Method and device for verifying message safety
A security and message technology, applied in the field of communication, can solve the problems of delay in detection timing, cumbersome manual configuration, complex implementation, etc., and achieve the effect of preventing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
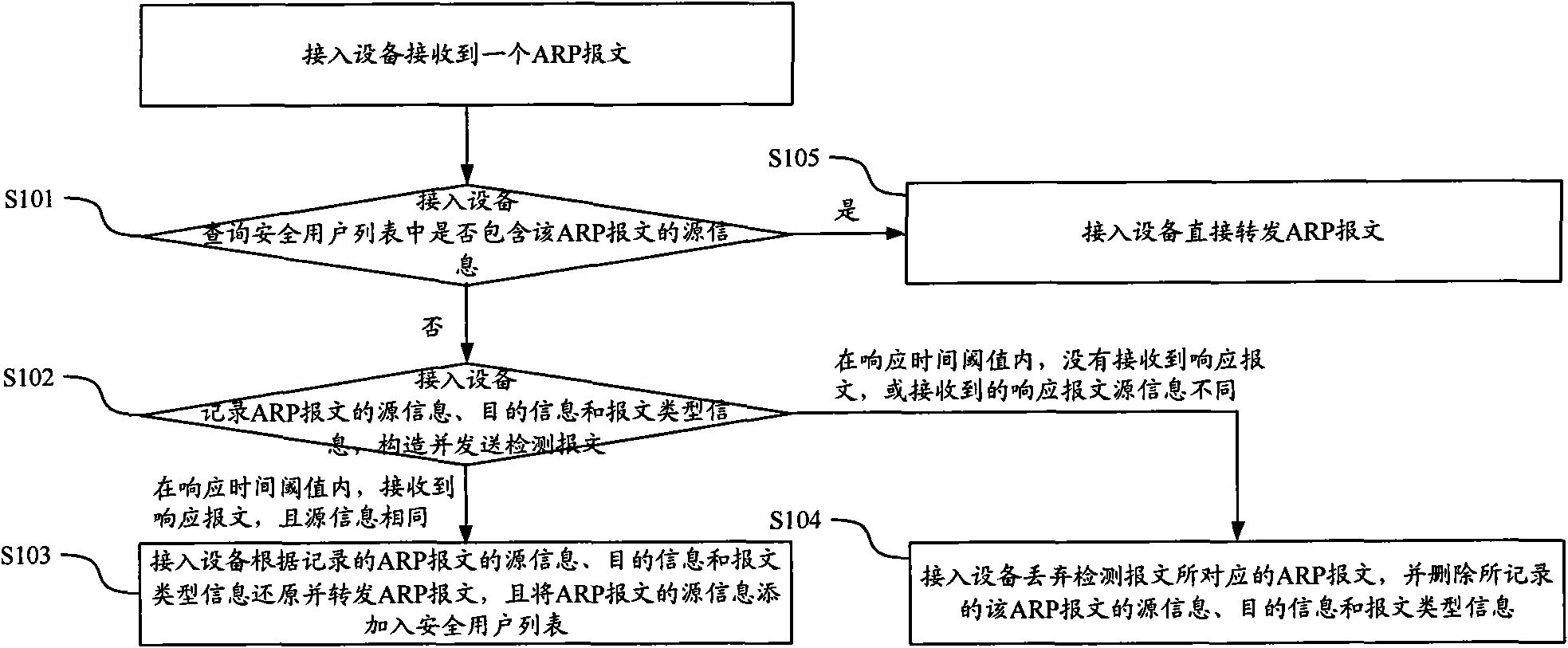
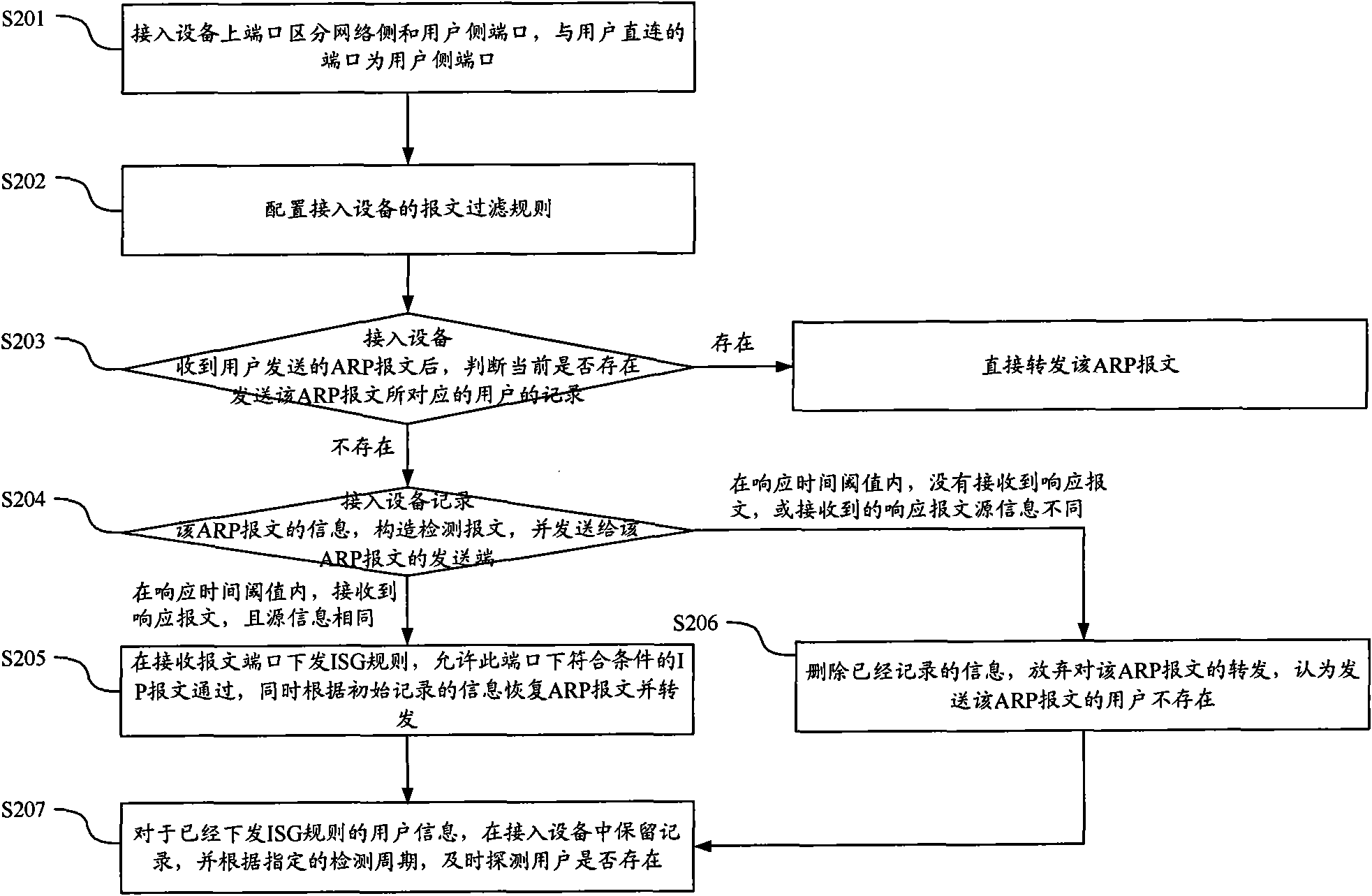
[0060] Aiming at the deficiencies in the background technology, the present invention proposes a method for message security verification, which implements a method on the access device to verify user legitimacy by detecting ARP messages, and realizes user authentication by issuing ACL rules. Security filtering, thereby reducing the impact of user counterfeiting IP address attacks on the uplink network.
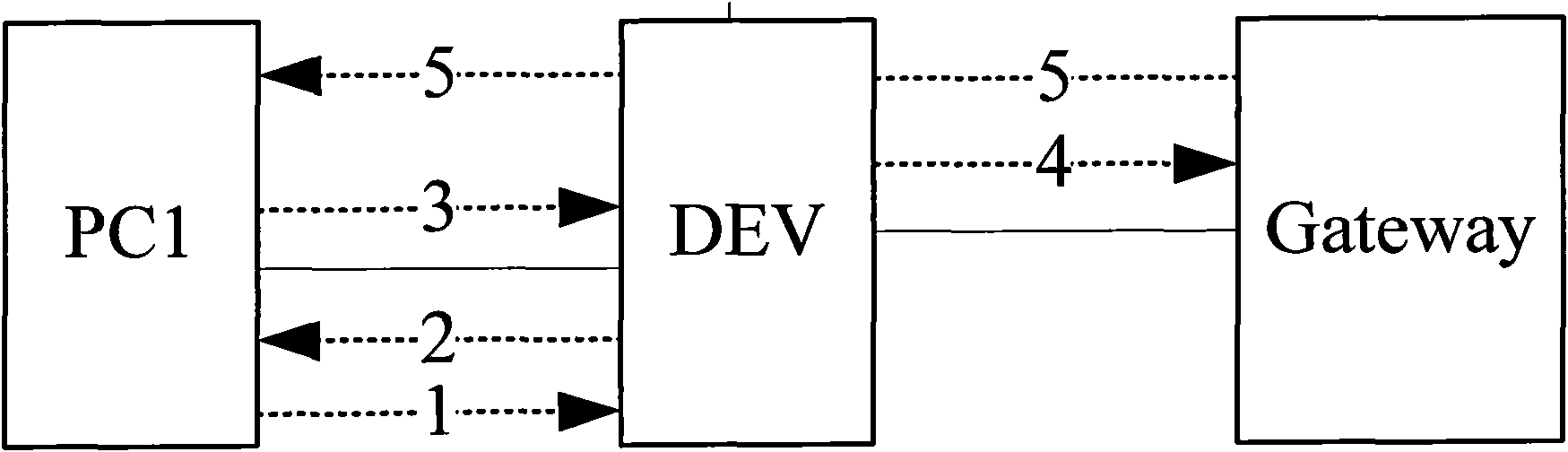
[0061] Such as figure 1 As shown in FIG. 1 , it is a schematic flowchart of a method for message security verification proposed by the present invention, and the method is applied to a system including at least one access terminal and one access device.
[0062] Wherein, a secure user list is established in the access device, and the secure user list is used to store information of secure access terminals, and the access device only checks the IP packets sent by the access terminal In the initial state of the access device, the established security user list is empty, thus, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com