Efficient verifiable multi-keyword sequencing searchable encryption method supporting preference search and logic search
An encryption method, multi-keyword technology, applied in the field of information security, can solve problems such as need for further research, gap, single function, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
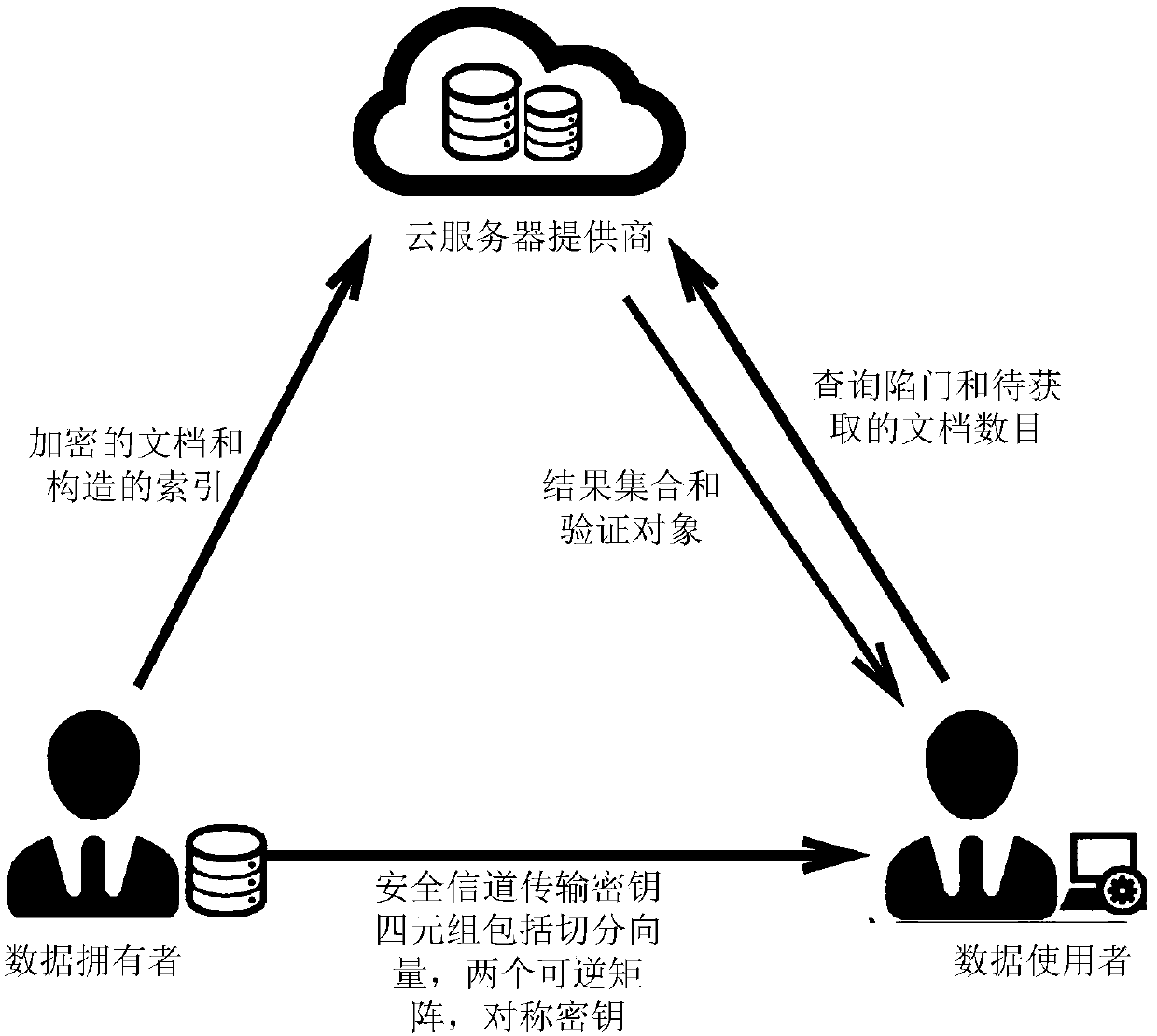
[0072] This embodiment discloses an efficient and verifiable multi-keyword sorting and searchable encryption method that supports preference search and logical search, including the following three parts:
[0073] a) Data owner
[0074] The data owner is the owner of the data. It mainly performs searchable encryption preprocessing, including several steps such as key generation, document encryption, index generation, and summary generation. In order to ensure the confidentiality of the data held, the data owner needs to encrypt the document data held to obtain the ciphertext document set E. In order to make the encrypted documents searchable and ensure the efficiency of the search, the data owner needs to base on the document Set FS to build a security index At the same time, the data owner will also generate a message digest to facilitate the data user to verify the integrity and accuracy of the search results. Then, the data owner will send the encrypted ciphertext documen...
Embodiment 2
[0147] The following uses a specific example to illustrate the specific process of multi-keyword preference search. The scheme of logical search is basically similar. The formal proof of its search correctness is also given above, so I won’t go into details here. The diagonal matrix is mainly used to reduce the amount of calculation, and the calculation steps are basically the same, so I won't go into details here.
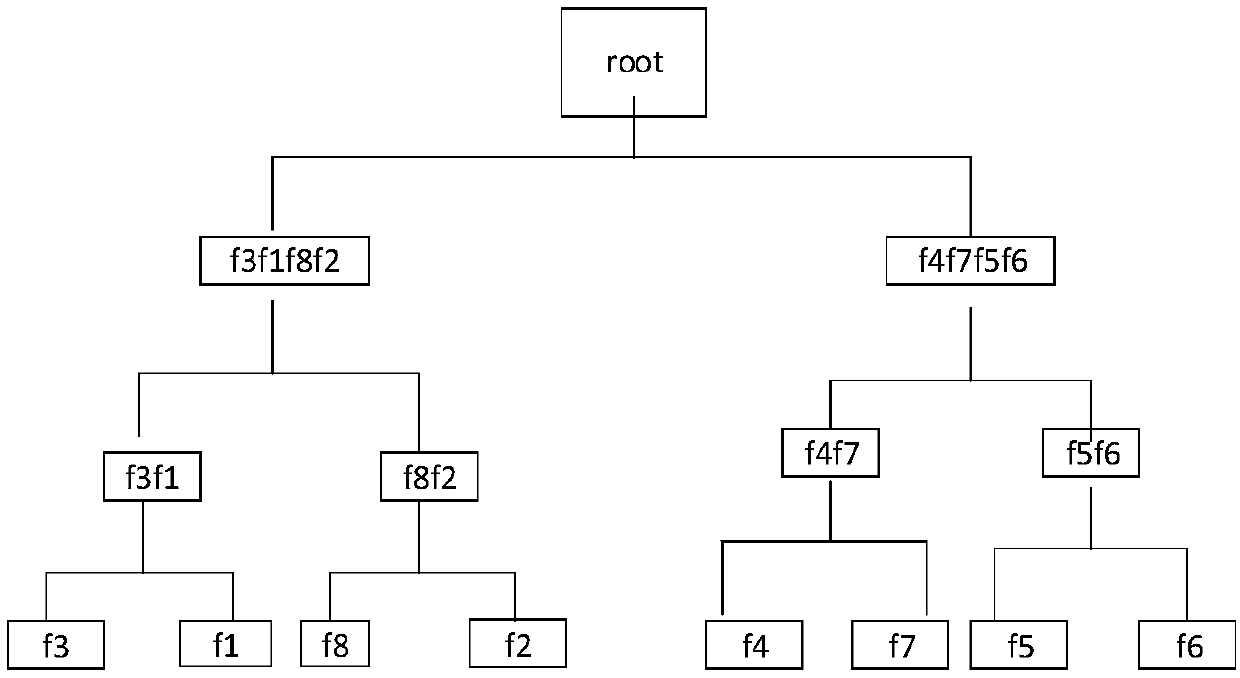
[0148] (1) The content of each document in the document collection FS is as follows. It is convenient to explain the flow of the program here, and each document is very small. The entire dictionary has only 6 keywords, and 2 redundant keywords are introduced. So the entire generated dictionary size is 8.
[0149] f1.txt: python java
[0150] f2.txt: java go
[0151] f3.txt:python go
[0152] f4.txt:cpp
[0153] f5.txt:c
[0154] f6.txt:javascript
[0155] f7.txt: python cpp c
[0156] f8.txt: python go java
[0157] (2) After the generated dictionary is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com