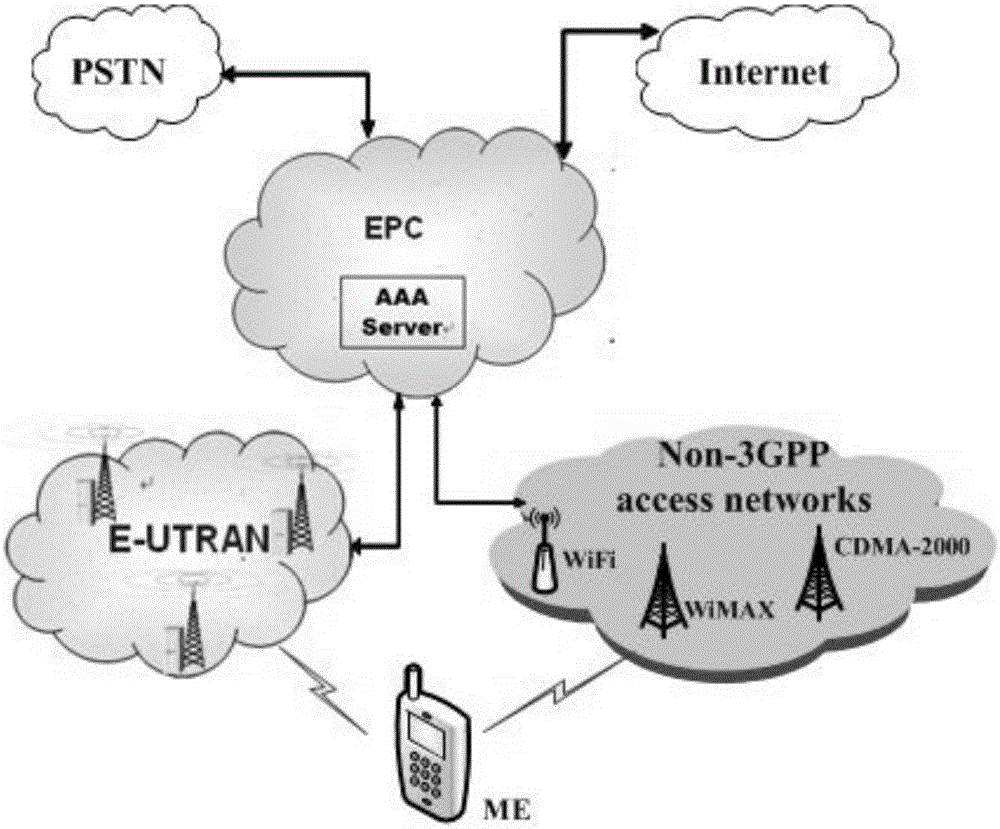
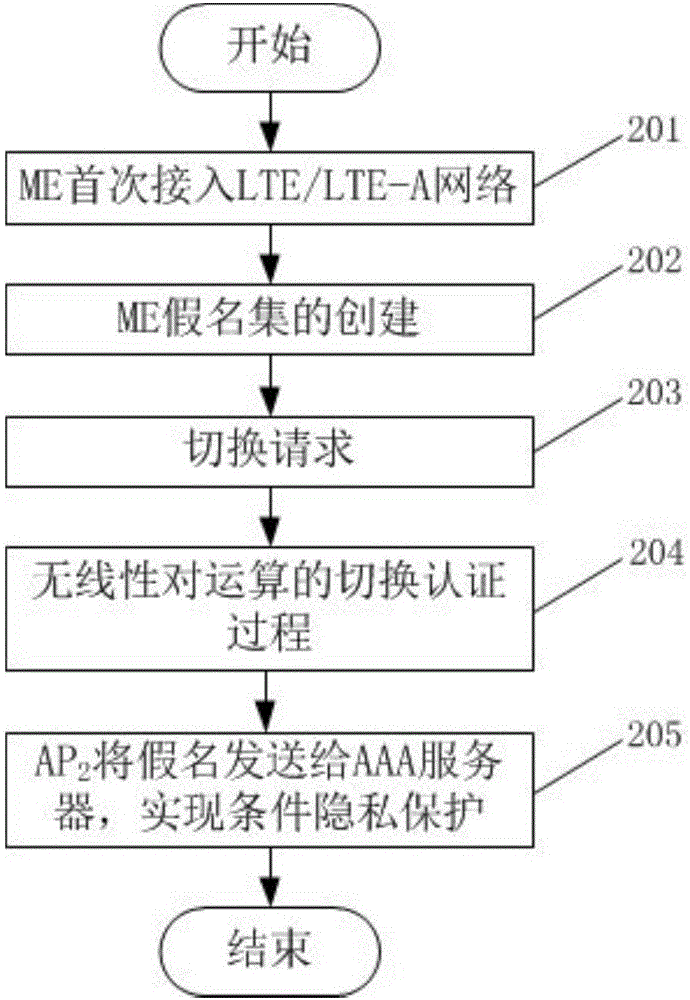
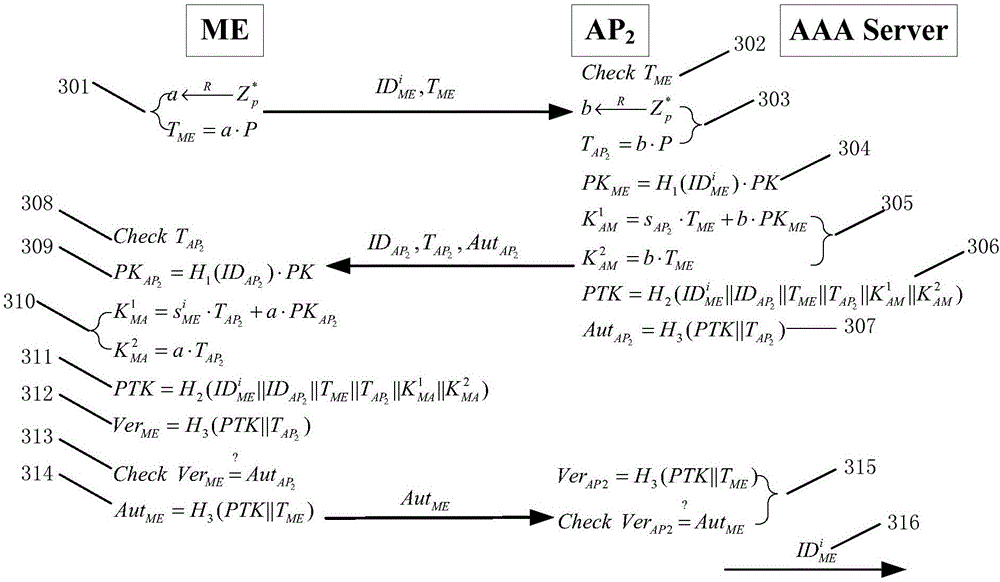
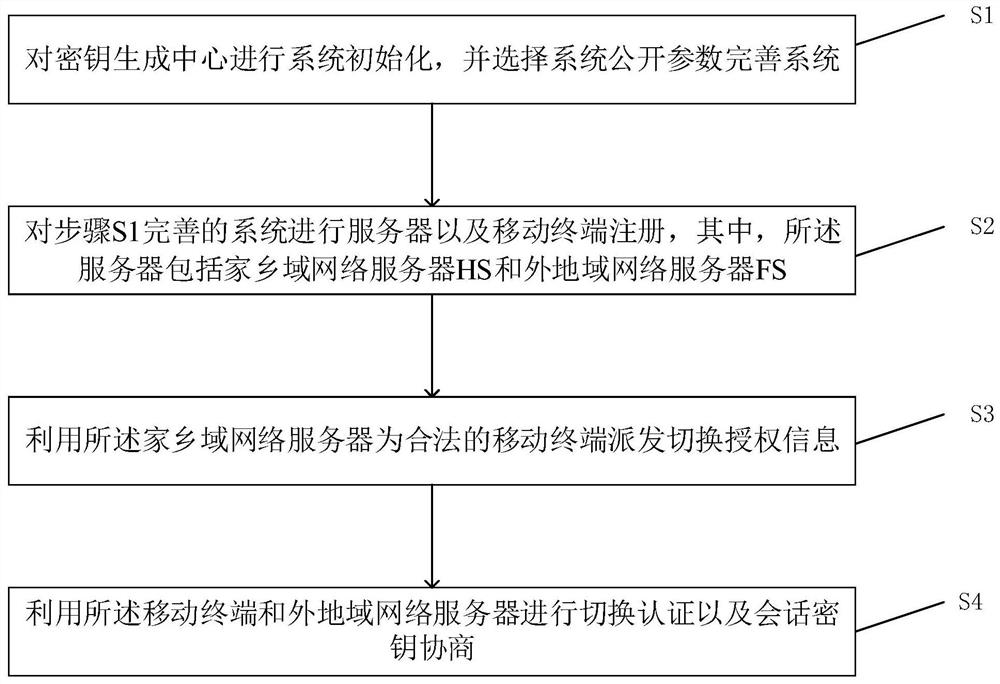
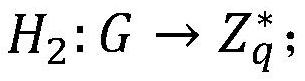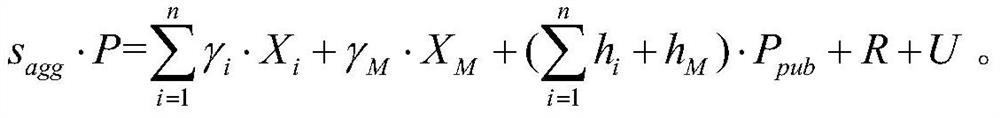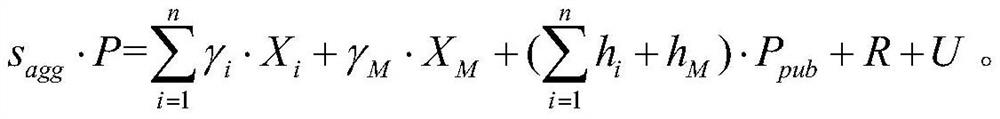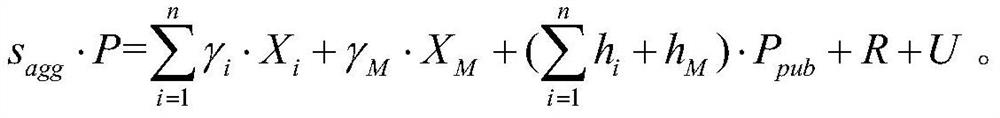Patents
Literature
41 results about "Handover authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
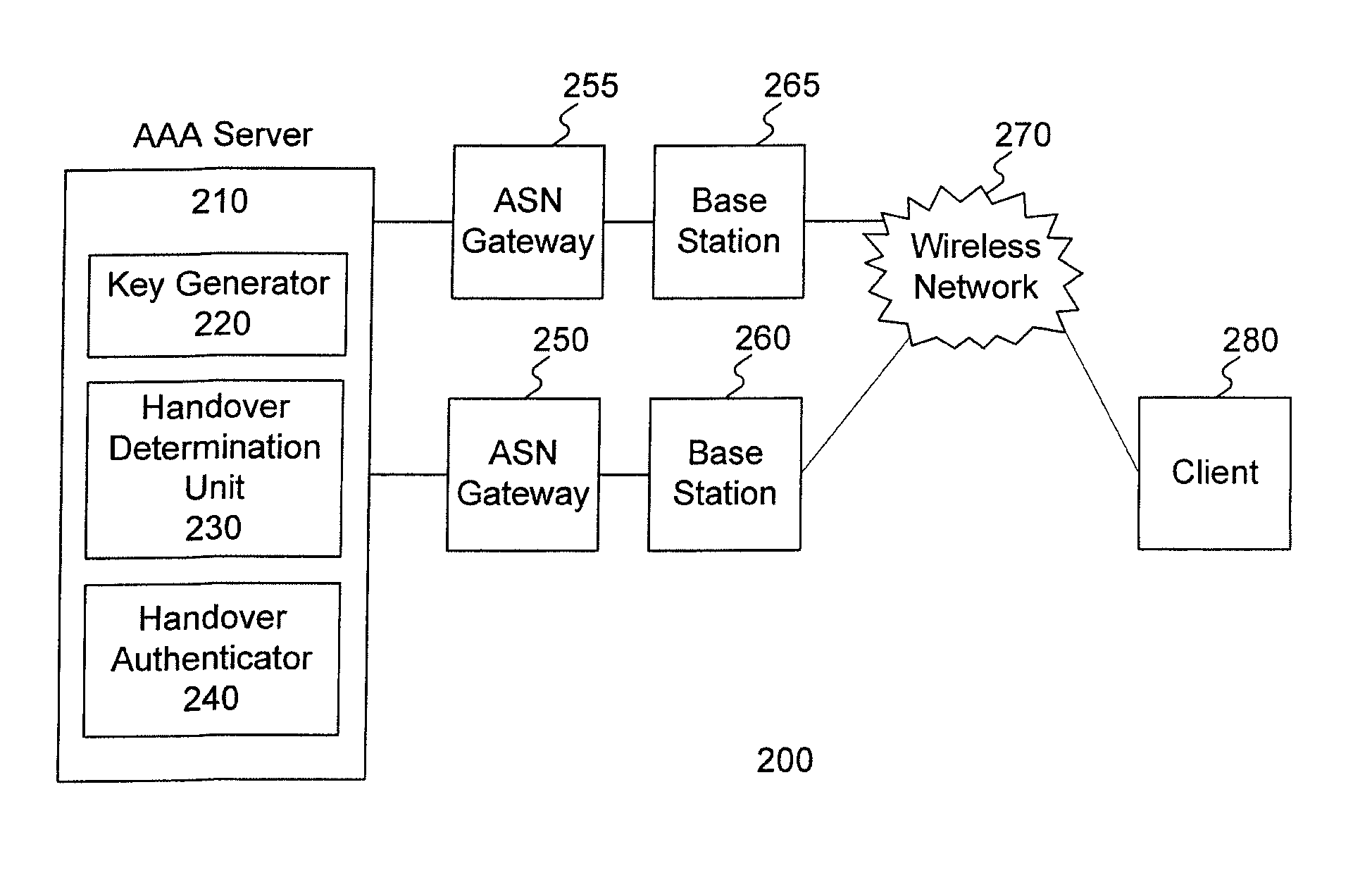
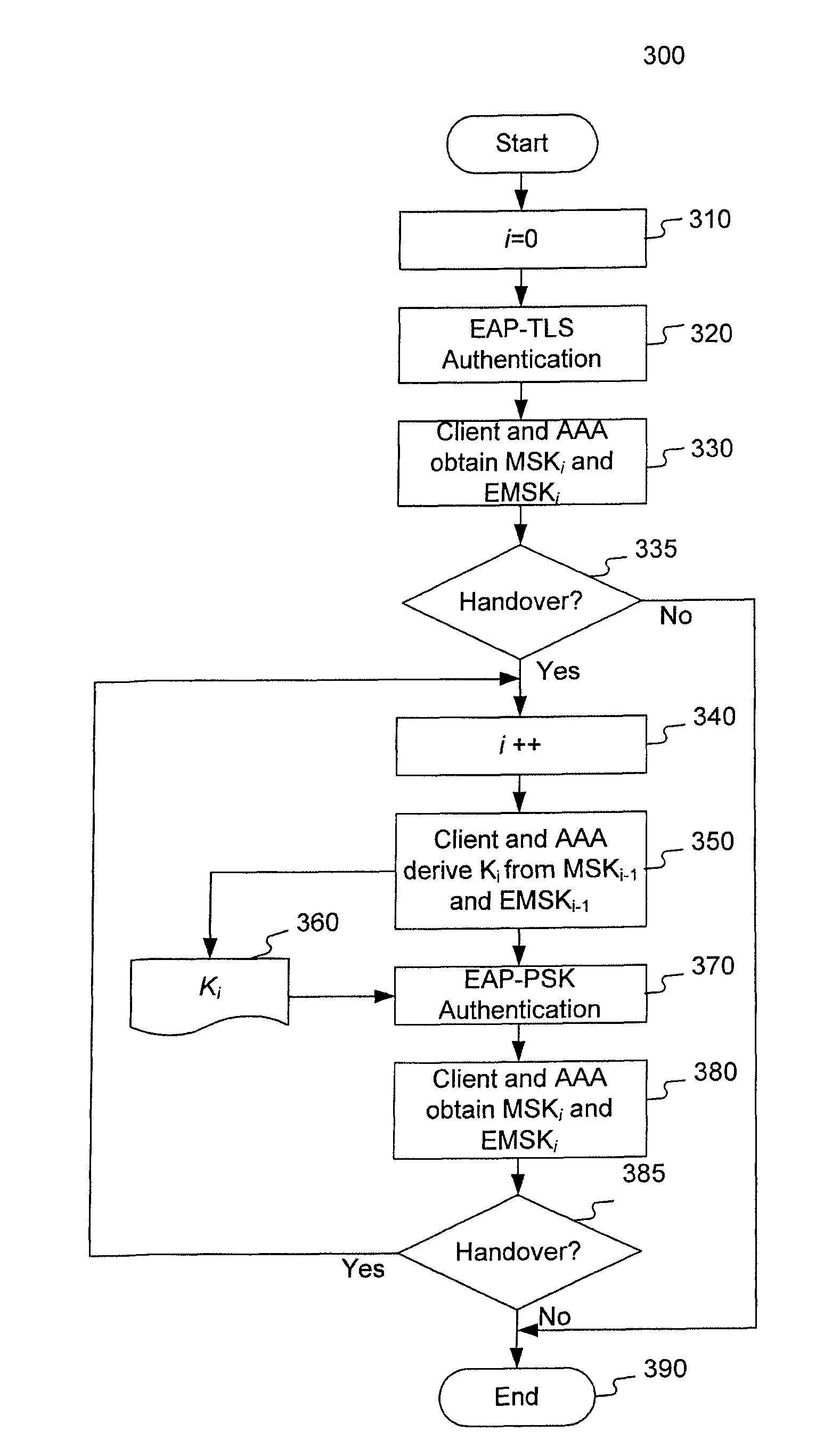
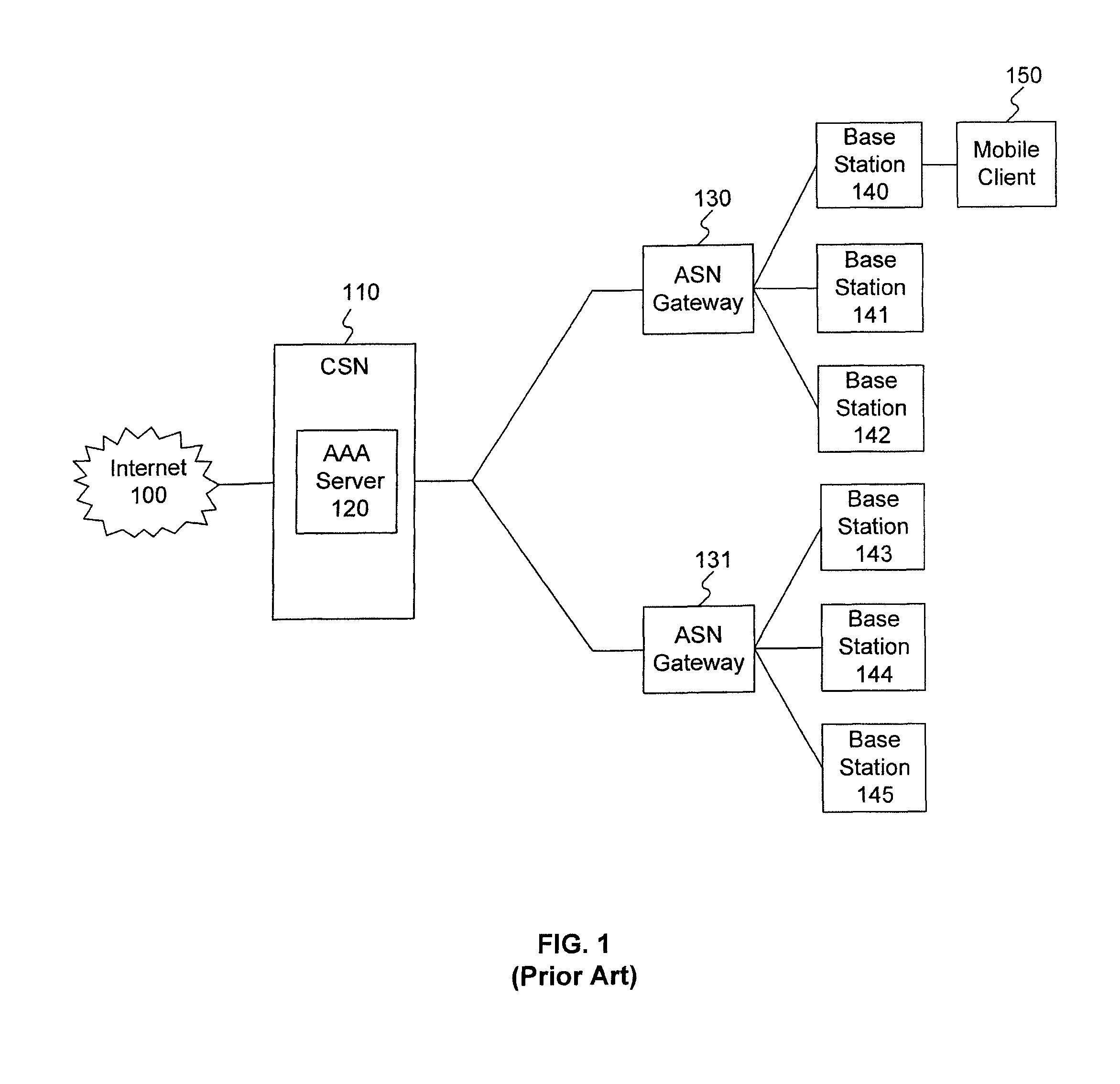
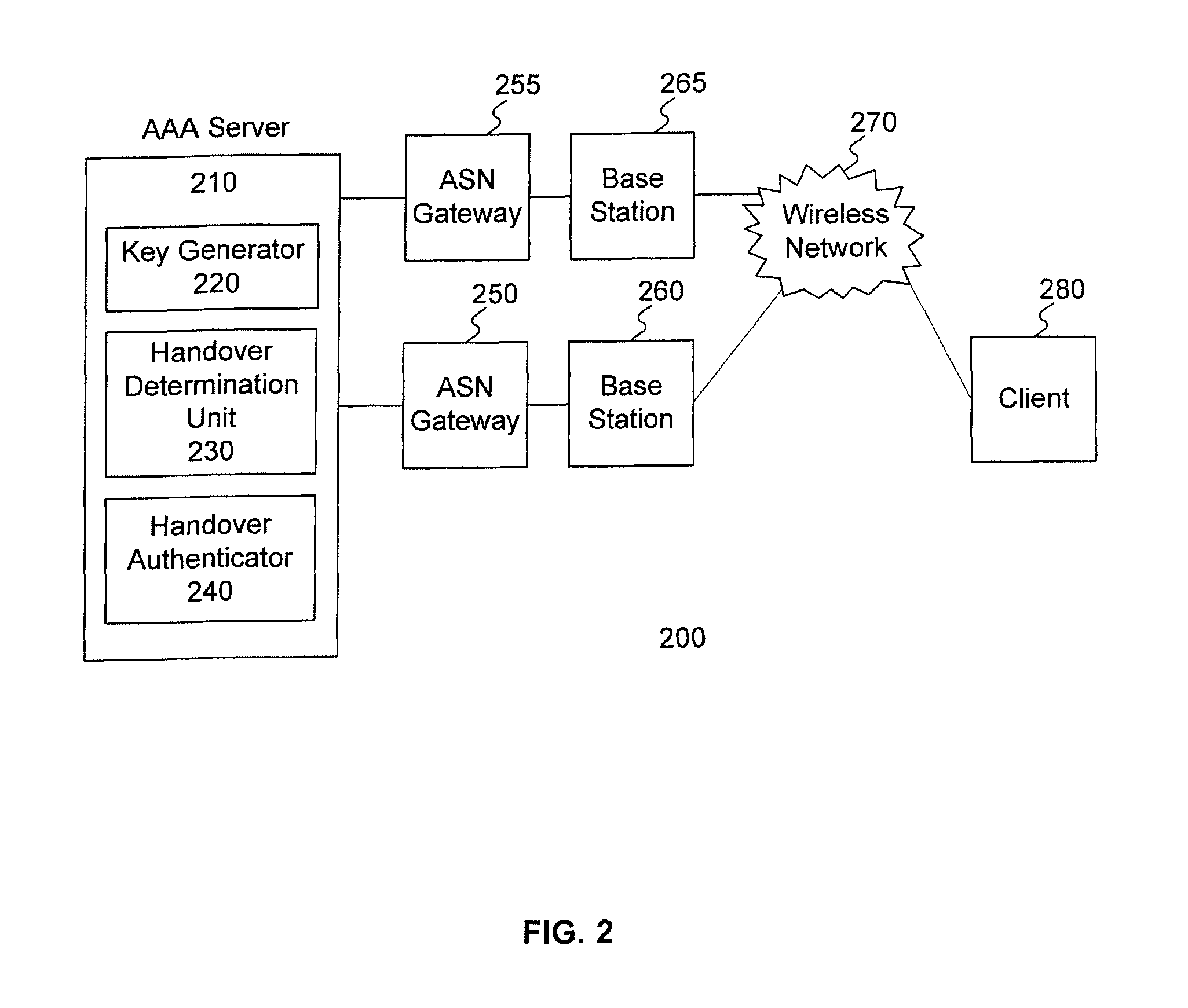
Method and system for handover authentication
ActiveUS20100046467A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsClient-sideNetwork service
A handover authentication method includes performing, by a wireless network server, a first authentication between a client and the wireless network server via a first network gateway; obtaining first authentication keys for the wireless network server and the client based on the first authentication; determining, by the wireless network server, a need to handover the client from the first network gateway to a second network gateway; deriving, by the wireless network server and from the first authentication keys, a handover authentication key shared by the client and the wireless network server; obtaining, by the wireless network server, second authentication keys for the network server and the client; and serving, by the wireless network server, the client via the second network gateway.
Owner:IND TECH RES INST
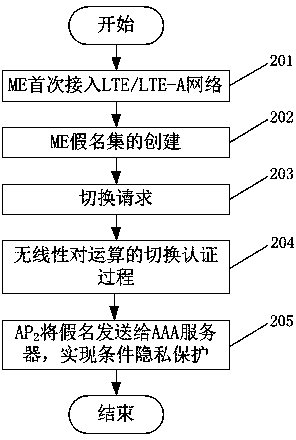
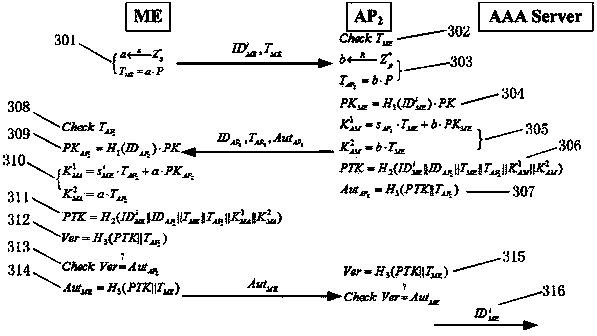
Authentication switching method with privacy protection in LTE (long term evolution)/LTE-A (LTE-advanced) network
InactiveCN103781067ARealize privacy protectionReduce handover authentication delaySecurity arrangementKey exchangeHash function
The invention discloses an authentication switching method with privacy protection in an LTE (long term evolution) / LTE-A (LTE-advanced) network. After ME (mobile equipment) is accessed to the LTE / LTE-A network for the first time and successfully finishes access authentication with an AAA (authentication, authorizing and accounting) server, the AAA server generates a pseudonym set for the ME. When the ME needs to be switched to a new AP (access point) due to movement, only one unused pseudonym needs to be selected from the pseudonym set to perform identity authentication, the real identity of the ME does not need to be provided, so that leakage of a user identity and position privacy can be avoided, and anonymity and untraceability are realized. In the authentication switching process, key agreement is realized based on a Diffie-Hellman key exchange algorithm, the mutual authentication process is finished by hash function value verification, bilinear pairing operation is omitted, and authentication delay is reduced.
Owner:NANJING UNIV OF SCI & TECH
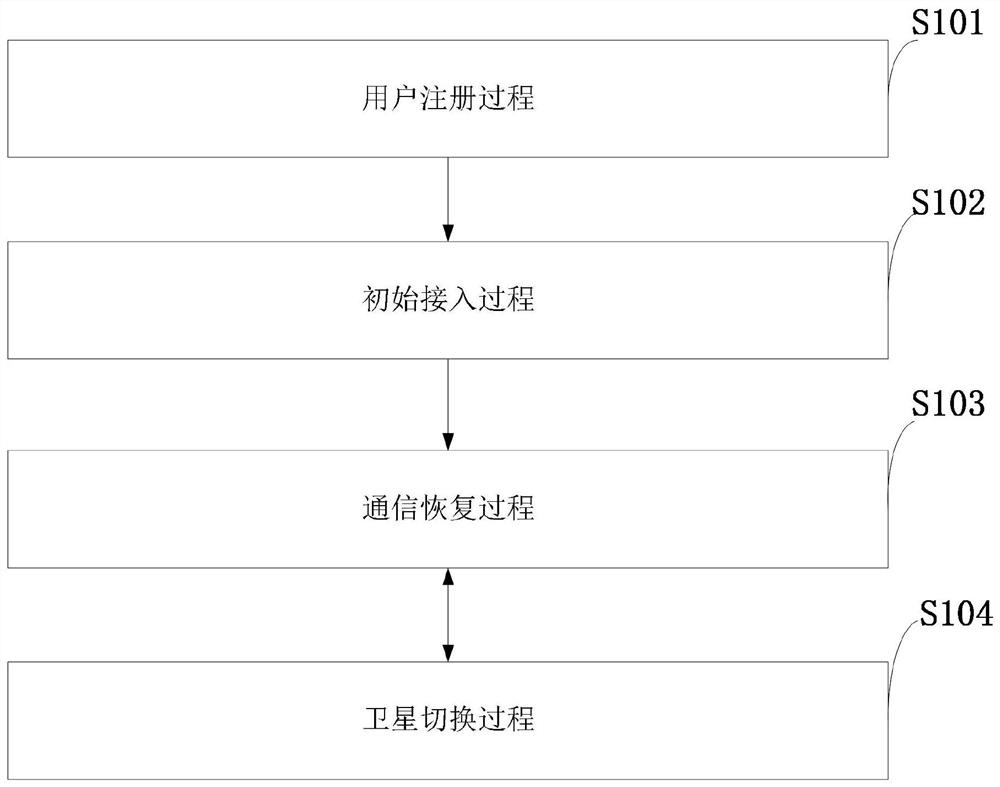
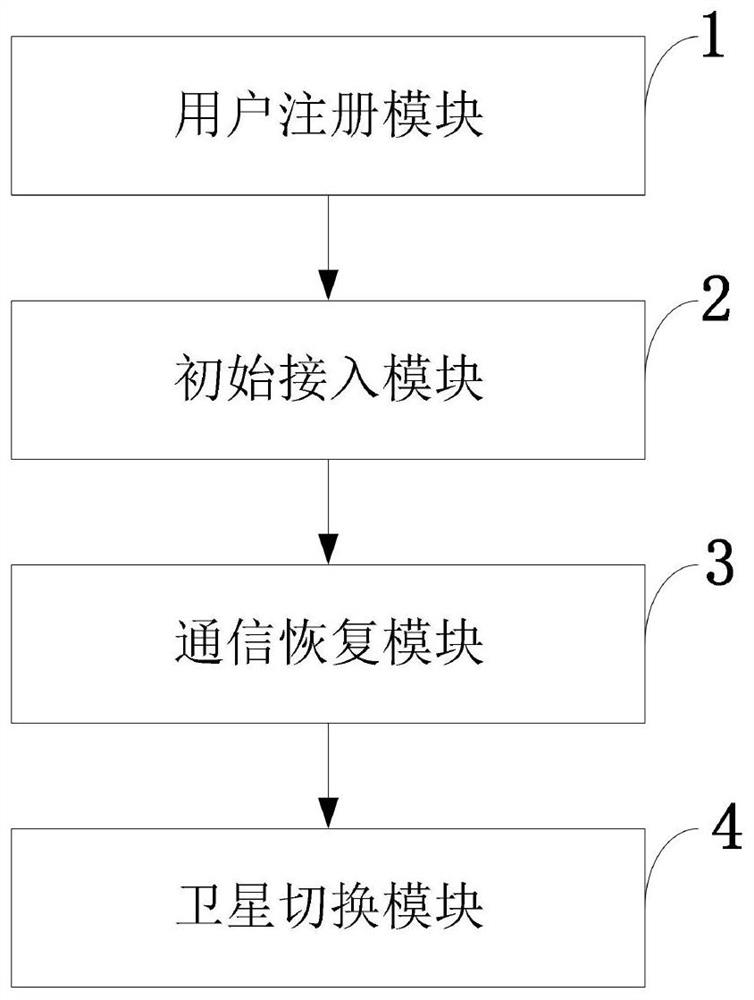
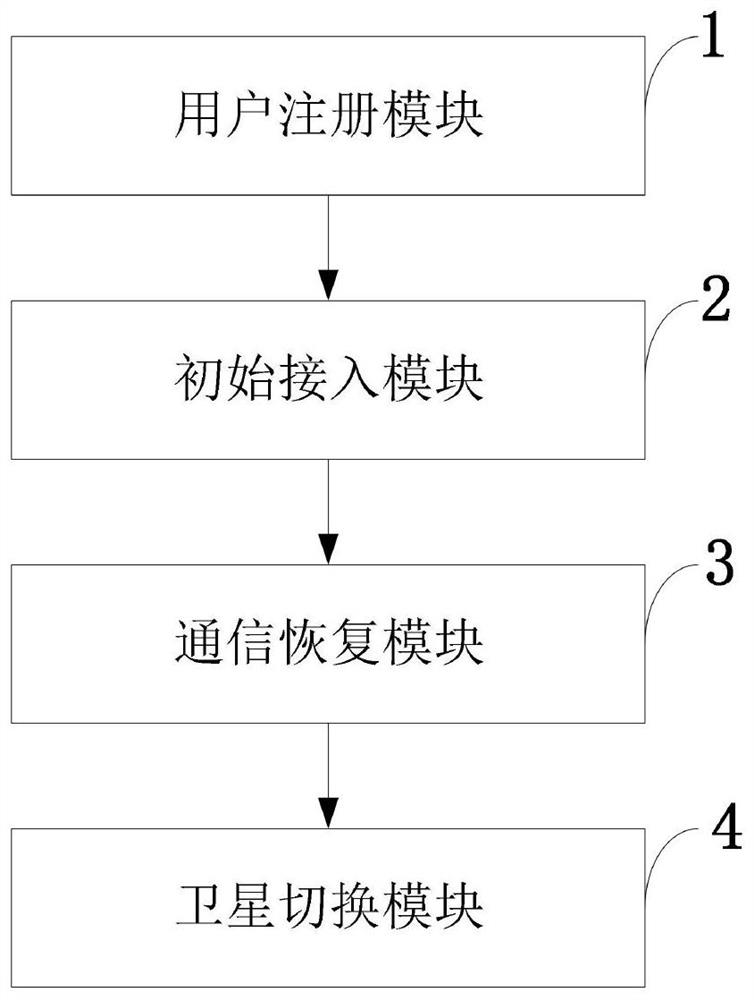
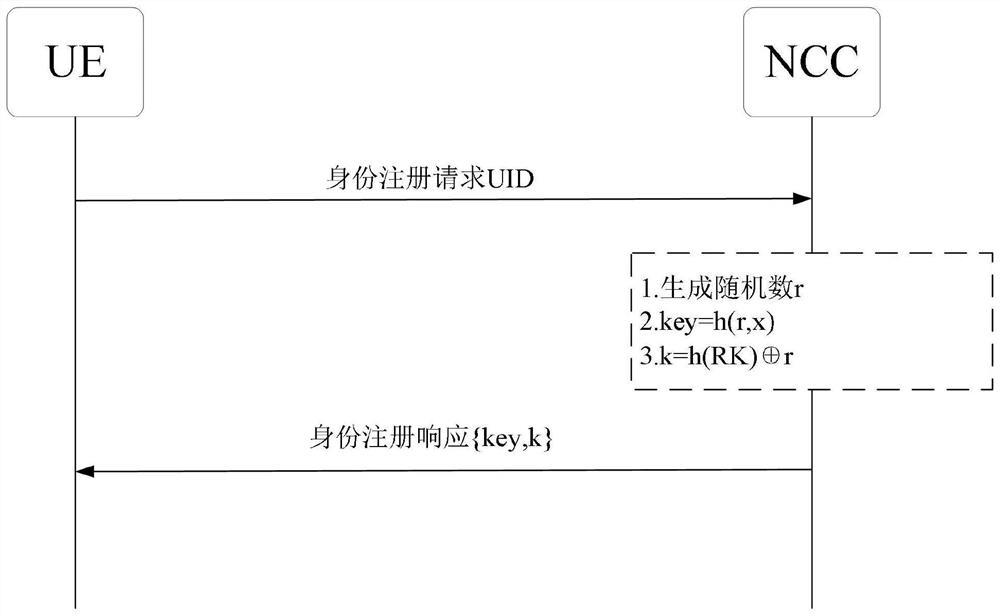
Access and switching authentication method and system in satellite network intermittent connection scene
ActiveCN112087750ASafe and efficient access authentication processReduce the number of interactionsNetwork topologiesSecurity arrangementHash functionTimestamp
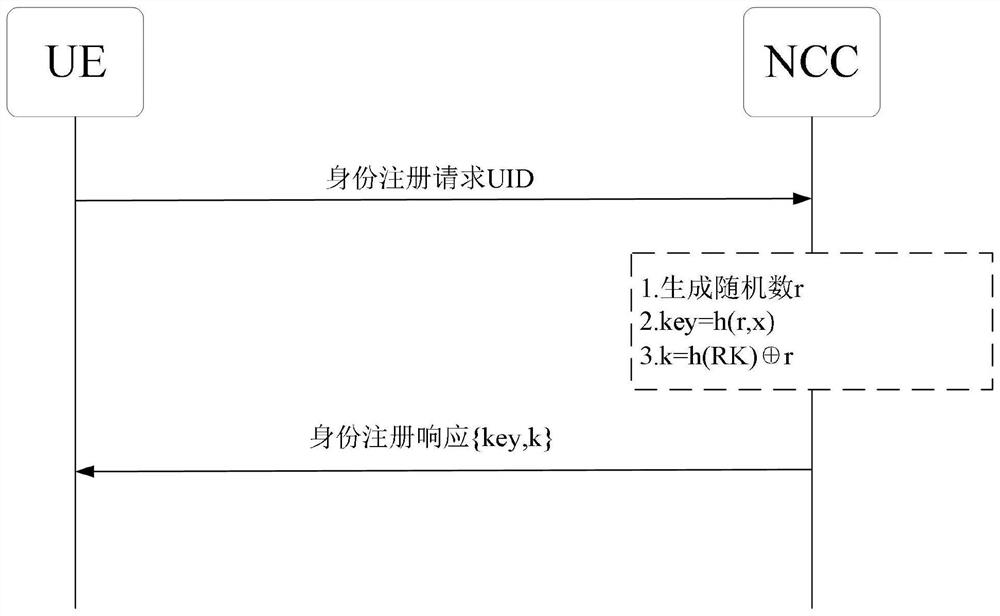
The invention belongs to the technical field of network security communication, and discloses an access and switching authentication method and system in a satellite network interrupted connection scene. The access and switching authentication method has the advantages that: simple hash and XOR operations are used for operation, and meanwhile, a terminal is guaranteed to be safely accessed to a satellite network through using a timestamp, a message authentication code, a random number and RES, and bidirectional authentication is realized while the communication overhead and the calculation overhead are reduced; based on a current session key of a mobile user UE and a satellite network, rapid communication recovery authentication after the UE and the satellite network are disconnected is realized, the unnecessary access authentication frequency is reduced, and the burden of the system is reduced; safe switching is achieved through utilizing random numbers and hash functions, and safe switching is achieved while the communication cost in the satellite switching process is reduced; and the user achieves anonymity by generating a temporary identity, and each successful authentication is refreshed for the next authentication.
Owner:XIDIAN UNIV
Identity-based authentication method for space-based network
ActiveCN113079016ASmall message sizeAvoid transmissionKey distribution for secure communicationUser identity/authority verificationTelecommunicationsEngineering
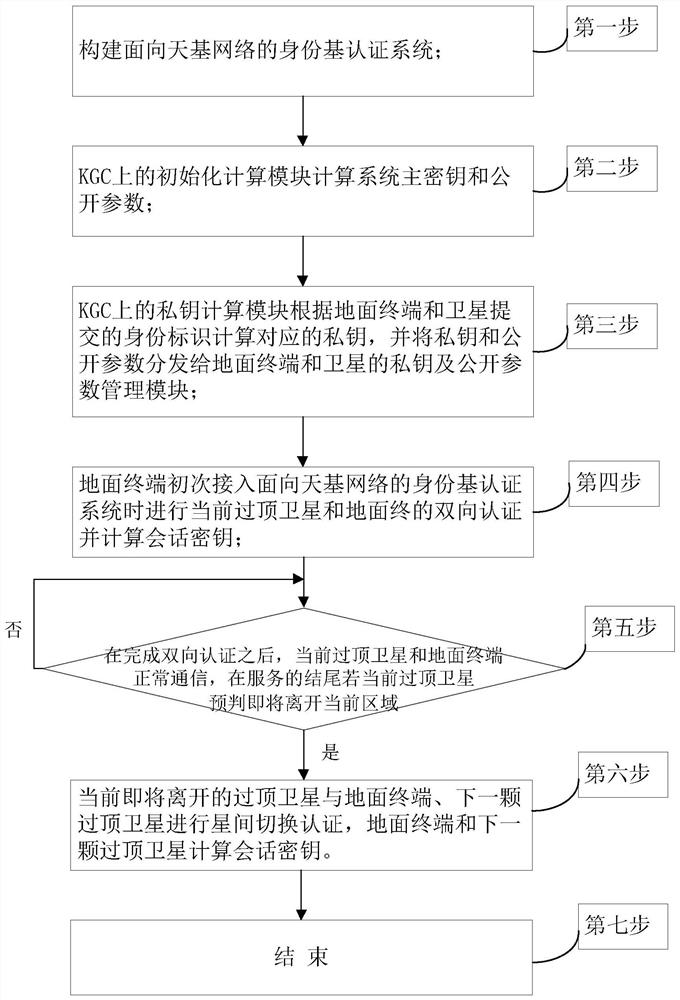
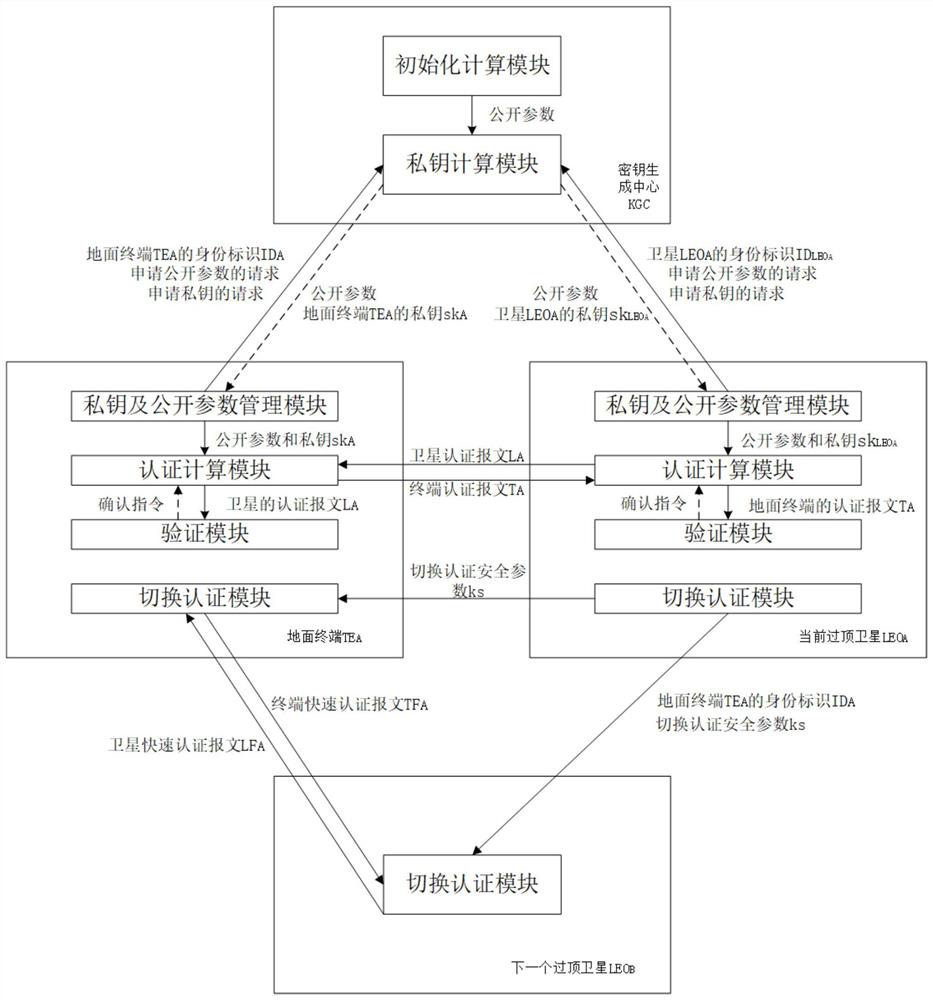
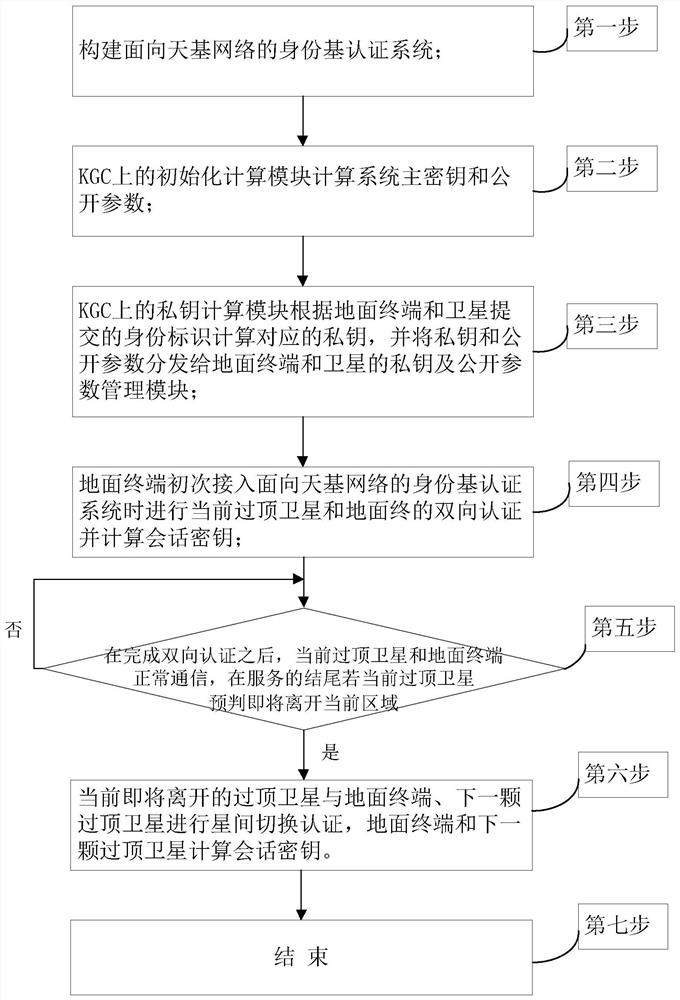
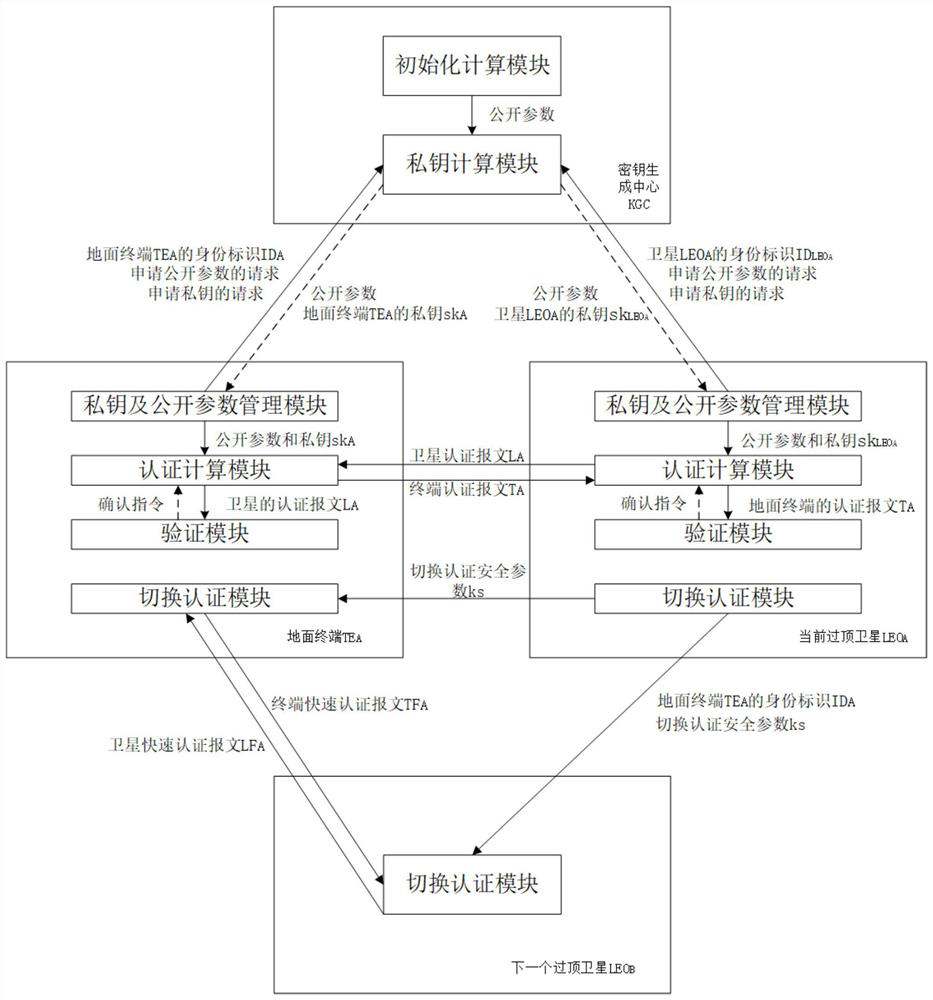
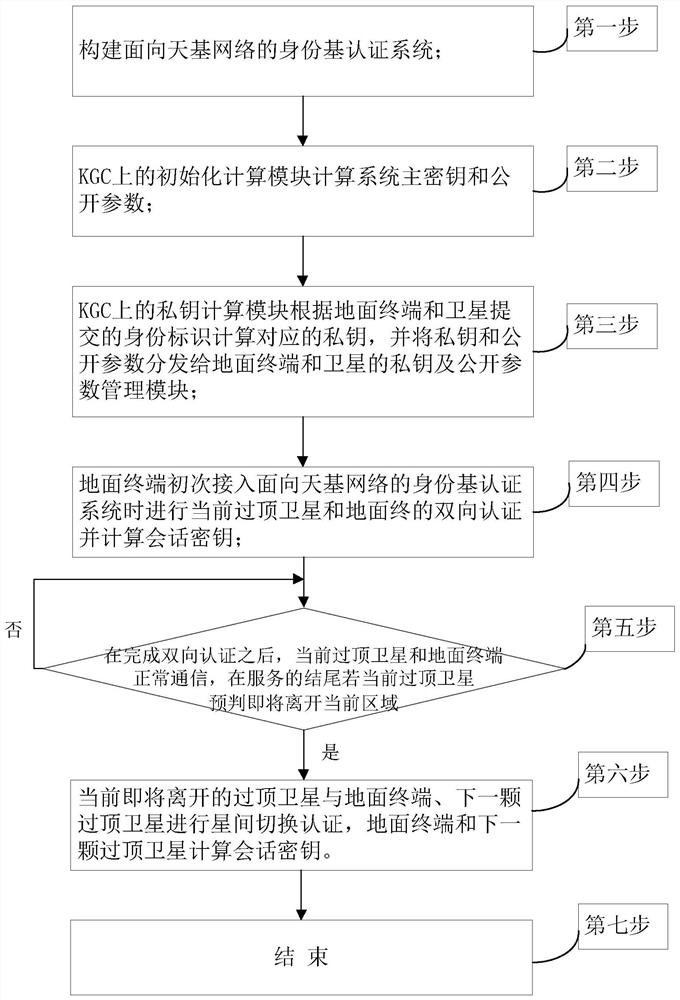
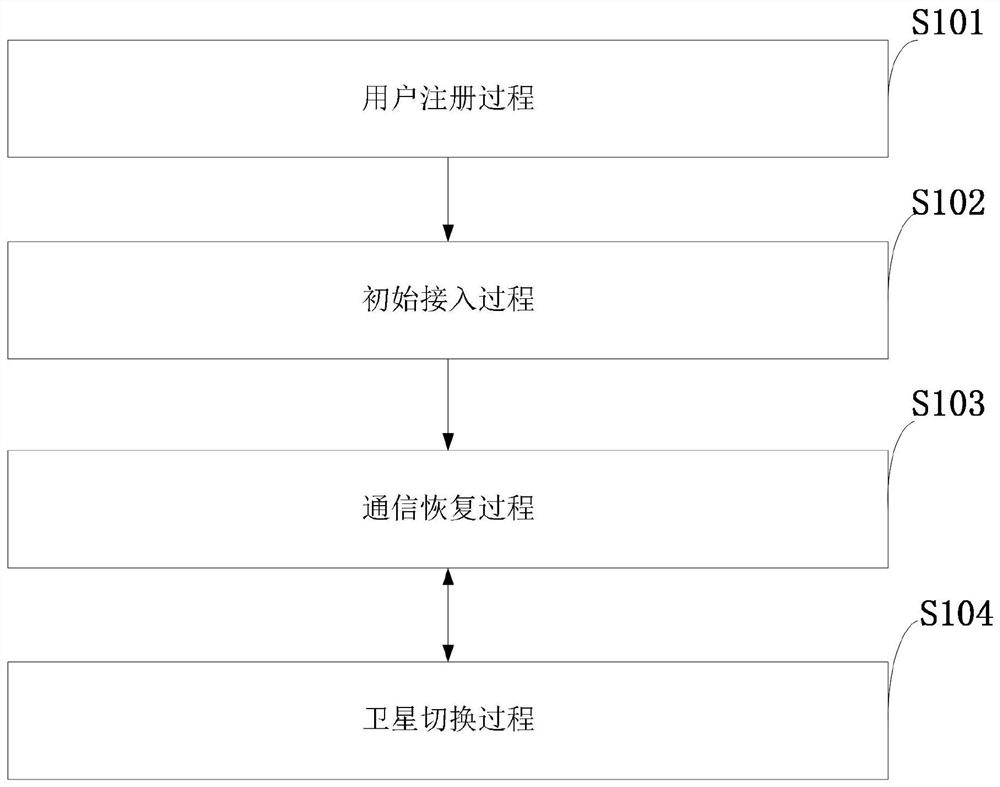
The invention discloses an identity-based authentication method for a space-based network, and aims to solve the problem of security authentication of a ground terminal and a satellite in the space-based network and improve the security of space-based network communication. According to the technical scheme, the method comprises the following steps: firstly, constructing an identity-based authentication system for a space-based network consisting of a ground terminal, a key generation center (KGC) and a low-orbit satellite; by an initialization calculation module of the KGC, calculating a system master key and public parameters; and by a private key calculation module of the KGC, calculating a corresponding private key and distributing the private key and the public parameters to the ground terminal and the satellite. When a terminal TEA gets access, bidirectional authentication and session key negotiation of a current overhead satellite LEOA and the TEA are carried out, then the LEOA and the TEA normally communicate with each other, if the LEOA determines that the LEOA is about to leave a current area at the end of service, inter-satellite switching authentication is carried out, if the LEOA determines that the LEOA is not about to leave the current area at the end of service, the LEOA and the TEA continue to communicate with each other. According to the invention, the size of the transmitted message is effectively reduced, and fast switching authentication and session key negotiation are realized while the security is ensured.
Owner:NAT UNIV OF DEFENSE TECH
Combined handover authentication method and system used for goods escorting
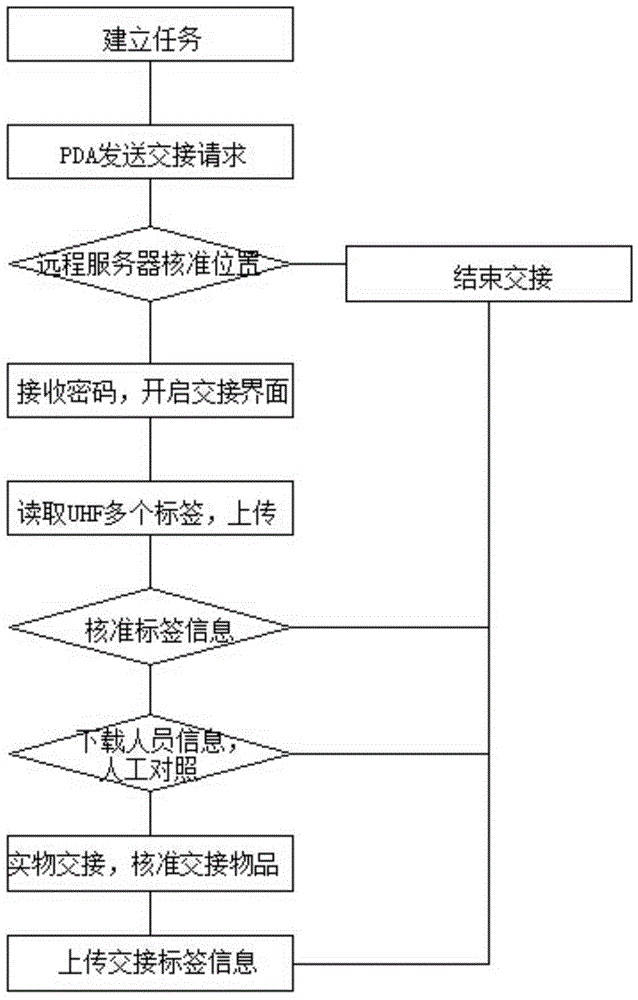
InactiveCN104392339AAvoid private transfersStrong process controllabilityLogisticsSecret codeGeolocation
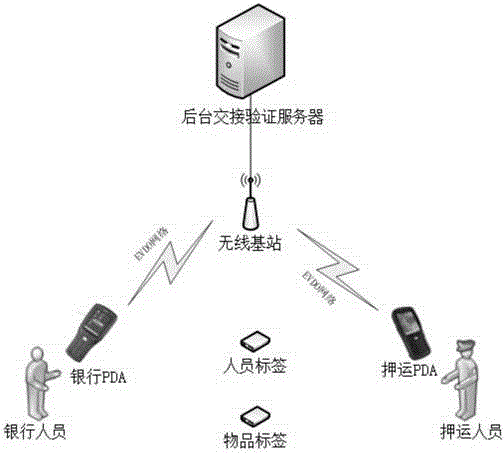
The invention discloses a combined handover authentication method and system used for goods escorting. The method is characterized by including the following steps that: (a) handover task information is pre-stored to a remote server; (b) handheld terminals transmit handover requests through a wireless network, detect geographic positions where signals are transmitted, and after conformation between the geographic positions and geographic positions pre-stored in the remote server are confirmed, opening codes are send back; (c) the handheld terminals open authentication interface display, and read several pieces of authentication tag information, are coupled with the remote server through the wireless network, and judge whether the obtained authentication tag information is correct or not through comparison, at the same time, download personnel information, and the method enters a manual authentication phase; and (d) physical handover is performed, and tag information of handover items is uploaded, and the handover terminates. The system can keep real-time communication with the remote server through the wireless network. According to the combined handover authentication method and system, an electronic fence is set, and information can be uploaded and downloaded on line, and the controllability, timeliness and reliability of a handover process can be ensured, and situations such as handover errors and omissions can be avoided; and the whole handover process has traceability, so that the whole handover process is safer and more reliable.
Owner:SUZHOU UNIV
Quick switching authentication method for low-orbit satellite communication network
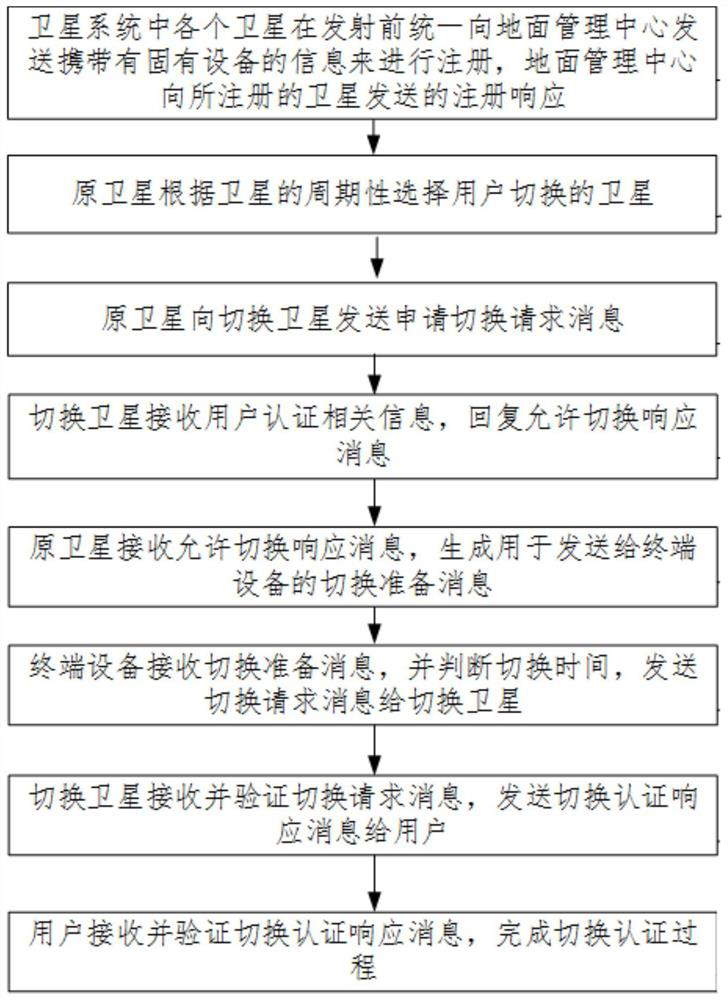
ActiveCN112332900AReduce overheadGuaranteed continuityUser identity/authority verificationRadio transmissionTelecommunicationsHandover authentication
The invention discloses a quick switching authentication method for a low-orbit satellite communication network, which comprises the following steps that: a user terminal and a satellite terminal carry satellite inherent equipment information to register in a ground management center, and an original satellite selects a satellite switched by the user terminal according to the periodicity of the satellite to send a switching application request message; if successfully decrypting the authentication information of the user terminal, the switching satellite repliess a switching permission response message to the original satellite; the original satellite receives the switching permission response message of the switching satellite, generates switching preparation information and sends the switching preparation information to the user terminal; the user terminal receives the switching preparation message, determines the switching time, and sends a switching authentication request message to the switching satellite; the switching satellite receives the switching authentication request message and sends switching authentication response information to the user terminal; the user terminalreceives and verifies the switching authentication response information to complete a switching authentication process; According to the method, the security of the switching authentication process of the user terminal is ensured while the switching authentication time delay and the calculation overhead are reduced.
Owner:GUIZHOU AEROSPACE INST OF MEASURING & TESTING TECH
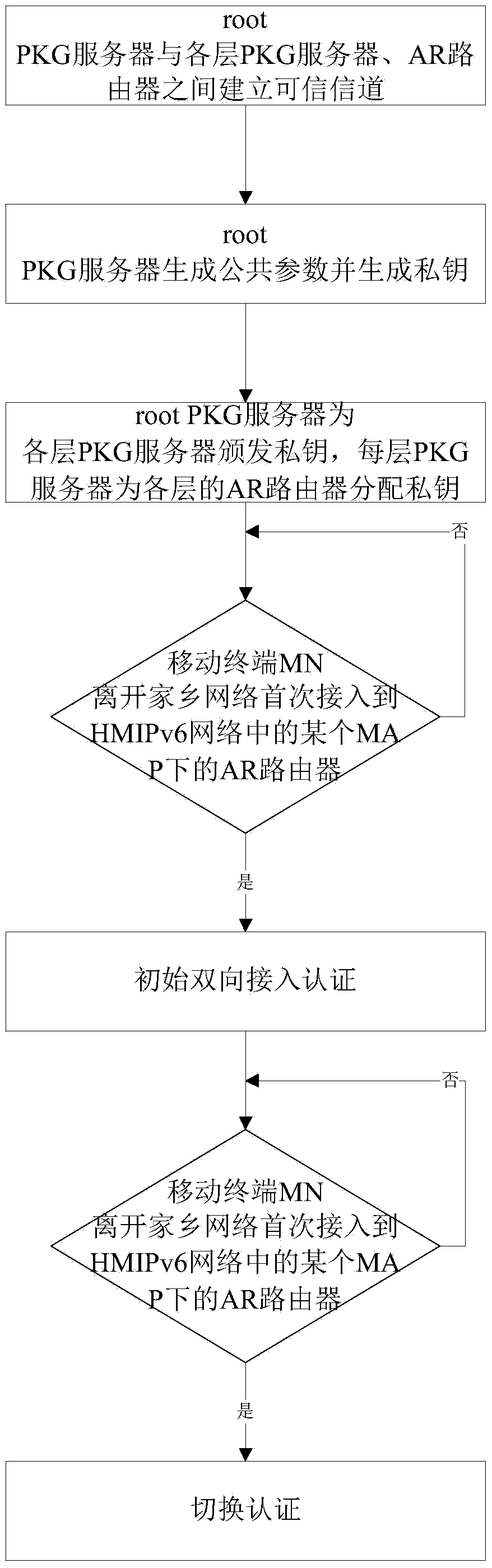
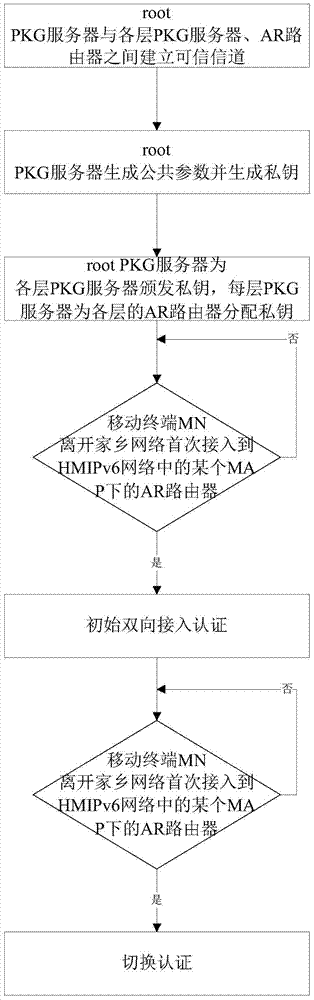
Two-way access authentication method for multi-layer-MAP oriented HMIPv6 network
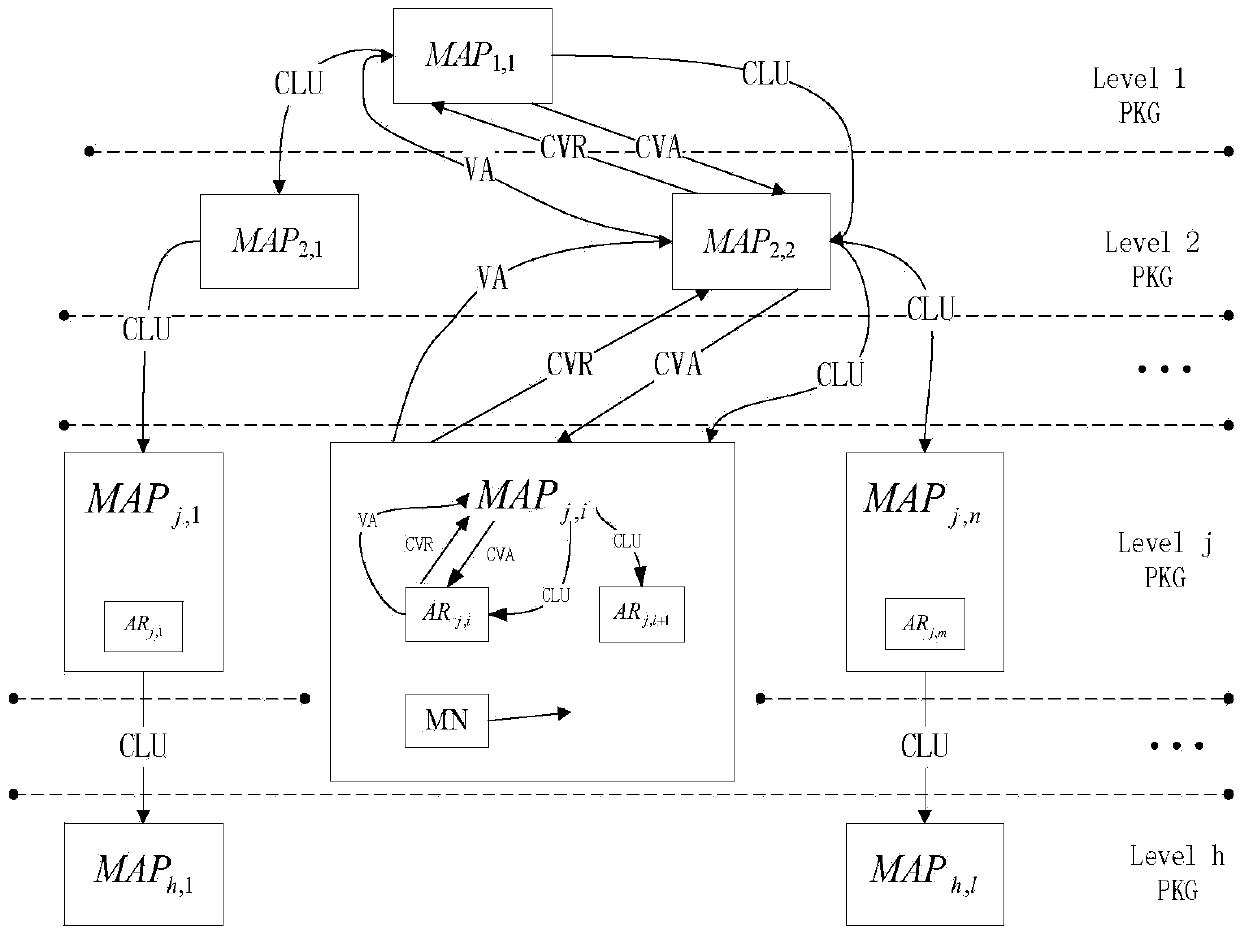
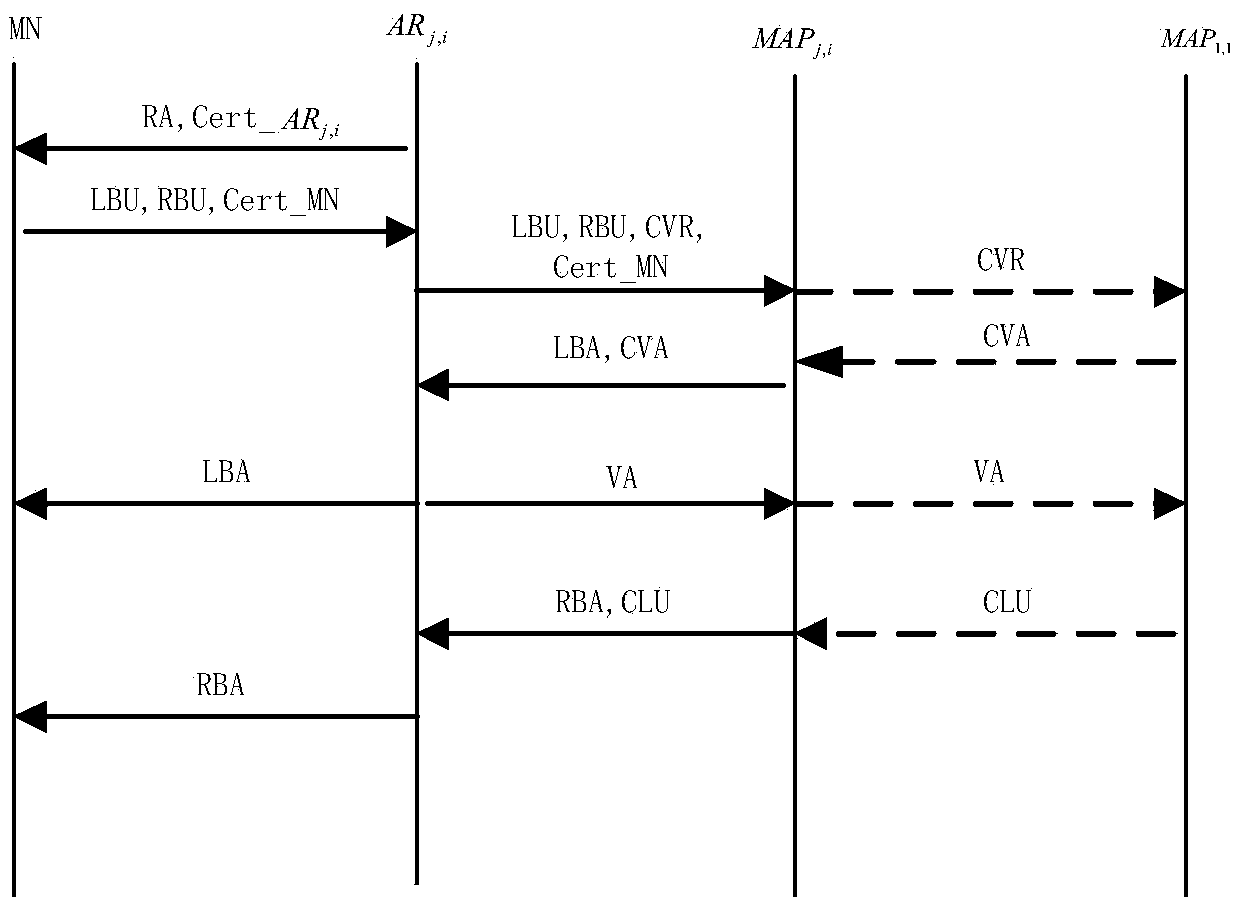
ActiveCN105376230AShorten the lengthImplement two-way authenticationTransmissionSecurity arrangementShort signatureTrusted third party
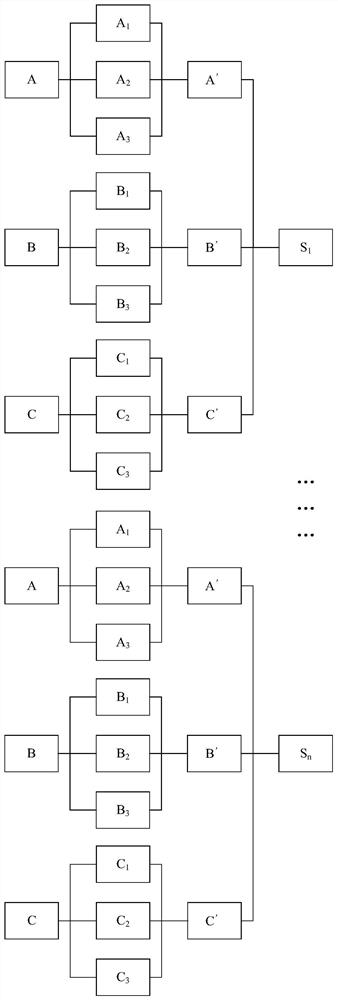
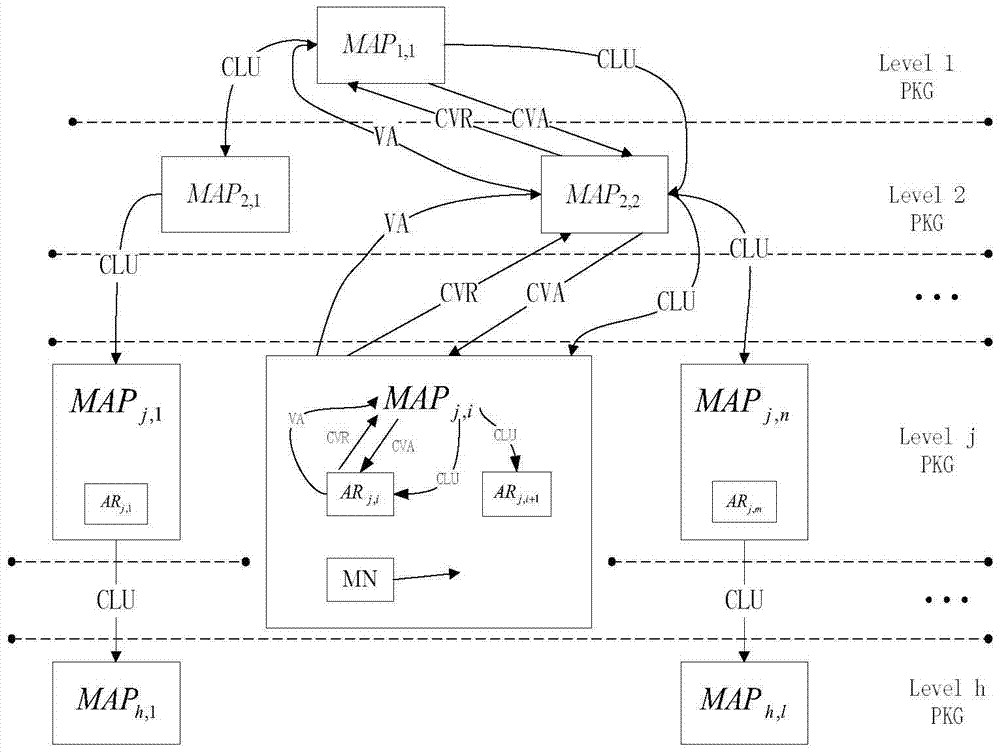
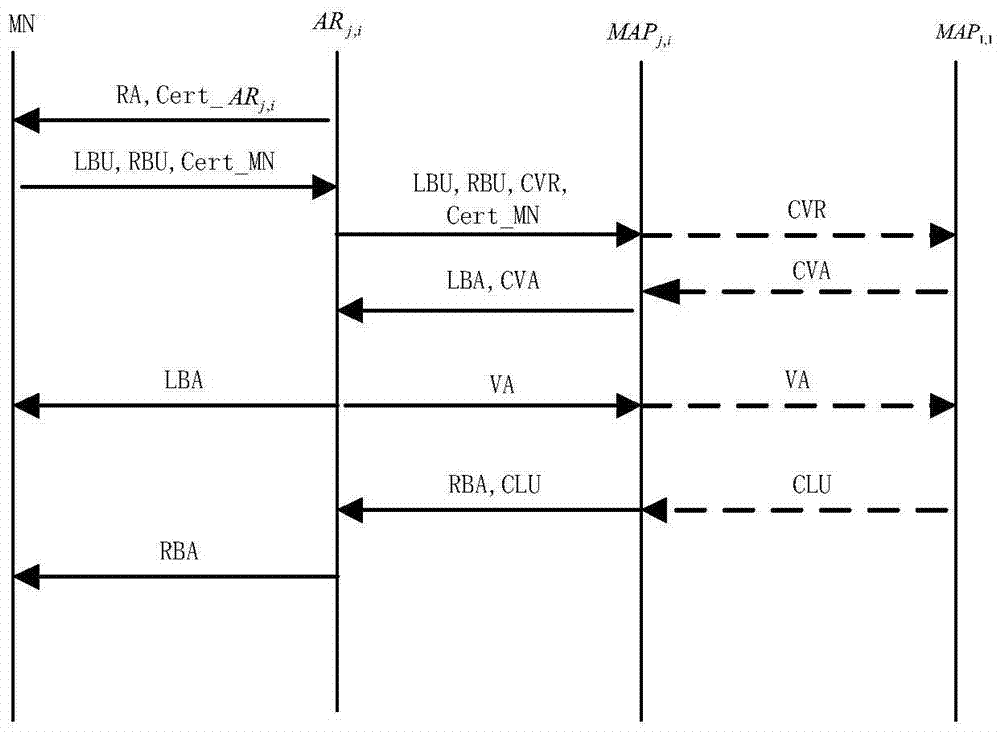
The invention provides a two-way access authentication method for a multi-layer-MAP oriented HMIPv6 network. The two-way access authentication method comprises the following steps that: a root PKG server is used as a trusted third party; a trusted channel is established among the root PKG server, PKG servers and AR routers in various layers; the root PKG server generates common parameters and private keys; the root PKG server issues the private keys to the PKG servers in the various layers according to identity information of the PKG servers in the various layers; the PKG server in each layer distributes the private key to the AR router in this layer according to identity information of the AR router in this layer; when a mobile node MN leaves a home homework and is accessed to the AR router under a certain MAP in the HMIPv6 network for the first time, initial two-way access authentication is carried out; and, when the mobile node MN is in a currently accessed foreign network and the AR router in the current MAP domain is switched into another MAP domain or another AR router, switching authentication is carried out. The invention provides a short signature scheme based on node certificate hierarchical identity; the security is based on the h-CDH problem; the short signature scheme has the advantages that: the lengths of the private keys are reduced along with increasing of hierarchical levels; and the lengths of the private keys are independent of the hierarchical levels.
Owner:NORTHEASTERN UNIV
Data feedback method and system
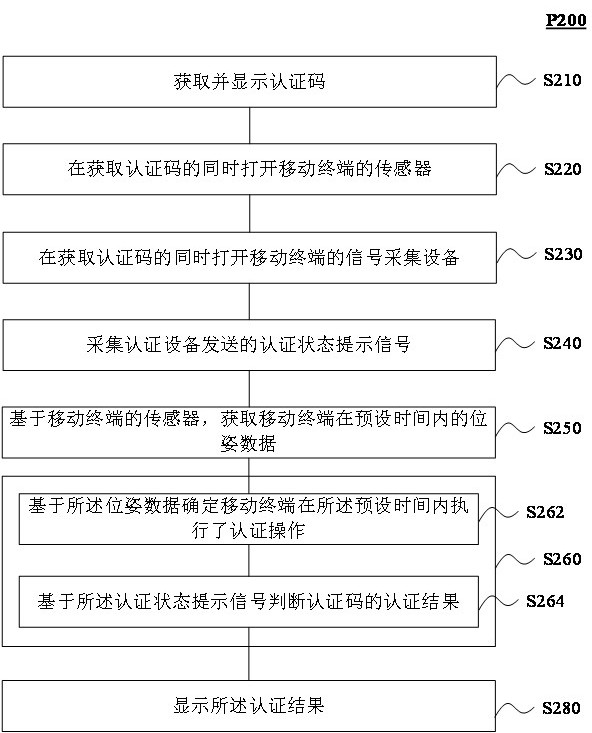
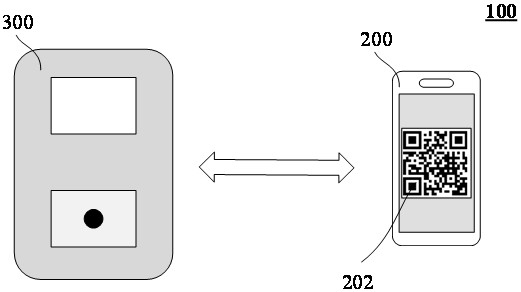
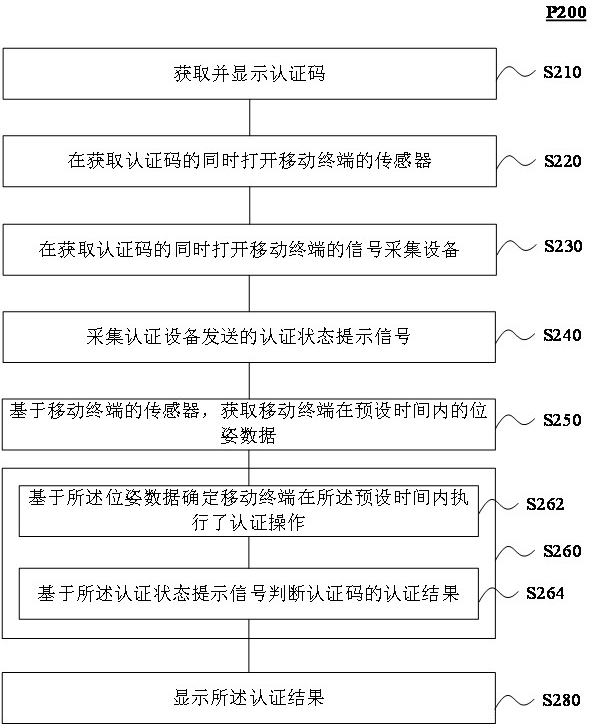
ActiveCN111738736AImplement feedbackImprove experienceDevices with sensorCo-operative working arrangementsEmbedded systemHandover authentication
According to the data feedback method and system provided by the invention, after the mobile terminal calls out the authentication code, the pose data of the mobile terminal is acquired through the sensor of the mobile terminal, and the code scanning authentication state prompt signal of the authentication equipment is acquired through the signal acquisition equipment of the mobile terminal; whether the mobile terminal performs a code scanning authentication action or not is judged according to the pose data; and a code scanning authentication result is judged according to the acquired code scanning authentication state prompt signal, and the authentication result is displayed on a page of the mobile terminal. According to the method and the system, the code scanning authentication resultcan be fed back to the mobile terminal in real time in an offline state of the authentication equipment or the mobile terminal, and the mobile terminal is prompted to switch the authentication code after the code scanning is failed. Therefore, real-time feedback of data in an offline state is realized, and the user experience is improved.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
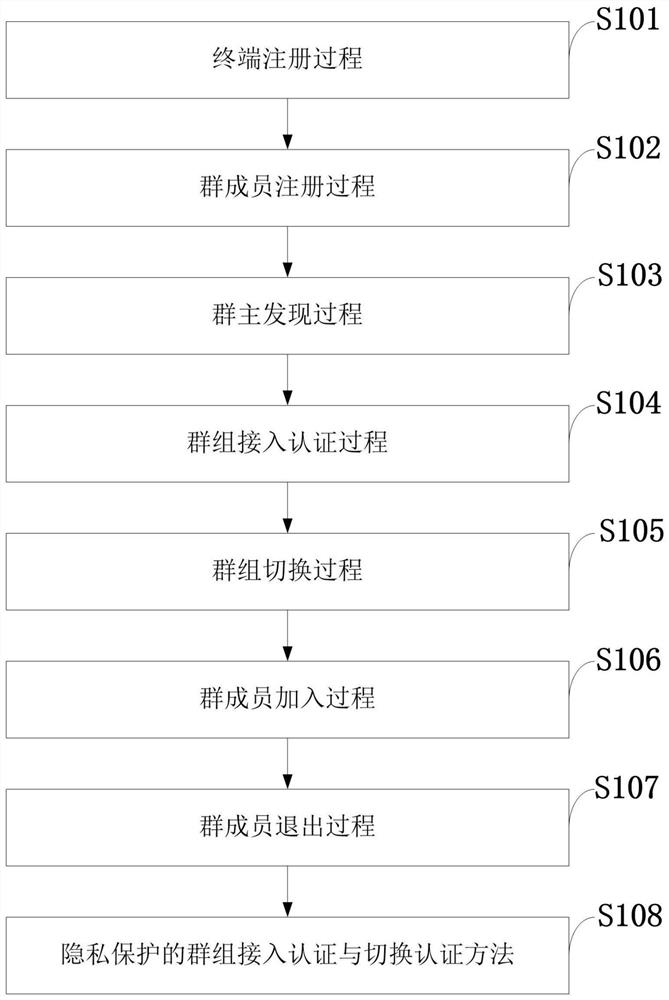
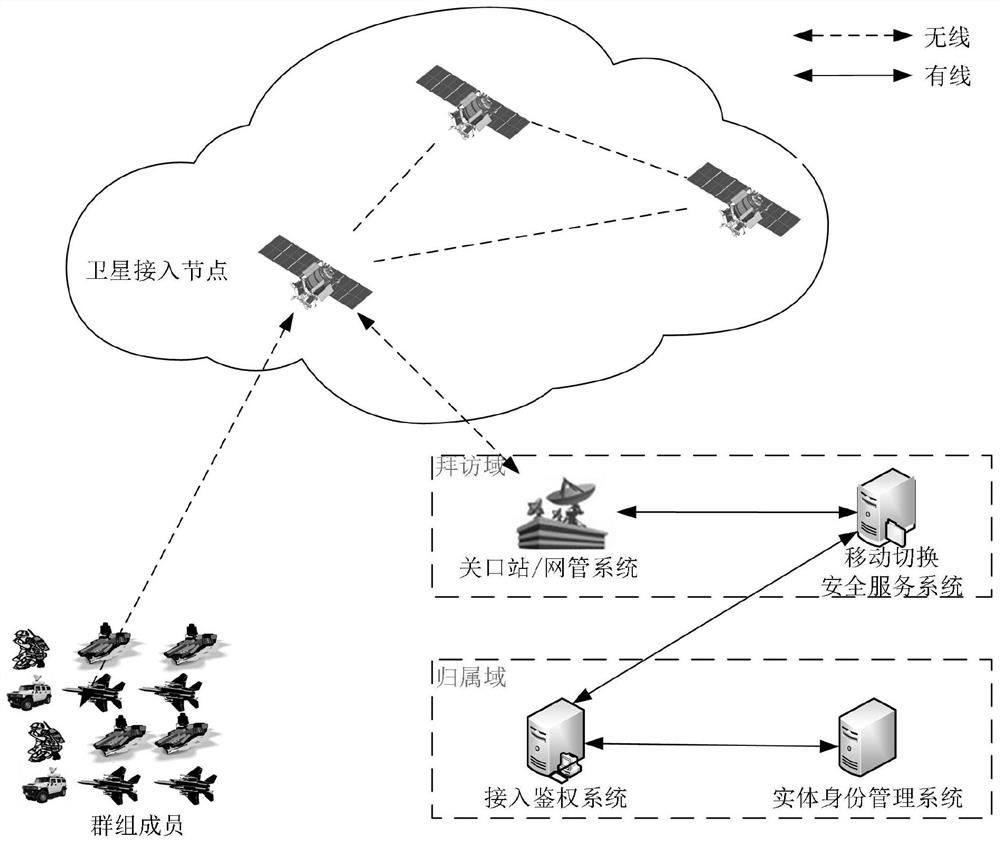
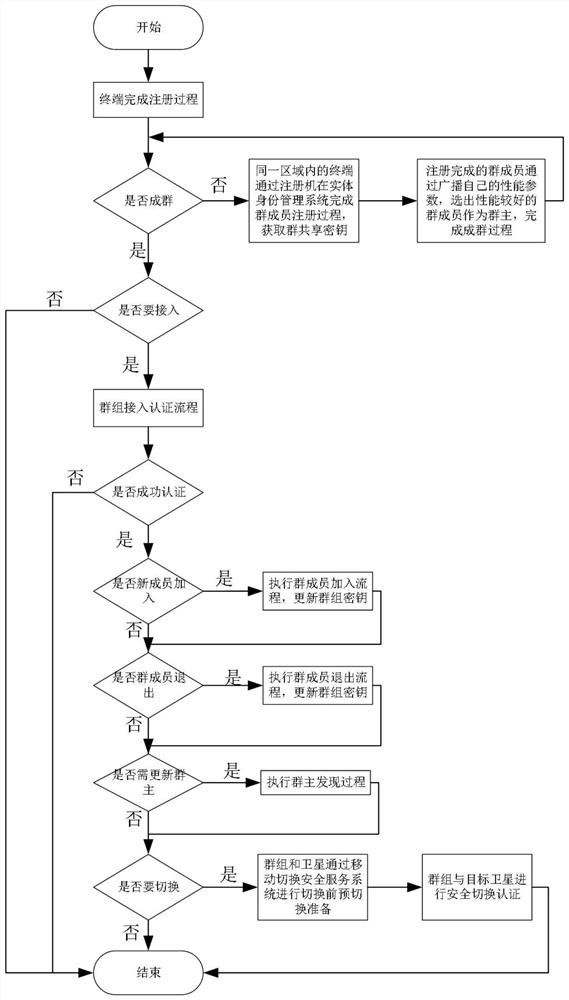
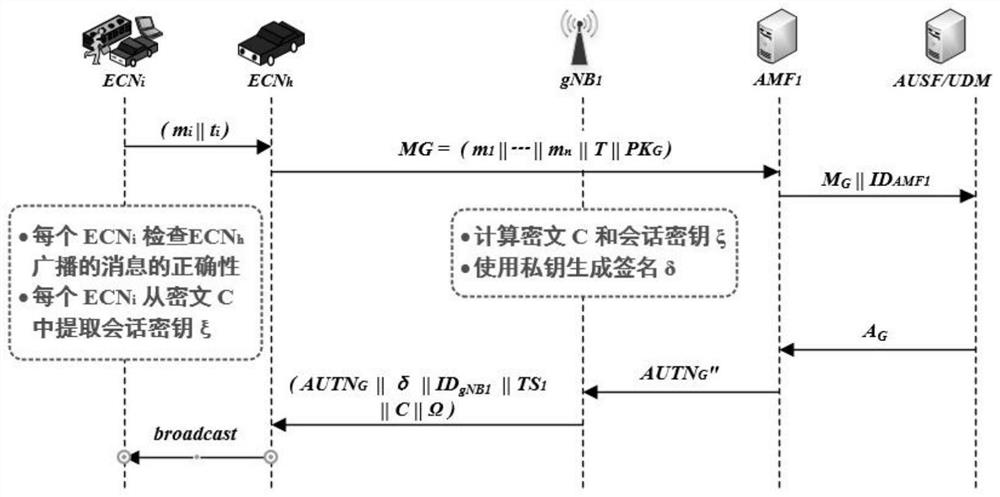
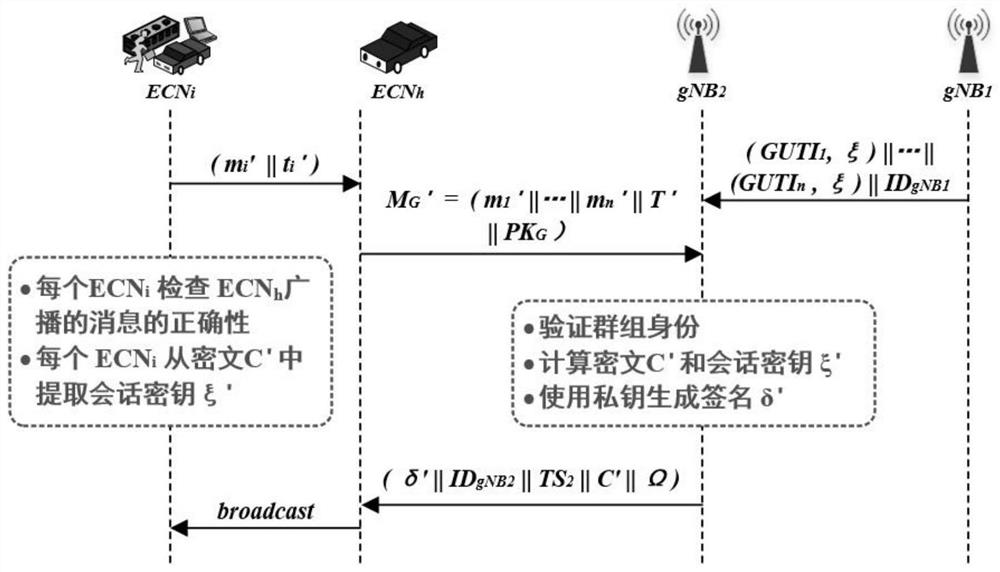
Group access authentication and switching authentication method and application suitable for space-ground integration
ActiveCN112243235APrivacy protectionImprove authentication efficiencyNetwork topologiesSecurity arrangementPrivacy protectionEngineering
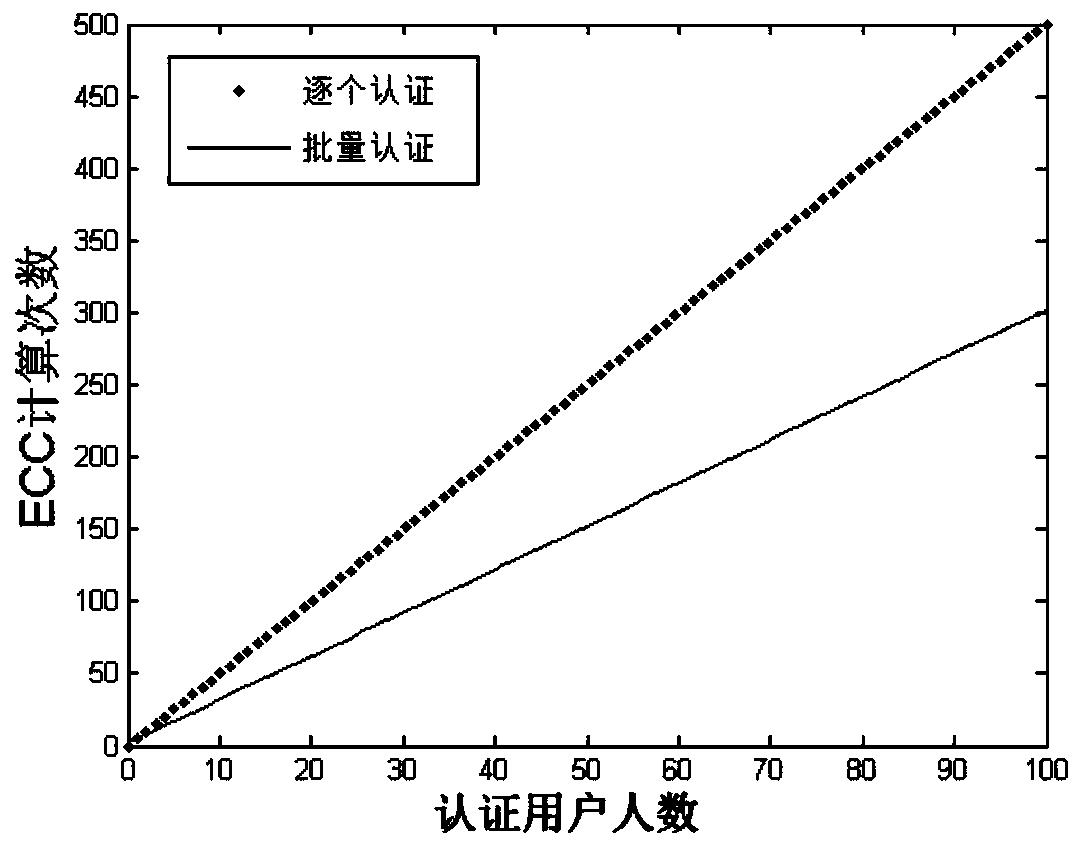
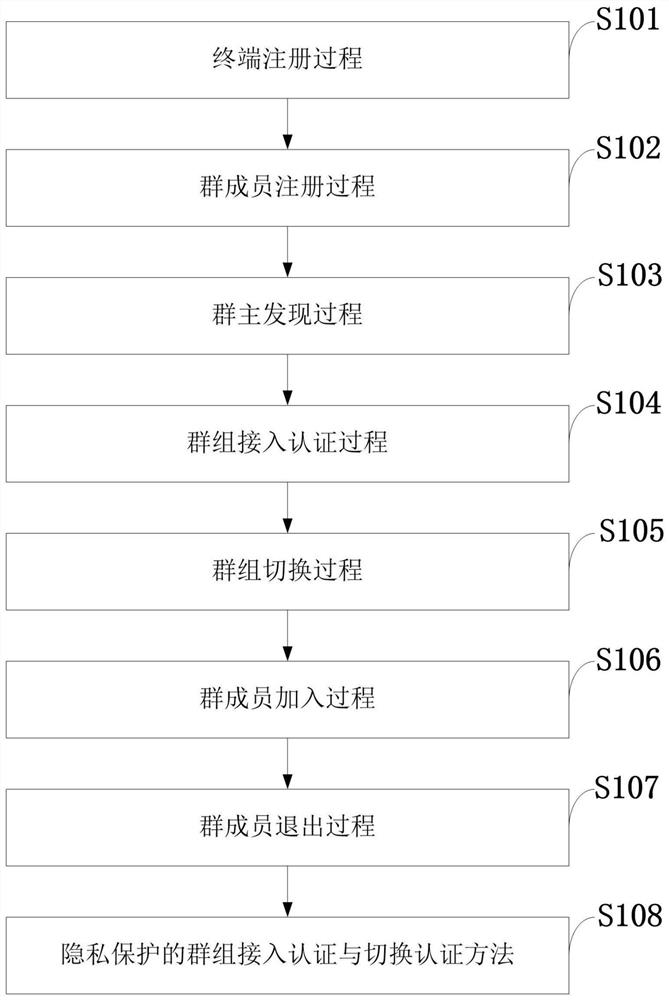
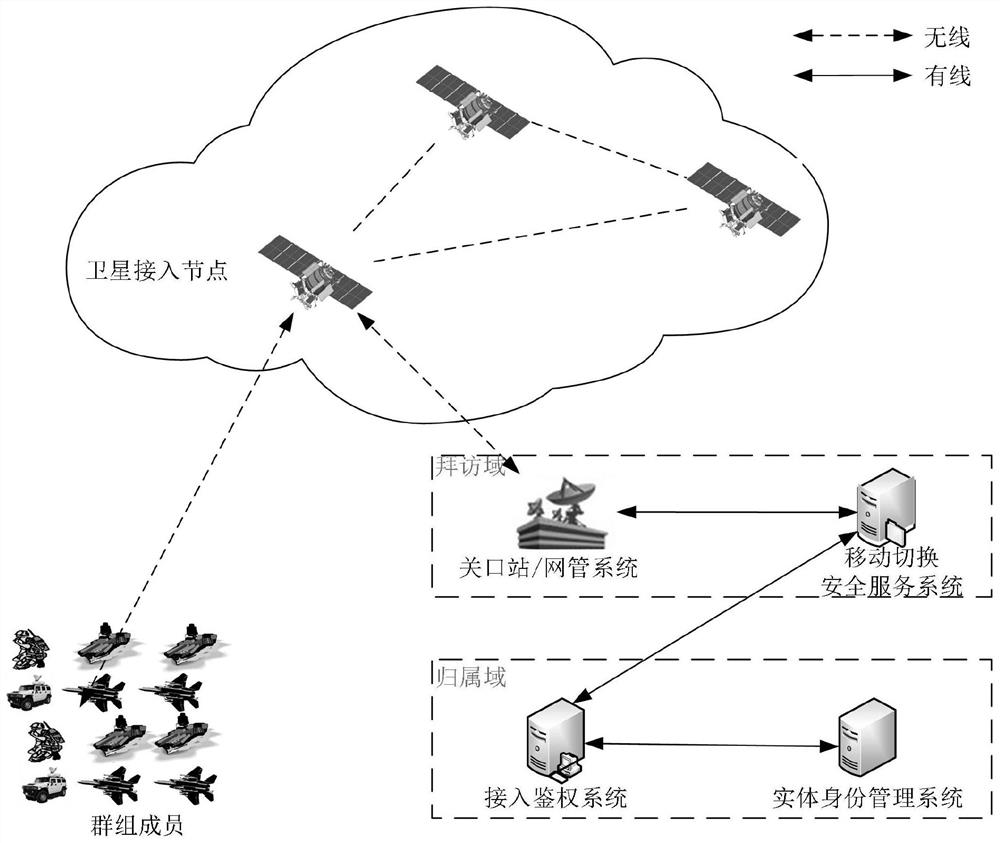
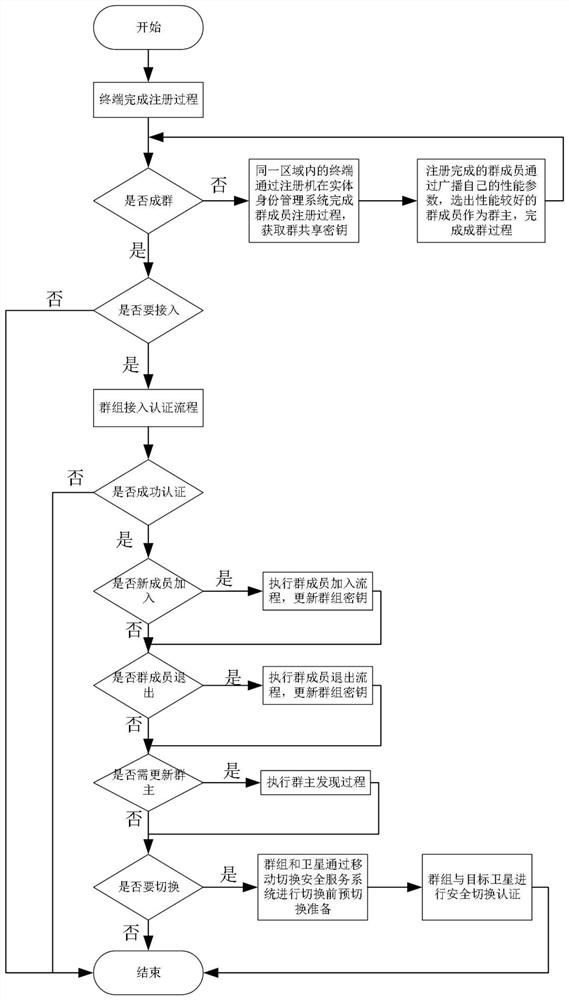
The invention belongs to the technical field of communication network security, and discloses a group access authentication and switching authentication method and application suitable for space-ground integration; the method comprises a terminal registration process, a group member registration process, a group owner discovery process, a group access authentication process, a group switching process, a group member joining process, and a group member quitting process. The invention discloses a privacy-protected group access authentication and switching authentication method. The method can beapplied to space-ground integrated group access authentication and switching scenes; the group owner discovery process is executed offline, so that the group owner can be selected regularly; massiveterminal access authentication and switching authentication are supported; joining and quitting of members in the group can be supported through the joining and quitting process of the group members,and the flexibility of the system is improved; through group authentication, the communication overhead, the calculation overhead and the signaling overhead can be effectively reduced; in addition, the privacy of the identity information of the terminal can be realized through a privacy-protected group access authentication and switching authentication method.
Owner:XIDIAN UNIV
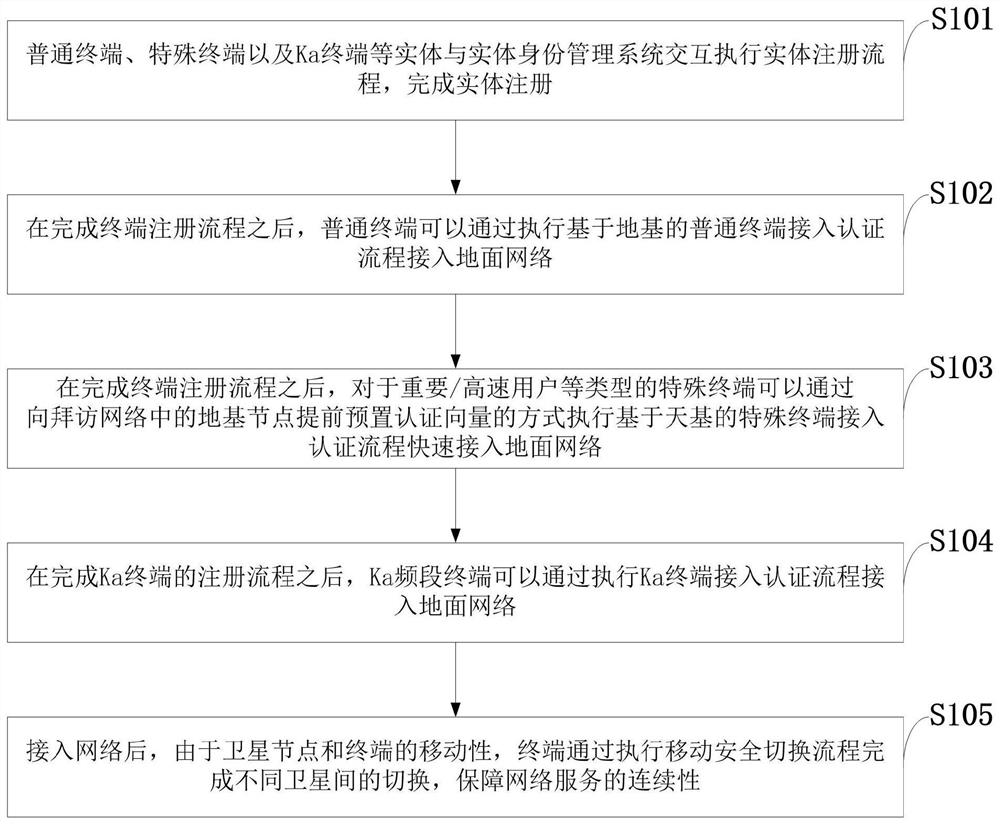
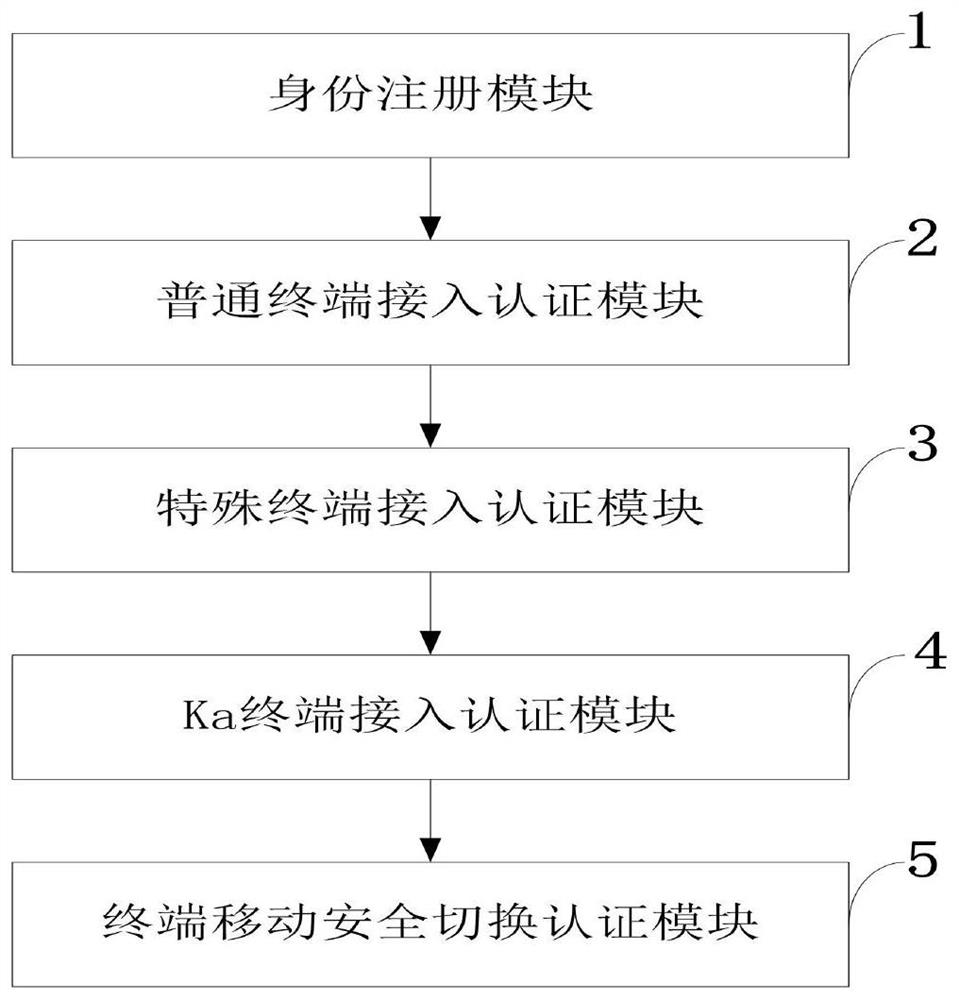
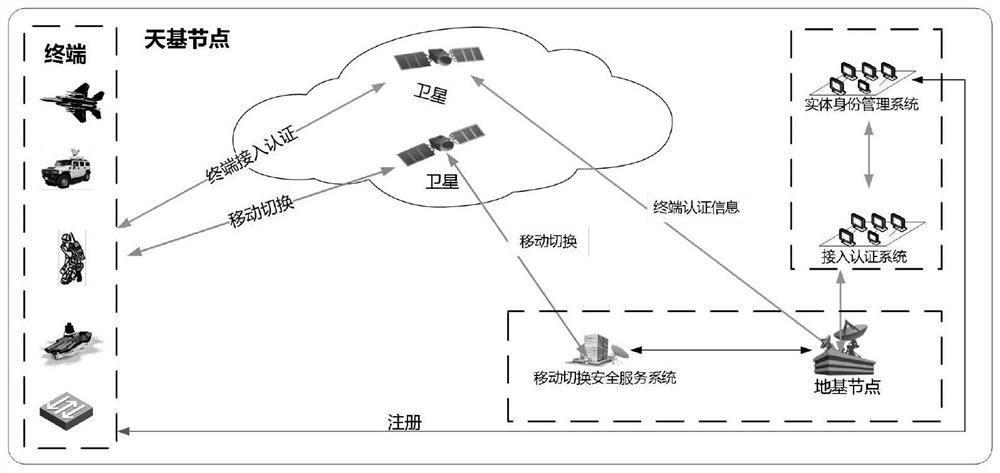
Multi-type terminal access and handover authentication method and system, equipment and application
ActiveCN112235792AEnhanced anonymityDefense against replay attacksAssess restrictionNetwork topologiesAccess networkEngineering
The invention belongs to the technical field of communication network security, and discloses a multi-type terminal access and handover authentication method and system, equipment and application. Themethod comprises the steps of entity registration; ground-based common terminal access authentication; space-based special terminal access authentication; ka terminal access authentication; terminalhandover authentication. According to the method, a common terminal can safely and efficiently access a ground network by executing a ground-based common terminal access authentication process; for special terminals, such as important / high-speed users and the like, a space-based special terminal access authentication process can be used to quickly access a network by presetting an authentication vector in advance without participation of a home network, so that the problem that network service cannot be provided due to faults of the home network is avoided; the access authentication process based on the Ka terminal is used for the Ka terminal, so that high reliability of network access of the Ka terminal is guaranteed, the access authentication efficiency is greatly improved, and access authentication and handover of various different types of terminals are realized.
Owner:XIDIAN UNIV
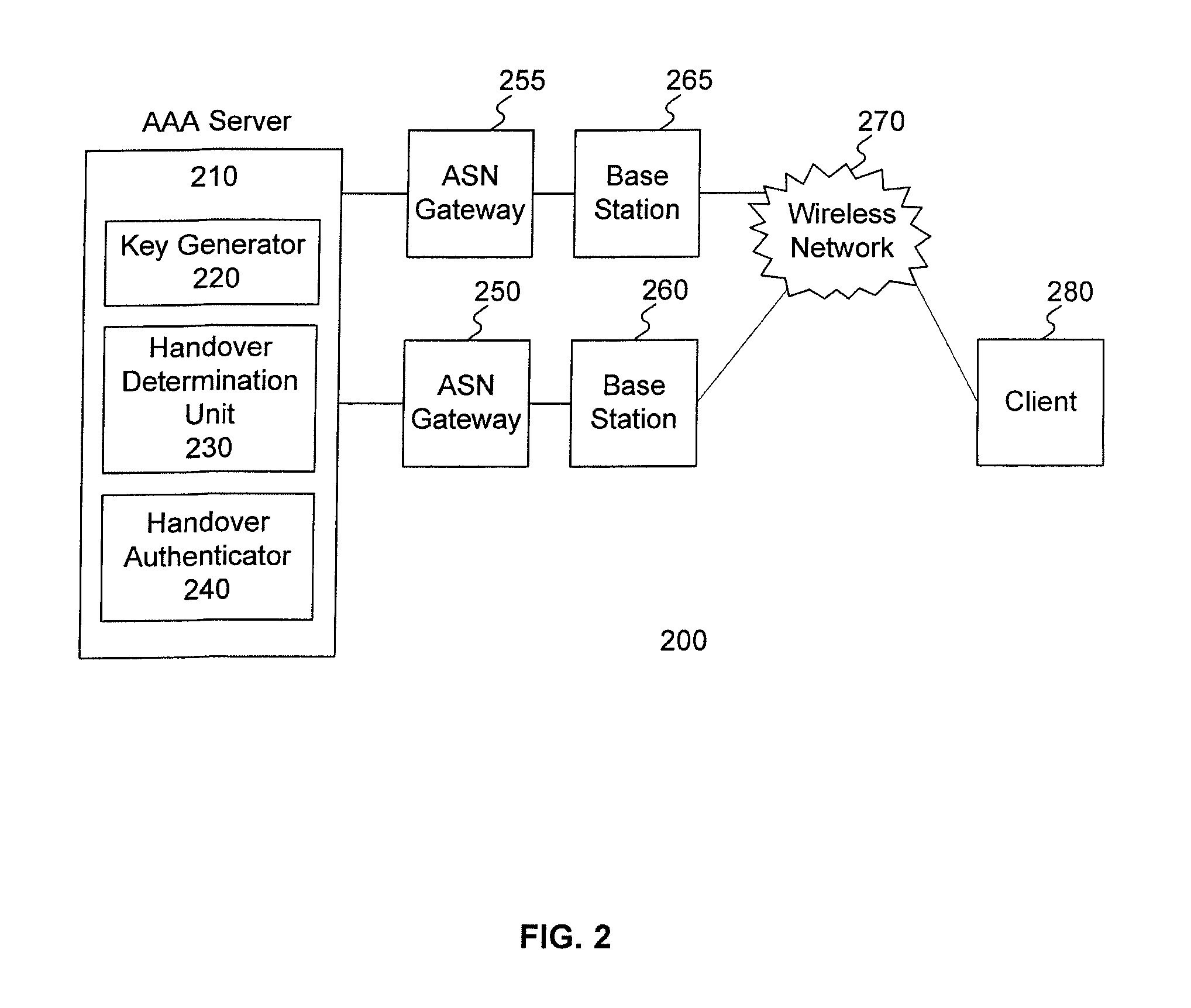
Method and system for handover authentication
ActiveUS8131296B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsClient-sideNetwork service
A handover authentication method includes performing, by a wireless network server, a first authentication between a client and the wireless network server via a first network gateway; obtaining first authentication keys for the wireless network server and the client based on the first authentication; determining, by the wireless network server, a need to handover the client from the first network gateway to a second network gateway; deriving, by the wireless network server and from the first authentication keys, a handover authentication key shared by the client and the wireless network server; obtaining, by the wireless network server, second authentication keys for the network server and the client; and serving, by the wireless network server, the client via the second network gateway.
Owner:IND TECH RES INST
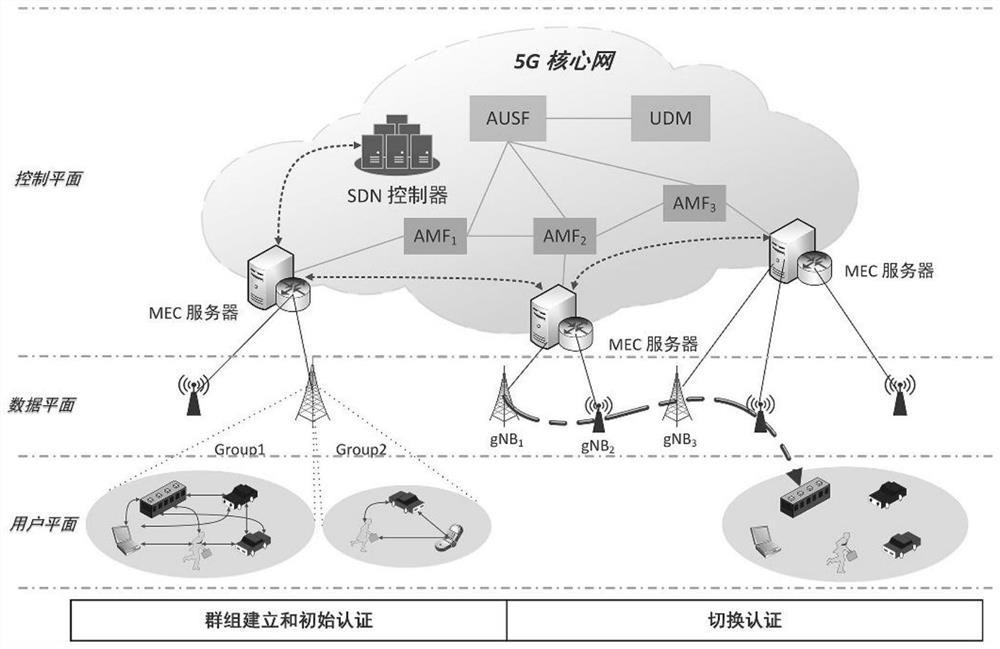
Multi-user authentication method and system for mobile communication scene and information processing terminal
PendingCN114286334AReduce the probability of congestionImprove securitySecurity arrangementNetwork architectureEngineering
The invention belongs to the technical field of network communication, and discloses a multi-user authentication method and system for a mobile communication scene and an information processing terminal. An initial authentication stage; and switching the authentication stage. According to the method, a multi-user authentication scheme is designed by using an aggregation message authentication code with a detection function and a contribution-based broadcast encryption technology based on MEC and SDN technologies, so that the channel congestion probability is reduced, the calculation overhead and communication overhead of switching authentication are reduced, the switching authentication time delay is reduced, and the safety performance of group authentication is improved. According to the invention, the network architecture integrated by the SDN and the MEC server can monitor the network state in real time according to the dynamic topology of the user in advance to make a switching decision, a large amount of calculation overhead can be completed before switching authentication, and the switching authentication time delay is effectively reduced. And the group messages are aggregated, so that the number of times of signaling interaction can be effectively reduced, and the possibility of channel congestion is reduced.
Owner:XIAN UNIV OF POSTS & TELECOMM
Handover Authentication Method with Privacy Preservation in LTE/Lte‑A Networks
InactiveCN103781067BRealize privacy protectionReduce handover authentication delaySecurity arrangementKey exchangeHash function
The invention discloses a handover authentication method with privacy protection in an LTE / LTE-A network. After an ME accesses the LTE / LTE-A network for the first time and successfully completes access authentication with an AAA server, the AAA server generates a Pseudonym set; when ME needs to switch to a new AP due to movement, it only needs to select an unused pseudonym from the pseudonym set for identity authentication without providing the real identity of ME, thereby avoiding the leakage of user identity and location privacy , to achieve anonymity and untraceability. In the handover authentication process, the method negotiates keys based on the Diffie-Hellman key exchange algorithm, completes the mutual authentication process through hash function value verification, does not use bilinear pairing operations, and reduces authentication delay.
Owner:NANJING UNIV OF SCI & TECH
Security authentication method based on chameleon hash function
ActiveCN113890740AGuarantee authenticityAvoid Malicious OperationsKey distribution for secure communicationUser identity/authority verificationCommunications securityHash function
The invention discloses a safety certification method based on a chameleon hash function, which relates to the field of wireless communication safety certification of heterogeneous wireless networks and mainly comprises the following operation steps of: firstly, system initialization is performed on a key generation center to select the system public parameters and finish system establishment; the home domain network server HS completes registration; the foreign region network server FS completes registration; the mobile terminal MT completes registration; the home domain network server HS distributes switching authorization information to a legal and credible mobile terminal MT; and the mobile terminal MT and the foreign region network server FS complete authentication switching and session key negotiation. According to the method, the security real-time authentication of the mobile terminal and the foreign region network in the heterogeneous wireless network can be effectively realized, and the identity privacy of the mobile terminal and the resistance to temporary private key leakage and replay attacks are ensured. Moreover, in the authentication process, the mobile terminal consumes less resources.
Owner:SOUTHWEST JIAOTONG UNIV
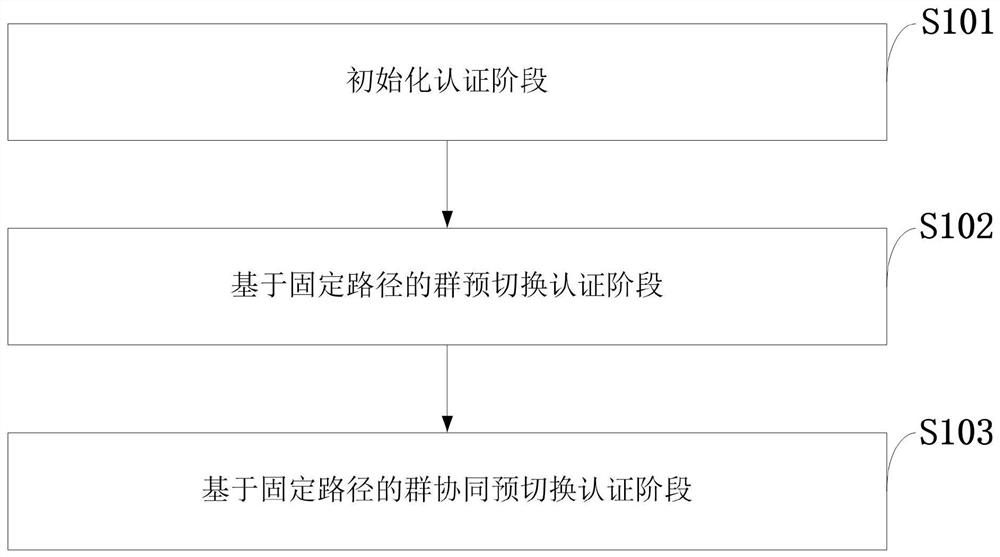
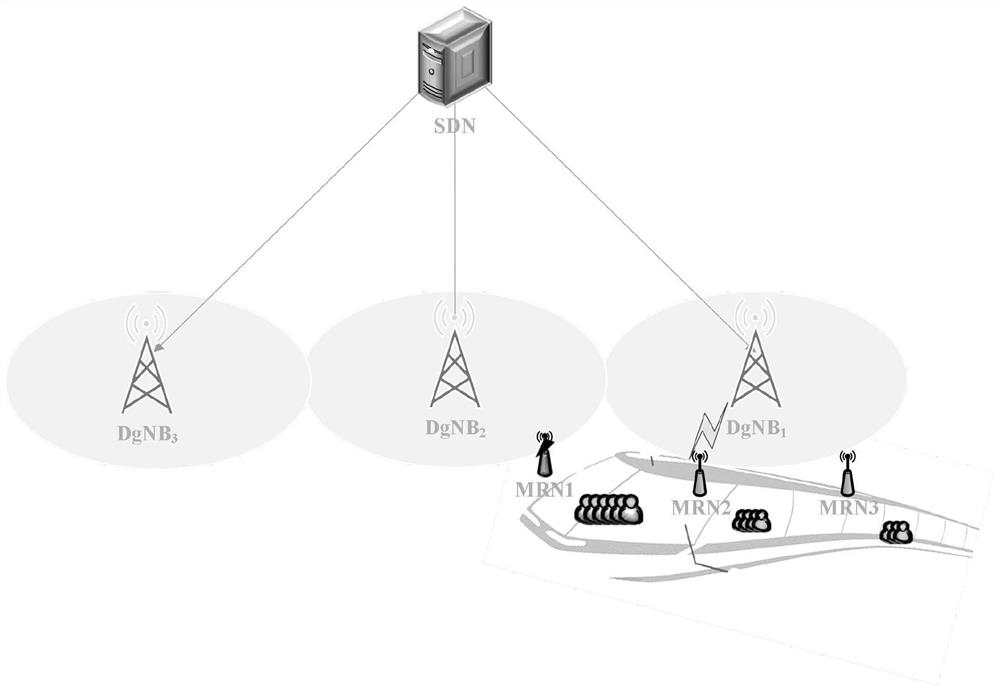
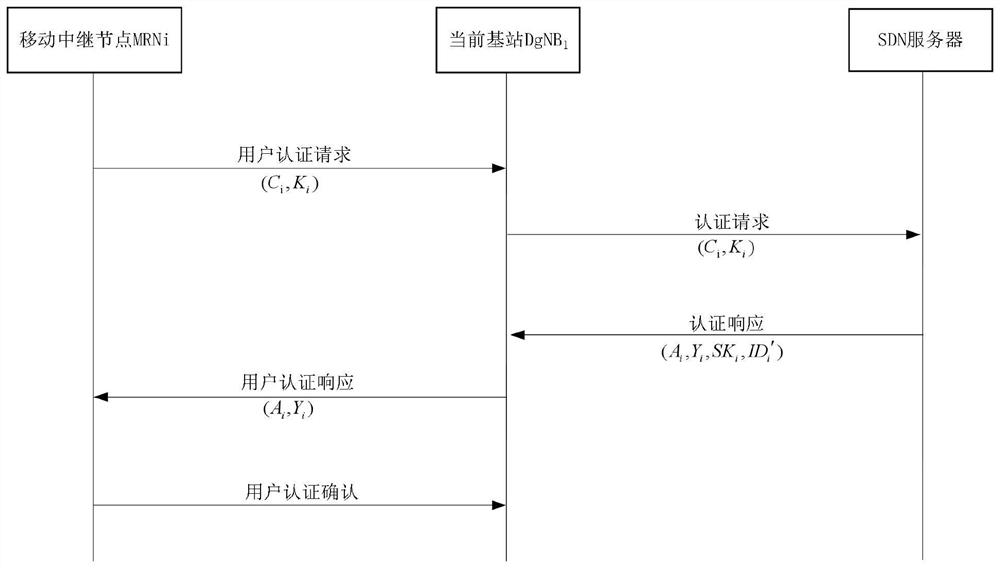
Group pre-handover authentication method based on fixed path, high-speed rail network communication platform
ActiveCN109769248BCorrect valid hashReduce switching overheadKey distribution for secure communicationUser identity/authority verificationPathPingEngineering
Owner:XIDIAN UNIV
Method and system for data feedback
ActiveCN111738736BImplement feedbackImprove experienceDevices with sensorCo-operative working arrangementsEngineeringHandover authentication
The data feedback method and system provided in this manual, after the mobile terminal calls out the authentication code, collect the pose data of the mobile terminal through the sensor of the mobile terminal, and collect the code scanning authentication status prompt signal of the authentication device through the signal collection device of the mobile terminal ; and judge whether the mobile terminal has made an action of scanning code authentication according to the pose data; judge the result of code scanning authentication according to the collected code scanning authentication status prompt signal, and display the authentication result on the page of the mobile terminal. The method and system can immediately feed back the code scanning authentication result to the mobile terminal when the authentication device or the mobile terminal is offline, and prompt the mobile terminal to switch the authentication code after the code scanning fails. In this way, real-time feedback of data in an offline state can be realized, and the user experience can be improved.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Ticket-based access layer handover authentication method for LTE-R vehicle-ground communication
ActiveCN108337661BAvoid participationReduce complexityKey distribution for secure communicationParticular environment based servicesCommunications securityIn vehicle
A kind of LTE-R vehicle-ground communication access layer switching authentication method based on ticket, its step mainly is: A, apply for ticket: vehicle-mounted mobile unit applies for and preserves target ticket and target base station ticket; B, X2 interface handover authentication: vehicle-mounted The mobile unit uses the target base station ticket to complete the authentication and key negotiation process with the target base station safely and efficiently, realizing fast handover across base stations and avoiding the participation of the source base station; The management entity completes the authentication process safely and efficiently, and completes the authentication and key negotiation process with the target base station with its help, avoiding the participation of the source mobile management entity and the source base station, and quickly realizing handover across mobile management entities; this method effectively realizes In the LTE-R system, the secure real-time access layer handover authentication of vehicle-ground wireless communication improves the efficiency of handover authentication on the basis of ensuring security.
Owner:SOUTHWEST JIAOTONG UNIV
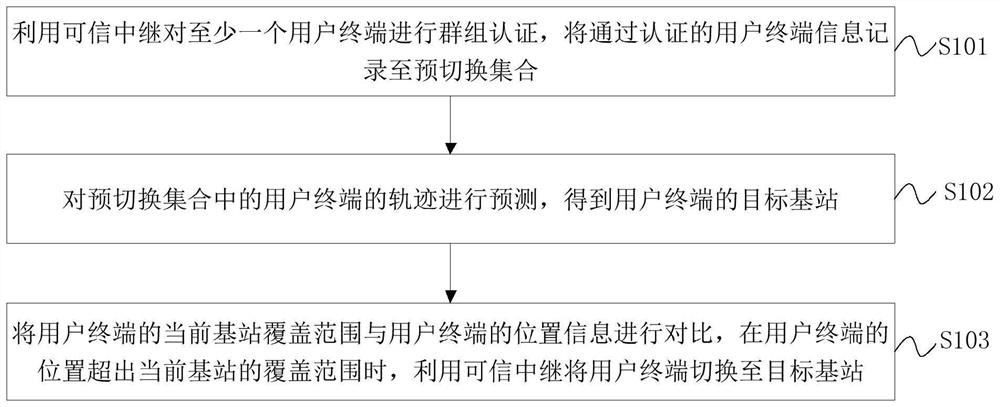
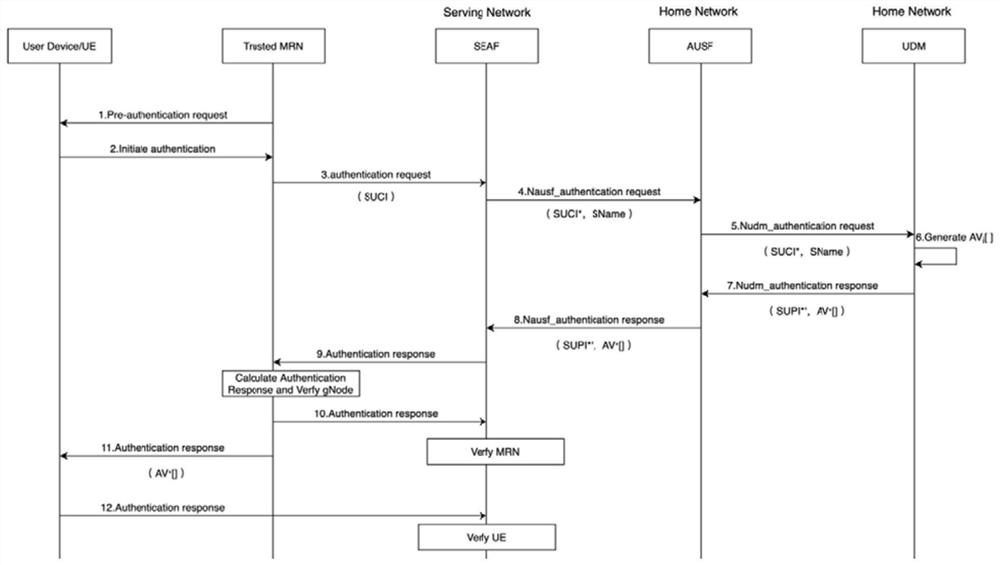
Group pre-switching authentication method and device based on trusted relay
ActiveCN114390516AAchieve mutual authenticationPromote sustainable developmentSecurity arrangementTerminal equipmentTrunking
The invention discloses a group pre-switching authentication method and device based on a trusted relay, and the method comprises the steps: carrying out the group authentication of a user terminal through the trusted relay, and recording the information of the user terminal passing the authentication to a pre-switching set; predicting the track of the user terminal in the pre-switching set to obtain a target base station of the user terminal; and comparing the current base station coverage range of the user terminal with the position information of the user terminal, and switching the user terminal to a target base station by using a trusted relay when the position of the user terminal exceeds the current base station coverage range. The group pre-switching technology and the trusted execution technology are combined, group switching can be rapidly and safely carried out, it is guaranteed that the 5G network can provide smooth and safe communication experience for users in the train running process, the switching problem of mass terminal devices in the current 5G network in the high-speed moving process is solved, and the user experience is improved. The method is high in applicability and safety, and switching overhead consumption is reasonable.
Owner:BEIHANG UNIV
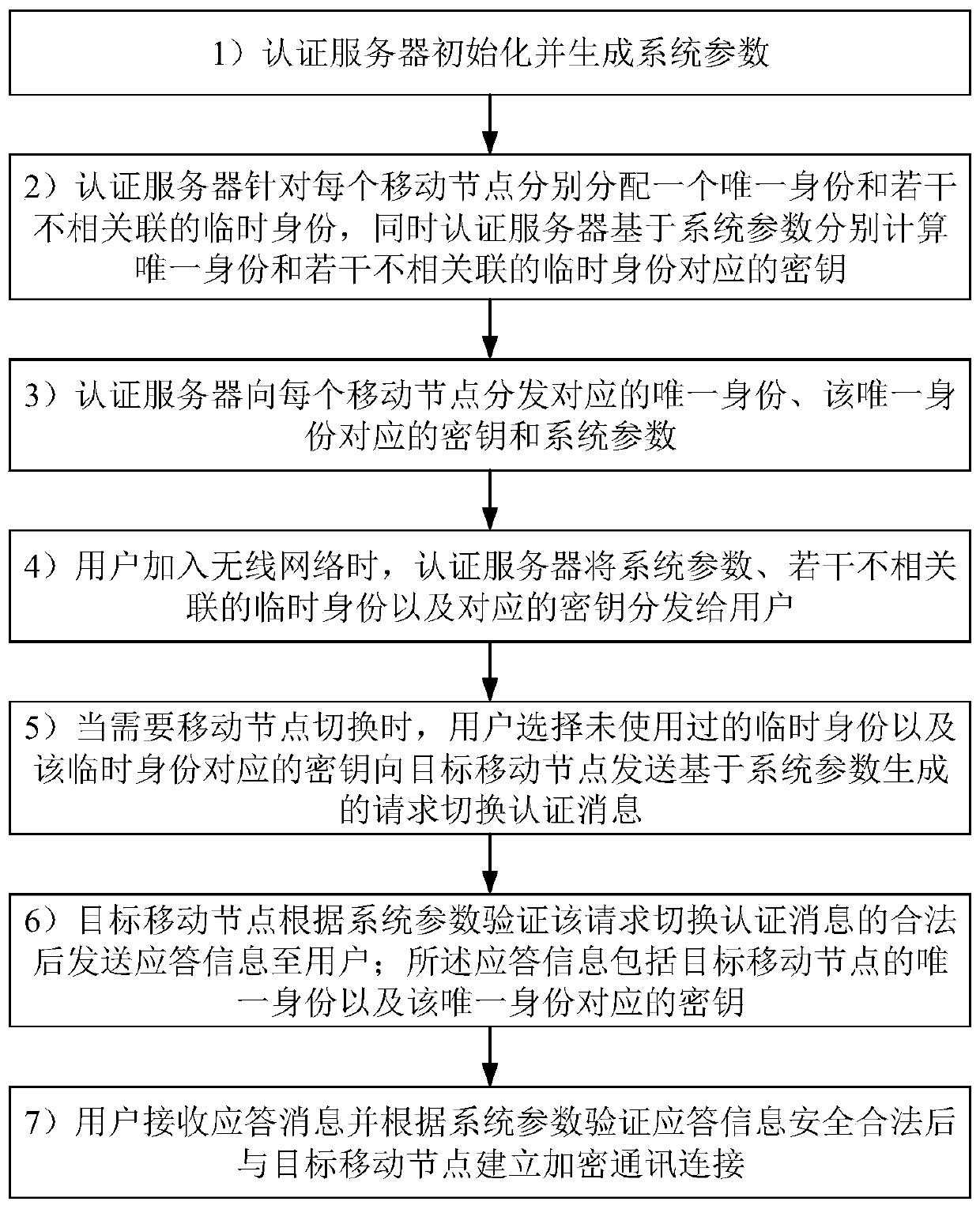
An anonymous handover authentication method based on false identity in wireless network
ActiveCN106856605BSolve anonymous authenticationImplement a batch authentication strategyTransmissionSecurity arrangementThird partyInternet privacy
The invention discloses a false identity based wireless network anonymous switching authentication method, which comprises the steps that 1) an authentication server generates system parameters; 2) the authentication server respectively allocates a unique identity and temporary identity and a corresponding key for each mobile node; 3) the authentication server distributes the system parameters and the corresponding unique identities and keys to the mobile nodes; 4) the authentication server distributes the system parameters, the temporary identities and the keys to users; 5) the user sends a switching authentication request message to a target mobile node by selecting an unused temporary identity and key; 6) the target mobile node verifies the legitimacy of the switching authentication request message and then sends a response message to the user; and 7) the user verifies the response message to be safe and legal and then establishes encrypted communication connection with the target mobile node. According to the invention, participation of a third-party is not required, anonymous switching authentication is completed through twice handshaking, privacy information of the users is protected, batch authentication is supported, and the efficiency of simultaneous authentication requested by multiple users is improved.
Owner:福建中信网安信息科技有限公司
Group access authentication and handover authentication methods and applications applicable to space-ground integration
ActiveCN112243235BPrivacy protectionImprove authentication efficiencyNetwork topologiesSecurity arrangementPrivacy protectionEngineering
Owner:XIDIAN UNIV
An identity-based authentication method for space-based networks
ActiveCN113079016BSmall message sizeAvoid transmissionKey distribution for secure communicationUser identity/authority verificationEngineeringNetwork communication
Owner:NAT UNIV OF DEFENSE TECH
Access and handover authentication method and system in satellite network intermittent connection scenario
ActiveCN112087750BSafe and efficient access authentication processReduce the number of interactionsNetwork topologiesSecurity arrangementTimestampMessage authentication code
Owner:XIDIAN UNIV
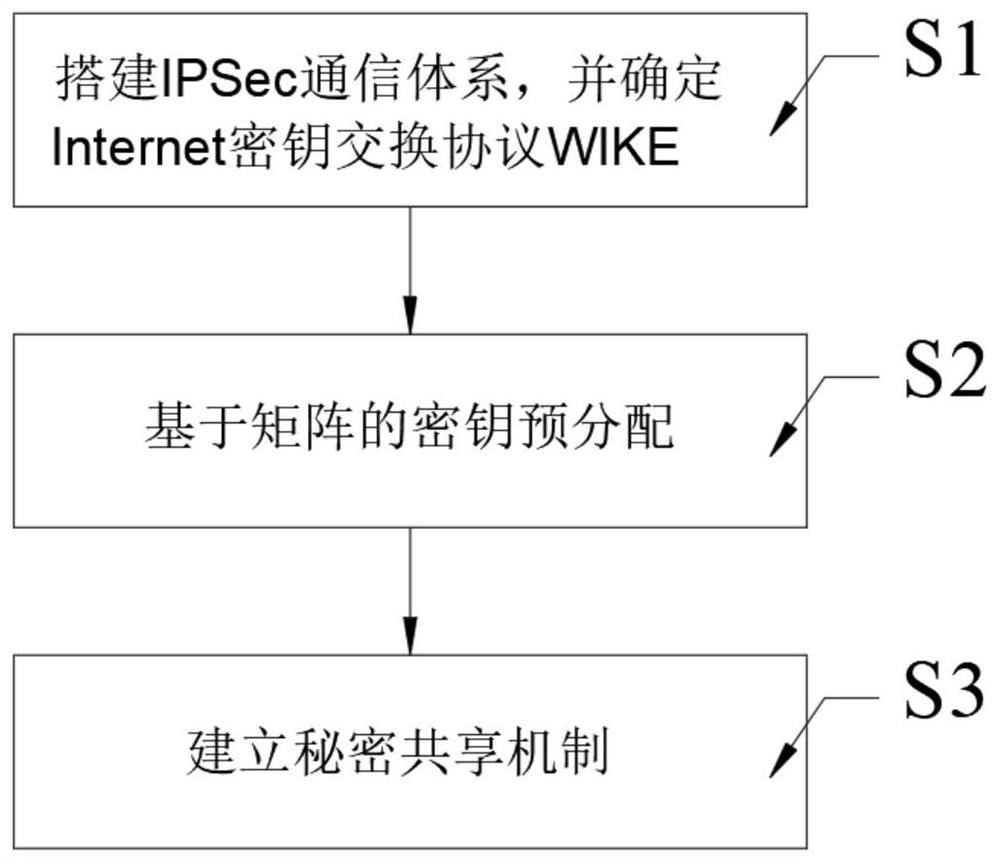
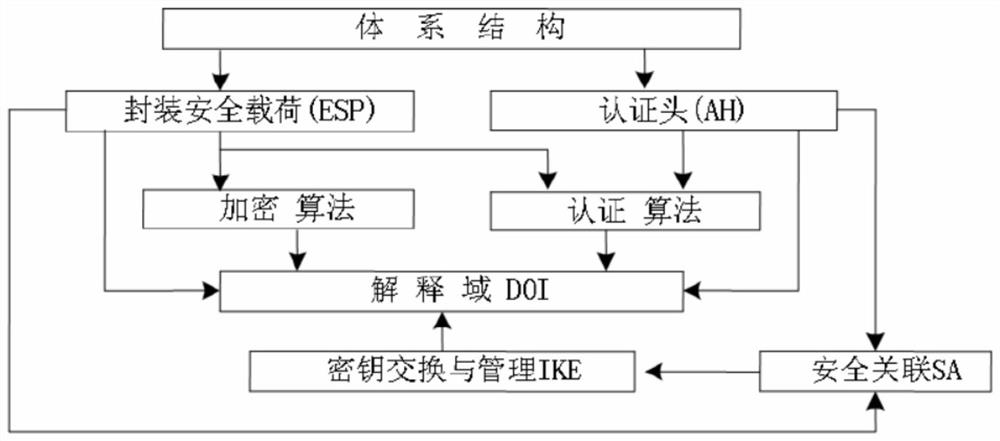
Network security authentication method
InactiveCN111935708AObvious performance advantageSolve the problem of fast switching authentication failureSecurity arrangementWireless mesh networkEngineering
The invention discloses a network security authentication method. The method comprises the following steps: S1, establishing an IPSec communication system; S2, carrying out matrix-based key pre-distribution; and S3, establishing a secret sharing mechanism. The beneficial effects are as follows: the method is suitable for an IKEv2 initial exchange process improvement protocol in a wireless networkenvironment. The protocol has obvious performance advantages. The method can be applied to a wireless Internet network environment; in addition, a quick switching authentication method based on a neighbor graph and a pre-distribution method based on a matrix key are adopted, a rapid switching authentication scheme of the wireless Mesh network is provided, the problem of quick switching authentication failure caused by the mobility of the Mesh access point can be solved, through a self-healing group key distribution scheme, a safety channel does not need to be established between a group administrator and each group member to distribute personal secret information of the group members, and safety of storage overhead and communication overhead is achieved.
Owner:HEZE UNIV
Key agreement method for identity-unpaired wireless network cross-domain handover authentication
ActiveCN107360567BEfficiency improvement for switching authenticationReduce computational overheadSecurity arrangementAttackInternet privacy
Owner:SOUTHWEST JIAOTONG UNIV
LTE-R network group authentication key agreement method without certificate aggregate signature
InactiveCN110149214BReduce overheadReduce communication delayKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAccess networkTrunking
A kind of LTE-R network group authentication key negotiation method without certificate aggregation signature, its main operation steps are: A, system establishment and participant registration: the entity participating in authentication completes registration at the key generation center, and obtains public and private keys Information; B. Initial access authentication: when the user equipment is uniformly connected to the LTE-R network before the train departs, it executes a certificate-free signature algorithm to generate its own signature and sends it to the relay server, and the relay server executes the certificate-free aggregate signature algorithm. Realize rapid mutual authentication and negotiation of shared keys between user equipment, relay server and roadside base station; C. Handover authentication: During train operation, user equipment always maintains a stable connection with The roadside base station realizes fast and frequent switching authentication by implementing the certificateless signature algorithm; D. Terminate the session. The method has high authentication efficiency, small signaling overhead and good security.
Owner:CHINA ACADEMY OF RAILWAY SCI CORP LTD +1
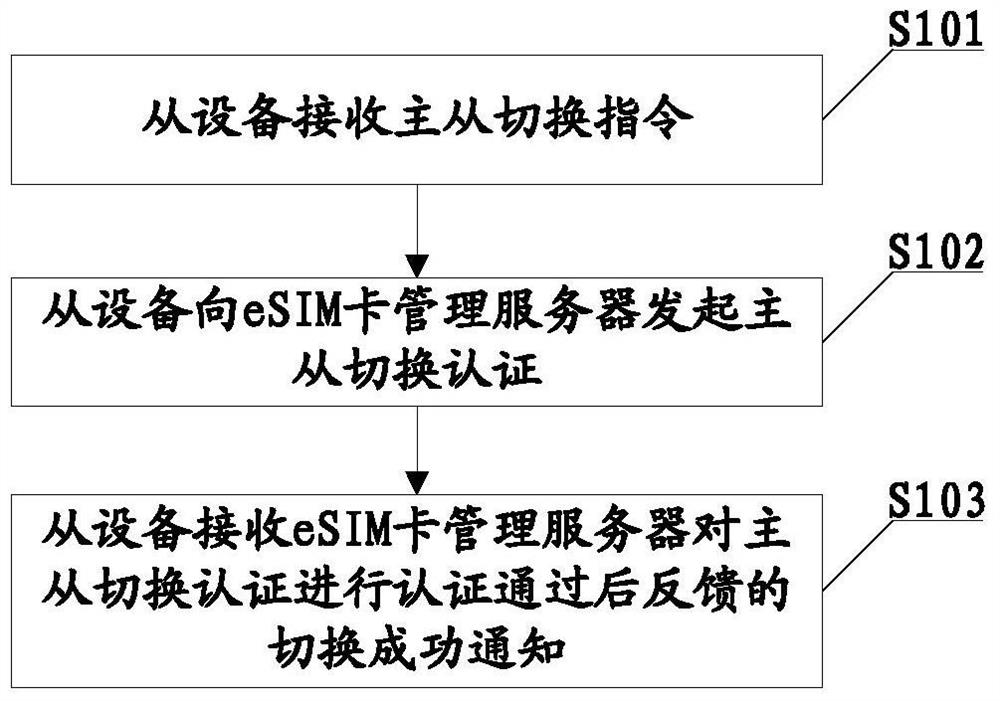
Master-slave device switching method of esim card, slave device and esim card management server
ActiveCN107548054BImprove satisfactionSecurity arrangementNetwork data managementUser deviceOperating system
The embodiment of the present invention provides a master-slave device switching method of an eSIM card, a slave device, and an eSIM card management server. The master device of the eSIM card and the eSIM card in the slave device use the same number; the slave device in the embodiment of the present invention can receive Master-slave switching command, after receiving the master-slave switching command, initiate a master-slave switching authentication to the eSIM card management server; after the eSIM card management server passes the authentication of the master-slave switching authentication initiated by the slave device, set the slave device as an eSIM card The master device, and send a handover success notification to the slave device. Therefore, when the user cannot use the master device, for example, the master device is out of power or the master device is not in the user device, etc., the user can send a master-slave switch command to the slave device to switch the slave device to the master device, so that the operation of the master device can be performed normally. , can improve user experience satisfaction, and is more conducive to the promotion and use of eSIM cards.
Owner:ZTE CORP
A WMN anonymous access authentication system and method based on proxy ring signature
ActiveCN105744522BAvoid Privacy LeakageReduce Authentication LatencySecurity arrangementCommunications securityRing signature
Owner:NORTHEASTERN UNIV LIAONING
Blockchain-based data encryption working method
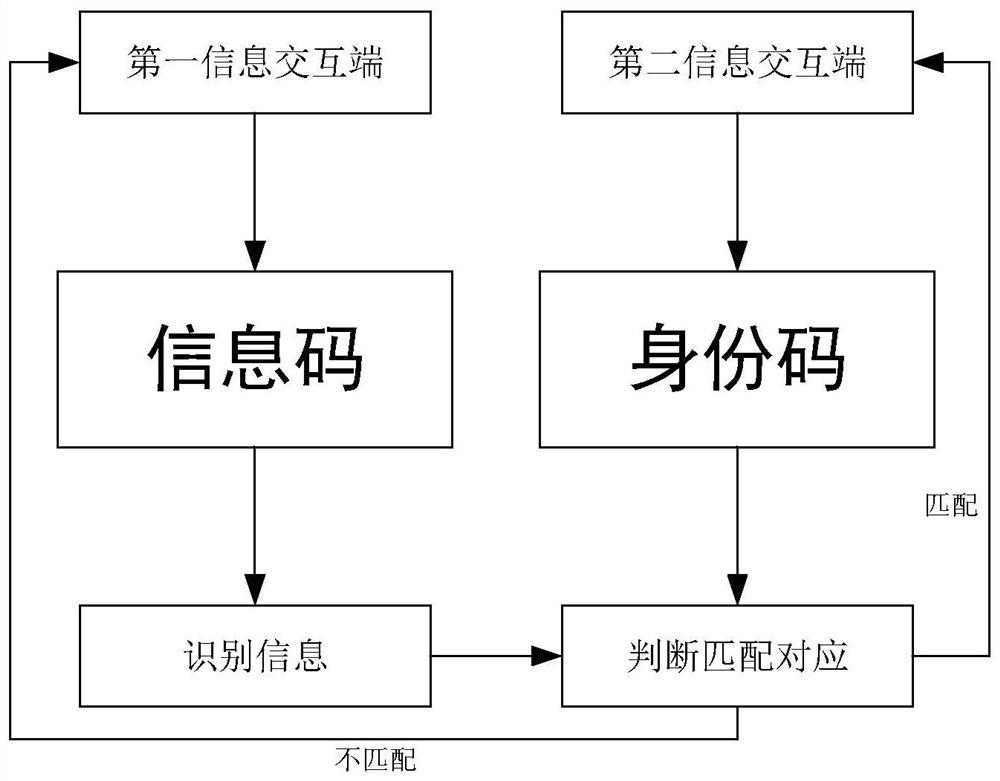
InactiveCN111767557BImprove matchImprove information securityDatabase distribution/replicationDigital data protectionEngineeringMaster key
The present invention proposes a blockchain-based data encryption working method, including: S1, establishing an encryption channel for each node in the blockchain network, and setting a first information interaction terminal and a second information interaction terminal for each encryption channel terminal, the first information interaction terminal is used to distribute instructions to encrypted information, and the second information interaction terminal is used to receive encrypted information and record the random number containing specific identification information in encrypted information; S2, the first information exchange terminal after passing the encrypted information authentication The second information interaction terminal opens the encryption channel, performs data call and data mining, S3, after encrypting the output, selects random numbers to update the encryption parameters through switching authentication, and forwards the information received by the second information interaction terminal to the smart terminal, through the hash operation Generate local parameters for the smart terminal master key, use the master key identity parameters to update the authentication key KEY, and encrypt and encapsulate the key.
Owner:王仁义
A two-way access authentication method for hmipv6 network oriented to multi-layer map
ActiveCN105376230BShorten the lengthImplement two-way authenticationTransmissionSecurity arrangementThird partyShort signature
The present invention provides a multi-layer MAP-oriented HMIPv6 network two-way access authentication method, comprising: the root PKG server acts as a trusted third party and establishes a trusted channel with the PKG server of each layer and the AR router; the root PKG server generates public parameters and generate a private key; the root PKG server issues a private key according to the identity information of each layer of PKG servers, and each layer of PKG servers distributes private keys to it according to the identity information of the AR router of this layer; when the mobile terminal MN leaves the home network for the first time and connects to When entering the AR router under a certain MAP in the HMIPv6 network, the initial two-way access authentication is performed; when the mobile terminal MN is in the foreign network currently connected, it is switched from the AR router in the current MAP domain to another MAP domain or When using an AR router, switchover authentication is performed. The present invention proposes a short signature scheme based on node certificate hierarchical identity, its security is based on the h-CDH problem, the advantage is that with the increase of the grading series, the length of the private key is reduced, and the signature length does not depend on the grading series .
Owner:NORTHEASTERN UNIV LIAONING
A Batch Handoff Authentication and Key Agreement Method for Heterogeneous Networks
ActiveCN111885602BEffective implementation of batch switching authenticationImprove authentication efficiencyUser identity/authority verificationNetwork topologiesAccess networkEngineering
Owner:鹏博士数智云集团有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com