Patents
Literature
115results about How to "Ensure network security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
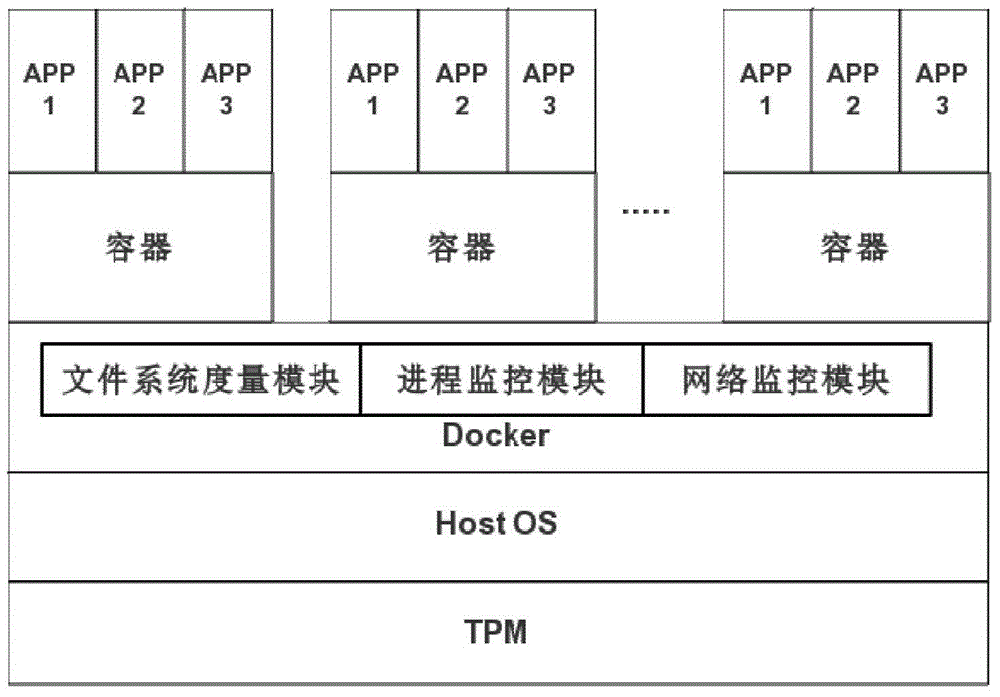
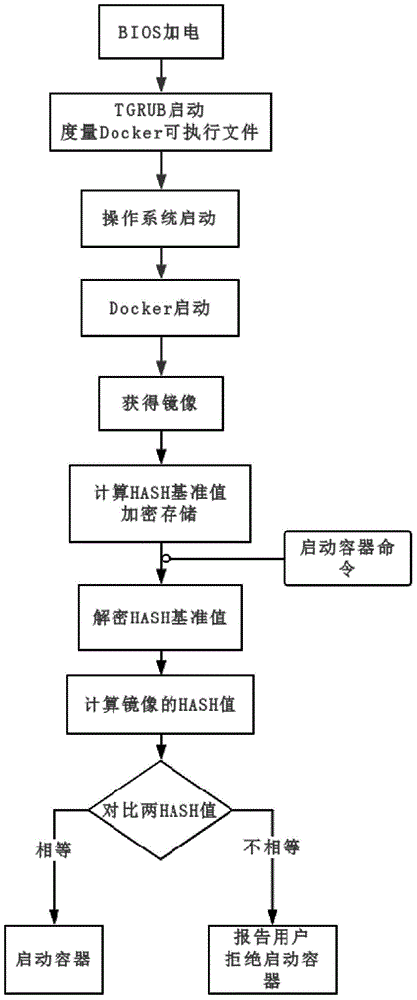
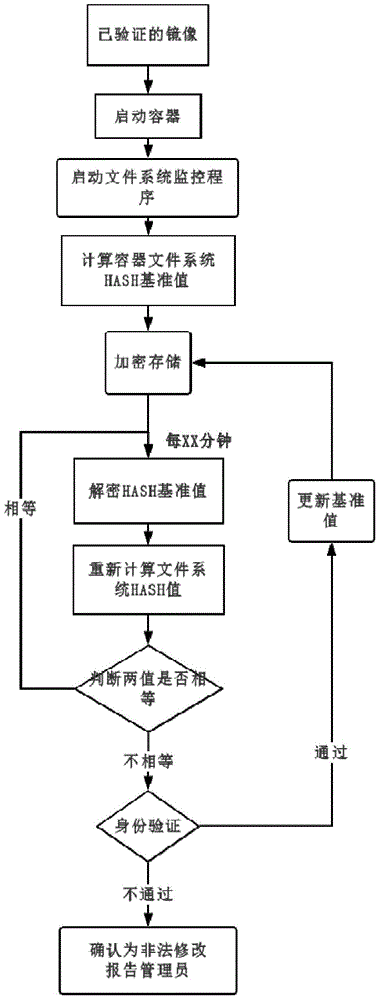
Security reinforcement method for credible container based on Docker
ActiveCN105069353ATrusted bootGuaranteed normal startupPlatform integrity maintainanceNetwork communicationMirror image
The invention discloses a security reinforcement method for a credible container based on Docker used for performing security reinforcement on a Docker container system, and realizes the credible container based on the Docker, as well is applied to a server cluster based on the Docker. The credible container based on the Docker comprises a container program Docker, a container credible measurement module, a progress monitoring module and a network communication monitoring module, wherein the container credible measurement module comprises a credible booting sub-module and a file measurement sub-module. The reinforcement method focuses on the credibility of the Docker container; a credible computing and integrity measurement technology is matched with a real-time monitoring module to reinforce the container system based on the Docker, so that the container and a mirror image are prevented from tampering; and meanwhile, a network communication behavior of the container is limited, and an inner progress of the container is monitored, so as to realize the security reinforced credible container.
Owner:WUHAN UNIV
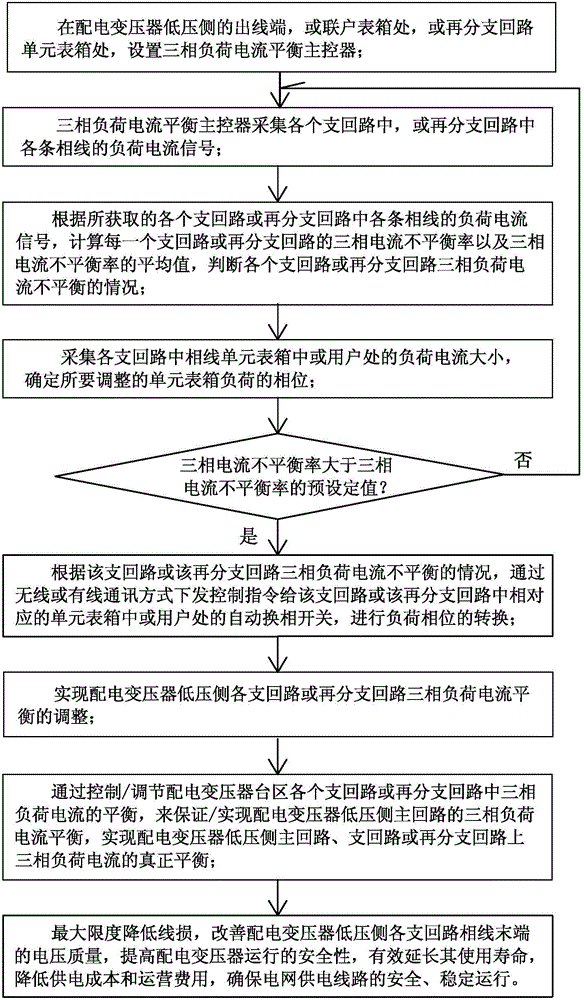
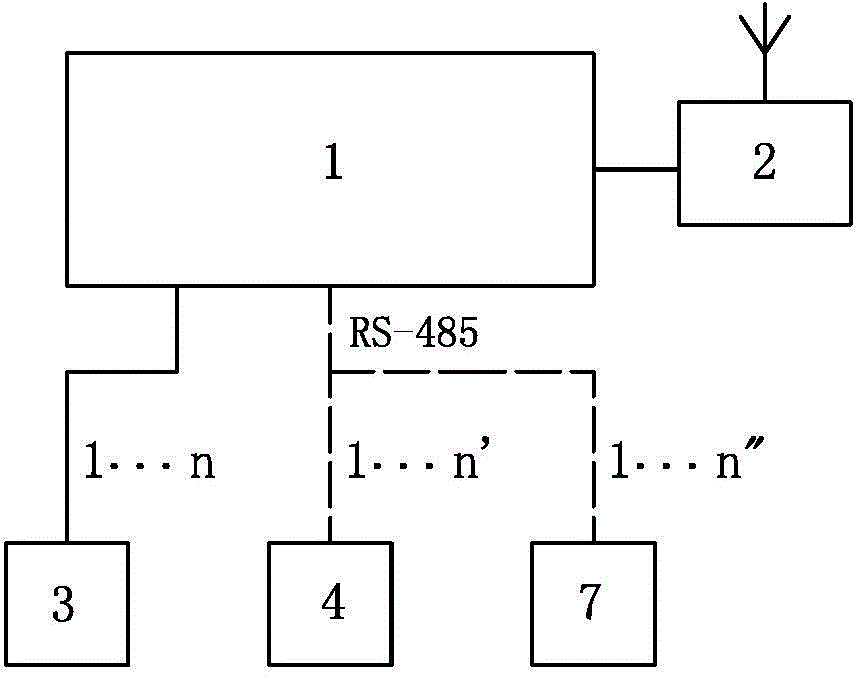
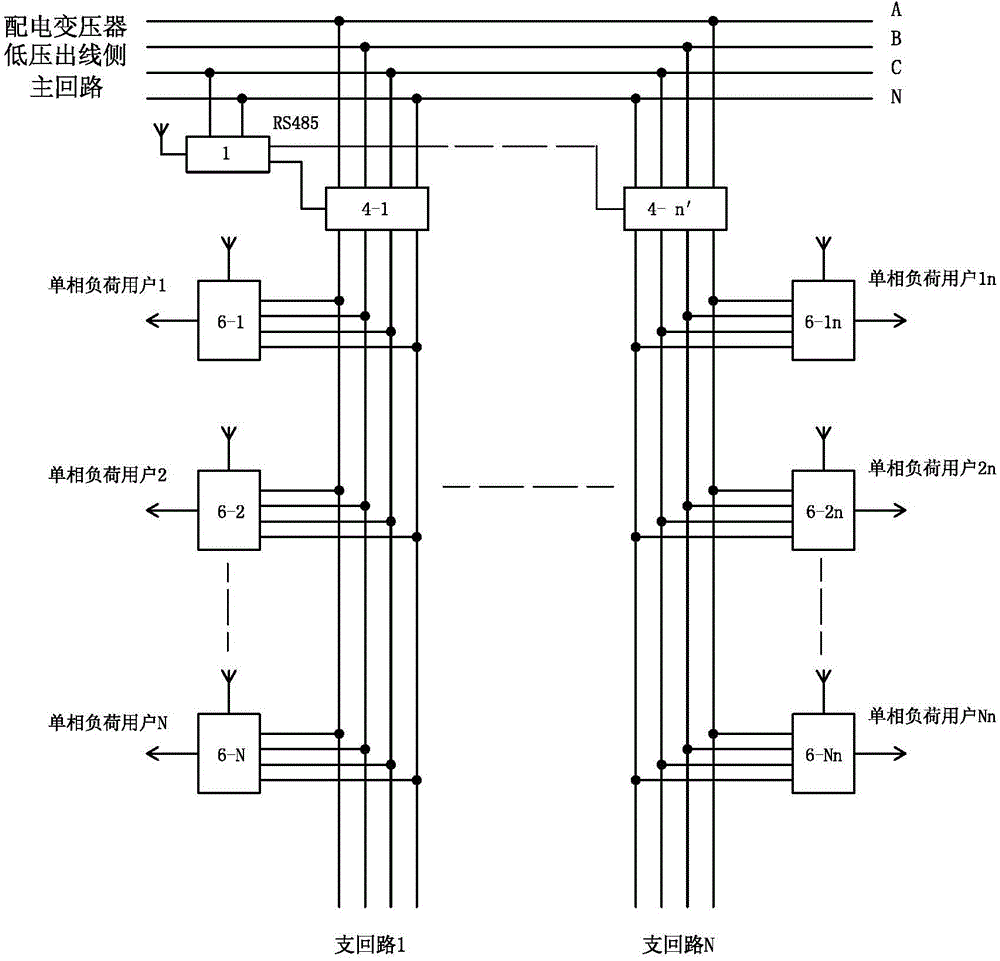
Distributed type power supply zone branch circuit three-phase load current balance monitoring method and device
ActiveCN104092229AImprove voltage qualityAchieve regulationPolyphase network asymmetry elimination/reductionPolyphase network asymmetry reductionDistribution transformerPower flow
The invention discloses a distributed type power supply zone branch circuit three-phase load current balance monitoring method and device and belongs to the field of power supply and distribution devices. At least one three-phase load current balance main controller is arranged, load current signals of each phase circuit in each branch loop are collected, according to the obtained load current signals of each phase circuit, the three-phase current unbalance rate or the mean value of the three-phase current unbalance rate of each branch loop is computed, and the unbalance situation of three-phase load current of each branch loop is judged. The magnitude of load current in each unit meter box of each branch loop is collected, and the phase of unit meter box load which needs to be adjusted is determined. According to the three-phase load current unbalance situation of a certain branch, a control instruction is issued to an automatic phase-changing switch in a unit meter box corresponding to the branch loop, converting of load phases is carried out, adjusting of three-phase load current balance of each branch loop on the low-voltage side of a distribution transformer is achieved, and the real balance of distribution transformer low-voltage side main loop three-phase load current is guaranteed.
Owner:宿迁卡诗博工贸有限公司
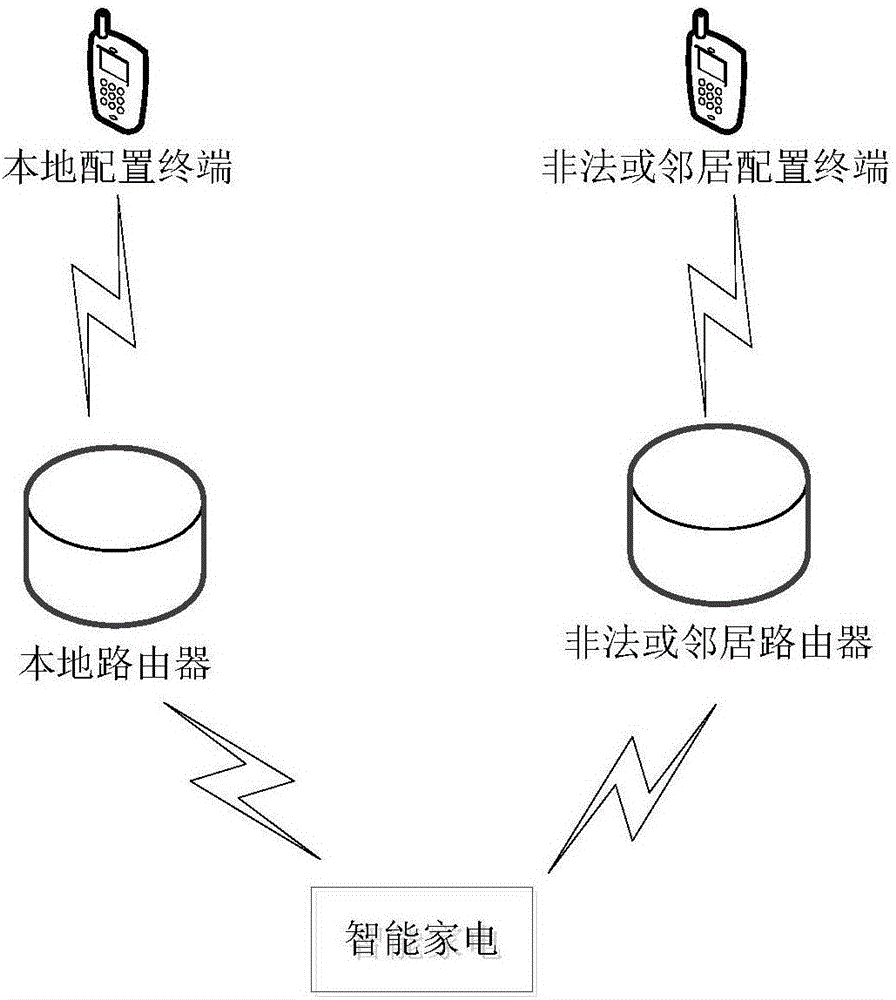
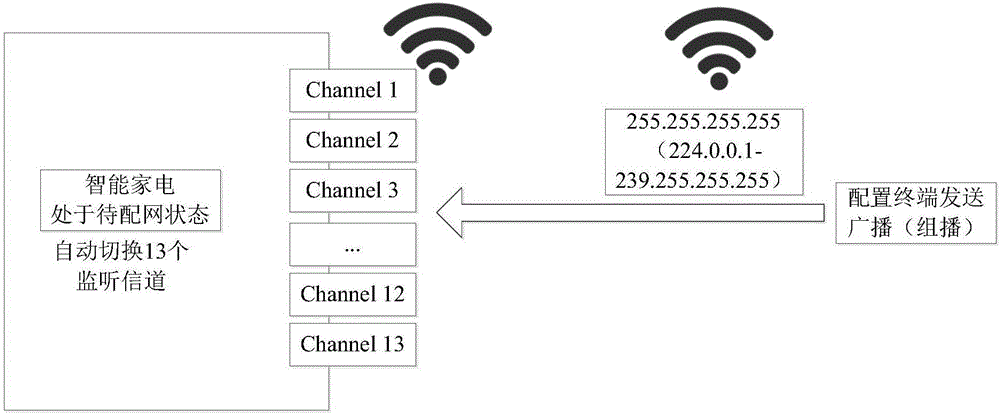
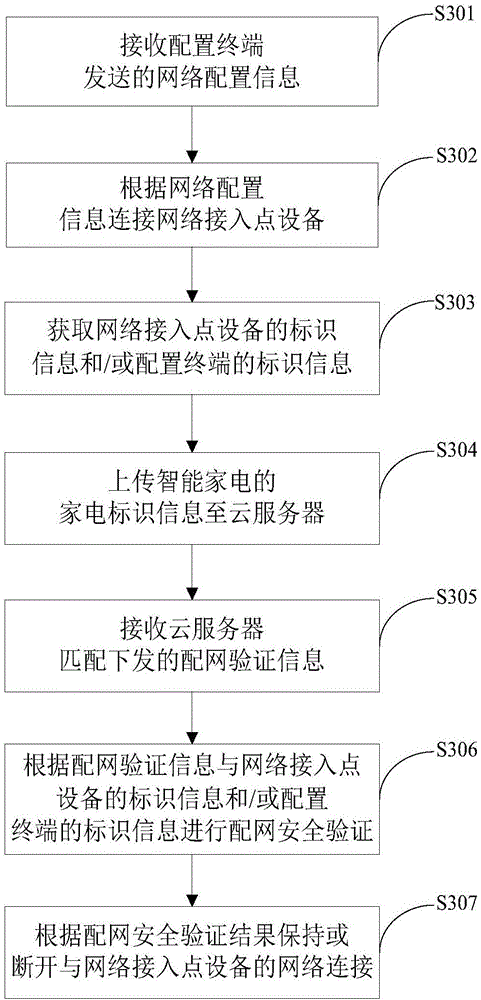
Intelligent household electrical appliance network access security control method
ActiveCN106789462AEnsure network securityGuaranteed binding securityHome automation networksNetwork connectionSecurity question
The invention discloses an intelligent household electrical appliance network access security control method, comprising the steps of receiving network configuration information sent by a configuration terminal; carrying out connection with a network access point device according to the configuration information; obtaining identification information of the network access point device and / or the identification information of the configuration terminal; uploading household electrical appliance information of an intelligent household electrical appliance to a cloud server; receiving distribution network verification information matched and issued by the cloud server; carrying out distribution network security verification according to the distribution network verification information and the identification information of the network access point device and / or the identification information of the configuration terminal; and keeping or disconnecting the network connection with the network access point device according to a distribution network security verification result. According to the intelligent household electrical appliance network access security control method provided by the invention, the operation of a user can be reduced and the security problem resulting from the fact that a device is configured and connected with an illegal router or is bound and controlled by the illegal user can be solved.
Owner:JOYOUNG CO LTD
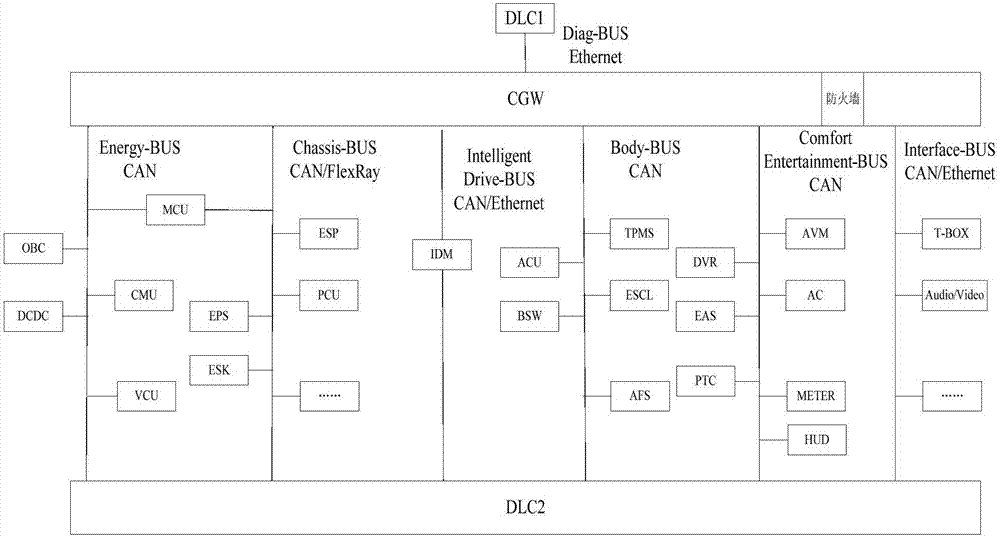
Network architecture of intelligent network connection vehicle and vehicle
The invention provides a network architecture of an intelligent network connection vehicle and the vehicle. The architecture is characterized in that a first OBD diagnosis port is connected to an external diagnostic apparatus and acquires an internal network access request input by the external diagnostic apparatus; a central gateway controller is connected to internal network segments of the vehicle and is connected to the first OBD diagnosis port so as to transmit interaction information among an information interface control network segment and other network segments in the internal network segments of the vehicle and acquire the internal network access request transmitted by the first OBD diagnosis port; the central gateway controller includes an access authentication module which is used for carrying out authentication on the internal network access request and transmitting a first internal network access request to the internal network segments of the vehicle when the request passes through the authentication; and a firewall is used for carrying out filtering processing on the interaction information and transmitting the filtered interaction information to the internal network segments of the vehicle so as to increase safety of an internal network of the vehicle.
Owner:BEIJING ELECTRIC VEHICLE
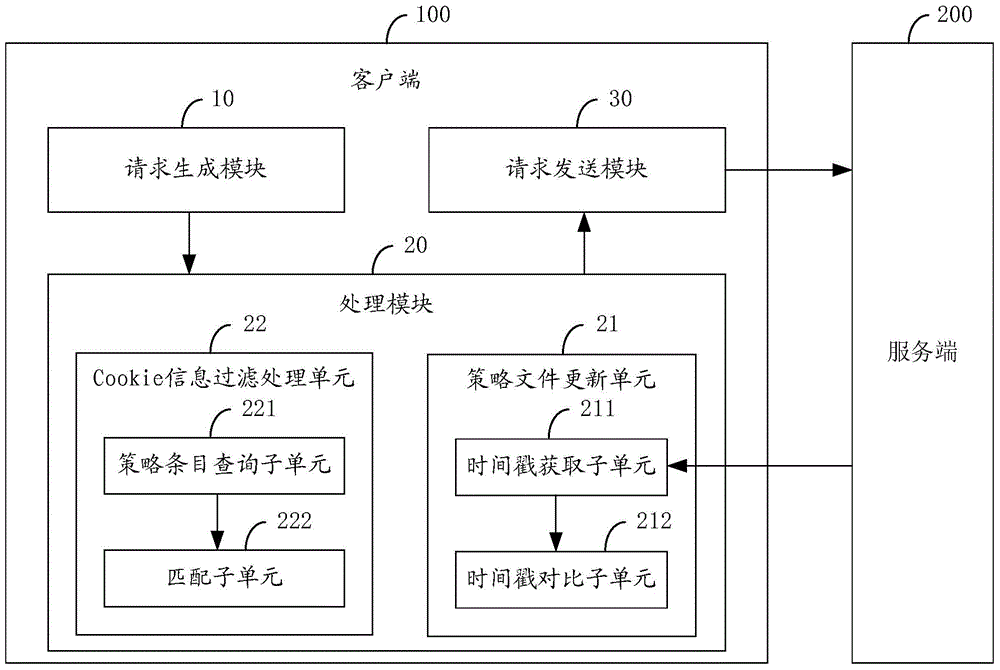
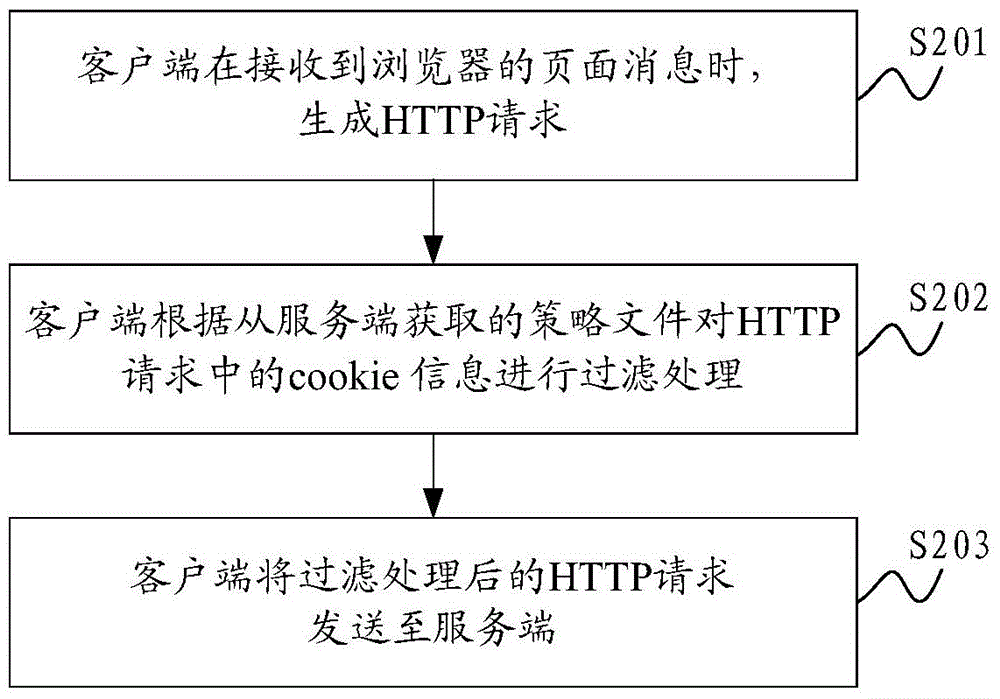
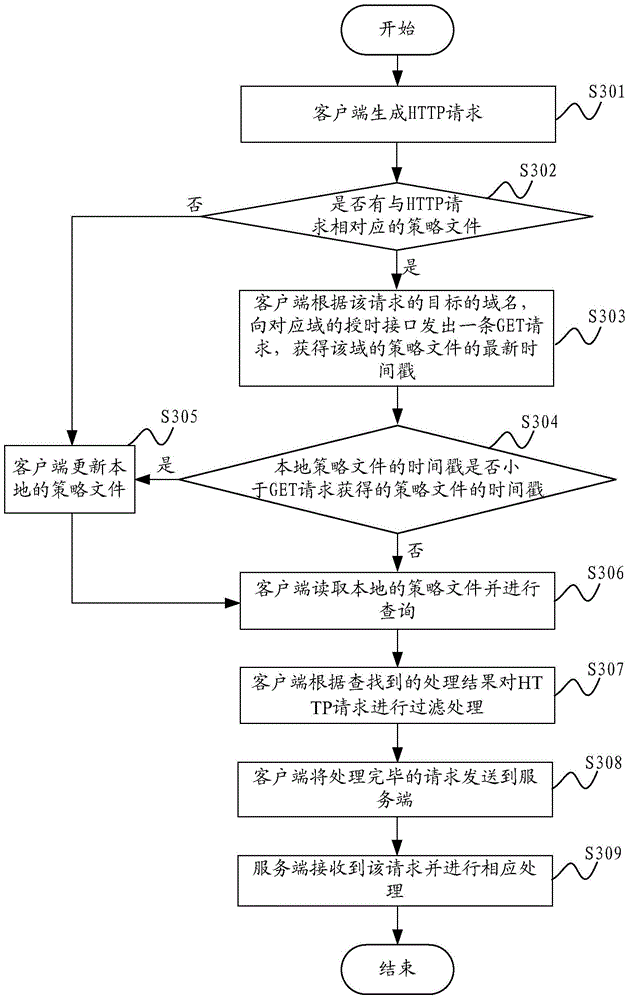
Method and system for preventing cross-site request forgery attack
The invention is applicable for the technical field of network safety, and provides a method and a system for preventing a cross-site request forgery attack. The method comprises the steps that: a client generates an HTTP request when page information of a browser is received; the client performs filtration treatment on cookie information in the HTTP request based on a strategy document obtained from a server-side; the client sends the HTTP request after subjected to the filtration treatment to the server-side. In the method and the system for preventing the cross-site request forgery attack, the strategy document is provided by the server-side, the server-side defines requests from which pages the service-side expects to receive exactly, and the client performs authenticity judgment on the HTTP request based on the strategy document, so that requests which are not allowed by the strategy document are guaranteed to not carry cookie of a user, requests which the server-side does not expect to receive cannot be sent by the client, and the network safety of the client is guaranteed.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
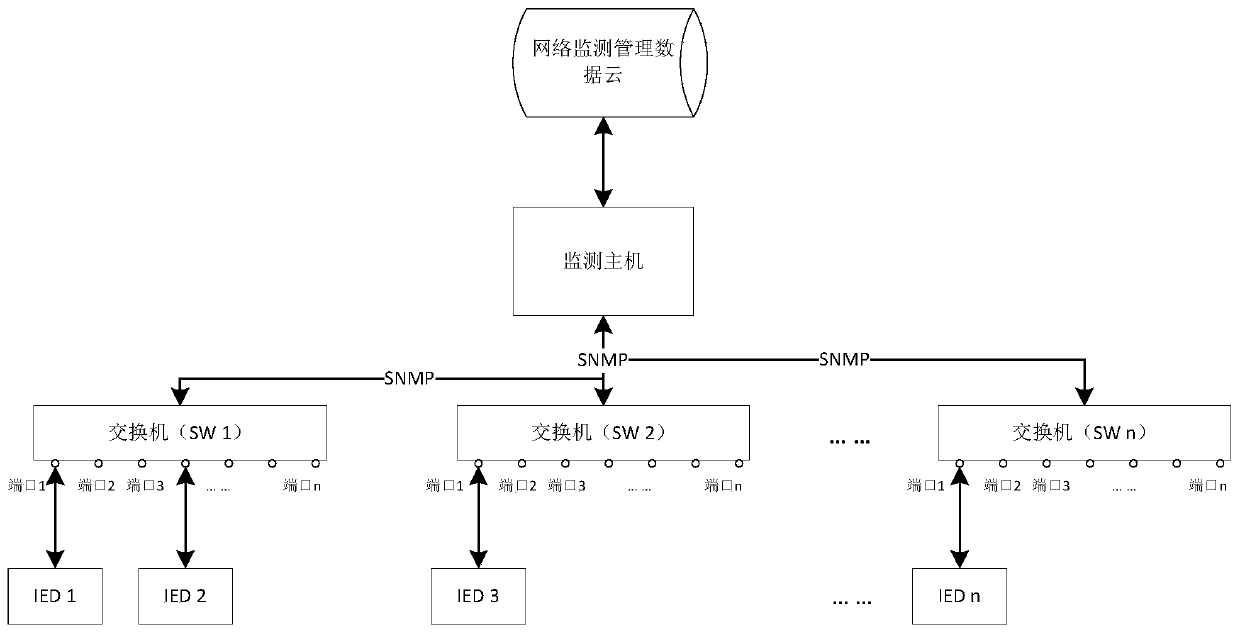
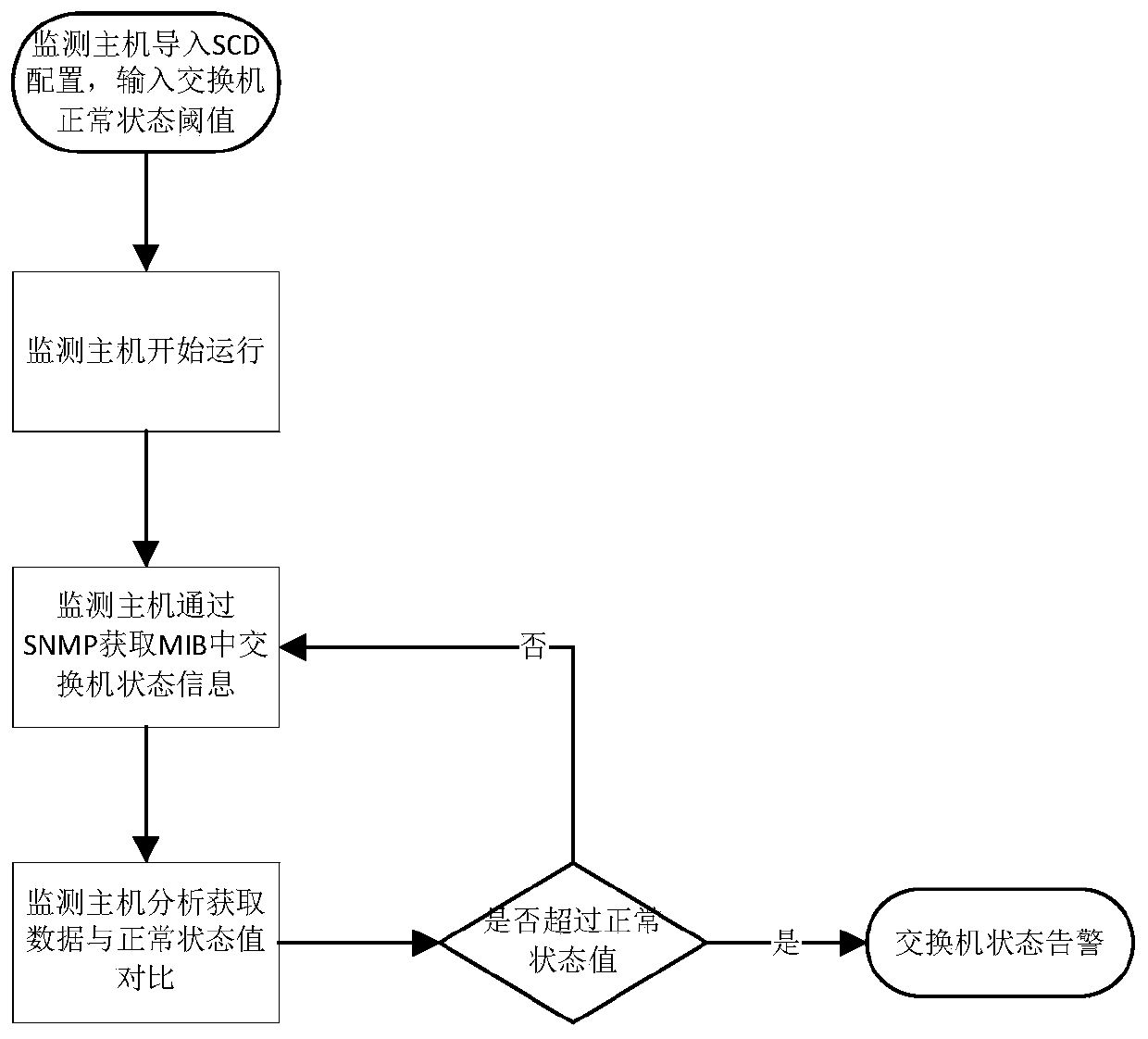
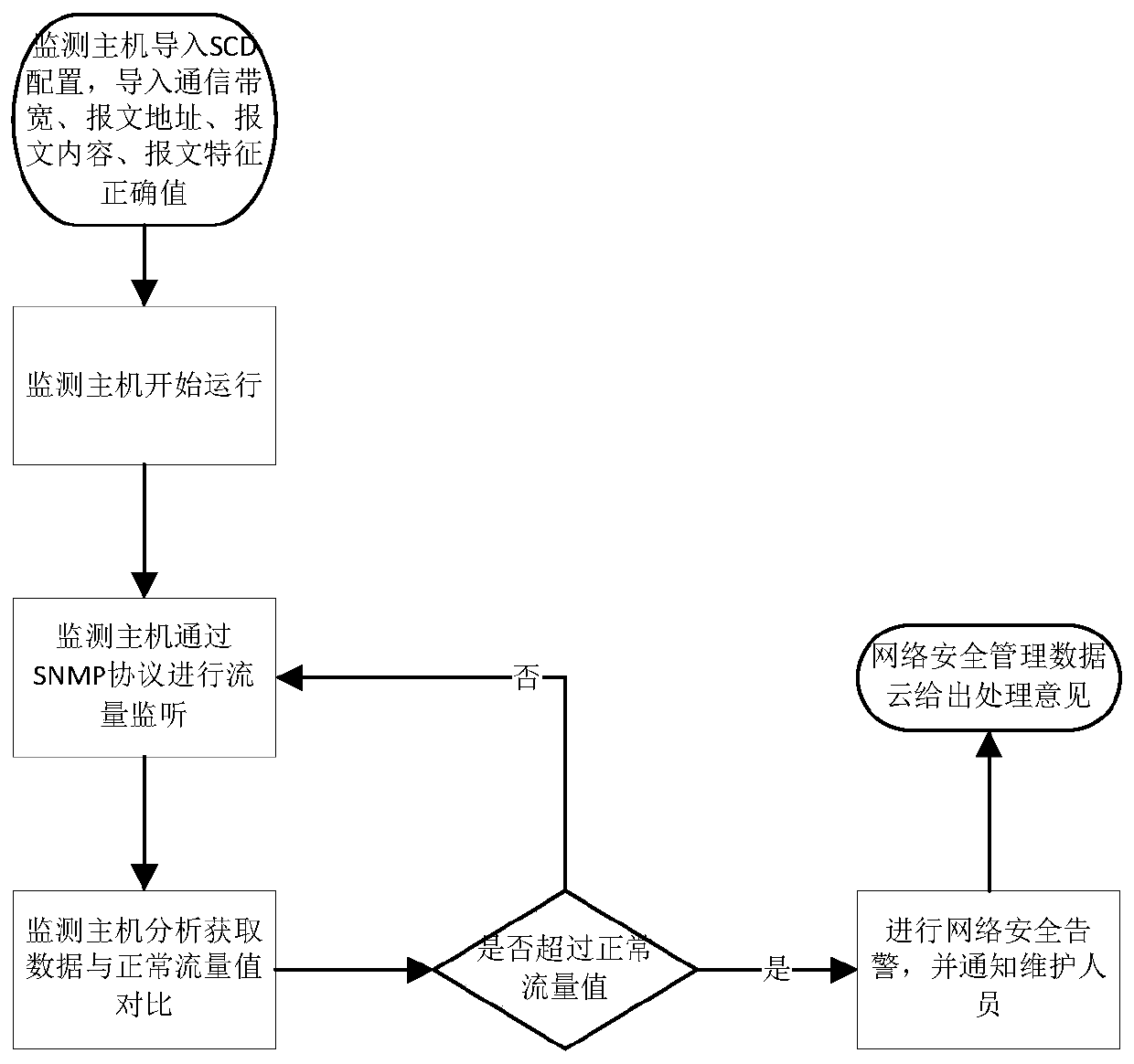
Intelligent substation process level network monitoring management system
ActiveCN110224894AEnsure network securityRealize visual location of faultsData switching networksSmart substationNetwork communication
The invention discloses an intelligent substation process level network monitoring management system. The system comprises a monitoring host, wherein the monitoring host generates preset process levelnetwork communication state information through SCD configuration of an intelligent substation; and the monitoring host acquires the operation state information of the process layer switch in real time, analyzes and processes the operation state information acquired in real time to obtain actual process layer network communication state information, and compares the actual process layer network communication state information with preset process layer network communication state information to realize operation state monitoring of the process layer switch. The intelligent substation process level network monitoring management can be rapidly and reliably completed in real time, monitoring data are complete and reliable, the alarm response speed is high, and the network security of the intelligent substation is ensured; and moreover, the mapping relation between the process layer network communication physical link and the virtual connection is graphically displayed, and the fault visual positioning of the process layer network physical link / virtual connection is realized.
Owner:STATE GRID SICHUAN ELECTRIC POWER COMPANY NEIJIANG POWER SUPPLY +4
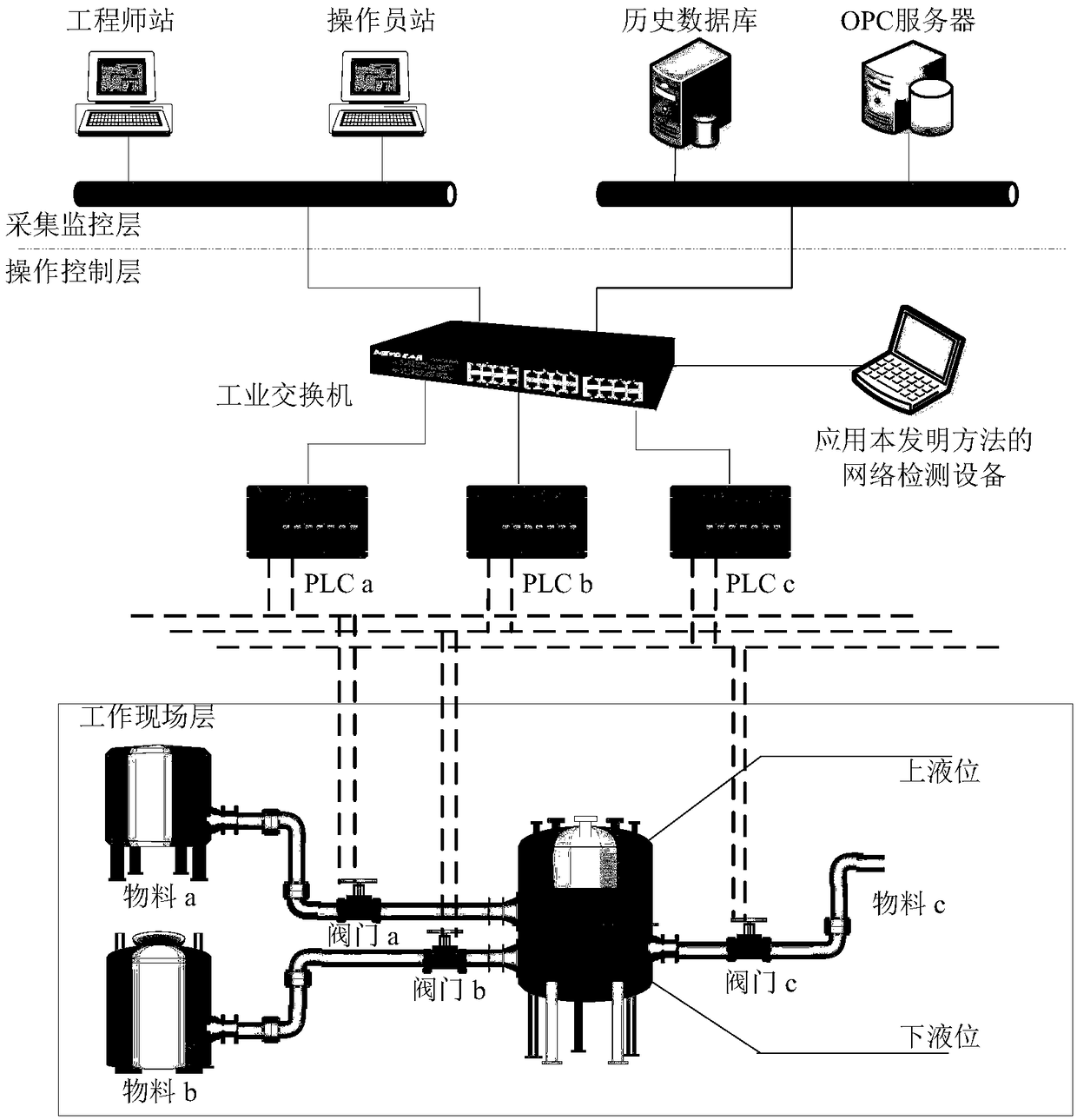
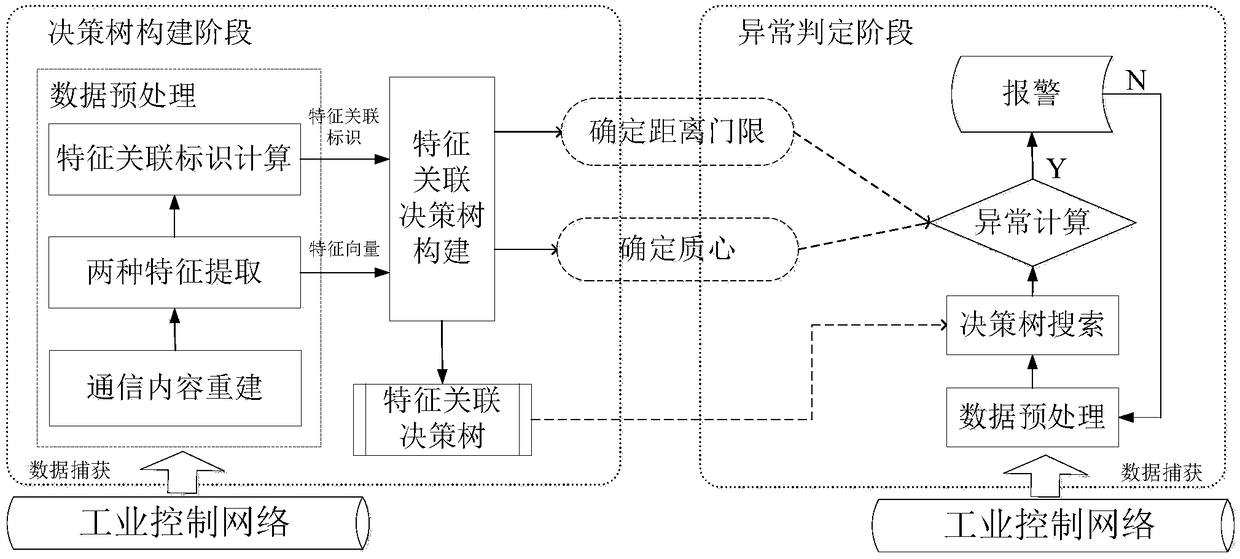
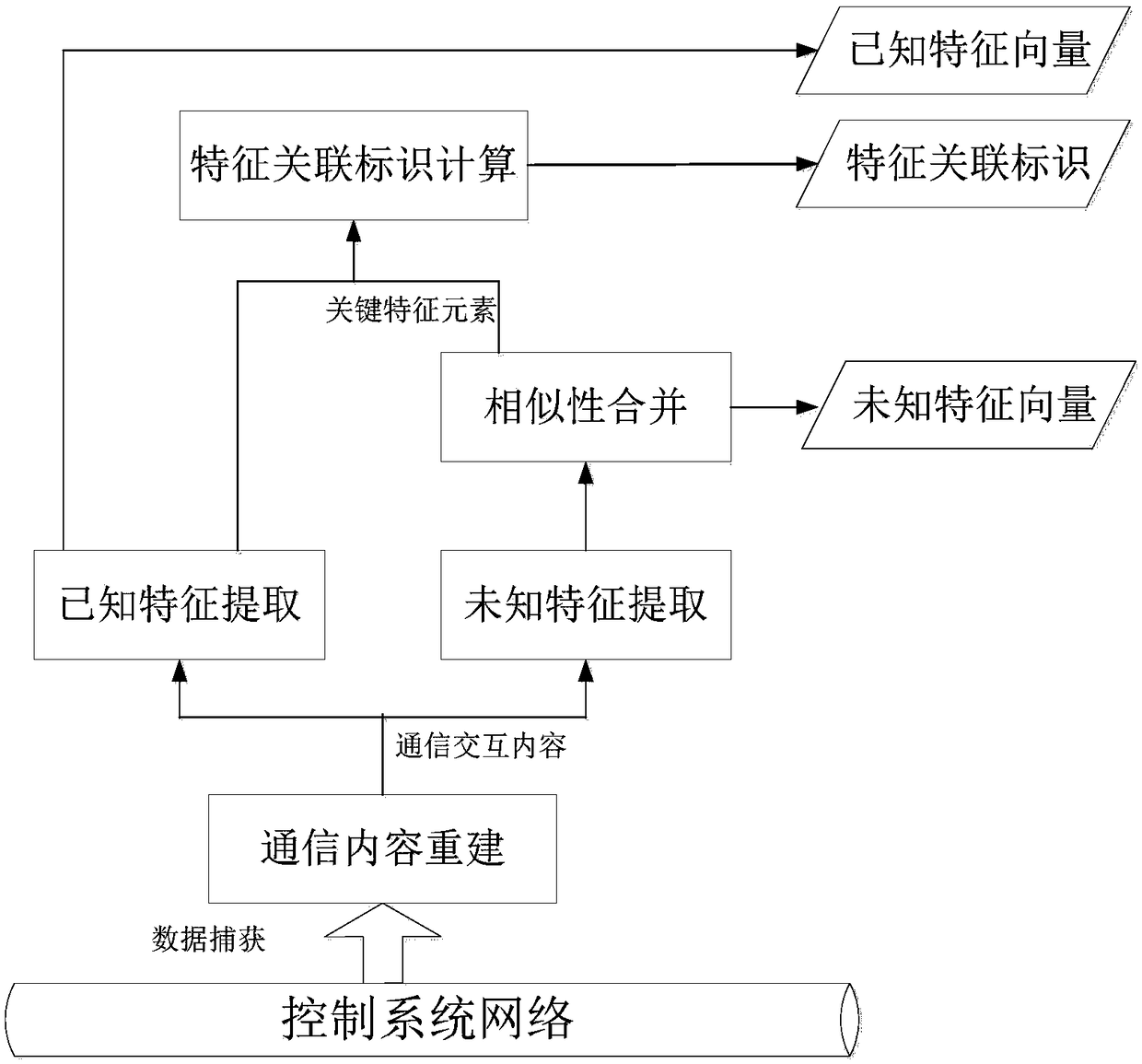
Limited known industrial communication protocol abnormal behavior detection method based on feature association
ActiveCN108737410AEnsure network securityUnusual changes foundData switching networksIndustrial communicationPhases of clinical research
The invention discloses a limited known industrial communication protocol abnormal behavior detection method based on feature association. For a feature that a message format of a limited known industrial communication protocol has a known part and an unknown part, through association of the two parts of information, abnormality detection is carried out on communication behaviors of the limited known industrial communication protocol. The method specifically comprises a decision tree establishment phase and an abnormality judgment phase. In the decision tree establishment phase, feature extraction is carried out on original communication data in a control system, known features and unknown features are bound through feature association identities, a feature association decision tree is established, and a mass center and a distance threshold of an unknown feature space are obtained. In the abnormality judgment phase, decision tree searching and mahalanobis distance calculation are carried out on data preprocessed feature information, and through comparison with the distance threshold, the abnormality detection is carried out on limited known protocol communication behaviors. According to the method, analysis, modeling and detection can be carried out on industrial control communication data, this kind of industrial communication behavior abnormalities can be discovered in real time, alarm is generated, and network security is ensured.
Owner:辽宁工控科技有限公司
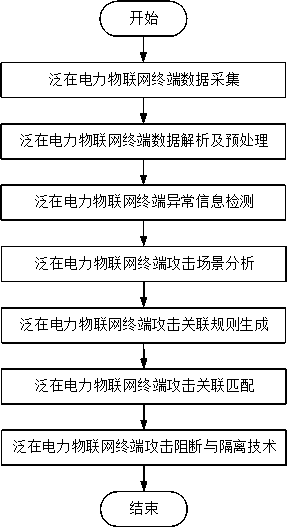
Safety protection method for ubiquitous power Internet of Things terminal in specific attack scene
InactiveCN111404914AEnsure safetyEnsure network securityCharacter and pattern recognitionArtificial lifeData packAttack
A safety protection method for a ubiquitous power Internet of Things terminal in a specific attack scene comprises the steps: firstly, forming a sensor network by combining a high-speed transmission technology with sensors, and collecting and uploading information such as temperature and humidity; secondly, preprocessing the acquired information; analyzing a data packet layer by layer to extract amessage instruction-level field, and detecting abnormal data; then, analyzing two attack scenes of a distributed denial service attack and a data tampering attack, associating abnormal events generated by the attacks, finding potential threats in time, and recognizing the attack scenes effectively; and finally, isolating and blocking the attacked terminal by using a power terminal attack blockingand isolating technology, so that the security of the ubiquitous power Internet of Things terminal is ensured. According to the method, specific attack scenes such as distributed denial of service attacks and distributed data tampering attacks which may be suffered can be effectively identified, measures such as blocking and isolation are taken to ensure the network security of the power terminal, and the method has relatively high engineering practical value.
Owner:NANJING ELECTRIC POWER ENG DESIGN +2
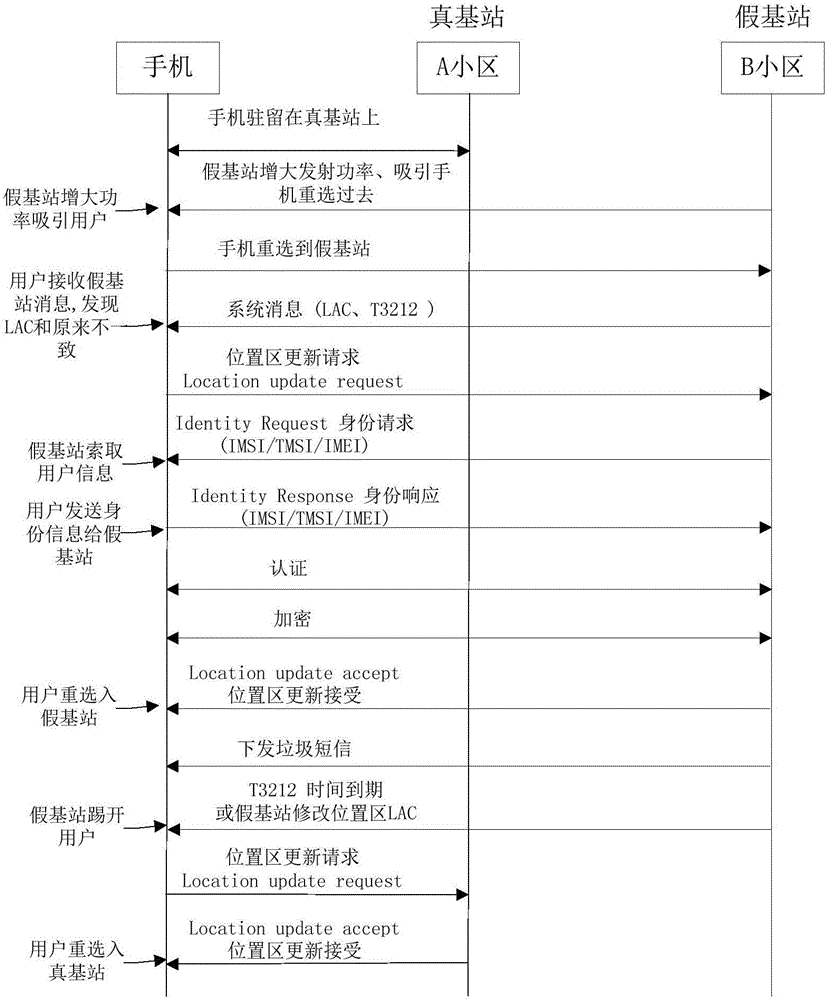
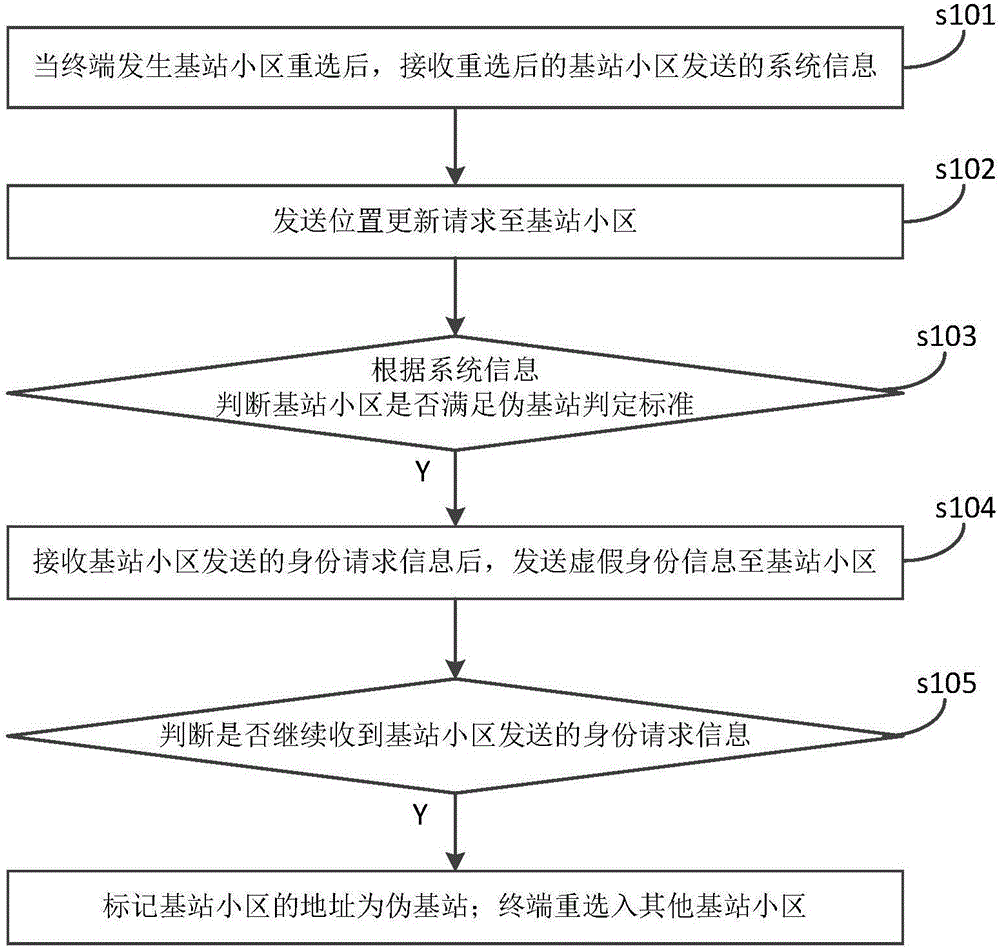
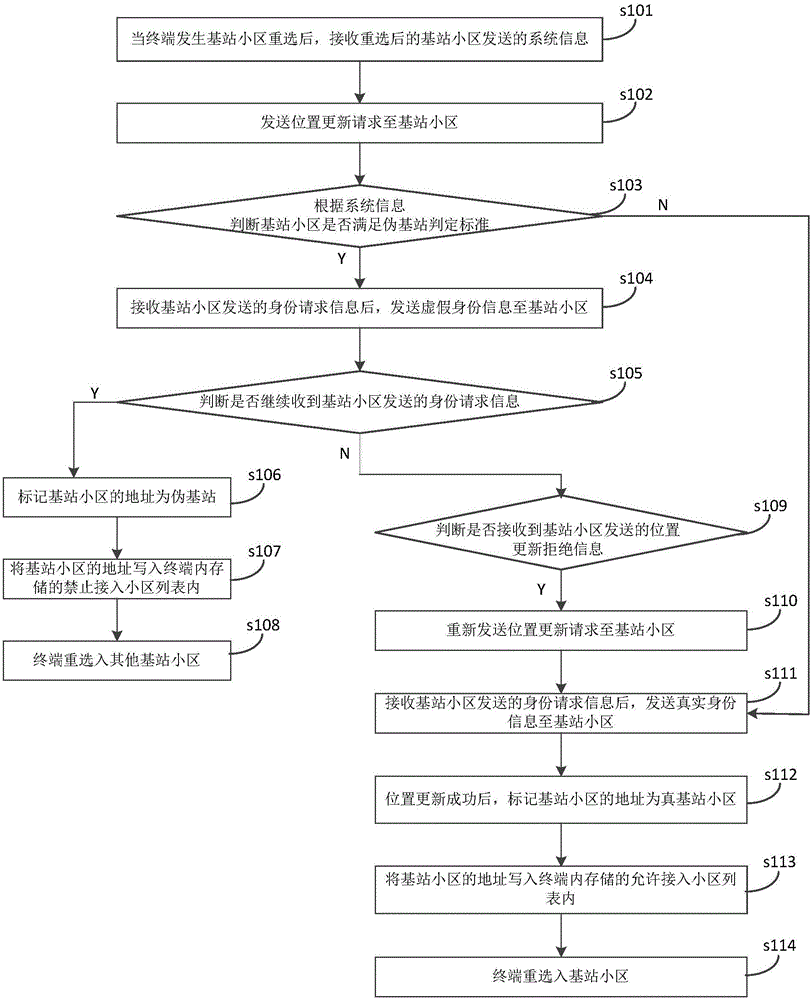
Terminal and method and system for recognizing pseudo base station
ActiveCN106211167AEnsure network securityPrevent leakageSecurity arrangementRecognition systemInformation leakage
The invention discloses a method and a system for recognizing a pseudo base station, which are used in a terminal. When base station cell reselection happens to the terminal, system information sent by a base station cell after reselection is received; a position updating request is sent to the base station cell; according to the system information, whether the base station cell meets a pseudo base station judging criterion is judged, and if yes, after identity request information sent by the base station cell is received, false identity information is sent to the base station cell; whether the identity request information sent by the base station cell is received continuously is judged, and if yes, the address of the base station cell is marked as pseudo base station; and another base station cell is reselected by the terminal. The pseudo base station can be recognized, information leakage of the terminal user during the recognition process can be avoided, and the network security of the terminal user is greatly ensured. The invention also provides a terminal comprising the above pseudo base station recognition system. The terminal also has the above beneficial effects which are not described any more.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
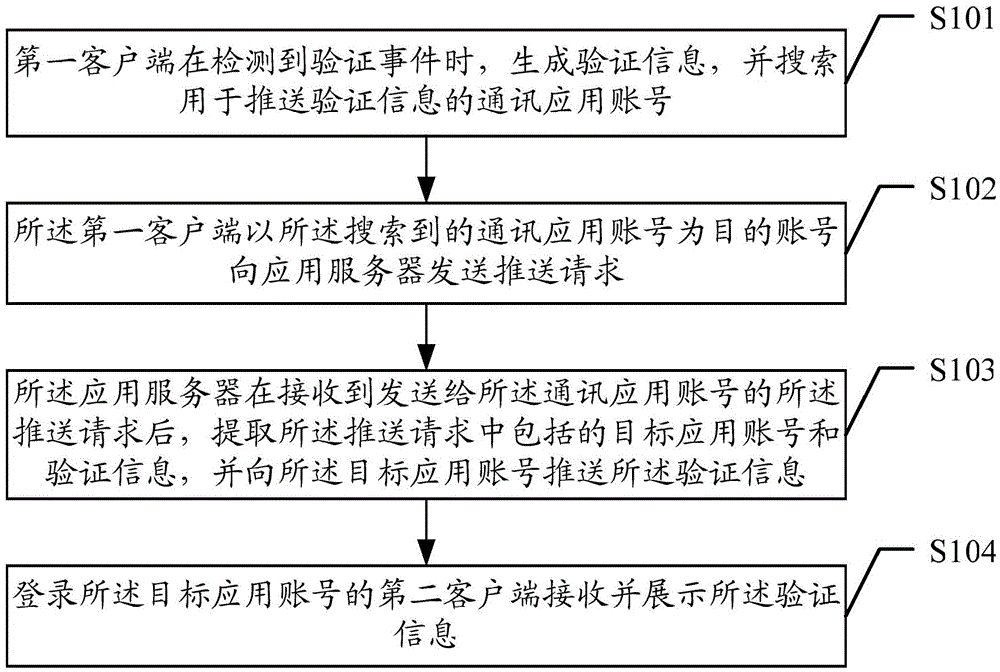
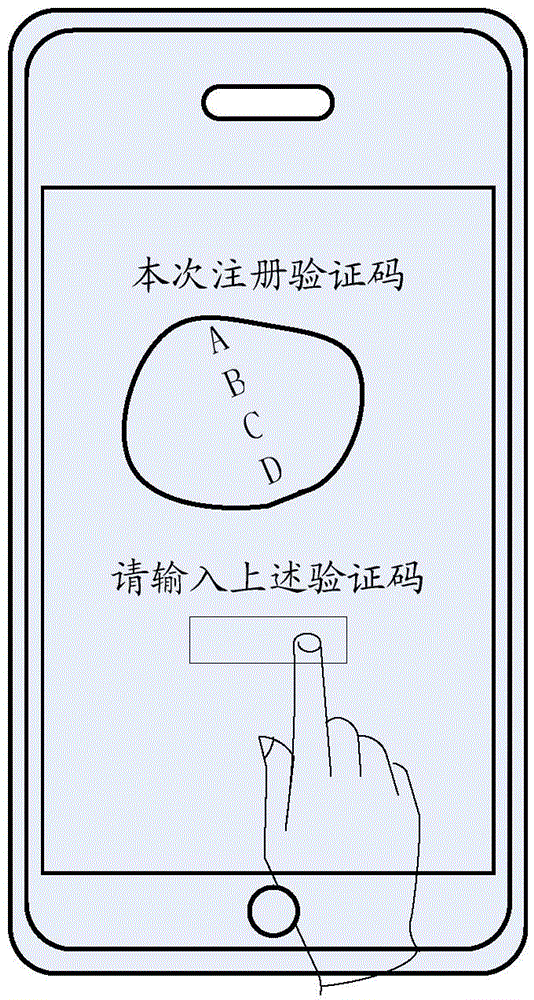
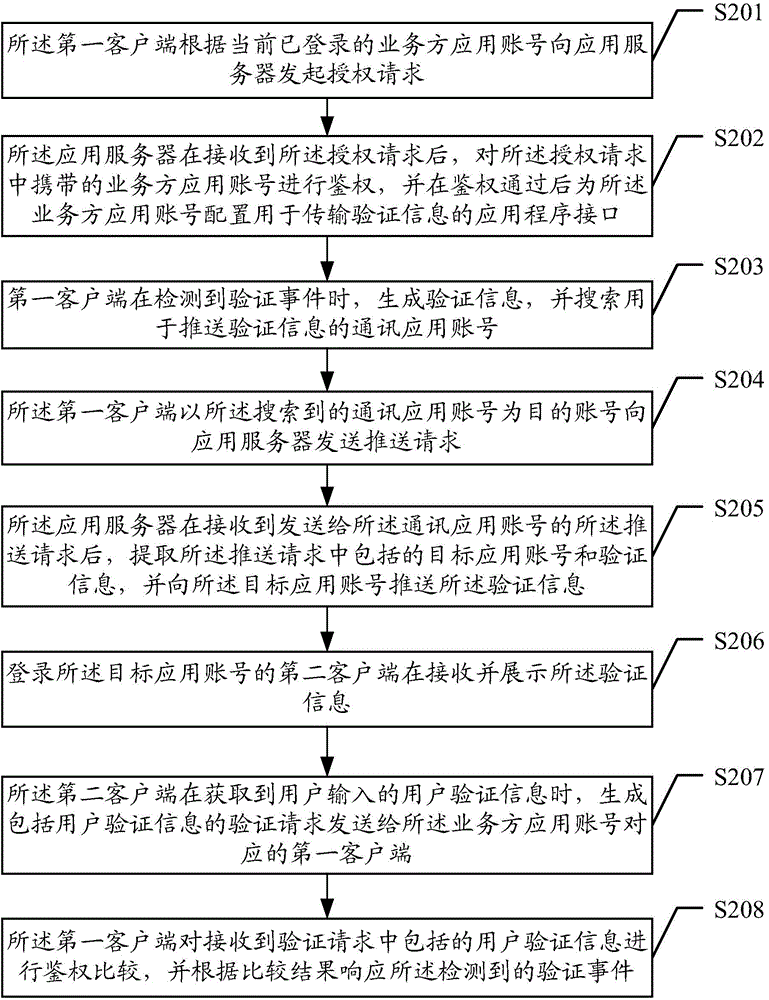
Method, device and system for verification information push, and method, device and system for information verification
ActiveCN104618315AEnsure safetyEnsure network securityServices signallingDigital data authenticationApplication serverClient-side
The embodiment of the invention discloses a method, a device and a system for verification information push, and a method, a device and a system for information verification. The method for verification information push comprises the steps that a first client side generates verification information when detecting a verification event, and searches a communication application account pushing the verification information; the first client side takes the searched communication application account as a target account and sends a push request to an application server, wherein the push request comprises a target application account and verification information corresponding to the verification event; the application server receives the push request sent to the communication application account, then extracts the target application account and verification information included in the push request, and pushes the verification information to the target application account; and a second client side of the target application account is logged in and the verification information is received and shown. Through adoption of the method, device and system for verification information push, verification information push in application scenes like instant messaging application and social messaging application is realized, and verification information safety and network safety are guaranteed.
Owner:TENCENT TECH (SHENZHEN) CO LTD
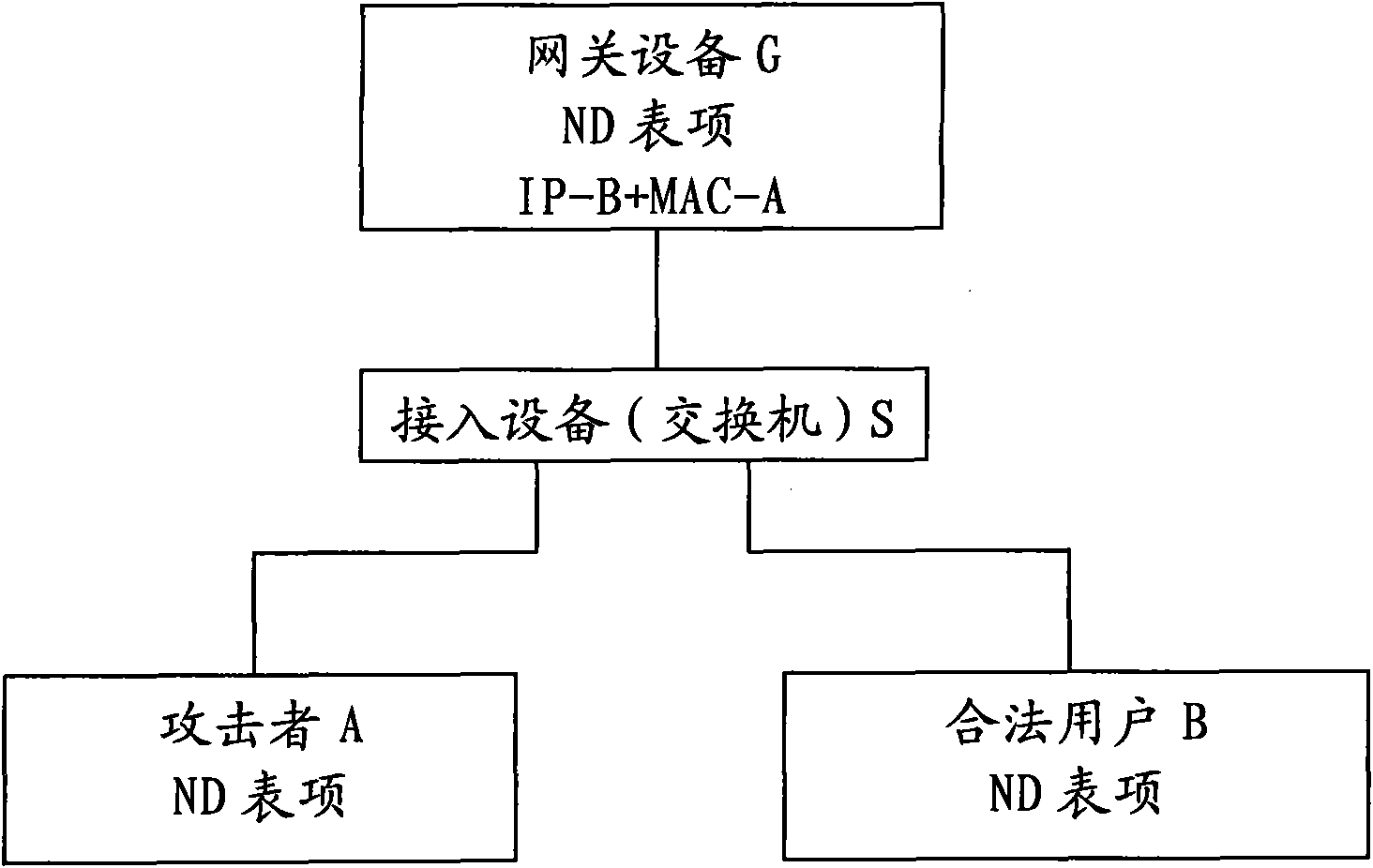
Method for preventing neighbor discovery protocol message attack and device
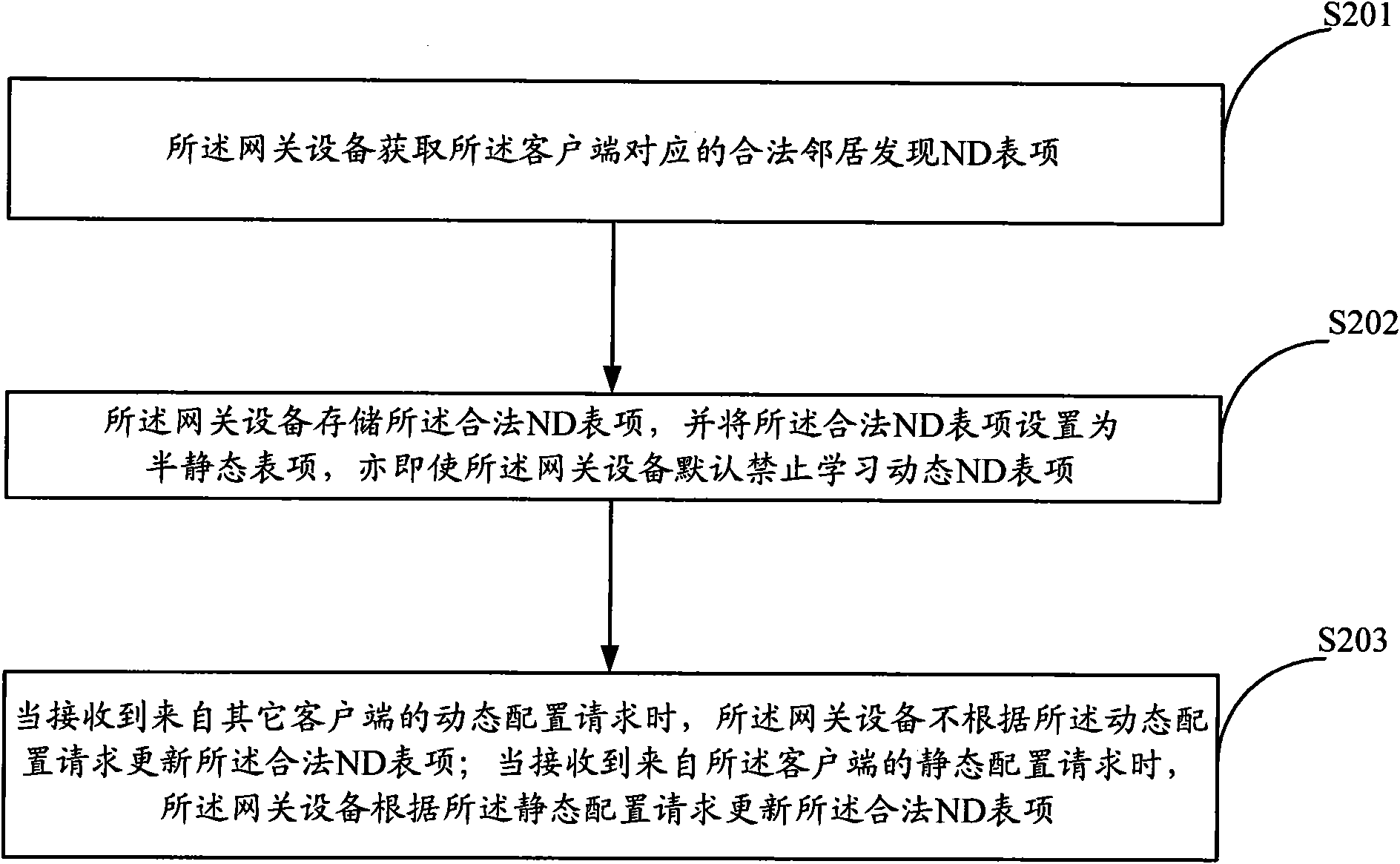
ActiveCN101577723AEnsure network securityImprove overall robustnessData switching networksClient-sideNeighbor Discovery Protocol
The invention discloses a method for preventing neighbor discovery protocol message attack, which is applied to a system comprising a client and a gateway device. The method comprises the following steps: the gateway device obtains a legal neighbor discovery ND list item corresponding to the client; the gateway device stores the legal ND list item and sets the legal ND list item as the semi-static list item; when receiving dynamic configuration requests from other clients, the gateway device does not update the legal ND list item according to the dynamic configuration requests; when receiving a static configuration request from the client, the gateway device updates the legal ND list item according to the static configuration request. The method improves the reliability of DHCPv6 network equipment, ensures the safety of neighbor list items and reduces invalid resource occupation. The invention also provides a device corresponding to the method of the invention.
Owner:NEW H3C TECH CO LTD
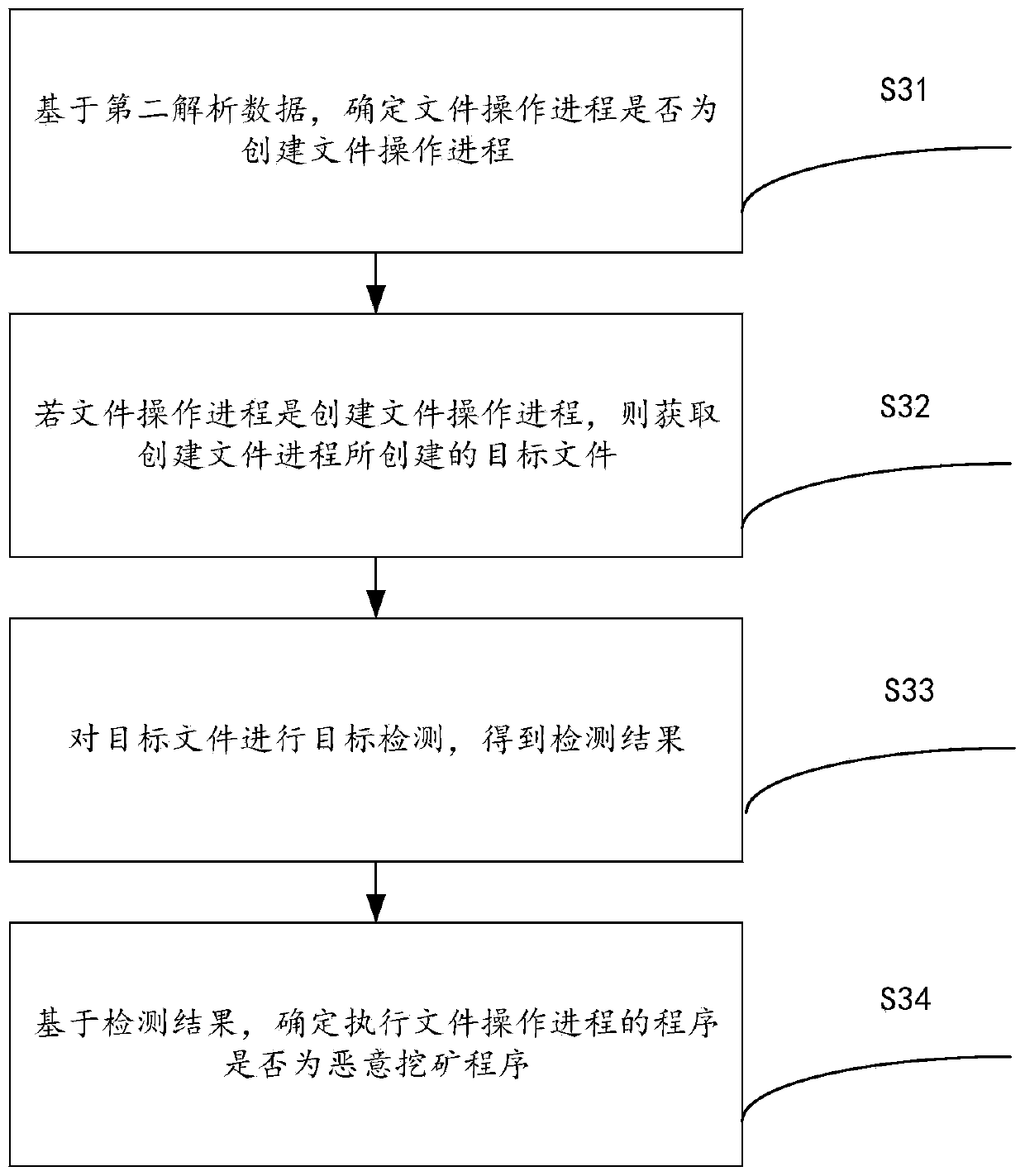
Malicious mining program active defense method and device
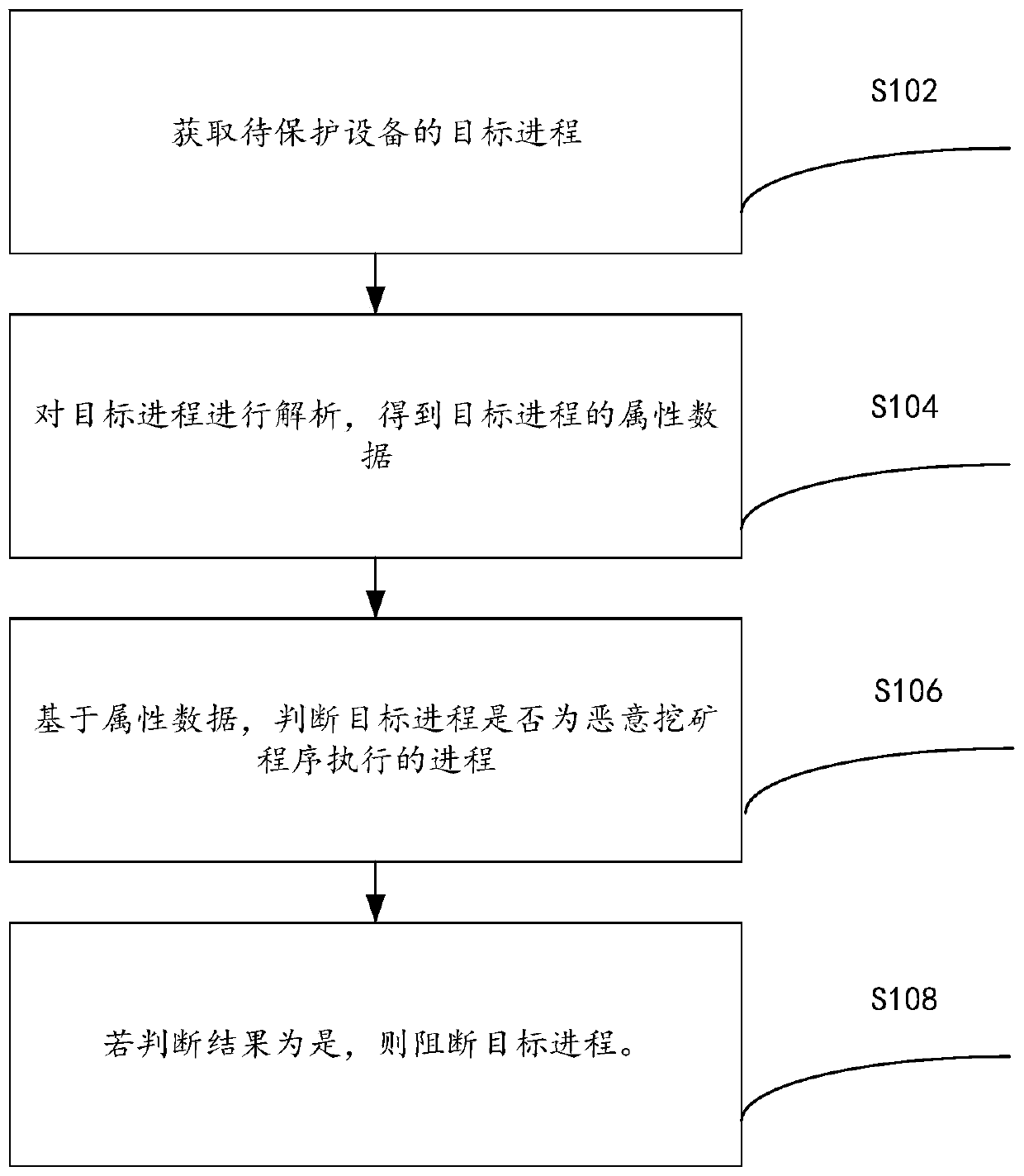
InactiveCN110619217ATo achieve the purpose of active defenseEnsure network securityPlatform integrity maintainanceActive DefenseNetwork security
The invention provides a malicious mining program active defense method and device, and relates to the technical field of network security, and the method comprises the following steps: obtaining a target process of to-be-protected equipment; analyzing the target process to obtain attribute data of the target process; judging whether the target process is a process executed by a malicious mining program or not based on the attribute data; and if the judgment result is yes, blocking the target process, thereby solving the technical problem that the malicious mining program cannot be actively defended in the prior art.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
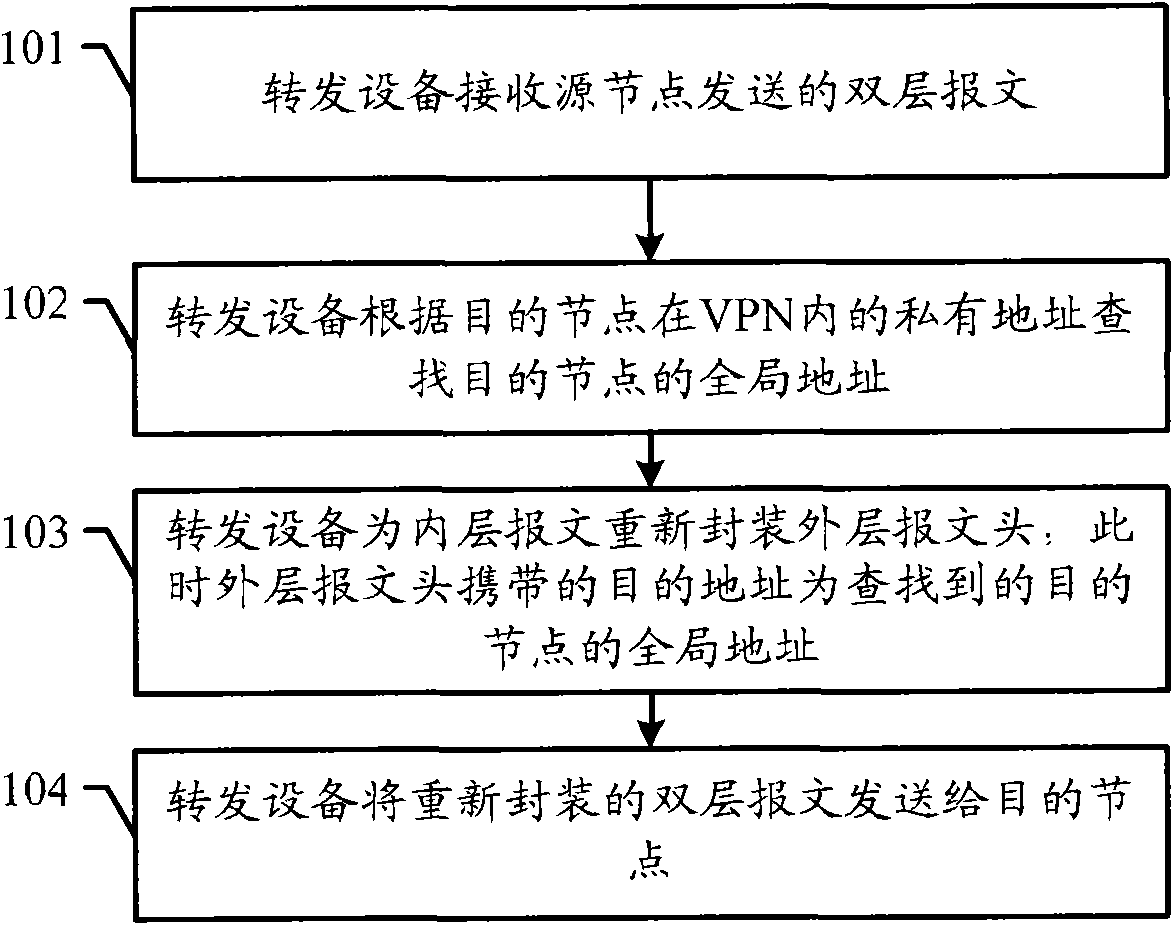
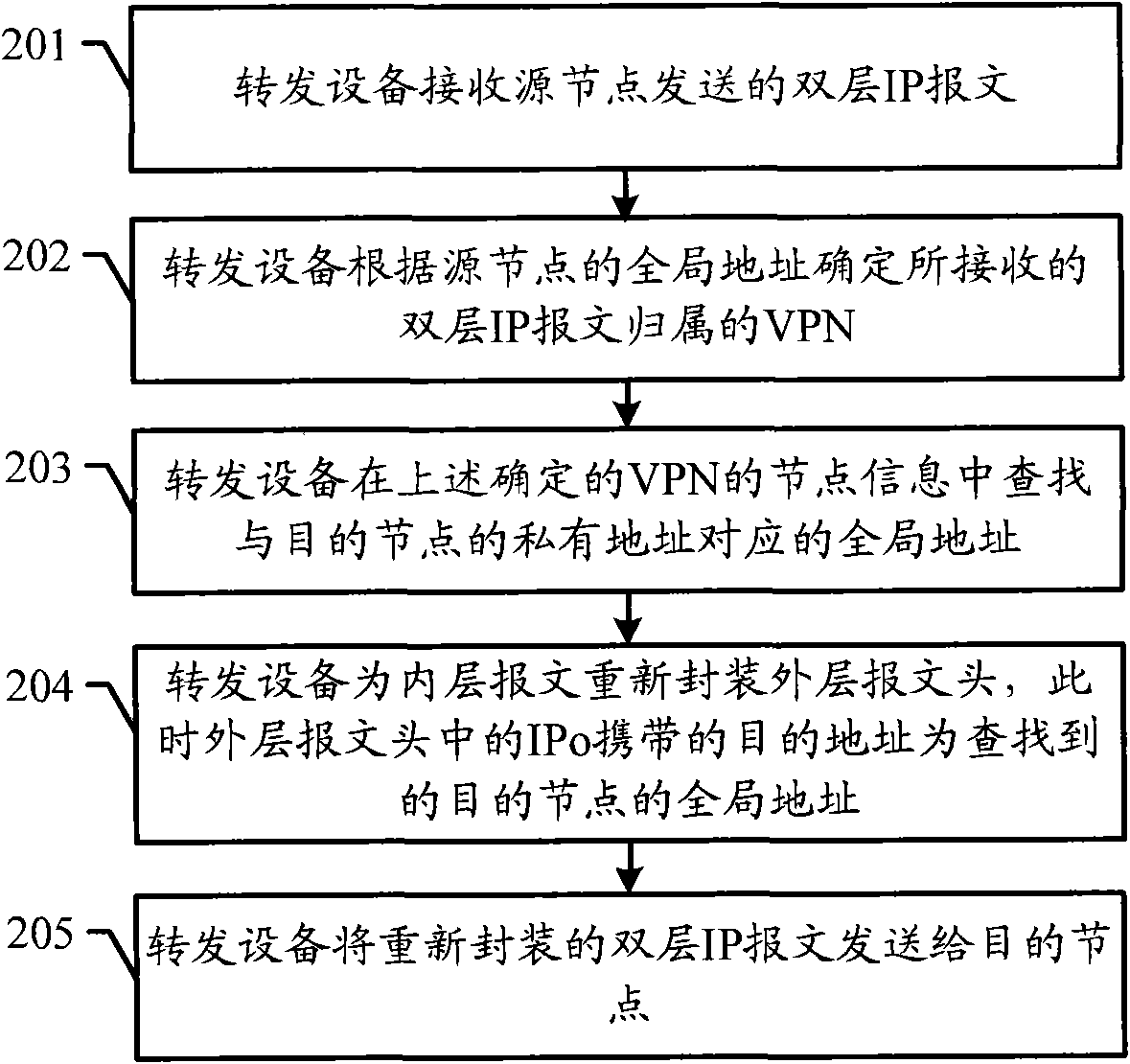
Message forwarding method, forwarding unit and network terminal equipment
The embodiment of the invention discloses a message forwarding method, a corresponding forwarding unit and network terminal equipment. The embodiment of the invention adopts the mode that based on the network message forwarding, a virtual private network is realized; nodes in the virtual private network needs the specific forwarding unit to forward the message so as to realize the intercommunication with each other, thus ensuring the network security of the virtual private network.
Owner:CHENGDU HUAWEI TECH
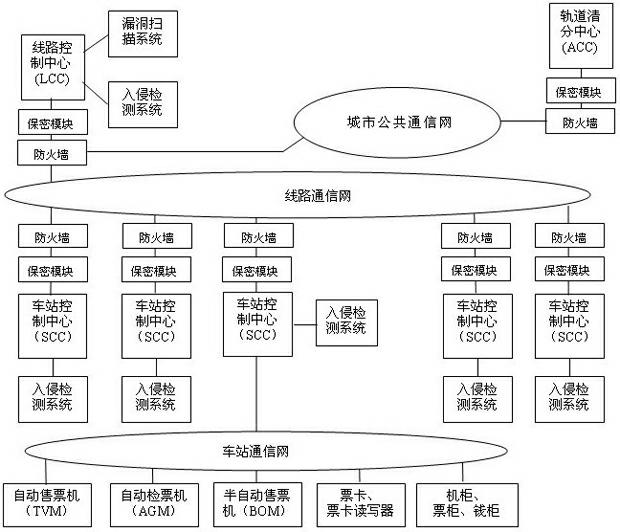
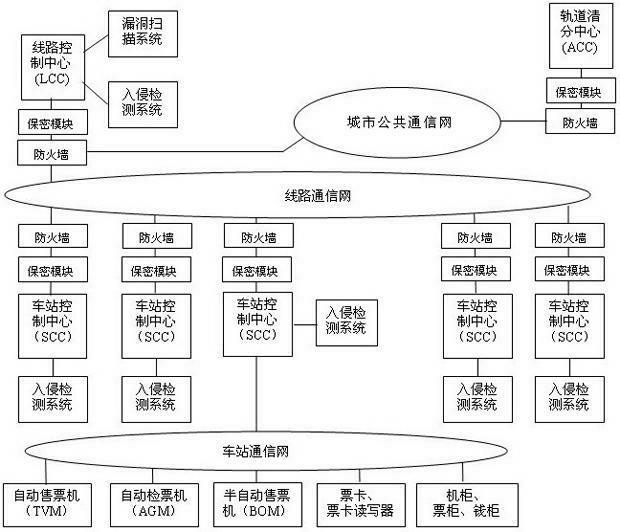
Track transportation automatic fare collection safety protection system and method thereof
InactiveCN102567668AEnsure network securityGuarantee data securityInternal/peripheral component protectionCollection systemSafety control
The invention discloses a track transportation automatic fare collection safety protection system and a method thereof. The track transportation automatic fare collection safety protection system comprises a station terminal device, at least one station control center, a line control center and a track clearing center. The station terminal device is connected with the station control centers through a station communication network respectively, a plurality of station control centers are connected with the line control center through the station communication networks, and the line control center is connected with the track clearing center through a city public communication network. The station terminal device is one or more of an automatic ticket vendor, an automatic ticket checker, a semi-automatic ticket vendor, a ticket card, a ticket card reader, a device cabinet, a ticket cabinet and a money cabinet. The station terminal device, the station control center and the line control center of the automatic fare collection system build a complete safety control system, safety of devices, networks and data of the track transportation automatic fare collection system is guaranteed, and personal safety, ticket card safety, property safety and the like are guaranteed accordingly.
Owner:四川久远新方向智能科技有限公司
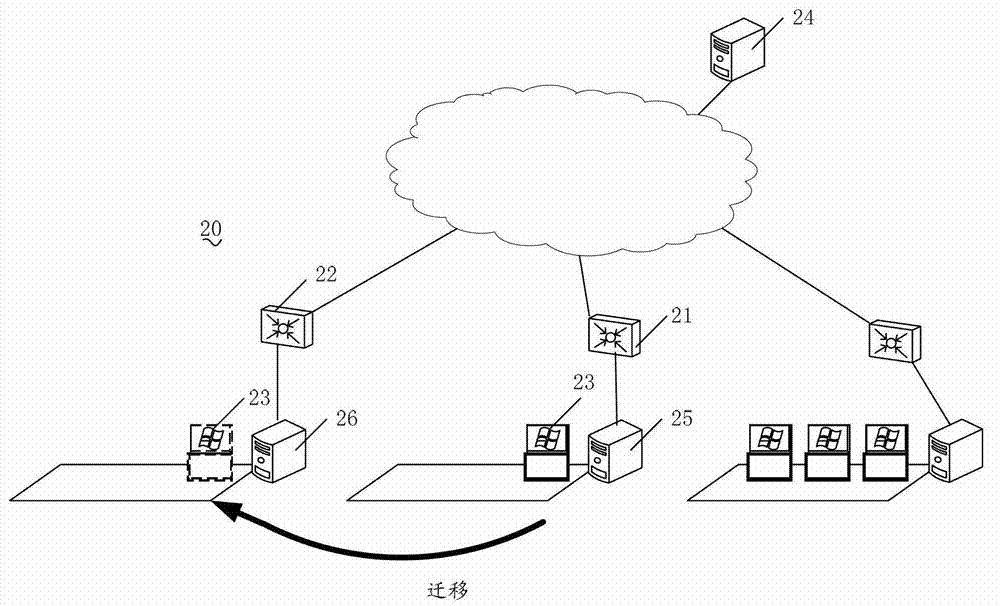
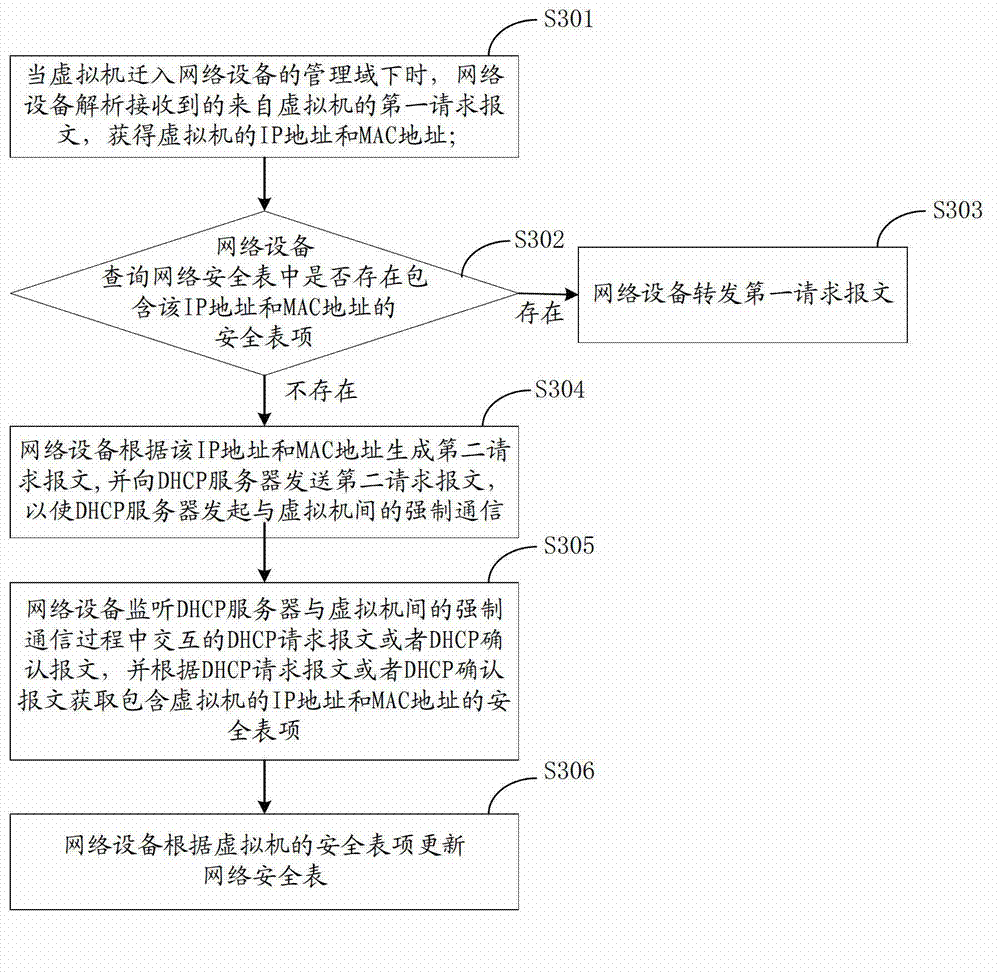
Method for updating network security table and network device and dynamic host configuration protocol (DHCP) server
InactiveCN103095722AGuaranteed reliabilityEnsure network securityTransmissionNetwork security policyMedia access control
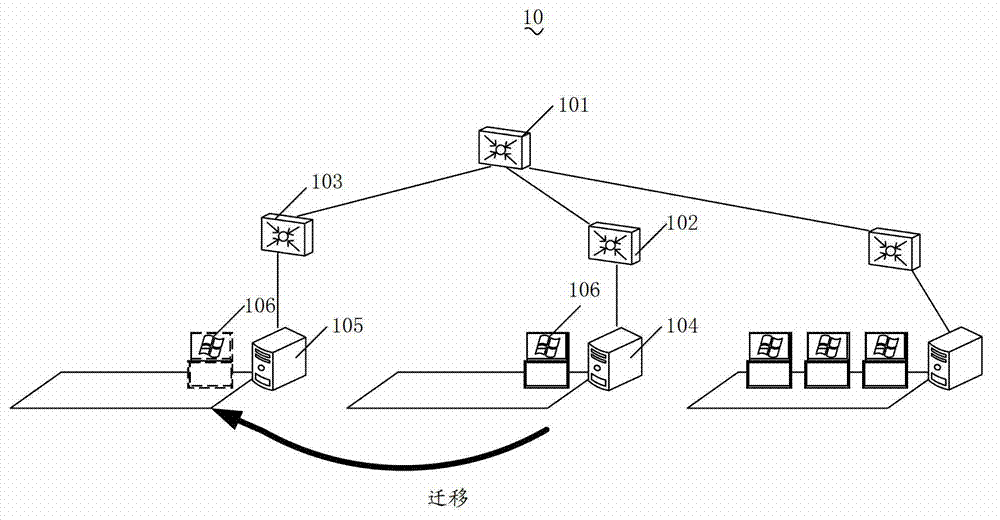
The invention discloses a method for updating network security table, a network device and a dynamic host configuration protocol (DHCP) server. When a virtual machine moves in a management domain of a network device, the network device analyses a first received request message from the virtual machine, an internet protocol (IP) address and a medium access control (MAC) address of the virtual machine are obtained, when a security table item including the IP address and the MAC address doesn't exist in a network security table of the network device, the network device sends a second request message generated according to the IP address and the MAC address to the DHCP server, so that the DHCP server is enabled to launch mandatory communication between the DHCP server and the virtual machine, the network device monitors an interactive message between the DHCP server and the virtual machine to obtain the security table item of the virtual machine, the network security table is updated according to the security table item. Through the above mode, the method for updating network security table, the network device and the DHCP server ensure that the virtual machine can access the network normally when the virtual machine moves in the management domain of the network device, reliability of the network security table is also ensured, and therefore network security is ensured.
Owner:HUAWEI TECH CO LTD
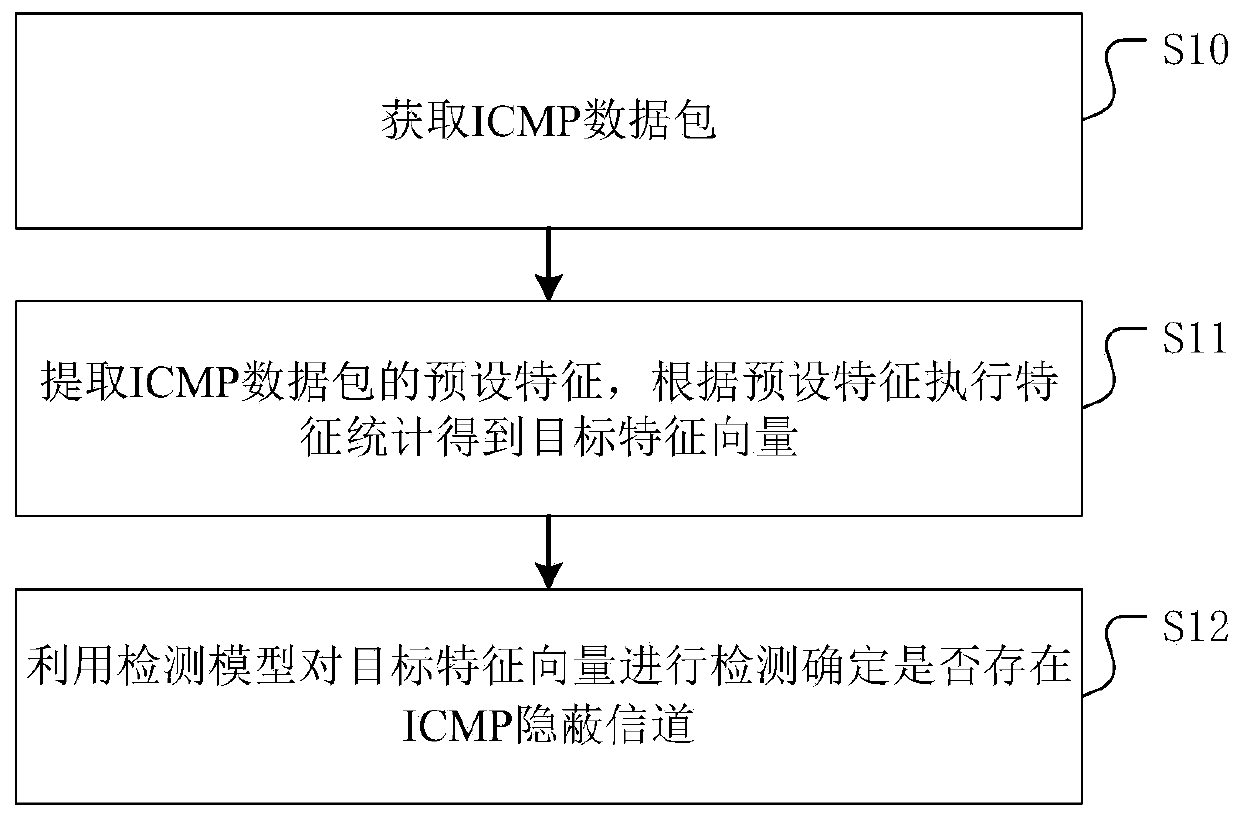
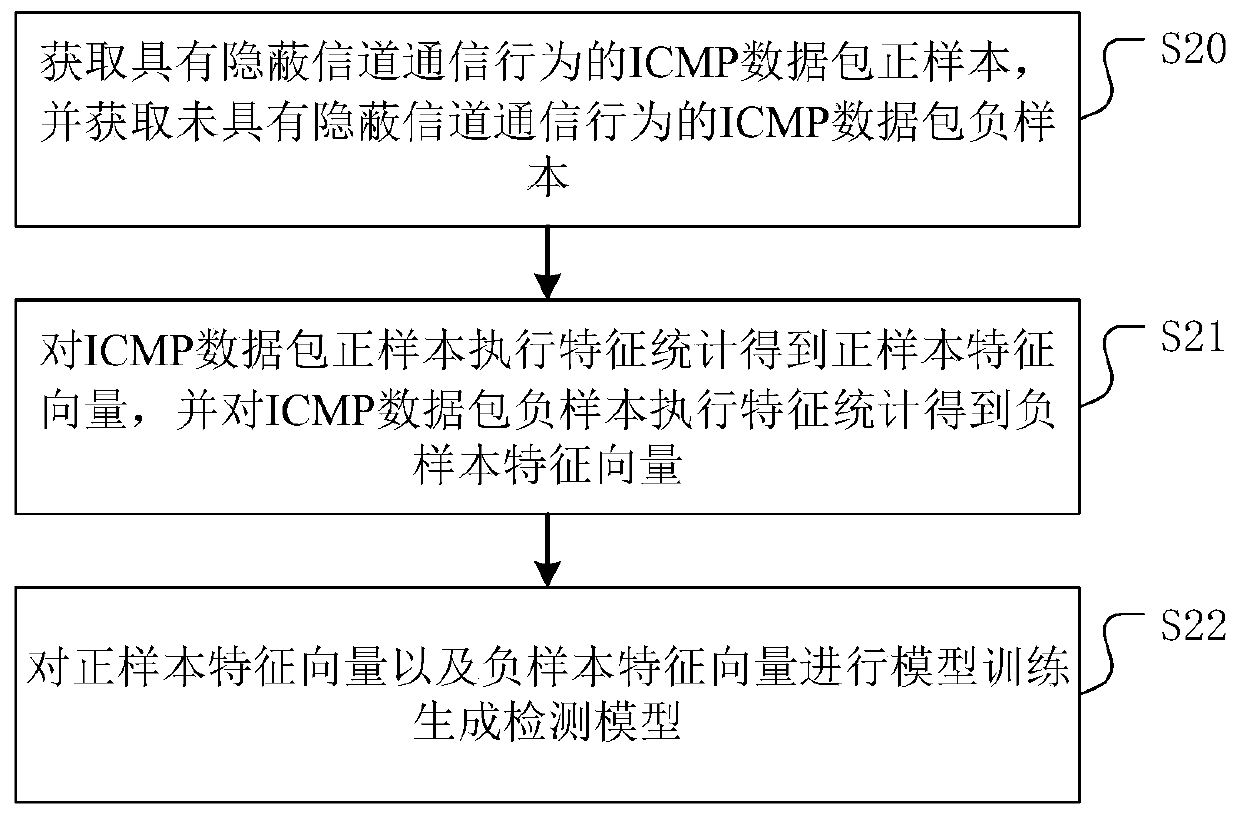
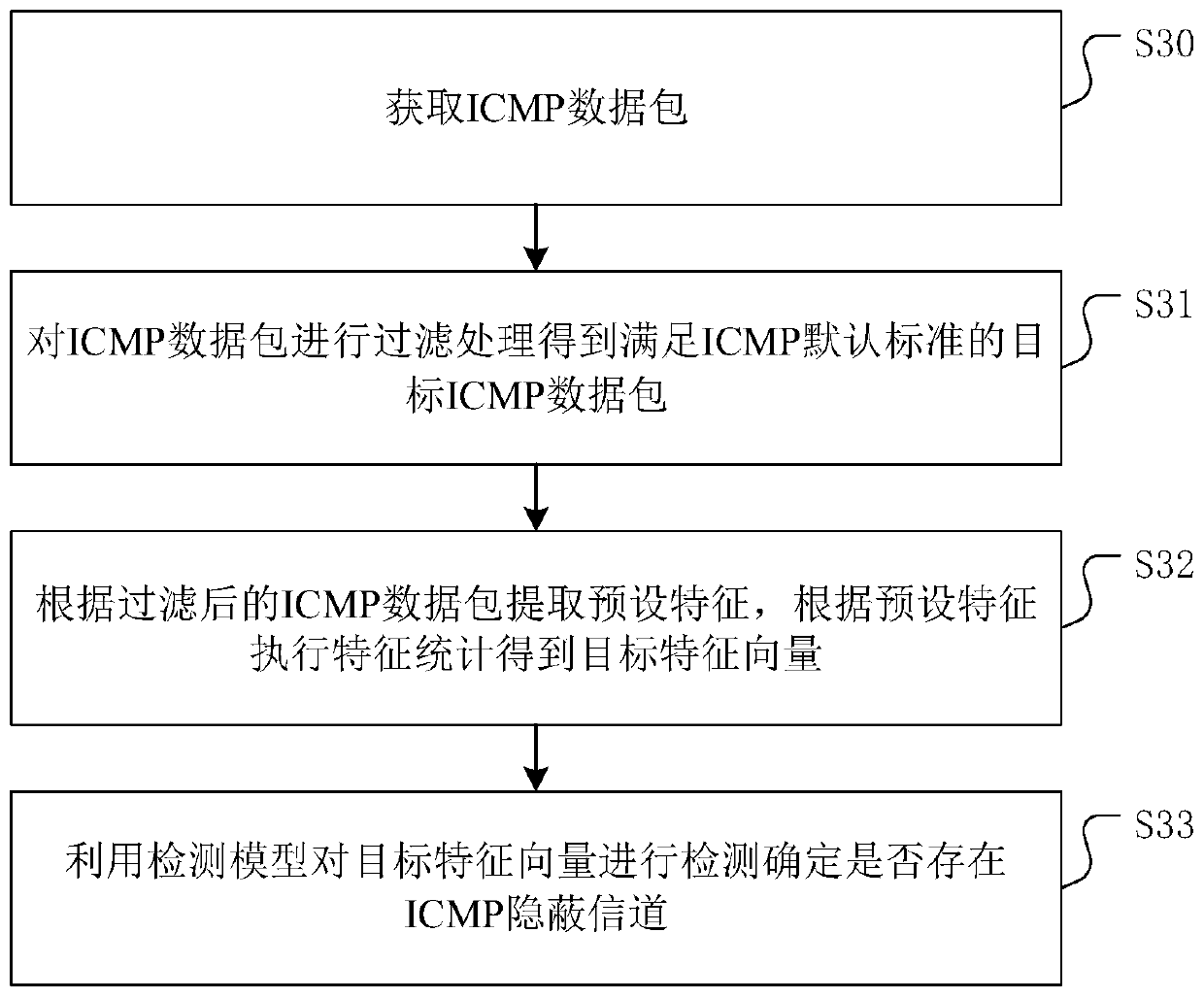
Covert channel communication detection method, device and equipment
The invention discloses a covert channel communication detection method, device and equipment. The method comprises the following steps: acquiring an ICMP data packet; extracting the preset feature ofthe ICMP data packet, and executing feature statistics according to the preset feature to obtain an execution feature statistics to obtain a target feature vector; and detecting the target feature vector by using the detection model to determine whether an ICMP covert channel exists or not. According to the method, the detection model is used for detecting the target feature vector to determine whether the ICMP covert channel exists or not, so that covert channel communication detection based on the ICMP data message is realized, and the network security of the user host is relatively ensured. In addition, the invention further provides a covert channel communication detection device and equipment based on ICMP and a storage medium, and the beneficial effects are as described above.
Owner:SANGFOR TECH INC
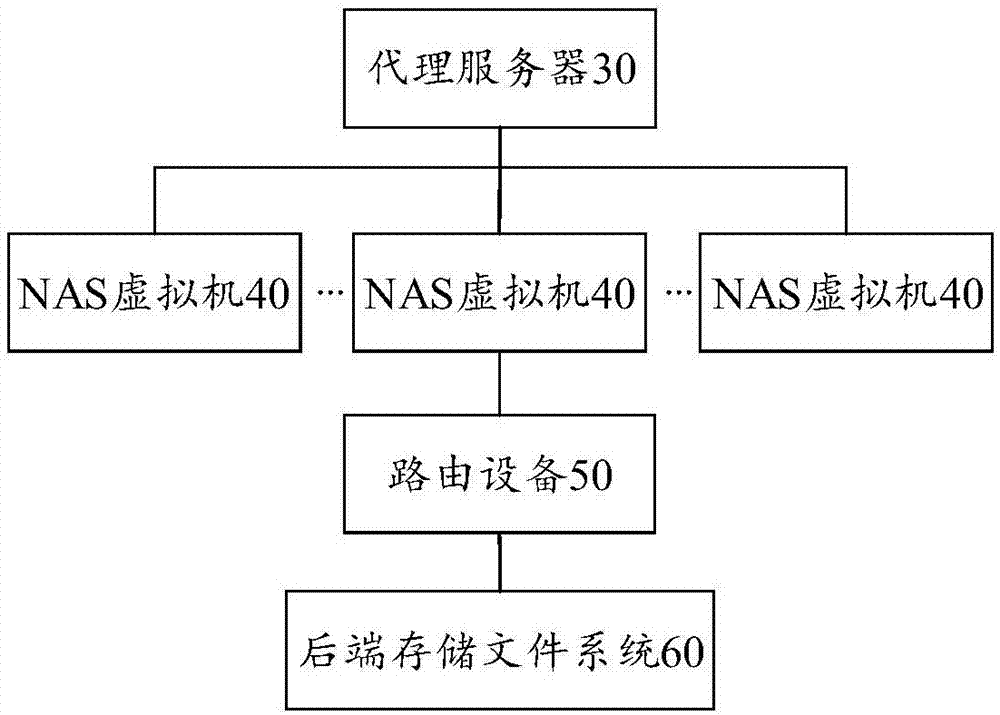
Distributed network attached storage method and system
ActiveCN106878457AEnsure network securityMake full use of network resourcesData switching networksClient-sideSystem service
The invention discloses a distributed network attached storage method and system. The distributed network attached storage method comprises the steps that a proxy server receives mounting requests initiated by clients, wherein the proxy server is connected to a plurality of NAS (Network Attached Storage) virtual machines, the plurality of NAS virtual machines are connected with the clients, and the plurality of NAS virtual machines are connected with a back-end storage file system through routing equipment; the proxy server distributes the mounting requests of different clients to different NAS virtual machines, and the selected NAS virtual machine acts as a file system server to provide network file system services for the corresponding client. In the invention, a plurality of NAS virtual machines provide services for users simultaneously, and only part of service ports are externally exposed, so that the network security is ensured; and distributed processing is performed on mounting requests of the users, so that network resources can be sufficiently utilized, and read-write bandwidth requirements of the users are met to the maximum extent.
Owner:CHINANETCENT TECH
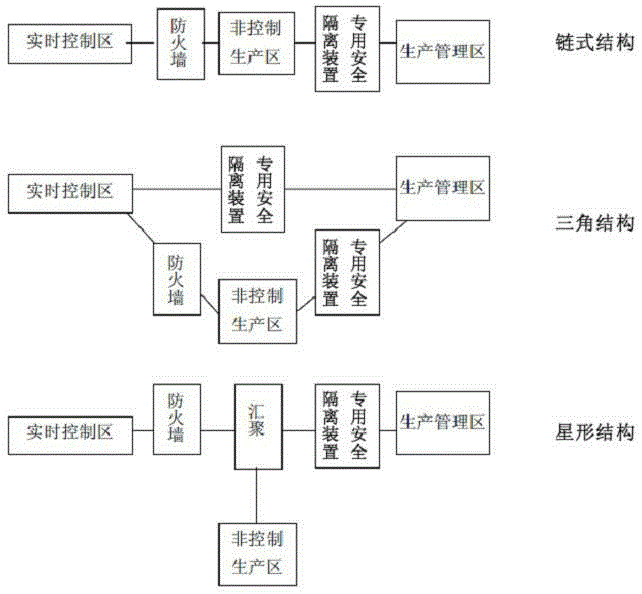
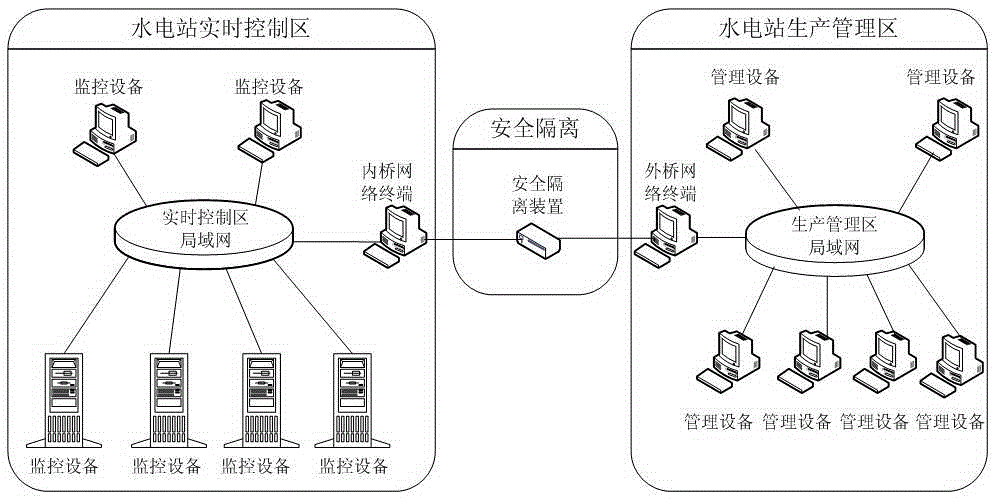
Hydropower station Ethernet-type security isolation device inside-outside universal data bridge
InactiveCN105391613AMeet the requirements of secondary securityAvoid attackNetworks interconnectionNetwork terminationManagement process
The invention discloses a hydropower station Ethernet-type security isolation device inside-outside universal data bridge comprising an inner bridge network terminal, an outer bridge network terminal, and a security isolation device. The inner bridge network terminal is mounted in a hydropower station real-time control area, and is used for collecting data of monitoring equipment in the hydropower station real-time control area. The security isolation device is used for realizing one-way transmission between the inner bridge network terminal and the outer bridge network terminal and physical isolation between the inside and outside of the Ethernet and transmitting the data collected by the inner bridge network terminal to the outer bridge network terminal in a one-way mode. The outer bridge network terminal is mounted in a hydropower station production management area, and is used for receiving the data from the inner bridge network terminal and transmitting the data to management equipment in the hydropower station production management area in real time. According to the invention, the hydropower station production management area can acquire the data of the hydropower station real-time control area in real time, and real-time production process data can be added in the management process to realize management and control integration.
Owner:四川中鼎自动控制有限公司
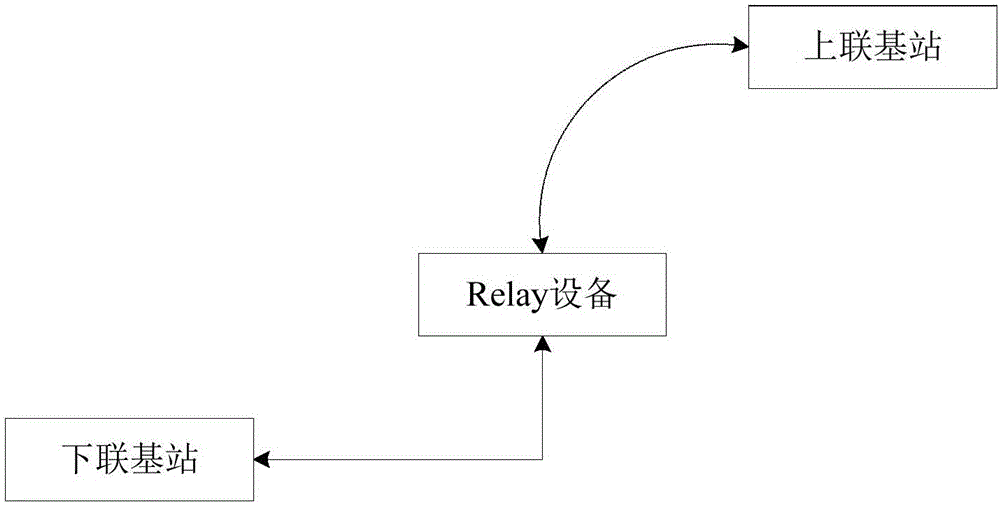
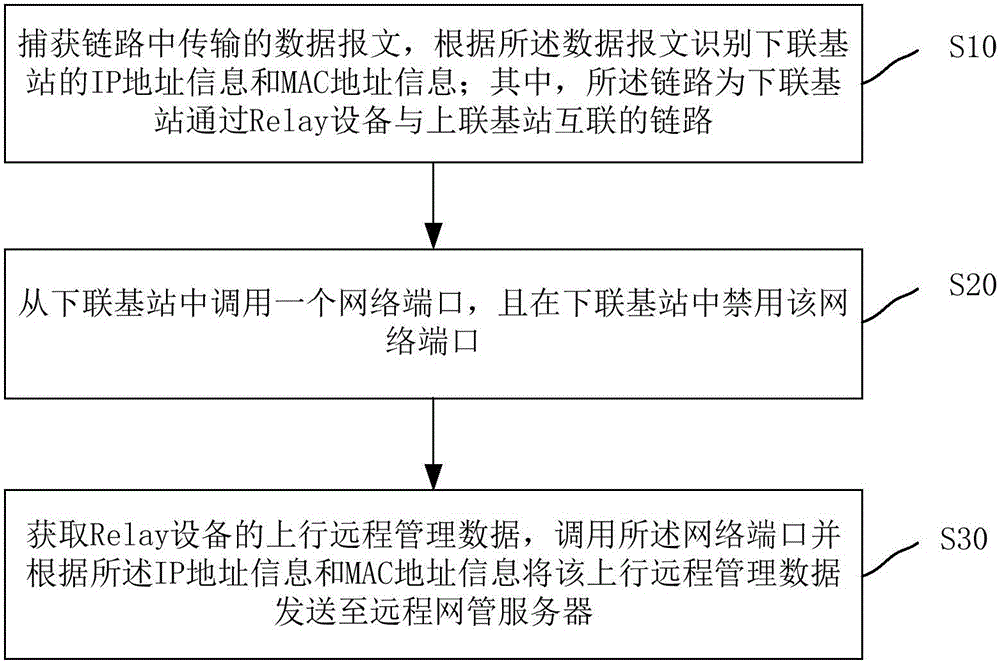
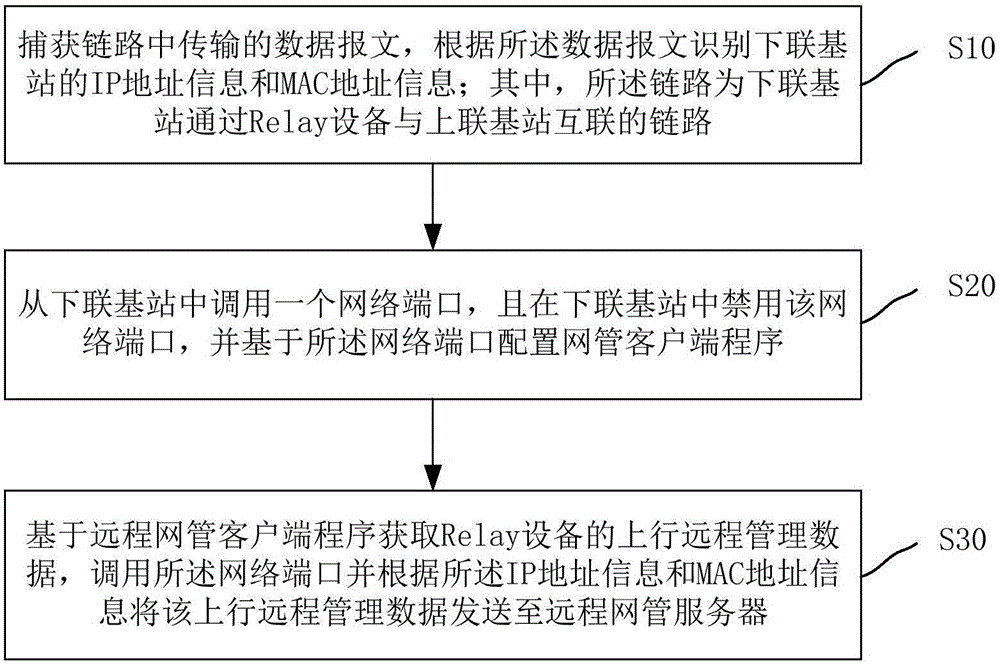
Method and system for connecting relay device with remote network management server, and the relay device
ActiveCN106413127AHigh feasibilityImprove maintainabilityConnection managementIp addressMaintainability
The invention relates to a method and system for connecting a relay device with a remote network management server, and the relay device. The method comprises the steps of capturing a data message transmitted in a link, and identifying IP address information and MAC address information of a subordinate base station according to the data message, wherein the link is the link for connecting the subordinate base station with a superior base station through the relay device; calling a network port from the subordinate base station and forbidding the network port in the subordinate base station; obtaining uplink remote management data of the relay device, calling the network port and sending the uplink remote management data to the remote network management server according to the IP address information and MAC address information. According to the method, the system and the device, the relay device can receive management maintenance of the remote network management server conveniently, the wide range layout feasibility and maintainability of the relay device can be improved, IP addresses of a public network can be saved, and the network security of the relay device can be ensured to the greatest extent.
Owner:COMBA TELECOM SYST CHINA LTD
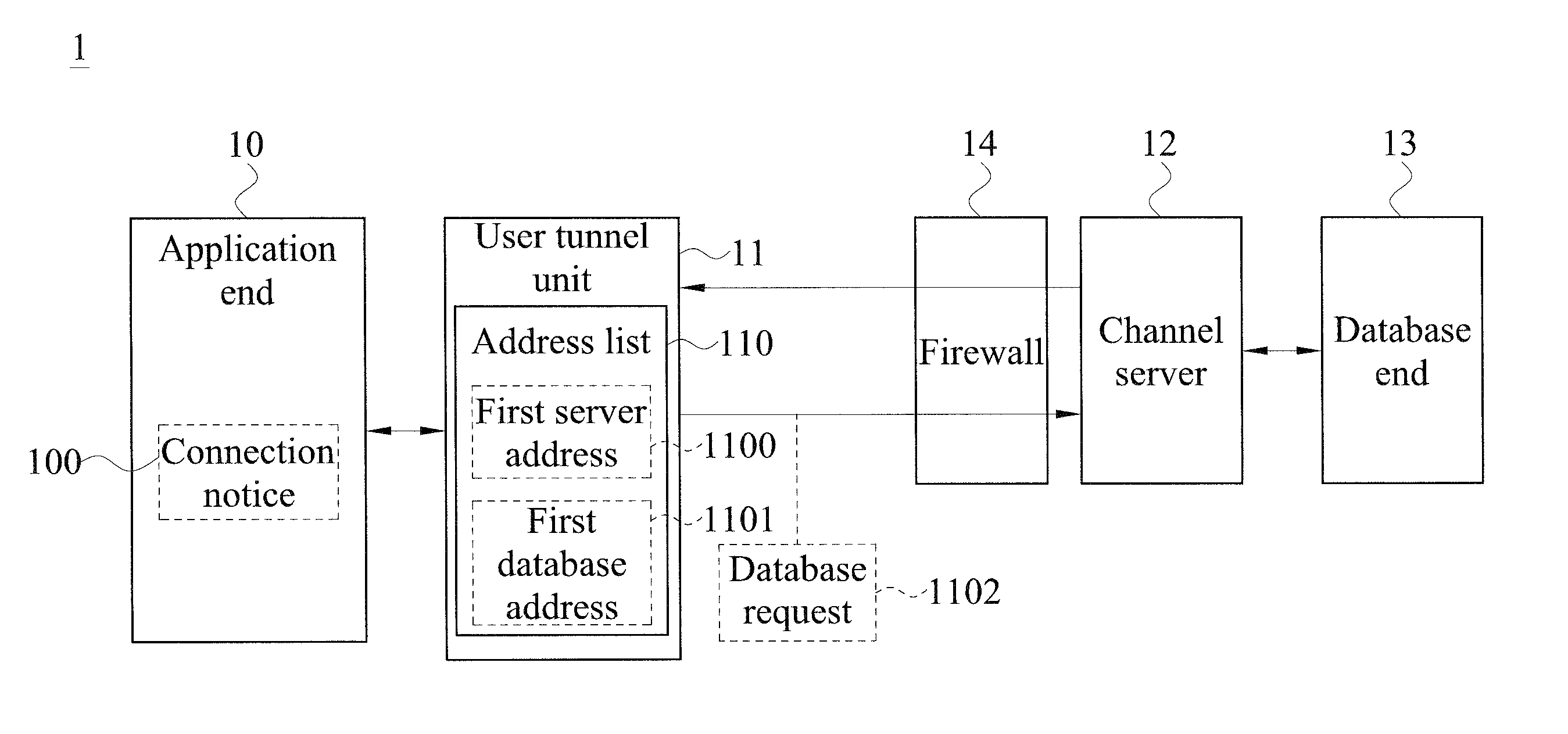
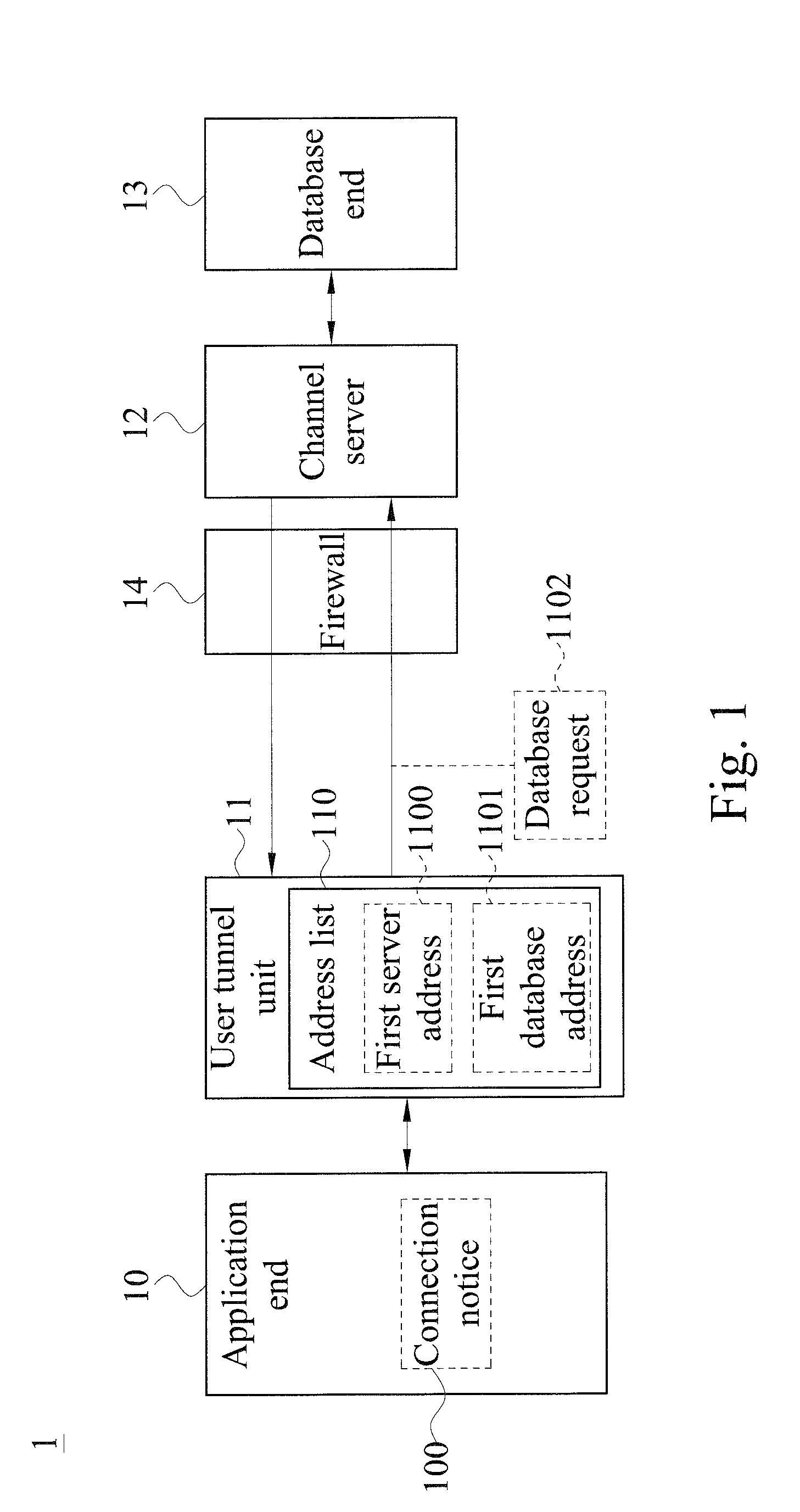
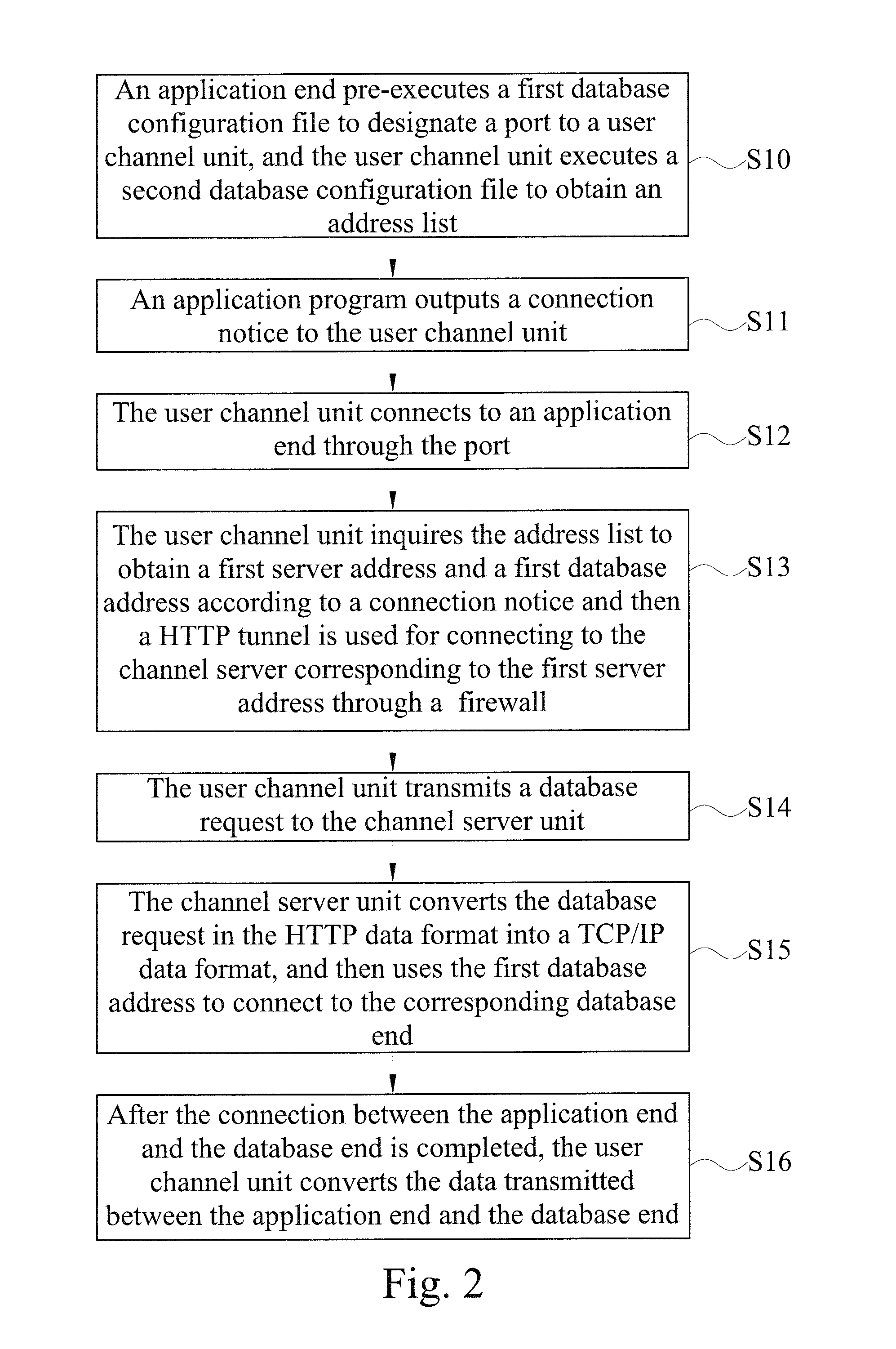
System for accessing data of cloud database using transparent technology
ActiveUS20150074794A1Improve operating convenience and using satisfactionEnsure network securityMultiple digital computer combinationsProgram controlHTTP tunnelThe Internet
Disclosed is a system for accessing data of a cloud database via transparent technology, and the system includes at least one channel server and at least one cloud database end. When a connection notice is outputted from an application end, the user channel unit detects a first server address and a first database address in a HTTP data format, and connects to a corresponding channel server via the HTTP tunnel to send a database request, so that the channel server can convert the first database address in the HTTP data format into a TCP / IP data format and then connect to a corresponding database end. Therefore, the application end can access data from the database behind the firewall via the Internet without modifying any program code.
Owner:SYSCOM COMP ENG
Method for controlling rapid login of wireless intelligent product
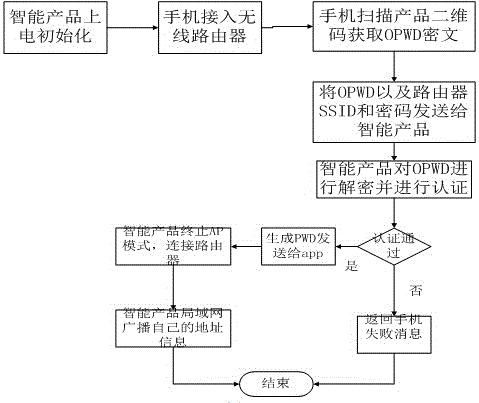
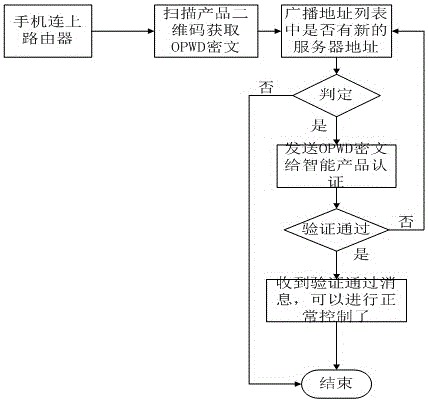
InactiveCN106211145AImprove network securityImprove experienceConnection managementTransmissionCiphertextPassword
The invention belongs to the field of intelligent household control, and relates to a method for controlling rapid login of a wireless intelligent product. Compared to a conventional control method, the method has the following advantages: login can be realized without a registered account, the operation is simple, the intelligent product can be configured for network access and connection simply through scanning, while application is facilitated, the network security of the intelligent product is improved through two security verification modes, i.e., a wifi router password and a unique identity code UPWD cyphertext of a two-dimensional code, the application is flexible, and user experience of the product is improved; and the control method can simplify the network access and login flow of the intelligent product, realizes multiple application through configuration at a time, reduces the complexity of product application to the maximum degree, at the same time, guarantees the network security of the intelligent product and enhances user experience.
Owner:JIANGXI HONGDU AVIATION IND GRP
FPGA (Field Programmable Gate Array)-based network security log processing method and device
ActiveCN102098291AAvoid Cybersecurity RisksEnsure network securityData switching networksIp addressReal-time computing
The invention provides an FPGA (Field Programmable Gate Array)-based network security log processing method and device. The device comprises a network data storage, a user rule storage and a feature comparator. The method comprises the steps of: receiving packets sent by an external network, and temporarily storing the packets in the network data storage; detecting source and target IP addresses, source and target ports and protocols of the network packets, and monitoring the control bit of a message; for packets in accordance with set source and target IP addresses, set source and target ports and a set protocol, filtering results according to rules for hit packets, analyzing packet header information and filtering actions, and judging whether to send a log packet and determining the type of the log packet; and when a feature value is accorded with, grouping the packets taken from the network data storage, and sending the grouped packets to a mainframe memory to be stored, and analyzing data. By means of the method and the device provided by the invention, packet contents on the network can be monitored in time, network security risks can be prevented from increasing, and the network security is guaranteed.
Owner:曙光网络科技有限公司
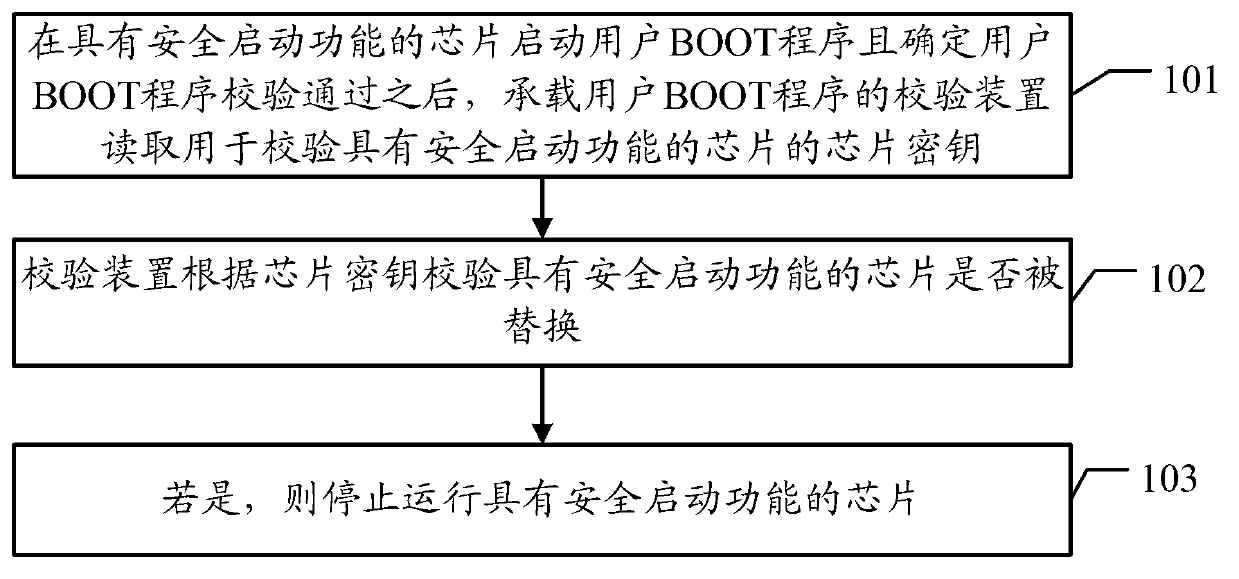
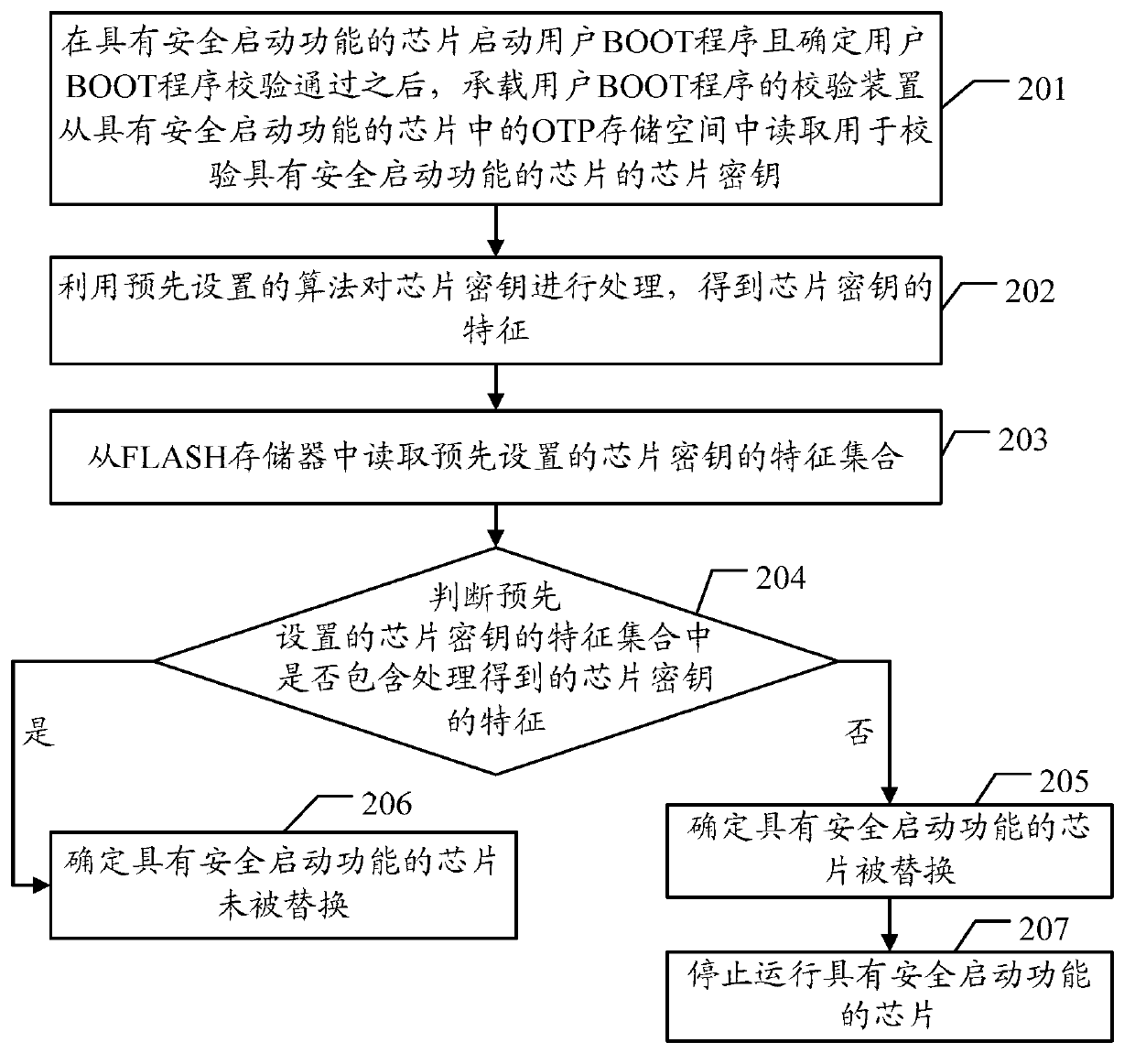
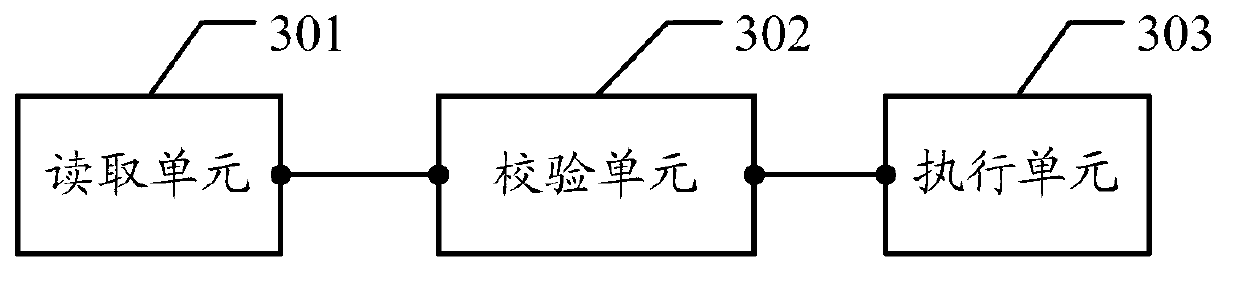
Validation method and validation device of chip with secure booting function
InactiveCN103279705AEnsure network securityEnsure safetyComputer security arrangementsBootingValidation methods
The invention discloses a validation method and a validation device of a chip with a secure booting function. The validation method of the chip with the secure booting function comprises the following steps that the validation device carrying BOOT procedures of a user reads a chip secret key used for verifying the chip with the secure booting function after the BOOT procedures guided by the user are started by the chip with the secure booting function and the BOOT procedures of the user are confirmed to be verified; the validation device judges whether the chip with the secure booting function is replaced or not according to the chip secret key; if the chip with the secure booting function is replaced, the chip of the secure booting function is stopped operating, a single board is prevented from starting, a network is prevented from being illegally embezzled and an operator network is prevented from being attacked, and therefore the safety of networks is guaranteed.
Owner:SHANGHAI HUAWEI TECH CO LTD
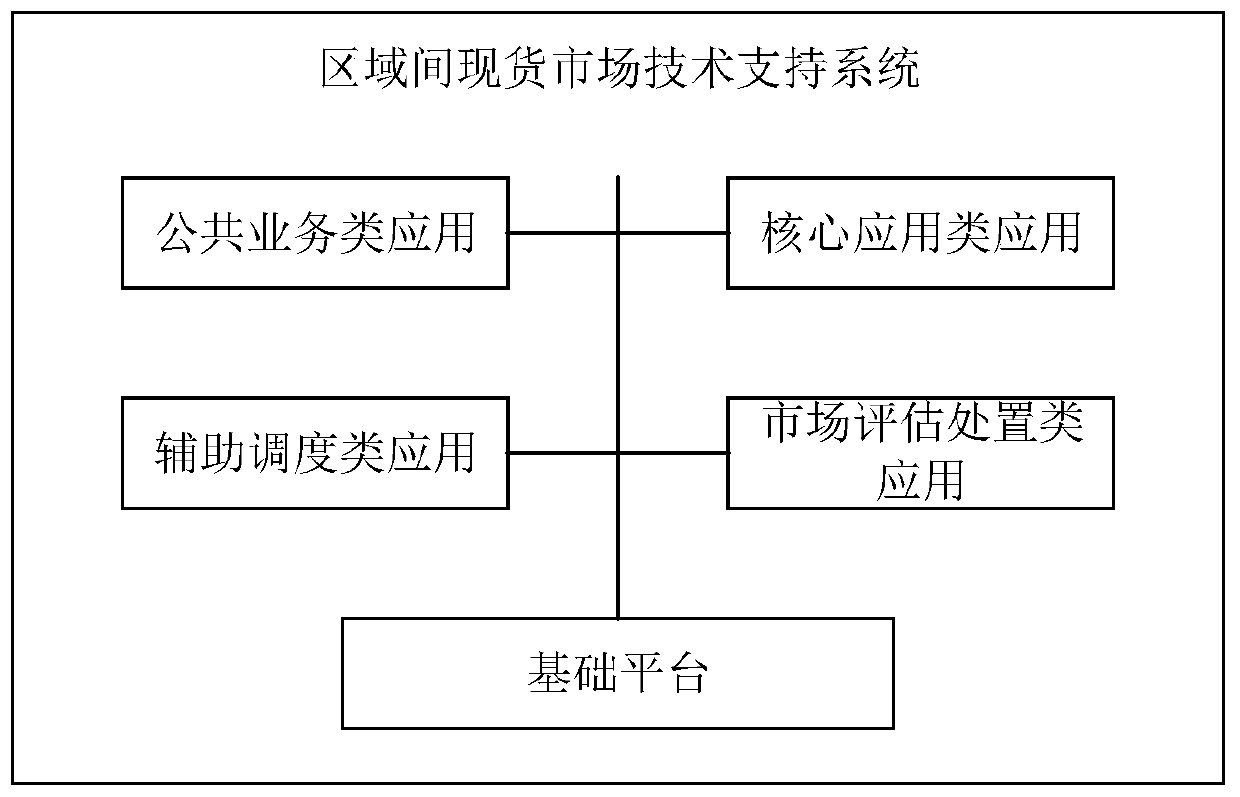
Inter-regional spot market technical support system
PendingCN110570083AMeet functional requirementsIntegrity guaranteedResourcesMarketingFunctional requirementComputer science
The invention provides an inter-regional spot market technical support system. The system comprises a basic platform, a public service application, a core application, an auxiliary scheduling application and a market evaluation disposal application. The inter-regional spot market technical support system provided by the invention meets the market rules and development goals of the inter-regional electric spot market, meets the functional requirements of spot market operation, and ensures the practicability and applicability of the system.
Owner:CHINA ELECTRIC POWER RES INST +2
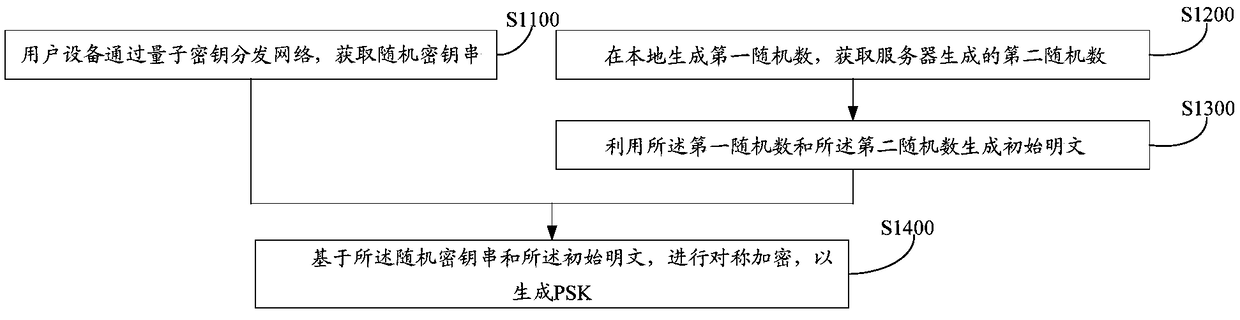
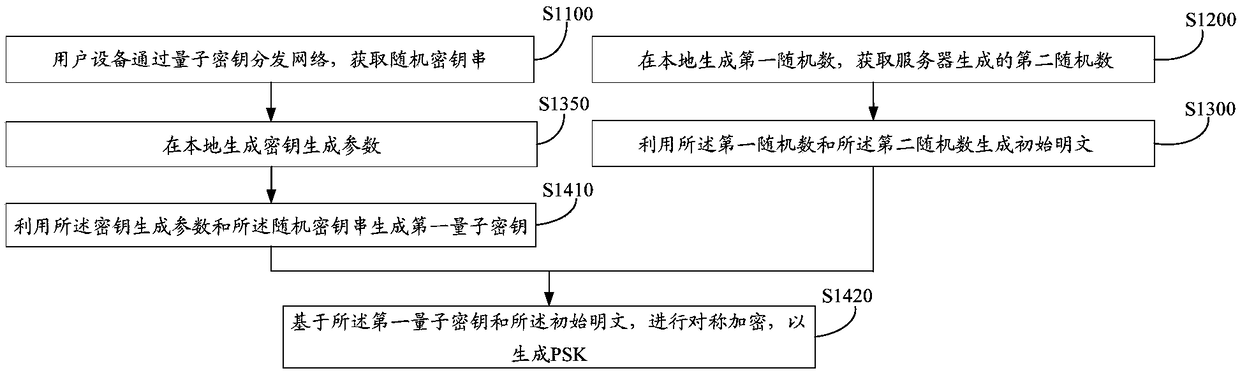
PSK generation method and apparatus, user equipment, server, and storage medium
ActiveCN108964912AEnsure network securitySmall amount of calculationKey distribution for secure communicationKey generationQuantum key distribution
The invention provides a PSK generation method and apparatus, user equipment, a server, and a storage medium. The method comprises the following steps: obtaining a random key string through a quantumkey distribution network; generating a first random number locally, and obtaining a second random number generated by the server; generating an initial plaintext by using the first random number and the second random number; and performing symmetric encryption based on the random key string and the initial plaintext to generate a PSK. According to the method, the random key string is obtained by using the quantum key distribution network with high security, and only symmetric encryption is adopted in the process of generating the PSK, so that the calculation amount of key generation can be reduced under the premise of ensuring the network security.
Owner:SANGFOR TECH INC
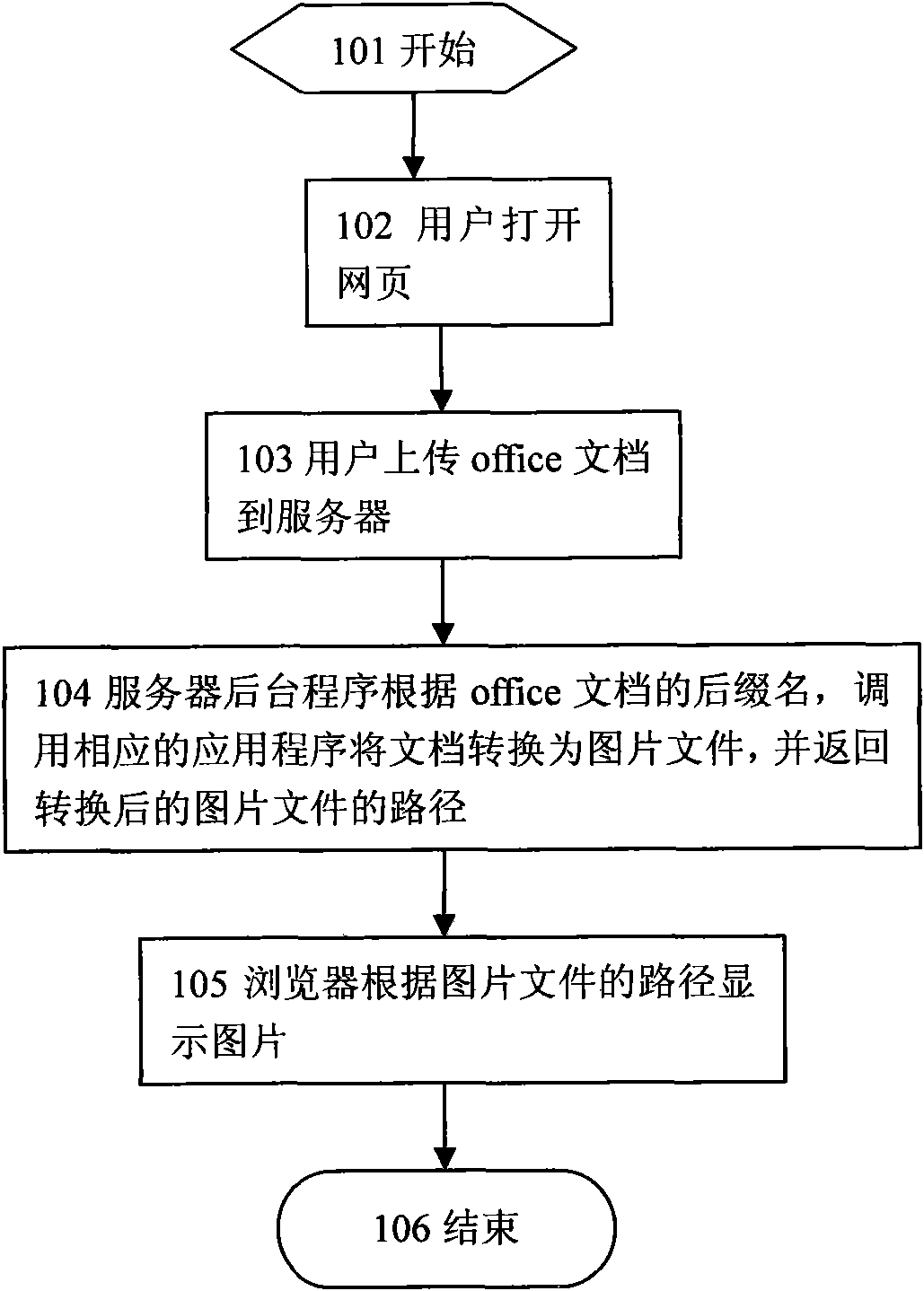
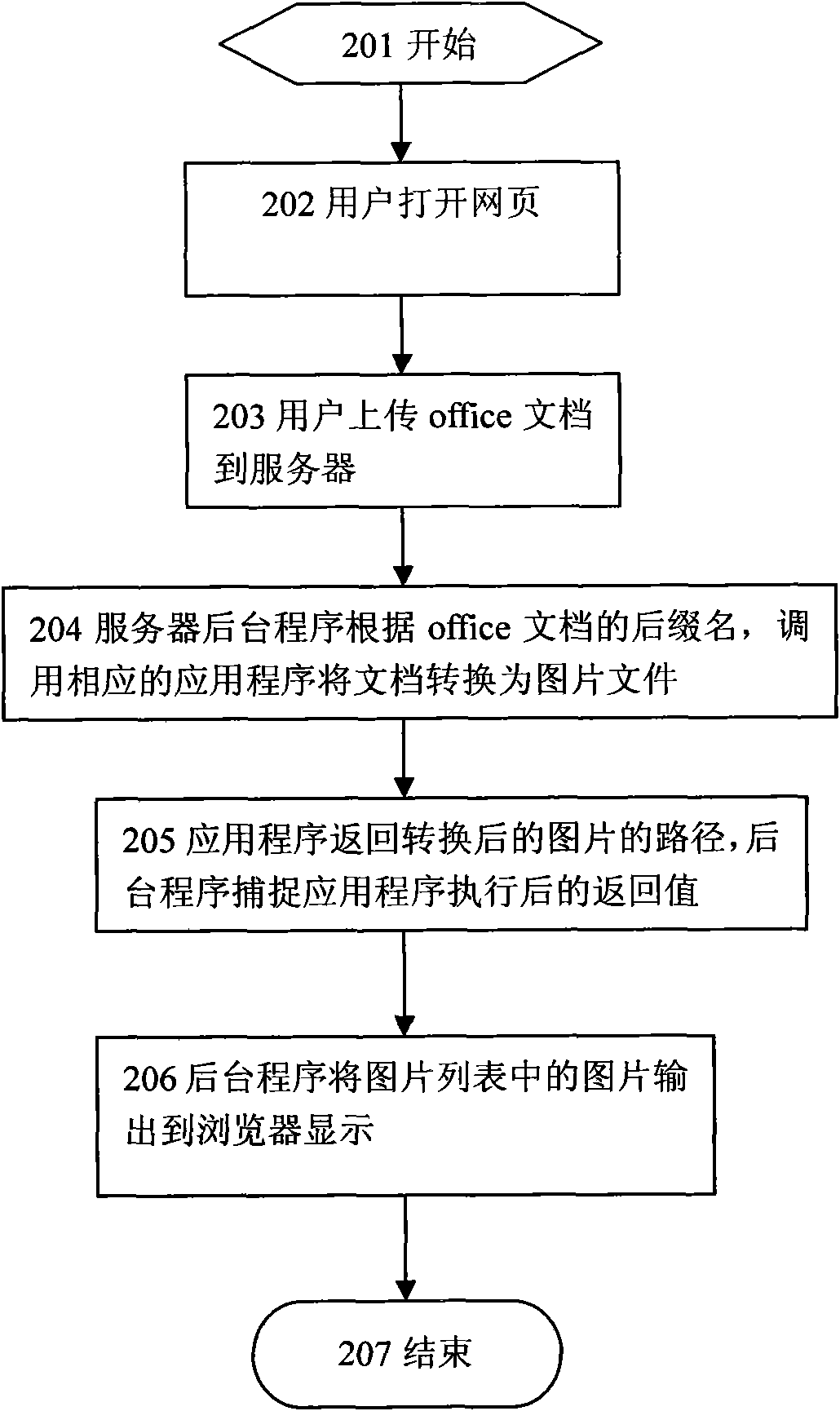
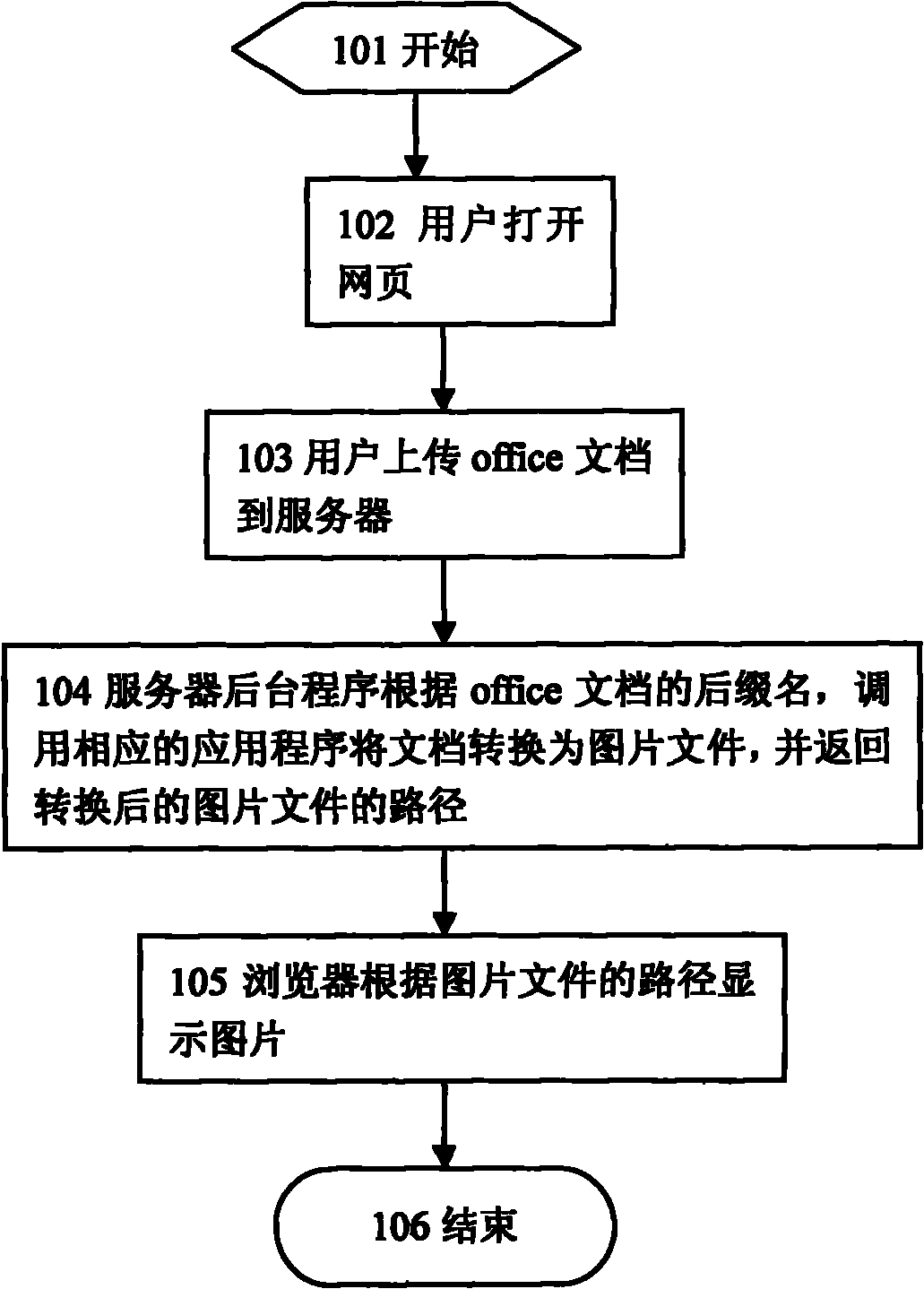
Method for converting document into image
InactiveCN102314470AMeet the need to view all content of the documentImprove bindingSpecial data processing applicationsWeb data browsing optimisationThird partyDocument preparation
Owner:SUZHOU CODYY NETWORK SCI & TECH
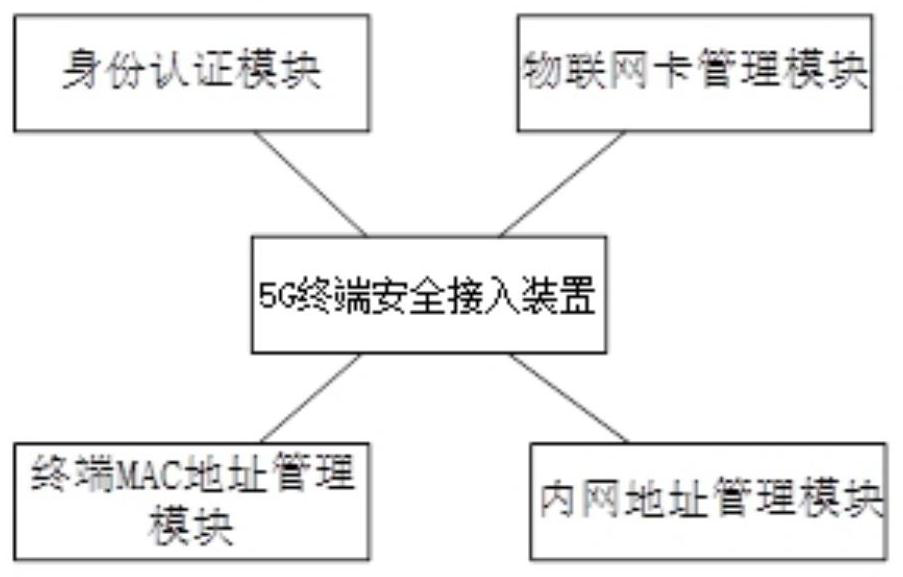
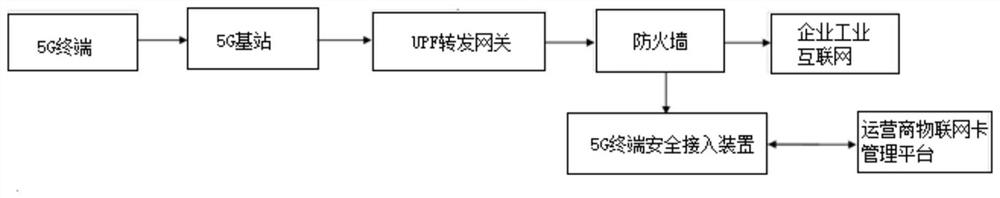
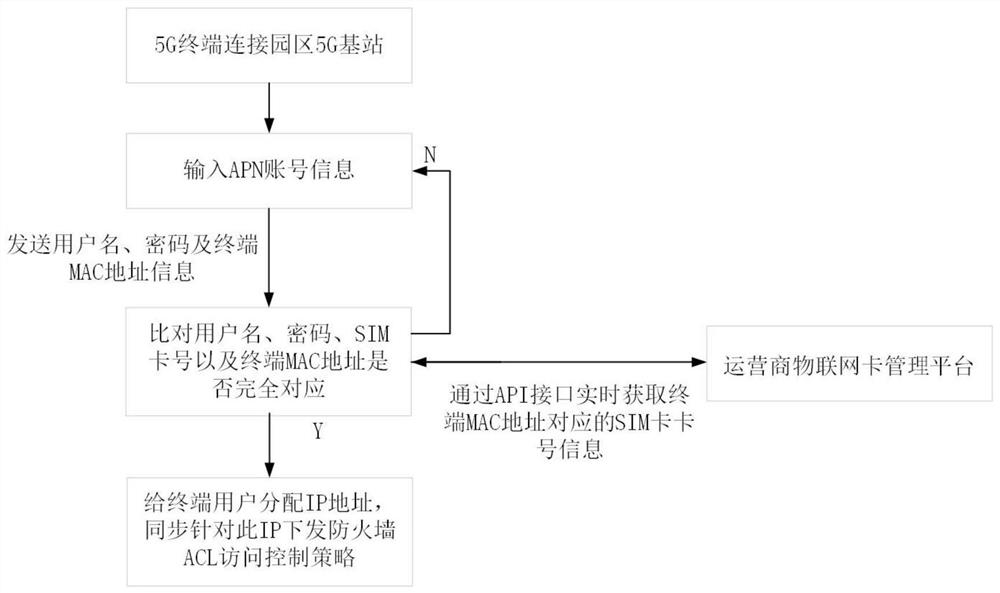
5G terminal security access device, system and equipment
ActiveCN112492602APrevent theftAvoid a series of information security risks such as being stolenSecurity arrangementHigh level techniquesNetwork addressingEngineering
The embodiment of the invention provides a 5G terminal security access device, system and equipment. The device comprises an identity authentication module used for identifying the identity of a user;the Internet of Things card management module is used for being in butt joint with an operator Internet of Things card management platform and obtaining SIM card information; the terminal MAC addressmanagement module is used for acquiring 5G terminal MAC address information; and the intranet address management module is used for issuing a network address and authorizing access to an internal system. According to the 5G terminal security access device, system and equipment provided by the embodiment of the invention, a series of information security risks such as loss of the 5G terminal, lossof an SIM card and stealing of an account can be avoided, and the network security of accessing the 5G terminal to an enterprise internal network is ensured to the greatest extent.
Owner:武汉武钢绿色城市技术发展有限公司
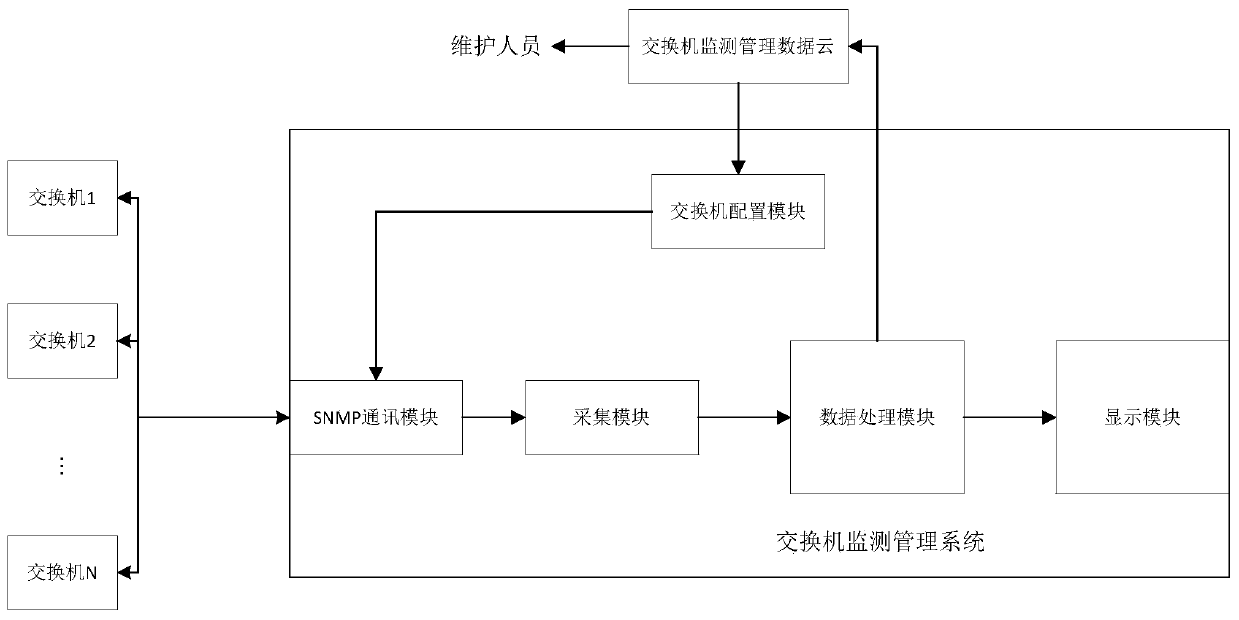
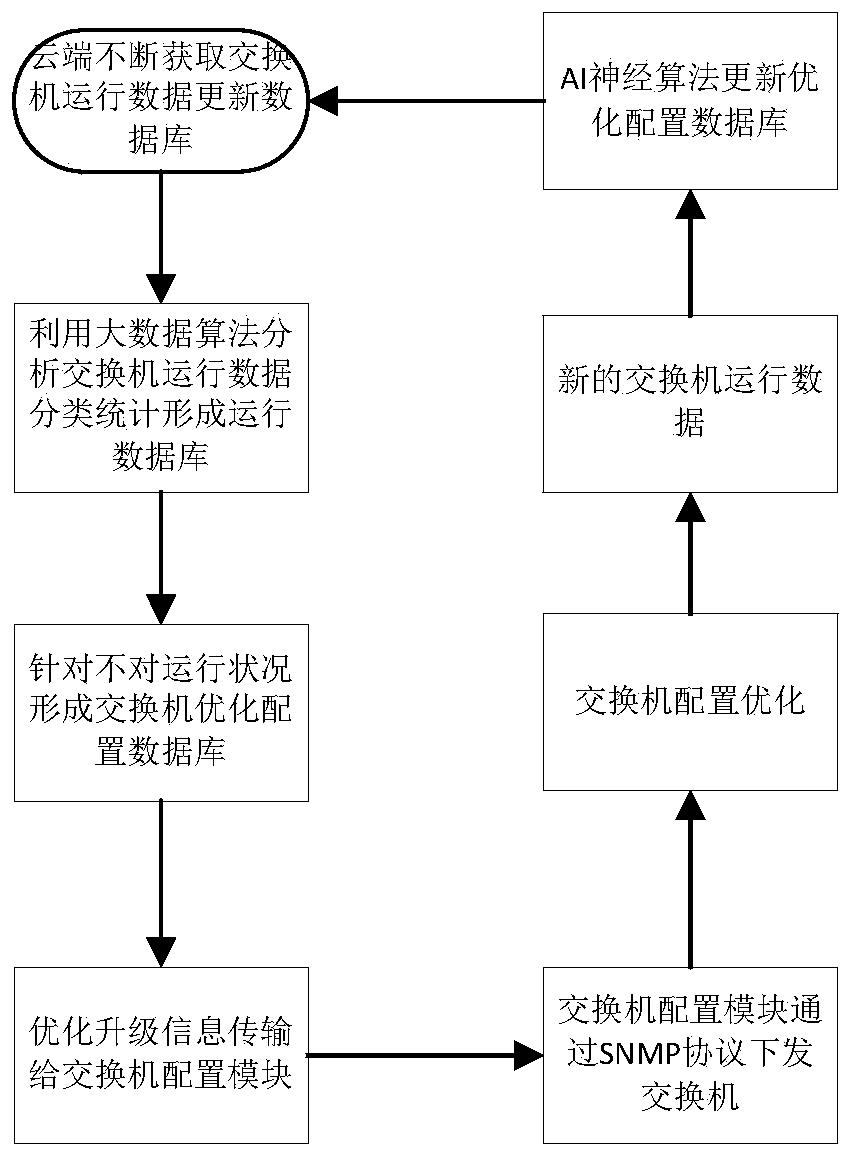
Intelligent substation switch online monitoring system
ActiveCN110247800AFast and convenient online monitoringEnsure network securityData switching networksSmart substationModular design
The invention discloses an intelligent substation switch online monitoring system. The system comprises a switch monitoring management system, a switch monitoring management data cloud and an intelligent substation switch, wherein the switch monitoring management system is in data transmission and communication with the intelligent substation switch; and the switch monitoring and management system is used for acquiring the operation state information of the intelligent substation switch in real time and analyzing and processing the operation state information to obtain switch operation monitoring state information and alarm information, and sending the switch operation monitoring state information and the alarm information to the switch monitoring and management data cloud for storage and optimal configuration. Online monitoring of the intelligent substation switch can be rapidly and conveniently completed, monitoring data are complete and reliable, the alarm response speed is high, and the network security of an intelligent substation is guaranteed; and modular design is adopted, the structure is reasonable, the response speed is high, and safety and reliability are achieved.
Owner:STATE GRID SICHUAN ELECTRIC POWER COMPANY NEIJIANG POWER SUPPLY +4
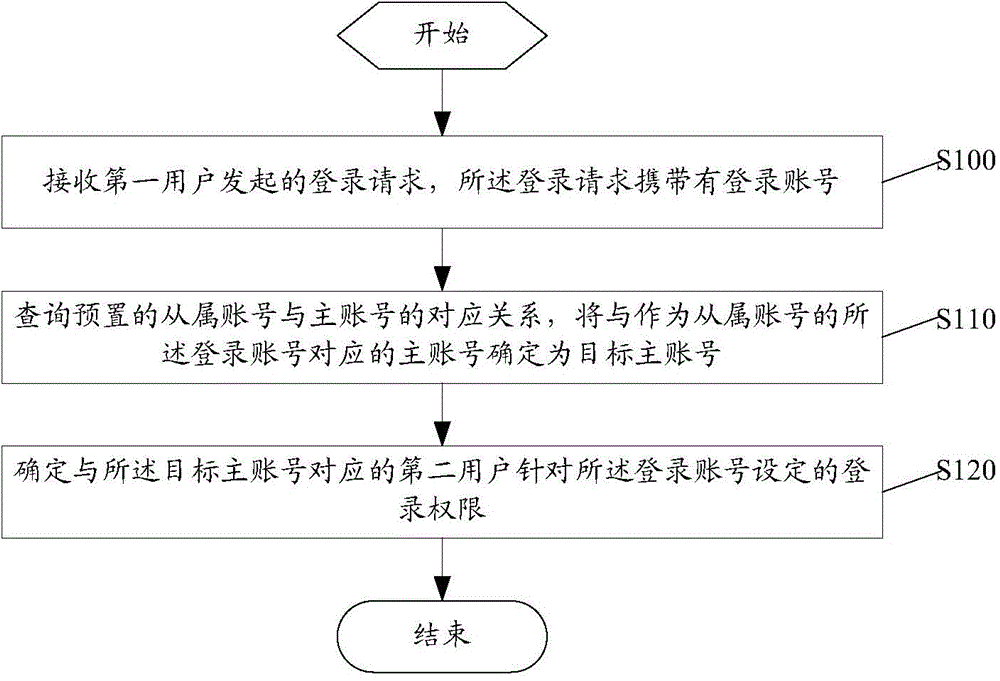
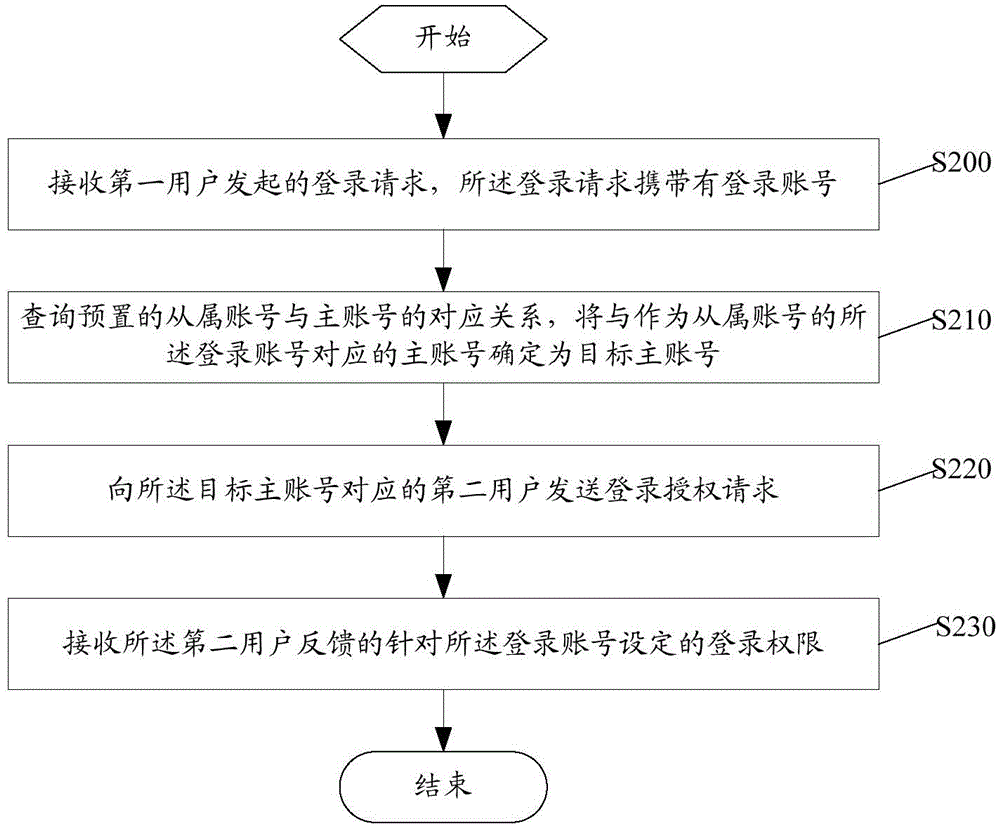
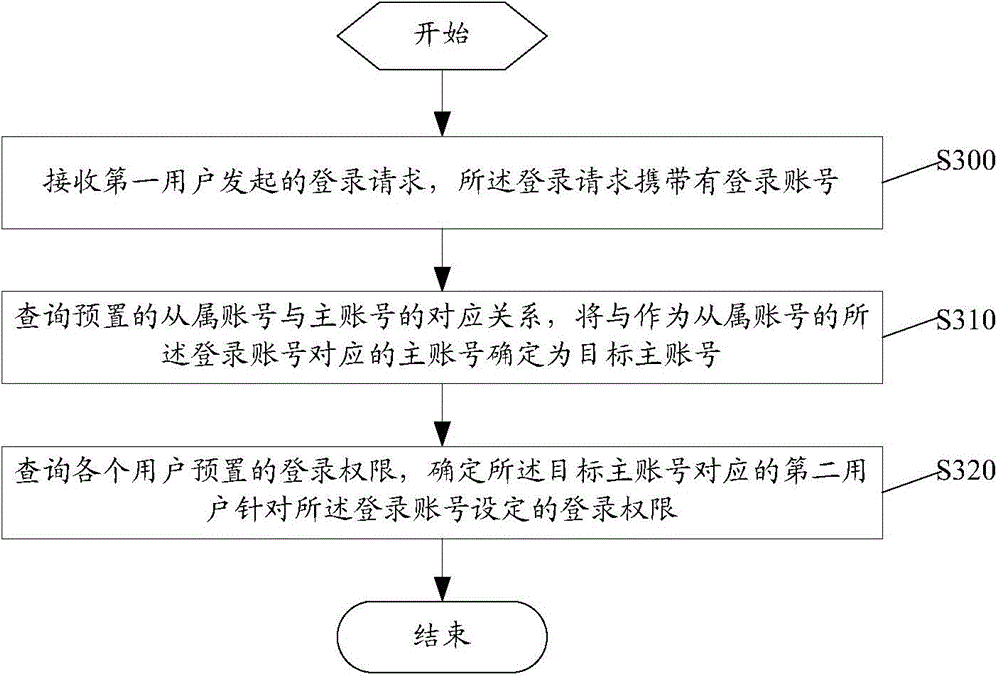
Account management method, device and system
InactiveCN106209955AEasy to implementEnsure network securityData switching networksBank accountDatabase
The application discloses an account management method, device and system. The method comprises the following steps: receiving a login request initiated by a first user, wherein the login request carries a login account; querying the corresponding relation of a preset subordinate account and a main account, determining the main account corresponding to the login account used as the subordinate account as the target main account; determining the login authority set aiming at the login account by a second user corresponding to the target main account, wherein the login authority is login permission or login rejection. Through the account management method disclosed by the application, the authority management is performed aiming at the condition that each account does not need to singly log in, each subordinate account can determine the login authority through a pre-bound main account in login, and the implementation mode is simpler and more convenient.
Owner:TENCENT TECH (SHENZHEN) CO LTD
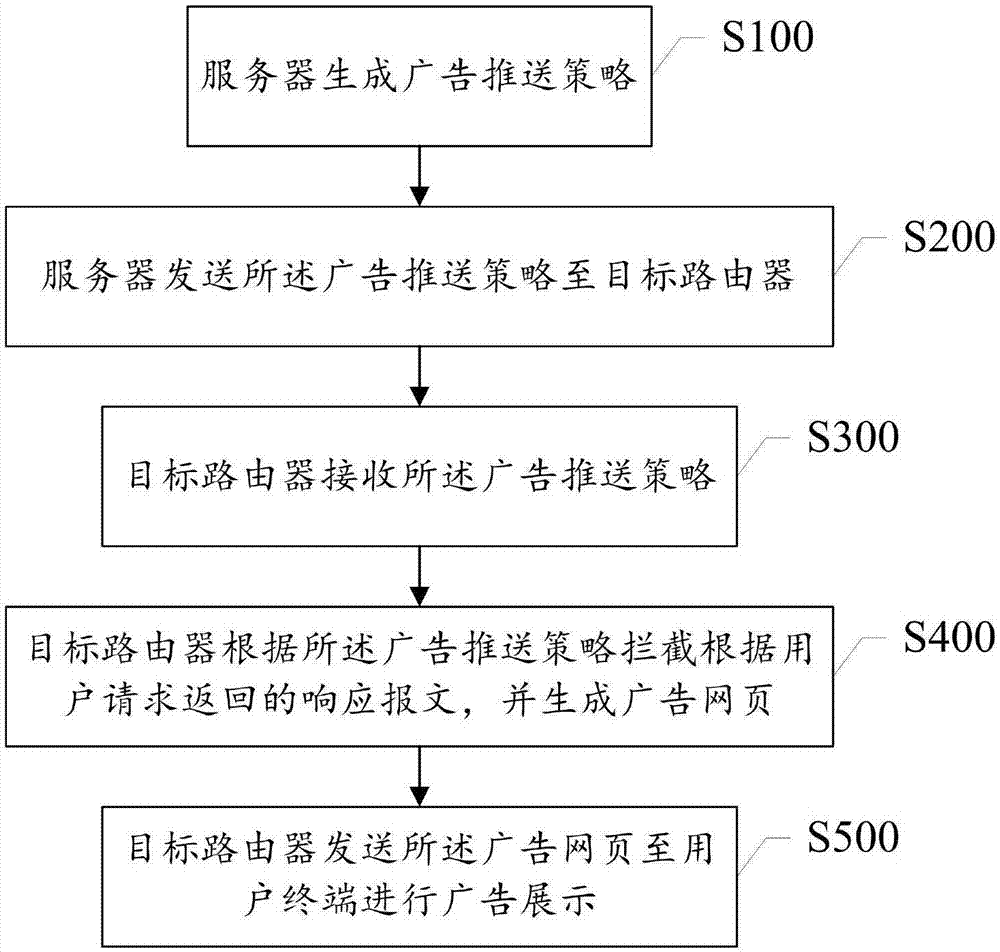
Advertisement pushing method and system
InactiveCN107977857APrecise deliveryReduce advertising costsAdvertisementsTransmissionComputer terminalWeb page
The invention provides an advertisement pushing method and system. The advertisement pushing method comprises that S100: a server generates an advertisement pushing strategy; S200: the server sends the advertisement pushing strategy to a target router; S300: the target router receives the advertisement pushing strategy; S400: the target router intercepts a response message returned according to auser request according to the advertisement pushing strategy and generates an advertisement webpage; and S500: the target router sends the advertisement webpage to a user terminal for advertisement display. According to the invention, aims of accurately putting the advertisement and reducing the advertisement cost are achieved, and advertisement display can be widely carried out on mobile terminals and desktop clients.
Owner:台州市吉吉知识产权运营有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com