Patents
Literature
174 results about "Message size" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
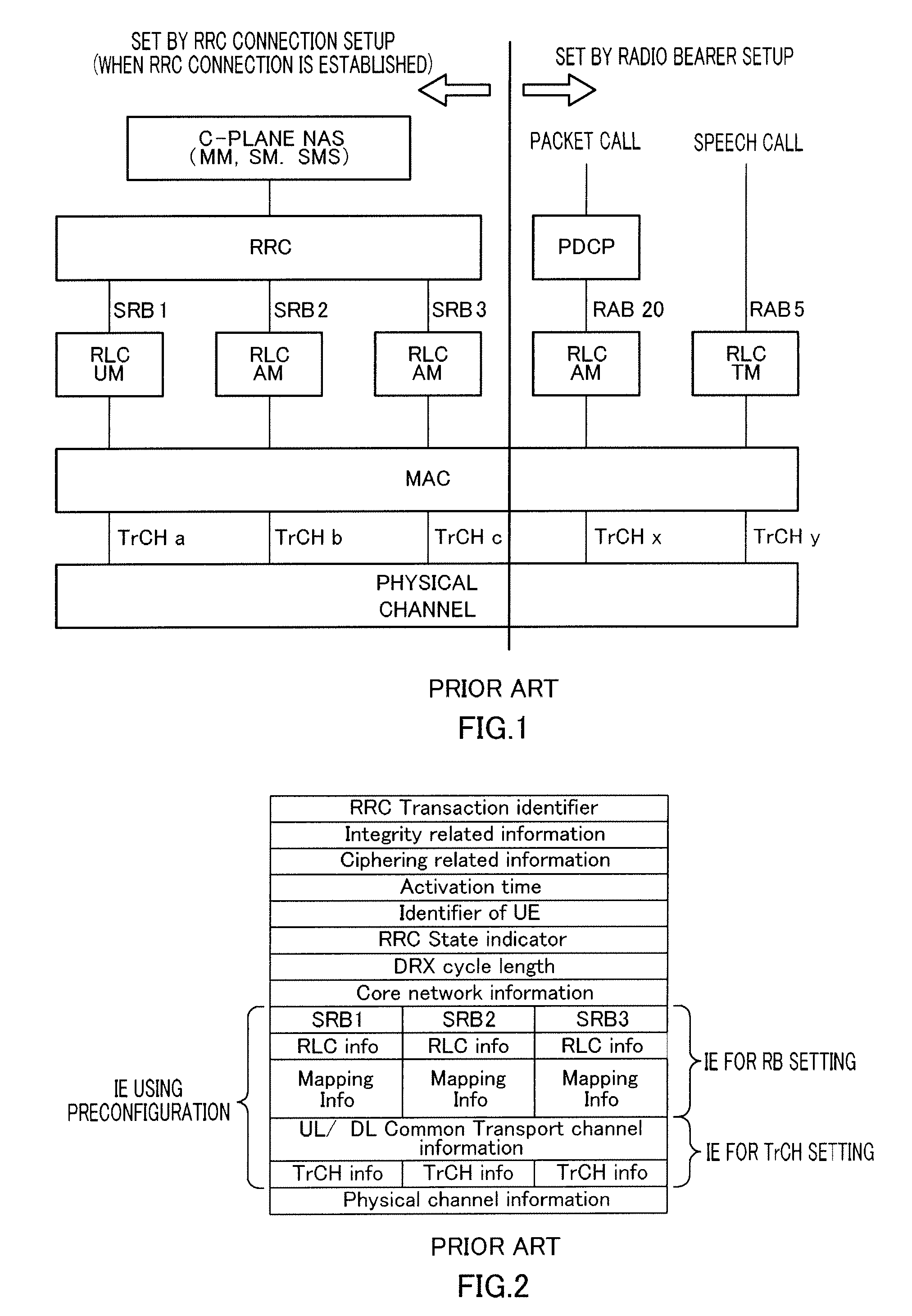
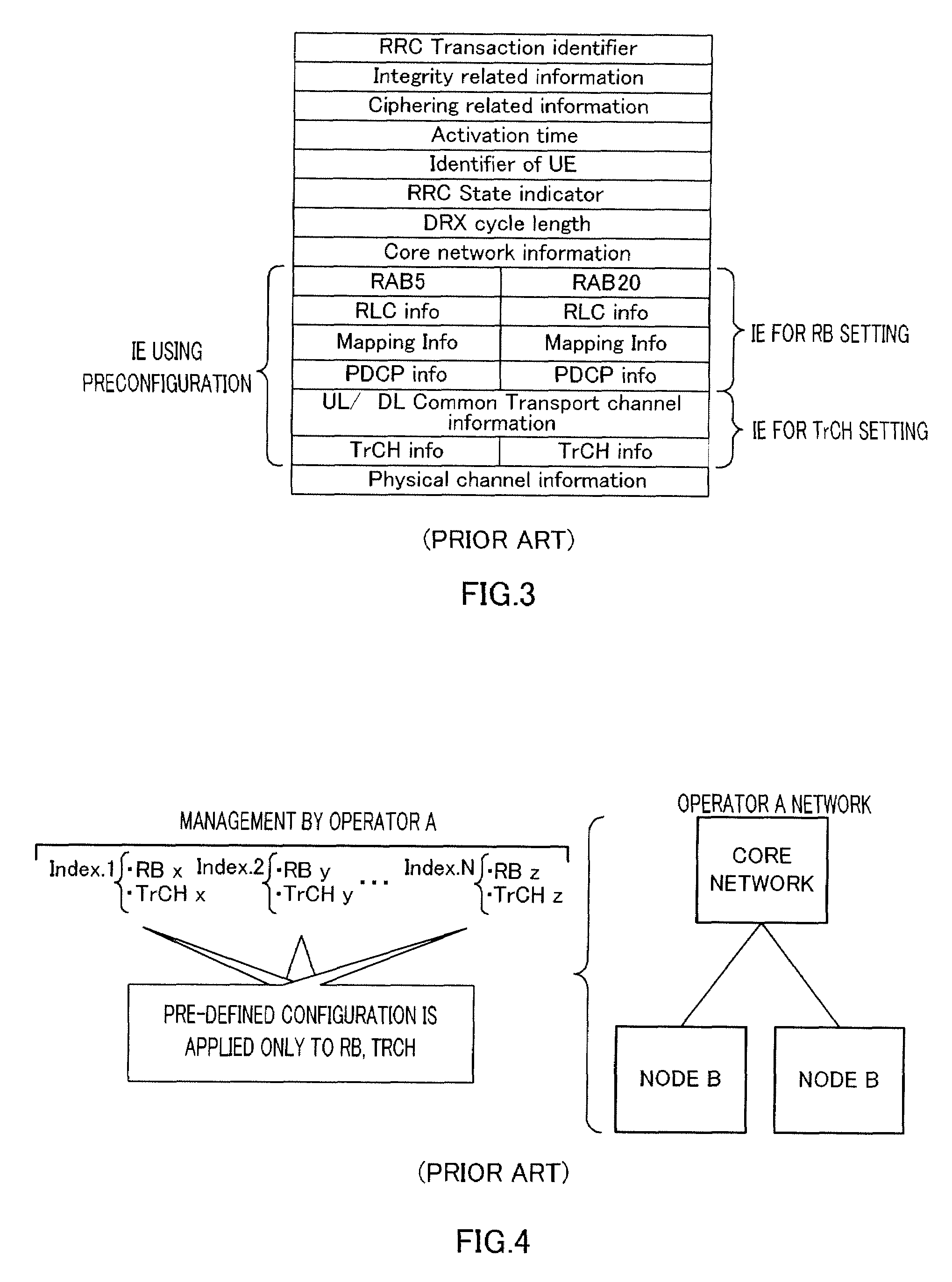
Message size is based on the message headers, the body of the message, and then any attachments associated to the mail message.
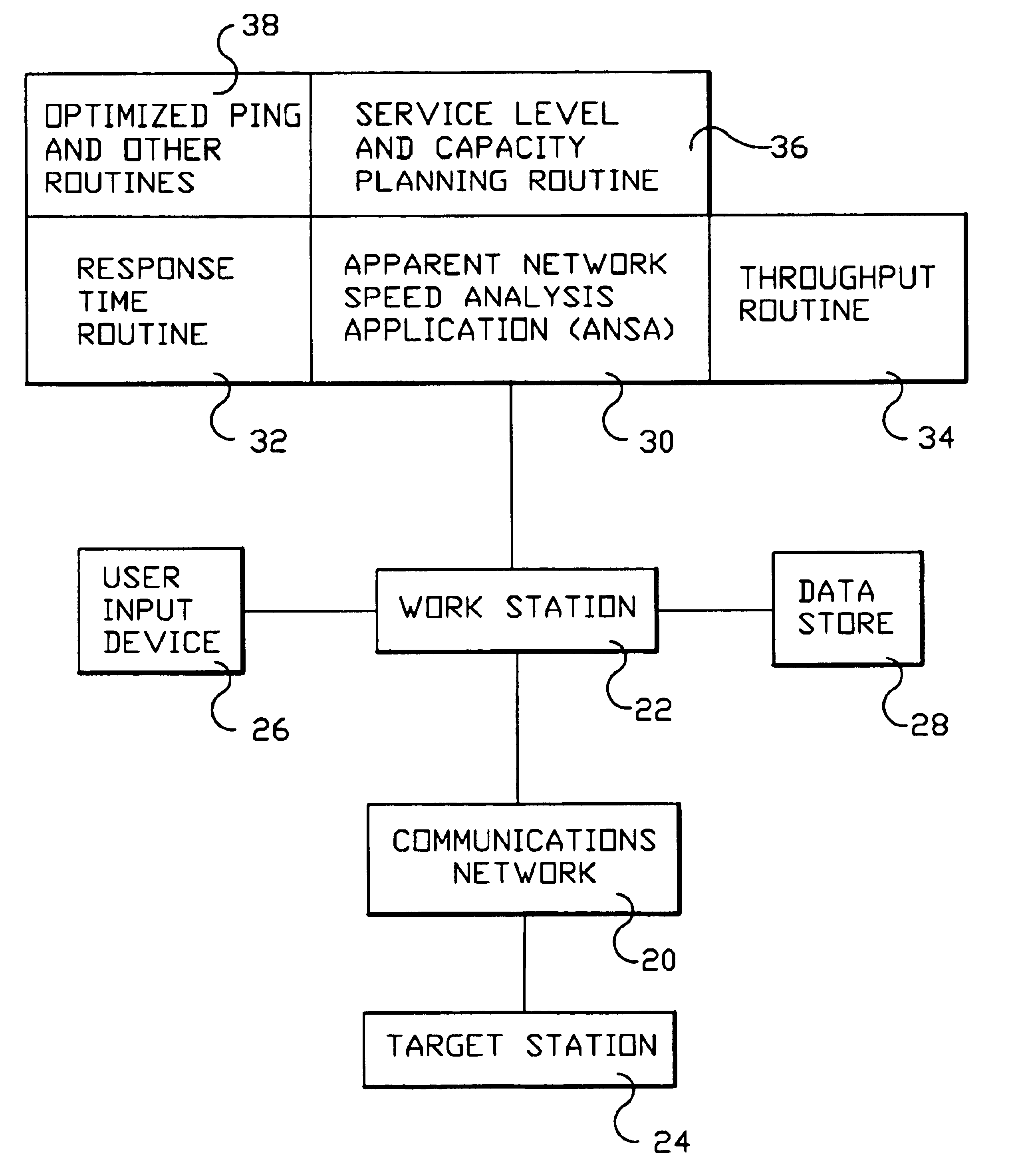
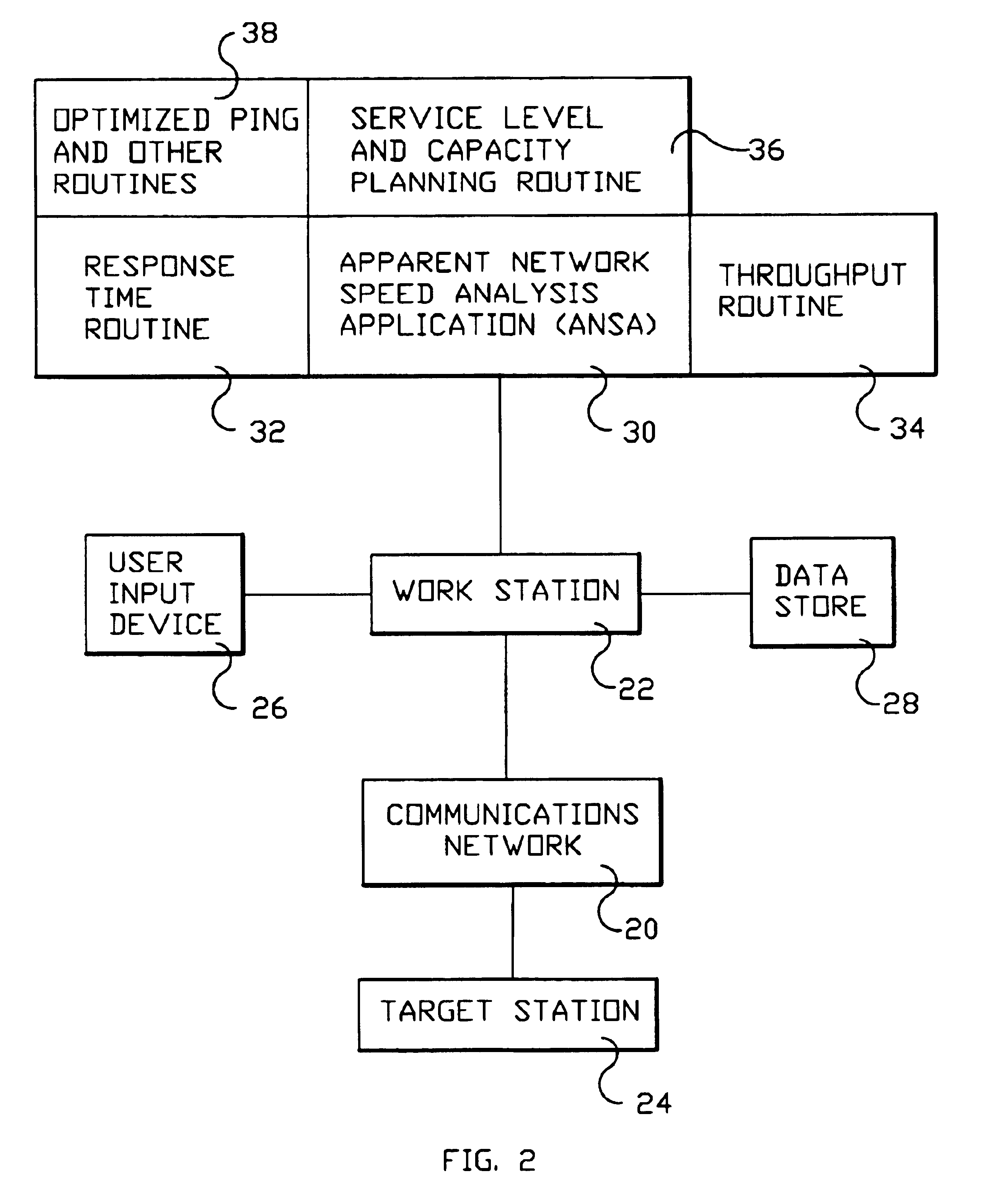
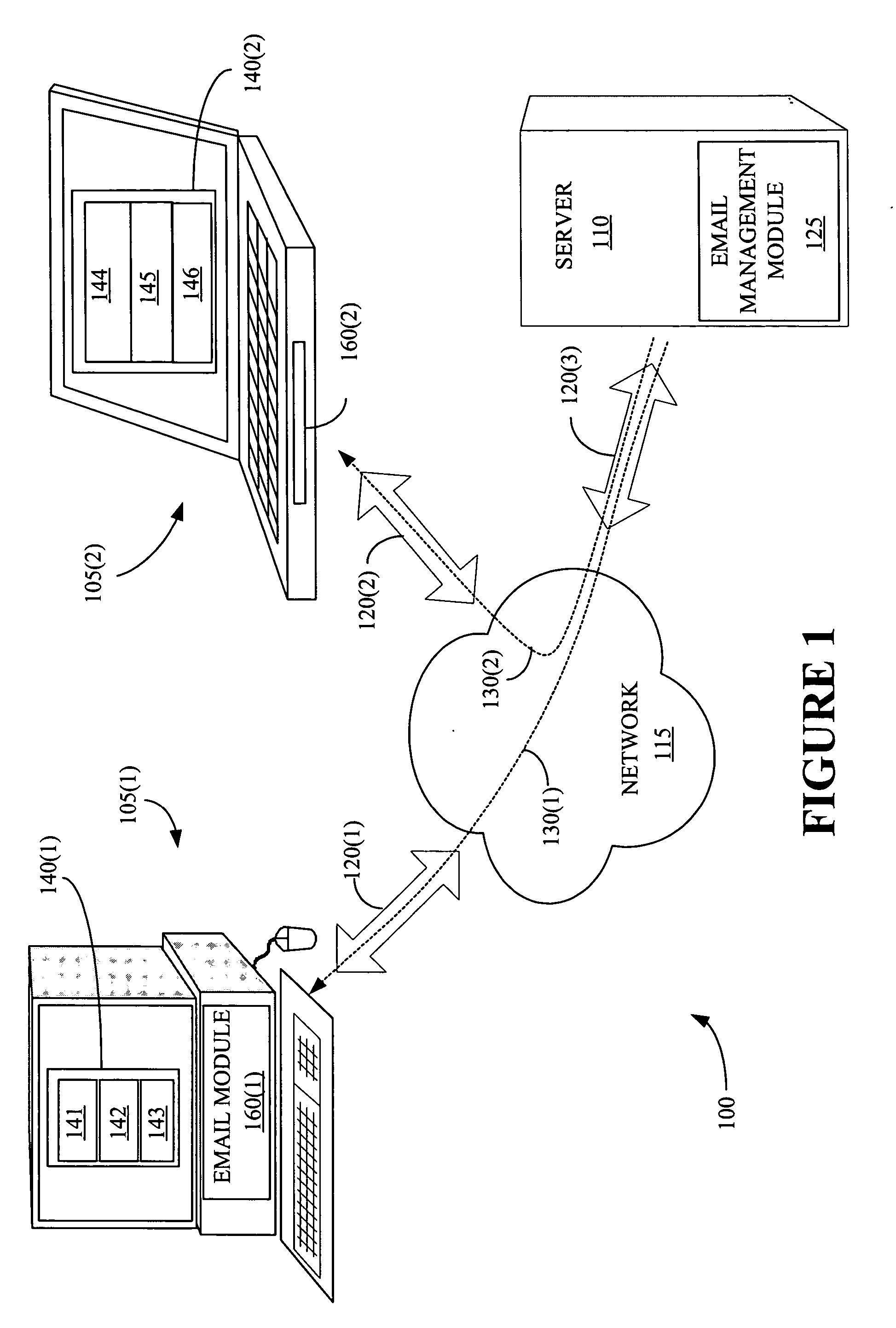
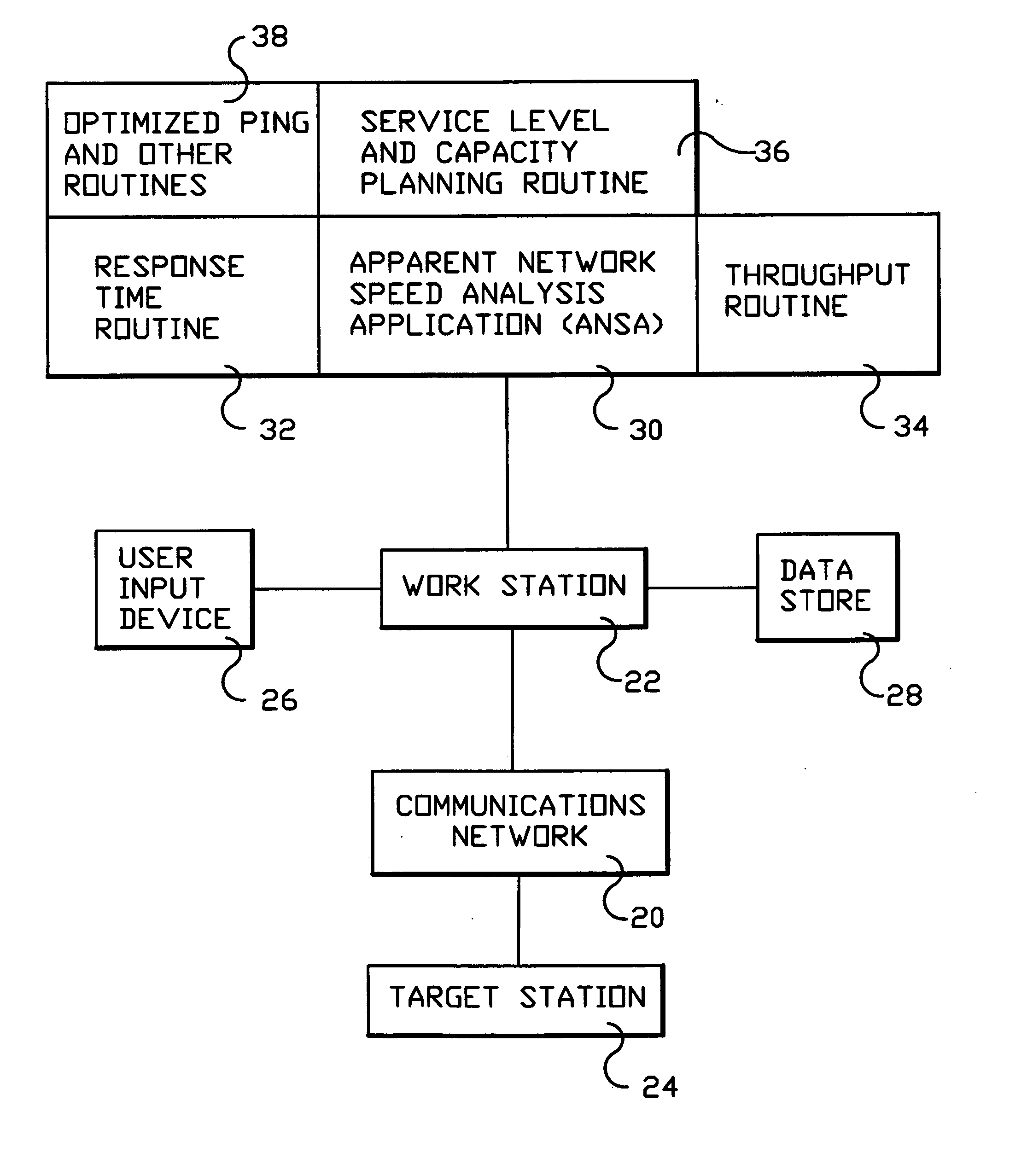
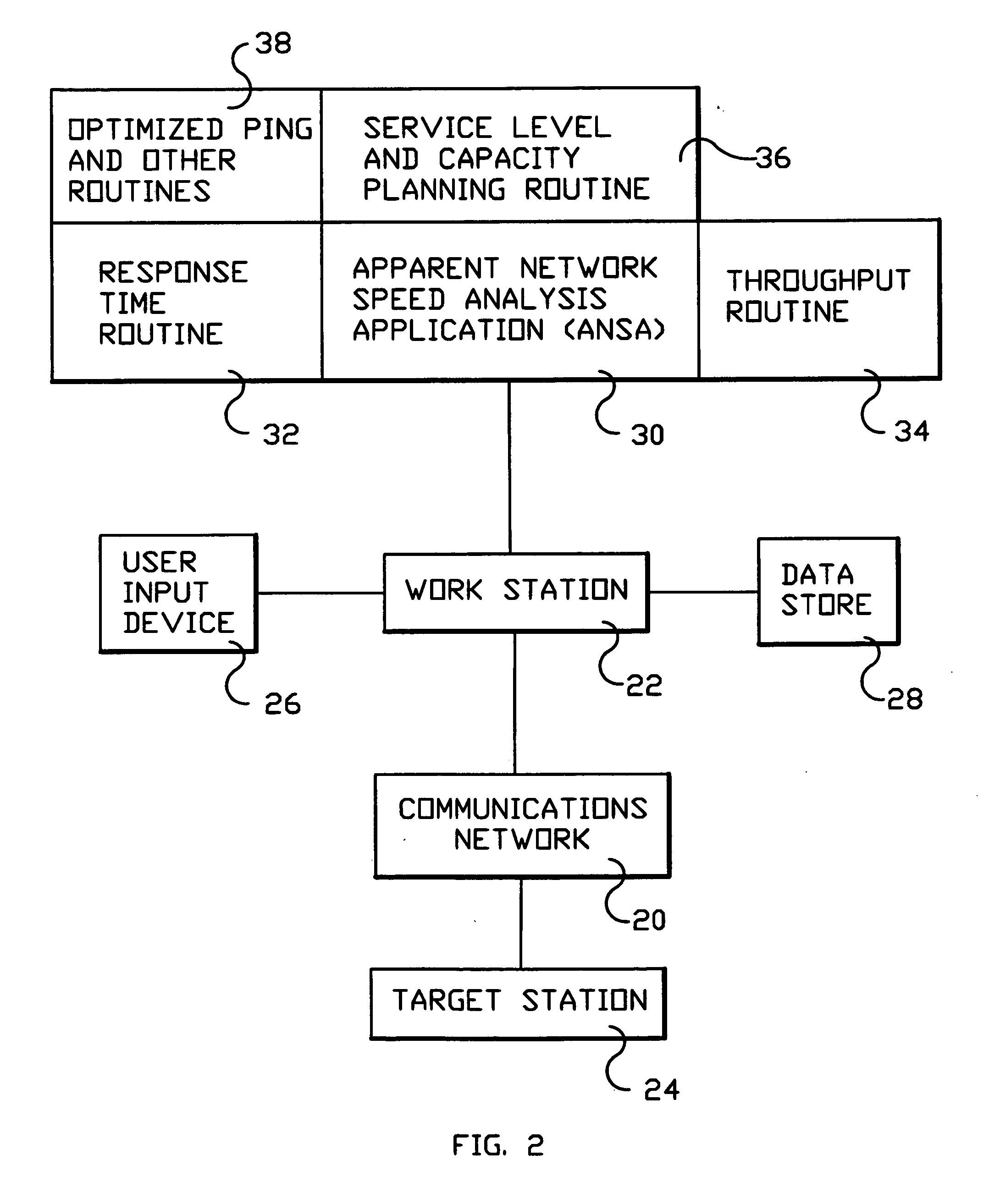
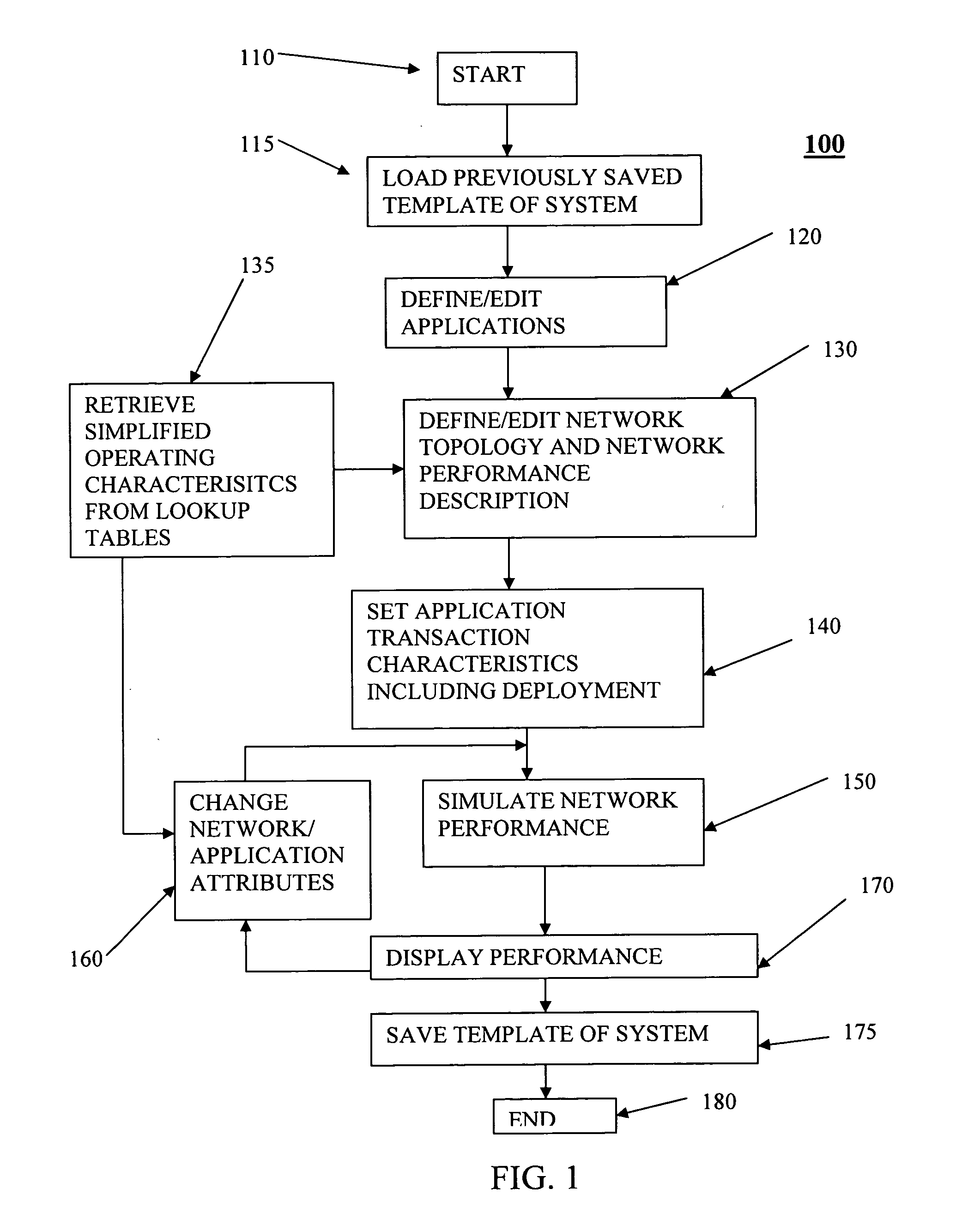
System and method for monitoring performance, analyzing capacity and utilization, and planning capacity for networks and intelligent, network connected processes
Analysis of networks and testing and analyzing intelligent, network connected devices. An instantaneous network utilization value is assigned for the worst surviving ping instance of between 90% and 99% (determined proportionately from the ratio of dropped test samples to surviving test samples), and then used to solve for average network message size and average utilization of the network. A plurality transactions of different types are transmitted across the network to intelligent end systems and the results mathematically evaluated to determine the portion of the total response time contributed by the network and by the end processors; the utilization of the end processor processing subsystems and of the end processor I / O subsystems; and the utilization of the end system as a whole; and of the network and end processors considered as a unitary entity. Steps include determining utilization of the network when test packets are dropped by the network; utilization of intelligent processor and other devices attached to the network when test transactions are dropped, and when not dropped; and response time for remote processes at both the network and processor level.
Owner:IBM CORP
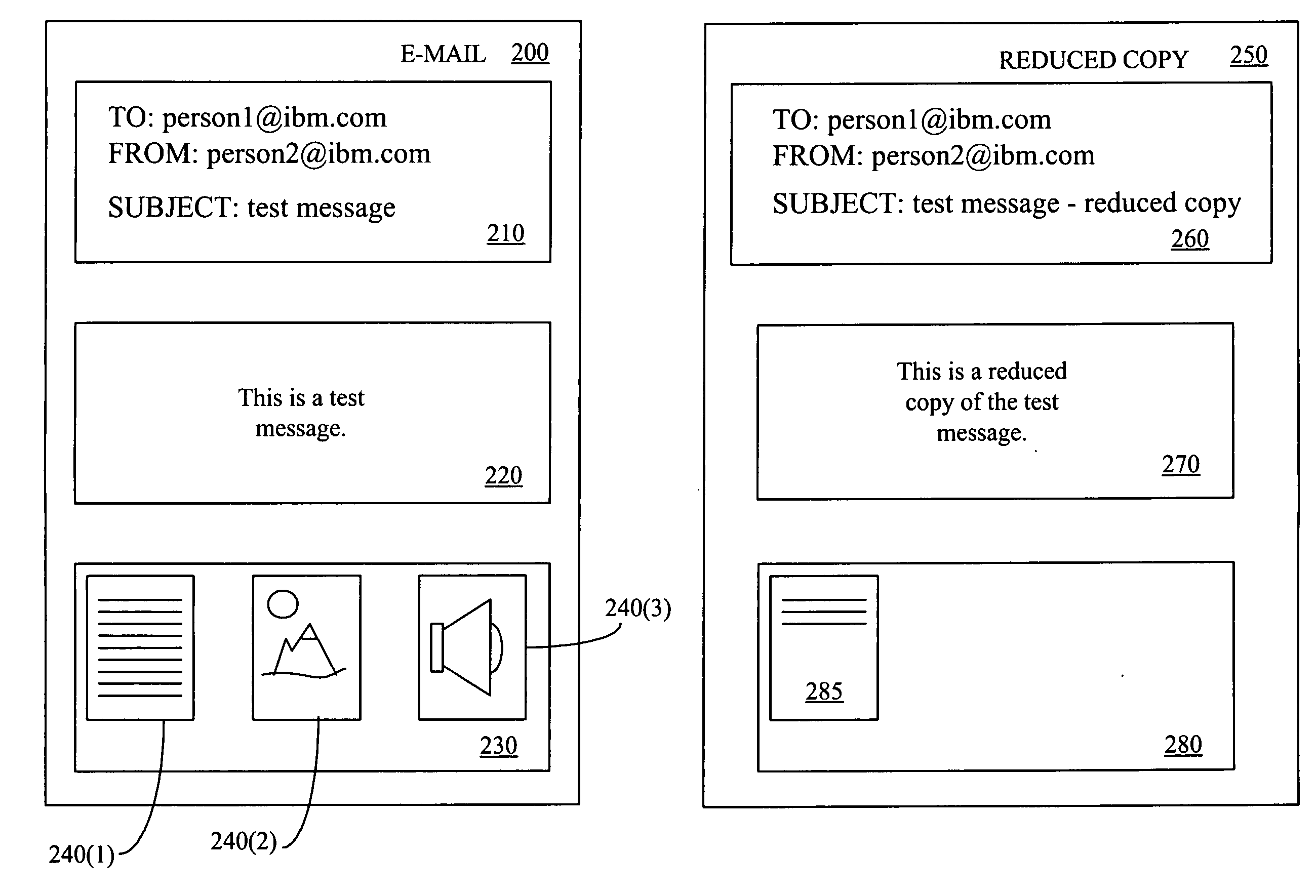
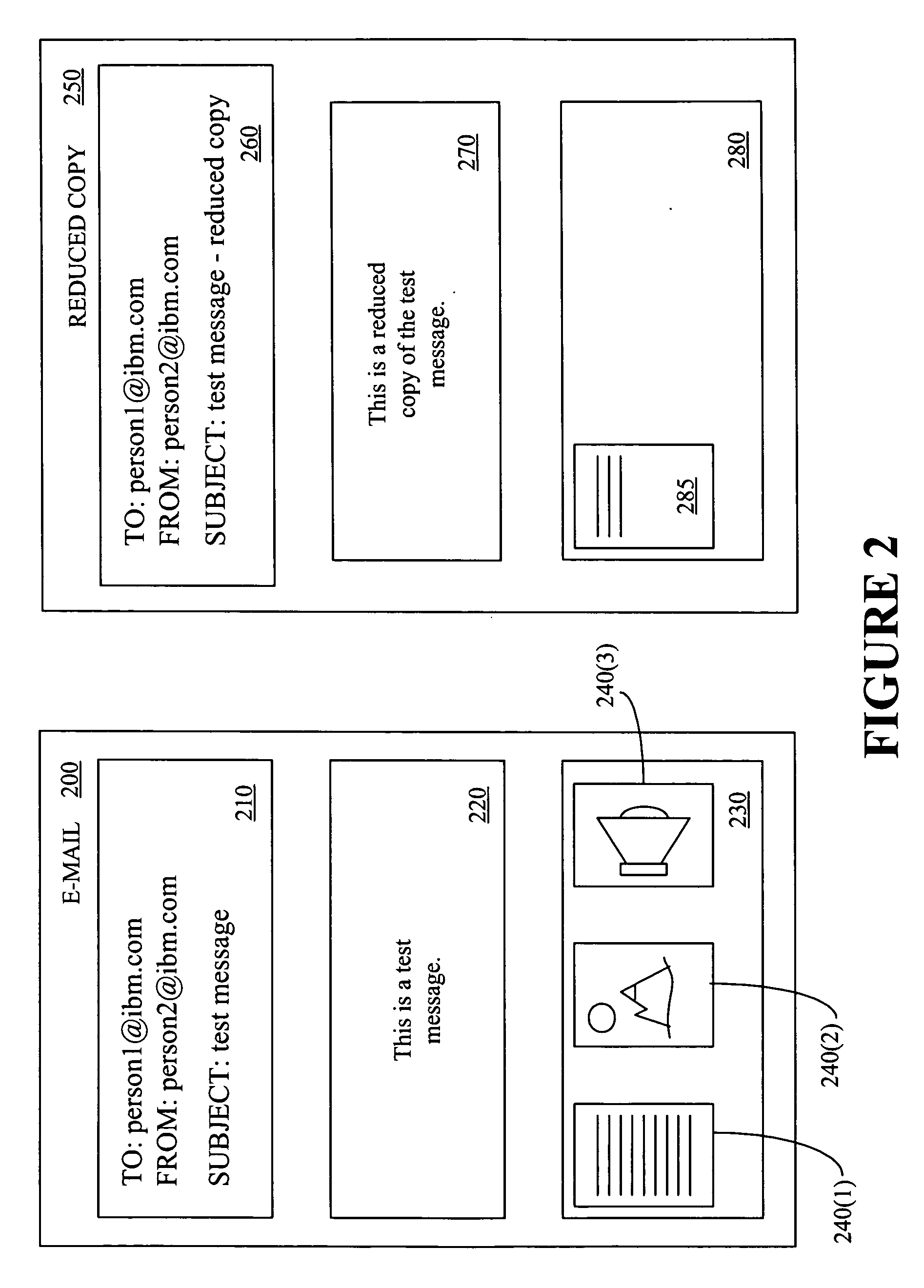
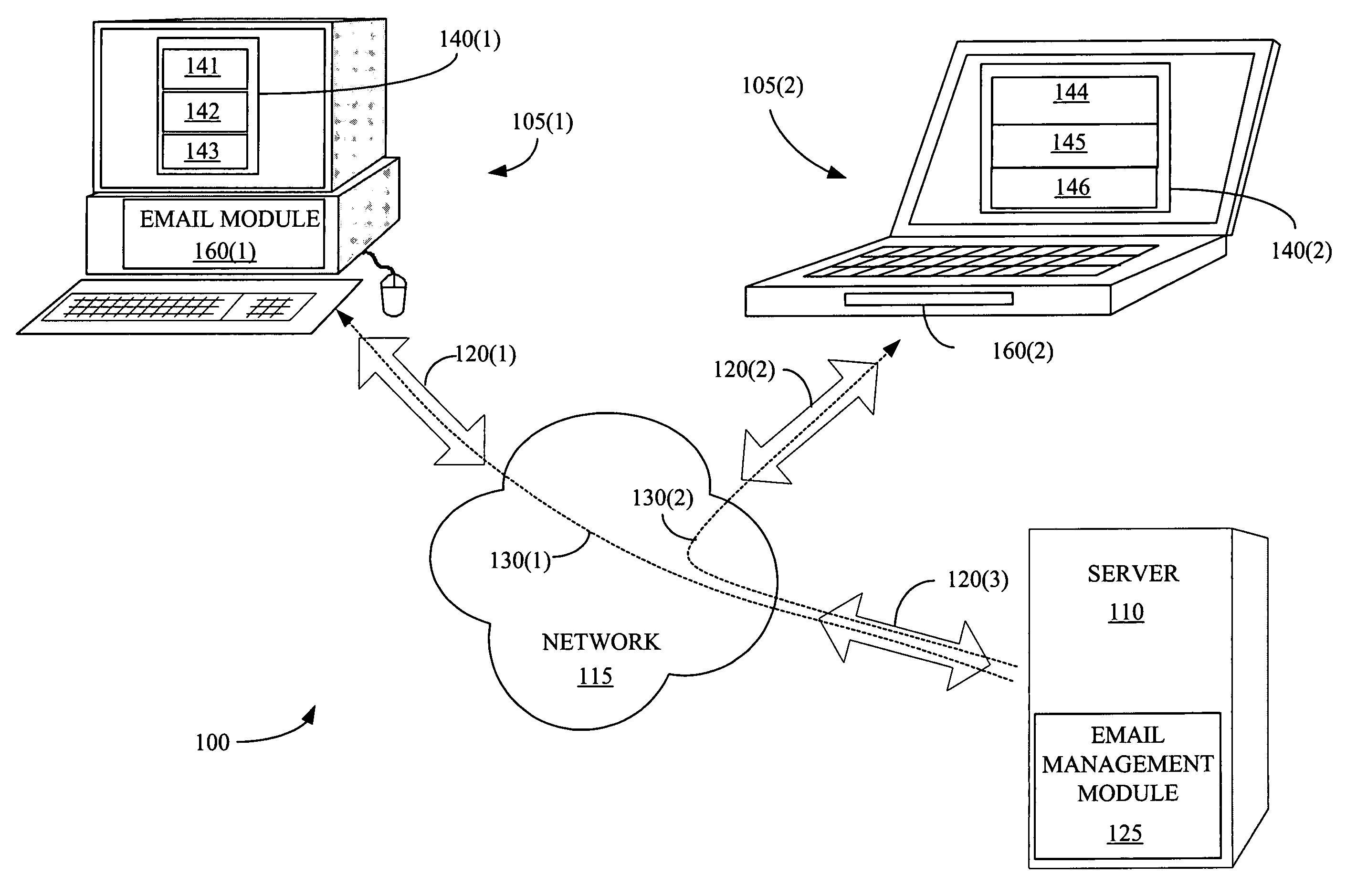
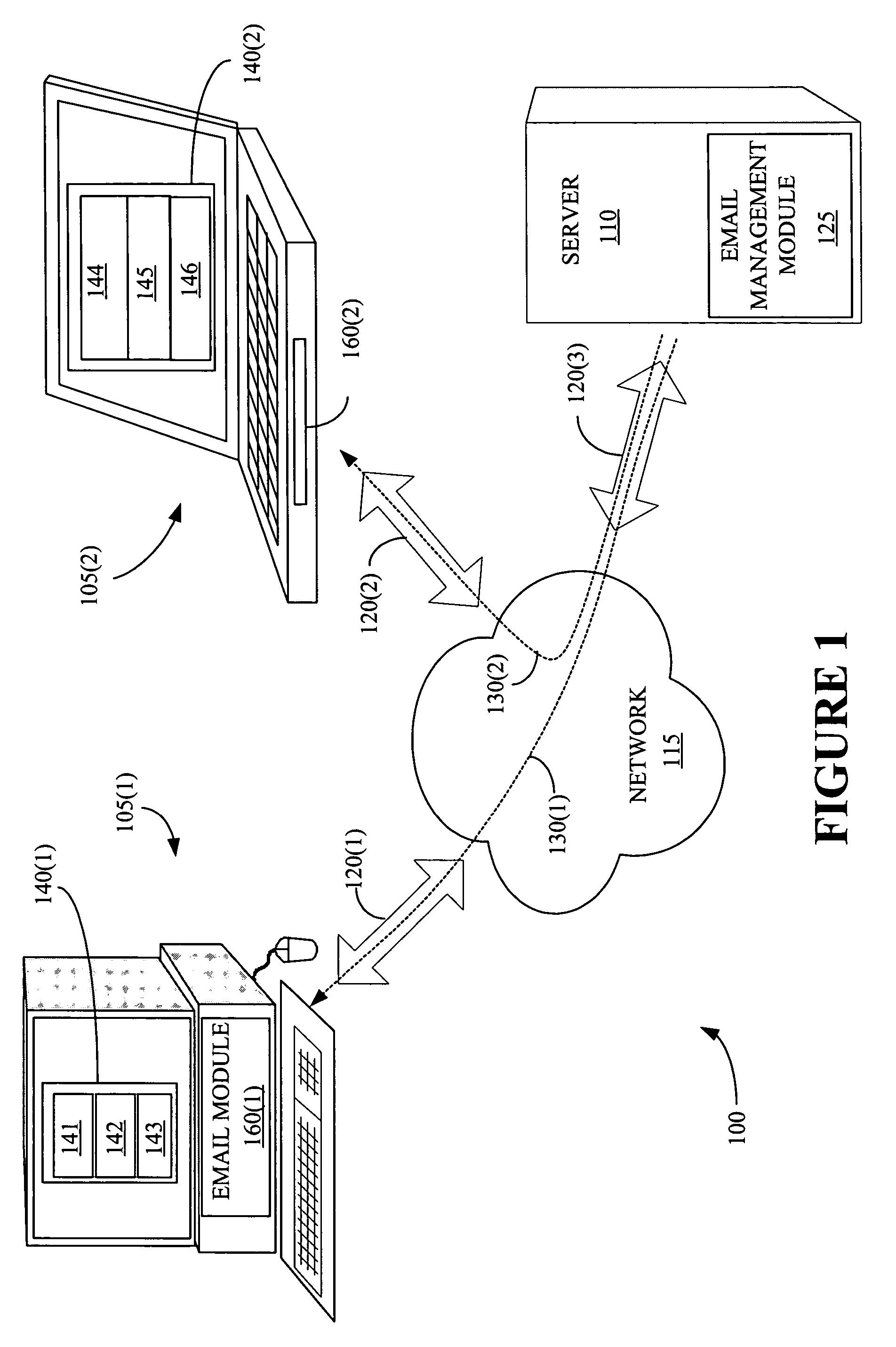
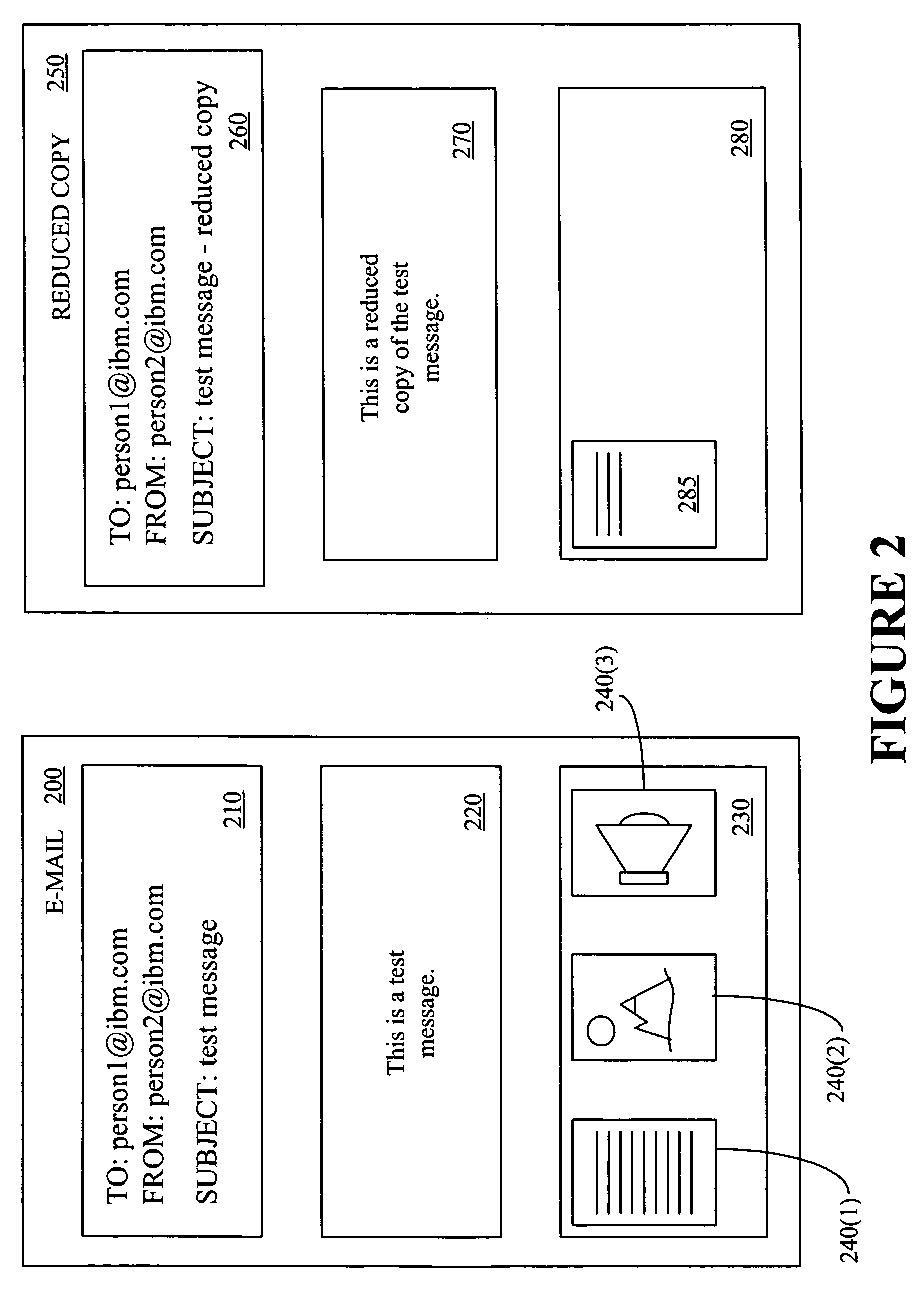
Providing a portion of an electronic mail message based upon a transfer rate, a message size, and a file format
ActiveUS20050193070A1Automatic call-answering/message-recording/conversation-recordingMultiple digital computer combinationsMessage sizeWorld Wide Web
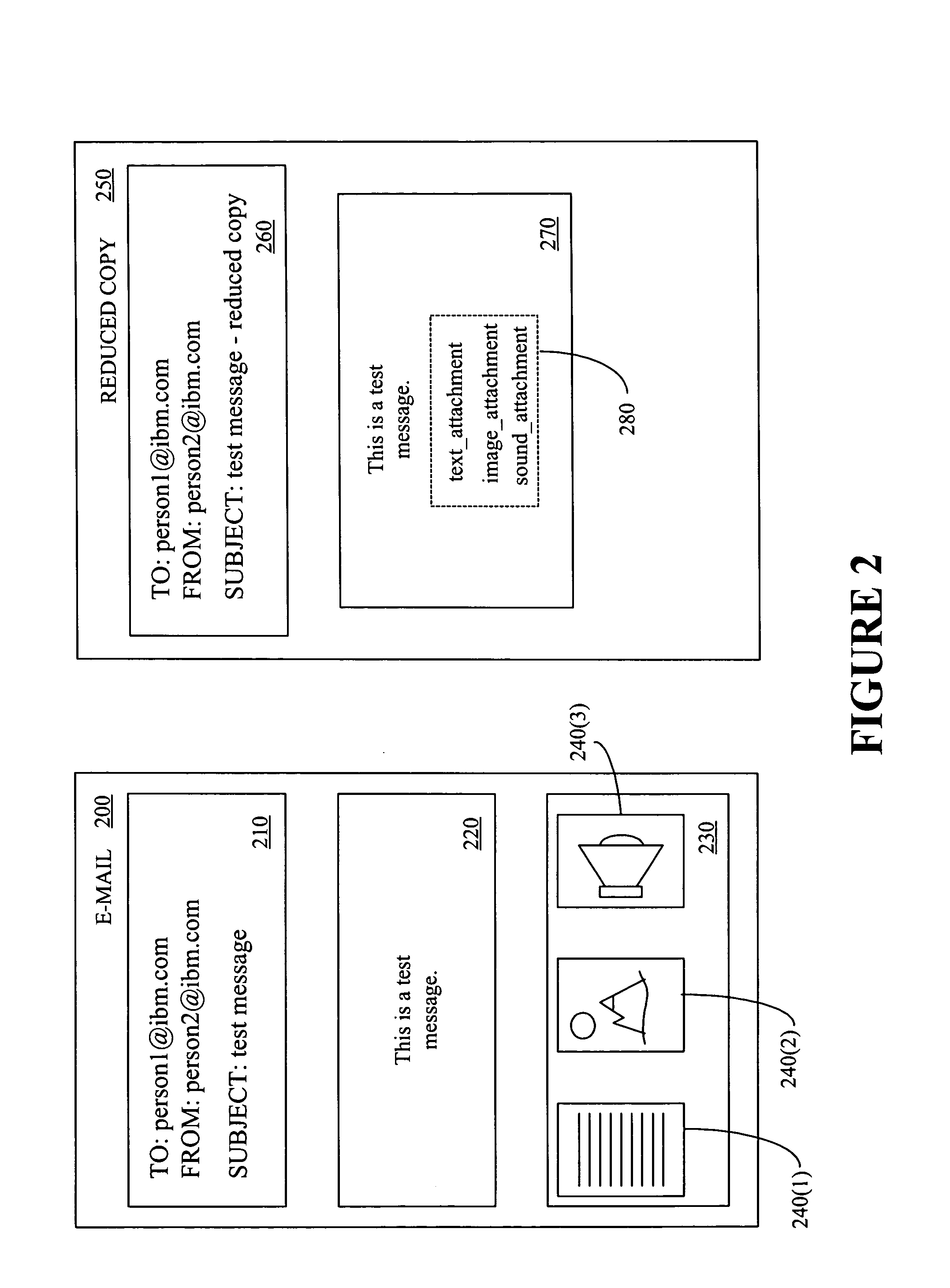
A method and an apparatus for providing a portion of an electronic mail message based upon a transfer rate, a message size, and a file format are presented. The method includes determining whether it is desirable to provide less than all of an electronic mail message and determining a format associated with the electronic mail message in response to determining that it is desirable to provide less than all of the electronic mail message. The method also includes selecting a portion of the electronic mail message using the determined format and providing the selected portion of the electronic mail message.
Owner:IBM CORP
System and method for monitoring performance, analyzing capacity and utilization, and planning capacity for networks and intelligent, network connected processes
InactiveUS20050018611A1Error preventionFrequency-division multiplex detailsTotal responseTest sample
Analysis of networks and testing and analyzing intelligent, network connected devices. An instantaneous network utilization value is assigned for the worst surviving ping instance of between 90% and 99% (determined proportionately from the ratio of dropped test samples to surviving test samples), and then used to solve for average network message size and average utilization of the network. A plurality transactions of different types are transmitted across the network to intelligent end systems and the results mathematically evaluated to determine the portion of the total response time contributed by the network and by the end processors; the utilization of the end processor processing subsystems and of the end processor I / O subsystems; and the utilization of the end system as a whole; and of the network and end processors considered as a unitary entity. Steps include determining utilization of the network when test packets are dropped by the network; utilization of intelligent processor and other devices attached to the network when test transactions are dropped, and when not dropped; and response time for remote processes at both the network and processor level.
Owner:IBM CORP
System and method for variable rate multiple access short message communications
ActiveUS20050259723A1Increase size of messageEasy to useModulated-carrier systemsMultiplex code generationComputer hardwareCommunications system
A communication system and receiver is provided that facilitates increased message size in a communication system that supports a large number of transmitters sharing a common frequency band. The communication system facilitates increased message size by incorporating a plurality of transmit bit sets in each burst of data. The additional transmit bit sets are incorporated into a plurality of transmit codes that are generated using at least one additional spreading code that is orthogonal to the base spreading code. The plurality of transmit codes are then combined into one composite message and the composite message is spread again using another scrambling sequence. The final composite spread message is transmitted to the receiver in the appropriate message time slot, resulting in CDM / TDMA burst signal that facilitates increased message size.
Owner:GENERAL DYNAMICS MISSION SYST INC
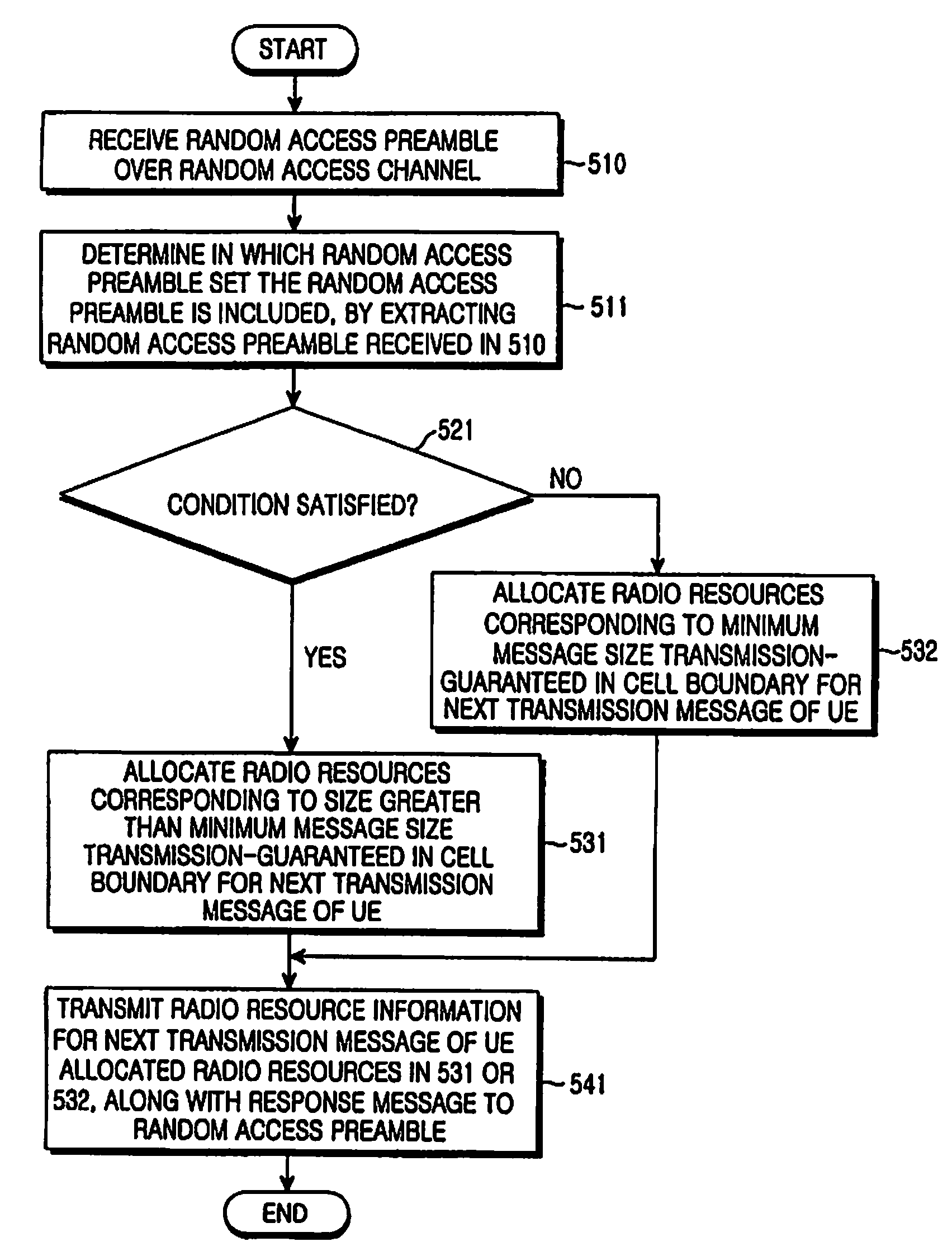
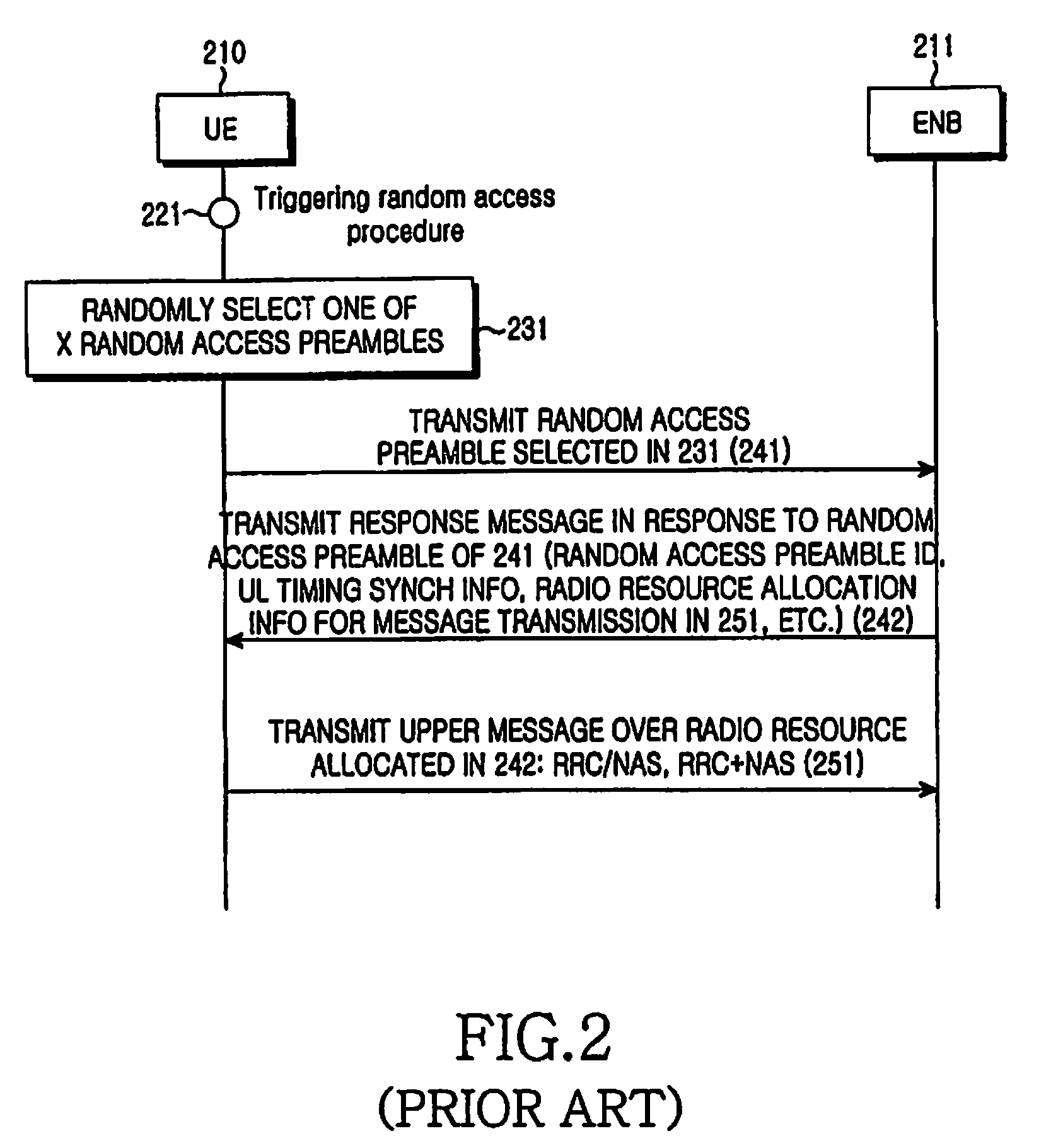
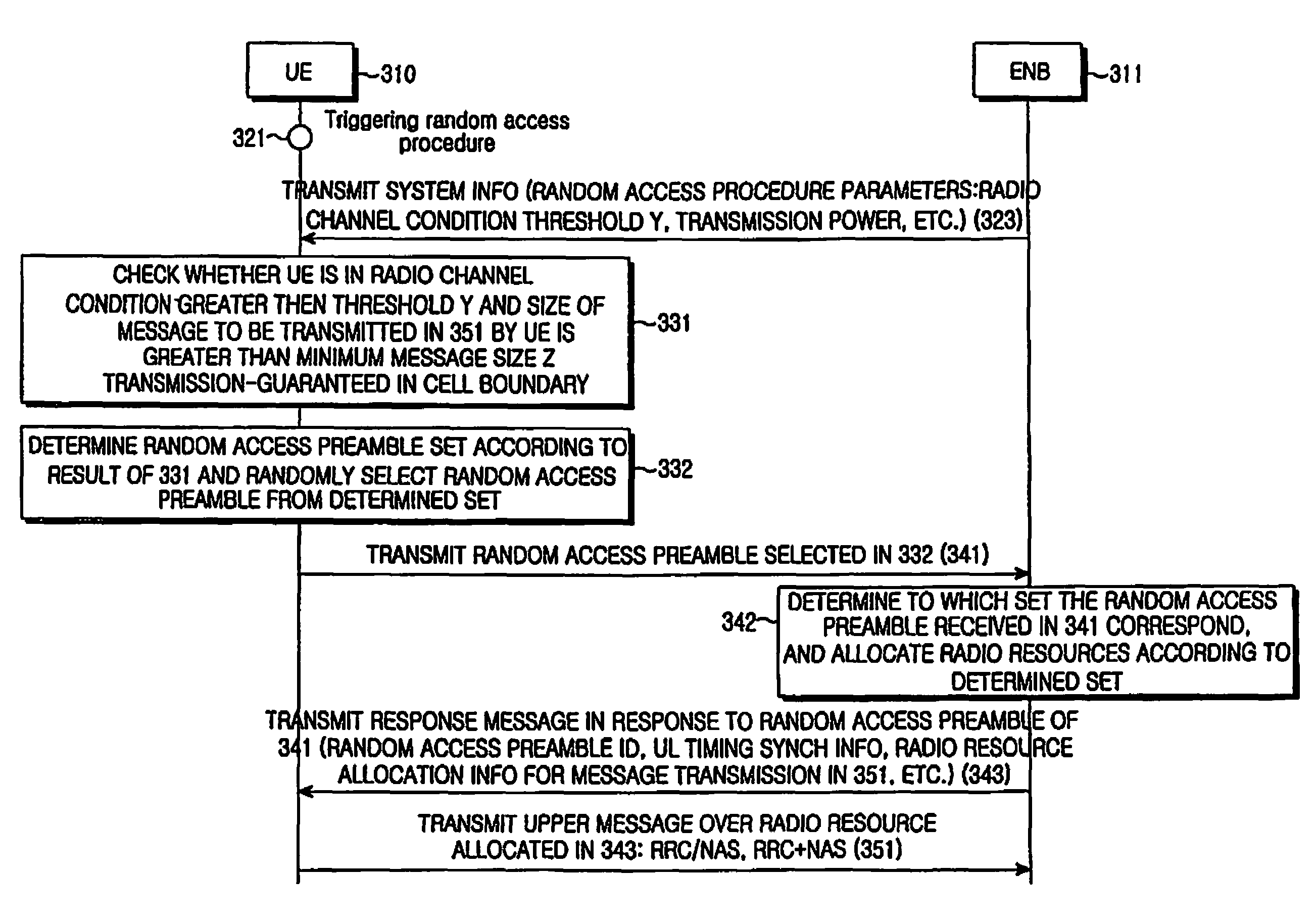
Method and apparatus for allocating radio resource using random access procedure in a mobile communication system
ActiveUS20080130588A1Effective distributionAssess restrictionNetwork topologiesTelecommunicationsRadio channel
A method for transmitting a random access preamble using a random access procedure in a mobile communication system. The random access preamble transmission method includes selecting, upon triggering of the random access procedure, one of random access preamble sets predefined between a User Equipment (UE) and an Evolved Node B (ENB) according to whether a radio channel condition is greater than a radio channel condition threshold and a size of a message that the UE will transmit after transmission of the random access preamble is greater than a minimum message size, randomly selecting a random access preamble from the selected random access preamble set, and transmitting the selected random access preamble to the ENB over a random access channel.
Owner:SAMSUNG ELECTRONICS CO LTD
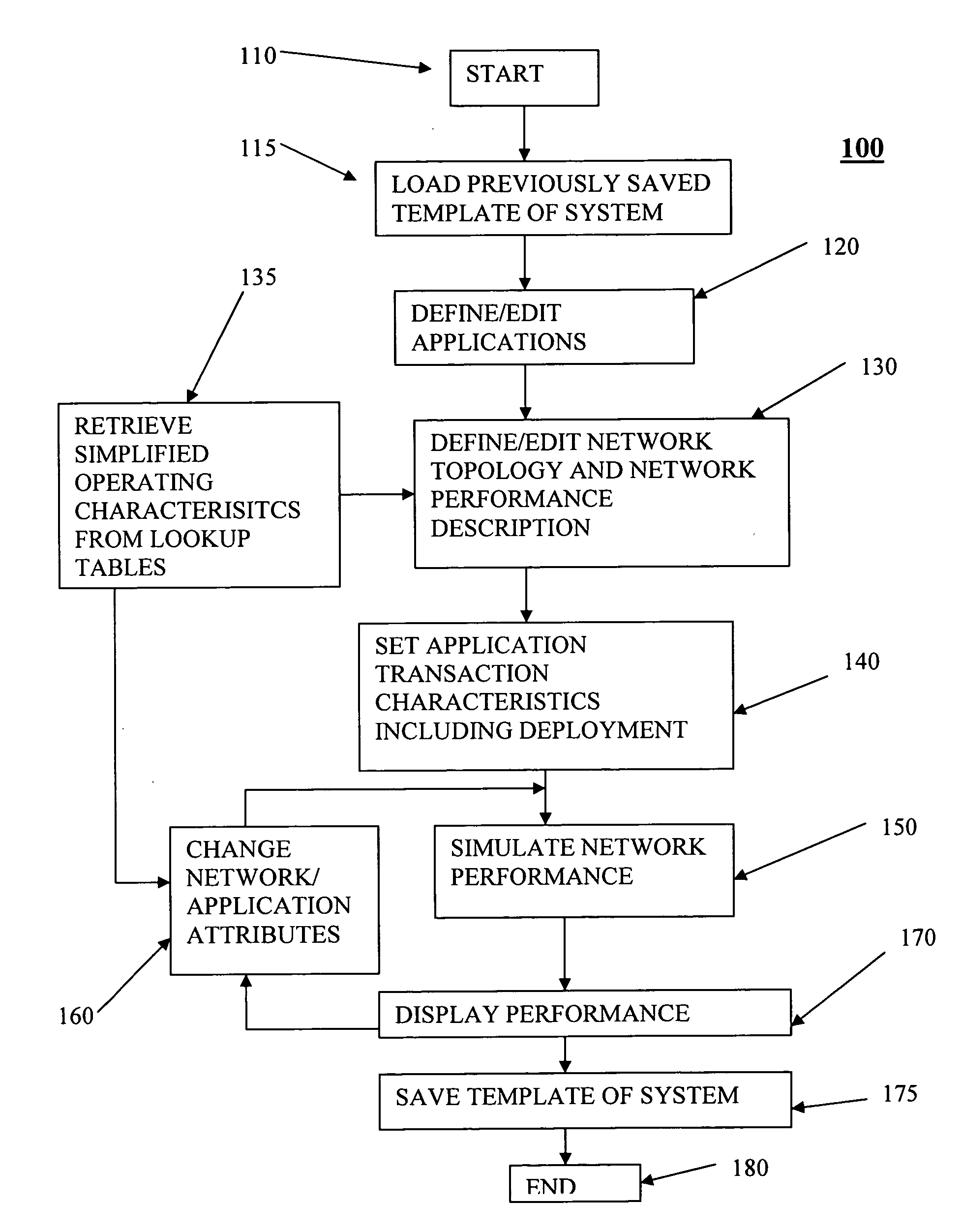
Network capacity planning
Data representing application deployment attributes, network topology, and network performance attributes based on a reduced set of element attributes is utilized to simulate application deployment. The data may be received from a user directly, a program that models a network topology or application behavior, and a wizard that implies the data based on an interview process. The simulation may be based on application deployment attributes including application traffic pattern, application message sizes, network topology, and network performance attributes. The element attributes may be determined from a lookup table of element operating characteristics that may contain element maximum and minimum boundary operating values utilized to interpolate other operating conditions. Application response time may be derived using an iterative analysis based on multiple instances of one or more applications wherein a predetermined number of iterations is used or until a substantially steady state of network performance is achieved.
Owner:OPNET TECH LLC
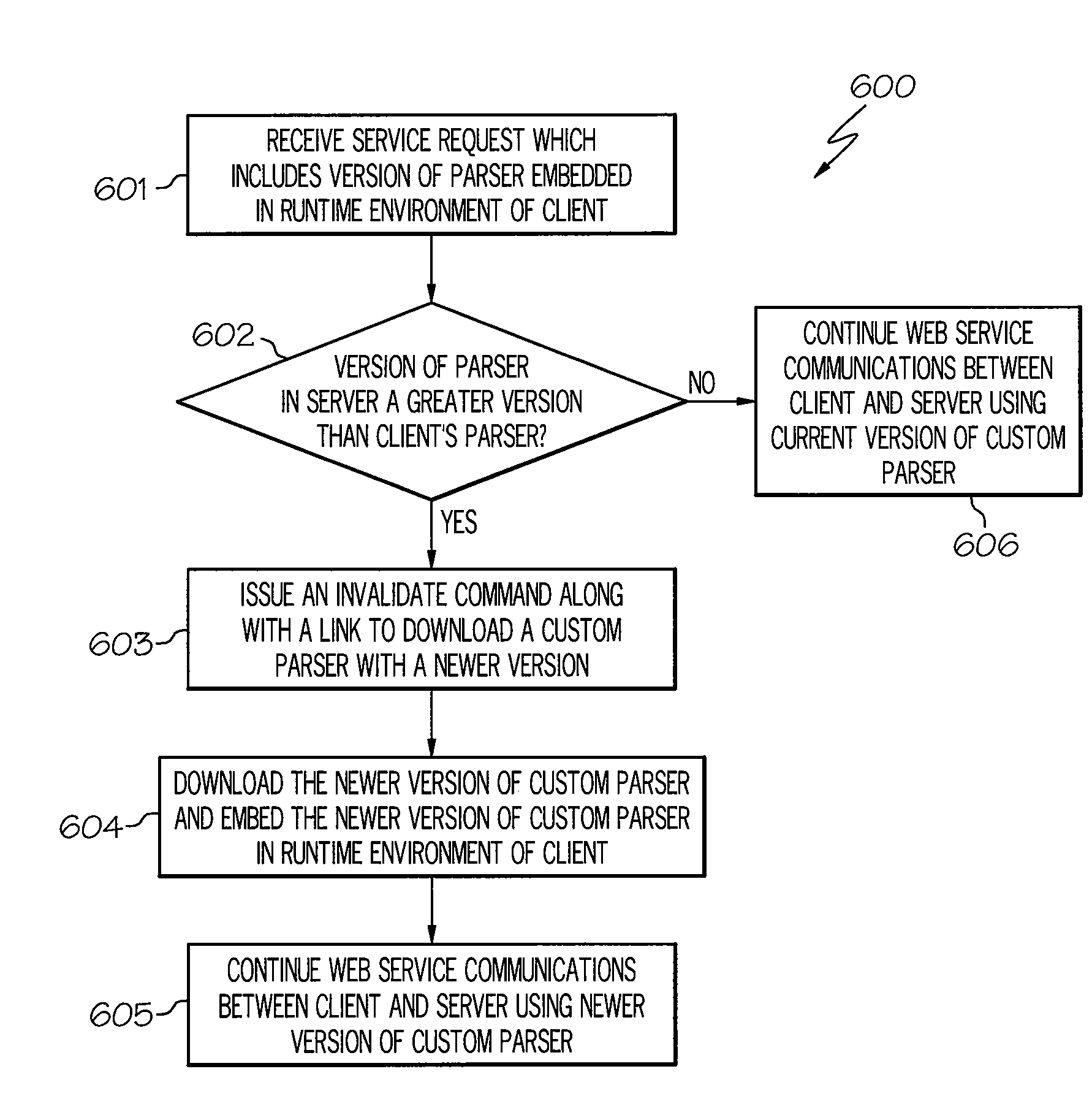
Optimize web service interactions via a downloadable custom parser
InactiveUS20080313267A1Efficient mannerMultiple digital computer combinationsTransmissionWeb serviceClient-side
A method, system and computer program product for optimizing web service interactions. A server receives a service request from a client, where the service request includes information that is used by the server to provide a customized parser to the client that allows optimal web service interactions. Upon the server providing a link to the client to download this customized parser, the client downloads the parser and embeds the parser into its runtime environment. The parser in the client is then able to receive and transmit communications from and to the server, respectively, in a most efficient manner. For example, the parser may reduce the size of the XML message size more considerably than compression algorithms. In another example, if the client and server communicate in different languages, the parser may translate the messages between the client and server so that the messages are understandable.
Owner:IBM CORP
Methods, Systems, and Apparatuses for Optimal Group Key Management for Secure Multicast Communication
InactiveUS20120257756A1Constant message sizeImmune to collusion attackKey distribution for secure communicationGroup controllerSecure multicast
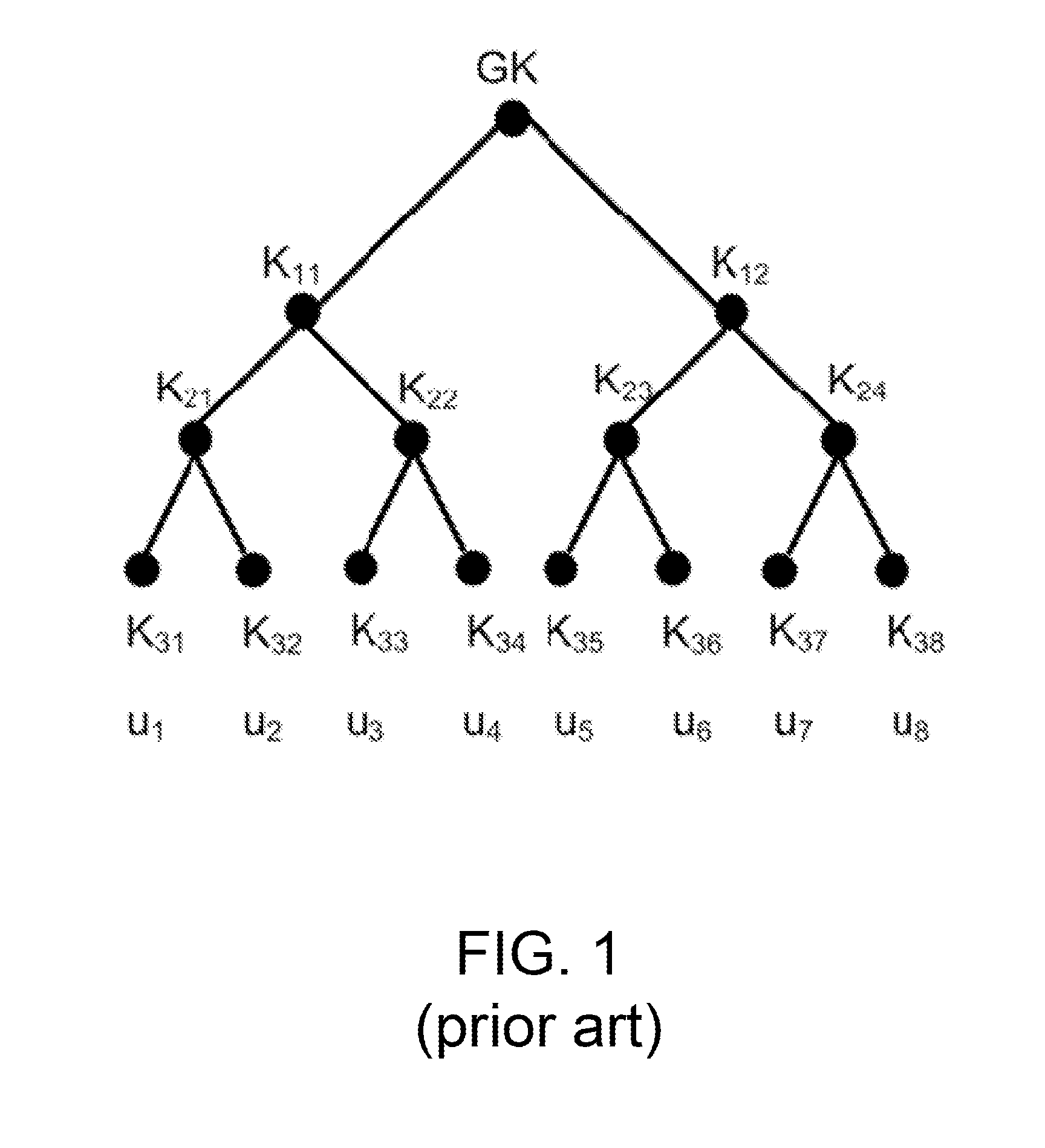
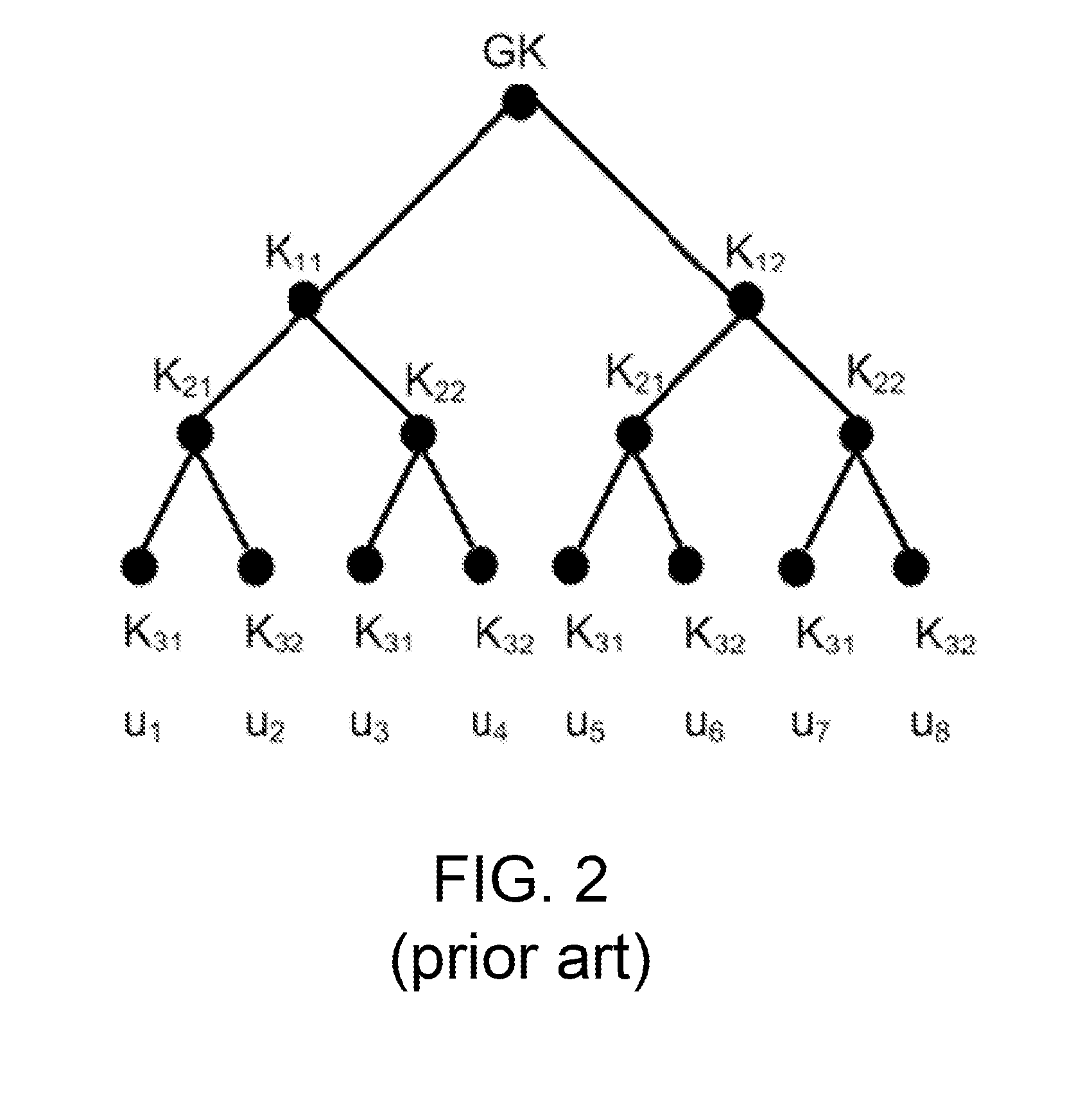
Apparatuses, systems, and methods for optimal group key (OGK) management that may achieve non-colluding and / or the storage-communication optimality are disclosed. In some embodiments, a group controller (GC) is responsible for key generation and distribution and the group data are encrypted by a group key. When joining the group, in some embodiments, each group member (GM) is assigned a unique n-bit ID and a set of secrets, in which each bit is one-to-one mapped to a unique secret. Whenever GMs are revoked from the group, in some embodiments, the GC will multicast an encrypted key-update message. Only the remaining GMs may be able to recover the message and update GK as well as their private keys. The disclosed OGK scheme can achieve storage-communication optimality with constant message size and immune to collusion attack and also may outperform existing group key management schemes in terms of communication and storage efficiency.
Owner:ARIZONA STATE UNIVERSITY
Providing a portion of an electronic mail message based upon a transfer rate, a message size, and a file format
ActiveUS7512658B2Automatic call-answering/message-recording/conversation-recordingMultiple digital computer combinationsMessage sizeWorld Wide Web
A method and an apparatus for providing a portion of an electronic mail message based upon a transfer rate, a message size, and a file format are presented. The method includes determining whether it is desirable to provide less than all of an electronic mail message and determining a format associated with the electronic mail message in response to determining that it is desirable to provide less than all of the electronic mail message. The method also includes selecting a portion of the electronic mail message using the determined format and providing the selected portion of the electronic mail message.
Owner:IBM CORP
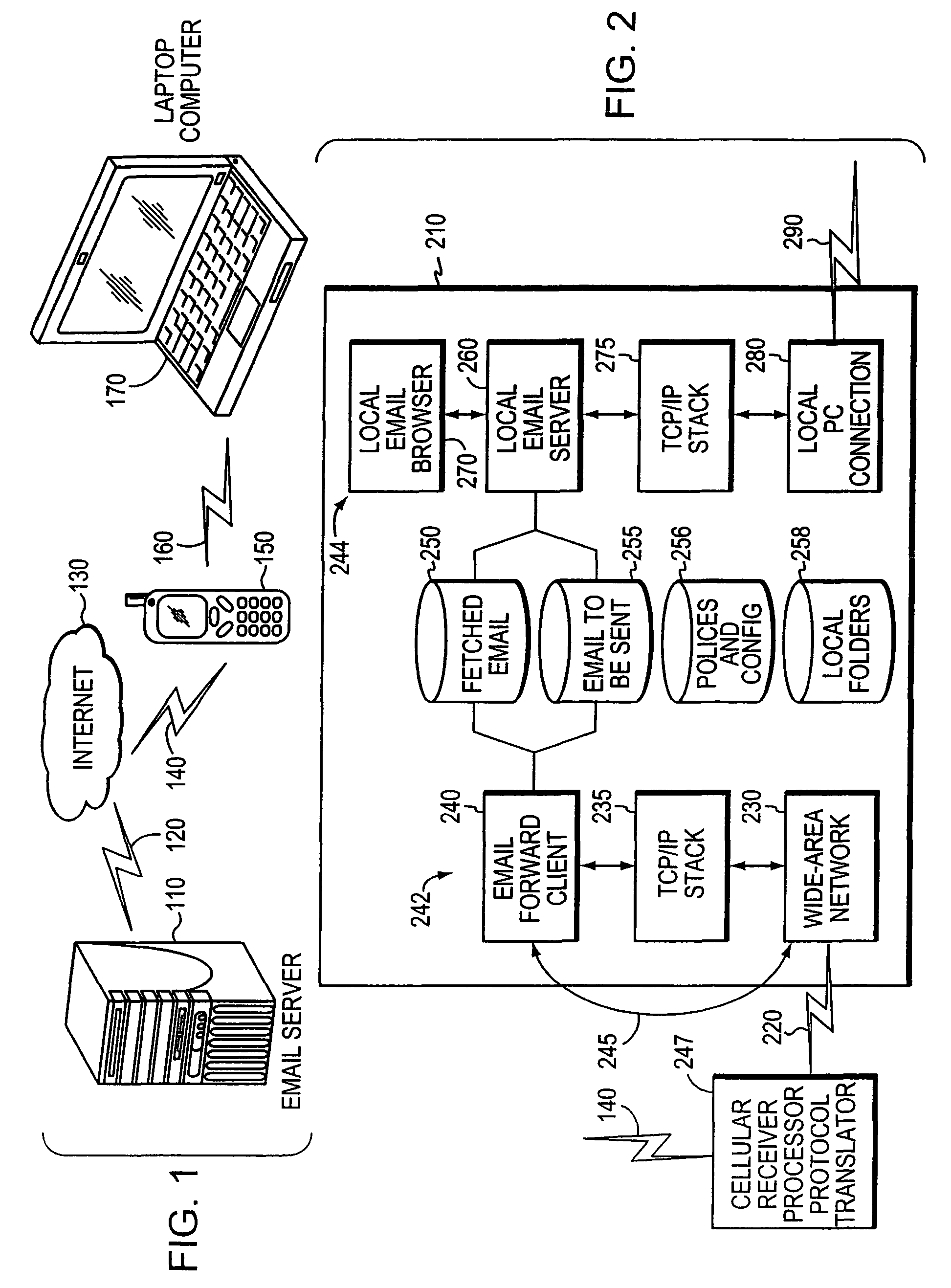
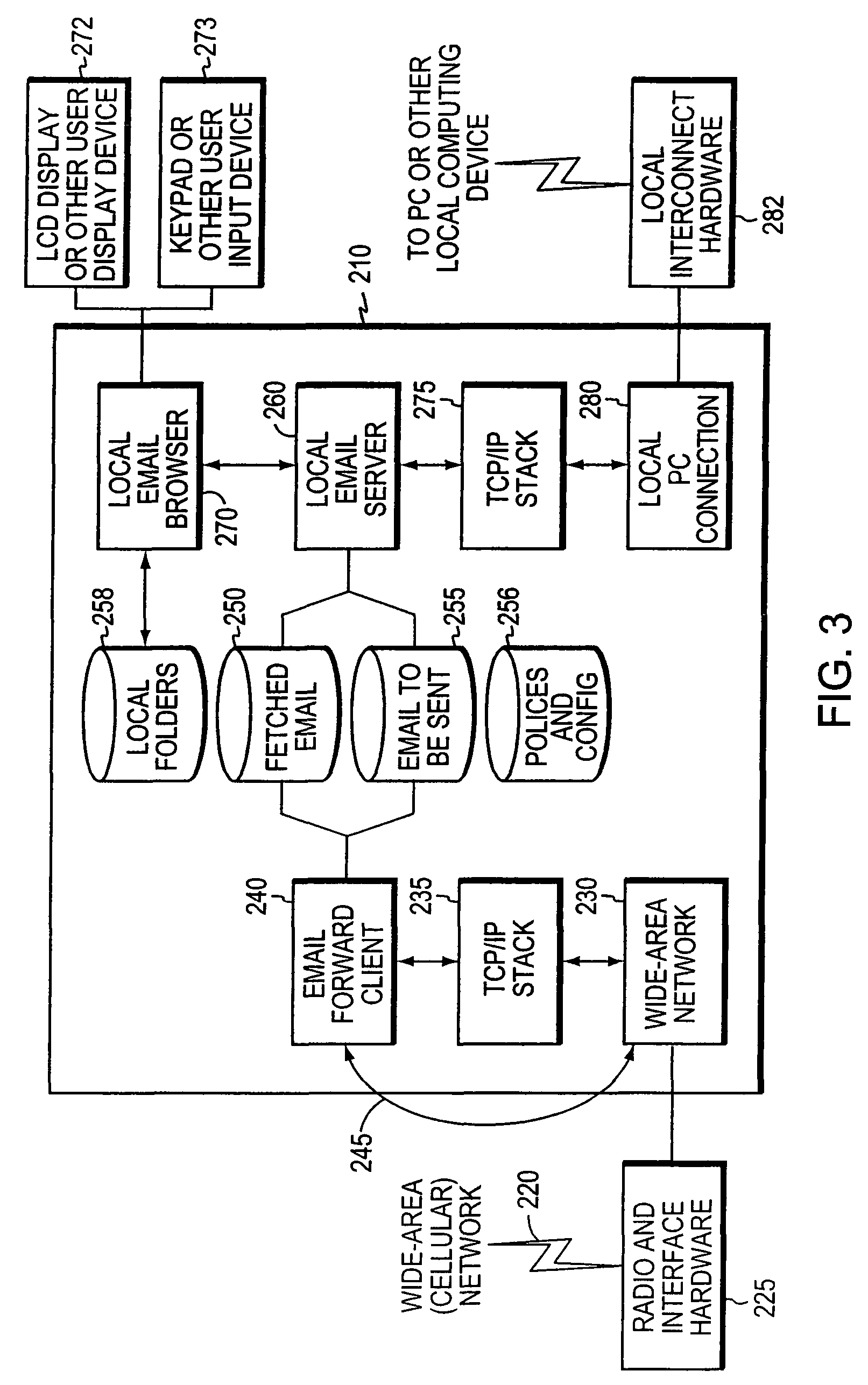
Integrated mobile messaging system and method
ActiveUS8117266B2Inadequate performanceMultiple digital computer combinationsSubstation equipmentOn boardShortest distance
Owner:MCCI CORP
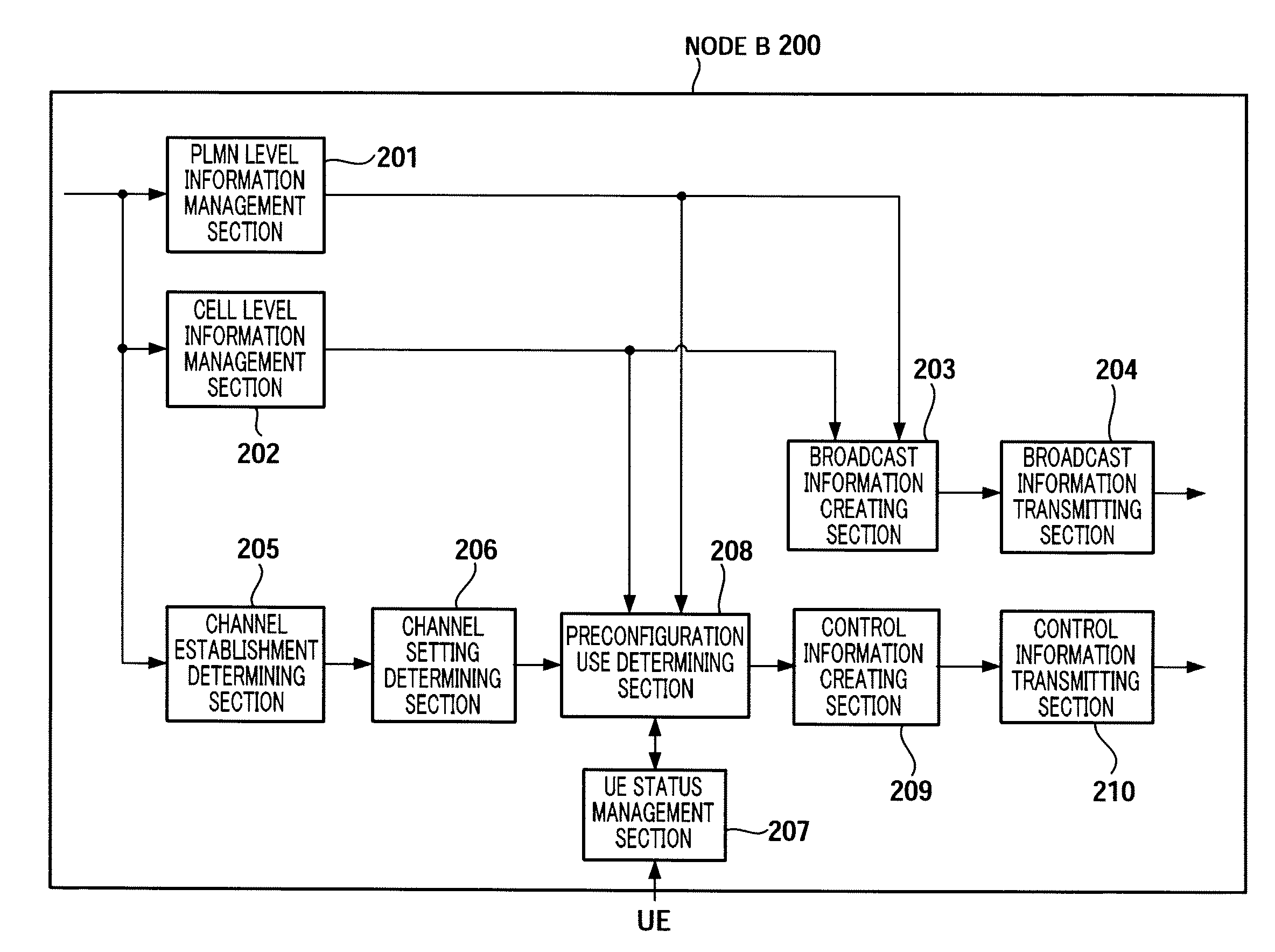
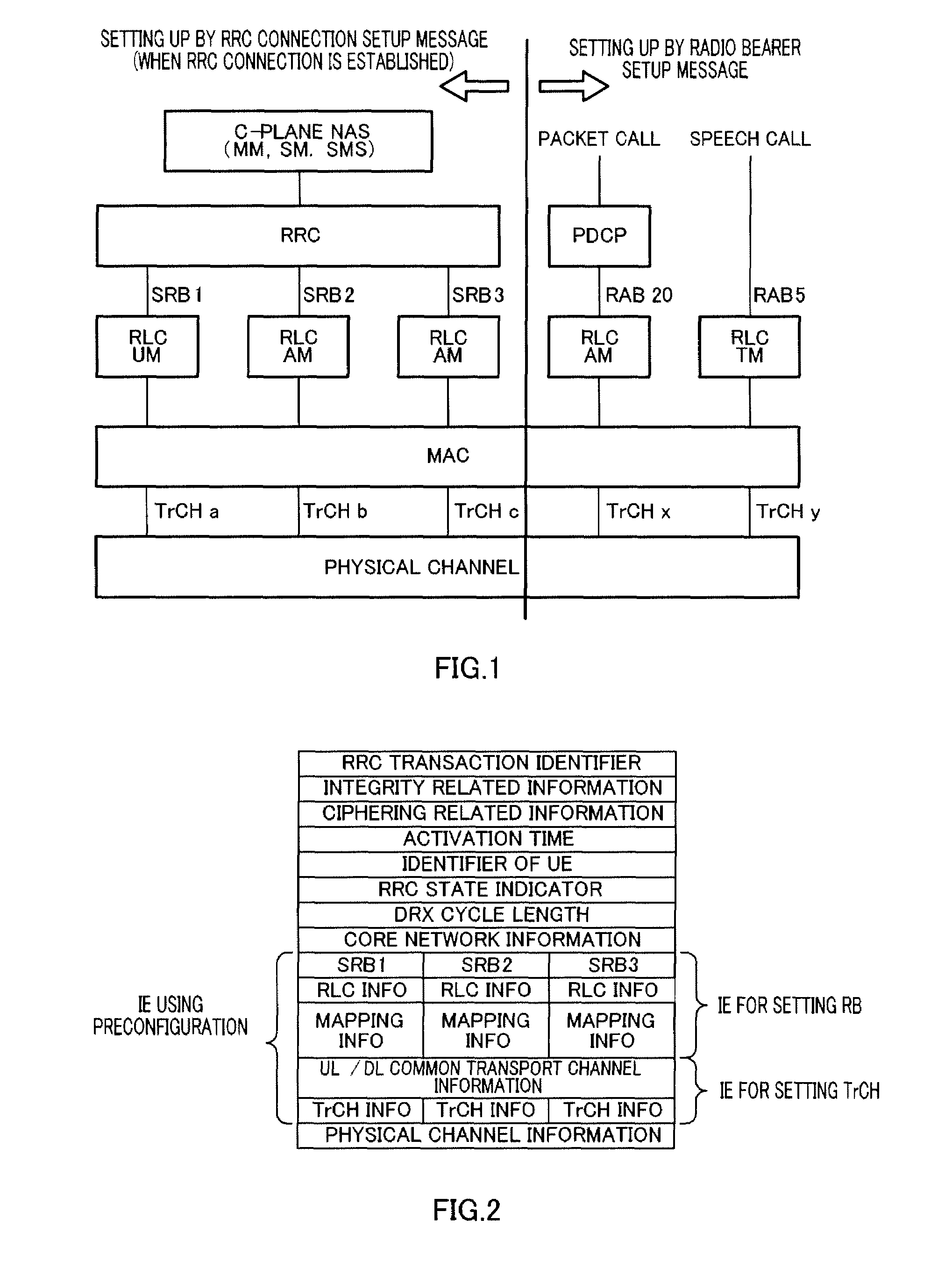
Radio communication base station device
InactiveUS20090247163A1Reduce message sizeAssess restrictionSubstation equipmentInformation transmissionMessage size
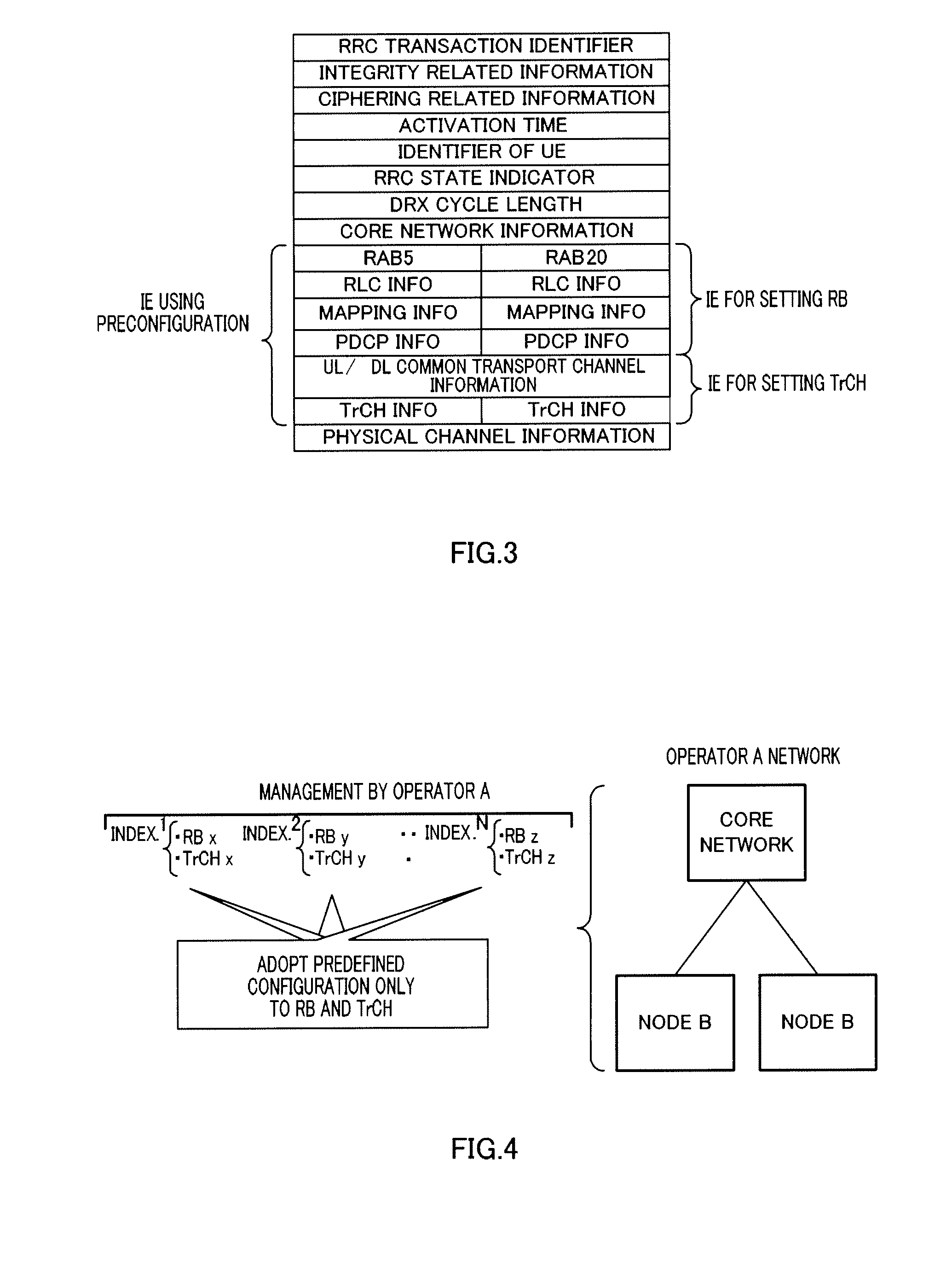
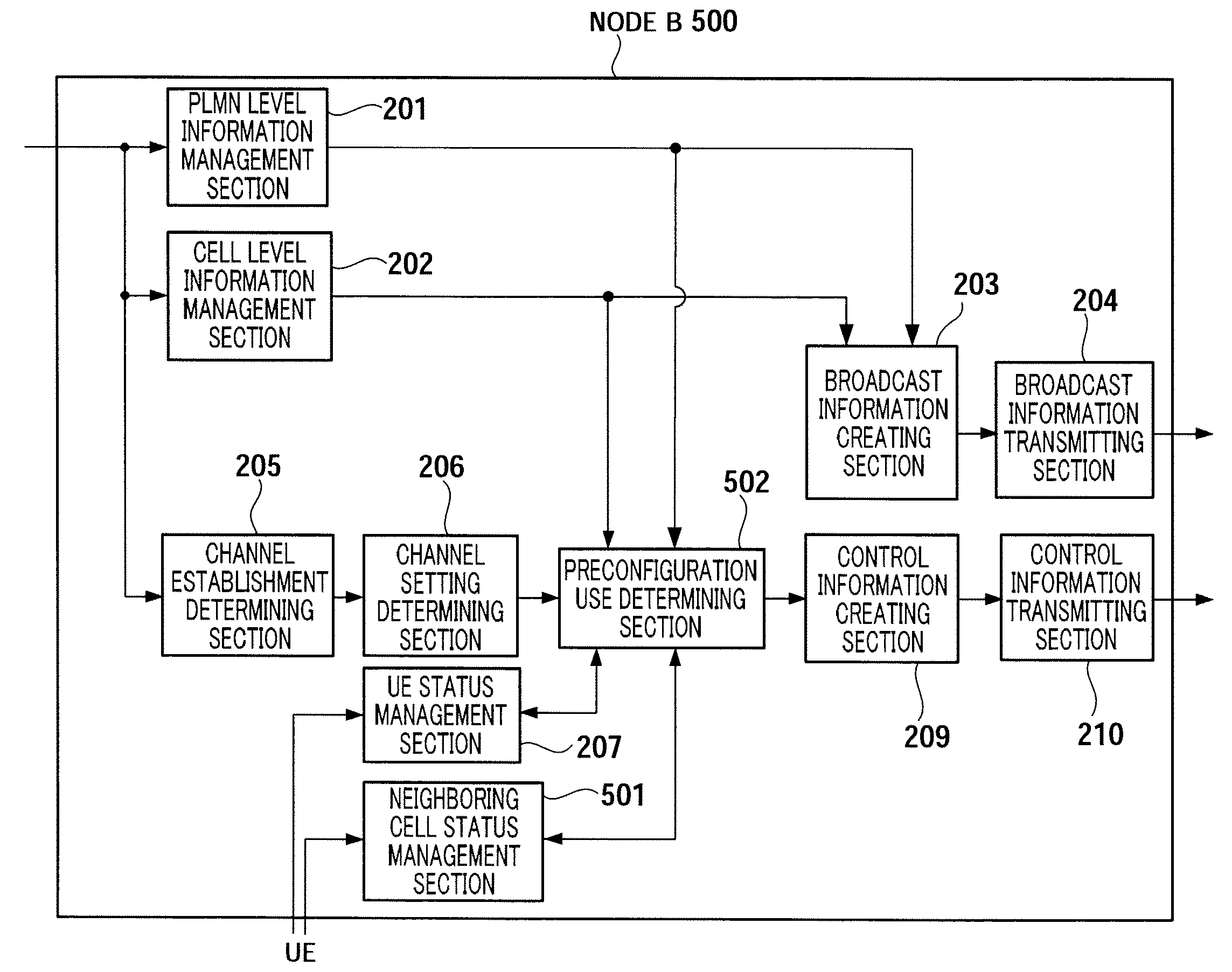
Provided is a radio communication base station device capable of reducing a message size in a call connection. In the device, a report information creation unit (203) creates report information by allocating cell level information as Preconfiguration information managed at a cell level and PLMN level information as Preconfiguration information managed at a PLMN level to different transmission units and the created report information is reported from a report information transmission unit (204) to UE. A Preconfiguration use decision unit (208) judges whether the UE which sets a channel can use Preconfiguration. If yes, a control information creation unit (209) includes the corresponding Index in control information and the control information is transmitted from a control information transmission unit (210) to the UE.
Owner:SOVEREIGN PEAK VENTURES LLC
Providing a portion of an electronic mail message based upon a transfer rate and a message size
InactiveUS20050193069A1Multiple digital computer combinationsData switching networksData transmissionMessage size
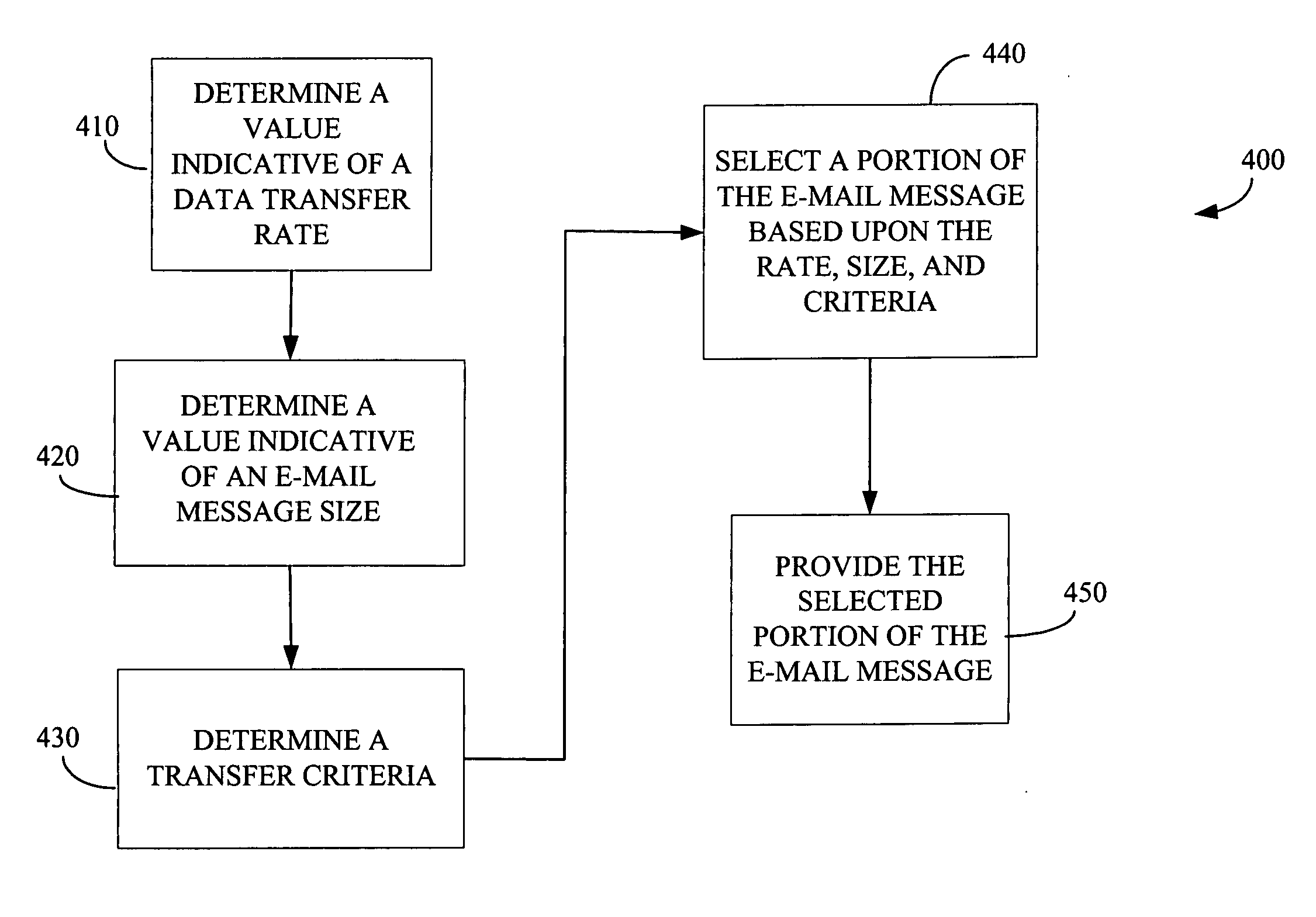
A method and an apparatus for providing a portion of an electronic mail message based upon a transfer rate and a message size are presented. The method includes determining a value associated with a data transfer rate, determining a value associated with a size of an electronic mail message, and determining mail transfer criteria. The method also includes selecting a portion of the electronic mail message based upon the determined transfer rate value, the determined value associated with the size of the electronic mail message, and the determined mail transfer criteria. The method further includes providing the selected portion of the electronic mail message.
Owner:IBM CORP
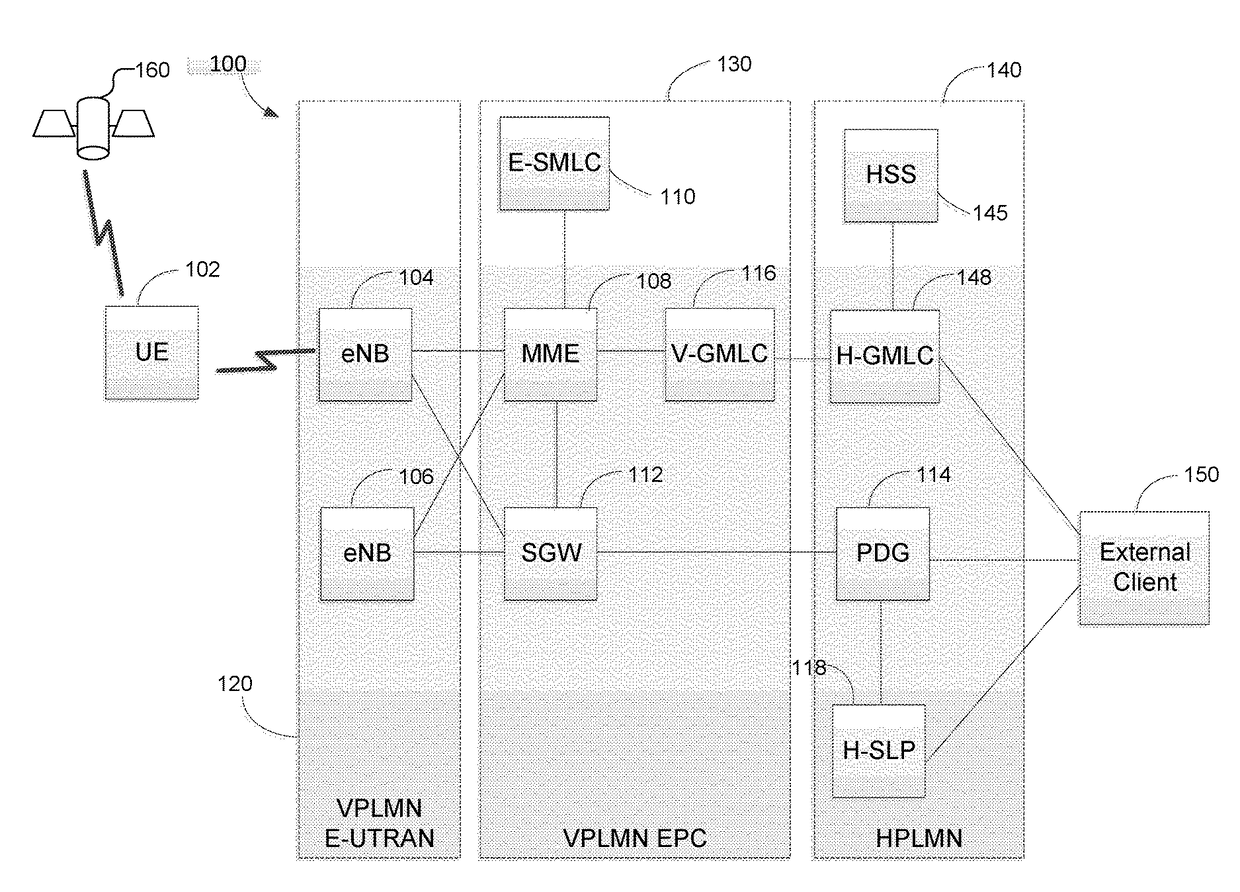
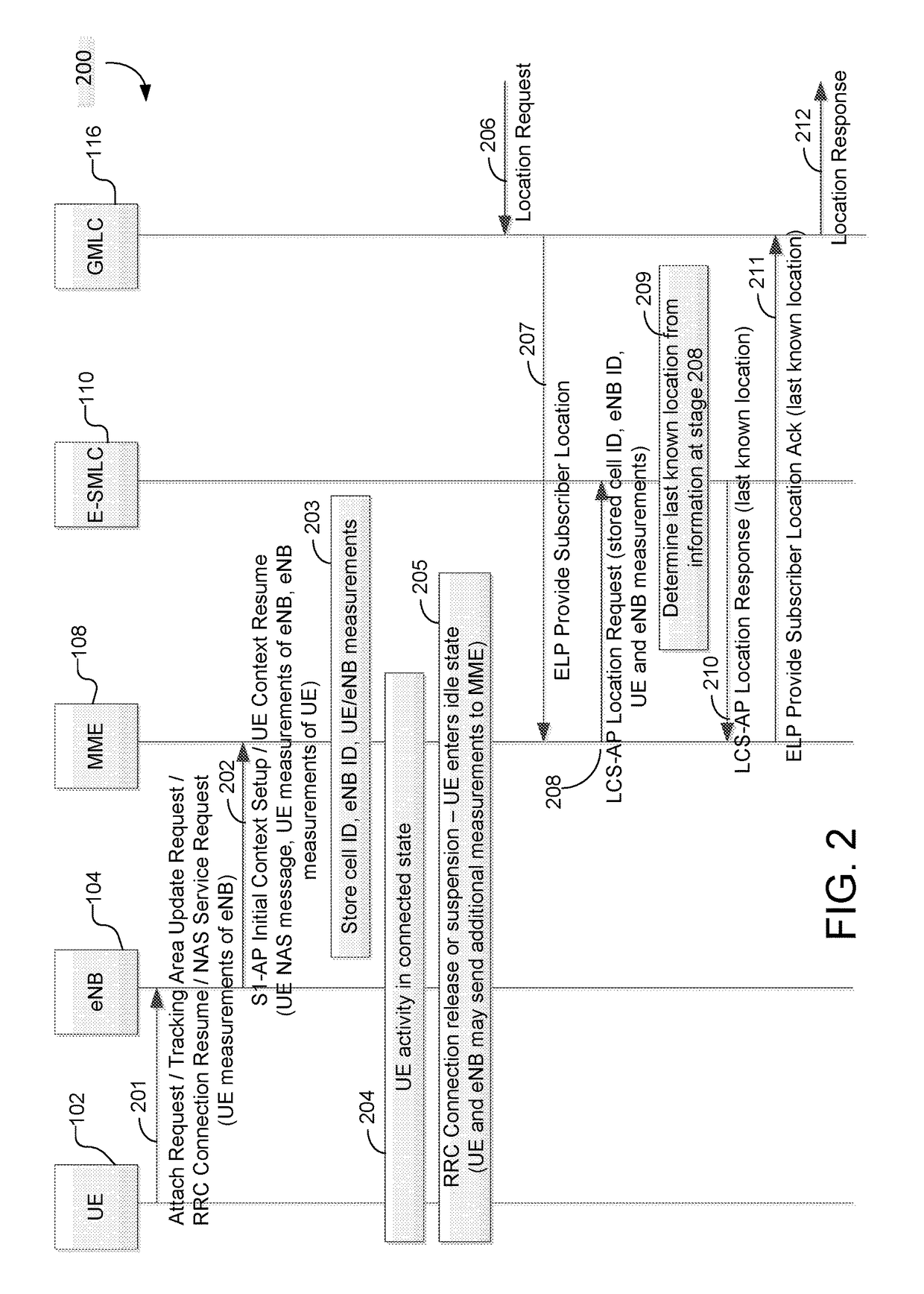
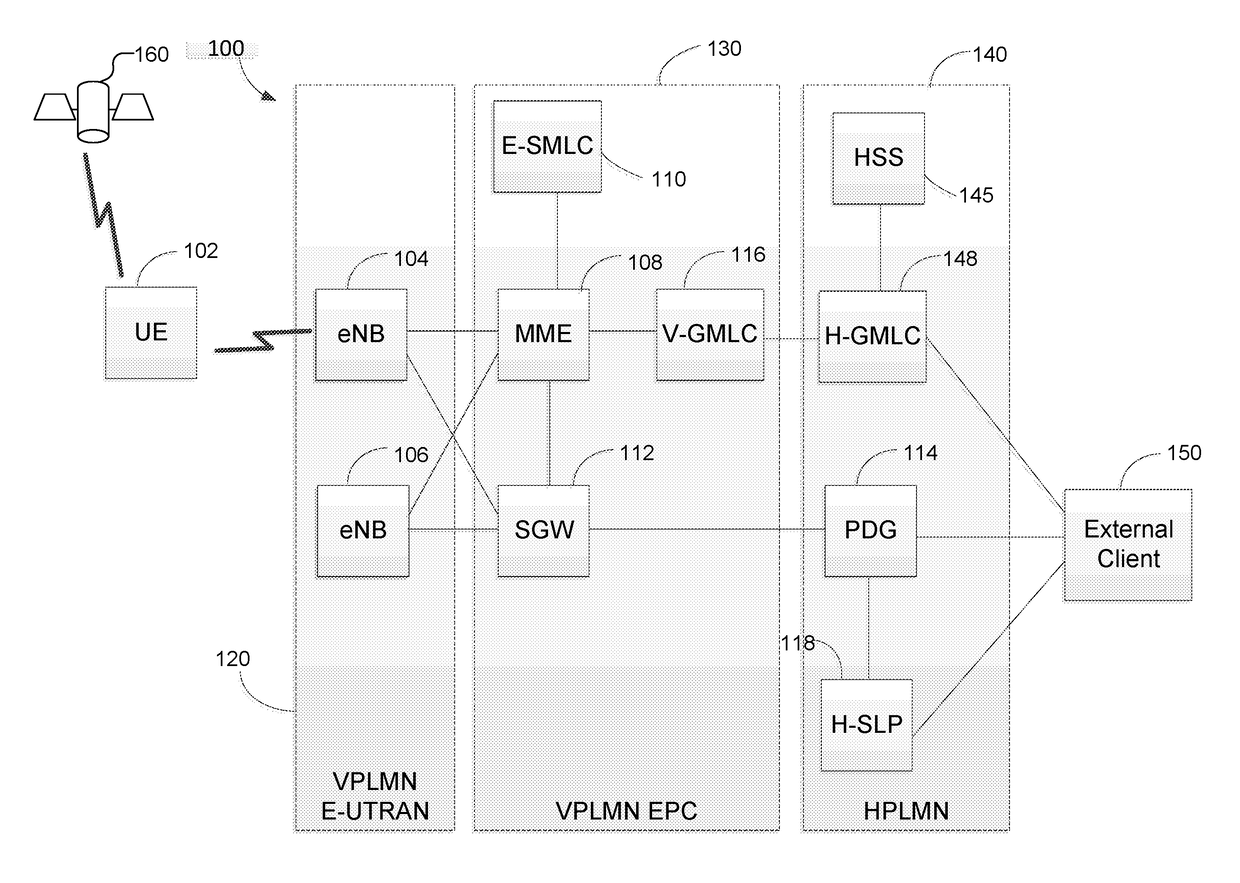
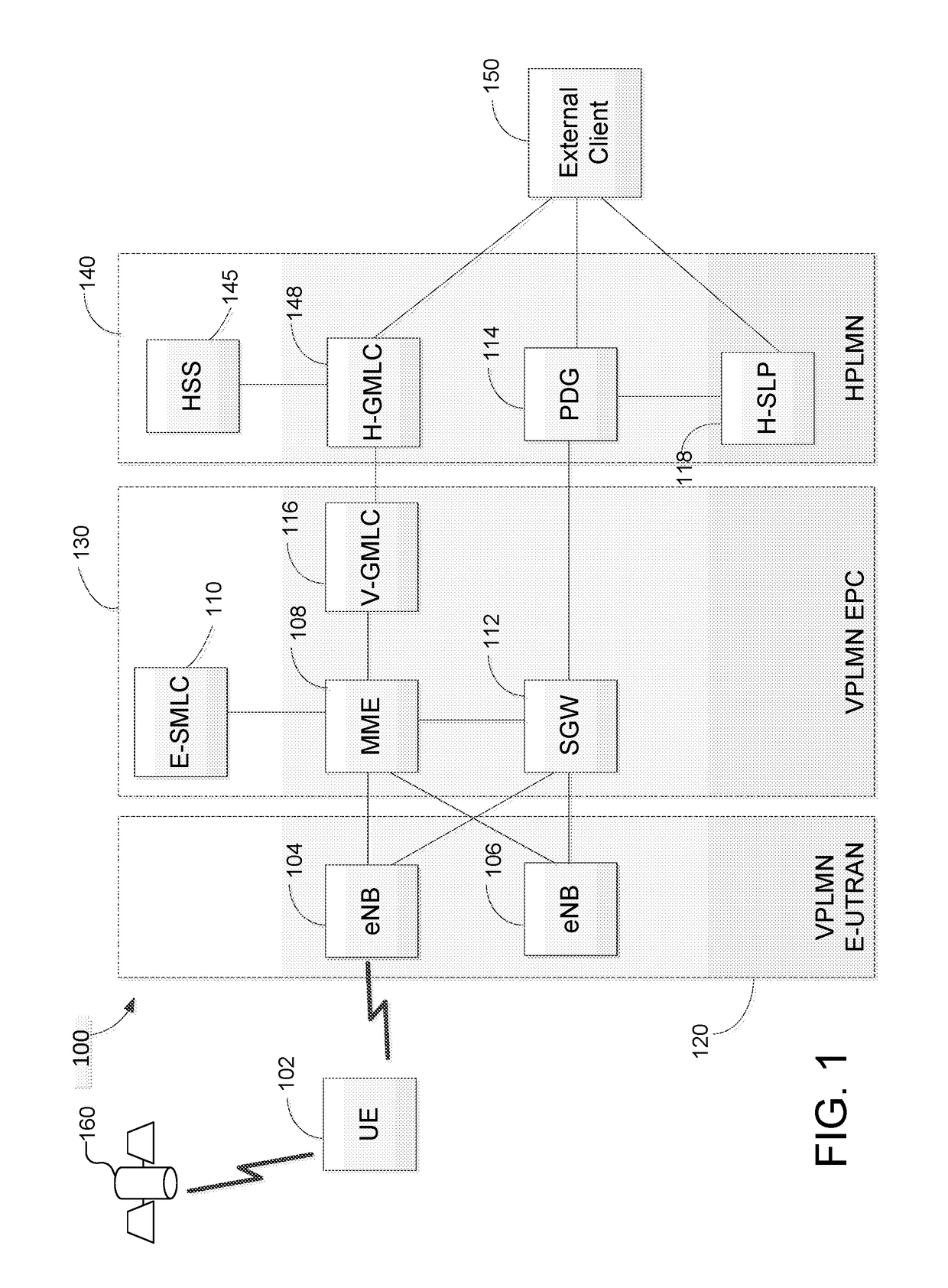
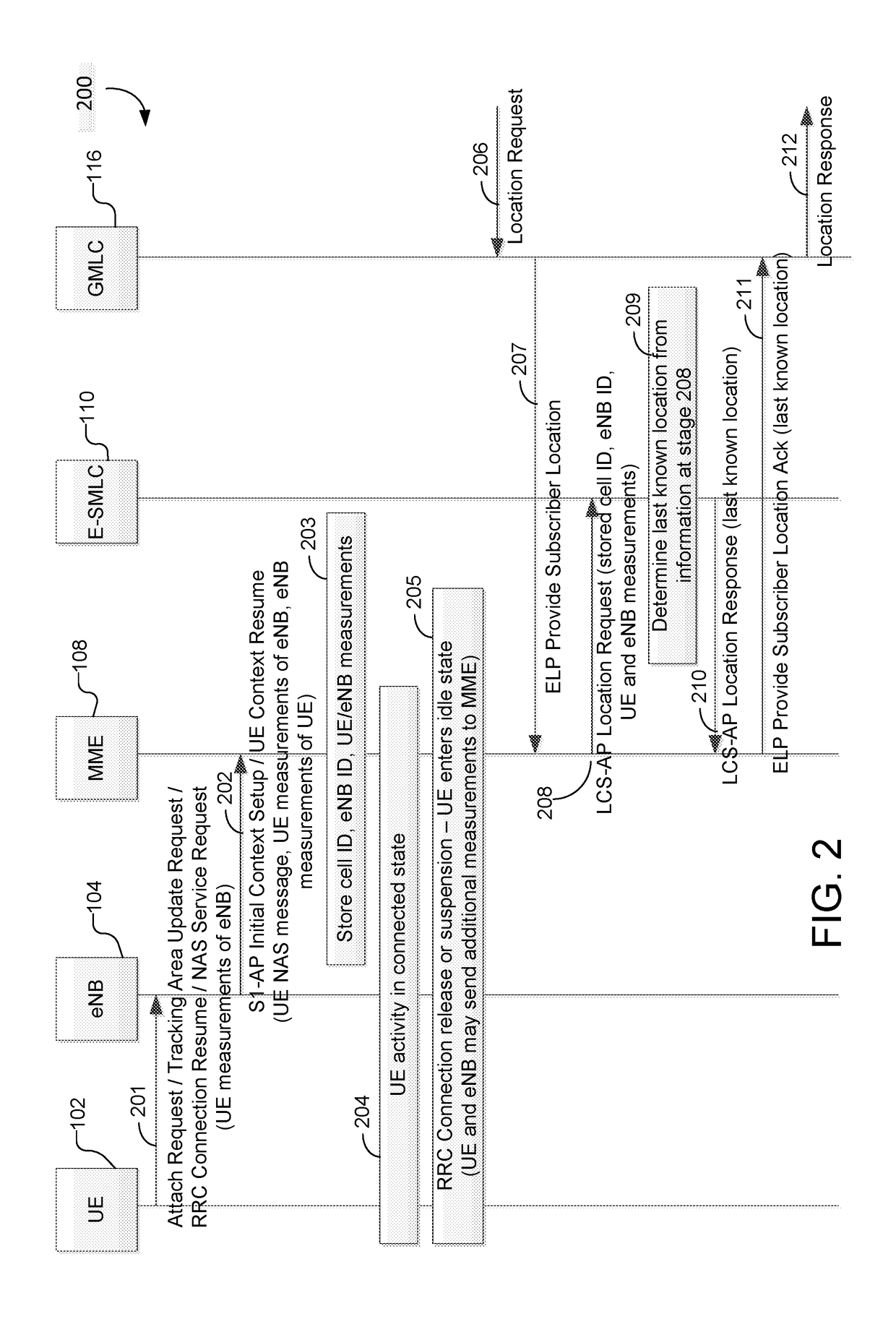
Methods and systems for support of location for the internet of things
PendingUS20180054796A1Large message sizeLong retransmissionConnection managementLocation information based serviceThe InternetMessage size
Methods and techniques are described for supporting location services for a user equipment (UE) that is using Narrowband Internet of Things radio access or Cellular Internet of Things features to access a wireless network. The techniques include enabling support for a last known location of a UE, using previously obtained location measurements, when a UE is not reachable from a wireless network for positioning. The techniques also include limiting positioning protocol interaction between a UE and a location server via a reduced maximum message size, reduced message volume and longer response and retransmission timers. The techniques further include enabling a UE to obtain location measurements when not connected to a wireless network, enabling periodic and triggered location of a UE in which a UE evaluates location triggers while not connected to a wireless network, enabling use of deferred location and enabling improved location security.
Owner:QUALCOMM INC
Improved semi-persistent resource allocation for v2v traffic
ActiveUS20190116609A1Simple methodParticular environment based servicesConnection managementRadio Base StationMessage size
The invention relates to an improved semi-persistent resource allocation for a mobile terminal (MT) for transmitting periodic data. The MT transmits information on the periodic data to the radio base station (BS), such that the BS determines the different possible transmission periodicities and / or the different possible message sizes of the data components of the periodic data. The MT receives from the BS plural semi-persistent resource (SPS) configurations, each being usable to transmit at least one of the supported data components. The MT indicates to the BS the data components that are to be transmitted by the MT. The MT receives from the BS an activation command to activate one or more of the SPS configurations to periodically allocate radio resources for the MT to transmit each of the indicated data components. The MT then transmits the one or more data components based on the radio resources and the transmission periodicity as configured by the activated one or more SPS configurations.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Methods and device for managing message size transmitted over a network
InactiveUS7275093B1Preventing message fragmentationReduce message fragmentationDigital computer detailsTime-division multiplexData sourceMessage size
Methods and a device for changing the message size broadcast over a network and furthermore preventing fragmentation in networks are provided. The device intercepts a message transported across a network, wherein the message is sent from a data source to a data receiver and changes the message size. In addition, the device may use the methods to change the message size of data transmitted over a network thus reducing fragmentation. As a result, network devices such as classifiers preferably avoid re-assembling fragments. More specifically by reducing re-assembling, network devices like a classifier can react more quickly to applications requiring information found in both of an IP and TCP / UDP header.
Owner:VALTRUS INNOVATIONS LTD +1
Simplified configuration of an internet-enabled device
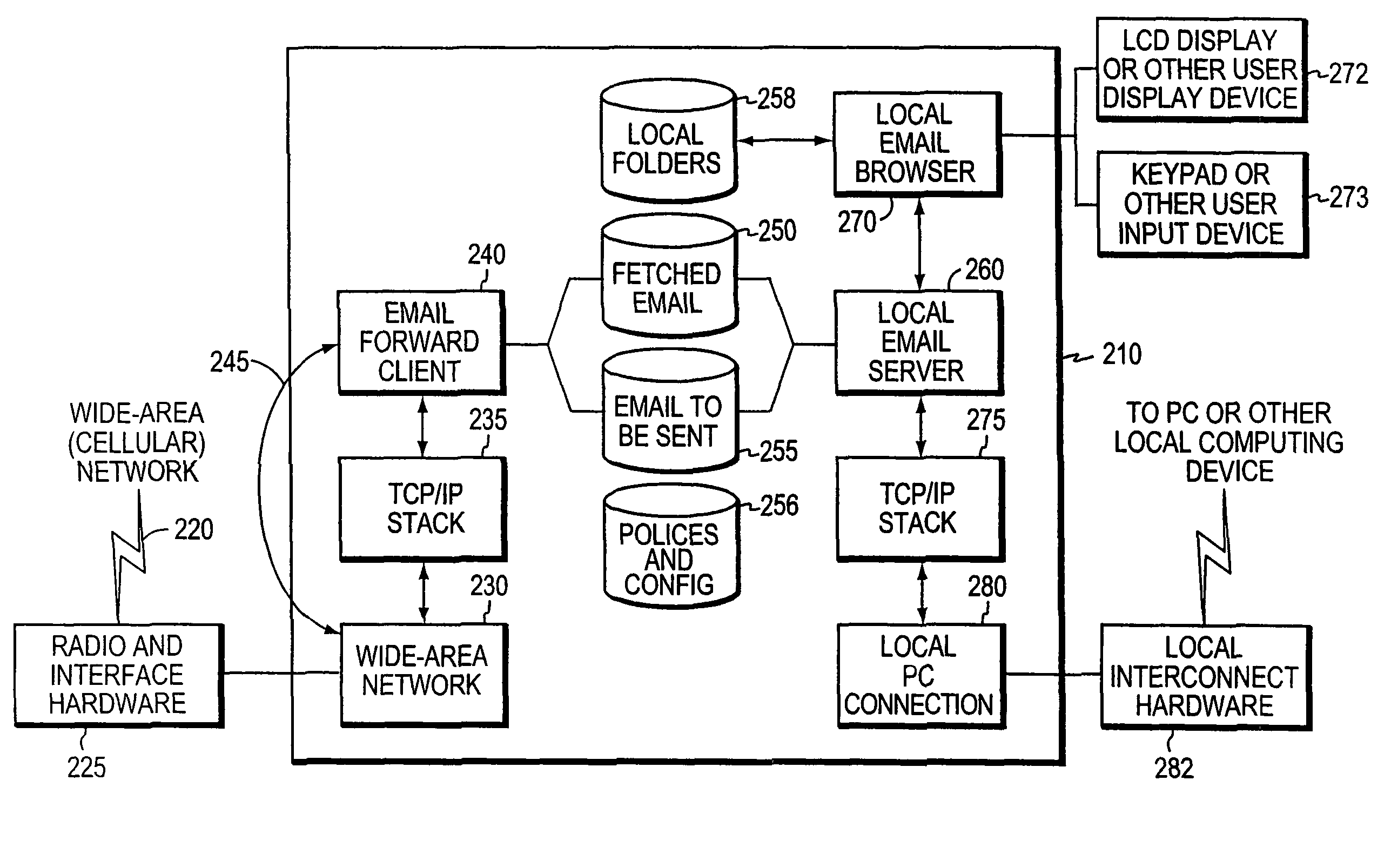
InactiveUS6898623B1OptimizationMinimal user interventionMultiple digital computer combinationsOffice automationEmail addressMessage size
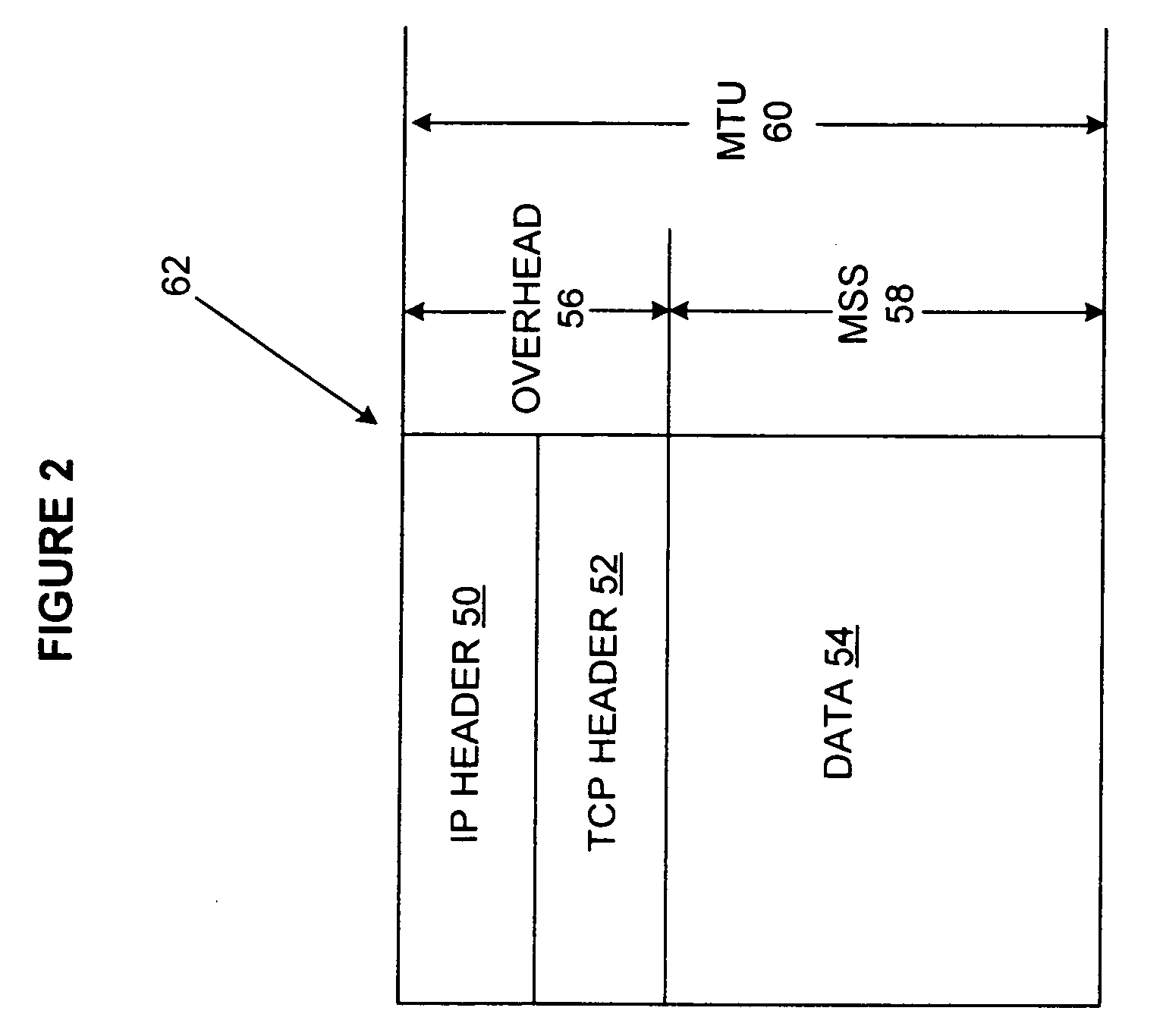
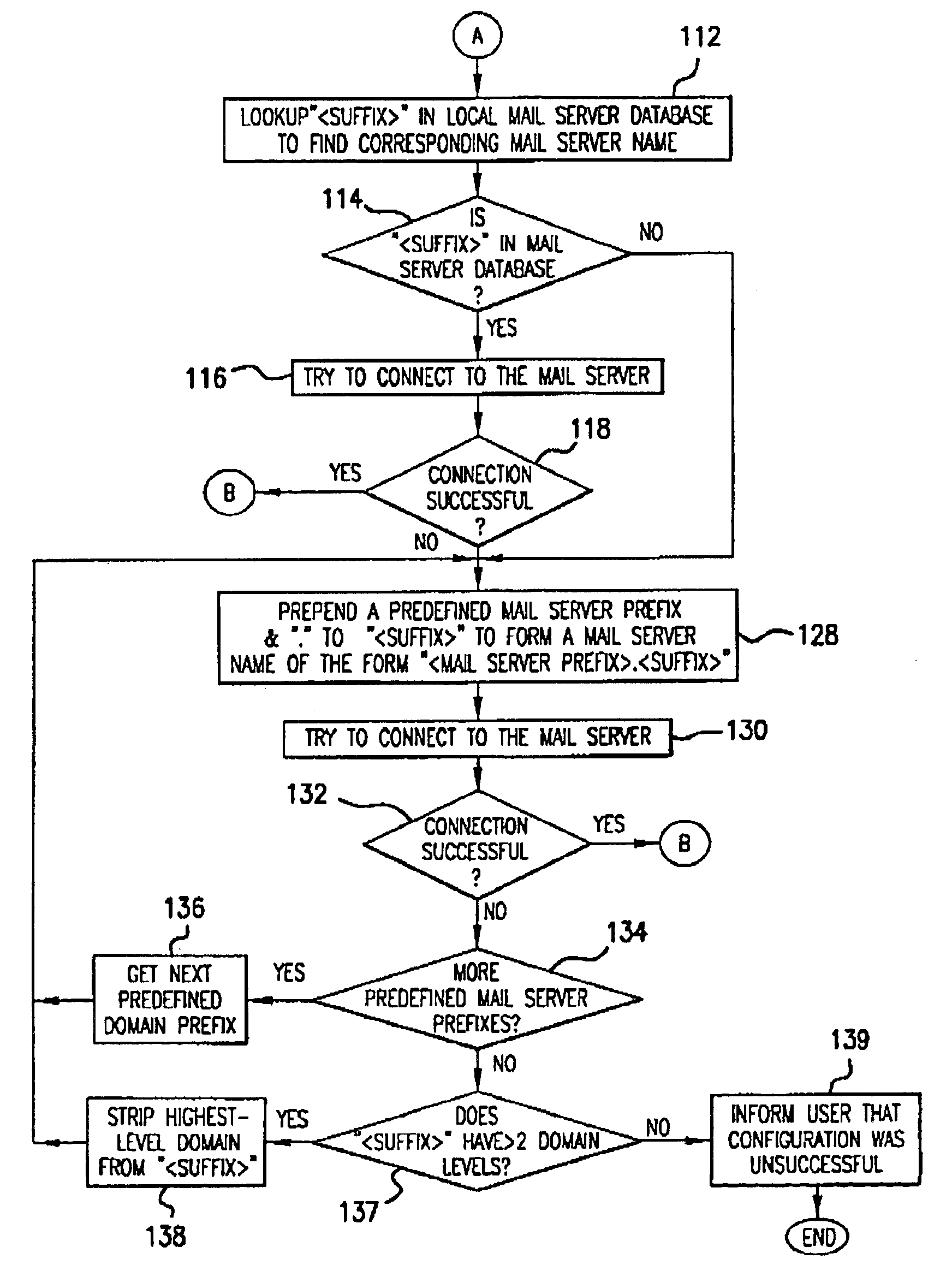
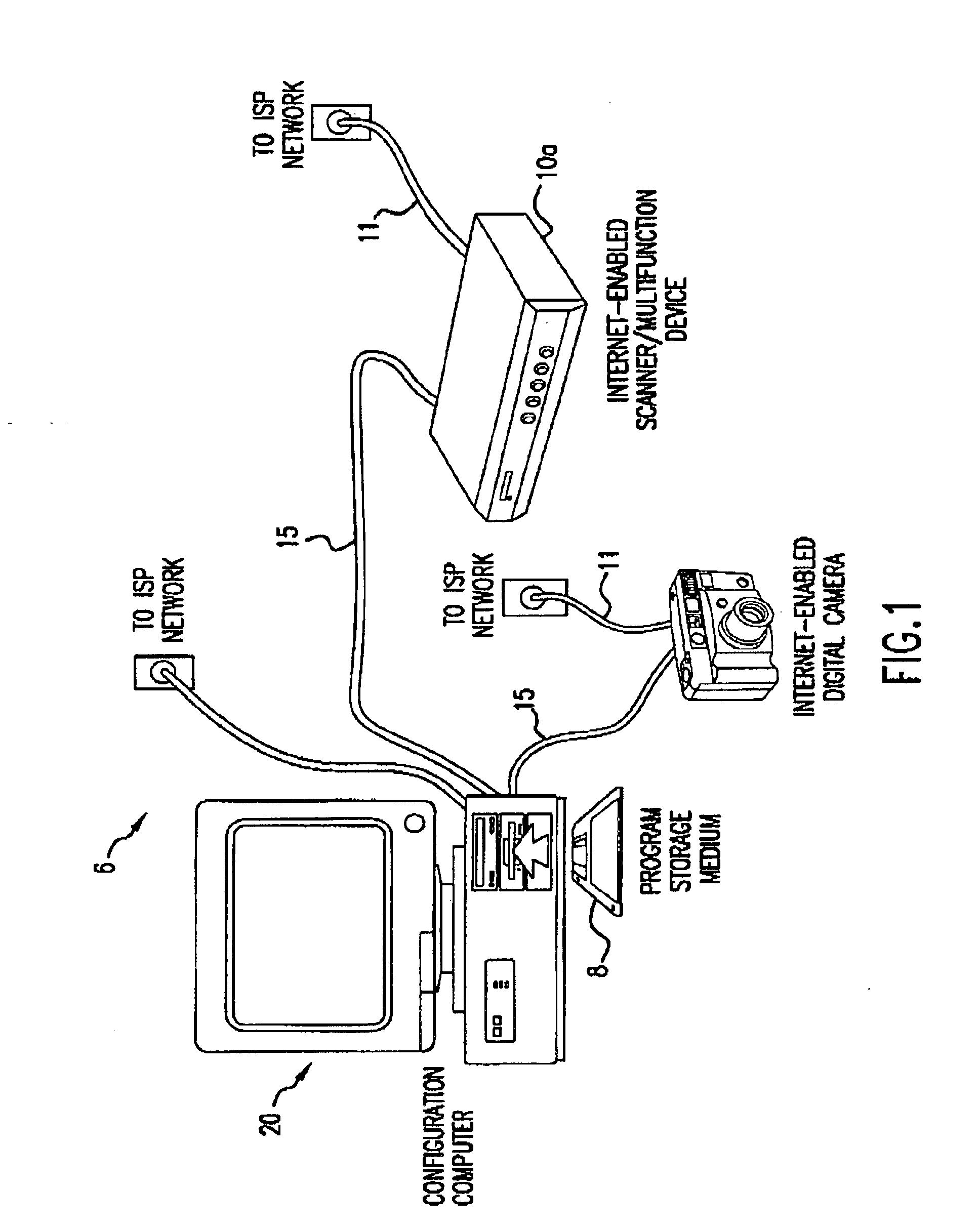
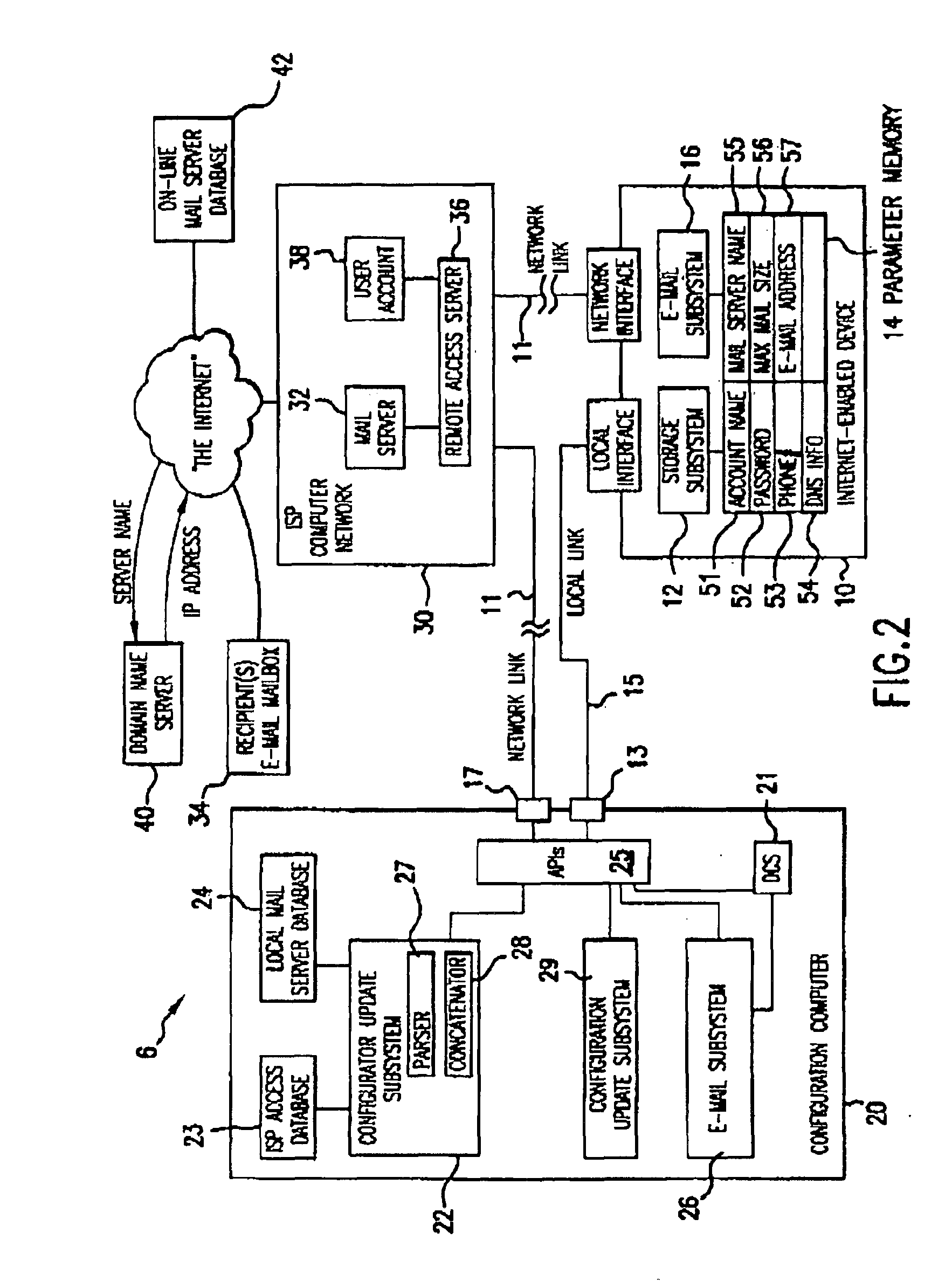
A system and method for configuring an Internet-enabled device to communicate with an unknown mail server so as to allow the device to send information as e-mail messages over the Internet using the resources of an Internet service provider (ISP). Such devices include scanners, multifunction peripherals, and digital cameras. A configuror program uses predetermined access parameters for the ISP to simplify the configuration of the device. From an e-mail address specified by the user during configuration, the configuror determines the mail server name that the device will use to send e-mail, and downloads the address, along with a portion of the access parameters and a maximum e-mail message size, to the device. After configuration, the device can directly connect to the ISP and send e-mail in a stand-alone manner. If the device is connected to a computer following installation, computer can update the device for any changes in ISP access, and the device can send e-mail messages through the computer rather than directly so as to avoid more than one simultaneous connection to the ISP.
Owner:HEWLETT PACKARD DEV CO LP
Methods and systems for support of location for the internet of things
ActiveUS20180054795A1Large message sizeLong retransmissionConnection managementLocation information based serviceThe InternetMessage size
Methods and techniques are described for supporting location services for a user equipment (UE) that is using Narrowband Internet of Things radio access or Cellular Internet of Things features to access a wireless network. The techniques include enabling support for a last known location of a UE, using previously obtained location measurements, when a UE is not reachable from a wireless network for positioning. The techniques also include limiting positioning protocol interaction between a UE and a location server via a reduced maximum message size, reduced message volume and longer response and retransmission timers. The techniques further include enabling a UE to obtain location measurements when not connected to a wireless network, enabling periodic and triggered location of a UE in which a UE evaluates location triggers while not connected to a wireless network, enabling use of deferred location and enabling improved location security.
Owner:QUALCOMM INC
Method and device for improving the data transmission security in a serial data transmission having flexible message size
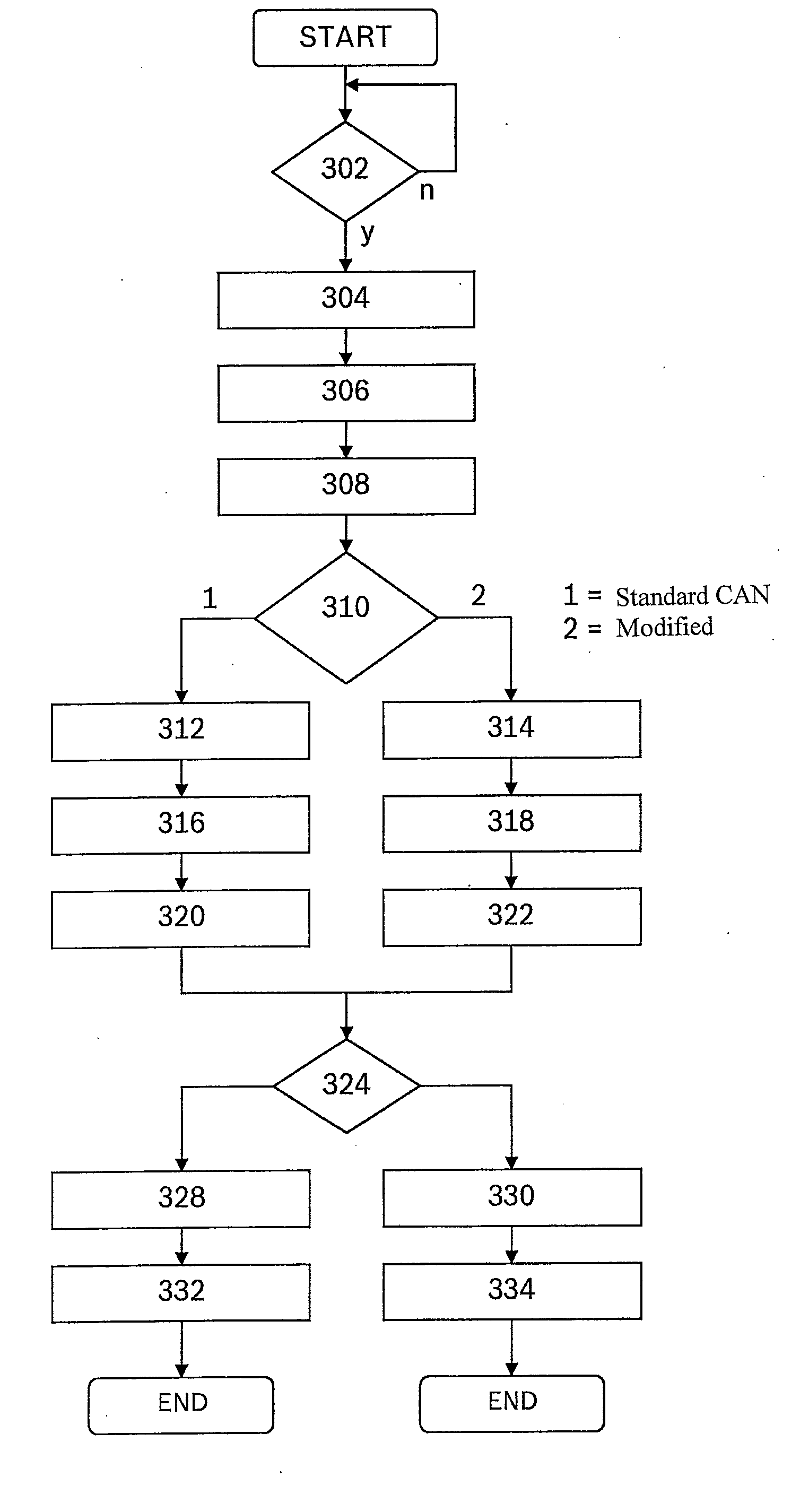
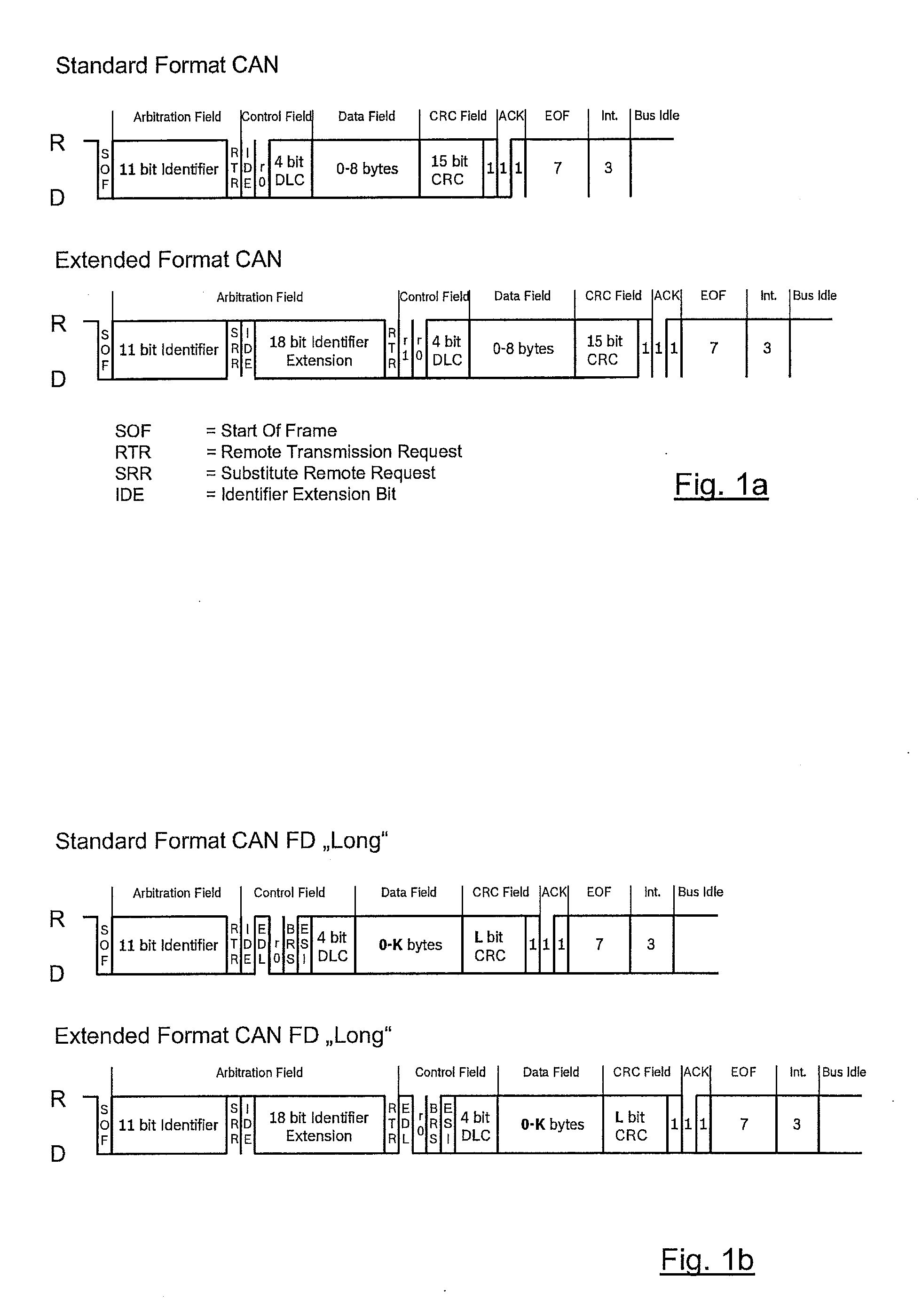
ActiveUS20140223258A1Speed advantageMinimally modifiedCode conversionCoding detailsData transmissionMessage size
A method is provided for serial data transmission in a bus system having at least two bus subscribers, which exchange messages via the bus, the send access to the bus for each message being assigned to a bus subscriber by the arbitration method according to CAN Standard ISO 11898-1; it being decided as a function of a suitable identification (EDL) which result from one of the CRC calculations started in parallel is used for checking the correct data transmission; for at least one value of the identification an additional condition being checked, and in response to its presence, fixed stuff bit sequences from one or more bits are inserted into the message by the sender, at least into parts of the message.
Owner:ROBERT BOSCH GMBH
Power control in communication systems
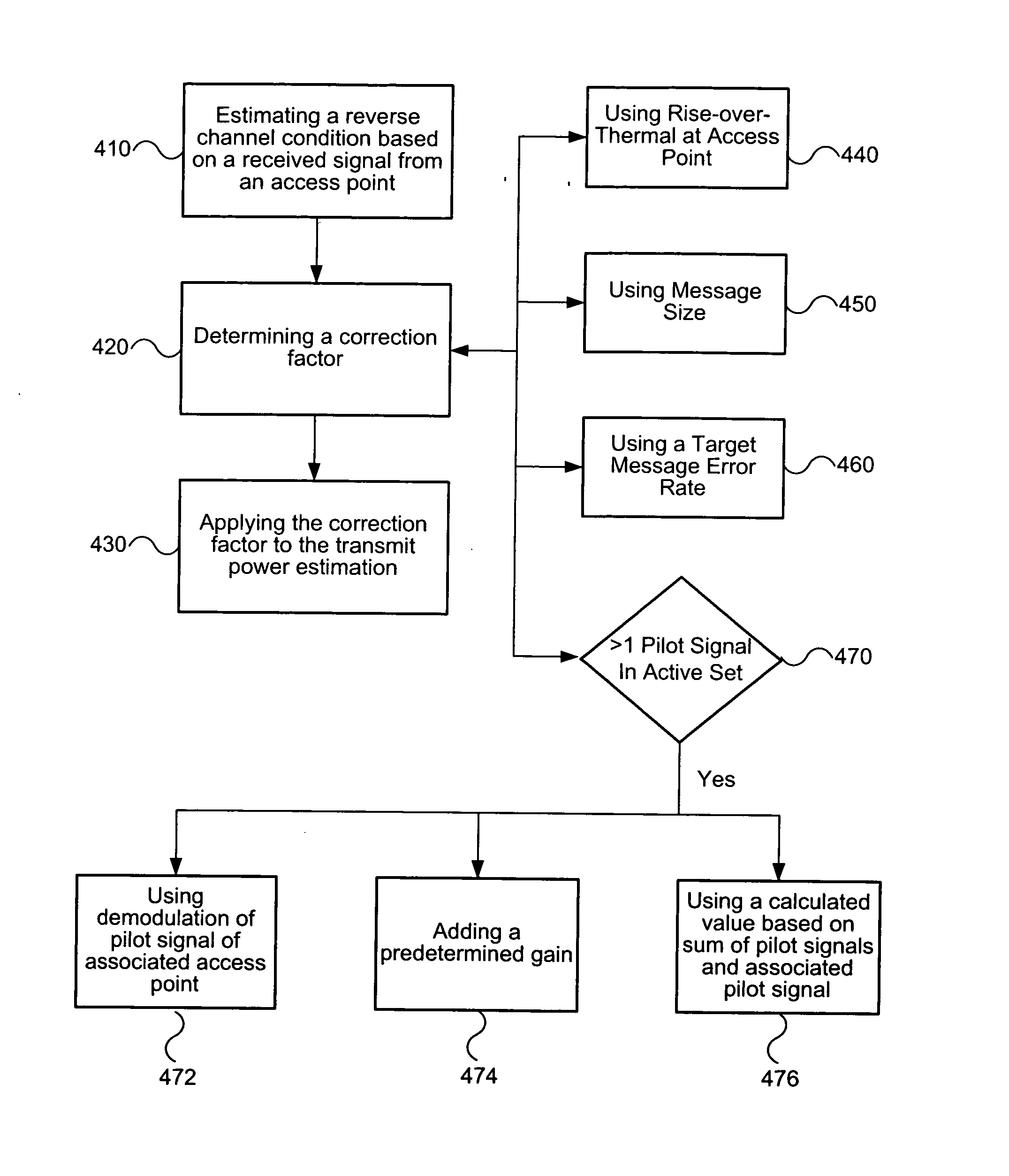
InactiveUS20070201405A1Convenient power controlPower managementRadio transmissionCommunications systemTransmitted power
Systems and methods for estimating transmit power in a communication system are disclosed. An estimate of a reverse channel condition is based on a received signal from an access point. A correction factor is determined based on at least one of the number of access points detected, a Rise-over-Thermal (RoT) at the access point, a message error rate, and a message size. Then the correction factor is applied to the transmit power determination.
Owner:QUALCOMM INC
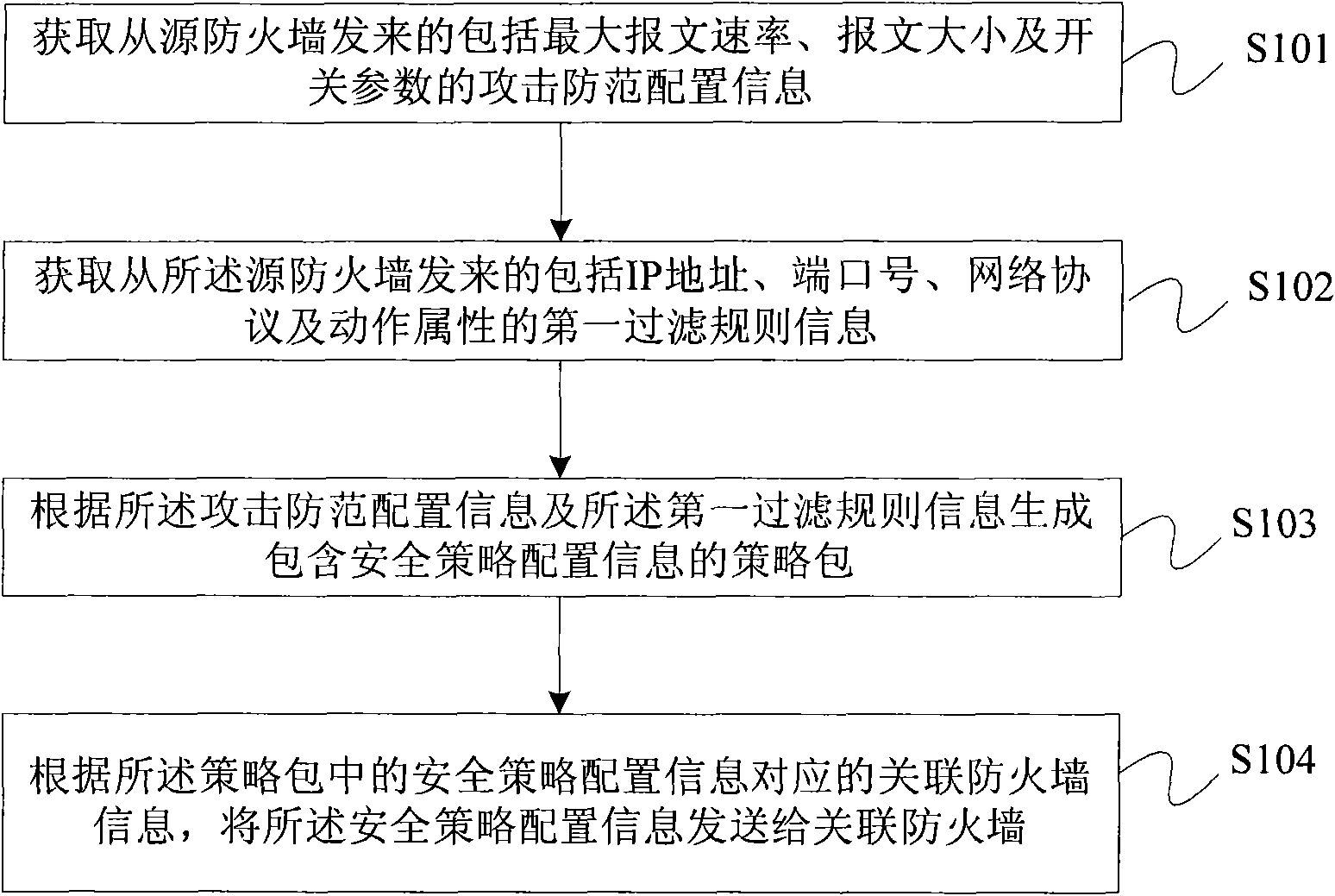
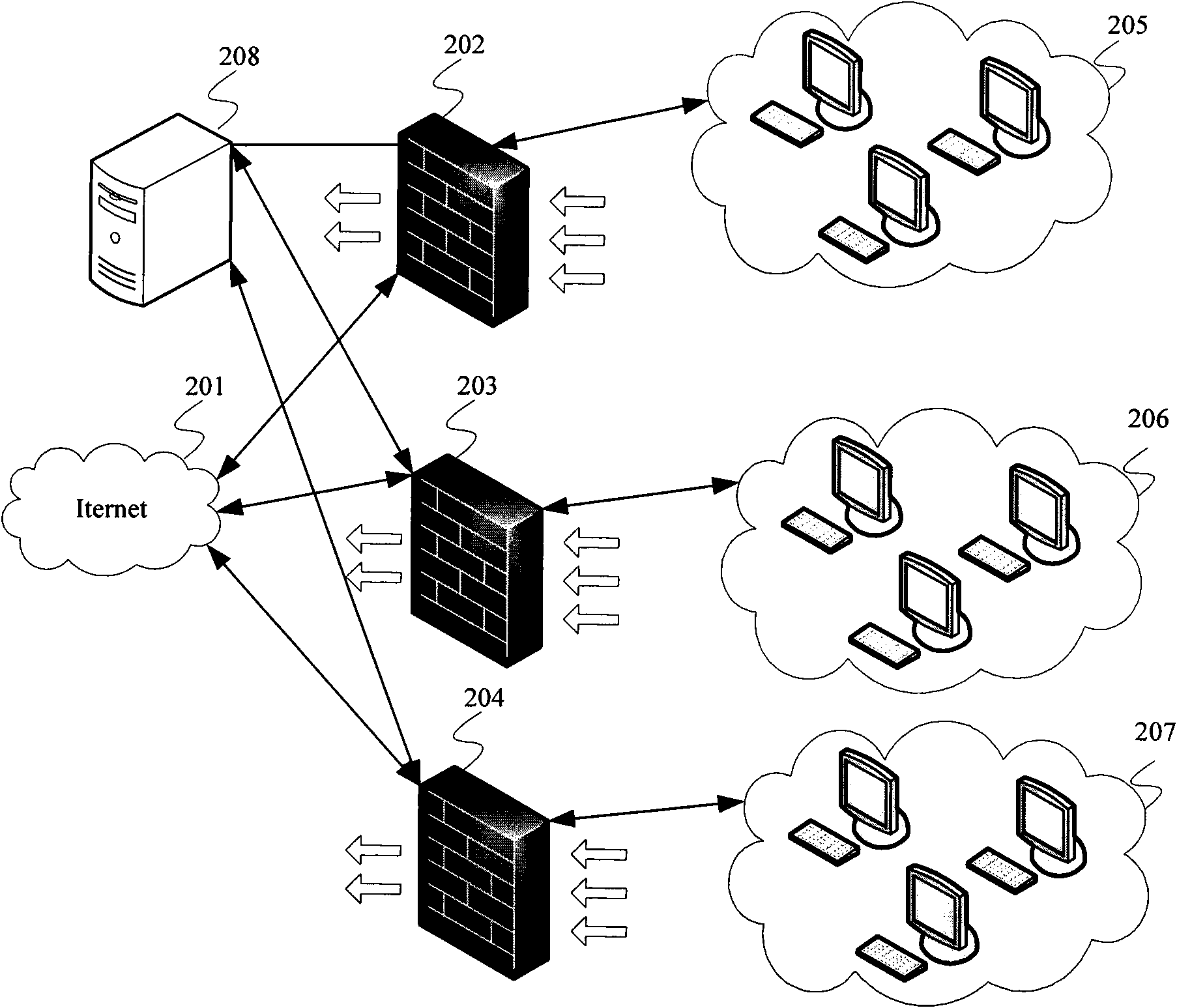
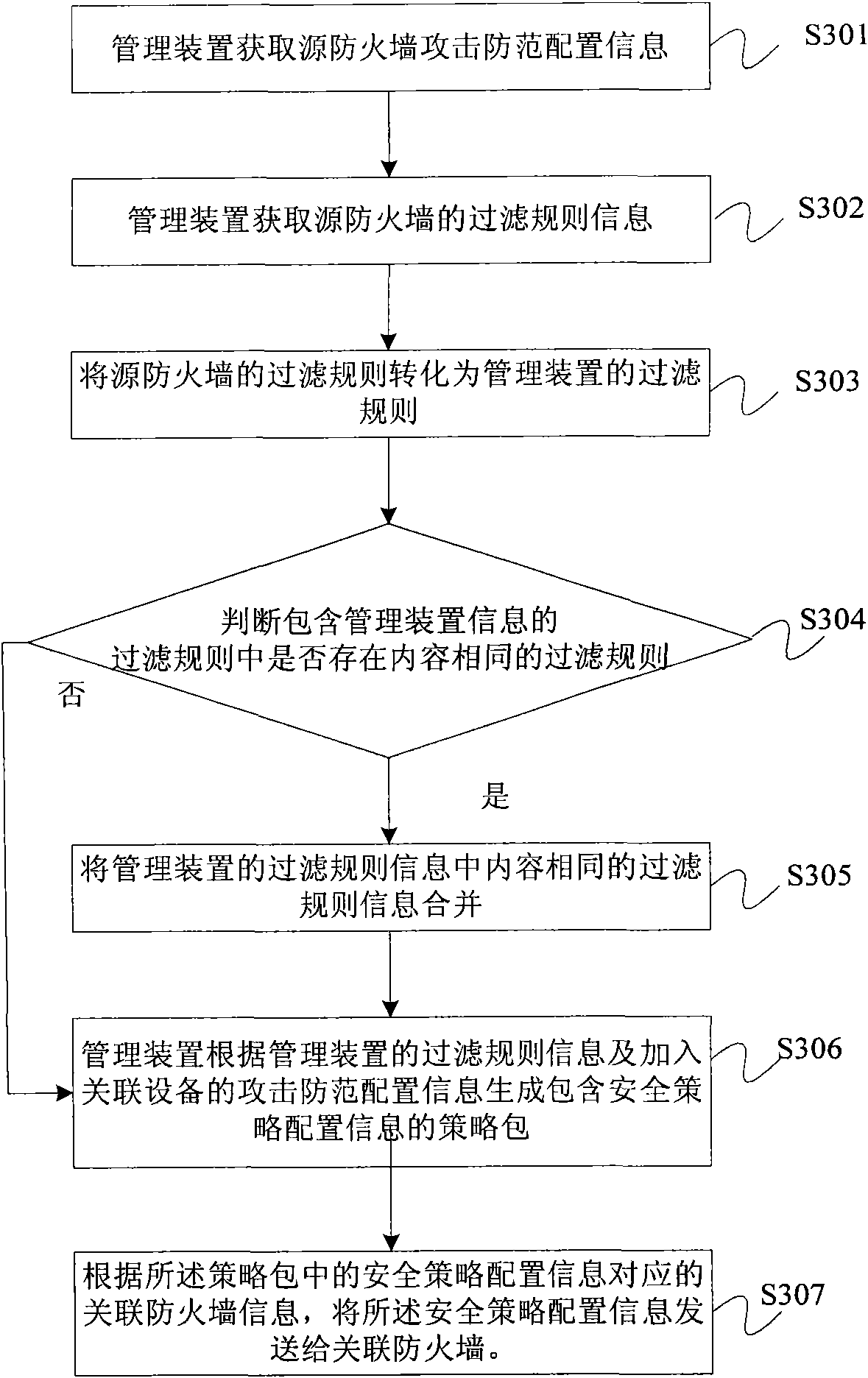
Firewall security policy configuration method and management unit
The invention provides a firewall security policy configuration method and a management unit. The method comprises the following steps of: obtaining attack prevention configuration information which includes maximum message rate, message size or an on-and-off parameter and is sent from the firewall; obtaining first filter rule information which includes an IP address, a port number, a network protocol and action attribute and is sent from the firewall; generating a policy package including security policy configuration information according to the attack prevention configuration information and the first filter rule information; and sending the security policy configuration information to the association firewall according to association firewall information corresponding to the security policy configuration information in the policy package. In the embodiment of the invention, the security policy of a single firewall is reversely reduced to the policy package, thus providing convenience for a user to conduct security policy configuration on the firewall.
Owner:CHENGDU HUAWEI TECH
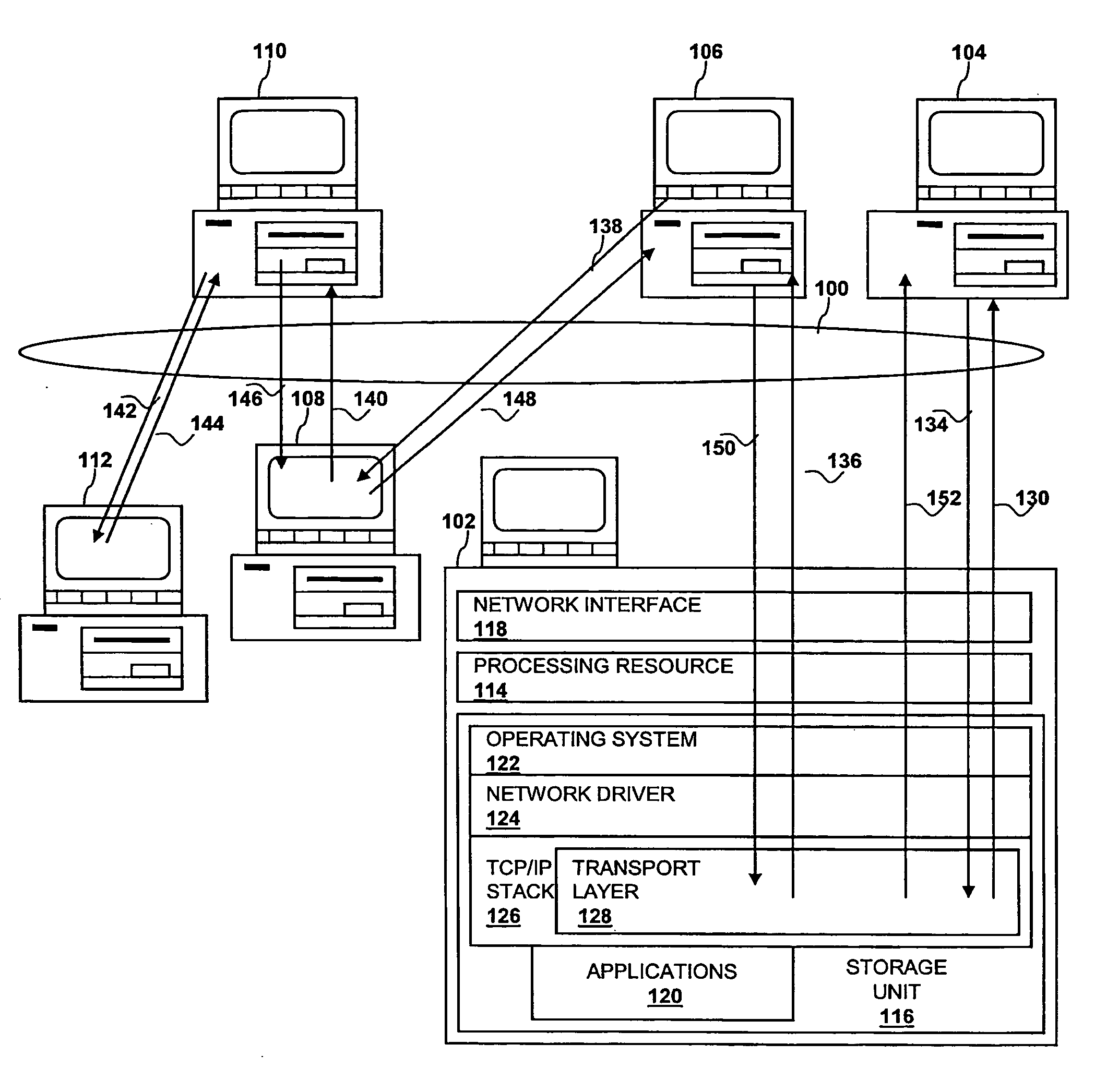
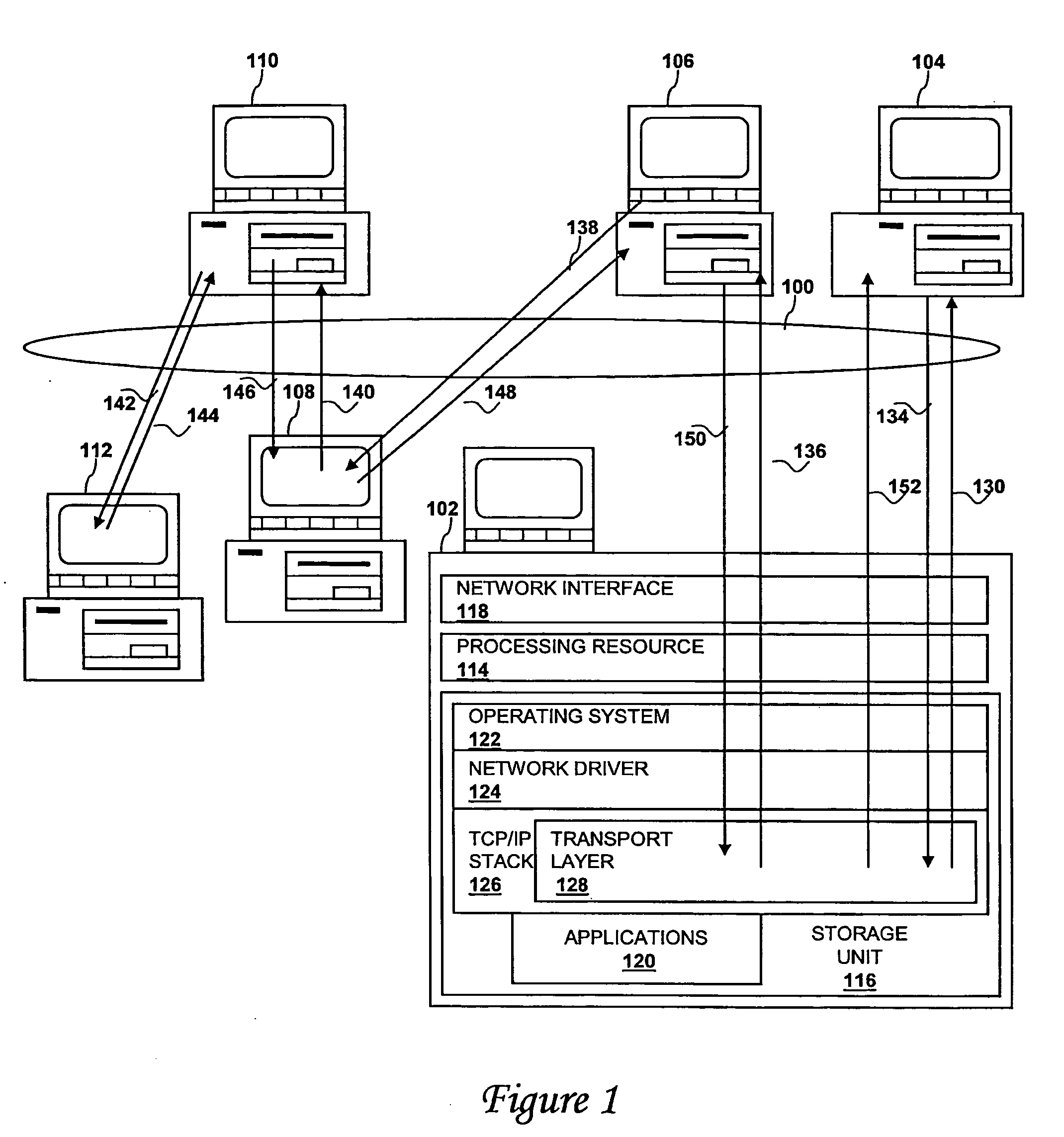
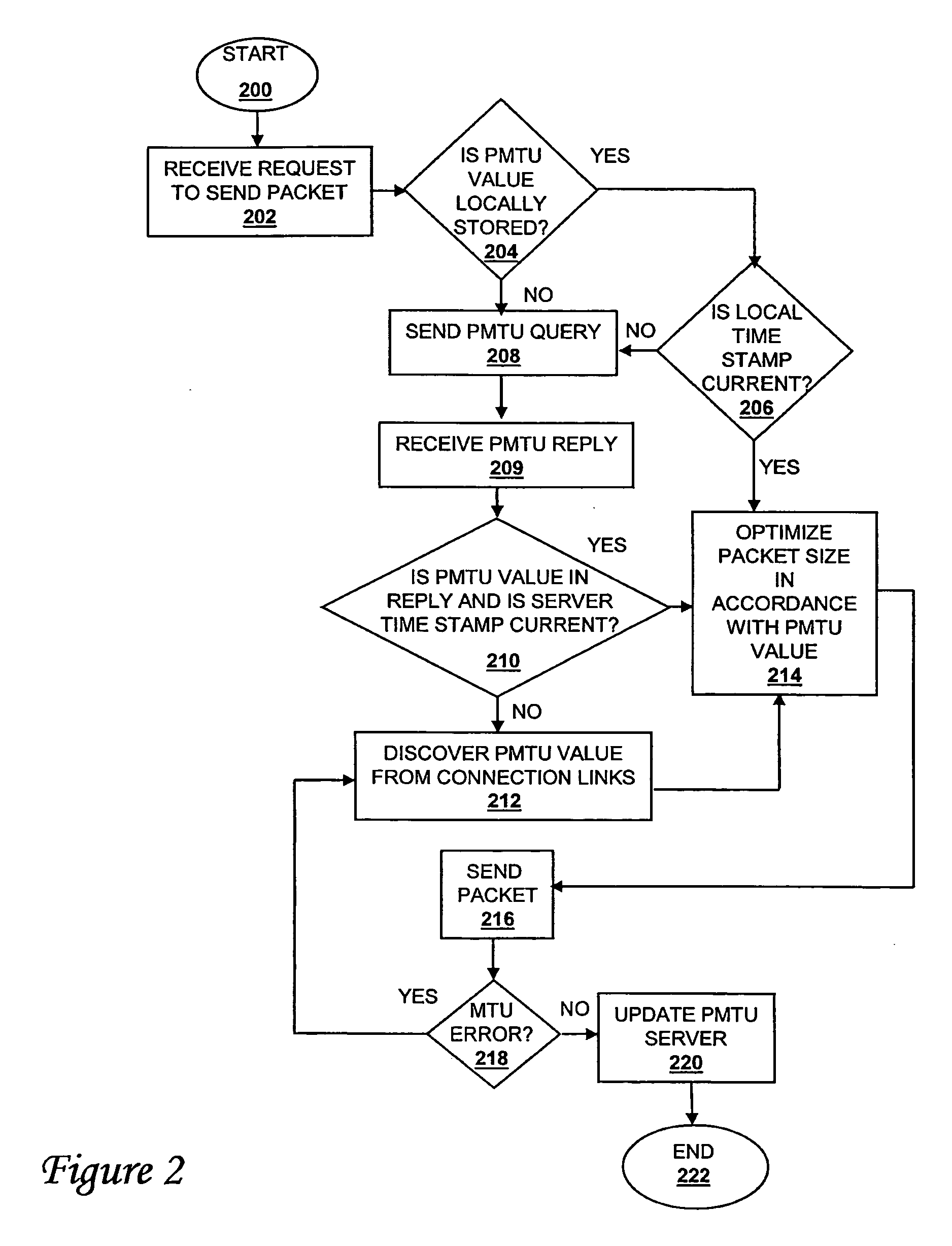
Method, system, and computer program product for remote storage and discovery of a path maximum transmission unit value on a network
A method, system, and computer program product for optimizing a message size for communication in a communication network are disclosed. The method comprises identifying a connection to a target, sending to a path maximum transmission unit value server (which is not the target) a request for a path maximum transmission unit value for the connection to the target, and, in response to receiving the path maximum transmission unit value for the connection to the target from the server, optimizing a communication by sending to the target a packet having a size in accordance with the value.
Owner:IBM CORP
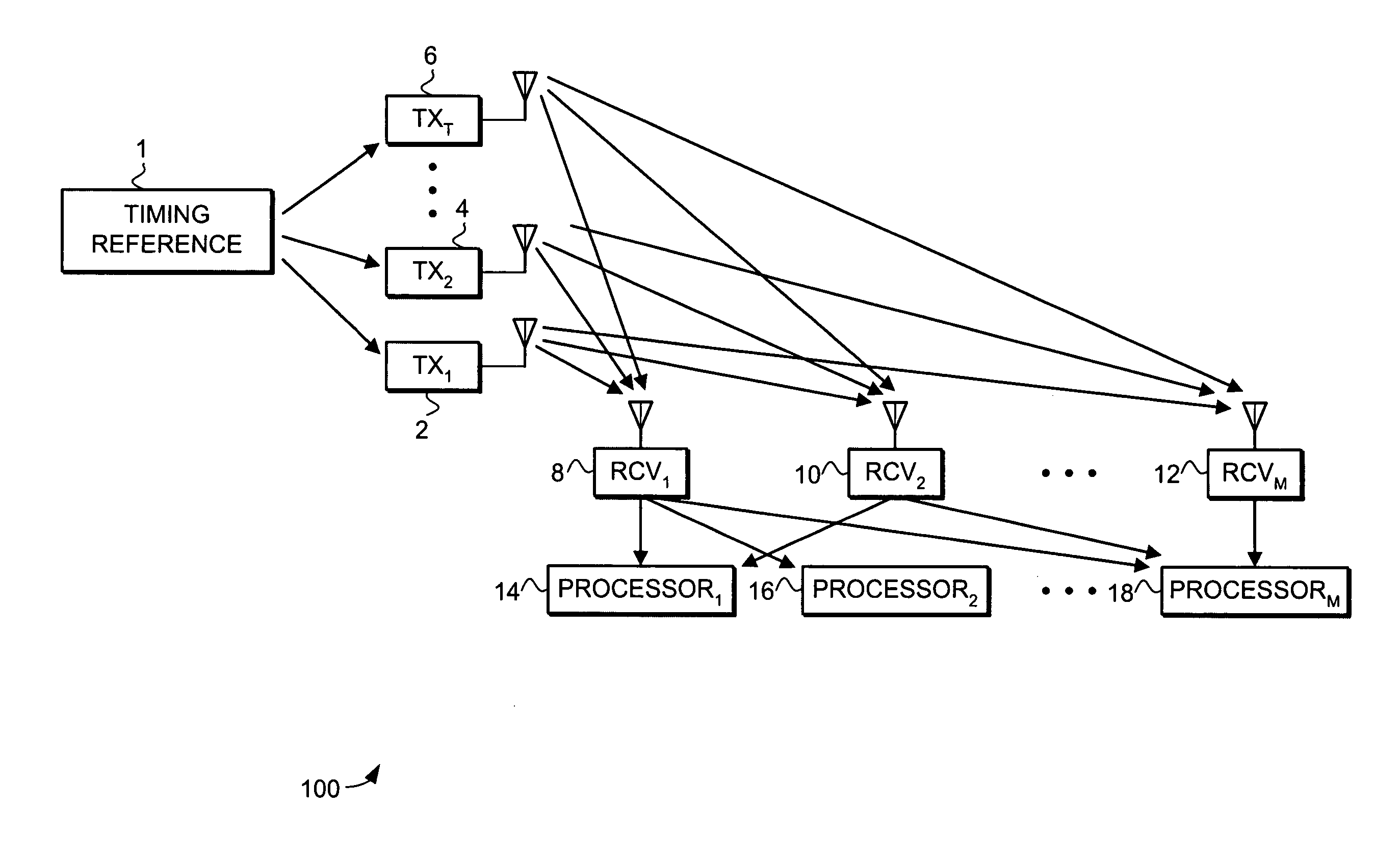
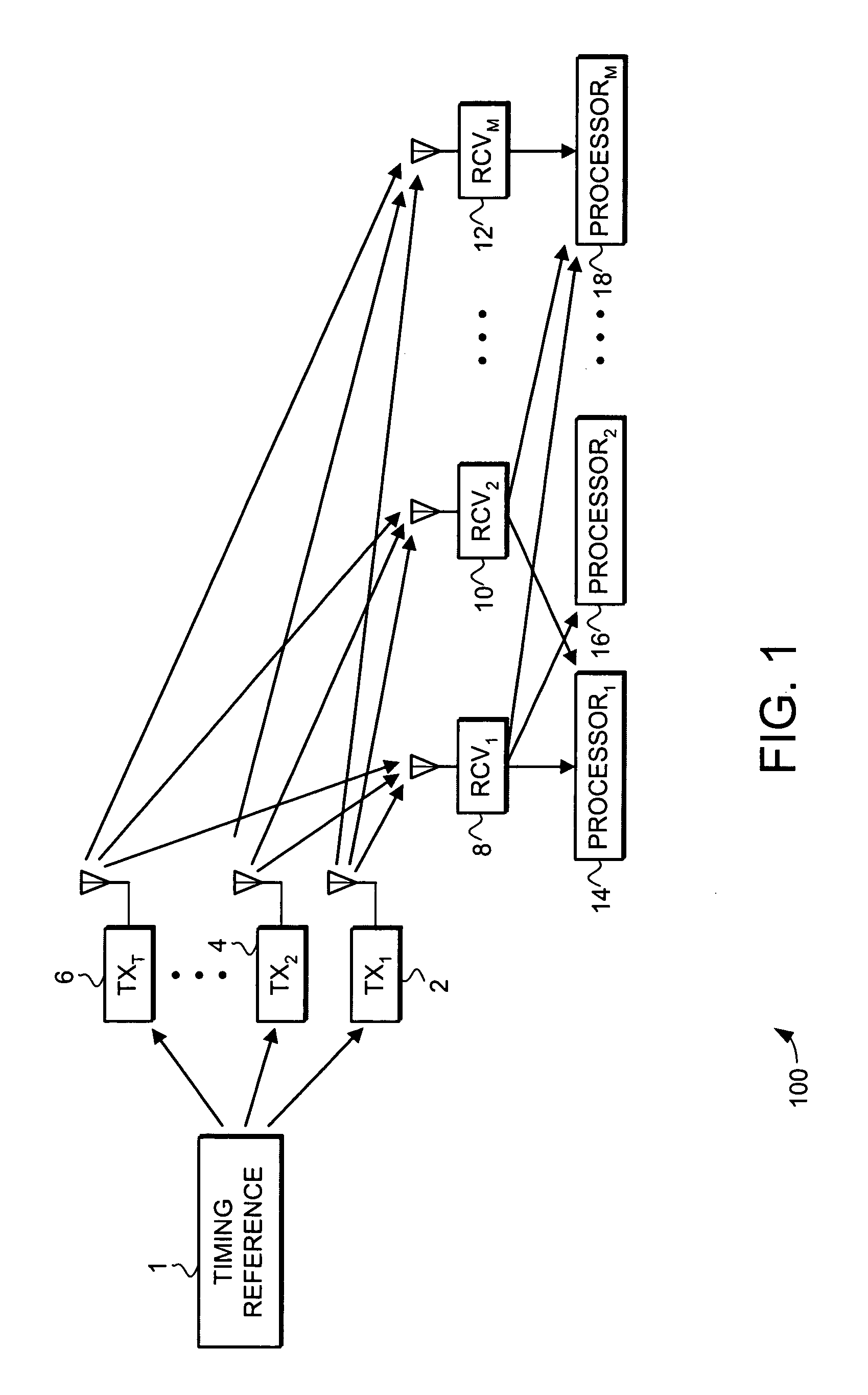
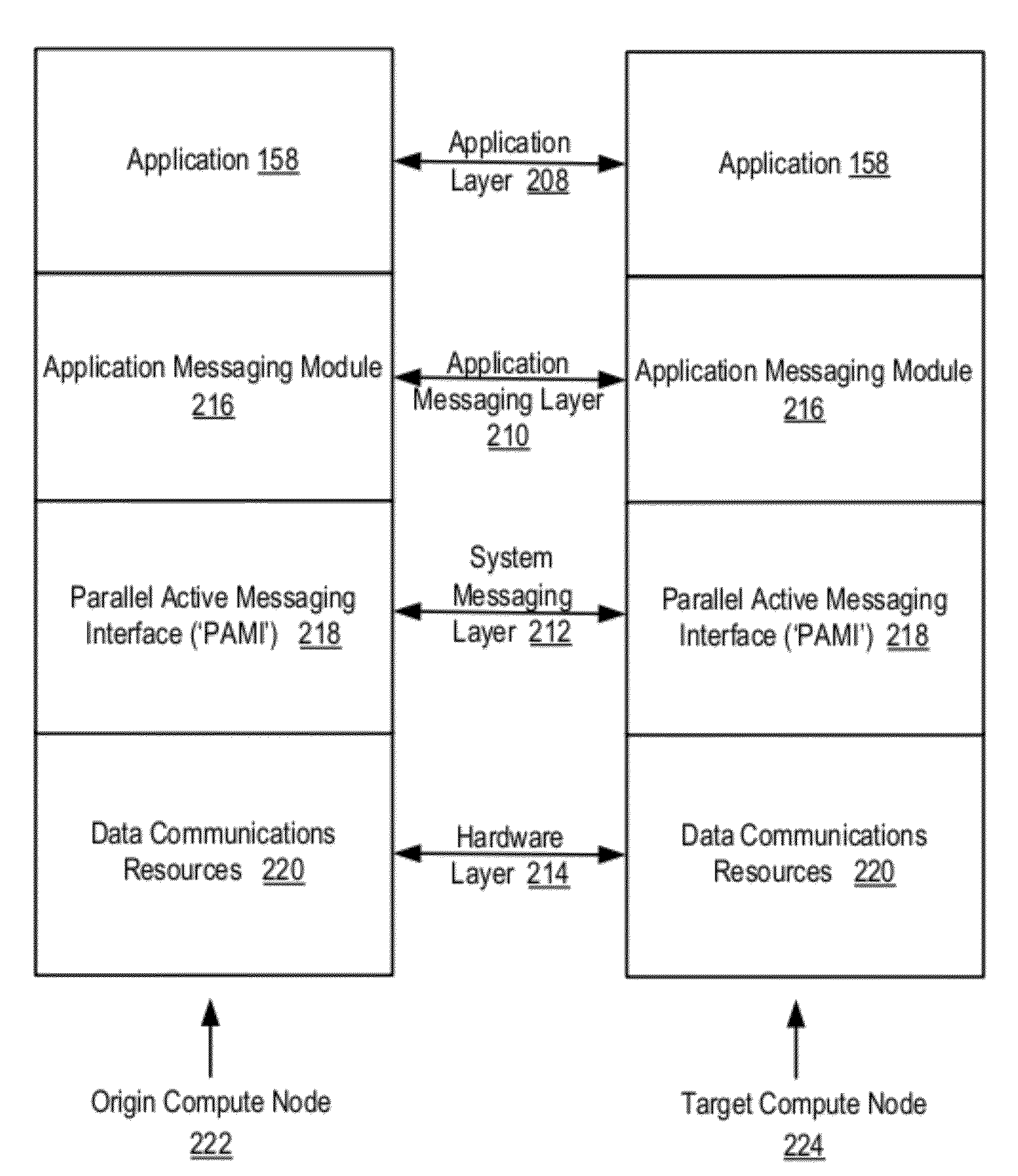
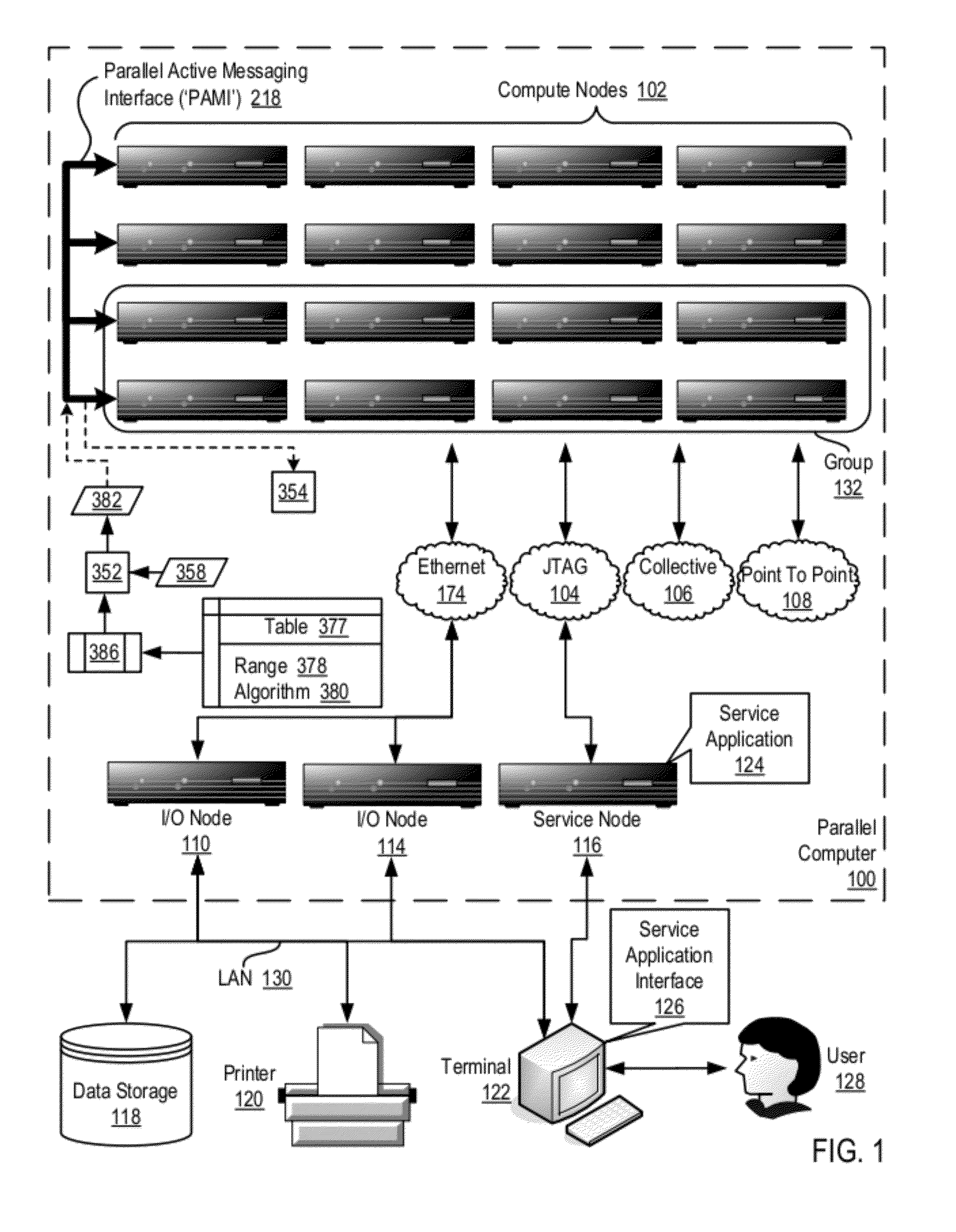
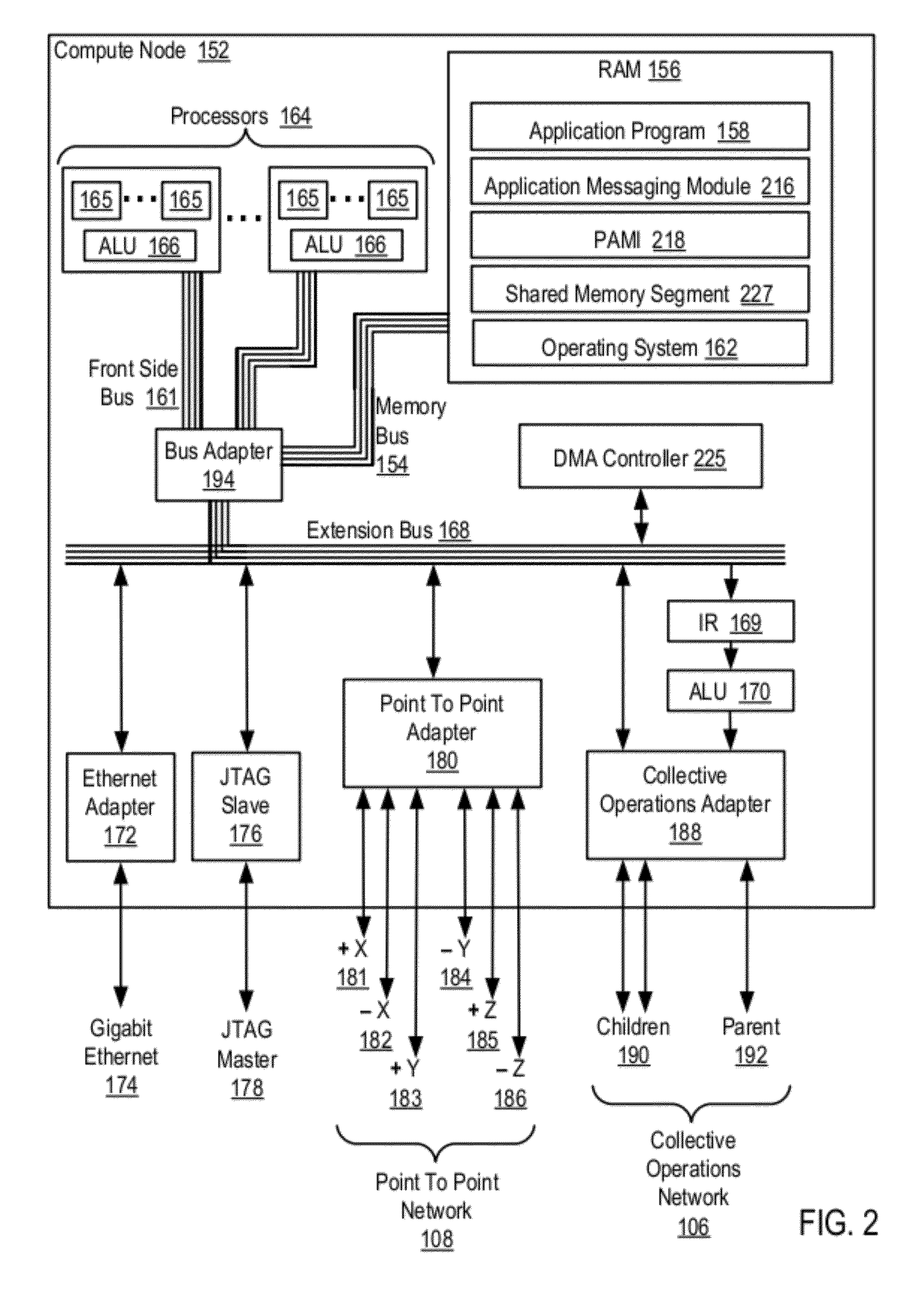
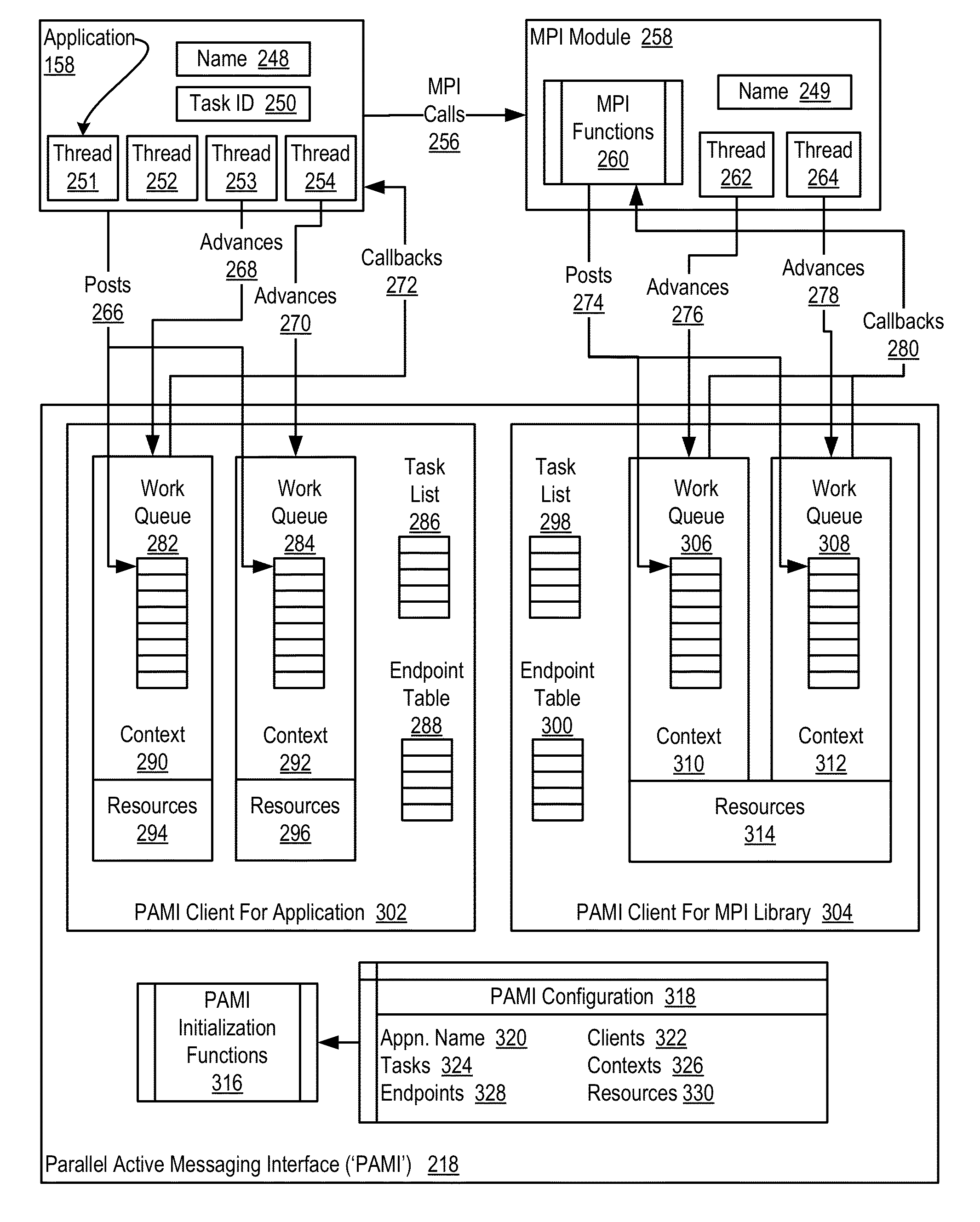
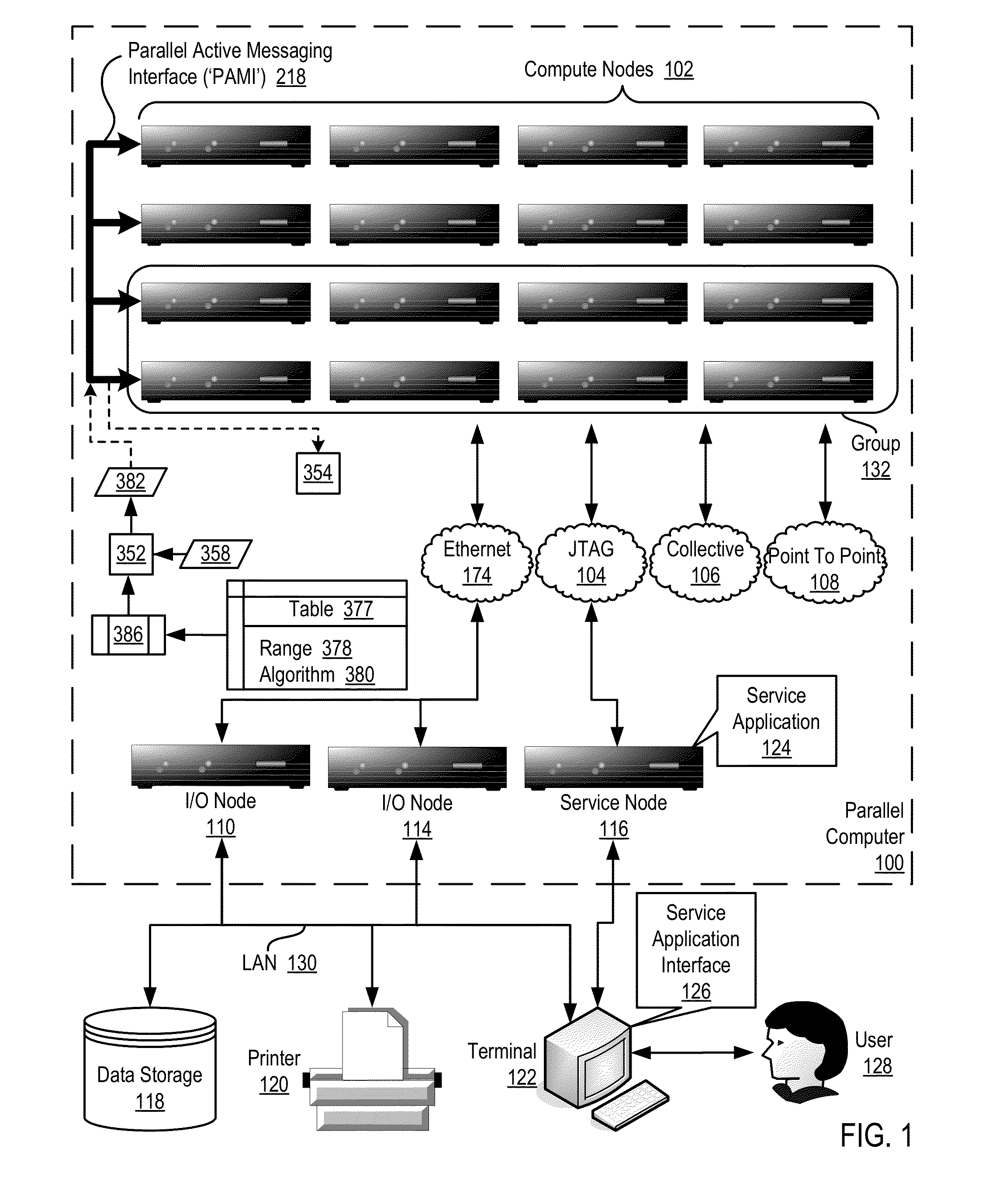
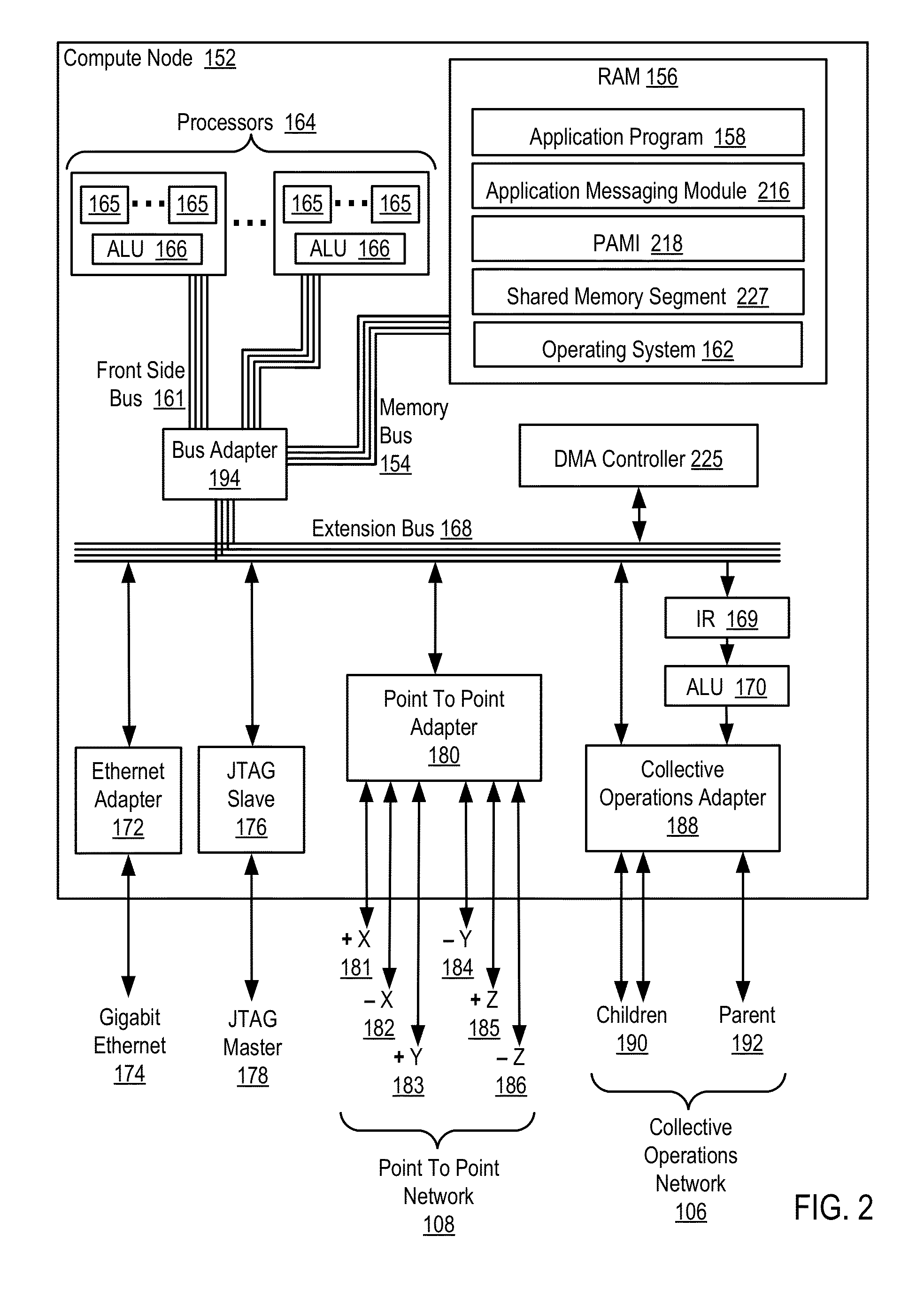
Data Communications In A Parallel Active Messaging Interface Of A Parallel Computer
InactiveUS20120144400A1Digital computer detailsMultiprogramming arrangementsCommunication endpointParallel computing
Algorithm selection for data communications in a parallel active messaging interface (‘PAMI’) of a parallel computer, the PAMI composed of data communications endpoints, each endpoint including specifications of a client, a context, and a task, endpoints coupled for data communications through the PAMI, including associating in the PAMI data communications algorithms and ranges of message sizes so that each algorithm is associated with a separate range of message sizes; receiving in an origin endpoint of the PAMI a data communications instruction, the instruction specifying transmission of a data communications message from the origin endpoint to a target endpoint, the data communications message characterized by a message size; selecting, from among the associated algorithms and ranges, a data communications algorithm in dependence upon the message size; and transmitting, according to the selected data communications algorithm from the origin endpoint to the target endpoint, the data communications message.
Owner:IBM CORP
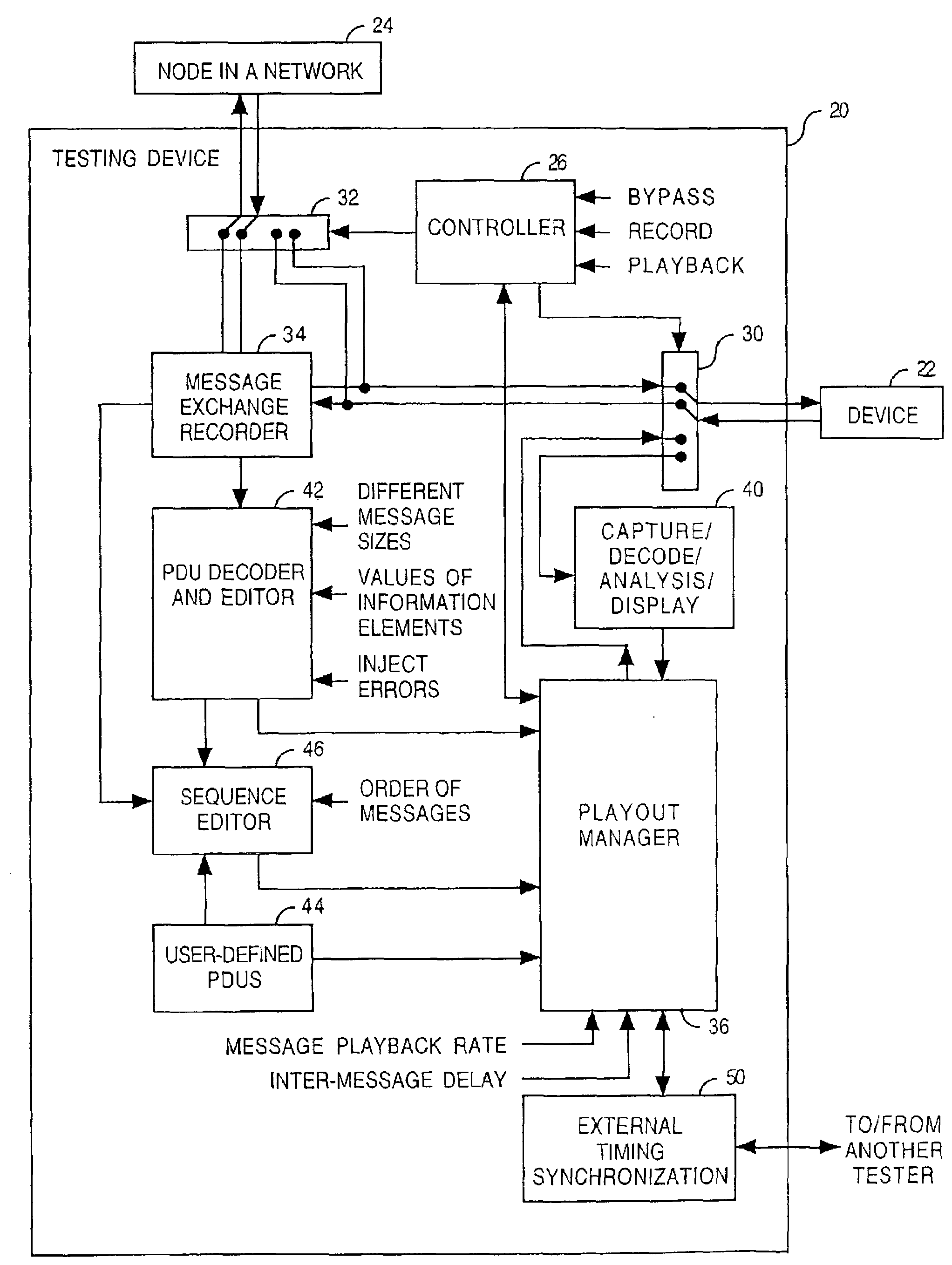
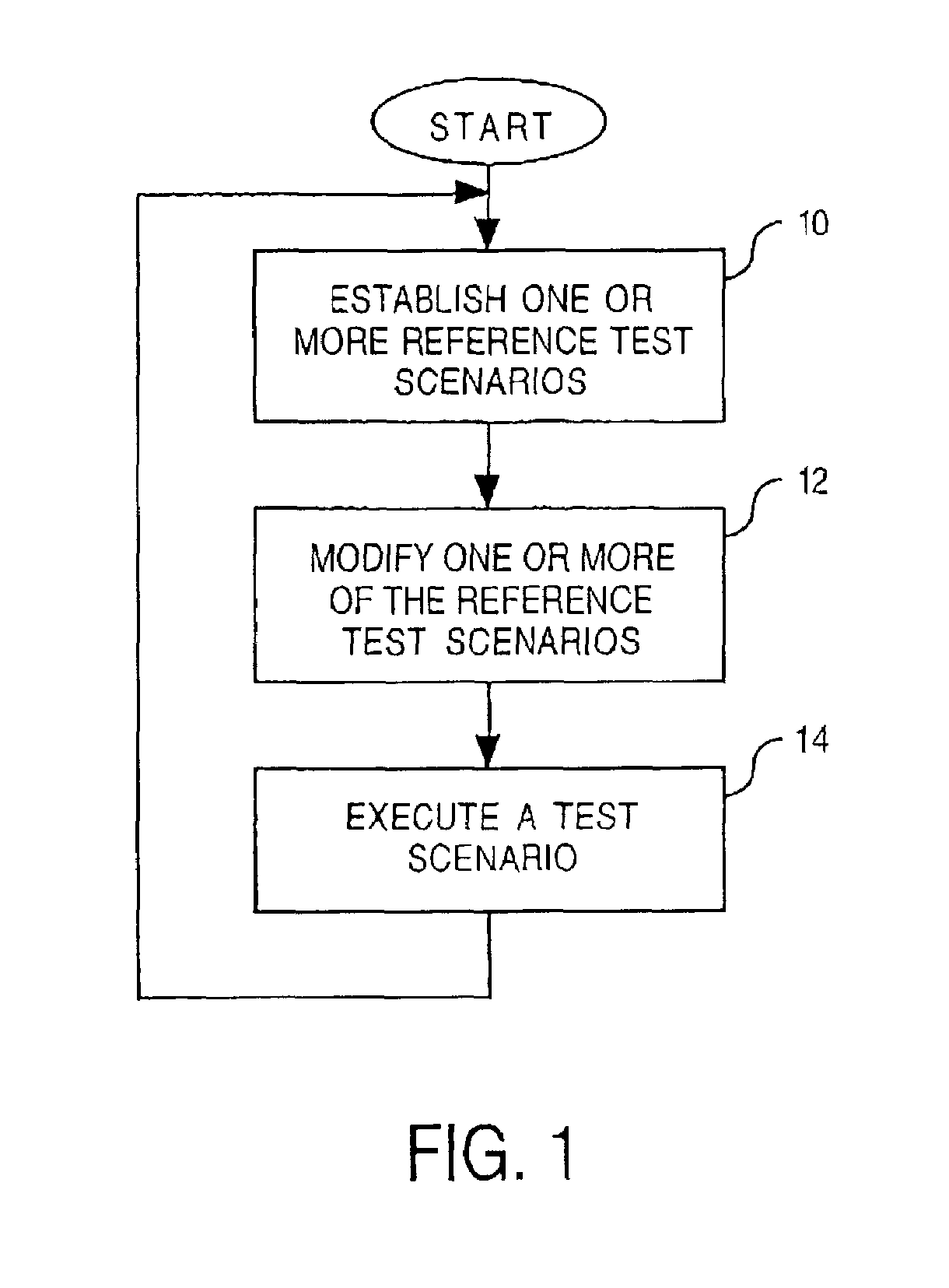
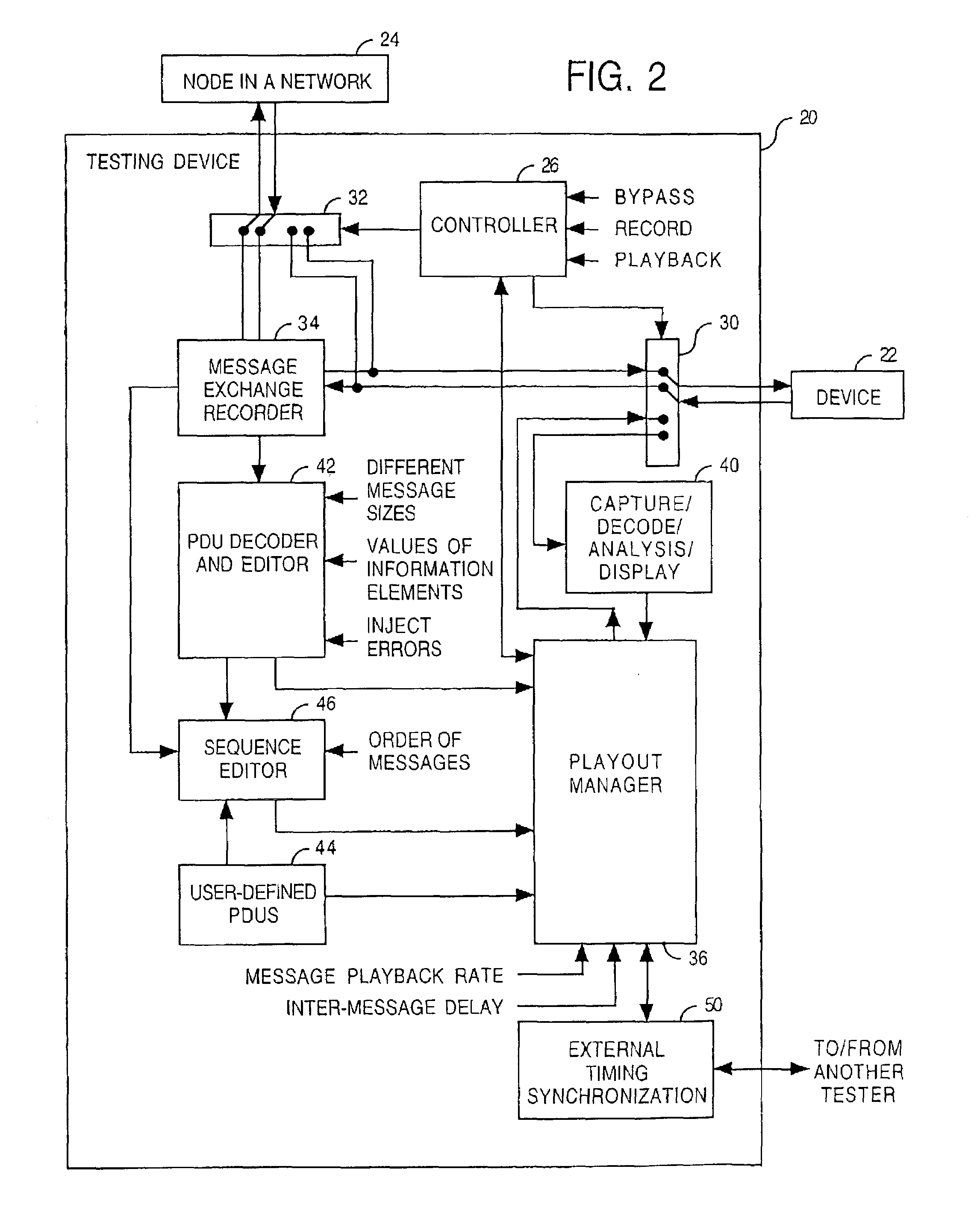
Controlled exception-based routing protocol validation
InactiveUS7342892B2Improve reliabilityError preventionTransmission systemsMessage sizeAdverse conditions
An implementation of a routing protocol in a device is tested by testing how the device reacts to messages and message sequences having potentially adverse conditions. Examples include messages either having a specified message size which is intentionally out-of-conformance with the routing protocol, having a repeated protocol field, absent a mandatory protocol field, or having an incorrect order of protocol fields. Examples also include message sequences having either a specific playback delay between at least one pair of adjacent protocol messages in the first sequence of protocol messages, a specific playback rate for the second sequence of protocol messages, or a modified message order.
Owner:AT&T INTPROP I L P
Data communications in a parallel active messaging interface of a parallel computer
InactiveUS20130061244A1Digital computer detailsMultiprogramming arrangementsCommunication endpointParallel computing
Algorithm selection for data communications in a parallel active messaging interface (‘PAMI’) of a parallel computer, the PAMI composed of data communications endpoints, each endpoint including specifications of a client, a context, and a task, endpoints coupled for data communications through the PAMI, including associating in the PAMI data communications algorithms and ranges of message sizes so that each algorithm is associated with a separate range of message sizes; receiving in an origin endpoint of the PAMI a data communications instruction, the instruction specifying transmission of a data communications message from the origin endpoint to a target endpoint, the data communications message characterized by a message size; selecting, from among the associated algorithms and ranges, a data communications algorithm in dependence upon the message size; and transmitting, according to the selected data communications algorithm from the origin endpoint to the target endpoint, the data communications message.
Owner:INT BUSINESS MASCH CORP
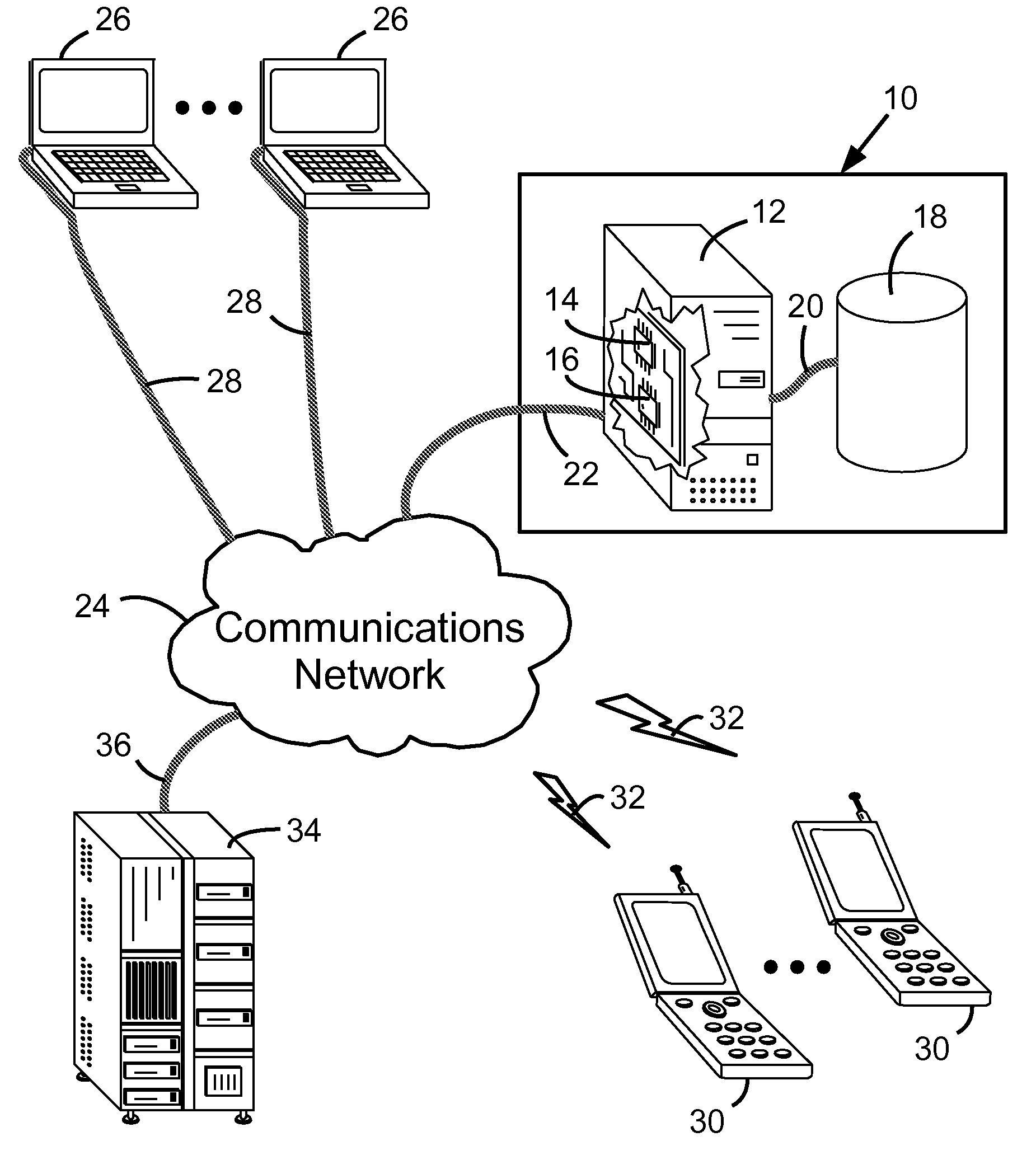
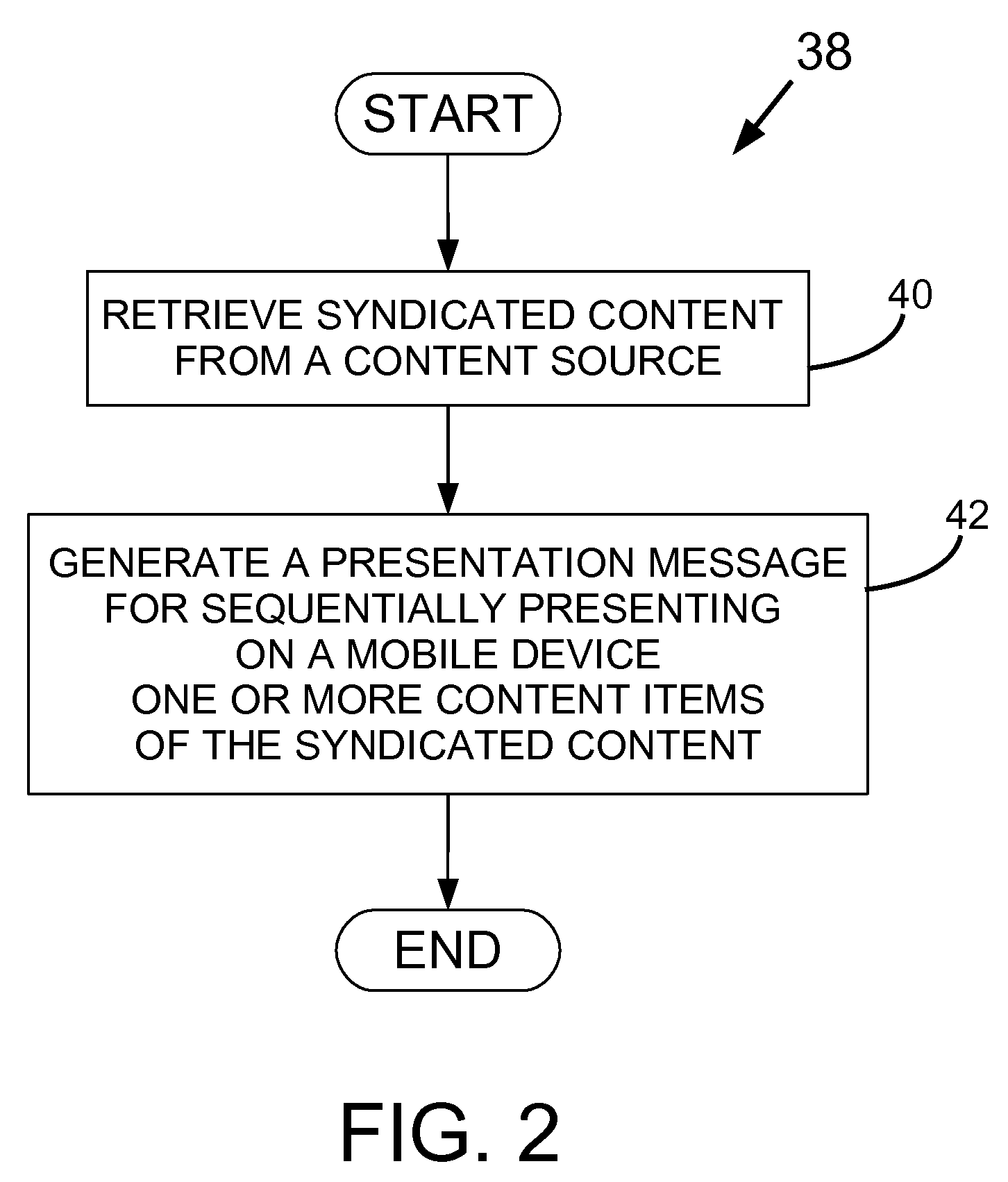
Method and system for producing a presentation message for a mobile device
InactiveUS20090300120A1Multiple digital computer combinationsData switching networksWeb feedMessage size
A method and system produces a presentation message for a mobile device. The method involves retrieving syndicated content from a content source; and generating from the syndicated content the presentation message for sequentially presenting on the mobile device one or more content items of the syndicated content. The syndicated content may be a RSS or ATOM web feed. The method may involve receiving a user selection of a web feed and an invocation parameter; determining supported media types, display dimensions, maximum presentation message size and presentation parameters; retrieving the syndicated content; selecting the one or more content items; converting the one or more content items to one or more presentation objects; assembling the presentation objects into the presentation message; and delivering the presentation message to the mobile device such that viewing the presentation message causes the presentation objects to be sequentially displayed on the mobile device.
Owner:CONTEC INNOVATIONS INC
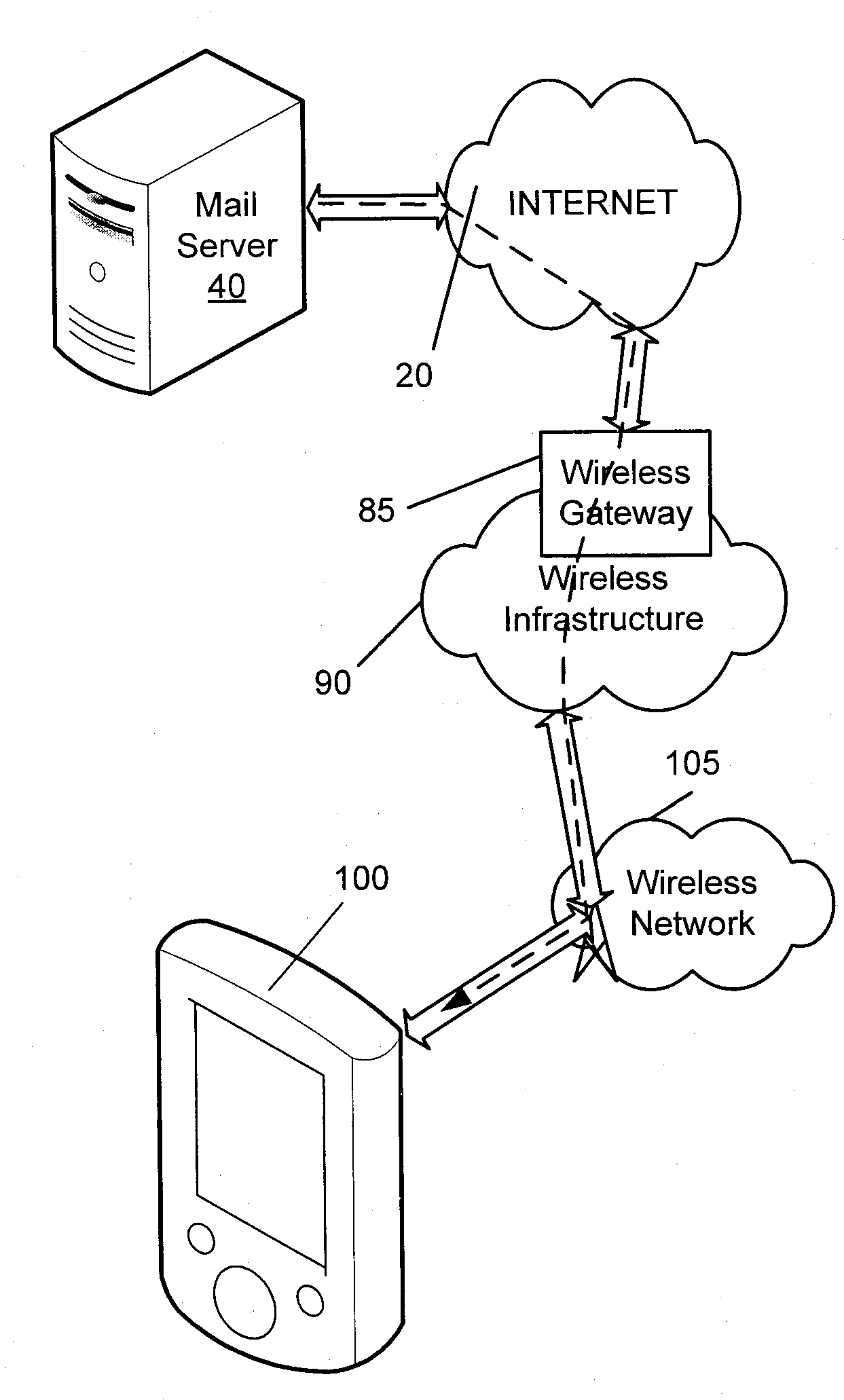
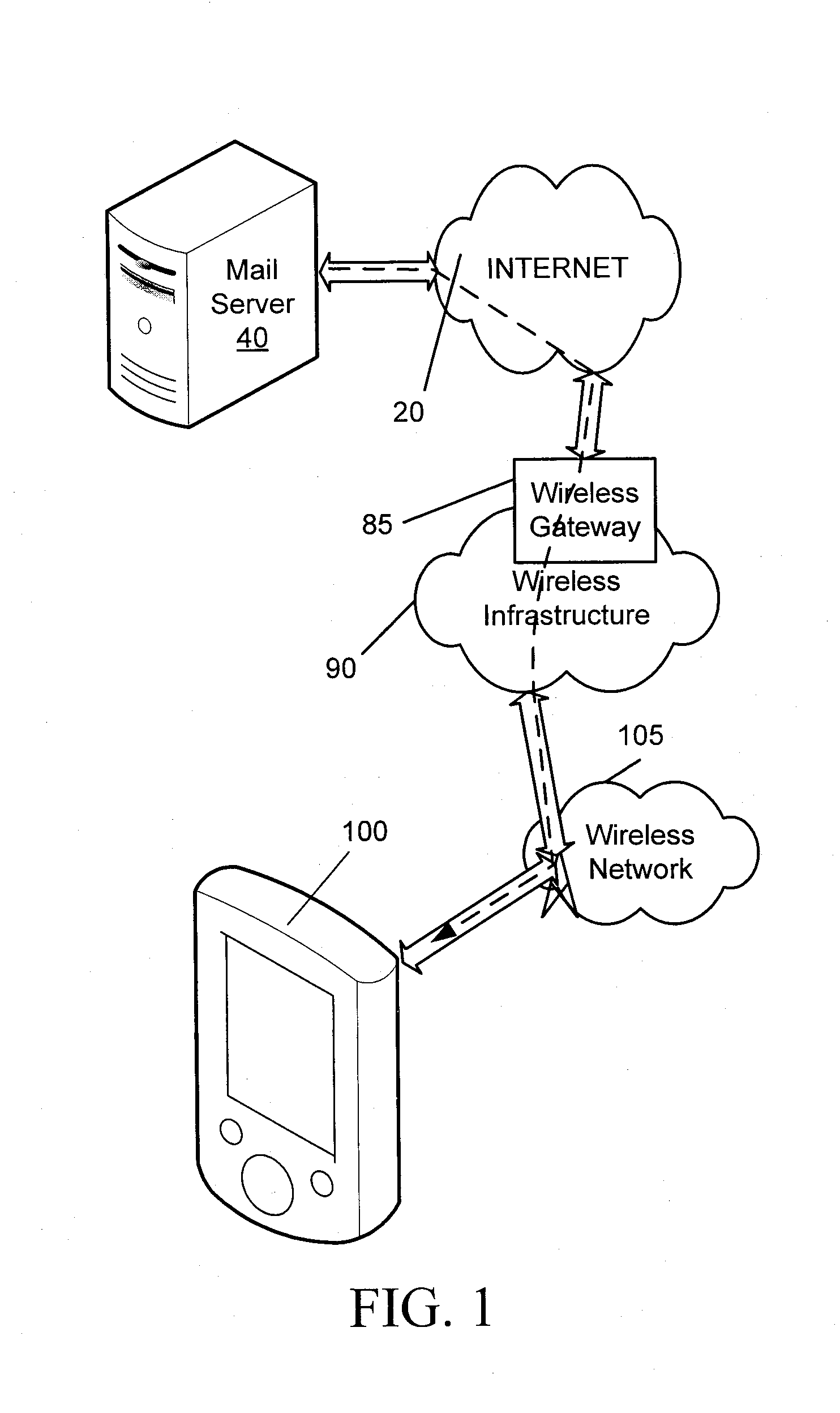
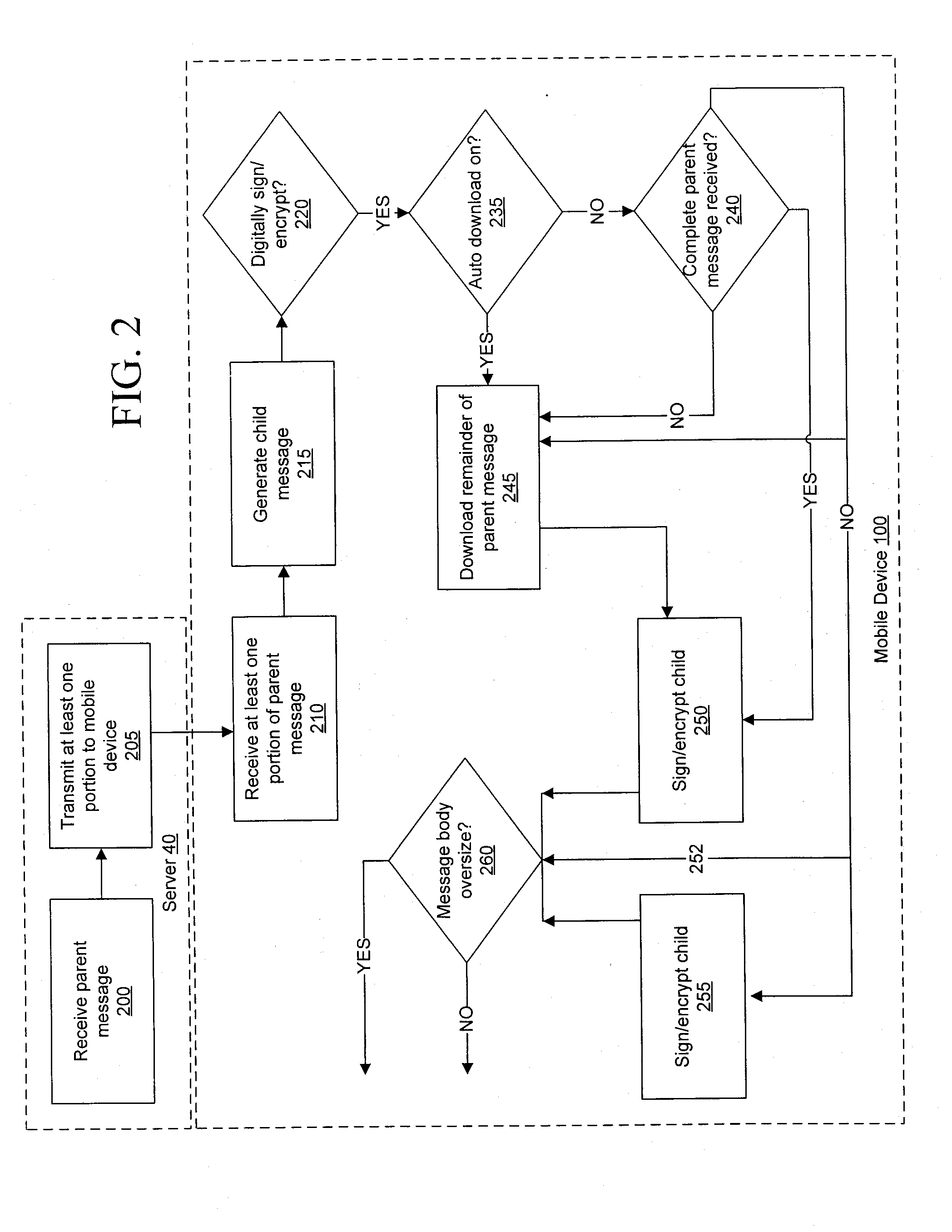
Secure message handling on a mobile device
ActiveUS20090034729A1Public key for secure communicationUser identity/authority verificationComputer hardwareMessage handling
Systems, methods, and software for providing digital security to a child message transmitted from a mobile device to a messaging server, where the mobile device typically does not transmit the parent message with the child message to the messaging server. Whether to apply digital security, such as encryption or a digital signature, or both, is determined, and if the mobile device does not include a complete copy of a parent message for insertion into the child message, the mobile device selectively downloads the parent message from the messaging server prior to the computation of a digital signature or prior to encryption. The systems and methods may also provide a check of the child message size, when the child message includes inserted parent content, to ensure that the child message does not exceed any prescribed limits on message size.
Owner:MALIKIE INNOVATIONS LTD
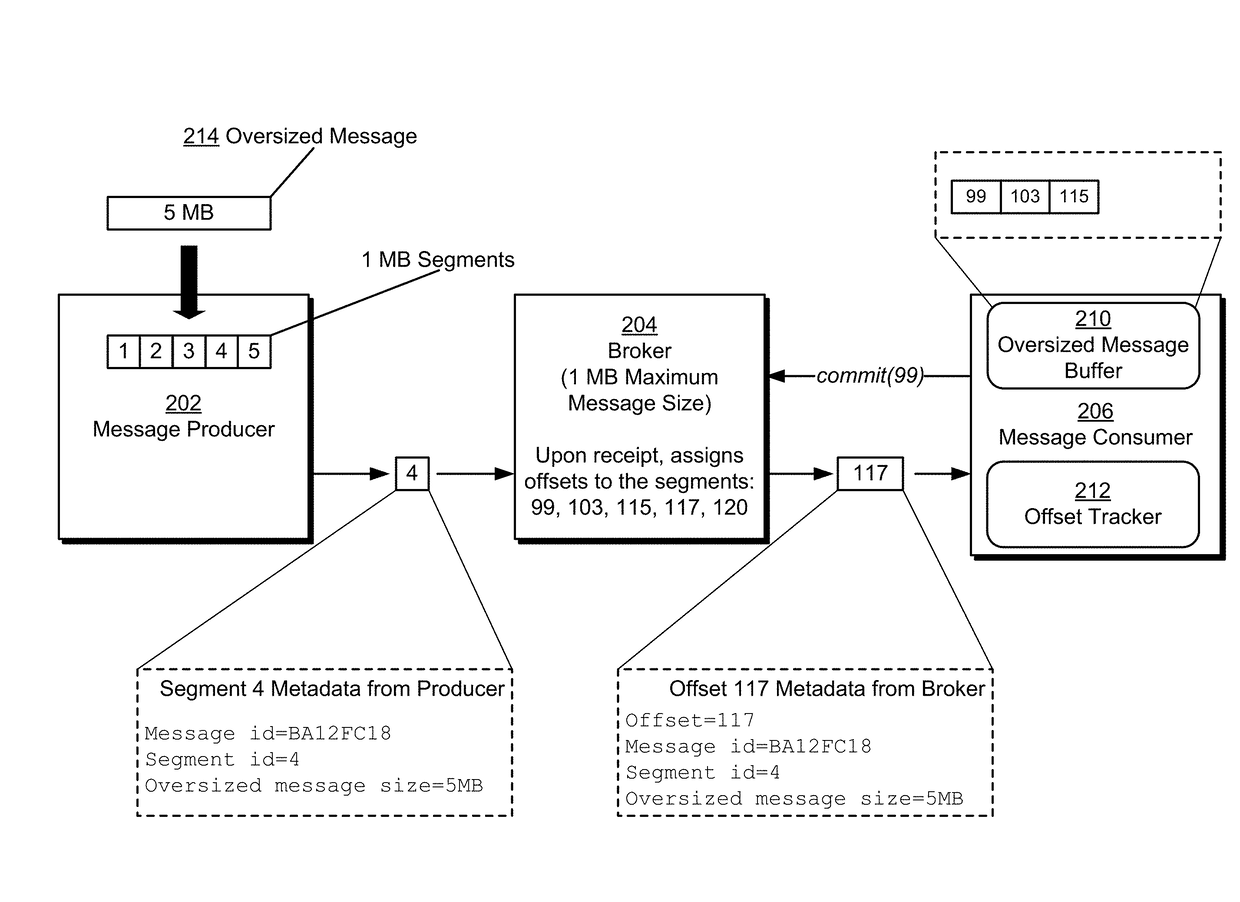
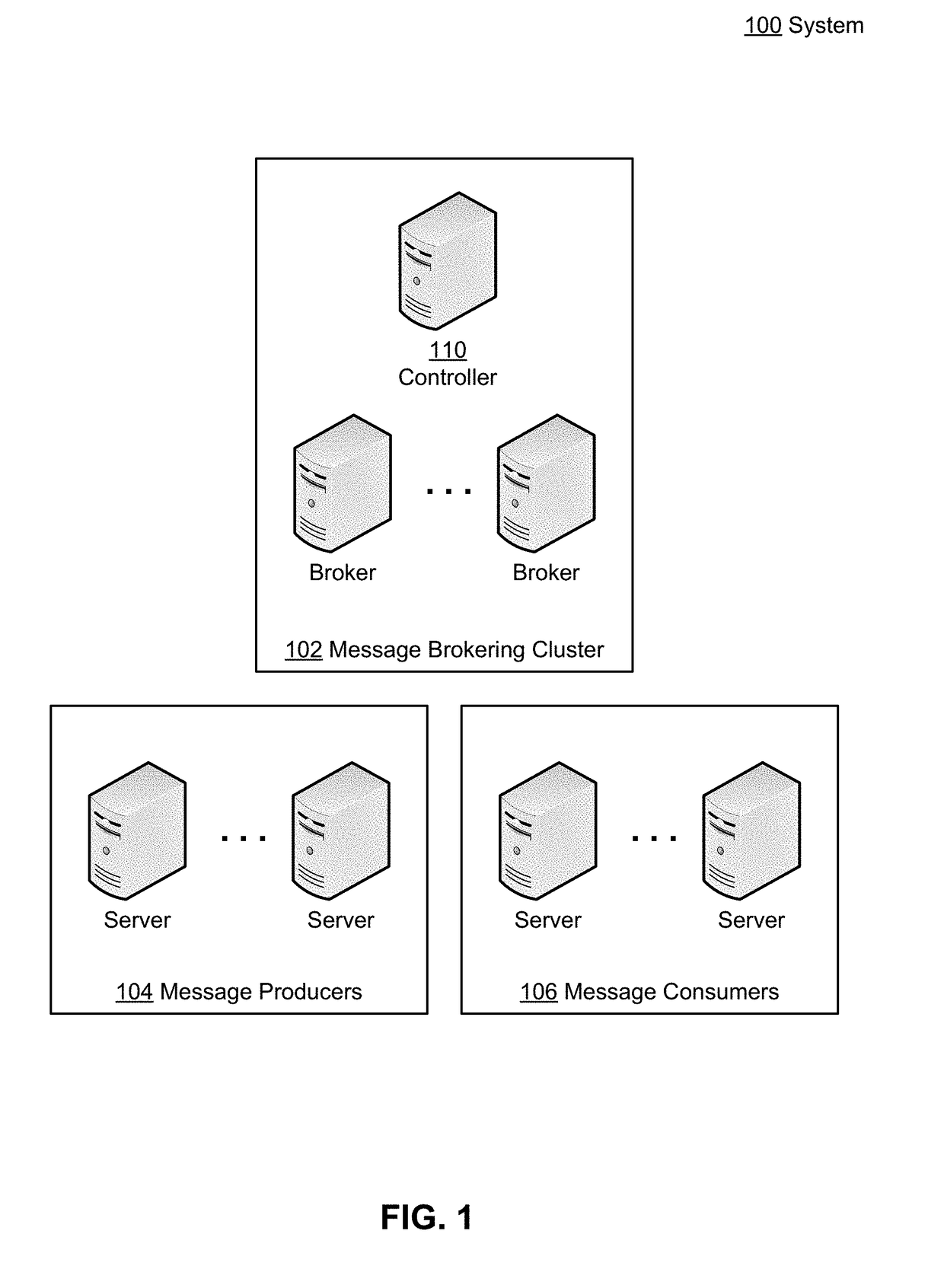
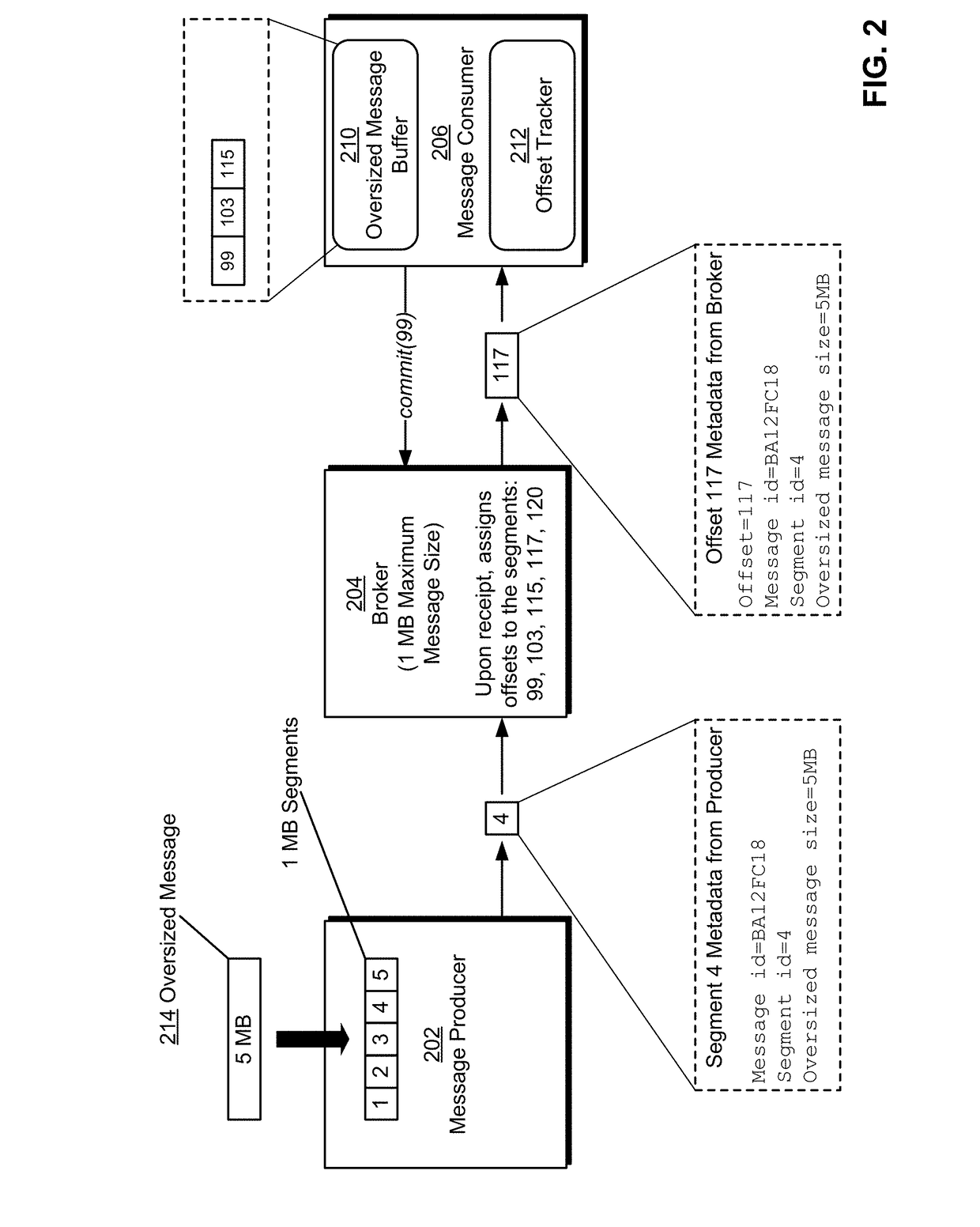
Large message support for a publish-subscribe messaging system
A system, apparatus, and methods are provided that support the passing of oversized messages within a publish-subscribe messaging system. During operation, the system subscribes to a message stream brokered by a message brokering cluster that imposes a maximum message size. Responsive to receiving a given message of the message stream, the system (1) determines an offset to commit to the message brokering cluster, wherein the determined offset is based on whether one or more segments of one or more oversized messages are buffered, and (2) commits the determined offset to the message brokering cluster. Responsive to recovering from a crash, wherein the offset at which to resume the receipt of messages from the message stream is unknown, the system then retrieves the determined offset from the message brokering cluster and resumes the receipt of messages from the message brokering cluster based on the determined offset.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for allocating radio resource using random access procedure in a mobile communication system
ActiveUS8451781B2Effective distributionAssess restrictionNetwork topologiesTelecommunicationsRadio channel
A method for transmitting a random access preamble using a random access procedure in a mobile communication system. The random access preamble transmission method includes selecting, upon triggering of the random access procedure, one of random access preamble sets predefined between a User Equipment (UE) and an Evolved Node B (ENB) according to whether a radio channel condition is greater than a radio channel condition threshold and a size of a message that the UE will transmit after transmission of the random access preamble is greater than a minimum message size, randomly selecting a random access preamble from the selected random access preamble set, and transmitting the selected random access preamble to the ENB over a random access channel.
Owner:SAMSUNG ELECTRONICS CO LTD
Wireless communication terminal apparatus, wireless communication base station apparatus, wireless communication system and telephone call connecting method
InactiveUS20090275319A1Reduce message sizeAssess restrictionConnection managementCommunications systemTerminal equipment
A wireless communication terminal apparatus, a wireless communication base station apparatus, a wireless communication system and a telephone call connecting method wherein the message size in a telephone call connection can be reduced. A broadcast information producing part (203) assigns cell level information, which is preconfiguration information managed by the cell level, and PLMN level information, which is preconfiguration information managed by the PLMN level, to different transmission units to produce broadcast information, which is then broadcasted from a broadcast information transmitting part (204) to UEs. A preconfiguration usage deciding part (208) determines whether a UE, which sets a channel, can use a preconfiguration. If the UE can use a preconfiguration, a control information producing part (209) causes control information to include the corresponding index, and then the control information is transmitted from a control information transmitting part (210) to the UE.
Owner:PANASONIC CORP
Encryption and signature schemes using message mappings to reduce the message size
ActiveUS20060159259A1Computationally efficientBandwidth-reduced ring signaturePublic key for secure communicationUser identity/authority verificationComputer hardwareRing signature
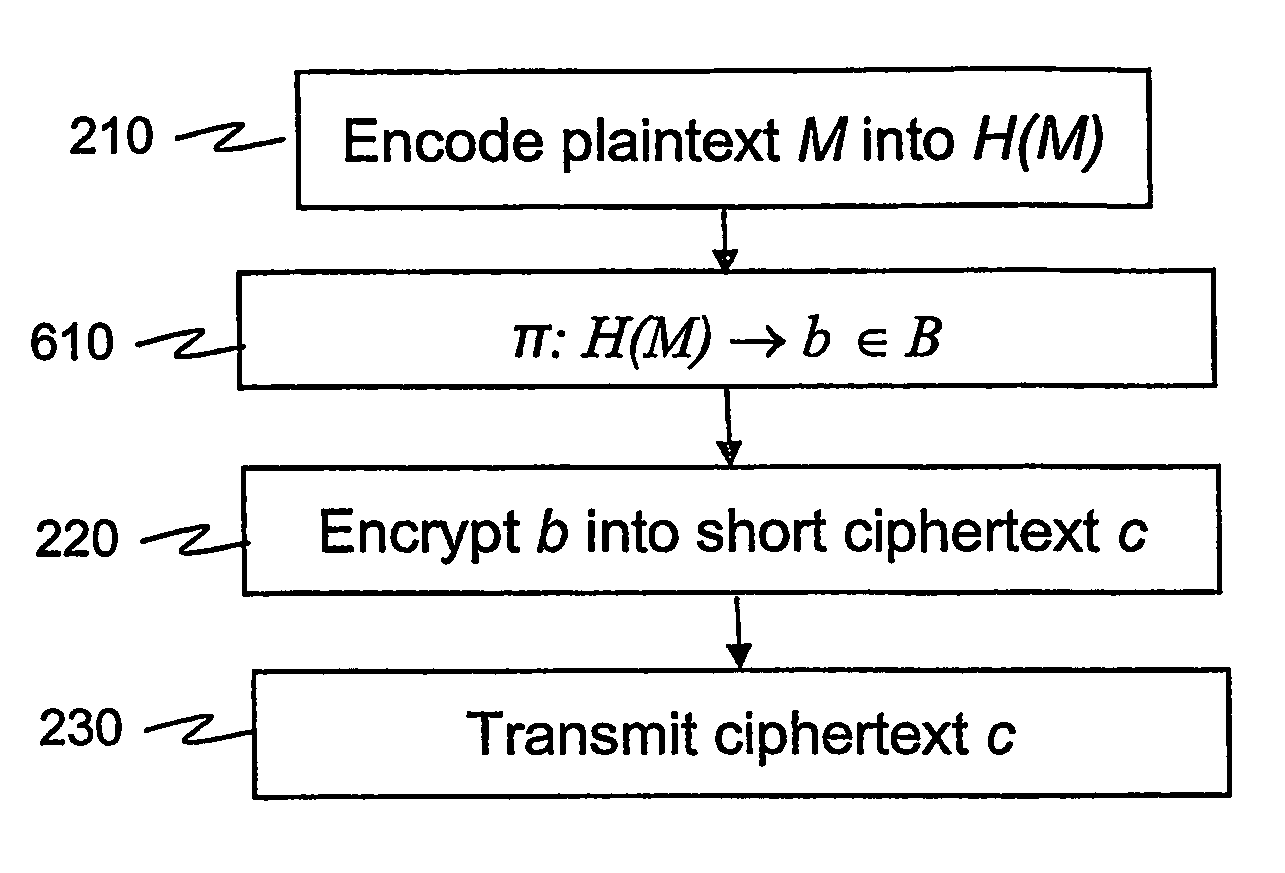
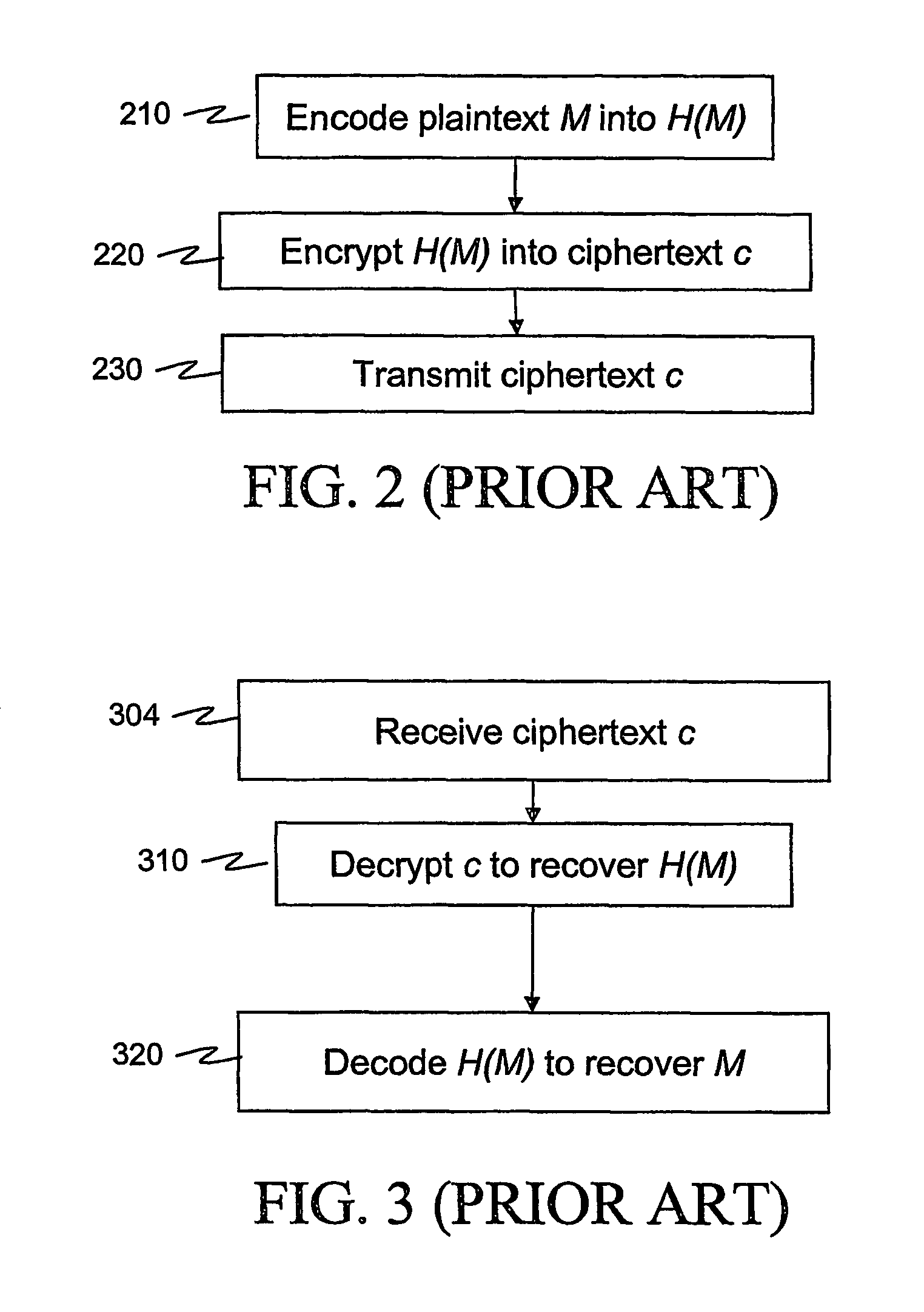
According to some embodiments of the invention, a message is processed before encryption so that the encryption method generates a short ciphertext. The message processing can be viewed as a mapping (610) that maps the message into another message that generates the short ciphertext. The mapping is reversible at least if the (possibly encoded) message (H(M)) is in a restricted set, e.g. a set [0,h?] of short messages. In some embodiments of the present invention, short signatures are provided by mapping the signature into a short signature. The mapping (810) is reversible at least if the original message (H(M)) used to generate the signature is short. Signcryption, aggregate signature, and ring signature outputs are also shortened.
Owner:NTT DOCOMO INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com