Method for protecting against attacks in a high-speed network
A high-speed network and network technology, applied in transmission systems, electrical components, etc., can solve problems such as inability to effectively prevent overflow attacks, and achieve the effect of preventing denial of service attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
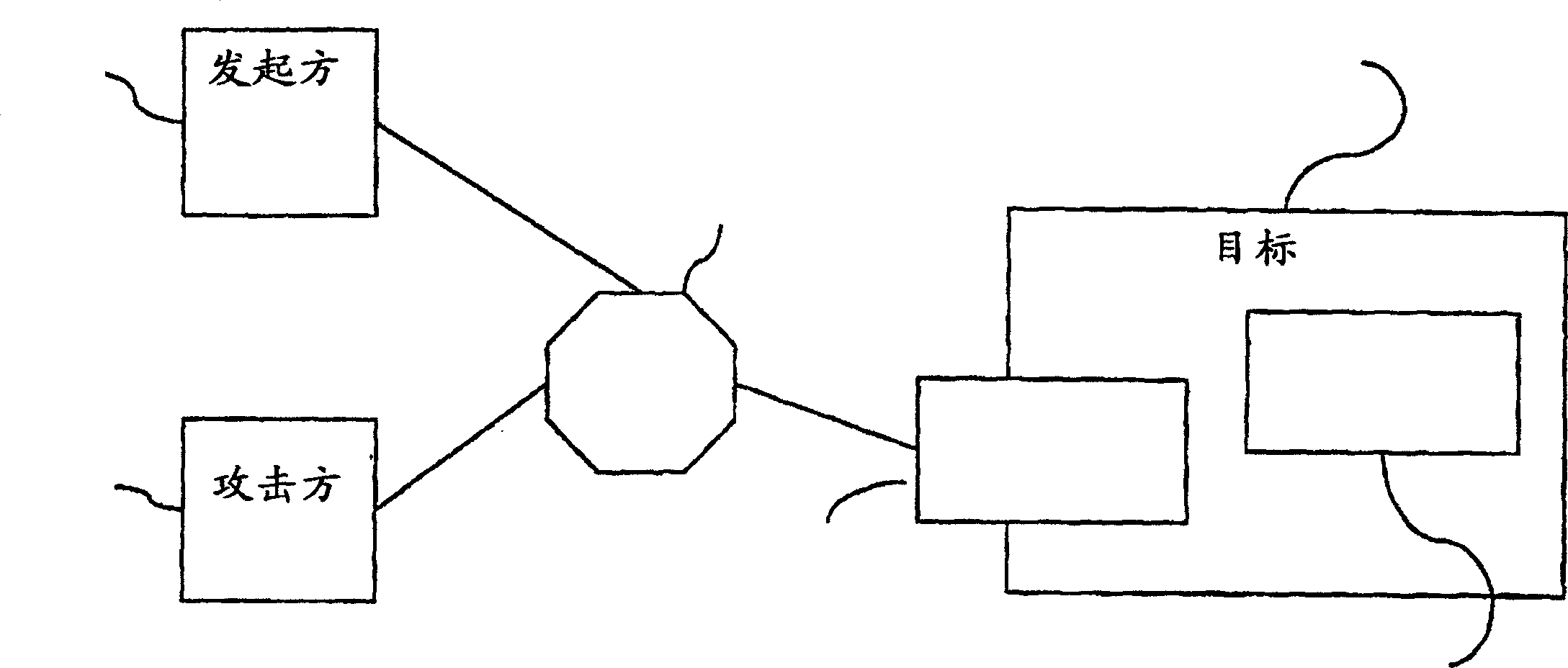
[0033] figure 1 A possible scenario of a denial of service attack is shown. The attacker 10 sends the request to the target 14 over the optical fiber 16 using the source ID of the authorized initiator 12 . According to the present invention, this request is evaluated in the hardware networking module 18 to ensure that the resources of the main CPU 20 in the target are not being used and to prevent the target from overflowing.
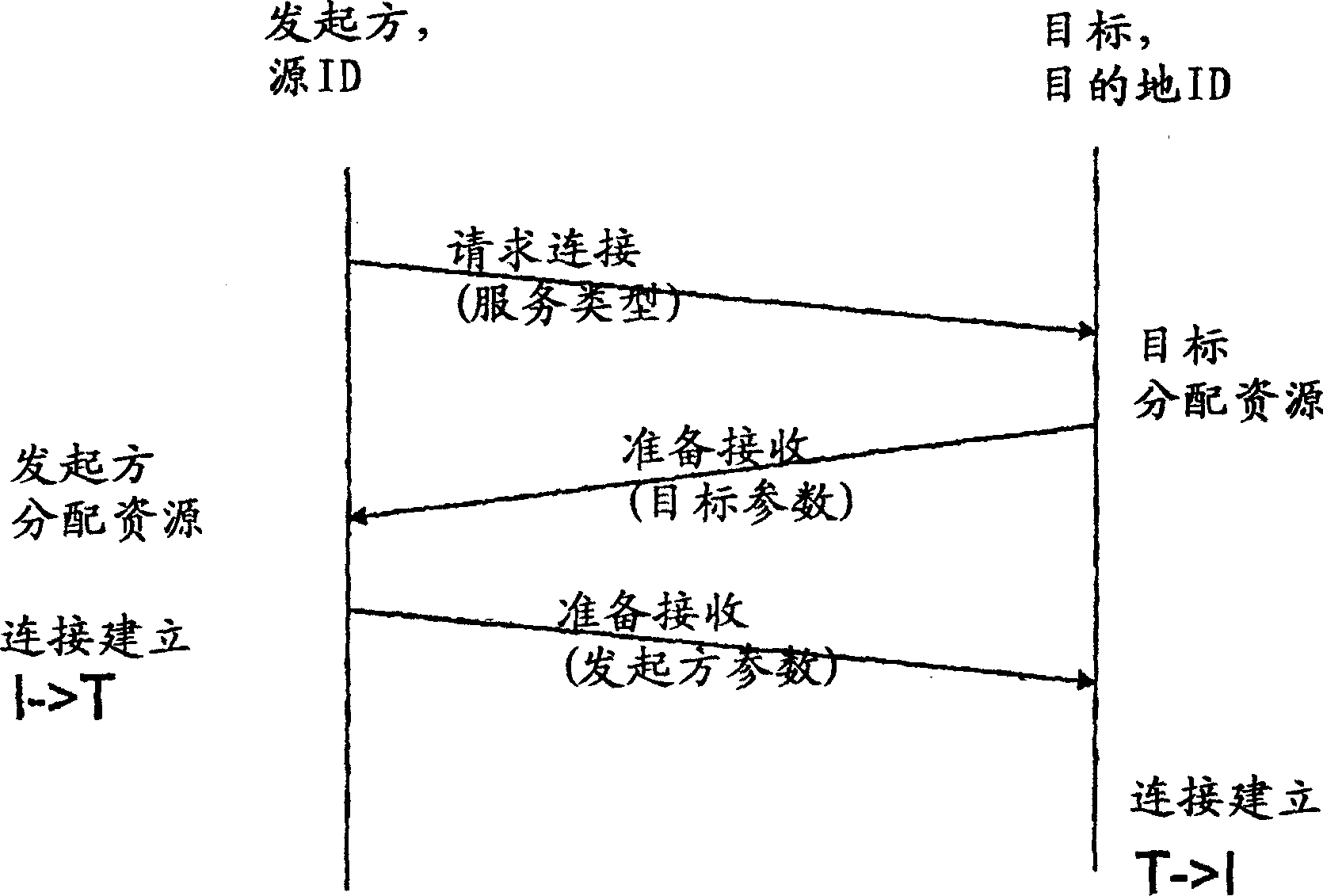
[0034] to see figure 2 , a 3-way handshake protocol is illustrated in the figure. The initiator identified by the source ID sends a request message to the target identified by the destination ID. A target postback includes a ready-to-receive message for the target parameter. To establish a connection, the initiator sends a Ready to Receive message containing the initiator parameters.
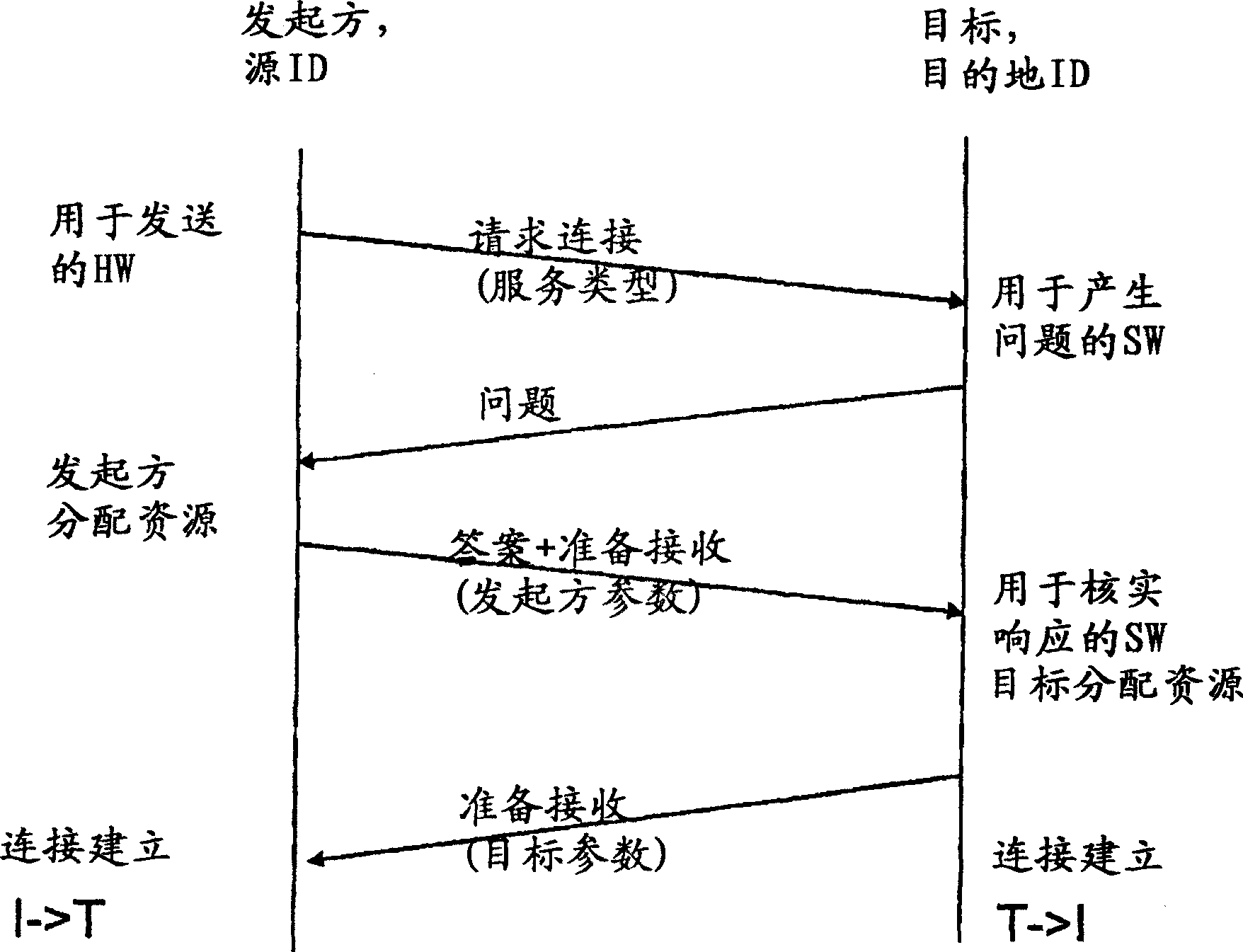
[0035] With this 3-way handshake protocol, an attacker using a spoofed address can flood the target with connection requests because the target allocates resources ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com