A method and device for enhancing Ad hoc network security and cooperation mechanism
A network security and mechanism technology, applied in the field of communication security, can solve the problems of intolerance of unintentional errors of nodes, incentivized node enthusiasm, heavy burden on nodes, etc., to reduce communication traffic and computational overhead, avoid denial of service attacks, and reduce system complexity. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
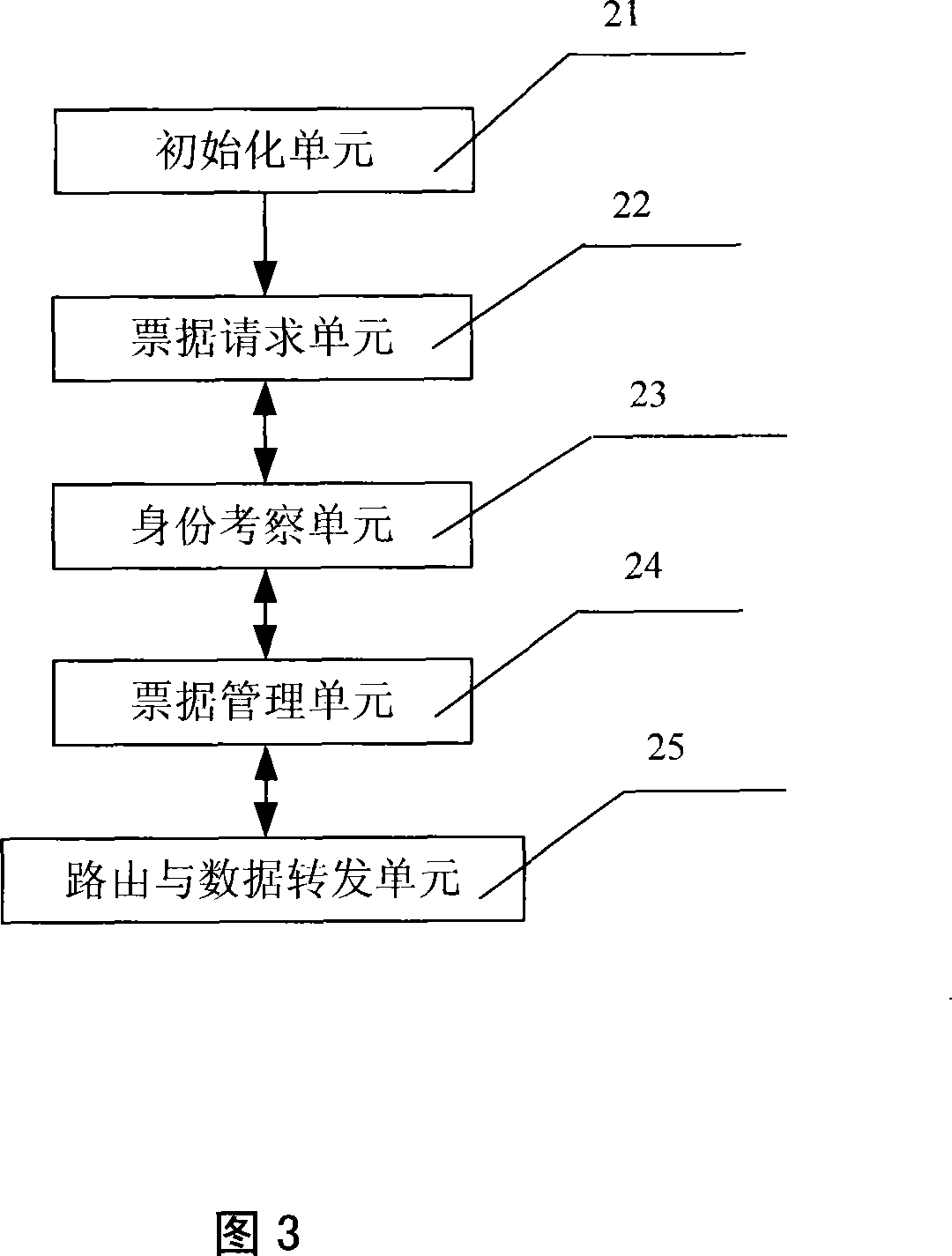
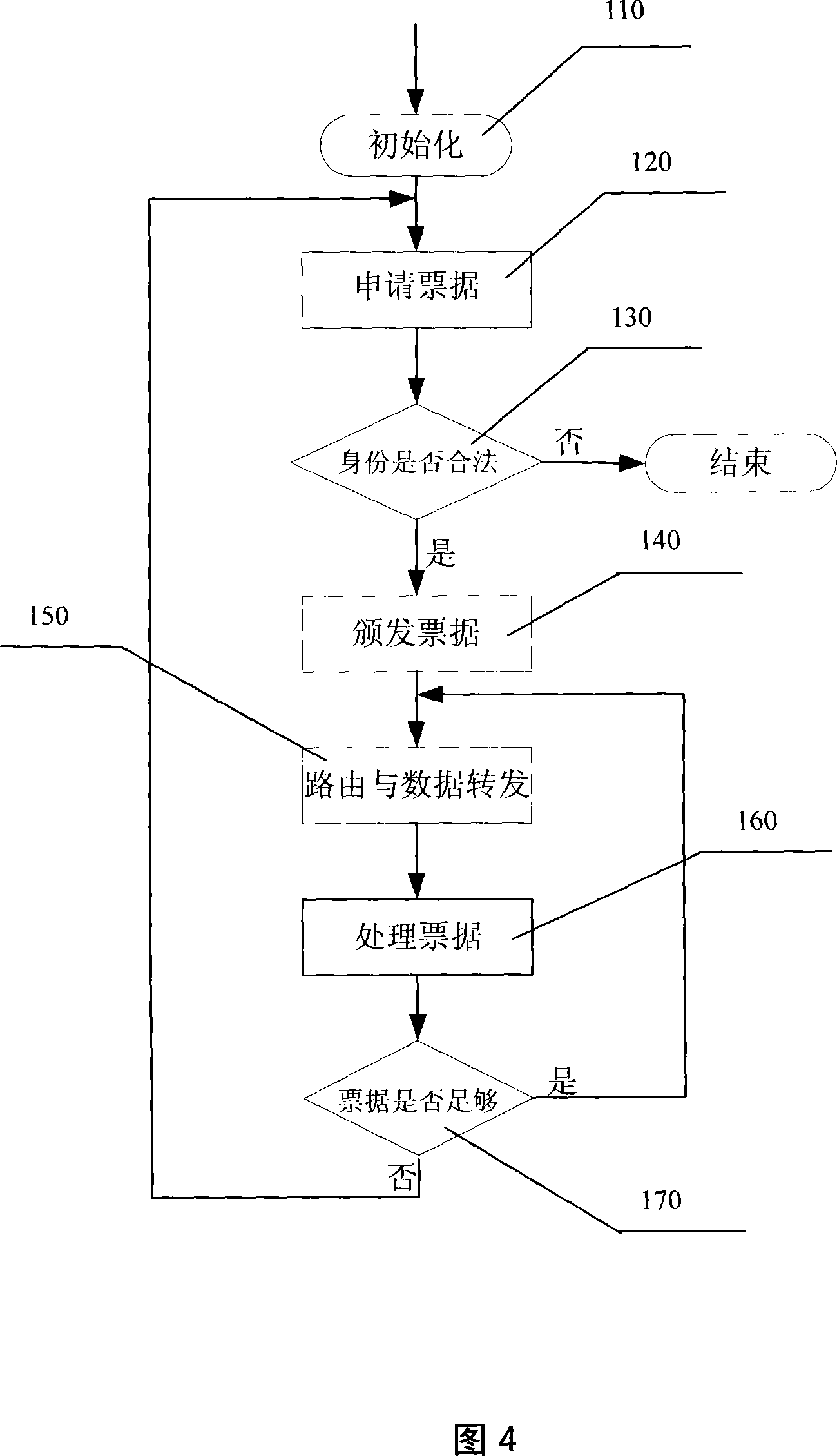
[0032] The method for enhancing Ad hoc network security and cooperation mechanism and the device for realizing the method of the present invention will be described in detail below with reference to the accompanying drawings.
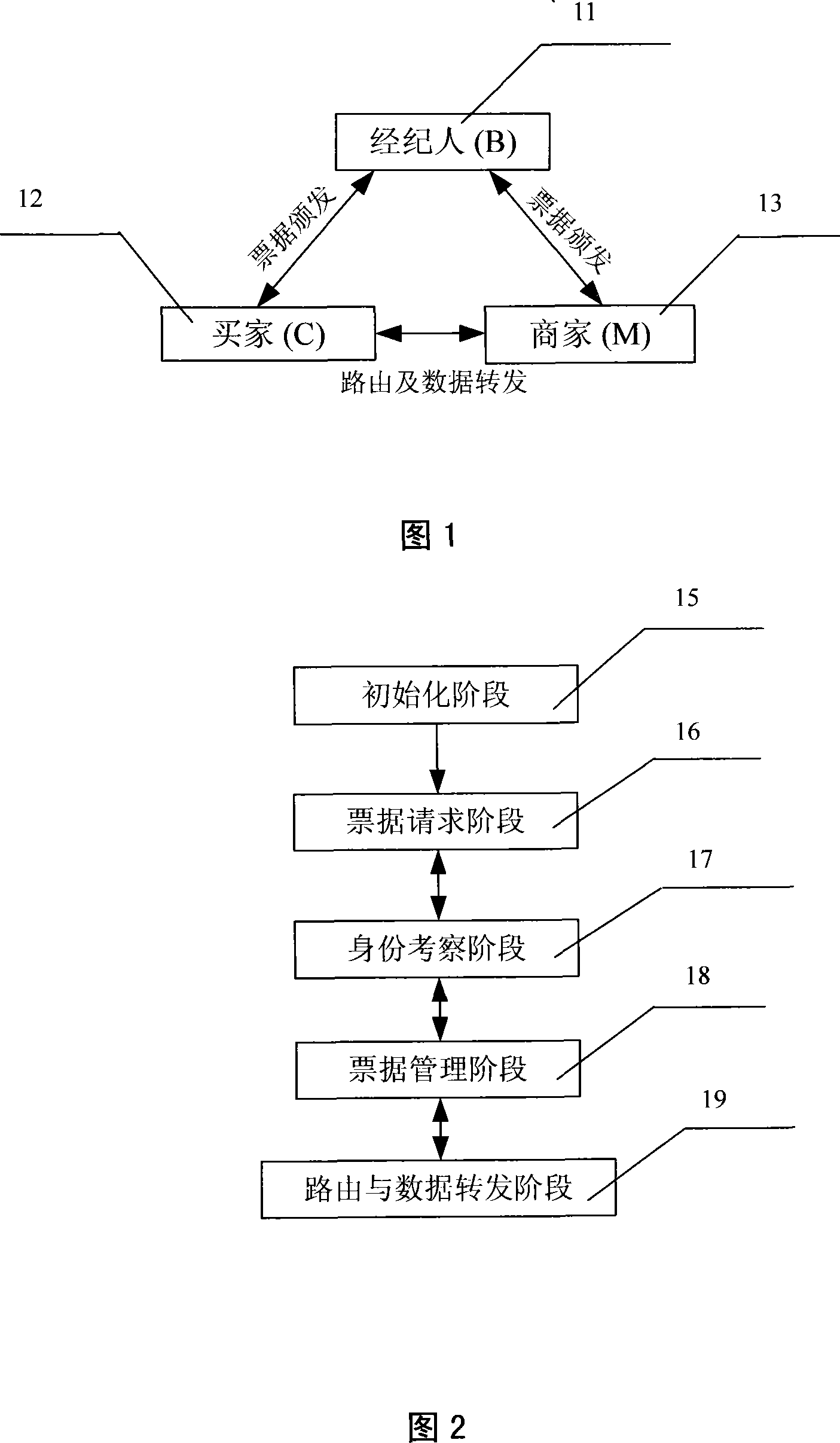
[0033] 1. Reference model
[0034] figure 1It is the reference model of the method for enhancing Ad hoc network security and cooperation mechanism of the present invention. It is a reference model for the reward mechanism based on micropayment, which is a kind of small electronic payment. In the Ad hoc network, nodes correspond to entities in the reference model, and nodes play different roles at different times to complete corresponding tasks in the model. The entities in the model are described as follows:
[0035] 1) Broker: The main task of a node in the identity of a broker is to monitor the behavior of its neighbor nodes, record its reputation value and be responsible for issuing tickets.
[0036] 2) Buyer: The main task of a node as a buyer i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com