Method and device for cross-sit request forgery (CSRF) defense authentication
A technology of cross-site request forgery and authentication method, applied in the field of CSRF defense and authentication of cross-site request forgery, can solve the problems of increasing development cost, unable to save session data at the front end, unable to use the SESSION verification mechanism, etc., to achieve the effect of preventing replay attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
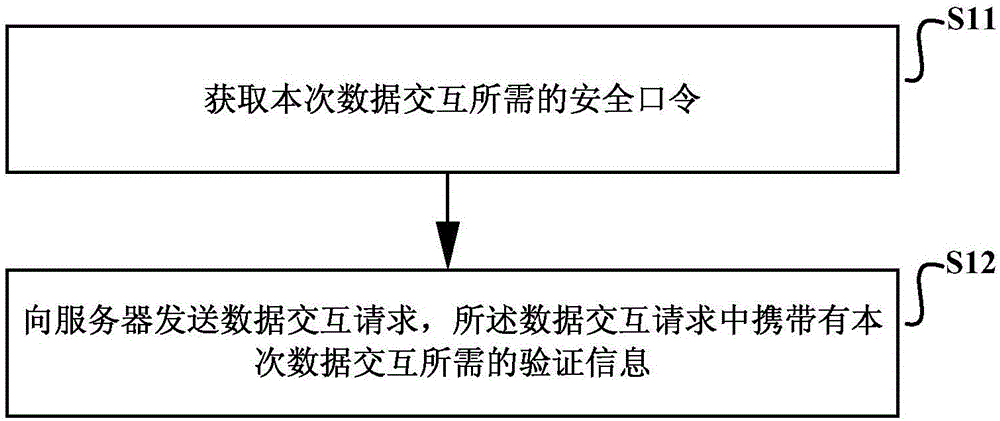
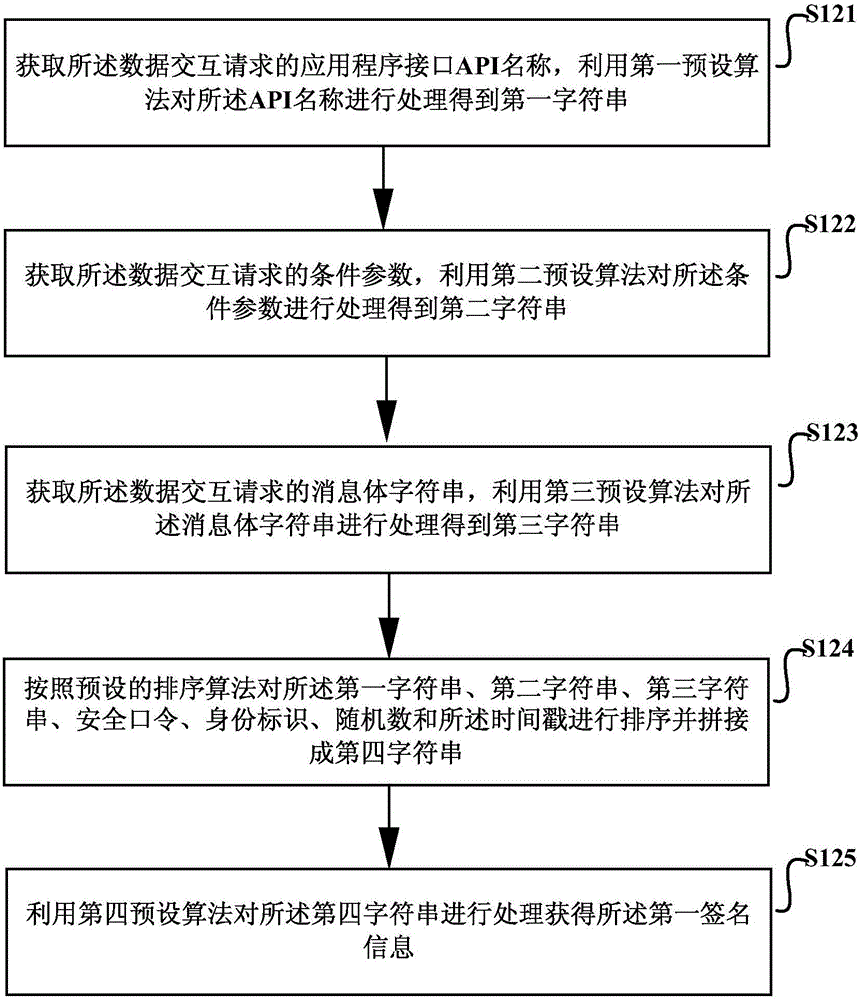
[0035] Such as Figure 1a As shown, it is a schematic diagram of the implementation flow of the cross-site request forgery CSRF defense authentication method provided by Embodiment 1 of the present invention, which may include the following steps:
[0036] S11. Obtain a security password required for this data interaction.
[0037] During specific implementation, the security password is obtained through a login request sent to the server, and the login request includes the user name and password required for this login.
[0038] Specifically, when the client sends a login request to the server (when the user logs in to the browser with a user name and password), it calls the API interface of the login request to send a login request to the server, and the server verifies the login request based on the user name and password required for this login. Whether this login is passed, if yes, return the security password required for data interaction to the client, recorded as Token...
Embodiment 2
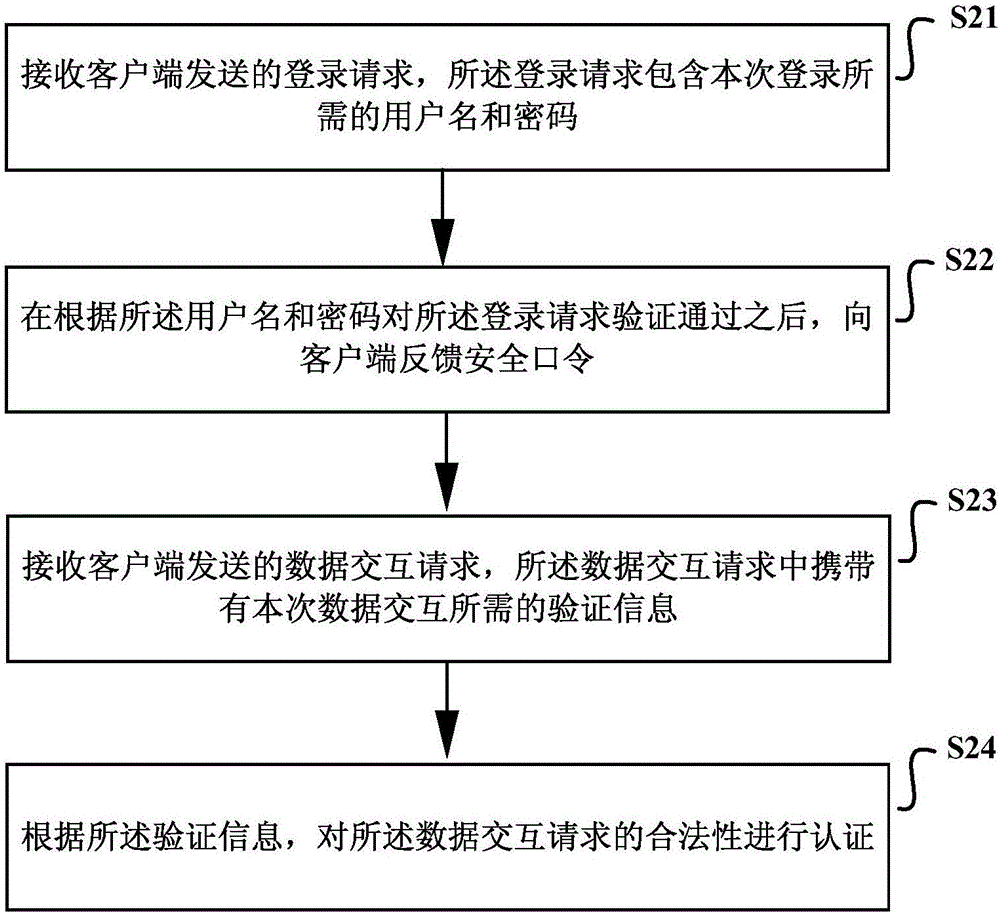
[0090] Such as Figure 2a As shown, it is a schematic diagram of the implementation flow of another cross-site request forgery CSRF defense authentication method provided by Embodiment 2 of the present invention, which may include the following steps:
[0091] S21. Receive a login request sent by the client, where the login request includes a username and password required for this login.
[0092] S22. Feed back a security password to the client after the login request is verified according to the user name and password.
[0093] Specifically, after receiving the login request sent by the client, the server can determine whether the login is successful according to the username and password used in the login request and from the pre-stored correspondence between the username and password, and if so, It is determined that the current login request is passed; otherwise, it is determined that the current login request fails.
[0094] After confirming that the login request is pas...
Embodiment 3
[0128] Based on the same inventive concept, an embodiment of the present invention also provides a cross-site request forgery CSRF defense authentication device. Since the principle of the above-mentioned device to solve the problem is similar to the cross-site request forgery CSRF defense authentication method, the implementation of the above-mentioned device can be found in the method The implementation of this method will not be repeated here.
[0129] Such as image 3 As shown, it is a schematic structural diagram of a cross-site request forgery CSRF defense authentication device provided by Embodiment 3 of the present invention, including: an acquisition unit 31 and a first sending unit 32, wherein:
[0130] The obtaining unit 31 is configured to obtain the security password required for this data interaction, the security password is obtained through a login request sent to the server, and the login request includes the user name and password required for this login;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com