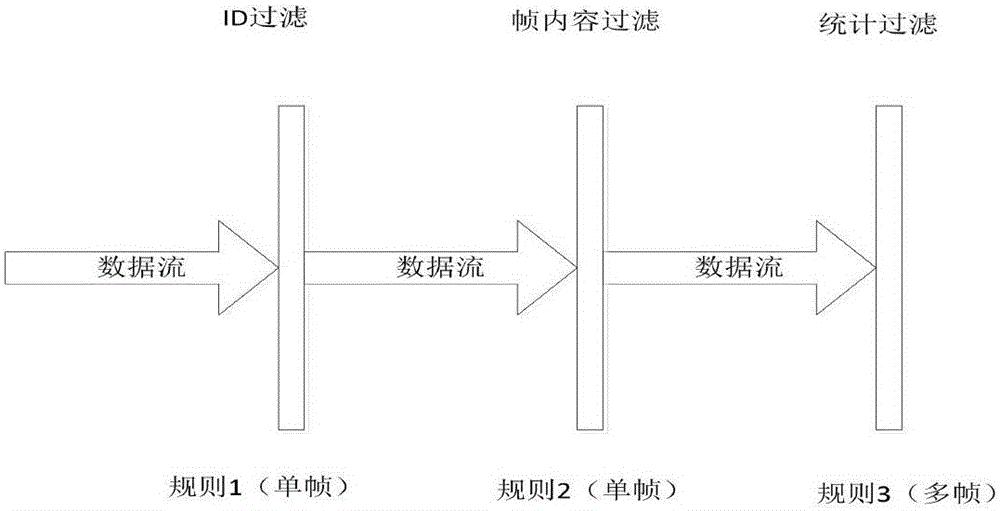
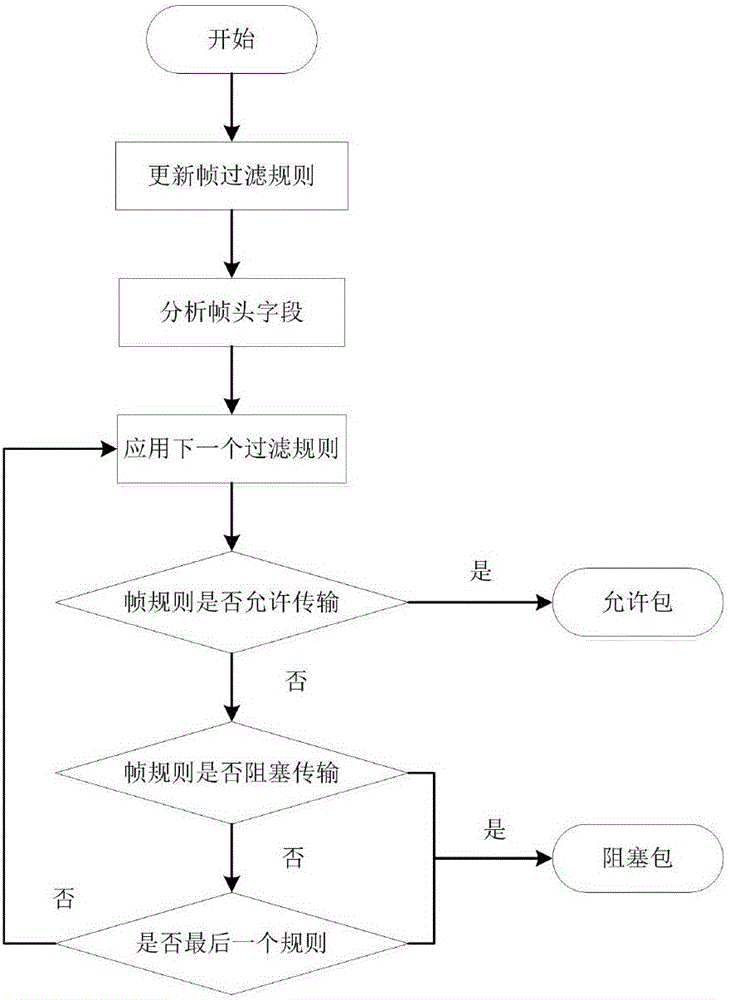
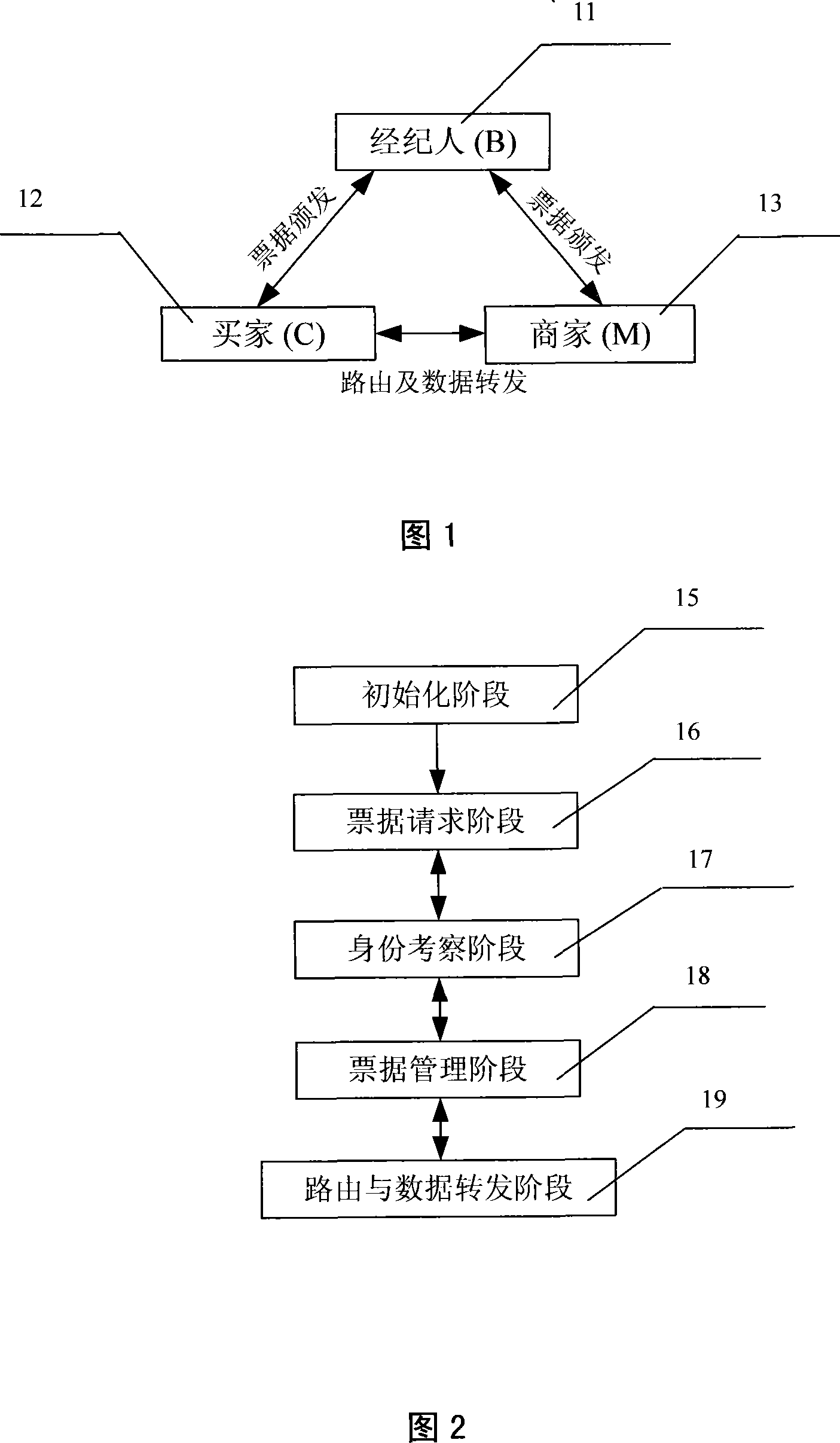
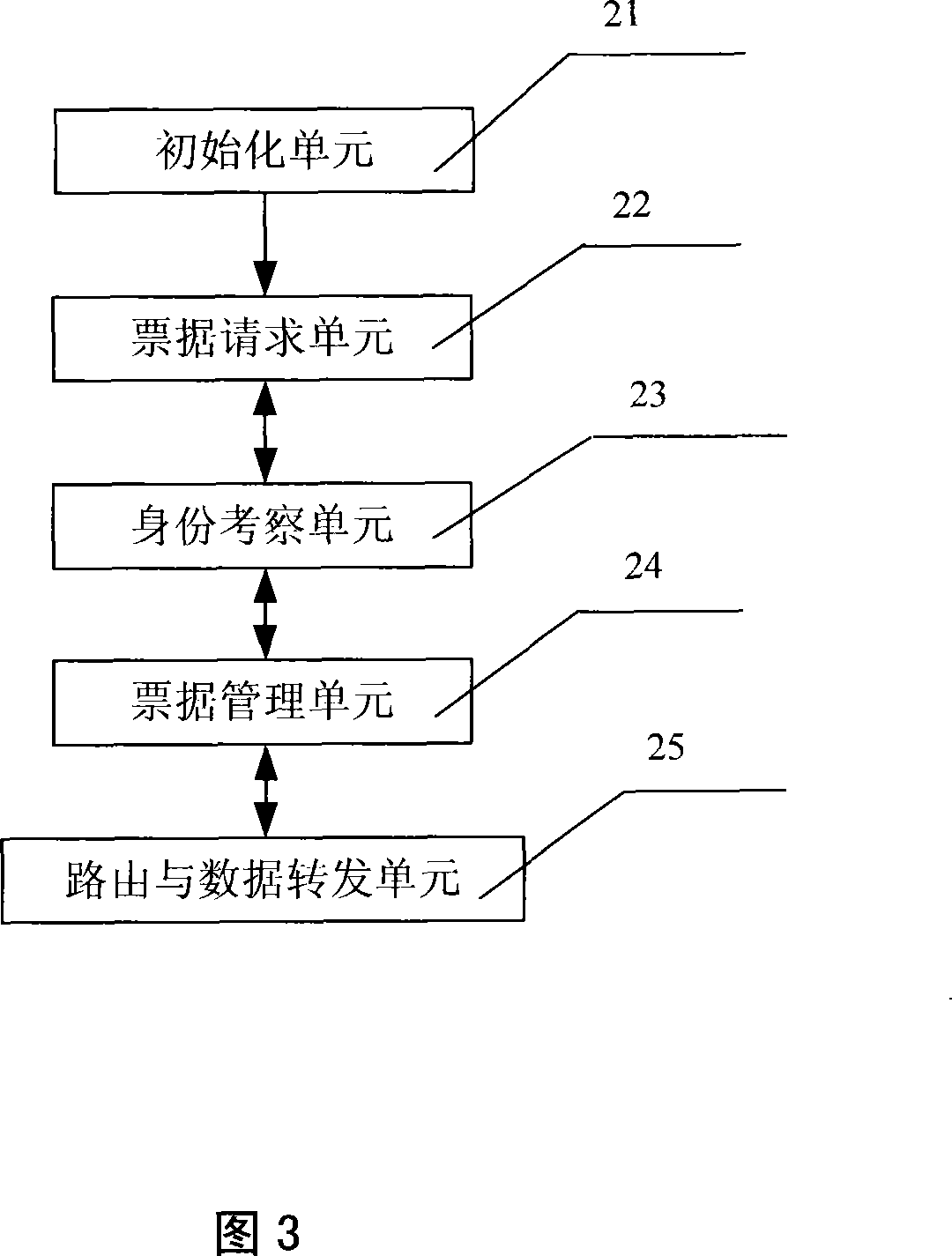
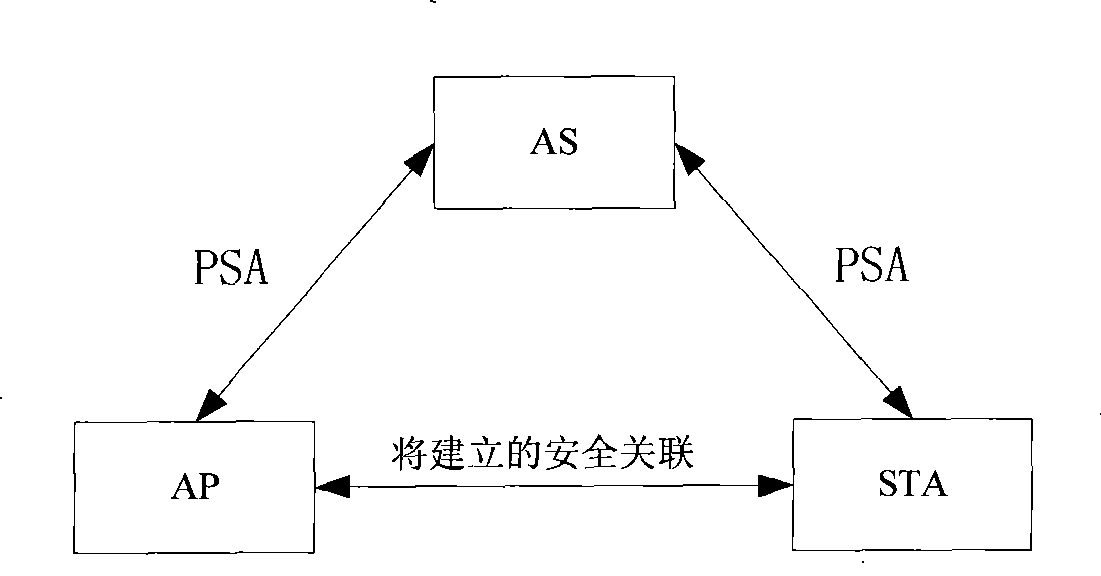
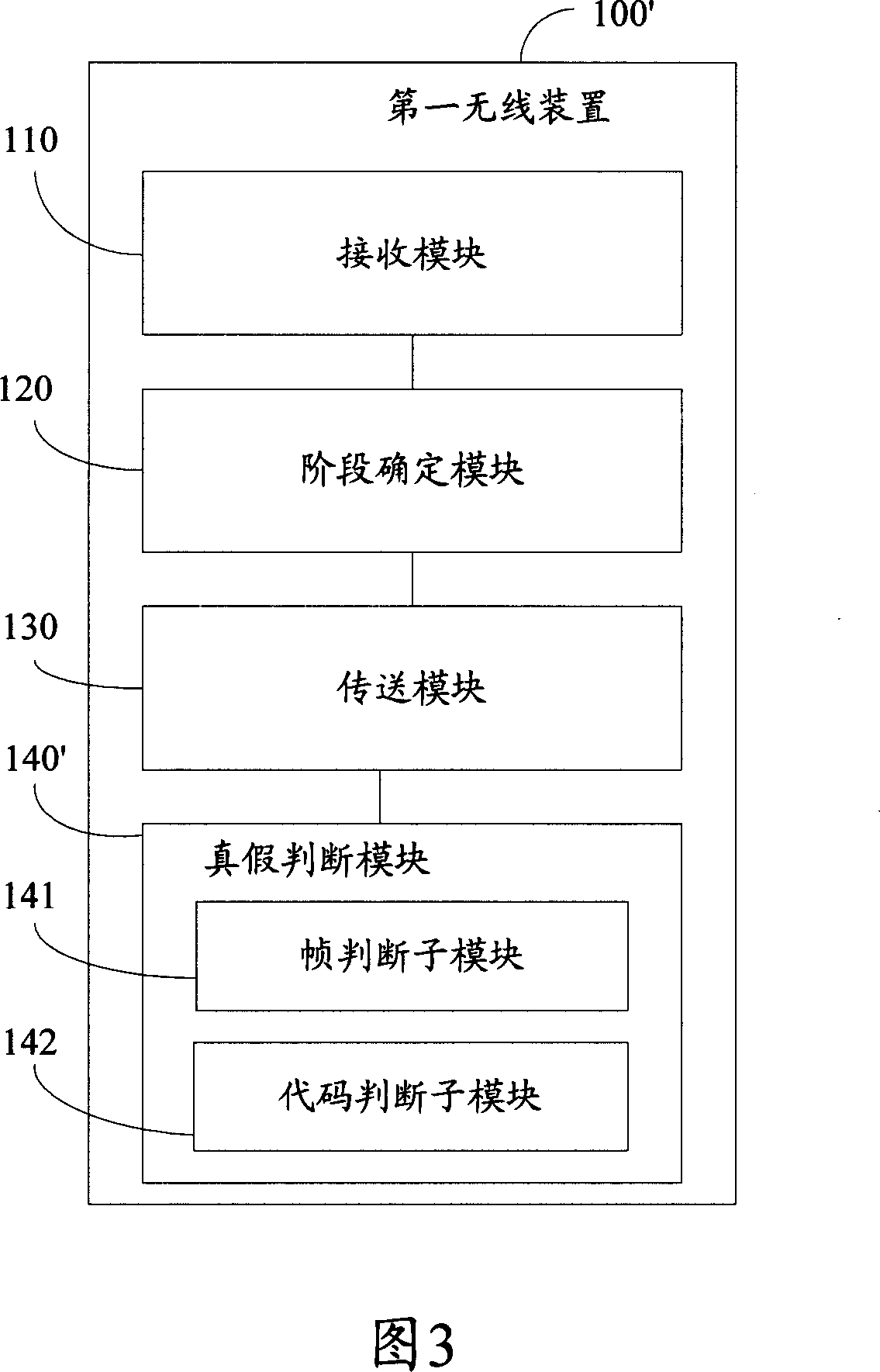
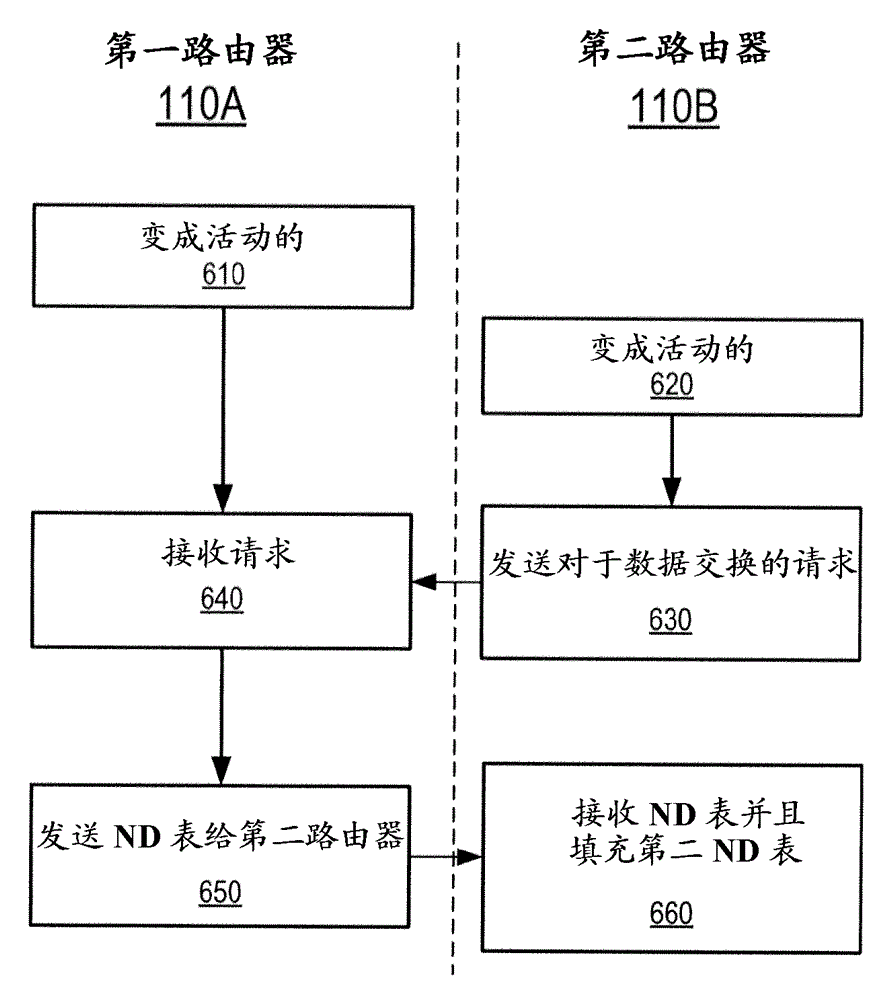
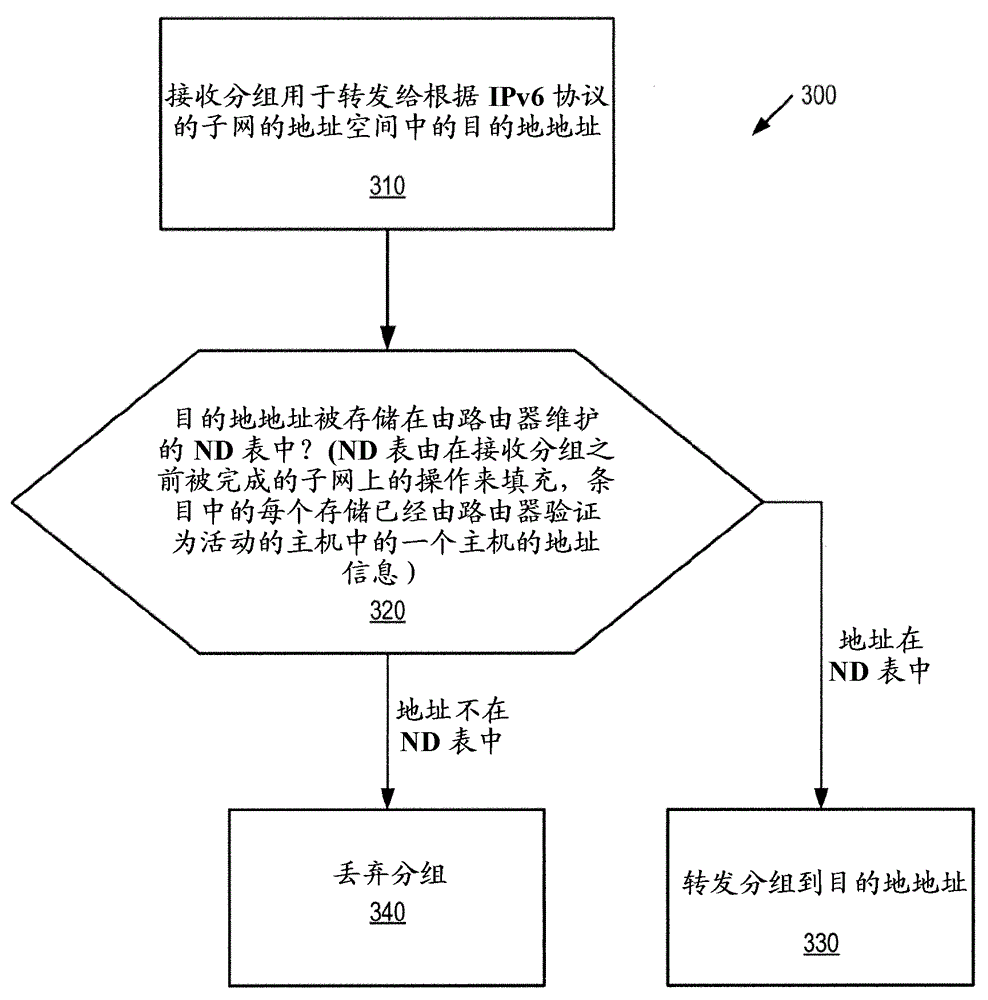
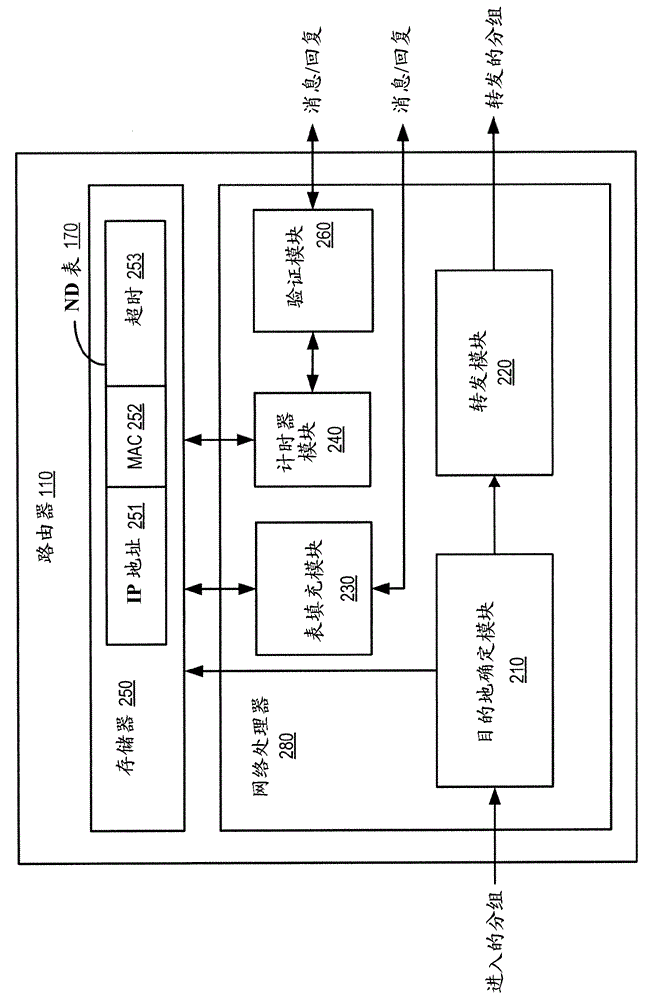
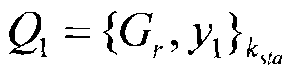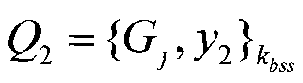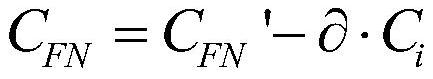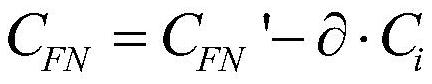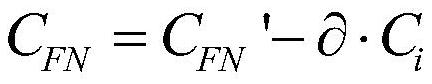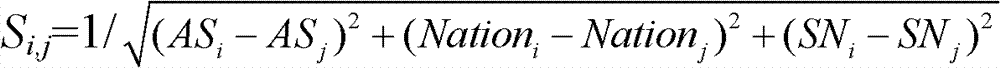Patents
Literature
37results about How to "Avoid Denial of Service Attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method and system for monitoring DDOS (distributed denial of service) attacks in small flow
ActiveCN102821081AMake up for the inability to detect low-rate DDoS attacksHigh false positive rateData switching networksSimilarity analysisProtocol Application
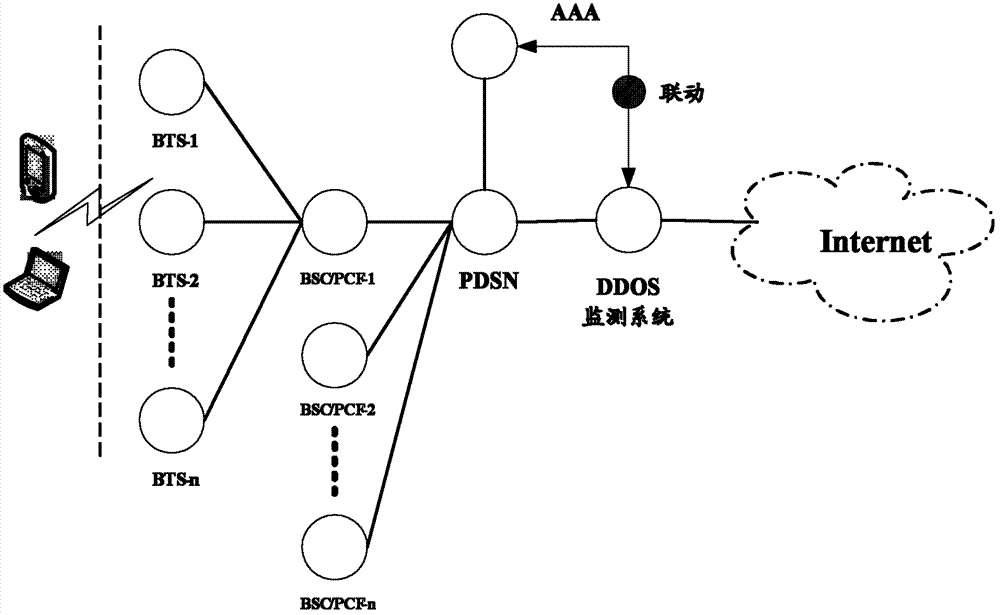
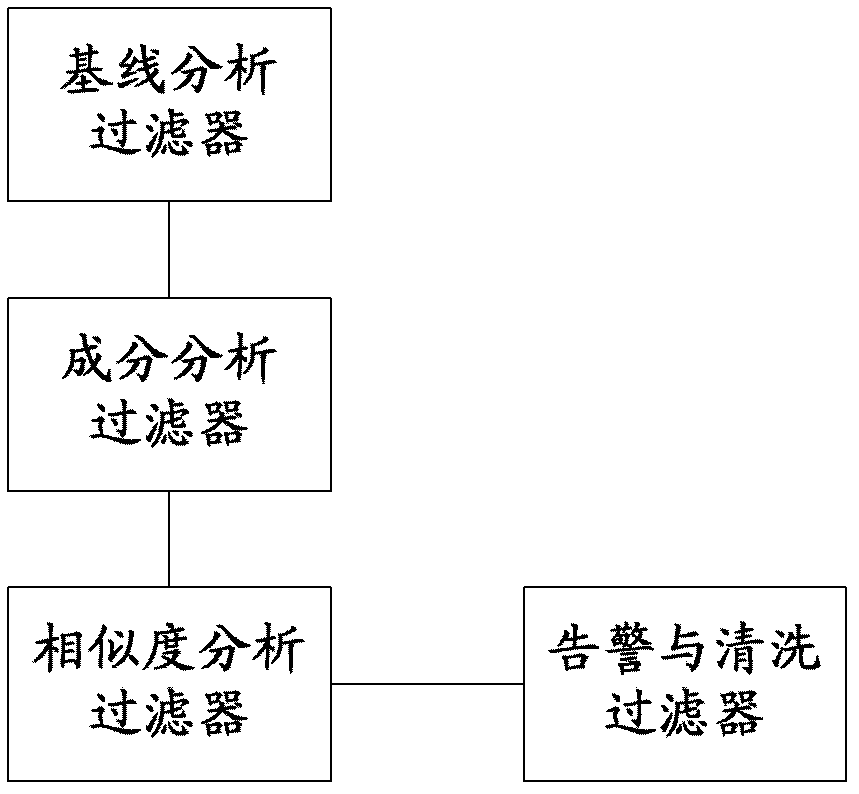
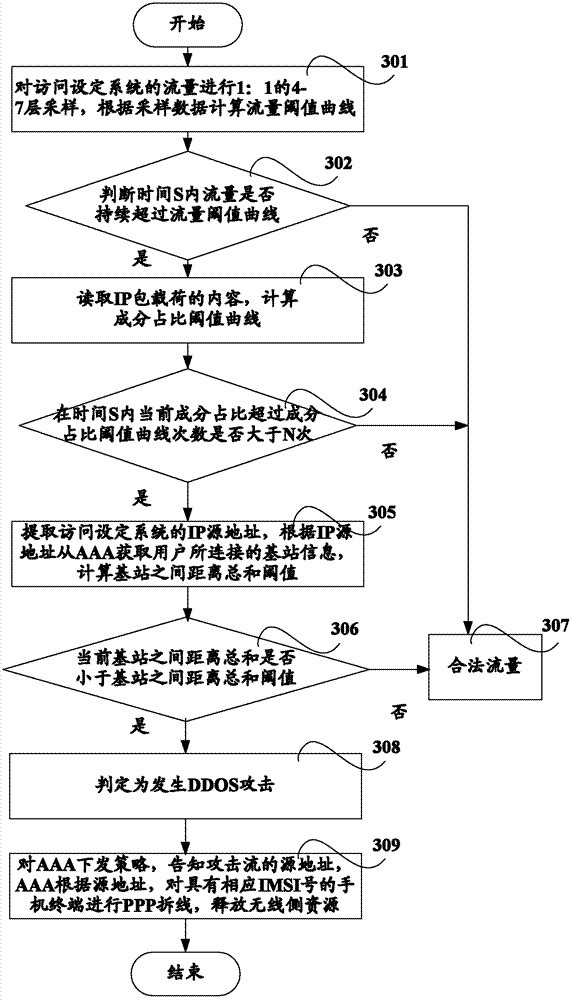
The invention discloses a method and a system for monitoring DDOS (distributed denial of service) attacks in small flow, solves the problems that the existing DDOS attack detection technology is high in cost, complex to implement and high in misjudgment rate, cannot respond to DDOS attacks aiming at an application layer and the like, and provides the monitoring scheme of an integrated DPI (dots per inch) technology. A baseline analysis, component analysis and similarity analysis method is used to establish a normal use model, characteristics are accurately matched to detect the attacks in small flow and the application layer attacks, deployment at one point of an operator network and complete coverage of the operator network are achieved, and detection accuracy is increased.
Owner:CHINA TELECOM CORP LTD
Firewall of vehicle-mounted information system of automobile
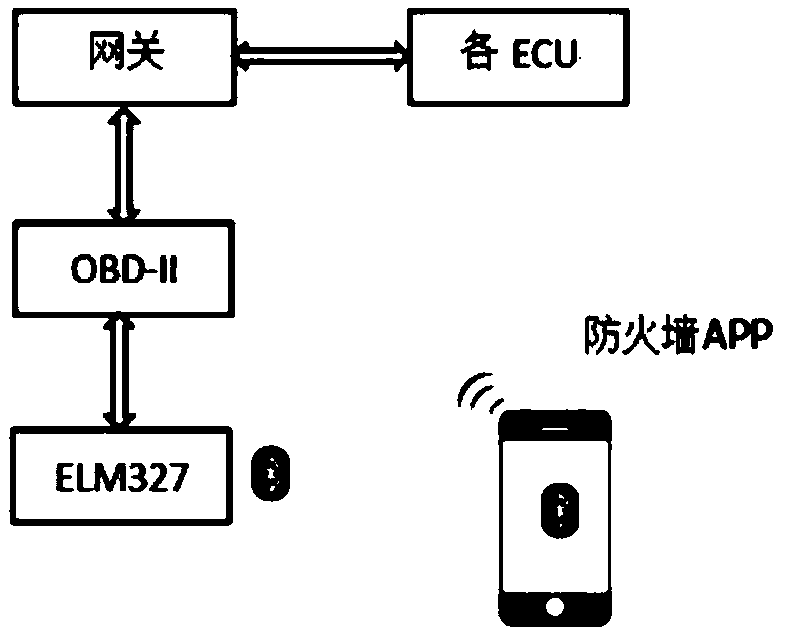
ActiveCN105871830ABlock network communicationPrevent Hong Fan AttackTransmissionIn vehicleSecurity rule
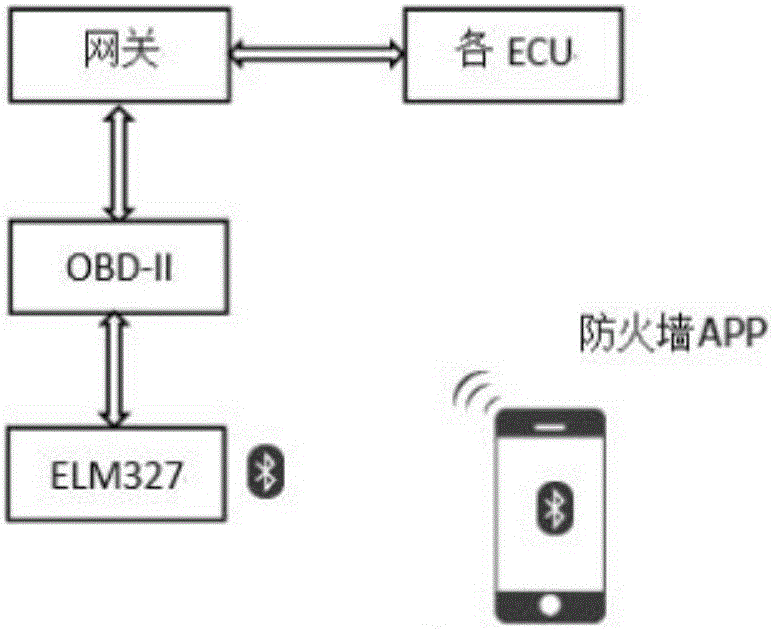
The invention discloses a firewall of a vehicle-mounted information system of an automobile. According to the firewall, a hardware platform is composed of a smart phone or a smart terminal connected with an external network. The firewall is an APP installed in the smart phone or the smart terminal. The firewall is the unique entry / exit for connecting the vehicle-mounted information system and the external network. Data enters a gateway in the automobile after passing through an ELM327 connected with the smart phone or terminal and then passing through an OBD-II connected with the ELC327. The data is forwarded to different intra-automobile buses by the gateway according to the features of the data. Finally the data enters corresponding ECUs for execution. The illegal data is filtered by security rules of the firewall and then is discarded. The firewall of the vehicle-mounted information system of the automobile comprises the ELM327, the OBD-II, the gateway, the ECUs and the firewall APP. According to the system, a flooding attack can be prevented and a service attack can be rejected through statistical rules; and a replay attack can be prevented through address filtration.
Owner:CHENGDU UNIV OF INFORMATION TECH
A method and device for enhancing Ad hoc network security and cooperation mechanism
InactiveCN101170410AReduce complexitySolve the node identity problemUser identity/authority verificationData switching networksNetwork security policyDistributed computing
Owner:HUAZHONG UNIV OF SCI & TECH
Optical network terminal, port speed limiting attribute configuration method and packet process method
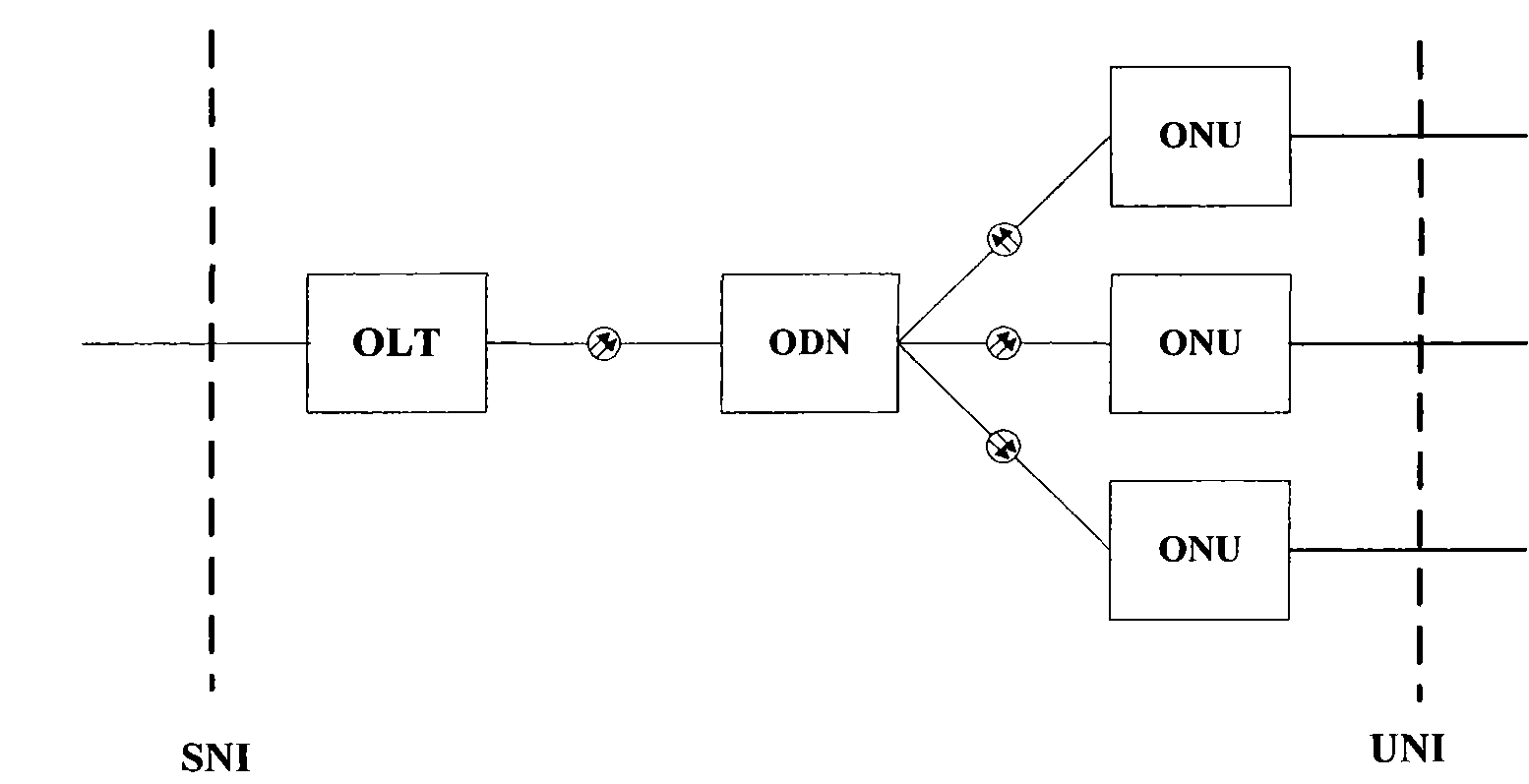
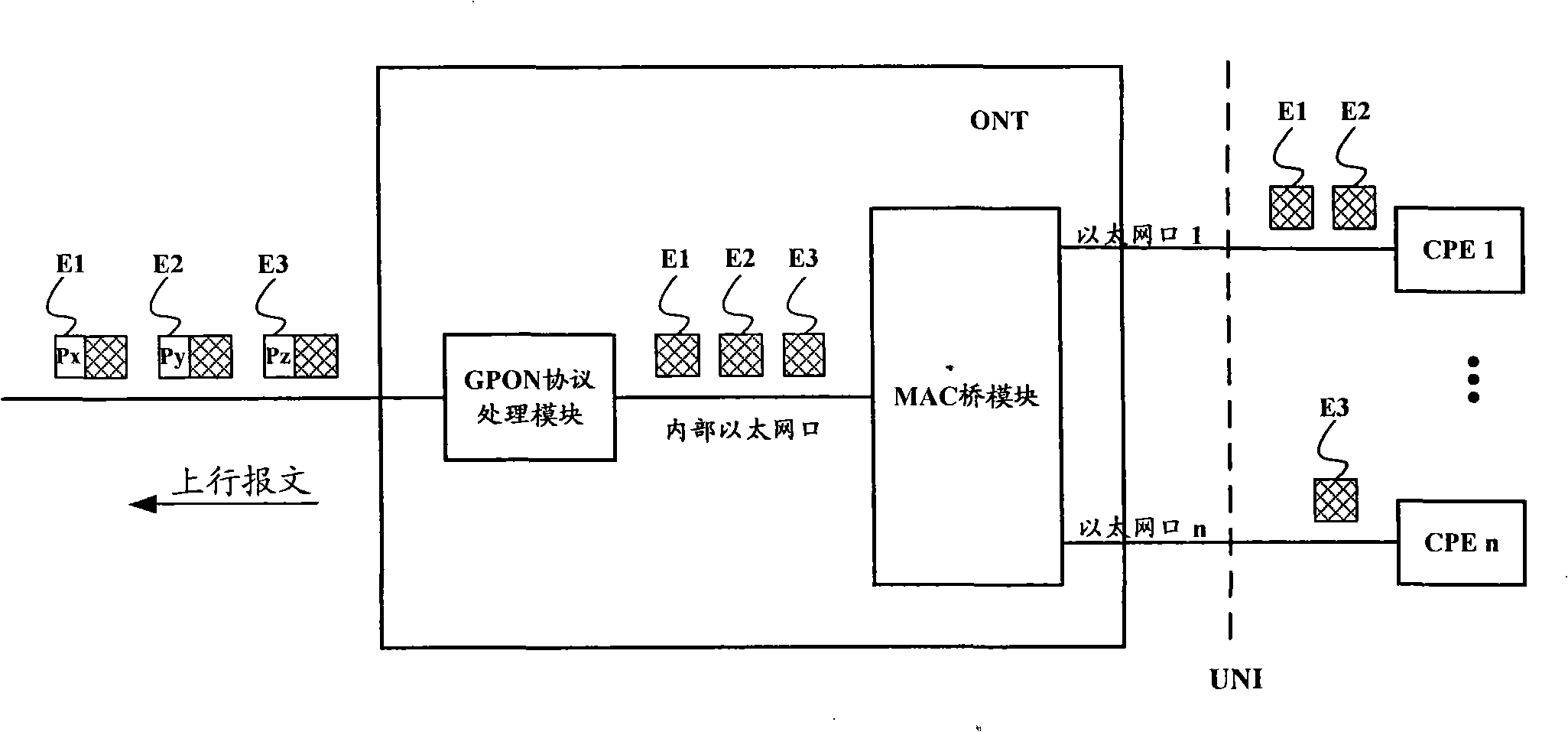
ActiveCN101453672APrevent overflowAvoid Denial of Service AttacksMultiplex system selection arrangementsData switching networksProtocol processingData rate
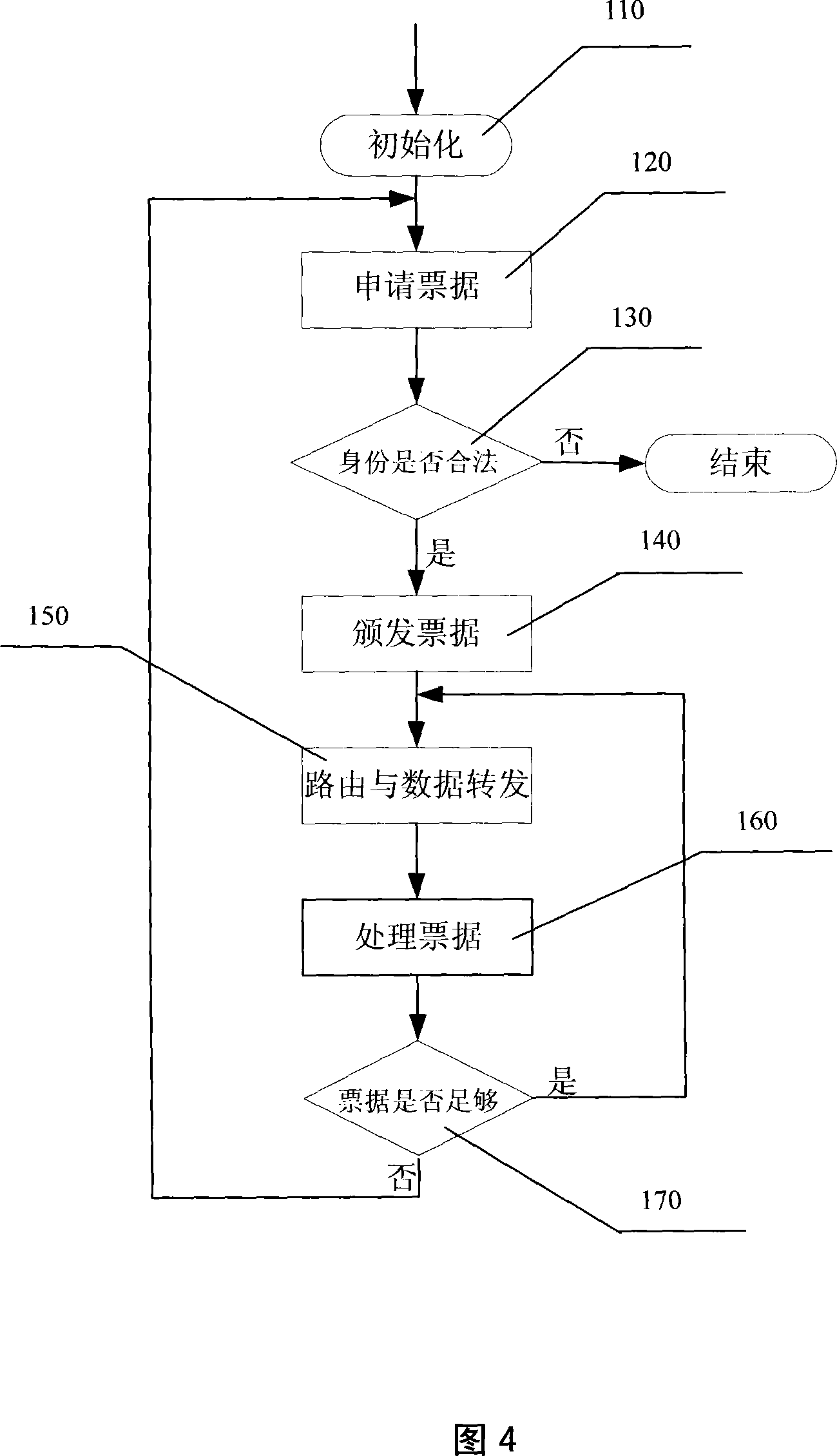
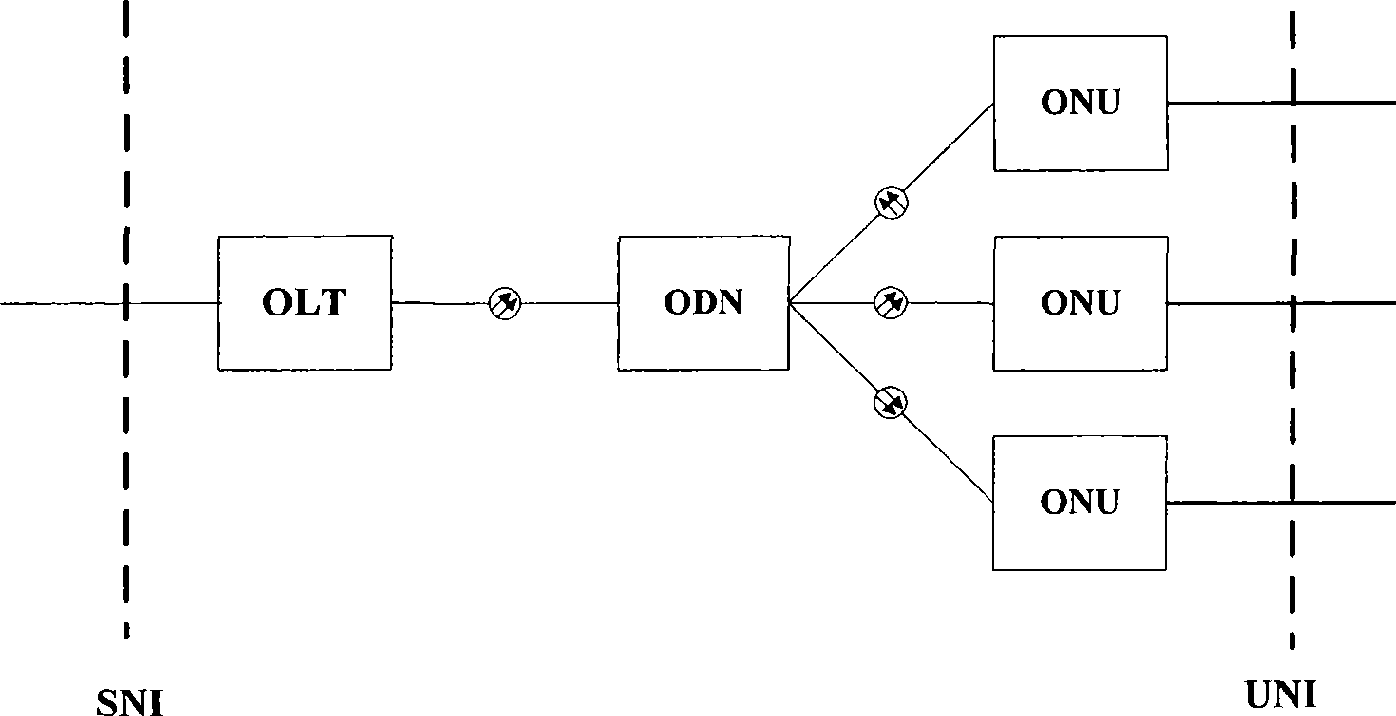
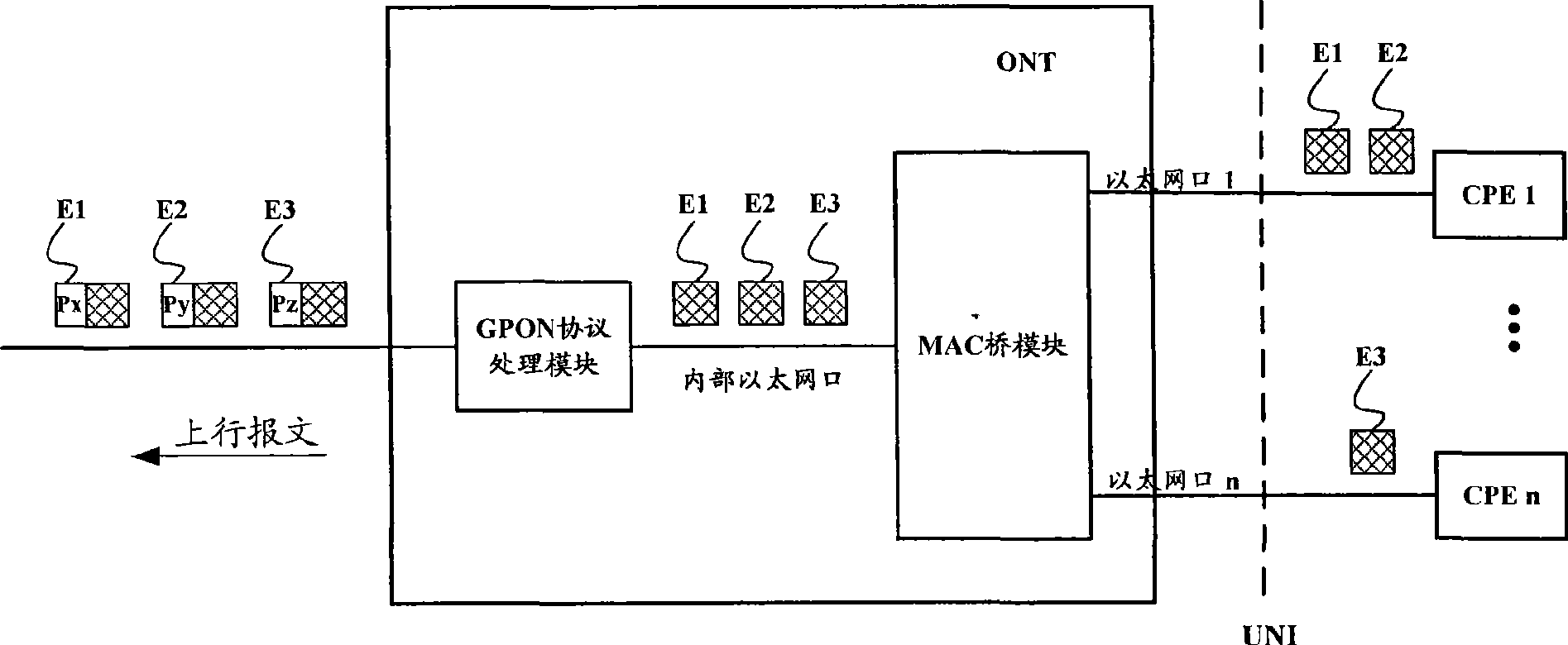
The invention relates to an optical network terminal ONT, a method for configuring port rate limit attribute and a method for processing a message thereof. The optical network terminal comprises a passive optical network (PON) protocol processing module and a user network interface functional module which are connected through an internal interface. The optical network terminal also comprises a port rate limit module connected with the user network interface, wherein the port rate limit attribute is stored in the port rate limit module. The method for configuring the port rate limit attributeof the ONT comprises the following steps: A, a configuring terminal transmits a port rate limit attribute configuring command to the ONT; and B, the ONT stores the port rate limit attribute in a management entity. The method for processing the message of the ONT comprises the following steps: determining whether data velocity transmitted by the user network interface exceeds a set value in the port rate limit attribute of the user network interface or not, if so, a step of flow control is carried out on the user network interface. The invention ensures that the ONT can realize the function ofport rate limit, can prevent overflowing of a receiving buffer inside the ONT, and prevent an illegal user from initiating denial of service attack.
Owner:HUAWEI TECH CO LTD
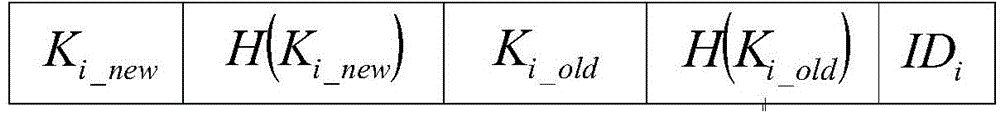
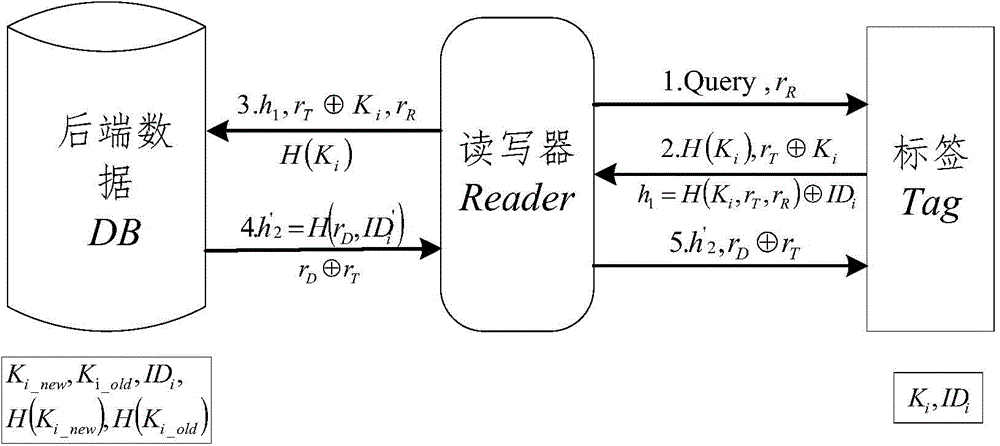
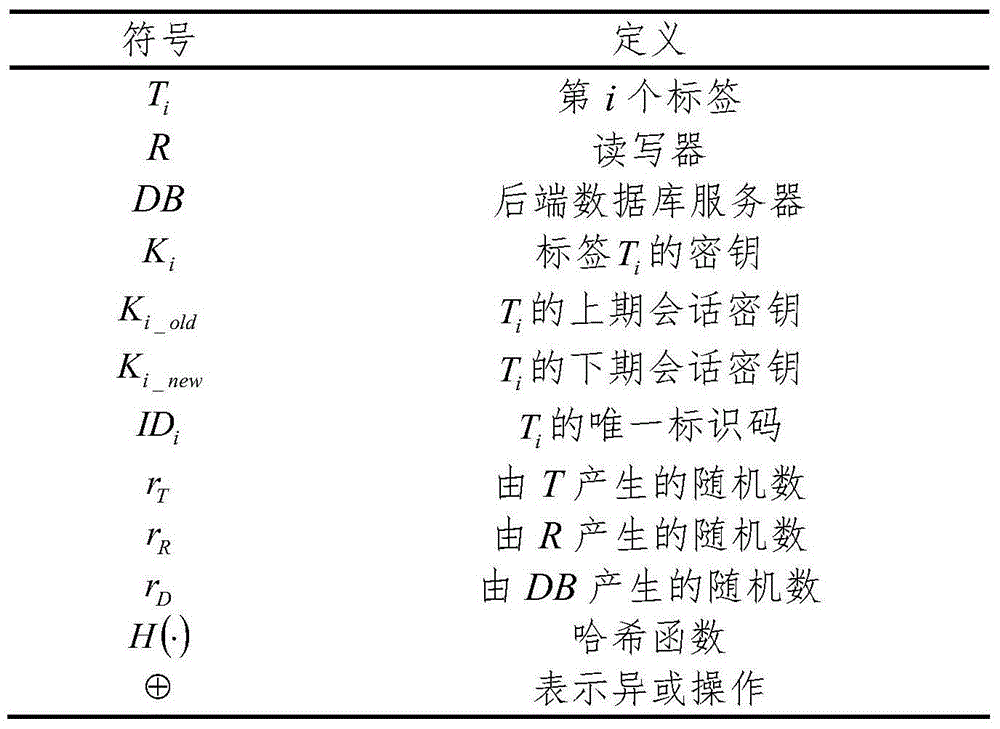
RFID two-way authentication method based on Hash function and capable of updating keys synchronously
ActiveCN104579688AGuarantee forward securityAvoid trackingUser identity/authority verificationCo-operative working arrangementsHash functionElectronic tagging
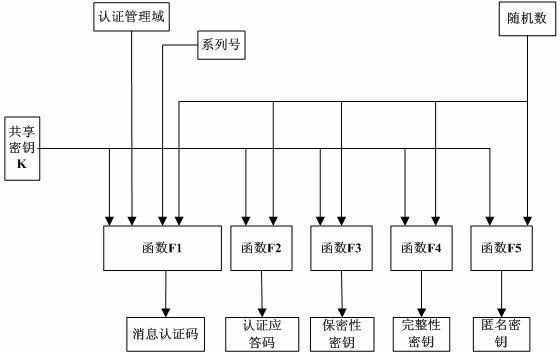
Provided is an RFID two-way authentication method based on a Hash function and capable of updating keys synchronously. A label key dynamic updating mechanism is introduced in the method, a self-synchronizing solution scheme is designed, and secondary authentication on an RFID label is achieved. Safety analysis and performance comparison are performed on an existing protocol, the analysis result shows that on the premise that label cost is not increased, the computing amount of the label and a rear-end database is reduced through new two-way authentication, the retrieval efficiency of the rear-end database is improved, the privacy protection and safety problem of an RFID system is effectively solved, meanwhile, the executing efficiency of RFID protocol identification is improved, and the method is more suitable for a low-cost RFID system and a large-scale electronic label system and has certain application value.
Owner:JIANGXI UNIV OF SCI & TECH
Method for realizing safety model of access authentication in mobile internet
InactiveCN102256252APrevent Malicious RegistrationReduce Authentication LatencyWireless network protocolsSecurity arrangementService flowEngineering
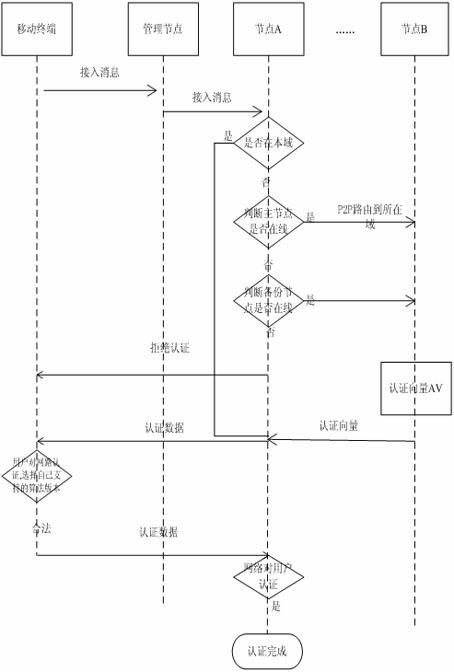
The invention relates to a method for realizing a safety model of access authentication in the mobile internet. In the method provided by the invention, an authentication server with a P2P (Peer 2 Peer) framework is arranged in the mobile internet; the access authentication safety of the mobile internet is solved by utilizing an AKA (Also Known As) authentication mechanism; the concrete flow of AKA in the mobile internet is described; the whole authentication course is realized through C knowledge programming by utilizing socket; the core framework of the mobile internet is realized by combining the distributed techniques such as a P2P technique and the like; an operator can establish a carrier-class network capacity platform capable of being expanded and providing multimedia applications and content applications; the framework based on the P2P technique can still provide the service for users under the condition of actual effects of a single node; the mobile internet can collect network bandwidth resources for the service through the P2P technique, thereby improving the throughput capacity of the service flow; and the P2P technique is the development direction of the mobile internet, thus the realization of the research for the AKA authentication mechanism based on the P2P framework extremely has reality significances.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method and apparatus for preventing disarmed service attack in network address converting
InactiveCN1949762AAvoid Denial of Service AttacksAvoid business interruptionData switching networksNetwork addressingNetwork address translation
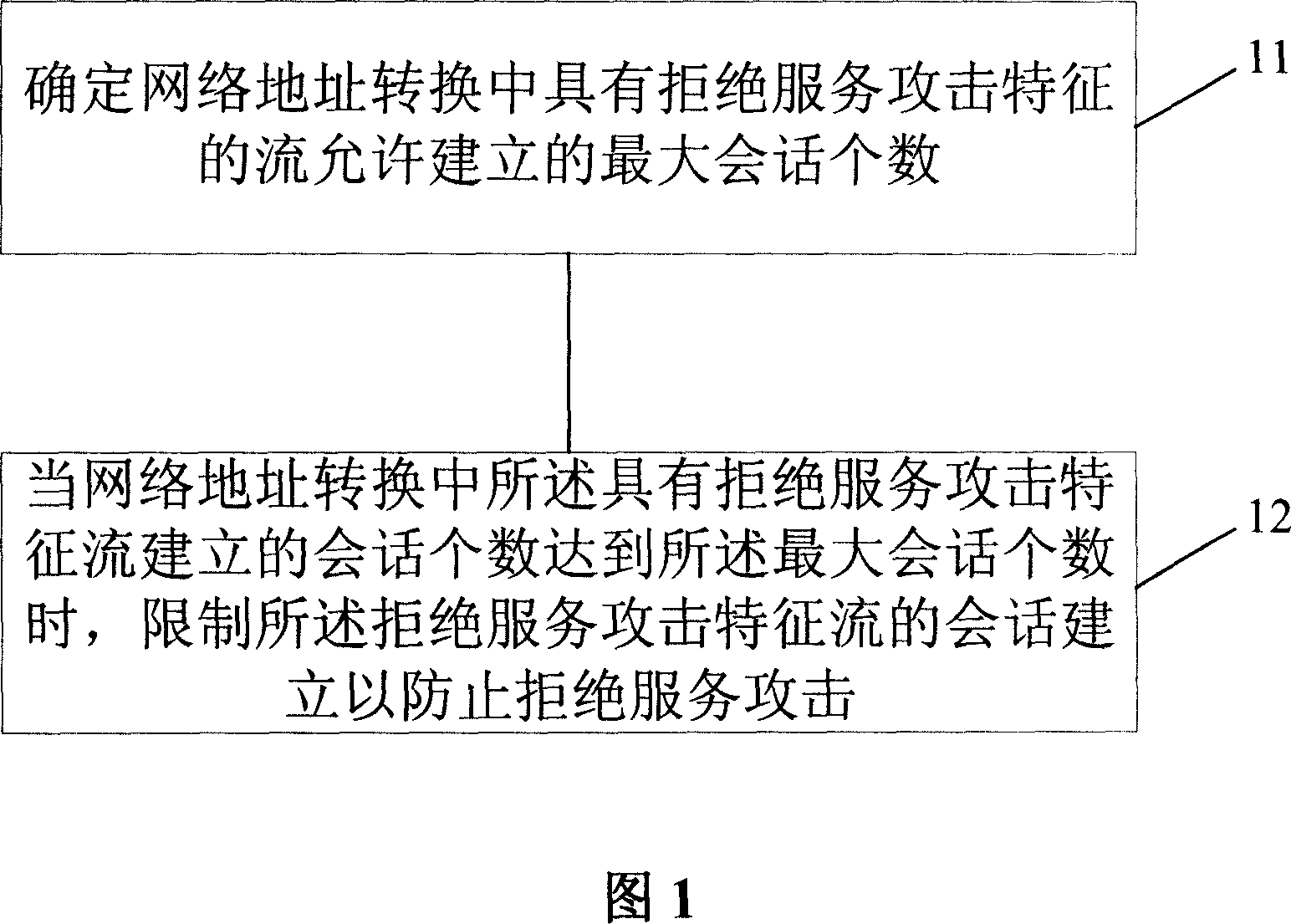
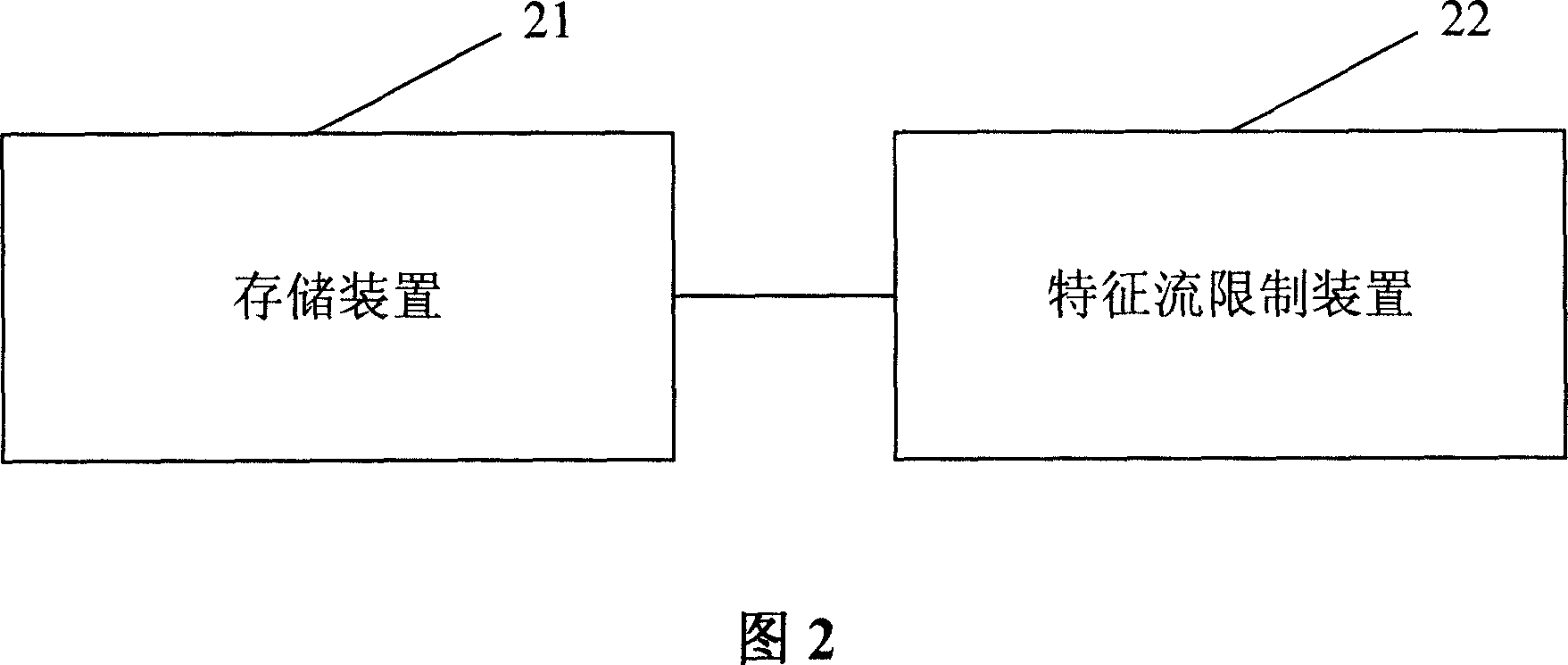
The invention discloses a method for preventing denial of service attack in network address conversion, comprising: determining the maximum number of sessions that the stream with the characteristic of denial of service attack is allowed to build in the network address conversion; when the number of sessions that the stream builds is up to the maximum session number in the netwrok address conversion, limiting the session building of the stream to prevent denial of service attack. In addition, the invention discloses a corresponding device. And the invention can assure normal user service.
Owner:HUAWEI TECH CO LTD
Wireless local area network switching authentication method based on elliptical curve
InactiveCN101489226ASimplify the distribution processReduce trust management overheadUser identity/authority verificationSecurity arrangementAuthentication serverMobile station
The present invention discloses a wireless local area network switching authentication method based on elliptic curve, and belongs to the filed of network switching authentication. The method comprises the following steps: initializing an authentication server, which includes establishing two prime number sets and one elliptic curve; initializing the access point and mobile station, which comprises calculating authentication server, establishing the common and private key pair by the base point of common and private key pair of broadcast access point and mobile station to the base point, the access point and mobile station according to the secret information transmitted by authentication server; and switching authentication, which comprises executing mutual authentication with target access point and common key of mobile station and establishing sharing key with an ECDH algorithm. The method of the invention can effectively defend all known wireless local area network attack comprising denial of service and domino effect attack, and furthermore effectively reducing the computing expenditure and transmission expenditure.
Owner:SOUTHEAST UNIV
Internet of Things security access control method based on blockchain and fog node reputation
ActiveCN113381975AImprove scalabilityImprove securityUser identity/authority verificationInternet privacyDigital signature
The invention discloses an Internet of Things security access control method based on a blockchain and fog node reputation. The method specifically comprises the following steps: carrying out fog node and cloud node registration, cloud service and Internet of Things equipment registration; enabling the Internet of Things equipment to initiate a request signal for accessing the cloud service to the proxy fog node; enabling the fog node to verify the identities of the Internet of Things equipment, the cloud node and the fog node after receiving the request signal of the Internet of Things equipment; detecting whether the reputation value of the fog node is qualified or not and whether the request behavior is legal or not, and if yes, sending a request of the fog node with a digital signature to the cloud node; enabling the cloud node to transmit the cloud service data to the server of the proxy fog node after verification; and enabling the server of the proxy fog node to transmit the data to the Internet of Things equipment. According to the invention, the Ethereum intelligent contract technology realizes decentration and expandable Internet of Things access control in a blockchain network, and the security of access control of Internet of Things equipment is ensured through a reputation mechanism and a behavior detection mechanism.
Owner:厦门吉快科技有限公司
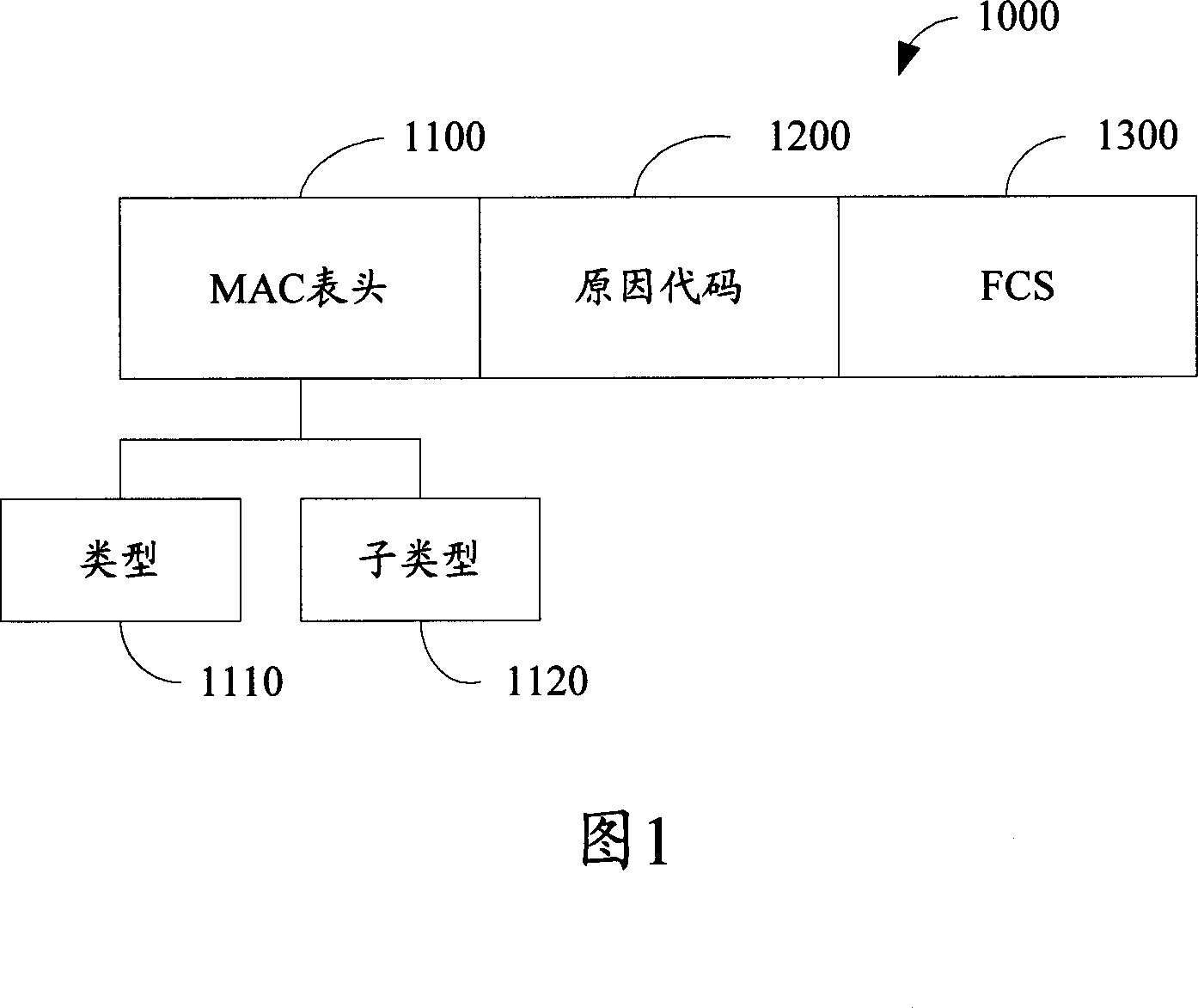
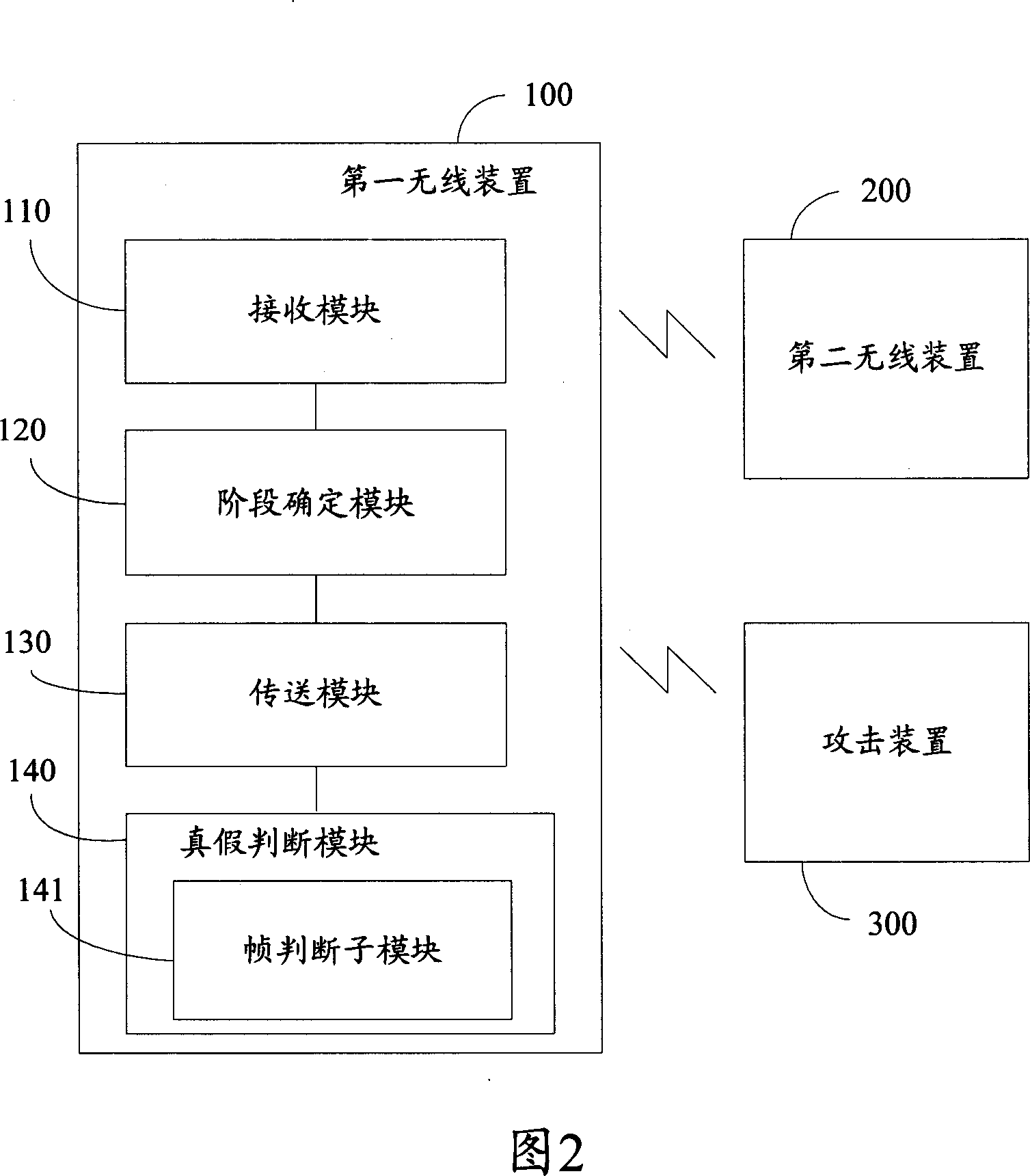
Wireless device and method for discriminating administrative frame
InactiveCN101075899AAvoid Denial of Service AttacksData switching networksReal-time computingDenial-of-service attack
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
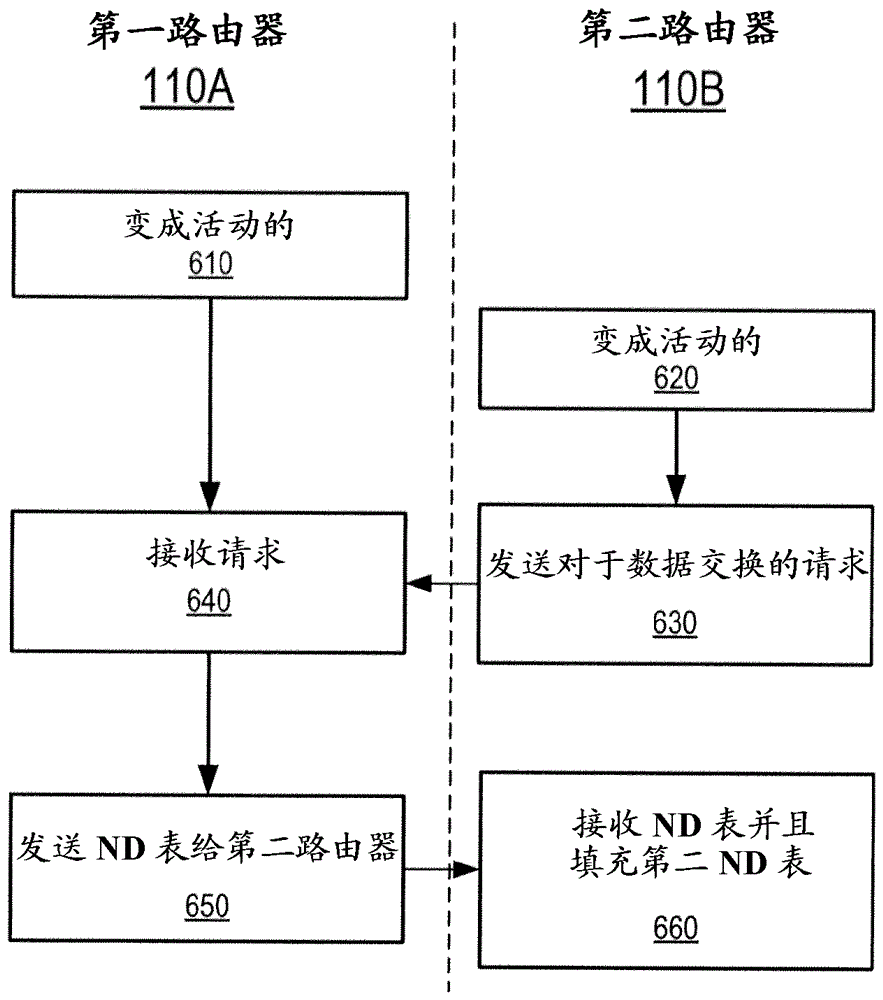
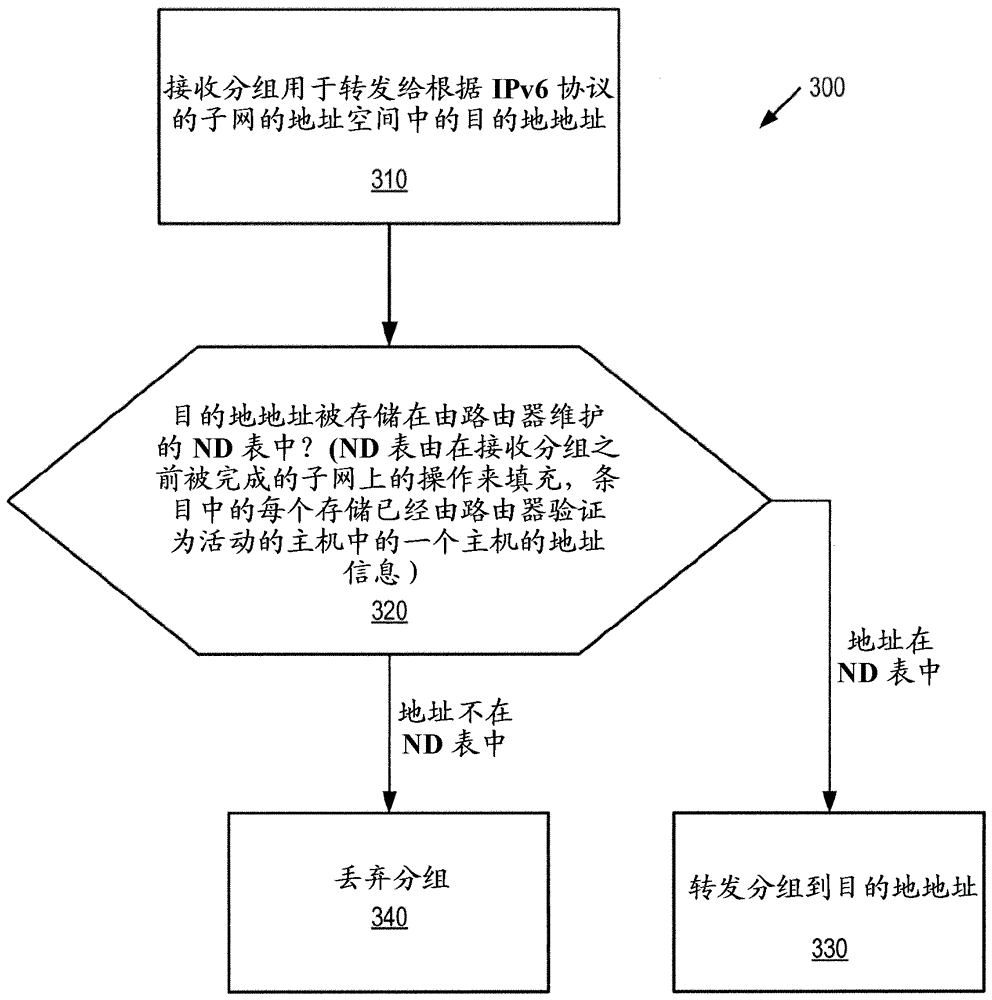
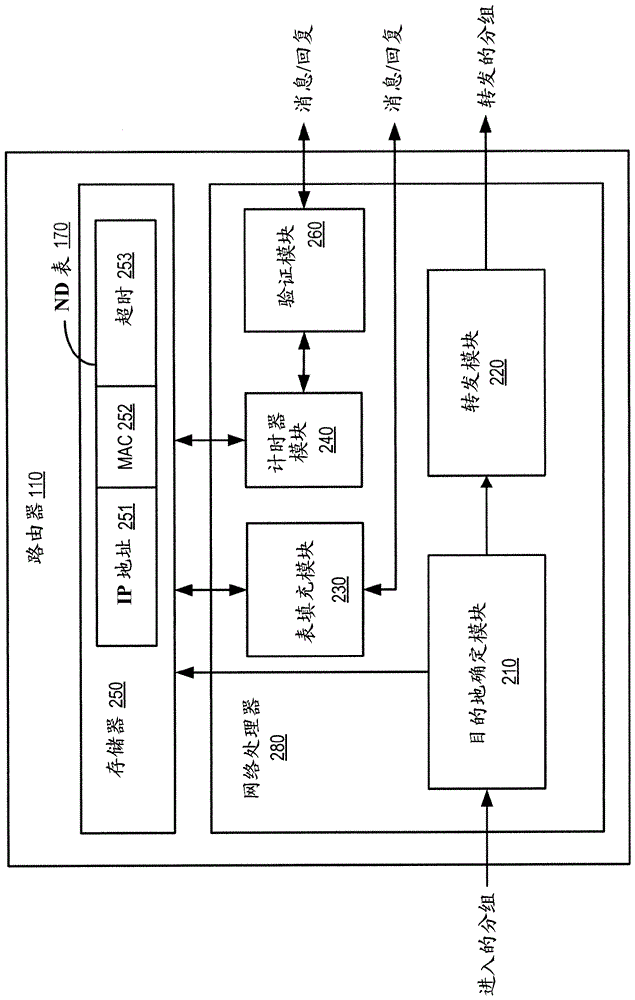
Preventing neighbor-discovery based denial of service attacks
ActiveCN103609089AAvoid Denial of Service AttacksTransmissionProtocol for Carrying Authentication for Network AccessComputer science
A method is provided for preventing denial-of-service attacks on hosts attached to a subnet, where the attacks are initiated by a remote node over an external network. The method is performed by a router which forwards packets between the external network and the subnet. The router receives a packet for forwarding to a destination address in an address space of the subnet according to the IPv6 protocol and looks up the destination address in a Neighbor Discovery (ND) table. The ND table is populated by operations on the subnet that were completed prior to receipt of the packet. Entries in the ND table store address information of the hosts that have been verified by the router to be active. The router forwards the packet to the destination address if the destination address is stored in the ND table. Otherwise, the packet is discarded.
Owner:TELEFON AB LM ERICSSON (PUBL)
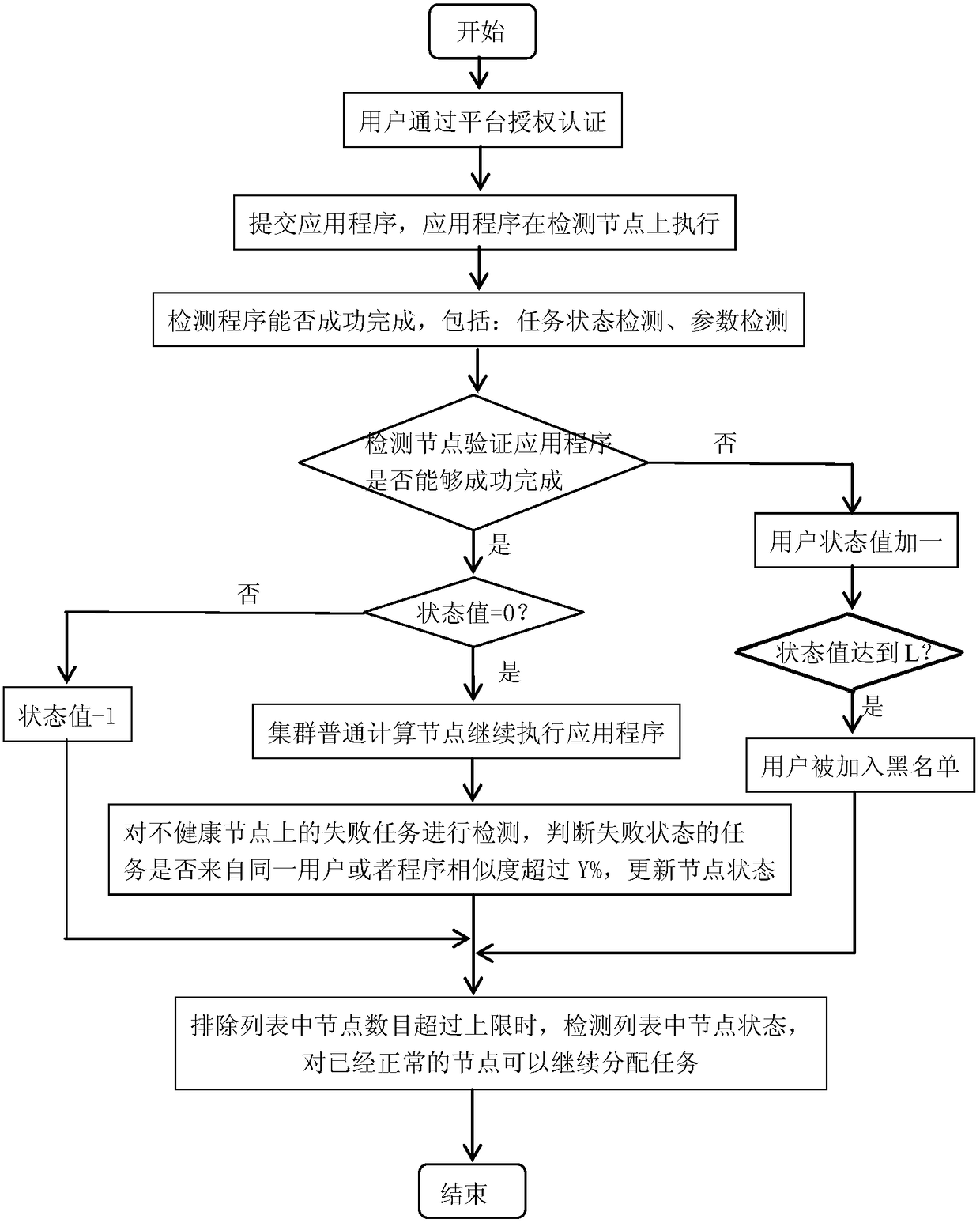
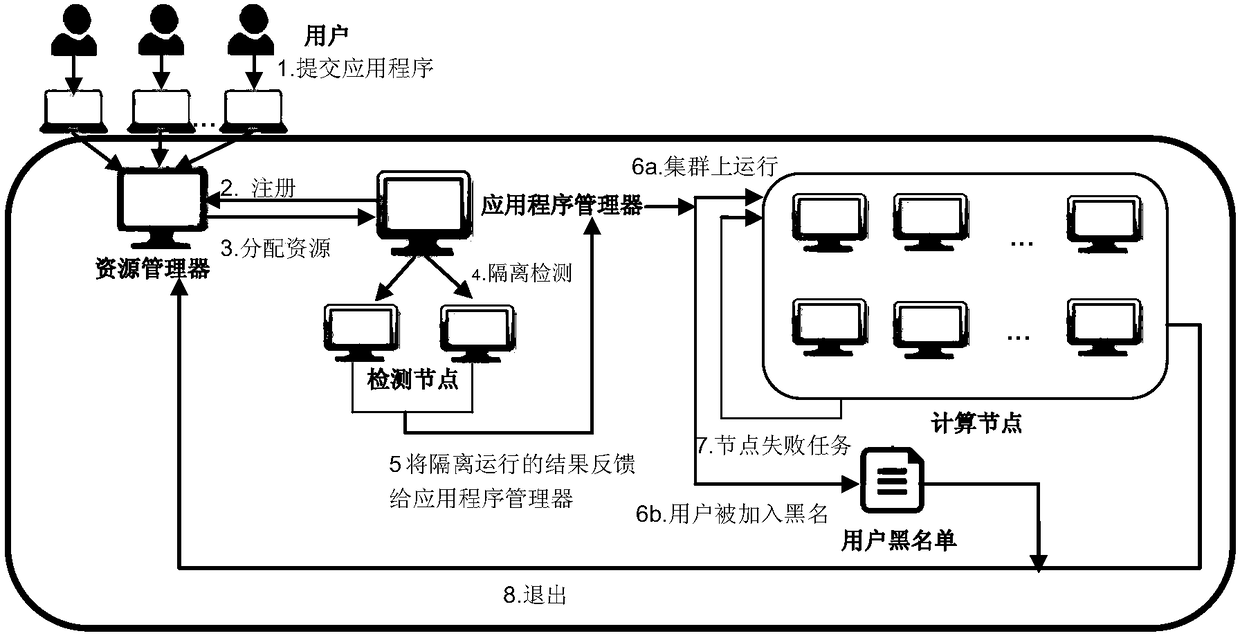
Service denial detection method for large data platform
InactiveCN105653928AAvoid Denial of Service AttacksPrevent vandalismDigital data authenticationPlatform integrity maintainanceData platformBlack list
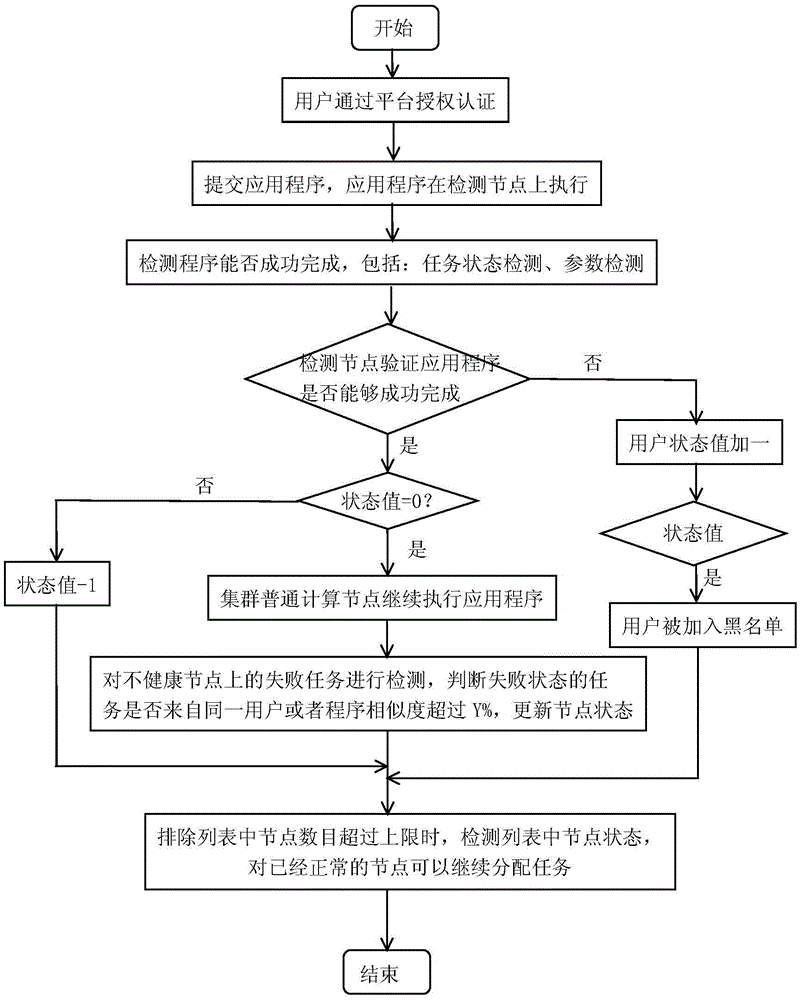
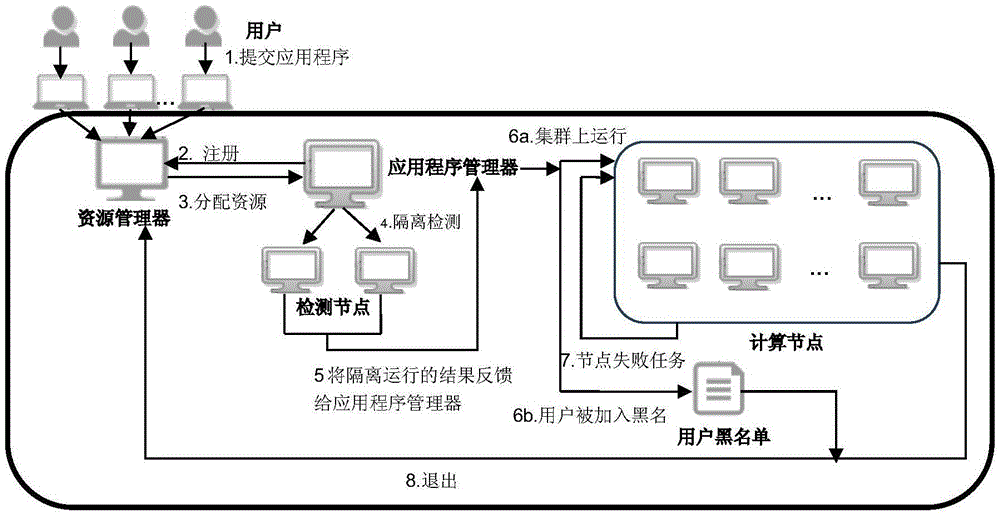
The invention discloses a service denial detection method for a large data platform. The method includes the steps that a plurality of nodes are selected in the large data platform and serve as detection nodes, and a plurality of nodes serve as calculation nodes; a user blacklist is set; secondly, a submitted application is firstly detected in the detection nodes; if any task is detected unqualified, the task and the application are both marked failed; if tasks are detected qualified, the application is allocated to the calculation nodes for continuous execution; thirdly, the nodes are detected, and when the number of the tasks marked failed on the nodes exceeds a set value P, the nodes are marked UNHEALTHY; when the number of the calculation nodes marked UNHEALTHY exceeds a set threshold, the tasks marked failed on the calculation nodes are detected, and if the tasks come from a same user or the similarity exceeds a set value, the calculation nodes are added into an exclusion list; if the ratio of the number of the nodes in the exclusion list exceeds N%, it is judged that attack of service denial exists.
Owner:PEKING UNIV
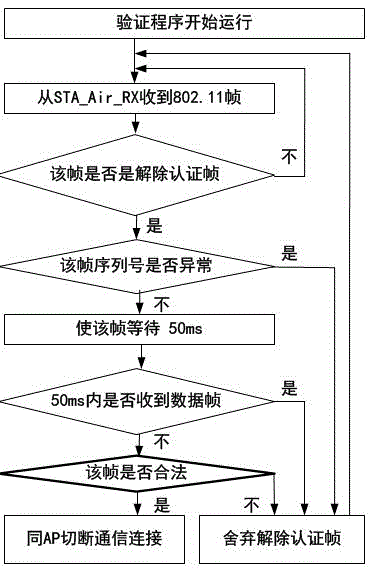
Novel method for proofing 802.11 wireless deauthentication frame flood DoS
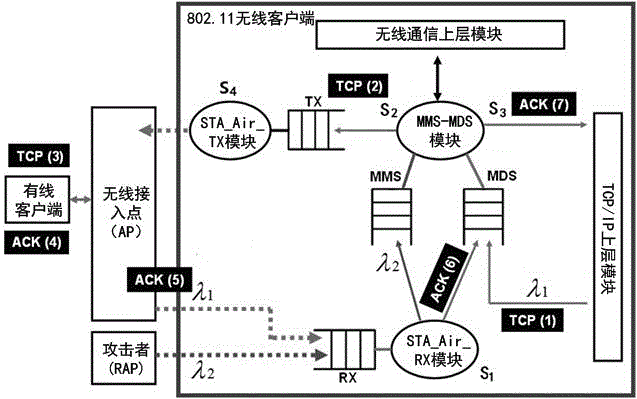
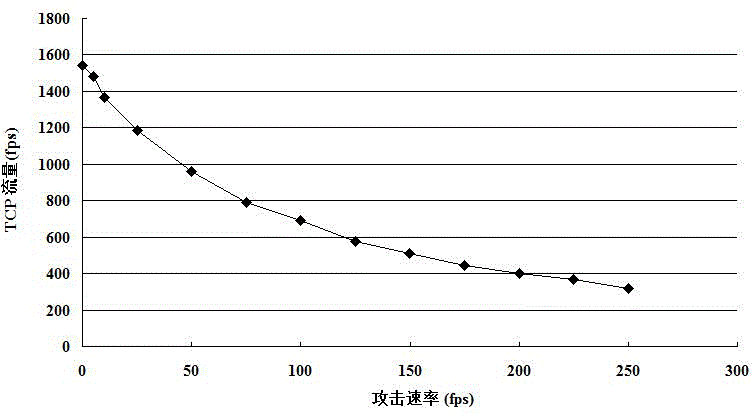
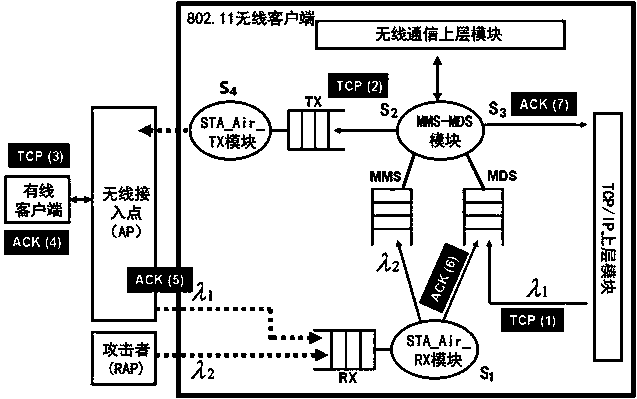
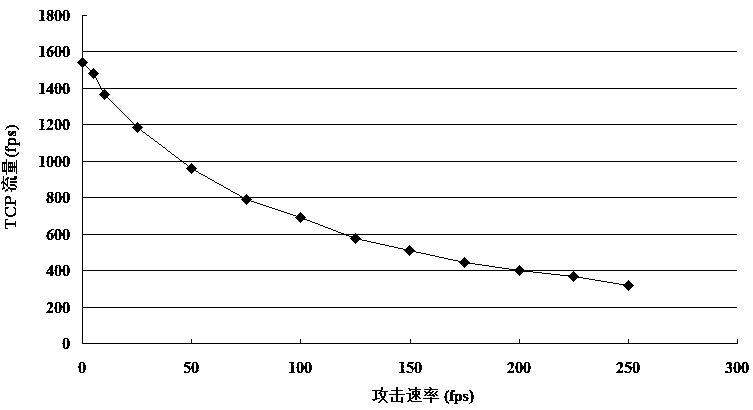
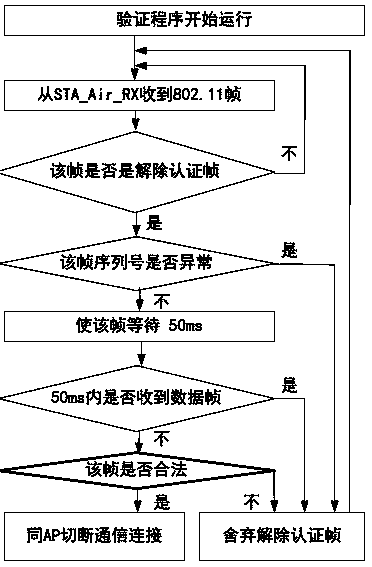
ActiveCN105282144AEffective protectionImprove performance against denial-of-service attacksTransmissionSecurity arrangementRogue access pointWireless
The invention relates to a novel method for proofing 802.11 wireless deauthentication frame flood DoS, and provides a queuing model based on a 802.11 wireless client. The queuing model includes a TCP / IP upper-layer module, an MMS-MDS module, an STA_Air_TX module, and an STA_Air_RX module. The TCP / IP upper-layer module of the wireless client sends TCP data frames to an MDS queue to successively wait for the processing of the MMS-MDS module; when the wireless client prepares to send the data frames for communication, the MMS-MDS module processes the TCP data frames and then forwards the TCP data frames to a TX queue, the STA_Air_TX module sends the TCP data frames to an access point AP; a Rogue Access Point (RAP) sends a deauthentication frame to the wireless client at a speed rate of lambda2, the STA_Air_TX module receives, verifies the deauthentication frame, and determines whether the deauthentication frame should be forwarded to an MMS queue or be directly and immediately abandoned; the STA_Air_TX module receives TCP-ACK and forwards the TCP-ACK to an MDS queue; and the MMS-MDS module completes the verification of the deauthentication frame within the time of S2. The method can prevent a Wireless Local Area Network (WLAN) from deauthentication DoS under low-attack and high-attack speed rates.
Owner:SANMING UNIV
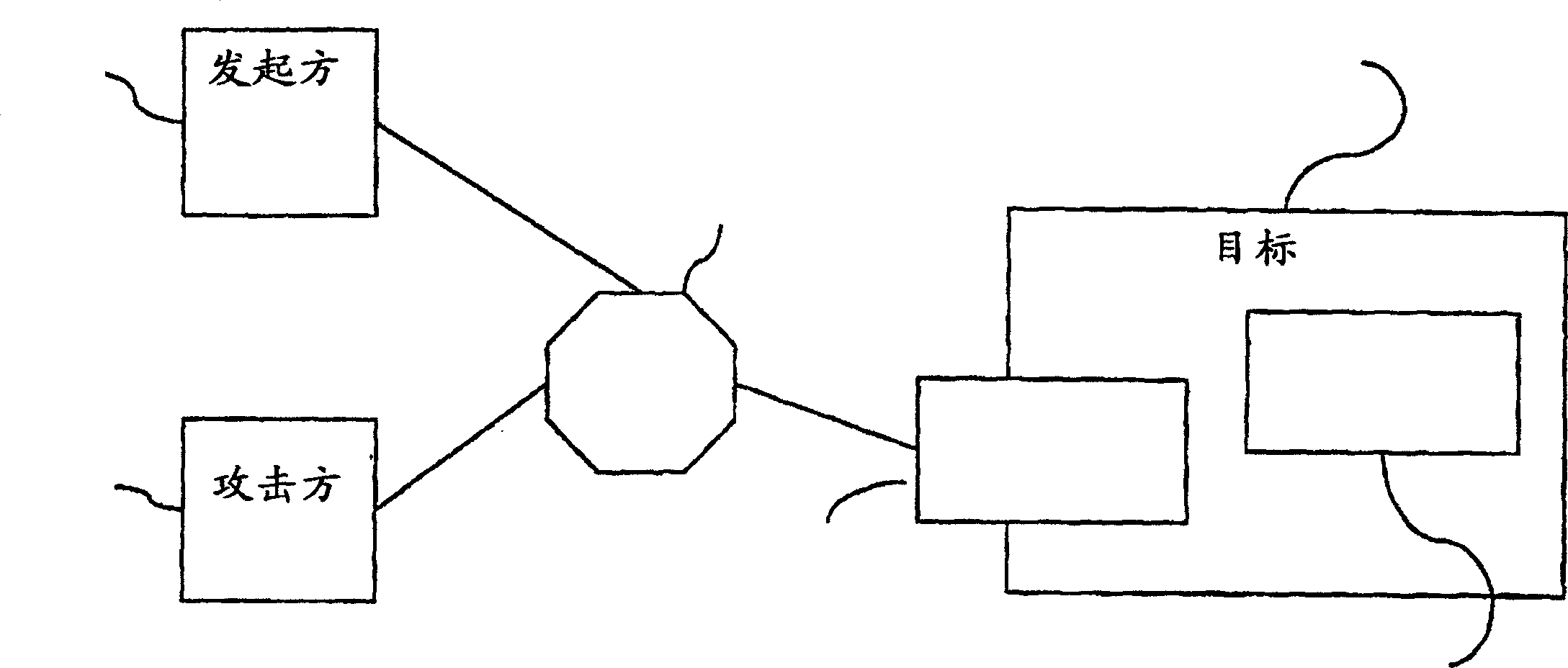
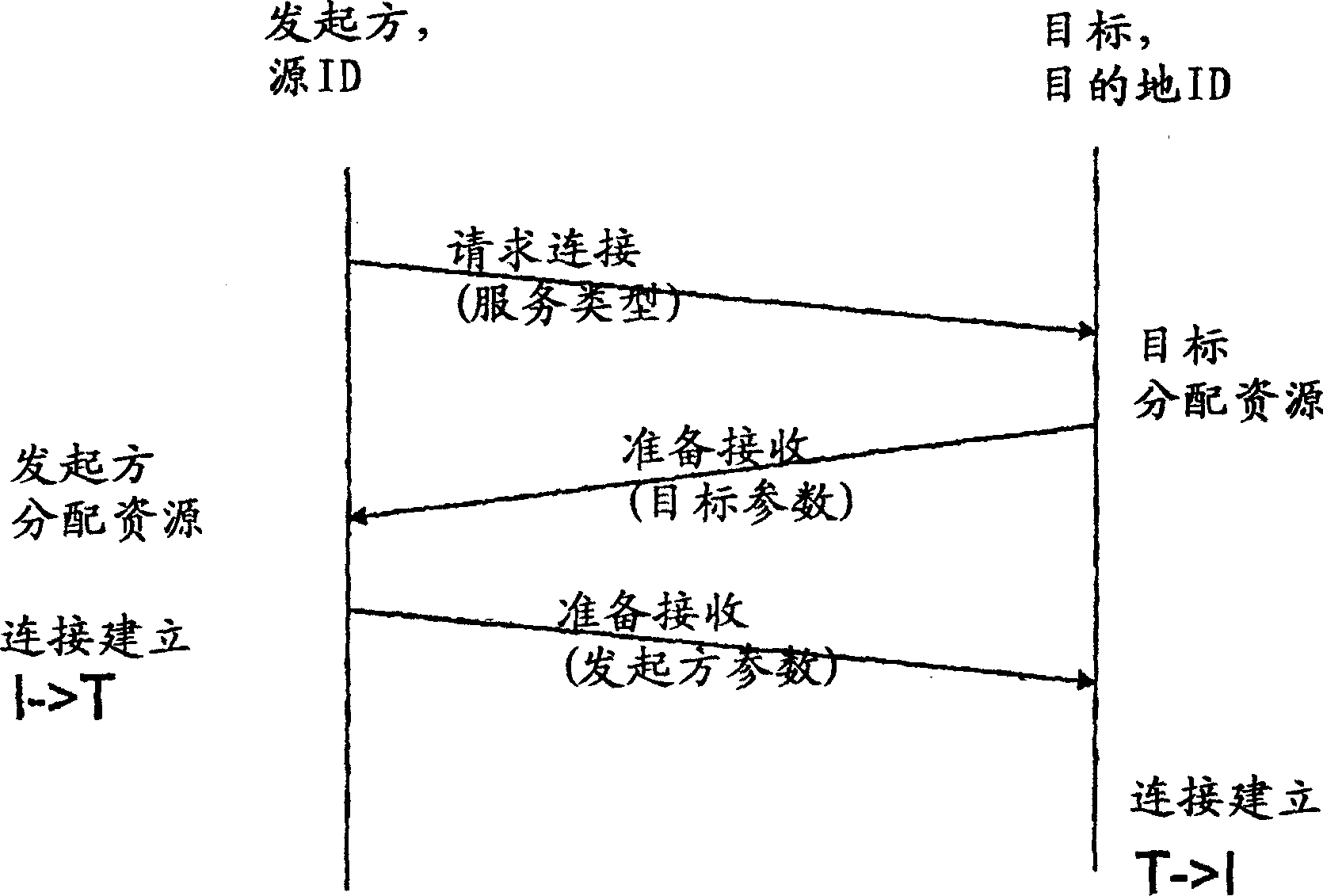
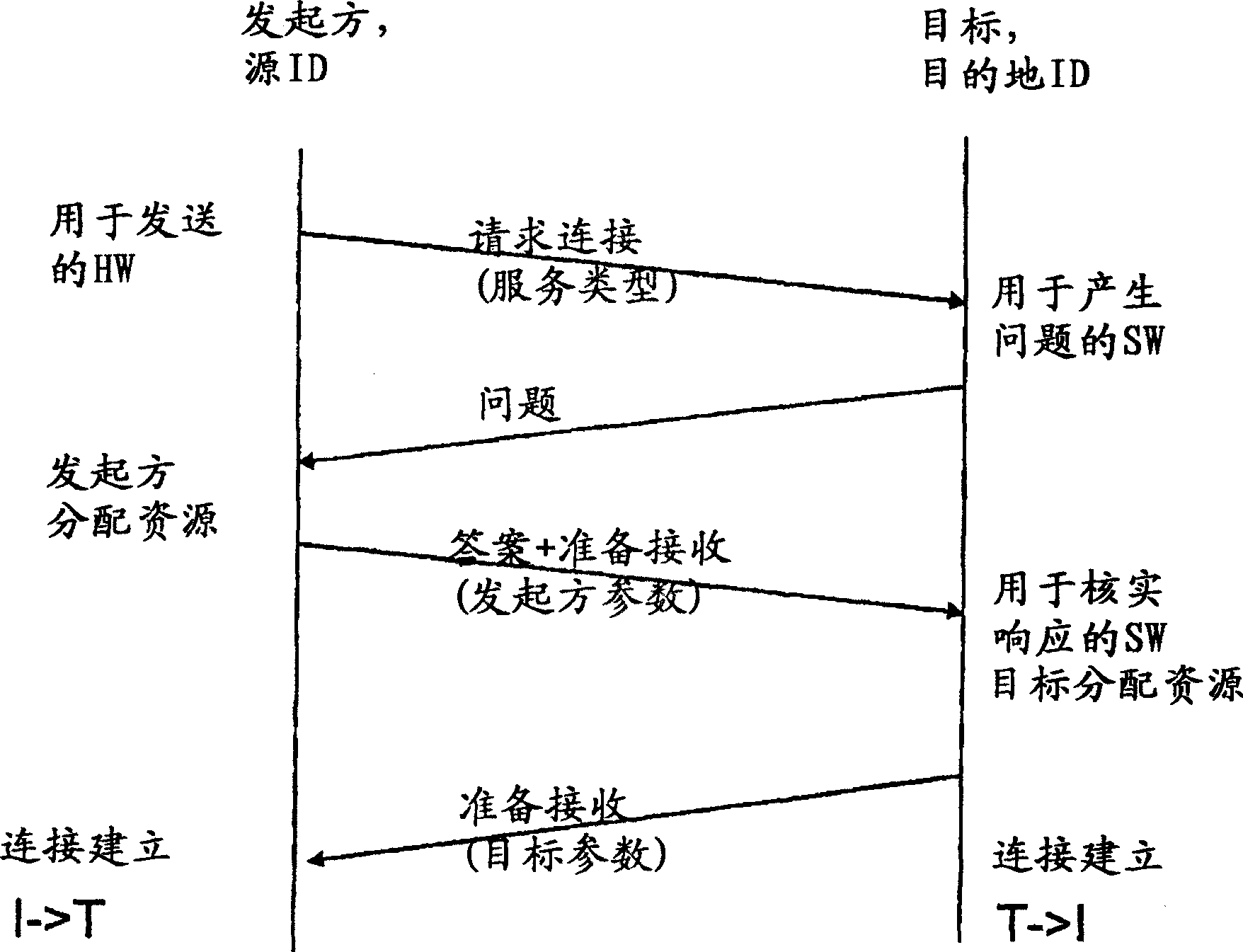
Method for protecting against attacks in a high-speed network
InactiveCN1820483AAvoid Denial of Service AttacksProcessing speedPlatform integrity maintainanceTransmissionComputer networkAttack
A method, module and computer program for protecting a target against attacks in a high-speed network. The method according to the invention comprises the steps of generating a question, after having received a request from an initiator identified by a sourcelD associated to a certain node in the network, sending the question to the node identified by the sourcelD, in case that an answer to the question is received, evaluating the answer, and in case that a proper answer has been received, enabling communication between the initiator and the target by sending a further message from the target to the initiator.
Owner:IBM CORP
A method and device for enhancing Ad hoc network security and cooperation mechanism
InactiveCN101170410BReduce complexitySolve the node identity problemUser identity/authority verificationData switching networksTicketEngineering
Owner:HUAZHONG UNIV OF SCI & TECH
A denial of service detection method for big data platform
InactiveCN105653928BAvoid Denial of Service AttacksPrevent vandalismDigital data authenticationPlatform integrity maintainanceData platformBlack list
The invention discloses a service denial detection method for a large data platform. The method includes the steps that a plurality of nodes are selected in the large data platform and serve as detection nodes, and a plurality of nodes serve as calculation nodes; a user blacklist is set; secondly, a submitted application is firstly detected in the detection nodes; if any task is detected unqualified, the task and the application are both marked failed; if tasks are detected qualified, the application is allocated to the calculation nodes for continuous execution; thirdly, the nodes are detected, and when the number of the tasks marked failed on the nodes exceeds a set value P, the nodes are marked UNHEALTHY; when the number of the calculation nodes marked UNHEALTHY exceeds a set threshold, the tasks marked failed on the calculation nodes are detected, and if the tasks come from a same user or the similarity exceeds a set value, the calculation nodes are added into an exclusion list; if the ratio of the number of the nodes in the exclusion list exceeds N%, it is judged that attack of service denial exists.
Owner:PEKING UNIV
Method, equipment and system for checking temporary key negotiation information
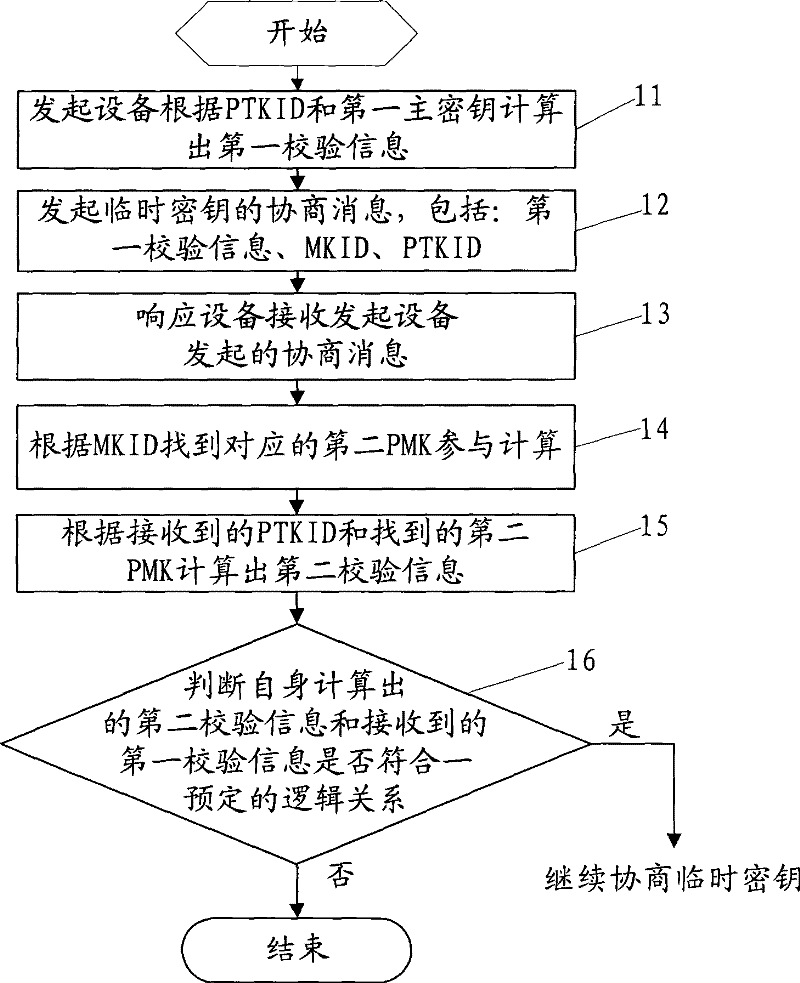
ActiveCN101686226BWill not occupyNormal communication serviceSecuring communicationData miningEphemeral key
The embodiment of the invention discloses a method, equipment and a system for checking temporary key negotiation information, which relates to the field of communication and avoids the problem that a large amount of resources of response equipment are occupied and consumed by attacking equipment. In the embodiment of the invention, an initiator calculates first checking information firstly according to a first derivation key of a first main key and a temporary key label and transmits temporary key negotiation information comprising the first checking information and the like to a responser; the responser calculates the second checking information, judges whether the second checking information and the received first checking information conform to a preset logical relationship or not, and verifies whether the temporary key negotiation information of the initiator is legal or not; and when a condition that the negotiation information is legal is judged, a temporary key and a temporarykey integrality code are calculated, and the temporary key is installed. The embodiment of the invention is mainly used in systems of various negotiating temporary keys.
Owner:HUAWEI TECH CO LTD
A Novel Anti-802.11 Wireless Deauthentication Frame Flood Denial of Service Attack Method
ActiveCN105282144BEffective protectionImprove performance against denial-of-service attacksTransmissionSecurity arrangementWireless lanWireless access point
Owner:SANMING UNIV
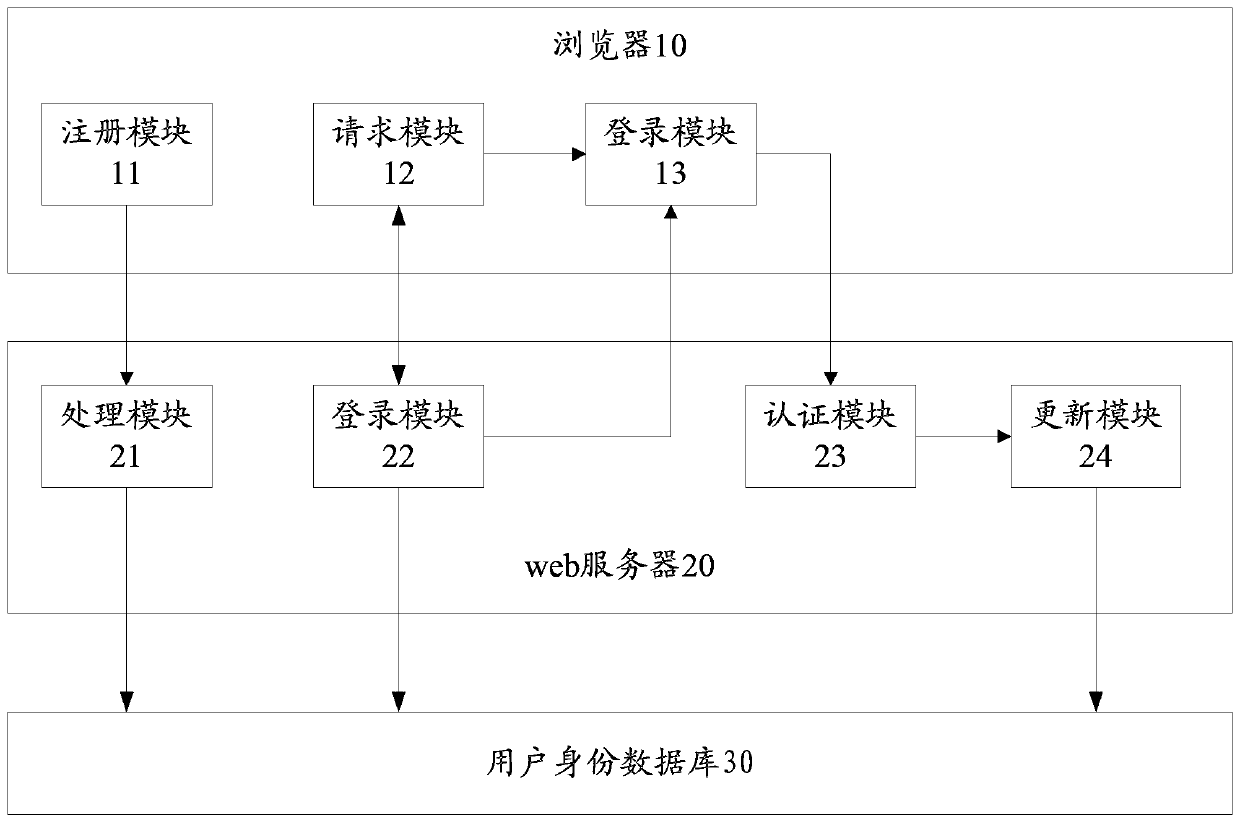
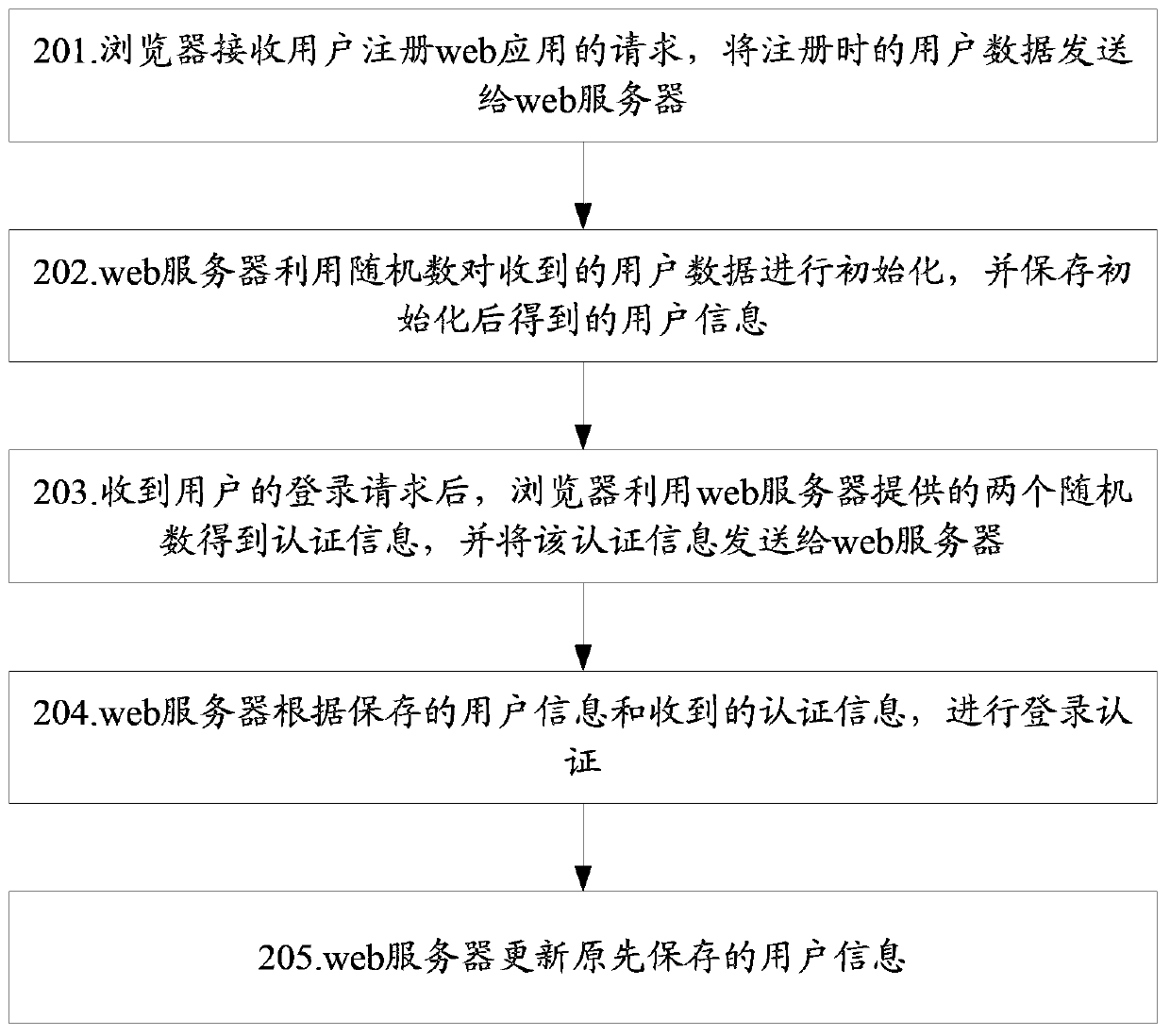
A login authentication method and system for web applications
ActiveCN103581121BPrevent tamperingPrevent eavesdropping attacksTransmissionWeb applicationWeb service
The invention discloses a log-in authentication method on web application. The method includes the following steps that after a log-in request of a user is received, a browser obtains authentication information by means of two random numbers provided by a web server and sends the authentication information to the web server; the web server carries out log-in authentication according to the stored user information and the received authentication information. The invention further provides a log-in authentication system on the web application. According to the technical scheme, data tampering, intercepting attract, decimal attract, dictionary attack, replay attract and denial of service attack can be prevented.
Owner:ZICT TECH CO LTD
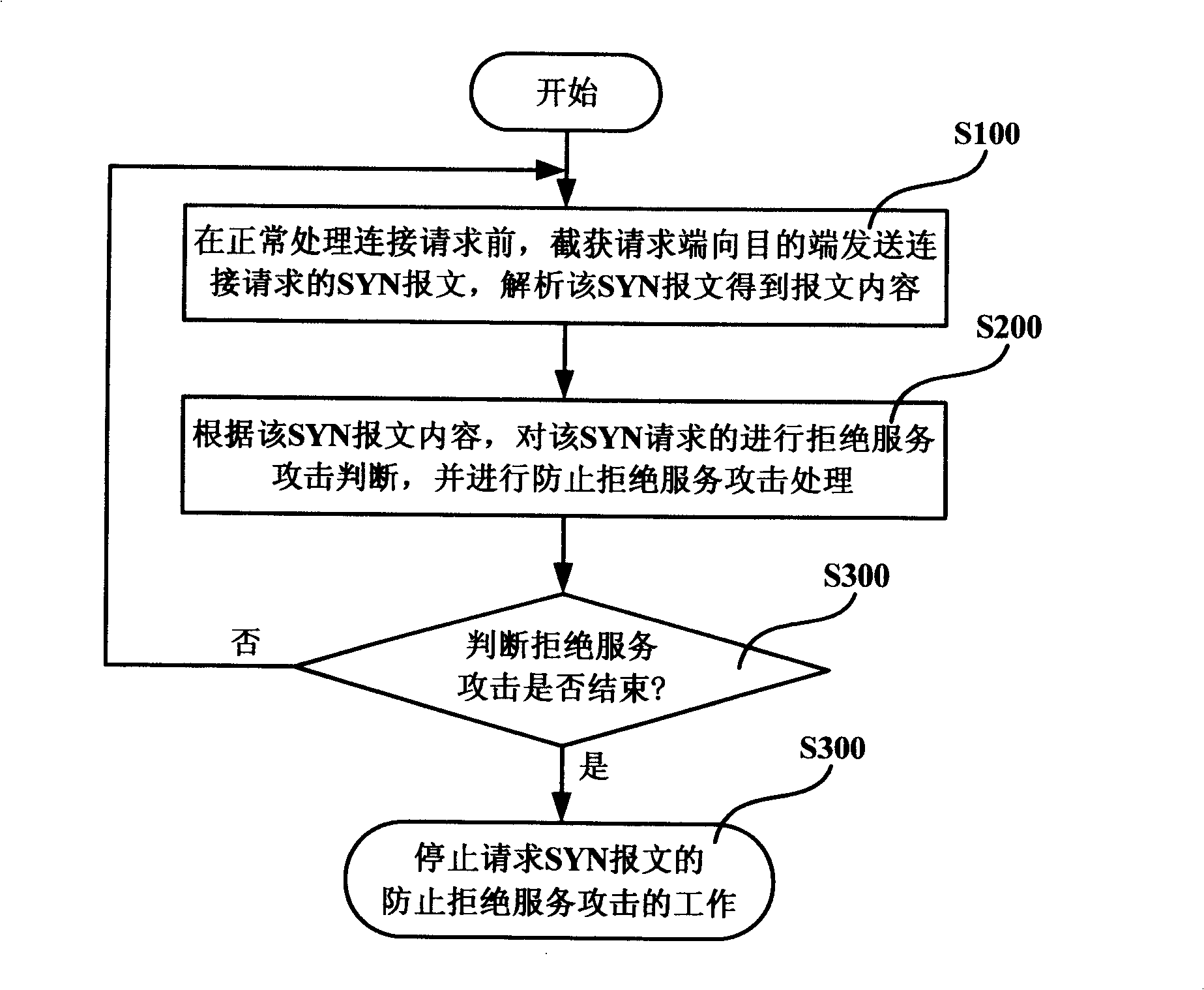
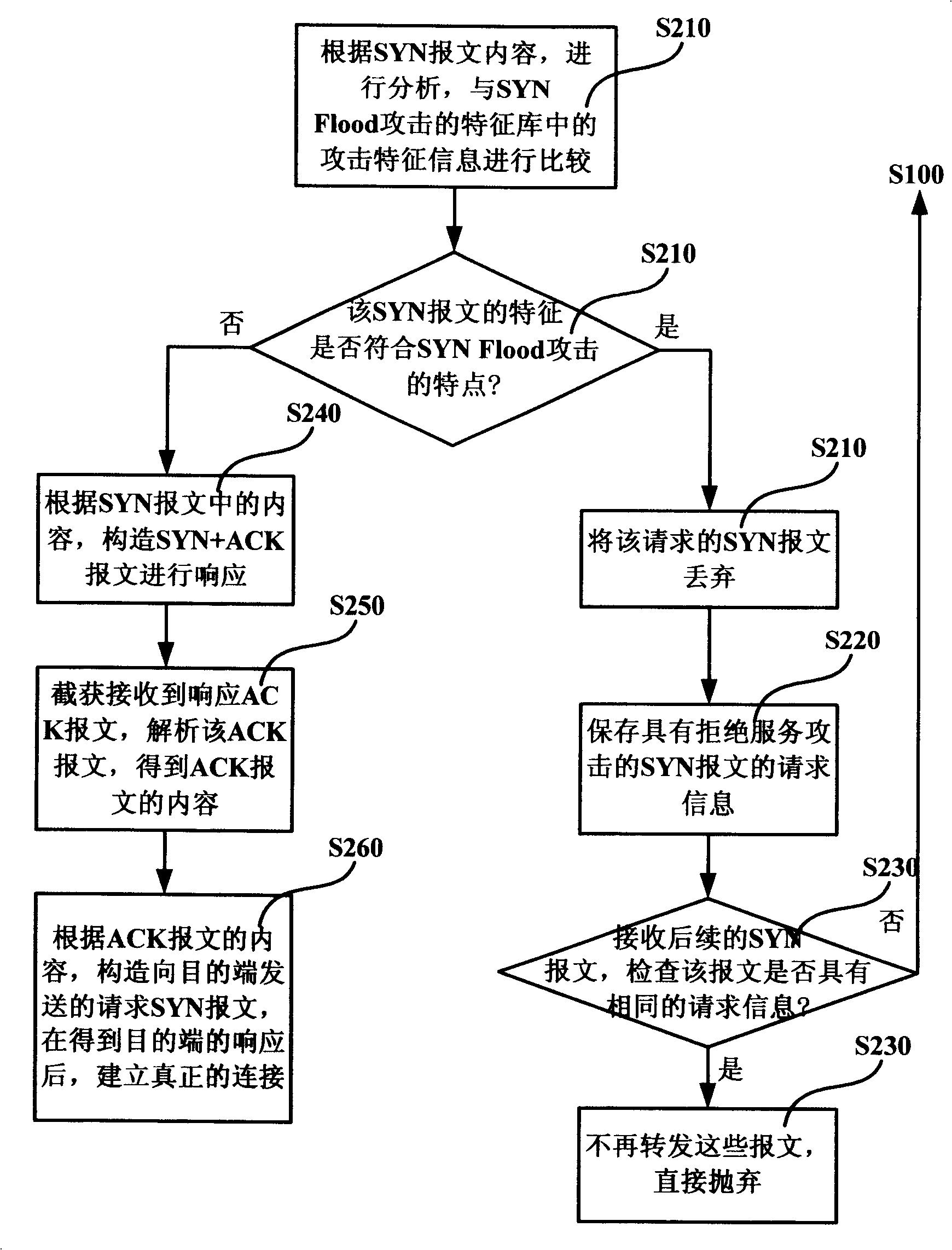
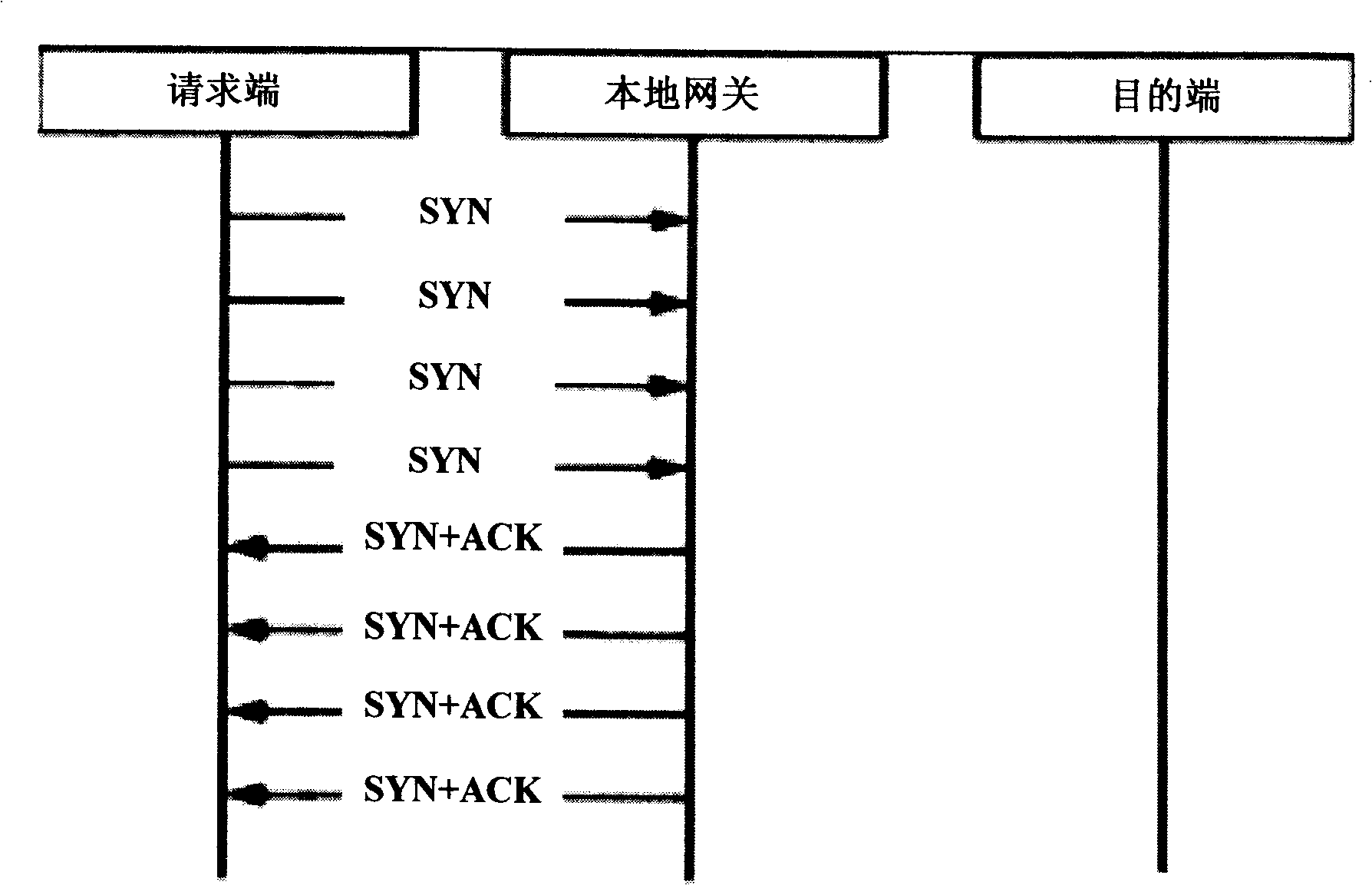
Method and system for preventing refusal service attack
ActiveCN101202742BForwarding is not affectedUnaffected by interferenceData switching networksWork statusDenial-of-service attack
The invention discloses a method and a system for preventing the attack of a denial service. The method includes the following steps: step A, before a connection request is processed normally, a message transmitted from an initiator to a target terminal is intercepted and captured and the message content of the message is analyzed; step B, the attack of the denial service is judged according to the message content and treatment for preventing the attack of the denial service is carried out. The invention can effectively prevent the attack of denial service in a normal working state.
Owner:ZTE CORP
Firewall of a car information system
ActiveCN105871830BBlock network communicationPrevent Hong Fan AttackTransmissionIn vehicleSecurity rule
The invention discloses a firewall for a vehicle-mounted information system. The firewall is composed of a smart phone or an intelligent terminal connected to an external network to form a hardware platform. The firewall is an APP installed on the mobile phone or an intelligent terminal. The only import and export, the data enters the gateway inside the car through the ELM327 connected to the smart phone or terminal, and then enters the gateway inside the car through the OBD‑II connected to the ELM327; then the gateway forwards it to different in-car buses according to the characteristics of the data, and finally enters the corresponding The ECU is executed; illegal data is filtered by the security rules of the firewall and discarded. The firewall of the vehicle on-board information system includes: ELM327, OBD-II, gateway, each ECU, firewall APP. The invention can prevent flood attacks and denial of service attacks through statistical rules. Address filtering can prevent replay attacks.
Owner:CHENGDU UNIV OF INFORMATION TECH
Access control method and system for wireless local area network
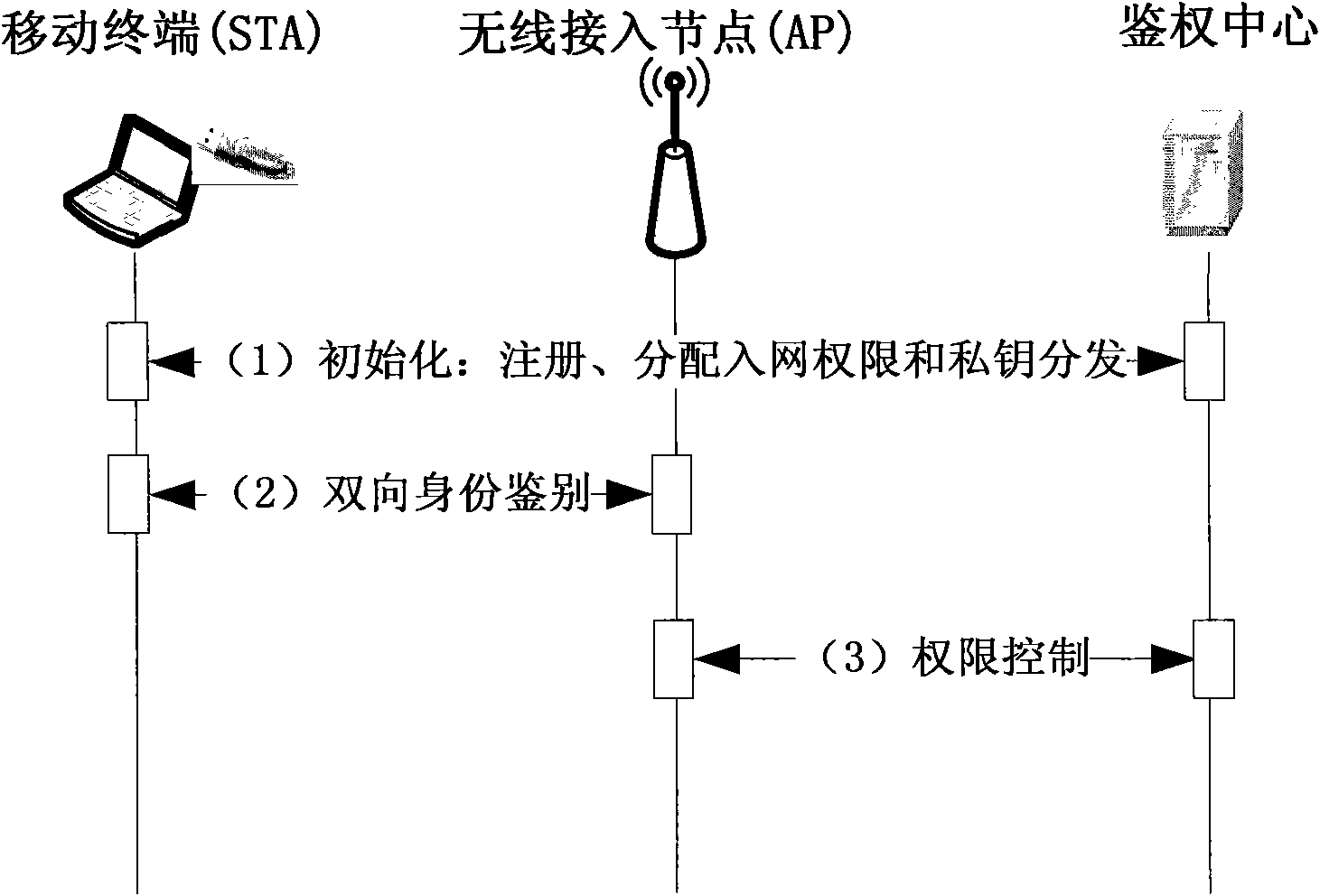
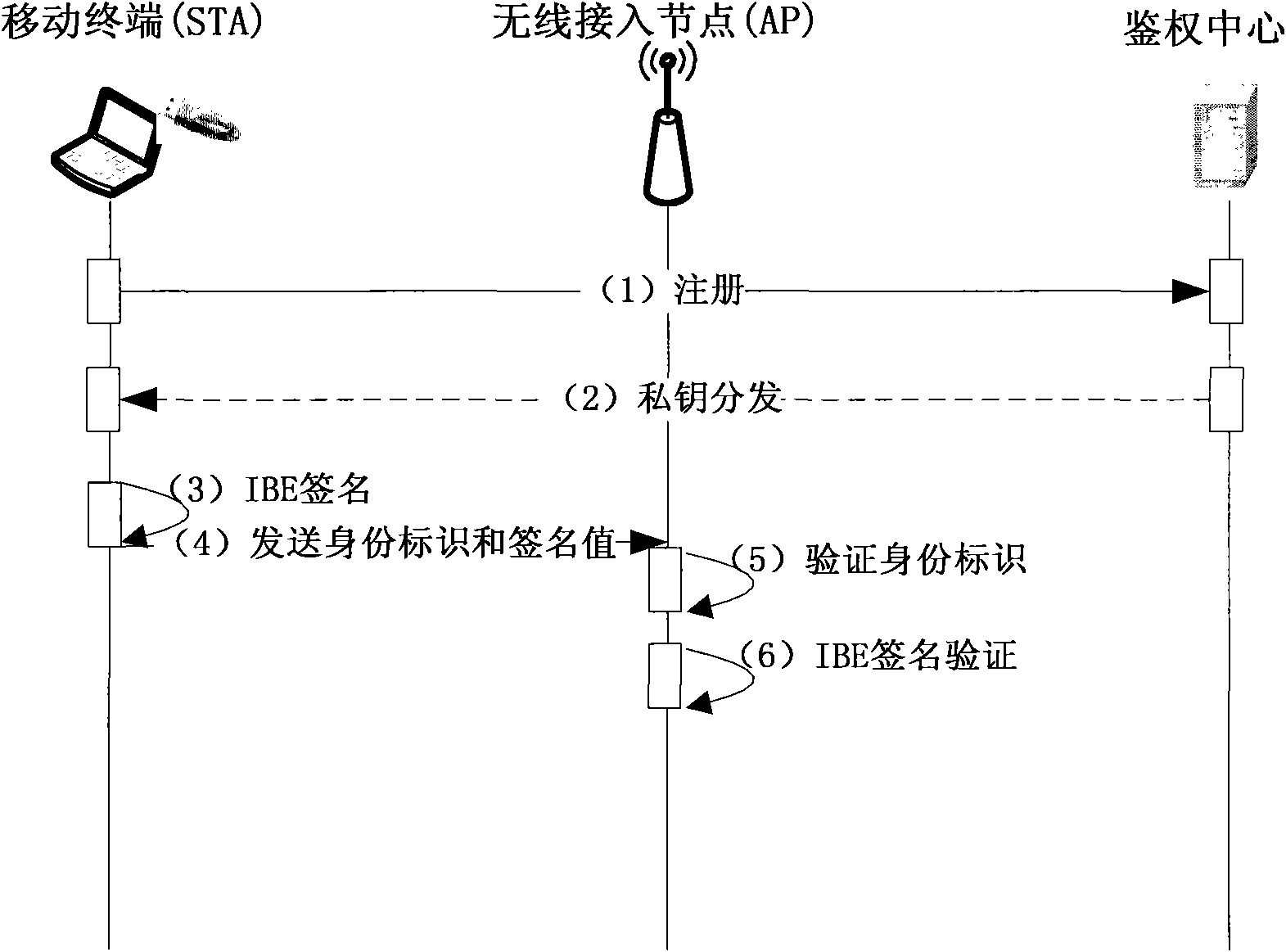
ActiveCN101951603BAvoid blockingSave bandwidthSecurity arrangementMan-in-the-middle attackControl system
The invention discloses an access control method for a wireless local area network. The method comprises the following steps of: A, arranging a user identity token USB-KEY for storing an identity identifier and a private key on a mobile terminal and performing the operation of an IBE algorithm; B, performing identity authentication on the mobile terminal to be subjected to network entry by adopting the identity-based encryption technology, namely IBE technology, and if the authentication is not passed, not allowing users to access the network; and C, determining the resource access permissionof the mobile terminal, and controlling the network access action of the mobile terminal according to the resource access permission. The method introduces the authentication control of specific application resources accessed by the users, adapts to the development tendency of taking application as the center in the wireless local area network, and simultaneously, improves the safety of the access control scheme of the wireless local area network and avoids man-in-the-middle attack and the attack of denial of service. The invention also discloses a system for the access control of the wireless local area network correspondingly.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Method and device for preventing denial of service (DoS) attacks
A method for preventing denial-of-service (DOS) attacks includes: a user is set as a restricted state if the hit-rate of the user is lower than a hit-rate threshold and / or the non-hit number of the user is higher than a non-hit number threshold; a packet is judged whether it is a non-hit packet, if yes, the state of the user transmitting the packet is queried, and if the user is in the restricted state, then the packet is discarded. An apparatus for preventing denial-of- service attacks is provided by this invention, and the apparatus includes: a user data reception unit, a local mapping list query unit and a first-package attack identification and control unit. It is realized by this invention that the DOS / Distributed-Denial-Of-Service (DDOS) attacks caused by a malicious user transmitting the first-package continually are able to be controlled. The limit of the first-package attack is able to adjusted according to the circumstance of system startup, system over loading, especial users and user logging, et al, thereby it is able to assure that in the above especial scenarios, the first-package attack is avoided in the system and simultaneously the user is able to use the network normally.
Owner:昆山乐凯锦富光电科技有限公司
Grouping rerouting method for anonymous communication system
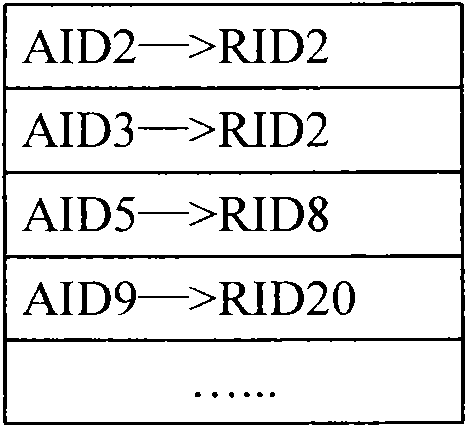
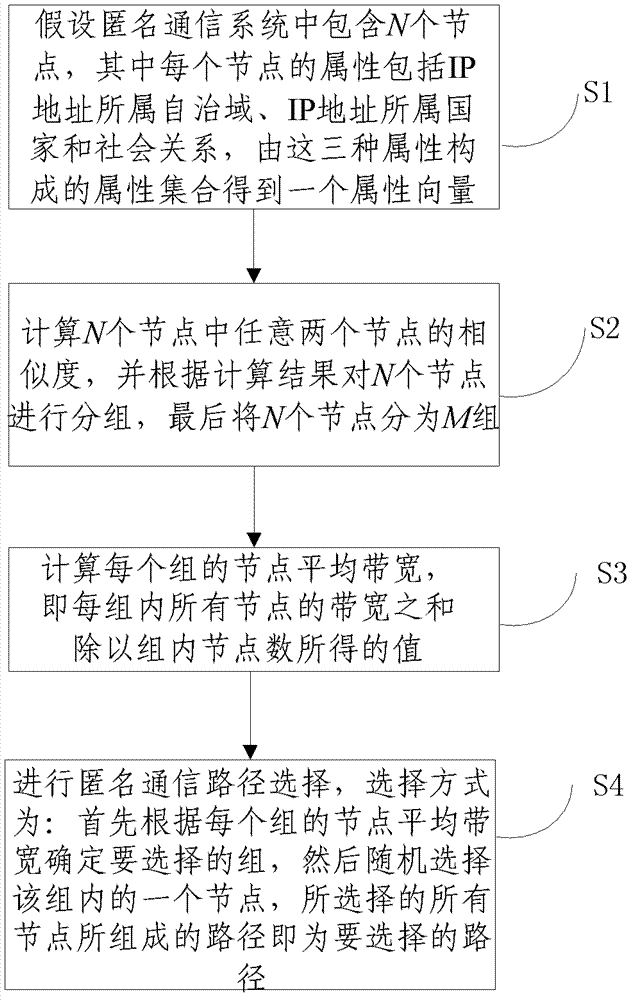
ActiveCN102238090BImprove securityAvoid passive aggressionData switching networksCommunications systemIp address
The invention relates to the fields of information security and anonymous communication, and discloses a grouping rerouting method for an anonymous communication system. The method comprises the following steps of: 1, supposing that the anonymous communication system comprises N nodes of which each has the attributes of the home autonomous system of an Internet protocol (IP) address, the home nation of the IP address and social relations, and obtaining an attribute vector by using an attribute set consisting of the three attributes; 2, computing similarity between any two of the N nodes, and grouping the N nodes into five according to computational results; 3, computing the average node bandwidth of each group, namely computing a value obtained by dividing the number of the nodes in each group by using the summation of bandwidths of all the nodes in the group; and 4, performing anonymous communication path selection. By the method, the resistance of the anonymous communication system to a plurality of active and passive attacks can be improved, the security performance of the system is greatly improved, and simultaneously, the overall efficiency and performance of the system are combined.
Owner:TSINGHUA UNIV
Incentive method and system for ad hoc network autonomous node data forwarding cooperation
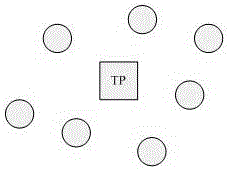
The invention discloses an excitation method and system for cooperation of data forwarding of self-governing nodes of an Ad hoc network. A micro-payment means is utilized to excite the self-governing nodes in the Ad hoc network to carry out data forwarding and to set the behavior of a third party confidence mechanism TP for supervising the nodes to manage virtual currency, the nodes with unusual behaviors are detected and isolated, the TP can construct conversation chain table assemblies according to conversation reports, and dependency for specific type DSR routing protocols is overcome. According to the excitation method and system, IP address identifications of source nodes and target nodes are utilized to have conversations, and the system can be compatible with the routing protocols of any types.
Owner:武汉华天通力科技有限公司
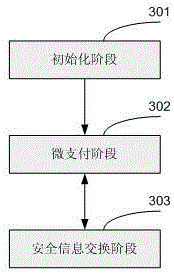
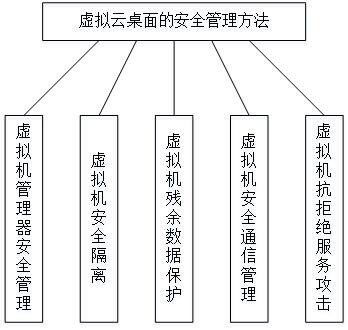
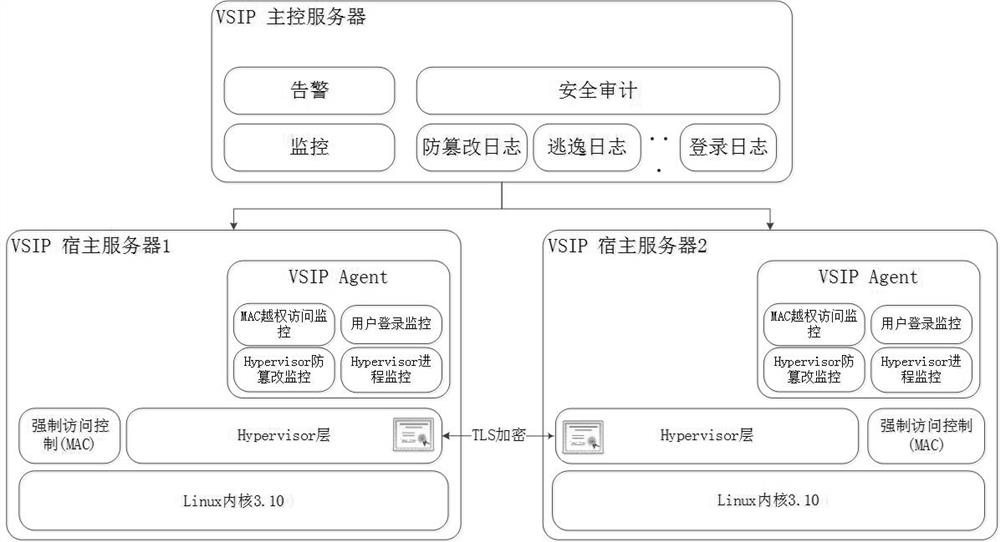
Safety management method of virtual cloud desktop
PendingCN111966458AImprove securityPrevent direct executionResource allocationSoftware simulation/interpretation/emulationVirtualizationSecure communication
The invention discloses a safety management method of a virtual cloud desktop. The safety management method comprises one or more of the following safety management methods: namely safety management of the virtual machine manager: collecting monitoring and auditing log information of a preset type in a virtual desktop management server, and generating tamper-proof auditing information according tothe monitoring and auditing log information; safety isolation of the virtual machine: performing safety isolation on the virtual machine, the storage device and the network; protecting the residual data of the virtual machine: respectively clearing the residual data of the virtual machine memory and the virtual machine disk; virtual machine secure communication management: encrypting data transmission between subsystems of the virtualization platform system; the virtual machines resist denial of service attacks; an independent virtual switch is allocated to each virtual machine, and each virtual machine switch is bound with a physical network port. According to the invention, the safety performance of the virtual cloud desktop is improved.
Owner:INFORMATION & TELECOMM COMPANY SICHUAN ELECTRIC POWER
Optical network terminal, port speed limiting attribute configuration method and packet process method
ActiveCN101453672BPrevent overflowAvoid Denial of Service AttacksData switching networksNetwork terminationProtocol processing
The invention relates to an optical network terminal ONT, a method for configuring port rate limit attribute and a method for processing a message thereof. The optical network terminal comprises a passive optical network (PON) protocol processing module and a user network interface functional module which are connected through an internal interface. The optical network terminal also comprises a port rate limit module connected with the user network interface, wherein the port rate limit attribute is stored in the port rate limit module. The method for configuring the port rate limit attributeof the ONT comprises the following steps: A, a configuring terminal transmits a port rate limit attribute configuring command to the ONT; and B, the ONT stores the port rate limit attribute in a management entity. The method for processing the message of the ONT comprises the following steps: determining whether data velocity transmitted by the user network interface exceeds a set value in the port rate limit attribute of the user network interface or not, if so, a step of flow control is carried out on the user network interface. The invention ensures that the ONT can realize the function ofport rate limit, can prevent overflowing of a receiving buffer inside the ONT, and prevent an illegal user from initiating denial of service attack.
Owner:HUAWEI TECH CO LTD
Hadoop framework cloud platform risk assessment and pre-warning method
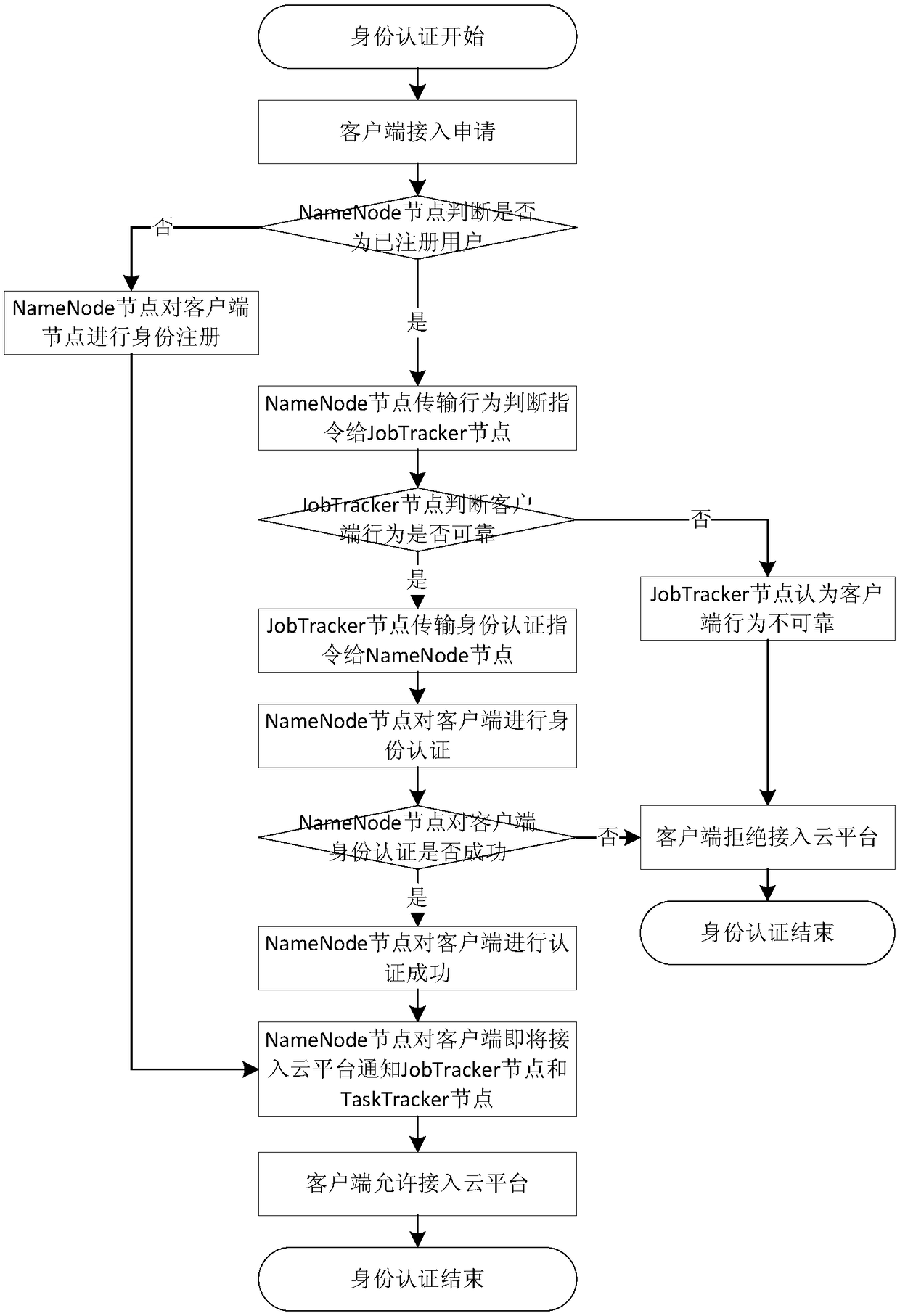
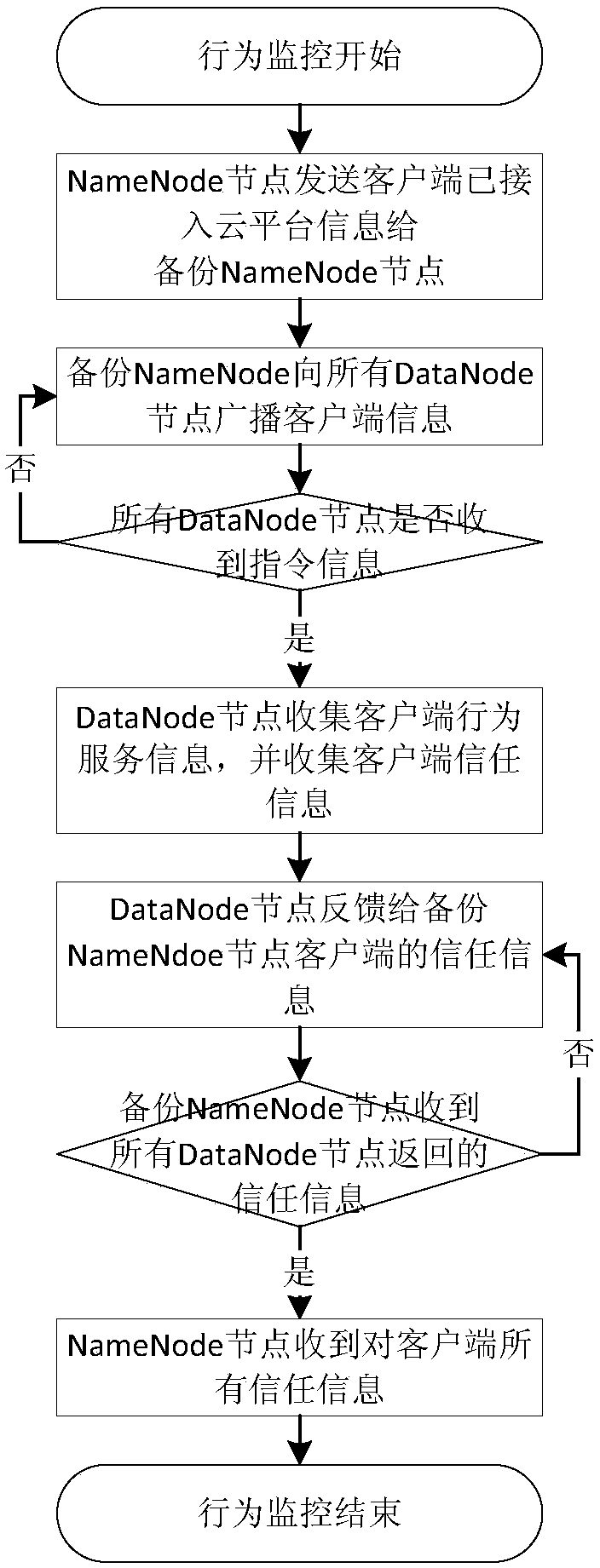
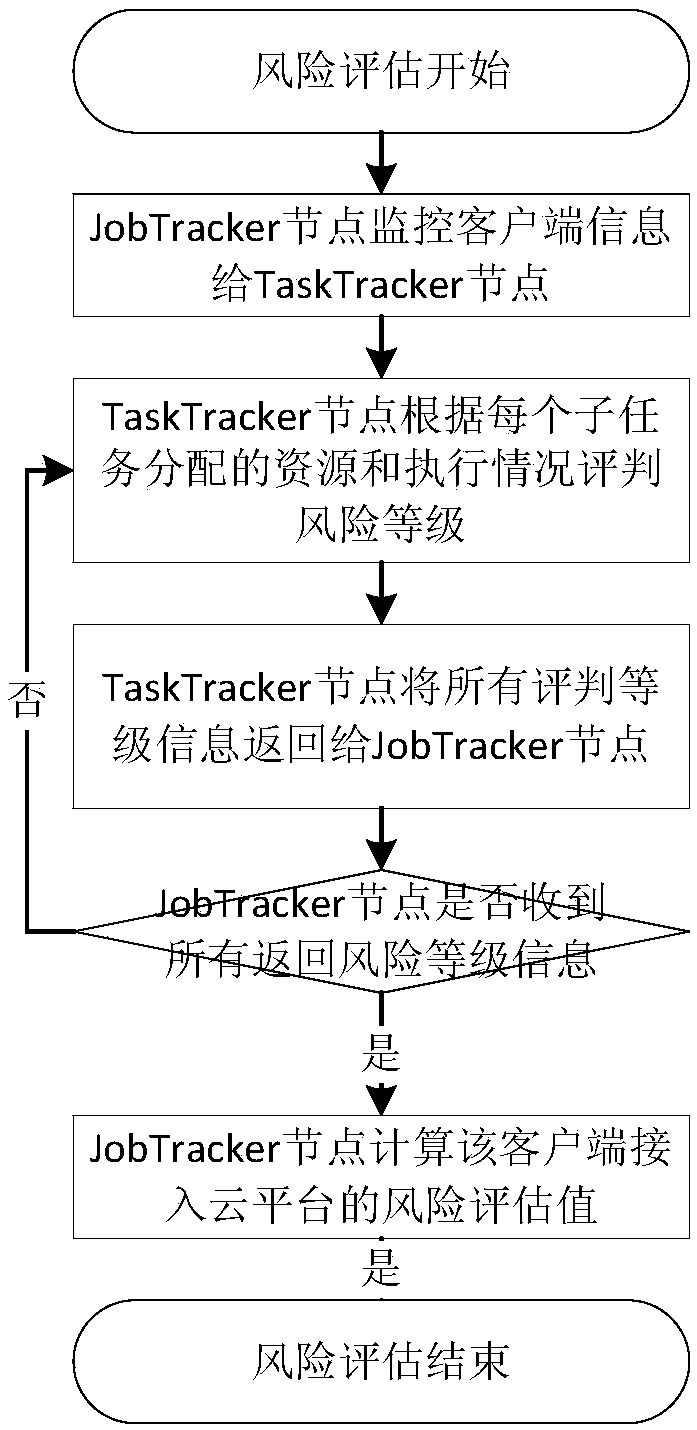
ActiveCN108134697AImprove service qualityAvoid Denial of Service AttacksData switching networksQuality of serviceDependability
The invention discloses a Hadoop framework cloud platform risk assessment and pre-warning method. Risk assessment and pre-warning of a Hadoop framework cloud platform are achieved by an identity authentication module, a behavior monitoring module, a risk assessment module and a system pre-warning module jointly; the identity authentication module, the behavior monitoring module, the risk assessment module and the system pre-warning module are achieved by a NameNode, a backup NameNode, a DataNode, a JobTracker node and a TaskTracker jointly. Aiming at the problem that the client access servicebased on the Hadoop framework cloud platform is unreliable in behavior; the invention builds security management modules, including the identity authentication module, the behavior monitoring module,the risk assessment module and the system pre-warning module, in the cloud platform, the group can be effectively prevented from rejecting service attacks, and the quality of service of the cloud security platform is improved.
Owner:四川铁道职业学院
A method and apparatus for preventing denial of service attacks on hosts attached to a subnet
A method is provided for preventing a denial of service attack on a host (120) attached to a subnet (150), wherein the attack is initiated by a remote node (139) through an external network (160). The method is performed by a router (110) forwarding packets between an external network (160) and a subnet (150). The router (110) receives the packet for forwarding to a destination address in the address space of the subnet (150) according to the IPv6 protocol and looks up the destination address in a neighbor discovery ND table (170). The ND table (170) is populated by operations on the subnet (150) that are completed prior to receiving the packet. Entries in the ND table (170) store address information for hosts (120) that have been verified as active by the router (110). If the destination address is stored in the ND table (170), the router (110) forwards the packet to the destination address. Otherwise, the packet is discarded.
Owner:TELEFON AB LM ERICSSON (PUBL)
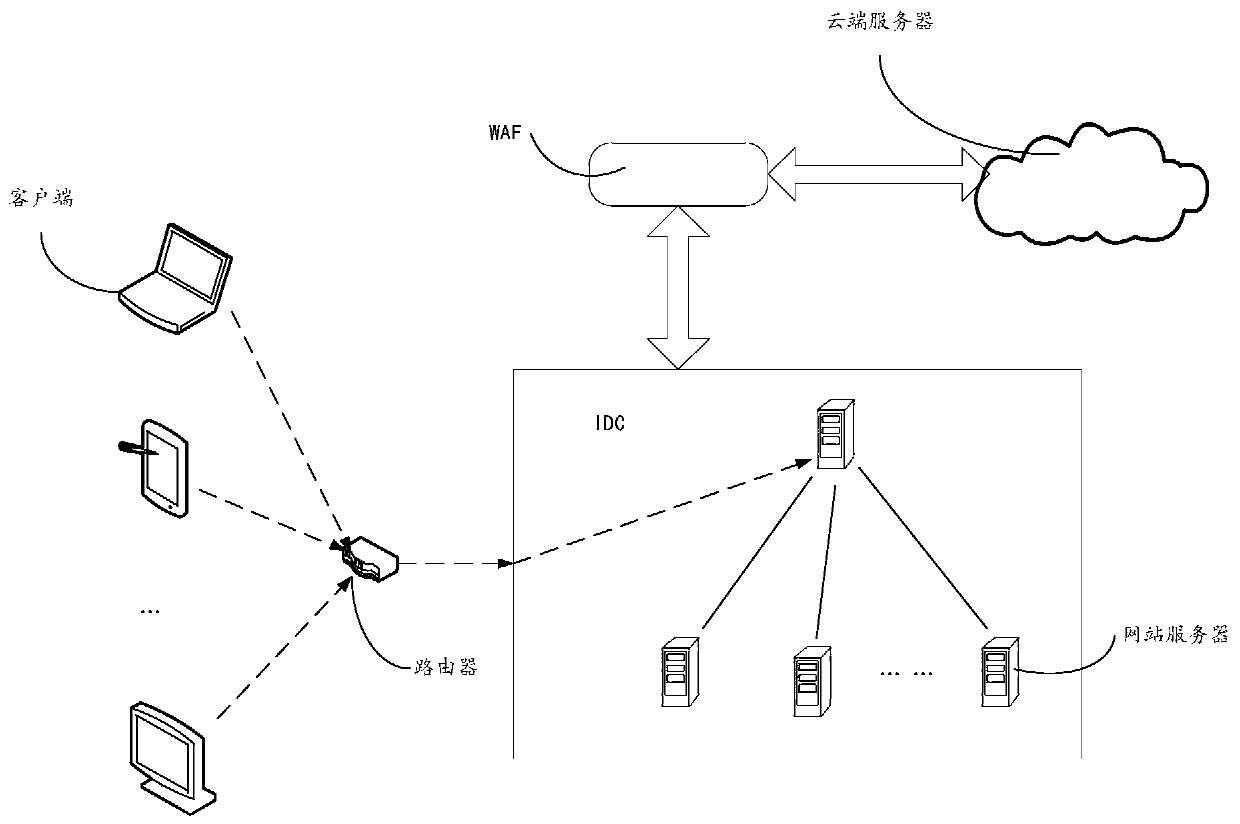
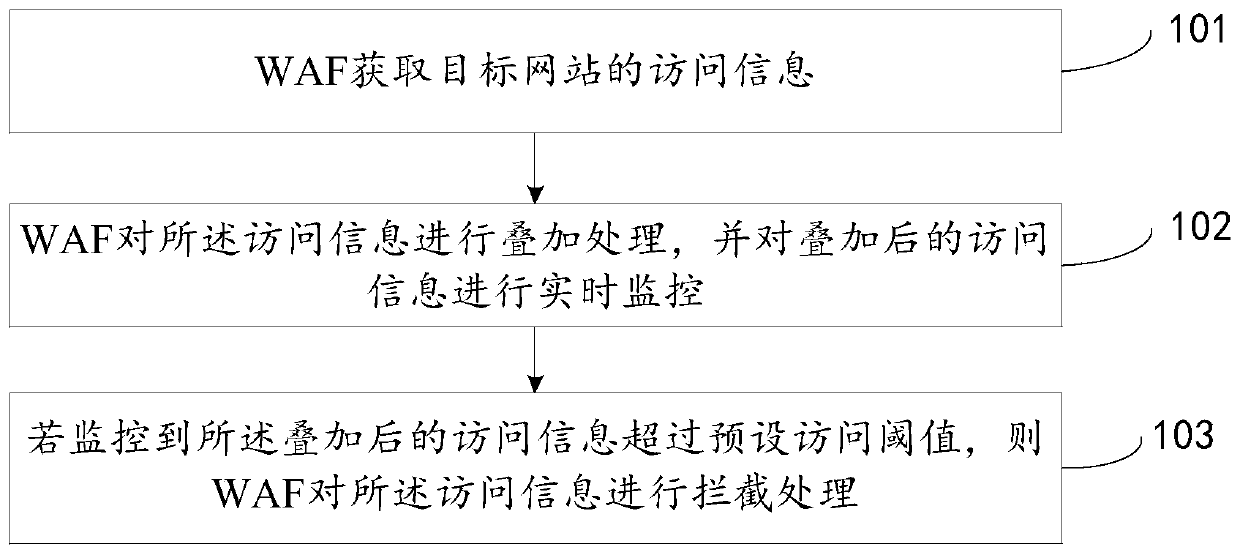
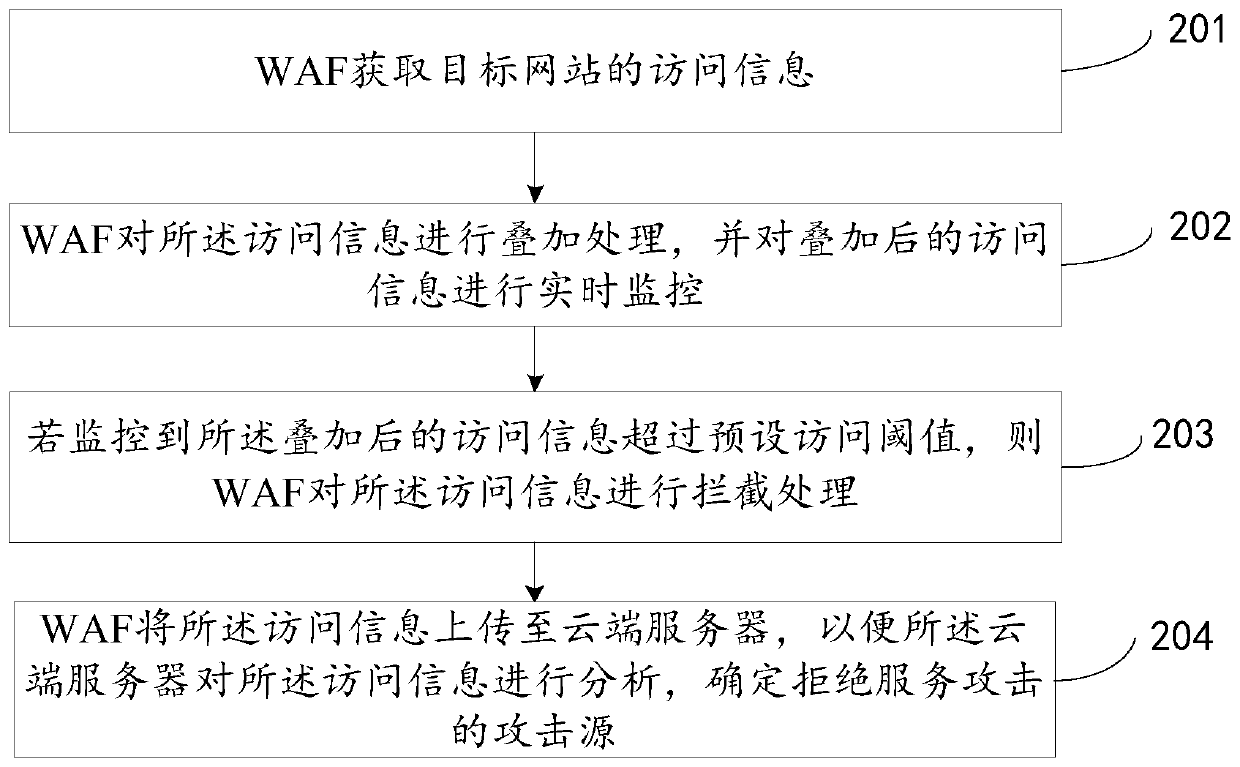
Processing method, waf, router and system for denial of service attack
The invention discloses a processing method and system of a denial of service attack, a Web application firewall (WAF), and a router, is mainly applied to a CC attack process, and relates to the technical field of Internet, mainly for the purpose of solving the problem of threatening security of a target website when the target website is attacked in a time interval of cloud protection performed by a cloud server in the prior art. The method provided by the technical scheme comprises the following steps: a WAF obtaining access information of the target website; performing superposing processing on the access information and performing real-time monitoring on the superposed access information; and if it is monitored that the superposed access information exceeds a preset access threshold, performing interception processing on the access information.
Owner:BEIJING QIHOO TECH CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com