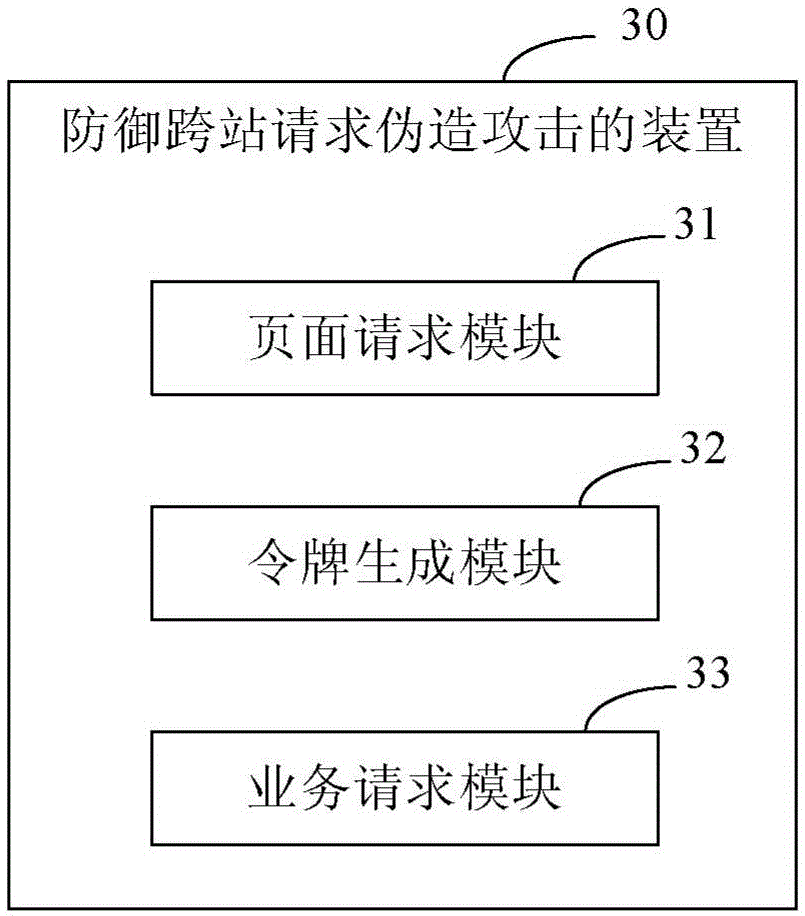
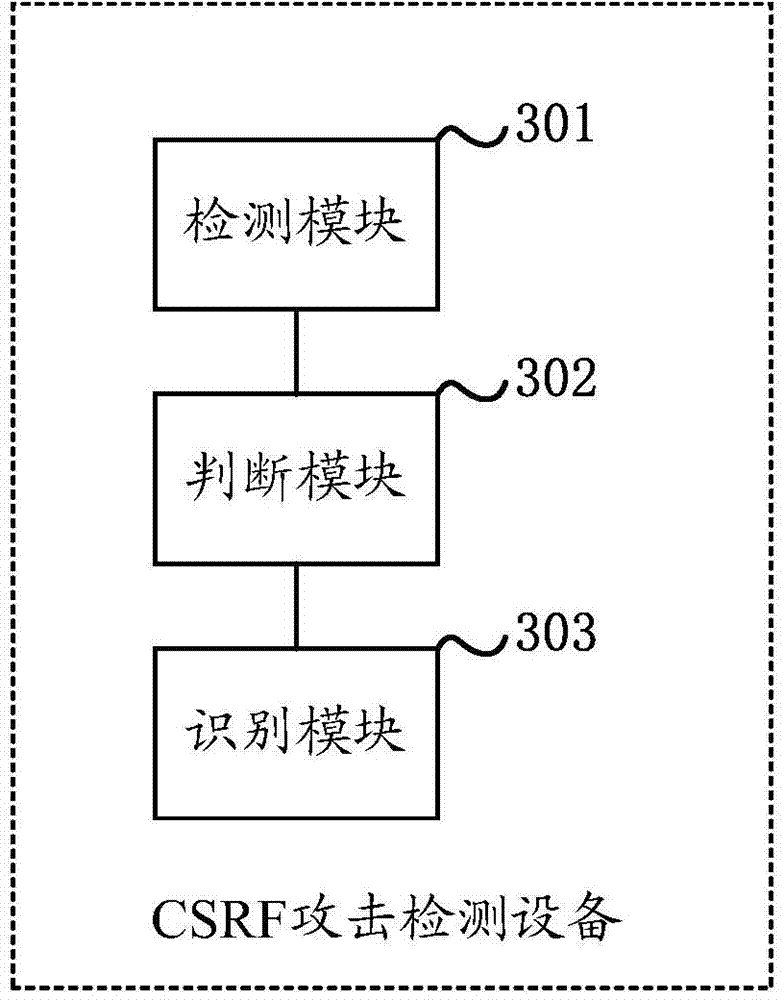
Patents
Literature
38 results about "Cross-site request forgery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
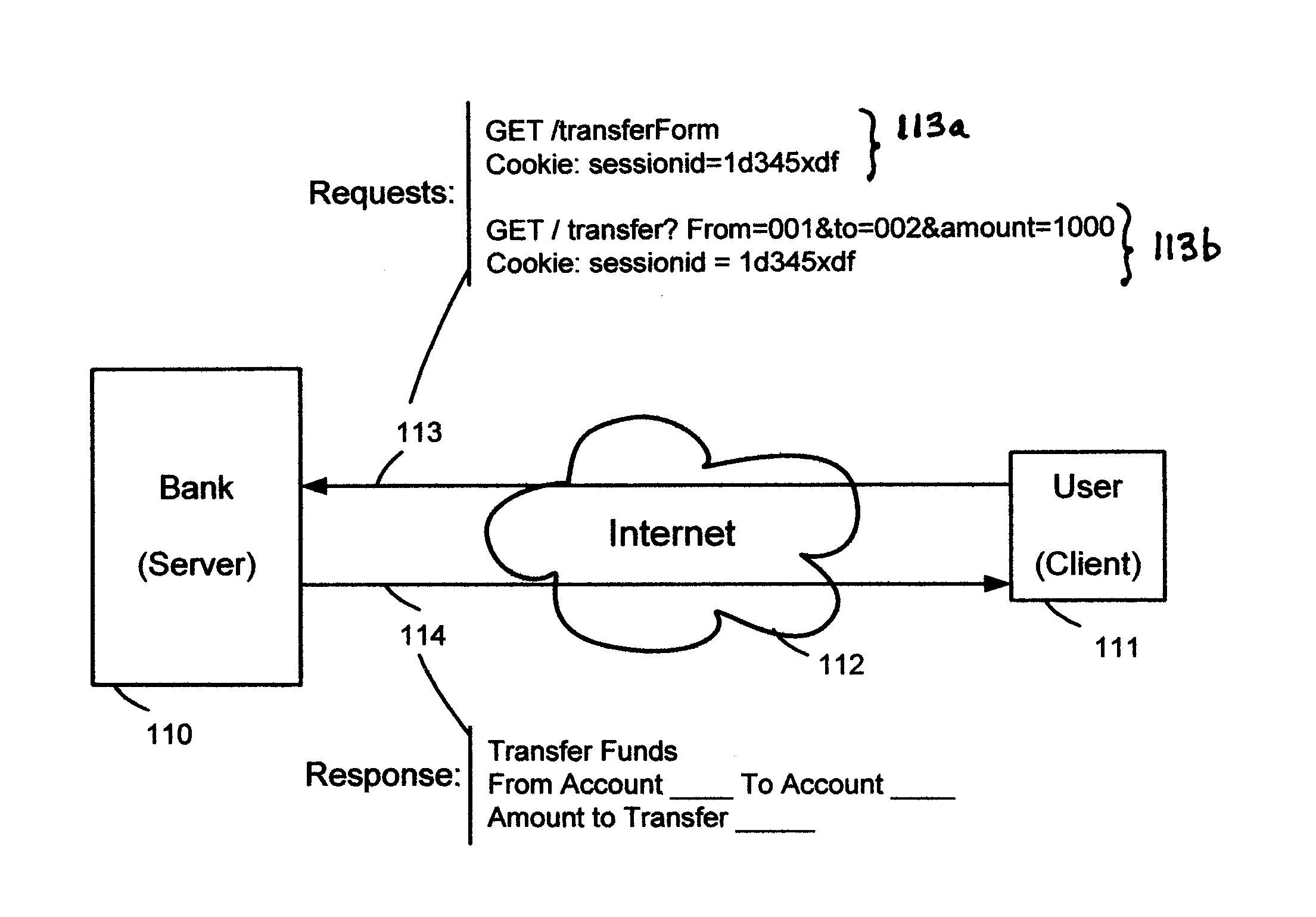
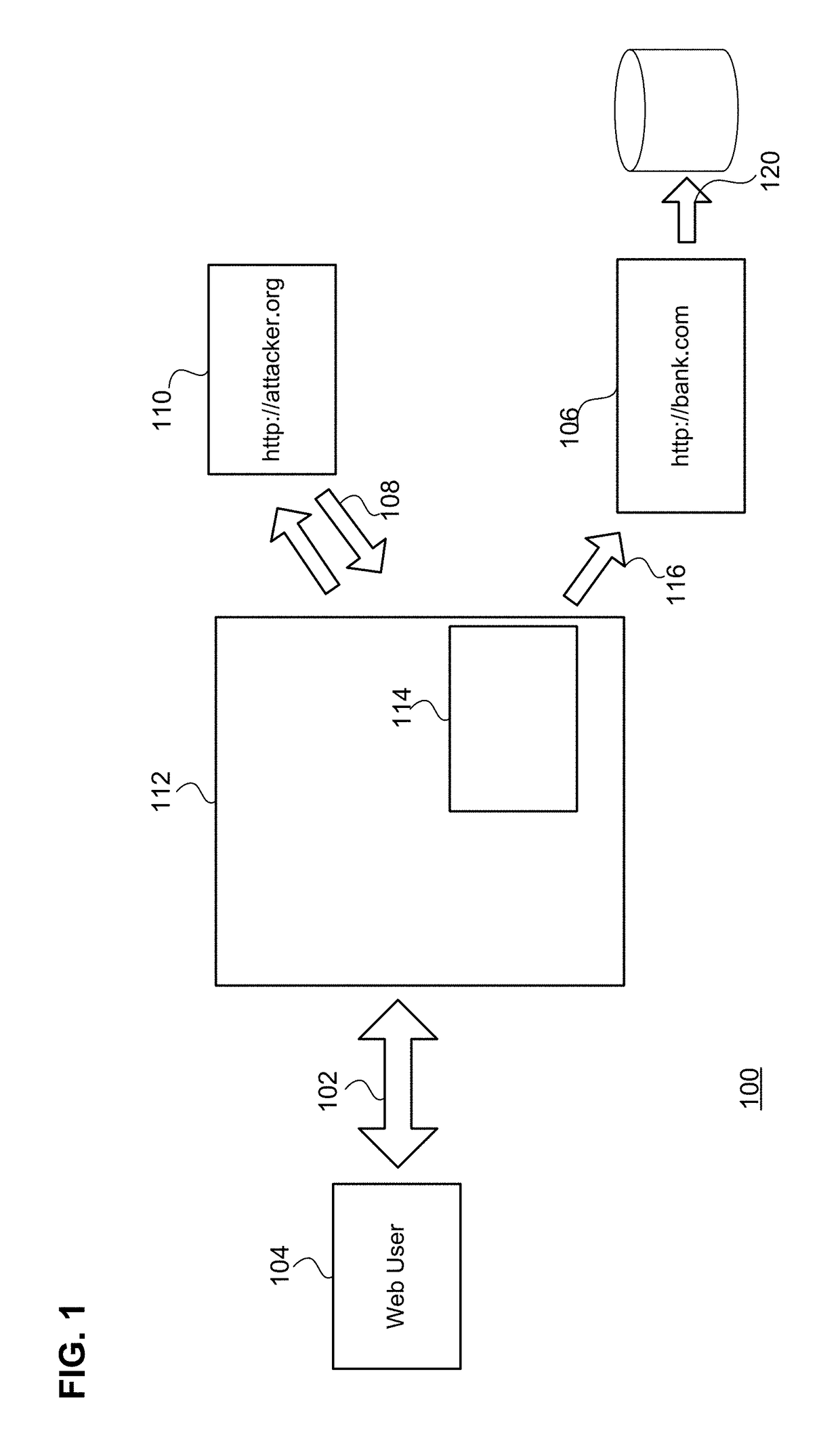
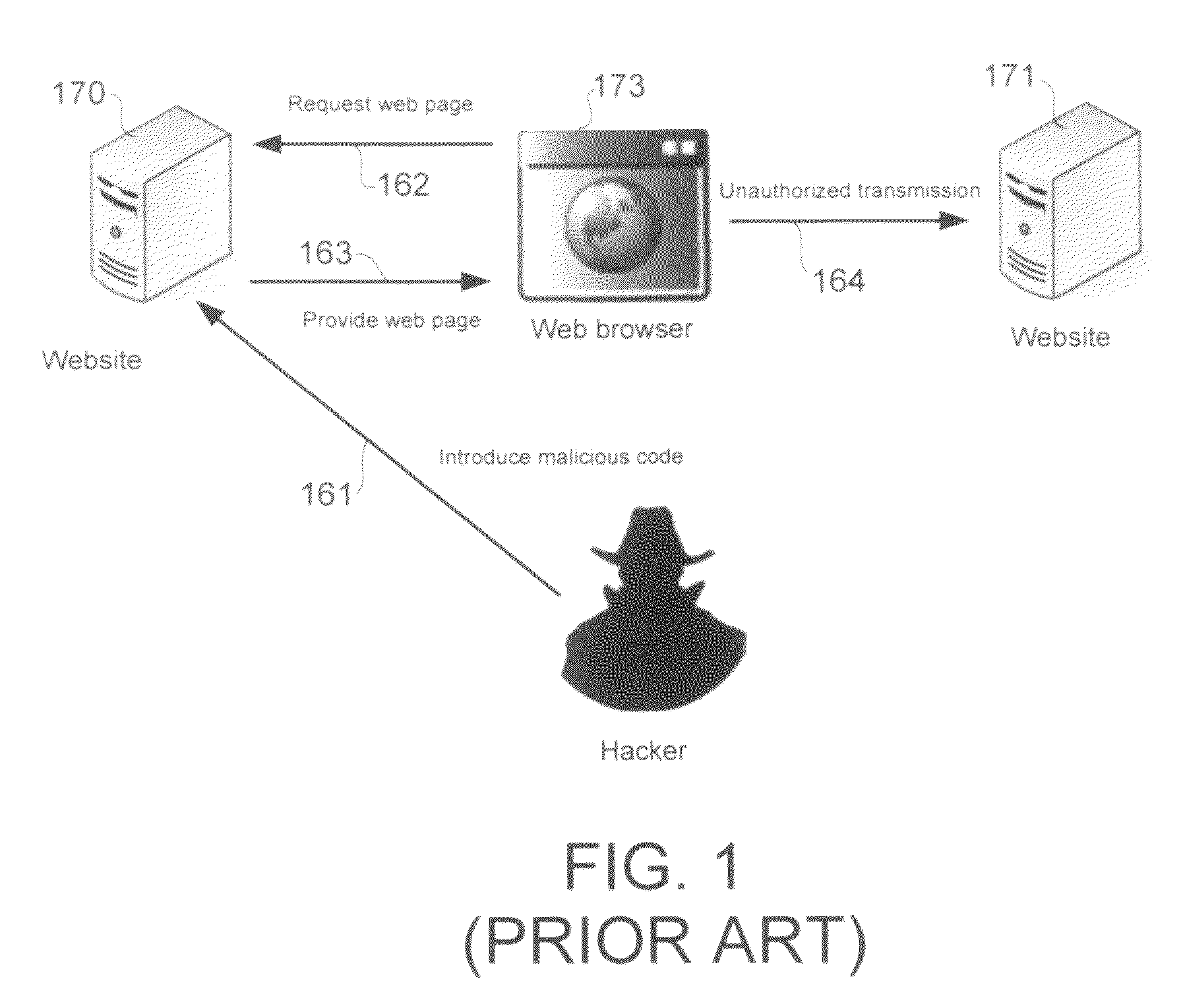
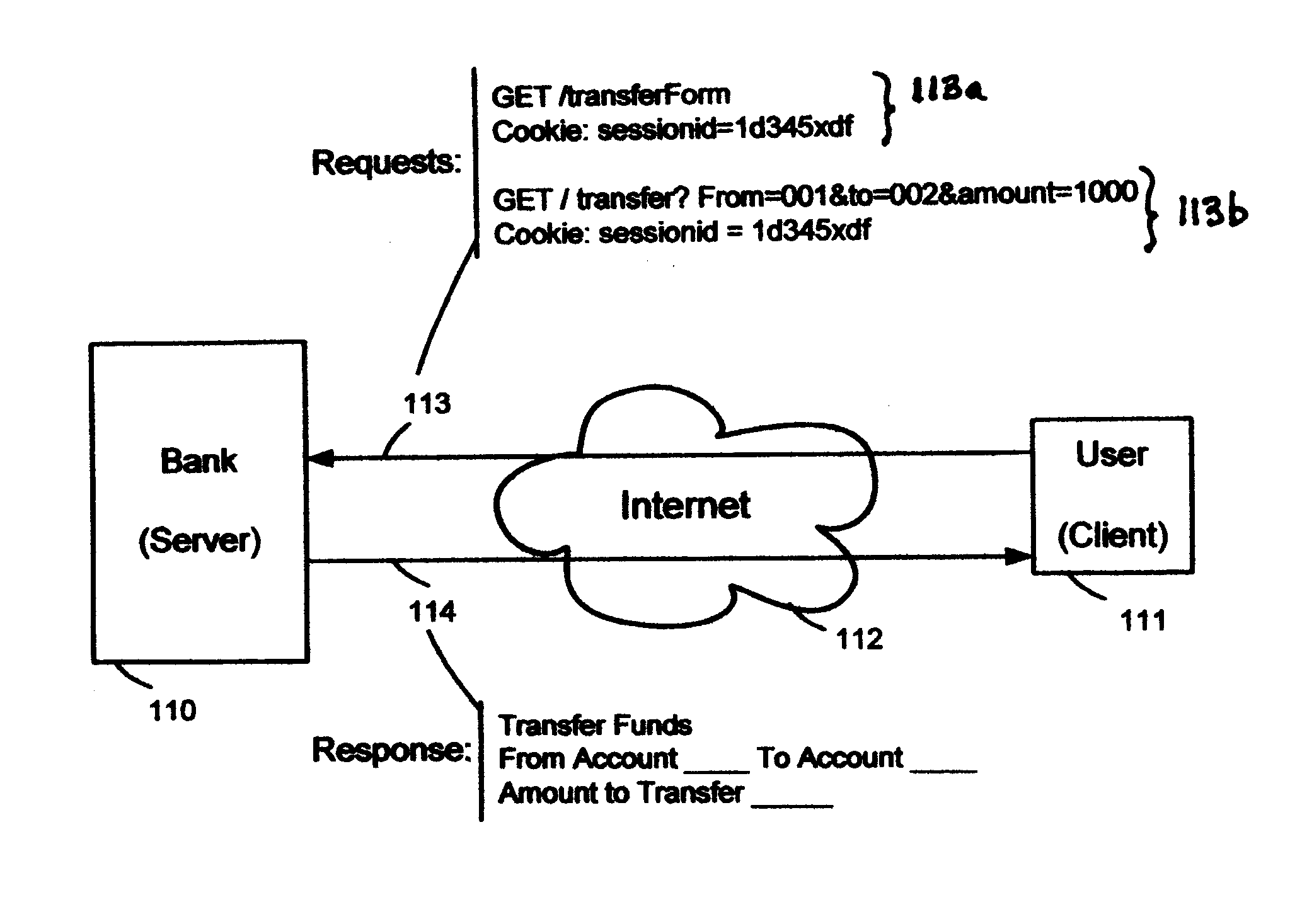
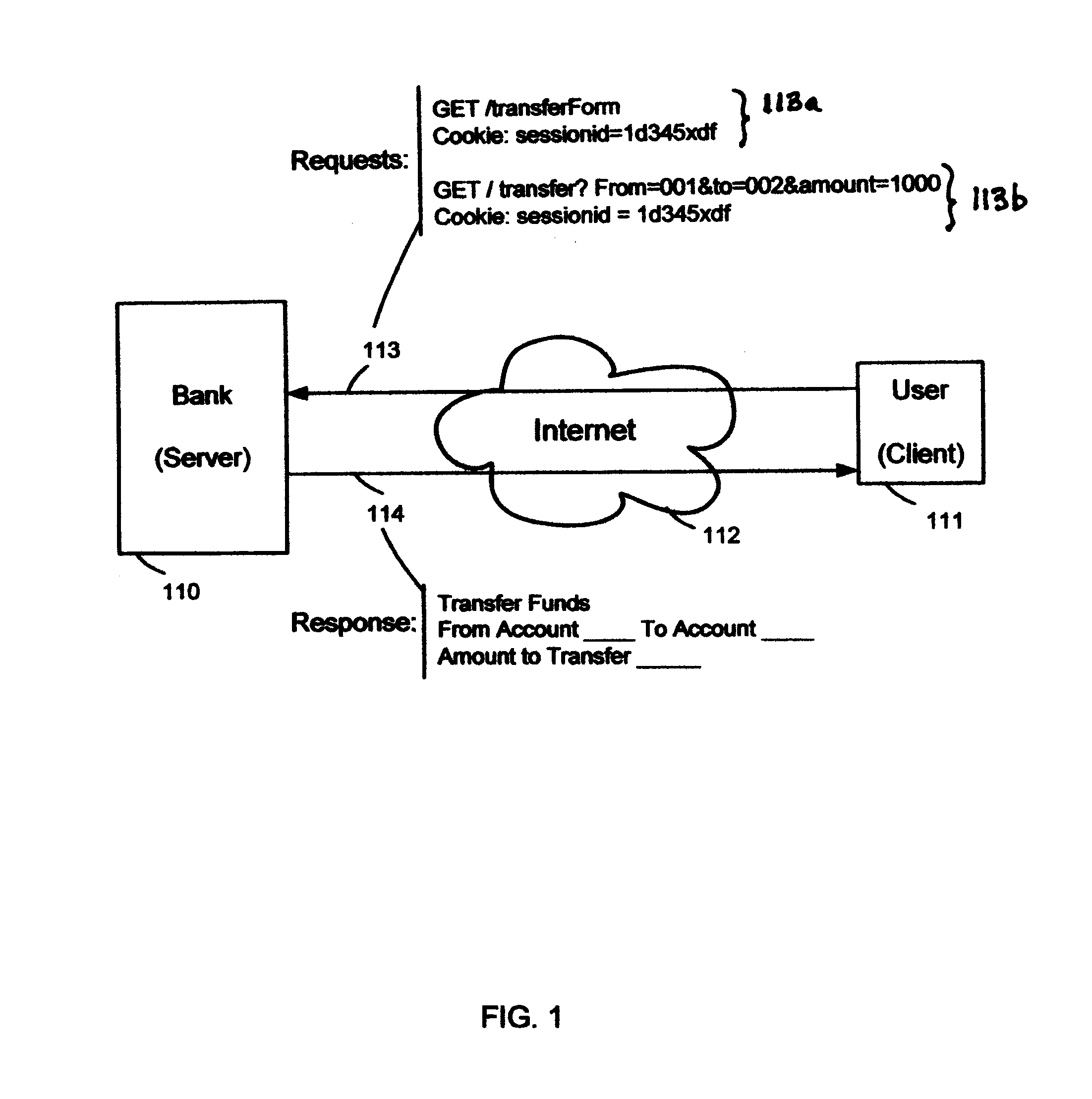
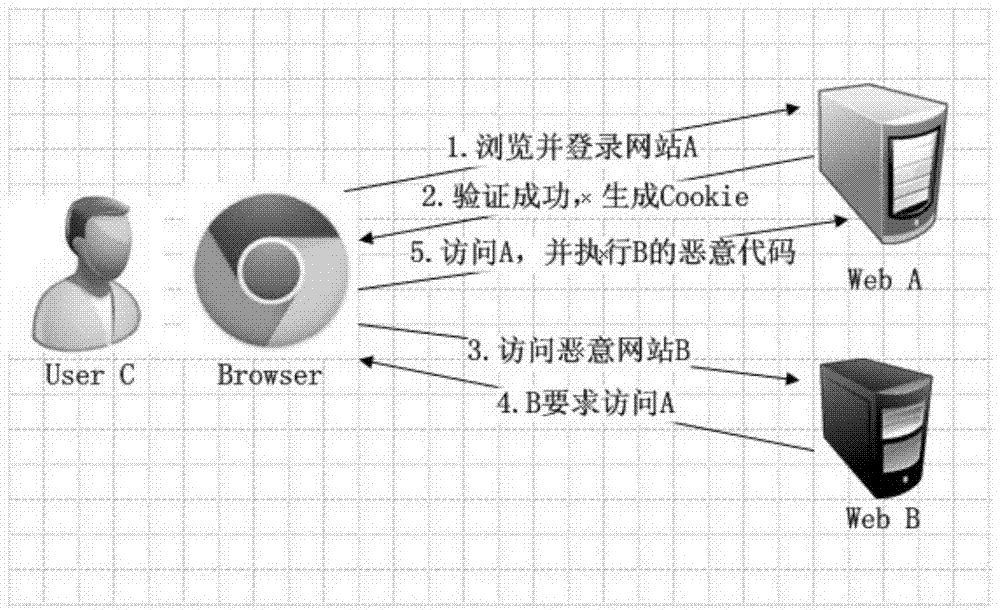
Cross-site request forgery, also known as one-click attack or session riding and abbreviated as CSRF (sometimes pronounced sea-surf) or XSRF, is a type of malicious exploit of a website where unauthorized commands are transmitted from a user that the web application trusts. There are many ways in which a malicious website can transmit such commands; specially-crafted image tags, hidden forms, and JavaScript XMLHttpRequests, for example, can all work without the user's interaction or even knowledge. Unlike cross-site scripting (XSS), which exploits the trust a user has for a particular site, CSRF exploits the trust that a site has in a user's browser.
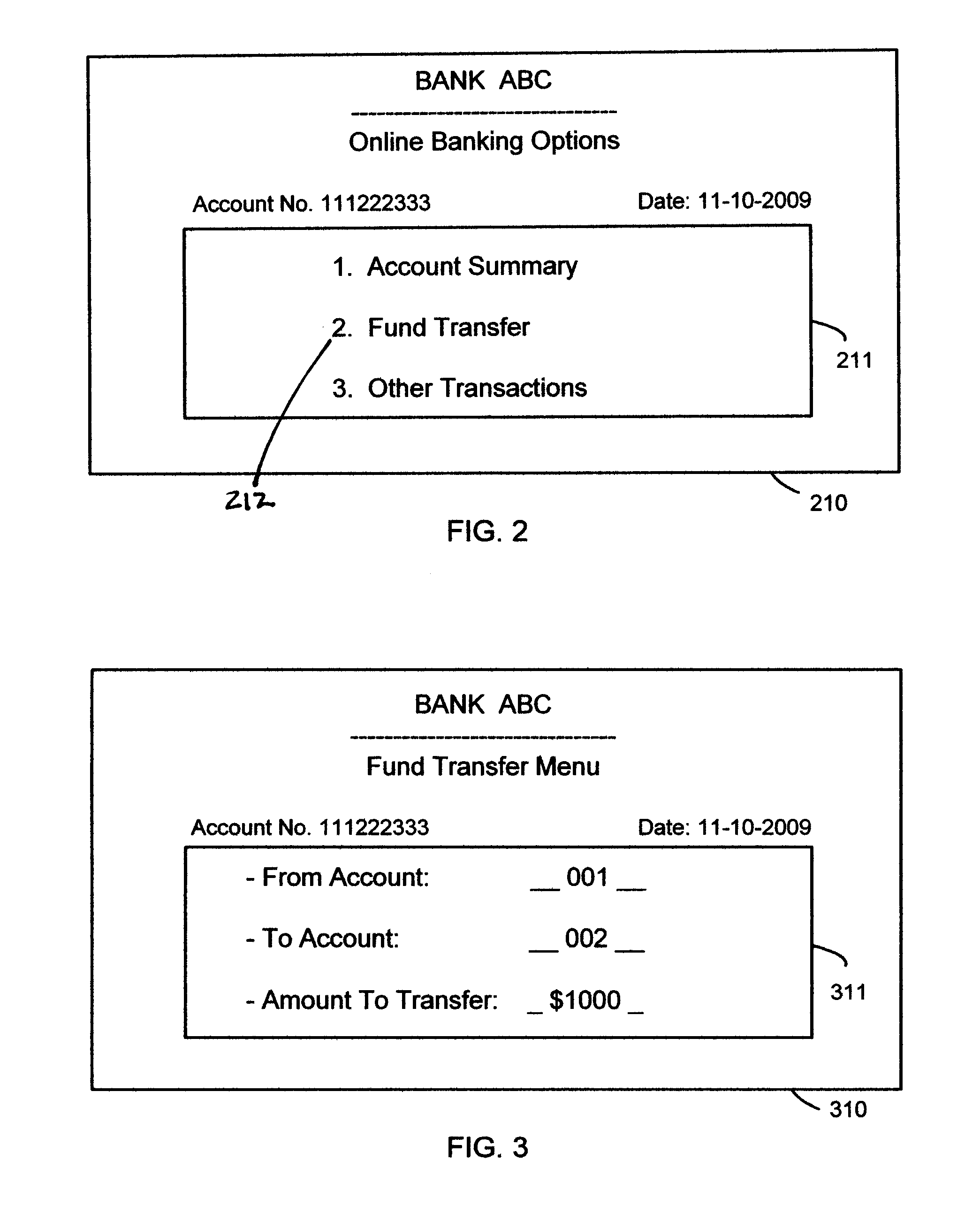
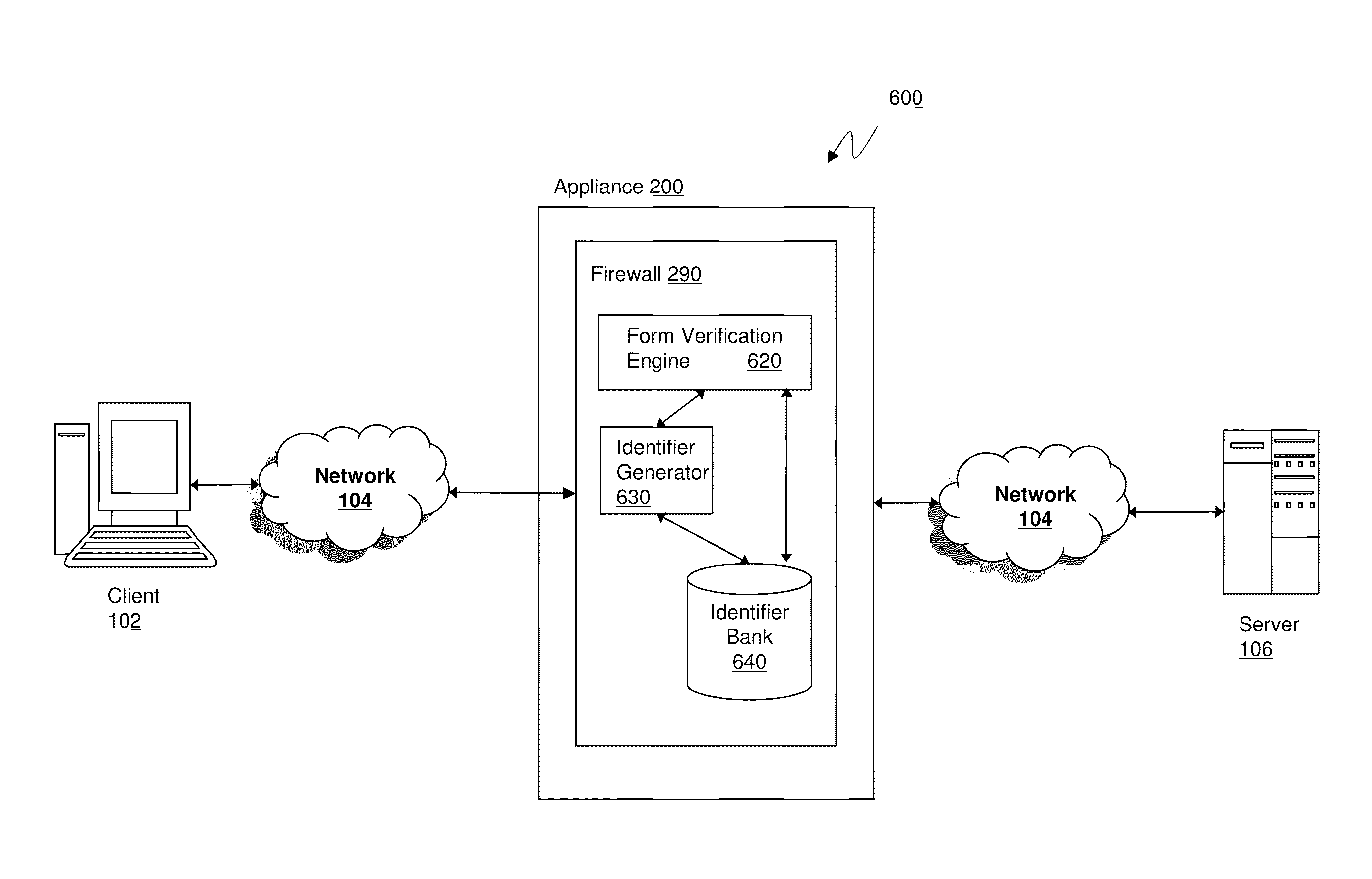
Systems and methods for cross site forgery protection
ActiveUS20110154473A1Digital data protectionMultiple digital computer combinationsThird partyCross-site request forgery
The present solution described herein is directed towards systems and methods to prevent cross-site request forgeries based on web form verification using unique identifiers. The present solution tags each form from a server that is served out in the response with a unique and unpredictable identifier. When the form is posted, the present solution enforces that the identifier being returned is the same as the one that was served out to the user. This prevents malicious unauthorized third party users from submitting a form on a user's behalf since they cannot guess the value of this unique identifier that was inserted.
Owner:CITRIX SYST INC
Systems and methods for protecting web based applications from cross site request forgery attacks
InactiveUS20100100927A1Digital data processing detailsUser identity/authority verificationCross-site request forgeryWeb service
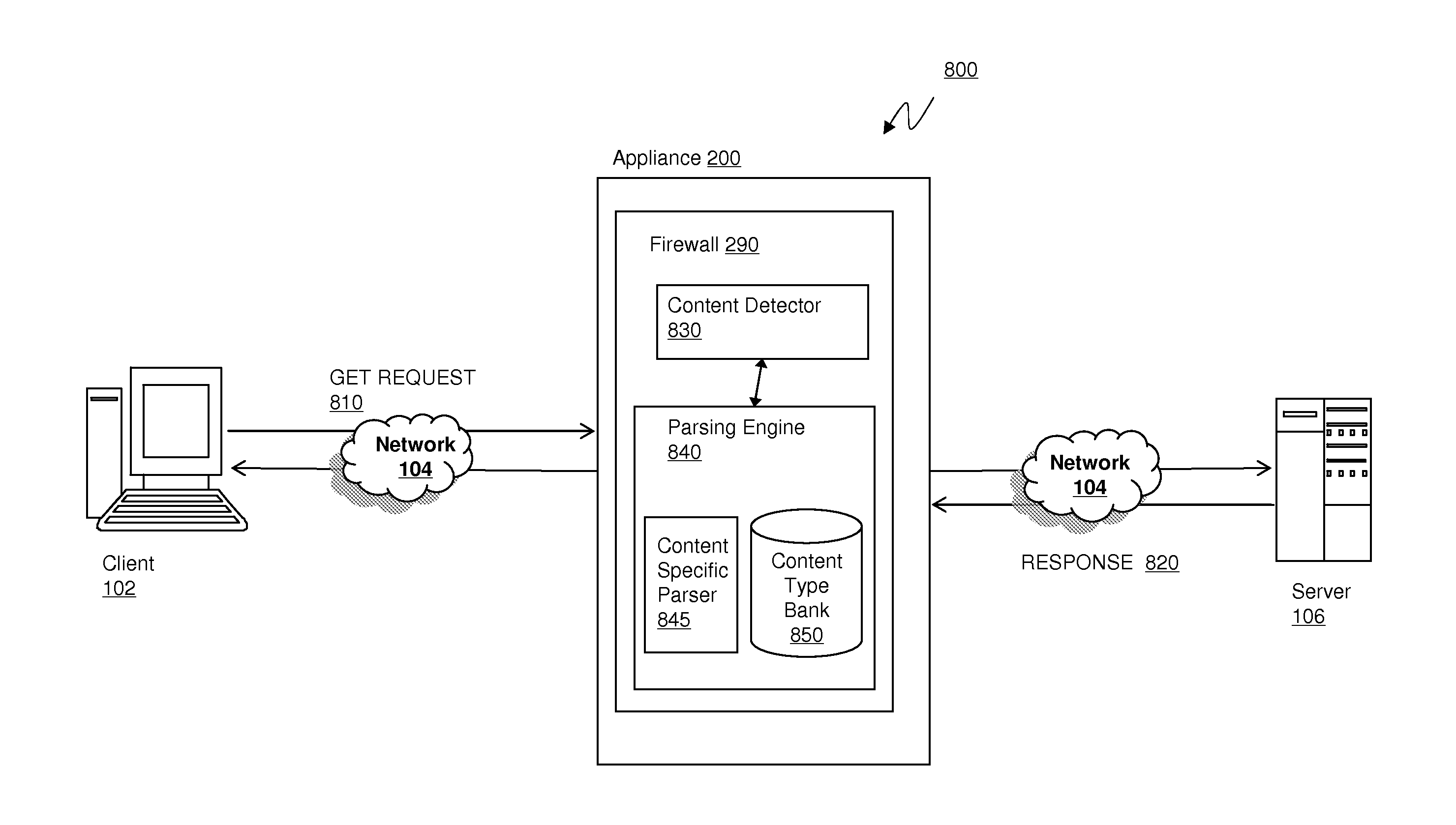
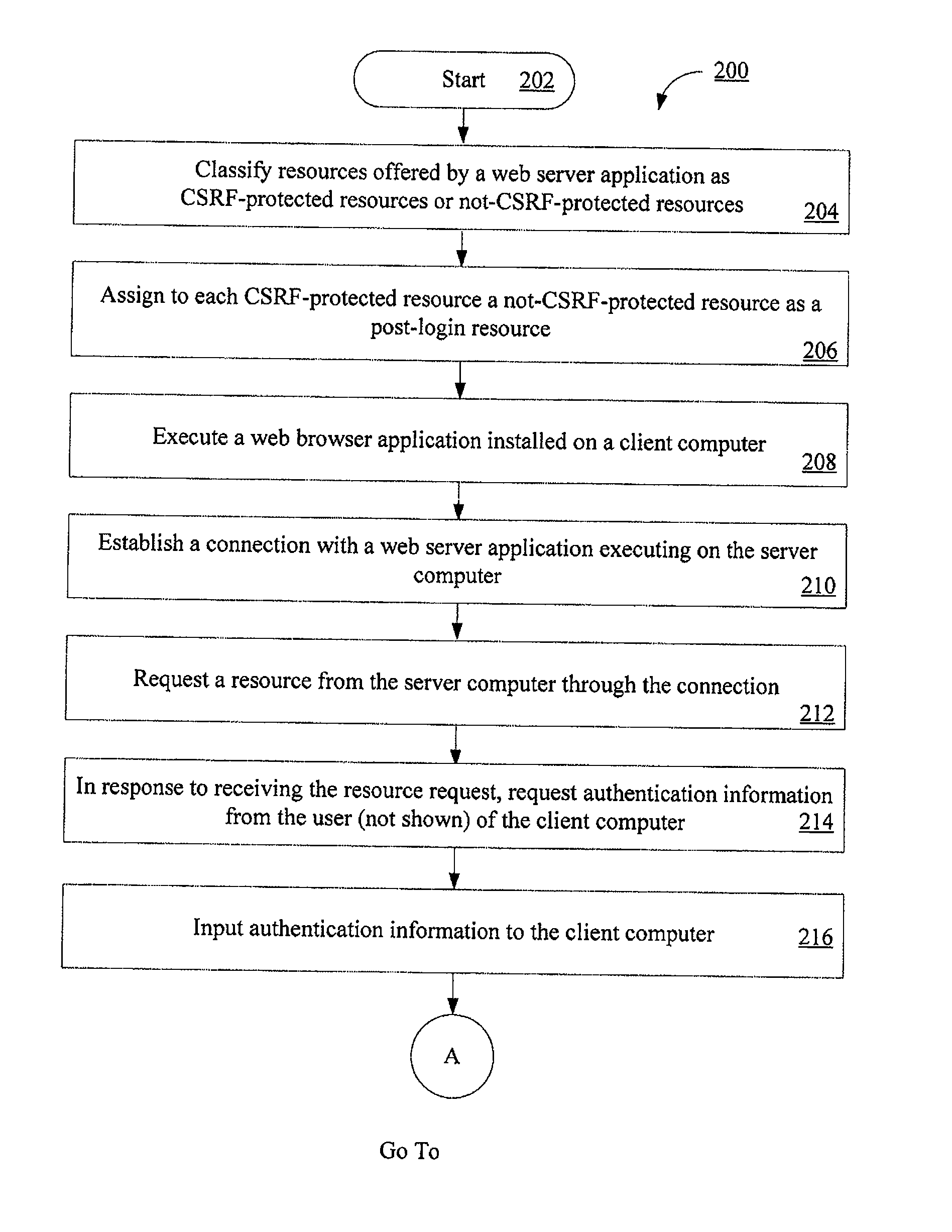
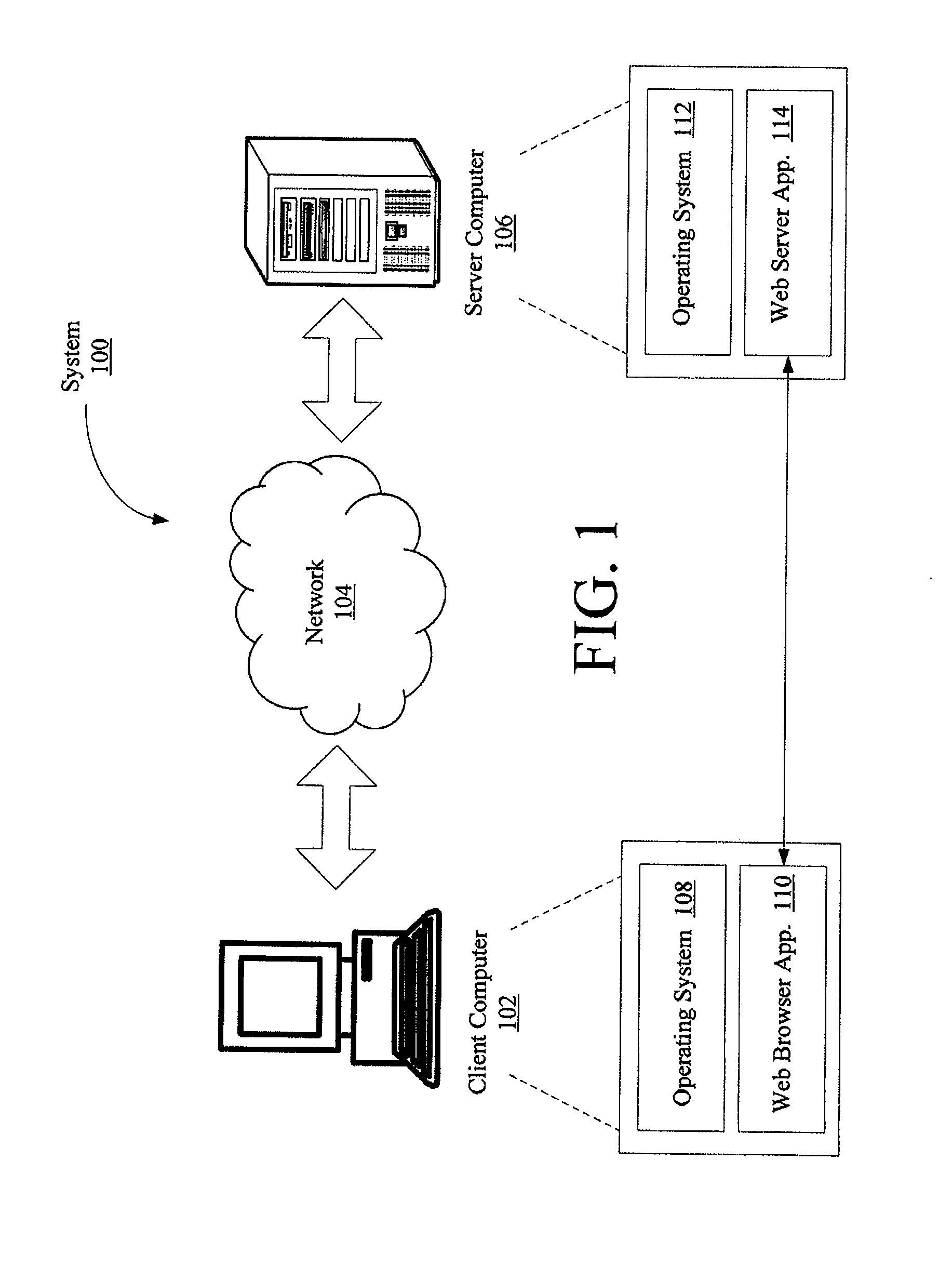
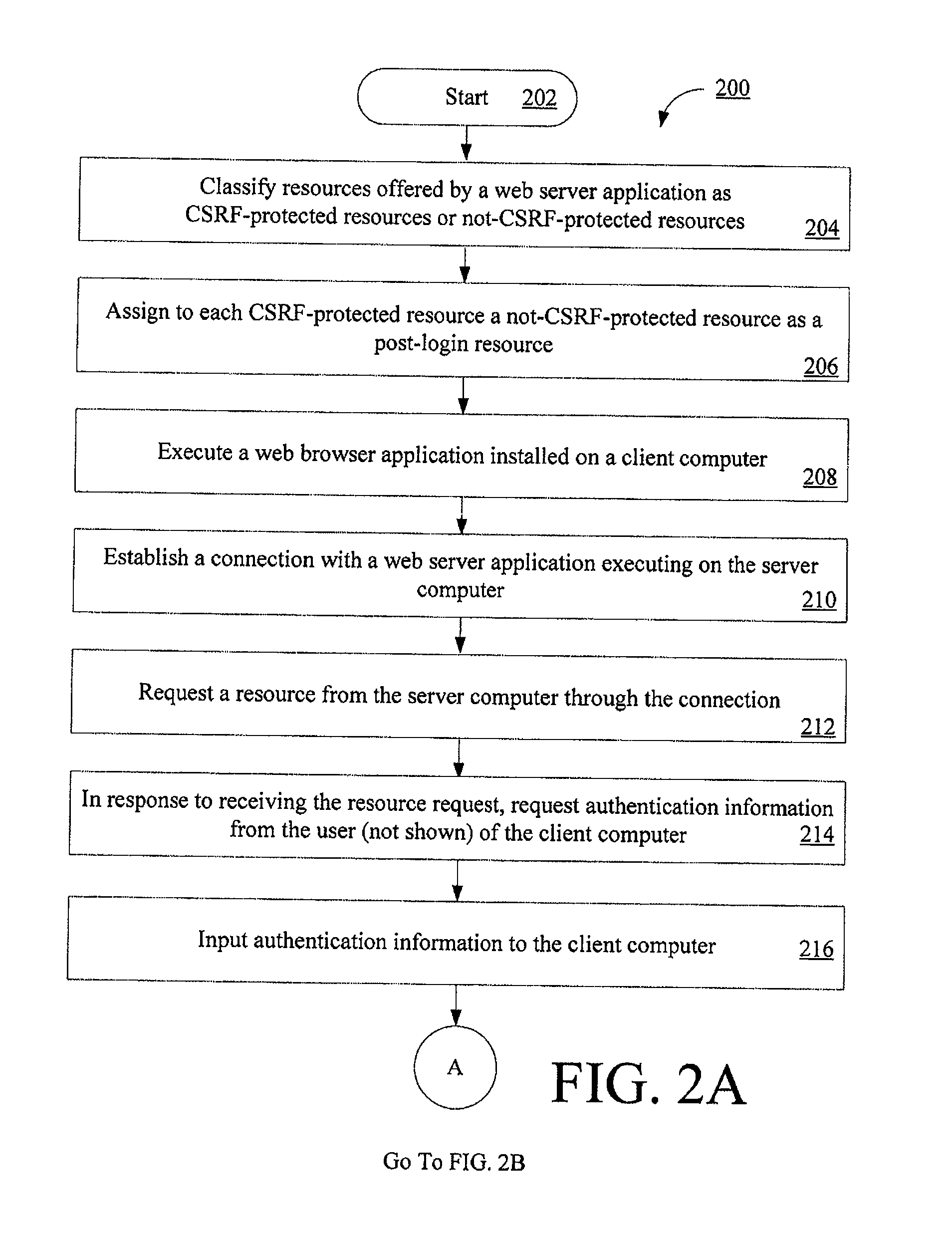
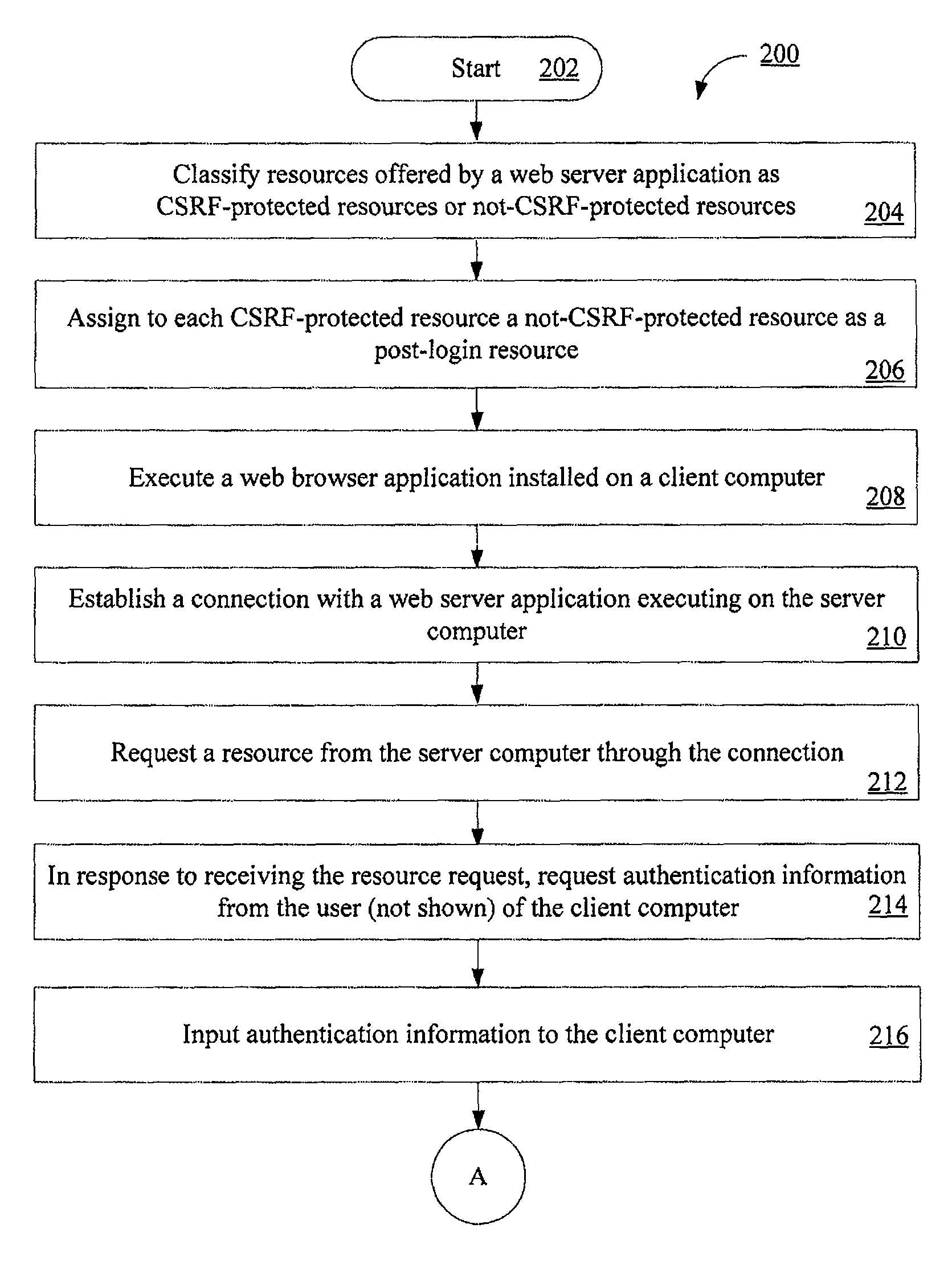
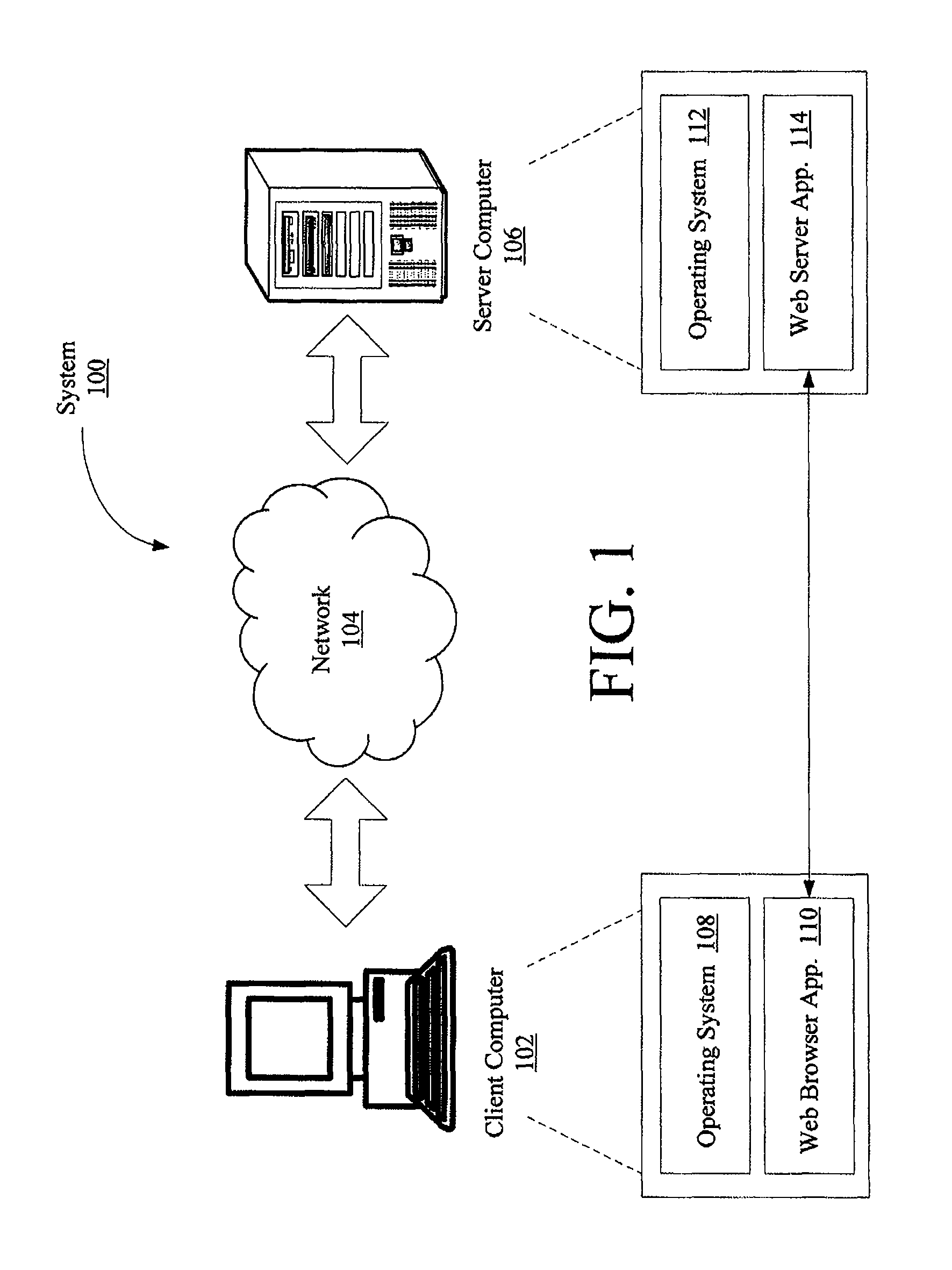
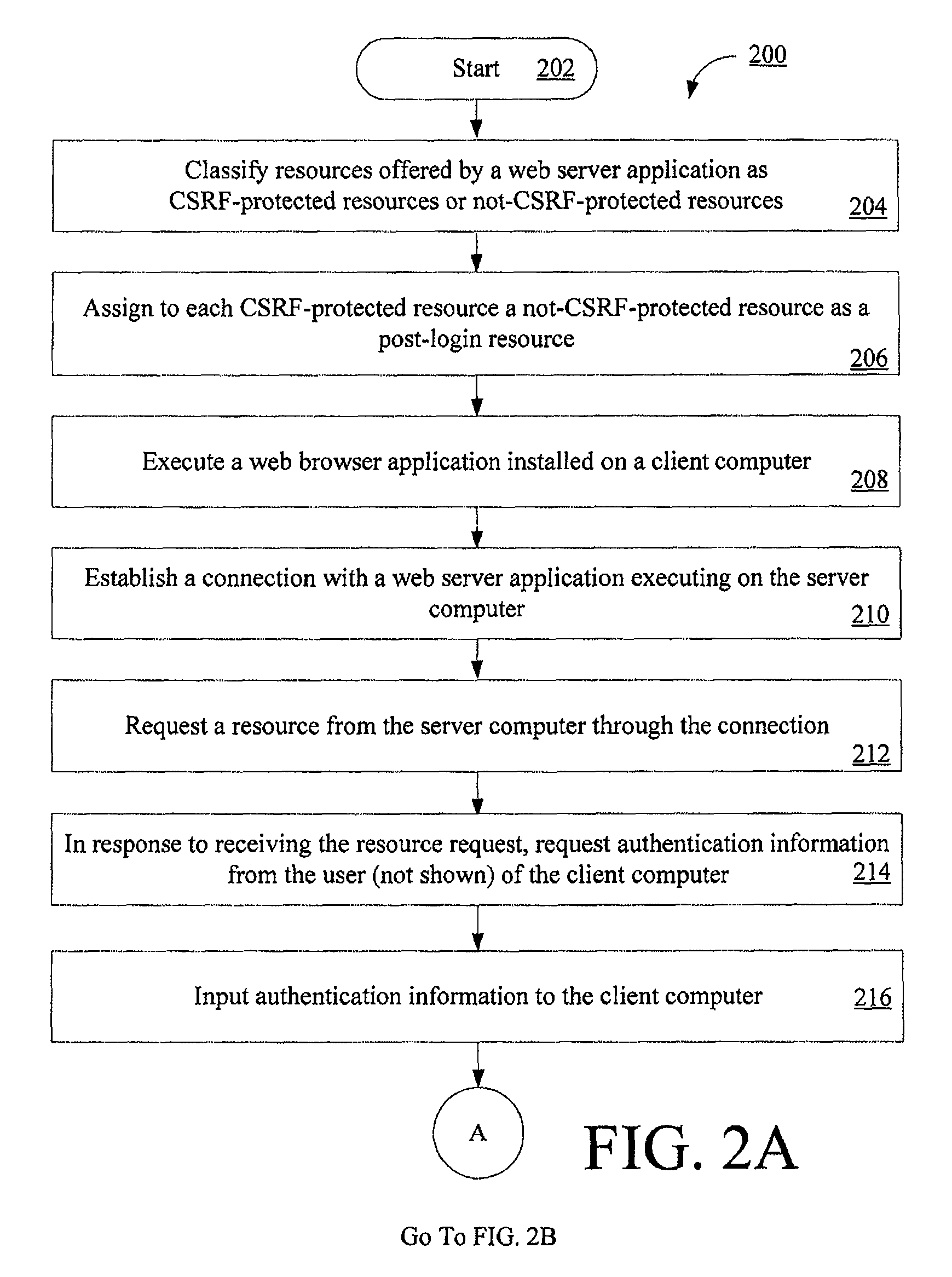
Computer implemented methods (200) for protecting web based applications (110, 114) from Cross Site Request Forgery (CSRF) attacks. The methods involve (204) classifying each resource offered by a web server application as a CSRF-protected resource or a not-CSRF-protected resource. The methods also involve (214, . . . , 222) performing a user authentication, (224) initializing an authentication-token, and (226) initializing a CSRF protection secret that is used to validate CSRF protection parameters contained in resource identifiers for the resources. The methods further involve (228) performing a server-side rewriting process (300) to add the CSRF protection parameter to the resource identifiers for the resources and / or (230) performing a client-side rewriting process to add the CSRF protection parameter to a resource identifier for a second resource (e.g., a resource created at a client computer (102)).
Owner:IBM CORP
Systems and methods for protecting web based applications from cross site request forgery attacks
InactiveUS8020193B2Digital data processing detailsAnalogue secracy/subscription systemsCross-site request forgeryWeb service
Computer implemented methods (200) for protecting web based applications (110, 114) from Cross Site Request Forgery (CSRF) attacks. The methods involve (204) classifying each resource offered by a web server application as a CSRF-protected resource or a not-CSRF-protected resource. The methods also involve (214, . . . , 222) performing a user authentication, (224) initializing an authentication-token, and (226) initializing a CSRF protection secret that is used to validate CSRF protection parameters contained in resource identifiers for the resources. The methods further involve (228) performing a server-side rewriting process (300) to add the CSRF protection parameter to the resource identifiers for the resources and / or (230) performing a client-side rewriting process to add the CSRF protection parameter to a resource identifier for a second resource (e.g., a resource created at a client computer (102)).
Owner:INT BUSINESS MASCH CORP
Webpage request safe processing method and system
ActiveCN102685081ATo achieve the purpose of defending against CSRF attacksRetrofit smallTransmissionCross-site request forgerySafe handling
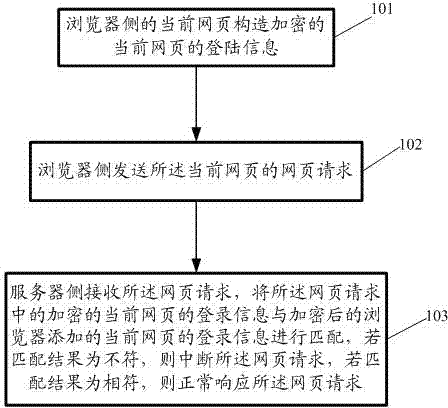
The embodiment of the invention discloses a webpage request safe processing method and a webpage request safe processing system; the method comprises the following steps that: the current webpage on a browser side constructs the encrypted log-in information of the current webpage; the browser side sends the webpage request of the current webpage; the webpage request comprises the encrypted log-in information of the current webpage and the log-in information of the current webpage that a browser adds; a server side receives the webpage request, and matches the encrypted log-in information of the current webpage in the webpage request with the log-in information of the current webpage that the browser adds after encryption; if the matching result is inconsistent, the webpage request is interrupted; and if the matching result is consistent, the webpage request is normally responded to. After the invention is adopted, the identification and the prevention to cross-site request forgery (CRSF) attack are realized when the reform to the whole system is small.
Owner:云南腾云信息产业有限公司
Method and device for forwarding hyper text transport protocol (HTTP) request
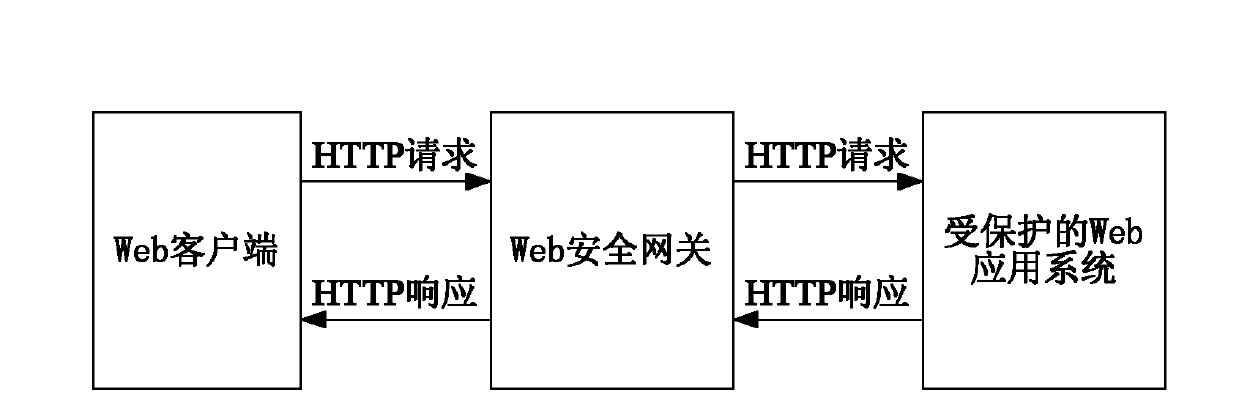
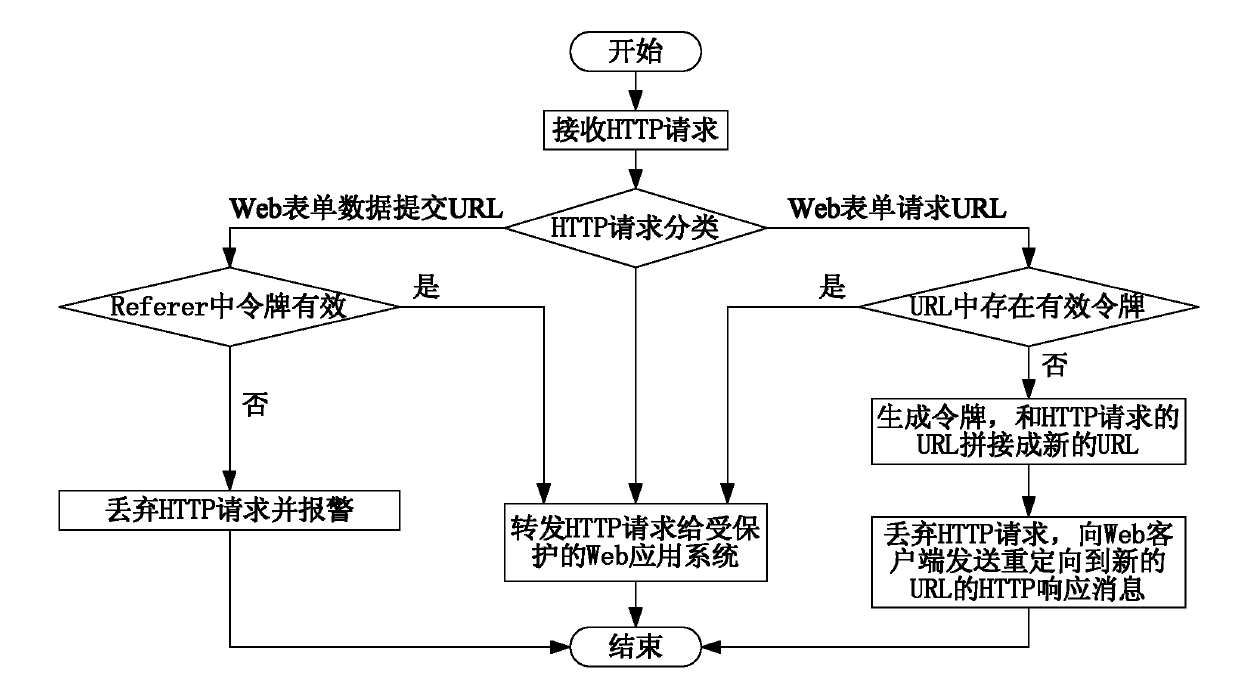
InactiveCN102571846AReduce computational overheadReduce computing pressureTransmissionCross-site request forgeryClient-side
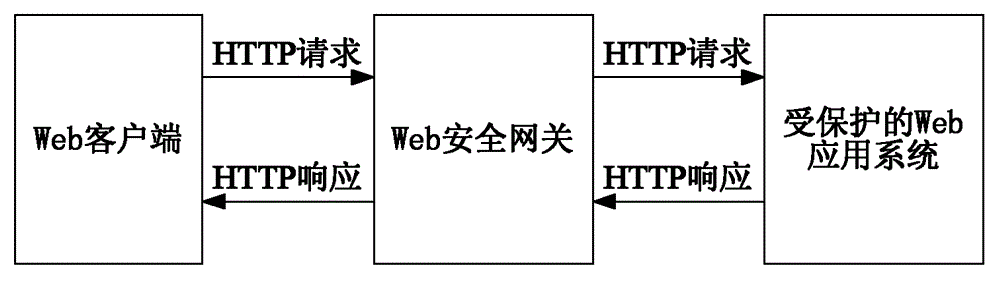
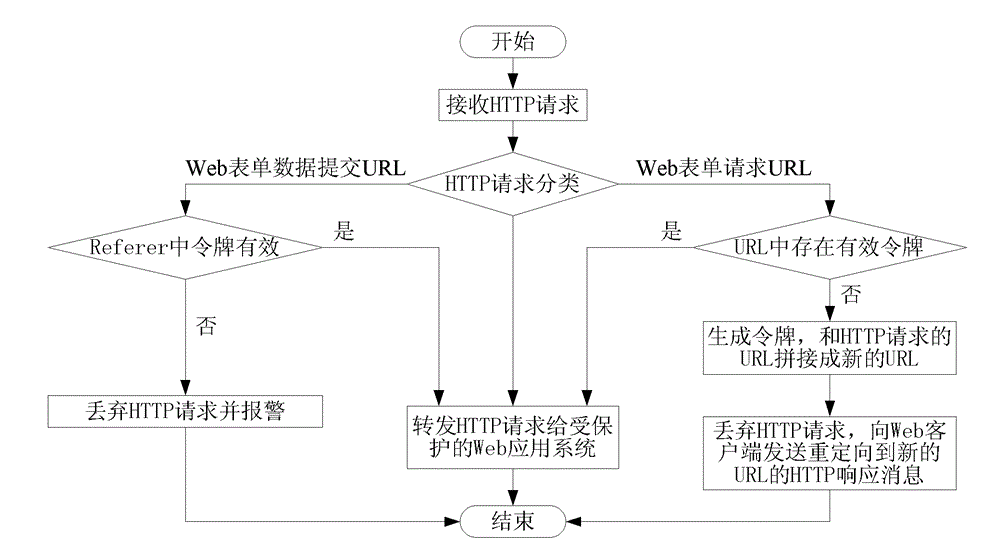
The invention relates to a method and a device for forwarding a hyper text transport protocol (HTTP) request. The method comprises the steps of: judging whether a uniform resource locator (URL) of the HTTP request of a Web client is a URL requested by a Web form or a URL submitted by Web form data or not; forwarding the HTTP request when the URL of the HTTP request is the URL requested by the Web form and effective tokens are carried in parameters of the URL of the HTTP request; randomly generating a unique token if the token is not carried, splicing the URL of the HTTP request and the generated token into a new URL, discarding the HTTP request, and sending an HTTP response message requesting the redirection to the new URL to the Web client; and forwarding the HTTP request when the URL of the HTTP request is the URL submitted by Web form data, the HTTP request has the referrer value and the effective token can be extracted from the referrer. The method and the device have the advantages that the effective defense on cross site request forgery (CSRF) attack can be realized, and the computation overhead on a Web security gateway is greatly reduced.
Owner:BEIJING VENUS INFORMATION TECH +1
Preventing Cross-Site Request Forgery Attacks on a Server
ActiveUS20110225234A1Preventing CSRF security attackPrevents CSRF security attackDigital data processing detailsComputer security arrangementsCross-site request forgeryClient-side
Preventing Cross-Site Request Forgery (CSRF) security attacks on a server in a client-server environment. In one aspect, this comprises embedding a nonce and a script in all responses from the server to the client wherein, when executed, the script adds the nonce to each request from the client to the server; sending the response with the nonce and the script to the client; and verifying that each request from the client includes the nonce sent by the server from the server to the client. The script preferably modifies all objects, including dynamically generated objects, in a server response that may generate future requests to the server to add the nonce to the requests. The server verifies the nonce value in a request and optionally confirms the request with the client if the value is not the same as the value previously sent by the server. Server-side aspects might be embodied in the server or a proxy between the server and the client.
Owner:IBM CORP
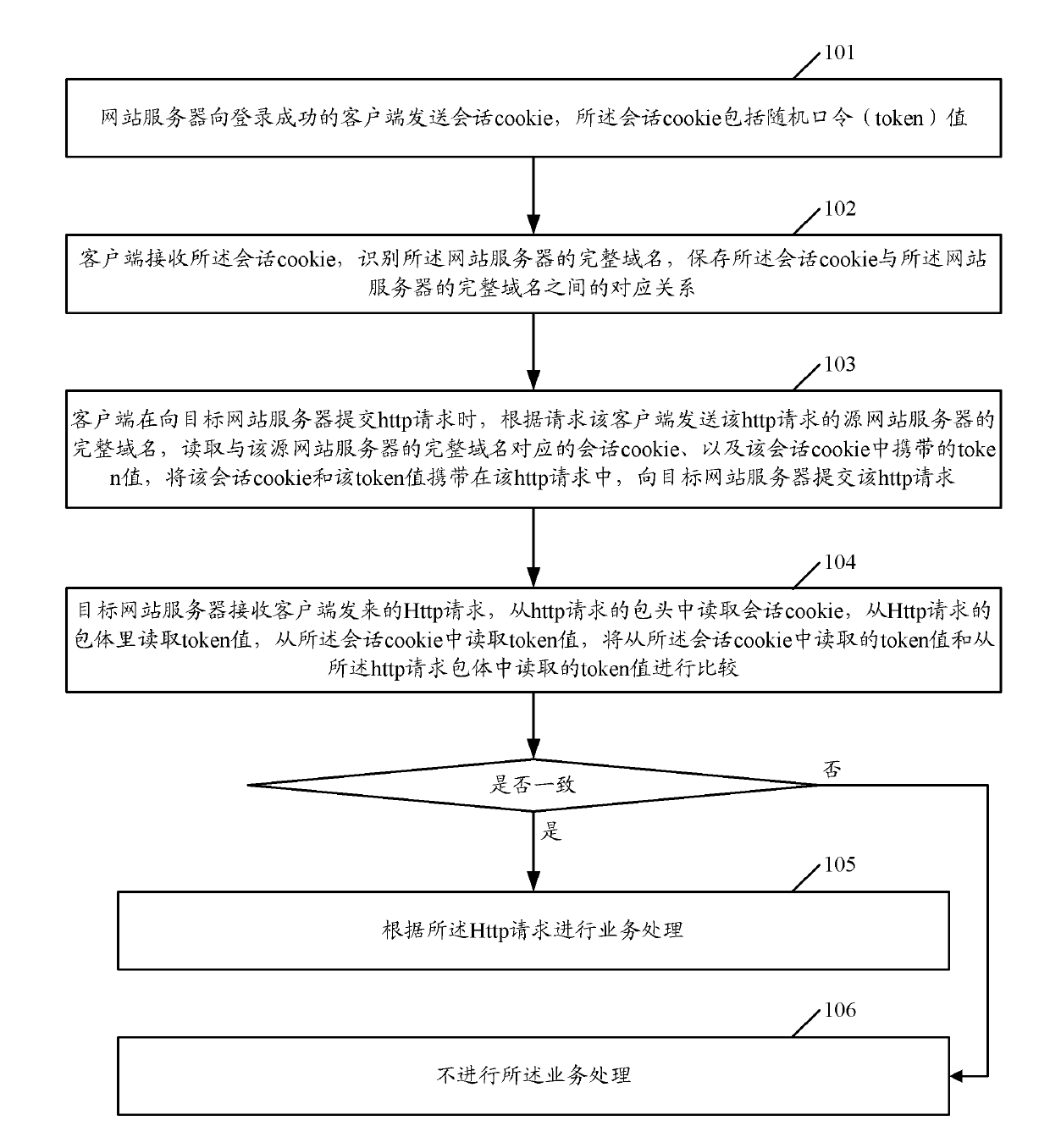
Method, system and device for preventing CSRF (cross site request forgery) attack
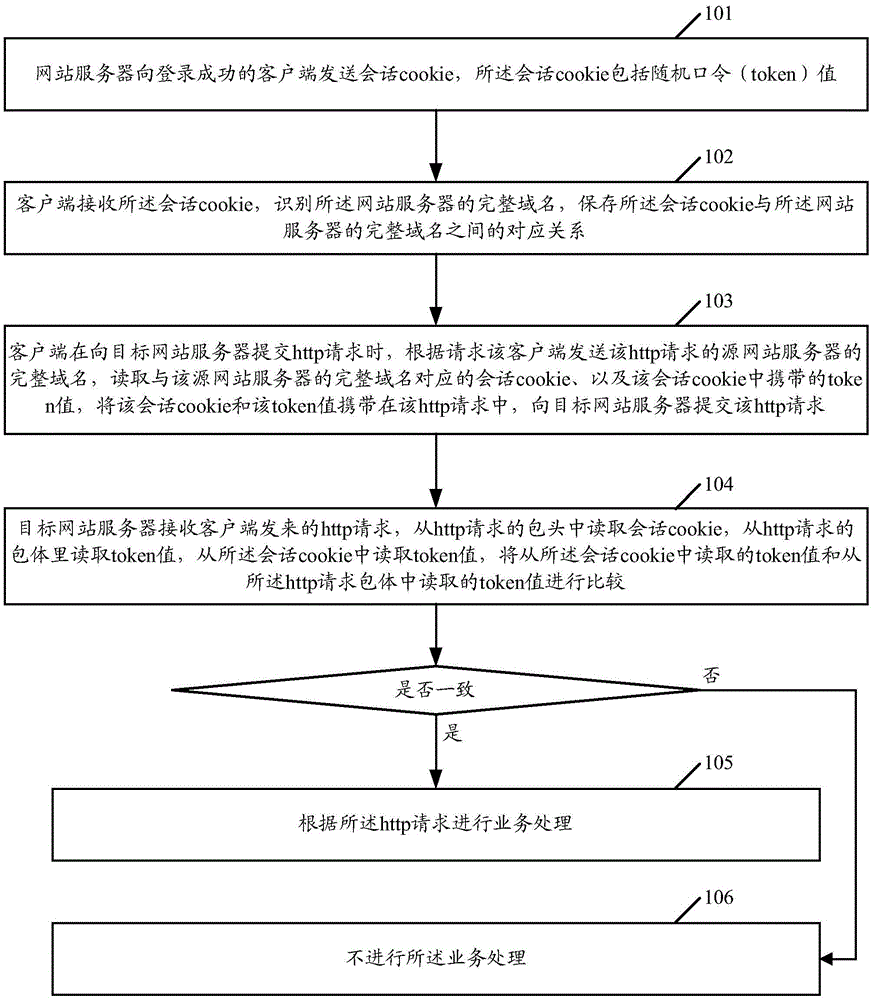
The embodiment of the invention discloses a method, a system and a device for preventing a CSRF (cross site request forgery) attack. The method comprises the following steps: a web server sends a session cookie to a client with successful logging in and the session cookie comprises a token value; the client, according to a complete domain name of a source web server, reads the session cookie corresponding to the complete domain name and reads the token value in the session cookie; the session cookie is included in a packet header of an Http request and the token value is included in a packet body of the Http request; the Http request is sent to a target web server; the target web server compares the token value of the cookie and the token value read from the packet body of the Http request; and if the token value of the cookie and the token value read from the packet body of the Http request are inconsistent, or the token value cannot be read from the cookie, an operation processing is not carried out. The method, the system and the device of the invention can be applied to prevent the CSRF attack.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Systems and methods for cross site forgery protection
ActiveUS8640216B2Digital data processing detailsUser identity/authority verificationCross-site request forgeryThird party
Owner:CITRIX SYST INC
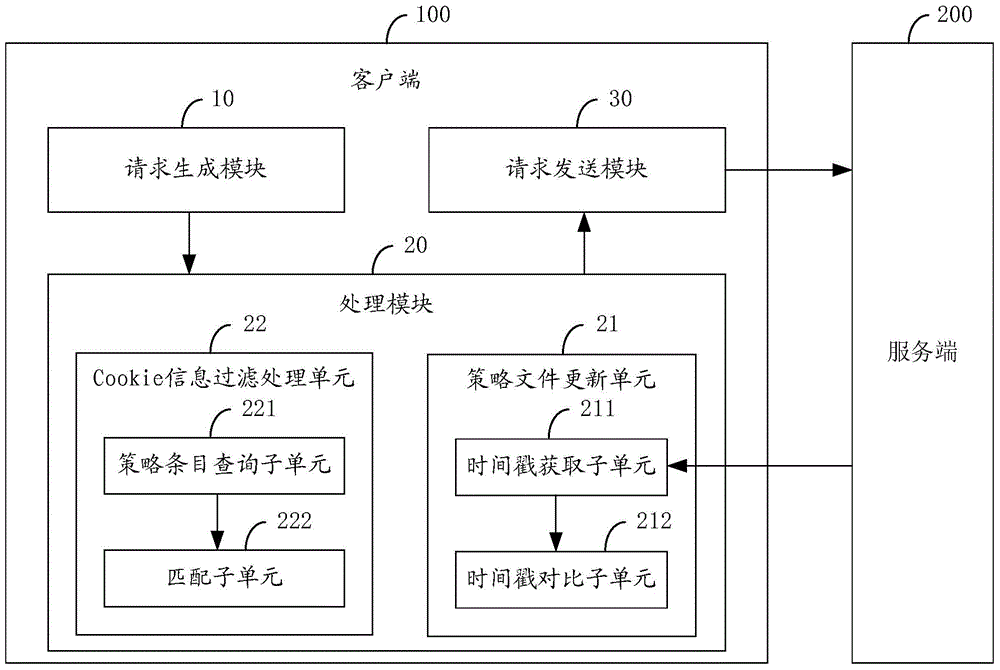
Method and system for preventing cross-site request forgery attack
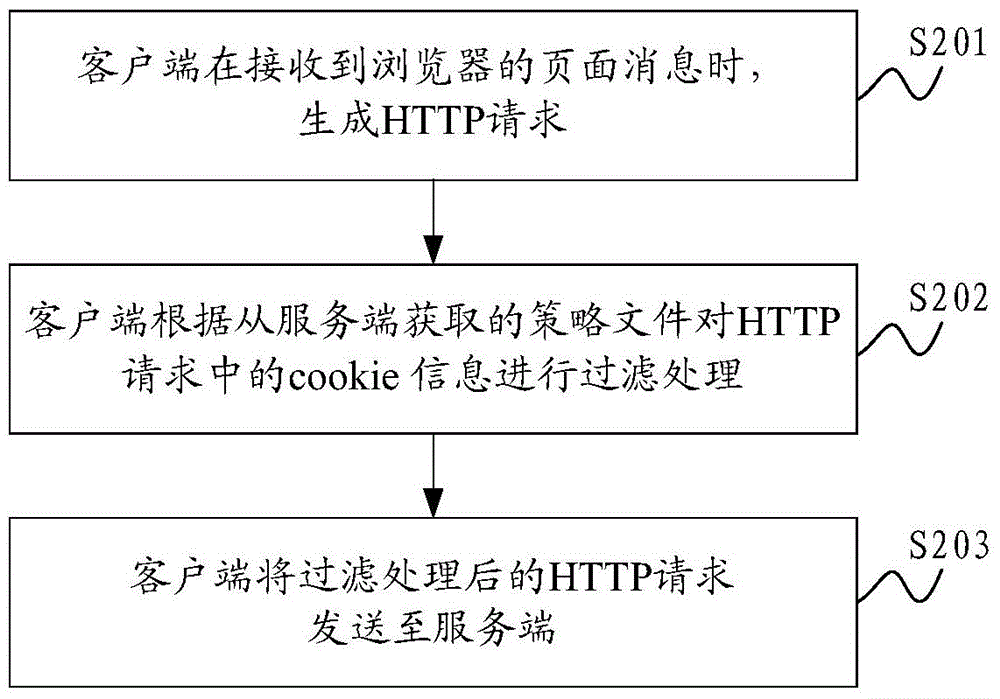
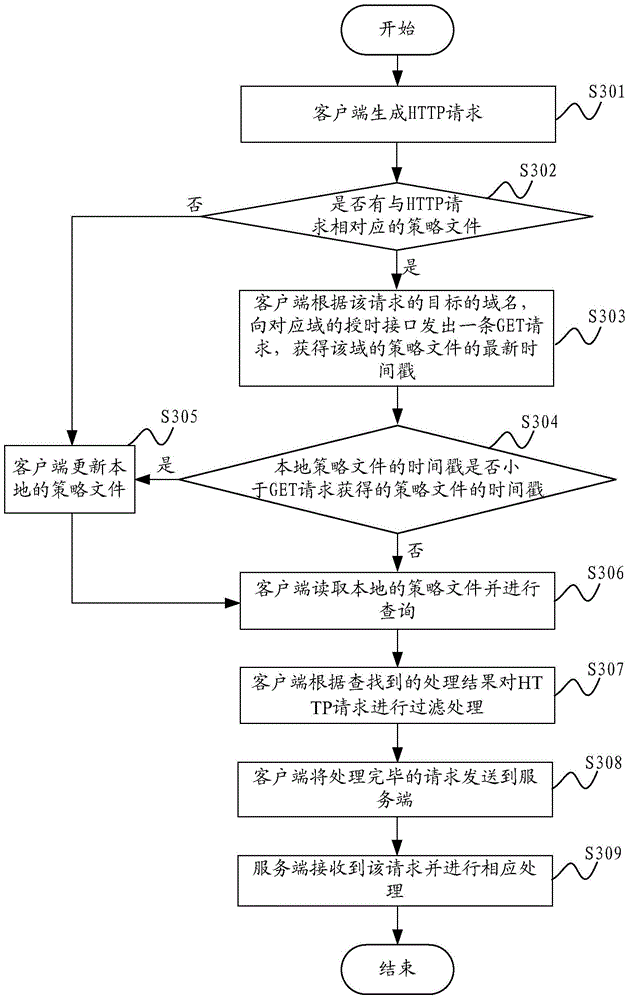
The invention is applicable for the technical field of network safety, and provides a method and a system for preventing a cross-site request forgery attack. The method comprises the steps that: a client generates an HTTP request when page information of a browser is received; the client performs filtration treatment on cookie information in the HTTP request based on a strategy document obtained from a server-side; the client sends the HTTP request after subjected to the filtration treatment to the server-side. In the method and the system for preventing the cross-site request forgery attack, the strategy document is provided by the server-side, the server-side defines requests from which pages the service-side expects to receive exactly, and the client performs authenticity judgment on the HTTP request based on the strategy document, so that requests which are not allowed by the strategy document are guaranteed to not carry cookie of a user, requests which the server-side does not expect to receive cannot be sent by the client, and the network safety of the client is guaranteed.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method and device for cross-sit request forgery (CSRF) defense authentication
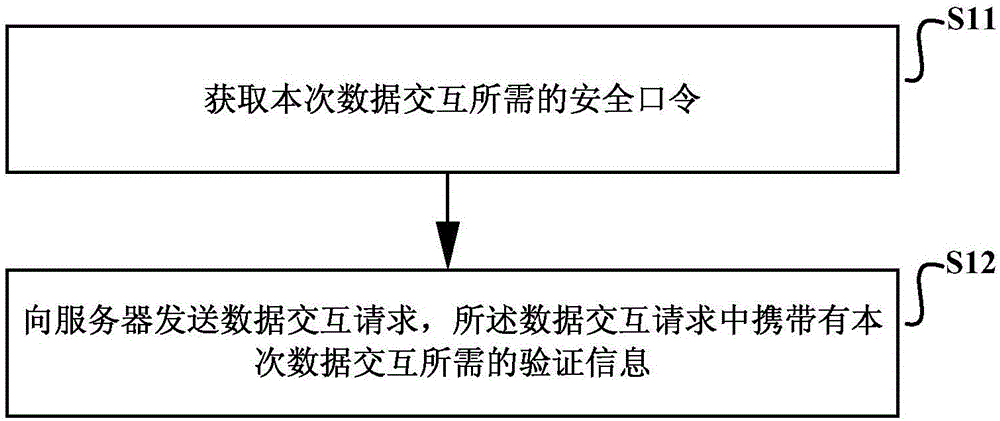
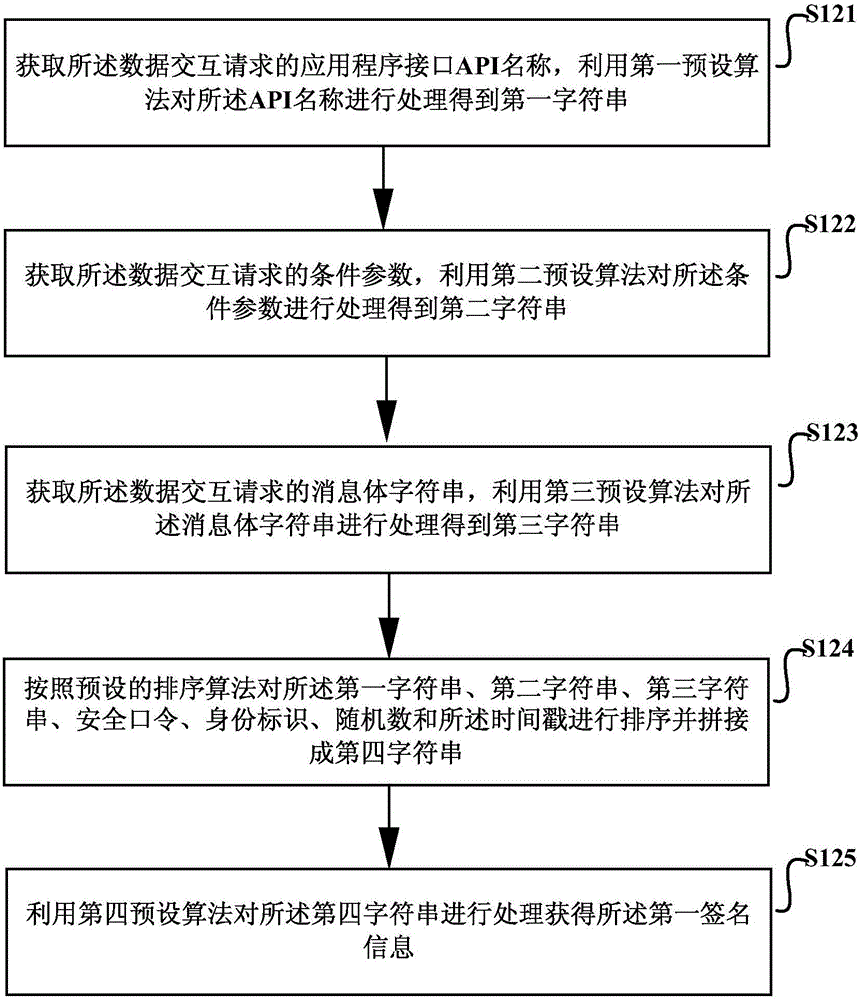
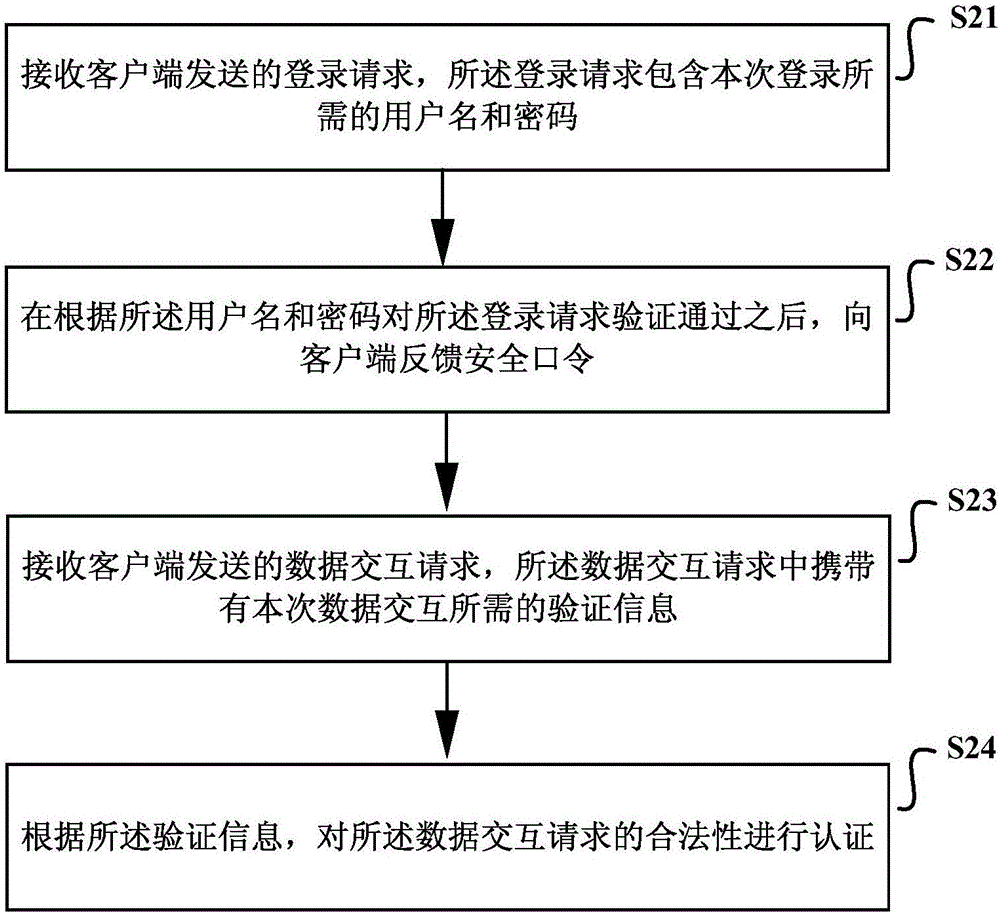
The invention discloses a method and device for CSRF authentication. The method comprises the following steps: acquiring a secure password needed for this data interaction and sending data interaction requests to the server. The secure password is obtained by a login request sent to the server, which includes the user name and password required for the login. The data interaction request carries authentication information needed for the data interaction and the authentication information is used to indicate that the server authenticates the validity of the data interaction request, wherein the authentication information is determined according to the secure password. By adopting the method provided by the CSRF authentication defense method and device, not only can the protection of the CSRF attack be effectively realized, but also the tamper proof effect is achieved. To a certain extent, the CSRF defense authentication method and device can protect replay attacks and is more versatile.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Guarding against cross-site request forgery (CSRF) attacks
Cross-Site Request Forgery attacks are mitigated by a CSRF mechanism executing at a computing entity. The CSRF mechanism is operative to analyze information associated with an HTTP request for a resource. The HTTP request typically originates as an HTTP redirect from another computing entity, such as an enterprise Web portal. Depending on the nature of the information associated with the HTTP request, the HTTP request may be rejected because the CSRF mechanism determines that the request is or is likely associated with a CSRF attack. To facilitate this determination, the approach leverages a new type of “referer” attribute, a trustedReferer, which indicates that the request originates from a server that has previously established a trust relationship with the site at which the CSRF mechanism executes. The trustedReferer attribute typically is set by the redirecting entity, and in an HTTP request header field dedicated for that attribute.
Owner:IBM CORP
Methods and systems for cross site forgery protection
ActiveCN102763368AData taking preventionDigital data protectionCross-site request forgeryThird party
Owner:CITRIX SYST INC
Cross-site request forgery (CSRF) vulnerability detection
ActiveUS20180351986A1Error detection/correctionDigital data protectionCross-site request forgeryVirtualization
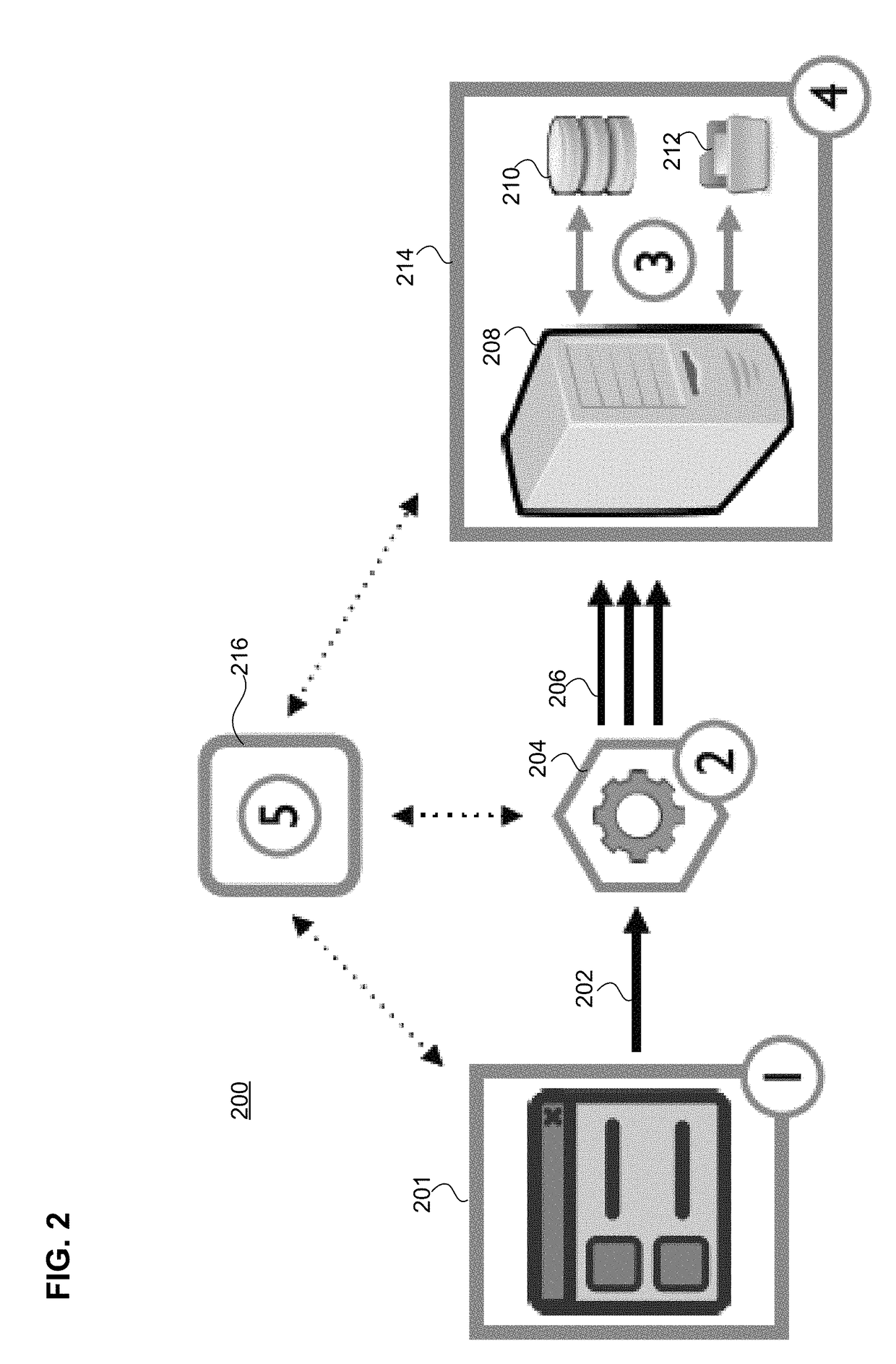
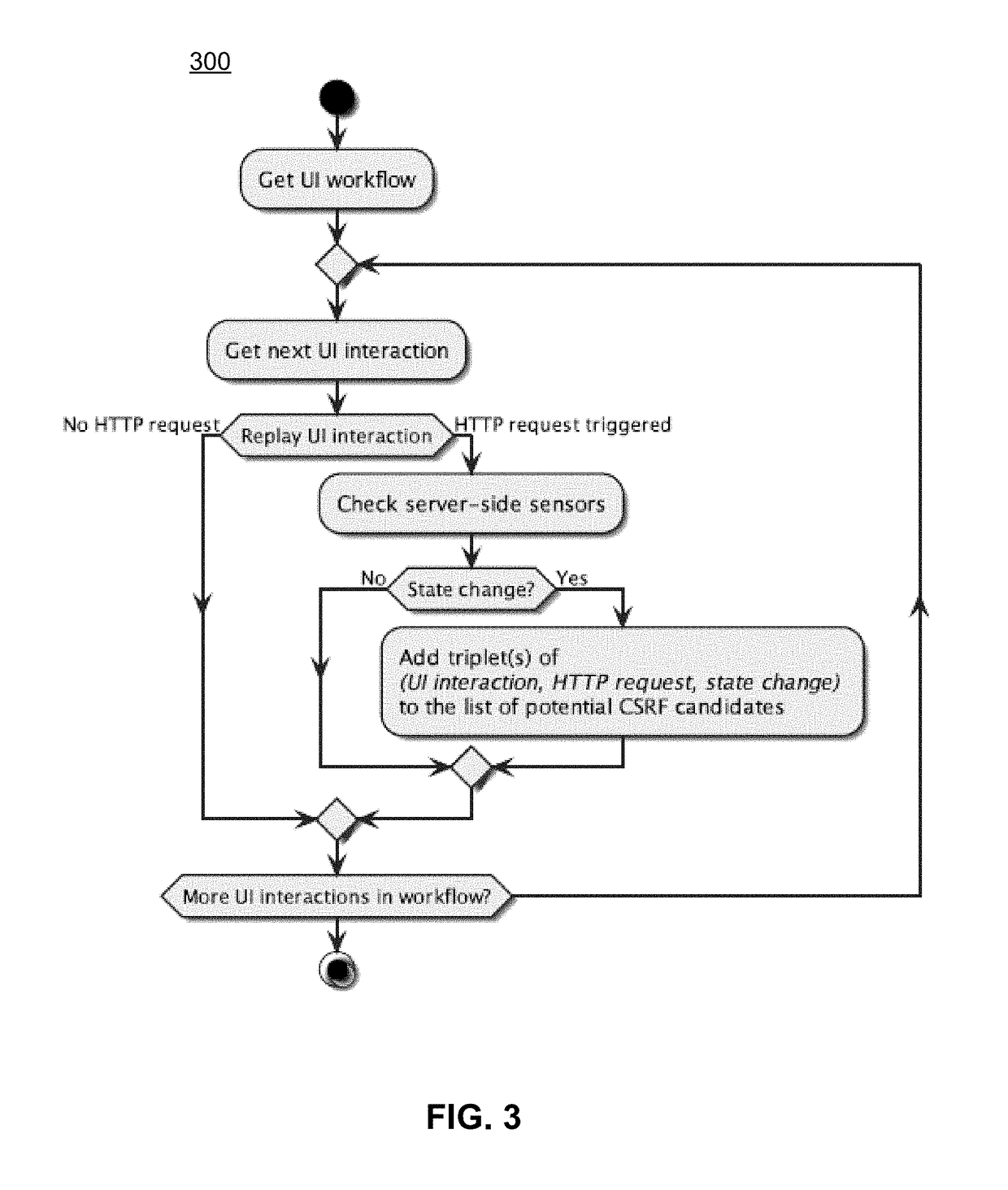
Embodiments detect cross-site request forgery (CSRF) attacks by monitoring, mutation, and analysis of suspect requests that are received by an application server. An engine observes UI interaction, HTTP traffic, and server-side changes in order to create an initial list of CSRF candidates (e.g., HTTP requests that could indicate a CSRF vulnerability). Embodiments may feature a virtualized server-side platform including sensors deployed for application persistence monitoring. Using inter-trace analysis, these CSRF candidates are de-composed into their semantic components (e.g., parameter values and classes). By performing value mutation operations on these components and repeated replay of the resulting HTTP requests, CSRF candidates are tested to see if the underlying HTTP request could be utilized in the context of a CSRF attack. Subsequent validation and exploitability assessment may reduce the initial list of suspect candidate requests to only those exploitable cases for which a proof-of-vulnerability demonstration exploit can be created.
Owner:SAP AG
Detection of cross-site request forgery attacks
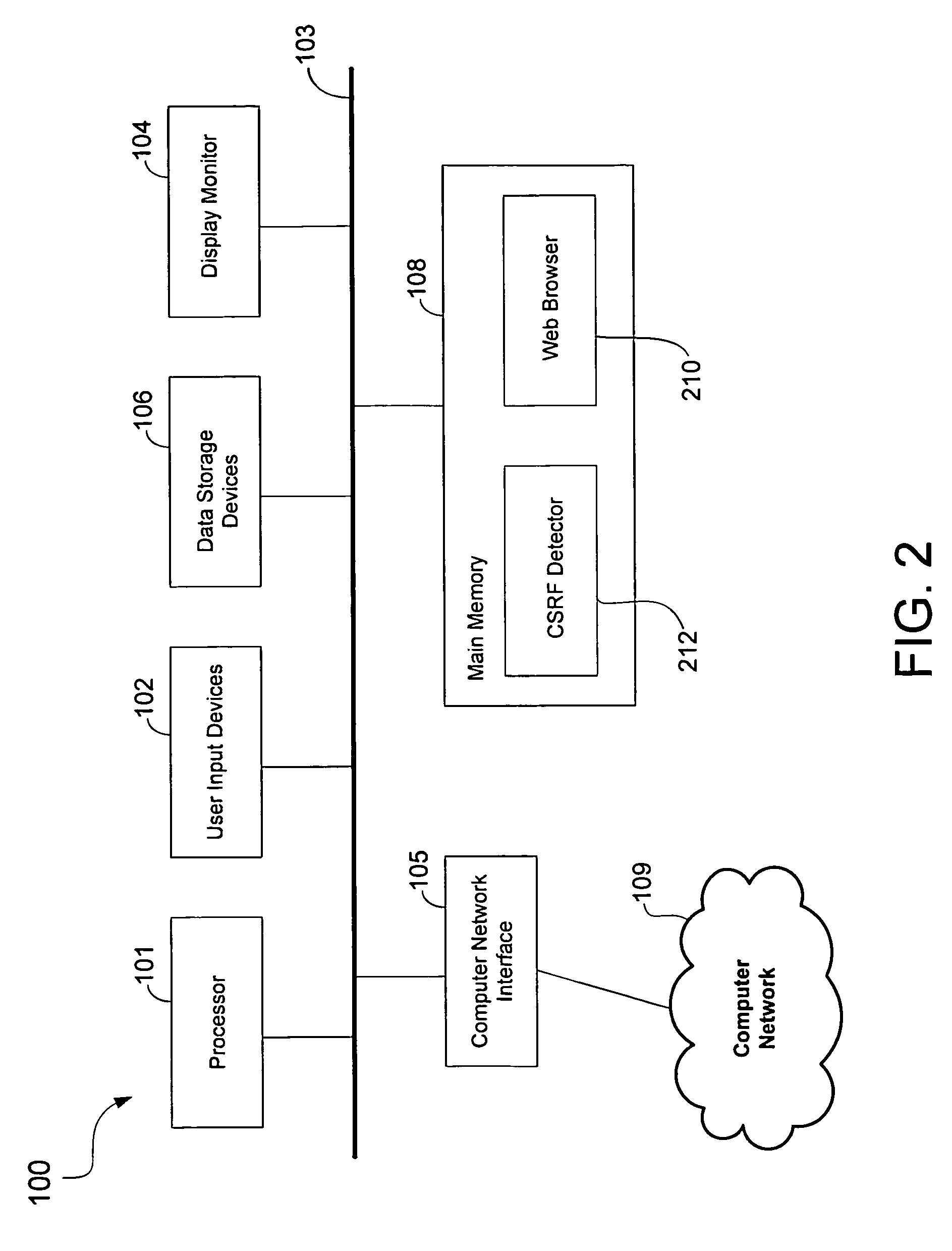
ActiveUS8893270B1Memory loss protectionError detection/correctionCross-site request forgeryWeb browser
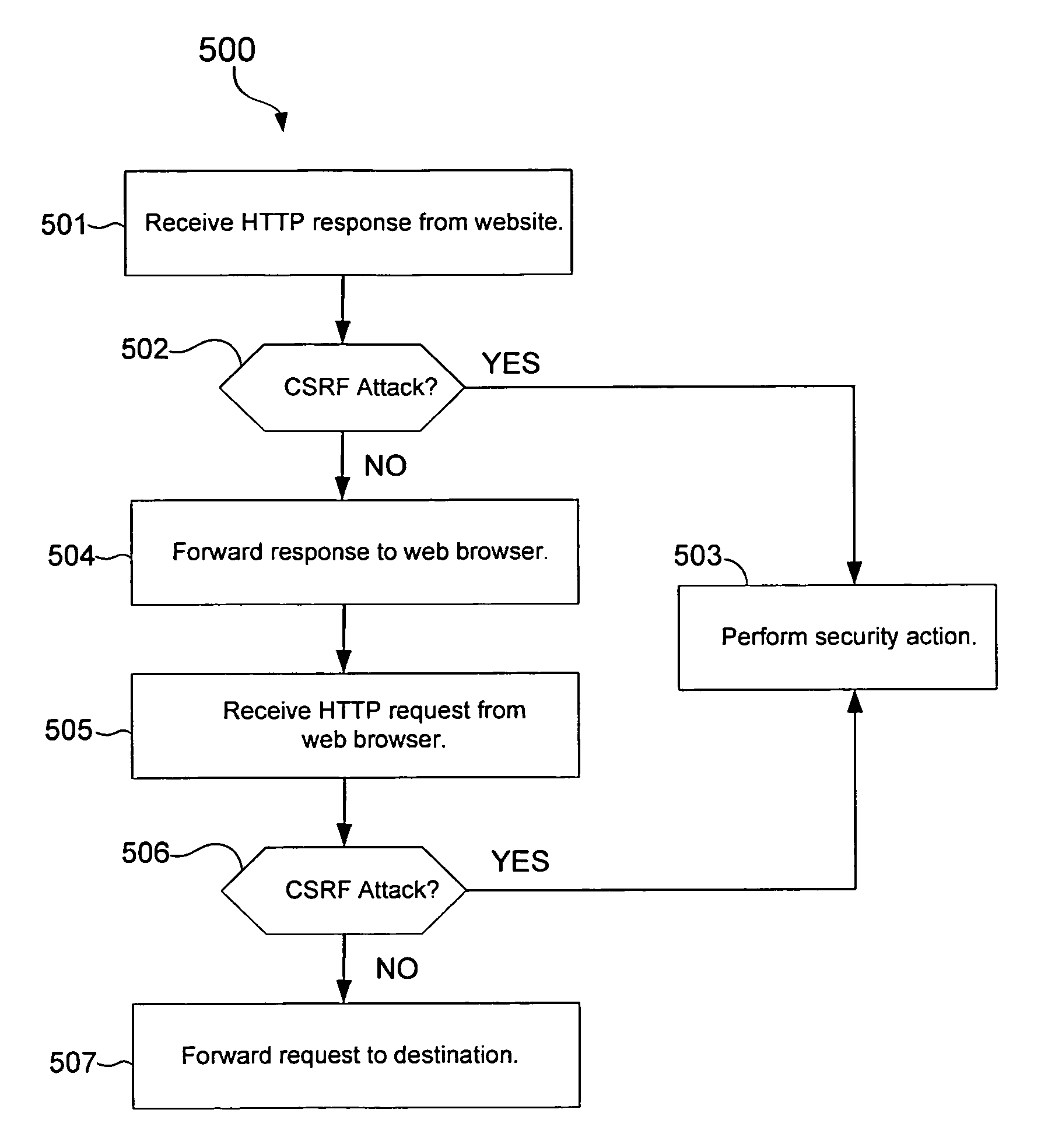
Methods and apparatus for detecting cross-site request forgery (CSRF) attacks include a CSRF detector that analyzes HTTP communications for information indicative of a CSRF attack. The CSRF detector may analyze HTTP responses from a website for CSRF code that automatically performs unauthorized access of an online account of a user of a user computer upon receipt and execution of the CSRF code in the user computer. The CSRF detector may also analyze HTTP requests from a web browser for information indicative of a CSRF attack.
Owner:TREND MICRO INC
Preventing Cross-Site Request Forgery Attacks on a Server
ActiveUS20120180128A1Preventing CSRF security attackPrevents CSRFMemory loss protectionError detection/correctionCross-site request forgeryClient-side
Preventing Cross-Site Request Forgery security attacks on a server in a client-server environment. In one aspect, this comprises embedding a nonce and a script in all responses from the server to the client wherein, when executed, the script adds the nonce to each request from the client to the server; sending the response with the nonce and the script to the client; and verifying that each request from the client includes the nonce sent by the server to the client. The script preferably modifies all objects, including dynamically generated objects, in a server response that may generate future requests to the server to add the nonce to the requests. The server verifies the nonce value in a request and optionally confirms the request with the client if the value differs from the value previously sent. Server-side aspects might be embodied in the server or a proxy.
Owner:INT BUSINESS MASCH CORP
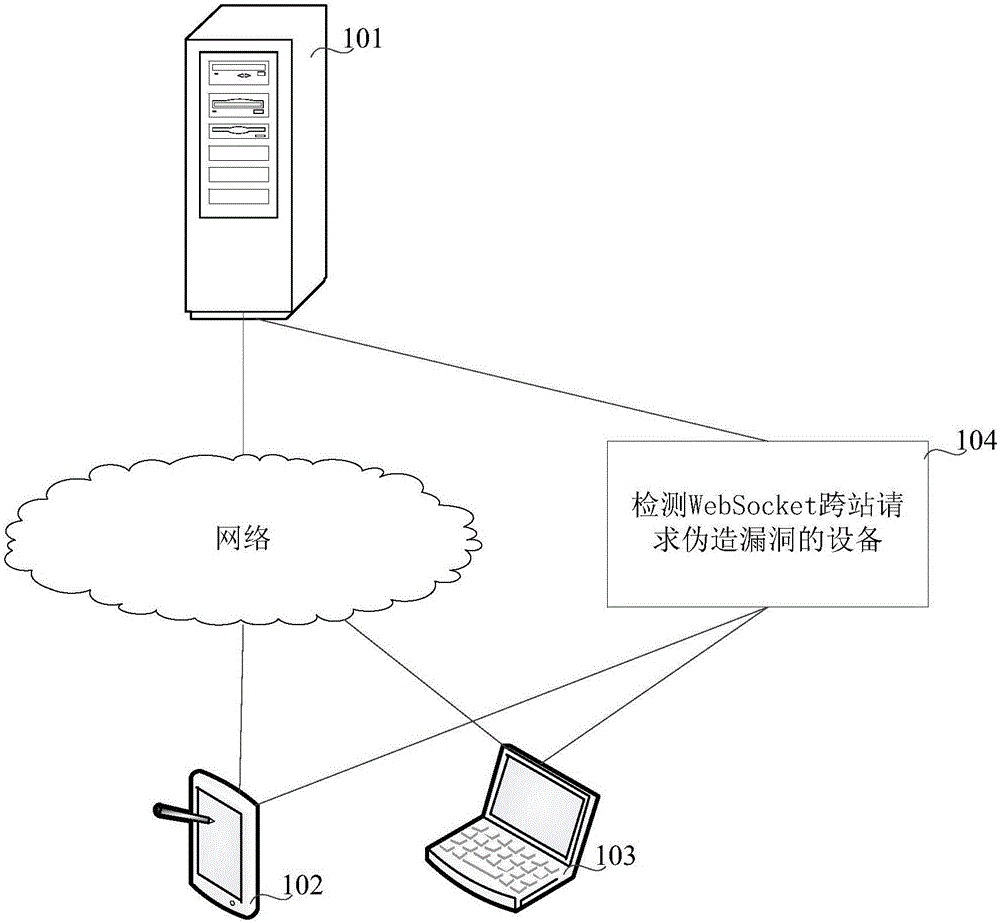
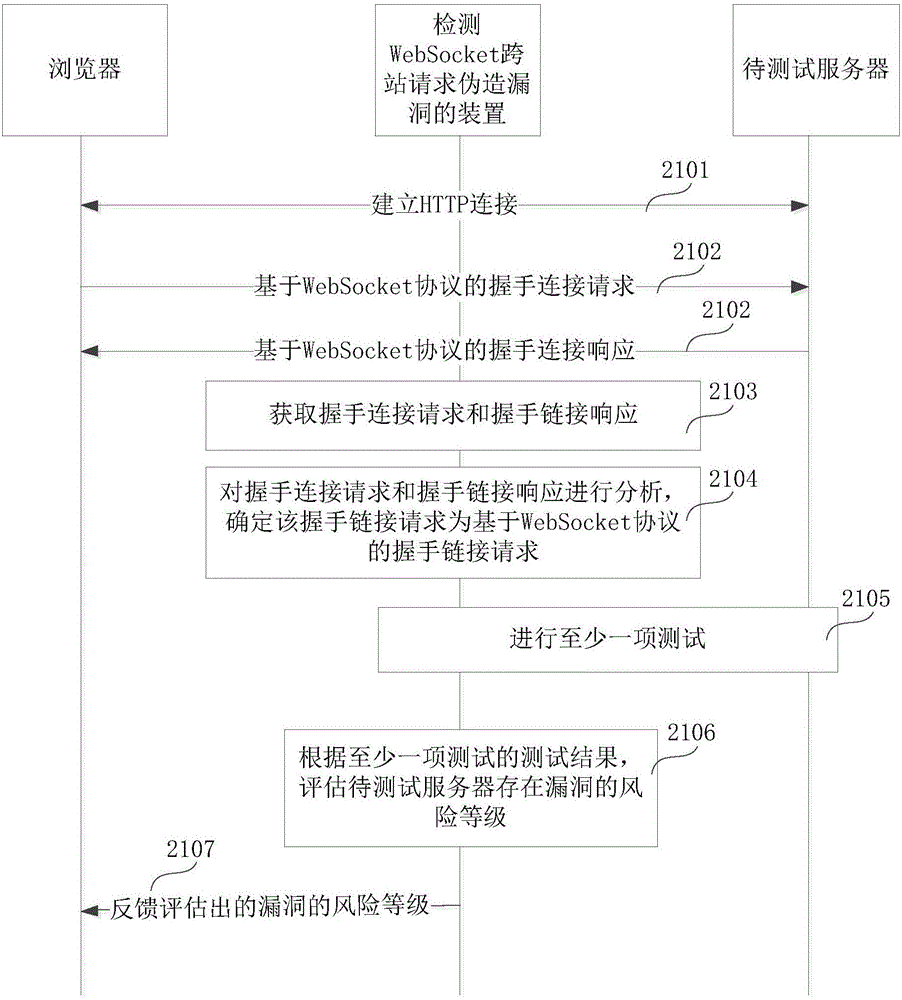
Method and apparatus for detecting loophole of WebSocket cross-site request forgery
The embodiments of the invention relate to the field of telecommunication, and in particular to a method and apparatus for detecting a loophole of a WebSocket cross-site request forgery, aiming at detecting whether a to-be-tested server has the loophole of WebSocket cross-site request forgery. According to the embodiments of the invention, the method comprises the following steps: when it is determined that a handshake connection request is based on the WebSocket protocol, based on the handshake connection request, generating at least one forgery request based on the WebSocket protocol, transmitting the at least one forgery request to a to-be-tested server, determining whether the to-be-tested server may be deceived by the forgery request based on the WebSocket protocol so as to verify whether the to-be-tested server has the loophole of WebSocket cross-site request forgery and the risk level of the loophole.
Owner:CHINA UNIONPAY
Method, device and system for preventing cross-site request forgery
InactiveCN106549925AGuaranteed online securityPrevent CSRFTransmissionCross-site request forgeryTerminal equipment
Owner:ALIBABA GRP HLDG LTD
Cross site request forgery vulnerability detection method and device
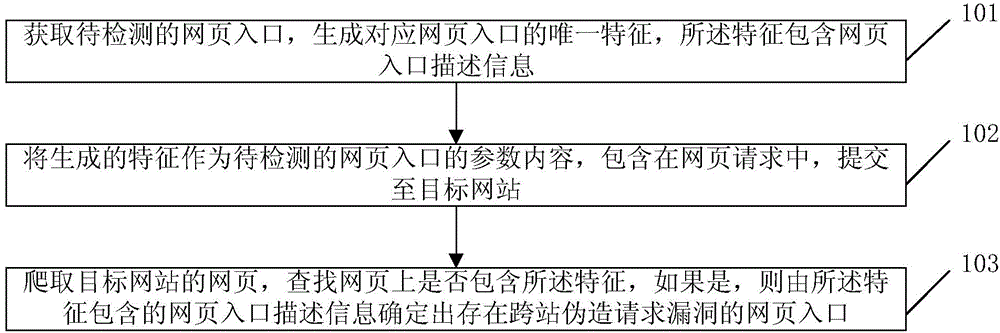
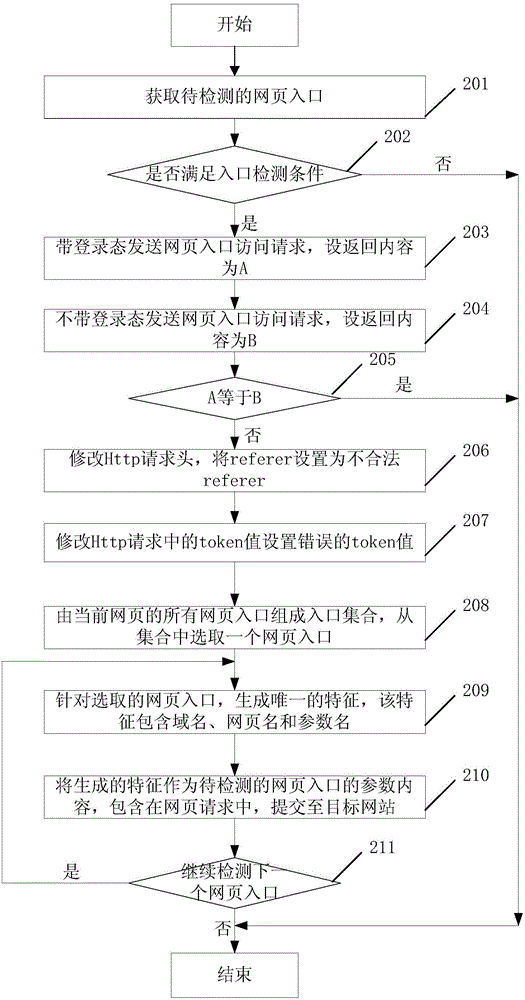
ActiveCN104660556AAutomatic detectionAccurate detectionTransmissionCross-site request forgeryWeb page
The invention discloses a cross site request forgery vulnerability detection method and device. The method comprises the following steps: acquiring a webpage entrance to be detected, and generating a unique feature corresponding to the webpage entrance, wherein the feature comprises webpage entrance description information; taking the generated feature as the parameter content of the webpage entrance to be detected, including the generated feature in a webpage request, and submitting the webpage request to a target website; and crawling a webpage of the target website, looking up whether or not the feature is included on the webpage or not, and if so, determining a webpage entrance on which cross site request forgery vulnerability exists according to the webpage entrance description information included in the feature. Through adoption of the scheme of the invention, the accuracy of cross site request forgery vulnerability detection can be increased.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Method and system for authenticating a rich client to a web or cloud application
ActiveUS9699168B2Digital data processing detailsUser identity/authority verificationCross-site request forgeryApplication server
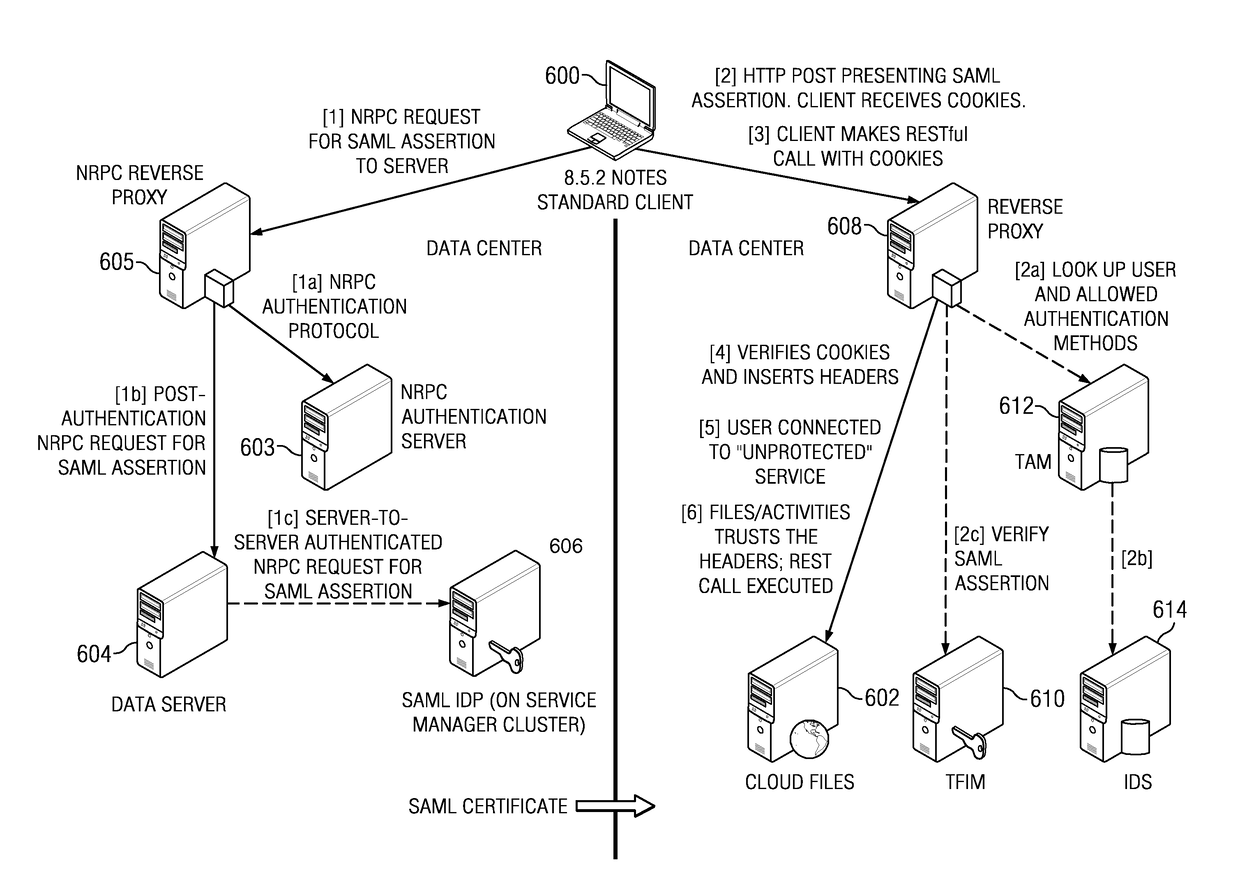
A rich client performs single sign-on (SSO) to access a web- or cloud-based application. According to the described SSO approach, the rich client delegates to its native application server the task of obtaining a credential, such as a SAML assertion. The native server, acting on behalf of the user, obtains an assertion from a federated identity provider (IdP) that is then returned to the rich client. The rich client provides the assertion to a cloud-based proxy, which presents the assertion to an identity manager to attempt to prove that the user is entitled to access the web- or cloud-based application using the rich client. If the assertion can be verified, it is exchanged with a signed token, such as a token designed to protect against cross-site request forgery (CSRF). The rich client then accesses the web- or cloud-based application making a REST call that includes the signed token. The application, which recognizes the request as trustworthy, responds to the call with the requested data.
Owner:IBM CORP
Method and device for defending cross-site request forgery attacks
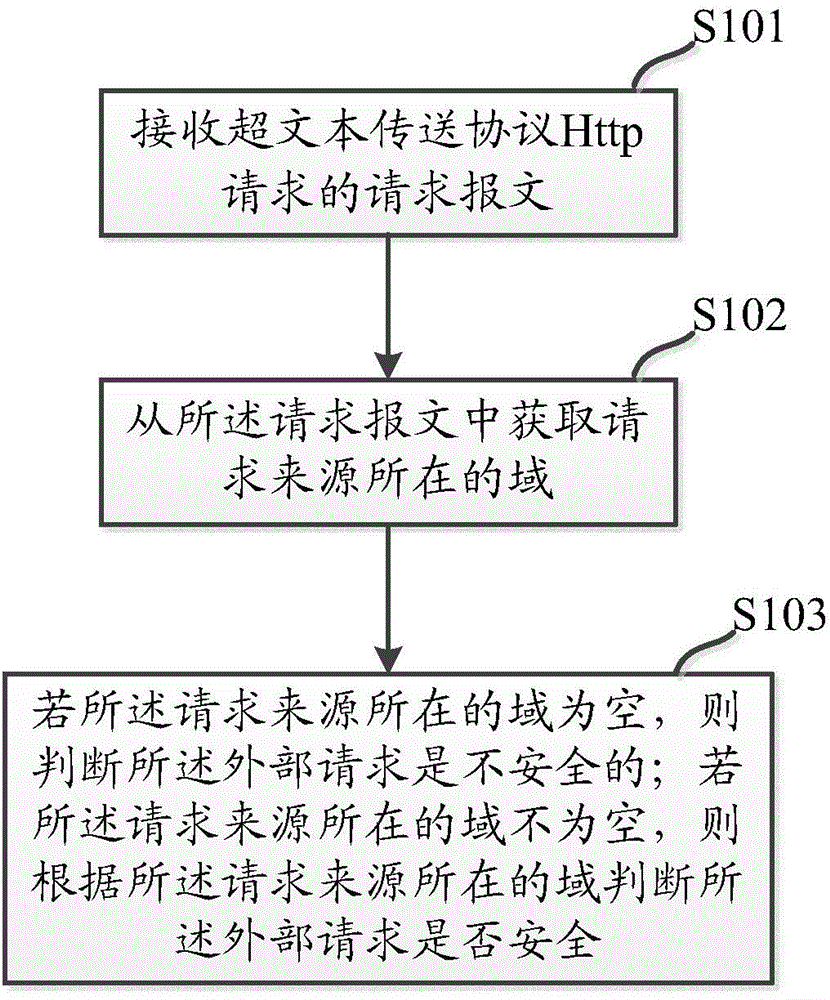
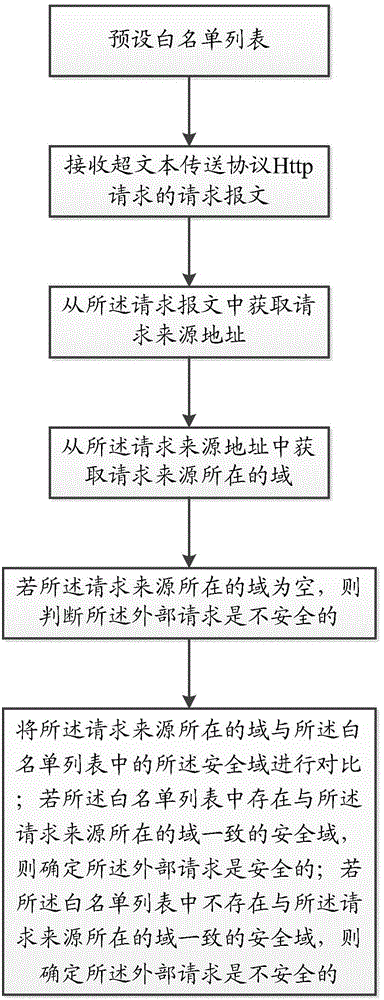
The invention discloses a method for defending cross-site request forgery attacks. The method comprises the steps of: receiving a request packet Hypertext Transfer Protocol Http requests; message requesting source to obtain the domain from where the request; if the source of the request is located field is empty, it is determined that the hypertext transfer protocol Http request is unsafe; domain if the request source is located is not empty, then the field is determined according to the request source where the hypertext transfer protocol Http request is security. Therefore, the defense cross-site request forgery attack the present application provides a method of defense can effectively cross-site request forgery attacks.
Owner:MICRO DREAM TECHTRONIC NETWORK TECH CHINACO
Network request protection method and network communication system
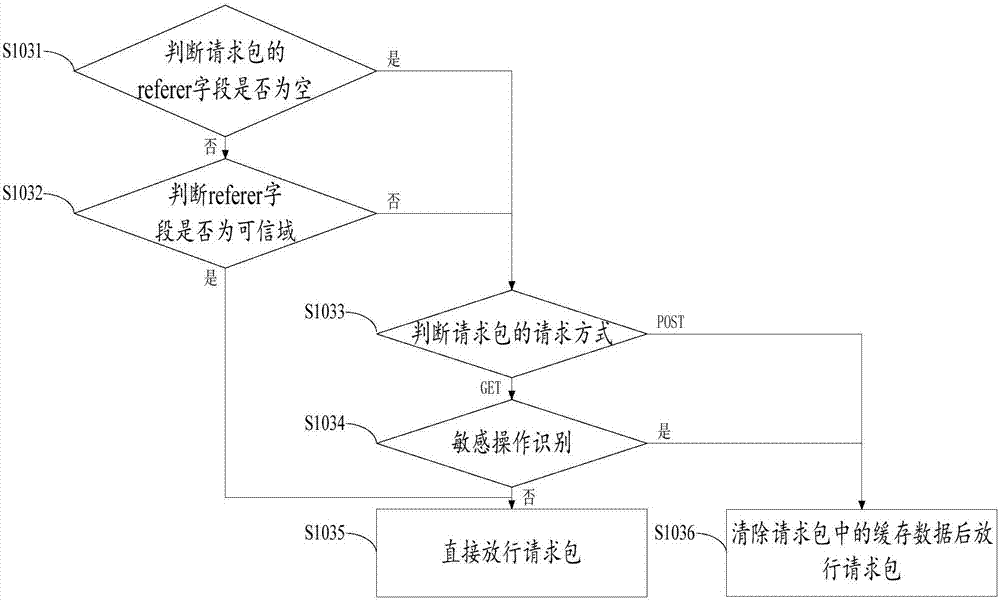
The invention provides a network request protection method and a network communication system. The network communication system comprises a server and a a user terminal that communicate with each other. The method comprises the following steps: acquiring a first HTTP request sent by the user terminal by the server; replacing a preset character in the first HTTP request by the server to obtain a second HTTP request, and detecting whether a preset sensitive keyword is included in the second HTTP request; and if not, then acquiring and verifying whether a Referer value in the first HTTP request starts with a preset domain name by the server, and verifying that a token value in the first HTTP request is a preset value. Thus, the sensitive keywords in the HTTP requests are shielded, and the requests are verified by combining a Referer field and a token, so that cross-site scripting attacks and cross-site request forgery can be recognized and excluded, so that the safety of data interactionbetween a legal user terminal and the server is improved.
Owner:CHENGDU NEUSOFT UNIV
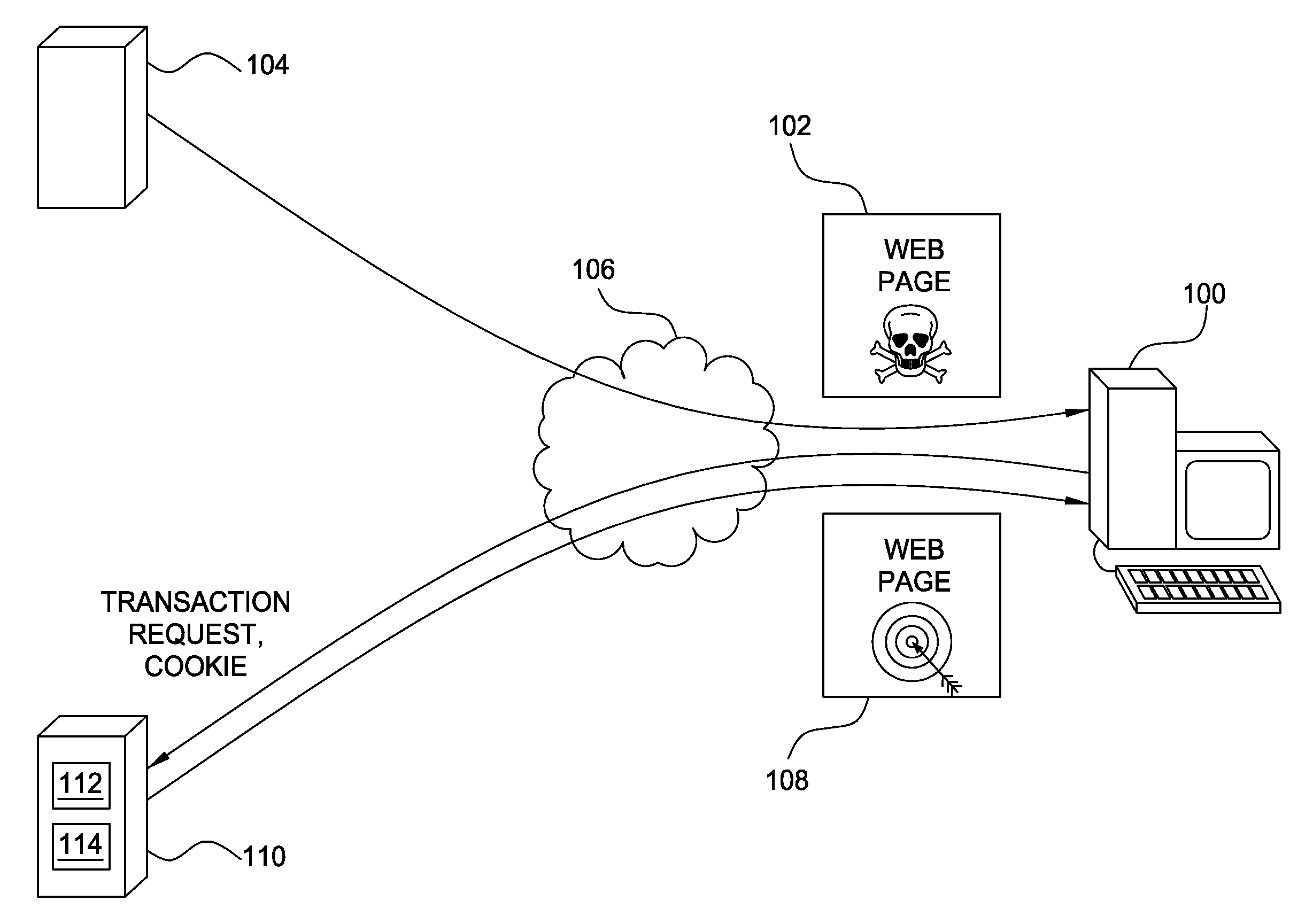
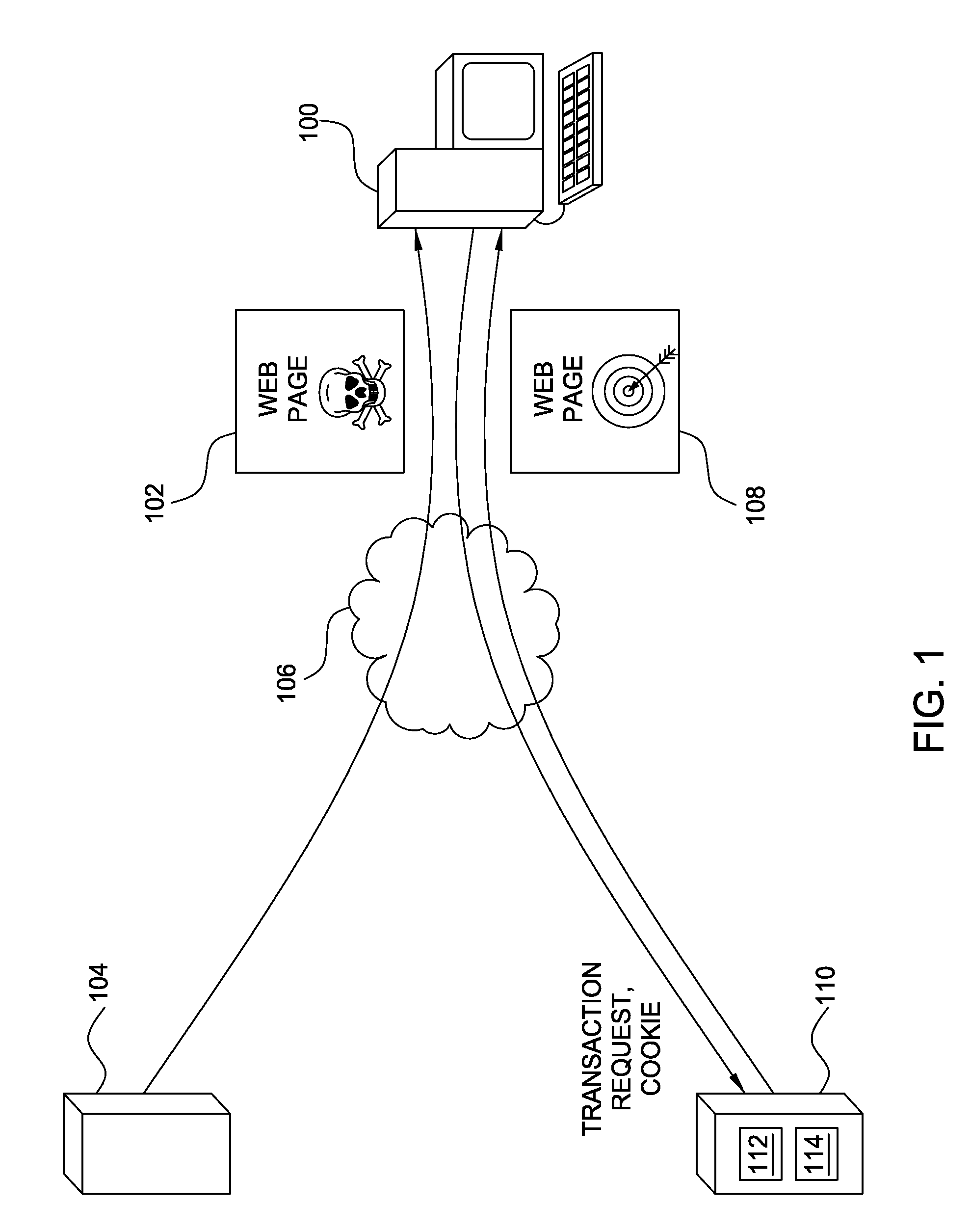
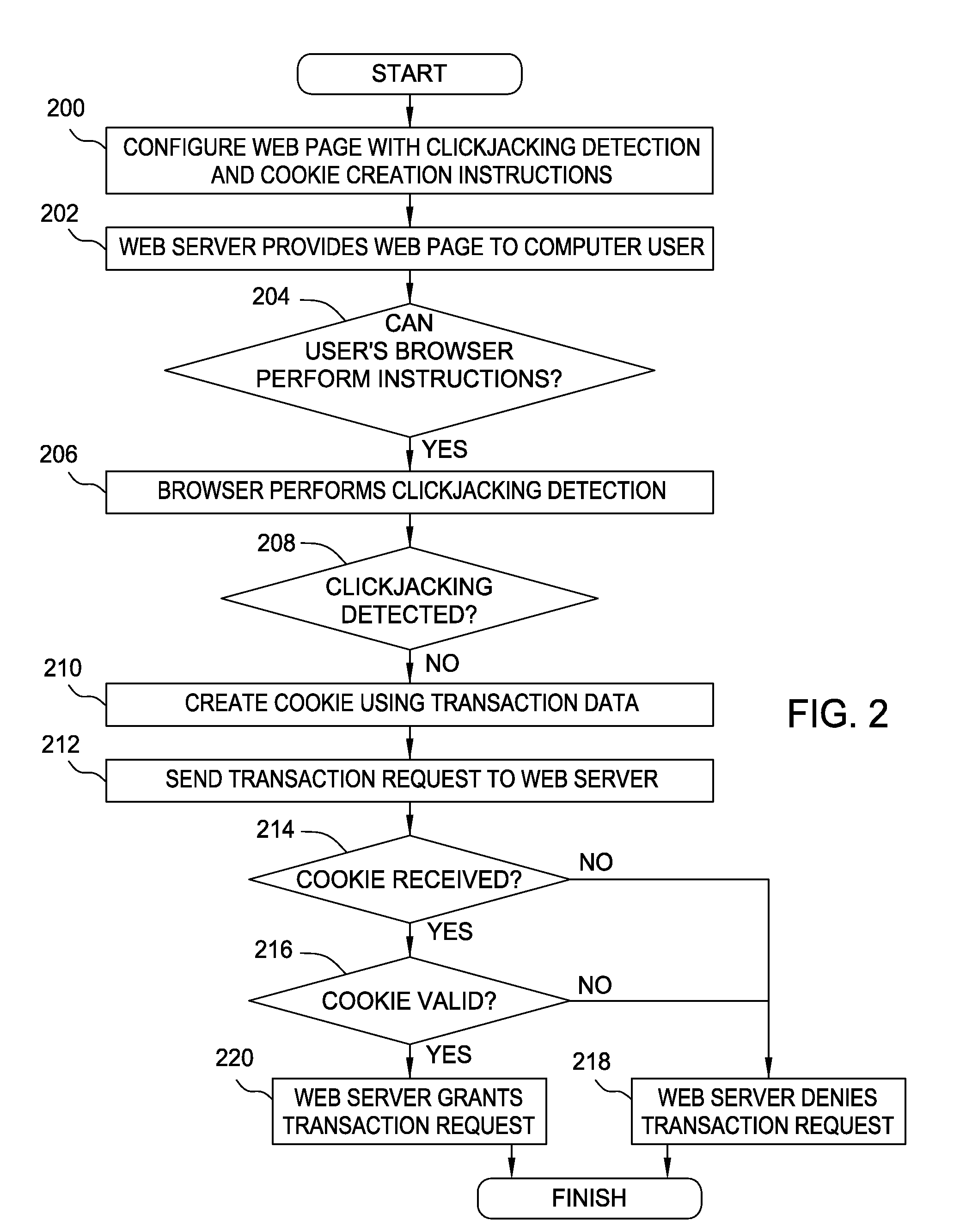
Thwarting cross-site request forgery (CSRF) and clickjacking attacks
ActiveUS8813237B2Memory loss protectionError detection/correctionCross-site request forgeryClickjacking
Embodiments of the invention generally relate to thwarting fraud perpetrated with a computer by receiving a request from a computer to perform a transaction. Embodiments of the invention may include receiving the request together with transaction data and a cookie, where the transaction data are separate from the cookie; determining in accordance with predefined validation criteria whether the cookie includes a valid representation of the transaction data; and performing the transaction only if the cookie includes a valid representation of the transaction data.
Owner:INT BUSINESS MASCH CORP
Method and device for defending cross-site request forgery attack
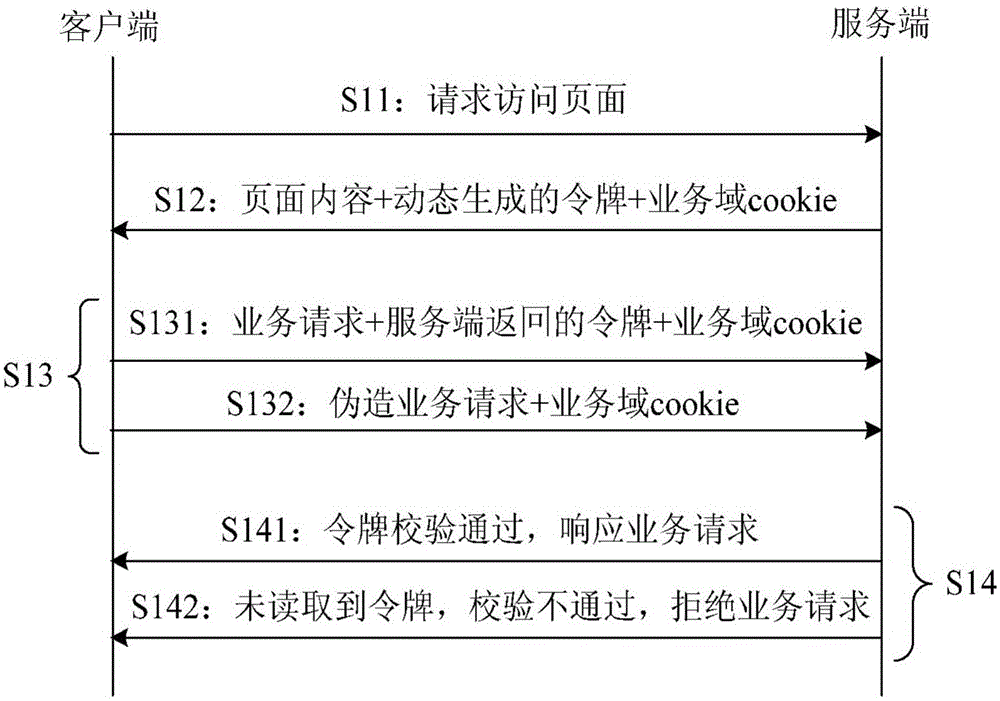
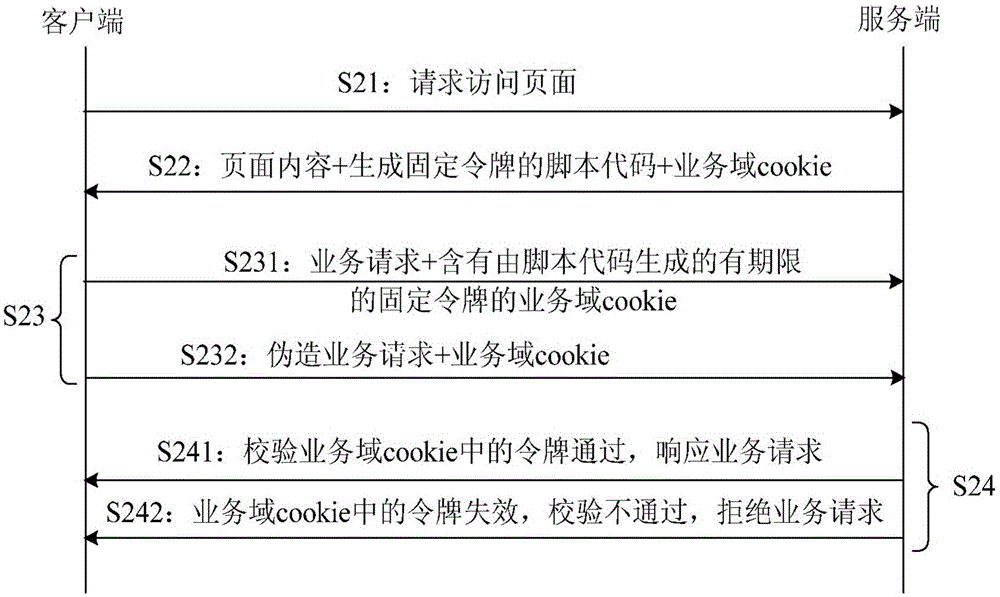
ActiveCN106341370AShort expiration timeRelieve pressureUser identity/authority verificationCross-site request forgeryExpiration Time
The invention provides a method and device for defending a cross-site request forgery attack, thereby being conducive to enabling a token calibration method to be small in code modification amount, and thus achieving the purpose of being simple in function realization and small in pressure brought about for a server. The method for defending the cross-site request forgery attack comprises the steps that a client asks a server for a page and then receives page content, a script code and a service domain cookie which are returned by the server; the client operates the script code so as to generate a fixed token, writes the fixed token into the service domain cookie and sets the expiration time of the token; and the client sends a service request and the service domain cookie to the server, then receives response content of the server and displays the response content.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
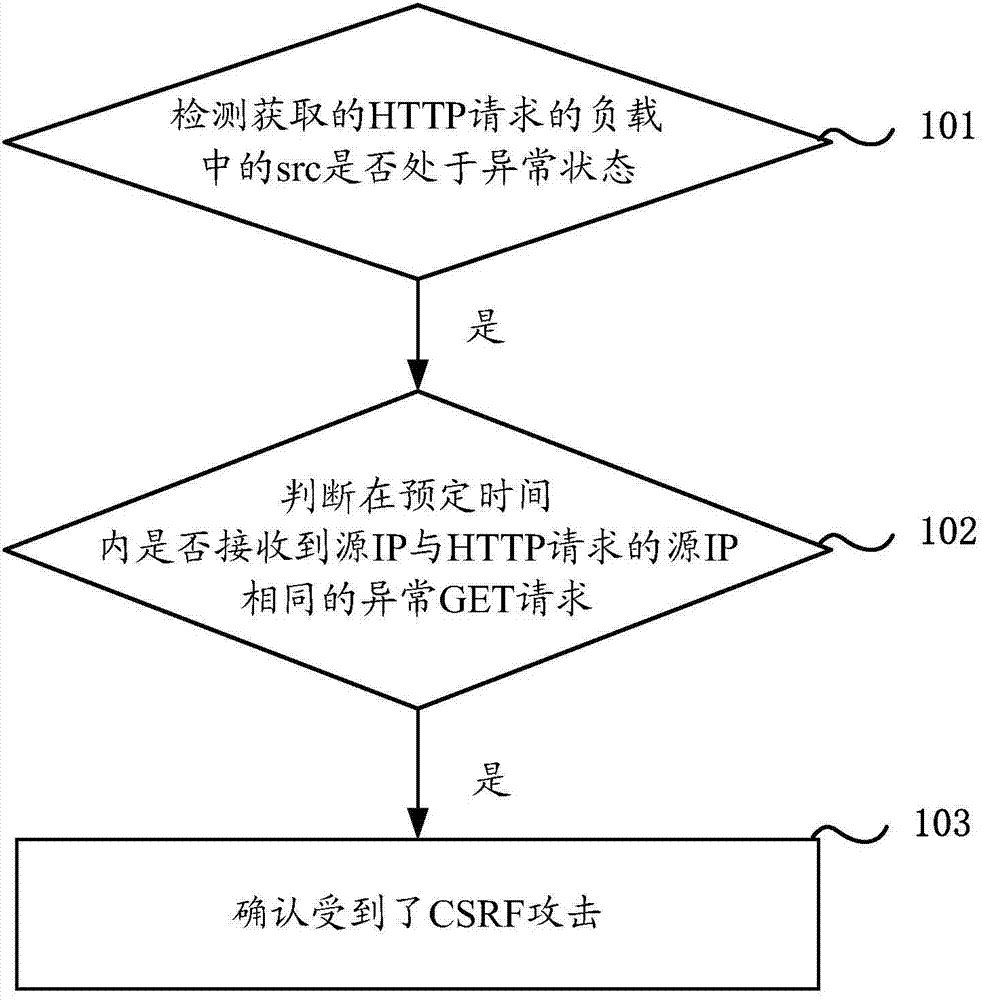
Cross-site request forgery CSRF attack recognition method and device
The present invention discloses a cross-site request forgery CSRF attack recognition method and device. When a source src in a load of an obtained HTTP request is detected to be at an abnormal state, whether an abnormal GET request whose source IP is the same as a source IP of the HTTP request is received within a preset time is determined, and if is, a CSRF attack is confirmed. By this means, srcs at abnormal states and the abnormal GET requests are continuously detected to commonly confirm whether CSRF attacks based on forged srcs are received, thereby realizing recognition of the CSRF attacks based on the forged srcs.
Owner:NEW H3C TECH CO LTD
CSRF protection method and system based on cloud platform
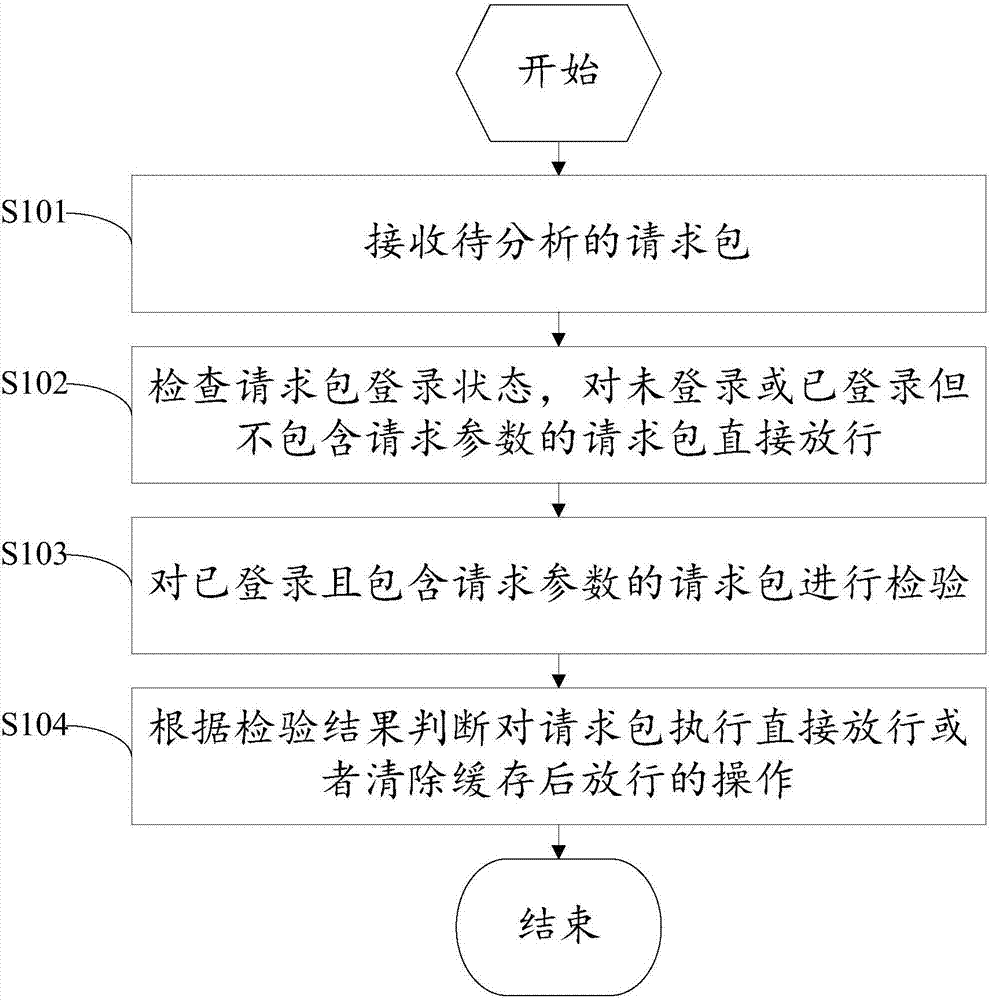
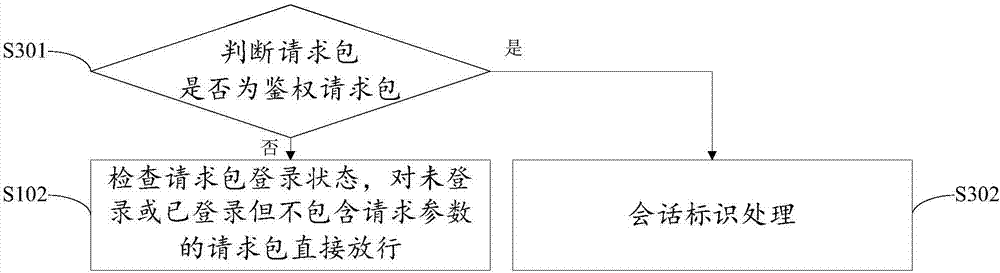
ActiveCN107294994ALittle impact on performanceReduce false blocking behaviorTransmissionCross-site request forgeryOperating system
The invention discloses a CSRF (Cross-Site Request Forgery) protection method and system based on a cloud platform. The method comprises the following steps: receiving a request packet to be analyzed; checking the login state of the request packet, and directly releasing the request packet which does not log or has logged and does not include a request parameter; checking the request packet which has logged and includes a request parameter; and judging whether the request packet is directly released or released after the cache is cleared according to the checking result. The CSRF protection method and system based on the cloud platform have the advantages: by judging the login authority of a request access system, erroneous intercepting behaviors on open operating interfaces can be reduced, the detection efficiency can be improved, and the influence on the performance of the cloud platform can be reduced; and by recognizing the request mode, configuring sensitive operation parameters and performing relevant processing on the requested referer, CSRF protection on the whole website can be realized, the configuration is simple and convenient, and the requirement for the profession of operators is low.
Owner:CHINANETCENT TECH
Secure client-server communication
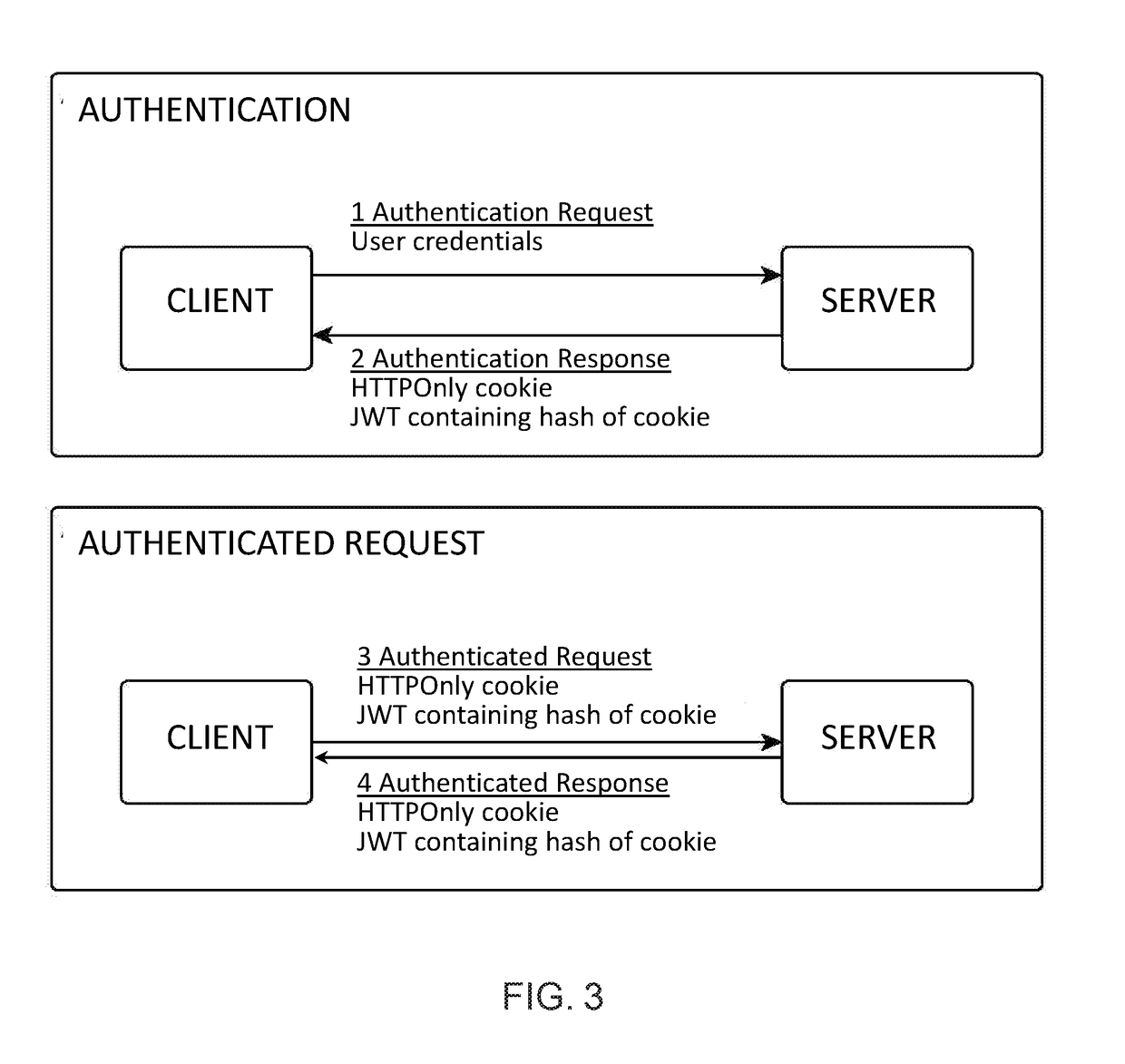
ActiveUS20190068602A1TransmissionLocation information based serviceCross-site request forgeryRepresentational state transfer
A secure client-server connection method compatible with RESTful (REpresentational State Transfer) APIs (Application Programming Interface) that is resistant to cross-site scripting (XSS) and cross-site request forgery (CSRF) attacks. The server generates a token for the client and a random value which it pairs with the token. The random value is hashed. The hash value is transmitted to the client contained in the token and the random value is transmitted to the client contained in an HTTPOnly cookie. Even if an attacker steals the token and / or the hash, security is maintained, since the server verifies communications from the client by validating the token on the basis of its hash value. Validation is performed by the server hashing the random value contained in the HTTPOnly cookie paired with the token to obtain a further hash value, and checking that this further hash value matches the token's hash value.
Owner:GREEN MARKET SQUARE LTD
A method, system and device for defending against cross-site request forgery (csrf) attacks
The embodiment of the invention discloses a method, a system and a device for preventing a CSRF (cross site request forgery) attack. The method comprises the following steps: a web server sends a session cookie to a client with successful logging in and the session cookie comprises a token value; the client, according to a complete domain name of a source web server, reads the session cookie corresponding to the complete domain name and reads the token value in the session cookie; the session cookie is included in a packet header of an Http request and the token value is included in a packet body of the Http request; the Http request is sent to a target web server; the target web server compares the token value of the cookie and the token value read from the packet body of the Http request; and if the token value of the cookie and the token value read from the packet body of the Http request are inconsistent, or the token value cannot be read from the cookie, an operation processing is not carried out. The method, the system and the device of the invention can be applied to prevent the CSRF attack.
Owner:TENCENT TECH (SHENZHEN) CO LTD
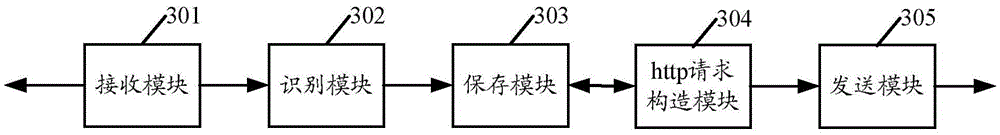
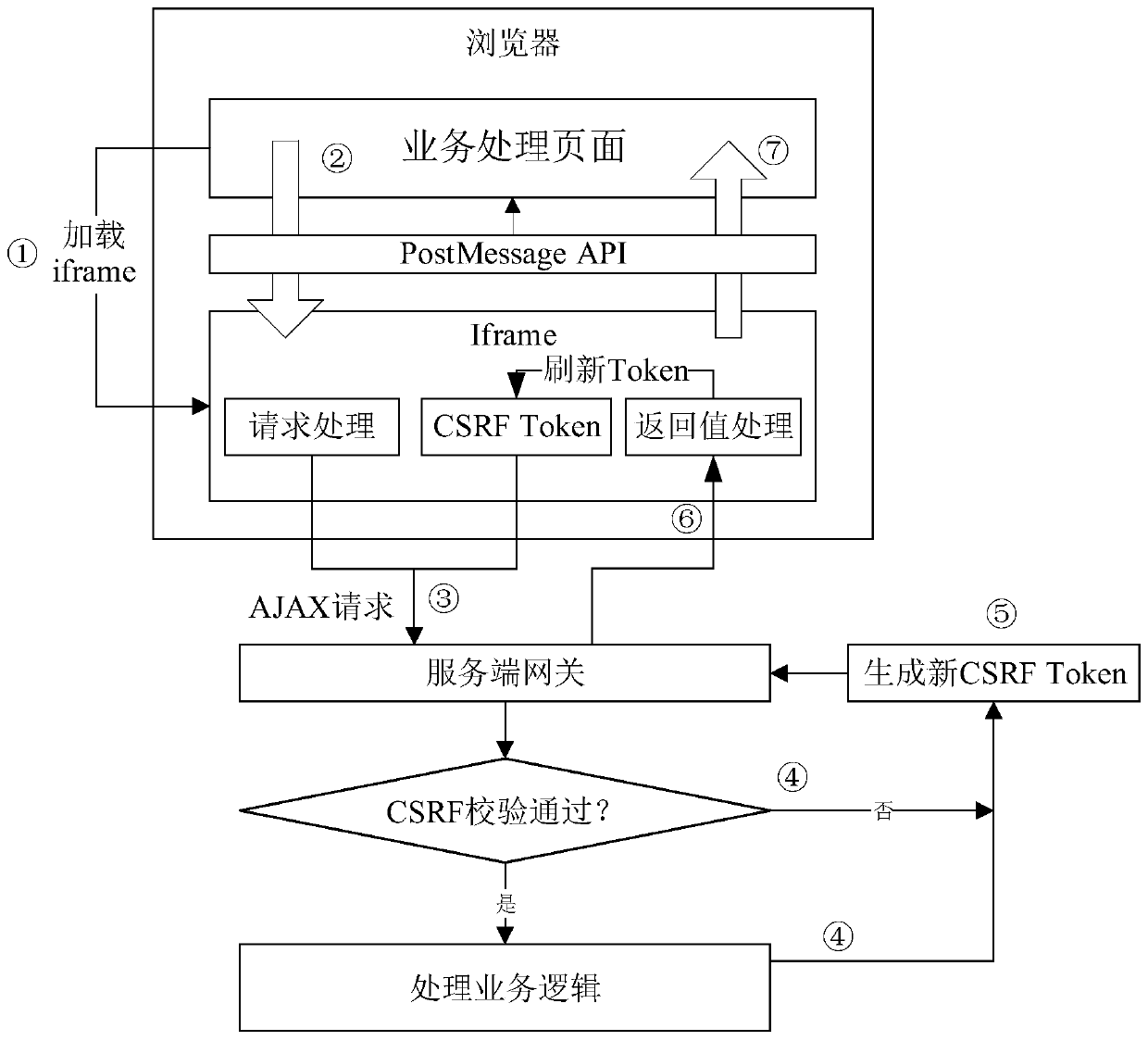
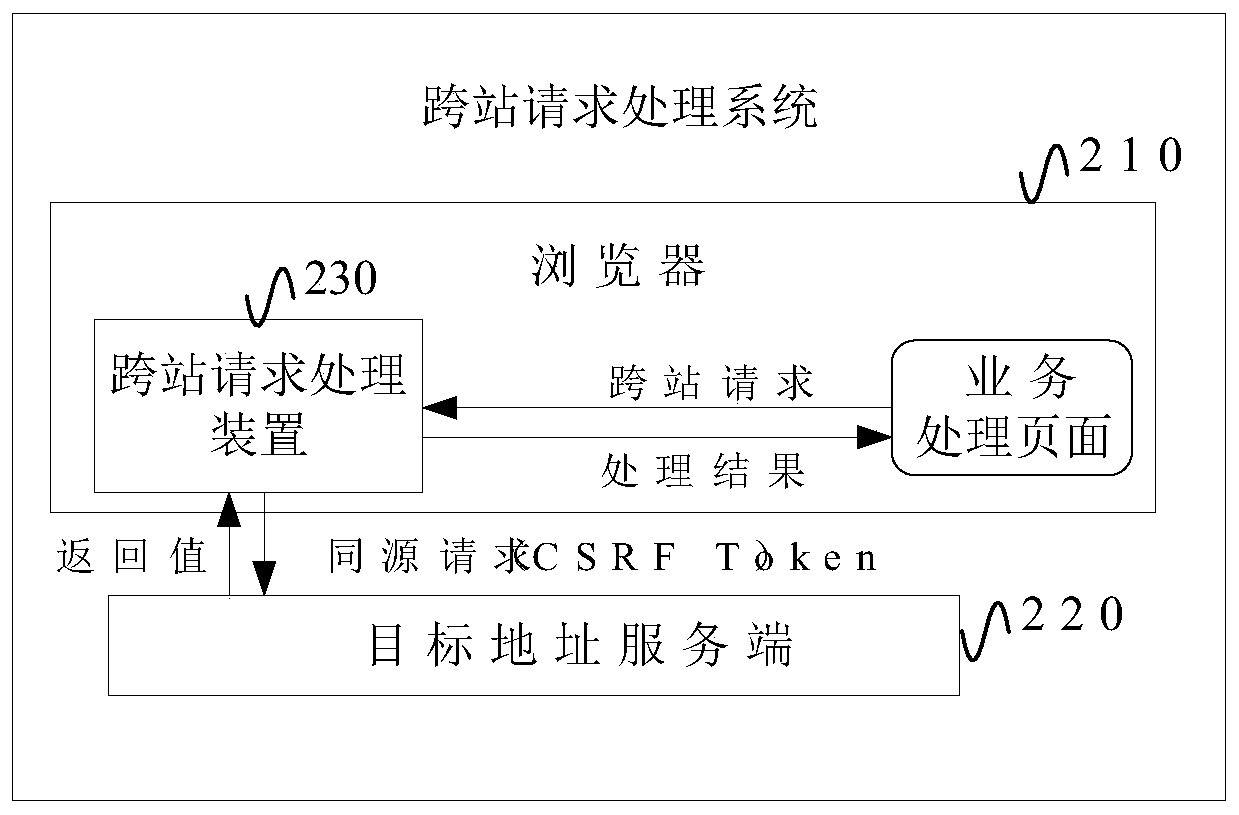
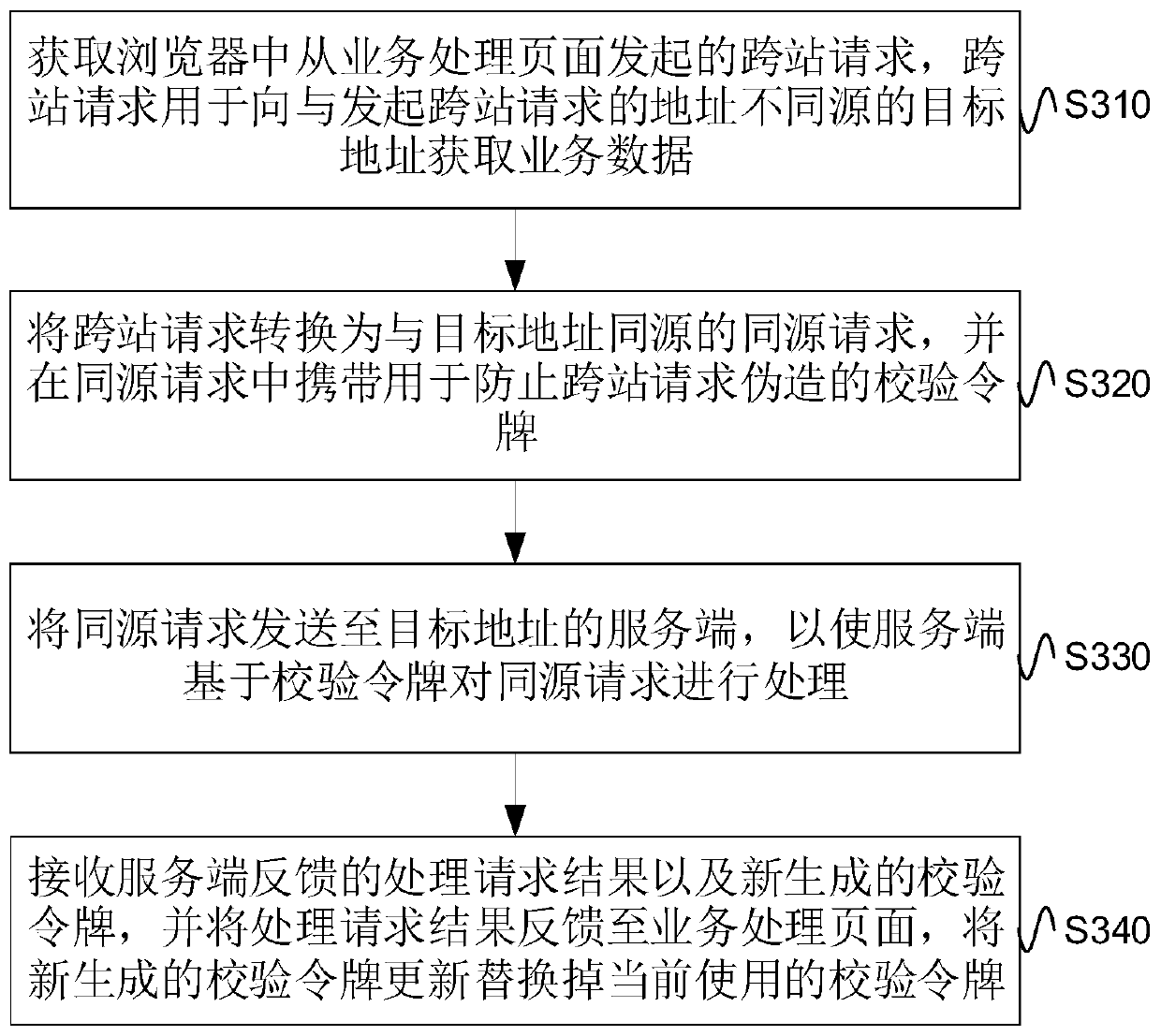
Cross-station request processing method and device and electronic equipment
The embodiment of the invention provides a cross-site request processing method and device and electronic equipment, and the method comprises the steps: obtaining a cross-site request initiated from abusiness processing page in a browser, and enabling the cross-site request to be used for obtaining business data from a target address which is different from the address where the cross-site request is initiated; converting the cross-site request into a homologous request homologous with the target address, and carrying a verification token for preventing the cross-site request from being forged in the homologous request; sending the homologous request to a server of the target address, so that the server processes the homologous request based on the verification token; and receiving a processing request result fed back by the server and a newly generated verification token, feeding back the processing request result to the service processing page, and updating the newly generated verification token to replace the currently used verification token. According to the scheme of the embodiment of the invention, the cross-station request service can be processed on the premise of effectively preventing the CSRF.
Owner:ALIBABA GRP HLDG LTD
Method and device for forwarding hyper text transport protocol (HTTP) request
InactiveCN102571846BReduce computational overheadReduce computing pressureTransmissionCross-site request forgeryHyper text transport protocol
The invention relates to a method and a device for forwarding a hyper text transport protocol (HTTP) request. The method comprises the steps of: judging whether a uniform resource locator (URL) of the HTTP request of a Web client is a URL requested by a Web form or a URL submitted by Web form data or not; forwarding the HTTP request when the URL of the HTTP request is the URL requested by the Web form and effective tokens are carried in parameters of the URL of the HTTP request; randomly generating a unique token if the token is not carried, splicing the URL of the HTTP request and the generated token into a new URL, discarding the HTTP request, and sending an HTTP response message requesting the redirection to the new URL to the Web client; and forwarding the HTTP request when the URL of the HTTP request is the URL submitted by Web form data, the HTTP request has the referrer value and the effective token can be extracted from the referrer. The method and the device have the advantages that the effective defense on cross site request forgery (CSRF) attack can be realized, and the computation overhead on a Web security gateway is greatly reduced.
Owner:BEIJING VENUS INFORMATION TECH +1
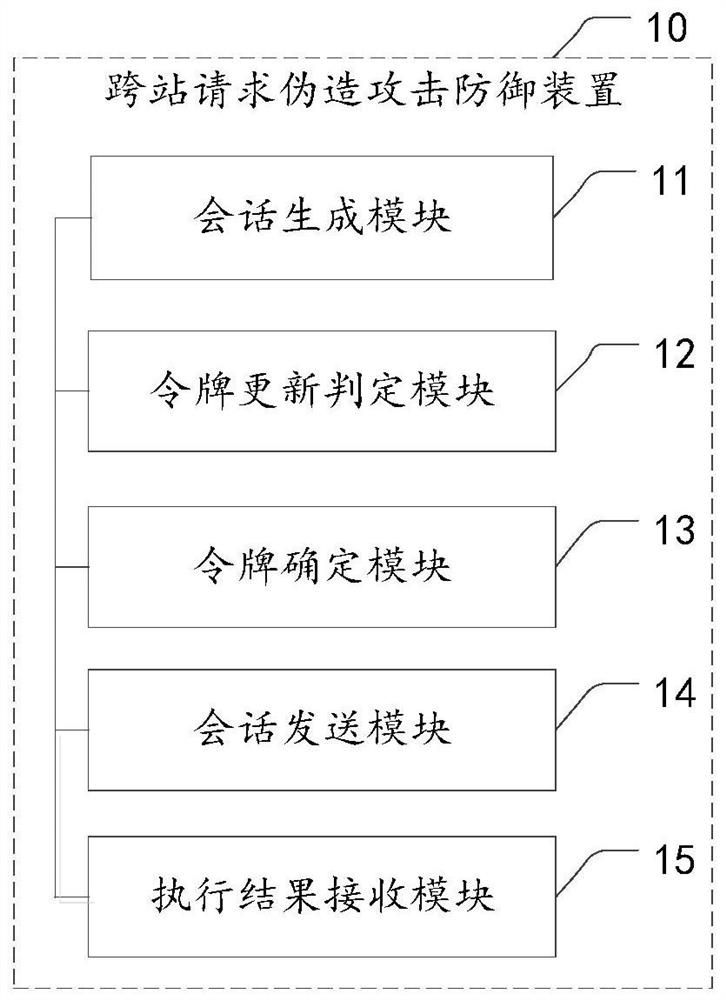
Cross-site request forgery attack defense method and device, electronic device and storage medium
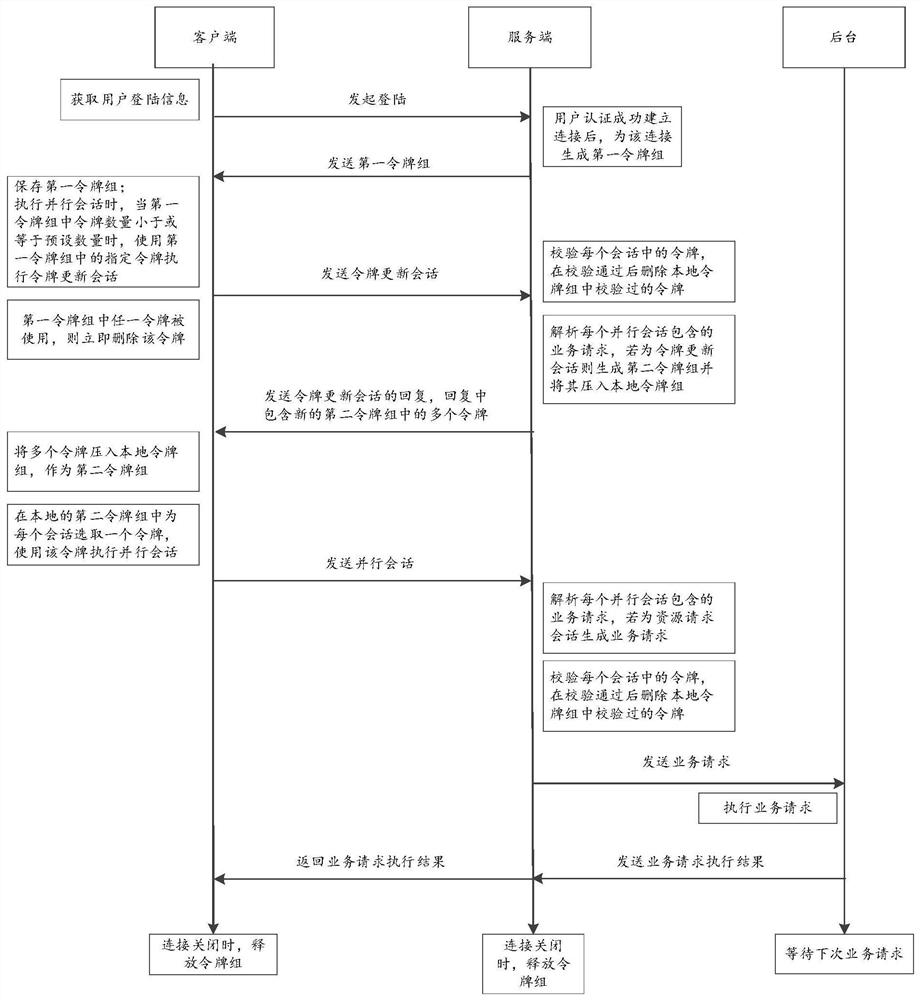
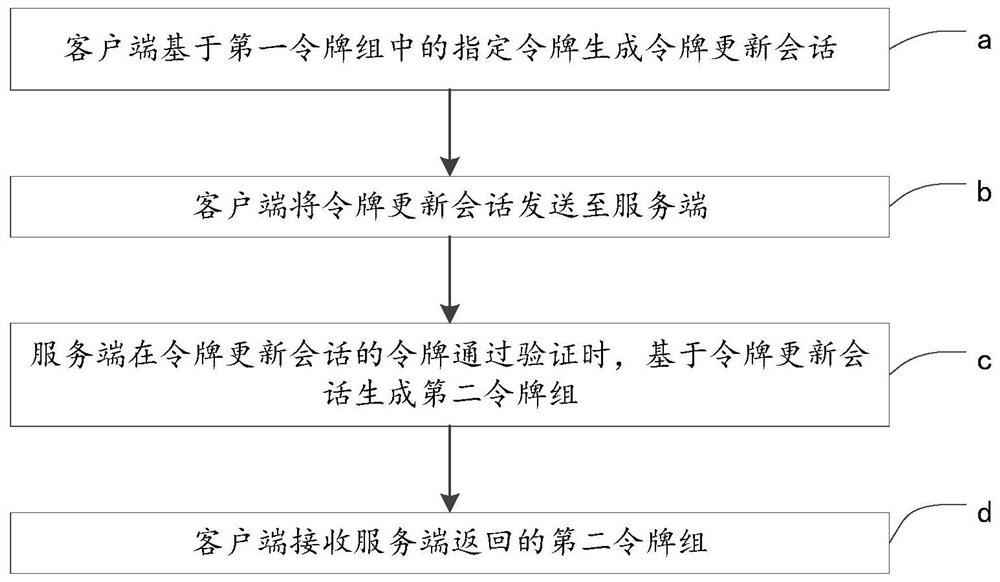
The invention provides a cross-site request forgery attack defense method and device, an electronic device and a storage medium, and relates to the technical field of information security. The method applied to the client comprises the following steps: generating a parallel session based on a request of a user; determining whether token group updating needs to be carried out or not based on the number of tokens in a first token group stored by the client; when the token group needs to be updated, obtaining a second token group, and determining a token corresponding to the parallel session in the second token group; the parallel session containing the token corresponding to the parallel session is sent to the server side, so that the server side generates a service request based on the parallel session when the token of the parallel session passes verification, and obtains a service request execution result from the background based on the service request; and receiving a service request execution result returned by the server. According to the method, available tokens are ensured when a client needs to perform a session through a token group updating means, and the service stability is improved while cross-site request forgery attack defense is ensured.
Owner:BEIJING TOPSEC NETWORK SECURITY TECH +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com