Fuzzy query encryption method supporting dynamic verification in unreliable cloud computing environment
A computing environment and dynamic verification technology, applied in computing, computer security devices, special data processing applications, etc., can solve the problem that there is no way to support encrypted data fuzzy query, verification results and dynamic updates at the same time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
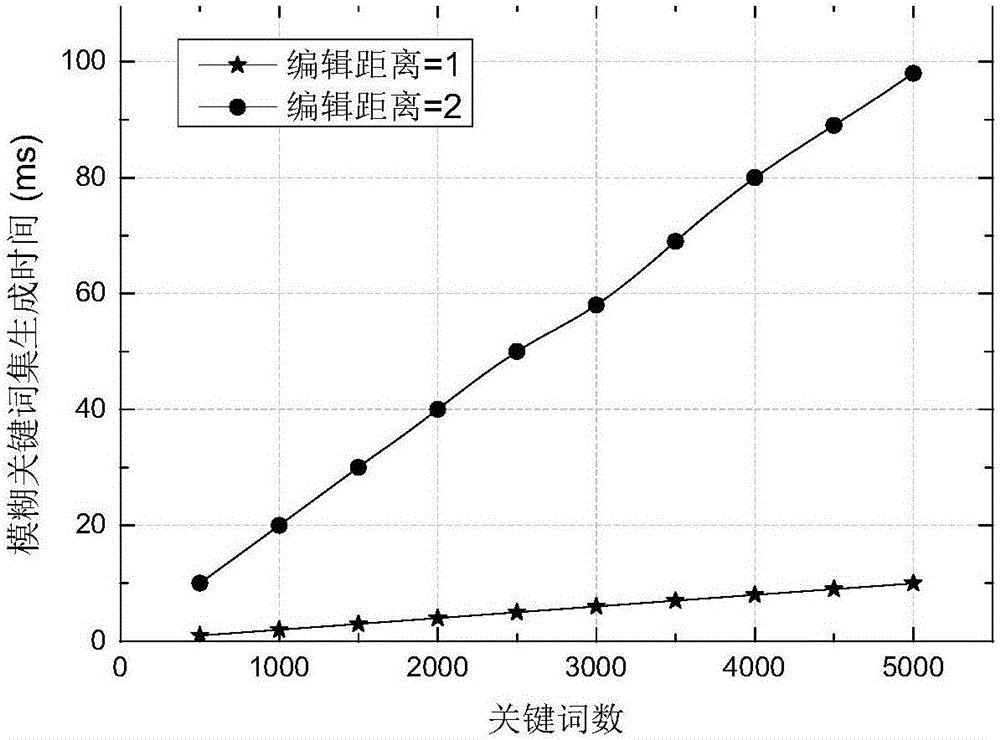
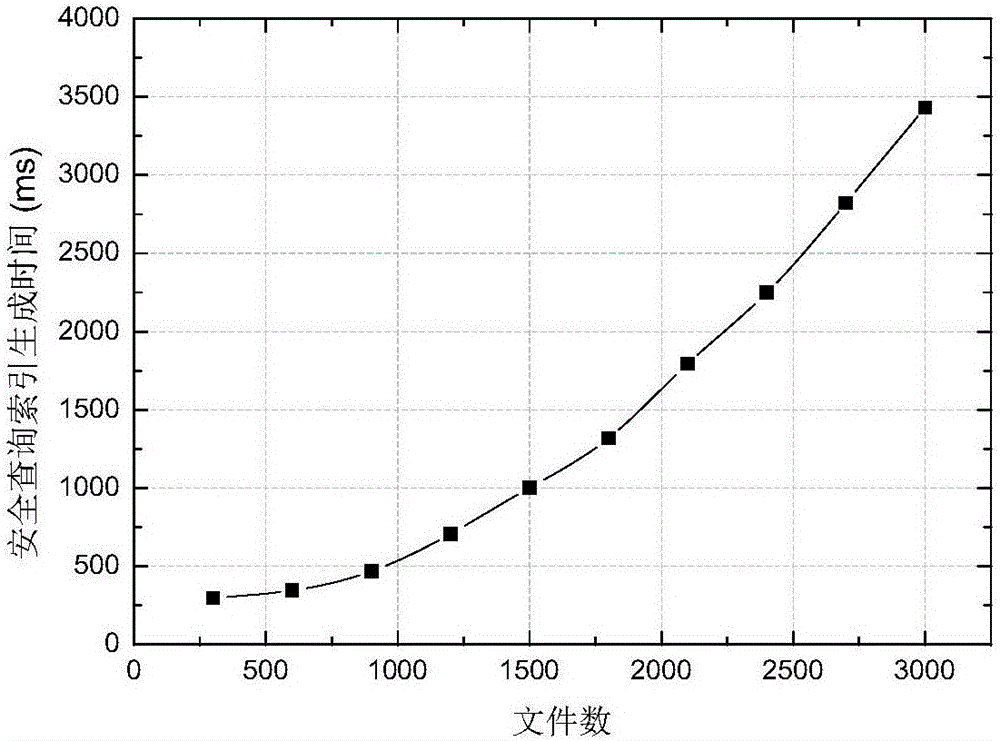
[0053] The experimental hardware environment is Windows 7 operating system, the CPU is Intel Core i5-4590 (3.30GHz), the memory is 4GB, and it is implemented by Java programming language. The data set is a collection of IEEE INFOCOM papers in the past 10 years, containing more than 3,500 articles. By extracting the keywords contained in the documents, a keyword set is formed. The experiment uses the 256-bit AES symmetric encryption algorithm to encrypt and decrypt the document, uses the RSA accumulator with a key length of 1024 bits to generate verification evidence, and uses SHA-256 as the hash function.
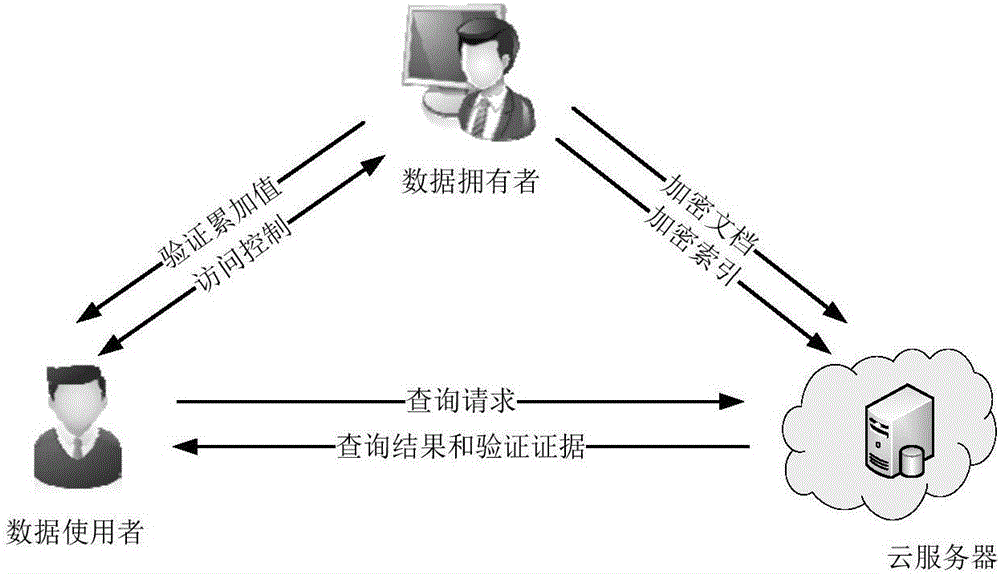
[0054] A fuzzy query encryption method that supports dynamic verification in an untrusted cloud computing environment. The overall architecture is as follows: figure 1 shown, including the following steps:
[0055] Step 1: The data owner uses the k...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com