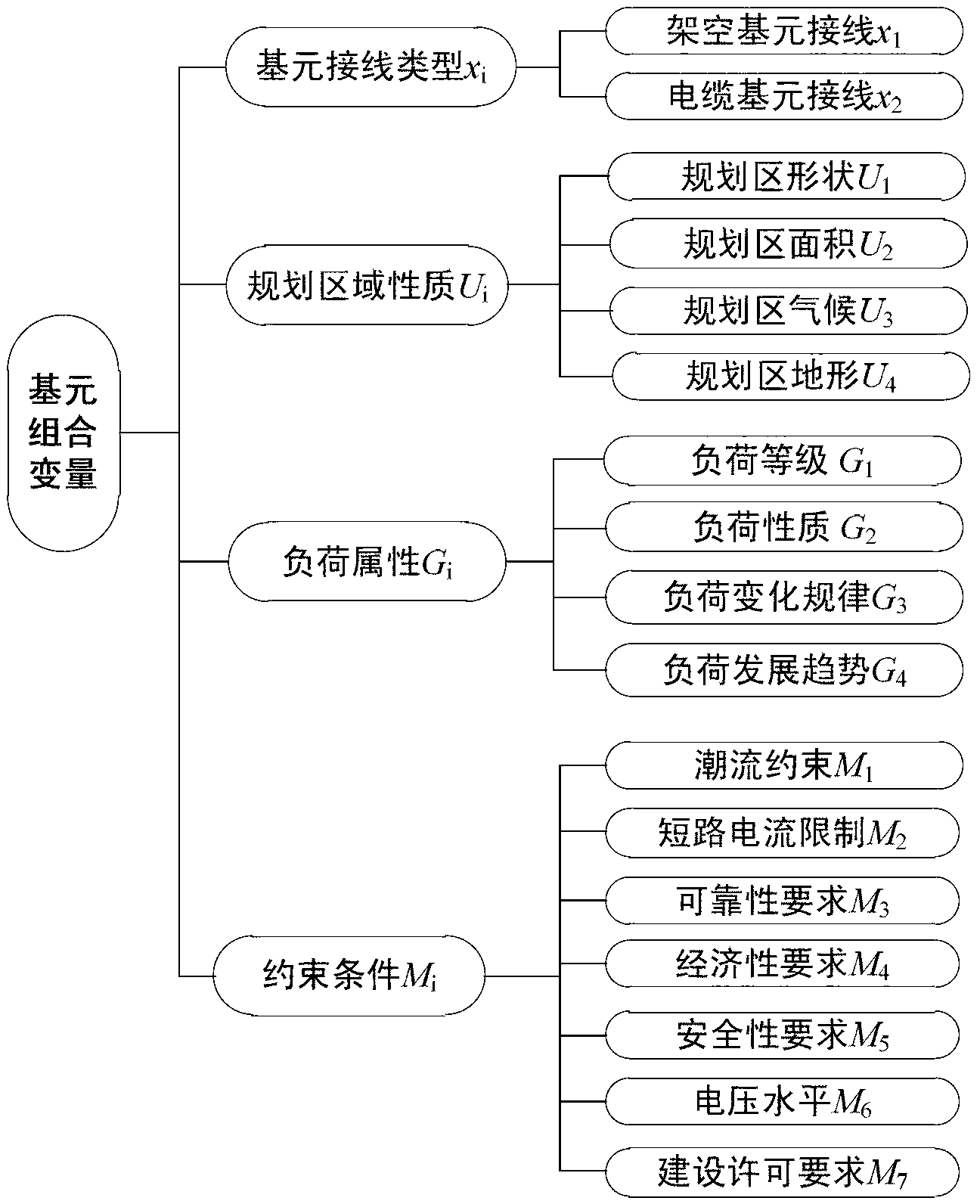
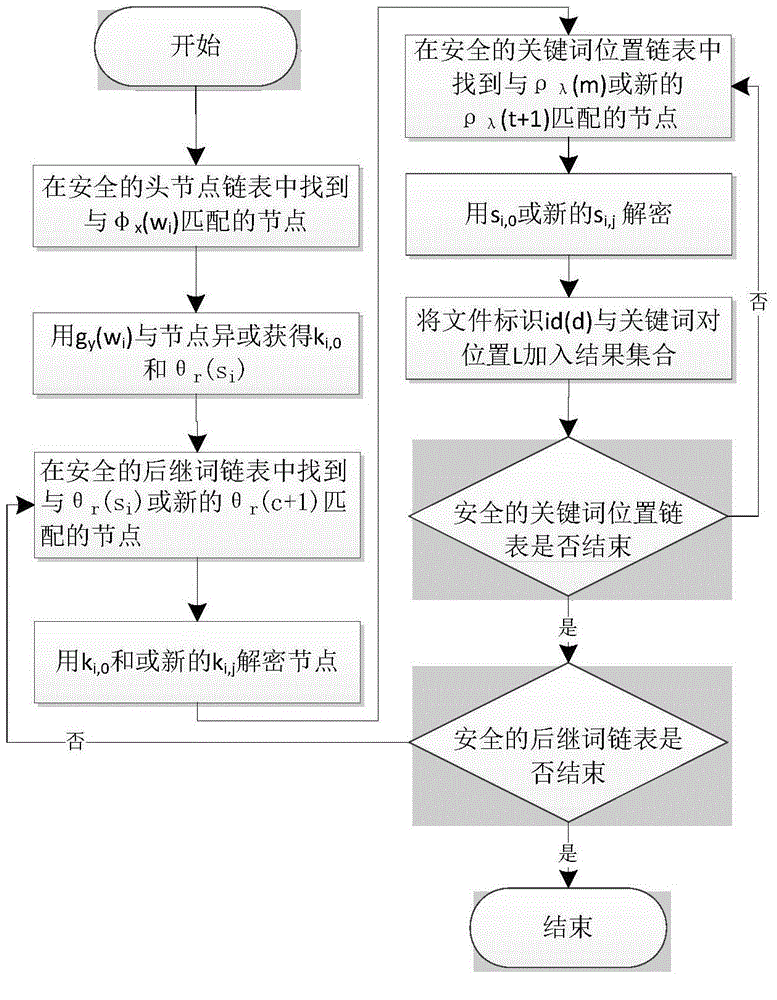
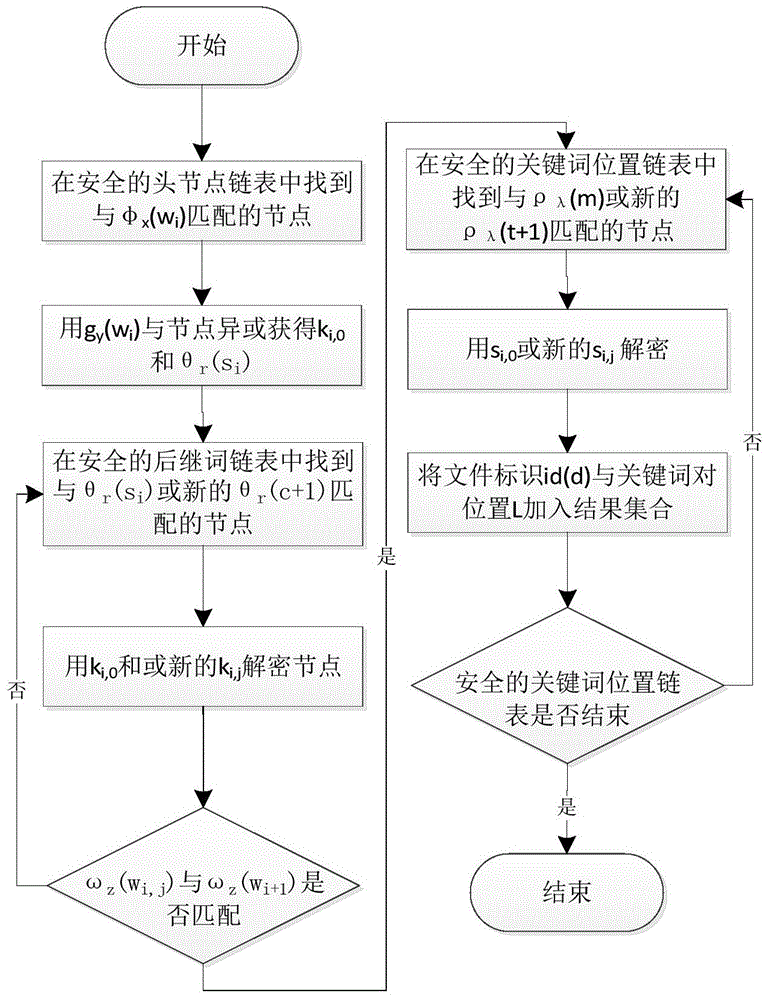
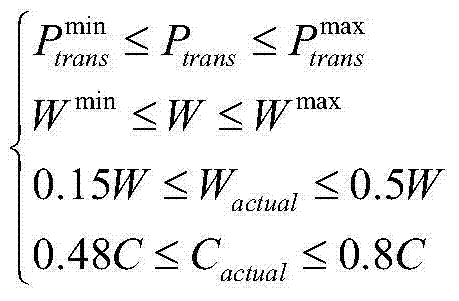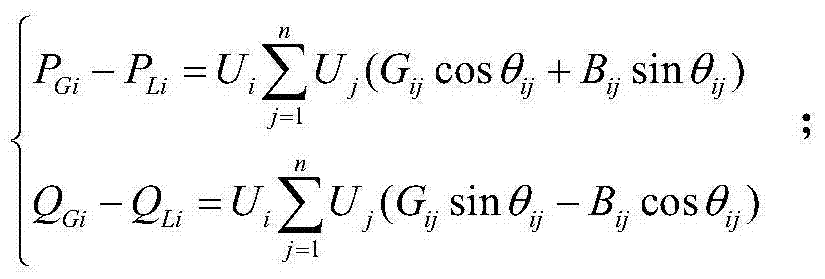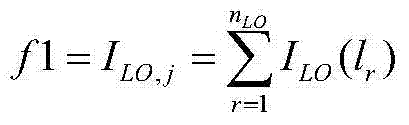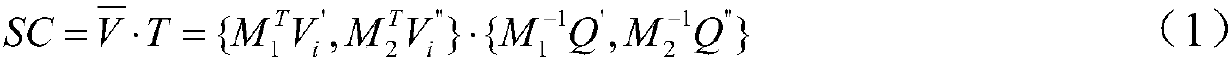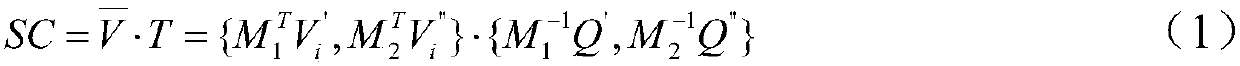Patents
Literature
149 results about "Security index" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Reserve Index/Security Index. The Security Index pertained to the FBI list of dangerous individuals who might commit acts inimical to the national defense and public safety of the United States in time of emergency. The list also included those who could be arrested upon the order of a U.S. President invoking the Emergency Detention Program.
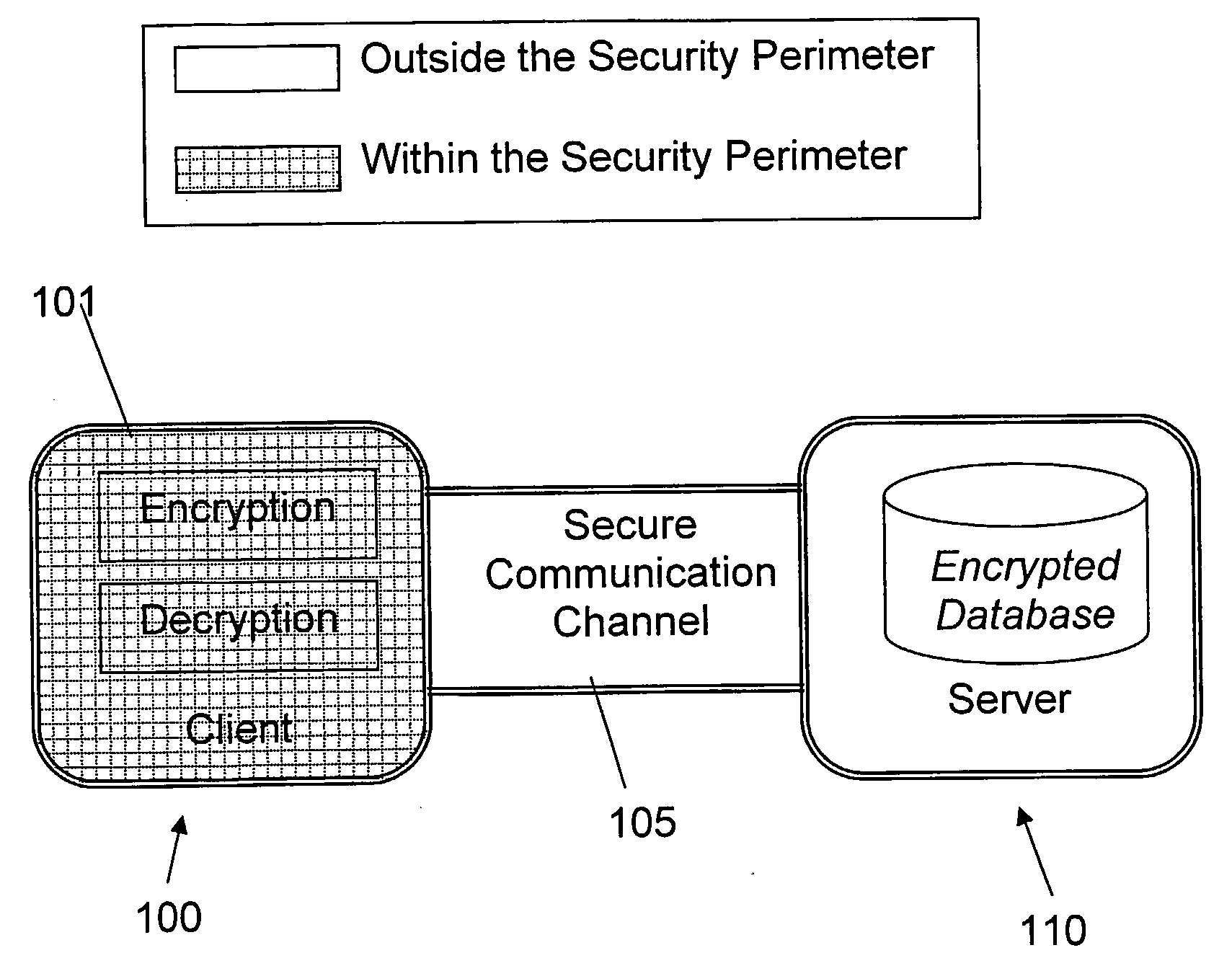
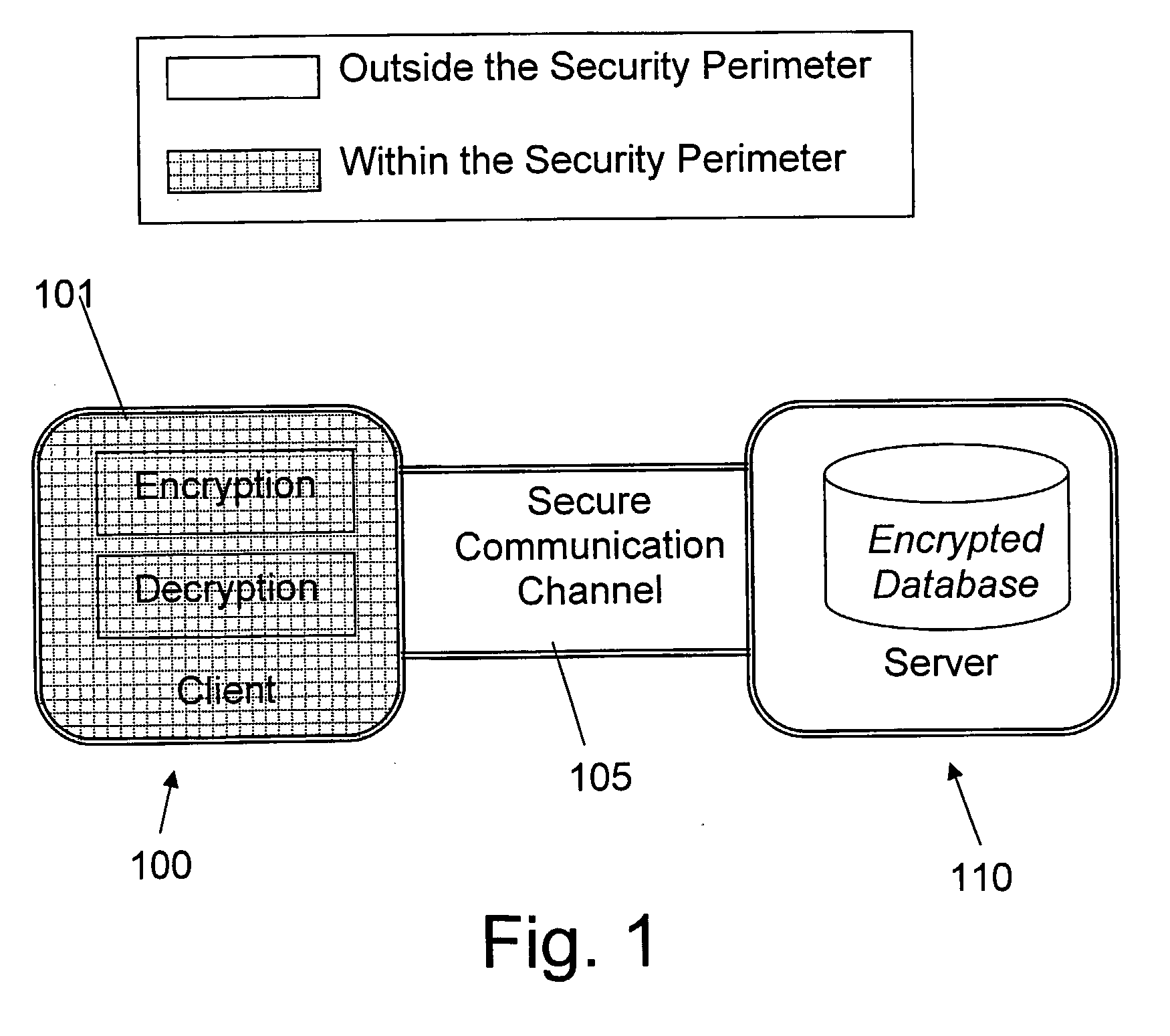
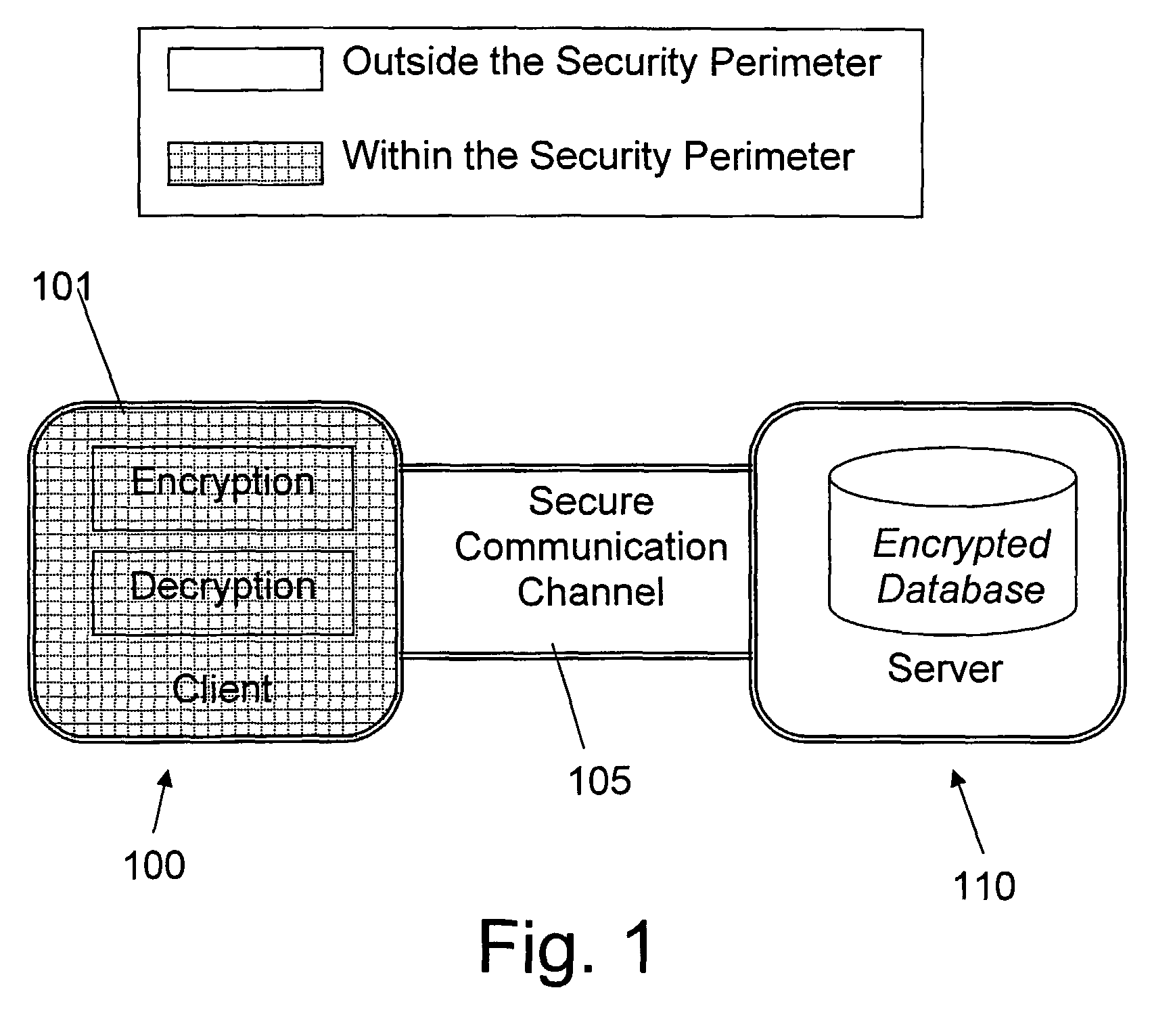
Structure Preserving Database Encryption Method and System
ActiveUS20080133935A1Easy accessAvoid contactKey distribution for secure communicationMultiple keys/algorithms usageDatabase indexMulti user environment
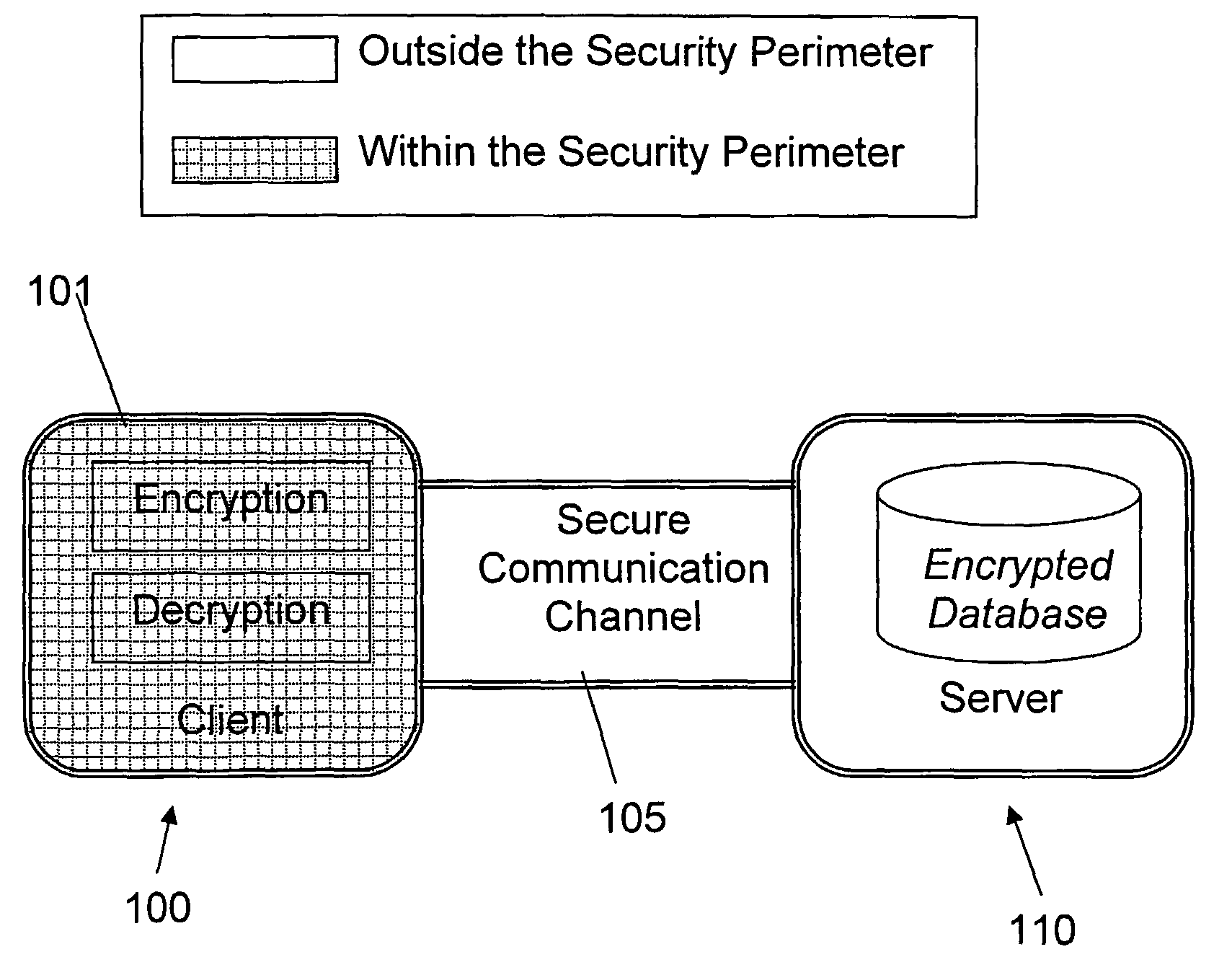
A database encryption system and method, the Structure Preserving Database Encryption (SPDE), is presented. In the SPDE method, each database cell is encrypted with its unique position. The SPDE method permits to convert a conventional database index into a secure one, so that the time complexity of all queries is maintained. No one with access to the encrypted database can learn anything about its content without the encryption key. Also a secure index for an encrypted database is provided. Furthermore, secure database indexing system and method are described, providing protection against information leakage and unauthorized modifications by using encryption, dummy values and pooling, and supporting discretionary access control in a multi-user environment.
Owner:BEN GURION UNIVERSITY OF THE NEGEV
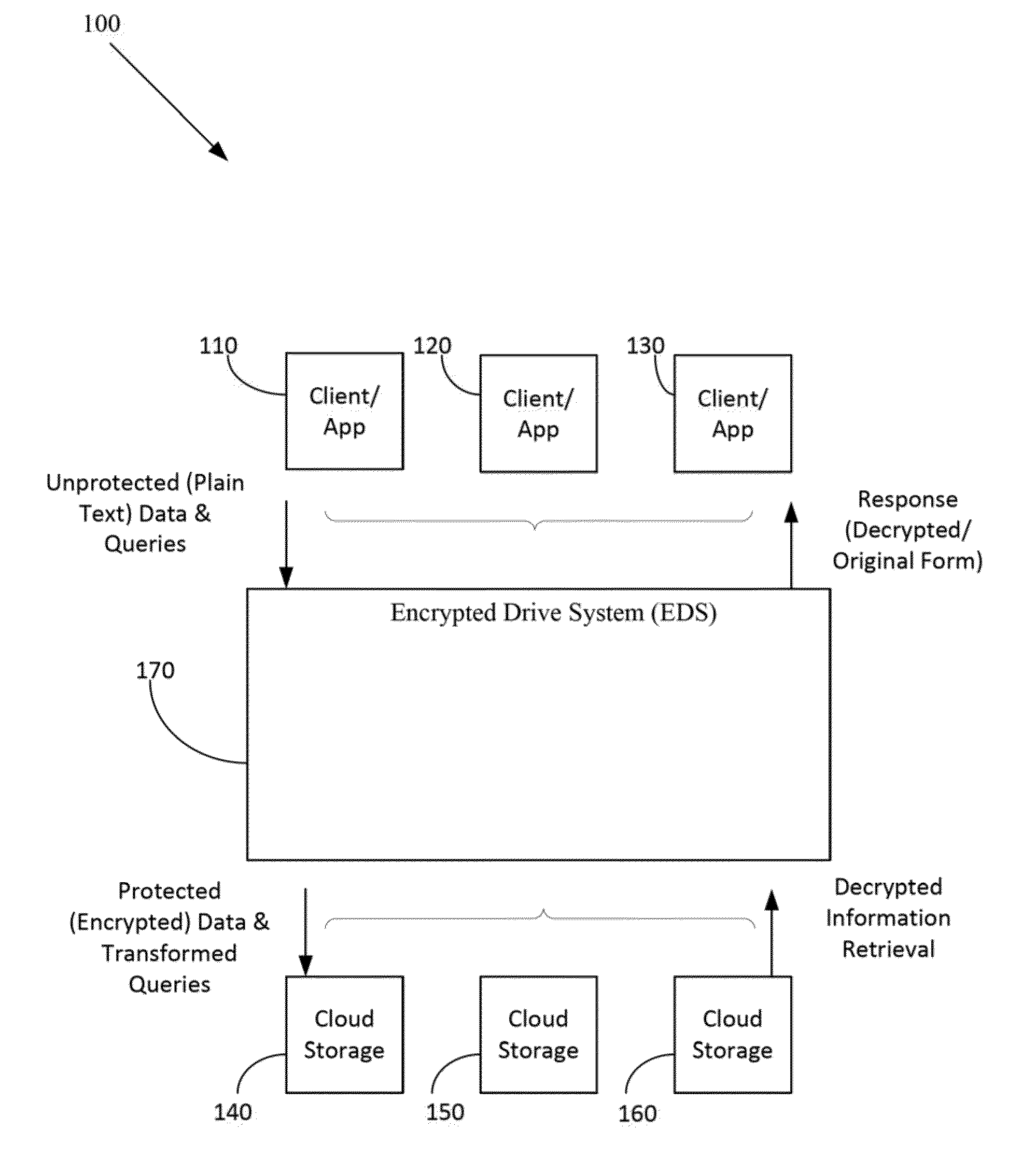
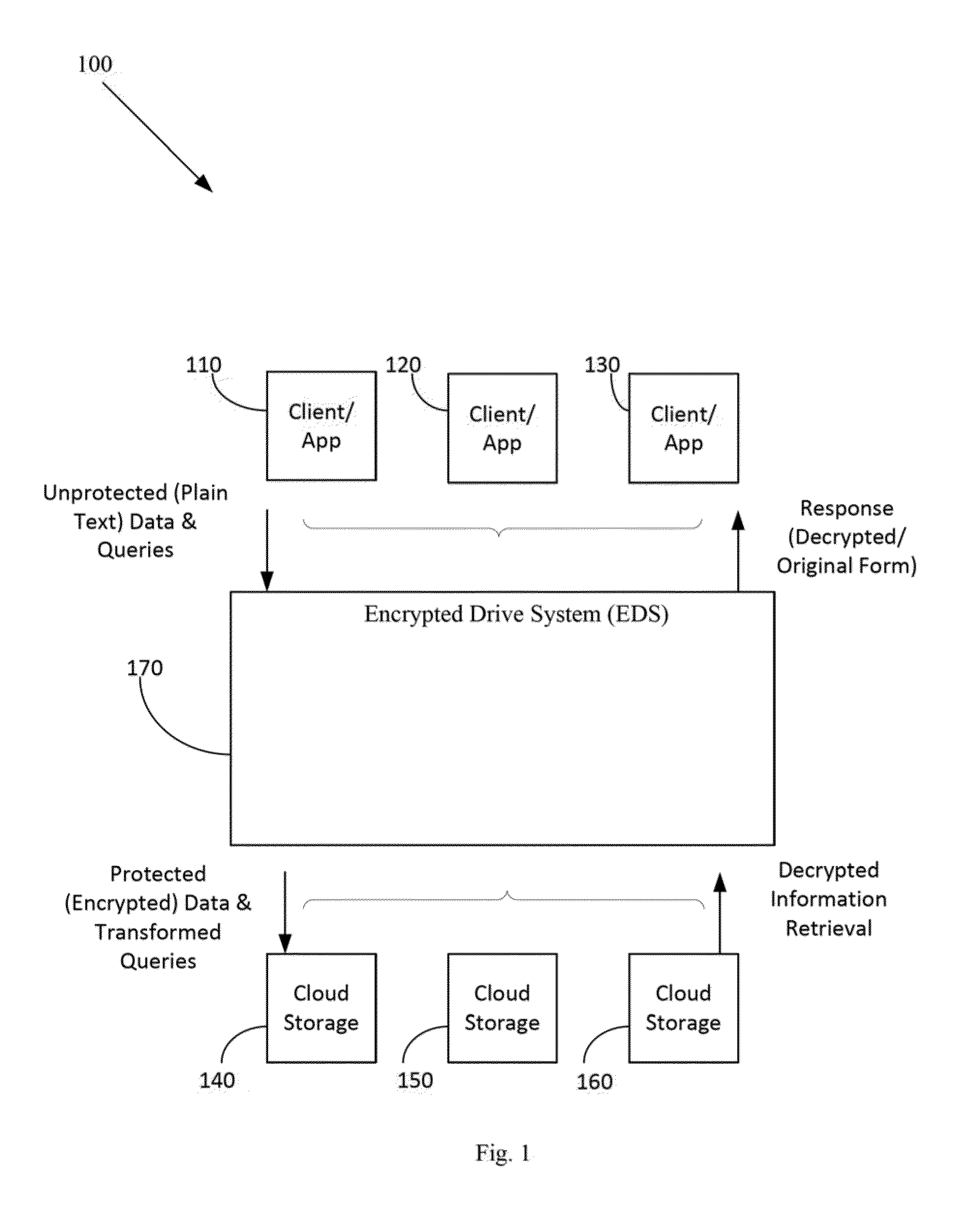
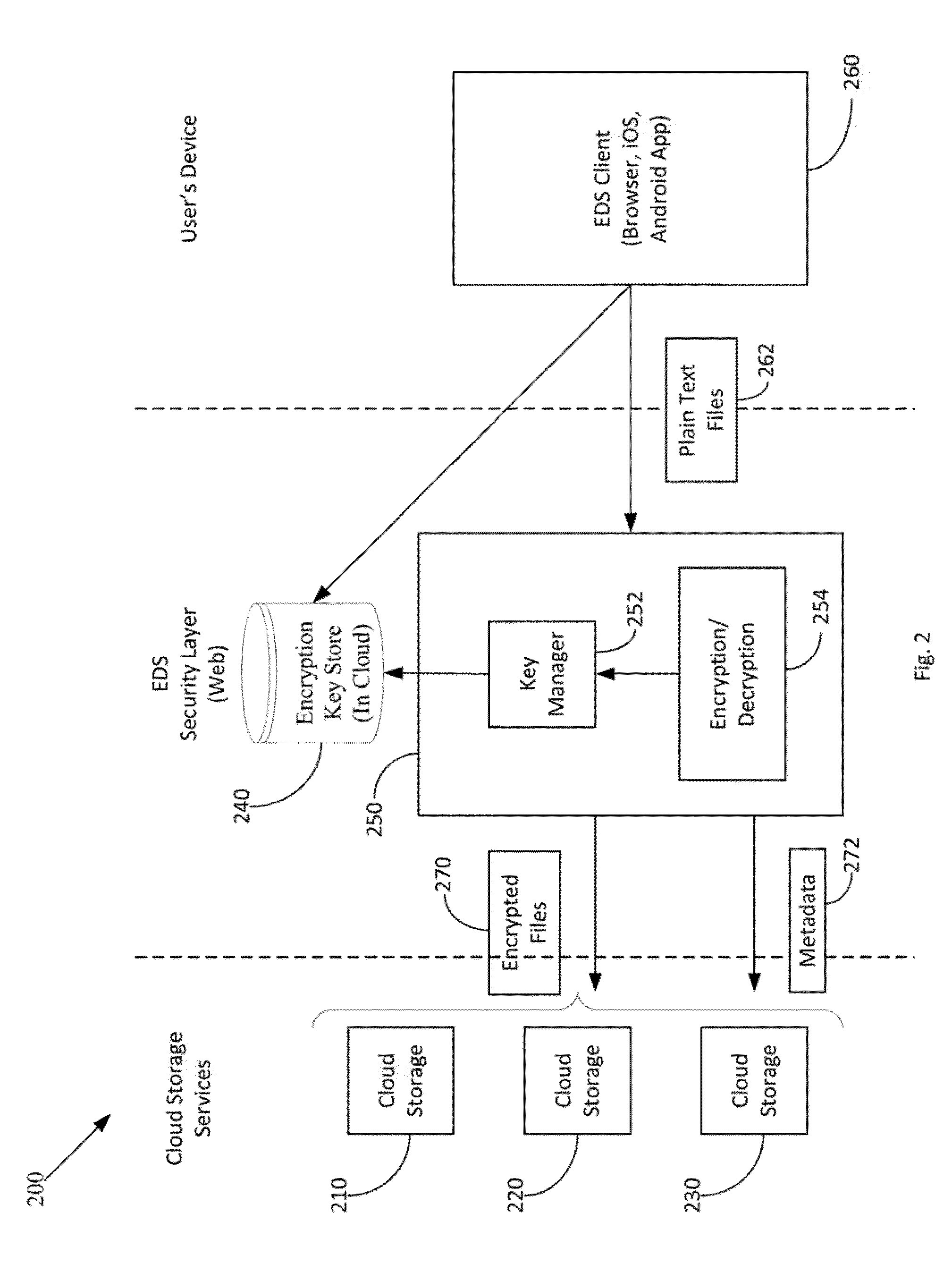
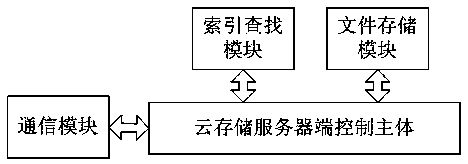
Method and apparatus for securing sensitive data in a cloud storage system
ActiveUS20150365385A1Protection attackImprove security levelEncryption apparatus with shift registers/memoriesSecurity indexData file
In one aspect, relates to a system and method of seamlessly encrypting data files before uploading them to a public cloud storage system by providing an encrypted drive system (EDS) that forms a security layer around existing cloud storage services to provide enhanced protection to data. The EDS also provides a convenient interface to specify data protection policies across connected cloud storage applications. The EDS implements standard functionalities like accessing, search and sharing directly on the encrypted data using secure indexing and querying of encrypted data. The EDS is able to guarantee a much higher level of security for data in the cloud without the user having to compromise on the features of the various applications.
Owner:GARBLECLOUD INC
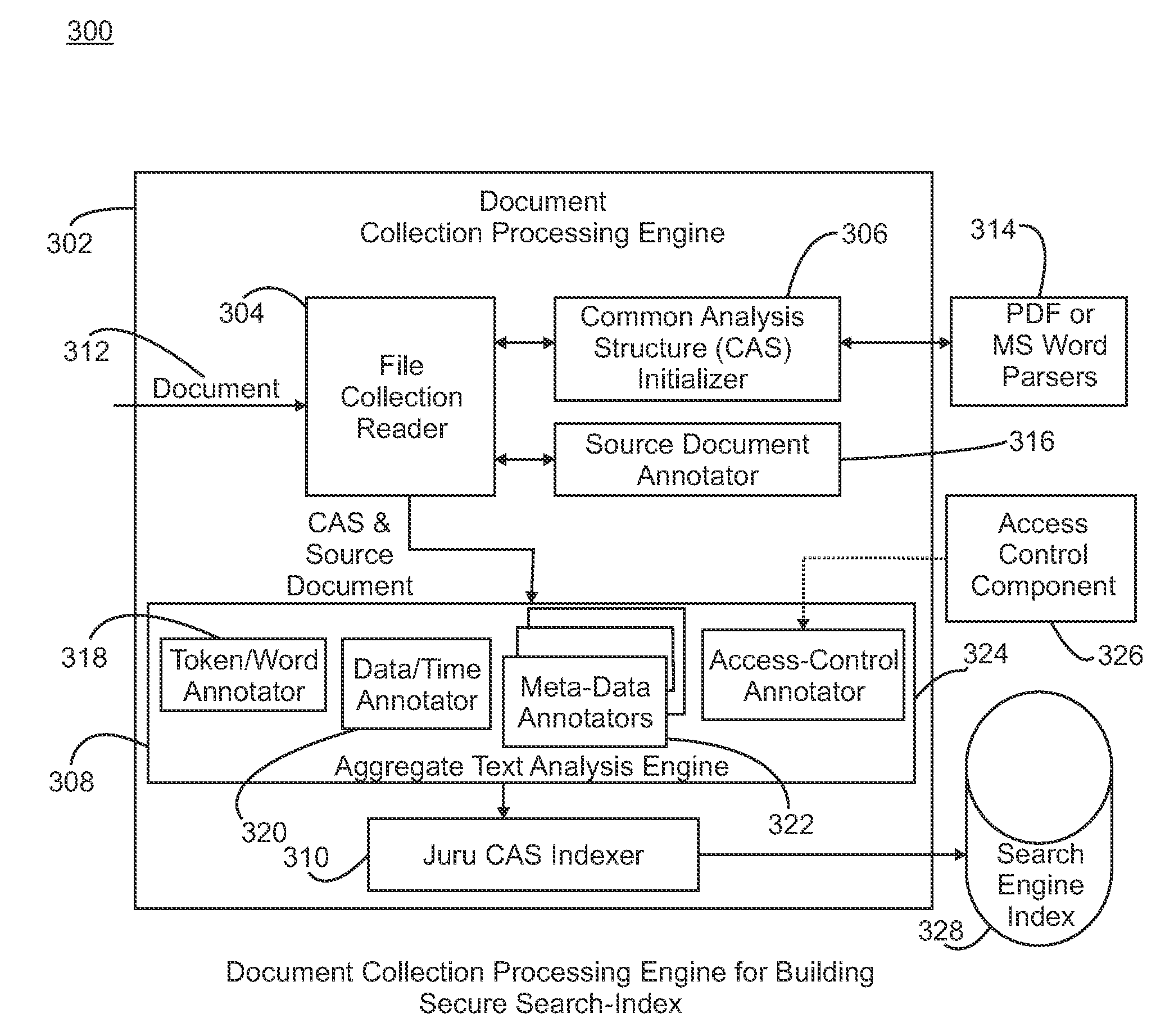
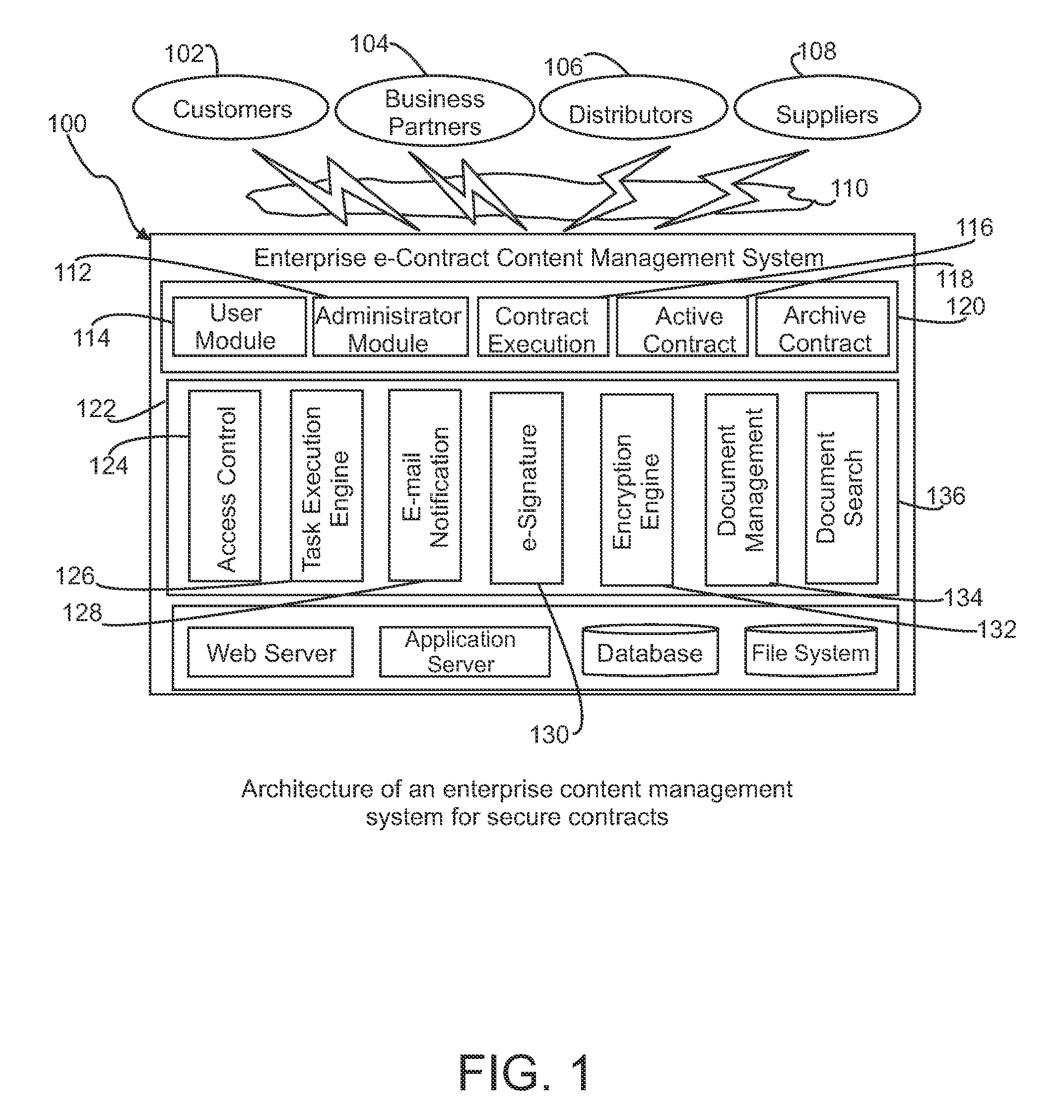
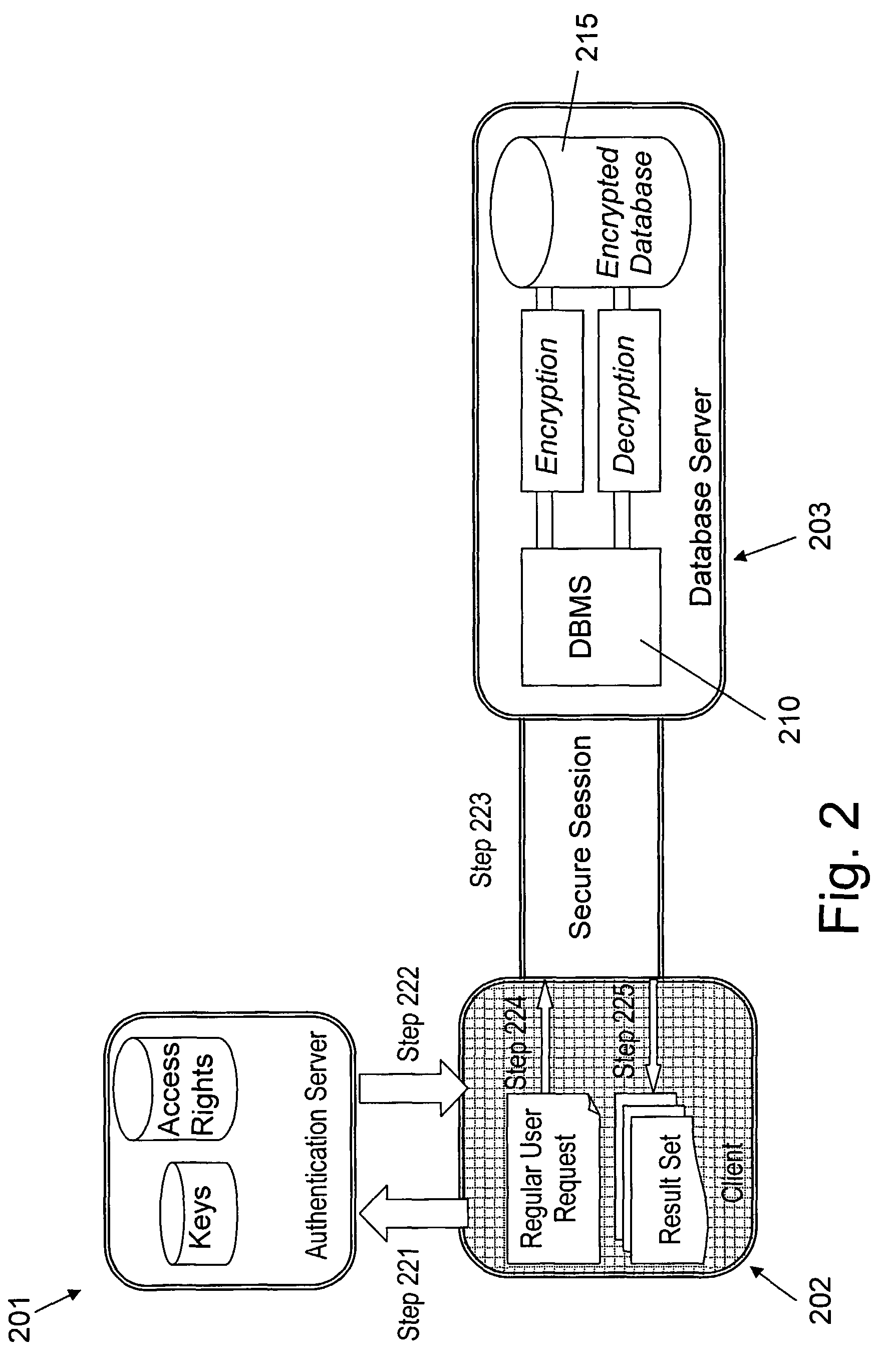
Secure search of private documents in an enterprise content management system
InactiveUS20090106271A1Efficient use ofEfficient retrievalText database queryingSpecial data processing applicationsDocument analysisEnterprise content management
An enterprise content management system such as an electronic contract system manages a large number of secure documents for many organizations. The search of these private documents for different organizational users with role-based access control is a challenging task. A content-based extensible mark-up language (XML)-annotated secure-index search mechanism is provided that provides an effective search and retrieval of private documents with document-level security. The search mechanism includes a document analysis framework for text analysis and annotation, a search indexer to build and incorporate document access control information directly into a search index, an XML-based search engine, and a compound query generation technique to join user role and organization information into search query. By incorporating document access information directly into the search index and combining user information in the search query, search and retrieval of private contract documents can be achieved very effectively and securely with high performance.
Owner:IBM CORP
Symmetrical searchable encryption method for supporting result high-efficiency sequencing in hybrid cloud storage
InactiveCN104765848AImplement a repetitive redundancy removal mechanismImprove storage space utilizationDigital data protectionSpecial data processing applicationsCiphertextData retrieval
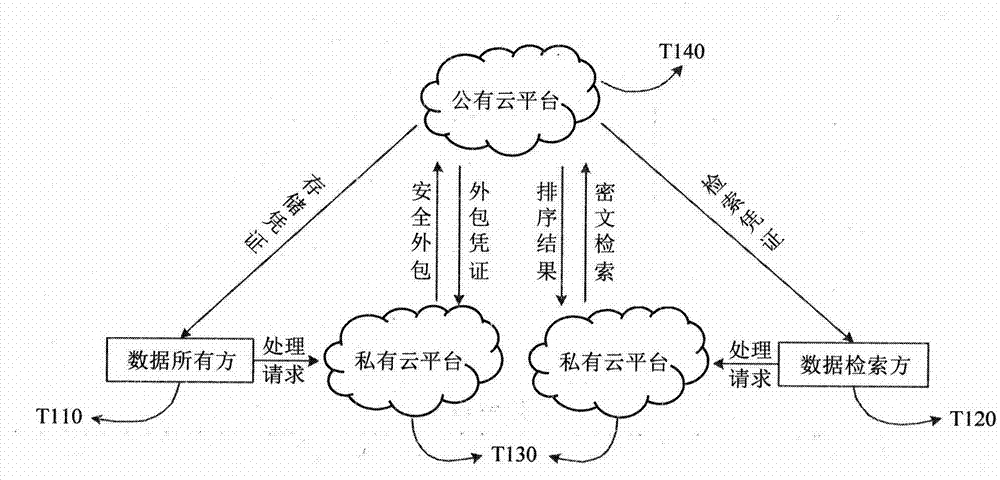
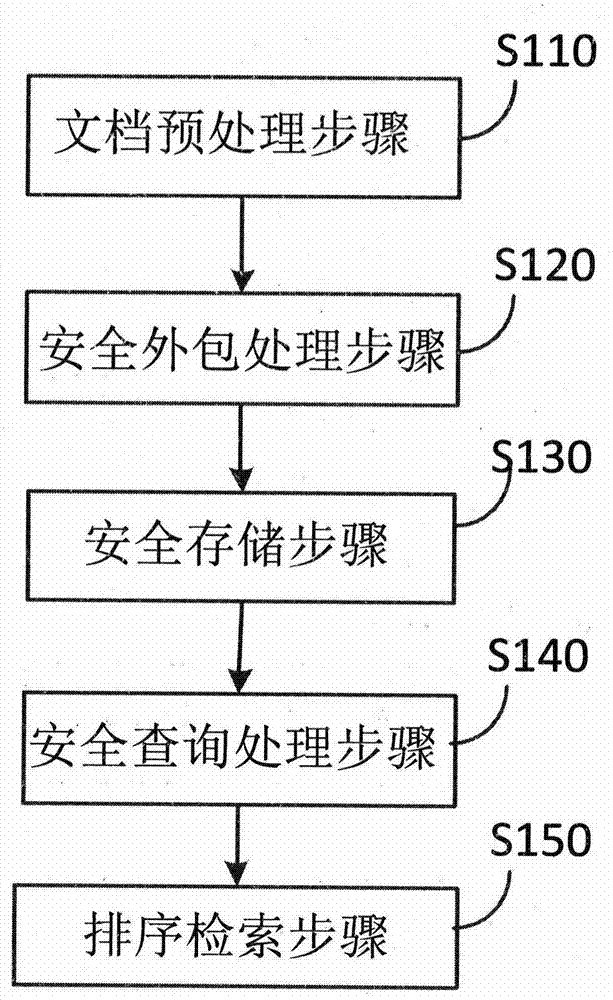
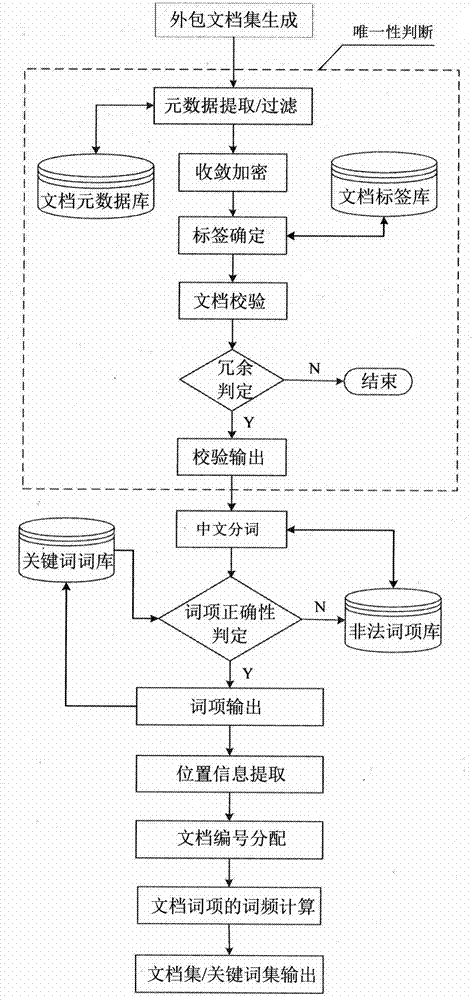
Provided is a symmetrical searchable encryption method for supporting result high-efficiency sequencing in hybrid cloud storage. A hybrid cloud storage system based on a data owning party, a data retrieving party, a private cloud platform and a public cloud platform is involved in the steps of design file preprocessing, security packing, file security storage, security inquiring and sequencing ciphertext retrieving, and the security packing and high-efficiency retrieving of a mass of file sets are organically integrated. Dual-layer security indexes are established to serve high-efficiency sequencing of ciphertext retrieving, and operations of adding, deleting, inquiring and changing dynamic indexes can be supported; the retrieving history and retrieving interests of a data user serve as subjective characteristics of ciphertext search sequencing and participate in the sequencing computation of retrieving results; the file uniqueness testing step is added to the file preprocessing step, and therefore a data repetitive deletion redundancy mechanism is achieved, the high efficiency of packing the file sets of the data owning party is ensured, and the technical support is provided for increasing the utilization rate of storage space of public cloud.
Owner:PLA AIR FORCE AVIATION UNIVERSITY
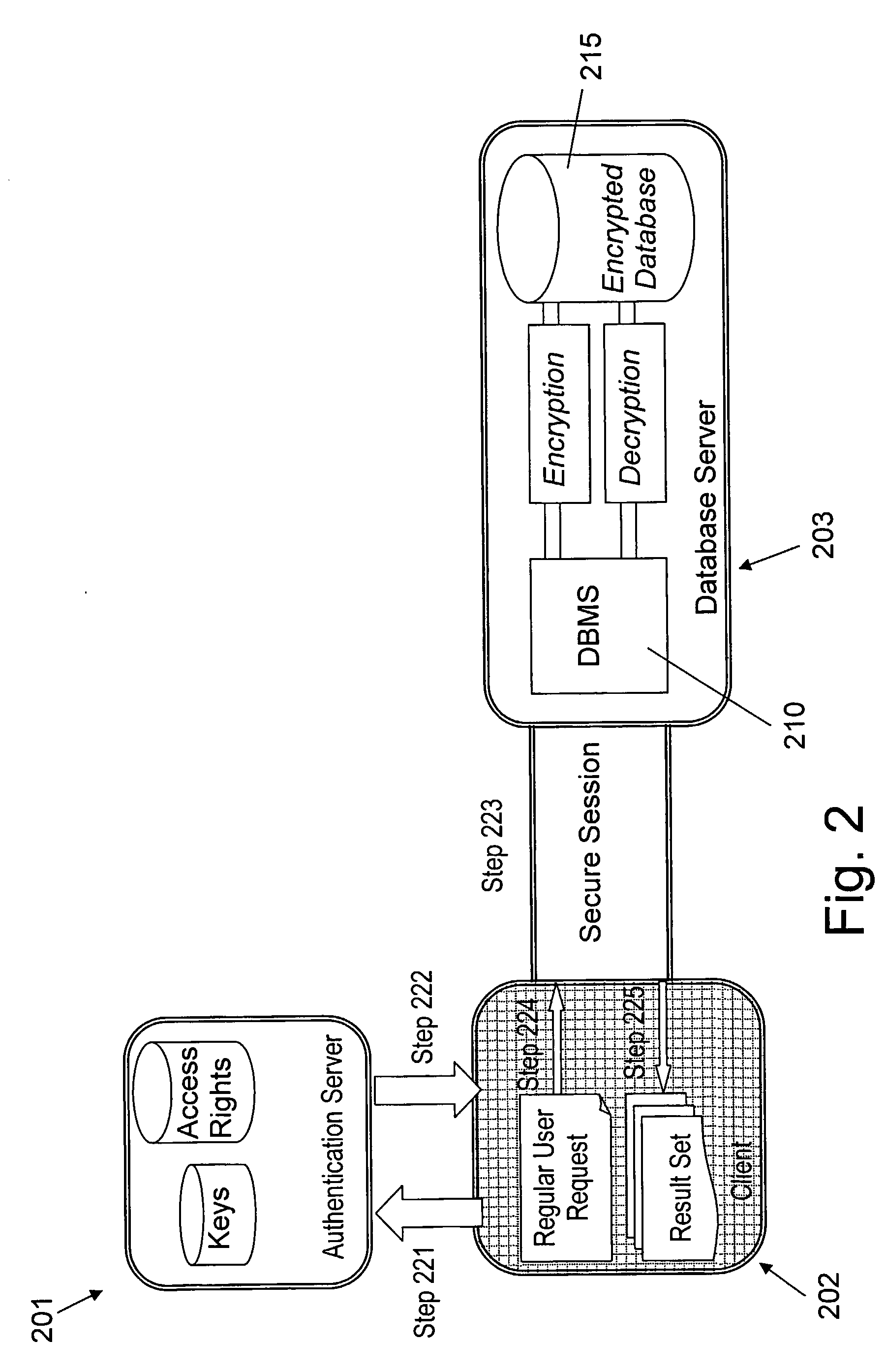
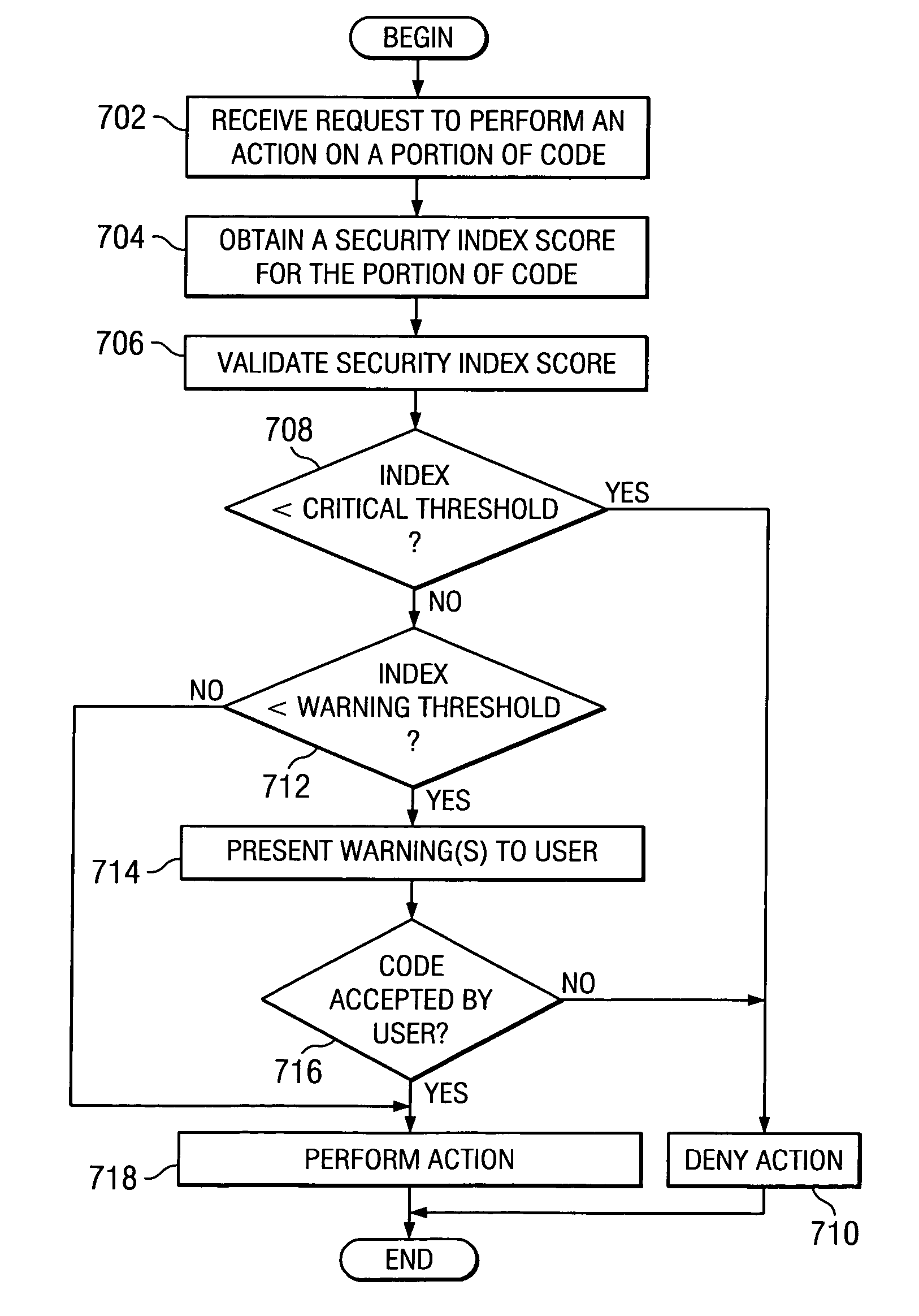
System for managing security index scores
InactiveUS20050283622A1Lower security levelUnauthorized memory use protectionHardware monitoringSafety indexDigital signature
A system for managing security index scores is provided. A security index that rates the security level of a portion of code is associated with the code. Development tools, such as packaging utilities, compilers, integrated development environments, and the like, may warn the user if the security level of the portion of the code is low. Source code repository tools, such as concurrent versioning systems, may deny submitted source code if the security index is below a threshold or below a previous version. Installation tools may warn a user or refuse to install a software package if an associated security index is low. Security index scores may be maintained and digitally signed by a trusted third party.
Owner:IBM CORP
Key escrow-free secure multi-keyword sorting and searching system
ActiveCN108632032ADoes not affect search resultsExpandable and flexibleKey distribution for secure communicationUser identity/authority verificationCiphertextSecurity index
The invention relates to a key escrow-free secure multi-keyword sorting and searching system. The system comprises a key generation center, a cloud server, a data owner and a data user; the key generation center is used for achieving interactive computing with the cloud server to jointly generate a public parameter of the system and a property public key-private key pair of the data user; the cloud server is used for storing a file of the data owner and responding to a searching query request of the data user; the data owner extracts a keyword set from the file, encrypts the keyword set into asecure index, encrypts the file, makes an access strategy and embeds the access strategy into ciphertext; and the data user defines the searched keyword set and generates a trap door by using the property private key of the data user to search for the encrypted file stored in the cloud server. According to the system, the key escrow problem is solved, flexible authorization keyword searching andfine-grained data access authorization are achieved, multi-keyword subset searching is supported, and the searching result is not influenced by changes of the keyword query order.
Owner:FUZHOU UNIV
Method for keyword searchable encryption based on bilinear pairs in cloud storage
ActiveCN104021157AEnsure safetyImprove efficiencyDigital data protectionTransmissionCiphertextMulti user environment
The invention discloses a method for keyword searchable encryption based on bilinear pairs in cloud storage. The method includes the steps that firstly, system parameters are initialized; users are added; thirdly, encryption and security indexes for files are generated; fourthly, search tokens, relative to keywords, of the users are generated; fifthly, a cloud storage server is searched for keywords relative to ciphertexts; sixthly, the ciphertexts are decrypted by the users; seventhly, the users are logged out. According to the method, the authorized users can look for the encrypted files through a trap door connected with the keywords. The keywords used by the users for search cannot be known even by the cloud storage server, so that security of user information can be guaranteed; Compared with an existing scheme, the comprehensive efficiency of the aspects of communication and calculation cost, namely the aspects of the search speed of the size of the trap door, the encryption and search speed of the keywords, of the provided scheme is improved, and the method is suitable for multi-user environments.
Owner:广州爱范儿科技股份有限公司
Dynamic and Adaptive Configurable Power Distribution System
ActiveUS20160099567A1Easy to measureIncreases stability guaranteeMechanical power/torque controlLevel controlPower qualityTransient state
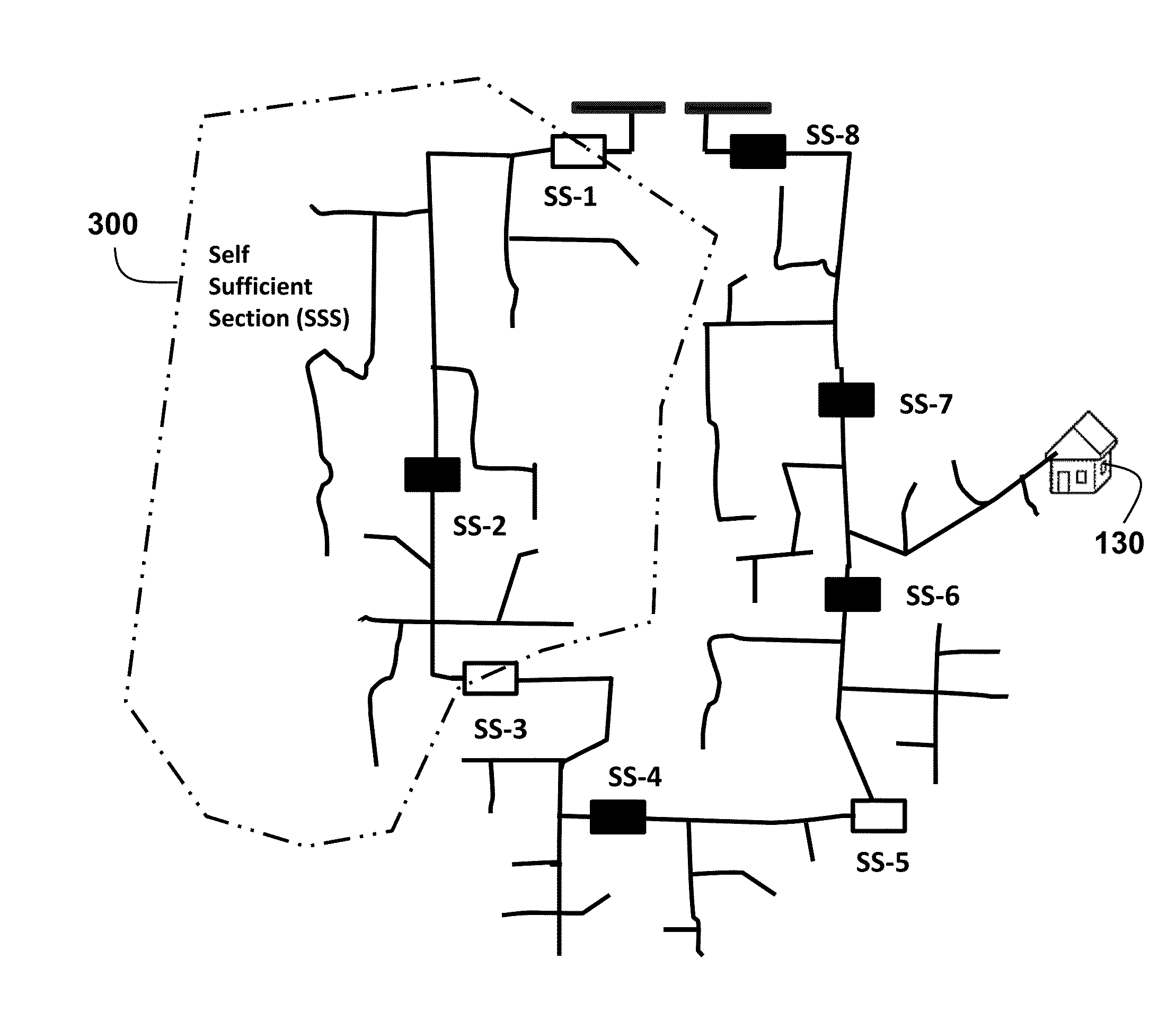
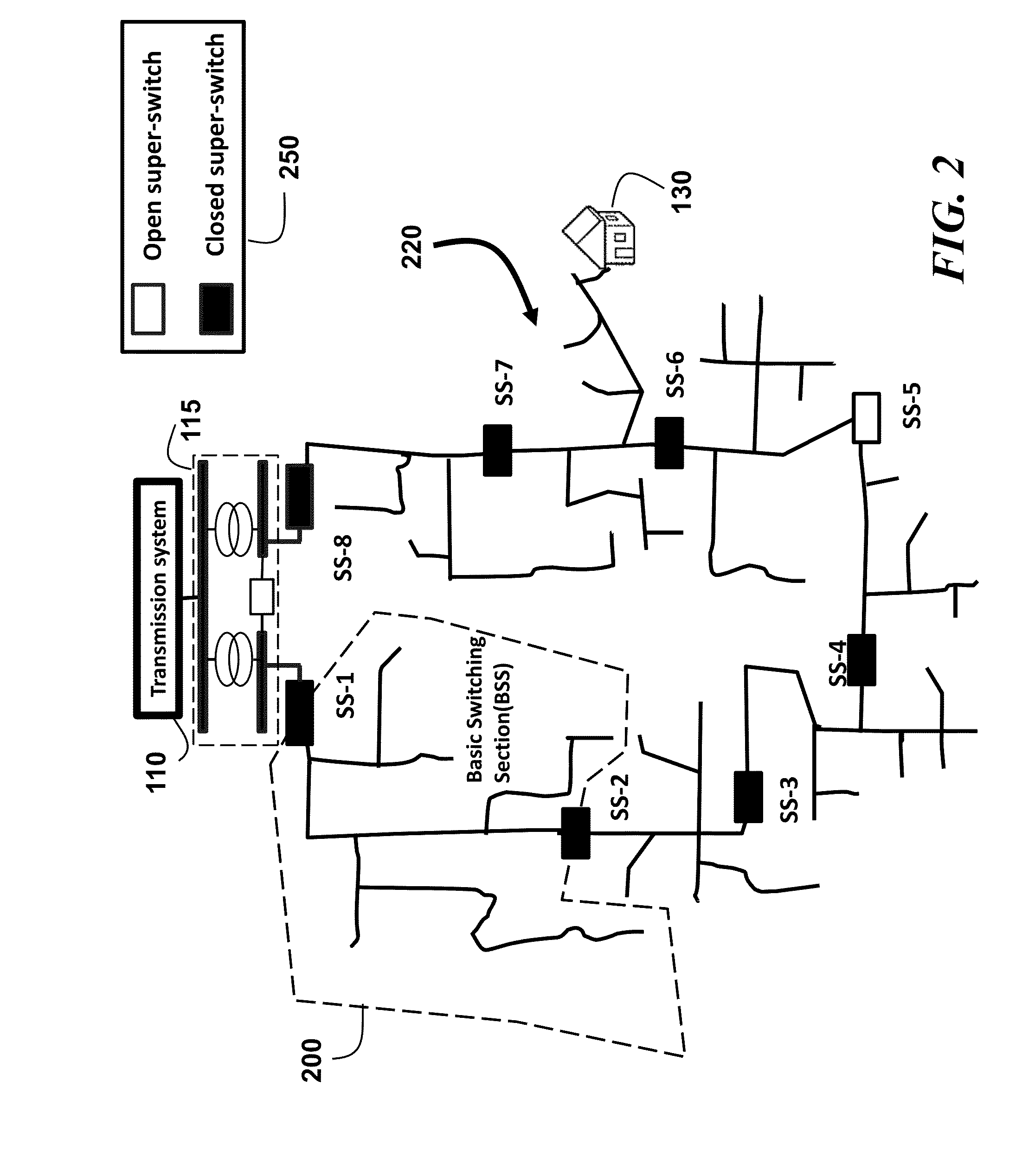
A power distribution system is dynamically and adaptively configured in real-time to improve energy efficiency, reliability and power quality, particularly if the system includes renewable sources and storages. An optimal multi-objective scheduling and partitioning method is provided to partition the system into self-sufficient sections (SSS) through optimally combination of adjacent basic switching sections (BSS). The SSSs enable system operating at a lower cost, with less power losses, more energy efficiency, improved power quality, and sufficient transient security. The method uses two storage based transient security indices, storage compensation power margin (SCPM) and storage compensation energy margin (SCEM) evaluate the transient stability margin of distribution system. A minimal stability margin is used to ensure that the system remains stable when subject to large unexpected load deviations.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Fuzzy multi-keyword retrieval method of encrypted data in cloud environment
ActiveCN106326360AAchieve retrievalImprove securityDatabase queryingTransmissionDimensionality reductionCiphertext
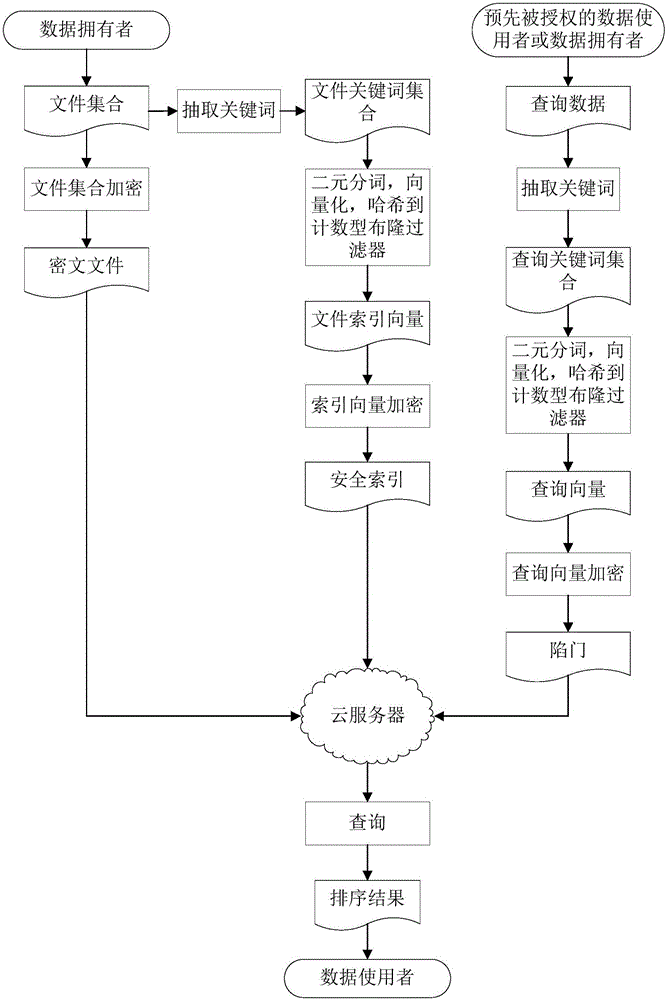
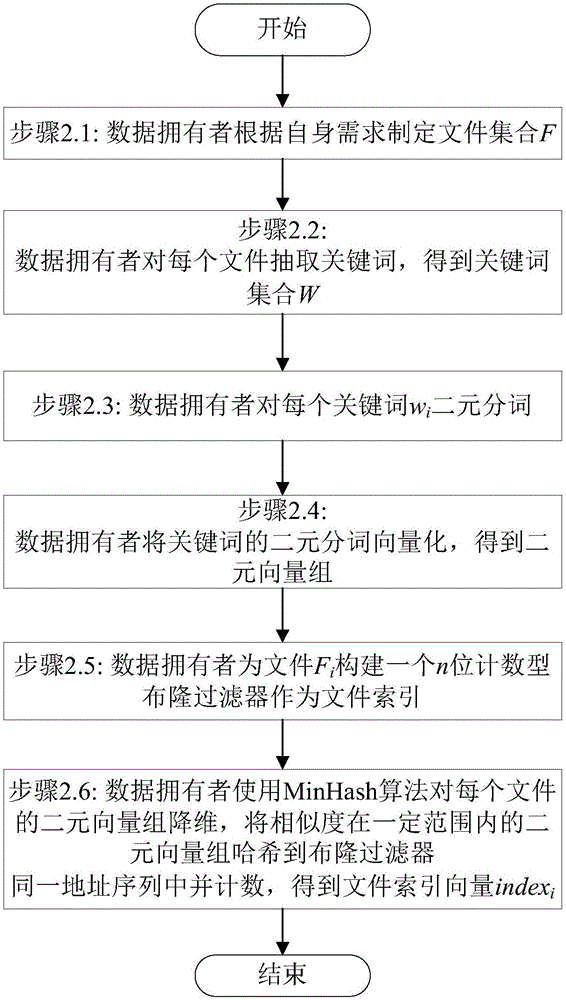
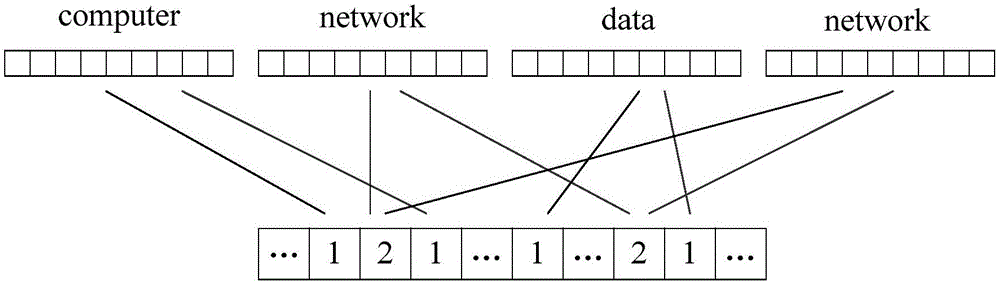
The invention discloses a fuzzy multi-keyword retrieval method of encrypted data in cloud environment. A file is subjected to set encryption by a data owner to generate a ciphertext file; keywords are extracted from each file; the keywords are subjected to binary segmentation and vectorization to obtain a binary vector group; the binary vector group is subjected to dimensionality reduction and is then inserted into a counting type bloom filter to generate index vectors; each index vector is encrypted to obtain a security index; the ciphertext file and the security indexes are sent to a cloud server; a pre-authorized data user or the data owner extracts the keywords from query data; binary segmentation and vectorization are performed to generate a query vector; encryption is performed to obtain a trap door; the trap door is sent to the cloud server; the cloud server obtains a certain number of files with the highest relevancy degree through query according to the trap door and the security index; after sorting, the files are returned to the data owner. The large data volume of ciphertext multi-keyword retrieval is supported; compared with the prior art, the method has the advantages that the index building and query processes are more efficient; the sorting result is more accurate; the data privacy is effectively protected.
Owner:WUHAN UNIV OF SCI & TECH
Structure preserving database encryption method and system
ActiveUS8639947B2Provide protectionKey distribution for secure communicationMultiple keys/algorithms usageDatabase indexMulti user environment
A database encryption system and method, the Structure Preserving Database Encryption (SPDE), is presented. In the SPDE method, each database cell is encrypted with its unique position. The SPDE method permits to convert a conventional database index into a secure one, so that the time complexity of all queries is maintained. No one with access to the encrypted database can learn anything about its content without the encryption key. Also a secure index for an encrypted database is provided. Furthermore, secure database indexing system and method are described, providing protection against information leakage and unauthorized modifications by using encryption, dummy values and pooling, and supporting discretionary access control in a multi-user environment.
Owner:BEN GURION UNIVERSITY OF THE NEGEV
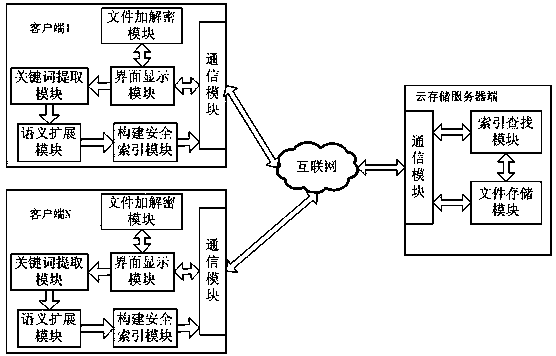
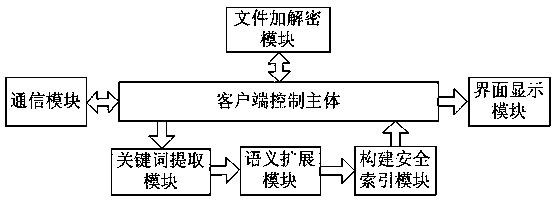
Method and system for designing searchable encrypted cloud disc with fuzzy semantics
InactiveCN103955537AAdd deleteEasy to operateSpecial data processing applicationsSecuring communicationCiphertextSecurity index
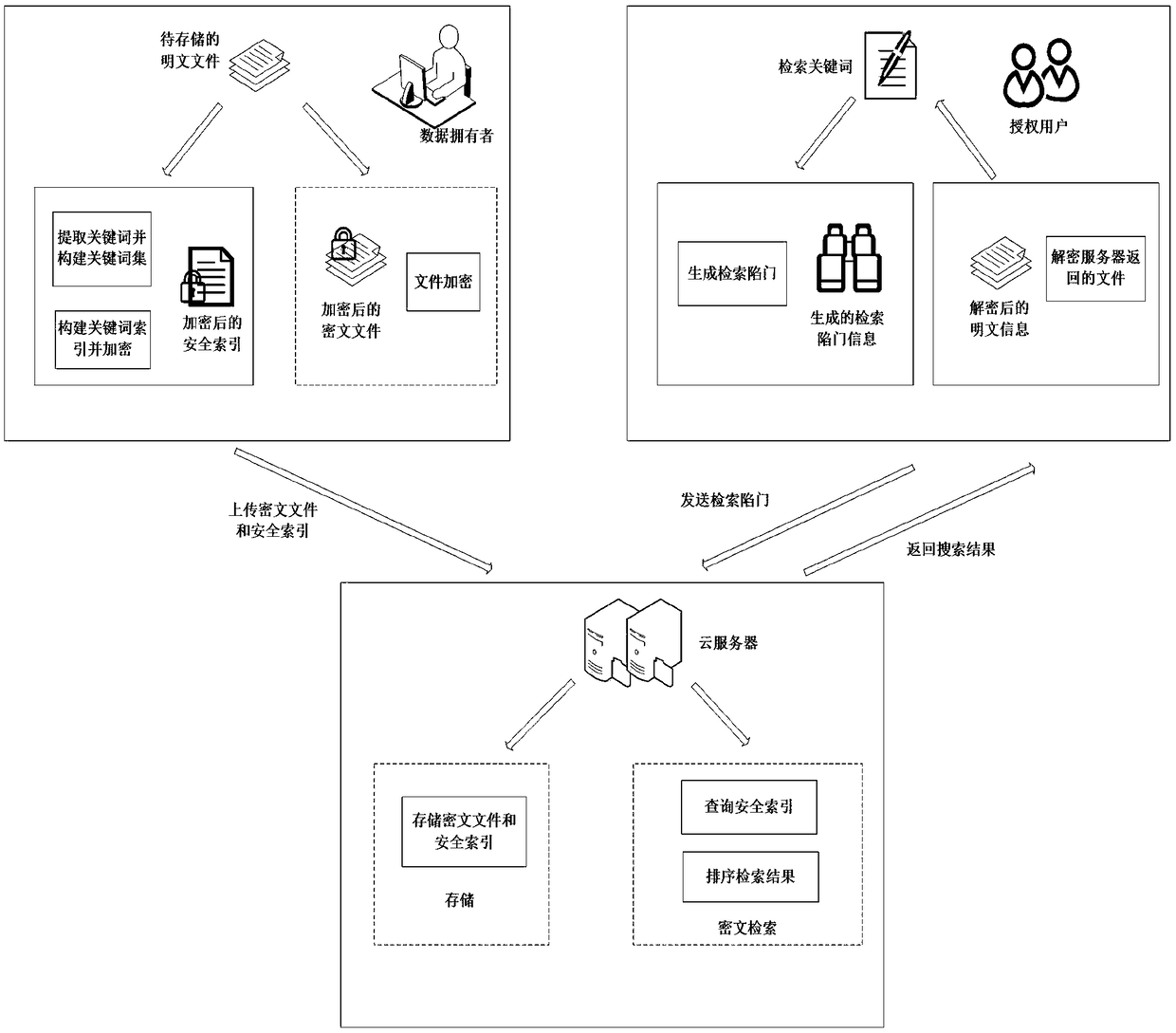
The invention relates to a method and a system for designing a searchable encrypted cloud disc with fuzzy semantics. The method comprises the following steps: firstly, inputting a key pair to encrypt a file which is needed to be uploaded by a user through a client side; extracting keywords of the encrypted file, and carrying out semantic extension to build a synonym set; secondly, building a safety index to the built synonym set by a bloom filter, and uploading the safety index to a cloud storage server side; generating a keywords trap door according to the key input by the user by the client side, and submitting the trap door to the cloud storage server side; finally, searching for a corresponding file by the safety index according to the keywords trap door submitted by the user by the cloud storage server side, and returning the file back to the client side; decrypting the file returned by the cloud storage server side through the key pair by the client side. The method and the system are mainly used for providing the synonyms semantic fuzziness search function for the information search of the cipher text file, and supporting the search of many keywords, so that the file can be updated with higher efficiency.
Owner:FUZHOU UNIV
Multi-user multi-keyword searchable encryption method in cloud storage
InactiveCN104023051AGuaranteed privacyImprove efficiencySpecial data processing applicationsSecuring communicationCiphertextData information
The invention discloses a multi-user multi-keyword searchable encryption method in cloud storage, comprising the following steps: Step 1, system parameter initialization; Step 2, addition of users; Step 3, file encryption by a file owner and generation of security index; Step 4, generation of keyword search token by users; Step 5, search of ciphertext keyword by a cloud storage server; Step 6, decryption of ciphertext by users; and Step 7, cancellation of users. According to the method, an authorized user can search an encrypted file by the utilization of a trap door linked with a keyword; a data user encrypts his / her own data and stores the data into the cloud storage server; and the required encrypted data can be searched through a keyword search token when the data is needed, and download and decryption are carried out. Meanwhile, the cloud storage server doesn't know about the user's search keyword, thus guaranteeing data information privacy for the user. The method is suitable for a multi-user environment.
Owner:XIAN UNIV OF TECH
Smart power grid distributed ciphertext retrieval method and system model based on alliance block chain
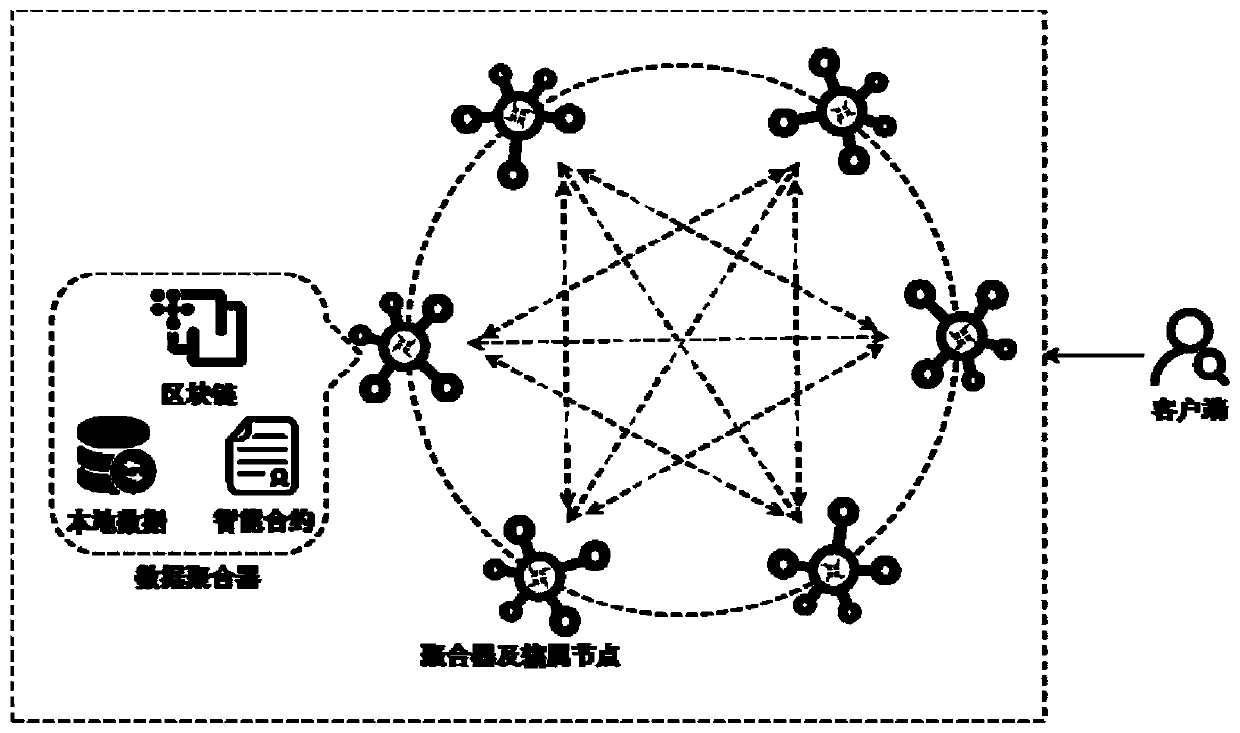
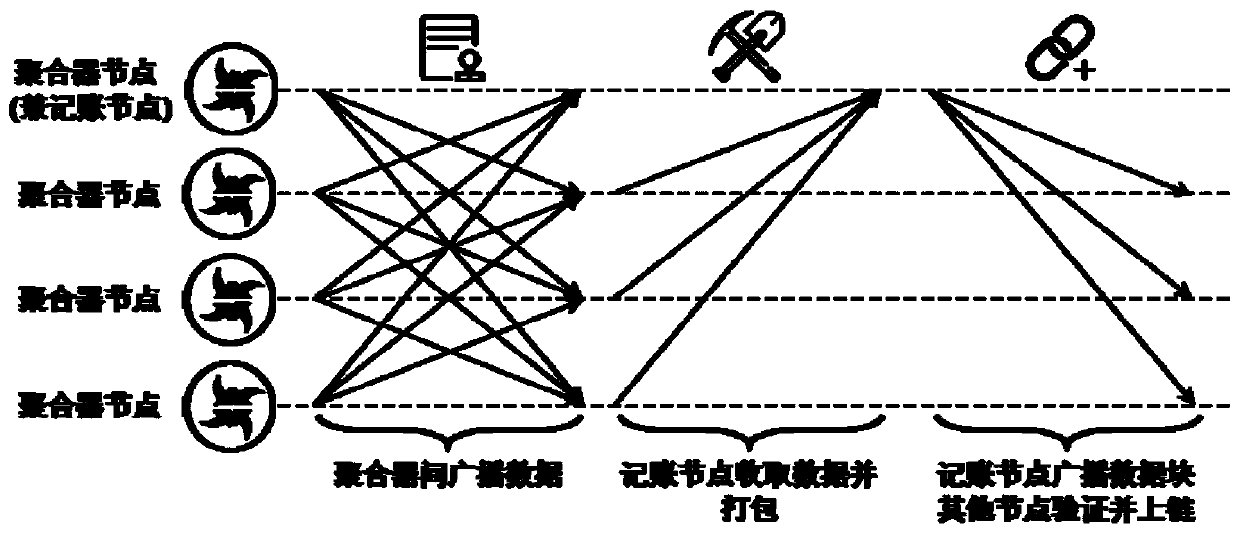
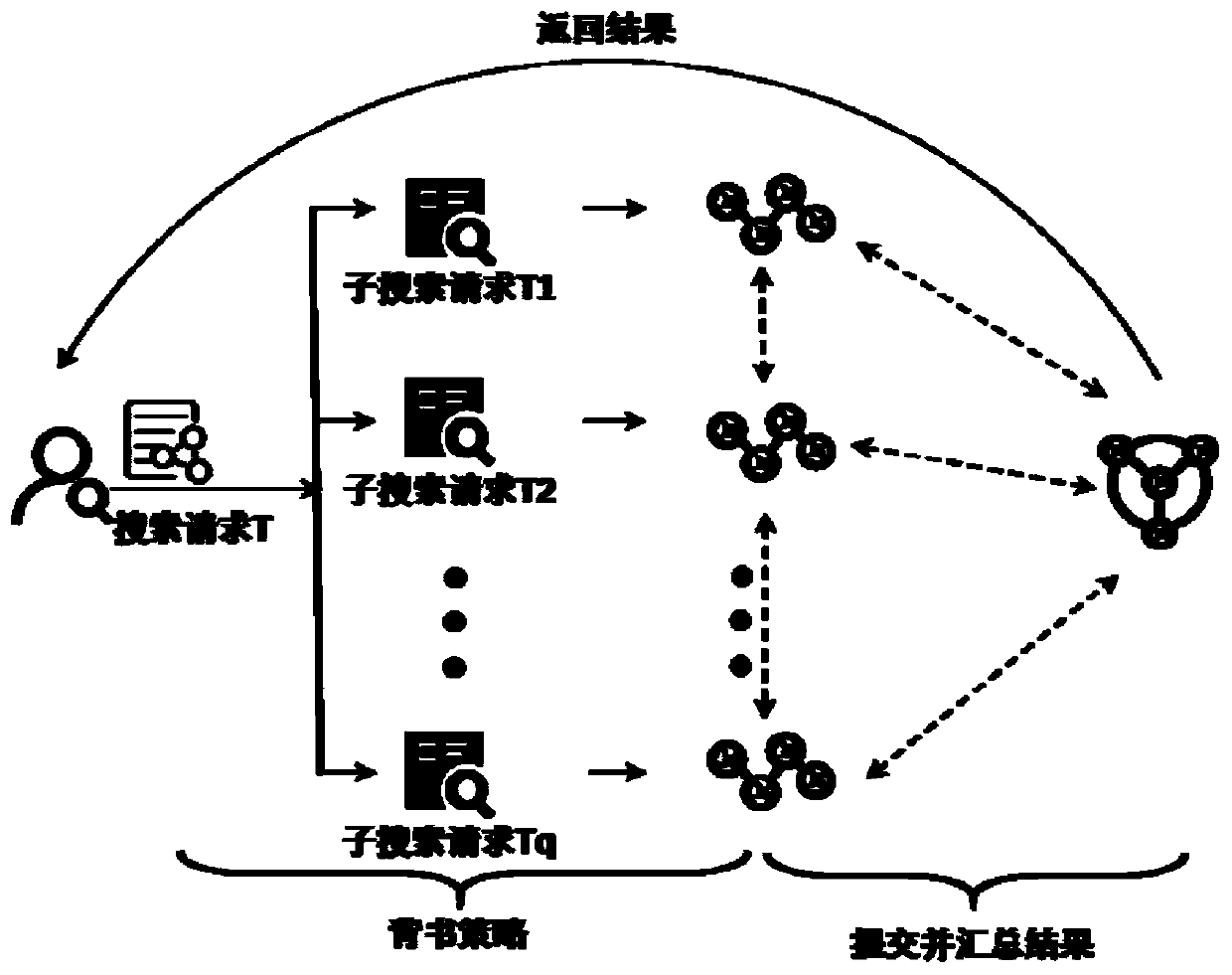
ActiveCN110032891ARetrieval is safe and trustedSearch Safe and TrustedEncryption apparatus with shift registers/memoriesUser identity/authority verificationCiphertextSmart grid
The invention discloses a smart power grid distributed ciphertext retrieval method and system model based on an alliance block chain. The smart power grid distributed ciphertext retrieval method basedon an alliance block chain comprises the following steps of: 1) initializing a system; 2) generating a security index; 3) uploading and storing the index; 4) generating and releasing a search token;5) enabling the intelligent contract to execute a search operation; 6) returning search results. According to the smart power grid distributed ciphertext retrieval method based on the alliance block chain, safe and credible search on sensitive data is realized by utilizing the public, distributed calculation is performed on a search algorithm through an intelligent contract, dynamic division is performed on transactions according to the number of records in an account book, the number of return results in user query, node states in a network and other information, an adaptive endorsement strategy is formulated, and the optimal query efficiency is achieved.
Owner:CHINA ELECTRIC POWER RES INST +1
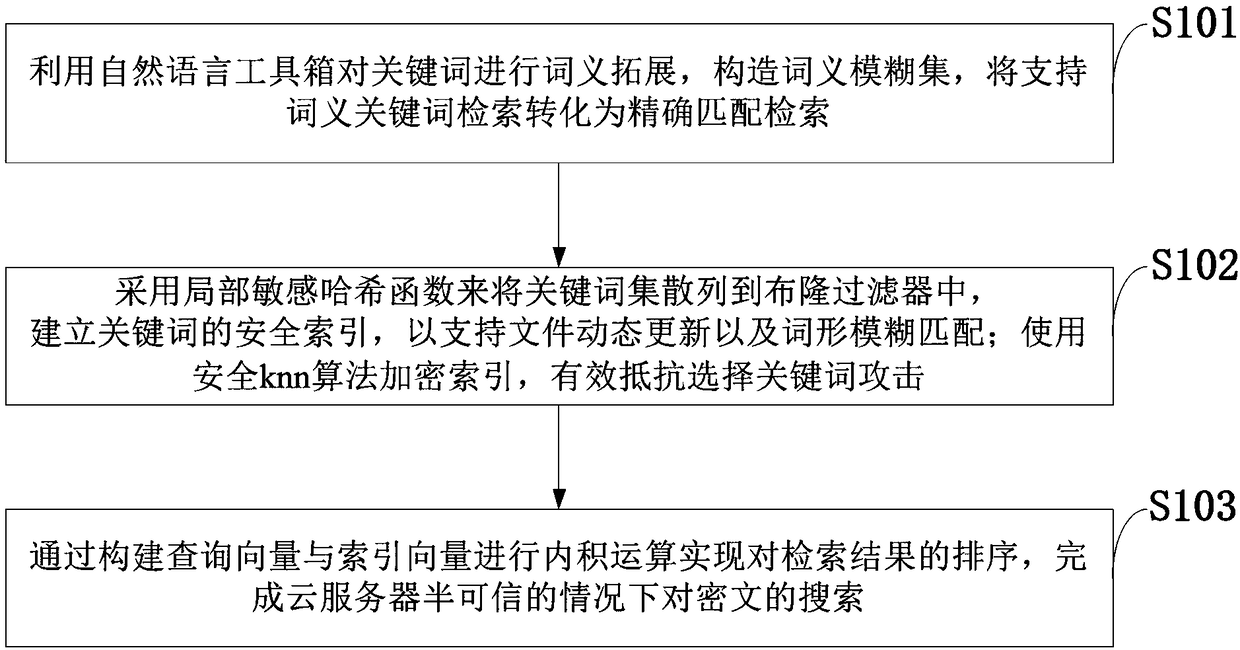
Searchable encryption method and system for supporting fuzzy retrieval of word morphology and word meaning in cloud environments
ActiveCN108712366AFuzzy retrieval implementationSearch Encryption SimplifiedKey distribution for secure communicationSpecial data processing applicationsHash functionCiphertext
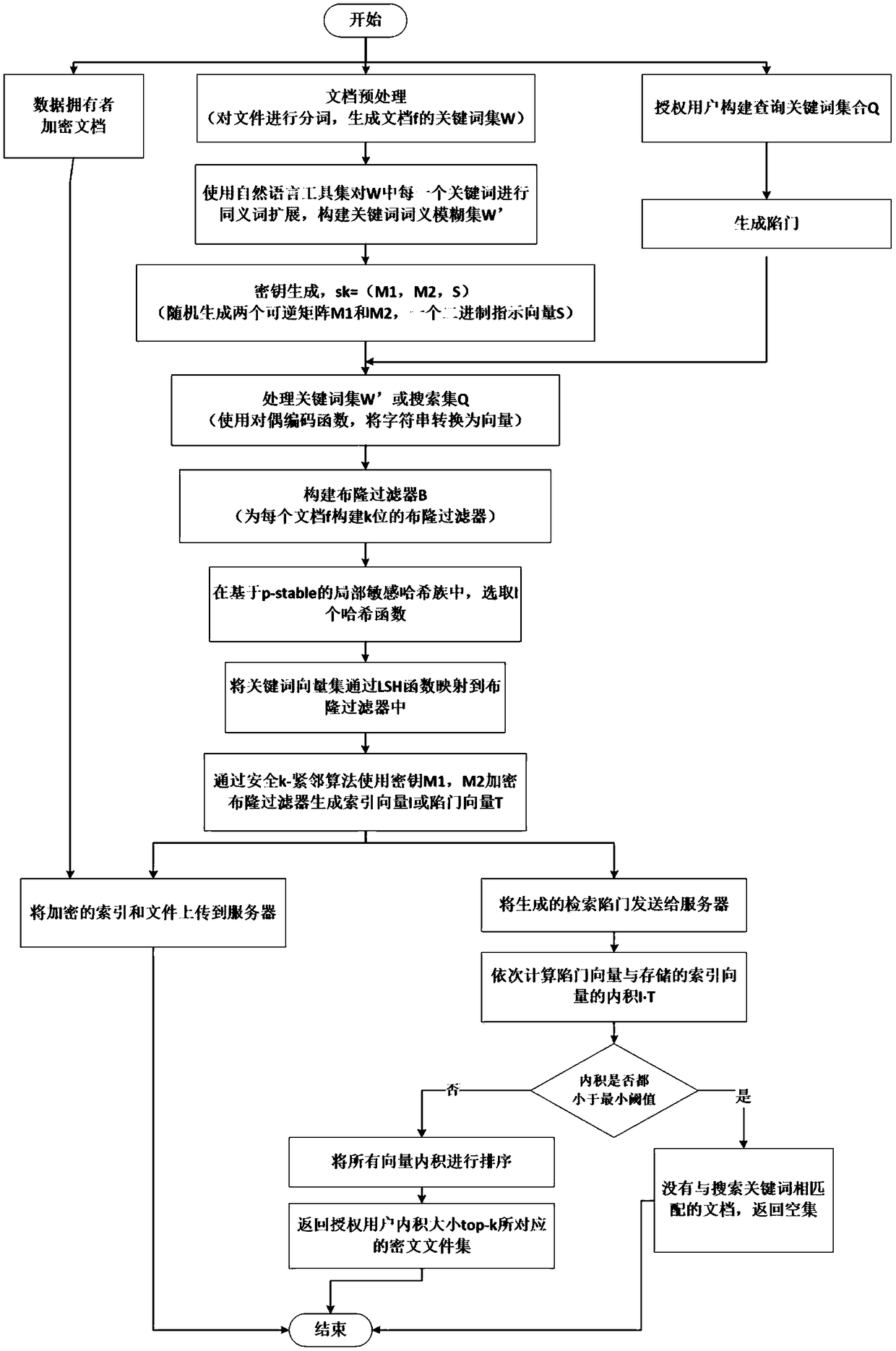
The invention belongs to the technical field of information security, and discloses a searchable encryption method and system for supporting fuzzy retrieval of word morphology and word meaning in cloud environments. The method includes establishing a security index by adopting a Bloom filter structure to support file dynamic update; accomplishing word morphology fuzzy matching by adopting a locally sensitive Hash function; performing word meaning expansion on keywords by using a natural language toolbox, constructing a word meaning fuzzy set, and inserting the word meaning fuzzy set into the established security index so that support word meaning keyword retrieval can be converted into accurate matching retrieval; performing inner product operation to realize the ordering of retrieval results by establishing query vectors and index vectors; and using the Hash function and a security knn algorithm to make the method and the system effectively resist selection keyword attacks so that thesearching of cryptograph on a cloud server under semi-trusted conditions. Cryptograph searching functions can be achieved; and the method and the system can support fuzzy retrieval of word morphologyand word meaning, multi-keyword retrieval, and dynamic adding and deleting files.
Owner:XIDIAN UNIV
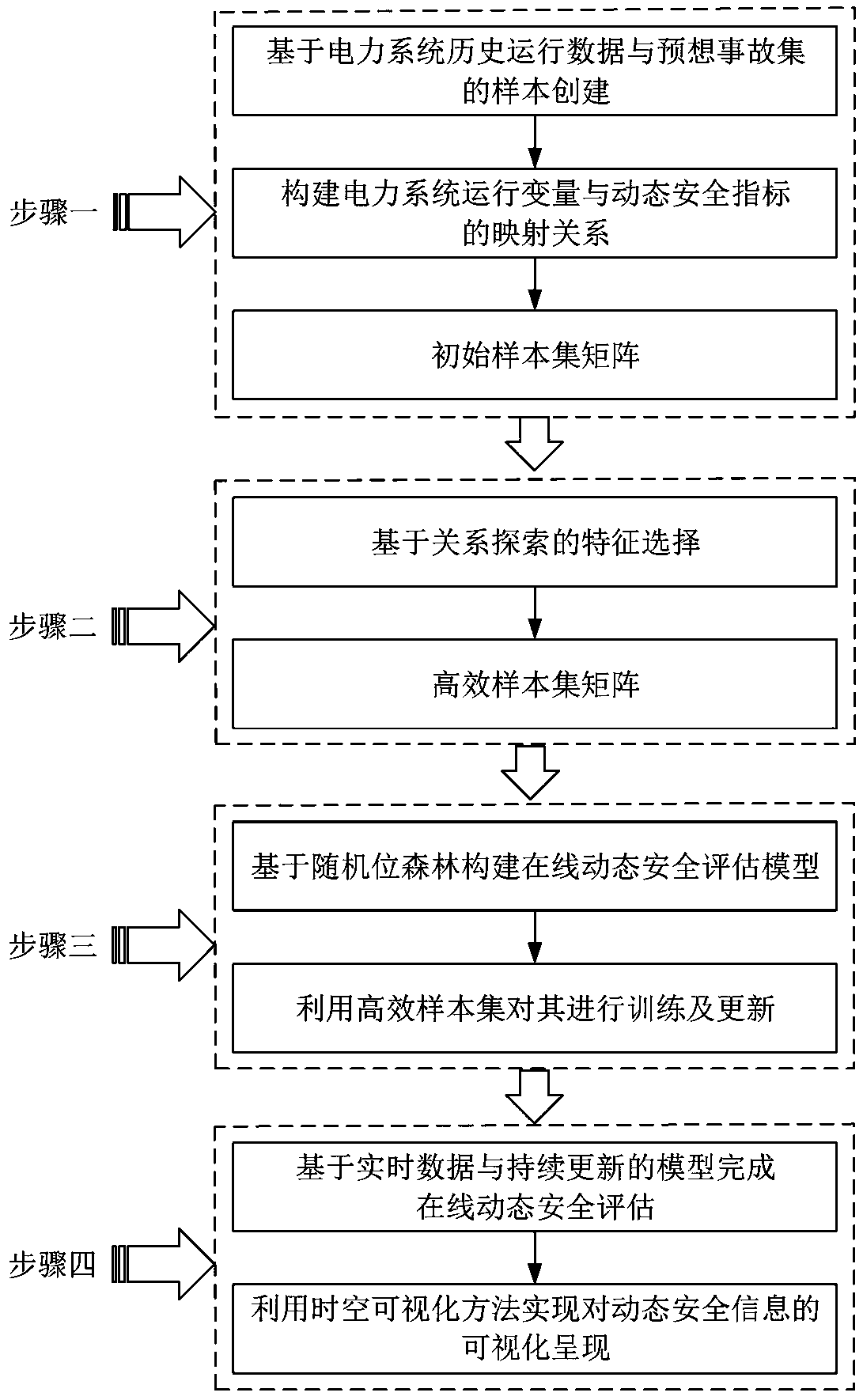
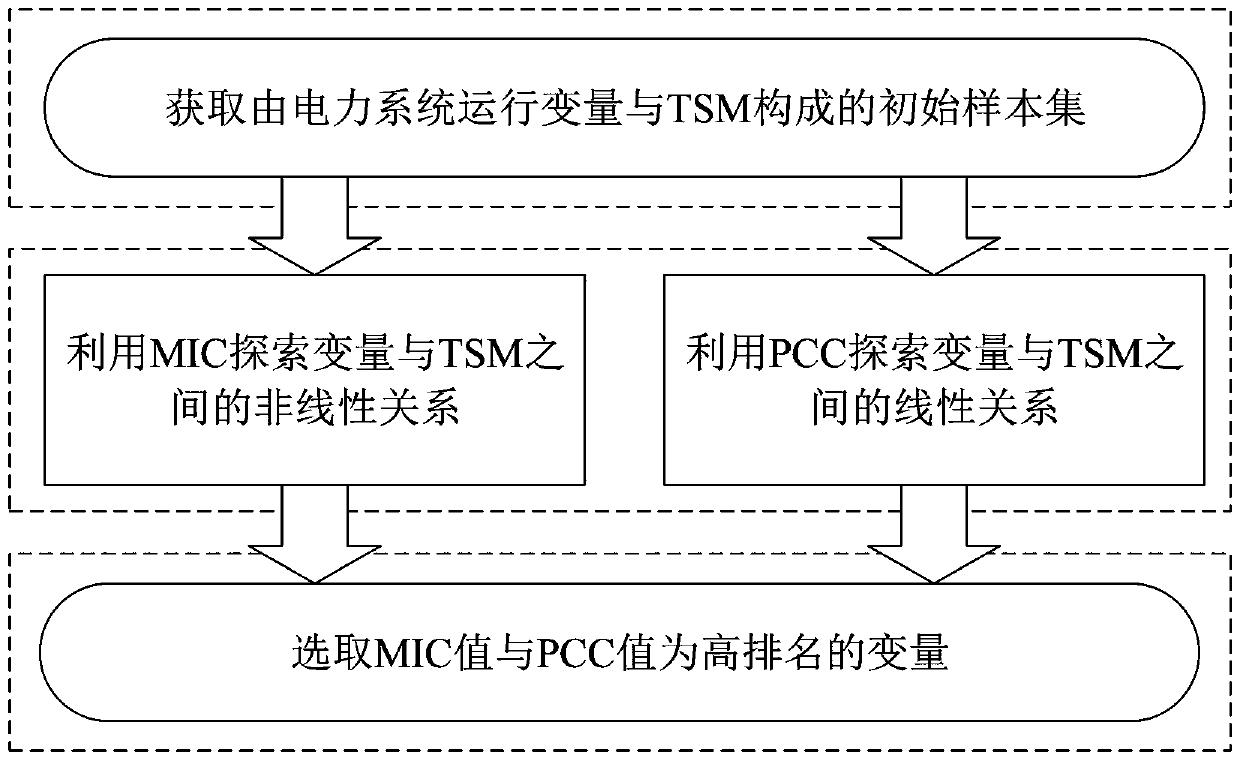
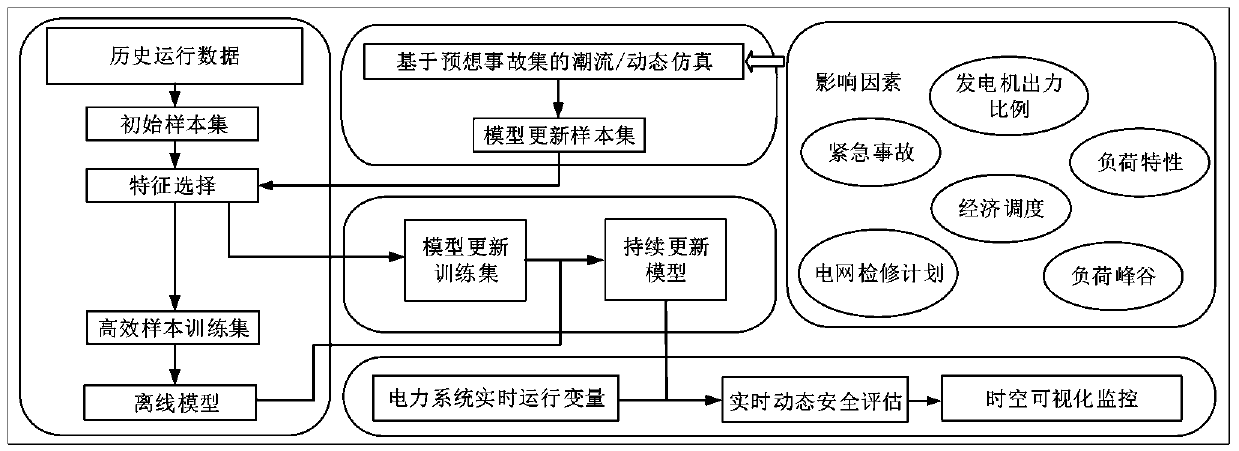
Power system dynamic security assessment comprehensive model and spatiotemporal visualization method
ActiveCN110311376ADescribe wellDimensional reductionSpecial data processing applicationsAc network circuit arrangementsVisual presentationSecurity index
The invention provides a power system dynamic security assessment comprehensive model and a spatiotemporal visualization method. The method comprises the following steps: constructing a dynamic security index and establish an initial sample set for dynamic security assessment based on the historical operation data of a power system and a predicted accident set; 2) constructing a feature selectionframework, performing feature selection on the initial sample set and forming a processed high-efficiency sample set; 3) constructing an online dynamic security assessment comprehensive model based ona random bit forest and performing offline training and updating on the model by using the high-efficiency sample set; and 4) using the continuously updating dynamic security assessment model to complete the online assessment of the dynamic security state and using the spatiotemporal visualization method to realize the visual presentation of the dynamic security information. The purpose of the present invention is to provide the online dynamic security assessment comprehensive model and the spatiotemporal visualization method which are beneficial to the system operators to take timely preventive and control measures, avoid large power outage caused by accidents and improve the secure operation level of the power grid.
Owner:CHINA THREE GORGES UNIV
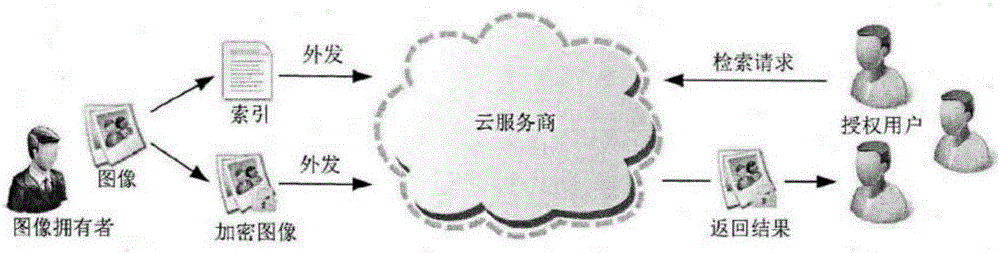
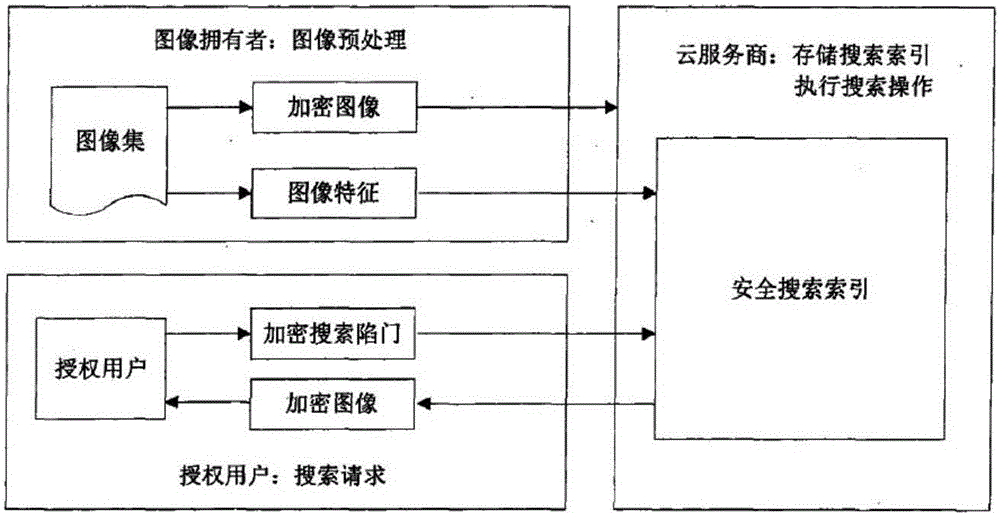
Cloud computation-based internet education platform resource library image retrieval method
InactiveCN106599311AReduce construction costsEnsure safetyWeb data indexingDigital data protectionThe InternetSecurity index
The invention belongs to the technical field of cloud computation, and particularly relates to a cloud computation-based internet education platform resource library image retrieval method. The method comprises the following steps of: data pre-processing: extracting image features by an image owner by using an image feature extraction algorithm, constructing a safety index by using the image features, encrypting images in an image library, and finally sending the safety index and the encrypted image library to a cloud server provider; retrieval: authorizing a user to construct a search trap door and submitting the search trap door to the cloud service provider; and searching an index file by the service provider according to a retrieval request so as to obtain image identifiers matched with the retrieval request, and sorting the sorting results according to relevancy. According to the method, a global image feature-based encrypted image retrieval method is used for realizing the efficient and convenient using of image data under cloud computing environment.
Owner:GUANGZHOU AVA ELECTRONICS TECH CO LTD
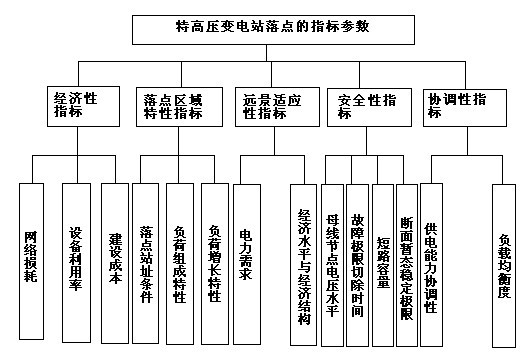
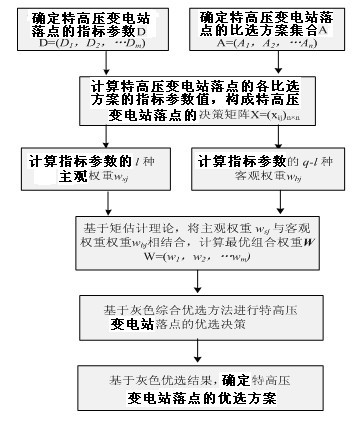
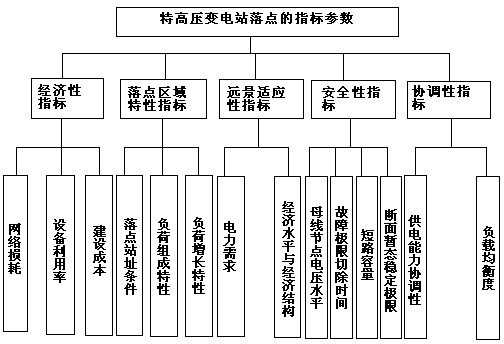
Optimal selection method of extra-high voltage transformer substation location
The invention relates to an optimal selection method of an extra-high voltage transformer substation location. The method is characterized by: firstly, establishing an index parameter which is used to plan an extra-high voltage transformer substation location layout; carrying out a system comprehension assessment on the location of the extra-high voltage transformer substation from five aspects of an economic index parameter, a security index parameter, a location area characteristic index parameter, a perspective adaptability index parameter and a coordination index parameter; according to the assessment, providing an extra-high voltage location grey integration optimization selection method based on a moment estimation theory; through the moment estimation theory, considering a subjectivity of a decision maker and objectivity than weight changes as time flies; finally, through the grey integration optimization selection method, carrying out optimization selection of a decision scheme. The method of the invention provides an important theory guidance for the extra-high voltage location program and possesses scientificity and rationality.
Owner:STATE GRID HUBEI ELECTRIC POWER COMPANY +1
Searchable encryption method of multiple keywords at specified location in cloud storage
ActiveCN105049196AImprove search speedUndo implementationKey distribution for secure communicationSpecial data processing applicationsCiphertextSecurity index
The invention discloses a searchable encryption method of multiple keywords at the specified location in cloud storage. The method is implemented specifically according to the following steps: Step 1, system parameter initialization; Step 2, user adding; Step 3, file encryption and security index generation by a file owner; Step 4, index re-encryption by a server; Step 5, generation of keyword search token by a user; Step 6, search of ciphertext keywords by a cloud storage server; Step 7, decryption of ciphertexts by the user; and Step 8, user revocation. By the method, the problem that keyword search cannot be realized after cloud storage data encryption in the prior art is solved.
Owner:佛山市明茂网络科技有限公司
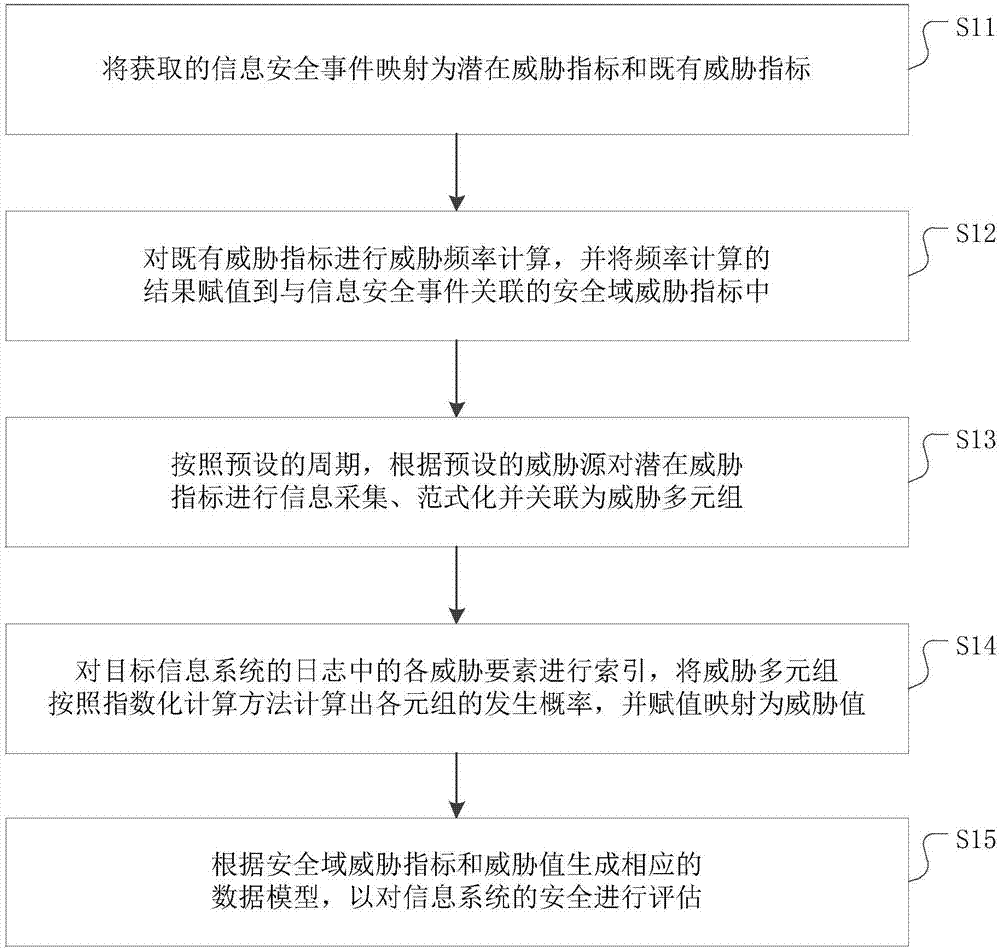
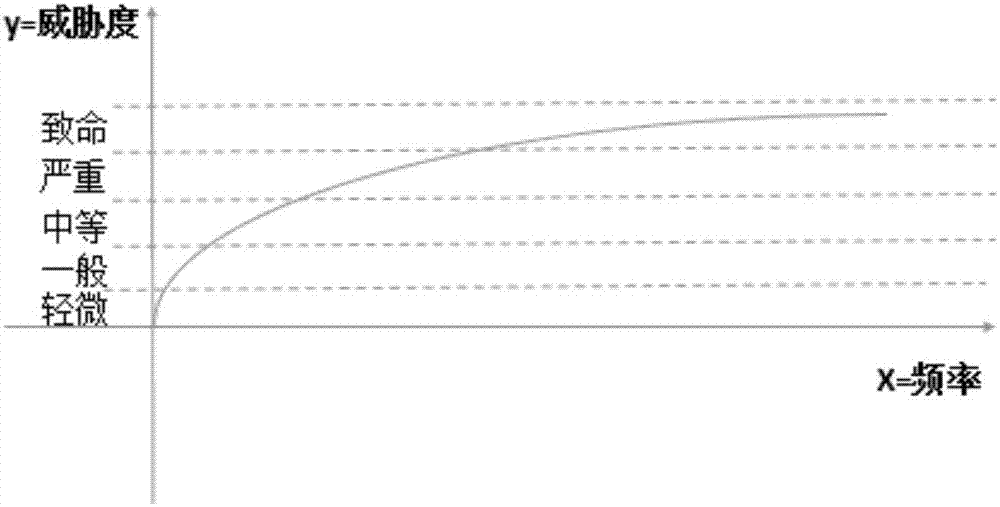
Threat data processing method for information system
The invention discloses a threat data processing method for an information system. The method comprises the steps that an obtained information security incident is mapped into a potential threat index and an existing threat index; threat frequency calculation is performed on the existing threat index, the result of the frequency calculation is assigned to the security index threat index related to the information security incident; according to a preset period, information collection, formation and correlation are performed on the potential threat index according to a preset threat source to obtain a threat multi-component system; each threat element in a log of a target information system is indexed, the threat multi-component system is used for working out the occurrence probability of the multi-component system on the basis of an indexation calculation method, and assignment and mapping are performed to obtain a threat value; according to the security domain threat index and the threat value, a corresponding data model is generated so as to evaluate the security of the information system. By building the data model, a user can conveniently and visually observe the occurrence probability of each threat in the information security incident, and the threat with which the information system is faced can be evaluated objectively.
Owner:国家电投集团河南电力有限公司 +1
Fuzzy query encryption method supporting dynamic verification in unreliable cloud computing environment
InactiveCN106776904AProtect query privacyImprove query experienceDigital data protectionTransmissionUser needsFuzzy query
The invention discloses a fuzzy query encryption method supporting dynamic verification in an unreliable cloud computing environment. The method achieves protection of user query privacy in a cloud computing environment, and improves a query experience of an encrypted data in the cloud computing environment. The method defines a similarity between keywords by editing a distance, a fuzzy keyword set is constructed by using wildcards, and a security index is constructed based on an inverted index, which enables users to query fuzzy keyword. A verifiable set is constructed using verifiable techniques to verify whether nor not a server tampers with query results and to verify whether or not the query results returned by the cloud server are correct and complete. In order to solve the problem that users need to update a lot of data in the cloud computing environment, the data is updated efficiently. The method supports the users to do the fuzzy query, update the encrypted data dynamically, verify the correctness and integrity of the query results, and improves the users' query experience under the premise of protecting data privacy.
Owner:CENT SOUTH UNIV
Transmission capacity and wind and fire bundling transmission optimization method of extra-high voltage channel
InactiveCN104751236AEasy to calculateEasy for quantitative analysisForecastingElectricity priceMathematical model
The invention relates to a transmission capacity and wind and fire bundling transmission optimization method, and in particular relates to the transmission capacity and wind and fire bundling transmission optimization method. The invention firstly establishes an index system considering receiving end power grid electricity power demand, static security index, transient stability index, economic index and power transmission electrovalence. The indexes are quantized for establishing mathematical model of multi-objective functions and the multi-objective optimization algorithm is adopted for computing. During the solving process, multi-objective functions are solved simultaneously and computed for obtaining alternative solution meeting constraint condition, and the entropy function method is adopted for confirming the optimal compromise solution. The index system considering receiving end power grid electricity power demand, static security index, transient stability index, economic index and power transmission electrovalence is adopted, the evaluation index is convenient to compute and analyze in a quantitative manner, the transmission capacity of the electric transmission line and the influence to the receiving end power grid from sending end wind and fire bundling ratio can be reflected synthetically.
Owner:STATE GRID CORP OF CHINA +4
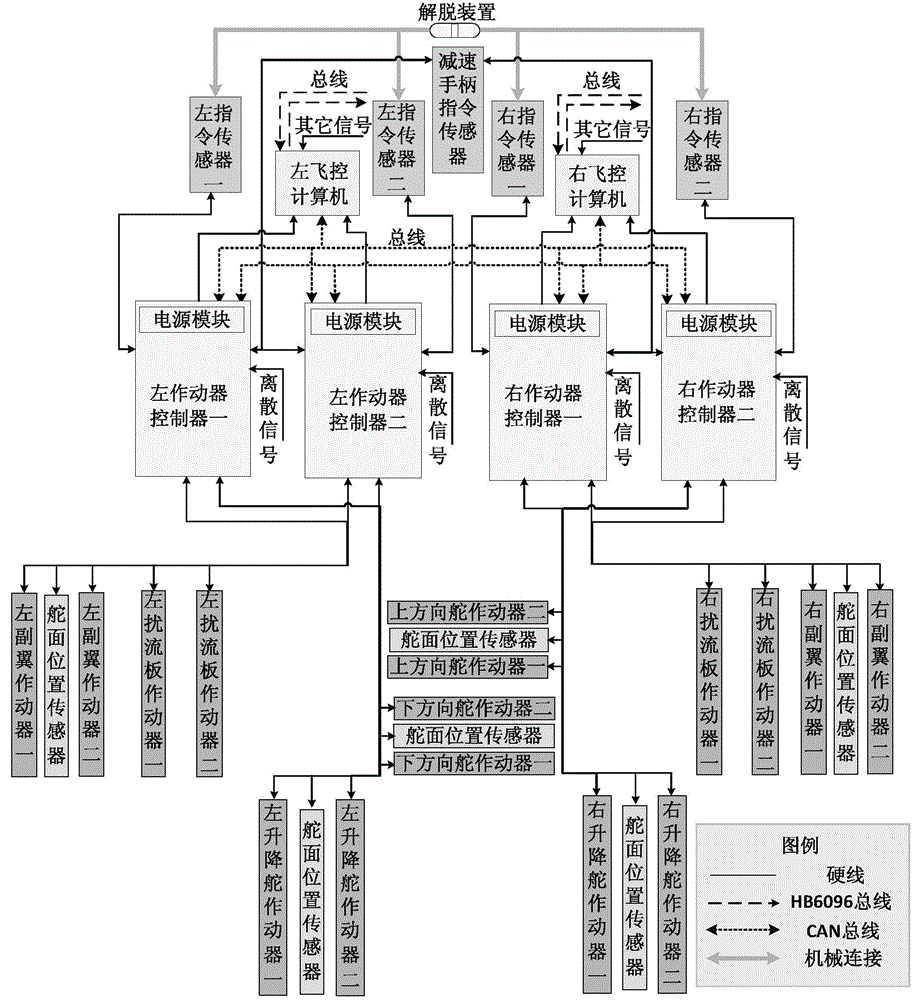
Flybywire control system with high safety and low cost
ActiveCN105446329AReduce in quantityMeet safety requirementsVehicle position/course/altitude controlPosition/direction controlFlight control modesControl system design
The present invention belongs to the field of the airplane flight control system design, and relates to a flybywire control system with high safety and low cost. The technical scheme of the system provided by the invention comprises the following steps: performing reasonable allocation of a command sensor, an actuator controller, a flight control computer, an actuator, a control plane position sensor and the type and the quantity of cables, and at the same time centralizing the functions of devices and performing optimal design of the interface relations of the devices. The security index is realized, the weight of the system is mitigated, the number of functional spare parts is reduced, the arrangement length of cables is decreased, and the cost of the flybywire control system is effectively reduced.
Owner:XIAN AIRCRAFT DESIGN INST OF AVIATION IND OF CHINA
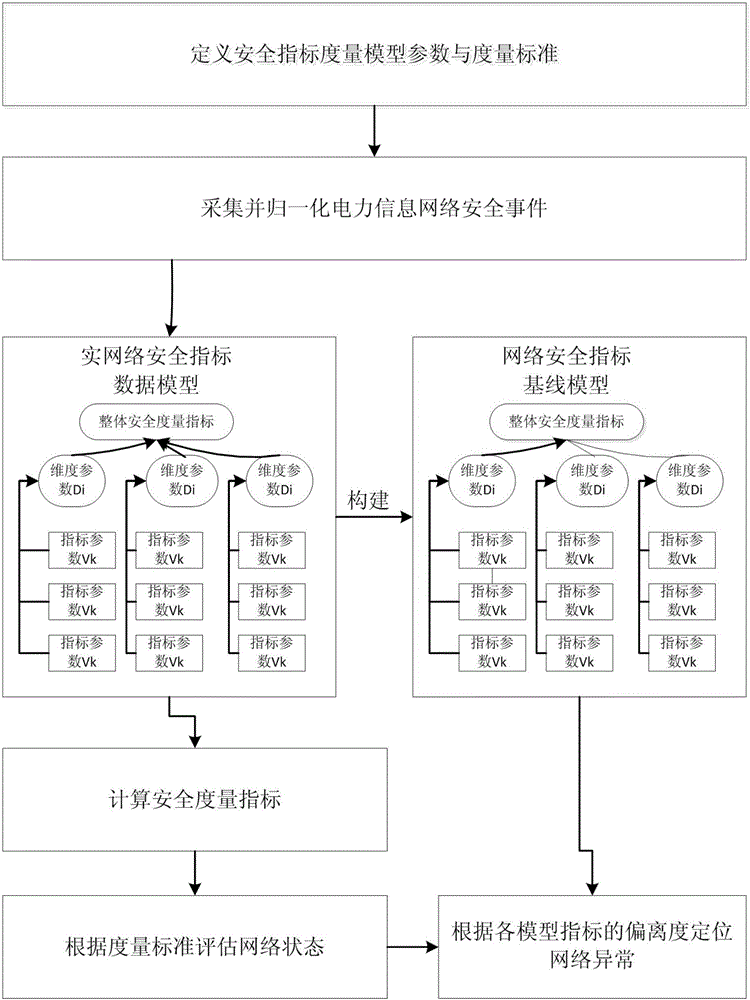
Electric power information network security measuring method based on security log data mining
The invention provides an electric power information network security measuring method based on security log data mining. The electric power information network security measuring method comprises the steps of defining a security index measurement model parameter and a measurement standard; acquiring electric power information network heterogeneous security events, normalizing the security events by means of an extensible security event standard format which is defined based on a template, and buffering the security events, thereby forming standard security events; in mass standard security events, grouping the security events according to a dimension parameter Di, extracting a parameter which reflect network safety operation condition according to an index parameter Vk, and obtaining a real-time network security index data model; dynamically updating the network security index data baseline model according to fitting between the network security index historical data and the network security index real-time data; calculating a network security measurement index; and obtaining a network abnormity position through the network security measurement index. The electric power information network security measuring method settles the technical problems such as low accuracy, low efficiency and no effective facility for performing security problem positioning in prior art.
Owner:GUIZHOU POWER GRID INFORMATION & TELECOMM
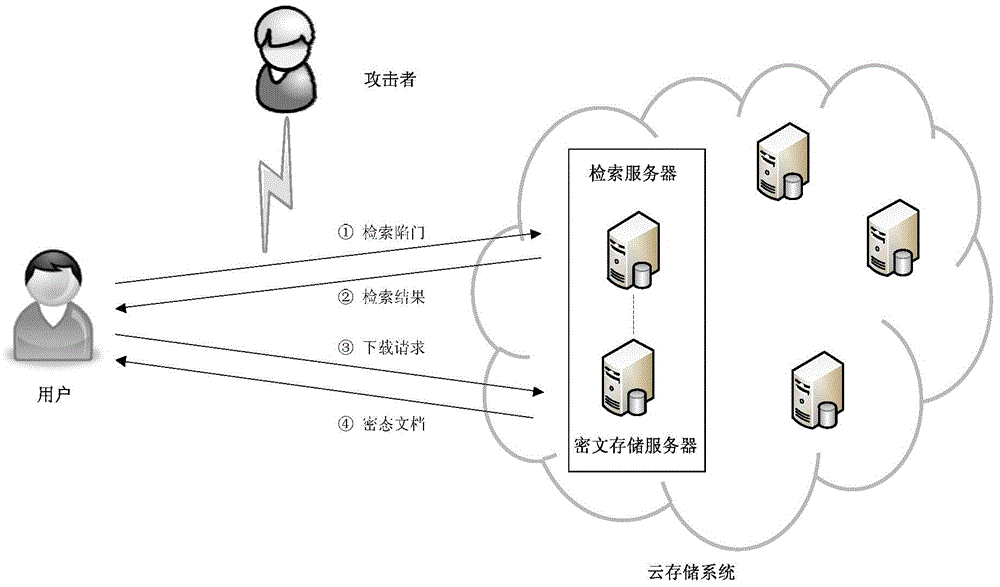
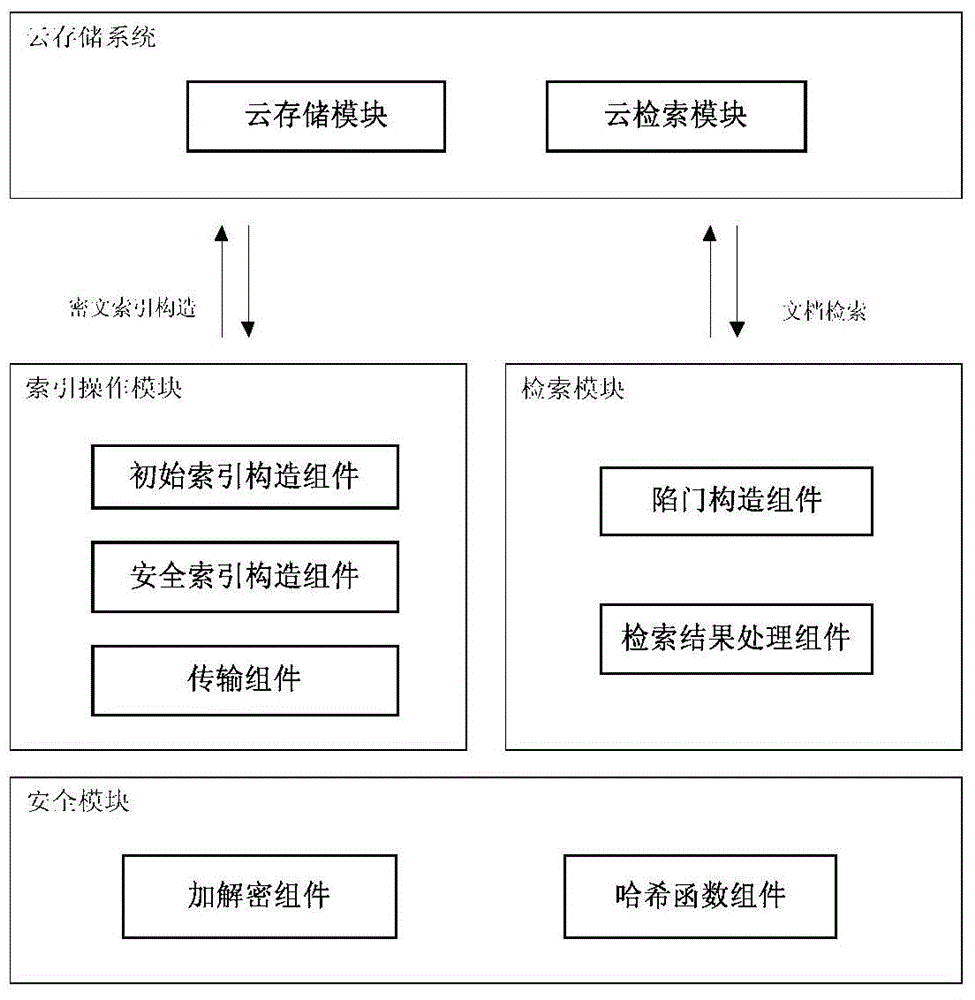
Safe electronic medical system for cloud storage
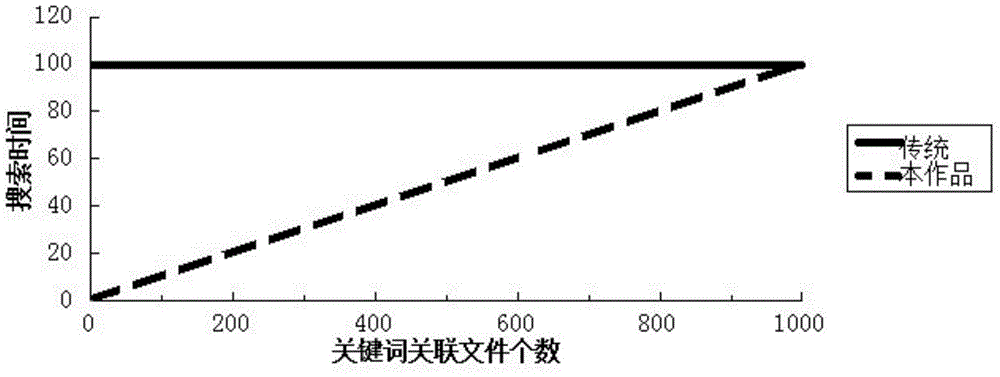
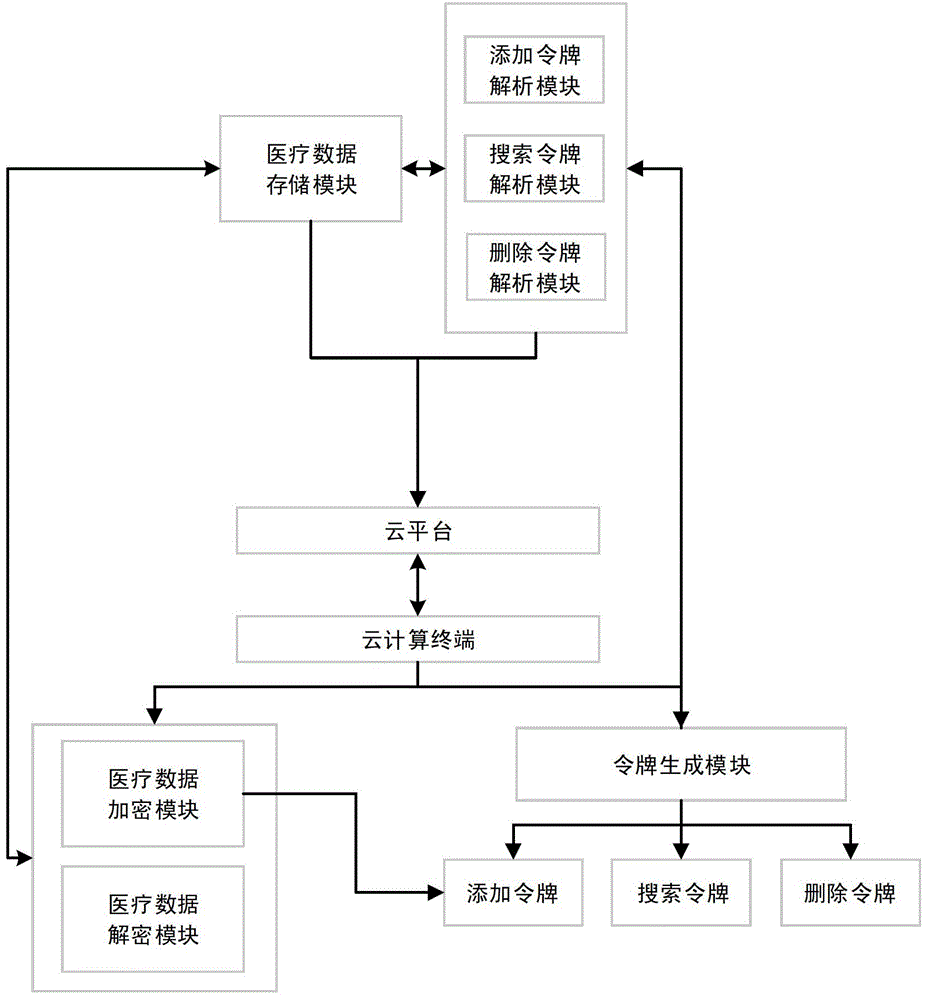
InactiveCN103607420AConvenient and effective storageEasy to manage effectivelyDigital data authenticationTransmissionPatient needConfidentiality
The invention relates to a safe electronic medical data management system for cloud storage, and the safe electronic medical data management system can be applied to the field of cloud storage. The safe electronic medical data management system comprises a cloud storage server terminal and a cloud computing terminal. The cloud storage server terminal is used for storing encrypt files uploaded by users, and generating and modifying a safe index for users to search, and dynamically updating encrypted medical data. The cloud computing terminal comprises a doctor terminal and a patient terminal, doctors and patients login the system through different roles in a website the patients need U shields to carry out identity authentication during login, and a user can login successfully and enter the website to have a look only when double factor authentication of a login password of the user and a data certificate of the U shield is passed. According to the invention, a cloud storage technology is employed to conveniently and effectively store and manage electronic medical data, and the confidentiality of the electronic medical data is guaranteed. A safe and effective electronic medical data search function and a dynamic update scheme are provided, and the scheme is an electronic medical data management scheme advantaged by safety, high efficiency, strong feasibility and good practicability.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
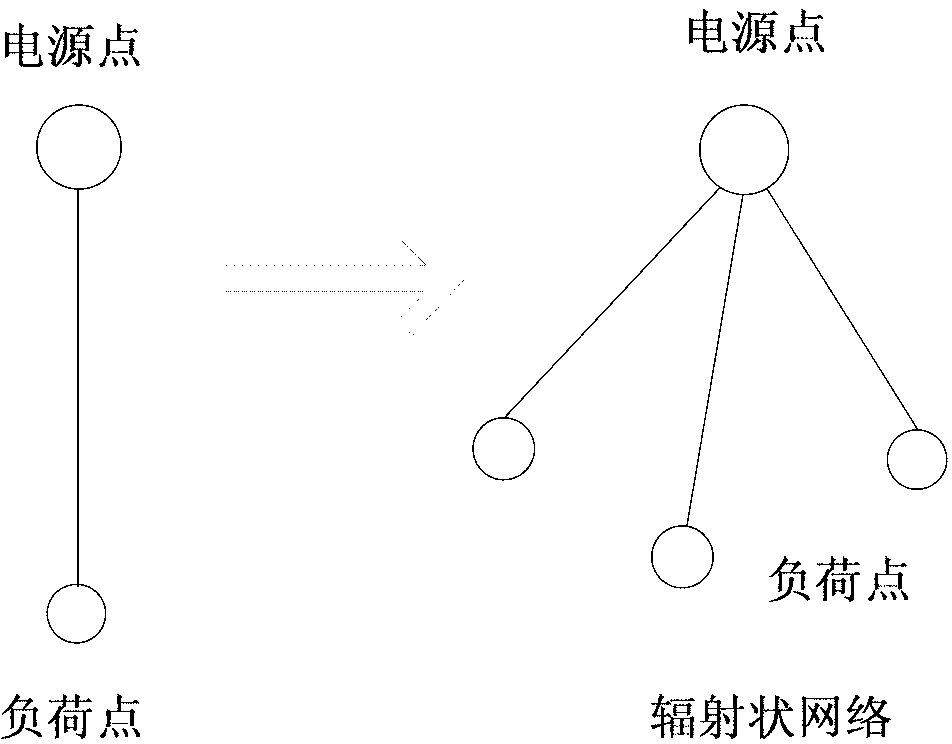
Distribution network connection method
InactiveCN103066596ASolve the problem of inconsistent index dimensionsAc network circuit arrangementsConnection typeSecurity index
The invention relates to a distribution network connection method and belongs to the distribution network method technical field. The distribution network connection method adopts that a primitive connection type is the basic unit of the distribution network transmission electric energy; a point-to-point connection type from a power supply to a load comprises an overhead primitive connection and a cable primitive connection. The distribution network connection method identifies the types and magnitudes of the primitive connection, forms the distribution network connection method in an inferring mode, and accesses the types of the distribution network connection. The appraisal types of the distribution network comprise a reliability access, an economic access, and a security access. The distribution network connection method chooses an optimized connection model, introduces obscure subordinating degree function to solve the problem of inconformity of all kinds of index dimensions, and achieves selecting the optimized connection type under different emphasis through dynamic weighting. The distribution network connection method has the advantages of avoiding a former inherent flaw of the connection type, improving the security index, an obscure subordinating degree and a weighting thought, providing novel synthetic evaluation module for the distribution network connection, and has a significant practical value and referential meaning on construction of the distribution network by introducing an obscure inference method to constitute the distribution network connection type.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
Phrase-based searchable symmetric encryption method
ActiveCN104899517AGuaranteed confidentialityAvoid transmissionDigital data protectionSpecial data processing applicationsSafety indexConfidentiality
A phrase-based searchable symmetric encryption method comprises steps of initializing a client end, generating a keyword index, generating a safety index and uploading to a cloud end server, generating an inquiry trapdoor and uploading to the clod end server, and executing inquiry and returning a result by the cloud end server. An encrypted ciphertext and the encrypted safety index are stored in the cloud end server, only file numbers and trapdoor information are mastered, during storage and inquiry operation of a cloud end, information of user storage data and information of inquired sentences are not leaked, confidentiality of the user data and an inquiry mode are ensured, the inquiry process has only one interaction, the trapdoor is uploaded, the file numbers containing the inquiry sentences are returned, a user downloads specific files to local for decryption as required, transmission of unnecessary files in a network is avoided and network expenditure is saved. The invention has the advantages of good security, less network expenditure and the like and is suitable for use in a low wideband environment.
Owner:SHAANXI NORMAL UNIV
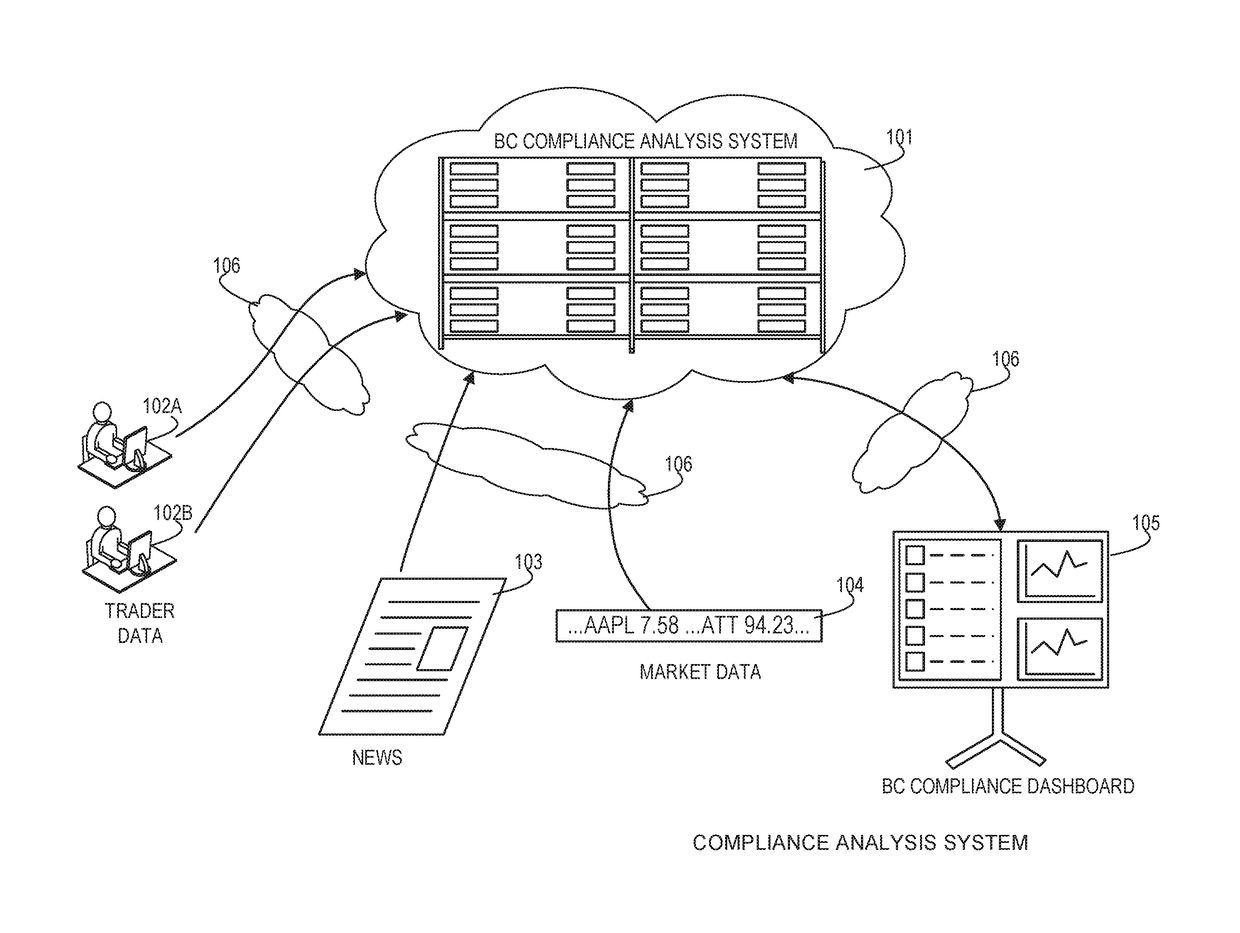
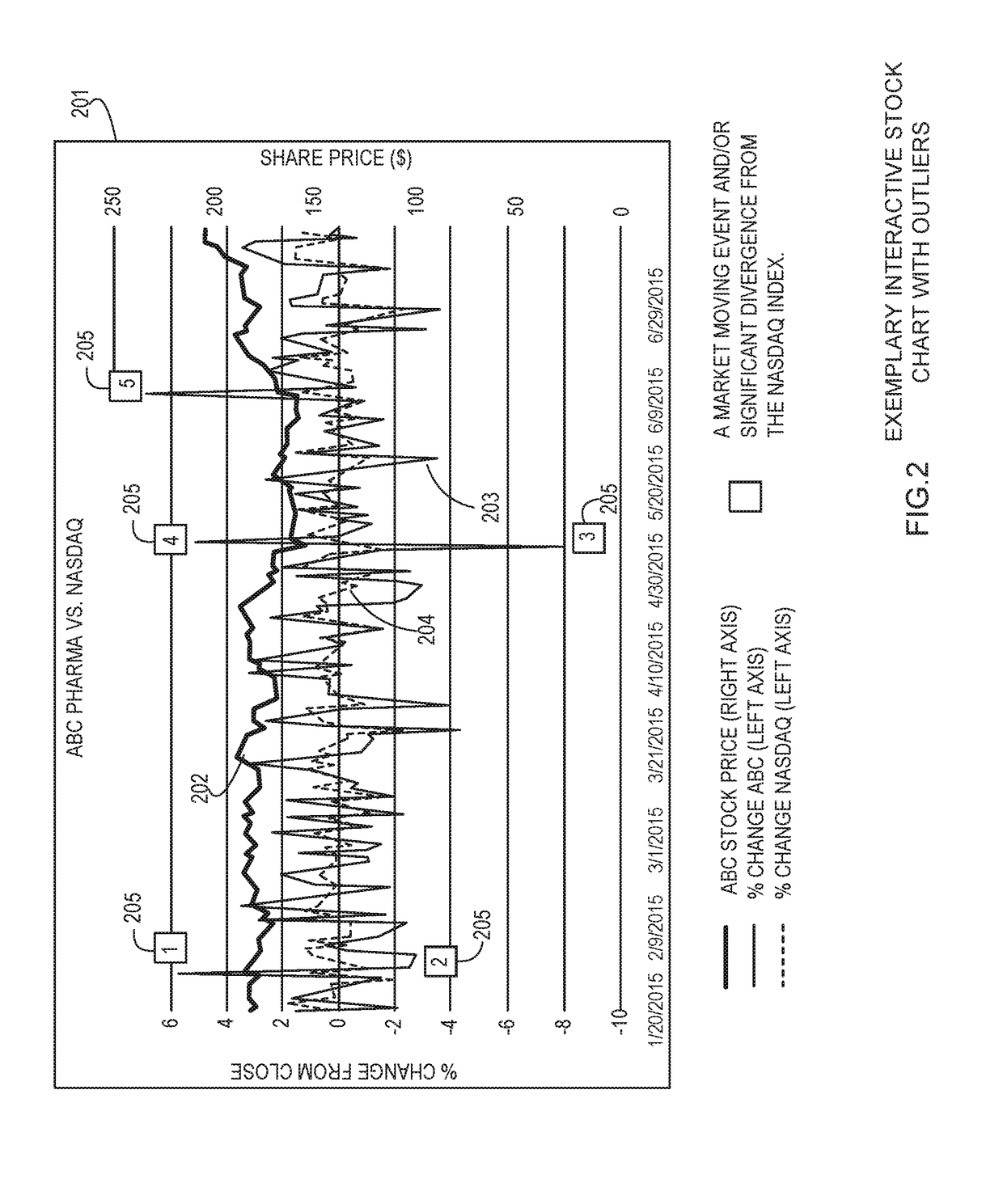
Systems and methods for identification and analysis of securities transactions abnormalities
System and methods for analyzing and making actionable stock and securities data, and more particularly to analyzing securities data and purchases in connection with news events to identify and analyze abnormalities in securities purchases relating to insider trading. A module comprised of market data as well as news and events related to securities and multiple Z-score market move mechanisms. Embodiments of the module also include historical pricing, historical percentage change, and historical volume for securities. In addition, the historical percentage change is also included for security indices and benchmarks. Market data is pulled into the module automatically then normalized to determine the output. The module calculates whether or not financial transactions are potentially nefarious to investment firms by applying targeted trades to market movements. Associated security news and events are produced and published to a dashboard and alert screen in an interactive format.
Owner:BASISCODE TECH LLC
Searchable encryption method based on semantic sorting of keywords
InactiveCN109063509AImprove retrieval efficiencyImplement Semantic Ranked SearchDigital data protectionSpecial data processing applicationsPlaintextDocument similarity
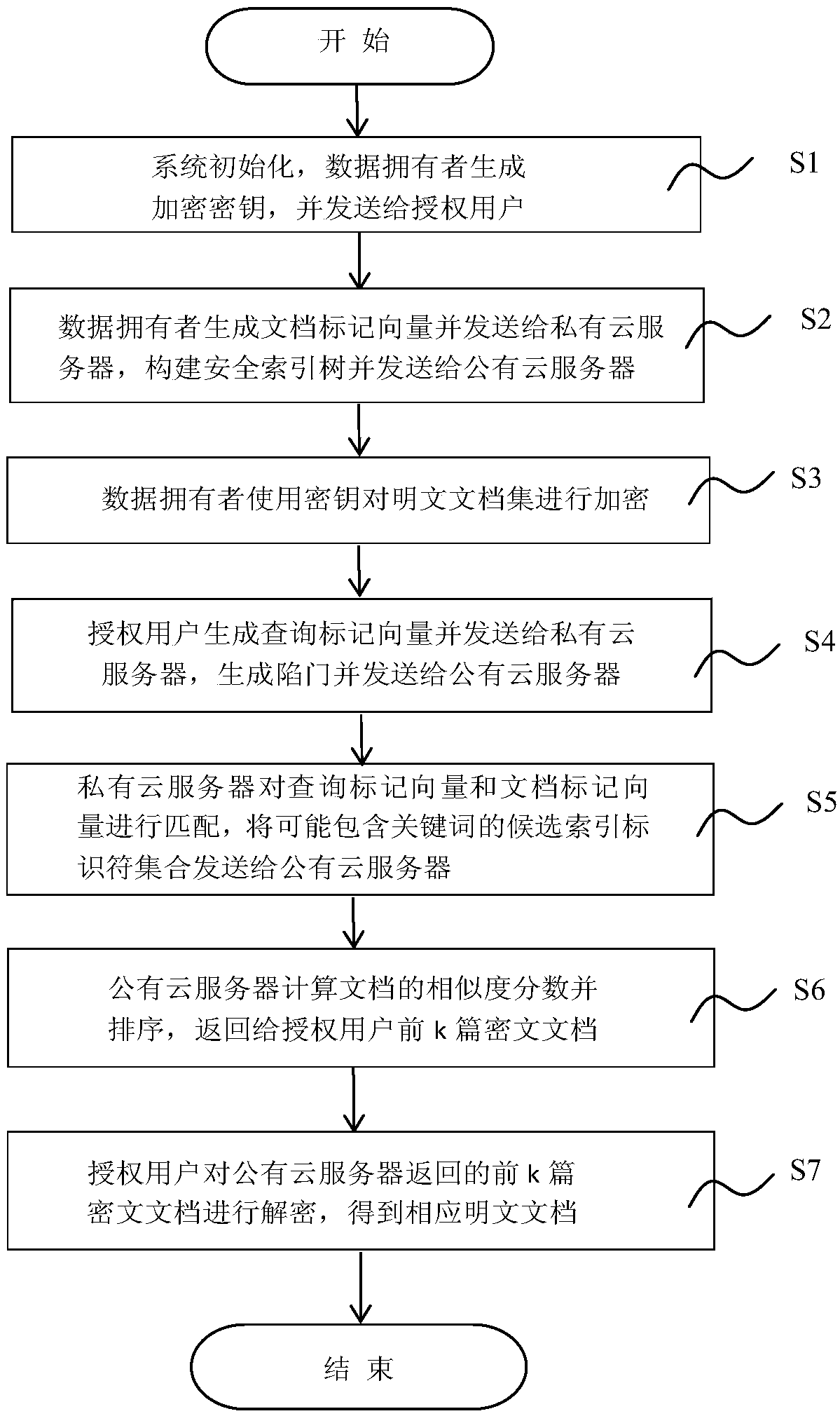
The invention discloses a searchable encryption method based on semantic sorting of keywords, includes such steps as generating encryption key by data owner and sending it to authorized user, extracting keywords from plaintext document set, constructing document mark vector according to keywords and sending it to private cloud server, creating secure index tree and sending it to public cloud server; The authorized user sends the query mark vector generated by the search keyword to the private cloud server, and sends the generated query trap to the public cloud server. The private cloud servermatches the query tag vector with the document tag vector, and sends the set of security index identifiers that may satisfy the user's query request to the public cloud server. The public cloud servercalculates document similarity, sorts the calculation results, and returns the set of ciphertext documents with the highest similarity to the authorized users. By realizing the multi-keyword semanticsorting method, the invention not only ensures the data privacy safety, but also effectively improves the retrieval efficiency.
Owner:SHANGHAI MARITIME UNIVERSITY
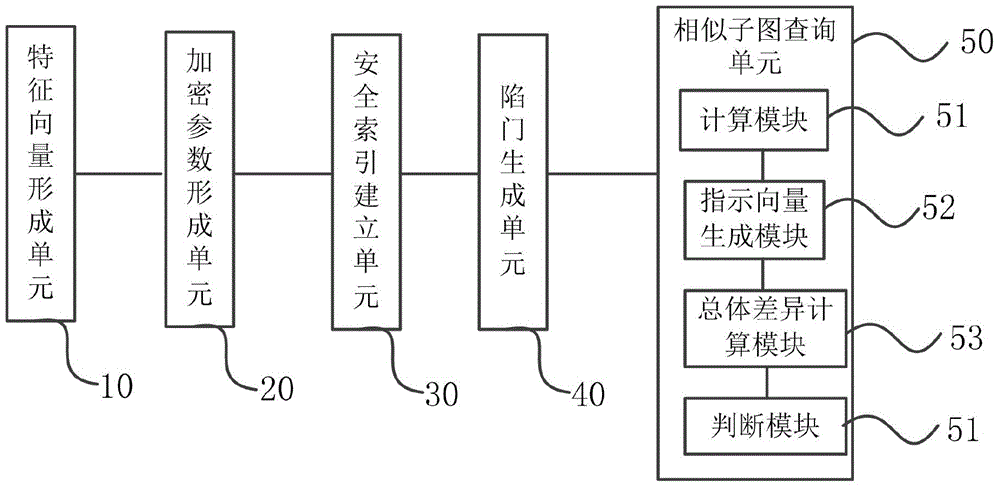
Similar sub-image inquiring method and system for protecting privacy under cloud computing environment
InactiveCN104408070ADigital data protectionSpecial data processing applicationsSafety indexFeature vector
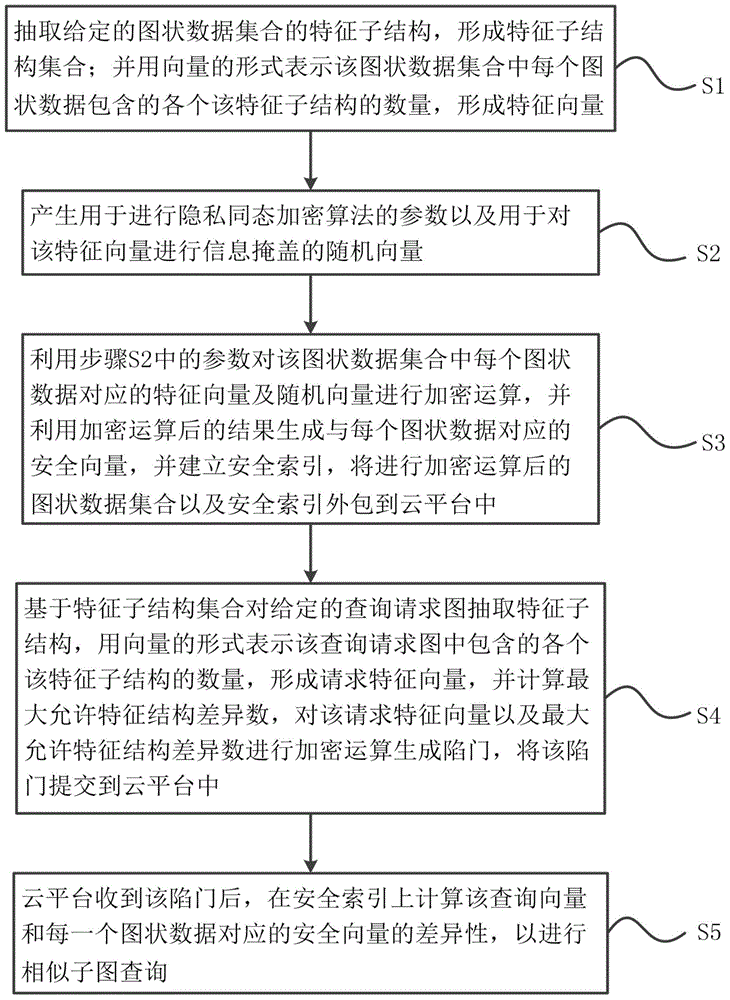
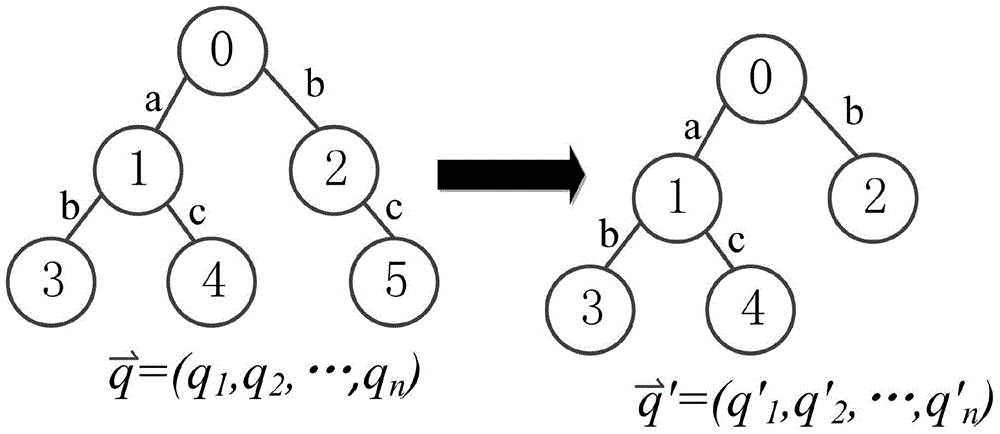
The invention provides a similar sub-image inquiring method and system for protecting privacy under a cloud computing environment. The similar sub-image inquiring method comprises the following steps: extracting characteristic sub-structures of an image shape data set; representing the quantity of each characteristic sub-structure contained in each image datum by using a characteristic vector; generating a parameter for encrypting and a random vector, and carrying out encryption calculation on the characteristic vector and the random vector of each image shape datum to generate a safety vector and establish a safety index; outsourcing the encrypted image shape data set and safety index into a cloud platform; extracting a characteristic sub-structure from an inquiry request image, and representing the quantity of each characteristic sub-structure contained in the inquiry request image by using a request characteristic vector; calculating a maximum allowable characteristic structure difference number, and generating a trap door and submitting the trap door to the cloud platform; after the cloud platform receives the trap door, calculating the difference between the request characteristic vector and the safety vector corresponding to the image shape data on the safety index to further inquire a similar sub-image. According to the similar sub-image inquiring method and system, the safety of privacy information referred in a similar sub-image inquiring process can be protected.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Rapid ciphertext retrieval method and system capable of resisting statistical analysis attack
ActiveCN104636462AImprove securityEffectively hideDigital data protectionSpecial data processing applicationsSafety indexCiphertext
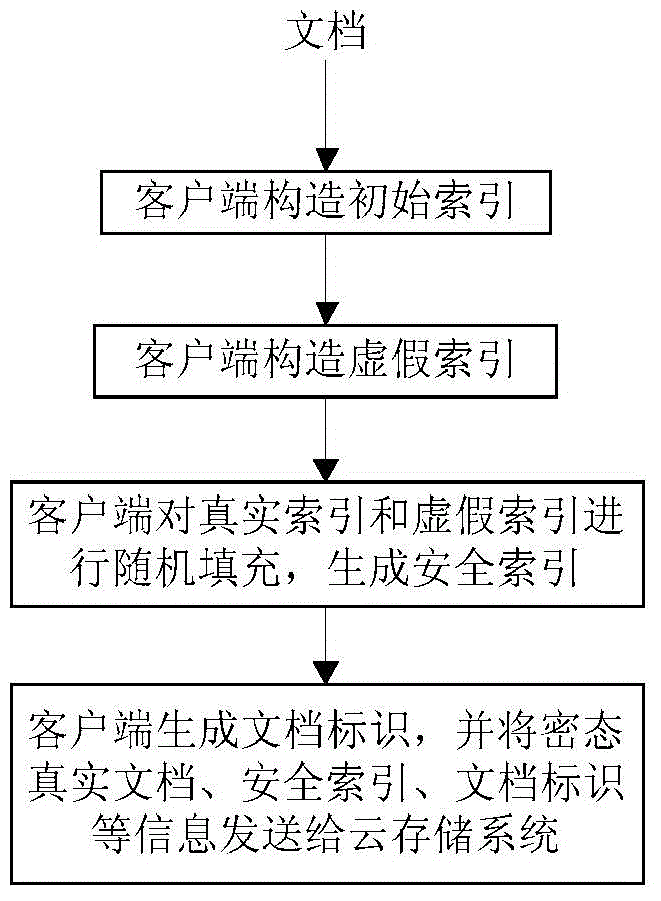
The invention discloses a rapid ciphertext retrieval method and system capable of resisting a statistical analysis attack, and belongs to the technical field of information safety. According to the method and system, rapid retrieval of mass of ciphertext documents can be achieved, and the statistical analysis attack can be effectively resisted. The system comprises a cloud storage system and a plurality of client sides, and the client sides are connected with the cloud storage system through a network. On the basis of the principle, after the client sides carry out initial index setting on documents hopefully uploaded by users on client sides, a false index is firstly set up, then, random filling is carried out on a real index and the false index to generate a safety index, and therefore statistical information of the documents can be effectively hidden, and the aim of resisting the statistical analysis attack is achieved. The method specifically comprises (1) system initialization, (2), ciphertext index setting and (3) document retrieval. The system and method have the advantages that the retrieval efficiency is high, accuracy is high, the communication cost is low, the statistical information of the documents can be effectively hidden, and the statistical analysis attack can be resisted.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com