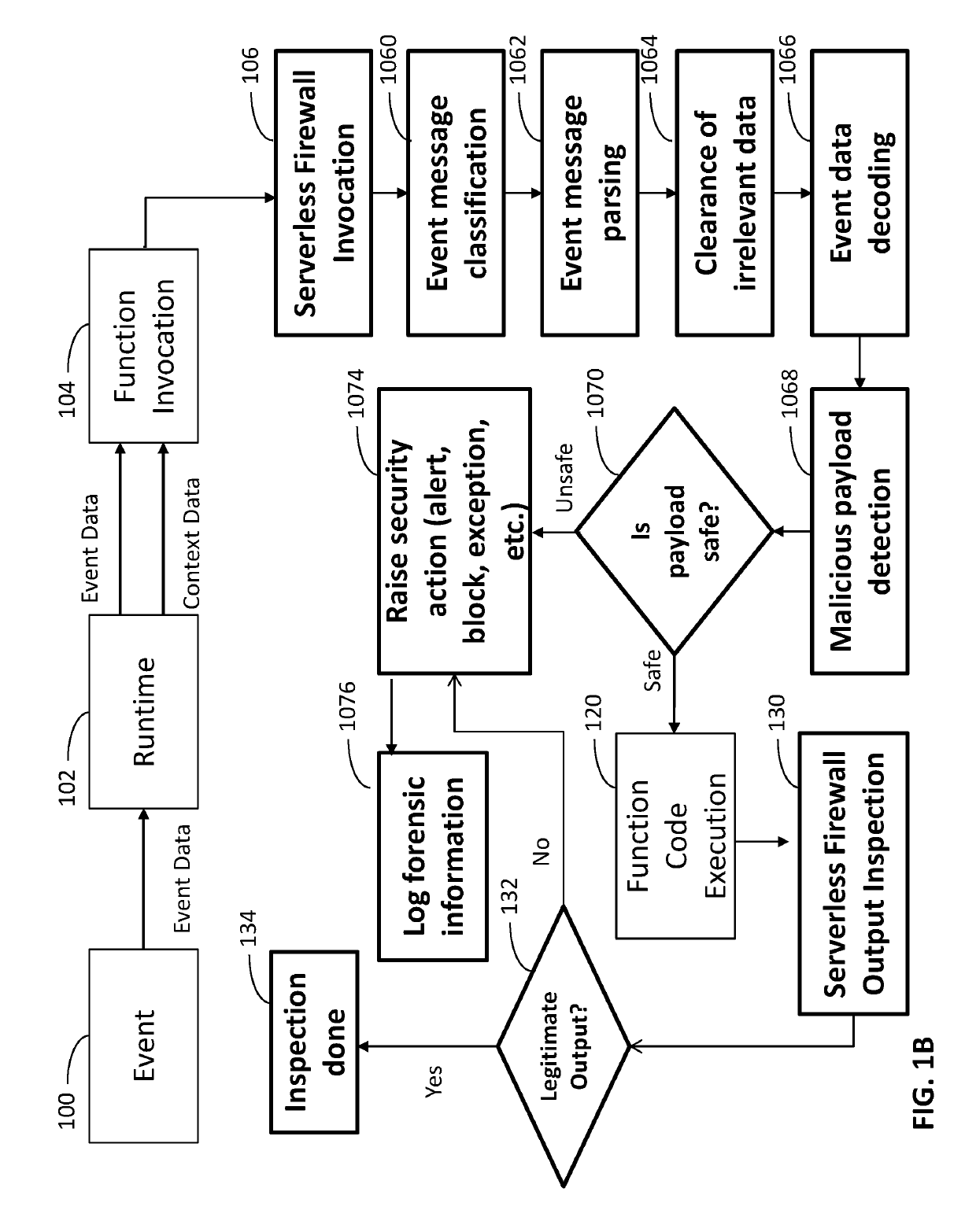
System and method for protecting serverless applications
A system and methods for protecting a serverless application, the system including: (a) a serverless application firewall configured to inspect input of the serverless function so as to ascertain whether the input contains malicious, suspicious or abnormal data; and (b) a behavioral protection engine configured to monitor behaviors and actions of the serverless functions during execution thereof.
Owner:TWISTLOCK LTD
Cloud-based WEB application firewall system and security protection method thereof
The present invention provides a cloud-based WEB application firewall system which is formed by a cloud firewall engine and a firewall control center. The firewall control center configures and manages a cloud firewall engine which is arranged in a cloud formed by multiple extendible high-performance servers. The cloud firewall engine detects and intercepts the attack to an application layer. Compared with the prior art, the system has the advantages that: (1) the WEB application firewall system deployment can become effective only after a user reconfigures a DNS, which is convenient and fast, (2) the safety officer of a WEB application firewall system provider carries out unified configuration upgrade, and novel attack can be intercepted earlier than that of a traditional WEB application firewall, (3) when the WEB application firewall system performance has a bottleneck, only buying more cloud resources is needed, and buying equipment again to carry out redeployment is not needed. The invention also provides a security protection method with the use of the WEB application firewall system.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD
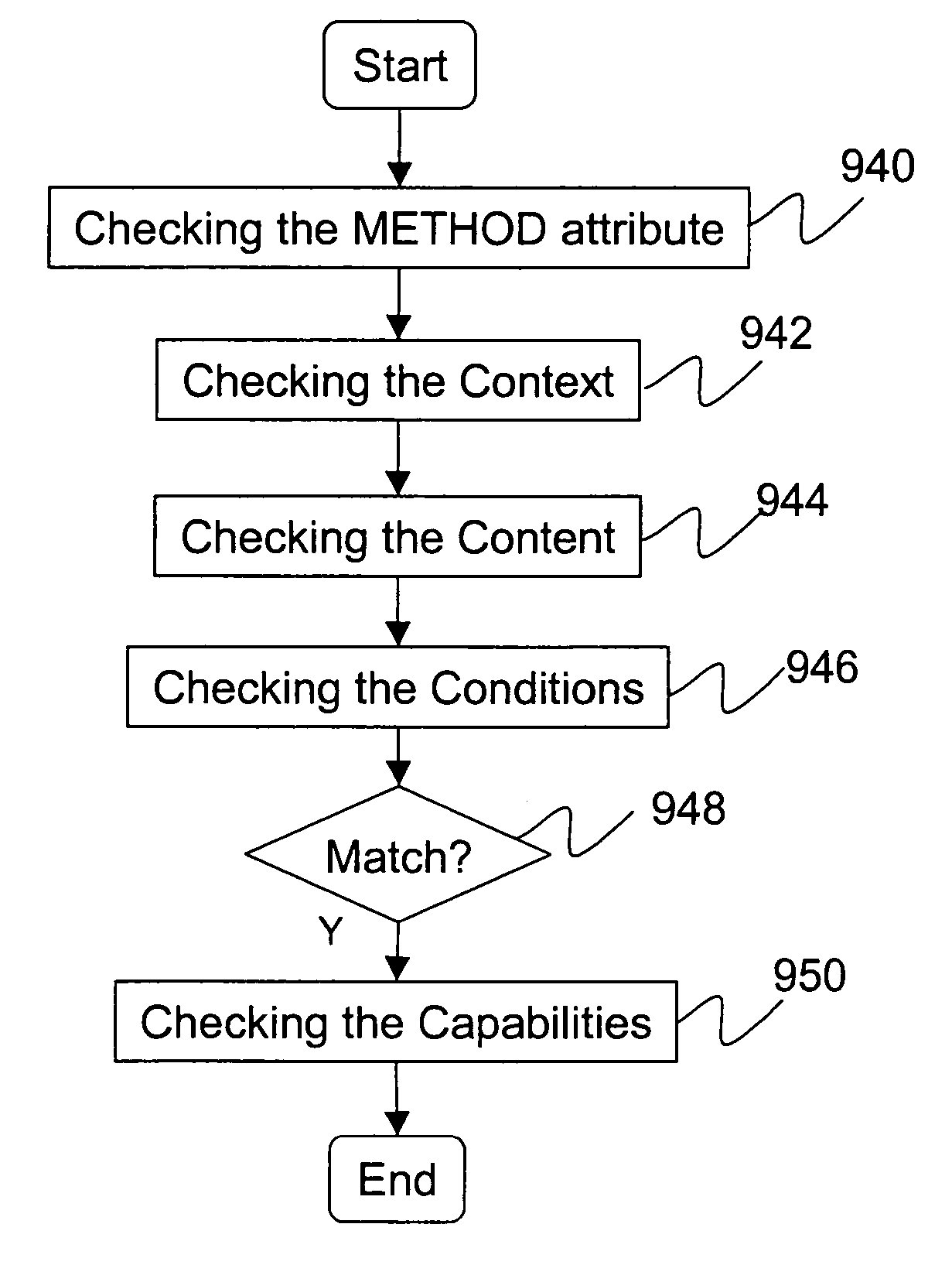
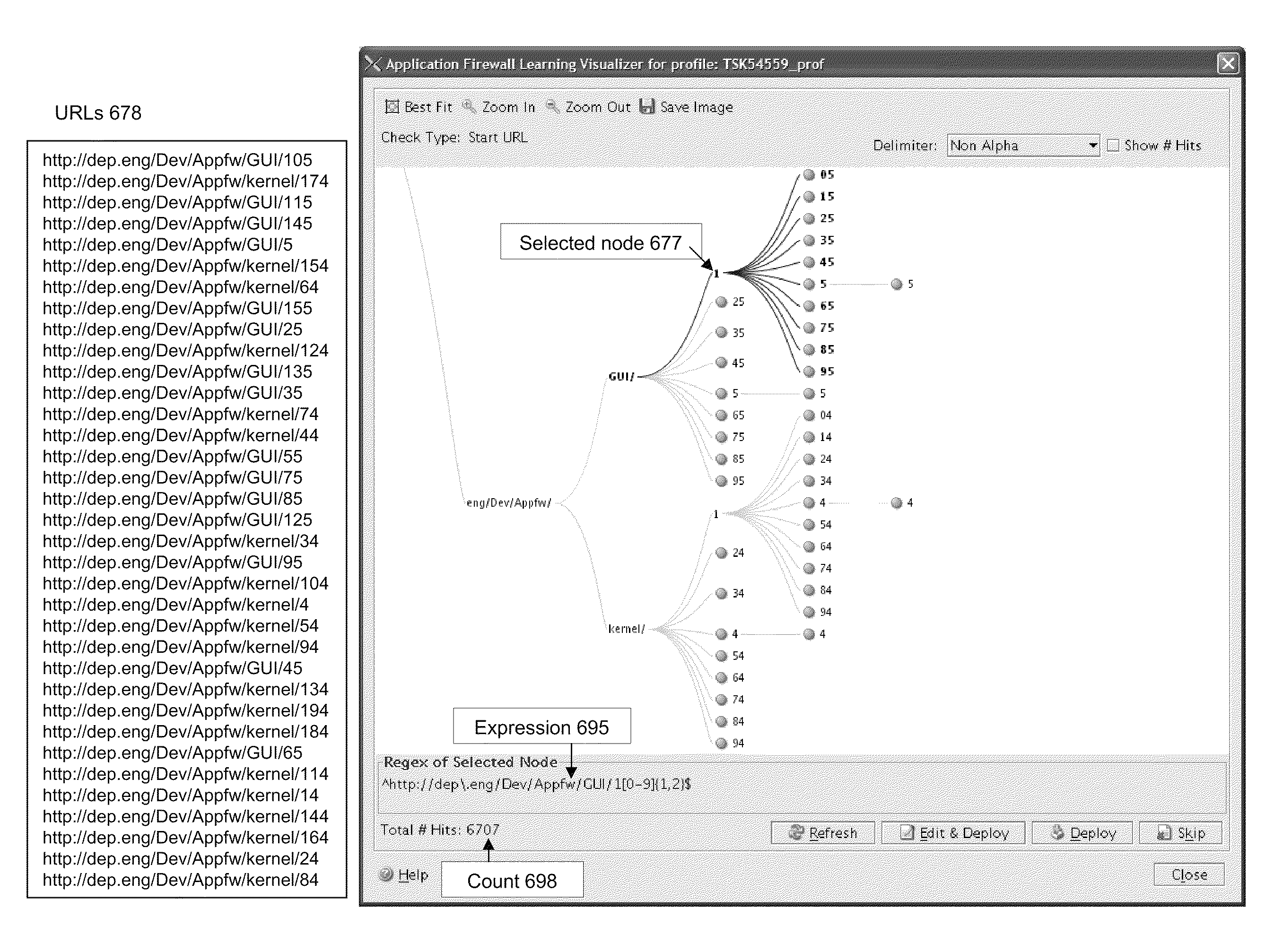
Systems and methods for providing a visualizer for rules of an application firewall
ActiveUS9215212B2Multiple digital computer combinationsProgram controlWeb serviceUniform resource locator
The present invention is directed towards systems and methods for generating a representation a plurality of learned rules from a learning engine of an application firewall. The representation may be generated based on a history of URL communications with a web server. A learning engine of an application firewall may determine a plurality of learned rules based on a history of URL communications with a web server. Each of the plurality of learned rules mat be assigned a URL string. A visualizer can categorize a subset of the plurality of learned rules under a first check type of a plurality of check types. The visualizer may further generate a tree representation of URL strings of the subset of learned rules. Each node of the tree corresponds to a segment of the URL strings identified based on a delimiter for the URL strings.
Owner:CITRIX SYST INC
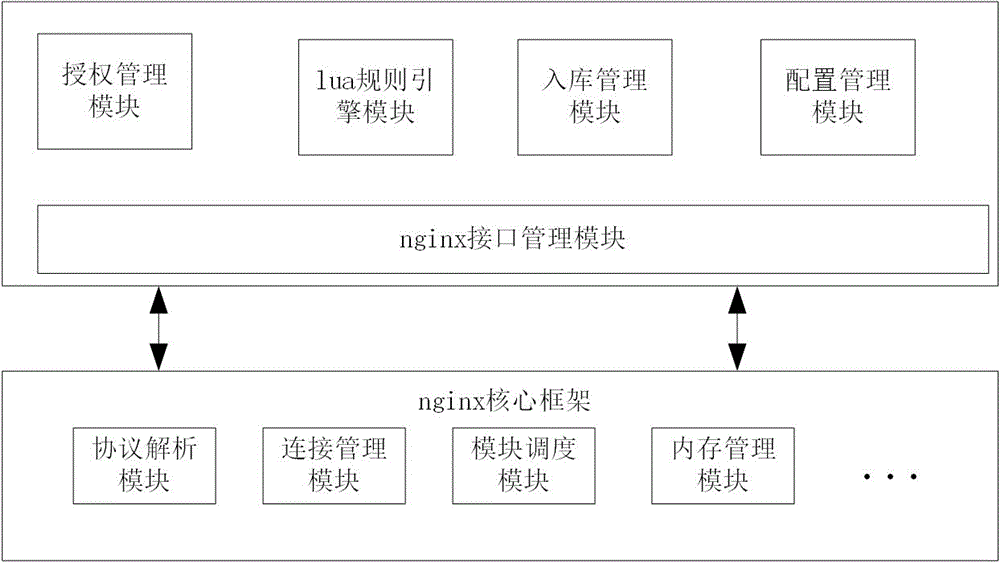
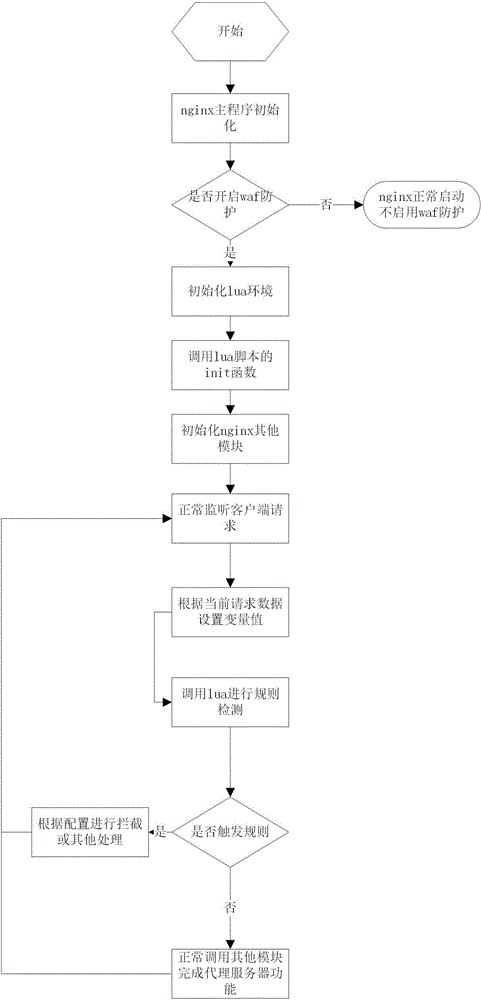
Web application firewall system based on nginx + Lua and implementation method thereof
InactiveCN105227571AImprove scalabilityImprove performanceTransmissionInternal memoryWeb application
The invention relates to a web application firewall system based on nginx + Lua. The web application firewall system comprises a nginx HTTP proxy layer and a service layer; the nginx HTTP proxy layer comprises a protocol analysis module, a connection management module, a module scheduling module and an internal memory management module; the service layer comprises an authorization management module, a lua rule engine module, a storage management module, a configuration management module and a nginx interface management module; the nginx HTTP proxy layer and the service layer are connected through the nginx interface management module. The web application firewall system provided by the invention can effectively and flexibly defend web application attacks.
Owner:FUZHOU BOKE WANGAN INFORMATION TECH CO LTD
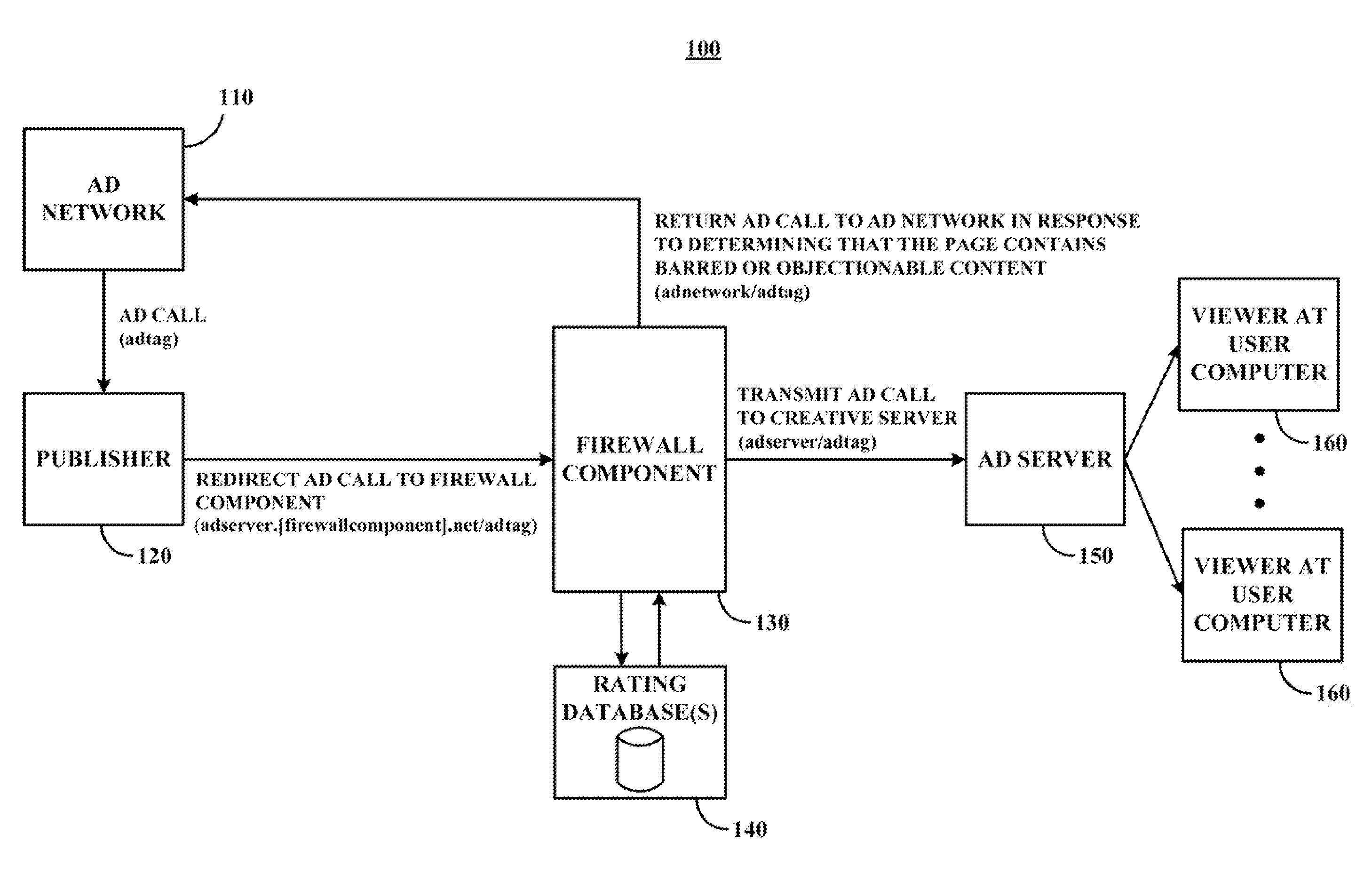
Content management systems, methods, and media using an application level firewall
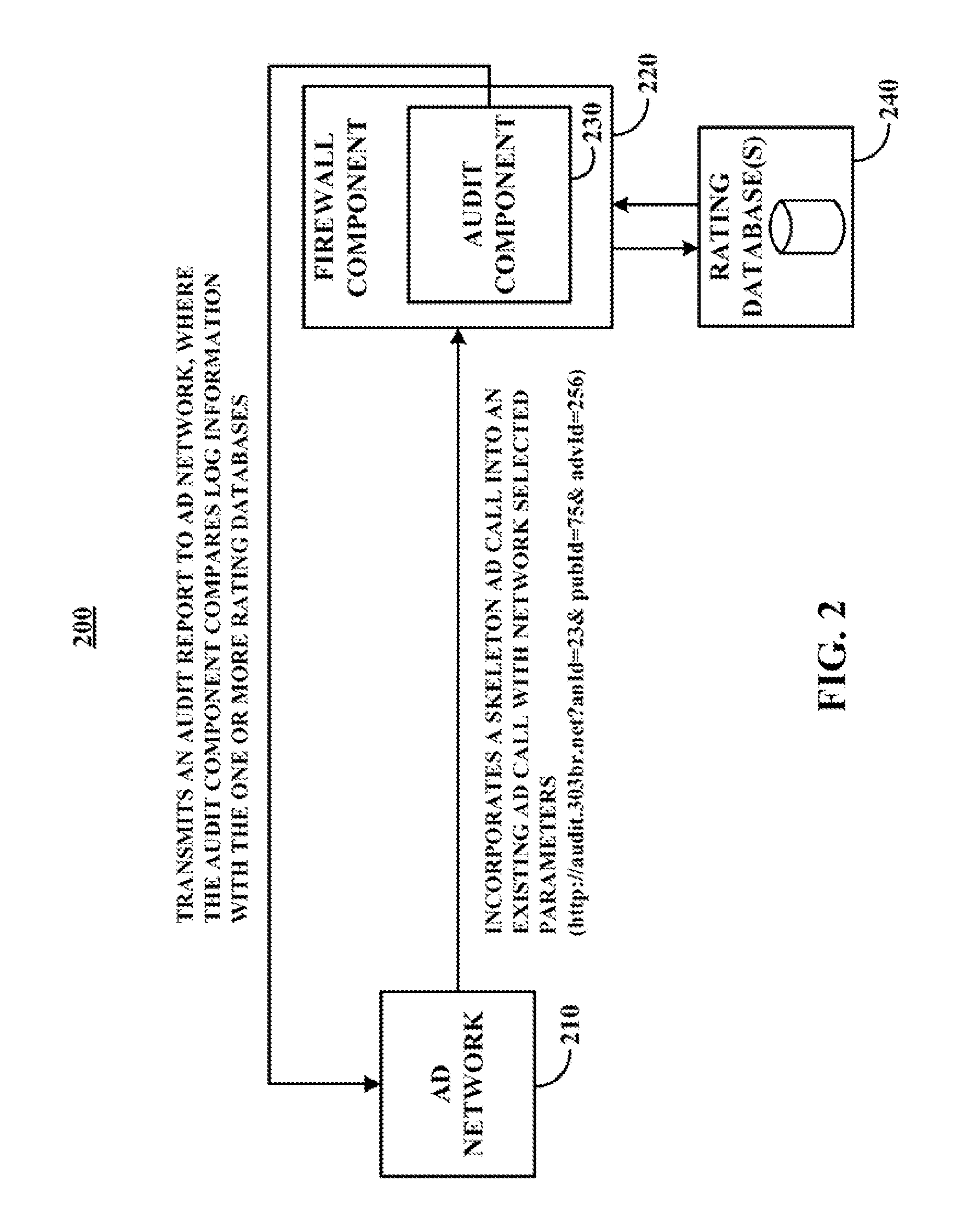
Content management systems, methods, and media using an application level firewall are provided. In accordance with some embodiments of the disclosed subject matter, the system for managing advertisement adjacencies comprises: a firewall component in an application layer comprising a processor and a memory, wherein the firewall component is configured to operate in an advertisement call stack of the application layer and wherein the processor is programmed to: receive an advertisement call for publishing an advertisement in an advertisement server on a web page, wherein a verification tag is inserted in the advertisement call that redirects the advertisement call to the firewall component prior to transmission to the advertisement server; determine whether the web page associated with the advertisement call contains objectionable content; and, in response to determining that the web page does not contain objectionable content, transmit the advertisement call to the advertisement server for publishing the advertisement on the web page.
Owner:INTEGRAL AD SCI
Web application protection method and system, and Web application firewall
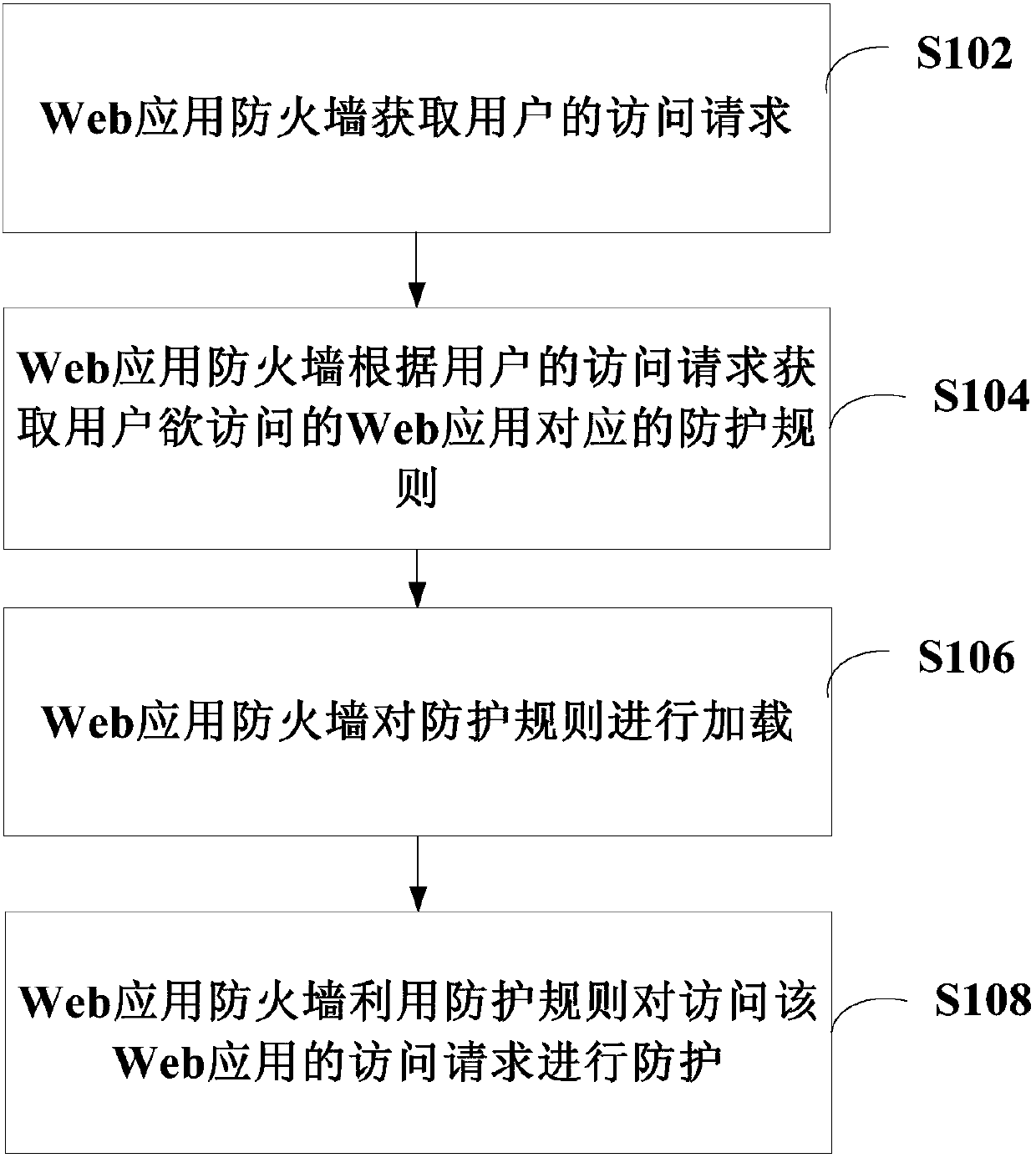
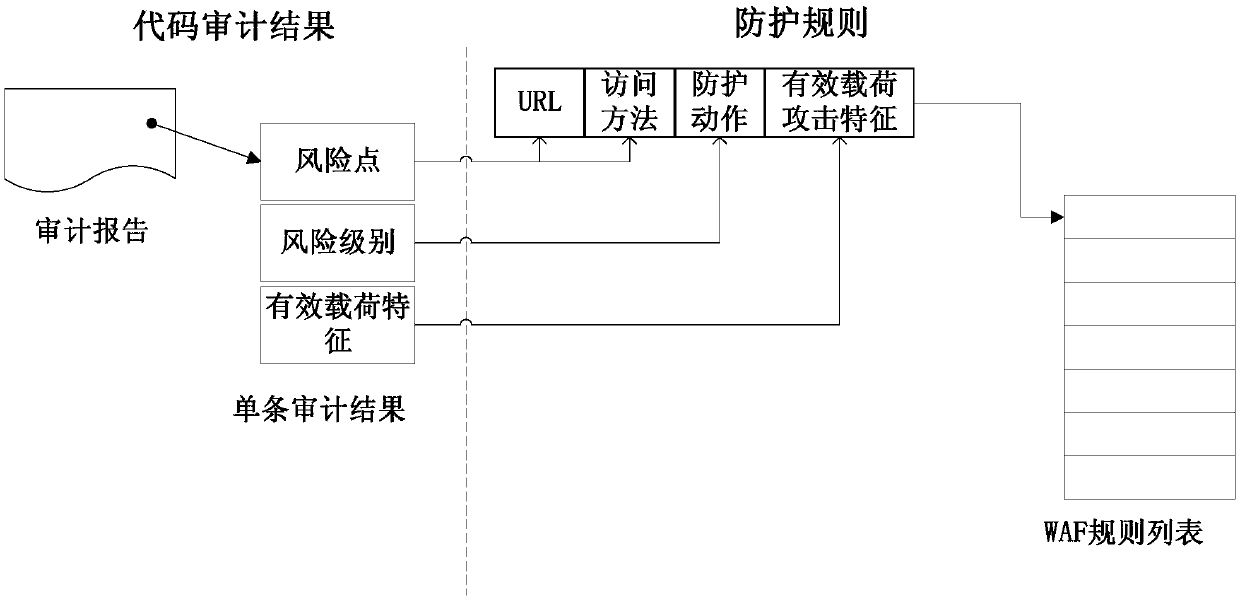
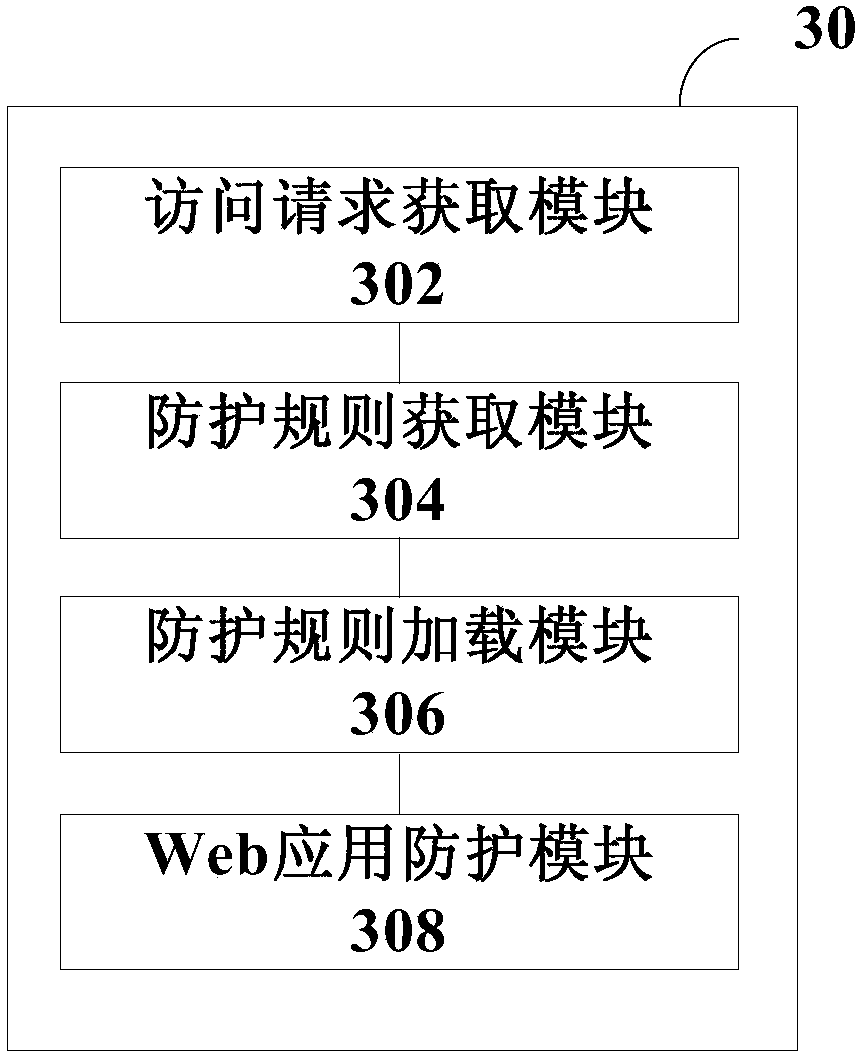
ActiveCN108023860AImprove the protective effectSupport concurrent accessTransmissionWeb applicationThe Internet
The invention discloses a Web application protection method and system, and a Web application firewall, and relates to the technical field of the Internet. The method disclosed by the invention comprises the following steps: the Web application firewall obtains an access request of a user, obtains a corresponding protection rule of a Web application to be accessed by the user according to the access request of the user, loads the protection rule, and uses the protection rule to protect the access request of accessing the Web application. In the Web application protection method and system disclosed by the invention, corresponding protection rules are flexibly set for different Web applications, the WAF does not uniformly configure all protection rules, and when an access request arrives, the WAF obtains the protection rule of the Web application to be accessed by the access request, dynamically loads the protection rule and finally uses the protection rule to perform protection processing on the access request. As the WAF neither needs to configure full rules, nor needs to perform full-rule matching protection for each request, concurrent access can be better supported, and the protection performance of the WAF is improved.
Owner:CHINA TELECOM CORP LTD
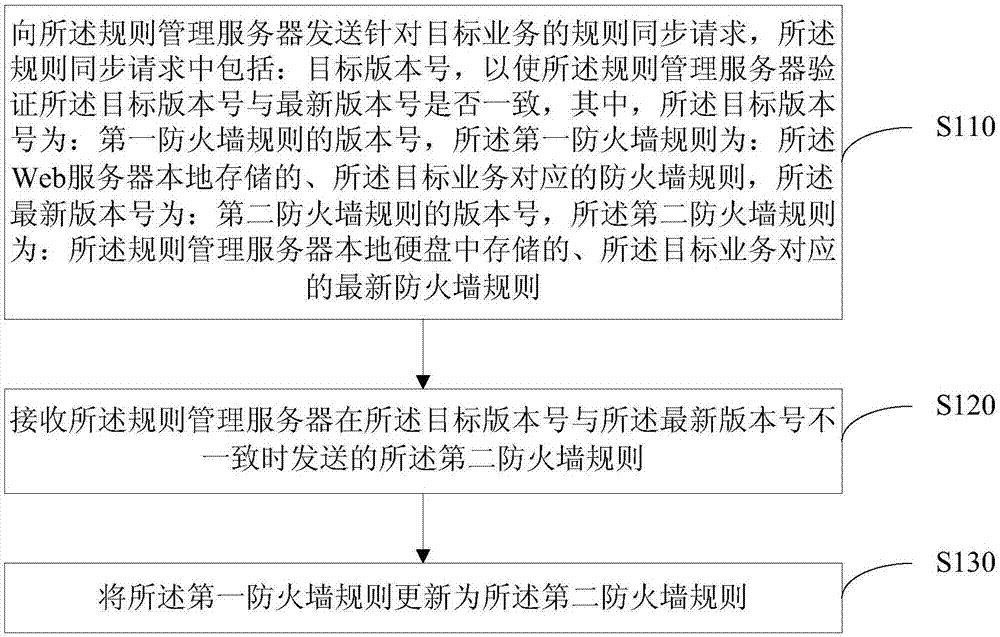
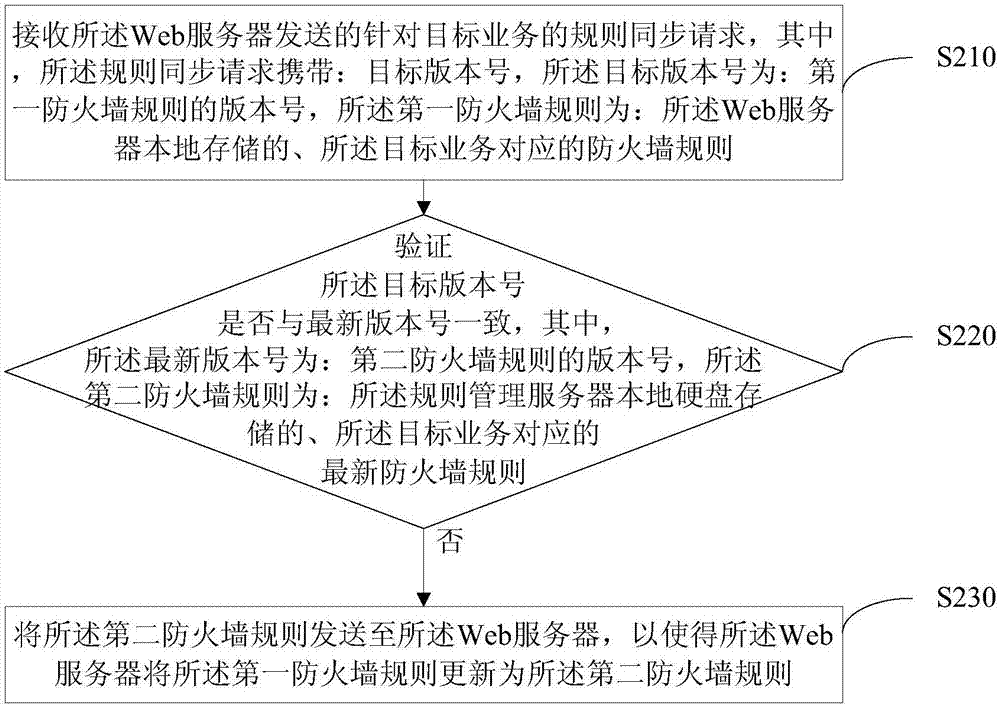
Web application firewall rule updating method, device and system
The invention discloses a Web application firewall rule updating method, device and system. The method disclosed by the embodiment of the invention comprises the following steps: firstly, a Web server sends a rule synchronization request for a target service to a rule management server; and then, the rule management server verifies whether a target version number in the rule synchronization request is consistent with the latest version number, wherein the target version number is the version number, which is locally stored by the Web server, of a first firewall rule corresponding to the target server; and the latest version number is the version number, which is stored in a local hard disk of the rule management server, of the latest firewall rule corresponding to the target service; if the target version number and the latest version number are inconsistent, a second firewall rule is sent to the Web server; the Web server receives the second firewall rule sent by the rule management server; and the first firewall rule is updated as the second firewall rule. By use of the technical scheme provided by the embodiment of the invention, the updating of the firewall rule can be realized in real time.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
Network application firewall system and realization method thereof
InactiveCN105871919AAvoid damageAvoid access performance impactTransmissionApplication serverReal-time data
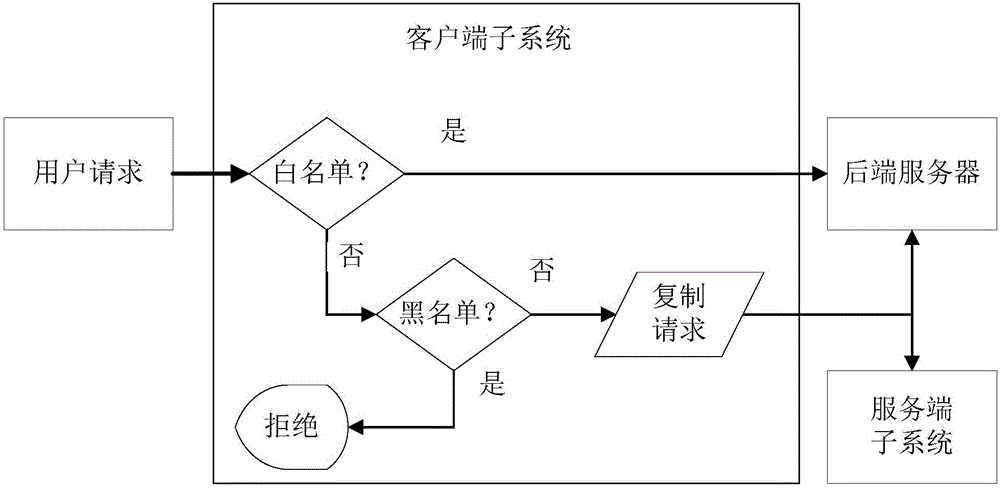
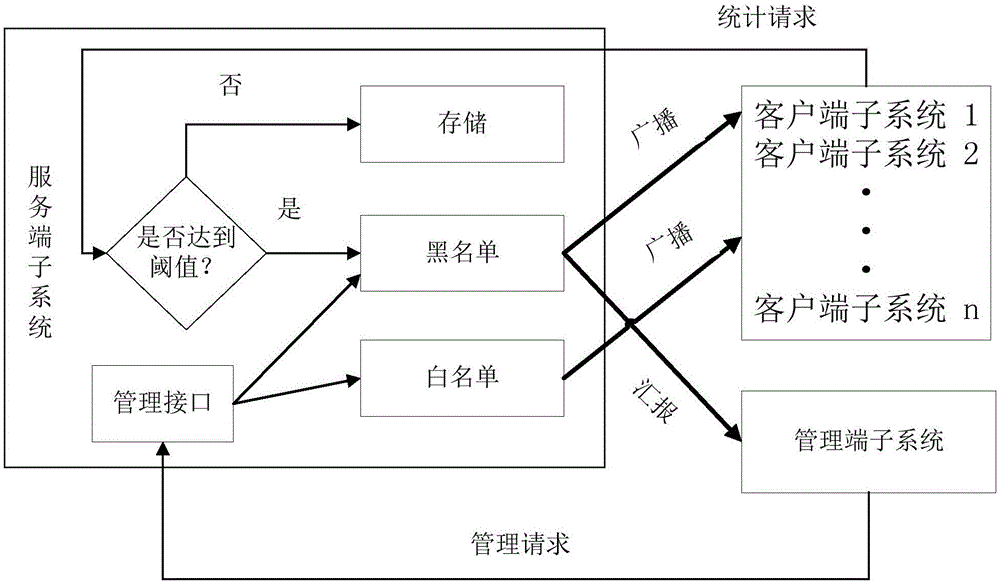
The invention discloses a network application firewall system and its realization method. The system includes: a client subsystem, which runs on an Internet portal server, and is used to receive user requests from the external network, and compare user request characteristics with locally stored black and white List comparison: when the user is in the whitelist, skip the follow-up logic directly and forward the user request to the backend application server; when the user is in the blacklist, interrupt the user request; the service subsystem is used to realize real-time data Analysis and storage: By sending data to the client subsystem, real-time statistical analysis is performed according to the predefined analysis logic, and the analysis results are stored; when the analysis results reach the preset threshold, the blacklist logic is automatically triggered. By adopting the present invention, complex client logic can be realized and customizability can be improved, so that it is suitable for network video and live broadcast services.
Owner:北京花房科技有限公司
Application firewall validation bypass for impromptu components
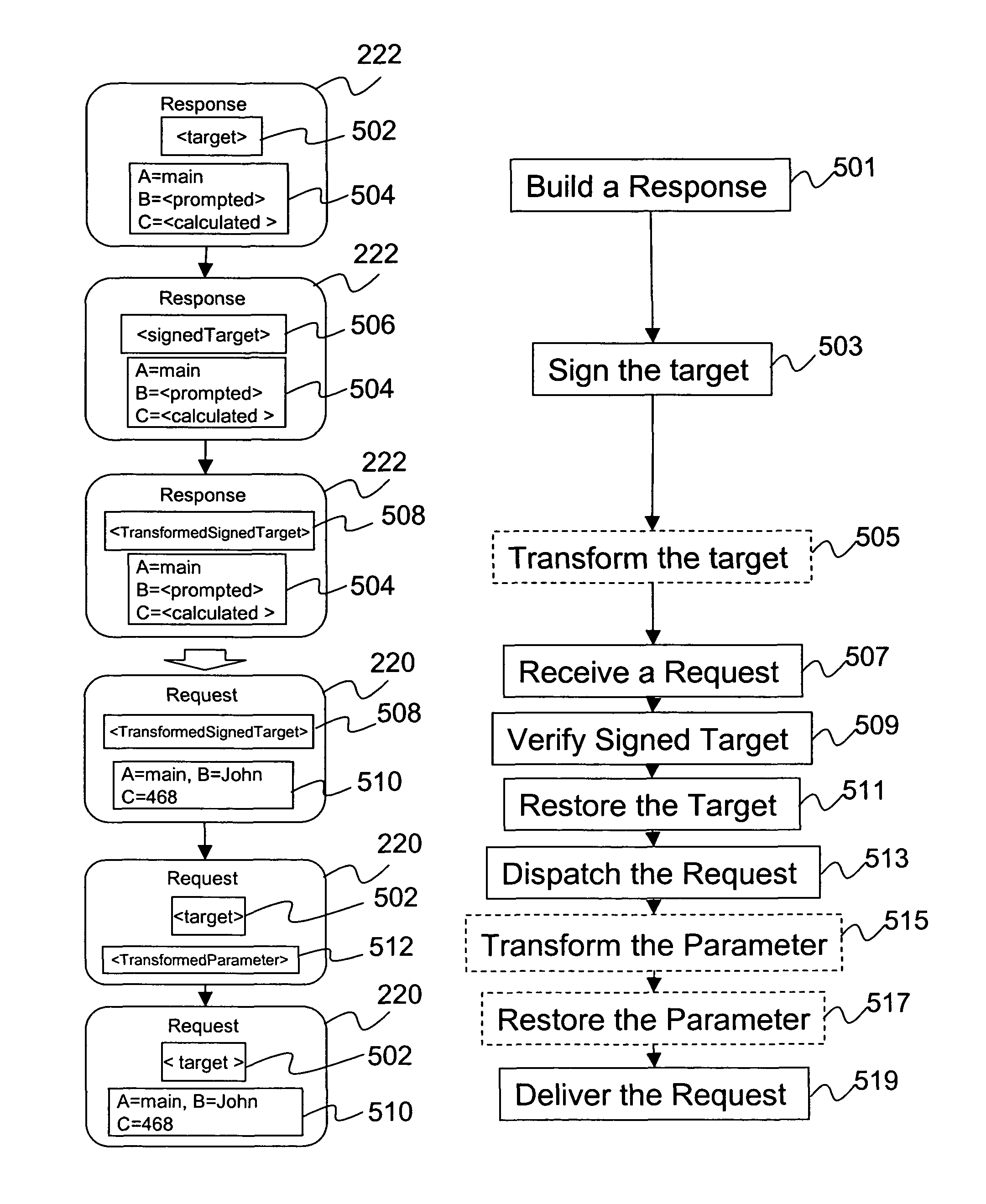
A method of controlling data transfer between a Web client and a Web application by building a response with a target. The target indicates a destination to an impromptu component of the Web application. The target is signed when a response is built. After receiving the response by the Web client; the corresponding a request from the Web client includes the signed target. The request is received by an entry point of the Web application. The entry point has existing validation rules. The validation rules are by-passed when the signed target is verified. The target is restored in the request to the original state; and dispatched to the impromptu component.
Owner:INT BUSINESS MASCH CORP
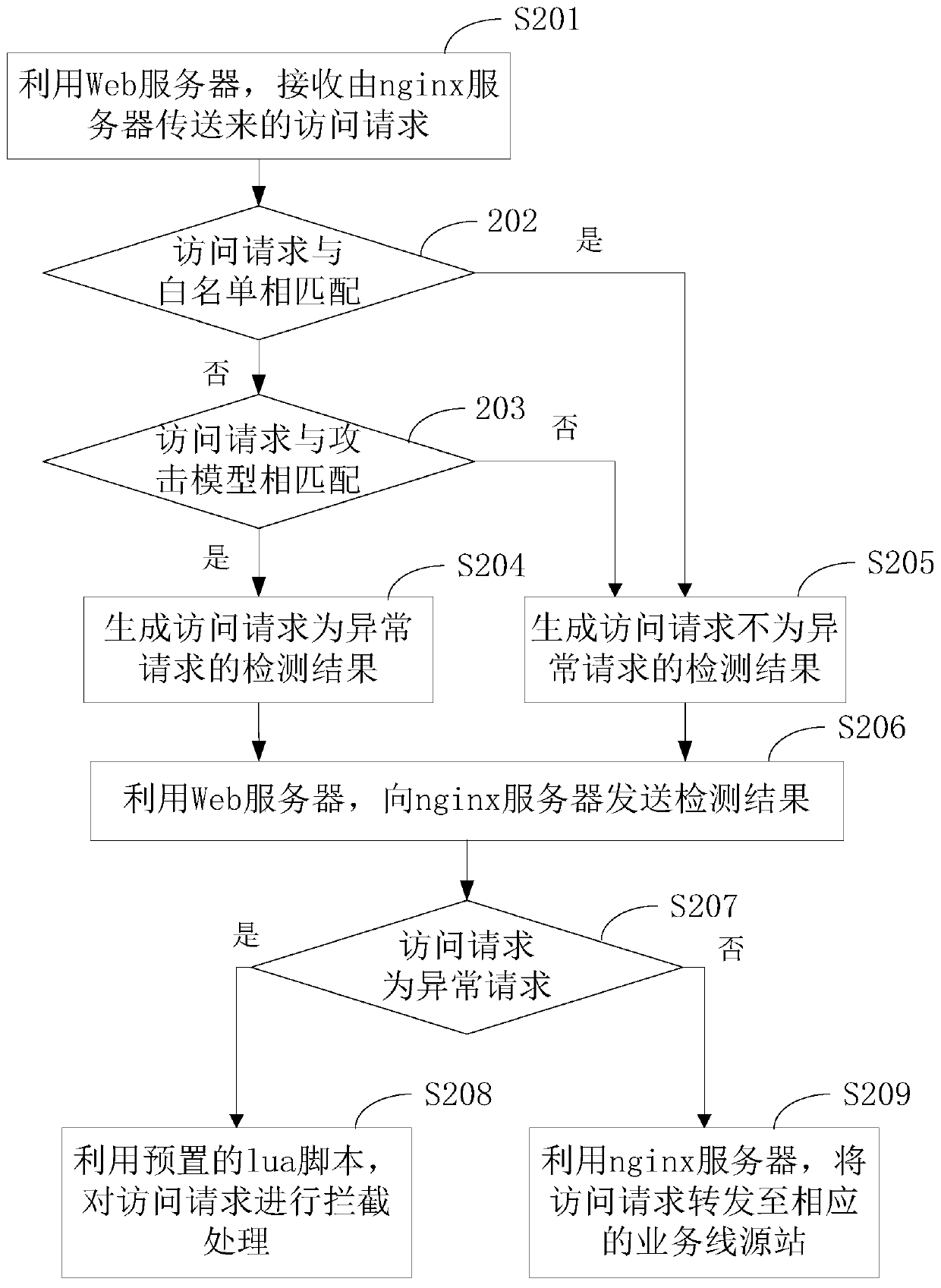
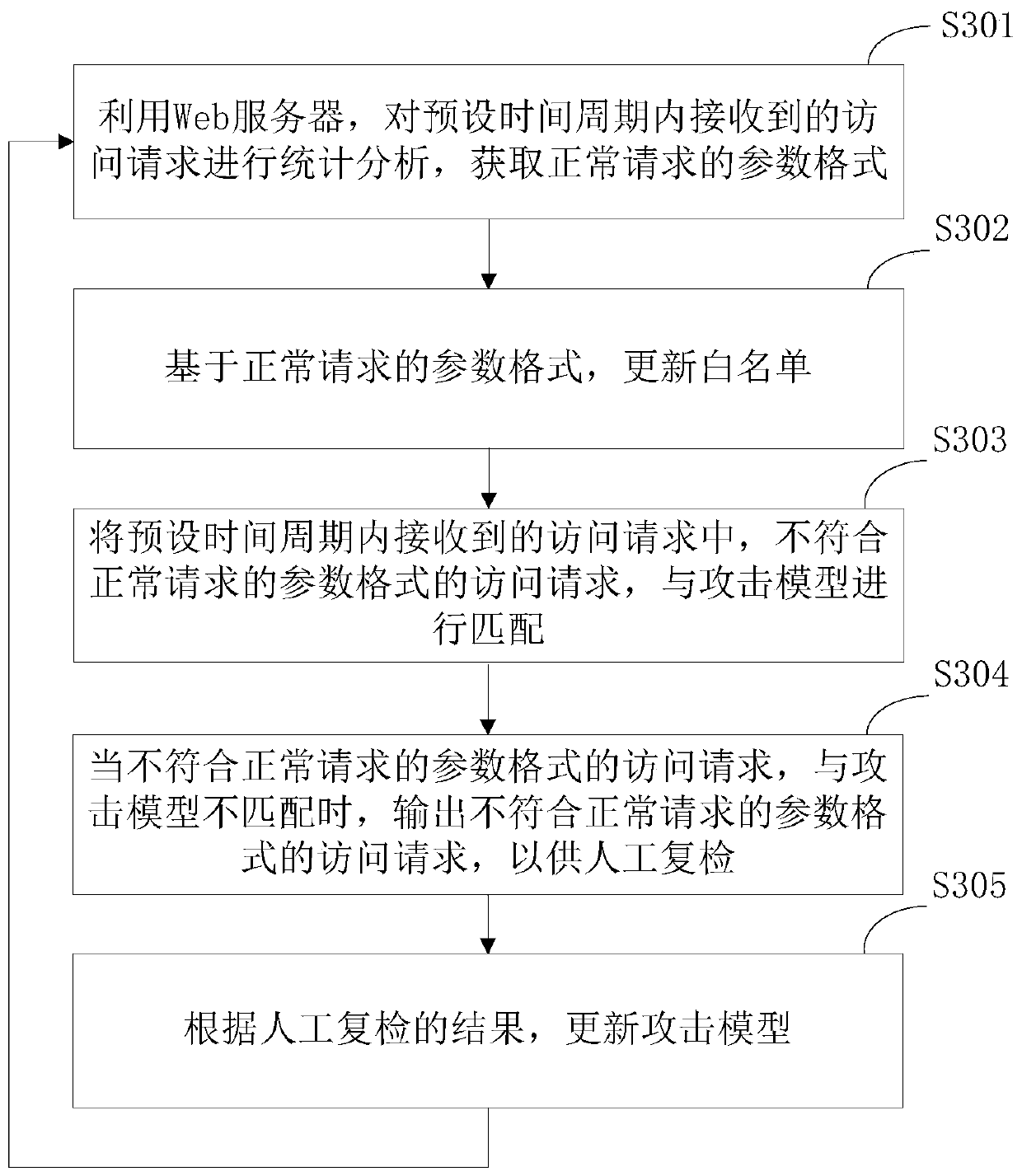
Web application security protection method and a Web application firewall system
The invention provides a Web application security protection method and a WAF system. The WAF system comprises a Web server and an nginx server. The method comprises the following steps of building the Web server by adopting a python tornado framework; detecting whether the access request transmitted by the nginx server is an abnormal request or not by utilizing the Web server to obtain a detection result; using the Web server to send a detection result to the lua script in the nginx server; reading a detection result of the input lua script by using the nginx server to determine whether the access request is an abnormal request or not; if the access request is an abnormal request, intercepting the access request by using a lua script; and otherwise, forwarding the access request to the corresponding service line source station by using the nginx server. According to the WAF system, when Web application security protection is realized, excessive server resources are not occupied, and the occupancy rate of the WAF system on the server resources is reduced.
Owner:BEIJING SOHU NEW MEDIA INFORMATION TECH
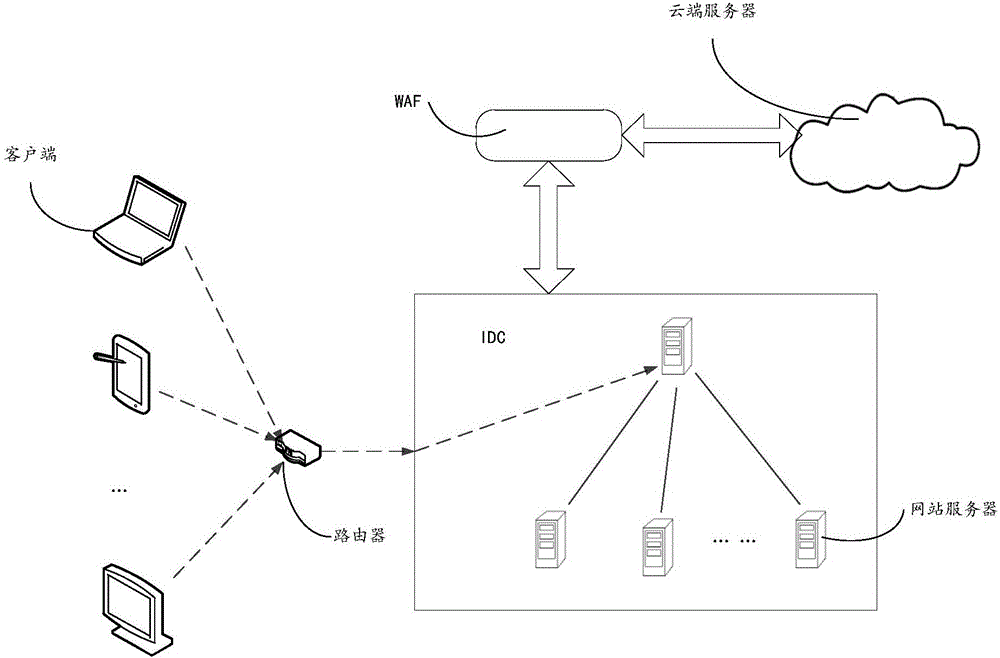
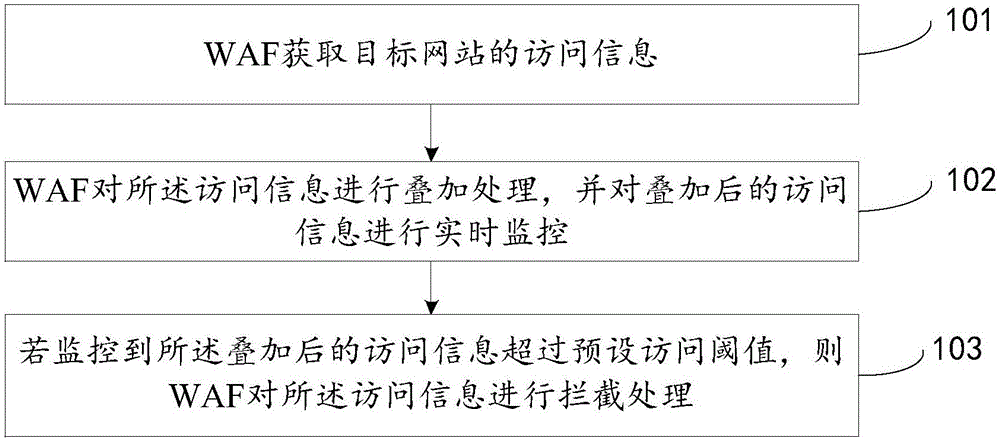
Processing method and system of denial of service attack, Web application firewall (WAF), and router
The invention discloses a processing method and system of a denial of service attack, a Web application firewall (WAF), and a router, is mainly applied to a CC attack process, and relates to the technical field of Internet, mainly for the purpose of solving the problem of threatening security of a target website when the target website is attacked in a time interval of cloud protection performed by a cloud server in the prior art. The method provided by the technical scheme comprises the following steps: a WAF obtaining access information of the target website; performing superposing processing on the access information and performing real-time monitoring on the superposed access information; and if it is monitored that the superposed access information exceeds a preset access threshold, performing interception processing on the access information.
Owner:BEIJING QIHOO TECH CO LTD +1
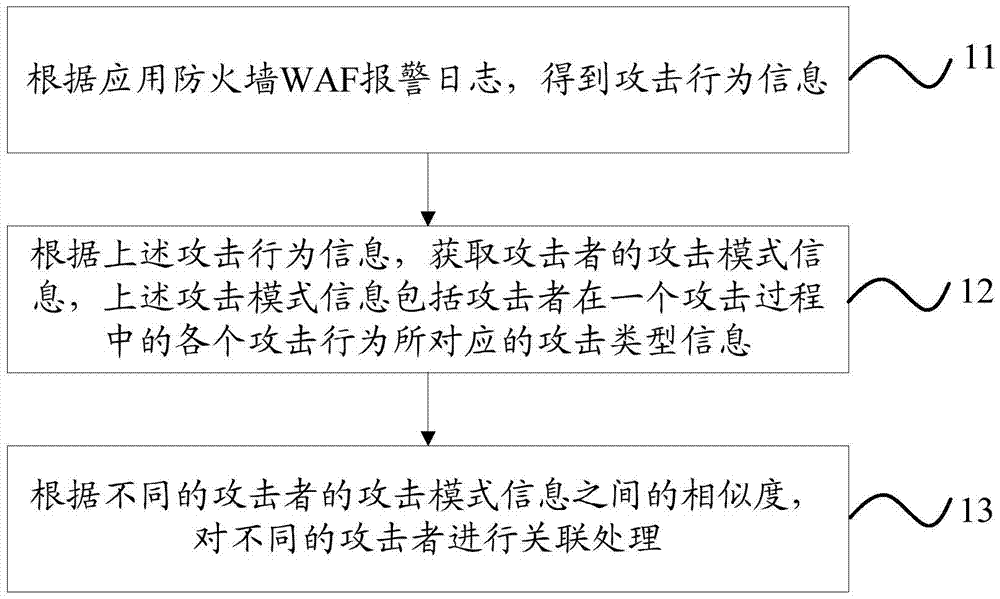
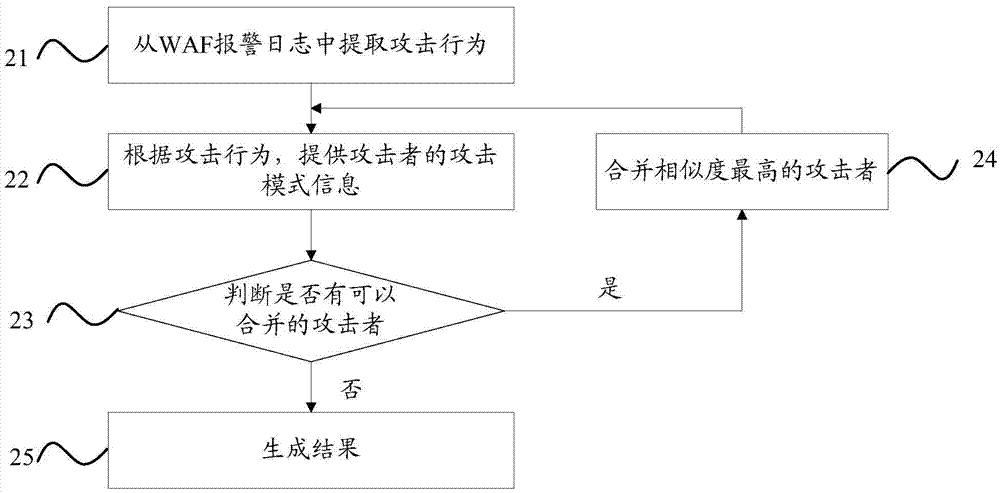
Warning association method and device
Owner:CHINA MOBILE COMM GRP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com