Cross-site request forgery CSRF attack recognition method and device
A forged request, cross-site technology, applied in the field of communication, can solve the problems of attack failure, unrecognizable attack based on forged srcCSRF, permission theft, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
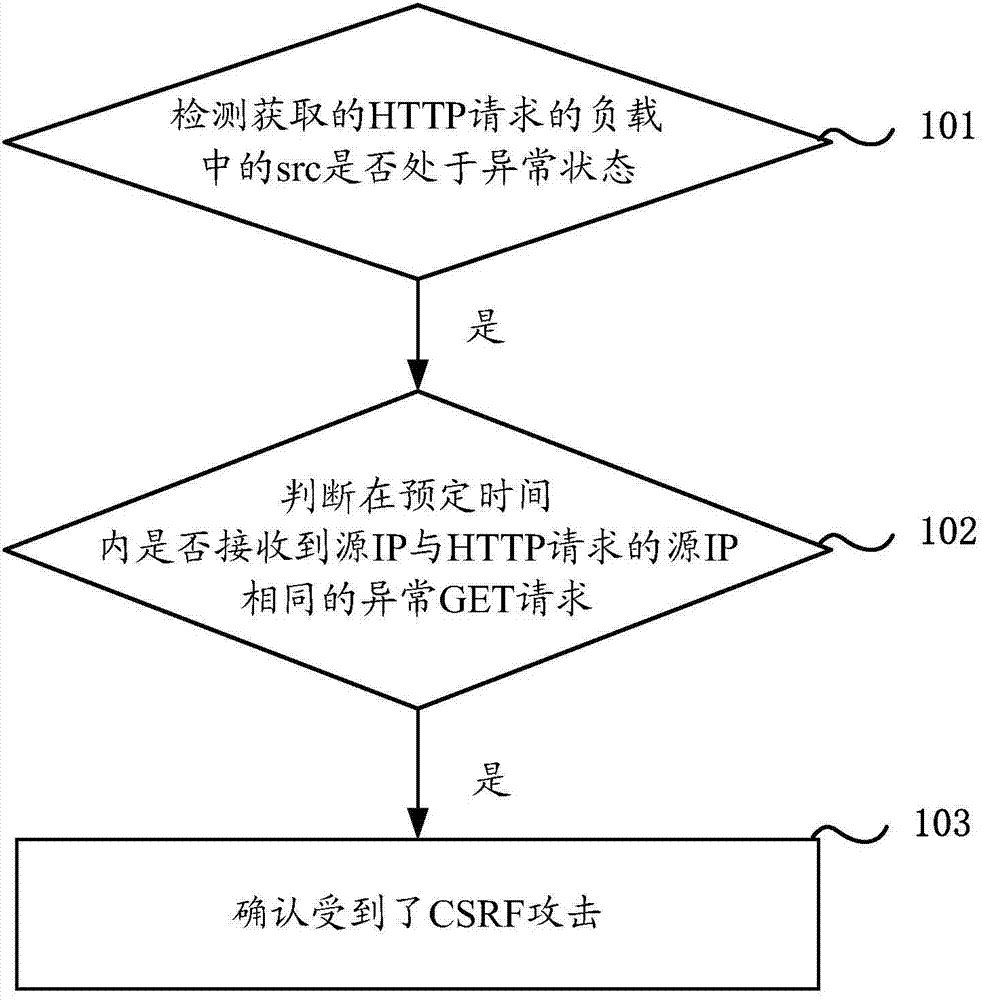
[0049] Aiming at the above-mentioned problems existing in the prior art, the embodiment of the present invention provides a CSRF attack detection method for a cross-site forgery request, such as figure 1 shown, including the following steps:
[0050] Step 101, detecting whether the src in the acquired HTTP request payload is in an abnormal state.
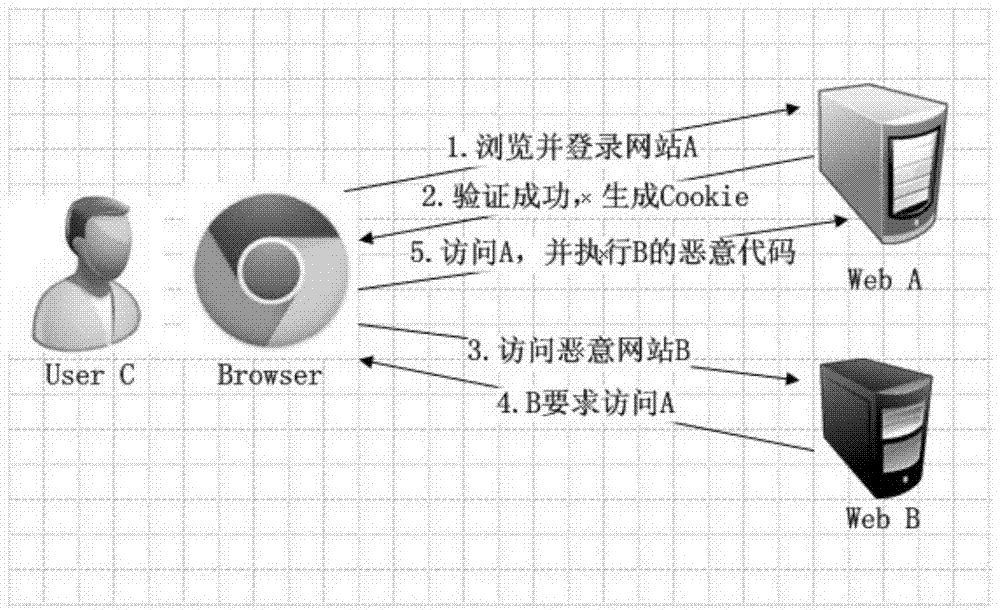
[0051] by figure 2Let’s take the environment as an example to illustrate. After user C visits the normal website A through the browser and passes the verification, website A returns the cookie information to the browser. Within the validity period of the cookie information, user C visits website B again. , at this time, website B will return the HTTP (HyperText Transfer Protocol, hypertext transfer protocol) request to user C, and step 101 in the present invention is to continuously detect all obtained HTTP requests, and further analyze and obtain in the HTTP request load Whether the src is in an abnormal state.
[0052] In an e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com