Firewall security policy configuration method and management unit
A technology of security policy and management device, applied in the field of network security, which can solve the problems of ineffective utilization, error-prone, troublesome, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
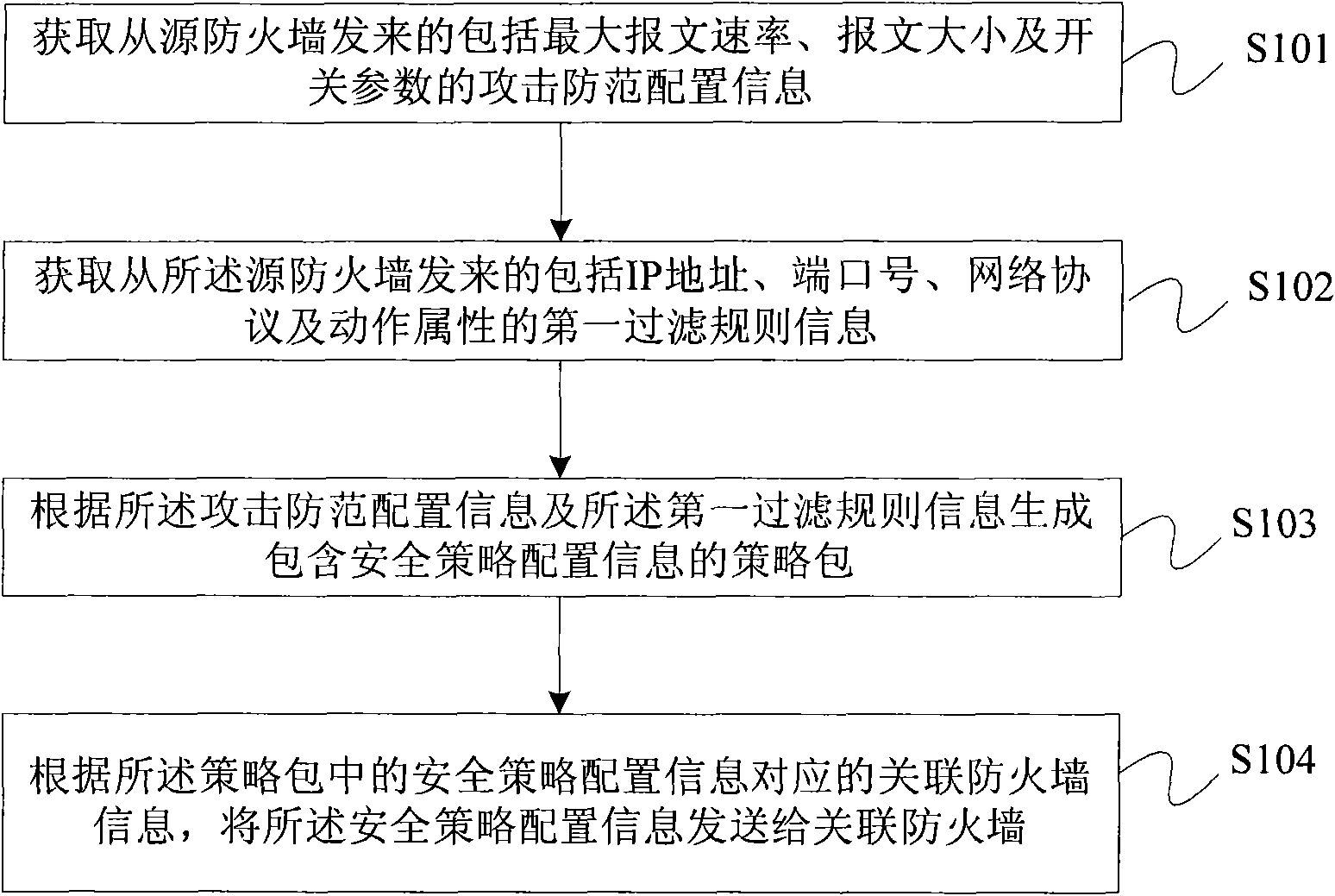
[0028] figure 1 It is a schematic flowchart of a firewall security policy configuration method according to an embodiment of the present invention, and the method includes:
[0029] Step S101: Obtain attack defense configuration information including maximum packet rate, packet size or switch parameters sent from the source firewall;
[0030] Step S102: Obtain the first filtering rule information including IP address, port number, network protocol and action attribute sent from the source firewall;
[0031] Step S103: Generate a policy packet containing security policy configuration information according to the attack defense configuration information and the first filtering rule information;
[0032] Step S104: Send the security policy configuration information to the associated firewall according to the associated firewall information corresponding to the security policy configuration information in the policy package.
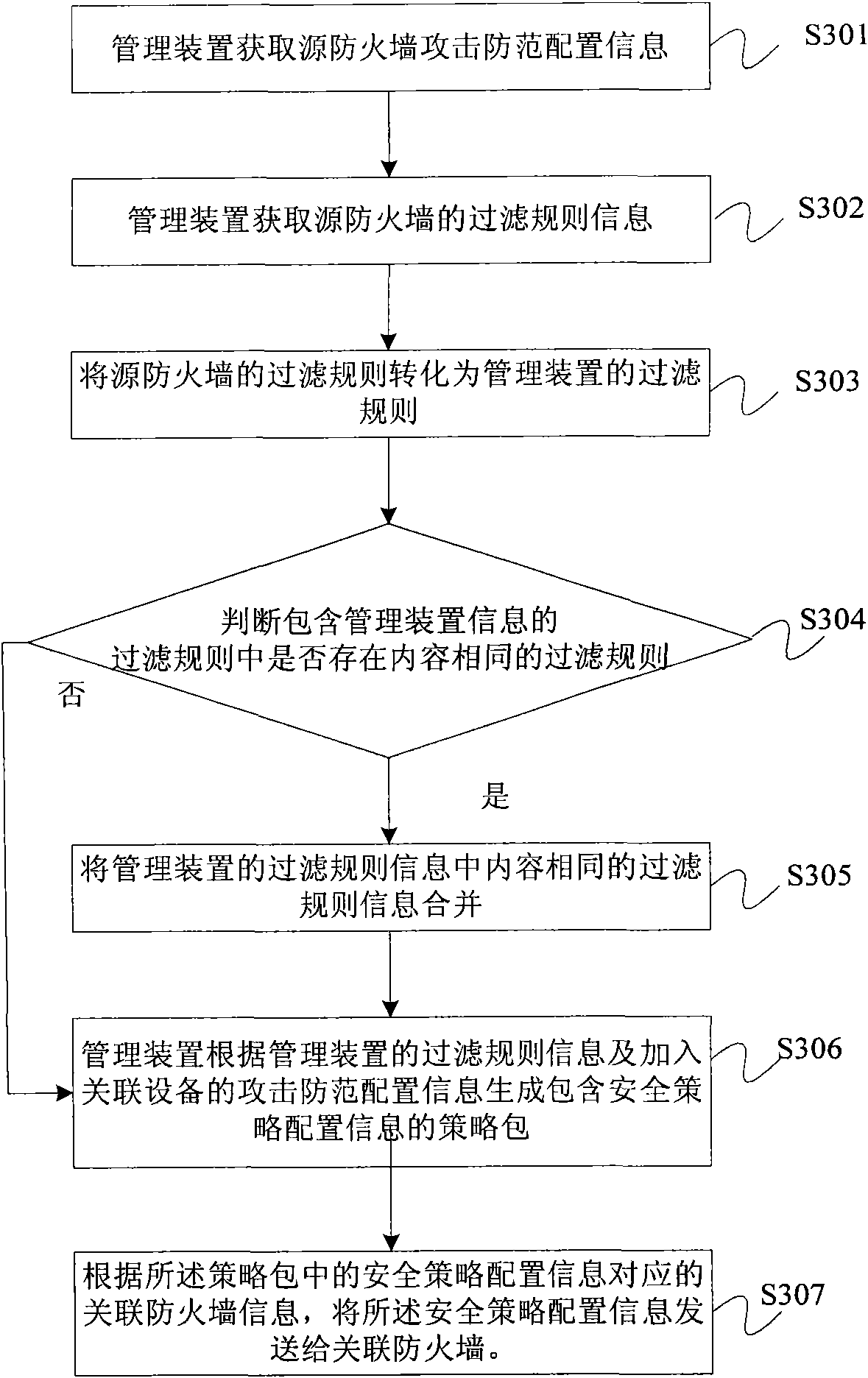
[0033] The method further includes: sending security...
Embodiment 2
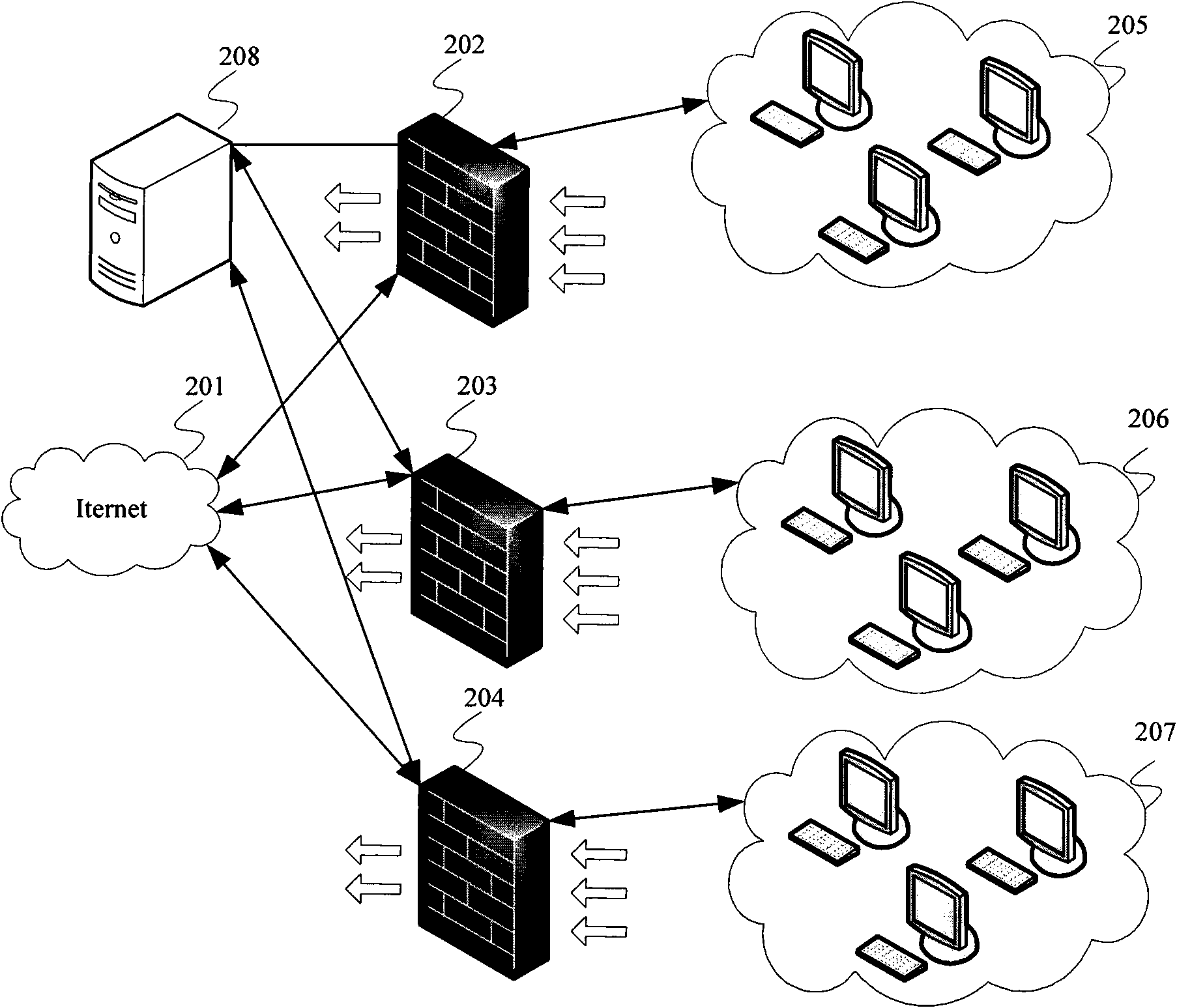
[0075] Figure 13 It is a schematic structural diagram of a management device according to an embodiment of the present invention. Such as Figure 13 As shown, the management device includes: a configuration information acquisition unit 1301, a rule information acquisition unit 1302, a policy package generation unit 1303 and an information sending unit 1304, wherein:
[0076] The configuration information obtaining unit 1301 is used to obtain the attack defense configuration information that includes the maximum packet rate, packet size or switch parameters sent from the source firewall; The firewall sends a command requesting attack defense configuration information, and receives the attack defense configuration information including the maximum packet rate, packet size or switch parameters returned by the source firewall through the communication protocol after receiving the command. The configuration information obtaining unit 1301 may also obtain information from the sou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com