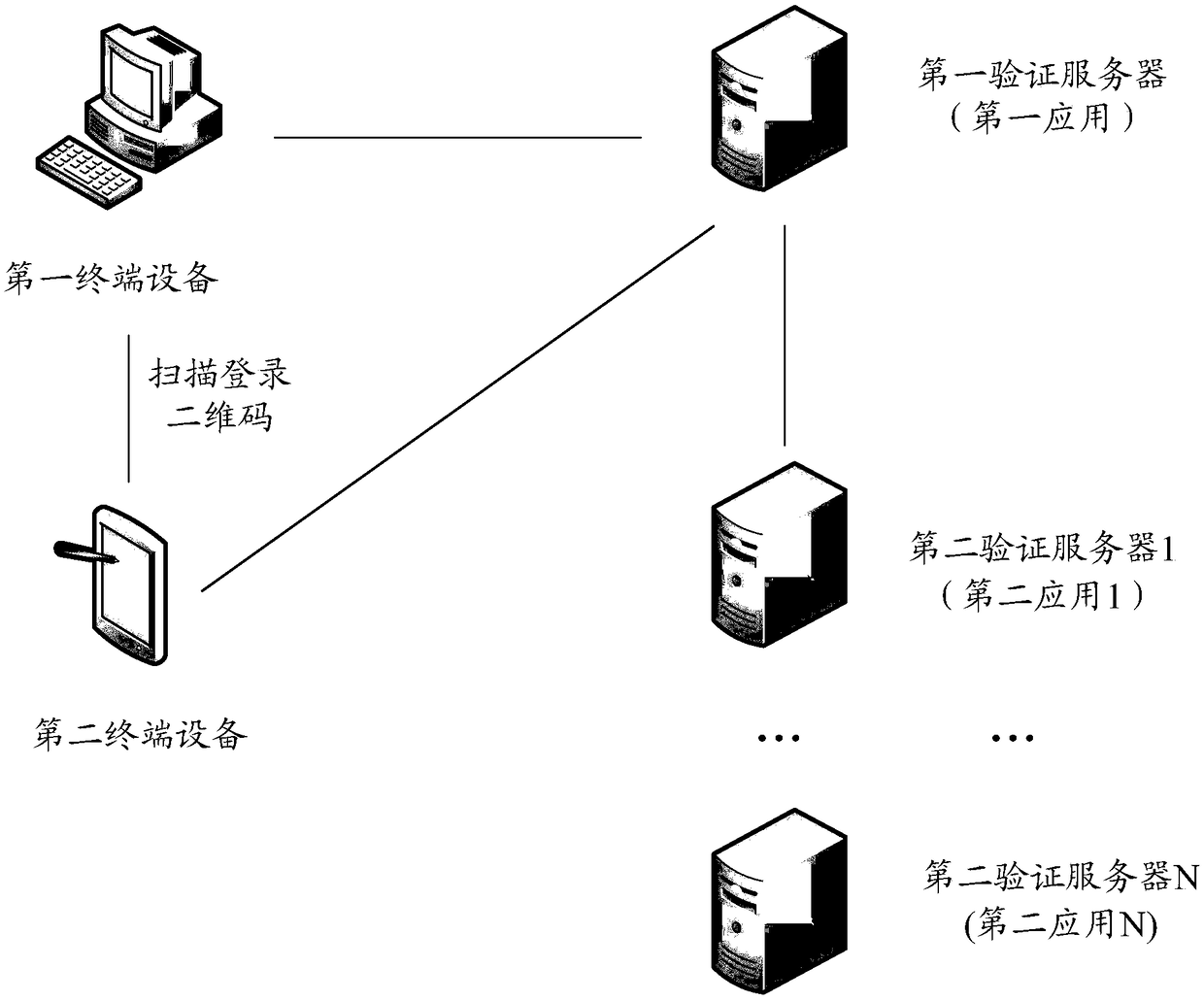
Multi-application login method and device
A login method and multi-application technology, applied in the computer field, can solve problems affecting user experience and inflexible login methods, and achieve the effect of improving user experience and flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
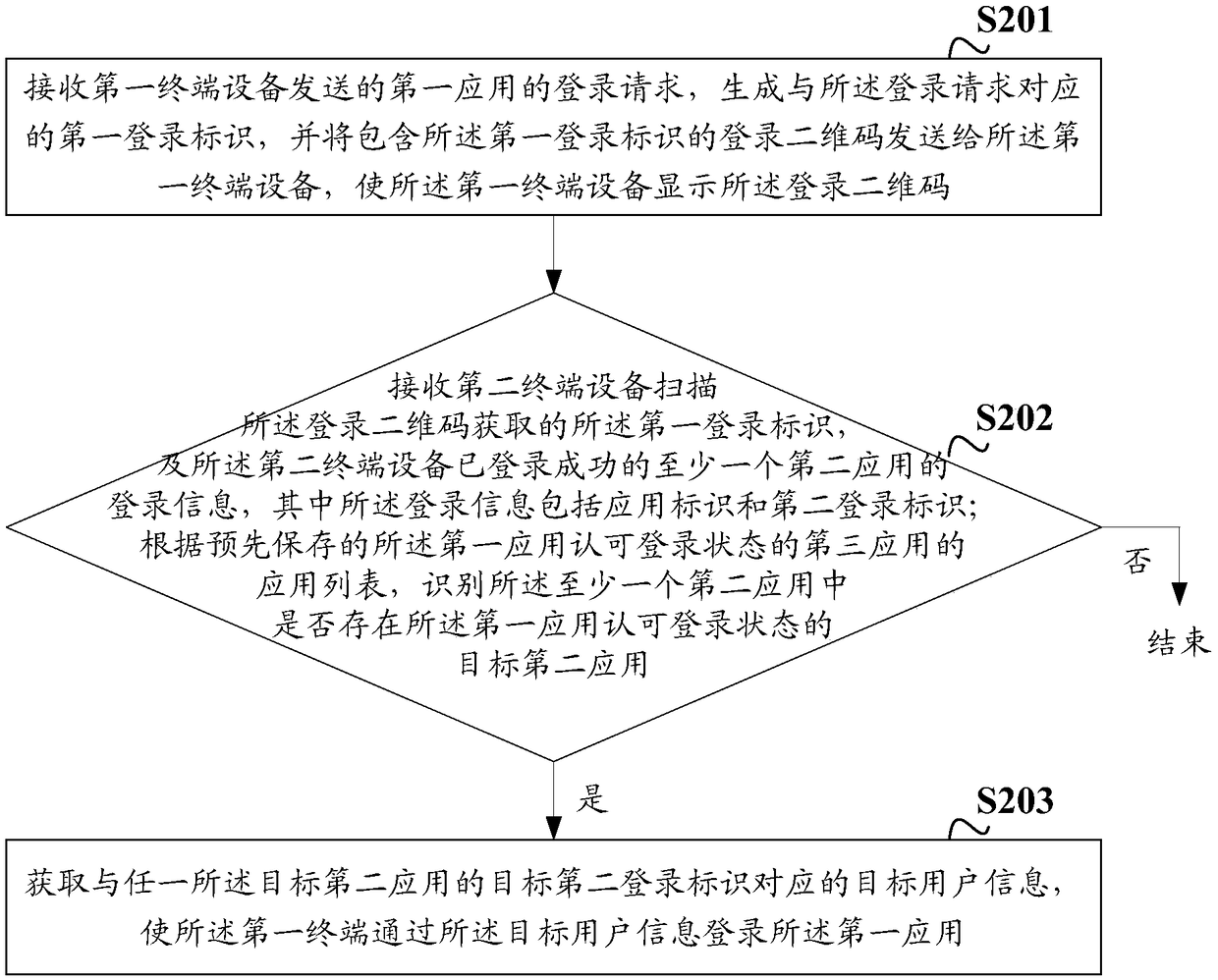
[0051] figure 2 It is a schematic diagram of a multi-application login process provided by an embodiment of the present invention, and the process includes:
[0052] S201: Receive a login request of the first application sent by the first terminal device, generate a first login ID corresponding to the login request, and send a login QR code containing the first login ID to the first terminal device, enabling the first terminal device to display the login QR code.
[0053] In the embodiment of the present invention, the verification server will generate a login ID uniquely corresponding to the login request for each received application login request to identify the login request. For example, the login request ID can include the global A unique identifier (Globally Unique Identifier, GUID) and the like are used to ensure the uniqueness of the login request identifier.
[0054] In addition, in practical applications, the user can trigger the first terminal device to send a l...
Embodiment 2
[0070] In order to improve the reliability of login, on the basis of the above embodiments, in the embodiment of the present invention, if the public key and private key of each application are pre-configured, the login information also includes the private key signature, and the acquisition and Before the target user information corresponding to the target second login identifier of any of the target second applications, the method further includes:
[0071] Verifying the signature of the private key of the target second application according to the public key of the target second application;
[0072] If the signature verification is passed, the step of acquiring target user information corresponding to the target second login ID of the target second application is performed.
[0073] In the embodiment of the present invention, each application can also be configured with a public key and a private key, and publicize the public key.
[0074]Specifically, before the first ve...
Embodiment 3
[0078] image 3 It is a schematic diagram of a multi-application login process provided by an embodiment of the present invention, and the process includes:
[0079] S301: Scan the login QR code of the first application displayed on the first terminal device to obtain the first login ID included in the login QR code, where the first login ID is the first login ID corresponding to the first application. Generated by the verification server according to the login request of the first application sent by the first terminal device.
[0080] In the embodiment of the present invention, the verification server will generate a login ID uniquely corresponding to the login request for each received application login request to identify the login request. For example, the login request ID can include a GUID etc. are used to ensure the uniqueness of the logon request ID.
[0081] Specifically, after receiving the login request of the first application sent by the first terminal device, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com