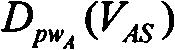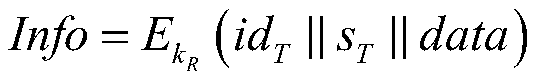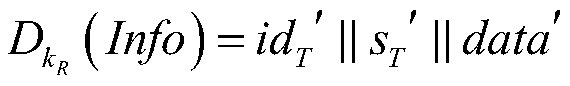Patents
Literature
74results about How to "Achieve mutual authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
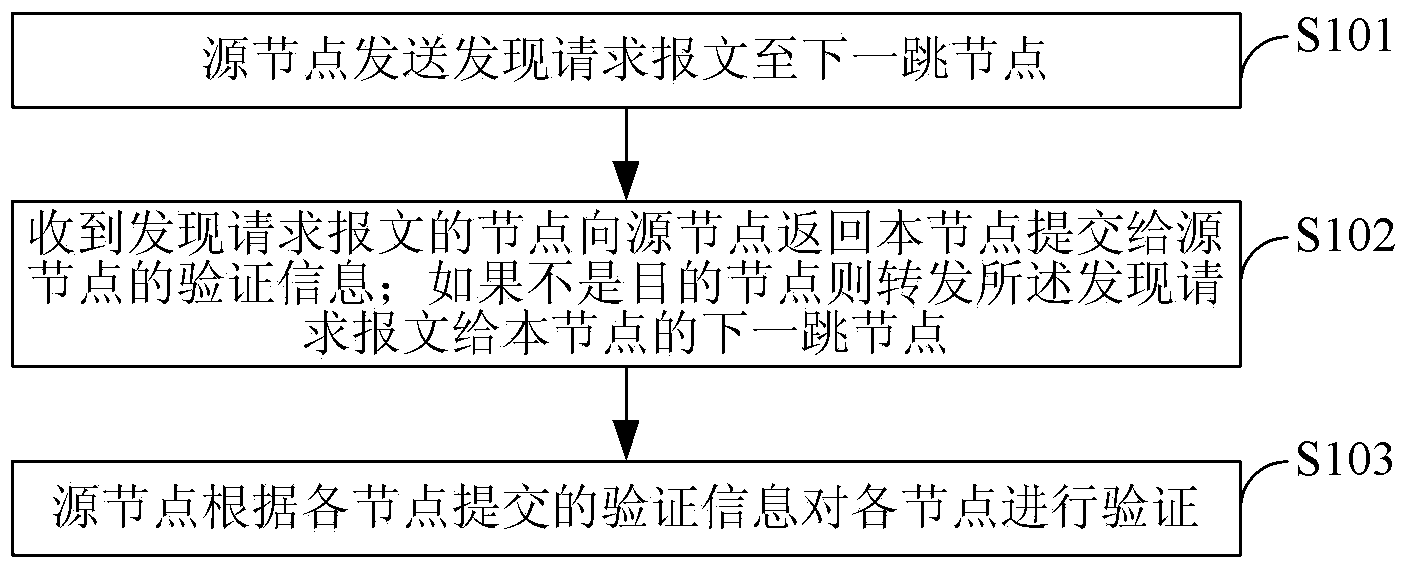
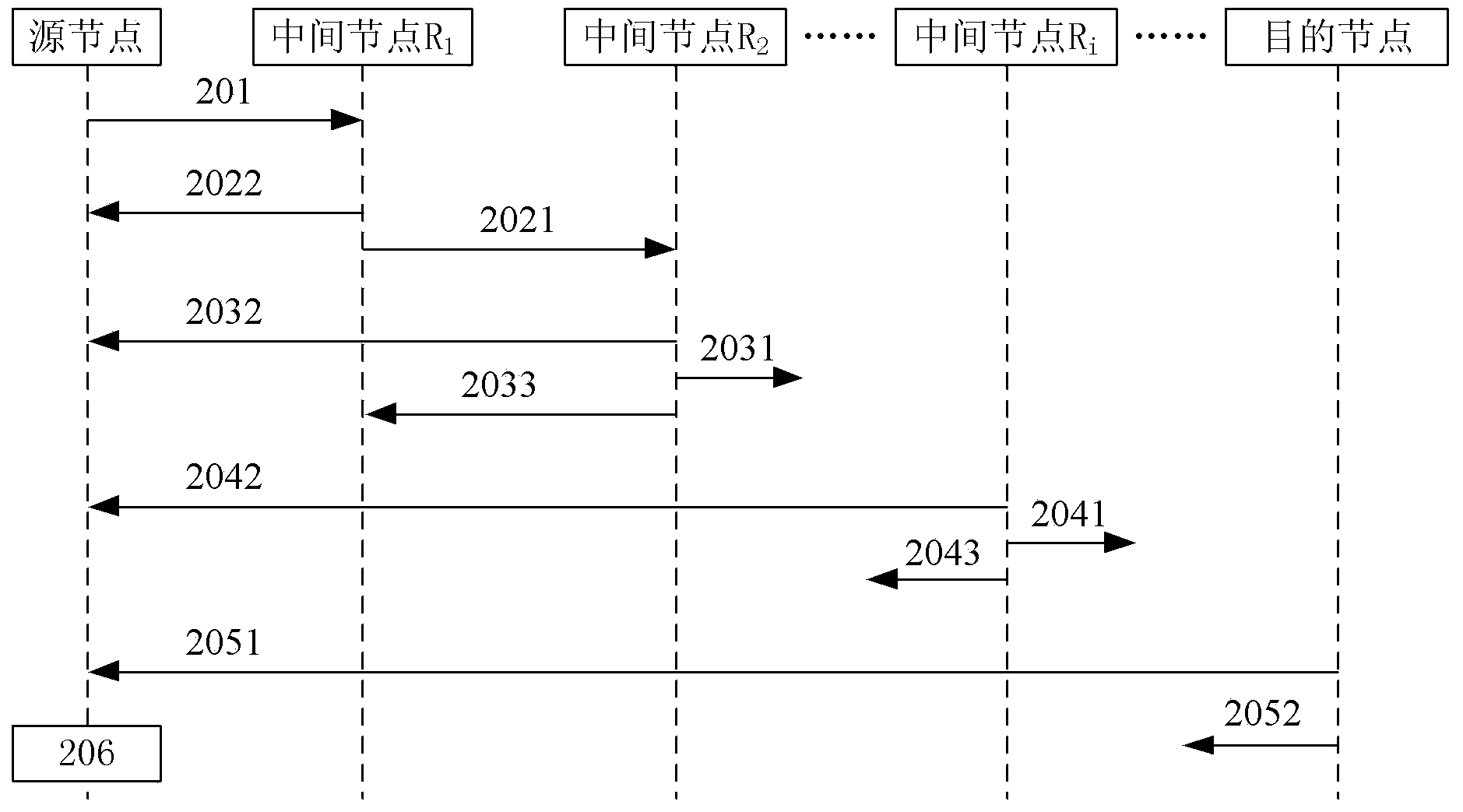
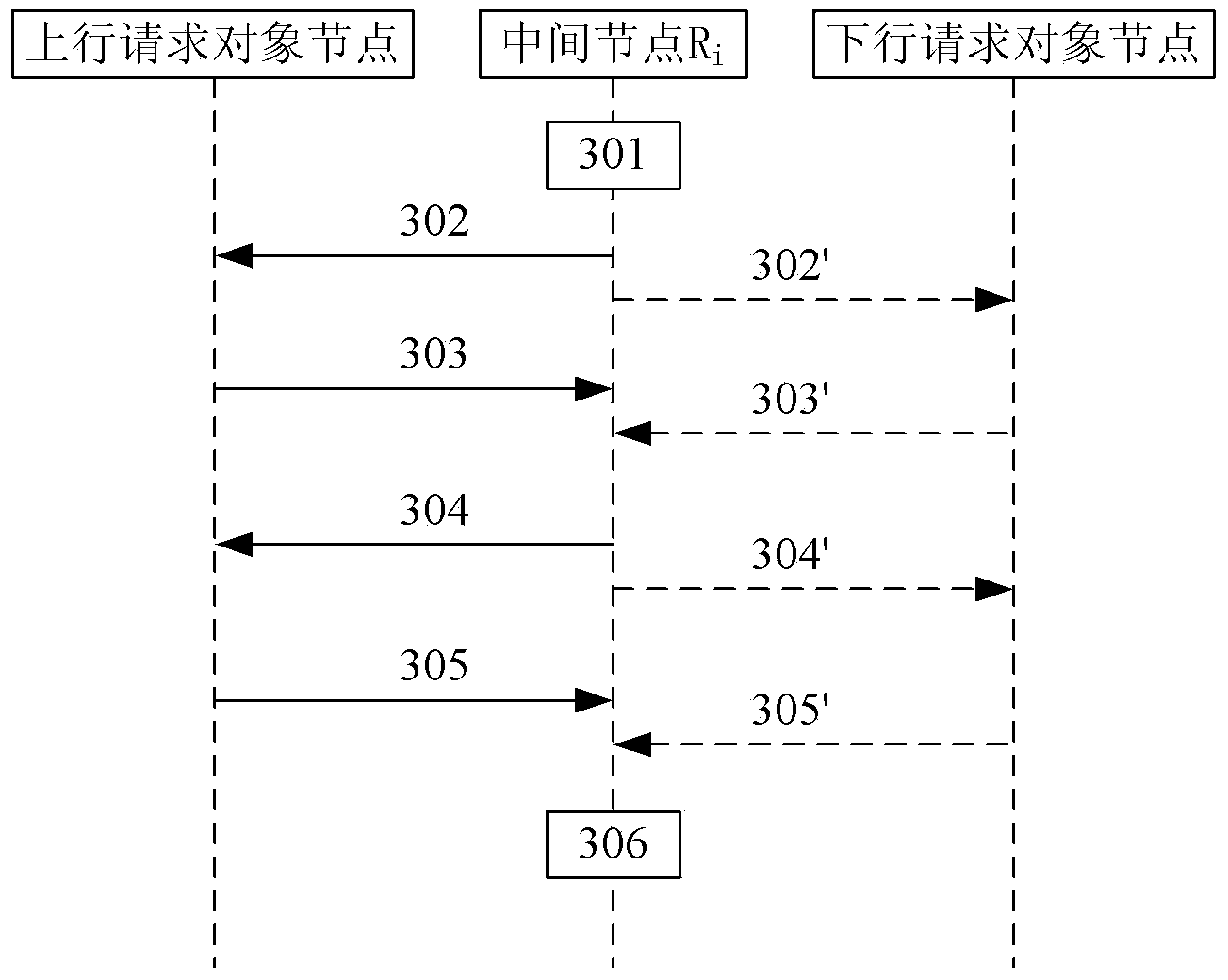
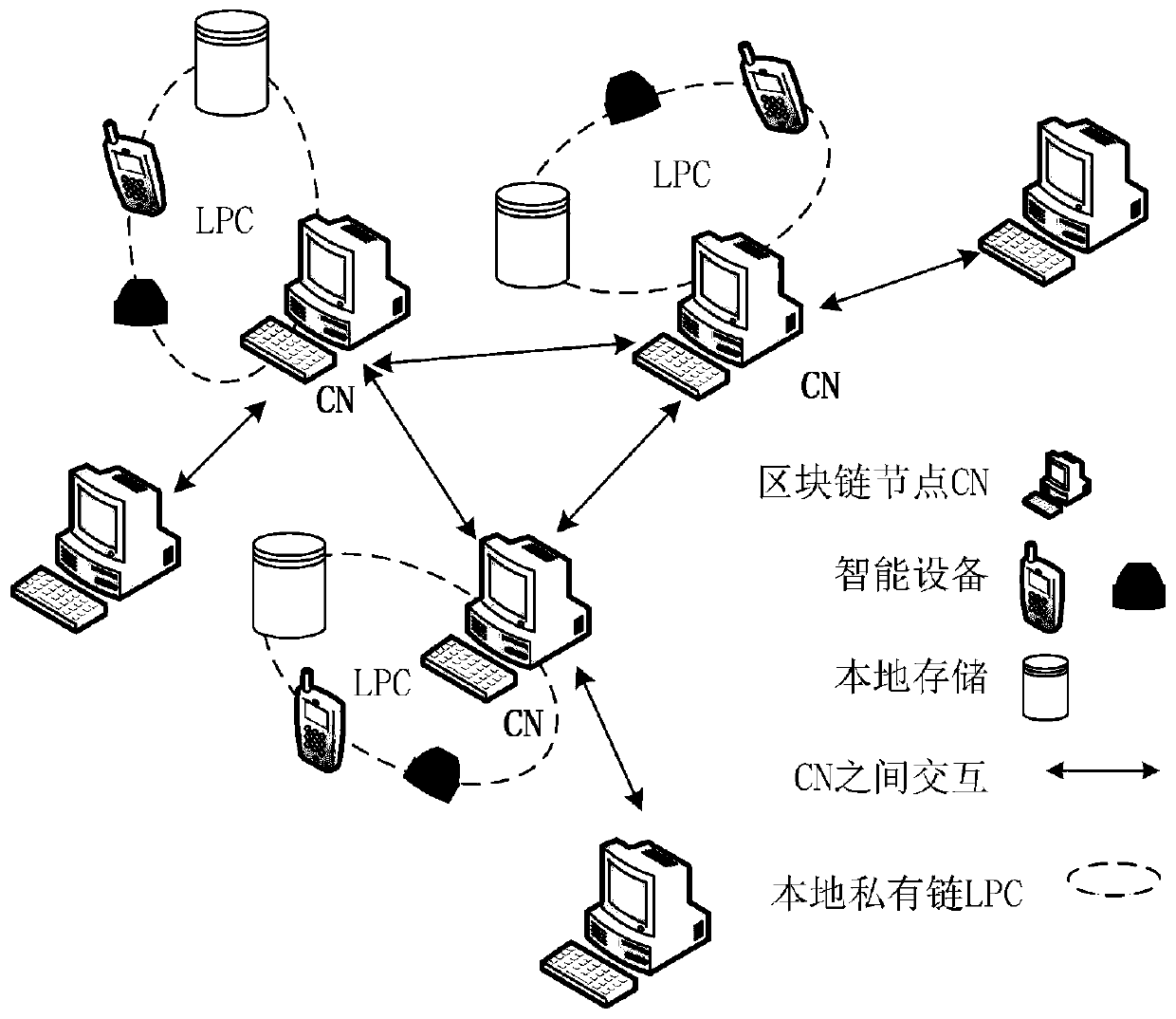
Node discovering method and system in communication network
ActiveCN103701700AAchieve mutual authenticationSafe and reliable communication transmissionUser identity/authority verificationData switching networksComputer networkComputer science
The invention provides a node discovering method and a node discovering system in a communication network. The method comprises the following steps that a source node sends discovery request messages to a next hop of node, and the discovery request messages carry the address information of the source node, the identity information of the source node, the address information of a target node and the challenge value generated by the source node; a node receiving the discovery request messages returns verification information, submitted to the source node by the node, to the source node; whether the node is a target node or not is judged according to the address information, and if the node is not the target node, the discovery request messages are transferred to the next hop of node of the node; after the source node receives the verification information returned by the target node, each node is verified according to the verification information submitted by each node; if the verification is completely passed, each node is determined to be trusted nodes. The method and the system provided by the invention have the advantages that the safety and the reliability of the communication transmission between network equipment can be ensured, and the communication delay is reduced.
Owner:INST OF INFORMATION ENG CAS +1
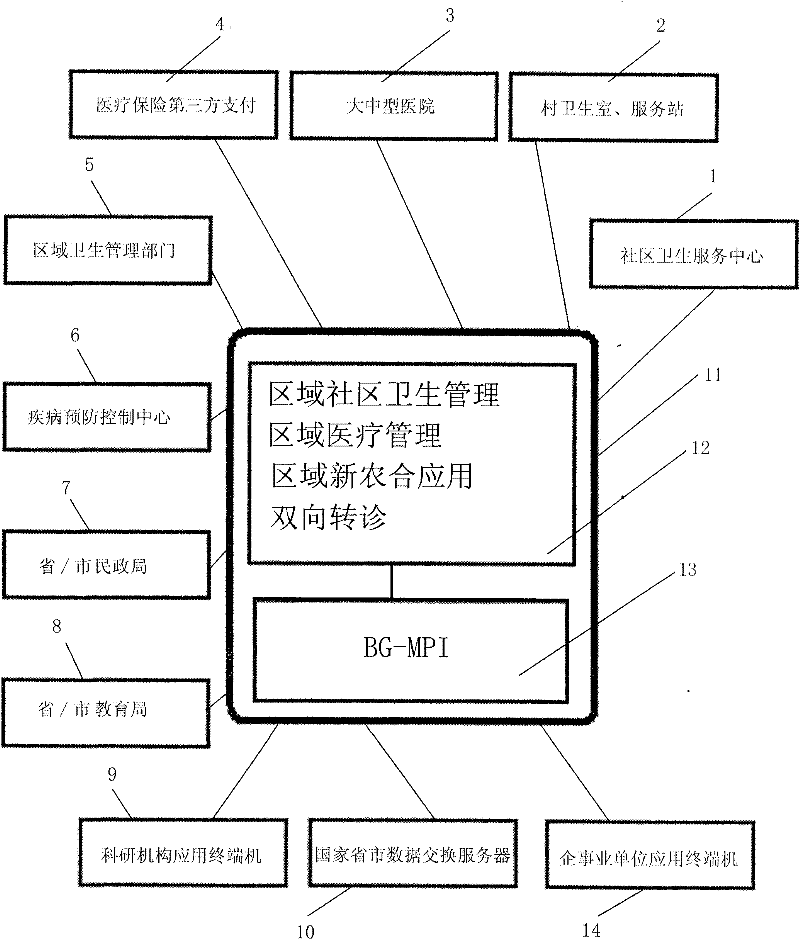
Regional health information sharing network system
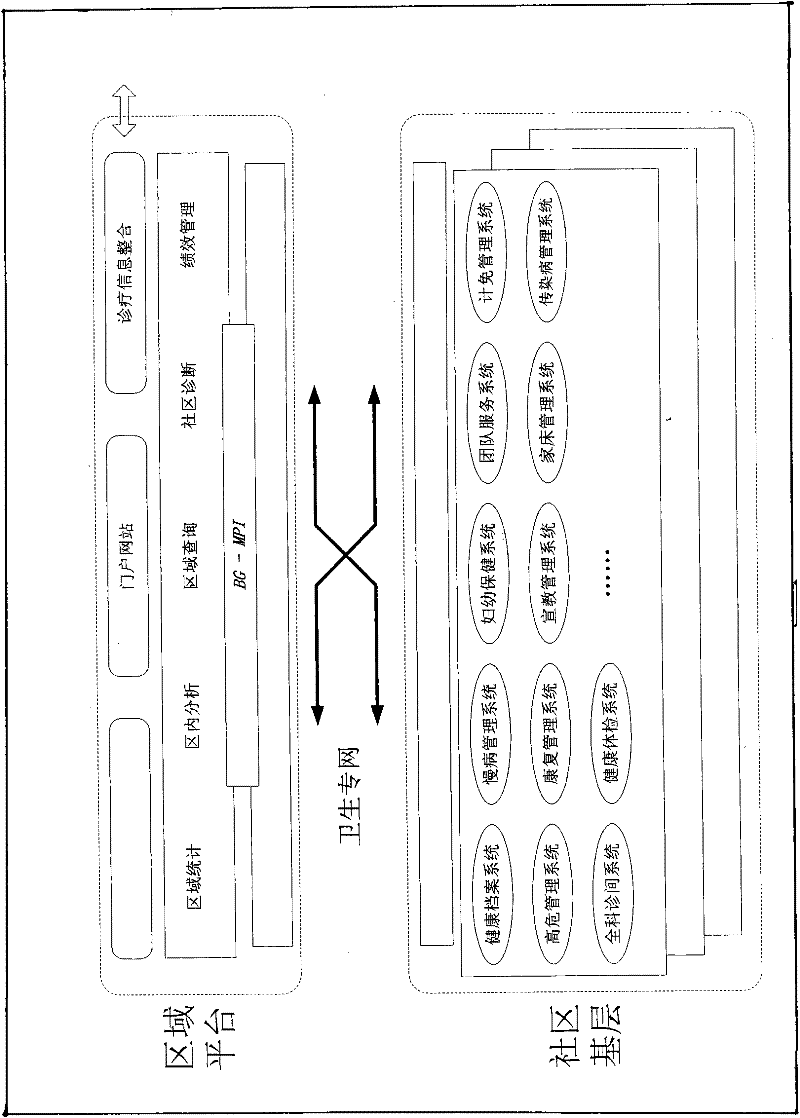
InactiveCN102236874ASolve the problem of shared interactionAchieve mutual authenticationData processing applicationsSpecial data processing applicationsData connectionData integration
The invention discloses a regional health information sharing network system, which is characterized in that an application terminal device of a community health service center, an application terminal device of a village clinics / service station, an application terminal device of a large and medium-sized hospital, and an application terminal device of a third party pay for medical insurance are all in two-way data connection with a medical health information sharing platform. The system is suitable for establishing cross-platform data sharing in a certain scope mainly based on residents, and builds up a perfect platform for the construction of regional health information. Based on the platform, a plurality of application systems of different fields and different structures can be added, thus the platform has excellent expansibility, and regional health information is shared and interacted. The system has strong data integration performance; a BG-MPI module provides a strong data pairing mechanism with high accuracy; and mutual authentication of multiple service modules can be realized. Compared with the prior art, the system has outstanding substantive characteristics and remarkable improvement.
Owner:上海新致百果信息科技有限公司 +1
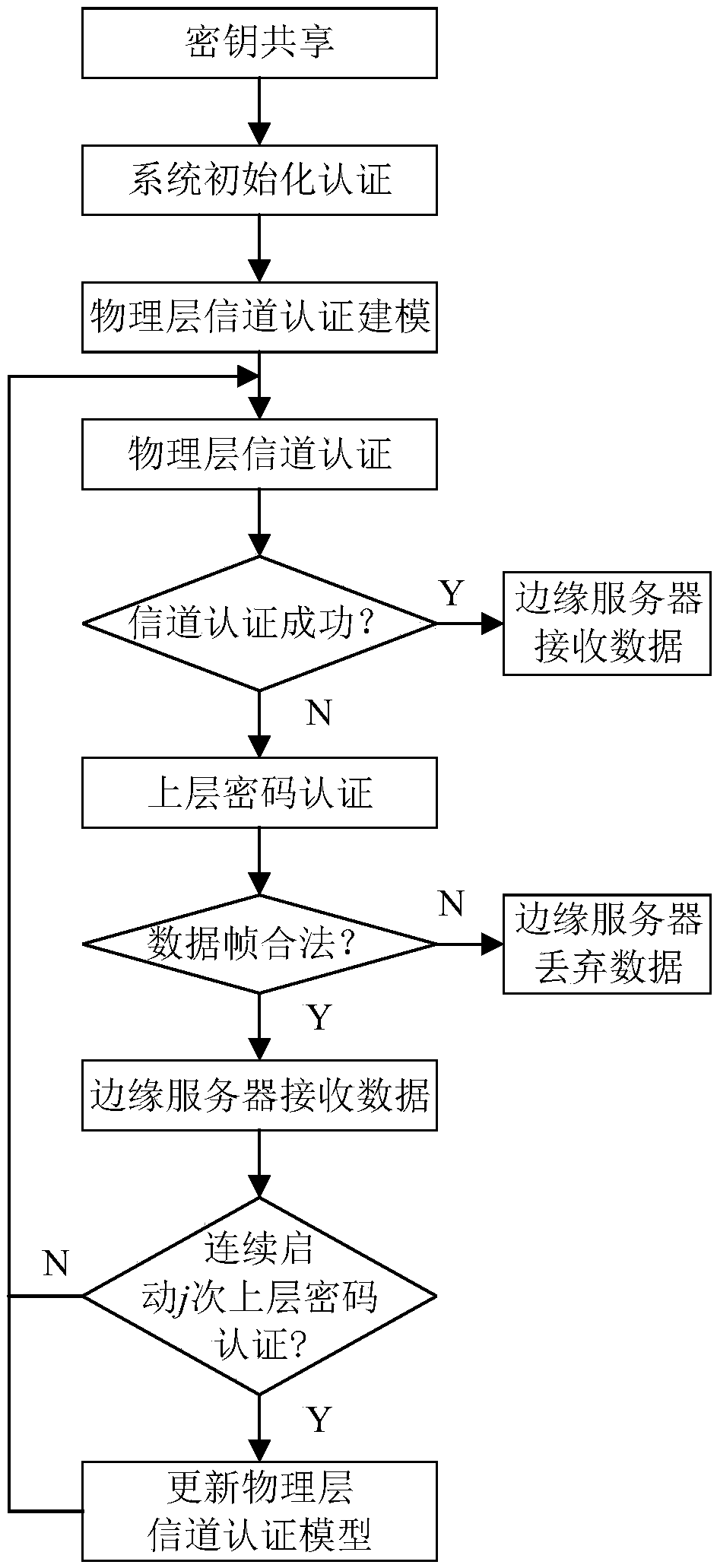
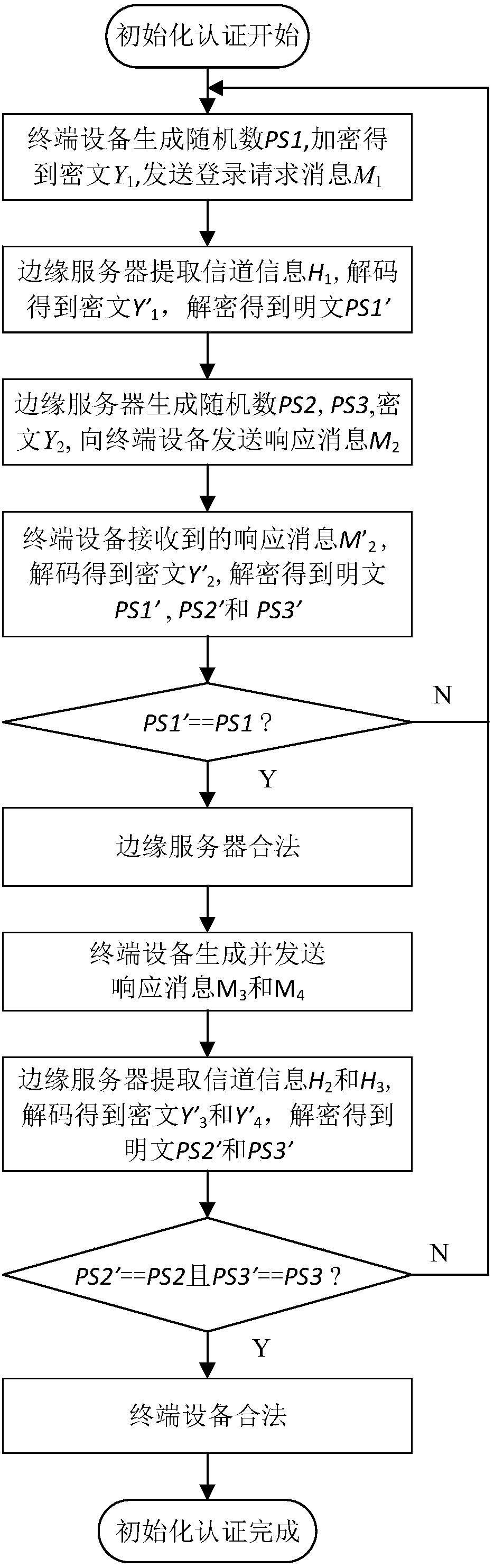
Terminal equipment access authentication method and system based on edge computing
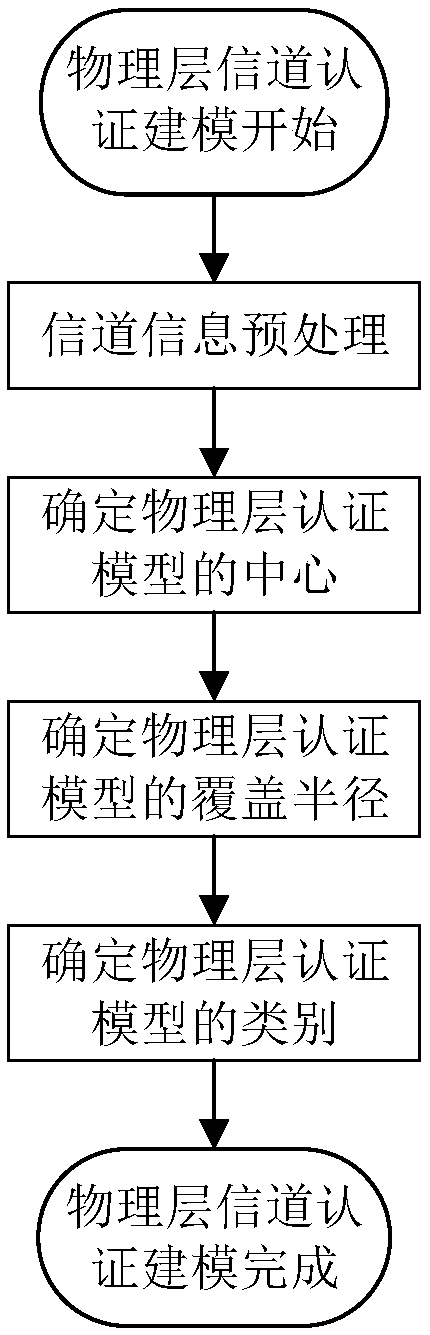
ActiveCN108810026AReduce complexityReduce overheadTransmissionLightweight cryptographyEdge computing
The invention discloses a terminal equipment access authentication method and system based on edge computing. The method comprises the following steps: S1, key sharing, sharing a key between the terminal equipment and the edge computing server; S2, system initialization authentication: accomplishing mutual initial identity authentication between the terminal equipment and the edge computing serveraccording to the key and the lightweight cryptography algorithm; S3, physical layer channel authentication modeling: verifying the data legality from the fourth-frame data by the edge computing server; S5, upper cryptography authentication: starting the upper cryptography authentication if the legality of the received data frame cannot pass the model authentication at the non-initialization authentication stage; and S6, physical layer channel authentication model updating: updating the physical layer channel authentication model when j data frames continuously received by the edge computing server in the coherent time need to start the upper cryptography authentication. Through the method disclosed by the invention, the complexity of the terminal equipment identity authentication is reduced, and the security and the authentication rate of the identity authentication are improved.
Owner:CERTUS NETWORK TECHNANJING
Improved anonymous authentication method based on conditional privacy protection
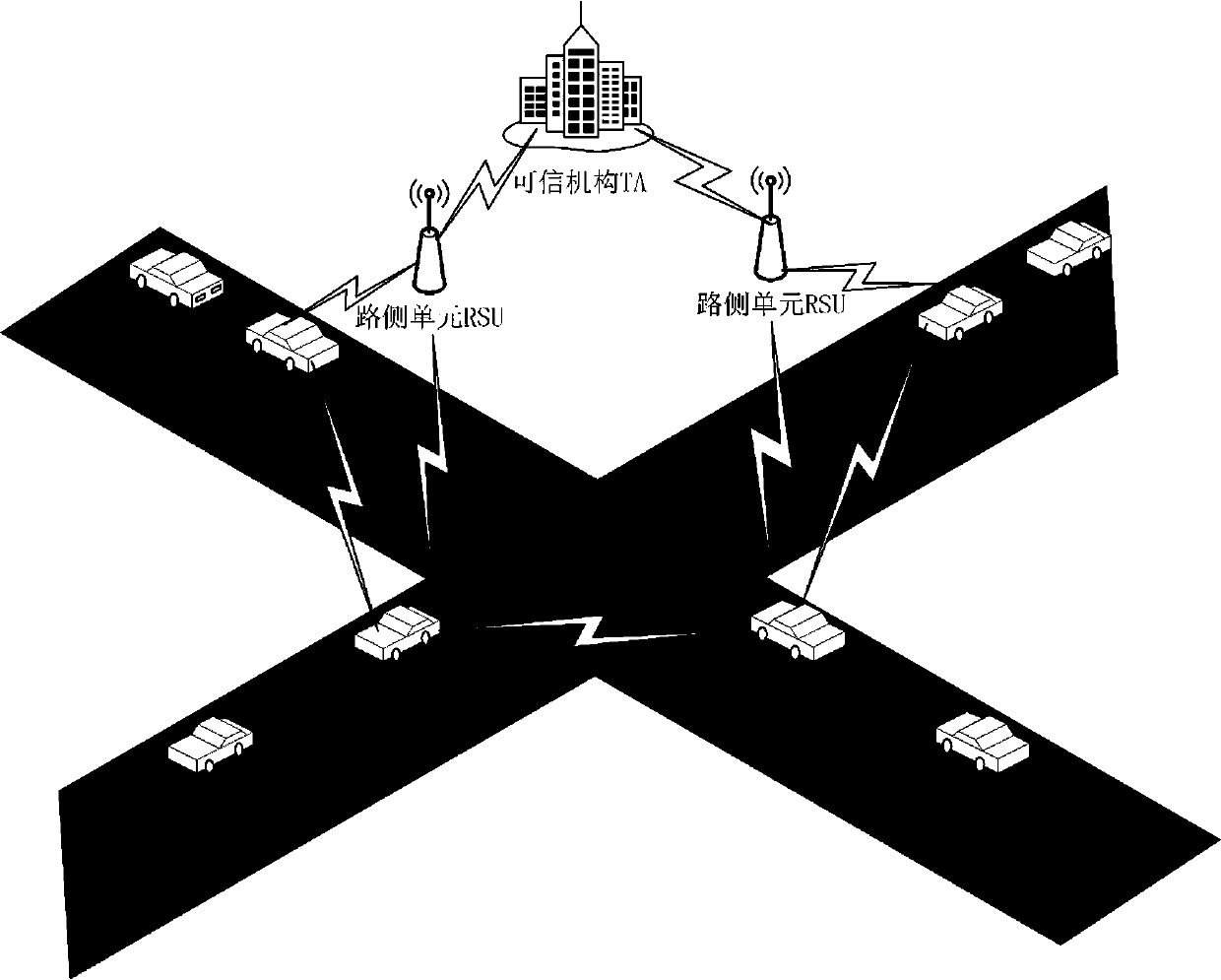
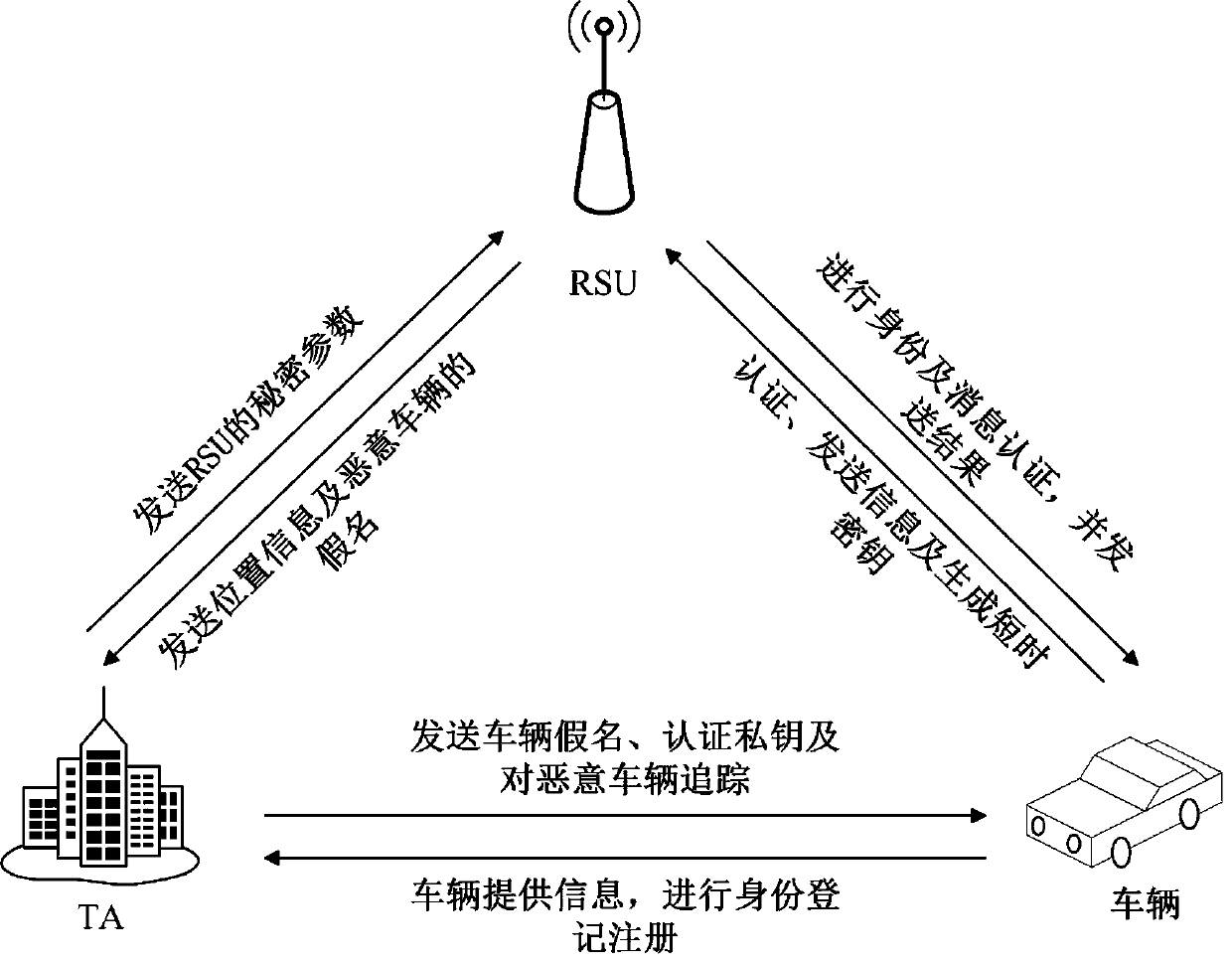
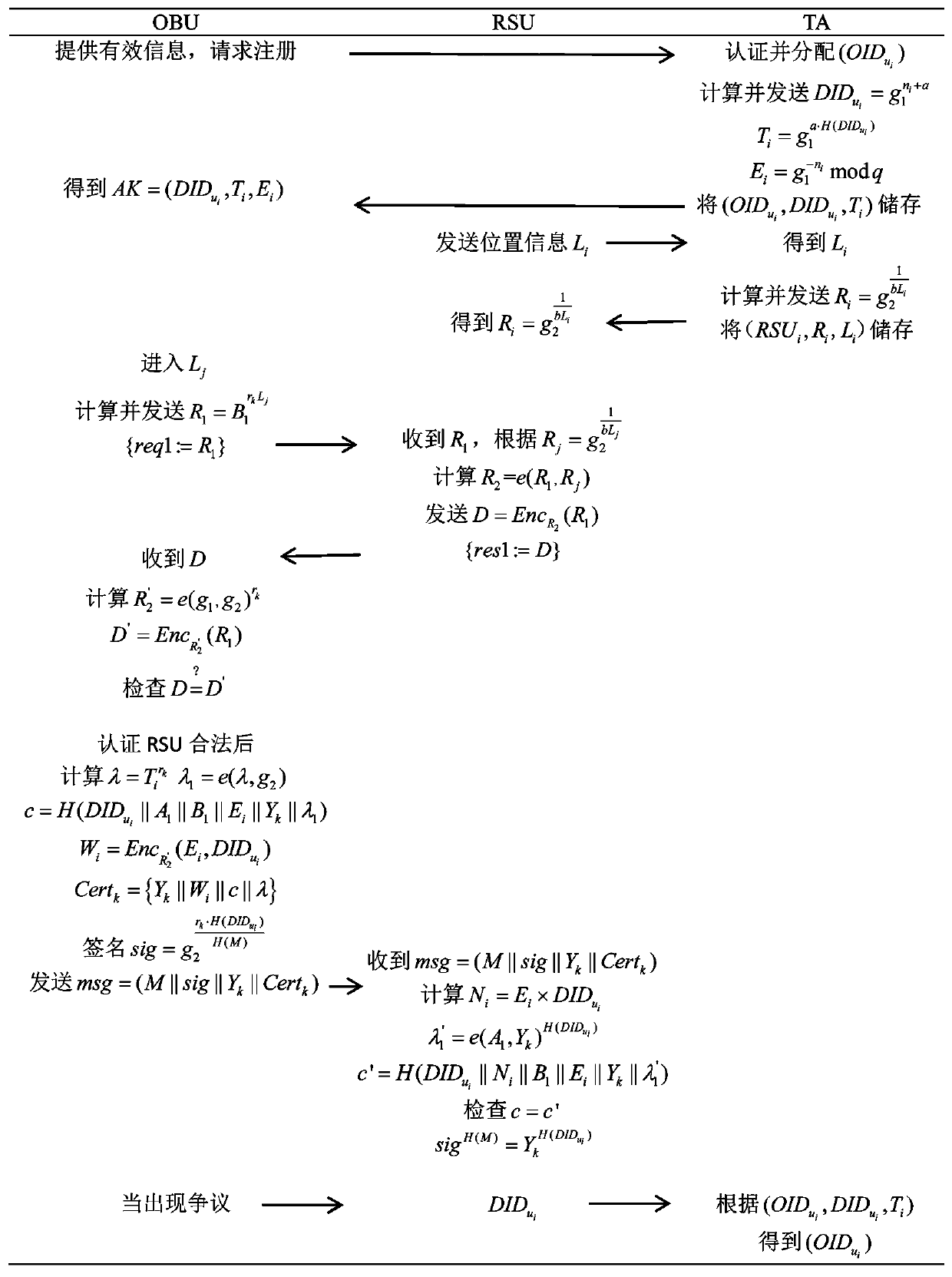
ActiveCN110022542AQuick searchJudgment of invalidityKey distribution for secure communicationParticular environment based servicesPrivacy protectionAnonymous authentication
The invention discloses an improved anonymous authentication method based on conditional privacy protection, which is characterized by comprising the following steps: 1) initializing a system; 2) registering vehicles; 3) registering RSU; 4) generating a short-time secret key; 5) generating an anonymous certificate; 6) performing message signing; 7) authenticating the anonymous certificate and themessage; 8) carrying out conditional tracking. According to the method, mutual authentication between the OBU and the RSU is realized; the identity information in the vehicle anonymity certificate ischanged; an attacker cannot monitor and track the identity information of the vehicle; the method can quickly find out the real identity information of a malicious vehicle and judge the invalidation of an illegal vehicle, has identity authentication, anonymity, non-linkability, privacy protection and traceability, and improves the authentication efficiency.
Owner:GUILIN UNIV OF ELECTRONIC TECH
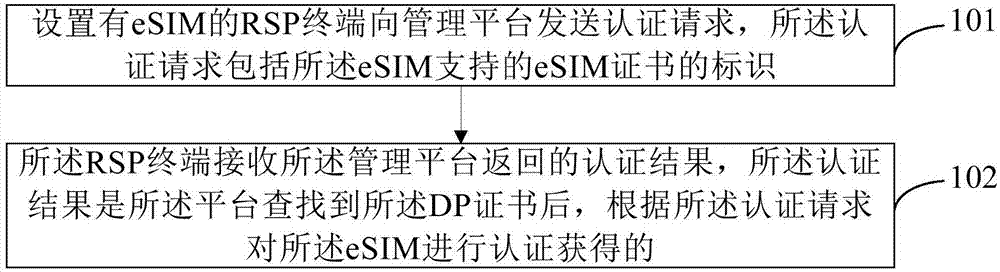
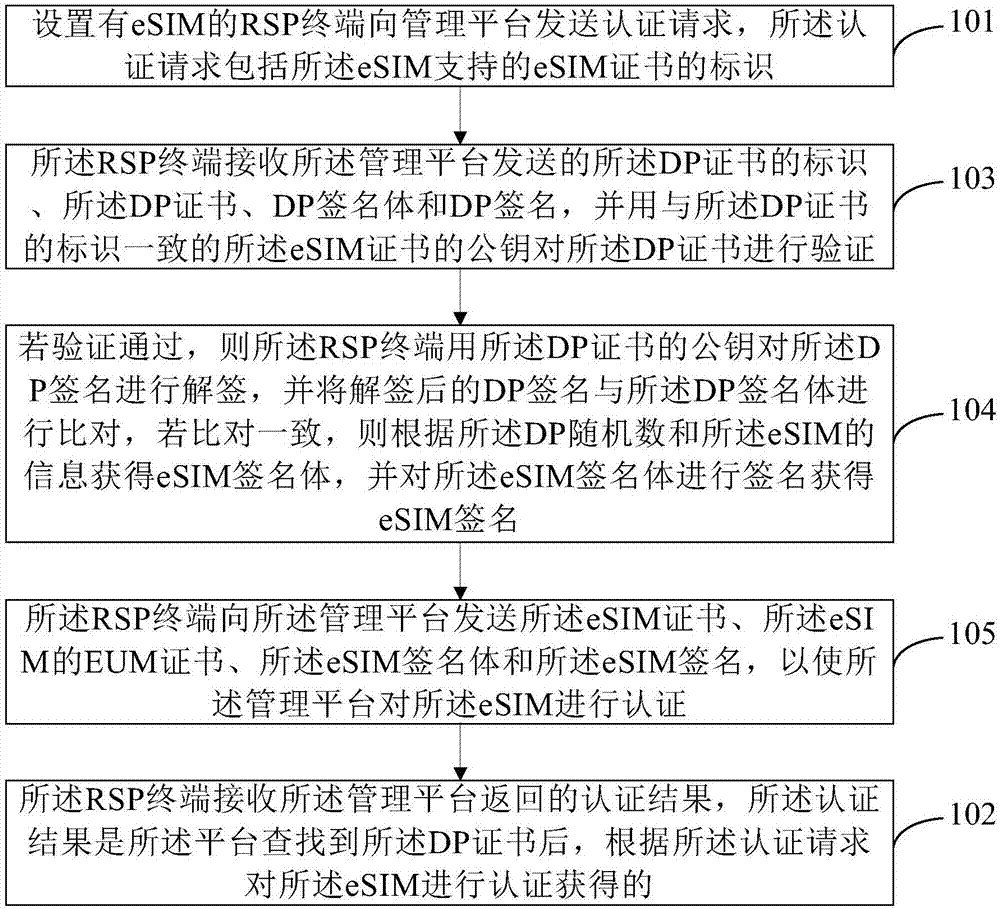
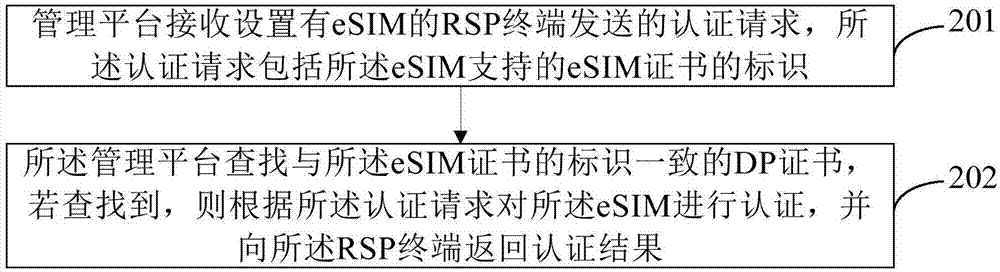
Authentication method applied to eSIM, RSP terminal and management platform
ActiveCN107547573AAchieve mutual authenticationImprove authentication efficiencyUser identity/authority verificationSecurity arrangementMutual authentication
The invention provides an authentication method applied to eSIM, an RSP terminal and a management platform. The method comprises the steps that the RSP terminal provided with the eSIM sends an authentication request to the management platform, wherein the authentication request comprises identification of an eSIM certificate supported by the eSIM, and the identification of the eSIM certificate isused for the management platform to seek a DP certificate consistent with the identification of the eSIM certificate; the RSP terminal receives an authentication result returned by the management platform, the authentication result is obtained by authenticating the eSIM according to the authentication request after the platform seeks the DP certificate. According to the scheme, the certificates supported by two parties are confirmed before the authentication process is conducted, mutual authentication between the management platform and the RSP terminal is achieved, and the authentication efficiency is improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
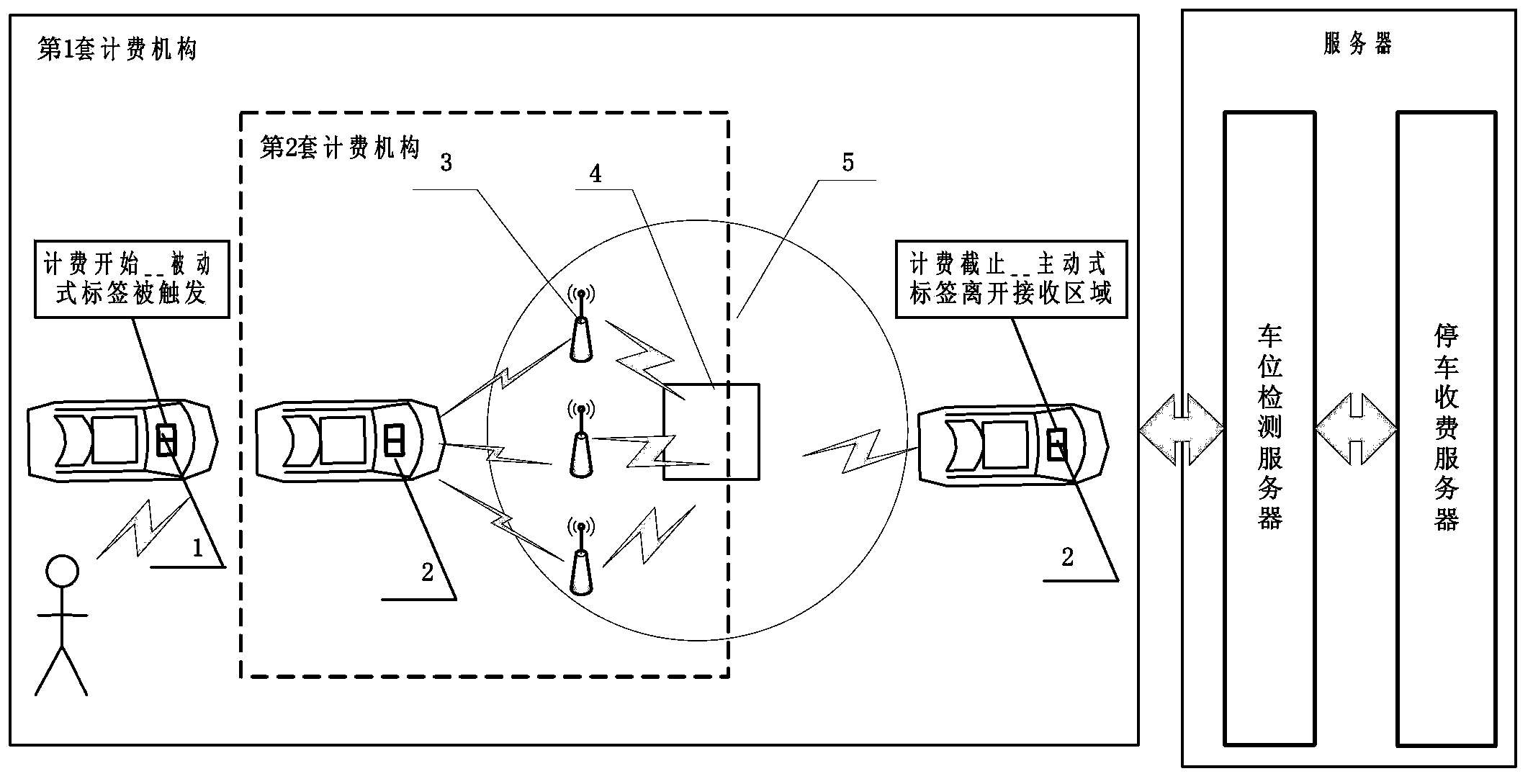
Open-type parking lot charging system based on vehicle-mounted composite tag and method thereof
The invention relates to an open-type parking lot charging system based on a vehicle-mounted composite tag and a method thereof. The open-type parking lot charging system is technically characterized in that the system consists of the vehicle-mounted composite tag, a parking stall information collector and a server which are connected to achieve charging of an open-type parking lot. The method judges the billing start time of parking, taking the passive tag triggering time as the main reference and the vehicle drive-in time detected by a parking stall detector as the extra reference; the method judges the billing stop time of parking, taking information collection range that the active tag leaves the region as the main reference and the vehicle drive-out time detected by the parking stall detector as the extra reference. Through coordination of supervisors and intelligent equipment of the parking lot, vulnerability probably caused by human factors is compensated, irresistible congenital defects and shortcomings of the intelligent equipment are avoided and the problem of misjudgment of the open-type parking lot is solved.
Owner:东莞市帕马智能停车服务有限公司
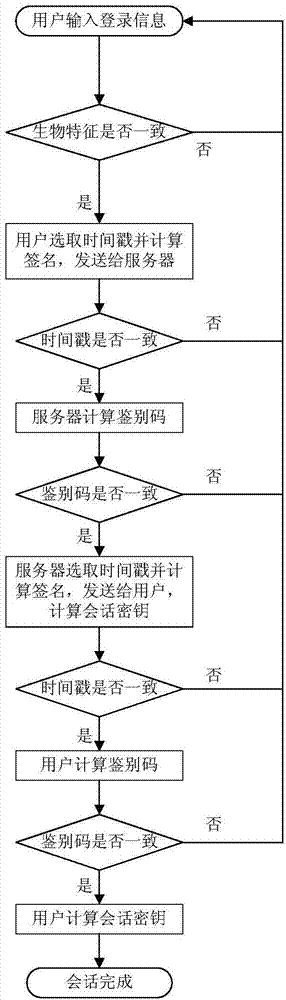
Identity-based authentication method and identity-based authentication system with secret key negotiation
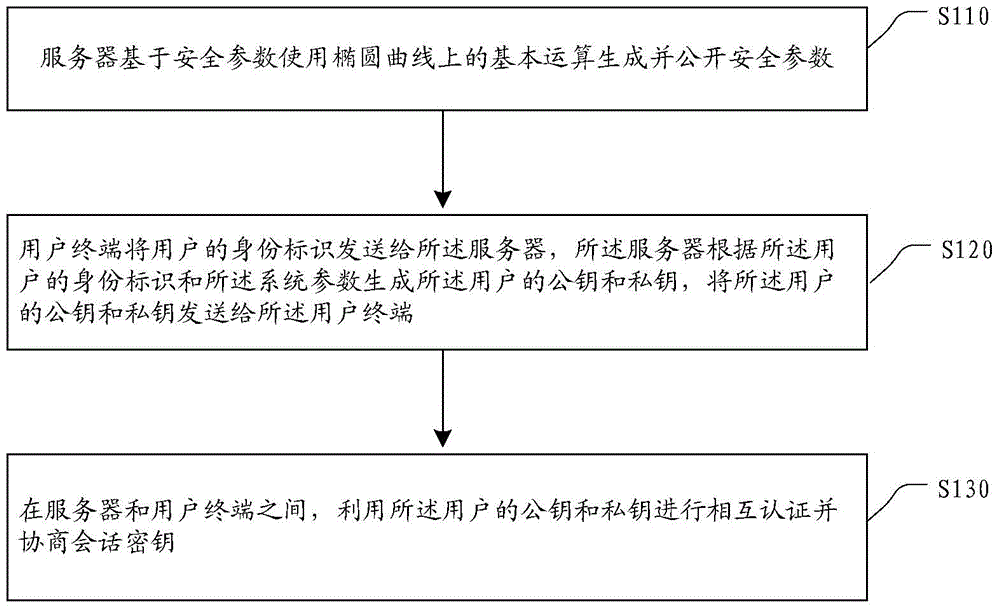
ActiveCN105577377AAchieve mutual authenticationKey distribution for secure communicationUser identity/authority verificationE-commerceComputer terminal
An embodiment of the invention provides an identity-based authentication method and an identity-based authentication system with secret key negotiation. The identity-based authentication method mainly comprises the steps of generating and disclosing a system parameter by a server based on a safety parameter; transmitting identity identification of a user to the server by user terminal, generating the public key and the private key of a user by the server according to the identity identification and the system parameter of the user, and transmitting the public key and the private key of the user to the user terminal; and performing mutual authentication and session key negotiation by means of the public key and the private key of the user between the server and the user terminal. The embodiment of the invention provides the identity-based authentication method and the identity-based authentication system with secret key negotiation. The identity-based authentication method and the identity-based authentication system can realize mutual authentication between the client and the server. Furthermore in the mutual authentication process, session key is negotiated and authentication can be effectively and safely realized by means of basic operation on an elliptical curve. The identity-based authentication method and the identity-based authentication system can be widely applied in electronic commerce.
Owner:AEROSPACE INFORMATION
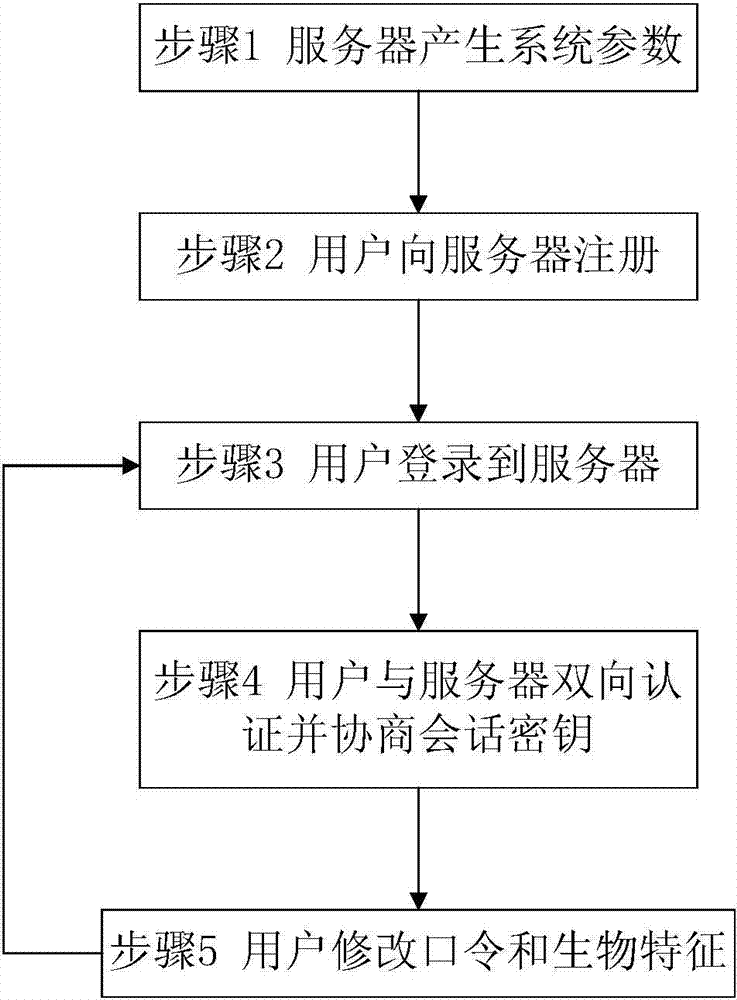
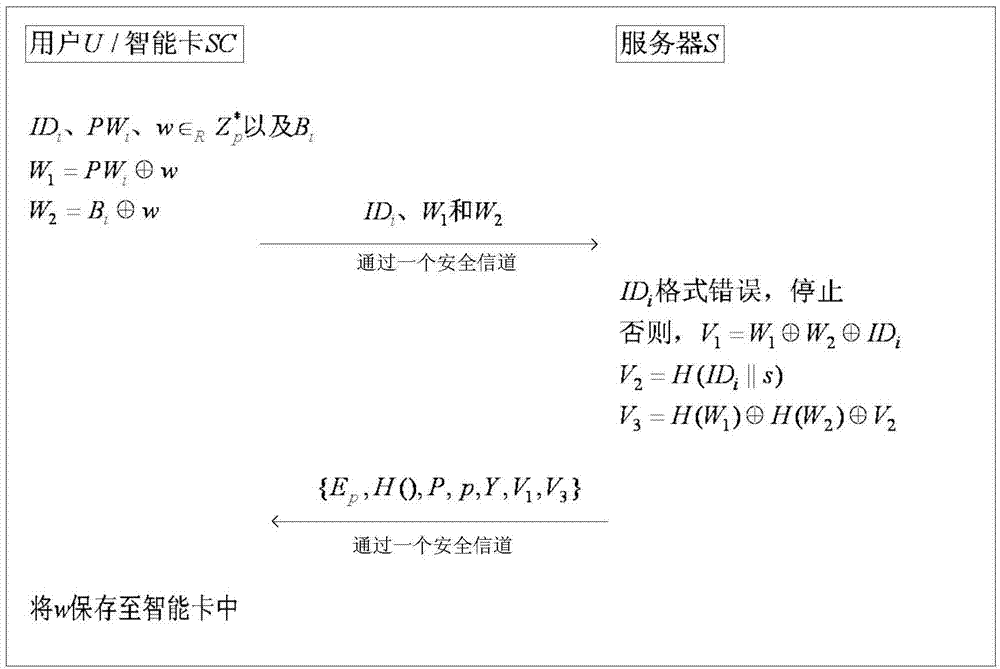
Remote authentication protocol method based on password and intelligent card
ActiveCN104901809AEnhanced anonymityReach deliveryUser identity/authority verificationArray data structurePassword
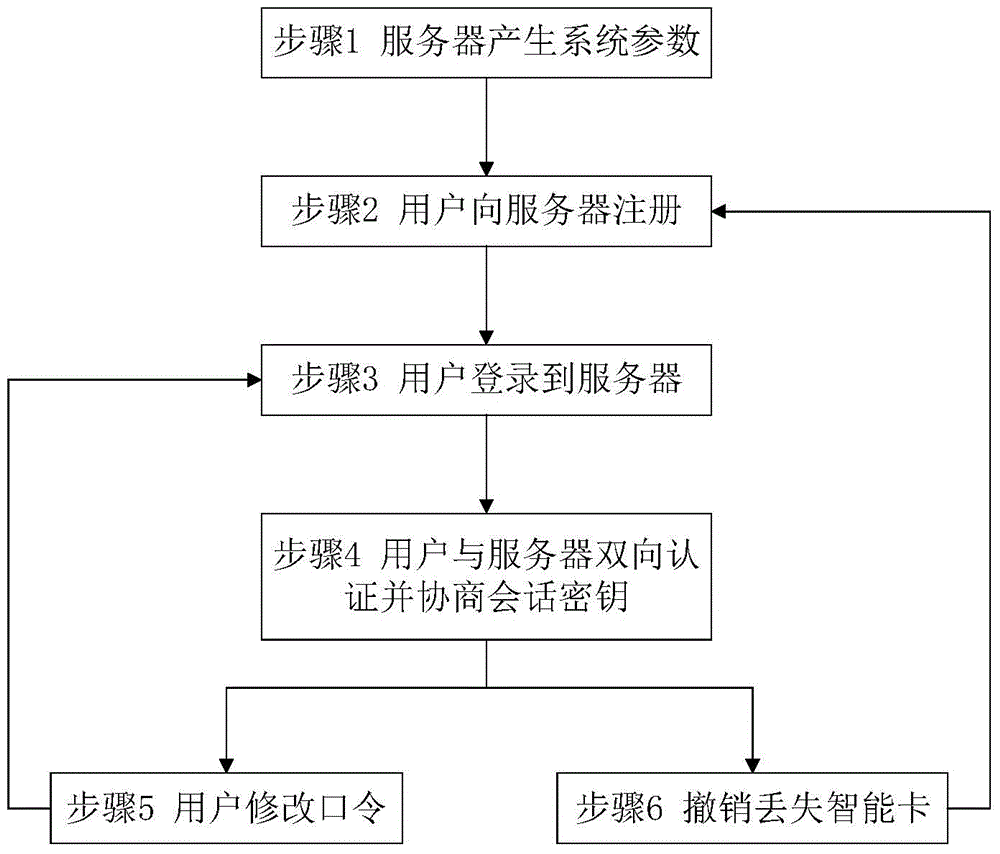
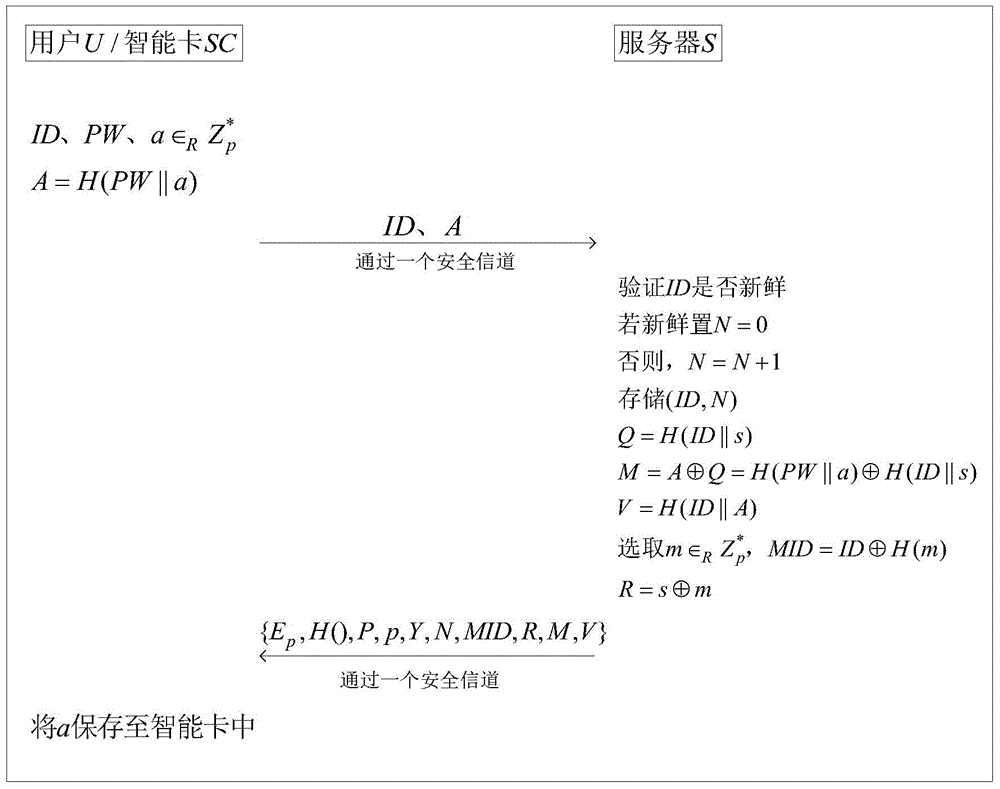
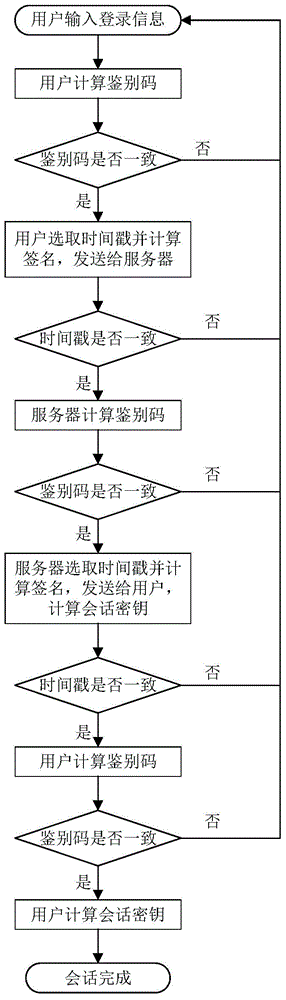
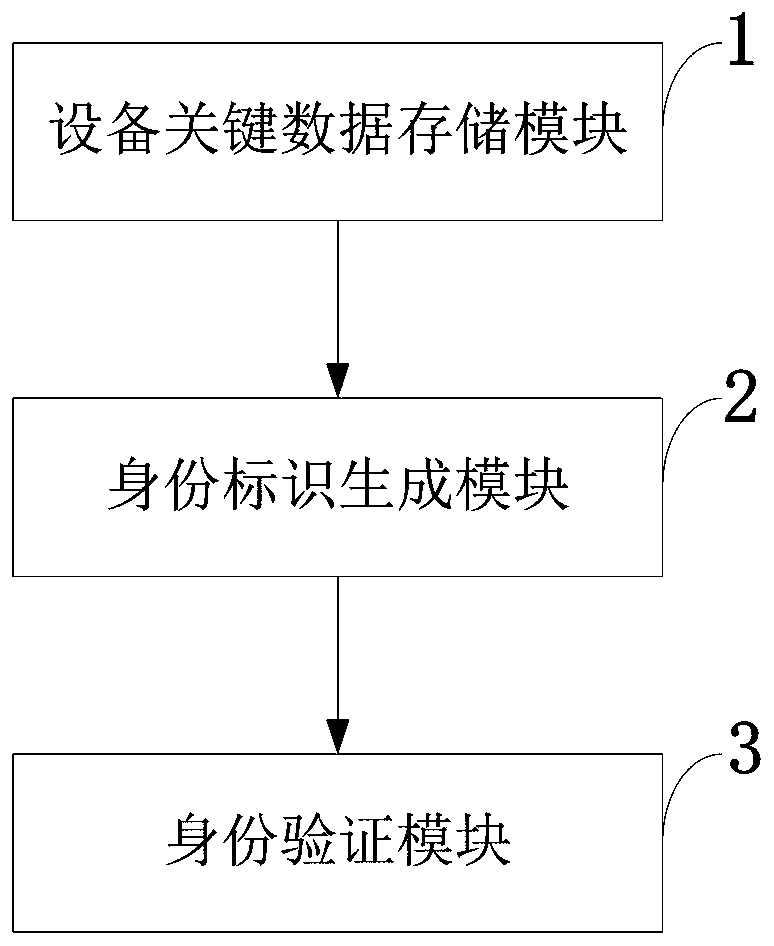
The invention provides a remote authentication protocol method based on password and an intelligent card, and belongs to the field of information safety. The protocol employs an optimized elliptical curve algorithm, a counting set and authentication codes are embedded, password can be modified, and the lost intelligent card can be canceled. The anonymity of a user is ensured, the method is safe and efficient, mutual authentication and negotiation of session key of the user are realized via twice interaction, and the method is suitable for remote authentication systems as e-cash, online education and remote medicine.
Owner:BEIHANG UNIV
Lightweight authentication method and system based on Ethereum IoT entity, and intelligent terminal
ActiveCN111147228AFast and secure mutual authenticationReduce communication overheadKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHash functionAttack
The invention belongs to the technical field of network security communication, and discloses a lightweight authentication method and system based on Ethereum IoT entity, and an intelligent terminal.The method comprises the following steps: performing an Ethereum-based IoT entity hierarchical architecture deployment stage; performing an intelligent device registration stage; sending authentication request information; verifying the request information for the chameleon hash function and sending authentication information and response information; sending an authentication confirmation message; performing IoT inter-entity interaction information. The method and system are applied to all Internet of Things scenes, the consensus reaching time of the blockchain node is greatly reduced, and the trouble caused by the limitation of the processing capacity of the intelligent equipment is also solved; the hash value of the key information of the equipment is subjected to whole-network backup in the blockchain, so that the security of the identity of the terminal equipment is ensured; mutual authentication between entities of the Internet of Things is realized by utilizing the characteristics of the chameleon hash function, so that the authentication efficiency is improved, and all currently known attacks can be resisted.
Owner:XIDIAN UNIV
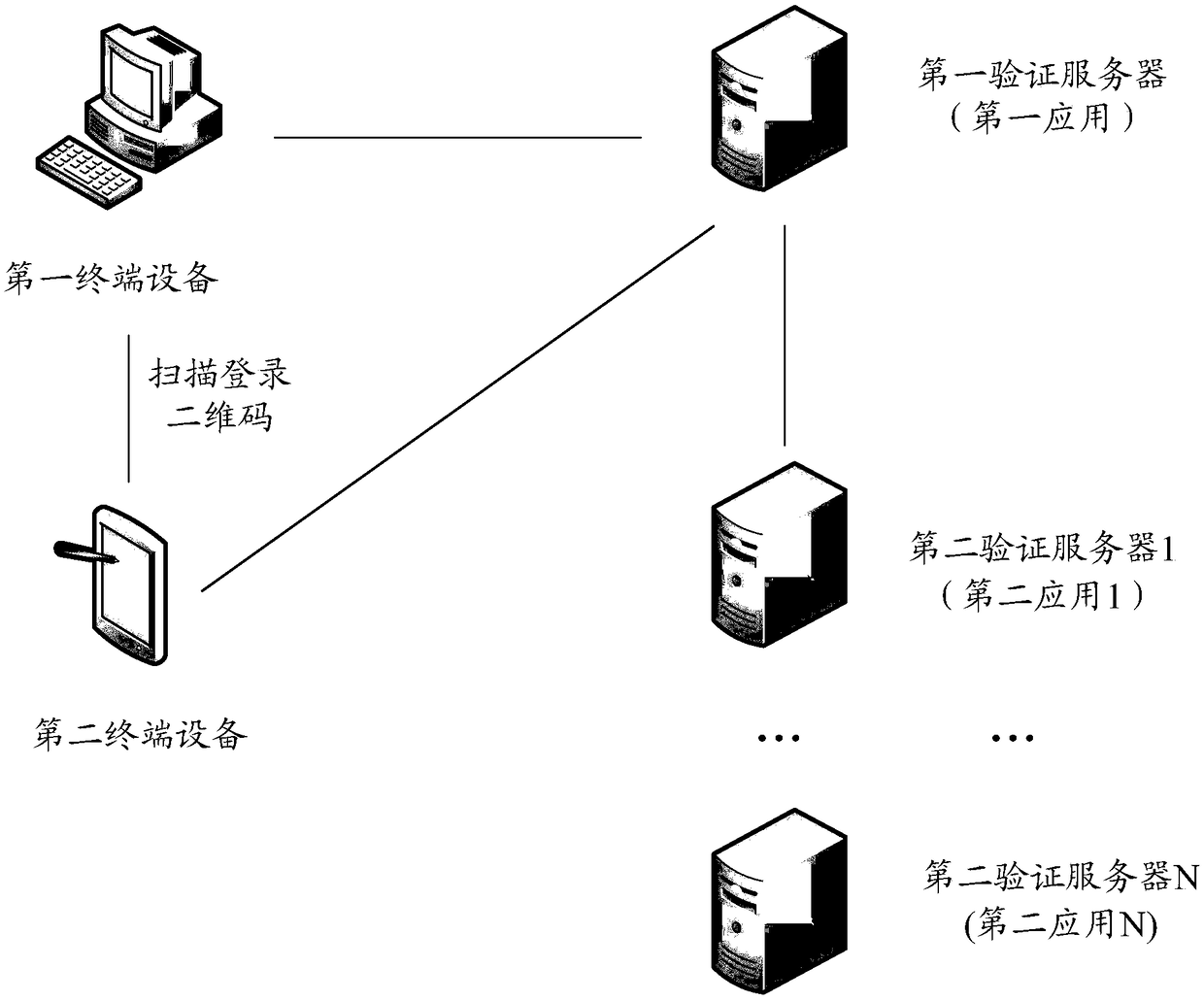
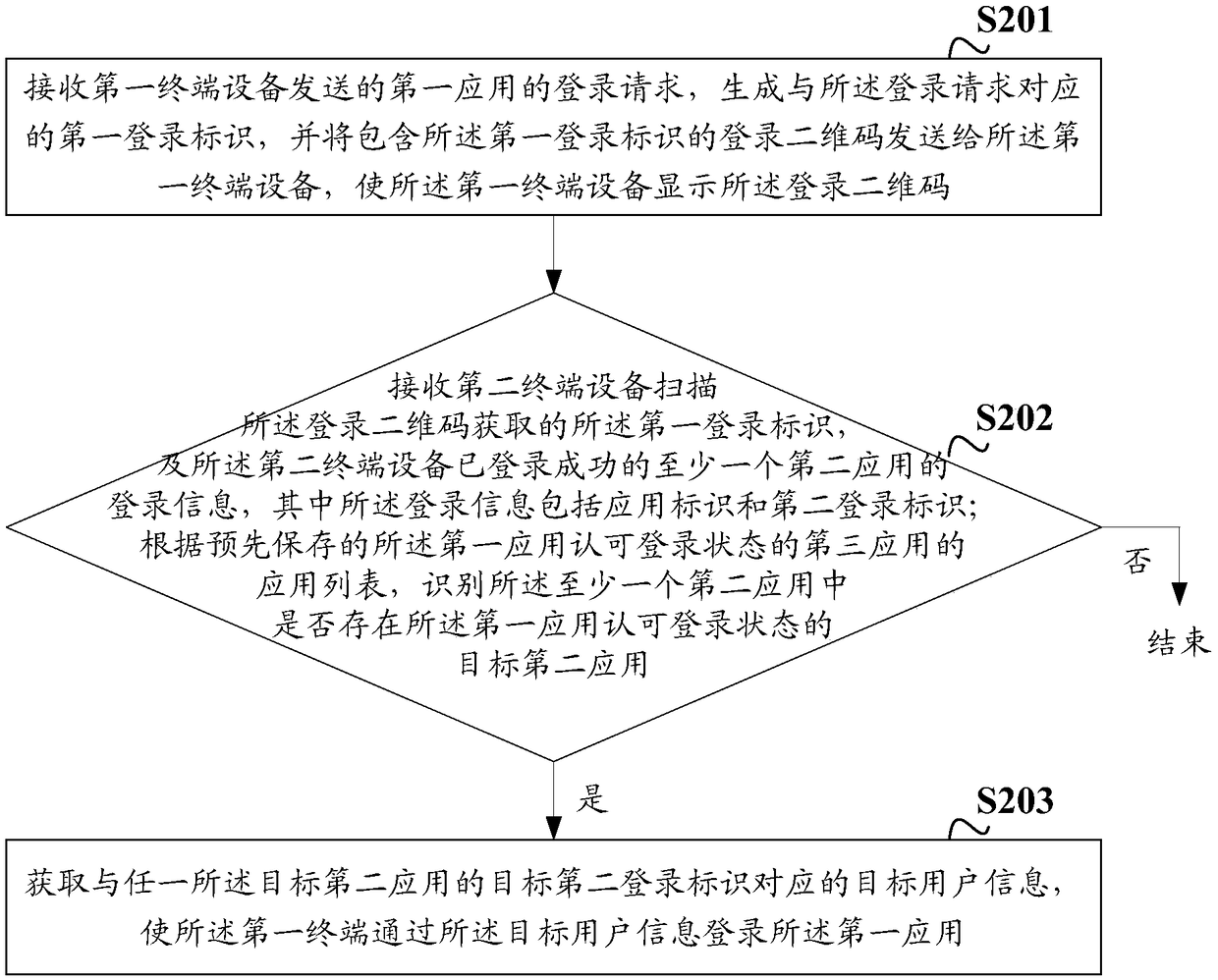
Multi-application login method and device
ActiveCN109413096AImprove experienceAchieve mutual authenticationUser identity/authority verificationDigital data authenticationTerminal equipmentComputer terminal
The invention discloses a multi-application login method and device. The method comprises the steps of receiving a login request of a first application sent by first terminal equipment by using a first verification server, and generating a login two-dimensional code including a first login identifier corresponding to the login request; displaying the login two-dimensional code by using the first terminal equipment; receiving a first login identifier acquired by second terminal equipment through scanning the login two-dimensional code and login information of at least one second application that is successfully logged in; when the target second application with the login state accepted by the first application in the at least one second application is recognized according to an applicationlist of third applications of which the login states are accepted by the first application, acquiring target user information corresponding to the target second login identifier of any target second application, thus allowing the first terminal to log in the first application via the target user information. The invention provides a login scheme which can achieve mutual authentication between thedifferent applications.
Owner:BEIJING HAITAI FANGYUAN HIGH TECH
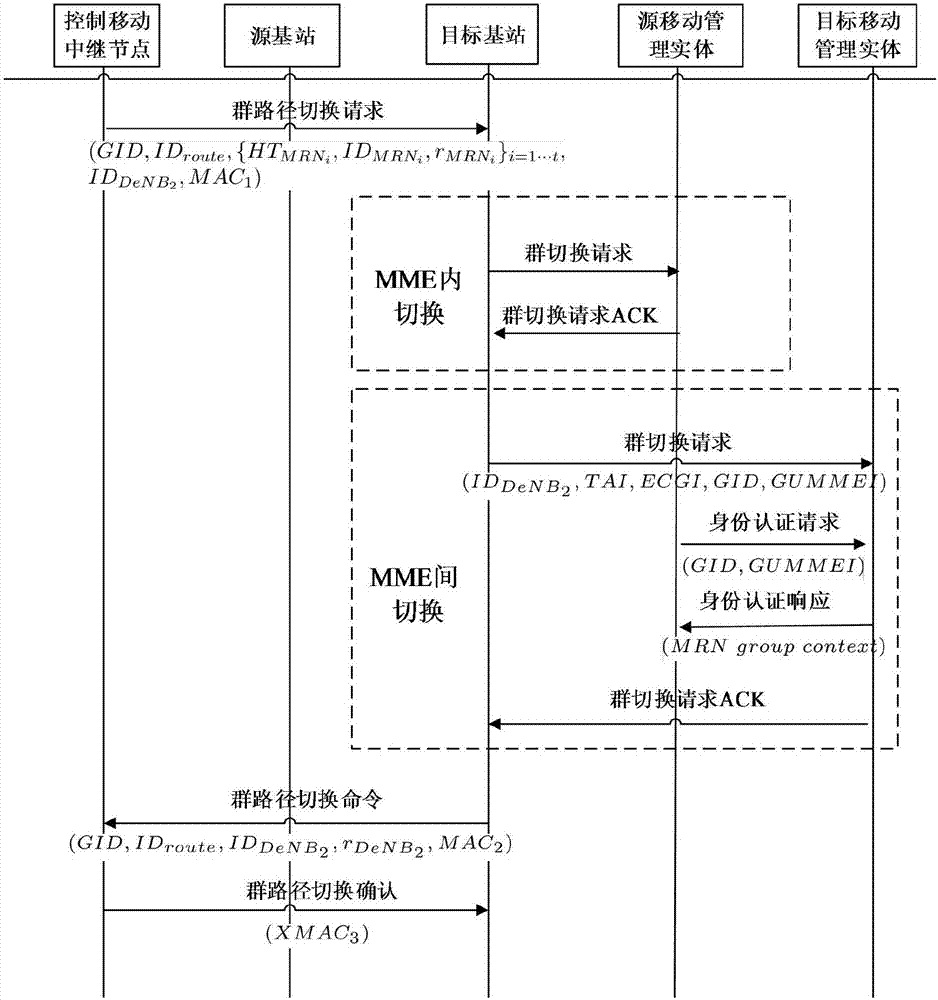
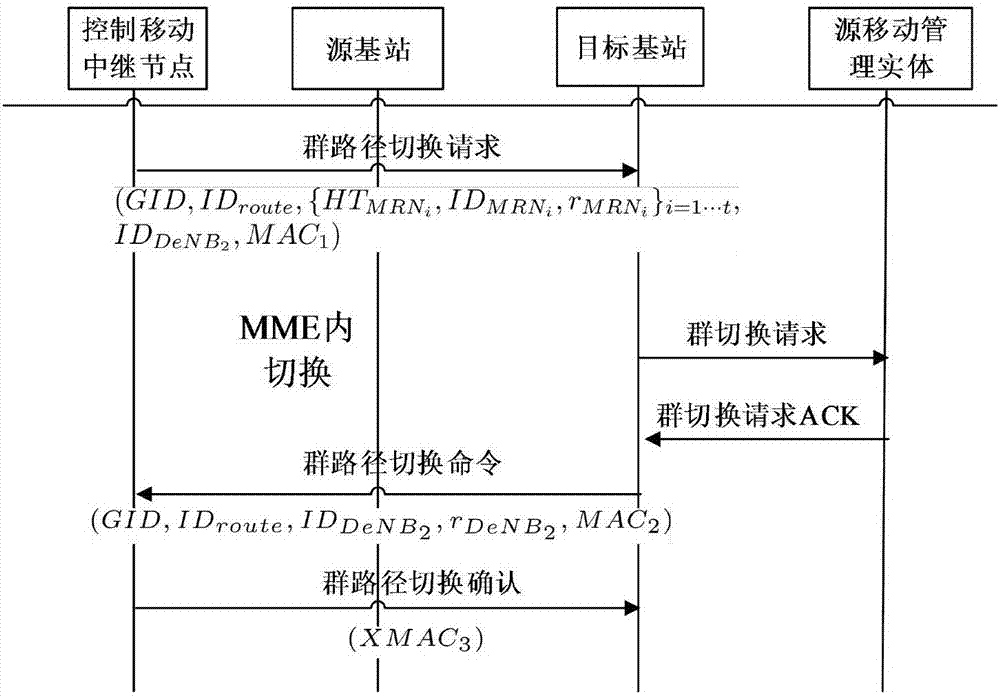
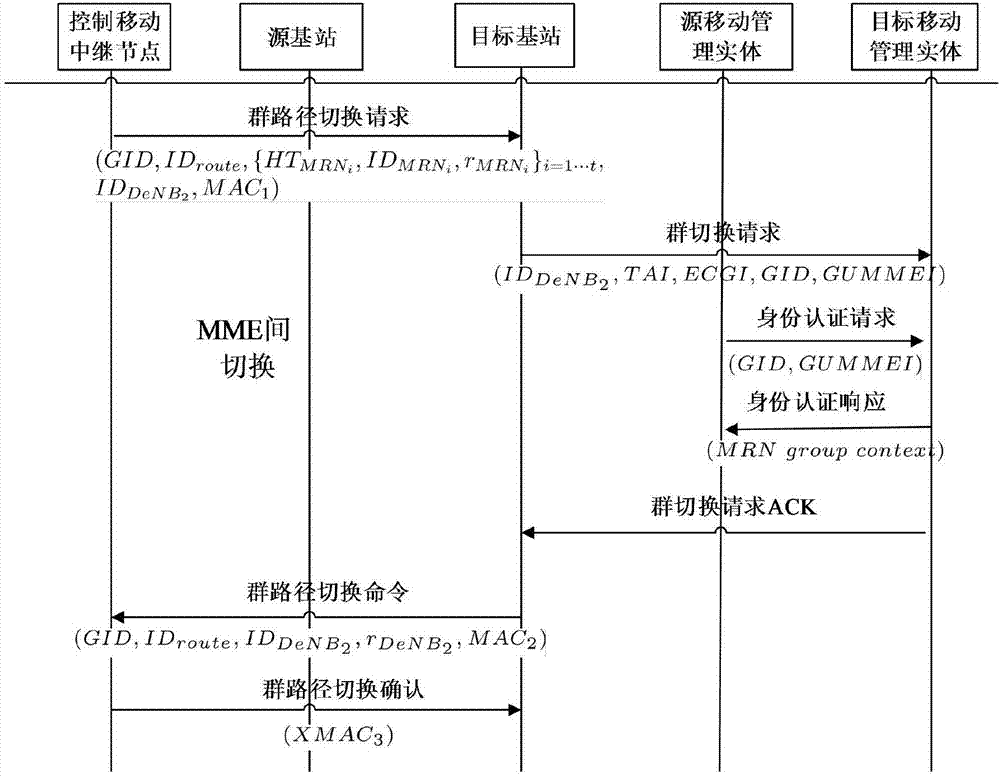
Group path mobile handover authentication method based on mobile relay
ActiveCN106961682AReduce signaling trafficReduce communication costsSecurity arrangementTraffic volumeMutual authentication
The invention discloses a group path mobile handover authentication method based on a mobile relay, which is characterized by comprising the following steps of: S1, executing a stage of carrying out initial authentication; S2, executing a stage of carrying out switching authentication on the basis of a group path; S3, executing an internal switching process aiming at MMEs; S4, executing an inter-switching process aiming at the MMEs; S5, sending group switching command information; and S6, sending a group switching confirmation message. According to the group path mobile handover authentication method disclosed by the invention, the scheme is designed according to a 3GPP standard, and thus, communication equipment in the standard does not need to be changed, and the group path mobile handover authentication method can be applied to networks of all LTE-A mobile scenes; massive switching information can be integrated into one piece of group switching information, and signaling traffic between all the equipment and the MMEs is greatly saved, so that switching communication cost is greatly reduced, and signaling congestion on a link between a service network and a home network is reduced; and mutual authentication between a group of MRNs and a base station DeNB can be directly implemented, and all currently known attacks can be resisted to.
Owner:XIDIAN UNIV
Remote protocol authentication method based on biological features
ActiveCN104767624AEnhanced anonymityStable deliveryUser identity/authority verificationDigital data authenticationUser needsPassword
The invention provides a remote protocol authentication negotiation protocol method based on biological features and belongs to the field of information safety. An efficient elliptic curve coding system is adopted. The method comprises the following steps that (1) system initialization is carried out to generate elliptic curve data; (2) a user submits register information to a server through a safe channel, and the server conducts data processing and then stores the information into an intelligent card and sends the information to the user through the safe channel; (3) a user needs to calculate login information and sends the login information to the server; (4) the purpose of authentication and key negotiation between the user and the server can be achieved through two times of hand shaking, and a session key is generated; (5) the user can achieve the purposes of changing a password and the biological features through the operation of the intelligent card without the assistance of the server. By means of the design, the protocol is high in safety, all mentioned known attacks can be resisted, meanwhile, dynamic identity is adopted, the anonymity of the user is protected, and the calculation performance is also greatly improved. The method is suitable for online education, remote medical and other remote authentication systems.
Owner:BEIHANG UNIV
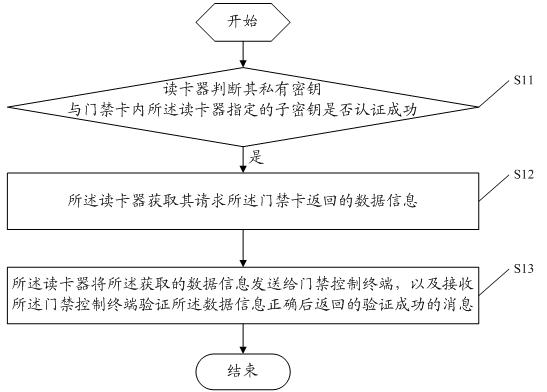
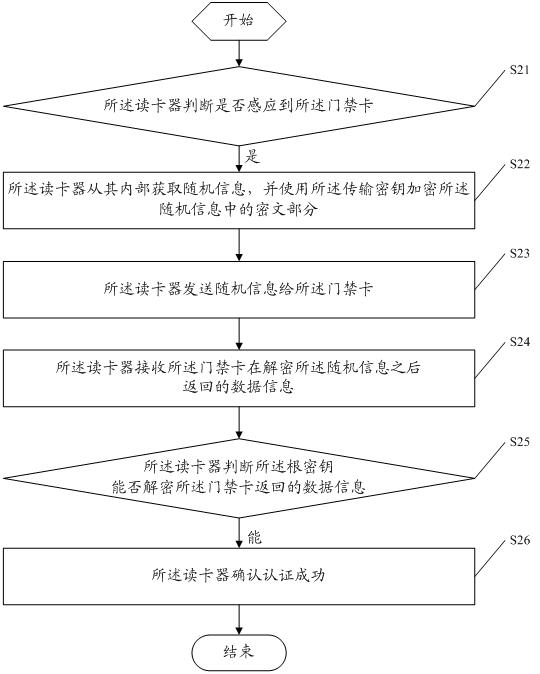
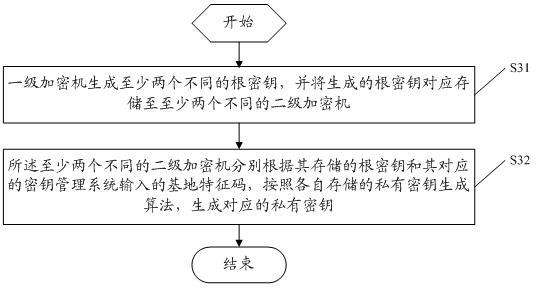
Entrance guard authentication method and system
ActiveCN102542645AAchieve mutual authenticationRealize all-in-one cardDigital data authenticationSensing record carriersAuthentication systemData information
The embodiment of the invention discloses an entrance guard authentication method, which comprises the following steps that: a card reader judges whether private keys of the card reader and sub-keys specified by the card reader in an entrance guard card are successfully authenticated, wherein at least two sub-keys with a shared master key are stored in the entrance guard card; the card reader acquires data information which is required to be returned by the entrance guard card if the authentication is successful; and the card reader transmits the acquired data information to an entrance guard control terminal and receives authentication passing information returned after the entrance guard control terminal verifies the correctness of the data information. The embodiment of the invention also discloses an entrance guard authentication system. By the method and the system, the entrance guard card and a plurality of card readers are mutually authenticated; and therefore, nuclear power personnel using the entrance guard card can pass various nuclear power plants under the same nuclear power enterprise by using the same card.
Owner:CHINA NUCLEAR POWER TECH RES INST CO LTD +1
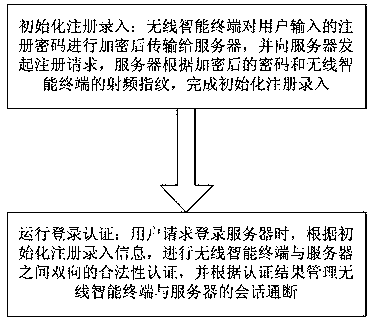
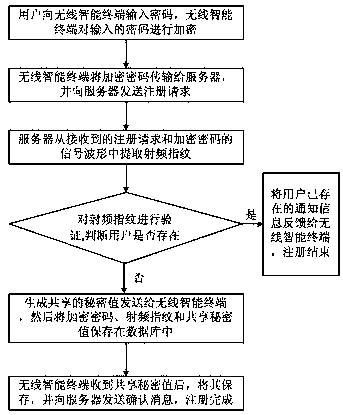
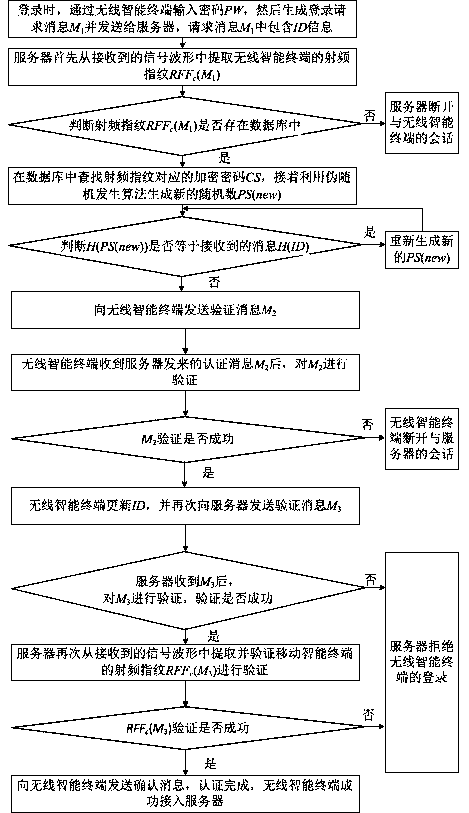
Radio frequency fingerprint (RFF)-based wireless intelligent terminal access authentication method and RFF-based wireless intelligent terminal access authentication system
ActiveCN107612949AReduced complexity and overheadMeet the need for anonymityTransmissionAuthentication systemRadio frequency
The invention discloses a radio frequency fingerprint (RFF)-based wireless intelligent terminal access authentication method and an RFF-based wireless intelligent terminal access authentication system. The method comprises the following steps: S1, initialized registration entry: using a wireless intelligent terminal to encrypt a registered password input by a user, then transmitting the encryptedpassword to a server, and initiating a registration request to the server; using the server to complete the initialized registration entry according to the encrypted password and the RFF of the wireless intelligent terminal; S2, running login authentication: when the user requests to log in to the server, performing two-way legitimacy certification between the wireless intelligent terminal and theserver according to the initialized registration entry information, and managing the connection and disconnection of session between the wireless intelligent terminal and the server according to thecertification result. The RFF-based wireless intelligent terminal access authentication method and the RFF-based wireless intelligent terminal access authentication system which are provided by the invention can realize the mutual authentication between the wireless intelligent terminal and the server, thus reducing the complexity of identity authentication of the wireless intelligent terminal andimproving the safety of the identity authentication.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
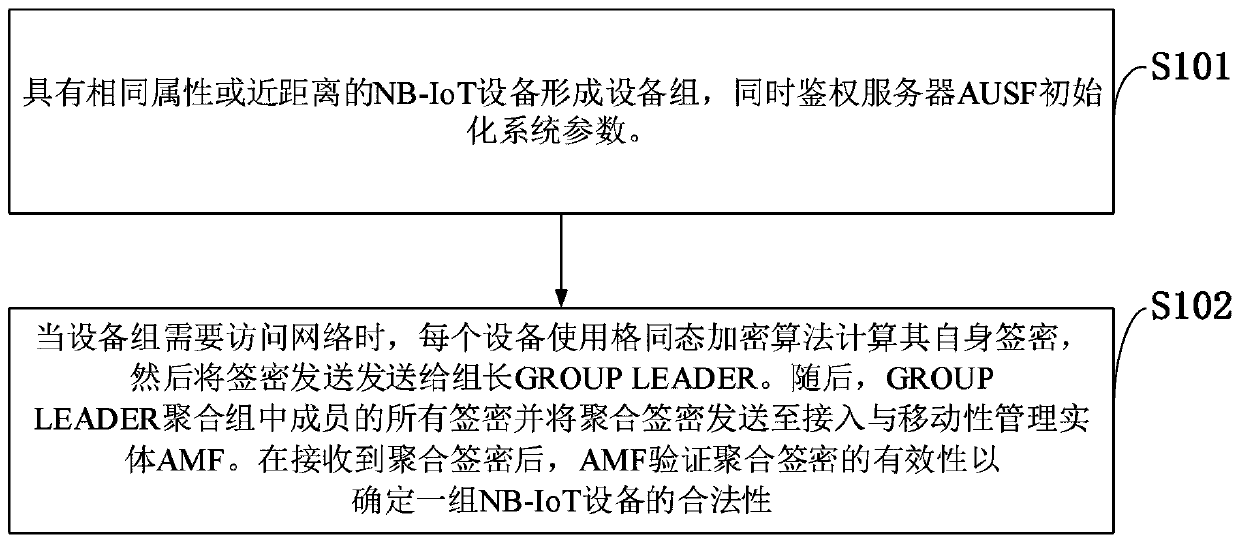
anti-quantum rapid authentication and data transmission method for mass NB-IoT equipment
ActiveCN109756877AAchieve mutual authenticationVerify legitimacyNetwork traffic/resource managementSecurity arrangementShortest distanceSigncryption
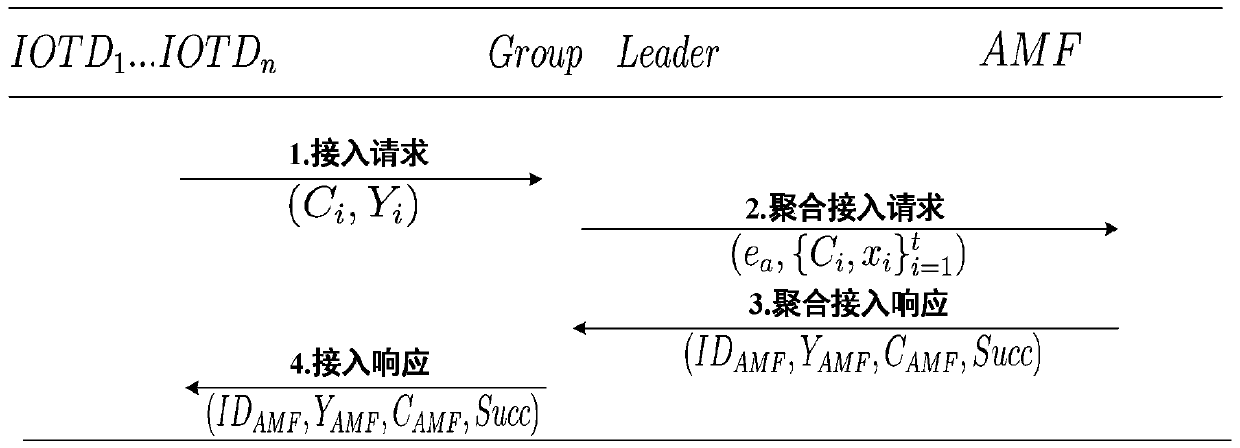
The invention belongs to the technical field of communication network security, and discloses an anti-quantum rapid authentication and data transmission method for mass NB-IoT equipment. NB-IoT equipment with the same attribute or short distance forms an equipment group, and when the equipment group needs to access the network, each equipment calculates own signcryption by using a lattice homomorphic encryption algorithm; the signcryption is sent to the group leader GROUP LEADER. Then, all signatures of members in the GROUP LEADER aggregation group are signed, and the aggregation signatures are sent to an access and mobility management entity AMF; and after the aggregation signcryption is received, the AMF verifies the validity of the aggregation signcryption to determine the legality of the group of NB-IoT devices. According to the invention, access authentication and data transmission of a group of NB-IoT devices can be realized at the same time based on the homomorphic encryption technology of the cells without establishing a data bearer, so that the signaling flow is simplified. Compared with the prior art, the authentication and data transmission cost is lower.
Owner:XIDIAN UNIV
GNSS satellite clock state of health monitoring method
InactiveCN108563108ARealize real-time monitoringAchieve mutual authenticationRegulating apparatusPhase fittingState of health
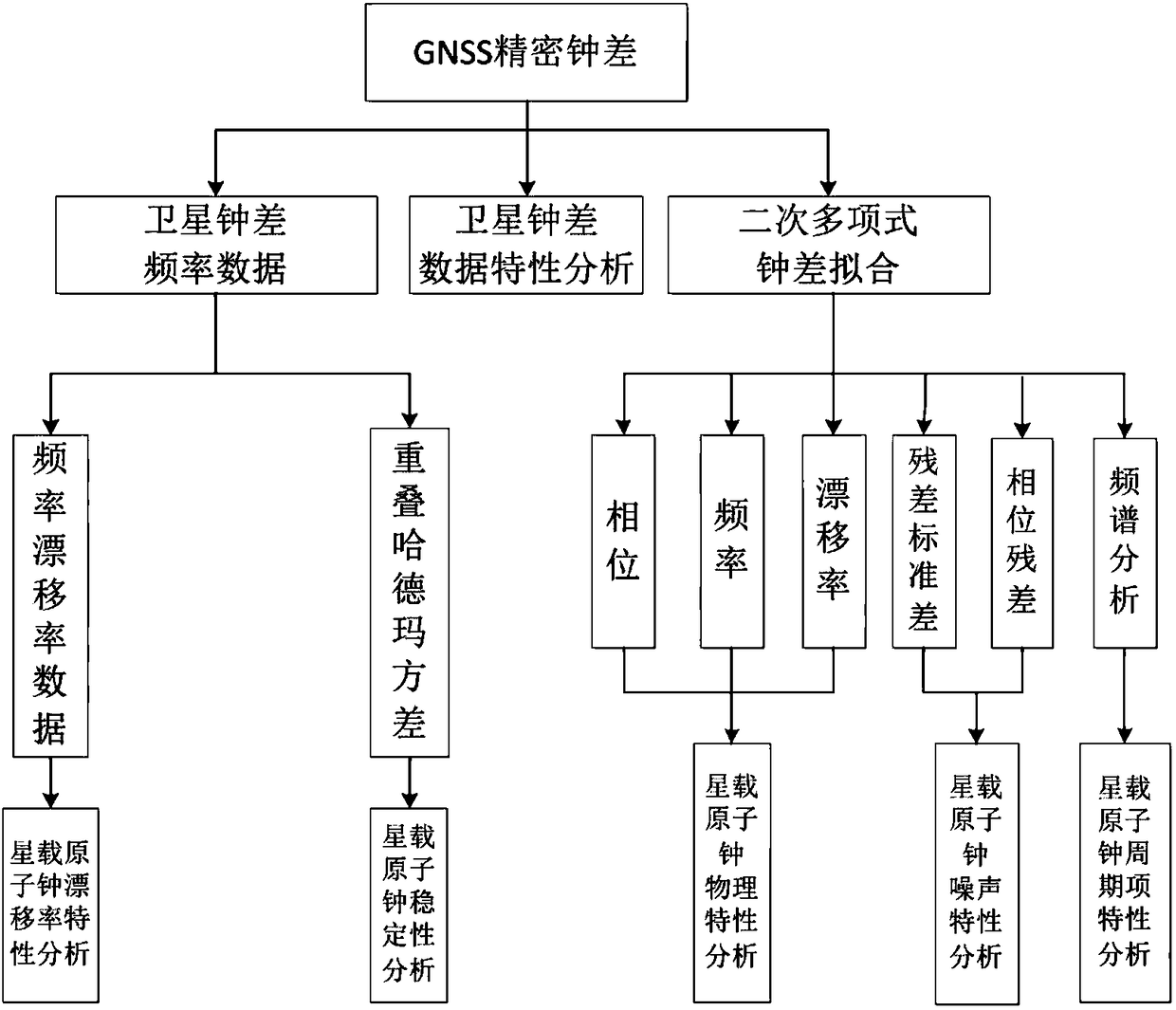
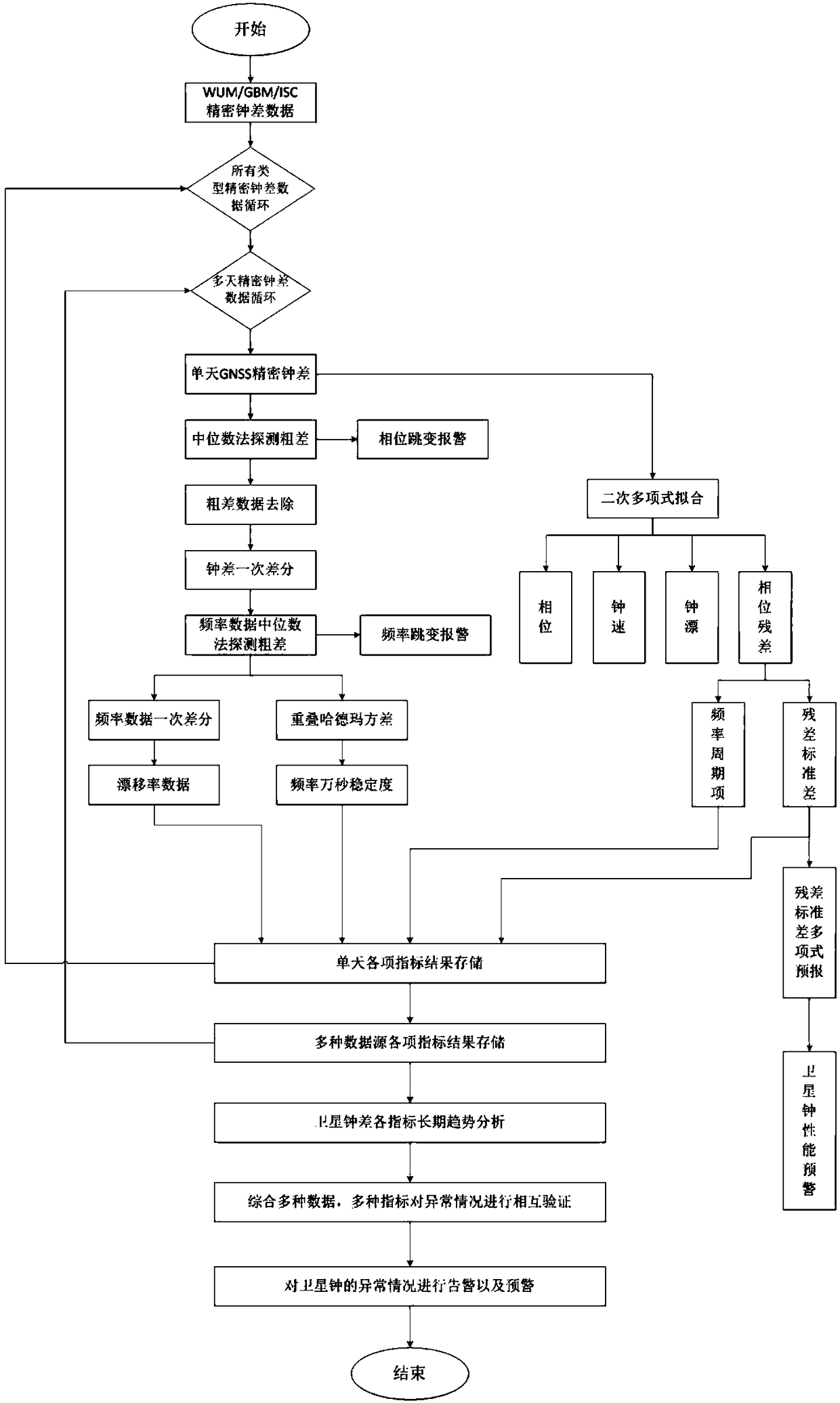
The invention discloses a GNSS satellite clock state of health monitoring method. Mutual effective verification can be performed for the satellite clock abnormal state by using multiple satellite clock difference data so that the problems of fault location difficulty, false alarm, early warning difficulty and poor timeliness causing various abnormal phenomena of the satellite clock can be solved,and long-term real-time monitoring of the state of health of the satellite clock can be realized. The method comprises the steps that the frequency and drift rate data are acquired through the primaryand secondary differential precision clock difference data, and the phase and frequency hop is detected by using the median method; fitting of the clock difference is performed by using the quadraticpolynomial so as to acquire the long time phase residual and the residual standard deviation; statistics of the frequency stability of the satellite clock is performed by using overlap hadamard variance; and finally various indexes are comprehensively evaluated, and the early warning information of the change of the satellite clock performance and the alarm information of the frequency and phasehop are given. The result proves that the satellite atomic clock state of health monitoring method using phase fitting residual based on multiple data sources is feasible.
Owner:SPACE STAR TECH CO LTD
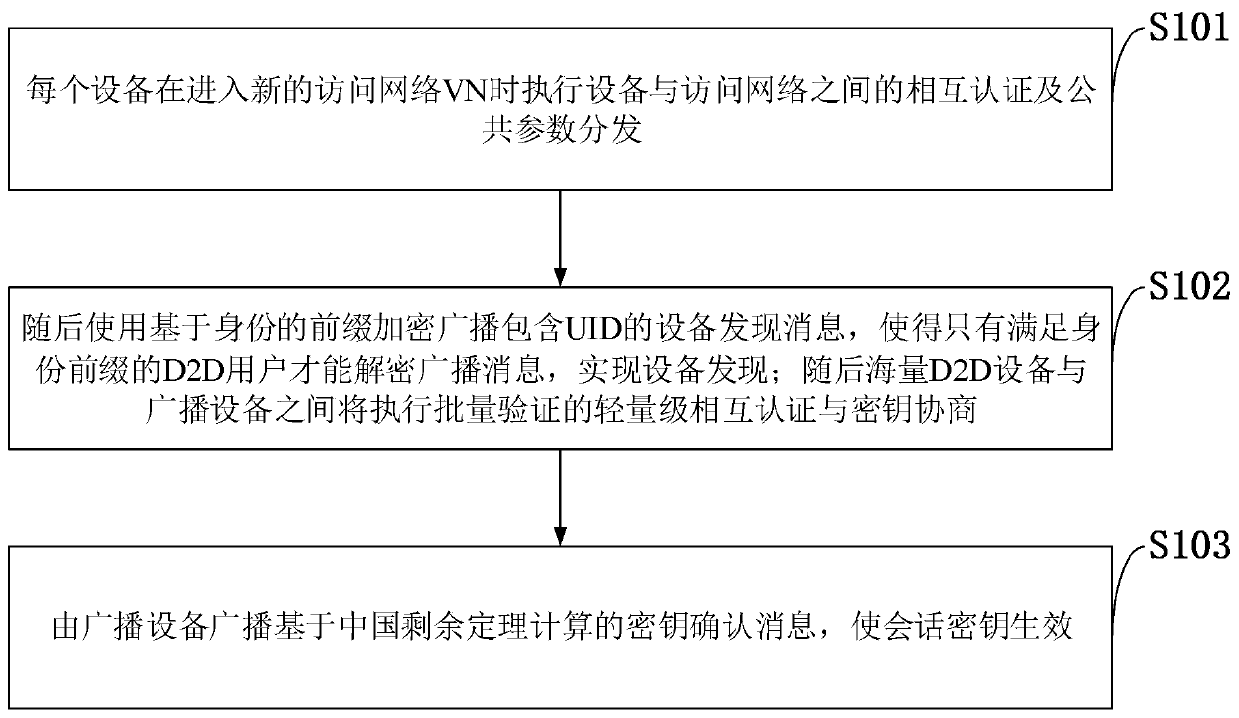
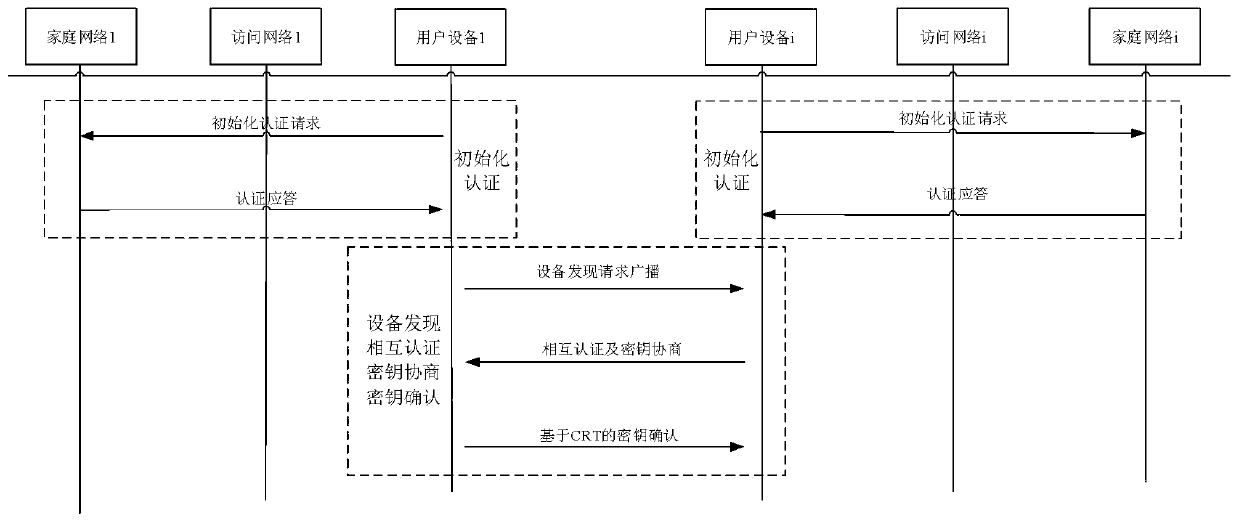
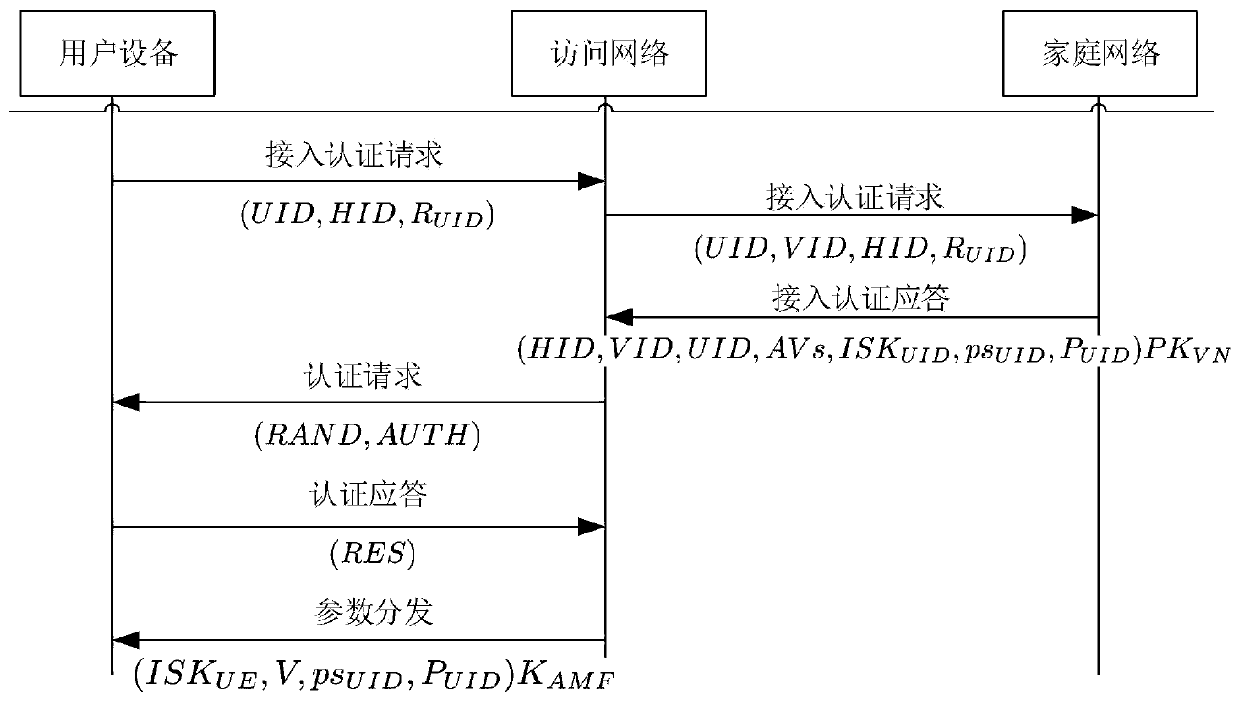
Mass D2D anonymous discovery authentication and key negotiation method
ActiveCN109768861AReduce communication overheadReduce computational overheadKey distribution for secure communicationSecurity arrangementCRTSIdentity privacy
The invention belongs to the technical field of communication network security, and discloses a mass D2D anonymous discovery authentication and key negotiation method. The method includes an initialization authentication stage; an anonymous device discovery stage based on prefix encryption; a mutual authentication and key negotiation stage based on batch verification; and a key confirmation stage.According to the scheme design carried out according to the 3GPP standard, communication equipment in the standard does not need to be changed, and the method can be applied to networks of all LTE-A / 5G mobile scenes; the general structure of the equipment discovery and authentication mechanism provided by the invention can realize discovery, mutual authentication, key negotiation and identity privacy protection of adjacent equipment; according to the rapid key confirmation method based on the CRT mechanism provided by the invention, the signaling number is effectively reduced; the signaling overhead, the communication overhead and the transmission overhead are reduced; direct mutual authentication between a large number of D2D devices can be directly realized, and all known attacks at present can be resisted.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
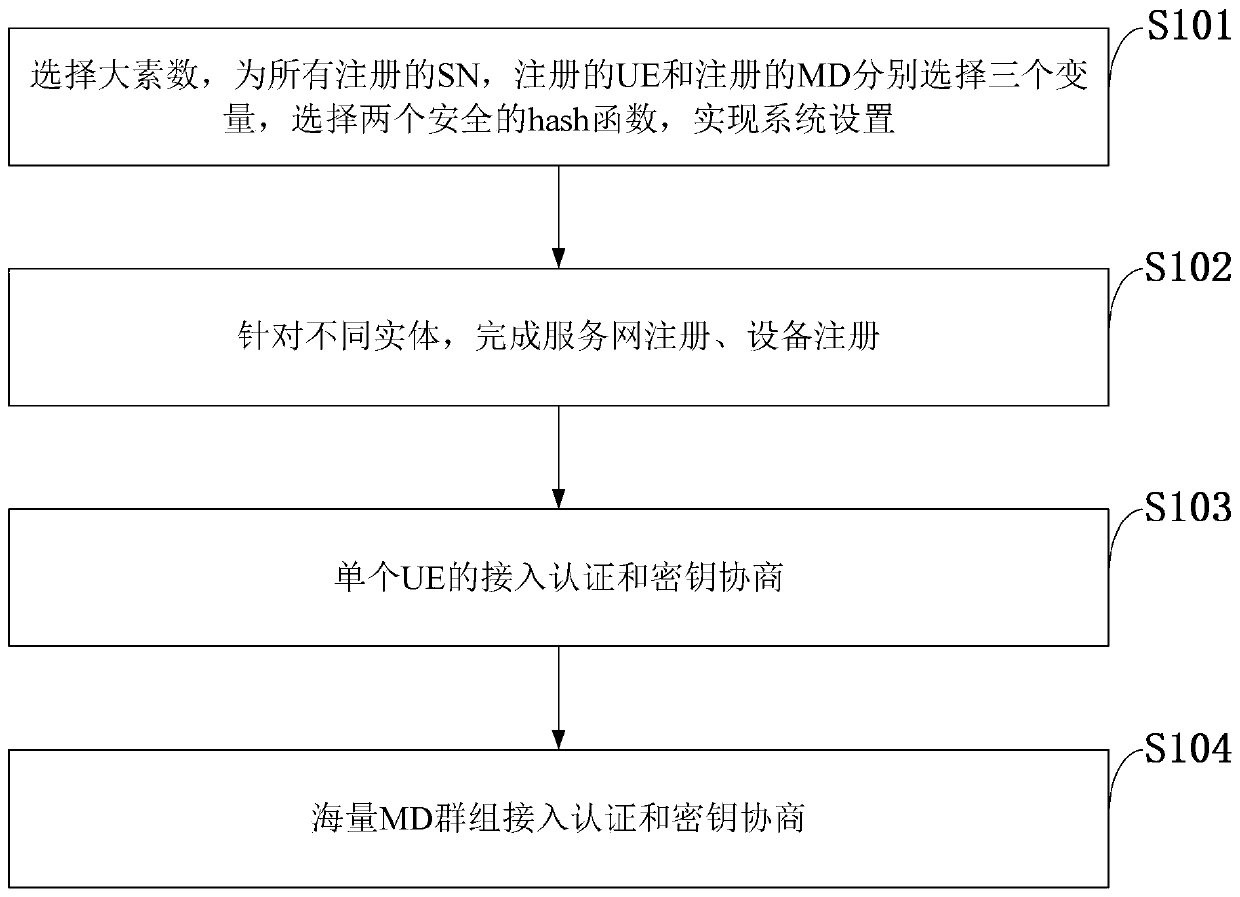
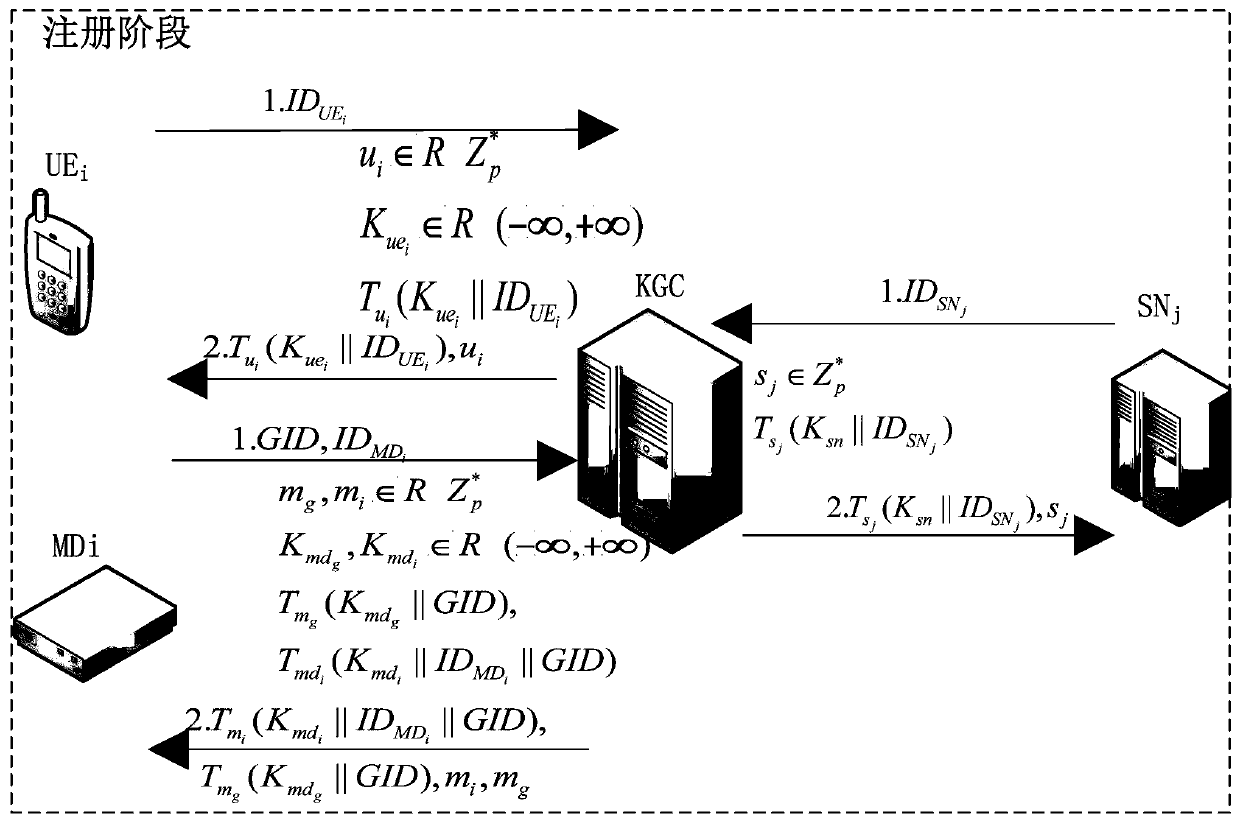
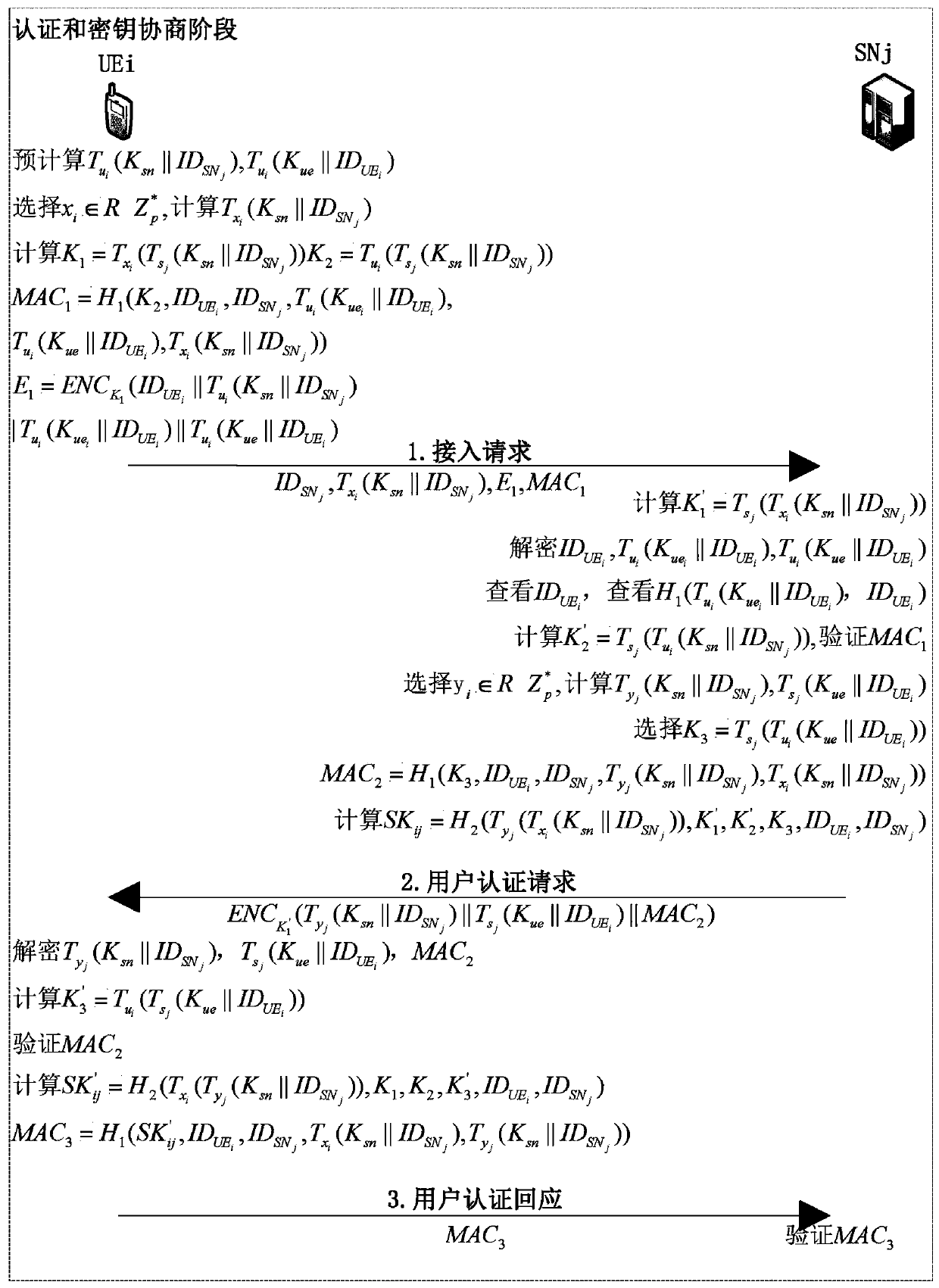
Lightweight security access authentication method and application suitable for 5G network equipment
ActiveCN110768954AAchieve mutual authenticationStrong Security PropertiesKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHash functionEngineering
The invention belongs to the technical field of communication network security, and discloses a lightweight security access authentication method suitable for 5G network equipment and an application,comprising the following steps: selecting a large prime number, respectively selecting three variables for all registered SNs, registered UEs and registered MDs, and selecting two secure hash functions to realize system setting; completing service network registration and equipment registration for different entities; realizing access authentication and key agreement of a single UE; and realizingmass MD group access authentication and key agreement. According to the invention, the signaling cost, the communication cost and the storage cost are reduced, signaling overhead can be effectively reduced, and signaling conflicts can be avoided; in the LSAA protocol for massive MDs, the SN can complete the authentication of a group of MDs by directly verifying the aggregated message verificationcode, thereby effectively reducing the communication and calculation overhead. Extended Chebyshev chaotic mapping is used, each MD can securely negotiate a different session key with the SN and consume less overhead.
Owner:XIDIAN UNIV
PCR primer group and kit for detecting African swine fever viruses based on double genes and application
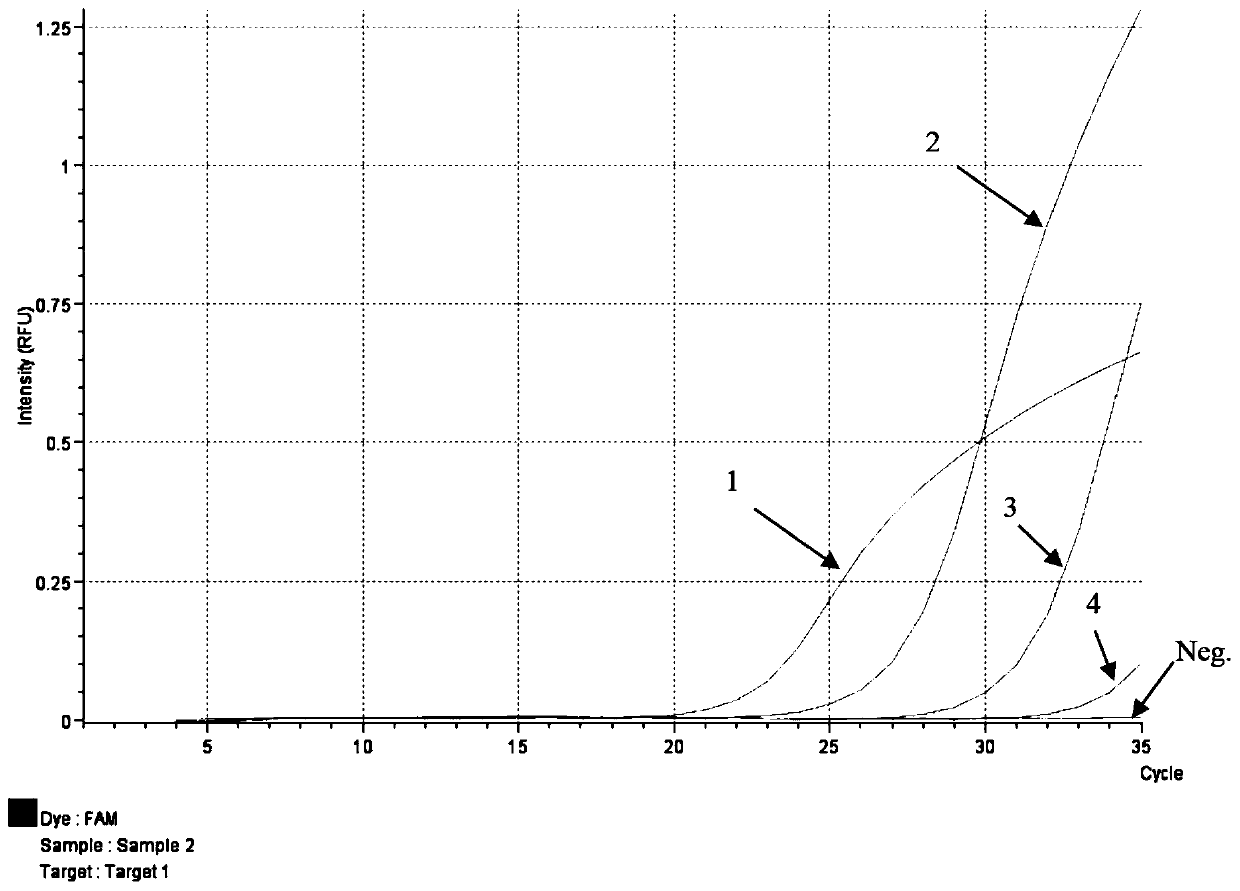
ActiveCN111218528AGuaranteed Sensitivity and SpecificityStrong specificityMicrobiological testing/measurementMicroorganism based processesAfrican swine feverVirus detection
The invention relates to the technical field of virus detection, in particular to a PCR primer group and kit for detecting African swine fever viruses based on double genes and application. The primergroup and method are high in detection specificity, good in repeatability and high in sensitivity, and meanwhile have the advantages of being easy and convenient to operate, short in detection time and the like, false positive results can be effectively reduced, the influence of positive control on a detection environment is reduced, and the primer group and the kit have high application value inrapid detection of the African swine fever viruses.
Owner:SHANDONG BINZHOU ANIMAL SCI & VETERINARY MEDICINE ACADEMY
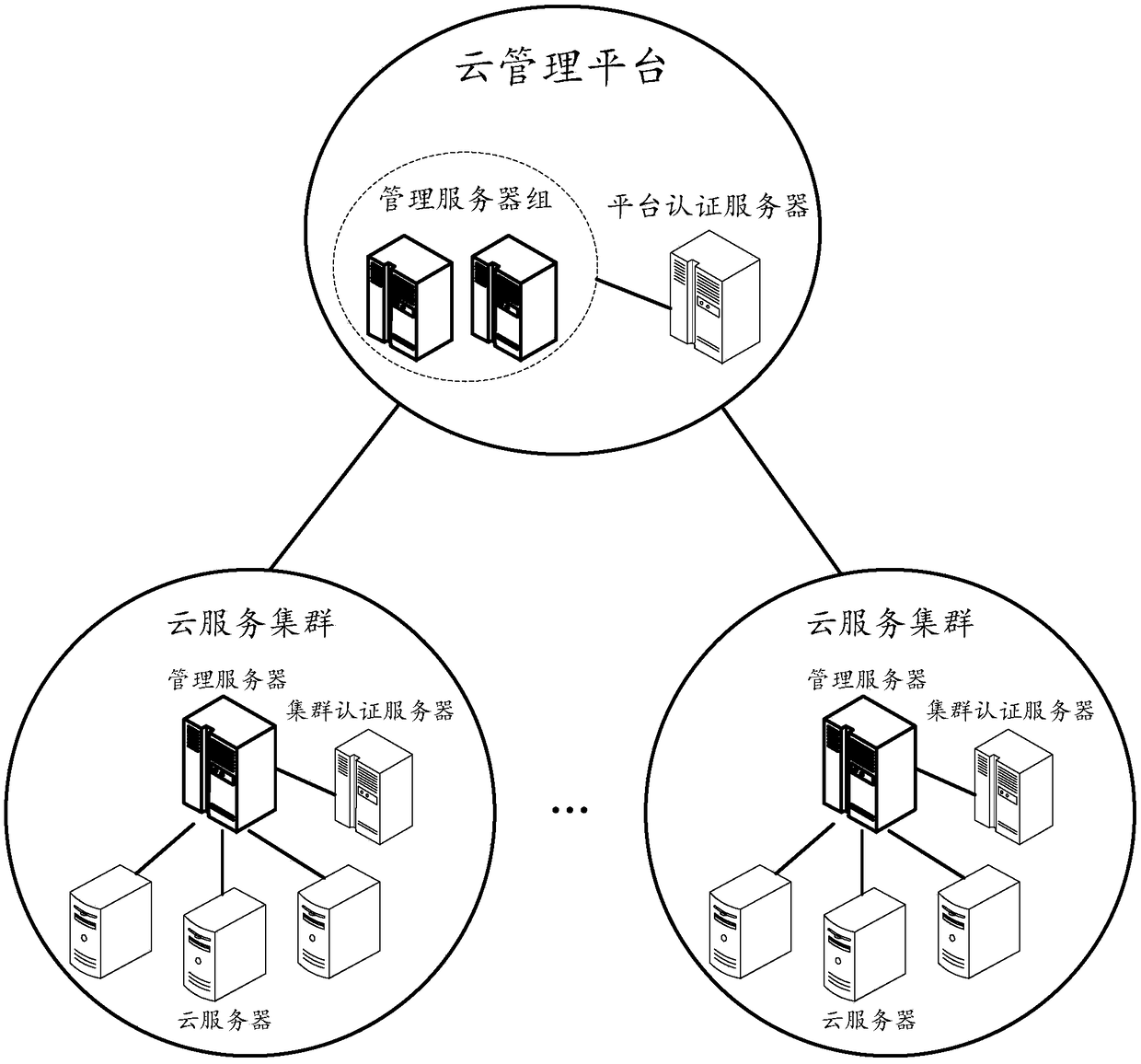
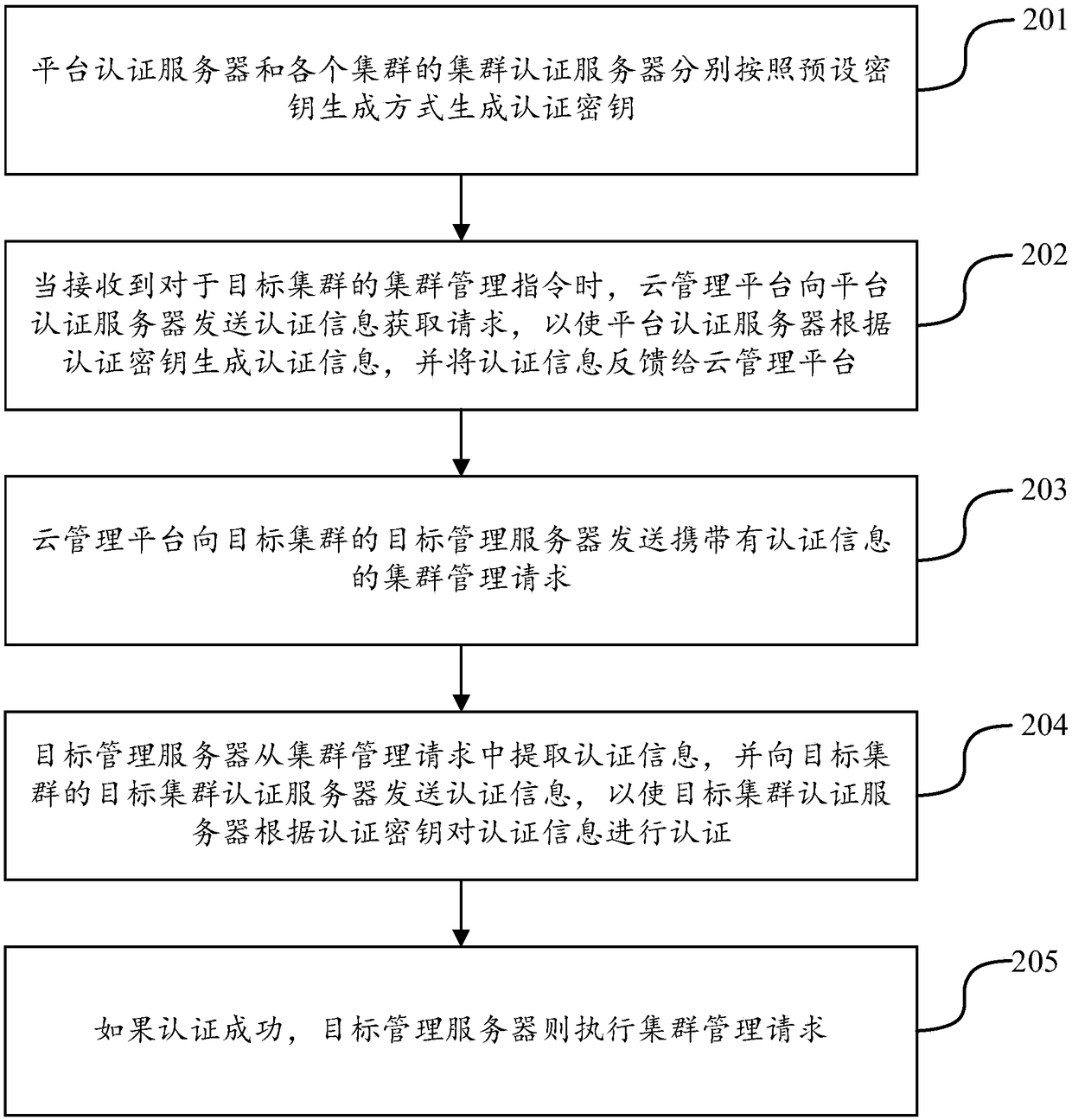
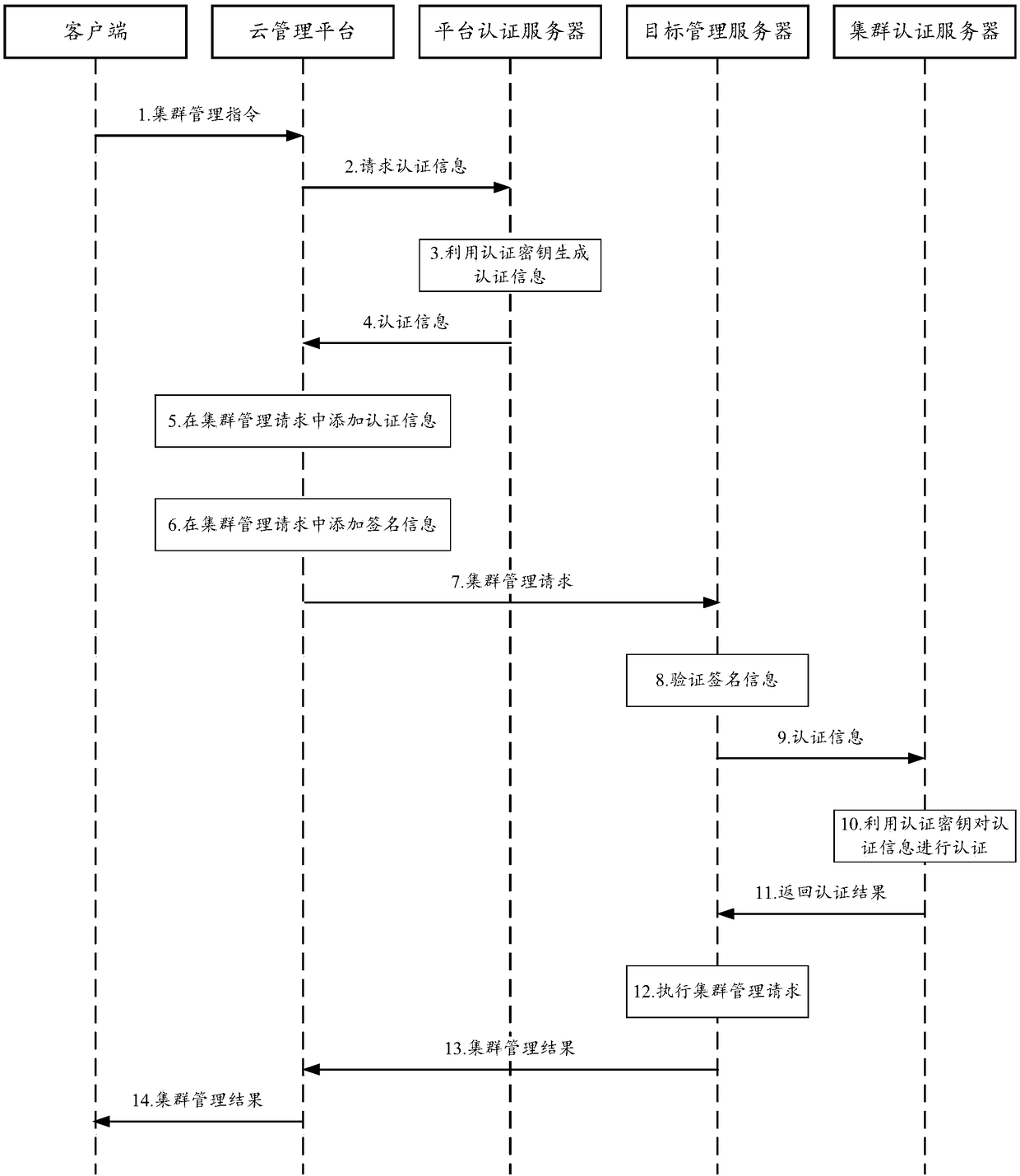
Cloud service cluster management method and system
InactiveCN108737171AImprove securityAchieve mutual authenticationKey distribution for secure communicationUser identity/authority verificationAuthentication serverComputer science
The invention belongs to the technical field of cloud computing, and discloses a cloud service cluster management method and system. The method comprises the following steps: a platform authenticationserver and cluster authentication servers of clusters generate authentication keys according to a preset key generation mode; when receiving a cluster management command for a target cluster, a cloudmanagement platform sends an authentication information acquisition request to the platform authentication server, so that the platform authentication server can generate authentication information according to the corresponding authentication key and feed the authentication information back to the cloud management platform; the cloud management platform sends a cluster management request with the authentication information to a target management server of the target cluster; the target management server sends the authentication information to a target cluster authentication server of the target cluster, so that the target cluster authentication server can authenticate the authentication information according to the corresponding authentication key; and if authentication is successful, the target management server executes the cluster management request. The method and system provided by the invention has the advantage that the authentication service safety can be improved.
Owner:CHINANETCENT TECH
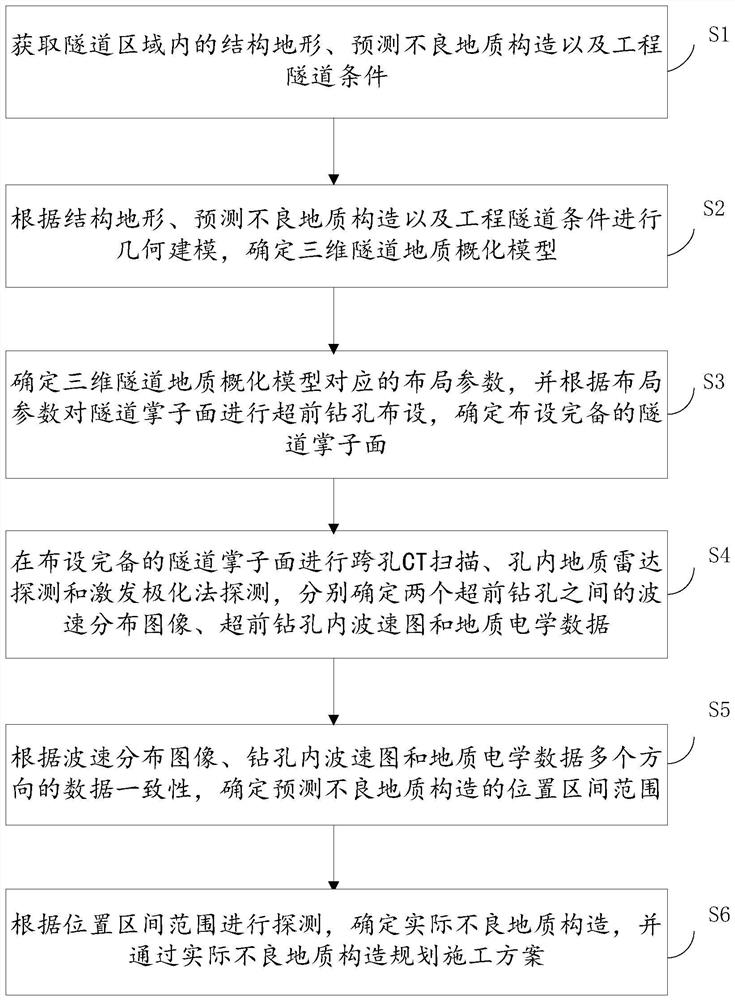
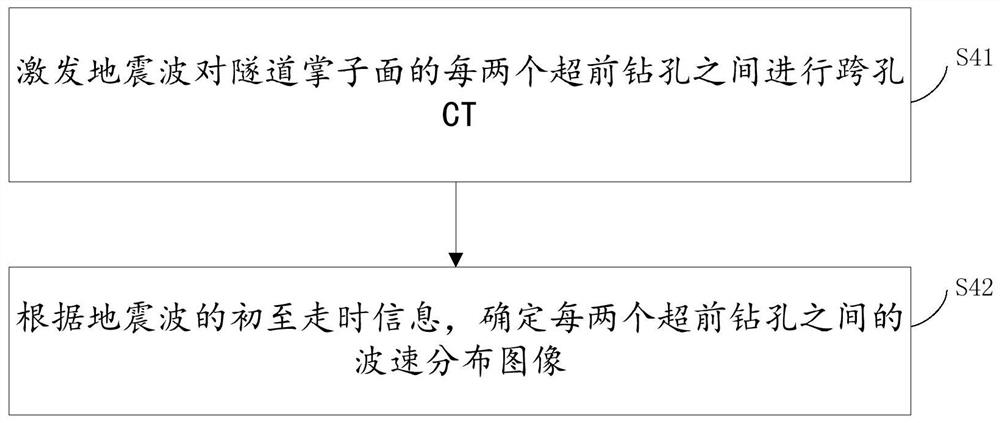
Multi-means advanced detection method for water-rich karst tunnel
PendingCN112965136AReduce construction riskAchieve mutual authenticationMaterial analysis using wave/particle radiationSeismic signal processingTerrainGeological exploration
The invention relates to a multi-means advanced detection method for a water-rich karst tunnel. The multi-means advanced detection method comprises the steps of: acquiring a structural terrain in a tunnel region, and predicting an unfavorable geological structure and an engineering tunnel condition; carrying out geometric modeling, and determining a three-dimensional tunnel geological generalization model; determining corresponding layout parameters, and carrying out advance drilling layout on the tunnel face; performing cross-hole CT scanning, in-hole geological radar detection and induced polarization method detection on the completely-arranged tunnel face, and determining a wave velocity distribution image between two advance drill holes, a wave velocity map in the advance drill holes and geoelectricity data respectively; determining a position interval range for predicting the unfavorable geological structure according to the data consistency of the wave velocity distribution image, the in-hole wave velocity map and the geoelectricity data in multiple directions; and detecting according to the position interval range, and planning a construction scheme. Multi-means advanced geological exploration is adopted, information of seismic waves, electromagnetic waves and an electrical method is combined, the tunnel construction risk is effectively reduced, and safe construction is ensured.
Owner:云南楚大高速公路投资开发有限公司 +1
Single sign-on authentication method based on inadvertent pseudo-random function and signcryption
ActiveCN110784305AReduce the difficulty of identity maintenanceEfficient storageKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextAttack
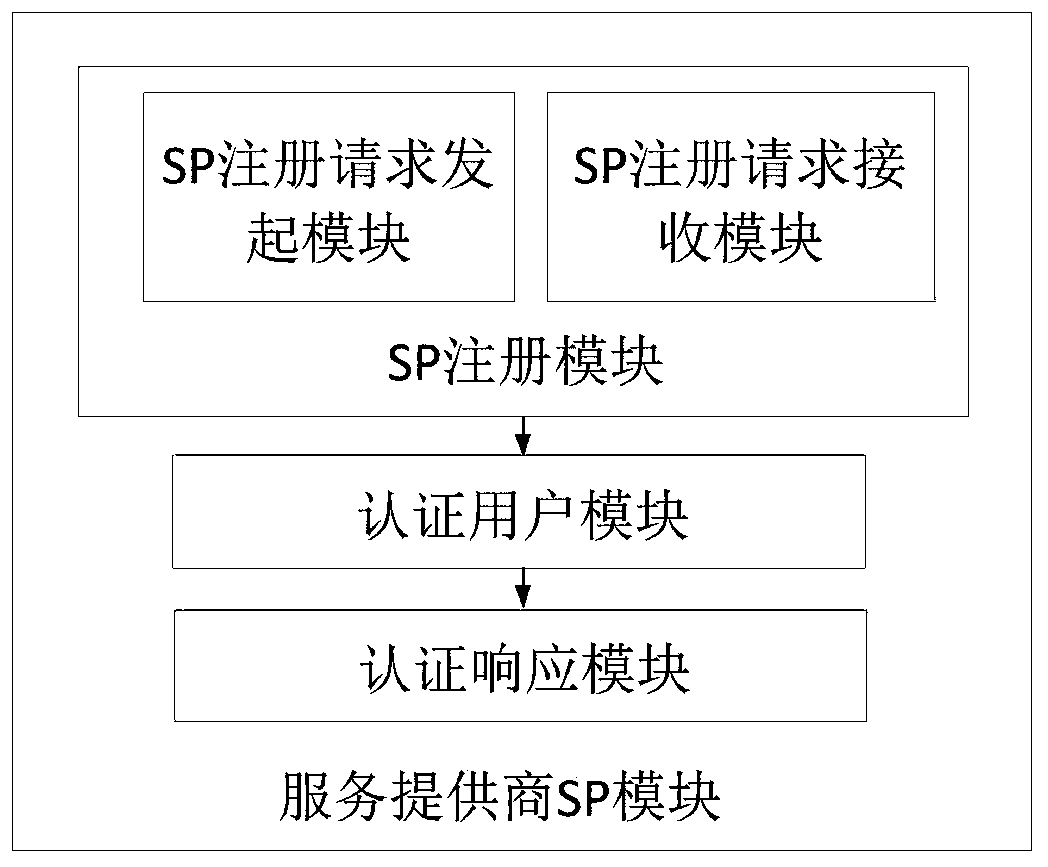
The invention belongs to the technical field of information security, and discloses a single sign-on (SSO) authentication system and method based on an inadvertent pseudorandom function (OPRF) and signcryption. The single sign-on authentication method includes a system initialization parameter stage, a user / service provider (SP) registration stage, an information retrieval stage and a user and SPbidirectional authentication stage. According to the invention, the OPRF and the signcryption scheme are combined, i.e., the OPRF value is obtained by blinding the password of the user through the OPRF and is used for encrypting the signcryption private key of the user, and the ciphertext is stored in the storage provider end. Before login, the user recovers the OPRF value and decrypts the retrieved ciphertext to obtain the signcryption private key, thereby realizing bidirectional authentication with the SP. The invention provides a security enhancement function for password leakage threats, an SP does not store a password or a password derivative value, a client accidentally leaks the password, and an enemy cannot counterfeit the password as the SP to deceive a user. According to the invention, common attacks in an SSO authentication system can be resisted and bidirectional authentication can be completed efficiently.
Owner:XIDIAN UNIV
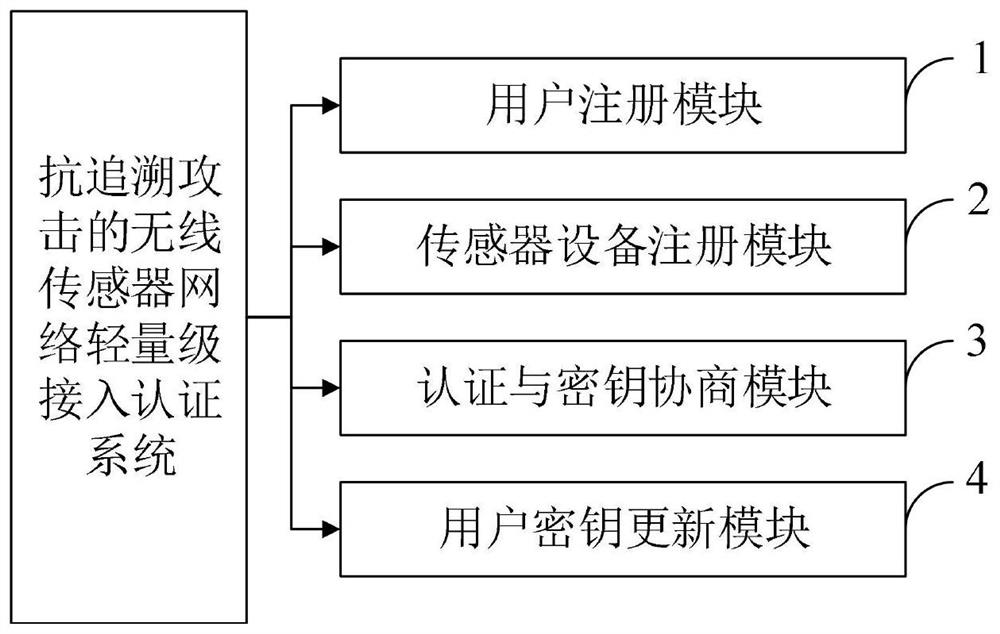
Anti-traceability-attack wireless sensor network lightweight access authentication method and system
ActiveCN112954680AGood attackReduce computational overheadSecurity arrangementInstrumentsAttackPassword
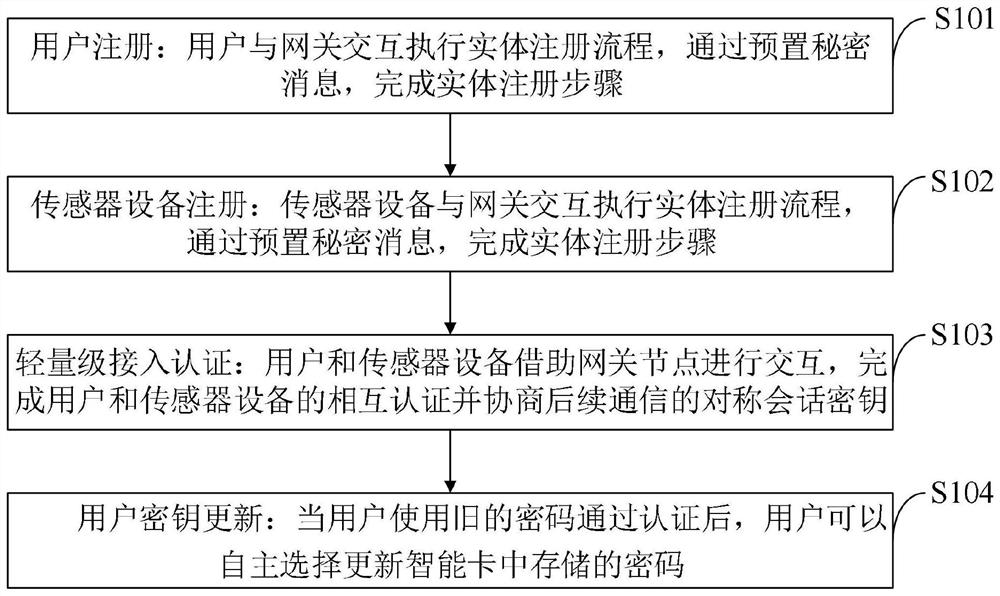
The invention belongs to the technical field of communication network security, and discloses an anti-traceability-attack wireless sensor network lightweight access authentication method and system, and the method comprises the steps: a user interacts with a gateway node to complete registration; the sensor device interacts with the gateway node to complete registration; after the user and the sensor equipment are registered, authentication and key negotiation are carried out with the help of the gateway node; and after the user node completes authentication by using the old password, the user node autonomously selects an updated password. The method can be better applied to resource-limited Internet of Things access equipment, has relatively low calculation overhead, resists common attacks, has good user anonymity and non-traceability, ensures that mutual authentication of a user and sensor equipment and session key negotiation can be effectively realized in an access authentication process, and improves the user experience. The method can have lower calculation overhead, and is more suitable for being applied to the scene of Internet-of-Things resource limited equipment.
Owner:XIDIAN UNIV
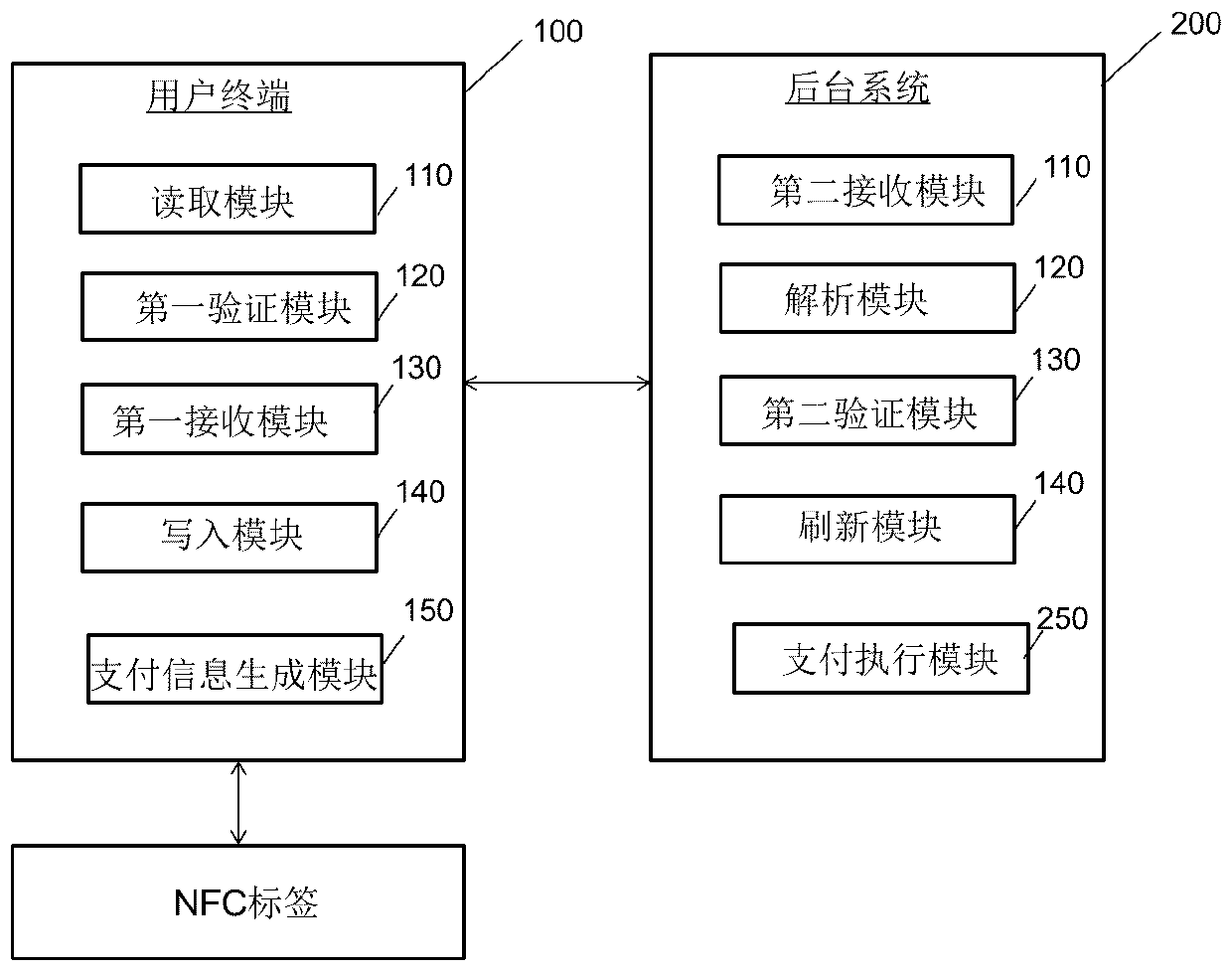
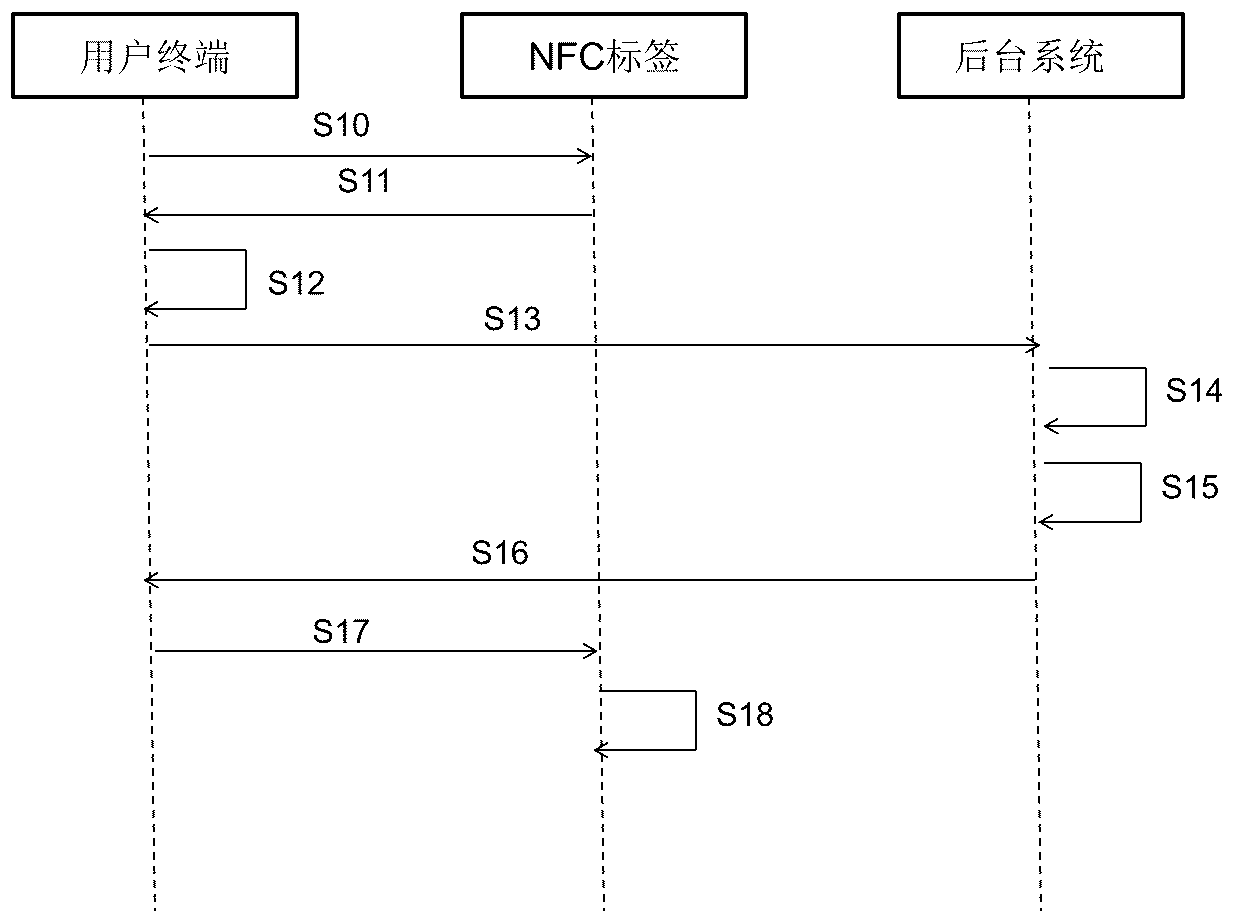
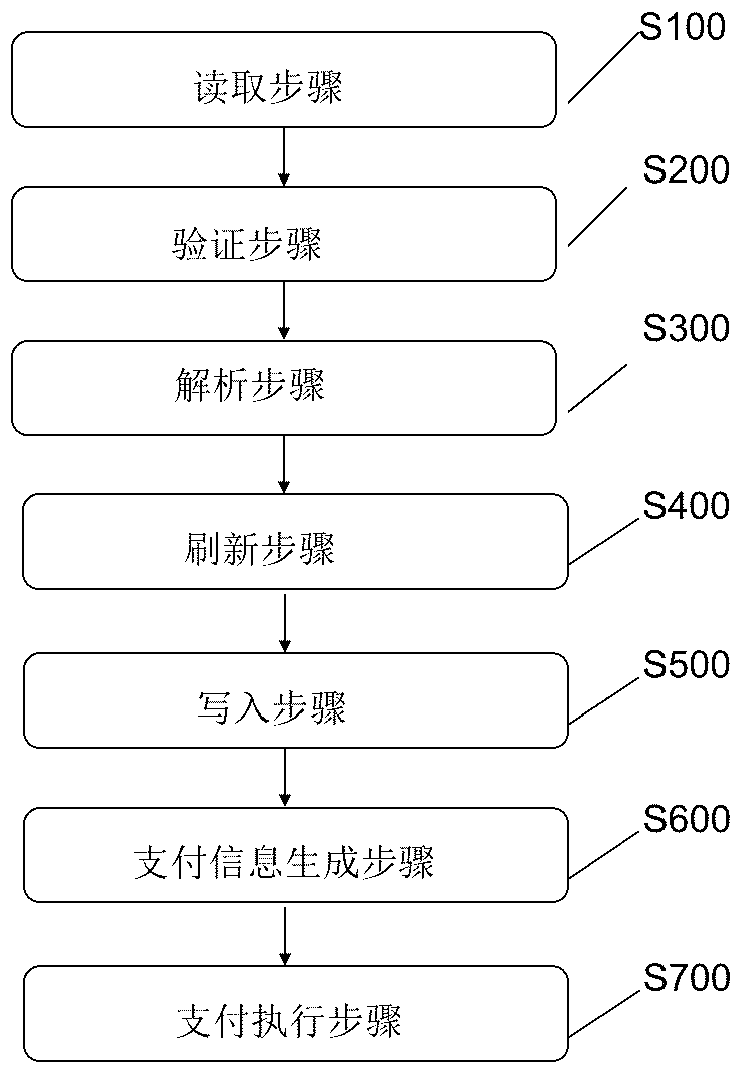
Label data refreshing method and system and payment method and system
ActiveCN111092719AAchieve mutual authenticationImprove experienceKey distribution for secure communicationUser identity/authority verificationRoot certificatePayment
The invention relates to a label data refreshing method. The method comprises the steps that a user terminal reads NFC label data from an NFC label; the user terminal verifies whether the read institution public key certificate is legal or not by utilizing a pre-stored CA root certificate, and sends the label identifier and the ciphertext data to a background system after the verification is passed; the background system parses the ciphertext data by using a pre-stored label private key, encrypts and signs the parsed ciphertext data, generates updated NFC label data, and sends the updated NFClabel data to a user terminal; and the user terminal writes the updated NFC label data into the NFC label. According to the invention, the NFC label data can be dynamically updated, and payment can berealized based on the dynamically updated NFC label, so that the payment security can be ensured, and the payment efficiency and the user experience can be improved.
Owner:CHINA UNIONPAY
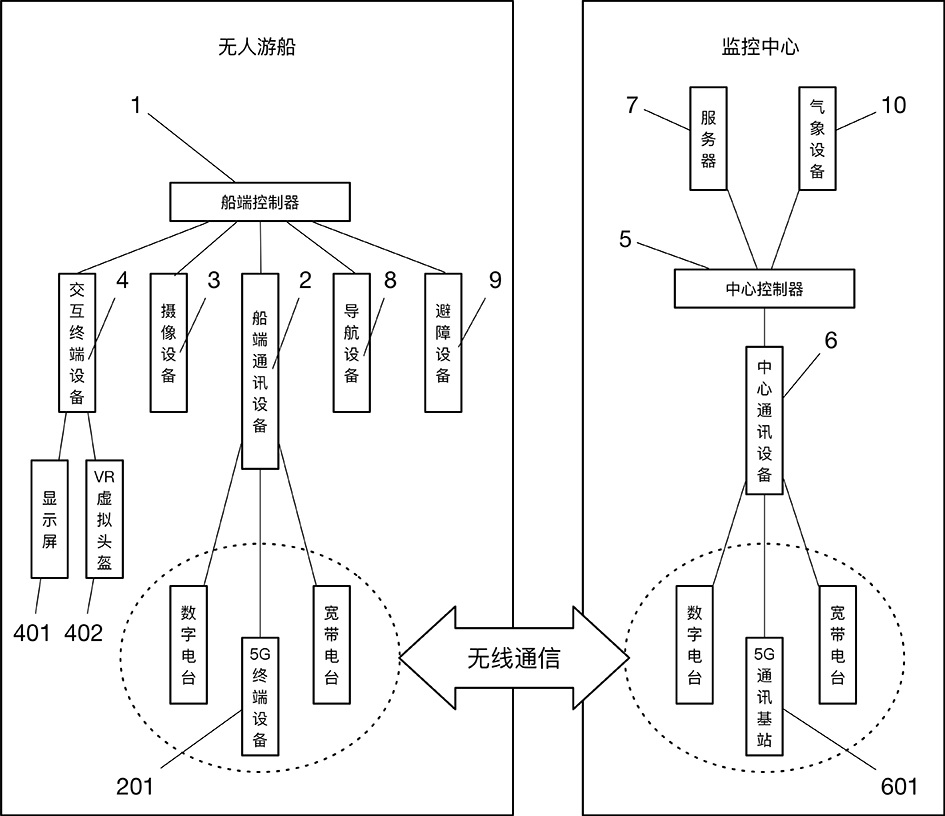
Unmanned sightseeing boat cluster monitoring system and information sharing method
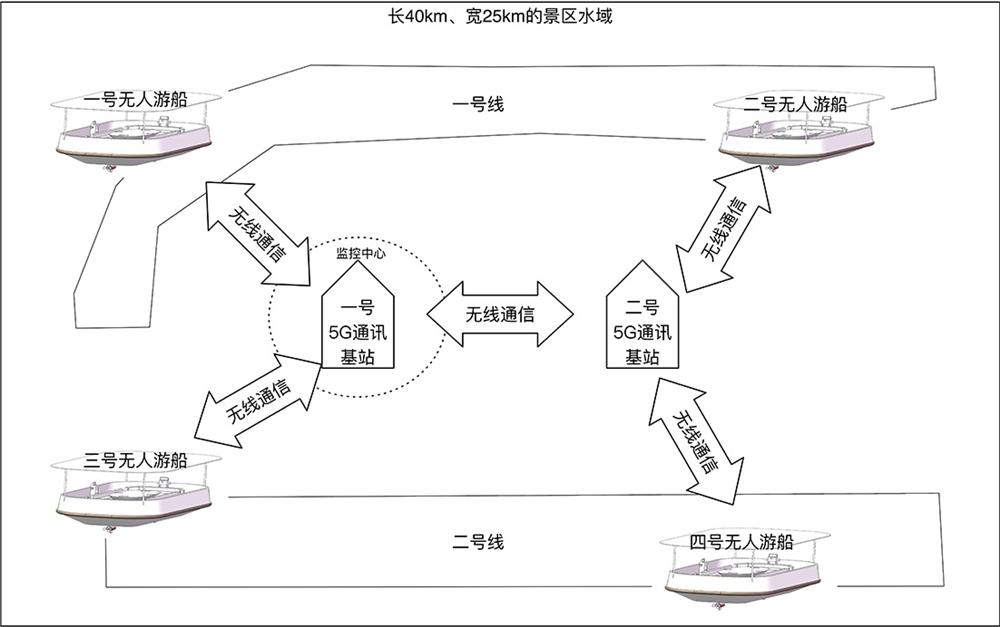
PendingCN112688975ASatisfy curiosityMeet the needs of big data exchangeWaterborne vesselsParticular environment based servicesInformation sharingTerminal equipment
The invention discloses an unmanned sightseeing boat cluster monitoring system and an information sharing method, the unmanned sightseeing boat cluster monitoring system comprises an unmanned sightseeing boat and a monitoring center, the unmanned sightseeing boat is provided with a boat end controller, boat end communication equipment, navigation equipment, obstacle avoidance equipment, camera equipment and interactive terminal equipment, and the monitoring center is provided with a central controller, central communication equipment and a server. The unmanned sightseeing boat exchanges data with the monitoring center through the communication device. The interactive terminal device plays image information or tour guide information of the unmanned pleasure boat; the central controller is used for monitoring the operation of each unmanned pleasure boat in an overall planning manner according to the monitoring data of the navigation equipment and the obstacle avoidance equipment; unmanned sightseeing boat cluster scheduling is realized through sharing navigation data, the recognition capability of water area obstacles is improved through sharing obstacle avoidance data, live-action sharing among multiple unmanned sightseeing boats is realized through a 5G communication technology, the requirement of passengers for multi-line sightseeing during single-time boat taking is met, the safety of the sightseeing boats can be ensured, and the performance of the unmanned sightseeing boats is maximized.
Owner:青岛无疆技术有限公司
Password-based three-party key exchange method
InactiveCN101938491AAgainst various attacksPerfect forward securityKey distribution for secure communicationThree partyKey exchange
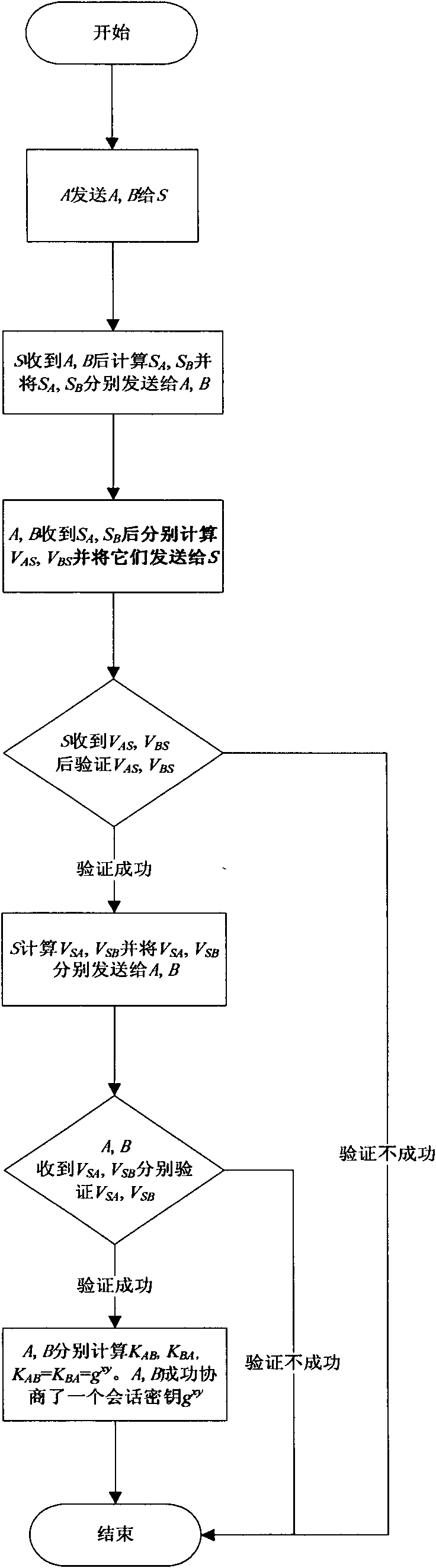
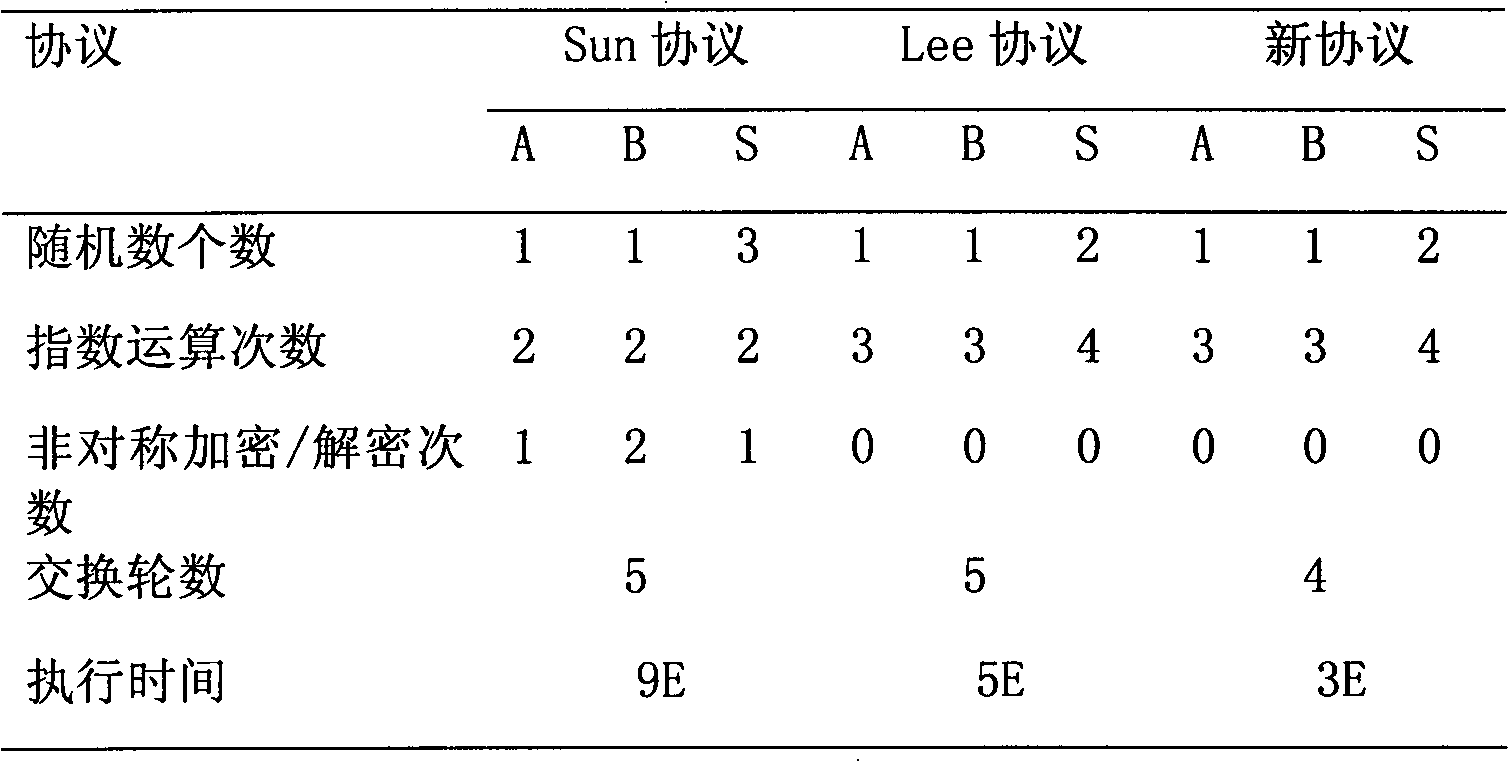
The invention discloses a password-based three-party key exchange method, which comprises the following steps that: S verifies VAS sent by A and the VAS sent by B, and if h(g<ax>, A, B, S) is equal to the second half part of DpwA(VAS) and h(g<by>, A, B, S) is equal to the second half part of DpwB(VBS), g<x> and g<y> in the h(g<ax>, A, B, S) and the h(g<by>, A, B, S) adopt the first half parts of the DpwA(VAS) and the DpwB(VBS) respectively, and the VSA is sent to A and the VSB is sent to B; and A and B verify the VSA sent by S, and if Dg<ax>(VSA) contains g<x> and Dg<by>(VSB) contains g<y>, A and B perform calculation respectively to establish a mutually unified session key g<xy>. The key exchange method not only can effectively resist various attacks and provide perfect forward security, but also achieves improvements on both the exchange turn number and the communication time.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
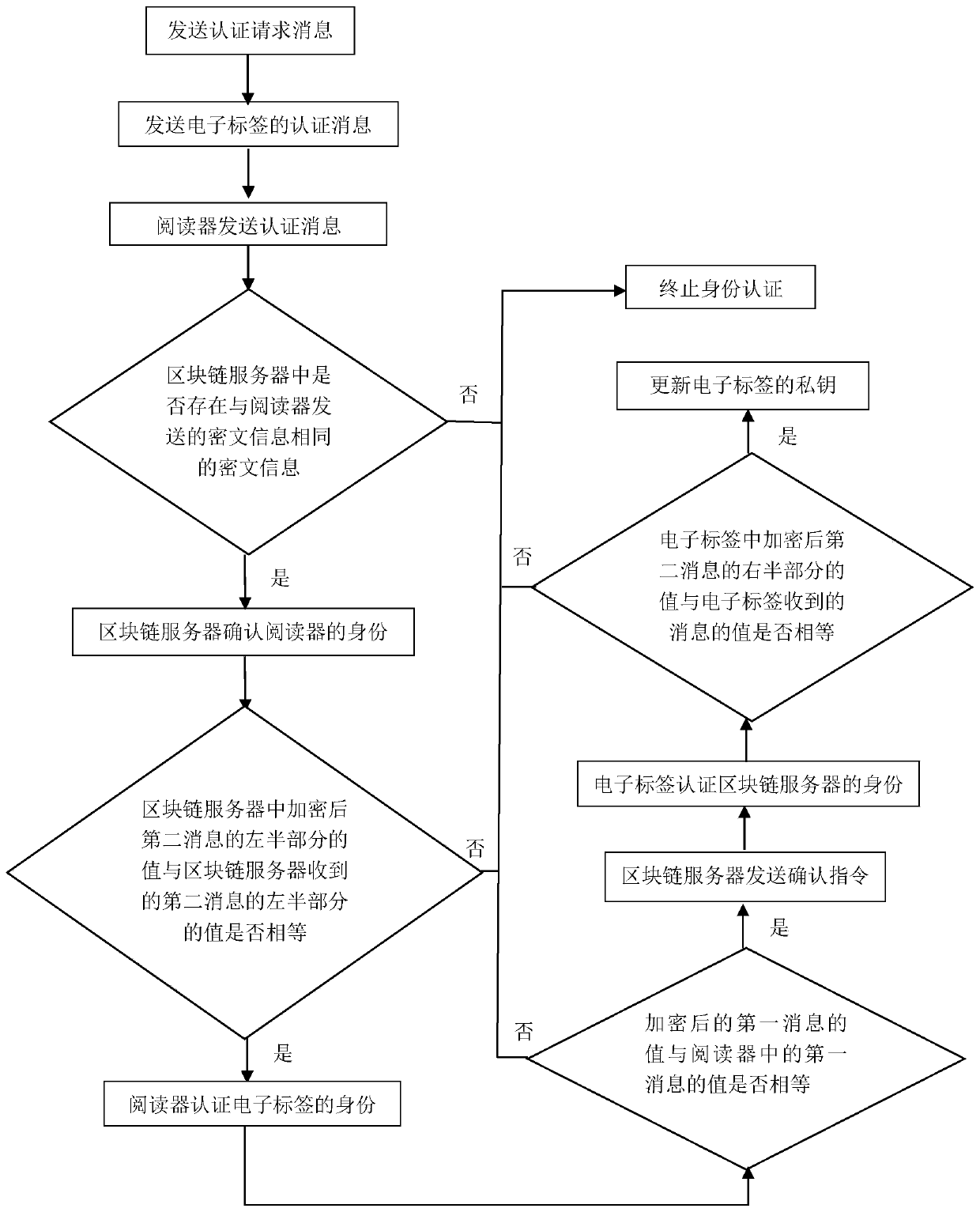
A bidirectional identity authentication method based on radio frequency identification for a block chain
ActiveCN109788465AImprove efficiency and safetyAchieve mutual authenticationUser identity/authority verificationSecurity arrangementBlockchainElectronic tagging
The invention discloses a bidirectional identity authentication method based on radio frequency identification for a block chain, and mainly solves the problems that a background database in the priorart is small in storage capacity, low in safety and efficiency, limited in electronic tag storage resource and poor in computing power. The method comprises the following implementation steps: (1) anauthentication request message is sent; (2) the blockchain server authenticates the reader; (3) the blockchain server authenticates the electronic tag; (4) the reader authenticates the electronic tag; (5) the electronic tag authenticates the blockchain server; Compared with the prior art, the identity information and data of the electronic tag are inquired through the block chain server, the calculated amount and occupied resources of the electronic tag are reduced, and bidirectional identity authentication between the electronic tag and the reader is achieved.
Owner:XIDIAN UNIV
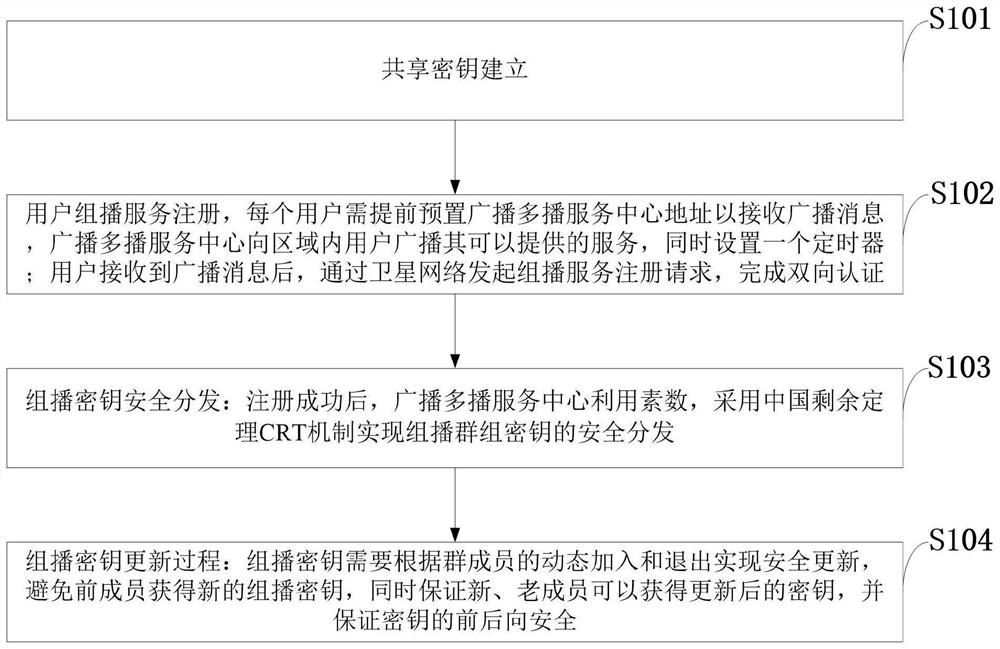
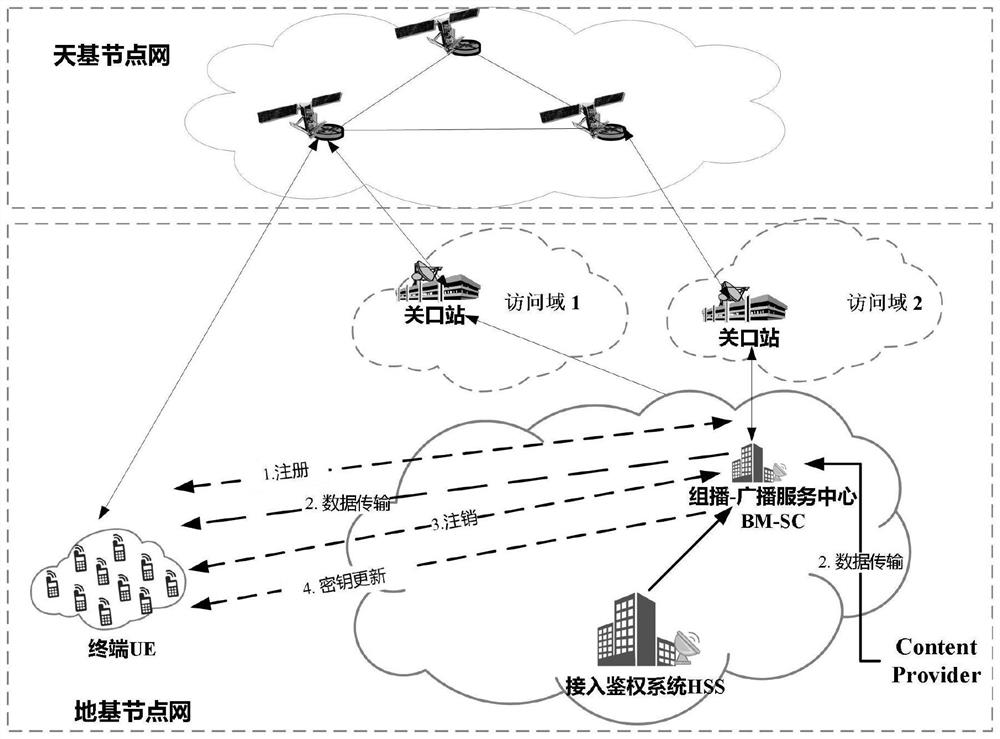
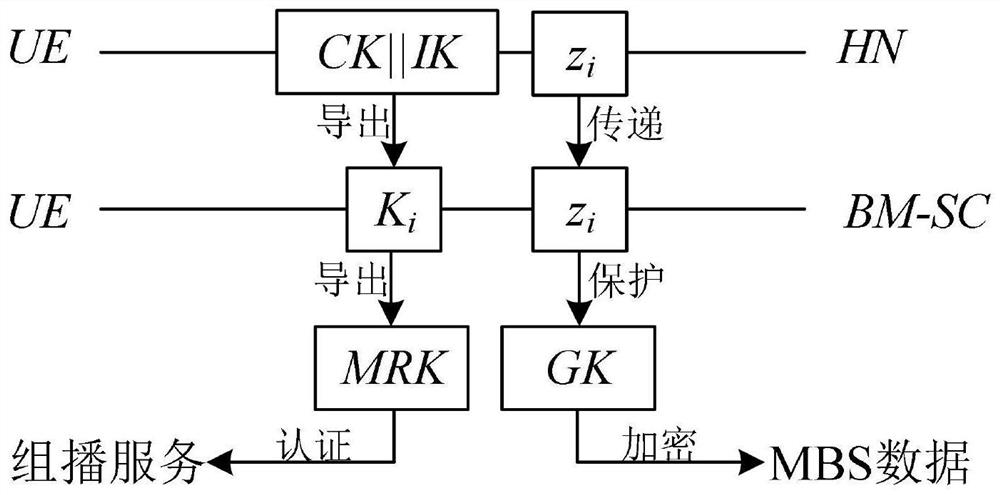
Method, system and equipment for implementing multicast service effective authentication and key distribution protocol
ActiveCN114466318AAvoid signaling conflictsReduce overheadBroadcast service distributionRadio transmissionEngineeringKey distribution
The invention belongs to the technical field of satellite communication information security, and discloses a multicast service effective authentication and key distribution protocol implementation method, system and equipment, and the multicast service effective authentication and key distribution protocol implementation method adopts a 5GAKA mechanism to realize deduction of a shared key between UE and BM-SC; a group multicast service registration mechanism is adopted; distributing and updating a multicast service group key based on the Chinese remainder theorem CRT; mutual identity verification and a key protocol between the UE and the BM-SC are safely realized in multicast service registration, and a key is updated when a group member relationship changes. According to the invention, the communication overhead and the calculation overhead are reduced, and the problem of signaling conflict when massive users access the BM-SC at the same time to obtain the multicast service is avoided; the key management efficiency is improved, and meanwhile, the security of multicast service data transmission can be ensured; and the previous and later multicast service data cannot be obtained under the condition that the new member joins and the old member quits.
Owner:XIDIAN UNIV
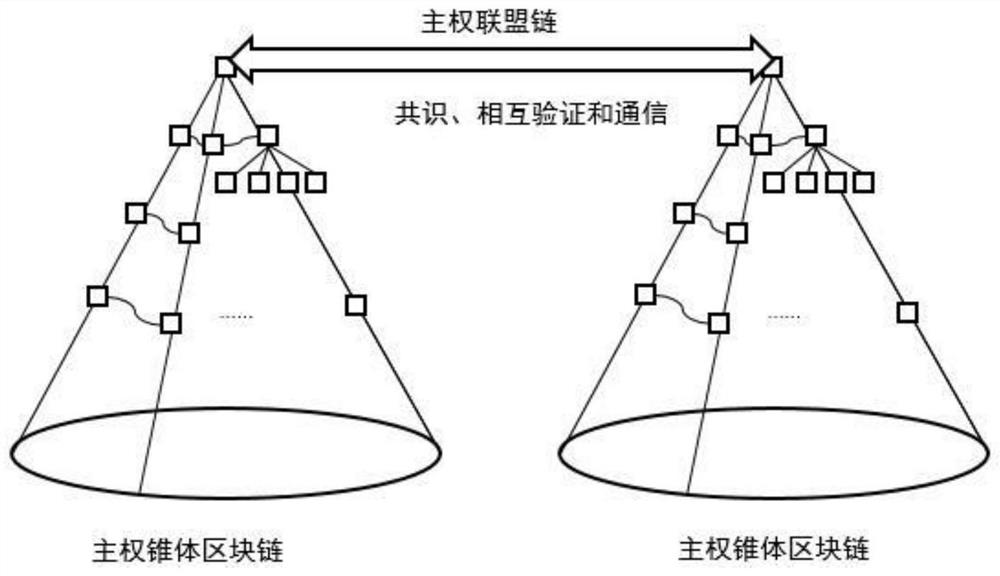
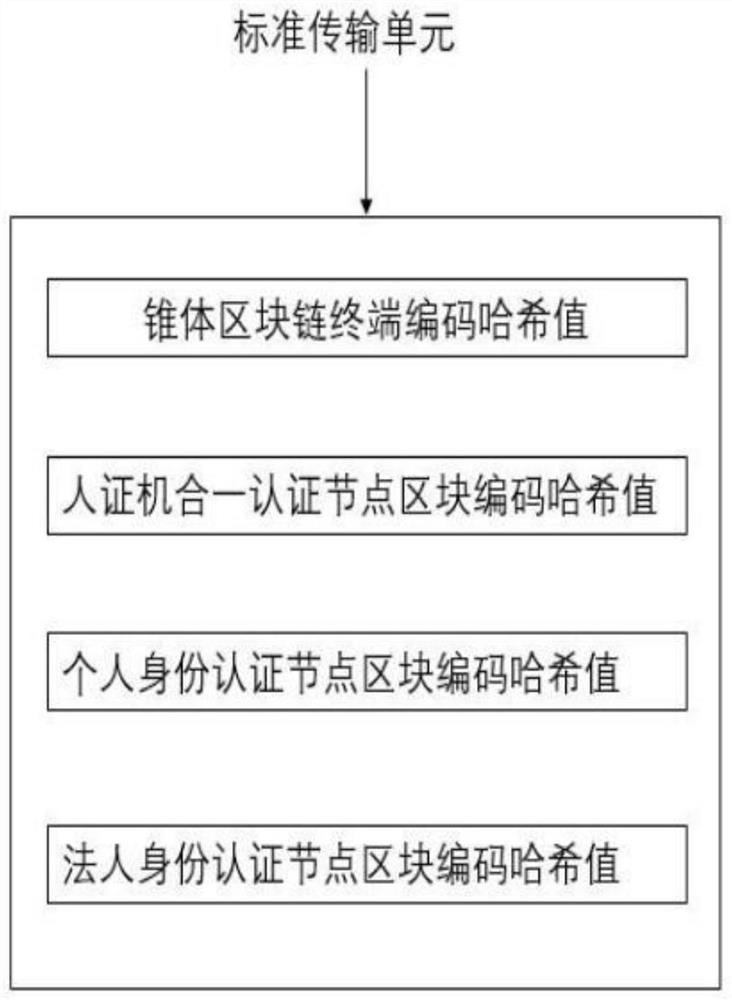
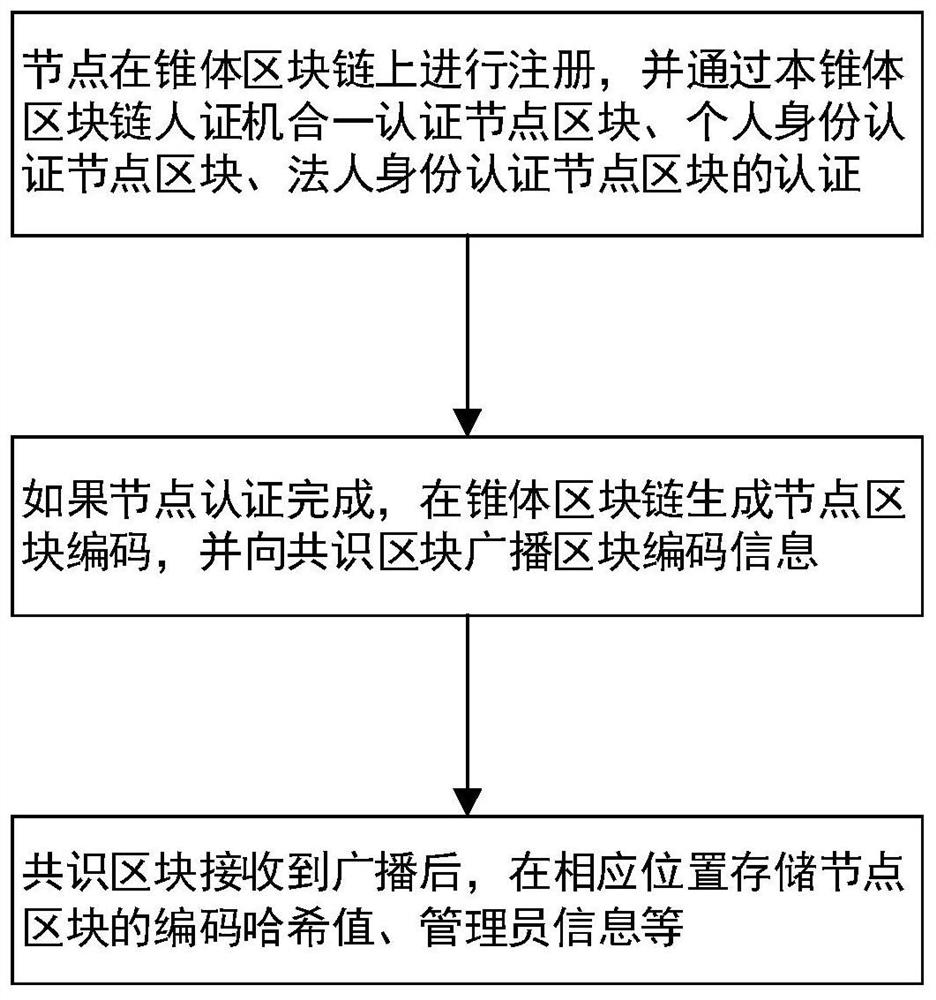
Prosomatic alliance chain of cone block chain
ActiveCN112769917AAchieve mutual authenticationRealize communicationFinanceUser identity/authority verificationBlockchainEngineering
The invention belongs to the technical field of blockchain, and particularly relates to a sovereign alliance chain of cone blockchain, each cone blockchain is a cone sovereign chain, and consensus is achieved among the cone sovereign chains to form the sovereign alliance chain; information transmission and authentication are carried out among the cone sovereign chains through a plurality of consensus blocks; point-to-point data communication is carried out between the cone main weight chains through the standard transmission unit, and broadcast information is sent to the consensus block. A cone alliance chain is formed through consensus of a plurality of sovereign cone block chains, information transmission and information authentication of a plurality of consensus blocks among the sovereign cone block chains are performed through a standard transmission unit of the cone block chains, a sovereign chain and an alliance chain which are equal and free and can be supervised by a government can be constructed, and mutual verification and communication of the alliance chain can be realized.
Owner:GLOBAL PRESTIGE INFORMATION TECH CO LTD
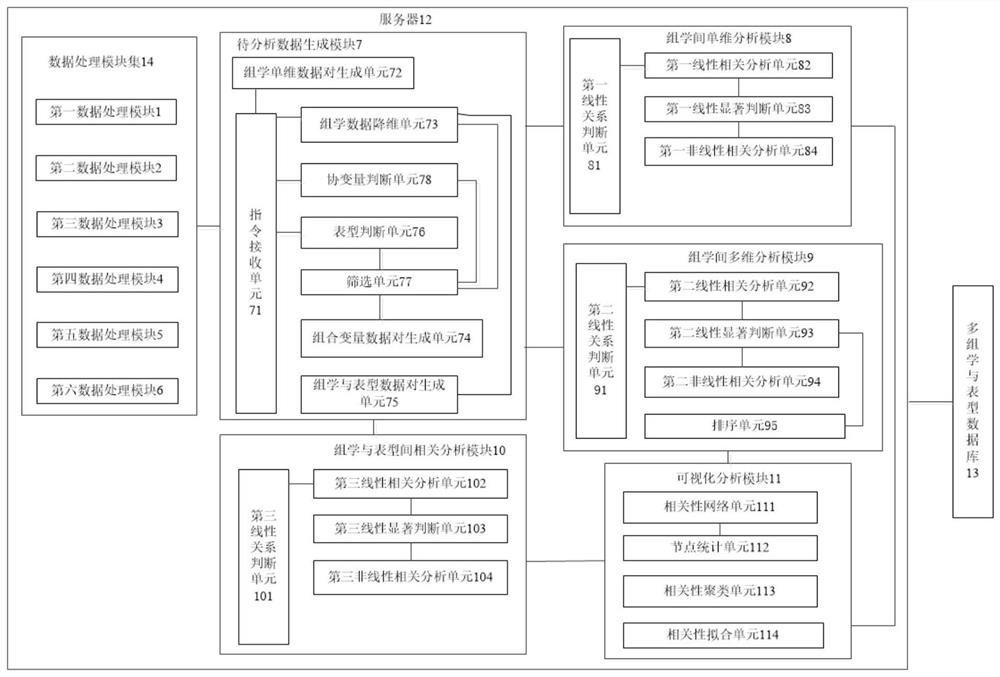
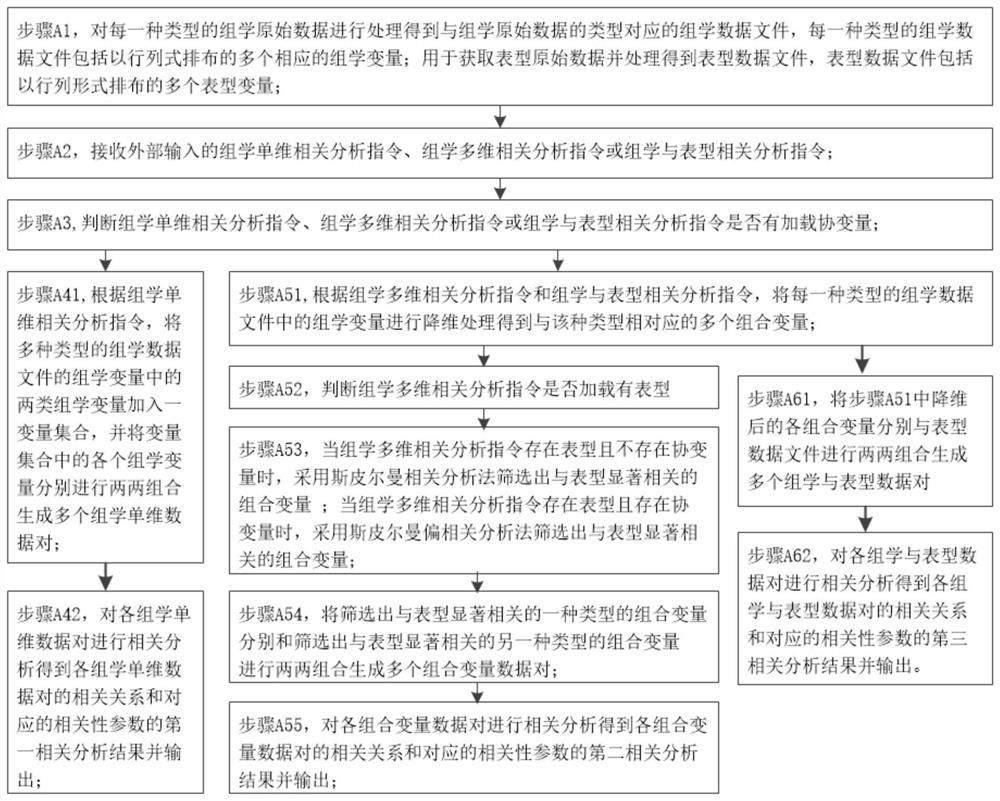
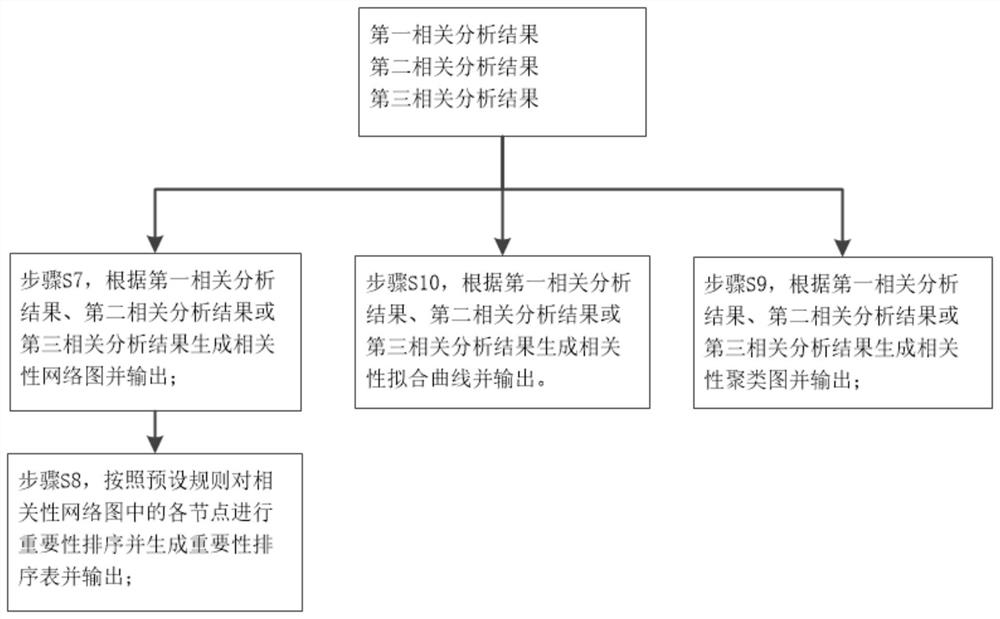
Integration system and method for correlation analysis among multiple omics data sets
InactiveCN111863136AAchieve mutual authenticationRich functionalityData visualisationBiostatisticsData setLinear correlation
The invention provides an integration system and method for correlation analysis among multiple omics data sets. The method comprises the following steps: processing each type of omics original data to obtain an omics data file corresponding to the type of the omics original data, and processing phenotypic original data to obtain a phenotypic data file; adding two types of omics variables in the omics variables of the various types of omics data files into a variable set, and combining the omics variables in the variable set in pairs to generate a plurality of omics single-dimensional data pairs; performing dimension reduction processing on each type of omics data file to obtain a combined variable corresponding to the type; combining the various types of combined variables in pairs to generate a plurality of combined variable data pairs; combining the various types of combined variables with the phenotypic data files in pairs to generate a plurality of omics and phenotypic data pairs;and performing correlation analysis on the omics single-dimensional data pairs, the combined variable data pairs and the omics and phenotype data pairs to respectively obtain respective correlation relationships and corresponding correlation parameters, and outputting the respective correlation relationships and the corresponding correlation parameters. The invention provides an effective methodfor comprehensively analyzing the biological information of the system and is capable of discovering the linear correlation relationship among the multiple omics data and finding out the nonlinear correlation pair with the function relationship and without the function relationship, thereby having comprehensive functionality.
Owner:SHANGHAI SIXTH PEOPLES HOSPITAL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com