Patents
Literature
134results about How to "Verify legitimacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
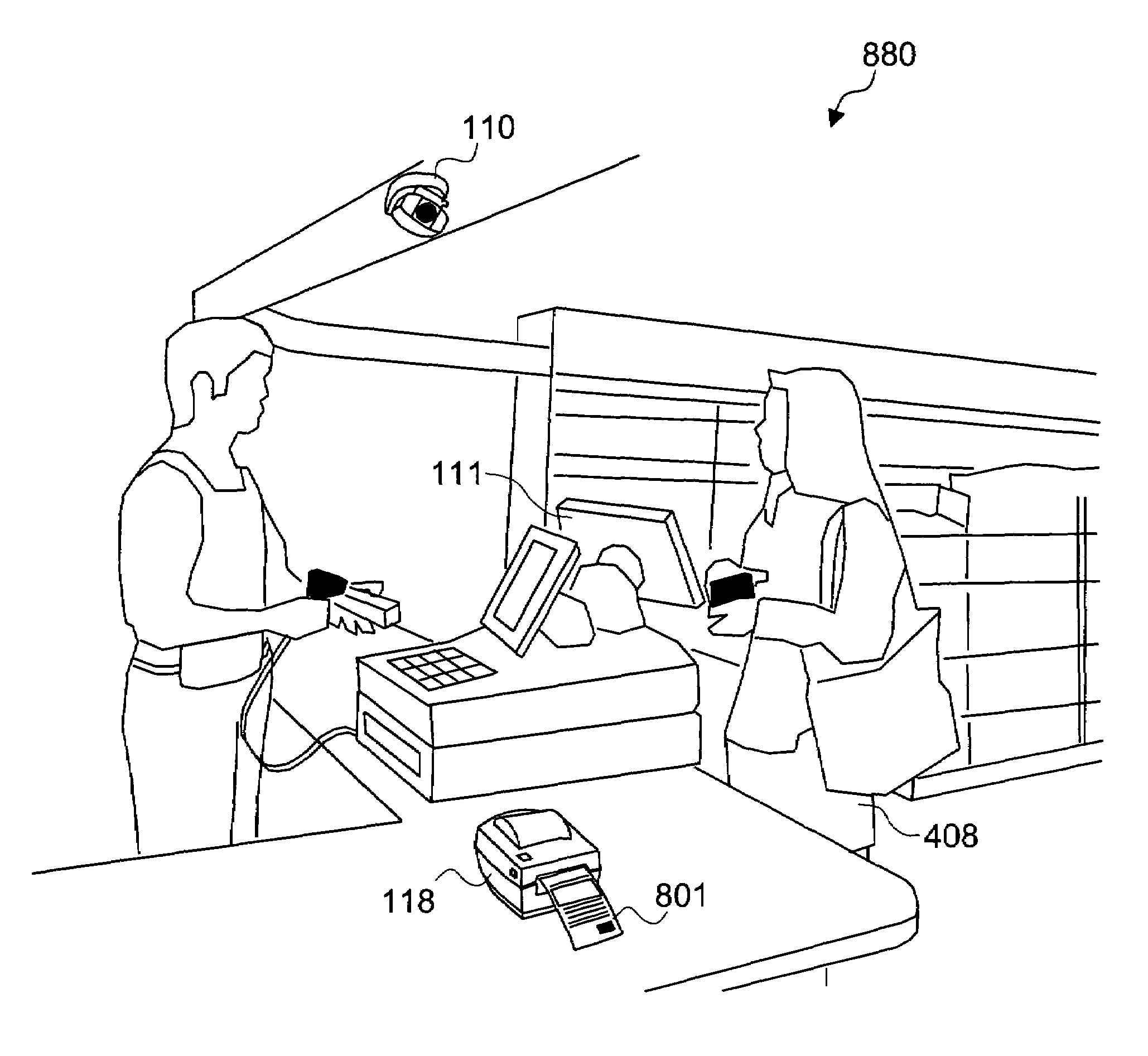
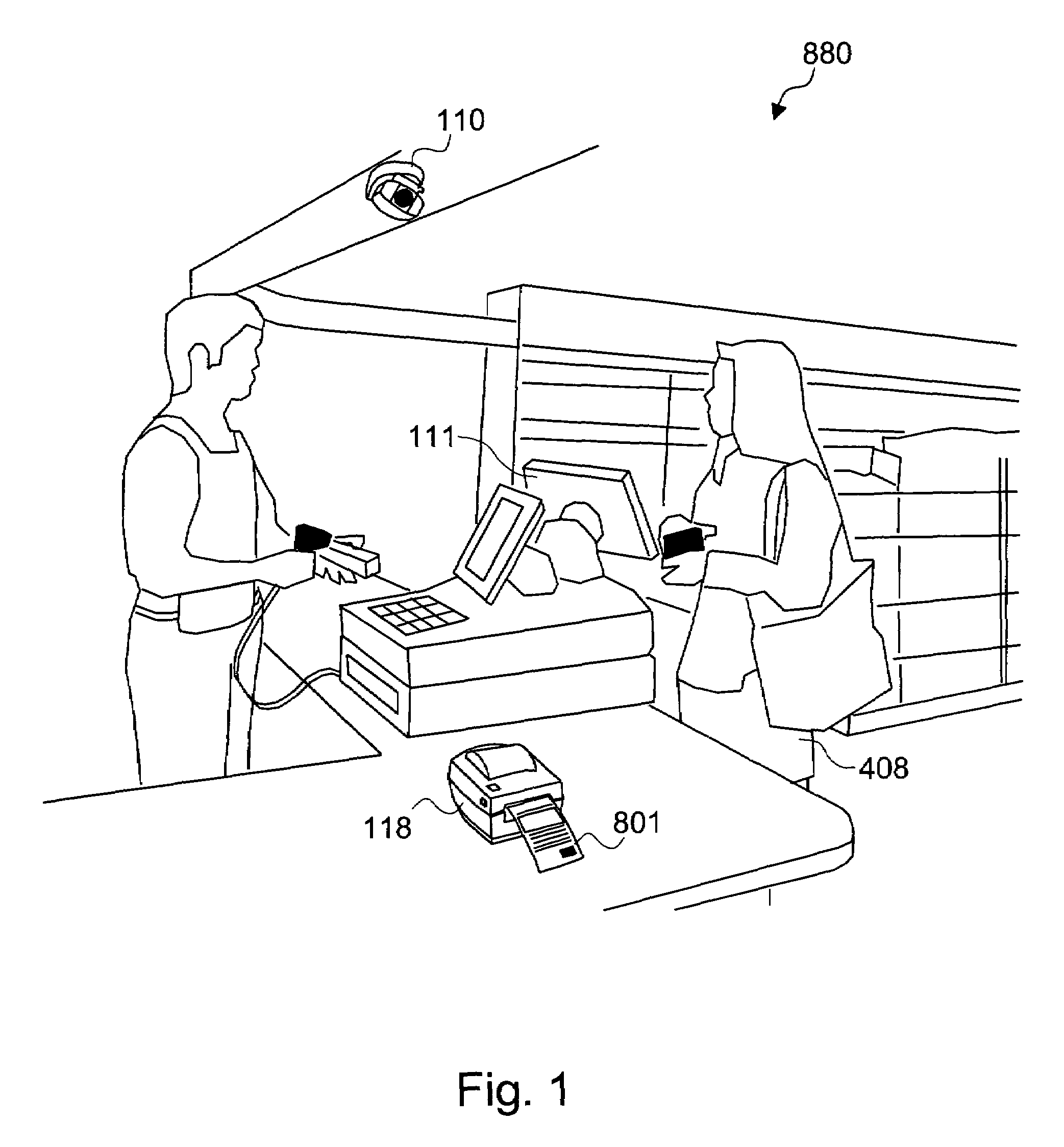
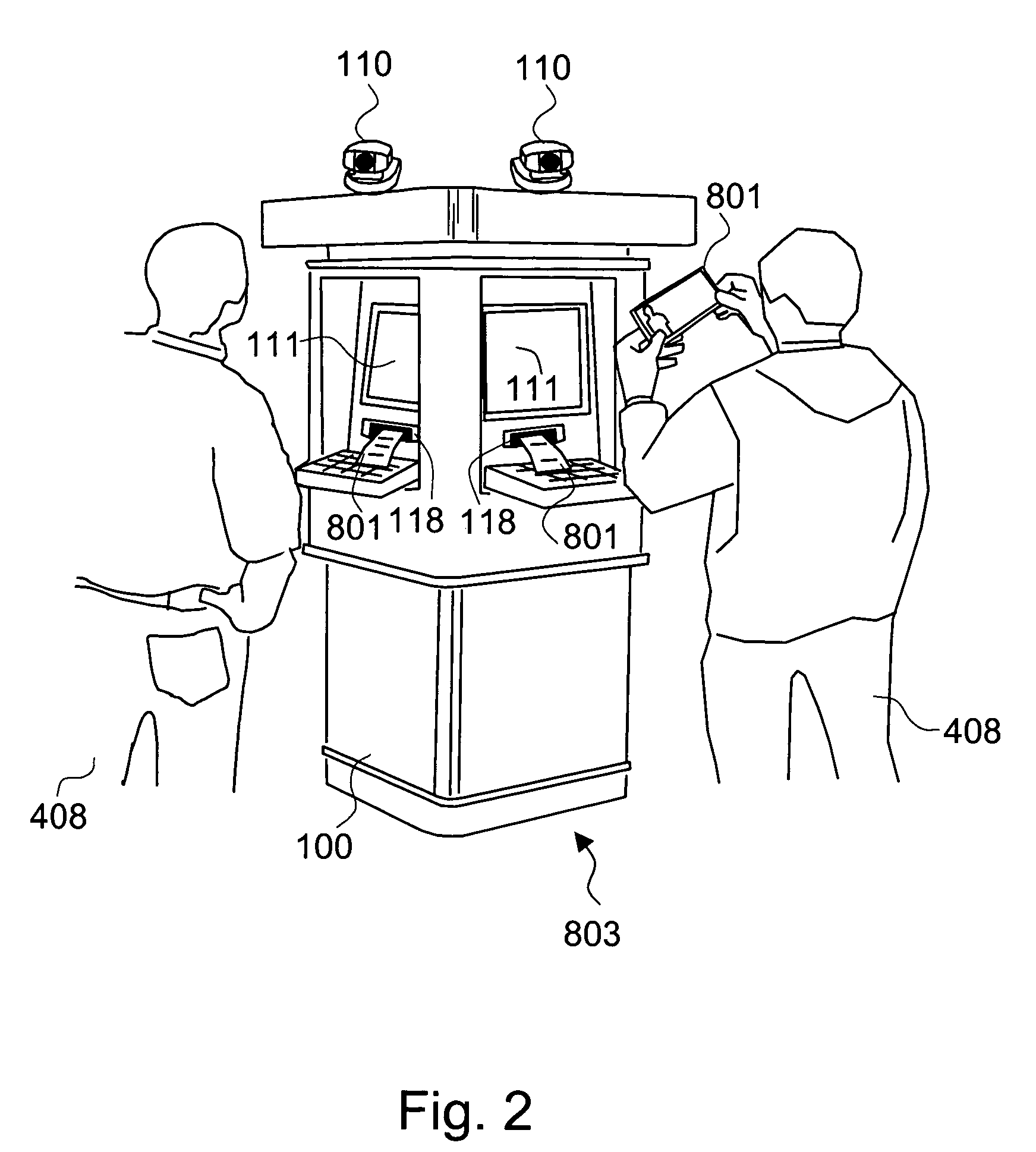
Method and system for printing of automatically captured facial images augmented with promotional content
ActiveUS7283650B1Verify legitimacyAvoid problemsAdvertisementsCharacter and pattern recognitionPublic placeComputer graphics (images)
The present invention is a system and method for printing facial images of people, captured automatically from a sequence of images, onto coupons or any promotional printed material, such as postcards, stamps, promotional brochures, or tickets for movies or shows. The coupon can also be used as a means to encourage people to visit specific sites as a way of promoting goods or services sold at the visited site. The invention is named UCOUPON. A plurality of Computer Vision algorithms in the UCOUPON processes a plurality of input image sequences from one or a plurality of means for capturing images that is pointed at the customers in the vicinity of the system in an uncontrolled background. The coupon content is matched by the customer's demographic information, and primarily, the UCOUPON system does not require any customer input or participation to gather the demographic data, operating fully independently and automatically. The embodiment of the UCOUPON system can be integrated into any public place that requires the usage of coupons, such as existing checkout counters of the retail store environment. The UCOUPON can also be integrated into a stand-alone system, such as a coupon Kiosk system.
Owner:F POSZAT HU
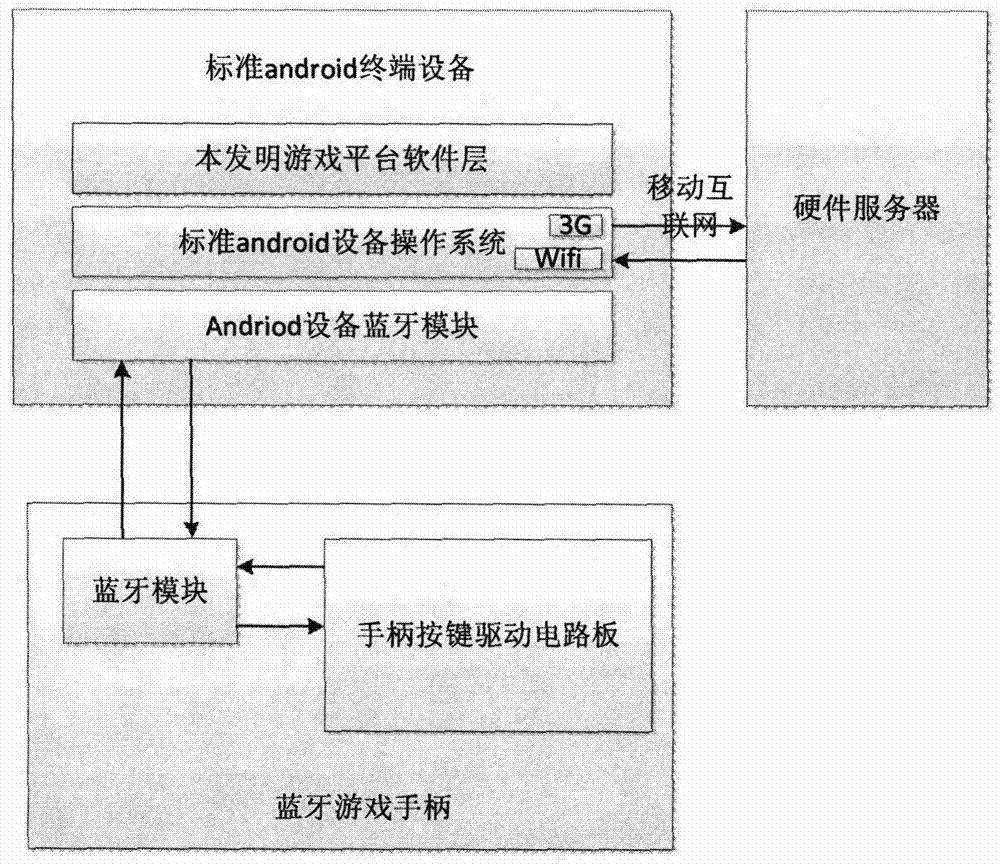
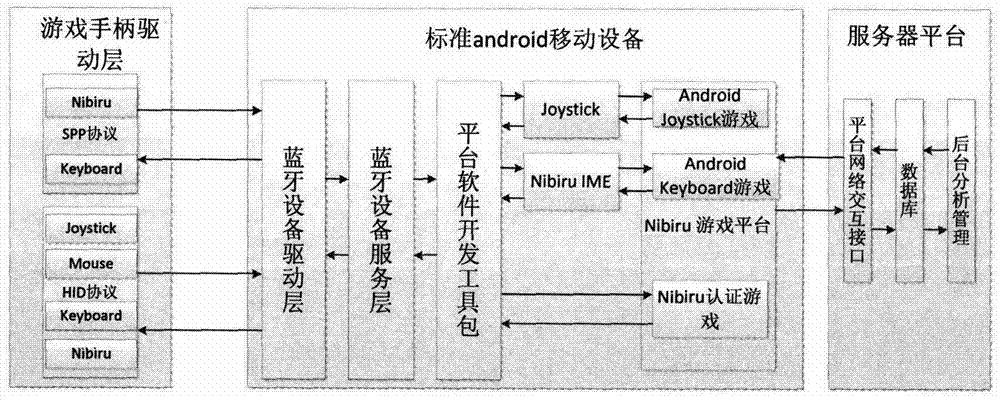
Android device gas platform system based on Bluetooth handle and implementation method of Android device gas platform system
ActiveCN103316472AReduce performance overheadReduce dependenceVideo gamesSpecific program execution arrangementsThe InternetSoftware engineering
The invention discloses an Android device gas platform system based on a Bluetooth handle and an implementation method of the Android device gas platform system. The interactive protocols of different Bluetooth handles on the market are unified, so that handles in different modes on the market can uniformly and conveniently have an access to a game platform and use the server technology, and the game platform is connected to a game content server through a network and can provide rich game resources so as to improve the user experience and the value of games. The game platform disclosed by the invention can be mounted on almost all Android devices so as to enable a common Android device mounted with the Android device gas platform system to become a game machine controlled by the handle in the Internet era.
Owner:NANJING RUIYUE INFORMATION TECH
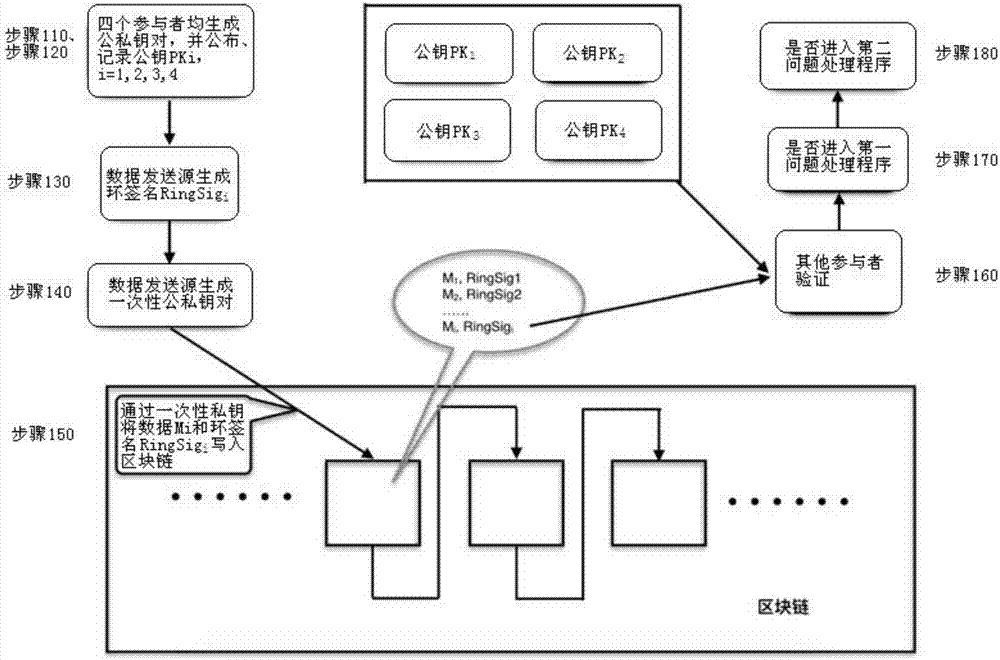
Multiparty data sharing method and system for protecting privacy data sending source
ActiveCN107453865AGuaranteed not to be exposedIdentity privacy data is not exposedKey distribution for secure communicationMultiple keys/algorithms usageBlockchainData sharing
The invention discloses a multiparty data sharing method for protecting privacy of a data sending source. A plurality of participants are jointly connected with a block chain and share data. The method comprises the steps that S1, the participants generate public and private key pairs; S2, the participants publish public keys corresponding to own identities and record all published public keys; S3, the data sending source generates a ring signature based on all public keys, a private key of the data sending source and to-be-sent data and writes the data and the ring signature into a block chain through a one-time private key; and S4, other participants reads the data and the ring signature, verify the ring signature based on the public keys, the data and the ring signature, employ the data if the verification result indicates legality, and do not employ the data if the verification result indicates illegality. The invention also discloses a corresponding system. According to the method and the system, the identity privacy data of a data sharer is prevented from being exposed, and data receivers believe that the data sharer really has the data sharing authority or even realizes responsibility investigation.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD
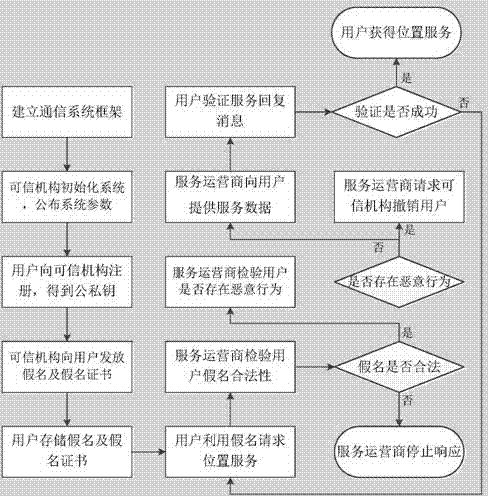
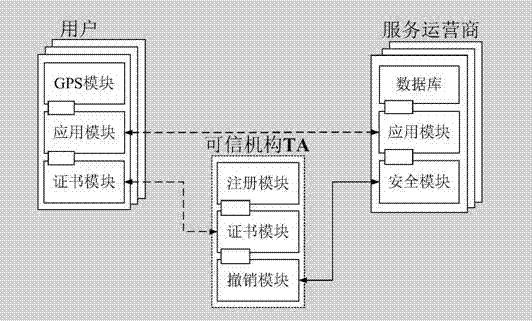
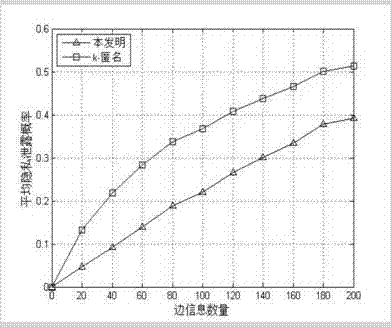
Position privacy protection method based on dynamic pseudonyms
ActiveCN103618995AAddress privacy breachesIncreased level of privacyLocation information based serviceSecurity arrangementCommunications systemSide information
The invention discloses a position privacy protection method based on dynamic pseudonyms. The position privacy protection method mainly overcomes the defect that the position privacy protection degree in an existing position pseudonym method based on position services is too low. The position privacy protection method comprises the steps that a communication system composed of users, a credible mechanism and a service provider is built; the system is initialized through the credible mechanism; the users sign in the credible mechanism on line to obtain public and private keys; the credible mechanism updates the pseudonyms and pseudonym certificates of the users regularly; the users use the dynamic pseudonyms to request position services from the service provider; the service provider provides service data for legal users and requests the credible mechanism to revoke malicious users; the legal users obtain the position service data. According to the position privacy protection method, identity anonymity is achieved by using the dynamic pseudonyms, the relation between identity information and spatiotemporal information is cut off, and therefore it is difficult for the service provider to speculate position information of the specific users by means of side information, position privacy of the users is protected effectively, and the position privacy protection method can be used for position privacy protection based on the position services in social networking services.
Owner:XIDIAN UNIV
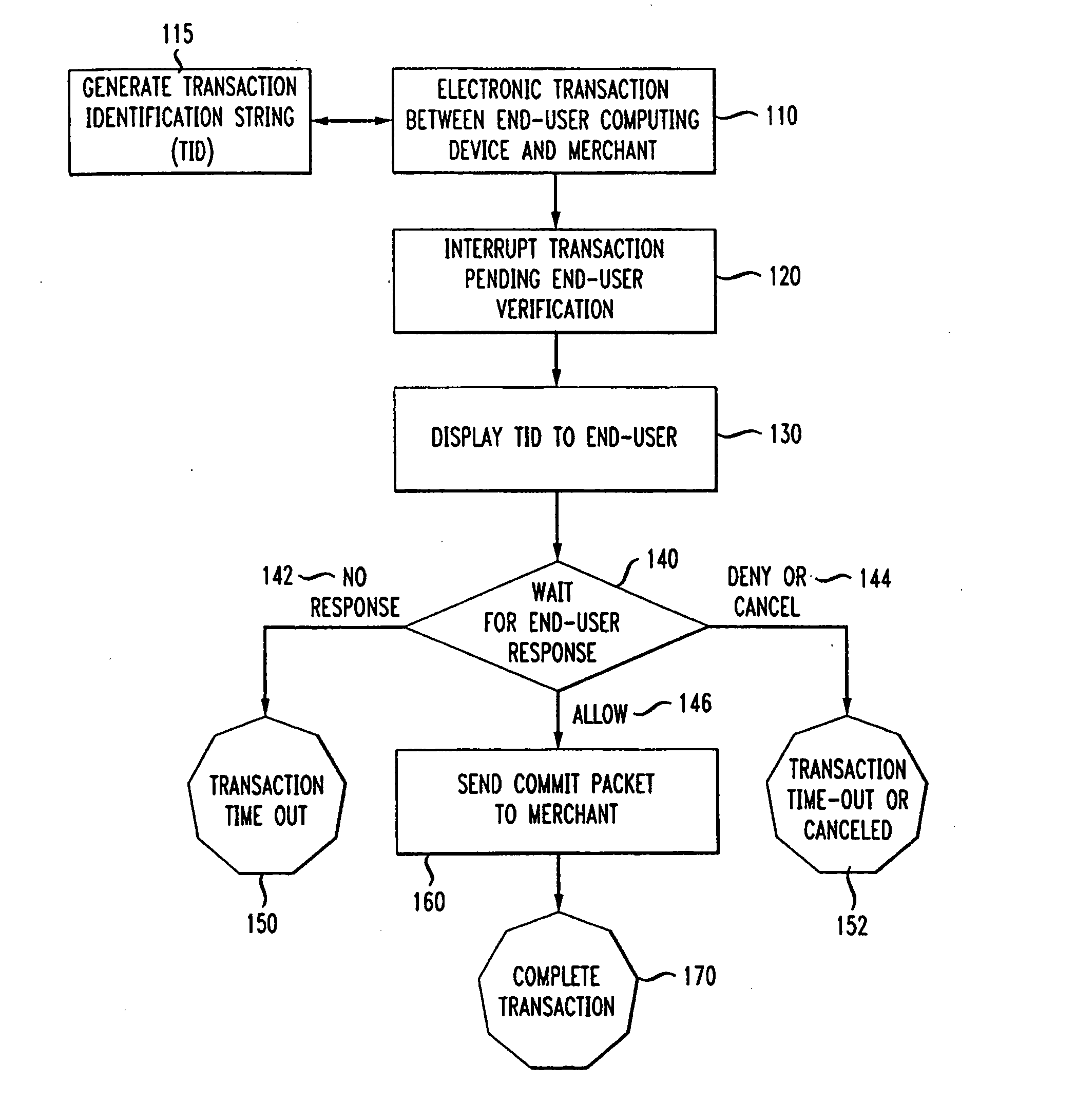
Method and Device for End-User Verification of an Electronic Transaction
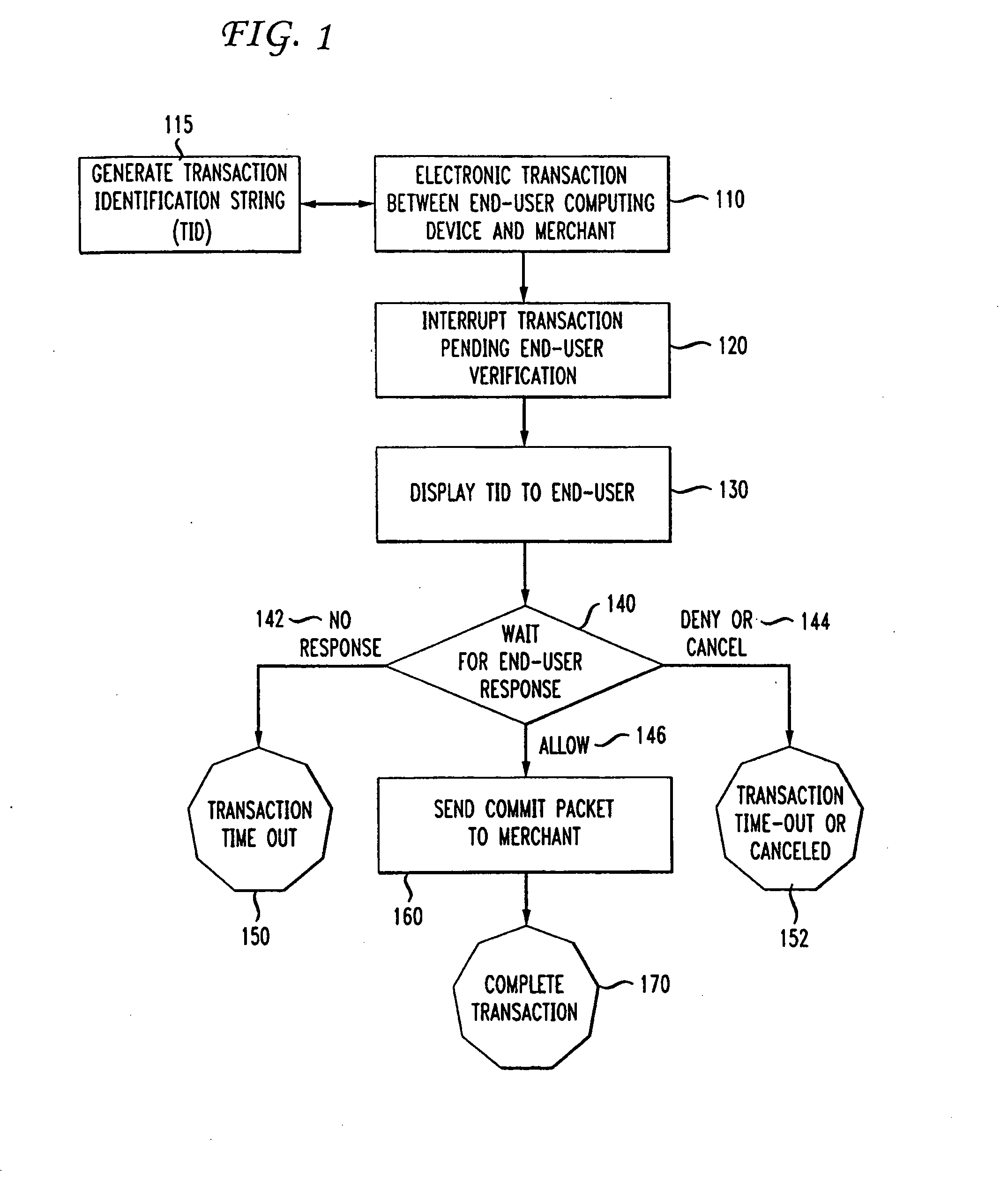
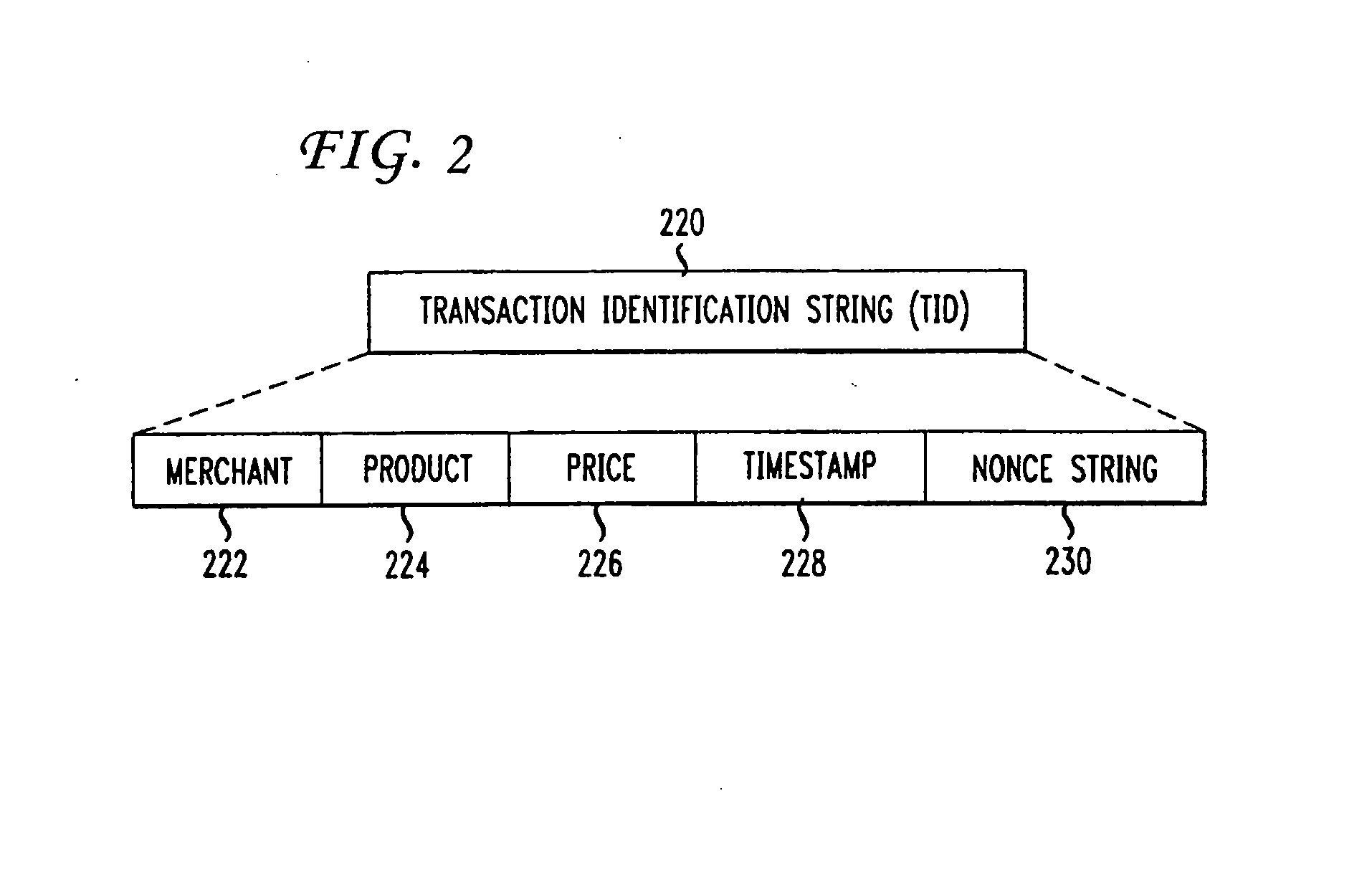
ActiveUS20150170146A1Verify legitimacyPrevent fraudulent transactionAcutation objectsFinanceOperational systemFinancial transaction
The present invention provides methods and apparatuses for verifying that a transaction is legitimate. The methods and apparatuses use protected memory space, such as kernel space of an operating system, or a separate memory space, such as is available on a SIM card of a cellular phone. The method of the invention proceeds by creating a transaction identification string (TID) and associating the TID with a transaction. The TID contains data relevant to or associated with the transaction and is typically readable by an end-user. The transaction is then interrupted until a user responds in the affirmative to allow completion of the transaction. Methods and devices used in the invention are particularly well suited to M-commerce, where transactions originating from a device are typically recognized by a merchant as coming from the owner of the device without further authentication.
Owner:AT&T INTPROP I LP
Data processing method and device and computer readable storage medium
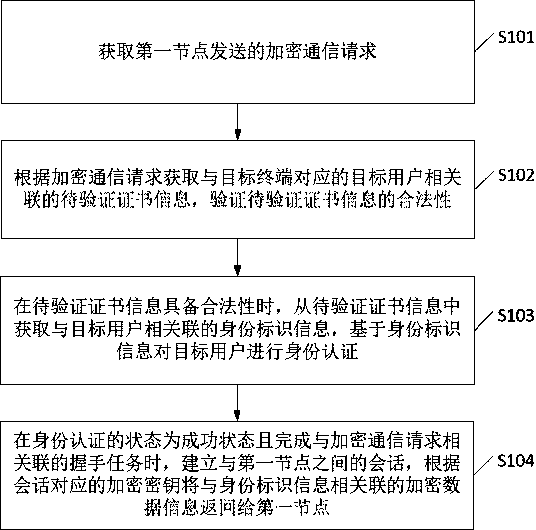
ActiveCN110708170AVerify legitimacyImprove privacyUser identity/authority verificationNetwork connectionsEngineeringData transmission
The invention discloses a data processing method and device and a computer readable storage medium. The method comprises the steps of a gateway node acquiring an encrypted communication request sent by a first node; wherein the first node is a node associated with the target terminal in the blockchain network; obtaining to-be-verified certificate information associated with a target user corresponding to the target terminal according to the encrypted communication request; when the to-be-verified certificate information has legality, obtaining identity identification information associated with the target user from the to-be-verified certificate information, and performing identity authentication on the target user based on the identity identification information; and when the identity authentication state is a successful state and a handshake task associated with the encrypted communication request is completed, establishing a session with the first node, and returning encrypted datainformation associated with the identity identification information to the first node according to an encryption key corresponding to the session. By adopting the method and the device, the privacy ofdata pulling can be enhanced, and the security of data transmission can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
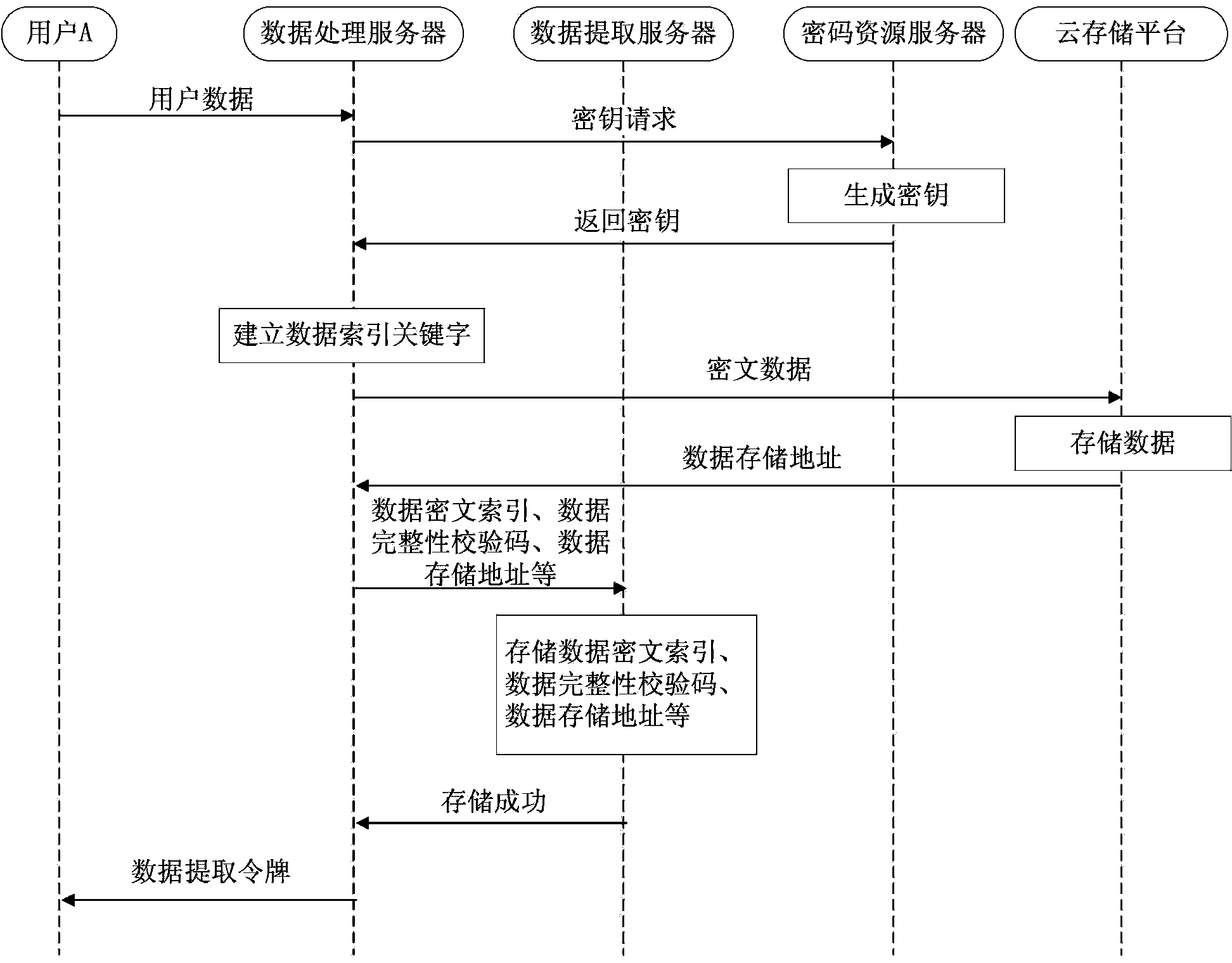
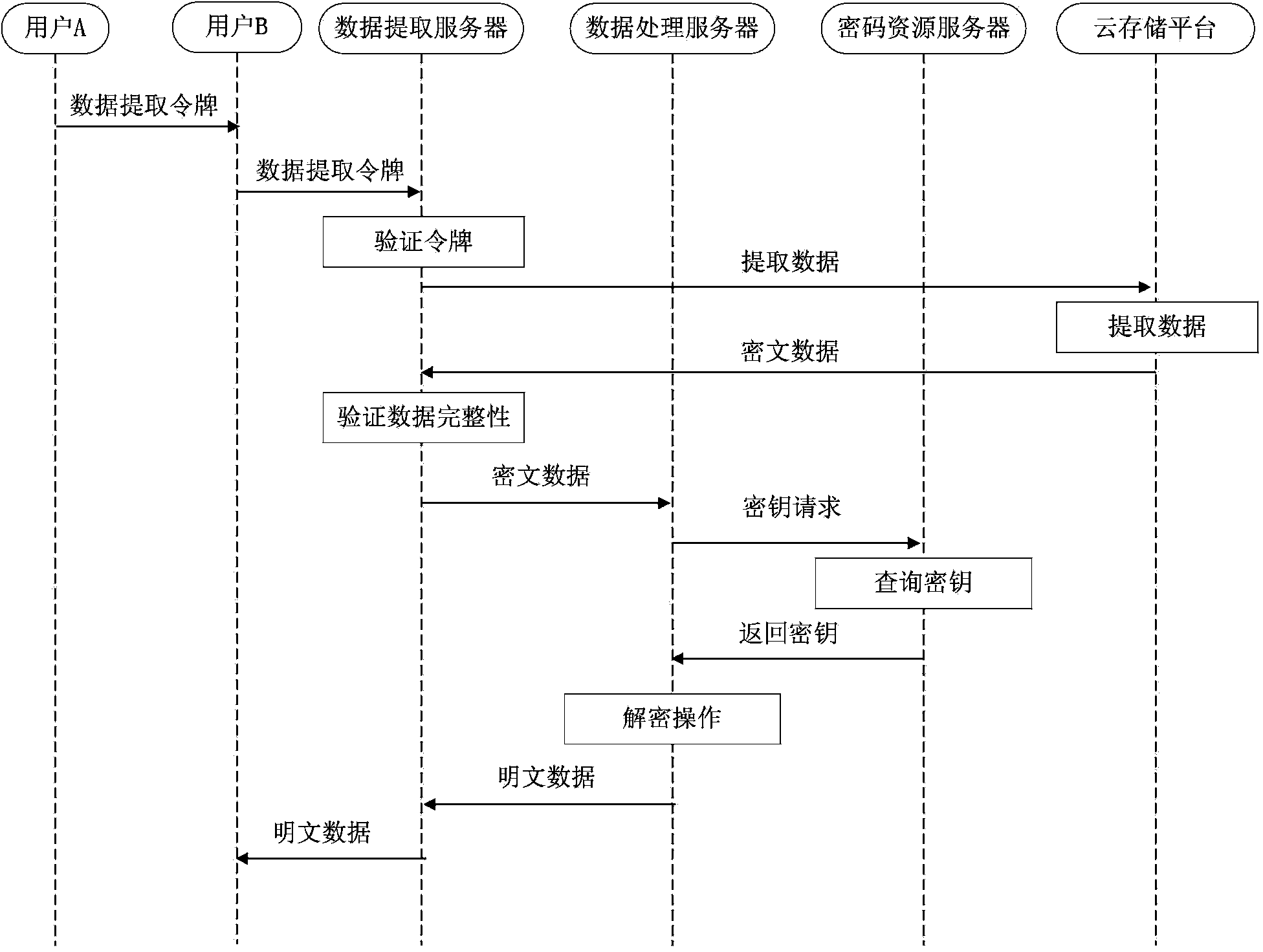
Data sharing method and system under cloud computing environment
ActiveCN103457733AImprove securityReduce duplicationUser identity/authority verificationData ingestionCiphertext
The invention relates to a data sharing method and system under the cloud computing environment. The method comprises the user data encryption storage step and the user data extraction step. The user data encryption storage step comprises the particular steps that a data processing server sets up data index keyword information for user data and generates a matched data ciphertext index and a matched data extraction token, the user data are stored in a cloud storage platform after being encrypted, the data ciphertext index and a data storage address are stored in a data extraction server, and the data extraction token is transmitted to a user. The user data extraction step comprises the particular steps that after receiving the data extraction token, the data extraction server verifies the legality of the data extraction token, extracts data from the cloud storage platform according to the data storage address, and the data are returned to the user by the data extraction server after being decrypted by the data processing server. According to the data sharing method and system, the data storage safety under the cloud computing environment is ensured, and meanwhile the problem of user data sharing is conveniently solved.
Owner:CEC CYBERSPACE GREAT WALL
Electronic medical record sharing method and system based on block chain
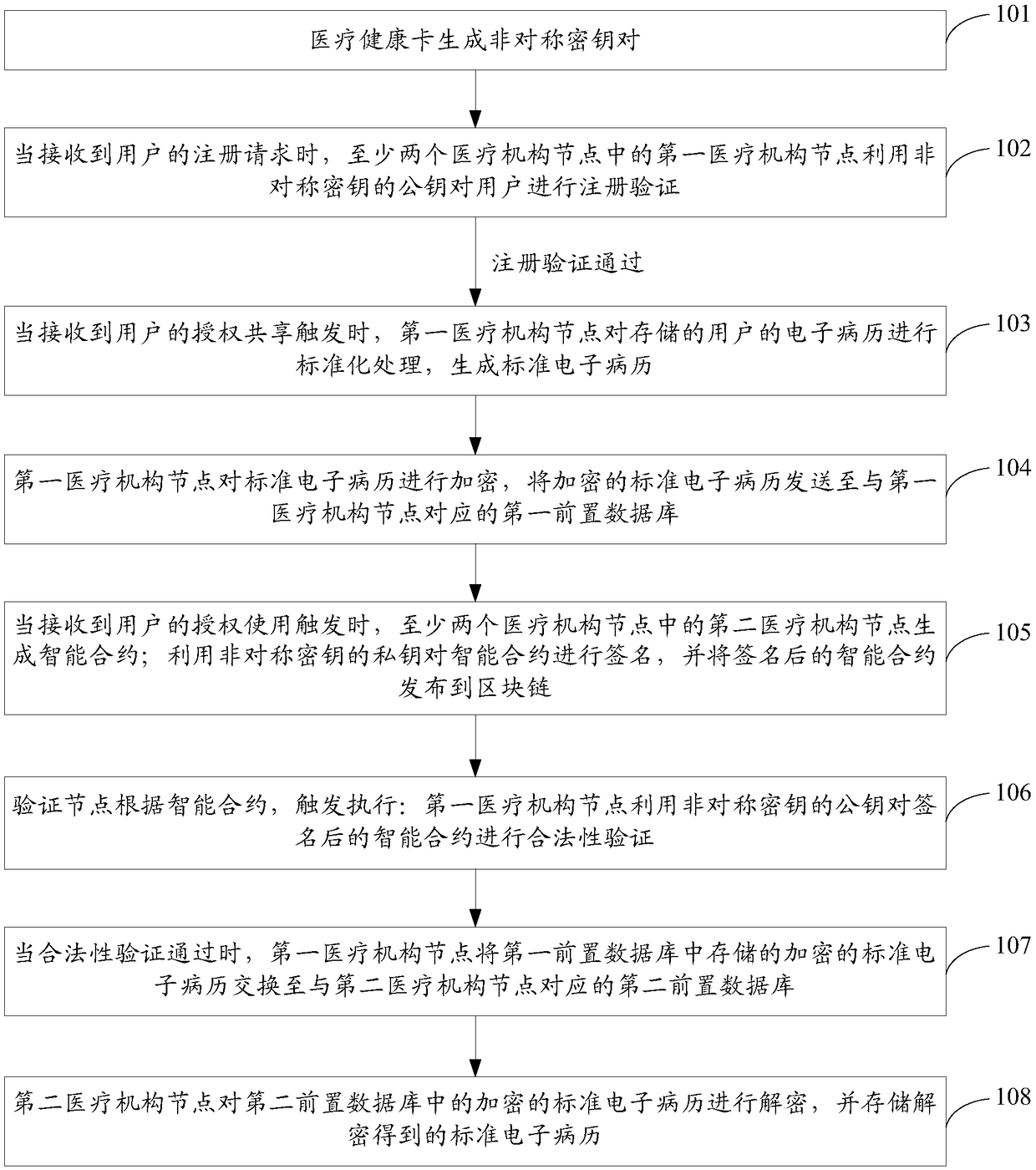
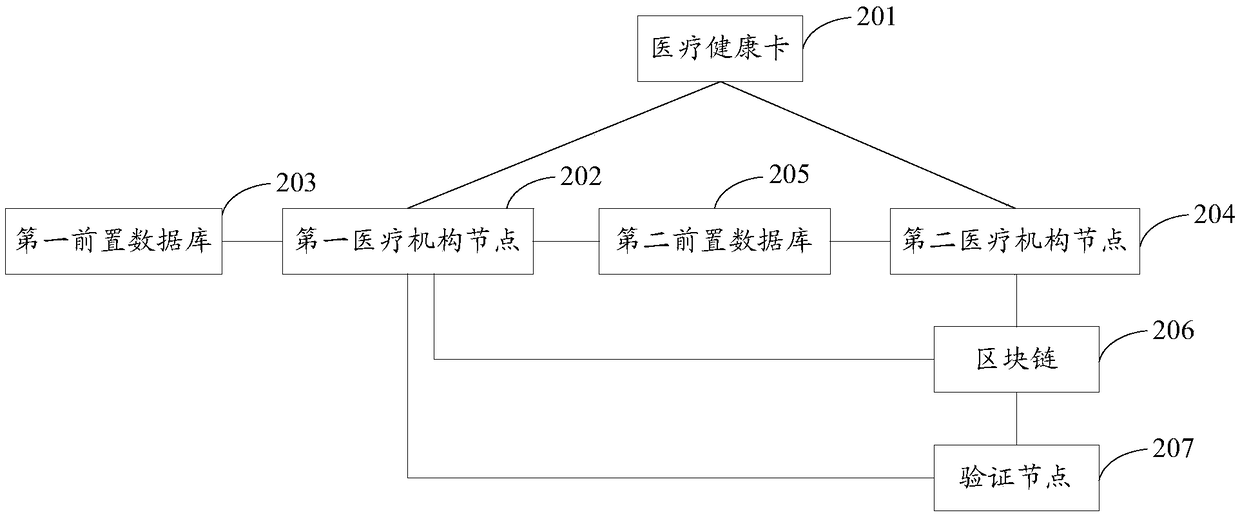
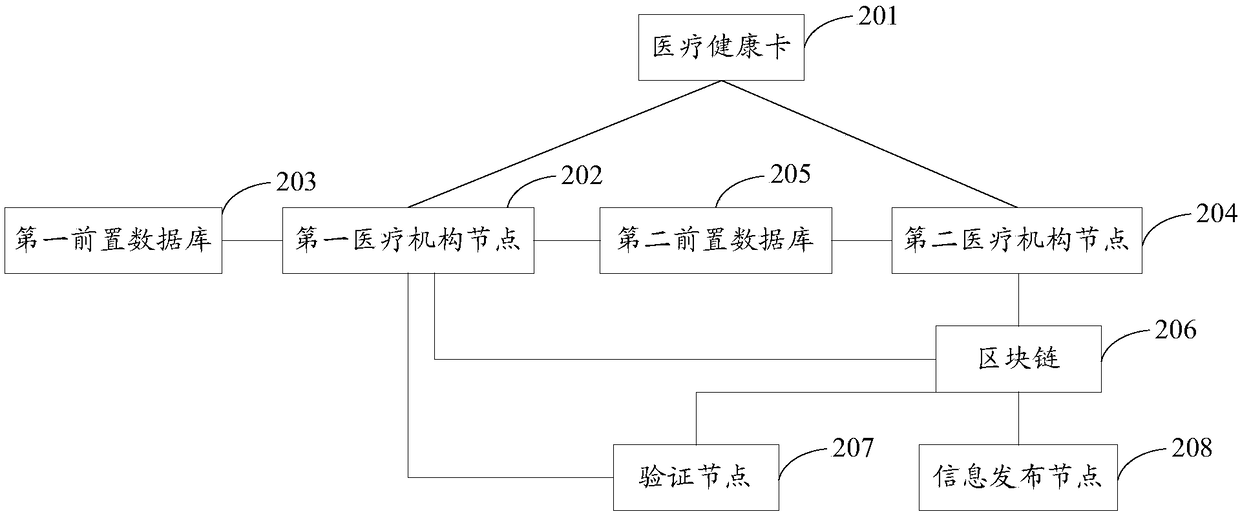
InactiveCN108449359AProtect patient privacyImprove sharing efficiencyUser identity/authority verificationPatient-specific dataMedical healthSmart contract
The invention provides an electronic medical record sharing method and system based on a block chain, wherein the method comprises the following steps: a medical health card generates an asymmetric secret key pair; the first medical institution node performs registration verification on the user by utilizing the asymmetric secret key, and when the verification is passed, a first medical institution node uses the asymmetric secret key to perform registration verification on a user; when the verification is passed, the steps are carried out as follows: when an authorized sharing trigger is received, the first medical institution node performs standardized processing on the electronic medical record, and the encrypted standard electronic medical record is sent to a first front-loaded database; when an authorized use trigger of the user is received, the second medical institution node generates an intelligent contract and the signed intelligent contract is issued to a block chain; a verification node, according to the intelligent contract, triggers the execution as follows: the first medical institution node conducts validity verification on the signed intelligent contract; when the verification is passed, an encrypted standard electronic medical record is exchanged to a second front-loaded database; the second medical institution node decrypts the encrypted standard electronic medical record to obtain a standard electronic medical record. According to the scheme, the sharing process of the electronic medical record can be simplified.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
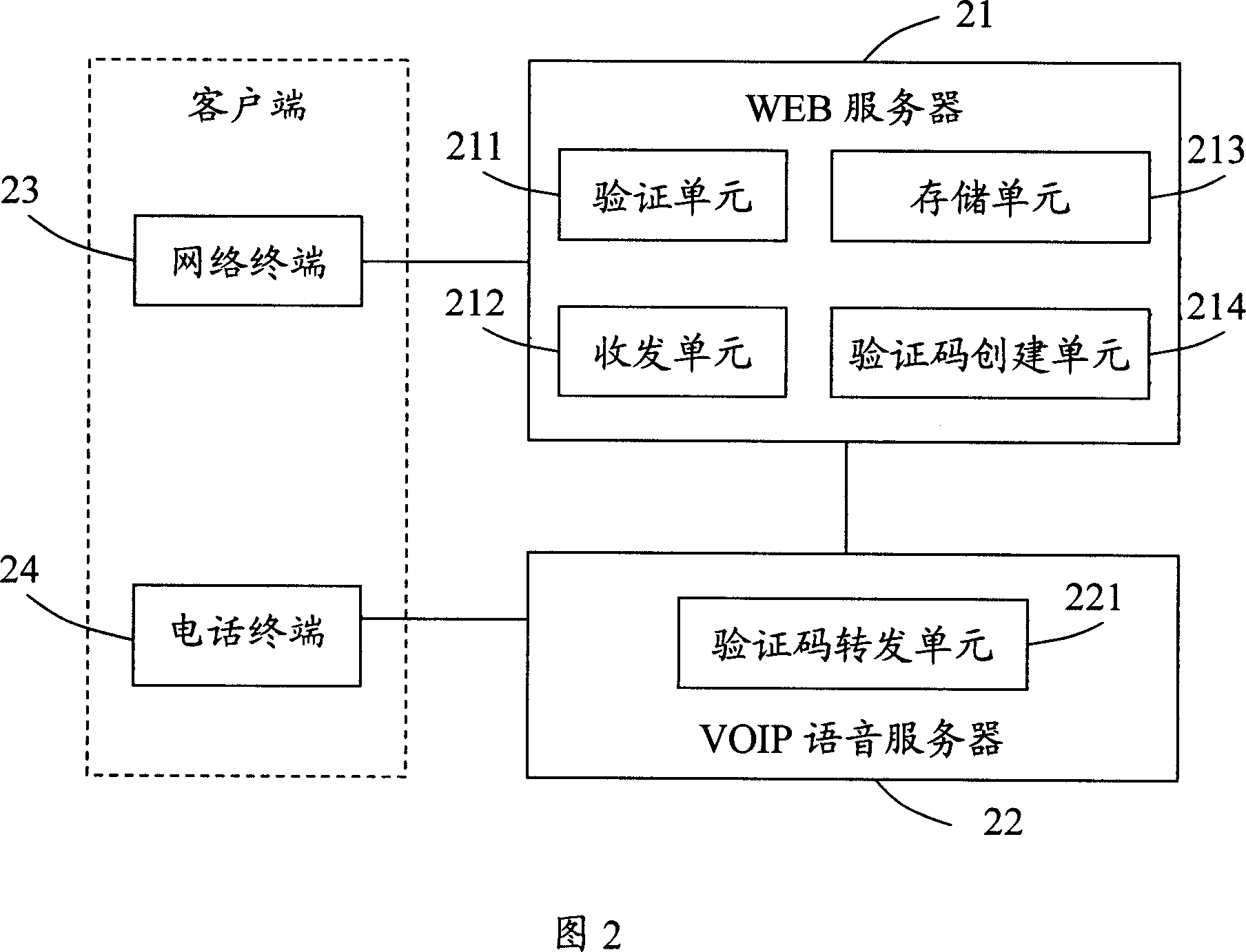
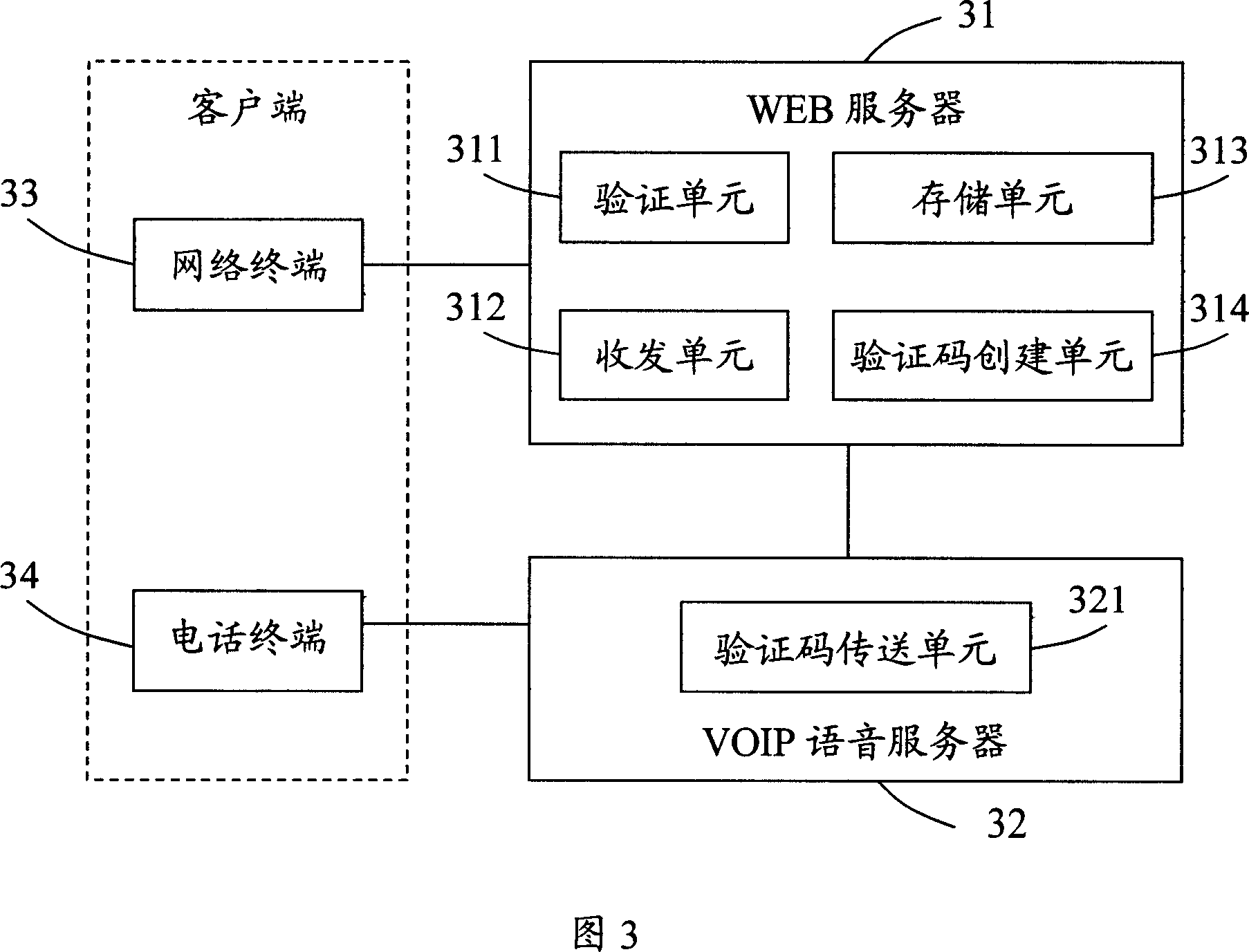
A number verification system and its method
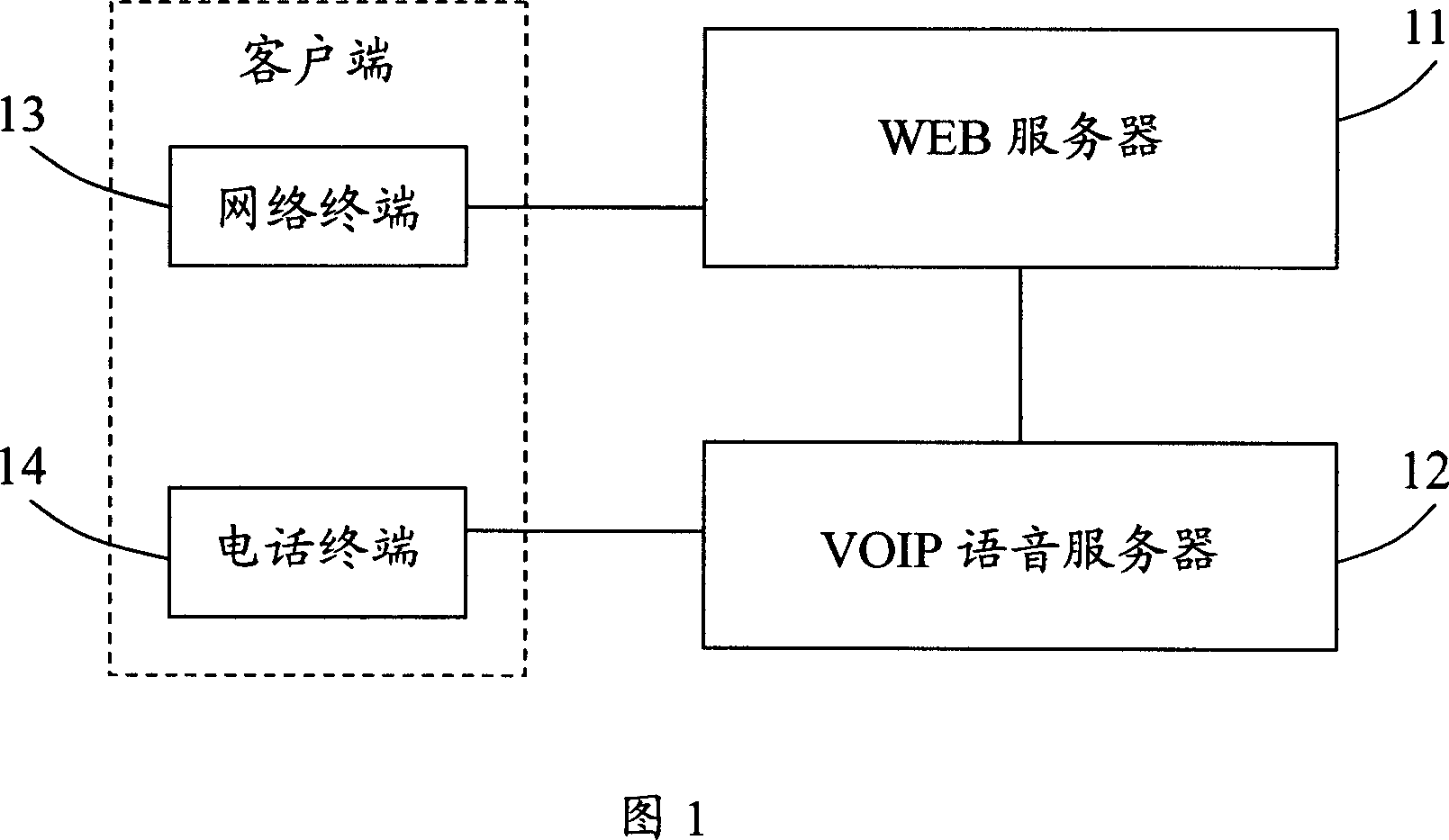
ActiveCN101079931ALow costVerify legitimacyInterconnection arrangementsUser identity/authority verificationVerification systemWeb server
This invention discloses a verification system for phone numbers including a WEB server and a VOIP phone server, in which, said WEB server includes: a T-R unit used in receiving phone numbers from the network terminals and sending verification codes to the terminals or sending the verification codes via the VOIP phone server, a verification code setting-up unit used in generating verification codes based on the received numbers, a storage unit used in storing the corresponding relation of the verification codes and the phone numbers and a verification unit used in receiving verification codes from the network terminals or the VOIP server by the T-R unit to verify phone numbers. This invention also provides a verifying method for corresponding phone numbers.
Owner:TENCENT TECH (SHENZHEN) CO LTD
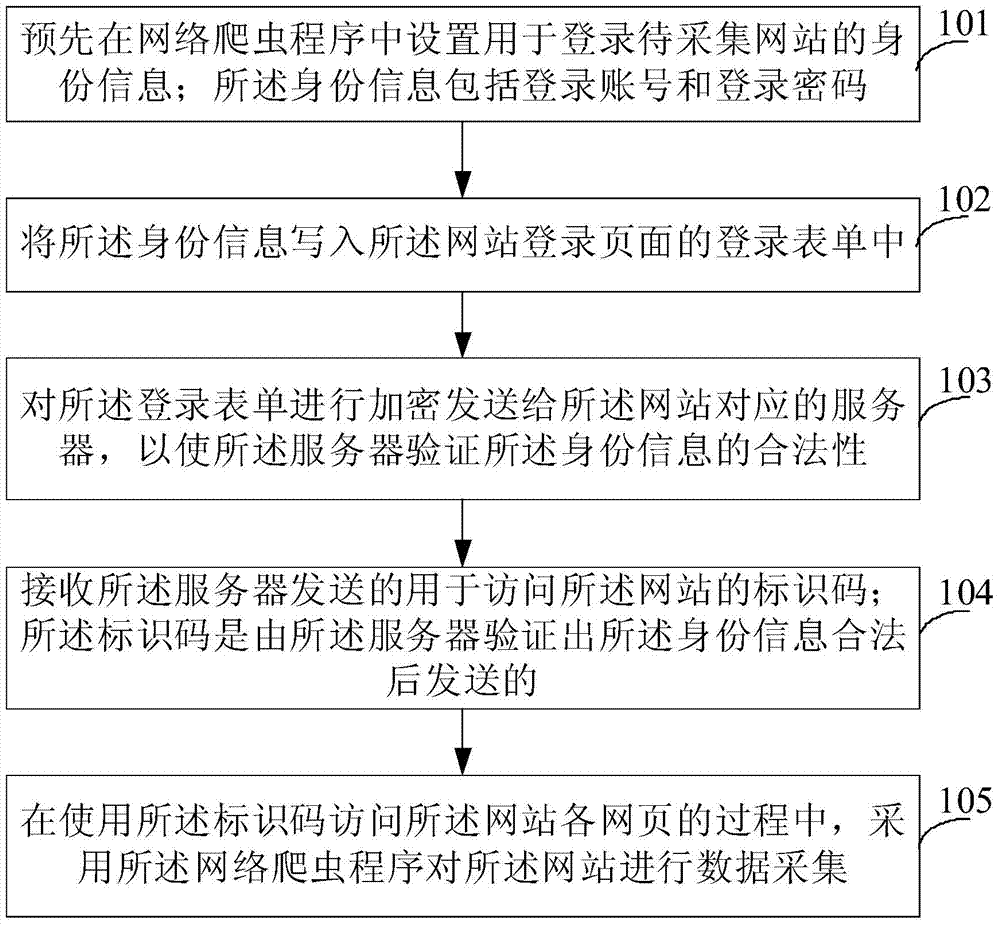
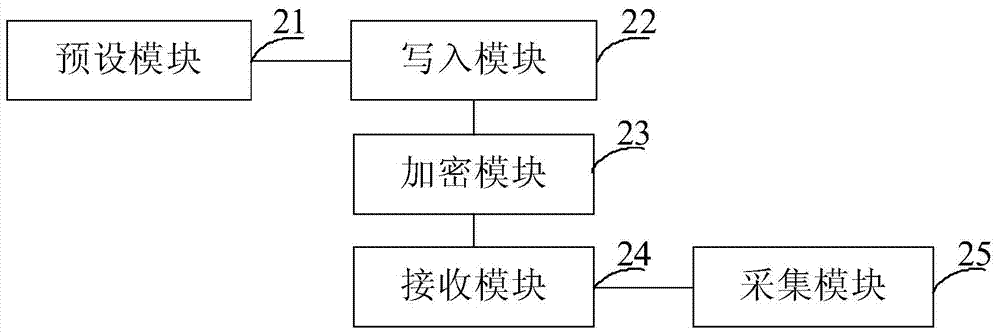
Website data acquisition method and device
The invention provides a website data acquisition method and device. The method comprises the first step of setting identity information used for logging in on a website to be acquired in a web spider program in advance, wherein the identity information comprises a log-in account and a log-in password, the second step of writing the identity information in a log-in form of the log-in page of the website, the third step of enciphering the log-in form and sending the log-in form to a server corresponding to the website so that the validity of the identity information can be authorized through the server, and the fourth step of receiving identification codes which are used for having access to the website and sent by the server, wherein the identification codes are sent after the server authorizes that the identity information is valid, and data acquisition is performed on the website by adopting the web spider program when the identification codes are used for having access to all the webpages of the network. According to the website data acquisition method and device, the identity information used for logging in on the website to be acquired is stored in the web spider program in advance, the identification codes are obtained from the server through the identity information, and then the web spider program accesses all the webpages of the website based on the identification codes so that data acquisition on the website can be achieved.
Owner:BEIJING PEOPLE ONLINE NETWORK
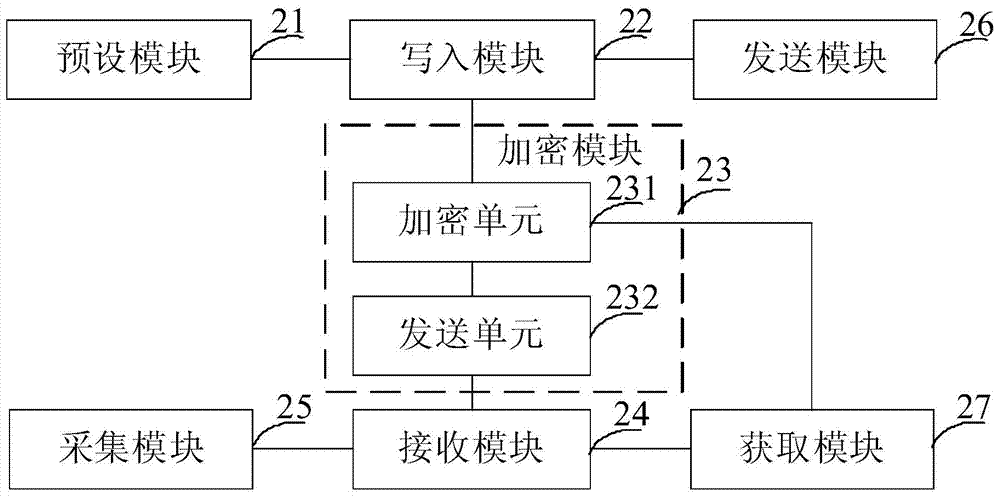
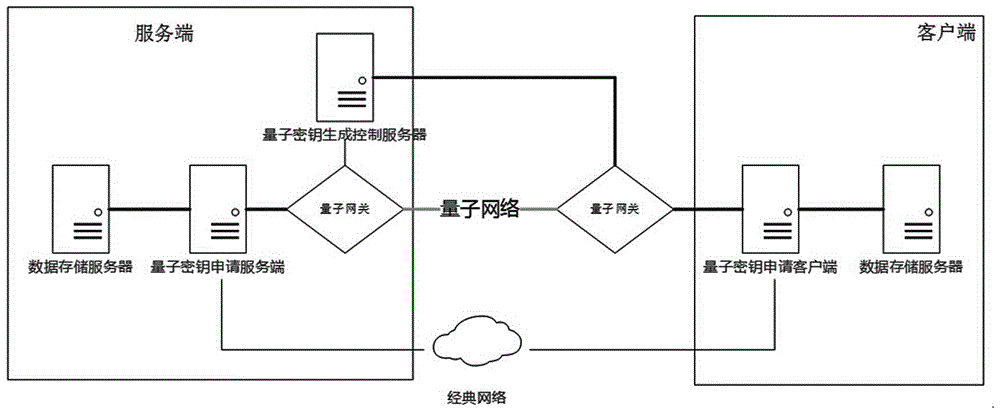
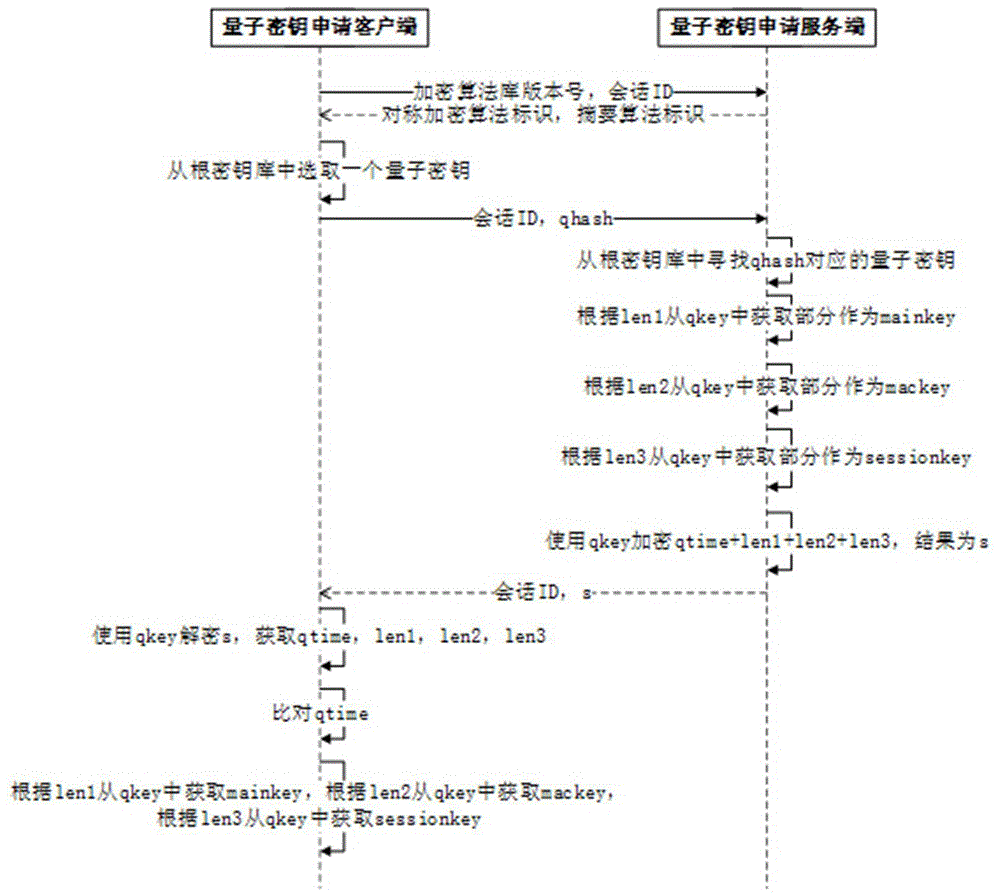
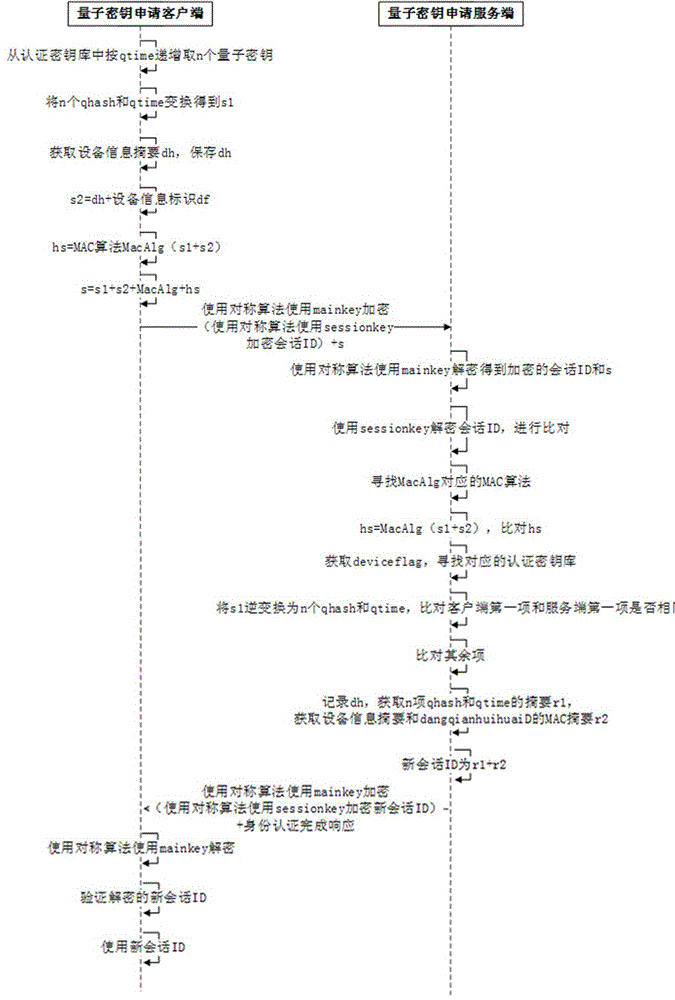
Identity authentication method during quantum secret key application process
ActiveCN105763563AEnsure safetySecurity updateKey distribution for secure communicationInformation transmissionVia device
The invention discloses an identity authentication method during a quantum secret key application process. The identity authentication method includes the steps: a quantum network deployment phase, a preparation initial phase, a secret key preparation phase, an identity authentication phase and a secret key application phase. During an abstract extraction process, as the identity authentication method uses a quantum secret key and the quantum secret key is provided with true randomness, the difficulty for performing reverse operation on the abstract can be further reduced and the safety for information transmission can be improved; and at the same time, after accomplishment of one time of session identity authentication, only a device for identity authentication is allowed to apply for a secret key, so that the safety is further improved through verification of the device information, and during the process, a session ID is in continuous changing state and depends on a plurality of factors, so that a large amount of impersonation attack can be timely eliminated through verification of the session ID. For the identity authentication method during a quantum secret key application process, the secret key is applied to the quantum secret key application process to verify the legal identity between two parties for communication, so that verification of the legal identity of the opposite side between the two parties for communication can be realized and the required data for verification has absolute safety during the transmission process in the network.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
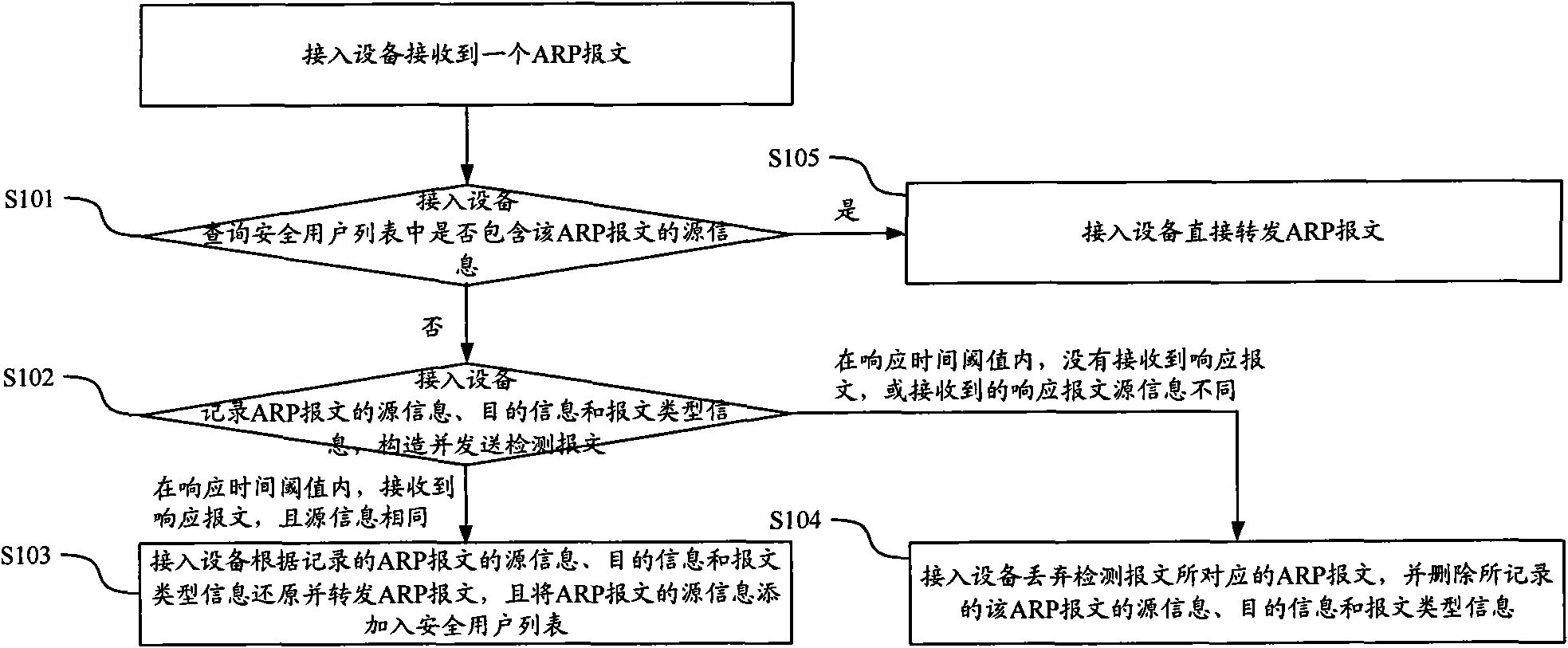
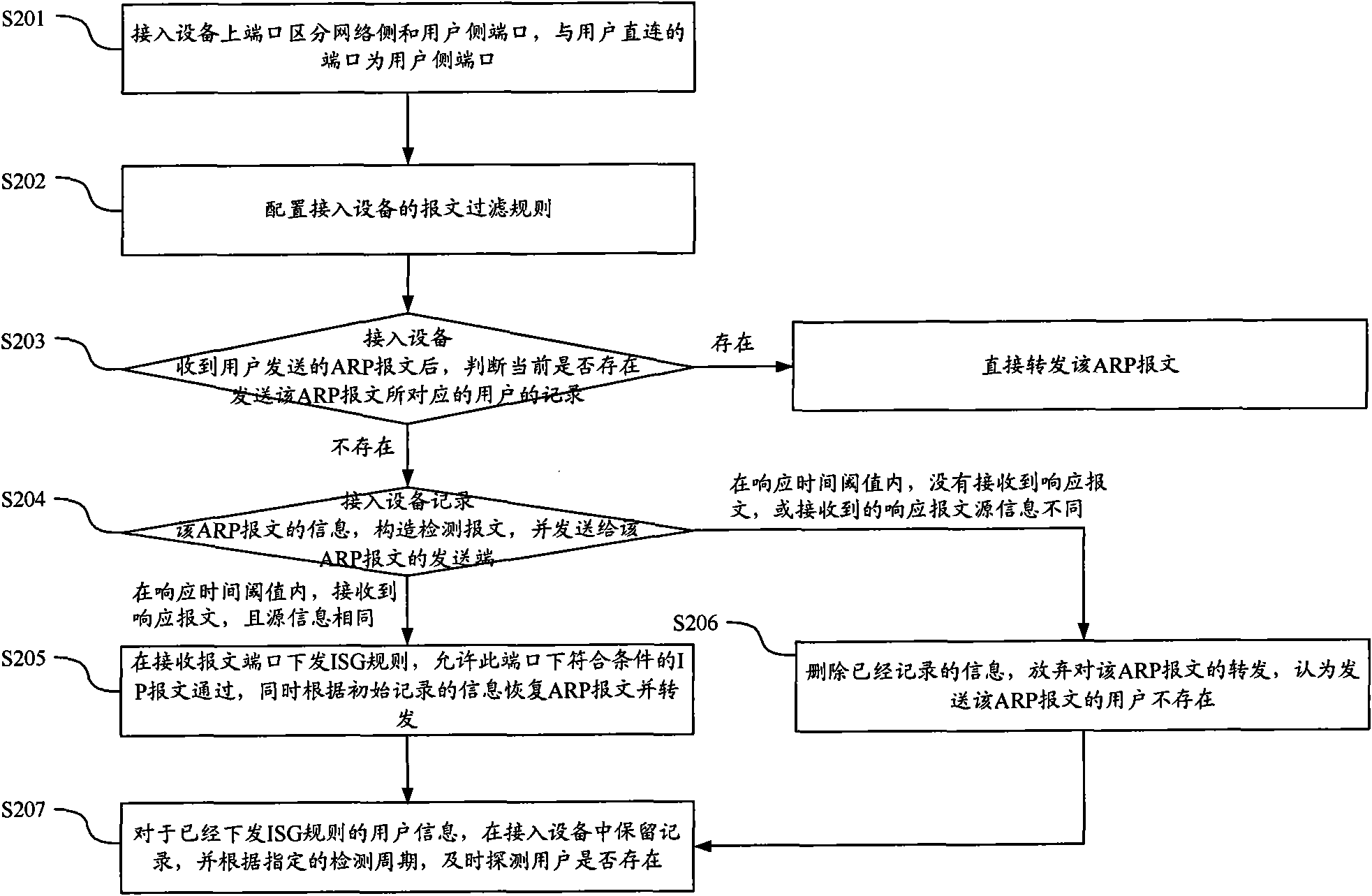
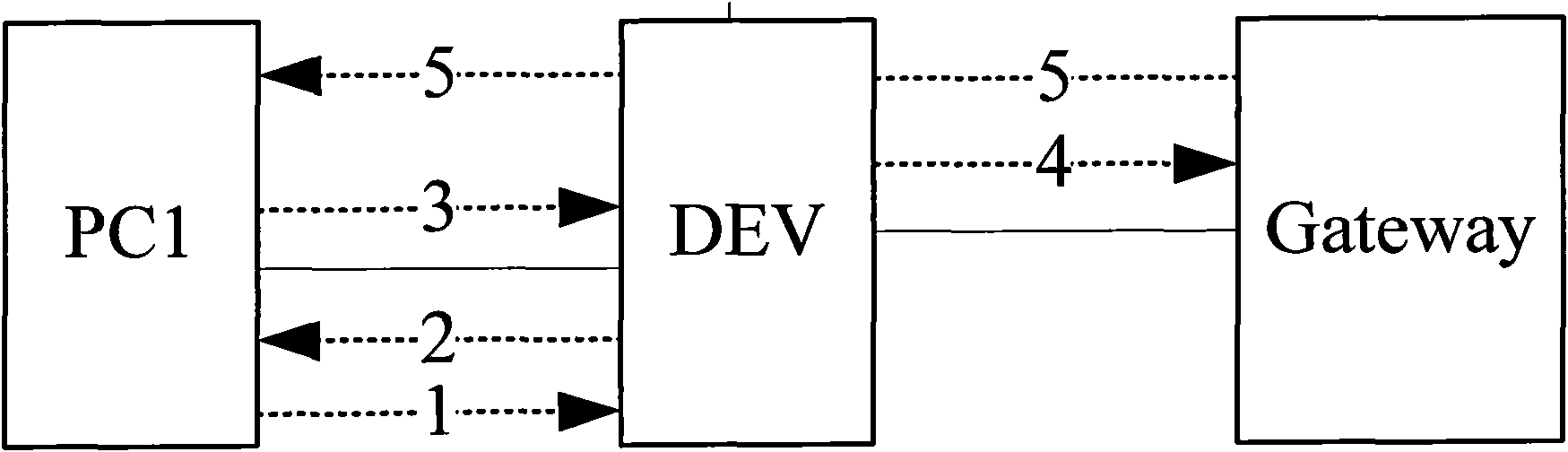
Method and device for verifying message safety
ActiveCN101820396AVerify legitimacyAvoid aggressive behaviorData switching networksComputer securityComputer science
The invention discloses a method and a device for verifying message safety. By using the technical scheme of the invention, simple user validation judgment can be carried out on an access device to effectively verify the user validation at a position closest to a user, thereby preventing the attack of a message with a user-forged IP on an uplink network at an end point.
Owner:NEW H3C TECH CO LTD
Application cloud safety certification method based on third-party service
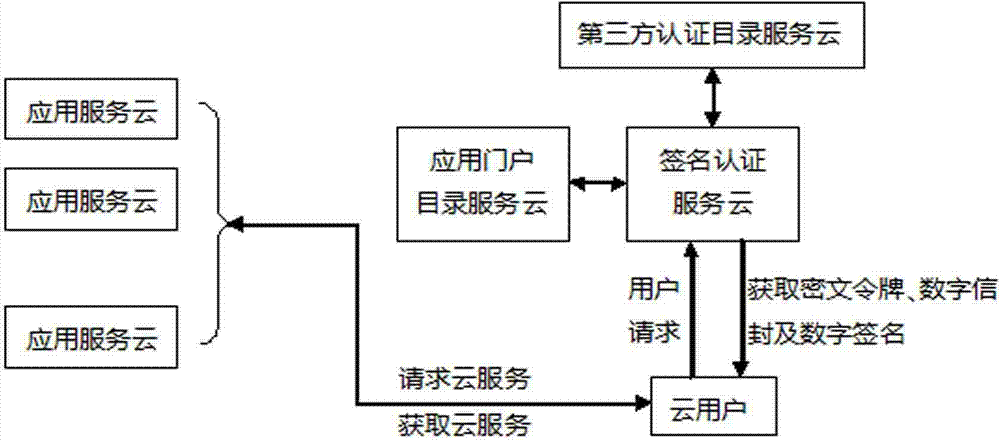
InactiveCN103490899AVerify authenticityVerify legitimacyUser identity/authority verificationThird partyInformation transmission
The invention provides an application cloud safety certification method based on a third-party service. The application cloud safety certification method based on the third-party service specifically comprises the steps that (1) a cloud user submits service demand information to a signature certification service cloud; (2) the signature certification service cloud receives the service demand information of the cloud user, and verifies validity of a certificate of the cloud user according to a third-party catalogue certification service cloud, carries out sign and issue on a ciphertext user login token and a digital envelope through an application portal catalogue service cloud, carries out certification service sign on the ciphertext user login token signed and issued through the application portal catalogue service cloud and the digital envelope signed and issued through the application portal catalogue service cloud, and sends the ciphertext user login token and the digital envelope back to the cloud user; (3) the cloud user carries out user sign on the obtained ciphertext user login token, the digital envelope and the certification service sign information, and submits the ciphertext user login token, the digital envelope and the certification service sign information to an application service to demand for the corresponding service; (4) the application service provides the corresponding service for the cloud user after being verified. Compared with the prior art, the application cloud safety certification method based on the third-party service ensures authenticity and non-repudiation of information sources, and improves safety of the process of information transmission.
Owner:INSPUR QILU SOFTWARE IND
An identity identification method for digital TV broadcast signal
ActiveCN101193266AConvenient and quick mapping relationshipVerify legitimacyPulse modulation television signal transmissionGHz frequency transmissionComputer hardwareTime information
The invention discloses a method of personal identification of digital TV broadcasting signal, which applies part or all of program content, time information and channel identification information of digital TV to generate personal identification code of a broadcasting TV signal on a transmission front end of the digital TV broadcasting signal, then the personal identification code of the broadcasting TV signal is placed in a self-defined data code flow which meets the standard of digital TV code flow and the self-defined data code flow reuses the transmission together with the former digital TV transmission flow; the illegal signal can be identified effectively through judging the legitimacy, effectiveness and integrity of the received content by selecting and detecting the personal identification code of the digital TV signal on a transmission receiving end of the digital TV broadcasting signal. Each part of information of personal identification code provided by the invention has a uniformed simple block structure, and the receiving end can carry out the analysis conveniently. The invention can reasonably choose the corresponding signature information to generate the personal identification code according to different safety protection requirements, thus realizing the higher performance cost ratio on the premise of guaranteeing the system requirements.
Owner:ACAD OF BROADCASTING SCI SARFT
Method and system for realizing smart card application and deployment
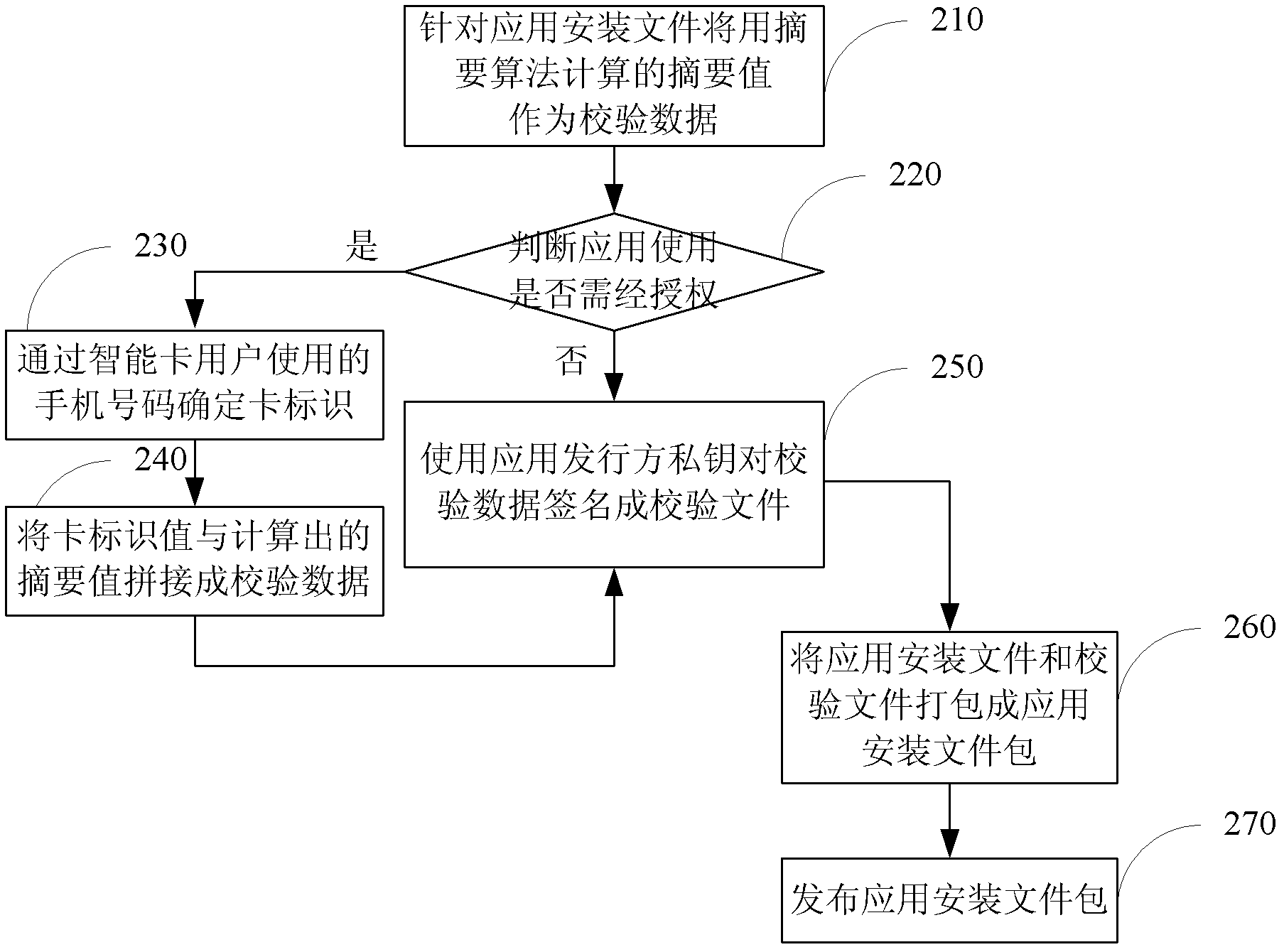
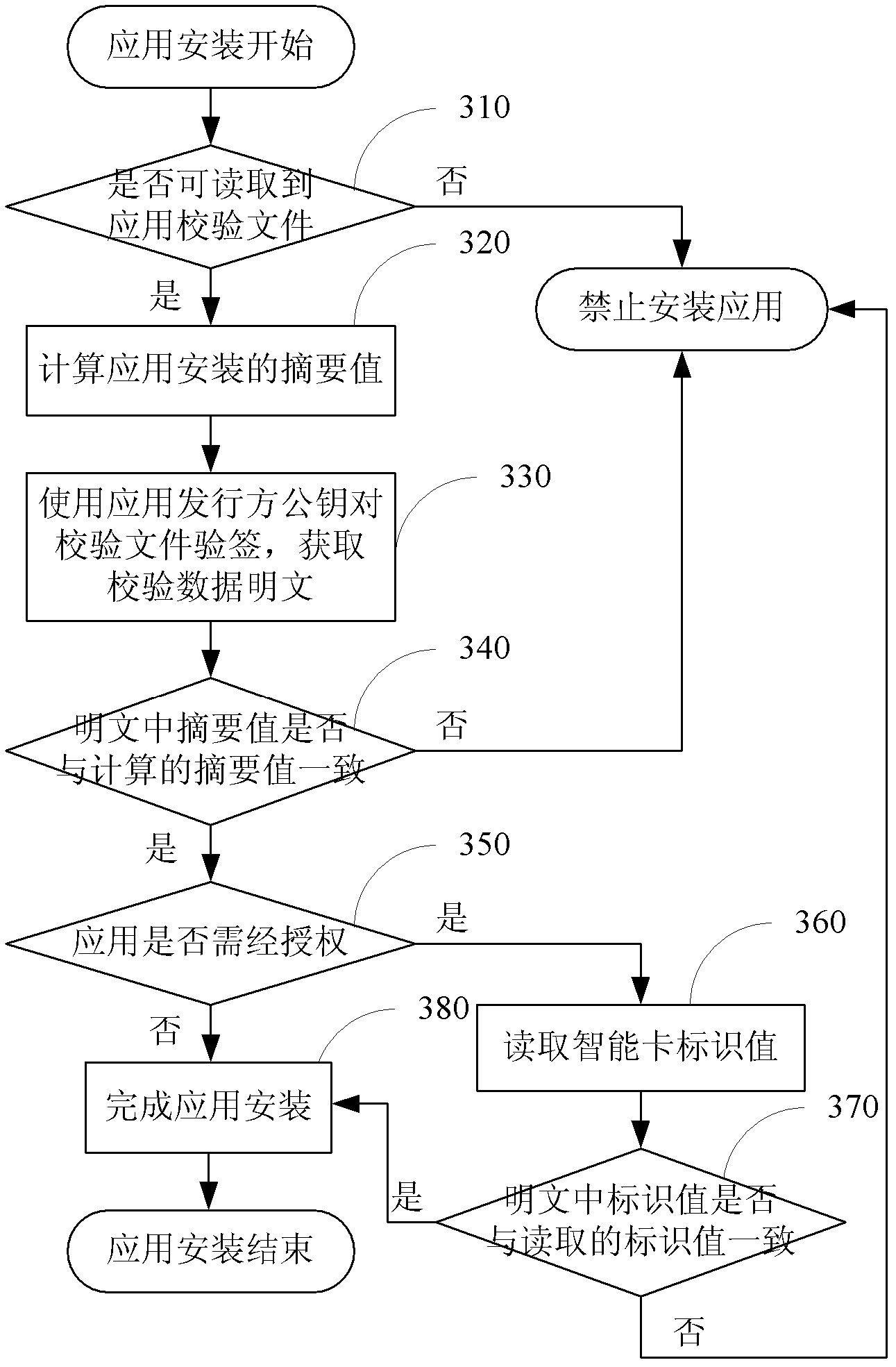
InactiveCN102663292AVerify integrityProtection of legitimate interestsUser identity/authority verificationComputer security arrangementsPlaintextSmart card
The invention discloses a method and a system for realizing smart card application and deployment, wherein the method comprises that application installation documents and checking documents are packed as an application installation document wrap to be published when application is published. When the application is installed, if the application installation document wrap is checked out without a checking document wrap, or the calculated abstract value is not consistent with the abstract value of the checking data plaintext decrypted from the checking documents, or users which need to be authorized are unauthorized, the application installation must be prohibited, otherwise, the installation is allowed. The method and the system have the advantages of guaranteeing the legitimate interests of application suppliers effectively, prohibiting installation of all the incomplete or tampered application by means of checking the completeness of the application, and supporting the authorized application installation, so that the legitimate interests of the installation suppliers and the authorized users are guaranteed in the meanwhile.
Owner:DATANG MICROELECTRONICS TECH CO LTD
Authentication method, device, authentication center and system
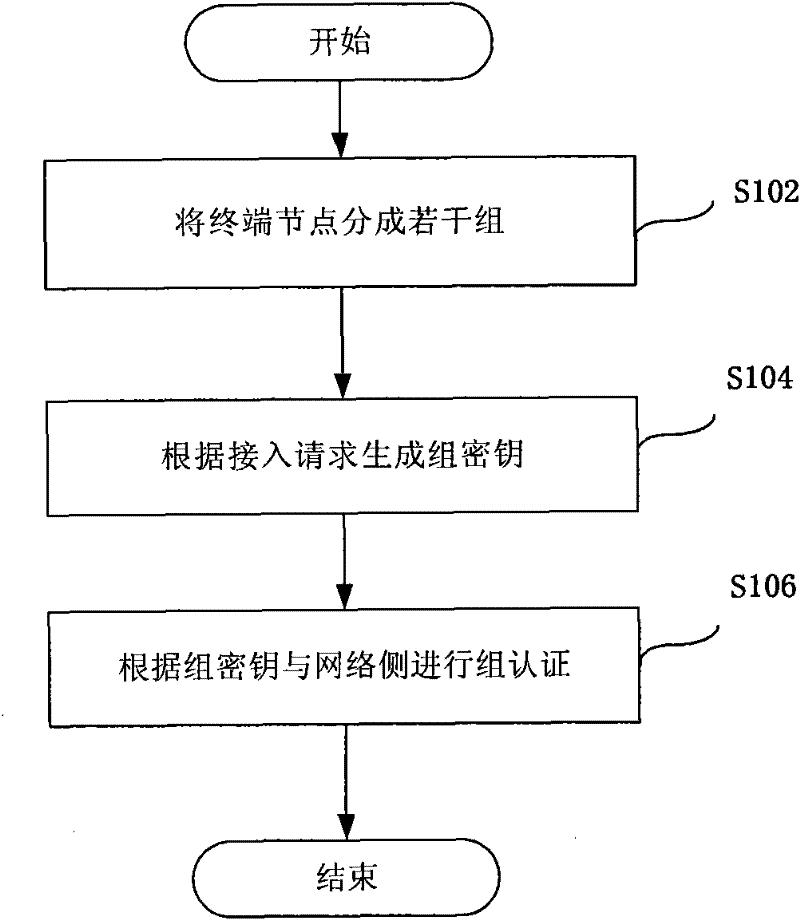
ActiveCN102238146AAddressing technical deficiencies in network loadImprove usabilityKey distribution for secure communicationSecurity arrangementThe InternetComputer terminal
The invention discloses an authentication method, an authentication device, an authentication center and an authentication system. The method comprises the following steps of: receiving at least one access request, and acquiring sub-key information from the access request; generating a group key according to the acquired sub-key information; and performing interaction with a network side to realize group authentication according to the group key. By the authentication method, the authentication device, the authentication center and the authentication system, the problem of network burden caused by one-to-one authentication in the prior art can be solved, and a plurality of nodes can be authenticated at a time so as to reduce seized network resources, the calculation resources of a server and the network burden; applicability to the authentication of terminal nodes in the Internet of things can be achieved; and the availability of services of the Internet of things can be greatly improved.
Owner:CHINA MOBILE COMM GRP CO LTD
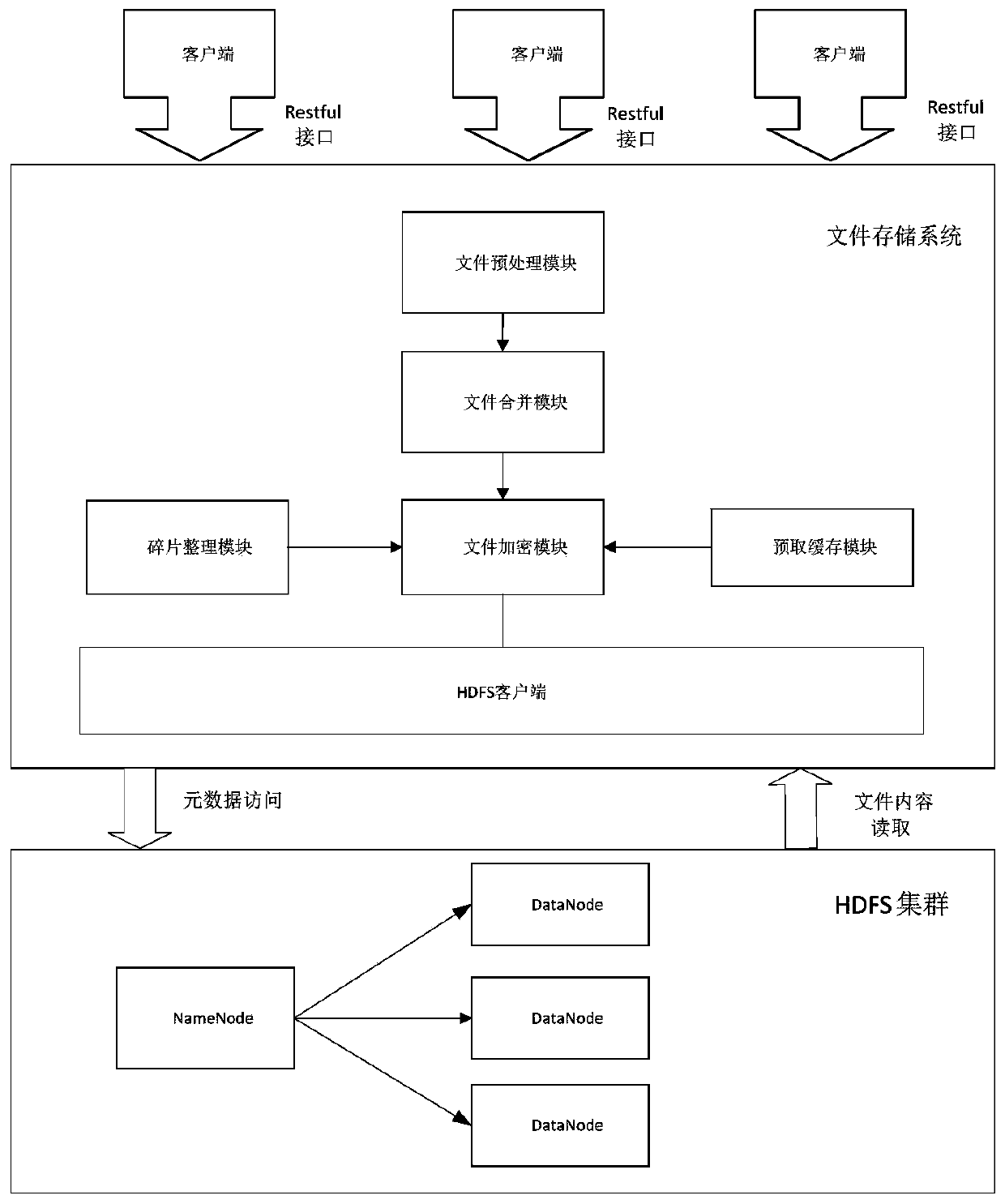
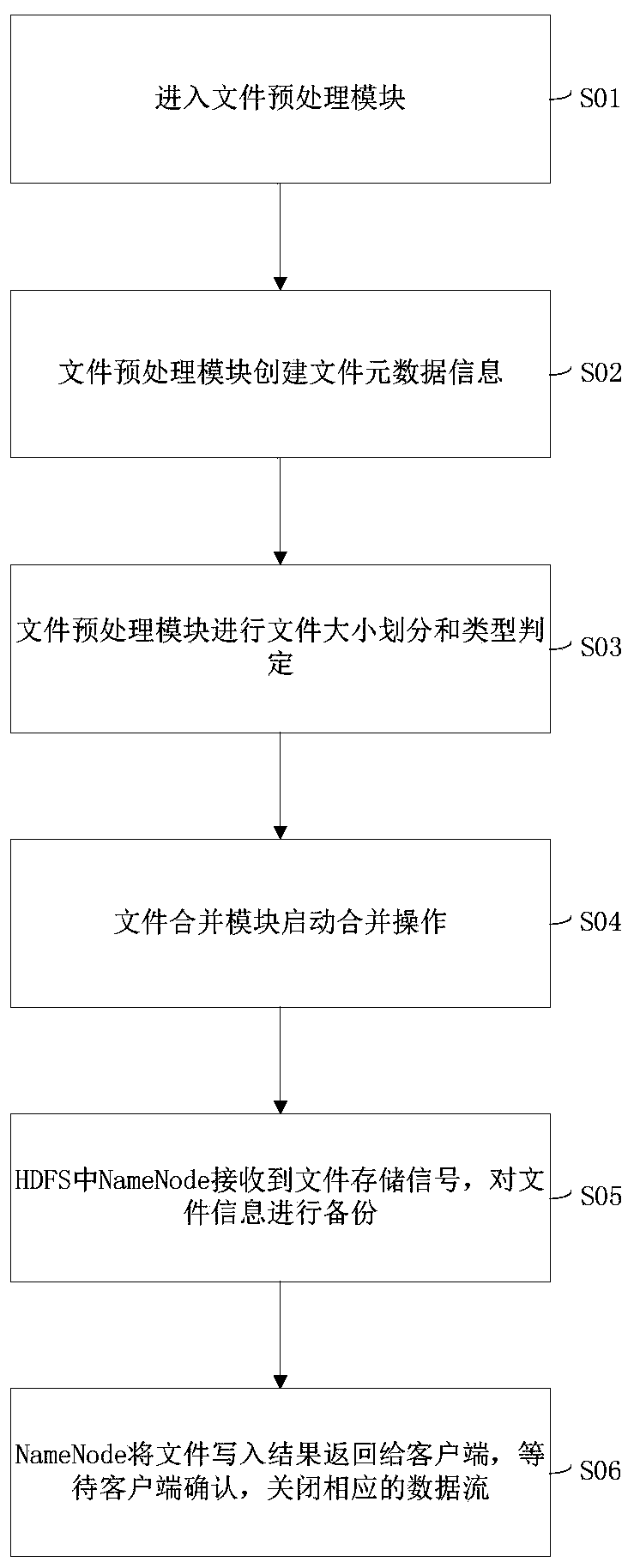
High-performance file storage and management system based on HDFS
PendingCN110647497AImprove retrieval efficiencyAvoid wastingFile system administrationSpecial data processing applicationsShardDistributed File System
The invention provides a high-performance file storage and management system based on an HDFS. A file preprocessing module and a file merging module are provided for overcoming the defect that an HDFS(Hadoop Distributed File System) supports small file storage, a pre-fetching cache module is provided for improving the file reading efficiency, a fragmentation module is provided for improving the overall space utilization rate, and a data encryption module is provided for protecting private files of a user. The invention provides a universal small file merging strategy and an HDFS client optimization scheme, and combines the advantages of an HAR file archiving method and a MapFile method so as to be suitable for any type of files. Specifically, the system optimizes a small file merging strategy and provides a defragmentation mechanism which is easy to update so as to improve the space utilization rate of an HDFS cluster. Meanwhile, a hotspot file strategy based on frequency statistics improves the reading speed of data, and improves the safety of a user account and a private file based on MD5 login encryption and AES file encryption.
Owner:GUANGDONG UNIV OF TECH
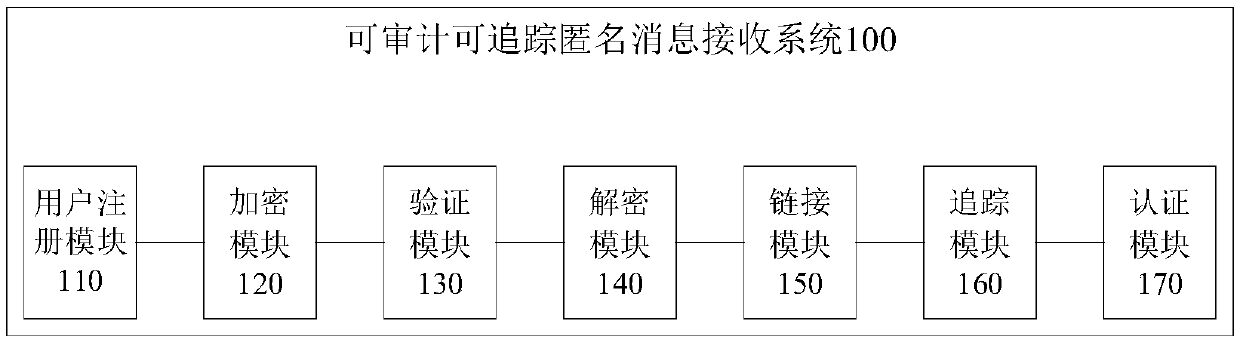
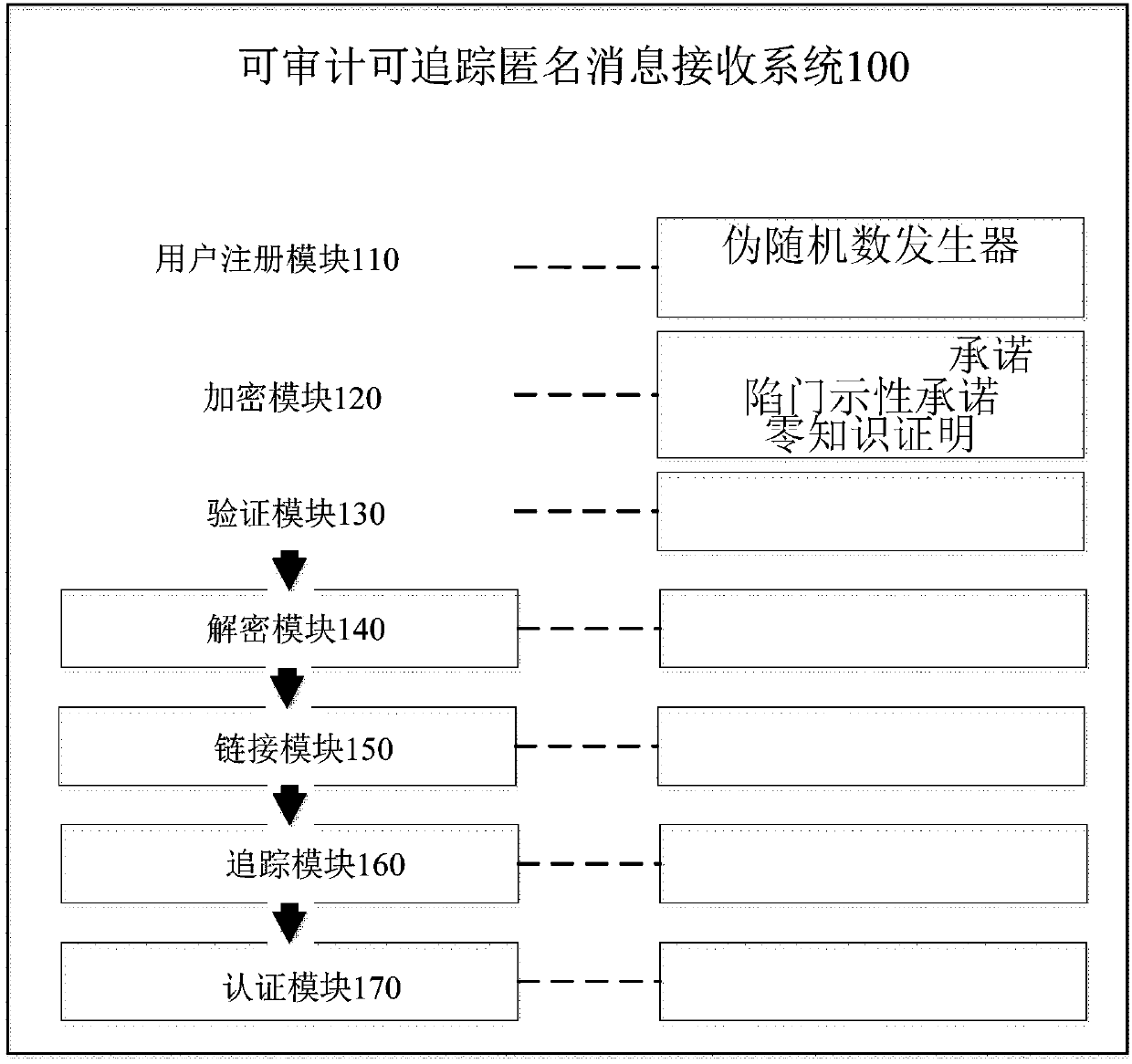
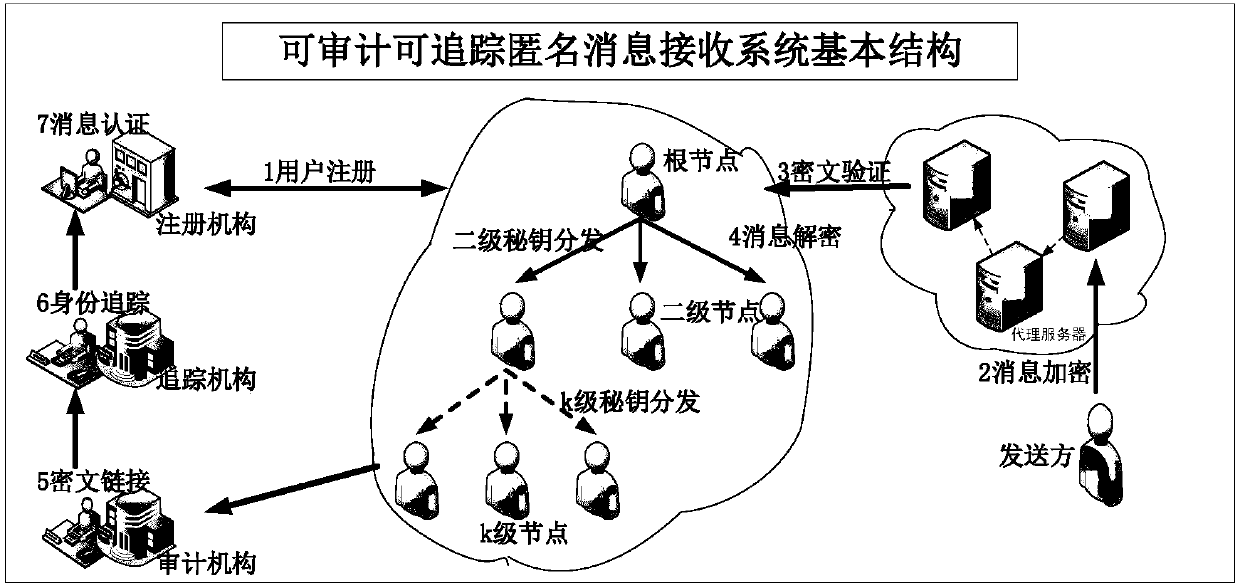
Auditable and traceable anonymous message receiving system and method
ActiveCN107733870AAvoid the problem of too much centralization of powerRealize privacy protectionKey distribution for secure communicationUser identity/authority verificationRegistration authorityCommunications system
The invention discloses an auditable and traceable anonymous message receiving system and method. The auditable and traceable anonymous message receiving system comprises a user registration module used for generating public and private keys and a public key certificate of a user through the interaction between the user and a register in an entity institution; an encryption module used for transmitting messages of the user in a communication system confidentially; a verification module used for verifying the legality of verification ciphertext messages in the communication system; a decryptionmodule used for decrypting ciphertext messages of an anonymous receiver; a link module used for judging whether any two messages are transmitted to the same receiver; a tracking module used for tracking an associated user of an abnormal ciphertext message; and an authentication module used for authenticating message contents received by an abnormal user. The auditable and traceable anonymous message receiving system provided by the invention can discover the malicious behavior of the user without affecting the privacy of the user, and then track the malicious behavior and even open user information, thereby effectively realizing the privacy protection of information sinks in the communication system and supporting the functions of a tracking mechanism for auditing, tracking and authenticating anonymous information sinks.
Owner:HANGZHOU INNOVATION RES INST OF BEIJING UNIV OF AERONAUTICS & ASTRONAUTICS
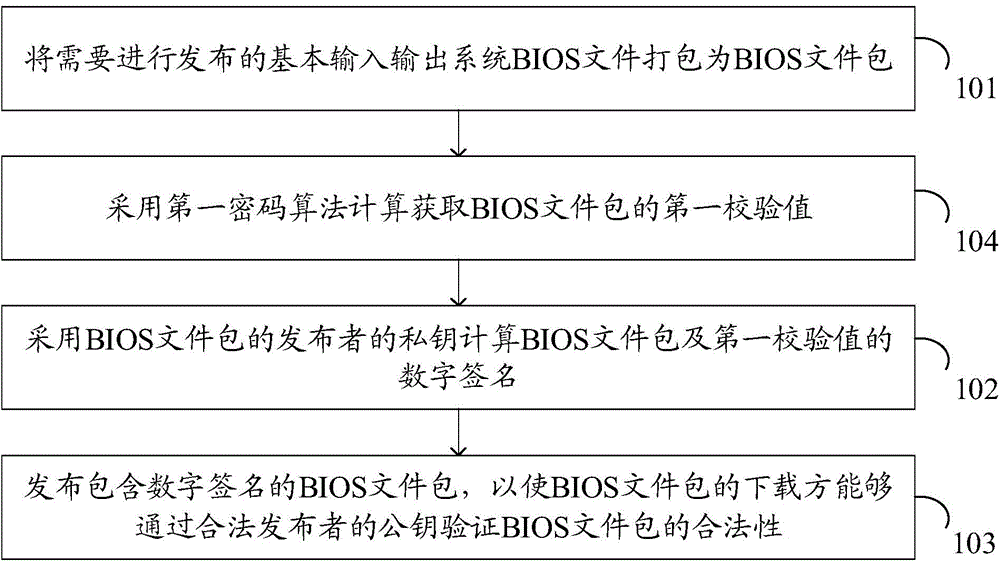
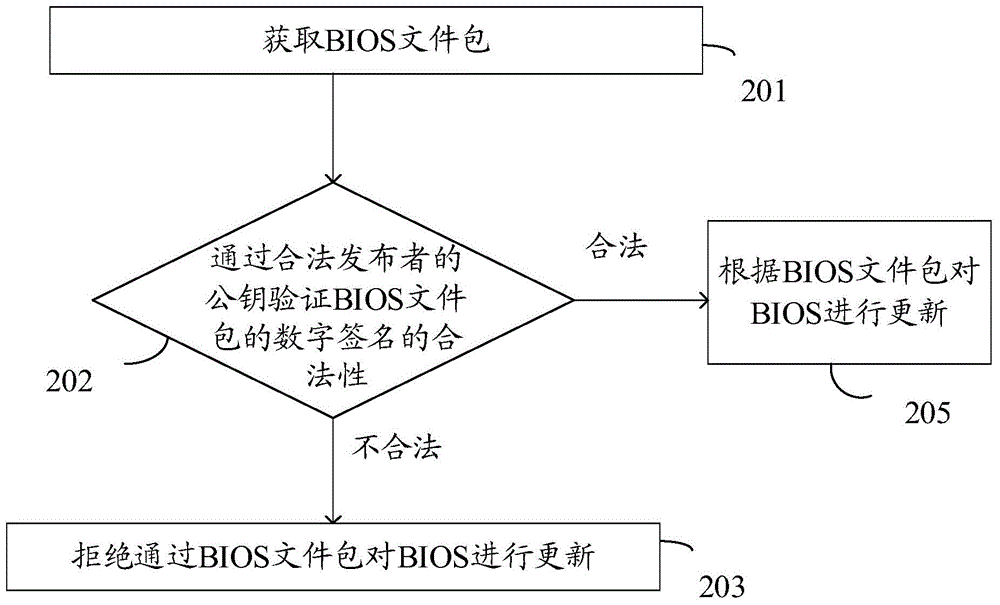
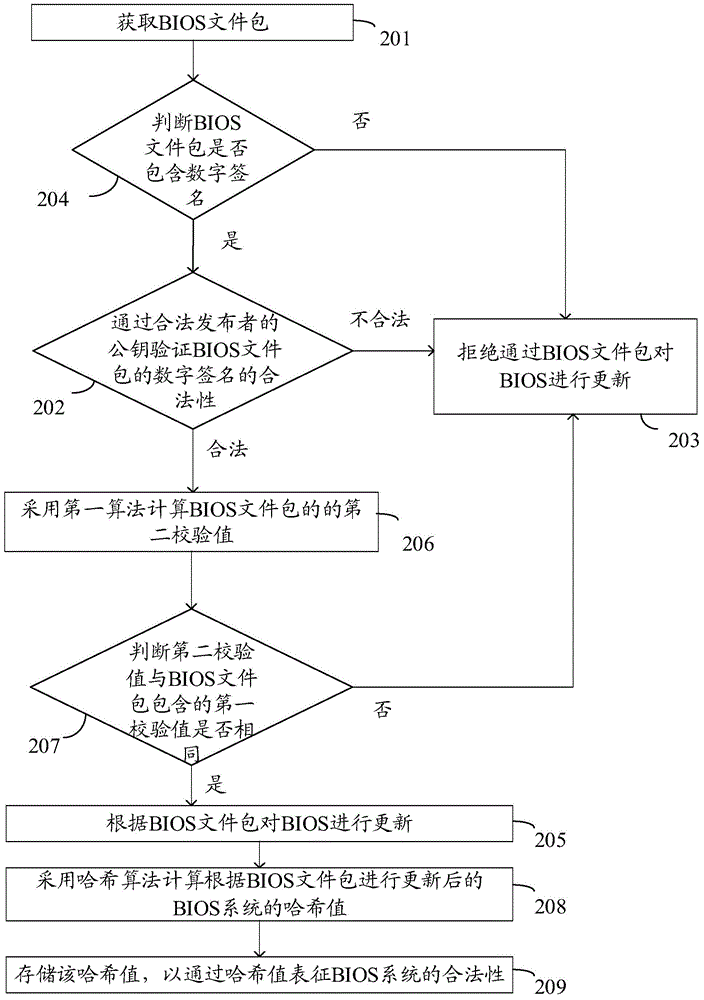
Data processing method and electronic equipment
InactiveCN104915591AImprove securityIrreversibleDigital data authenticationDigital signatureData treatment
The invention discloses a data processing method and electronic equipment. The method is used for solving the technical problem that an existing BIOS updating security authentication mechanism cannot ensure the security of BIOS updating files. The method is applied to the electronic equipment with a BIOS. The method comprises the steps of obtaining a BIOS file package; verifying the legality of a digital signature of the BIOS file package through a public key of a legal publisher; if the verifying result shows that the digital signature of the BIOS file package is illegal, rejecting updating of the BIOS through the BIOS file package.
Owner:LENOVO (BEIJING) LTD
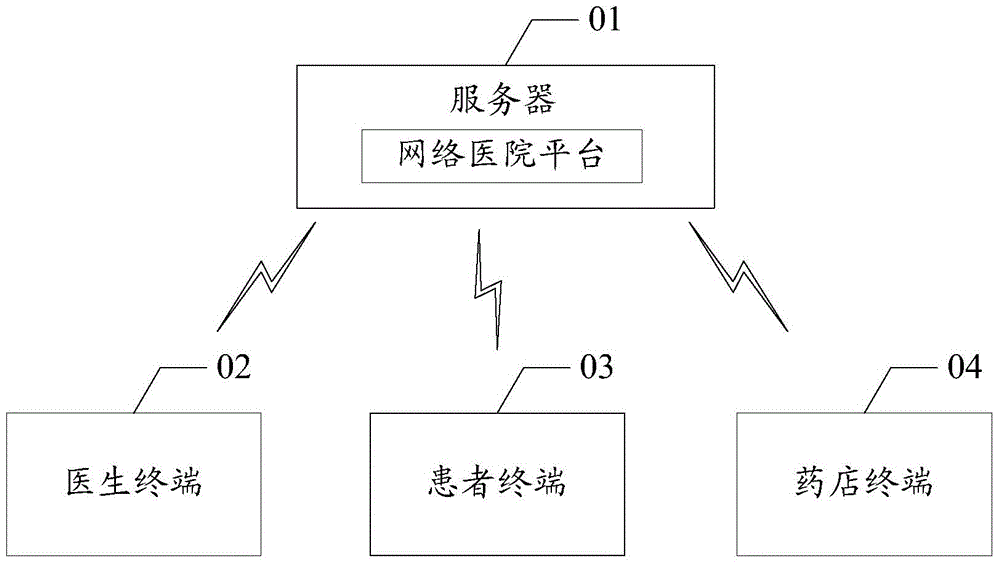
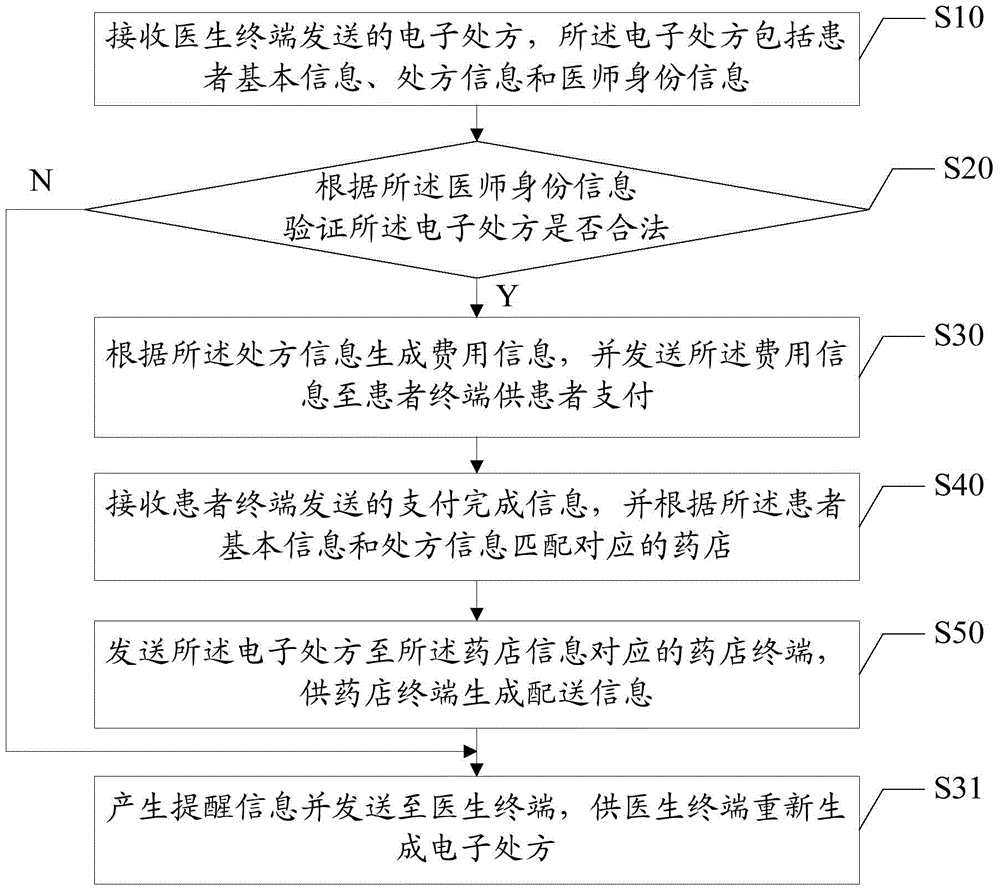
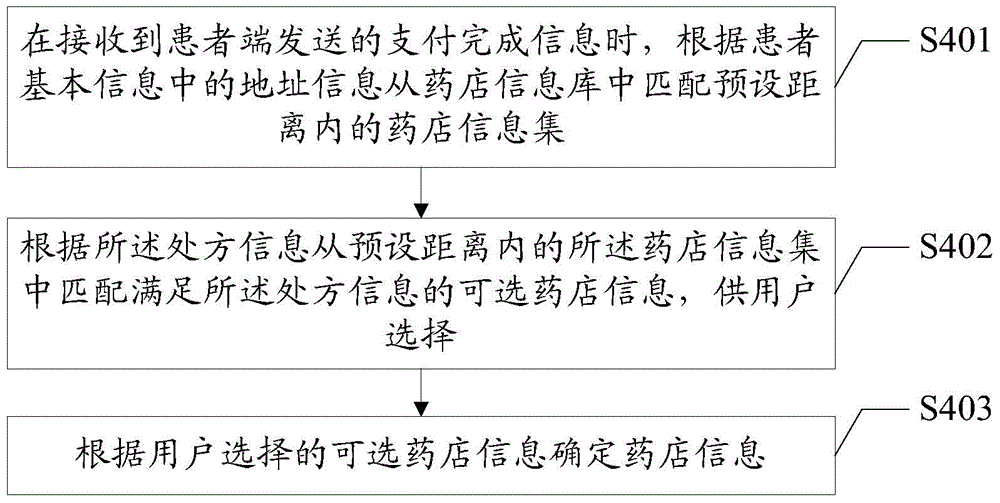
Medicine unified distribution method based on network hospital and network hospital platform
InactiveCN105005956AVerify legitimacyRealize unified deliveryOffice automationTransmissionPaymentDistribution method
The invention discloses a medicine unified distribution method based on a network hospital. According to the method, electronic prescriptions sent by doctor terminals are received via a network hospital platform, after the electronic prescriptions are verified to be legal, cost information is generated according to the prescription information, and when payment accomplishing information sent by patient terminals is received, the electronic prescriptions are sent to pharmacy terminals corresponding to the pharmacy information according to patient basic information and pharmacy information corresponding to matched prescription information. The invention also discloses a network hospital platform. According to the medicine unified distribution method, based on the electronic prescriptions and the network hospital platform, the legitimacy of the electronic prescriptions is verified via the reception of the electronic prescriptions sent by the doctor terminals, the cost information is generated according to the prescription information after verification so that the patient terminals can accomplish the payment, unified pricing is realized at the network hospital platform via the electronic prescriptions, the corresponding pharmacy information is matched after the patients accomplish the payment, and unified distribution of medicine on the network hospital platform according to the condition information of the patients is realized.
Owner:ANYCHECK INFORMATION TECH +3
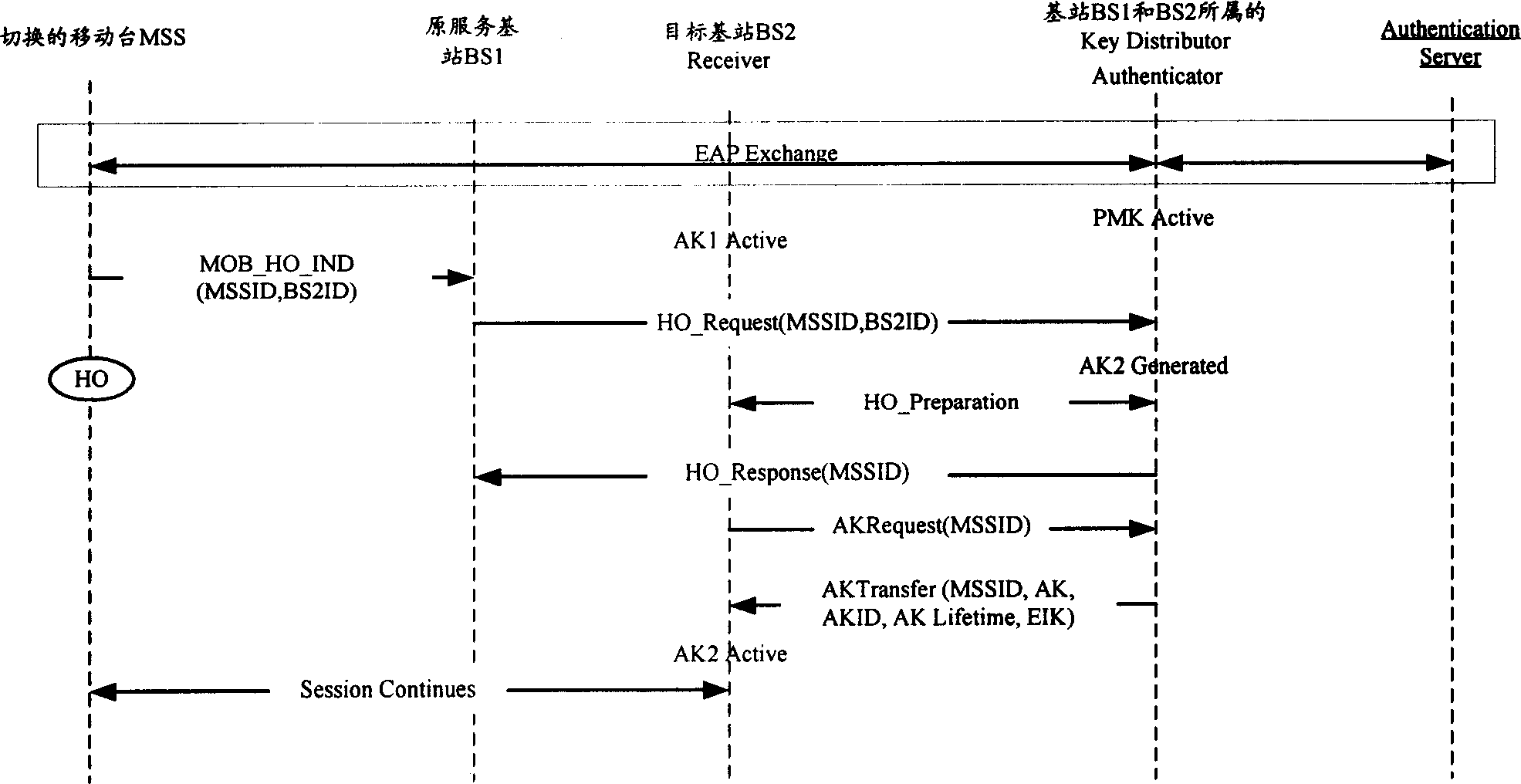
Method for acquring authentication cryptographic key context from object base station
InactiveCN1819698AVerify legitimacyEnsure safetyRadio/inductive link selection arrangementsTransmissionComputer hardwareSecure communication
The invention involves the mobile communication field, a method that the aiming base station gets the context information of the identified-right secret key, to solve the inconsistent problem in the relating sequence number of the aiming base station identified-right secret key context and the mobile terminal in the existing technology. The method including: the identified righter / the provider of the secret key create the context information of the identified-right secret key when the mobile terminal request cut, the context information includes the current sequence number of the identified-right secret key, the sequence number of the upward managing information authentication code and / or the current sequence number of the downward managing information authentication code; the identified righter / the provider of the secret key send the identified-right secret key and the relating sequence number to the aiming base station when the aiming base station that the mobile terminal ready to cut request the identified-right secret key. Thus maintained the continuity of the sequence number information, ensure the secure communication with the mobile terminal, and prevent effectively the possibly appearing replay attack, ensure the conversation security after restore.
Owner:HUAWEI TECH CO LTD
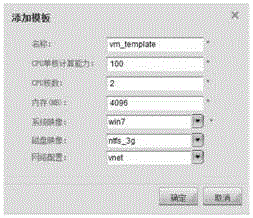
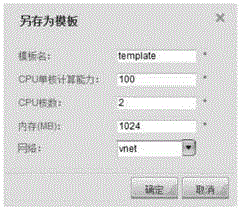
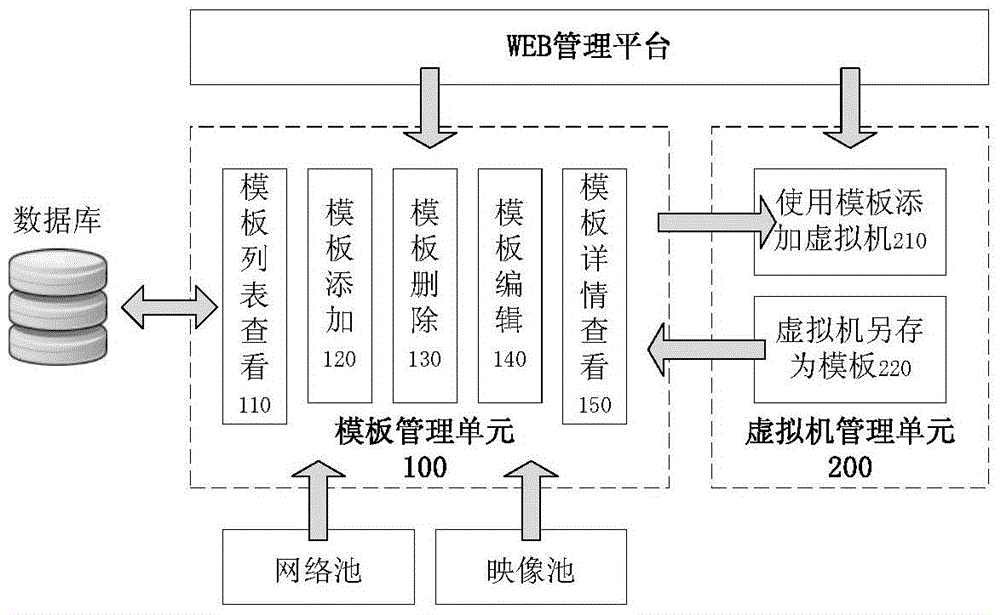
Cloud computing based virtual machine template management system and method
InactiveCN105740047AVerify legitimacyEasy to manageSoftware simulation/interpretation/emulationManagement systemCloud computing
The invention discloses a virtual machine template management system and method based on cloud computing. Through the system and method provided by the present invention, the operator can add, delete, edit, check the template list, check the details of the template, can use the template to quickly add a virtual machine, and can also save the virtual machine as a template, which effectively solves the virtual machine template management problem, which facilitates the management of the virtual machine by the user.
Owner:CHINA STANDARD SOFTWARE
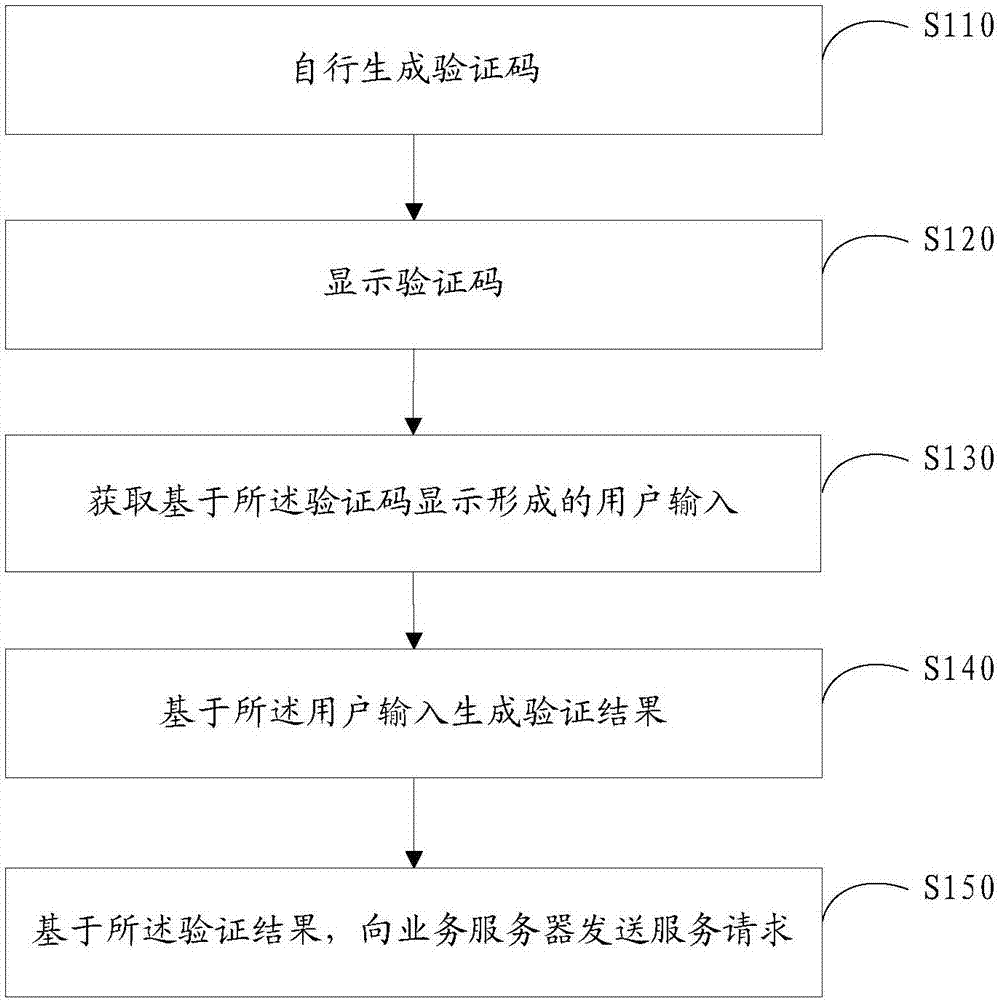
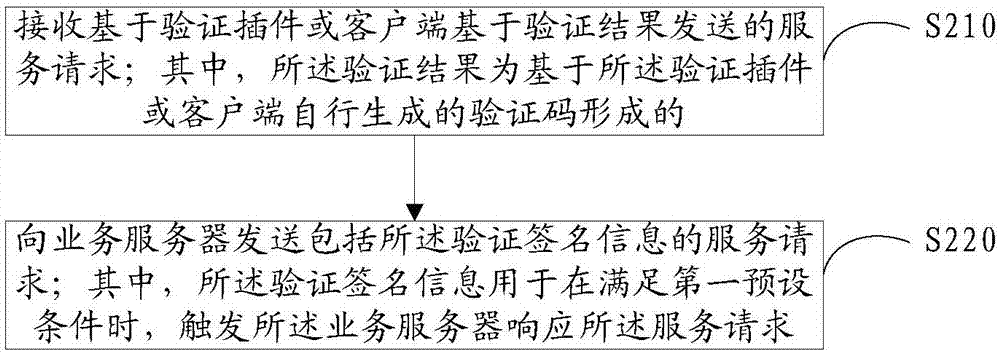
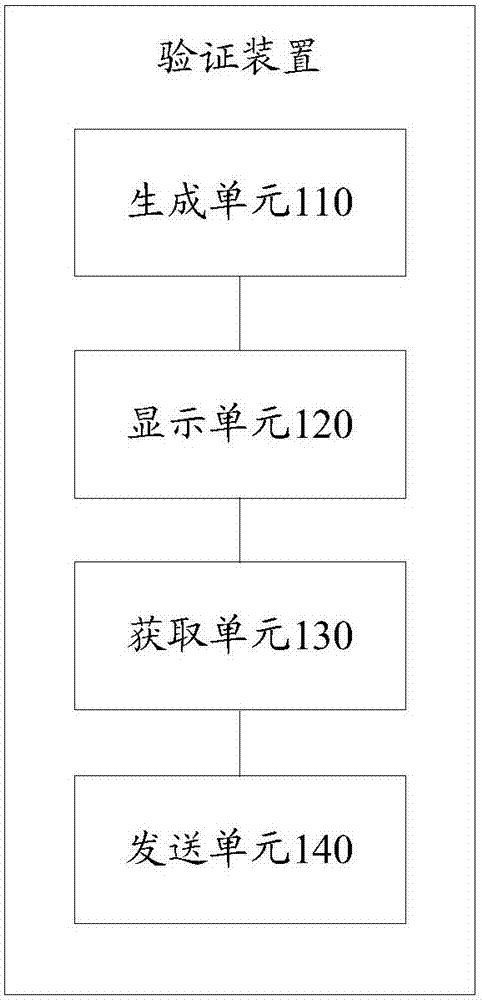
Verification method and device
ActiveCN107979467AVerify legitimacyReduce latencyUser identity/authority verificationDigital data authenticationTime delaysOperating system
Embodiments of the invention disclose a verification method and device. The method is applied to a verification plugin or a client. The method comprises the steps of generating a verification code automatically; displaying the verification code; acquiring a user input formed based on display of the verification code; generating a verification result based on the user input; and based on the verification result, sending a service request to a service server. Through adoption of the method, the verification code can be generated automatically and verified offline without using an authenticationserver, so that cases that verification time delay is long or verification cannot be performed caused by large load or faults of the authentication server are prevented.
Owner:CHINA MOBILE COMM LTD RES INST +1
Access method, related device and access apparatus
InactiveCN105657706AVerify legitimacyImprove securityAssess restrictionSecurity arrangementAccess methodWifi network
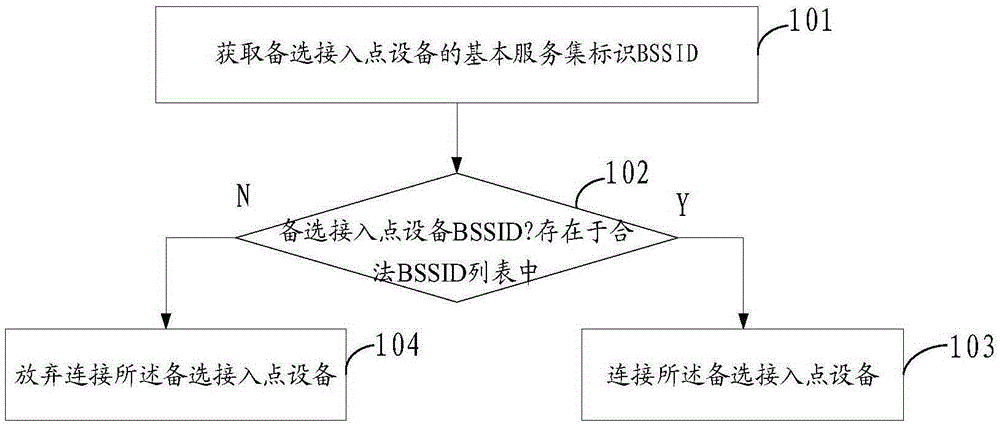
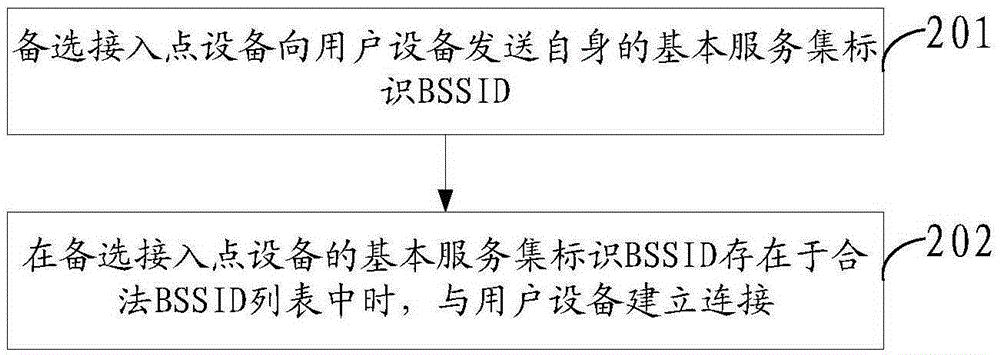
The invention discloses an access method, a related device and an access apparatus. The access method comprises the following steps: obtaining a basic service set identifier BSSID of an alternative access point device; and judging whether the basic service set identifier BSSID of the alternative access point device exists in a basic service set identifier BSSID list, and if so, connecting the alternative access point device. Since the basic service set identifiers BSSID of all legal alternative access point devices having the same basic service set identifier BSSID are pre-stored in the basic service set identifier BSSID list, before establishing a connection with the alternative access point device, whether the basic service set identifier BSSID of the alternative access point device exists in the legal basic service set identifier BSSID list is judged to verify the legality of the alternative access point device, when surfing the internet via a public WIFI network, a user can be guaranteed to access the legal alternative access point device, and thus the networking security via the public WIFI network is improved.
Owner:DONGGUAN COOLPAD SOFTWARE TECH
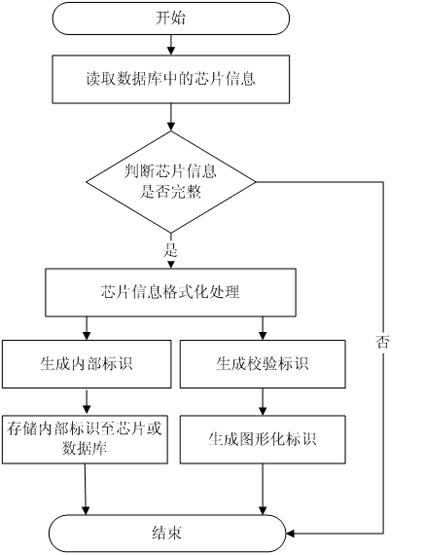
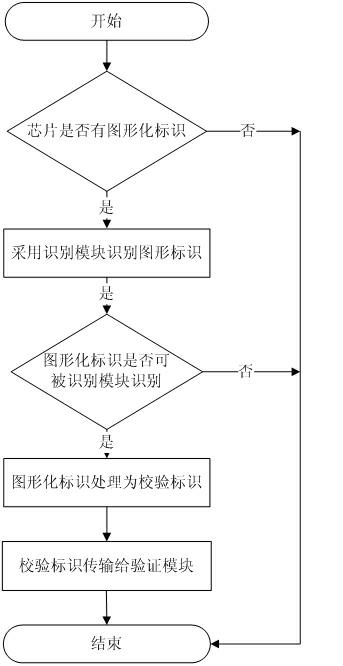
Method and system for validating chip validity by utilizing graphical chip
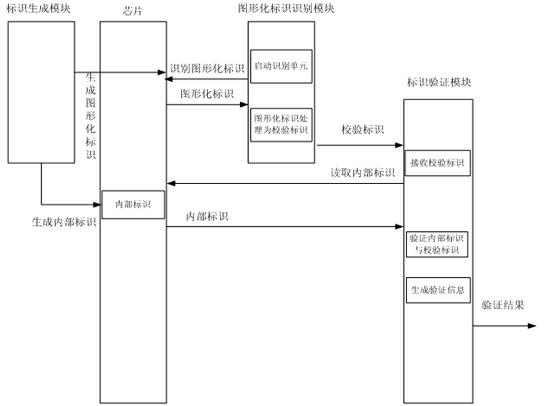
ActiveCN102375941AFacilitate automatic identification and managementVerify legitimacyInternal/peripheral component protectionComputer securityApplication software
The invention relates to a system and method for validating the chip validity by utilizing a graphical chip. The system comprises an identifier generation module, a graphical identifier identification module and an identifier validation module. The method for validating the chip validity comprises three basic work flows, namely a graphical identifier generation flow, a graphical identifier identification flow and a graphical identifier validation flow. When validating the chip validity, a user uses the graphical identifier on an identification chip of the graphical identifier identification module, and the graphical identifier is reduced into a verification identifier, the verification identifier is transmitted to the identifier validation module, the identifier validation module compares the verification identifier with an internal identifier which is saved in a chip, the graphical identifier of the chip is falsified if the validation identifier is not in accordance with the internal identifier, and the user can determine whether the chip is counterfeited or illegal or not and further forbids the user to download an application program; and the chip is legal if the validation identifier is in accordance with the internal identifier.
Owner:NATIONZ TECH INC
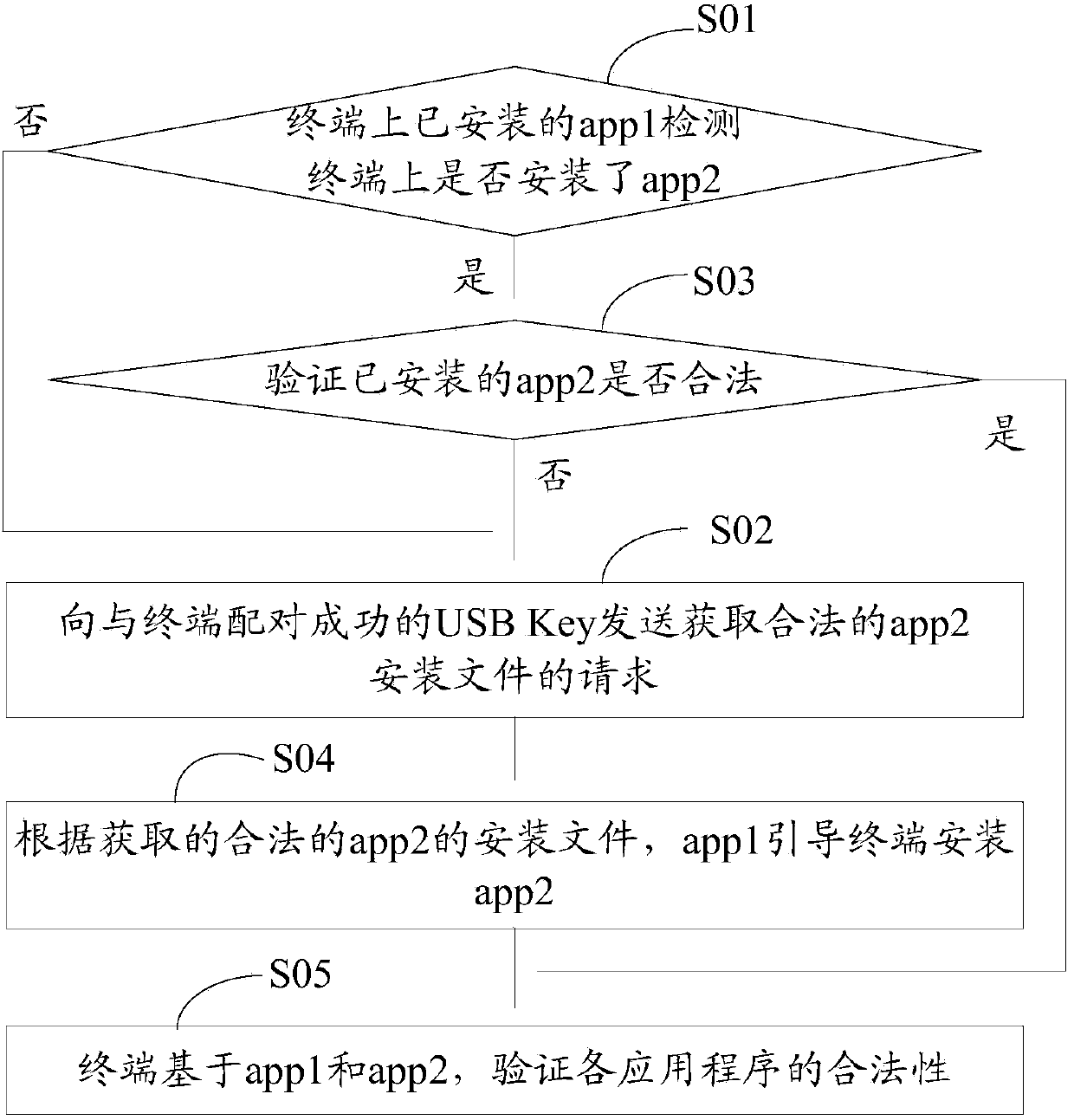
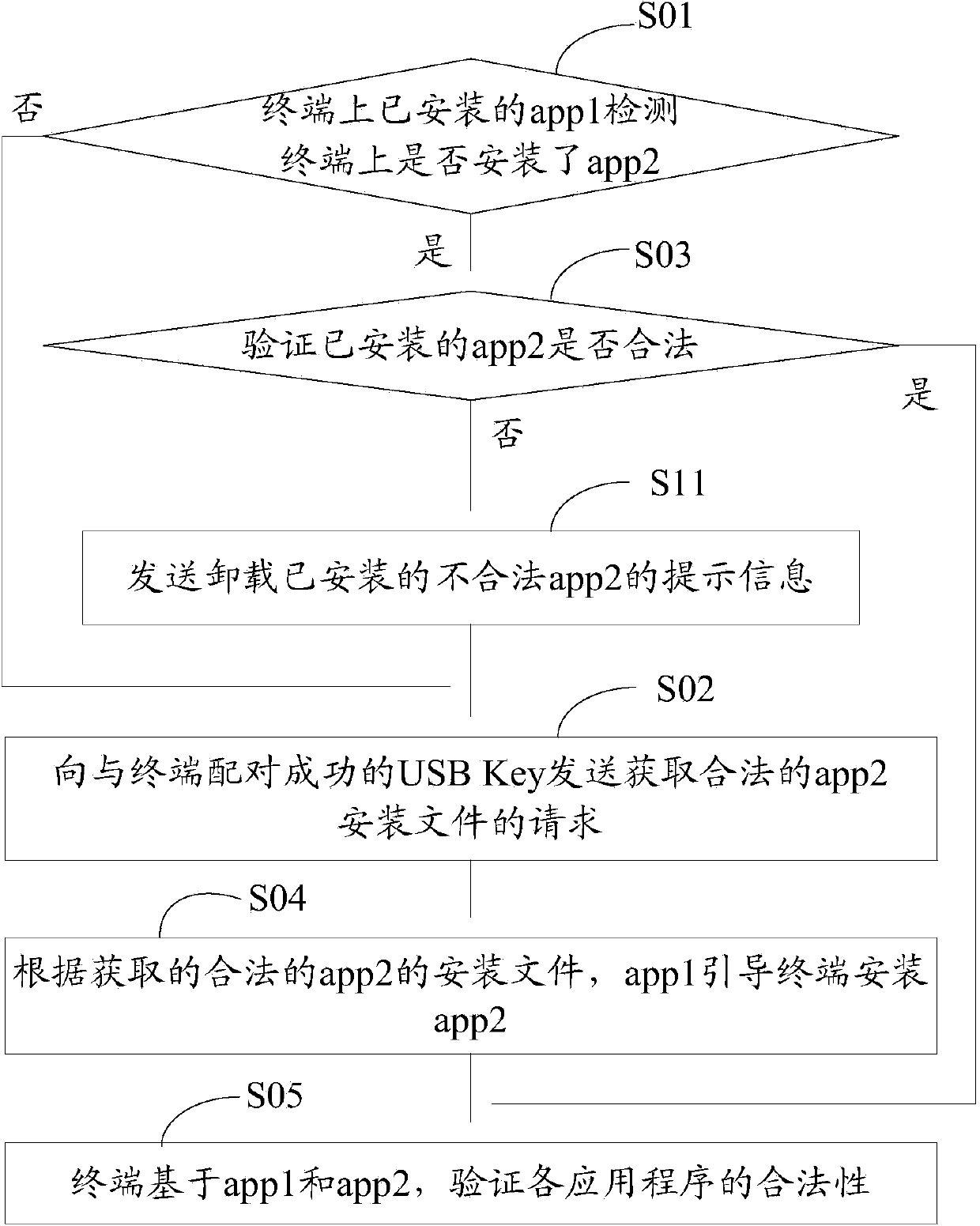
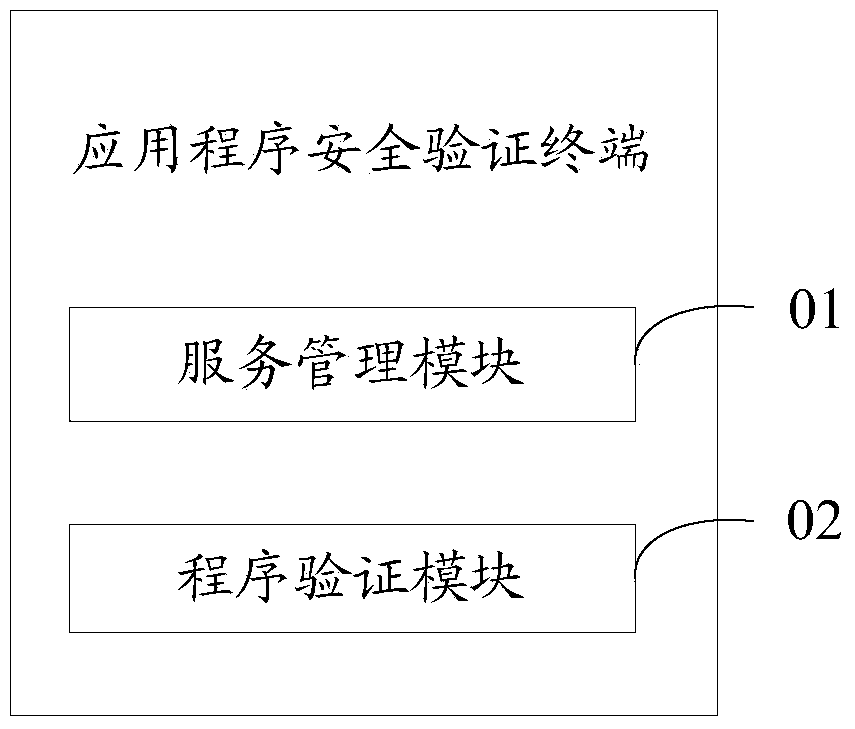
Application program security verification method and terminal
ActiveCN103473498AVerify legitimacyVerify securityDigital data authenticationTransmissionValidation methodsProgram security
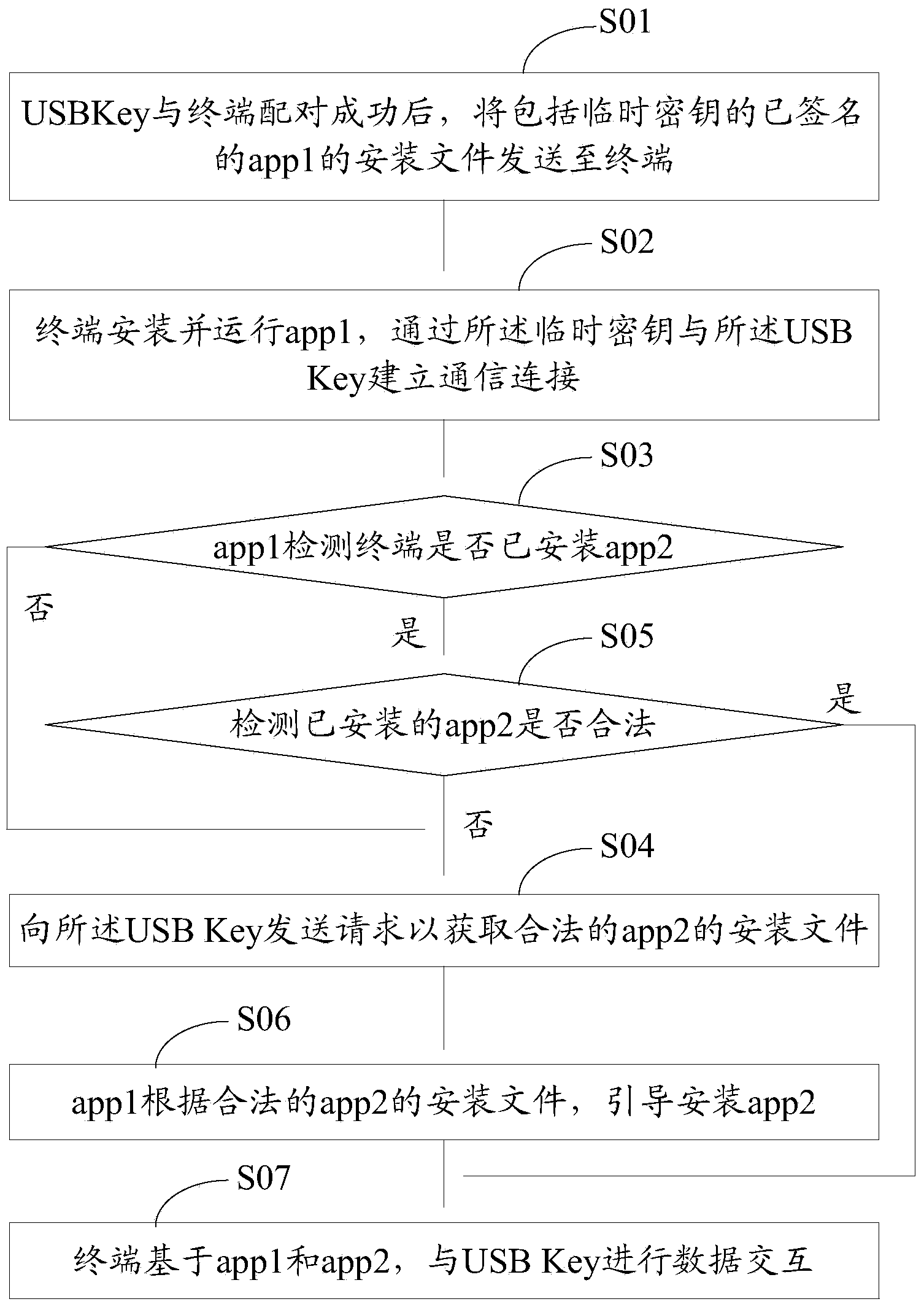
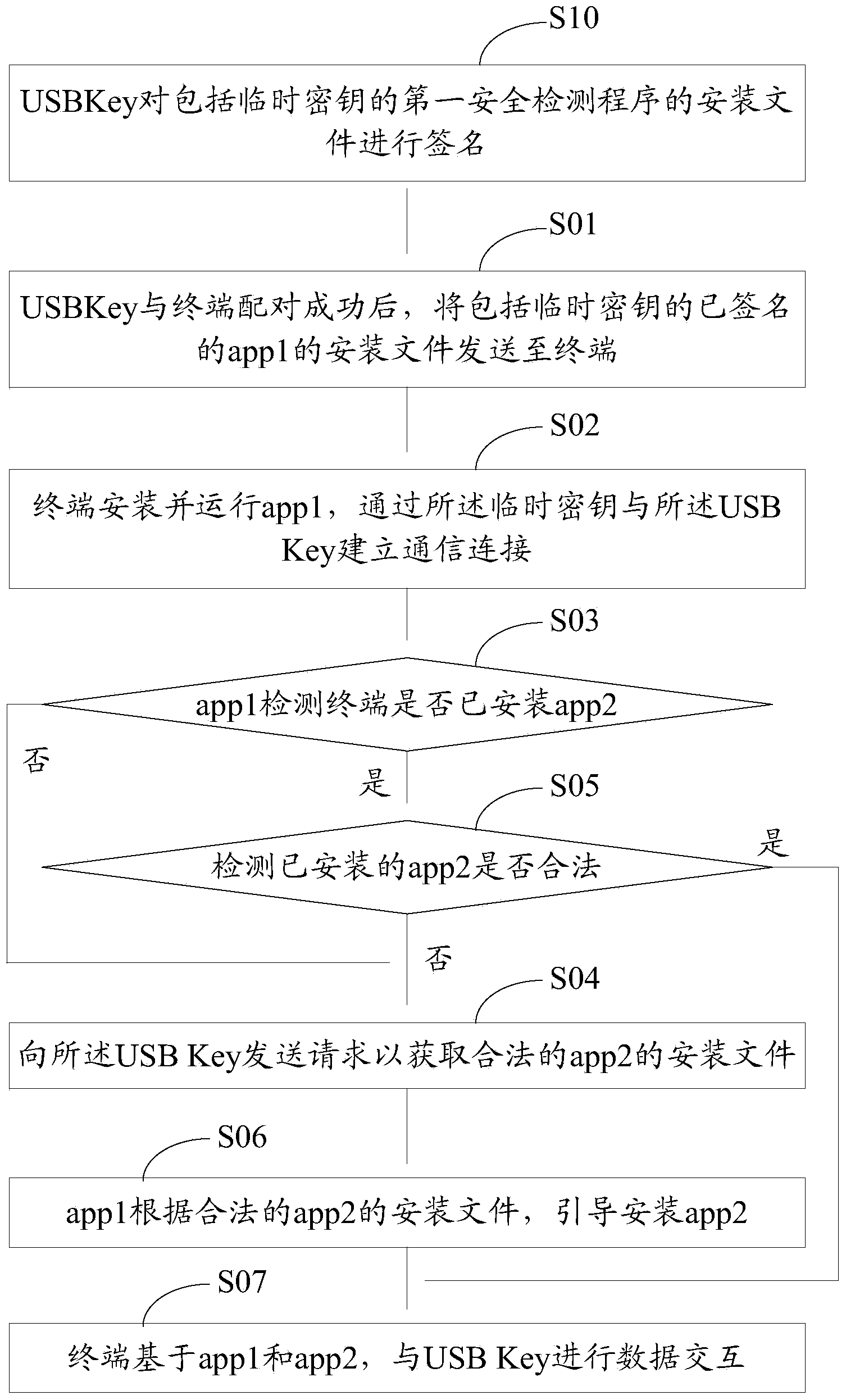
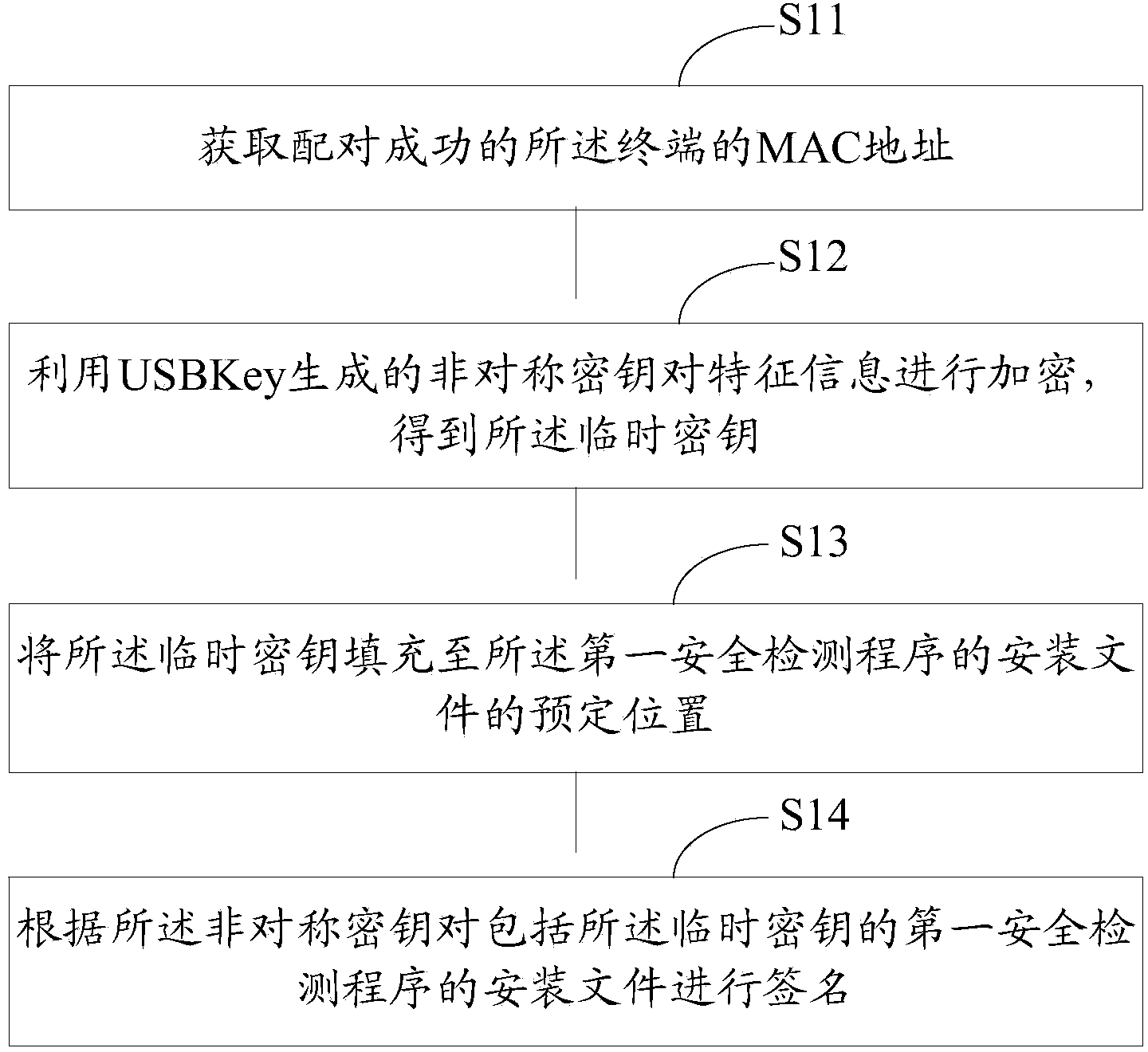
The invention discloses an application program security verification method and a terminal. A reliable application program, namely a service management program is provided by a USB (universal serial bus) Key and used for verifying other application programs such as a security detection program on the terminal, so that validity and security of the application programs on the terminal are effectively verified, and the problem of security risks due to incapability of verifying validity of traditional application program download and installation is solved. The method has the advantages that security of the application programs on the terminal is improved, and further, security of personal information of users is ensured.
Owner:北京明华联盟科技有限公司
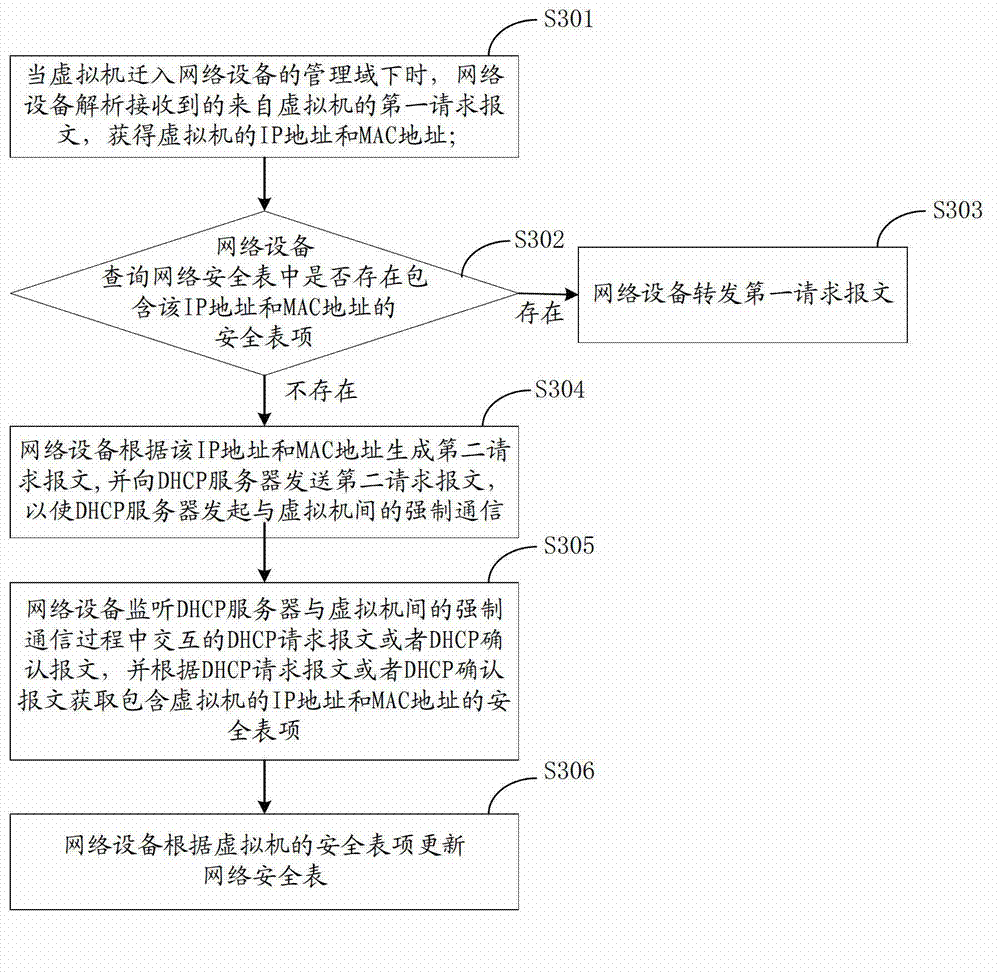
Method for updating network security table and network device and dynamic host configuration protocol (DHCP) server
InactiveCN103095722AGuaranteed reliabilityEnsure network securityTransmissionNetwork security policyMedia access control
The invention discloses a method for updating network security table, a network device and a dynamic host configuration protocol (DHCP) server. When a virtual machine moves in a management domain of a network device, the network device analyses a first received request message from the virtual machine, an internet protocol (IP) address and a medium access control (MAC) address of the virtual machine are obtained, when a security table item including the IP address and the MAC address doesn't exist in a network security table of the network device, the network device sends a second request message generated according to the IP address and the MAC address to the DHCP server, so that the DHCP server is enabled to launch mandatory communication between the DHCP server and the virtual machine, the network device monitors an interactive message between the DHCP server and the virtual machine to obtain the security table item of the virtual machine, the network security table is updated according to the security table item. Through the above mode, the method for updating network security table, the network device and the DHCP server ensure that the virtual machine can access the network normally when the virtual machine moves in the management domain of the network device, reliability of the network security table is also ensured, and therefore network security is ensured.
Owner:HUAWEI TECH CO LTD
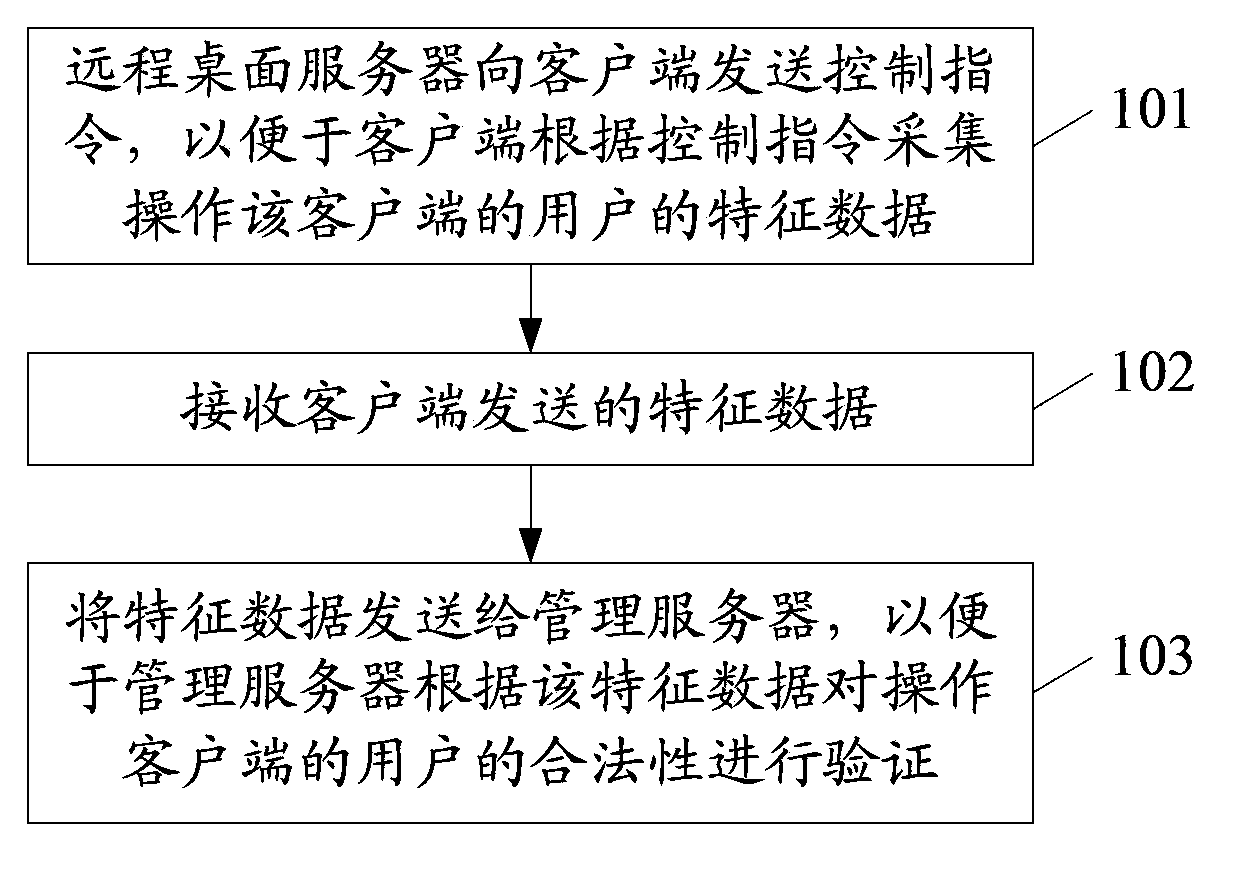
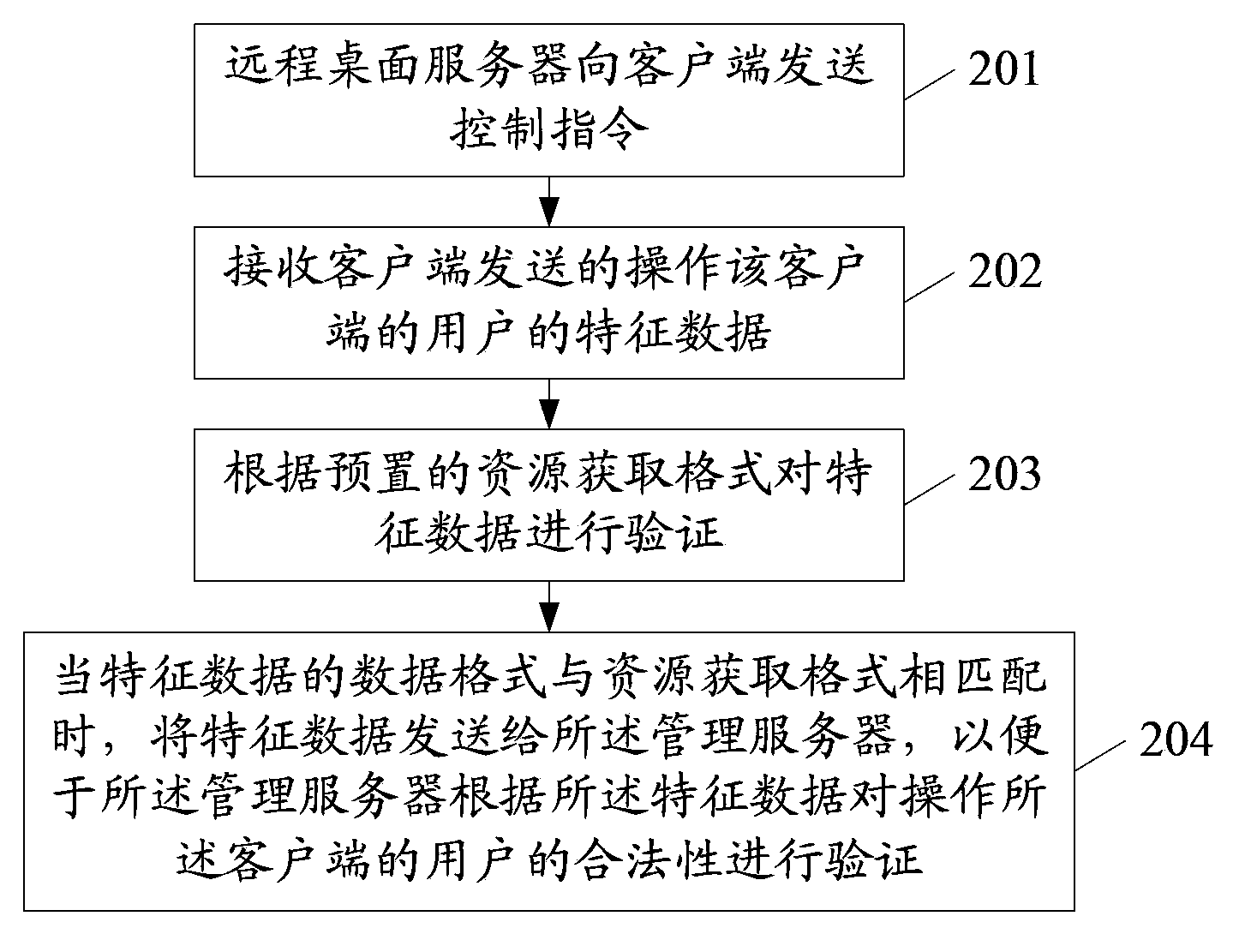
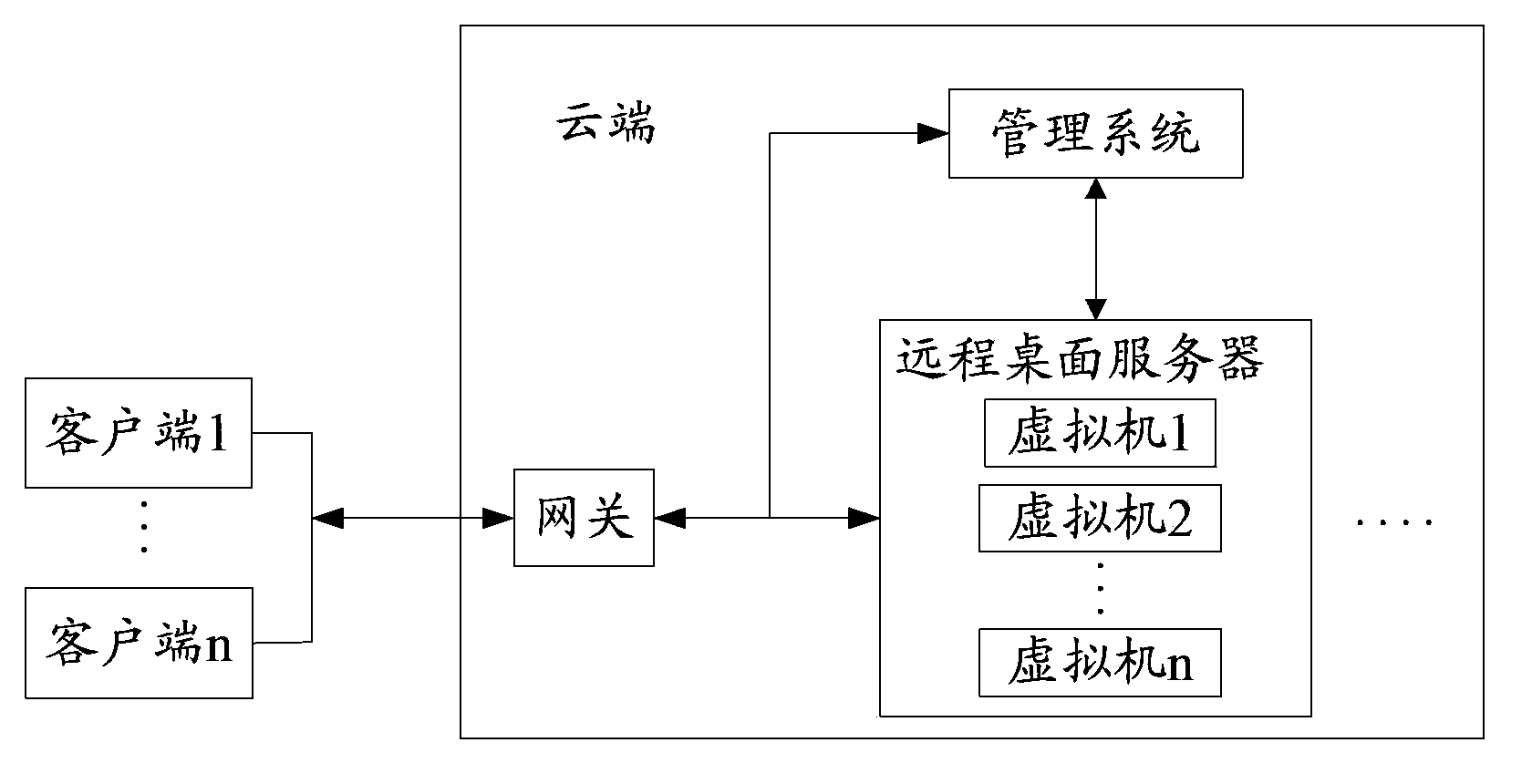
Method and system for improving security of remote desktop, and remote desktop server
The embodiment of the invention, which relates to the communication field, discloses a method and system for improving security of a remote desktop, and a remote desktop server, thereby improving system security in a virtual desktop infrastructure virtual (VDI) environment. According to the concrete scheme, the remote desktop server sends a control instruction to a client, so that the client collects feature data of user operating the client conveniently according to the control instruction; the feature data sent by the client are received; and the feature data are sent to a management server, so that the management server can verify validity of the user operating the client conveniently according to the feature data. According to the invention, the method, the system and the remote desktop server can be applied to the monitoring process of the remote desktop.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
Information safety protecting method and system
InactiveCN103491080AVerify legitimacyIncrease legitimacyProgram/content distribution protectionSecuring communicationApplication securityUSB
The invention discloses an information safety protecting method and system. According to the information safety protecting method and system, a reliable application program, namely a first safety detection program, is provided through a USB Key, other application programs on a terminal are verified through the reliable application program, then the legality of the application programs on the terminal is effectively verified, the problem that potential safety hazards exist due to the fact that the legality of downloading and installation of traditional application programs can not be verified is avoided, safety of the application programs on the terminal is improved, and furthermore safety of personal information of a user is guaranteed.
Owner:SHENZHEN EXCELSECU DATA TECH
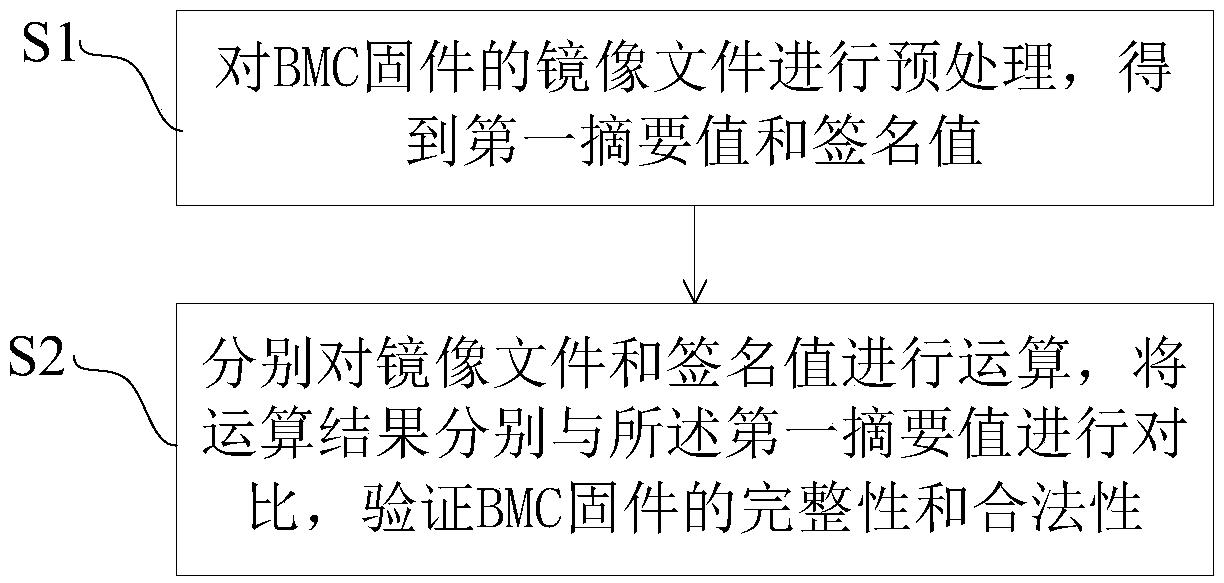
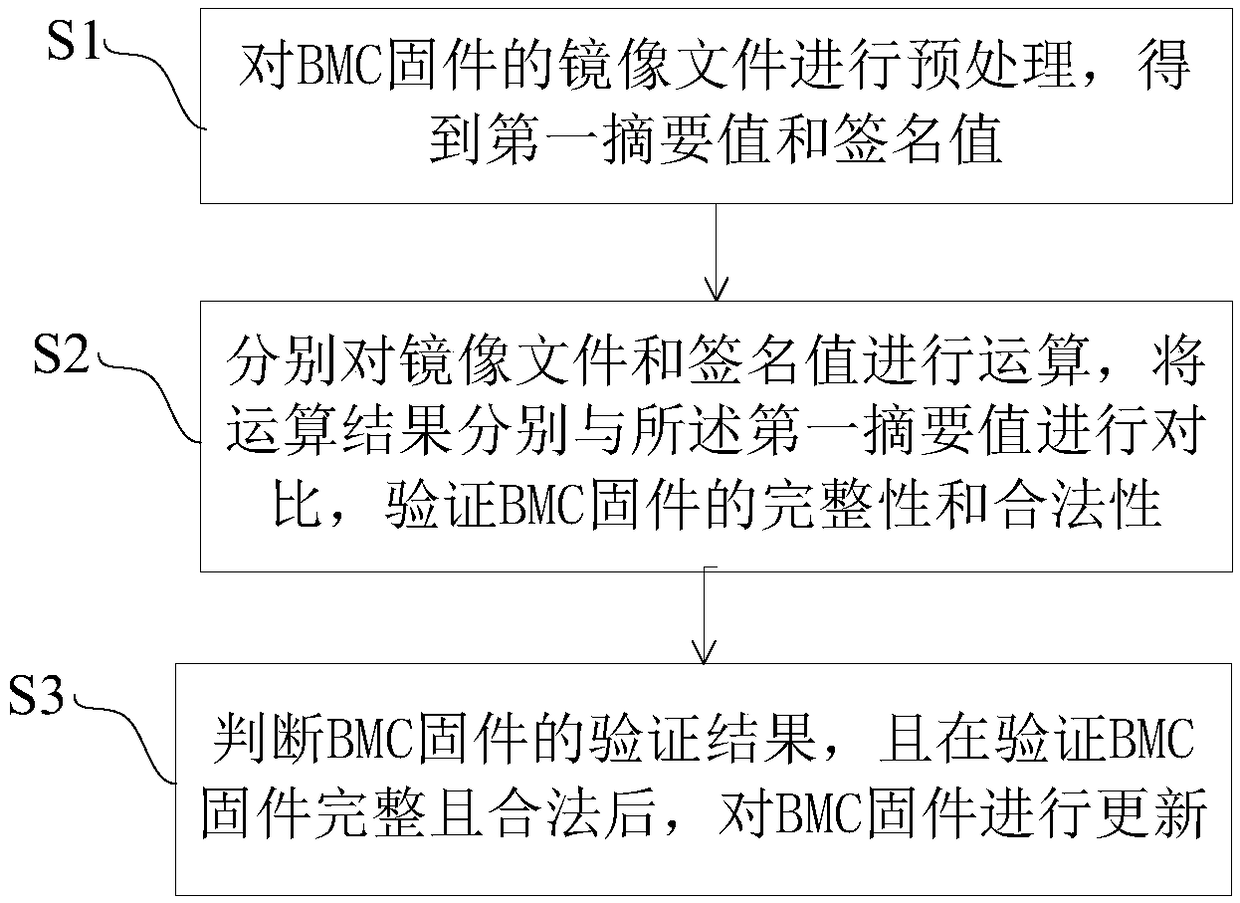
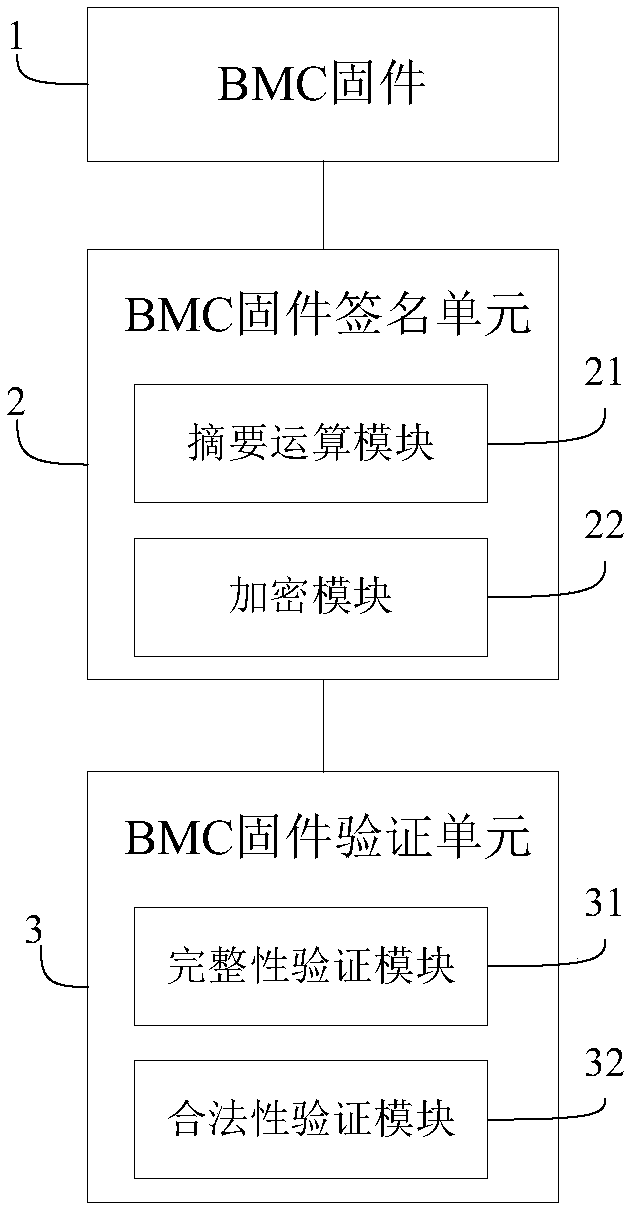
Security verification method and system of BMC firmware
InactiveCN109063470AVerify integrityVerify legitimacyPlatform integrity maintainanceSoftware deploymentComputer securityFirmware
The invention provides a BMC firmware security verification method and system. The method comprises the following steps: preprocessing a mirror image file of the BMC firmware to obtain a first digestvalue and a signature value; The image file and the signature value are calculated respectively, and the operation results are compared with the first digest value to verify the integrity and legitimacy of the BMC firmware. The system comprises a BMC firmware and a BMC firmware signature unit, which is used for preprocessing the mirror file of the BMC firmware to obtain a first digest value and asignature value; The BMC firmware verification unit calculates the image file and the signature value respectively, compares the operation result with the first digest value respectively, and verifiesthe integrity and legitimacy of the BMC firmware. At the same time, the invention verifies the integrity and legitimacy of the BMC firmware, and ensures the security of the BMC firmware to be updated.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com