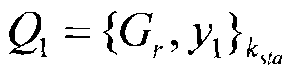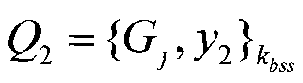Wireless local area network switching authentication method based on elliptical curve
A wireless local area network, elliptic curve technology, applied in wireless communication, user identity/authority verification, security devices, etc., can solve the domino effect attack, can not meet the switching certification, can not save switching time and other problems, to avoid the domino effect Attacks, reducing trust management overhead, and taking into account the effects of efficiency and security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
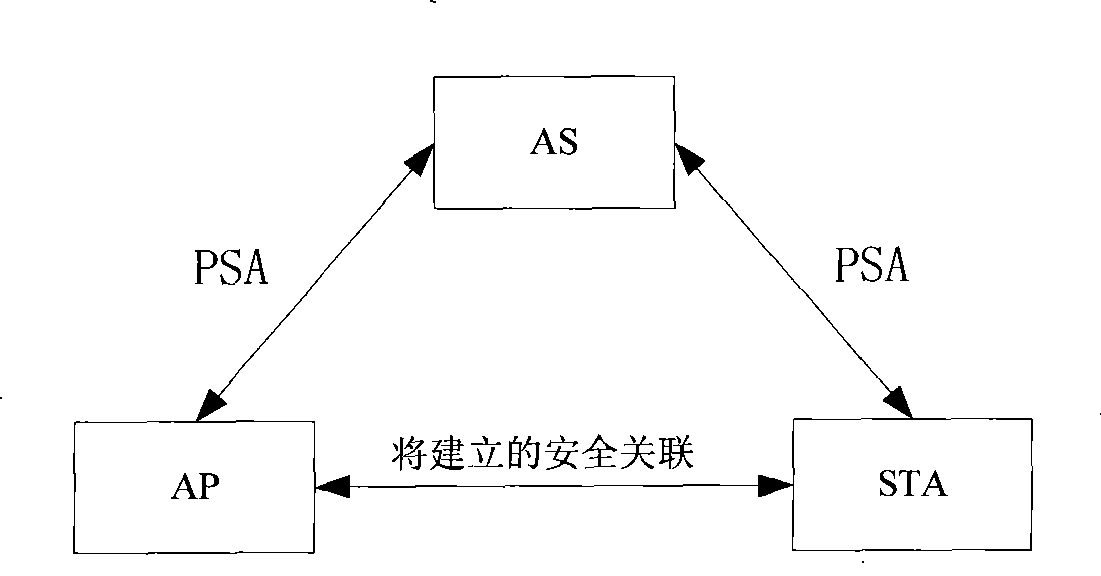
[0034] Such as figure 1 The schematic diagram of the trust model between the authentication server, access point and mobile station in the shown wireless LAN, the authentication server is responsible for maintaining the initial trust relationship, that is, we assume that the authentication server and each access point, the authentication server and each mobile station Secure channels are built respectively. When applying the method of the present invention, the authentication server must first initialize itself, each access point, and each mobile station, and then when the mobile station needs to switch authentication, it only needs to authenticate each other between the mobile station and the target access point.
[0035] A kind of wireless local area network handover authentication method based on elliptic curve, comprises the steps:
[0036] Step 1: Initialization
[0037] (1) Authentication server initialization
[0038] The authentication server creates the first set o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com