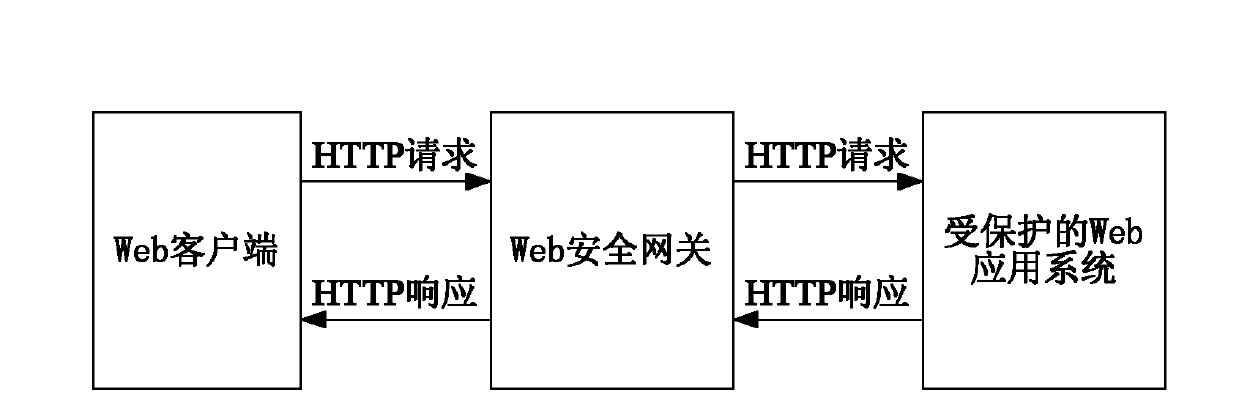
Method and device for forwarding hyper text transport protocol (HTTP) request
A unique and token technology, which is applied in the field of network security, can solve problems such as difficult to implement and reduce the performance of web security gateways, and achieve the effects of reducing computing pressure, easy deployment, and reducing computing overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
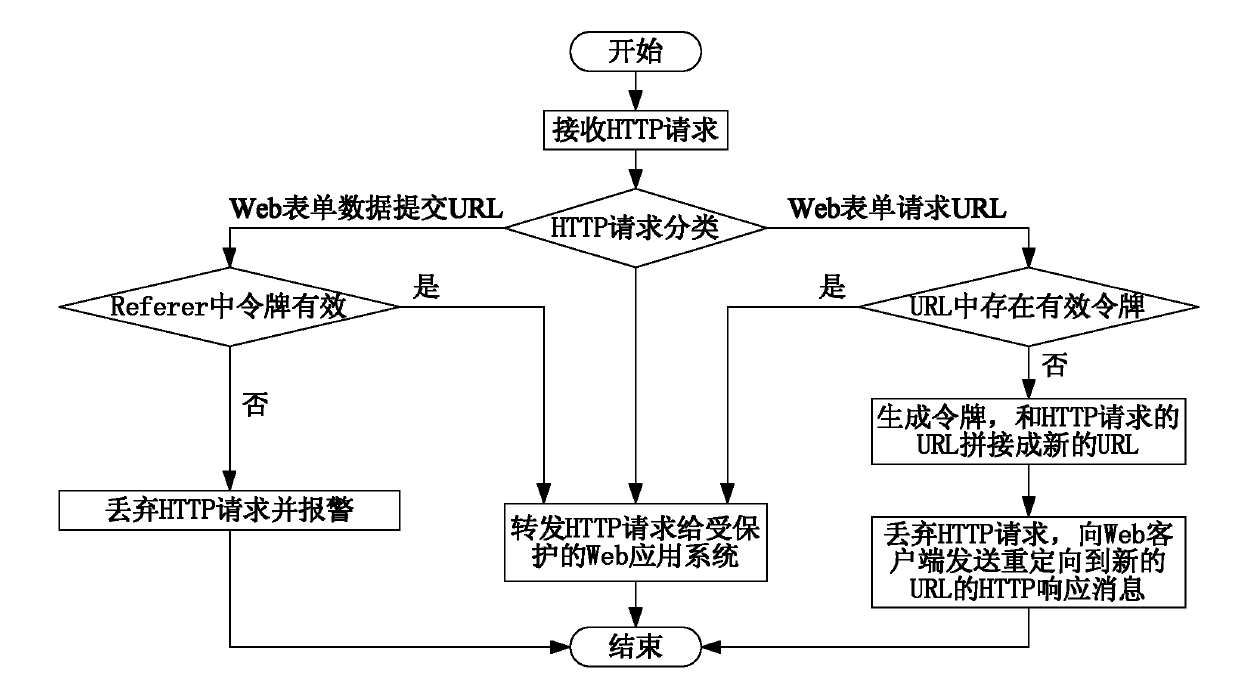
[0071] Embodiment 1, a method for forwarding an HTTP request, which can be applied to a web security gateway, includes:
[0072] Determine whether the URL of the HTTP request of the Web client is a Web form request URL or a Web form data submission URL;
[0073] When the URL of the HTTP request is a Web form request URL, if a valid token is carried in the URL parameter of the HTTP request, the HTTP request is forwarded; if the token is not carried, a unique token is randomly generated, and the The URL of the HTTP request and the generated token are spliced into a new URL, discarding the HTTP request and sending a request redirection to the HTTP response message of the new URL to the Web client;
[0074] When the URL of the HTTP request is a Web form data submission URL, if the HTTP request has a Referer value and a valid token can be extracted from the Referer, the HTTP request is forwarded.
[0075] In this embodiment, the method may also include:
[0076] When the URL of...
Embodiment 2
[0154] Embodiment 2, a device for forwarding HTTP requests, can be applied on the Web security gateway, such as Figure 4 shown, including:
[0155] The HTTP request classification module is used to judge whether the URL of the HTTP request of the Web client is a Web form request URL or a Web form data submission URL;
[0156] Web form request processing module, for when the URL of described HTTP request is Web form request URL, if carry effective token in the URL parameter of this HTTP request, then forward this HTTP request; If not carrying token then random Generate a unique token, splicing the URL of the HTTP request and the generated token into a new URL, discarding the HTTP request and sending a request to the Web client to redirect to the HTTP of the new URL response message;
[0157] The Web form data submission processing module is used for forwarding the HTTP request if the HTTP request has a Referer value and a valid token can be extracted from the Referer when th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com